Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
65 results about "Proprietary format" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A proprietary format is a file format of a company, organization, or individual that contains data that is ordered and stored according to a particular encoding-scheme, designed by the company or organization to be secret, such that the decoding and interpretation of this stored data is easily accomplished only with particular software or hardware that the company itself has developed. The specification of the data encoding format is not released, or underlies non-disclosure agreements. A proprietary format can also be a file format whose encoding is in fact published, but is restricted through licences such that only the company itself or licencees may use it. In contrast, an open format is a file format that is published and free to be used by everybody.
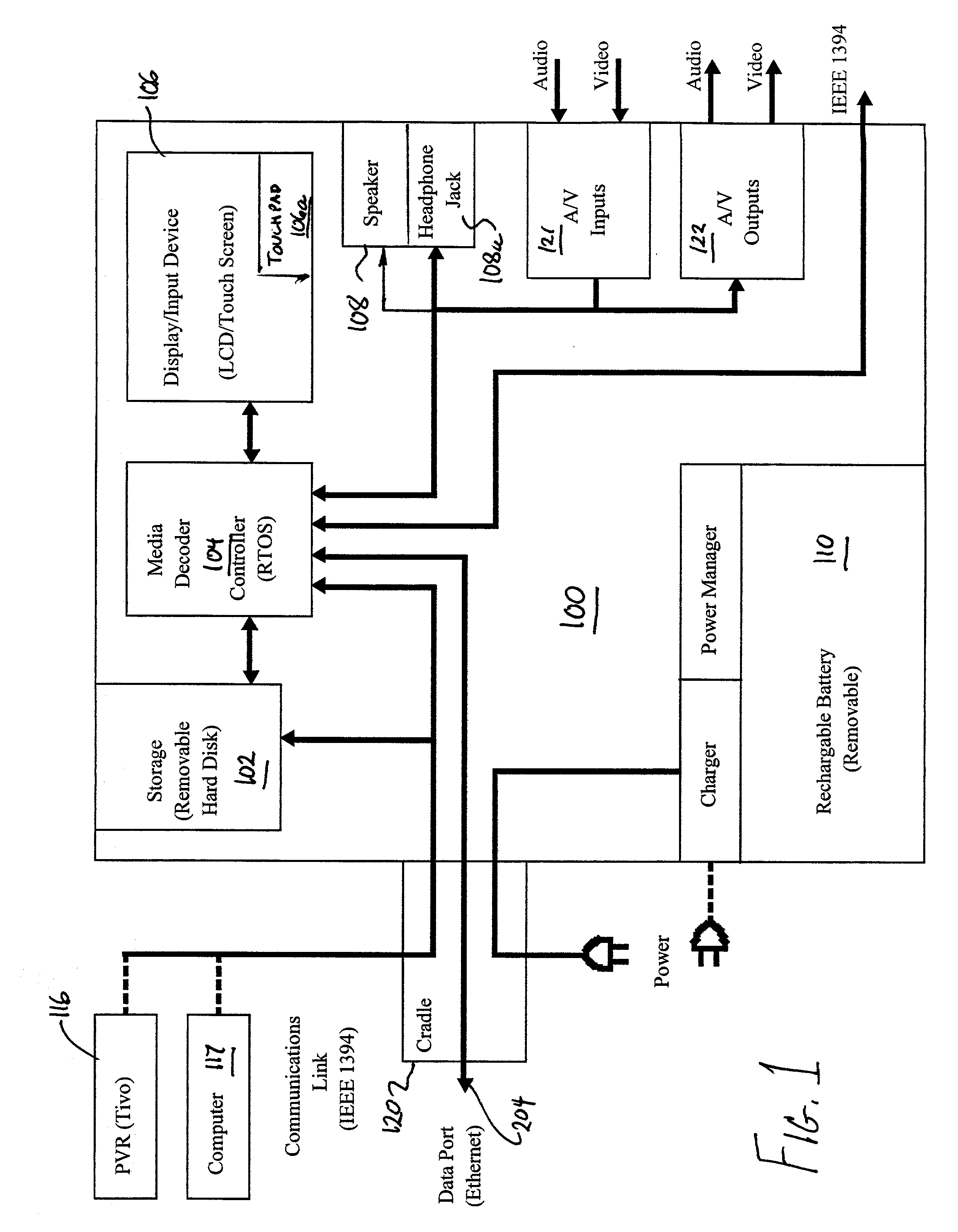
Portable player for personal video recorders
ActiveUS7239800B2Low costTelevision system detailsColor television signals processingProprietary formatDigital video
A low-cost portable digital video player receives proprietary compressed data from a source such as a personal video recorder (PVR), and displays the data on an integral display. A rewritable non-volatile memory of the player stores the data and a media decoder of the player transforms and decompresses the data. According to one embodiment the decoder transforms the data to a non-proprietary format, prior to storing the data. According to a second embodiment, the memory stores the data in the proprietary format, and decoder transforms and decompresses the data in response to an instruction from a user input device, and transfers the decoded data to a display. A cradle for the player provides communications to the PVR, a power supply and optionally further storage capacity.
Owner:INTELLECTUAL VENTURES ASSETS 186 LLC
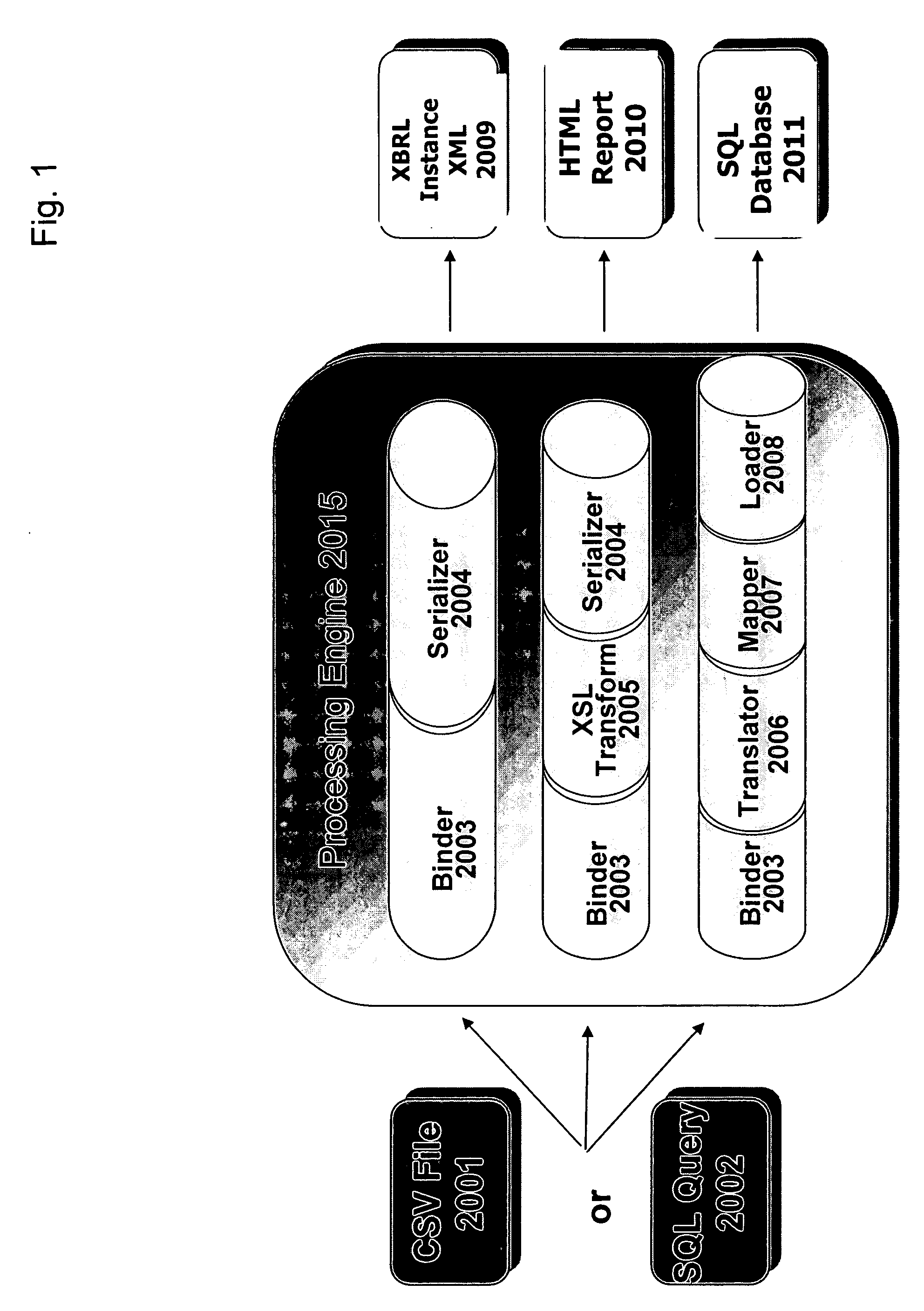
XBRL data conversion
InactiveUS20070078877A1Optimize dataDigital data processing detailsNatural language data processingXBRLData conversion
A system, method and machine-readable medium are provided for converting data to, from, and between standard and proprietary formats using XBRL. The present invention provides a capability for extracting data from databases of a proprietary system and representing the extracted data using a standard format that can be interpreted and processed by any compliant application. The systems and methods of the present invention can provide a bridge application between information systems that use incompatible formats for storing data or that cannot otherwise exchange data
Owner:DYNAMIC ACCESS SYST
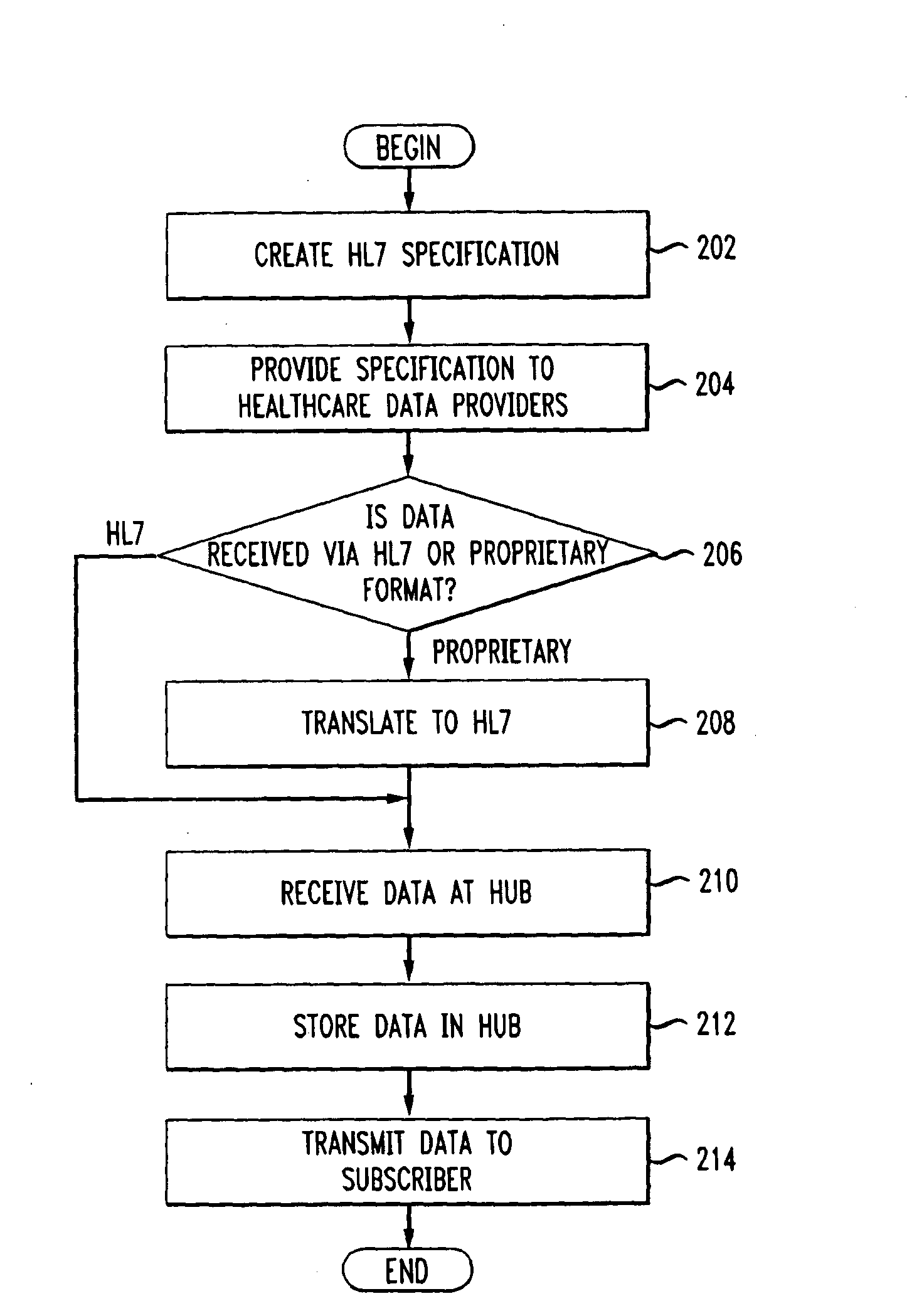
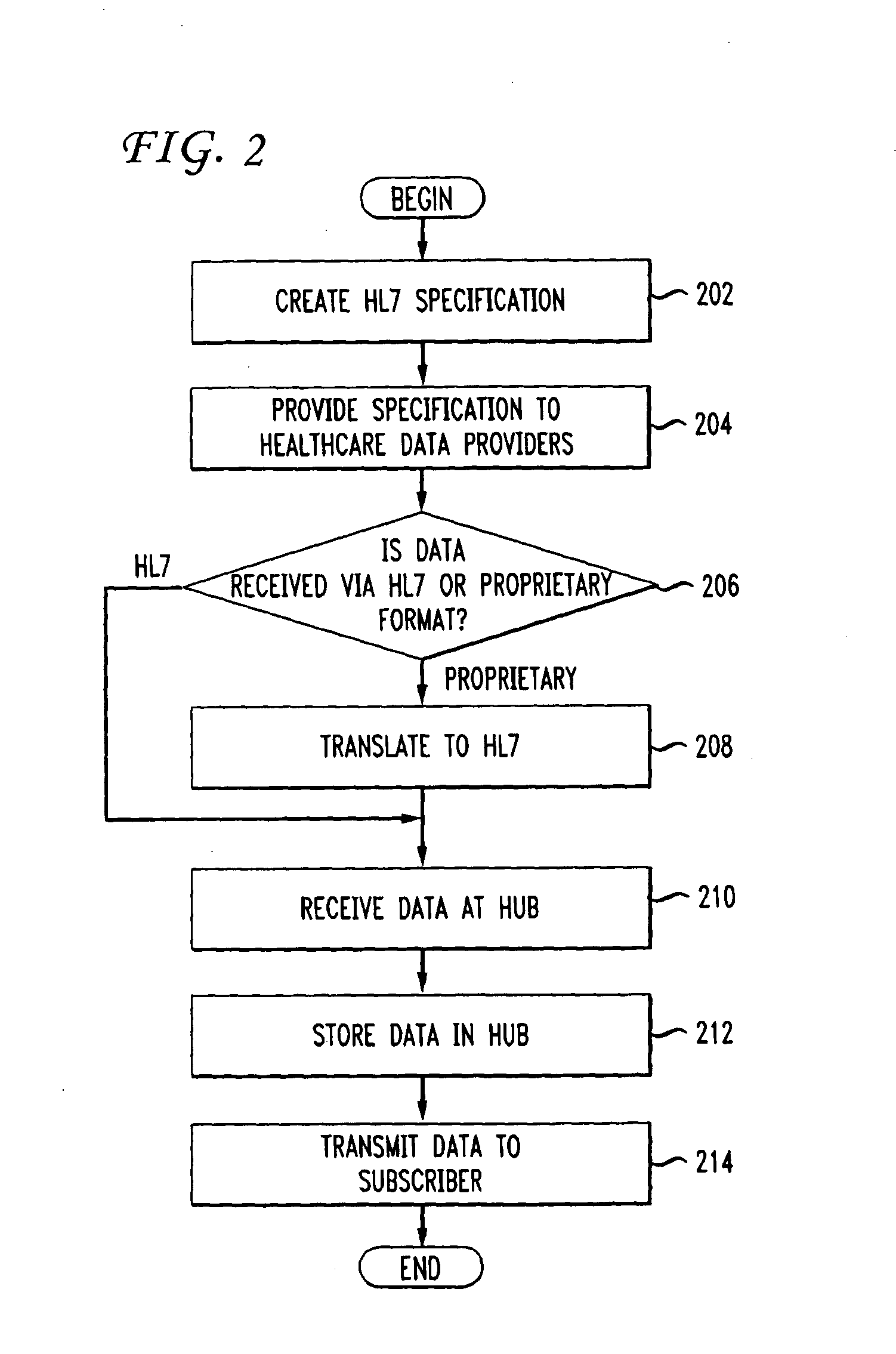
Standardized health data hub
A central health data repository stores health data from various data providers and provides data to various data consumers. The data hub is a standardized central repository that conforms to various standards, such as Health Level Seven (HL7). The data is received according to the HL7 specification and is transmitted to the various data providers using HL7. The data may also be transmitted as a continuous data feed. In this manner, a large volume of health data may be collected, stored, and disseminated using the data hub as a standardized service. A computer system includes one or more processors, an output network interface and an input network interface, a memory for storing multiple personal health records having fields for storing data in a proprietary format or in a standard format. The memory may also include an HL7 translation module and a data insertion / retrieval code module, wherein the computer system performs as a standardized health data repository for various entities in the healthcare industry.
Owner:IMETRIKUS
Methods and Systems for Providing Translations of Data Retrieved From a Storage System in a Cloud Computing Environment
ActiveUS20100199037A1Memory adressing/allocation/relocationProgram controlCloud computingVirtual storage
A method for providing translations of data retrieved from a storage system in a cloud computing environment includes receiving, by an interface object executing on a first physical computing device, a request for provisioning of a virtual storage resource by a storage system. The interface object requests, from a storage system interface object, provisioning of the virtual storage resource. The interface object receives, from the storage system interface object, an identification of the provisioned virtual storage resource. The interface object translates the identification of the provisioned virtual storage resource from a proprietary format implemented by the storage system interface object into a standardized format by accessing an interface translation file mapping each of a plurality of proprietary formats with the standardized format. The interface object responds to the request received from the second physical computing device, with a translation of the received identification.
Owner:CITRIX SYST INC
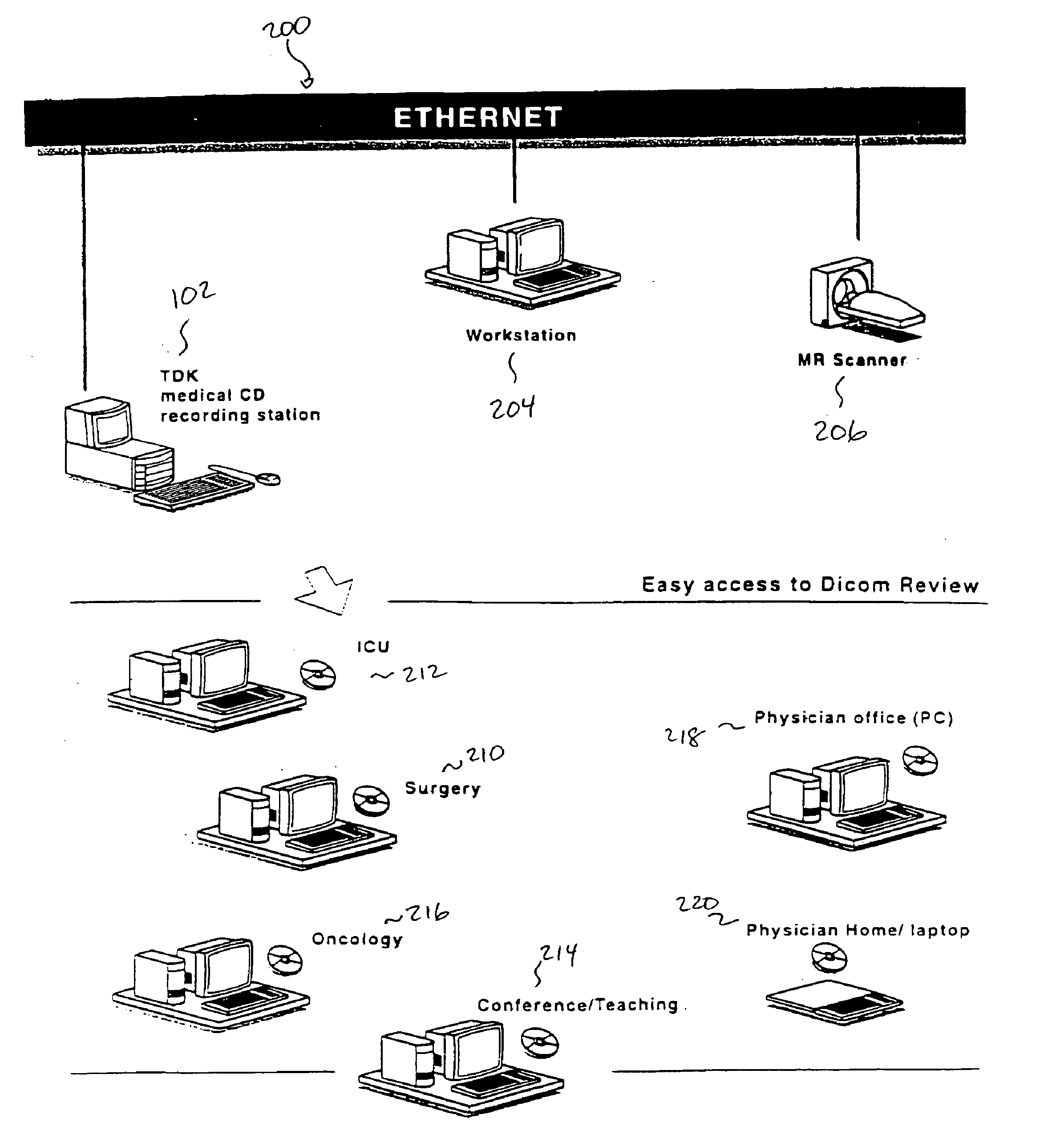
Removable media recording station for the medical industry
InactiveUS6954802B2Easy accessImprove distributionData processing applicationsCharacter and pattern recognitionIt investmentRemovable media
A removable medium recording station records medical image data in a format and removable medium that are widely accepted. The removable medium recording station can be used to effectively replace an installed storage device on an existing stand-alone medical image workstation. Storage onto removable media is transformed into an outboard operation. This transformation enables a hospital to migrate existing medical imaging systems to new formats and media without sacrificing a large portion of their initial investment. Additionally, the removable medium recording station can be attached as a peripheral on an existing medical modality network. In this capacity, the removable medium recording station enables an operator on the medical modality network to store medical images in a selected format and on a selected type of removable medium regardless of the proprietary format used by the enterprise level archive server. The removable medium recording station enables a hospital to add new functionality without sacrificing their investment in their enterprise solution.
Owner:TDK US CORP
Web-based collaborative document review system
A method of collaboratively editing a document includes converting an originating document to a web document comprising segmented files in a markup language; storing the web document on a server; retrieving the web document to generate edits thereto from a first participant; transmitting the first participant edits to the server and associating the first edits with the web document; retrieving the web document including first participant edits to generate additional edits thereto from a second participant; transmitting the second participant edits to the server and associating the second participant edits with the web document and the first participant edits; reviewing edits from all participants by a document administrator, accepting or rejecting edits, including conflicting edits, until desired changes are made to the web document; and converting the web document including first and second participant edits into an edited document into a proprietary format.
Owner:ZULIMAR
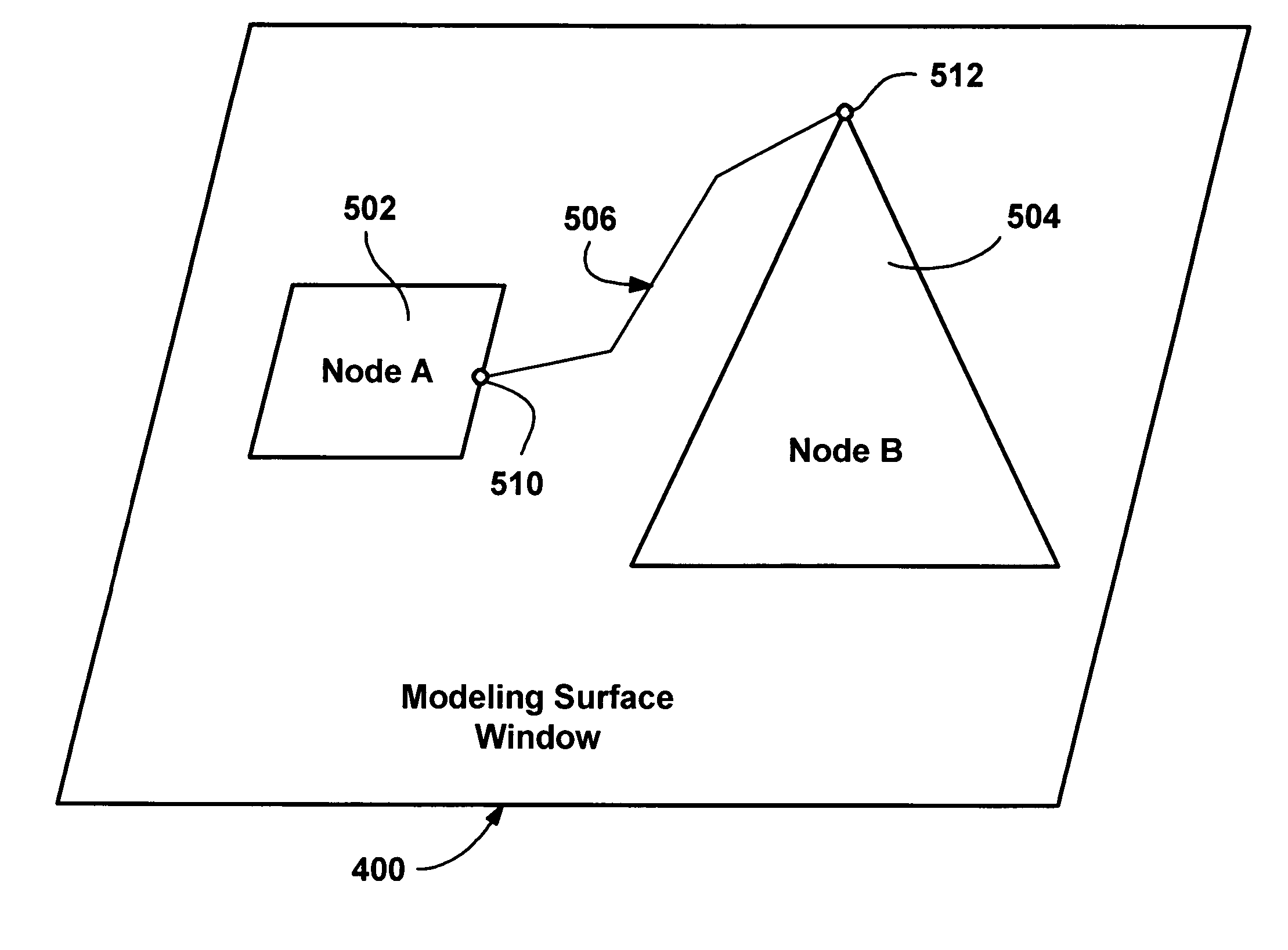
Dynamic, live surface and model elements for visualization and modeling
InactiveUS7196712B2Cathode-ray tube indicatorsExecution for user interfacesWeb siteDocumentation procedure
Described is a method and system providing a dynamic, live (active) surface and / or model elements to complement and enhance what is being modeled or visualized, enabling the addition of new features and functionality to visualization and modeling tools. A dynamic surface is accomplished by extending traditional HTML, rendering APIs and / or components to enable visualization and modeling functionality. The surface background and model elements may comprise HTML elements, and the surface can include a Web site. The model elements are HTML elements layered dynamically atop the surface, as the user interacts with them, and completed designs may be saved in a non-proprietary format, (e.g., HTML). The live surface bases its services on HTML rendering engine services, and further provides a visualization and modeling engine that wraps and extends the rendering engine through multiple interfaces. Interfaces can enumerate modeling elements and their relationships, add, delete or change connections between model elements and states, and initialize the surface, including loading an existing diagram such as saved as an HTML document.
Owner:MICROSOFT TECH LICENSING LLC
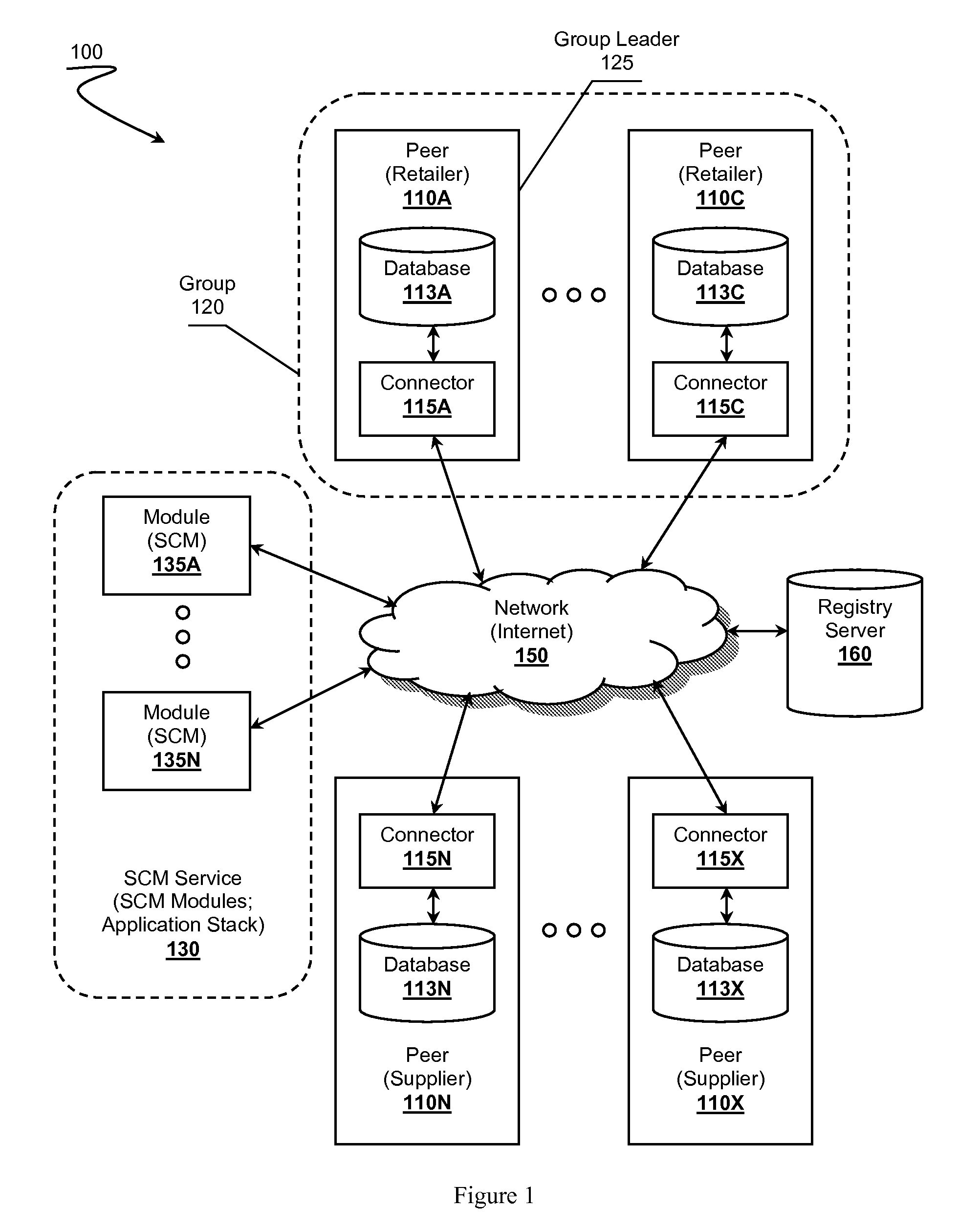
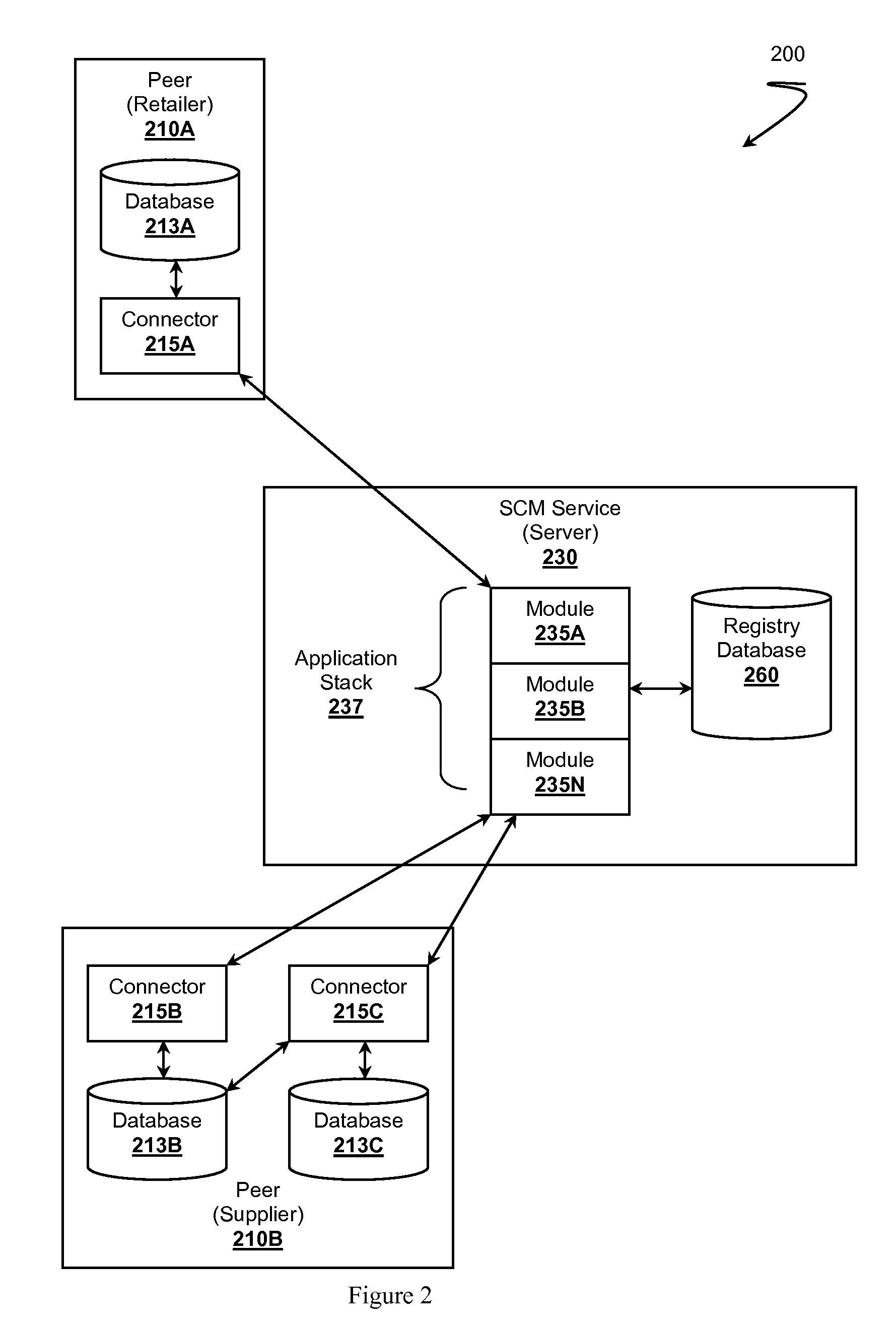
Supply Chain Management Systems and Methods
InactiveUS20100094674A1Expand databaseReduce waiting timeDigital data processing detailsResourcesApplication softwareData format
Supply chain management (SCM) systems and methods are presented. In SCM ecosystems having multiple independent trading partners that can functions as peers, the trading partners likely lack a “single version of truth” with respect to retail data formats or transactions. The partners can utilize database connectors to interact with other peer partners by converting the partner's retail data from proprietary formats to a common transaction format understood by all connectors or by an SCM application stack constructed from SCM modules. The connectors can use a registry server to discover other connectors capable participating in a requested transaction relationship. SCM modules can be configured to support a transaction relationship according to the transaction relationships available to the peers' connectors.
Owner:RETAIL NAVIGATOR
Method and apparatus for displaying non-standard-compliant images
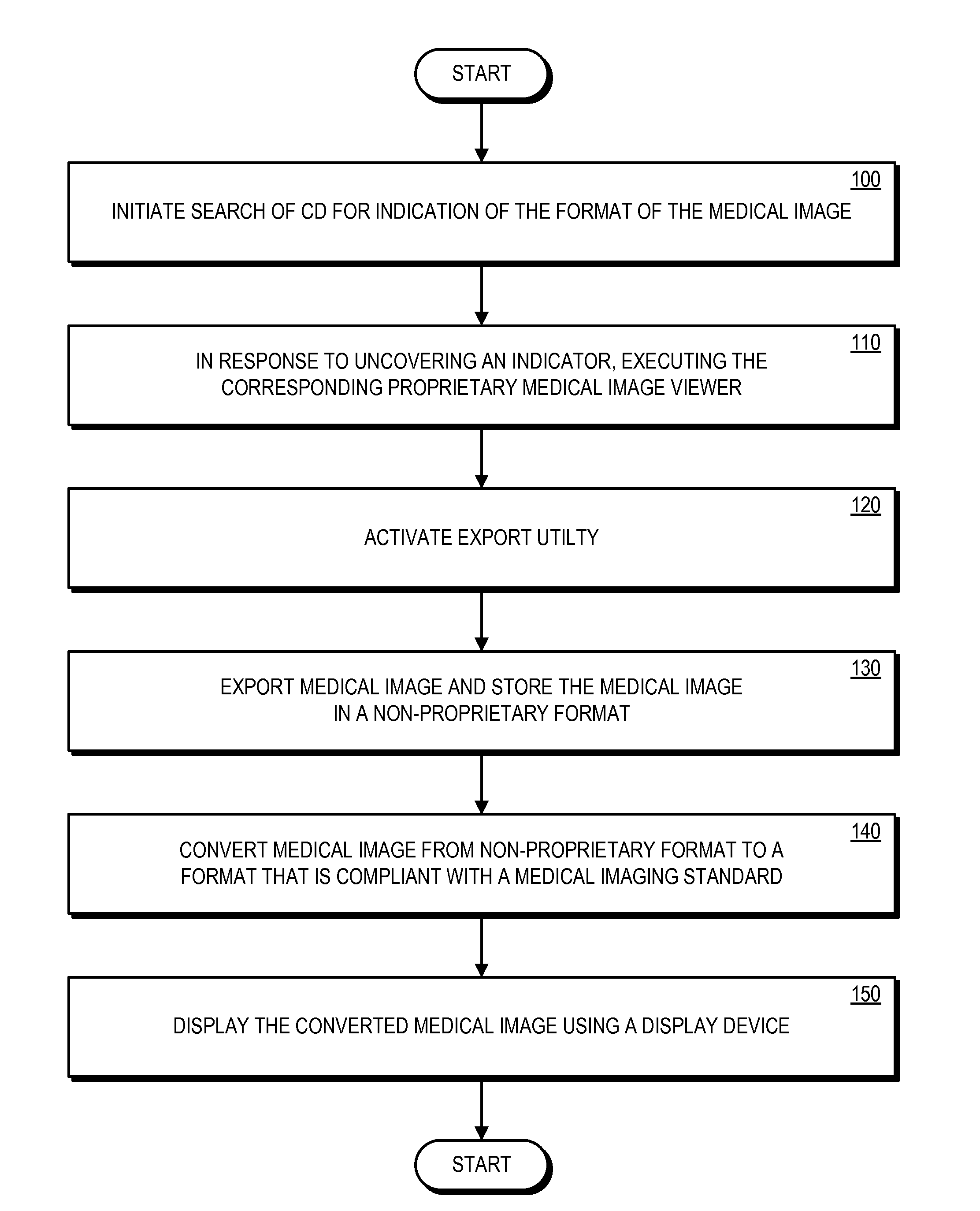
InactiveUS8825680B2Digital data information retrievalDigital data processing detailsComputerized systemDisplay device
Provided is a method of converting a medical image used in a network at a patient care facility, the network including an enterprise network storage solution optionally dedicated for storing medical images in a standardized medical imaging format that are to be retrieved over the network. The method includes us a computer system to search a portable computer-readable medium for an indication that the medical image is stored in a proprietary format on the portable computer-readable medium. The proprietary format of the medical image is identified, using the computer system, based on the indication. The medical image is converted into a format that is compliant with a standardized medical-imaging format, transmitted in the standardized medical-imaging format to be: (i) subsequently displayed by a display device without requiring prior storage of the medical image in an enterprise storage solution for medical images, and / or (ii) stored in the enterprise storage solution.
Owner:CODONICS
Security badge arrangement
InactiveUS20050229005A1Improve interoperabilityEasy to identifyDigital data processing detailsComputer security arrangementsThird partyDigital signature
A method and computer program product which comprises storing at least one data file inside a portable device such as security token or flash memory drive associated with a security badge. The data file includes sufficient information to allow a third party to verify the identity of an assignee of the security badge. The identity of the assignee is based at least in part on the information included in the data file by the third party without having to rely on a presentation affixed to one or more exterior surfaces of the security badge. Other embodiments of the invention comprises operatively coupling the security token to a security system, authenticating the assignee to the security token, generating a digital signature of the data file using a private key, and sending the digital signature, the data file and a digital certificate associated with the private key to said security system. The sufficient information comprises a digital photograph of the assignee, the assignee's name, the assignee's employer name, a logo of the employer or a security badge number and instructions for reading the data file when provided in a proprietary format. Final verification of the assignee's identity is performed by a security officer.
Owner:ACTIVCARD
Architecture of a bridge between a non-IP network and the web
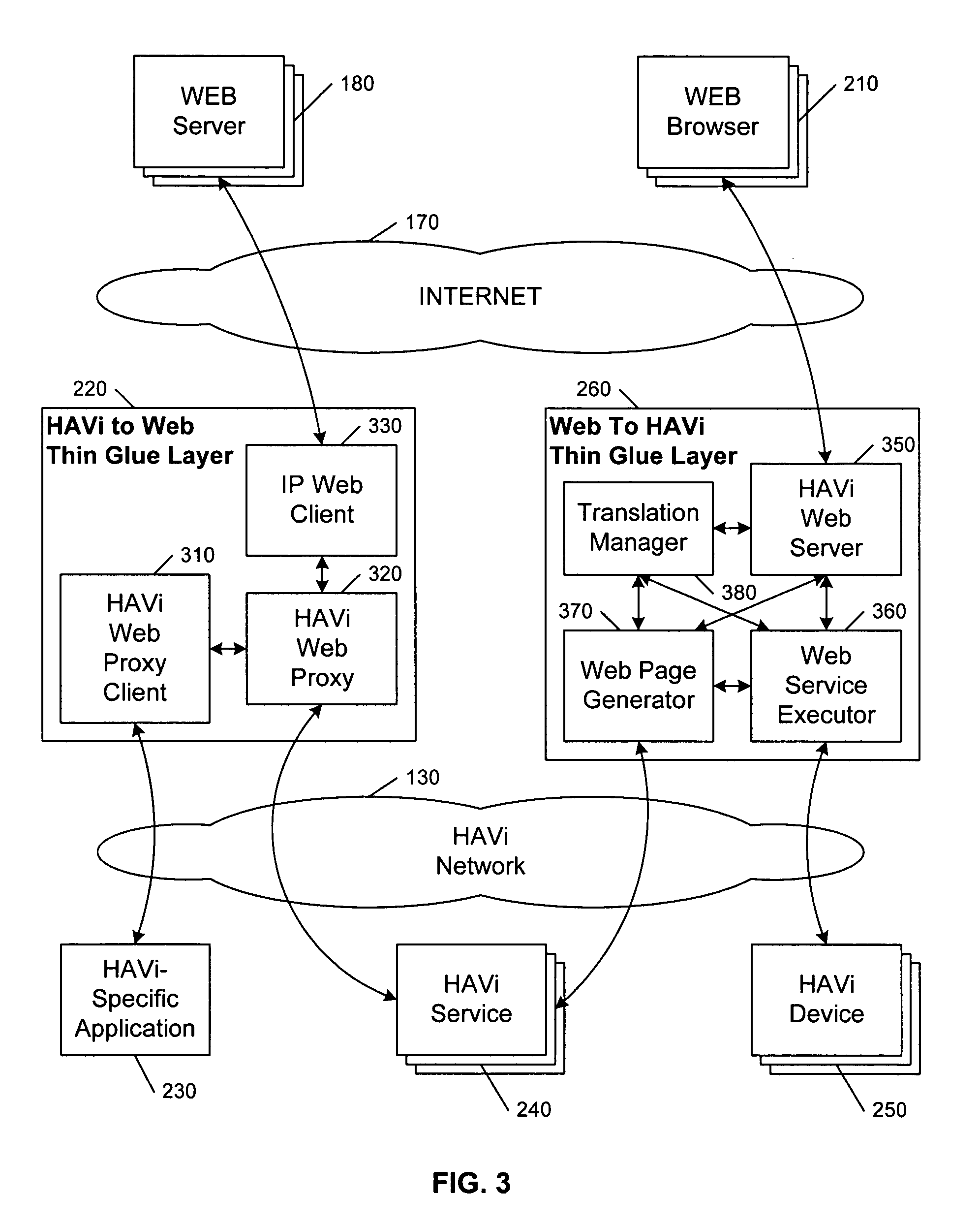
InactiveUS7111079B2Simple and efficientTelevision system detailsColor television detailsApplication softwareXML
Thin glue layers bridge a Non-IP network and the Internet Web. Existing services in both networks are used directly wherever feasible, thereby achieving simplicity and efficiency. A Non-IP-specific application can use a Non-IP API to access Internet services, and an IP-based Internet browser can use commands encoded in HTTP, XML, Java, or proprietary formats to access Non-IP services and to control Non-IP devices. In this manner, changes are not required to the Internet browser. The glue layers translate between the IP protocol and Non-IP API, but also allow commands and responses to tunnel between end applications in the Internet and the Non-IP network without interpretation.
Owner:U S PHILIPS CORP +1
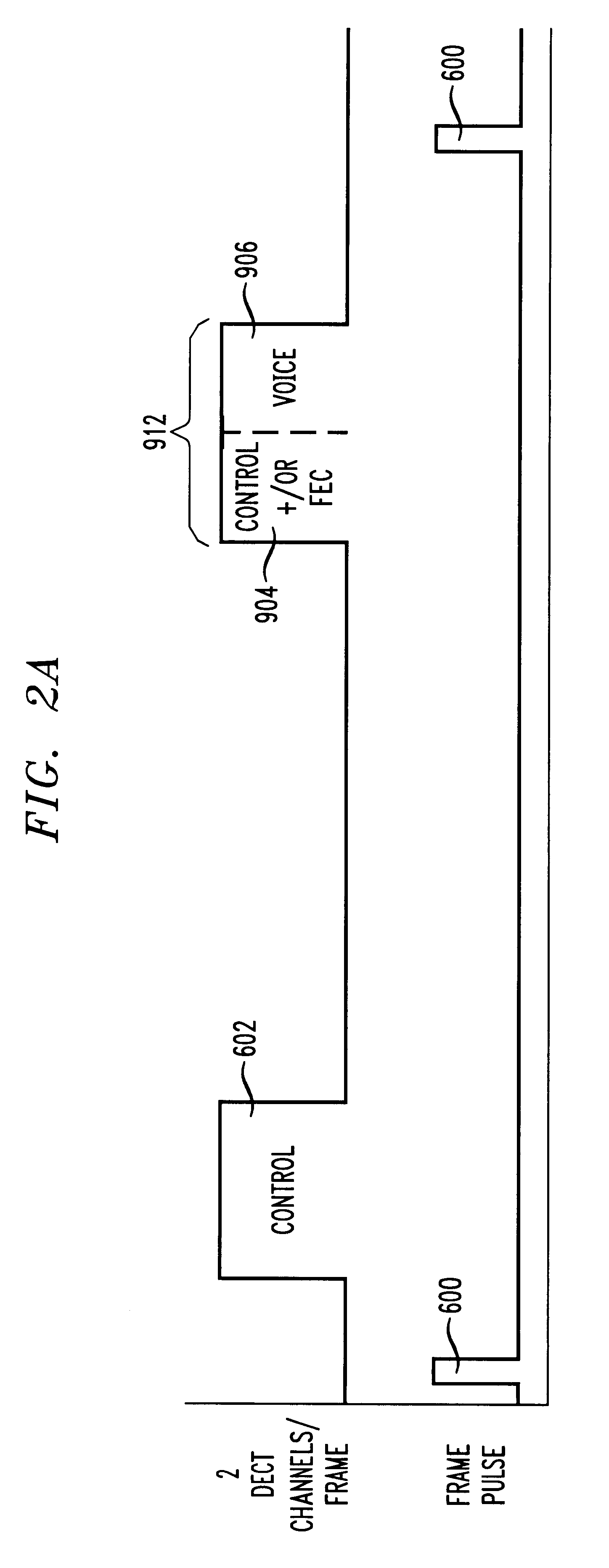
Method, apparatus, and communication protocol for transmitting control data with an improved error correction capability in a digital cordless telephone system
A more robust error correction capability is provided for the control data passed between a remote handset and its base unit in a DECT digital cordless telephone. According to the DECT standard as implemented in digital cordless telephones, one communication channel is used for control data and another is used for the voice data. While the DECT standard allows proprietary formats to be transmitted in the voice data channel, it fixes the information transmitted in the control data to ensure interoperability. In accordance with the principles of the present invention, the data rate of the voice data is reduced from a conventional 32 kb / s to provide bandwidth for error protection information. The error protection information may include, e.g., a redundant copy of the control data to provide the basis for a diversity scheme to improve the reliability of the control data transmission. Additionally, or alternatively, the error protection information may include error correction information, e.g., forward error correction information, relating to the control data and / or to the voice data to improve the reliability of the control data and / or voice data being transmitted. The error protection information may be combined with the voice data in the single communication channel time slot by, e.g., multiplexing, or apportioning of the time slot.
Owner:BELL NORTHERN RES LLC
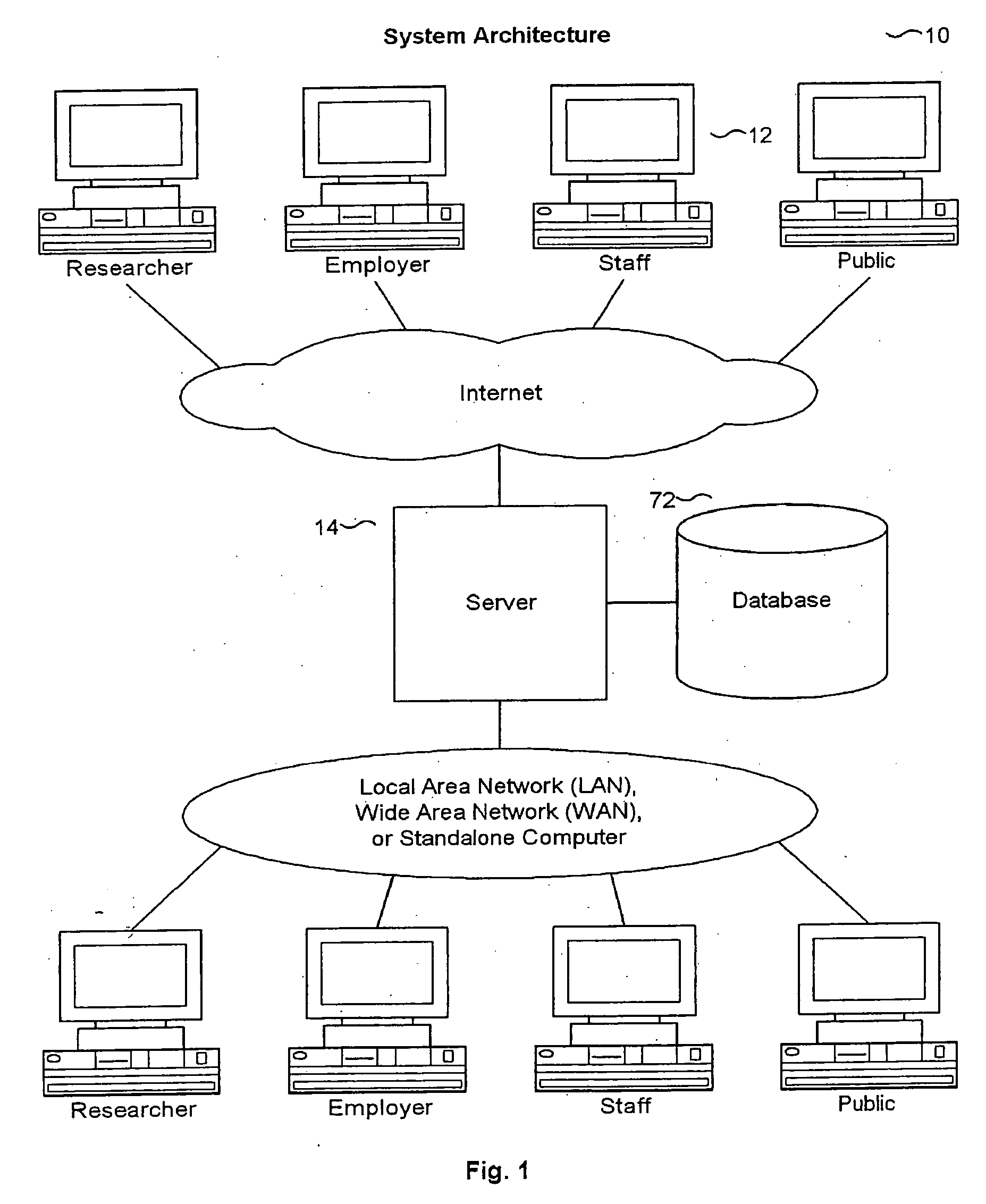
Labor market information analyzer system for researchers, employers, staff, and others
InactiveUS7054864B1Easy and efficient to manufactureReduce manufacturing costData processing applicationsSpecial data processing applicationsClient-sideData mining
A computerized information system for analyzing labor market information comprising: a server having a plurality of categorizing and processing services for researchers, employers, staff, and the like; a database of standard and proprietary format data and optional stored procedures operatively coupled with the server; and a plurality of input / output client devices operatively coupled with the server.
Owner:TOOMEY PAUL
Storage server with embedded communication agent
ActiveUS8756338B1Digital data information retrievalMultiple digital computer combinationsStorage Management Initiative – SpecificationProgram planning
A storage server receives a data access request in a standard communication format, such as the Storage Management Initiative-Specification (SMI-S). A single mode request is received at a disk module of the storage server and a cluster mode request is received at a management host of the storage server. The request is forwarded to a communication agent in a management module of the storage server. The communication agent translates the request from the standard communication format to a proprietary format used by the storage server to communicate with an attached storage subsystem. The storage server services the request from the attached storage subsystem through a disk module. In cluster mode, the request is forwarded to corresponding disk modules in each storage server in the cluster.
Owner:NETWORK APPLIANCE INC
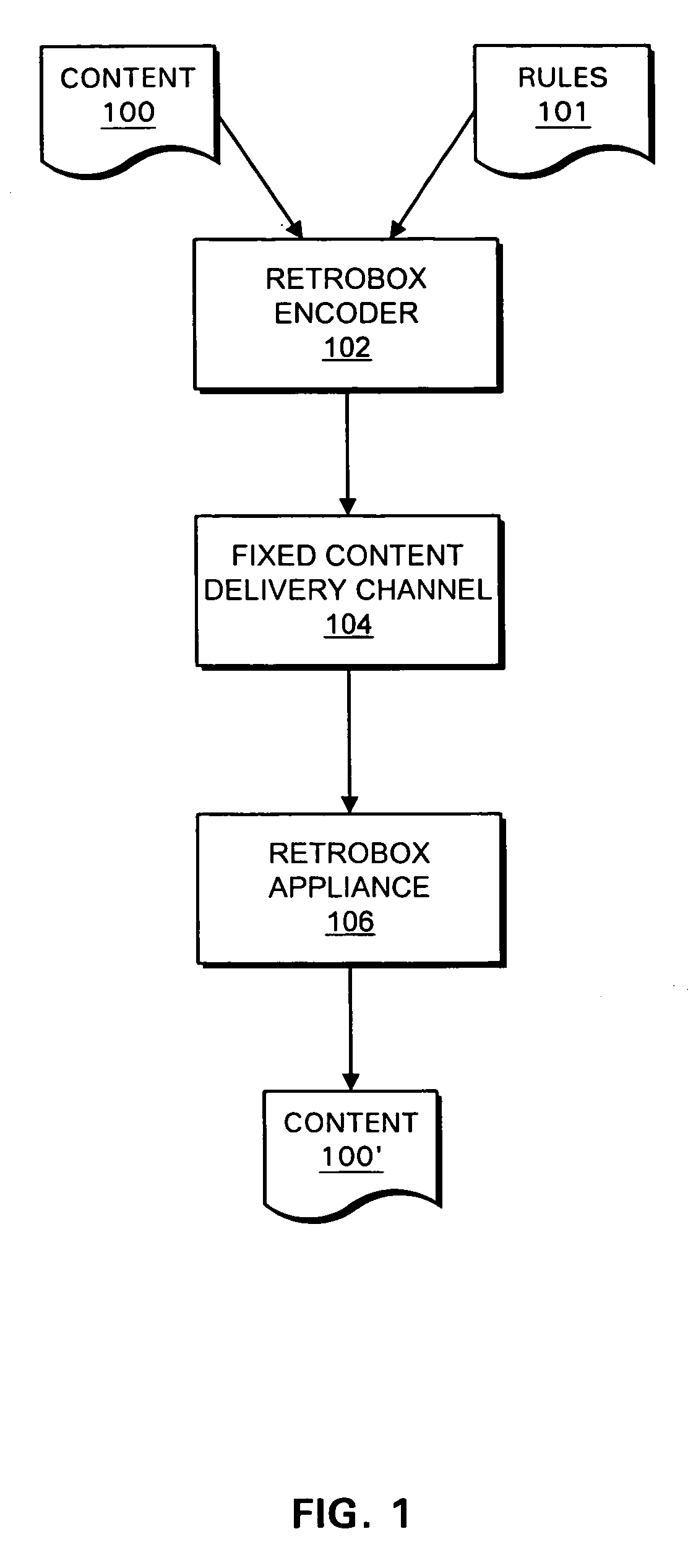
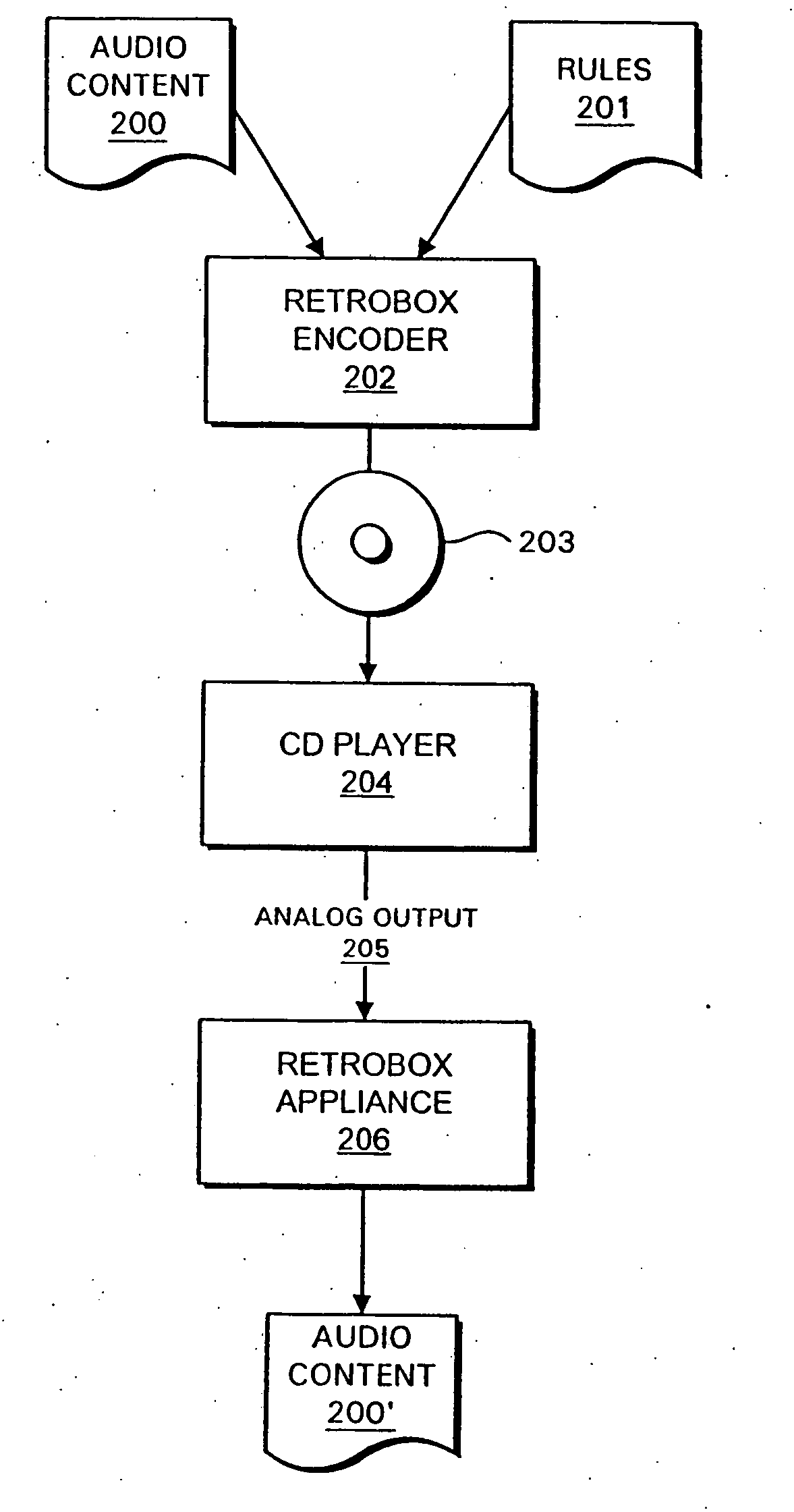
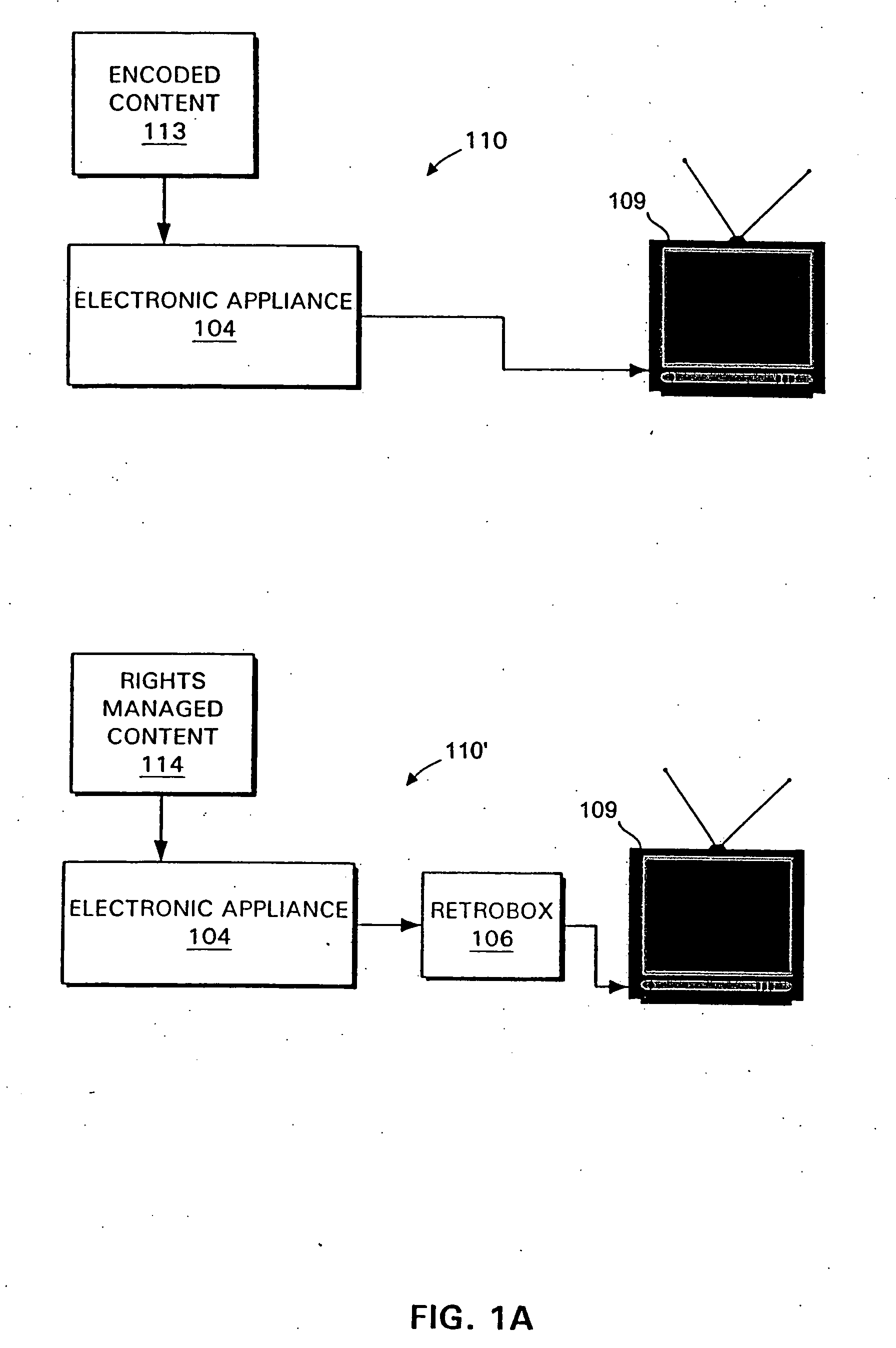
Systems and methods for retrofitting electronic appliances to accept different content formats
InactiveUS7050586B1Television system detailsUsing non-detectable carrier informationThird partyContent format
Systems and methods are disclosed for using an arbitrary fixed channel to carry third-party information. In one embodiment, the present invention provides systems and methods for enabling existing content rendering devices to accept content encoded in a proprietary format, such as an encoding format used by a digital rights management system. The encoded content is rendered by the device in the normal manner, and decoded by a retrofitting appliance connected to the device's output. The retrofitting appliance may apply decoded rules and controls to the decoded content, thereby managing use of the content.
Owner:INTERTRUST TECH CORP
Dynamic, live surface and model elements for visualization and modeling
InactiveUS20050041042A1Cathode-ray tube indicatorsExecution for user interfacesWeb siteComputer graphics (images)
Described is a method and system providing a dynamic, live (active) surface and / or model elements to complement and enhance what is being modeled or visualized, enabling the addition of new features and functionality to visualization and modeling tools. A dynamic surface is accomplished by extending traditional HTML, rendering APIs and / or components to enable visualization and modeling functionality. The surface background and model elements may comprise HTML elements, and the surface can include a Web site. The model elements are HTML elements layered dynamically atop the surface, as the user interacts with them, and completed designs may be saved in a non-proprietary format, (e.g., HTML). The live surface bases its services on HTML rendering engine services, and further provides a visualization and modeling engine that wraps and extends the rendering engine through multiple interfaces. Interfaces can enumerate modeling elements and their relationships, add, delete or change connections between model elements and states, and initialize the surface, including loading an existing diagram such as saved as an HTML document.
Owner:MICROSOFT TECH LICENSING LLC
Realtime processing of streaming data
ActiveUS20160004578A1Maximize data capture performanceImprove data collection efficiencyInterprogram communicationProgram loading/initiatingStreaming dataProcessing
The invention described here is intended for enhancing the technology domain of real-time and high-performance distributed computing. This invention provides a connotative and intuitive grammar that allows users to define how data is to be automatically encoded / decoded for transport between computing systems. This capability eliminates the need for hand-crafting custom solutions for every combination of platform and transport medium. This is a software framework that can serve as a basis for real-time capture, distribution, and analysis of large volumes and variety of data moving at rapid or real-time velocity. It can be configured as-is or can be extended as a framework to filter-and-extract data from a system for distribution to other systems (including other instances of the framework). Users control all features for capture, filtering, distribution, analysis, and visualization by configuration files (as opposed to software programming) that are read at program startup. It enables large scalable computation of high velocity data over distributed heterogeneous platforms. As compared with conventional approaches to data capture which extract data in proprietary formats and rely upon post-run standalone analysis programs in non-real-time, this invention also allows data streaming in real-time to an open range of analysis and visualization tools. Data treatment options are specified via end-user configuration files as opposed to hard-coding software revisions.
Owner:FISHEYE PROD
Browser on test equipment
InactiveUS7092947B2Give flexibilityImprove performanceData processing applicationsSubstation equipmentComputer hardwareWireless Application Protocol
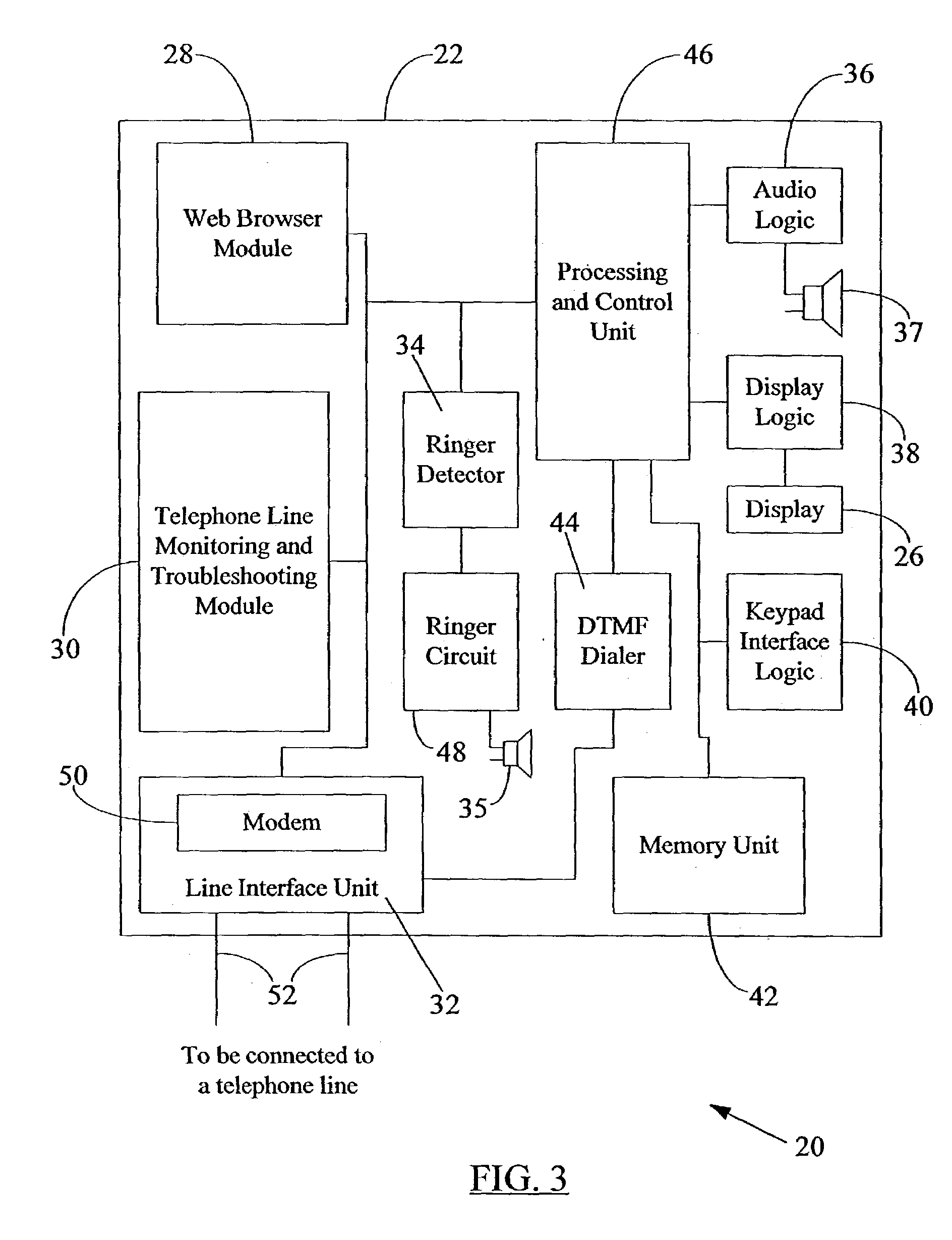
A portable telecommunication test set, such as a telephone line butt set, with a web browser incorporated therein. A standard HTML (Hyper Text Mark-up Language) or WAP (Wireless Application Protocol) browser may be incorporated within the portable test set, allowing a network technician to access the Internet as well as other remotely-located sources of information to retrieve data and other useful technical information while in the field for communication network or telephone line maintenance, troubleshooting or repair. The test set may contain memory to locally store certain technical information, e.g., telephone line-specific data or circuit information, that may be retrieved and “read” by the built-in browser module when prompted by the network technician. The web browser may display the content of the requested information on a display provided on the test set. Line-specific (as well as manufacturer-specific) test information need not be in a manufacturer-dictated proprietary format, but, instead, may be in a generally available text format, e.g., the HTML format or the WML (Wireless Mark-up Language) format. Testing-related data may thus be supplied (as hardware or software plug-in modules) by a vendor other than the manufacturer of the test set.
Owner:BELLSOUTH INTPROP COR
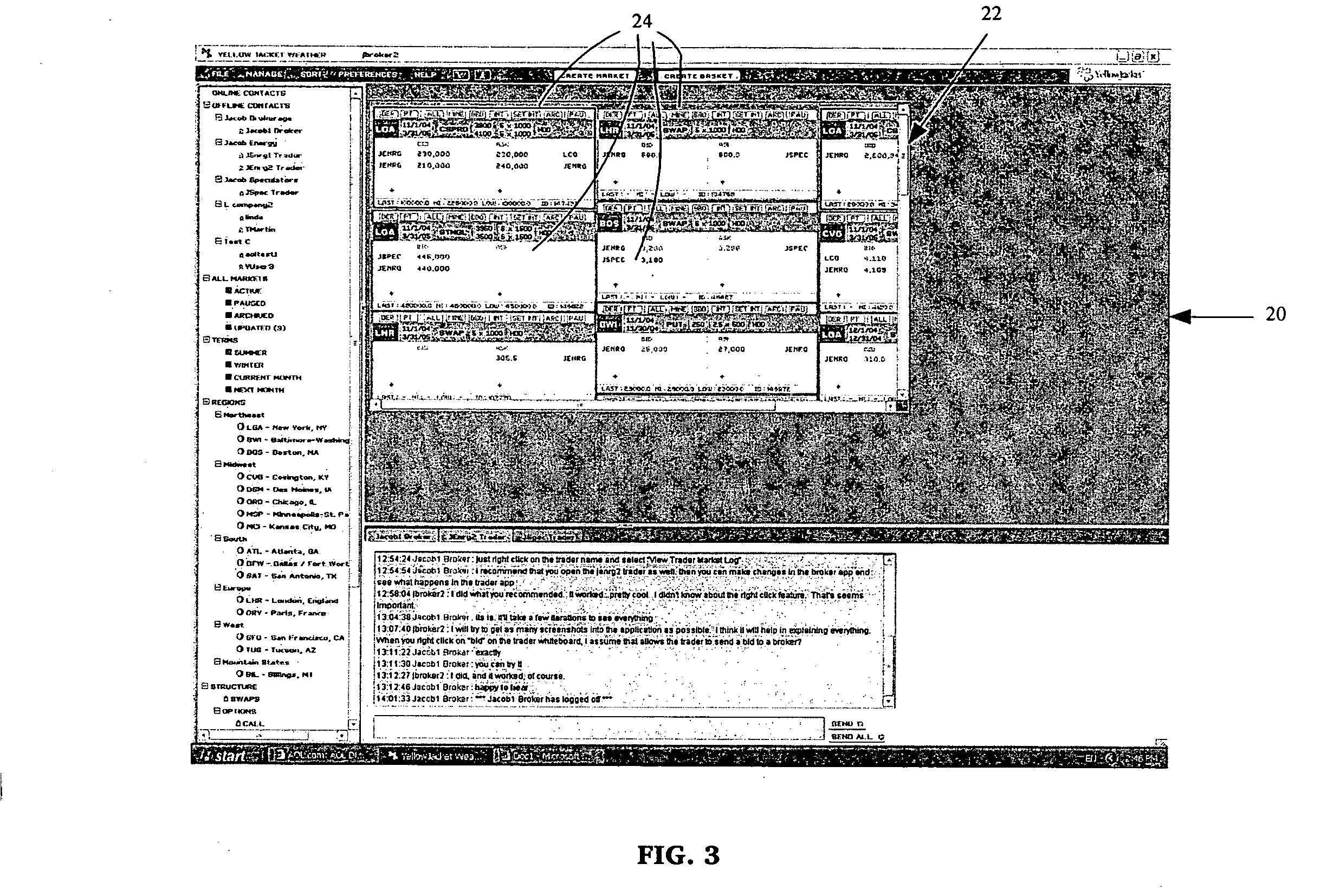
Virtual over-the-counter financial product exchange system
A virtual over-the-counter exchange system that allows brokers to negotiate and complete exchanges of financial products between traders within a plurality of financial product markets includes a data converter that converts financial product market information received from a broker into a standard financial product data format, a virtual broker database that stores the financial product market information in the standard financial product data format, a plurality of virtual trader databases, each virtual trader database storing, in the standard financial product data format, at least a portion of the financial product market information selected by the broker to be distributed to a corresponding one of a plurality of traders, and a data distributor that distributes the at least a portion of the financial product market information in each of the virtual trader databases to a corresponding one of the plurality of traders in one of a plurality of proprietary formats.
Owner:ICE DATA
Generation and Management of Logic
ActiveUS20080127163A1Specific program execution arrangementsMemory systemsComputer programProprietary format
Included are embodiments of a description language program stored in a computing device for updating a first version of a computer program. In at least one embodiment, the first version of the computer program is written in a universal format and the program includes logic configured to receive an updated version of the computer program. Other embodiments include logic configured to retrieve the first version of the computer program and logic configured to translate the updated version of the computer program from a proprietary format to the universal format. Still other embodiments include logic configured to utilize the at least one tag to compare the translated updated version of the computer program with the first version of the computer program.
Owner:VIA TECH INC
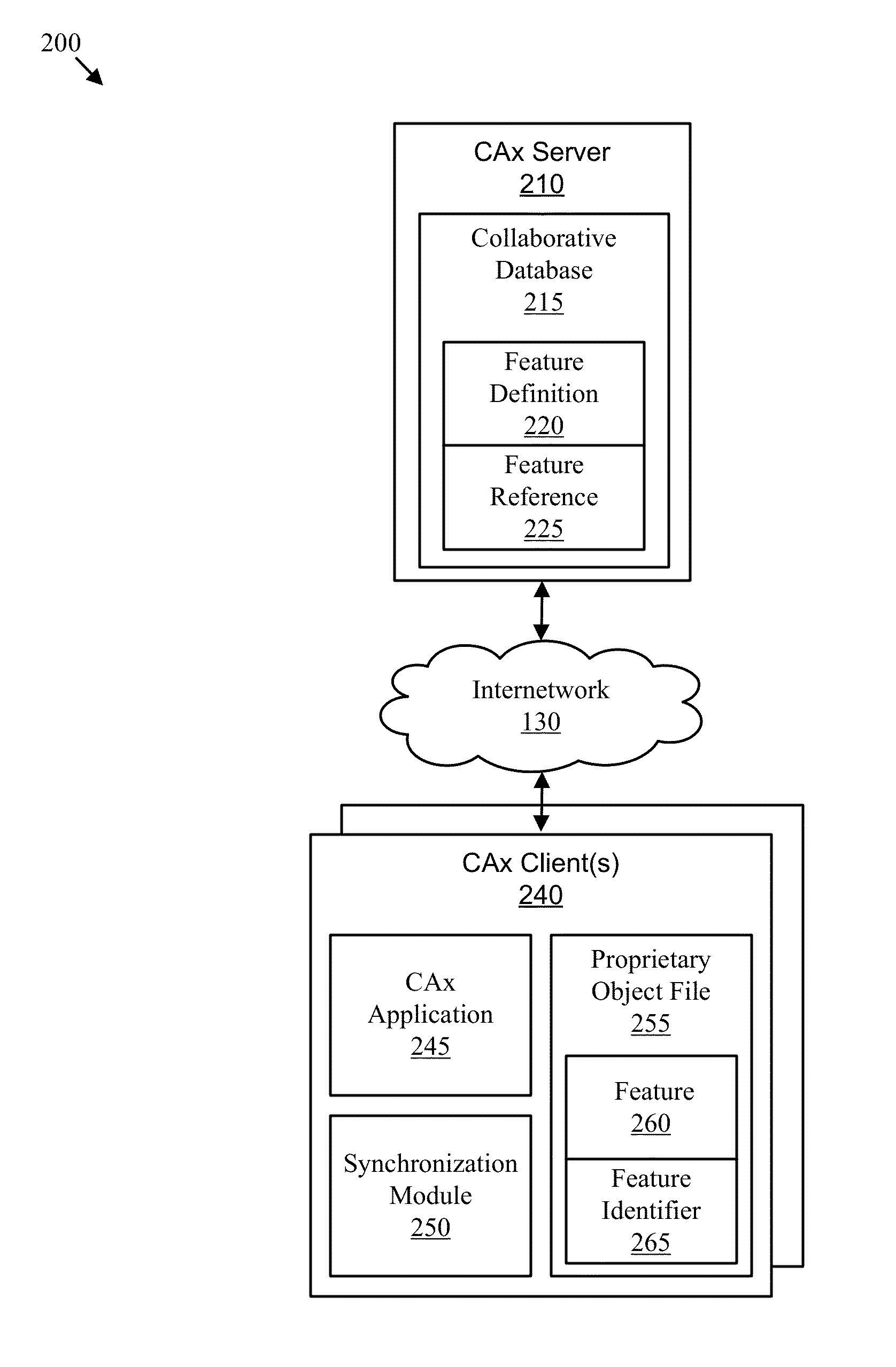
System, method, and apparatus for collaborative cax editing
A method for collaborative CAx editing may include storing a model of an engineering object comprising a plurality of features and encoded in a vendor-neutral format within a collaborative data store, detecting updates to the model of the engineering object stored on a first CAx client and encoded in a first proprietary format, converting the updates to feature changes, and updating the model of the engineering object encoded in the vendor-neutral format with the feature changes. The method may also include detecting feature changes for the model of the engineering object encoded in the vendor-neutral format, converting the feature changes to updates for the model of the engineering object encoded in a second proprietary format, and executing the updates for the model of the engineering object encoded in the second proprietary format. A corresponding apparatus, system, and computer-readable medium are also disclosed herein.
Owner:BRIGHAM YOUNG UNIV
Distributed and secured method and system for protecting and distributing audiovisual flows
ActiveUS7613182B2Color television signals processingRecord information storageComputer networkProprietary format
A process for secure distribution of digital audiovisual streams according to a standard, normalized or proprietary format, on which streams a separation of the stream into two parts is made prior to transmission to equipment of an addressee to generate a modified main stream having a format of the original stream and complementary information of any format including digital information suitable to permit reconstruction of the original stream, wherein a transmission is made, by separate paths during distribution of the modified main stream from a distribution server and of the complementary information to the equipment of the addressee from a secure central server passing via at least one local server connecting the equipment of the addressee to the local server via at least one access point.
Owner:OL SECURITY LIABILITY CO
Secure distributed process and system for the protection and distribution of audiovisual streams
ActiveUS20070189531A1Color television signals processingRecord information storageComputer networkComputer science
A process for secure distribution of digital audiovisual streams according to a standard, normalized or proprietary format, on which streams a separation of the stream into two parts is made prior to transmission to equipment of an addressee to generate a modified main stream having a format of the original stream and complementary information of any format including digital information suitable to permit reconstruction of the original stream, wherein a transmission is made, by separate paths during distribution of the modified main stream from a distribution server and of the complementary information to the equipment of the addressee from a secure central server passing via at least one local server connecting the equipment of the addressee to the local server via at least one access point.
Owner:OL SECURITY LIABILITY CO
Method of secure file transfer
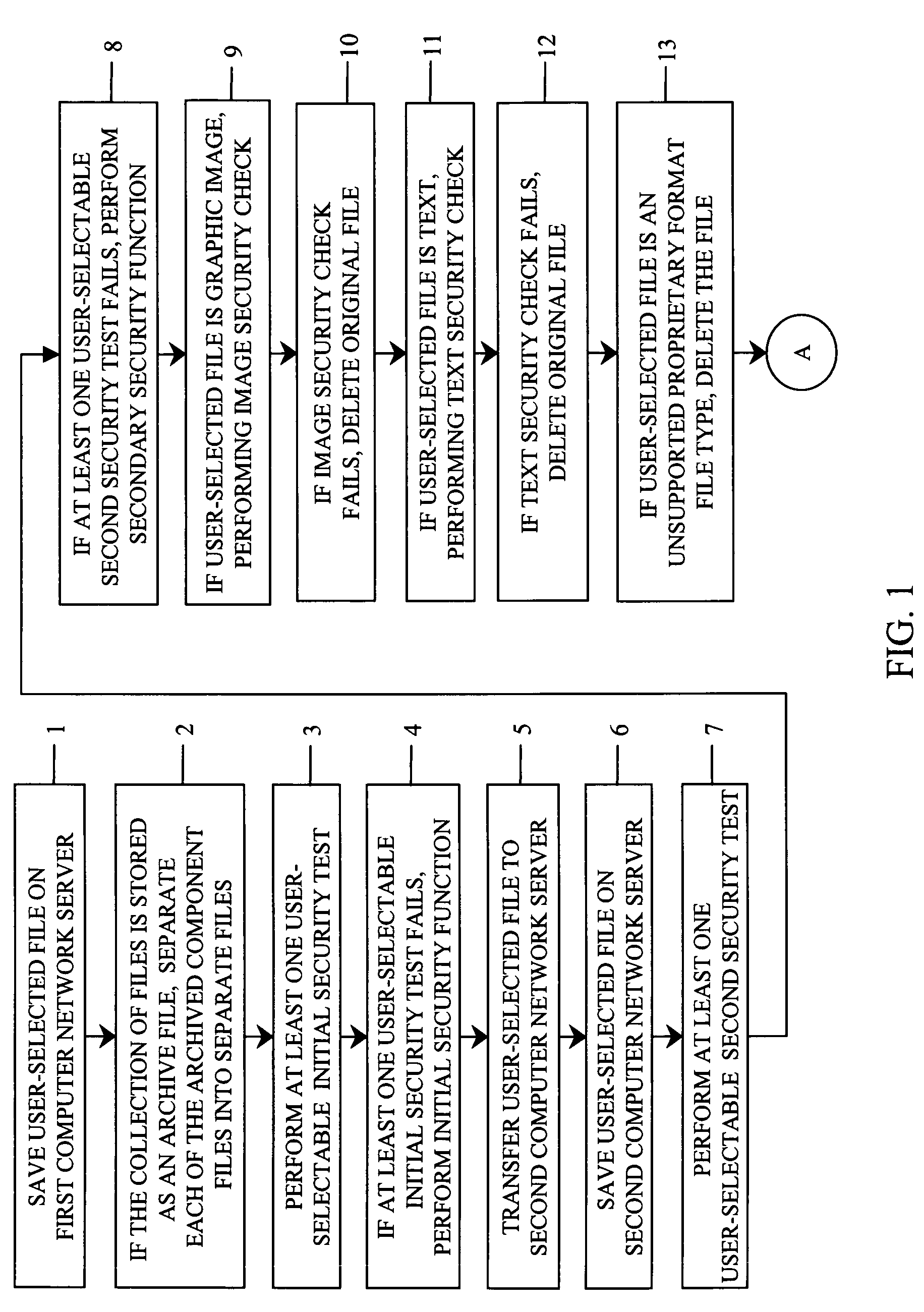
InactiveUS7930538B1Reduce threatMitigate the threat of malicious codeDigital data processing detailsAnalogue secracy/subscription systemsFilename extensionFile size
A method of securely transferring files from an un-trusted to a trusted network is disclosed. A file that is an archive file of many component files is separated into constituent files. Each file is stored on a first computer connected to an un-trusted network, and a series of initial checks, such as virus, file size, and file extension are performed. If the files pass, the file is transferred to a second server using a one-way file transfer mechanism. A series of secondary checks, similar to the initial checks is performed on each file transferred. For text files or images, a simplified security rule is applied. An open format transform is performed on proprietary format type files, and embedded file components are separated out. A user-definable security rule set is performed on each open format transform component. If all security tests pass, the file is reassembled and transferred to the trusted network.
Owner:NATIONAL SECURITY AGENCY
Method of secure file transfer
InactiveUS8069349B1Digital data processing detailsAnalogue secracy/subscription systemsSecurity ruleVirus
A method of securely transferring files from an un-trusted to a trusted network is disclosed. A file that is an archive file of many component files is separated into constituent files. Each file is stored on a server connected to an un-trusted network, and a series of initial checks, such as virus, file size, and file extension are performed. If the files pass, additional, file format specific security rules are applied. An open format transform is performed on proprietary format type files, and embedded file components are separated out. A user-definable security rule set is performed on each open format transform component. If all security tests pass, the file is reassembled and saved as a trusted file in the same format as the original file.
Owner:NATIONAL SECURITY AGENCY +1
MULTI-BIOMETRIC IoT BRIDGE
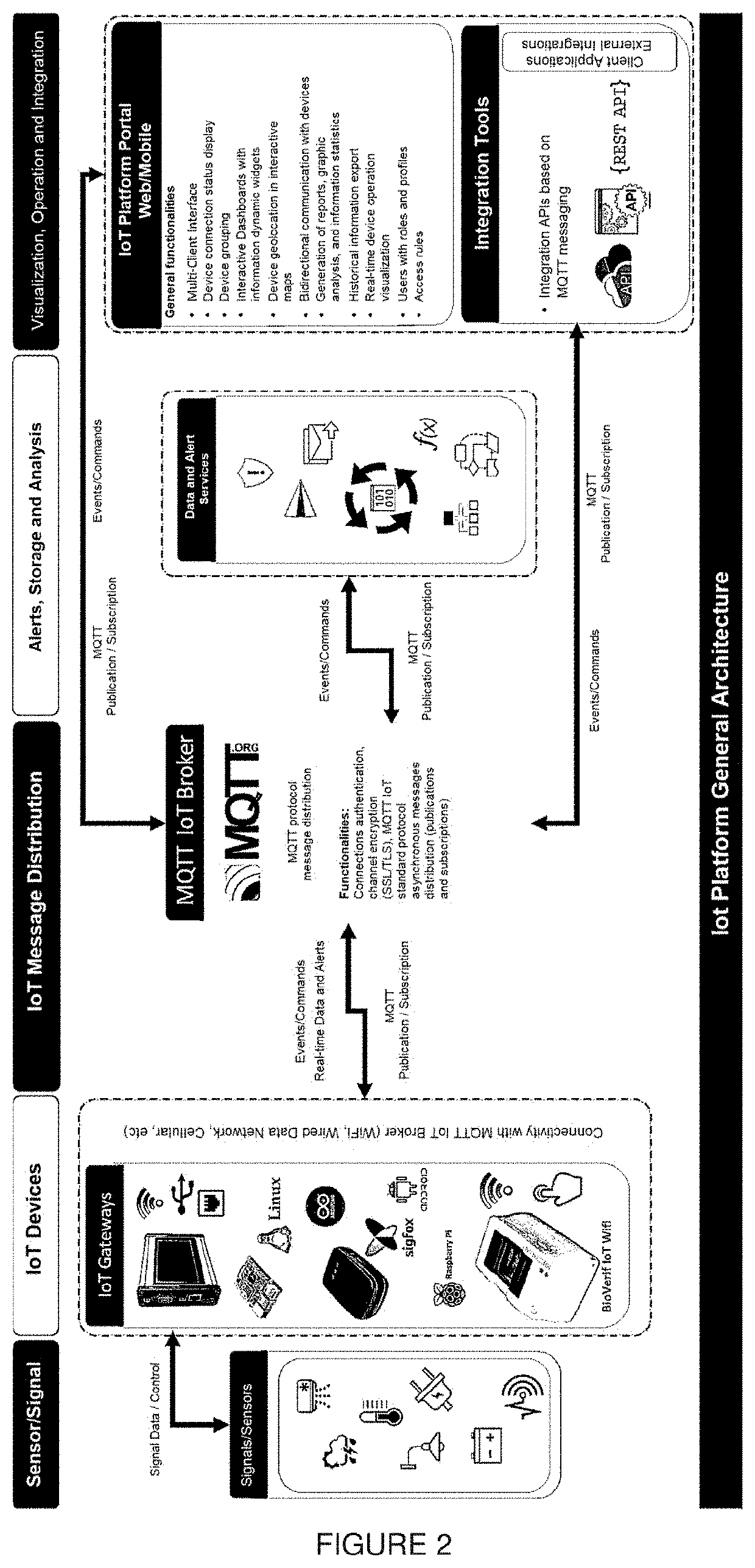
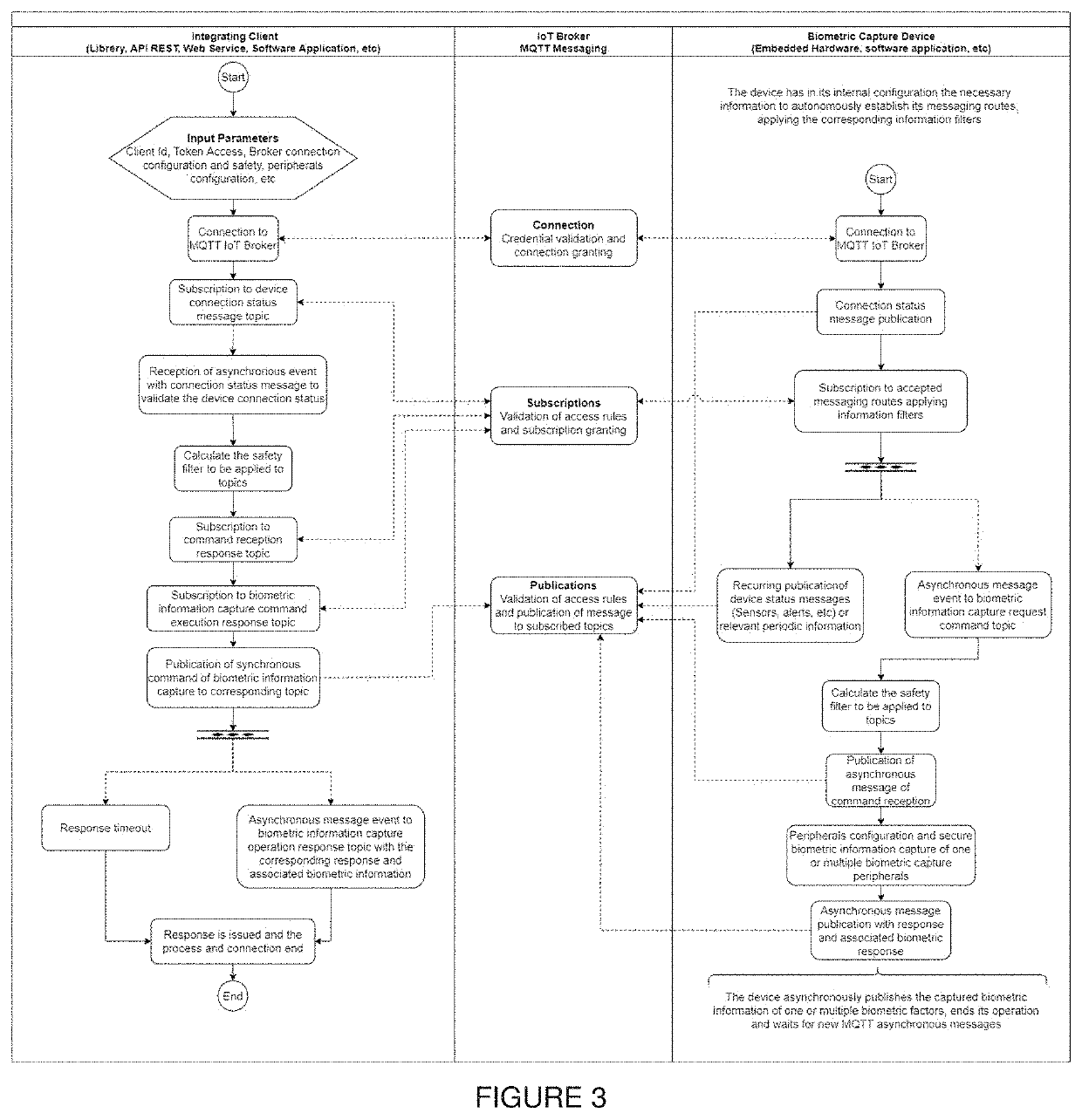
PendingUS20210211515A1Solve needsConducive to diversificationDigital data processing detailsTransmissionProprietary formatMQTT
A method is provided for the capture of biometric or multi-biometric information using: a standard Internet of Things (IoT) data broker in an efficient and distributed IoT architecture. The MQTT information protocol is used in combination with mobile or fixed devices that manage one or more peripherals for capturing biometric information. An IoT platform is provided that allows information to be viewed in real time along with historical information and statistics regarding the use and operation of the devices to be obtained. The invention provides a method based on standard integration protocols and tools for M2M communication in IoT architectures, which acts as an information bridge, facilitating implementation to capture any type of biometric or multibiometric information, which information can be in any format (biometric templates or images in standard or proprietary formats), so that the captured information can be used in any type of biometric process.
Owner:INVERSIONES TECHCAS DE AMERICA SA
Systems and methods for retrofitting electronic appliances to accept different content formats
InactiveUS20070230698A1Television system detailsDigital data processing detailsThird partyContent format
Systems and methods are disclosed for using an arbitrary fixed channel to carry third-party information. In one embodiment, the present invention provides systems and methods for enabling existing content rendering devices to accept content encoded in a proprietary format, such as an encoding format used by a digital rights management system. The encoded content is rendered by the device in the normal manner, and decoded by a retrofitting appliance connected to the device's output. The retrofitting appliance may apply decoded rules and controls to the decoded content, thereby managing use of the content.
Owner:INTERTRUST TECH CORP
Labor market information analyzer for researchers, employers, staff and others
InactiveUS20060195346A1Easily and efficiently manufactured and marketedLow priceDigital data processing detailsSpecific program execution arrangementsClient-sideStored procedure
A computerized information system for analyzing labor market information consisting of a server having a plurality of categorizing and processing services for researchers, employers, staff and the like, a database of standard and proprietary format data and optional stored procedures operatively coupled with the server, and a plurality of input / output client devices operatively coupled with the server.
Owner:GEOGRAPHIC SOLUTIONS
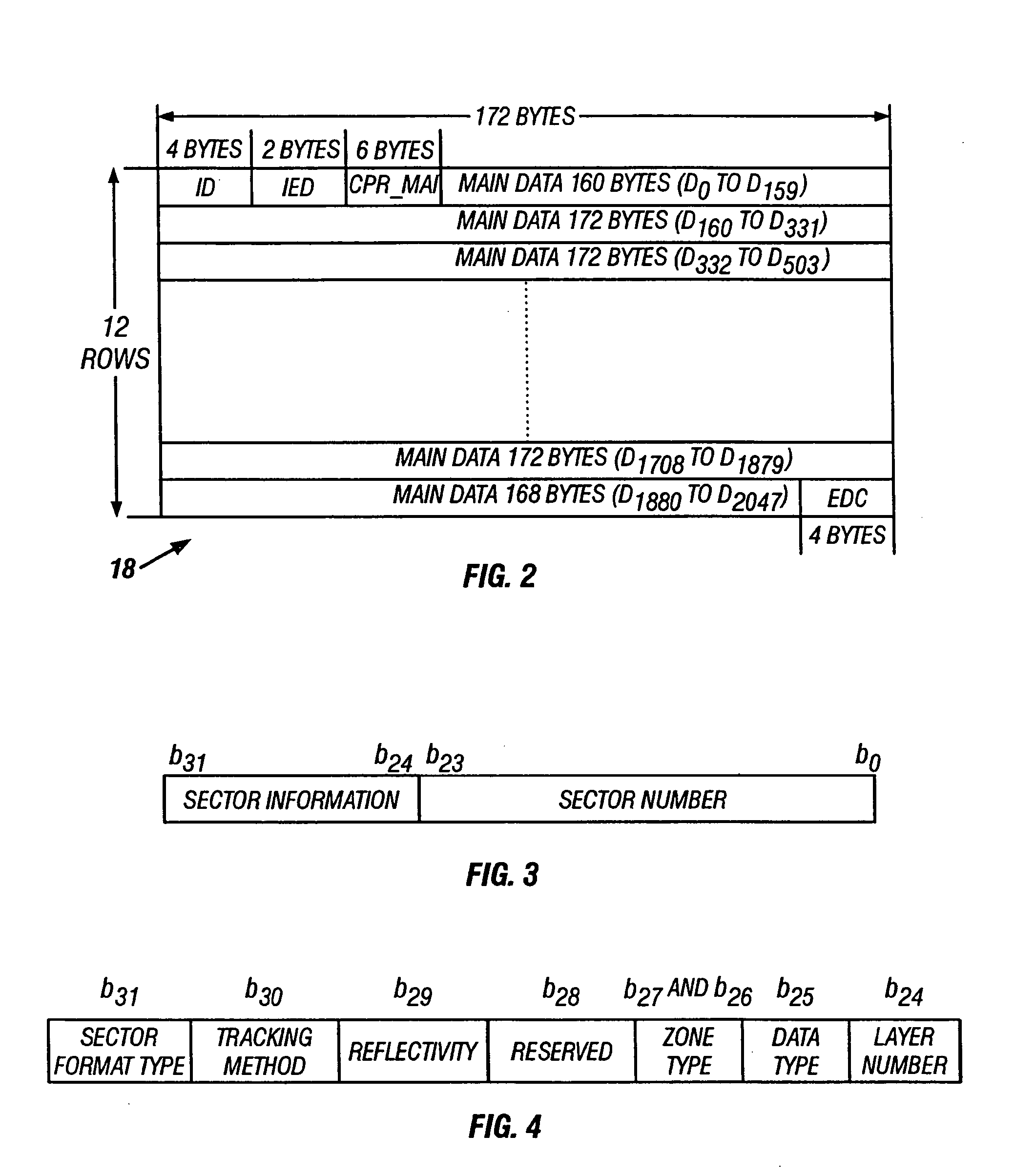
Secure digital video disk and player
InactiveUS20050108612A1Easy and inexpensive implementationInformation arrangementCode conversionShift registerDigital video
A method for recording data on an optical medium is disclosed. In one embodiment, the method includes receiving main data from a data source, determining a plurality of data frame values in response to the main data, inverting at least one selected bit in at least one of the data frame values to generate a plurality of encoded data frames, scrambling the encoded data frames by a feedback shift register to generate scrambled data frames, generating ECC values in response to the scrambled data frames, adding the ECC values to the scrambled data frames to generate an ECC block, rearranging the ECC block to generate a plurality of recording frames, encoding the recording frames by an eight-to-sixteen modulation (ESM) encoder to generate code words, adding sync values to the code words to generate a plurality of physical sectors, and recording the physical sectors on the optical medium. A complementary method for reading and decoding data from an optical medium is also disclosed. These complementary encoding and decoding schemes provide a method for creating and reading proprietary format DVDs which may not be read or copied by conventional DVD players. These encoding and decoding schemes result from relatively minor modifications to existing DVD standards, allowing many standard system components to be used and thereby making the encoding / decoding system relatively easy and inexpensive to implement.
Owner:MACROVISION CORP
Programming language translation systems and methods
ActiveUS8079027B2Specific program execution arrangementsMemory systemsHuman languageComputer program
Included are embodiments of a description language program stored in a computing device for updating a first version of a computer program. In at least one embodiment, the first version of the computer program is written in a universal format and the program includes logic configured to receive an updated version of the computer program. Other embodiments include logic configured to retrieve the first version of the computer program and logic configured to translate the updated version of the computer program from a proprietary format to the universal format. Still other embodiments include logic configured to utilize at least one tag to compare the translated updated version of the computer program with the first version of the computer program.
Owner:VIA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com