Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
573 results about "File Transfer Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network. FTP is built on a client-server model architecture using separate control and data connections between the client and the server. FTP users may authenticate themselves with a clear-text sign-in protocol, normally in the form of a username and password, but can connect anonymously if the server is configured to allow it. For secure transmission that protects the username and password, and encrypts the content, FTP is often secured with SSL/TLS (FTPS) or replaced with SSH File Transfer Protocol (SFTP).
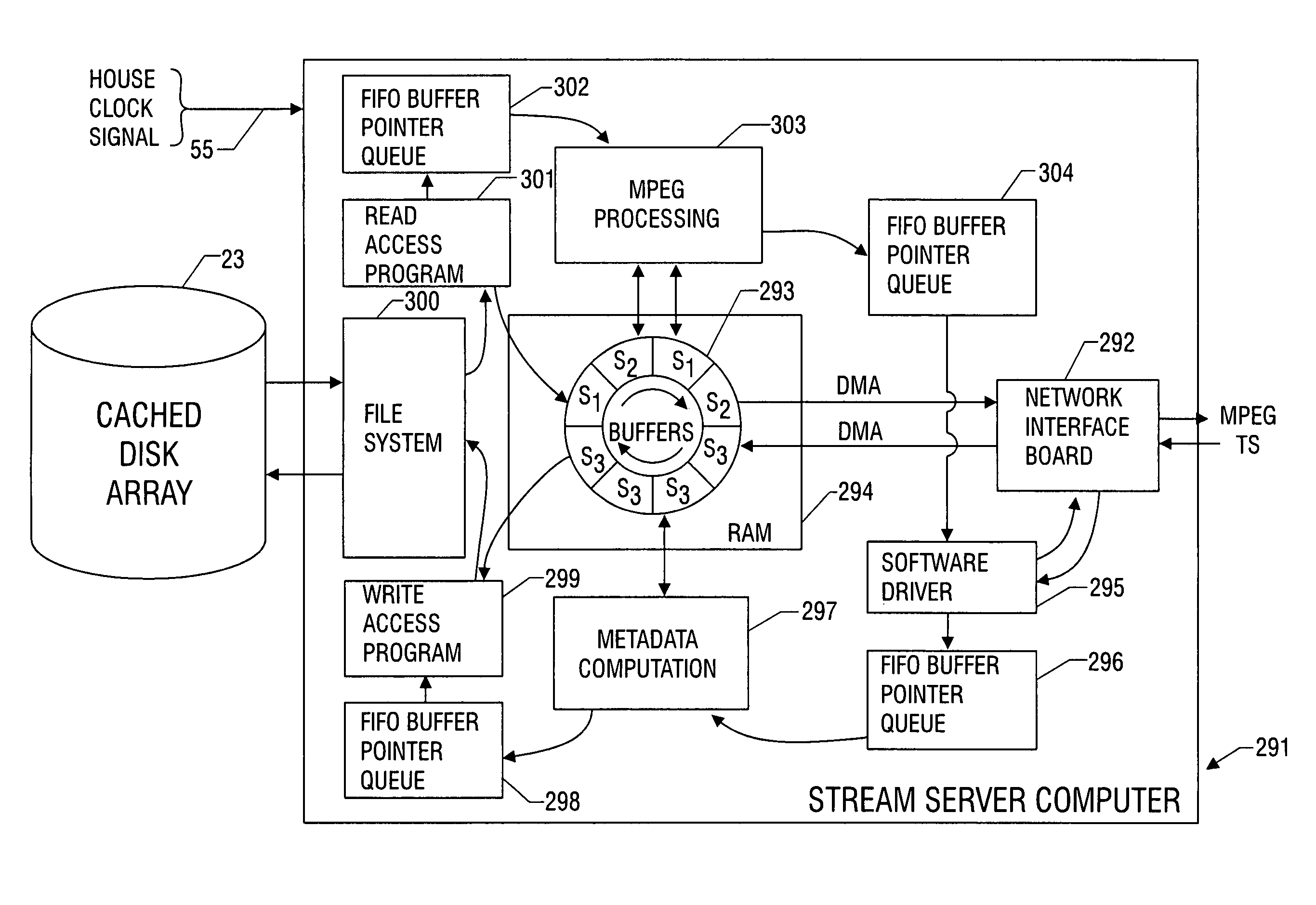
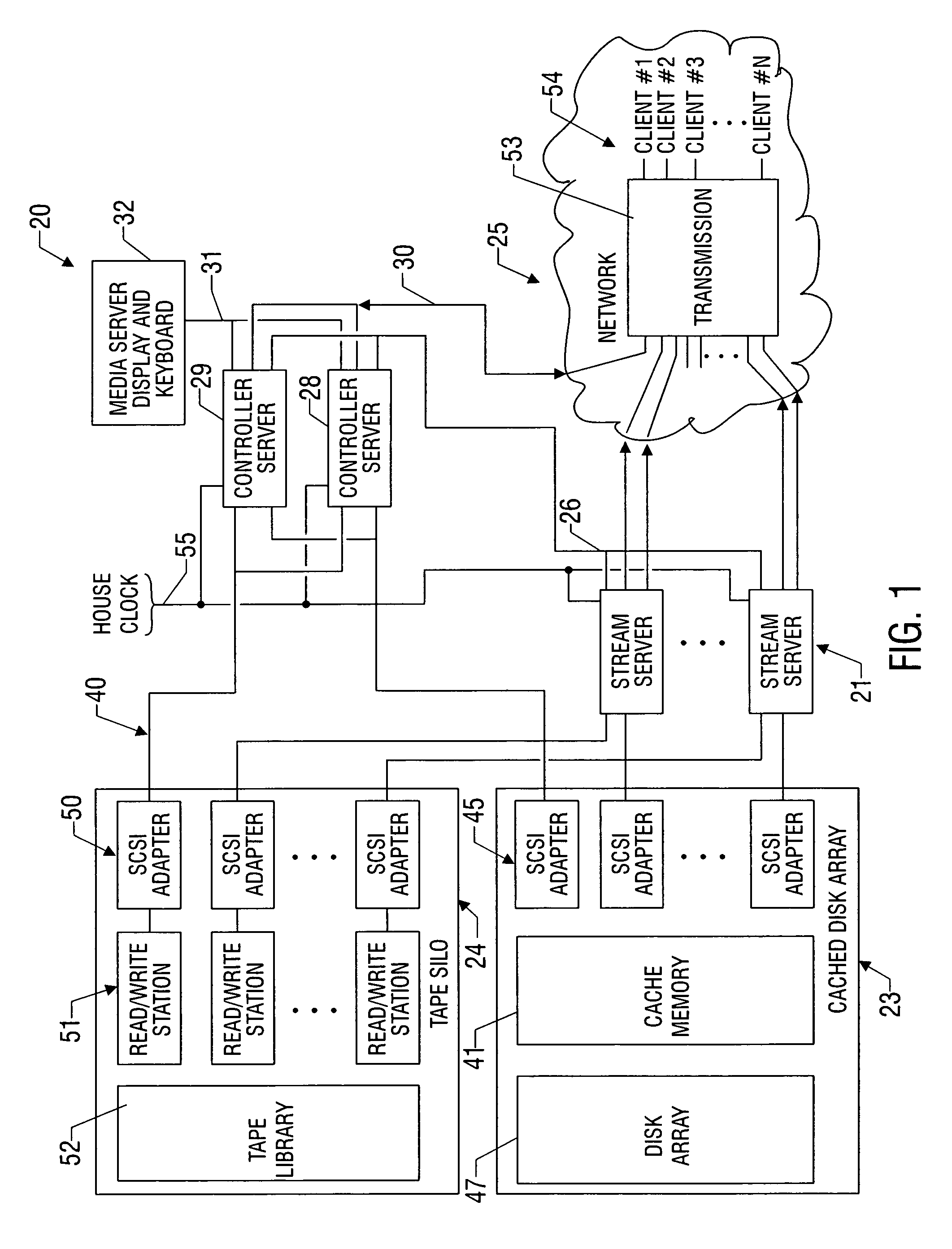
Preparation of metadata for splicing of encoded MPEG video and audio
InactiveUS7096481B1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningMPEG transport streamData stream
Metadata for splicing of an encoded digital motion video stream (such as an MPEG Transport Stream) is prepared in real time while recording at the encoding bit rate and faster than encoded bit rate for off line encoding independent of the bit rate and mechanisms for ingestion of the data stream into data storage. Preprocessing is performed during a metered file transfer protocol (FTP) and includes pseudo real-time encoding. The preprocessing includes Group of Pictures (GOP) level pre-processing of splicing In Points and results in an intimate linkage between metadata and the file system in which the video data is stored. The preferred file system enables access to metadata in parallel to writing the data on disk. The pre-processing is performed simultaneous to writing the data to the disk using a carousel type buffer mechanism.
Owner:EMC IP HLDG CO LLC +1
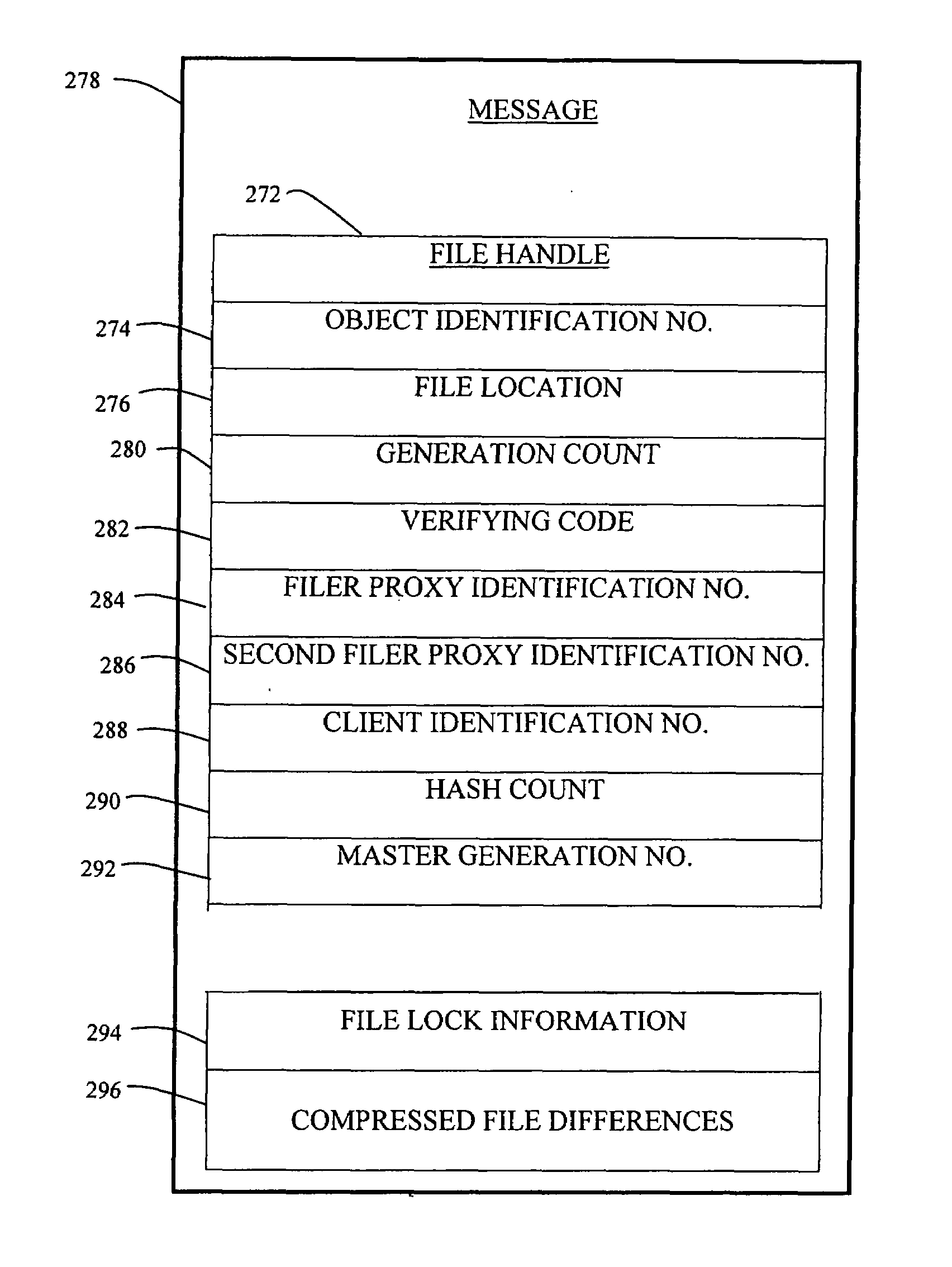
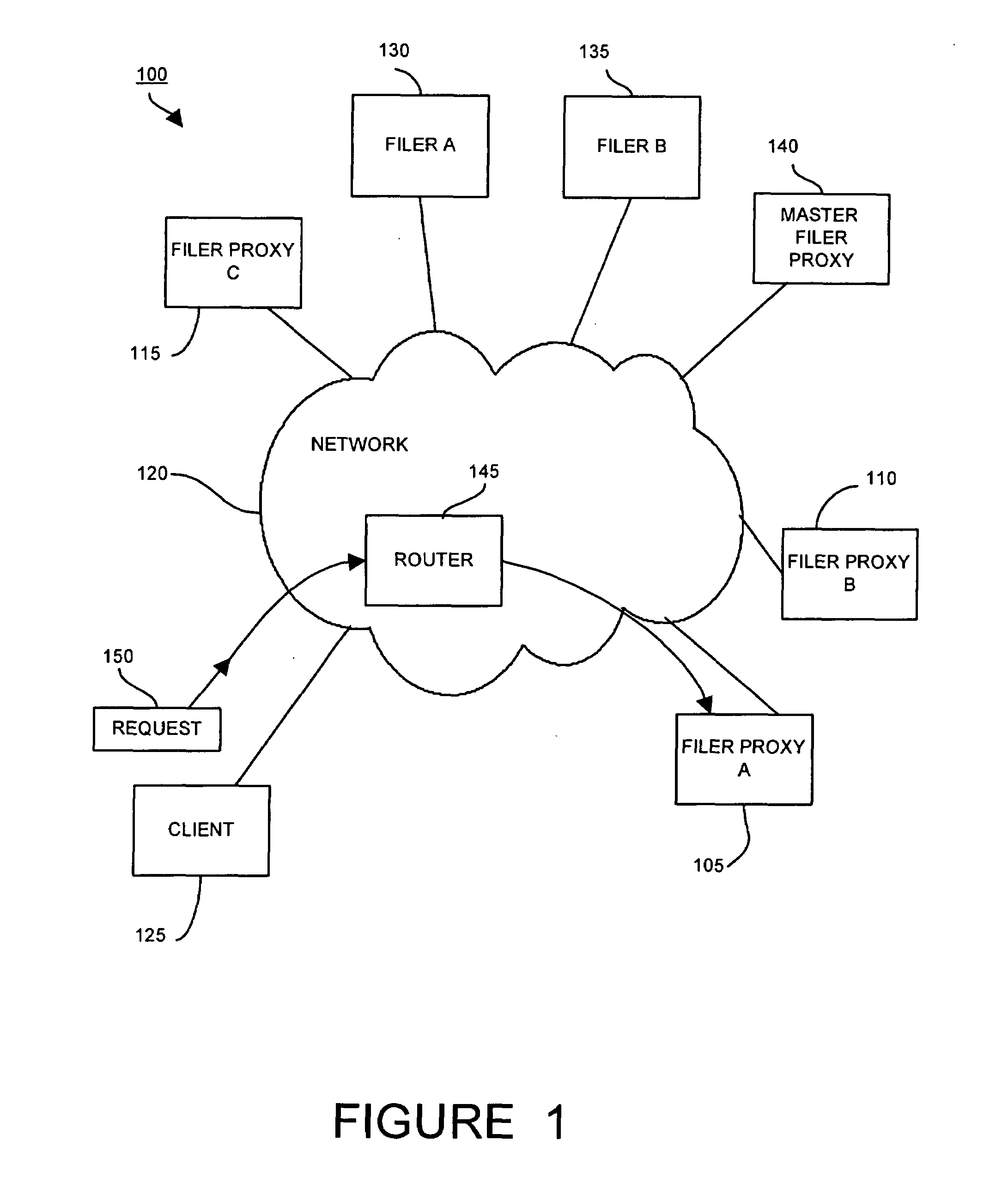
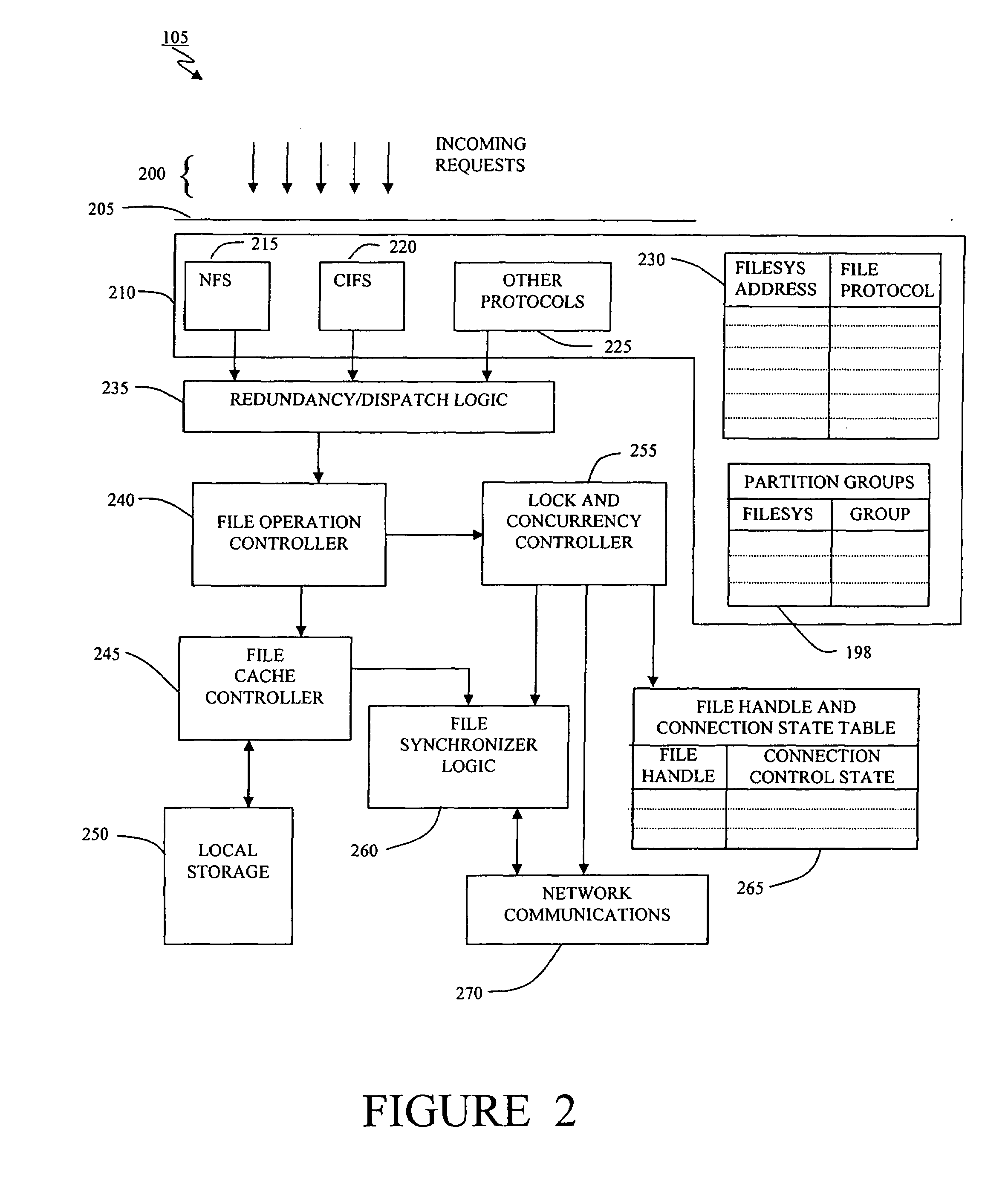
Method and apparatus for transparent distributed network-attached storage with web cache communication protocol/anycast and file handle redundancy
ActiveUS7254636B1Data processing applicationsDigital data processing detailsContent distributionNetwork connection
A distributed network-attached storage network provides content distribution using conventional file transfer protocols such as NFS and CIFS. A filer proxy accepts a client request and translates the client request to a file transfer protocol accepted at the file system having the file requested in the client request. The filer proxy generates a file handle for the file containing redundant filer proxy information to be used for failover to a backup filer proxy in the event of a network error or failure of an original filer proxy. The file handle also contains information for network security purposes such as detection of forged file handles.
Owner:CISCO TECH INC
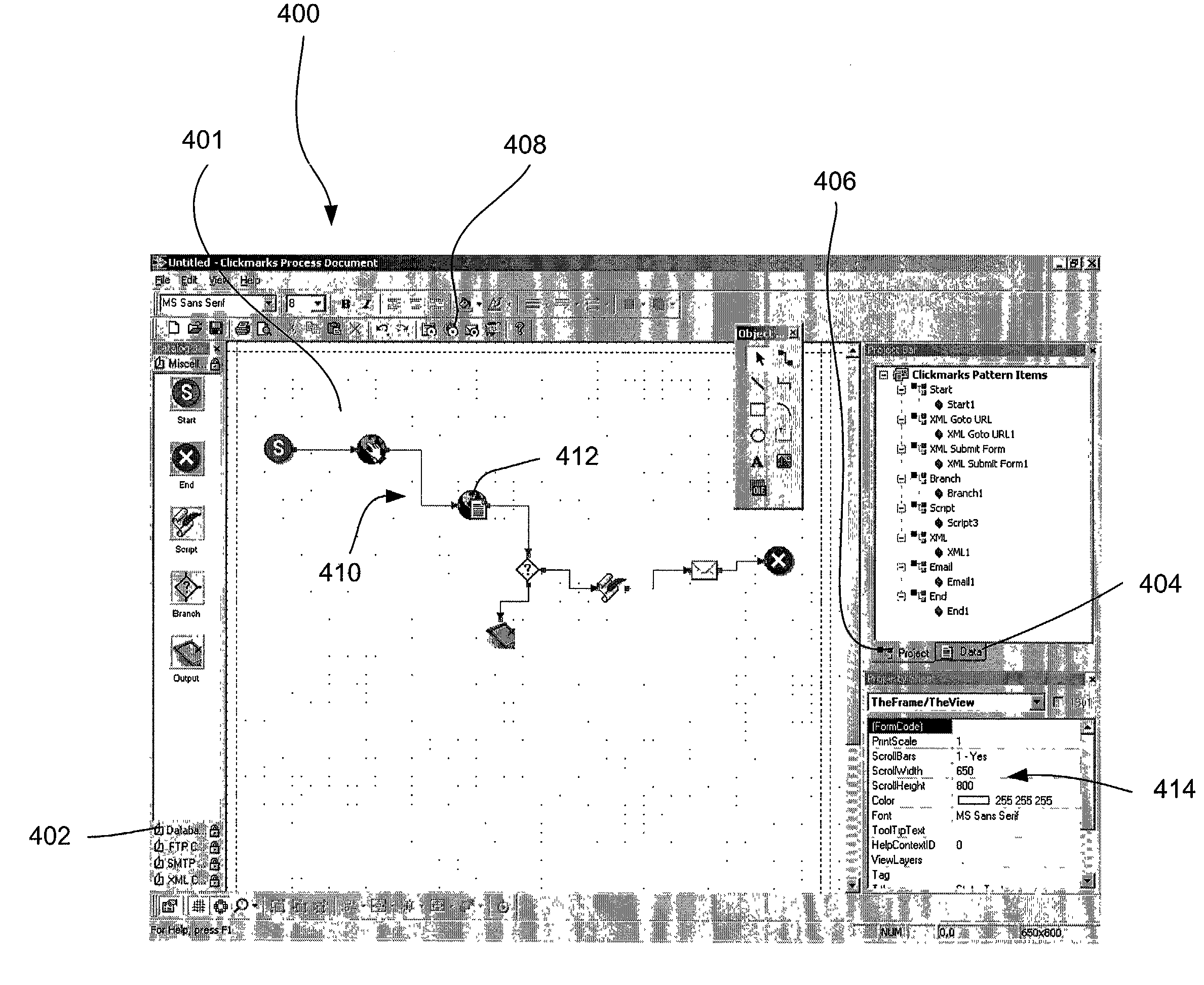
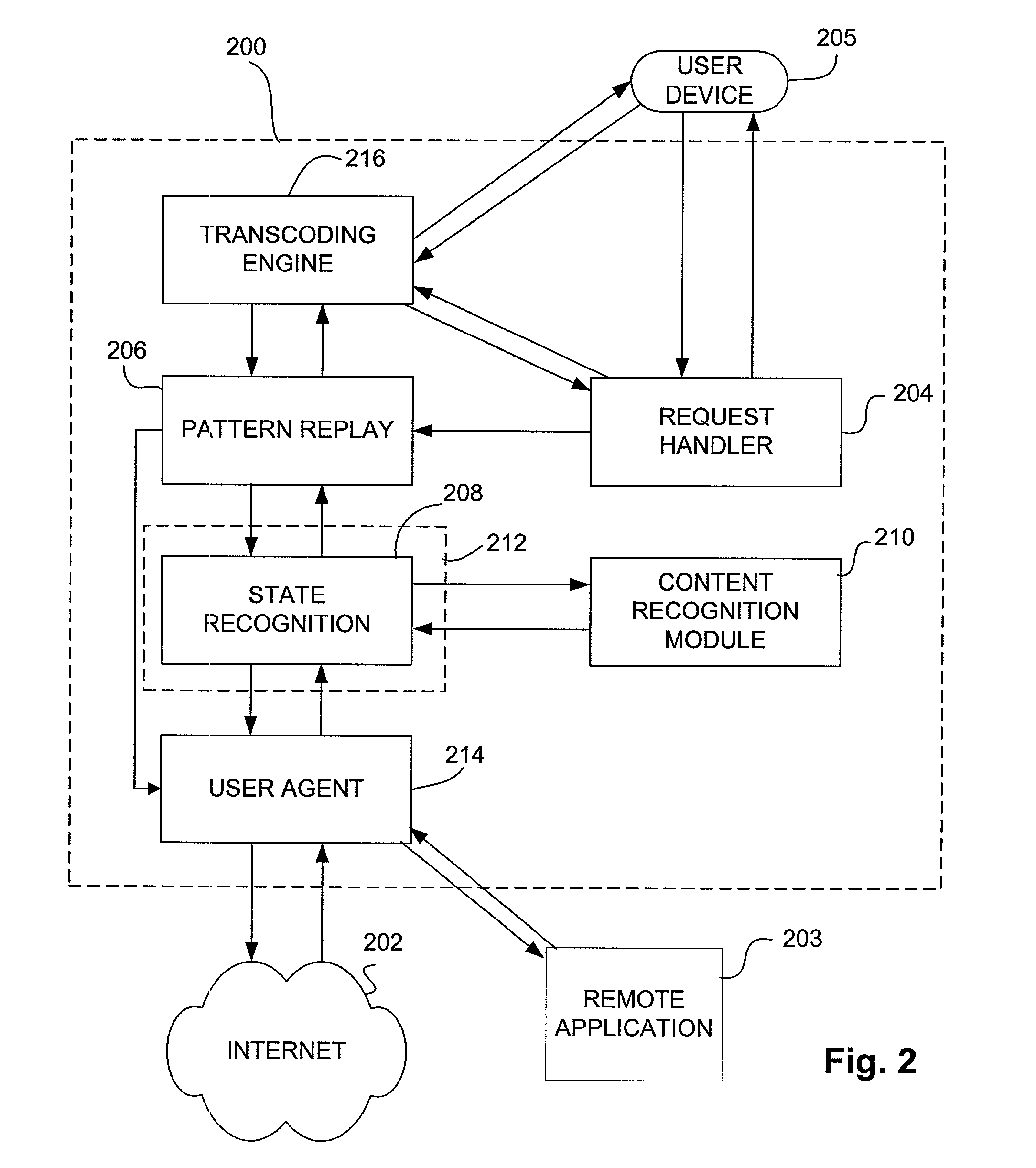
Interface for mobilizing content and transactions on multiple classes of devices
ActiveUS7185286B2Multiple digital computer combinationsSpecial data processing applicationsGraphicsGraphical user interface
A graphical user interface (GUI) for visual representation and manipulation of a transaction pattern. The GUI includes a workplace view for receiving user specification of content and / or a transaction for a transaction pattern, a pattern view for manipulating properties of the pattern, a device editor view for specifying pattern-related output on a client device, and a script view that allows a user to utilize scripting. A system, method and article of manufacture for recording a transaction pattern utilizing a graphical user interface are also provided. An interface is displayed. A user is allowed to specify interactions with content via the interface. The interactions are recorded. A pattern is generated based on the recorded interactions. The pattern, which includes a graphical representation of each interaction, is displayed on a GUI. Methods for recording an interaction with a database, recording a File Transfer Protocol (FTP) interaction, and generating a template for an electronic mail message are provided.
Owner:NVIDIA INT
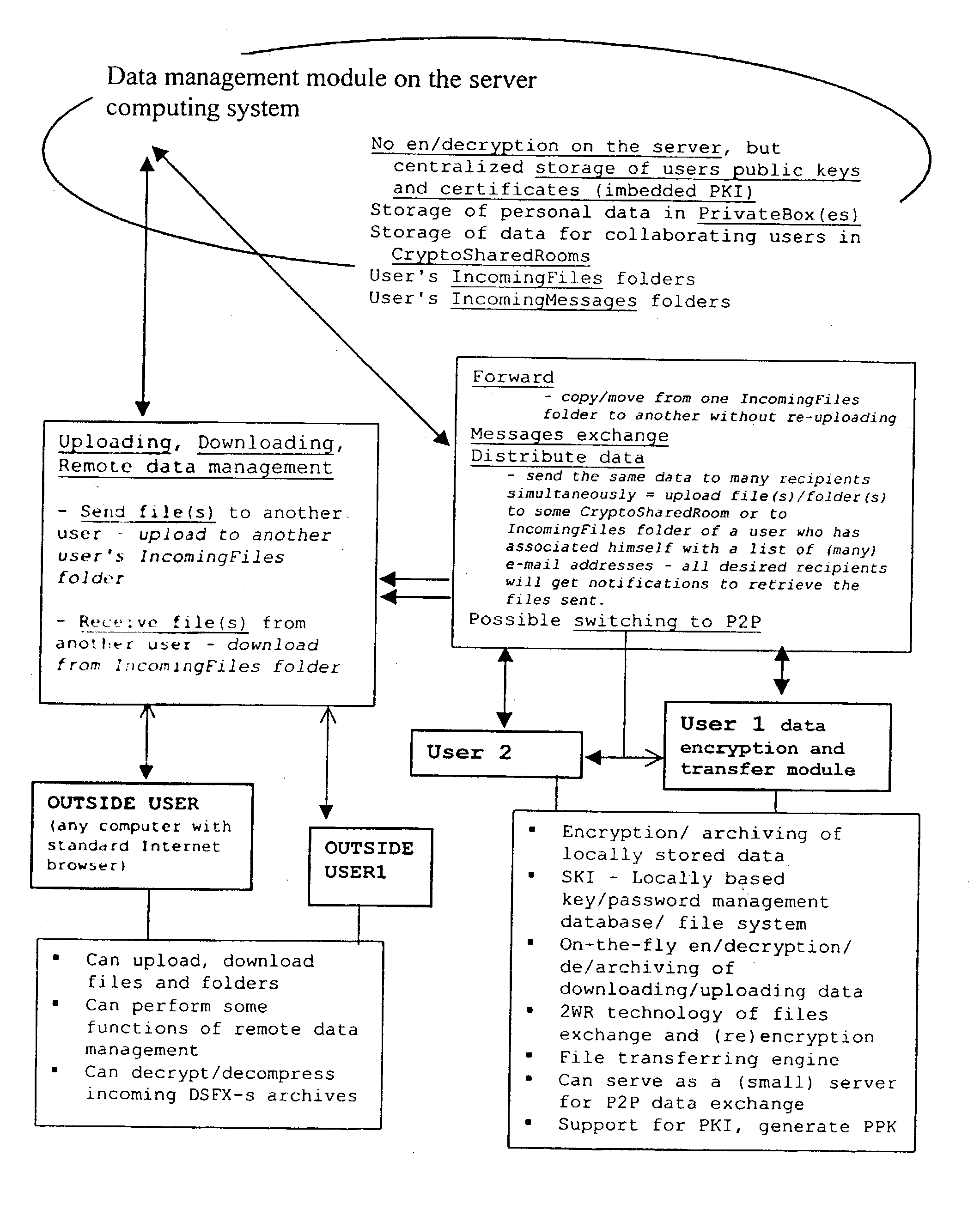
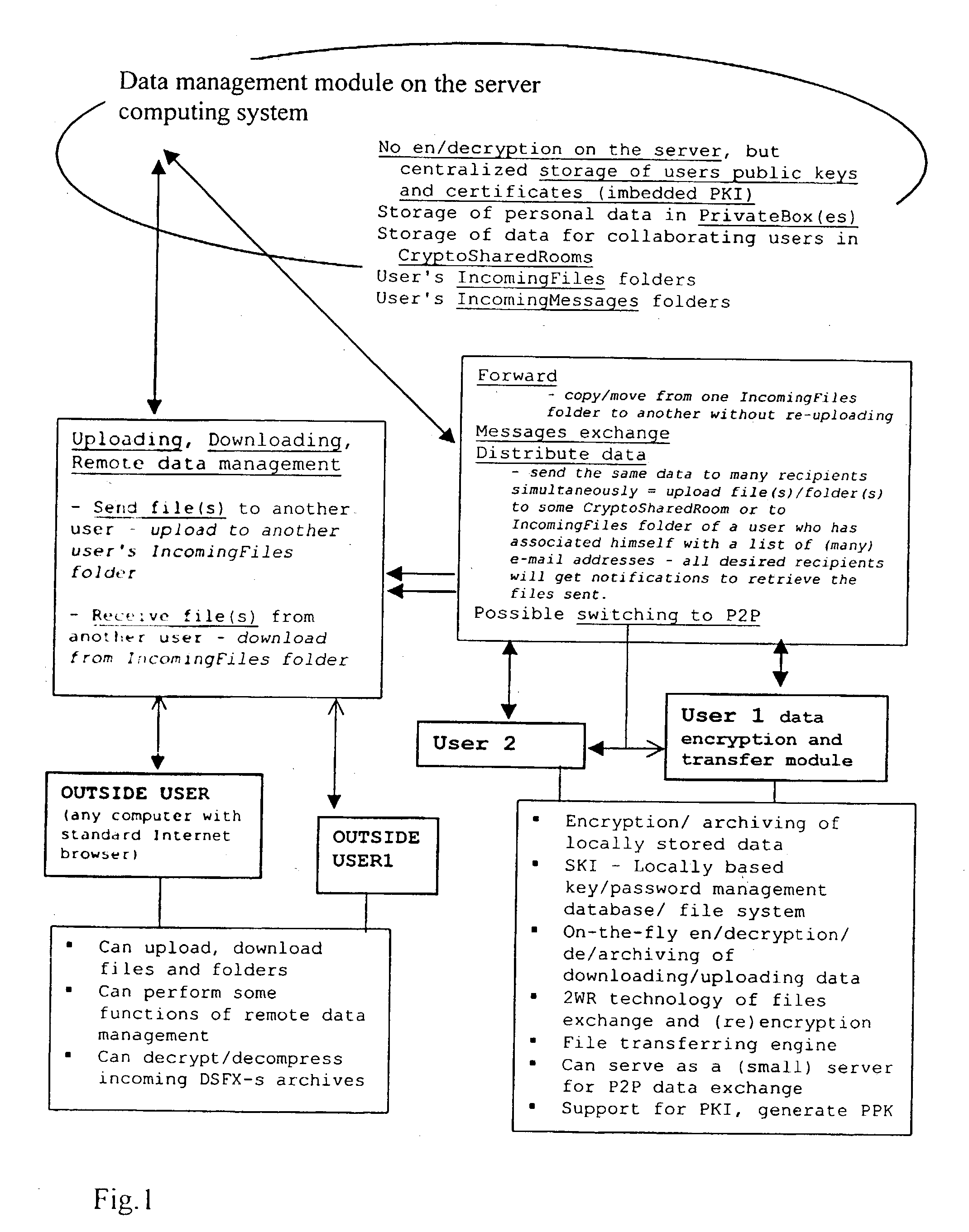
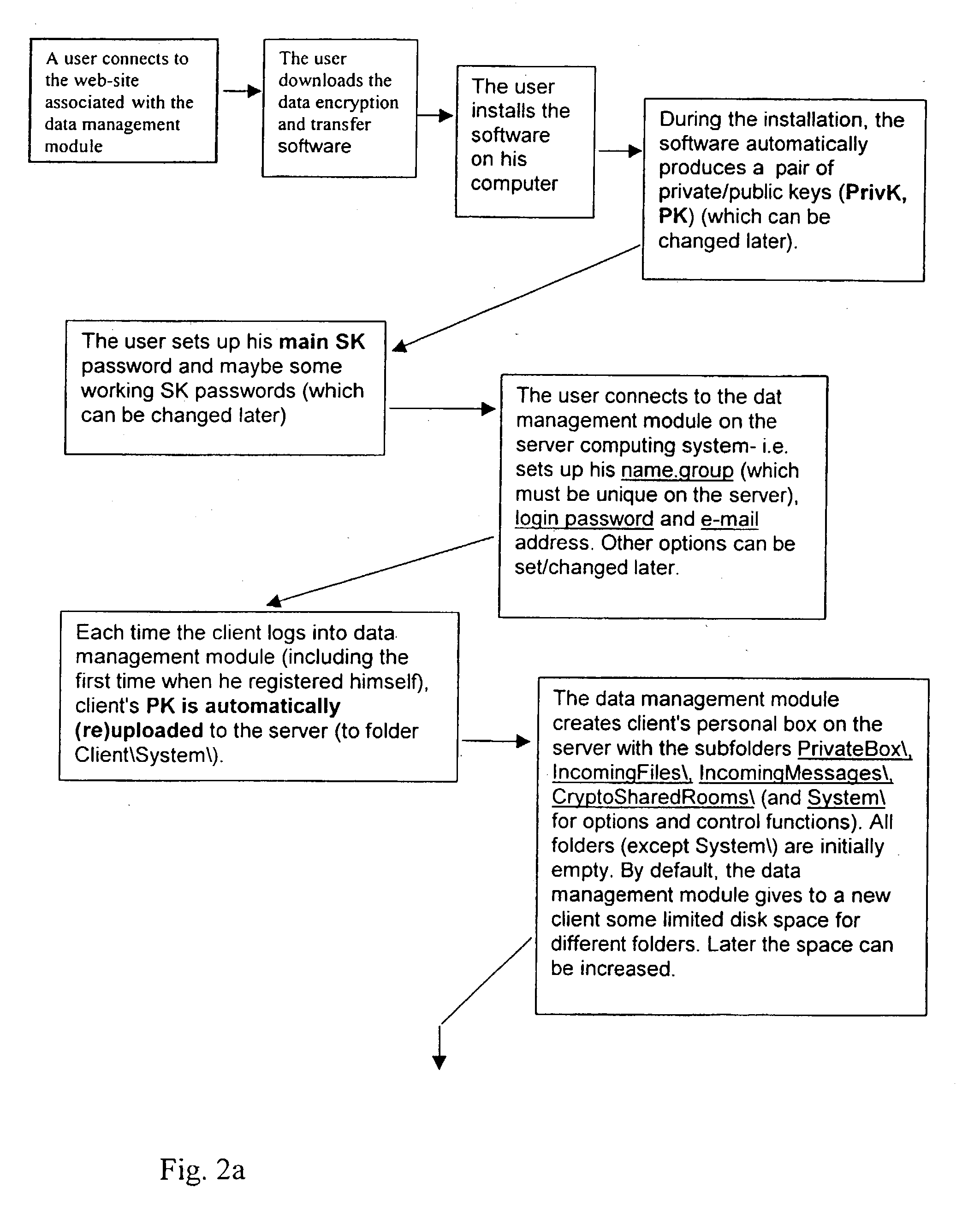
Data transfer and management system
InactiveUS20030177422A1Easily and securely managedEasily downloadableReliability increasing modificationsError preventionMegabyteData file
A system for the secure transfer of data and data management on the Internet has a data encryption and transfer module operable in a user computing system, a data management module operable in a server computing system, the transfer of data between the user and server computing systems being effected on the user computing system through use of the data encryption and transfer module, by moving the data to or from a first desktop window, associated with the user computing system, from or to a second desktop window, associated with the server computing system, each window being associated with a password, such that the step of moving the data from one window to the other causes the data to be encrypted / re-encrypted from one associated password to the other. The system also includes a password management module operable in the user computing system for managing the passwords, which are required to be used by a user of the system. The system uses symmetric key encryption coupled with file transfer protocol (FTP) data transfer and allows for the secure transfer of large data files of 100 megabytes or more.
Owner:HERBERT STREET TECH
Data transfer apparatus and data transfer method
InactiveUS20050105530A1Data switching by path configurationMultiple digital computer combinationsData shippingData transmission
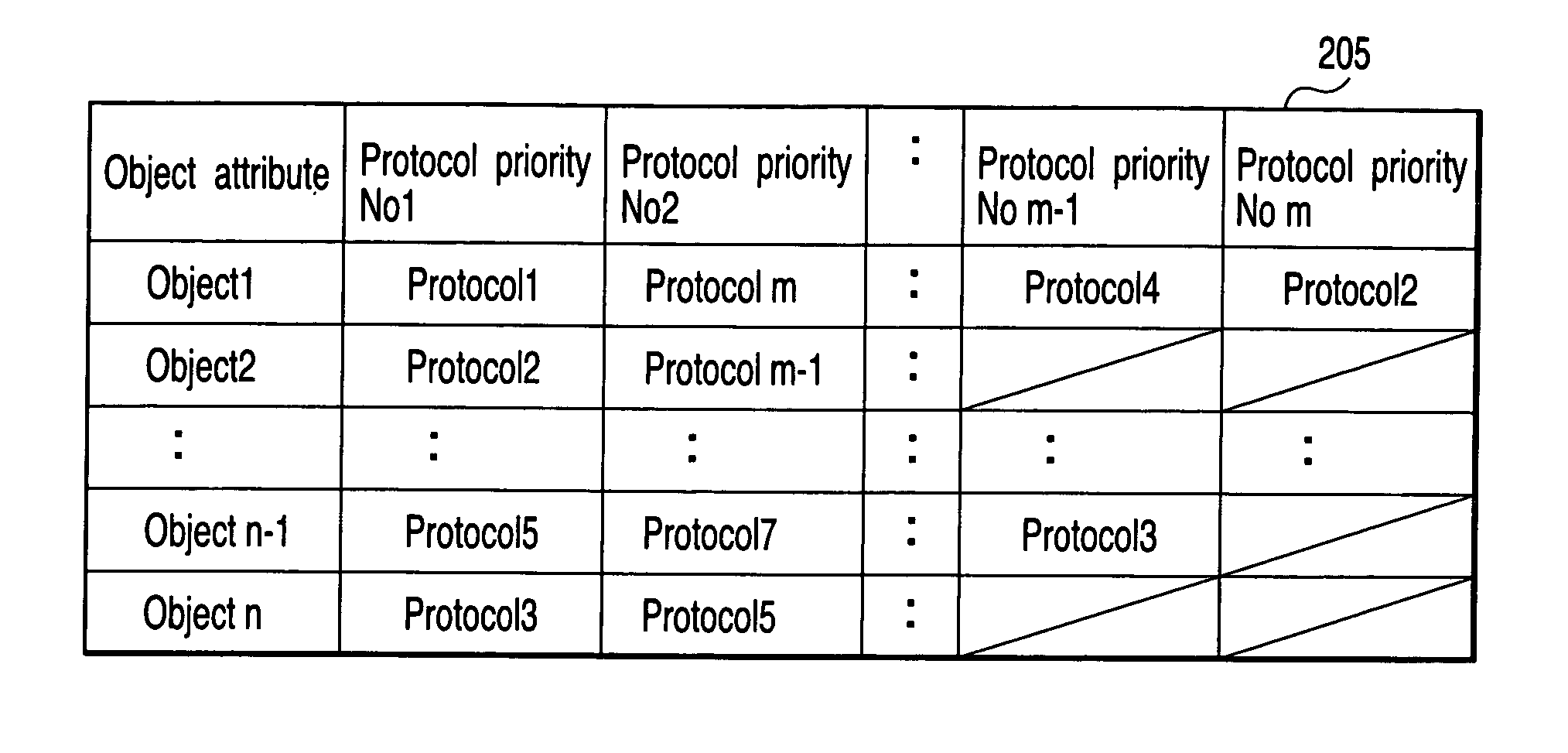
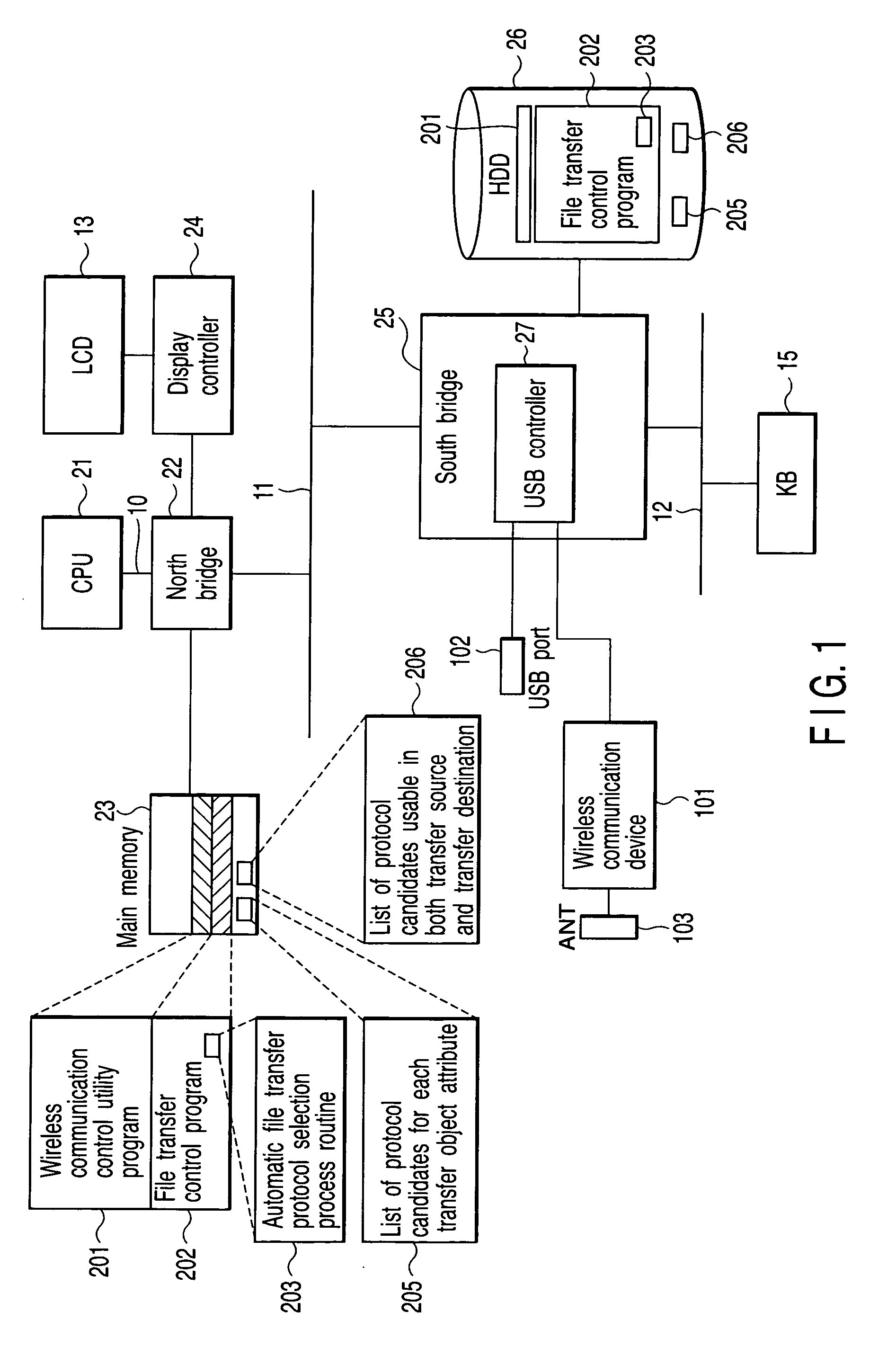
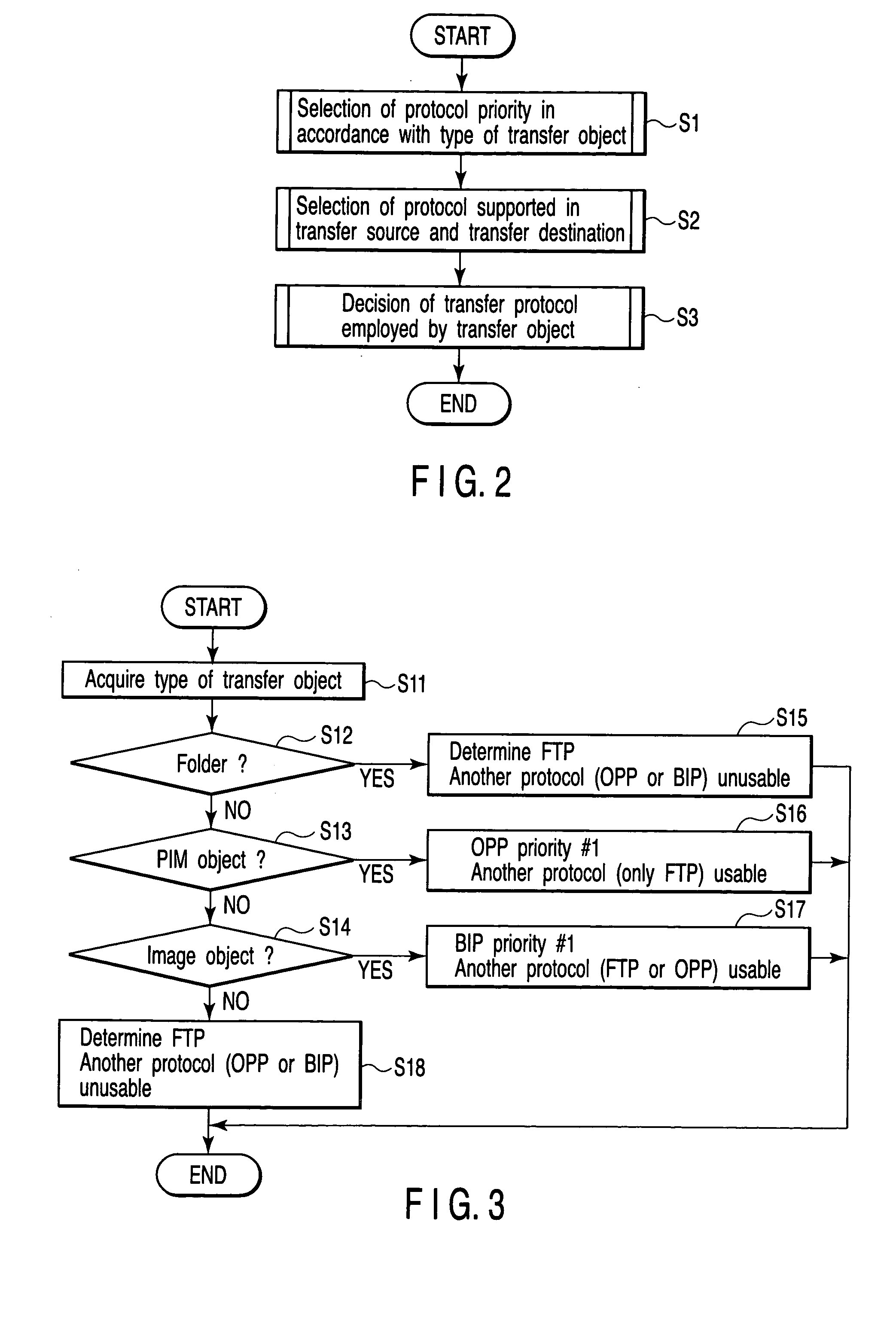
A data transfer apparatus according to this invention executes a protocol priority determination process of selecting usable transfer protocols in accordance with the type of transfer object and determining the priorities of the transfer protocols in accordance with the process of an automatic file transfer protocol selection process routine. The data transfer apparatus then executes a protocol selection process of selecting transfer protocols commonly usable in the transfer source apparatus and transfer destination apparatus of the transfer object. The data transfer apparatus executes a transfer protocol determination process of determining a transfer protocol for use on the basis of the transfer protocol and its priority which are determined in the protocol priority determination process, and the transfer protocols selected in the protocol selection process.
Owner:KK TOSHIBA
Cloud storage file transfer protocol (CFTP)
The invention discloses a novel cloud storage file transfer protocol (CFTP), which is a method for transferring files with a user terminal by using a cloud terminal provided with a cloud computation or storage environment, wherein after a terminal sends a file transfer request, a target file is split into a plurality of data blocks to be sent to a storage node of the cloud terminal for caching, a cloud terminal server is used for calculating out an optimum path and sending the optimum path to the terminal, and the user terminal acquires optimum download and upload speeds.
Owner:杨文军
Thread based view and archive for simple mail transfer protocol (SMTP) clients devices and methods
InactiveUS7516186B1Data processing applicationsMultiple digital computer combinationsView basedTimestamp
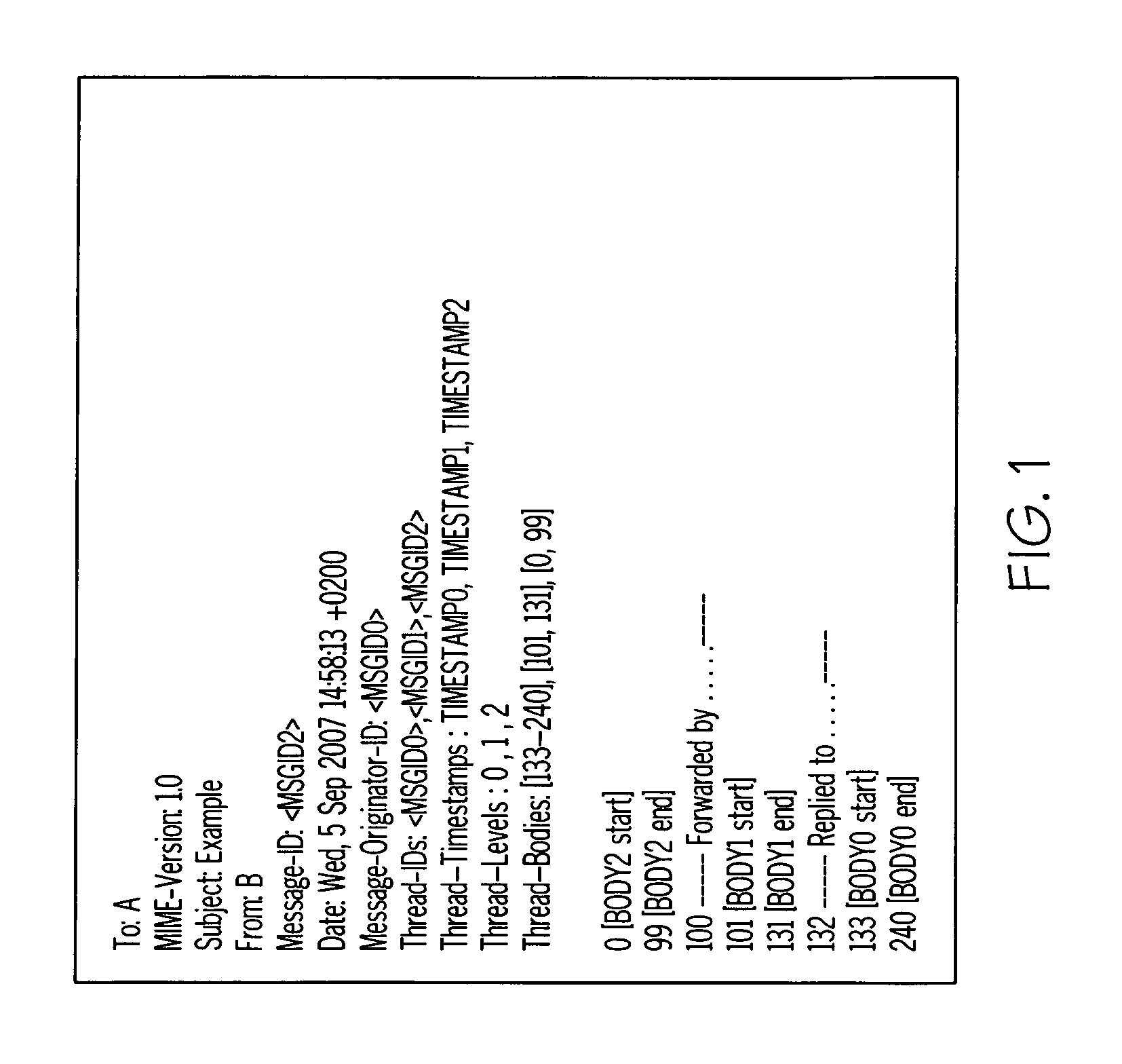
A method for local archiving of e-mail messages in an e-mail client application according to various exemplary embodiments can include generating a mail thread including at least two e-mail messages transmitted and received between a message originator and at least one recipient; appending e-mail identification data into a header of the at least two e-mail messages when transmitted. The method may also include archiving related e-mail messages within the mail thread in an e-mail client application, comprising: searching for the related e-mail messages by identifying each e-mail message having a same message originator field; and merging non-redundant segments of each e-mail message into a single message document hierarchically by response level and timestamp. The method may further include displaying, on a display screen, the single message document according to a conversational view based upon a perspective of the response level of a user within the mail thread.
Owner:IBM CORP
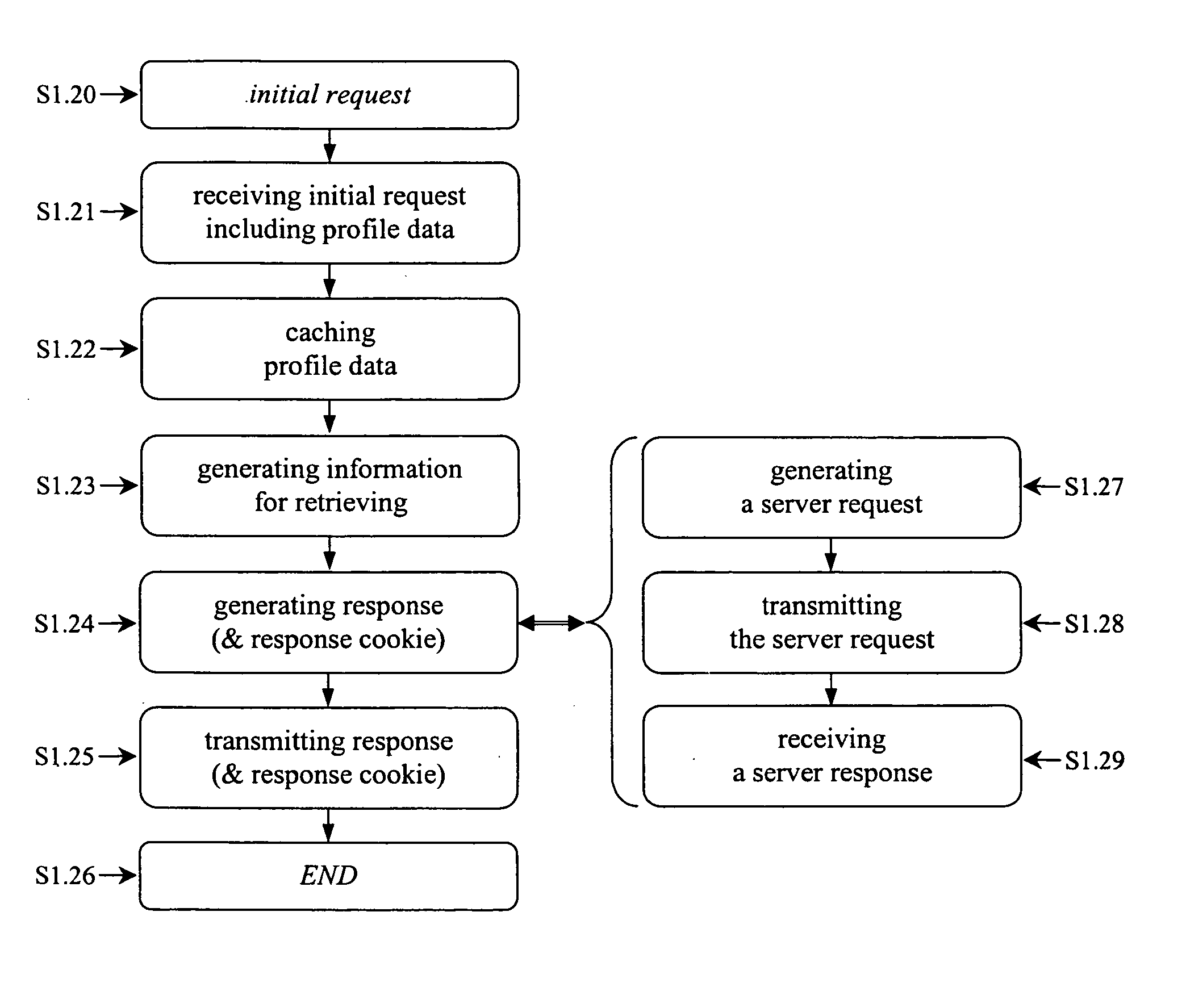
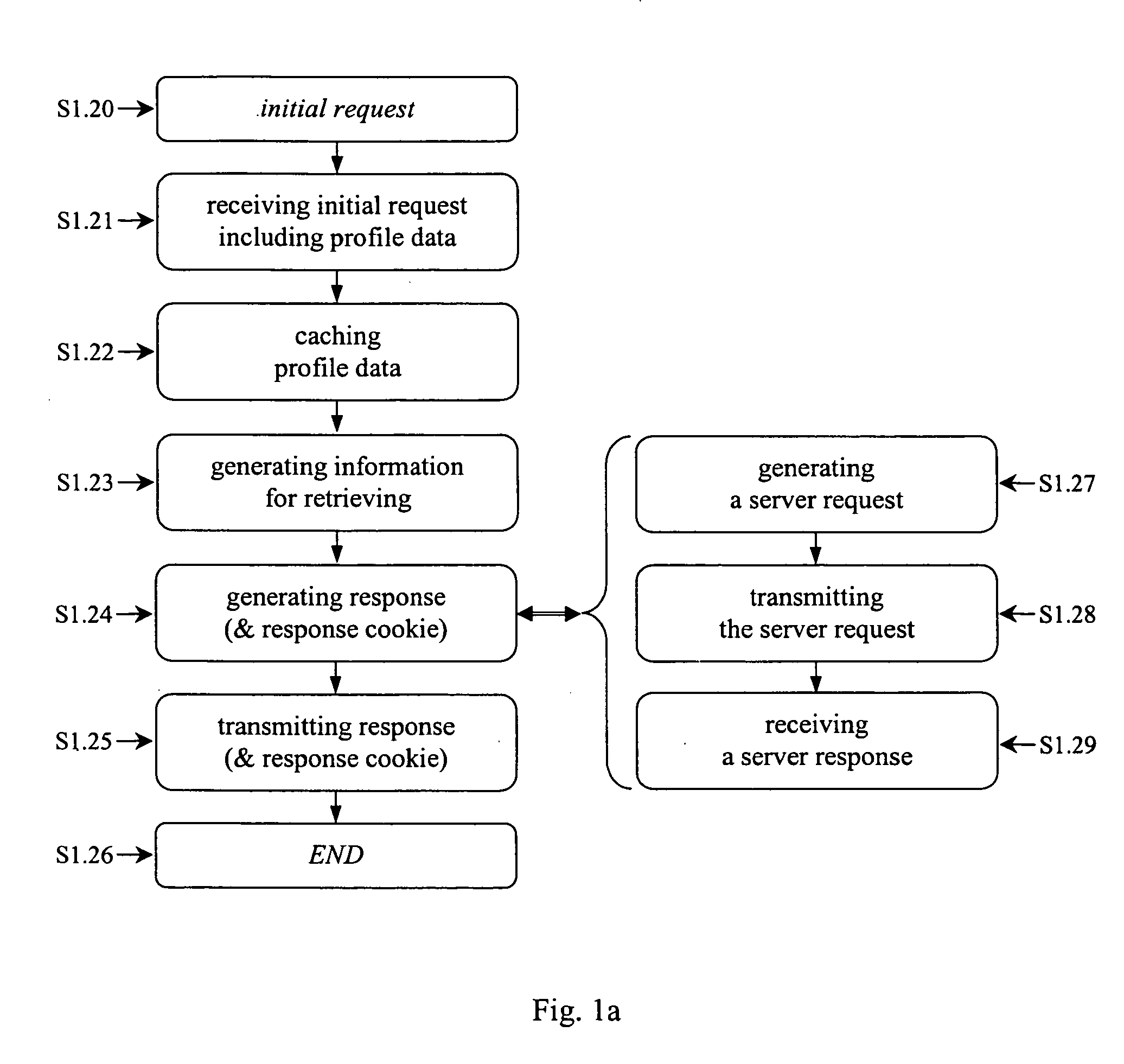
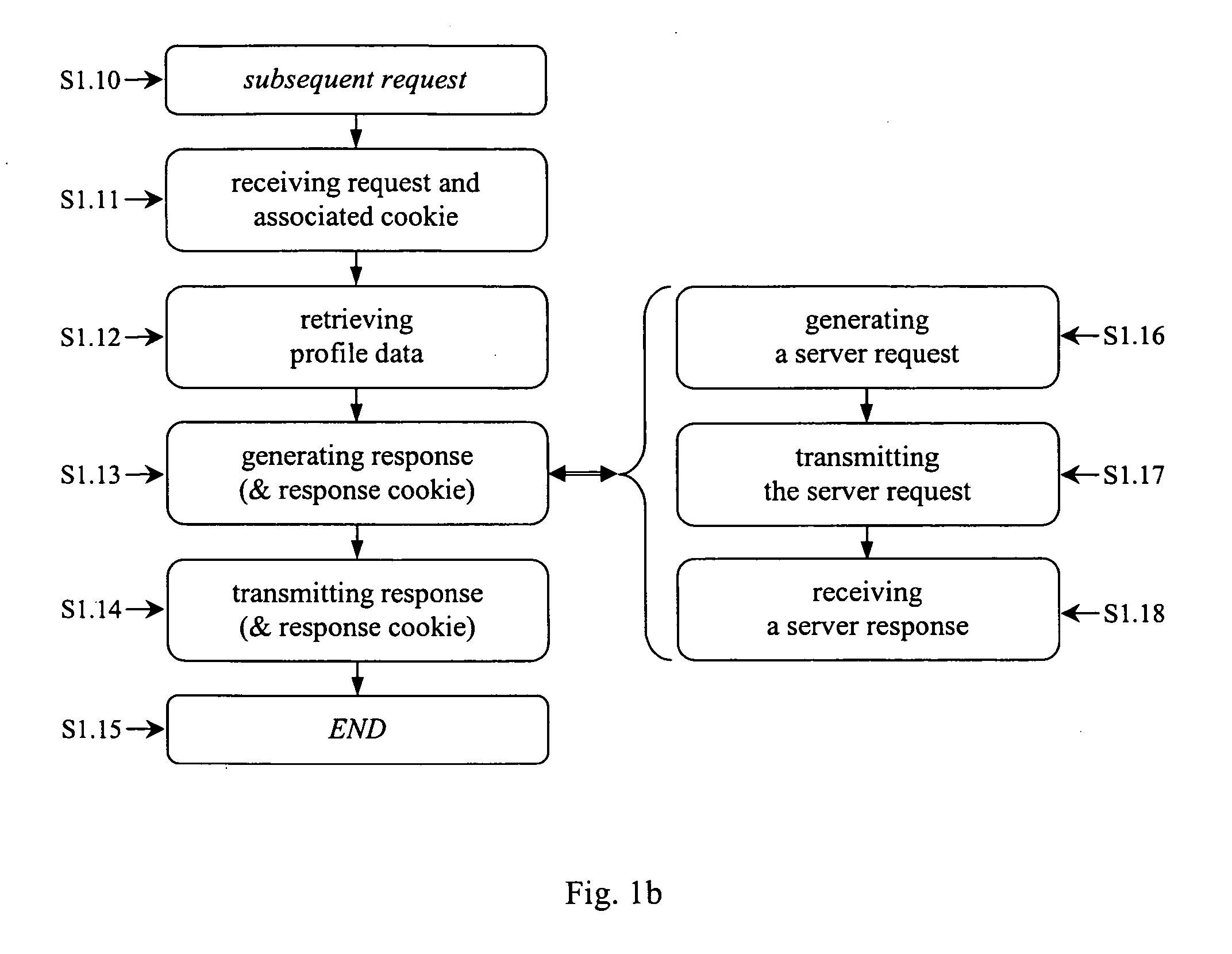
Method, network device and system for providing profile data applicable to hypertext transfer protocol (http)
InactiveUS20050120091A1Multiple digital computer combinationsSecuring communicationWireless Application ProtocolNetwork communication
The present invention is based on a concept to provide session and profile management for network communication, especially over hypertext transfer protocol (HTTP), employing available communication methods. Session and profile management is available and standardized for mobile communication by the means of the wireless session protocol (WSP) employable for wireless application protocol (WAP) communication. This wireless session protocol (WSP) is limited to mobile communication. The analog communication standard hypertext transfer protocol (HTTP) available and standardized for wireline communication does not offer a session and profile management. The present invention offers a method to establish an analog session and profile management by the means of cookies or modified uniform resource locators (URL) even over the hypertext transfer protocol (HTTP) without requiring substantial changes to the hypertext transfer protocol (HTTP) standard.
Owner:NOKIA CORP
Method and aparatus for plug-and-play webserver
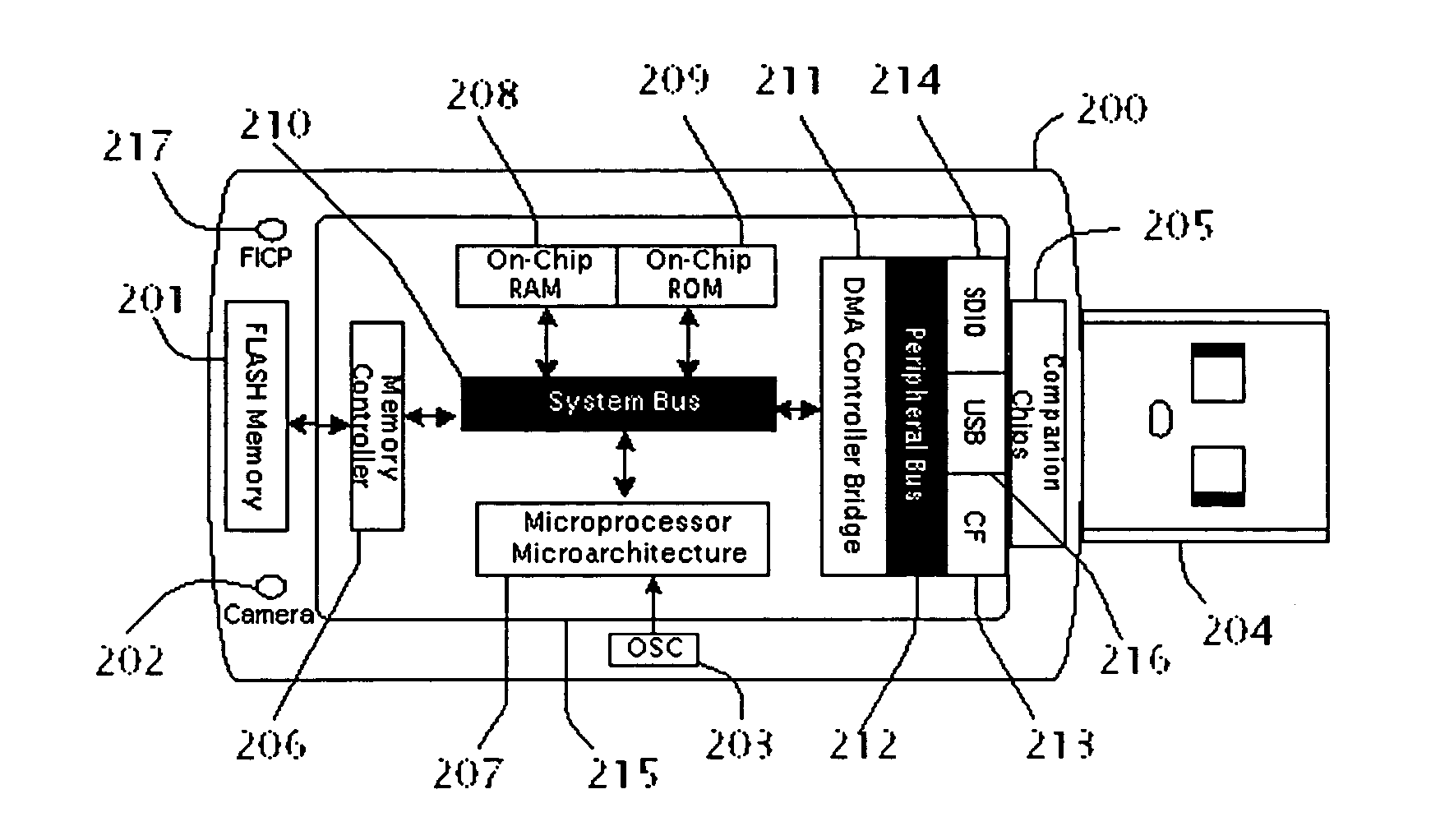
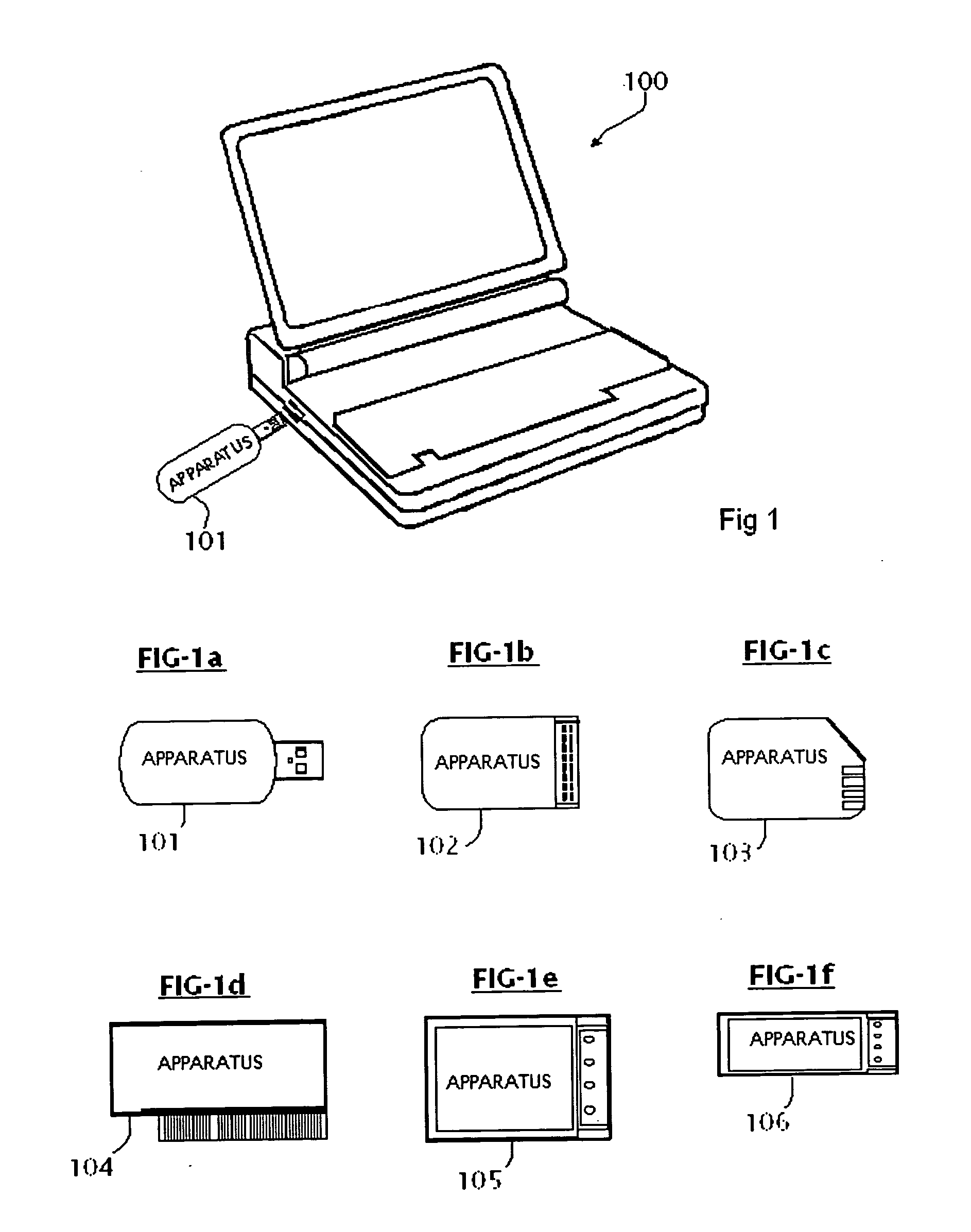
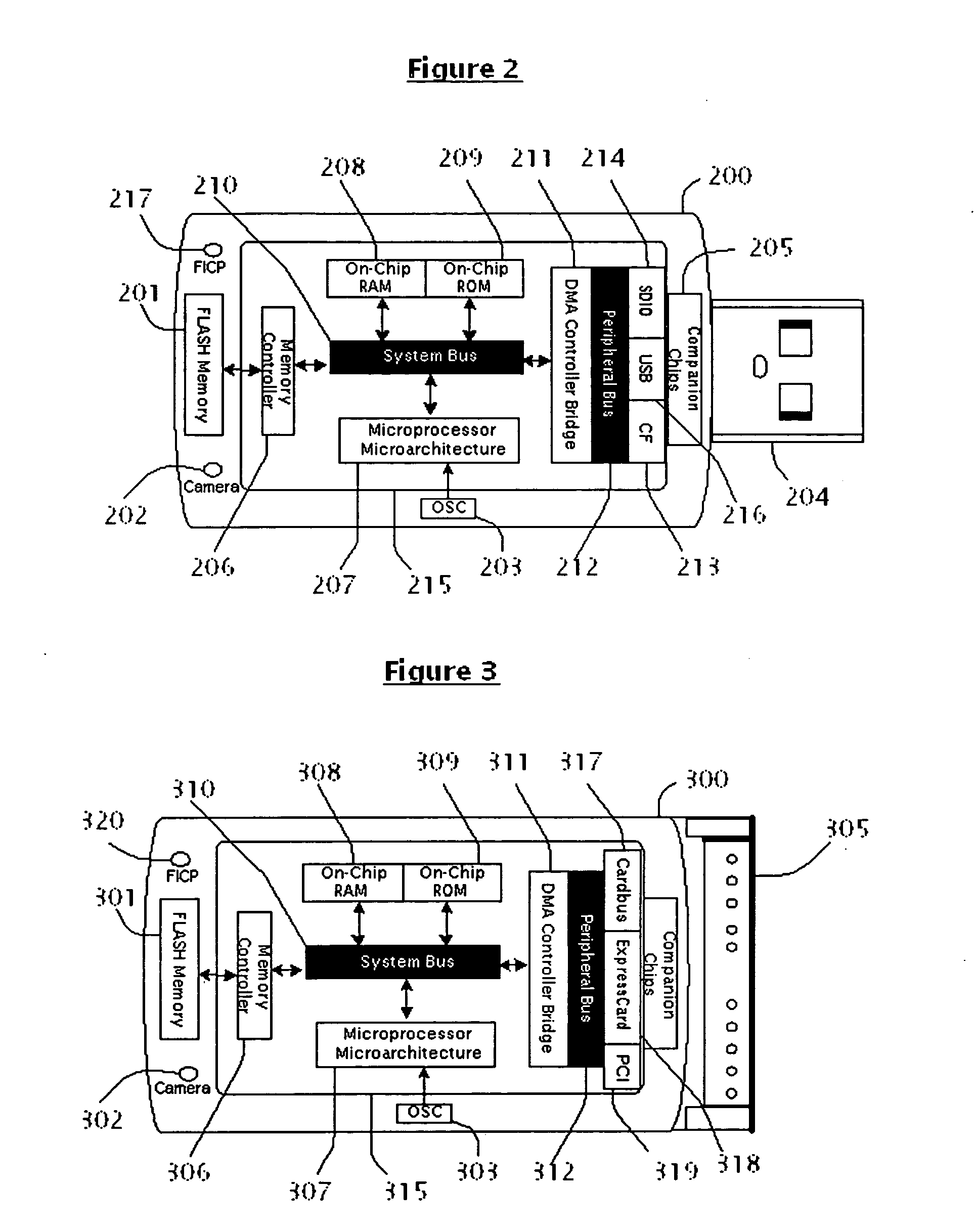
InactiveUS20060075174A1Simplify the development processEasy to adaptComponent plug-in assemblagesProgram loading/initiatingPCI ExpressUSB
A system, method and computer program for an apparatus is described. An apparatus is a very convenient, plug-and-play, ultra small, smart device that lets the end-users to host their websites at computer peripheral port. When said device is plugged in one of the computer peripheral ports: Universal Serial Bus (USB), Secure Digital Input and Output (SDIO), Compact Flash (CF), Cardbus, Peripheral Component Interconnect (PCI), PCI-Express and ExpressCard; it shall function as a dedicated web hosting device powerful and robust enough to handle web hosting functions for Personal Home Page, File Transfer Protocol (FTP) Files Server, Streaming media, Common Gate Interface (CGI) scripts, Active Server Pages, or Game Server.
Owner:MR VUONG CORY THANG
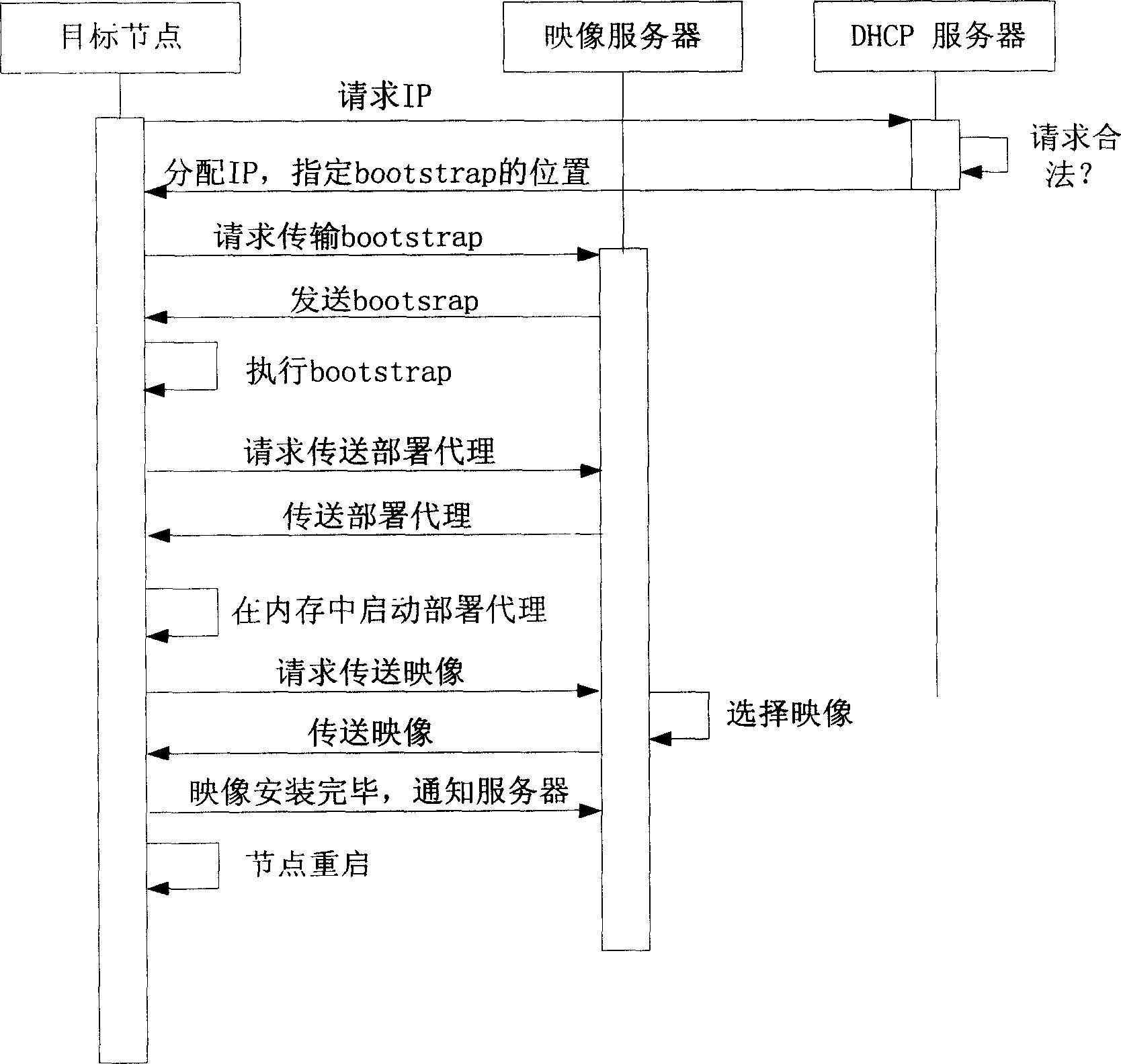
Automated quick deployment method for large-scale computer cluster node
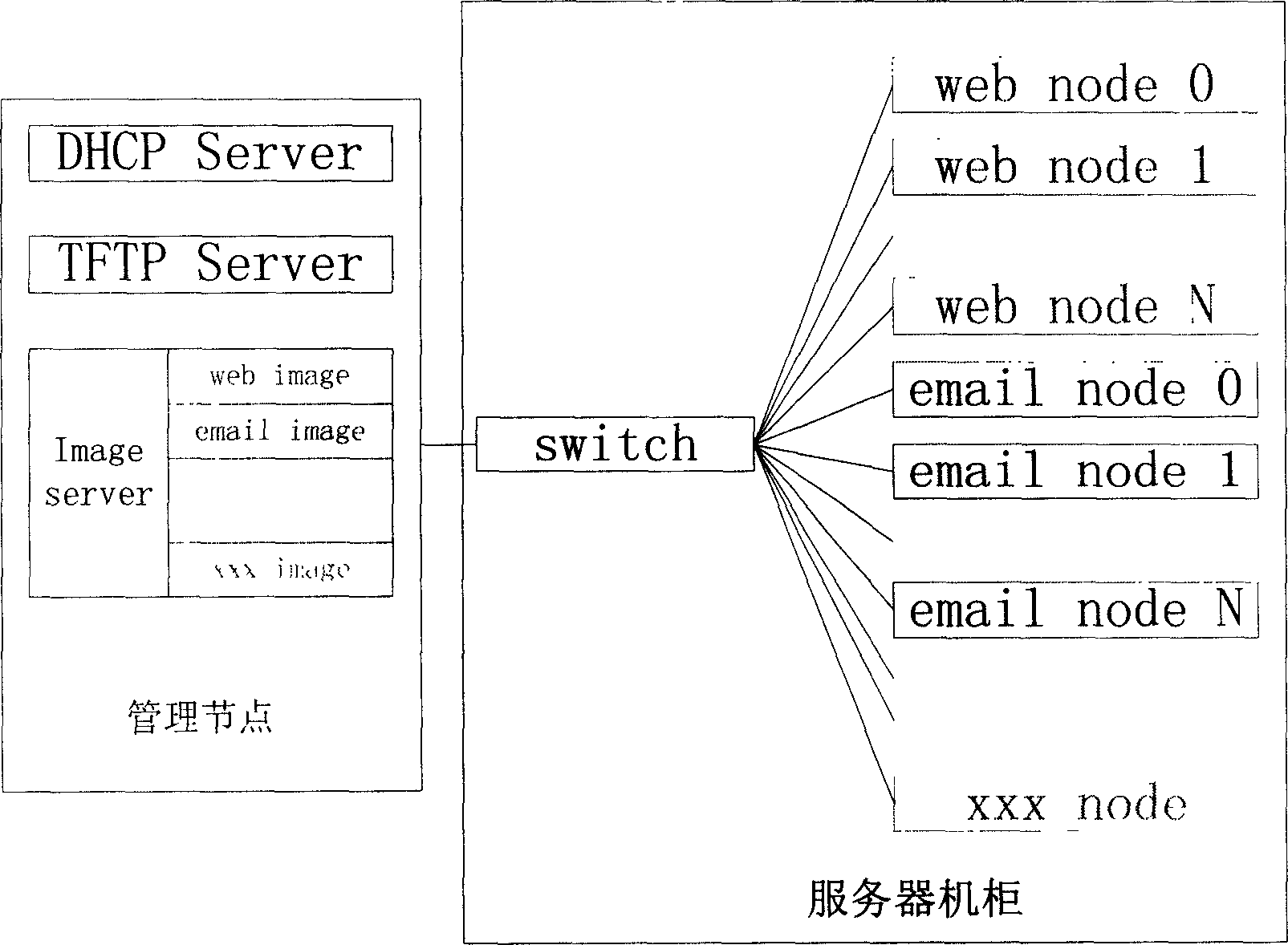
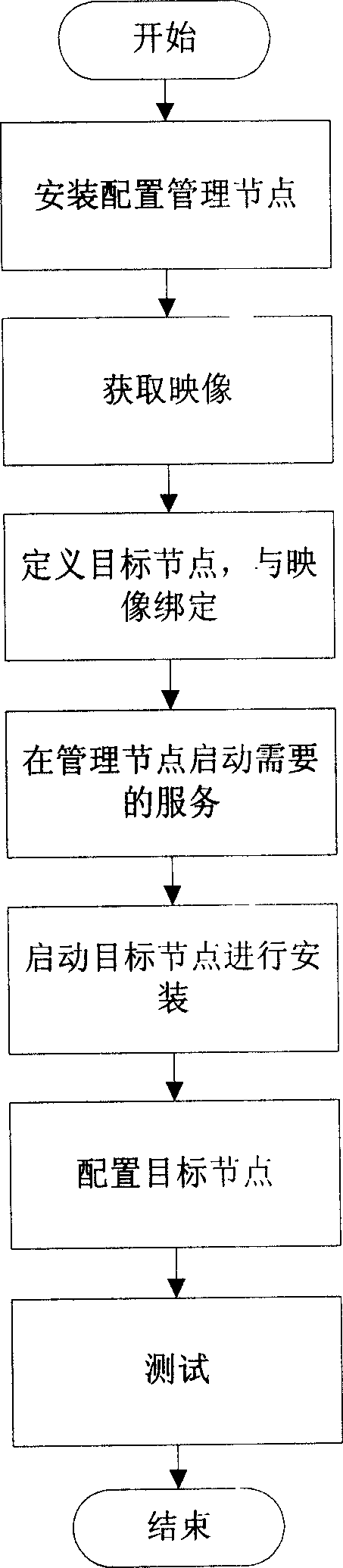
InactiveCN1731738ASuitable for installationNo human intervention requiredData switching networksSpecial data processing applicationsComputer clusterFile Transfer Protocol
This invention relates to method for automatically and rapidly allocating the system nodes of large-scale computer colony, which adopts image-based installing ways, customer machine / server structure, Pre-conducting executing surroundings PXE protocol, dynamic host configuring protocol DHCP, simple files-transferring protocol TFTP and wakeup on lan to realize the automatic and rapid allocation in large-scale colony system. This method comprises the five steps: attaining image, bonding the image with the aim nodes, installing the aim nodes, allocating the aim nodes, testing and so on, which actualizes the completely automation in the course of installing nodes in colony system. Compared with traditional way, the invention largely simplifies the installing course and improves work efficiency.
Owner:XI AN JIAOTONG UNIV +1
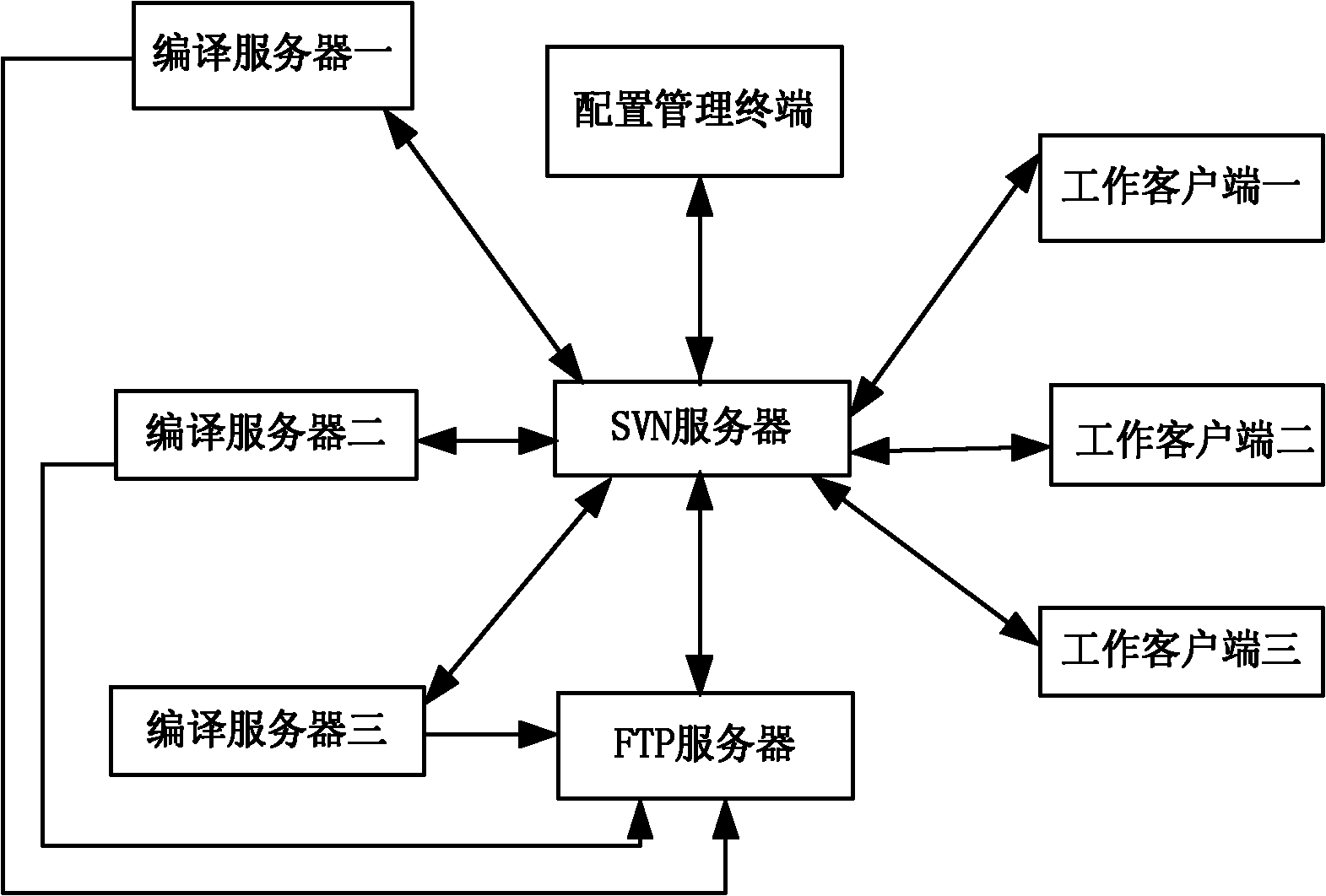
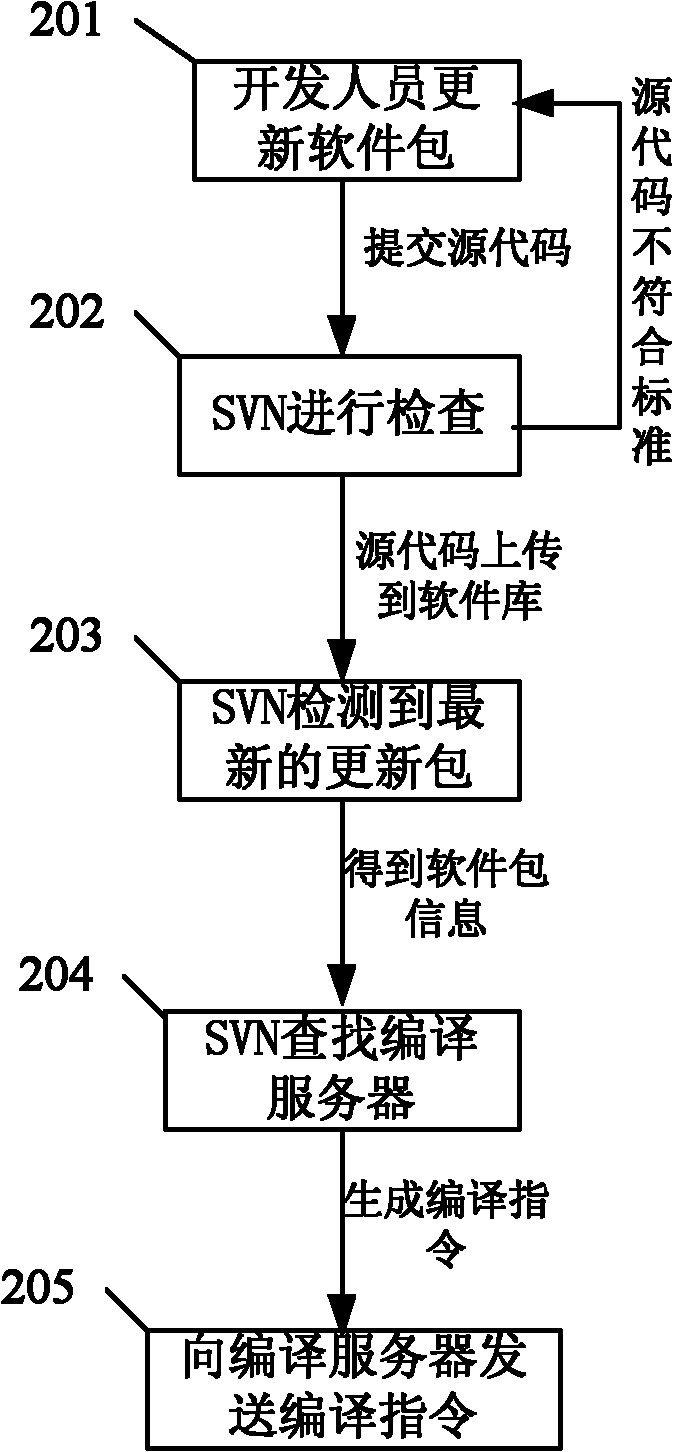
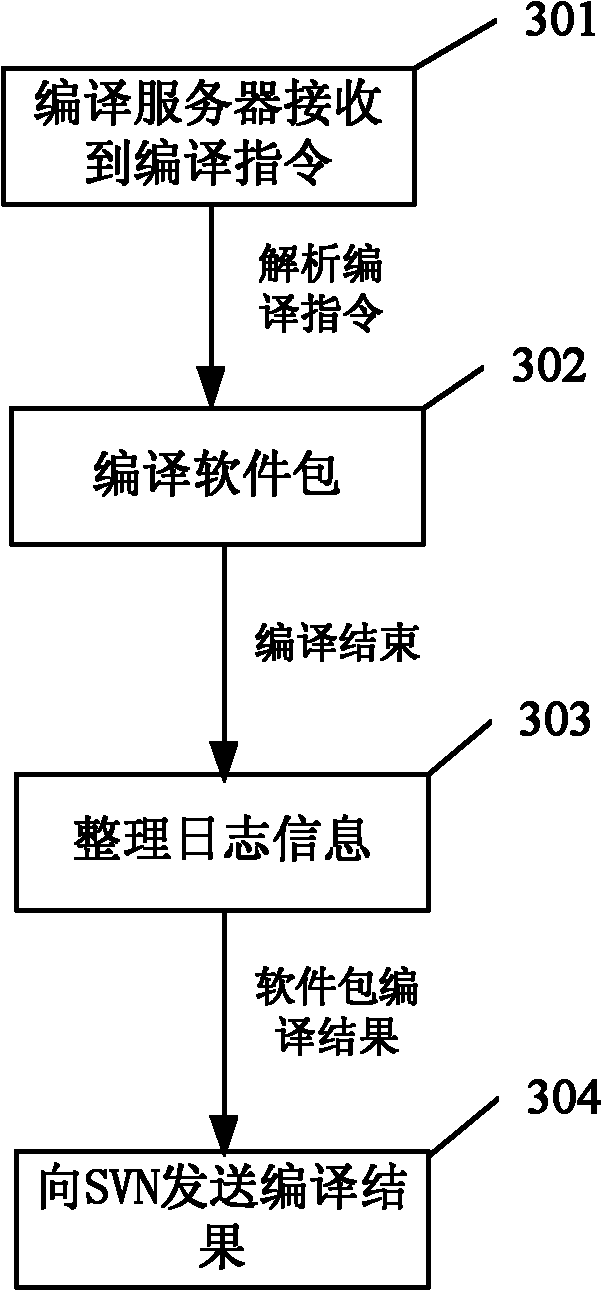
System and method for automatically releasing operating system version and automatically updating software package
InactiveCN102035892ASmooth updateReduce workloadTransmissionSpecific program execution arrangementsOperational systemProgram planning
The invention discloses a system and a method for automatically releasing an operating system version and automatically updating a software package. The system mainly comprises a switched virtual network (SVN) server, a compile server, a file transfer protocol (FTP) server, a working client and a configuration management terminal. In the method for automatically releasing the version and automatically updating the software package provided by the system, software packages of multiple items can be stored in one SVN server, the update conditions of the software packages can be automatically detected, the software packages can be automatically transmitted to a corresponding compile server for compiling, the compiled result is timely fed back to a configuration manager and a developer, and the configuration manager can make a system release plan in advance so as to timely and automatically release the system. The workload of the configuration manager can be obviously reduced, the software package compiling efficiency is greatly improved, and the probability of generating a human error is obviously reduced in the process of software package management and system release.
Owner:ZHONGKE FANGDE SOFTWARE CO LTD
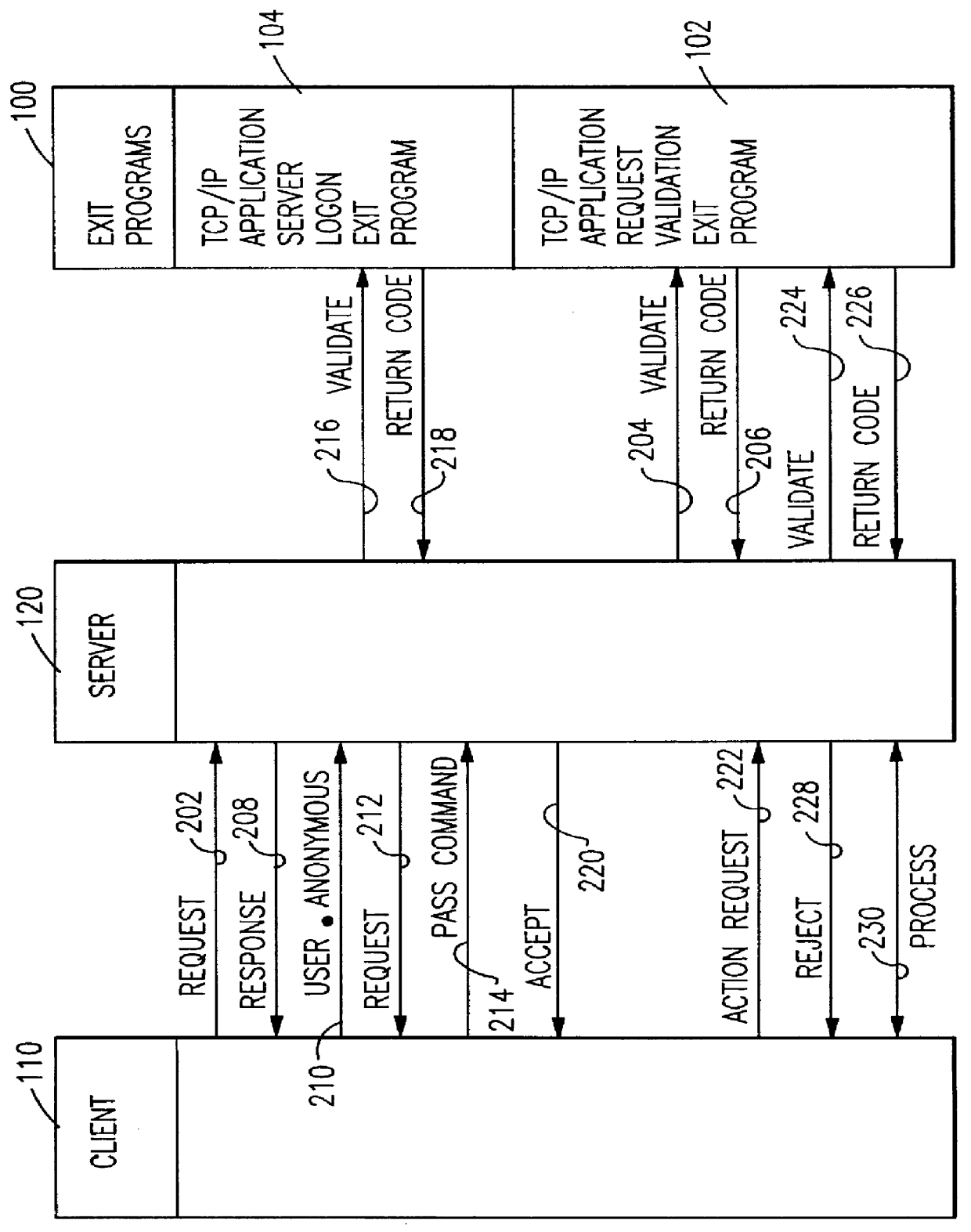
System and method for enabling and controlling anonymous file transfer protocol communications
InactiveUS6092198ADigital data processing detailsMultiple digital computer combinationsTransmission protocolNetwork addressing
Control of anonymous file transfer protocol server using exit programs: FTP and anonymous FTP communications are enabled and controlled by operating a server logon exit program to deny or authorize a logon request based on any combination of a user authentication string and / or client network address; and operating a request validation exit program to deny or authorize an action request based on any combination of type of request, user, client network address, and specific data requested.
Owner:IBM CORP
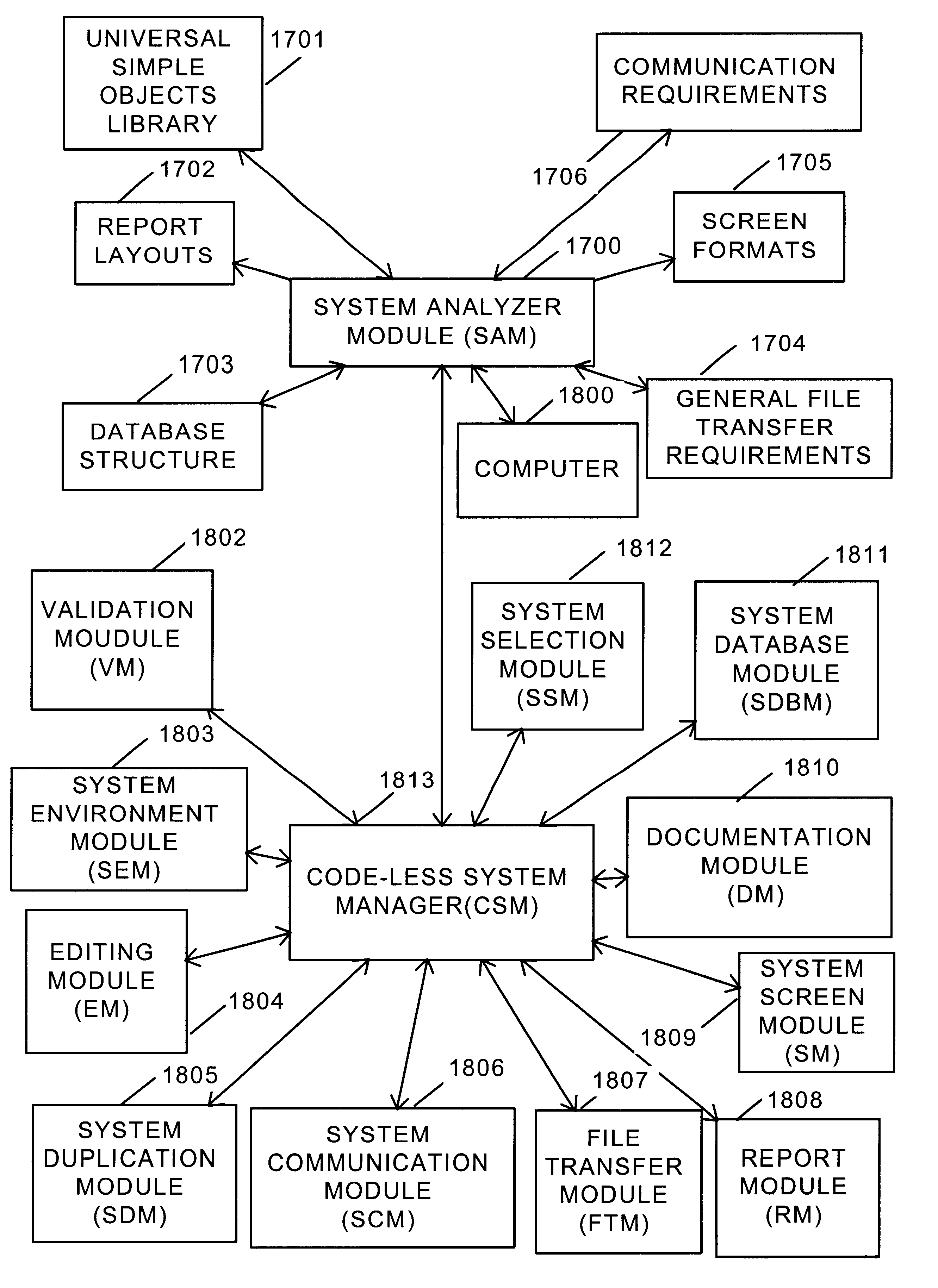
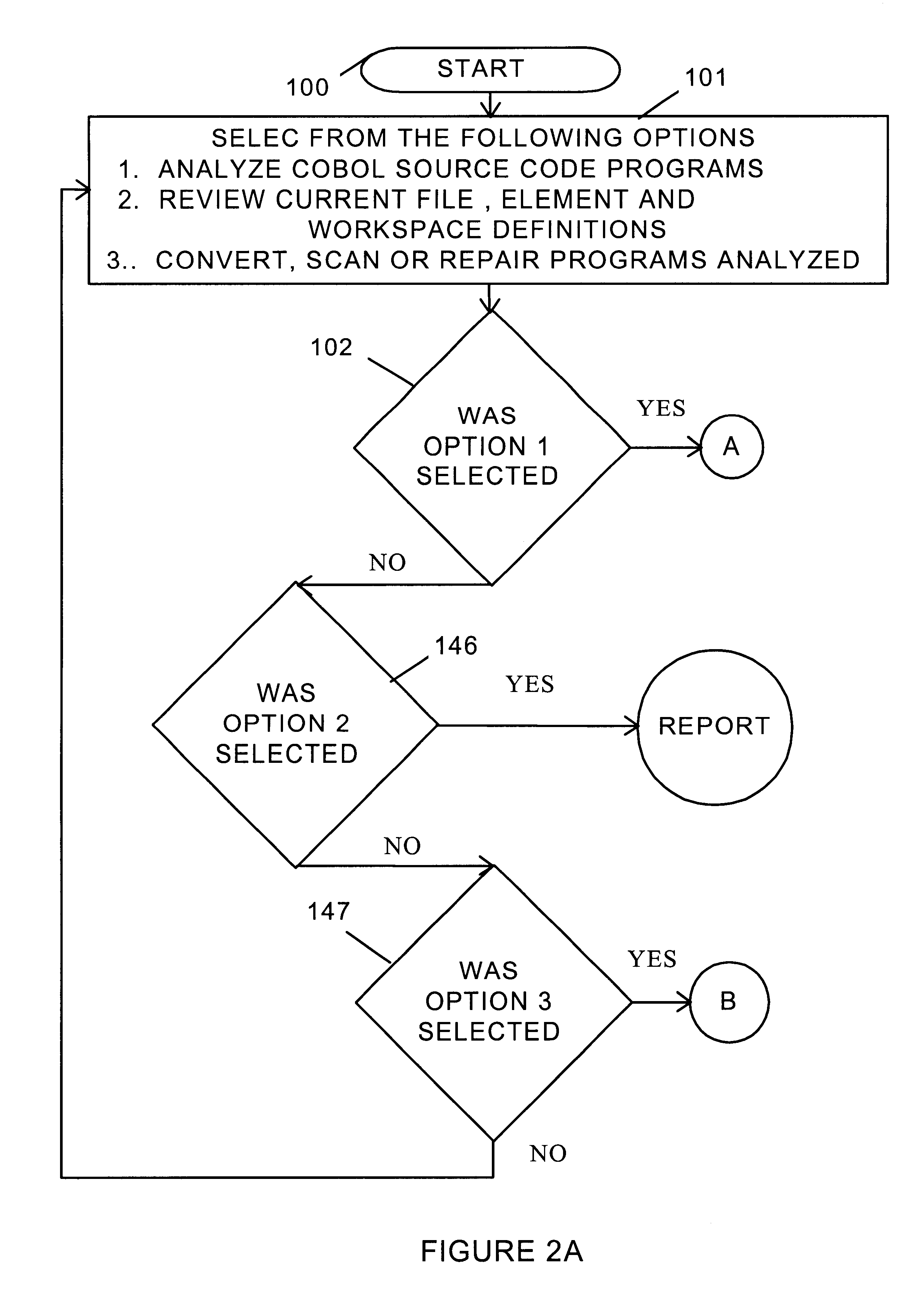
Software re-engineering system
InactiveUS6269474B1Improve system performanceSoftware maintainance/managementProgram loading/initiatingData fileApplication software
An optimization system including an option to convert existing code to a code-less environment or to create a codeless environment by the establishment of all essential application elements in files. The code-less environment is created through a design and analysis step, an environmental step and an installation step. An application map is prepared during the design and analysis step which defines where information enters into the system, where information is used, and where used information is changed. The application map is also used to verify that all information is accounted for. The design and analysis step also includes the generation of default database structures, screen formats, print layouts, file transfer protocols, validation tables and communication specifications. The environmental step includes modifying specifications in accordance with user preferences, simulating performance of the specifications with test data, preparing existing data files for conversion to the code-less system, and implementing parallel processing. The installation step includes final testing of selected hardware platforms and maintenance on a development system.
Owner:INT VERONEX RESOURCES
Fault Localization and Fiber Security in Optical Transponders
ActiveUS20120224846A1Accurate locationTransmission monitoringElectromagnetic transmission optical aspectsDigital signal processingFiber
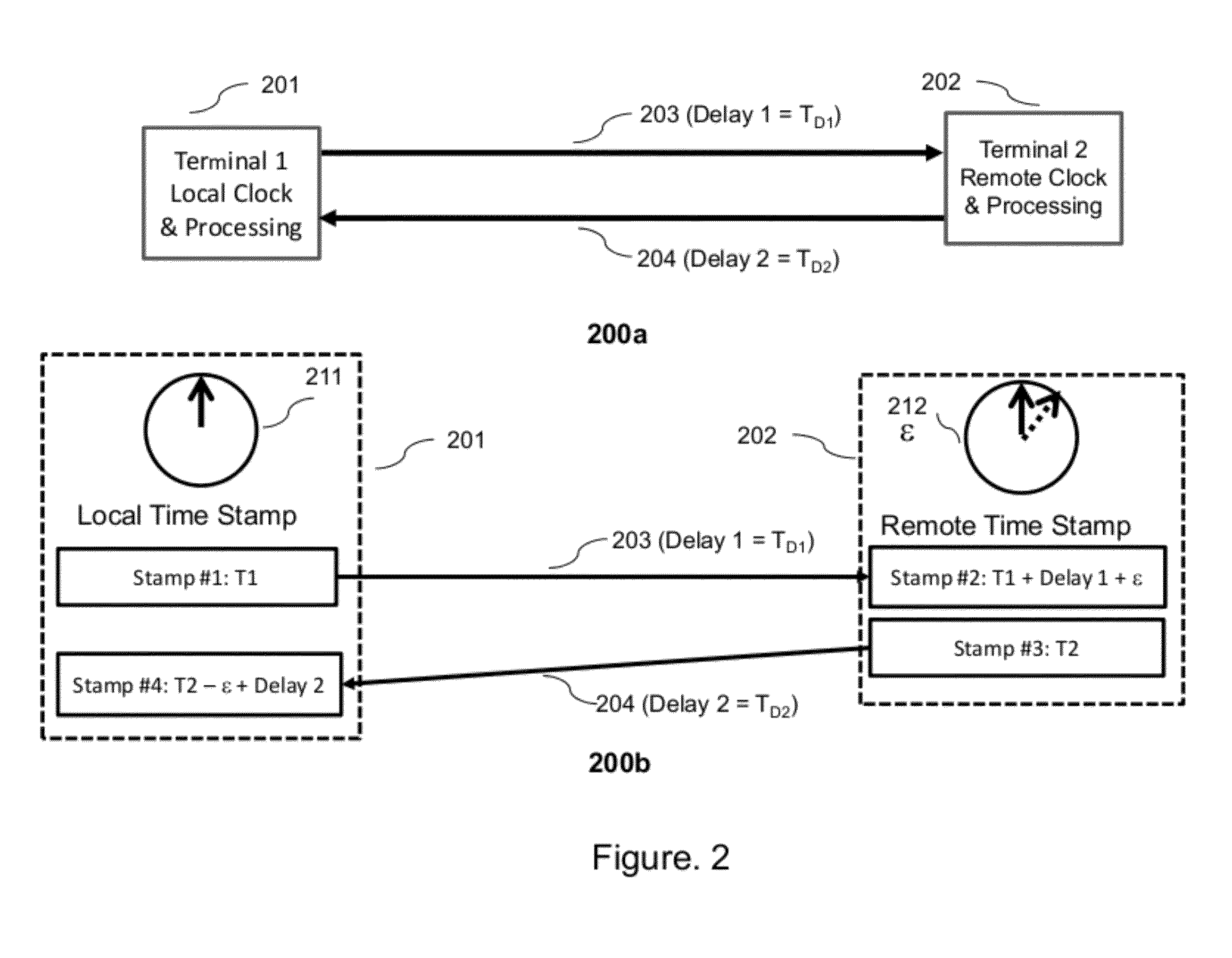
Designs, methods, and applications for fault localization and fiber security in optical transponders is described. In one embodiment a two-way time transfer protocol or other suitable method for synchronizing clocks between distant transponders is used. The clock synchronized transponders have digital signal processing to continually detect high precision time-histories of physical layer attributes in the transmission between the two transponders. Physical layer attributes can include: state-of-polarization changes, changes in polarization-mode-dispersion, change in propagation delay, changes or loss-of-light, changes in OSNR, changes in BER between the two nodes. By recording these physical layer changes and time-stamping them information on the magnitude and estimated location of the changes can be inferred by from the time records. In one aspect the method may be used in a distributed optical sensor for monitoring trespassing events that are a risk to fiber security of an optical transmission link.
Owner:ACACIA CHEM
Pre-positioning data in a network memory appliance
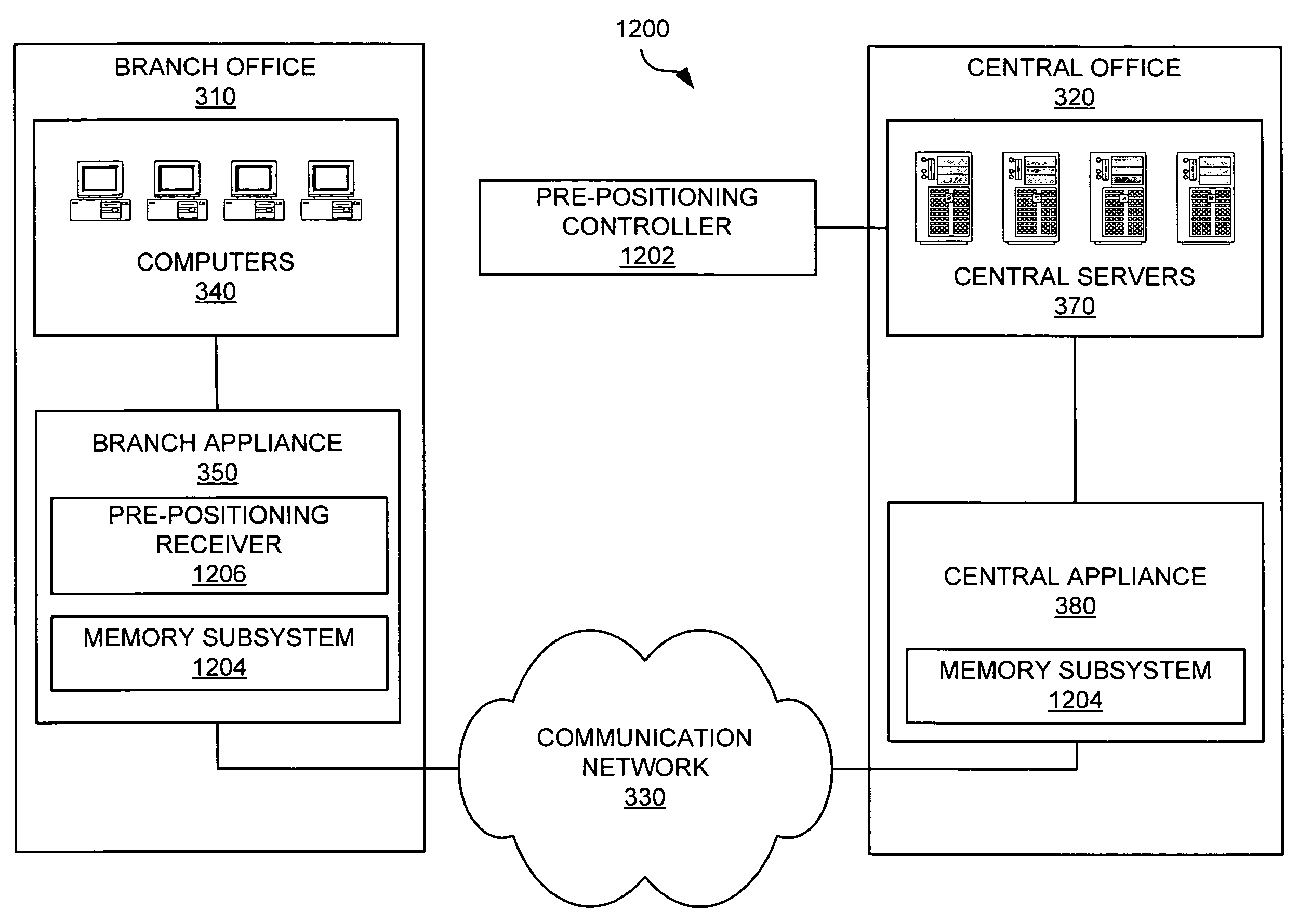
InactiveUS7698431B1Quick searchWithout license feeDigital computer detailsNetwork connectionsFile systemSoftware update
Systems and methods for pre-positioning data in a network memory are described. A pre-positioning command may be executed to position specific data at one or more network memory appliances before the data is requested at a branch office. For example, the first download of a software update over the communication network at a branch office may require several minutes. To make the first download of the software update faster, the software update may be downloaded previously to the branch appliance. According to various embodiments, the pre-positioning command may comprise a time of transfer and / or a schedule. The data may be received by a pre-positioning receiver such as a file system server, a hypertext transfer protocol server, a file transfer protocol server, or a virtual client.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Web-based file transfer protocol server enterprise manager with build-in database
InactiveUS20060179155A1Multiple digital computer combinationsTransmissionWeb browserBusiness management
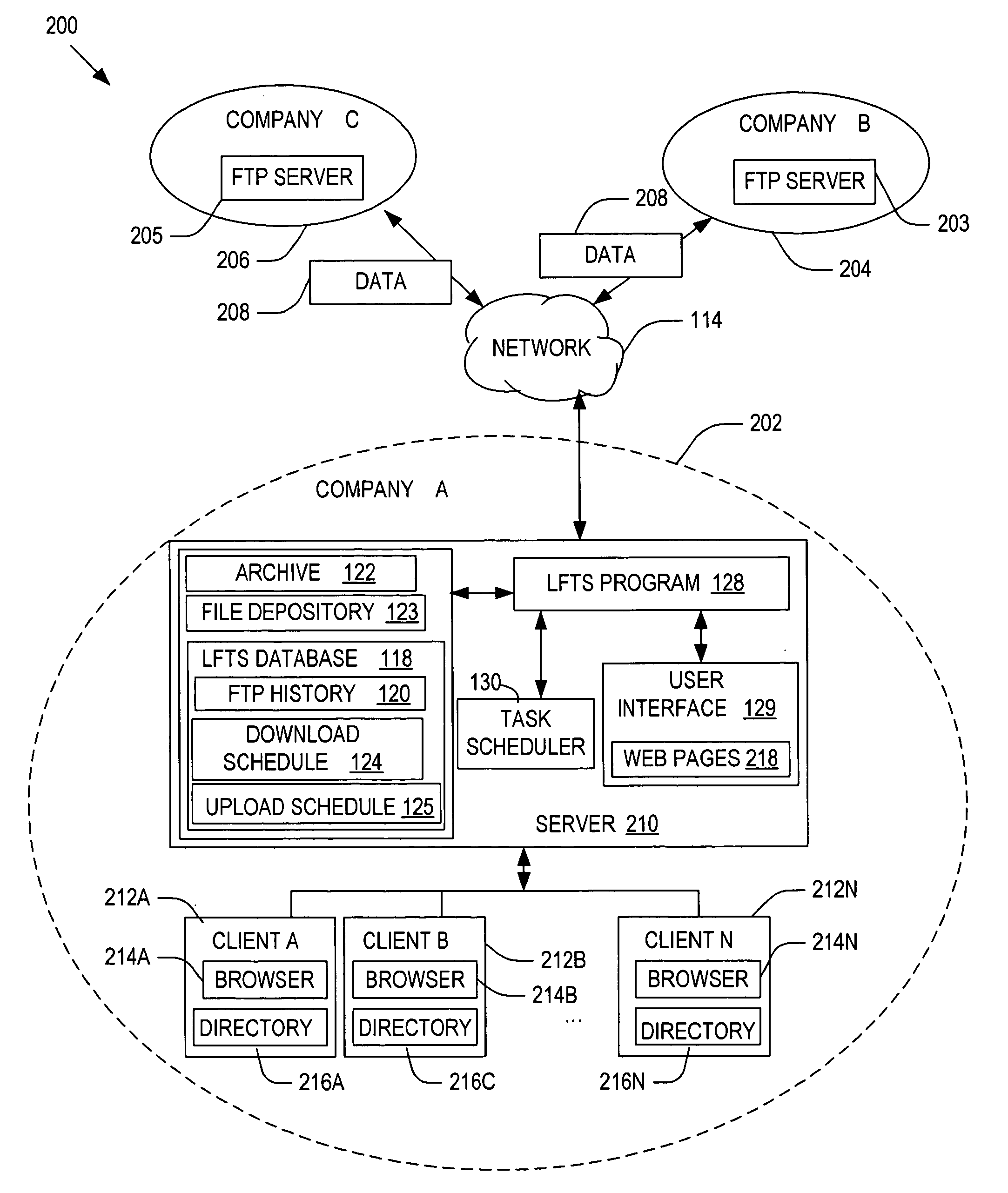
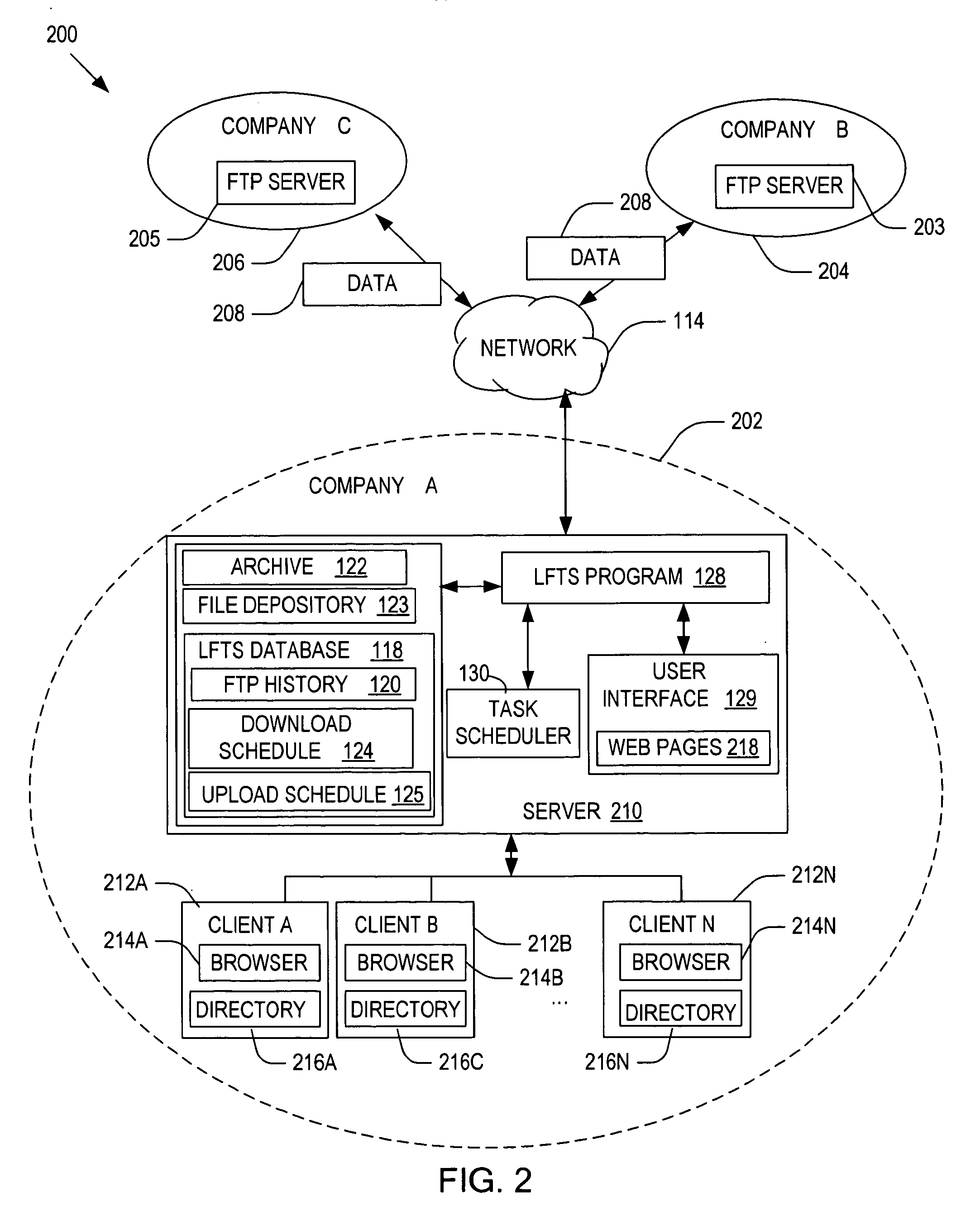
Methods, systems and computer readable media for downloading data to file depository managed on a server. A user locates a remote server that hosts a file to be downloaded to the file depository using a web browser. A download request is submitted to the download queue, wherein the download queue is executed to download the file into the file depository. The system checks remote FTP sites and updates its file depository at specific intervals set by users and downloads the latest version of its file and archives old versions. The system allows users to upload files from the file depository to remote servers and updates the file depository if the file transfer was successful. All file transfer history for downloads / uploads may be viewable by client users.
Owner:AGILENT TECH INC
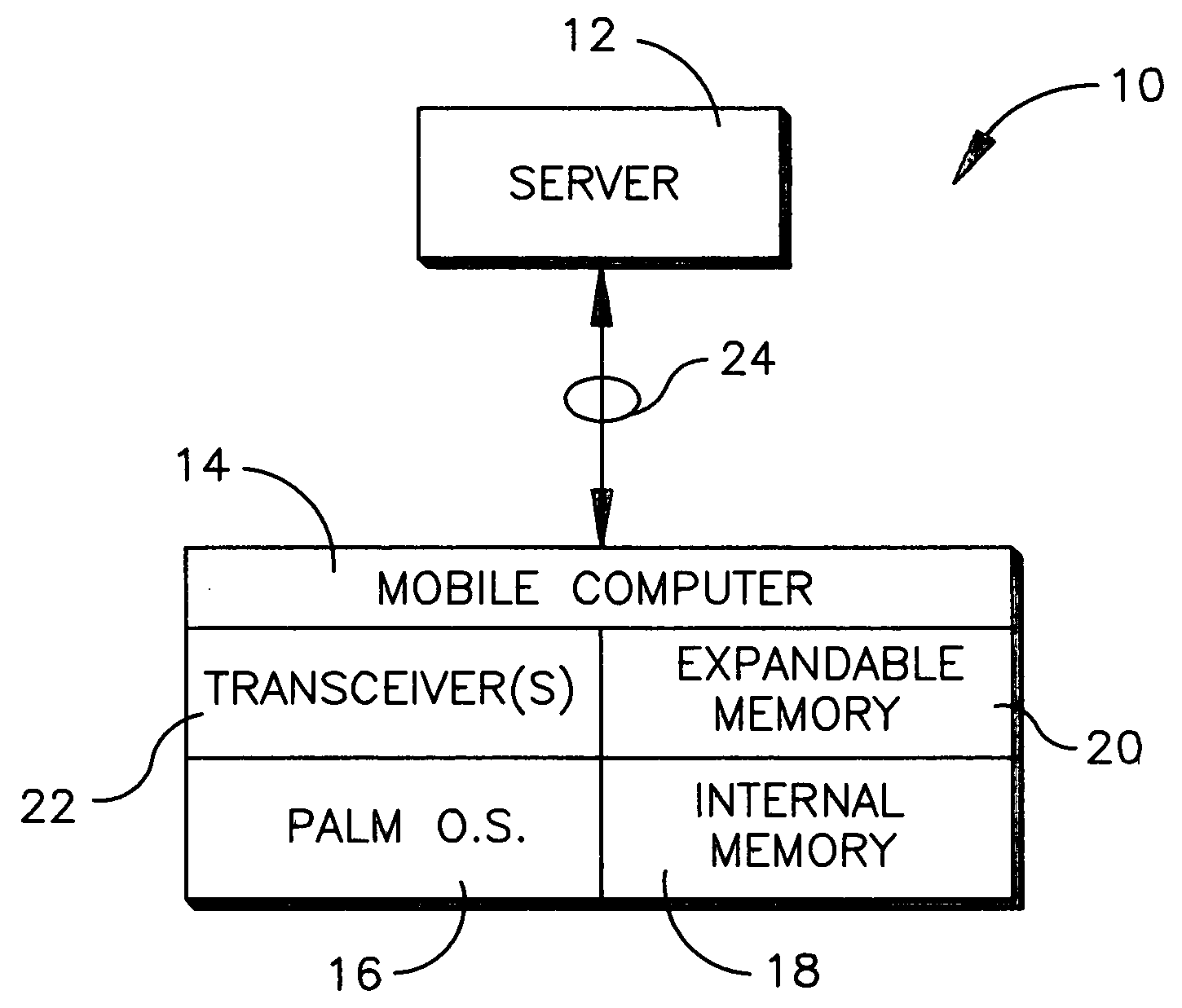
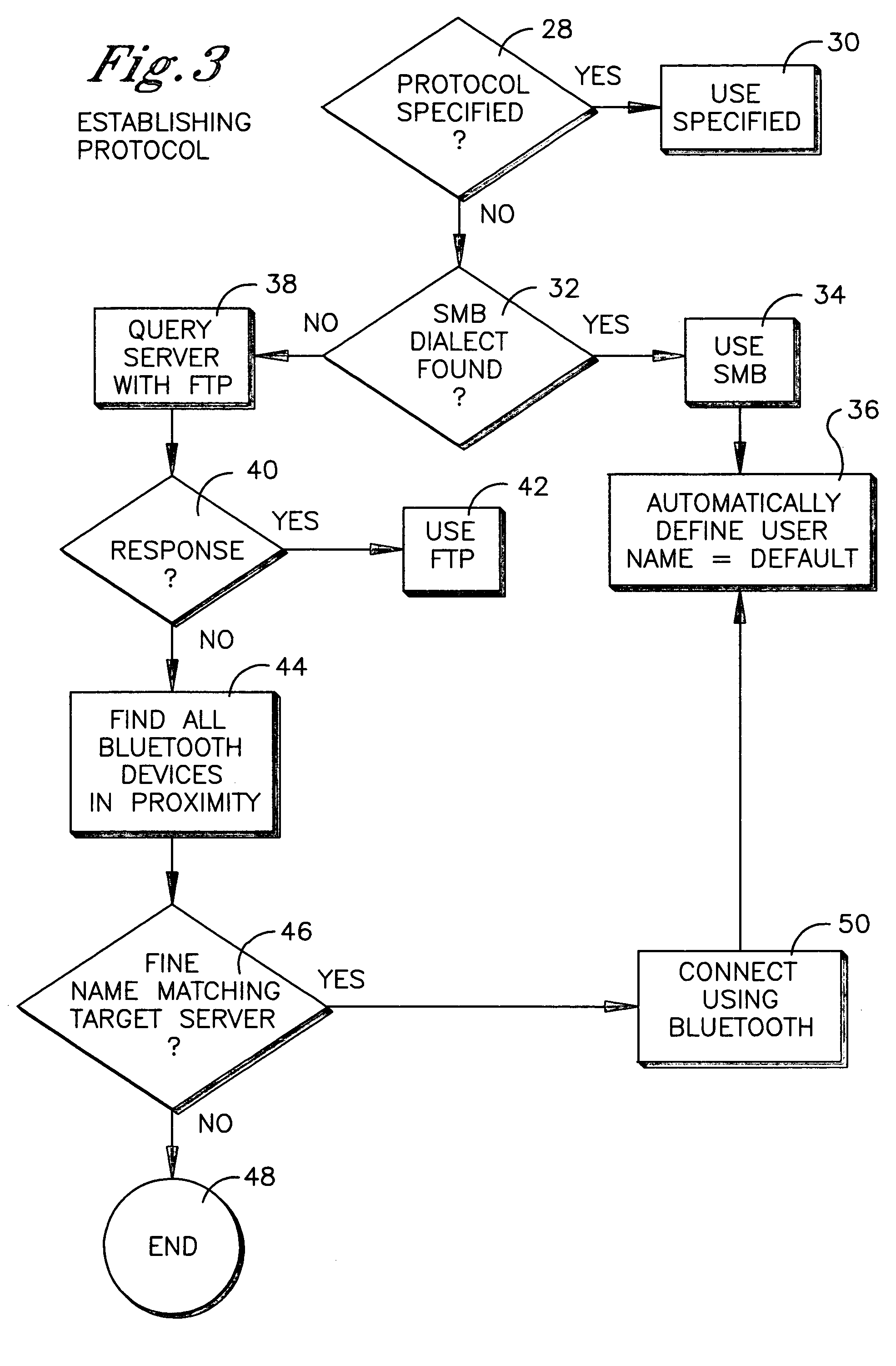
File transfer protocol for mobile computer
InactiveUS20050102537A1Digital data processing detailsPicture reproducers using cathode ray tubesInternal memoryBluetooth
A method is disclosed for communicating using a device having a Palm OS. SMB is preferentially used to communicate with a node, and if use of SMB is not possible, FTP is used, and if use of FTP is not possible, Bluetooth is used. If FTP or Bluetooth is selected as the protocol, file sharing between the device and node that entails a read or write is executed by temporarily copying a file to an internal Palm OS memory of the device, performing the read or write on the file, and then copying the file back to the node to overwrite a previous version of the file at the node. For non-Palm OS file transfer to the internal memory, the file is wrapped in a Palm OS stream in the internal memory for executing reads or writes. For file transfer to an expansion Palm OS memory card, byte-to-byte copying of the file is executed using the FAT of the expansion memory, with the file being transferred through an internal Palm OS memory of the device.
Owner:SONY CORP +1
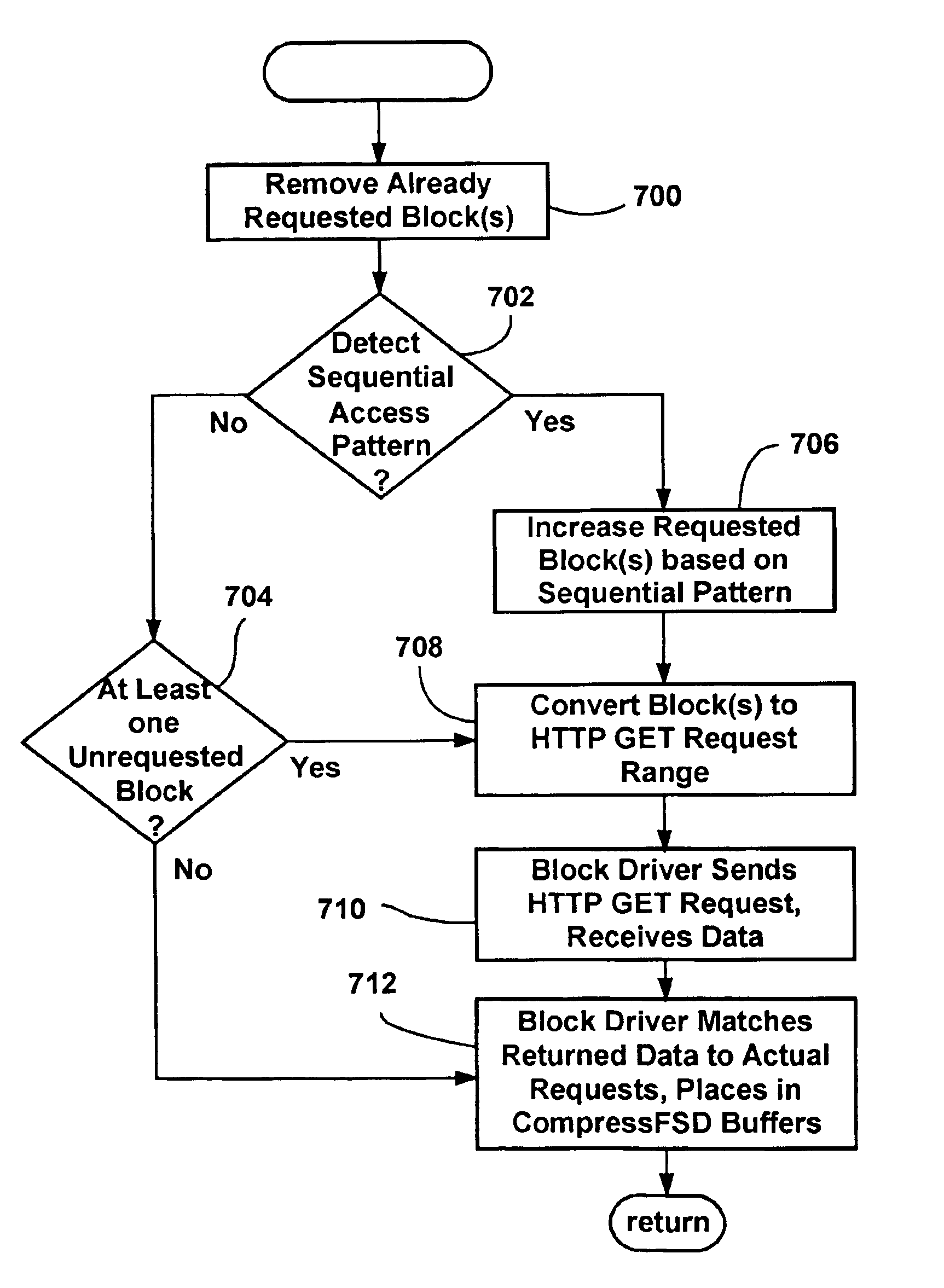
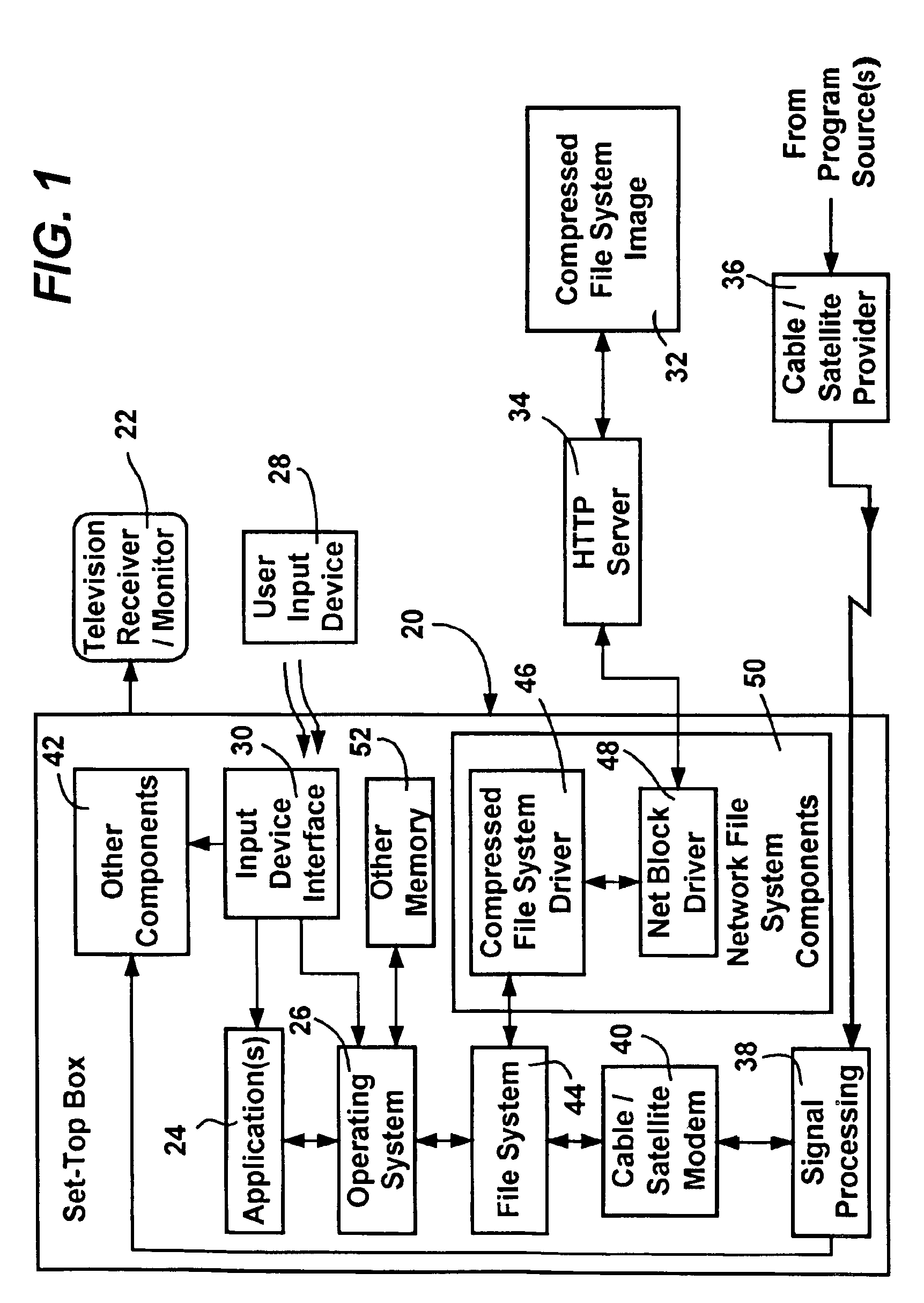
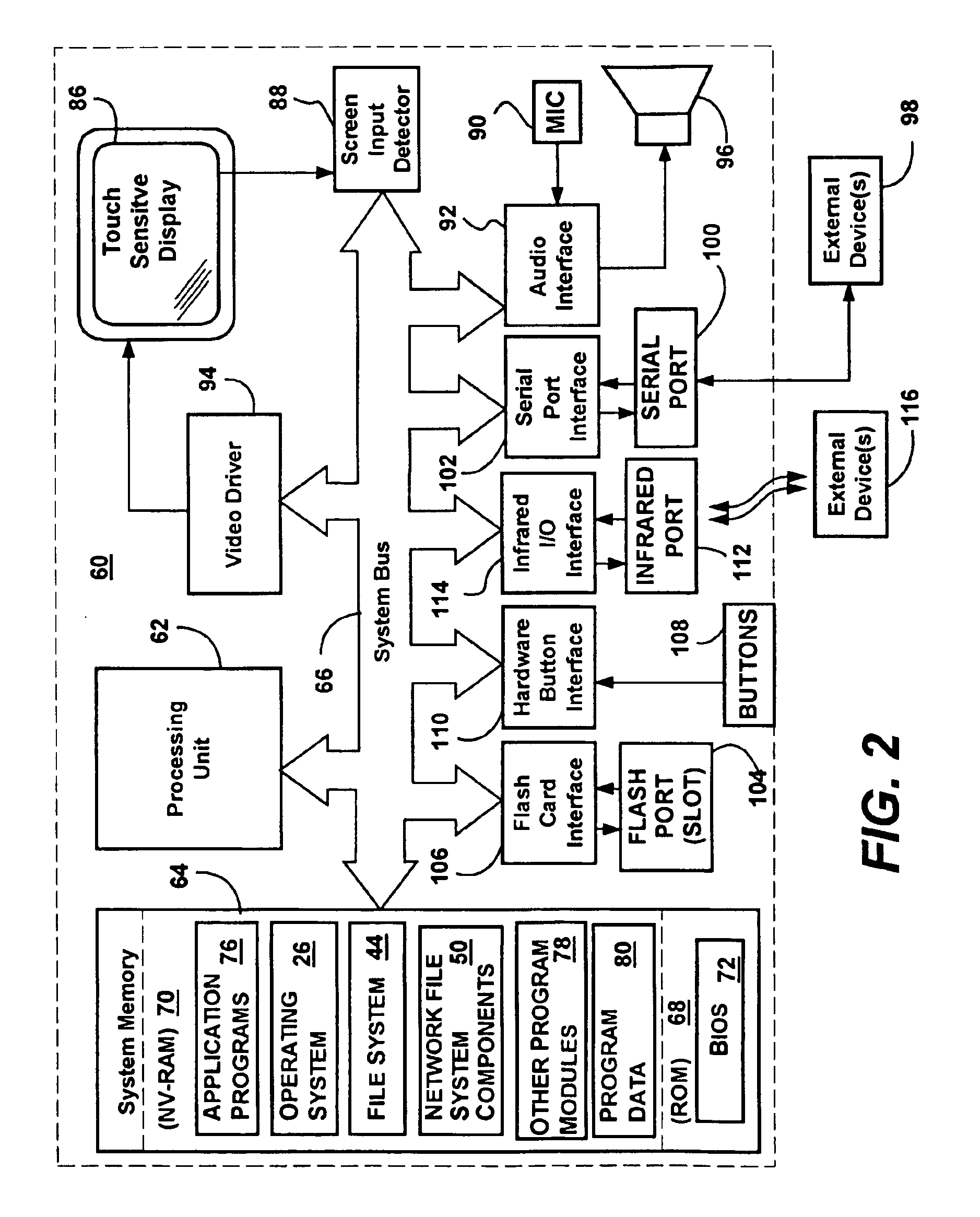
System and method for converting and reconverting between file system requests and access requests of a remote transfer protocol
InactiveUS6889256B1Minimized in sizeReduces seek requirementMultiple digital computer combinationsTransmissionTransmission protocolStreaming data
A method and system that combines efficient caching and buffering to provide a network file system, that may utilize data stored in one or more compressed image files of sequentially arranged byte stream data. As an application requests file opens and file reads of a file system, one or more drivers convert the block requests into HTTP: byte range requests or the like in order to retrieve the data from a remote server. As the data is received, it is reconverted and adjusted to match the application's request. Sequential block access patterns can be detected and used to request additional data in a single request, in anticipation of future block requests, thereby increasing efficiency. Local caching of received data, including caching after uncompressing received data that was compressed, further increases efficiency. A compressed file system format optimized for sequential access is also described that when used, further improves the efficient data access.
Owner:MICROSOFT TECH LICENSING LLC
Digital home movie library
InactiveUS20070186266A1Rule out the possibilityEliminates the trip to the storeTelevision system detailsGHz frequency transmissionHard disc driveData pack
The system and method of the present invention provides viewers access to a library of movies, or any other audio / video content available for viewing at anytime. Specifically, the method involves transmitting movies wirelessly to a set-top box in one's home and allowing movies to accumulate. A hard disk drive in the set-top box is used to store movies. In an exemplary embodiment, movies are wirelessly transmitted to the set-top box using a datacasting technology which allows data to be encoded onto standard television signals and transmitted using existing television transmitters and broadcast towers. Movies are transferred to the set-top box using a broadcast file transfer protocol and stored on the hard drive. Movies are “packetized” and these packets are continuously transmitted to the set-top box where they are incrementally reassembled. The user is not aware of what data is being sent to their set-top box. The movies are pushed down by the provider to reside passively in the box for a finite time period. Transmission of the data is controlled by the content or service provider. To ensure that movies are received in their entirety, the same movie may be broadcast to the set-top box several times. Any packets of data that were not received in the first attempt of transmission will be received with subsequent broadcasts. The set-top box is also connected to a phone line for billing purposes.
Owner:WATSON SCOTT F +1
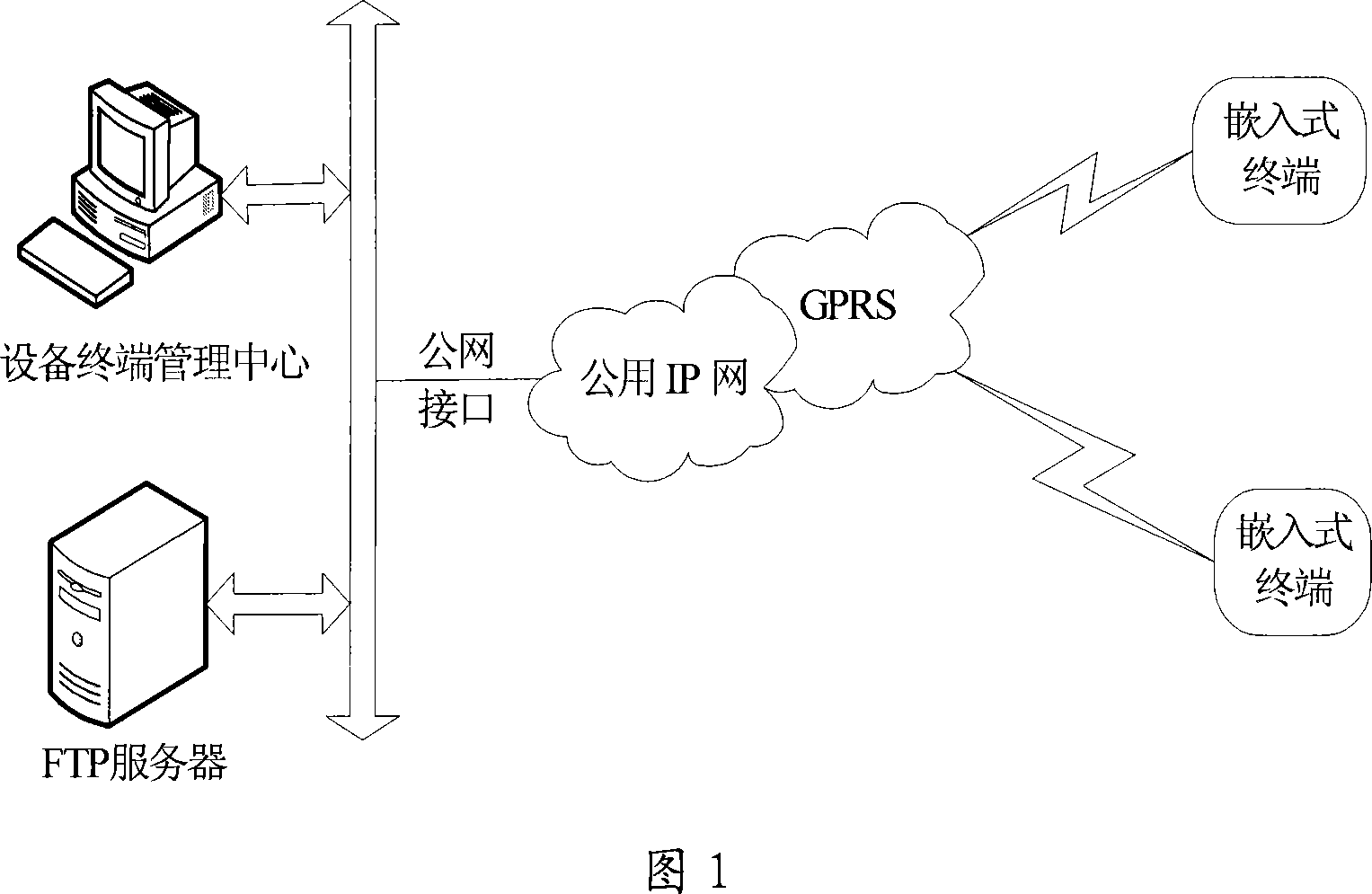
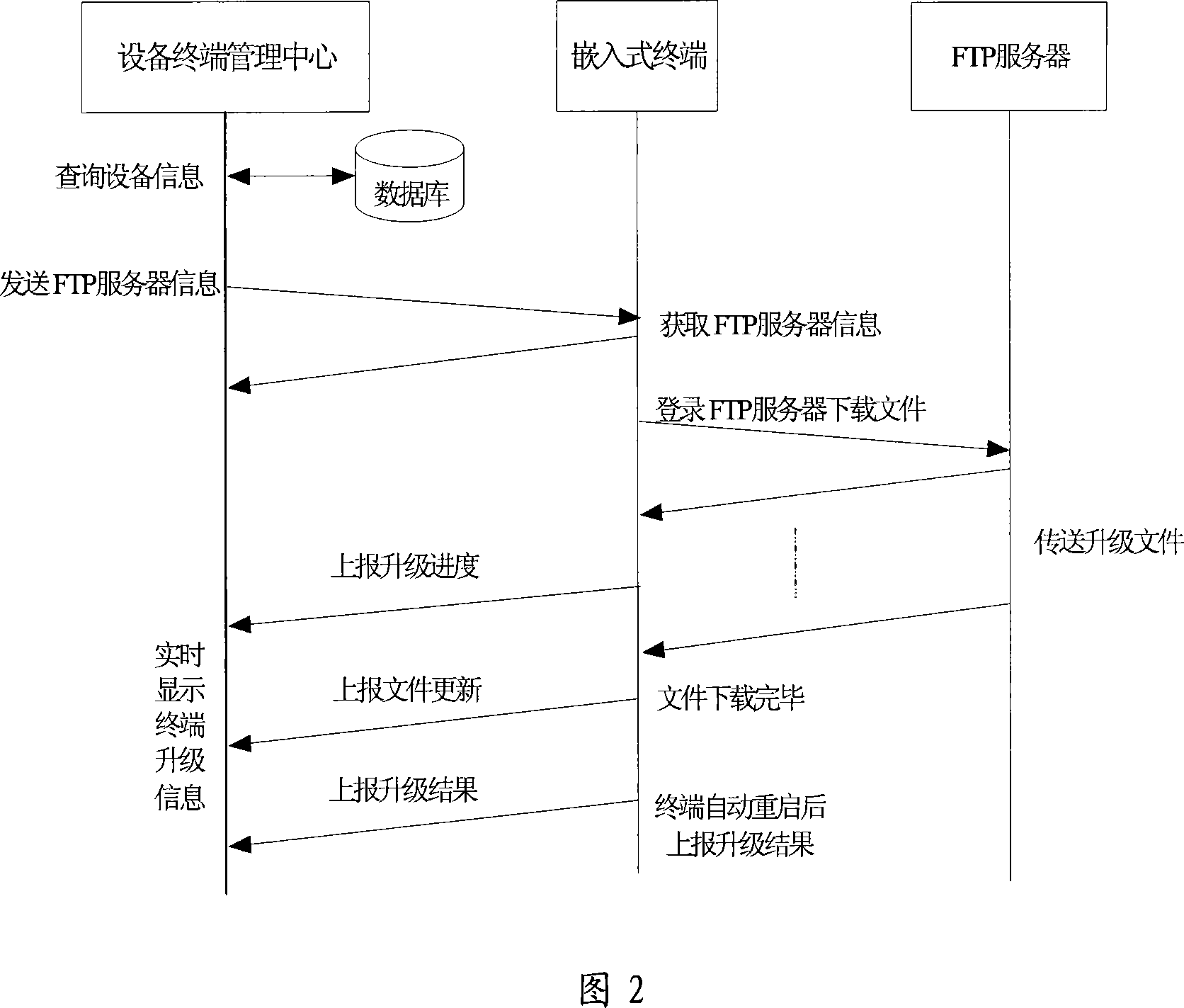
Remote upgrade method of built-in system software based on FTP protocol
The invention discloses a wireless remote updating method based on the embedded system software of FTP protocol, which comprises the following parts: management center of equipment terminal, FTP file server and embedded terminal, wherein the communication among the embedded terminal, management center of equipment terminal and FTP server is based on GPRS or CDMA1 wireless IP pattern, which supports multi-embedded terminals to update FTP remotely. The invention solves the defect of present updating pattern without defining complex wireless updating interactive protocol, which is an automatic remote updating method for software equipment.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
Synchronizing centralized data store from distributed independent data stores using fixed application programming interfaces
InactiveUS7484219B2Provide flexibilityData processing applicationsDigital data information retrievalApplication programming interfaceSemantics
A data transfer protocol utilizes a set of actions for affecting different objects that are stored in a data store. The data transfer protocol supports a set of application programming interfaces (APIs) that are applicable to the different objects. With the APIs, the data transfer protocol may synchronize a centralized data store with independent data stores. The data transfer protocol may support data that is hierarchical while maintaining referential integrity. Node objects may vary from nightly bulk uploads to interactive users uploading or querying smaller portions of the database. The data transfer protocol provides the semantics to carry out these operations with a fixed number of APIs for any arbitrary database. The data uploads may be sparse depending on what the remote data store holds and need not be in serial order.
Owner:MICROSOFT TECH LICENSING LLC
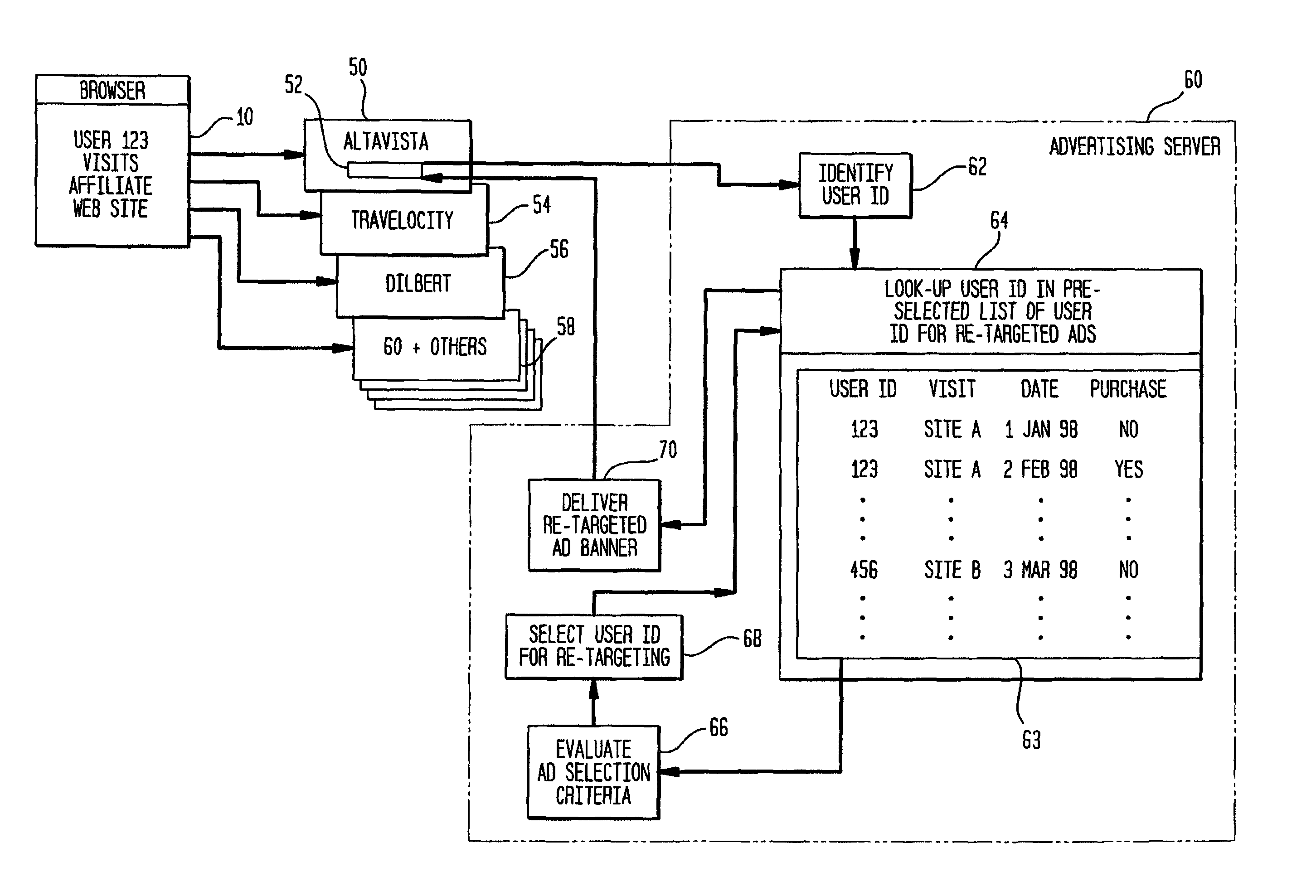
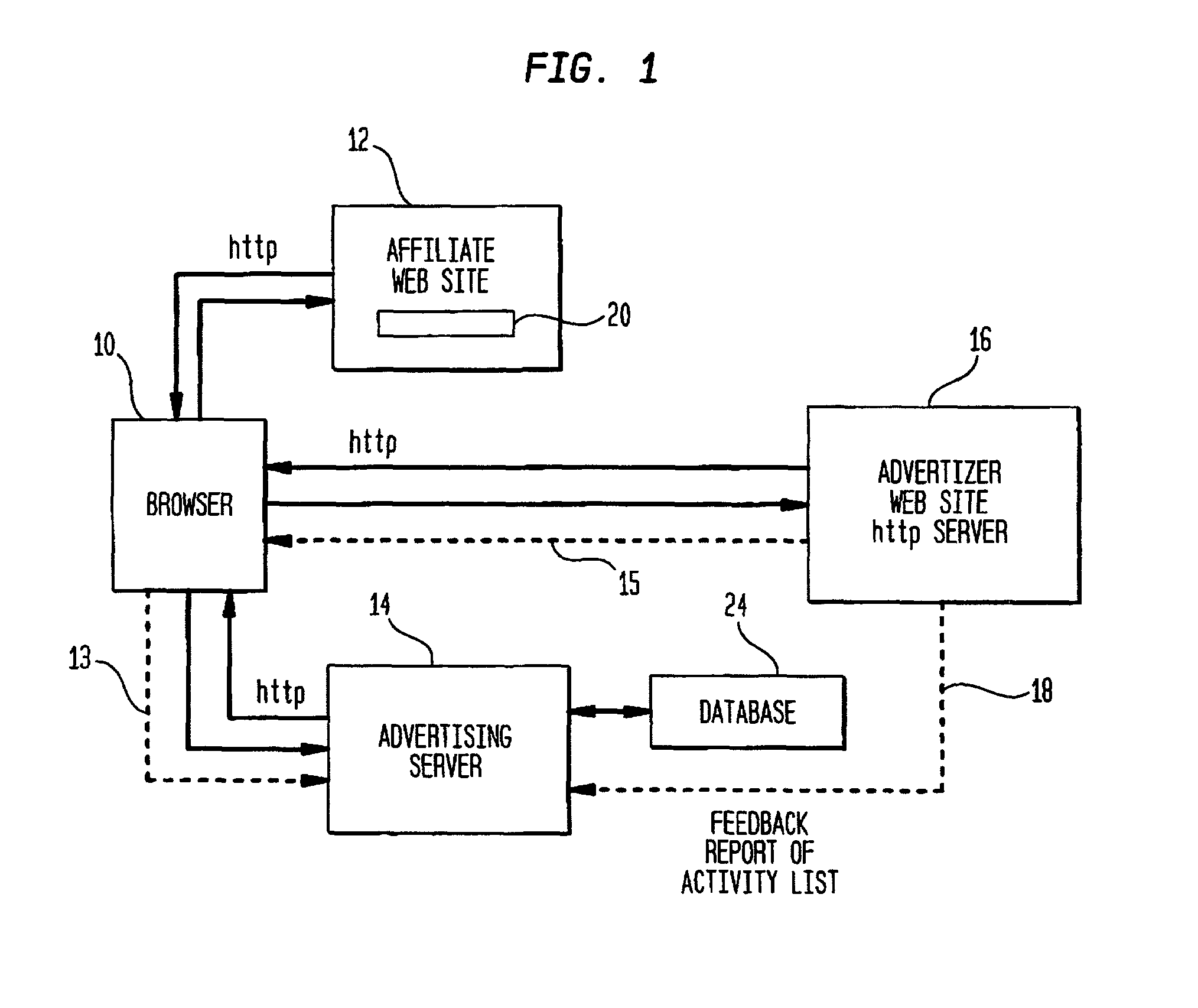
Network for distribution of re-targeted advertising
A computer system for automatic replacement of advertisements includes an advertising server for selecting an advertisement based on criteria related to the individual viewer. In particular, advertisements are selected for a given user, based on the past behavior of that specific given user. Advertiser web sites on the network are configured to anonymously report back user activity such as visit dates, purchases, specific product pages visited and the like. Alternative reporting embodiments include email, file transfer protocol and spotlight tags. User activity lists are processed to select candidates for re-targeting. Candidates for re-targeted advertisements are identified based on their own individual past activity, and stored in a list of candidate user ID's. When a candidate on the re-targeted list is identified at any network affiliate web site, a re-targeted advertisement is delivered to the candidate user.
Owner:GOOGLE LLC
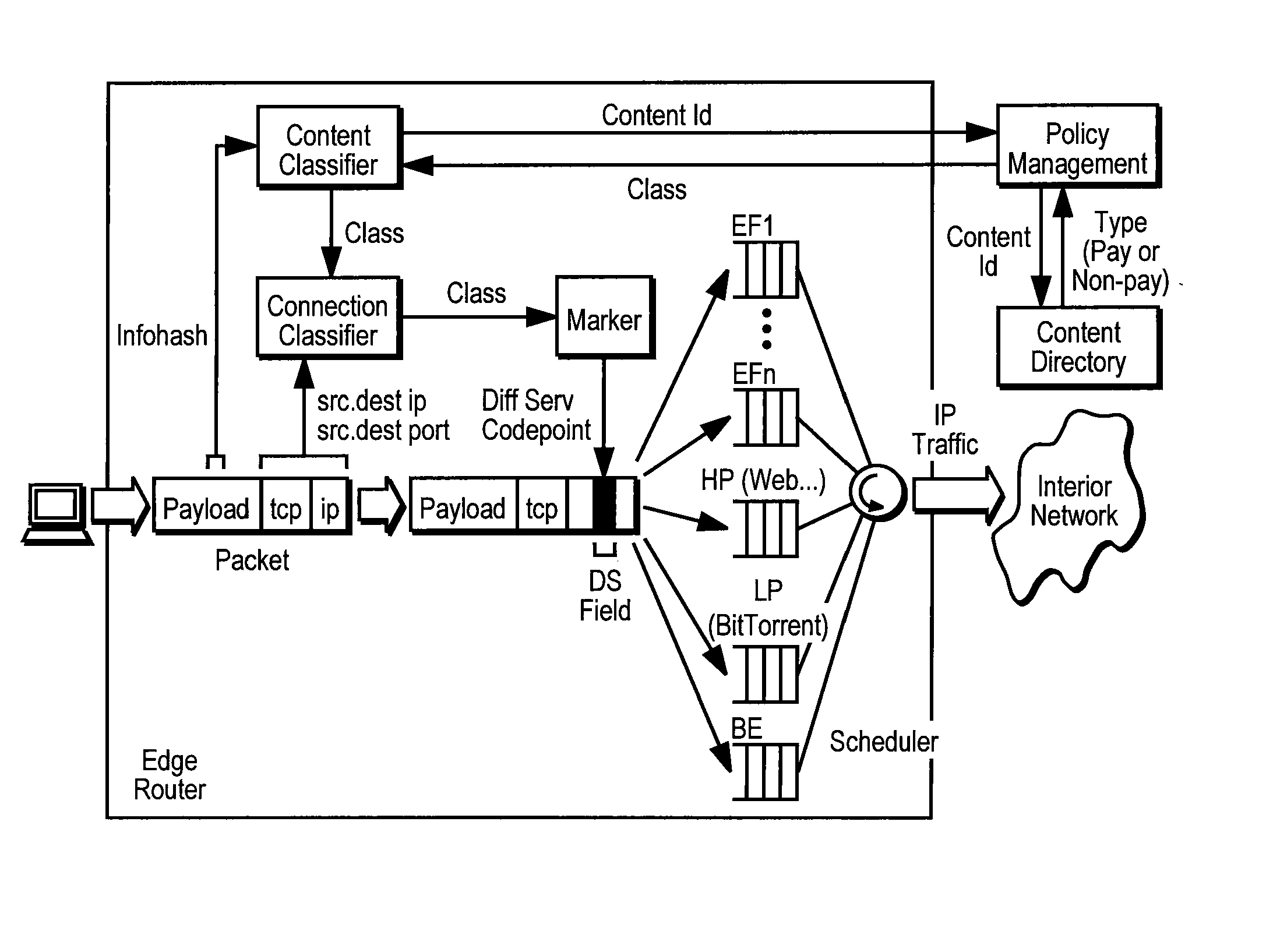
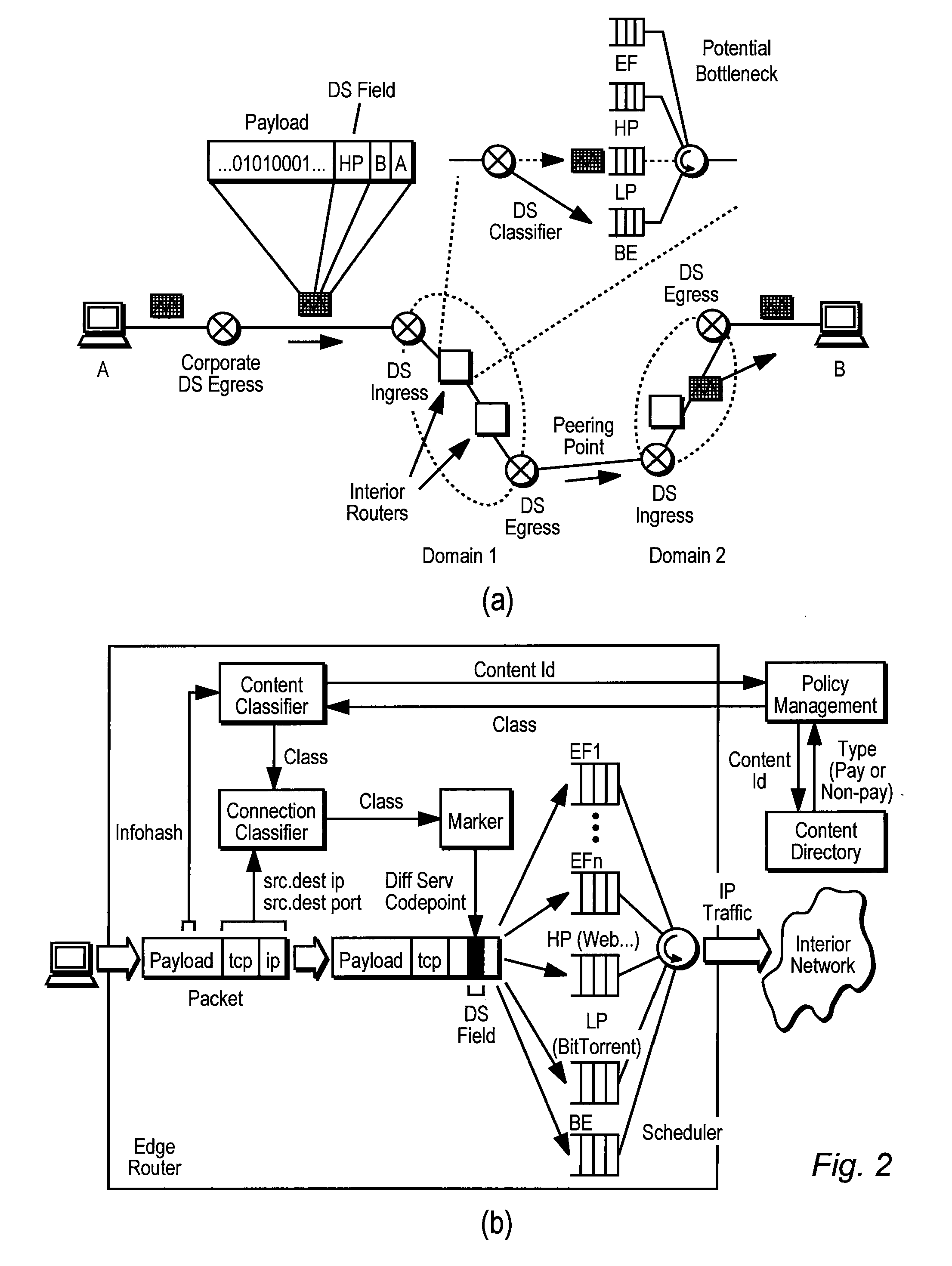
Classification and Verification of Static File Transfer Protocols
ActiveUS20070297417A1Reduce calculationImprove scalabilityError preventionFrequency-division multiplex detailsExtensibilityQuality of service
Classification and verification of static file transfer protocols is provided. A network node sitting in the path of packets classifies traffic according to its content, and then statistically verifies that the content actually matches the initial classification. Classification and verification are standard building blocks in networks systems that provide quality-of-service. However, unlike traditional quality-of-service building blocks, a system of the present invention takes a trust-but-verify approach, and thus can rely on longer-timescale statistical online or offline verification to reduce computational requirements. This improves scalability and reduces the cost and complexity that in part has prevented prior service differentiation systems from succeeding in the Internet. Internet Service Providers (ISPs) can combine the classification and verification building blocks with a networked directory service to allow further classification as to whether particular content is for pay.
Owner:BITTORRENT
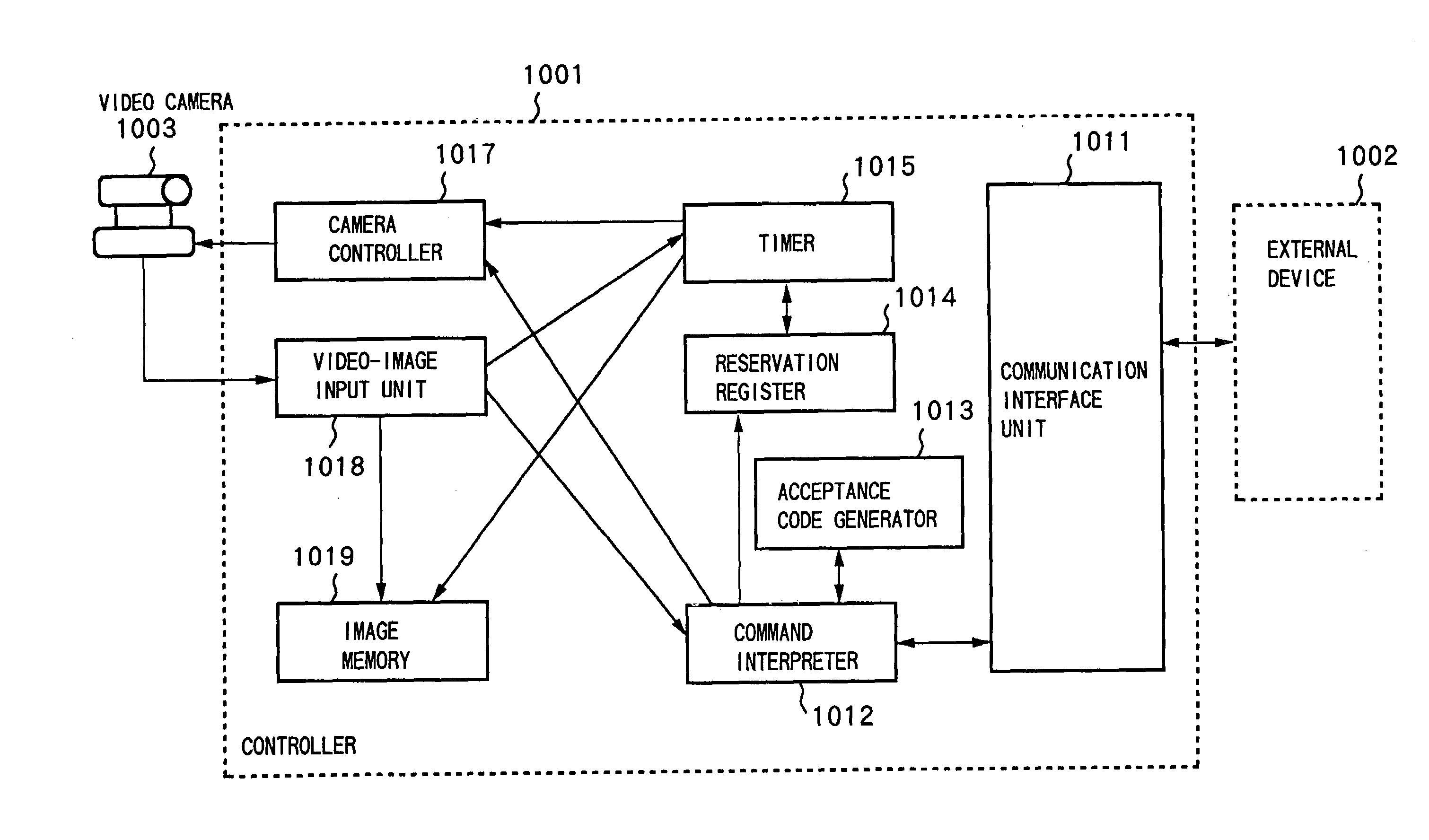
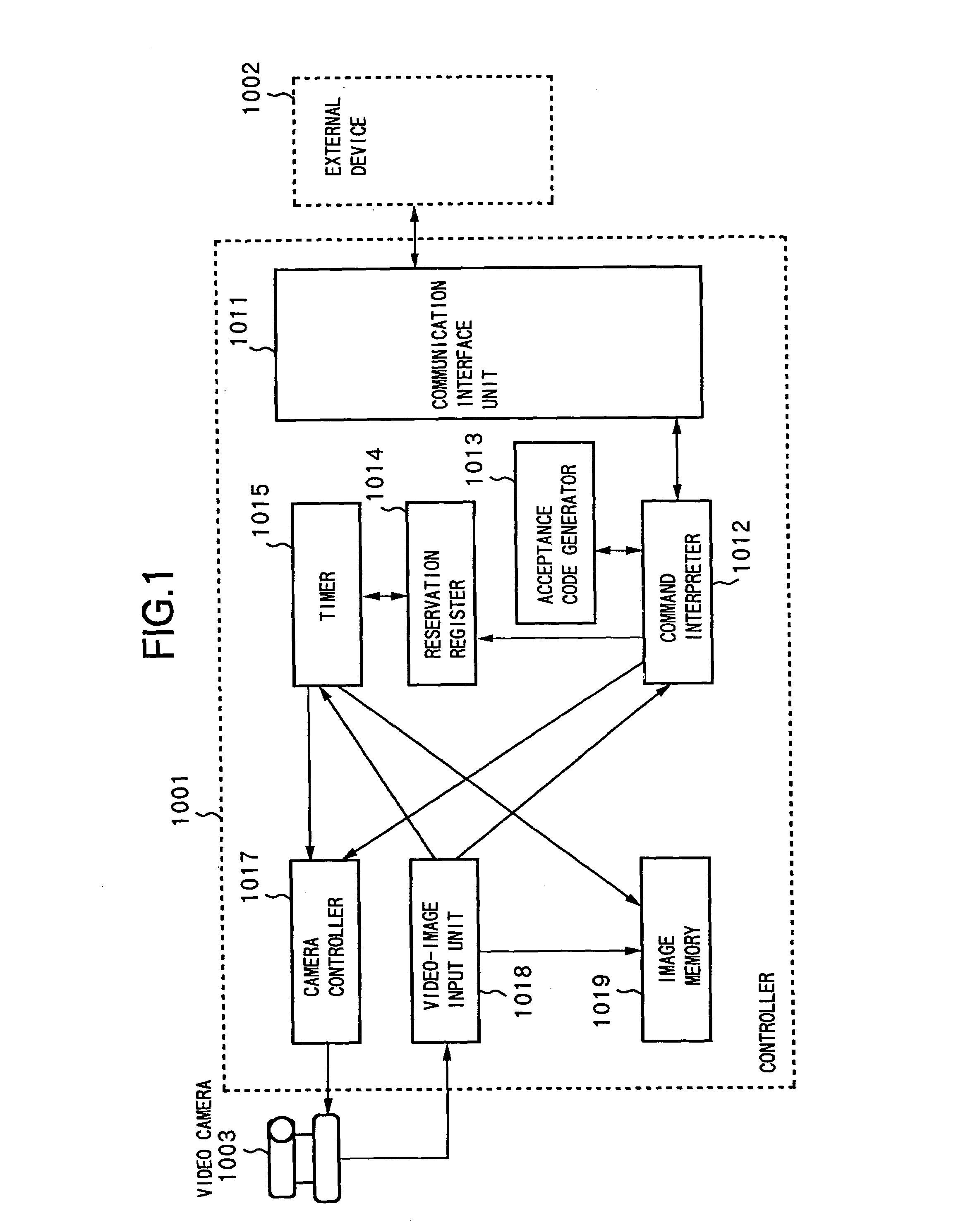
Communication method and apparatus, server and client on network, and program codes realizing communication thereof
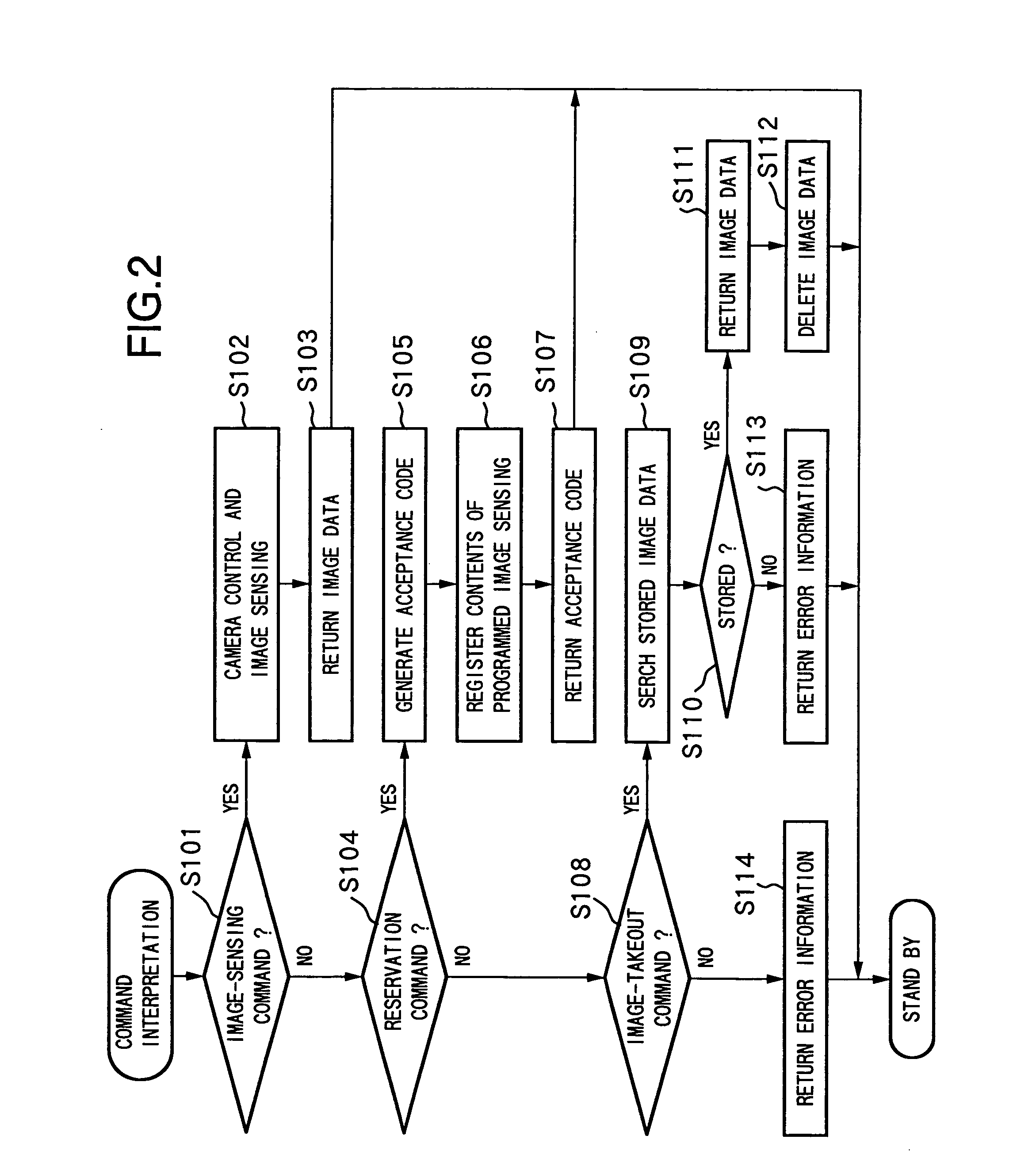
An end user is provided with an environment to easily remote-control a video camera via a general network such as the Internet. For this purpose, on a client side, the content of camera control is described in file-transfer protocol description, and the description is transferred to a camera server on the Internet via a browser. The camera server interprets the description, controls a camera in accordance with the designated content, to perform image sensing, and returns the obtained video image as the content of a file to the client. The client performs various controls while observing the video image. When a desired angle has been found, the client instructs to register the angle in a bookmark, then angle information displayed at that time is registered. Thereafter, when the user of the client can see the video image obtained on the same image-sensing conditions by merely select-designating the angle information registered in the bookmark.
Owner:CANON KK
Cross-platform mobile data management system and method
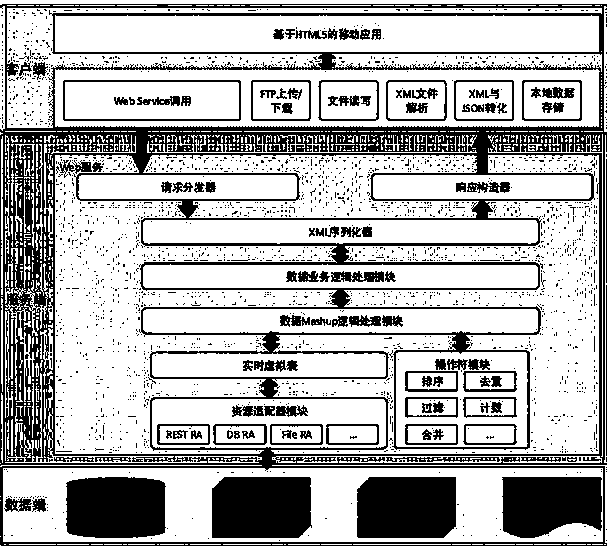
InactiveCN103645951ARealize mobile managementRealize visual managementProgram initiation/switchingTransmissionHTML5Web service
The invention discloses a cross-platform mobile data management system and method. The system comprises a client, a server side and a data side, wherein the client is used for providing a mobile operating entry, namely, an interface intersection window, for the mobile data management system, and the form of the client is based on HTML5 local mobile application; the server side is used for providing data service for the client of the mobile data management system, and the form of the data service mainly comprises Web service and FTP (file transfer protocol) service; and the data side is used for providing a data source for the mobile data management system, and the form of the data source comprises a database resource, a sensor Restful resource, a Web service resource and a file resource. With the adoption of the cross-platform mobile data management system and method, a system can use various smart mobile terminal platforms in a compatible manner, so that the effect that the business logic of a mobile application is compiled once and can operate on the various smart mobile terminal platforms is realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method and system for pay per use document transfer via computer network transfer protocols
InactiveUS7746496B2Reduce probabilityShorten the timeTelephonic communicationDigital computer detailsService provisionFacsimile transmission
A system includes a portion for receiving a transmission comprising a digitized document including a digitized computer network destination associated with a recipient from a user using a facsimile device, a portion for determining a telephone number for the facsimile device, an OCR portion for determining the computer network destination for the recipient from the digitized computer network destination for the recipient, a portion for determining an attachment from the digitized document, and a portion for sending the attachment to the computer network destination for the recipient including a service provider name, wherein the transmission is associated a pay-per-use service charge that may be asserted against the telephone number associated with the facsimile transmission device.
Owner:ADVANCED MESSAGING TECH INC
Job scheduling management system and method
ActiveCN103324539AEasy to integrateImprove computing powerResource allocationResource utilizationData center
The invention provides a job scheduling management system and method. The job scheduling management system structurally comprises an FTP (File Transfer Protocol) server, a client, a control node and a plurality of processing nodes. The job scheduling management method includes that a task node sends task running state information including middle progress state, error or exception of a task to the control node, and the control node executes exception processing or stopping according to an exception or error condition; the control node starts a heartbeat test to test whether a node is alive or not when the control node do not receive heartbeat information of the task node, and the control node reschedules all uncompleted tasks when the node crashes. Compared with the prior art, the job scheduling management system and method improves the level stack of large data processing software, enables Hadoop to break resources telescopic bottlenecks and business expansion limit of a single data center, promotes the integration of multiple data centers, and further expands computing capabilities and improves the resource utilization rate.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
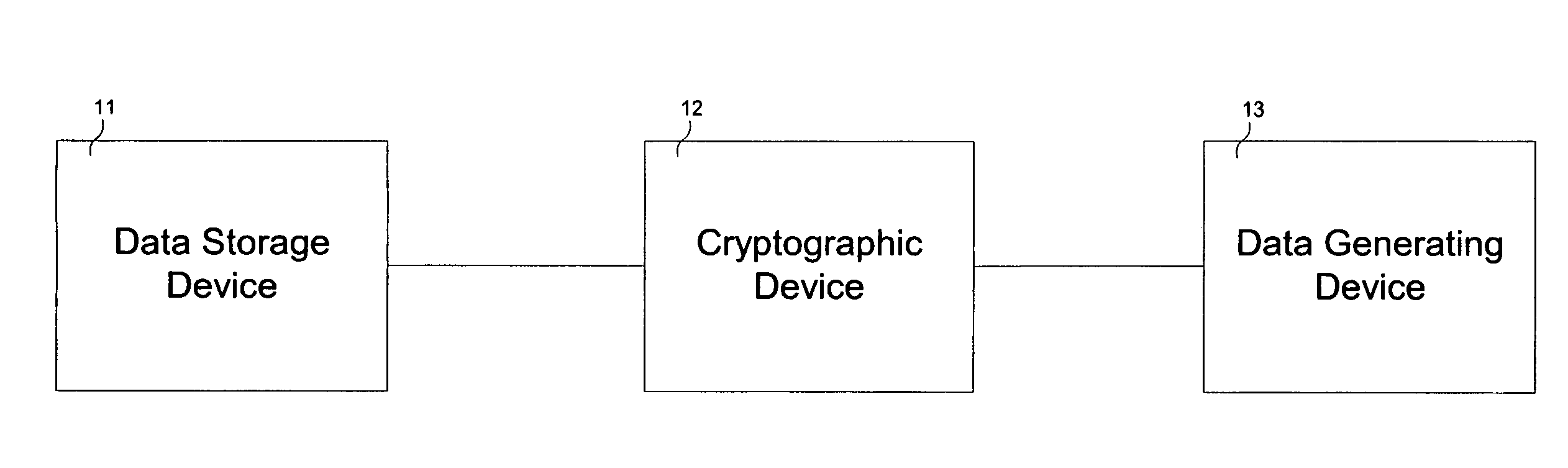
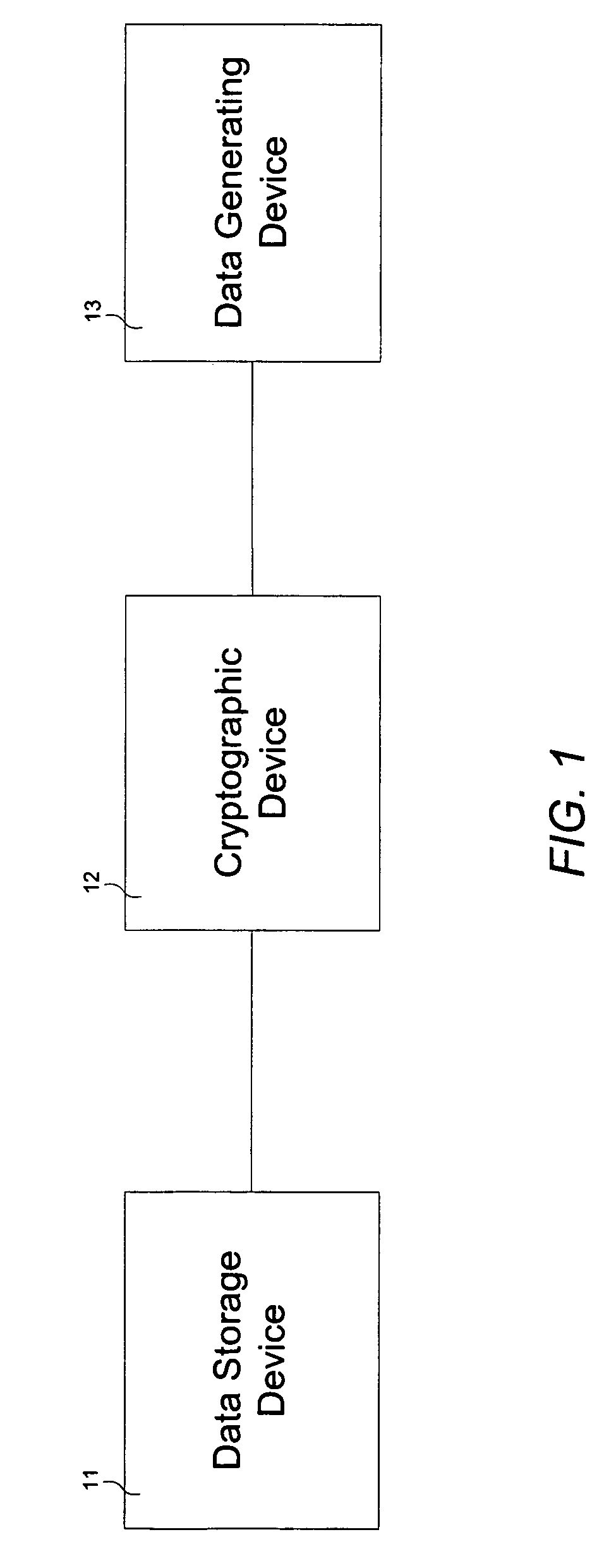
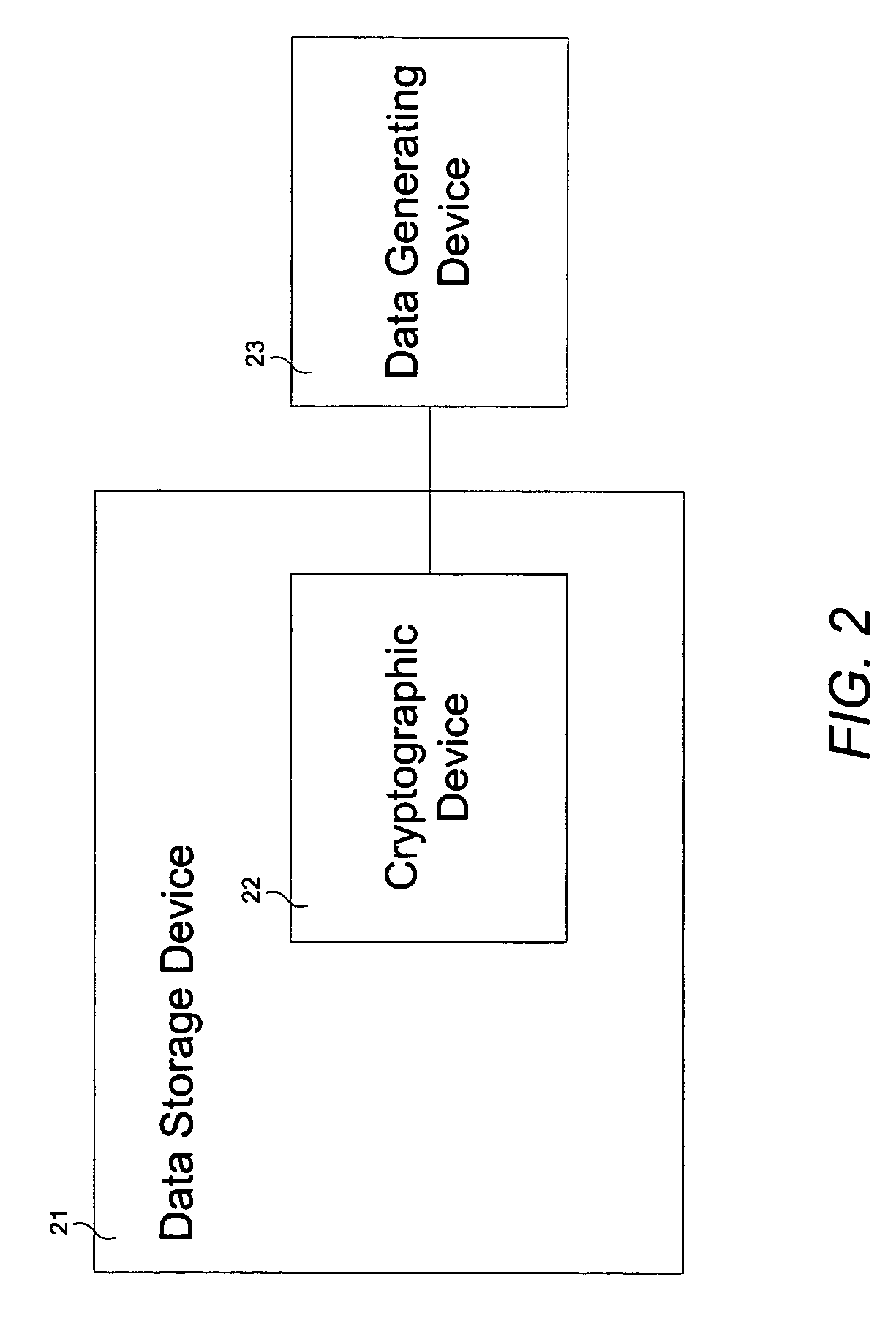
Cryptographic device
InactiveUS7136995B1Without compromising overall system performanceData stream serial/continuous modificationUnauthorized memory use protectionData streamControl store
A cryptographic device comprises a data stream interceptor, a main controller receiving input from the data stream interceptor, and a pair of data generating and storage controllers adapted to perform data transfer protocols with corresponding peer controllers of a data generating device and a data storage device, respectively, on command from the main controller. The cryptographic device further comprises a cipher engine programmed to transparently encrypt and decrypt data streams flowing between the data generating device and data storage device on command from the main controller. The cryptographic device does not utilize system resources associated with the data generating and storage devices during operation.
Owner:ENOVA TECH
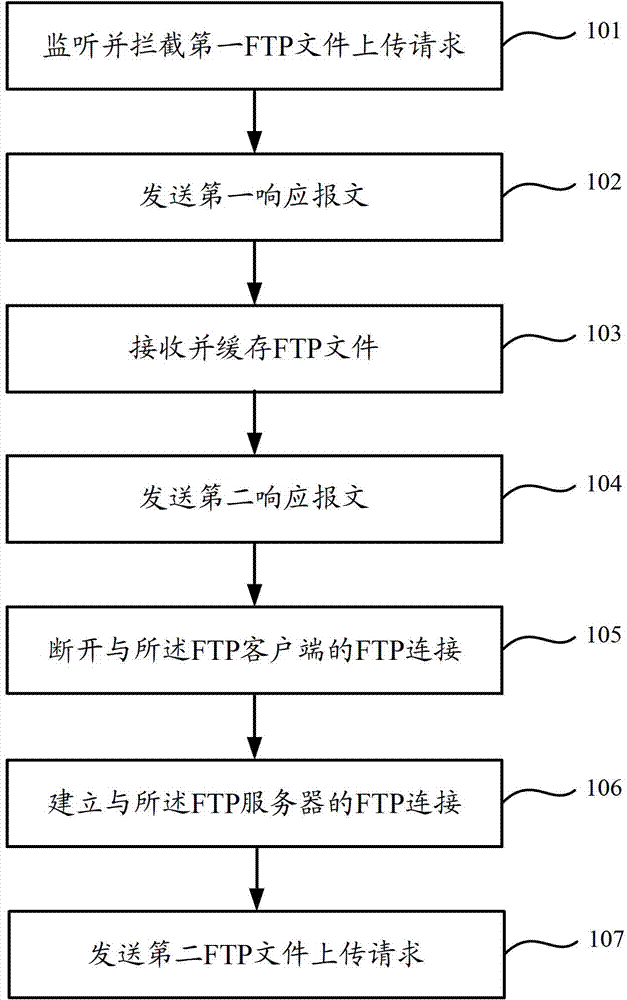
FTP (File Transfer Protocol) file uploading, downloading method and device
ActiveCN102833337AImprove experienceIncrease upload speedTransmissionClient-sideFile Transfer Protocol
The embodiment of the invention provides an FTP (File Transfer Protocol) file uploading, downloading method and device. The FTP file uploading method comprises the following steps of: responding, by client side accelerating equipment which pretends to be an FTP server, to a first FTP file uploading request of an FTP client side monitored by the client side accelerating equipment; receiving and caching, by the client side accelerating equipment, the FTP file uploaded by the FTP client side; and pretending to be the FTP server, and informing the FTP client side of the reception of the FTP file after the FTP file is received by the client side, and uploading the FTP file to the FTP server by the client side accelerating equipment. Thus, uploading operation of the FTP client side is finished in a local area network environment, and the FTP file uploading speed is increased. Meanwhile, the client side accelerating equipment is indicated to download the FTP file from other client side accelerating equipment for uploading the FTP file to be downloaded in a downloading reorientation mode. Thus, the FTP file being uploaded can also be downloaded in real time, the FTP file downloading speed is increased, and the connection stress of FTP file downloading on the FTP server can be reduced.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Data scanning network security technique
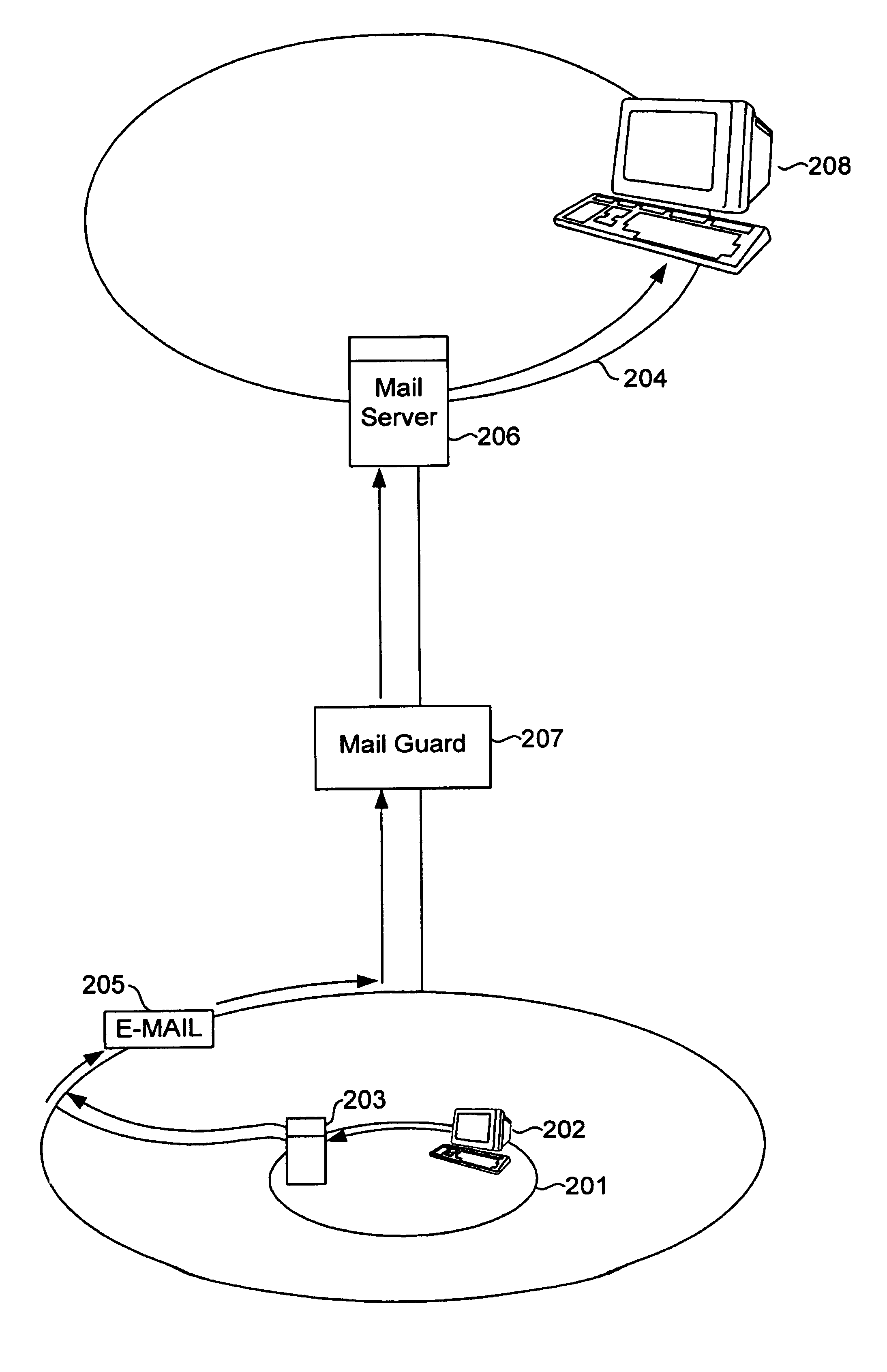
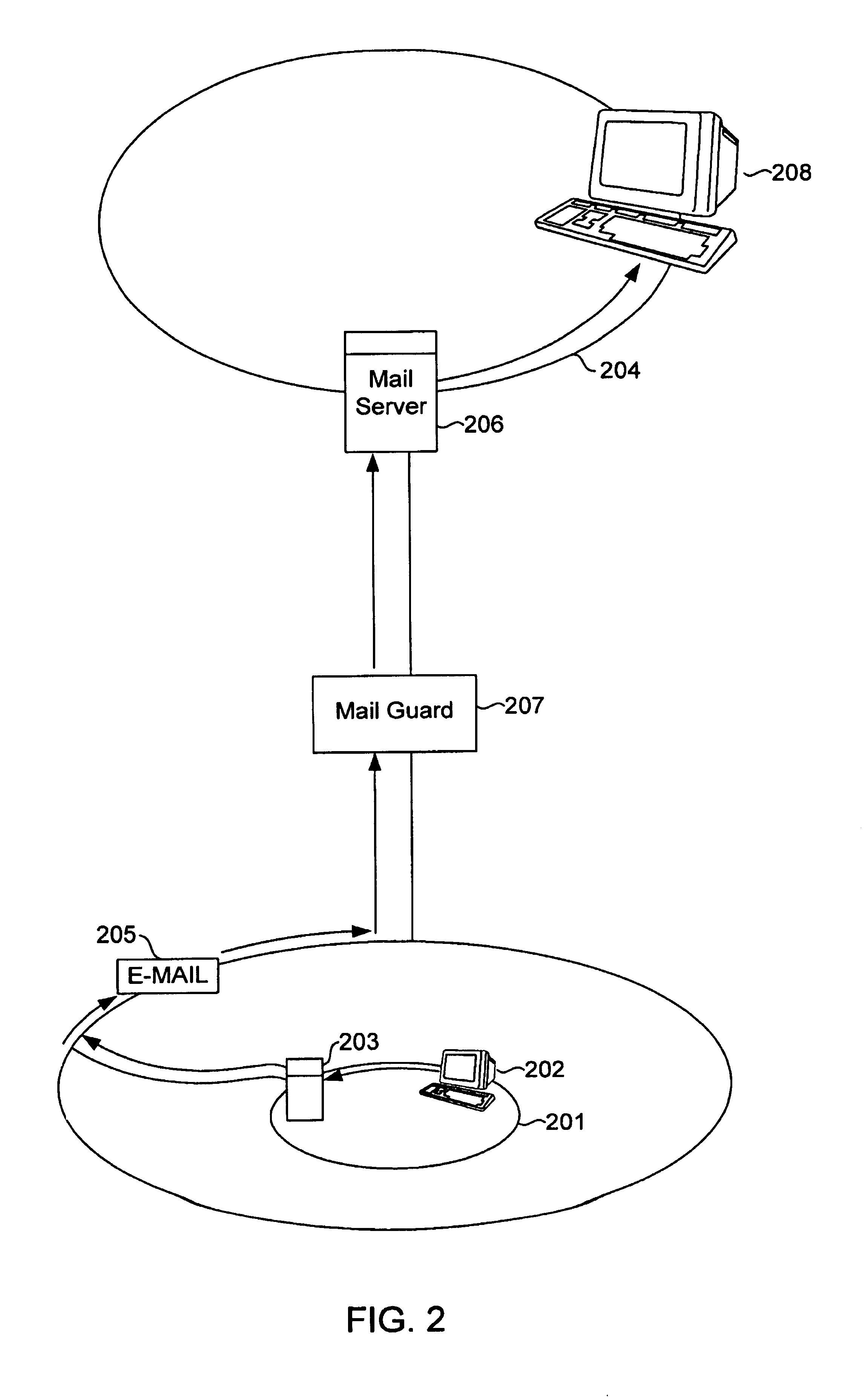
A system and method are disclosed for providing enhanced computer network security by scanning data, specifically electronic mail messages, sent to the network before the data is received and transmitted by the network's mail server. An e-mail message is received by a computer network configured to receive data and is checked as the data is received and before it is transmitted to a node on the computer network. The method includes determining whether an external source is attempting to establish a mail connection with the computer network configured to include a data scanning device that recognizes one or more data transfer protocols. Once the data is received the data scanning device begins evaluating the data by first determining whether the data is formatted according to one of the recognized protocols. The data scanning device begins scanning the data for acceptable content and format according to a rule set established by one of the recognized protocols. This is done at the same time as the data is received by the data scanning device. It is then determined whether the data should be sent to its destination on the computer network. If necessary, the data is translated before being passed to its destination on the computer network.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com