Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
297 results about "Physical computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
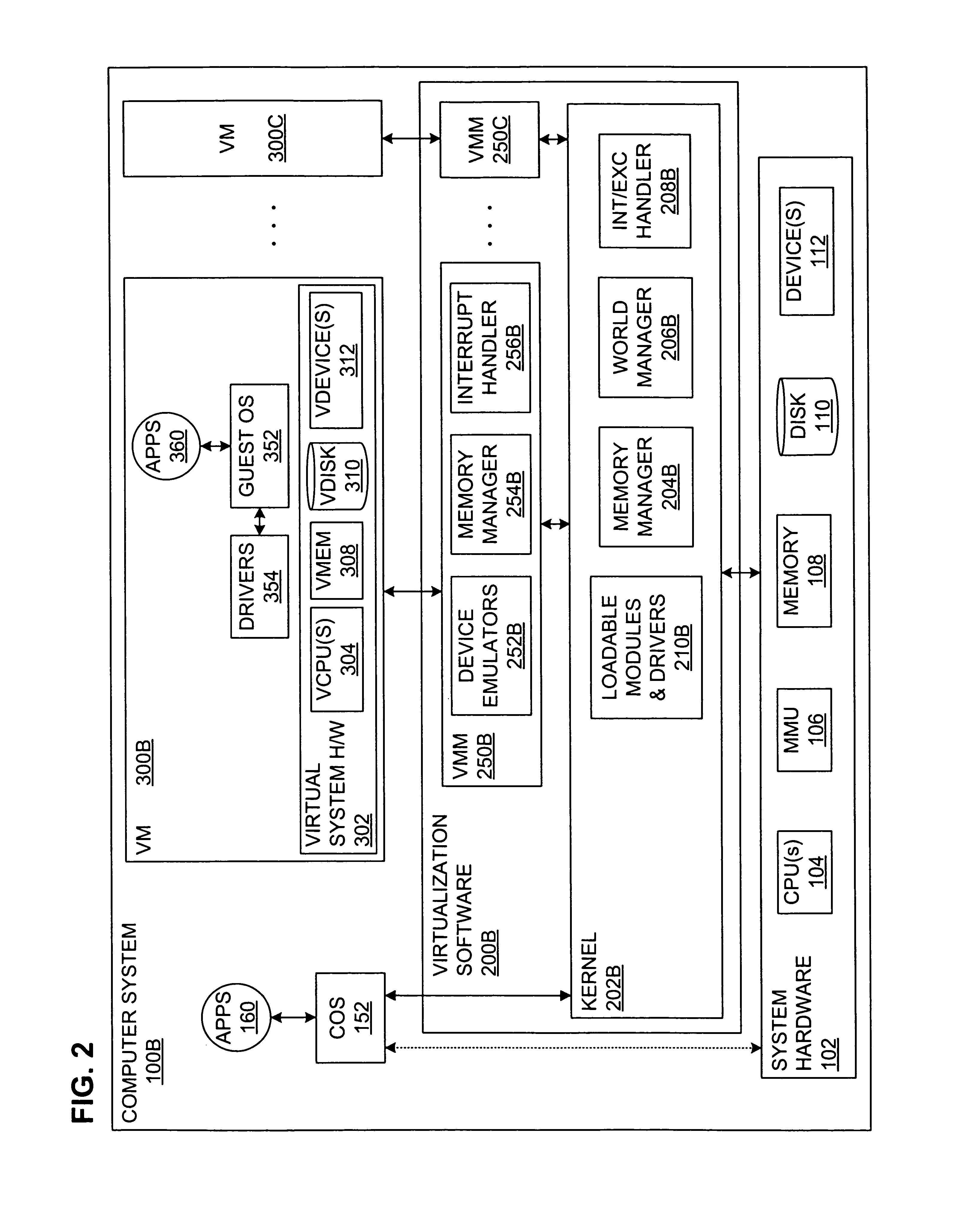
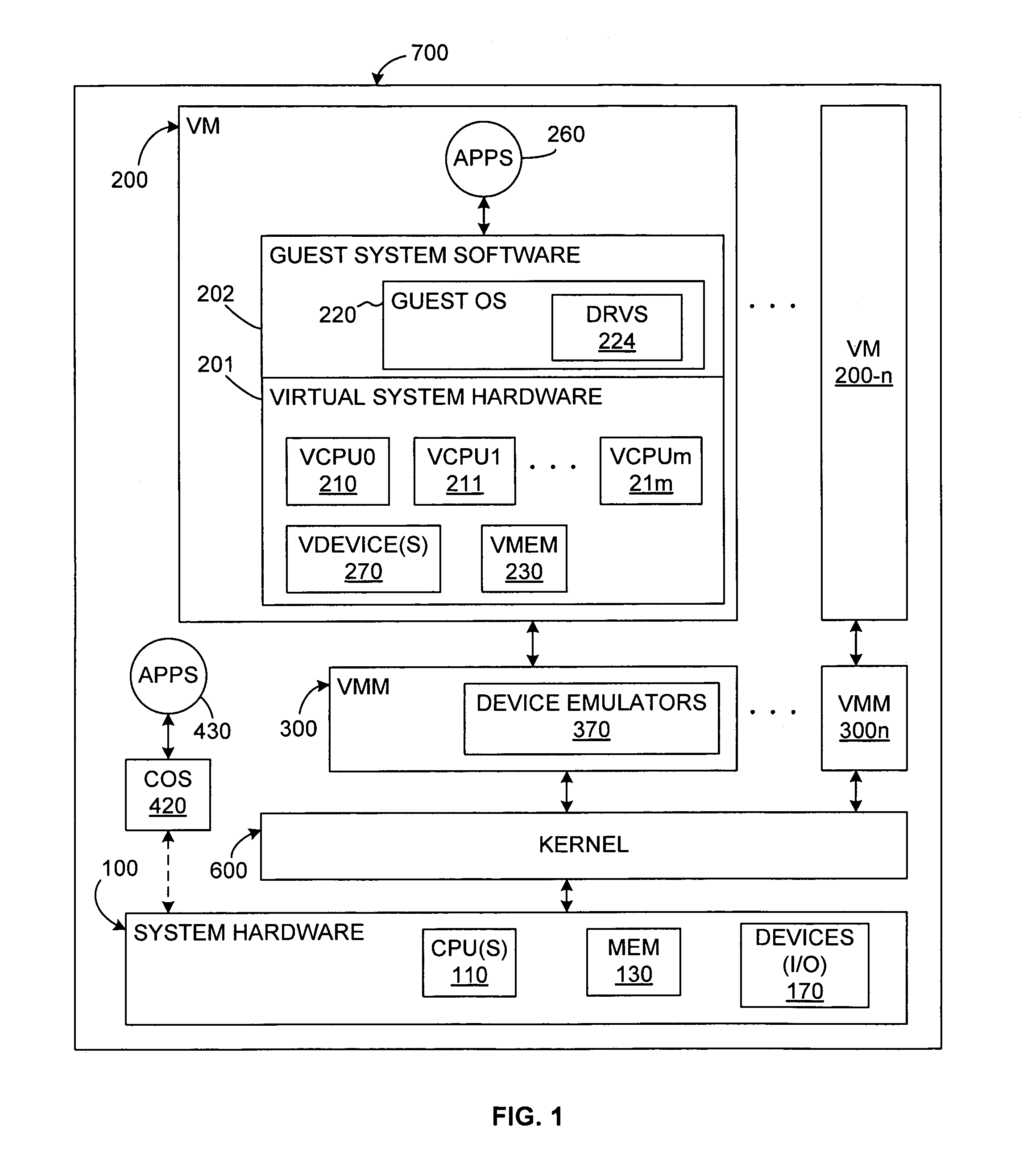
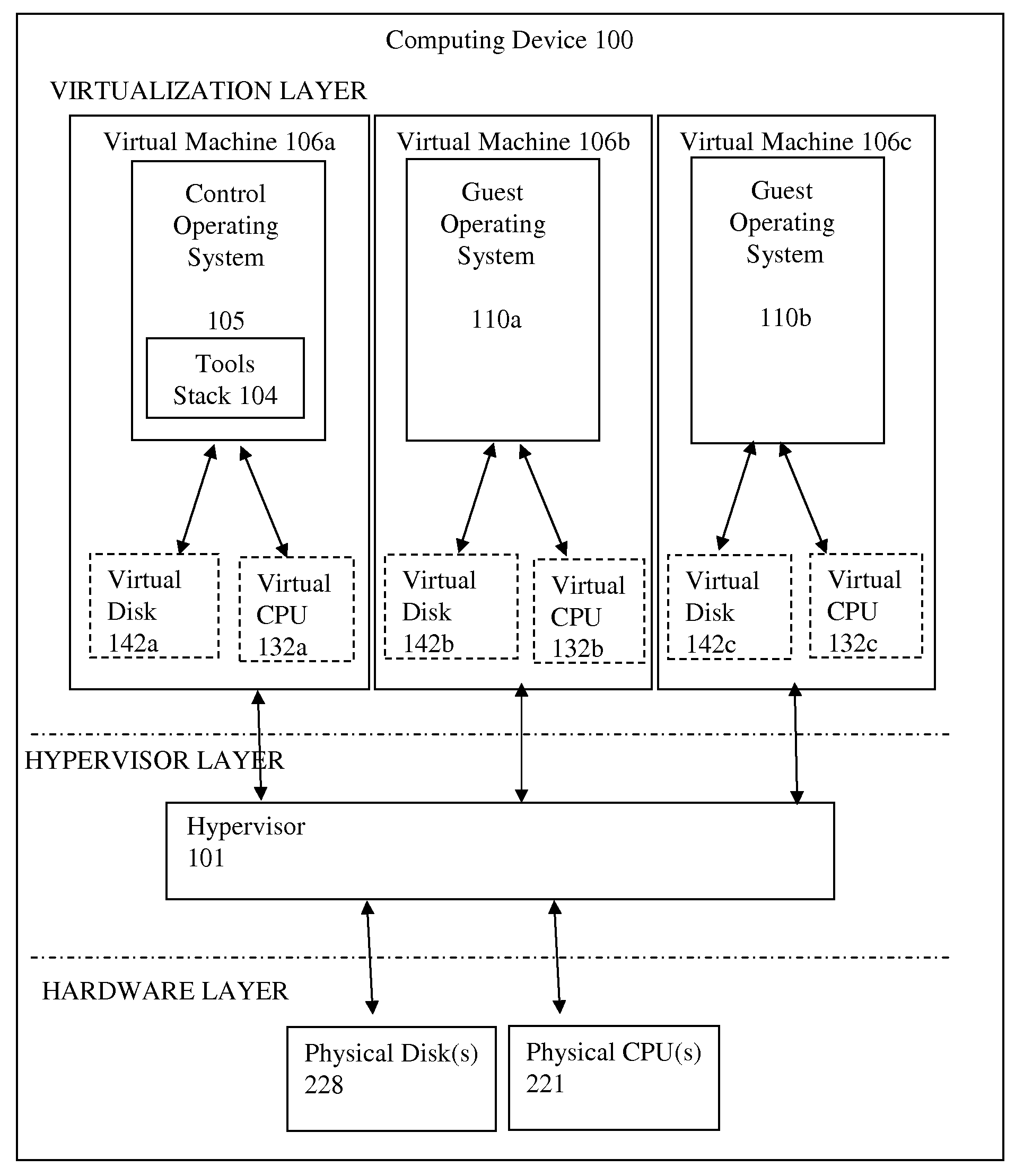
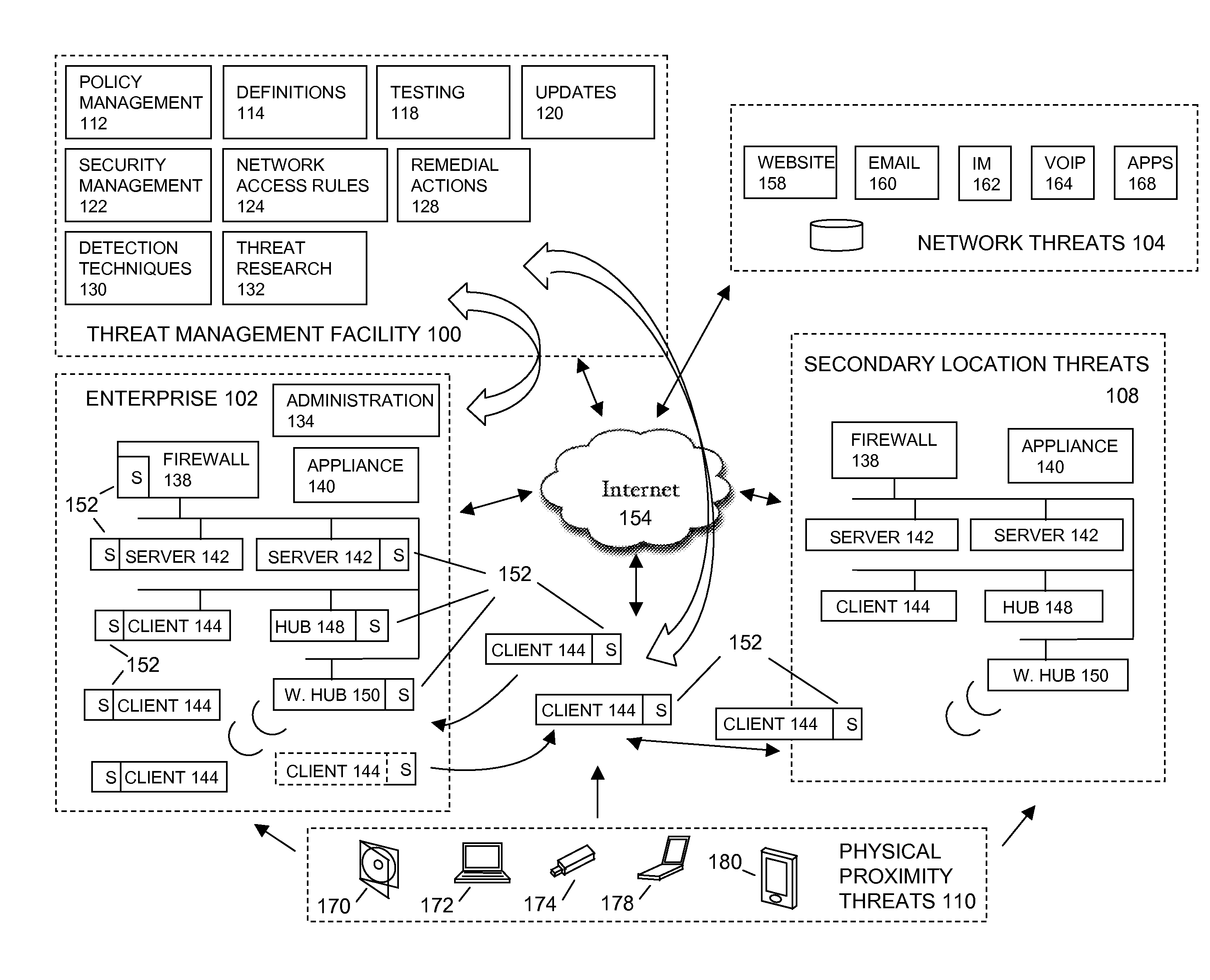
Physical computing means building interactive physical systems by the use of software and hardware that can sense and respond to the analog world. While this definition is broad enough to encompass systems such as smart automotive traffic control systems or factory automation processes, it is not commonly used to describe them. In a broader sense, physical computing is a creative framework for understanding human beings' relationship to the digital world. In practical use, the term most often describes handmade art, design or DIY hobby projects that use sensors and microcontrollers to translate analog input to a software system, and/or control electro-mechanical devices such as motors, servos, lighting or other hardware.
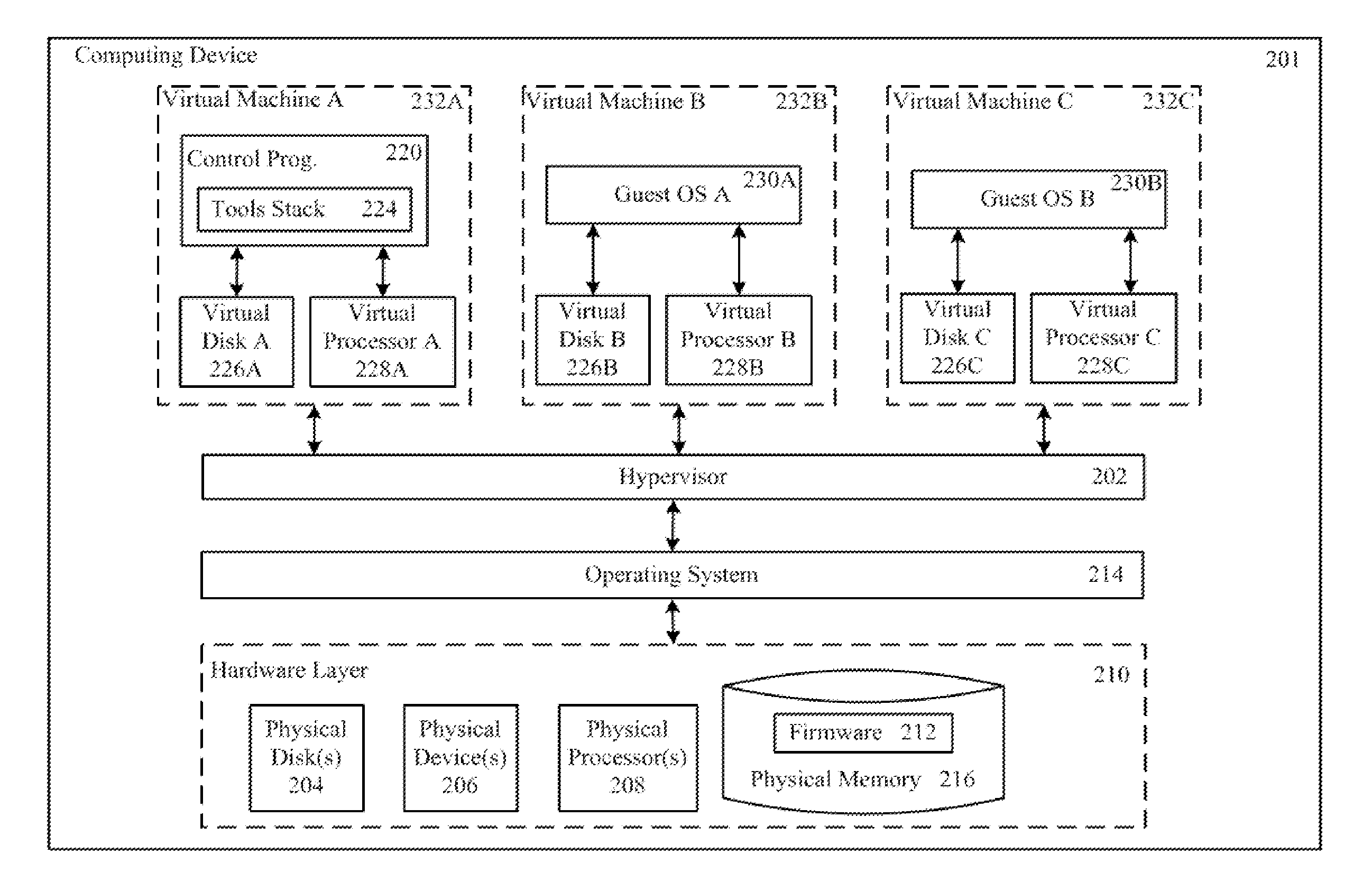
Virtual network in server farm
ActiveUS7802000B1Telephonic communicationUnauthorized memory use protectionTraffic capacityVirtual switch
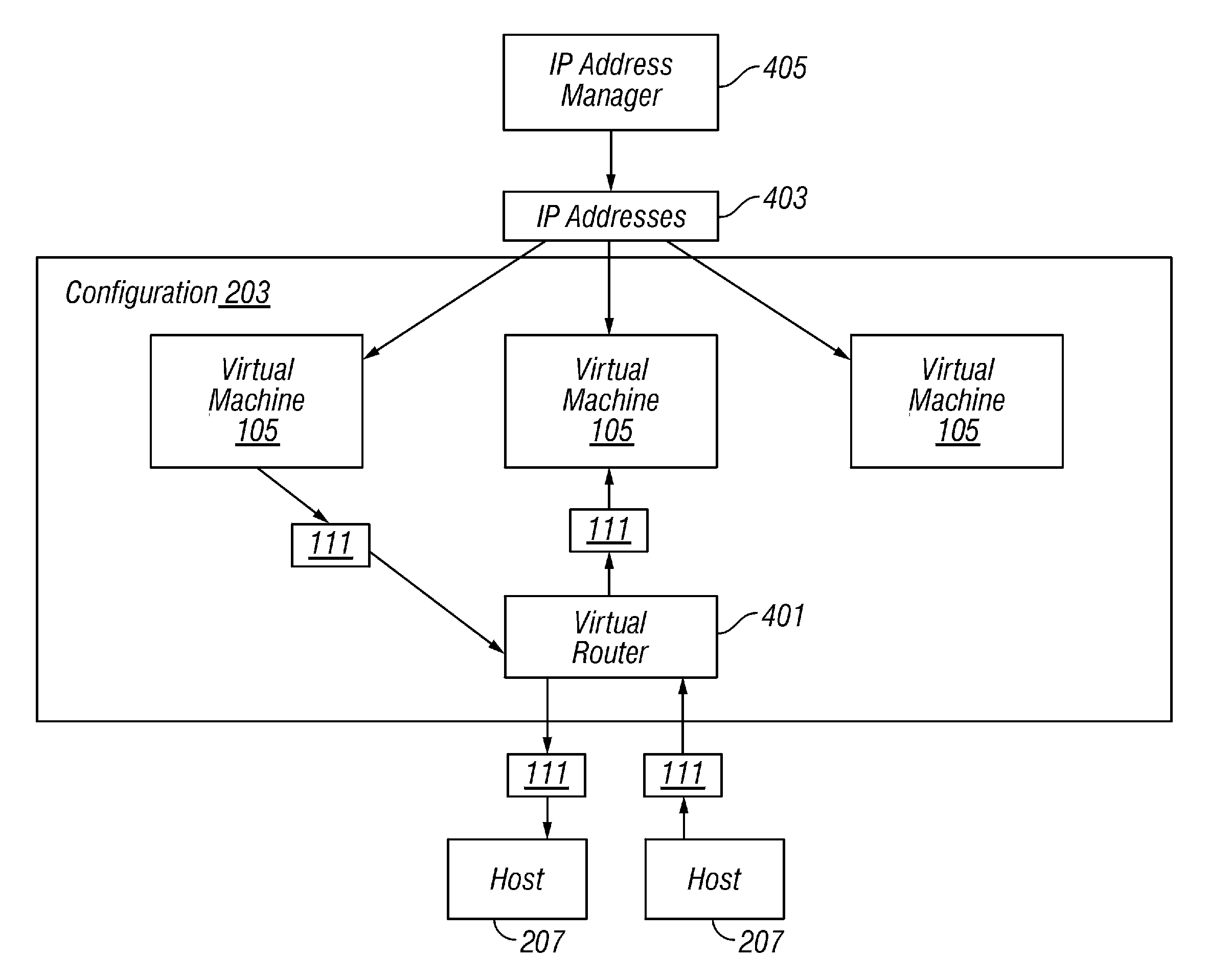
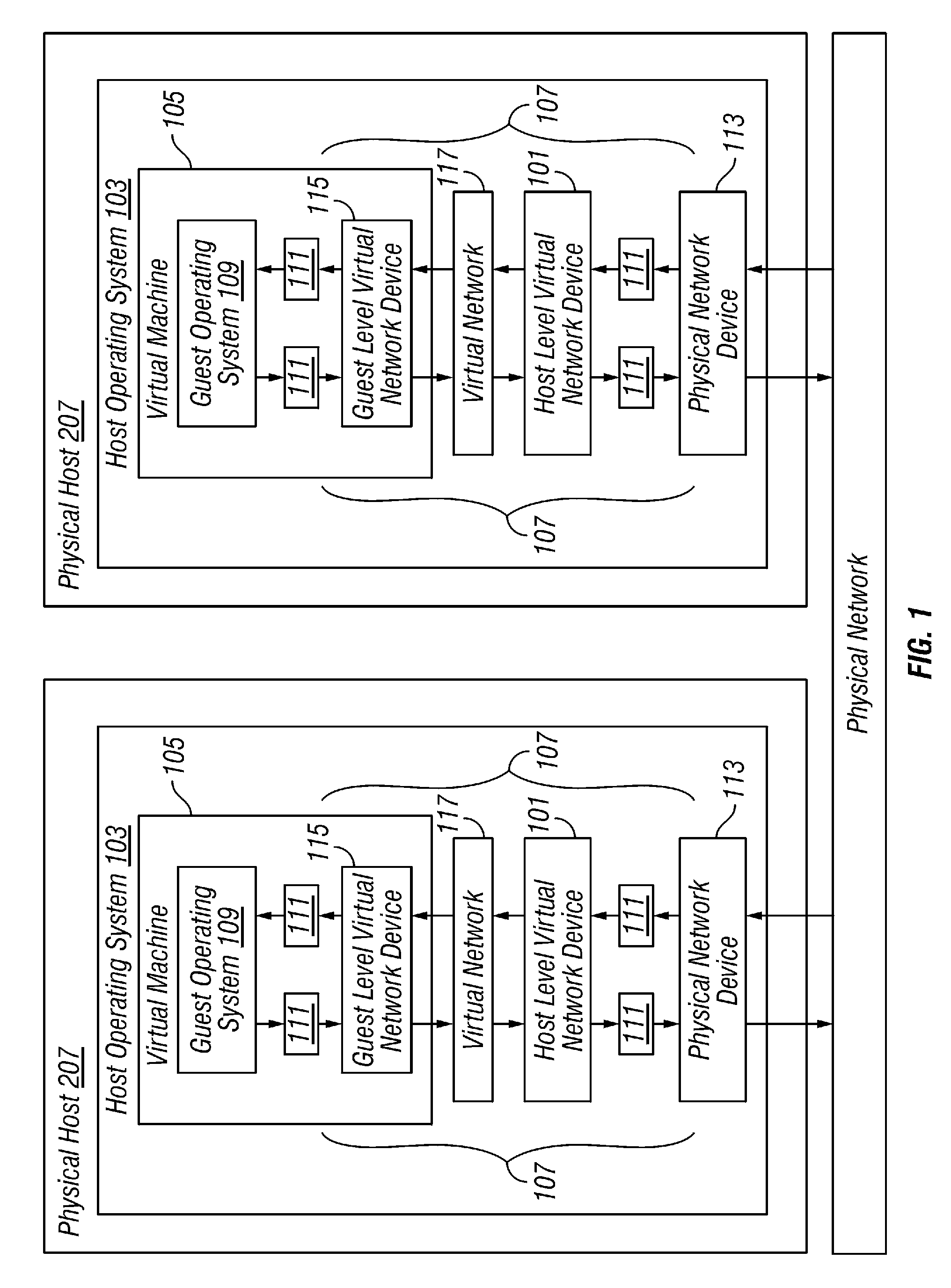
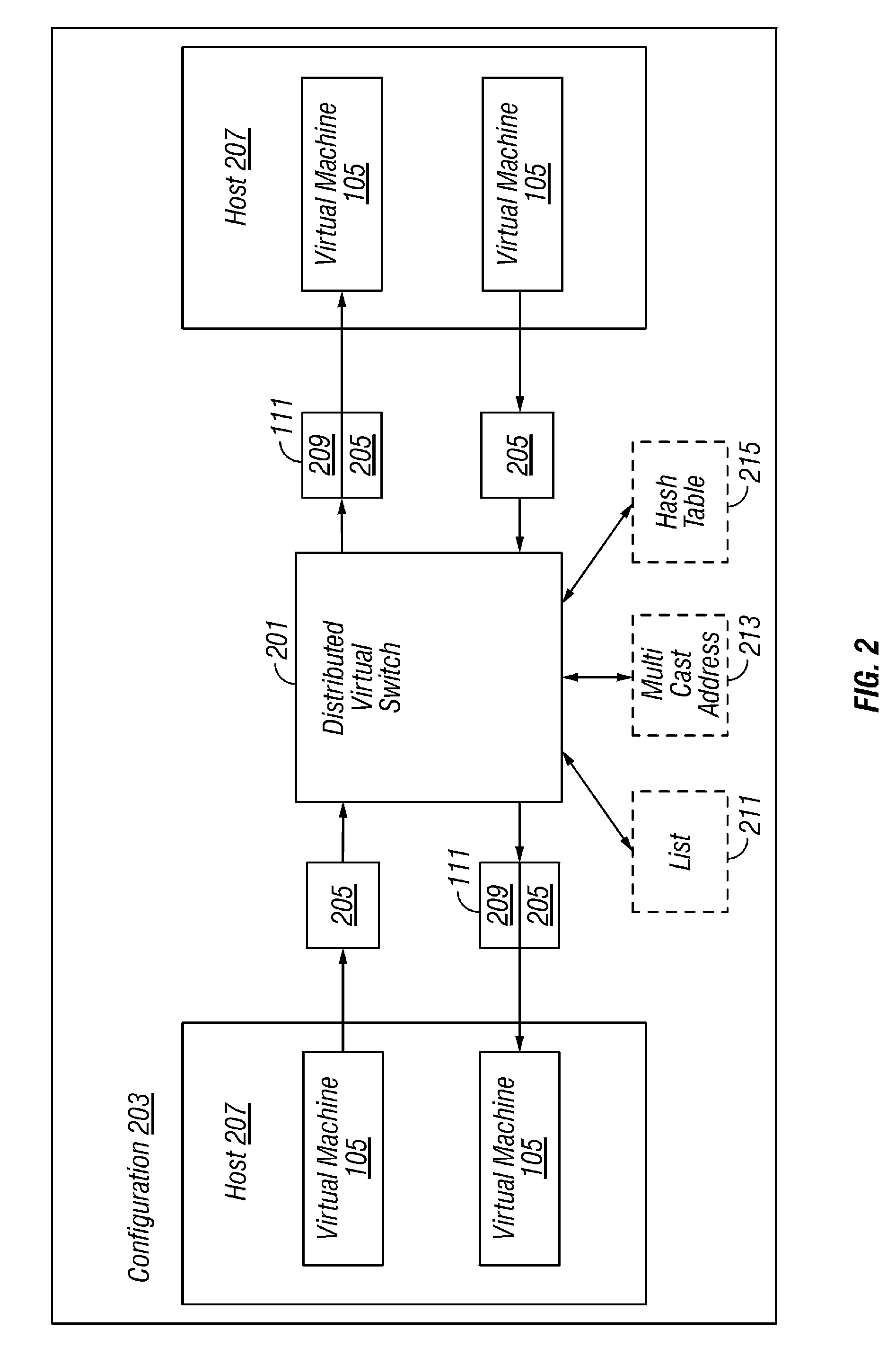
A plurality of virtual machines execute on a network of physical computers. The virtual machines are deployed in fenced and unfenced configurations across multiple physical computers. Host level virtual network devices execute on the physical computers, and intercept the virtual machine network traffic. For each fenced configuration of virtual machines, a distributed virtual switch transmits network traffic between the virtual machines deployed in that fenced configuration, and a virtual router routes network traffic between virtual machines deployed in that fenced configuration and external components.
Owner:VMWARE INC
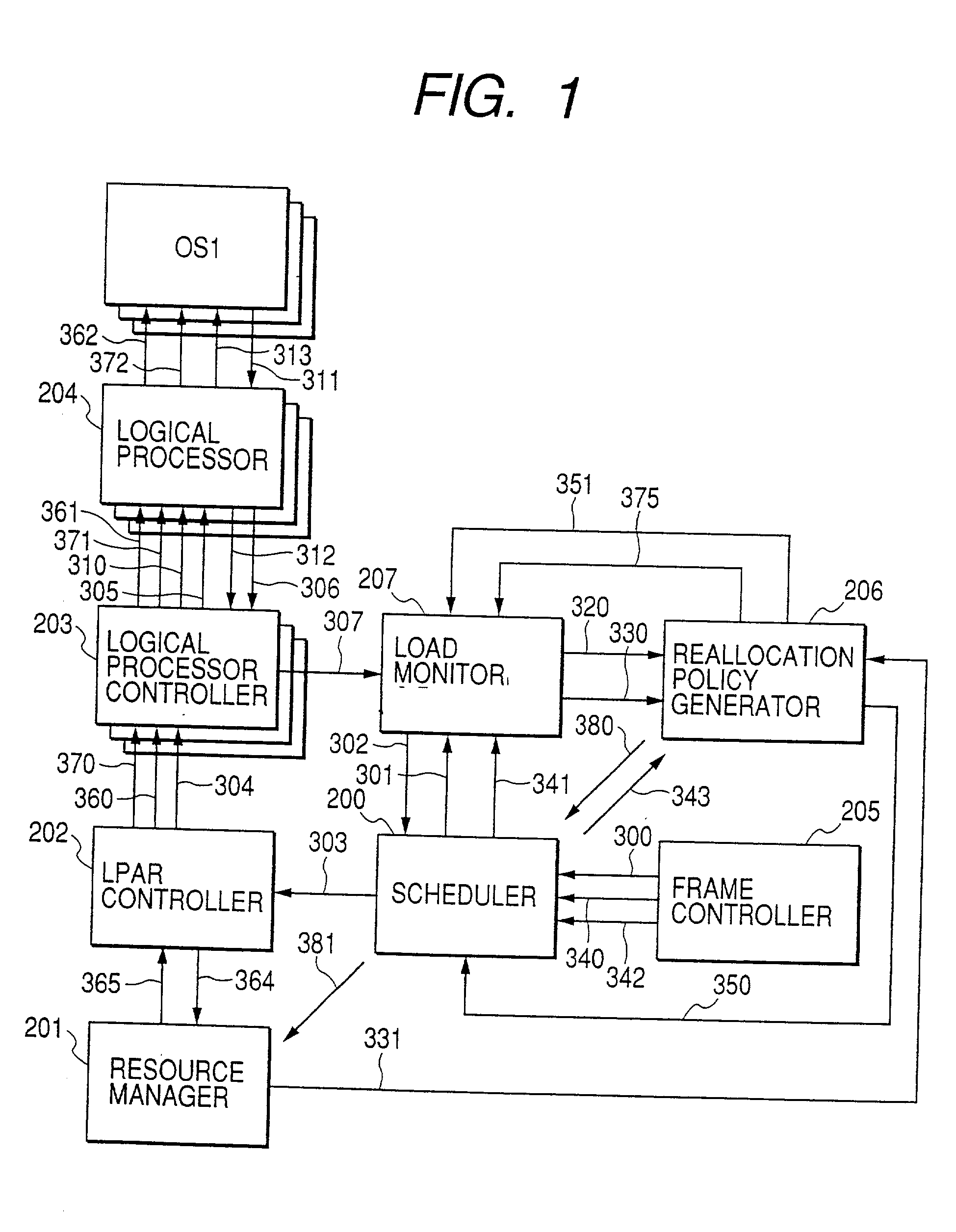
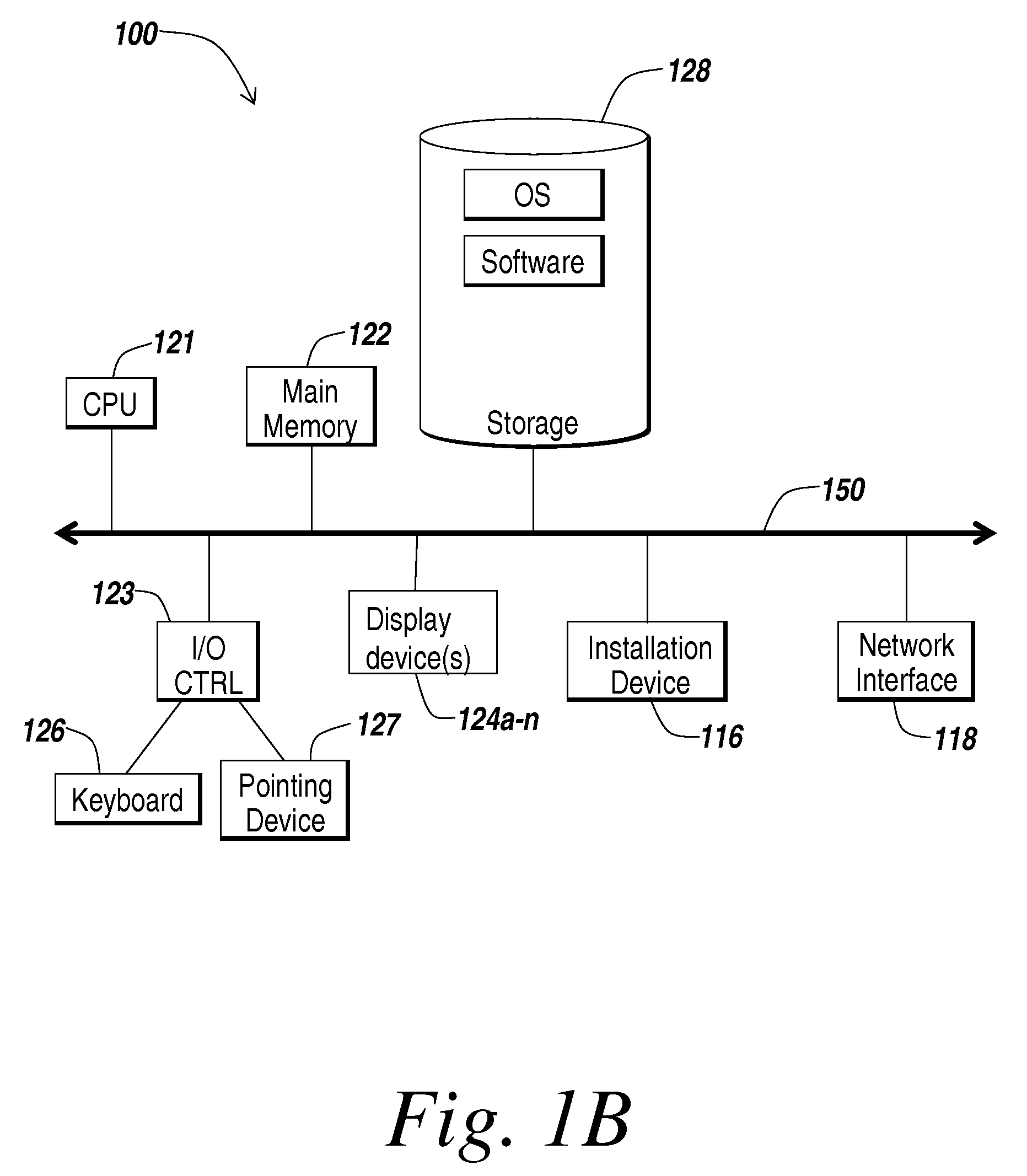
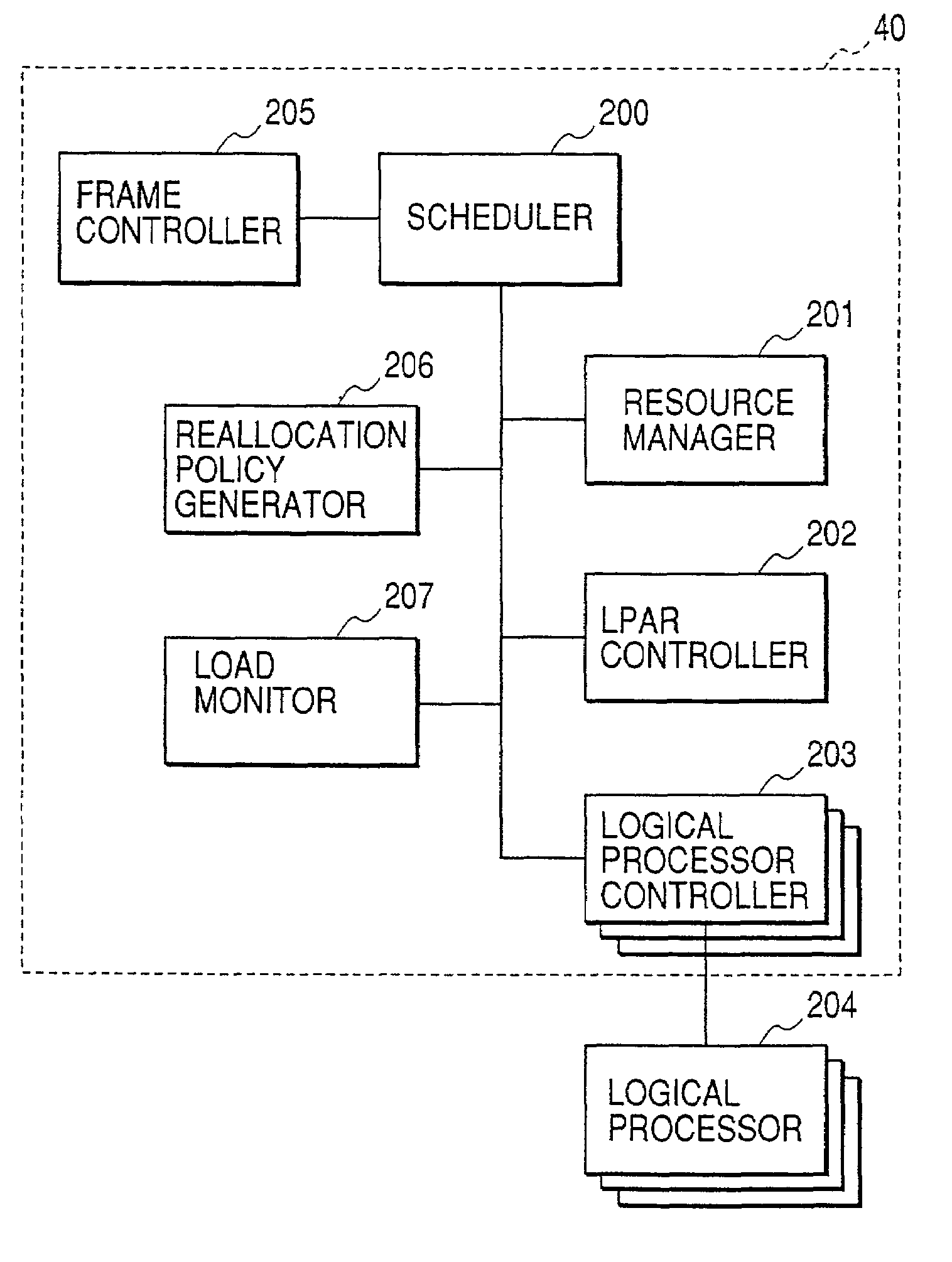
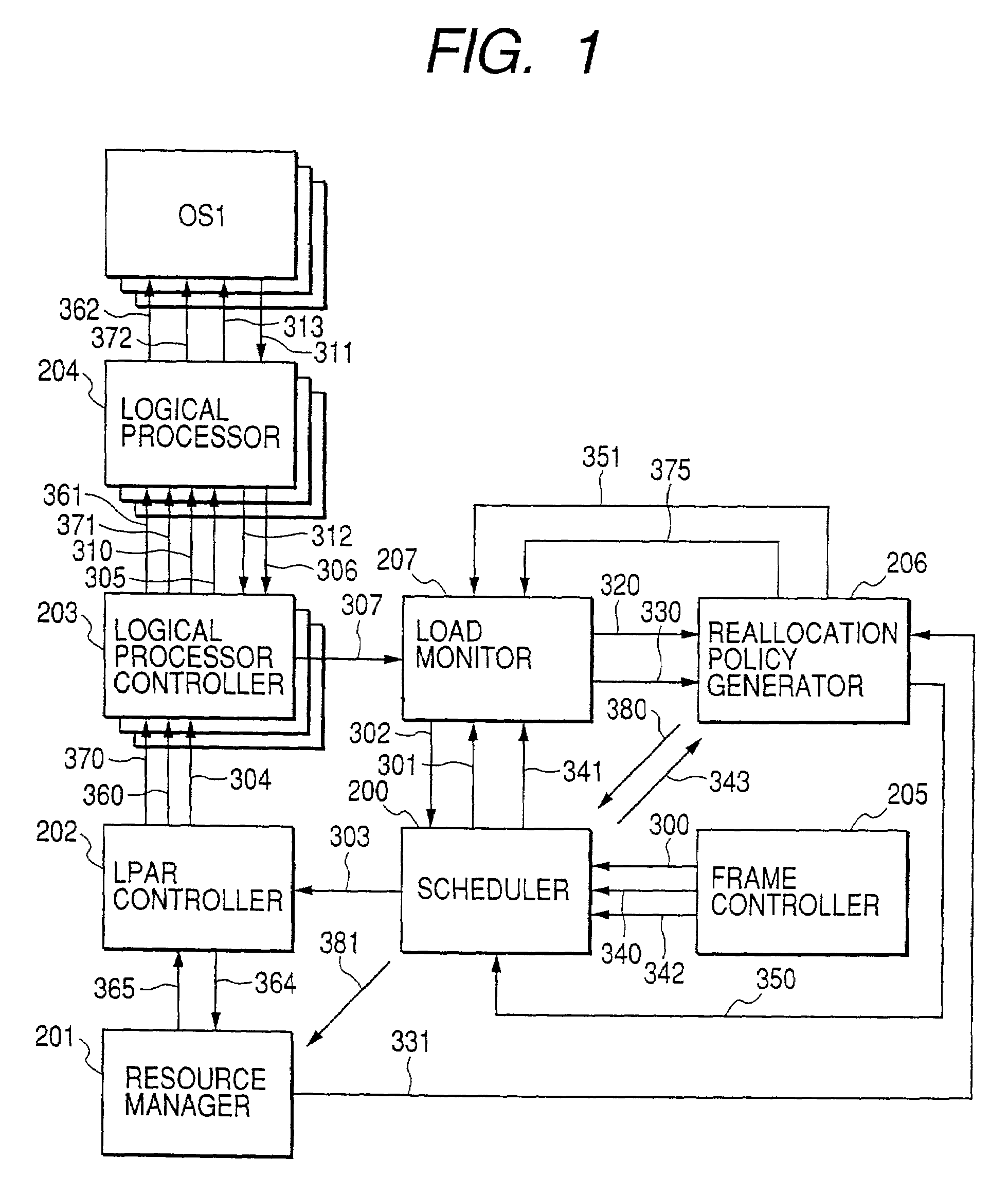
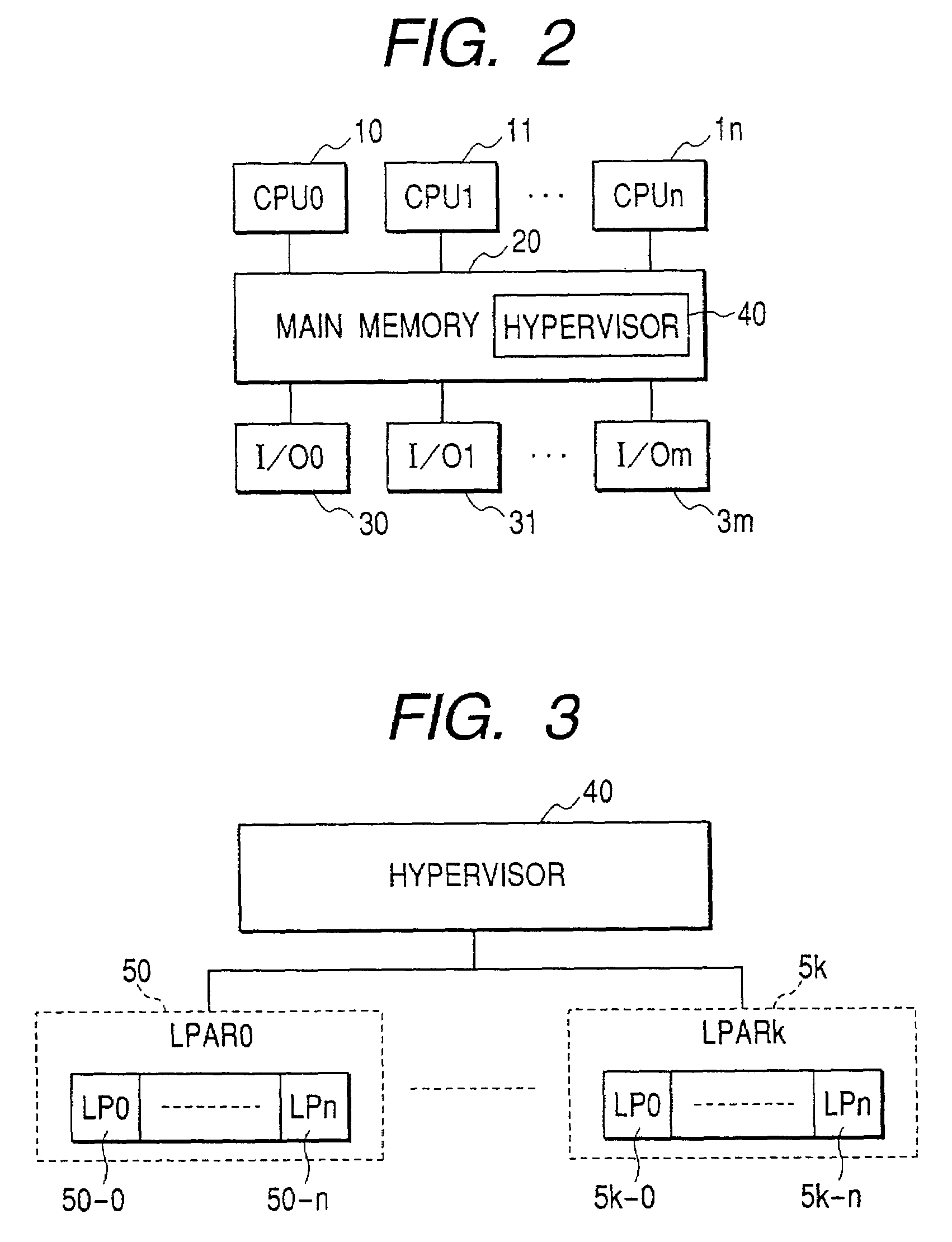
Virtual computer system with dynamic resource reallocation
InactiveUS20020087611A1Resource allocationError detection/correctionDynamic resourceVirtual computing
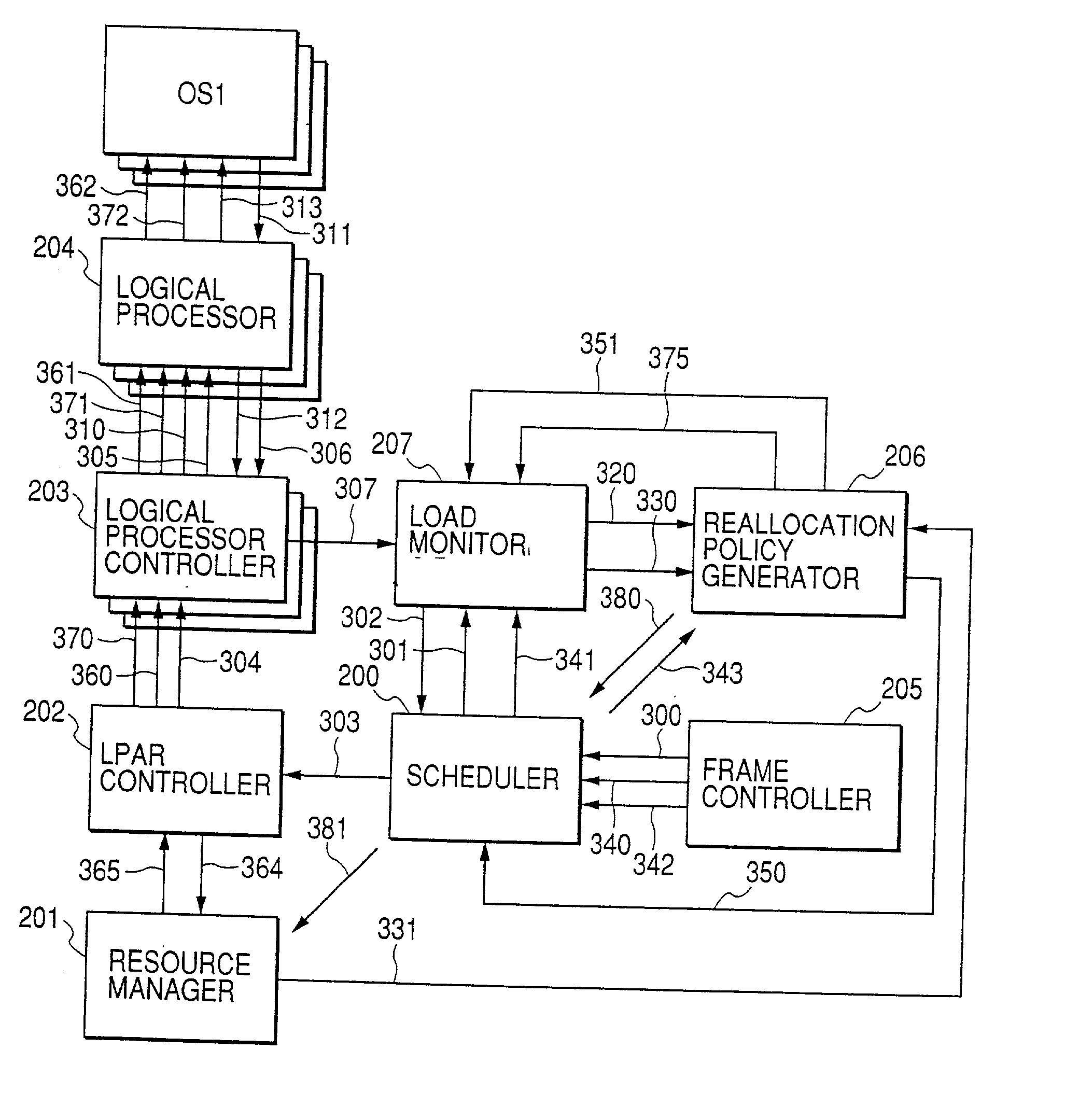
A virtual computer system including a reallocation means, in which a plurality of LPAR are operated by logically dividing physical resources composing a physical computer exclusively or in time dividing manner so as to dynamically change reallocation of physical resources among each of LPARs. Based on load conditions measured by an application or an OS of each LPAR, physical resource allocation to each LPAR is determined, thereby conducting reallocation of LPAR.
Owner:HITACHI LTD
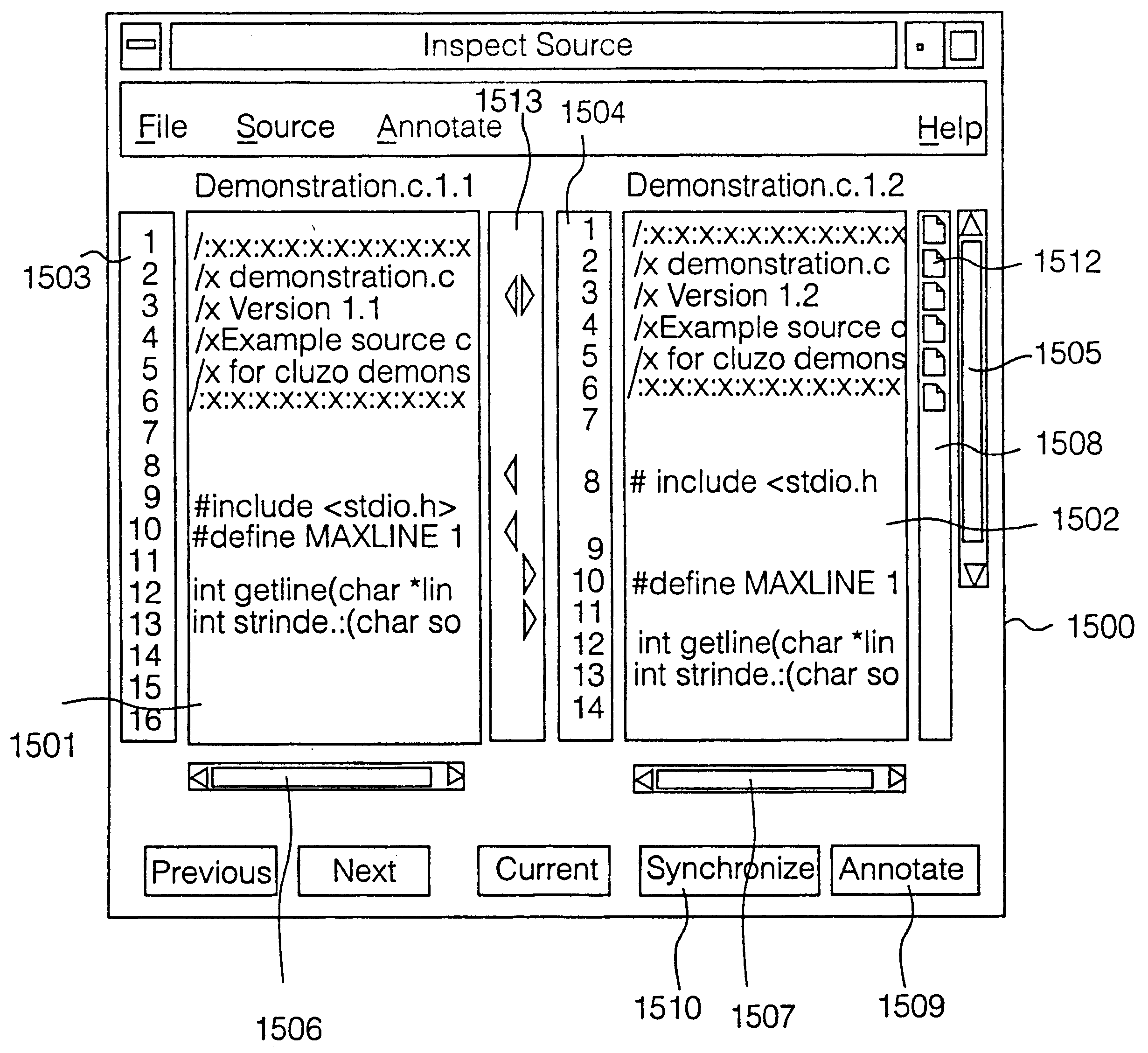
Interactive on line code inspection process and tool
InactiveUS6275223B1Data processing applicationsSpecific program execution arrangementsOnline codesDisplay device
A code inspection tool comprises a plurality of physical computing resources connected by a network facility, eg an LAN, intranet or internet, and a voice conferencing communications facility. The code inspection tool interfaces with a known configuration management system to load a quantity of original source code. A group of developers use a plurality of graphical user interfaces to inspect the code. All graphical user interfaces log into display views generated on a main graphical user interface, which is operated by a human controller of a code inspection session. The code inspection tool comprises means for allowing developers to compile annotation data and forward the annotation data from their respective graphical user interfaces to a centralized data store. Internal algorithms of the code inspection tool compile markers relating the annotation data files to individual lines of source code. During a code inspection session, all developers view a same display, which sets out original source code, side by side with new source code on a line by line basis, matching the line numbers of the original source code with those of the new source code. Changes to the original source code and new source code are visually identified by automatic generation of icons next to the appropriate source code lines on the display. Annotations to the source code lines are indicated by further icons next to the appropriate lines. The tool automatically generates data describing statistics of a code inspection process, for example number of lines inspected, during of a code inspection session, proportion of original and new code lines inspected. Code inspection reports may be generated in a variety of formats, eg plain text or HTML, and automatically distributed to individual developers over the networked facility.
Owner:RPX CLEARINGHOUSE
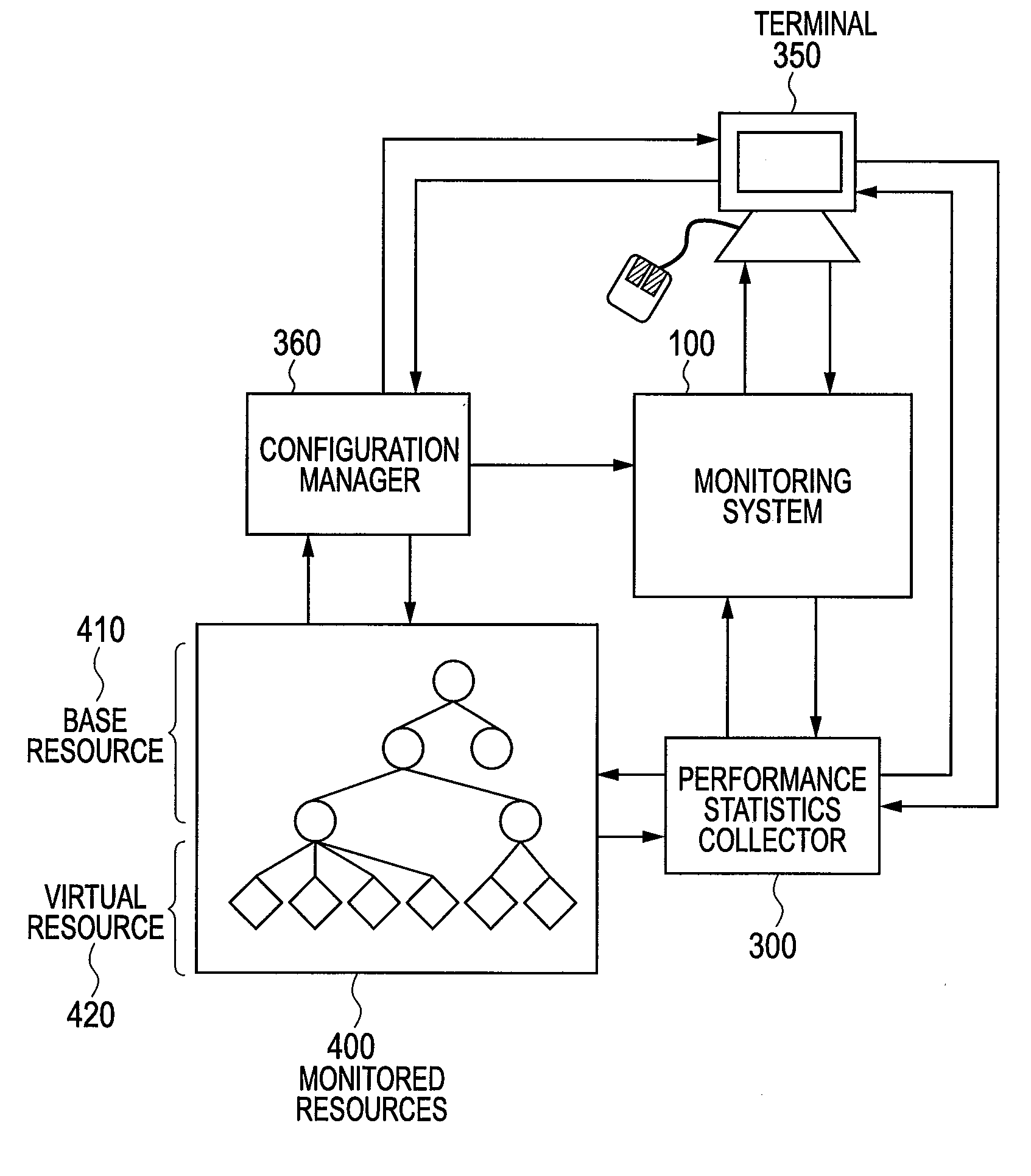
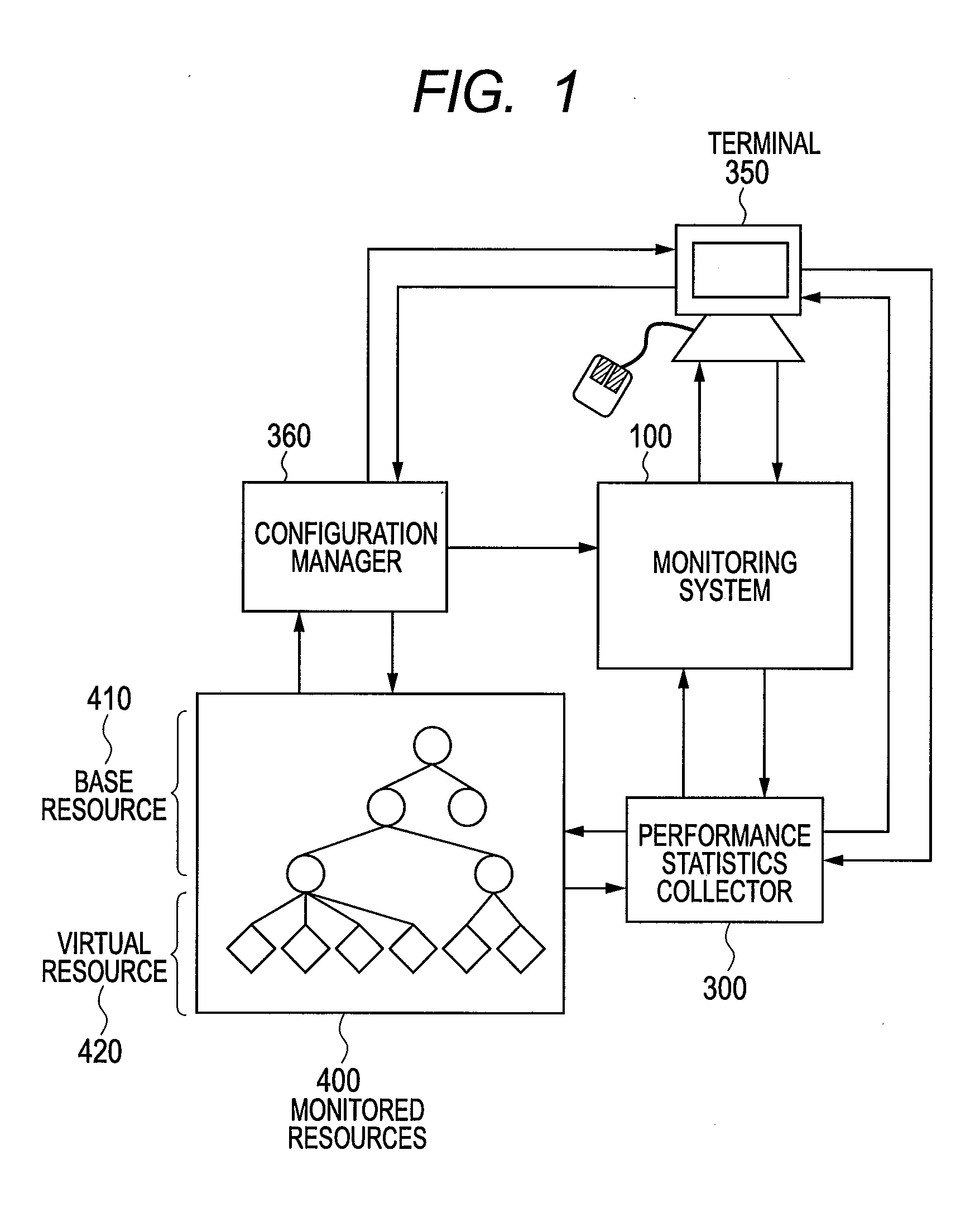
Monitoring system of computer and monitoring method
InactiveUS20120117226A1Low costEasy to analyzeDigital computer detailsProgram controlVirtualizationComputer resources
There is provided a monitoring system capable of representing relationships of computer resources that virtual servers use in a tree structure and aggregating the performance statistics of the virtual resources sharing physical resources. The monitoring system has: a virtualization module that makes virtual computers operate; and a monitoring module for monitoring the physical computers and components of the virtual computers. The monitoring module designates the physical computer and the components of the virtualizing module as base resources, manages the components of the virtual computers as virtual resources, generates a platform tree by extracting a tree structure from the virtual resources and the components of the base resources for predetermined platforms, generates a service provision tree by extracting a tree structure having the base or virtual resources as starting points, and establishes a reference relationship for the components contained in the platform tree and also contained in the service provision tree.
Owner:HITACHI LTD
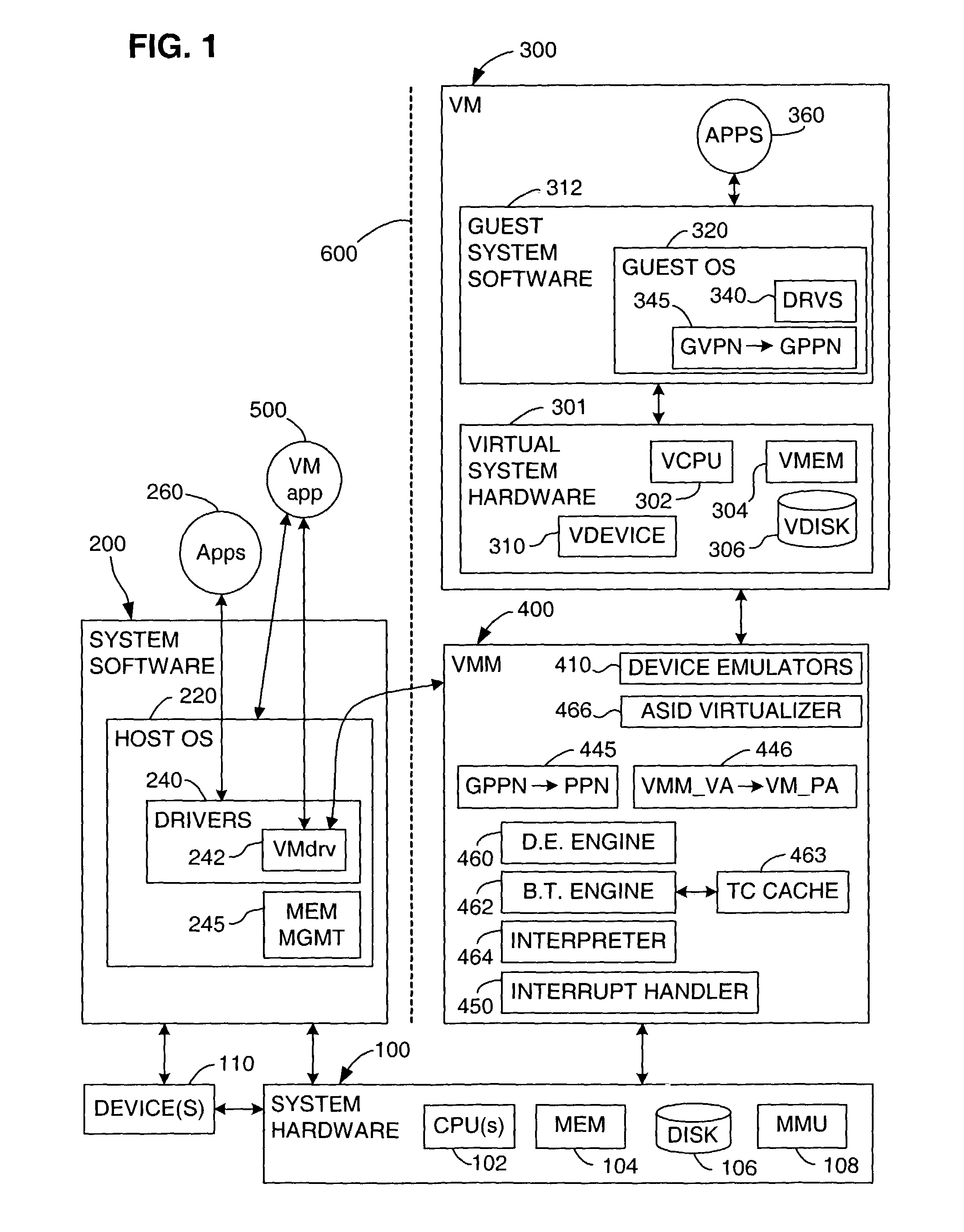
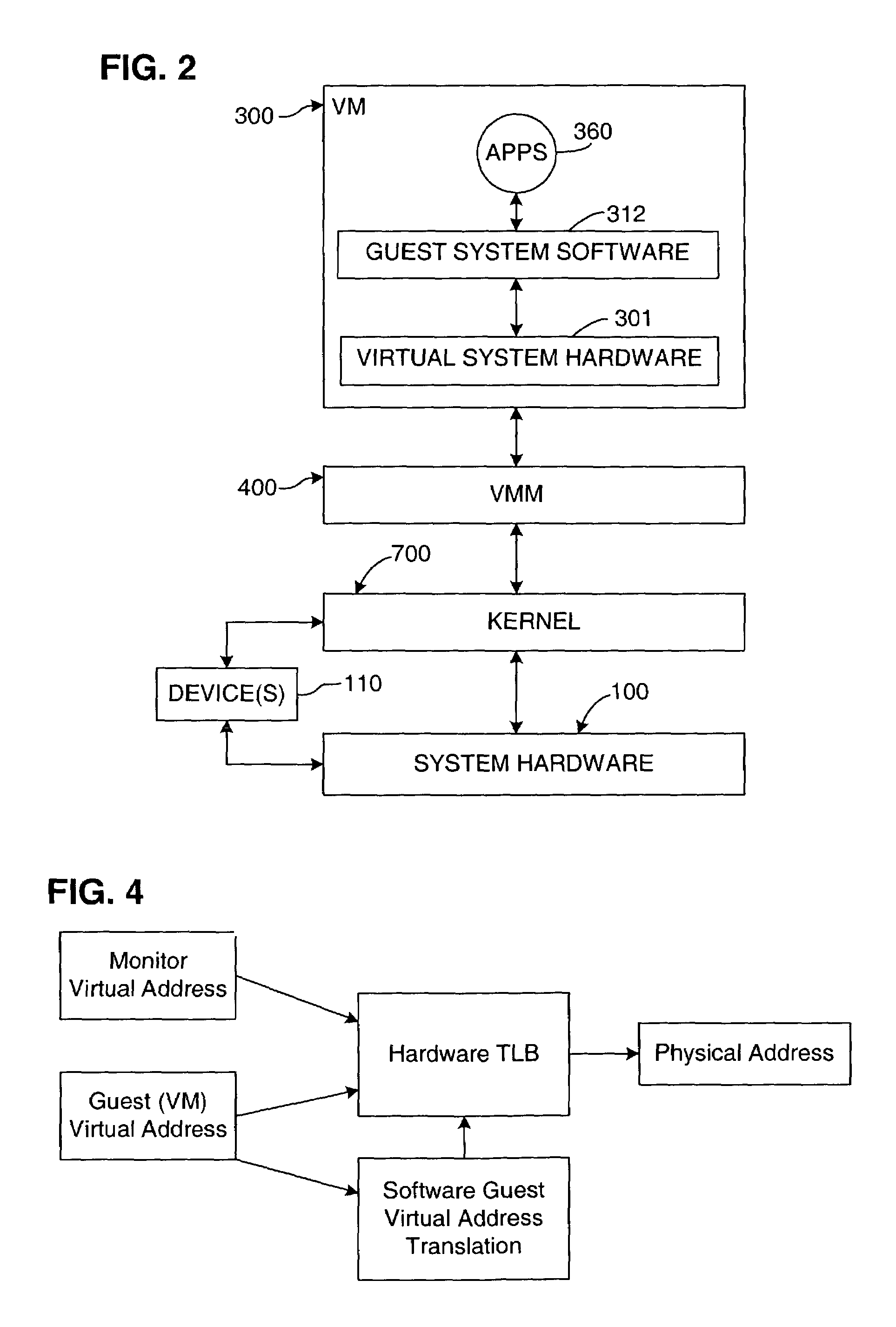
Virtualization system for computers that use address space indentifiers
A virtual computer system including multiple virtual machines (VMs) is implemented in a physical computer system that uses address space identifiers (ASIDs). Each VM includes a virtual translation look-aside buffer (TLB), in which guest software, executing on the VM, may insert address translations, with each translation including an ASID. For each ASID used by guest software, a virtual machine monitor (VMM), or other software unit, assigns a unique shadow ASID for use in corresponding address translations in a hardware TLB. If a unique shadow ASID is not available for a newly used guest ASID, the VMM reassigns a shadow ASID from a prior guest ASID to the new guest ASID, purging any entries in the hardware TLB corresponding to the prior guest ASID. Assigning unique shadow ASIDs limits the need for TLB purges upon switching between the multiple VMs, reducing the number of TLB miss faults, and consequently improving overall processing efficiency.
Owner:VMWARE INC
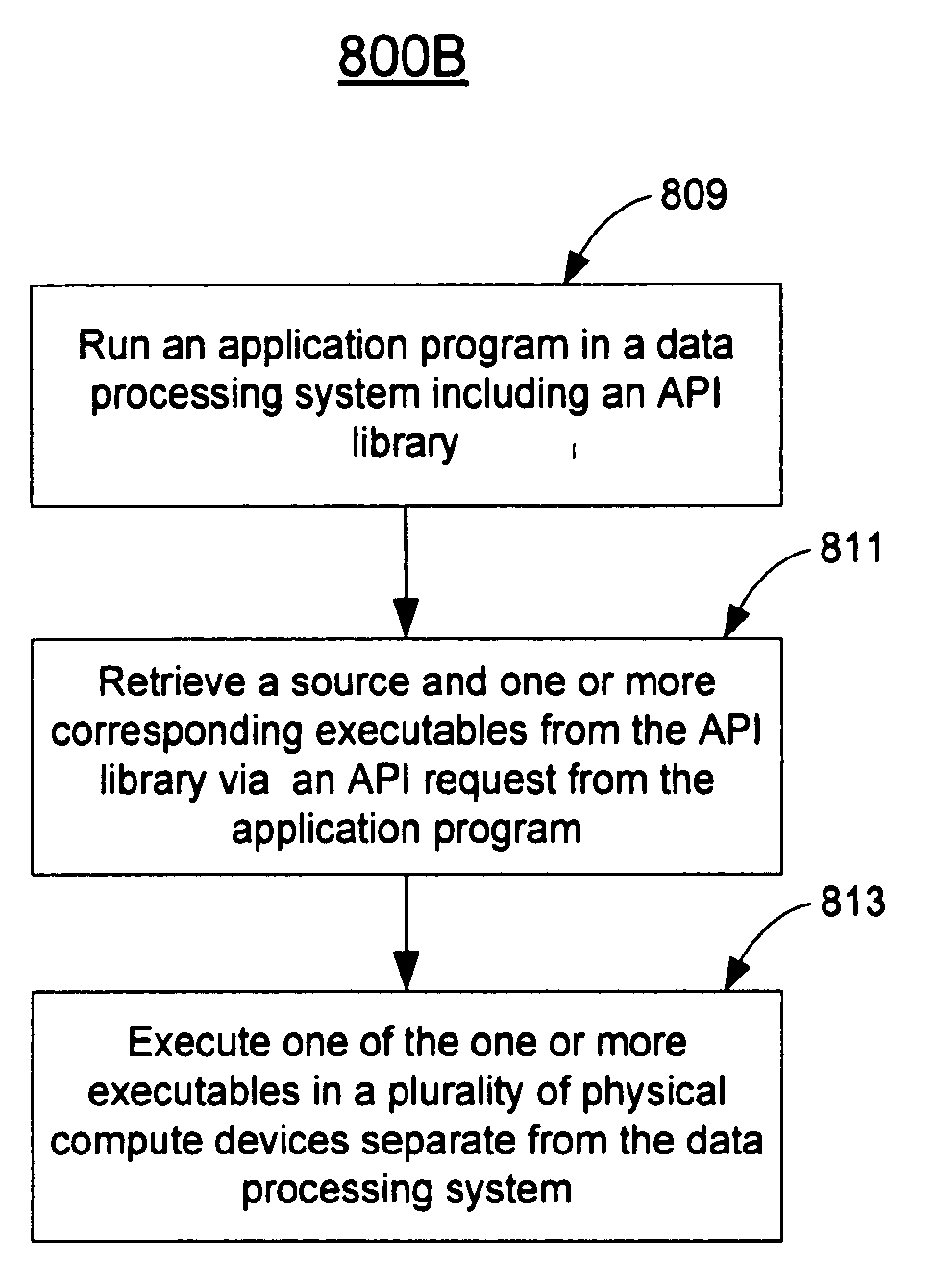
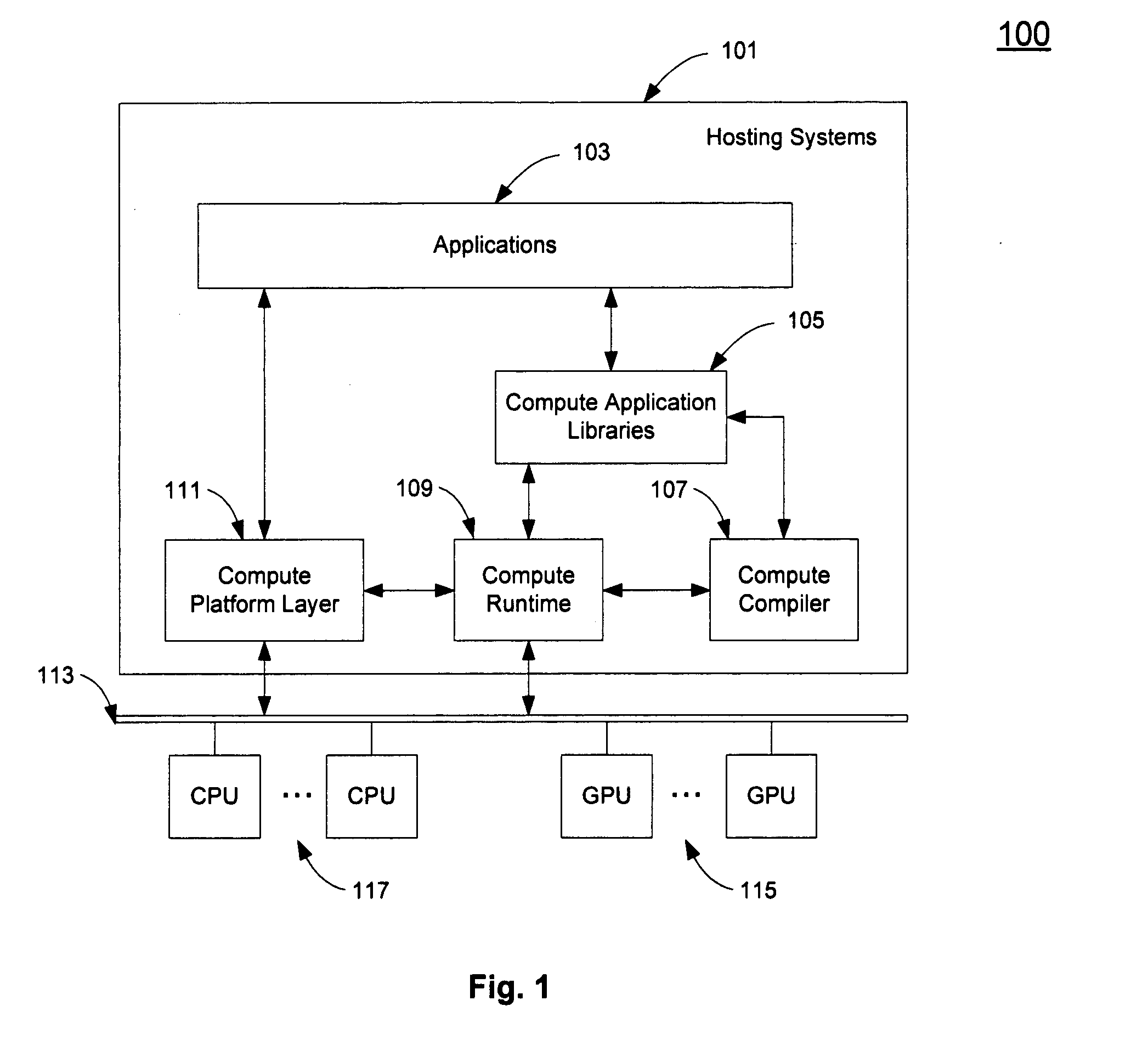
Parallel runtime execution on multiple processors
ActiveUS20080276262A1Multiprogramming arrangementsProgram loading/initiatingGraphicsParallel computing
A method and an apparatus that schedule a plurality of executables in a schedule queue for execution in one or more physical compute devices such as CPUs or GPUs concurrently are described. One or more executables are compiled online from a source having an existing executable for a type of physical compute devices different from the one or more physical compute devices. Dependency relations among elements corresponding to scheduled executables are determined to select an executable to be executed by a plurality of threads concurrently in more than one of the physical compute devices. A thread initialized for executing an executable in a GPU of the physical compute devices are initialized for execution in another CPU of the physical compute devices if the GPU is busy with graphics processing threads. Sources and existing executables for an API function are stored in an API library to execute a plurality of executables in a plurality of physical compute devices, including the existing executables and online compiled executables from the sources.
Owner:APPLE INC
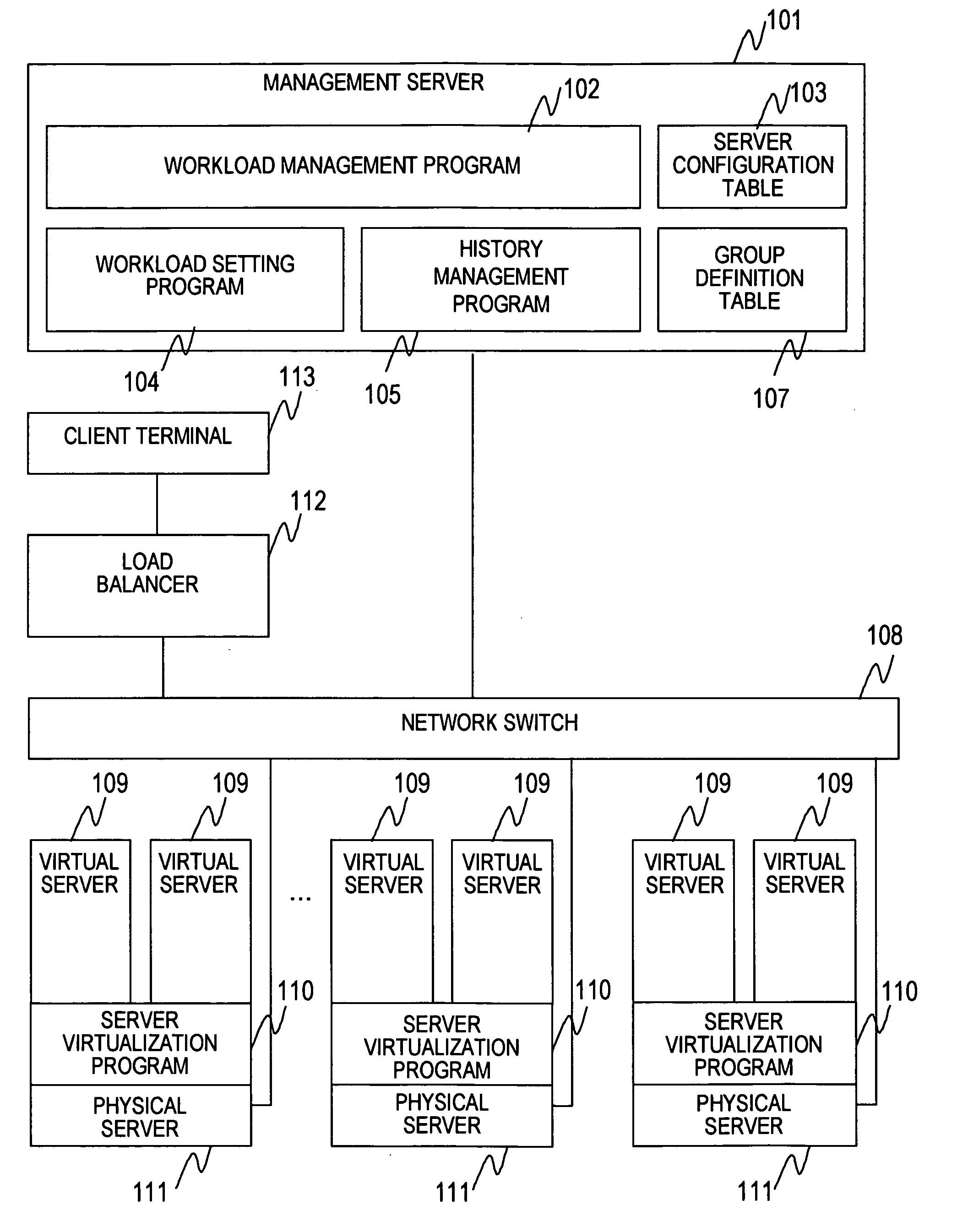
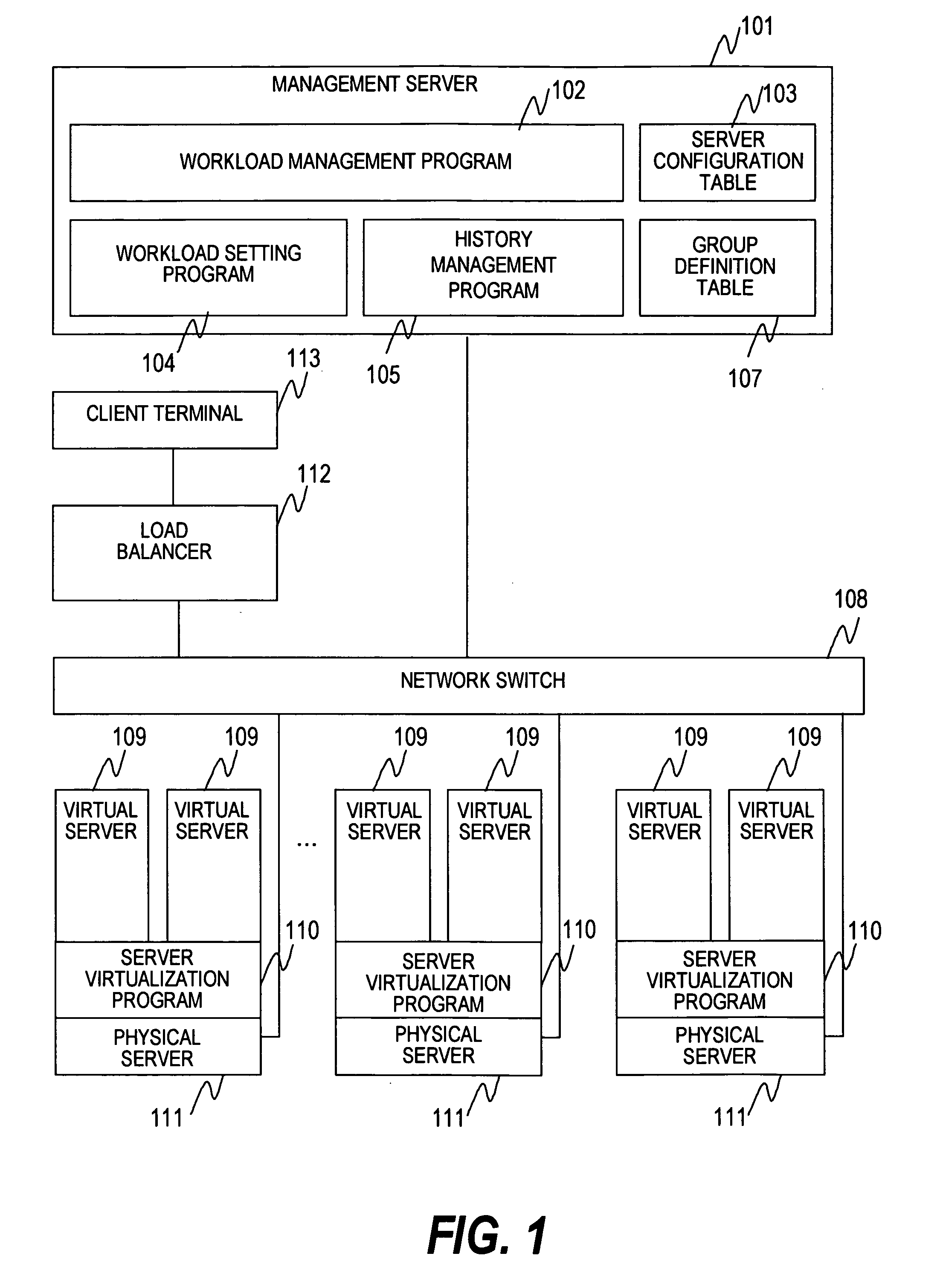
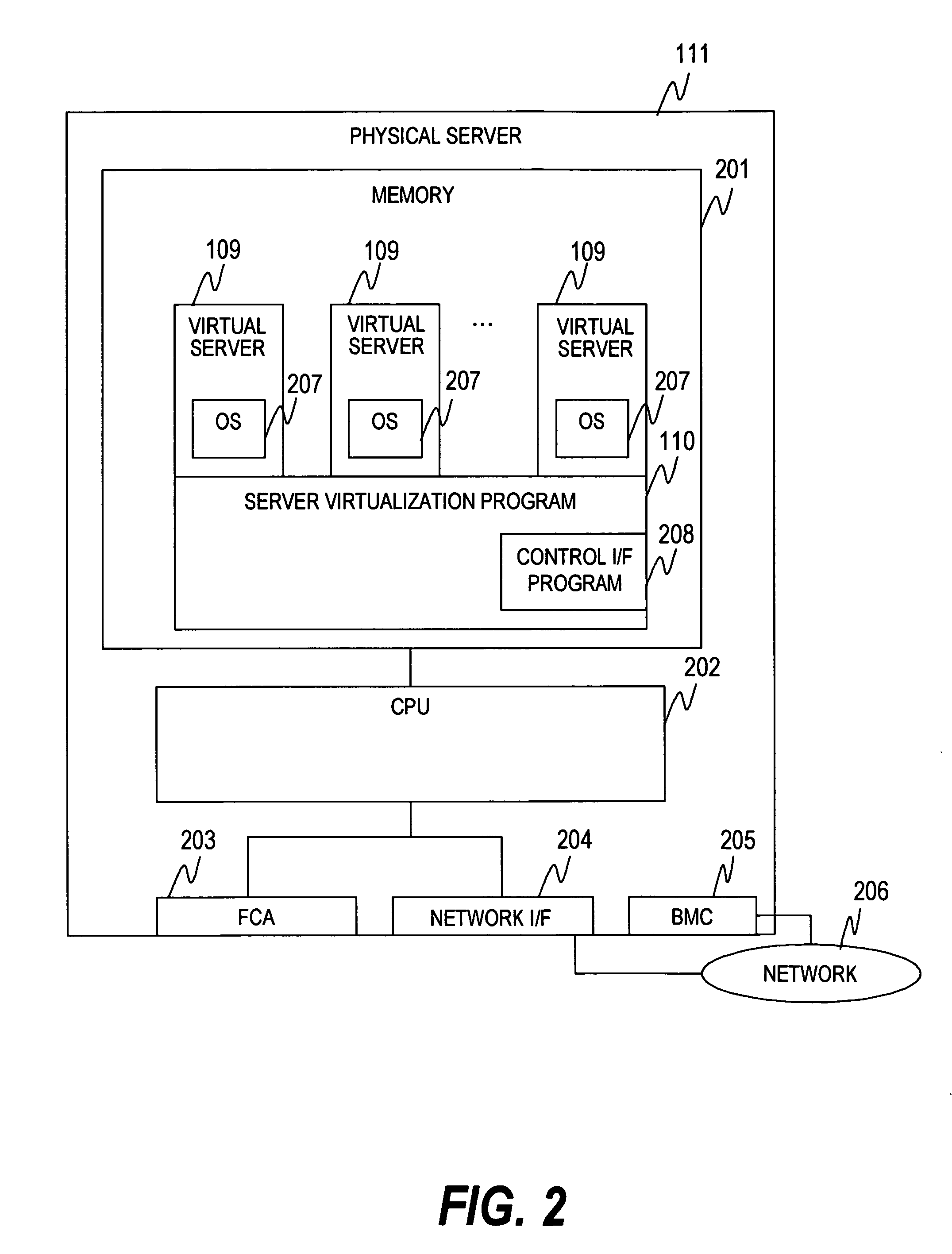
Method for workload management of plural servers
InactiveUS20070233838A1Easy to manageDigital computer detailsProgram controlComputerized systemVirtual computing
An object of this invention is to facilitate the workload management of a virtual server by an administrator in environment that a plurality of virtual computers configuring a single or a plurality of task systems are distributed among a plurality of physical computers. To achieve the object, there is provided a computer management method based upon a computer management method in a computer system having a plurality of physical computers, a plurality of virtual computers operated in the physical computer and a management computer connected to the physical computer via a network and characterized in that specification for performance allocated every group is accepted, the performance of the physical computers is acquired and the performance of the specified group is allocated to the virtual computers included in the group based upon the acquired performance of the physical computers.
Owner:HITACHI LTD
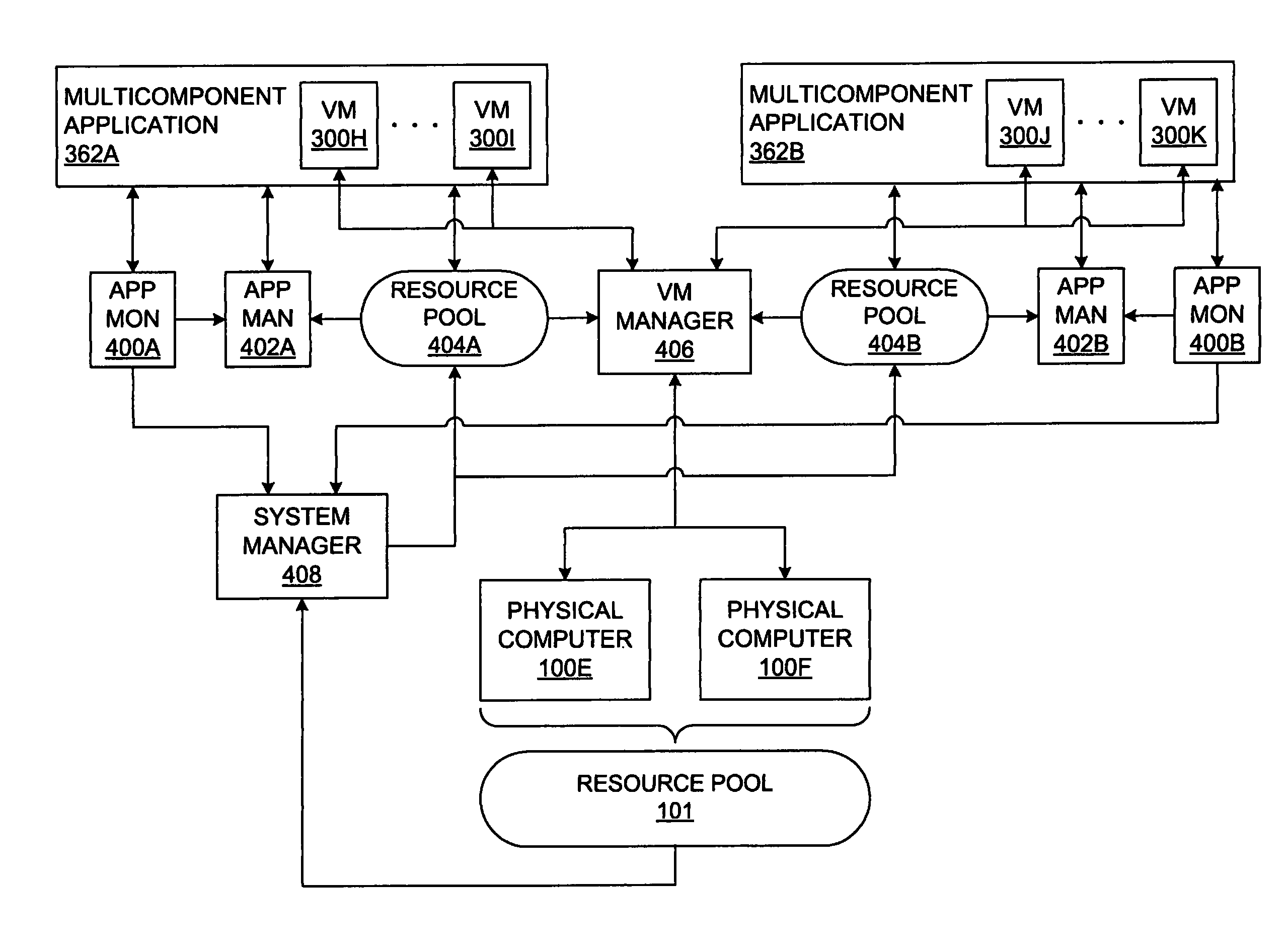
Executing a multicomponent software application on a virtualized computer platform
ActiveUS8286174B1Digital computer detailsMultiprogramming arrangementsVirtualizationHigh availability
A virtualized computer platform is established and maintained by virtualization software on one or more physical computers. A multicomponent software application may execute on the virtualized computer platform, with different components of the application executing in different virtual machines, which are supported by the virtualization software. The virtualization software may also provide, and / or facilitate the provision of, one or more services that may be beneficial to the operation of the multicomponent software application, such as automated provisioning, resource allocation, VM distribution, performance monitoring, resource management, high availability, backup, disaster recovery, alarms, security, etc. In some embodiments of the invention, some of these services are provided through coordinated efforts of a system resource manager, a VM manager, an application monitor and an application resource manager. In some of these embodiments, an application monitor and an application manager may be included with a multicomponent software application in a single installation package.
Owner:VMWARE INC
On-line replacement and changing of virtualization software
ActiveUS7814495B1Fast and non-disruptive and online updating and replacement and changingSoftware engineeringMultiprogramming arrangementsComputer supportedComputer support
In a virtualized system running one or more virtual machines on a first hypervisor, a second hypervisor is installed and control of the hardware resources of the physical computer supporting the virtualized system is migrated from the first hypervisor to the second hypervisor without interrupting the operation of the first hypervisor and the virtual machines. Initially a minimal set of hardware resources is hot-removed from control by the first hypervisor, and the second hypervisor is launched on the minimal set of hardware resources. Both the remaining hardware resources and the virtual machines are then migrated from the first hypervisor to the second hypervisor until all the virtual machines have been migrated over to the second hypervisor, while the virtual machines and the first hypervisor continue running largely unaffected by the migration process.
Owner:VMWARE INC
Methods and Systems for Dynamically Switching Between Communications Protocols
ActiveUS20100199276A1TransmissionSoftware simulation/interpretation/emulationStorage area networkNetwork Communication Protocols
A method for dynamically switching between communications protocols used in communicating with each of a plurality of physical computing devices includes configuring, by a storage delivery management service, a storage system in a storage area network, to communicate, according to a first communications protocol with a first physical computing device executing a virtual machine, the storage system providing, to the virtual machine, access to a virtual storage resource. The storage delivery management service receives a request to migrate the virtual machine from the first physical computing device to a second physical computing device. The storage delivery management service configures the storage system to communicate with the second physical computing device according to a second communications protocol. The storage delivery management service transmits, to the second physical computing device, an identification of the storage system providing access to the virtual storage resource for the virtual machine.
Owner:CITRIX SYST INC
Virtual computer system with dynamic resource reallocation
InactiveUS7290259B2Increase the number ofGuaranteed performanceResource allocationError detection/correctionDynamic resourceVirtual computing
A virtual computer system including a reallocation means, in which a plurality of LPAR are operated by logically dividing physical resources composing a physical computer exclusively or in time dividing manner so as to dynamically change reallocation of physical resources among each of LPARs. Based on load conditions measured by an application or an OS of each LPAR, physical resource allocation to each LPAR is determined, thereby conducting reallocation of LPAR.
Owner:HITACHI LTD
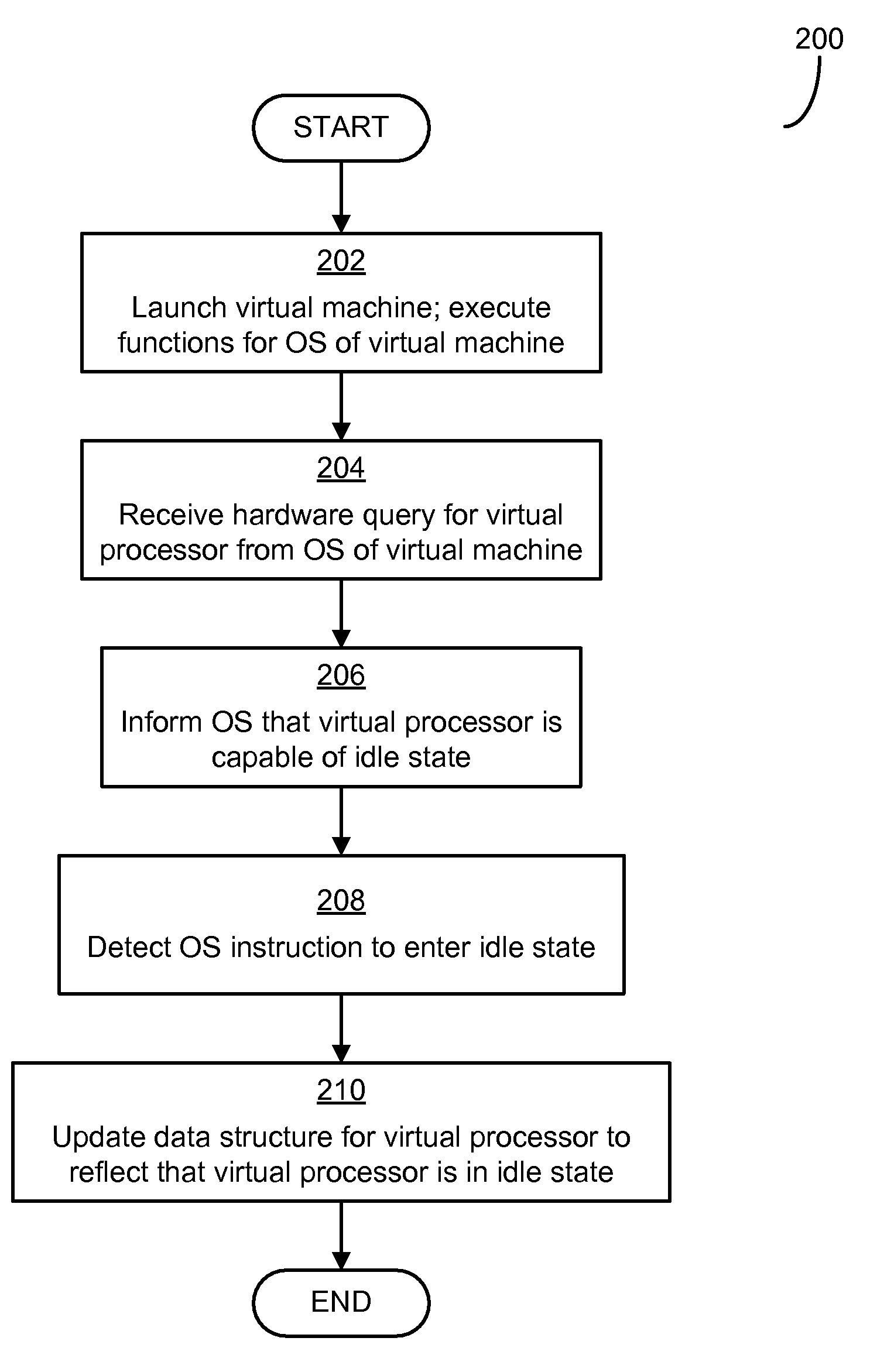
Power-saving operating system for virtual environment
ActiveUS20100218183A1Amount of timeReduce power consumptionEnergy efficient ICTEfficient power electronics conversionOperational systemComputer science
Principles for enabling power management techniques for virtual machines. In a virtual machine environment, a physical computer system may maintain management facilities to direct and control one or more virtual machines executing thereon. In some techniques described herein, the management facilities may be adapted to place a virtual processor in an idle state in response to commands from a guest operating system. One or more signaling mechanisms may be supported such that the guest operating system will command the management facilities to place virtual processors in the idle state.
Owner:MICROSOFT TECH LICENSING LLC
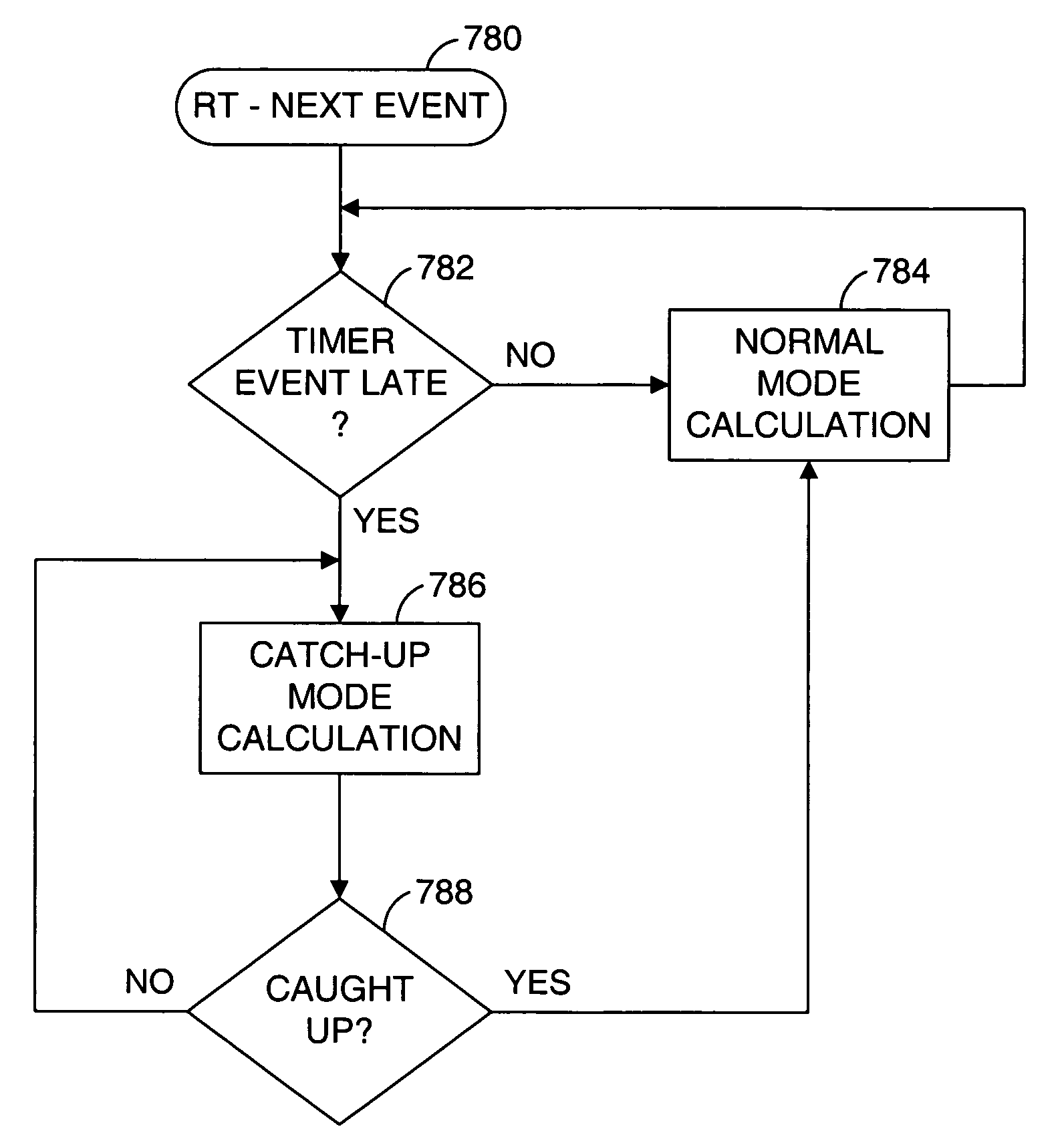
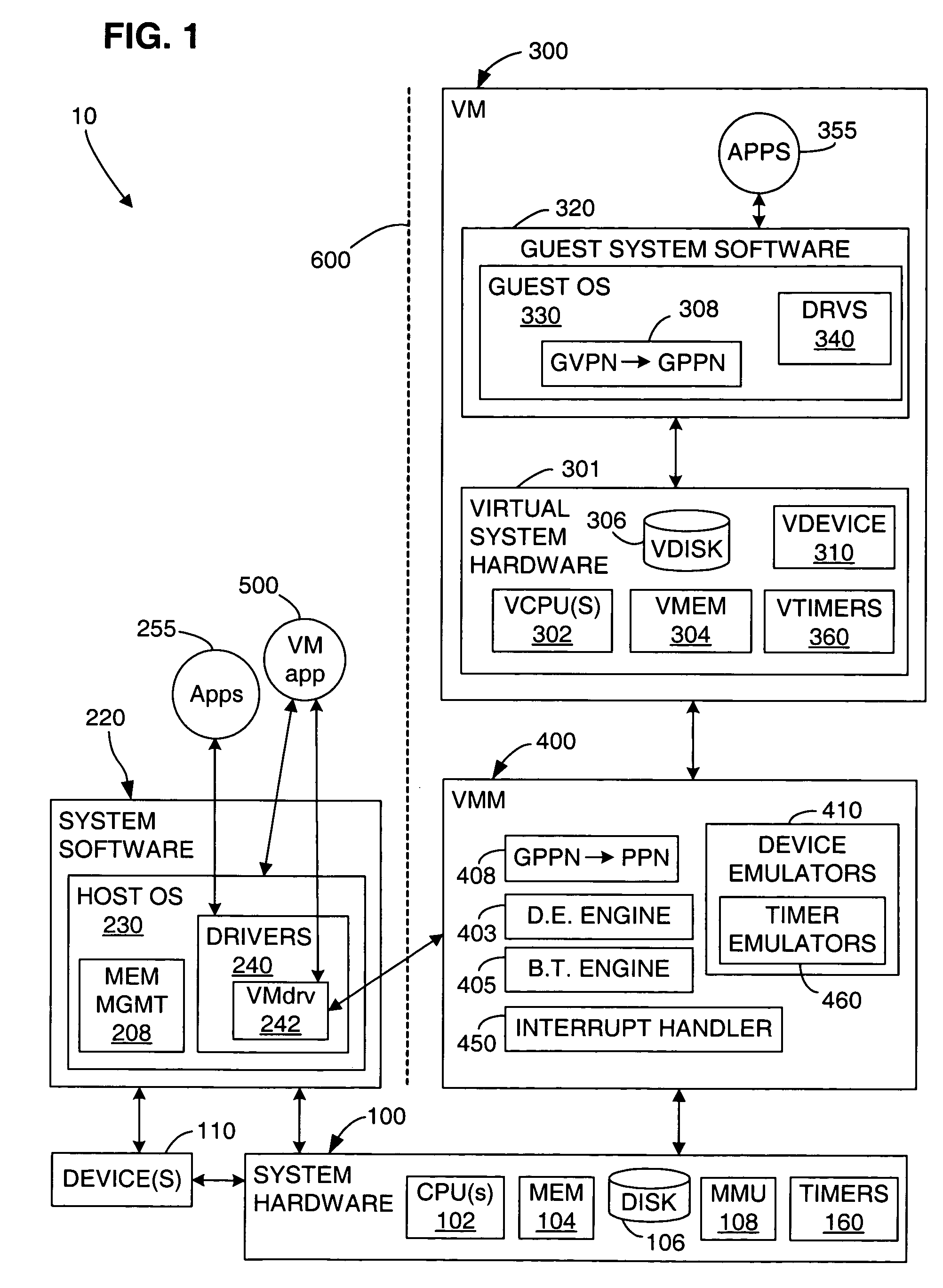
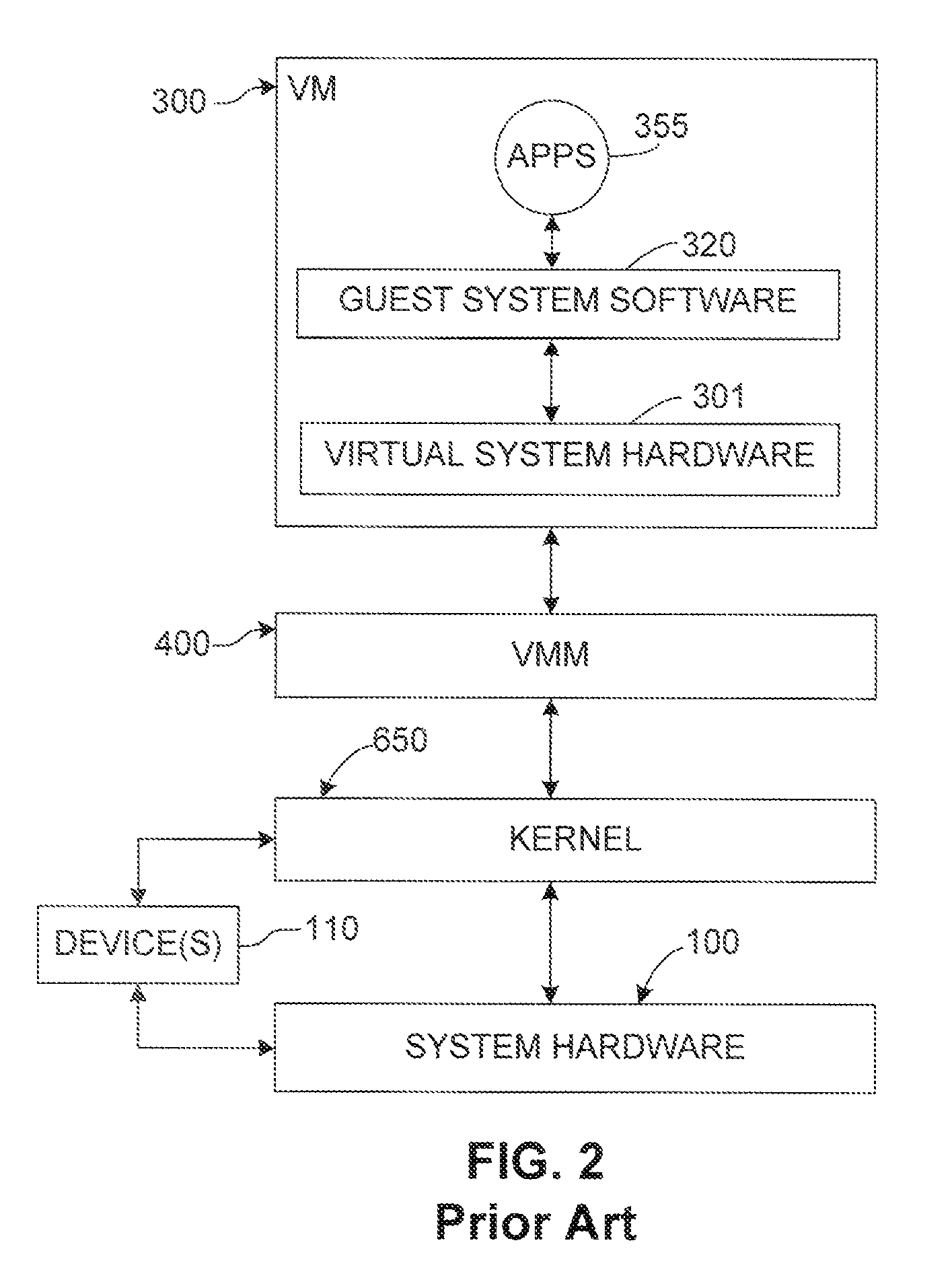
Method and apparatus for emulating multiple virtual timers in a virtual computer system when the virtual timers fall behind the real time of a physical computer system
ActiveUS7475002B1Generating/distributing signalsSoftware simulation/interpretation/emulationVirtual computingTimer
A virtual computer system includes multiple timer emulators for emulating multiple virtual timers in a virtual machine (VM). A time coordinator keeps track of an apparent time that is provided to the multiple timer emulators for presentation to the VM through the virtual timers. In particular, the time coordinator ensures that timer events generated by the multiple timer emulators are presented to the VM in an appropriate sequence and with substantially appropriate relative apparent times. Also, when guest software reads a count from a virtual timer, the time coordinator ensures that the apparent time presented to the guest software is substantially consistent with the apparent times represented by preceding and succeeding timer events. When the apparent time falls behind the real time of the physical computer system, the time coordinator speeds up the apparent time until it catches up to the real time.
Owner:VMWARE INC
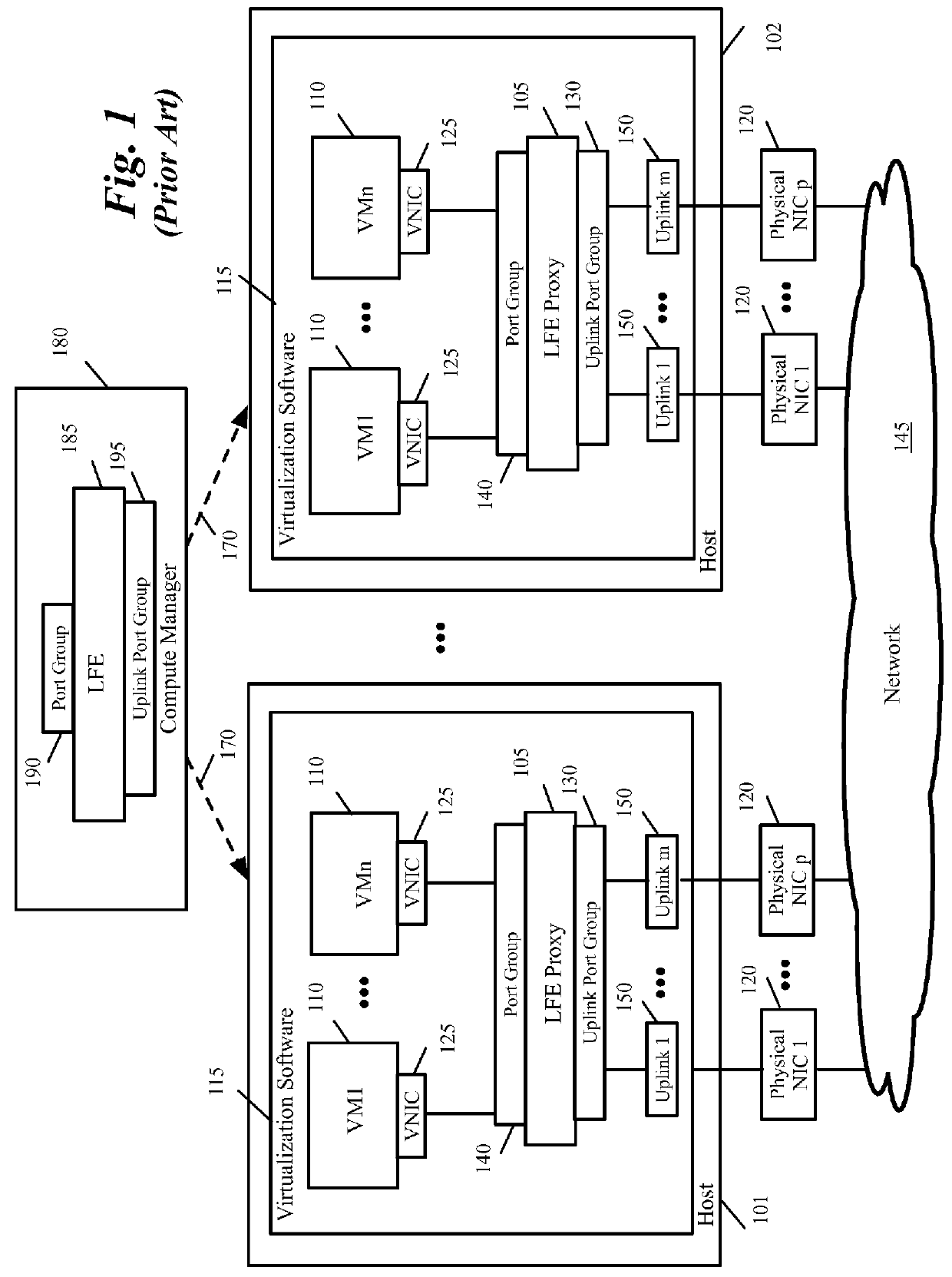
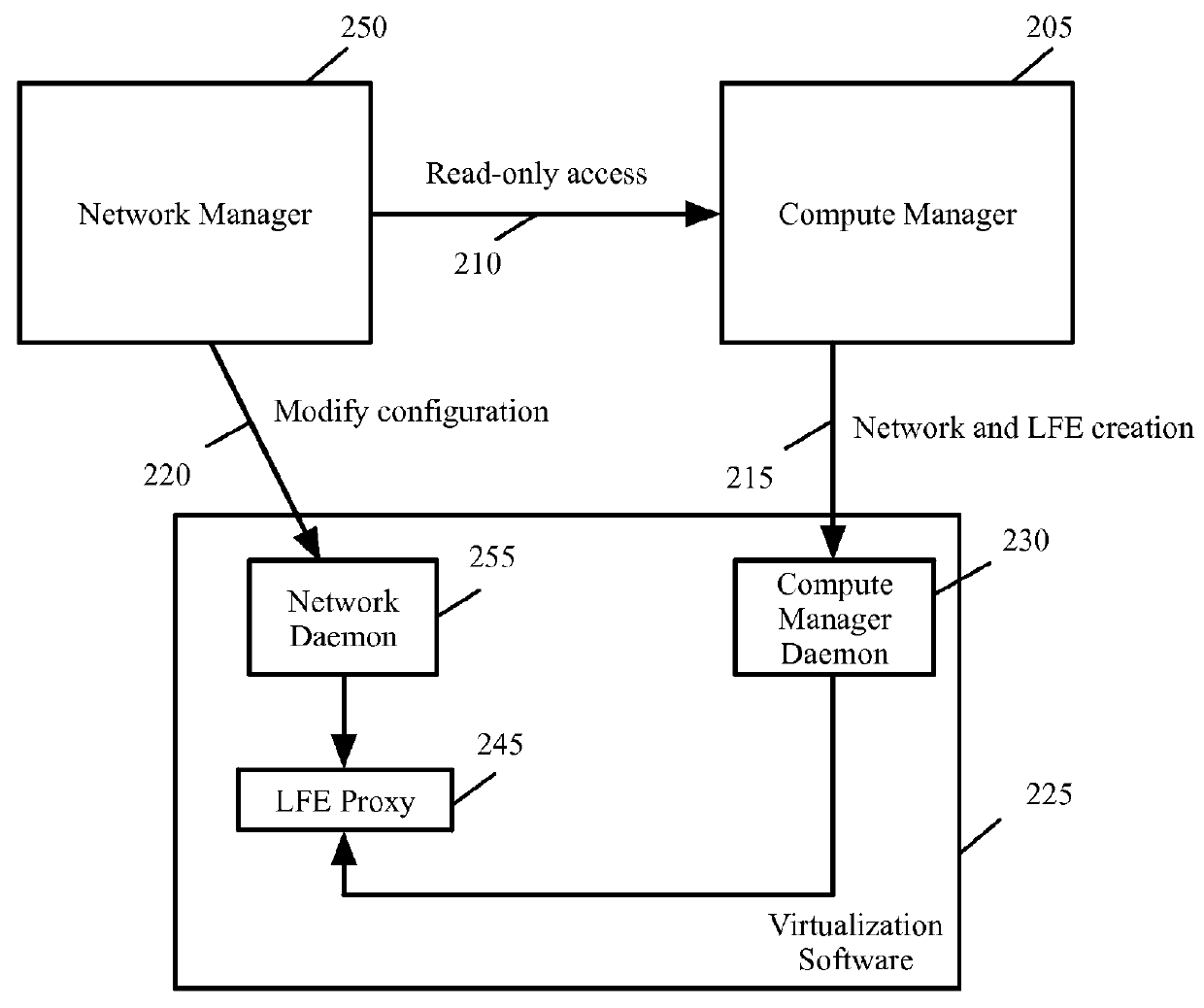
Enabling virtual machines access to switches configured by different management entities
A method of configuring a plurality of logical forwarding elements (LFEs) on a physical computing device comprising virtualization software and a plurality of data compute nodes (DCNs) is provided. The method provisions a first LFE configured and managed by a network manager of a datacenter on the physical computing device, the first LFE for performing OSI L3)packet forwarding between DCNs on one or more hosts, the first LFE comprising a plurality of logical ports configured and managed by the network manager, each logical port of the first LFE for connecting a DCN to a logical network configured and managed by the network manager. The method provisions a second LFE configured and managed by a compute manager of the datacenter on the physical computing device, the second LFE for performing OSI L3 packet forwarding between DCNs on one or more hosts, the second LFE comprising a plurality of logical port groups configured and managed by the compute manager, each logical port of the second LFE for connecting a DCN to a logical network configured and managed by the compute manager. The method configures a first DCN in the plurality of DCNs by the compute manager to connect to a logical network configured and managed by the network manager through a port of the first LFE. The method configures a second DCN in the plurality of DCNs by the compute manager to connect to a logical network configured and managed by the compute manager through a port of the second LFE.
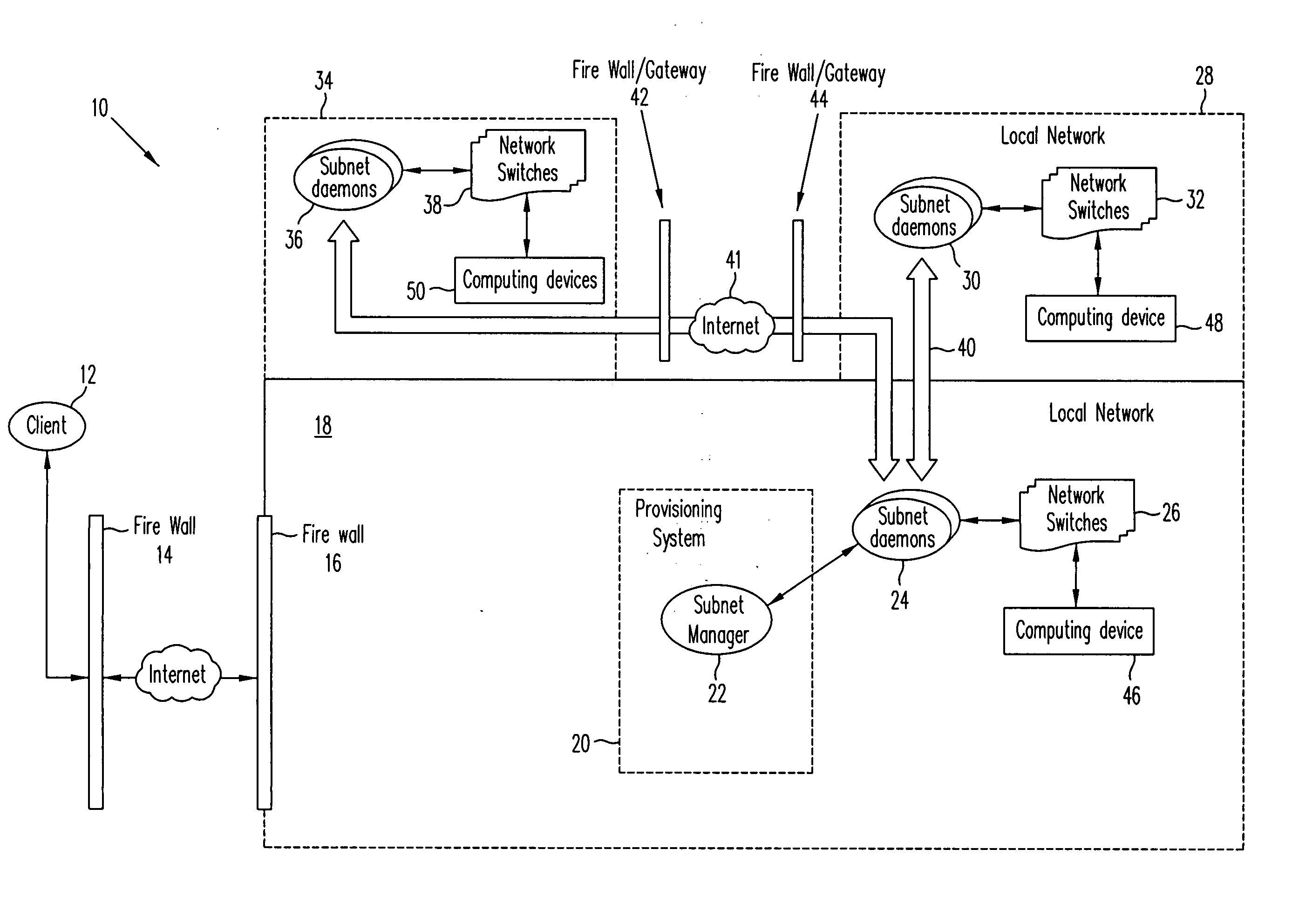
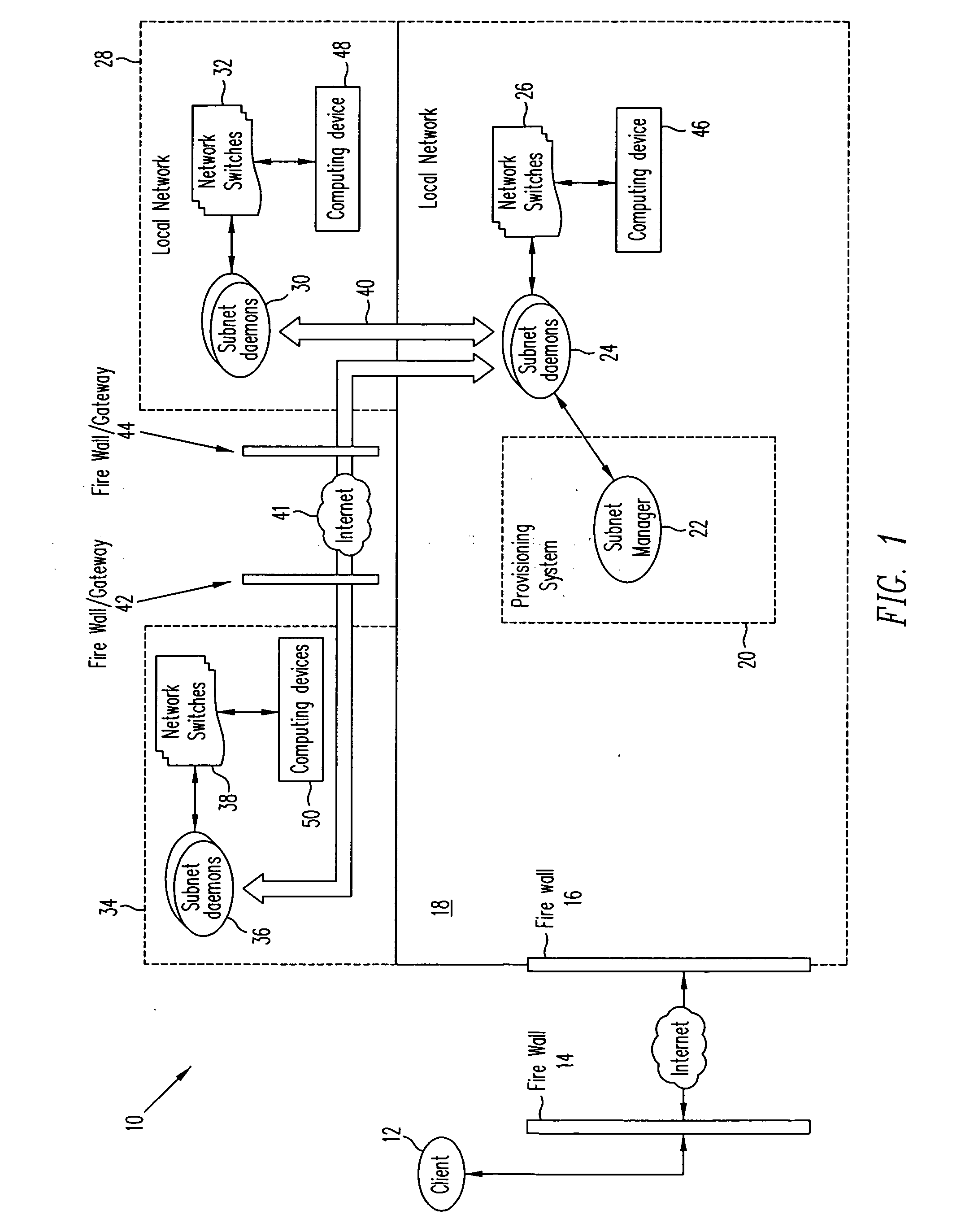
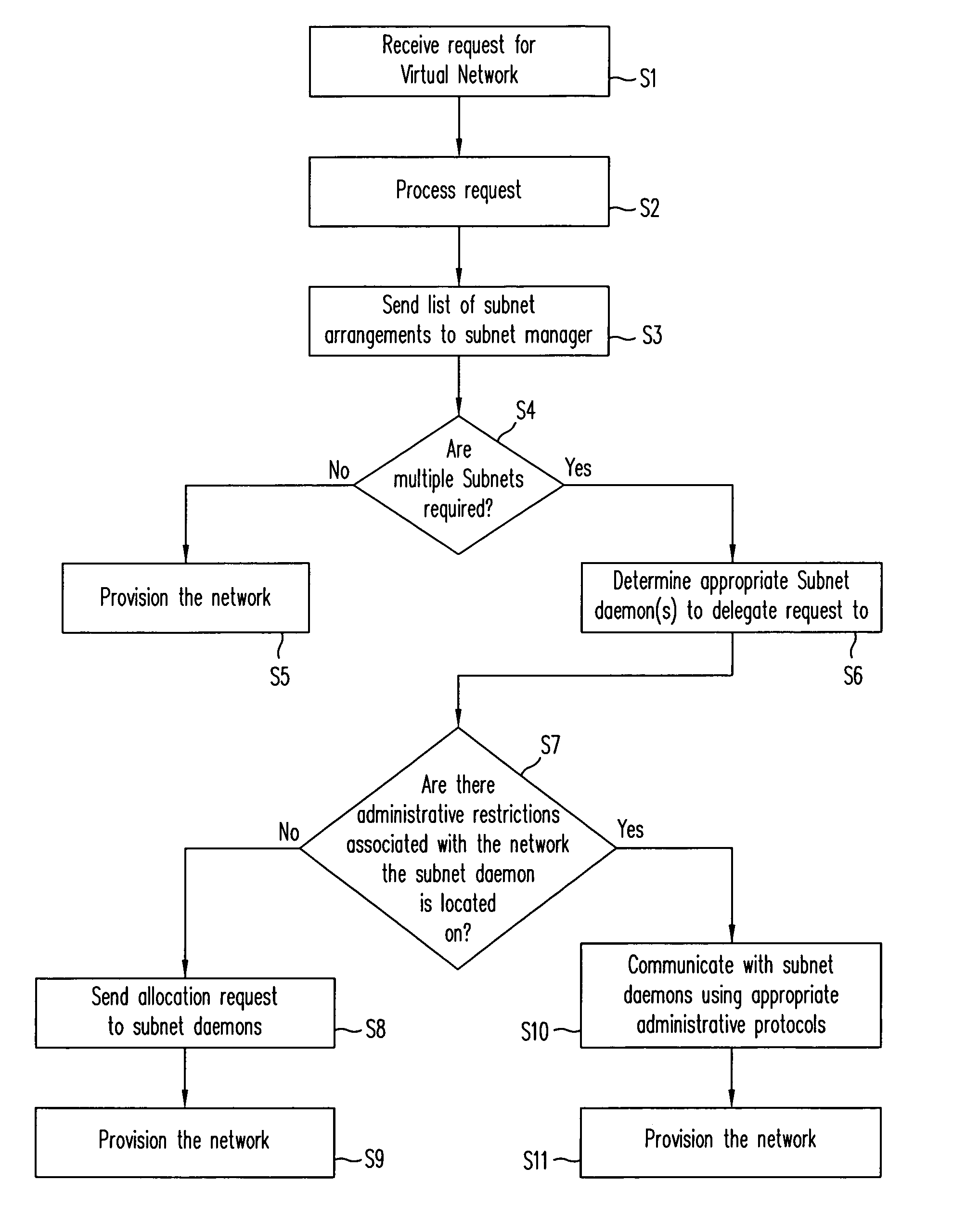
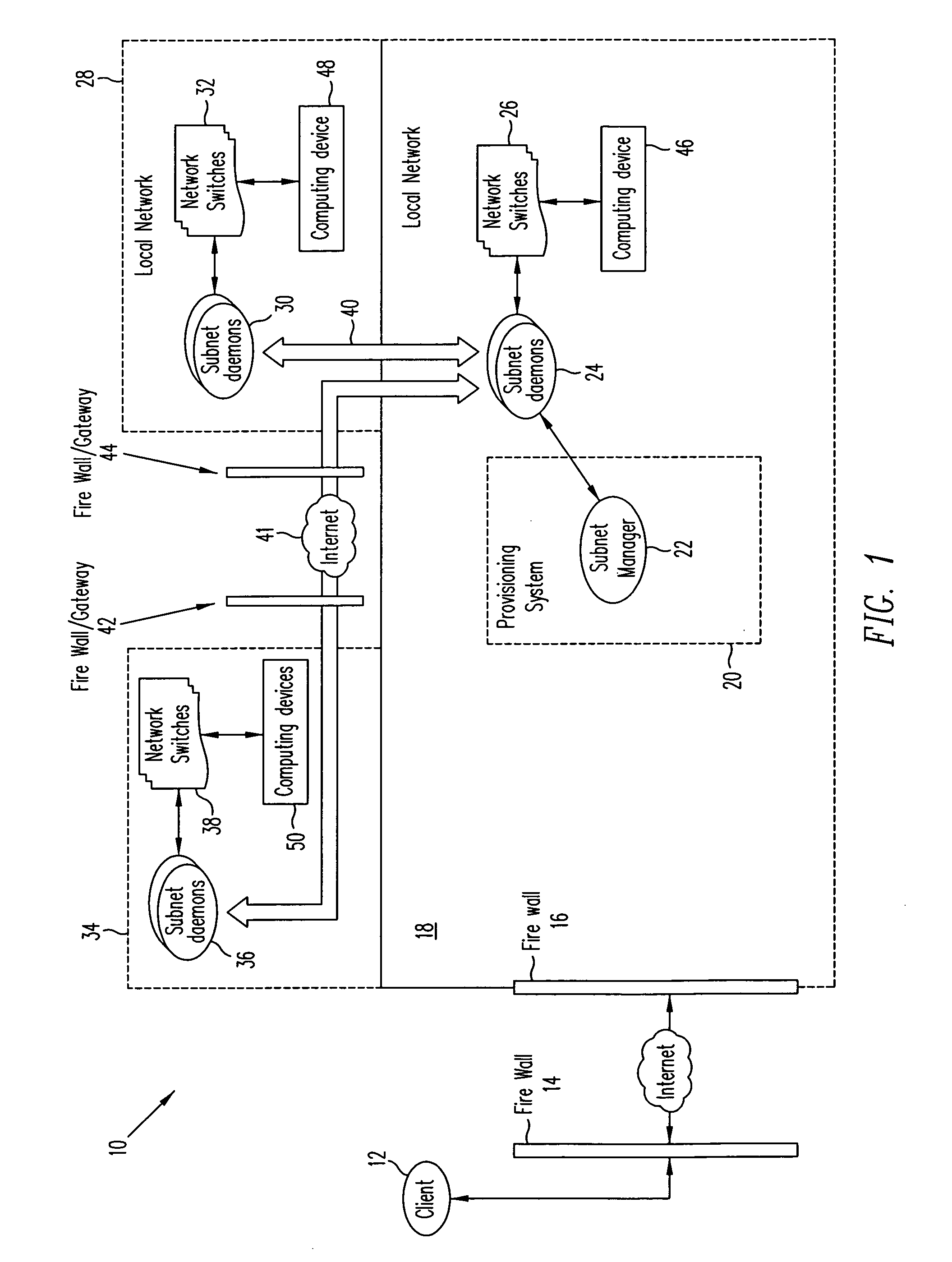
System for dynamic provisioning of secure, scalable, and extensible networked computer environments
InactiveUS20060114842A1Special service provision for substationData switching by path configurationTelecommunications linkPrivate network
A system and method for provisioning a virtual network is provided. Virtual networks can be automatically formed including switches in networks, such as local and private networks. Once the virtual networks are formed, virtual computing devices can be provisioned in place of physical computing devices that are connected to the switches. A system for provisioning a virtual network including a first virtual subnet and a second virtual subnet is provided. The system includes a first switch; a second switch; a first software process associated with first switch for provisioning the first virtual subnet; a second software process associated with the second switch for provisioning the second virtual subnet; and a communication link connecting the first switch and the second switch.
Owner:VERITAS TECH
System for dynamic provisioning of secure, scalable, and extensible networked computer environments
ActiveUS7027412B2Special service provision for substationMultiplex system selection arrangementsTelecommunications linkPrivate network
A system and method for provisioning a virtual network is provided. Virtual networks can be automatically formed including switches in networks, such as local and private networks. Once the virtual networks are formed, virtual computing devices can be provisioned in place of physical computing devices that are connected to the switches. A system for provisioning a virtual network including a first virtual subnet and a second virtual subnet is provided. The system includes a first switch; a second switch; a first software process associated with first switch for provisioning the first virtual subnet; a second software process associated with the second switch for provisioning the second virtual subnet; and a communication link connecting the first switch and the second switch.
Owner:SYMANTEC OPERATING CORP
Associating Virtual Machines on a Server Computer with Particular Users on an Exclusive Basis
ActiveUS20080201479A1Reduce usageError detection/correctionMultiple digital computer combinationsUser interfaceServer
A first computer of a plurality of computers in a server computer system may be associated with a first user on an exclusive basis. An administrator of the server computer system may utilize an administrative user interface in order to specify the association. Associating the first computer with the first user on the exclusive basis may prevent users other than the first user from using the first computer. In response to receiving a request from the first user to connect to the server computer system, the system may operate to determine that the first computer is associated with the first user on the exclusive basis and may assign the first computer to the first user. Once the first computer has been assigned to the first user, the first user can begin using the first computer. In some embodiments the first computer may be a physical computer. In other embodiments the first computer may be a virtual machine.
Owner:CITRIX SYST INC
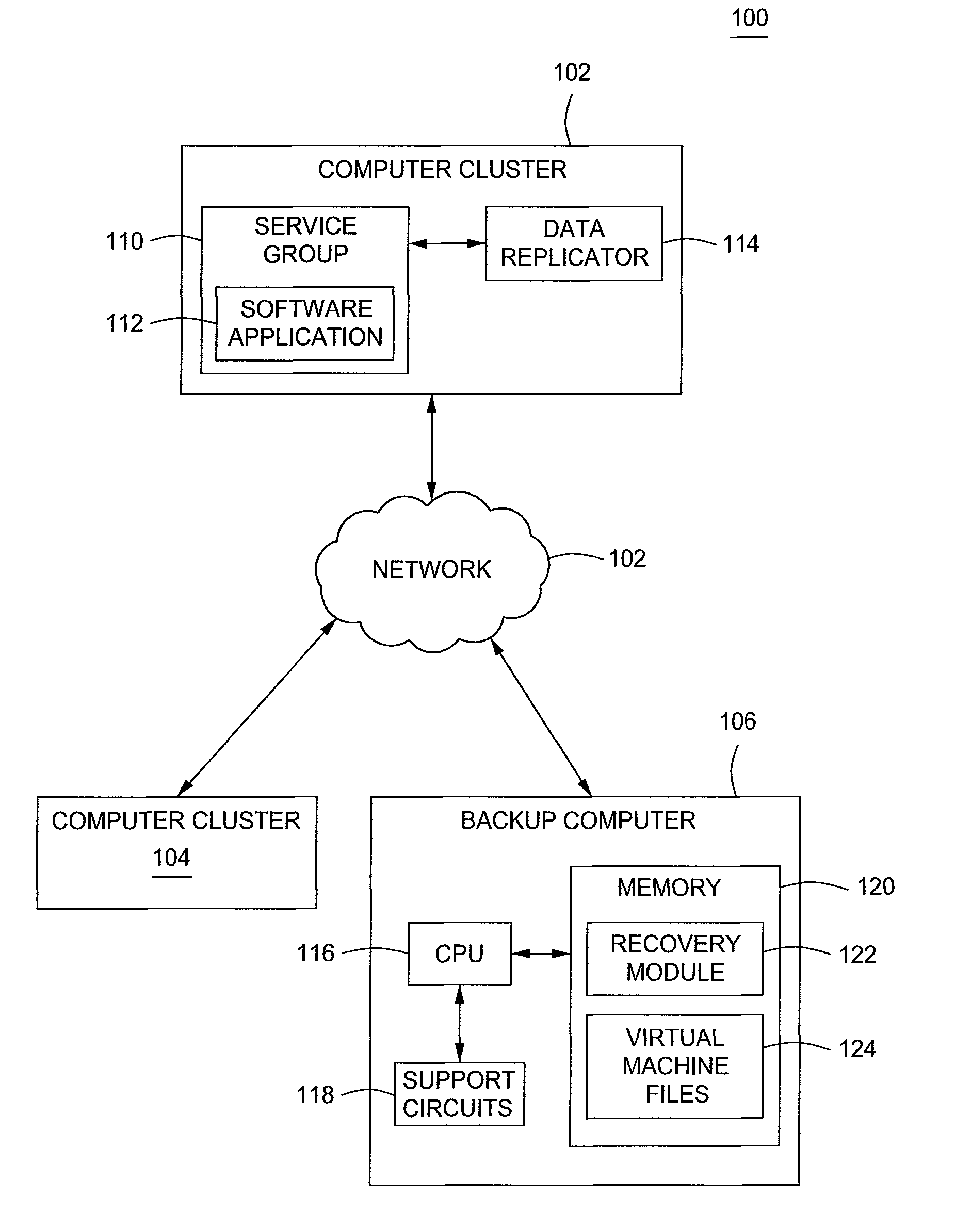
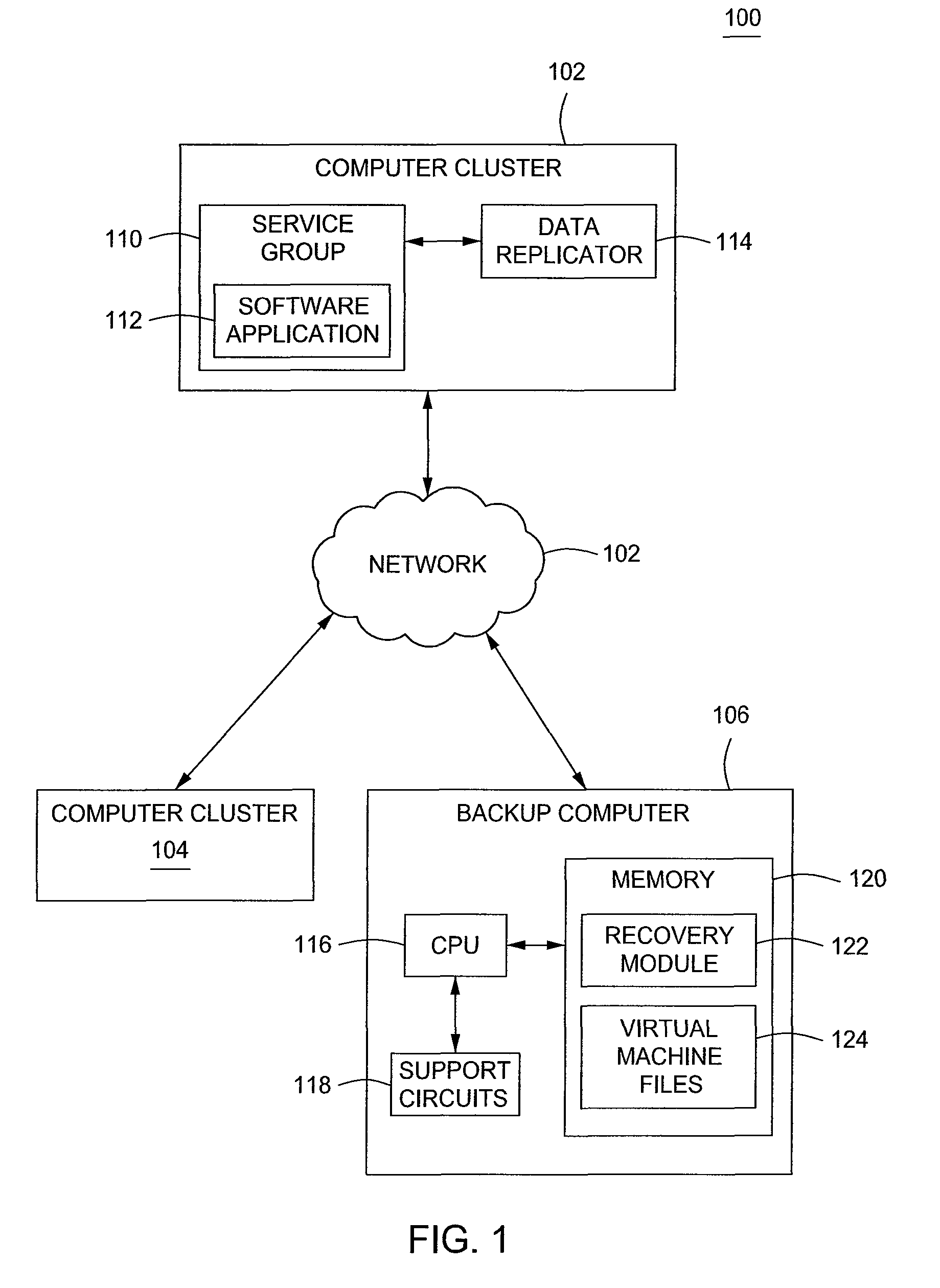
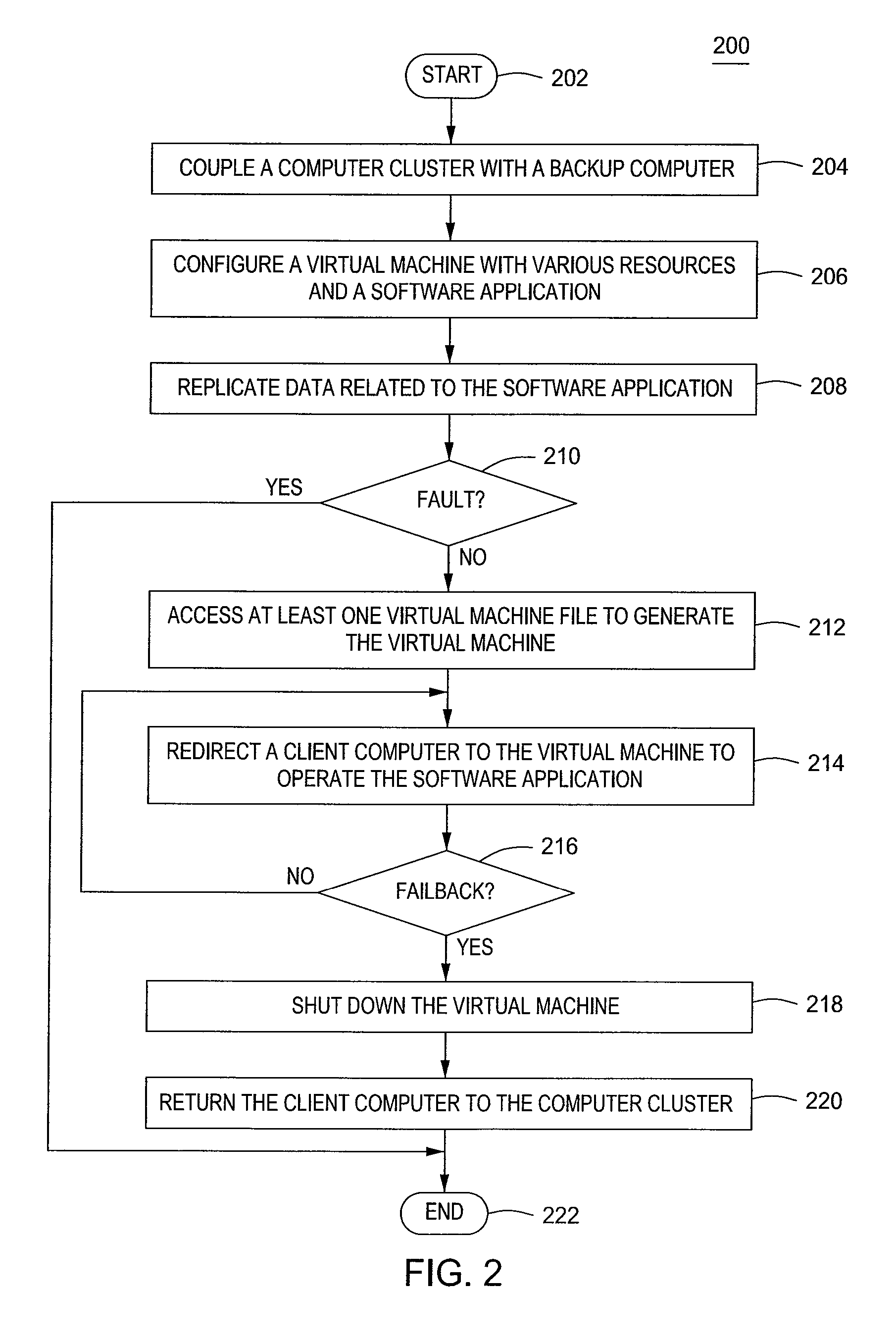
Method and apparatus for achieving high availability for an application in a computer cluster
A method and apparatus for achieving high availability in a computer cluster is provided. In one embodiment, a method for failing over a software application to a virtual machine from a physical computing environment comprises processing at least one virtual machine file at a backup computer, wherein the at least one virtual machine file is preconfigured with a software application that is hosted by a computer cluster and in response to an occurrence a fault at the computer cluster, accessing the at least one virtual machine file to operate the software application.
Owner:VERITAS TECH
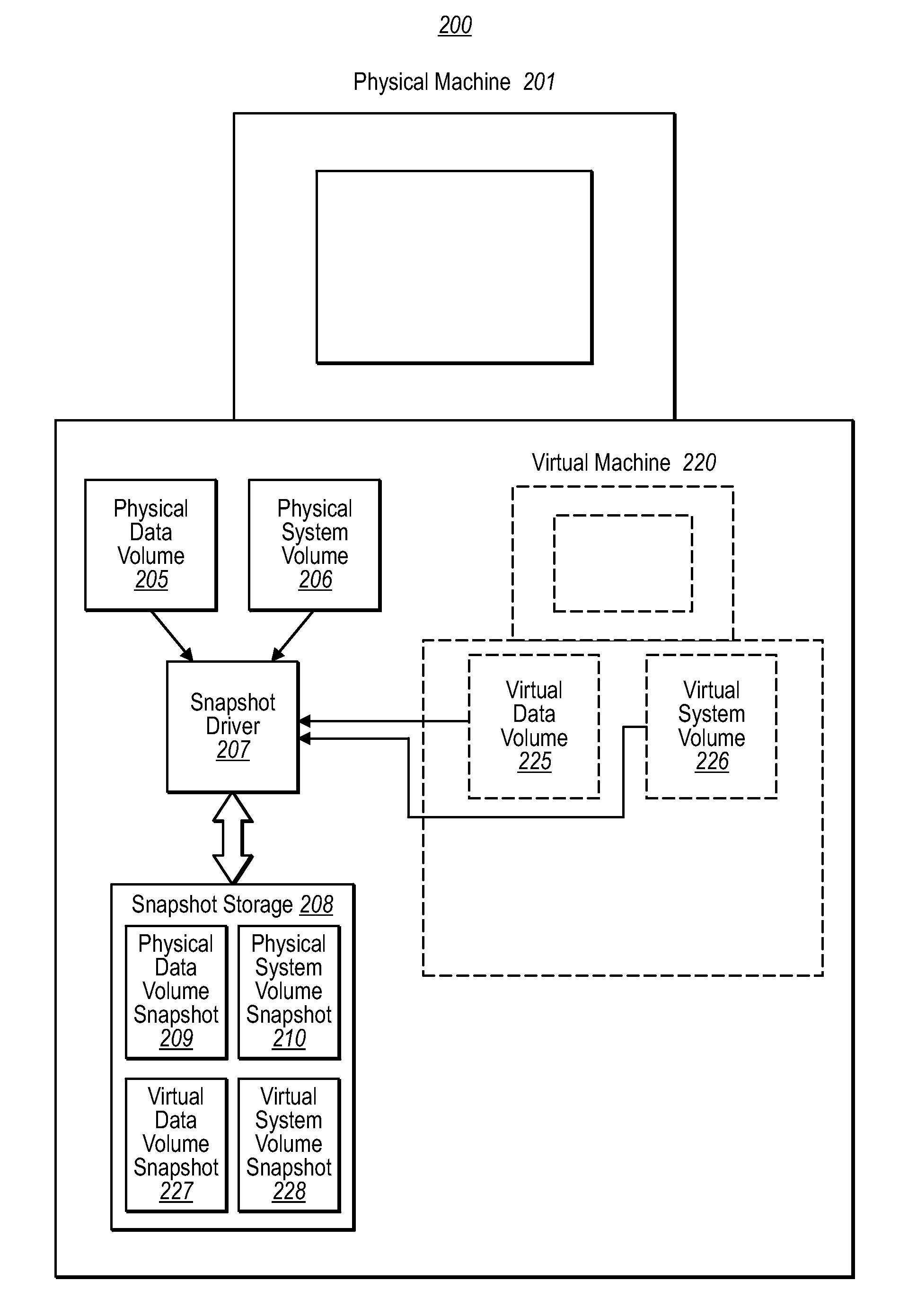
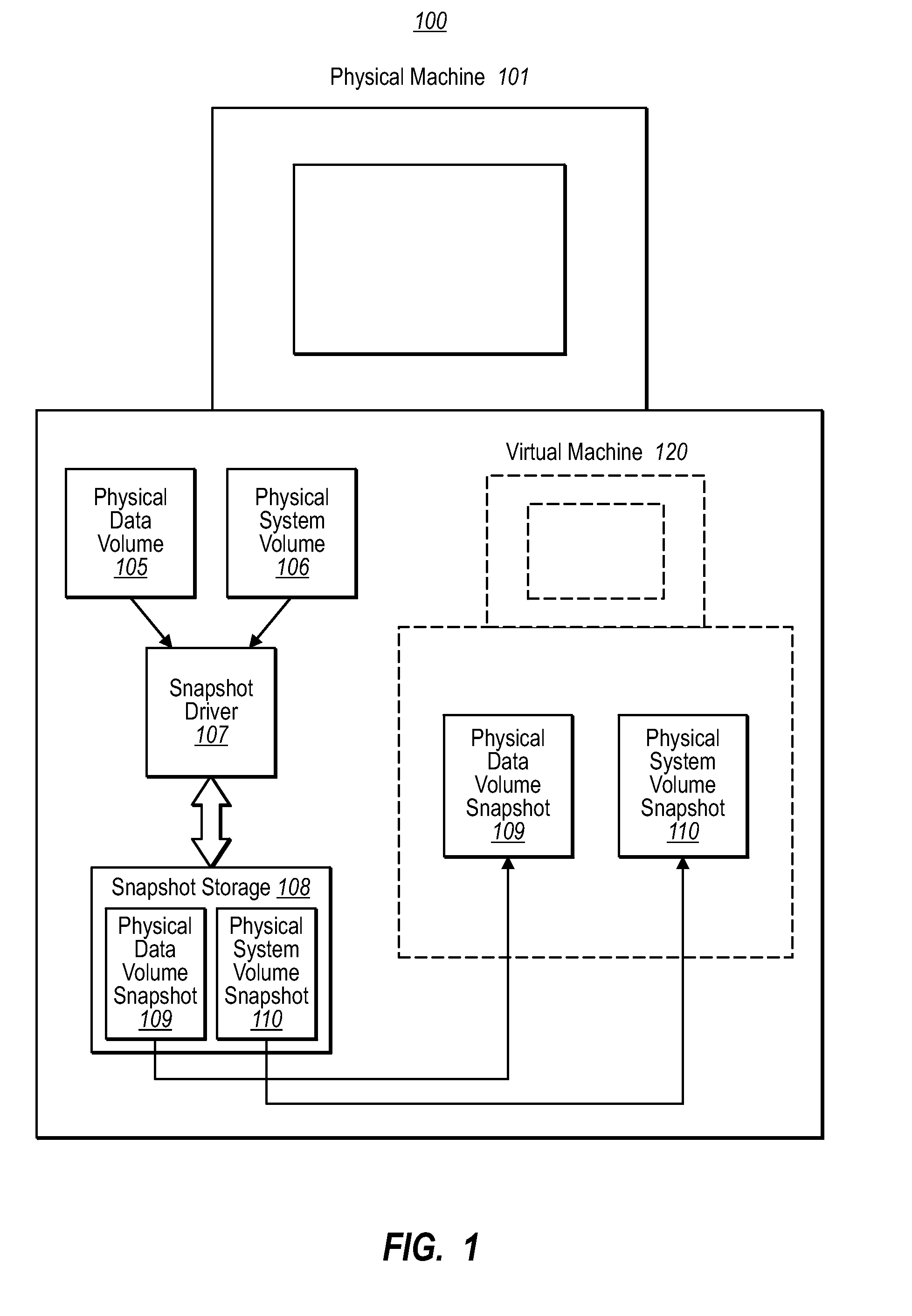
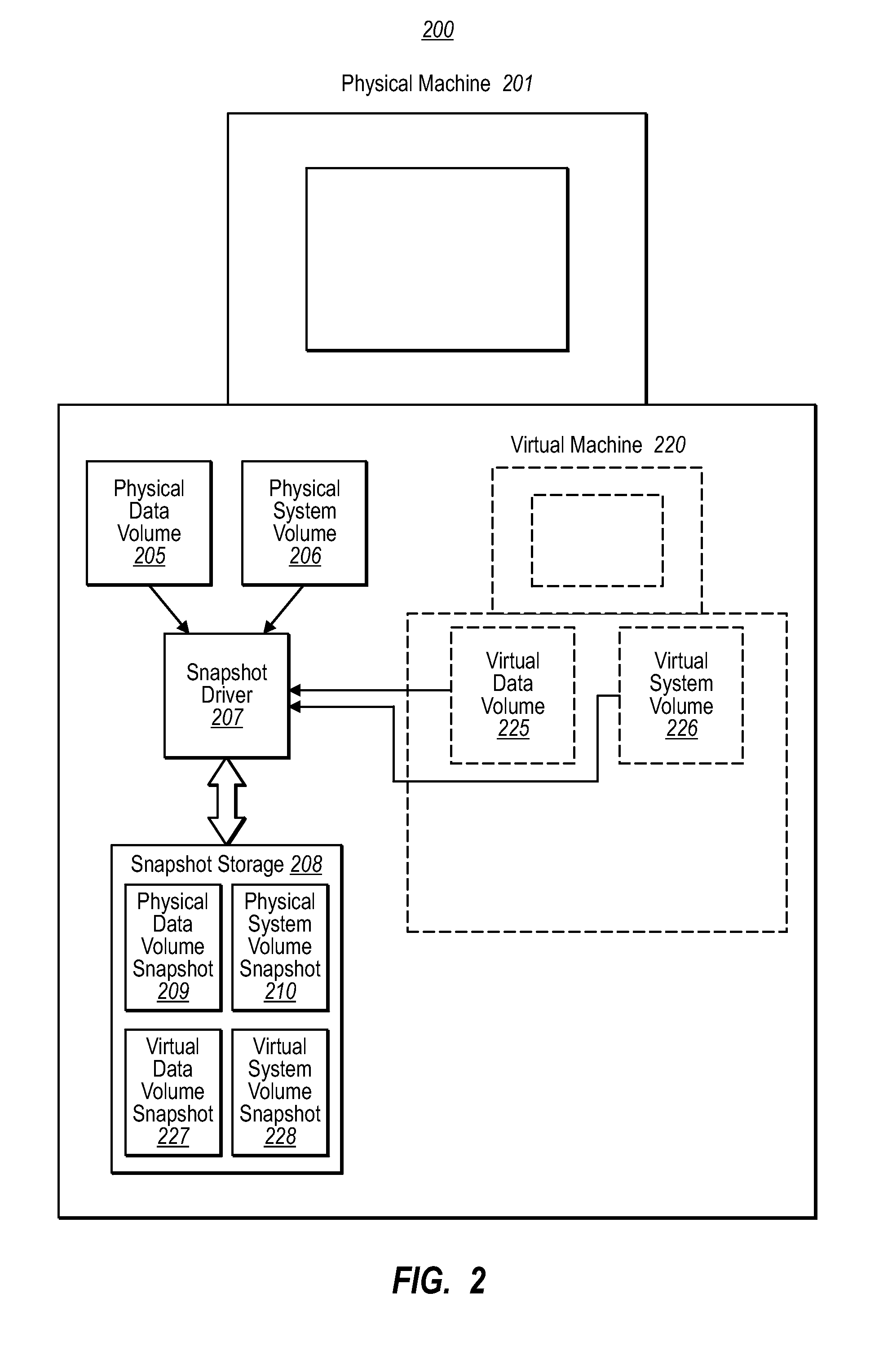
Running a virtual machine directly from a physical machine using snapshots
ActiveUS20080133208A1Well formedDigital computer detailsNon-redundant fault processingPhysical systemVirtual machine
Embodiments of the present invention are directed to the running of a virtual machine directly from a physical machine using snapshots of the physical machine. In one example, a computer system performs a method for running a virtual machine directly from a physical machine using snapshots of the physical machine. A snapshot component takes a snapshot of the physical system volume while the physical system volume is in an operational state. The virtual machine initializes using the physical system volume snapshot thereby allowing the physical system volume snapshot to be a virtual system volume snapshot representing an initial state of a virtual system volume. The physical system volume snapshot includes instances of all the files within the physical system volume at the time the snapshot was taken.
Owner:CA TECH INC
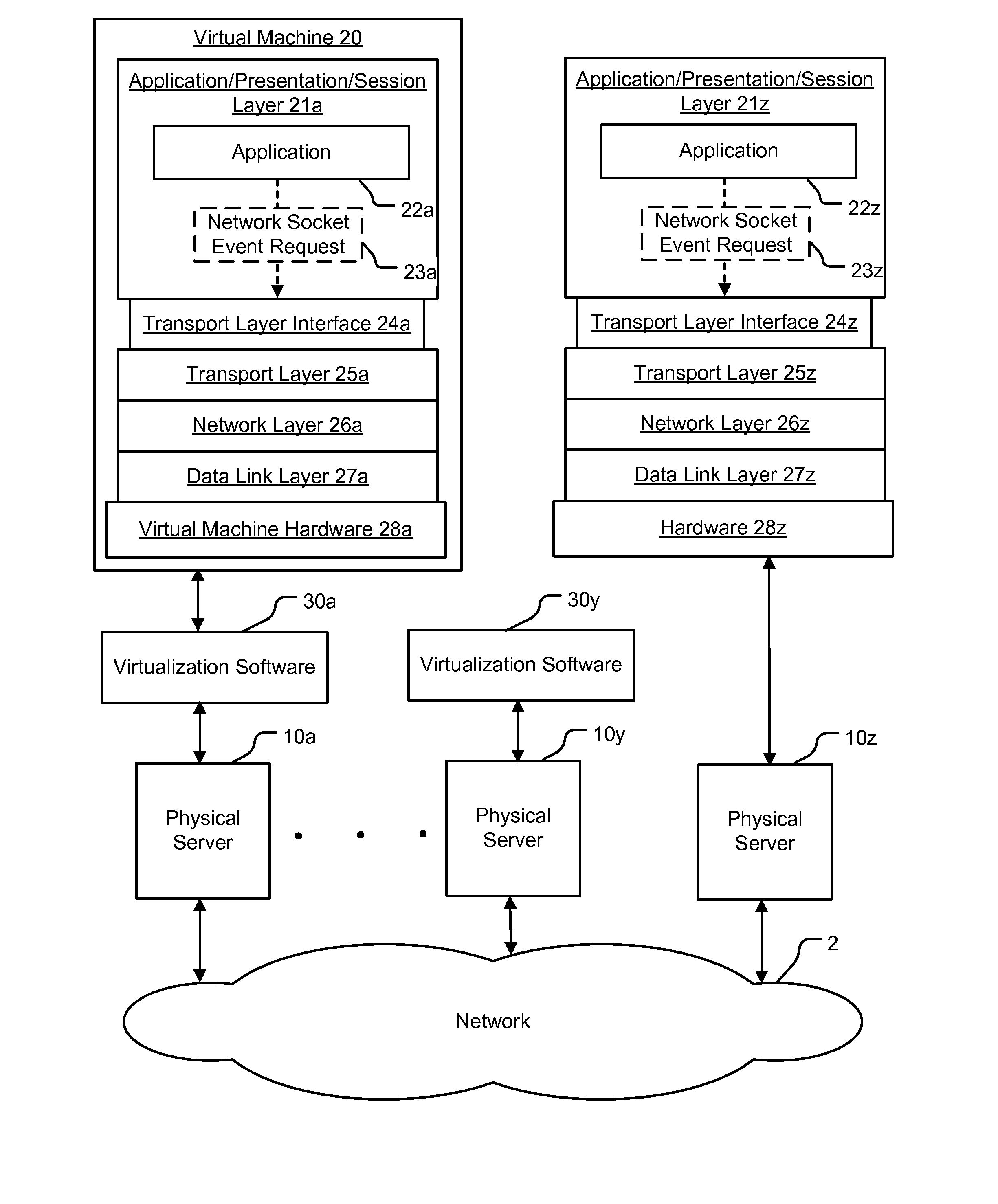
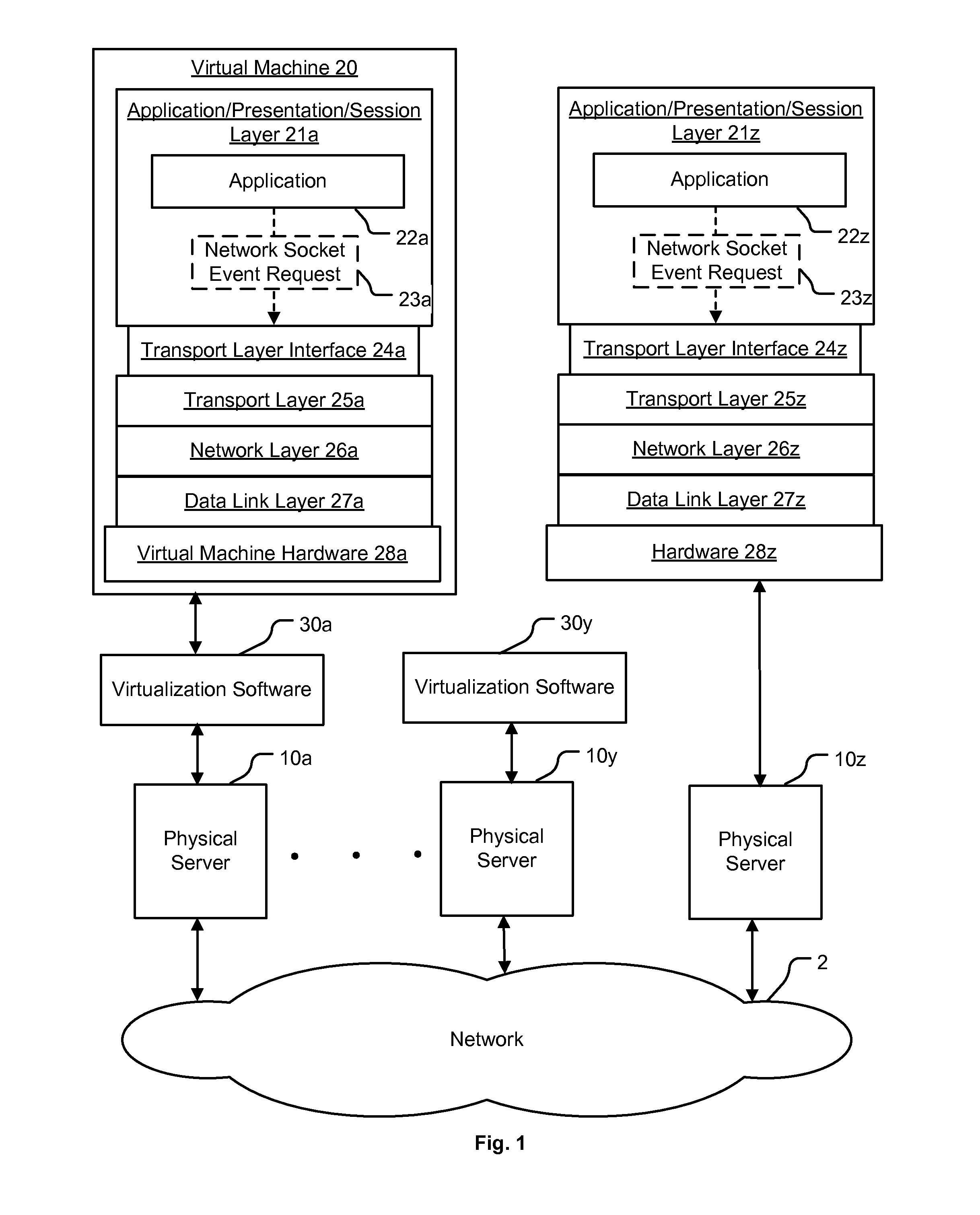
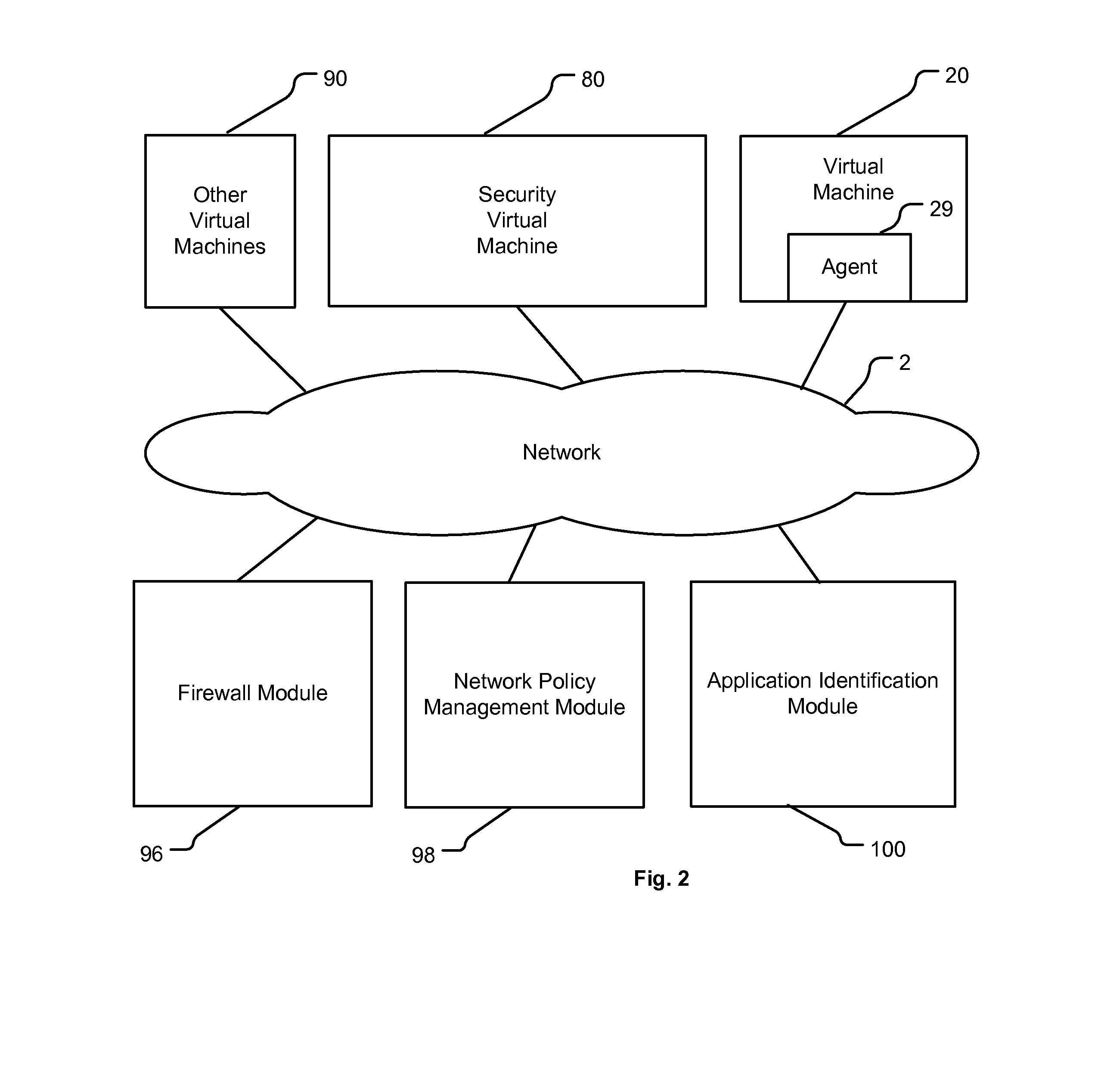
Method and apparatus for application awareness in a network
A method for enforcing a network policy is described herein. In the method, a network socket event request from an application executing in a first context is intercepted by an agent prior to the request reaching a transport layer in the first context. A context refers to virtualization software, a physical computer, or a combination of virtualization software and physical computer. In response to the interception of the request, the agent requests a decision on whether to allow or deny the network socket event request to be communicated to a security server executing in a second context that is distinct from the first context. The request for a decision includes an identification of the application. The agent then receives from the security server either an allowance or a denial of the network socket event request, the allowance or denial being based at least in part on the identification of the application and a security policy. The agent blocks the network socket event from reaching the transport layer when the denial is received from the security server. In one embodiment, the method is implemented using a machine readable medium embodying software instructions executable by a computer.
Owner:VMWARE INC
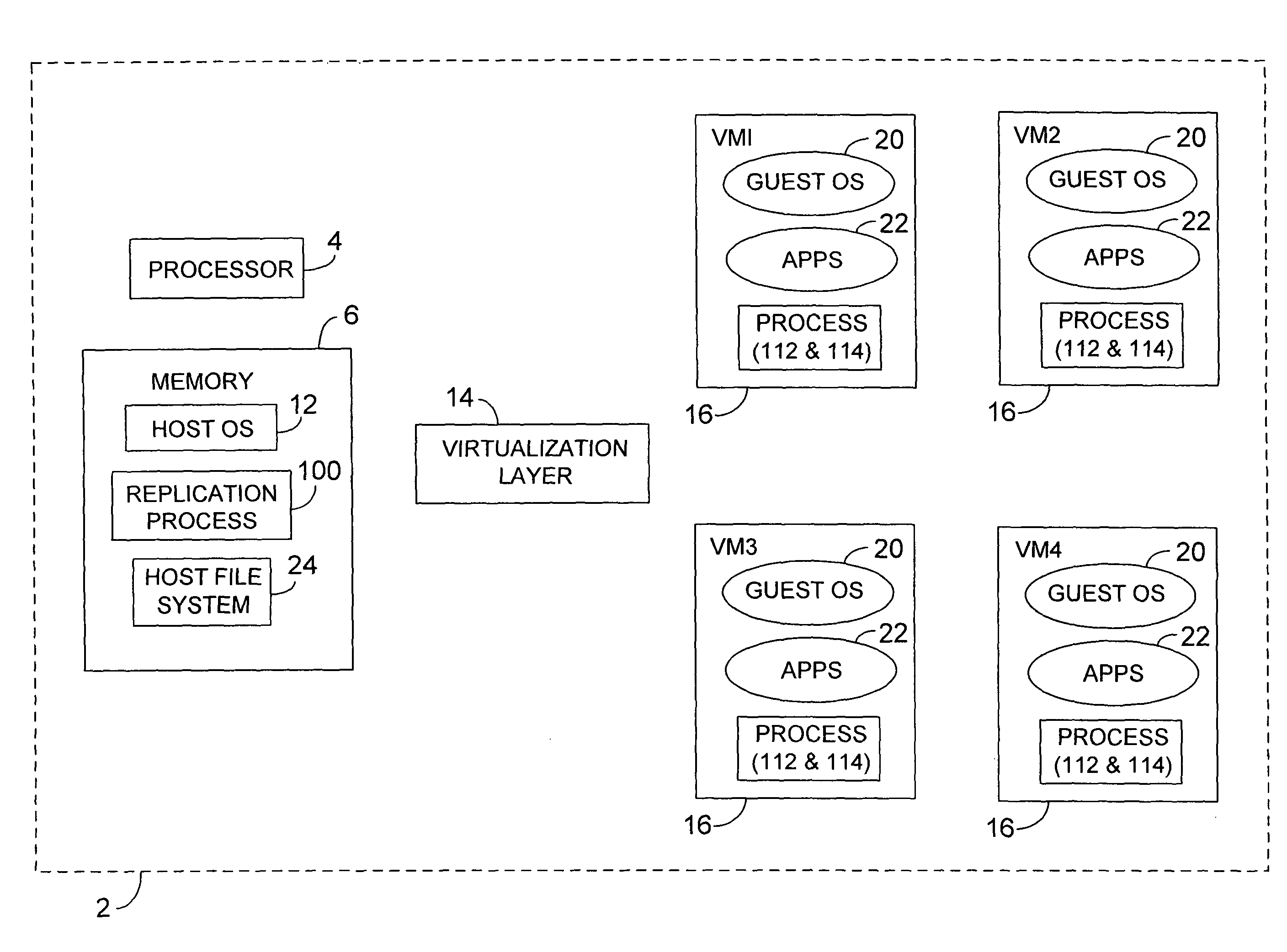
Platform independent replication
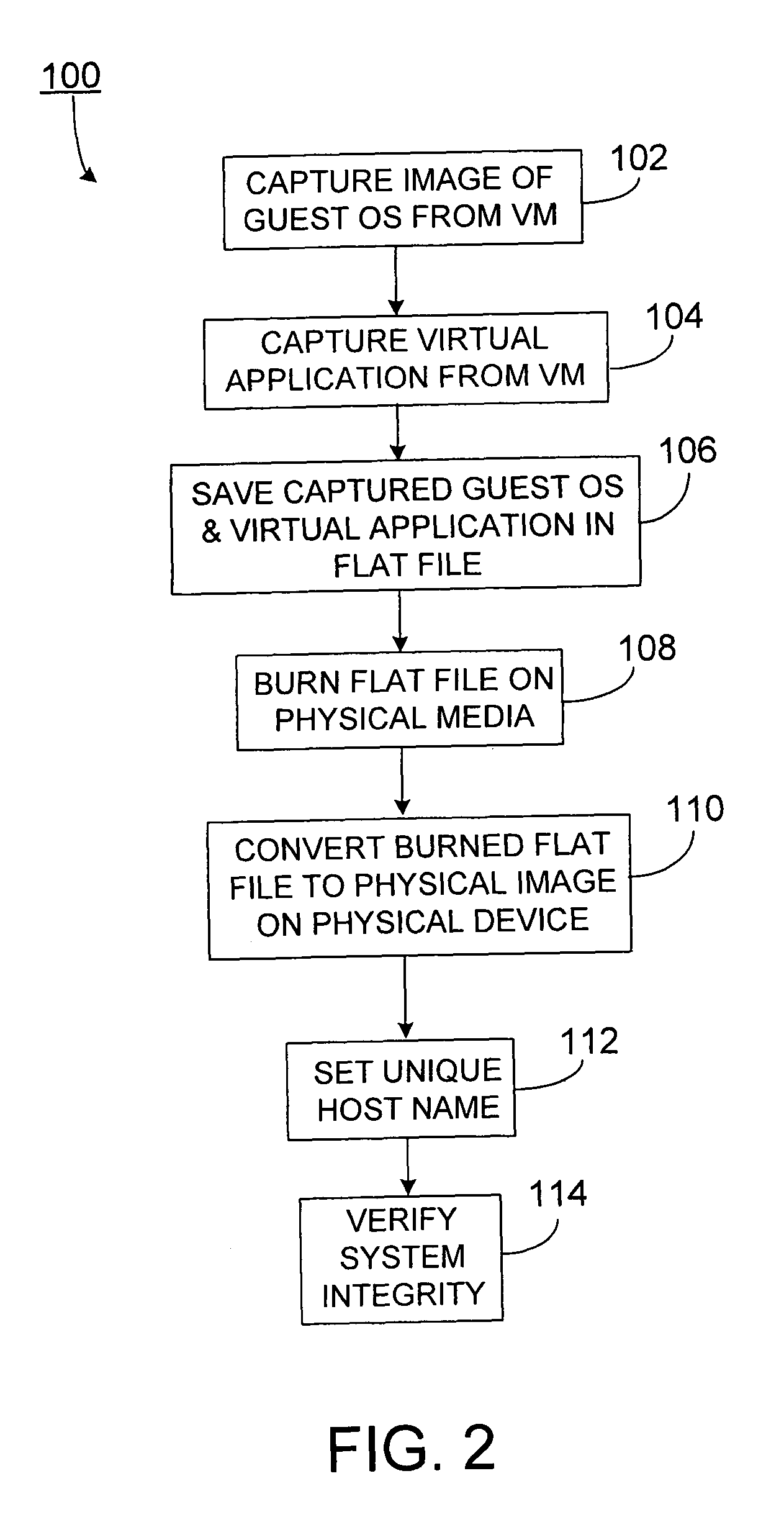
ActiveUS7725893B2Fast supplyReduce complexitySoftware simulation/interpretation/emulationMemory systemsVirtualizationOperational system
Methods and apparatus, including computer program products, for platform independent replication. Methods can include capturing a virtualized software application residing on a virtual machine, capturing a guest operating system residing on the virtual machine, and storing the captured virtualized software application including the guest operating system as a virtualization image in a flat file on a physical computing device.
Owner:SAP AG
Methods and Systems for Providing Translations of Data Retrieved From a Storage System in a Cloud Computing Environment
ActiveUS20100199037A1Memory adressing/allocation/relocationProgram controlCloud computingVirtual storage
A method for providing translations of data retrieved from a storage system in a cloud computing environment includes receiving, by an interface object executing on a first physical computing device, a request for provisioning of a virtual storage resource by a storage system. The interface object requests, from a storage system interface object, provisioning of the virtual storage resource. The interface object receives, from the storage system interface object, an identification of the provisioned virtual storage resource. The interface object translates the identification of the provisioned virtual storage resource from a proprietary format implemented by the storage system interface object into a standardized format by accessing an interface translation file mapping each of a plurality of proprietary formats with the standardized format. The interface object responds to the request received from the second physical computing device, with a translation of the received identification.
Owner:CITRIX SYST INC
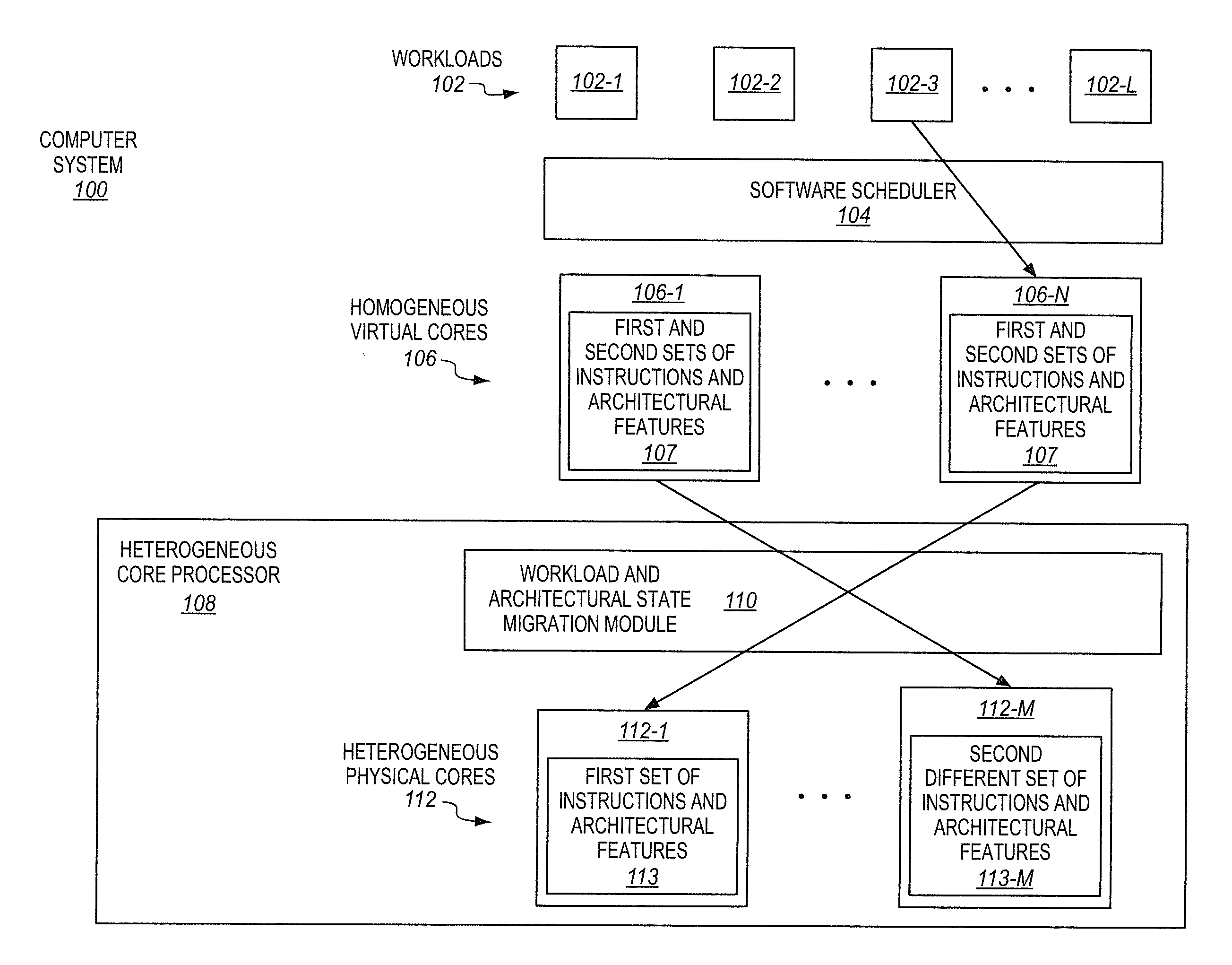
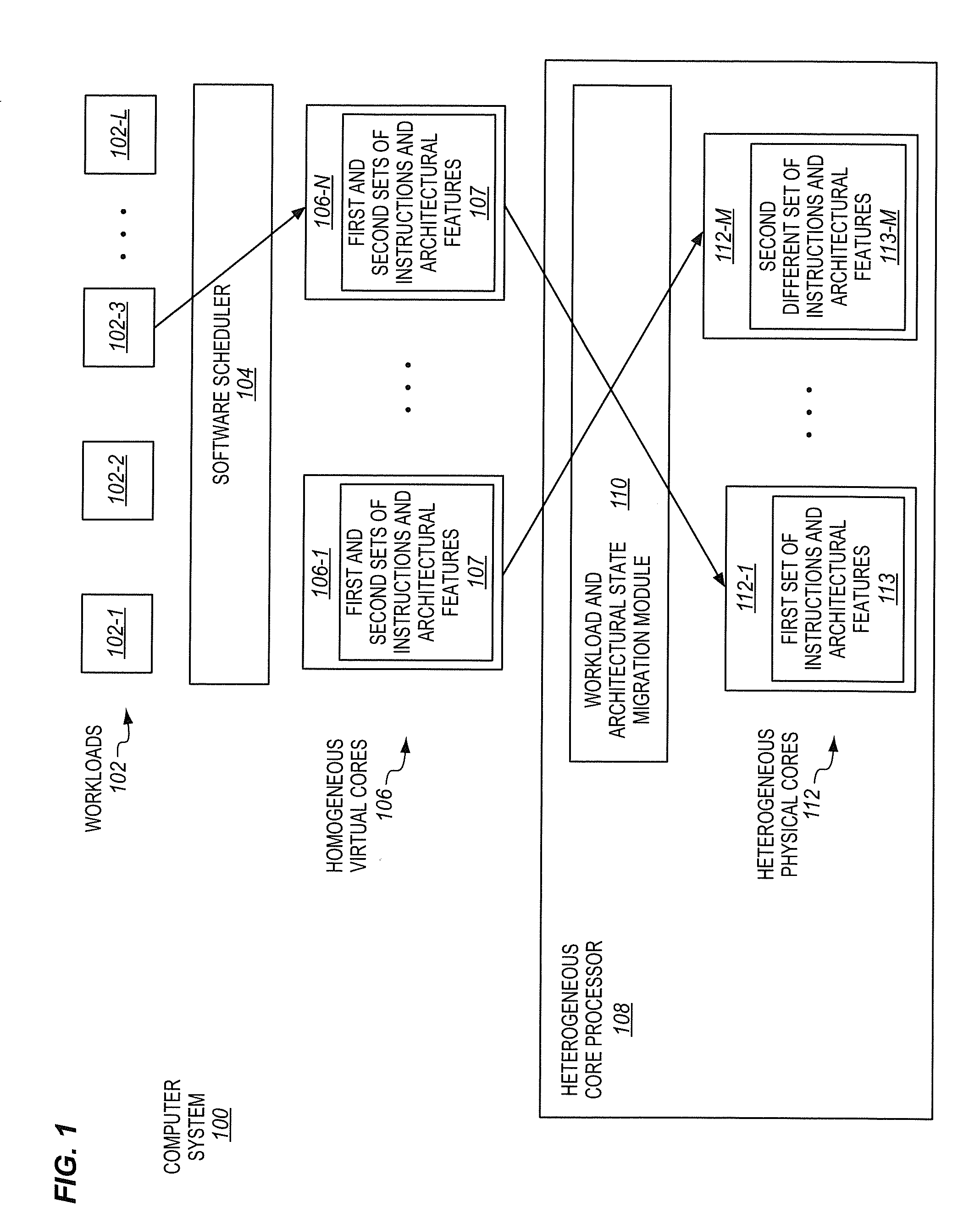
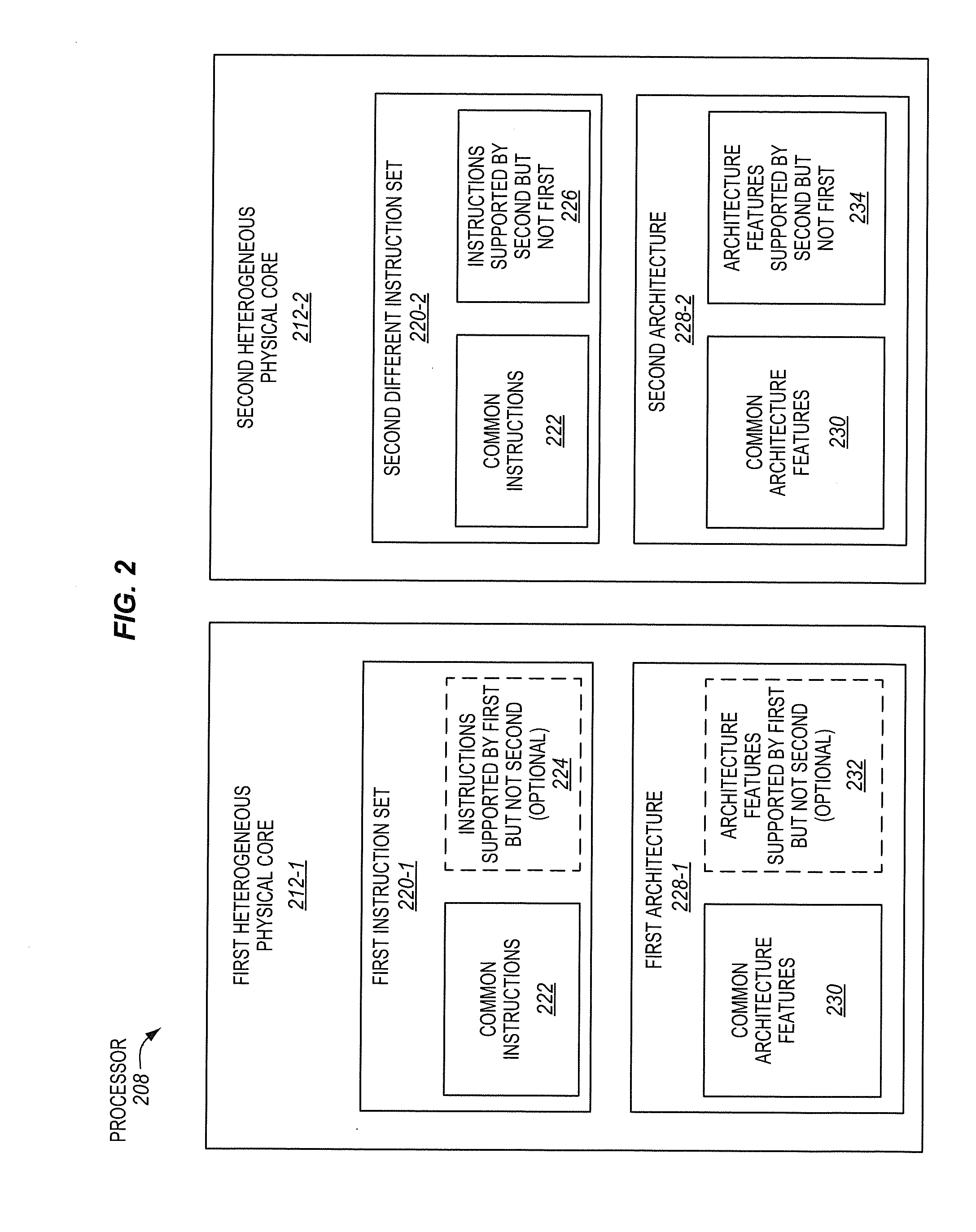
Processors having heterogeneous cores with different instructions and/or architecural features that are presented to software as homogeneous virtual cores
InactiveUS20150007196A1Resource allocationEnergy efficient computingParallel computingHeterogeneous network
A processor of an aspect includes a first heterogeneous physical compute element having a first set of supported instructions and architectural features, and a second heterogeneous physical compute element having a second set of supported instructions and architectural features. The second set of supported instructions and architectural features is different than the first set of supported instructions and architectural features. The processor also includes a workload and architectural state migration module coupled with the first and second heterogeneous physical compute elements. The workload and state migration module is operable to migrate a workload and associated architectural state from the first heterogeneous physical compute element to the second heterogeneous physical compute element in response to an attempt by the workload to perform at least one of an unsupported instruction and an unsupported architectural feature on the first heterogeneous physical compute element.
Owner:INTEL CORP
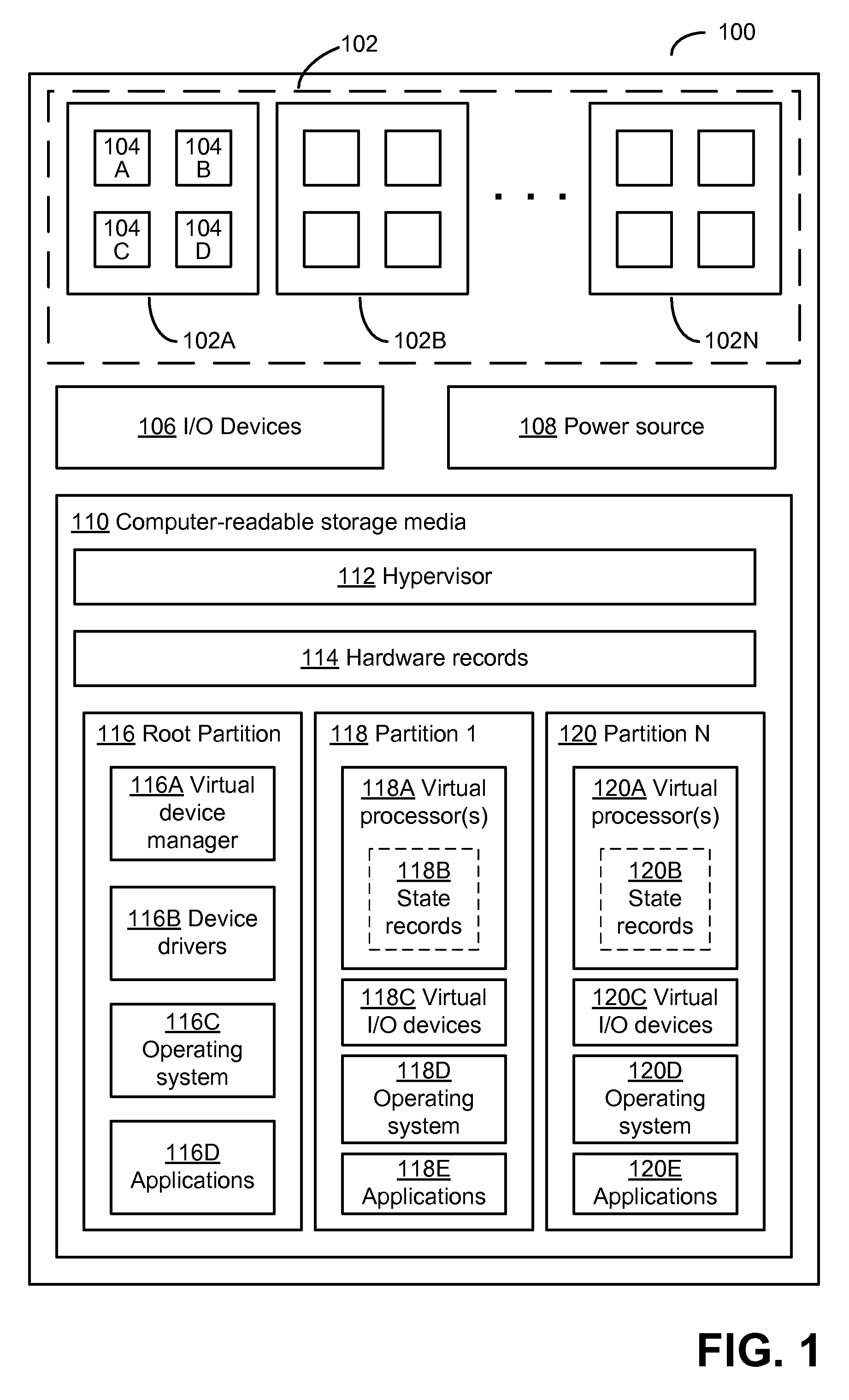
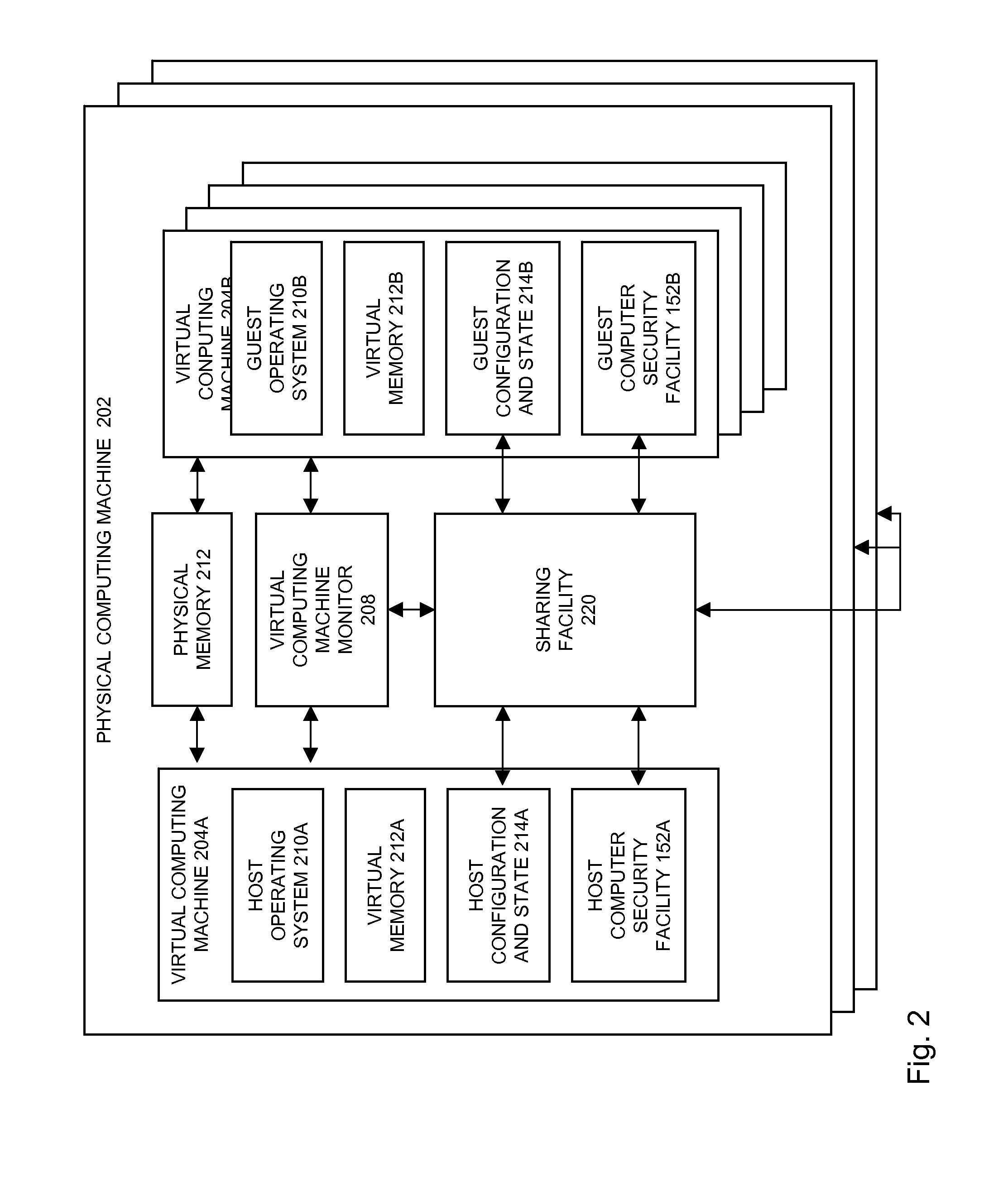
Virtual machine configuration sharing between host and virtual machines and between virtual machines
InactiveUS20090241194A1Access control be minimizedReduce controlMemory loss protectionError detection/correctionOperational systemVirtual computing
In embodiments of the present invention improved capabilities are described for presenting a physical computing machine including a virtual computer machine monitor and a one or more of virtual computing machines, where each of the virtual computing machines runs its own operating system, presenting one of the multiple virtual computing machines as a host, and the remaining multiple virtual computing machines as guests, and providing for a virtual machine protected environment, where suspicious file information is shared between the virtual machine protected environment and other virtual machines.
Owner:SOPHOS
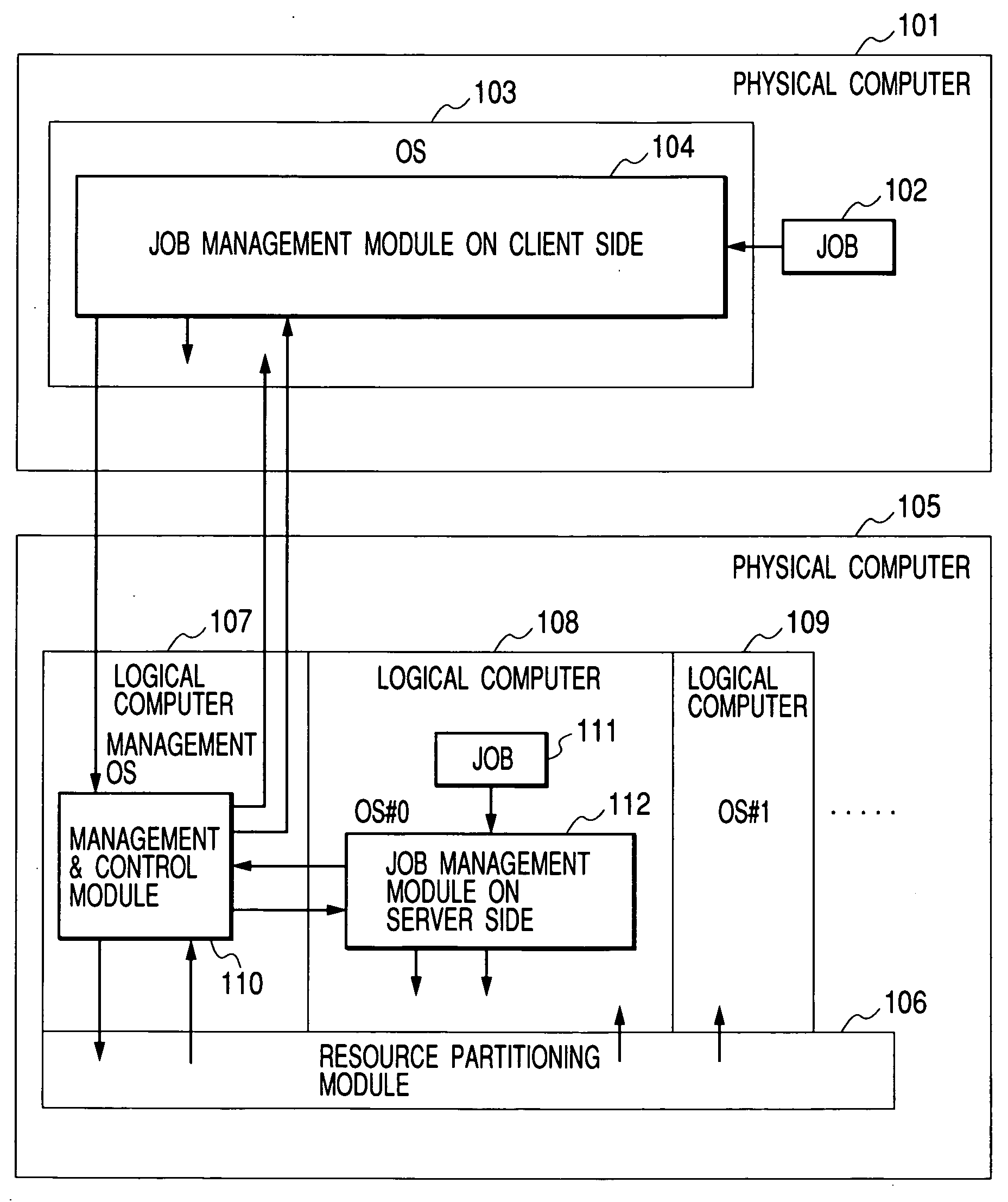
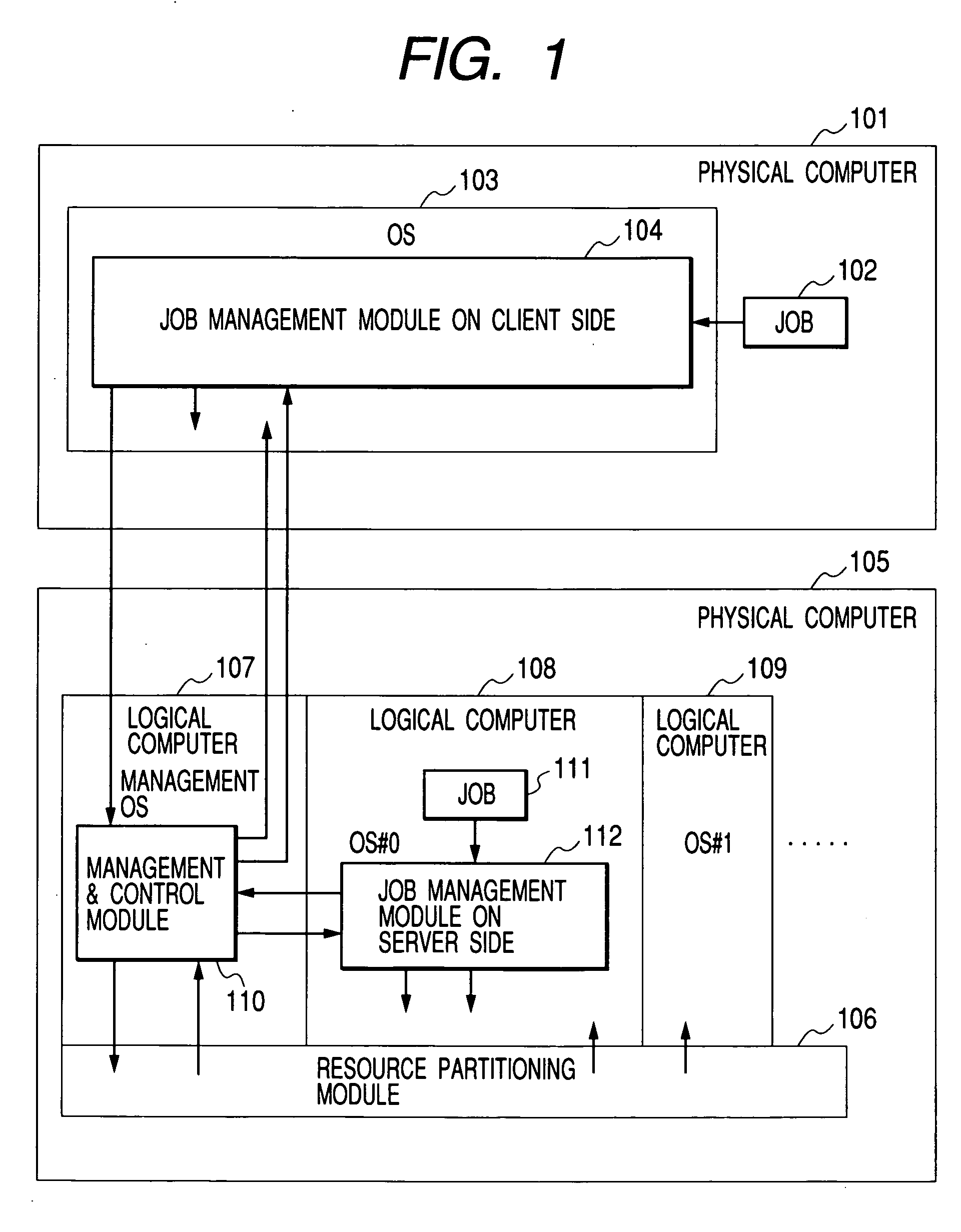
Method and program for executing a job in a remote computer in different computer environment
InactiveUS20050022188A1Reduce the burden onResource allocationMultiple digital computer combinationsOperational systemRemote computer
A client side physical computer into which the job is loaded issues a job execution request to a server side physical computer. The job execution request is accompanied by job execution statements and environment information. A management and control module on the server side starts an OS for a logical computer and exercises control to assign a server side volume corresponding to a client side volume and transfer the data on the client side volume to the server side volume. A server side job management module for the logical computer converts the original job execution statements and environment information to match the computer environment for the logical computer, and executes the requested job.
Owner:HITACHI LTD
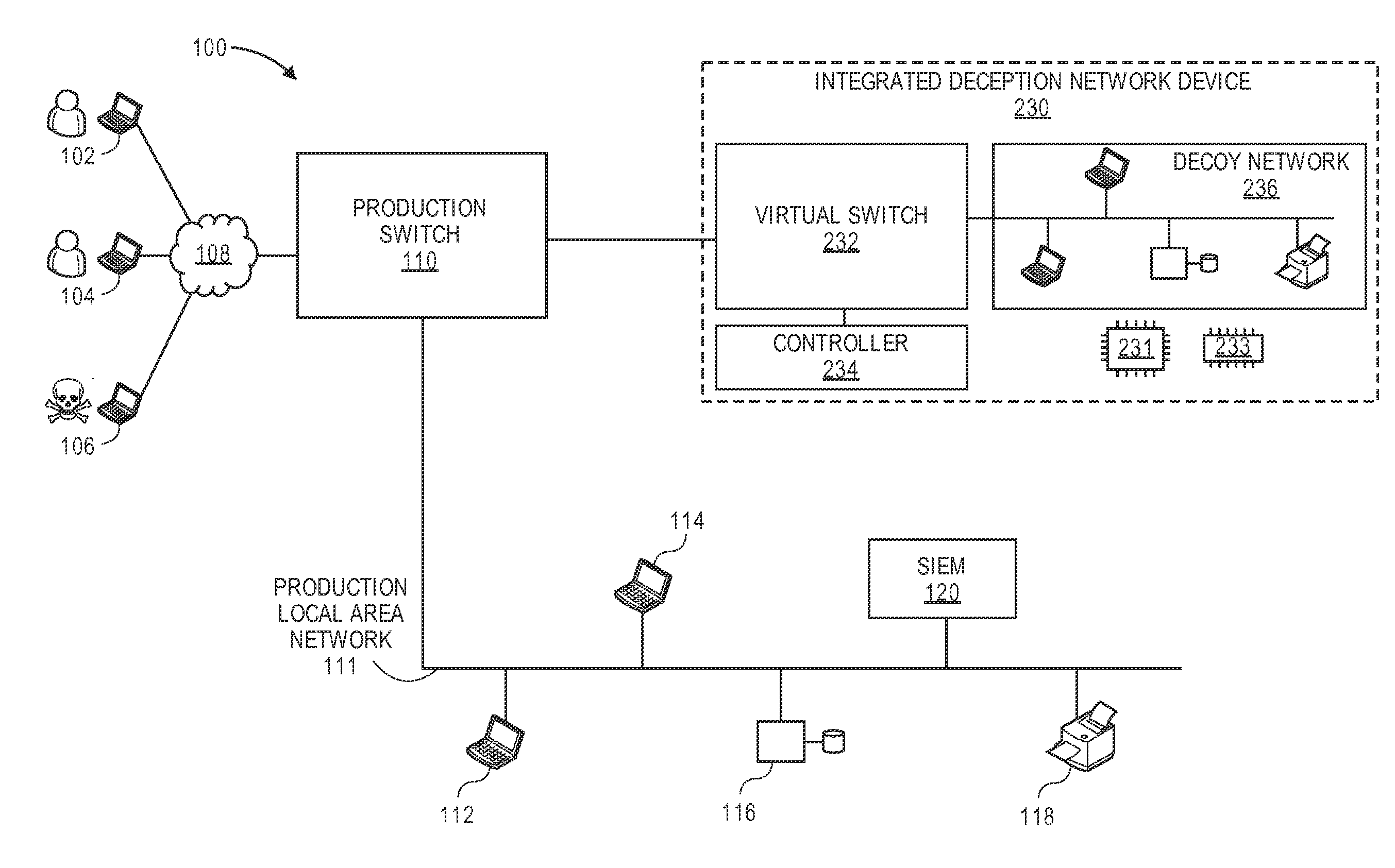
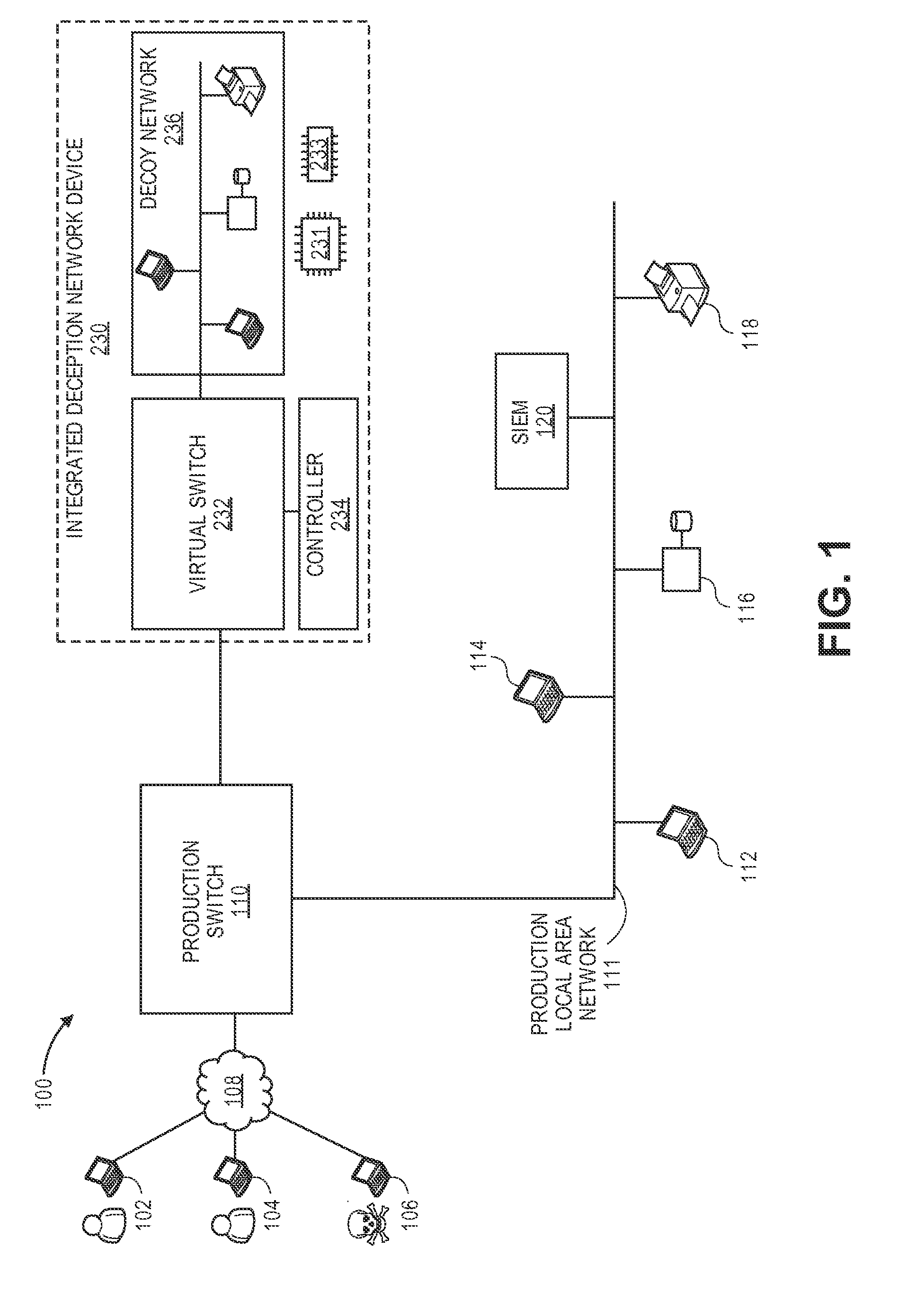
Network intrusion diversion using a software defined network
ActiveUS20160080415A1Avoid collisionMemory loss protectionError detection/correctionPacket collisionIp address
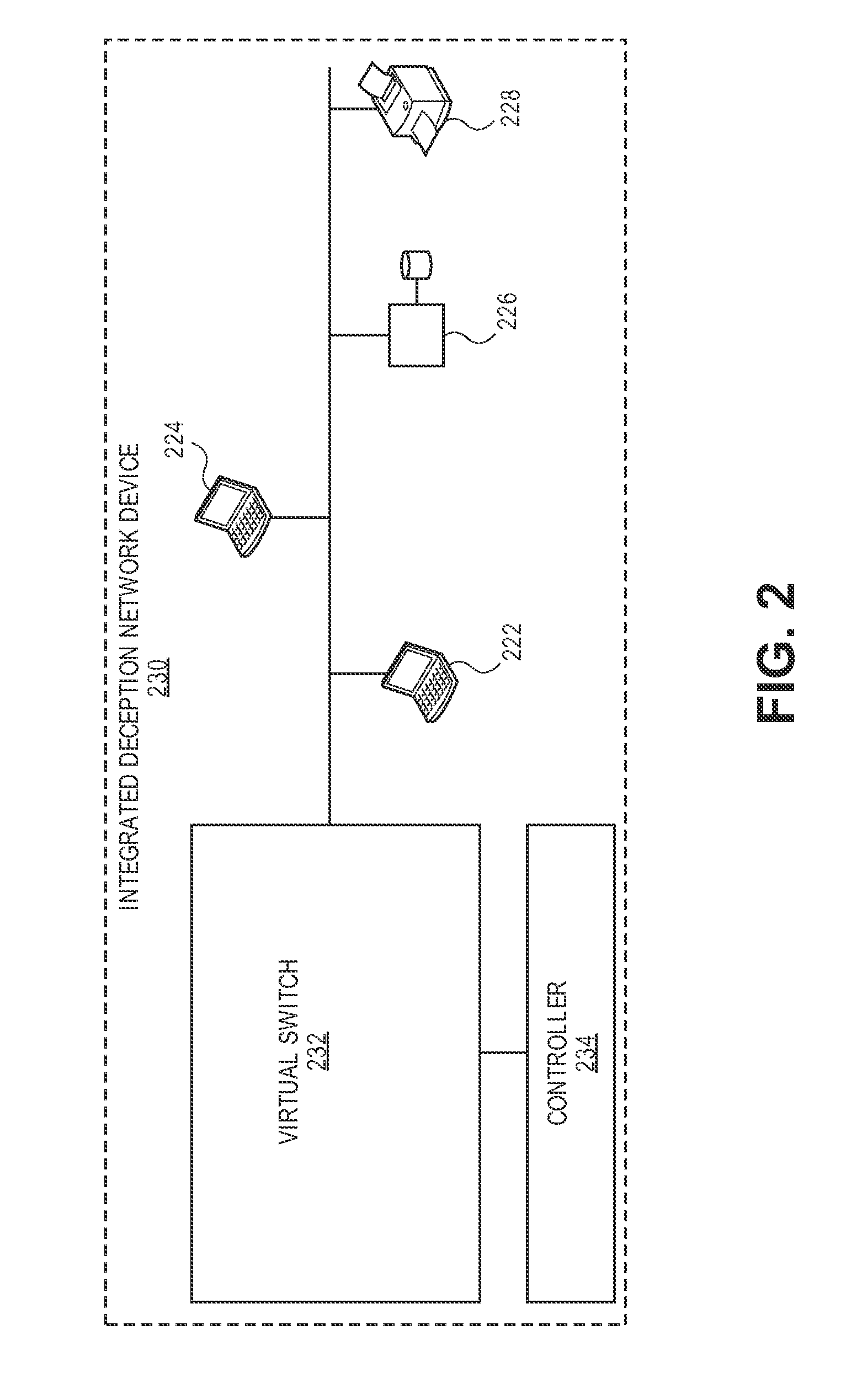
Methods, devices, and systems are described for diverting a computer hacker from a physical or other targeted production computer to a decoy software-based host emulator that emulates the physical computer. The decoy has the exact same IP address as the physical computer. In order to avoid packet collisions, a programmable physical switch and a virtual networking switch are employed, both of which can use software-defined networking (SDN). The virtual switch prevents packets from the decoy from flowing out of its virtual network until commanded. Upon a command, the physical switch redirects specific flows to the virtual switch, and the virtual switch opens specific flows from the decoy. The specific flows are those with packets containing the hacker's computer IP address, production computer IP address, and production computer port. The packets are associated with TCP connections or UDP sessions. The decoy host emulator can be a virtual machine (VM) running alongside many other VMs in a single computer. If the hacker performs a horizontal scan of the network, additional flows are diverted to other decoy host emulators.
Owner:ACALVIO TECH
Systems and methods for attaching a virtual machine virtual hard disk to a host machine
ActiveUS20060155667A1Digital data processing detailsComputer security arrangementsHard disc driveOperational system
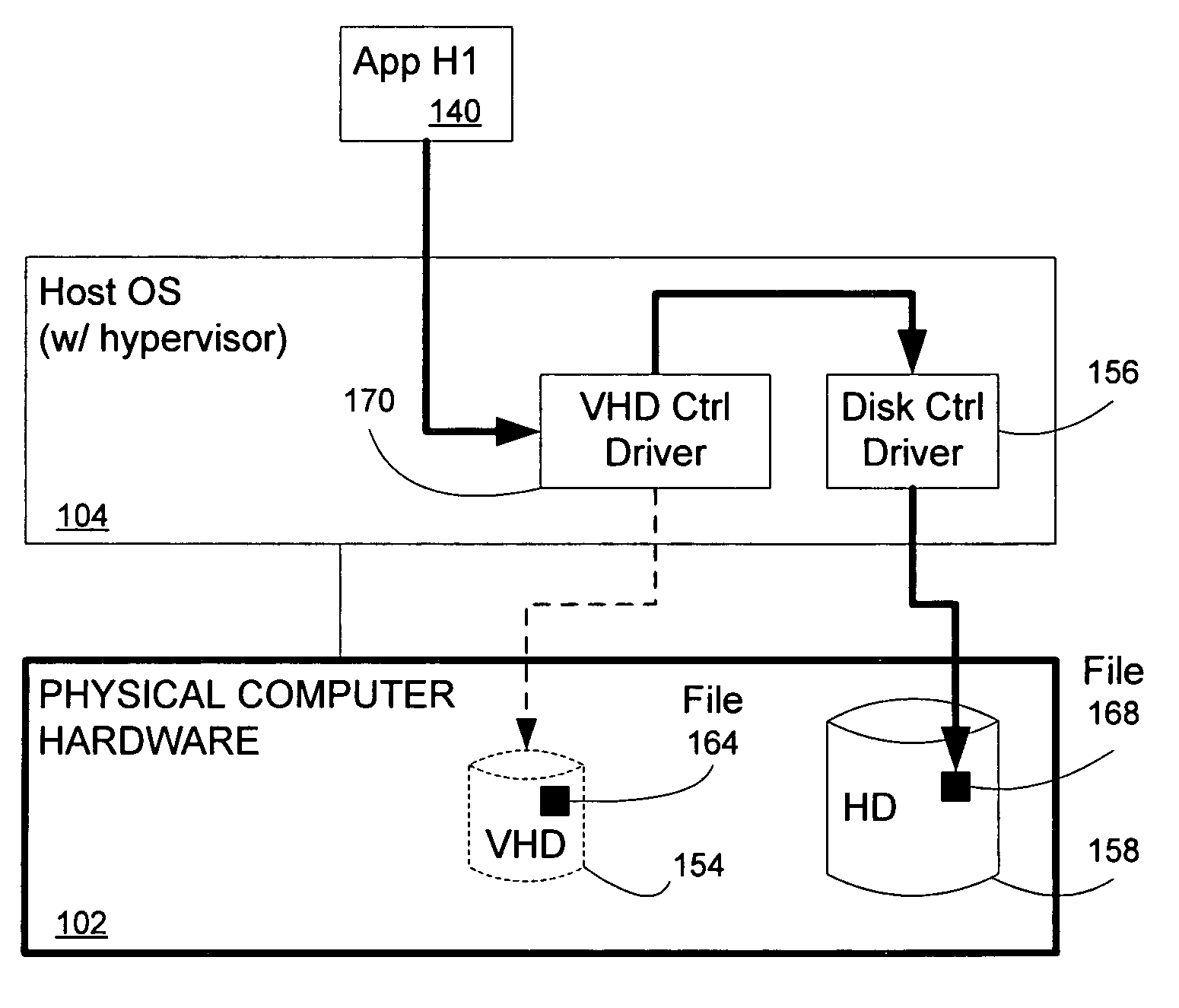
Various embodiments of the present invention are directed to systems and methods for “attaching” a virtual hard drive to the physical computer hardware by implementing a specialized disk controller driver for the host operating system that is recognized by the host operating system as a disk controller driver but which in fact also emulates the virtual hard disk it is “attached” to. When the host operating system sends requests to read and write sectors from the virtual hard drive, the specialized driver (the “virtual hard drive controller driver”) directly accesses and manipulates the back-end file mentioned above. Thus the virtual disk is “attached” and recognizable by the host operating system and can be manipulated thereby (and applications executing thereon).
Owner:MICROSOFT TECH LICENSING LLC
Methods and systems for providing to virtual machines, via a designated wireless local area network driver, access to data associated with a connection to a wireless local area network
ActiveUS20110145418A1Multiple digital computer combinationsInternal/peripheral component protectionNetwork connectionVirtual machine
The methods and systems described herein are directed to providing, to virtual machines, access to data associated with a connection to a wireless local area network, in a computing device executing a hypervisor hosting a first virtual machine and a second virtual machine. A first driver executed by a first virtual machine of the first physical computing device establishes a network connection to a second physical computing device, via a wireless local area network interface of the first physical computing device. The first driver receives from a second driver executed by a second virtual machine of the first physical computing device, a request for a characteristic of the network connection. The first driver provides, responsive to the request, data comprising the requested characteristic to the second driver.
Owner:CITRIX SYST INC
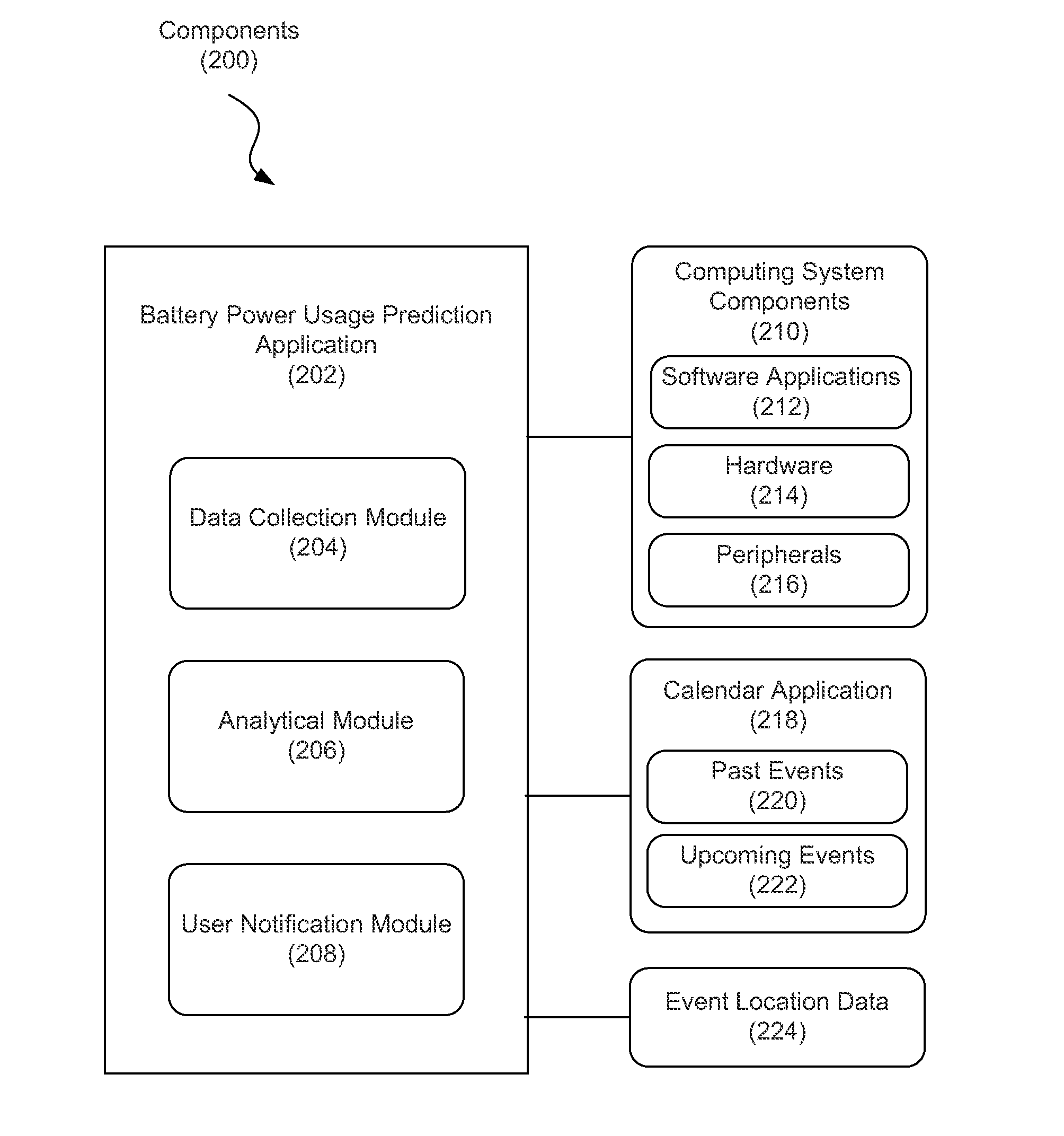
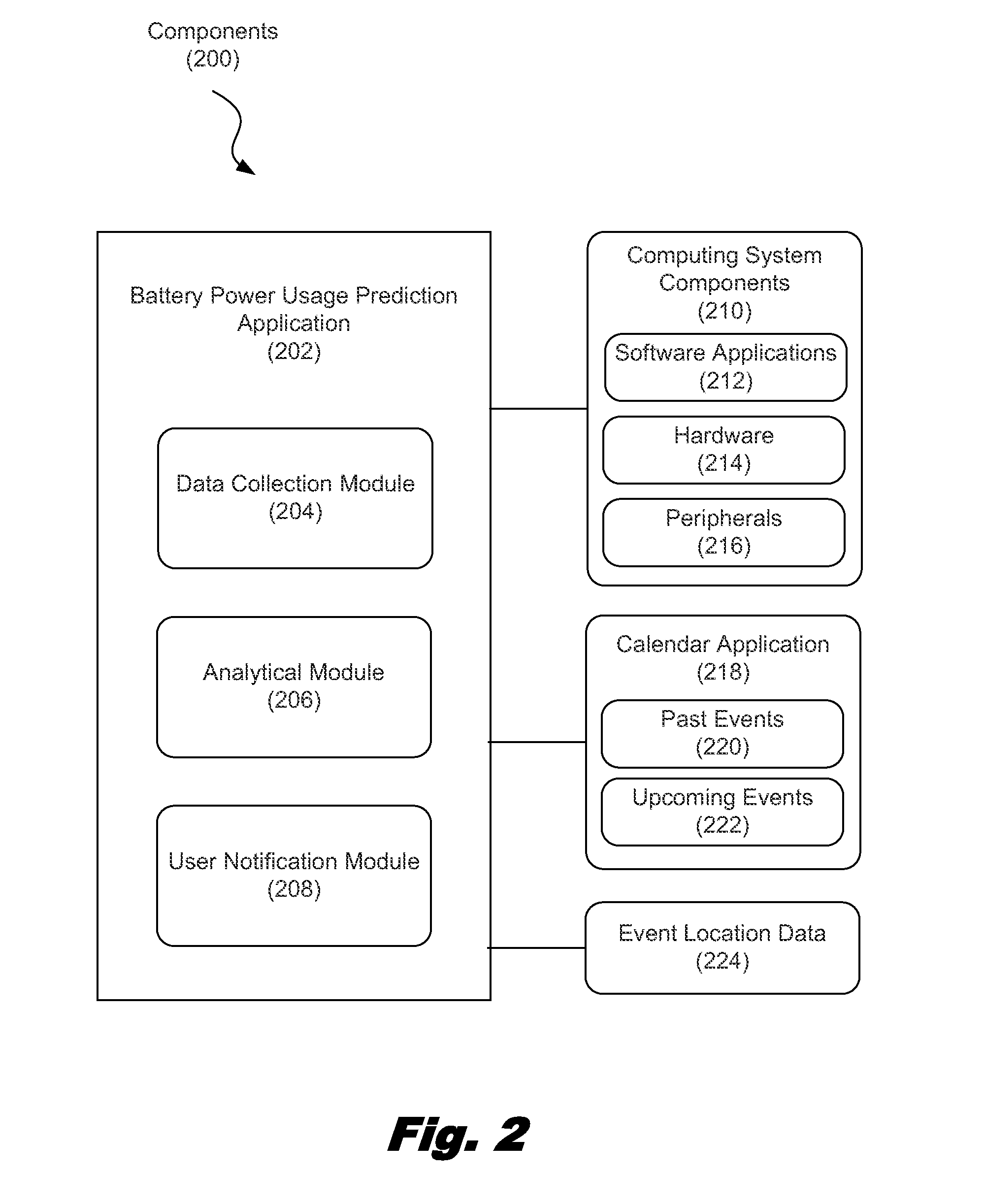
Predicting battery power usage
ActiveUS20120254634A1Volume/mass flow measurementPower supply for data processingElectrical batteryPower usage
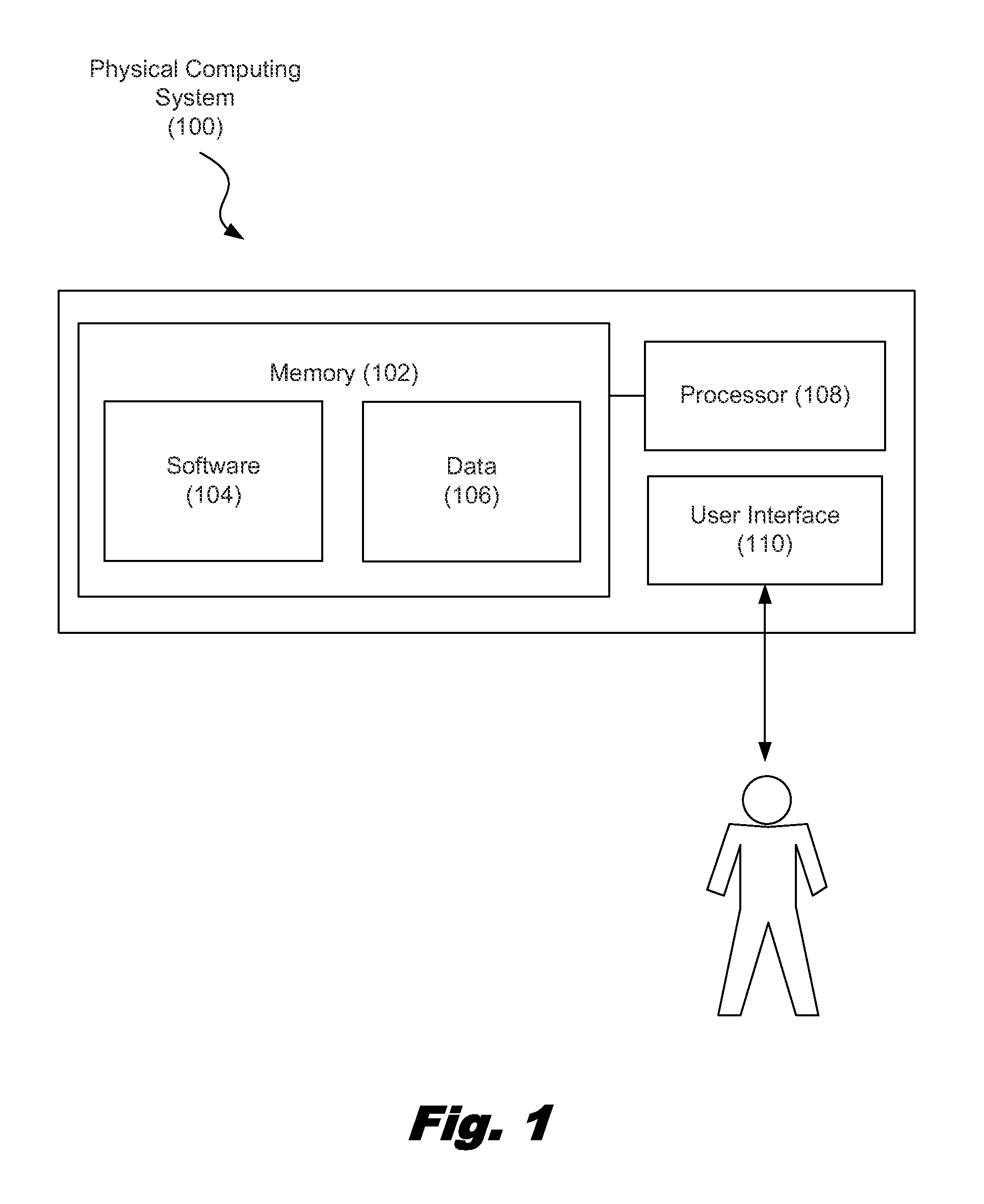
A method for predicting battery power usage includes, collecting information relating to battery power consumption due to tasks performed by the physical computing system powered by a battery, and notifying a user in response to a determination that tasks associated with an upcoming event stored in a calendar application of the physical computing system are projected to exhaust the battery. A computing system includes a processor, a memory communicatively coupled to the processor, and a battery to power the computing system. The processor is configured to collect information relating to battery power consumption due to tasks performed by the computing system, and notify a user in response to a determination that tasks associated with an upcoming event stored in a calendar application of the computing system are projected to exhaust the battery.
Owner:IBM CORP
Method for controlling a virtual machine and a virtual machine system
InactiveUS20090007112A1Improve performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationPhysics processing unit
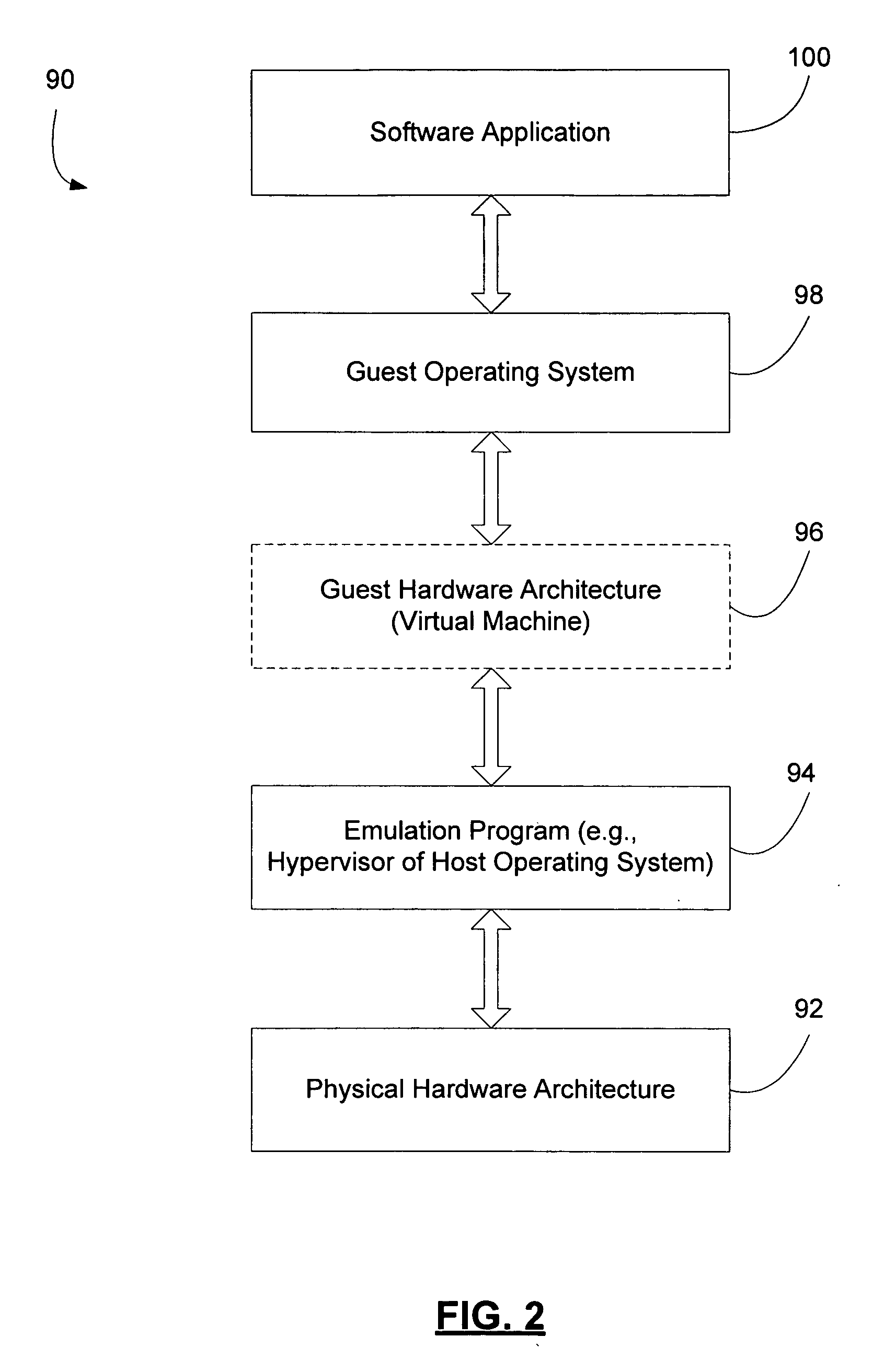
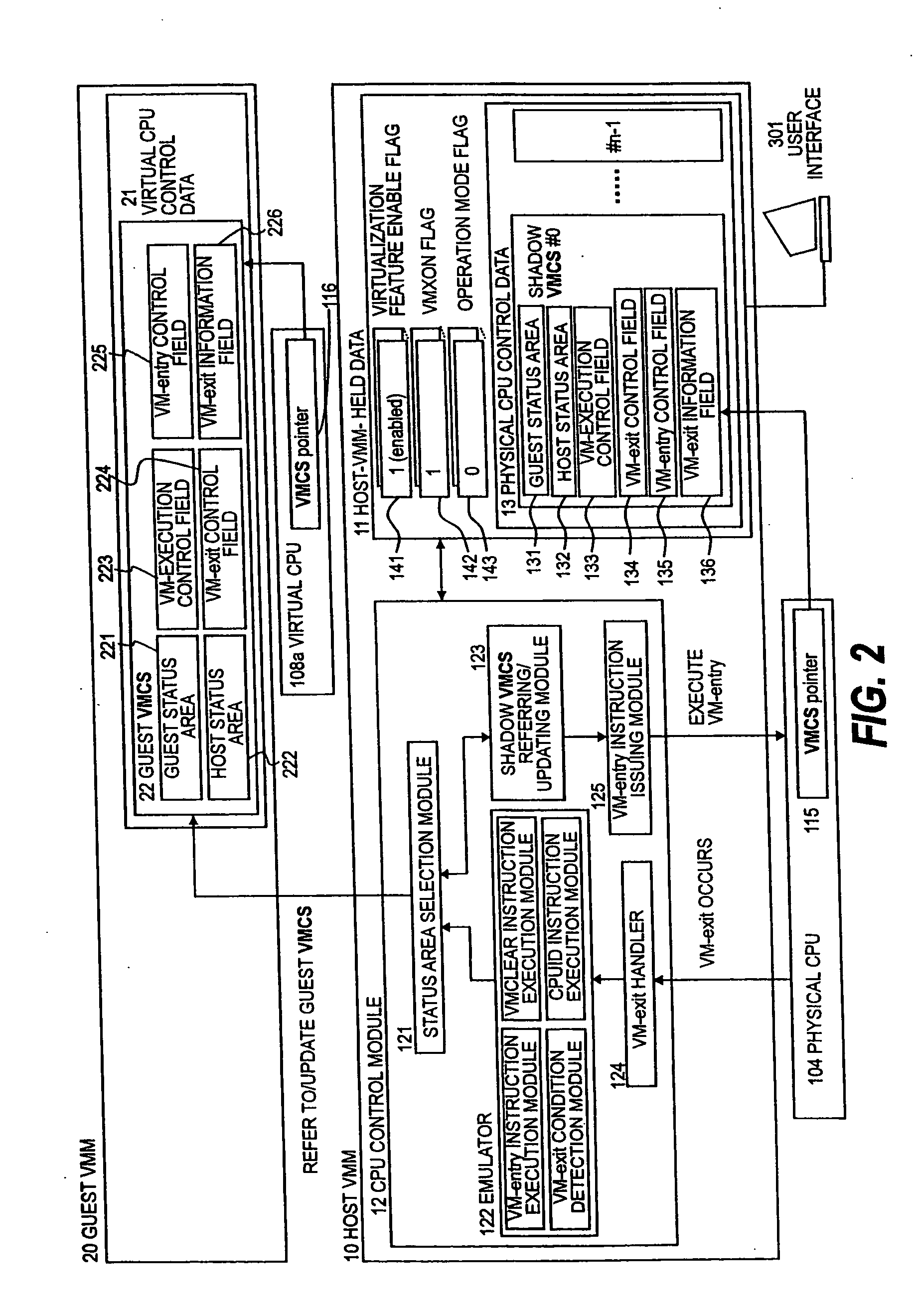
A next-generation OS with a virtualization feature is executed as a user program on a first virtual processor by selecting, in response to a cause of a call for a host VMM, one of a guest status area (221) for executing a user program on a second virtual processor and a host status area (222) for executing the guest VMM, and by updating a guest status area (131) of a shadow VMCS for controlling a physical processor. Accordingly, without a decrease in performance of a virtual computer, the next-generation OS incorporating the virtualization feature is executed on a virtual server, and the next-generation OS and an existing OS are integrated on a single physical computer.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com