Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
8833 results about "E infrastructure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
E-infrastructure facilitates competent equipment and favorable resources and opportunities that are essentially needed to for the safety, security, and development of a society. Further, e-infrastructure helps to integrate various technologies including different computer systems, internet broadband channels,...
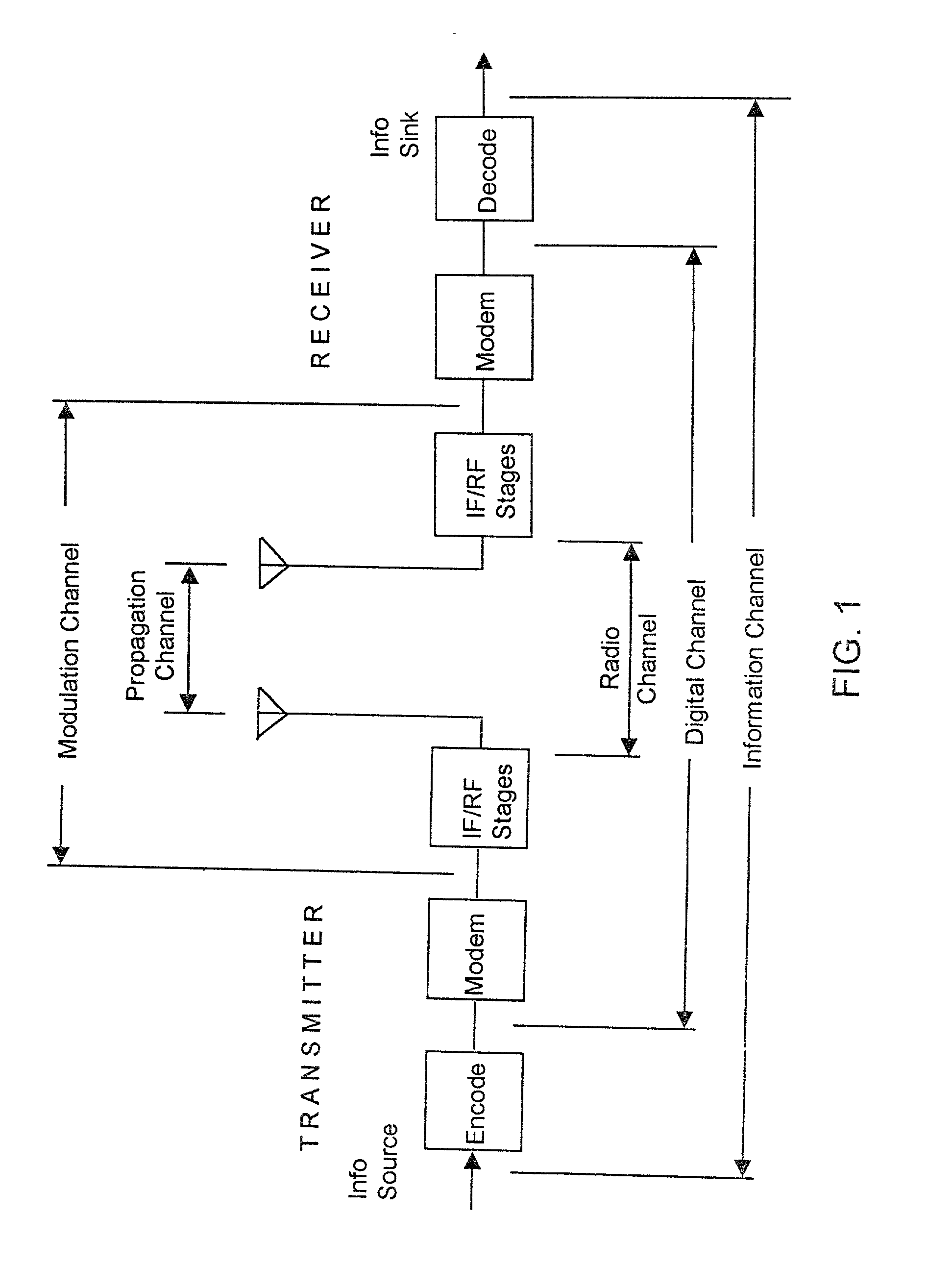
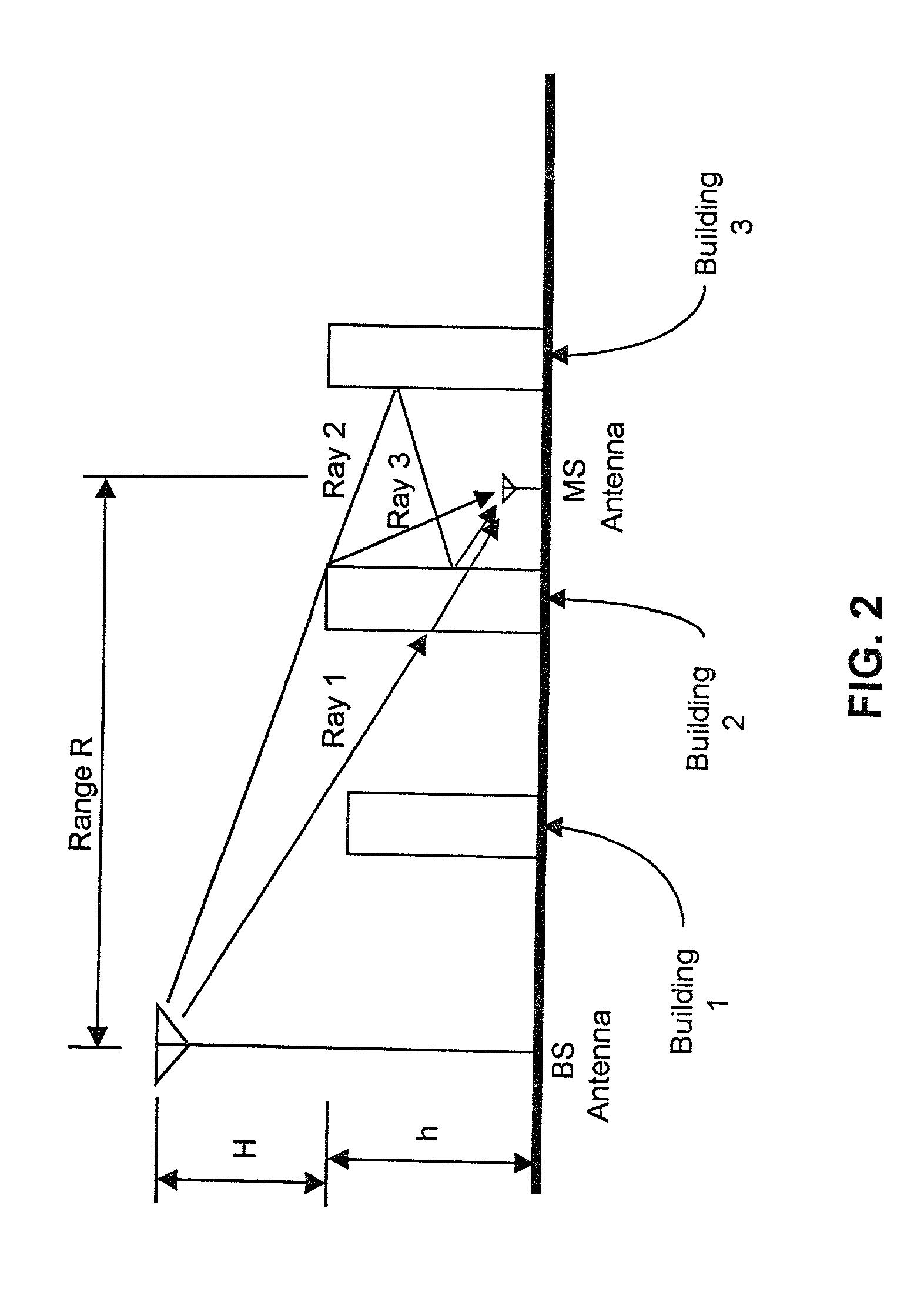
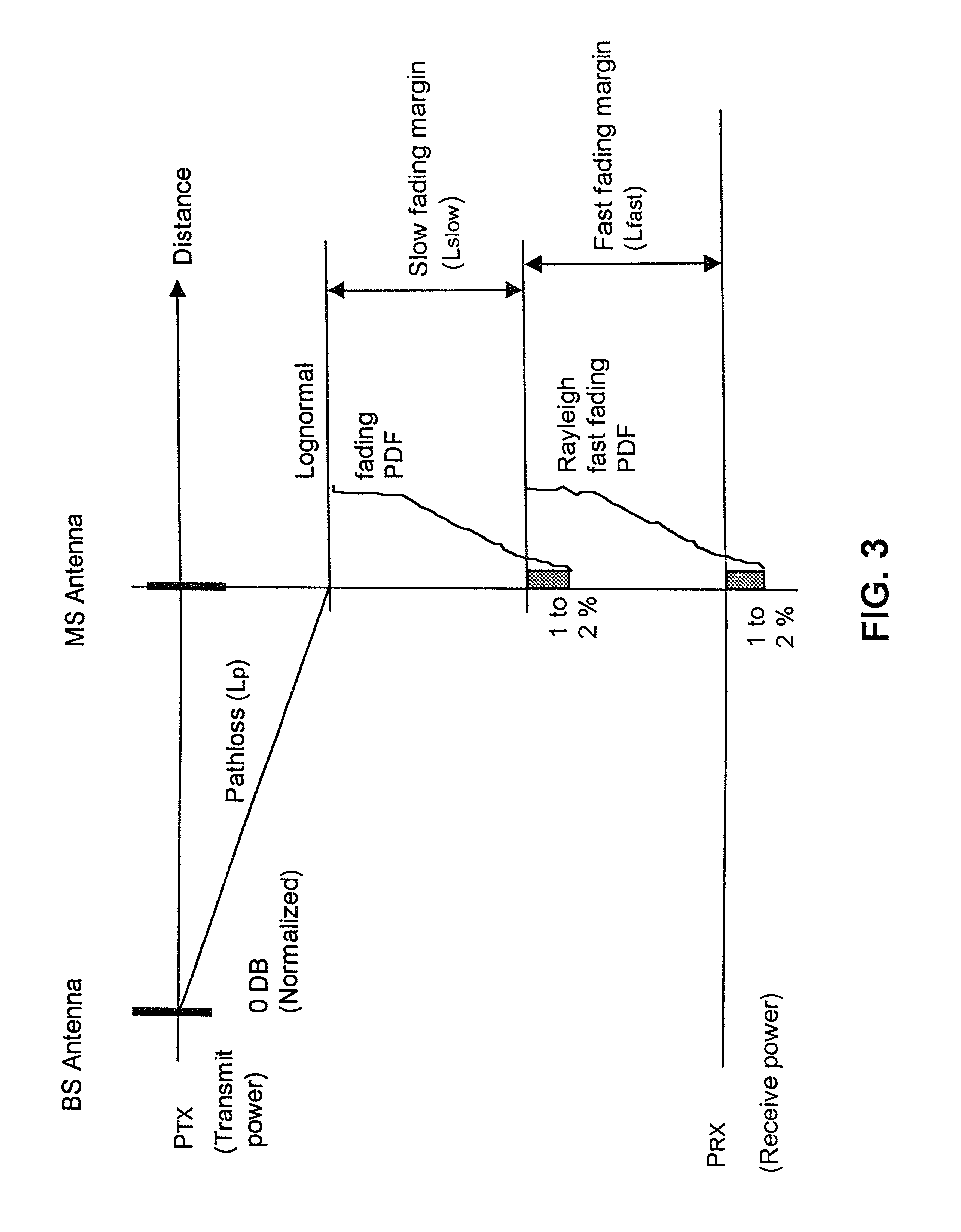
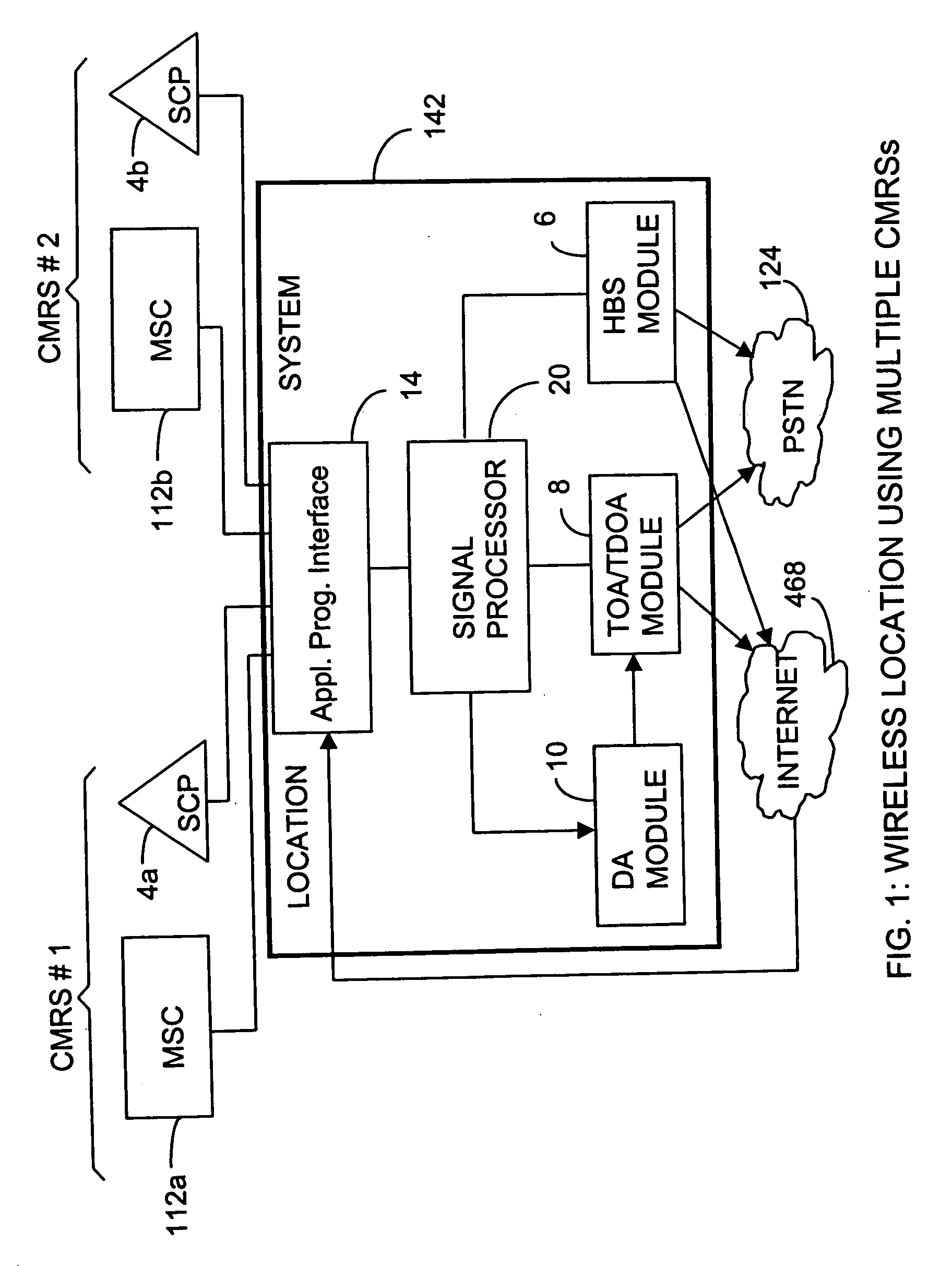
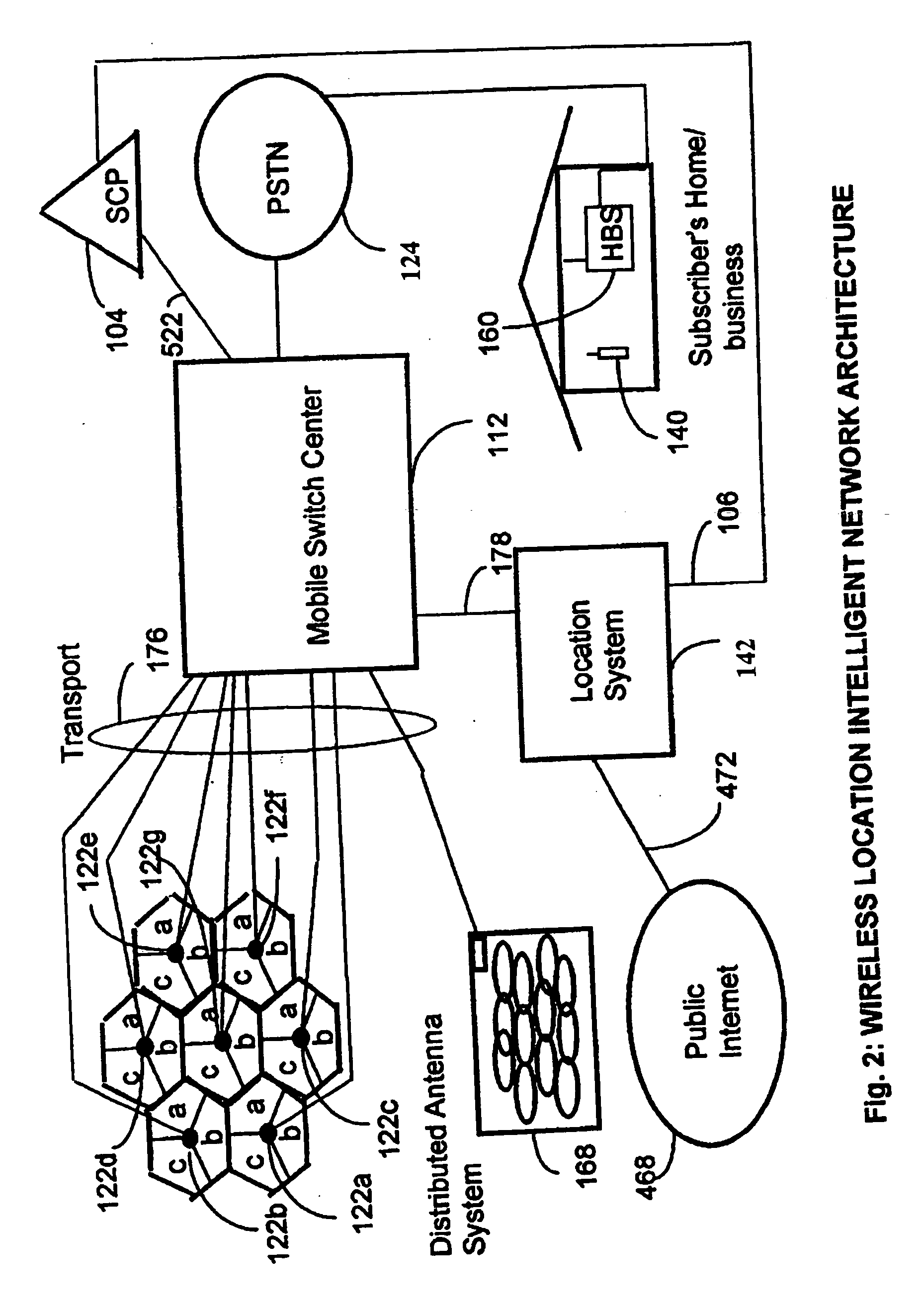
Wireless location using multiple location estimators
InactiveUS6249252B1Effectively and straightforwardly resolvedAmbiguity and conflictDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
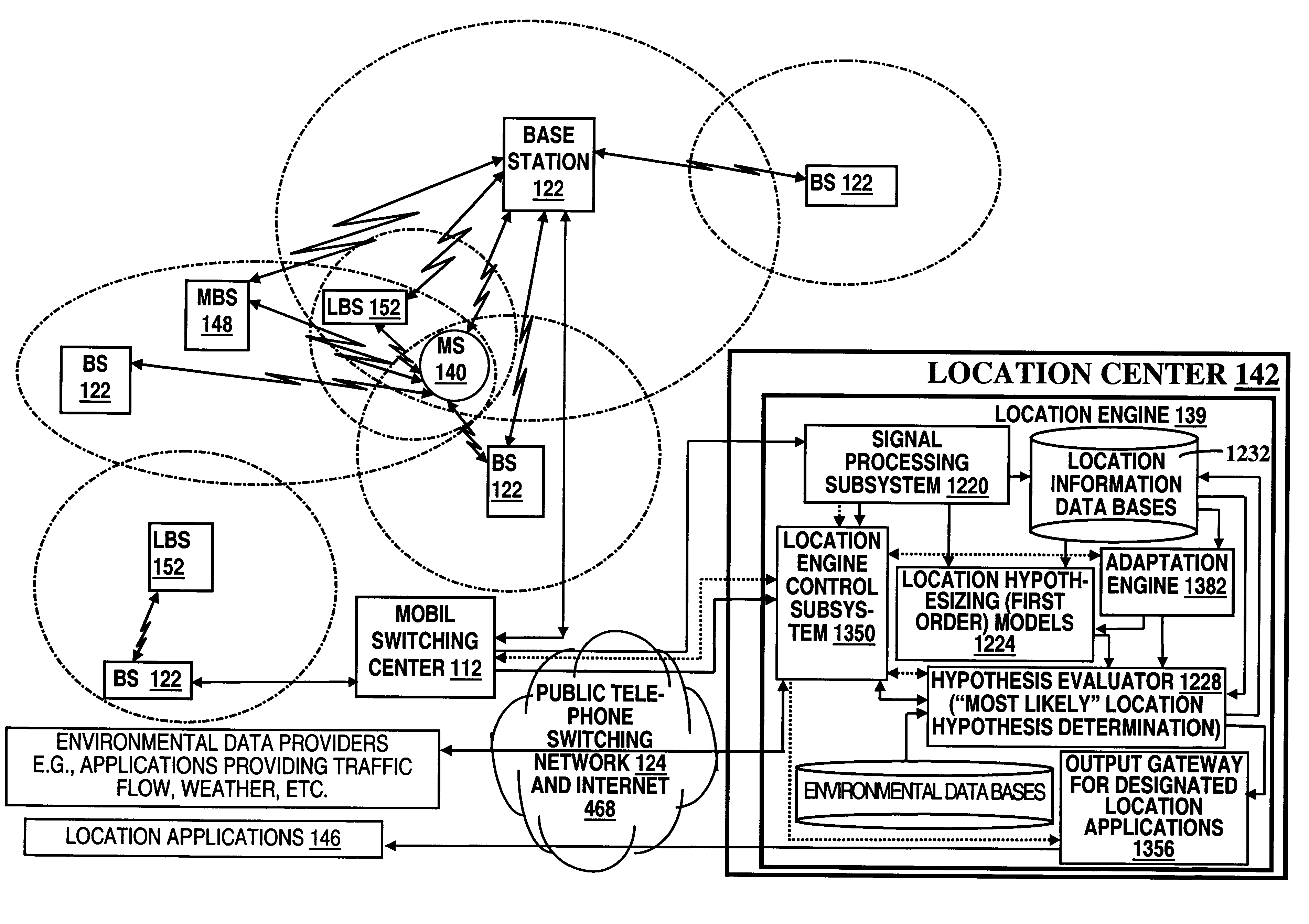
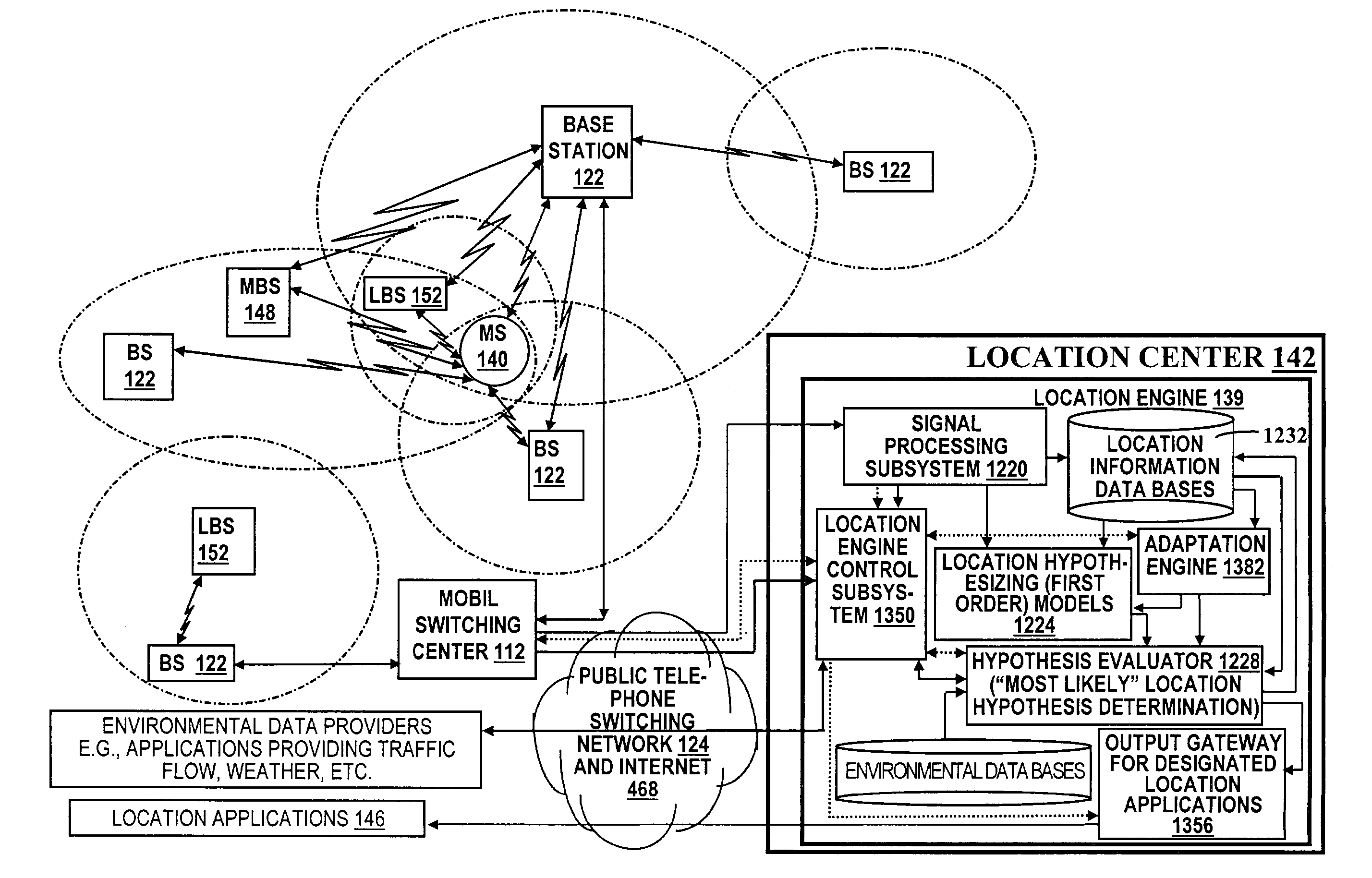
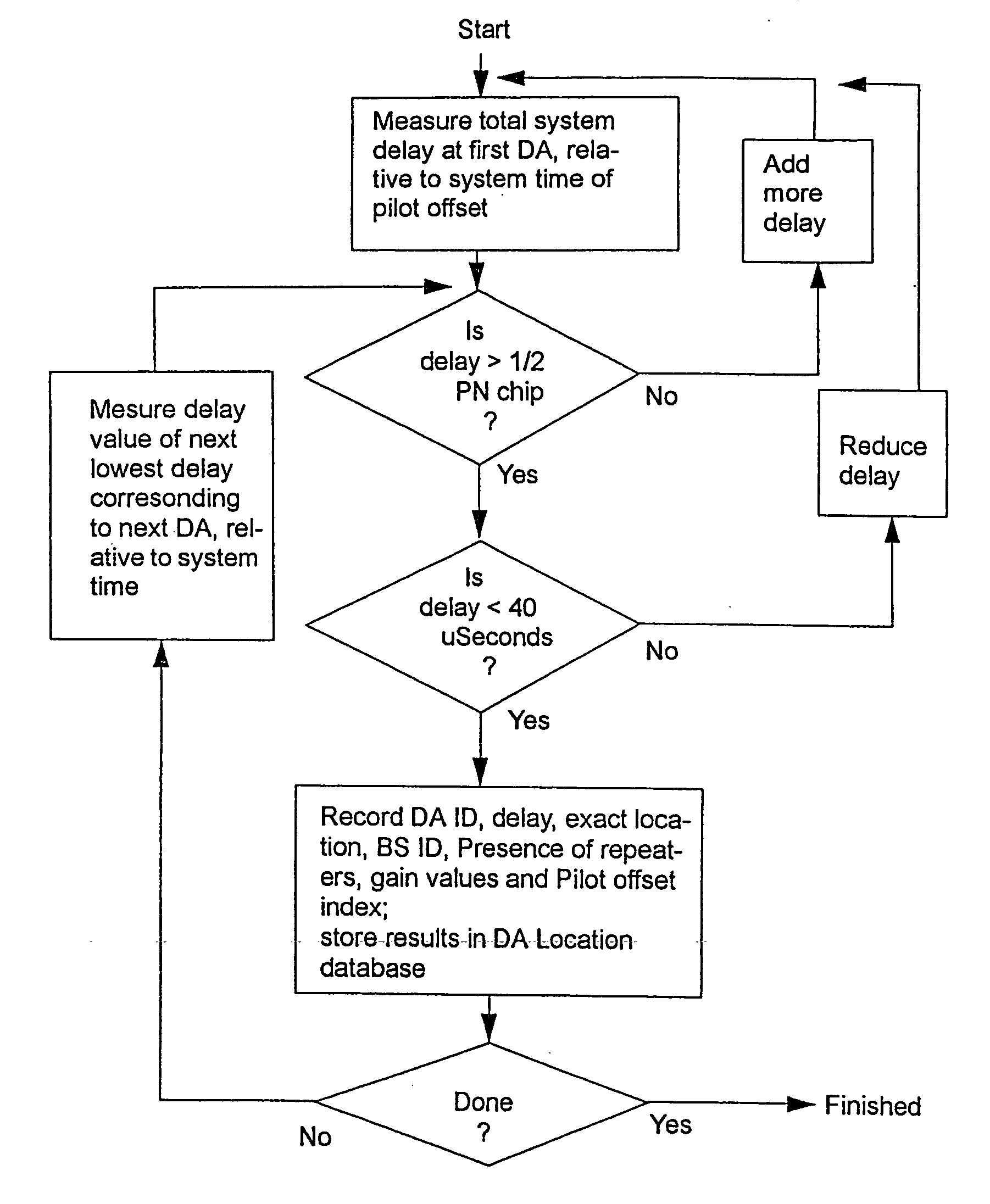
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signing environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
Applications for a wireless location gateway
InactiveUS20040198386A1Easy to implementEffectively and straightforwardly resolvedPosition fixationRadio/inductive link selection arrangementsTerrainInternet communication
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:DUPRAY DENNIS J
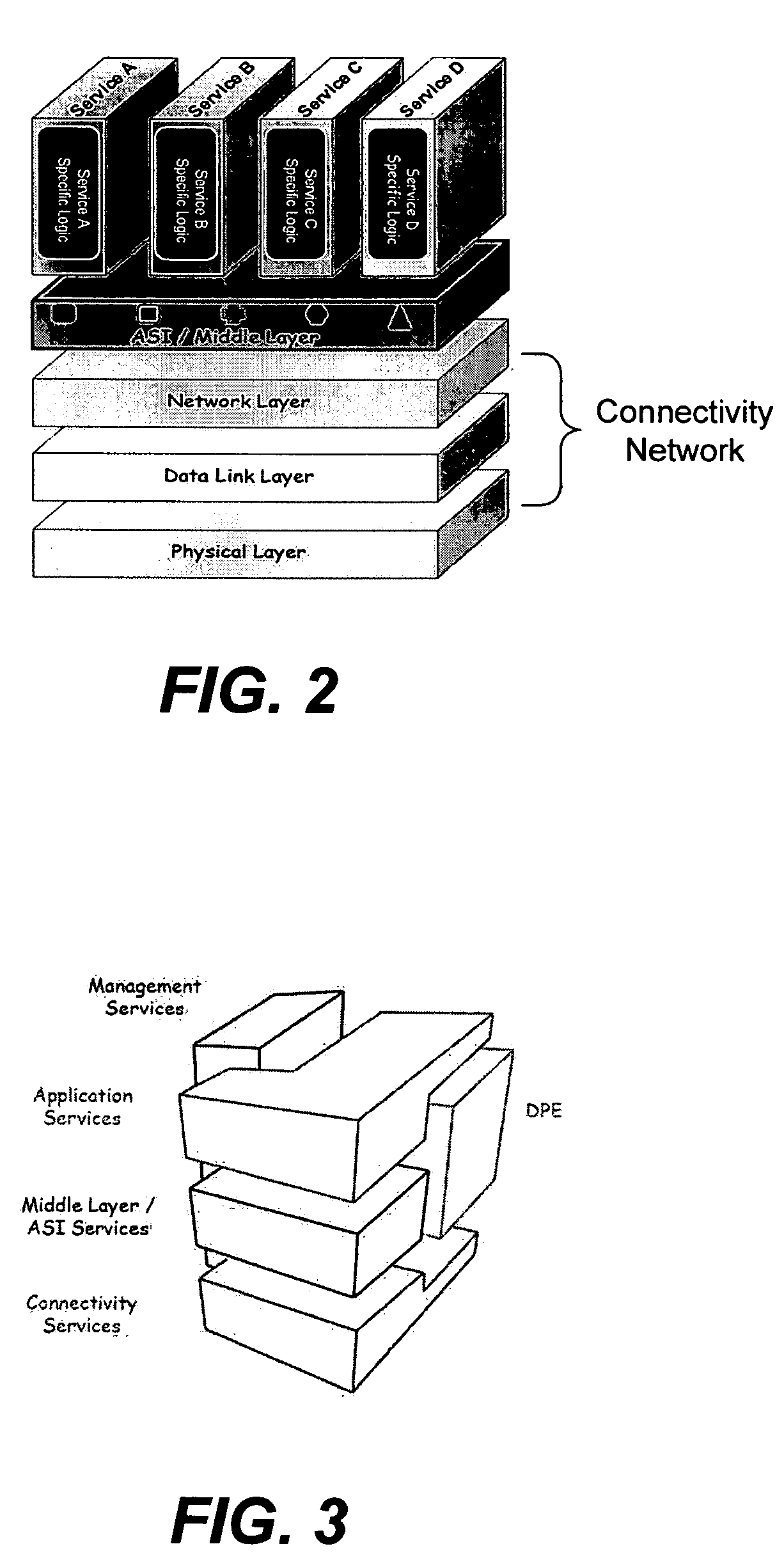
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
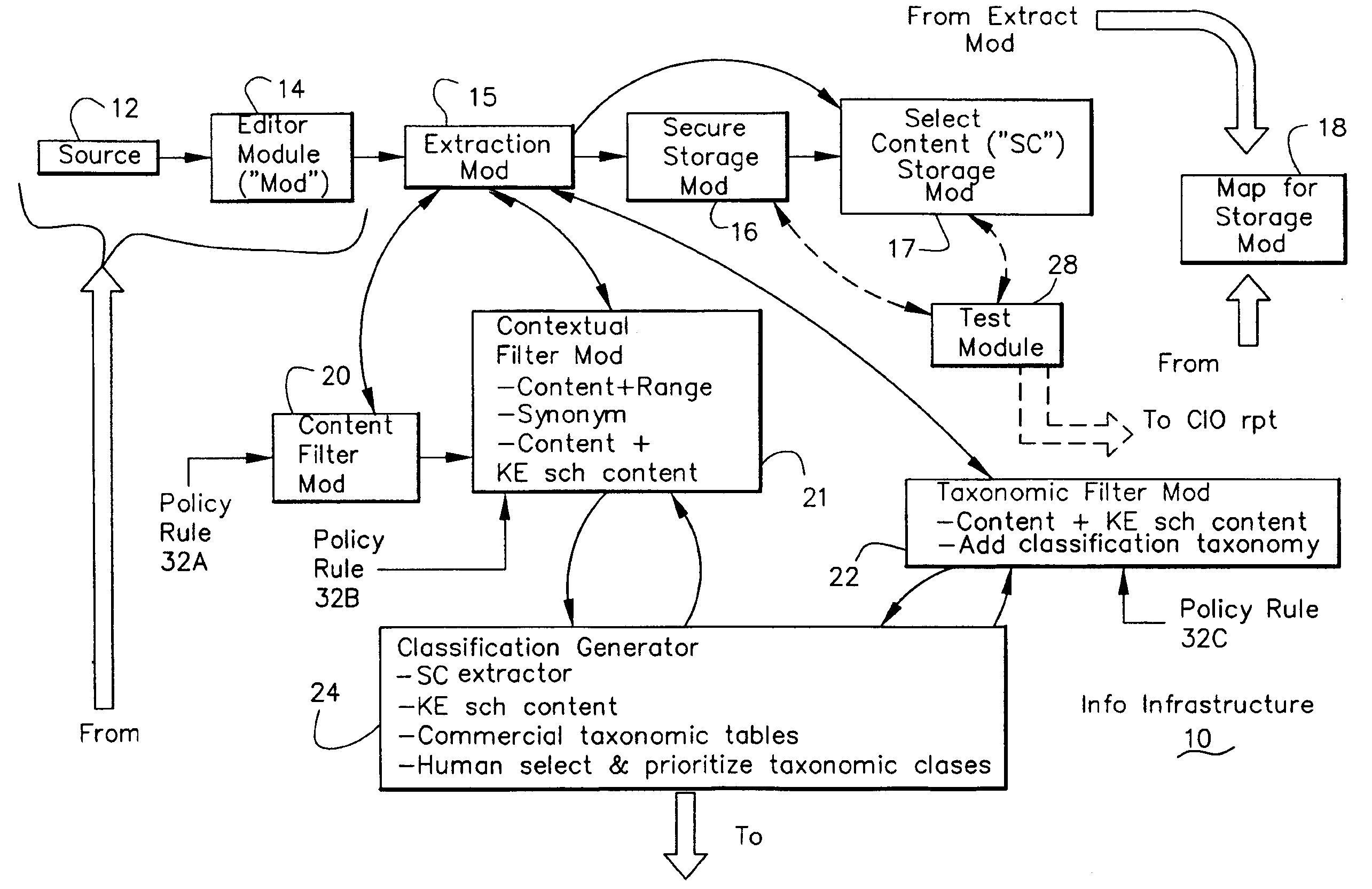
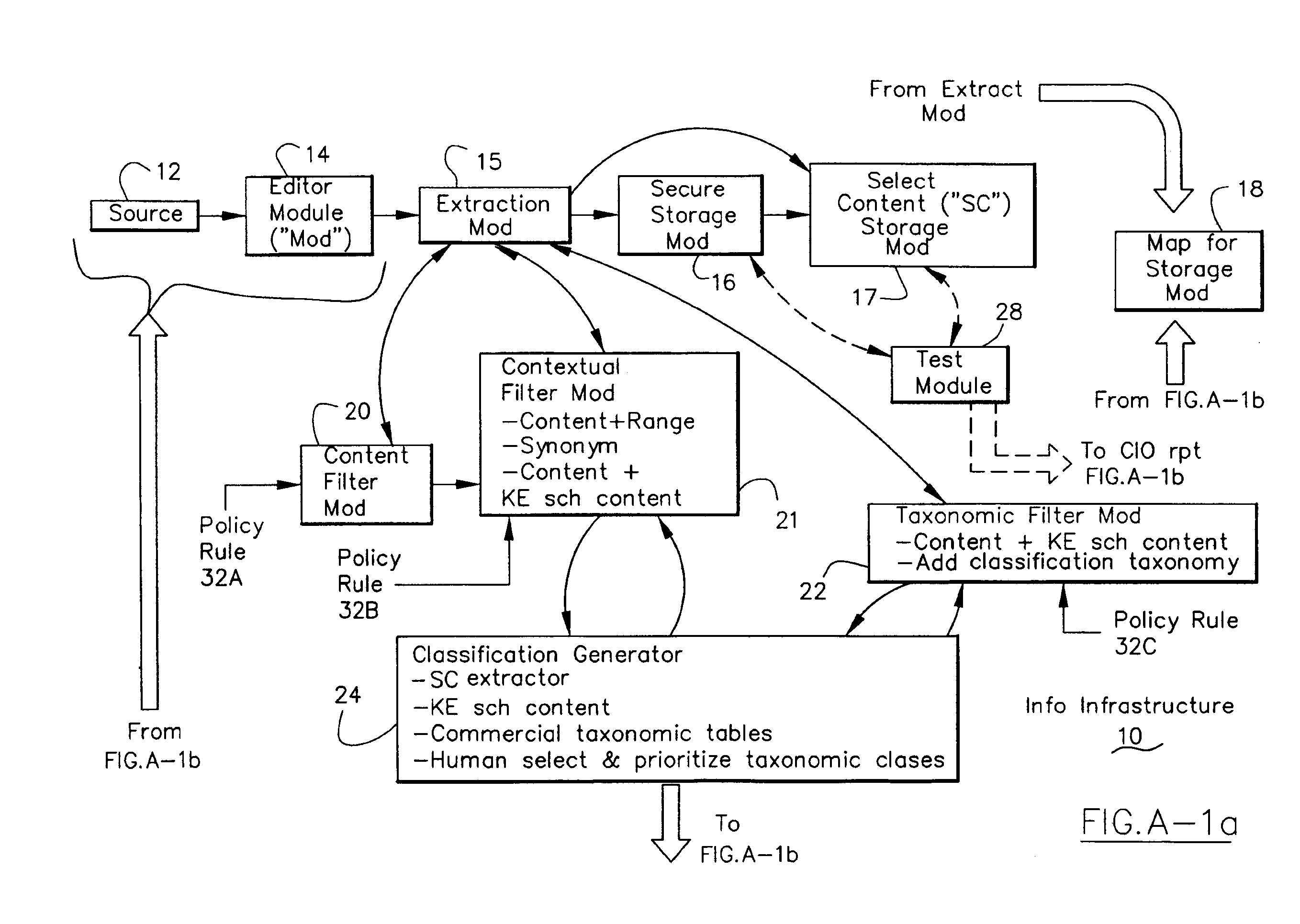
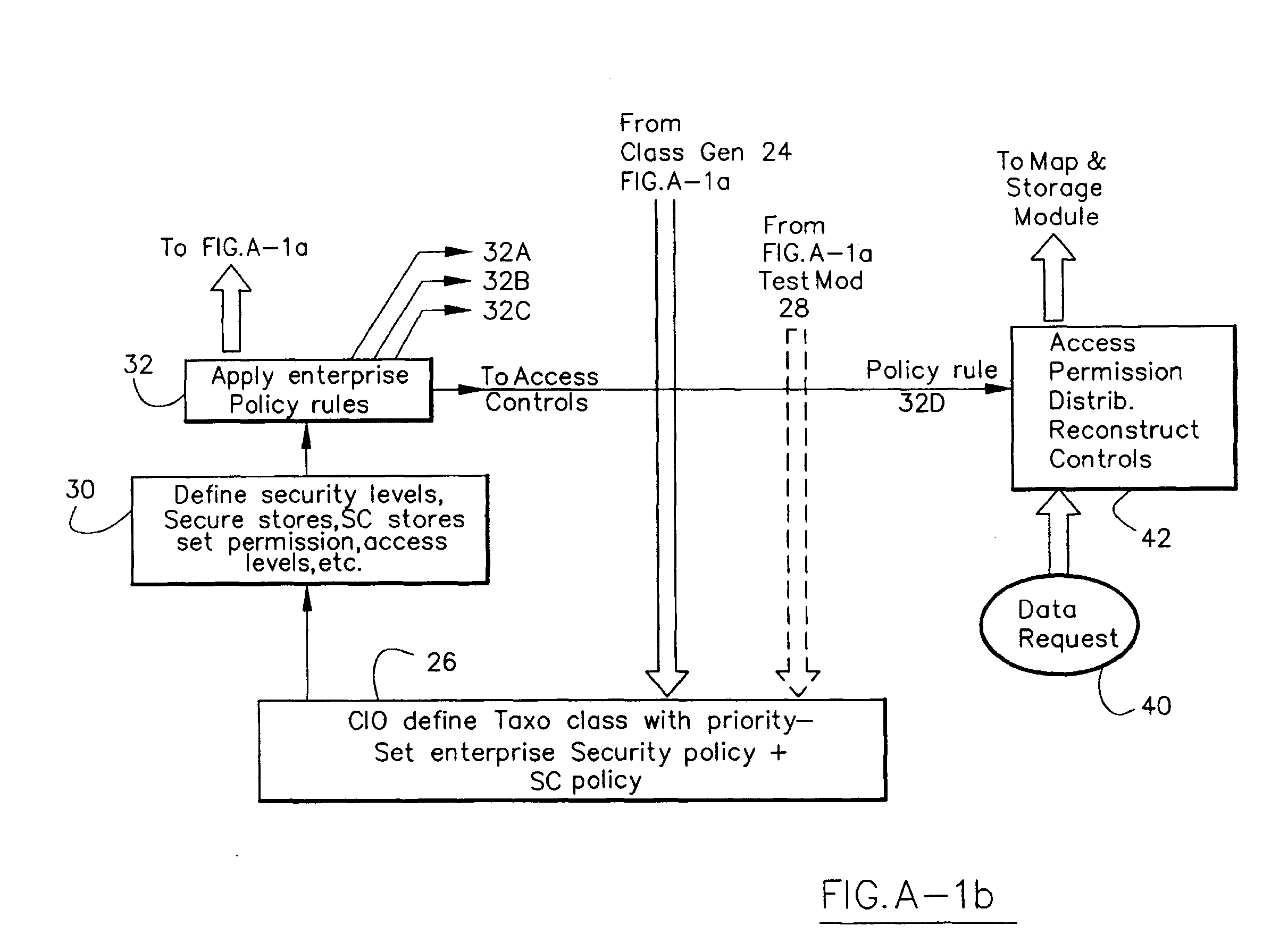
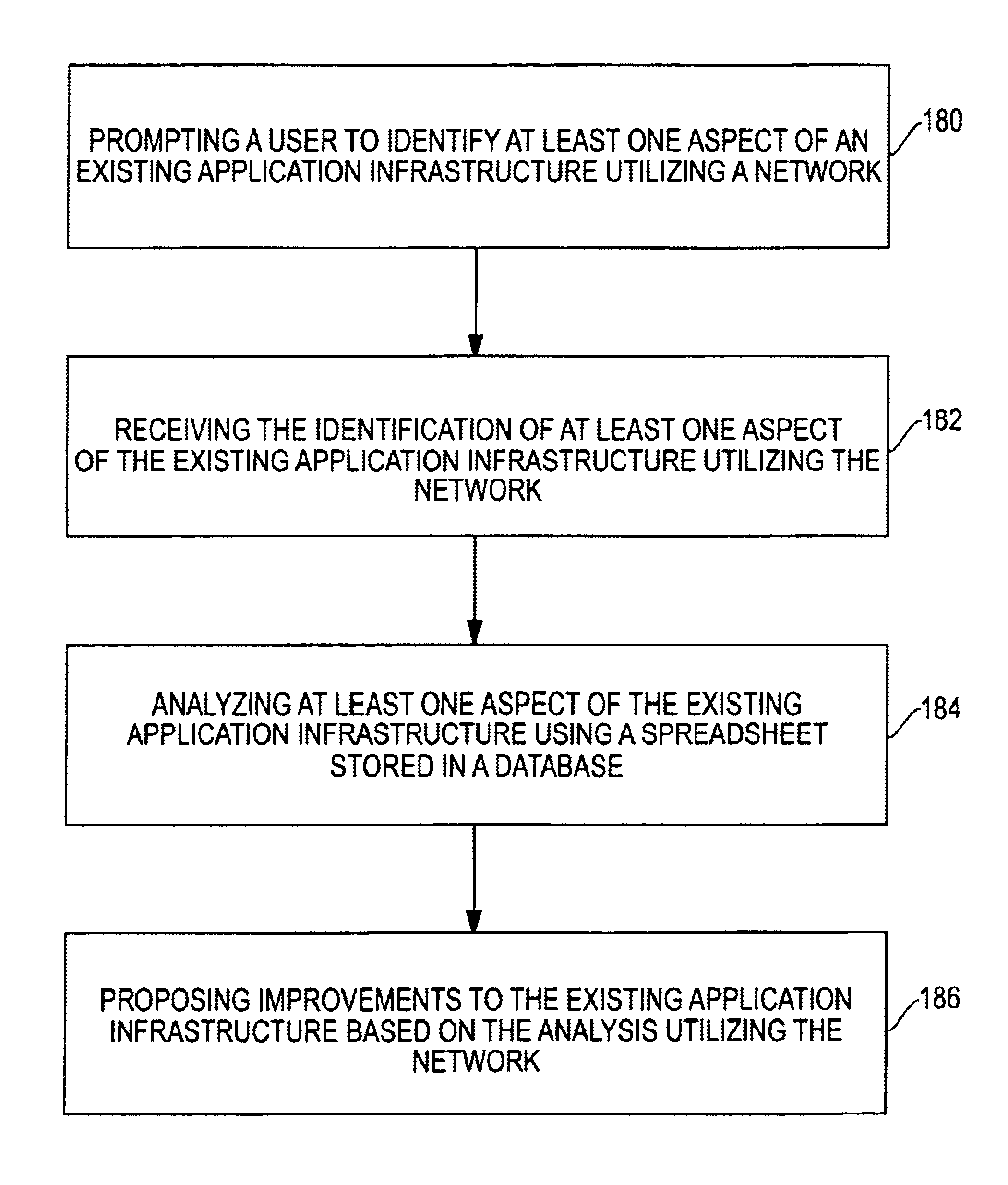
Information Infrastructure Management Tools with Extractor, Secure Storage, Content Analysis and Classification and Method Therefor
The present invention is a method of organizing and processing data in a distributed computing system. The invention is also implemented as a computer program on a computer medium and as a distributed computer system. Software modules can be configured as hardware. The method and system organizes select content which is important to an enterprise operating said distributed computing system. The select content is represented by one or more predetermined words, characters, images, data elements or data objects. The computing system has a plurality of select content data stores for respective ones of a plurality of enterprise designated categorical filters which include content-based filters, contextual filters and taxonomic classification filters, all operatively coupled over a communications network. A data input is processed through at least one activated categorical filter to obtain select content, and contextually associated select content and taxonomically associated select content as aggregated select content. The aggregated select content is stored in the corresponding select content data store. A data process from the group of data processes including a copy process, a data extract process, a data archive process, a data distribution process and a data destruction process is associated with the activated categorical filter and the method and system applies the associated data process to a further data input based upon a result of that further data being processed by the activated categorical filter utilizing the aggregated select content data.
Owner:DIGITAL DOORS
Wireless location using signal fingerprinting
InactiveUS20010022558A1Low costSpectrum efficiencyDirection finders using radio wavesBeacon systems using radio wavesInternet communicationCall tracing
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; and (4) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
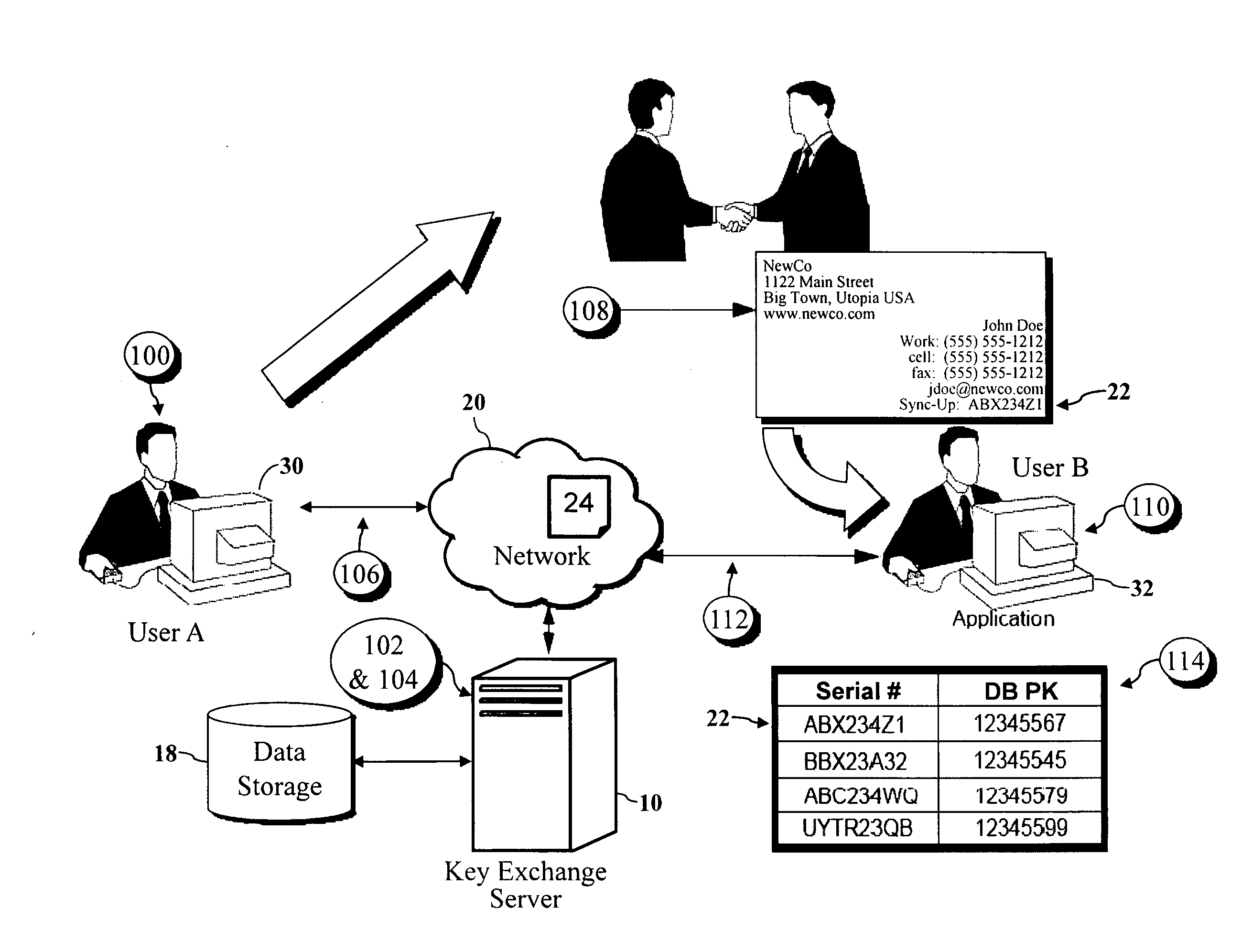
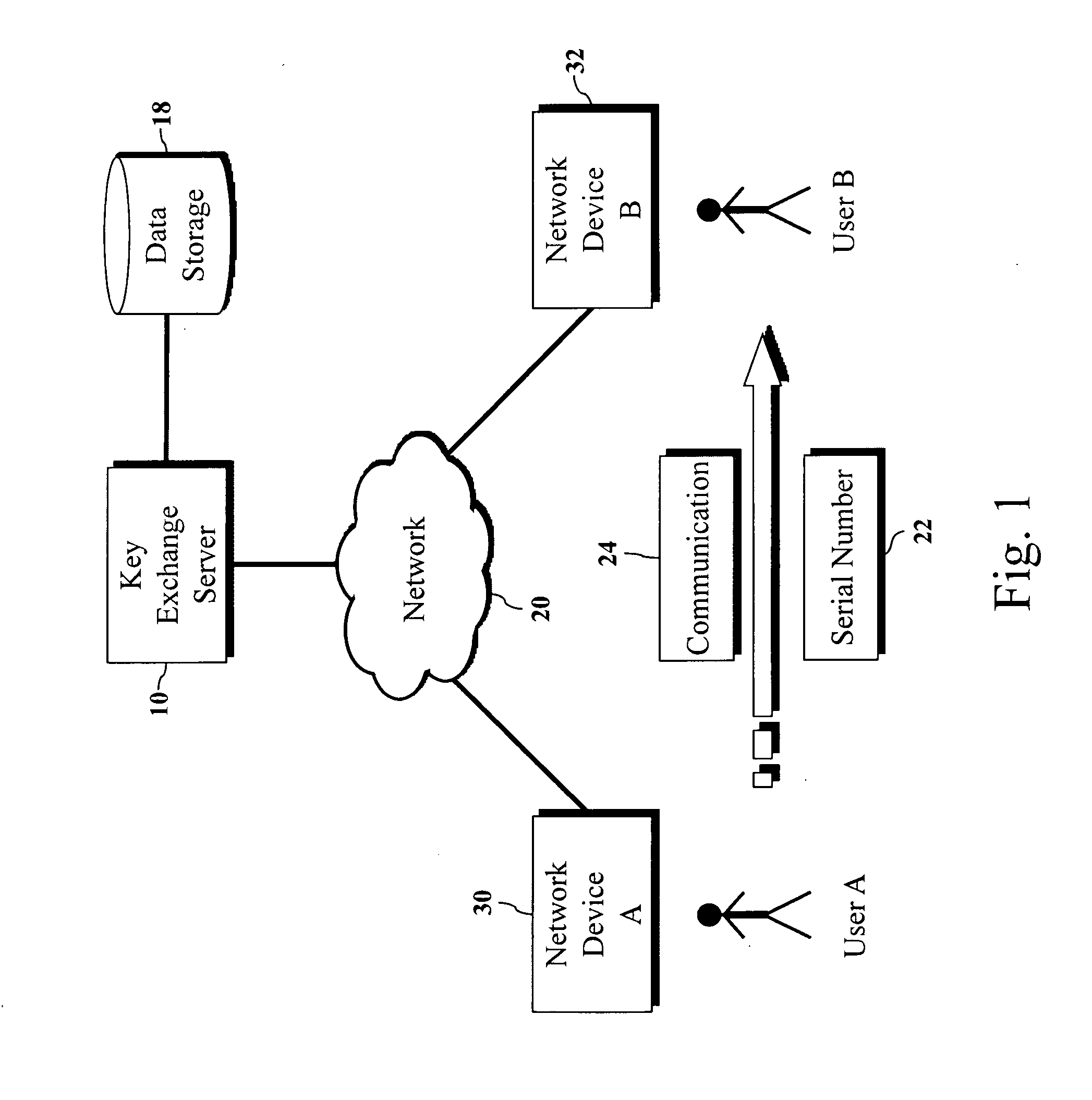
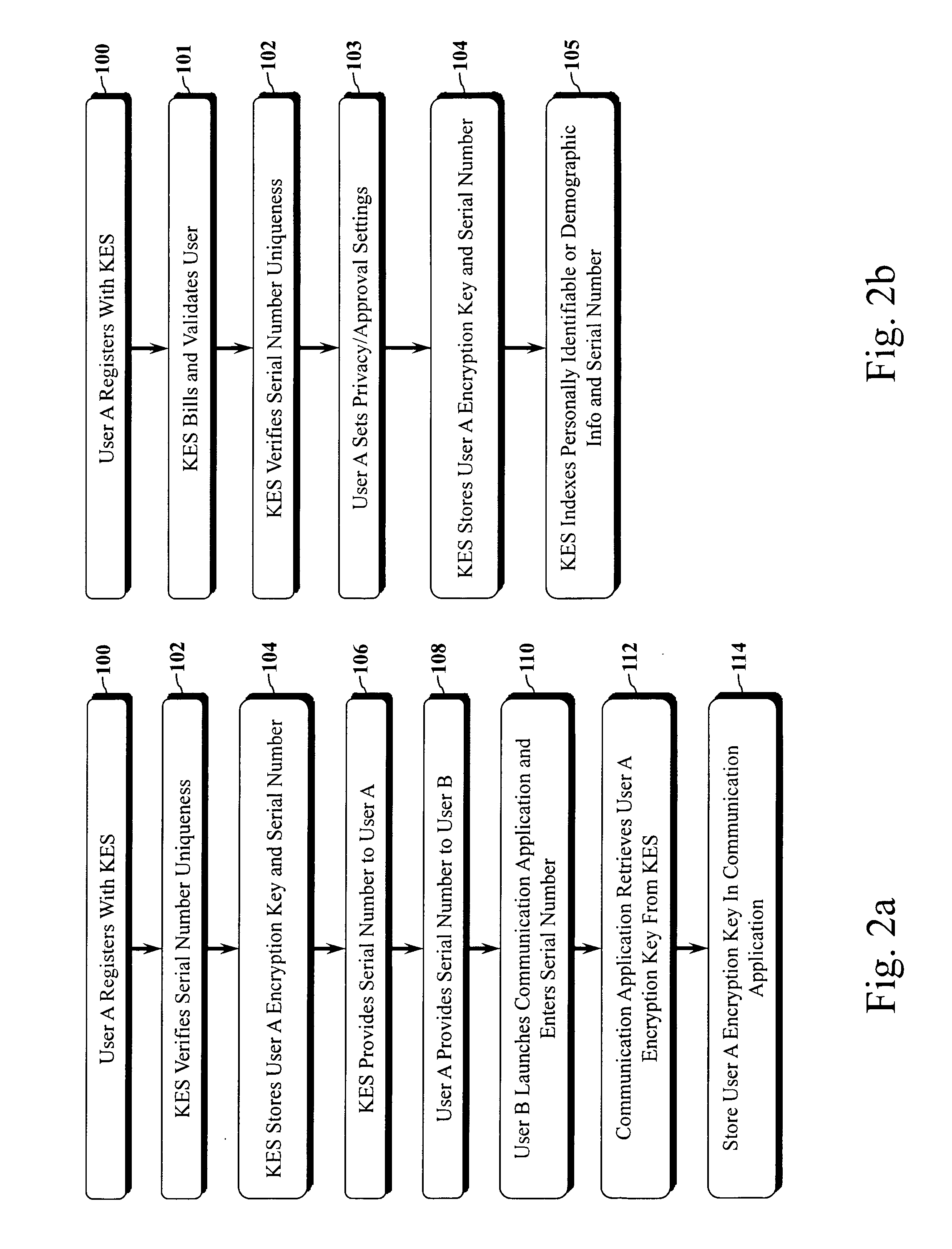
Encryption key exchange system and method
InactiveUS20120204032A1Improve usabilityUser identity/authority verificationPublic key infrastructure trust modelsUsabilityEncryption
The present invention is a computer-implemented key exchange system and methods for improving the usability of encryption technologies such as Public Key Infrastructure (PKI). One aspect of the present invention includes registering users, verifying user identity, and classifying users such that the users may send a communications such that communication recipients can verify the user identity and classification of the communication sender. Another aspect of the present invention includes users initiating relationships with other users, approving the establishment of relationships, and exchanging encryption keys between users after the establishment of a relationship.
Owner:SYNC UP TECH
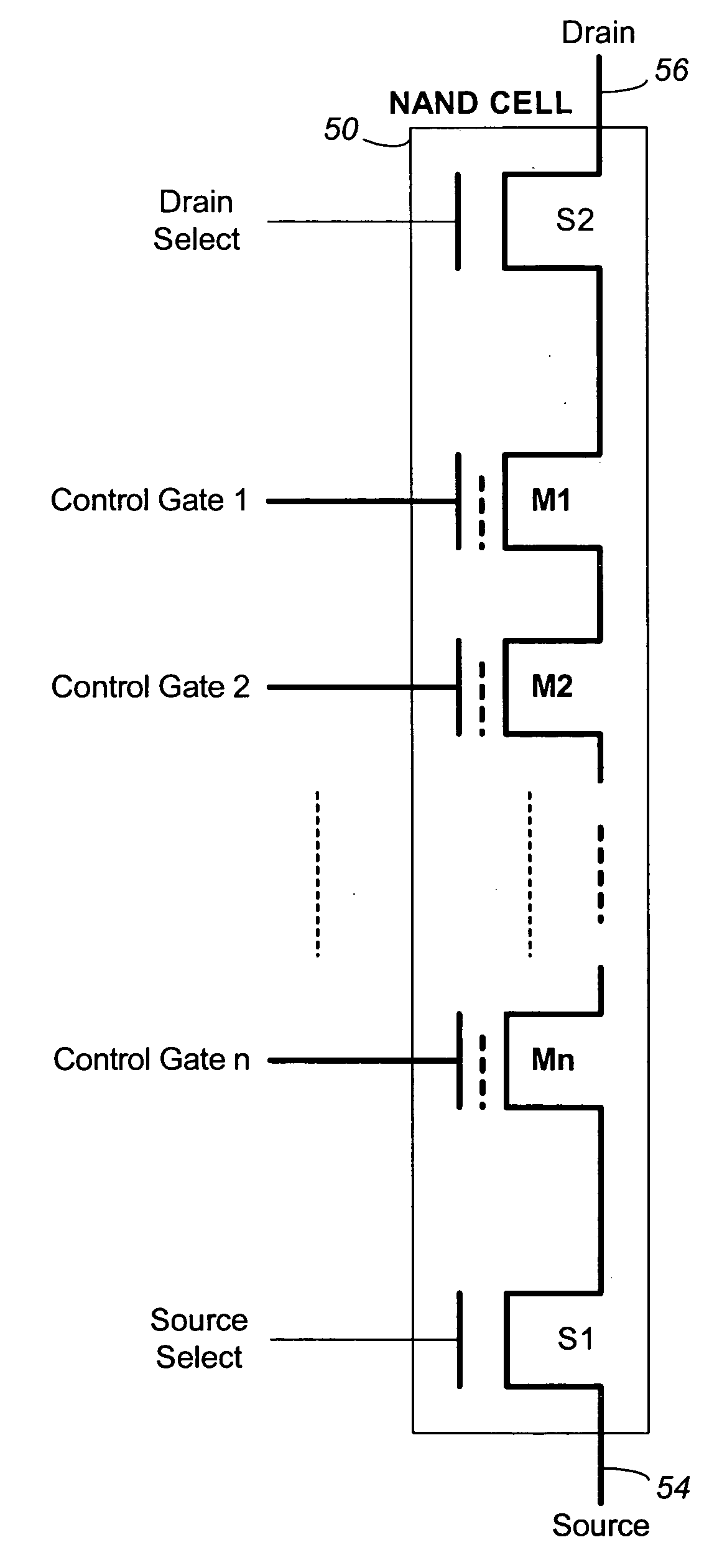
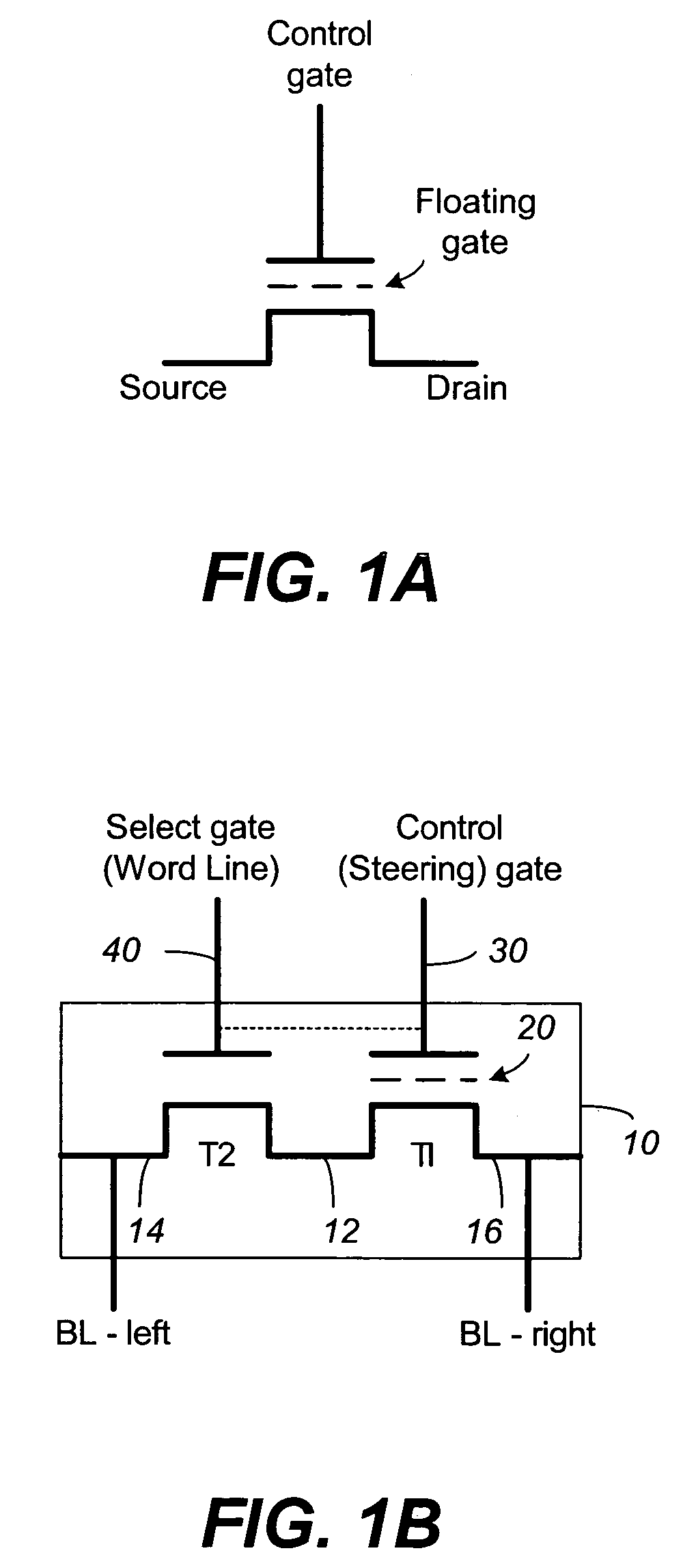
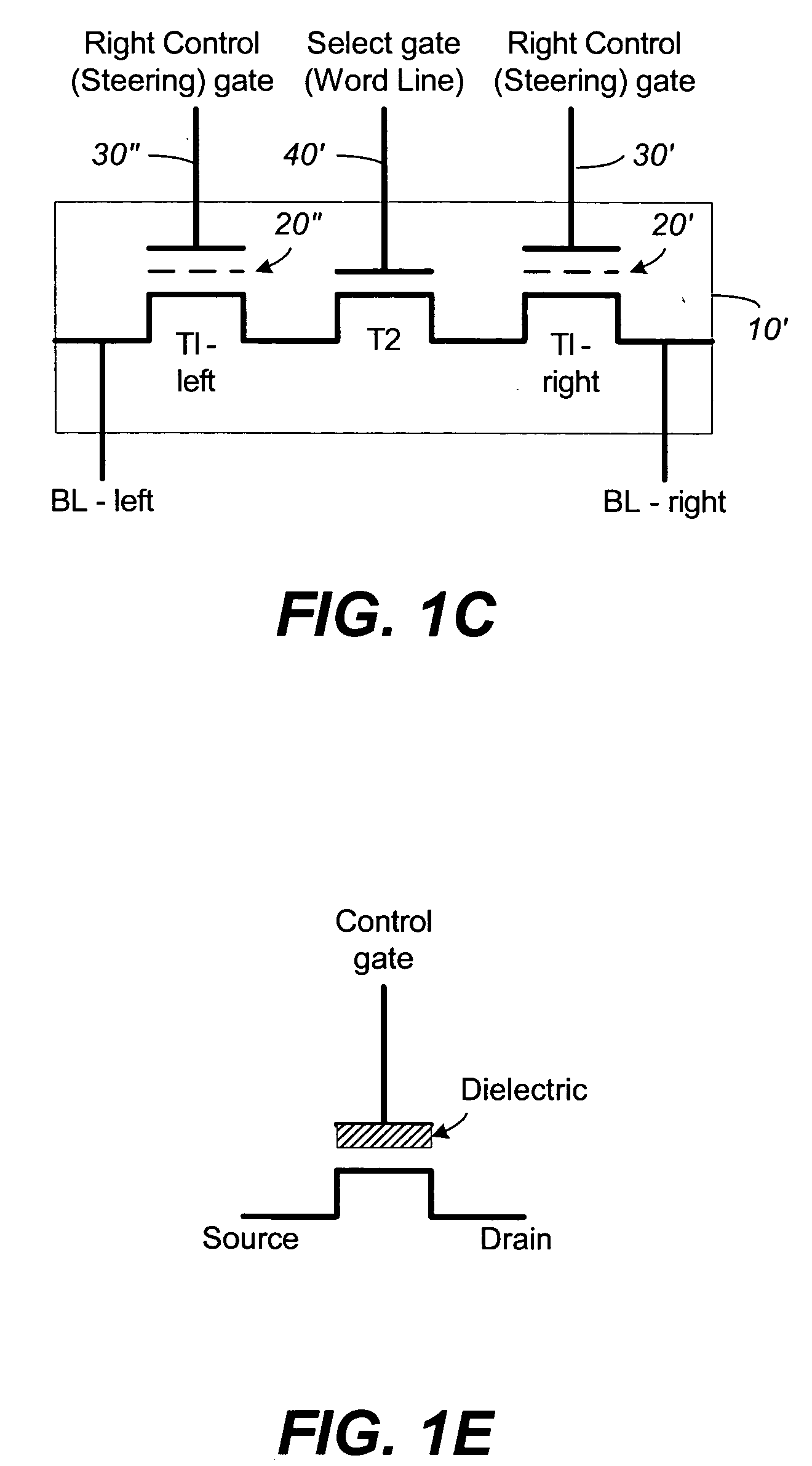
Non-volatile memory and method with shared processing for an aggregate of read/write circuits
InactiveUS20060140007A1Maximum versatilityMinimal componentRead-only memoriesDigital storageAudio power amplifierAssociative processor
A non-volatile memory device capable of reading and writing a large number of memory cells with multiple read / write circuits in parallel has an architecture that reduces redundancy in the multiple read / write circuits to a minimum. The multiple read / write circuits are organized into a bank of similar stacks of components. Redundant circuits such as a processor for processing data among stacks each associated with multiple memory cells are factored out. The processor is implemented with an input logic, a latch and an output logic. The input logic can transform the data received from either the sense amplifier or the data latches. The output logic further processes the transformed data to send to either the sense amplifier or the data latches or to a controller. This provides an infrastructure with maximum versatility and a minimum of components for sophisticated processing of the data sensed and the data to be input or output.
Owner:SANDISK TECH LLC
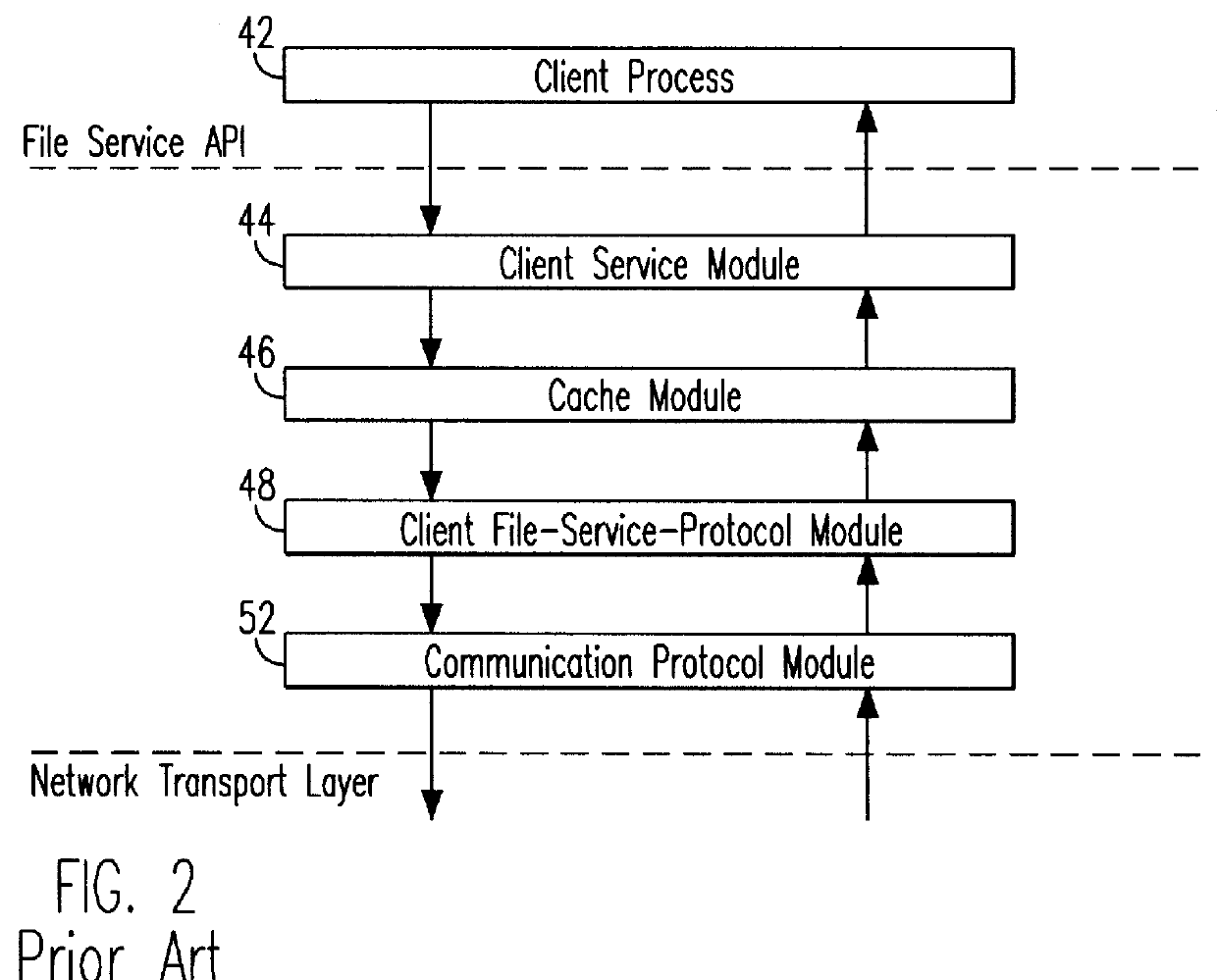
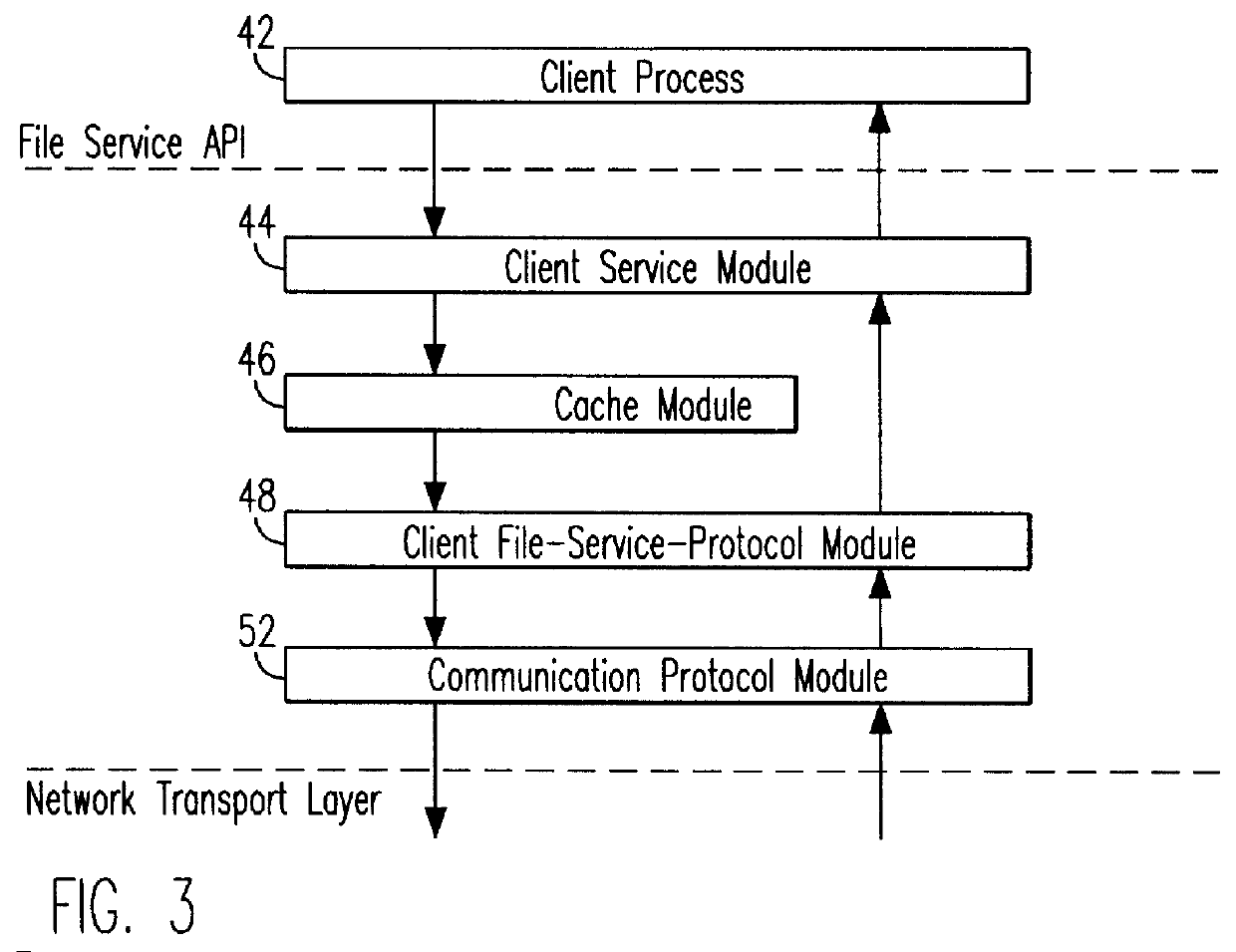
Remote file services network-infrastructure cache
InactiveUS6085234AMultiple digital computer combinationsMemory systemsService protocolSchema for Object-Oriented XML
A network-infrastructure cache ("NI Cache") transparently provides proxy file services to a plurality of client workstations concurrently requesting access to file data stored on a server. The NI Cache includes a network interface that connects to a digital computer network. A file-request service-module of the NI Cache receives and responds to network-file-services-protocol requests from workstations through the network interface. A cache, also included in the NI Cache, stores data that is transmitted back to the workstations. A file-request generation-module, also included in the NI Cache, transmits requests for data to the server, and receives responses from the server that include data missing from the cache.
Owner:MOSAID TECH +1
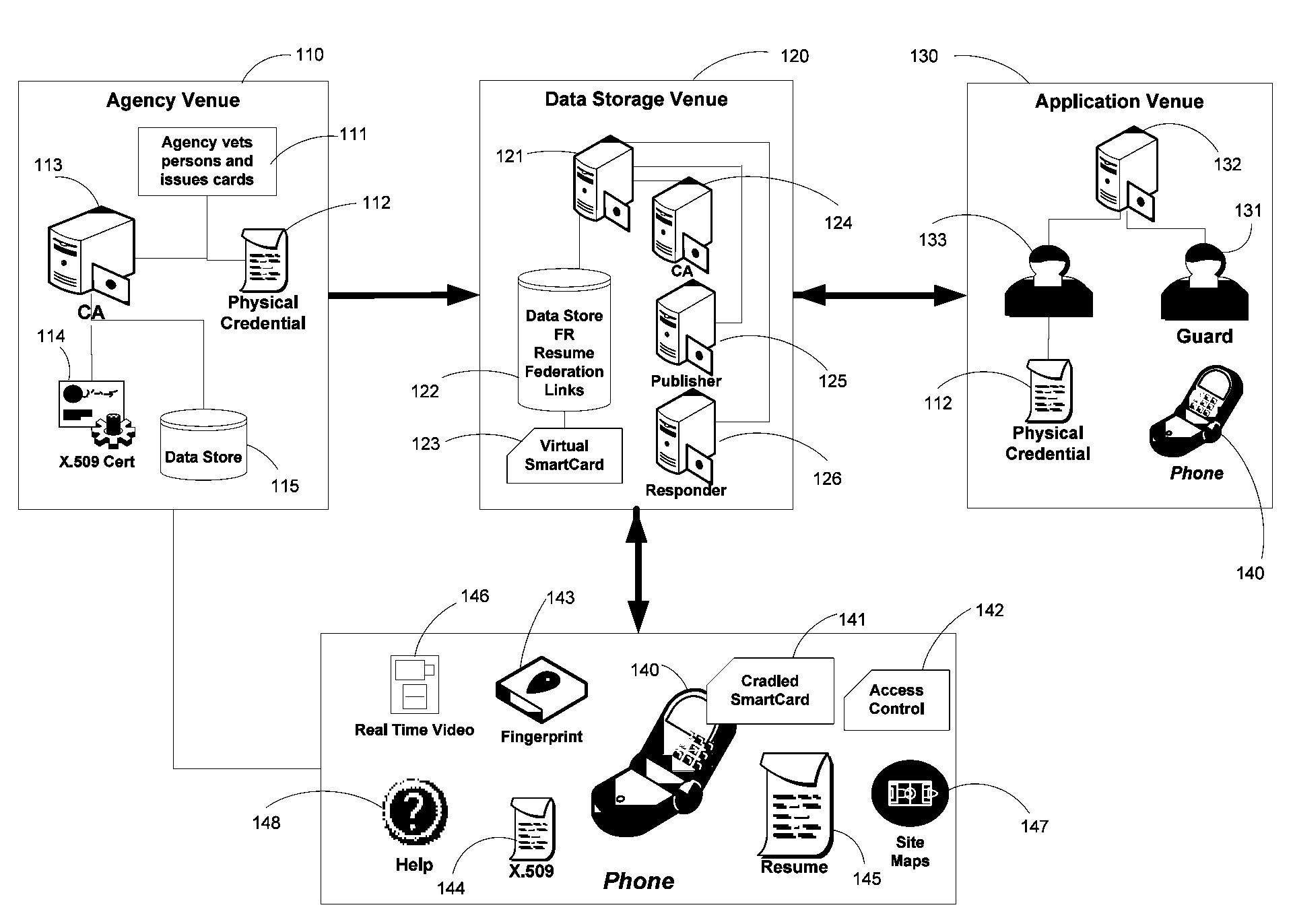
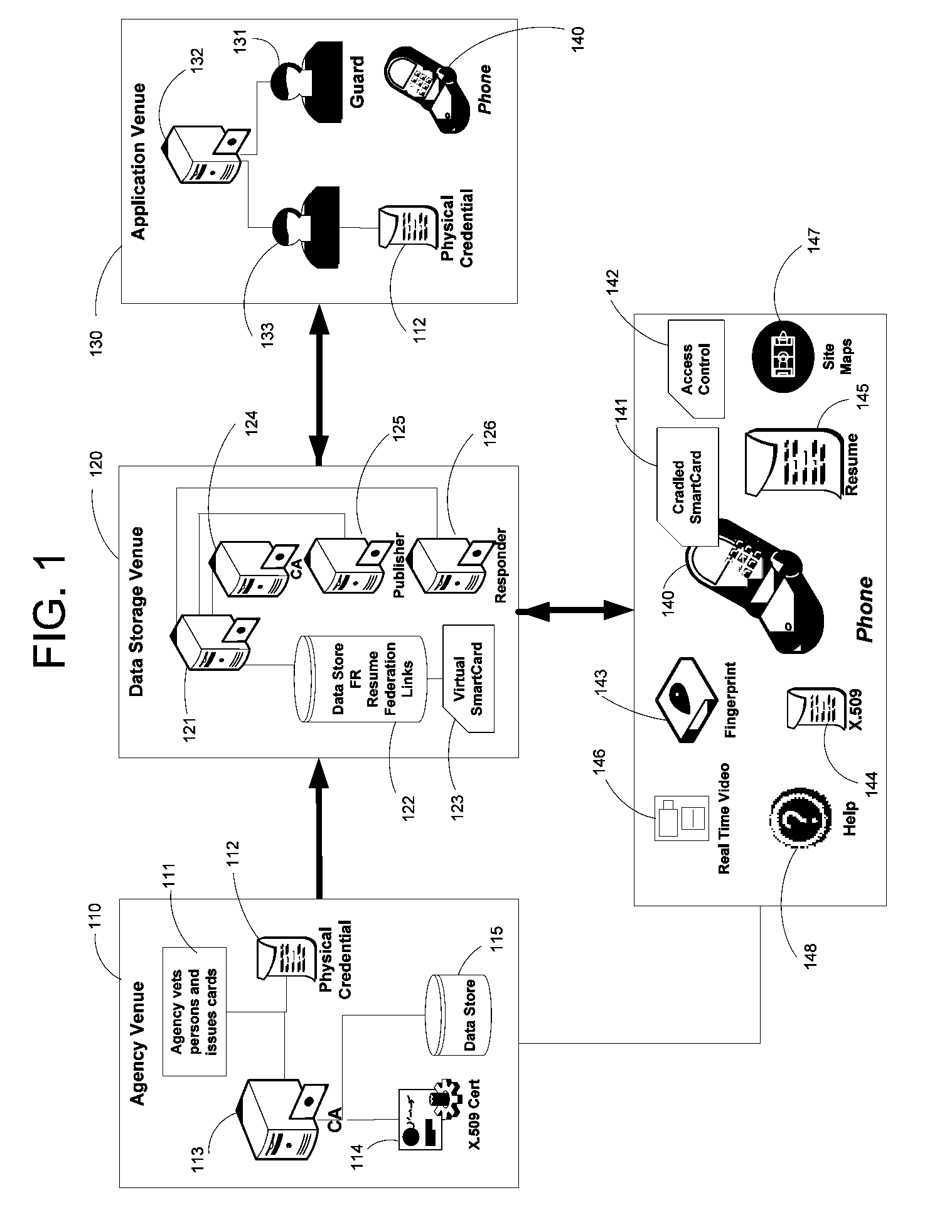
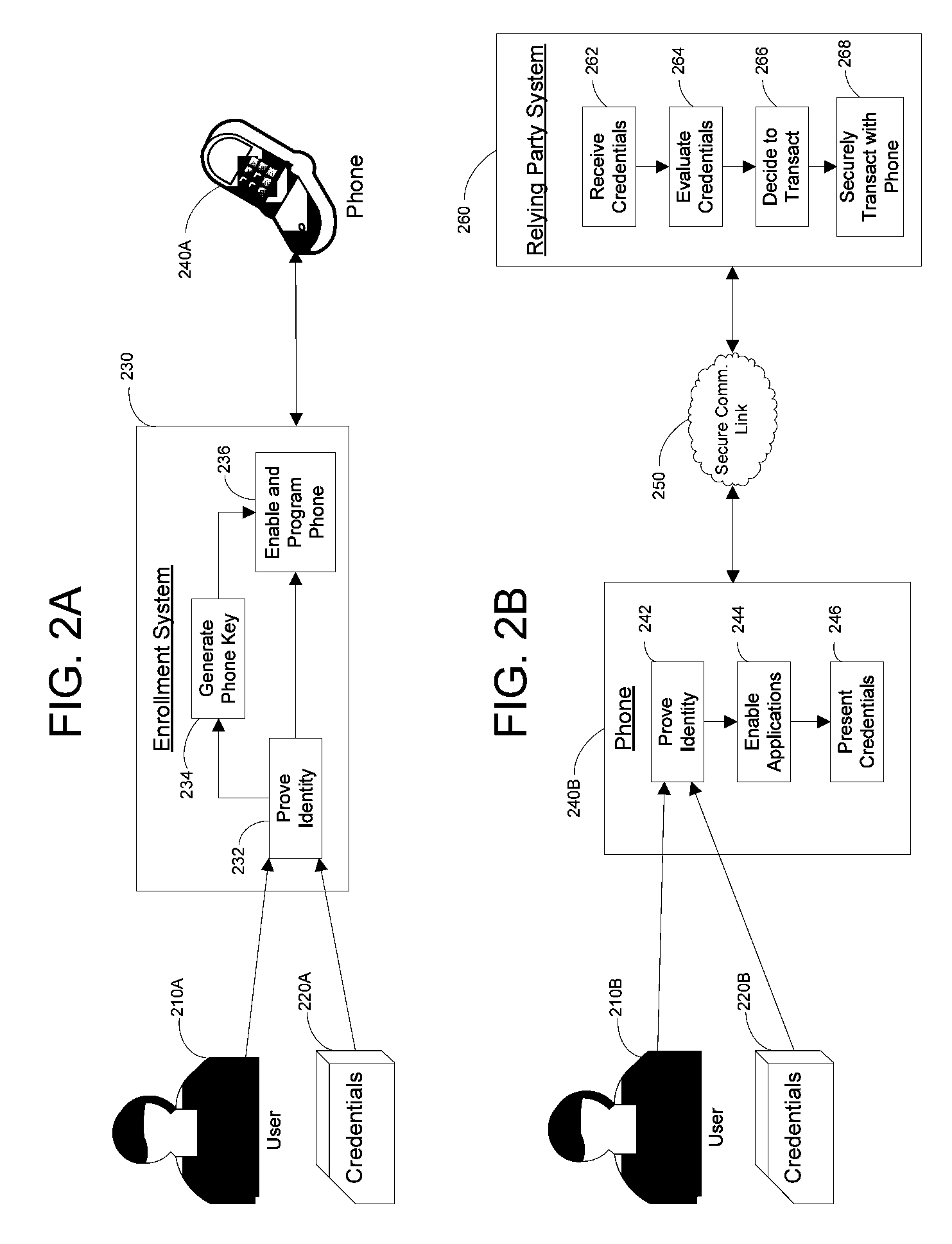
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
System and method for an application provider framework
InactiveUS6904449B1Broaden applicationMultiple digital computer combinationsOffice automationService provisionElectronic form
Owner:ACCENTURE GLOBAL SERVICES LTD
Distributed trusted virtualization platform
InactiveUS20090204964A1Key distribution for secure communicationMultiple digital computer combinationsVirtualizationEnd to end security
A platform architecture shifts the networked computing paradigm from PC+Network to a system using trusted mobile internet end-point (MIEP) devices and cooperative agents hosted on a trusted server. The MIEP device can participate in data flows, arbitrate authentication, and / or participate in implementing security mechanisms, all within the context of assured end-to-end security. The MIEP architecture improves platform-level capabilities by suitably (and even dynamically) partitioning what is done at the MIEP nodes, the network, and the server based infrastructure for delivering services.
Owner:MOTEGRITY +1
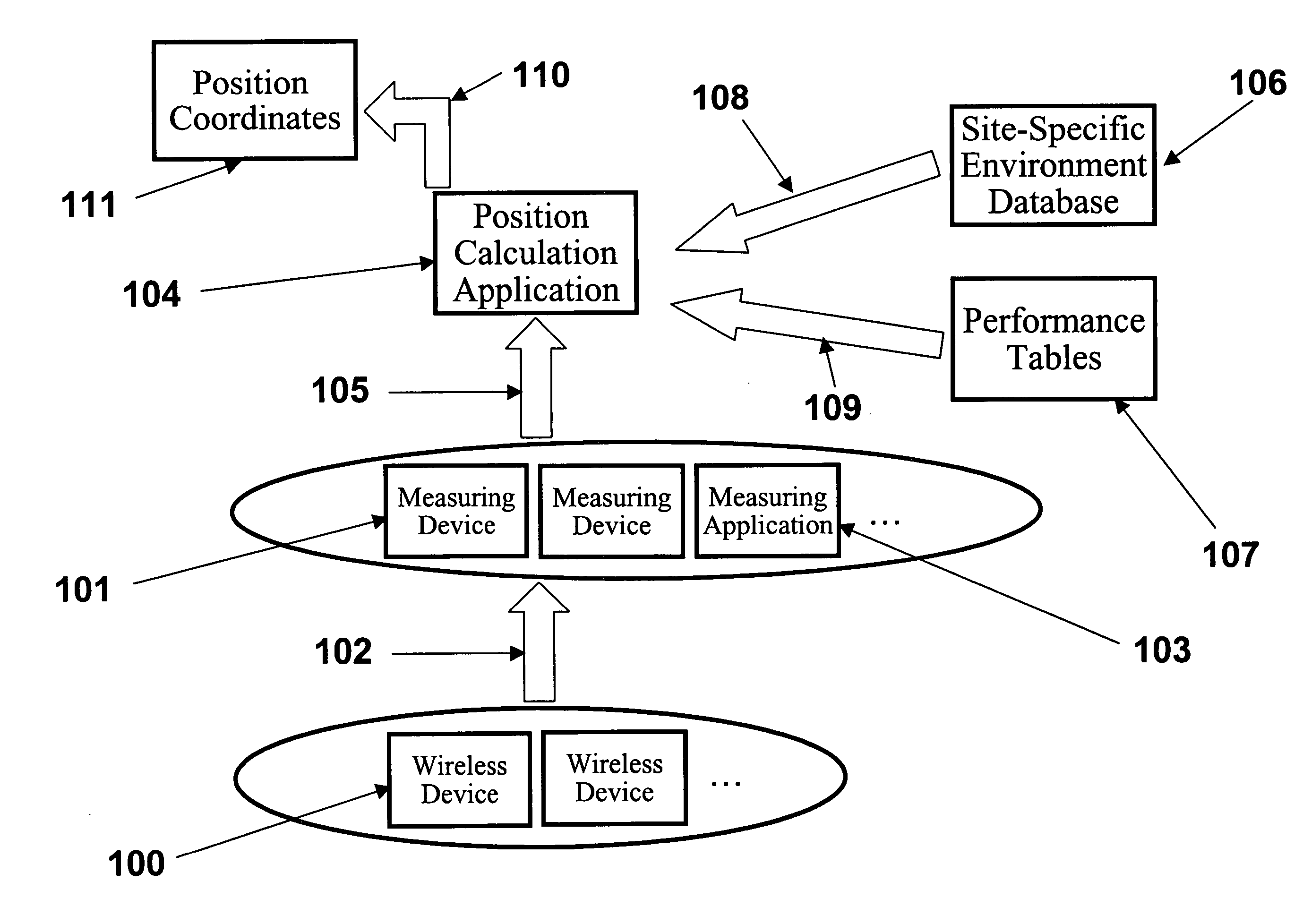
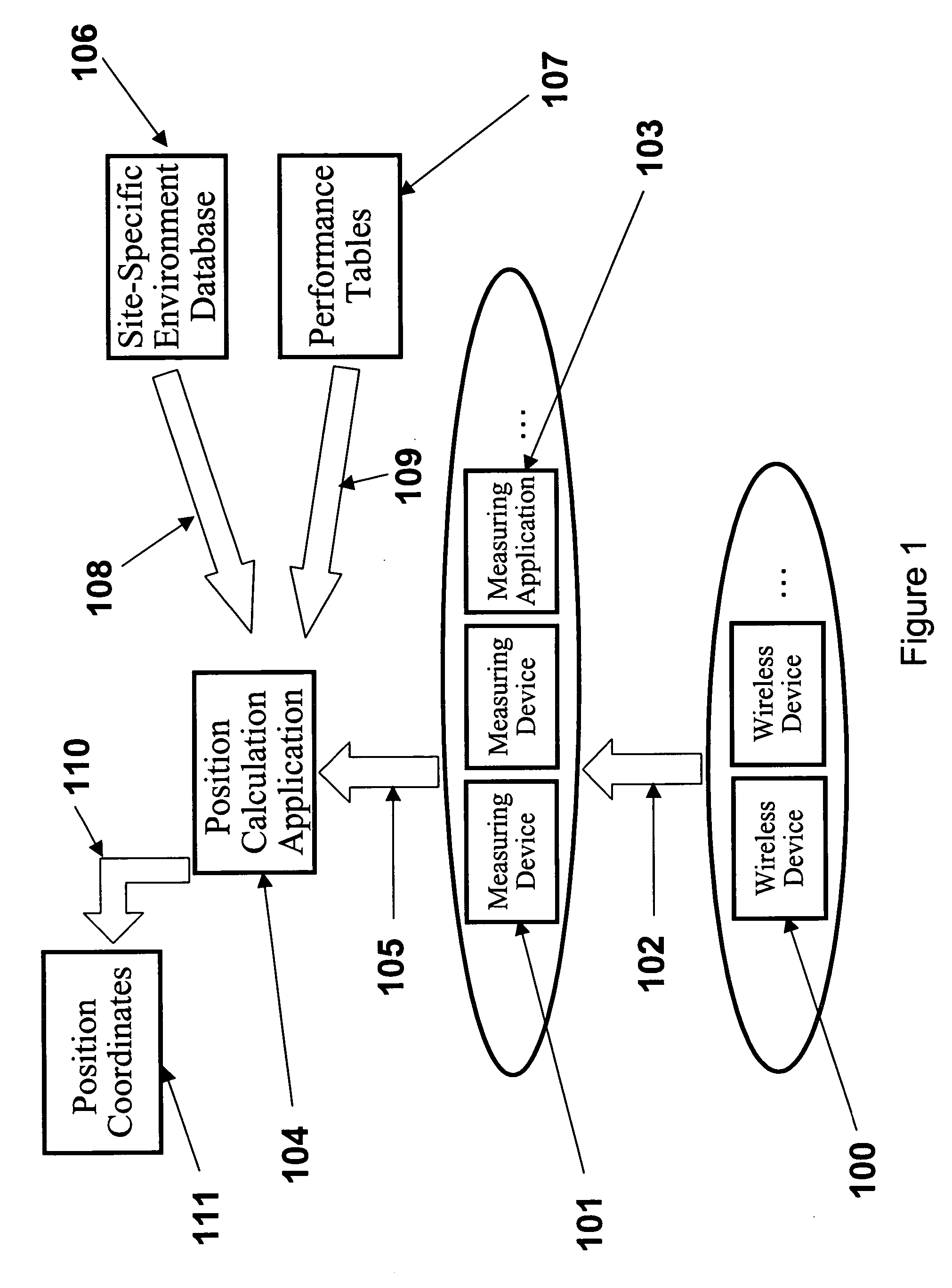
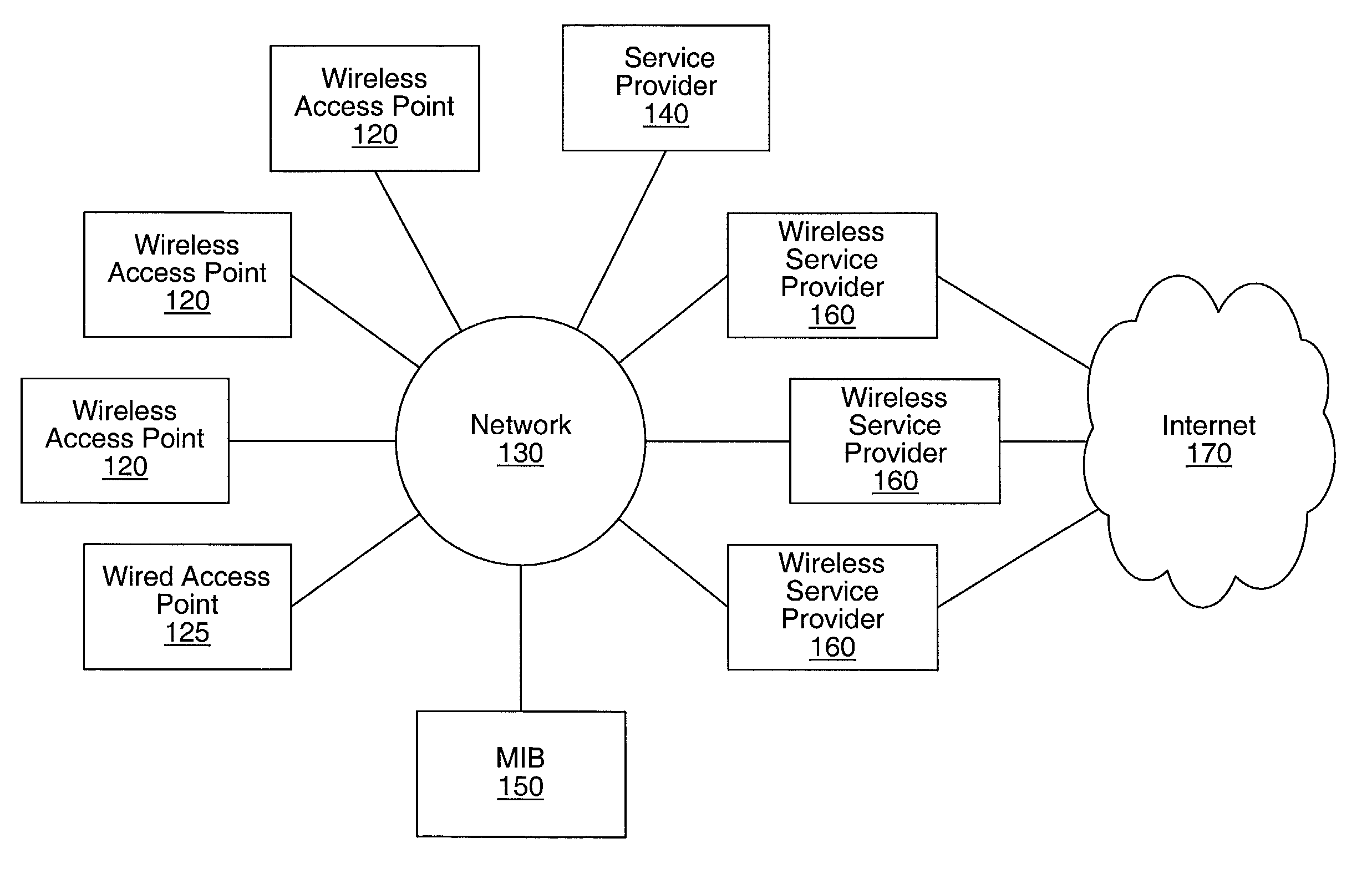
System, method, and apparatus for determining and using the position of wireless devices or infrastructure for wireless network enhancements
ActiveUS20060019679A1Increase network bandwidthHigh degreeDirection finders using radio wavesRoad vehicles traffic controlDevice typePredicting performance
A system and method for estimating the position of wireless devices within a wireless communication network combines measured RF channel characteristics for the wireless device with one or more predicted performance lookup tables, each of which correlates an RF channel characteristic to some higher order network performance metric and / or a position within an environmental model. Measured RF channel characteristics for wireless devices are compared against the performance lookup tables to determine the sent of lookup tables that most closely match the measured RF channel characteristics. The positions within the environmental model corresponding to the selected set of matching lookup tables are identified as possible locations for the wireless device. The performance lookup tables are uniquely constructed by site-specific location, technology, wireless standard, and equipment types, and / or the current operating state of the communications network.
Owner:EXTREME NETWORKS INC
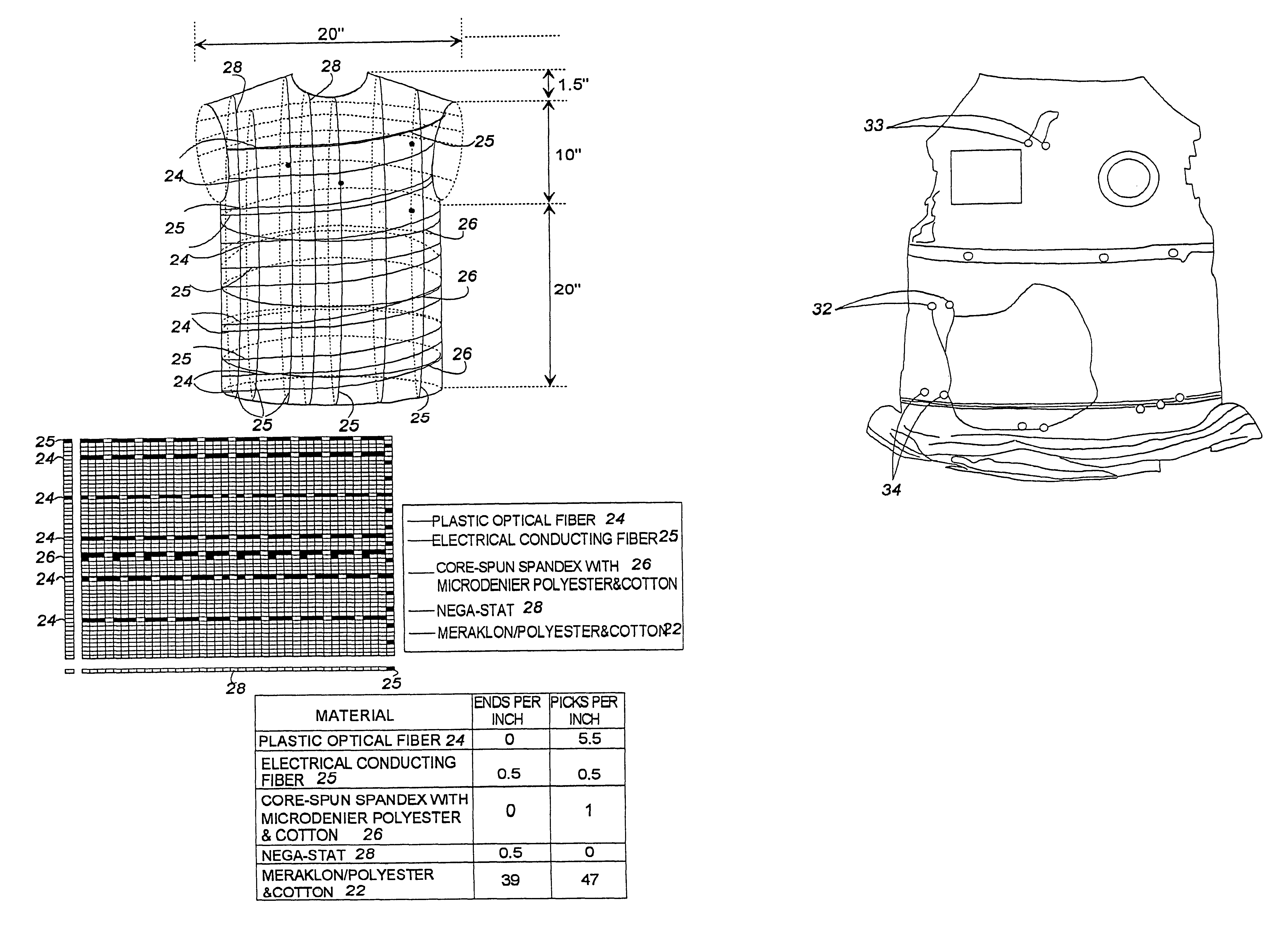
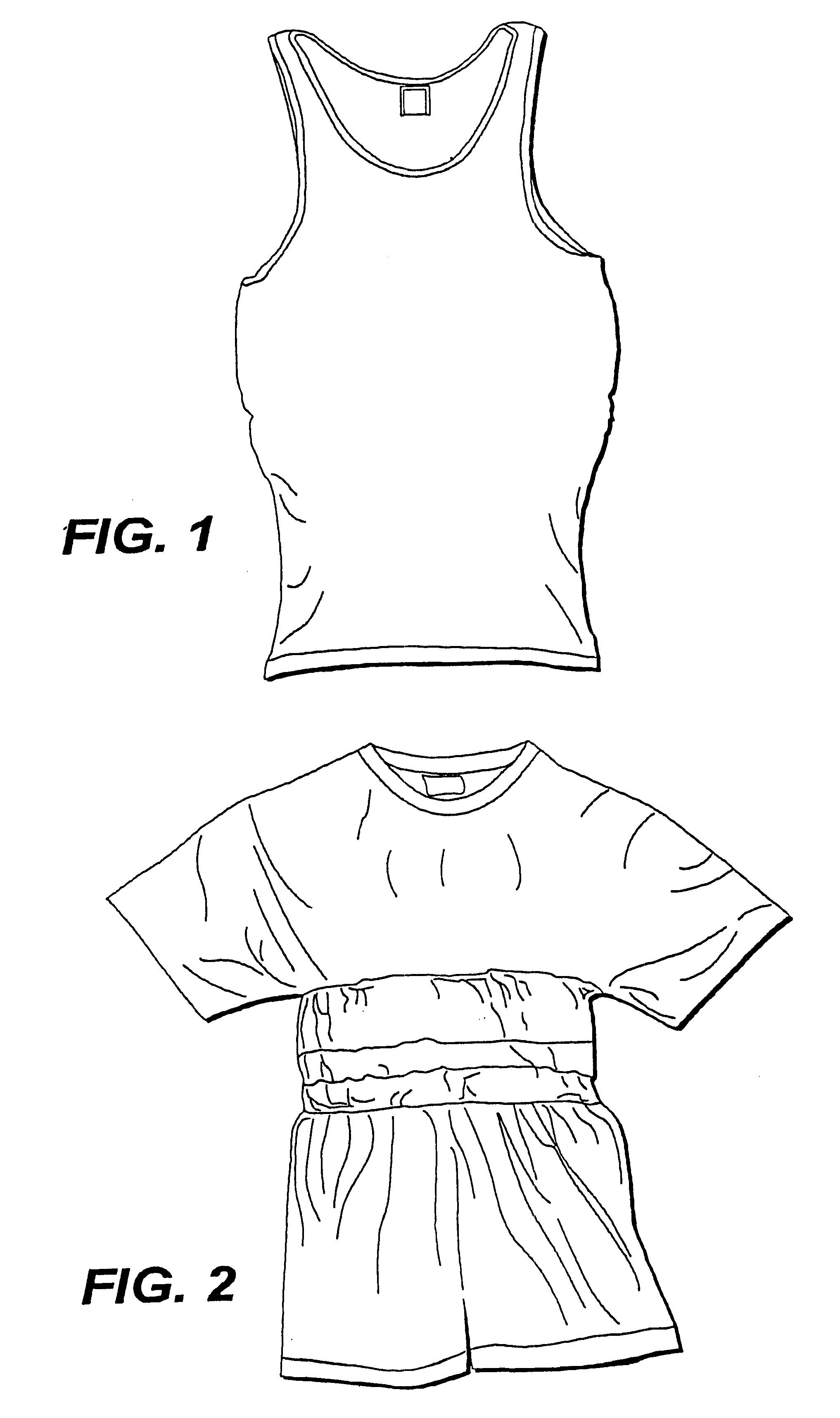
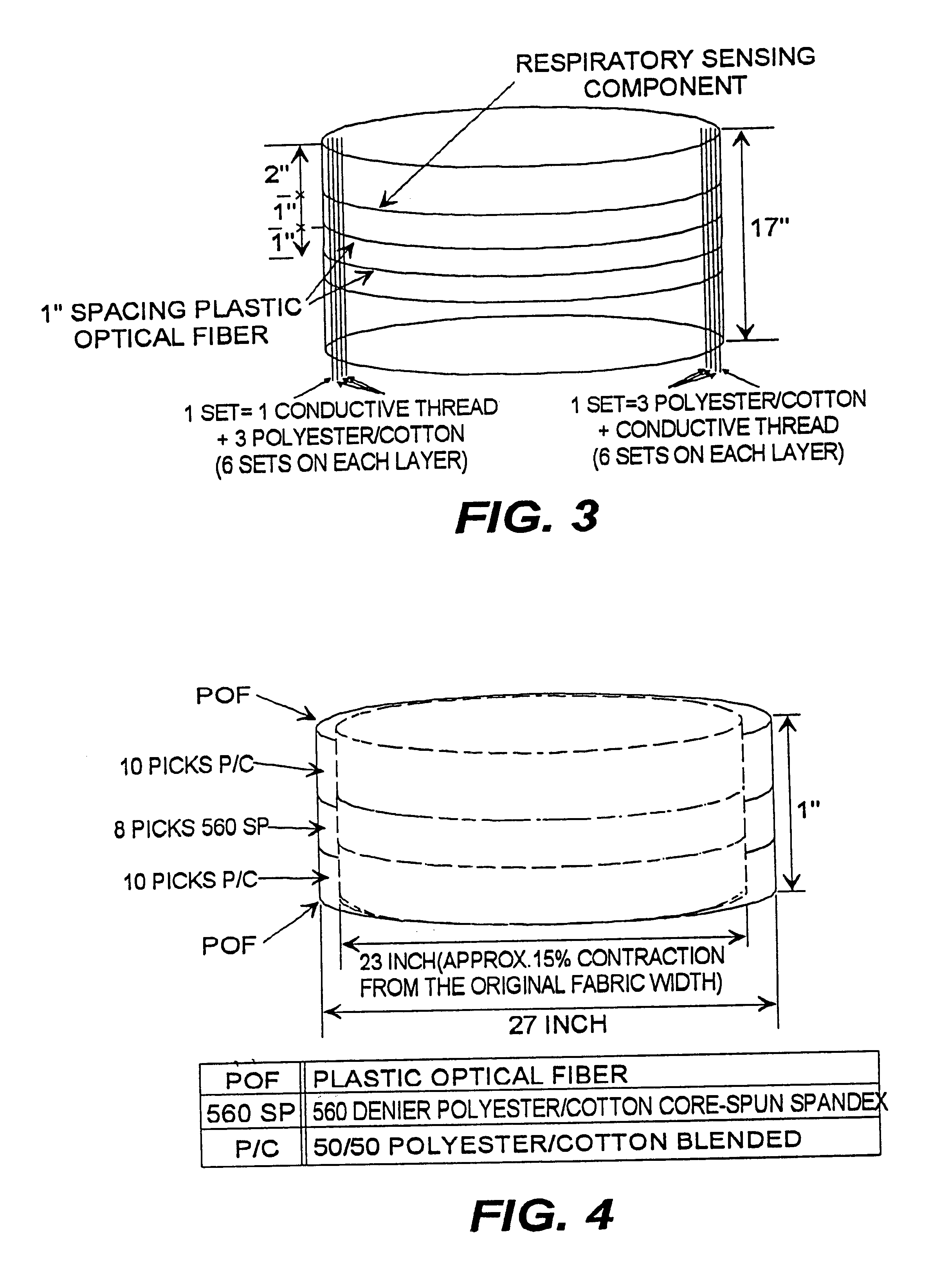
Fabric or garment with integrated flexible information infrastructure
InactiveUS6381482B1Raise the ratioImprove high temperature stabilityWeft knittingOrnamental textile articlesInformation processingEngineering
A fabric, in the form of a woven or knitted fabric or garment, including a flexible information infrastructure integrated within the fabric for collecting, processing, transmitting and receiving information concerning-but not limited to-a wearer of the fabric. The fabric allows a new way to customize information processing devices to "fit" the wearer by selecting and plugging in (or removing) chips / sensors from the fabric thus creating a wearable, mobile information infrastructure that can operate in a stand-alone or networked mode. The fabric can be provided with sensors for monitoring physical aspects of the wearer, for example body vital signs, such as heart rate, EKG, pulse, respiration rate, temperature, voice, and allergic reaction, as well as penetration of the fabric. The fabric consists of a base fabric ("comfort component"), and an information infrastructure component which can consist of a penetration detection component, or an electrical conductive component, or both. The preferred penetration detection component is a sheathed optical fiber. The information infrastructure component can include, in addition to an electrically conductive textile yarn, a sensor or a connector for a sensor. A process is provided for making an electrical interconnection between intersecting electrically conductive yarns. Furthermore, a process is established for sheathing the plastic optical fiber and protecting it.
Owner:GEORGIA TECH RES CORP
Medical device wireless adapter
The invention relates generally to a medical device wireless adapter, and more particularly, to a module that adapts an existing legacy or newly designed medical device to a healthcare provider's wireless infrastructure.
Owner:WELCH ALLYN INC
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
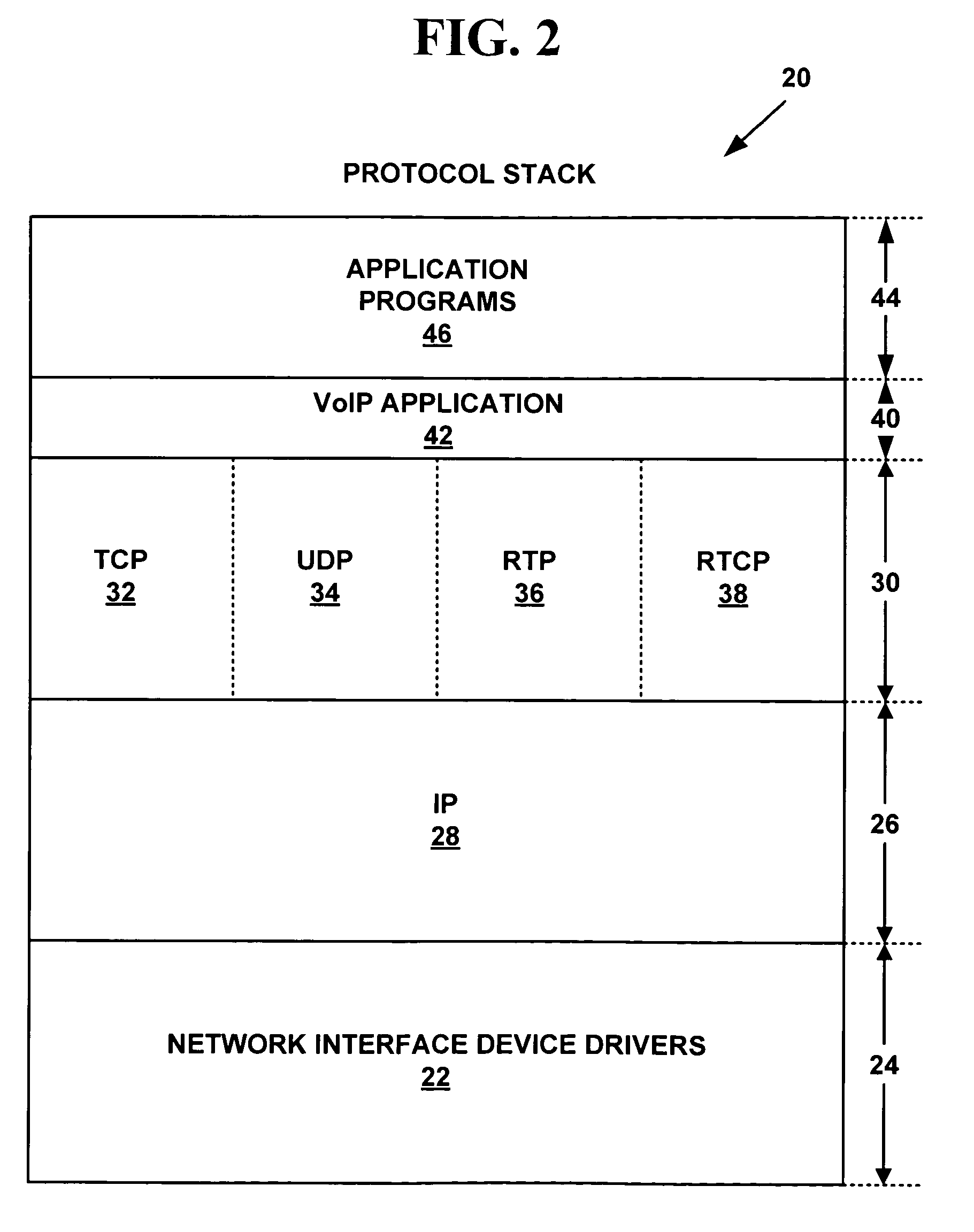
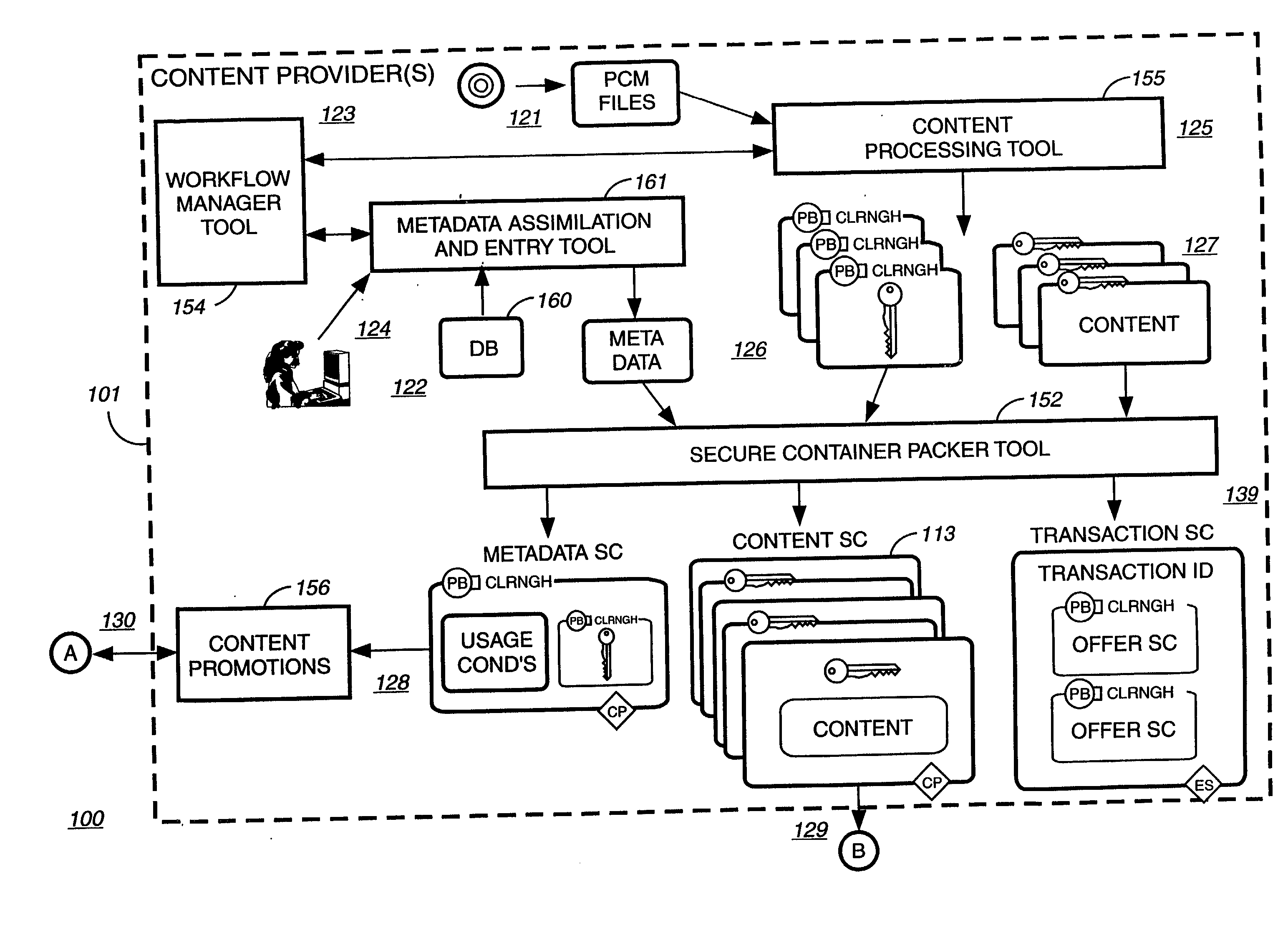
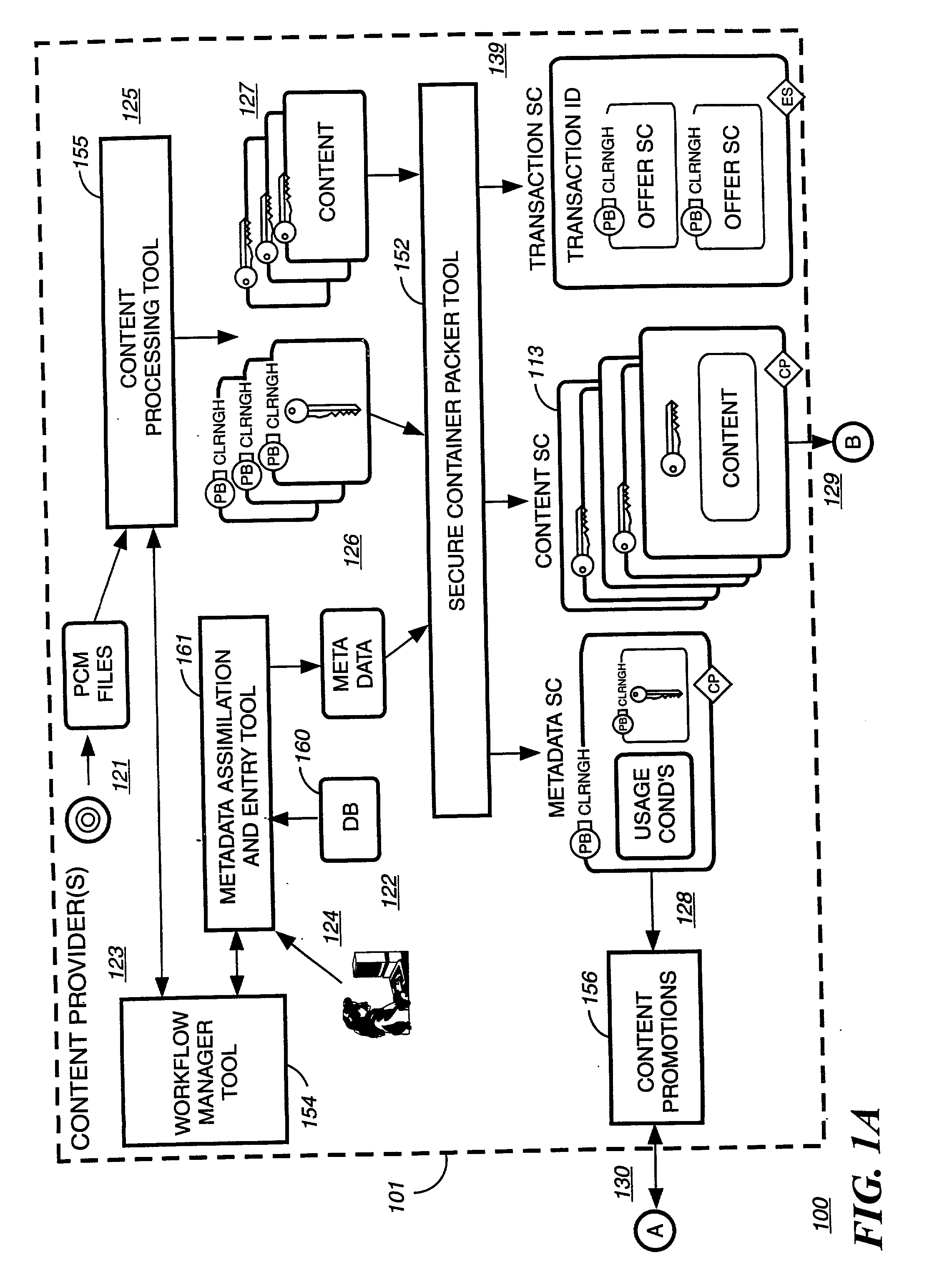
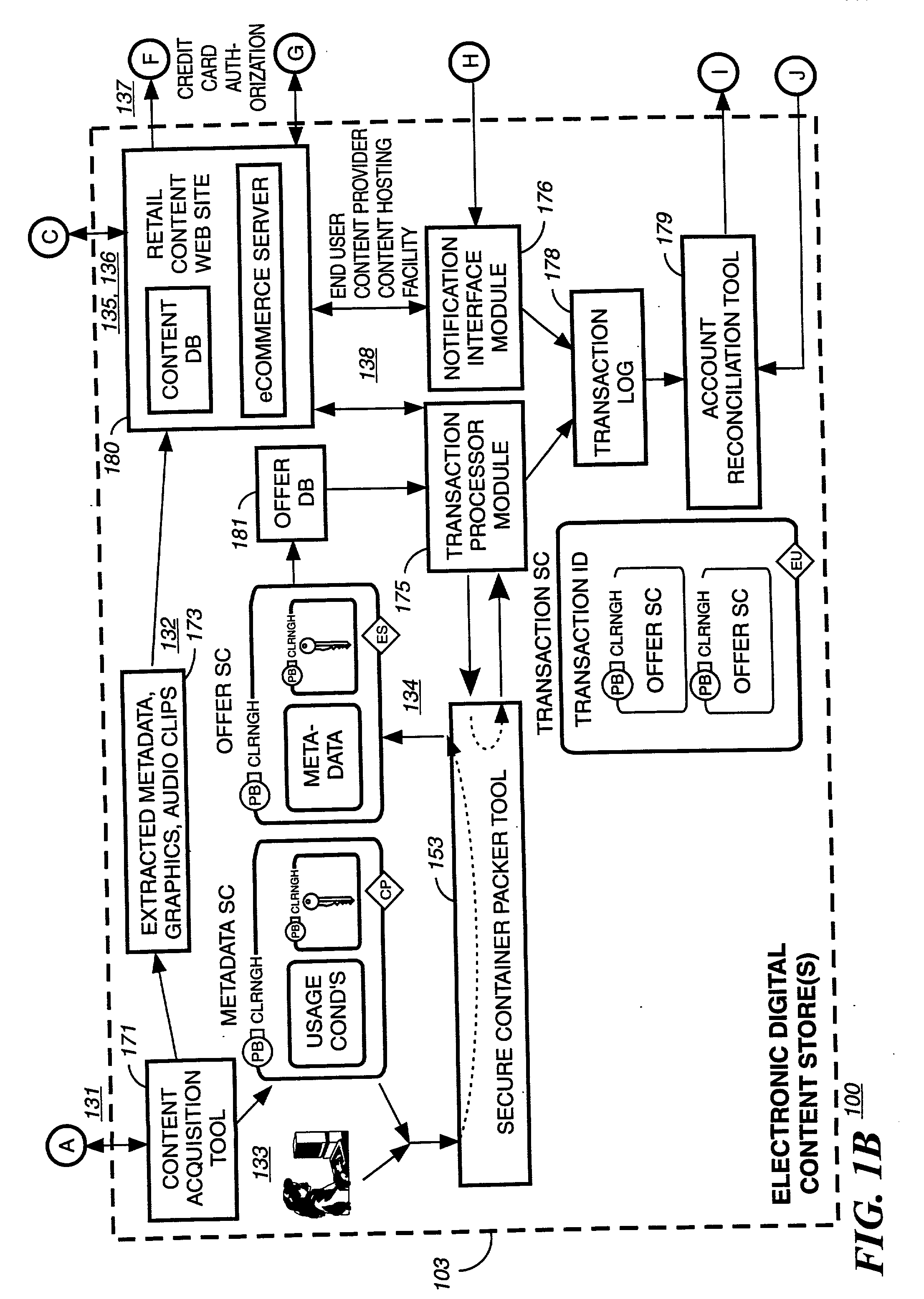
Digital content distribution using web broadcasting services
InactiveUS20030135464A1Website content managementElectronic credentialsBroadcast channelsDigital content
A method of securely receiving data on a user's system from a web broadcast infrastructure with a plurality of channels. The method comprising the steps of: receiving promotional metadata from a first web broadcast channel, the promotional metadata related to data available for reception; assembling at least part of the promotional metadata into a promotional offering for review by a user; selecting by a user, data to be received related to the promotional metadata; receiving data from a second web broadcast channel, the data selected from the promotional metadata, and wherein the data has been previously encrypted using a first encrypting key; and receiving the first decrypting key via a computer readable medium, the first decrypting key for decrypting at least some of the data received via the second web broadcast channel. In another embodiment, a method and system to transmit data securely from a web broadcast center is disclosed.
Owner:IBM CORP
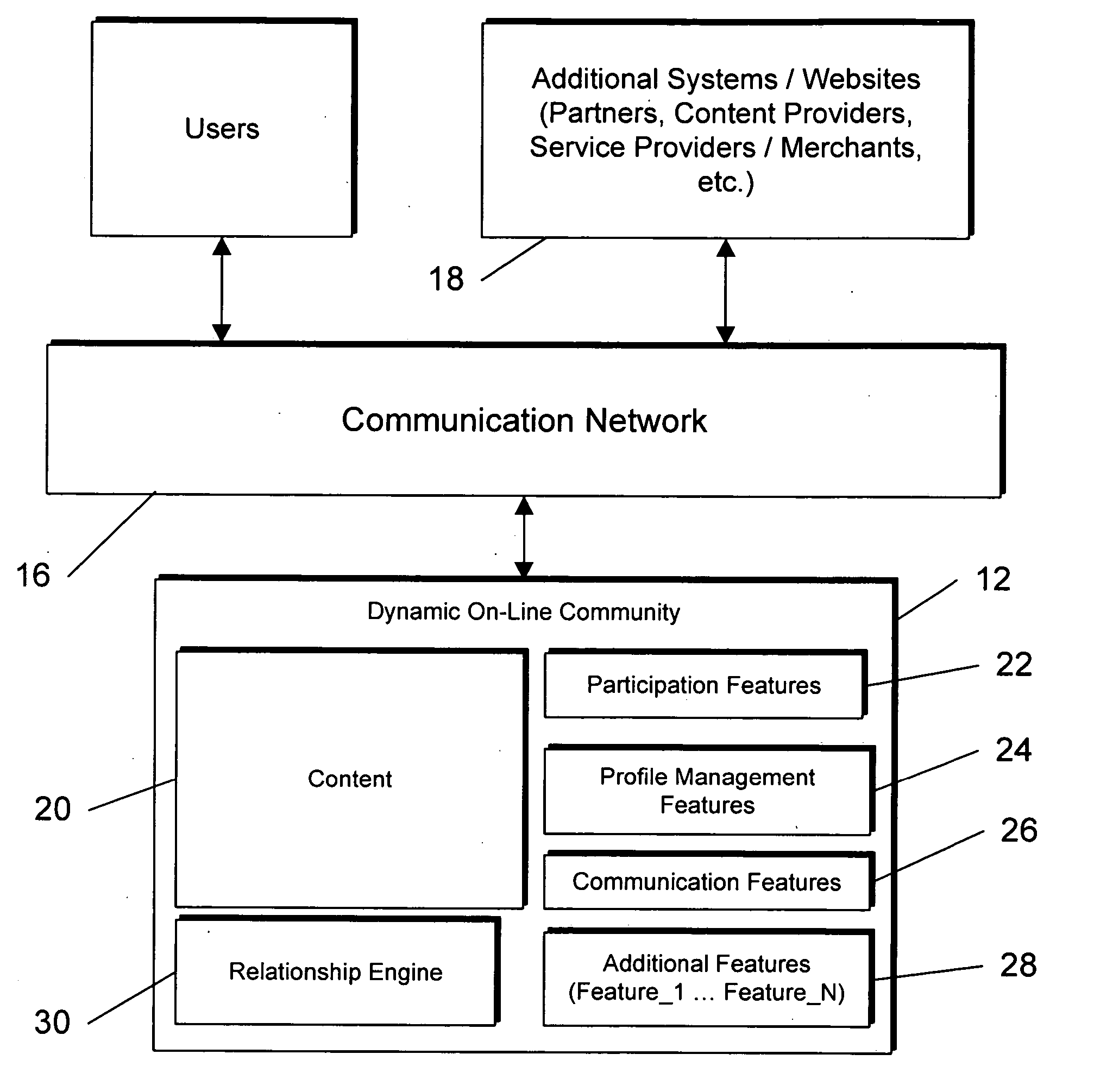
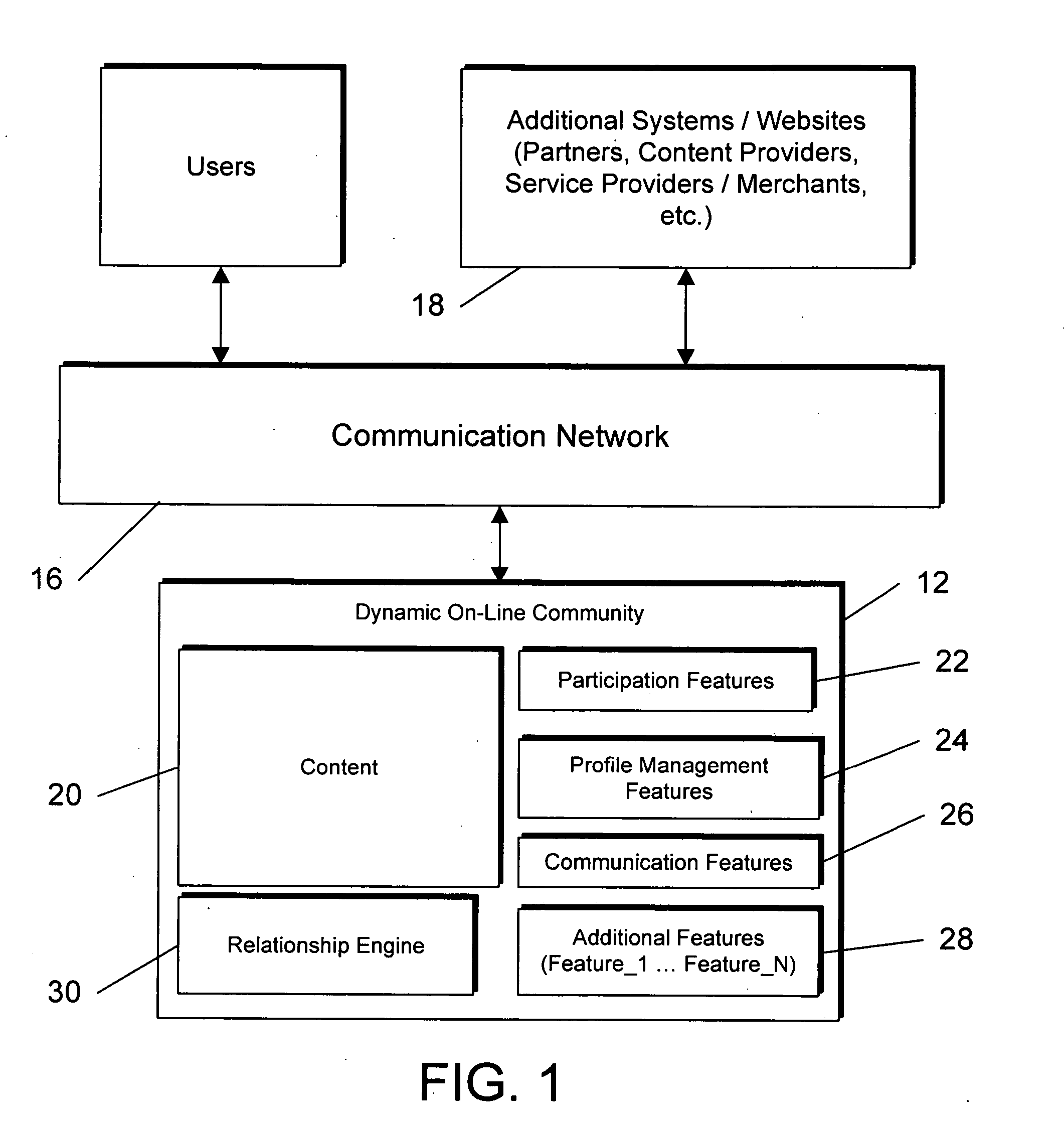
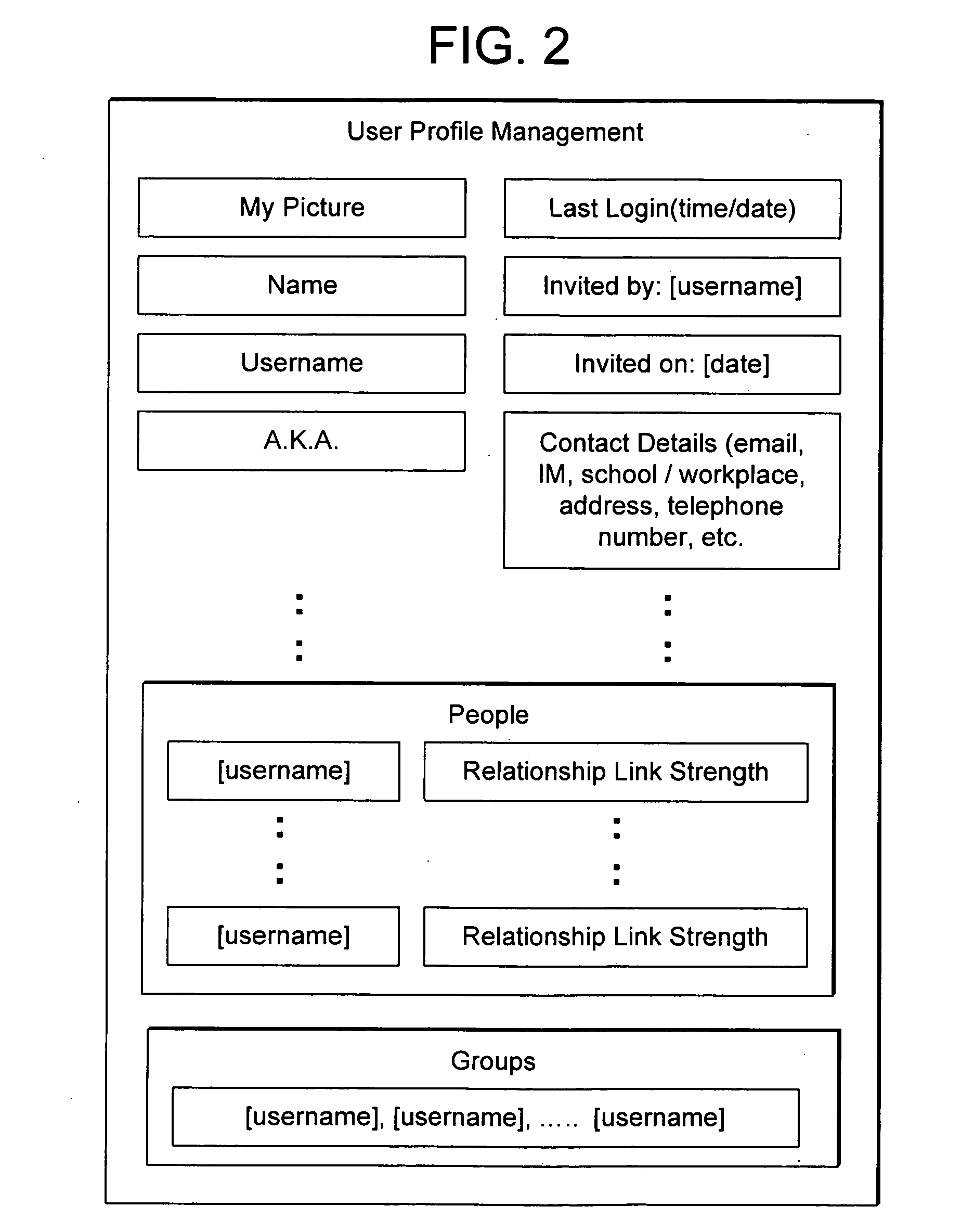
System and method for dynamically generating, maintaining, and growing an online social network
InactiveUS20060048059A1Grows and increase in functionalityOvercomes drawbackDigital data information retrievalCharacter and pattern recognitionCommunity systemSocial web
Owner:CONCERT TECH
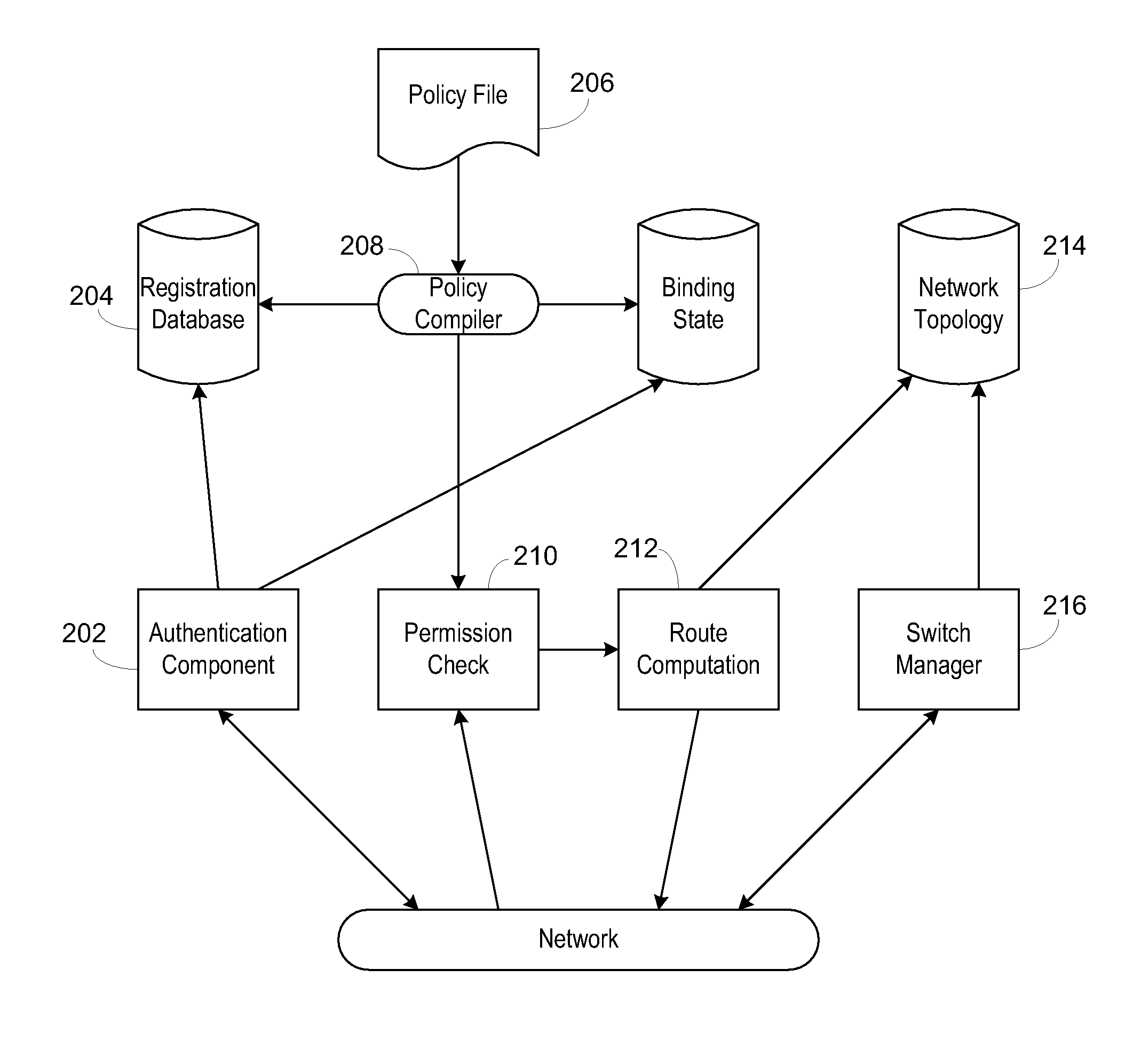
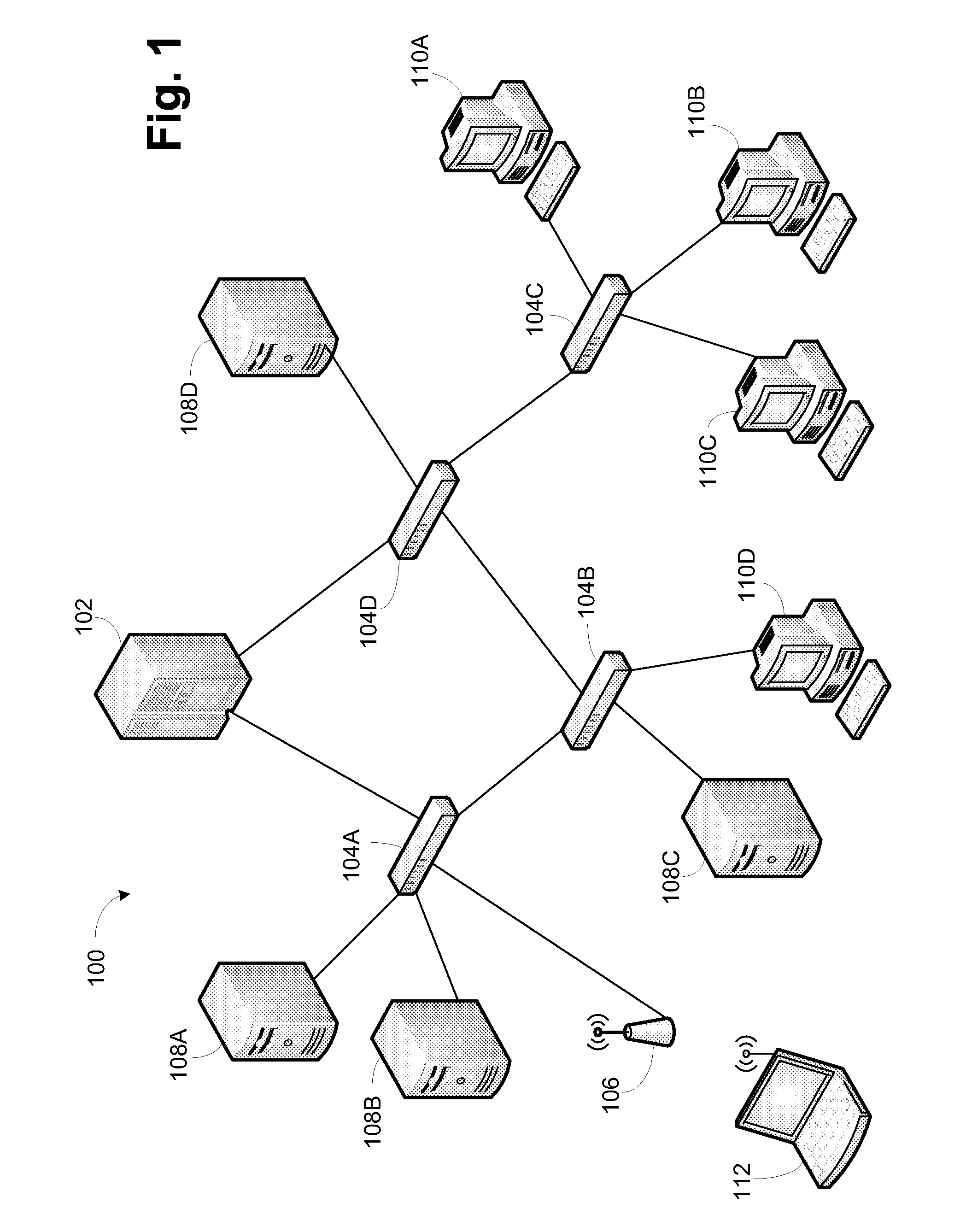
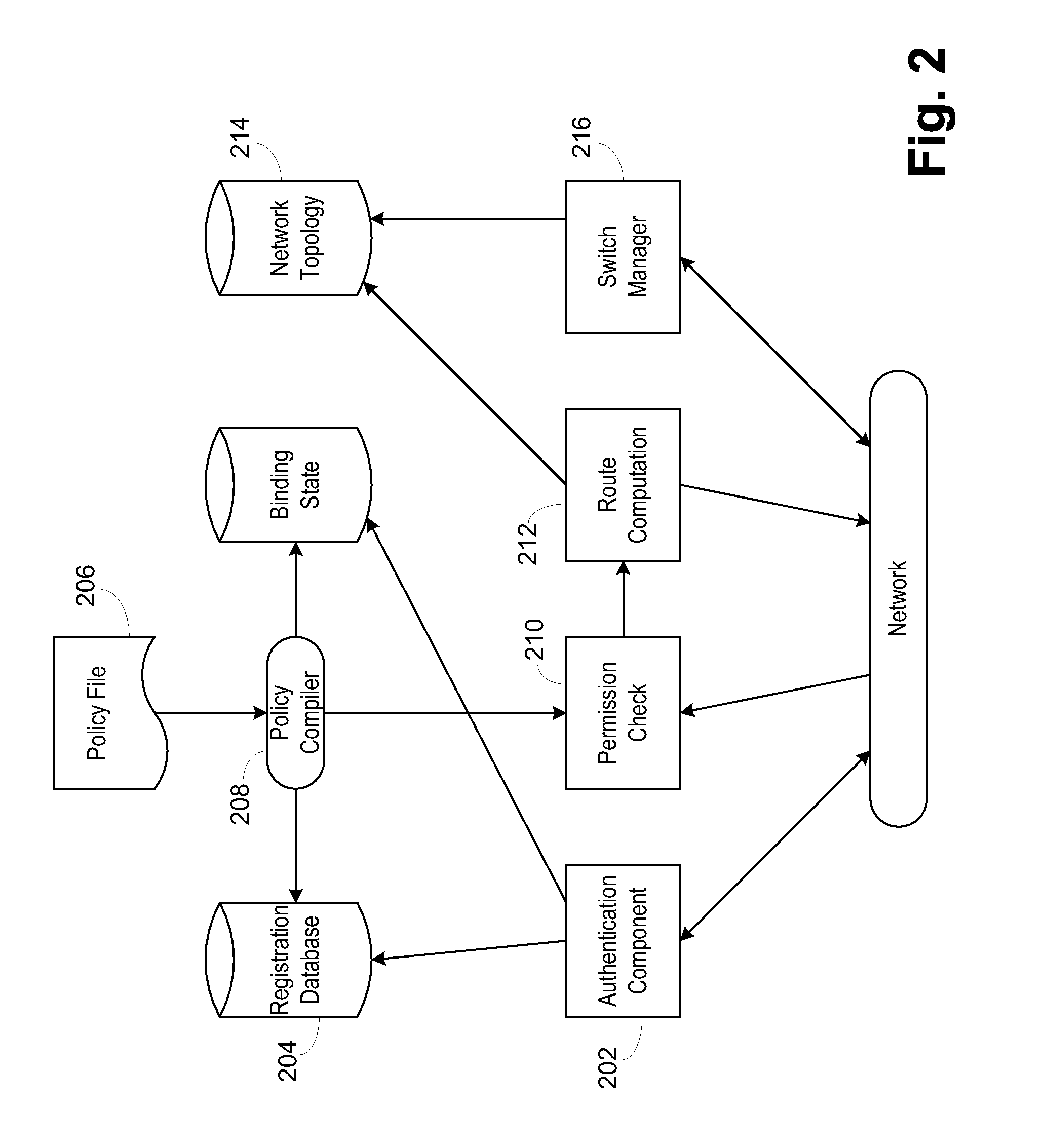
Secure network switching infrastructure
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Modular data center
Modular data centers with modular components suitable for use with rack or shelf mount computing systems, for example, are disclosed. The modular center generally includes a modular computing module including an intermodal shipping container and computing systems mounted within the container and configured to be shipped and operated within the container and a temperature control system for maintaining the air temperature surrounding the computing systems. The intermodal shipping container may be configured in accordance to International Organization for Standardization (ISO) container manufacturing standards or otherwise configured with respect to height, length, width, weight, and / or lifting points of the container for transport via an intermodal transport infrastructure. The modular design enables the modules to be cost effectively built at a factory and easily transported to and deployed at a data center site.
Owner:GOOGLE LLC
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
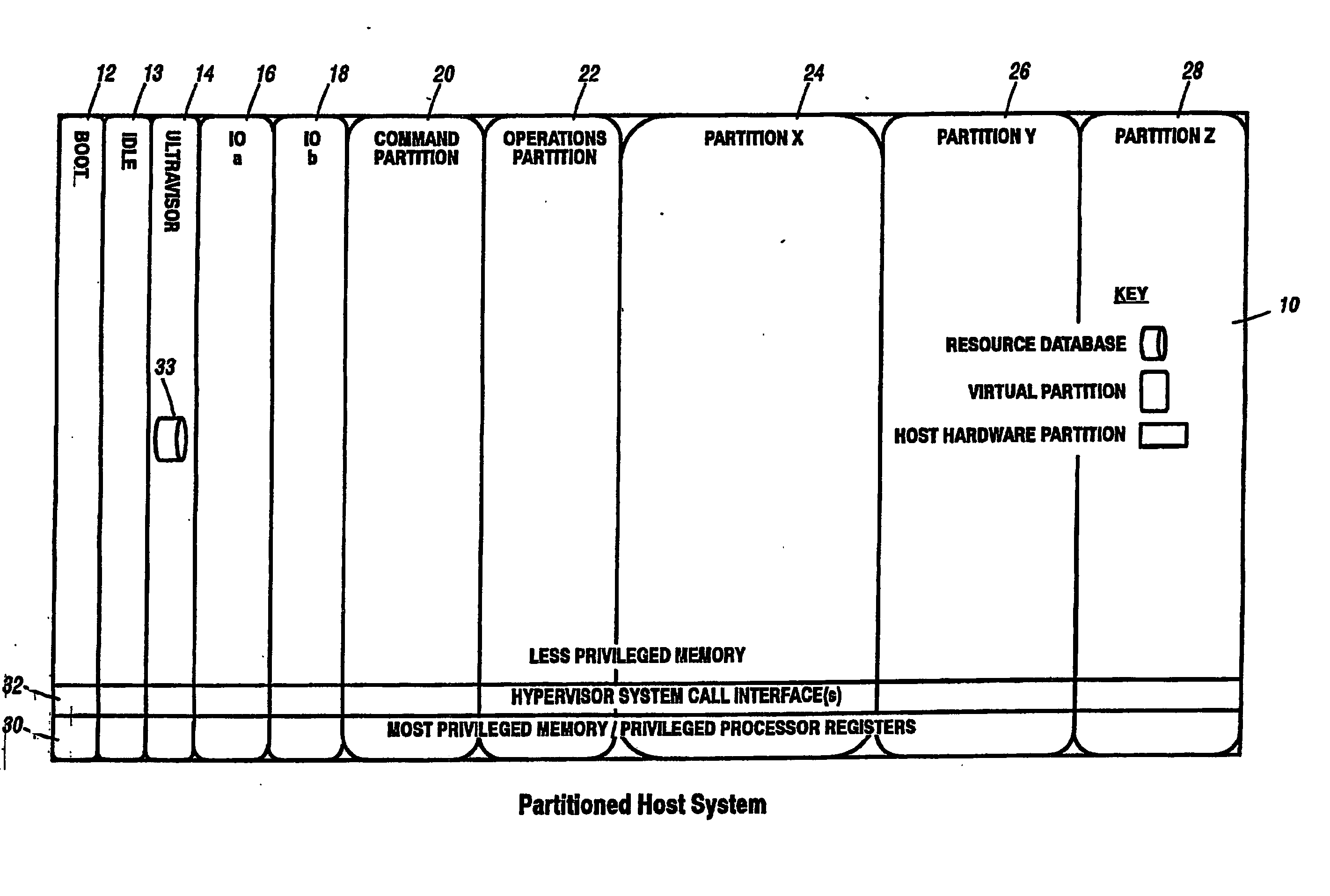
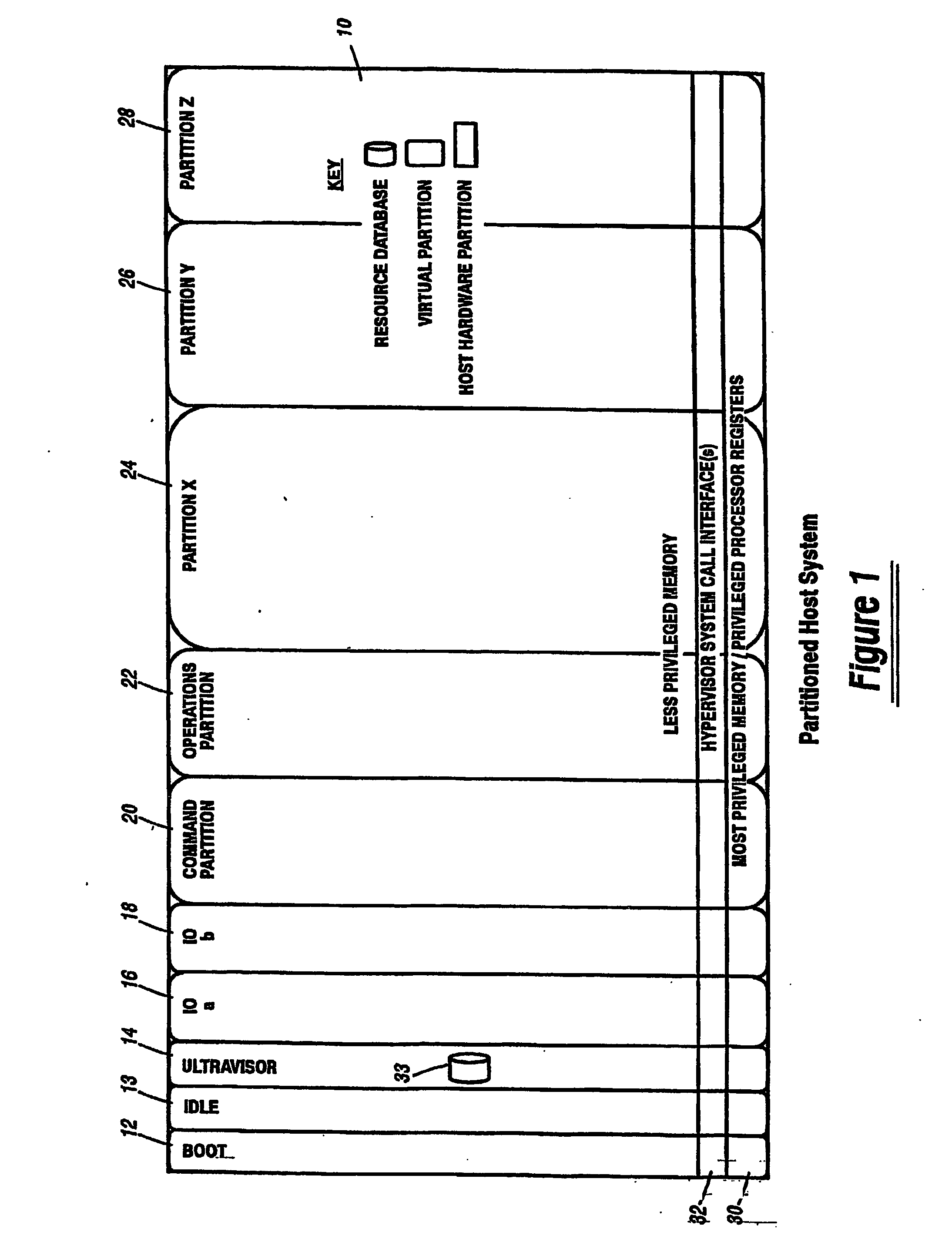
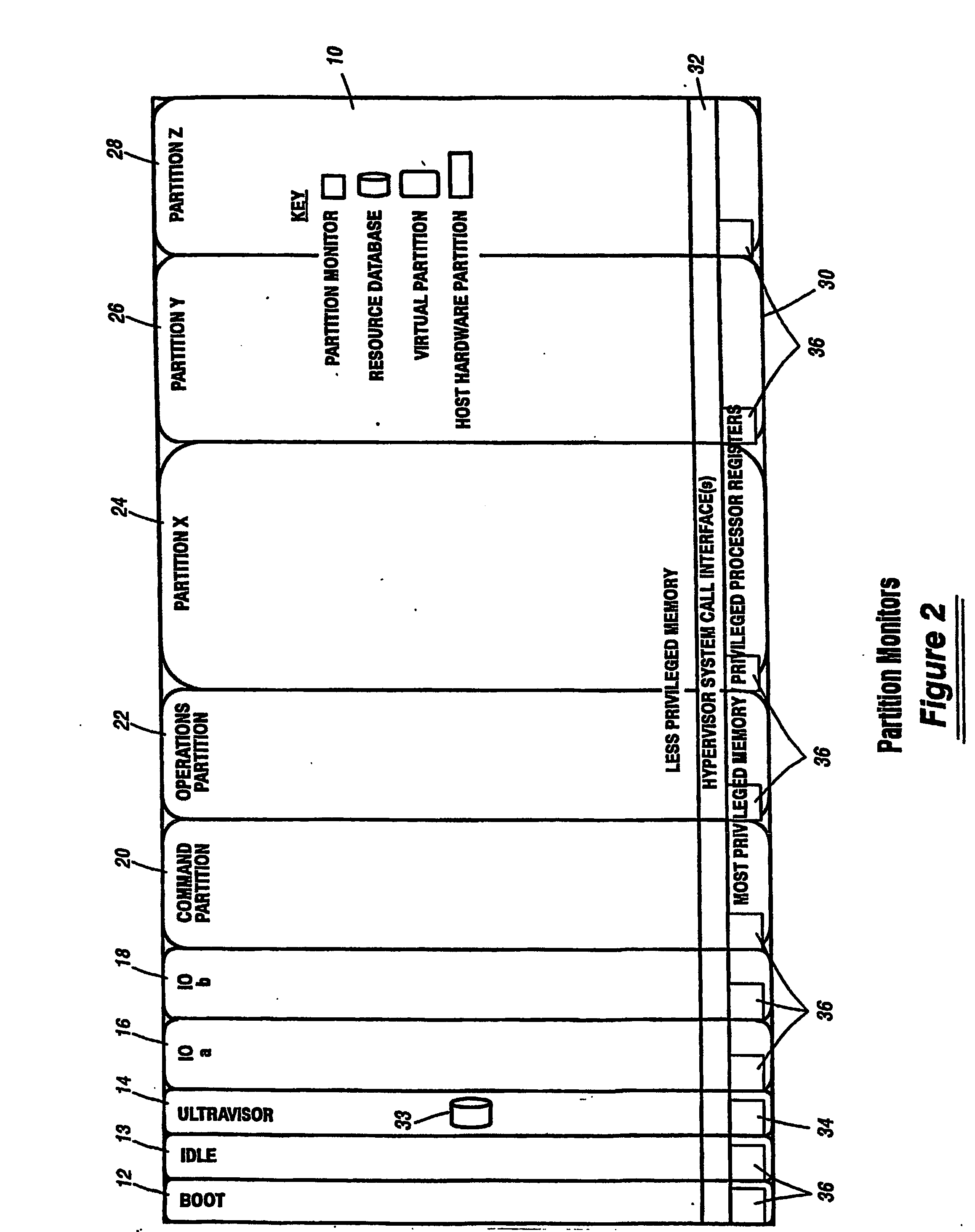
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
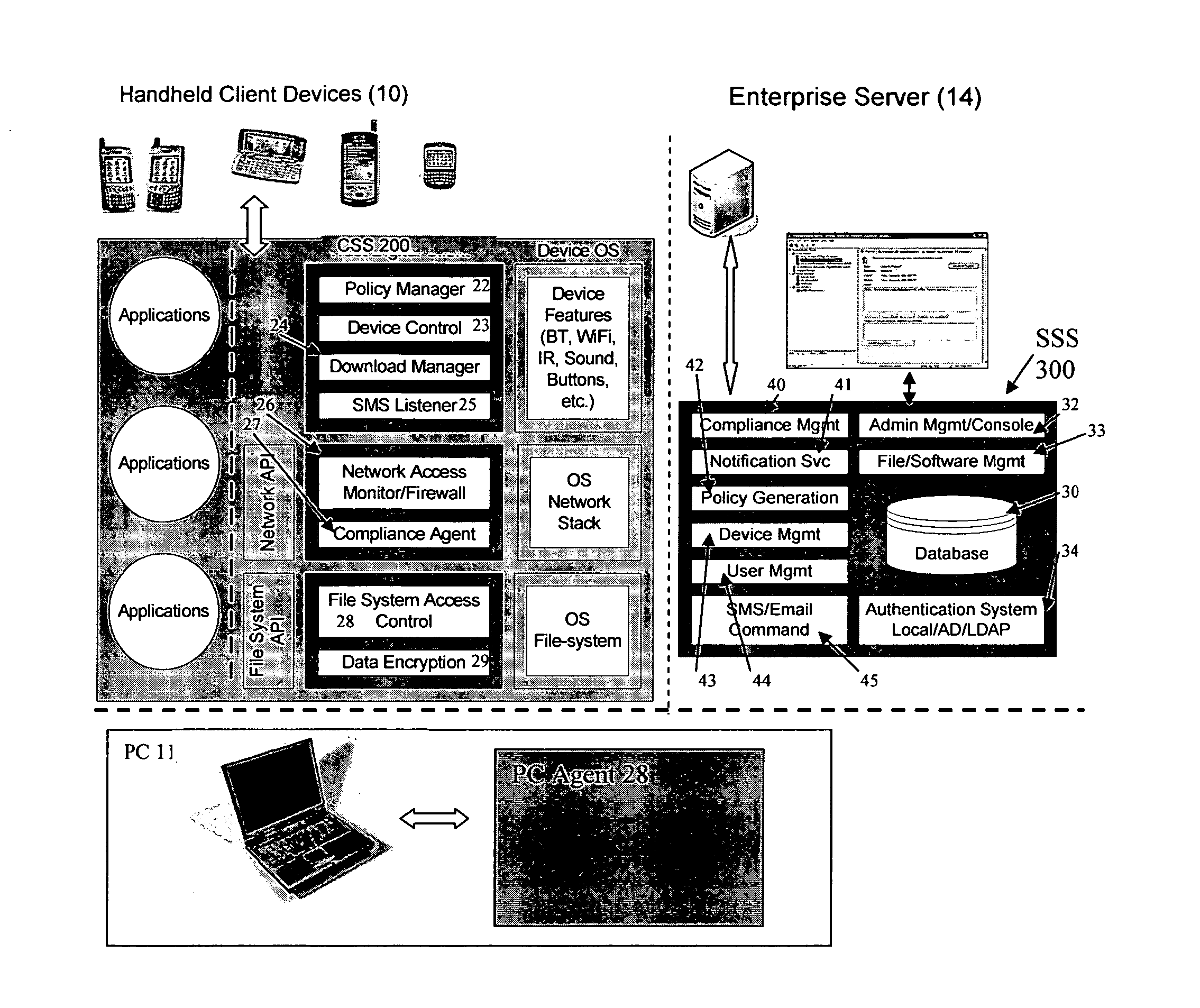
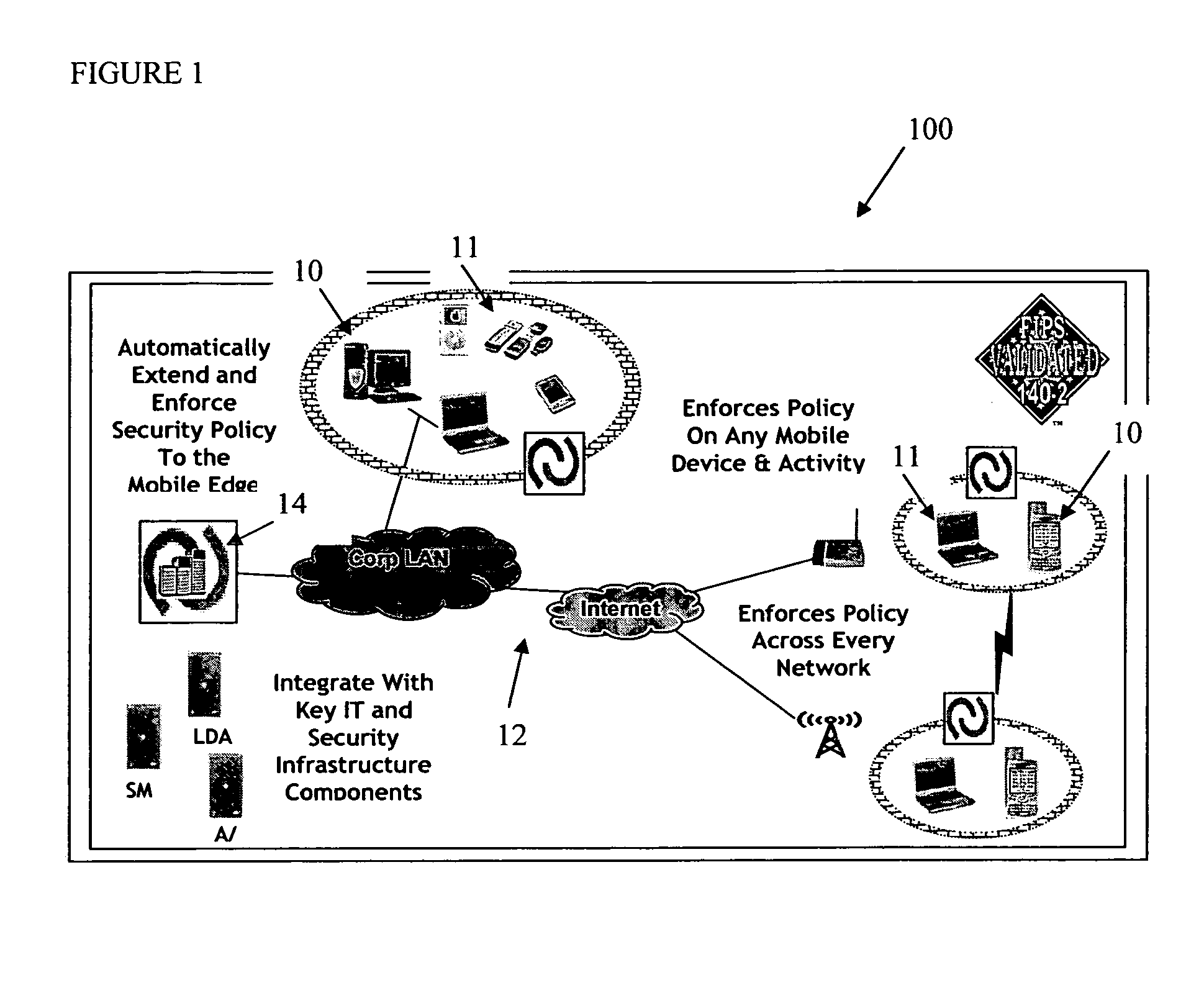
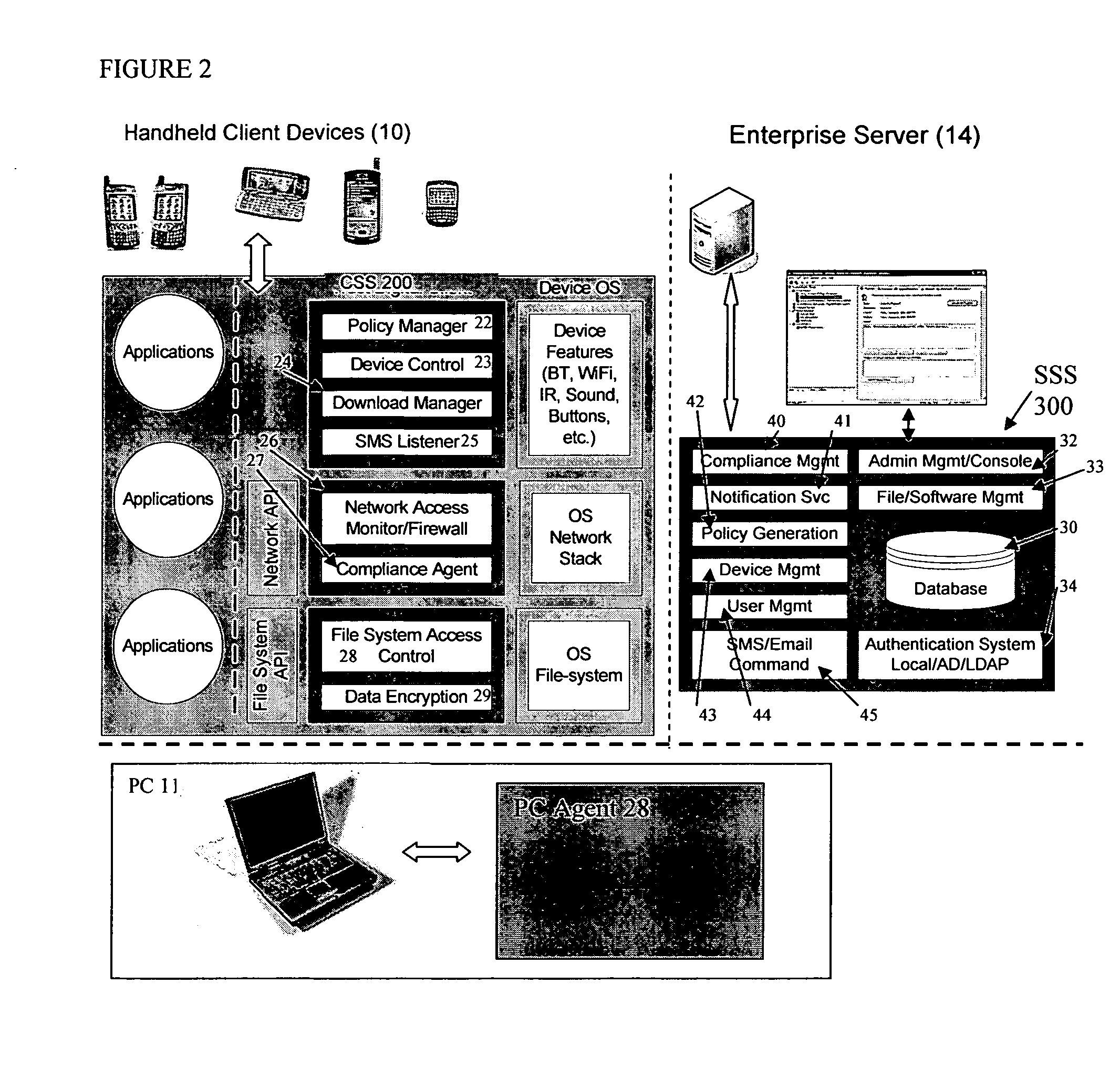
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
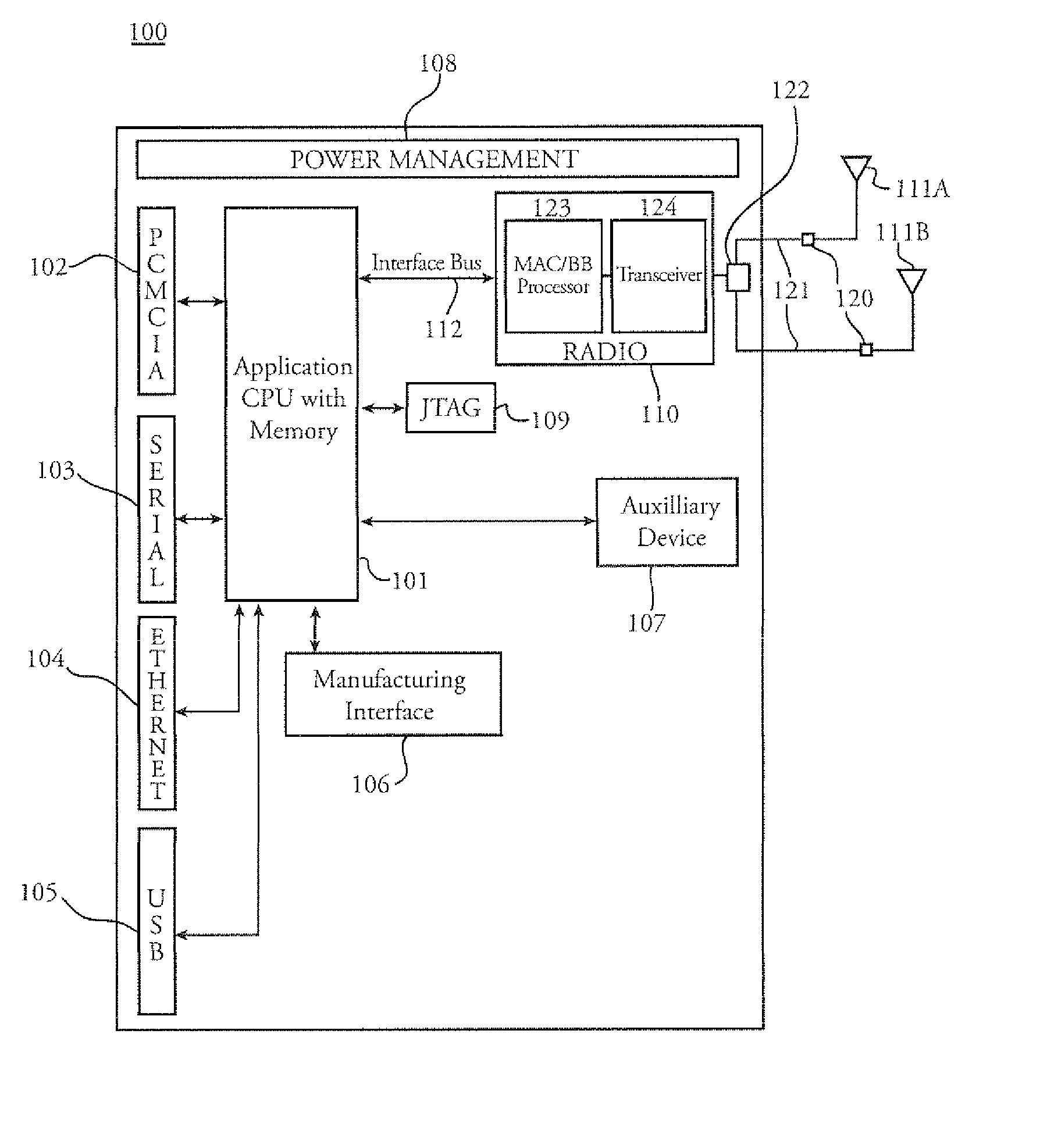
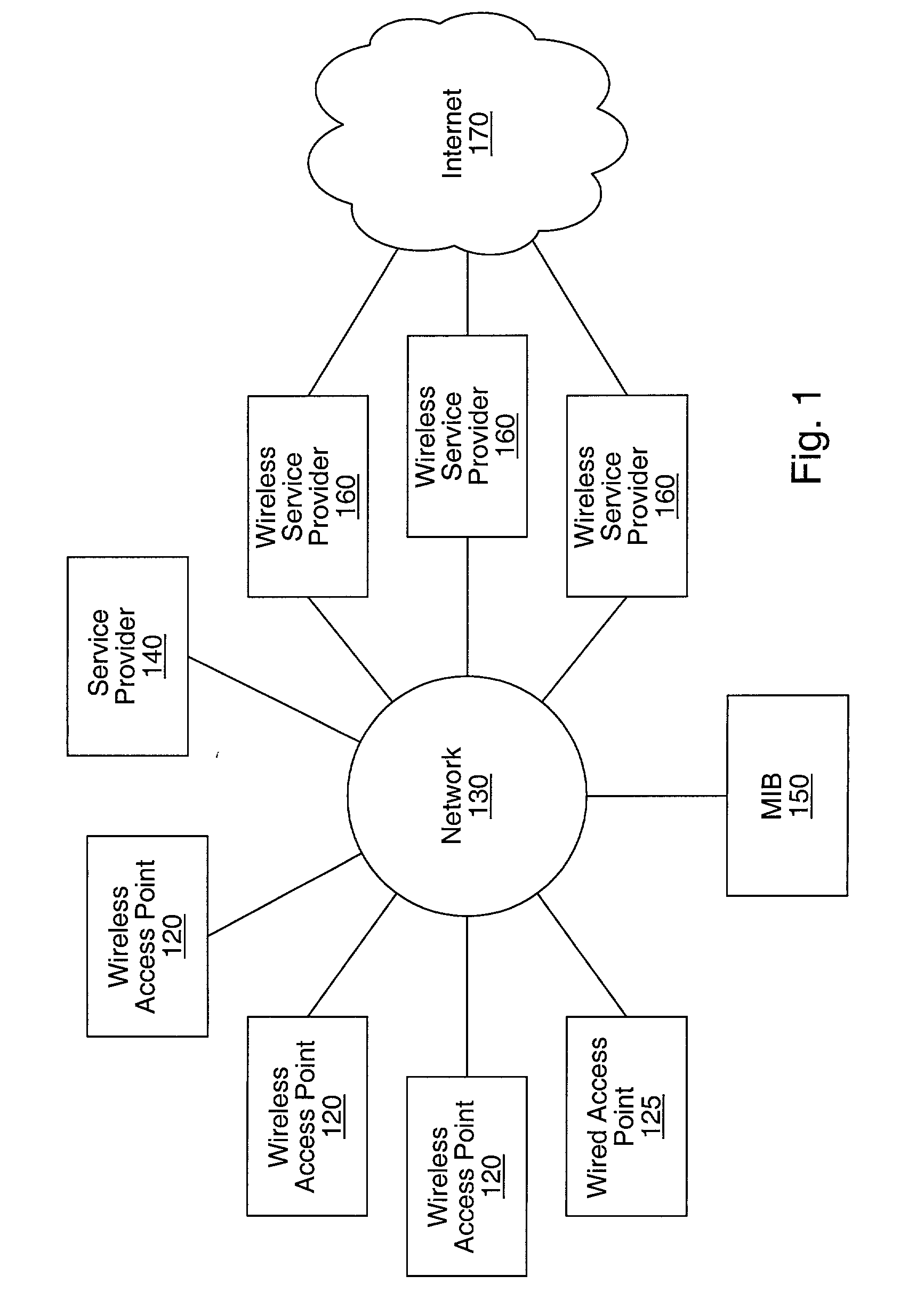
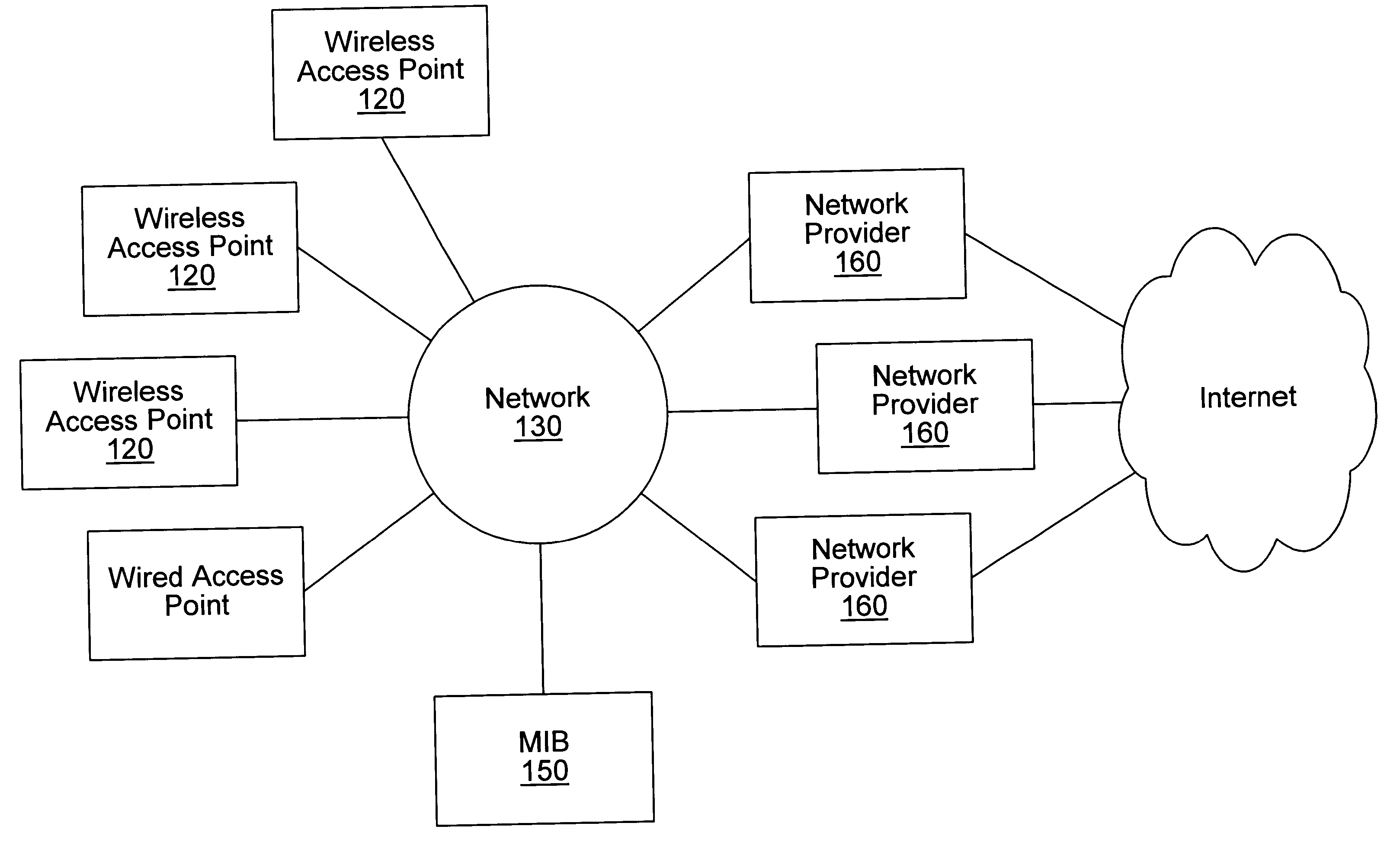
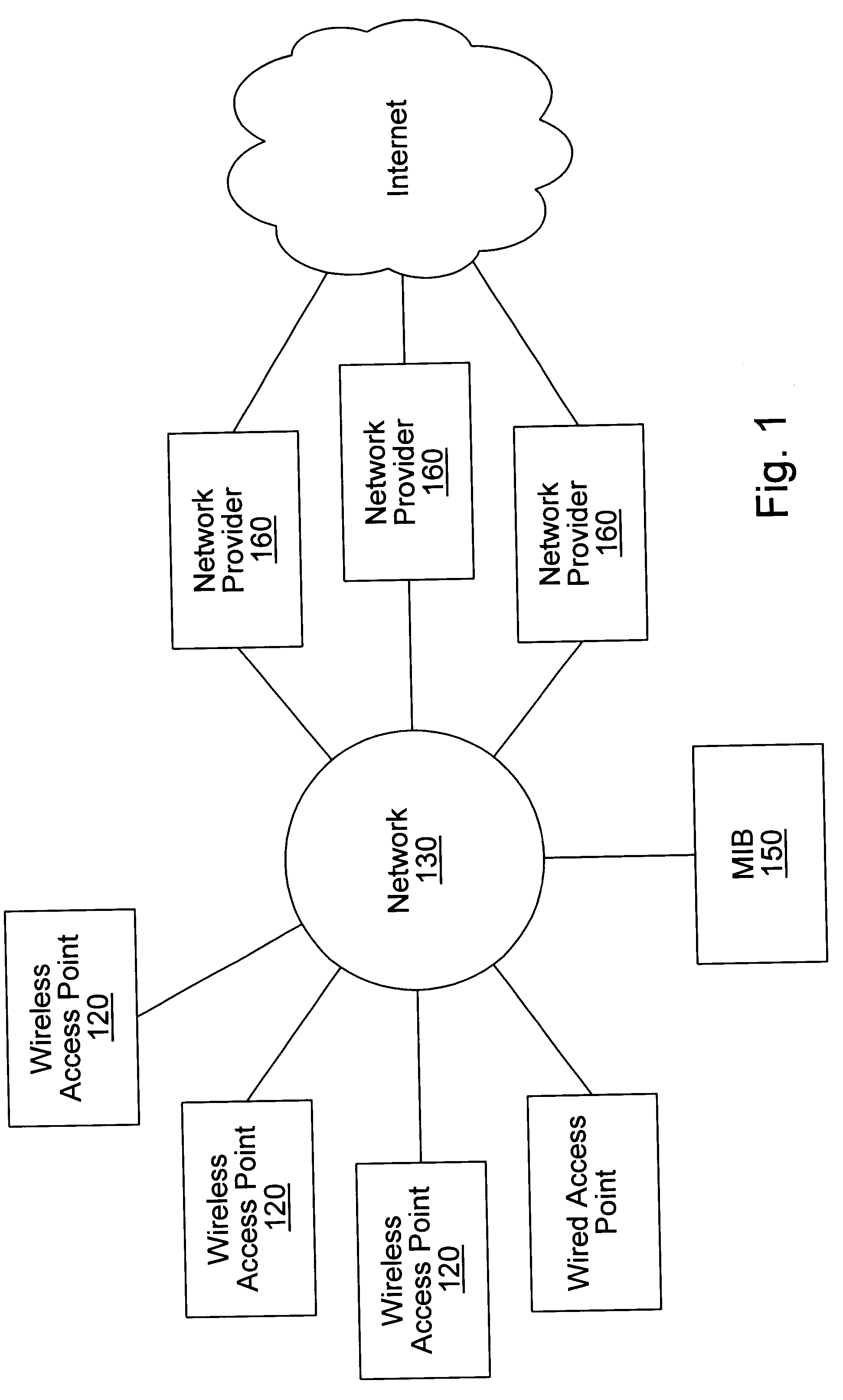
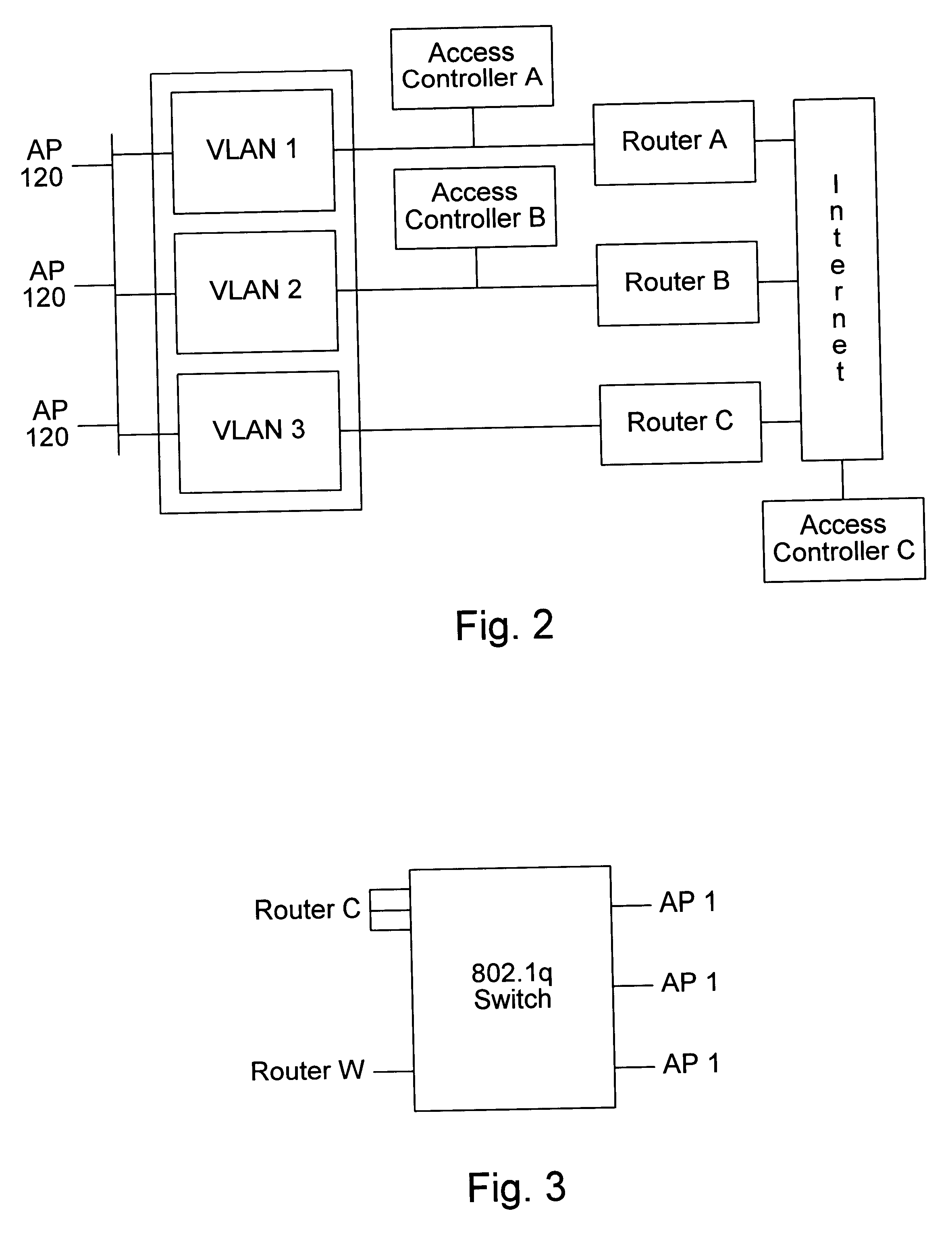
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
Locating a mobile station and applications therefor
InactiveUS20060025158A1Accurate locationEmergency connection handlingNetwork traffic/resource managementInternet communicationModularity
A location system is disclosed for wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location systems for outputting requested locations of hand sets or mobile stations (MS) based on, e.g., AMPS, NAMPS, CDMA or TDMA communication standards, for processing both local mobile station location requests and more global mobile station location requests via, e.g., Internet communication between a distributed network of location systems. The system uses a plurality of mobile station locating technologies including those based on: (1) two-way TOA and TDOA; (2) home base stations and (3) distributed antenna provisioning. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. The system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:FINETRAK LLC
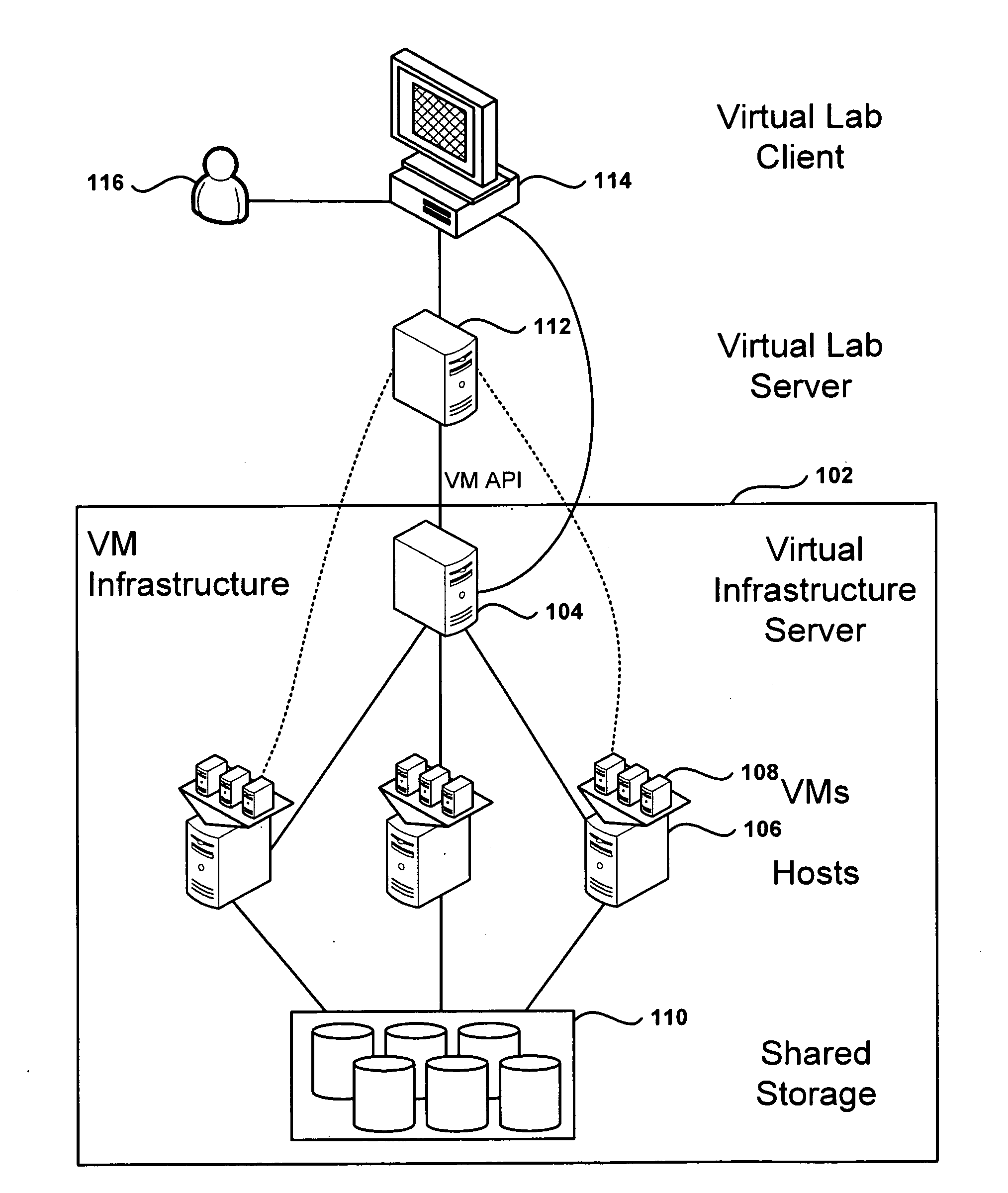
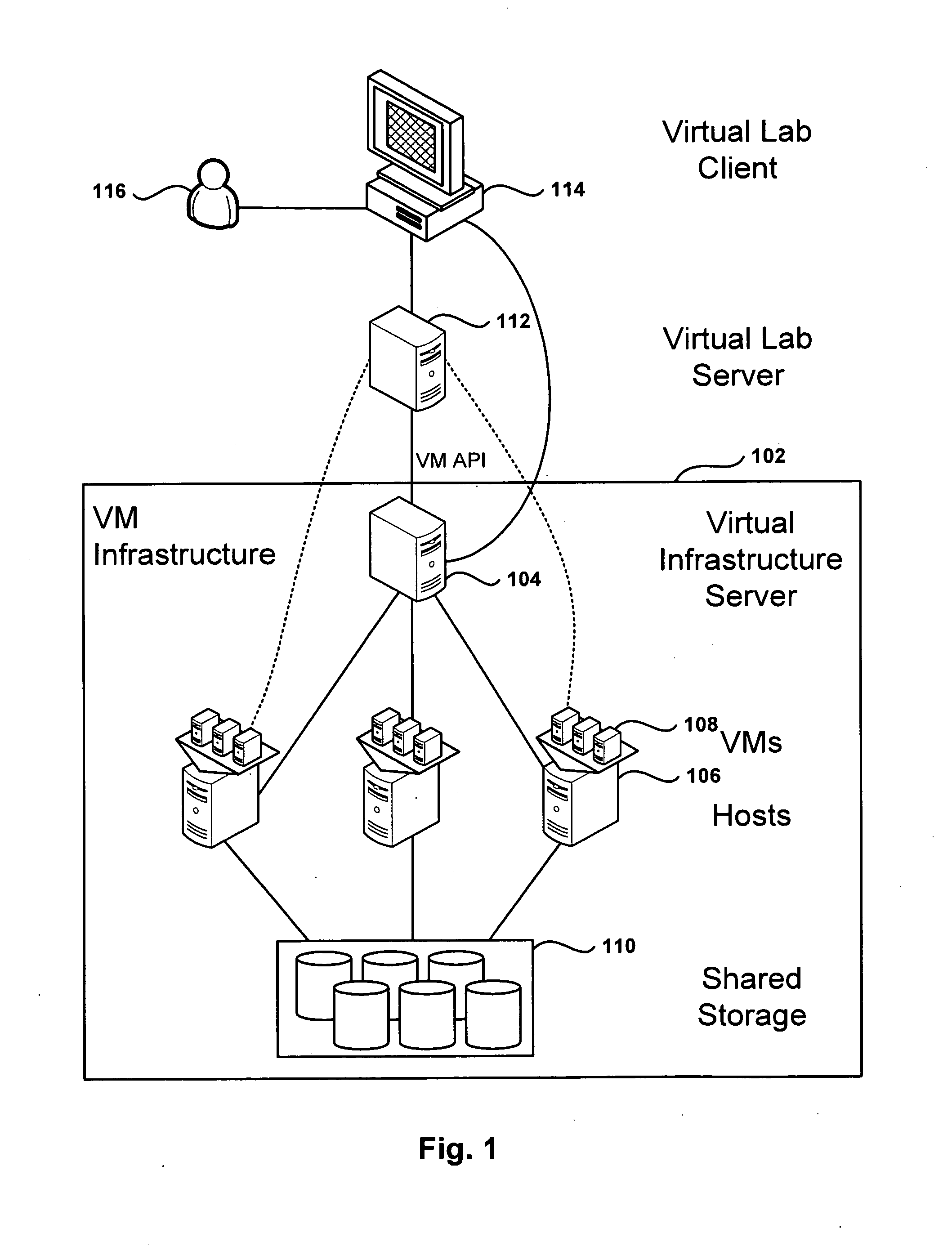
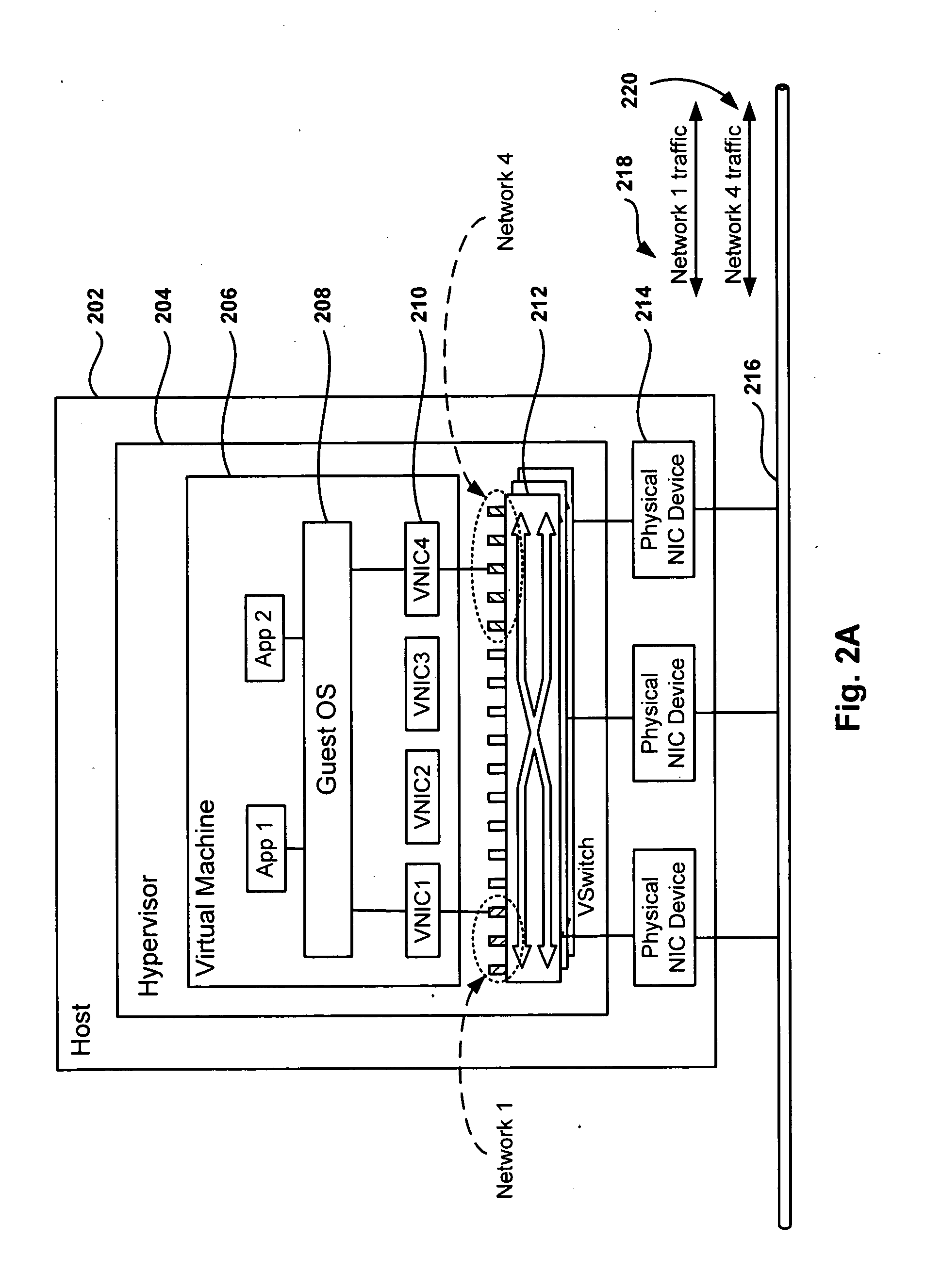
Management and Implementation of Enclosed Local Networks in a Virtual Lab
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
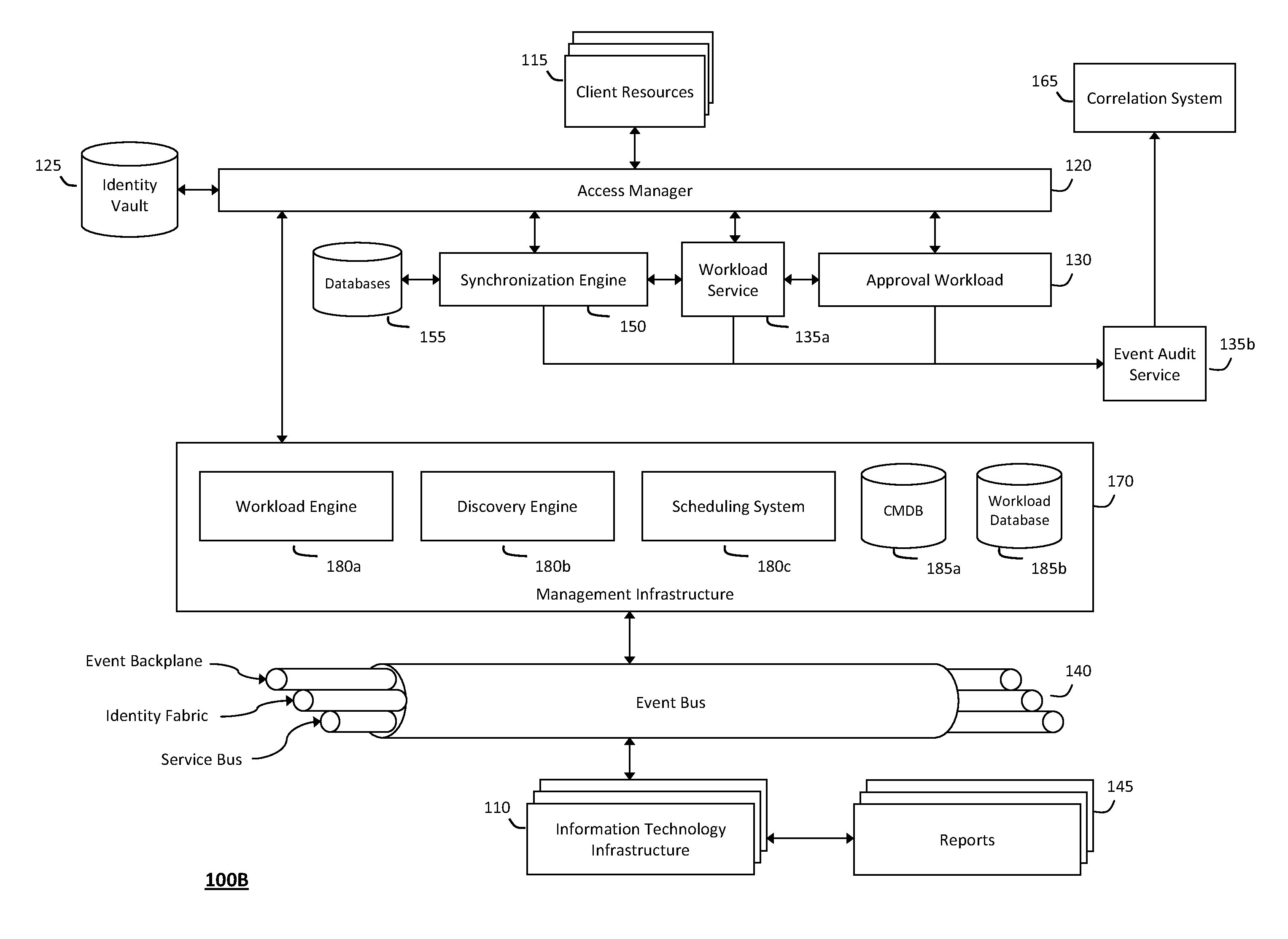
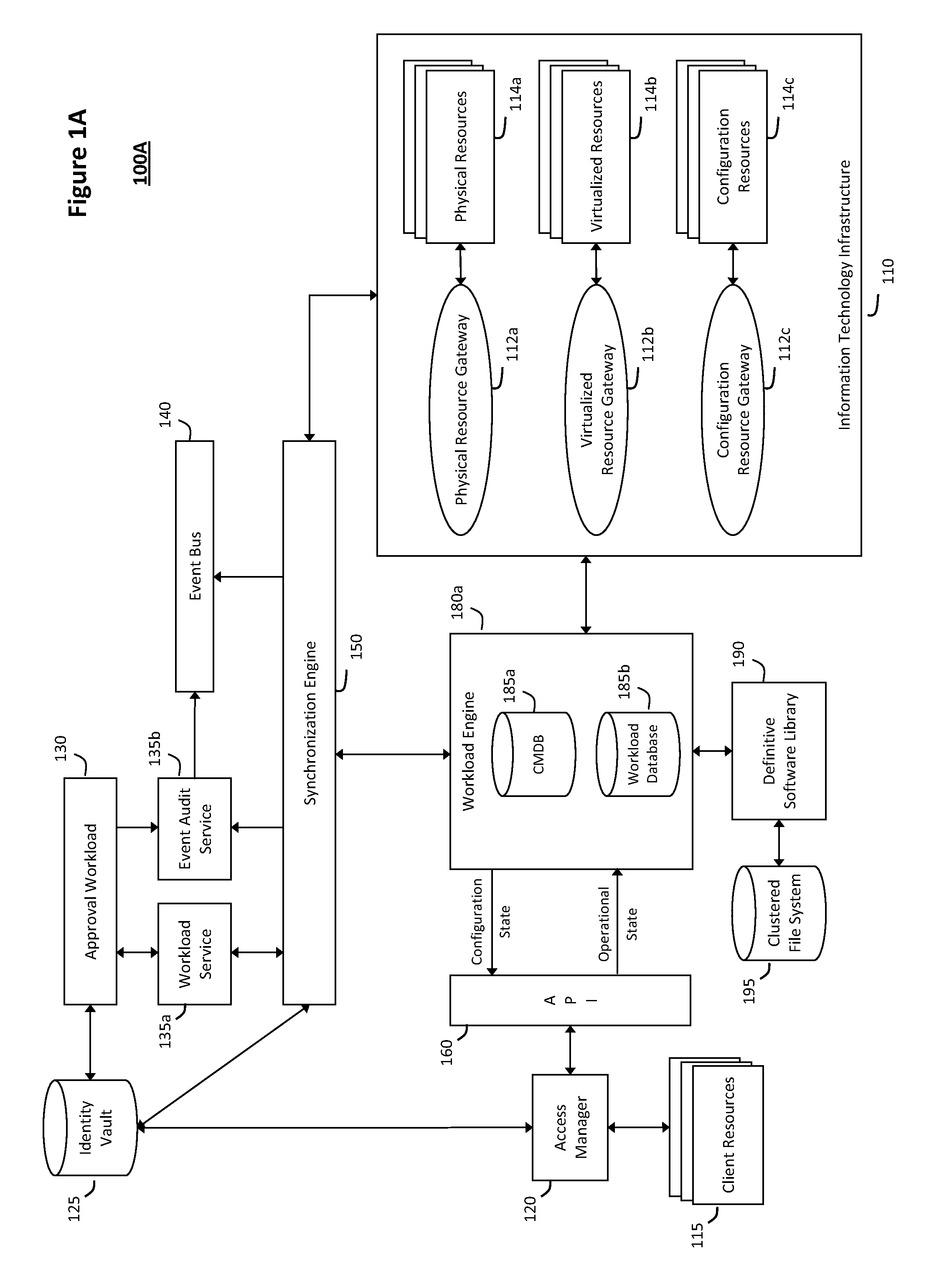
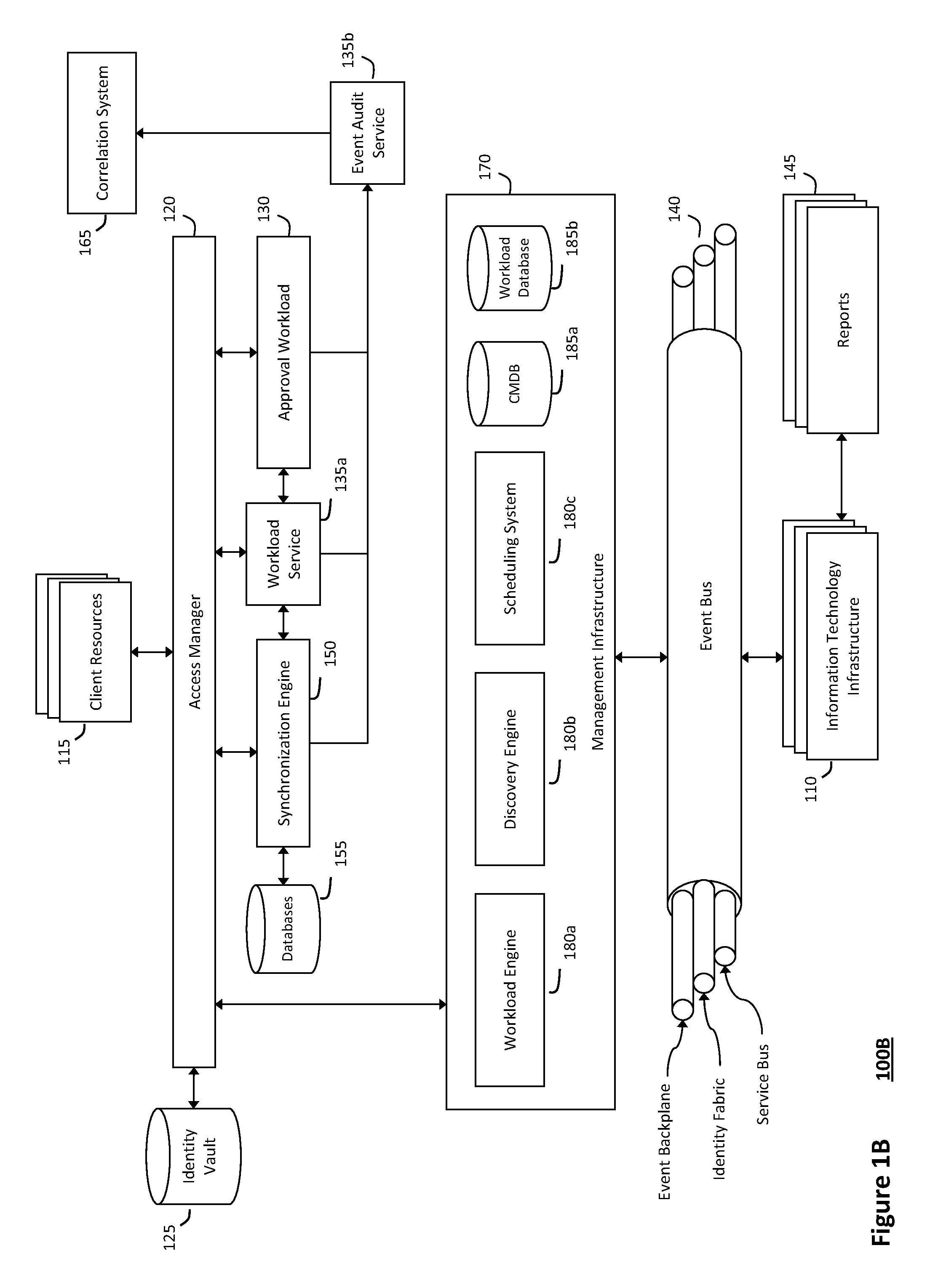
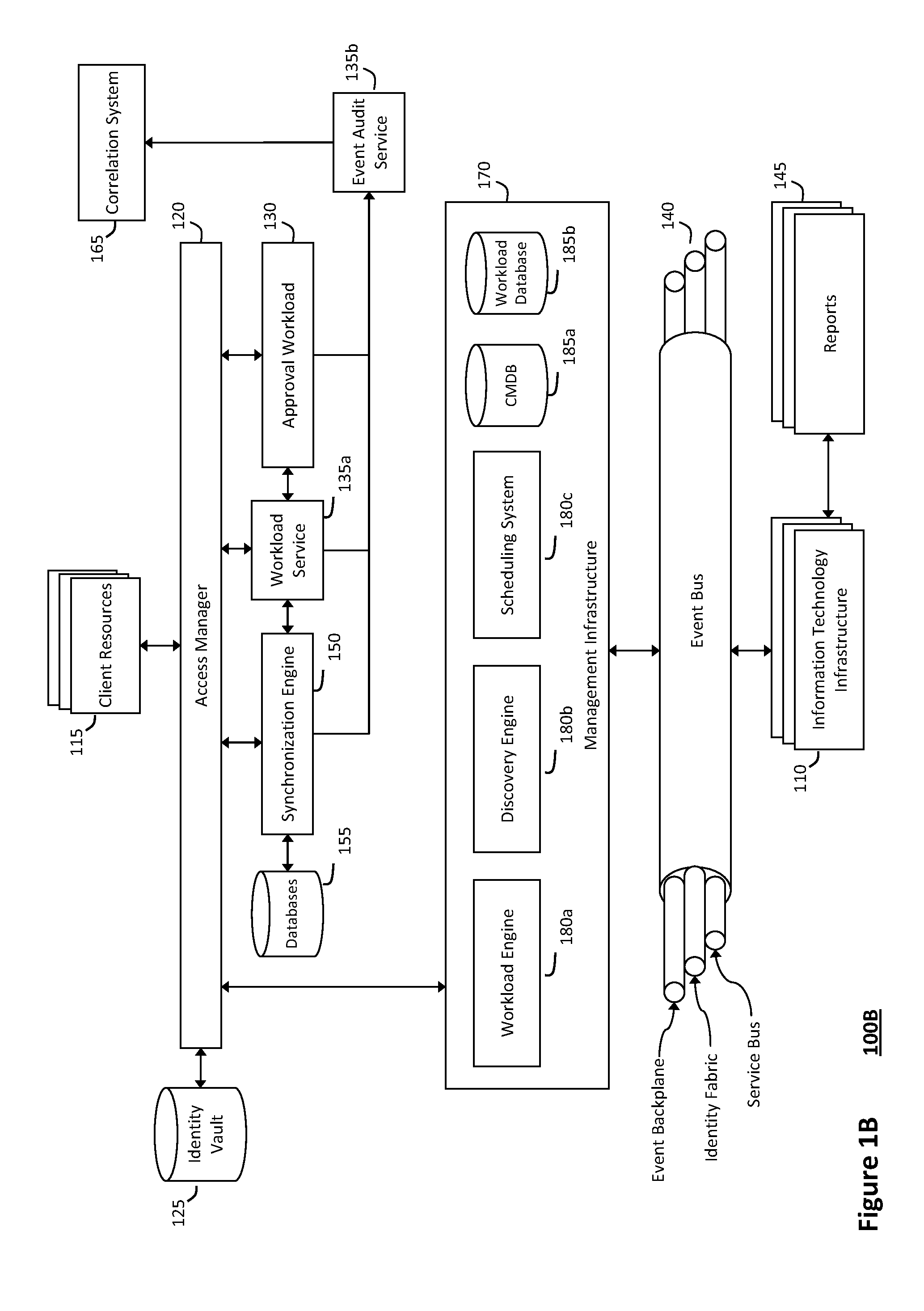
System and method for discovery enrichment in an intelligent workload management system
InactiveUS20110126275A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationVirtualizationService-oriented architecture
The system and method described herein for discovery enrichment in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing identities and access credentials, which may provide information that can enrich discovery of physical and virtual infrastructure resources. For example, a discovery engine may reference federated identity information stored in an identity vault and enrich a discovered infrastructure model with the federated identity information. Thus, the model may generally include information describing physical and virtualized resources in the infrastructure, applications and services running in the infrastructure, and information derived from the federated identity information that describes dependencies between the physical resources, the virtualized resources, the applications, and the services.
Owner:MICRO FOCUS SOFTWARE INC
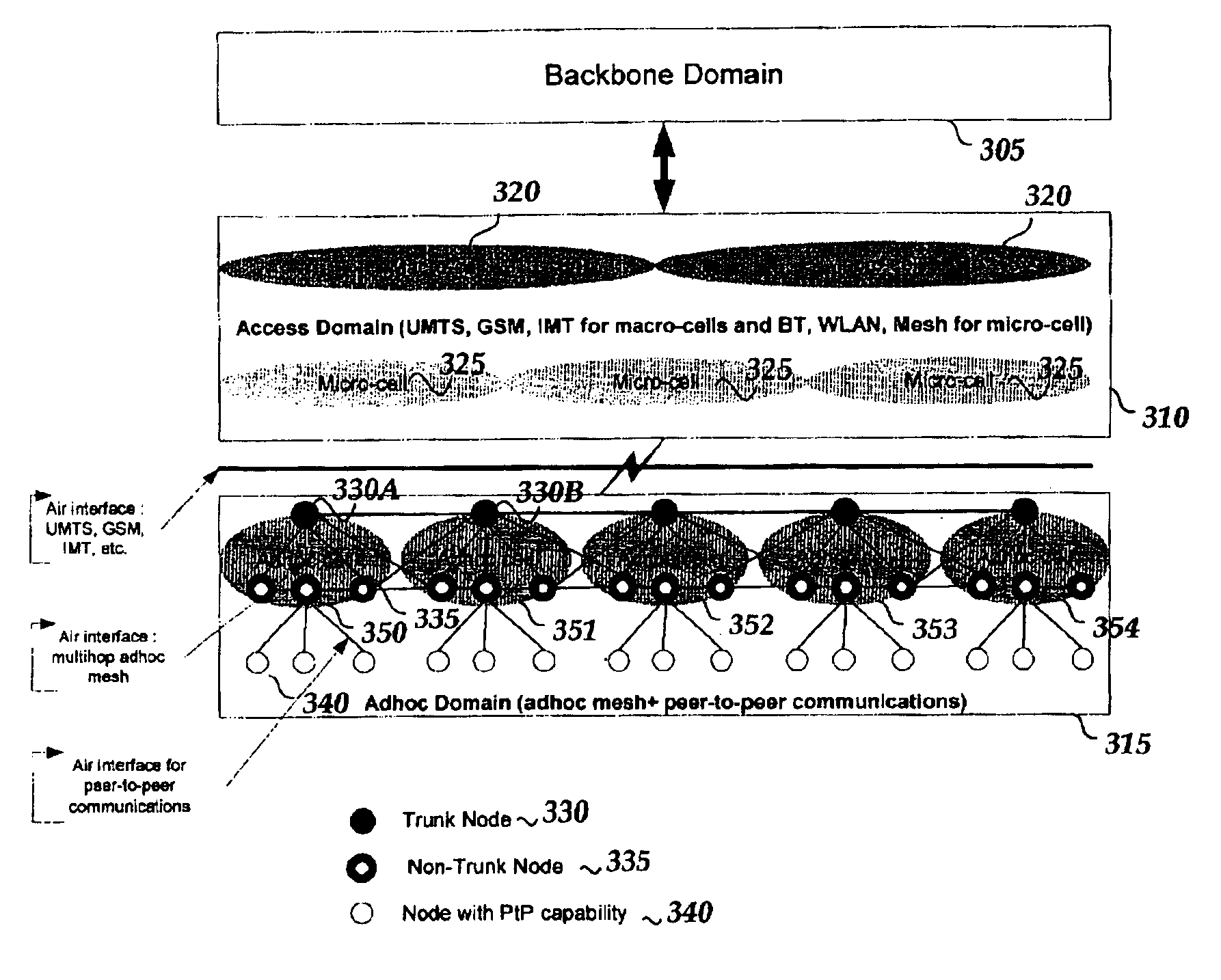
Mobile mesh Ad-Hoc networking
InactiveUS6879574B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCyber operationsAccess network
An architectural solution in which standalone ad-hoc network cells are used as an extension of the backbone infrastructure in terms of network architecture or / and its service capabilities is provided. These Ad-Hoc networks will integrate to the Internet via cellular and other access networks. This integration brings new possibilities to network operators and ISP's. In its extended architecture, it is envisaged that the mobility issues are handled by utilizing the IP mobility capabilities, taking into account the mobile mesh Ad-Hoc specific requirements.
Owner:NOKIA TECHNOLOGLES OY
System and method for intelligent workload management
ActiveUS20110125894A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationAuthentication serverService-oriented architecture
The system and method for intelligent workload management described herein may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads, wherein the management threads may converge information for managing identities and access credentials, enforcing policies, providing compliance assurances, managing provisioned and requested services, and managing physical and virtual infrastructure resources. In one implementation, an authentication server may generate authentication tokens defining access credentials for managed entities across a plurality of authentication domains, wherein the authentication tokens may control access to resources in an information technology infrastructure. For example, a management infrastructure may create service distributions for the managed entities, which may include virtual machine images hosted on physical resources. Further, the authentication tokens may be embedded in the service distributions, whereby the embedded authentication tokens may control access to the resources in the information technology infrastructure.
Owner:MICRO FOCUS SOFTWARE INC
Methods and systems for a mobile, broadband, routable internet
ActiveUS8060017B2Low costFast capacity expansionNetwork topologiesTime-division multiplexCellular telephonePeer-to-peer
In embodiments of the present invention improved capabilities are described for a mobile broadband routable internet (MBRI) providing for carrier-grade, networked, broadband, IP-routable communication among a plurality of mobile devices, where the mobile devices may represent a plurality of nodes that are linked together through a mobile ad-hoc network (MANET). Mobile devices may operate as peers in a peer-to-peer network, with full IP routing capabilities enabled within each mobile device, thereby allowing routing of IP-based traffic, including deployment of applications, to the mobile device without need for infrastructure conventionally required for mobile ad hoc networks, such as cellular telephony infrastructure. Full IP-routing to mobile devices may allow seamless integration to the fixed Internet, such as through fixed or mobile access points, such as for backhaul purposes. Thus, the MBRI may function as a standalone mobile Internet, without connection to the fixed Internet, or as an IP-routable extension of another network, whether it be the Internet, a local area network, a wide area network, a cellular network, a personal area network, or some other type of network that is capable of integration with an IP-based network.
Owner:POWERWAVE COGNITION INC
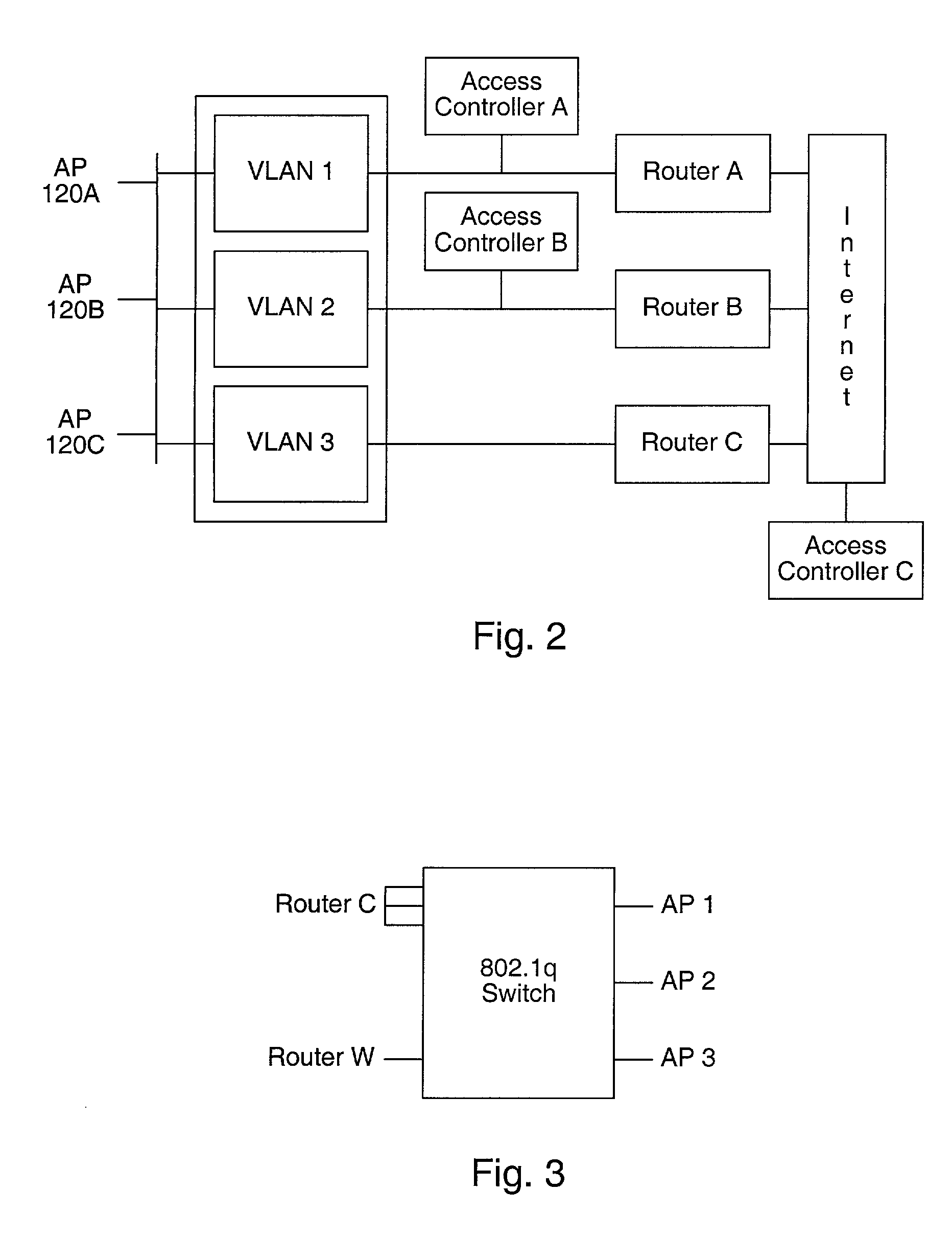
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
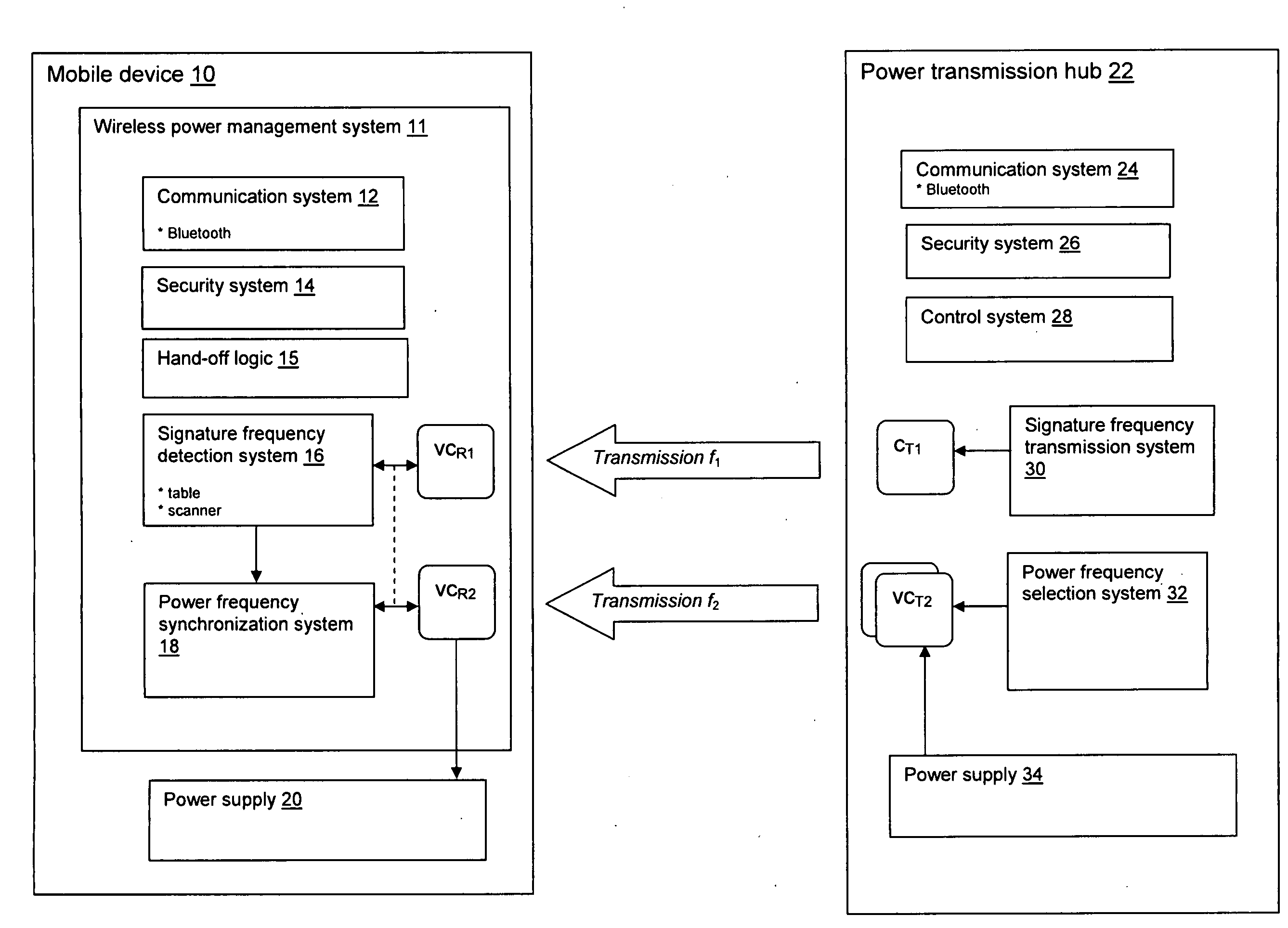
Wireless power infrastructure
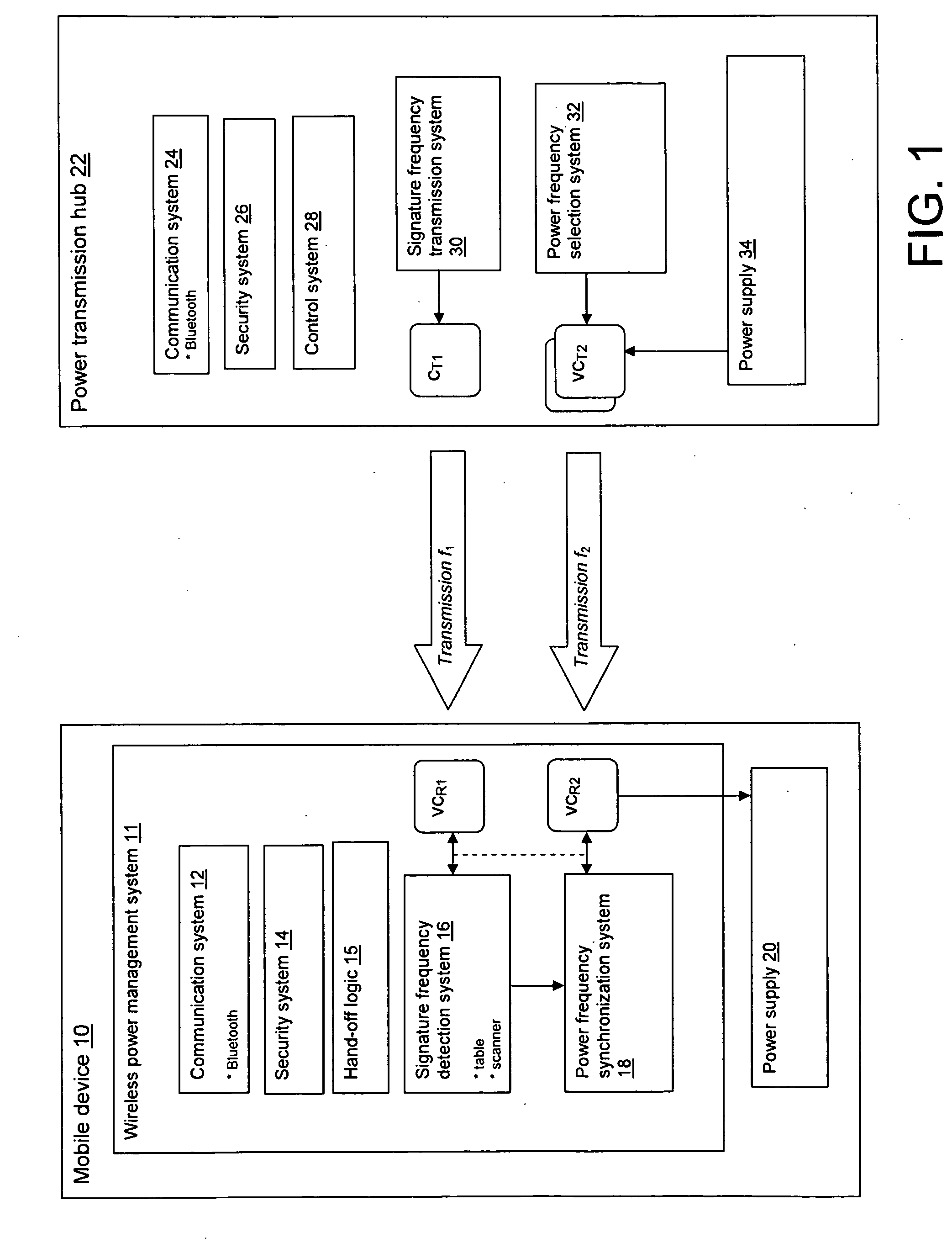
ActiveUS20100256831A1Mechanical power/torque controlLevel controlElectric power transmissionElectricity infrastructure
A wireless power infrastructure for delivering wireless power from a wireless network to mobile devices. The infrastructure includes a plurality of power transmission hubs, each hub having: a first capacitor for transmitting a signature frequency for a defined range; and a set of second capacitors, each for transmitting resonant wireless power within the defined range at a selectable frequency. A mobile device for obtaining wireless resonant the plurality of power transmission hubs is also described, and includes: a first variable capacitor for detecting a signature frequency associated with a proximately located power transmission hub; a second variable capacitor for receiving wireless resonant capacitor from the proximately located power transmission hub; and a synchronization system for setting the second variable capacitor to a frequency that is synchronized with a wireless resonant power transmission of the proximately located power transmission hub.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com