Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
509 results about "Computer support" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
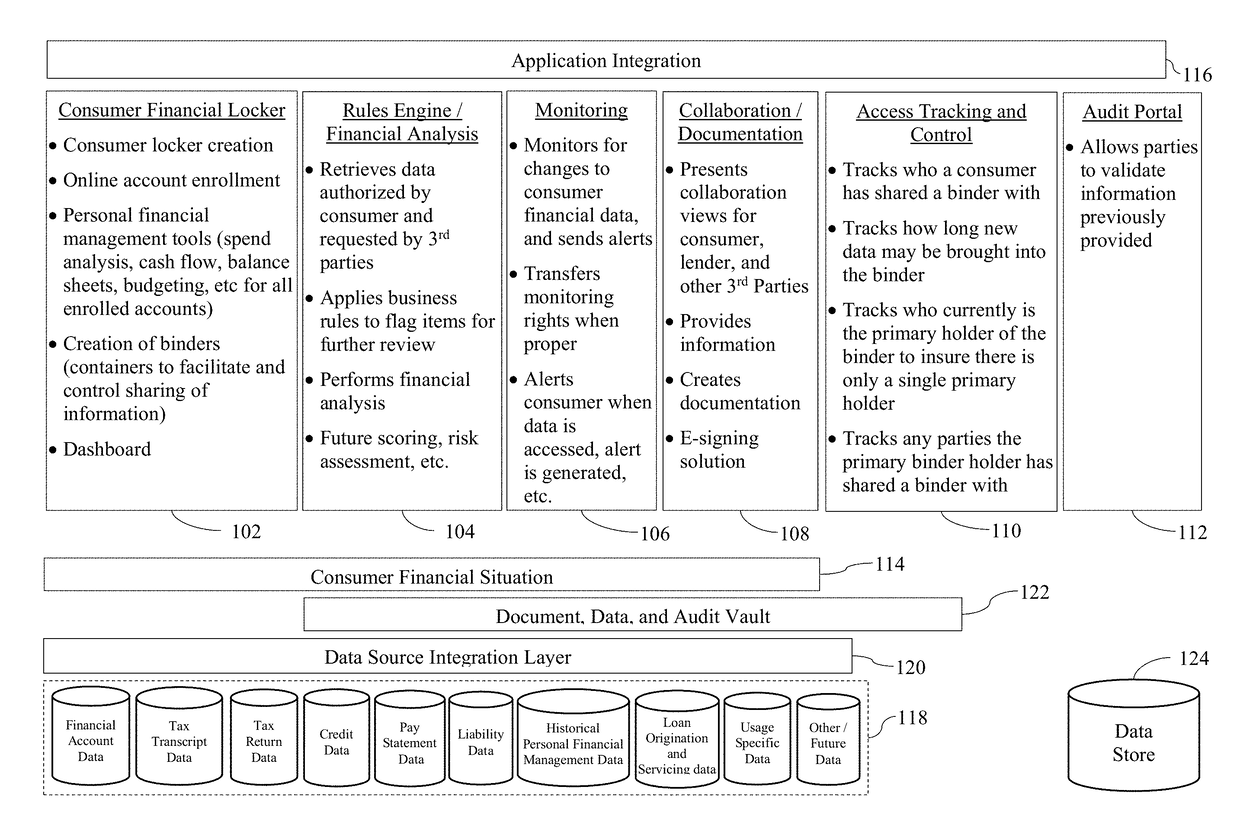
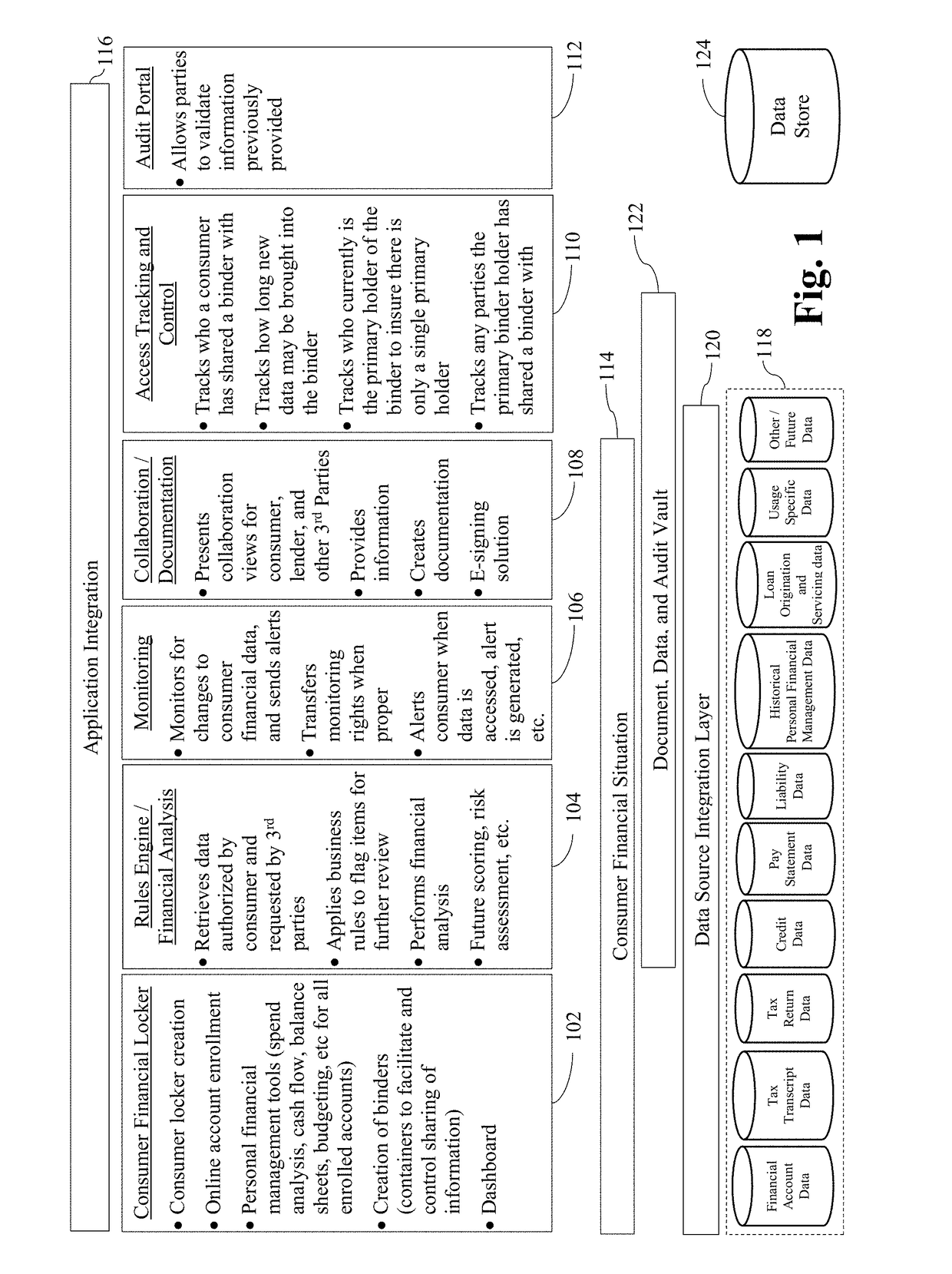
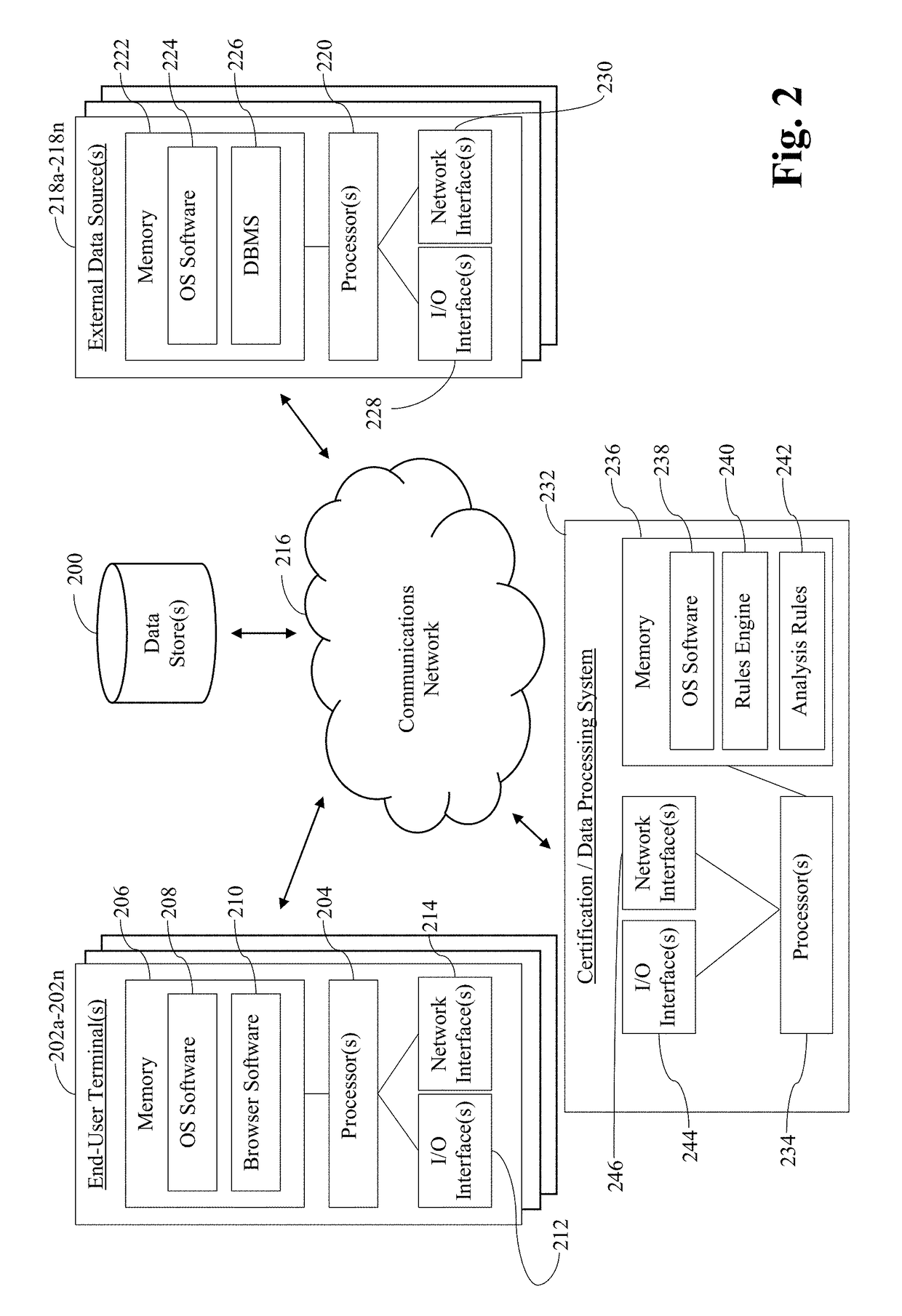
Systems and/or methods for enabling cooperatively-completed rules-based data analytics of potentially sensitive data
Certain example embodiments relate to systems and / or methods for providing enhanced control over potentially sensitive data sharable among and / or between different parties. For example, certain example embodiments provide views into computer-enabled workflows managed by external parties, including views into what sensitive data has been accessed, who has accessed it, etc., e.g., throughout the lifecycle of a product granted on the basis of an analysis of such data. A computer-enabled system for automatically assessing received sensitive data in accordance with one or more digitized rule sets also is provided in certain example embodiments, as are computer-mediated tools for helping to automatically, semi-automatically, and / or manually resolve issues detected in the assessments, e.g., via enhanced communication and collaboration, among and / or between parties to a transaction, as well as third-parties who indirectly are involved in the transaction. The data remains secure and traceable, e.g., in accordance with its provider's specifications.
Owner:FINLOCKER LLC
Collaborative diagnostic systems
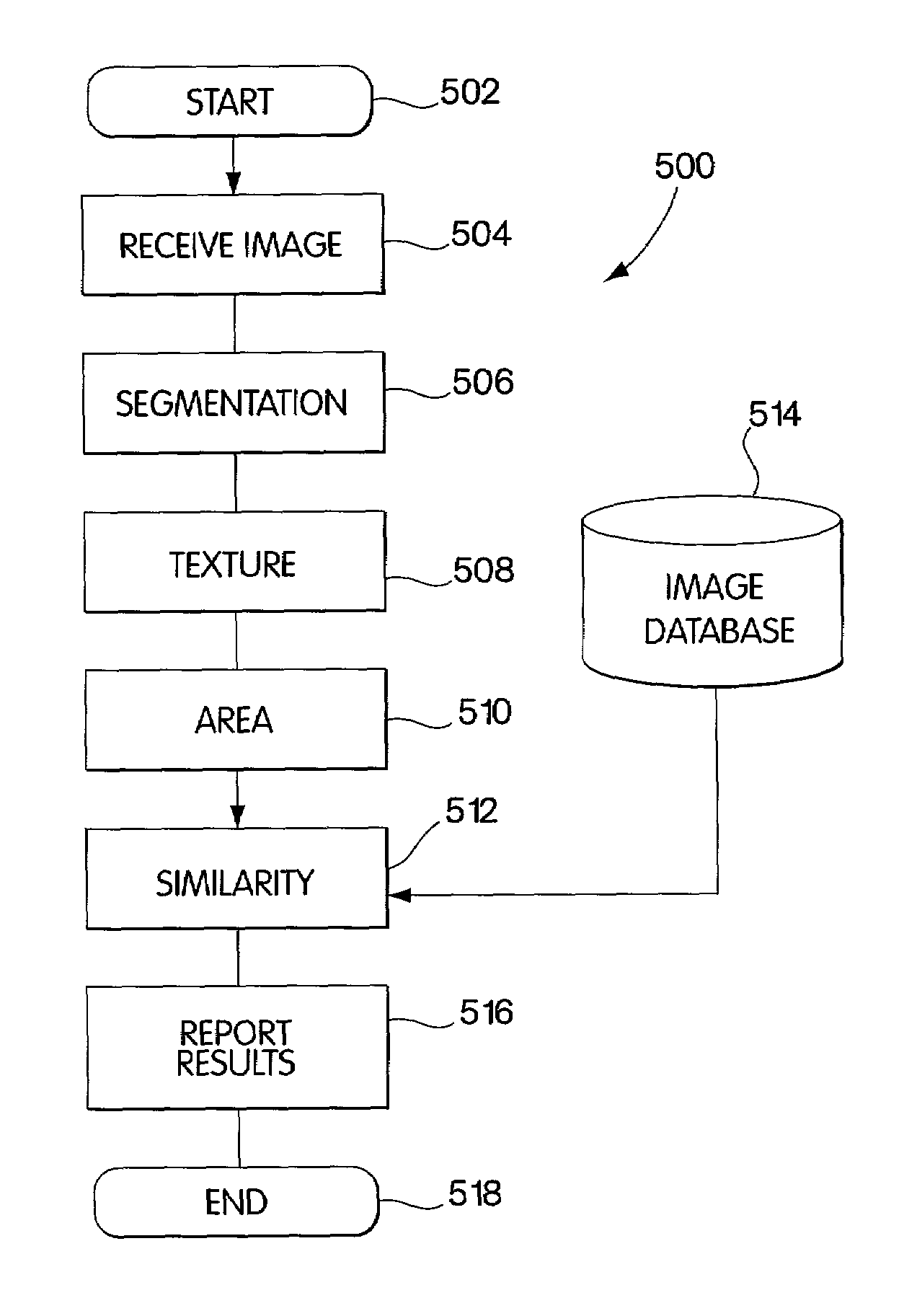
InactiveUS7027633B2Improve accuracyEasy to detectImage enhancementImage analysisHuman decisionData mining
The systems described herein include tools for computer-assisted evaluation of objective characteristics of pathologies. A diagnostic system arranged according to the teachings herein provides computer support for those tasks well suited to objective analysis, along with human decision making where substantial discretion is involved. Collaborative diagnosis may be provided through shared access to data and shared control over a diagnostic tool, such as a telemicroscope, and messaging service for clinicians who may be at remote locations. These aspects of the system, when working in cooperation with one another, may achieve improved diagnostic accuracy or early detection for pathologies such as lymphoma.
Owner:RUTGERS THE STATE UNIV
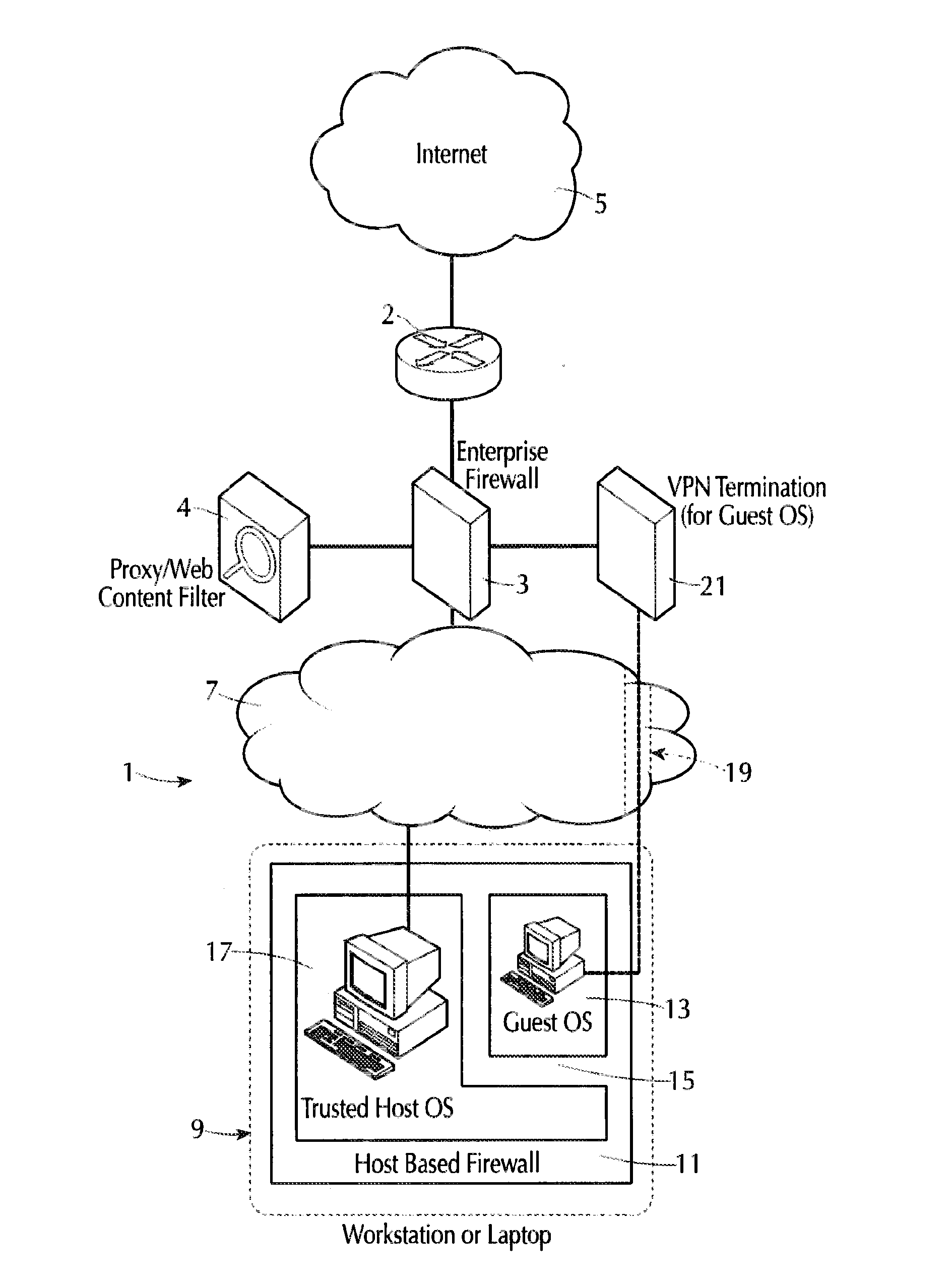
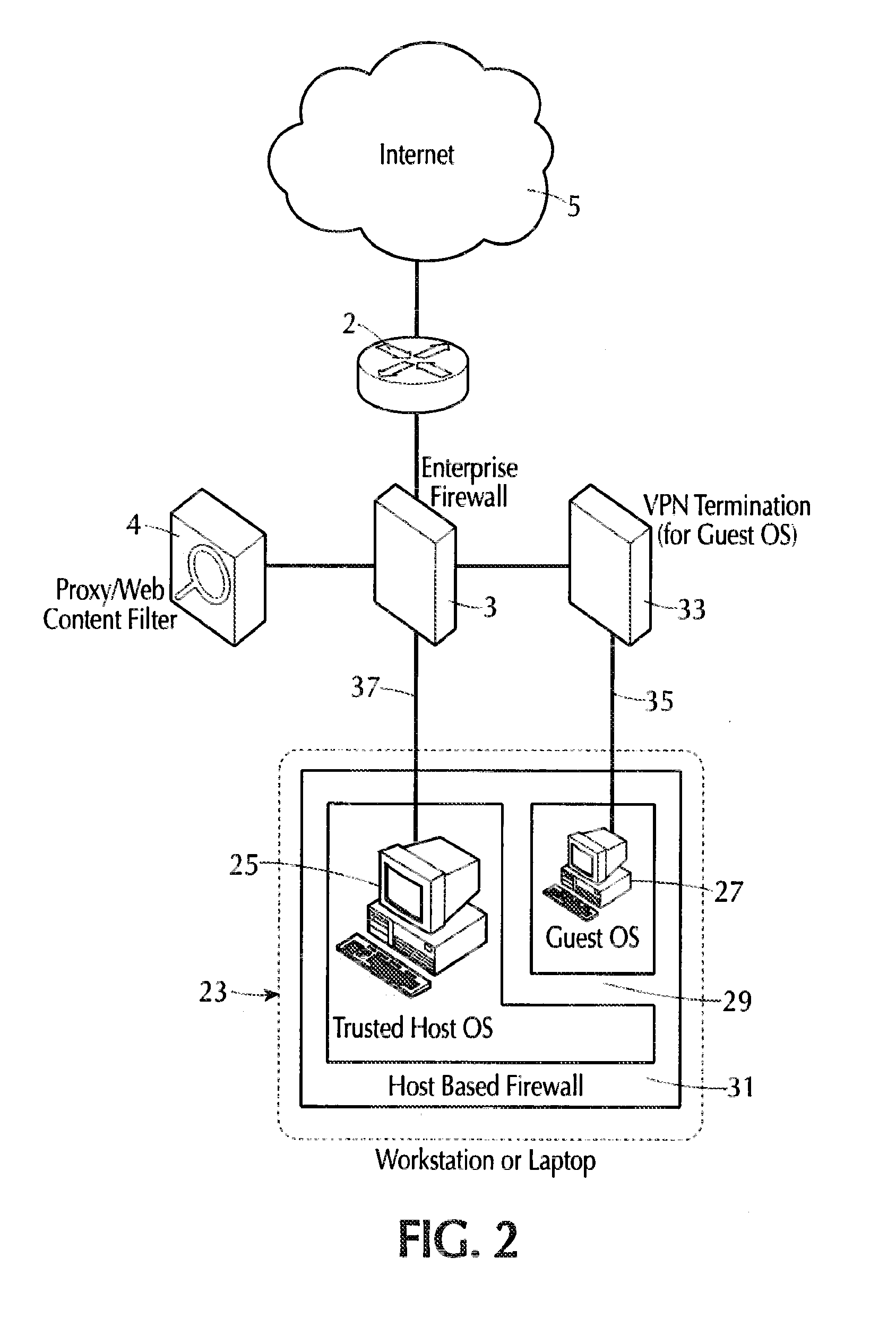
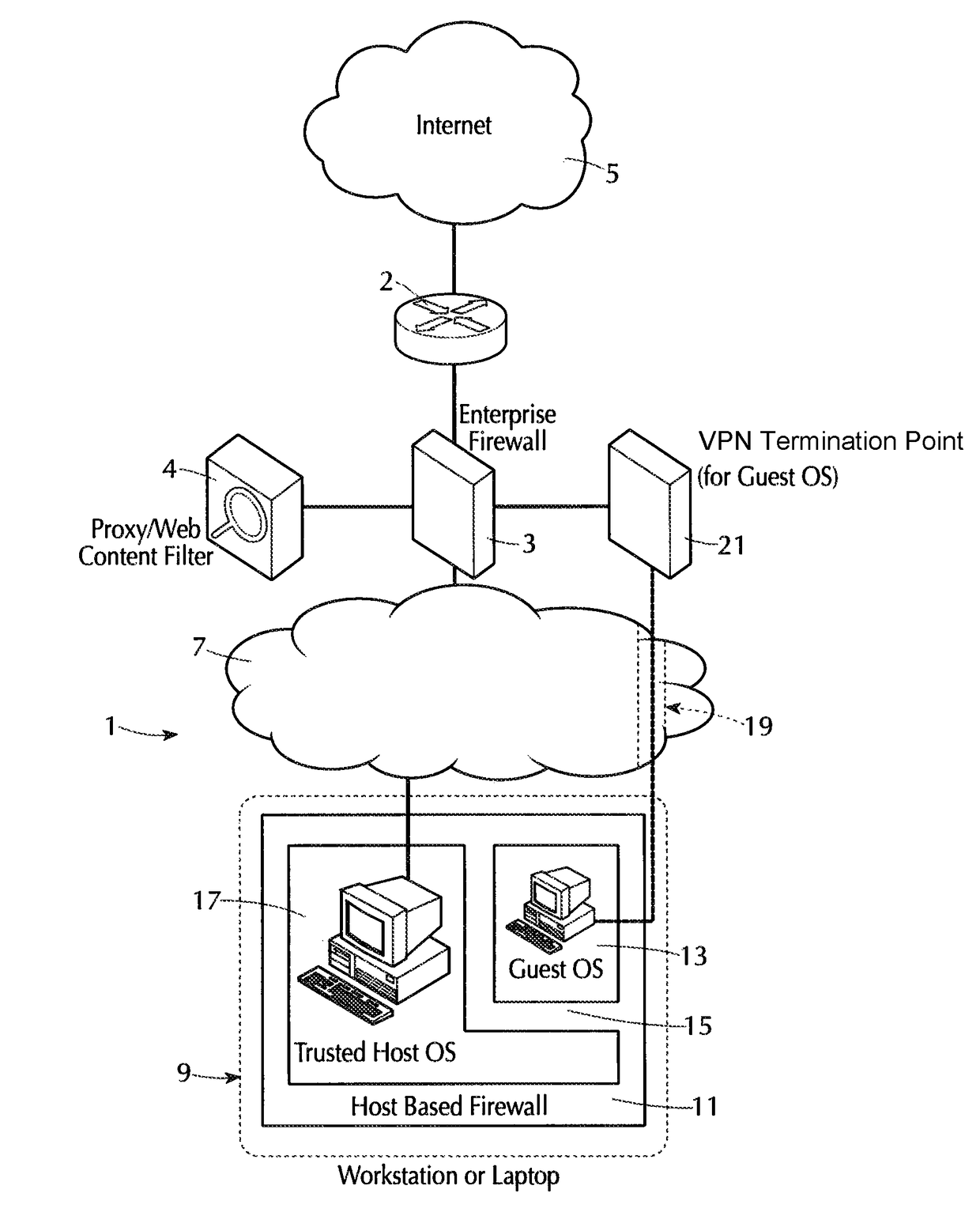
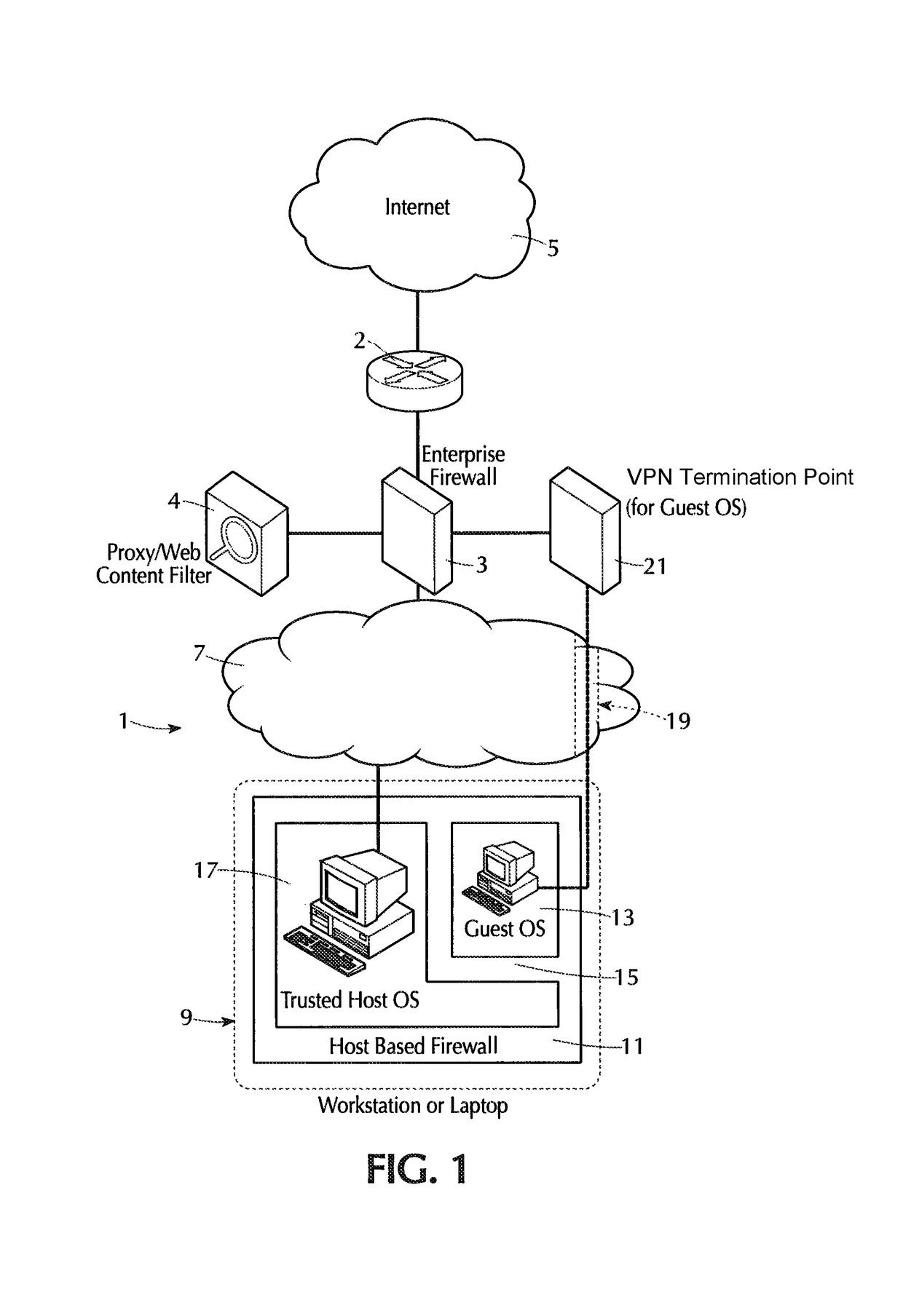
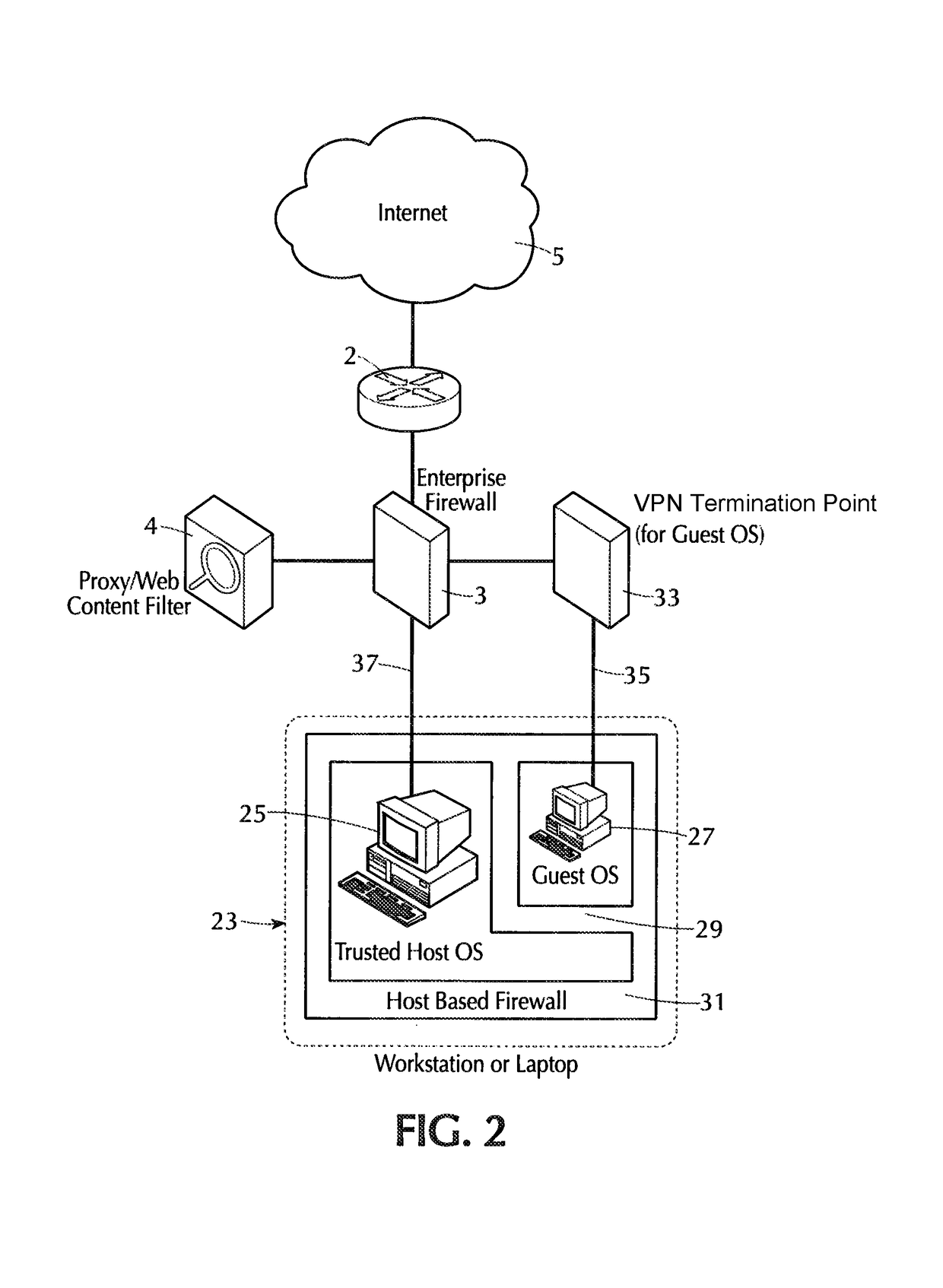
Internet isolation for avoiding internet security threats
ActiveUS20130318594A1Obviates abilityReduce the possibilityMultiple digital computer combinationsPlatform integrity maintainanceNetwork terminationPrivate network
A host computer supports a virtual guest system running thereon. The host system has a firewall that prevents it from communicating directly with the Internet, except with predetermined trusted sites. The virtual guest runs on a hypervisor, and the virtual guest comprises primarily a browser program that is allowed to contact the Internet freely via an Internet access connection that is completely separate from the host computer connection, such as a dedicated network termination point with its specific Internet IP address, or by tunneling through the host machine architecture to reach the Internet without exposing the host system. The virtual guest system is separated and completely isolated by an internal firewall from the host, and the guest cannot access any of the resources of the host computer, except that the guest can initiate cut, copy and paste operations that reach the host, and the guest can also request print of documents. The host can transfer files to and from a virtual data storage area accessible by the guest by manual operator action. No other transfer of data except these user initiated actions is permitted.
Owner:L3 TECH INC
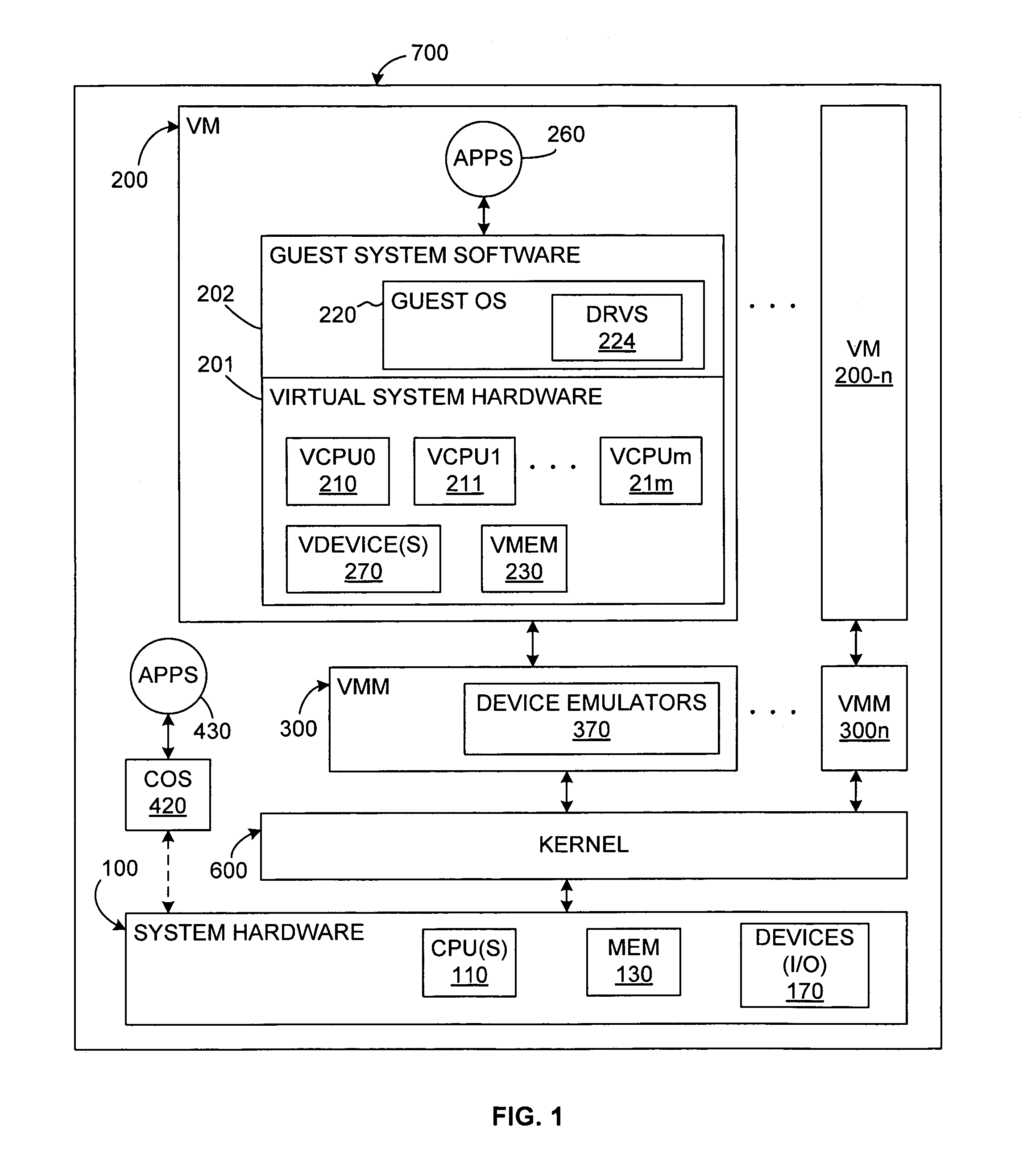
On-line replacement and changing of virtualization software
ActiveUS7814495B1Fast and non-disruptive and online updating and replacement and changingSoftware engineeringMultiprogramming arrangementsComputer supportedComputer support
In a virtualized system running one or more virtual machines on a first hypervisor, a second hypervisor is installed and control of the hardware resources of the physical computer supporting the virtualized system is migrated from the first hypervisor to the second hypervisor without interrupting the operation of the first hypervisor and the virtual machines. Initially a minimal set of hardware resources is hot-removed from control by the first hypervisor, and the second hypervisor is launched on the minimal set of hardware resources. Both the remaining hardware resources and the virtual machines are then migrated from the first hypervisor to the second hypervisor until all the virtual machines have been migrated over to the second hypervisor, while the virtual machines and the first hypervisor continue running largely unaffected by the migration process.
Owner:VMWARE INC
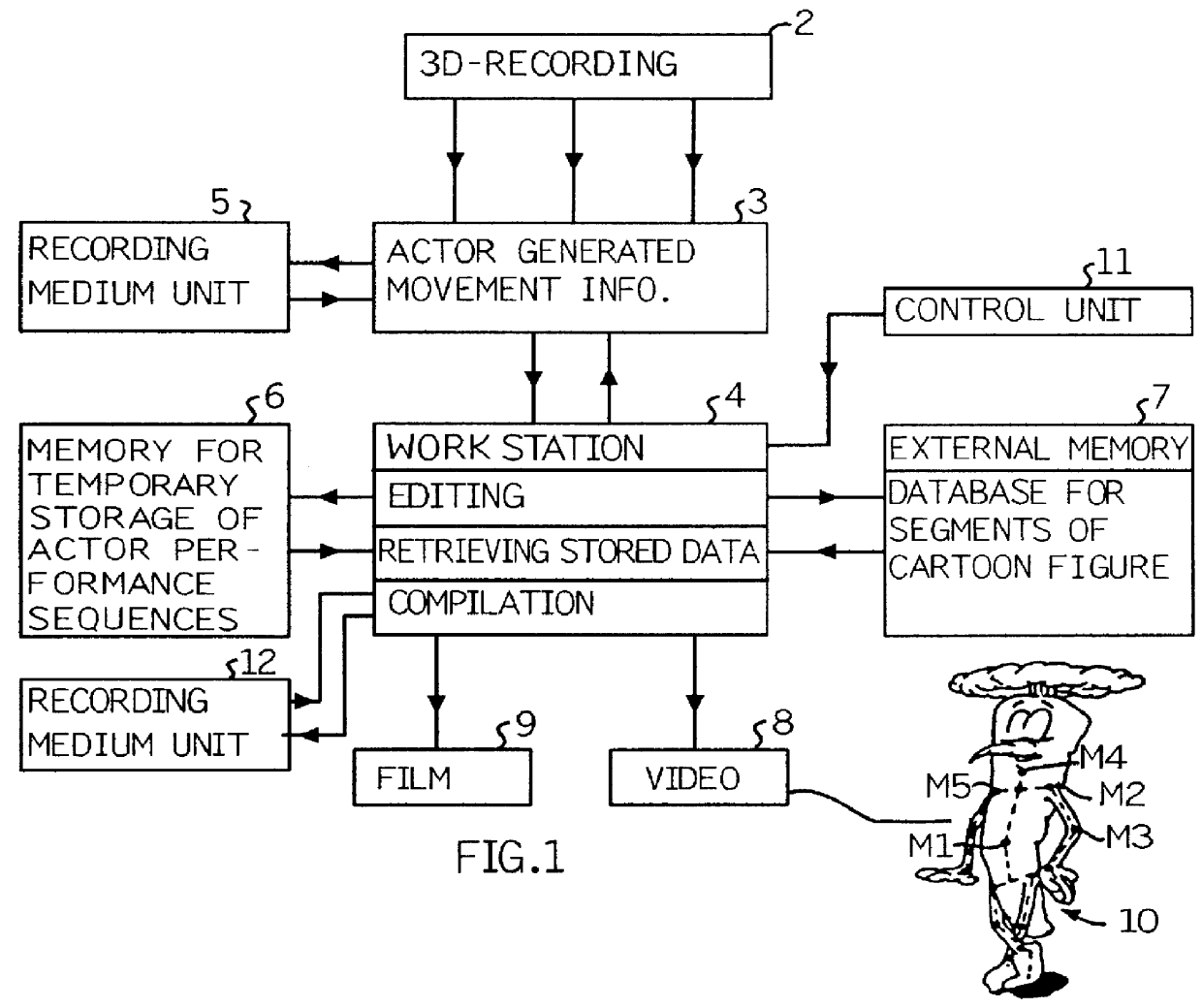
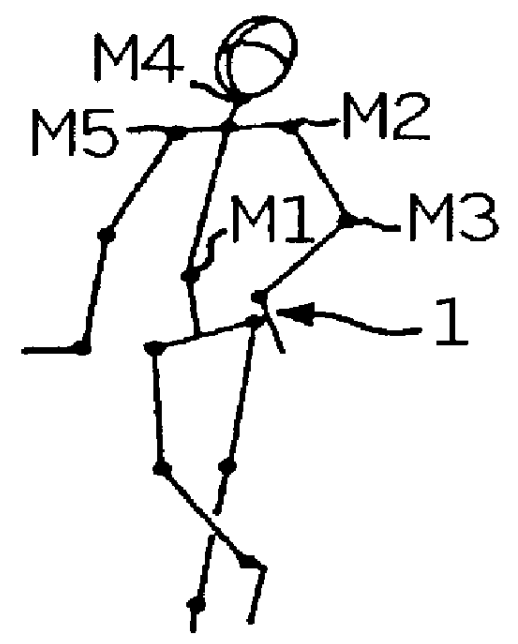
Method and apparatus for computer supported animation
A method for producing computer processed animation includes a work station composed of a computer and peripheral equipment which produces a graphic movement sequence for a cartoon figure, by compiling a recording of measured data from strategic parts of an actor, and storing in a memory information concerning the figure to be animated. The figure is divided into a plurality of sections which are movable in relation to one another. Prior to figure compilation for producing an image of the figure, the measured data recording for each section is obtained in the form of a space angle. Prior to compiling each section, a grouping of a predetermined number of perspective drawings is stored, in digitized form, in a respective area of the memory, each grouping in a plurality of mutually different space angle positions. A memory area of interest representing a perspective drawing of one of the sections can be addressed with the aid of information relating to the space angle obtained from the measured data recording for the section concerned. The figure is compiled in the compilation image in accordance with a predetermined sequential compilation schedule, section after section, where each subsequent section is added to the nearest proceeding section at a joint location, to build the sections.
Owner:STRANDBERG ORJAN
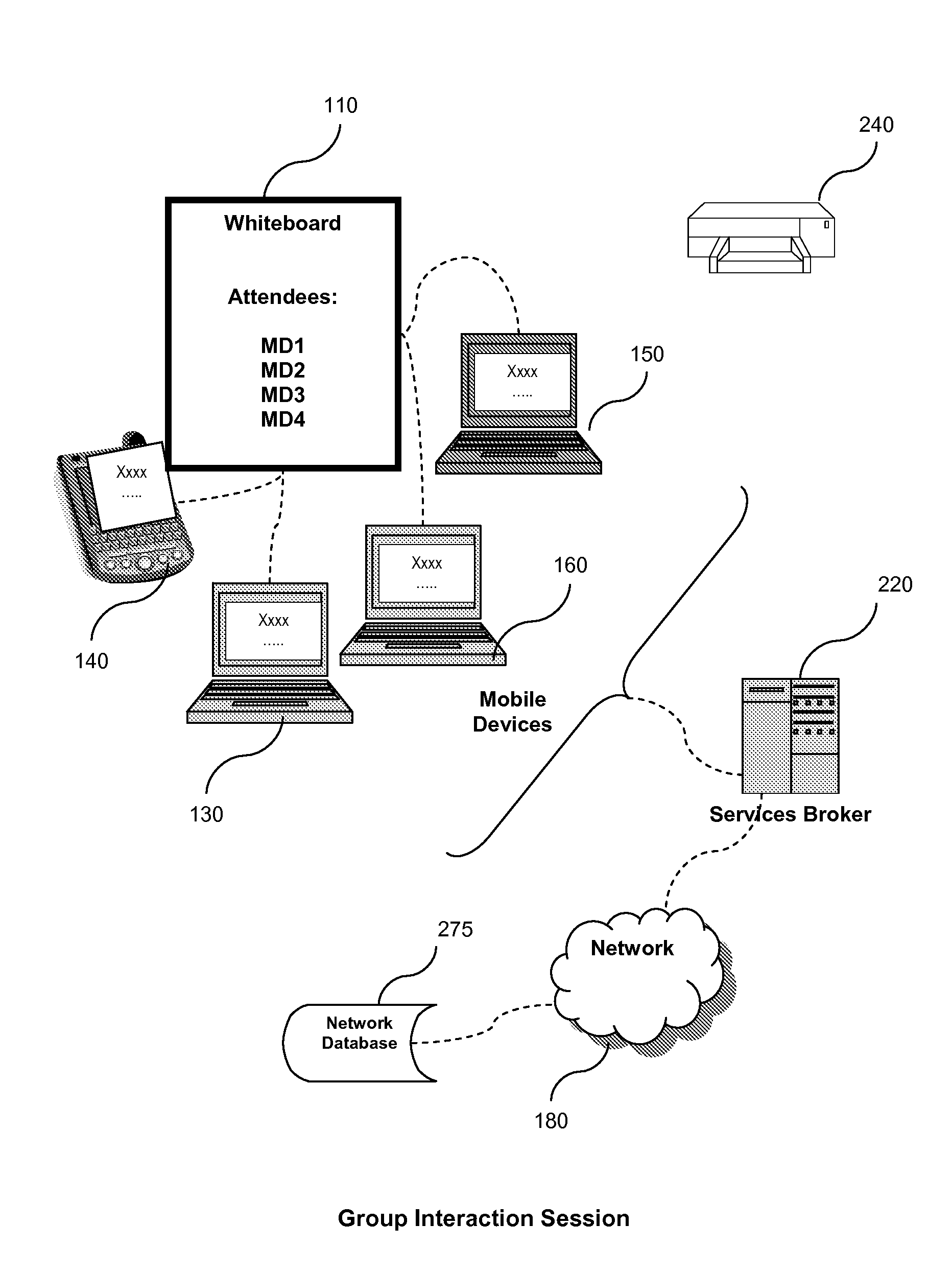
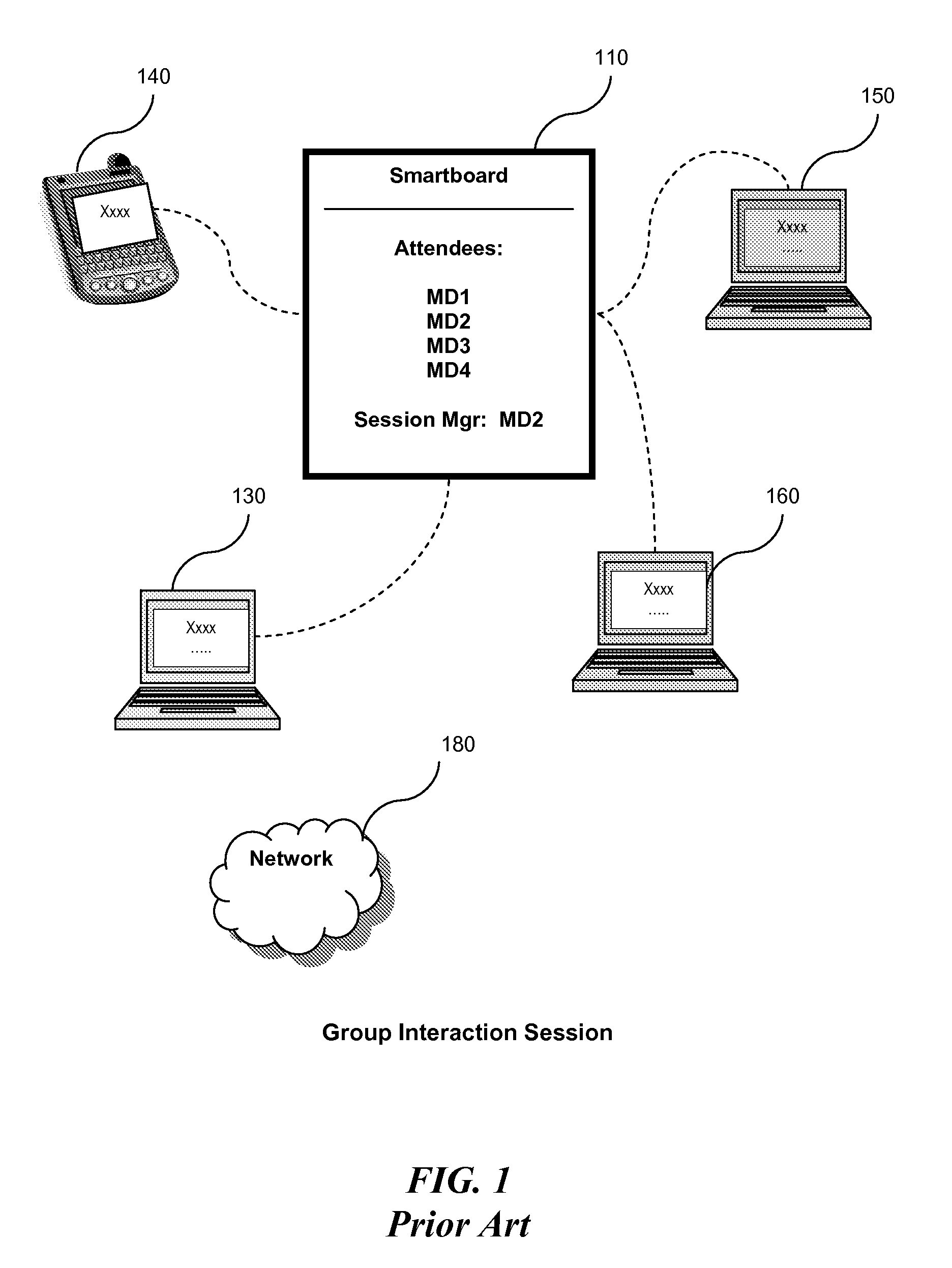
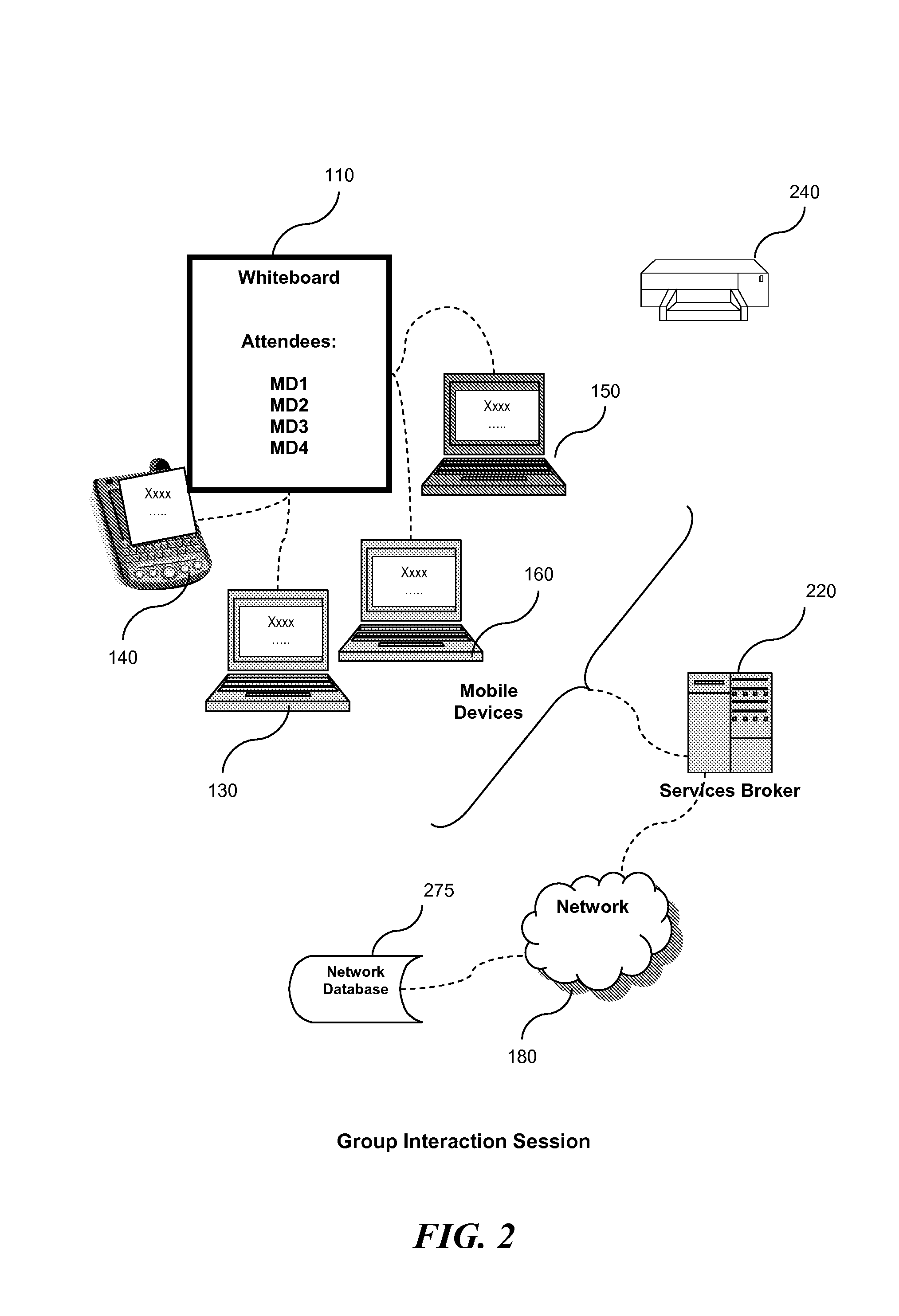
System and method for managing group interaction session states
ActiveUS20080189365A1Multiplex system selection arrangementsSpecial service provision for substationComputer supportedRecovery function
A services broker provides session suspend and resume capabilities to a computer-supported multi-user session made up of associations between a plurality of participants and the services broker. The services broker includes: a memory; an input / output subsystem for transmission of session data and for communicating with the plurality of participants; a processor, operatively connected to the memory, for carrying out instructions. The instructions cause the processor to: receive a trigger event from at least one of the plurality of participants, the trigger event for resuming a suspending session; verify that the suspending session can be resumed; transmit a resume request to the plurality of participants; and re-establish associations among the plurality of participants. Additionally, the services broker will transmit a stored session state and stored session data to at least one environmental device for resuming the suspended session at the point where the suspended session ended. The services broker also carries out instructions for suspending a joint session.
Owner:KOREA KEIT +2
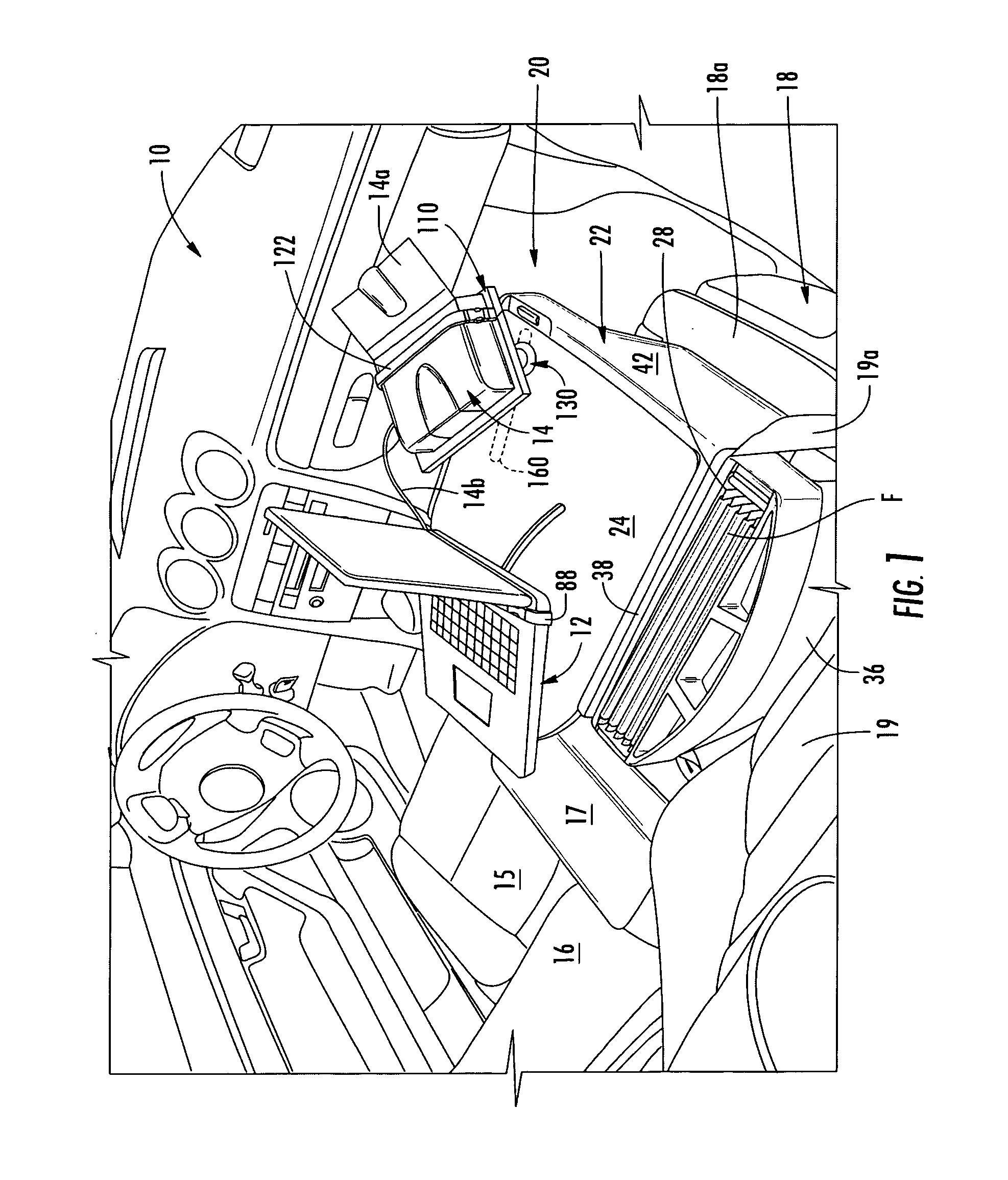
Portable Computer Support
InactiveUS20140085814A1Improved frictional body engagementRotational stability is reducedTravelling sacksTravelling carriersEngineeringComputer supported
A support for a pad computer and the like includes a body support strap which may be placed around the neck or shoulders of a user, and a body propping unit that positions a computer outwardly from the torso of the user. The body support strap connects to the body propping member preferably at a location proximately aligned with the center of gravity of the combined mass of the computer and computer support when the body popping member is deployed in its stand-off position. In a preferred variant the body propping member is a U-shaped strut assembly with two arms joined by a bridge. The body support strap connects to the arms. The arms are hinged at the sides of the computer. The bridge may be swung from an in-use orientation spacing the computer outwardly from a user, to a parked position wherein the bridge lies adjacent to an opposite transverse edge of the computer in the plane of the computer.
Owner:KIELLAND PETER J
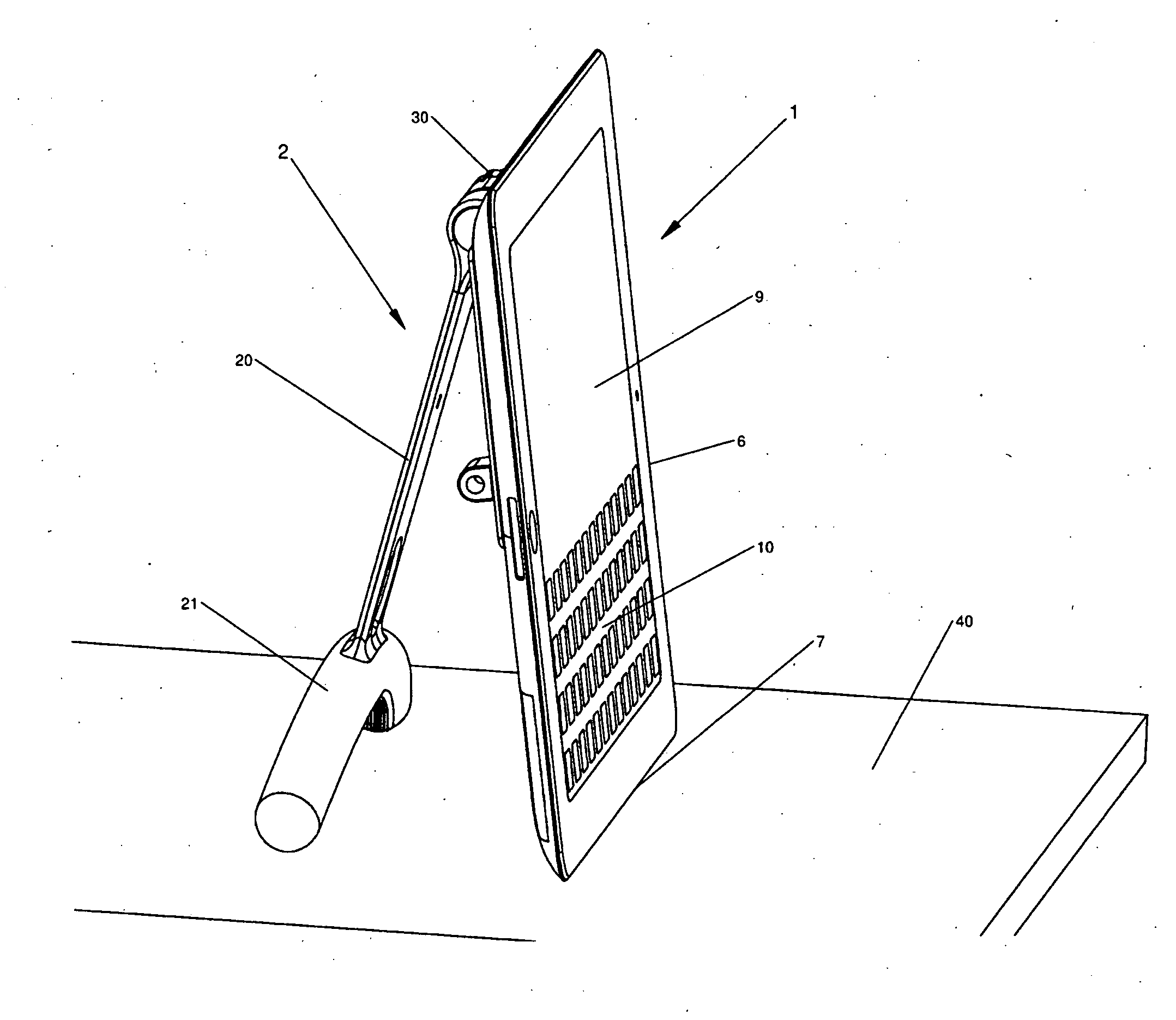
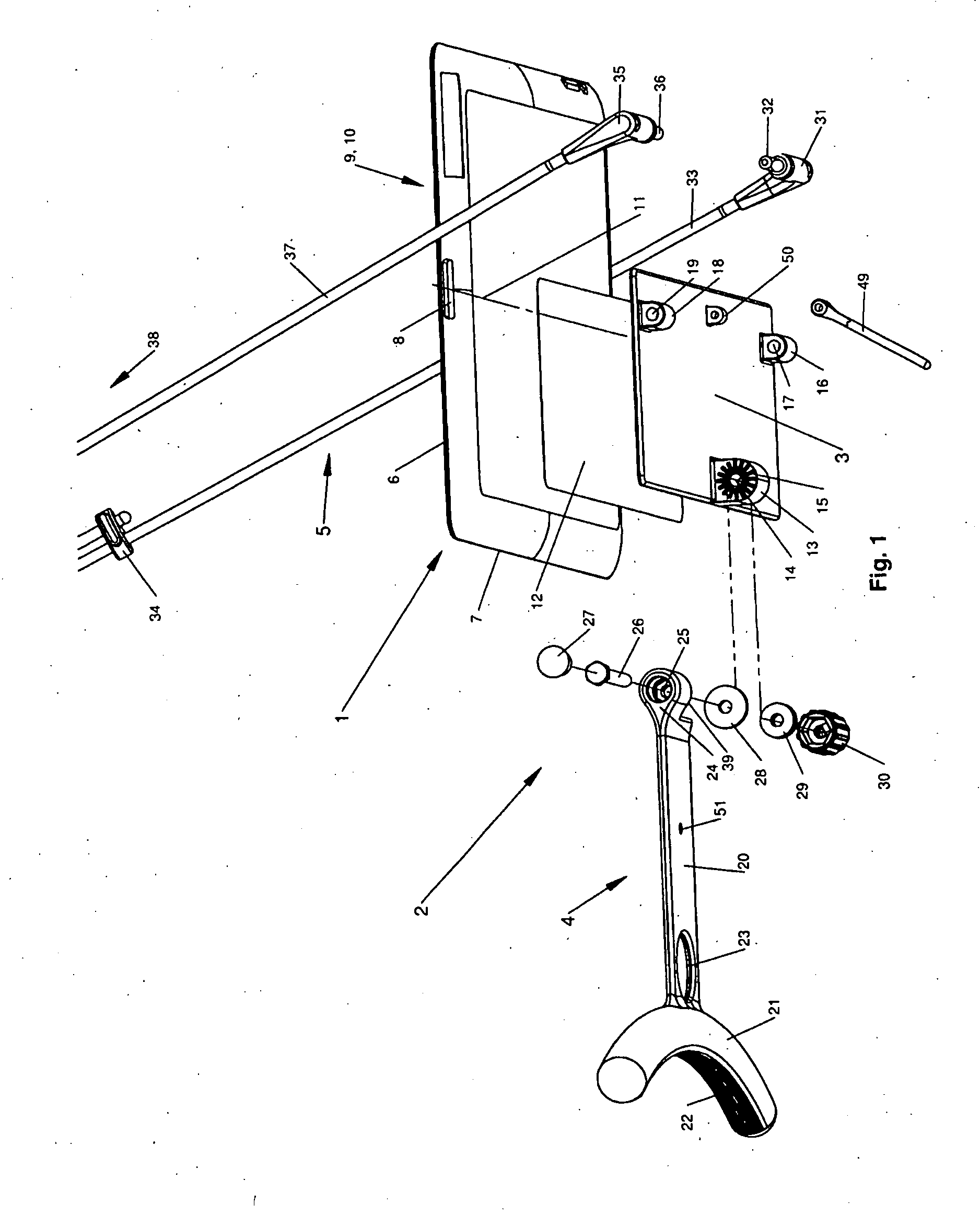
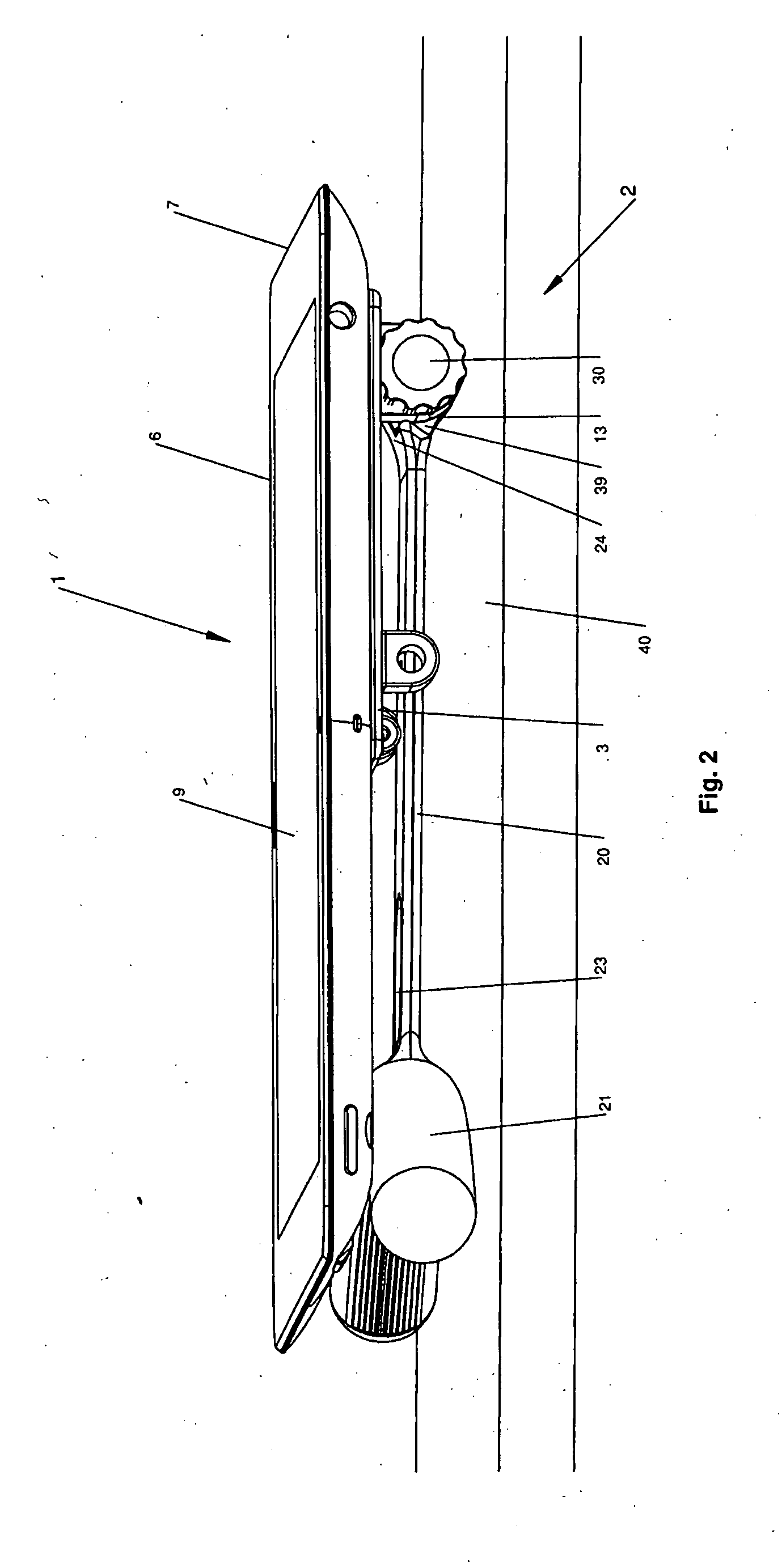
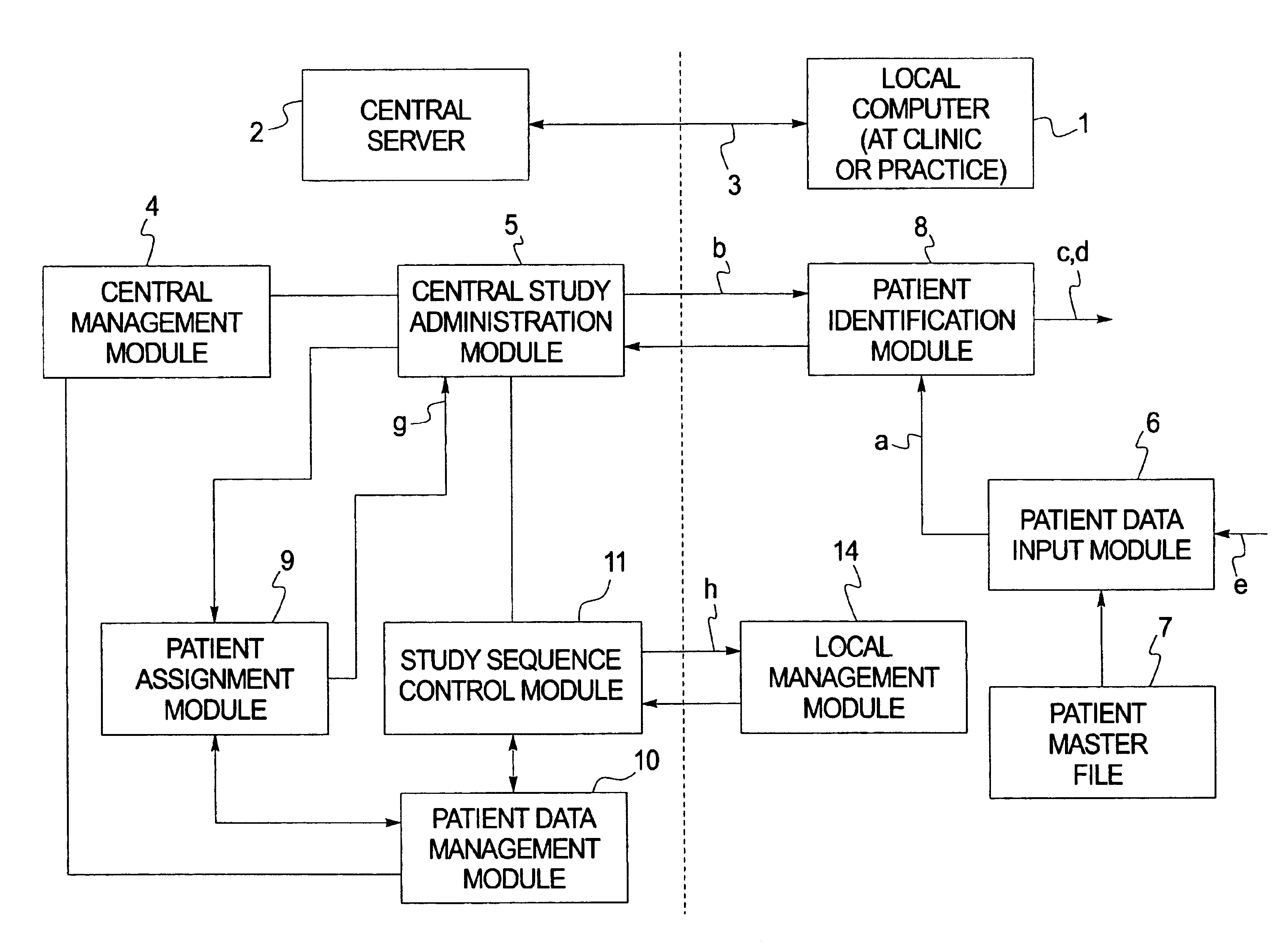
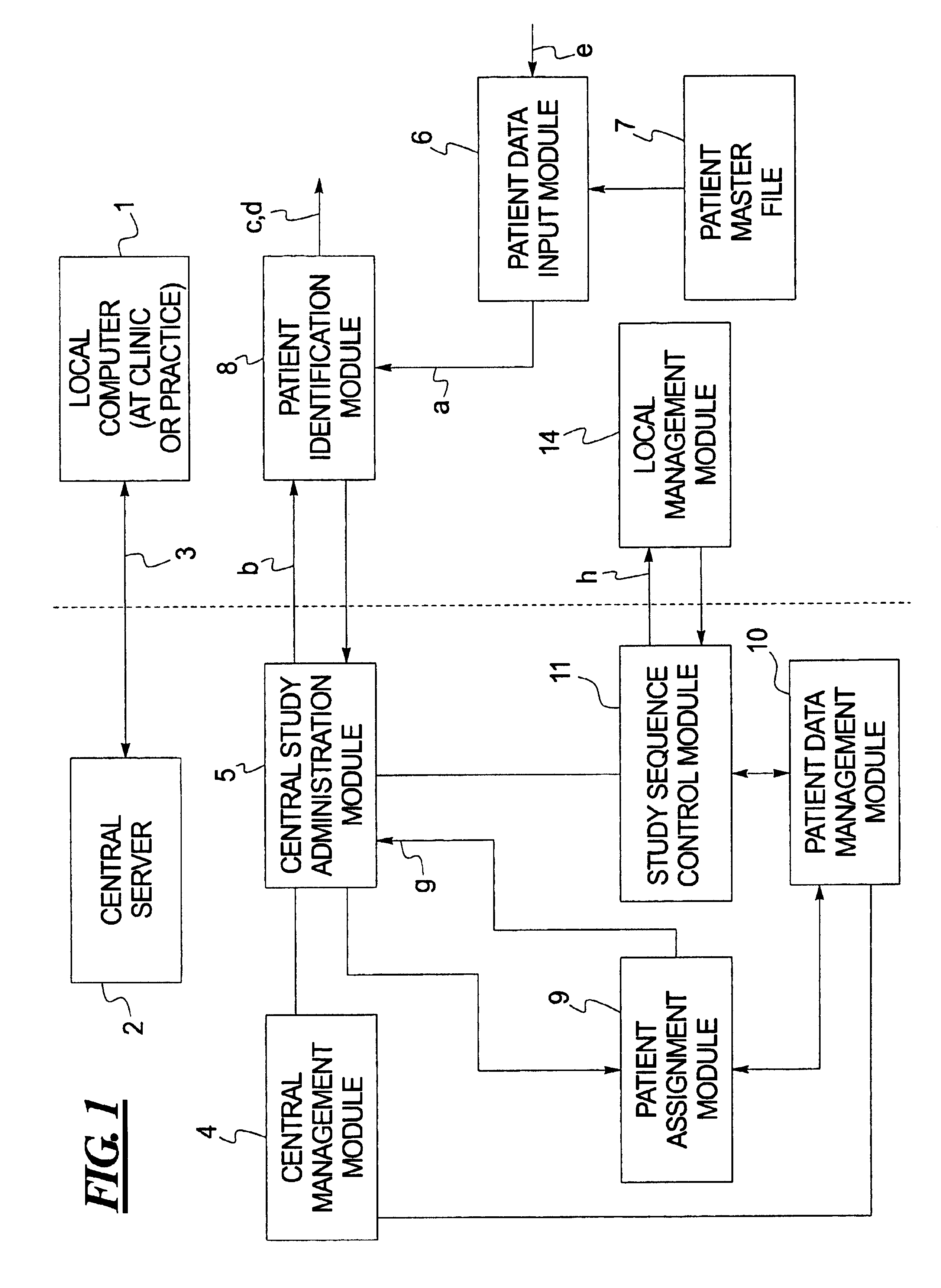
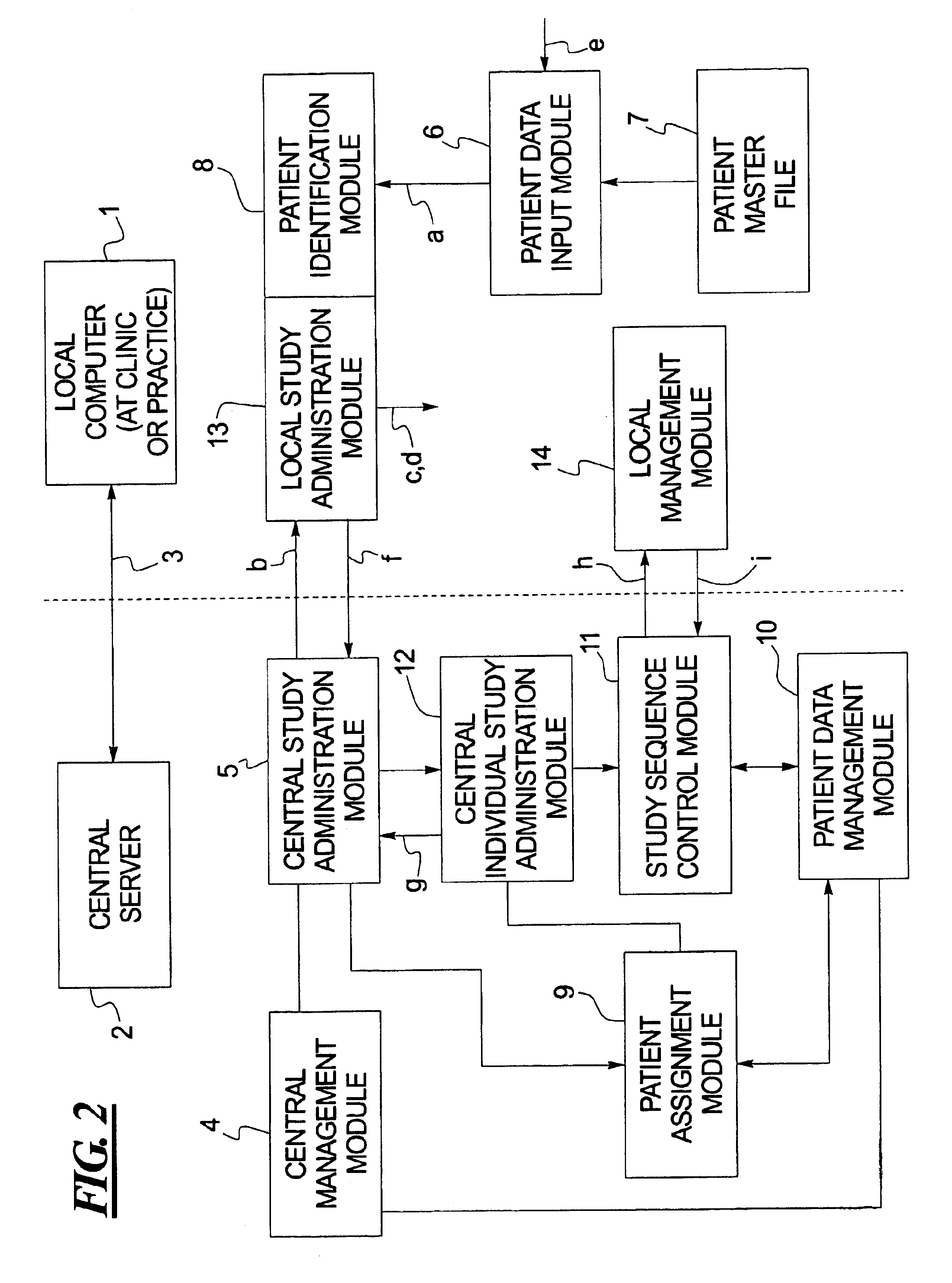
Computerized system for conducting medical studies
InactiveUS6839678B1Simpler and effective completionEasy to compareComputer-assisted medical data acquisitionElectric/electromagnetic visible signallingComputerized systemModularity
In a system for conducting medical studies a number of medical locations, such as clinics or medical practices, are connected to a central server via a computer network. The system is constructed in modular fashion, and it is automatically determined, with computer support within the system, whether a specific patient is eligible to participate in a medical study of the system, and if so, the sequence of the corresponding medical study is controlled centrally by corresponding modules, automatically and in a study-specific and patient-specific fashion.
Owner:SIEMENS HEALTHCARE GMBH
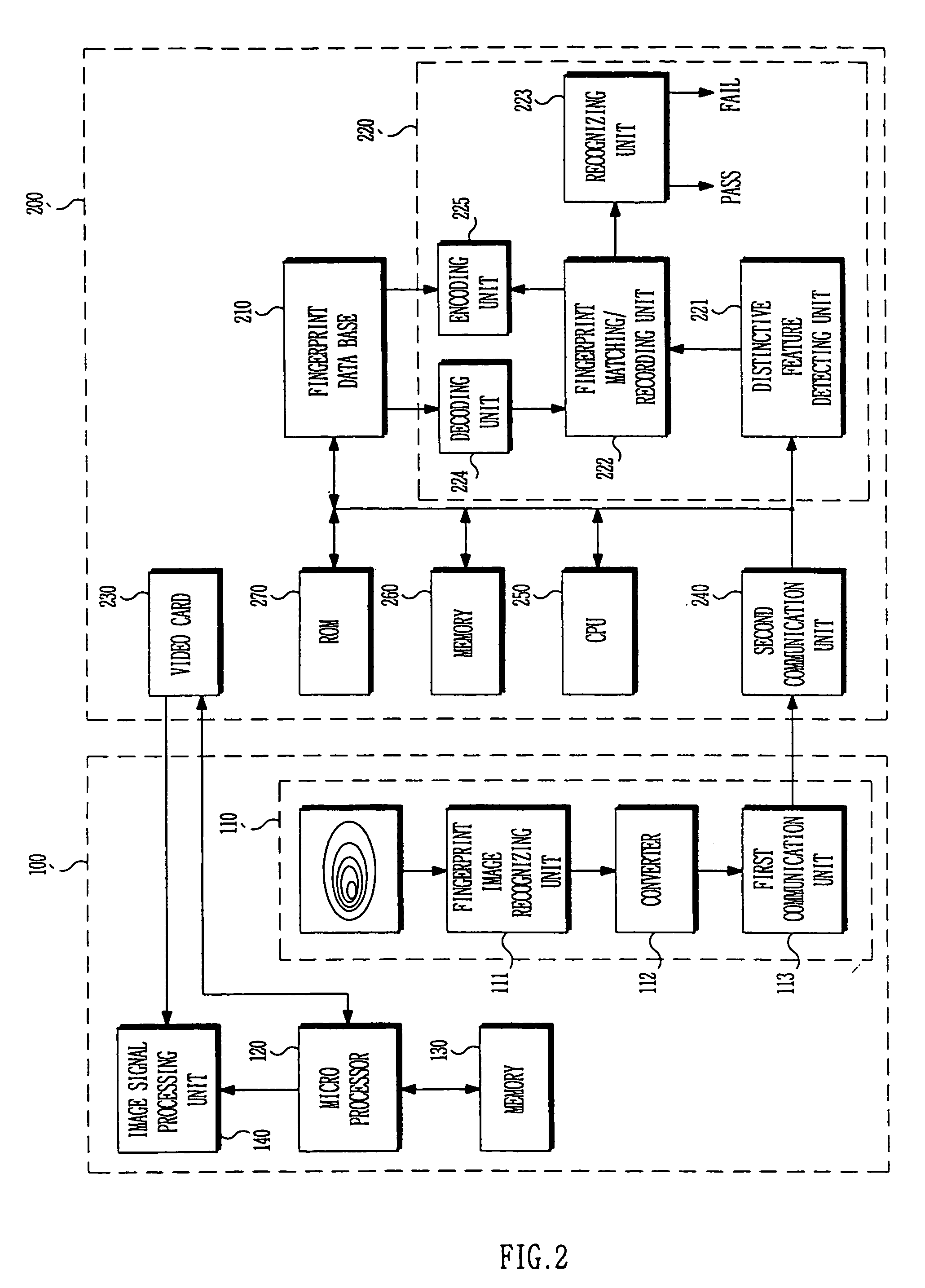
Fingerprint recognizing display and operating method thereof
InactiveUS7239728B1Digital data processing detailsCharacter and pattern recognitionDisplay deviceCommunication device
A fingerprint recognizing display system including fingerprint recognizing means in a panel of a display apparatus and an operating method thereof, wherein a fingerprint of an user is read and a program supported by a computer is allowed to be operated only if the read fingerprint is registered in fingerprint data of the computer. A display apparatus recognizes a fingerprint of the user through a fingerprint recognizing module included in the display apparatus and outputs recognized fingerprint data by using a communication device included in the fingerprint recognizing module. A computer main body includes a fingerprint data base having data of more than one fingerprint and a fingerprint verifying unit, and operates a program after deciding whether fingerprint data input from the display apparatus is an approved fingerprint through the fingerprint data base and the fingerprint verifying unit.
Owner:SAMSUNG ELECTRONICS CO LTD
Notebook computer support seat which can be conveniently folded and carried
InactiveUS20080029412A1Fixed securitySimple structureOffice tablesDigital data processing detailsEngineeringMechanical engineering
A notebook computer support seat which can be conveniently folded and carried is the support seat which is made by lightweight but stiff aluminum plates pivoted by hinges. A support arm on a base plate can be reversely inserted into an insertion hole of a front plate, projected support pieces can support the notebook computer, and insertion blocks at a tail end of a support plate or another coaxial inner support plate can be inserted into any set of insertion holes of the base plate according to an angle required by a user. The present invention can be folded into a plane shape, to facilitate being placed in a suitcase with the notebook computer, for carrying.
Owner:AIDMA ENTERPRISE
Dynamic negotiation of encryption protocols
ActiveUS20050198490A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesClient-sideComputer supported
Owner:MICROSOFT TECH LICENSING LLC
Method for displaying and/or processing image data of medical origin using gesture recognition
InactiveUS20090021475A1Good suitSterility can be maintainedLocal control/monitoringCathode-ray tube indicatorsData setComputer graphics (images)
A method for processing and / or displaying medical image data sets in or on a display device having a screen with a surface, including: detecting gestures performed on or in front of the screen surface; correlating the gestures to predetermined instructional inputs; and manipulating, generating, or retrieving, via computer support, the medical image data sets in response to the instructional inputs.
Owner:BRAINLAB
Multi-functional adjustable computer support stand
Owner:CHAN CHIN CHUNG +1
Multi-functional adjustable computer support stand
The present invention discloses a multifunctional adjustable computer support stand designed for disabled users. The present invention includes a movable base used to accommodate a computer host; two swing rods, formed on the bottom of the base; a retractable rod; a rotation member able to rotate to any desired angle; a support rod pivotally connected with the rotation member, including a shaft rod extending form the one end of the support rod; a rotatable base member, including a left U-shaped frame and a right U-shaped frame used to hold a monitor; an adjustment frame, U-shaped used to firmly hold a keyboard.
Owner:CHAN CHIN CHUNG +1
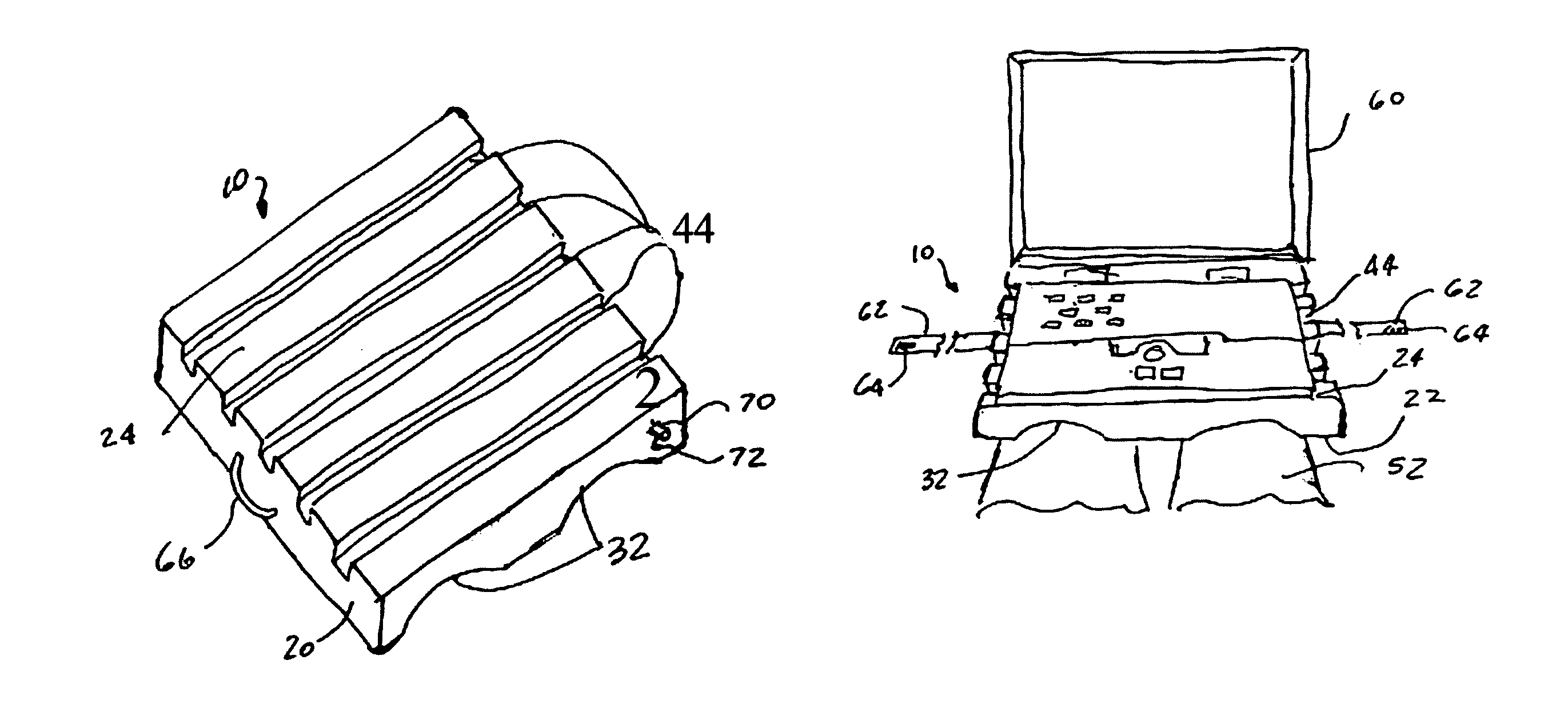
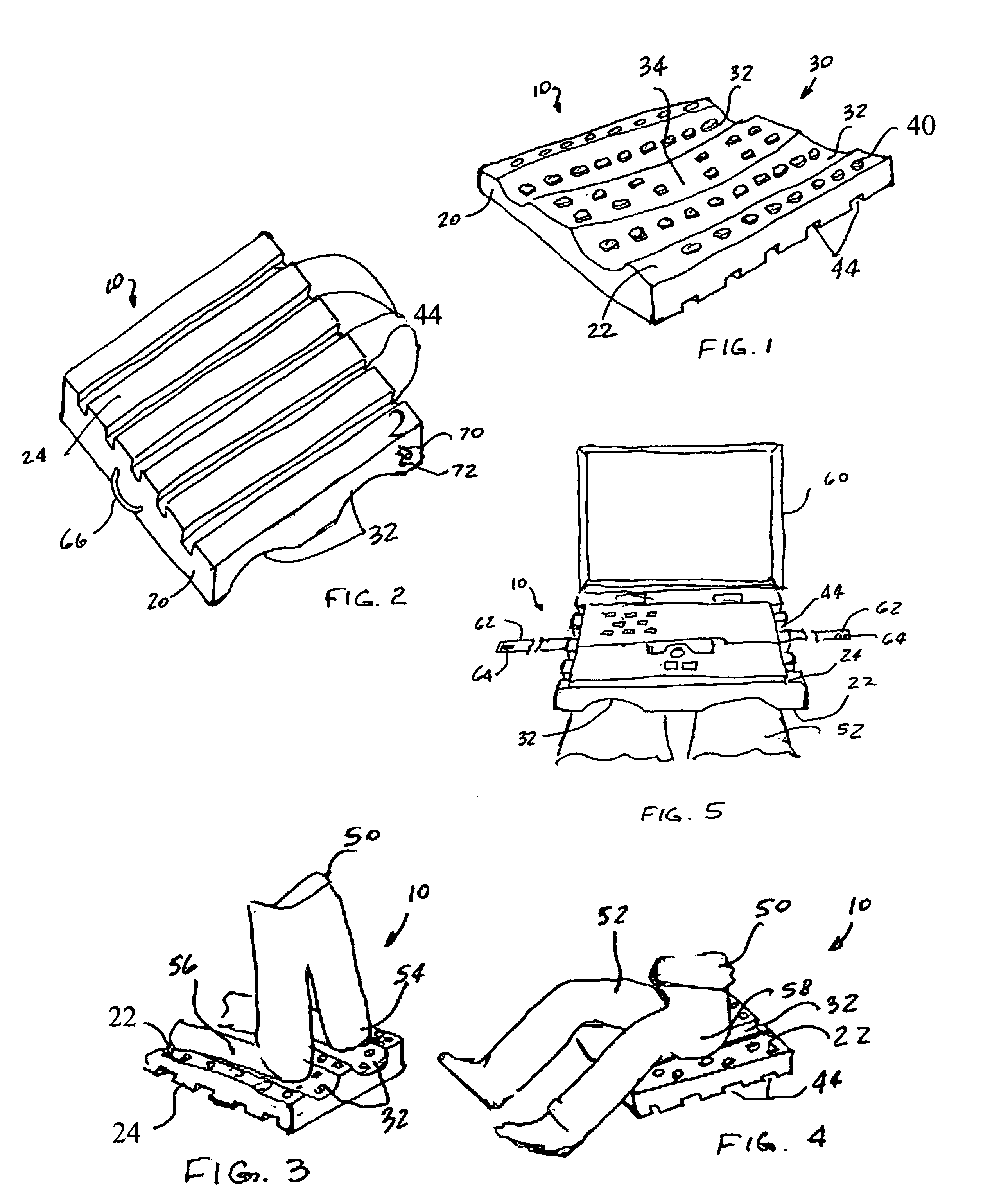
Combination notebook computer support and cushion
InactiveUS7322063B2Dissipate heat generatedEasy to manufactureSofasBed-tablesCushioningComputer supported
A cushioning and support device includes a unitary member having a predetermined size, a pair of cavities formed in a first surface of such unitary member for ergonomic engagement with at least one portion of a human body and a plurality of longitudinal grooves formed in an opposed second surface of such unitary member in a direction perpendicular to a direction of the pair of cavities for providing air ventilation under a load placed onto the second surface.
Owner:ESIMAI IFEANYI
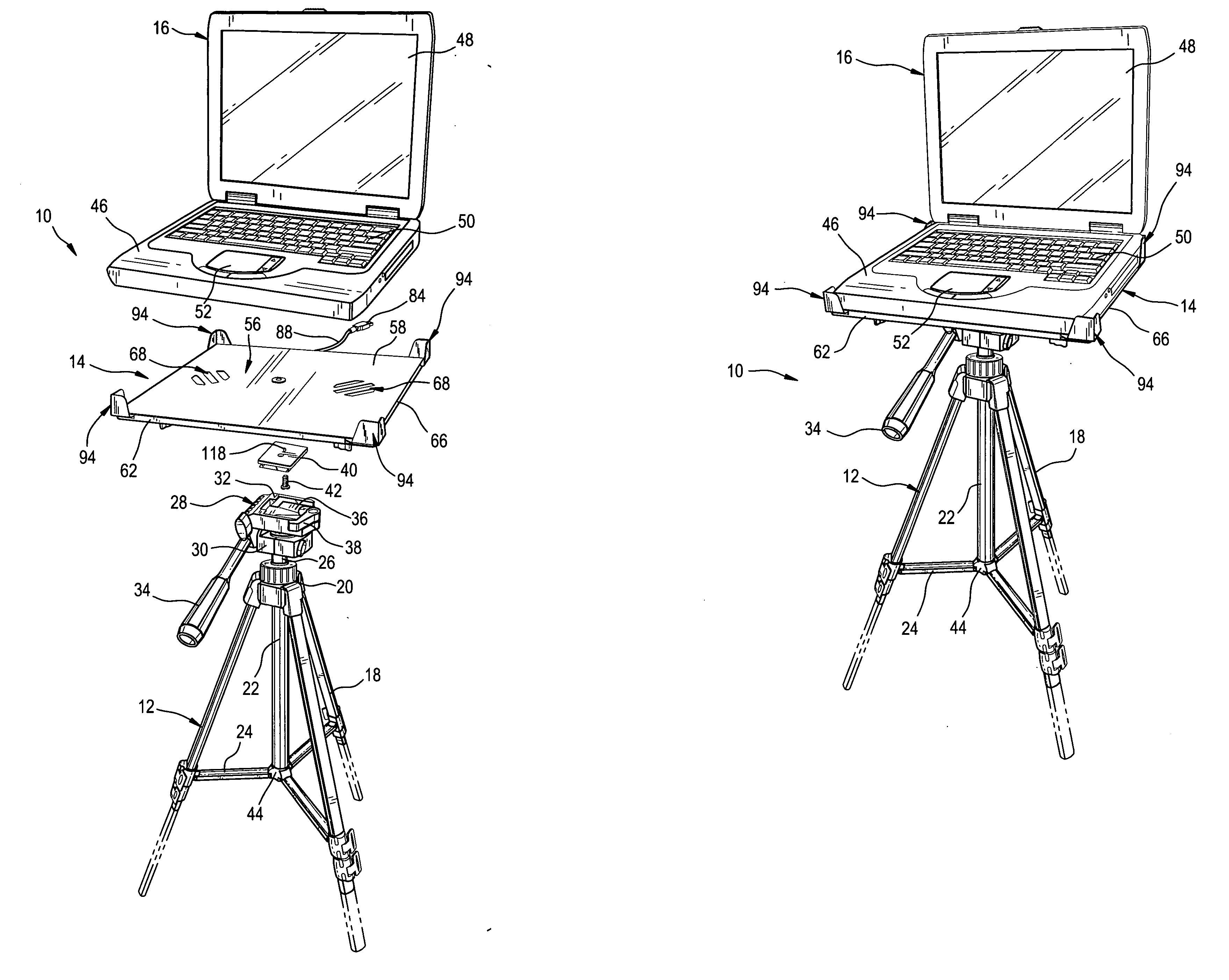
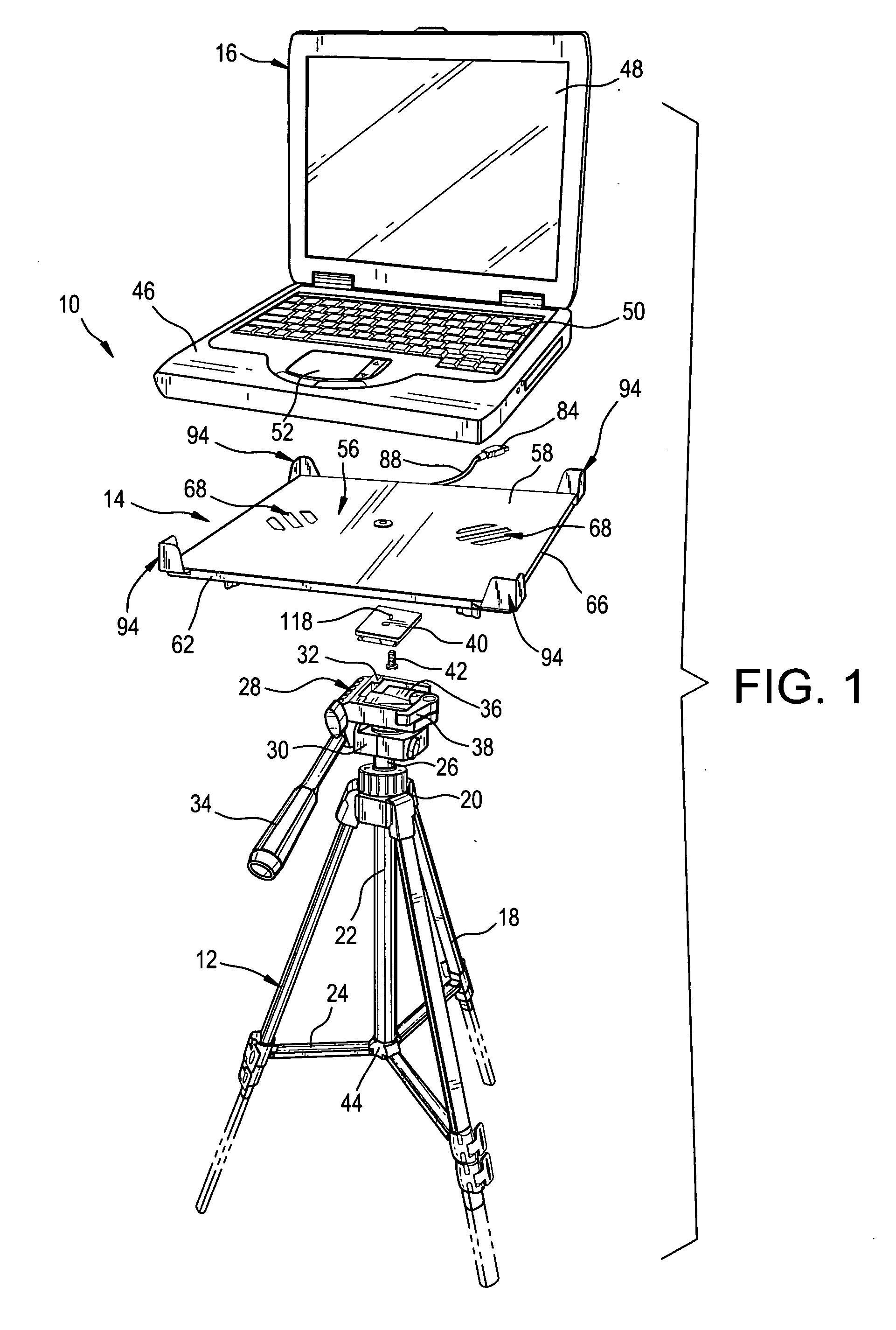
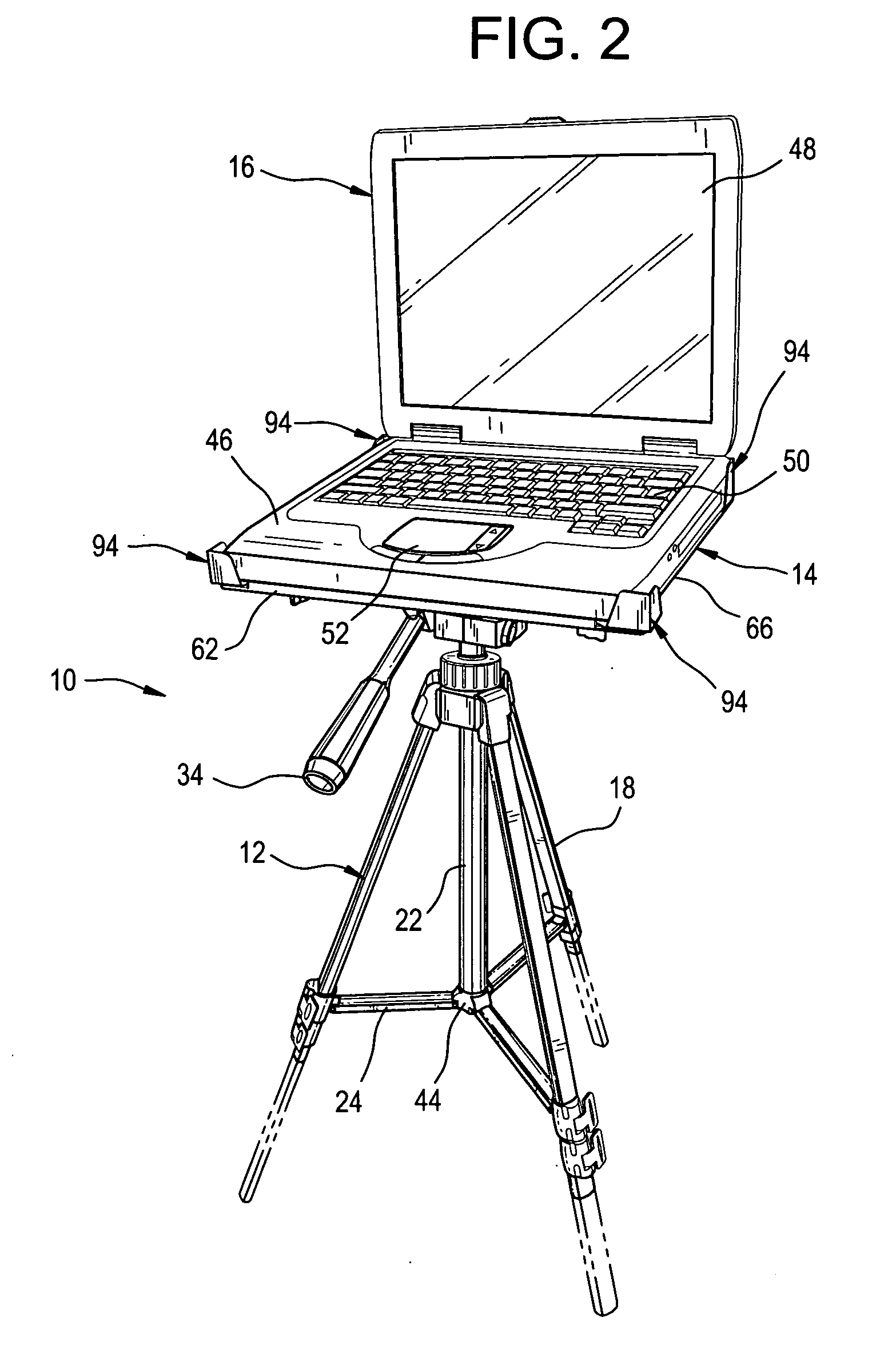
Laptop computer stand
InactiveUS20070131825A1Save battery powerEconomical and portableStands/trestlesKitchen equipmentEngineeringComputer supported
A laptop computer stand including a tripod and a platform releasably attached to the top of the tripod. The platform includes a base portion for supporting a laptop computer and a number of props radiating outwardly from the base portion for grasping the corners of the laptop computer supported by the base portion. Each of the props has a slide with an inner end and an outer end and a longitudinal channel in the inner end. A pair of upstanding fins is affixed to the outer end of the slide and projects above the top of the base portion. The fins are oriented at right angles to one another to form an inwardly directed concavity for receiving a corner of the laptop computer. A number of threaded fasteners, each respectively penetrating the base portion and one of the longitudinal channels, fix the positions of the props relative to the base portion.
Owner:SKRODZKI THOMAS
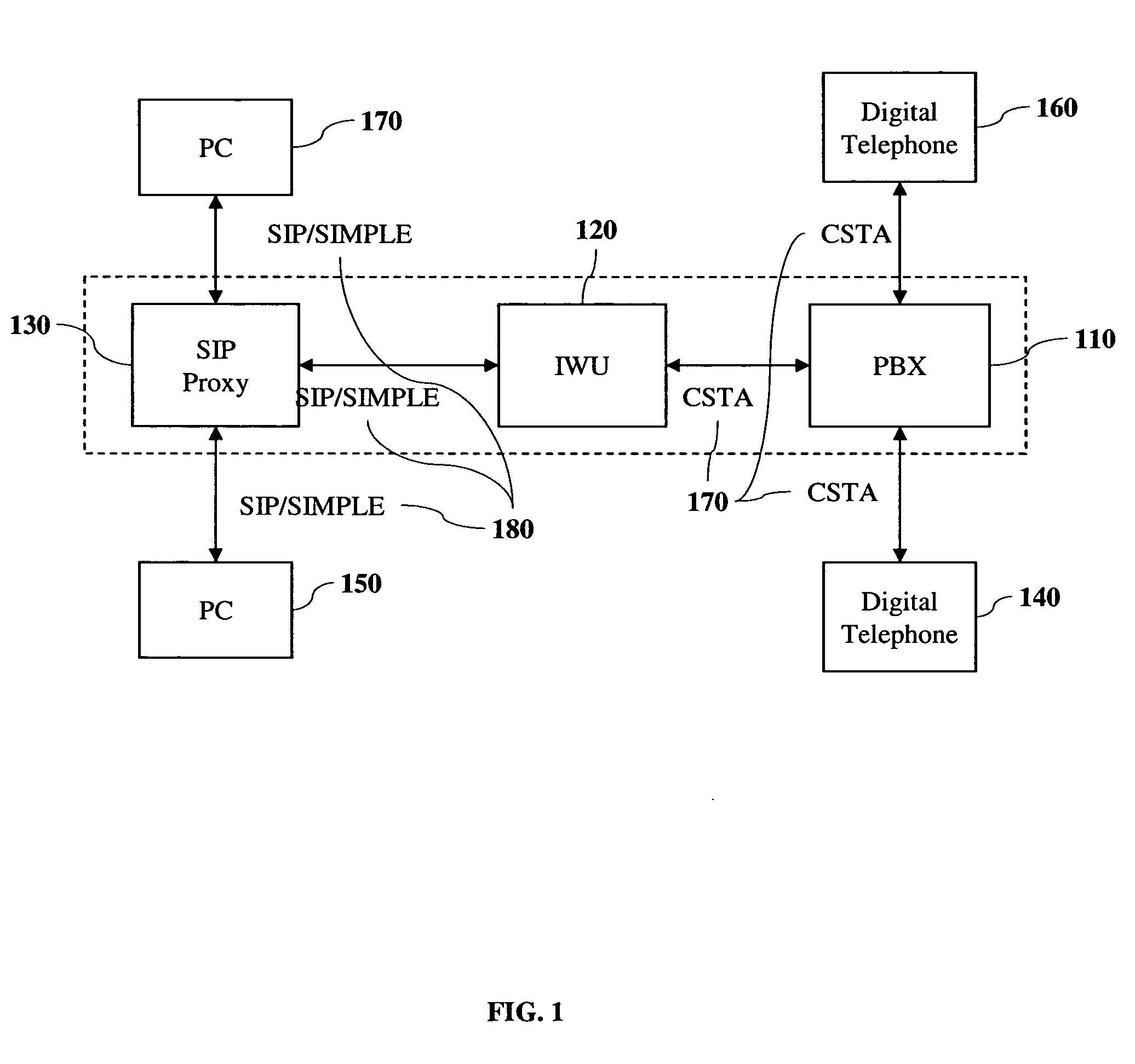
Instant messaging using telephone sets
InactiveUS20050198147A1Interconnection arrangementsSpecial service for subscribersSession Initiation ProtocolTelephone network
A method and an apparatus for providing Instant Messaging (IM) capability in digital telephone sets is disclosed. The invention allows telephone users to compose and display Instant Messages and to exchange contact lists with other telephone users or users of an Internet-based messaging system. The method of the invention in one embodiment allows digital telephones, with limited keys and display space, to support the full functionality of Instant Messaging. Quick compose and quick reply mechanisms allow sending common messages with minimum keypad button pushes. The invention also allows Computer Supported Telephony Application (CSTA) based messages to interface with the Session Initiation Protocol (SIP) messages, thus permitting IM exchanges between digital telephone set users and Window Messenger clients.
Owner:SIEMENS ENTERPRISE COMM GMBH & CO KG
Vertically-adjustable mobile computer workstation and method of using same
Mobile computer workstations must be sufficiently large in order to be stable, but small enough to be easily maneuverable through a work place. A vertically-adjustable mobile computer workstation of the present disclosure includes a pole rotatably attached to a base supported by a plurality of rotatable members. The pole includes a first arm rotatably attached to a second arm. A computer support is attached to the second arm and is moveable between a sitting user position and a standing user position, at least in part, by pivoting the arms of the pole with respect to one another and the moveable base.
Owner:STINGER INDS
Method for the computer-supported control of a ship
InactiveUS20120072059A1Accurate mappingHigh precisionDigital data processing detailsAnti-collision systemsProwStern
The positions and motions of a bow and a stern of the ship are detected using redundant devices and evaluated to automatically perform difficult maneuvers in ports or to generate recommendations for controlling the ship
Owner:GLAESER PHILIPP
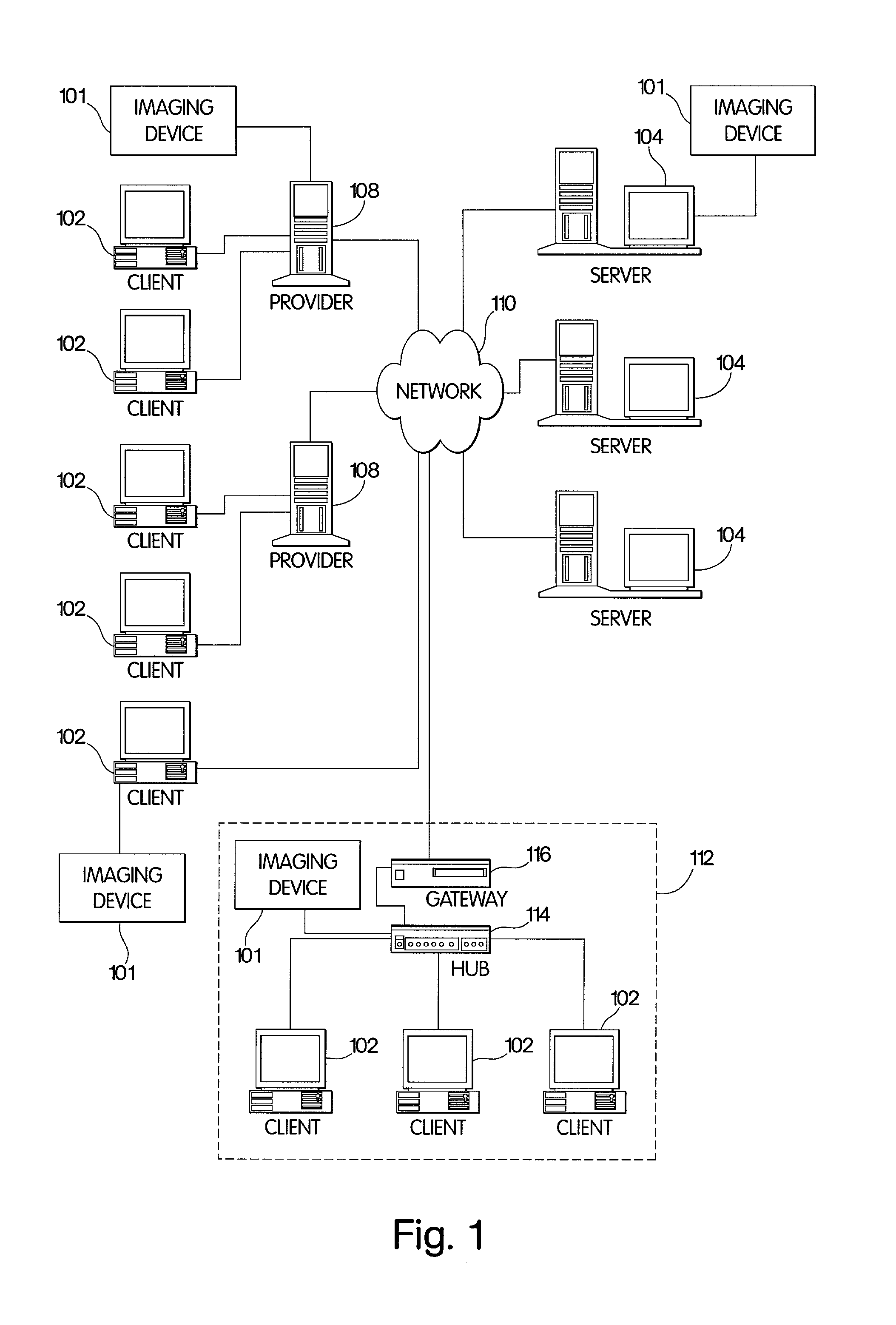
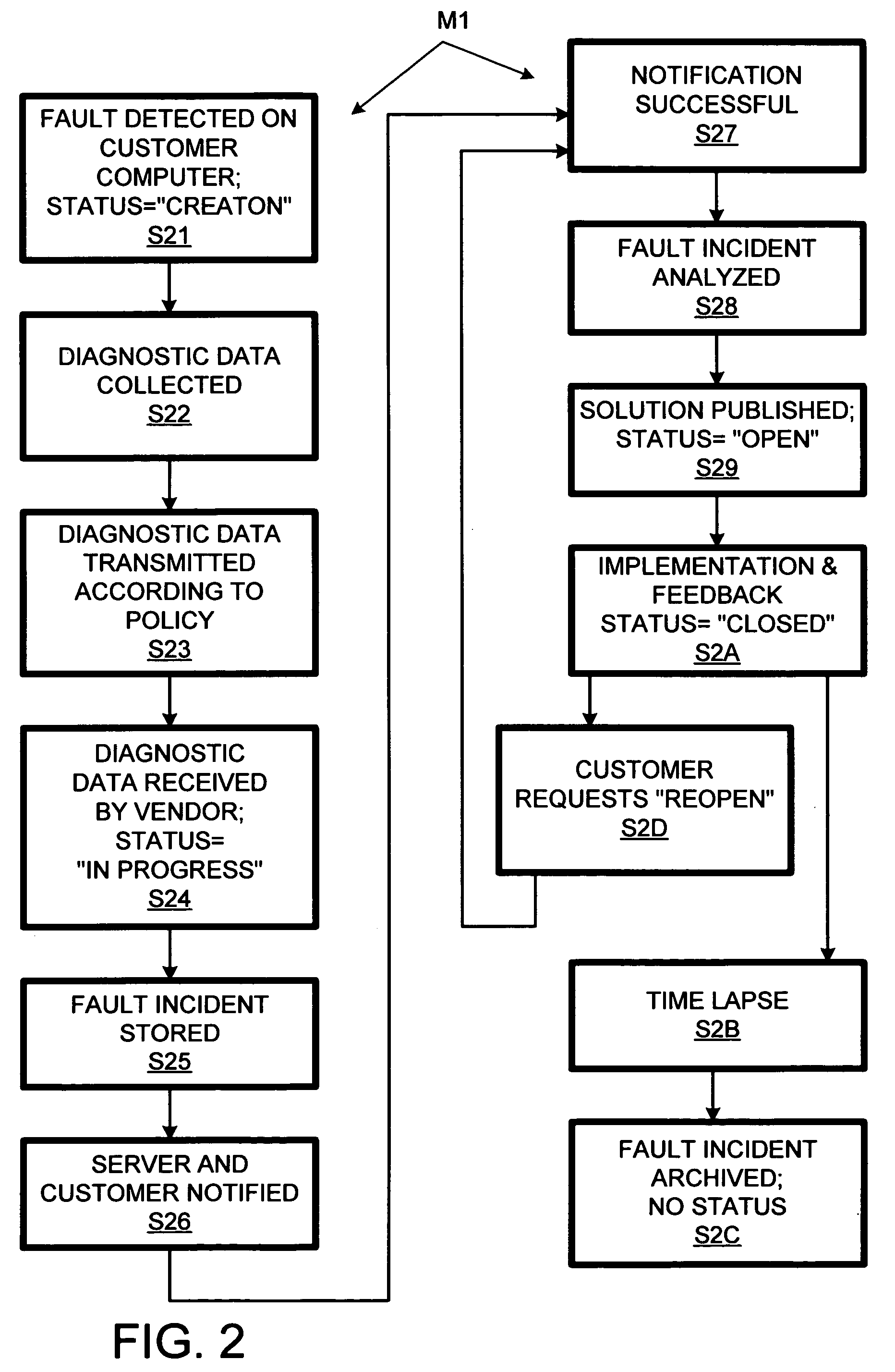
Computer support network with customer portal to monitor incident-handling status by vendor's computer service system
InactiveUS7373553B2Electronic circuit testingDetecting faulty hardware by remote testSupporting systemComputer supported
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
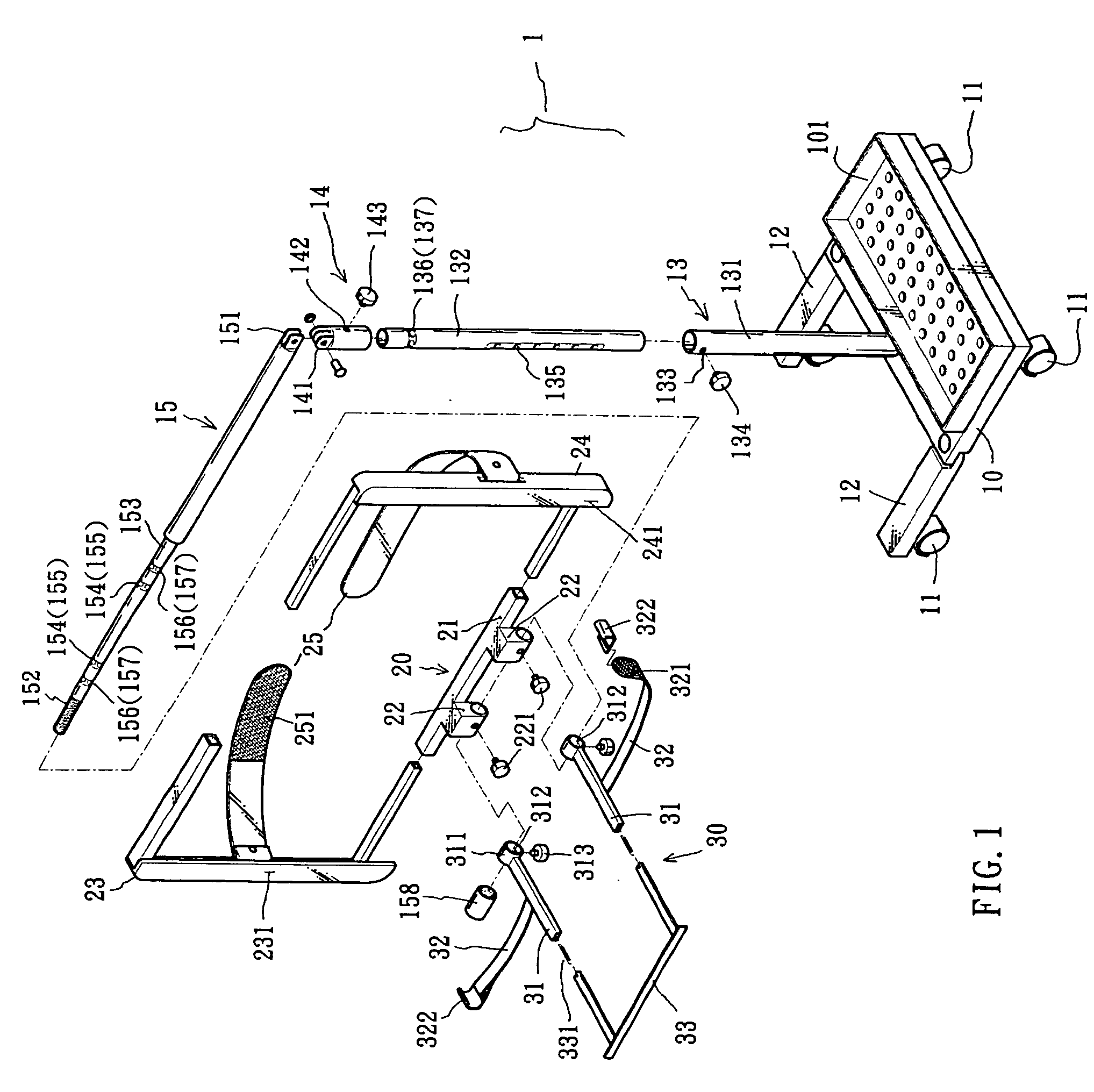
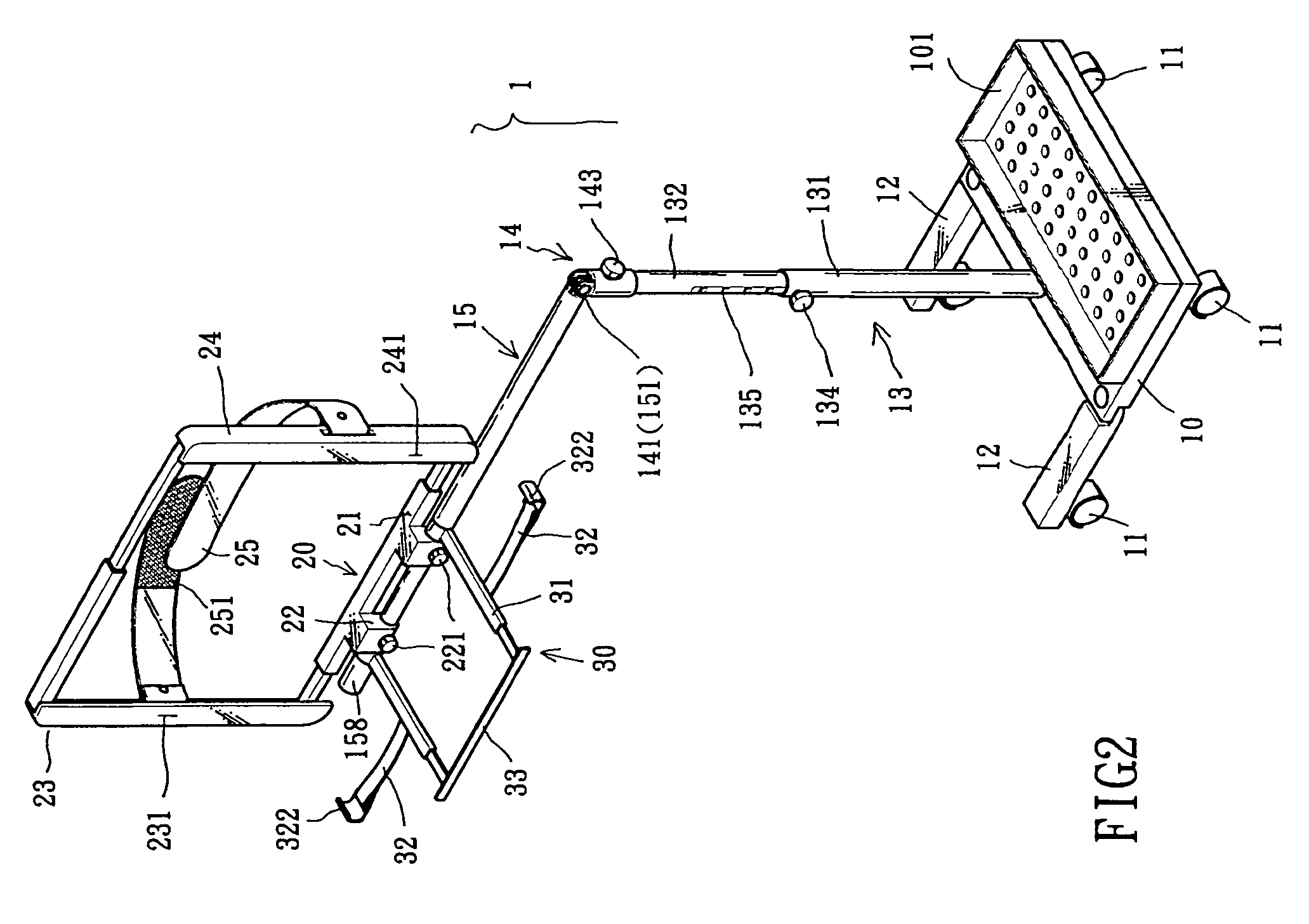
Multi-functional motivating exercise equipment
A multi-functional exercise machine, whose console has parts that can be slidden, rotated, extended, bended or unfolded so that the console can be transformed into an exercise workstation, comprising an arm supporting component and a computer supporting component for a user to efficiently work with a personal laptop computer free of distractions while doing exercise. The console can be transformed between a normal console and an exercise workstation, so that it can be used for both highly focused extensive exercise and moderate exercise with working or entertaining at same time, in either family or gym environment. The arm supporting component is specially designed to minimize upper body movements and the console supporting assembly is specially designed to minimize vibration and shaking during exercise. The equipment can further comprise a force adjustable body support to decrease load when standing on an exercise machine by supporting predetermined amount of weight, so that a user can do exercise longer while working with a computer.
Owner:LU ZHENYU
Portable desk and computer support
InactiveUS7793597B2Easy accessEasy to adjustVehicle arrangementsBed-tablesDriver/operatorVehicle driving
A portable desk adapted for use in temporary work areas such as a seat in a vehicle includes a main body having a work surface member at a position spaced from a support surface, a first support member adapted to receive a laptop or portable computer mounted on the work surface member for access by the vehicle driver when the portable desk is mounted in the front passenger seat of the vehicle, and a second support member adapted to receive a computer peripheral device, such as a printer, also for access to by the vehicle driver. Preferably, the work surface member is at the top surface of the portable desk, and the first support member may be adjustably positioned between a first position adjacent a driver of the vehicle and a second position spaced away from the vehicle driver.
Owner:AUTOEXEC
Accessory shelf mounting mechanism
InactiveUS7481170B2Easy tension adjustmentOffice tablesRevolvable tablesComputer supportedComputer support
A mounting mechanism useful for swivelly attaching a secondary work surface, such as a computer mouse platform or other accessory work shelf, to a primary work surface, such as a computer keyboard platform or a table or desk, and furniture, such as computer support furniture, having an accessory work shelf swivelly attached to a primary work surface. The mounting mechanism facilitates swivel movement of the accessory work shelf relative to the primary work surface while maintaining a constant but easily adjustable tension. A method for attaching both of said accessory work shelf and said primary work surface to a mounting mechanism.
Owner:HUMANSCALE CORP
Laptop computer support
An article for supporting a computer on a user's lap that cools the computer and isolates the user from heat, and methods of manufacture. Some embodiments include a body, a top surface, a bottom surface, a hollow area in between, an aperture through the top surface to the hollow area, and either a fan to move air through the aperture or an indentation in the top surface to allow air to circulate by the computer. Embodiments include a foam portion, a plastic portion that provides stiffness, a fabric covering and one or more side or rear openings to allow airflow. The fan may be powered from a USB port on the computer.
Owner:BELKIN INT
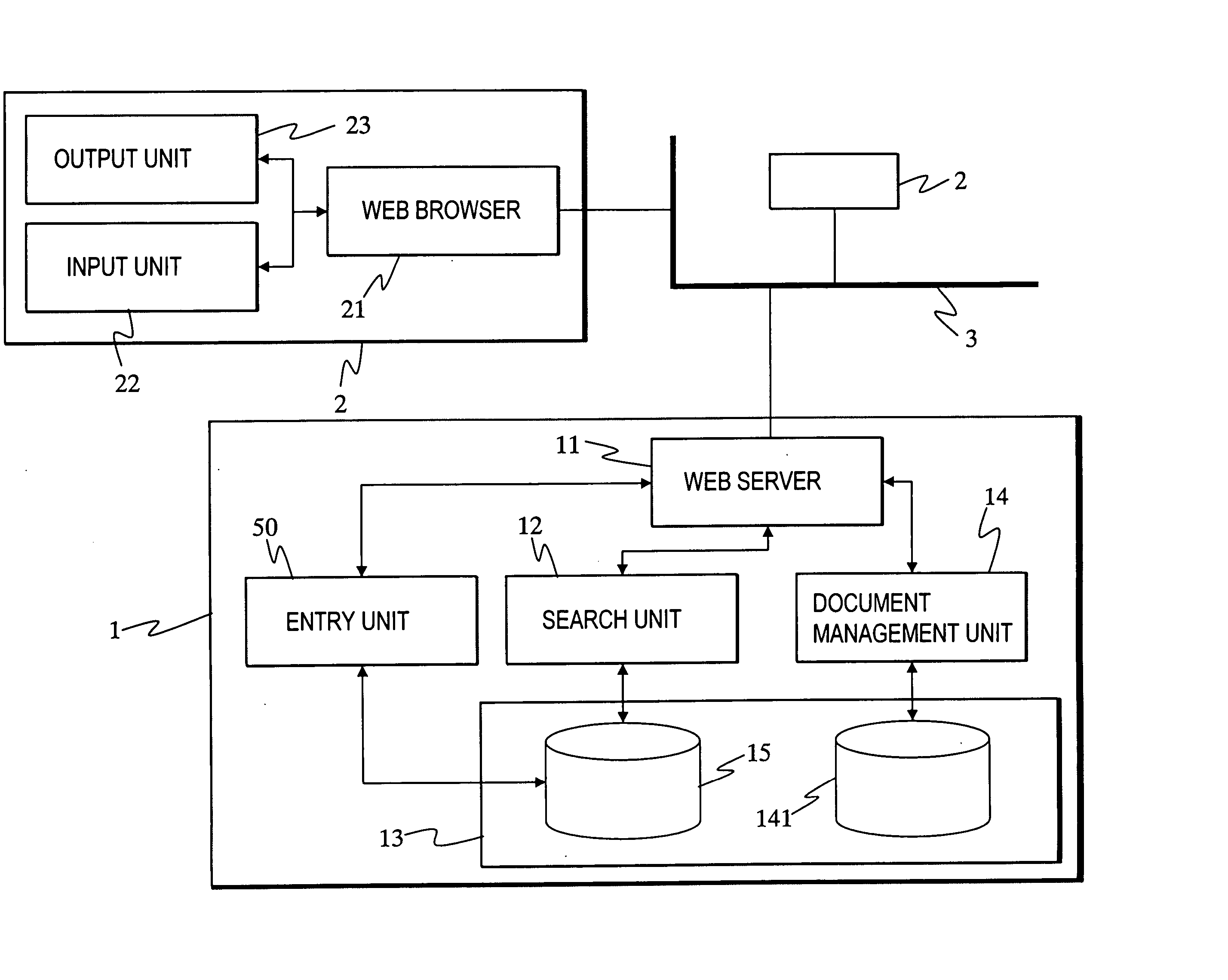
System for supporting introduction/operation of enterprise resource planning software
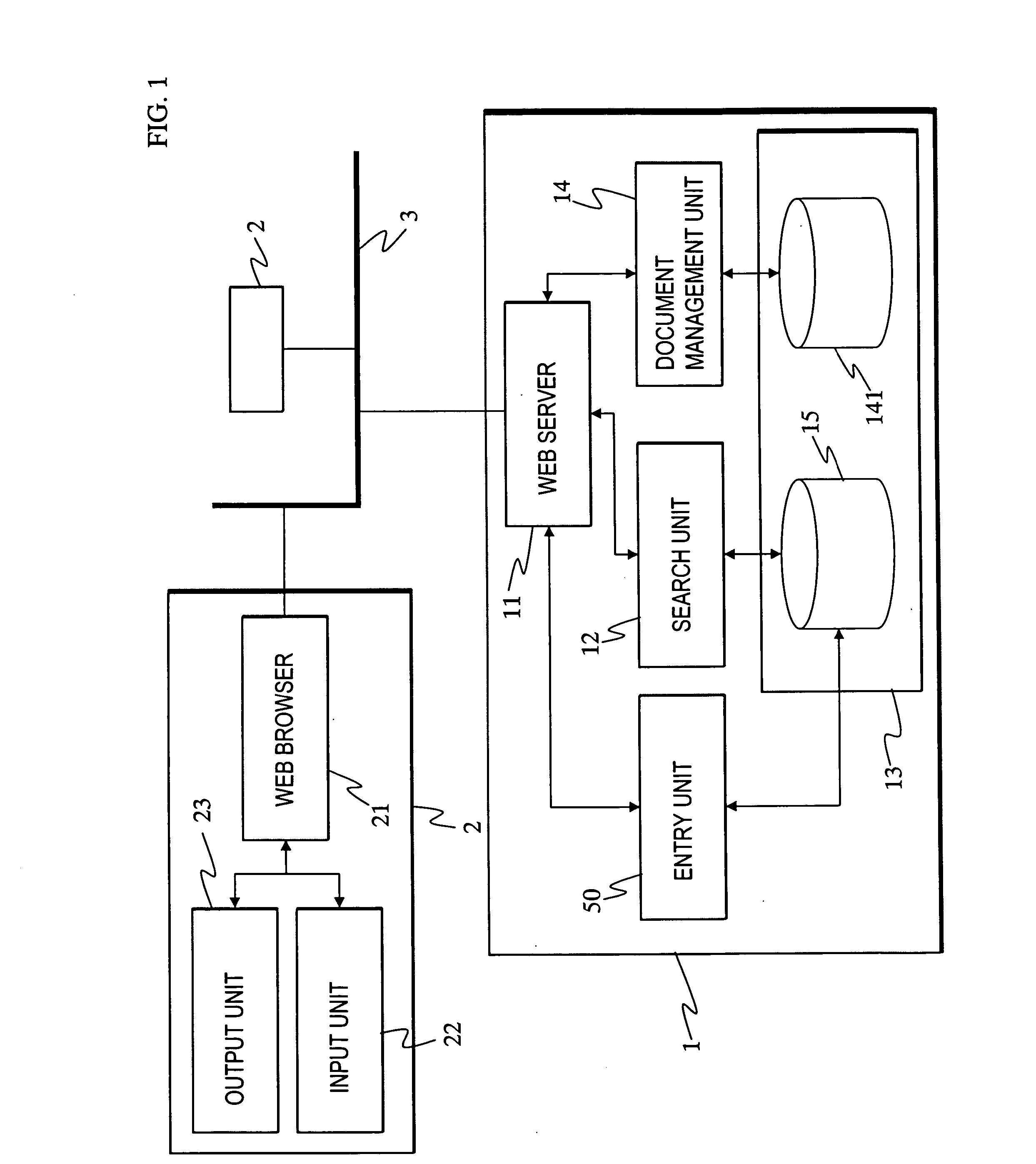
InactiveUS20070067338A1Office automationSpecial data processing applicationsManagement unitProgram planning
A system for supporting introduction / operation of Enterprise Resource Planning software by means of a computer. In this system, a document management unit (14) manages data for document including business flow diagrams expressing business flows by hierarchized business elements. A database (15) relates a business element to a customize item, its location, and a document. A search unit (12) searches the designated business element and a location of customize item corresponding to a designated business element and other business elements on a lower layer than the designated business element.
Owner:PANASONIC CORP
User interface with an input object and method for the computer-assisted control of a user interface
InactiveCN103858088AImprove experienceInteraction cancellationInput/output processes for data processingSensitive touchBall bearing
The invention relates to a user interface comprising a touch-sensitive touch screen, a special token being placed thereon. Said token comprises two disks which are interconnected by means of a ball bearing and which enable a rotation to be directly recorded by means of the token and by a rotation controller. The guiding of the rotation by the ball bearing enables the input object to have a particular haptic quality. Said ball bearing enables values to be modified rapidly up to a free running state when the upper element is accelerated and the rotation is continued once the user releases the input object based on the low friction resistance in the ball bearing, but also very precise, small adjustments in which the token provides a step-by step modification and / or screening of the rotation, such that the user receives, for each modified unit, a discrete haptic resistance via the finger-tips. Any parameters can be adjusted in a fast and efficient manner due to the tokens. The structure of a technical system can be reproduced on the touch screen, the parameters of corresponding elements of the technical system being visualized and can be modified by annular elements.
Owner:SIEMENS AG
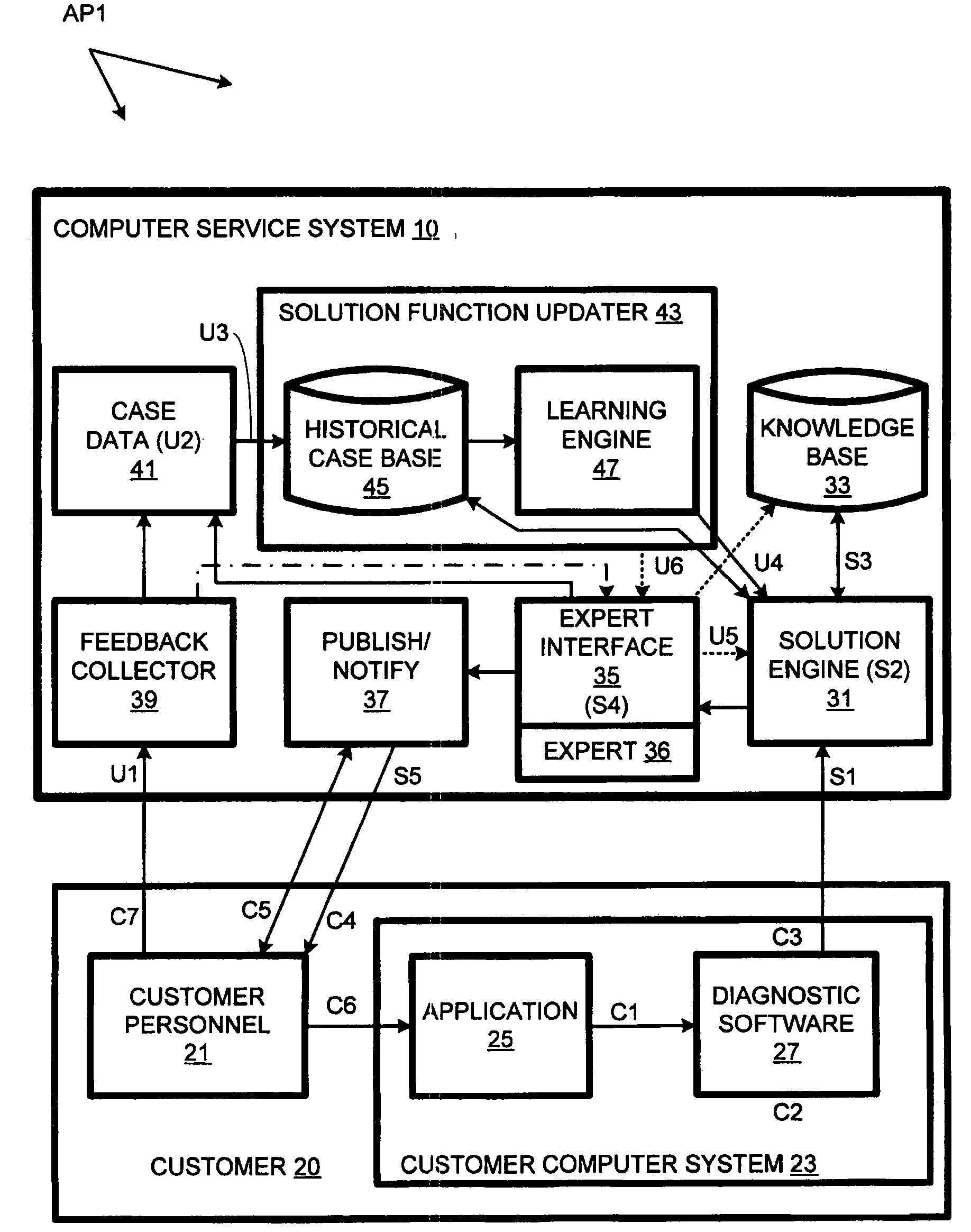
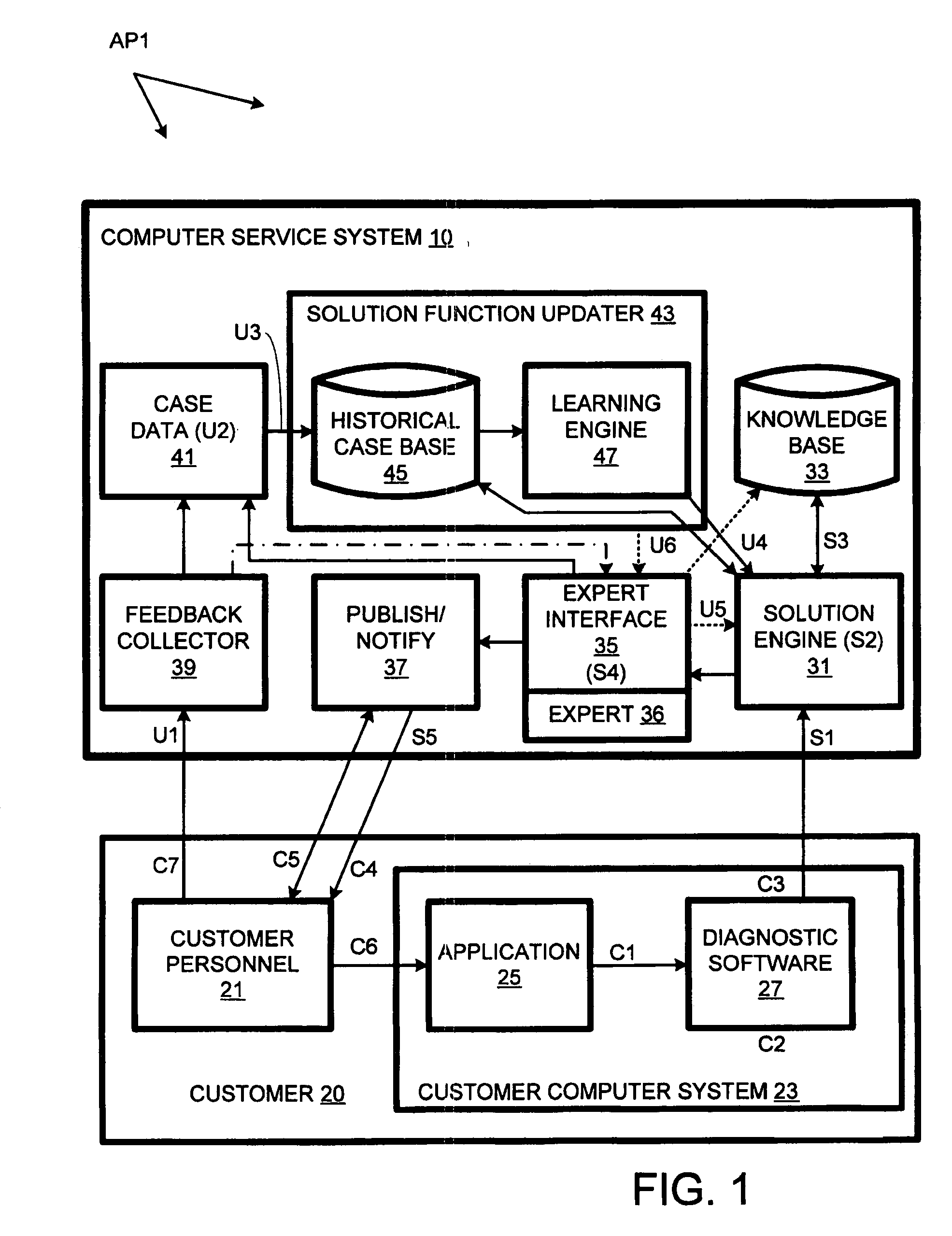
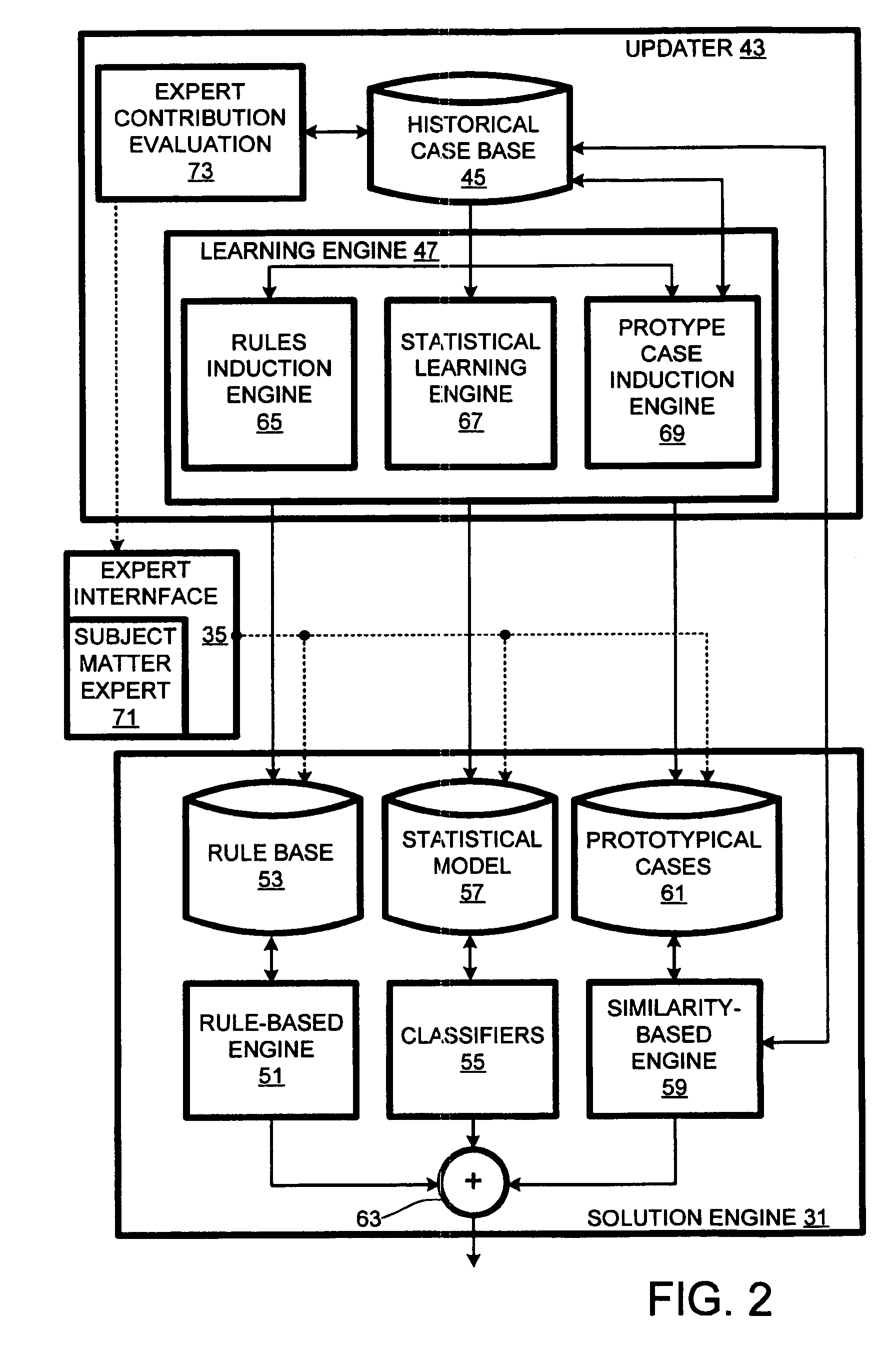
Computer support service with solution function updates as a function of pre-delivery expert changes to automatically generated solutions
A solution engine (31) of a vendor's highly-automated adaptive computer support system (10) for a remote customer (20) automatically generates proposed solutions, e.g., sets of support documents, as a function of diagnostic data received from a customer's computer system (23). The automatically generated solution can be subject to expert review (35) prior to publication (37) to the customer, e.g., when the automated system assigns a low confidence level to the solution. In addition, expert review can be triggered by feedback (39) from the customer once a proposed solution is communicated. The diagnostic data, solutions and feedback for an incident are packaged (at 41) as a “case” and entered into an historical case database (45). A solution function updater (43) updates the solution function as a function, at least in part, of the expert review and customer feedback.
Owner:MICRO FOCUS LLC
Serial interface controller supporting multiple transport protocols and control method
ActiveCN101599053ARealize functionElectric digital data processingData transmissionNetwork interface controller
The invention discloses a serial interface controller supporting multiple transport protocols, a control method and a computer supporting multiple transport protocols. The serial interface controller comprises a parameter storage unit, a variety setting unit, a bus data transport unit and a control logic processing unit, wherein the parameter storage unit is used for storing the information of control parameters of all the transfer protocols supported by the interface controller; the variety storage unit is used for setting the transport protocol variety abided by a serial interface to be controlled by the controller and generating transport protocol variety setting information; the bus data transport unit is used for transporting data between data processing equipment and the serial interface; the control logic processing unit is used for acquiring control parameter information which corresponds to the transport protocol variety setting information from the parameter storage unit according to the transport protocol variety setting information and controlling the serial interface according to the acquired control parameter information. The functions of a plurality of transport protocols following multiple transport protocols can be fulfilled by one physical serial interface.
Owner:LENOVO (BEIJING) CO LTD
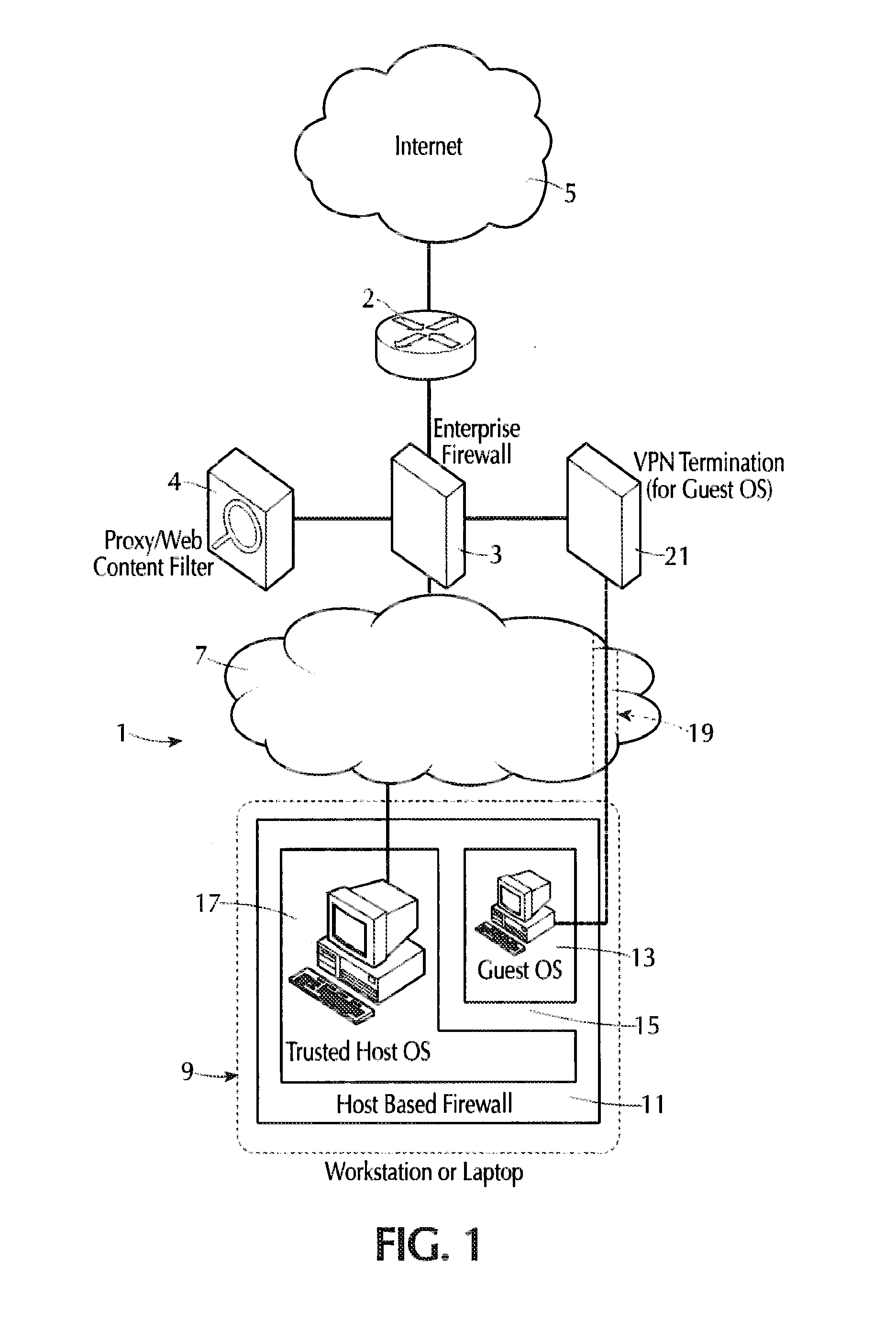
Internet isolation for avoiding internet security threats
ActiveUS9942198B2Obviates abilityReduce the possibilityMultiple digital computer combinationsPlatform integrity maintainanceNetwork terminationIp address
A host computer supports a virtual guest system running thereon. The host system has a firewall that prevents it from communicating directly with the Internet, except with predetermined trusted sites. The virtual guest runs on a hypervisor, and the virtual guest comprises primarily a browser program that is allowed to contact the Internet freely via an Internet access connection that is completely separate from the host computer connection, such as a dedicated network termination point with its specific Internet IP address, or by tunneling through the host machine architecture to reach the Internet without exposing the host system. The virtual guest system is separated and completely isolated by an internal firewall from the host, and the guest cannot access any of the resources of the host computer, except that the guest can initiate cut, copy and paste operations that reach the host, and the guest can also request print of documents. The host can transfer files to and from a virtual data storage area accessible by the guest by manual operator action. No other transfer of data except these user initiated actions is permitted.
Owner:L3 TECH INC
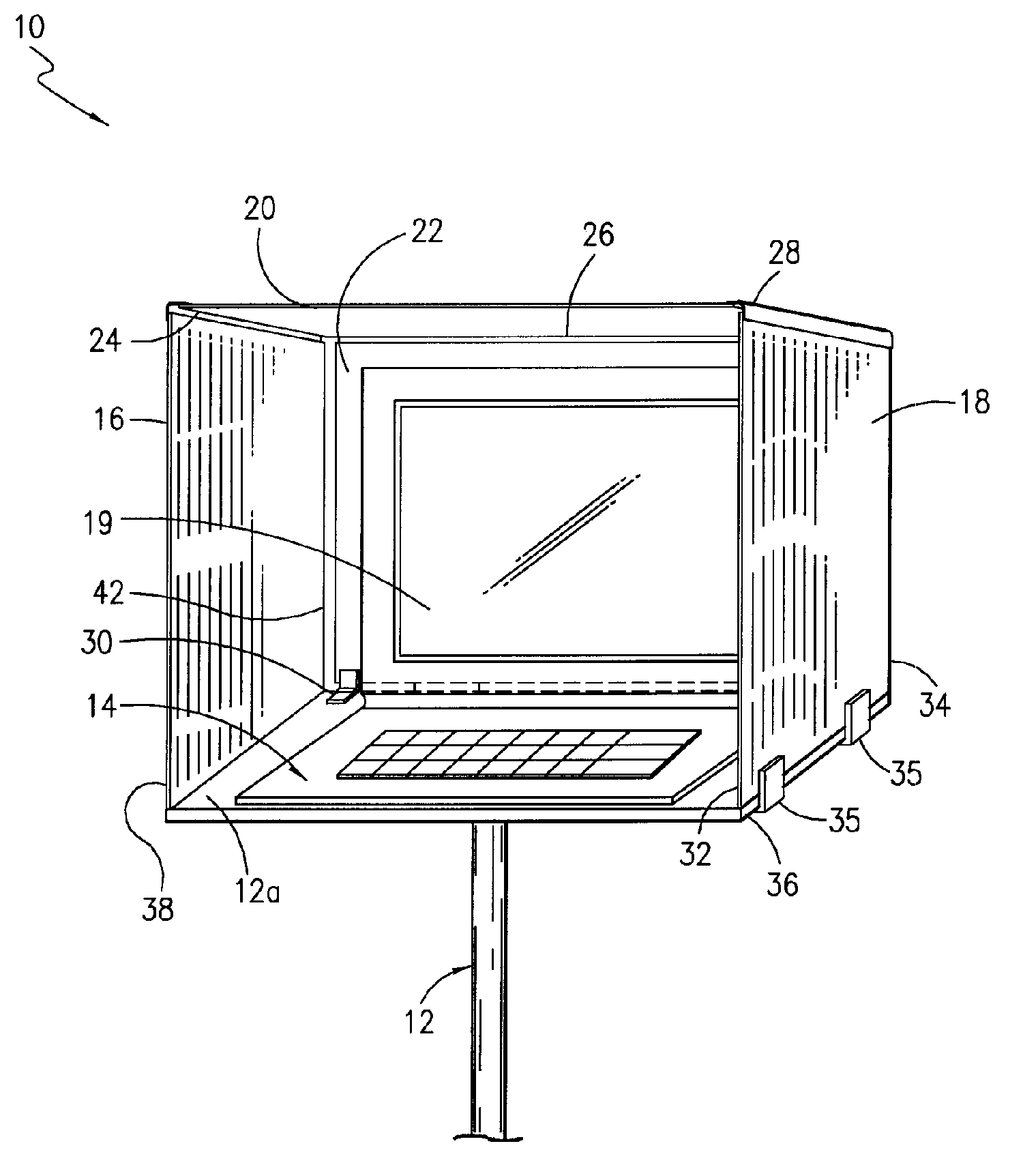
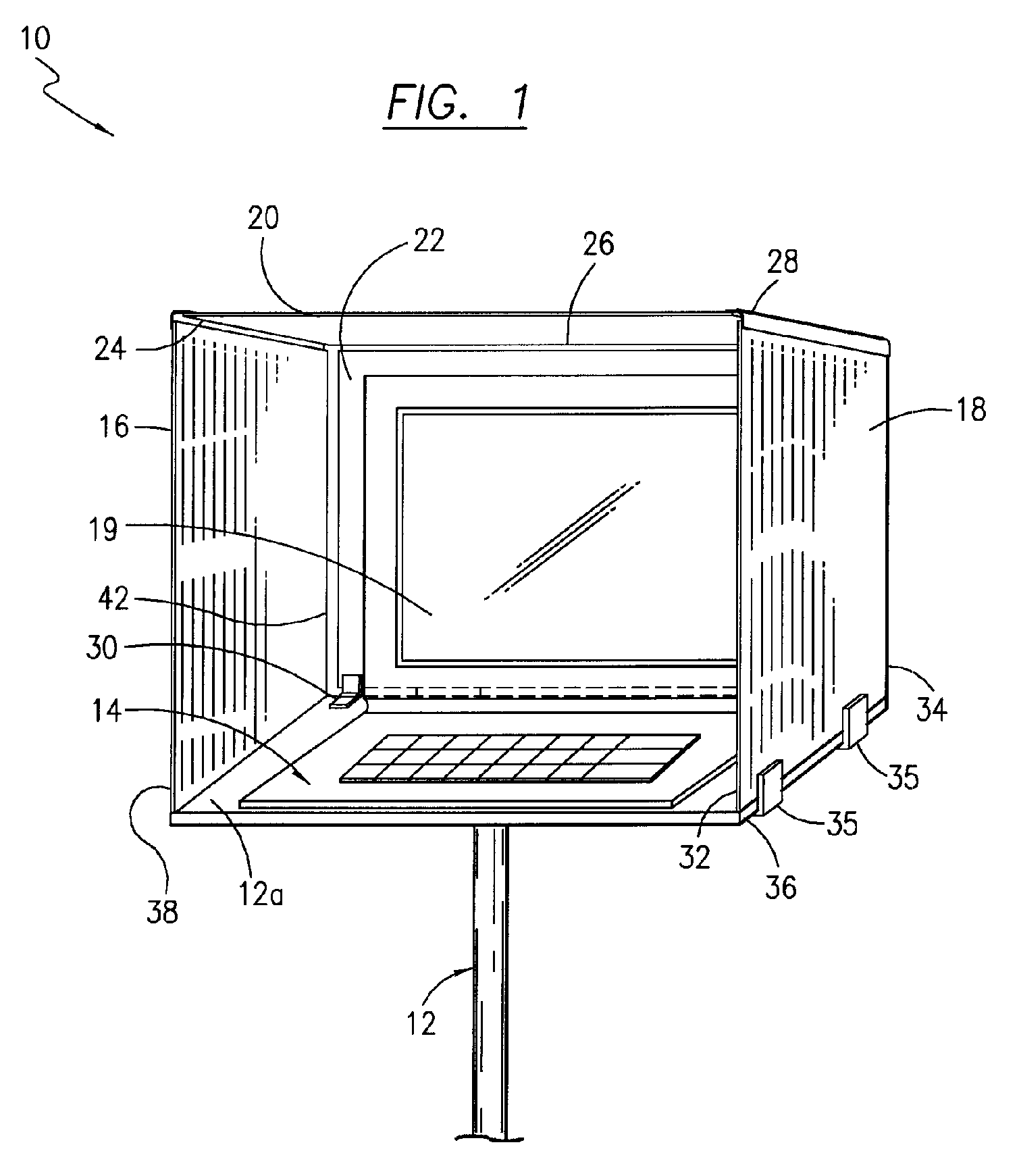
Outdoor laptop computer protector
InactiveUS7304839B1Reduce exposureImprove visibilityFoldable tablesStowable tablesDisplay deviceEngineering
A laptop computer outdoor protector attached to a laptop computer support surface for protecting a laptop computer during outdoor operation with the monitor disposed vertically to reduce glare from sunlight or other high intensity ambient light and to protect the laptop computer from wind, rain, snow or other objects such as tennis balls or golf balls. The protector may also be folded and stored while connected to the top of the laptop support surface when not in use.
Owner:BURNS JAMES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com