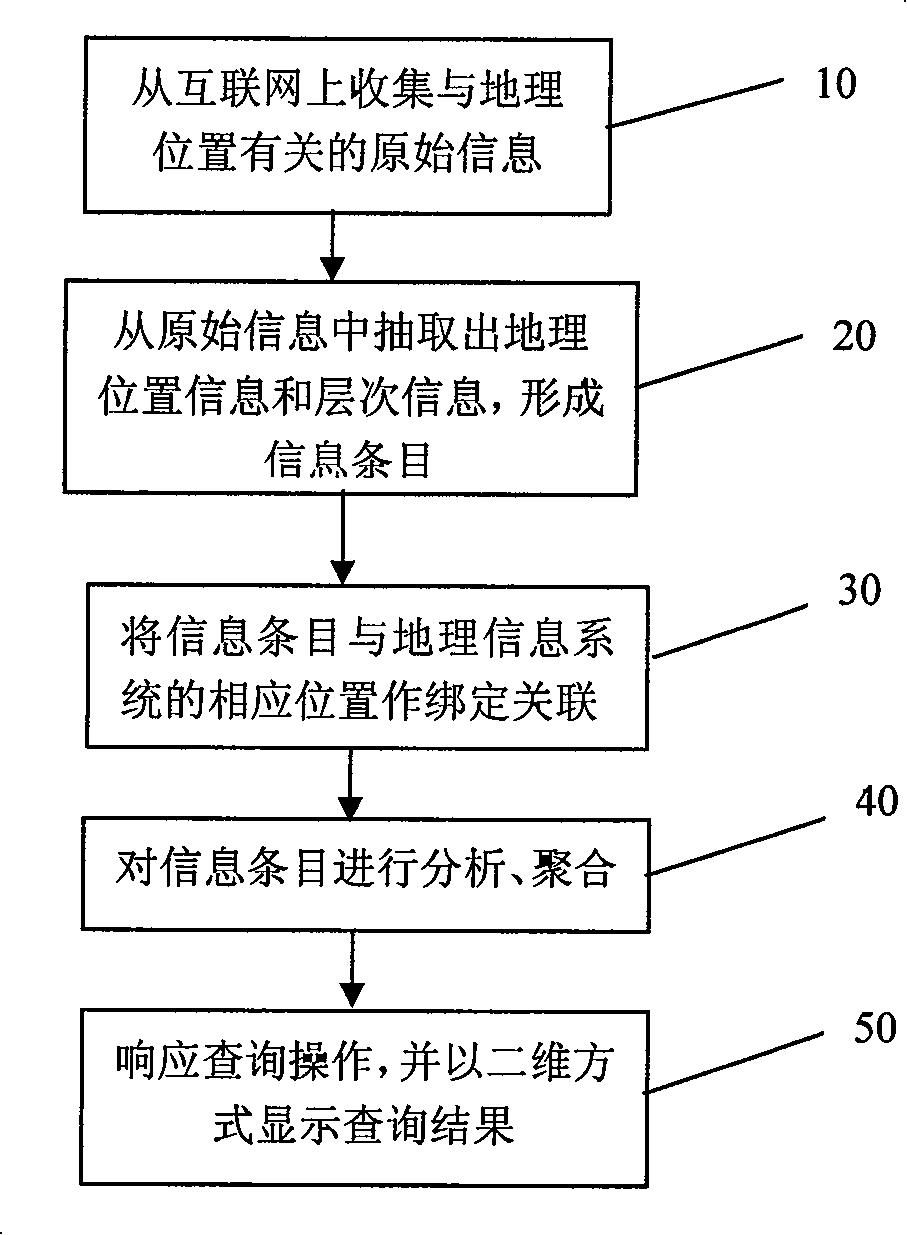
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
407 results about "Information aggregation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
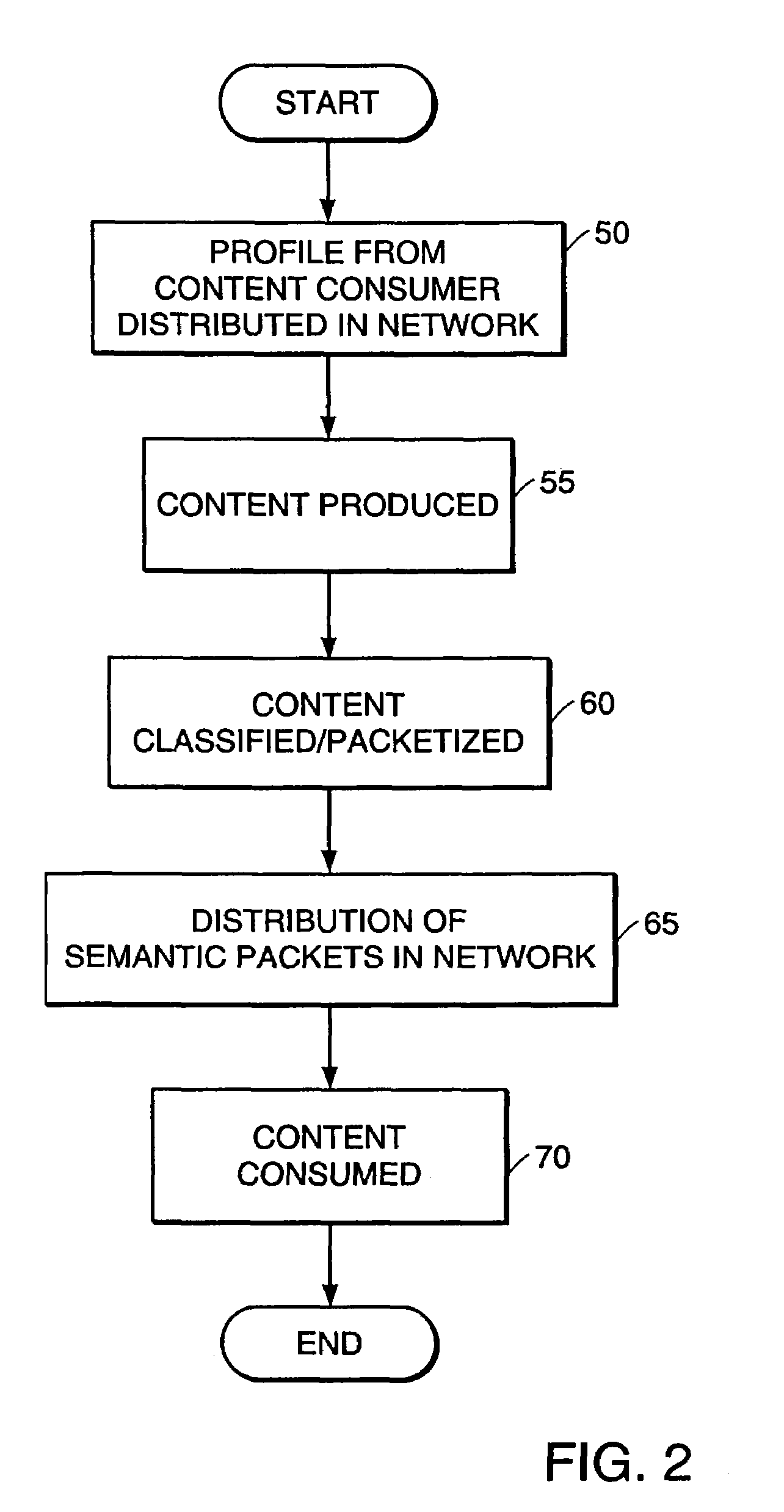
Data aggregation is any process in which information is gathered and expressed in a summary form, for purposes such as statistical analysis. A common aggregation purpose is to get more information about particular groups based on specific variables such as age, profession, or income. The information about such groups can then be used...
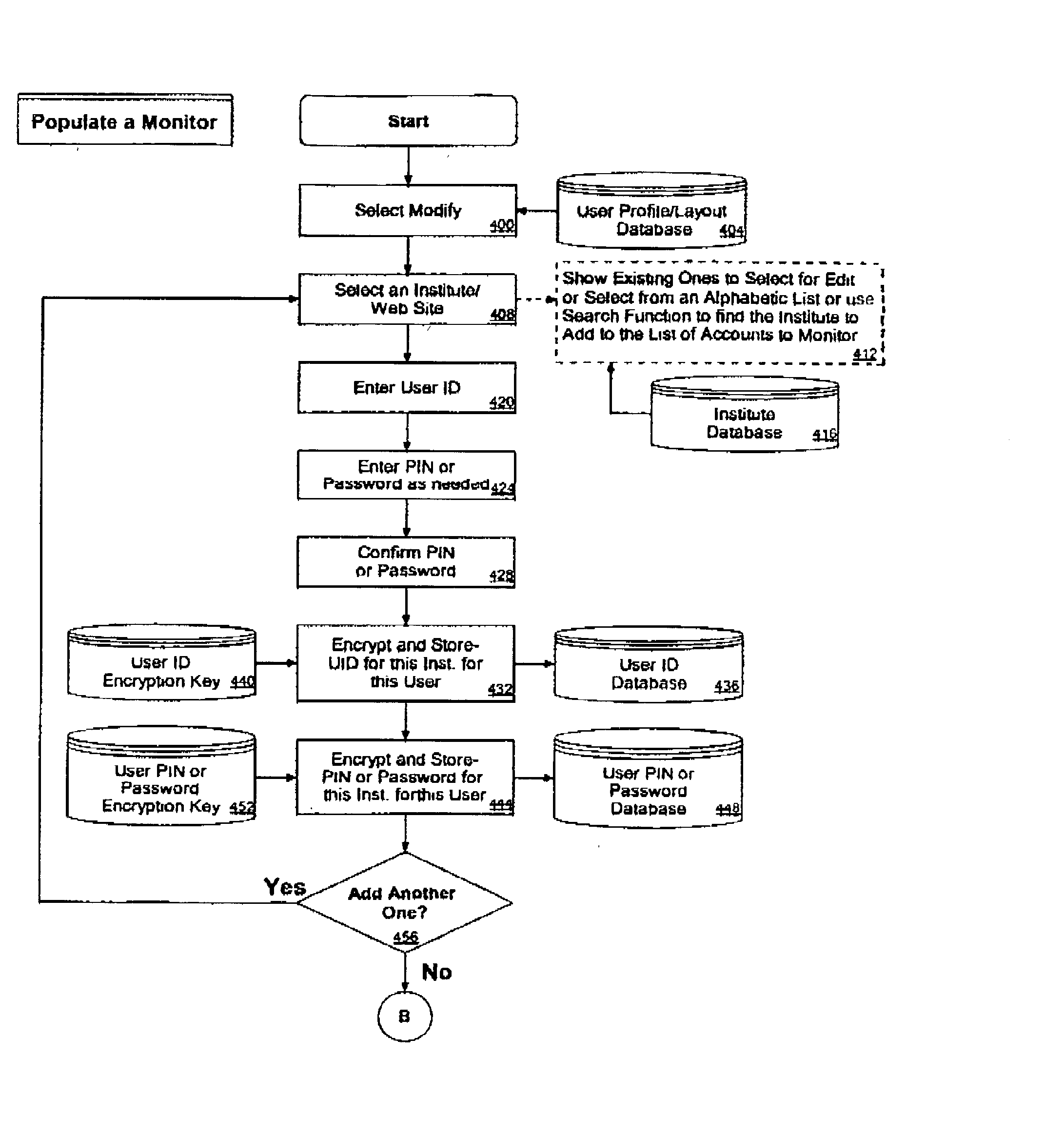
Secure selective sharing of account information on an internet information aggregation system
InactiveUS7120928B2Preserve security and confidentialityCommunication securityDigital data processing detailsUser identity/authority verificationThe InternetCode distribution
Owner:FINASTRA USA CORP
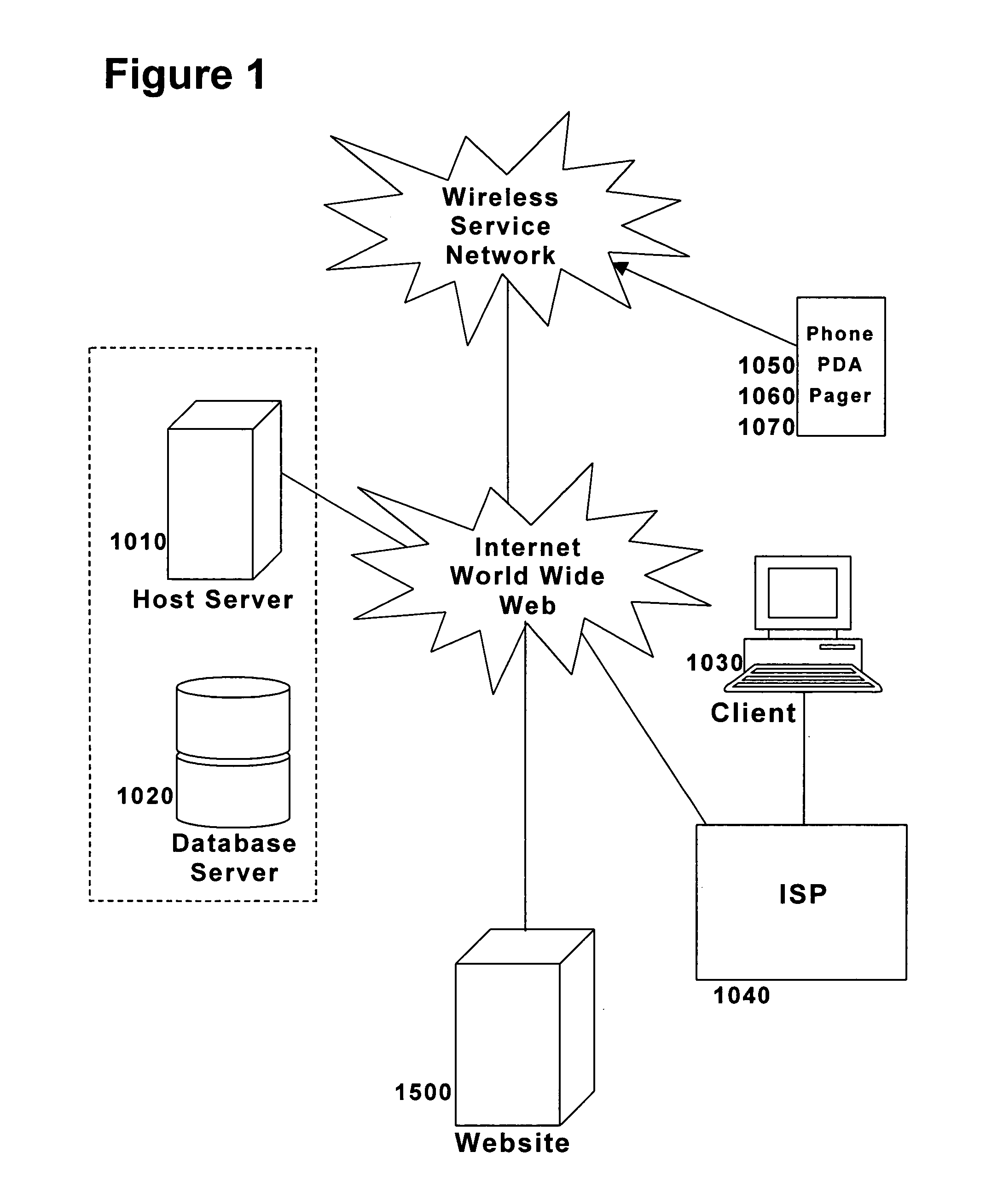
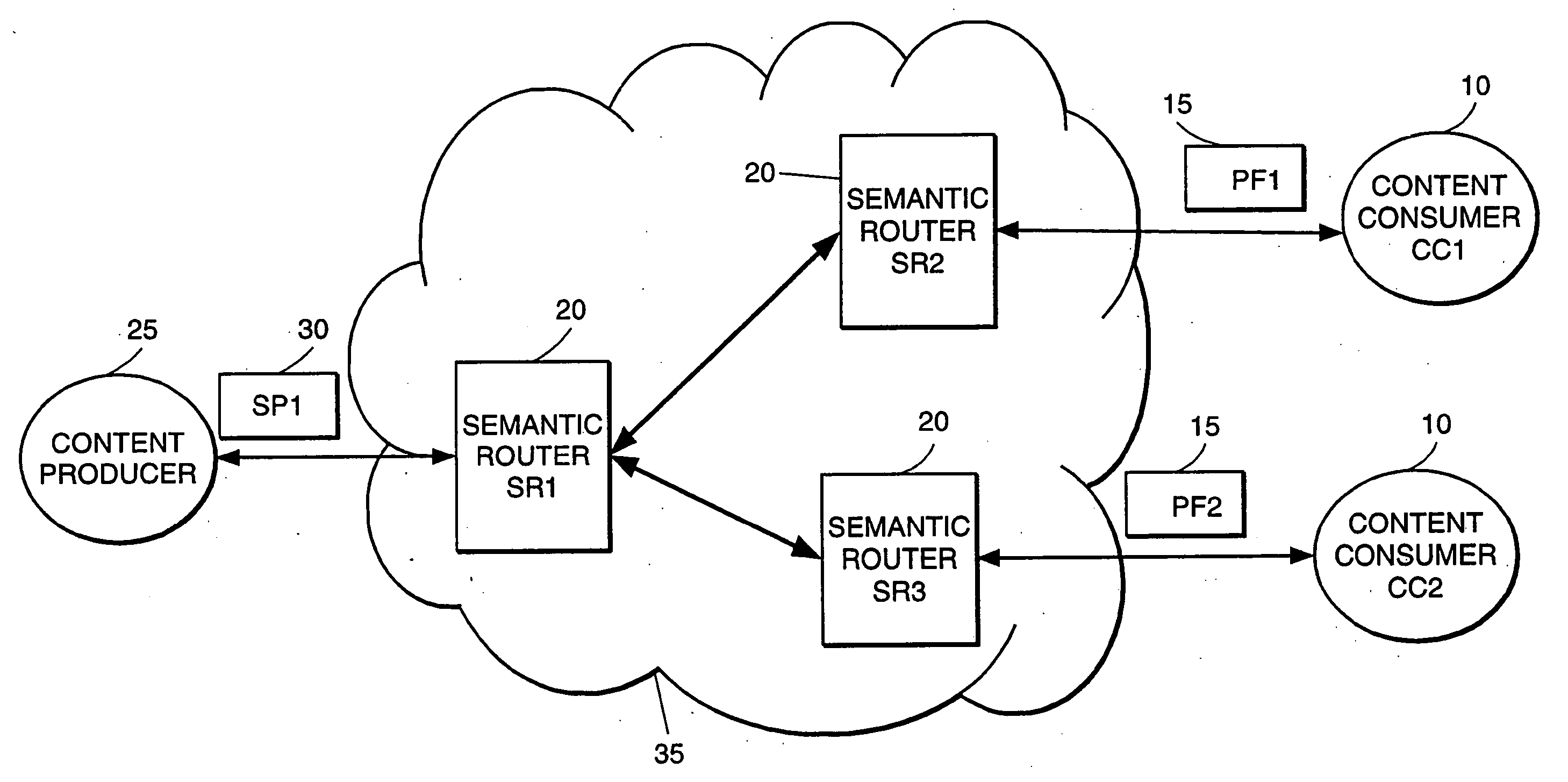
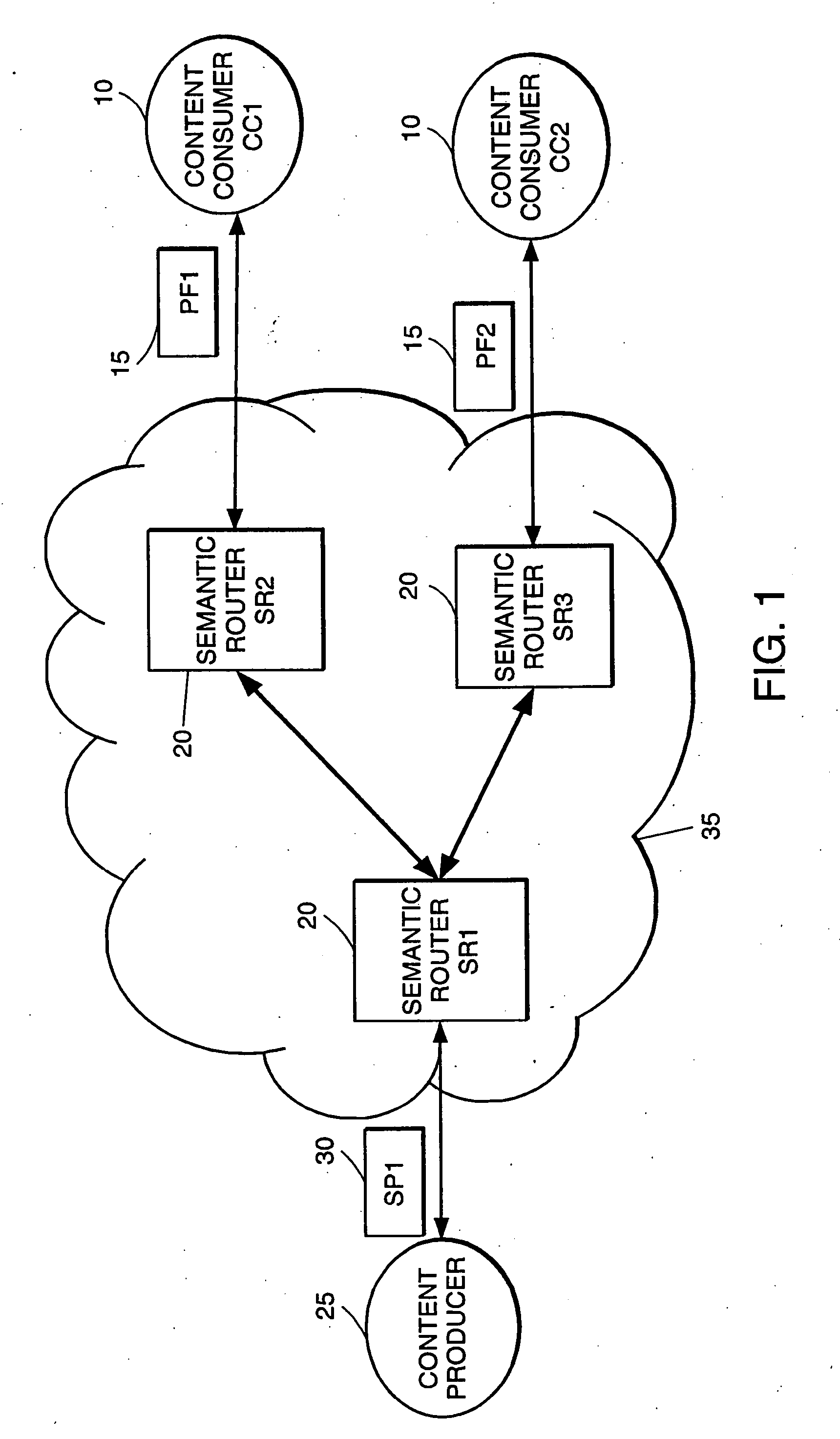
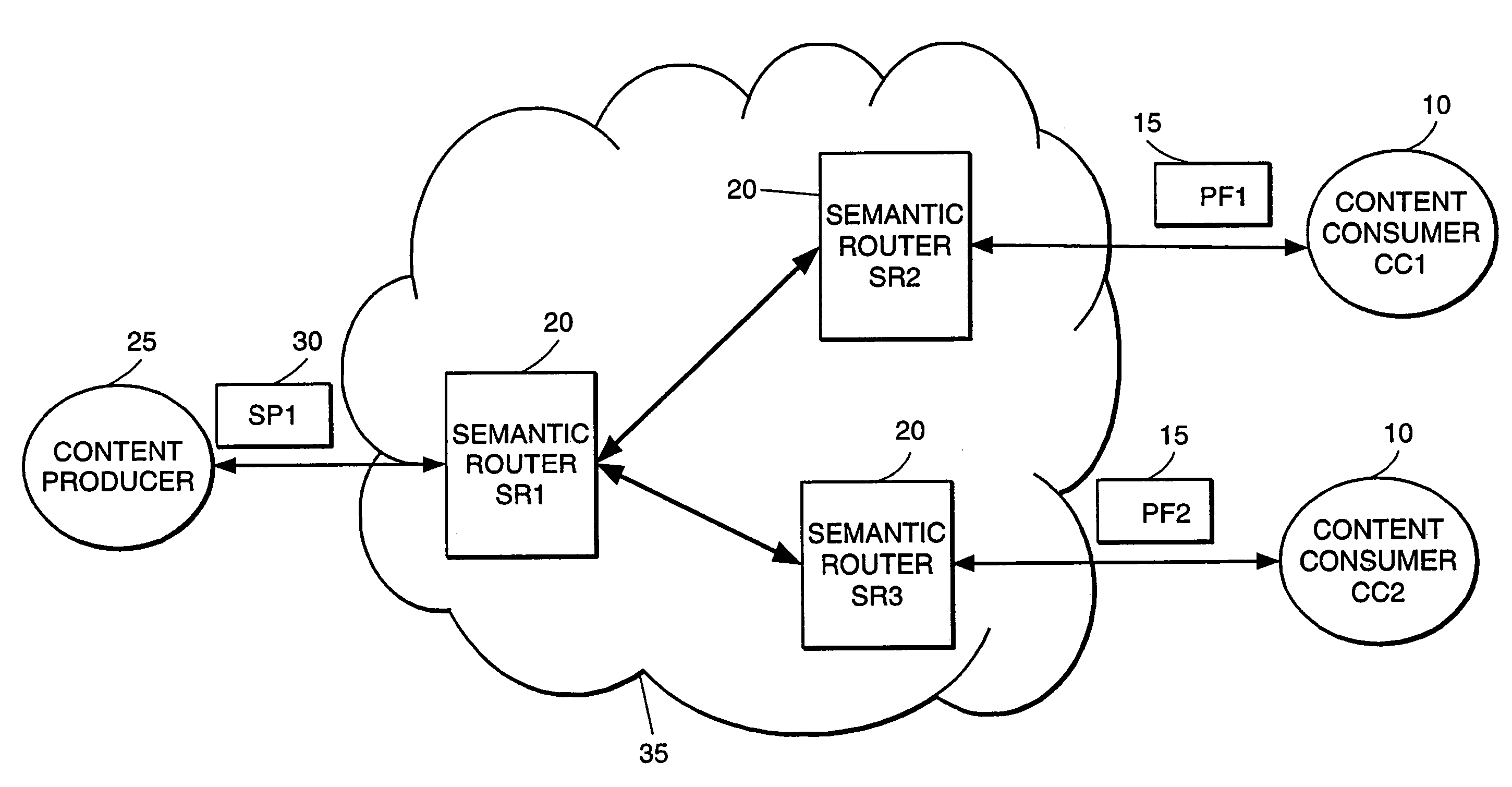
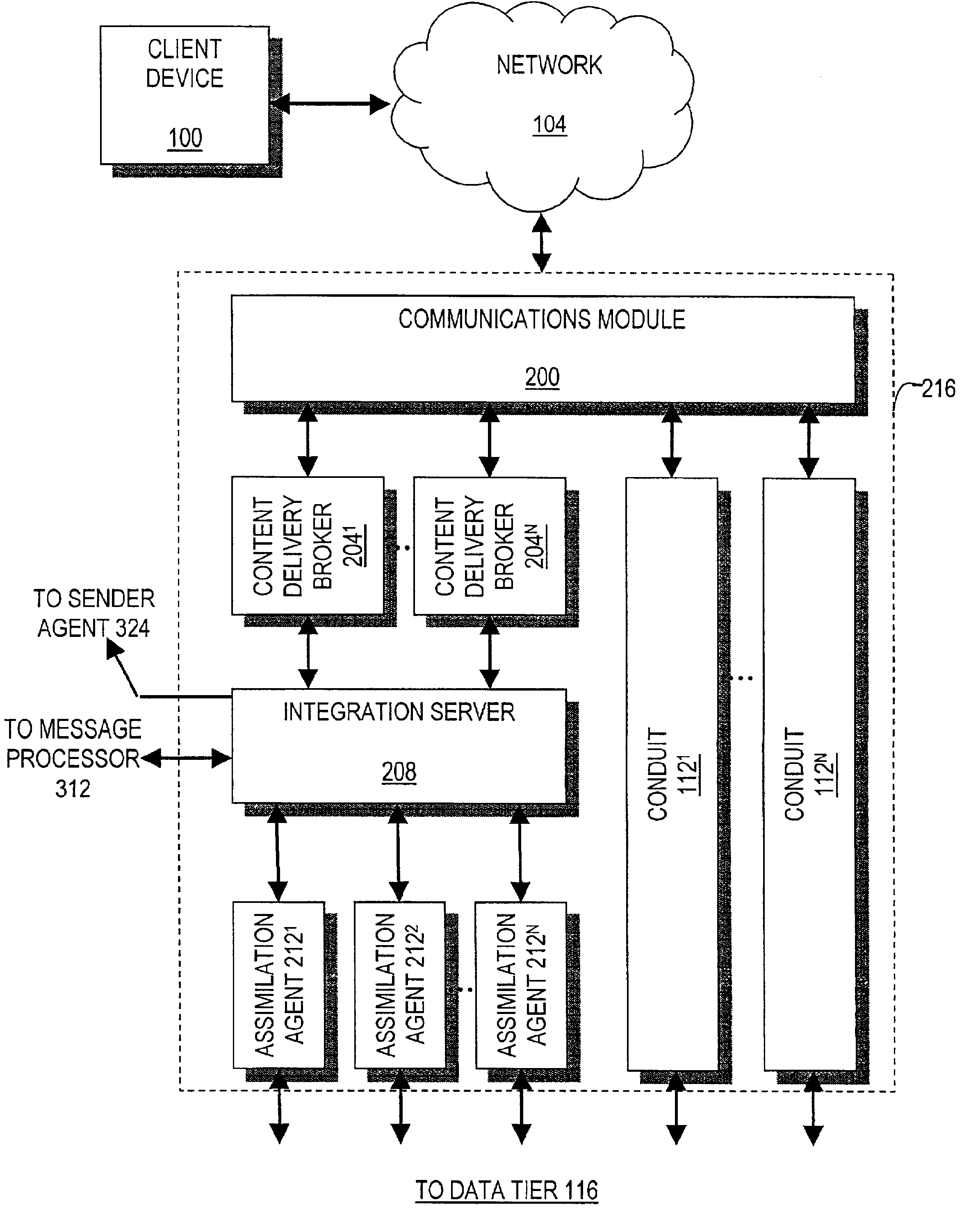
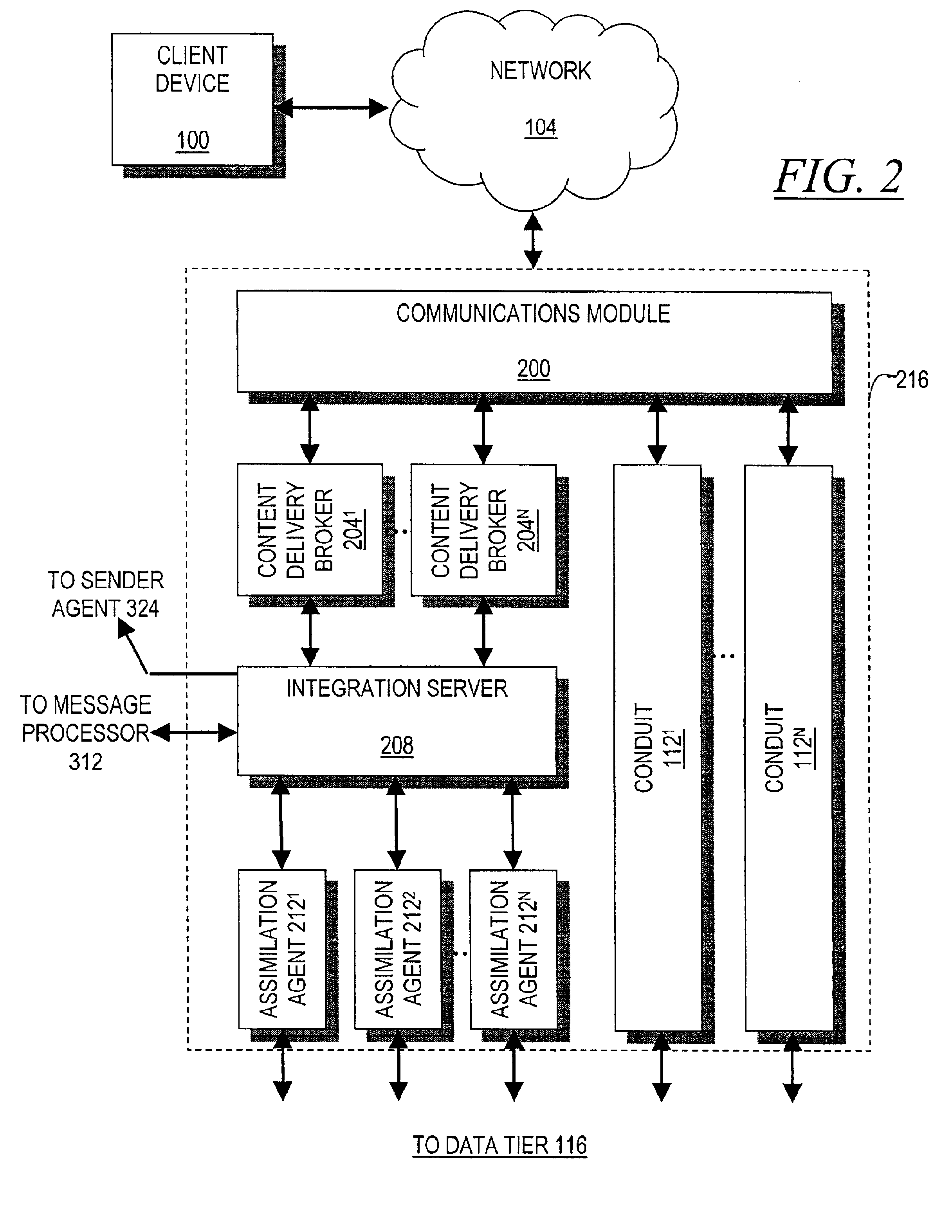
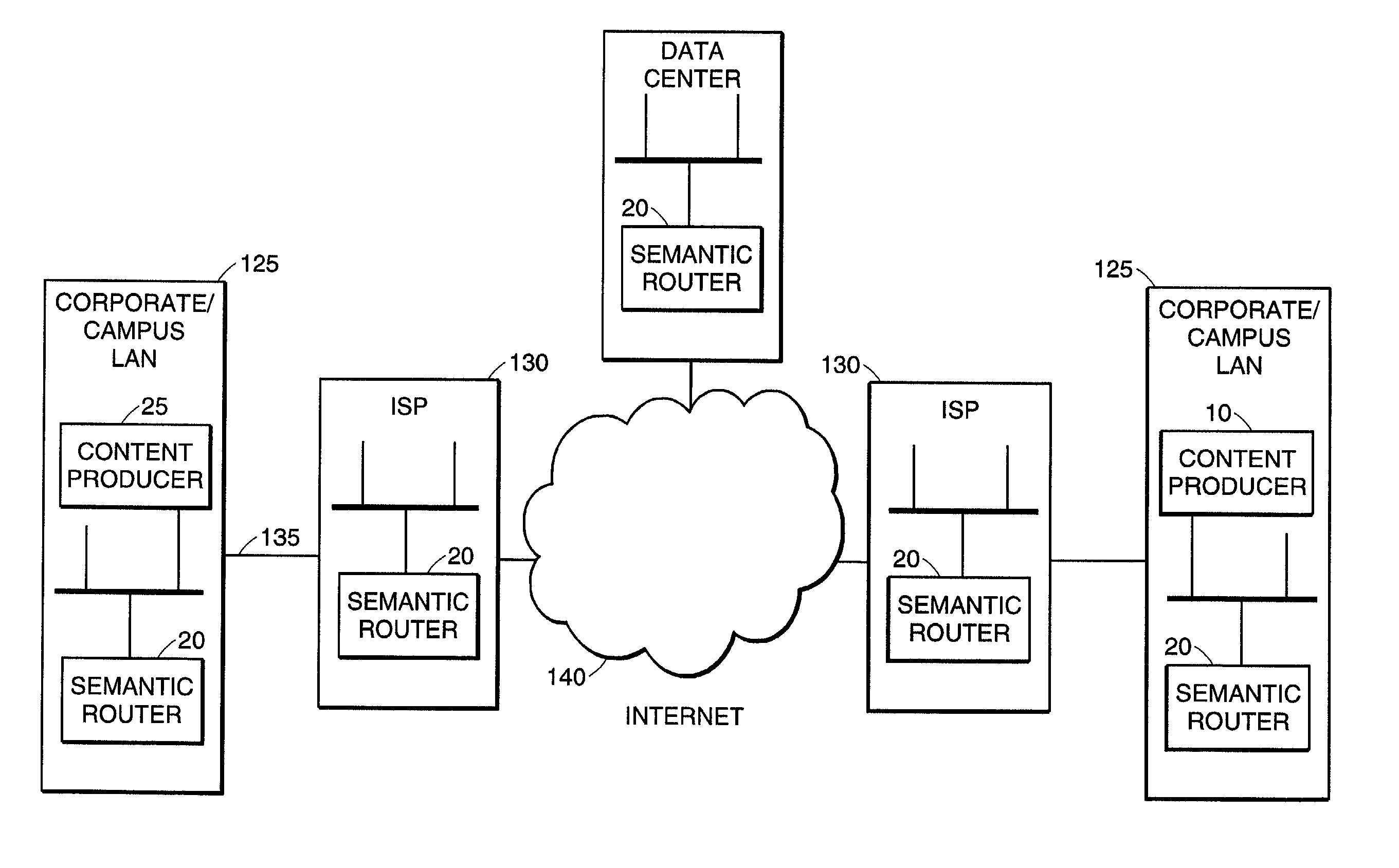
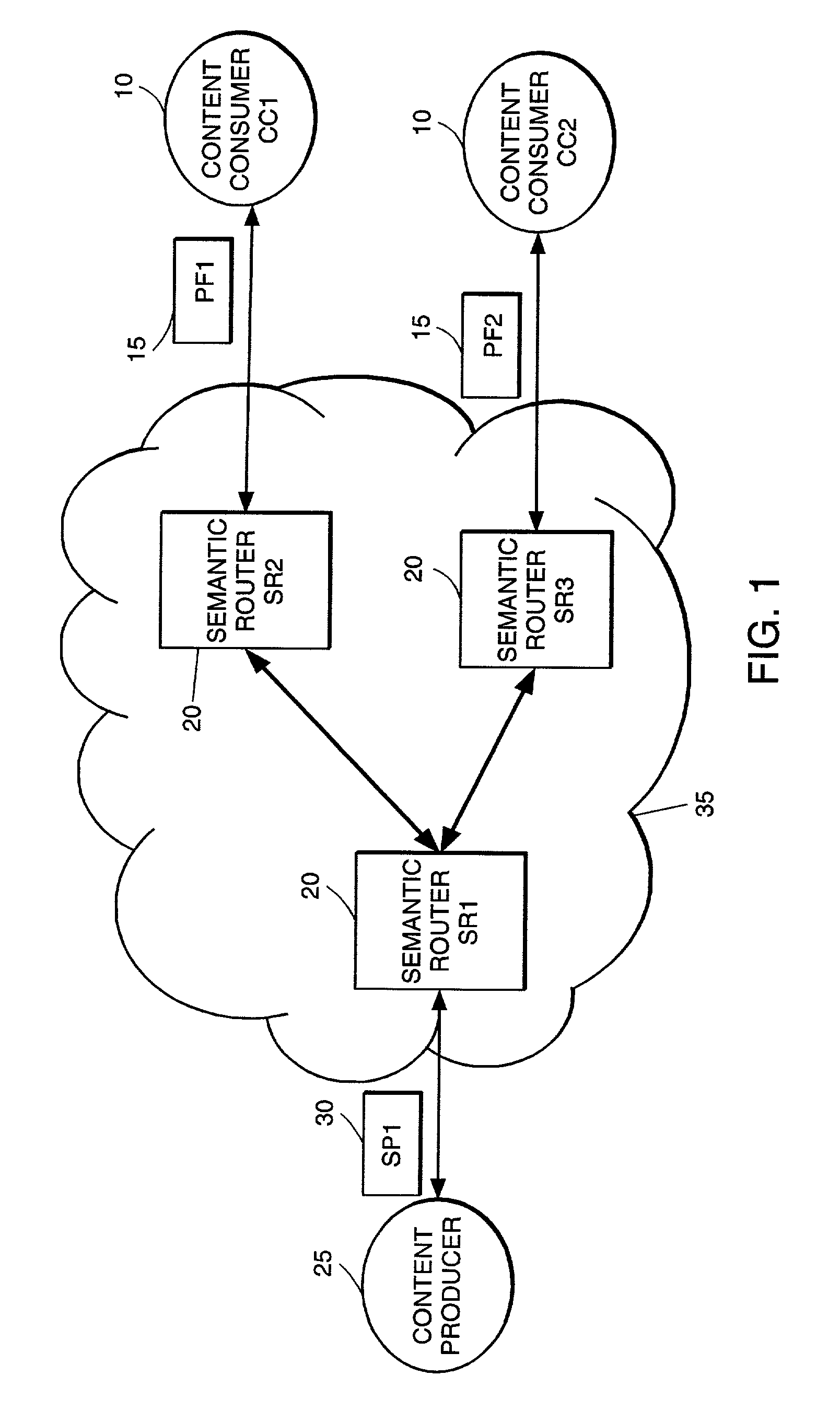
High-performance addressing and routing of data packets with semantically descriptive labels in a computer network
InactiveUS20070239892A1Reduce storageEasy to operateDigital computer detailsData switching networksRouting tableNetwork packet
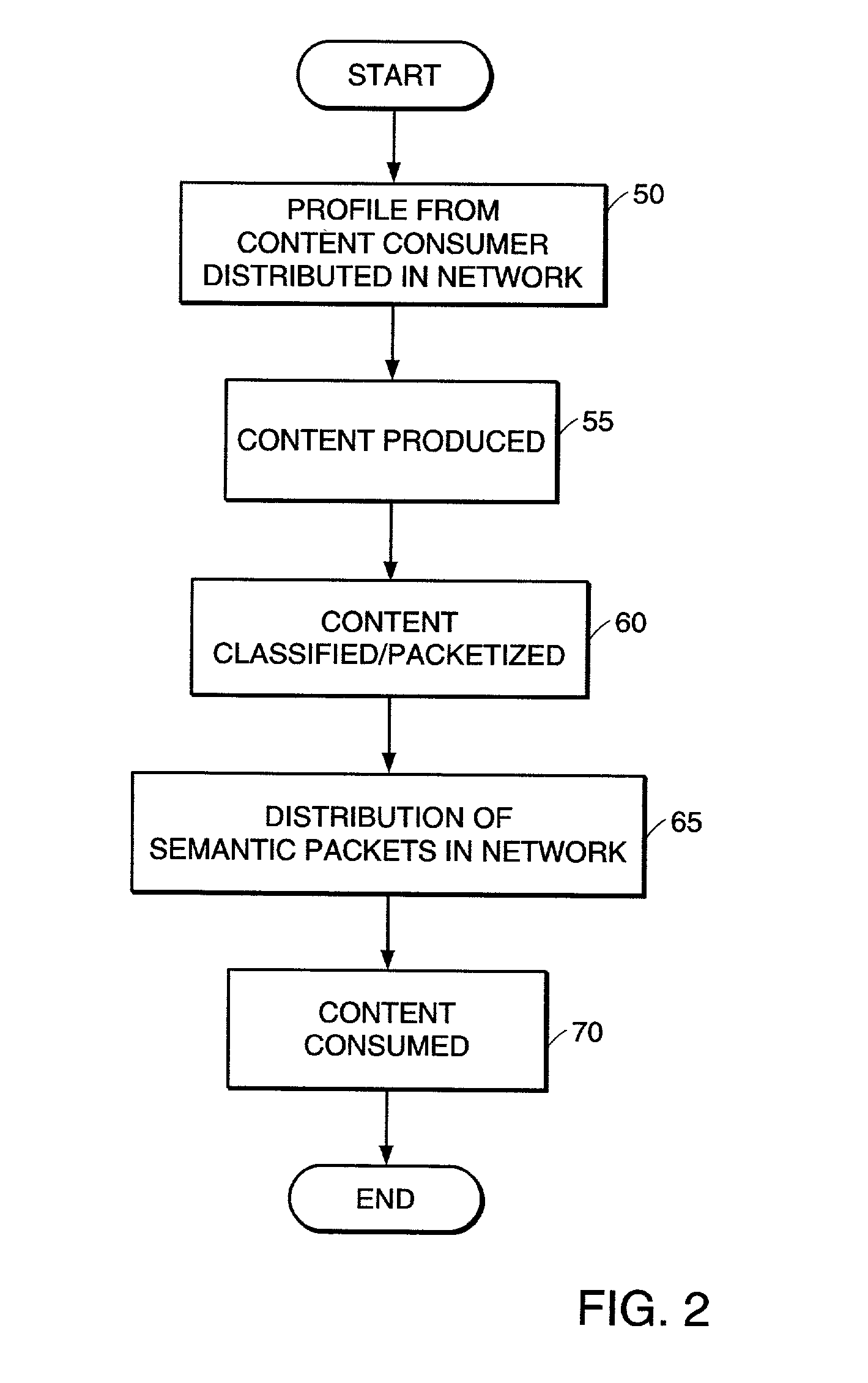
A method, system and apparatus for routing data through a network based on the content or semantics of the data. Semantic routing engines route the data through the network based upon information maintained in routing tables. The routing tables used to route the content through the network are derived by aggregating information about either content consumers or content producers into ontological
Owner:SEMANDEX NETWORKS
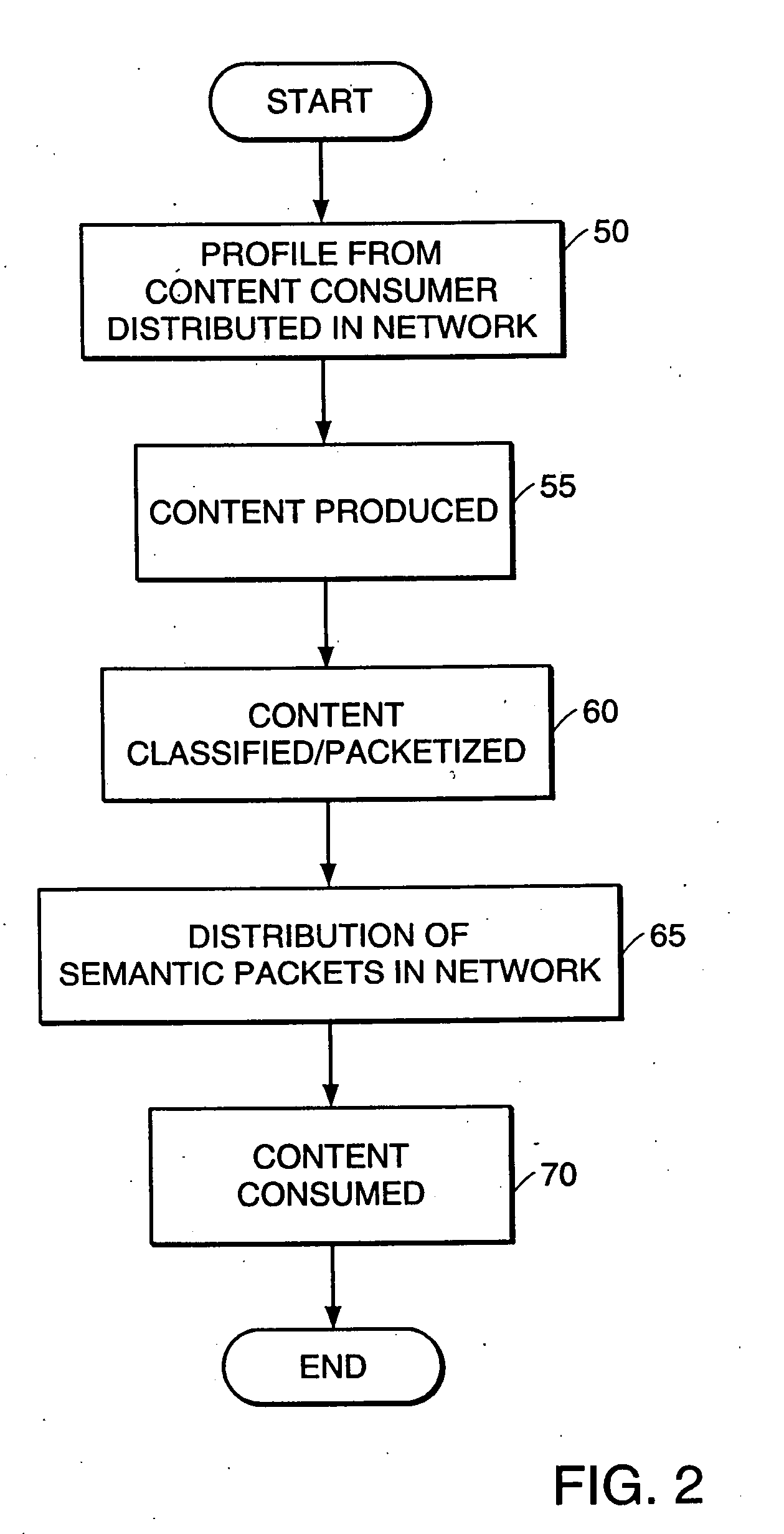
Information aggregation, processing and distribution system
InactiveUS20090094674A1Convenient and accurateEasy to useUser identity/authority verificationUnauthorized memory use protectionThird partyDistribution system
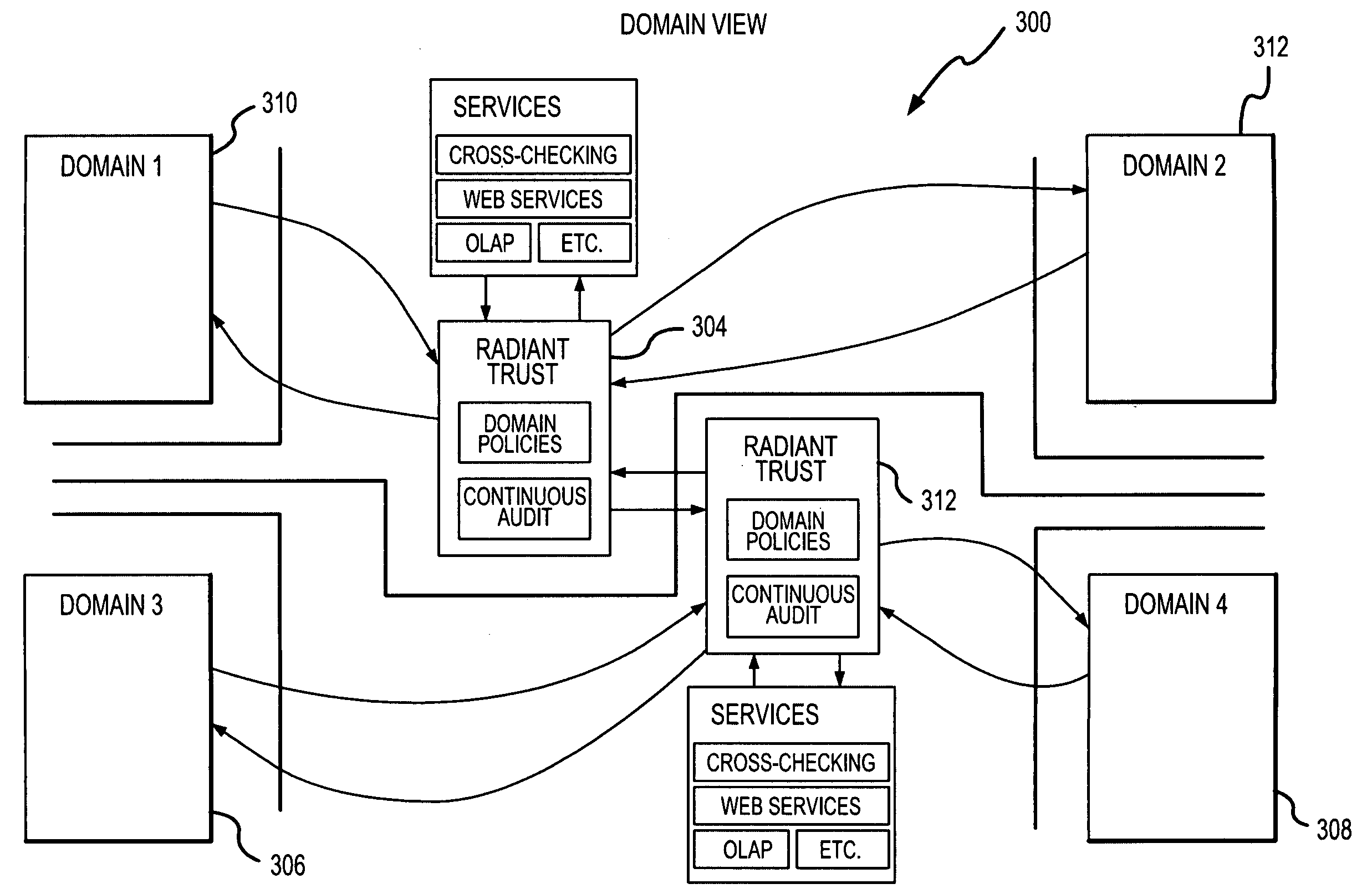
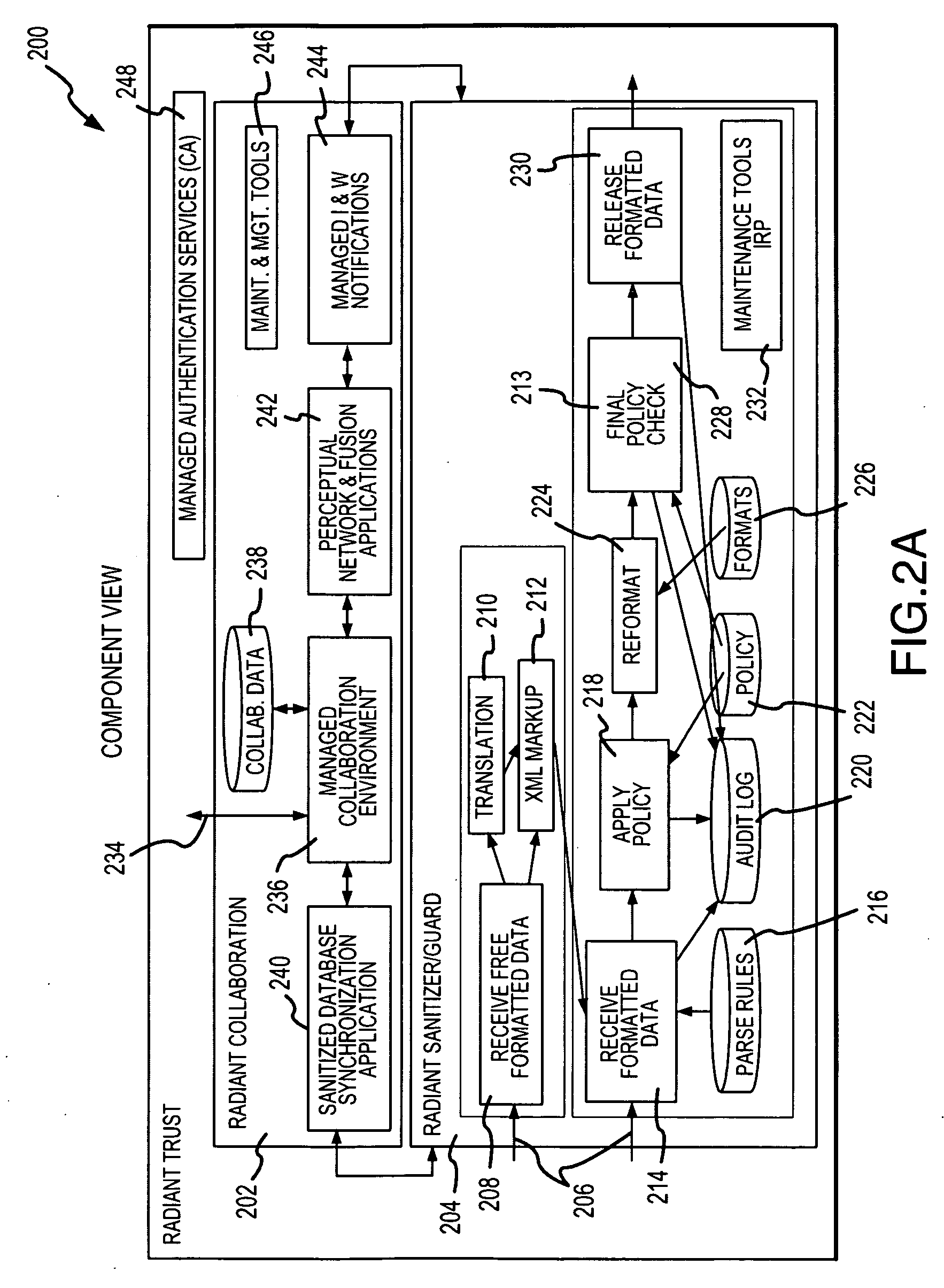
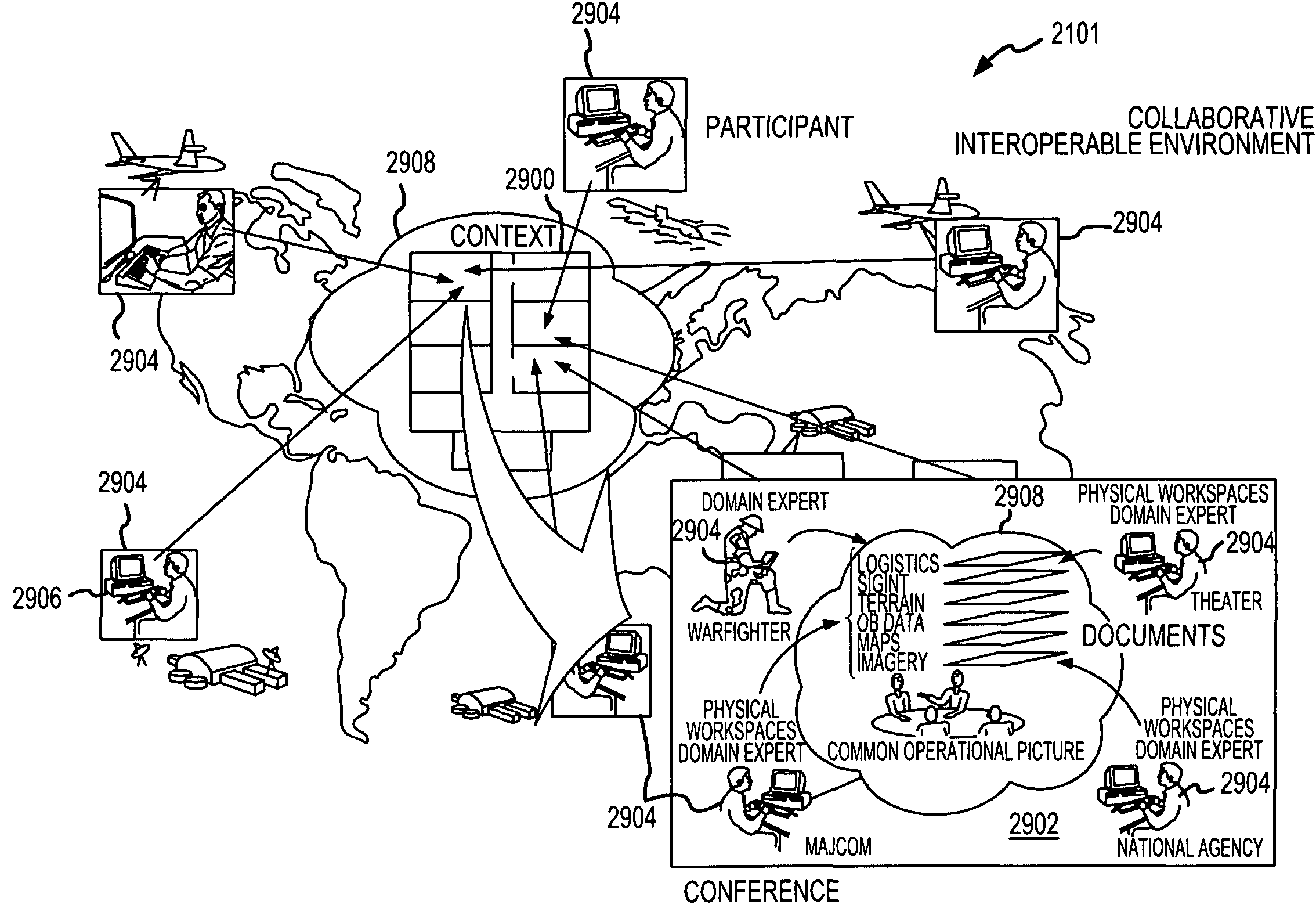
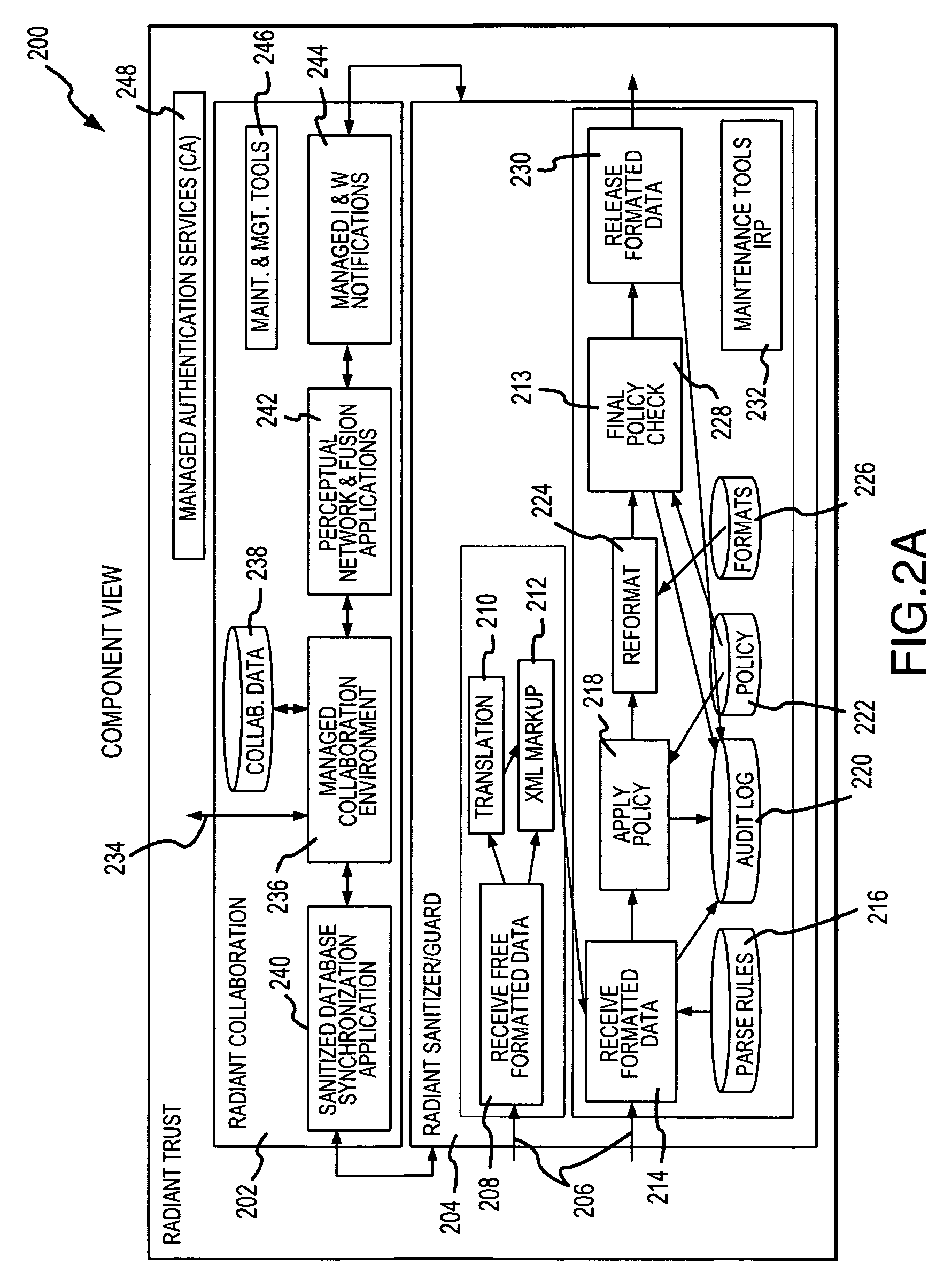
A utility is provided for managing exchanges of information within a context involving multiple users, for example, multi-user network collaboration. The invention enables automatic enforcement of a policy regarding sensitive information. The policy may be negotiated among the users and expressed as multiple rule sets that govern access to a use of sensitive information. The utility also logs activities involving sensitive information to ensure compliance with the policy. These logs can be audited by a third party or automatically processed for audit compliance by the utility. In this manner, an environment of trust is created which encourages fruitful collaboration.
Owner:LOCKHEED MARTIN CORP
Secure selective sharing of account information on an internet information aggregation system
InactiveUS20020194502A1Preserve security and confidentialityCommunication securityDigital data processing detailsComputer security arrangementsThe InternetMobile device
Owner:FINASTRA USA CORP
High-performance addressing and routing of data packets with semantically descriptive labels in a computer network
InactiveUS7555563B2Reduce storageEasy to operateDigital computer detailsData switching networksRouting tableNetwork packet
A method, system and apparatus for routing data through a network based on the content or semantics of the data. Semantic routing engines route the data through the network based upon information maintained in routing tables. The routing tables used to route the content through the network are derived by aggregating information about either content consumers or content producers into ontological.
Owner:SEMANDEX NETWORKS
Methods and apparatus for extendible information aggregation and presentation
InactiveUS6886046B2Reduce effortNatural language data processingMultiple digital computer combinationsExtensible markupClient-side
Methods and apparatus for arbitrarily extendible information aggregation and display. This functionality is achieved by abstracting the components of the system into individual modules which communicate using a platform-independent, extendible markup language such as extensible markup language (XML). A designer adds support for new information sources or client devices by abstracting and encapsulating messages to and from the information source or client device in a wrapper using a platform-independent, extendible markup language such as XML.
Owner:CITRIX SYST INC
Information aggregation, processing and distribution system
InactiveUS7809791B2Convenient and accurateEasy to useUser identity/authority verificationUnauthorized memory use protectionThird partyDistribution system
A utility is provided for managing exchanges of information within a context involving multiple users, for example, multi-user network collaboration. The invention enables automatic enforcement of a policy regarding sensitive information. The policy may be negotiated among the users and expressed as multiple rule sets that govern access to a use of sensitive information. The utility also logs activities involving sensitive information to ensure compliance with the policy. These logs can be audited by a third party or automatically processed for audit compliance by the utility. In this manner, an environment of trust is created which encourages fruitful collaboration.
Owner:LOCKHEED MARTIN CORP
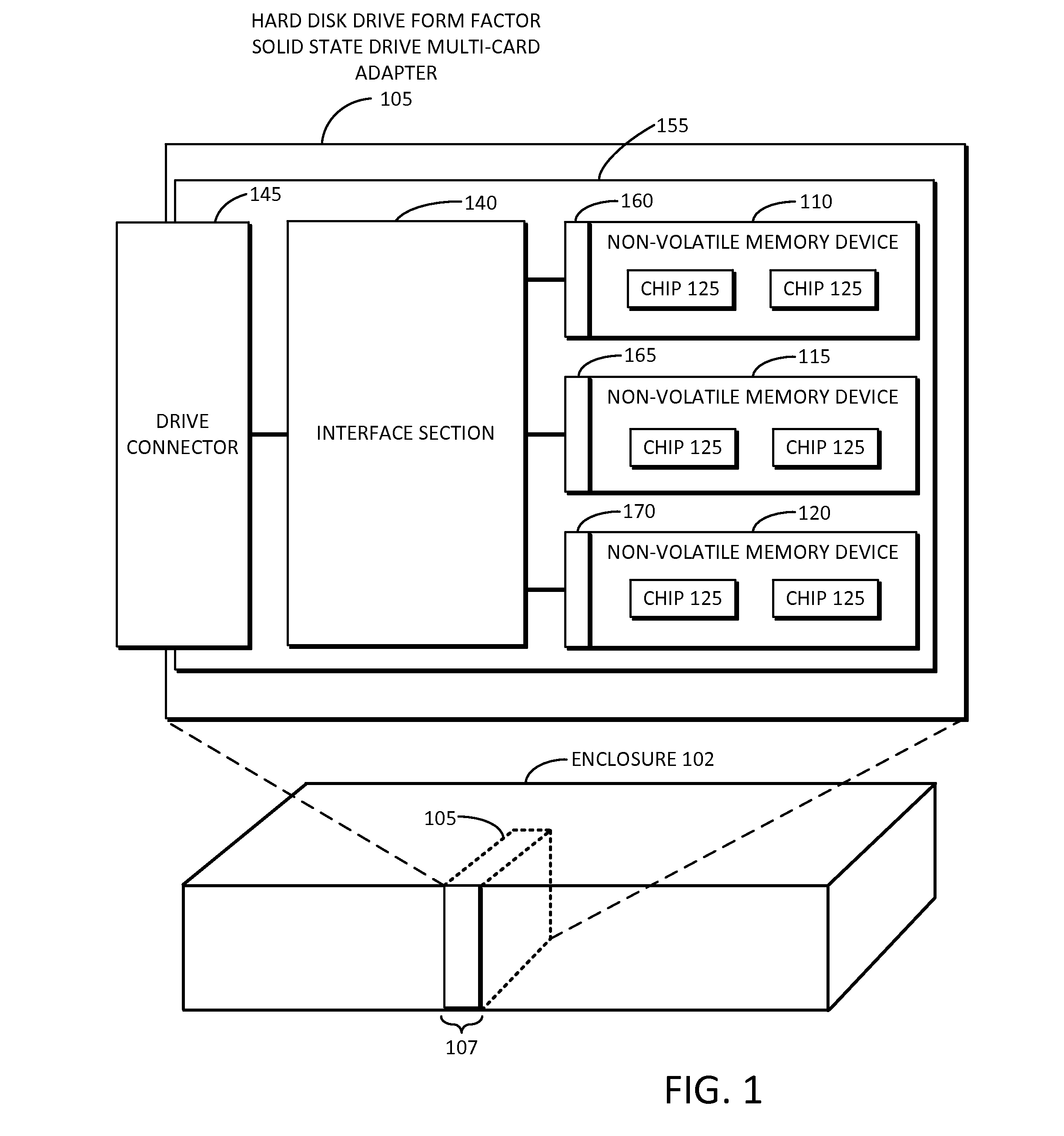
Solid state drive multi-card adapter with integrated processing
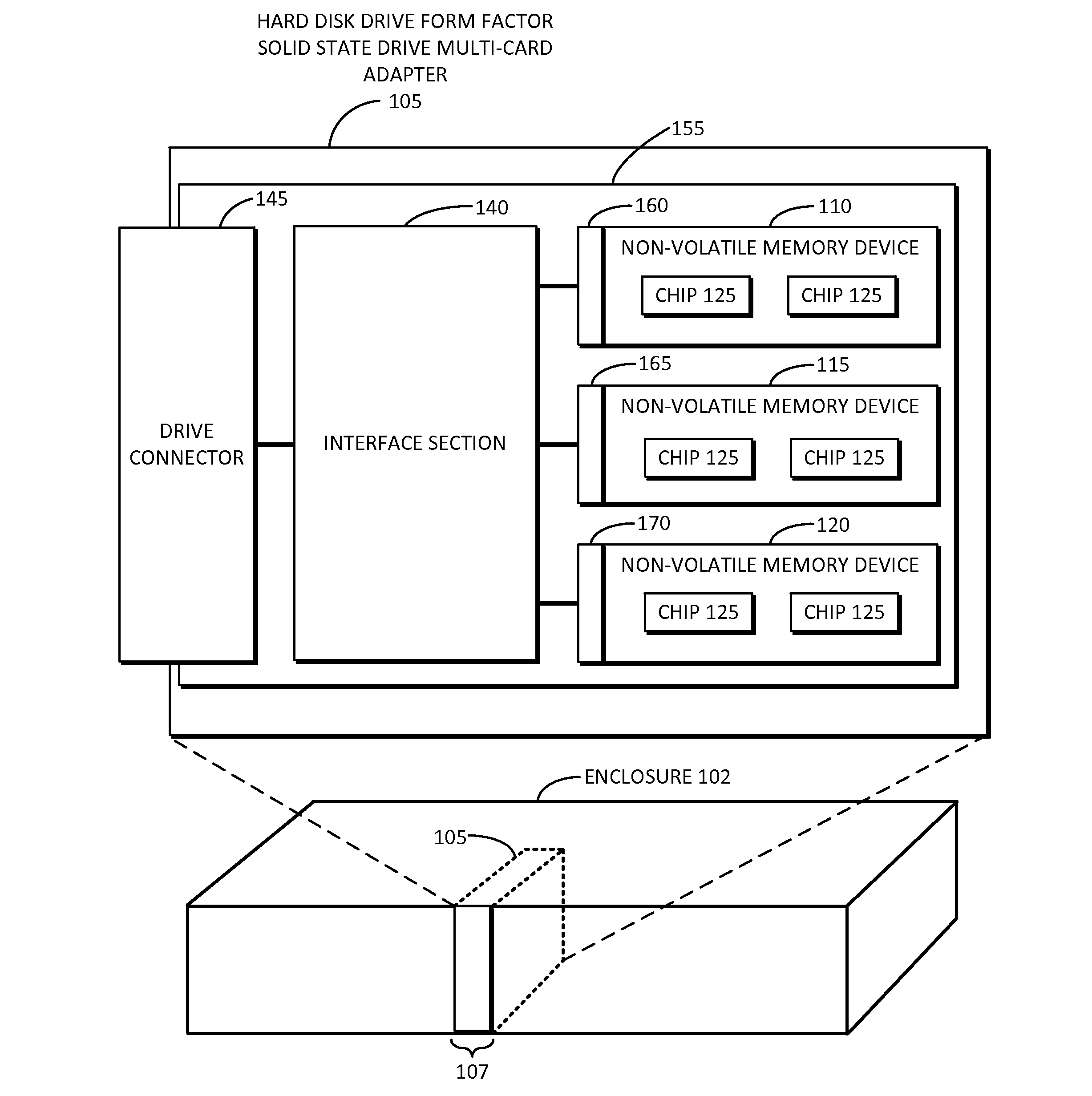
Embodiments of the inventive concept include solid state drive (SSD) multi-card adapters that can include multiple solid state drive cards, which can be incorporated into existing enterprise servers without major architectural changes, thereby enabling the server industry ecosystem to easily integrate evolving solid state drive technologies into servers. The SSD multi-card adapters can include an interface section between various solid state drive cards and drive connector types. The interface section can perform protocol translation, packet switching and routing, data encryption, data compression, management information aggregation, virtualization, and other functions.
Owner:SAMSUNG ELECTRONICS CO LTD
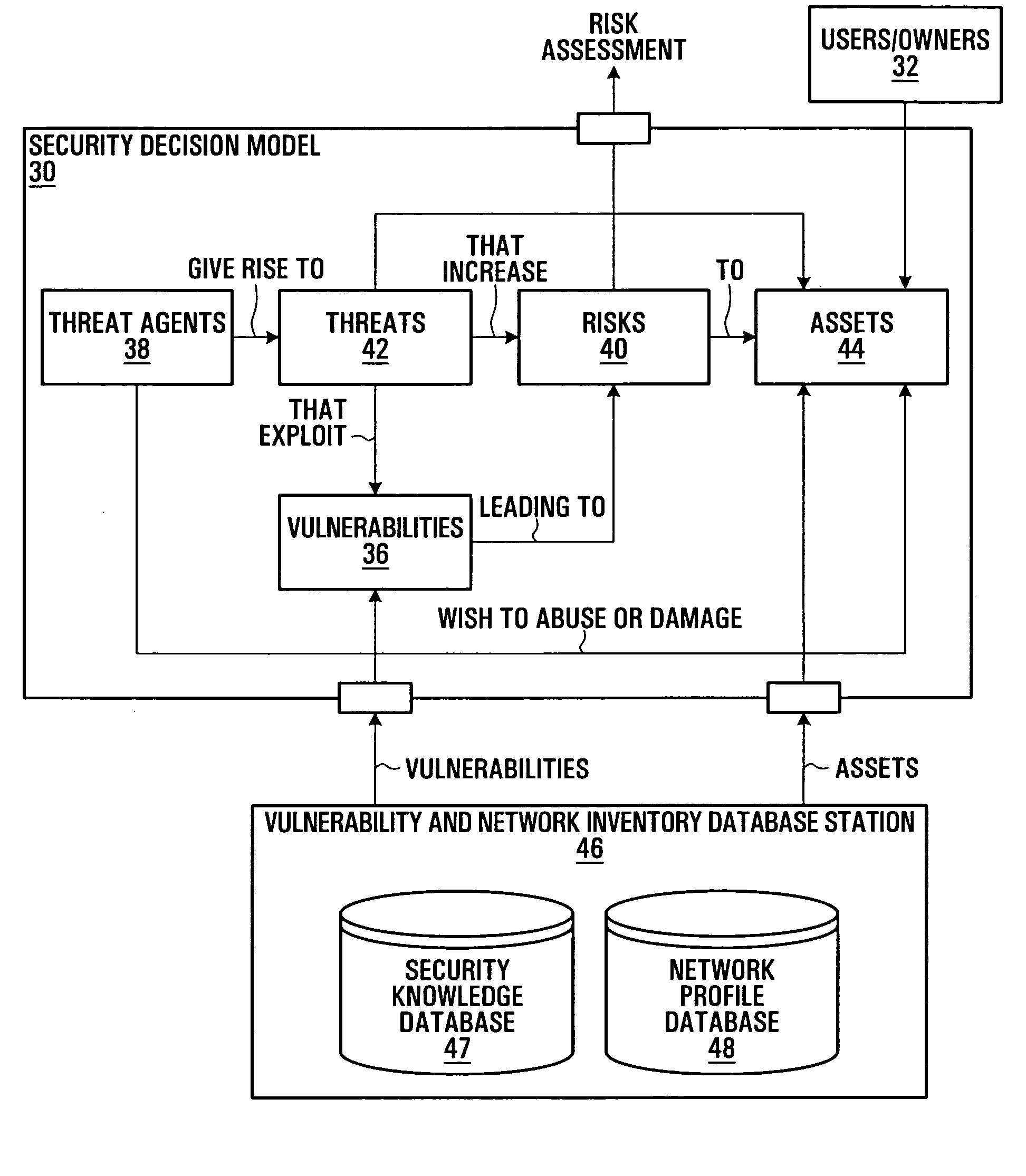
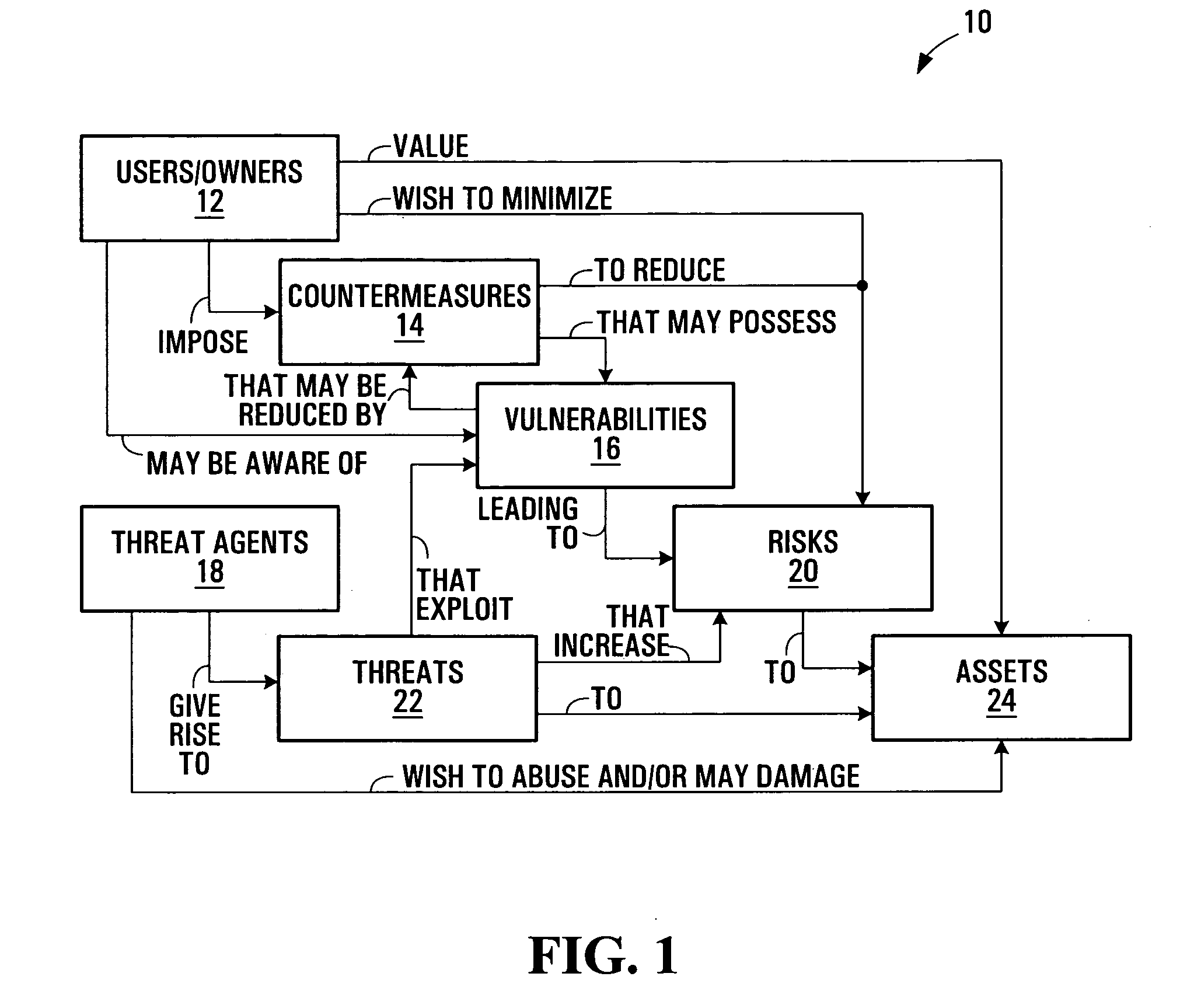
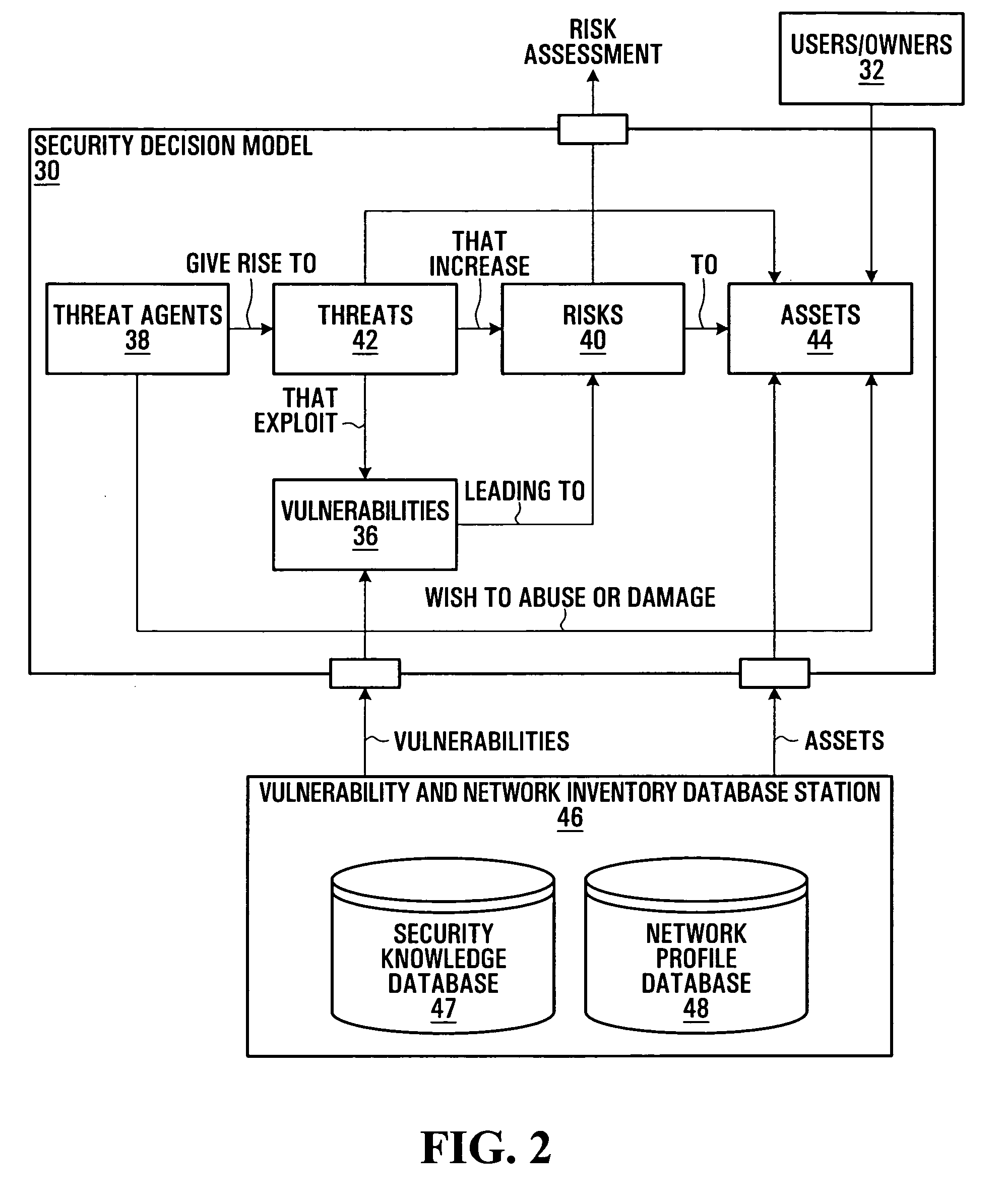
Security vulnerability information aggregation
InactiveUS20070067848A1Memory loss protectionError detection/correctionGraphicsGraphical user interface
Security vulnerability information aggregation techniques are disclosed. Vulnerability information associated with one or more security vulnerabilities is obtained from multiple sources and aggregated into respective unified vulnerability definitions for the one or more security vulnerabilities. Aggregation may involve format conversion, content aggregation, or both in some embodiments. Unified vulnerability definitions may be distributed to vulnerability information consumers in accordance with consumer-specific policies. Storage of vulnerability information received from the sources may allow the aggregation process to be performed on existing vulnerability information “retro-actively”. Related data structures and Graphical User Interfaces (GUIs) are also disclosed.
Owner:NOKIA TECHNOLOGLES OY
Scalable system for wide area surveillance
InactiveUS20080211915A1Character and pattern recognitionClosed circuit television systemsScalable systemWide area
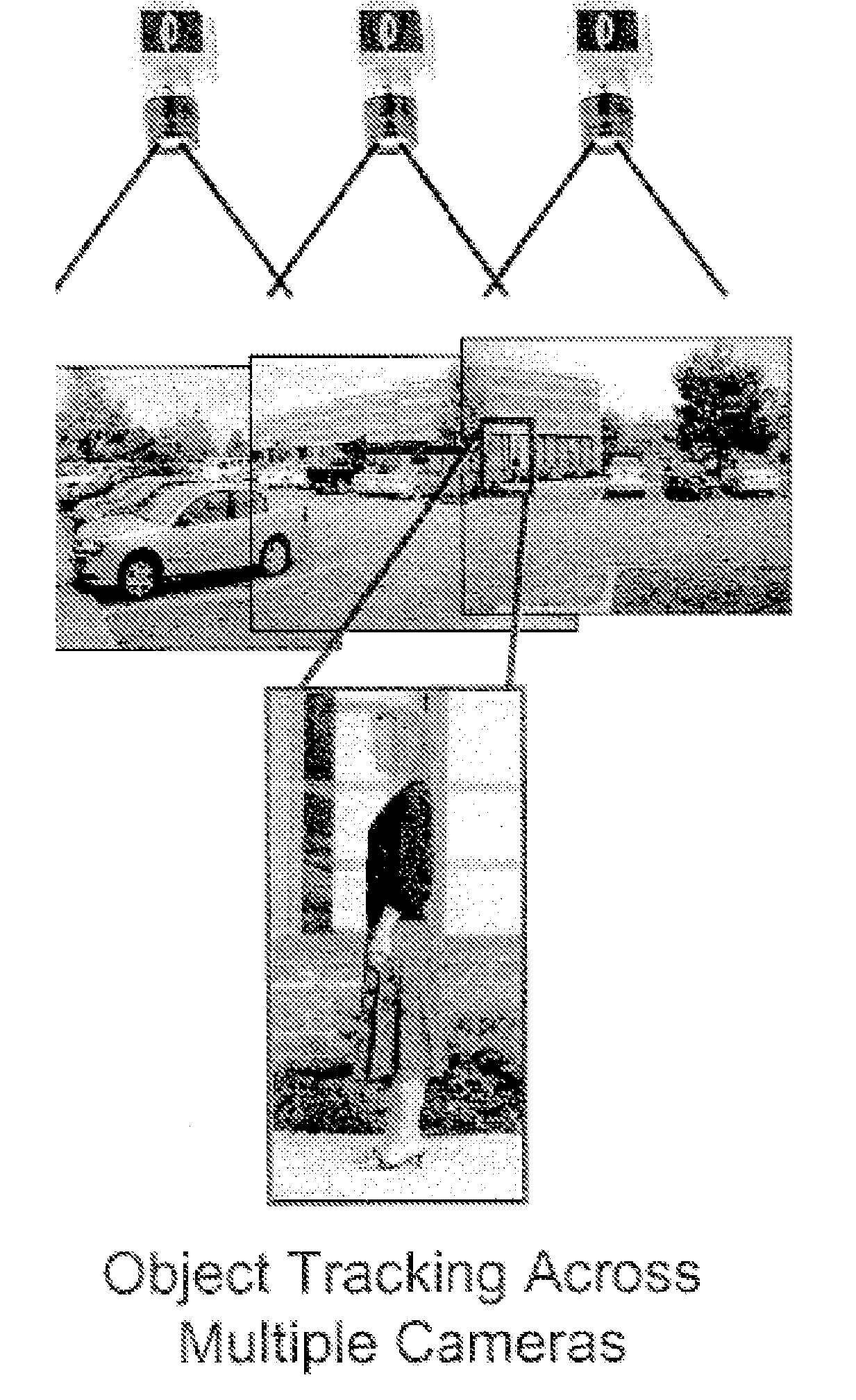
According to one embodiment, a controller for a surveillance system includes ports for coupling a camera, synchronization logic blocks coupled to the ports, an information aggregation logic block coupled to the camera ports, and an output port coupled to the information aggregation logic block. According to another embodiment, a method of scaling a surveillance system includes synchronizing a plurality of cameras, capturing images from the synchronized cameras, aggregating at least two processed synchronized images, and processing the aggregated synchronized images.
Owner:PIXEL VELOCITY
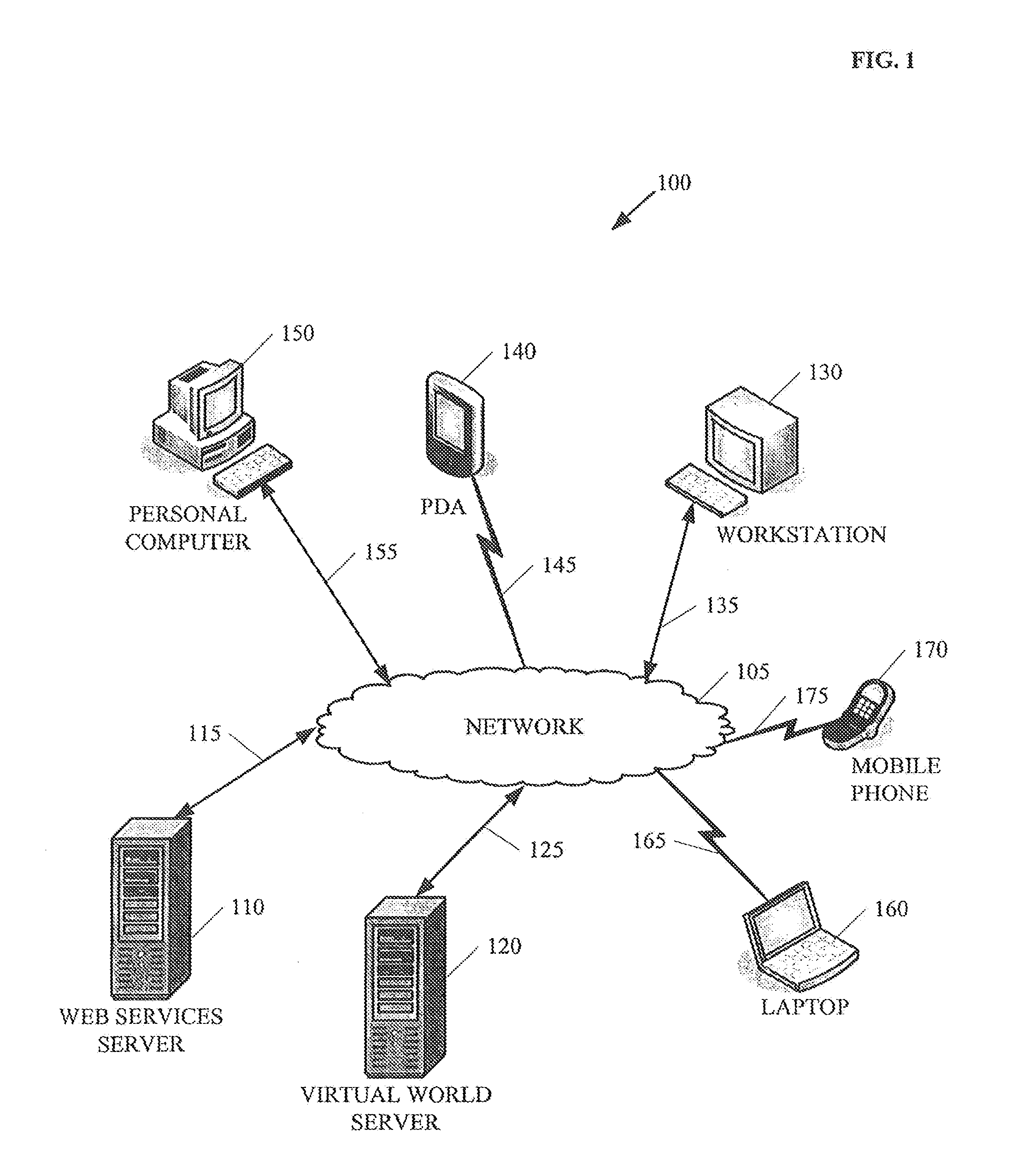
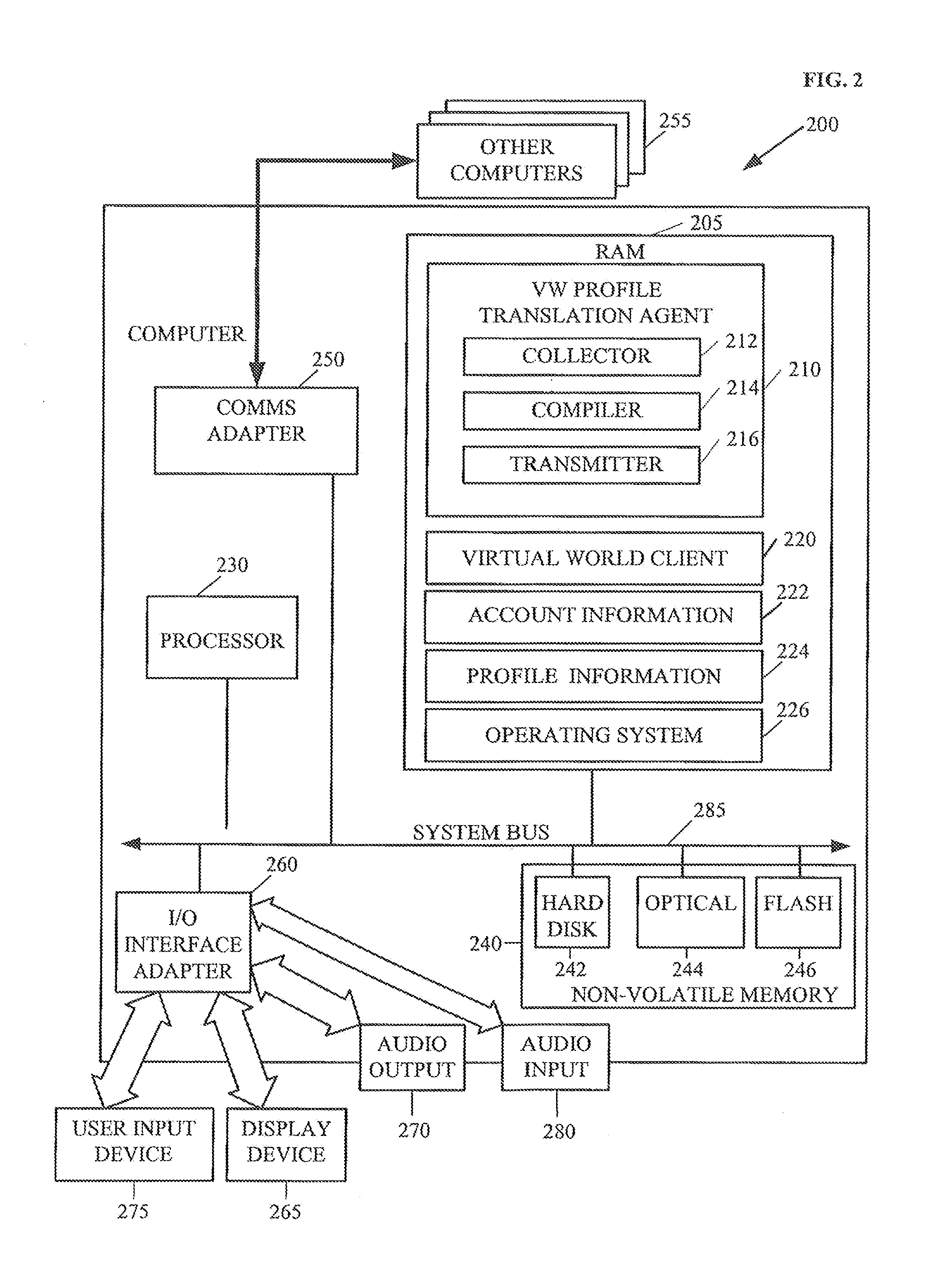
Developing user profiles in virtual worlds
Methods and arrangements of developing user profiles in virtual worlds are discussed. Embodiments include transformations, code, state machines or other logic to receive data from a software agent in a virtual world, directly or indirectly. The data may be based upon information automatically gathered from data stores outside the virtual world, including account data and user profile data. The embodiment may also involve developing a user profile of the user in the virtual world, based upon the data received from the software agent. An embodiment may also involve automatically gathering information from data stores external to the virtual world. The information may include user account data and user profile information. The embodiment may also include aggregating data for generating the user profile in the virtual world, based upon the information; and transmitting the data directly or indirectly to the virtual world.
Owner:ACTIVISION PUBLISHING
Method and subsystem for information acquisition and aggregation to facilitate ontology and language-model generation within a content-search-service system
ActiveUS20090083257A1Digital data processing detailsMetadata multimedia retrievalClassified informationTime range
Various embodiments of the present invention include information-aggregation-and-classification components of content-search-service systems which acquire information from information sources, aggregate and normalize the acquired information, and classify the acquired information prior to storing the normalized and classified information for use by language-model-builder components and ontology-builder components of the content-search-service systems. Additional embodiments of the present invention include the ontology-builder components, which builds ontologies from the normalized and classified information for specific dates, date / times, date ranges, or date / time ranges and for specific categories.
Owner:LIMELIGHT NETWORKS
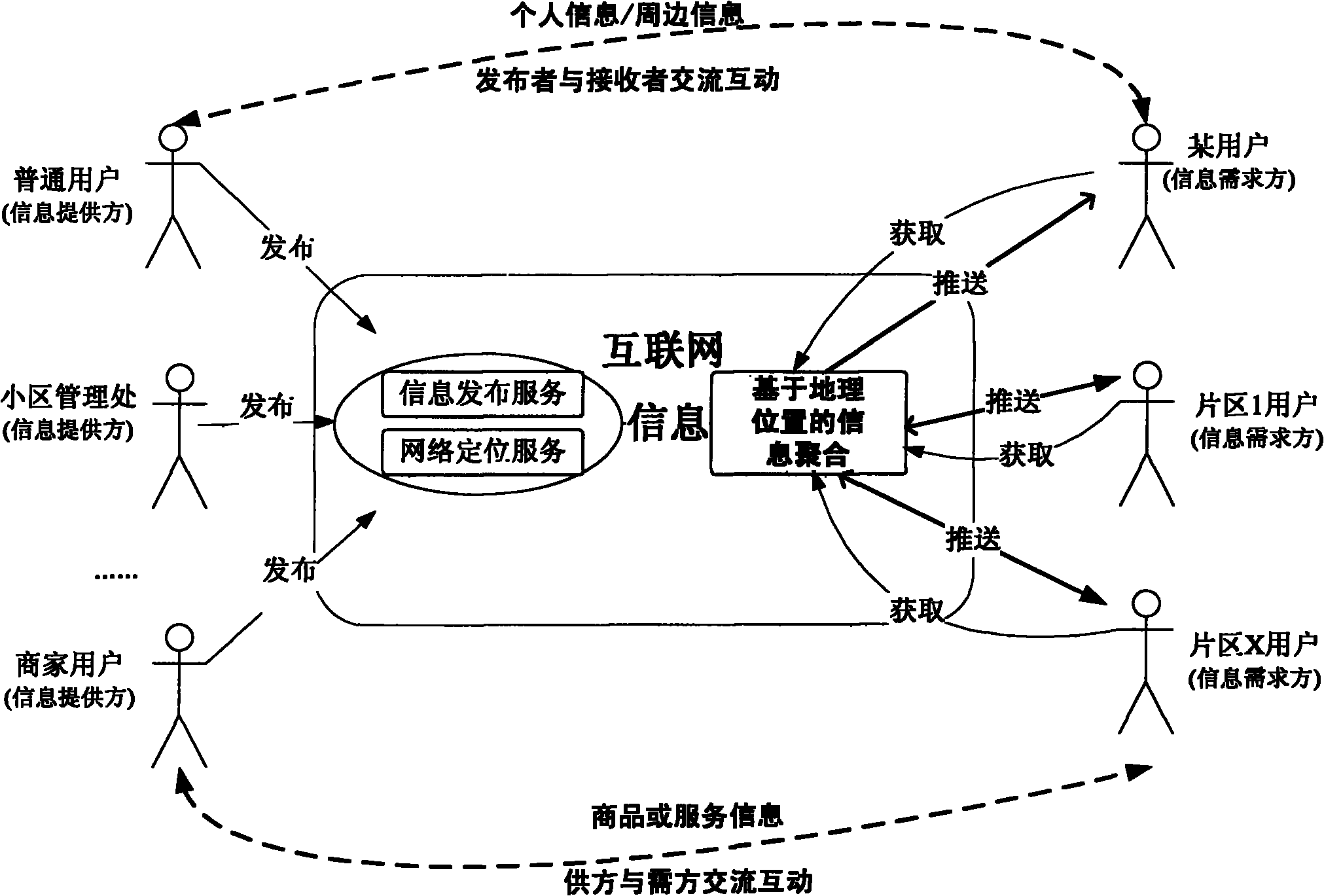
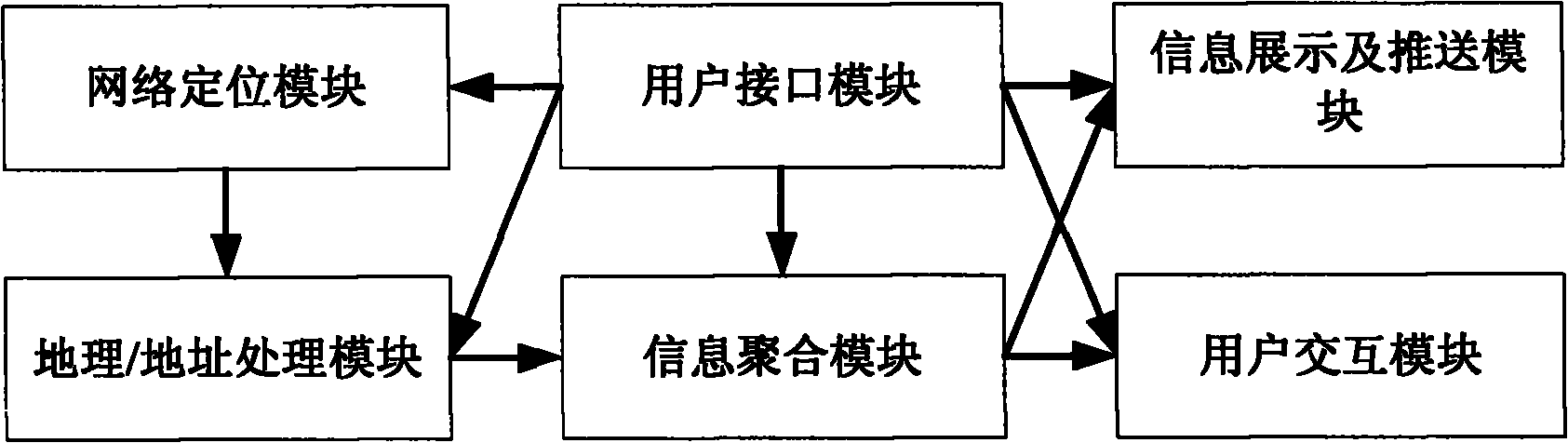
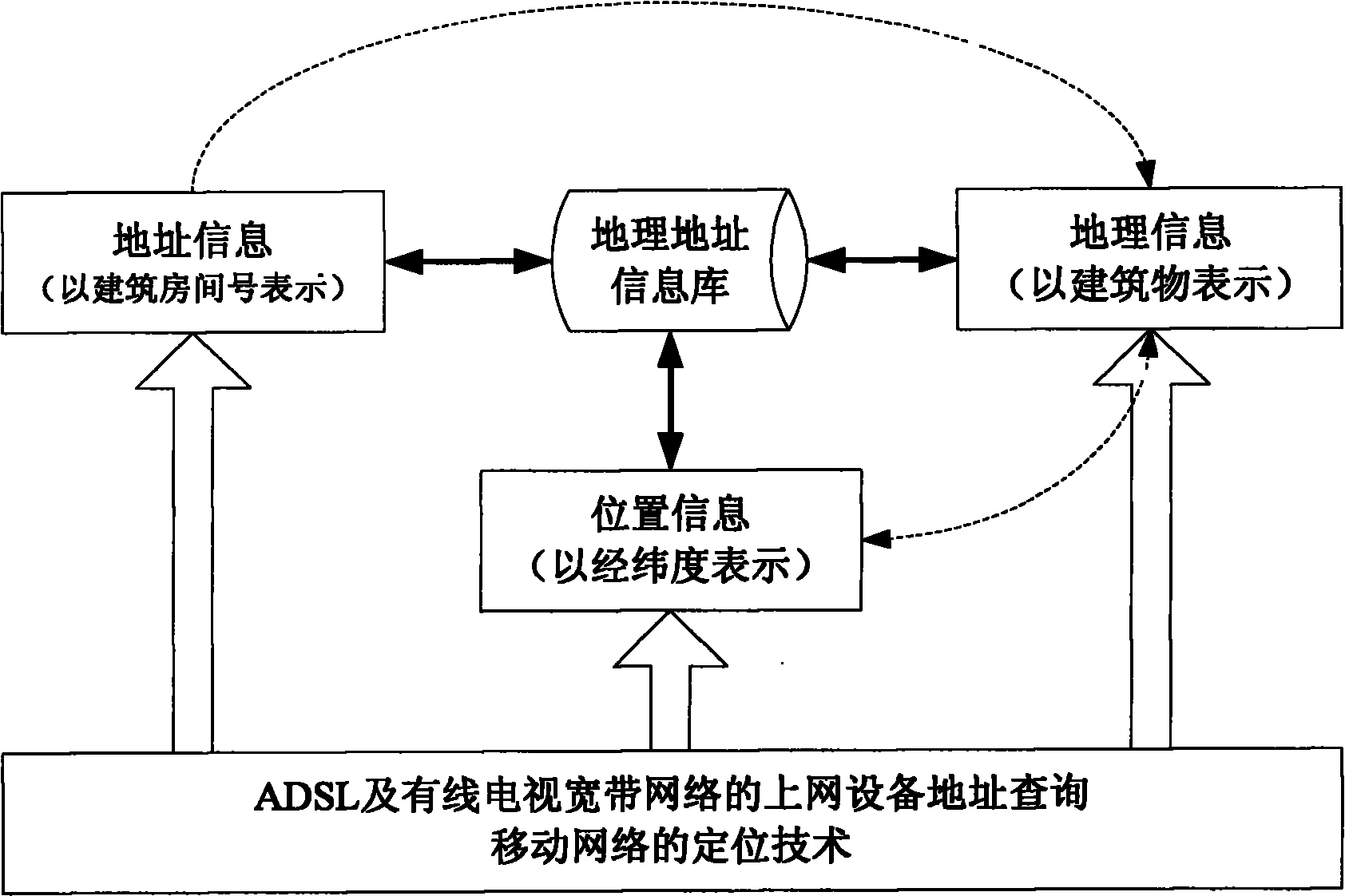
Geographic position-based internet information aggregating, pushing and interacting method
InactiveCN102147903APromote aggregationPrecise pushTransmissionCommerceGeographic siteWireless Application Protocol
The invention discloses a geographic position-based internet information aggregating, pushing and interacting method, which comprises the following steps of: acquiring position information or geographic information of a user who accesses the internet (including the mobile internet) by means of an asymmetrical digital subscriber loop (ADSL), cable televisions and a mobile network and the like by network positioning, wherein the position information, geographic information and user address information can be converted to form user geographic position information, an information application region and an information generation address; associating the information released by the user with the application region and the like and aggregating according to the geographic position and behavior characteristics; and showing the aggregated information according to the pre-set rules and actively pushing the aggregated information to the proper user, wherein the means of showing and pushing comprises webs, wireless application protocols (WAP), mobile phone messages, e-mails, micro-blogs, calls and the like, so the user can interact with the user or user cluster with the common hobbies on the basis of the aggregated information and the geographic information. The information aggregation mode provided by the invention can be applied to the occasions of information verification and direct selling of goods, services, hotels and the like.
Owner:李久进 +1
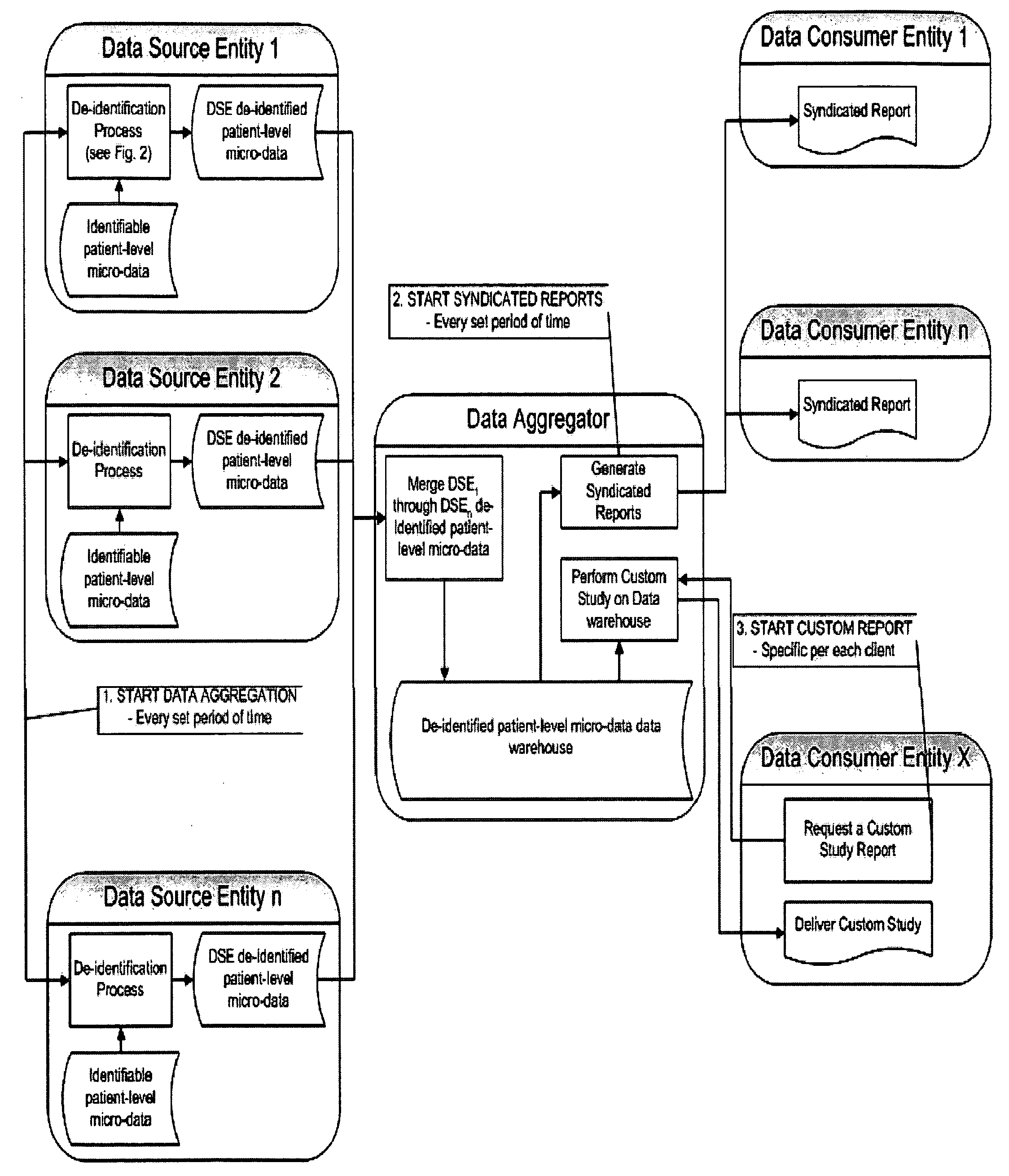
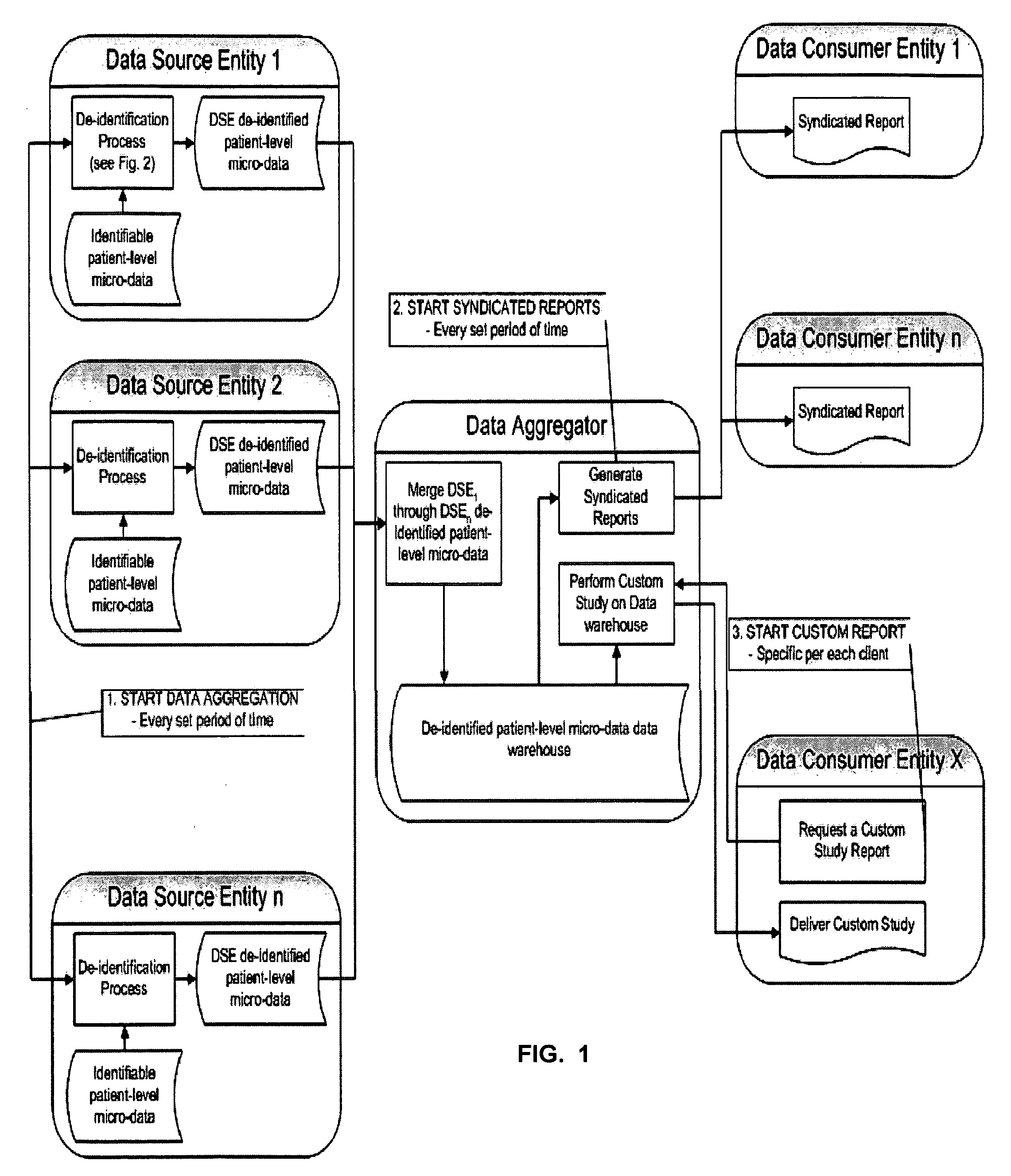
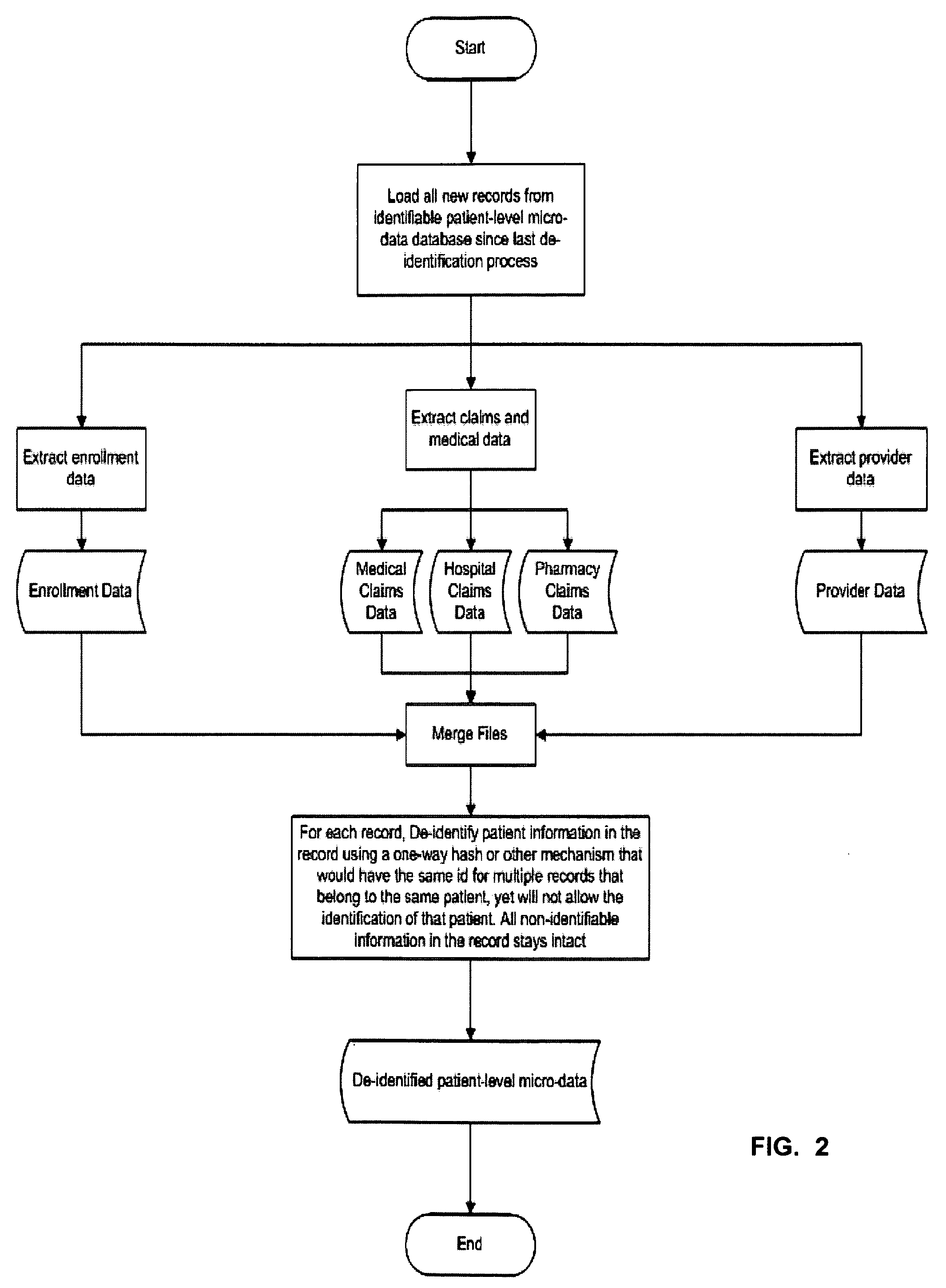
Double Blinded Privacy-Safe Distributed Data Mining Protocol
ActiveUS20090150362A1Easy to analyzeImplementation is particularly straightforwardMedical data miningDigital data processing detailsDouble blindData source
A Double Blinded Privacy-Safe Distributed Data Mining Protocol is disclosed, among an aggregator, a data consumer entity having privacy-sensitive information, and data source entities having privacy-sensitive information. The aggregator does not have access to the privacy-sensitive information at either the data consumer entity or the data source entities. The aggregator formulates a query without using privacy-sensitive information, and sends the query to the data consumer entity. The data consumer entity generates a list of specific instances that meet the conditions of the query and sends the list, encrypted, to the data source entities either directly or through the aggregator. The data source entities match the list against transactional data, de-identify the matched results, and send them to the aggregator. The aggregator combines results from data source entities and sends the combined result to the data consumer entity. This allows for privacy-safe data mining where both the data consumer entity and data source entities have privacy-sensitive information not available for the aggregator to see or use.
Owner:VEEVA SYST
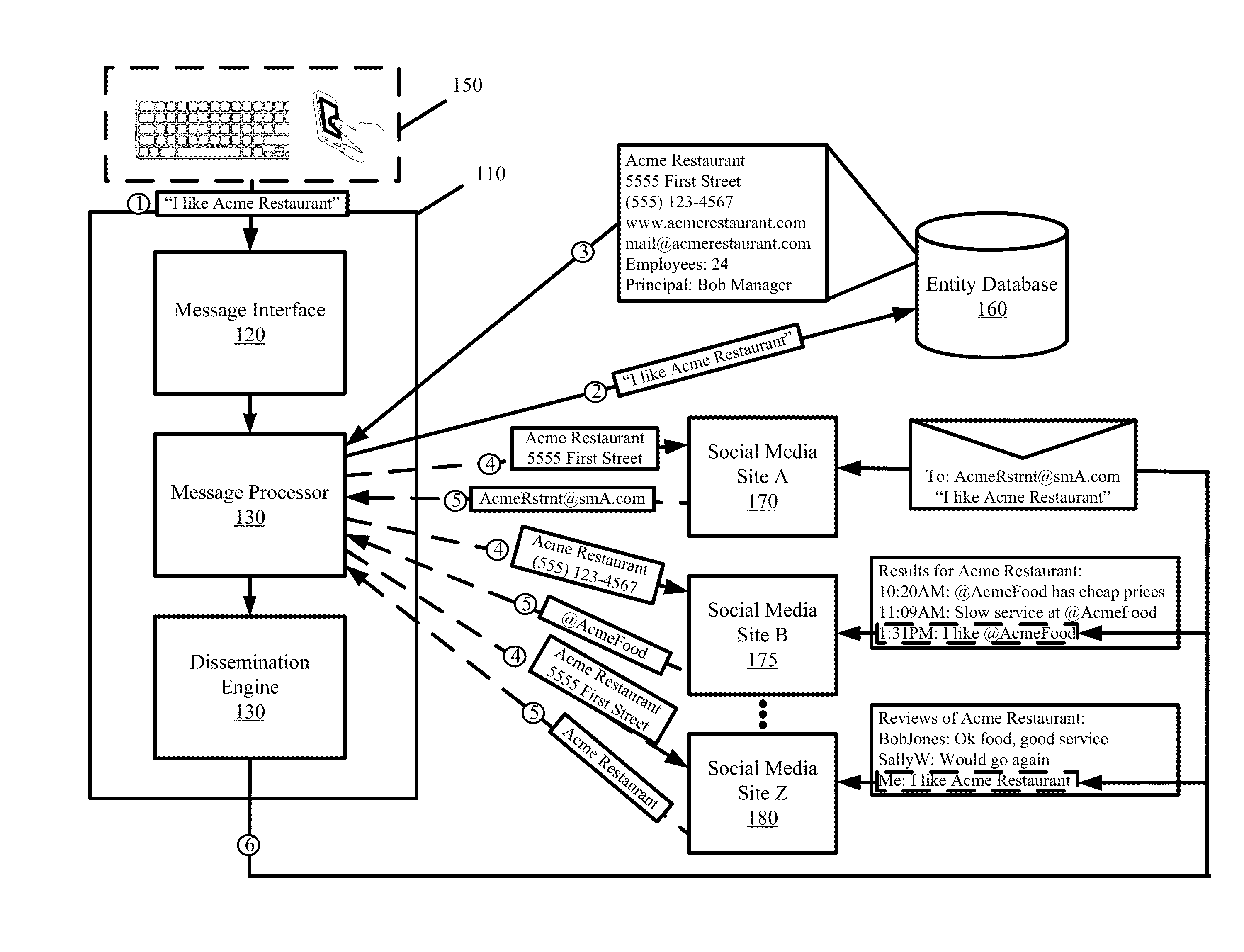
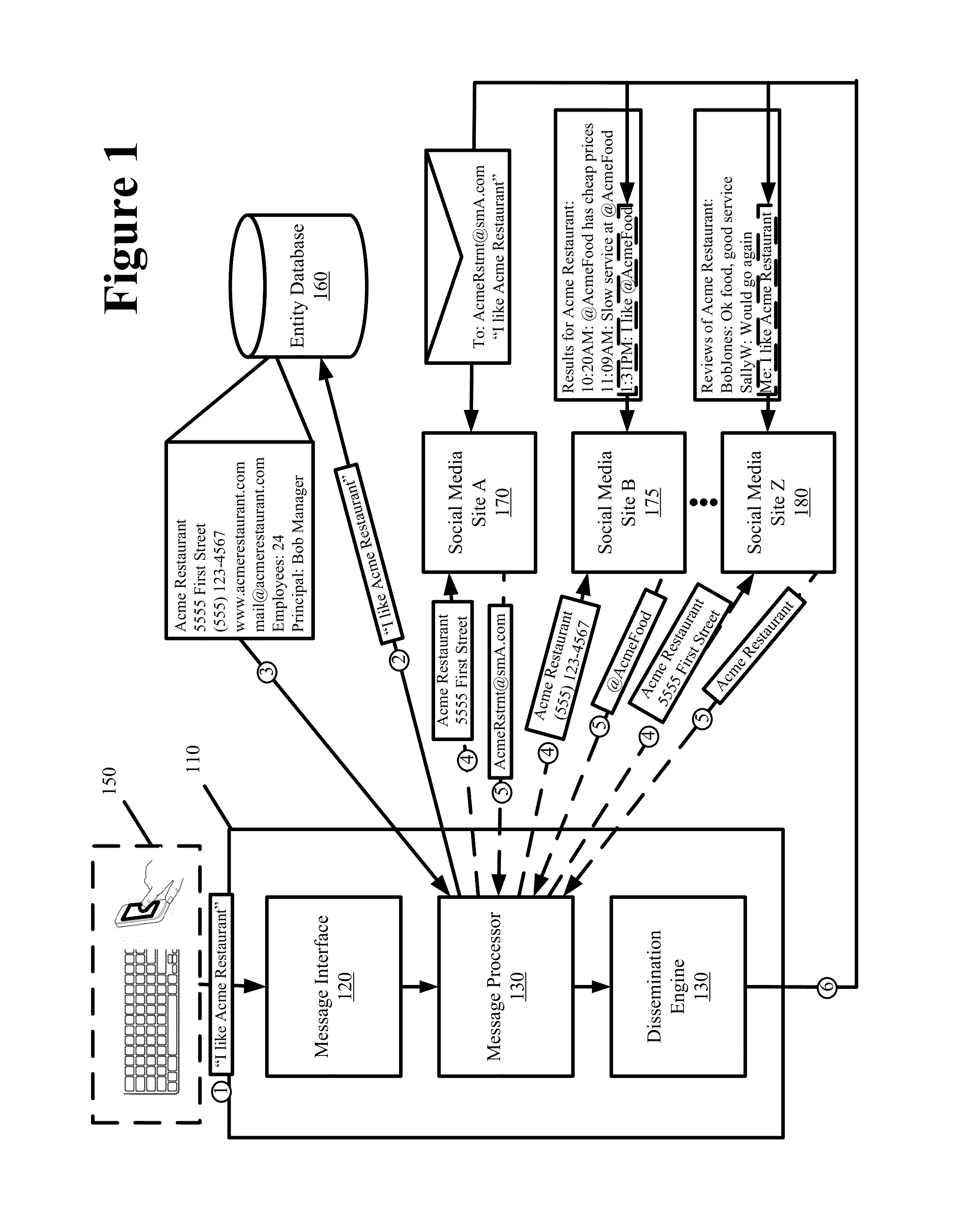
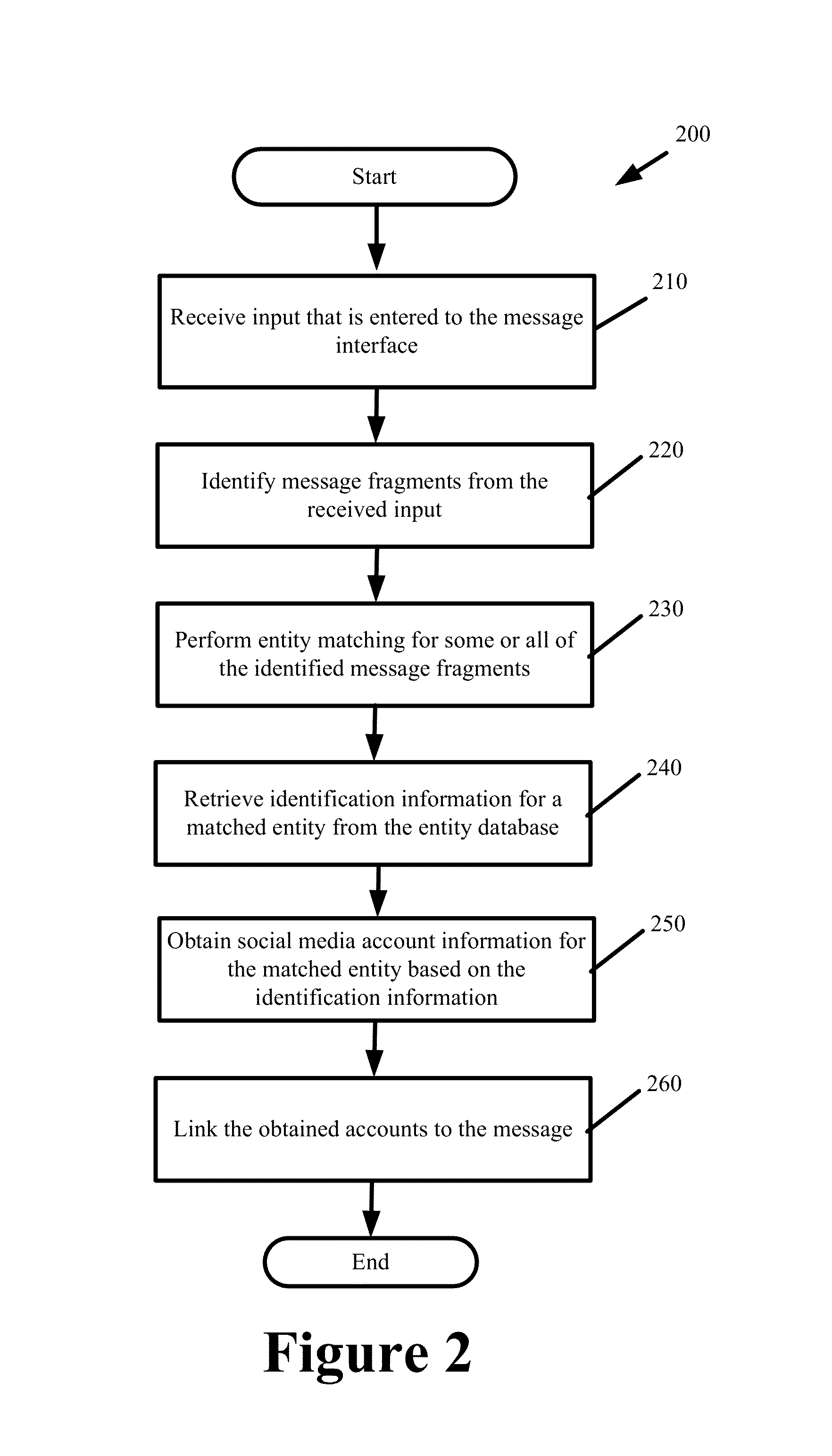
Method and system for directly targeting and blasting messages to automatically identified entities on social media
ActiveUS8380803B1Efficient and effectiveAccurately and efficiently determinedMultiple digital computer combinationsSubstation equipmentNews aggregatorData library
Some embodiments provide a communication tool that directly sends messages to accounts of different entities across different social media sites by automatically identifying and associating the accounts of the entities when the entities are referenced in the contents of the messages. Such identification and association is performed without the message originator manually specifying the accounts as intended recipients for the messages. The communication tool also automatically sends messages to different social media accounts of the message originator. The communication tool also blasts messages to an information aggregator that aggregates messages to develop a database from which the messages that target a particular entity can be presented irrespective of whether the particular entity has registered an account with any social media site, irrespective of which social media site the messages are originally destined for, and irrespective of whether a recipient is explicitly specified for the messages by the message originator.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
Information aggregation, processing and distribution system
InactiveUS7437408B2Convenient and accurateEasy to useUser identity/authority verificationUnauthorized memory use protectionThird partyDistribution system
A utility is provided for managing exchanges of information within a context involving multiple users, for example, multi-user network collaboration. The invention enables automatic enforcement of a policy regarding sensitive information. The policy may be negotiated among the users and expressed as multiple rule sets that govern access to a use of sensitive information. The utility also logs activities involving sensitive information to ensure compliance with the policy. These logs can be audited by a third party or automatically processed for audit compliance by the utility. In this manner, an environment of trust is created which encourages fruitful collaboration.
Owner:LOCKHEED MARTIN CORP
Information driven routing in ad hoc sensor networks
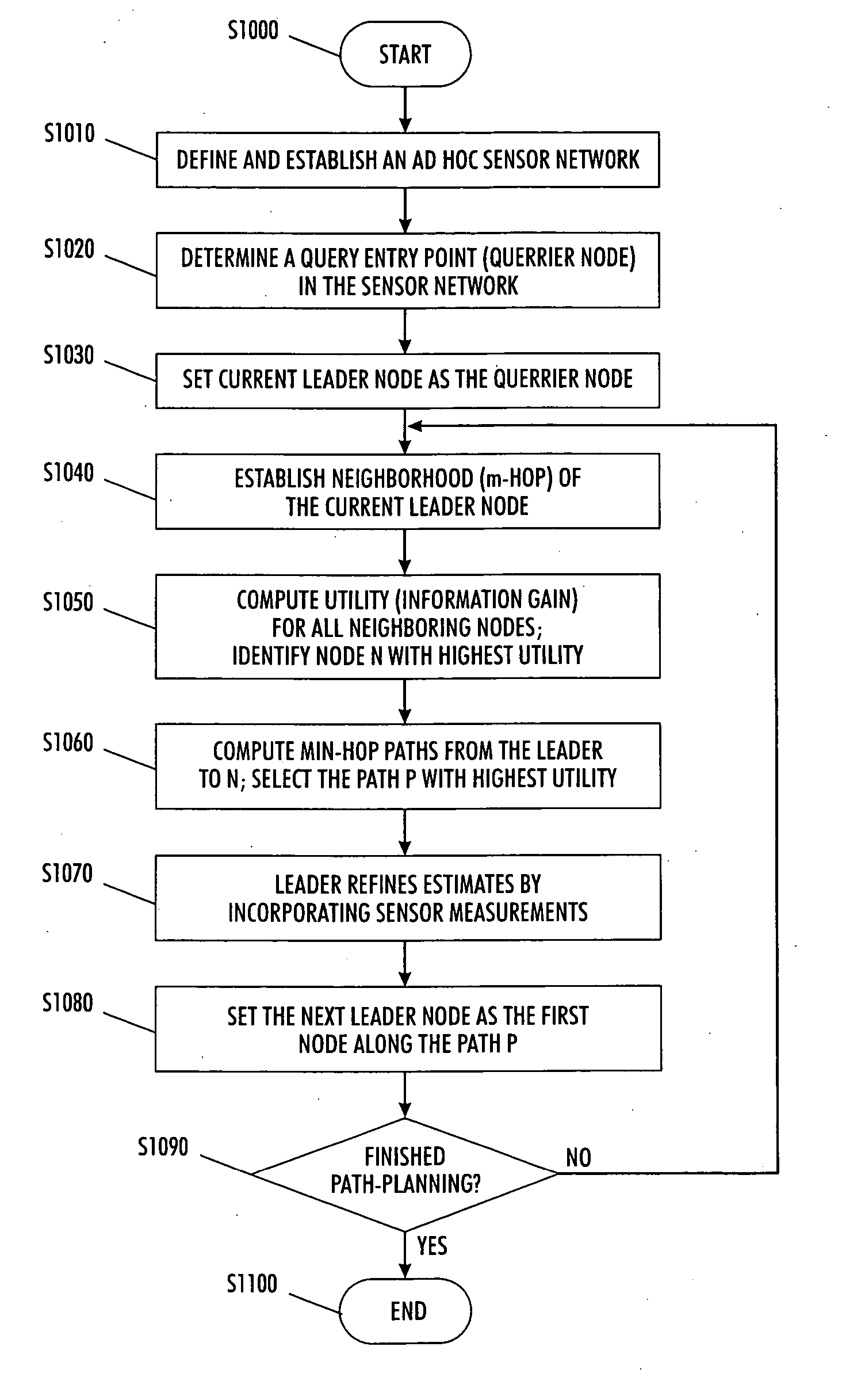
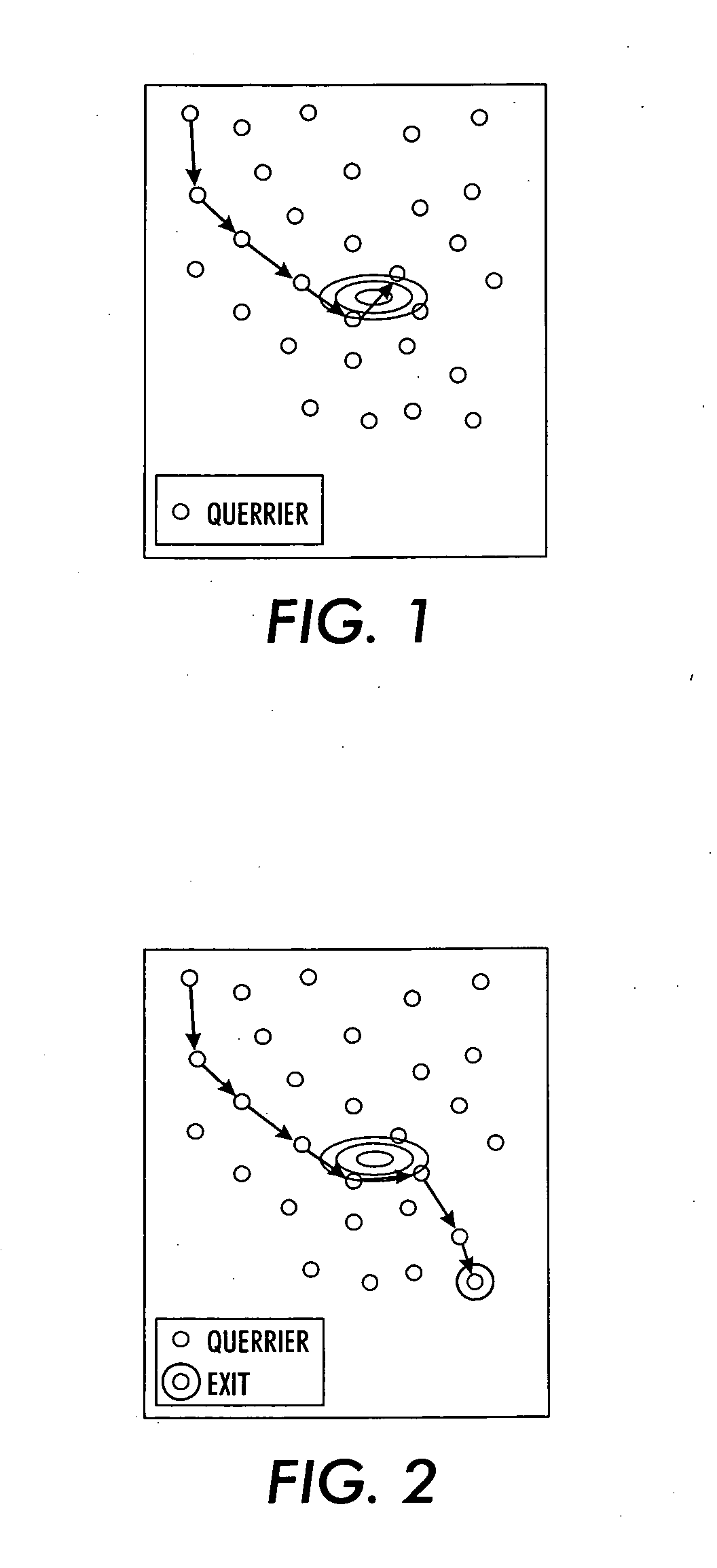
InactiveUS20050138200A1Improve performanceEnhanced informationError preventionTransmission systemsShort path algorithmEntry point
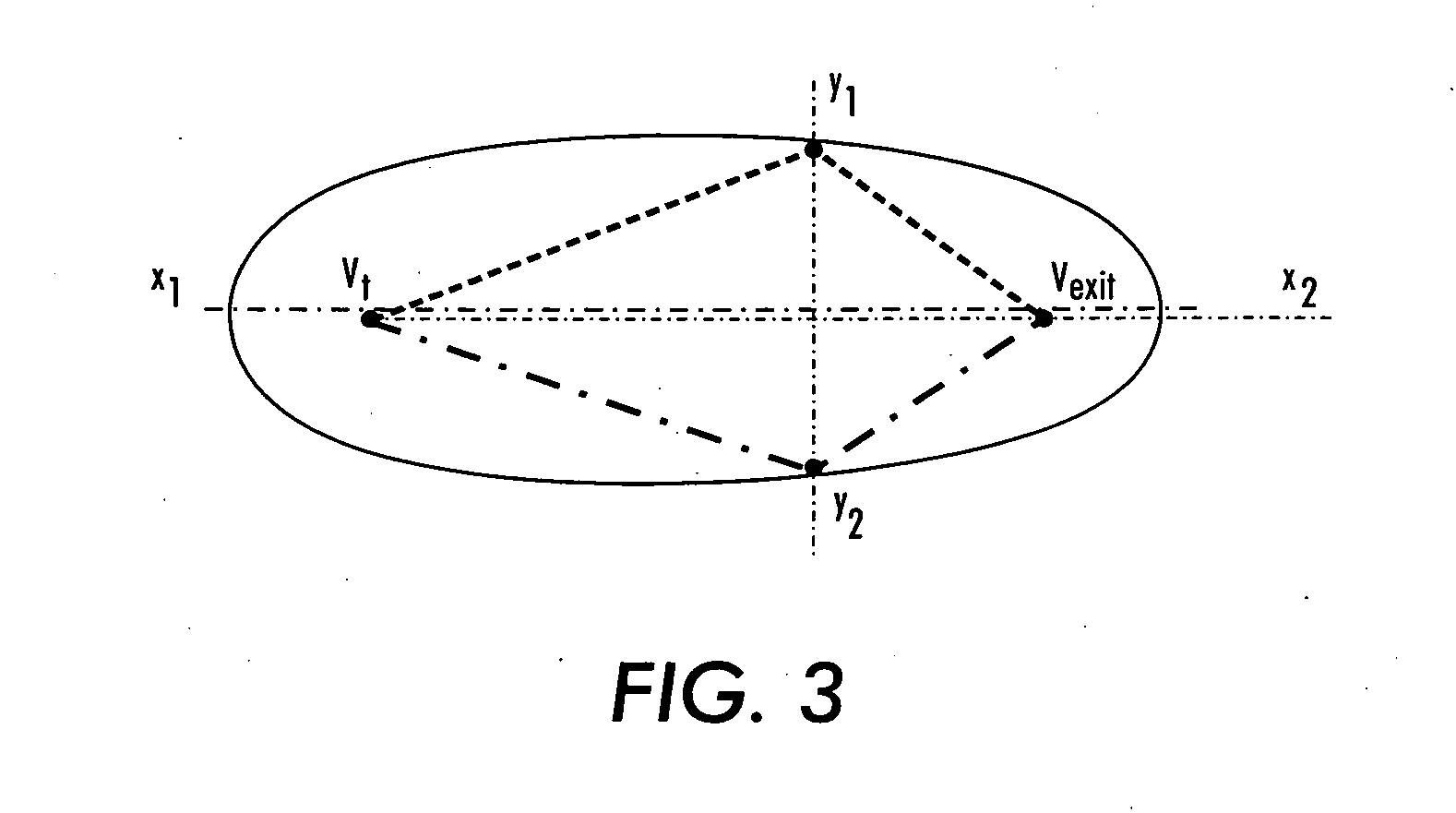
A sensor network routing is formulated as a joint optimization problem taking into account routing cost and information aggregation. Information gain is used explicitly to optimize the routing path. The optimization approach involves a shortest path algorithm in a modified network graph. A method is provided that routes queries from an arbitrary entry point to high activity network sensor regions using inputs from sensor nodes along the path to refine the message. The multiple step look-ahead approach provides deadlock avoidance and routing around sensor network holes. For point-to-point query routing, a method based on real-time A* (RTA*) search is provided to find a path which takes detours efficiently to maximize information aggregation. Future information expected to be gained along the path from an arbitrary node to an exit node may be estimated to allow the selection of a successor sensor node.
Owner:CISCO TECH INC
Location based services anonymous session tracking and anonymous information aggregation
InactiveUS20040093289A1Registering/indicating time of eventsRoad vehicles traffic controlIn vehicleInformation aggregation
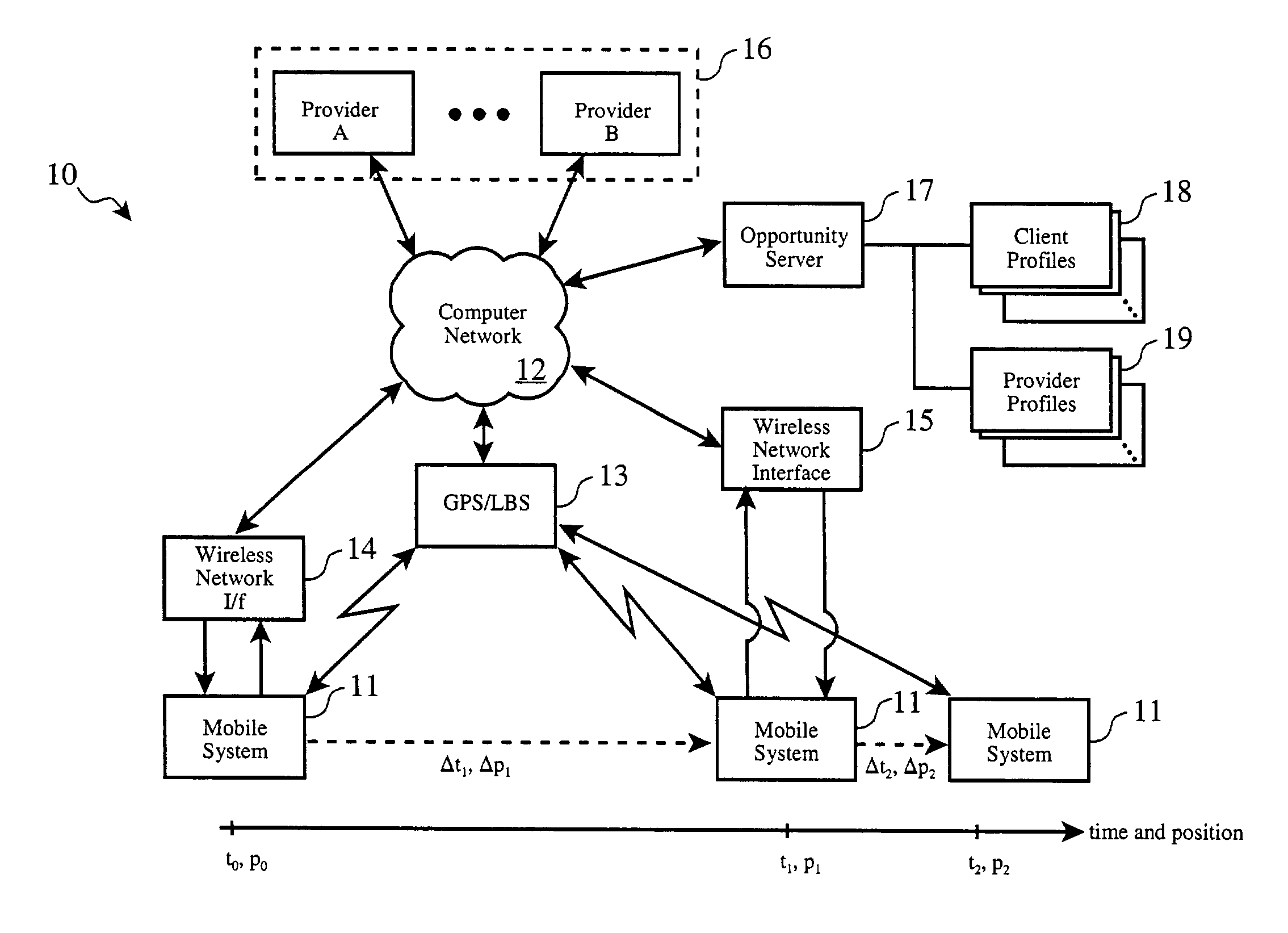
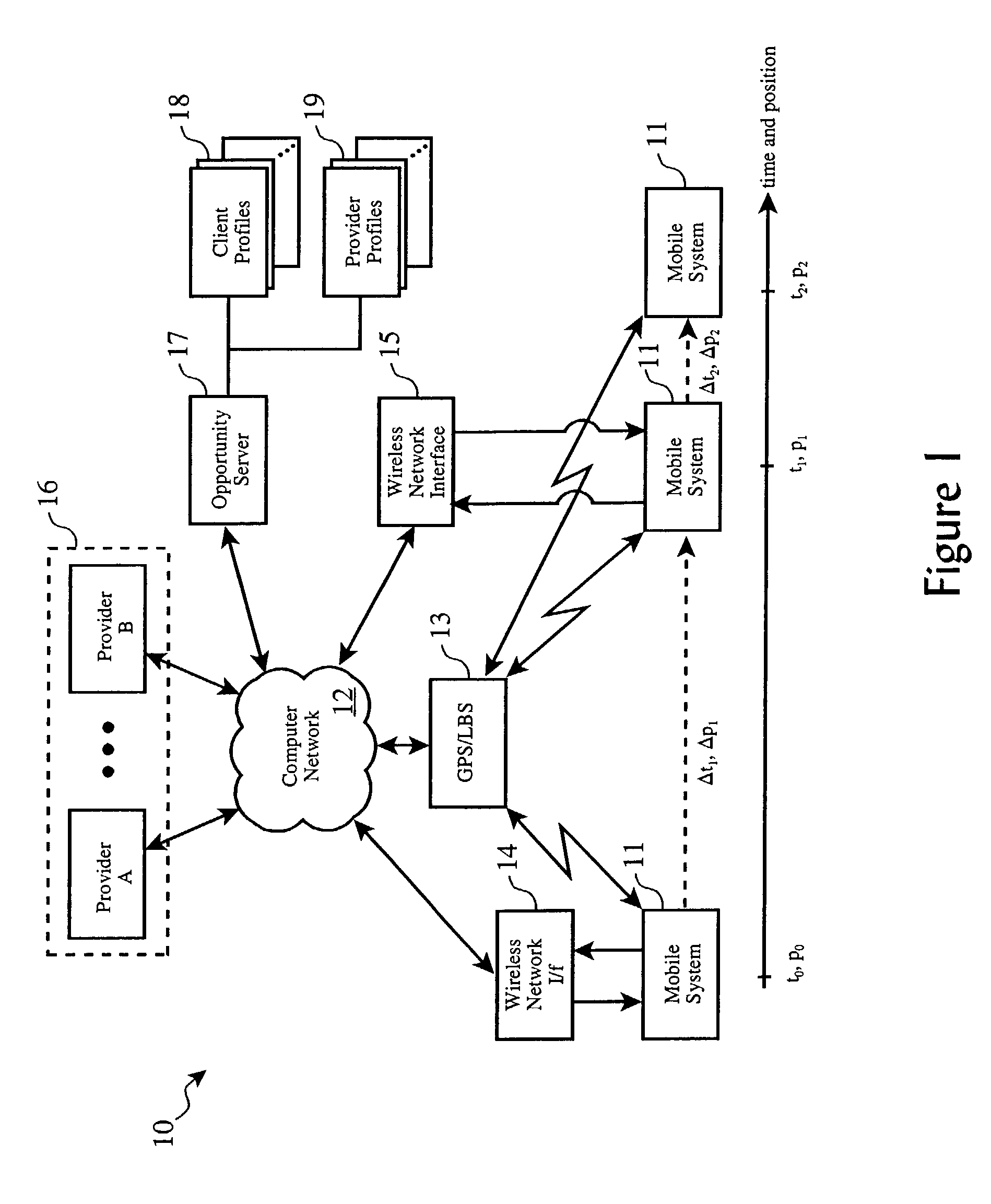
An opportunity server tracks in vehicle information system wireless web transactions using anonymous, reusable session identifiers, aggregates session records into classes of session data, and provides aggregated data to a plurality of data consumers in exchange for compensation. Credits are posted to share revenue and offset costs of OEM equipment and network access metered fees, thereby reducing the cost of said transactions by a user and promoting unfettered use of in vehicle information systems for a variety of services, purposes, and transactions.
Owner:IBM CORP
Information aggregation and enquiry method based on geographic coordinates
InactiveCN101192215AConvenient queryInquire in timeSpecial data processing applicationsGeolocationThe Internet
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
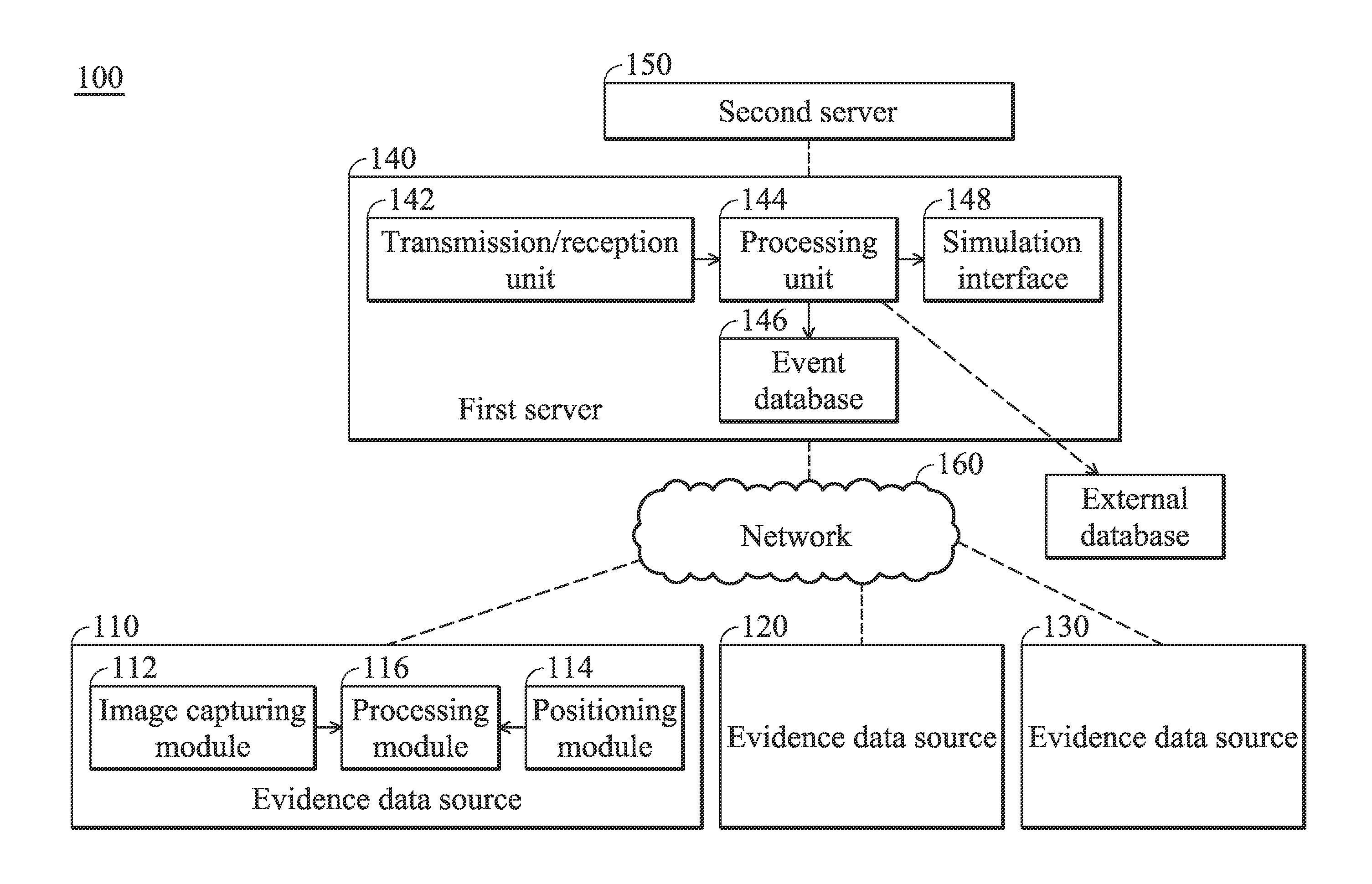
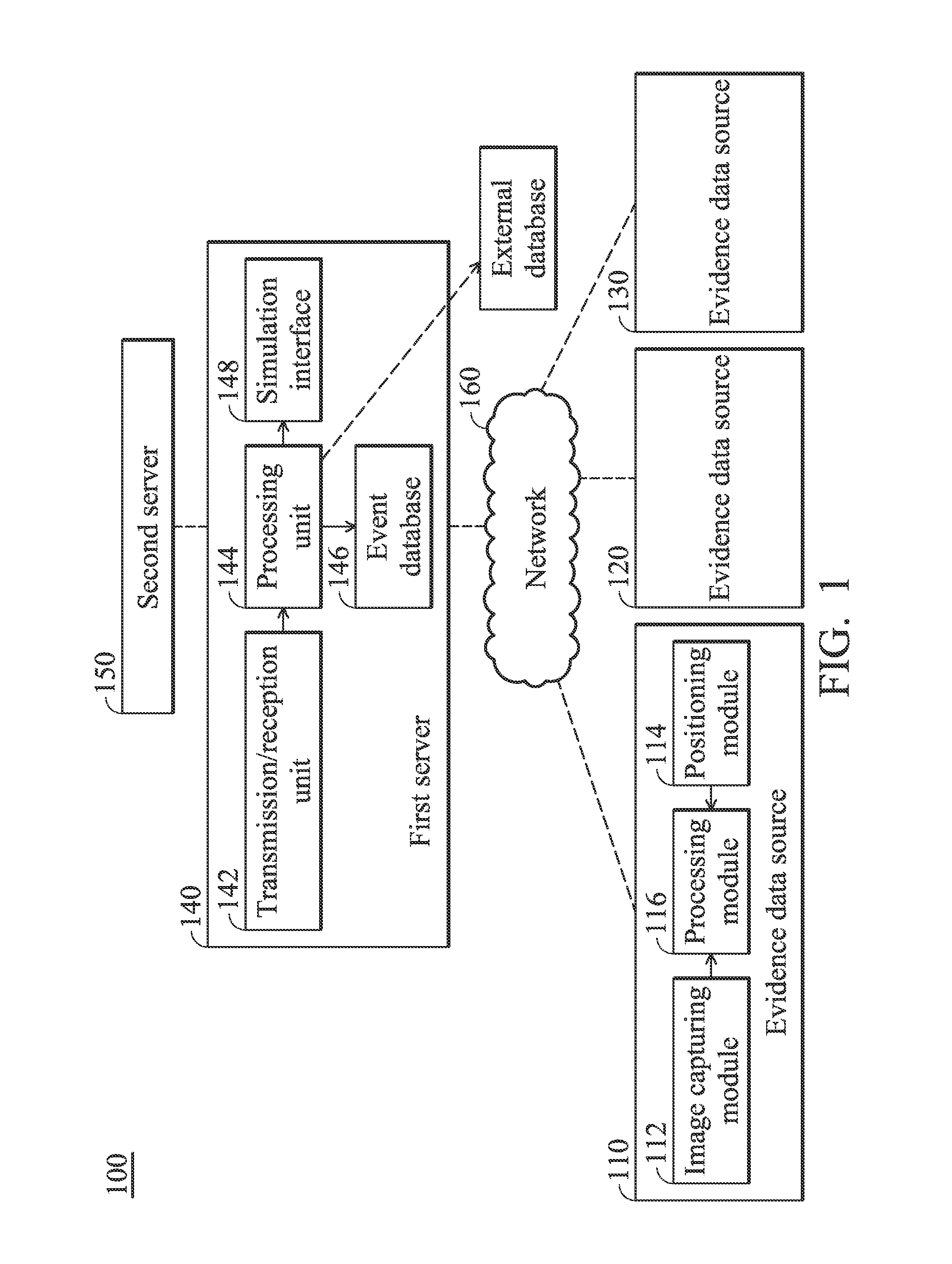
Accident information aggregation and management systems and methods for accident information aggregation and management thereof
ActiveUS20130086109A1Speed up the processDigital data processing detailsGeographical information databasesTemporal informationData source
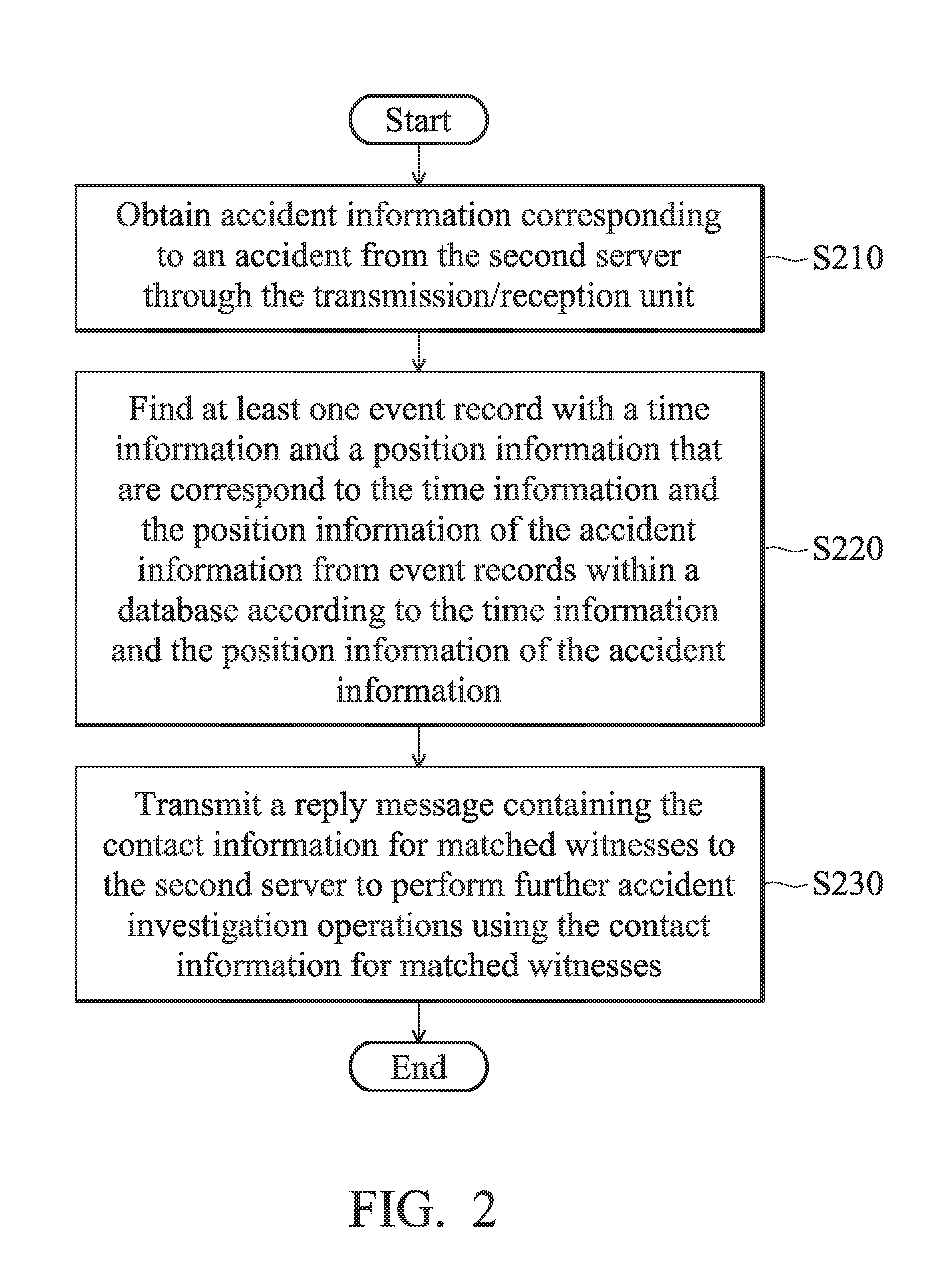
Accident information aggregation and management methods are disclosed. The Accident information aggregation and management method includes receiving an accident information from a first server, wherein the accident information includes a time information and a position information for an accident; searching whether any event data that is nearby the time information and the position information can be found in a database; if so, obtaining at least one witness information and evidence data source according to the found issue data; and providing the at least one witness information and evidence data source to the first server such that the first server can use the at least one witness information and evidence data source for further accident investigation.
Owner:QUANTA COMPUTER INC
System, method, and apparatus for connecting non-co-located video content viewers in virtual TV rooms for a shared participatory viewing experience
InactiveUS20090094656A1Two-way working systemsSelective content distributionCommunications systemMulti platform
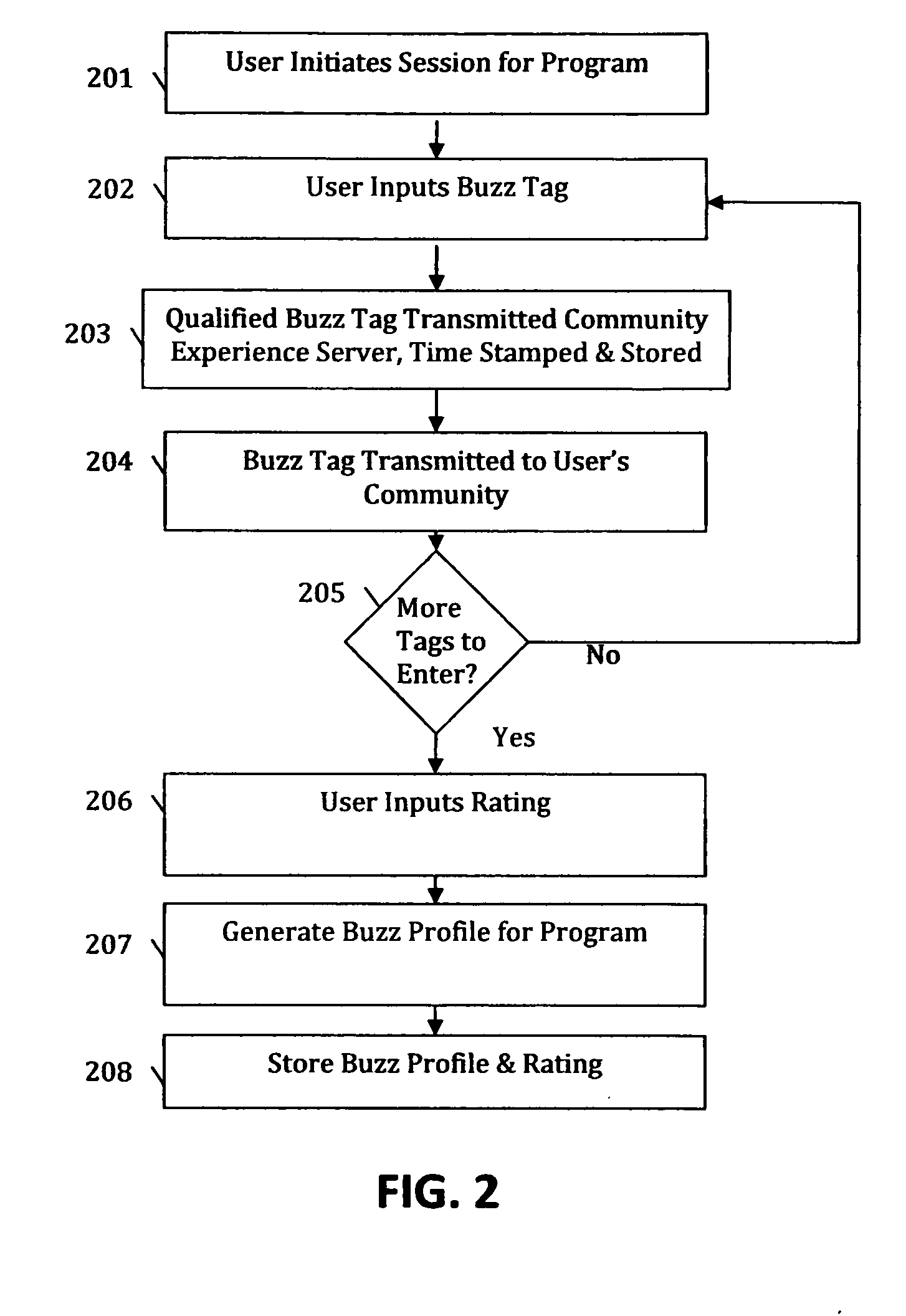
System, method and apparatus for connecting non-co-located video content viewers in Virtual TV Rooms for a shared participatory viewing experience. A multi-platform communication system allows viewers to connect across a plurality of video content delivery services in self-organized viewing communities to interact with each other as they enjoy the content as if they were in the same physical viewing location. A mechanism is provided to allow users to quickly see what their friends are currently watching and join them. In addition to exchanging text-based messages, viewers also share their impressions of the current video program via a defined set of single-key-click impressions called Buzz Tags™. A database and calculation process aggregates this information in to Buzz Profiles as a resource for users to find interesting content and fellow viewers with similar interests.
Owner:CARLUCCI JOHN B
Network device implementing two-stage flow information aggregation
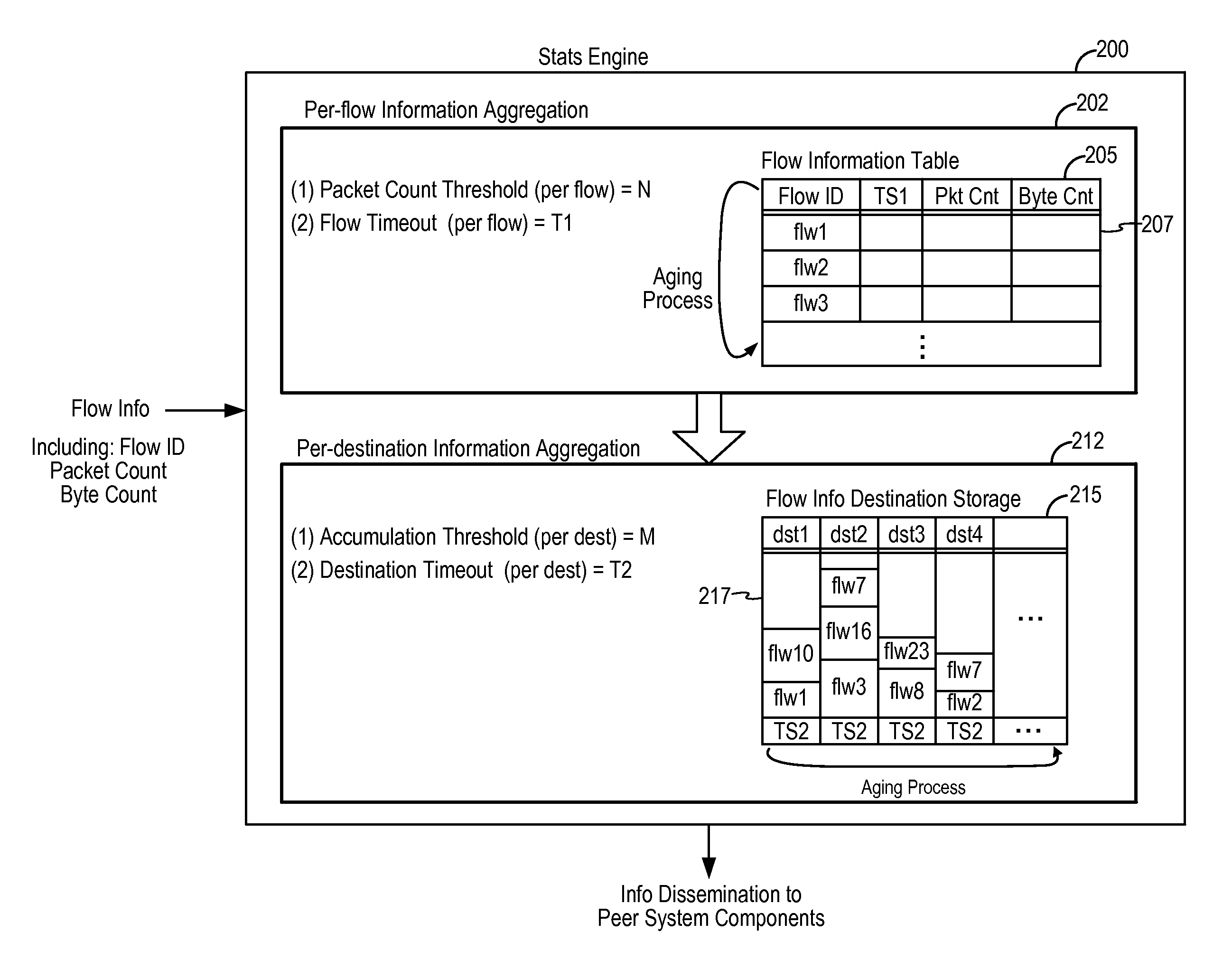
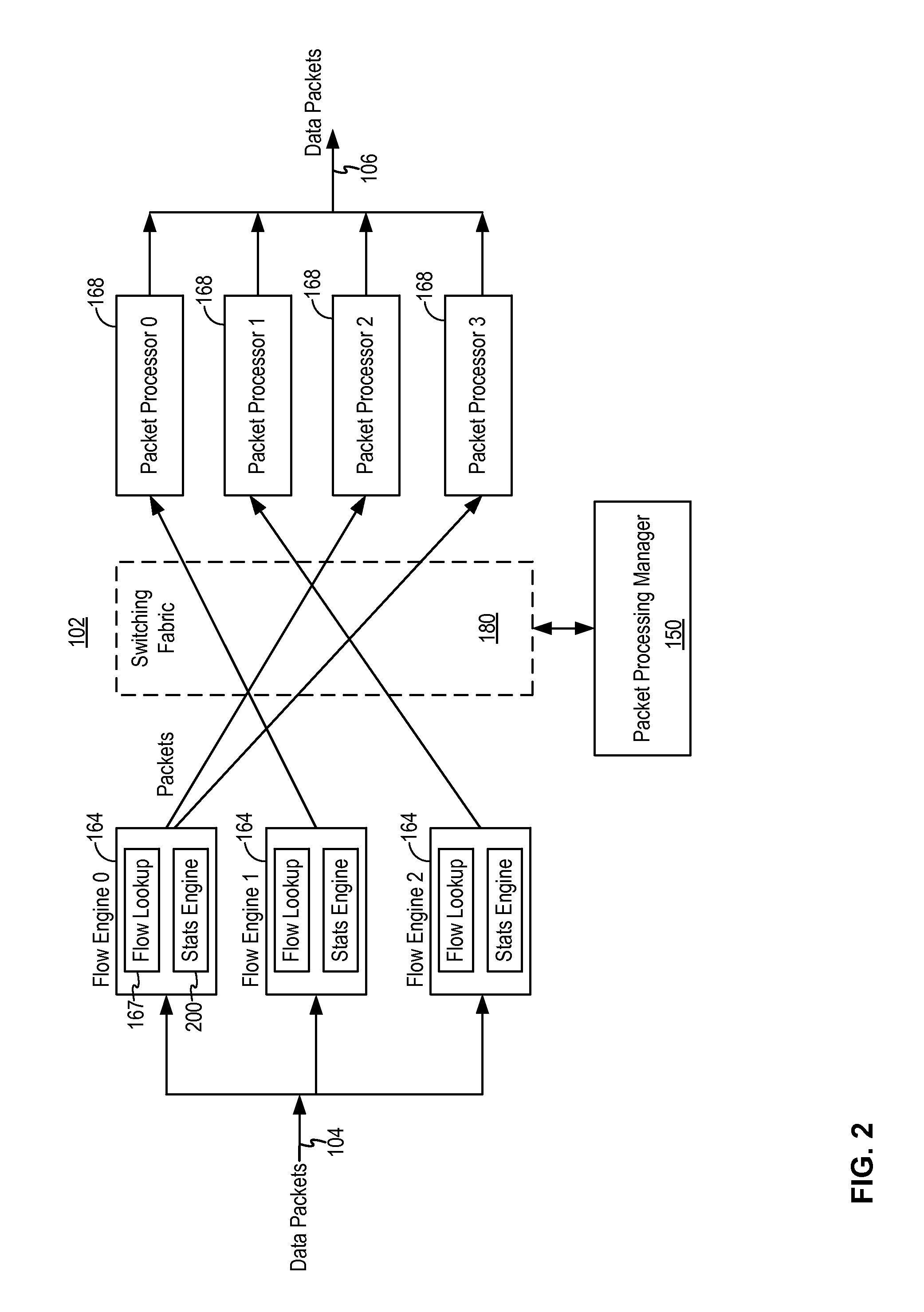
A network security device includes a network flow statistics processing engine to process network flow information related to network flows. The network flow statistics processing engine includes a first processing stage performing per-flow information aggregation and a second processing stage performing per-destination system component information aggregation, with each processing stage implementing a threshold-based data export scheme and a timer-based data export scheme. In this manner, up-to-date flow information is available to peer system components regardless of the varying flow rates of the network flow.
Owner:PALO ALTO NETWORKS INC
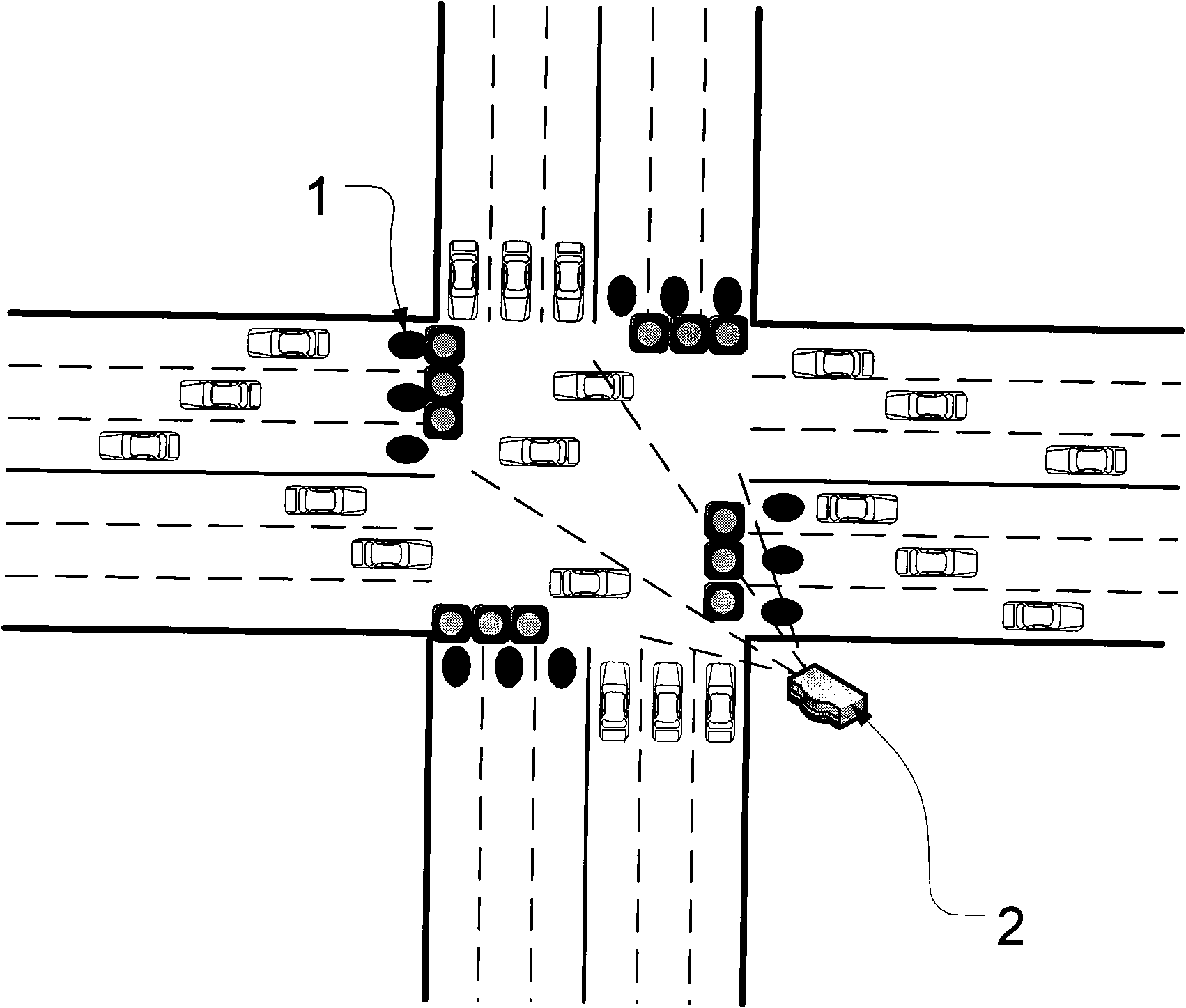
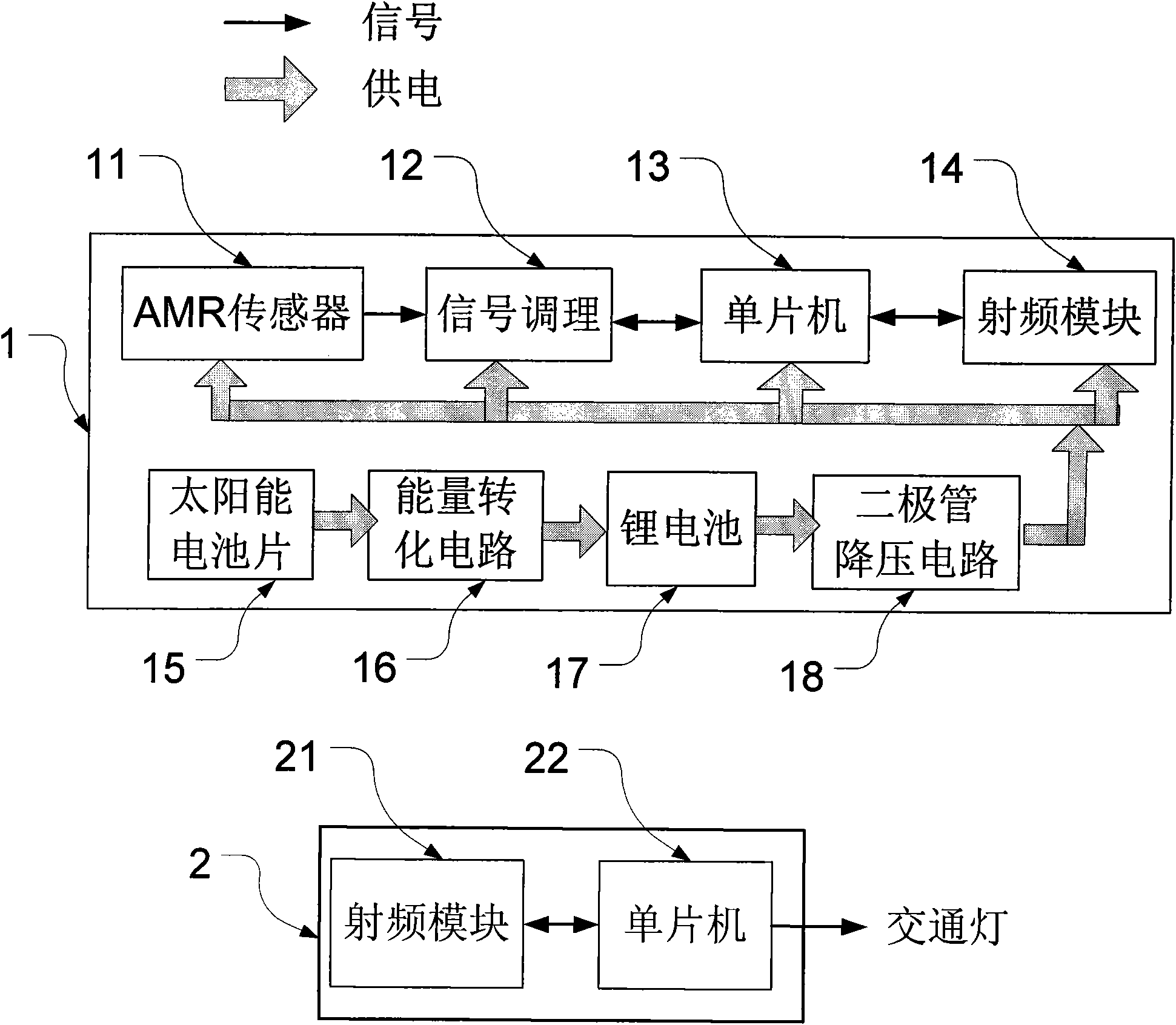
Vehicle flow detection system and traffic lamp control method
The invention provides a vehicle flow detection system and a traffic lamp control method. A traffic lamp can be controlled by a wireless network formed by adopting a plurality of information acquisition nodes and an information aggregation node according to actual vehicle flow. The information acquisition nodes are arranged in the middle of each vehicle passing traffic lane to acquire vehicle flow and transmit to the information aggregation node in a wireless mode; the information aggregation node controls the time delay of the traffic lamp by adopting a fuzzy theory according to vehicle flow information; and the information acquisition nodes ensure long-period stable operation by adopting a solar power supply and a sleep and wake-up mechanism. The invention can accurately detect the vehicle flow of various directions of a crossroad, increases road passing efficiency, improves crowded urban traffic condition and can overcome the defects that the traditional traffic lamp is controlled in time to waste time, and geomagnetic coils can not be popularized, and the like.
Owner:BEIHANG UNIV
Method and apparatus for extendible information aggregationand presentation
InactiveUS20050198393A1Reduce effortNatural language data processingMultiple digital computer combinationsClient-sideExtensible markup
Owner:CITRIX SYST INC
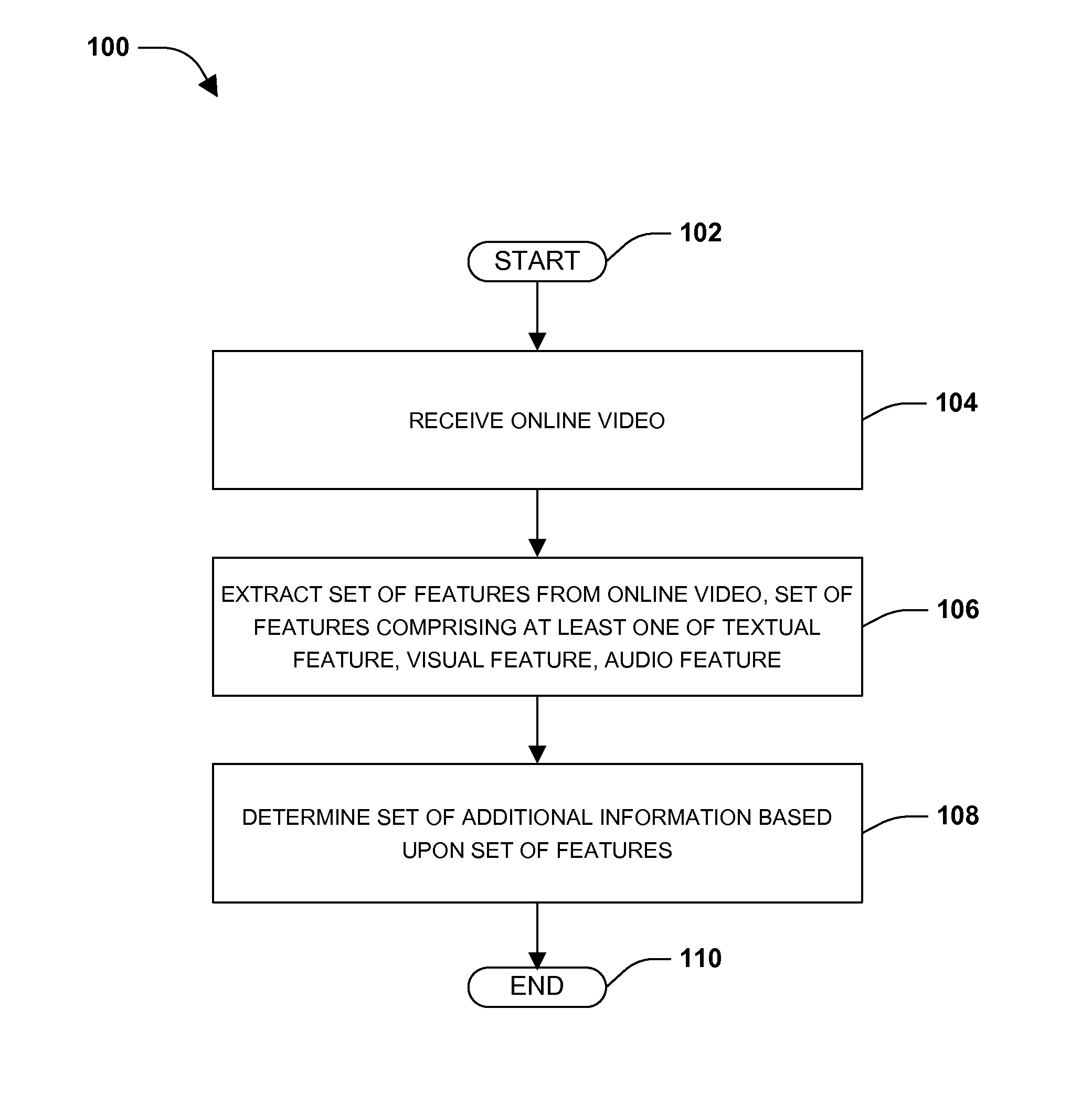
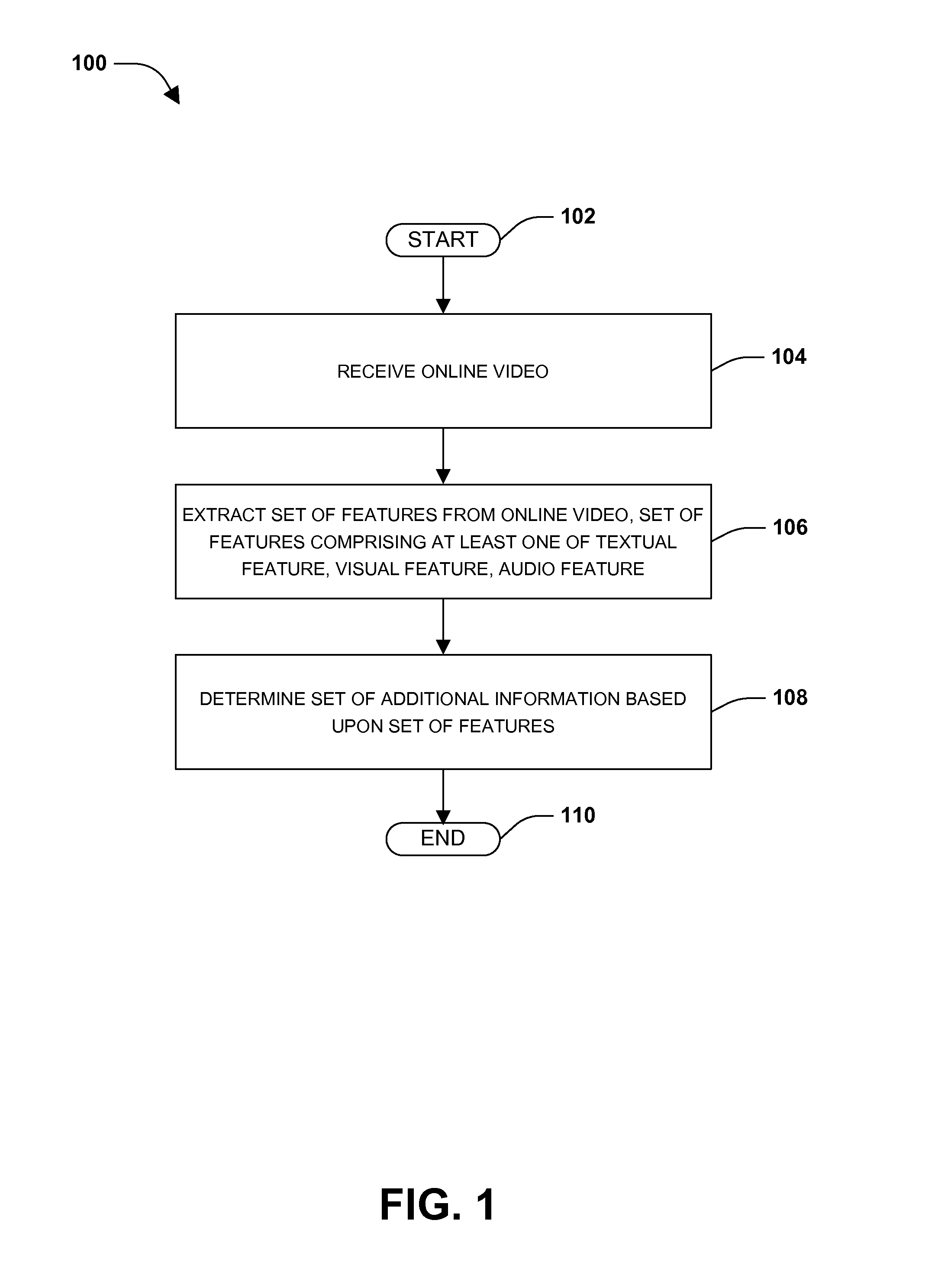
Enriching online videos by content detection, searching, and information aggregation
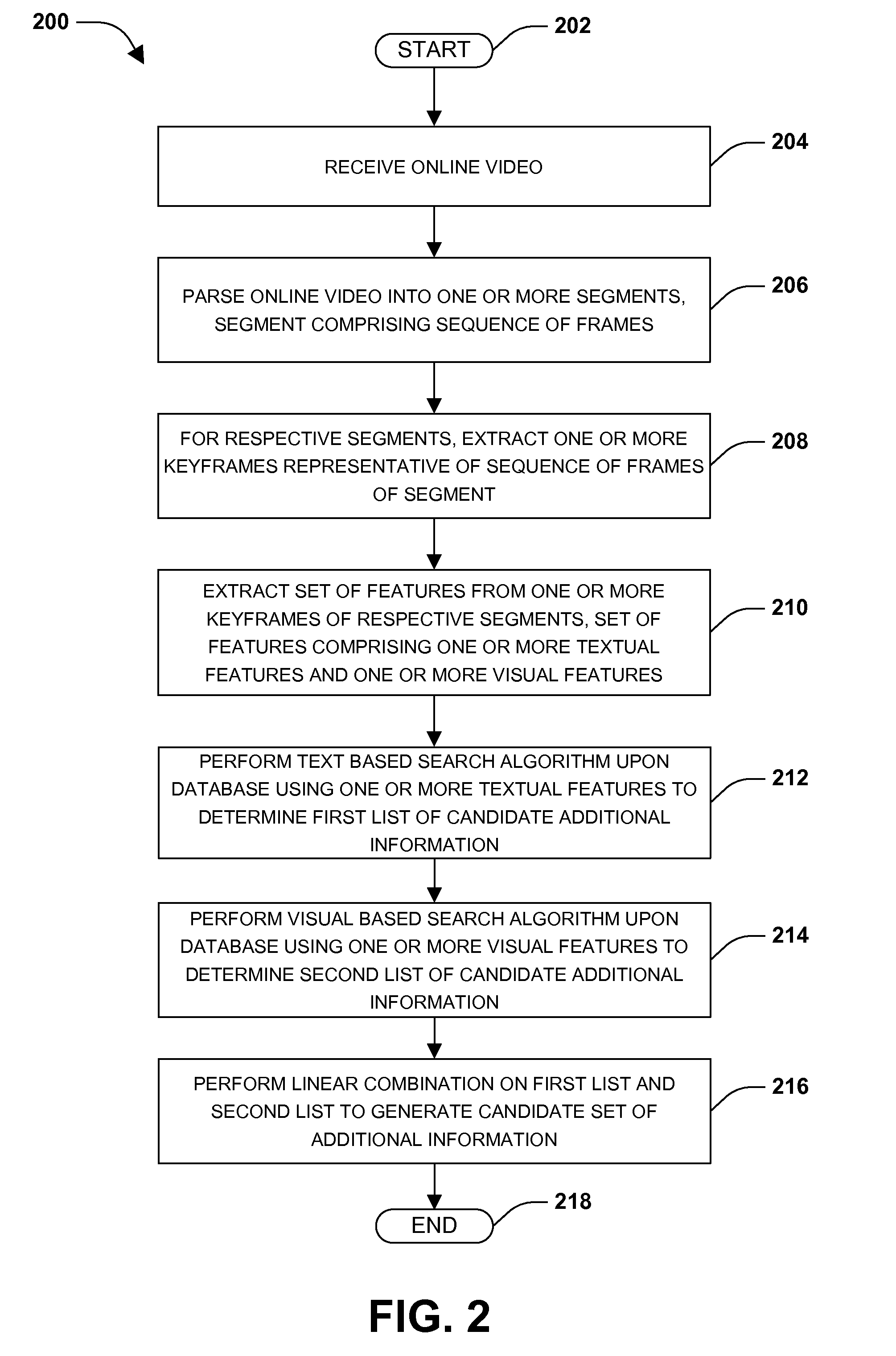
ActiveUS20110264700A1Well formedInput/output for user-computer interactionDigital data processing detailsInternet usersVisual perception
Many internet users consume content through online videos. For example, users may view movies, television shows, music videos, and / or homemade videos. It may be advantageous to provide additional information to users consuming the online videos. Unfortunately, many current techniques may be unable to provide additional information relevant to the online videos from outside sources. Accordingly, one or more systems and / or techniques for determining a set of additional information relevant to an online video are disclosed herein. In particular, visual, textual, audio, and / or other features may be extracted from an online video (e.g., original content of the online video and / or embedded advertisements). Using the extracted features, additional information (e.g., images, advertisements, etc.) may be determined based upon matching the extracted features with content of a database. The additional information may be presented to a user consuming the online video.
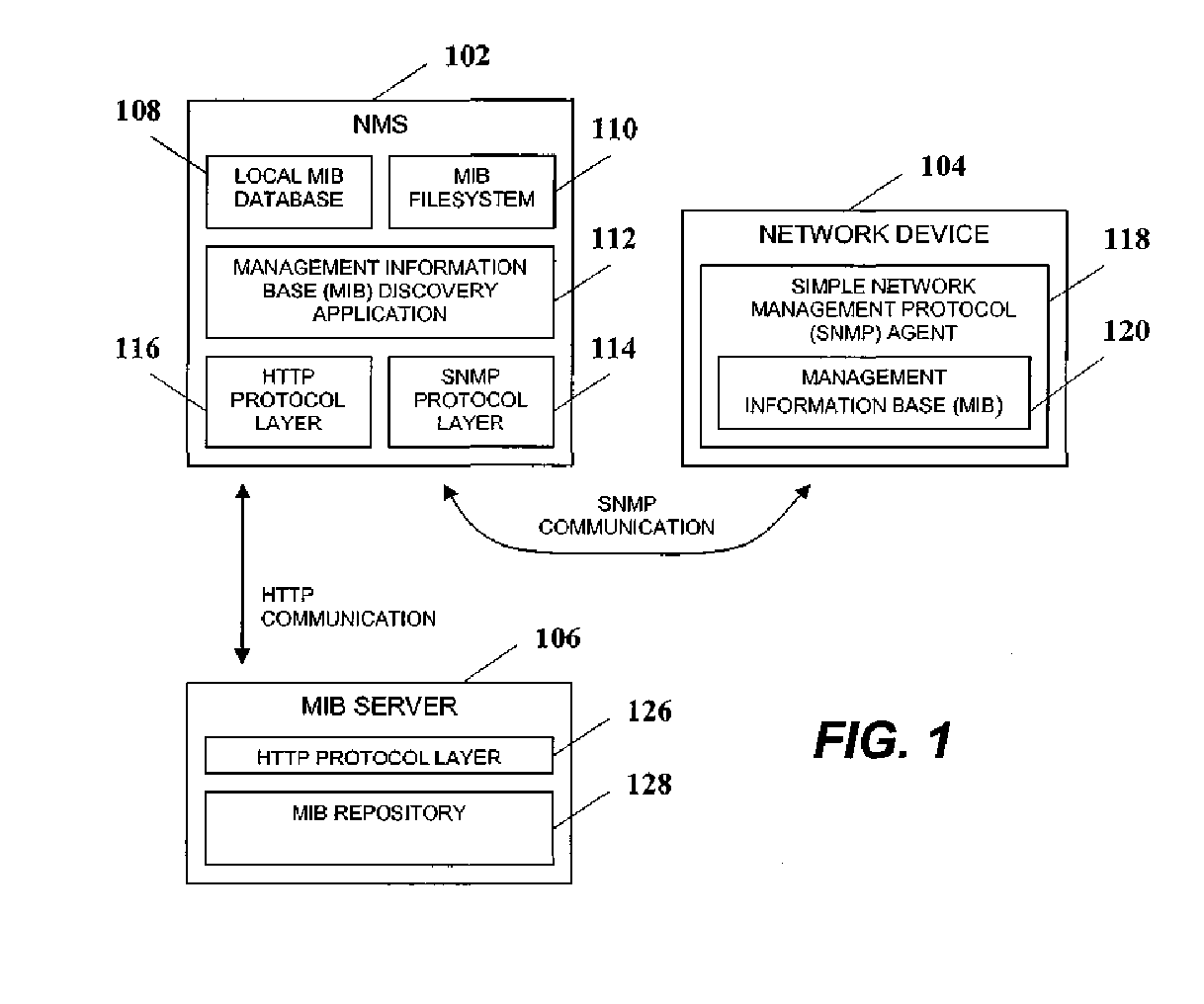
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for aggregating information in a wireless communication system
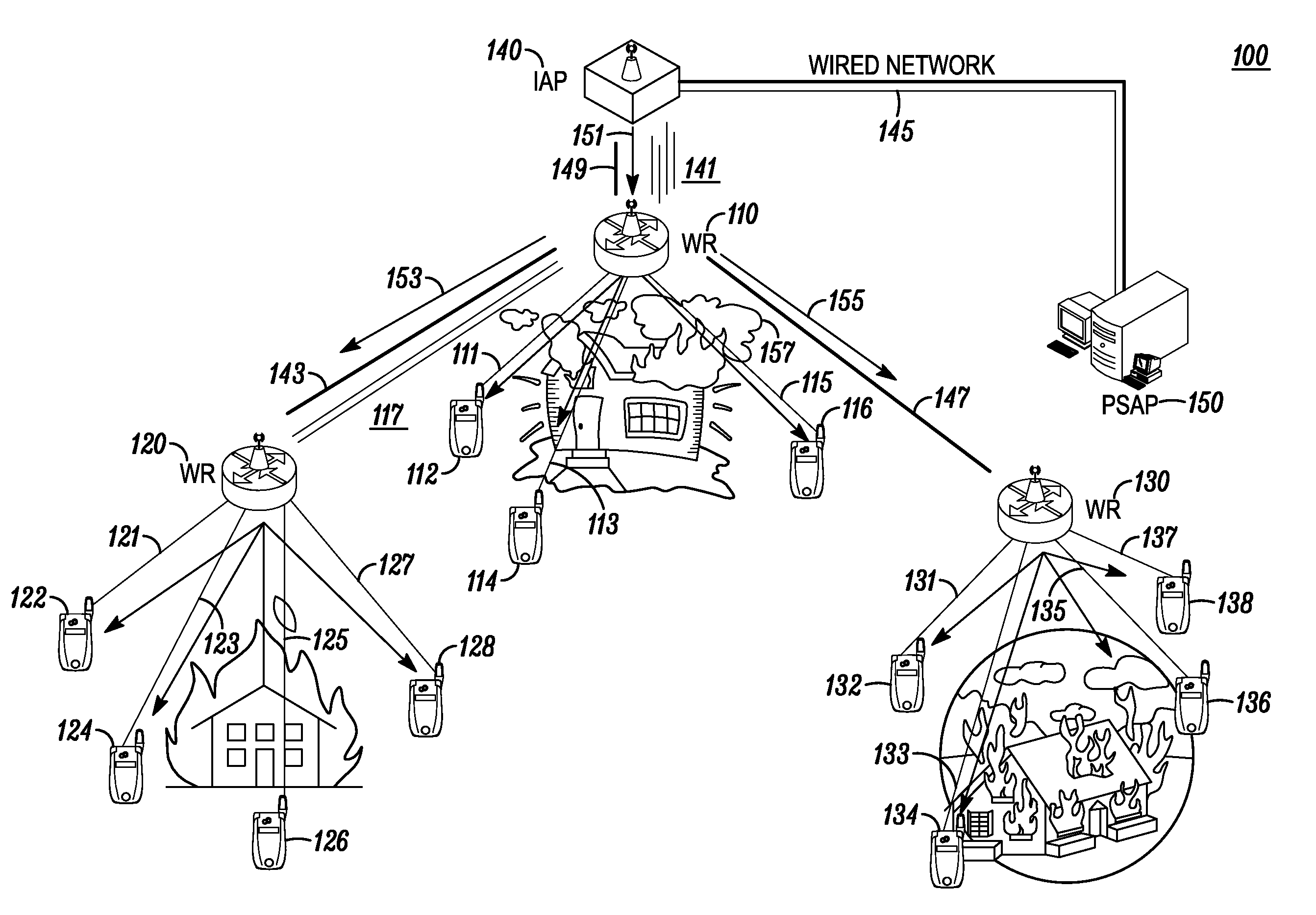
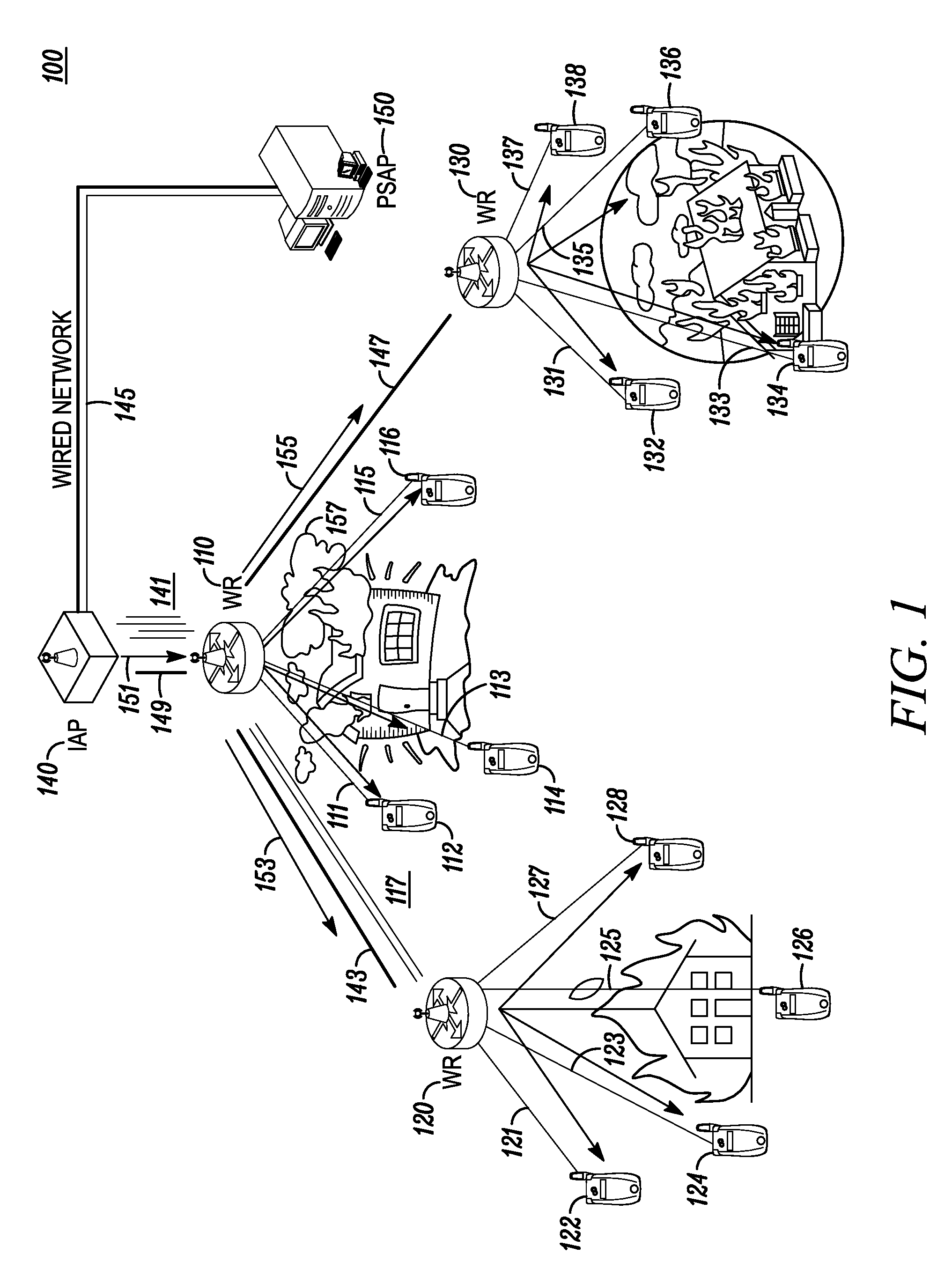
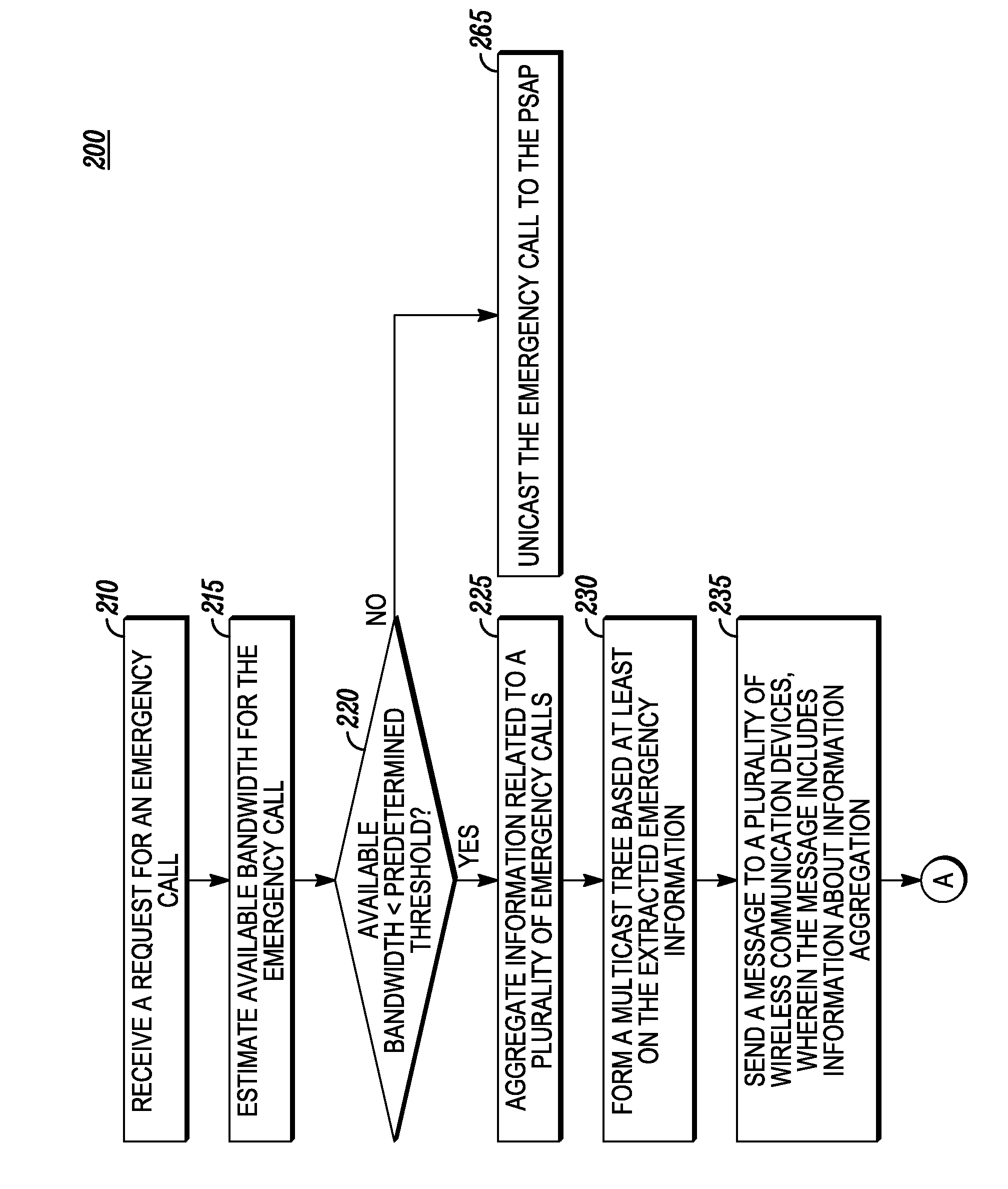
ActiveUS20100029243A1Emergency connection handlingTelephonic communicationWireless routerCommunications system
A Wireless Router (WR) aggregates information regarding the emergency calls based on their context and routes the aggregated emergency information to the correct portal which directs the aggregated emergency to appropriate Public Safety Answering Point (PSAP). The information aggregation is automatically triggered when the number of calls exceeds the multihop capacity to the egress point. The PSAP responds to the emergency situation by sending a response message via the Portal. The WR multicast / broadcasts the response message to the mobile devices which initiated the emergency calls. The response message generally includes emergency instructions based on incident type and location. Further, a call-back list is created for users whose emergency calls were not completed. By using the call-back list PSAP personnel can initiate calls to end users to provide assistance in emergency situations.
Owner:ARRIS ENTERPRISES LLC
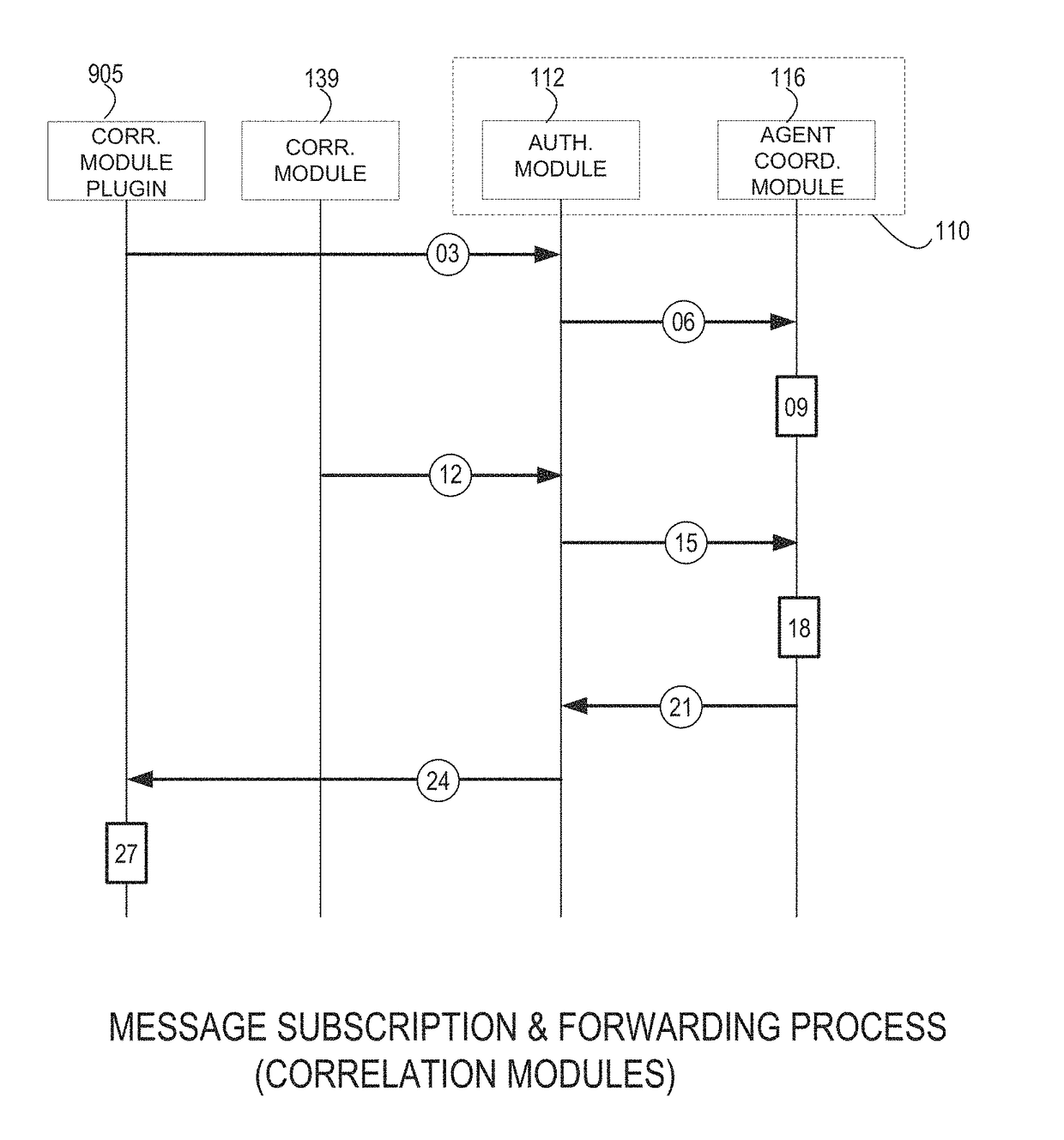
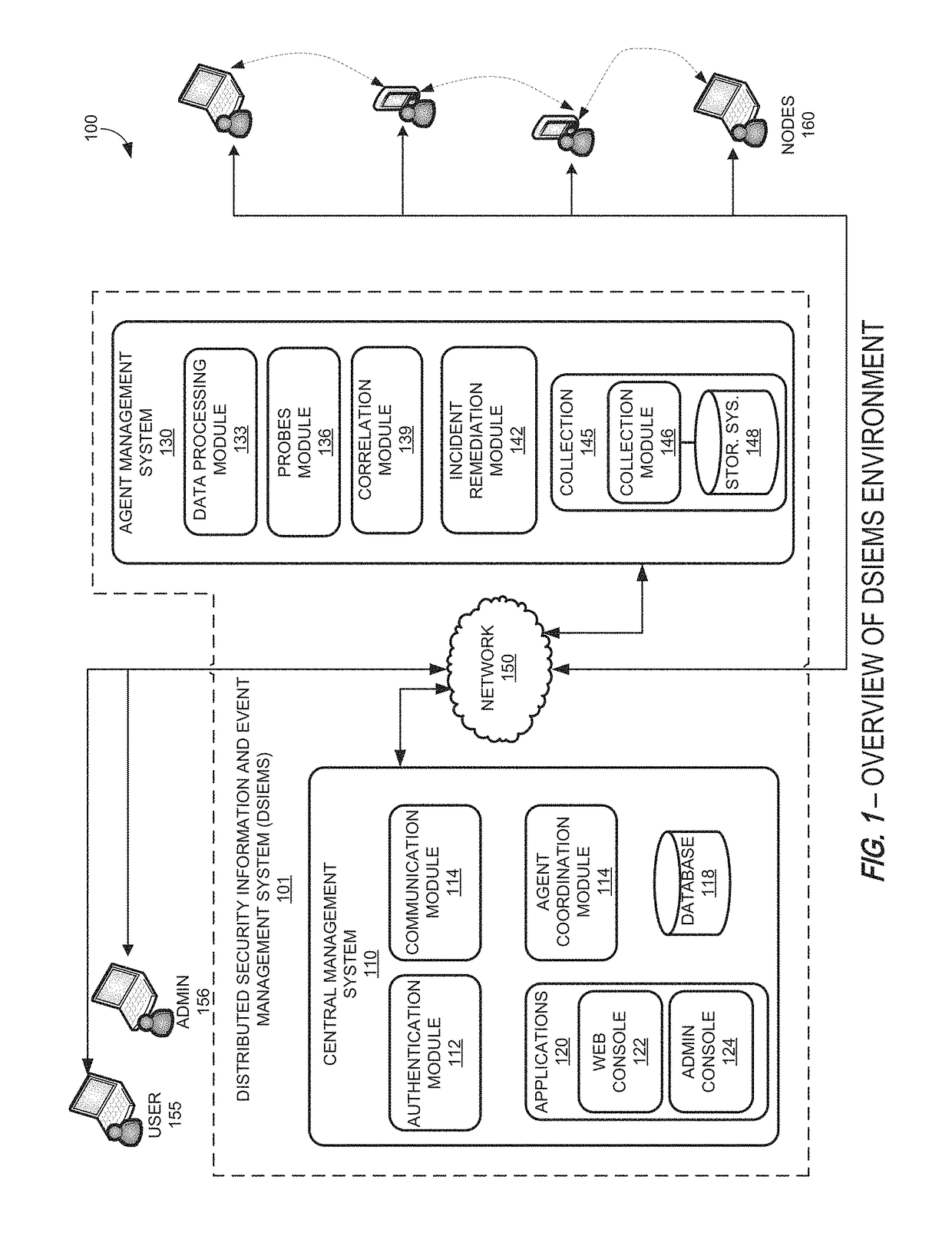
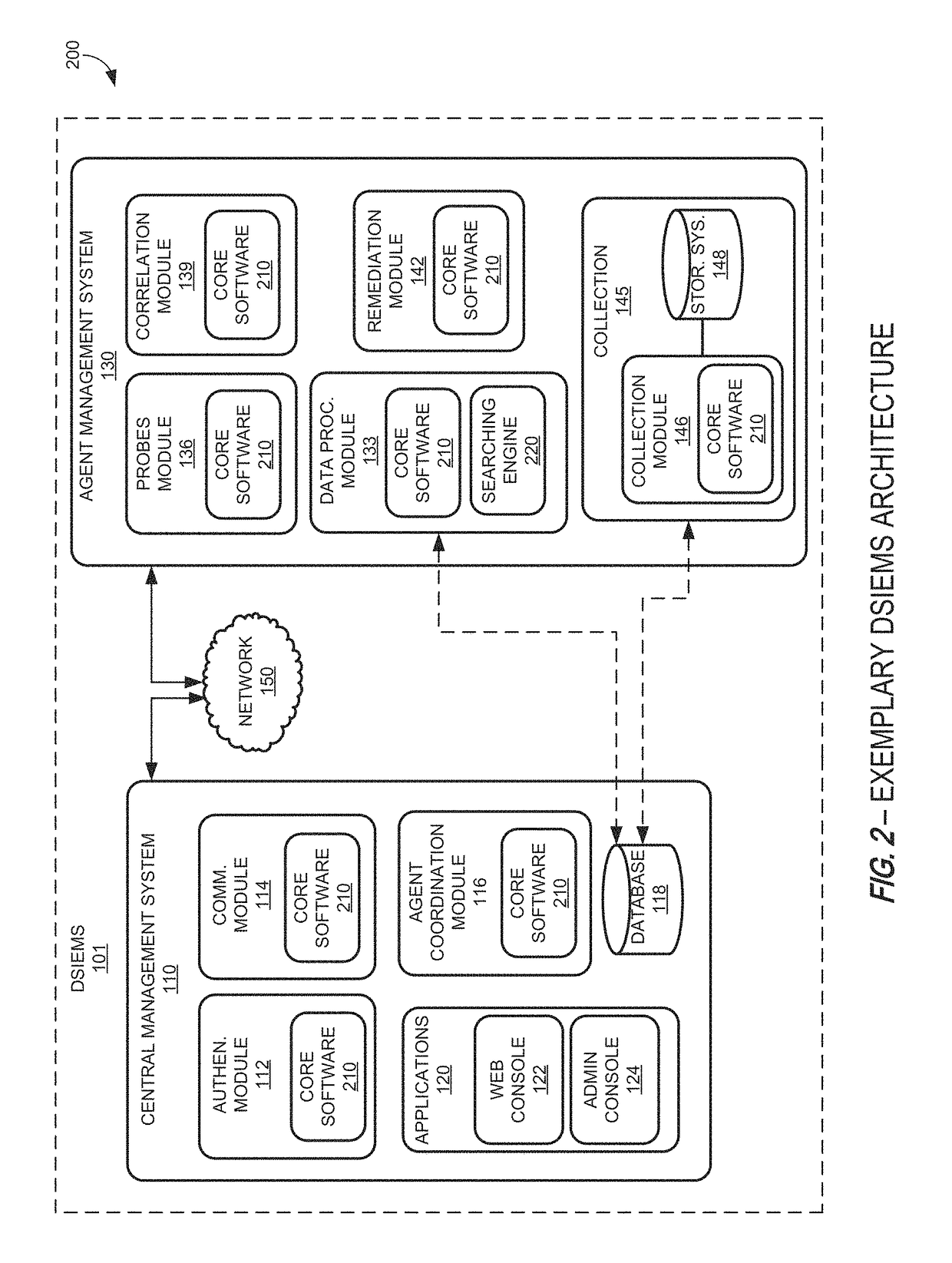
Systems and methods for providing a security information and event management system in a distributed architecture
ActiveUS9813449B1Quick installationEnables flexibilityTransmissionProgram/content distribution protectionSecurity information and event managementData access
A Distributed Security Information and Event Management System (DSIEMS) is a scalable, intelligent, security and fraud management platform that proactively collects information from a network's computer systems, applications, users, and external intelligence data feeds, and aggregates the information into a centralized repository where the information can then be analyzed and quickly acted upon when necessary. Further, according to one aspect, a DSIEMS analyzes aggregated information to discern patterns of potential attack, inappropriate data movement, and fraud from normal and legitimate network activity, account activity, user activity, and data access. According to one embodiment, aspects of the present disclosure are implemented in a distributed architecture. In particular, aspects of the present DSIEMS utilize an agent-based architecture in which intelligent software agents are deployed on each node (e.g., endpoint computing device) within the system.
Owner:LOOKWISE SL
High-performance addressing and routing of data packets with semantically descriptive labels in a computer network
ActiveUS7216179B2Reduce storageEasy to operateMultiple digital computer combinationsData switching networksRouting tableNetwork packet
A method, system and apparatus for routing data through a network based on the content or semantics of the data. Semantic routing engines route the data through the network based upon information maintained in routing tables. The routing tables used to route the content through the network are derived by aggregating information about either content consumers or content producers into ontological trees.
Owner:SEMANDEX NETWORKS
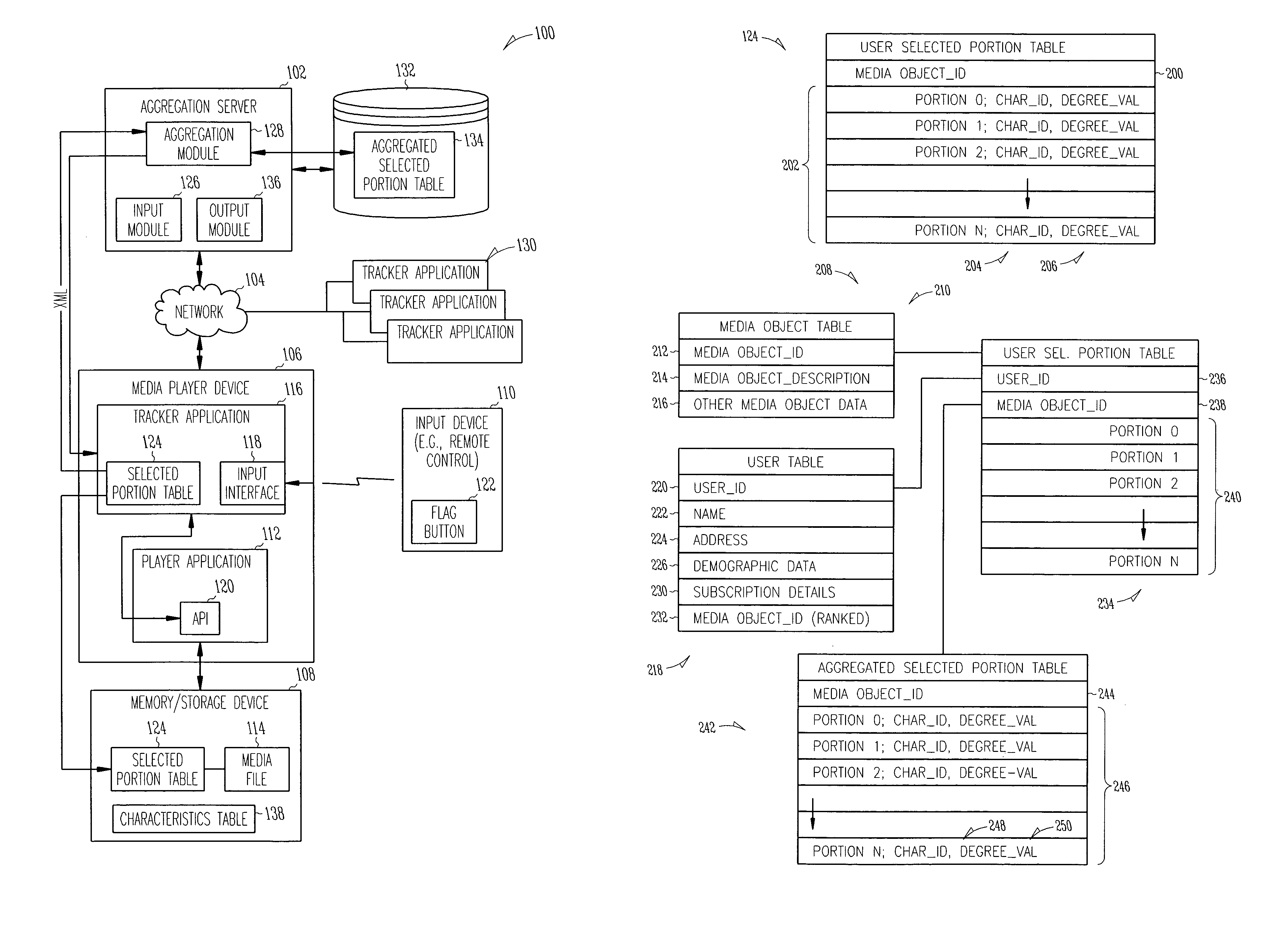
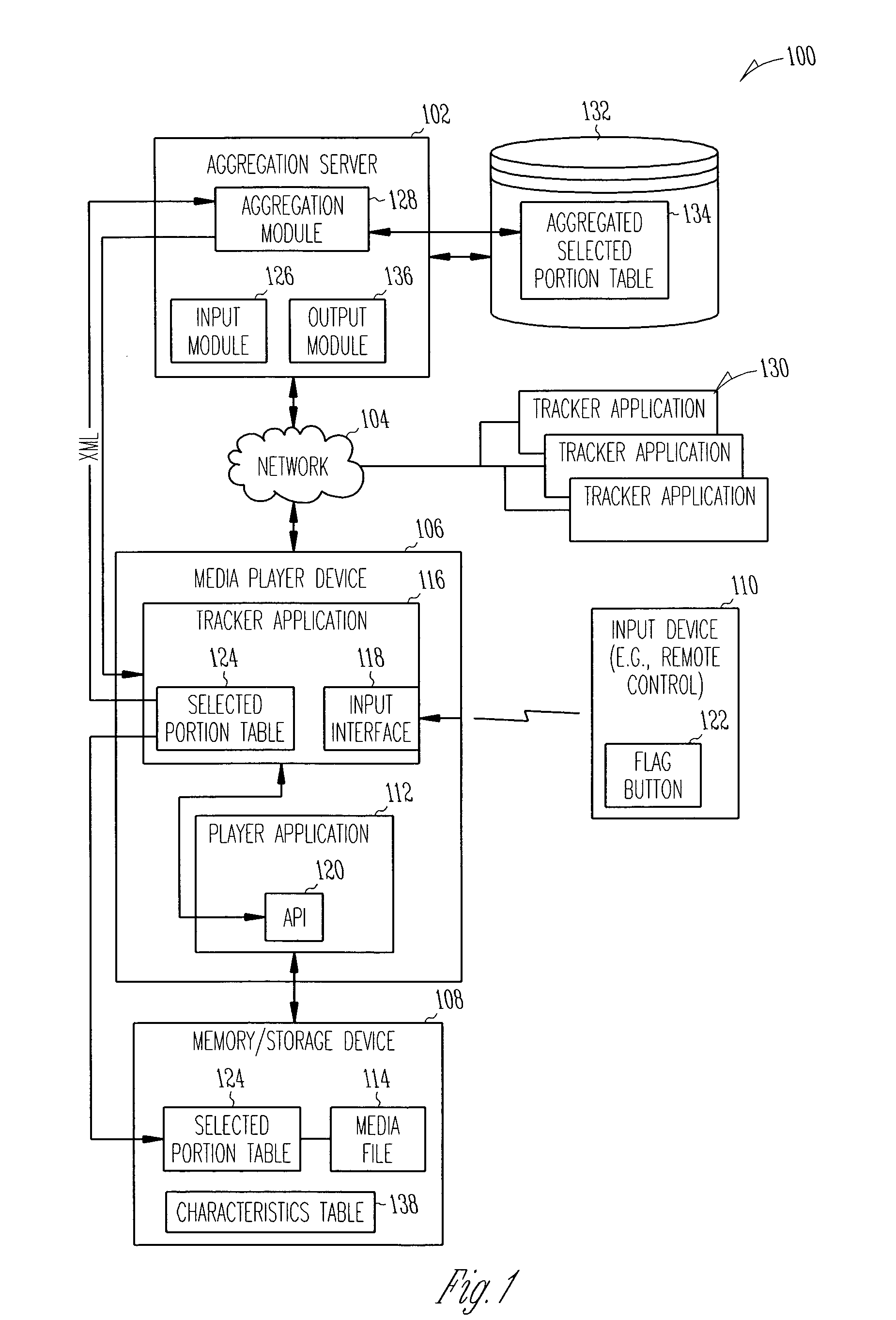
Aggregating characteristic information for digital content
ActiveUS8001143B1Digital data processing detailsMetadata multimedia retrievalDigital contentData mining
Owner:ADOBE SYST INC
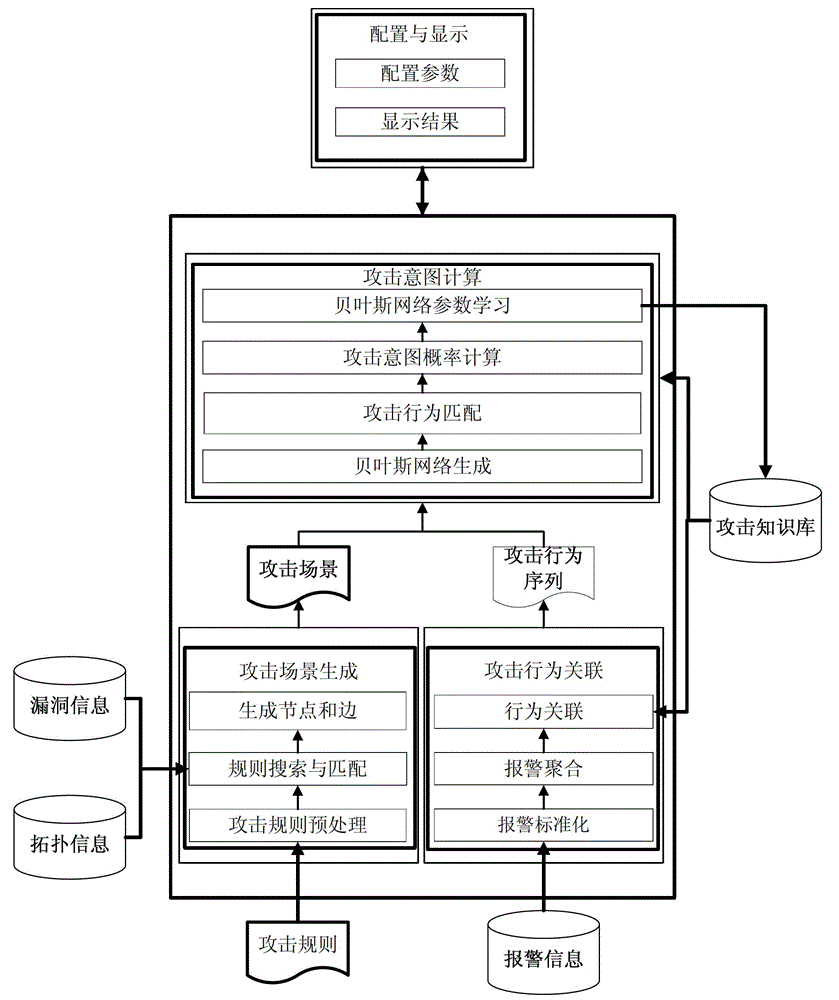
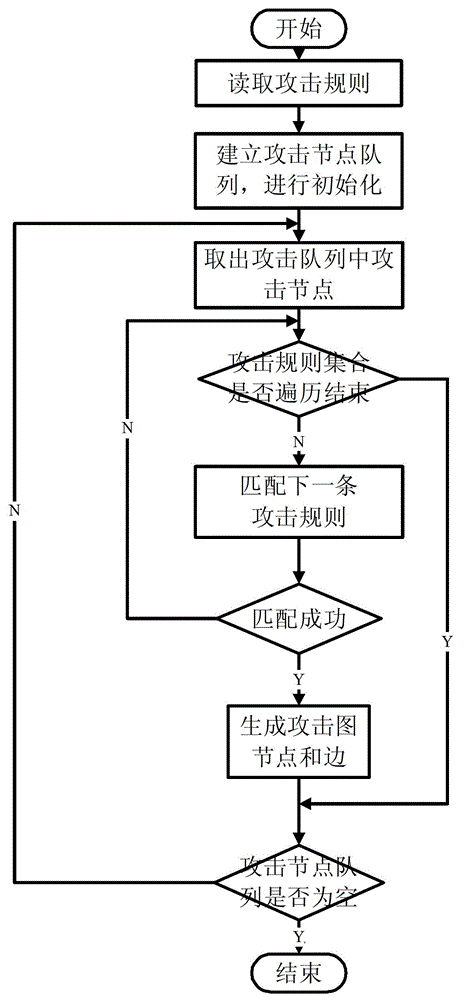
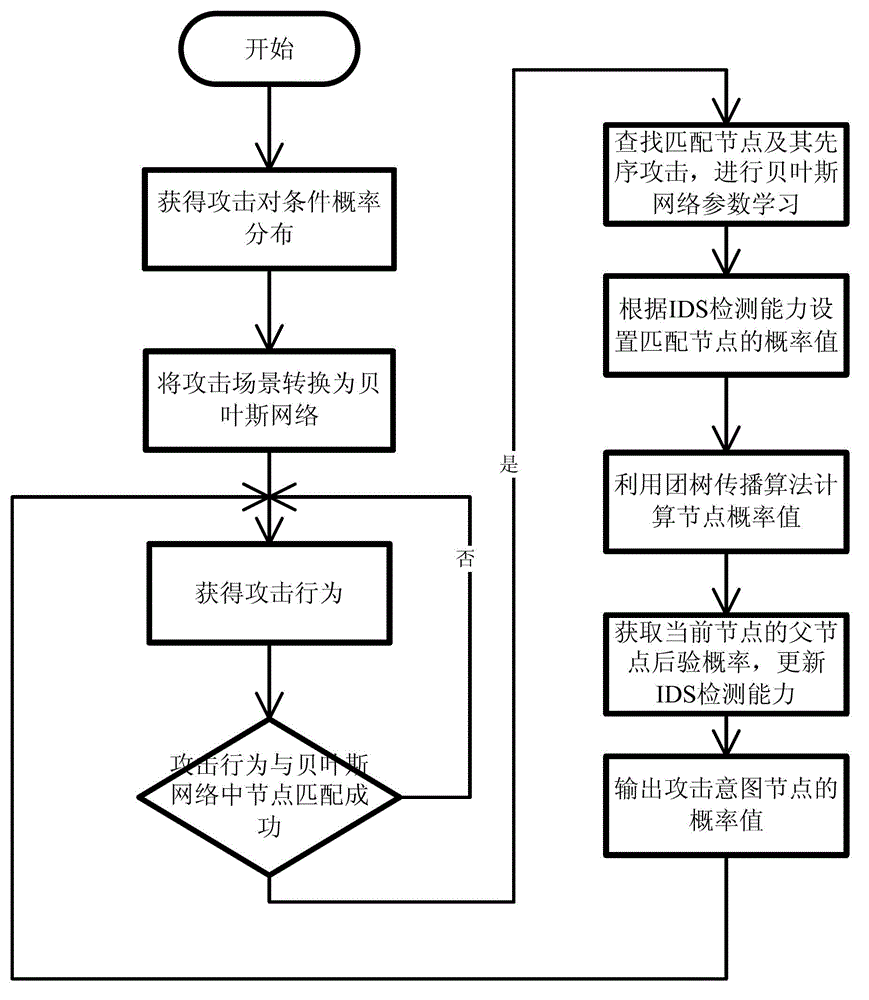
Attack intention recognition method based on Bayesian network inference
InactiveCN102724199AImprove scalabilityThe calculation result is accurateTransmissionPattern recognitionClique tree
The invention provides an attack intention recognition method based on Bayesian network inference. The attack intention recognition method is applied to the attack intention recognition of an intelligence and decision-making oriented system with a parameter learning mechanism in computer network self-organizing operation (CNSOO). The method can enable an intelligence system to recognize the attack intention of an attacker by using IDS (Intrusion Detection System) alarm information according to given host vulnerability information, network topological information and attack knowledge base and supply the attack intention to a decision-making system as a decision-making basis in a CNSOO environment. The attack intention recognition process comprises the following steps of: generating attacking scenes, fusing and matching IDS alarm information, updating conditional probability distribution caused by attacking behaviors, calculating the probability of attack intention nodes by using a clique tree propagation algorithm in the Bayesian network inference, and updating Bayesian network parameters and IDS detection capability. The calculation parameters are updated according to calculation results and historical information, so that the calculation results can be more accurate.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com