Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1342 results about "Data export" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data export. Data export is the process that executes a Kusto query and writes its results, making the query results available for later inspection. There are several methods for data export:
Dynamic presentation framework
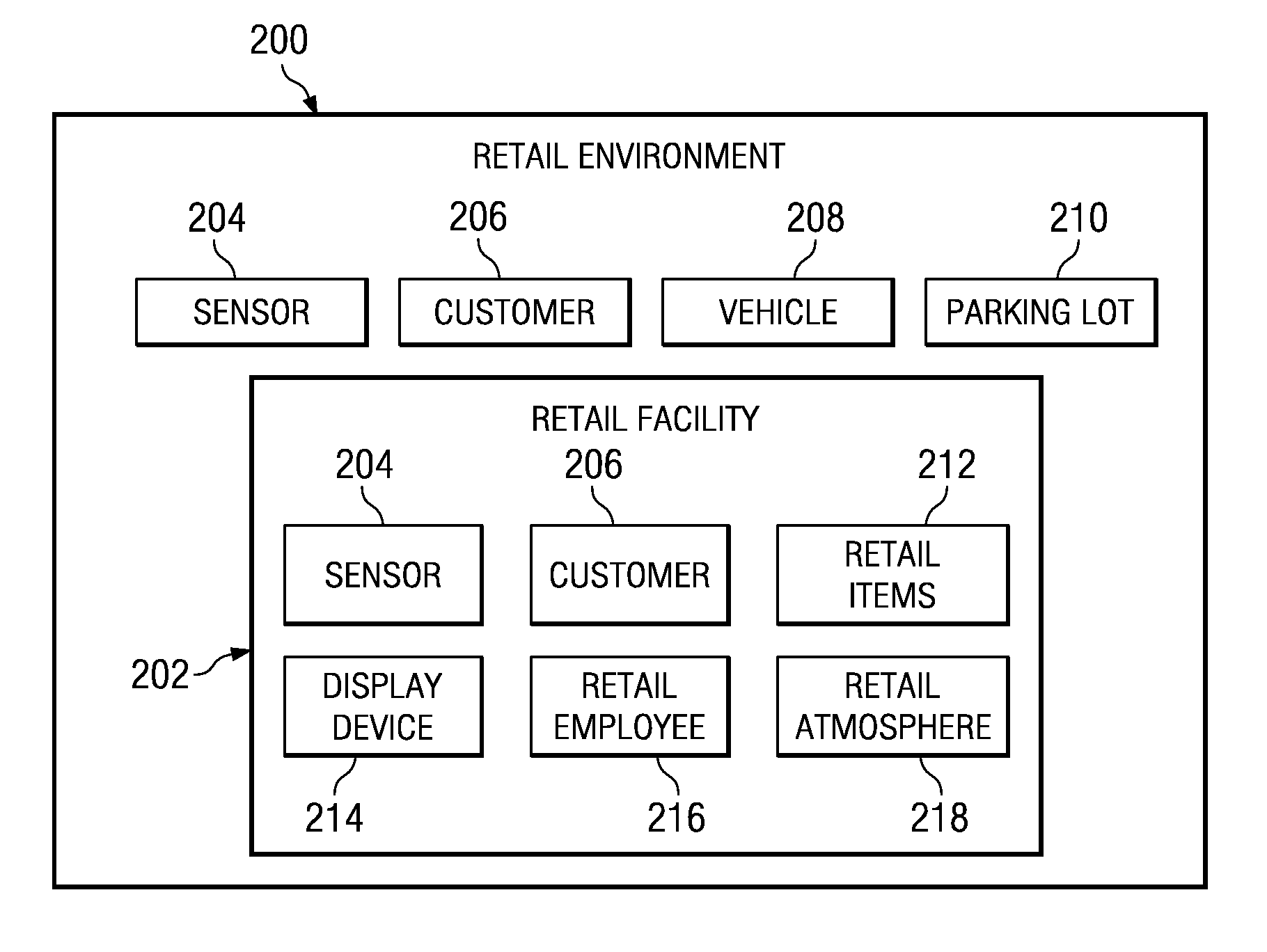
ActiveUS20110040804A1Eliminate the problemDigital data processing detailsMultimedia data retrievalDisplay deviceWorld Wide Web
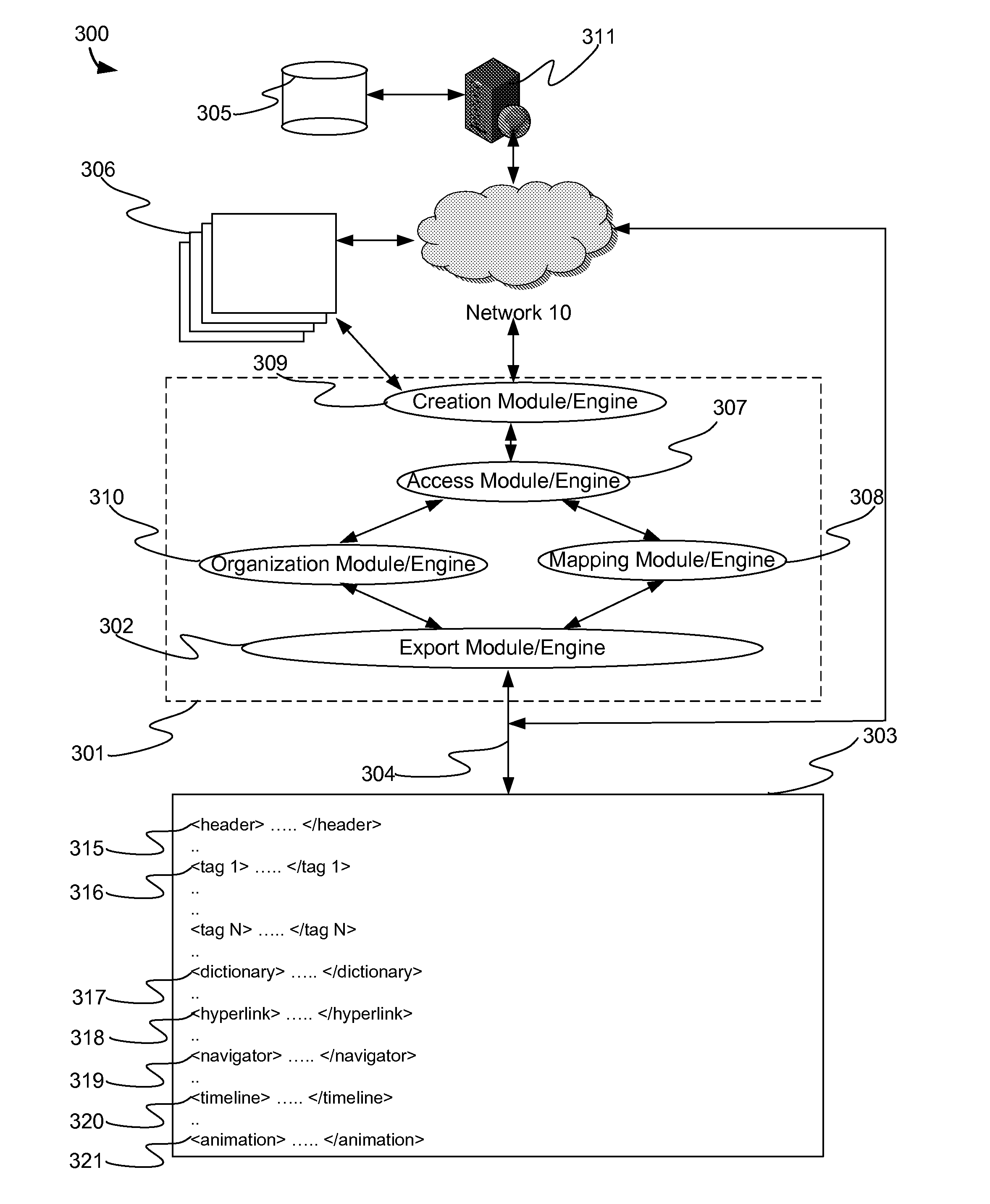
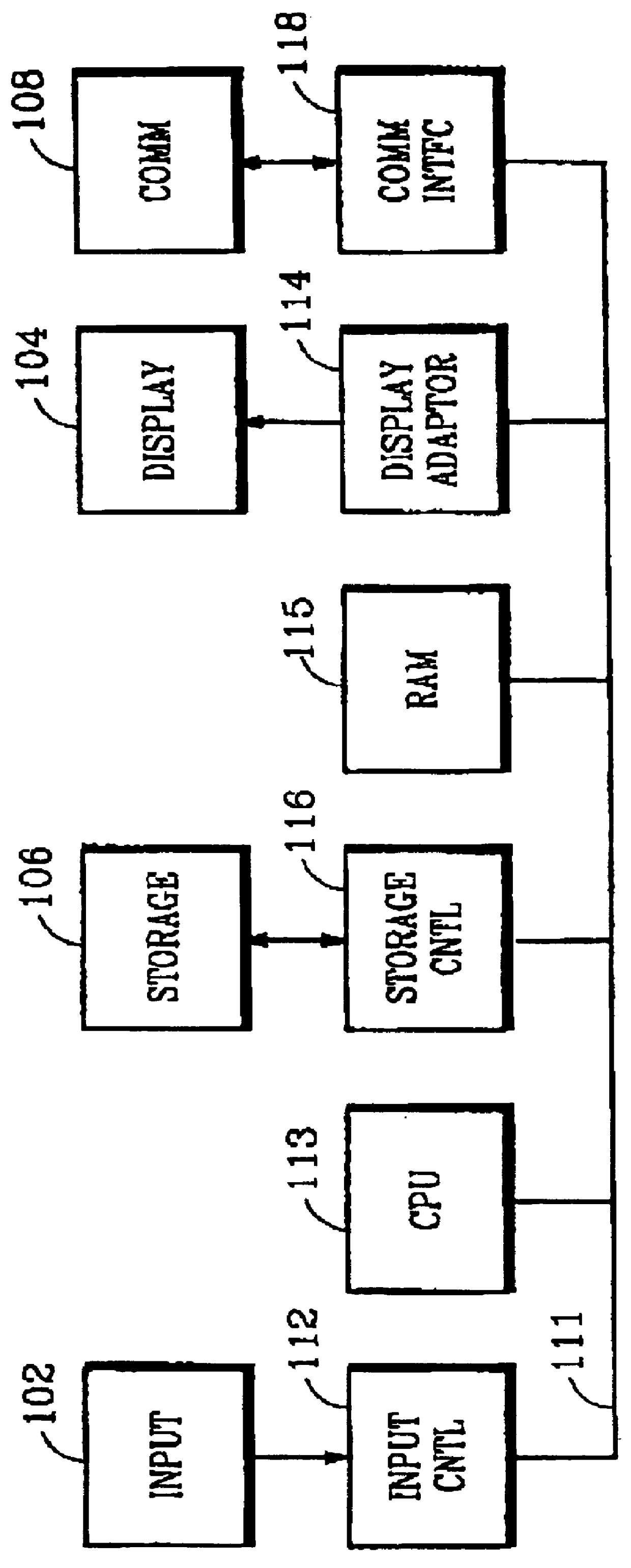
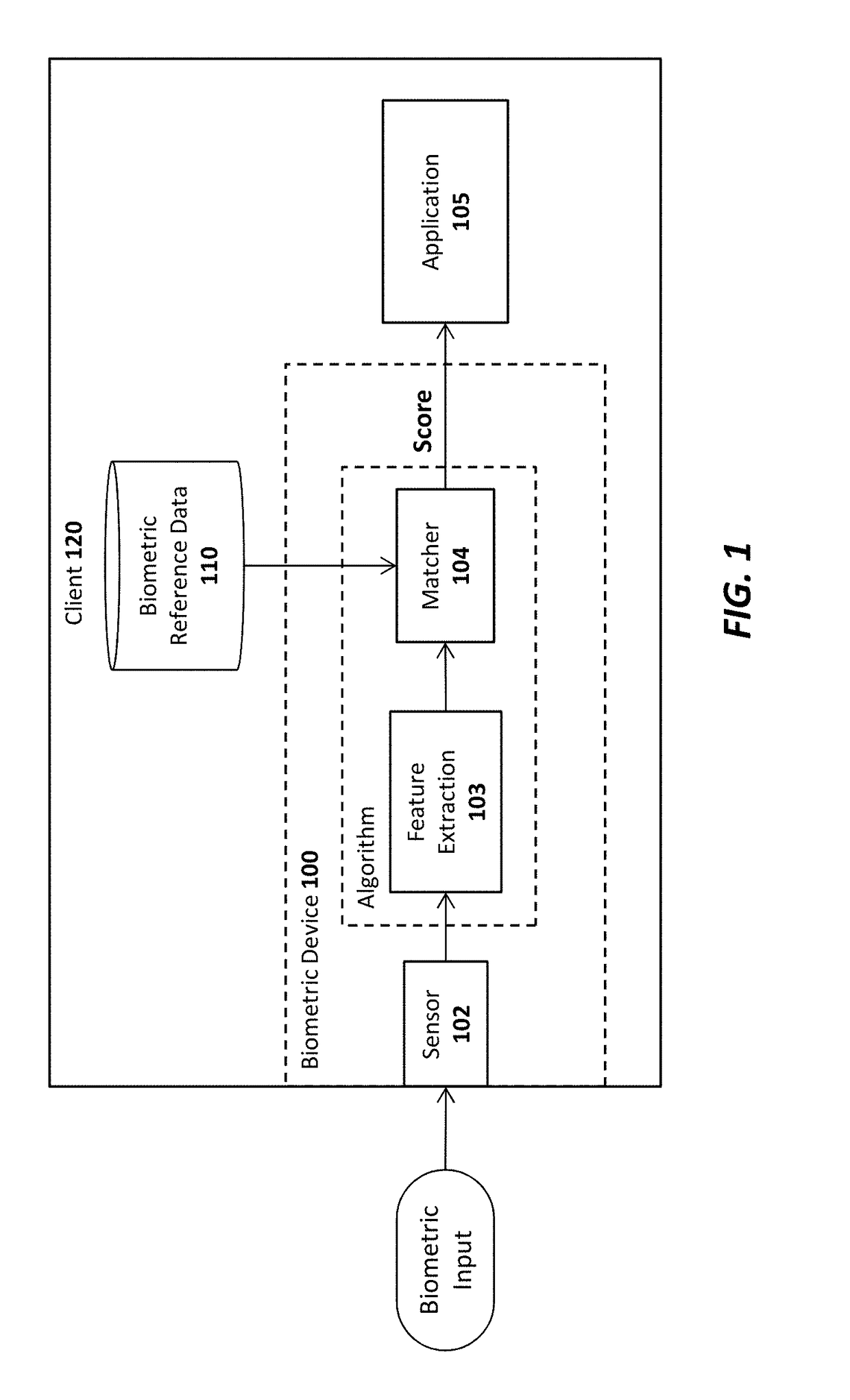
A system in accordance with the present invention may include one or more processors, memory from which the processor may fetch instructions according to a clock operating at a frequency, a display device, and one or more programs stored in the memory, with instructions to create a structured file for storing data related to the media presentation, access the data related to the media presentation from the presentation application, organize the data related to the media presentation according to an event, and export the organized data related to the media presentation to the structured file. These instructions may also be executed as steps of a method and may be fetched during the execution of one or more programs stored in a computer-readable storage medium.
Owner:APPLE INC
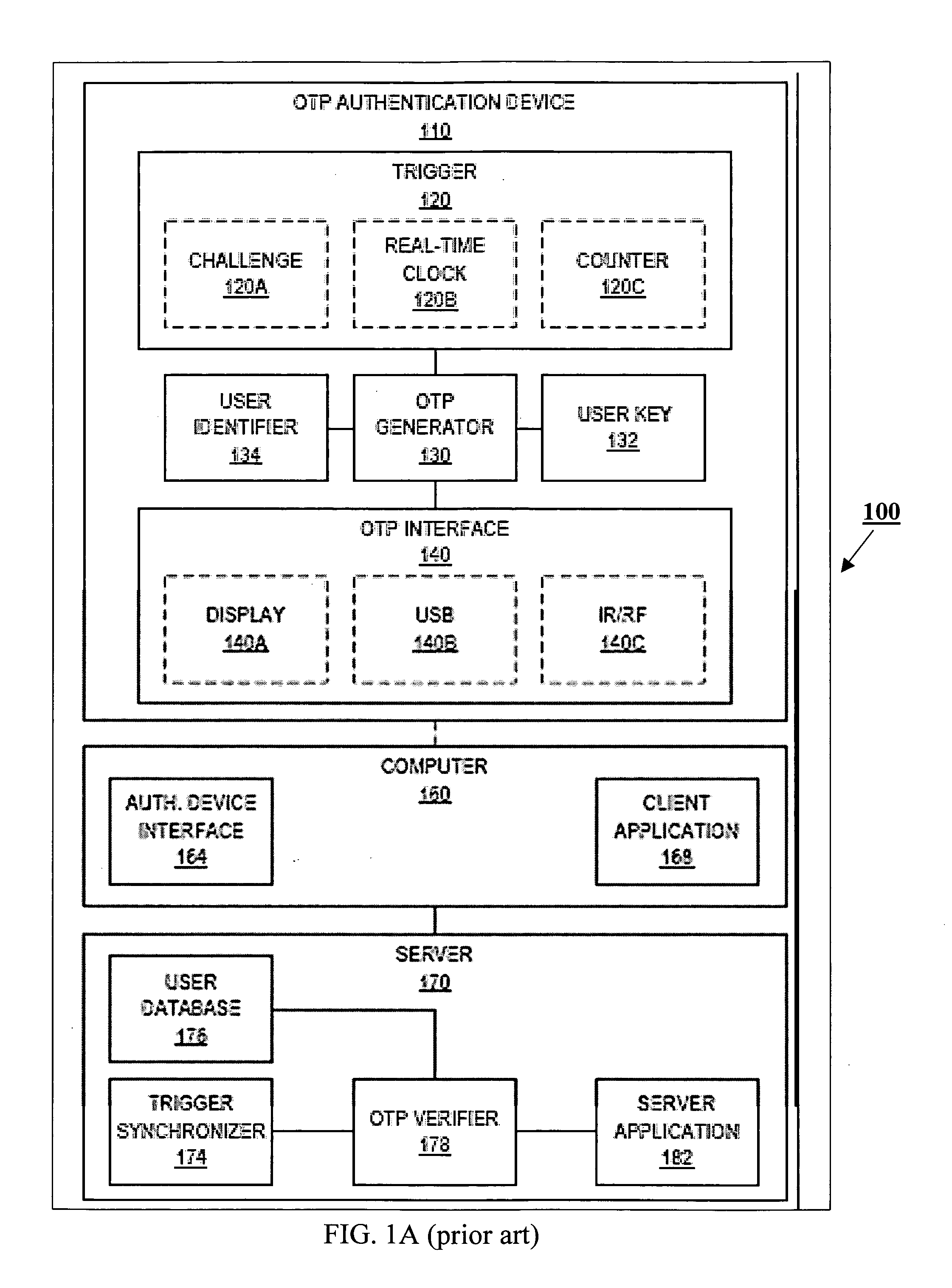
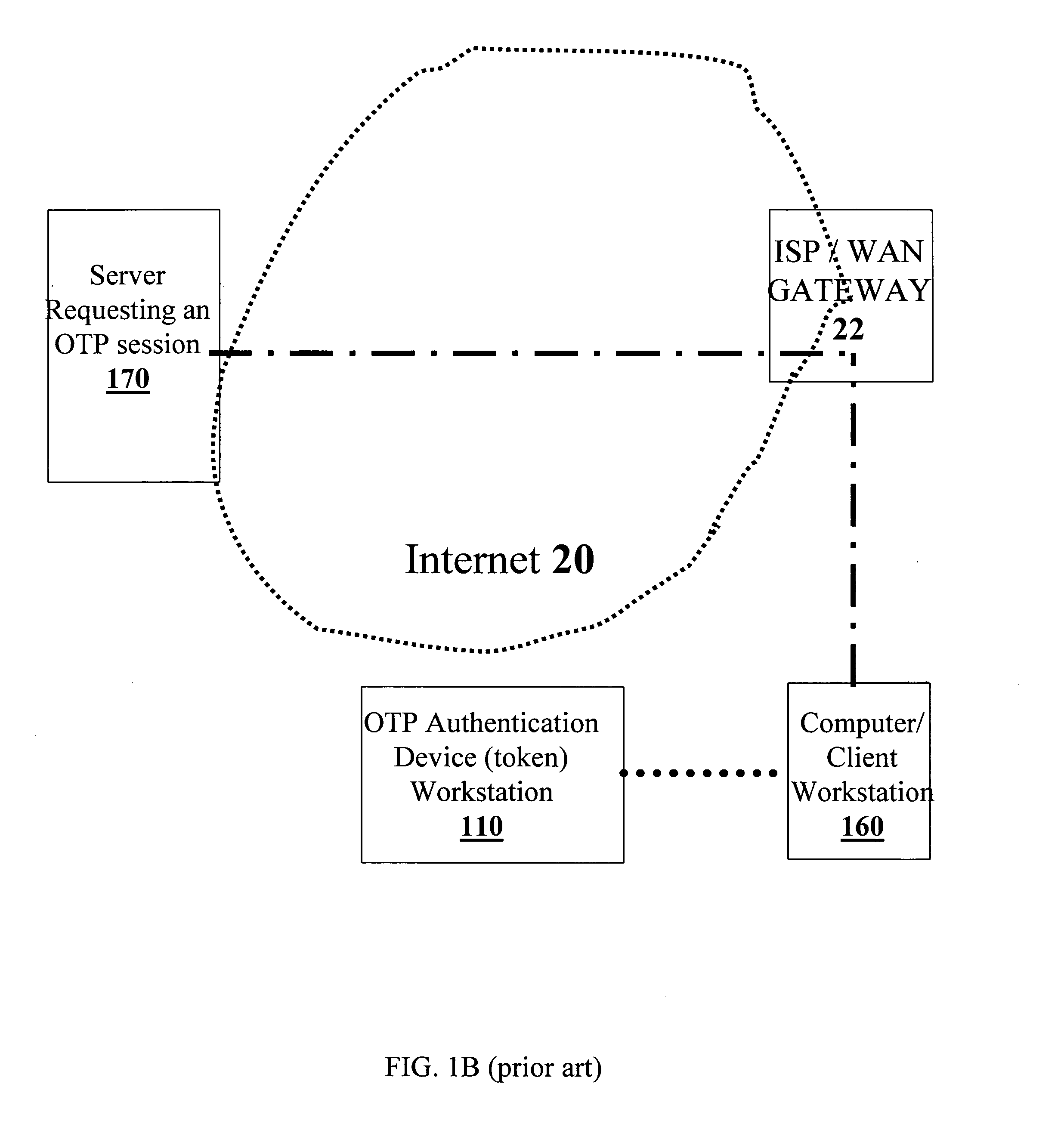
Extended one-time password method and apparatus
ActiveUS20070067828A1Vehicle testingKey distribution for secure communicationThe InternetUser authentication
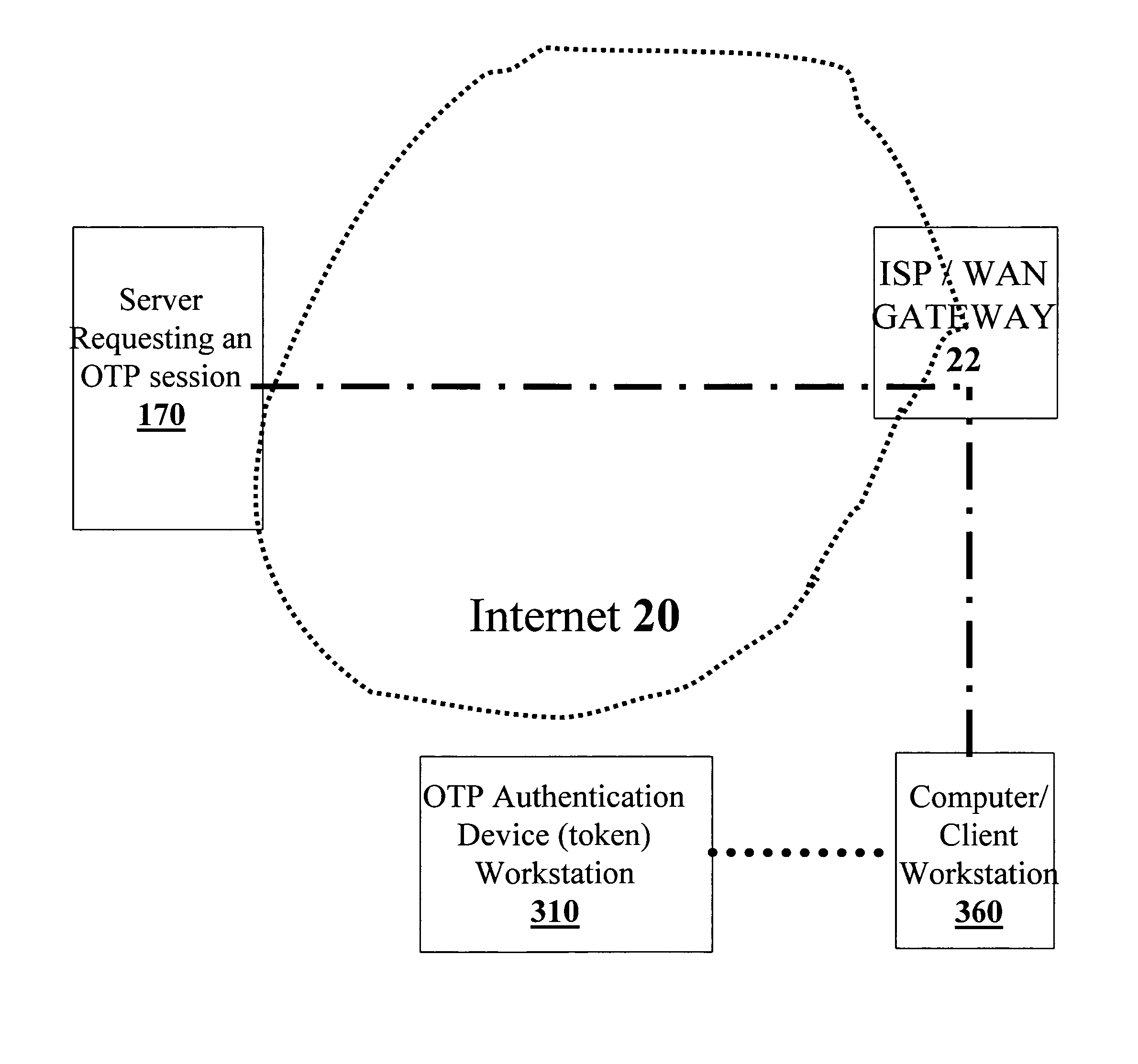
An OTP token for facilitating the authorizing of a client workstation to conduct a session with a server over the Internet is disclosed. Information at least partially identifying the server is provided to the OTP token and / or the client workstation, and a determination is made, using this identifying information, if the server is a legitimate server. In accordance with this determination, it is decided whether or not to transmit data indicative of a session OTP from the OTP token to the client workstation. In some embodiments, if the identifying information is indicative of a legitimate server, the data indicative of the session OTP is transmitted from the OTP token to the client workstation, and otherwise, the data indicative of the session OTP is withheld from the client workstation. Data indicative of the session OTP may include, in various embodiments, either multi-factor authentication data derived from user authorization data, or session OTP data that is independent of user authentication data.
Owner:WESTERN DIGITAL ISRAEL LTD
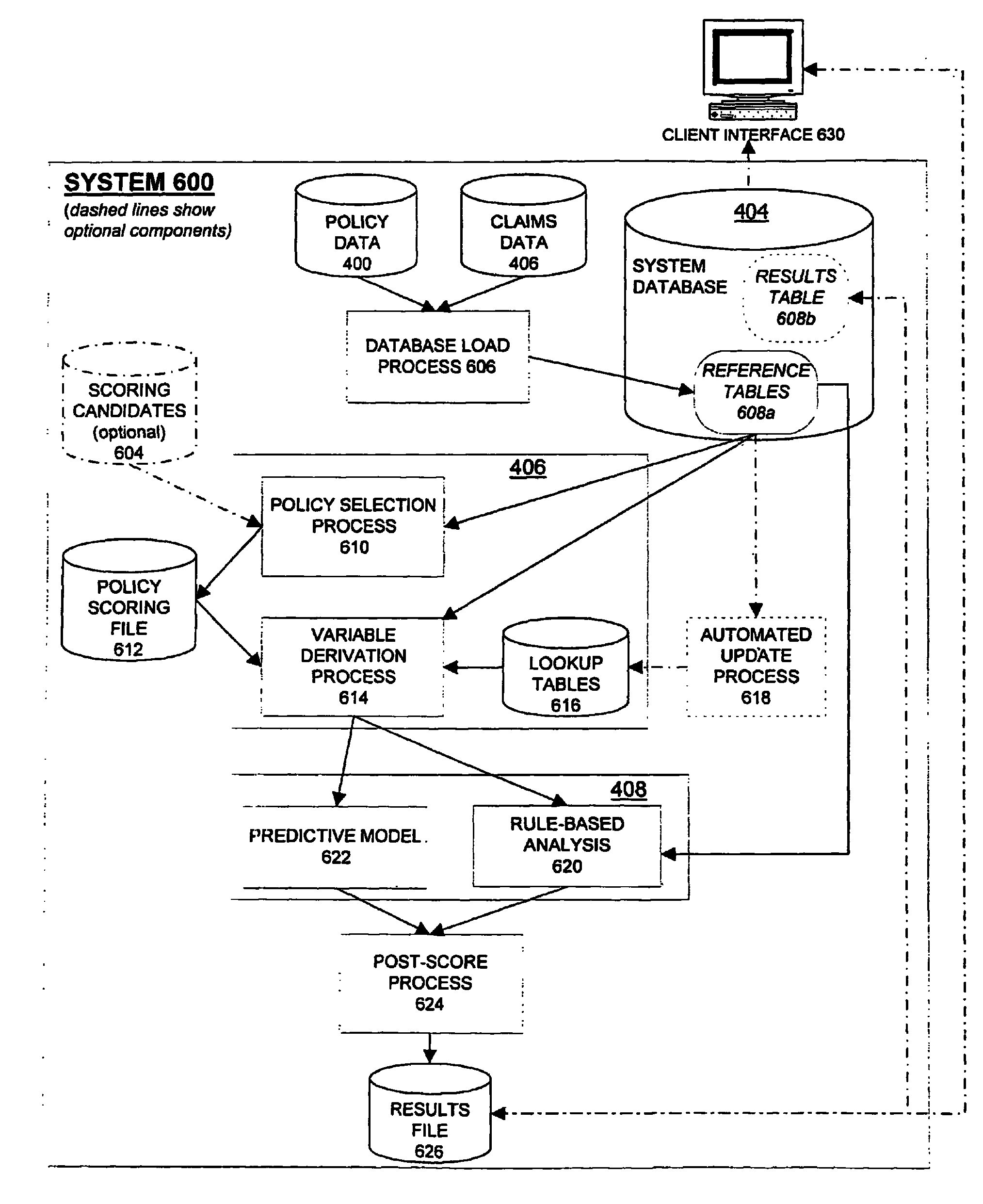
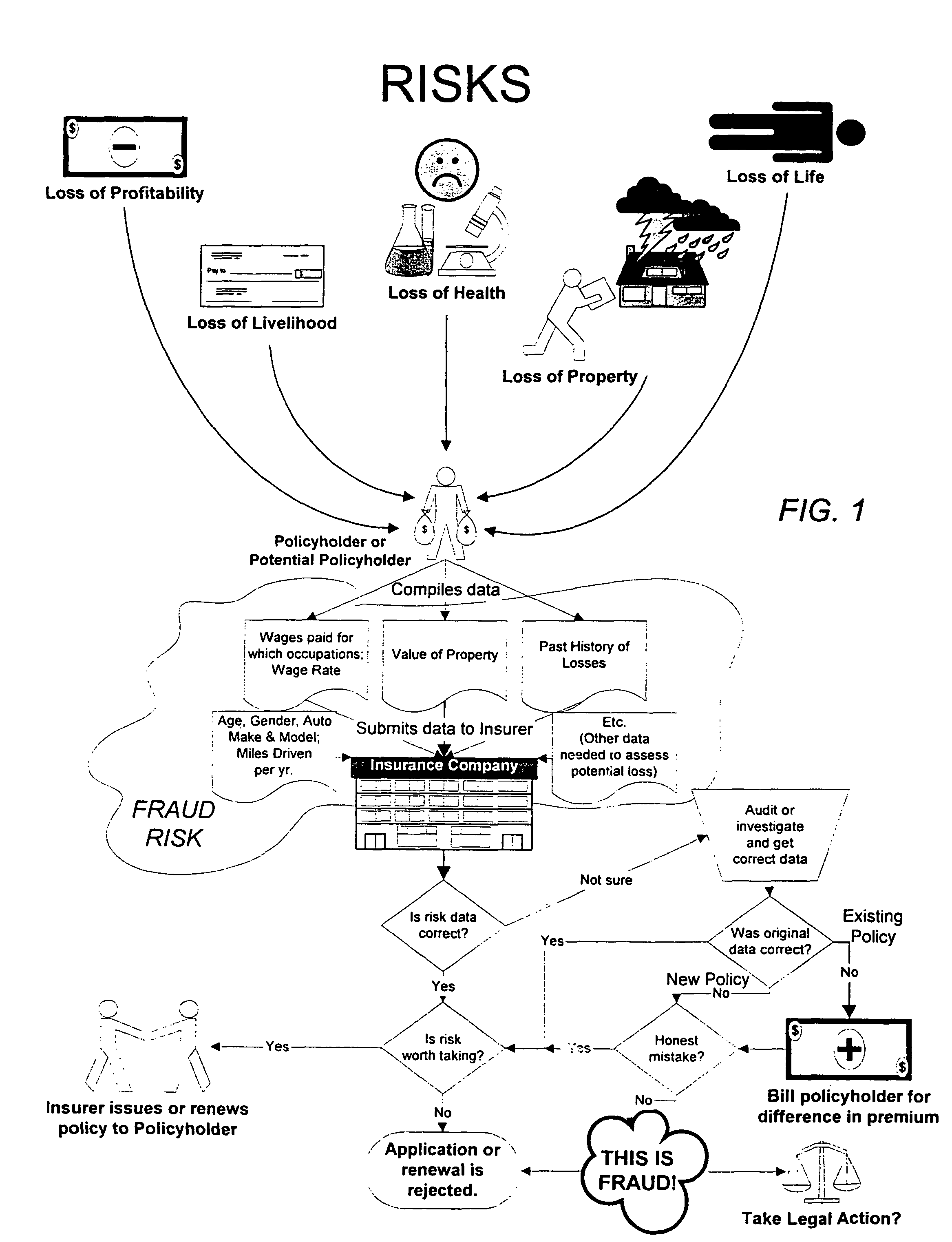
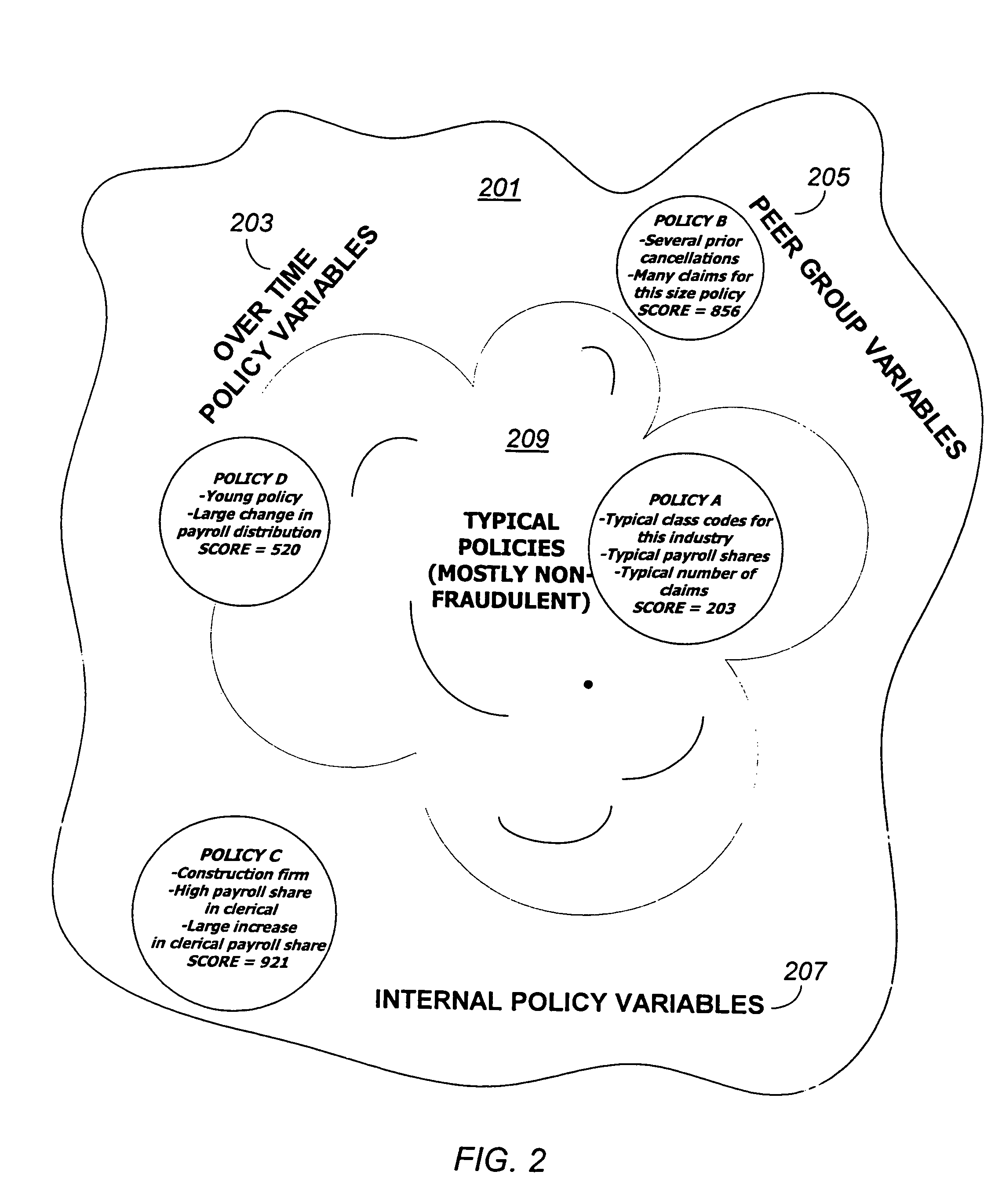
Detection of insurance premium fraud or abuse using a predictive software system
InactiveUS7813944B1Level of complexityIncrease ratingsFinanceOffice automationRelevant informationSoftware system
Detection of insurance premium fraud is provided by a predictive model, which uses derived variables to assess the likelihood of fraud for each policy. The predictive model produces a score, which is a measure of the likelihood of premium fraud or abuse. The predictive model is included in a system that accepts policies to be considered for scoring, selects which policies are appropriate for scoring, stores data about the policies in a database, uses the data to derive variables for the model, and processes and outputs the model scores and related information. A rule-based analysis, which detects specific inconsistencies in the data that are indicative of premium fraud, may also be part of the system. The model scores and red-flag indicators from the rule-based analysis may be further processed to provide customized output for users.
Owner:FAIR ISAAC & CO INC
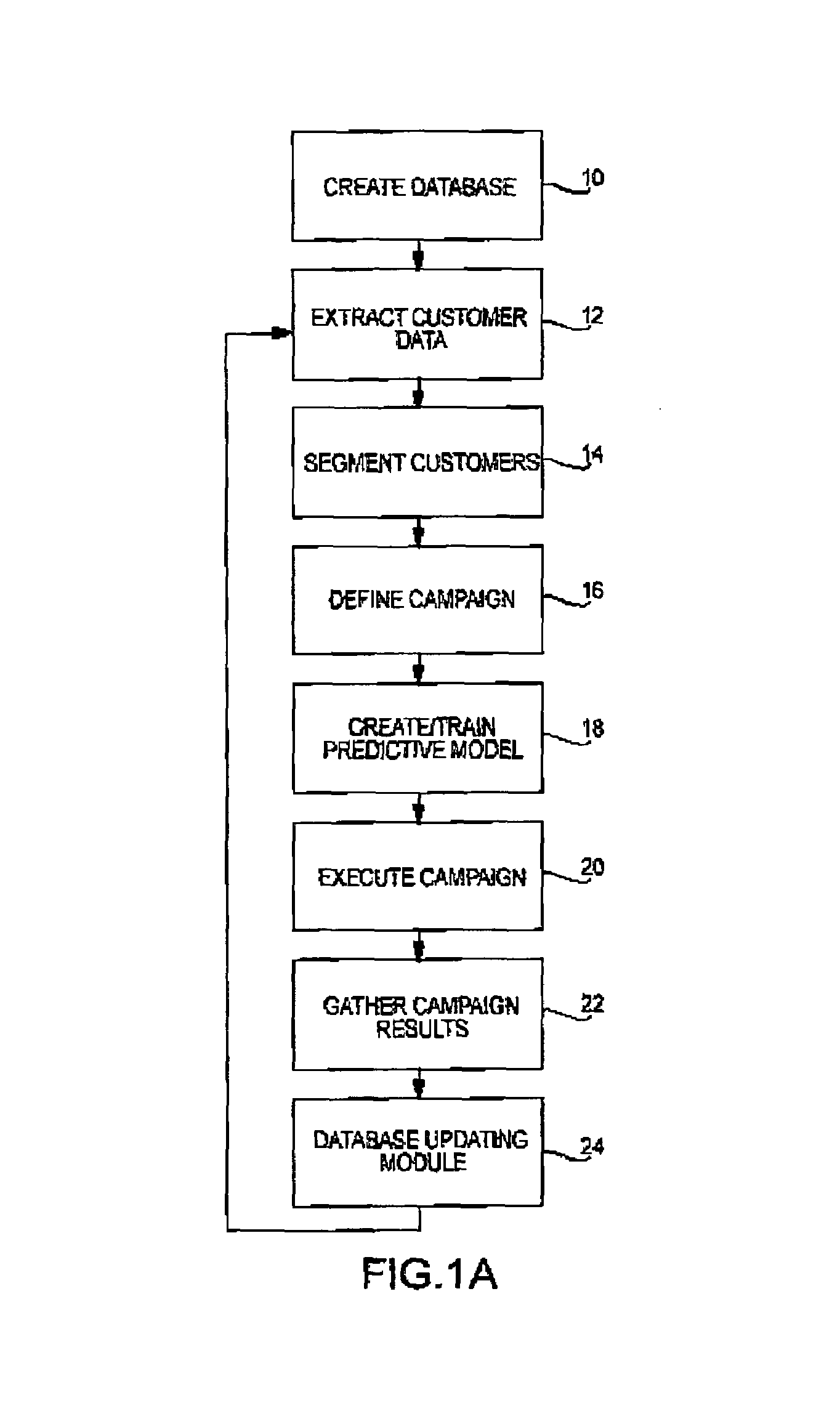
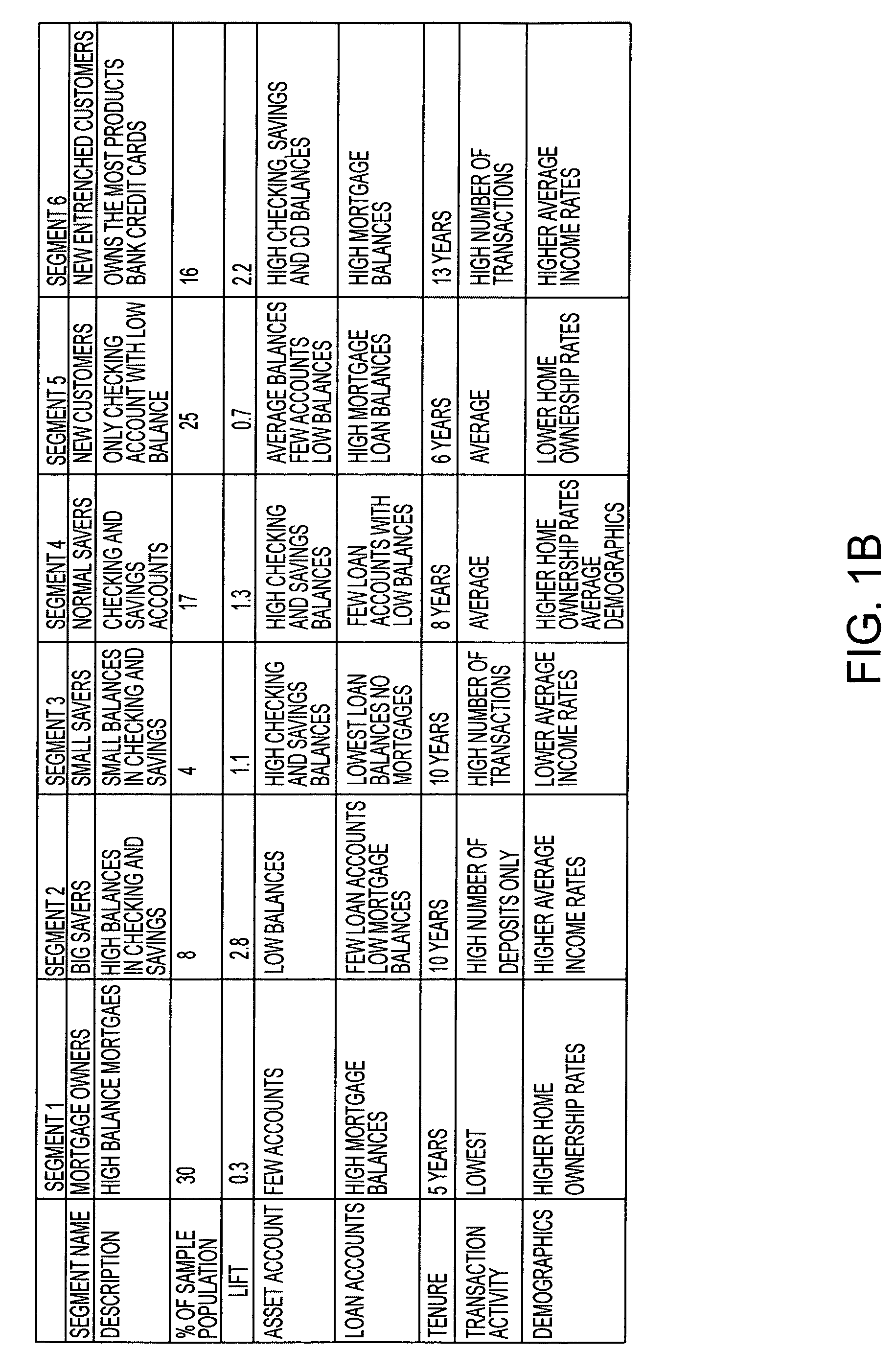
Standardized customer application and record for inputting customer data into analytic models
InactiveUS7047251B2Special data processing applicationsMarketingAnalytic modelDocumentation procedure
A system and method for creating virtual “flat” customer records derived from database customer data that may be used as standardized input for analytical models. A Customer Analytic Record (“CAR”) application may be created as a database object to extract, transform, and format all of the customer data needed for customer segmentation and predictive modeling. The CAR may be a set of database “views” that are defined using virtual stored queries and enabled using capabilities of a data base management system and a structured query language. The CAR is preferably a virtual “flat” record of the customer data needed for customer analytics. The customer data may be extracted by running one or more SQL queries against the database view(s). The CAR application may dynamically calculate additional variables using predetermined transformations, including custom transformations of an underlying behavior. If additional variables are created, the CAR may be modified to include the additional variables. The CAR is preferably a dynamic view of the customer record that changes whenever any update is made to the database. The definition of the CAR provides documentation of each data element available for use in models and analytics.
Owner:ACCENTURE GLOBAL SERVICES LTD
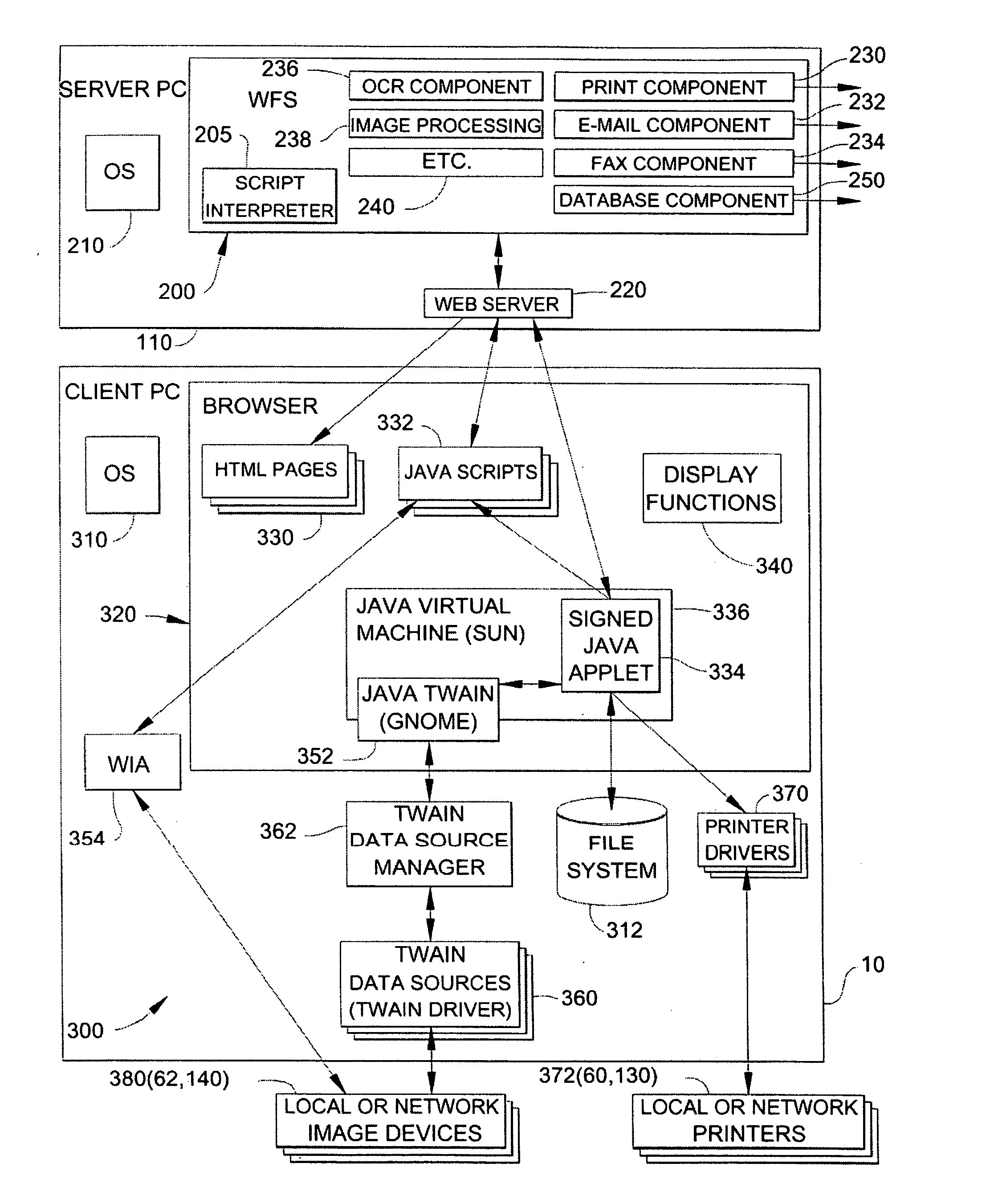
Method and apparatus for providing a work flow web application that receives image data via a web browser and exports the image data to a document processing server
InactiveUS20060085516A1Multiple digital computer combinationsOffice automationApplication softwareUniform resource locator
An improved image processing system is provided which receives image data at a computer and transfers that image data to a work flow server for image processing and document distribution. The system uses a work flow web application computer program that receives image data from a scanner, transfers that image data via a native interface or a driver on a client computer to a browser on the client computer, and then sends the data to a network document distribution server which is addressed from the client computer using URL's.
Owner:LEXMARK INT INC
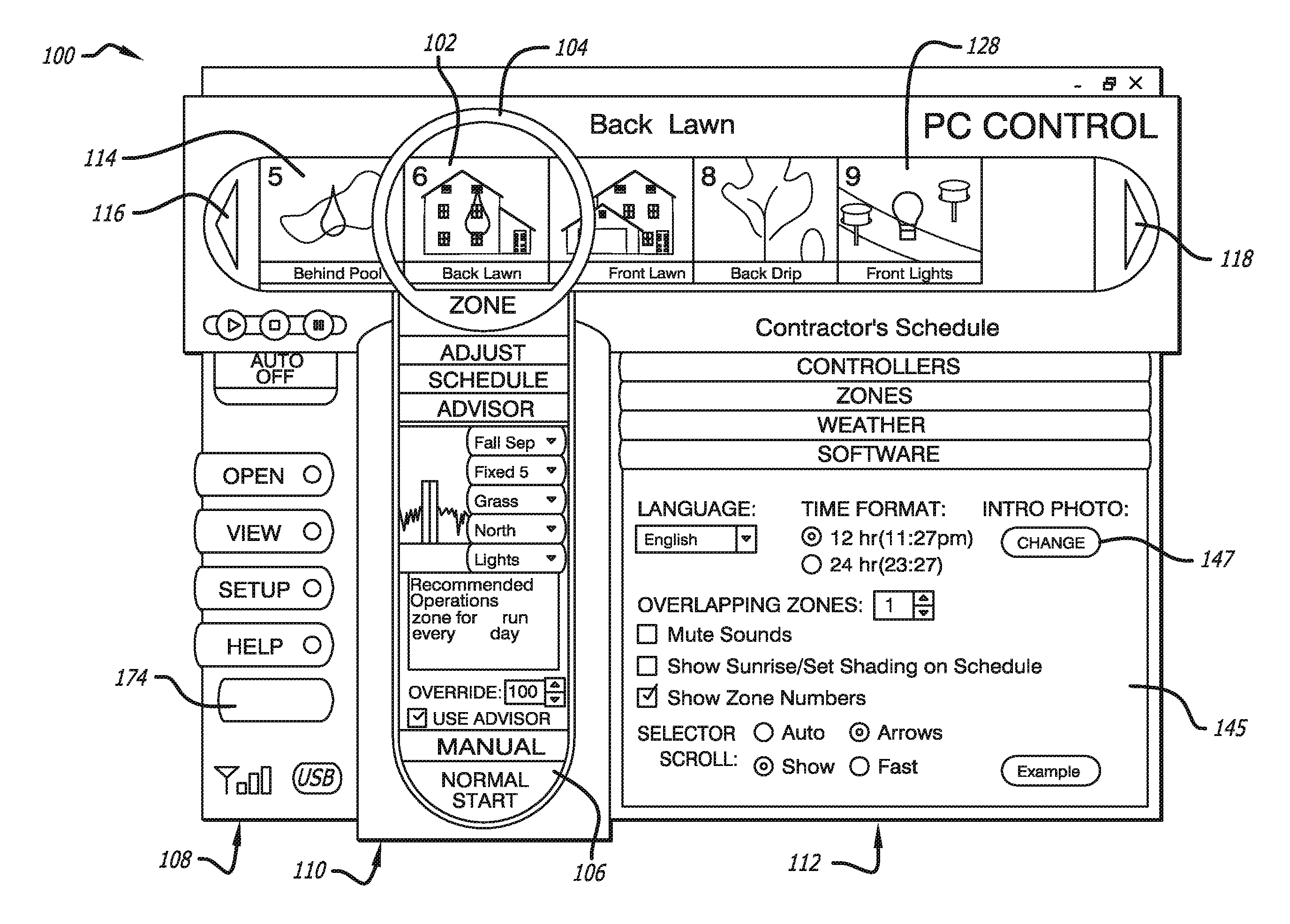
Computer-Operated Landscape Irrigation And Lighting System
A multi-zone landscape irrigation and lighting system includes a personal computer equipped with a detachable wireless remote, and a multi-station controller operating a plurality of irrigation valves and lighting circuits in accordance with schedules wirelessly transmitted to it by the computer through the remote. When detached from the computer, the remote can wirelessly operate selected irrigation or lighting zones manually. The computer has an intuitive graphic user interface capable of using actual zone photographs to identify individual zones in a strip of zone icons. The icon strip is movable past a lens-like window, the zone icon under the lens at a given time determining the zone currently programmable. A residential system can be operated by a contractor from the street, and the system can be programmed by e-mail from the contractor's shop. Fully automatic operation may be derived from data obtained over the Internet.
Owner:TORO CO THE
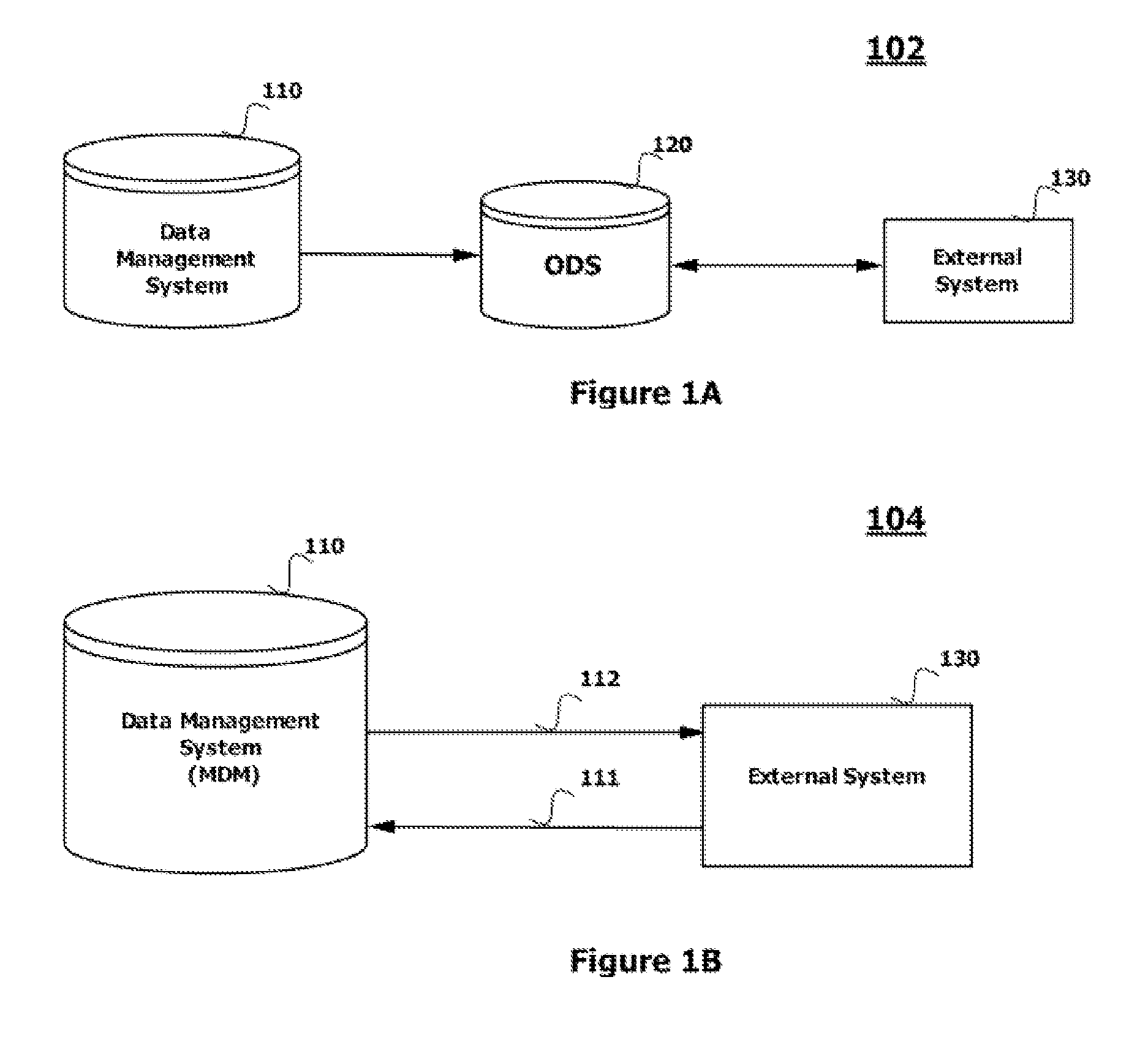
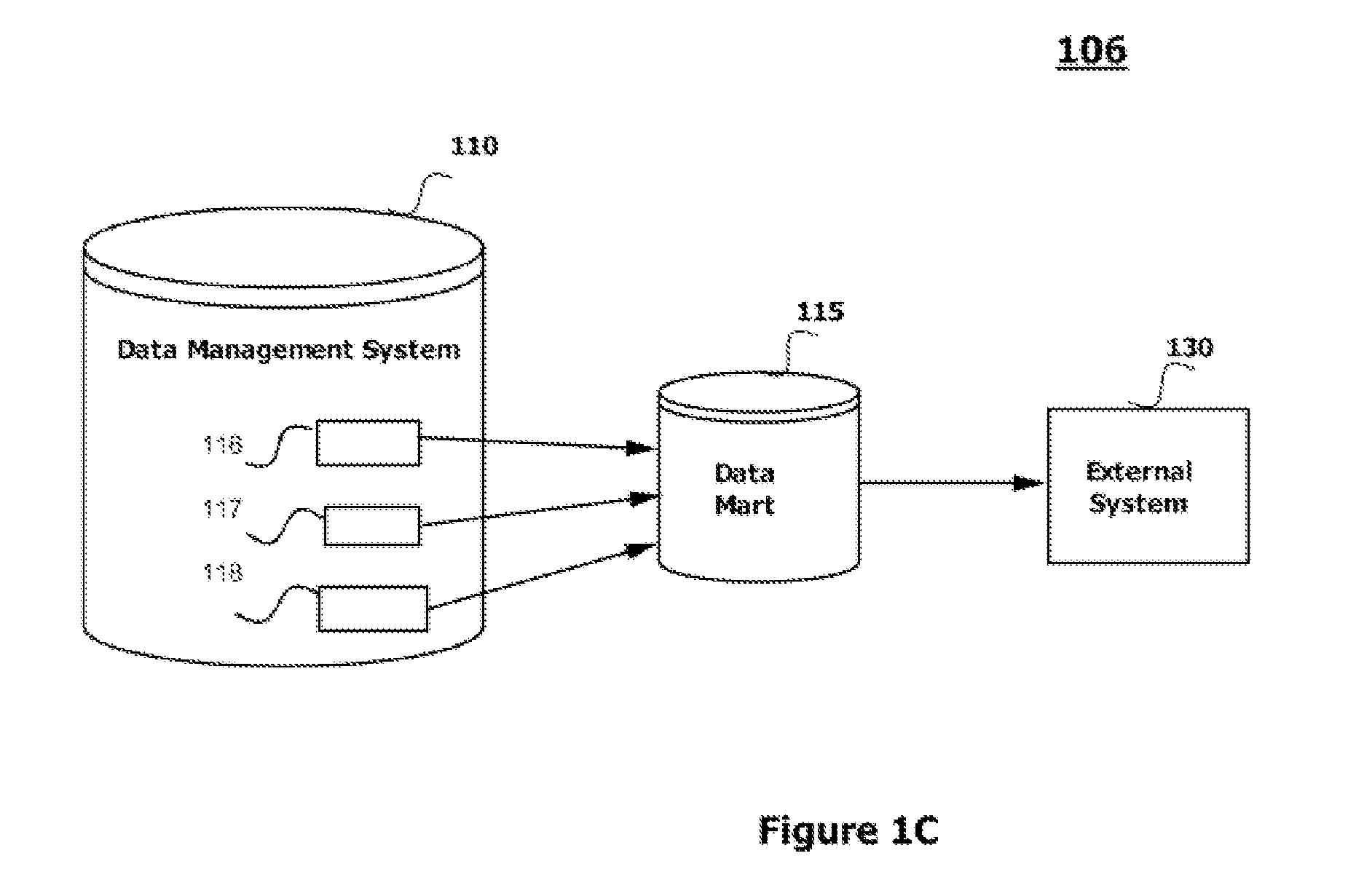
Data Synchronization Between a Data Management System and an External System
ActiveUS20110087632A1Digital data information retrievalDigital data processing detailsData synchronizationData management
A method, a system and a computer program of synchronizing data between a data management system and an external system are disclosed. The method includes creating a first database instance and a second database instance using an integration data model. The method further includes synchronizing data between the second database instance and the external system. A services framework is created and the first database instance and the second database instance are interfaced using the services framework which includes an entity definition repository, a change tracking repository, and a data export element. Also disclosed are a system and a computer program for synchronizing data between a data management system and an external system.
Owner:IBM CORP
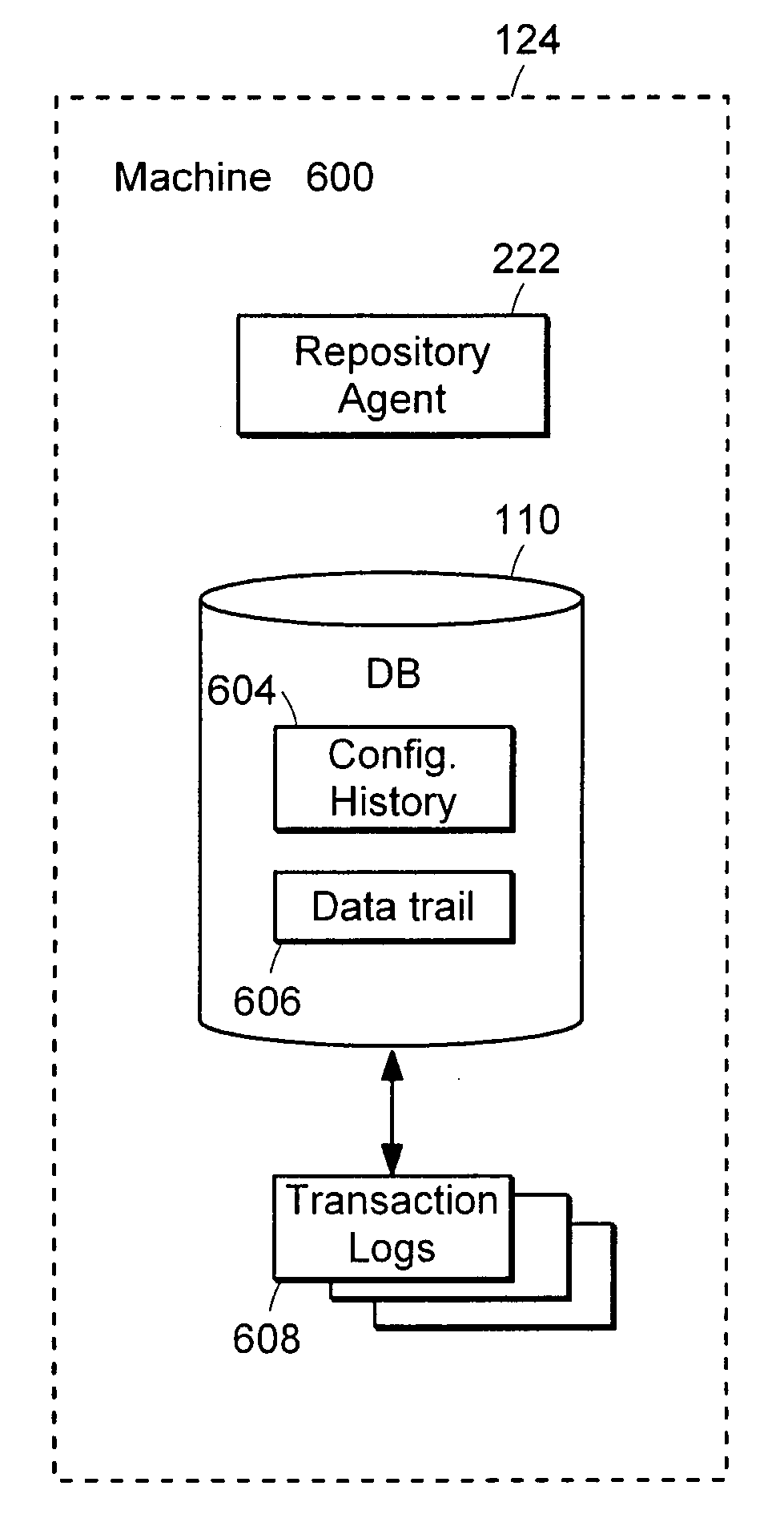
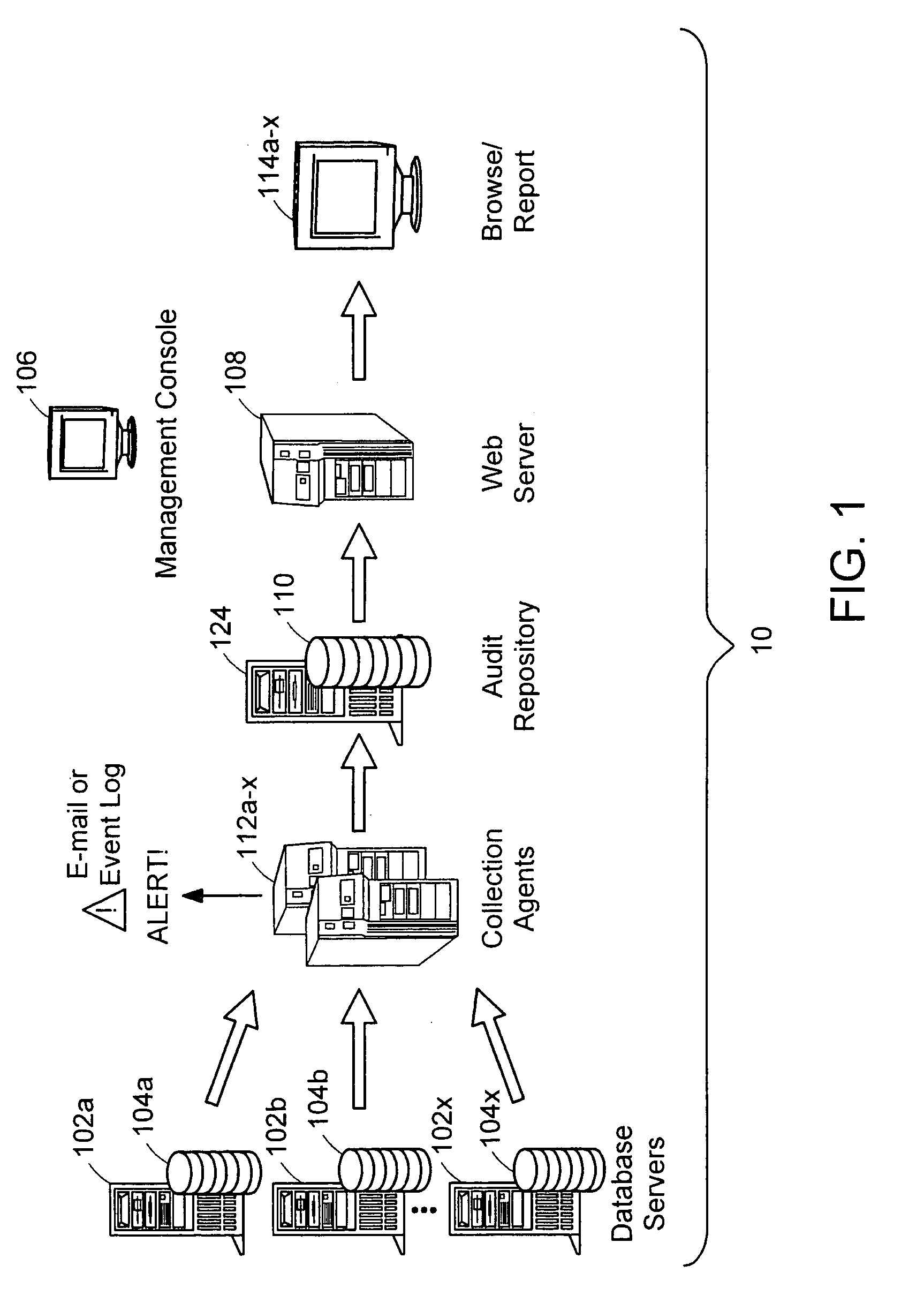
Data audit system
ActiveUS20050097149A1Digital data information retrievalComputer security arrangementsDatabase schemaCollections data
Described is a database audit system used to monitor, and optionally alert on database activity, providing a complete record of access to data and database structure. The data audit system may also provide an audit trail of data accesses and changes to database schema and permissions. A database audit may be performed by collecting data from database transaction logs and traces, exporting the collected data into a repository, and analyzing the data in the repository to create data audit reports and to provide data audit browsing capabilities.
Owner:BEYONDTRUST SOFTWARE INC
Method and apparatus for distributing over a network unsolicited information to a targeted audience
InactiveUS6119164AAvoid confictMultiple digital computer combinationsElectric digital data processingProgram instructionInformation transmission
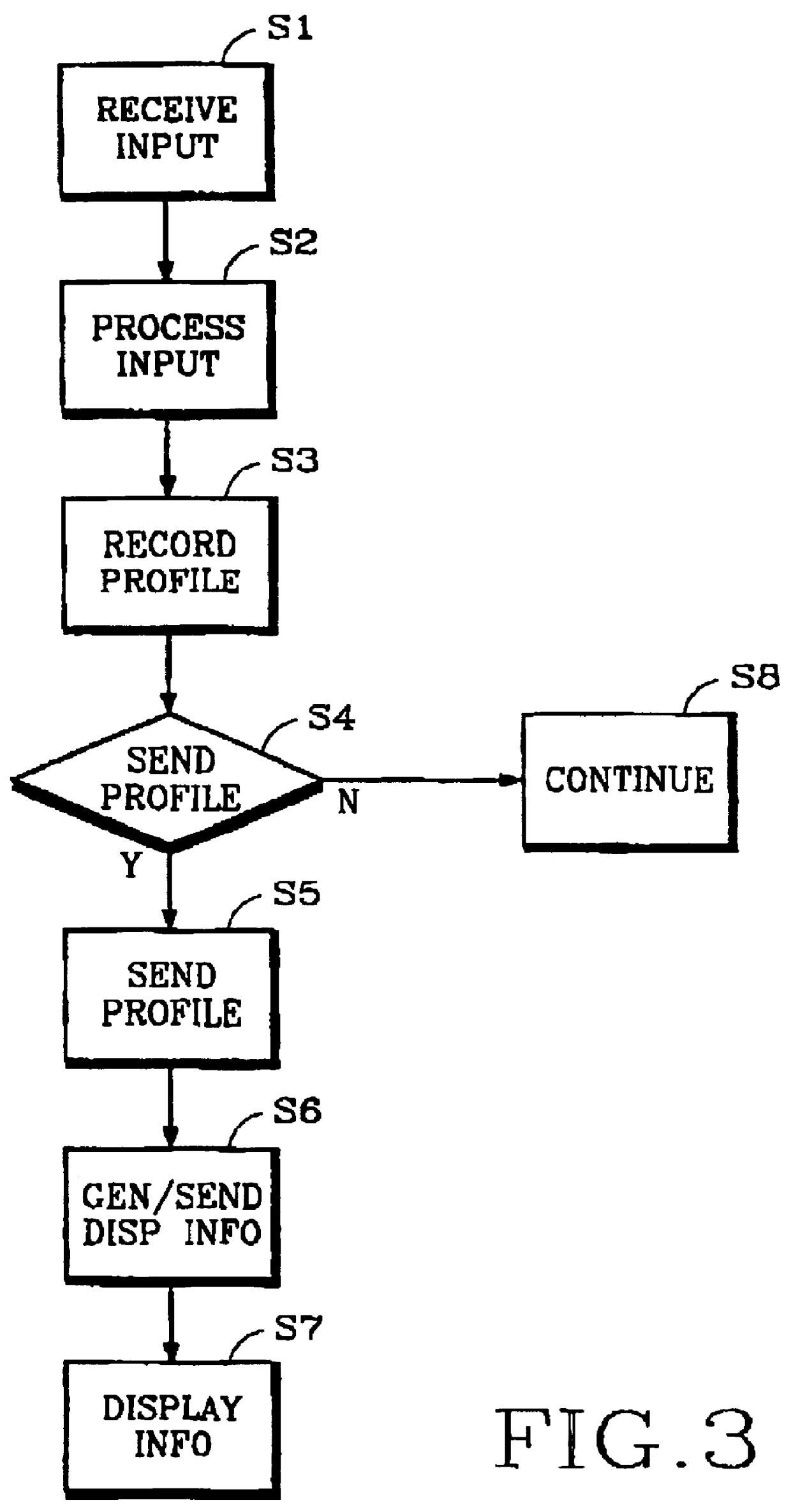
In response to input received from an operator, a workstation fully performs programmed instructions to carry out operator requests represented by the input. In addition, the workstation also records profile information derived from data representing operator choices and sends that profile information to a server along a communications path such as a telephonic link to a publicly-accessible network. The server analyzes the profile information, generates display information in response to the profile information, and returns display information along the communications path to the workstation. In turn, the workstation presents the display information to the operator. In this manner, information customized according to profiles can be delivered to people and organizations most likely to be interested in the information content.
Owner:FULL CIRCLE SOFTWARE
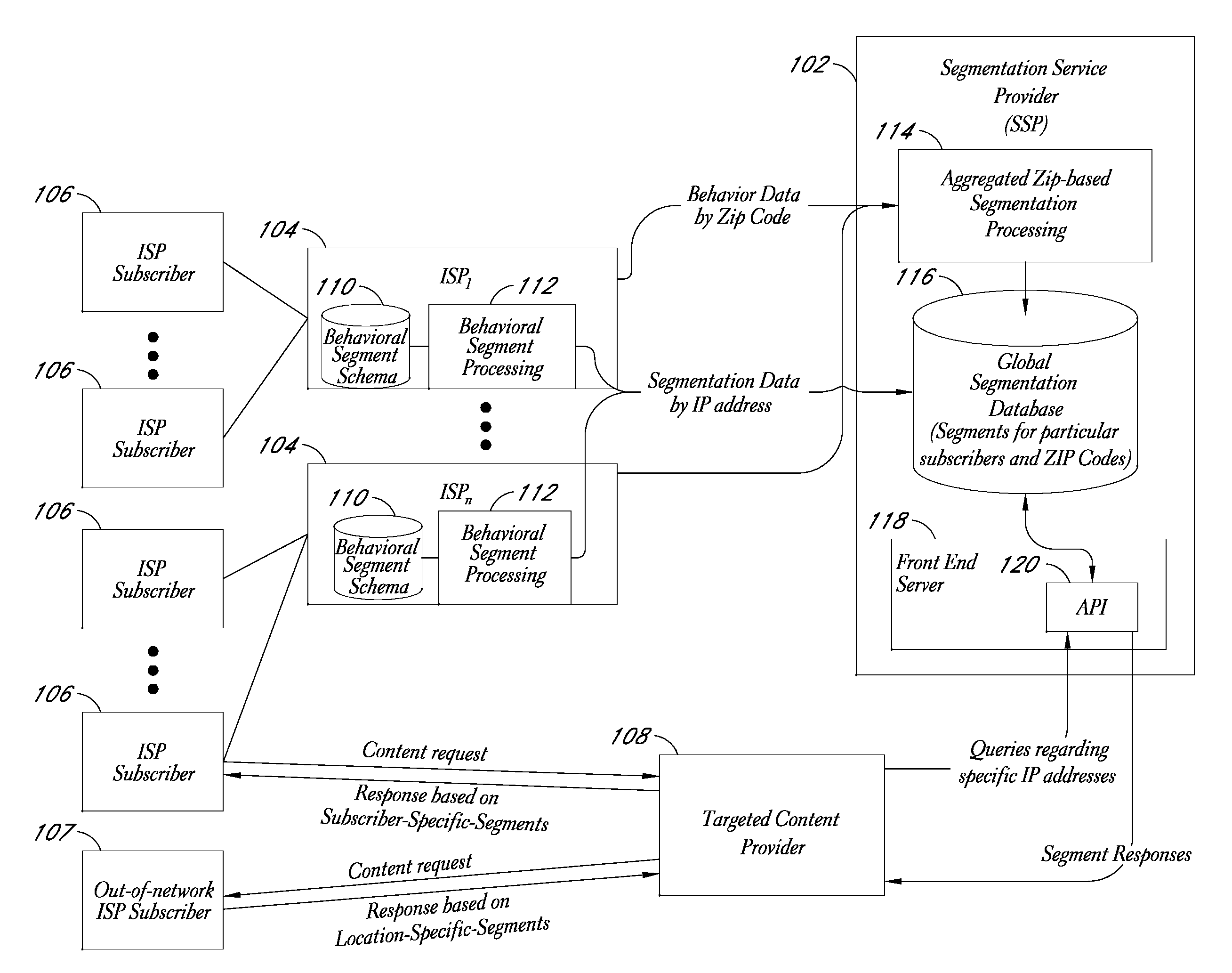
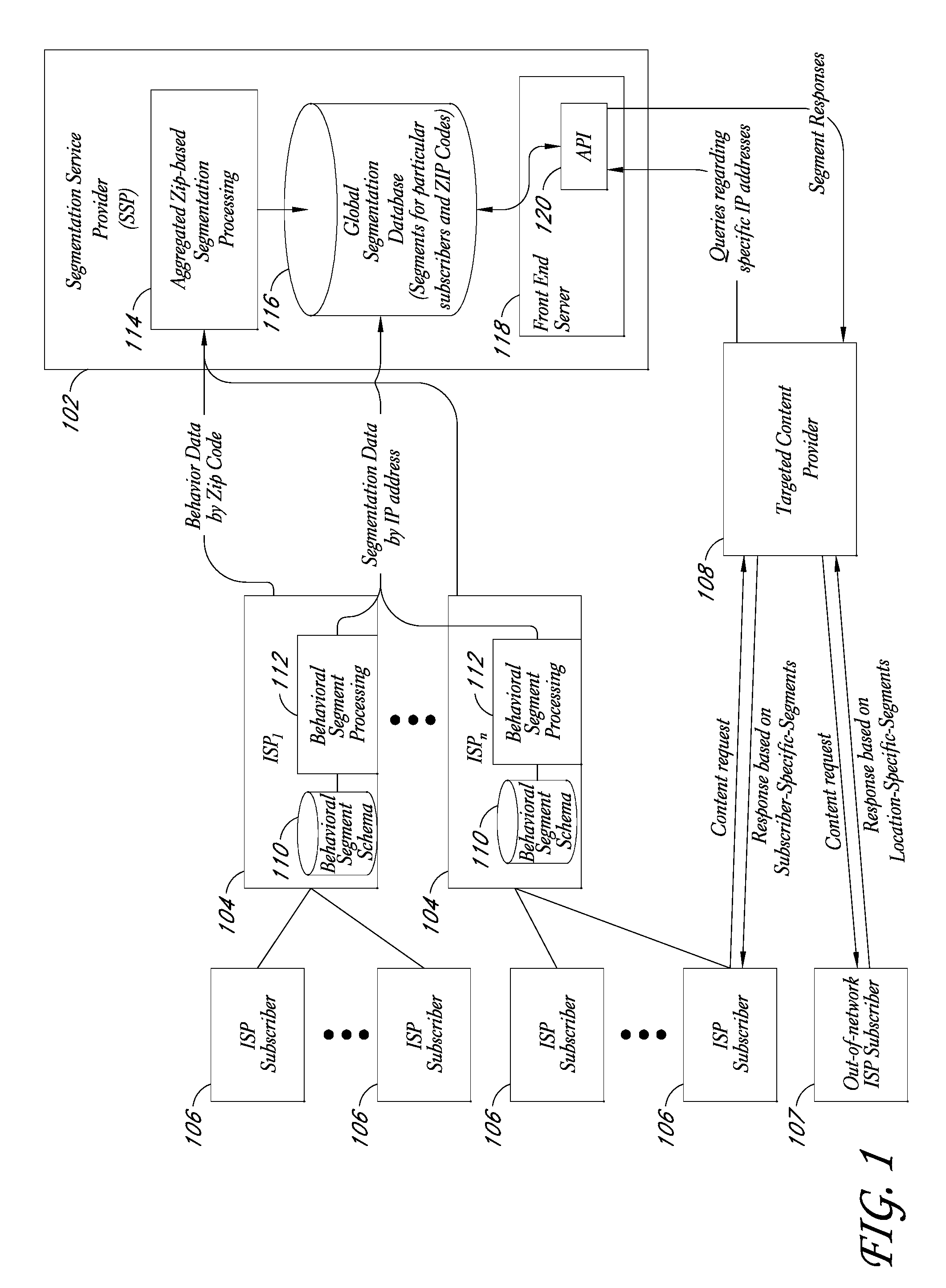
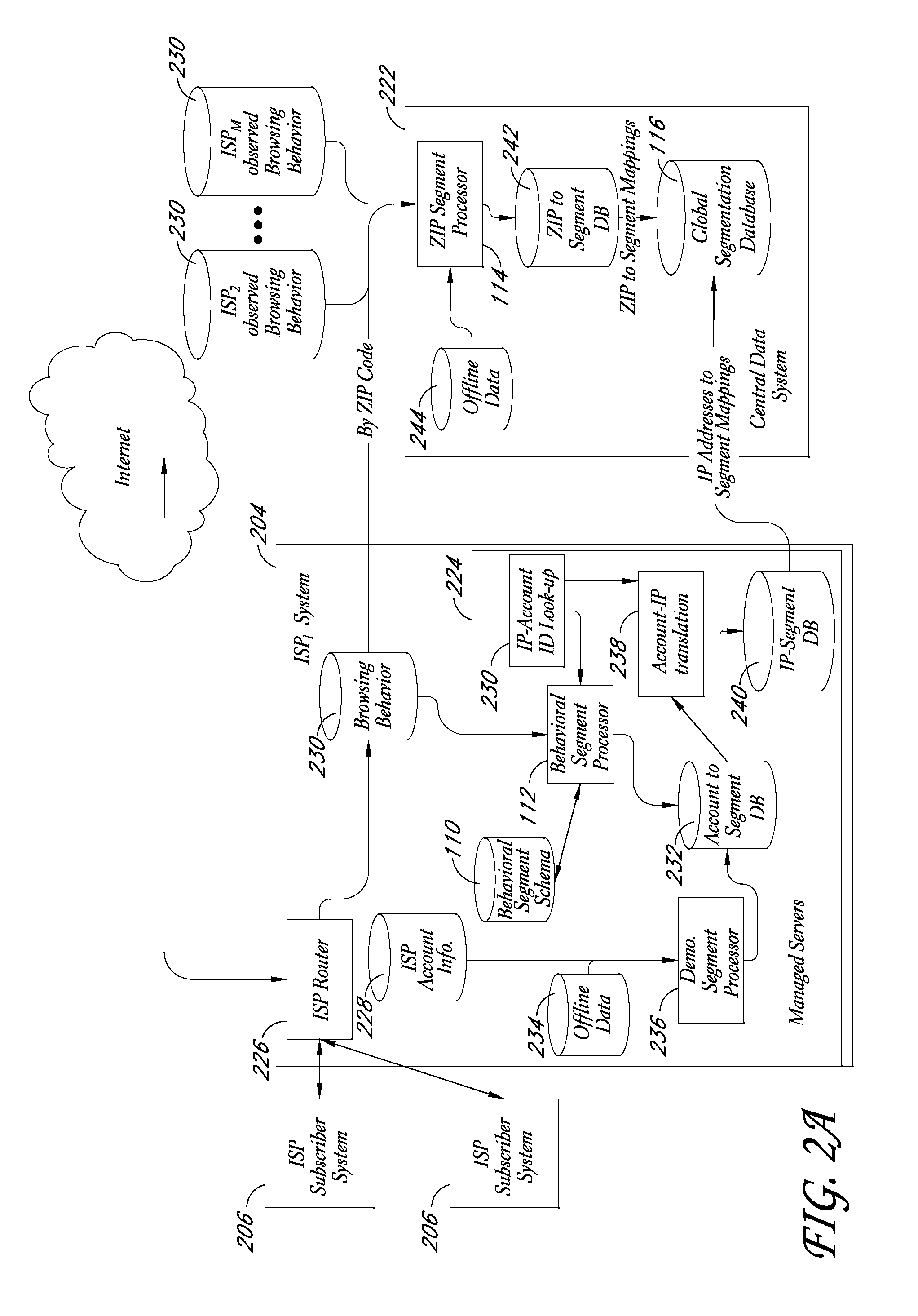
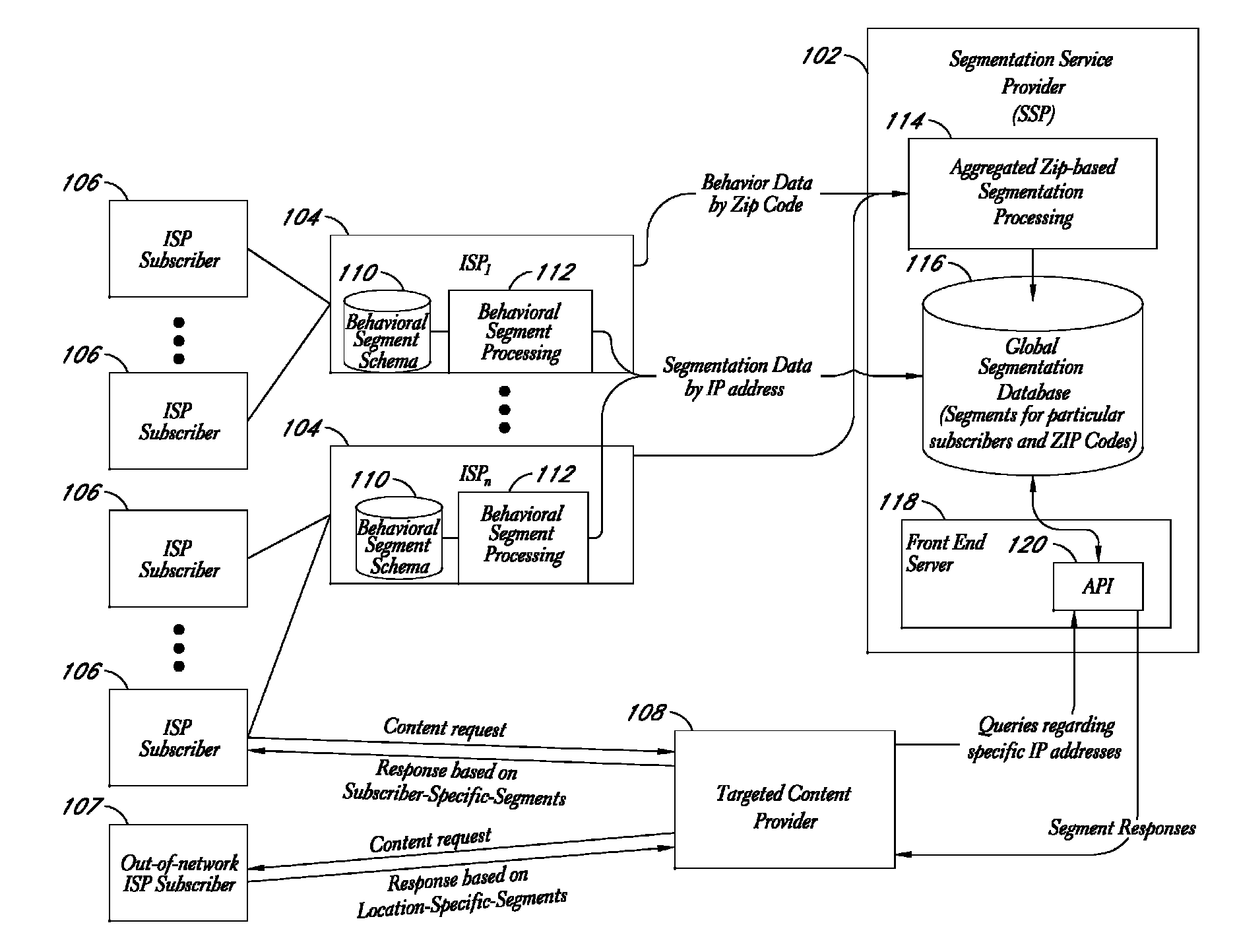
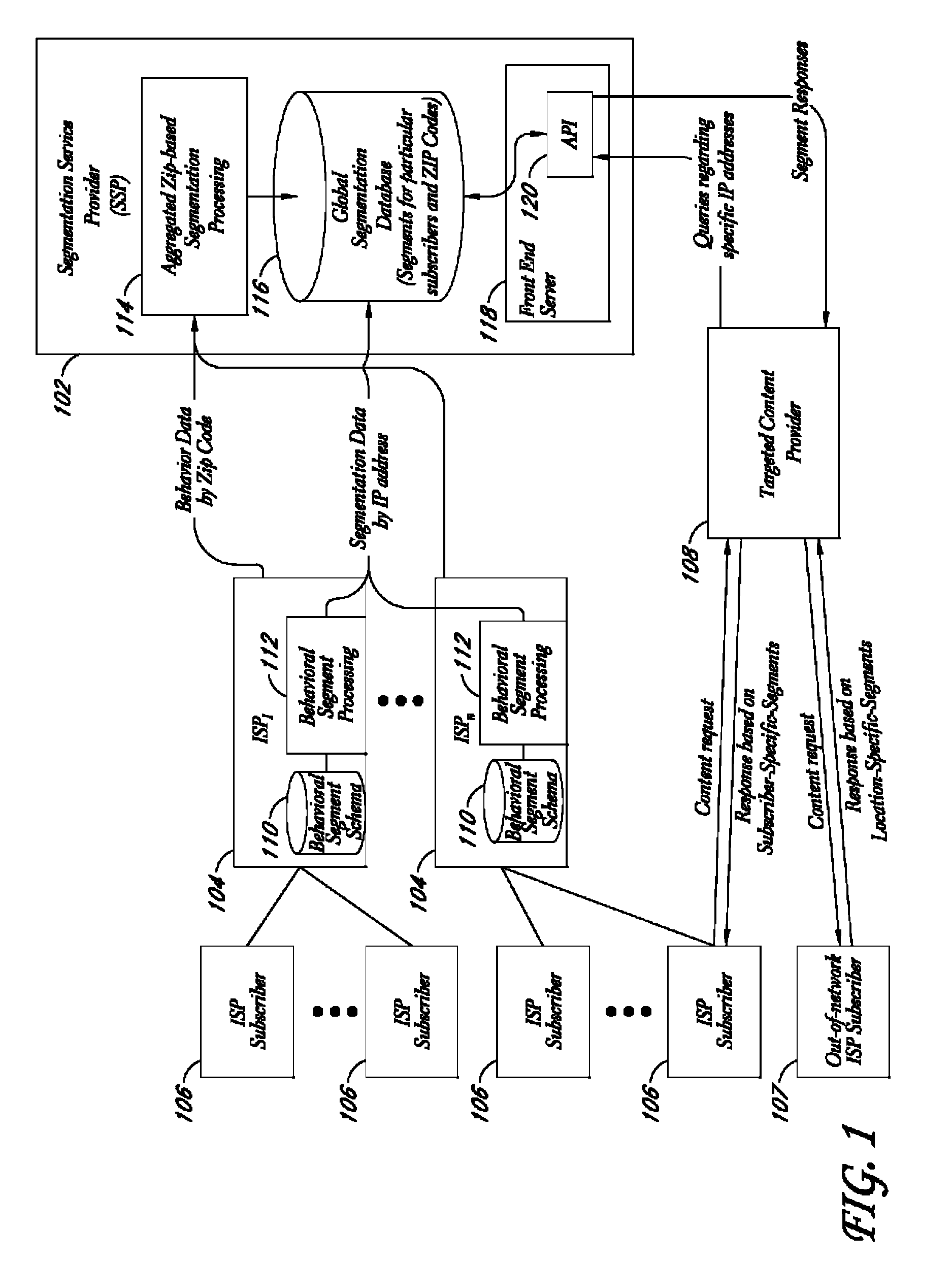
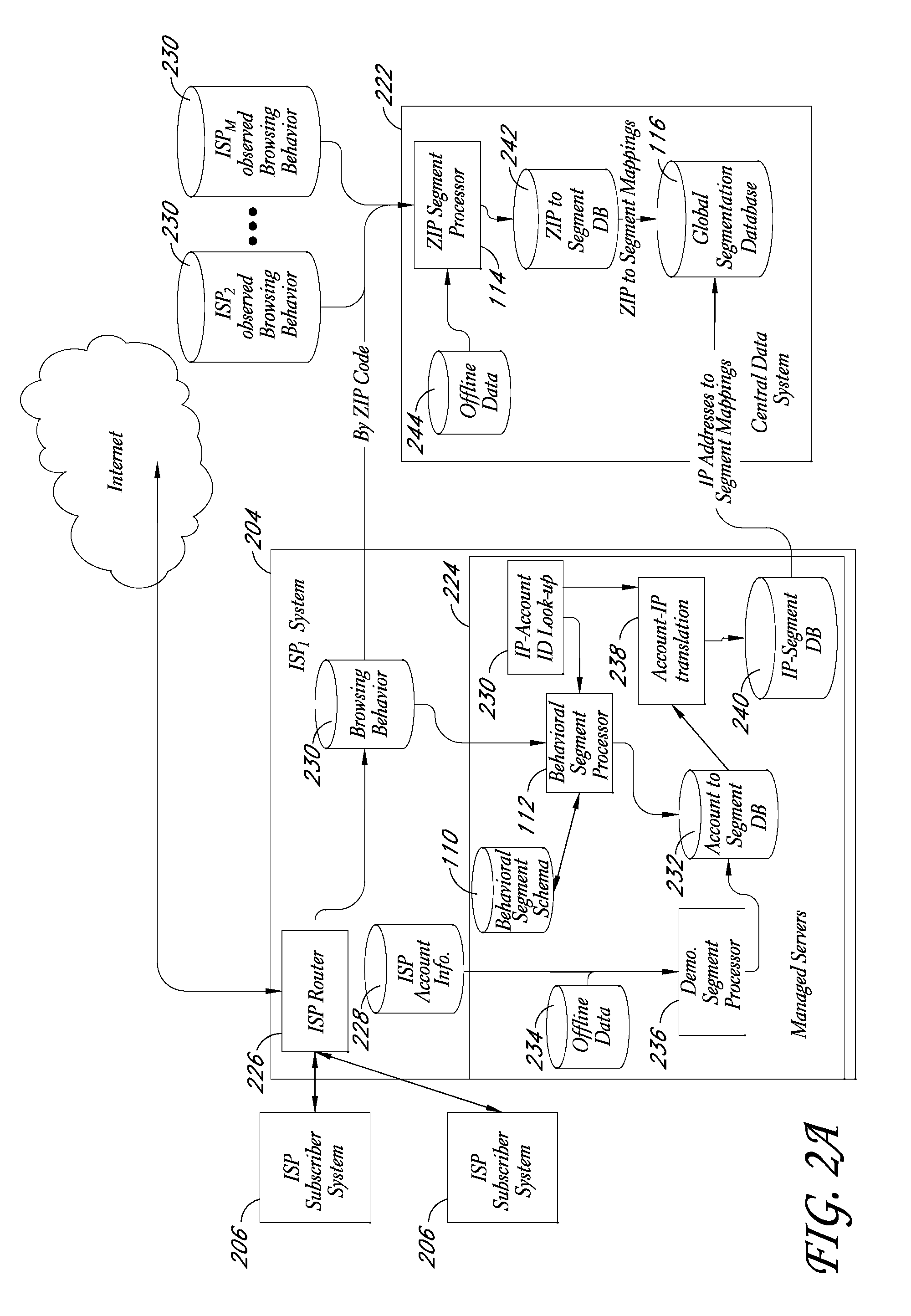
Behavioral segmentation using isp-collected behavioral data
InactiveUS20090132559A1Highly relevantExpand coverageDigital data processing detailsSpecial data processing applicationsWeb siteInternet searching
A system is disclosed that uses behavioral data collected by ISPs to categorize particular ISP subscribers. The behavioral data may, for example, include the identities of particular web sites and / or web pages accessed by particular subscribers, the search queries used by the subscribers to conduct Internet searches, and / or other types of behavioral information. The ISP subscribers are assigned to particular behavioral categories or “segments” using a behavioral segmentation schema that maps particular subscriber behaviors to particular behavioral segments. The ISP subscribers may also be mapped to other segment types, such as demographic segments derived from off-line data about the subscribers. The subscriber-to-segment mappings are made available to content targeting entities via a query interface that, for example, supports queries of the form “what are the segments associated with IP address X?”
Owner:EXPERIAN MARKETING SOLUTIONS
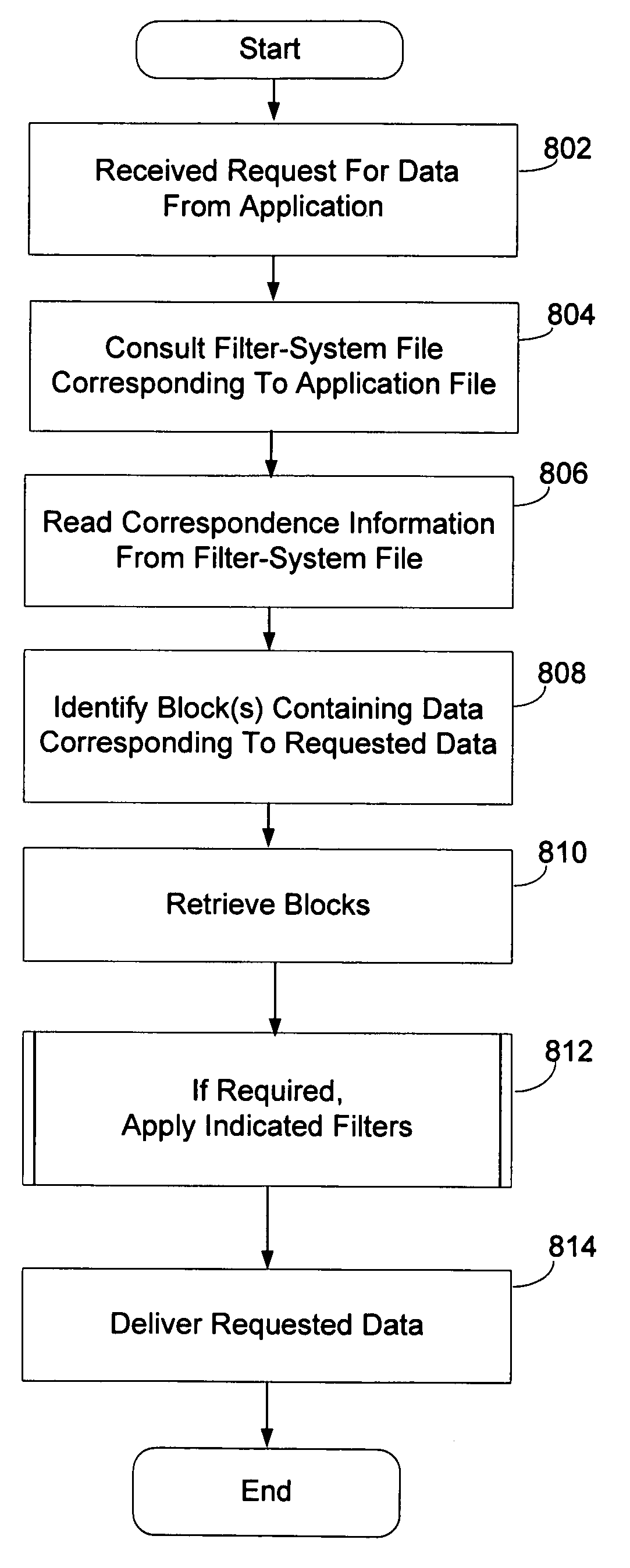
Filter file system
ActiveUS6970866B1Shorten delivery timeWithout sacrificing abilityData processing applicationsSpecial data processing applicationsFile systemFilter system
Methods and apparatus implementing a technique for retrieving requested data. In general, in one aspect, the technique includes receiving a request from an application to read a portion of an application file and consulting a filter-system file. The filter-system file contains processed data that corresponds to data in the application file and correspondence information indicating how the set of processed data corresponds to the data in the application file. The technique also includes deriving the requested portion of the application file from the processed data using the correspondence information, and delivering the requested portion of the application file to the application. In another aspect, the technique includes receiving data to be retrieved in response to a request from an application with reference to the application's view of the application file, processing the received data to generate processed data that corresponds to the received data, producing correspondence information indicating how the processed data corresponds to the received data is produced, and storing the processed data and the correspondence information in a filter-system file.
Owner:ADOBE INC
System and method for bootstrapping a user binding
A system, apparatus, method, and machine readable medium are described for bootstrapping an authenticator. For example, one embodiment of a method comprising: confirming an identity of a user by a first relying party using a first identity verification technique responsive to the user acquiring a device having an authenticator; generating or collecting initial user verification reference data upon verifying the identity of the user through the first identity verification technique; securely providing the initial user verification reference data or data derived from the initial user verification reference data to the authenticator; the authenticator implementing a second identity verification technique by comparing the initial user verification reference data or data derived from the initial user verification reference data to data collected from the user or data collected from a device provided to the user; and providing proof of a successful verification of the identity of the user to a second relying party during a registration request of the authenticator with the second relying party.
Owner:NOK NOK LABS
Method and apparatus for building and maintaining an object-oriented geospatial database
InactiveUS20050091223A1Easy to exportEasy and complete updatingData processing applicationsDigital data processing detailsData miningMetadata
An object-oriented system for building and maintaining a spatial data structure for use in topological applications. The data is organized in a database which incorporates spatial feature location, attributes, and metadata information in a relational framework across a hierarchy. The system provides for the instantiation of the objects and levels that make up the database and for spatially indexing the data among the objects across hierarchical levels. The data can be updated while preserving the spatial linking among objects and levels, and the data can be exported to a relational vector product format database.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Service for mapping IP addresses to user segments
ActiveUS7996521B2Expand coverageHighly relevantDigital data processing detailsDigital computer detailsInternet searchingWeb site
A system is disclosed that uses behavioral data collected by ISPs to categorize particular ISP subscribers. The behavioral data may, for example, include the identities of particular web sites and / or web pages accessed by particular subscribers, the search queries used by the subscribers to conduct Internet searches, and / or other types of behavioral information. The ISP subscribers are assigned to particular behavioral categories or “segments” using a behavioral segmentation schema that maps particular subscriber behaviors to particular behavioral segments. The ISP subscribers may also be mapped to other segment types, such as demographic segments derived from off-line data about the subscribers. The subscriber-to-segment mappings are made available to content targeting entities via a query interface that, for example, supports queries of the form “what are the segments associated with IP address X?”.
Owner:EXPERIAN MARKETING SOLUTIONS
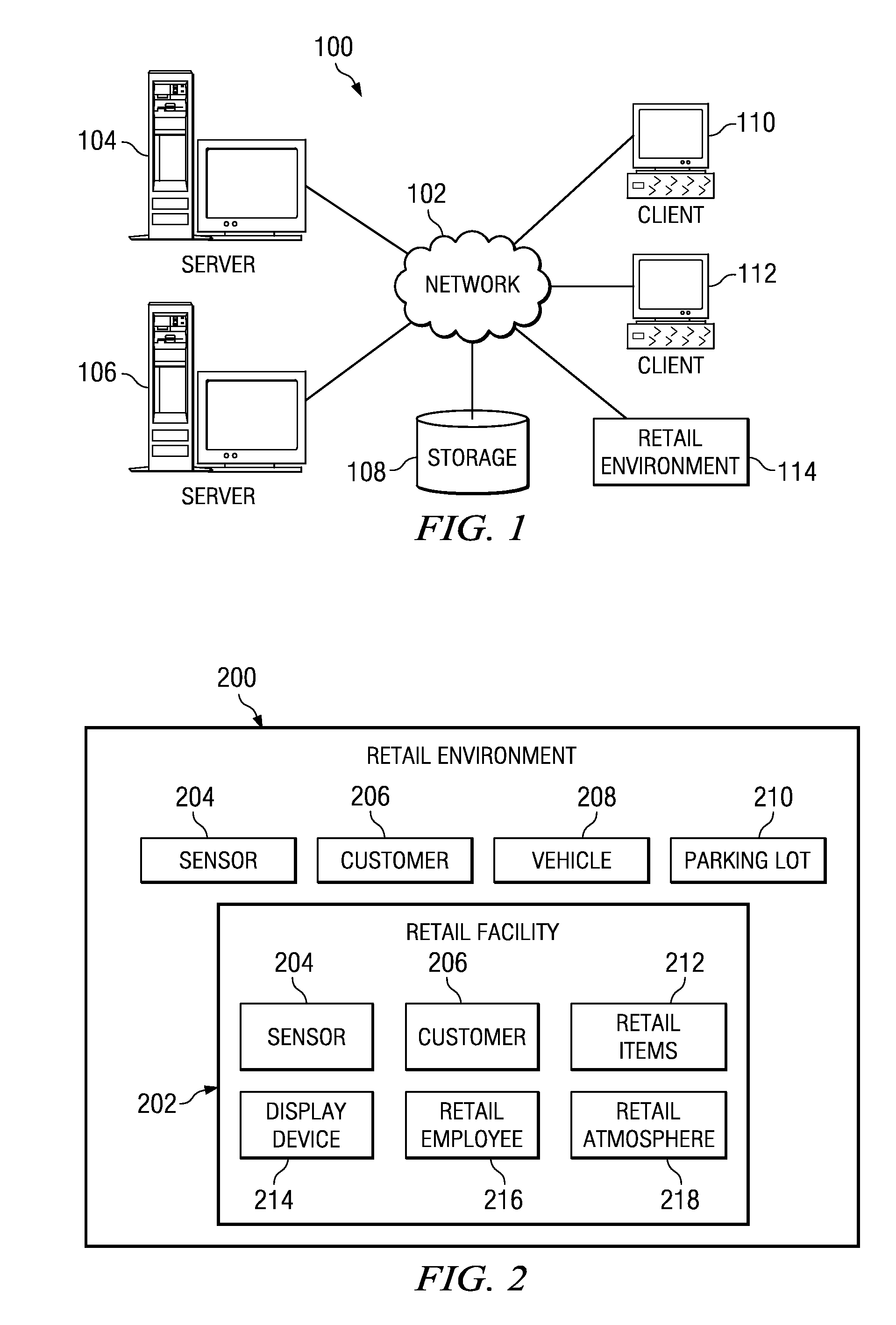
Method and apparatus for implementing digital video modeling to identify unexpected behavior
A computer implemented method, apparatus, and computer usable program product for identifying unexpected behavioral patterns. The process parses event data derived from video data to identify behavioral patterns, wherein the event data comprises metadata describing events occurring in a selected environment. The process analyzes the behavioral patterns to identify a set of expected behavioral patterns occurring in the selected environment, and generates an expected behavioral model using the expected behavioral patterns. Thereafter, the process forms a set of unexpected behavioral patterns from the behavioral patterns inconsistent with the expected behavioral model.
Owner:IBM CORP
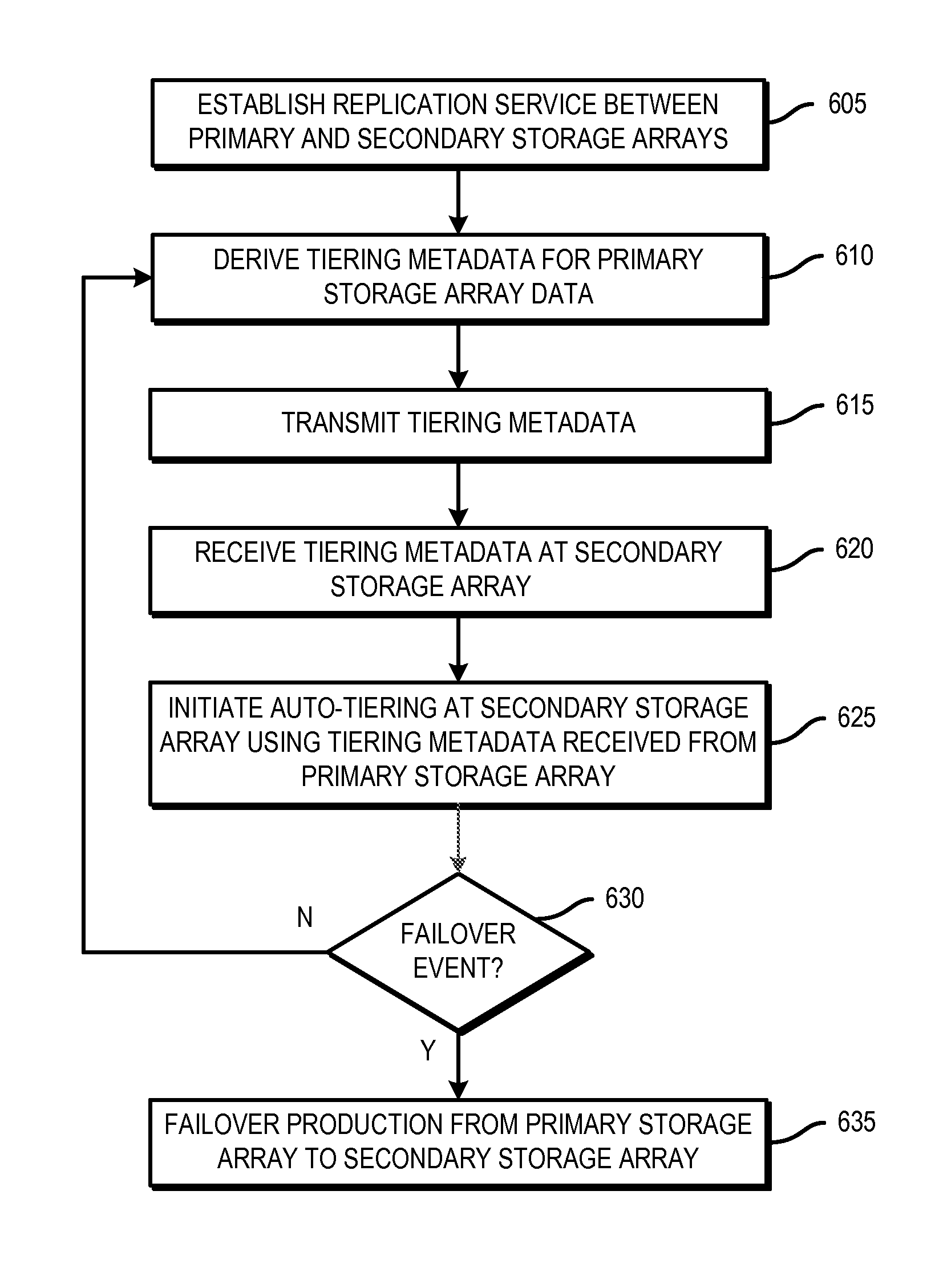
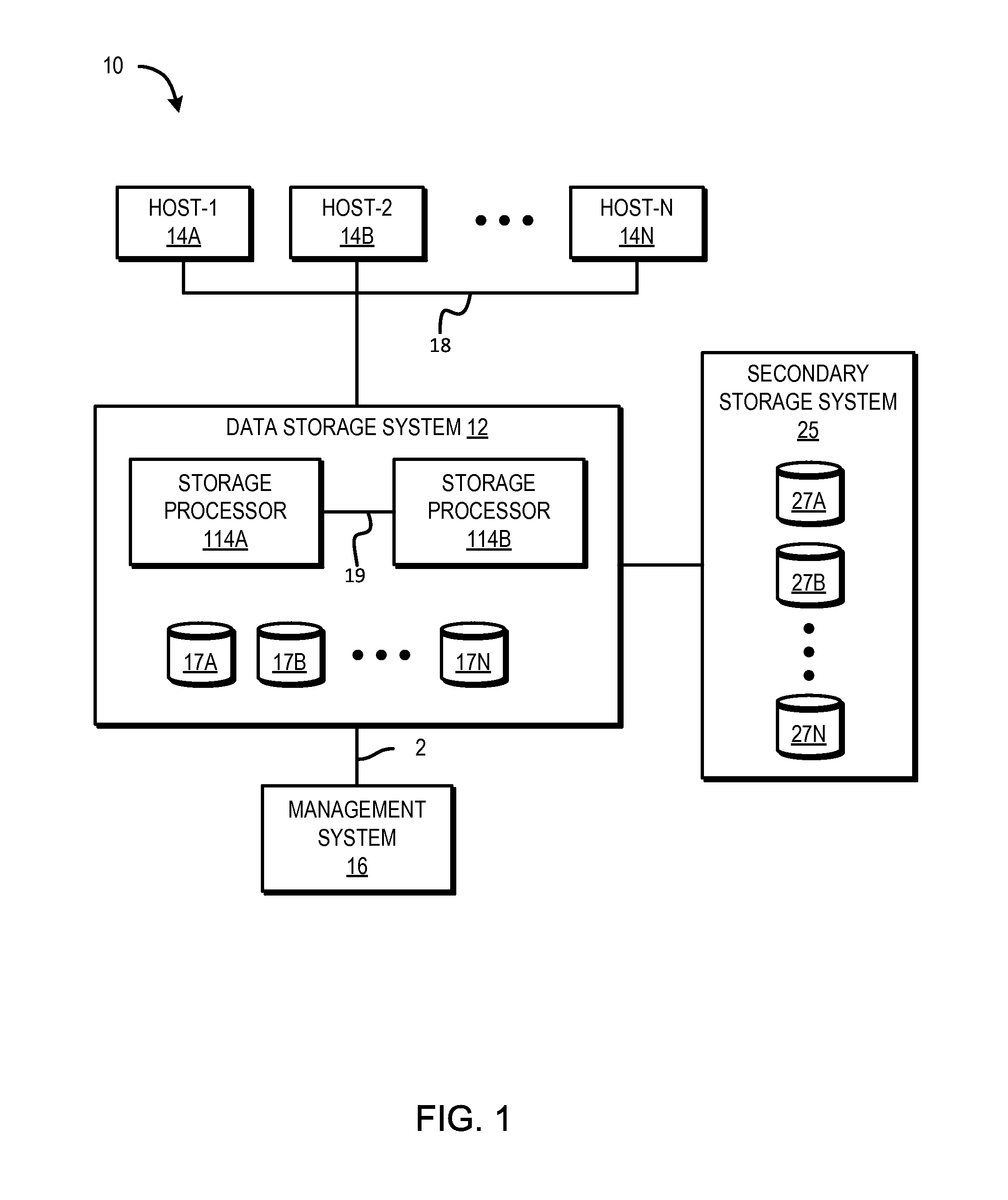
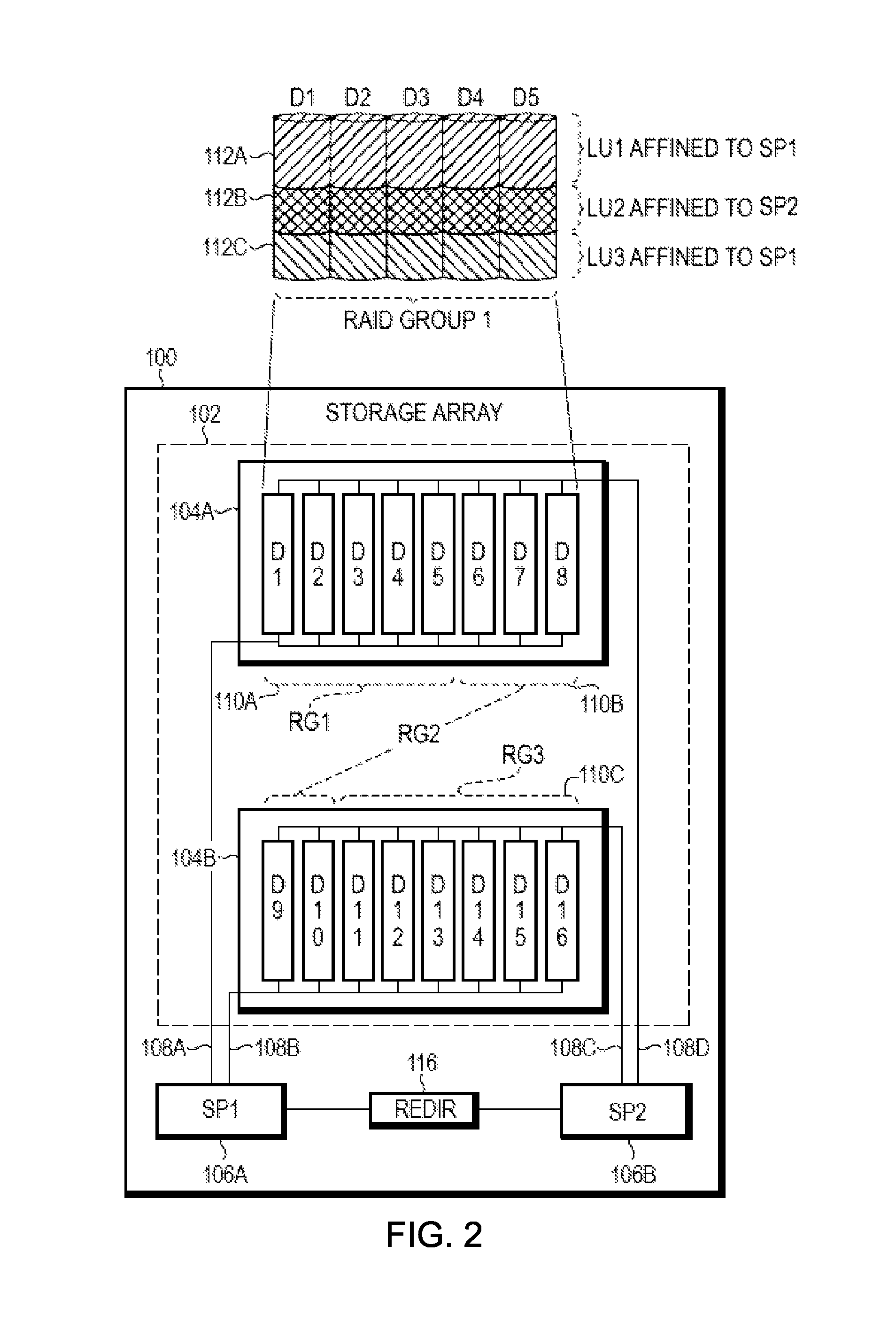
Optimizing data location in data storage arrays
ActiveUS9459809B1Memory architecture accessing/allocationInput/output to record carriersComputer hardwareObject store
A technique is used for optimizing data location in data storage arrays. A primary storage array is associated with a secondary storage array, the primary storage array and secondary storage array including auto-tiering functionality, where the secondary storage array is configured as a backup storage array for the primary storage array. Tiering metadata is derived for a storage object stored on the primary storage array. The tiering metadata is transmitted to the secondary storage array. Auto-tiering is initiated at the secondary storage array, where the received tiering metadata is provided as input to the secondary storage array's auto-tiering function when auto-tiering replicated storage object associated with the tiering metadata.
Owner:EMC IP HLDG CO LLC
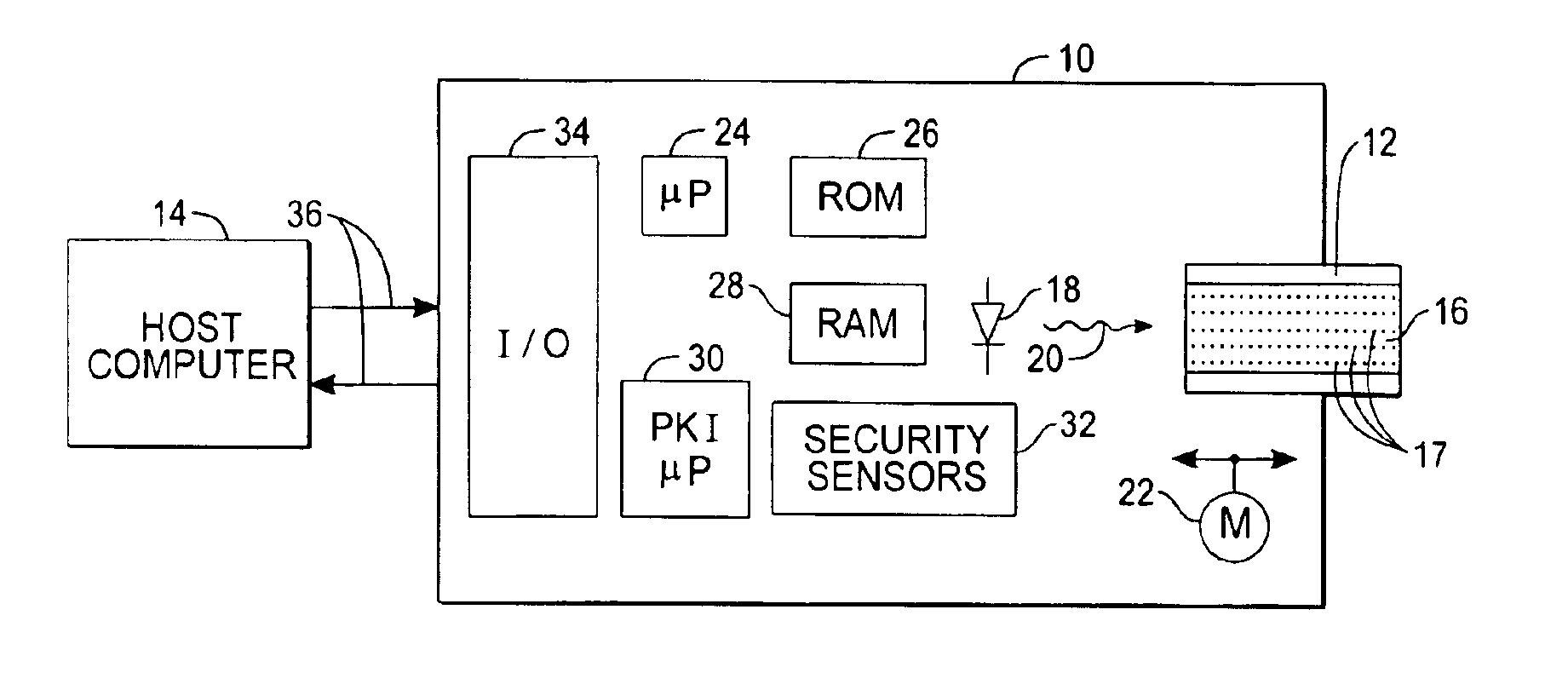
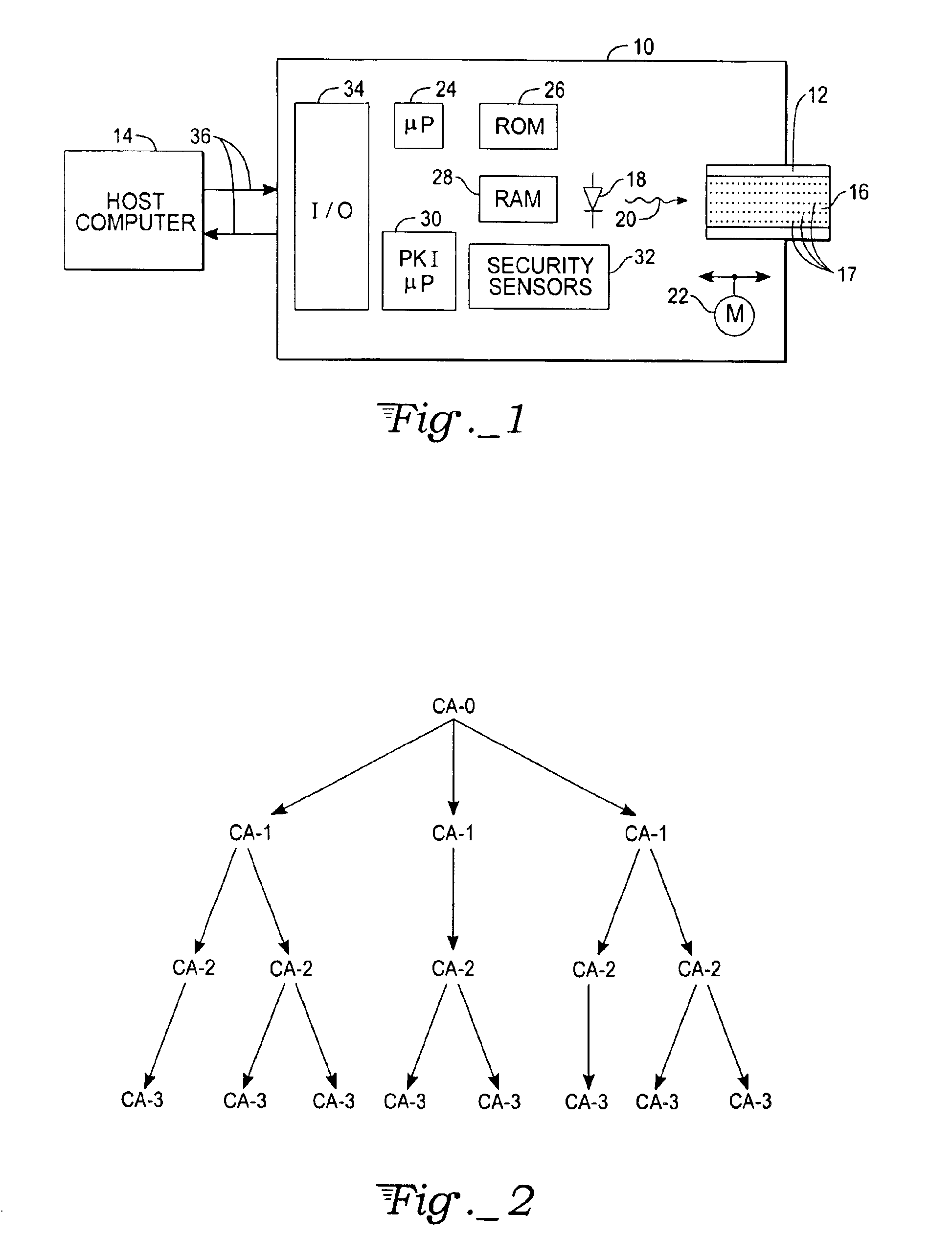
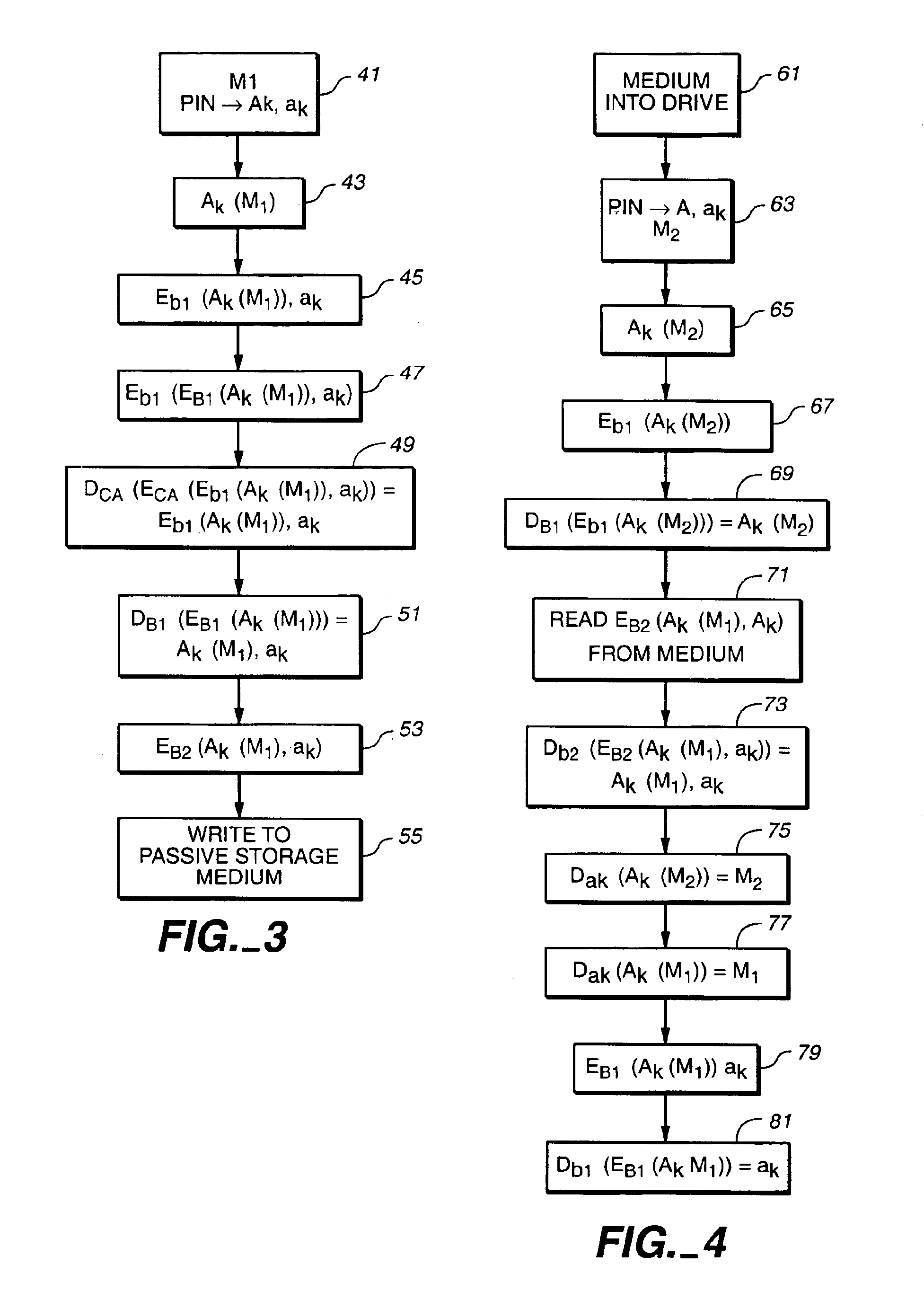
Secure transactions with passive storage media
InactiveUS6871278B1User identity/authority verificationUnauthorized memory use protectionBiometric dataPersonal identification number
A transaction system for use with passive data storage media, such as optical memory cards, uses secure protocols involving digital certificates for communication between a read / write drive and the medium and also for communication between the drive and a host computer. The drive is physically secured with tamper resistant features and stores cryptographic keys and firmware for executing the secure protocols. All messages (data or commands) passed between the drive and the passive medium or host computer not only are encrypted but also include at least one digital certificate for authenticating the message. Typically, asymmetric (public-private key) encryption is used and keys may be derived from an authorized user's password, personal identification number, or biometric data. The drive includes sensors to detect any attempted intrusions and a control unit that will destroy the critical information (keys and protocol code) in response to a detected intrusion. The keys and protocols stored in a drive can themselves be changed through appropriate use of a secure protocol involving digital certificates.
Owner:ASSA ABLOY AB
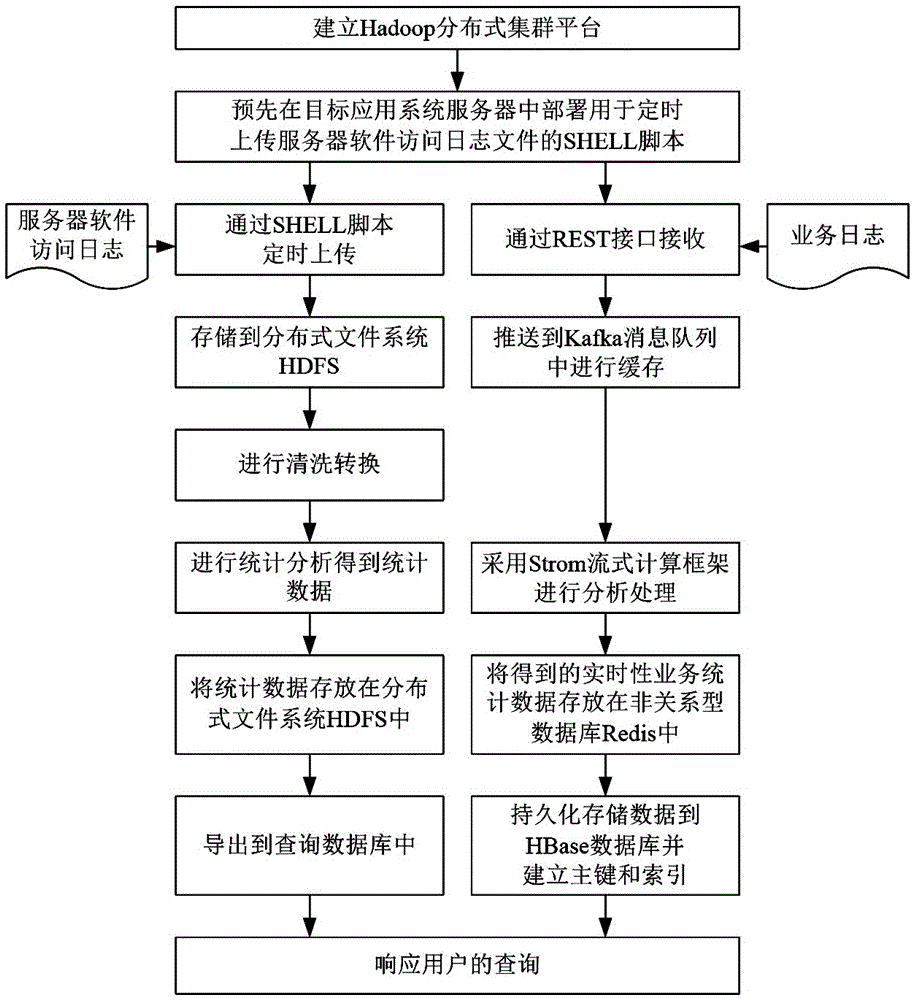
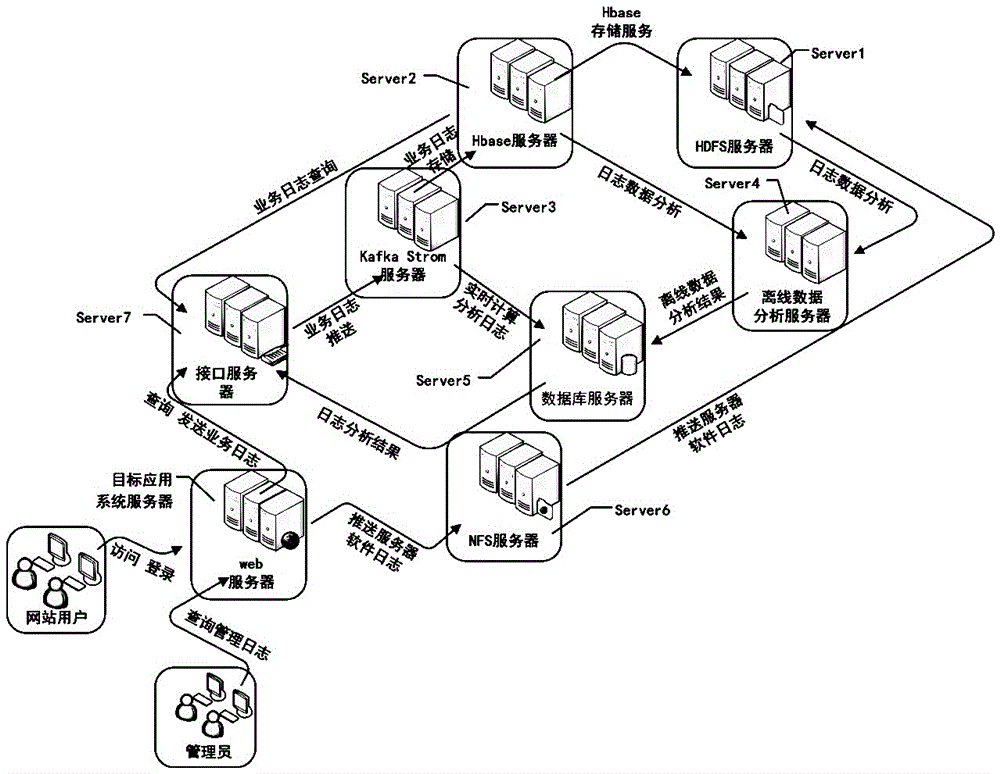
Hadoop-based mass log data processing method
InactiveCN106709003AEfficient collectionEasy to storeDatabase distribution/replicationSpecial data processing applicationsDistributed databaseData library
The invention discloses a Hadoop-based mass log data processing method. The method comprises the steps that on the basis of establishing a Hadoop distributed cluster platform, server software access logs and business logs in a target application system server are processed in a classified mode; log data collection, log data cleaning (limited to the server software access logs), log data analysis, log data storage and data export to an HBase distributed database or Mysql database are performed in sequence; then, a response is made to a query by a user based on the HBase distributed database or Mysql database in the Hadoop distributed cluster platform; and when a query request of the user is received, real-time business statistic data in the HBase distributed database or statistic data in the Mysql database is queried, and the query result is displayed. According to the method, log data can be collected from all application systems and centralized to be used for query, statistics and analysis, so that the processing speed and efficiency of application system logs are improved.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
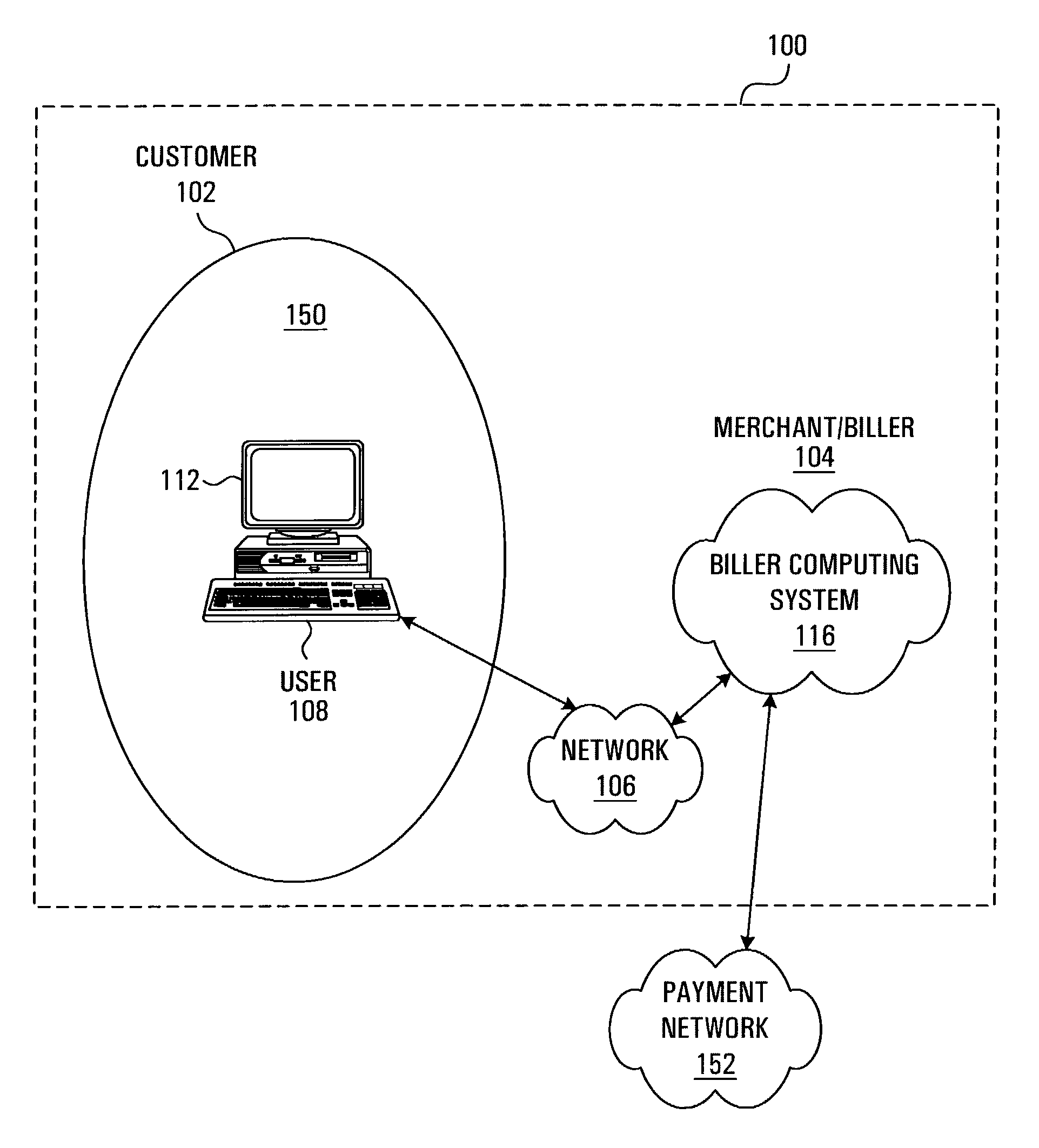
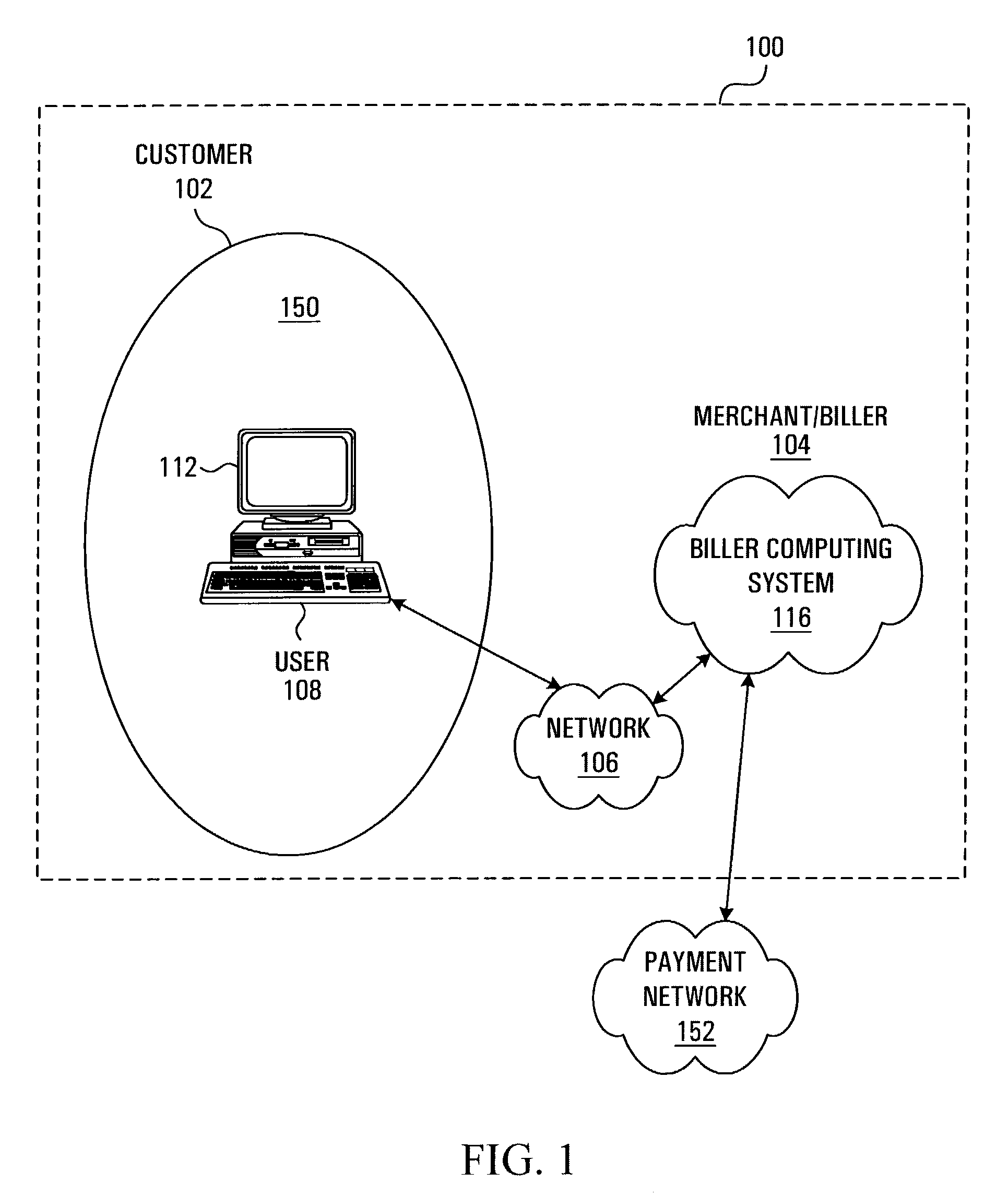
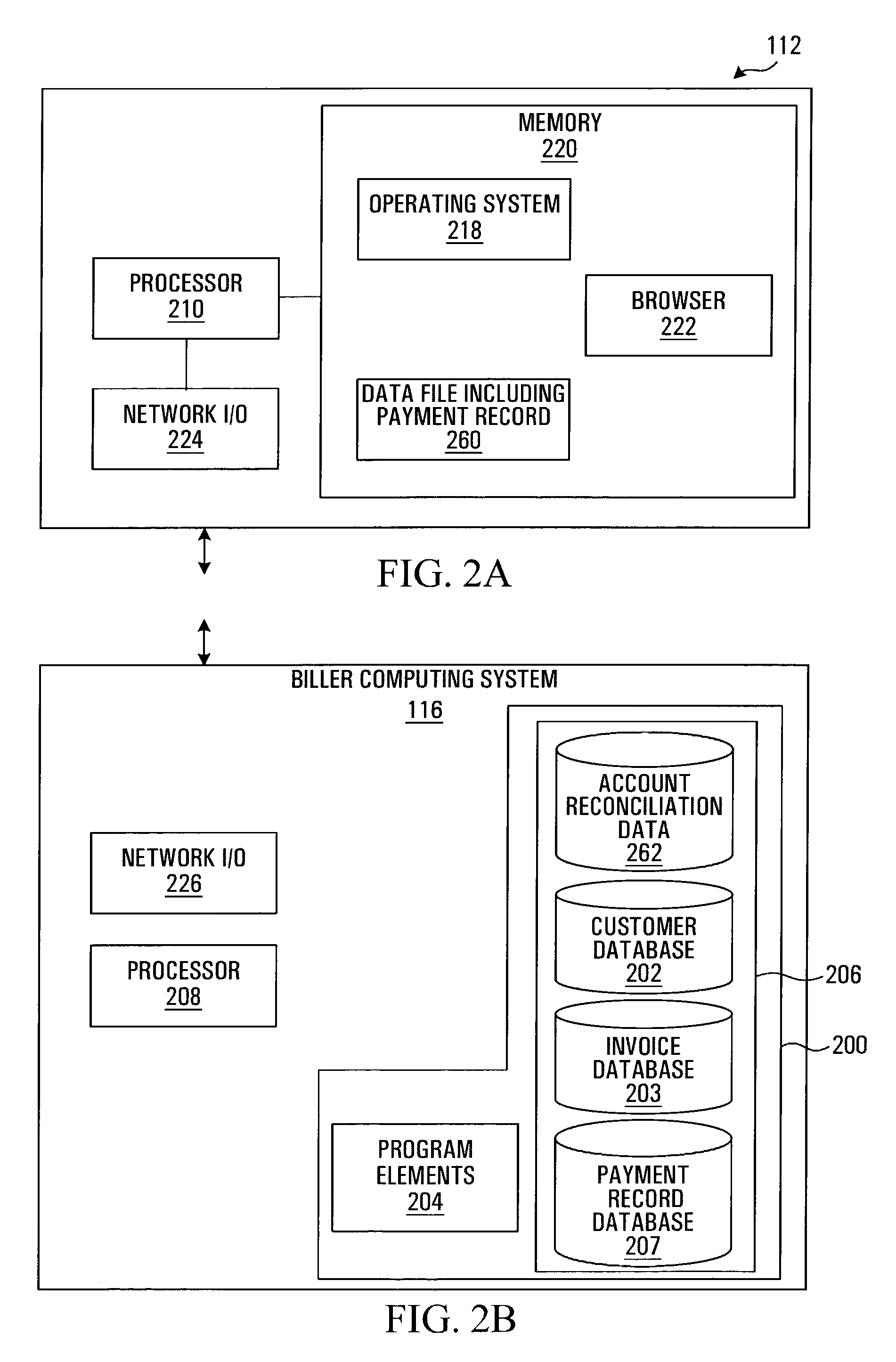
Method and system for generating account reconciliation data
ActiveUS7536325B2Allow accessSaving of time in-houseComplete banking machinesFinancePaymentData export
A method and system for providing information regarding a customer account are provided. The customer account includes a plurality of entries, each entry being indicative of a request for payment where the request for payment is being issued by a biller entity to a customer entity. A payment record including remittance detail data is received over a network account reconciliation data at least in part on the basis of the remittance detail data and the entries in the customer account. A signal suitable for causing information derived from the account reconciliation data to be displayed on a display screen is then transmitted.
Owner:CANADIAN NAT RAILWAY
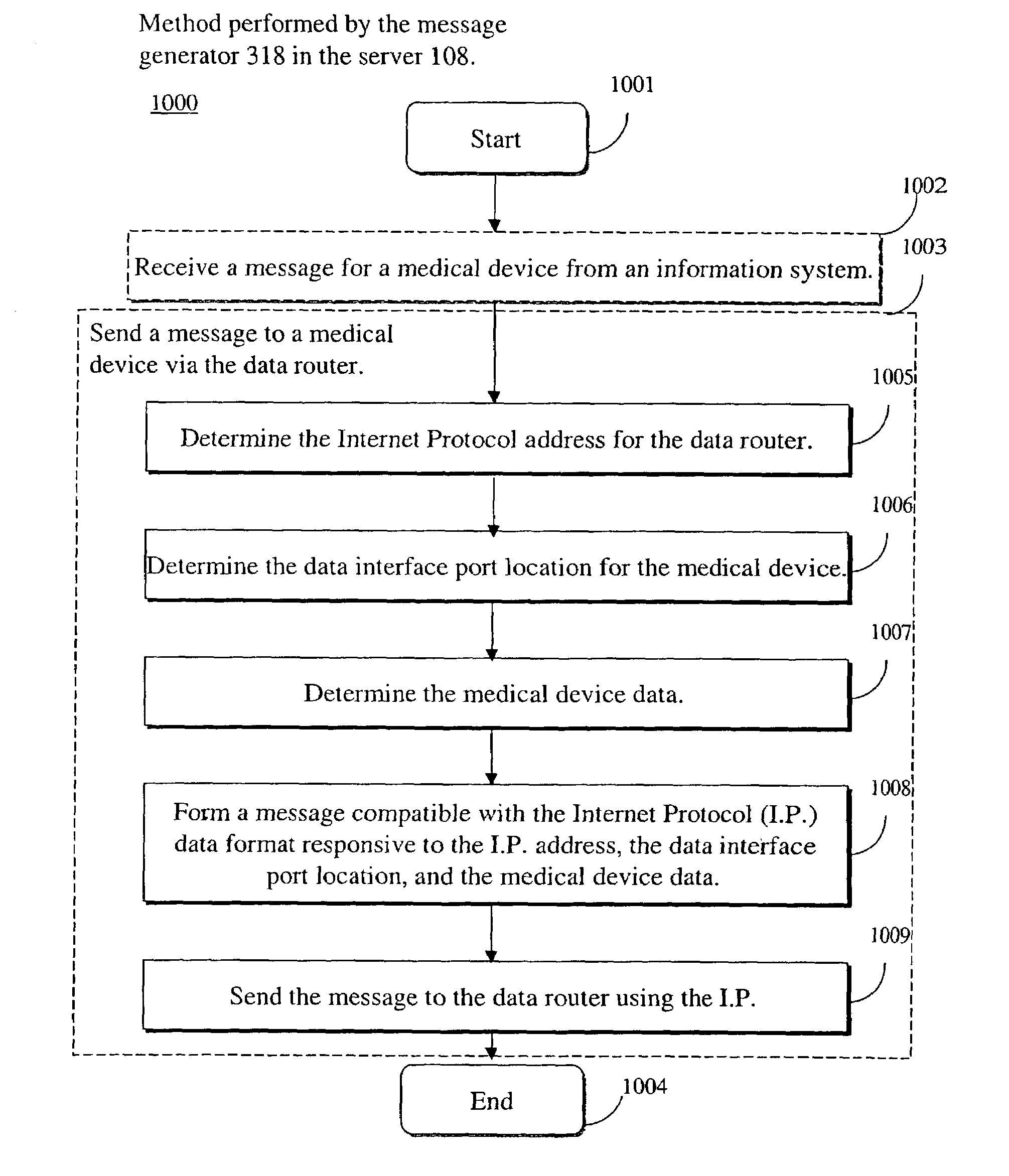
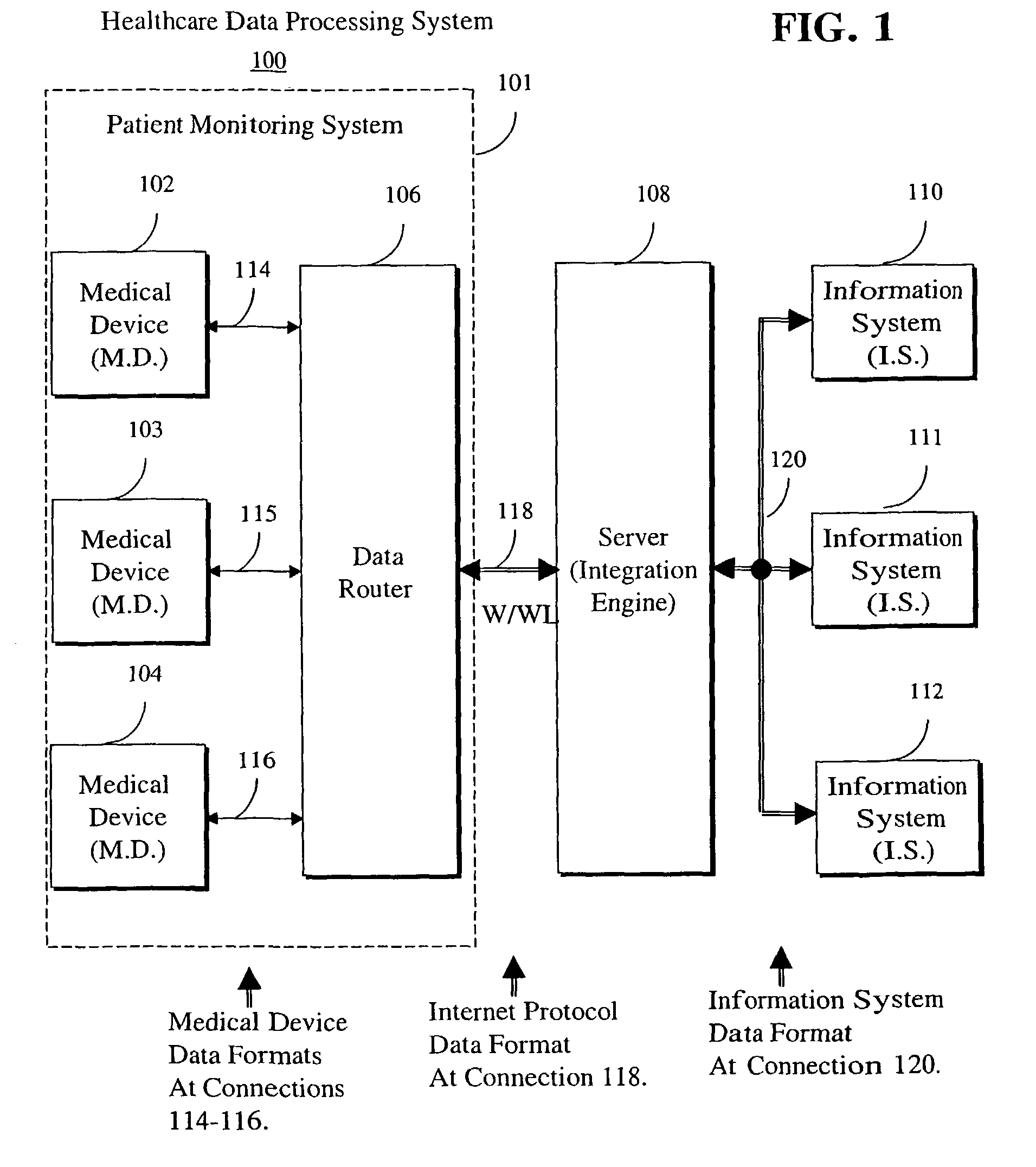
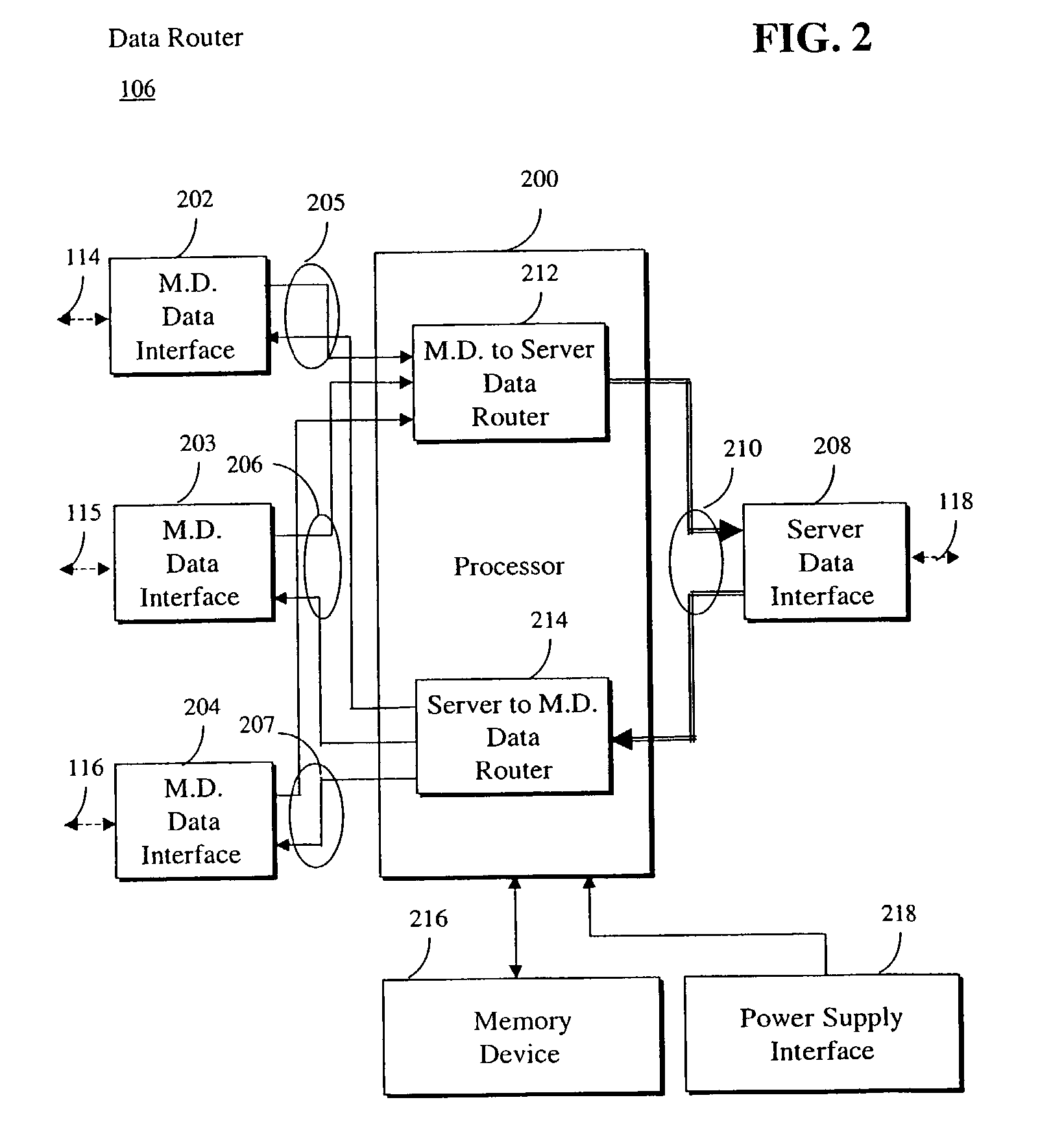
System for processing data acquired from multiple medical devices
A system and a corresponding method processes data acquired from multiple medical devices located at one of multiple patient bed stations. A first data interface bi-directionally communicates with multiple medical devices in acquiring data, including patient related information, and acquisition device type identifier information from one of the multiple medical devices using a communication protocol selected from multiple communication protocols associated with different medical devices. A data processor incorporates the acquisition device type identifier information derived from the acquired data into a message in an Internet compatible format for communication to a remote device. A second data interface bi-directionally communicates with the remote device to convey the acquisition device type identifier information to the remote device in the Internet compatible format message and employs a predetermined source Internet communication address usable by the remote device to identify a source location of the message from a map associating Internet communication addresses and source locations.
Owner:SHARED MEDICAL SYST CORP +2
Method and apparatus for implementing digital video modeling to generate a patient risk assessment model
A computer implemented method, apparatus, and computer program product for generating a risk assessment model for an assessment of a patient in a healthcare facility. The process retrieves event data for the patient, wherein the event data is derived from video data, and wherein the event data further comprises metadata describing events affecting the patient in a medical care facility, and parses the event data to form assessment data. The process then generates the risk assessment model using the assessment data.
Owner:IBM CORP
Method and system for migrating relational data to HBbase
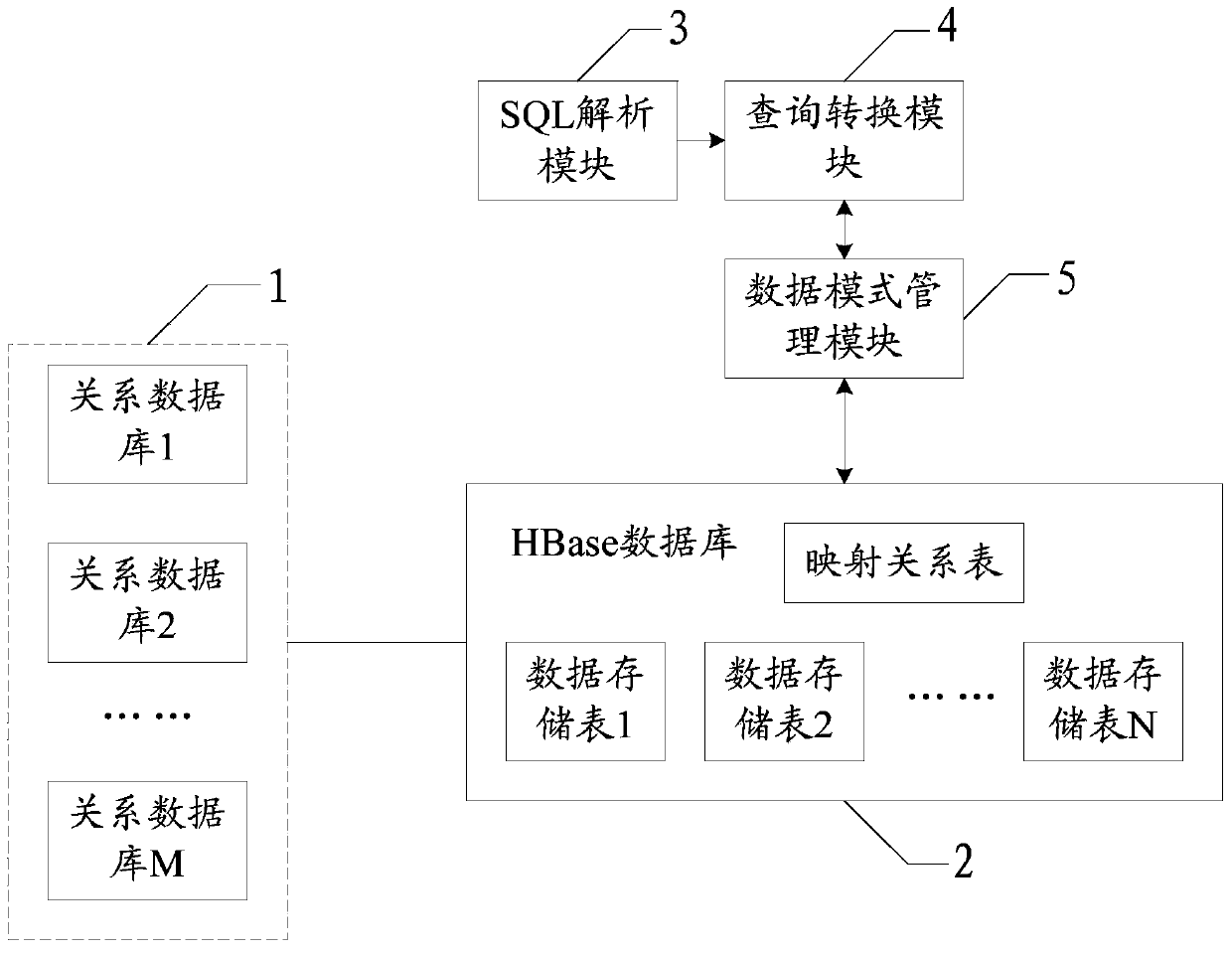
ActiveCN103631907ASmooth transitionFlexible configurationSpecial data processing applicationsRelational databaseQuery statement
The invention relates to a method and system for migrating relational data to the HBbase. The system comprises a relational data base, an HBase database, an SQL analysis module, a query conversion module and a data mode management module. As a mapping relation list is designed in the HBase database, a mapping relation of mode information in an original relation database and mode information in the HBase database is stored and mode information of a data form in the original relation database the is completely reserved, a mapping manner can be flexibly configured and more options are provided for users. Due to the efficient data organizing manner of the HBase, the access performance is greatly improved and the storage space is saved. Meanwhile, the data export function is provided and data interaction with other sub-systems is achieved. In addition, the data query function supports SQL query and converts an SQL query statement into a query statement of the HBase database, so that the users can transit to the HBbase database more smoothly.
Owner:INST OF INFORMATION ENG CAS
Method and apparatus for processing respiration data and assessing autonomic function
PendingUS20050251056A1High signal fidelityAccurate representationMedical data miningElectrocardiographyAutonomic functionSingle lead
Embodiments of the invention concern methods and apparatuses for deriving respiratory data from both single lead and multi-lead ECG data recordings. Other embodiments of the invention address the assessment of respiration rate from respiratory data such as respiratory data derived from ECG data. Still other embodiments of the invention address methods and apparatuses for the assessment of autonomic function. These last embodiments involve the derivation of respiratory data from ECG data, comparing the respiration rate to key threshold values, and the final derivation of one or more HRV parameters from the ECG data. The embodiments of the invention have implementations applicable to data previously recorded data as well as data recorded and processed in a real-time manner.
Owner:MEDDORNA
Building analytical models with standardized virtual flat files
A system and method for creating virtual flat customer records derived from database customer data that may be used as standardized input for analytical models. A Customer Analytic Record (“CAR”) application may be created as a database object to extract, transform, and format all of the customer data needed for customer segmentation and predictive modeling. The CAR may be a set of database views that are defined using virtual stored queries The CAR application may dynamically calculate additional variables using predetermined transformations, including custom transformations of an underlying behavior. The CAR is preferably a dynamic view of the customer record that changes whenever any update is made to the database. The definition of the CAR provides documentation of each data element available for use in models and analytics.
Owner:ACCENTURE GLOBAL SERVICES LTD
Malfunction Detection Method and System Thereof
InactiveUS20130173218A1High sensitivityAccurate expressionTesting/monitoring control systemsNuclear monitoringErrors and residualsE infrastructure
To allow early sensing of anomalies in a manufacturing plant or other infrastructure (plant), provided is a method that acquires data of runtime status of said plant from a plurality of sensors of said plant, makes a model from training data that corresponds to the regular runtime status of said plant, employs the training data thus modeled in computing a anomaly measure of the data acquired from the sensors, and detects anomalies. In computing the anomaly measure, the anomaly is detected by recursively carrying out: a derivation of a residual error from the training data thus modeled acquired from the plurality of sensors, a removal of a signal having a residual error that is greater than a predetermined value, and a computation of the anomaly measure for the data that is acquired from the plurality of sensors whereupon the signal having the large residual error is removed.
Owner:HITACHI LTD
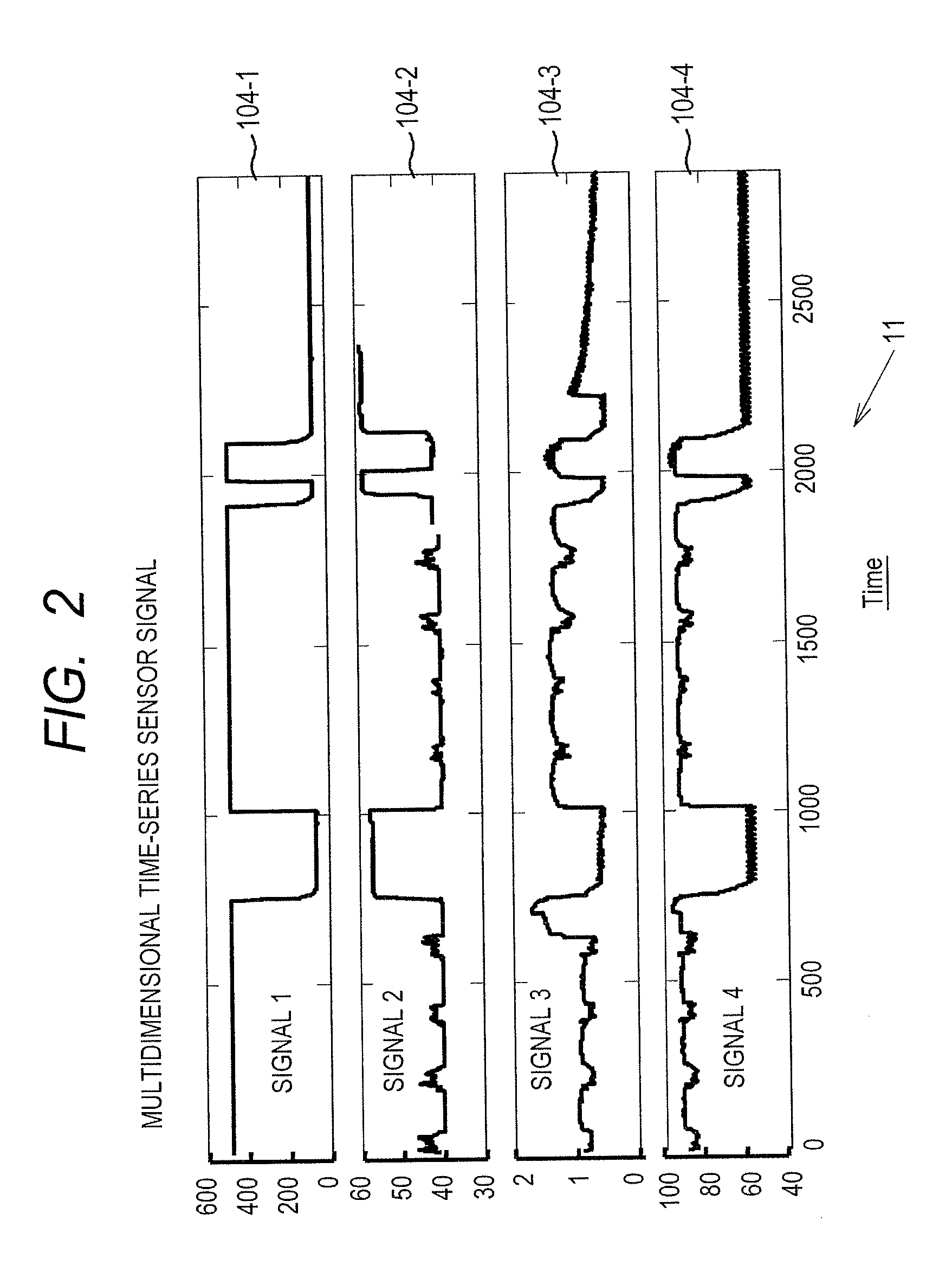
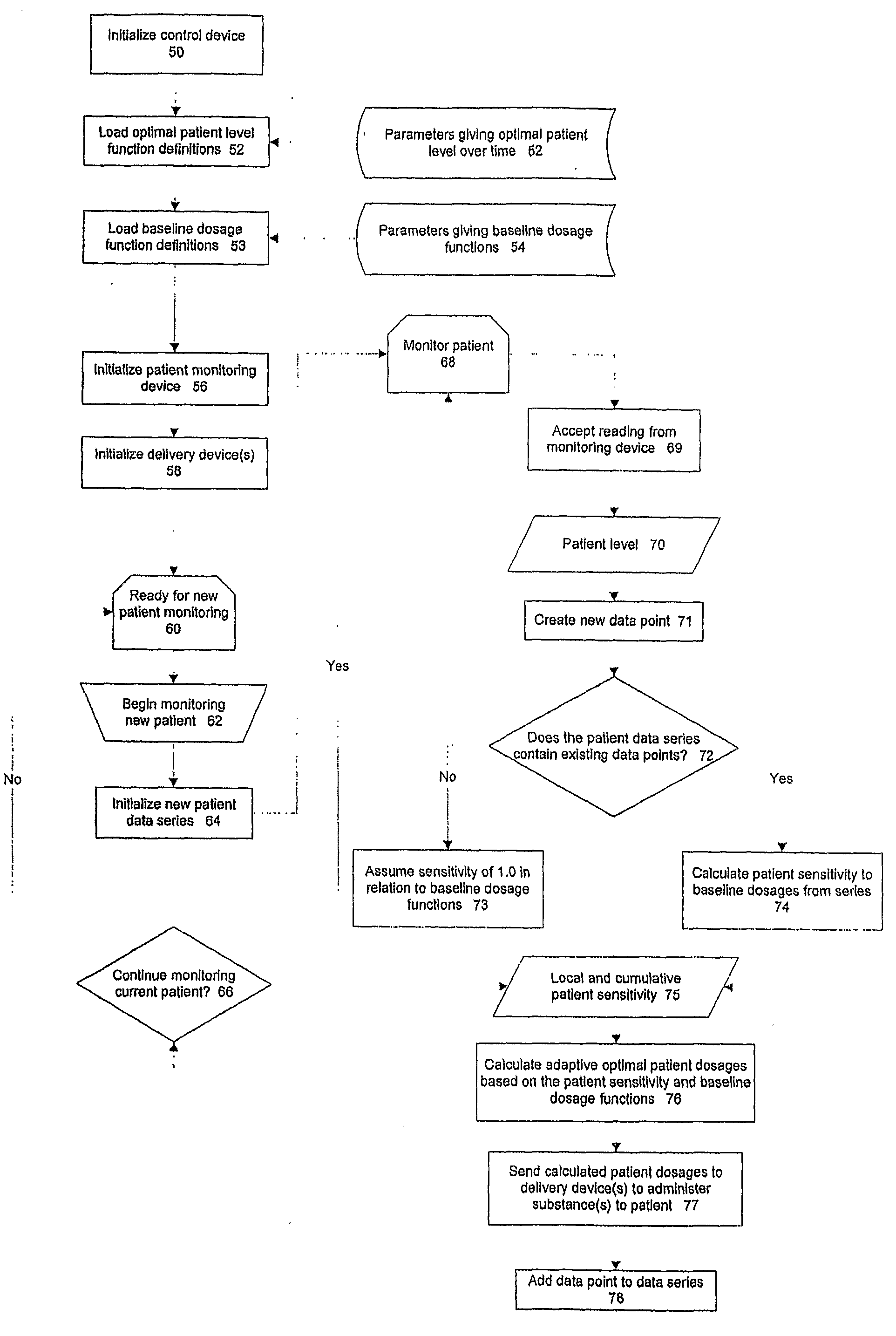
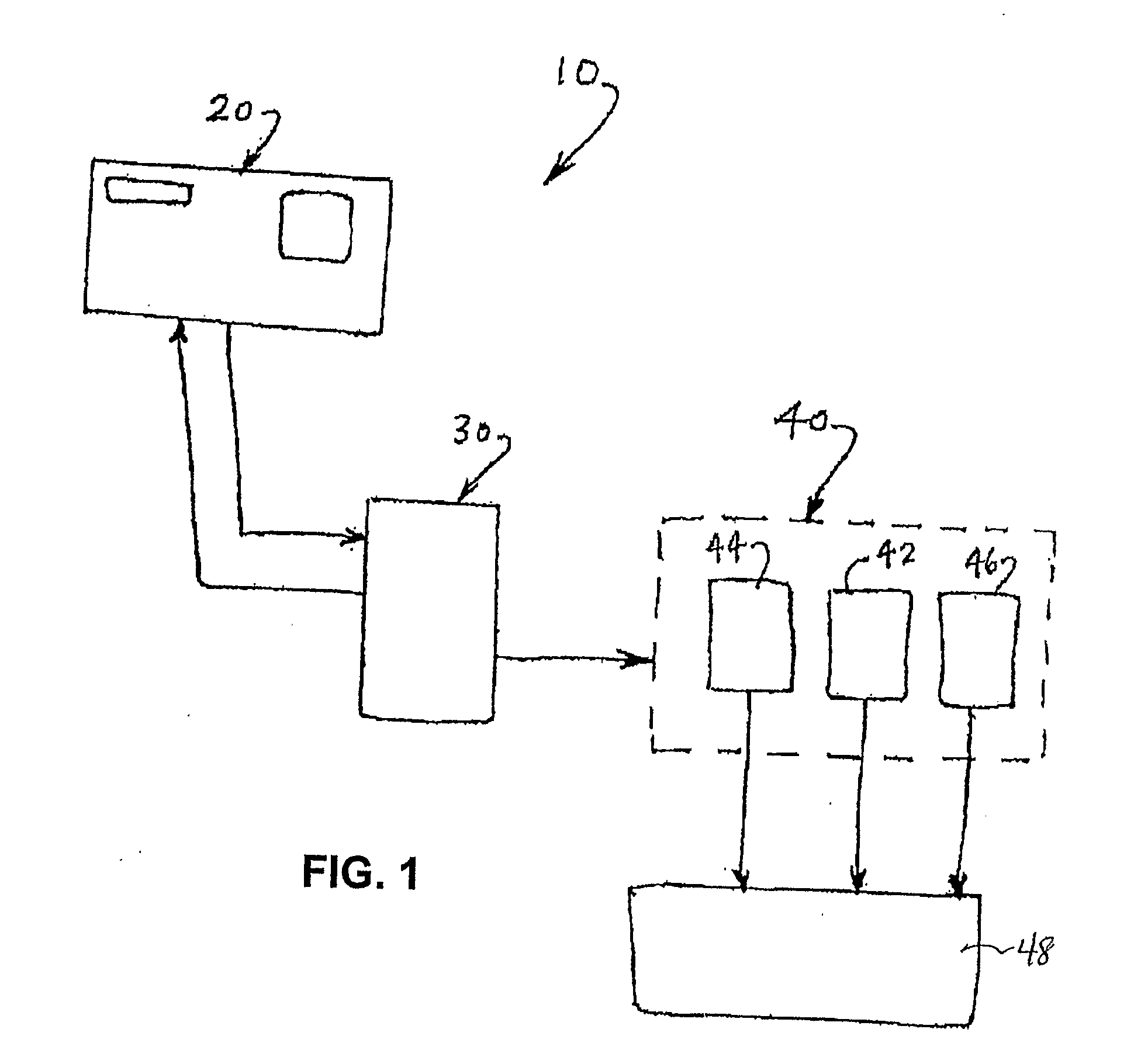
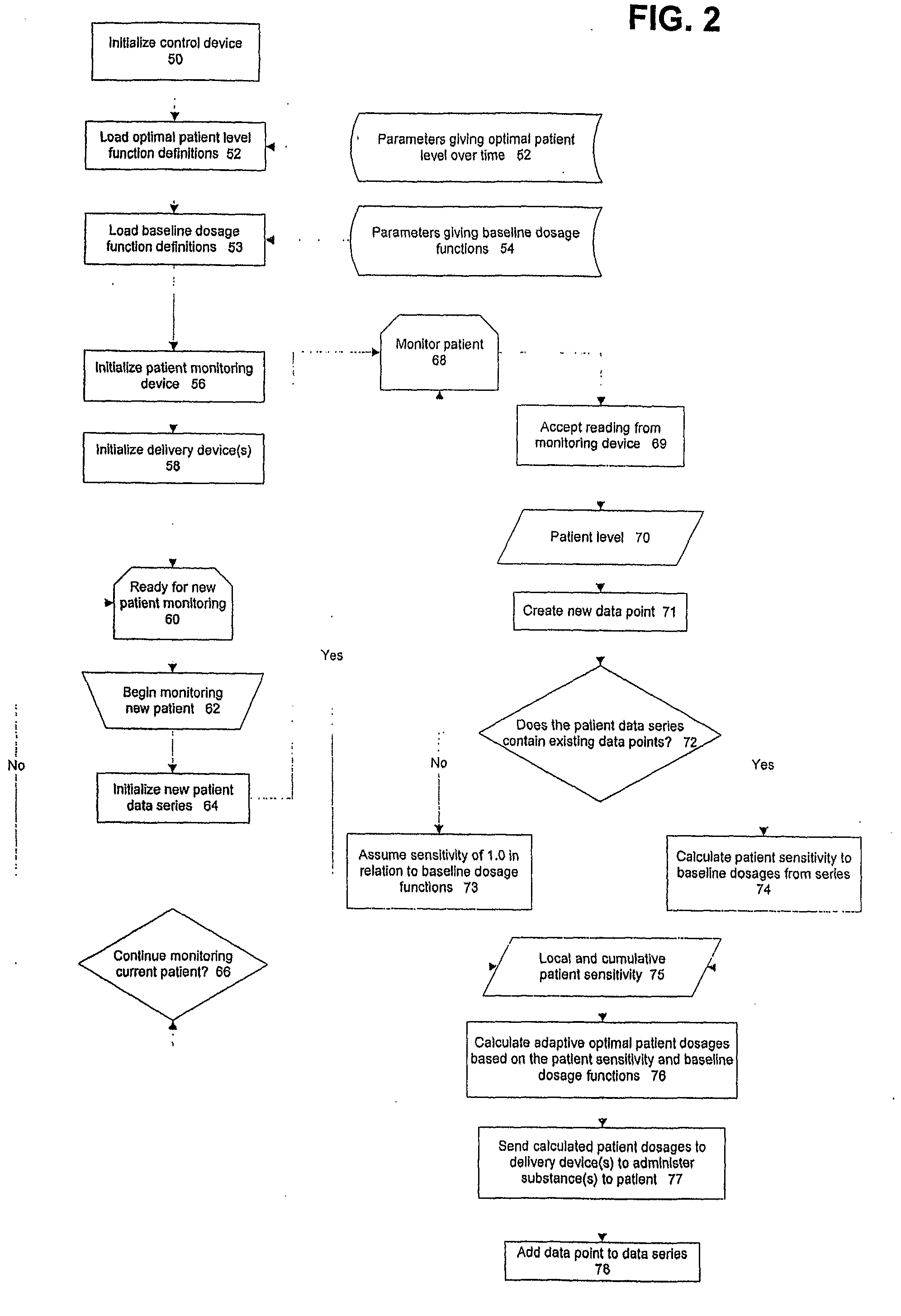
Balanced Physiological Monitoring and Treatment System
A system and method for providing balanced, automated regulation of a patient's physiological condition by monitoring at least one physiological parameter and, optionally, monitoring and controlling additional physiological parameters, is disclosed. The system includes a physiological parameter monitor, an intelligent control device and a multi-channel delivery device for providing controlled intravenous delivery of at least two medications that affect the physiological condition being controlled. Control logic in the intelligent control device is derived by an algorithm based on model predictive control. The control logic includes mathematically modeled systems, empirical data systems or a combination thereof. The system of the present invention is optionally included in a networked system to provide centralized data storage and archival of system information as well as data export and query capabilities that can be used for patient file management, health care facility management and medical research.
Owner:ADMETABYS CORP
Method and apparatus for identifying virtual body profiles
InactiveUS7242999B2Buying/selling/leasing transactionsSpecial data processing applicationsHuman bodyInformation processing
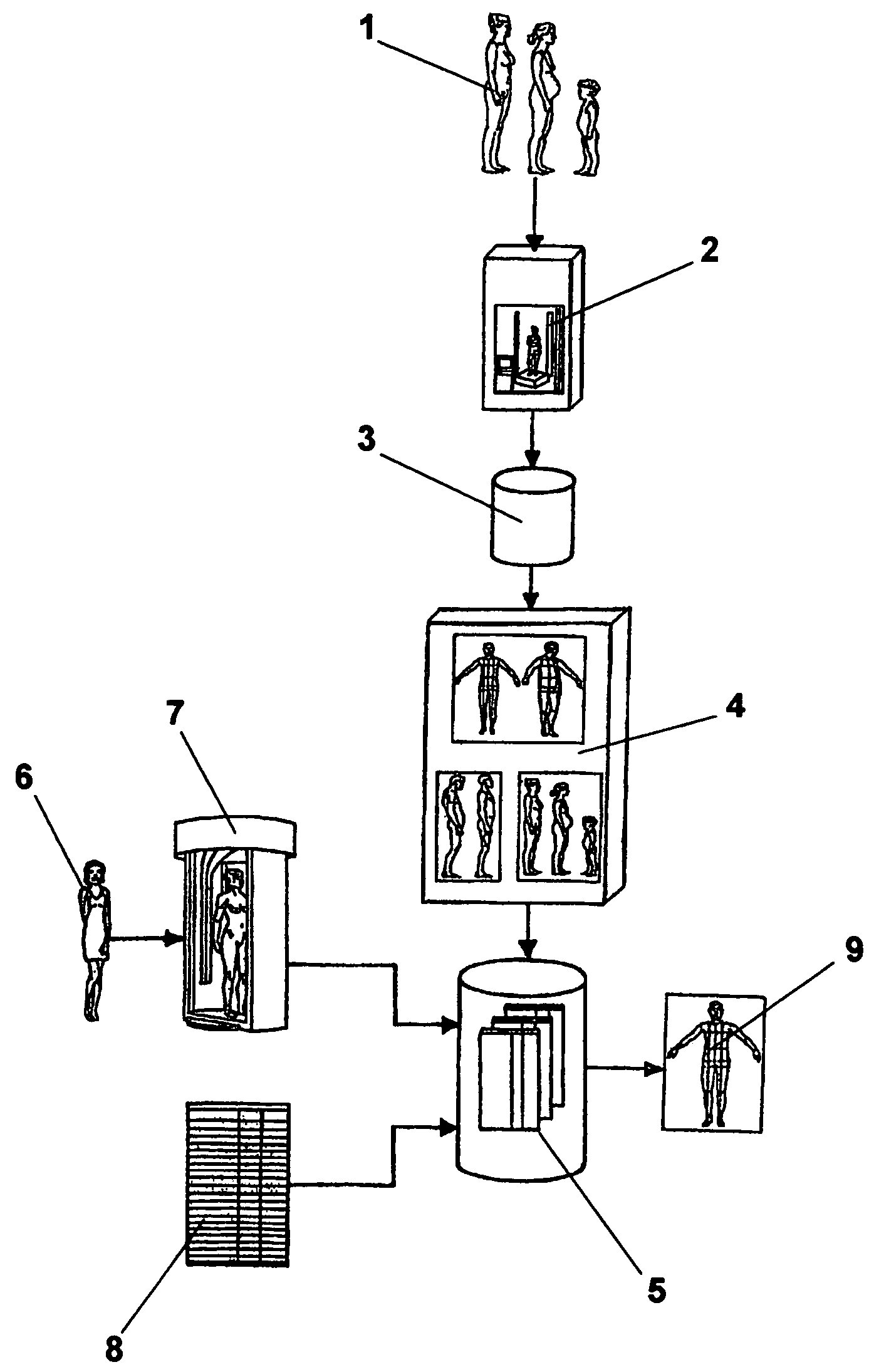
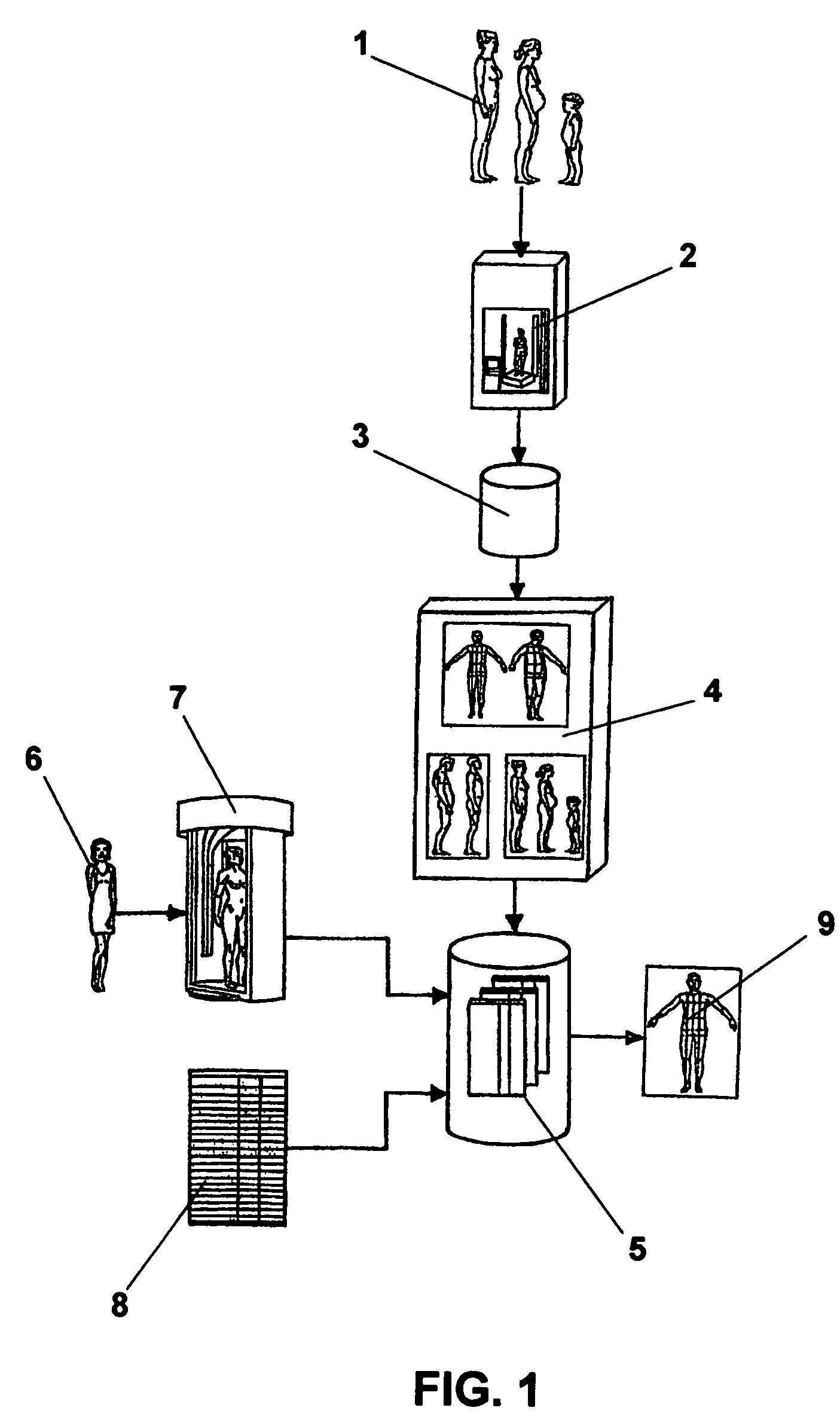
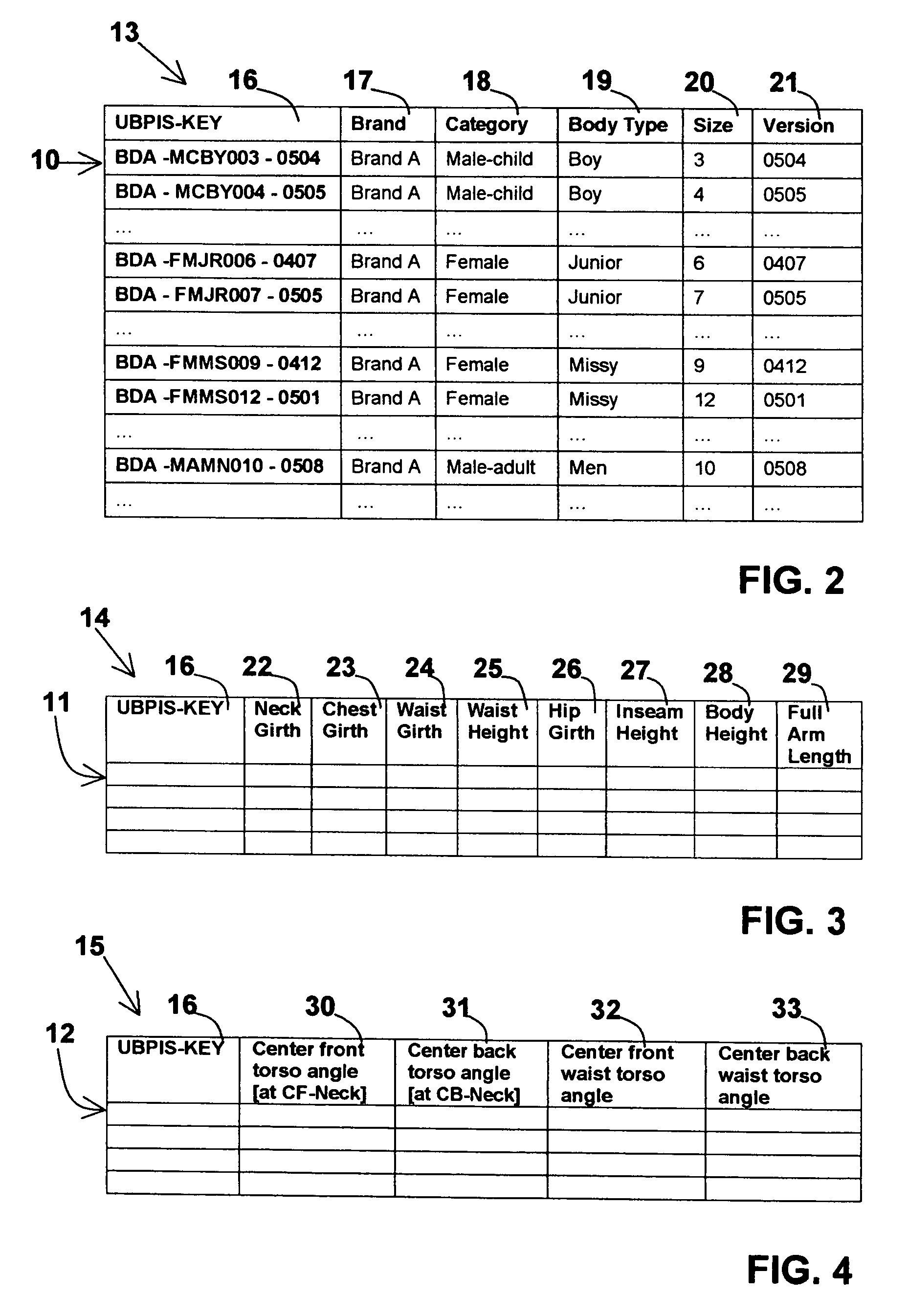
3D morphological data representative of reference size models of garment brands and respective categorizing data are introduced into an information processing system. These 3D morphological data are indexed by brand names, categorizing data, and volumetric, dimensional, and angular data derived from the morphological data in order to build a database of virtual human body profiles. For selecting a suitable profile matching a consumer's body, his / her personal measurements and categorizing data are introduced into the system, either directly if they are known, or acquired by scanning only a minimum numbers of points on the customer's body in a scanning booth so as to derive these measurements. Instead of methods of the prior art defining the body profiles of the consumers per se from the general population, this method attempts to categorize the body profiles of the specific brands' reference size human models, and all offered sizes, through the brands' grading rules.
Owner:WANG KENNETH KUK KEI
Method and apparatus for implementing digital video modeling to generate an optimal healthcare delivery model
A computer implemented method, apparatus, and computer program product for generating an optimal healthcare delivery model. The process parses event data derived from video data to identify patterns of events, wherein the event data comprises metadata describing events associated with a medical care facility. The process then identifies a subset of patterns of events from the patterns of events that achieves a target outcome to form a set of optimized patterns of events. The process generates an optimized healthcare delivery strategy using the set of optimized patterns of events to form the optimized healthcare delivery model for the medical care facility.
Owner:IBM CORP
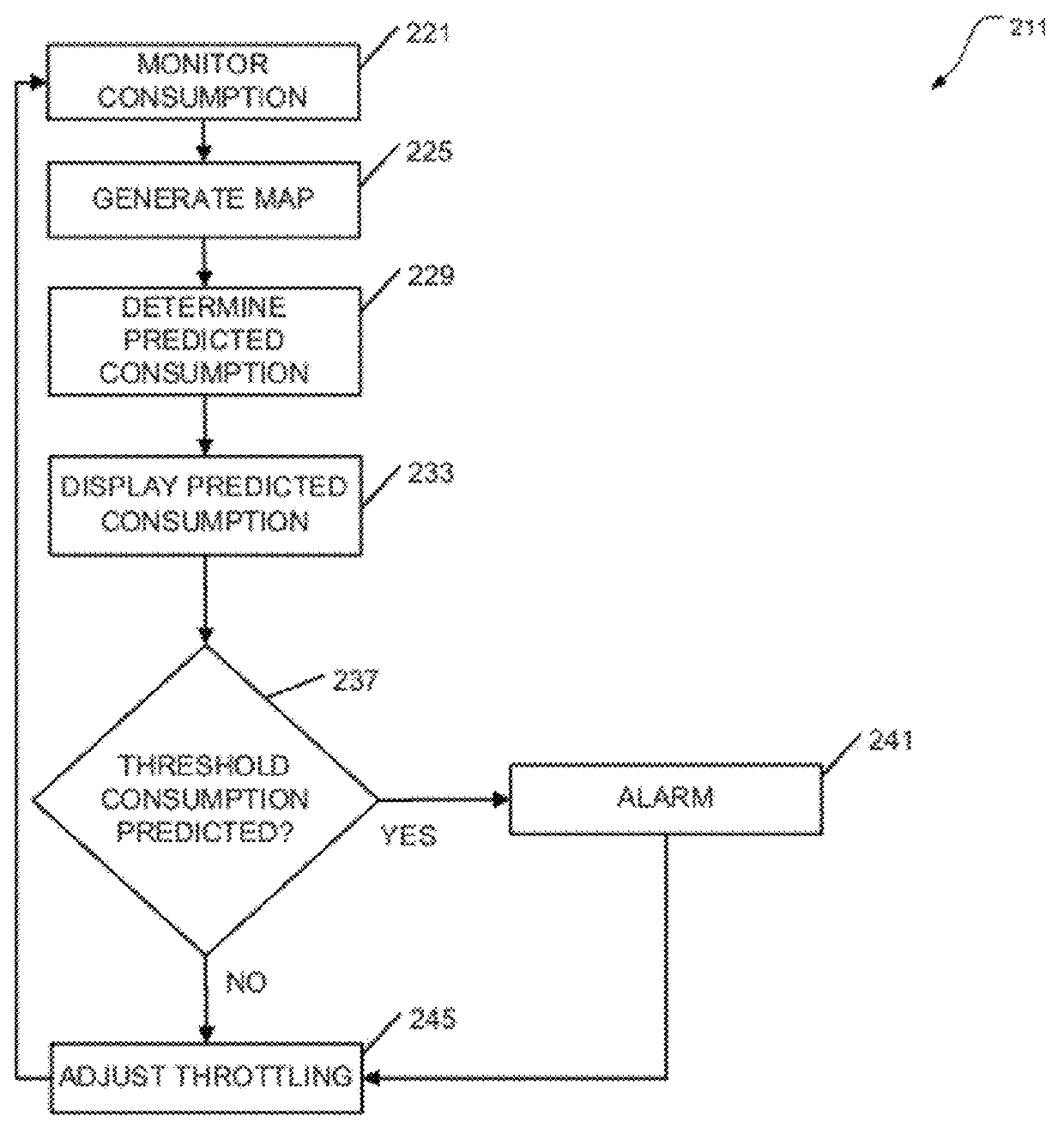
Predictive resource management
ActiveUS20120173477A1Digital data information retrievalDigital data processing detailsResource consumptionResource management
Apparatus, systems, and methods may operate to monitor database system resource consumption over various time periods, in conjunction with scheduled data loading, data export, and query operations. Additional activities may include generating a database system resource consumption map based on the monitoring, and adjusting database system workload throttling to accommodate predicted database system resource consumption based on the resource consumption map and current system loading, prior to the current database resource consumption reaching a predefined critical consumption level. The current system loading may be induced by data loading, data export, or query activity. Other apparatus, systems, and methods are disclosed.
Owner:TERADATA US
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com