Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
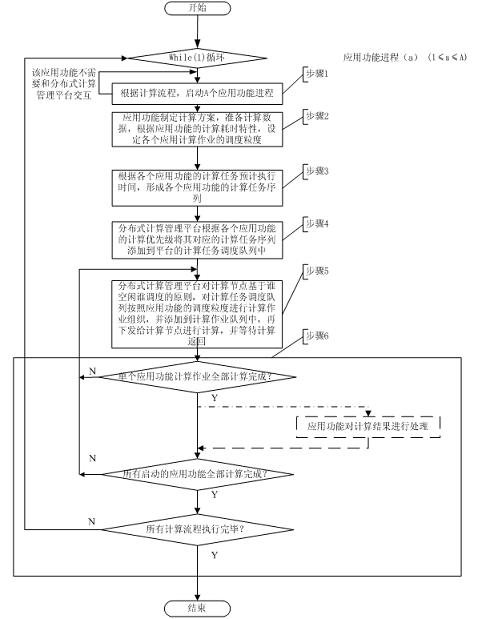
674 results about "Computer cluster" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
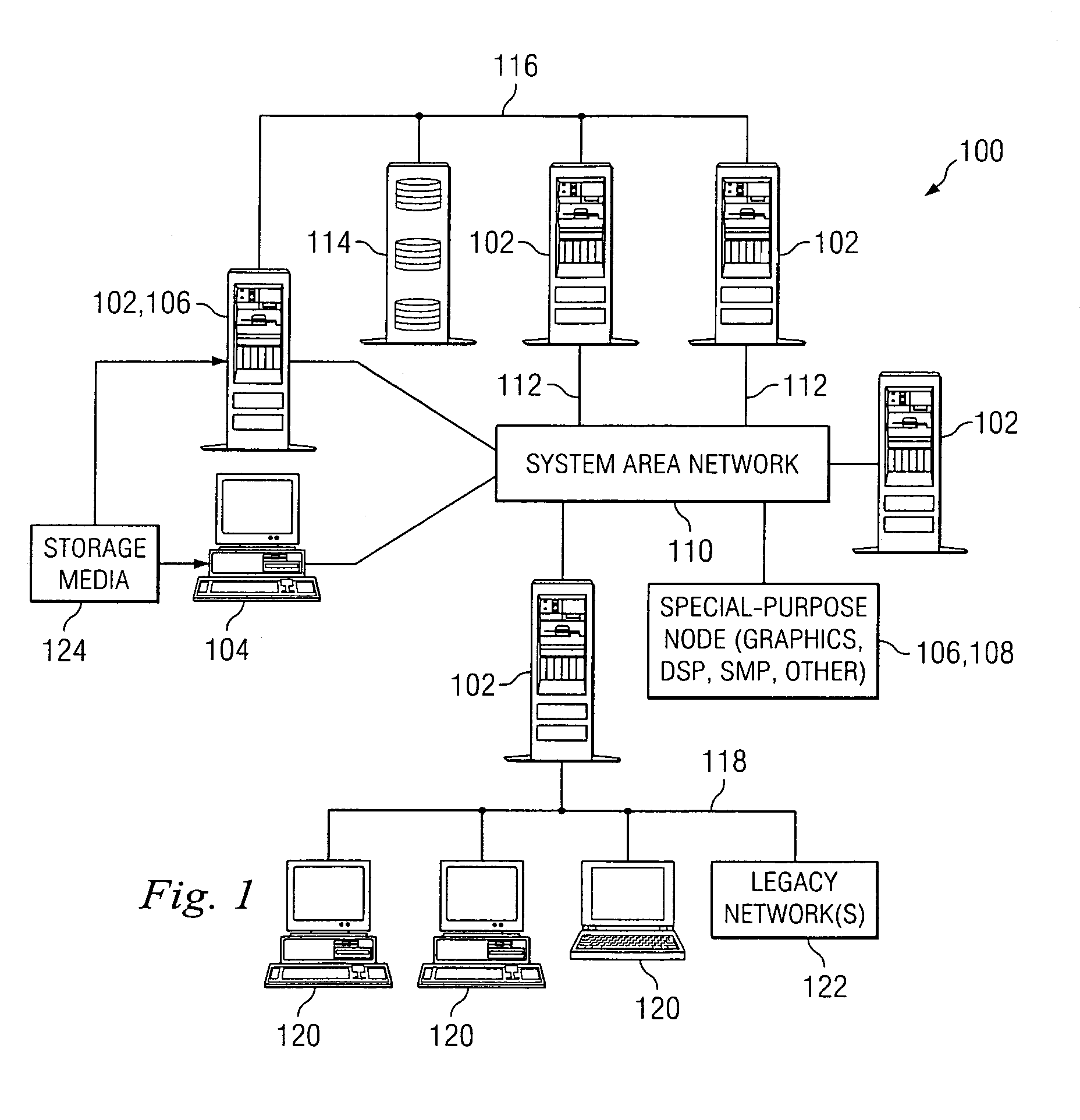
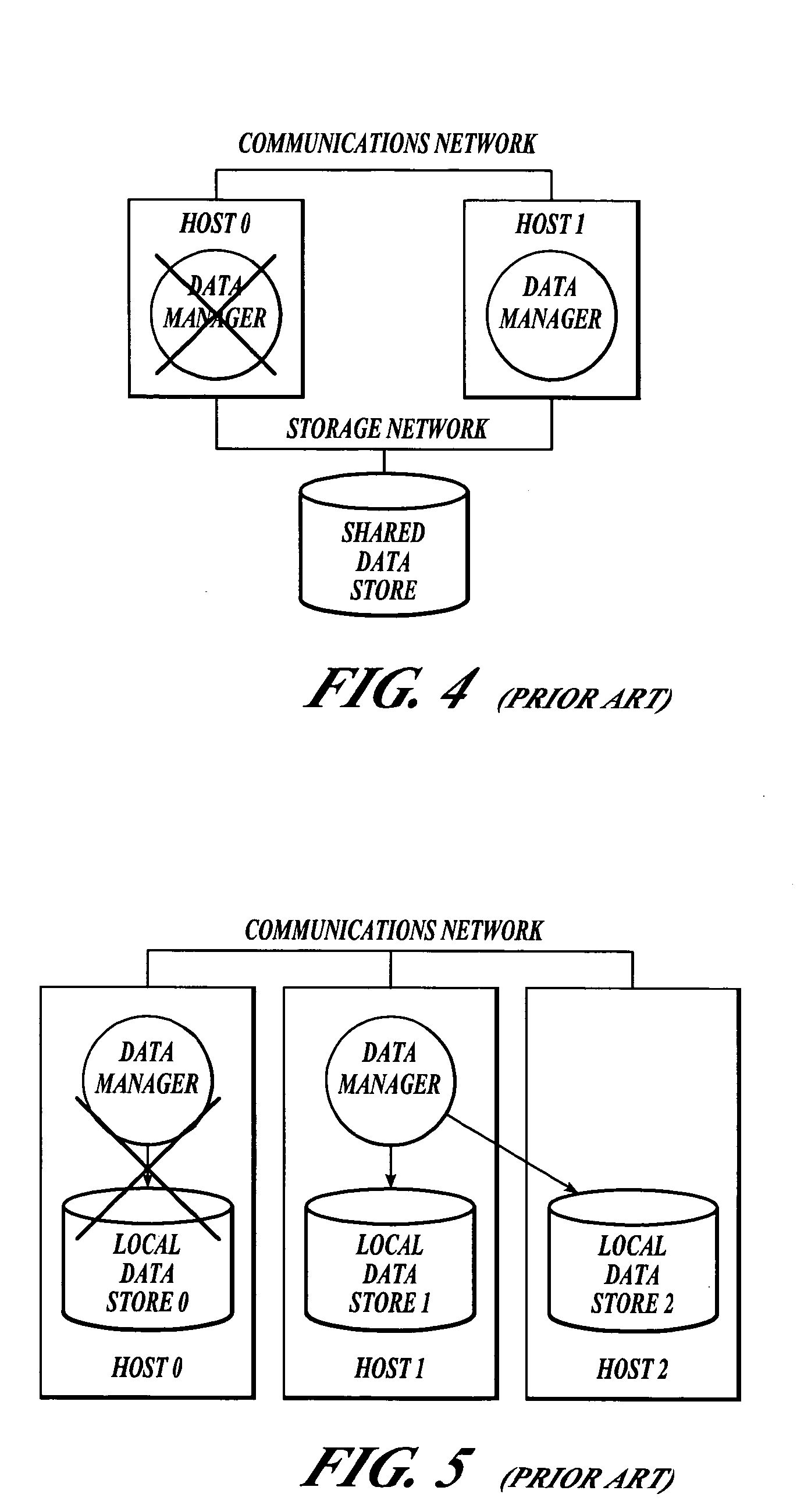
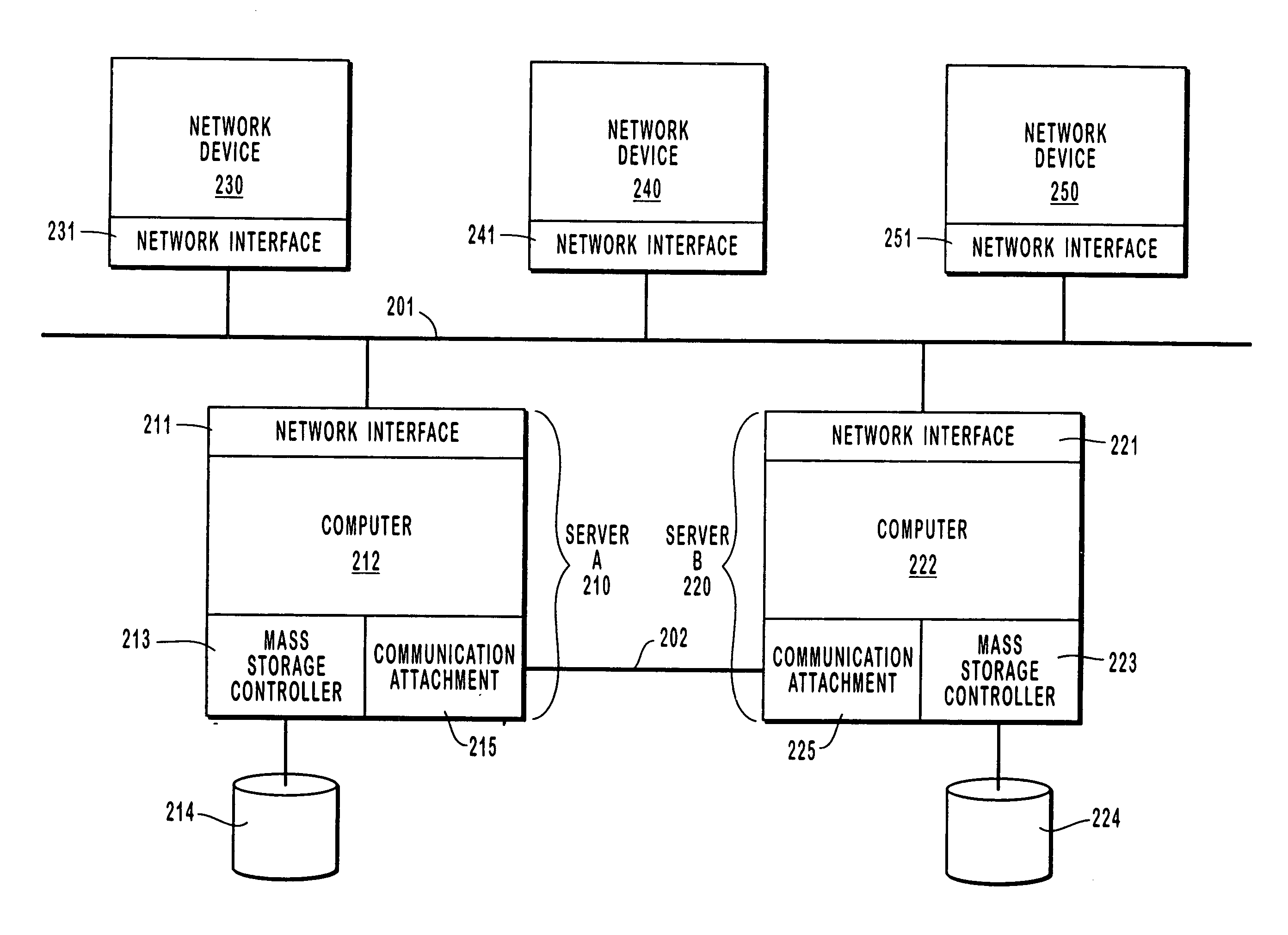
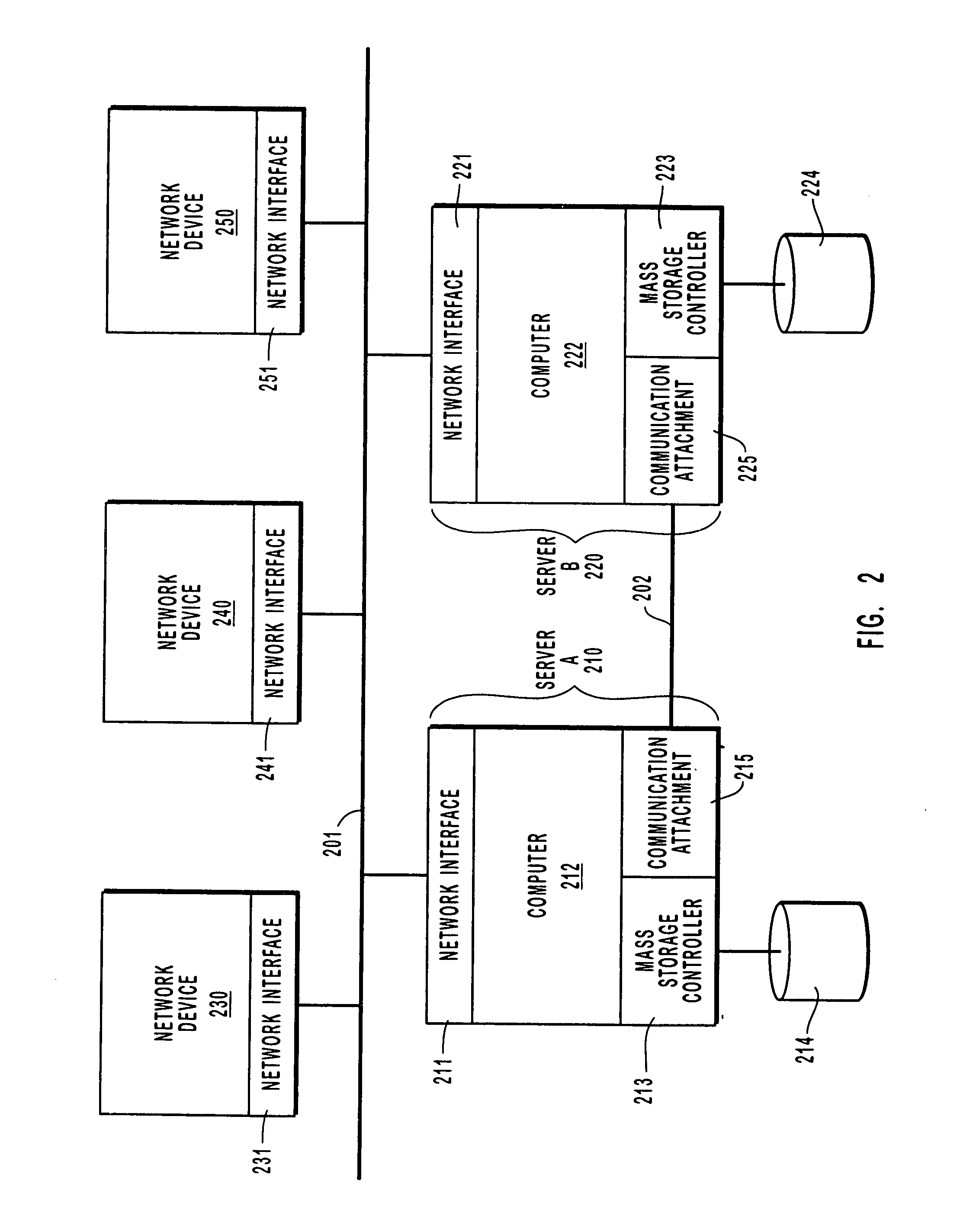
A computer cluster is a set of loosely or tightly connected computers that work together so that, in many respects, they can be viewed as a single system. Unlike grid computers, computer clusters have each node set to perform the same task, controlled and scheduled by software.
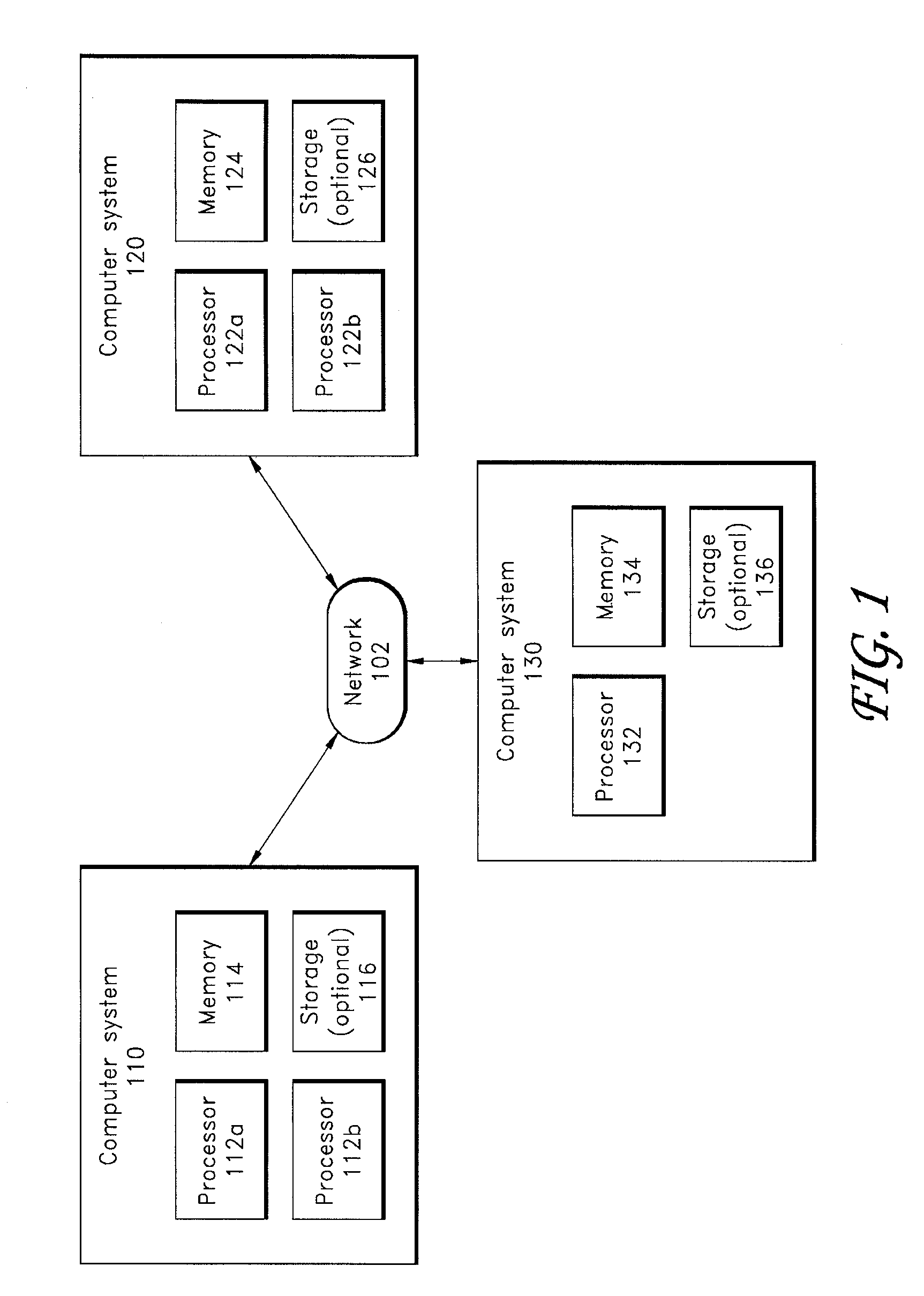
Clustered computer system with centralized administration
InactiveUS20060053216A1Digital computer detailsComputer security arrangementsOperational systemComputer cluster
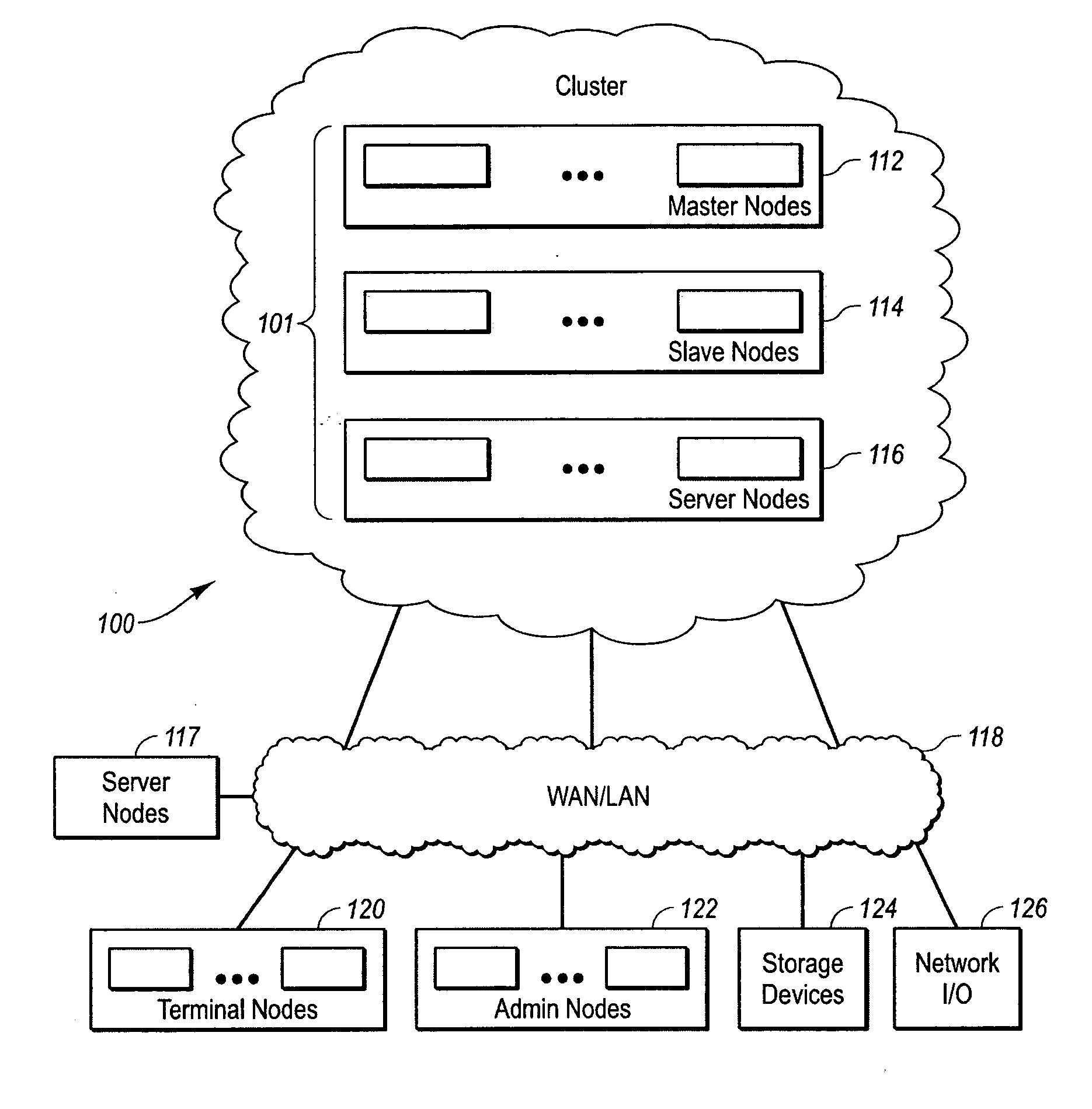
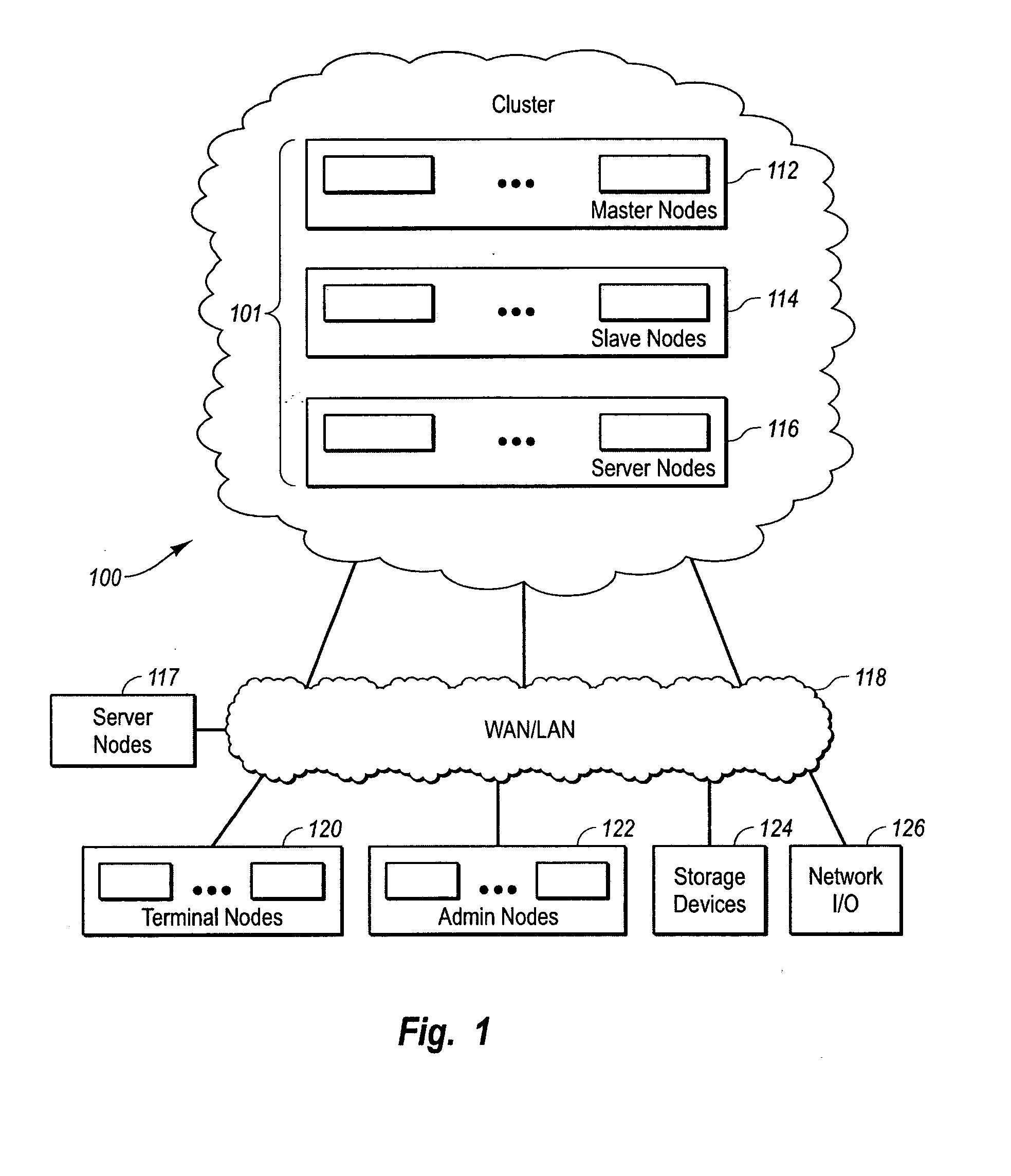
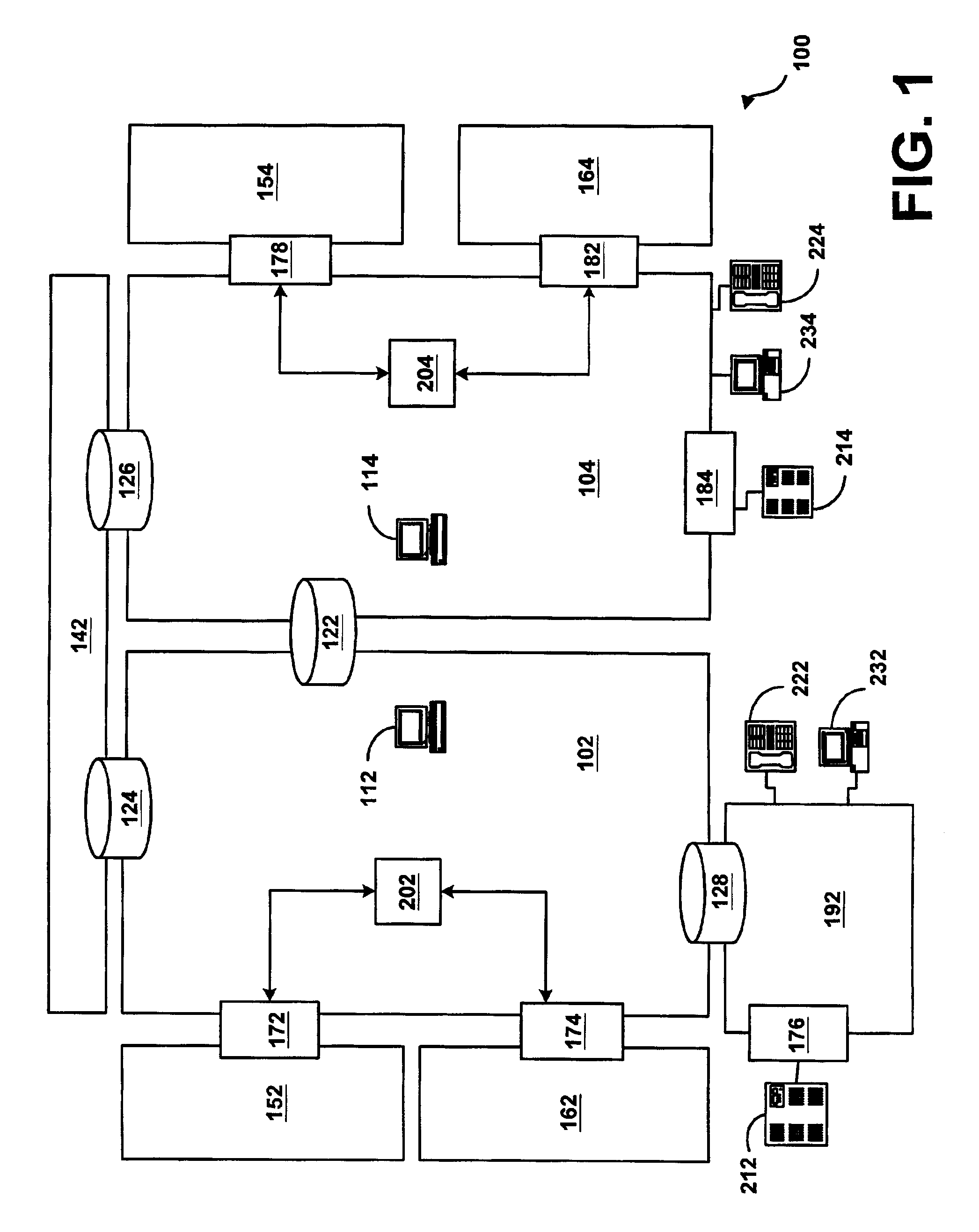
Systems and methods for a computer cluster and for conducting user sessions in a managed enterprise computer network. A cluster includes multiple inter-connected nodes with specific roles. Master nodes administer and monitor slave nodes and the slave nodes are used to conduct user sessions with users through terminal nodes that provide an interface to the cluster. The cluster also may include server nodes that provide network services. Master nodes also control admittance to the cluster of external nodes and sub-clusters. Admin nodes form a control plane used to control and administer the cluster through the master nodes. The cluster provides a virtual environment for the user session that is built from at least an operating system image, an application image and other data needed for the user session.
Owner:METAMACHINIX
System and method for assisting in controlling real-time transport protocol flow through multiple networks via use of a cluster of session routers
InactiveUS7002973B2Not easy to changeMultiplex system selection arrangementsInterconnection arrangementsTransceiverComputer cluster
A system for assisting in controlling real-time transport protocol flow through multiple networks via use of a cluster of session routers is disclosed. The system utilizes a first computer and a cluster of computers, wherein the cluster of computers comprises at least two associated computers that are connected to the first computer. Each of the associated computers comprises a second transceiver, a second memory having logic stored therein defining functions to be performed by the associated computers, and a second processor. The second processor is configured by the second memory to perform the functions of: performing an inbound screen on route information received by an associated computer, from the first computer, to determine if the received route information should be discarded; if the route information is not discarded, comparing the received and screened route information to a local policy defined within the cluster of computers; and performing an outbound screen on the received and screened information prior to transmitting the received and screened information outside the cluster of computers.
Owner:PRIMARY NETWORKS +1
Method and system for signing and authenticating electronic documents
InactiveUS7237114B1Complete private encryption key constructing and reconstructing can be avoidedPrevent steppingUser identity/authority verificationUnauthorized memory use protectionElectronic documentComputer cluster
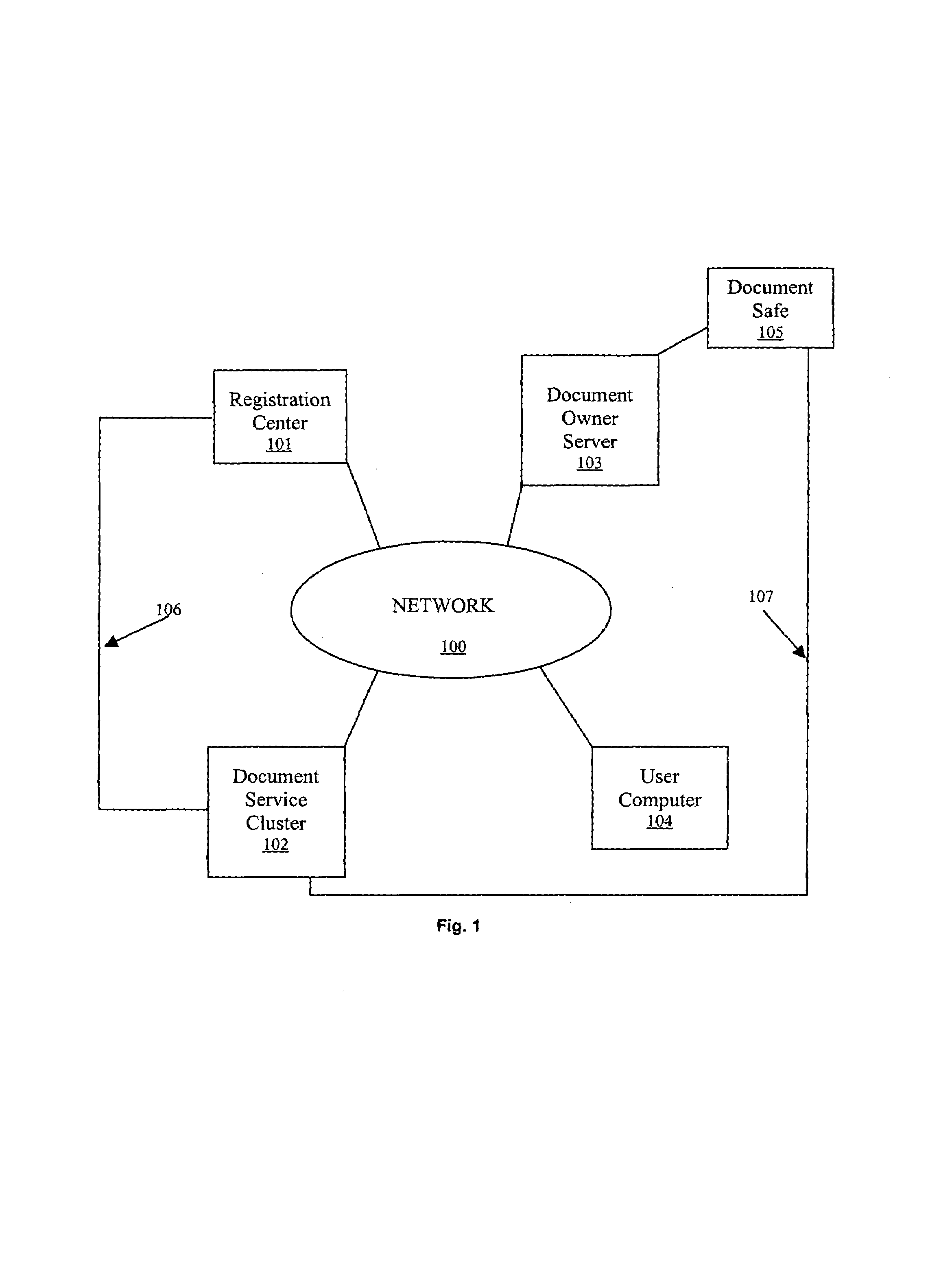
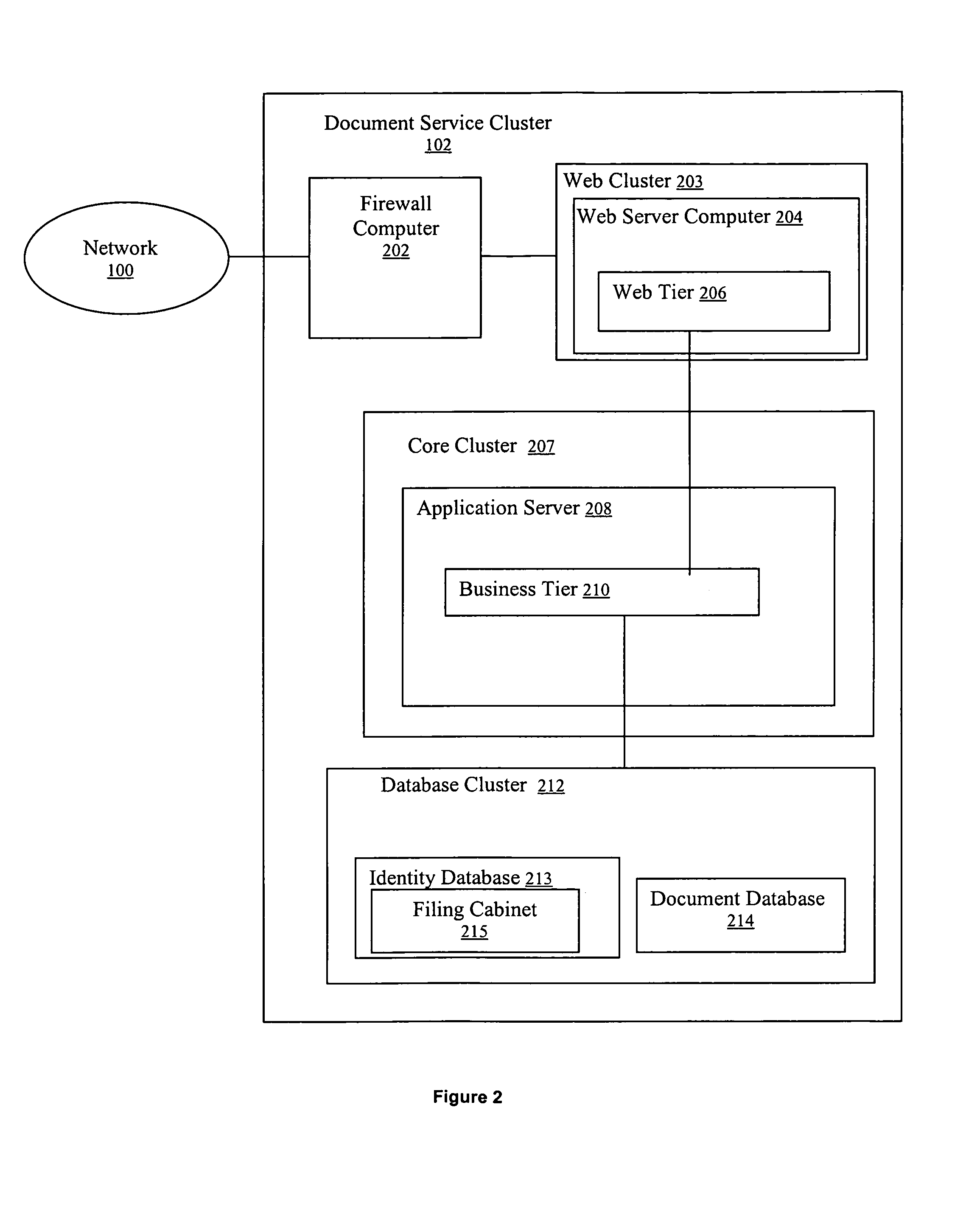
A system and method for signing, sorting, and authenticating electronic documents using public key cryptography. The system comprises a document service computer cluster connected to user computers, document owner server computers, and registration computers via a network such as for example, the internet or the world wide web. Document owners and system users can store electronic documents in an encrypted database located on the document service computer cluster, or on a document safe connected to the document owner server. Users can sign documents by identifying the document to be signed and sending a signing request to the document service computer cluster. The document service computer cluster retrieves the user's private key, which is located securely in a database on the cluster, and signs the identified document. No dedicated signing software need be installed on the user computer prior to accessing the document service computer cluster.
Owner:SIGNIX
System and method for providing dynamically alterable computer clusters for message routing
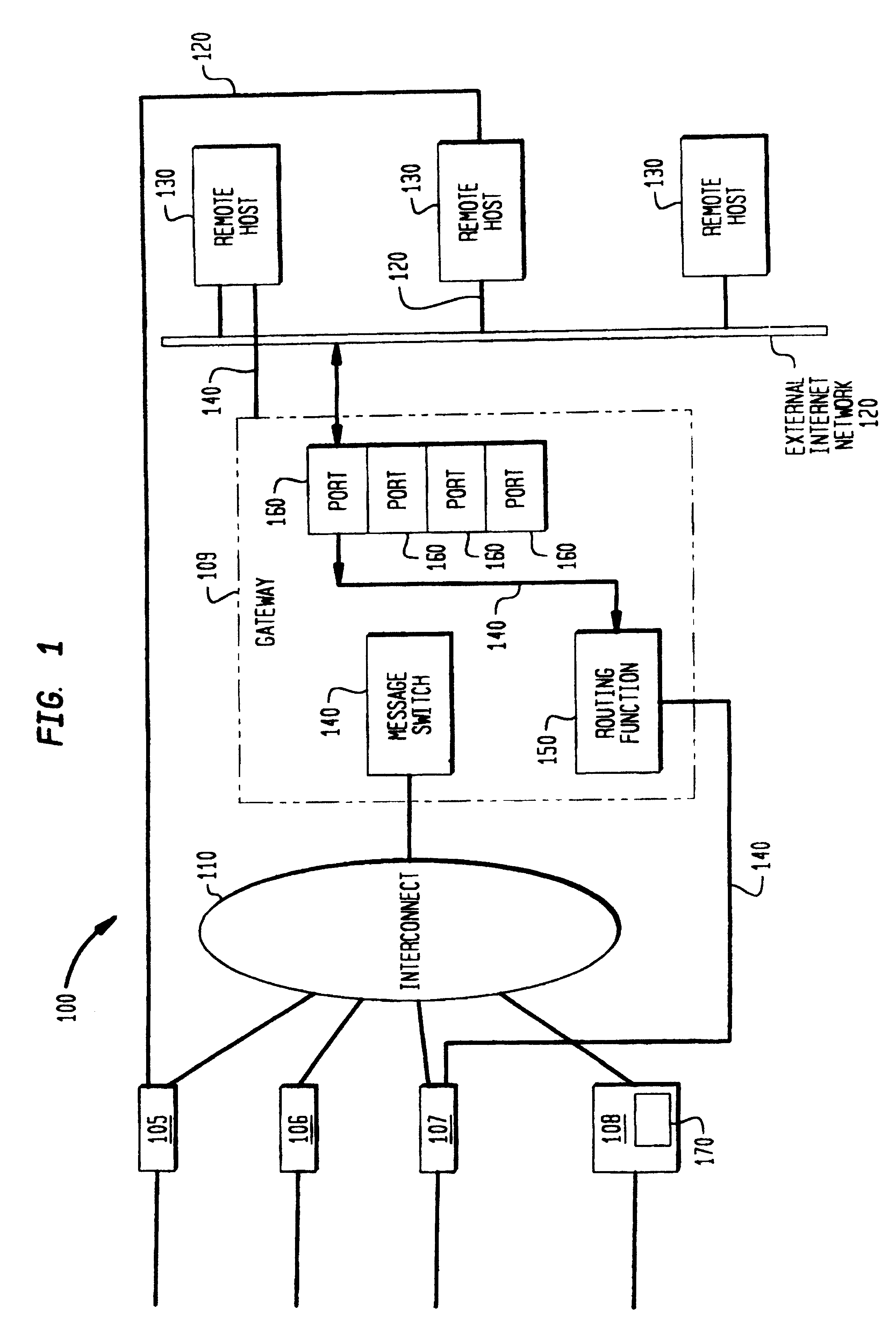
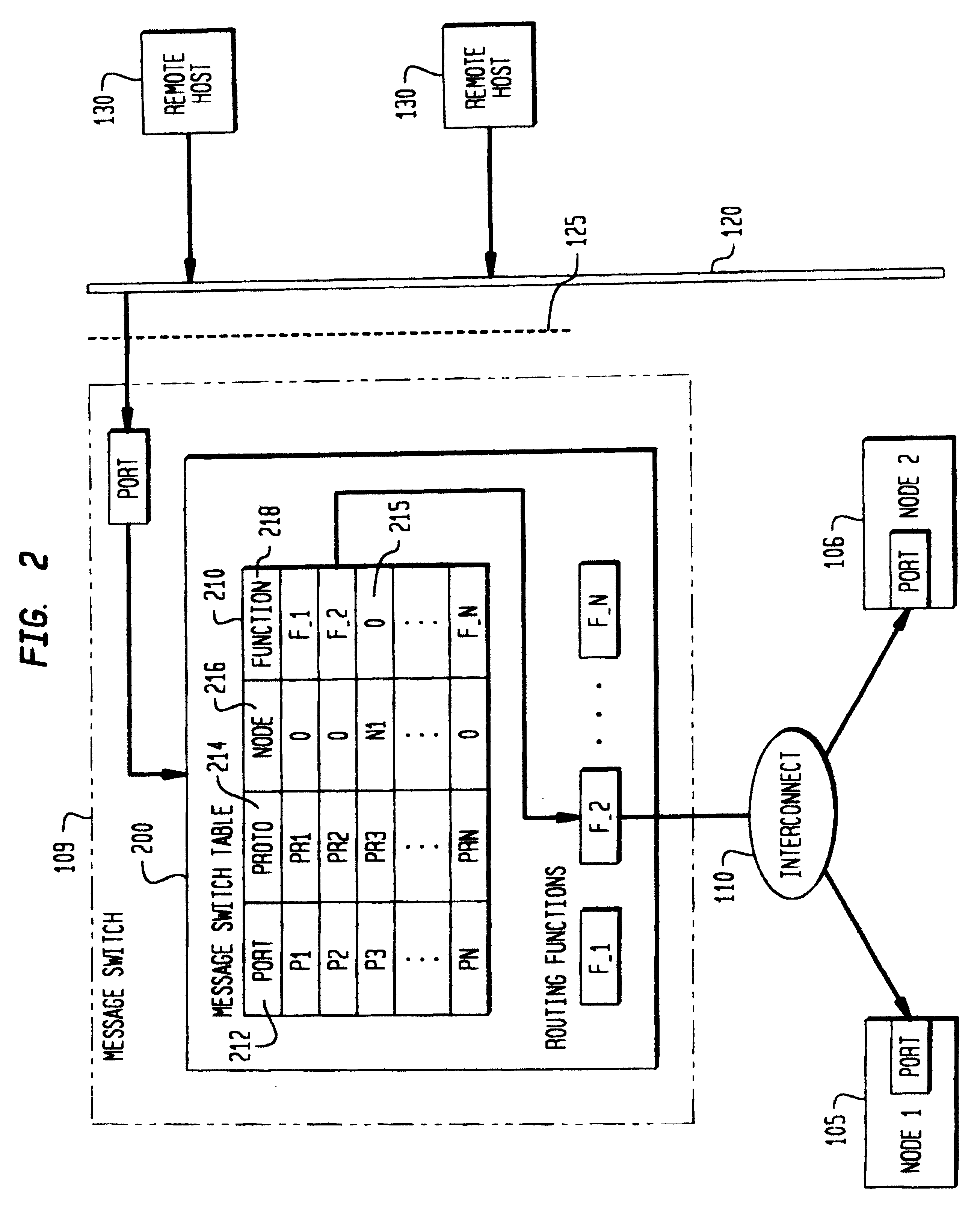
InactiveUS6496866B2Lower latencyAvoid problemsError detection/correctionDigital computer detailsComputer clusterMessage routing
Owner:INT BUSINESS MASCH CORP
Method for detecting and resolving a partition condition in a cluster
InactiveUS6965936B1Error detection/correctionMultiple digital computer combinationsComputer clusterTheoretical computer science
A method and system to detect and resolve a partition condition in a cluster of computers in a networked environment is described. The method can include: creating a scratch pad area accessible by the cluster of computers; dividing the scratch pad into a plurality of slots; recording in the plurality of slots, a generation number and a list of known nodes by each one of the plurality of notes, wherein an identifier is written in the list for each node that is known to a writing node; comparing each slot of the plurality of slots to ensure the generation number and the list of known nodes matches in each slot of the plurality of slots; and resolving the partition condition by creating a list of surviving nodes and re-allocating appropriate resources to each of the surviving nodes.
Owner:EMC IP HLDG CO LLC
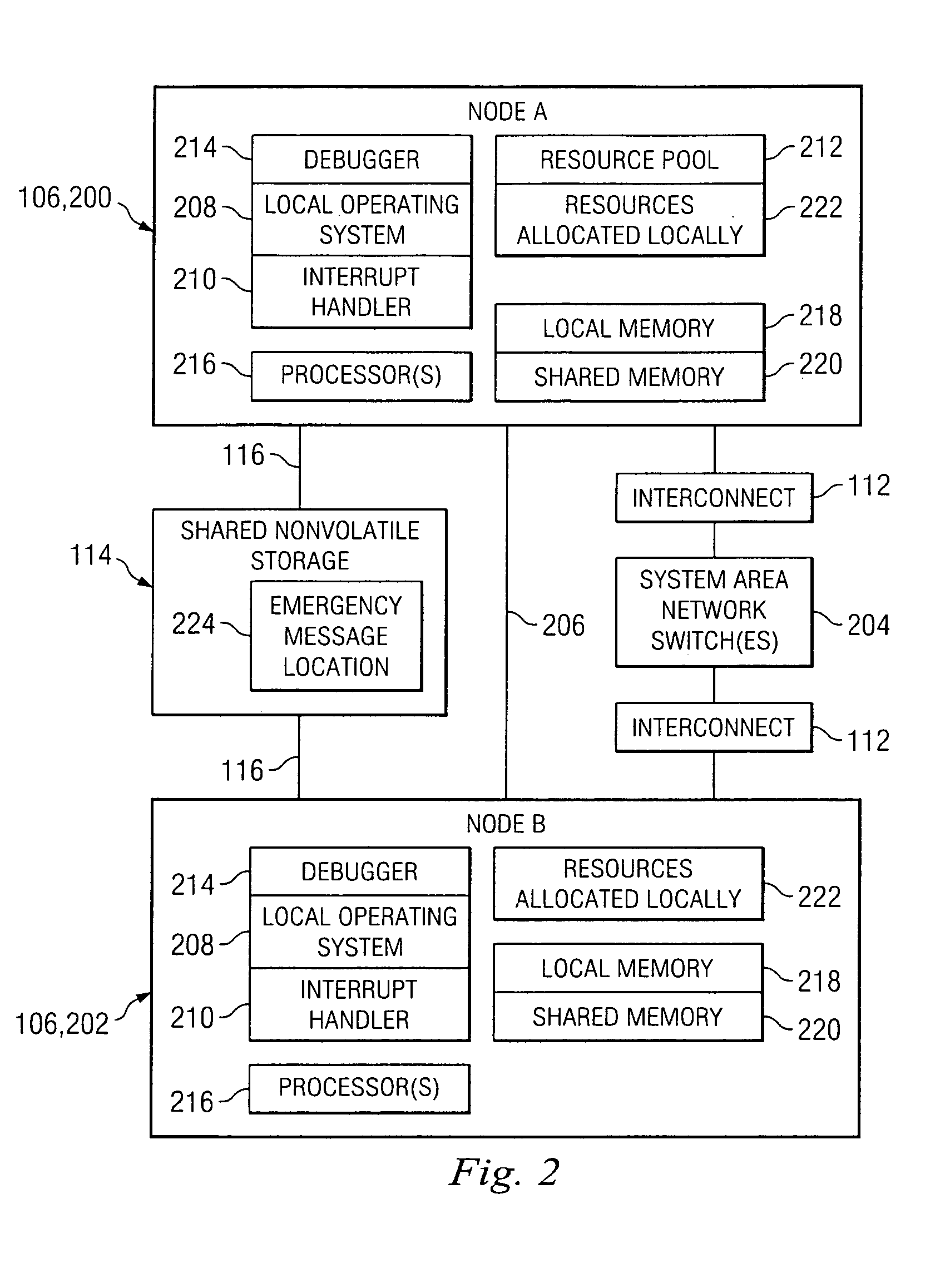
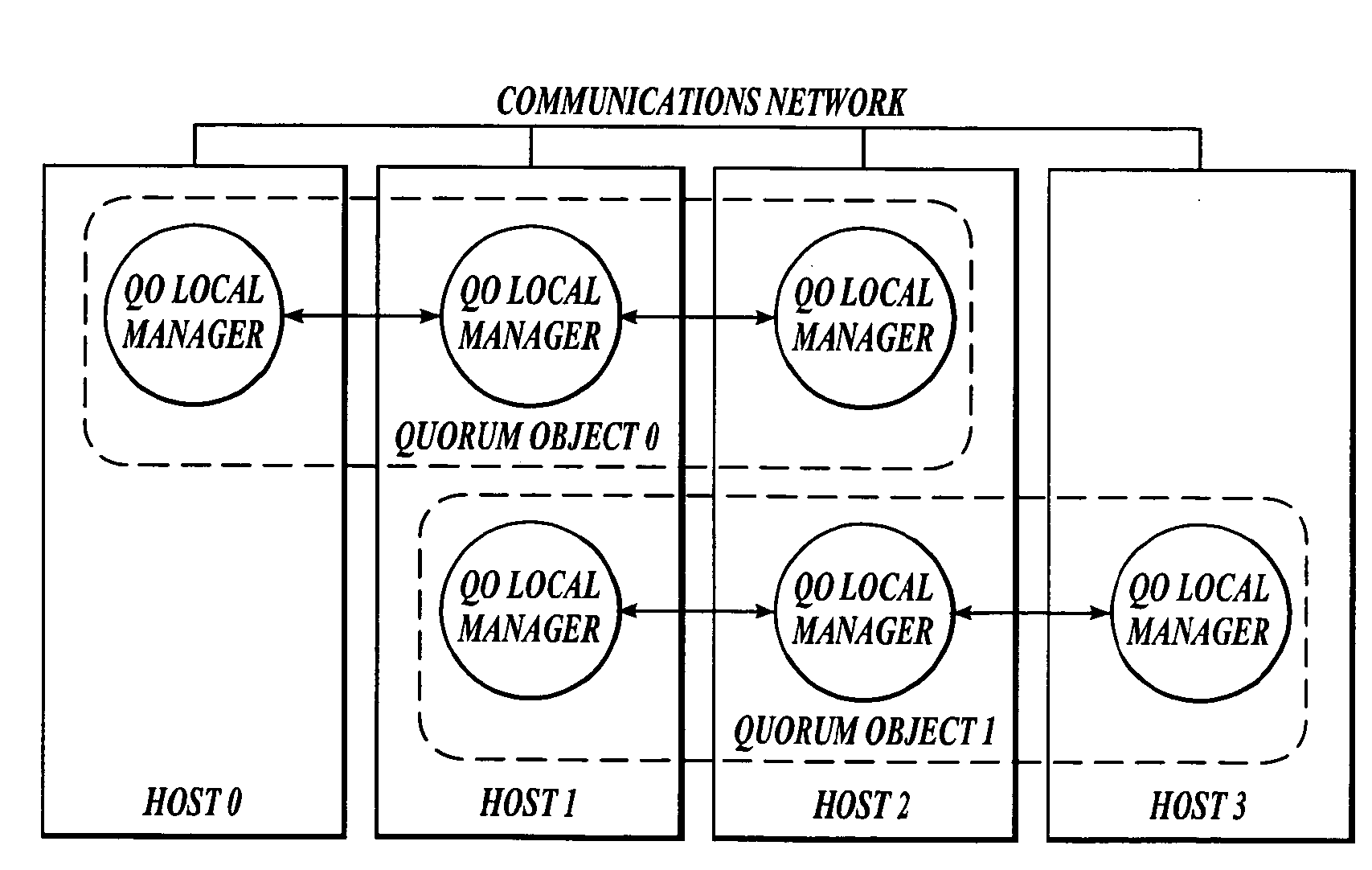
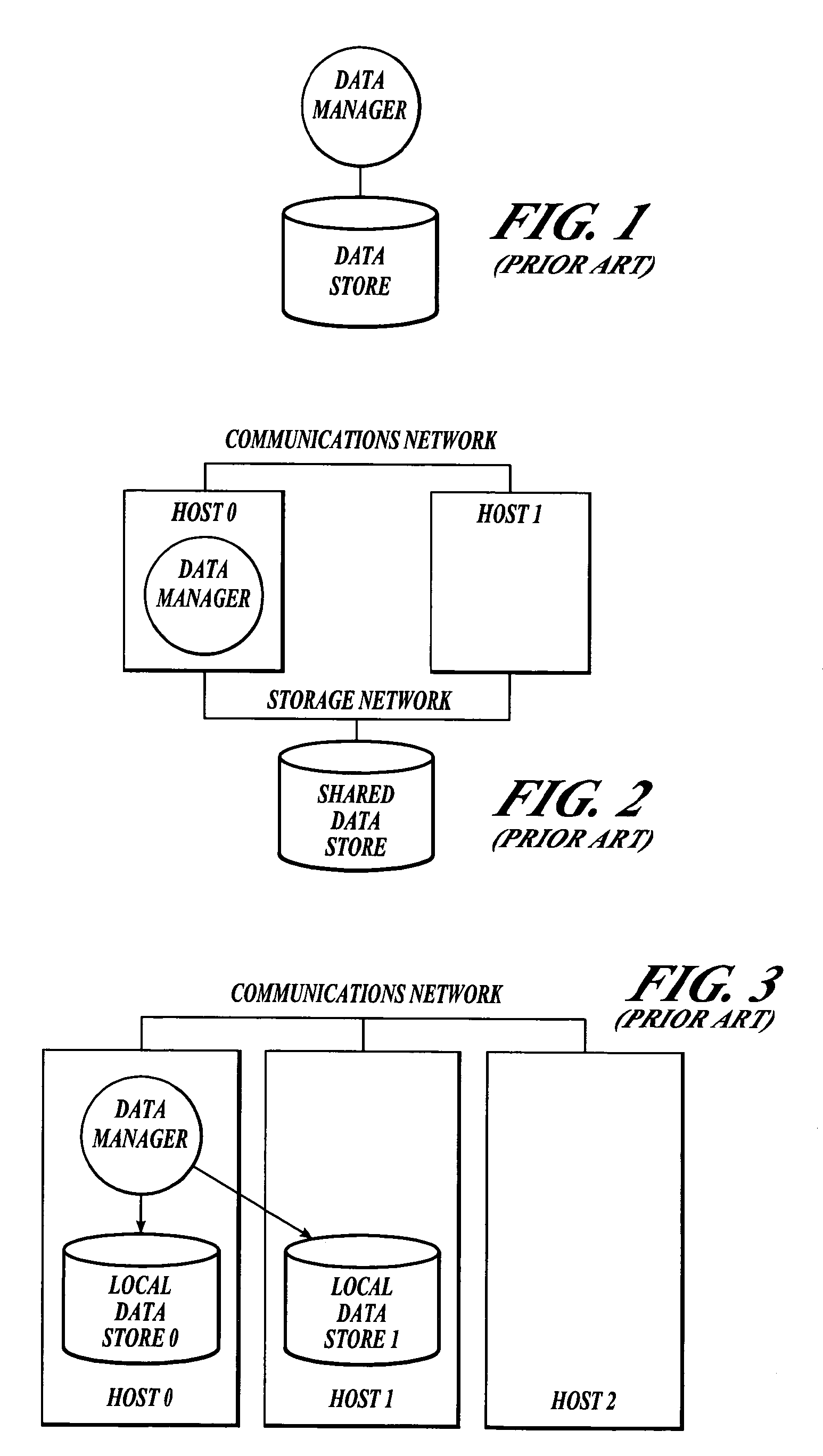
Scalable, software-based quorum architecture
A cluster of computers typically establishes a quorum, i.e., a software method for establishing agreement, to coordinate access to shared resources, such as a shared data store, in applications that must recover from the failure of one or more computers or their associated components. Prior art which associates a single quorum with an entire cluster, has inherent overheads that limit the size of the cluster to a small number of computers. The present invention comprises a scalable, software-based architecture for implementing a quorum mechanism to coordinate the actions of a cluster of computers. In contrast to prior art, the present invention advantageously encapsulates the quorum in a software construct, called a quorum object, which is disassociated from the cluster as a whole and spans a designated subset of the cluster's membership. By employing multiple quorum objects that are distributed across the cluster's membership, the cluster can uniformly scale to a large number of computers that handle a scalable processing workload, such as a partitioned database management system. The software methods that implement one embodiment of the present invention are described in detail.
Owner:SCALEOUT SOFTWARE
Automated quick deployment method for large-scale computer cluster node
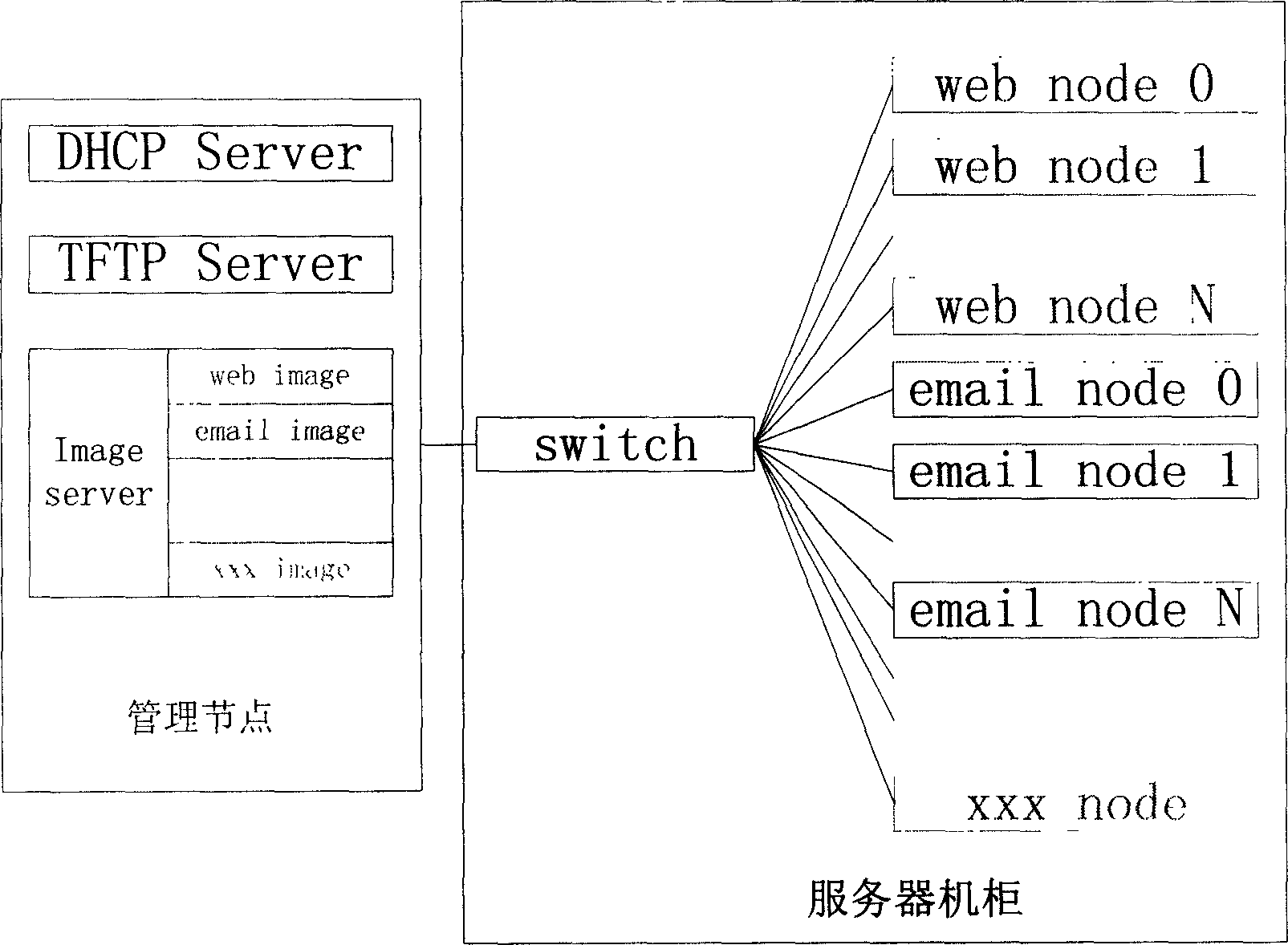
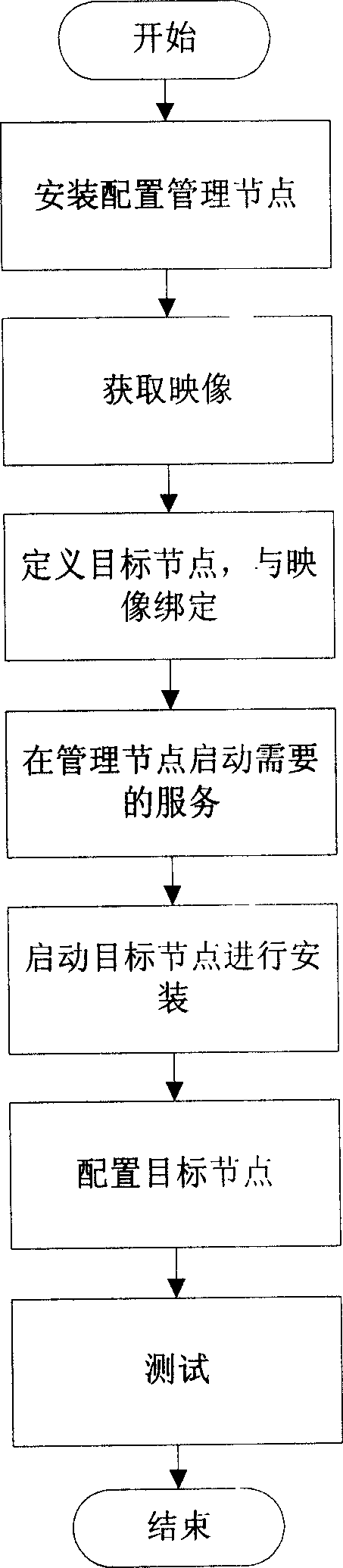
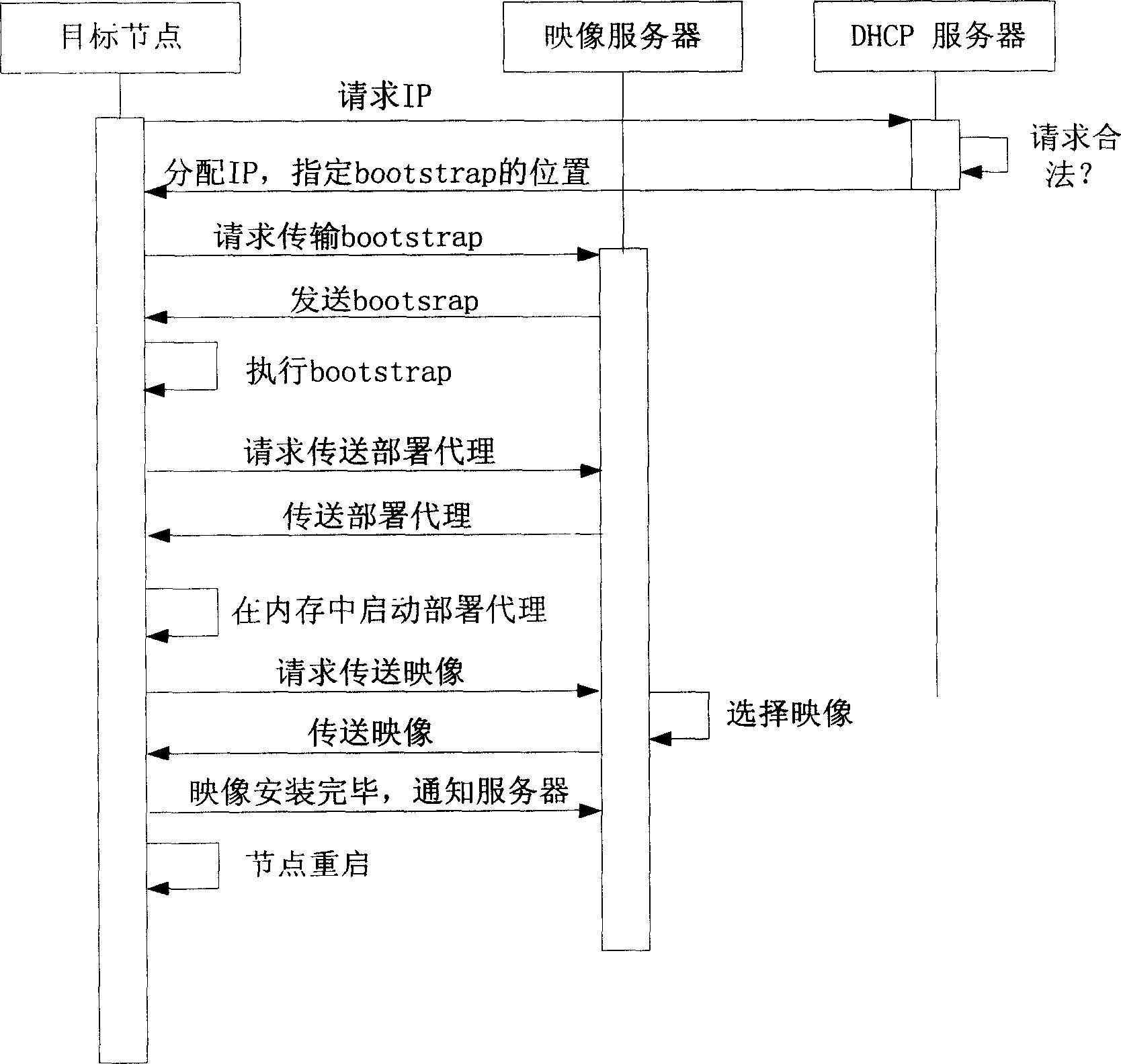
InactiveCN1731738ASuitable for installationNo human intervention requiredData switching networksSpecial data processing applicationsComputer clusterFile Transfer Protocol
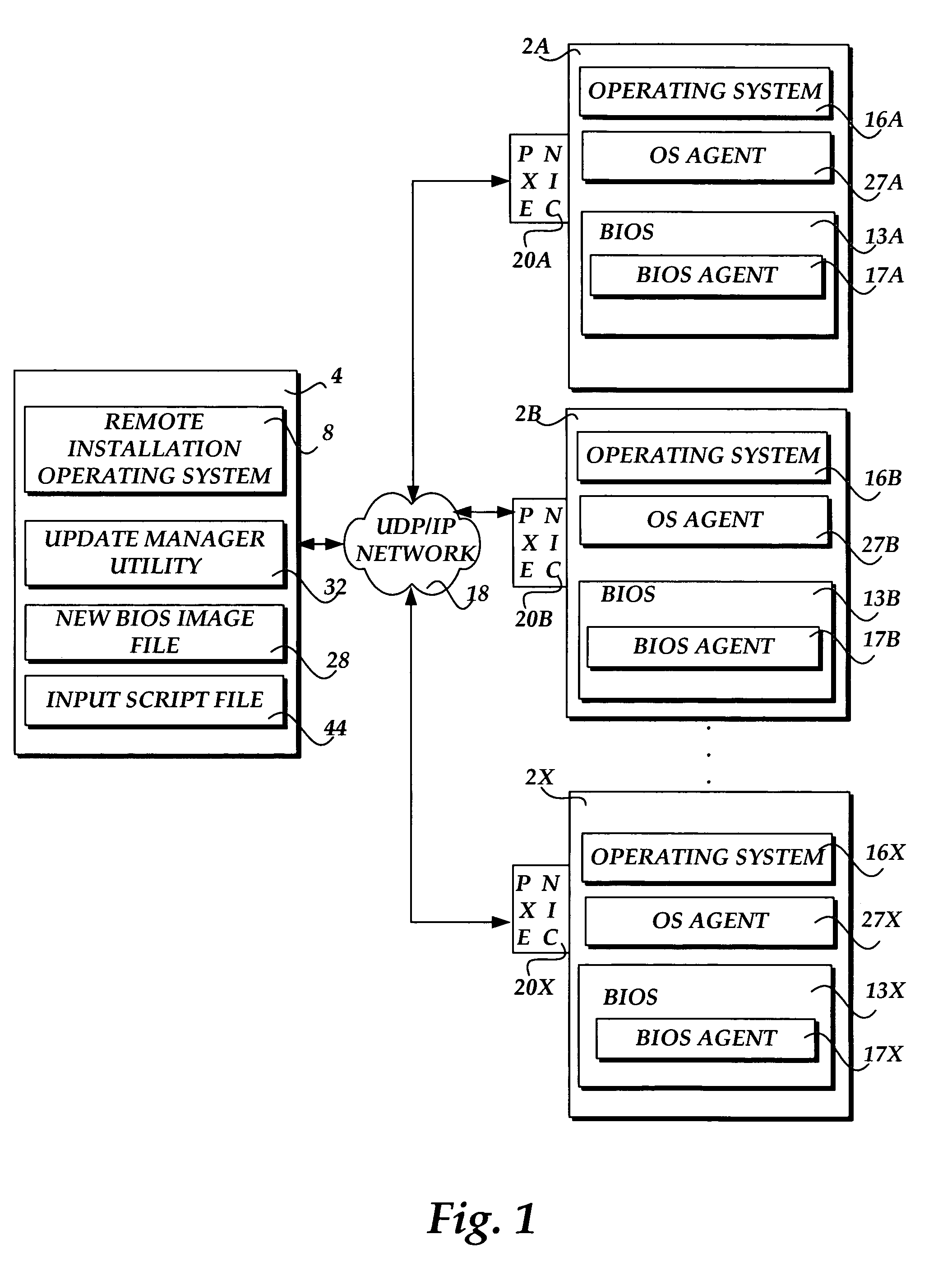
This invention relates to method for automatically and rapidly allocating the system nodes of large-scale computer colony, which adopts image-based installing ways, customer machine / server structure, Pre-conducting executing surroundings PXE protocol, dynamic host configuring protocol DHCP, simple files-transferring protocol TFTP and wakeup on lan to realize the automatic and rapid allocation in large-scale colony system. This method comprises the five steps: attaining image, bonding the image with the aim nodes, installing the aim nodes, allocating the aim nodes, testing and so on, which actualizes the completely automation in the course of installing nodes in colony system. Compared with traditional way, the invention largely simplifies the installing course and improves work efficiency.
Owner:XI AN JIAOTONG UNIV +1
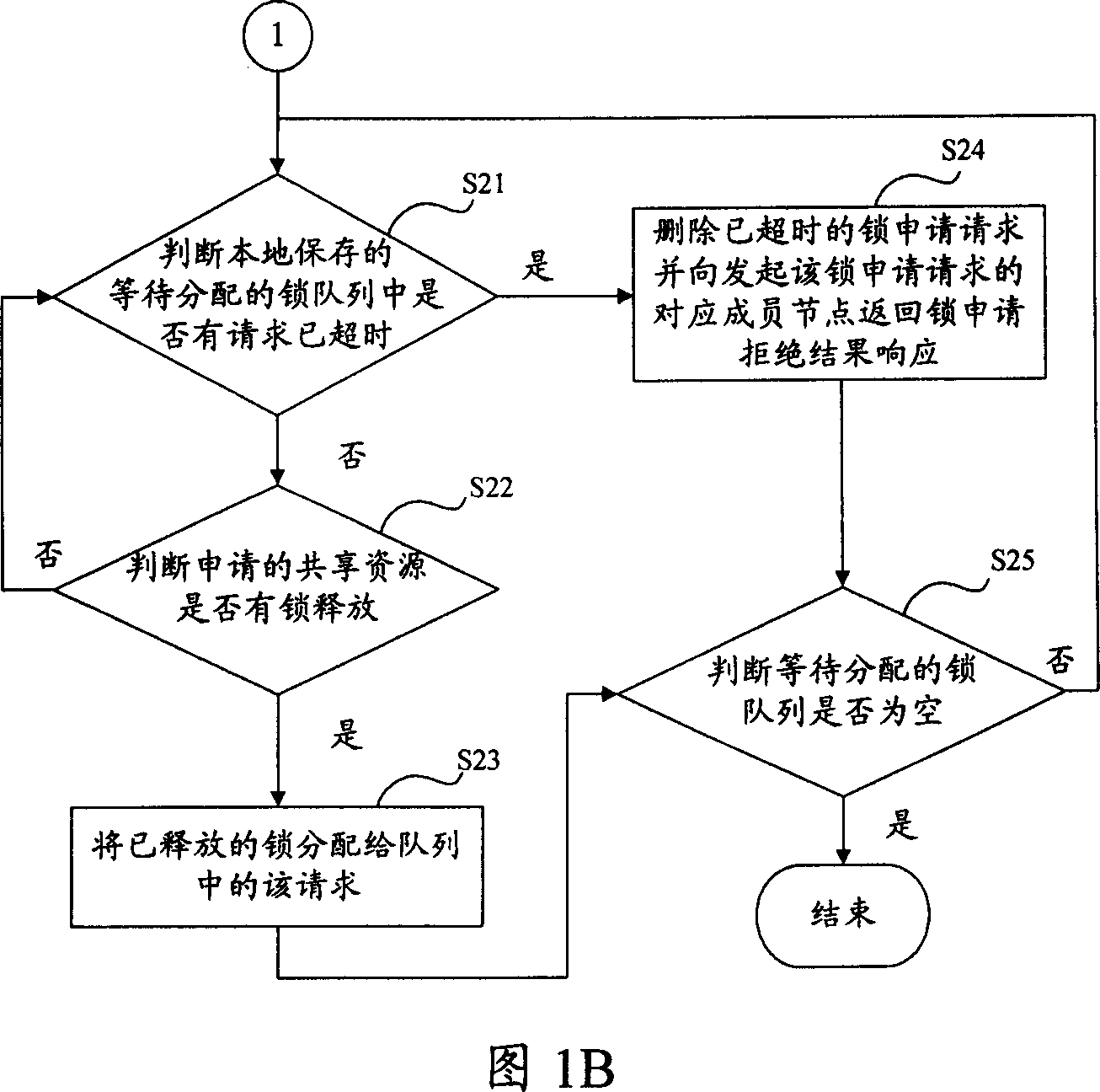
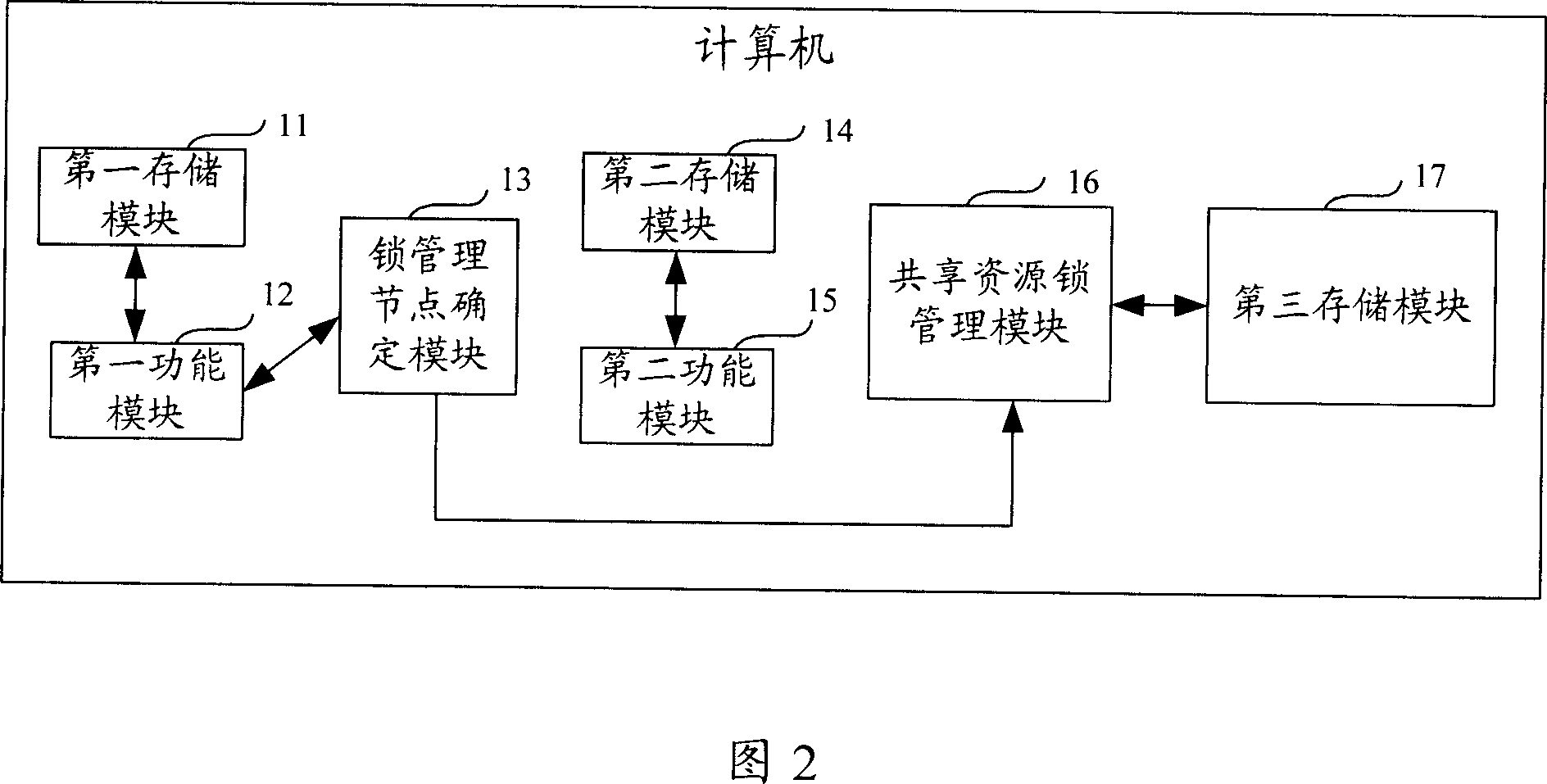
Method for distributing shared resource lock in computer cluster system and cluster system
ActiveCN1945539AAvoid performance bottlenecksTo achieve load balancingMultiprogramming arrangementsExtensibilityComputer cluster
This invention publishes a locked distribution method of shared resources in a type of computer integration system including: making more than one node of system members as locking management node of all the shared resources in the system, meanwhile each shared resource matches a locking management node; when one apply asks for applicant or release shored resources lock, and send applicant to the corresponding locking management node of this shored resources, the corresponding locking management node will finish the distribution and release of lock's applicant. This invention also publishes the corresponding structure of computer integration system. The invention can be used for realizing high usable locking service in the integration, and it has a high expansibility and realizes a balance of load.
Owner:HUAWEI TECH CO LTD +1
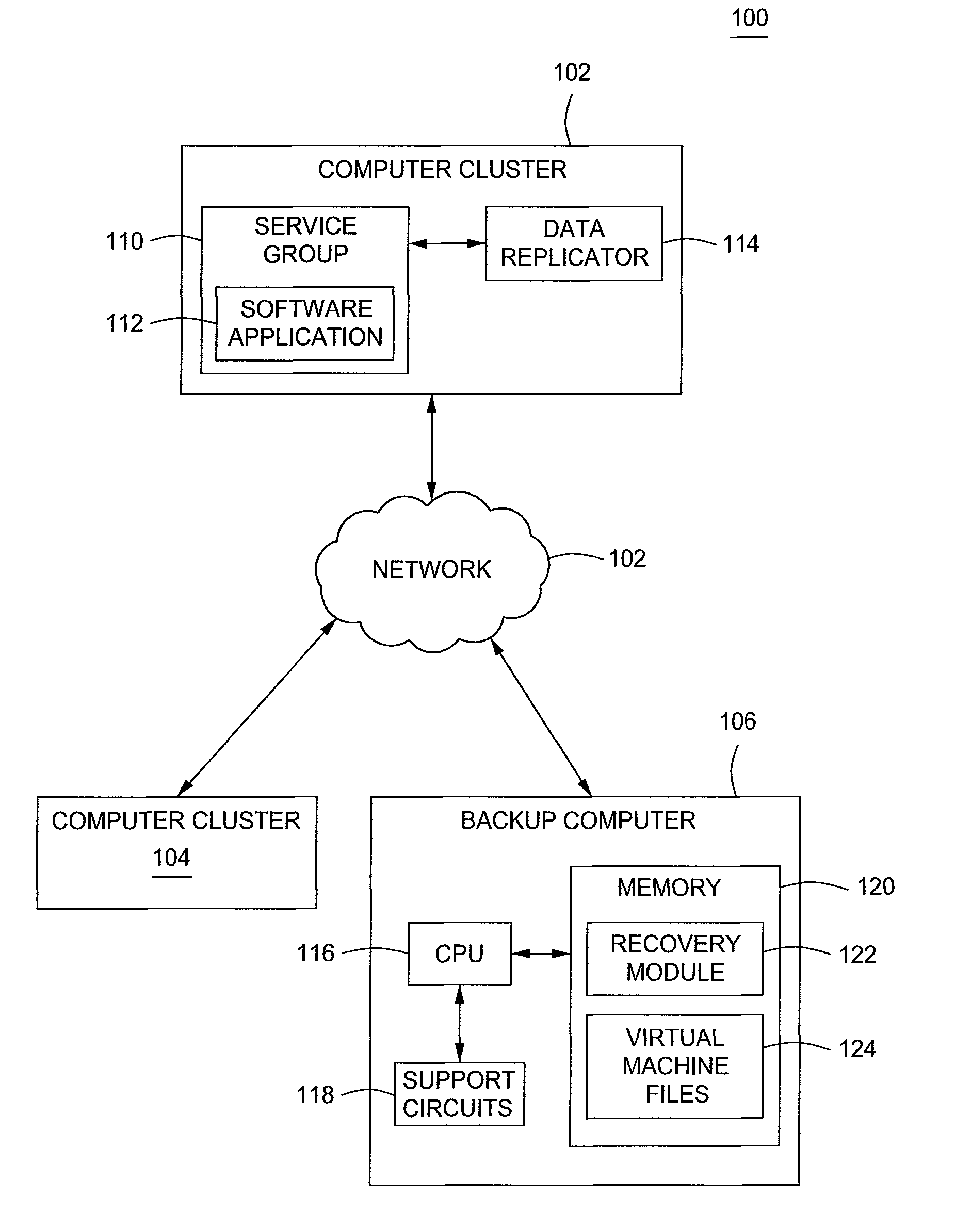
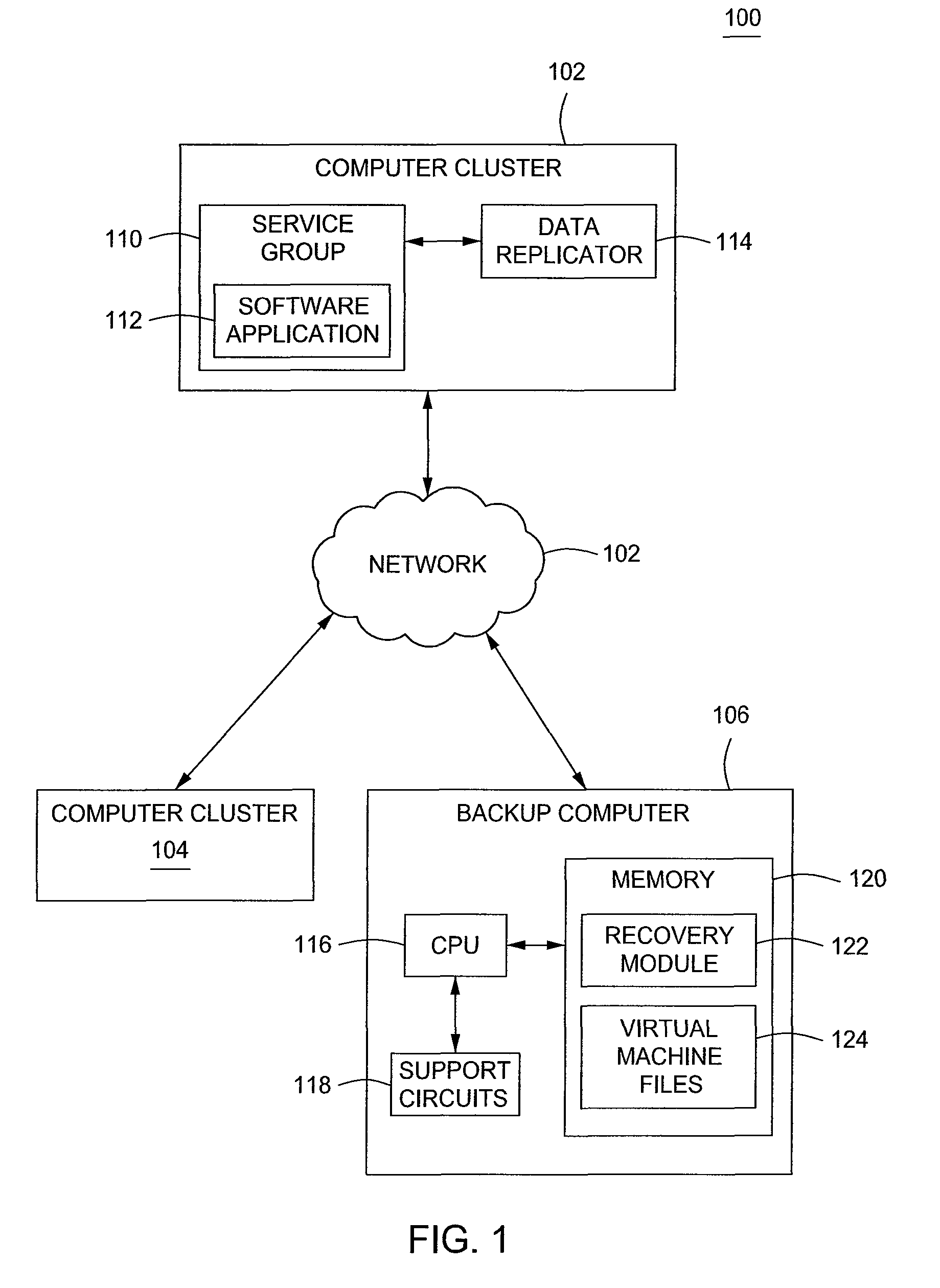
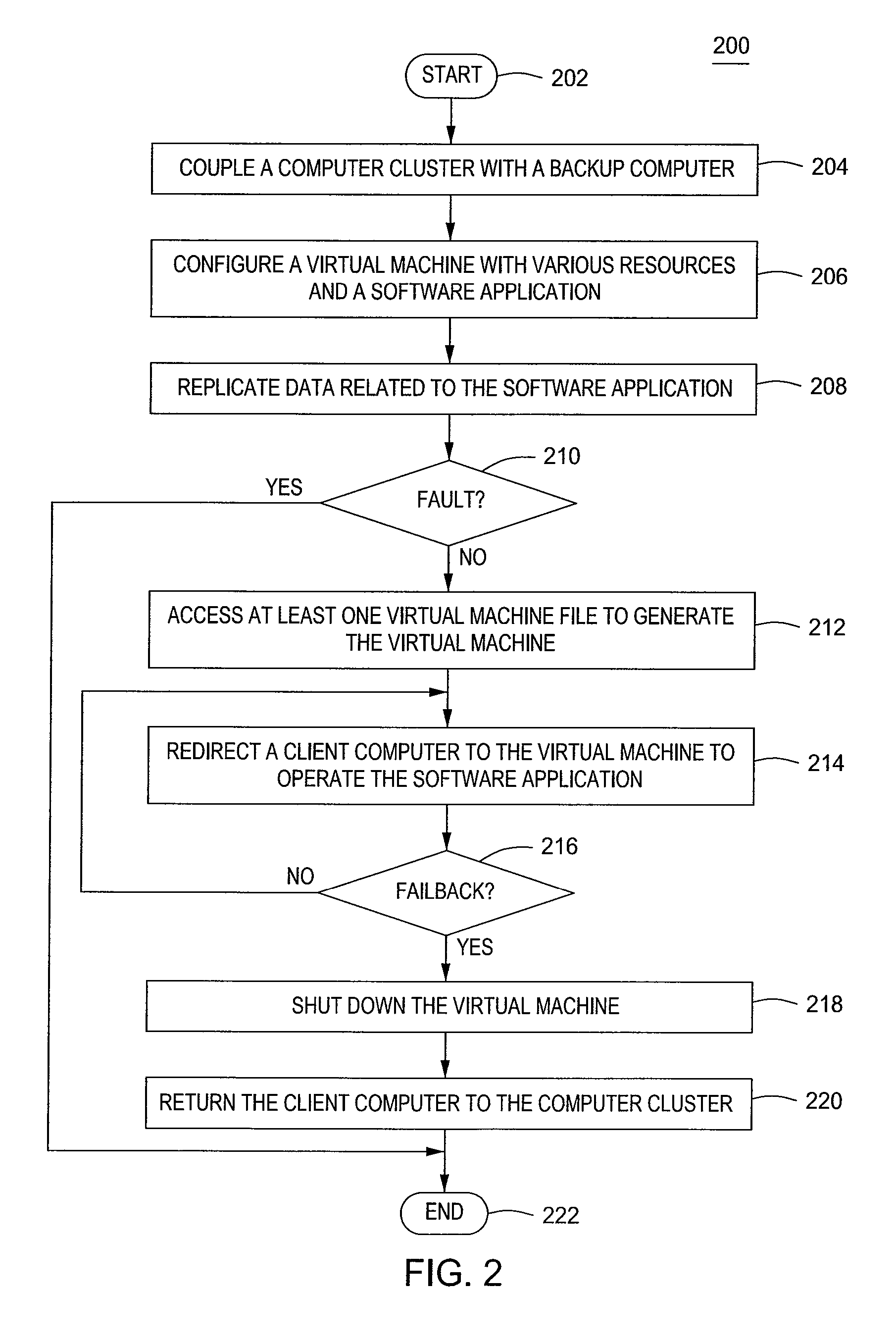
Method and apparatus for achieving high availability for an application in a computer cluster
A method and apparatus for achieving high availability in a computer cluster is provided. In one embodiment, a method for failing over a software application to a virtual machine from a physical computing environment comprises processing at least one virtual machine file at a backup computer, wherein the at least one virtual machine file is preconfigured with a software application that is hosted by a computer cluster and in response to an occurrence a fault at the computer cluster, accessing the at least one virtual machine file to operate the software application.
Owner:VERITAS TECH
Method of improving the availability of a computer clustering system through the use of a network medium link state function
InactiveUS20050033778A1Improve availabilityImprove reliabilityData processing applicationsDigital data processing detailsMass storageTelecommunications link
A method for improving the availability and reliability of a computer clustering system having first and second servers that are connected to each other by a communication link and that each have an associated mass storage device. In one implementation, the method begins when the first server detects a loss of communication over the communication link from the second server to the first server that prevents the servers from communicating with each other. The first server then analyzes the communication link to determine if the communication link is functioning properly. If the communication link is functioning properly, then the first server continues operation, assuming a right to survive without communicating with the second server or with the mass storage device of the first server or with the mass storage device of the second server, and the first server services network requests that would otherwise be serviced by the second server.
Owner:EMC CORP
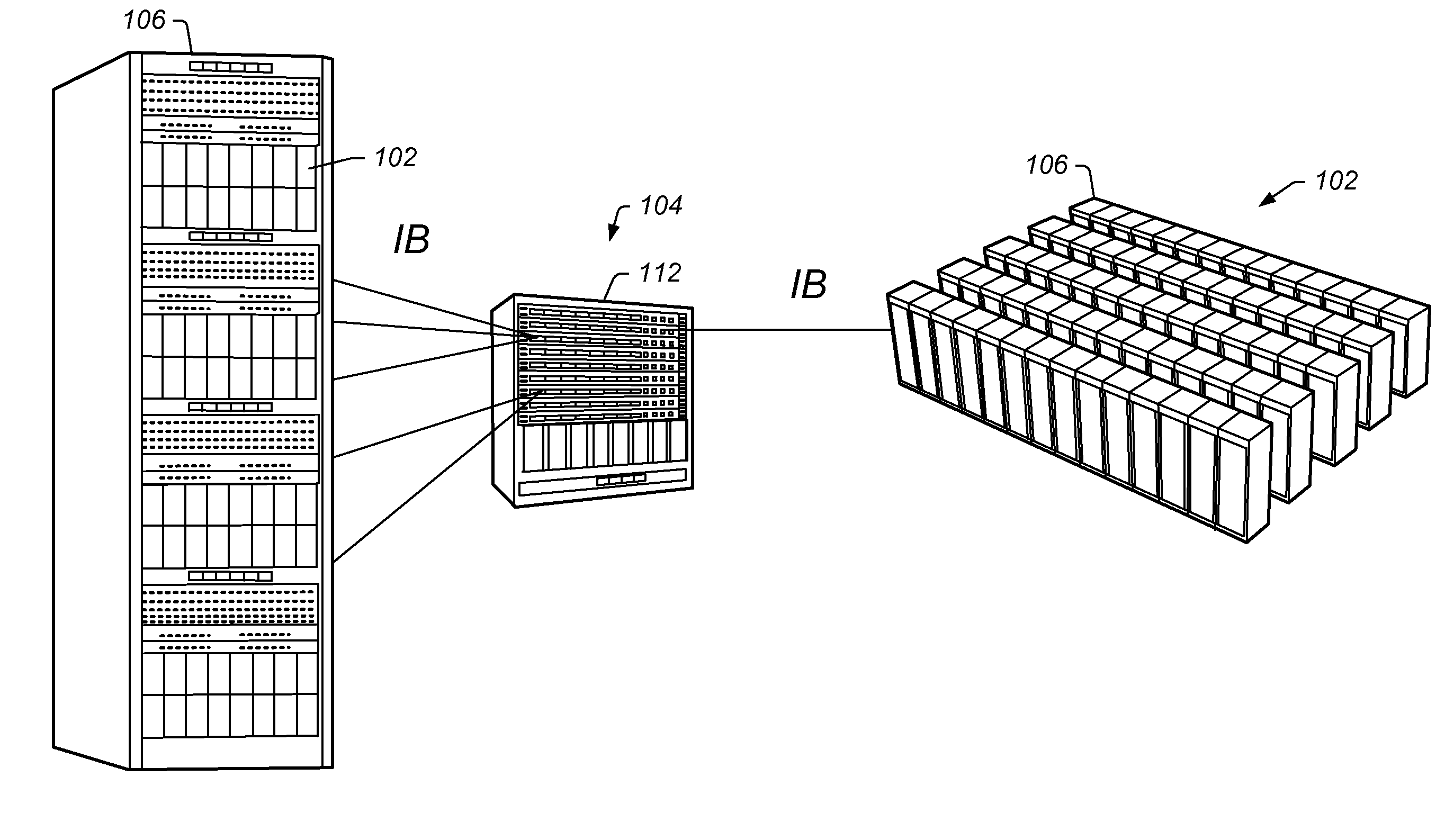
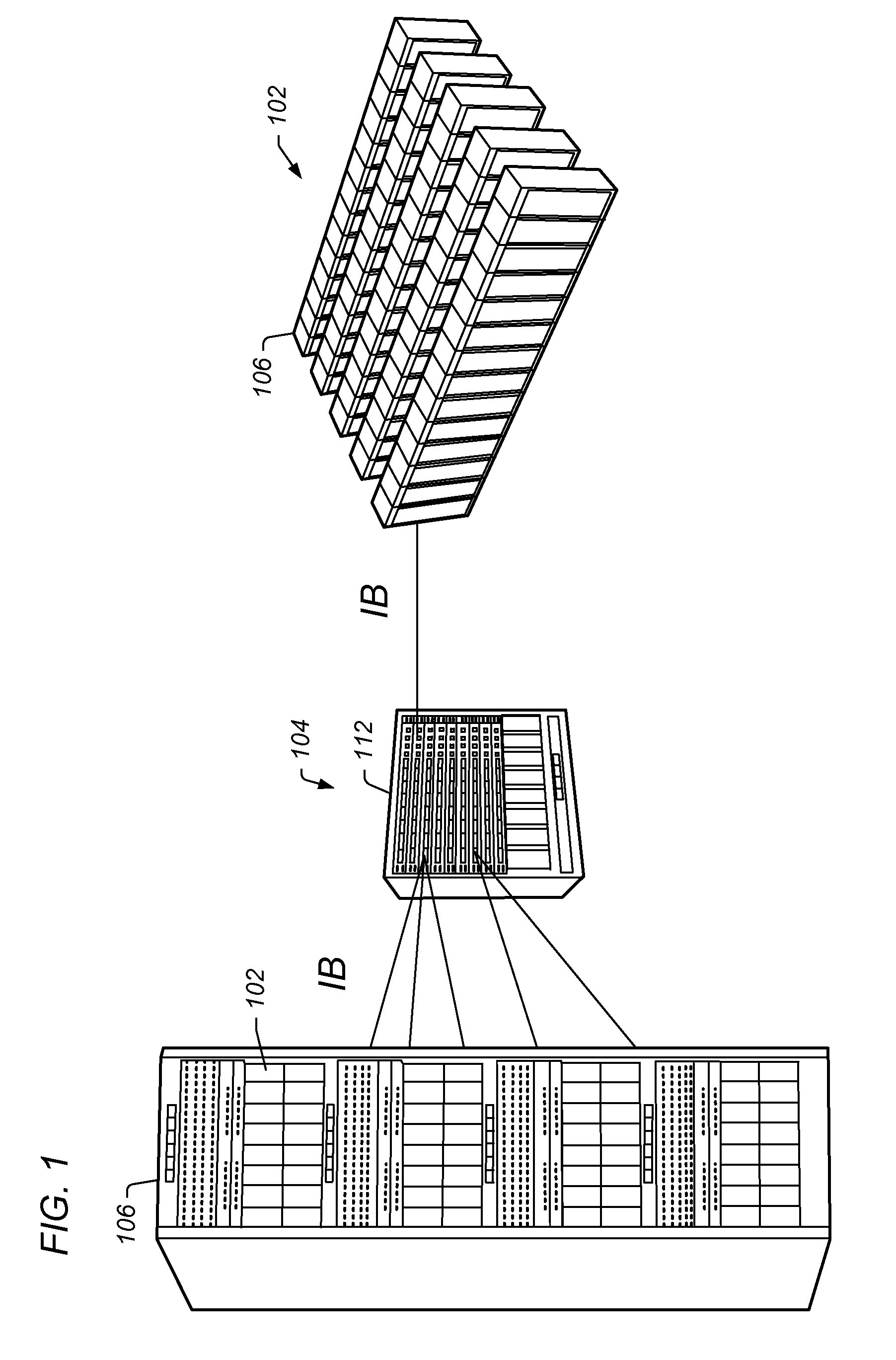
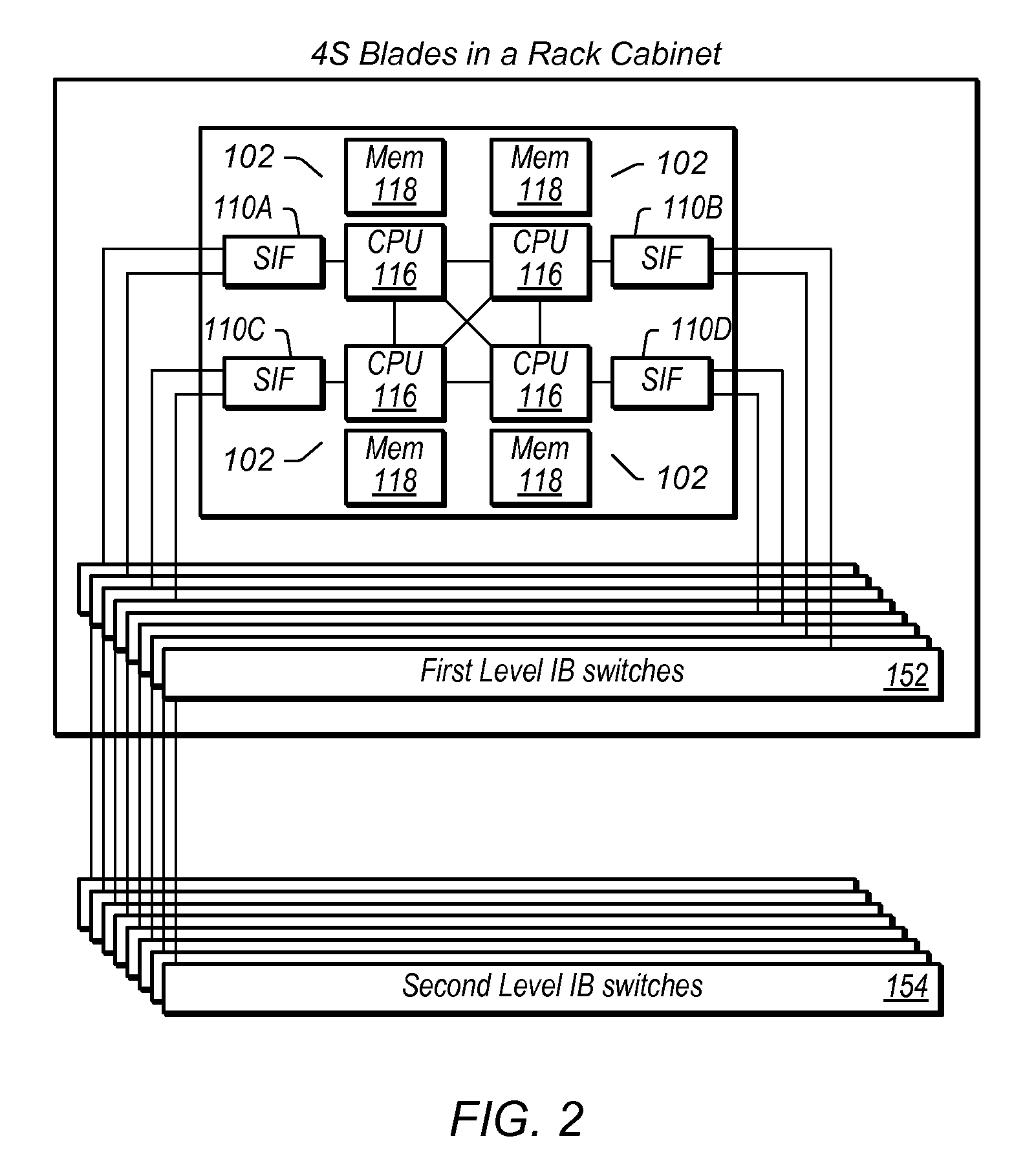
Scalable Interface for Connecting Multiple Computer Systems Which Performs Parallel MPI Header Matching
ActiveUS20100232448A1Improve clustering performanceImprove performanceDigital computer detailsData switching by path configurationComputer clusterMessage Passing Interface
An interface device for a compute node in a computer cluster which performs Message Passing Interface (MPI) header matching using parallel matching units. The interface device comprises a memory that stores posted receive queues and unexpected queues. The posted receive queues store receive requests from a process executing on the compute node. The unexpected queues store headers of send requests (e.g., from other compute nodes) that do not have a matching receive request in the posted receive queues. The interface device also comprises a plurality of hardware pipelined matcher units. The matcher units perform header matching to determine if a header in the send request matches any headers in any of the plurality of posted receive queues. Matcher units perform the header matching in parallel. In other words, the plural matching units are configured to search the memory concurrently to perform header matching.
Owner:ORACLE INT CORP
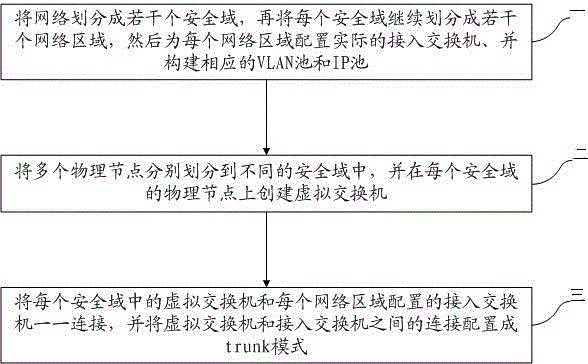
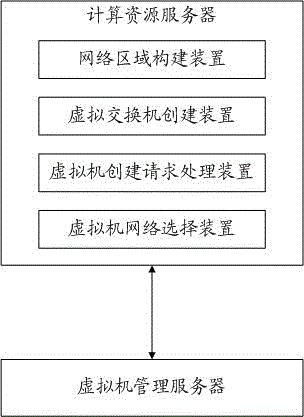
Virtual machine multi-network management system and method in cloud computing environment
ActiveCN103607308AImprove interoperabilityMeet diverse needsData switching networksSoftware simulation/interpretation/emulationCloud computingComputer cluster
Provided are a virtual machine multi-network management system and method in a cloud computing environment. The method comprises the steps that firstly, a network is divided into a plurality of security areas, each security area is continued to be divided into a plurality of network areas, then an actual receiving interchanger is configured for each network area, and a corresponding VLAN pool and an IP pool are constructed; secondly, multiple physical nodes are respectively divided into different safety areas, a virtual interchanger is constructed on a physical node of each security area, the physical nodes are one physical host or a computer cluster formed by multiple physical hosts, and the virtual interchangers comprise distributed interchangers and standard interchangers; thirdly, the virtual interchanger in each security area and the receiving interchanger configured in each network area are connected in a one-to-one mode, and connection between the virtual interchangers and the receiving interchangers is configured to be a trunk mode. The virtual machine multi-network management system and method belong to the technical field of network communication, and virtual machines can have access to multiple networks.
Owner:新讯数字科技(杭州)有限公司
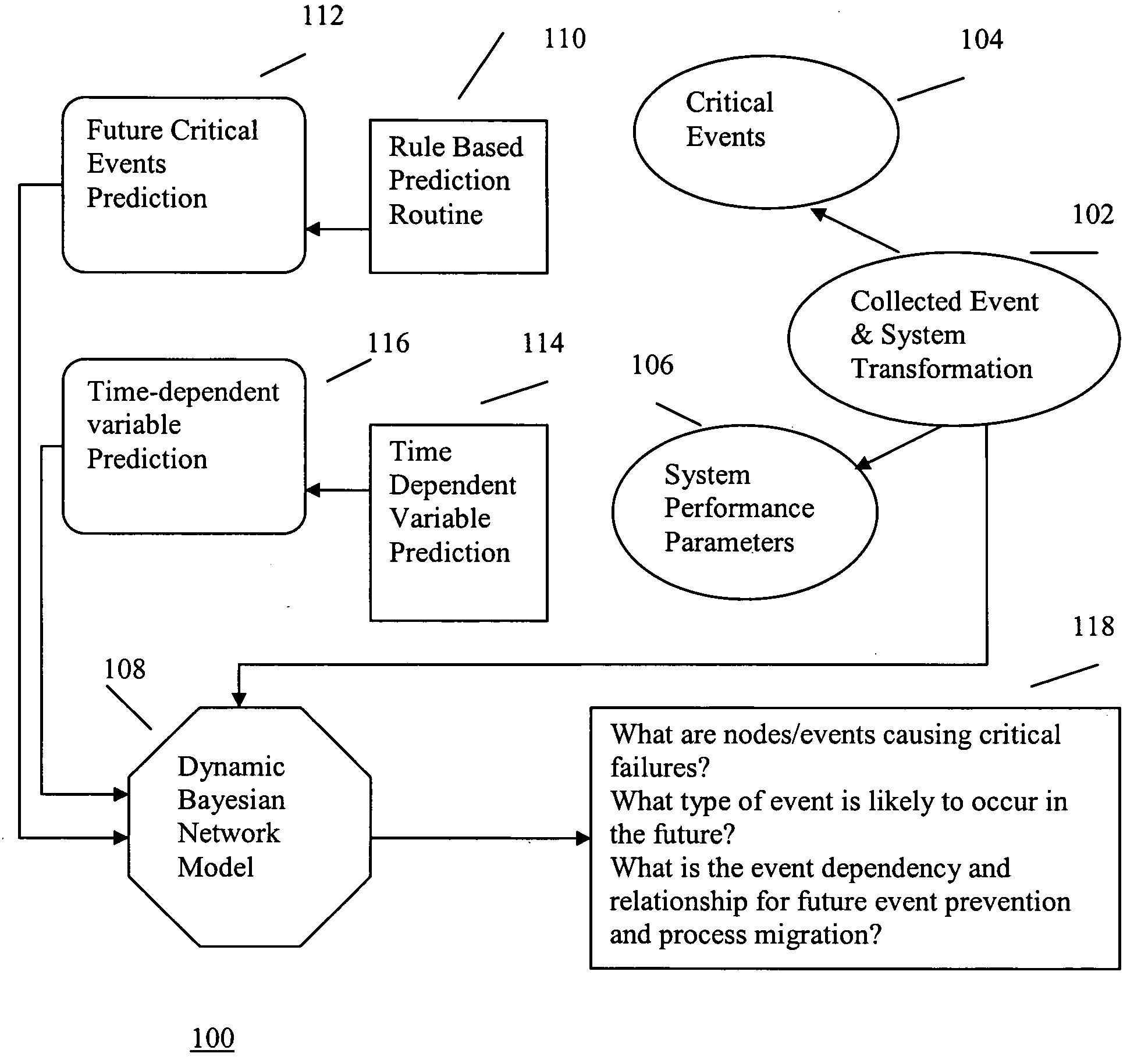
Hybrid method for event prediction and system control
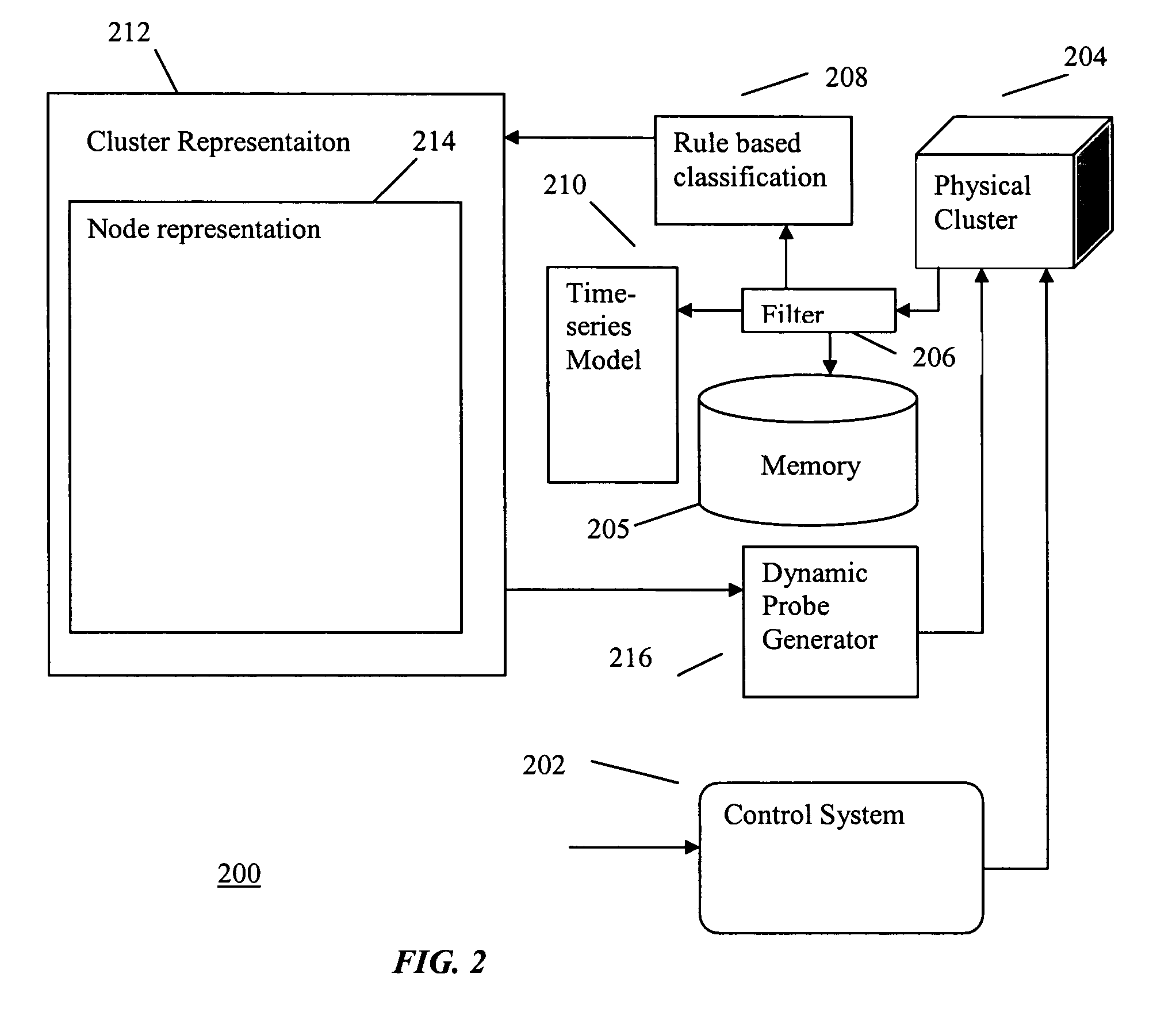
InactiveUS20050114739A1Data processing applicationsDigital computer detailsComputer clusterHybrid approach
A hybrid method of predicting the occurrence of future critical events in a computer cluster having a series of nodes records system performance parameters and the occurrence of past critical events. A data filter filters the logged to data to eliminate redundancies and decrease the data storage requirements of the system. Time-series models and rule based classification schemes are used to associate various system parameters with the past occurrence of critical events and predict the occurrence of future critical events. Ongoing processing jobs are migrated to nodes for which no critical events are predicted and future jobs are routed to more robust nodes.
Owner:GLOBALFOUNDRIES INC
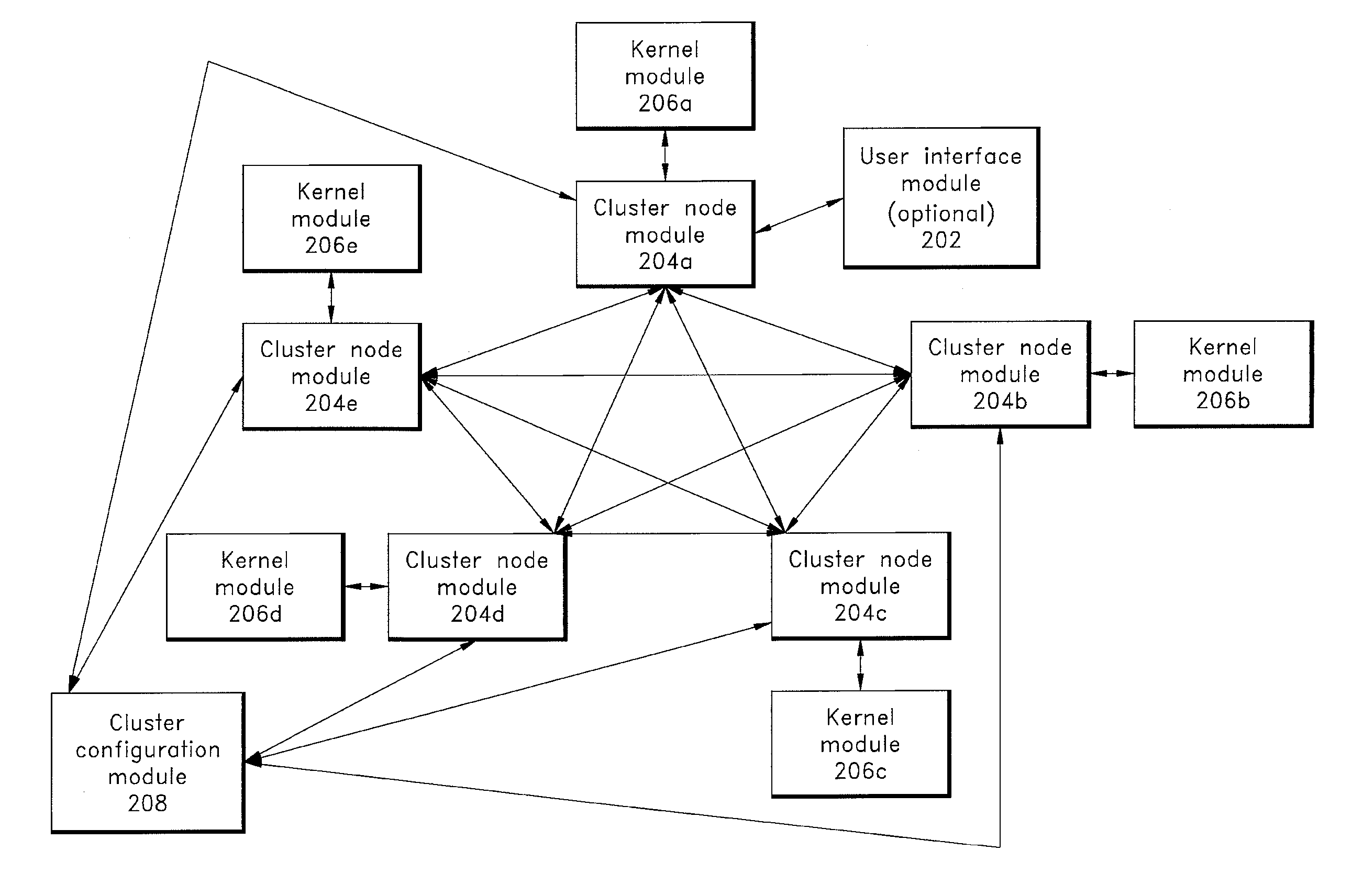
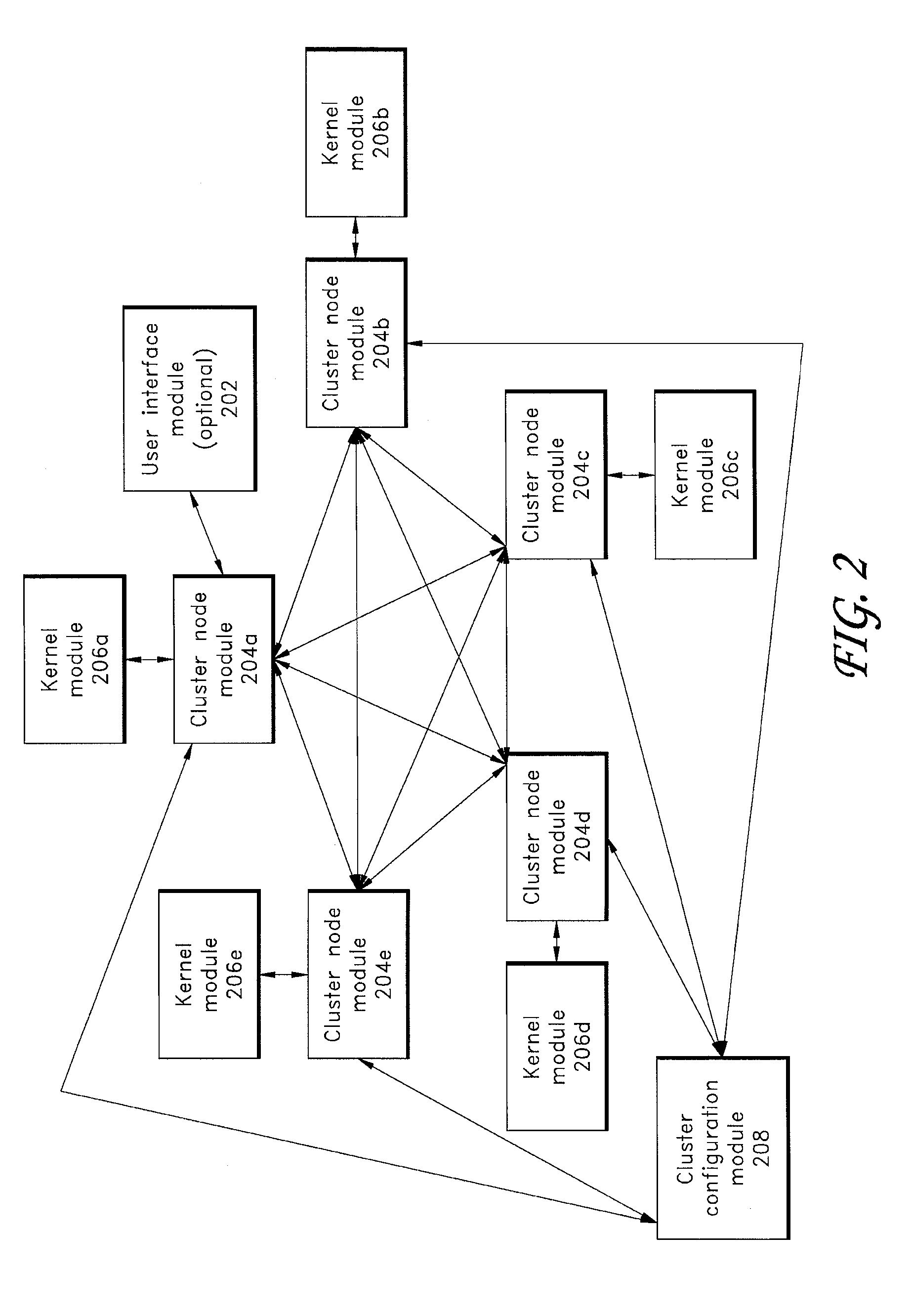
Cluster computing support for application programs
ActiveUS20070288935A1Conveniently addedImprove availabilityInterprogram communicationGeneral purpose stored program computerComputer clusterCluster Node
A computer cluster system comprising a plurality of nodes and a software package comprising a user interface and a kernel for interpreting program code instructions is provided. In one embodiment, a cluster node module is configured to communicate with the kernel and other cluster node modules. The cluster node module accepts instructions from the user interface and interprets at least some of the instructions such that several cluster node modules in communication with one another and with a kernel can act as a computer cluster.
Owner:ADVANCED CLUSTER SYST
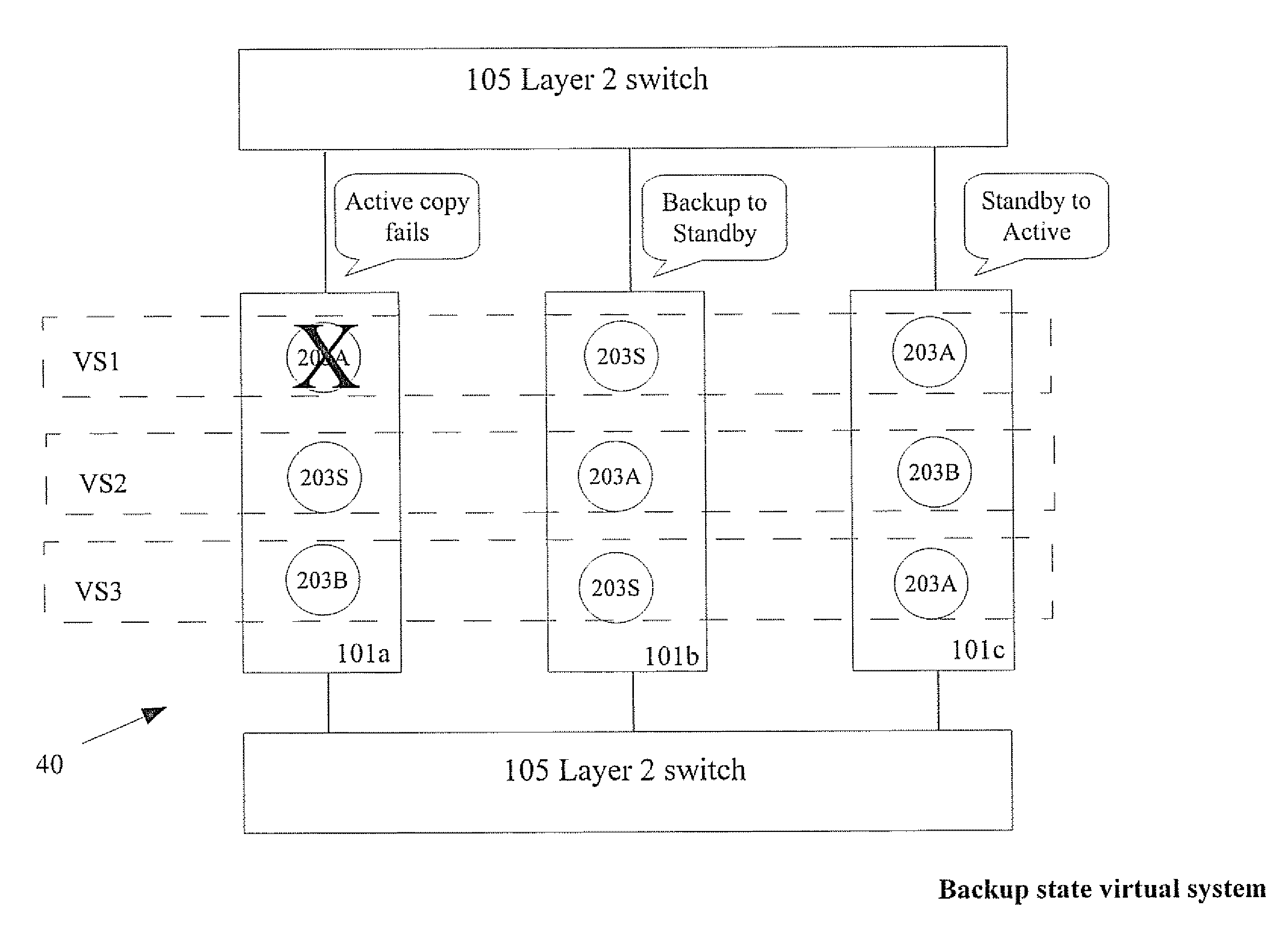
Application Cluster In Security Gateway For High Availability And Load Sharing
ActiveUS20080016386A1Improve usabilityTransmissionRedundant hardware error correctionComputer clusterState parameter
A method for load sharing and high availability in a cluster of computers. The cluster includes a first computer and a second computer which perform a task An active application runs in the first computer and a standby application is installed in the second computer. The active application and the standby application are included in an application group. A first plurality of applications is installed in the first computer; the first plurality includes the running active application. The active application performs the task and stores in memory of the first computer state parameters and a policy A synchronized copy of the state parameters and the policy pertaining to the task is maintained by storing in memory of the second computer. Preferably, the cluster is in a security gateway between data networks and performs a task related to security of one or more of the networks.
Owner:CHECK POINT SOFTWARE TECH LTD
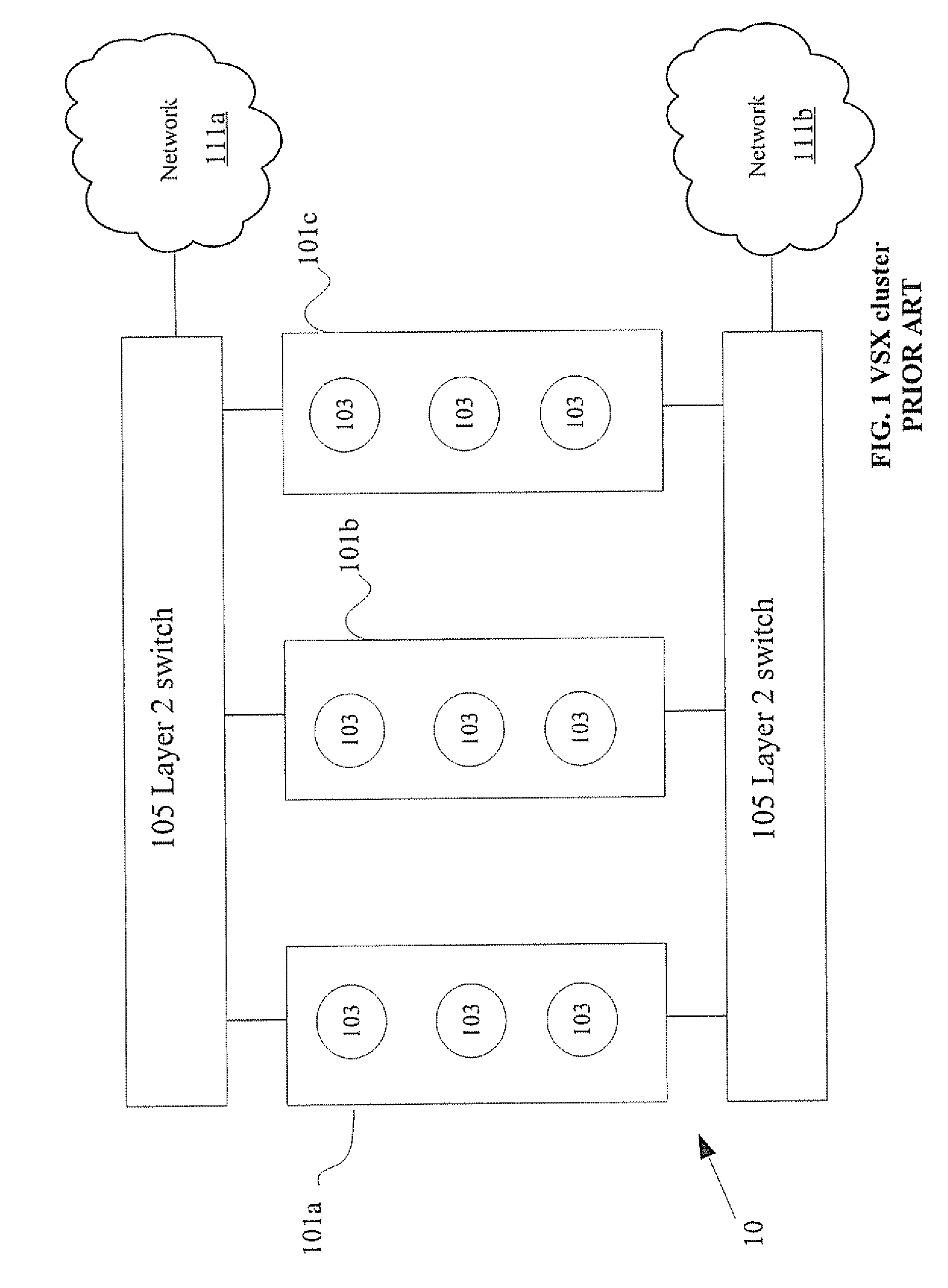
System and method for providing dynamically alterable computer clusters for message routing
InactiveUS20020166080A1Lower latencyError detection/correctionDigital computer detailsComputer clusterMessage routing
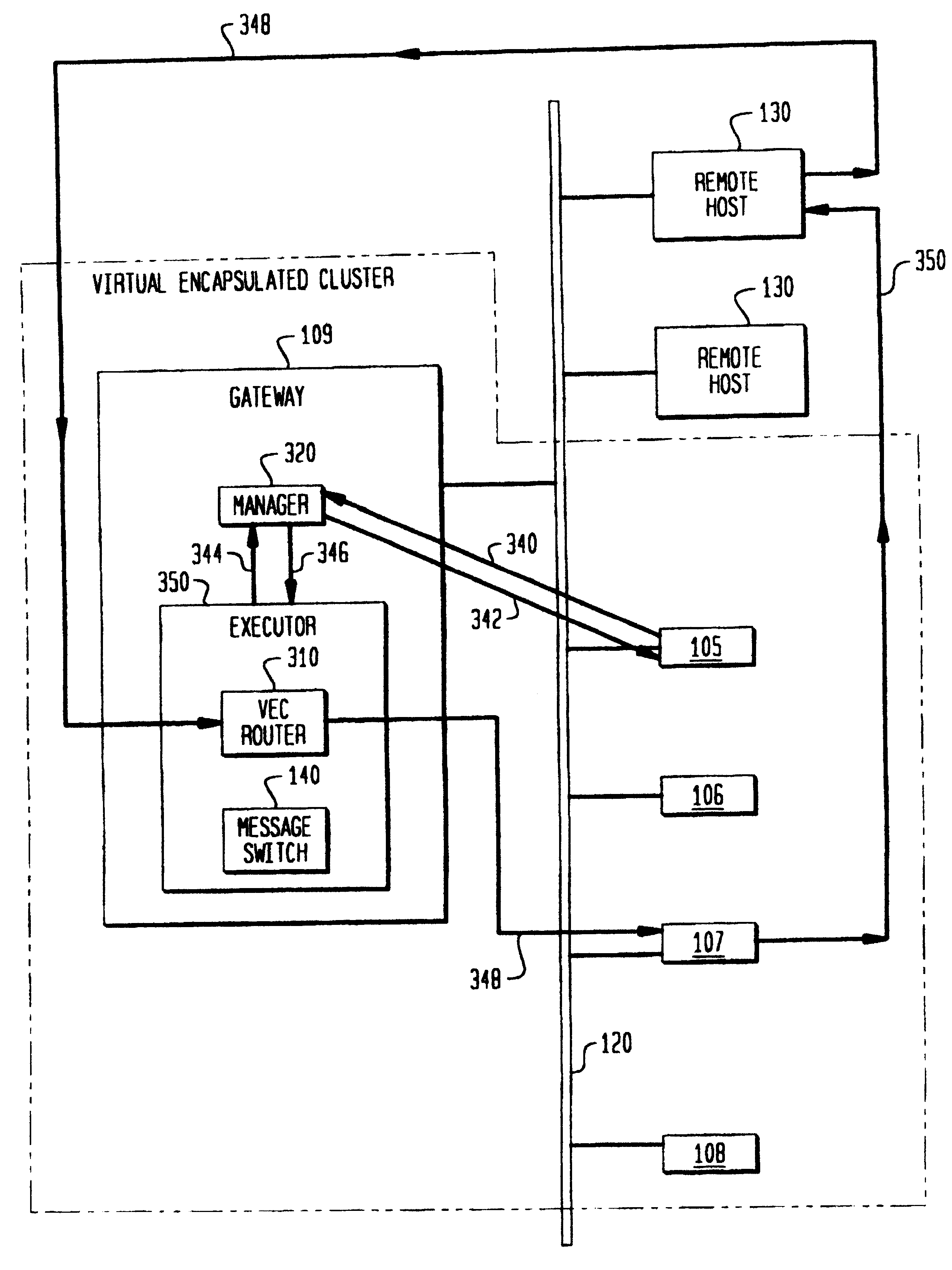
An object, of this invention is to improve the overall throughput of an Encapsulated Cluster. Another object of this invention is to reduce the aggregate delay of the remote service requests. A further object of this invention is to provide means for a designated node to take over the operation of a failed connection-router in such a way that network clients experience no interruption of service.
Owner:IBM CORP
Fault processing method of computer cluster system
InactiveCN103607297AReal-time monitoring statusReal-time monitoring of network statusData switching networksComputer clusterCluster systems
The invention discloses a fault processing method of a computer cluster system. The method comprises the following steps: (A) at least two nodes in the computer cluster system are selected and are set as management nodes which bear the fault processing and the management of the computer cluster system, one node in the management nodes is taken as a main node, and other nodes are taken as standby nodes, (B) a bottom monitoring service module of each node in the computer cluster system monitors the operation state of the node and software and hardware loads and judges whether a fault appears or not, and if so, the bottom monitoring service module notifies a message middleware service module to send a fault massage to a management center service module of the main node; and (C) the management center service module of the main node carries out fault processing according to the fault message. According to the technical scheme of the invention, in the condition that human intervention is not needed, the automatic processing function of the cluster computer system fault can be realized.
Owner:EISOO SOFTWARE
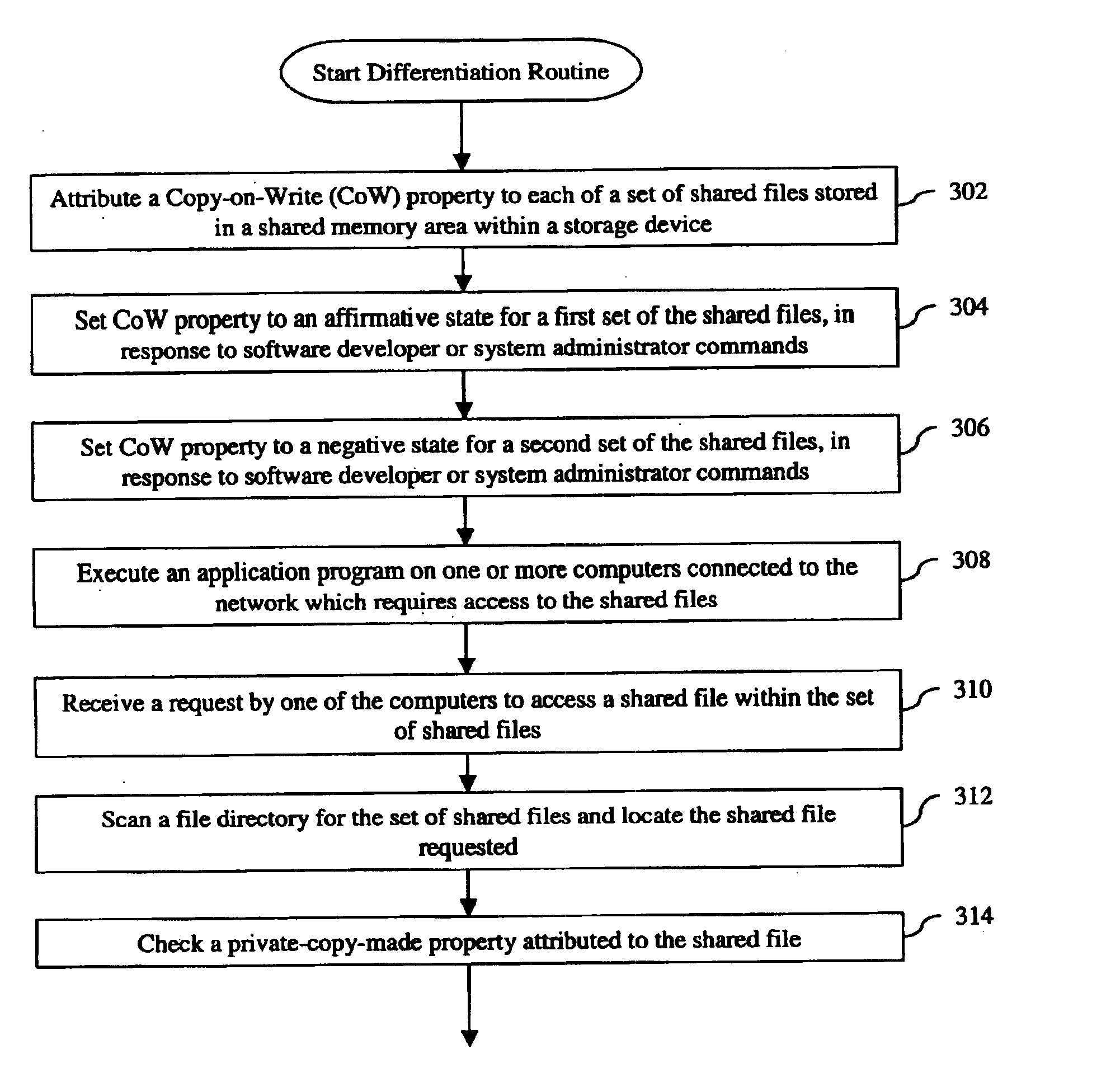
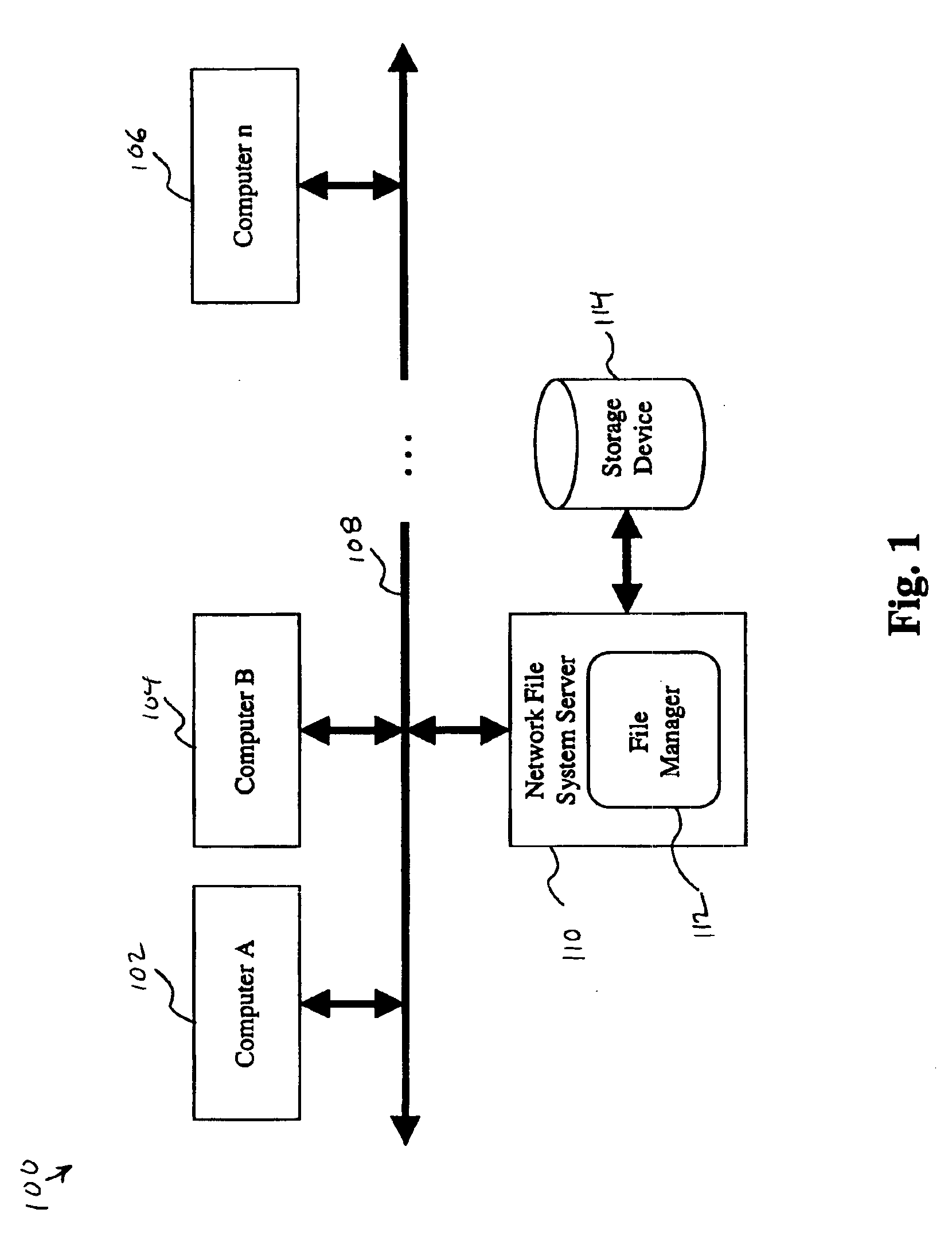
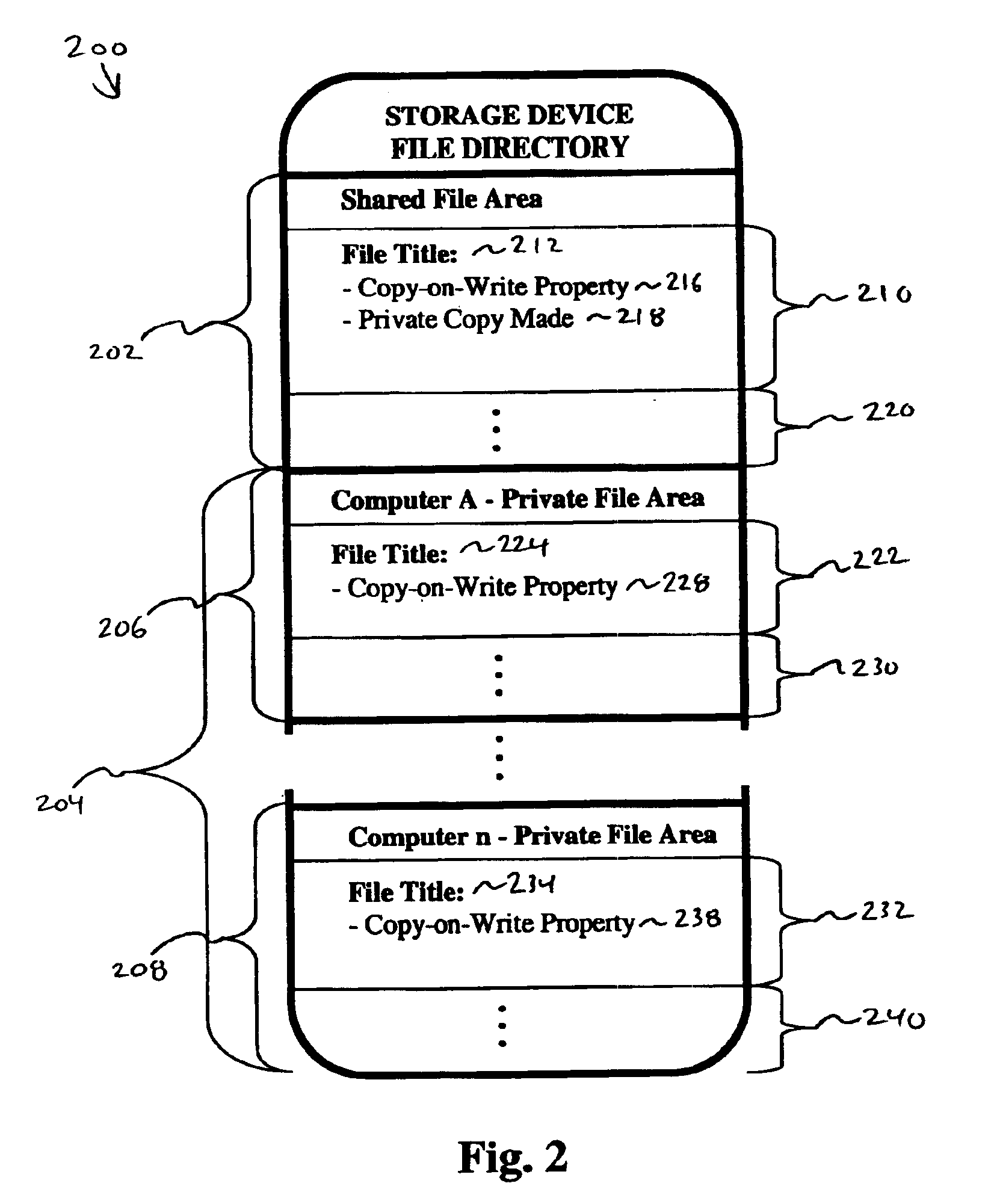
System and method for differentiating private and shared files within a computer cluster
InactiveUS6859812B1Data processing applicationsSpecial data processing applicationsComputer clusterComputer security
A system and method for differentiating private and shared files is disclosed. The invention includes the steps of: receiving a request from a computer for access to a shared file; providing the computer with access to a computer specific private copy of the shared file, if the private copy already exists; and creating the computer specific private copy of the shared file for the computer to access, if the private copy does not already exist and if write access to the shared file is requested.
Owner:HEWLETT PACKARD DEV CO LP
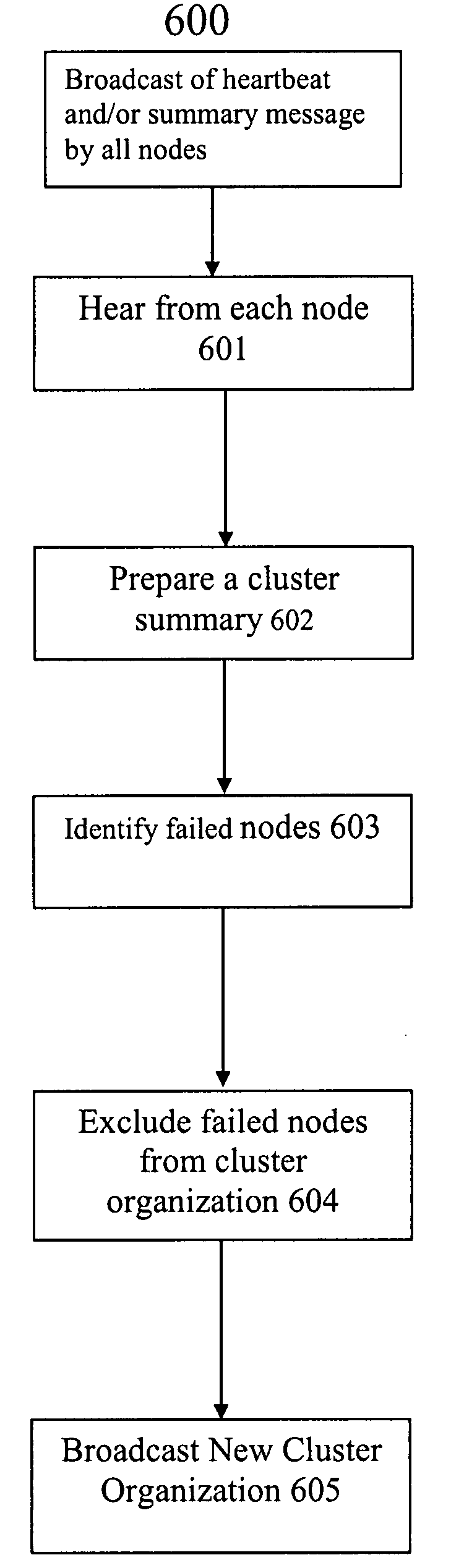
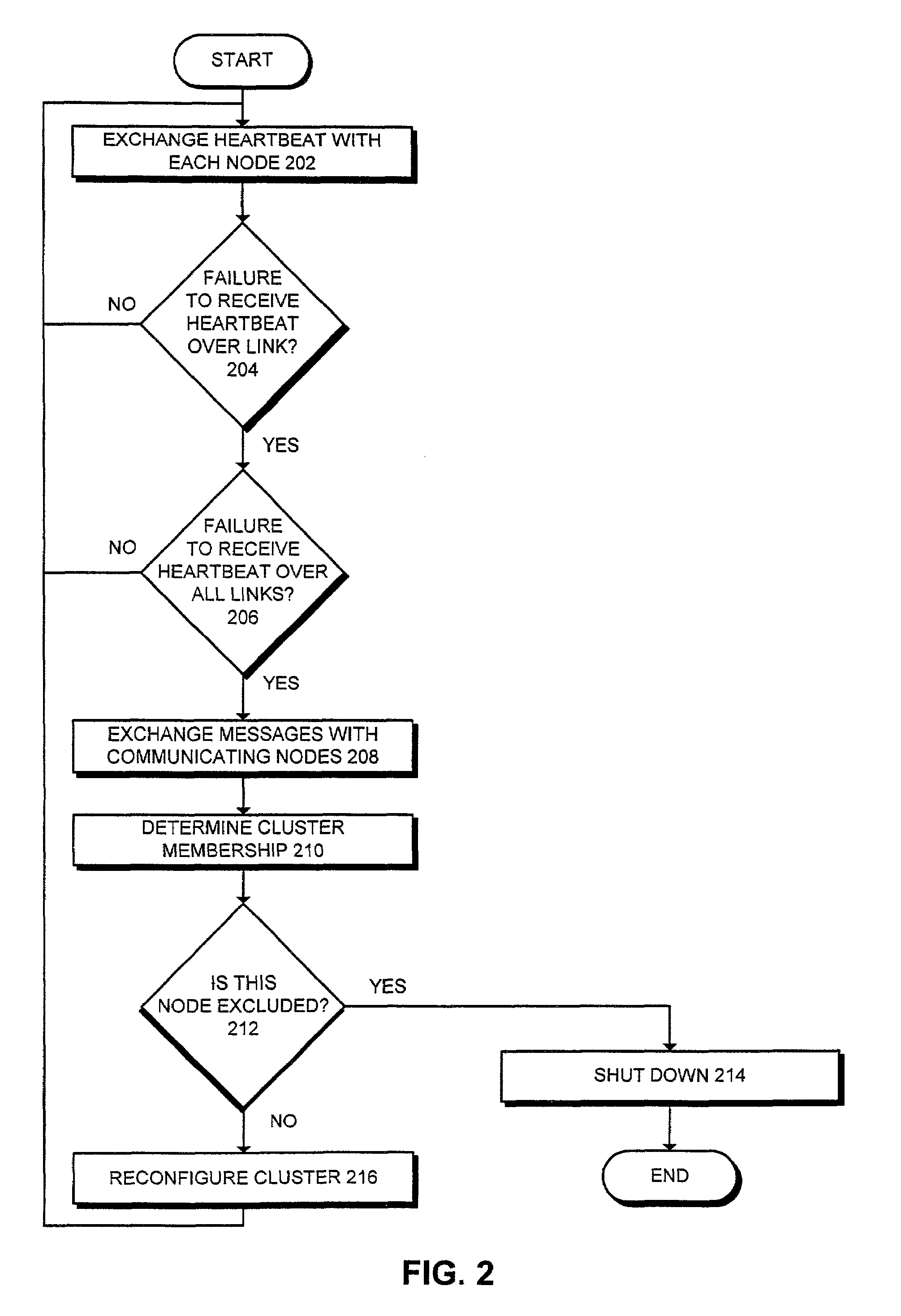
Method of managing nodes in computer cluster
A method is described of managing nodes in a computer cluster comprising: each node repeatedly broadcasting a cluster summary message; a cluster coordinator node identifying failed nodes by analysing cluster summary messages received from other nodes in the cluster; and the cluster coordinator node broadcasting an updated cluster organization status, if failed nodes are identified. In at least preferred embodiments, the broadcasts can be transmitted using an ad-hoc wireless network.
Owner:VALTRUS INNOVATIONS LTD +1
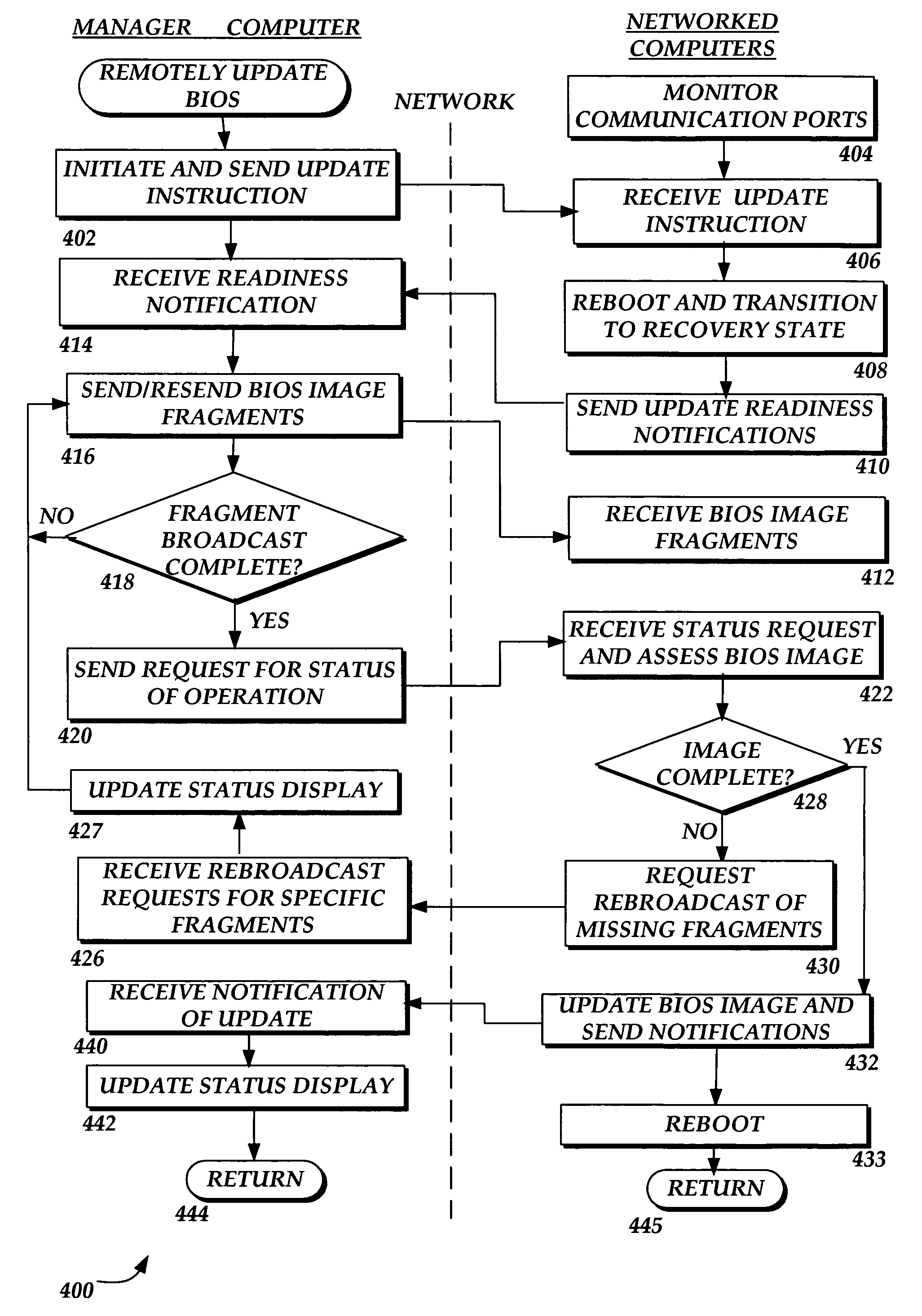
Methods and systems for updating the firmware on a plurality of network-attached computing devices
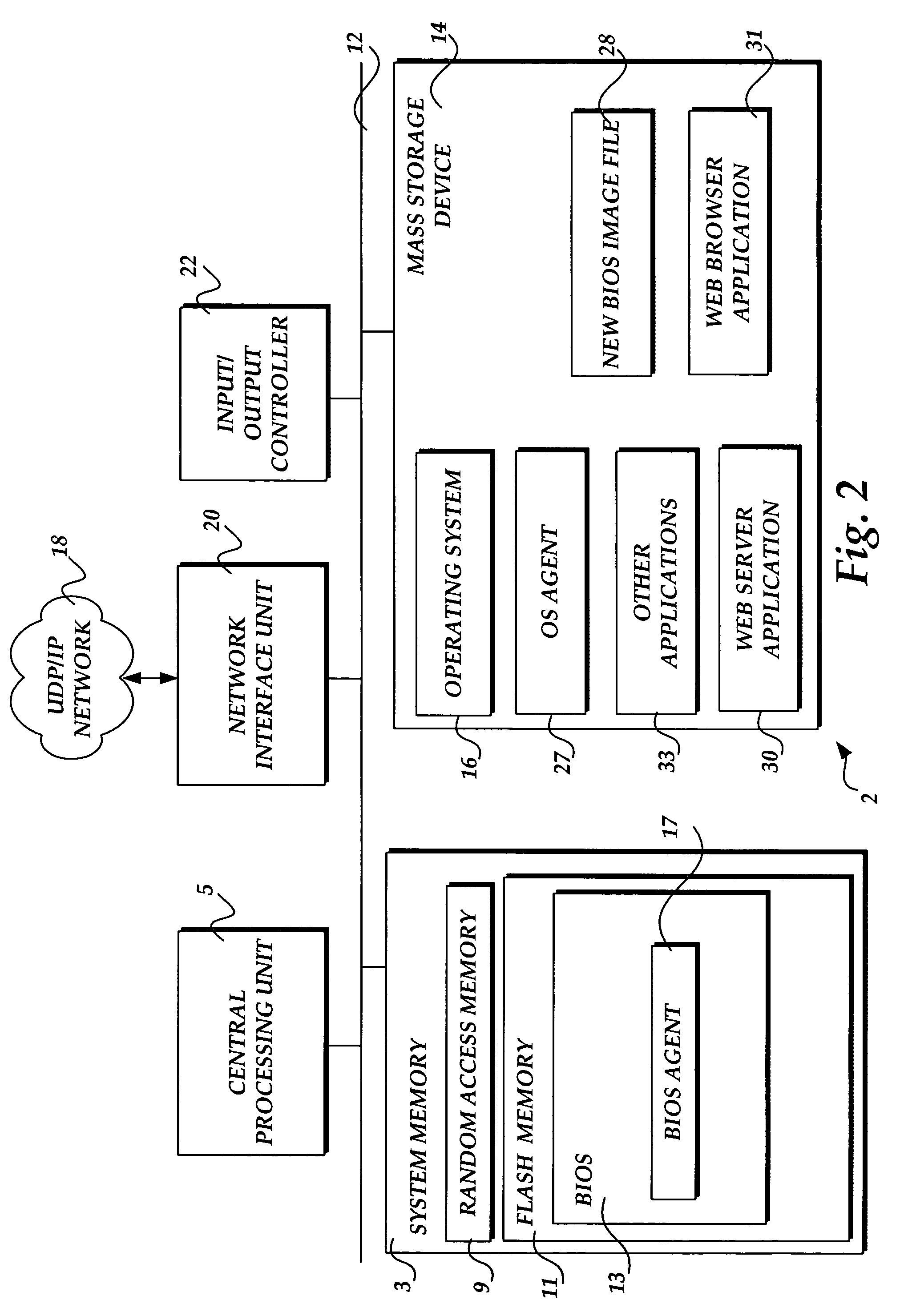
ActiveUS7421688B1Multiple digital computer combinationsTransmissionOperational systemComputer cluster
Methods and systems are provided for updating firmware on a plurality of networked computing devices via a distributed network. An instruction to update the firmware on a plurality of networked computing devices, such as nodes in a computer cluster, is sent from a manager computer to the computing devices monitoring for instructions. When the instruction is received, the computing devices transition to an operating system independent recovery state, receive a new firmware image over the distributed network, and update the firmware with the new firmware image.
Owner:AMERICAN MEGATRENDS
Hybrid method for event prediction and system control
InactiveUS7451210B2Data processing applicationsDigital computer detailsHybrid approachComputer cluster
Owner:GLOBALFOUNDRIES INC
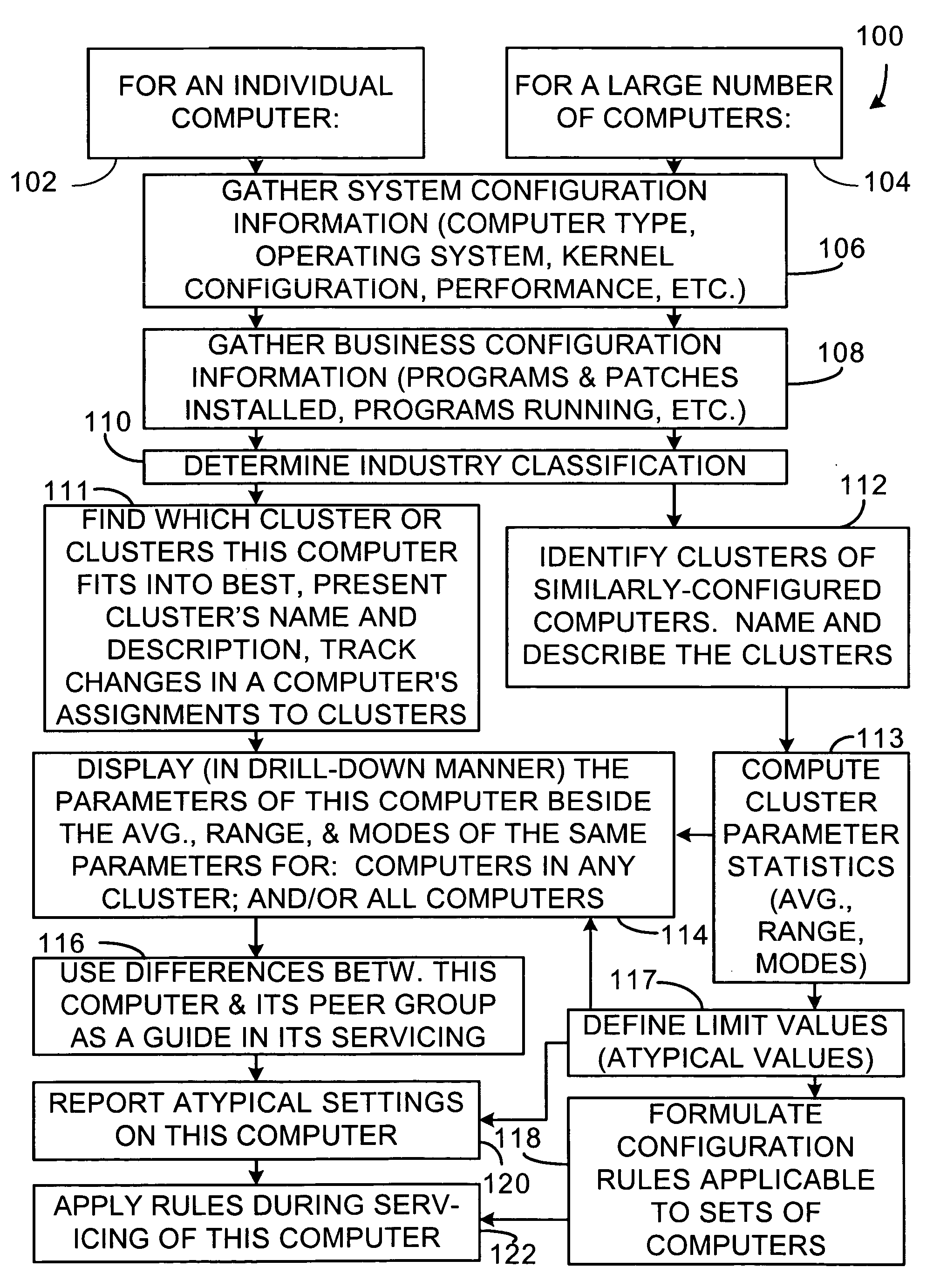
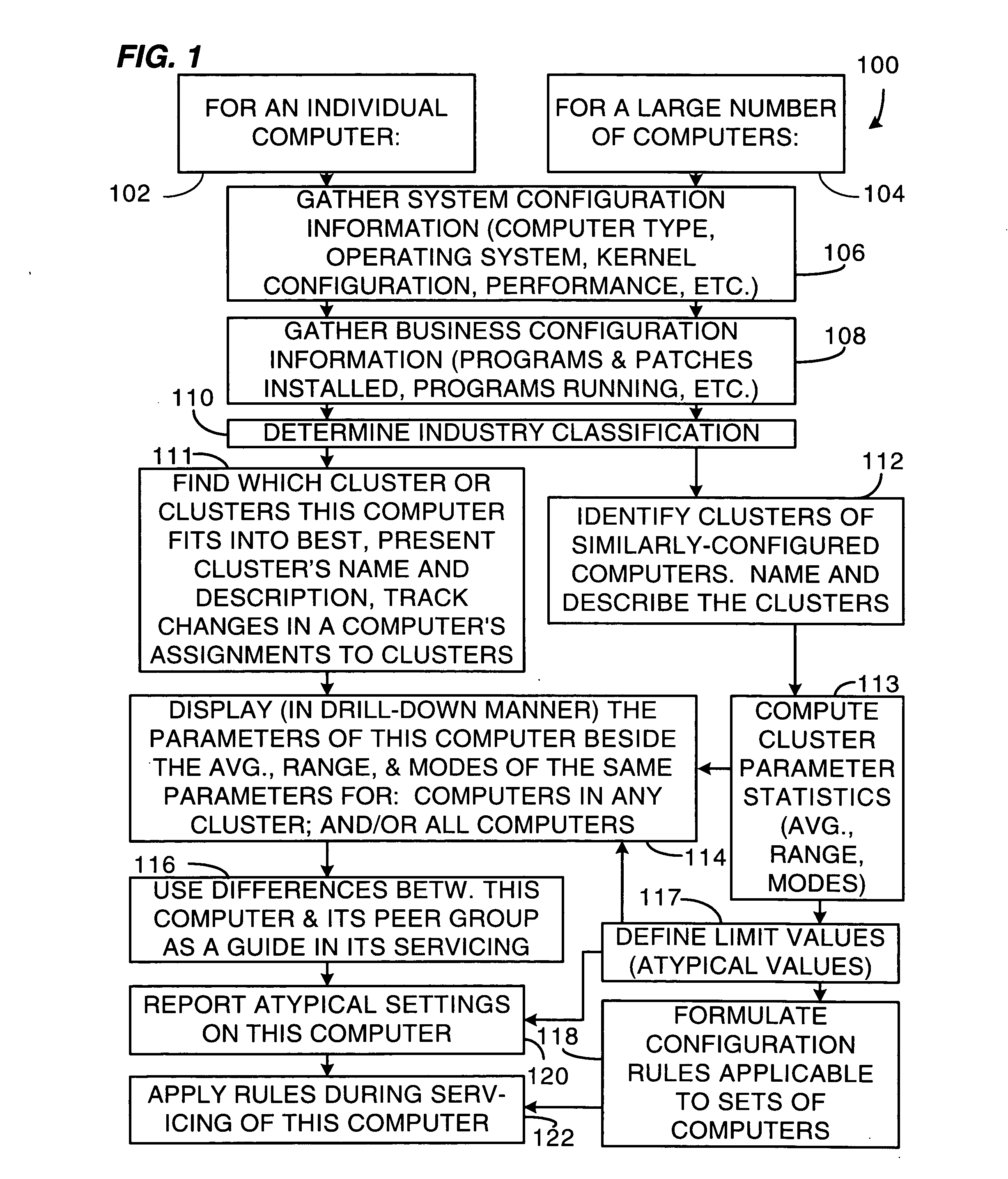
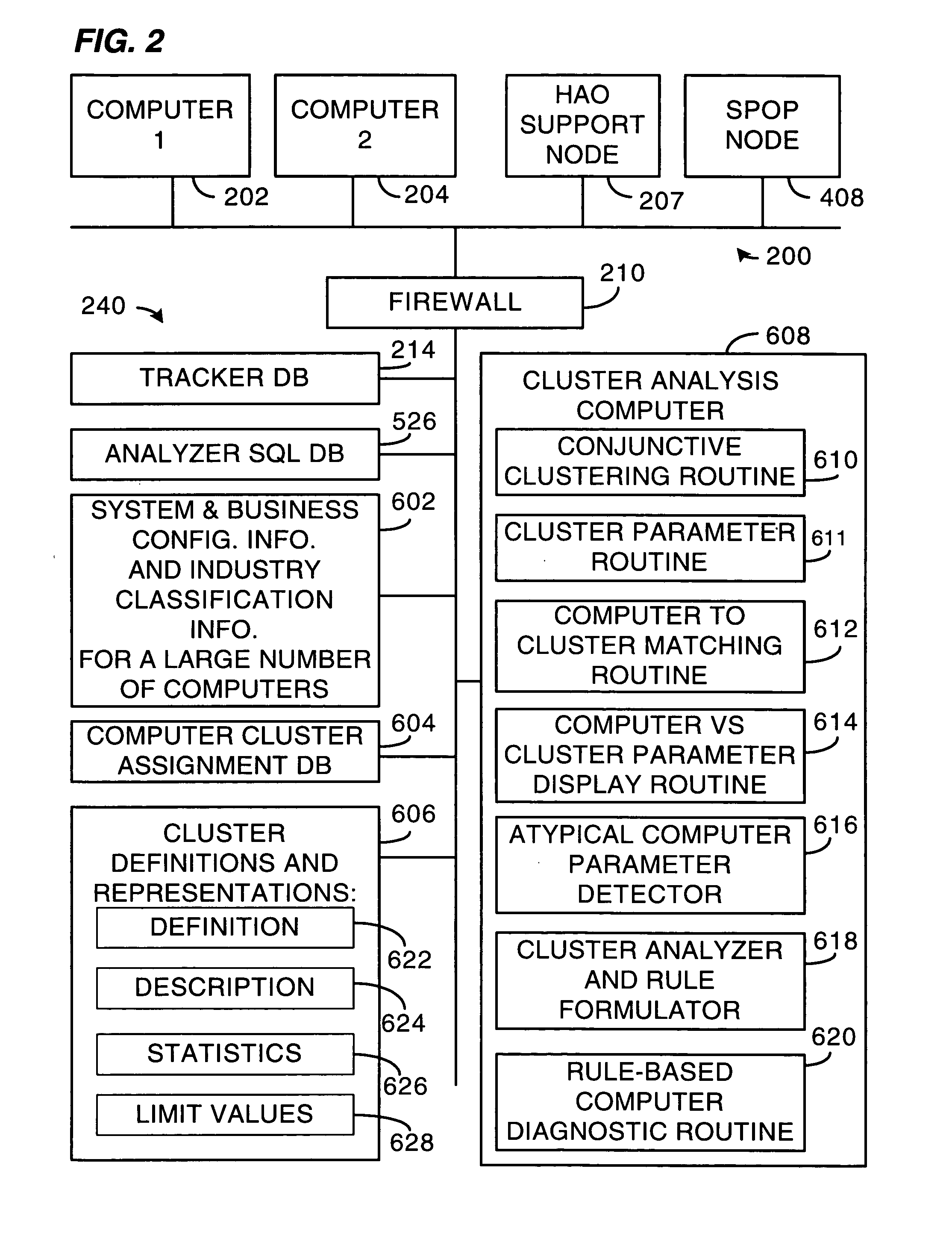
Method and system for comparing individual computers to cluster representations of their peers
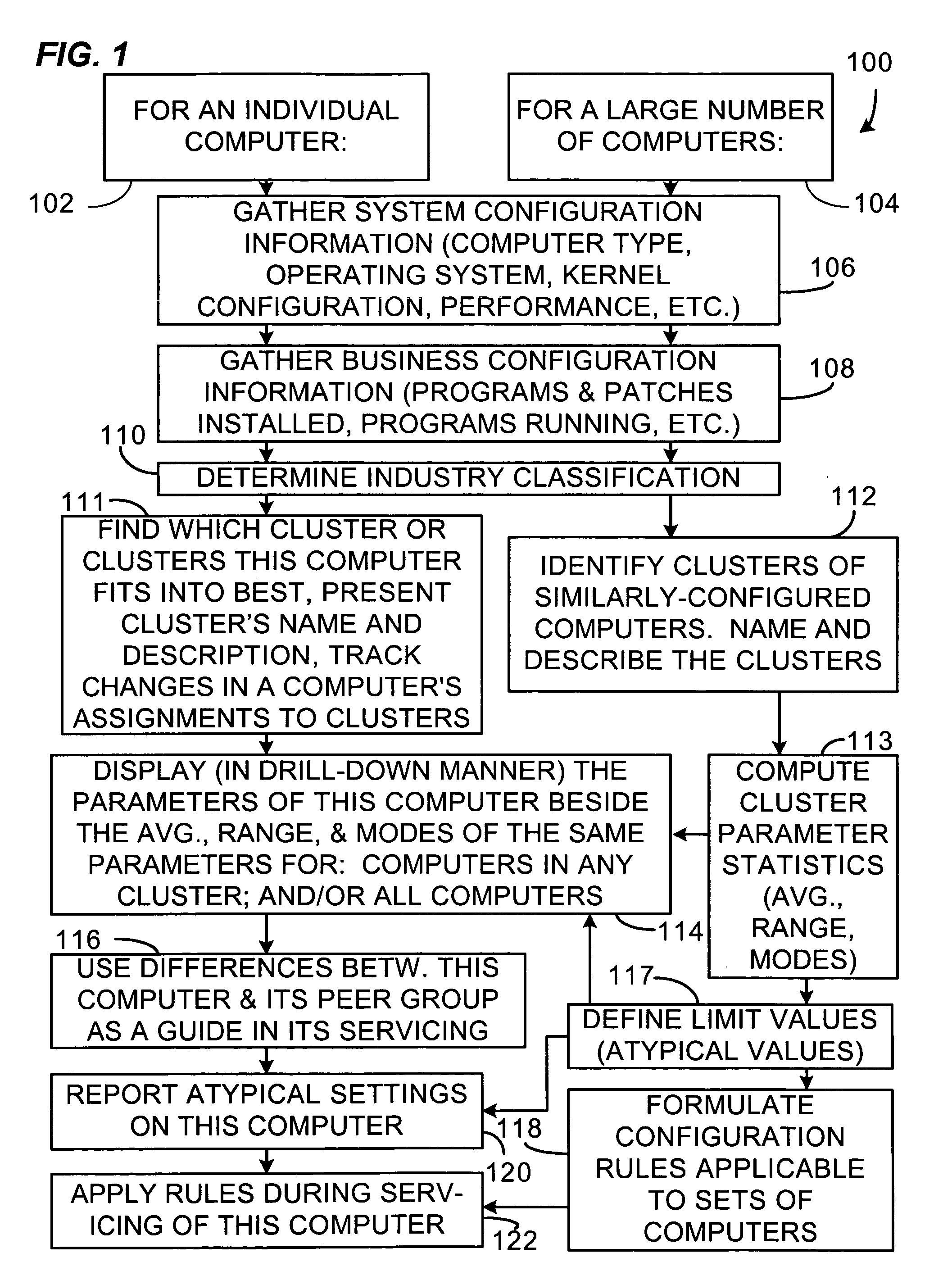
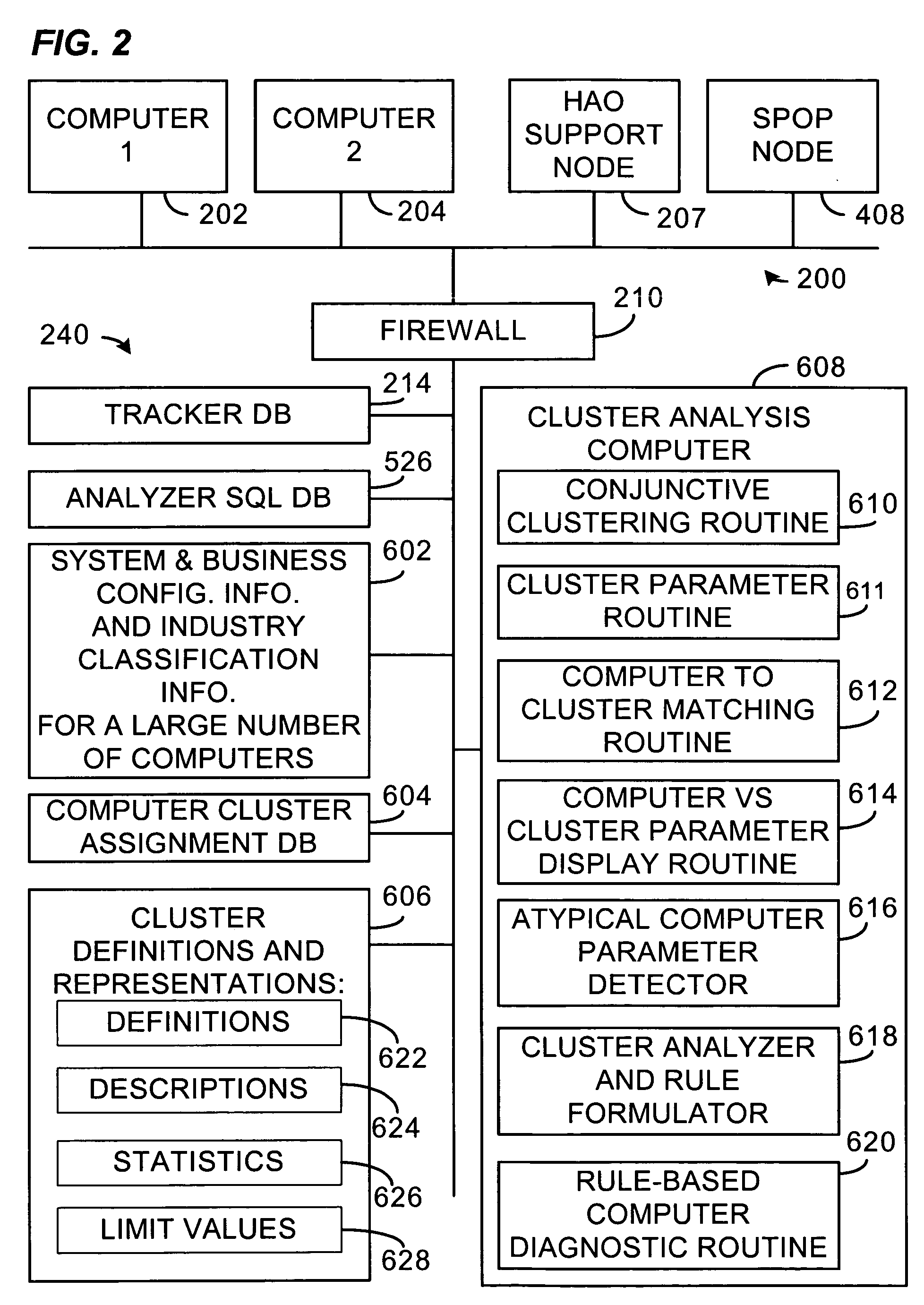
The present invention is a system or method for assisting in the maintenance and servicing of computers. The system, for example, comprises a cluster database containing information relating to one or more computer clusters, the information relating to each cluster comprising one or more cluster descriptions and one or more representations of configuration information values that characterize typical computer members of the cluster, and also a tracker database containing configuration information values gathered from and relating to one or more computers. The system further comprises a computer and cluster comparison routine having access to the cluster and tracker databases that compares one or more of the representations of configuration information values relating to one or more of the clusters to one or more of the corresponding configuration information values gathered from at least one given computer and that then indicates how closely the given computer's configuration conforms with the configuration of typical computer members of the one or more clusters.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
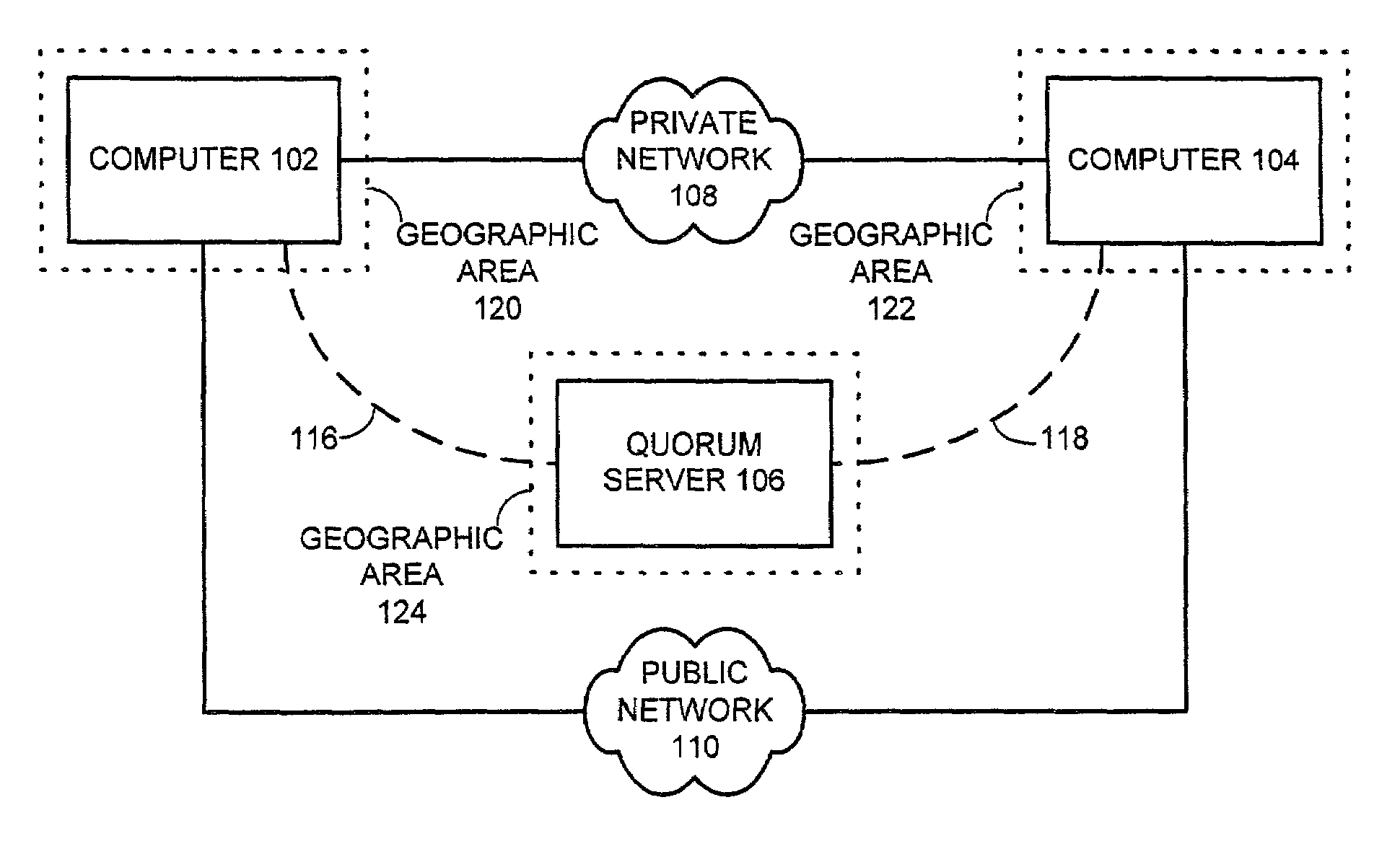
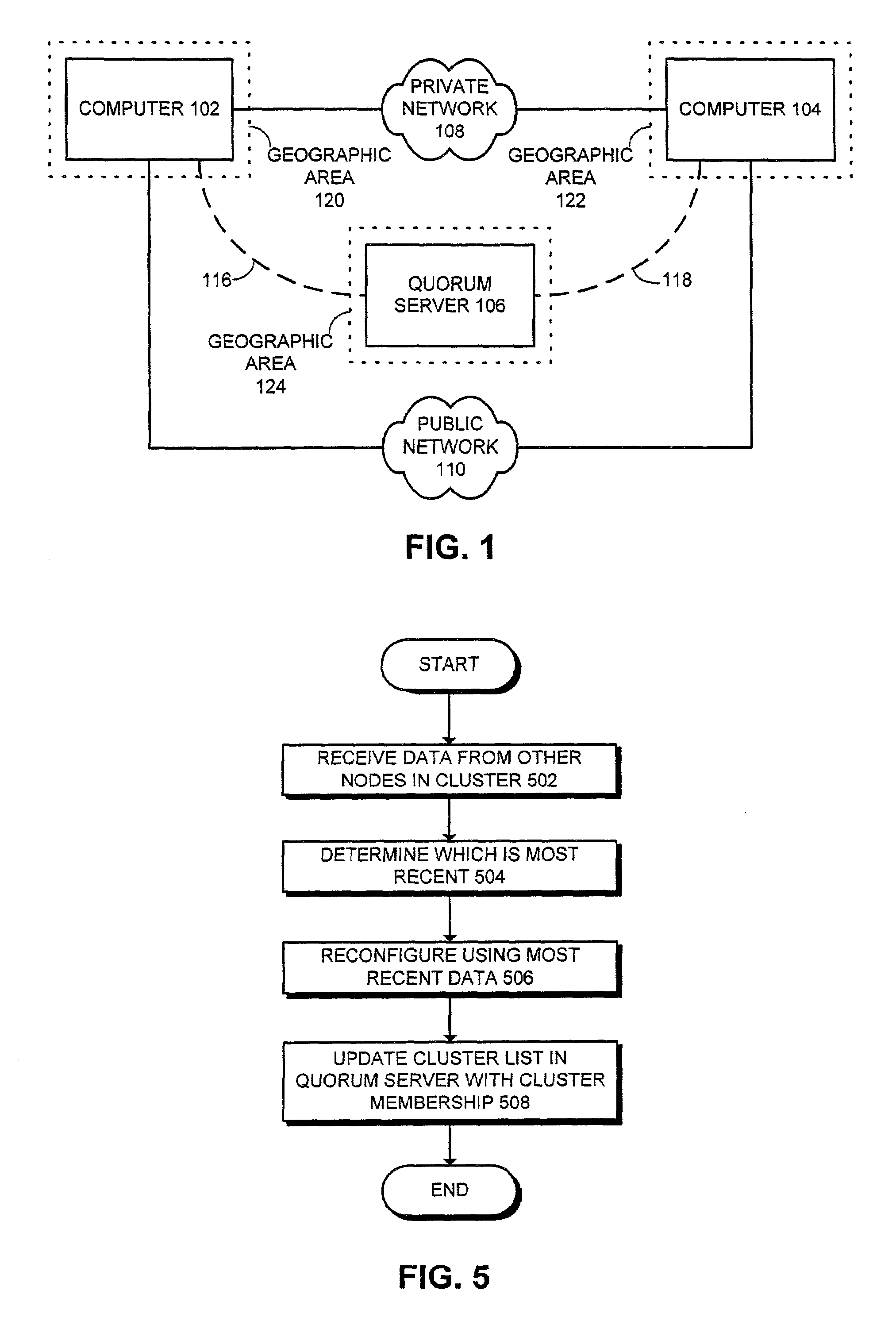
Method and system for establishing a quorum for a geographically distributed cluster of computers
ActiveUS7016946B2Facilitates establishing a quorumMultiple digital computer combinationsNon-redundant fault processingComputer cluster
One embodiment of the present invention provides a system that facilitates establishing a quorum for a cluster of computers that are geographically distributed. The system operates by detecting a change in membership of the cluster. Upon detecting the change, the system forms a potential new cluster by attempting to communicate with all other computers within the cluster. The system accumulates votes for each computer successfully contacted. The system also attempts to gain control of a quorum server located at a site separate from all computers within the cluster. If successful at gaining control, the system accumulates the quorum server's votes as well. If the total of accumulated votes is a majority of the available votes, the system forms a new cluster from the potential new cluster.
Owner:ORACLE INT CORP
Scalable data storage architecture and methods of eliminating I/O traffic bottlenecks
ActiveUS8347010B1Increase storage capacityImprove system performanceMemory systemsInput/output processes for data processingExtensibilityFiber
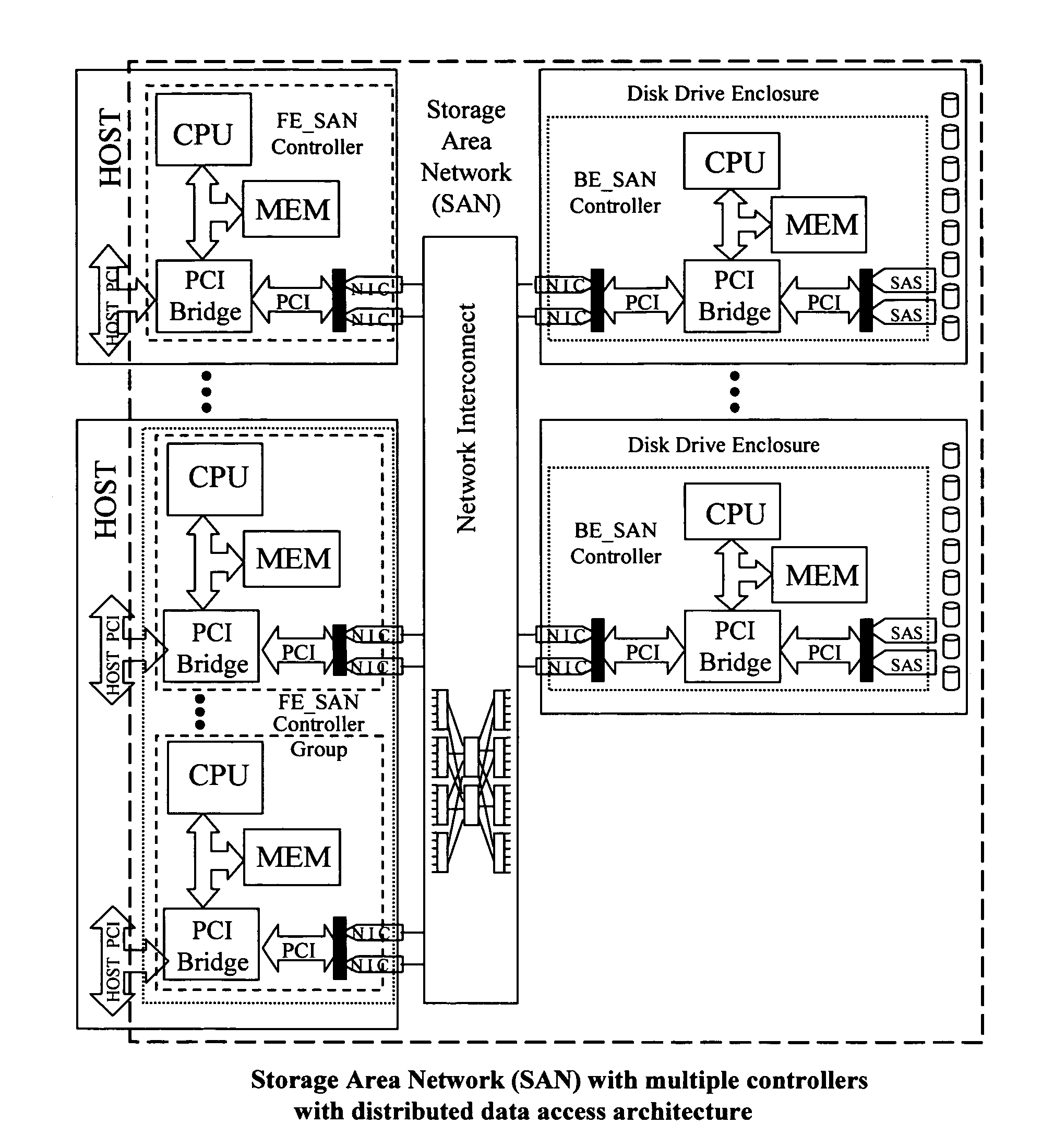
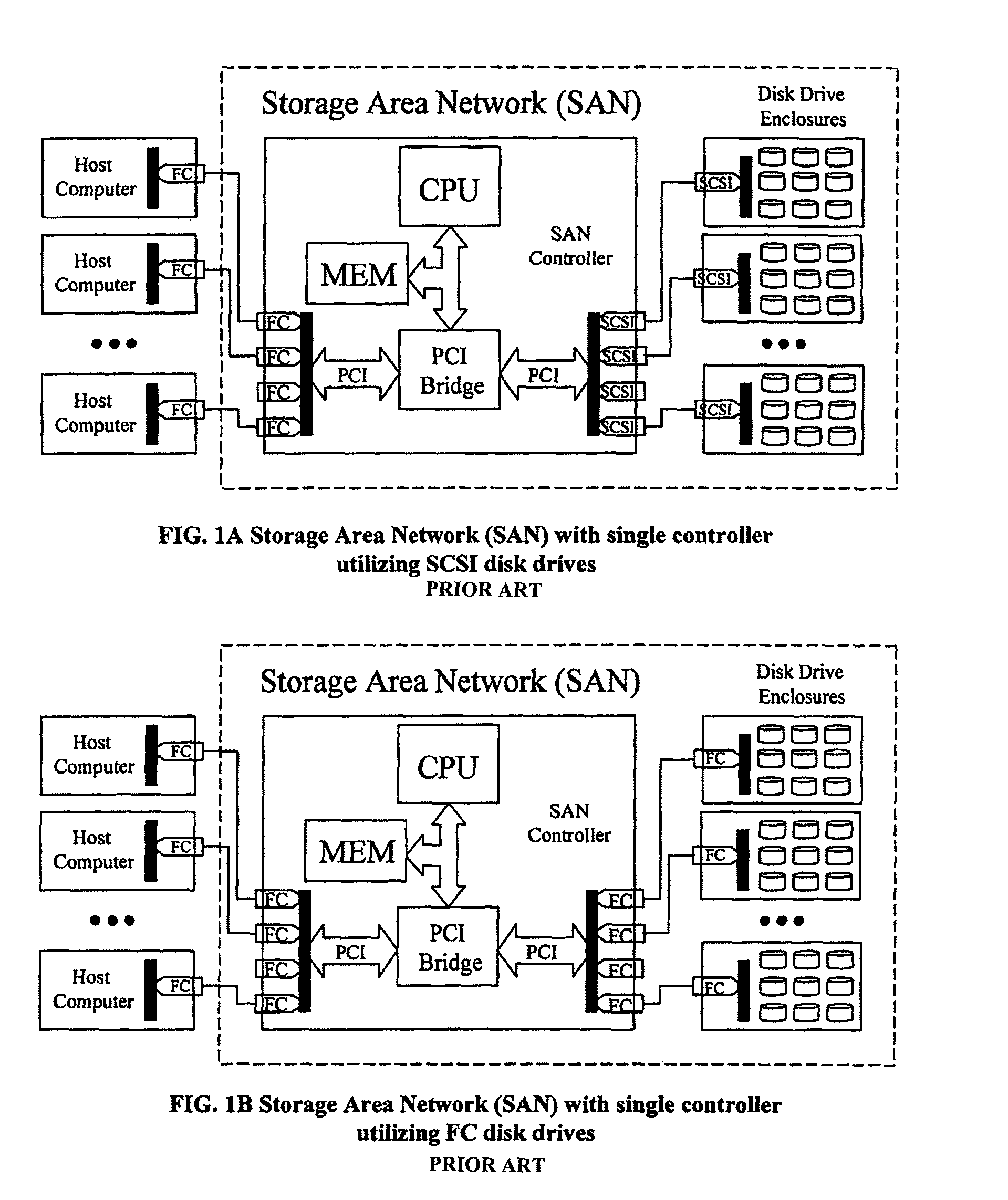
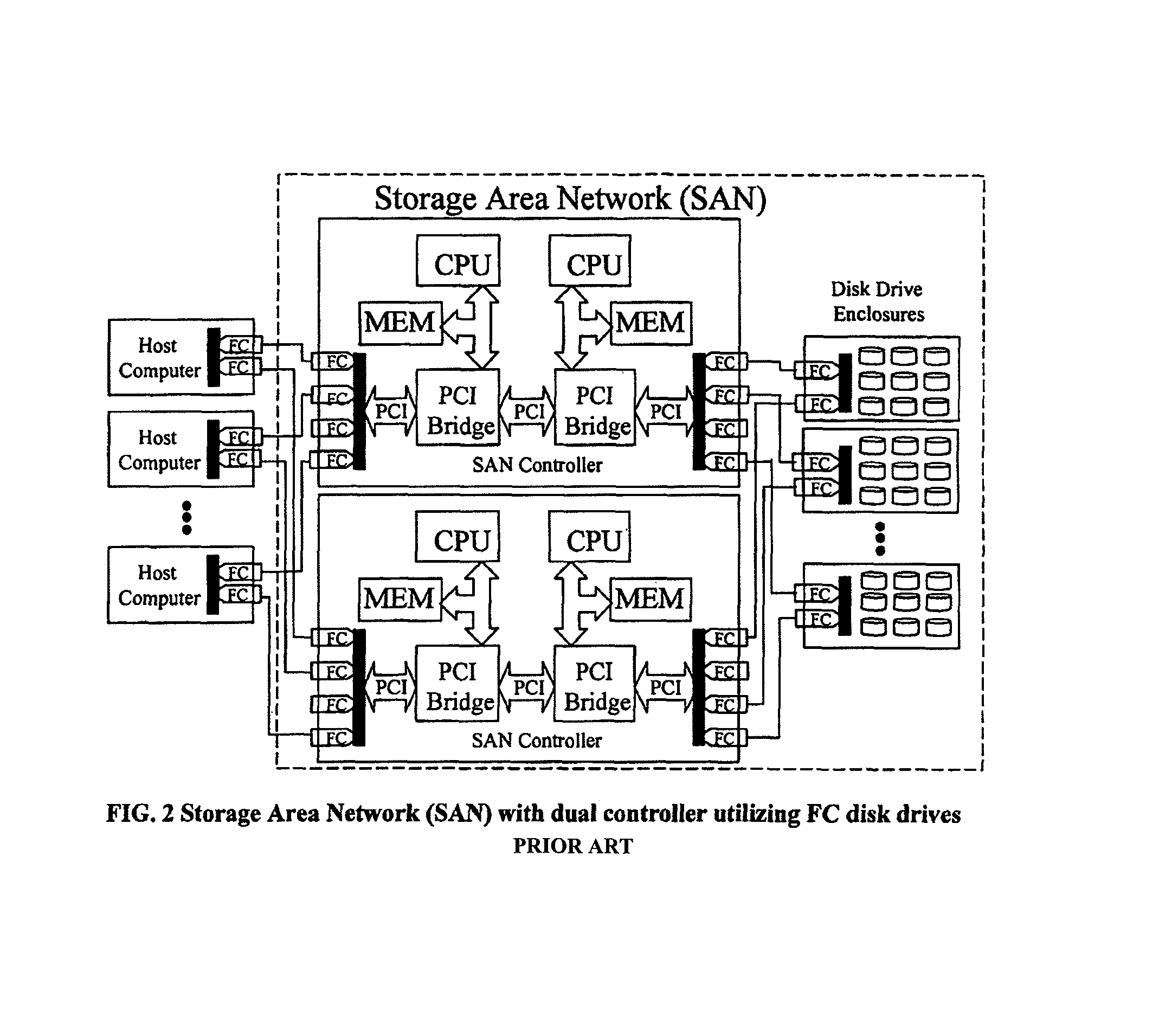
An apparatus and method implemented in hardware and embedded software that improves performance, scalability, reliability, and affordability of Storage Area Network (SAN) systems or subsystems. The apparatus contains host computers (application servers, file servers, computer cluster systems, or desktop workstations), SAN controllers connected via a bus or network interconnect, disk drive enclosures with controllers connected via network interconnect, and physical drive pool or cluster of other data storage devices that share I / O traffic, providing distributed high performance centrally managed storage solution. This approach eliminates I / O bottlenecks and improves scalability and performance over the existing SAN architectures. Although this architecture is network interconnect (transport) neutral, additional improvements and cost savings could be made by utilizing existing, of the shelf, low latency and high speed hardware such as Advanced Switching (AS) or Myrinet networks as a transport for data, Small Computer System Interface (SCSI) and other commands and messages. Using AS or Myrinet network as a replacement for Fiber Channel (FC) would significantly reduce the cost of such SAN systems and at the same time boost performance (higher data transfer rates and lower latencies). This invention is about defining hardware and software architectural solution that is specifically designed to eliminate I / O traffic bottlenecks, improve scalability, and reduce the overall cost of today's SAN systems or subsystems. This innovative solution, in addition to it's performance superiority compared to the existing solutions, should also provide 100% compatibility with the all existing Operating Systems (OS), File Systems (FS), and existing applications.
Owner:RADOVANOVIC BRANISLAV
Computer server cluster log monitoring method and monitoring platform
ActiveCN107943668AImprove real-time performanceSupport accessHardware monitoringStreaming dataComputer cluster
The invention relates to the technical field of computers, in particular to a computer server cluster log monitoring method and monitoring platform. The monitoring method includes step A of monitoringmassive machine code commands generated by a main board during the running of each server in a computer server cluster, and using a real-time stream data collection frame in a big data technology tocollect the machine code commands generated by the main board in real time; step B of performing data classification and transfer operations on the collected data, including real-time filtering, processing and storage; step C of performing real-time analysis and display of the data processed in step B to obtain real-time analysis results and store the results; step D of performing analysis by combination with the real-time analysis results and stored historical analysis results, obtaining potential abnormal results of the computer server, and performing early warning and notification. The computer server cluster log monitoring method and monitoring platform have the advantages of real time, expandability, automation, high availability and rich API extension.
Owner:江苏神威云数据科技有限公司
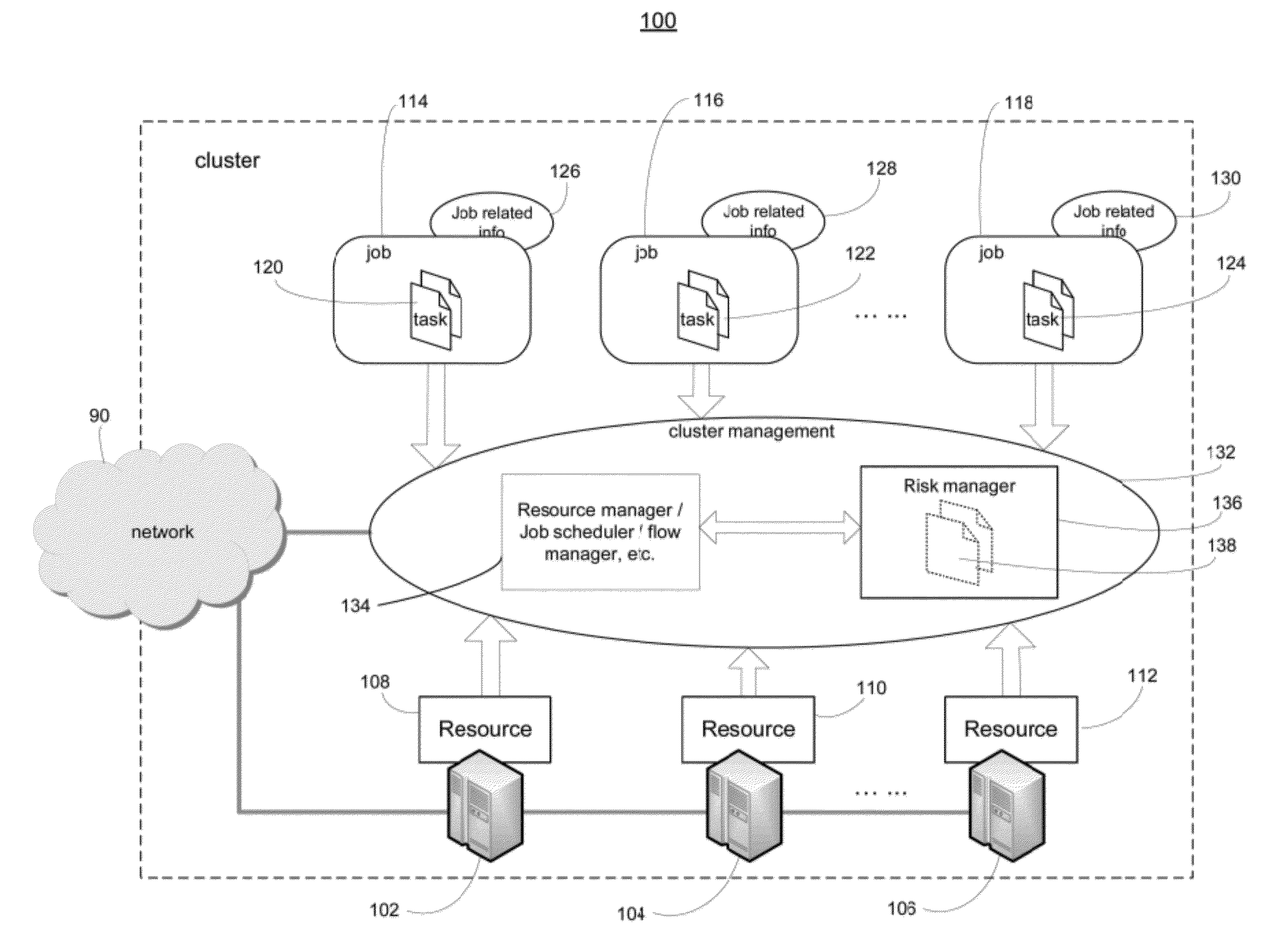
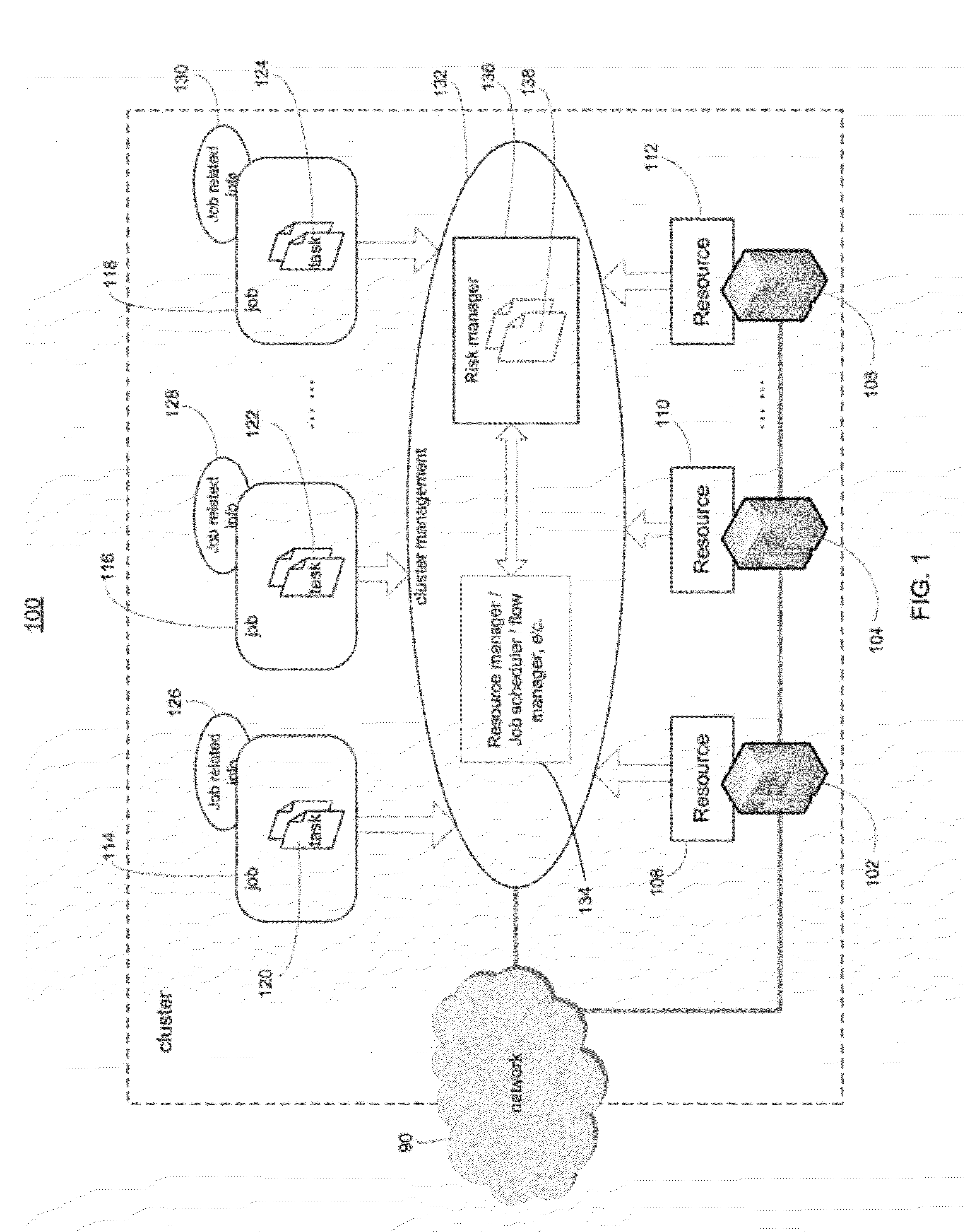
System and method of active risk management to reduce job de-scheduling probability in computer clusters
ActiveUS20120110584A1Minimize de-scheduling possibilityReduce executionMultiprogramming arrangementsReliability/availability analysisOperation schedulingComputer cluster
Systems and methods are provided for generating backup tasks for a plurality of tasks scheduled to run in a computer cluster. Each scheduled task is associated with a target probability for execution, and is executable by a first cluster element and a second cluster element. The system classifies the scheduled tasks into groups based on resource requirements of each task. The system determines the number of backup tasks to be generated. The number of backup tasks is determined in a manner necessary to guarantee that the scheduled tasks satisfy the target probability for execution. The backup tasks are desirably identical for a given group. And each backup task can replace any scheduled task in the given group.
Owner:GOOGLE LLC
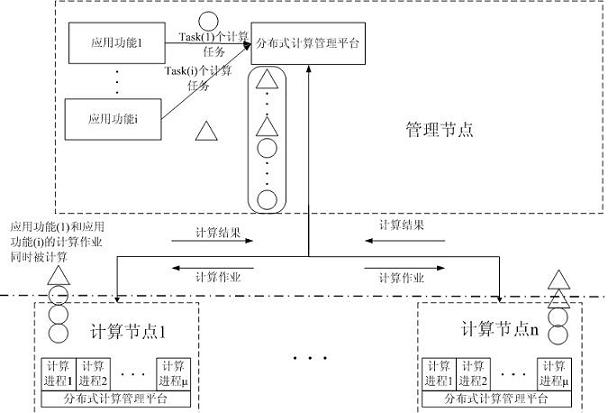
Distributed computing multiple application function asynchronous concurrent scheduling method
ActiveCN102063336AReduce overhead timeAvoid situations where it cannot be used by other application functionsProgram initiation/switchingResource allocationOperation schedulingComputer cluster
The invention belongs to the field of distributed computing, and provides a multiple application function asynchronous concurrent scheduling method, which is applied to a distributed computing management platform. The distributed computing management platform combines the time consumption characteristic and number of the computing tasks of each application function and the scale and performance information of a computer cluster node, realizes the computing operation of each application function by independently setting a proper computing operation scheduling grain size for each application function, and adds the computing operation into the scheduling sequence of the distributed computer management platform to realize the computing task asynchronous concurrent submission of the plurality of application functions, the uniform scheduling of the computing operation of the plurality of application functions and the computing result asynchronous recovery of the plurality of application functions, thereby fully utilizing the computing performance of the computer cluster and reducing computing time.
Owner:NARI TECH CO LTD
Method and device for dispatching job task
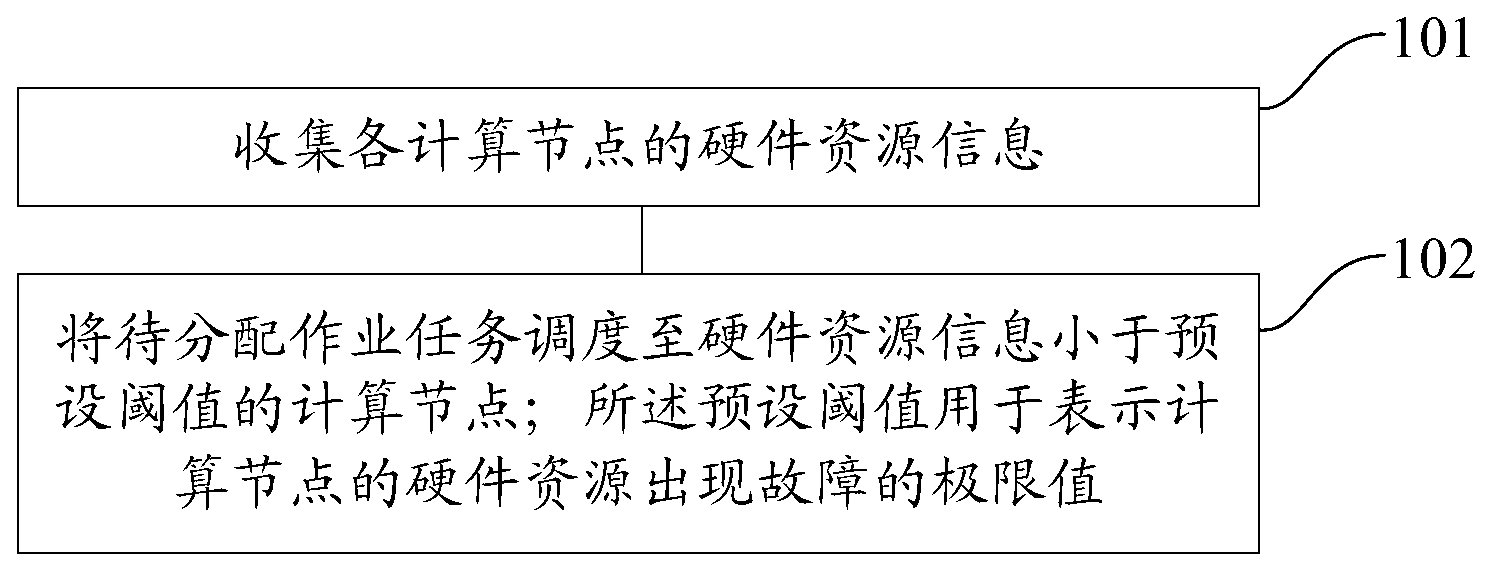
InactiveCN103019853AAvoid wastingTake advantage ofResource allocationComputer clusterResource information
The invention provides a method and device for dispatching a job task. The method particularly comprises the steps as follows: collecting hardware resource information of compute nodes; and dispatching the job task to be distributed to the compute node with the hardware resource information less than a preset threshold value, wherein the preset threshold value is used for representing a failure occurrence limit value of the hardware resource of the compute node. According to the method, the throughput rate of a computer cluster can be increased.
Owner:BEIJING IZP NETWORK TECH CO LTD
Method and system for clustering computers into peer groups and comparing individual computers to their peers
ActiveUS20050289071A1Maximizing numberDigital computer detailsNuclear monitoringComputer clusterCollection system
A method and system for identifying clusters of similarly-configured computers. The method, for example, comprises gathering system and business configuration information values from a set of computers. Next, at least a portion of the system and business configuration information values gathered from the set of computers is analyzed along with the numbers of computers that are configured in various ways. Then, using the result of the analysis as a guide, logical expressions of configuration information values are selected for use as definitions of one or more clusters of similarly-configured computers, the selection process generally maximizing the number of computers included within each cluster and also generally maximizing the number of configuration information value specifications included within the definition of each cluster. Then, for one or more clusters so defined and selected, one or more statistics or limit values are generated from one or more configuration information values or both gathered from the subset of computers included in the one or more clusters.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Distributed shared memory
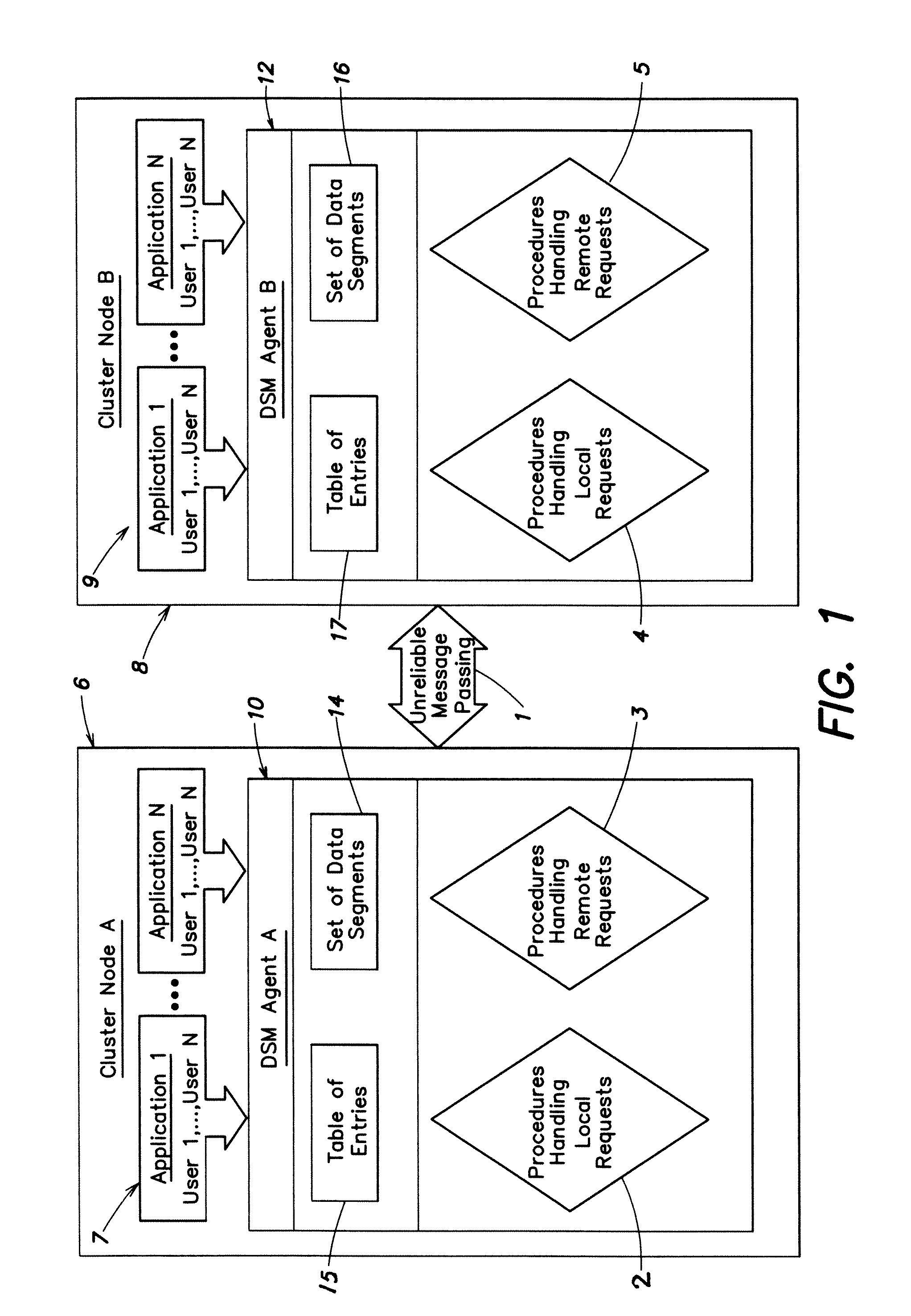
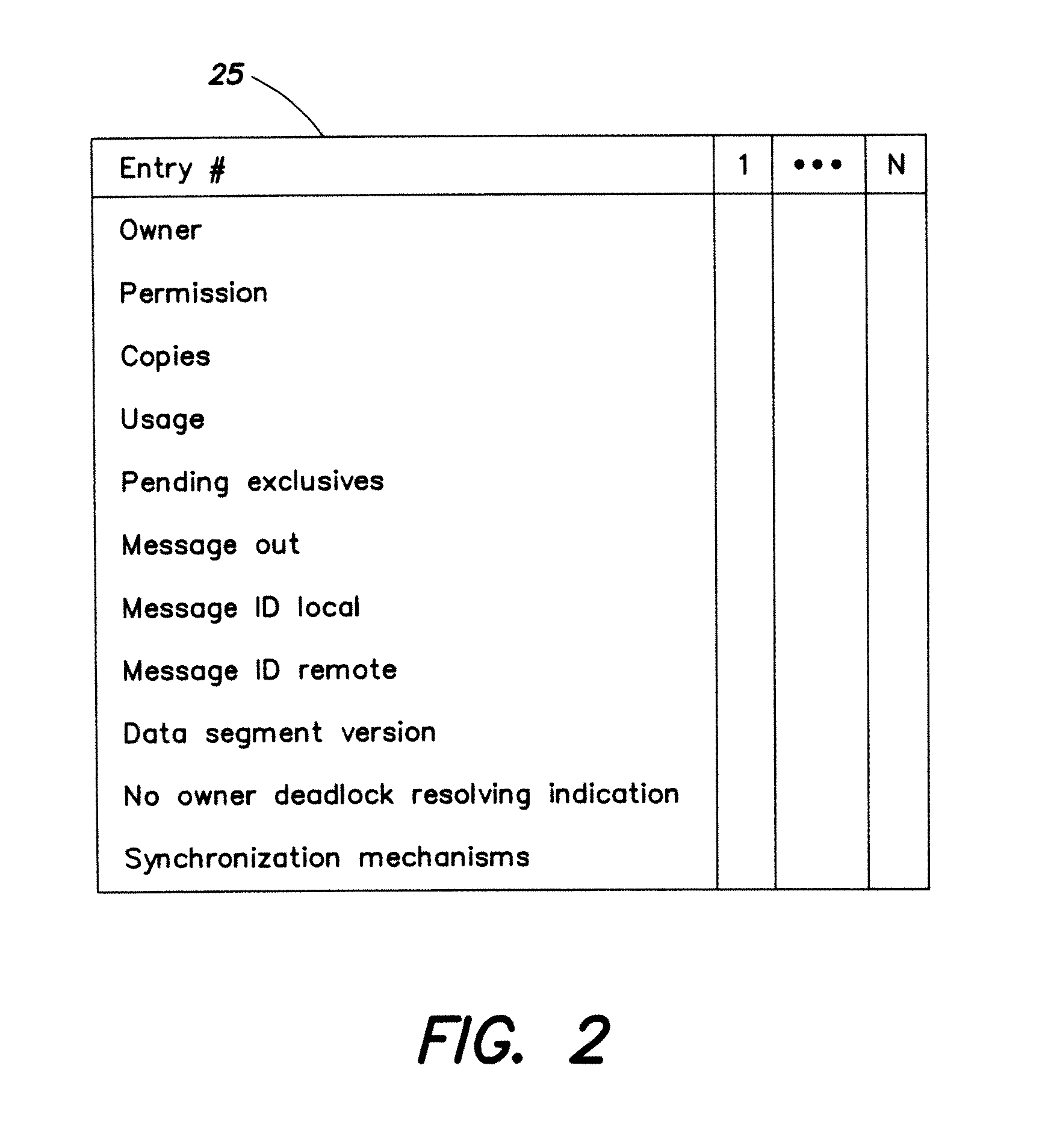
InactiveUS20120272012A1Memory architecture accessing/allocationMemory adressing/allocation/relocationData segmentComputer cluster
Systems and methods for implementing a distributed shared memory (DSM) in a computer cluster in which an unreliable underlying message passing technology is used, such that the DSM efficiently maintains coherency and reliability. DSM agents residing on different nodes of the cluster process access permission requests of local and remote users on specified data segments via handling procedures, which provide for recovering of lost ownership of a data segment while ensuring exclusive ownership of a data segment among the DSM agents detecting and resolving a no-owner messaging deadlock, pruning of obsolete messages, and recovery of the latest contents of a data segment whose ownership has been lost.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com