Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
526 results about "Enterprise level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Enterprise Level - as an organizational capability and competency. The Project Level - as a benefit realization and value creation measure applied on particular initiatives. The Individual Level - as an approach for enabling one person to change successfully.
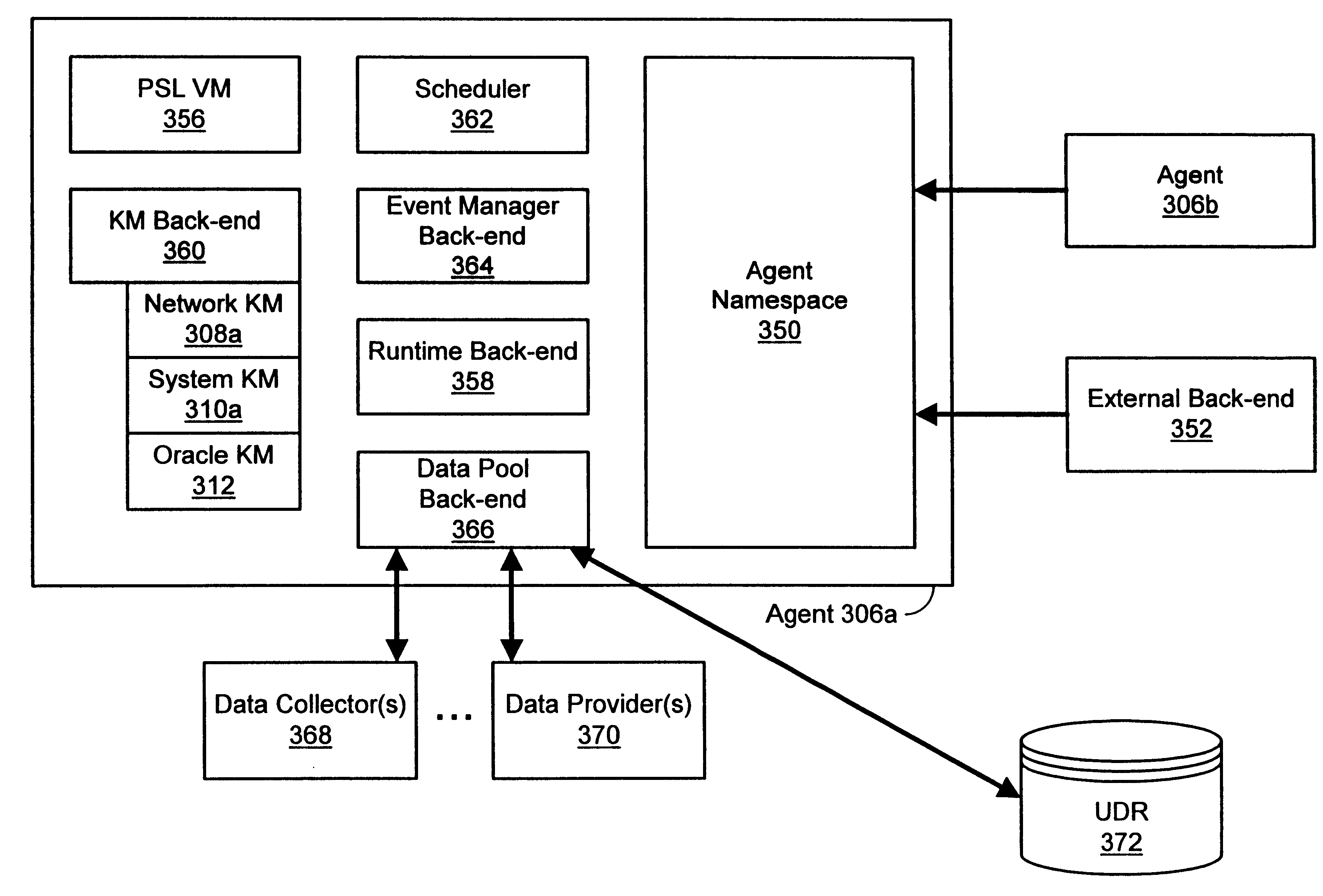
Enterprise management system and method which includes a common enterprise-wide namespace and prototype-based hierarchical inheritance
InactiveUS6895586B1Multiple digital computer combinationsTransmissionBusiness managementEnterprise level
A system and method for providing an improved namespace and object description system for enterprise management are disclosed. The system and method employ a hierarchical namespace with objects including prototypes and instances where an instance inherits traits from a prototype, such as attribute values and / or child objects.
Owner:BMC SOFTWARE
System and method of securing web applications across an enterprise
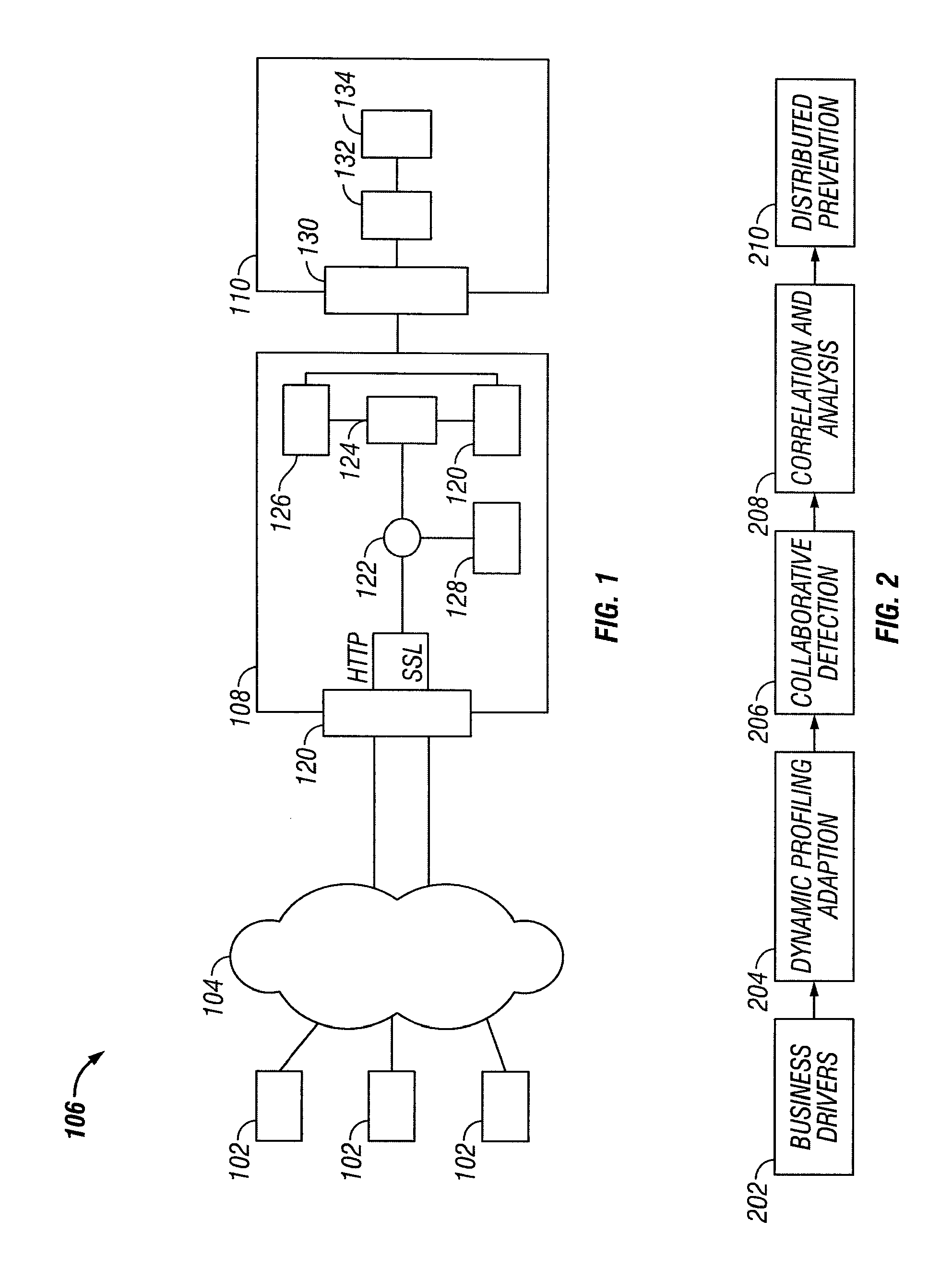
ActiveUS20080034425A1Avoid attackMemory loss protectionError detection/correctionTraffic capacityWeb application
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat
Owner:TRUSTWAVE HOLDINGS
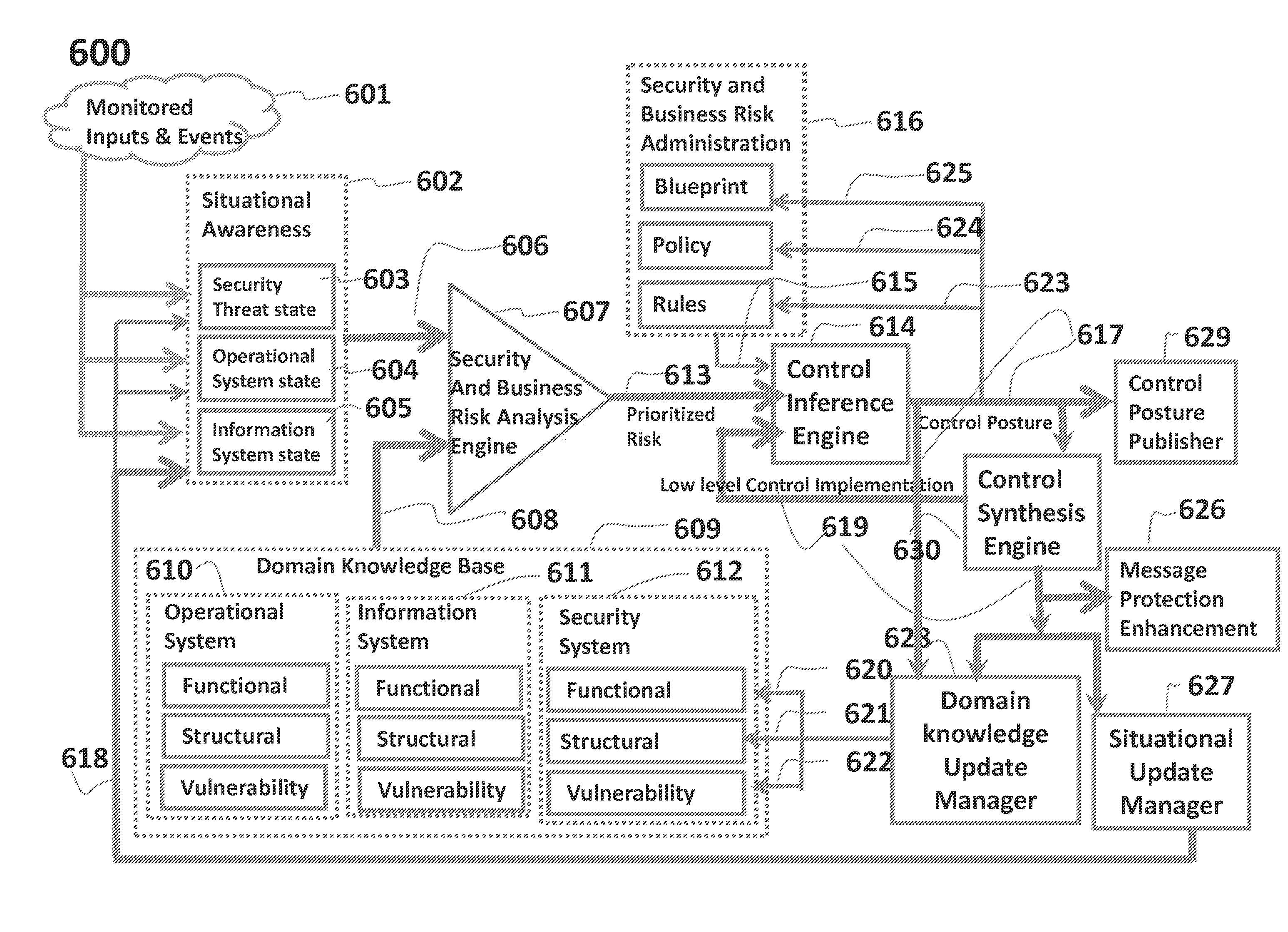
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
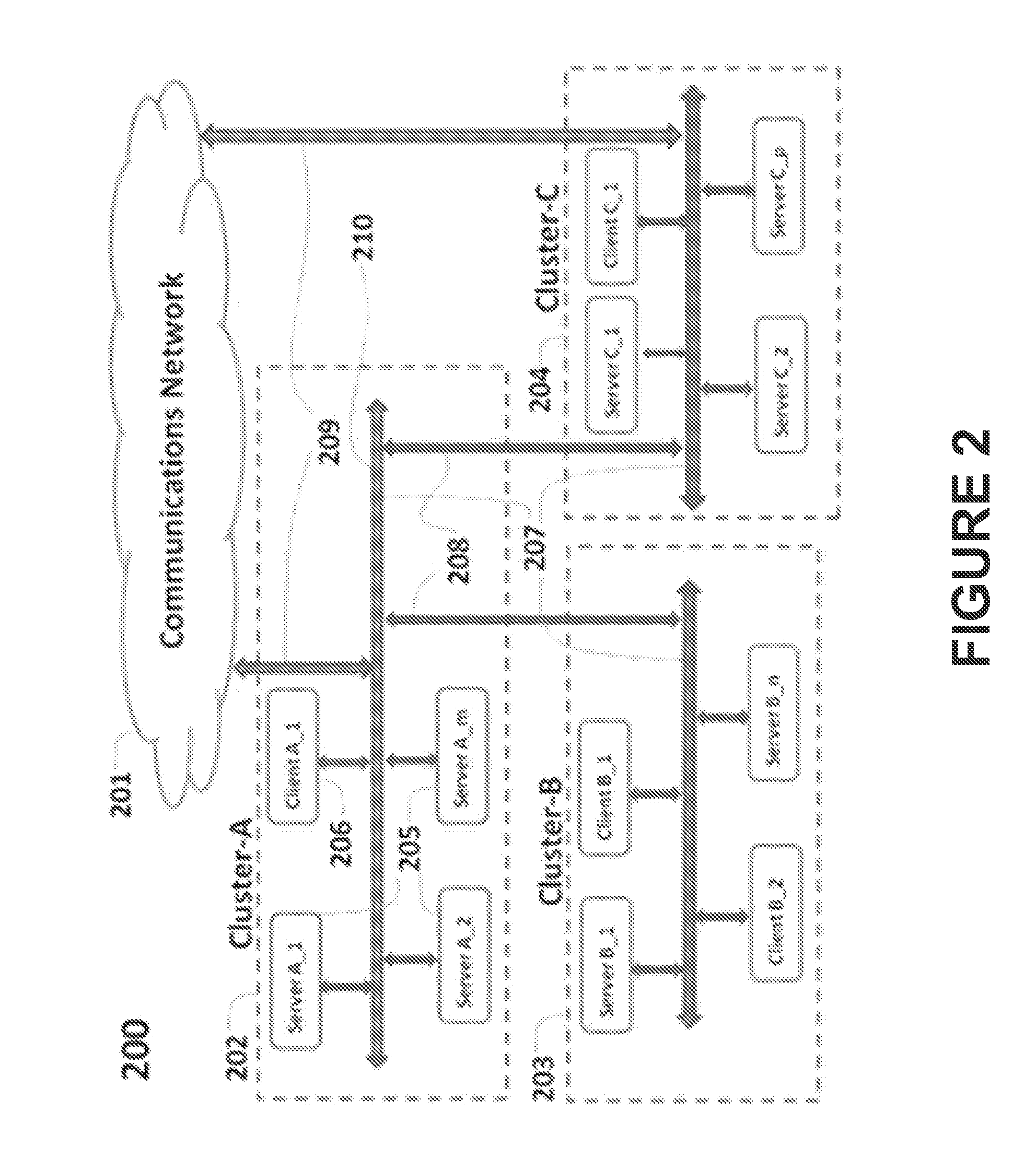
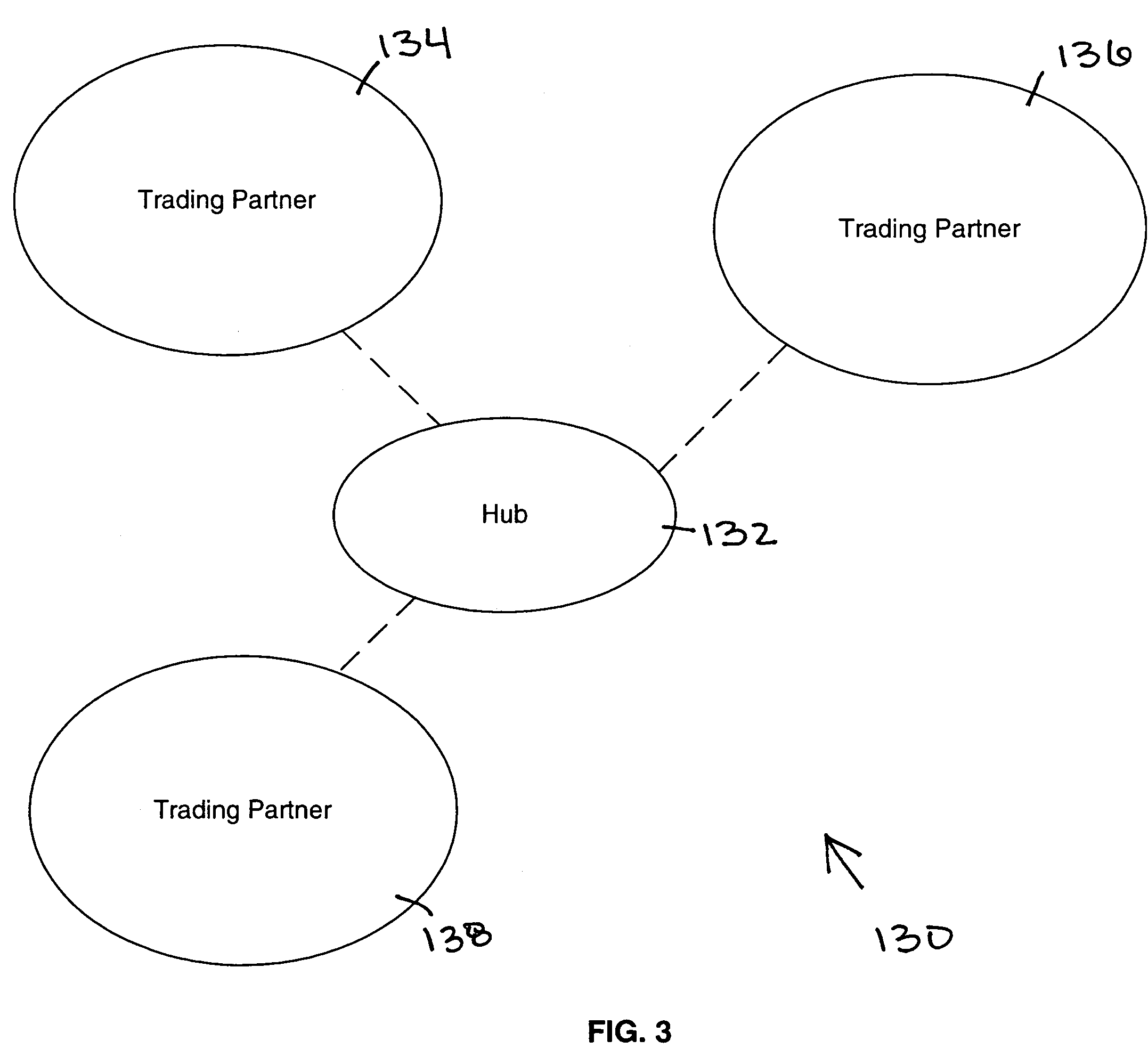
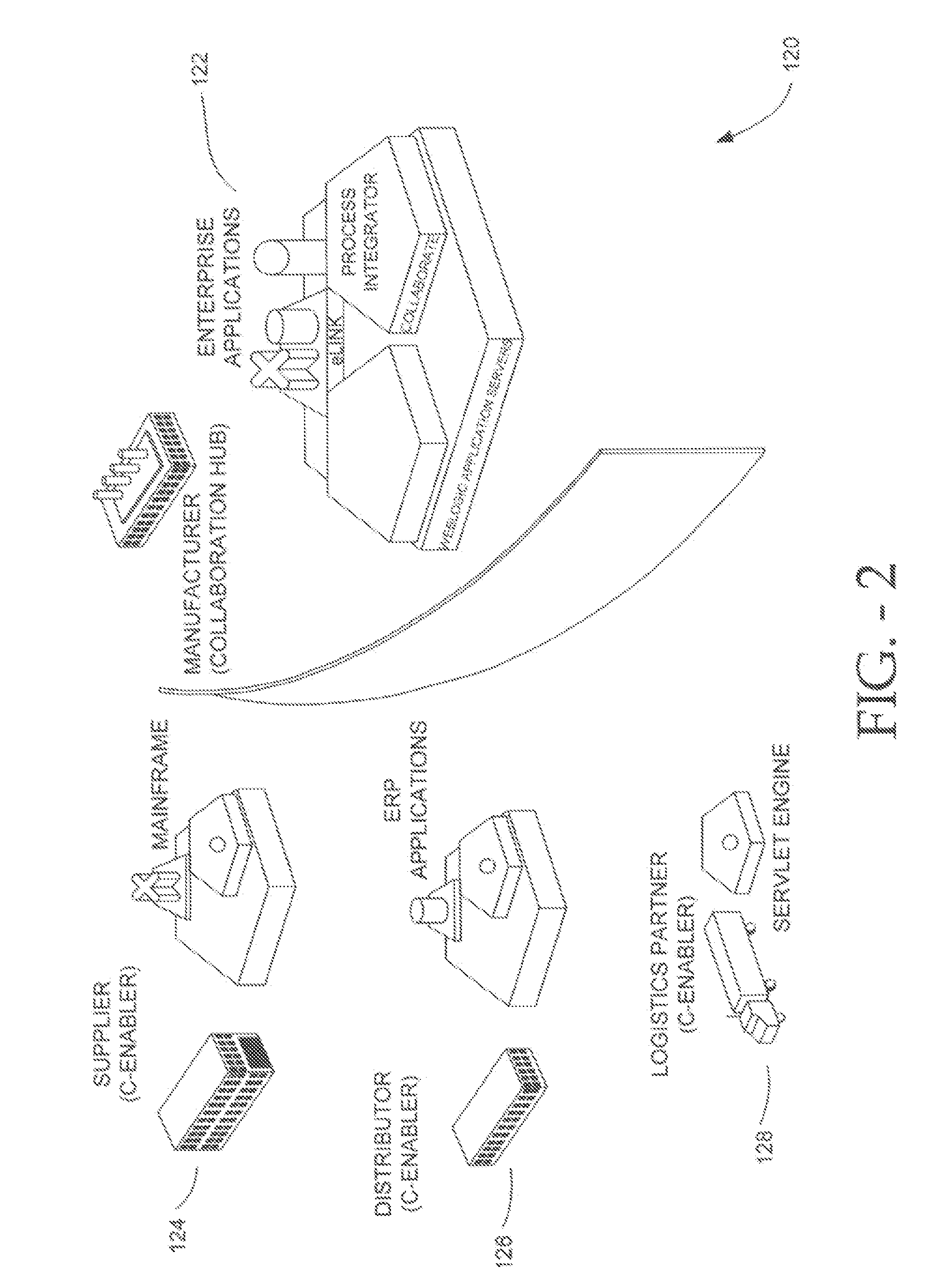
Workflow integration system for enterprise wide electronic collaboration
InactiveUS7051071B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsEnterprise levelElectronic business
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a workflow integration system for enterprise wide electronic collaboration. An embodiment of the invention includes a workflow integration system for a collaboration system that allows for sharing of workflow information between collaboration participants, comprising a collaboration server having stored thereon an enterprise workflow, a workflow server having stored thereon a participant workflow and an integration mechanism for allowing said enterprise workflow and said participant workflow to interact with one another.
Owner:ORACLE INT CORP
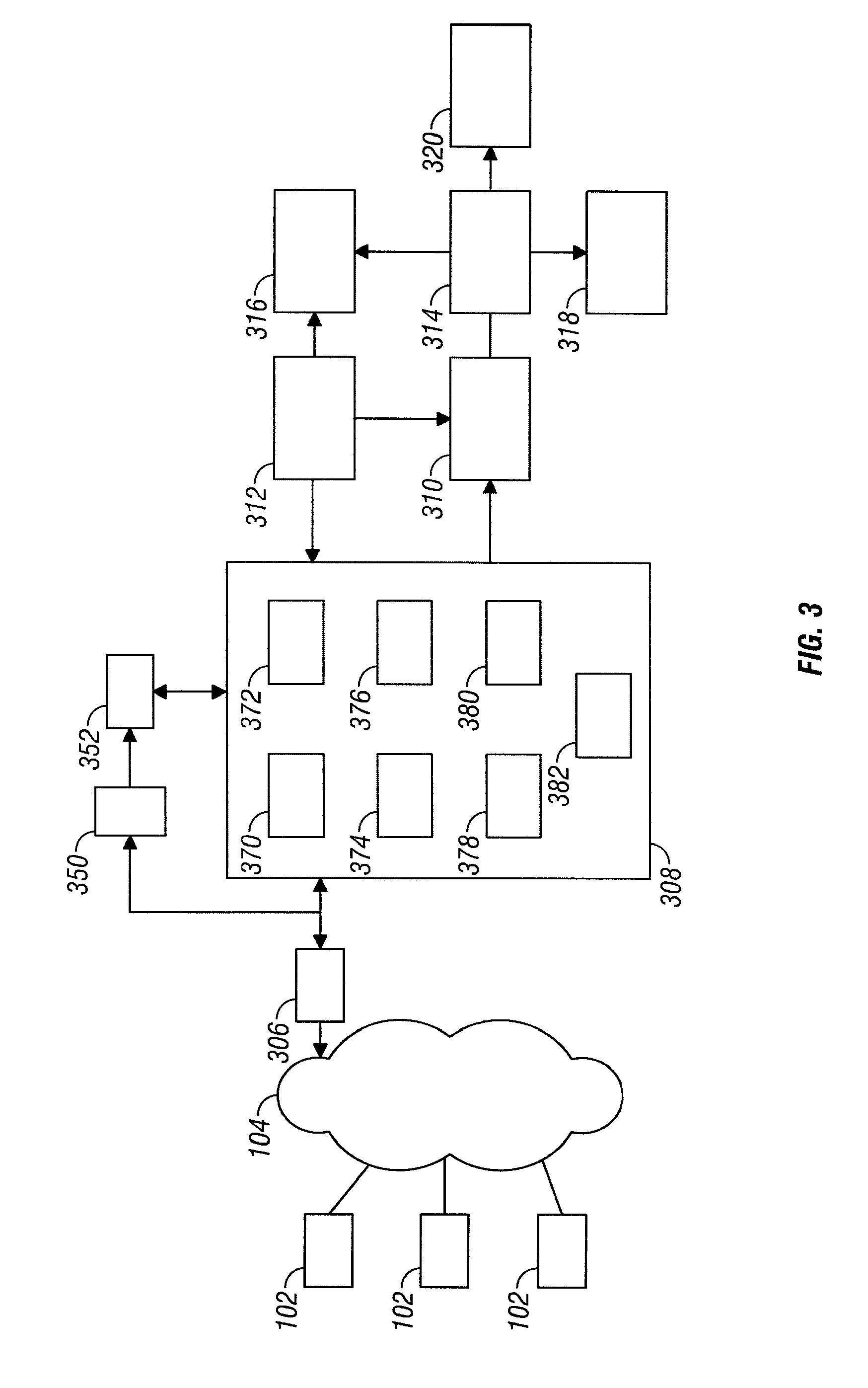
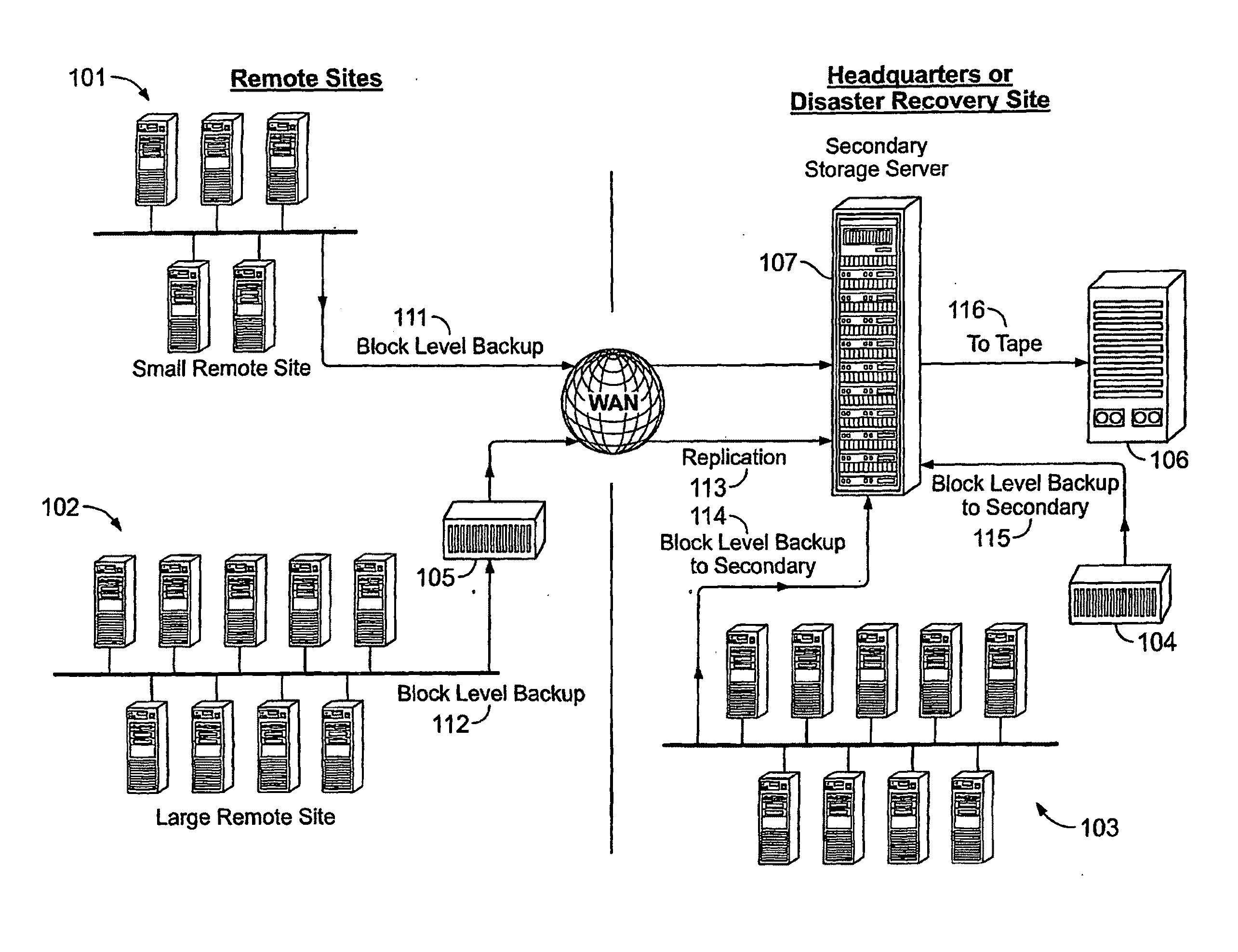
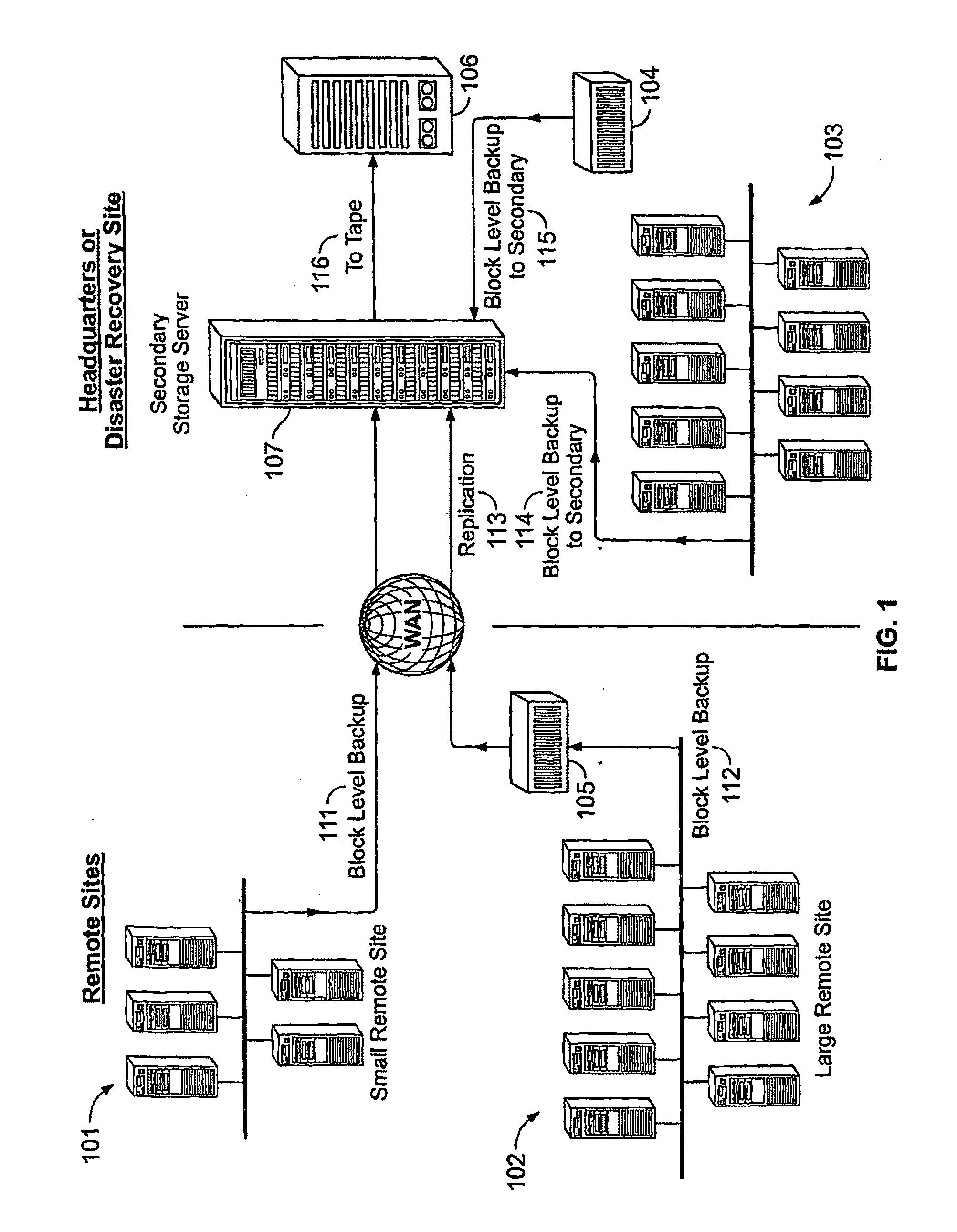
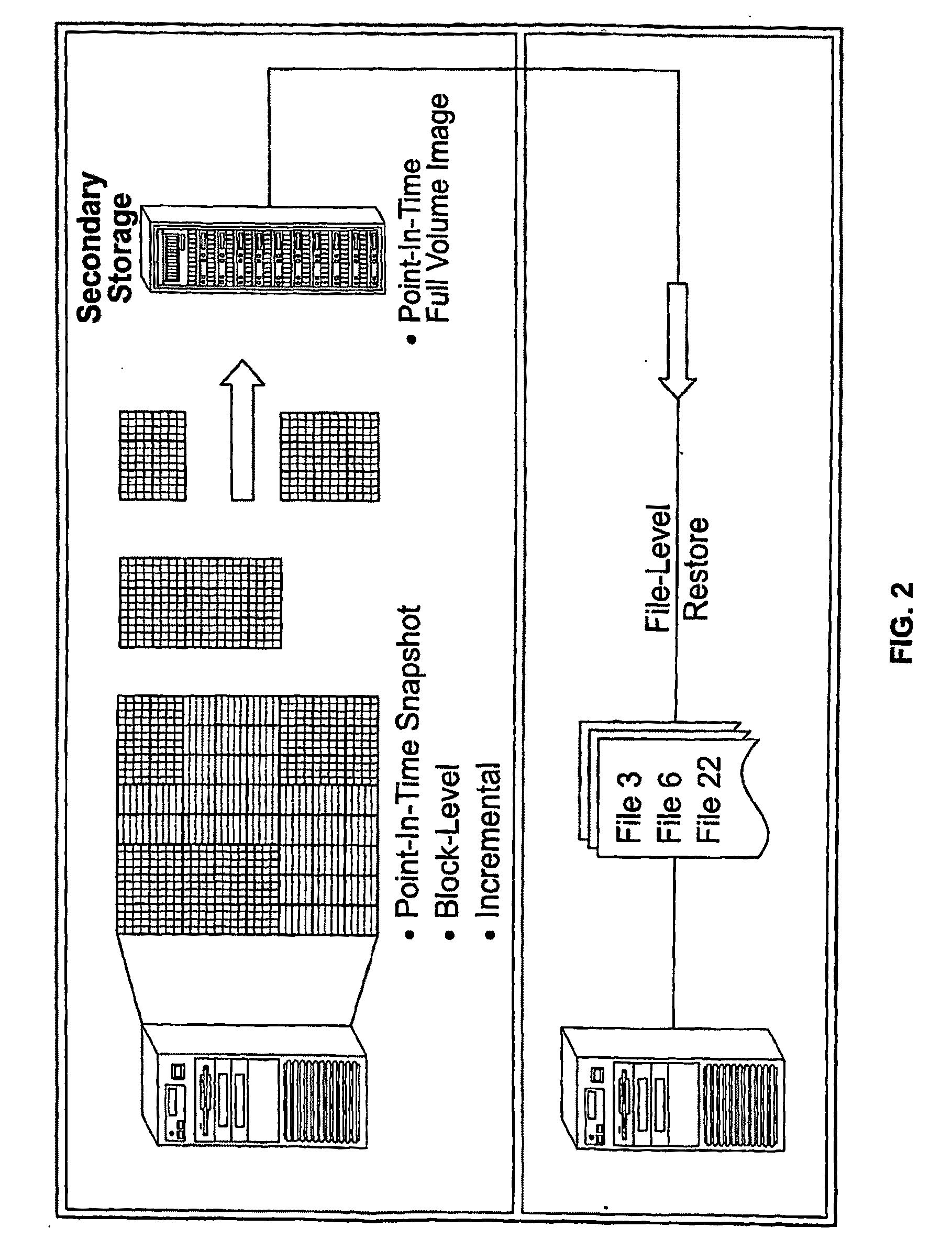
System And Method for High Performance Enterprise Data Protection
ActiveUS20100077160A1Improve performanceEliminate redundancyMemory loss protectionError detection/correctionOperational systemFile system
High performance, enterprise-level data protection system and method provides efficient block-level incremental snapshots of primary storage devices, and instant availability of such snapshots in immediately mountable form that can be directly used in place of the primary storage device. Related systems and applications are described, including an “Enterprise Image Destination” (EID) for backup images; a mirroring technique whereby a replacement physical primary facility may be created while working with a second storage unit as the primary source file system; and a technique for eliminating redundant data in backup images when multiple systems with partially common contents (e.g., operating system files, common databases, application executables, etc.) are being backed up. A number of examples showing “Fast Application Restore” (FAR) with the use of the invention are also provided.
Owner:CATALOGIC SOFTWARE
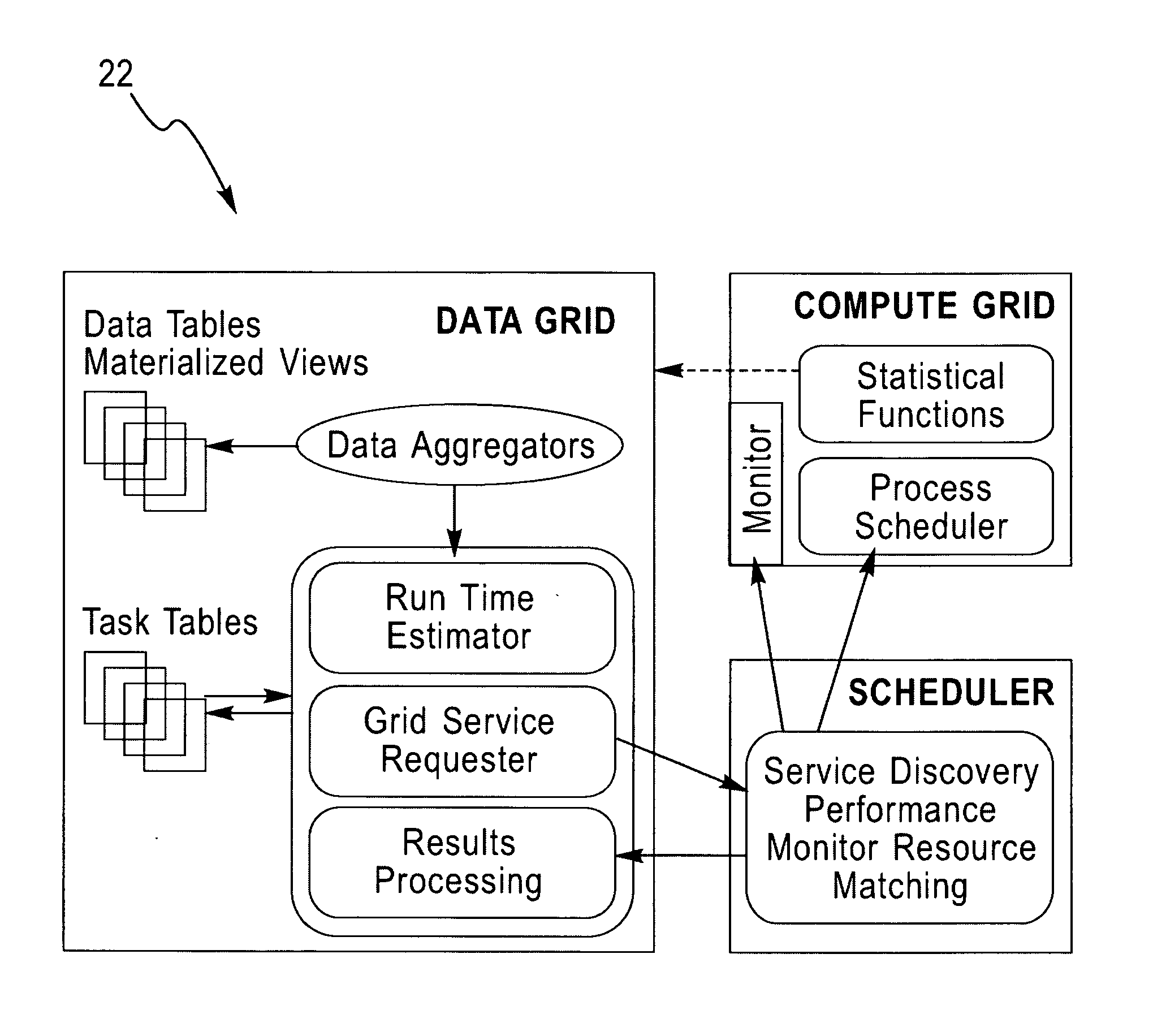
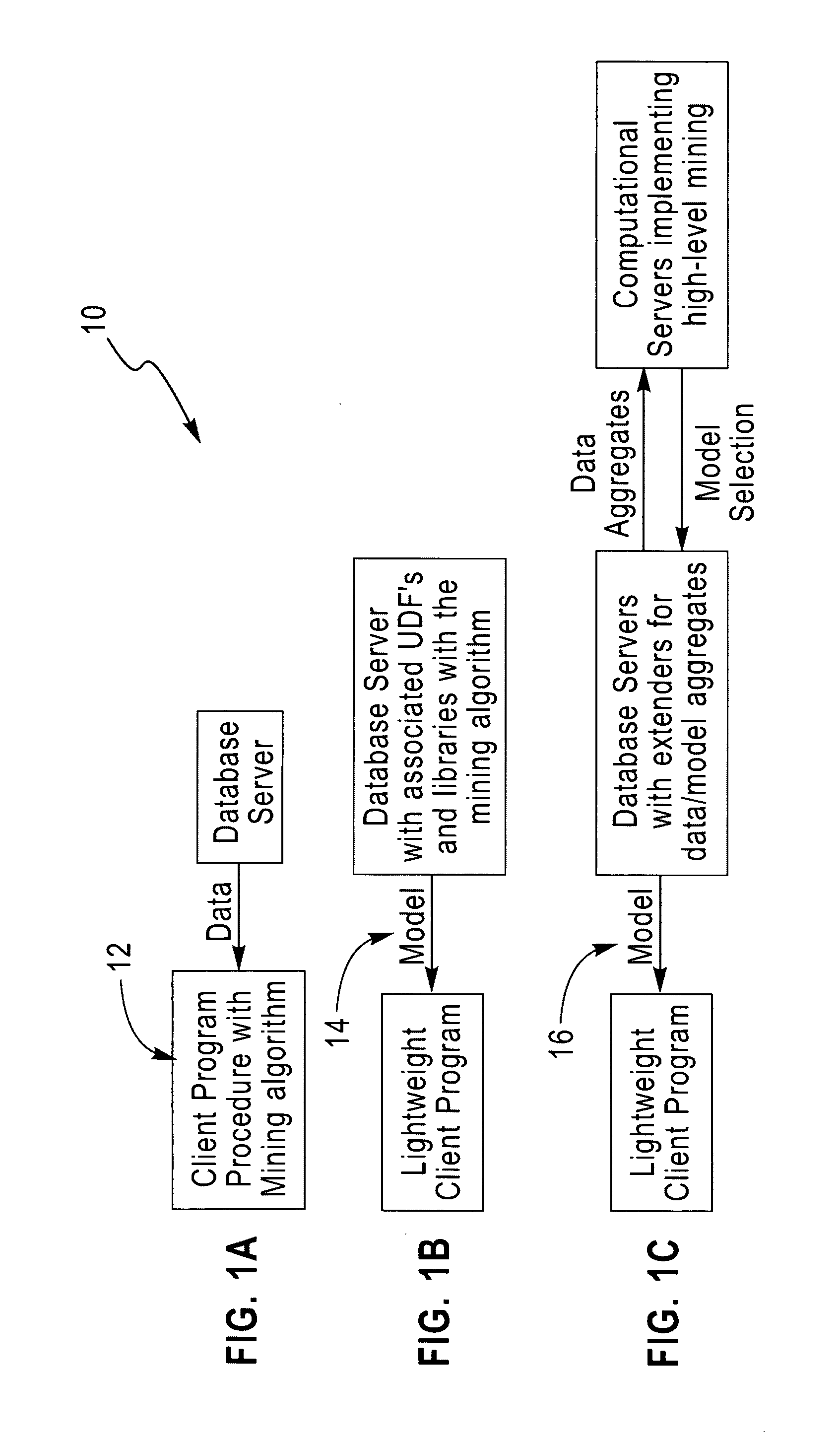
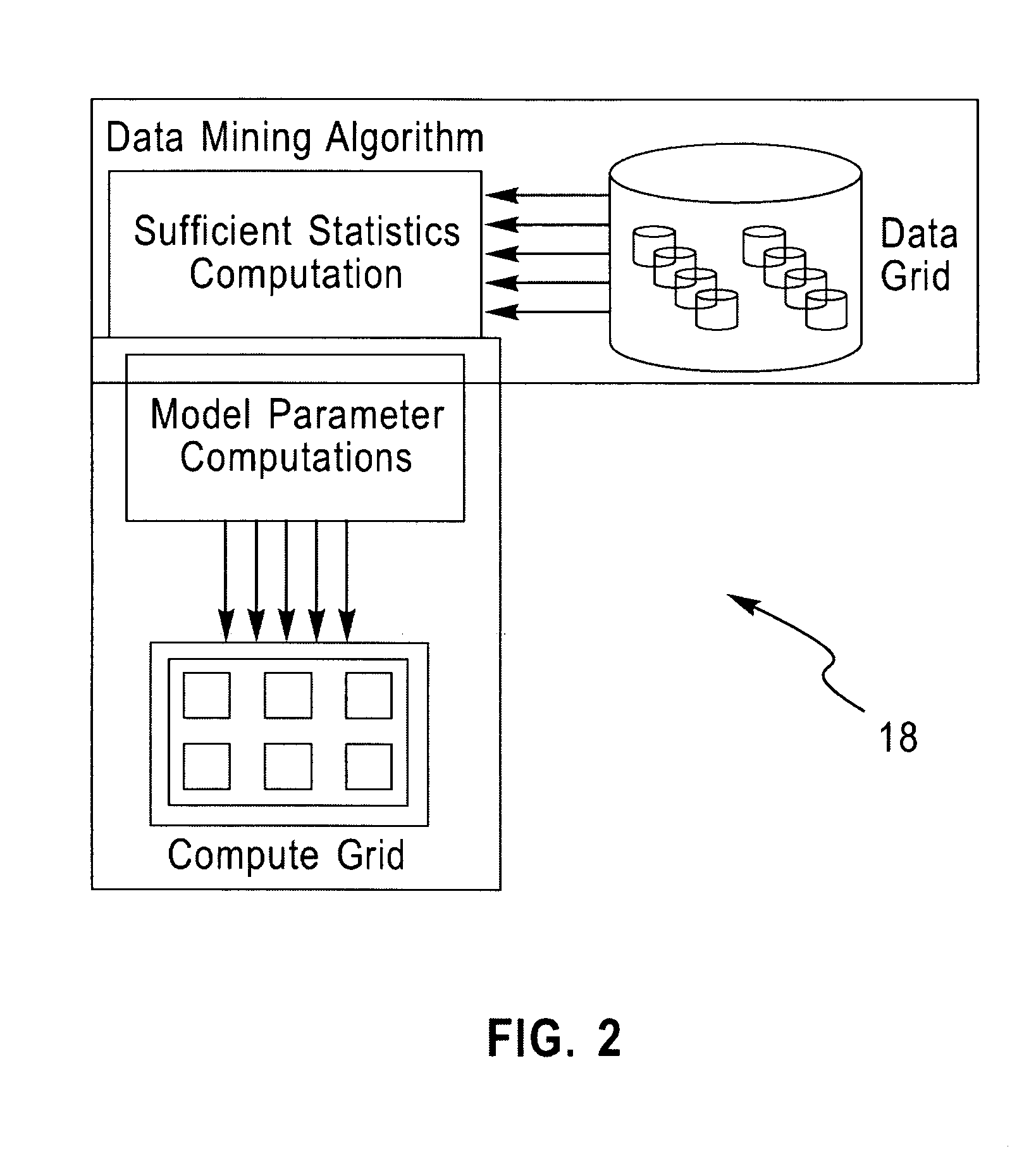
System and architecture for enterprise-scale, parallel data mining
InactiveUS20070174290A1Scalable storage and query performanceImprove robustnessDigital data information retrievalOffice automationQuality dataRelational database
A grid-based approach for enterprise-scale data mining that leverages database technology for I / O parallelism and on-demand compute servers for compute parallelism in the statistical computations is described. By enterprise-scale, we mean the highly-automated use of data mining in vertical business applications, where the data is stored on one or more relational database systems, and where a distributed architecture comprising of high-performance compute servers or a network of low-cost, commodity processors, is used to improve application performance, provide better quality data mining models, and for overall workload management. The approach relies on an algorithmic decomposition of the data mining kernel on the data and compute grids, which provides a simple way to exploit the parallelism on the respective grids, while minimizing the data transfer between them. The overall approach is compatible with existing standards for data mining task specification and results reporting in databases, and hence applications using these standards-based interfaces do not require any modification to realize the benefits of this grid-based approach.
Owner:IBM CORP
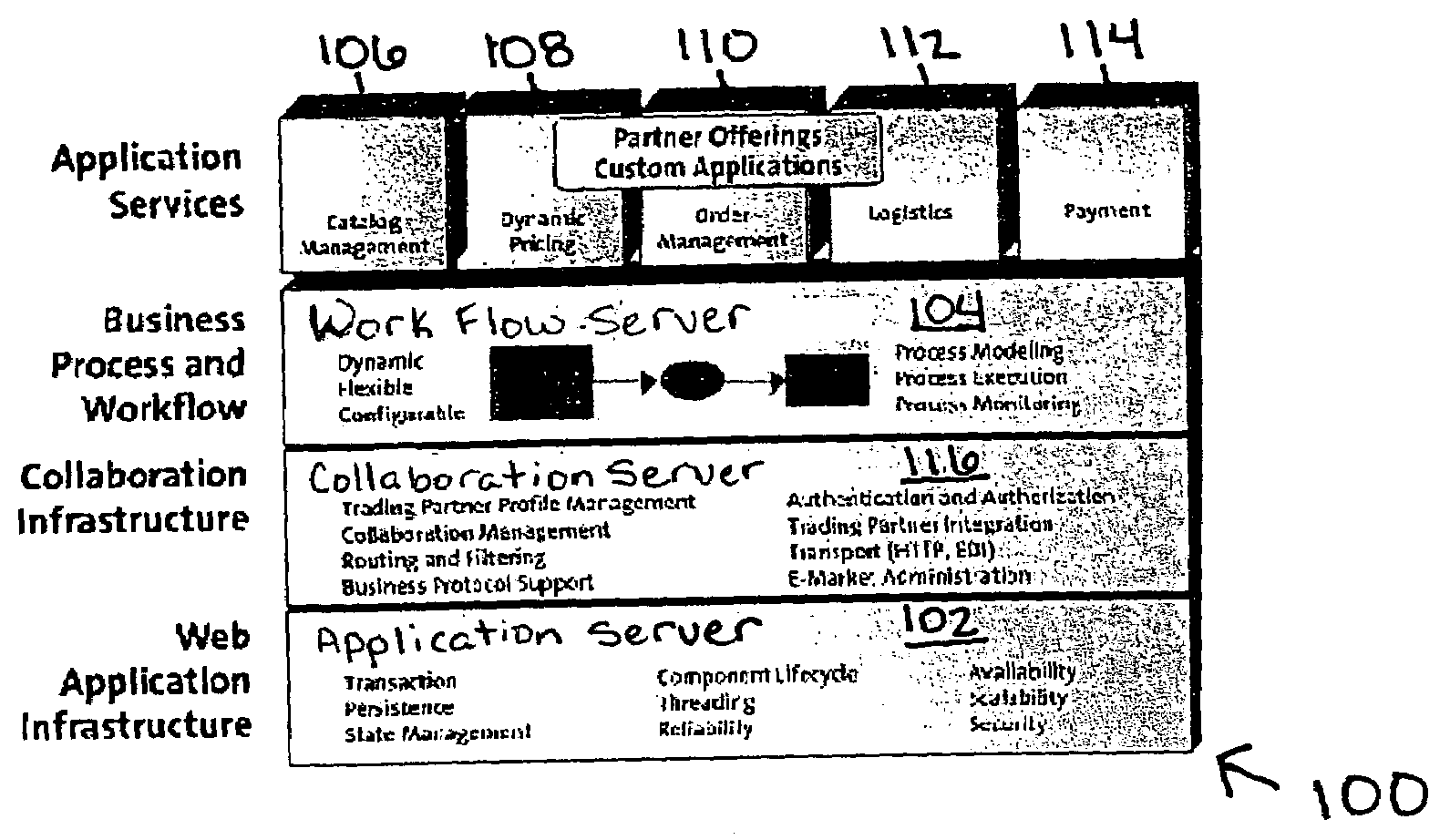
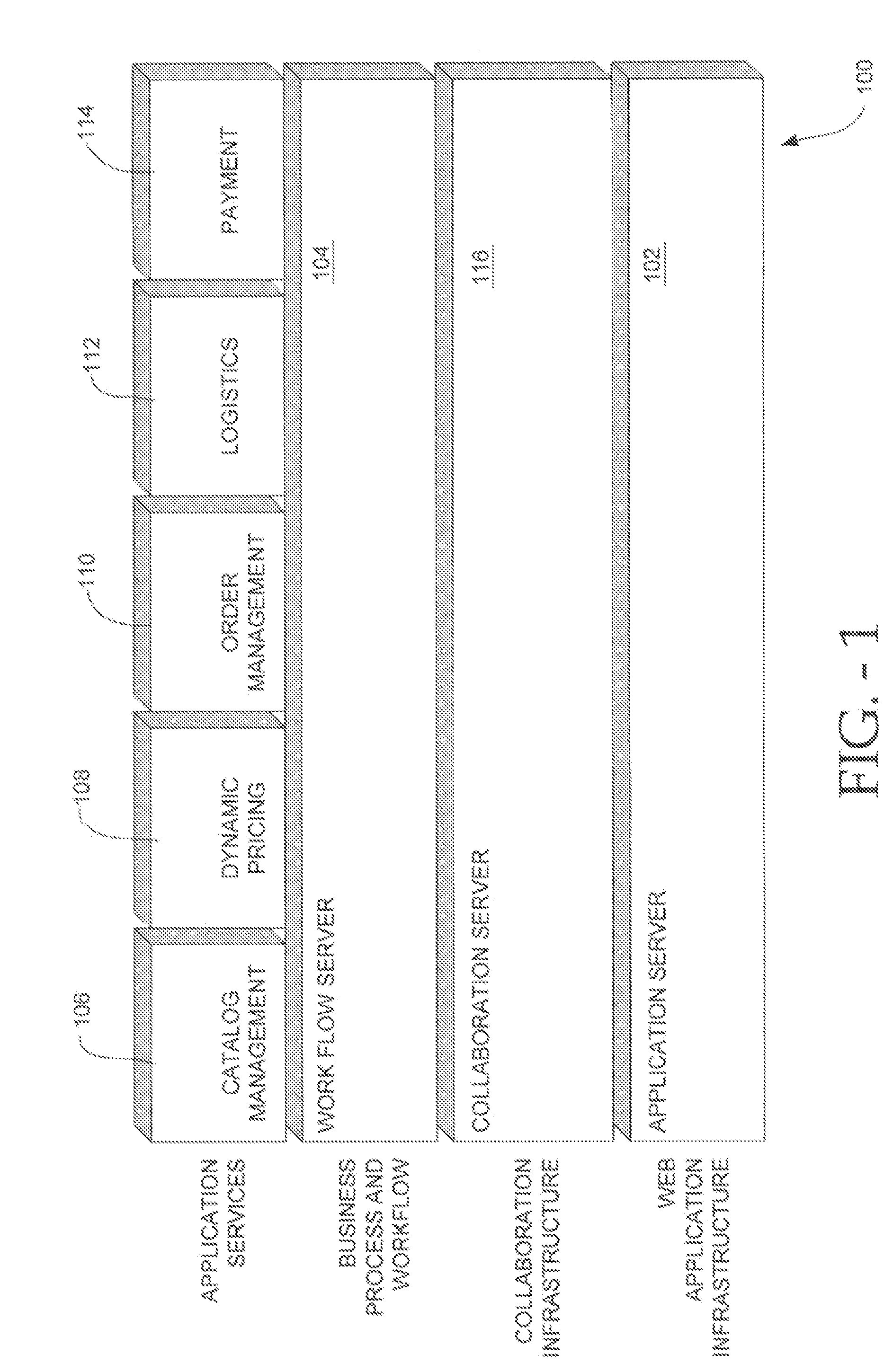
Providing a multi-tier enterprise level application
InactiveUS7945636B2Facilitate multi-tier applicationEasy to controlAdvertisementsMultiple digital computer combinationsApplication softwareEnterprise level
Systems and methods for providing a multi-tier enterprise level application. In particular, the present invention relates to systems and methods for providing an architecture and interface for delivering customizable music and advertisements to remote retail locations. A client player computer device is located at the retail location and a server system is located at a remote location. The server system selectively provides broadcast information when an active contract, an active advertisement, and an active schedule are available. The client player computer device establishes a contact with a server at a predetermined time or upon request by the server or another source. The client player computer device executes a broadcast or program schedule that includes music content and advertisements, wherein the advertisements have been purchased as blocks of time by entities and are scheduled to be broadcast at particular times. The music content and advertisements are selectively customizable to provide a dynamic service at the retail location.
Owner:IN STORE BROADCASTING NETWORK LLC
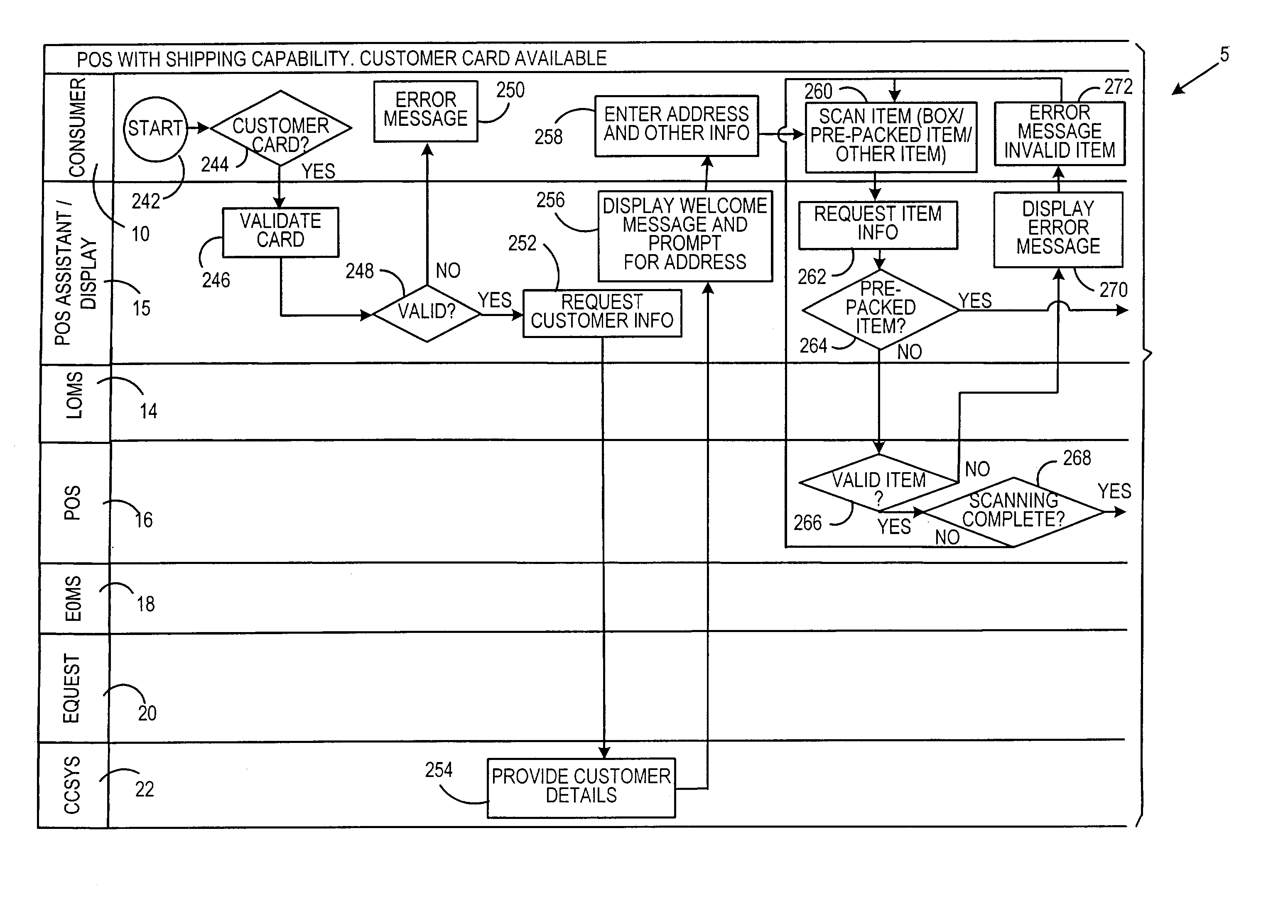
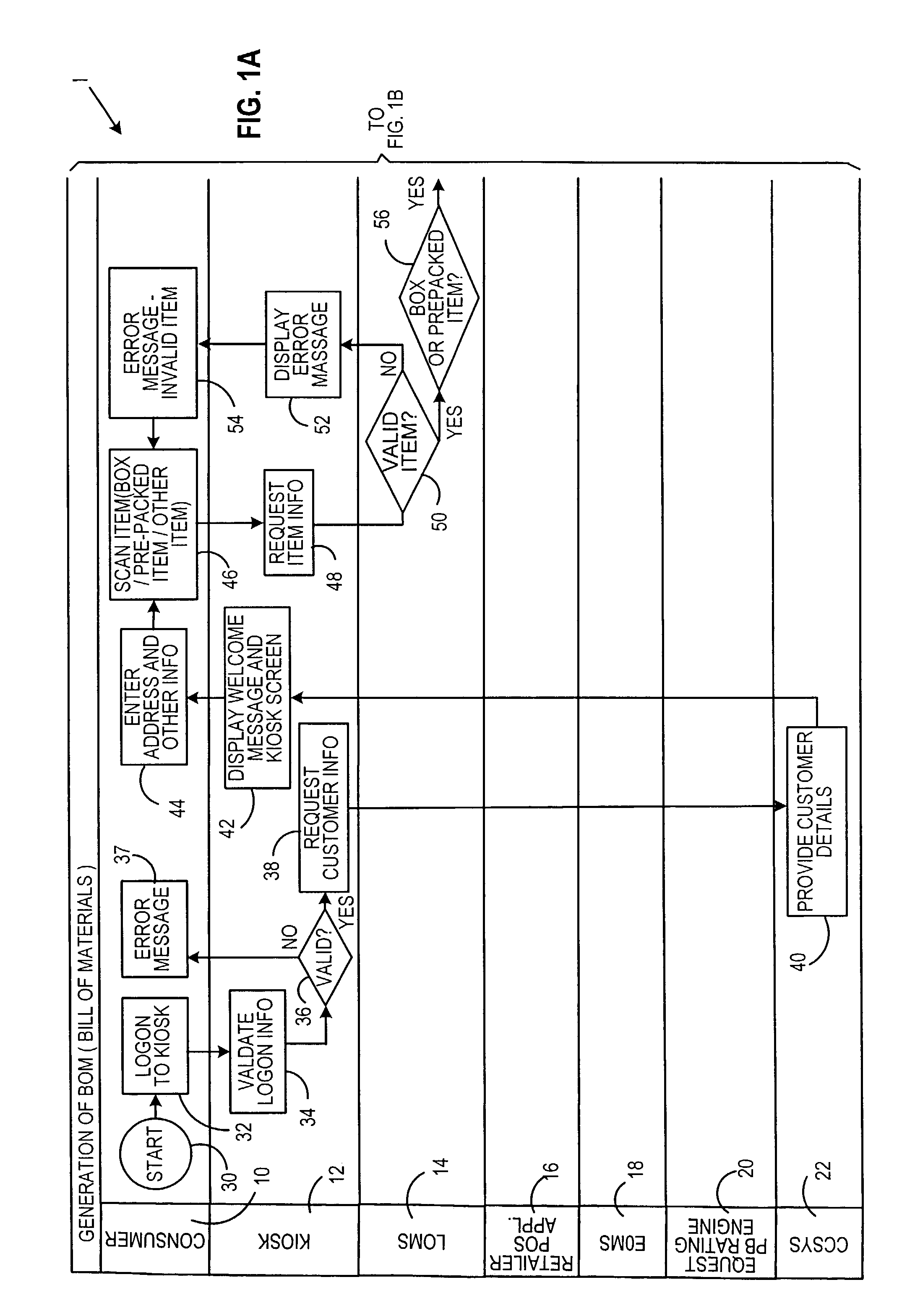
Method and system for enterprise-level unassisted customer shipping
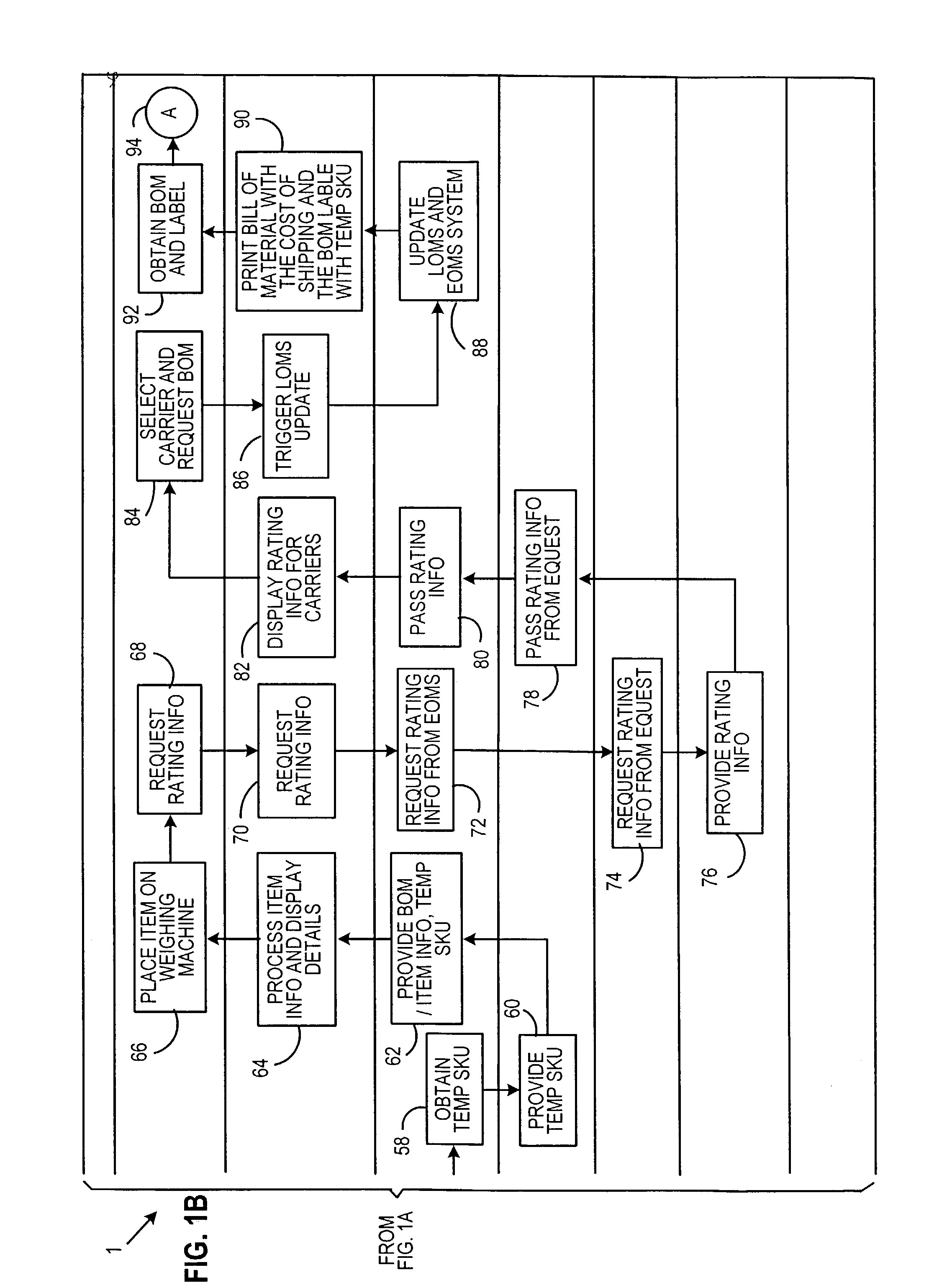
InactiveUS6970855B2Enhancing customer convenienceImprove integrityFranking apparatusLogisticsPaymentBill of materials
A system and method for unassisted enterprise-level unassisted customer shipping is described providing for payment of shipping and item costs in a single transaction. In one configuration, a customer utilizes a kiosk to process a shipping bill of materials for presentment at a point of sale terminal.
Owner:DMT SOLUTIONS GLOBAL CORP
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS8856936B2Minimize false positivesTrue to riskMemory loss protectionError detection/correctionApplication softwareBusiness process
Owner:ALBEADO
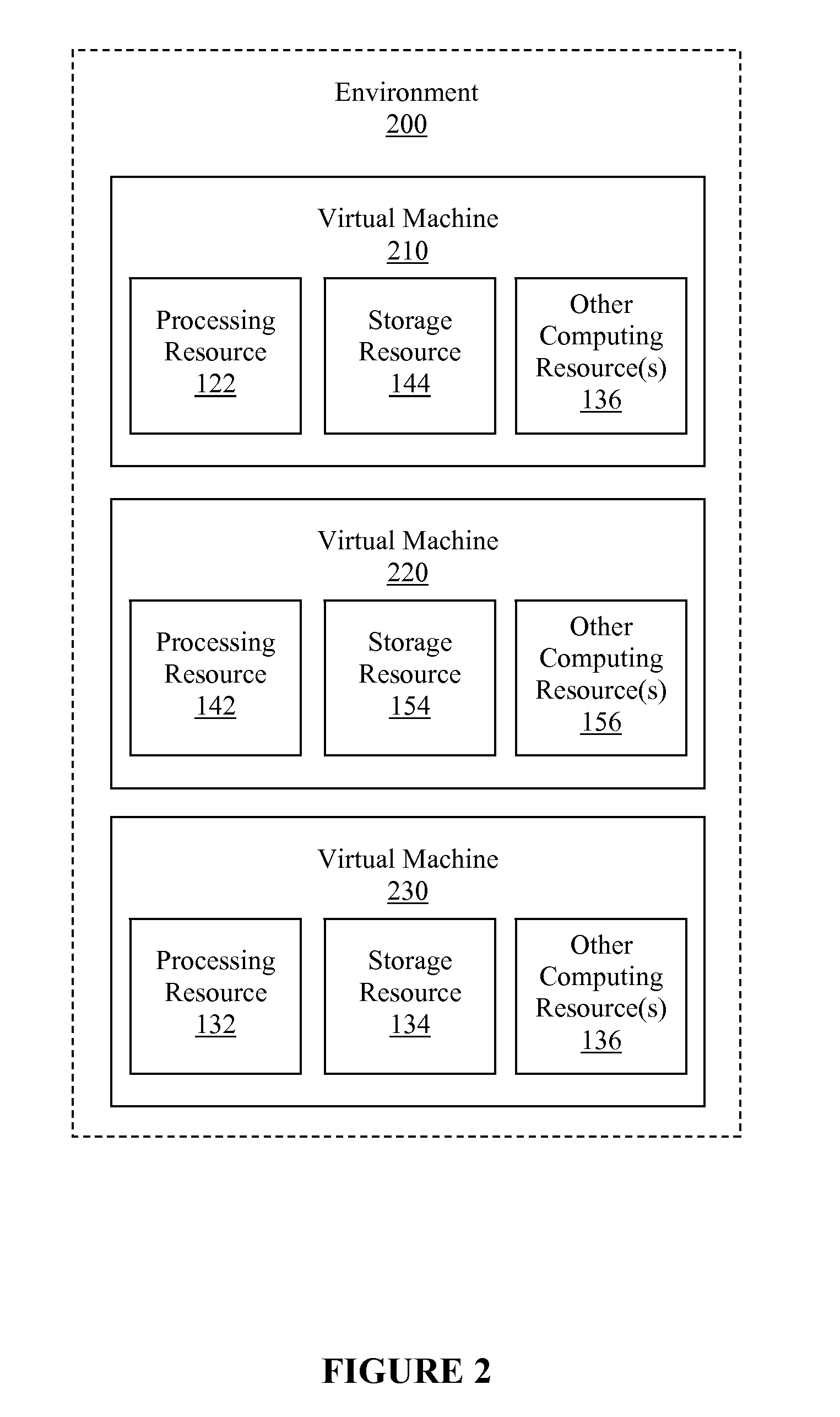
Enterprise-level management, control and information aspects of cloud console
ActiveUS20110055385A1Enabling and trackingInput/output for user-computer interactionError detection/correctionGraphicsGraphical user interface
A method, computer-readable medium, and system for monitoring usage of computing resources provisioned across multiple cloud providers and / or data centers are disclosed. Events associated with usage of a plurality of computing resources may be accessed, where the plurality of computing resources may implement a virtual machine, a plurality of virtual machines of a cloud computing environment, etc. The events may be associated with a start, a stop, a status change, etc., of the plurality of computing resources. The events may be used to generate usage data for the plurality of computing resources. The usage data may include historical data associated with previous usage of the plurality of computing resources. Additionally, the usage data may be displayed using a graphical user interface, thereby enabling monitoring and / or tracking of usage of computing resources provisioned across at least one cloud provider and / or at least one data center.
Owner:ACCENTURE GLOBAL SERVICES LTD
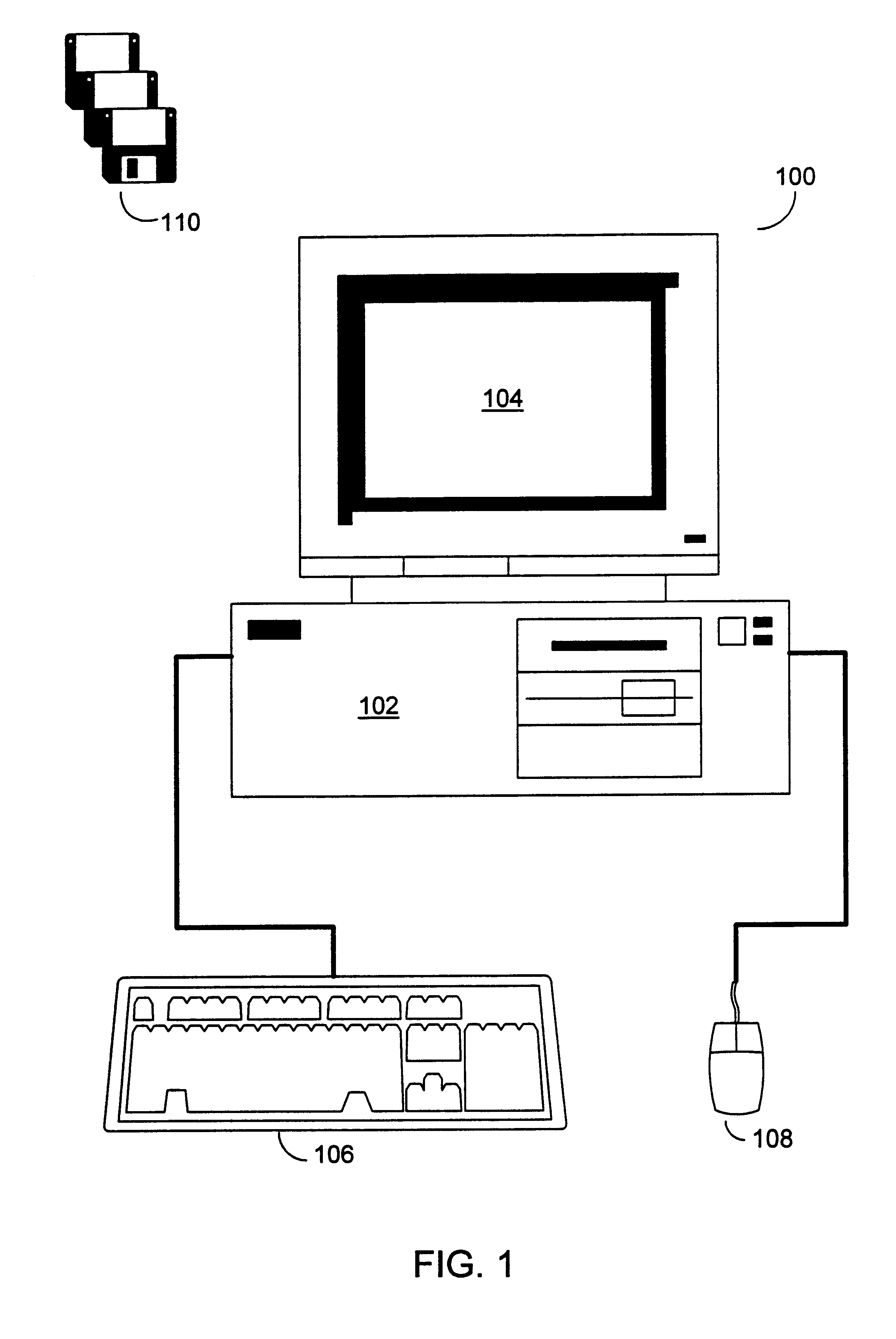
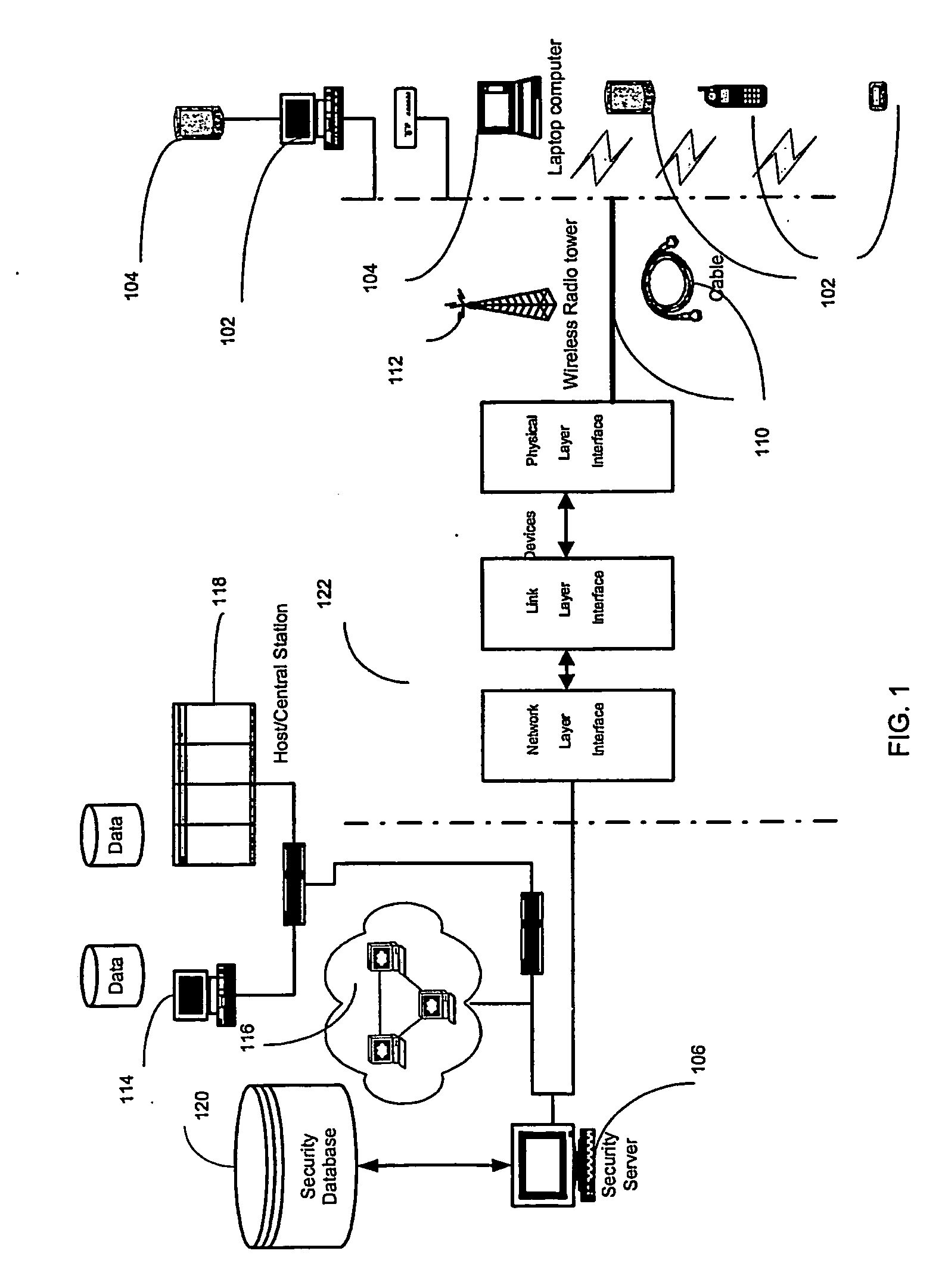
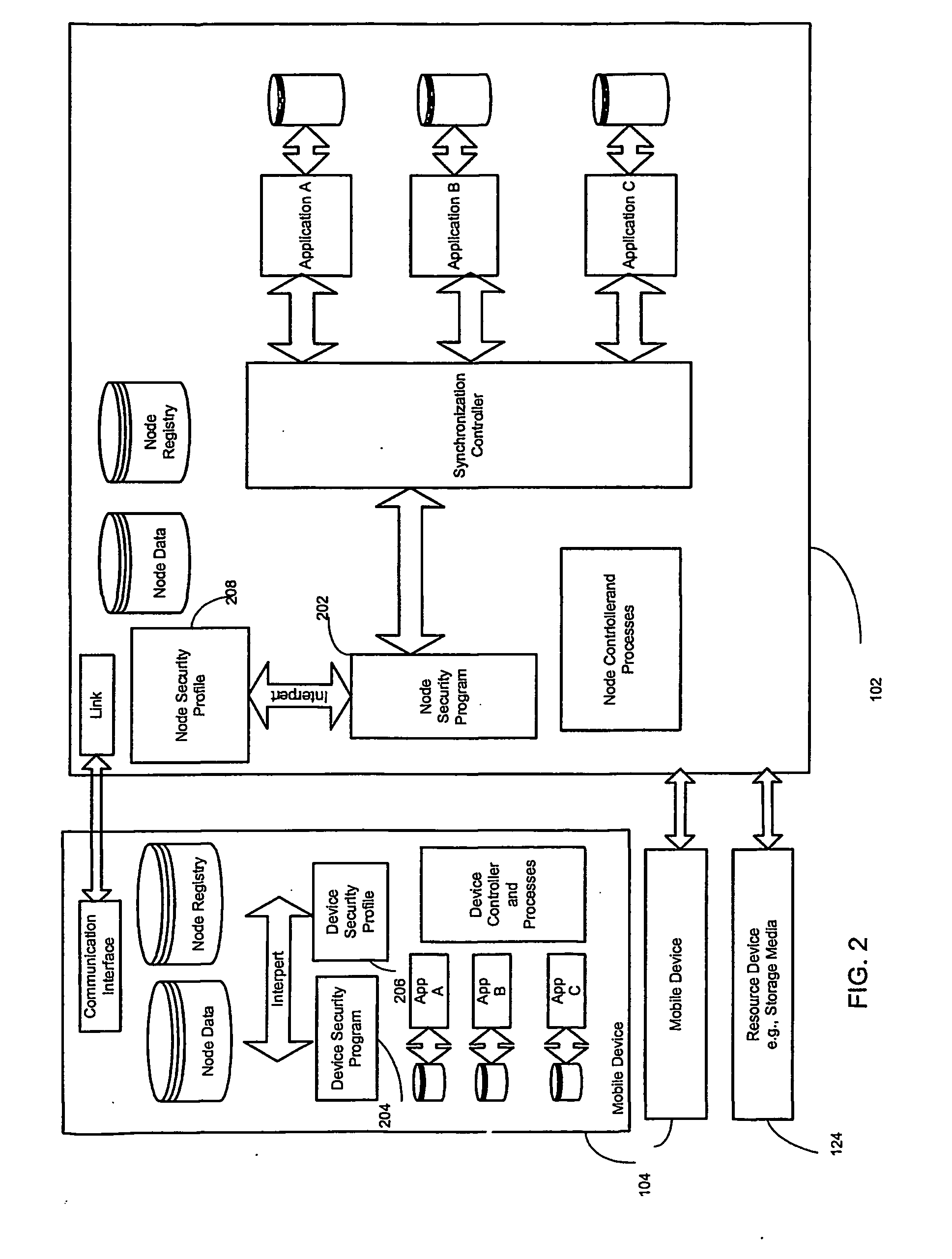
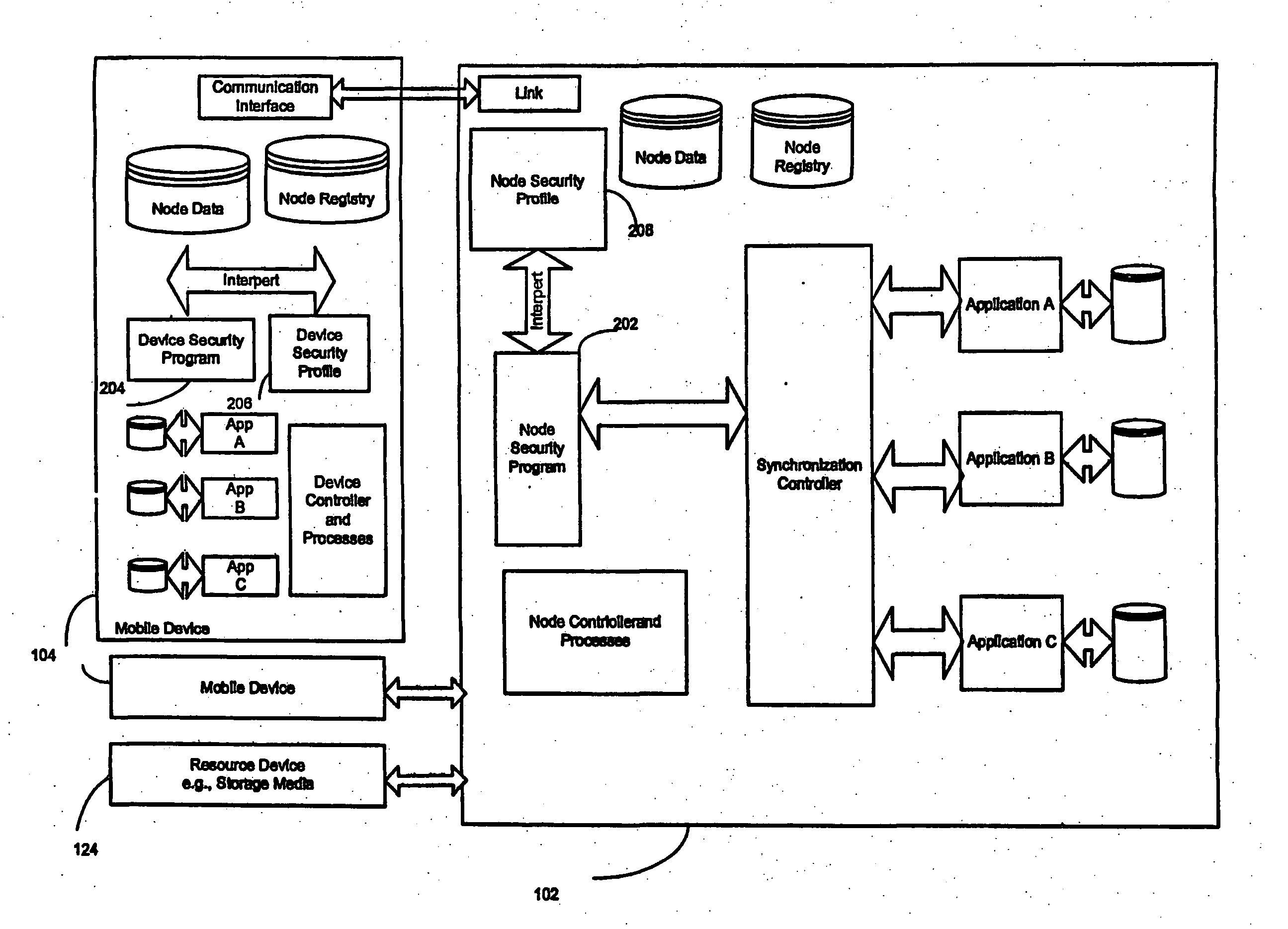
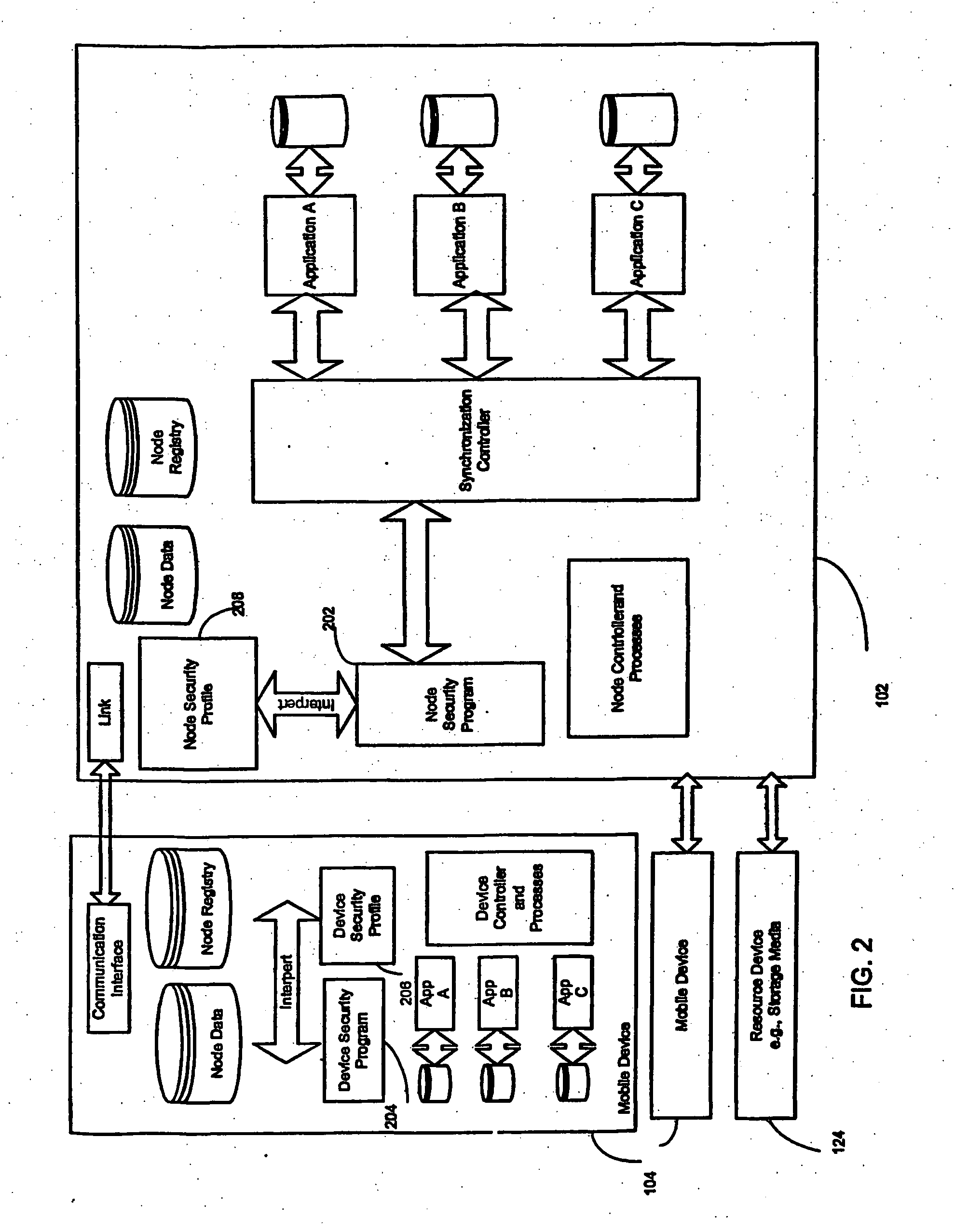
Enterprise-wide security system for computer devices
A system and method for securing data in mobile devices includes a computing node and a plurality of mobile devices. A node security program executed in the computing node interfaces with a device security program executed at a mobile device. The computing node is responsible for managing the security based on a node security profile interpreted by a node security program executed in the computing node. A device discovery method and arrangement also detects and locates various information about the mobile devices based on a scan profile.
Owner:TRUST DIGITAL +1
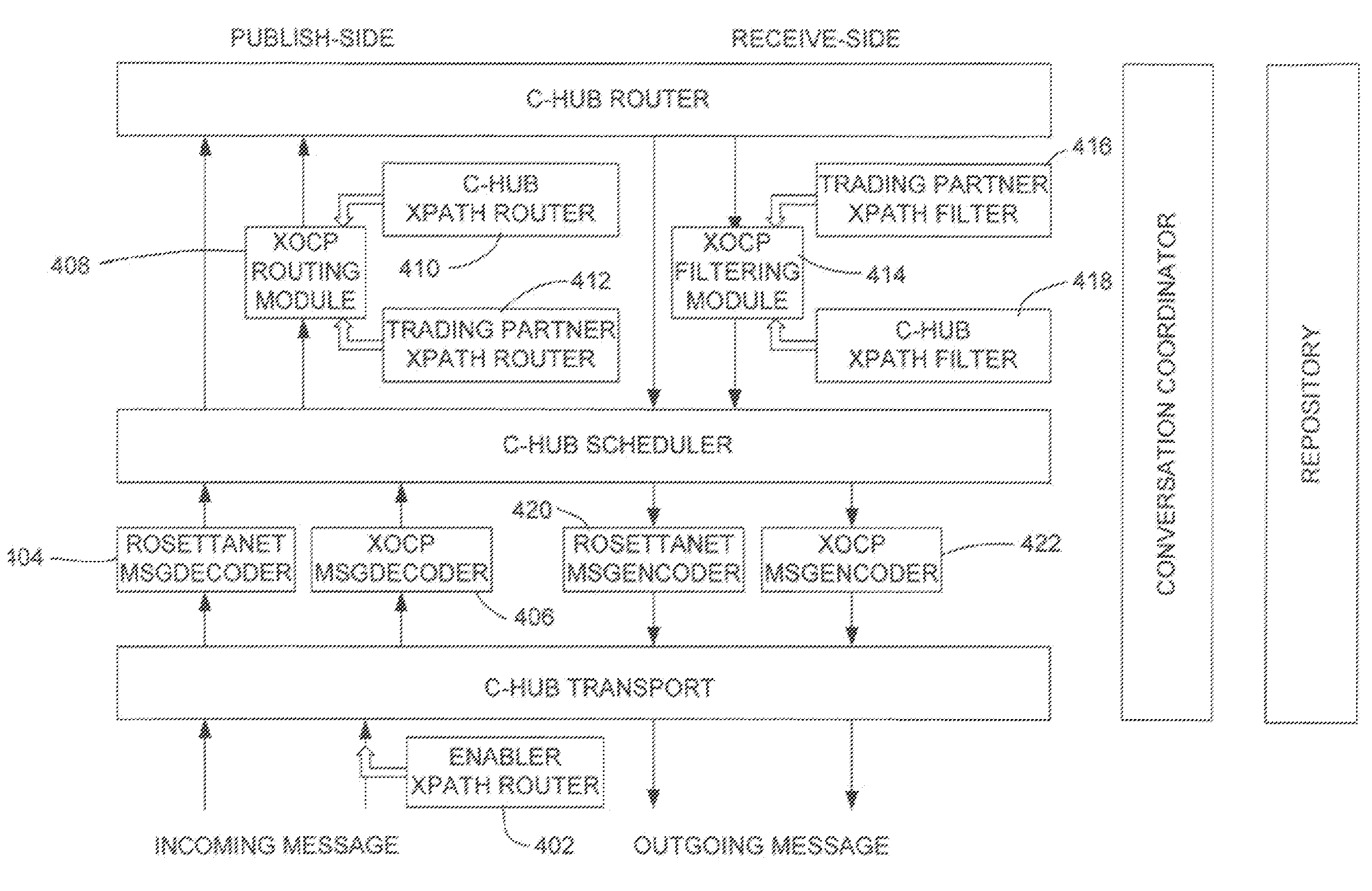
Pluggable hub system for enterprise wide electronic collaboration
InactiveUS7143186B2Increase speedEnsure qualityFinanceMultiple digital computer combinationsSession managementMessage flow
An enterprise wide electronic commerce system allows trading partners to act as participants in a complex trading process. Participants communicate with one another by joining conversations that are hosted in a collaboration space and managed by a collaboration hub. In this manner, the enterprise workflow may have an effect on, or be affected by, local workflows. The invention provides a pluggable hub system for enterprise wide electronic collaboration. An embodiment of the invention includes a collaboration hub for use with a collaboration system, comprising a hub transport for receiving messages from participants and sending messages to participants, a hub router for routing messages from a first participant to a second participant, a hub scheduler for scheduling the flow of messages between the hub router and the hub transport, a conversation manager for managing the flow of messages between participants, and a repository for storing conversation management data.
Owner:ORACLE INT CORP
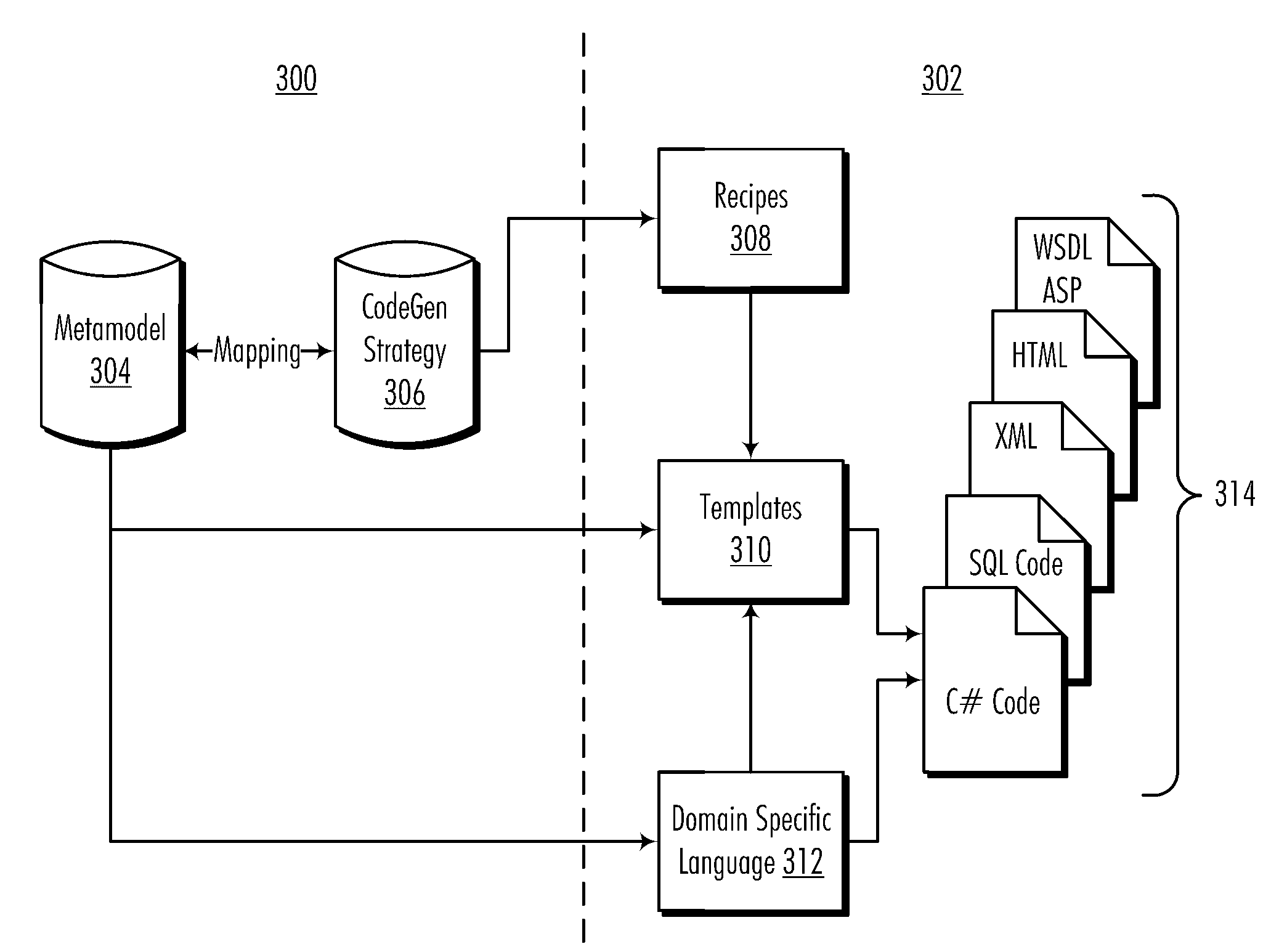
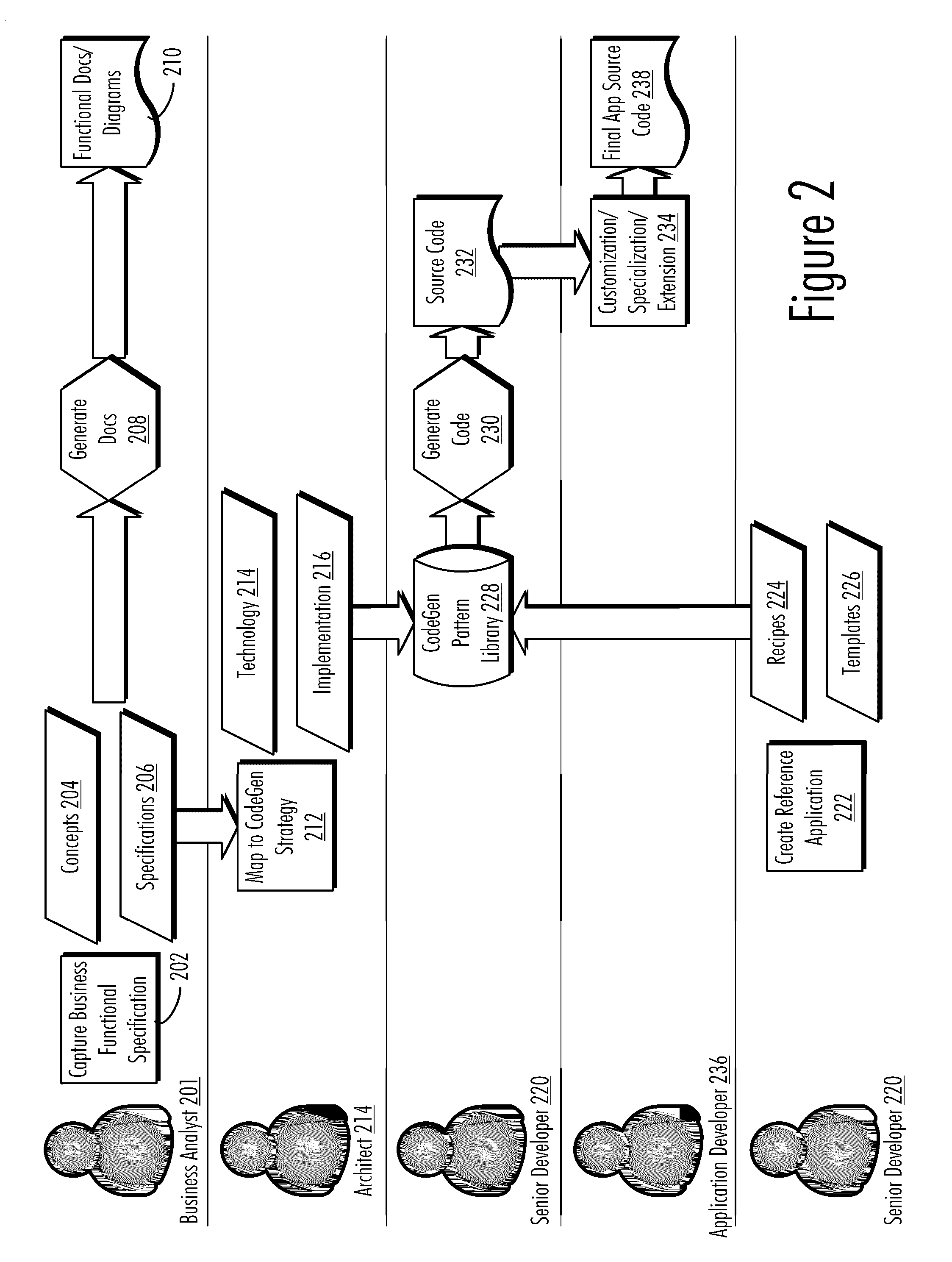
Enterprise-Scale Application Development Framework Utilizing Code Generation
InactiveUS20080127040A1Good compatibilityFacilitate functional comparabilityModel driven codeRequirement analysisData processing systemWeb service
Owner:BARCELLONA JON
System and method for enterprise modeling, optimization and control
A system and method for performing modeling, prediction, optimization, and control, including an enterprise wide framework for constructing modeling, optimization, and control solutions. The framework includes a plurality of base classes that may be used to create primitive software objects. These objects may then be combined to create optimization and / or control solutions. The distributed event-driven component architecture allows much greater flexibility and power in creating, deploying, and modifying modeling, optimization and control solutions. The system also includes various techniques for performing improved modeling, optimization, and control, as well as improved scheduling and control. For example, the system may include a combination of batch and continuous processing frameworks, and a unified hybrid modeling framework which allows encapsulation and composition of different model types, such as first principles models and empirical models. The system further includes an integrated process scheduling solution referred to as process coordinator that seamlessly incorporates the capabilities of advanced control and execution into a real time event triggered optimal scheduling solution.
Owner:ROCKWELL AUTOMATION TECH
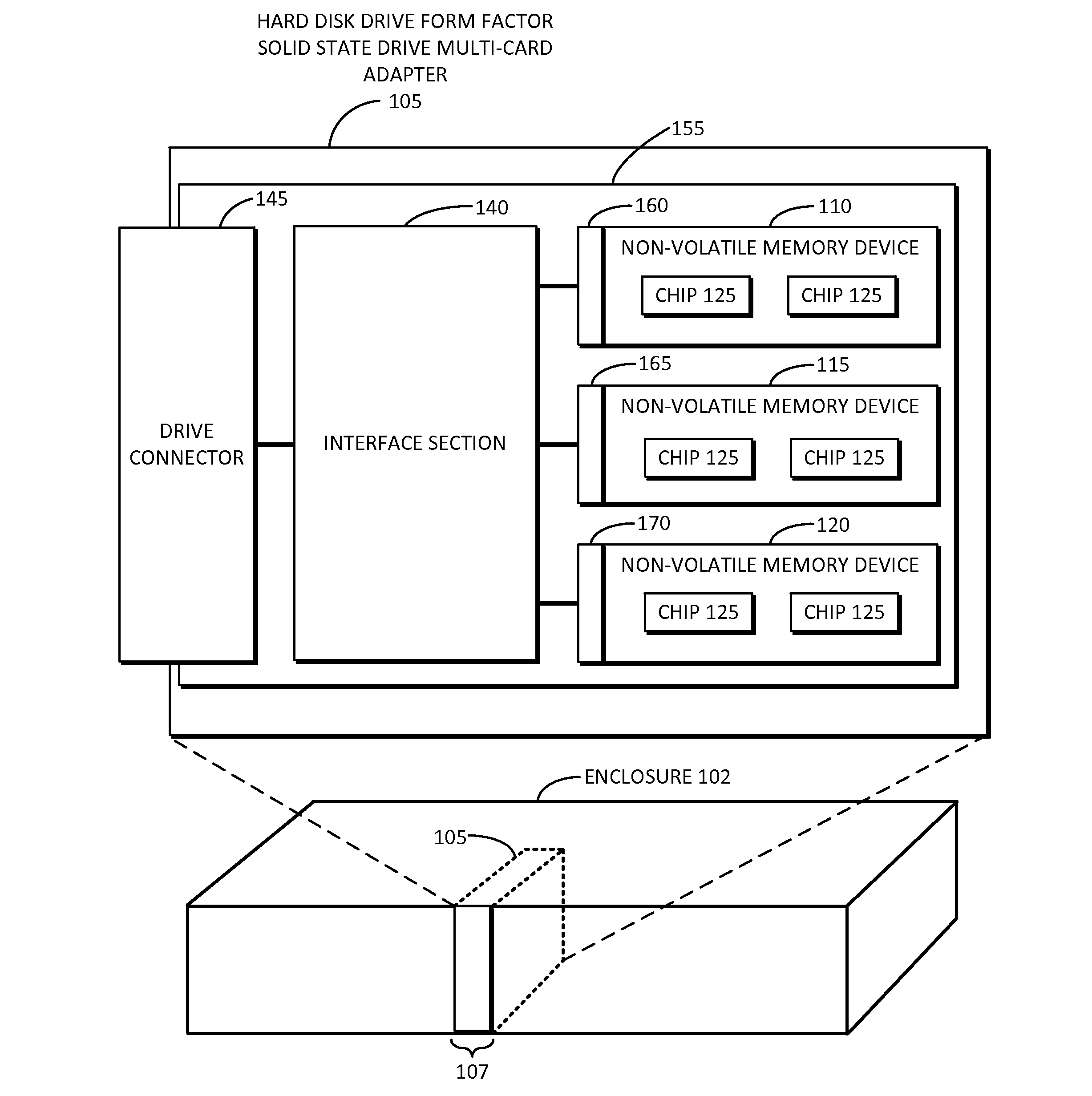
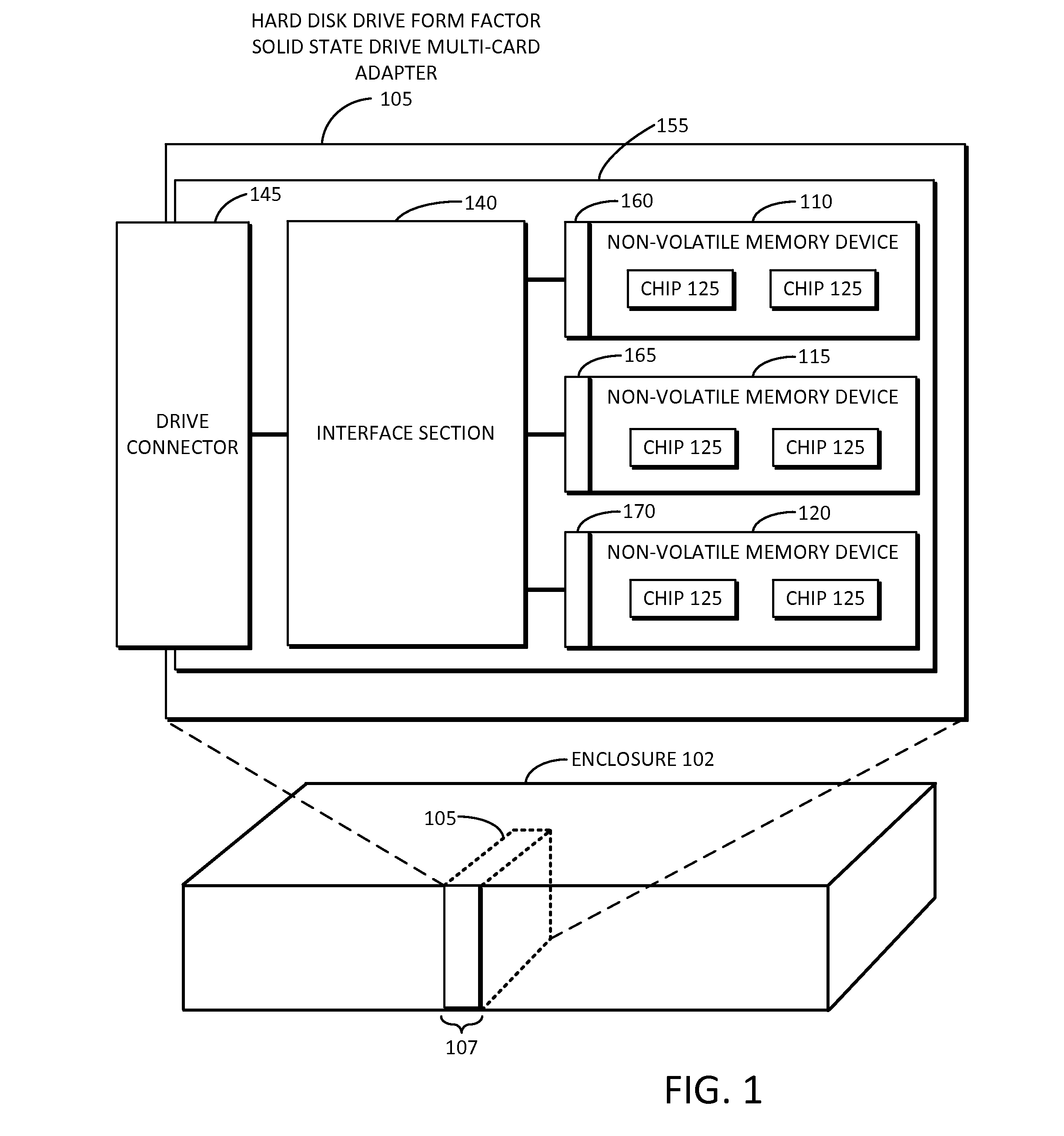
Solid state drive multi-card adapter with integrated processing
Embodiments of the inventive concept include solid state drive (SSD) multi-card adapters that can include multiple solid state drive cards, which can be incorporated into existing enterprise servers without major architectural changes, thereby enabling the server industry ecosystem to easily integrate evolving solid state drive technologies into servers. The SSD multi-card adapters can include an interface section between various solid state drive cards and drive connector types. The interface section can perform protocol translation, packet switching and routing, data encryption, data compression, management information aggregation, virtualization, and other functions.
Owner:SAMSUNG ELECTRONICS CO LTD
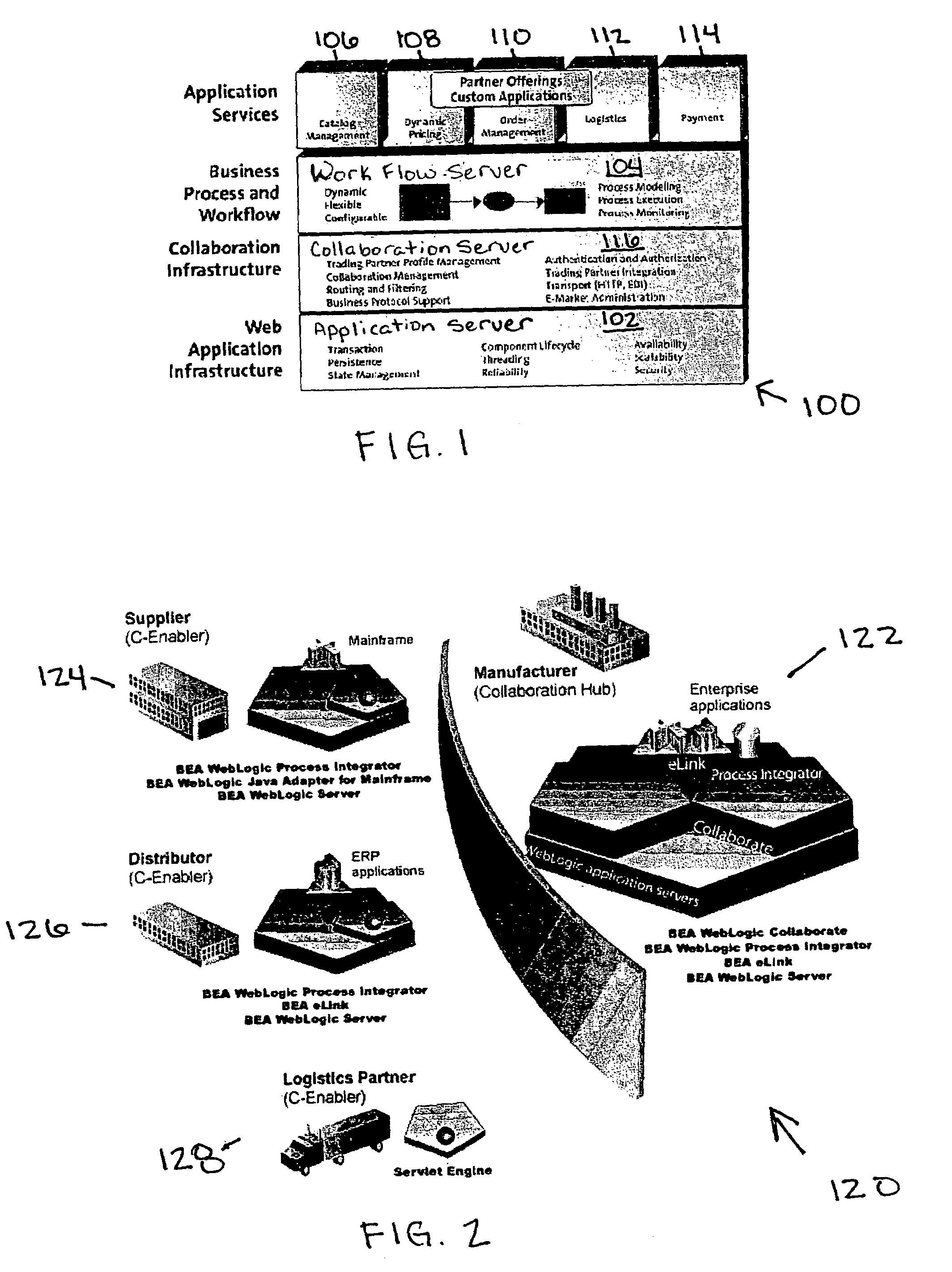
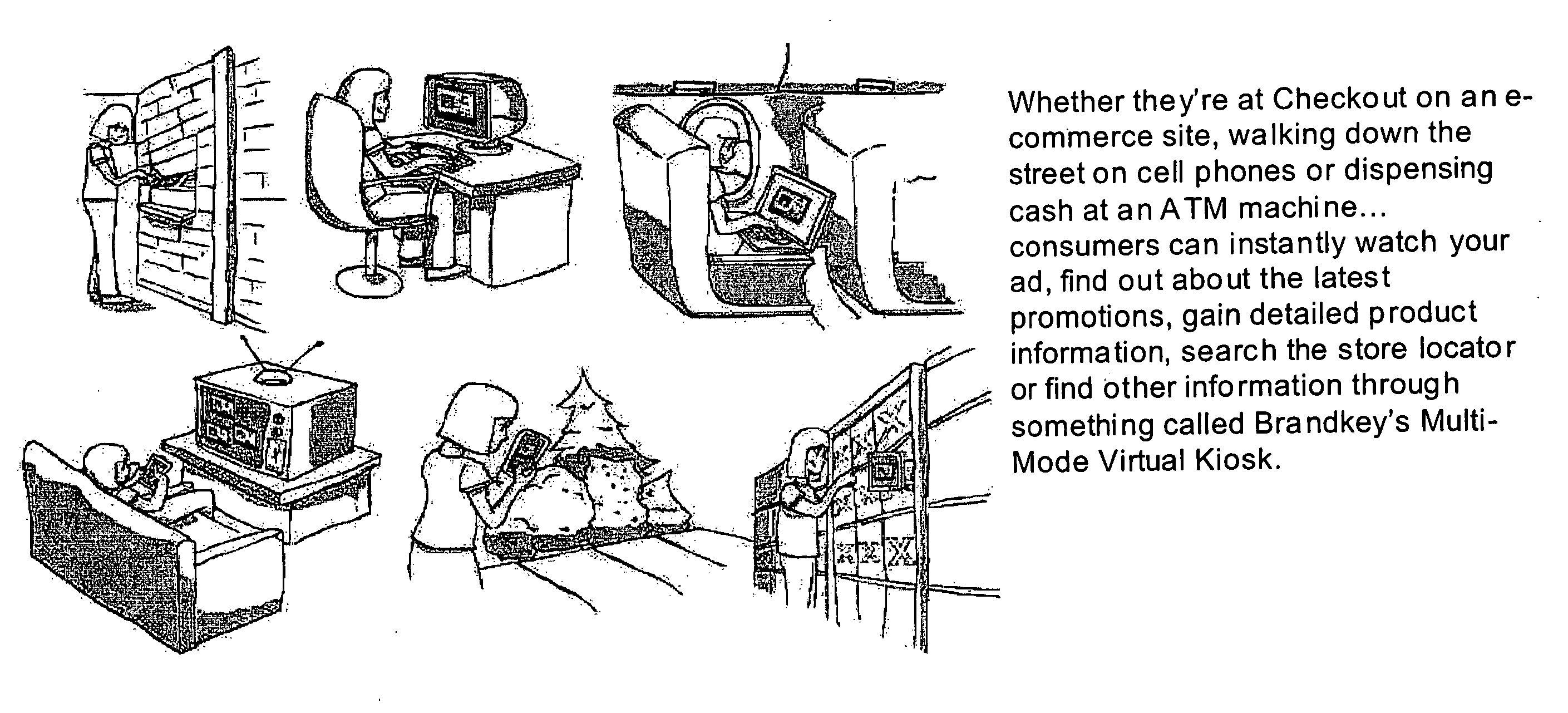
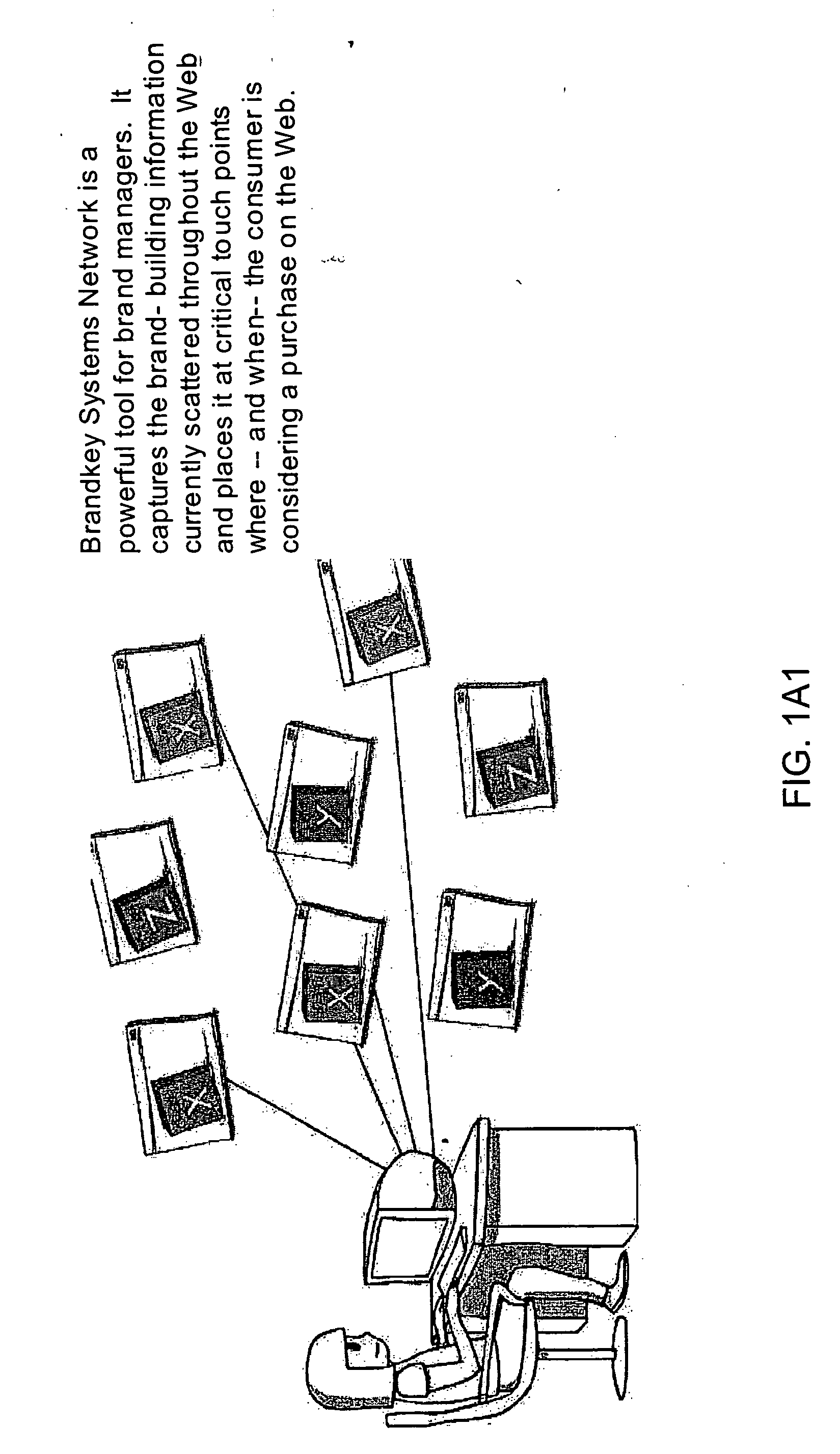
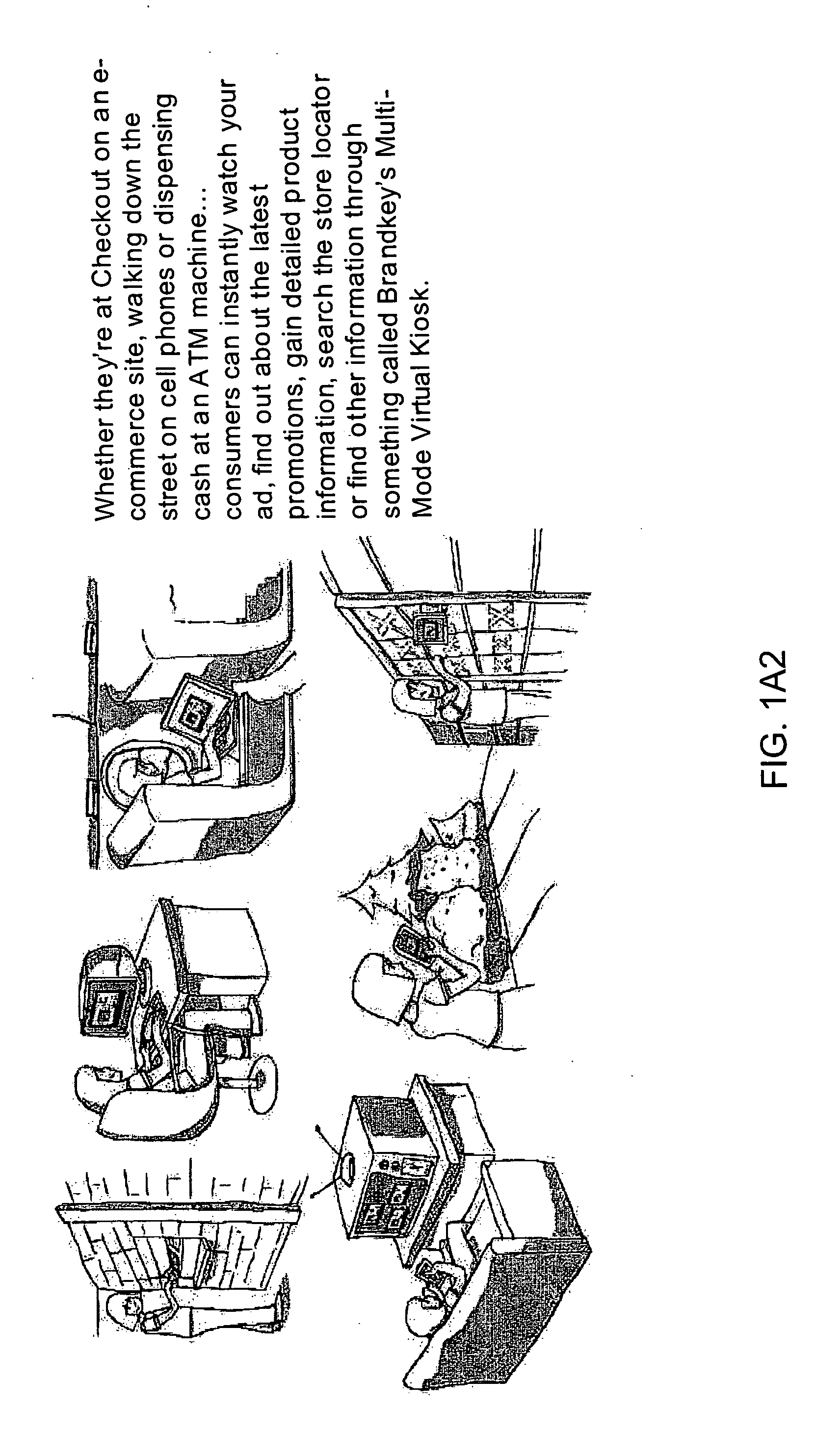
Inernet-based brand marketing communication network for enabling commission-based e-commerce transactions along the fabric of the world wide web (WWW) using server-side driven multi-mode virtual kiosks (MMVKs)
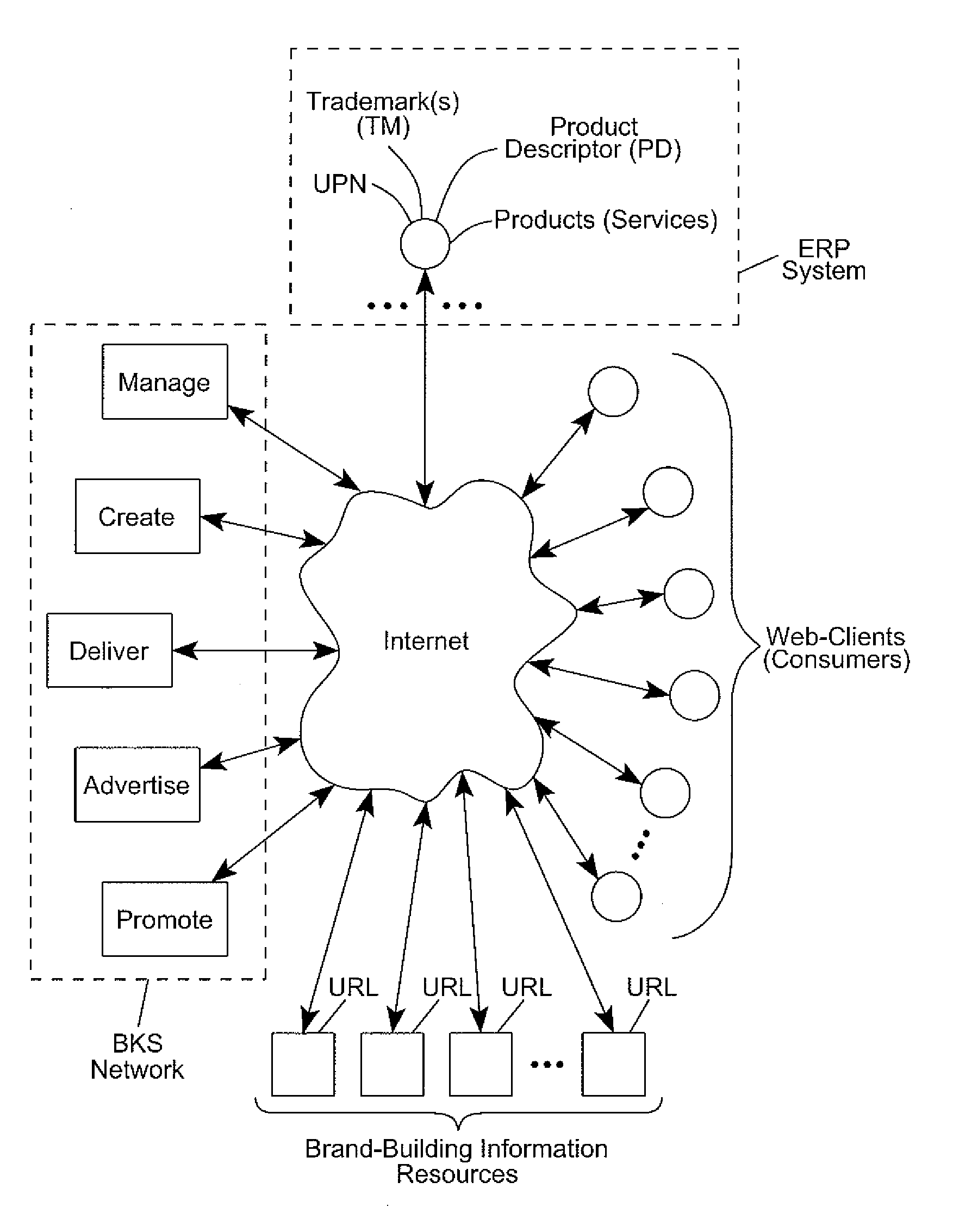
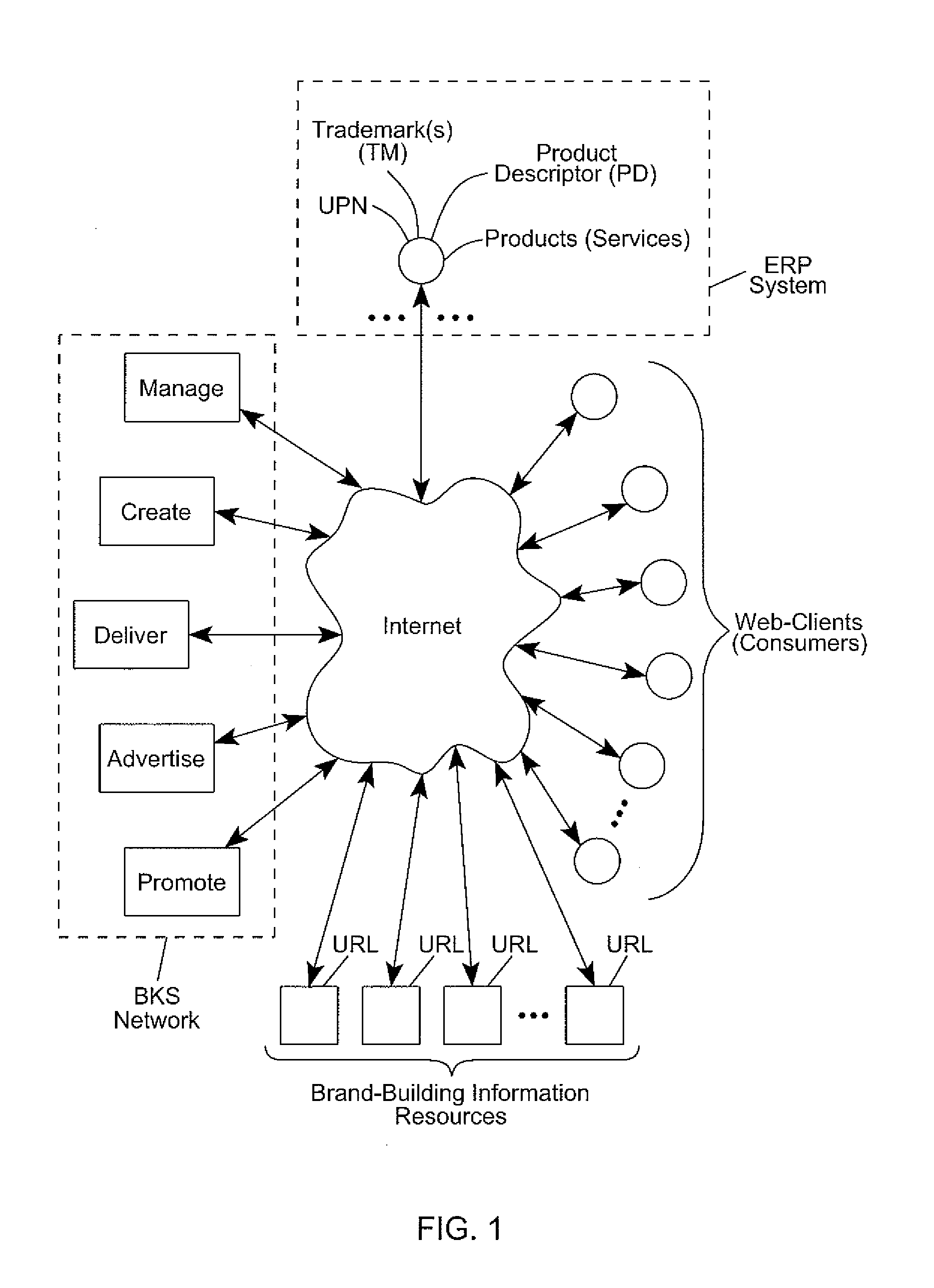
Internet-based Enterprise-Level Brand Management And Marketing Communication Network based on an innovative brand command, control and communication architecture (BC3), which gives brand owners complete command and control over the wide range of brand-building assets, messaging and promotions scattered throughout the Web, and how they are communicated to directly consumers at diverse Web touch points, with the efficiency and automation of supply-chain management solutions. The Network supports the deployment, installation and remote programming of brand-building server-side driven Multi-Mode Virtual Kiosks on the World Wide Web (WWW), and provide brand managers, their agents and online trading partners the power to build stronger online brands, drive sales and eliminate existing friction in the retail chain through a collaborative carrier-class, indutrial-strength e-marketing communication network.
Owner:BKS NETWORKS
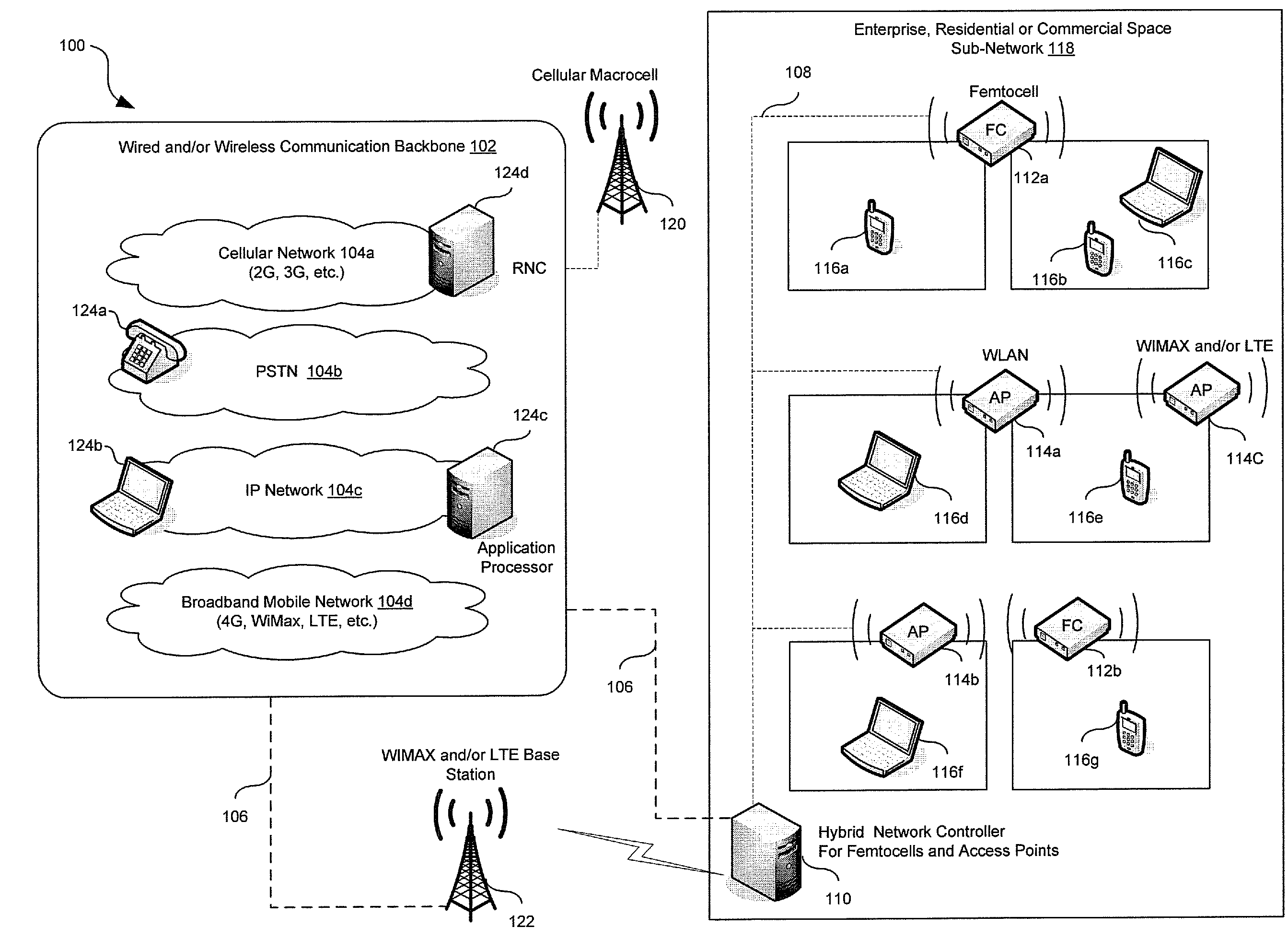
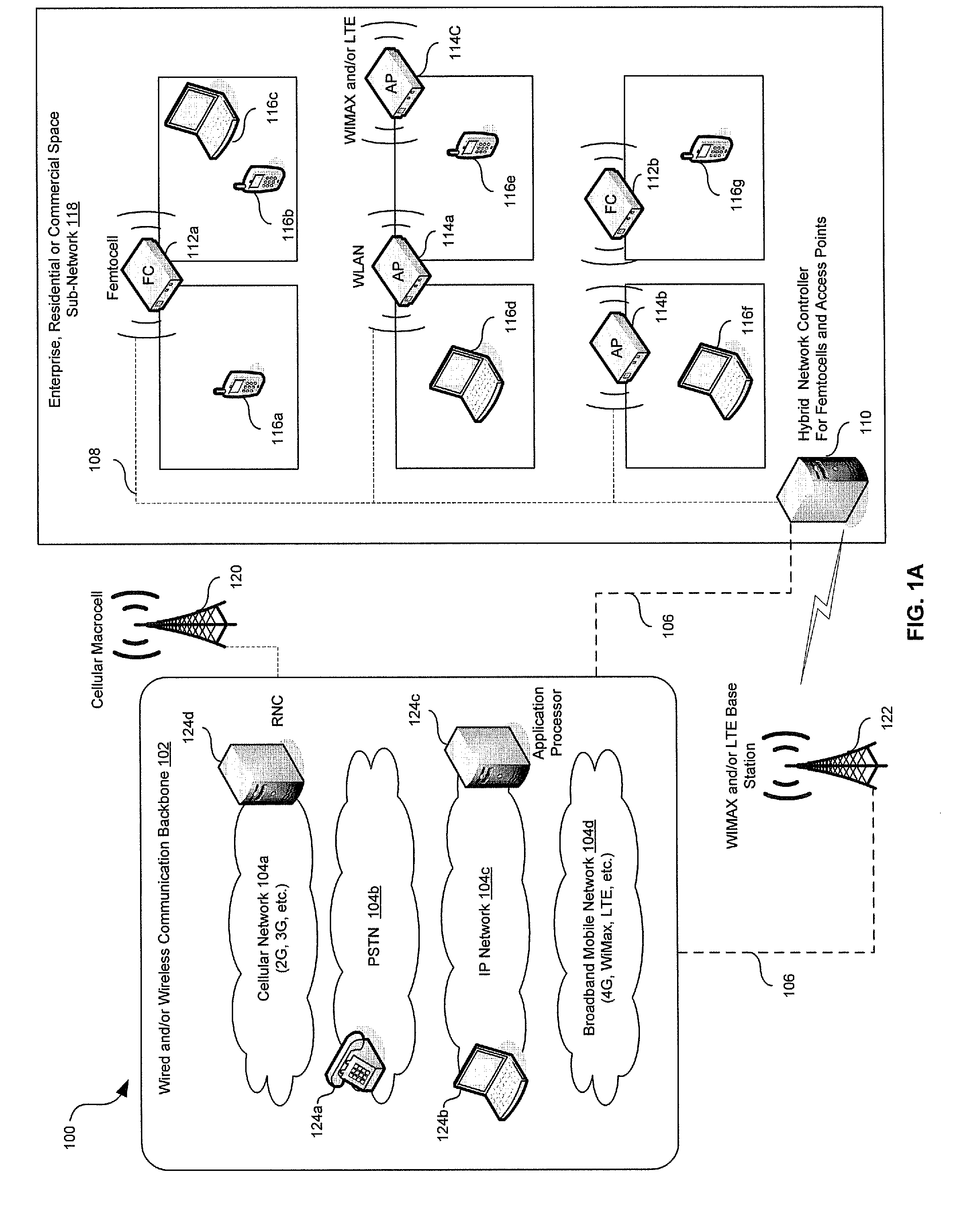
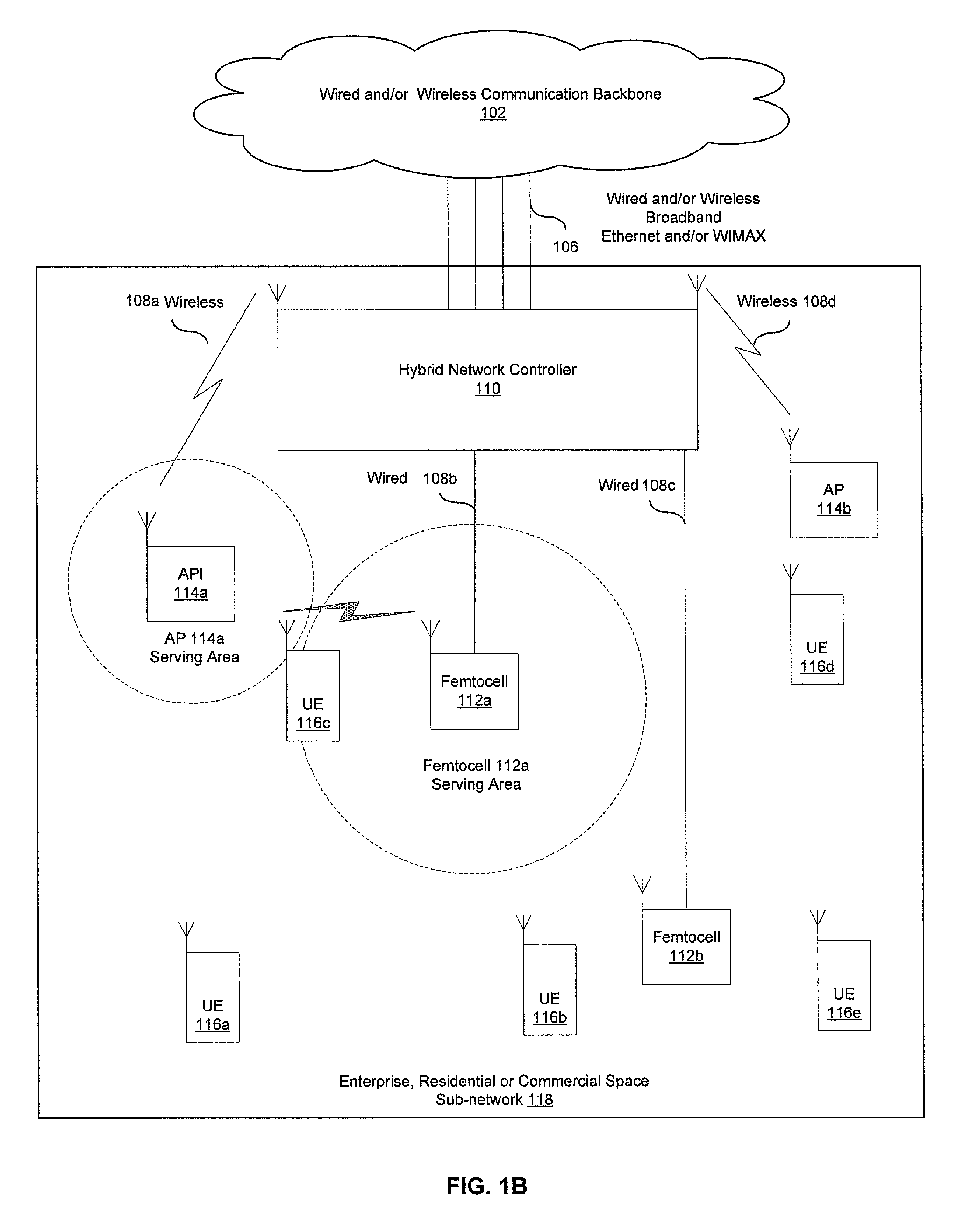
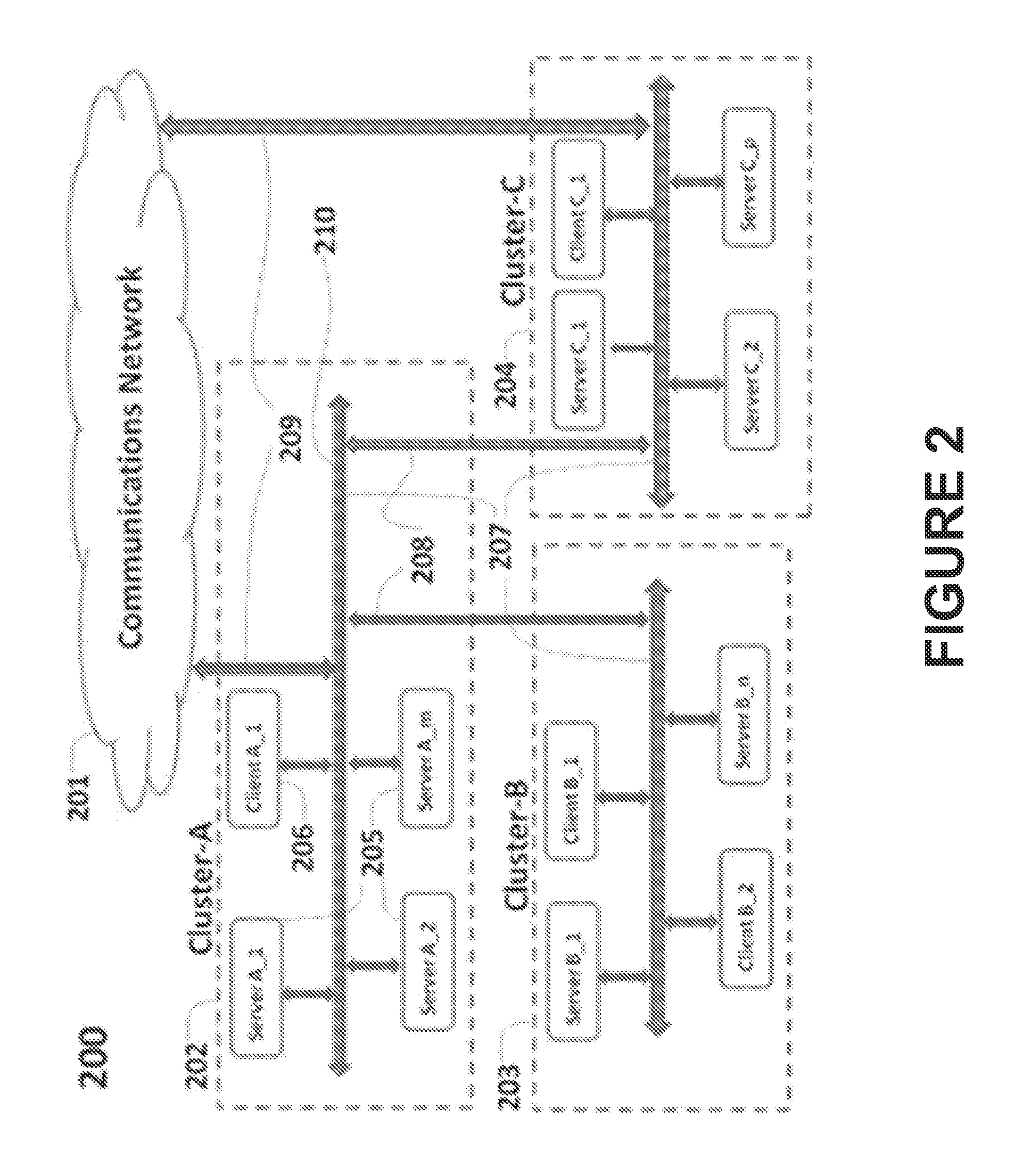
Enterprise Level Management in a Multi-Femtocell Network
Aspects of a method and system for enterprise level management in a multi-femtocell network are provided. In this regard, one or more endpoint devices may receive traffic management information from a hybrid network controller for enabling handoff of calls and / or communication sessions among femtocells and / or access points. The received traffic management information may comprise set-up instructions, handoff instructions, transmit power, neighbor list information, signal quality thresholds, frequency assignments, transmission time, code assignments and / or antenna pattern assignments. The endpoint device may control handoffs between a communication device external to the communication system and the femtocells, access points and / or end-point devices.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for monitoring an electrical network
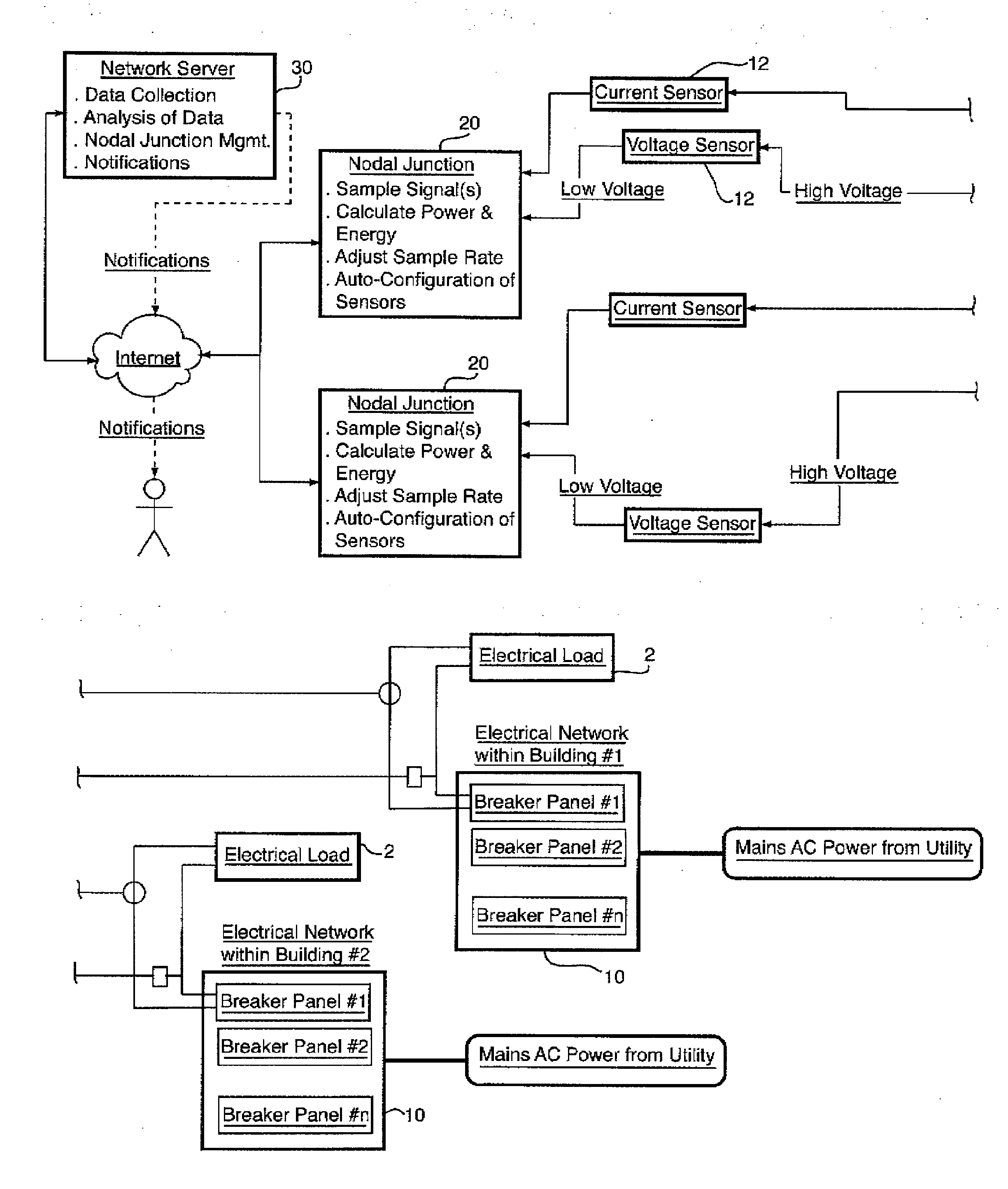
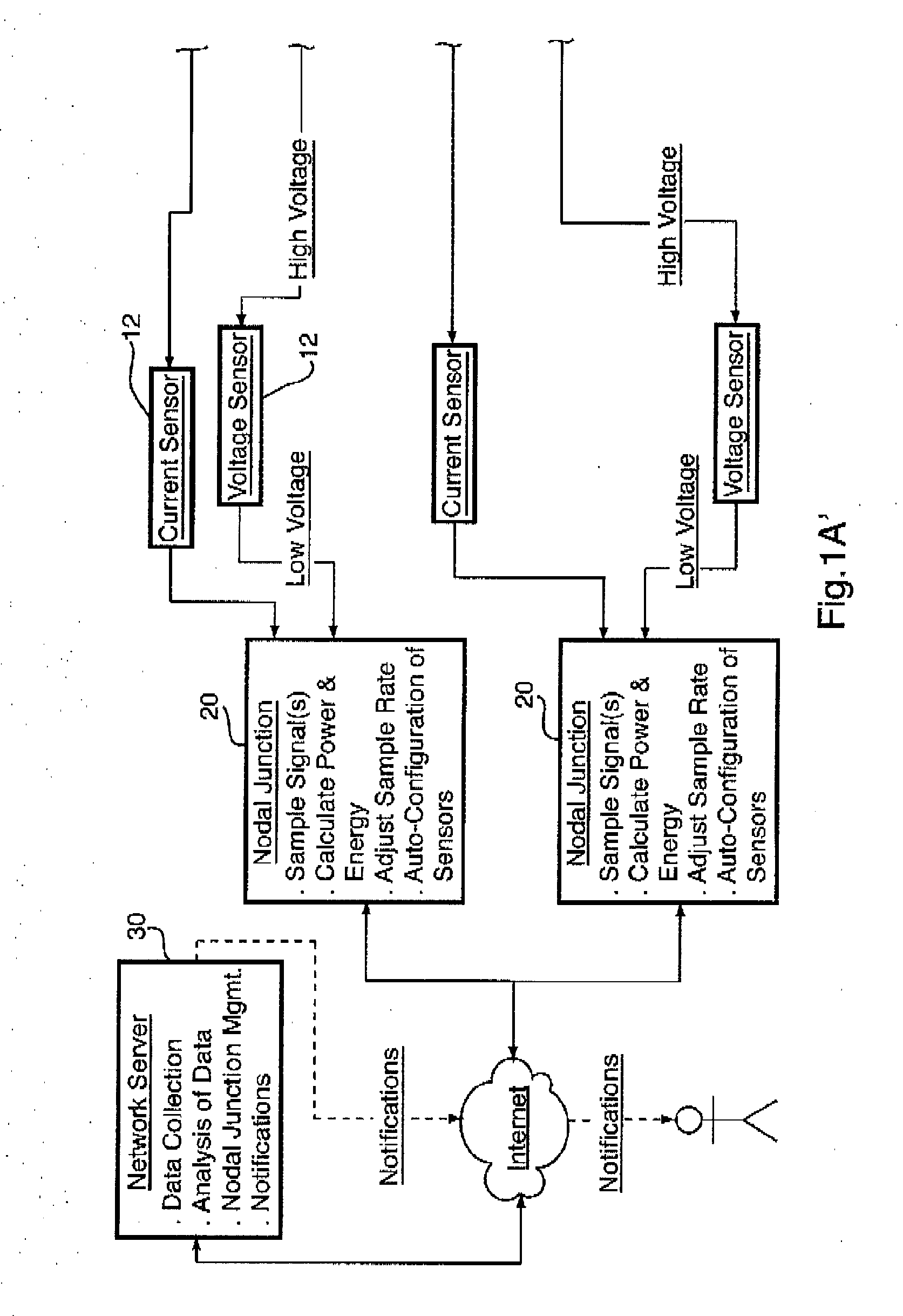
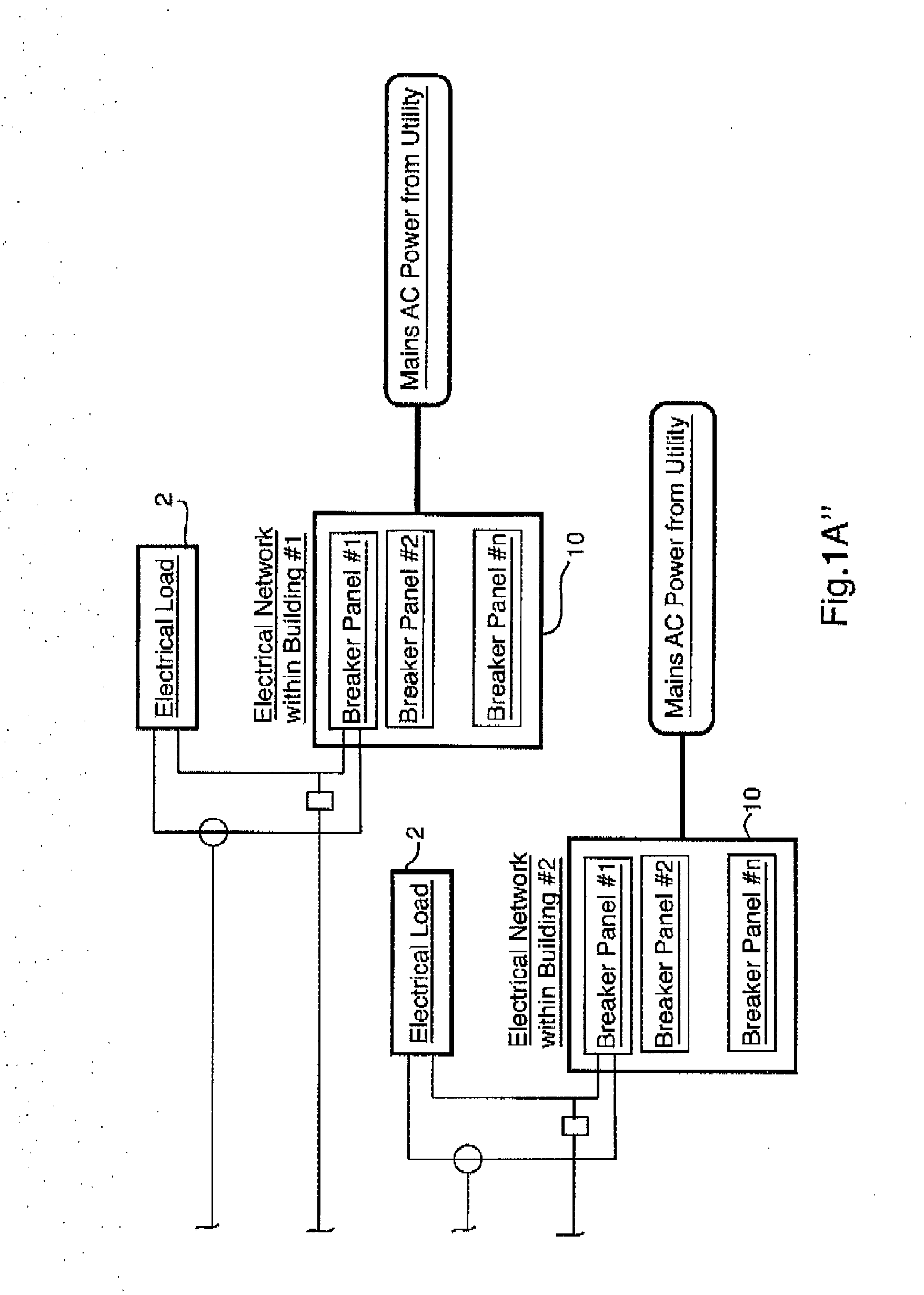
An energy monitoring system which in preferred embodiments employs at least one nodal junction receiving and creating data by analog to digital conversion from a plurality of local node sensors. Data accumulated by the nodal junction is used for analysis of wave patterns to detect anomalies in the local electrical network and / or loads connected to the local electrical network. Anomalies can be detected in various ways, including: comparison of data with historical data acquired from the local node sensors; comparison of data with known wave pattern profiles for similar loads; and comparison of data with data acquired from local node sensors at other locations. Thus, the accumulation of data in the system of the invention provides the ability to perform comparative analysis to a baseline or standard, and also the ability to perform comparative analysis at an enterprise level across different target locations.
Owner:CIRCUITMETER
Interactive large data analysis query processing method
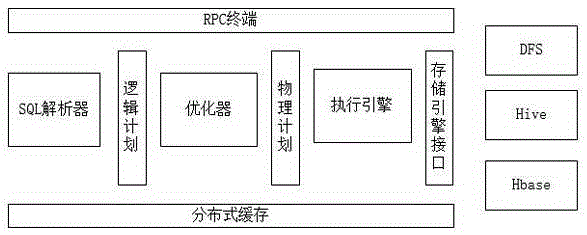
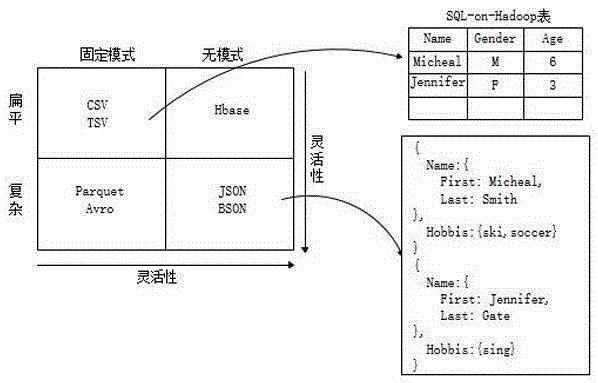
InactiveCN105279286AImprove query efficiencyImprove scalabilitySpecial data processing applicationsDatabase queryData set
The invention provides an interactive large data analysis query processing method. The interactive large data analysis query processing method comprises steps that, 1), a query request generated by a user or a machine is submitted to an SQL query analyzer; 2), the query quest is analyzed by the SQL query analyzer into a logic plan; 3), the logic plan is read by an optimizer and is converted into a physical plan, and interaction between a storage engine and a specific data source is realized; and 4), the physical plan is performed by a performing engine, and meta-data information is provided based on a meta-database query performing framework. For real-time interactive large data set analysis blank, P-byte data is processed under the condition of low delay response through the method according to design, multiple functions of other SQL-on-Hadoop engines are integrated, the query speed is greatly improved, and thereby Hadoop data query and enterprise-level large data analysis can be rapidly and efficiently carried out for enterprise users.
Owner:陕西艾特智慧信息技术有限公司
System and method of securing web applications across an enterprise
ActiveUS7934253B2Memory loss protectionDigital data processing detailsTraffic capacityWeb application
A system and method for protection of Web based applications are described. The techniques described provide an enterprise wide approach to preventing attacks of Web based applications. Individual computer networks within the enterprise monitor network traffic to identify anomalous traffic. The anomalous traffic can be identified by comparing the traffic to a profile of acceptable user traffic when interacting with the application. The anomalous traffic, or security events, identified at the individual computer networks are communicated to a central security manager. The central security manager correlates the security events at the individual computer networks to determine if there is an enterprise wide security threat. The central security manager can then communicate instructions to the individual computer networks so as to provide an enterprise wide solution to the threat.
Owner:TRUSTWAVE HOLDINGS
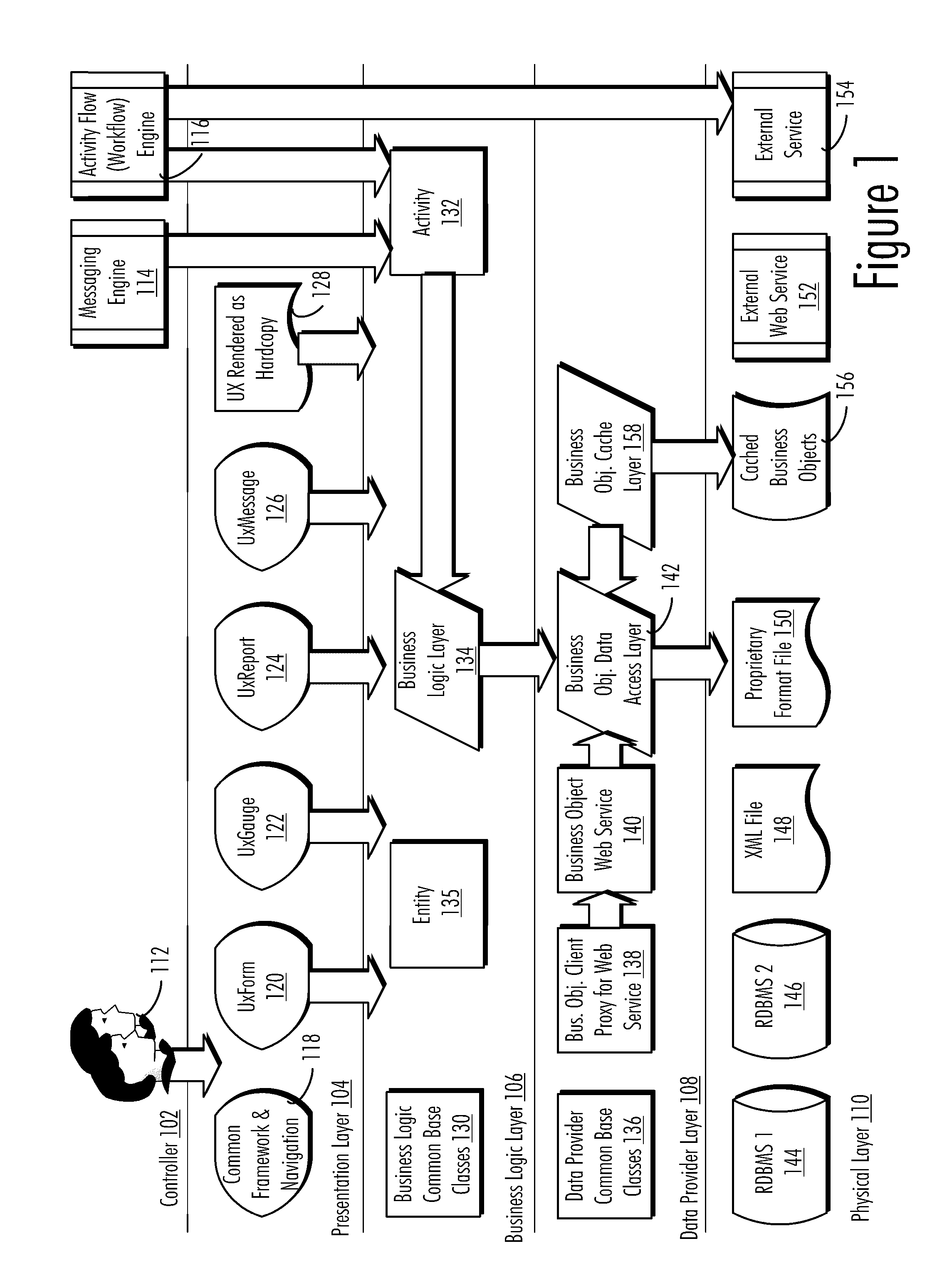
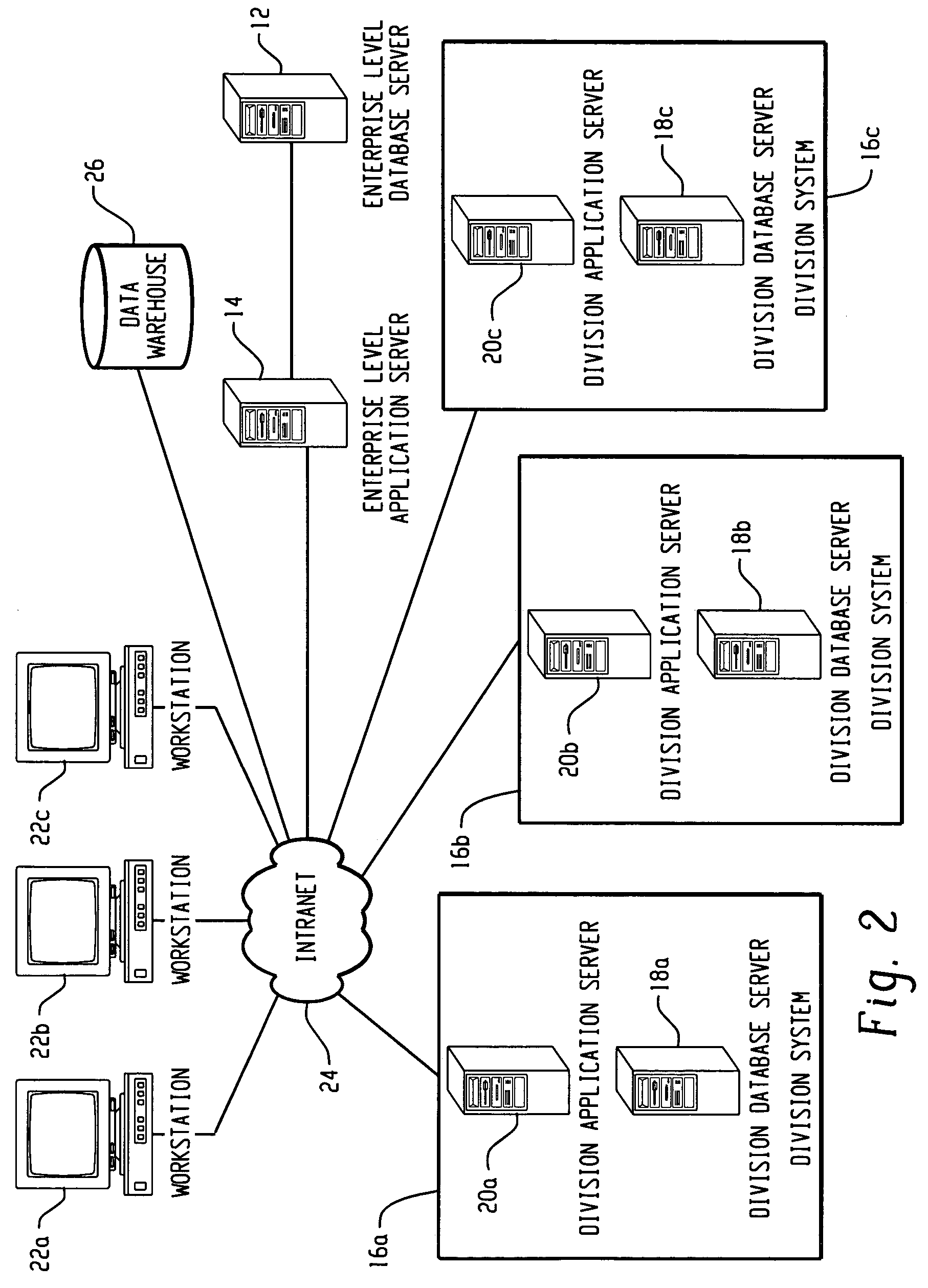
Master data management system for centrally managing cached data representing core enterprise reference data maintained as locked in true state read only access until completion of manipulation process
In one embodiment, a system is provided for centrally managing core enterprise reference data associated with an enterprise. A centralized master repository contains the core enterprise reference data. An internal services framework coupled to the centralized master repository provides internal services for managing the core enterprise reference data within the centralized master repository, one or more of the internal services having direct access to the core enterprise reference data stored in the centralized master repository for management purposes. An infrastructure services layer coupled to the centralized master repository provides for bulk data transfers of core enterprise reference data between the centralized master repository and one or more external operational systems according to one or more enterprise-level business workflows, the external operational systems being permitted indirect access to the core enterprise reference data stored in the centralized master repository for operational purposes.
Owner:BLUE YONDER GRP INC
Model for communication between manufacturing and enterprise levels
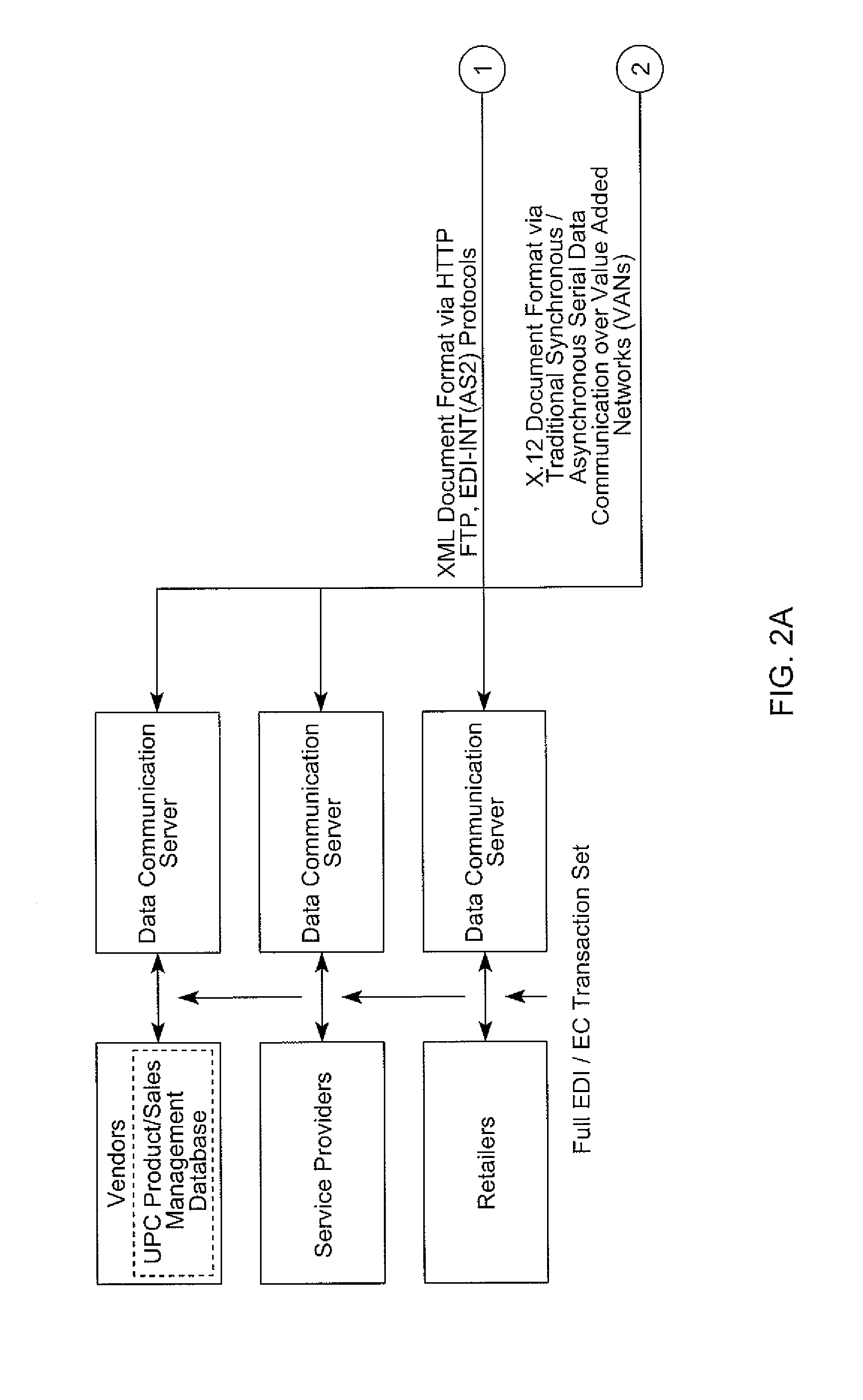
ActiveUS20050267882A1Programme controlData processing applicationsProgrammable logic controllerEnterprise level
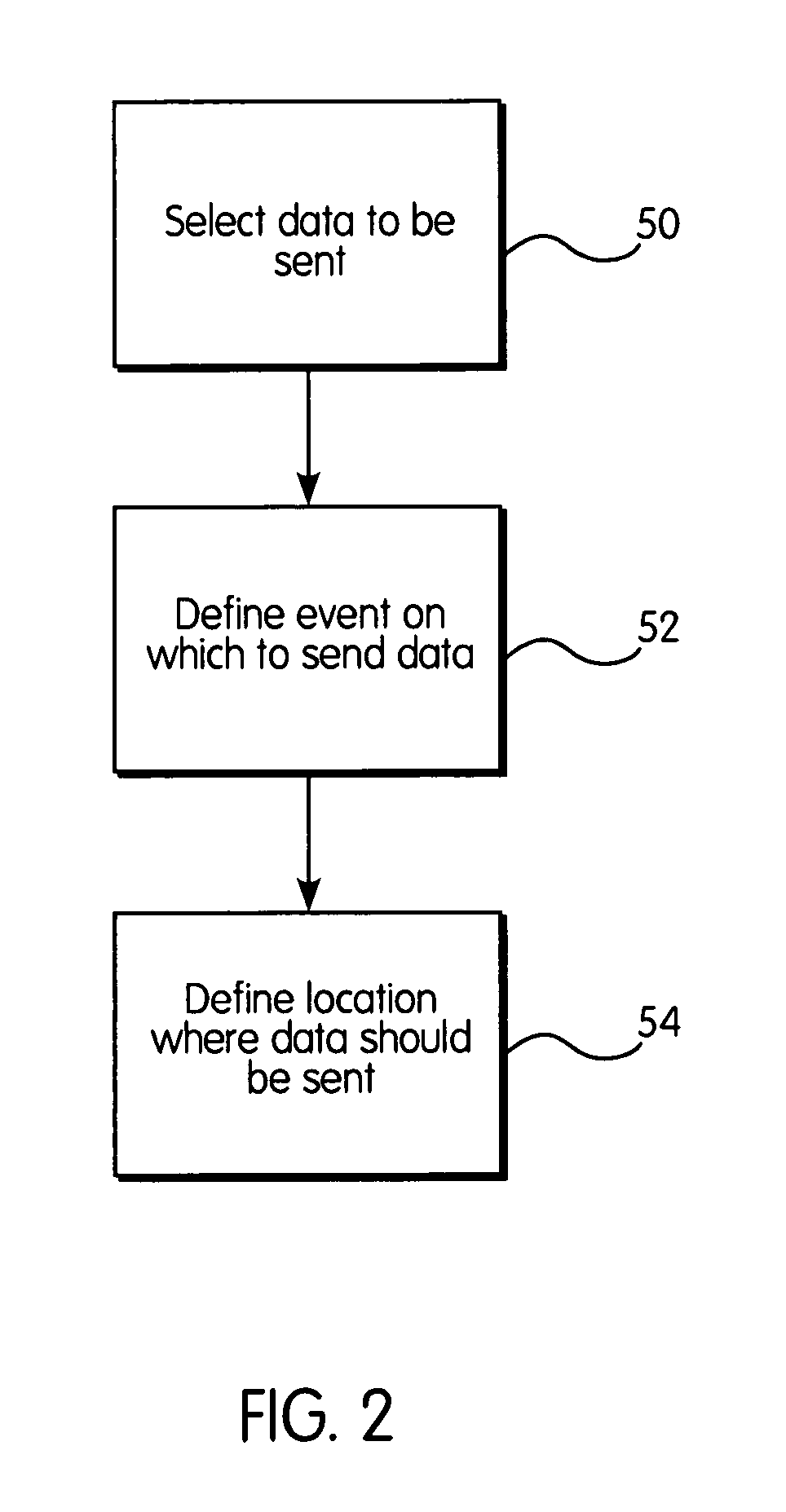
A device for communicating with low level controllers and sensors located on the production floor of an enterprise directly from the top level of the enterprise. The device comprises a controller which interfaces with programmable logic controllers (PLCs) via the backplane into which the PLCs are plugged. Users are able to define triggers that specify the circumstances under which data points within the PLCs are transported to the enterprise level where they may be stored in a database or sent directly to enterprise application via one of a number of possible transfer protocols. The invention also includes a software client which allows users to set up transfer triggers and view data points on the PLCs in real time.
Owner:TELIT TECH CYPRUS LTD
Enterprise application deployment and management system for multiple tenants
ActiveCN105323282AEasy to addFlexible Service Adaptation EngineData switching networksResource isolationComposite application
The invention relates to an enterprise application deployment and management system for multiple tenants. A container-based multi-tenant isolation mechanism is realized; the integration and migration of enterprise legacy systems are supported; rich enterprise-level services are provided; SOA architecture-based enterprise-level application development is supported; perfect self-service ability is provided; high availability of a platform can be provided; dynamic expansion and demand-based scalability can be realized; and pure asynchronous intelligent routing is realized. The objective of the invention is to solve problems in multi-tenant resource isolation, compatibility with existing applications and composite application construction in cloud computing technologies for enterprise applications. The enterprise application deployment and management system for multiple tenants has the advantages of multi-tenant safe isolation, seamless migration of enterprise applications and the scalability of applications.
Owner:DIGITAL CHINA INFORMATION SYST
Method for constructing data quanta space in network and distributed file storage system
ActiveCN101188569AEasy to monitorGuaranteed monitoringData switching networksElectric digital data processingTransfer procedureData file
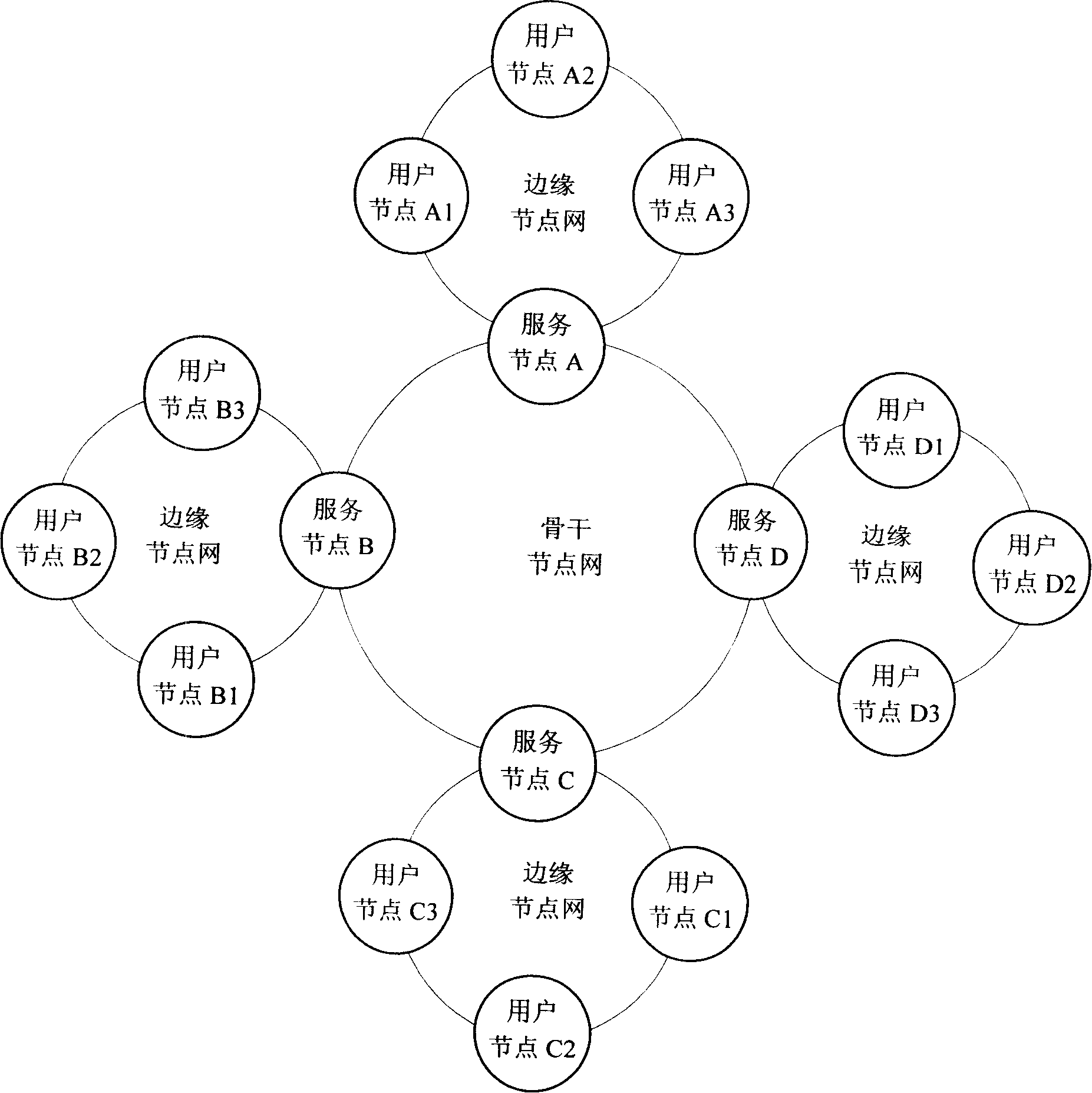
The invention relates to a method for data quantity subspace construction on the network and a distributed document storage system. Through the distributed document storage system, user nodes use service nodes to choose and upload data documents onto usable user nodes in the network, and the distributed nodes are formed; after the user nodes upload the data documents or during the transmission of the data documents, the service nodes adjust the usable nodes in the whole backbone nodes network automatically to distribute tasks which are undertaken, the data documents that the user requests to upload or transmit are distributed and stored in the sharing space of a plurality of user nodes through copying the data documents, a plurality of sharing nodes are formed to be used by the user nodes to download or transmit the documents, so a data storage and transmit quantity subspace is formed in the network. The invention can realize stable, high efficient and opened enterprise-level distributed storage application.
Owner:李明 +1
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20140380488A1Minimize false positivesTrue to riskMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
Data exchange and sharing technology among heterogeneous systems
InactiveCN101957865AReduce investmentNo human intervention requiredSpecial data processing applicationsData platformData source
The invention discloses data exchange and sharing technology among heterogeneous systems. Data and services in different systems can be accessed in a uniform mode. The data exchange and sharing technology can be implemented by the following steps of: 1, establishing an import data source; 2, establishing a data format template; 3, defining a transformation rule; 4, archiving the data format template; 5, importing the data; 6, exporting the data; 7, transforming formats; 8, sorting the data out; 9, recovering the data; 10, encrypting / decrypting and compressing / uncompressing the data; and 11, managing messages. The invention provides a data interface mechanism, enterprise-level data interaction in the systems can be realized by the mechanism, data exchange and sharing of each management system can be realized through an enterprise data platform, and a large number of memory spaces are not required when the data are processed, so that investment in memory equipment can be reduced; and data processing and transmission are performed on line without manual intervention, so that maintenance cost can be reduced.
Owner:杭州新中大科技股份有限公司
RFID with two tier connectivity, RFID in the PLC rack, secure RFID tags and RFID multiplexer system
InactiveUS20070143162A1Easy to integrateMaintain securityProgramme controlDigital data processing detailsMultiplexingMultiplexer
A device by which RFID data can pass from the RFID reader, or from the plant floor PLC and reader, to business applications at the enterprise level. The RFID tag date is easily integrated into a PLC for integration with other equipment. The security of the overall system is maintained by only allowing tag information to be available to authenticated users by means of active or passive tags and the use of certificates and encryption during the data transmission. Multiple RFID reader device drivers can be customized to support any number of readers available in the marketplace, with each RFID reader including its own data structure, protocol and handshaking methodology for communication. Additionally, a set of run time and configuration tools is provided which allow for an easier integration of RFID tag data into the enterprise architecture for use by other business applications.
Owner:ILS TECH INC
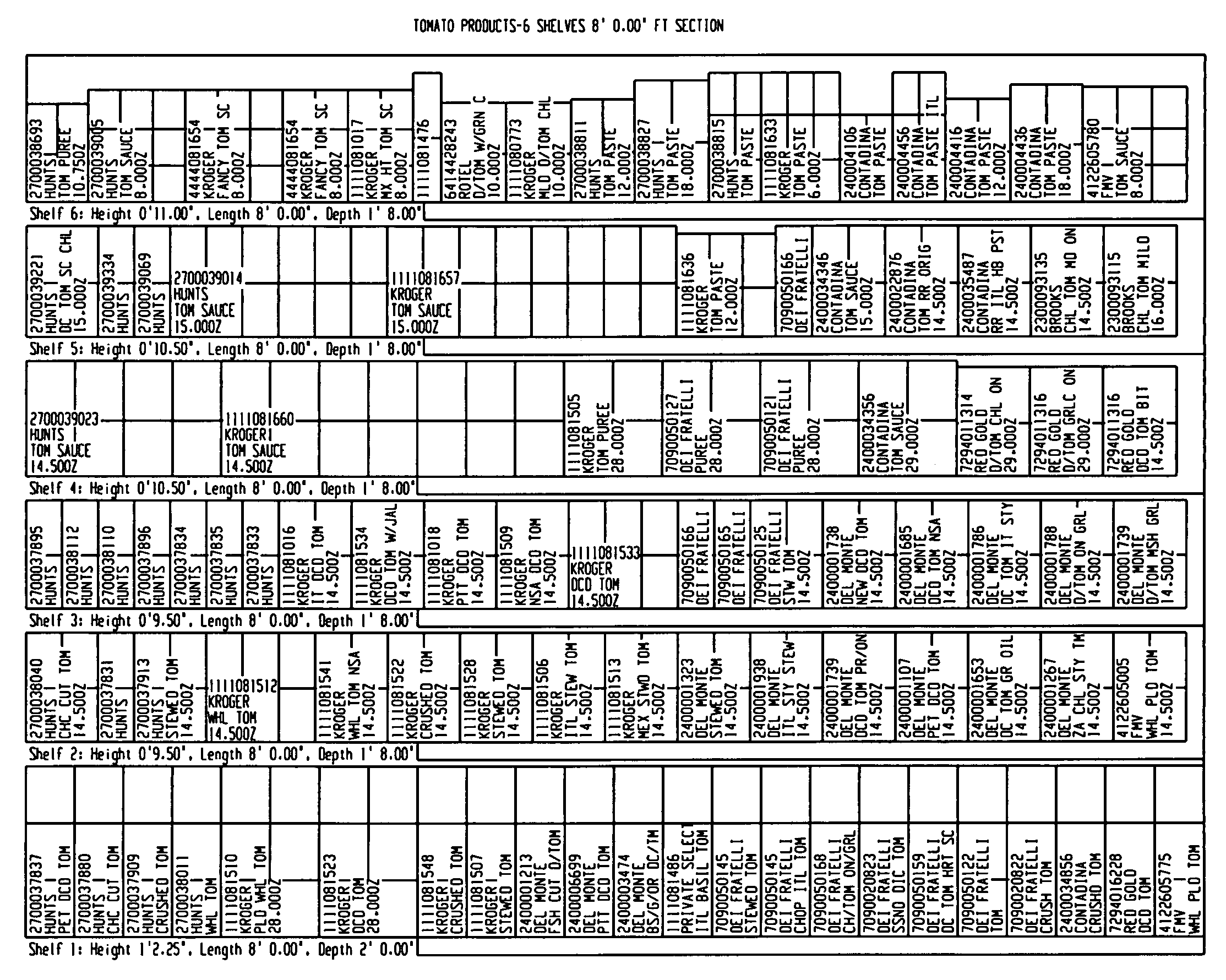
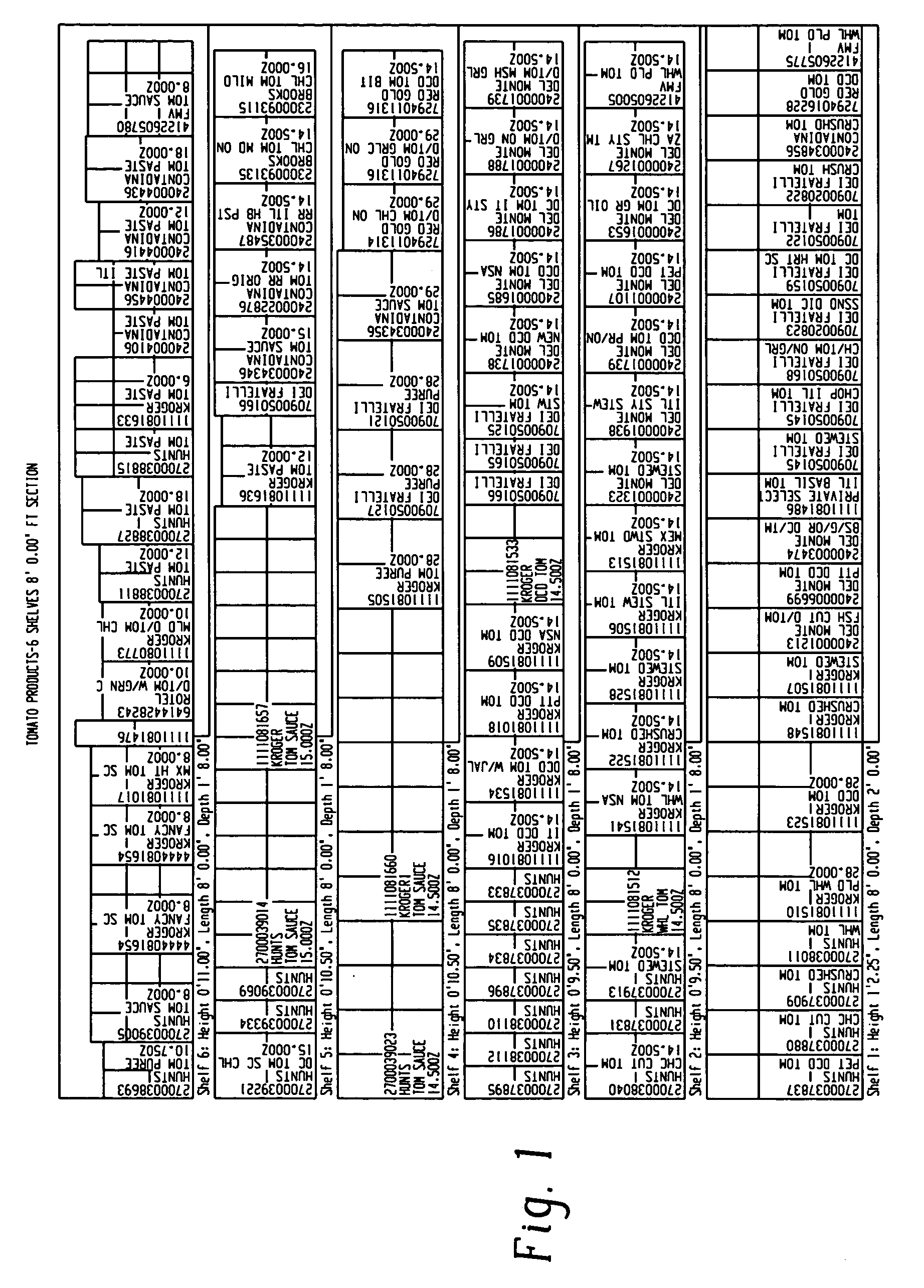
System and method for mapping of planograms
A method for storing and organizing item arrangement information for an enterprise is provided. Standardized item arrangement maps are generated at the enterprise level and disseminated to stores within the enterprise. Managers create store maps consisting of compilations of the item arrangement maps provided by the enterprise. The resulting store maps define the arrangement of all items within the store. The store maps may be used in conjunction with an inventory system to order items and stock the store. Additionally, store maps may be used with a location information system to provide item location information to consumers.
Owner:KROGER THE
Enterprise-wide security system for computer devices
InactiveUS20070186275A1Digital data processing detailsUser identity/authority verificationMobile deviceEnterprise level
A system and method for securing data in mobile devices (104) includes a computing mode (102) and a plurality of mobile devices (104). A node security program (202) executed in the computing node (102) interfaces with a device security program (204) executed at a mobile device (104). The computing node (102) is responsible for managing the security based on a node security profile (208) interpreted by a node security program (202) executed in the computing node (102). A device discovery method and arrangement (106) also detects and locates various information (120) about the mobile devices (104) based on a scan profile (206).
Owner:MUSARUBRA US LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com