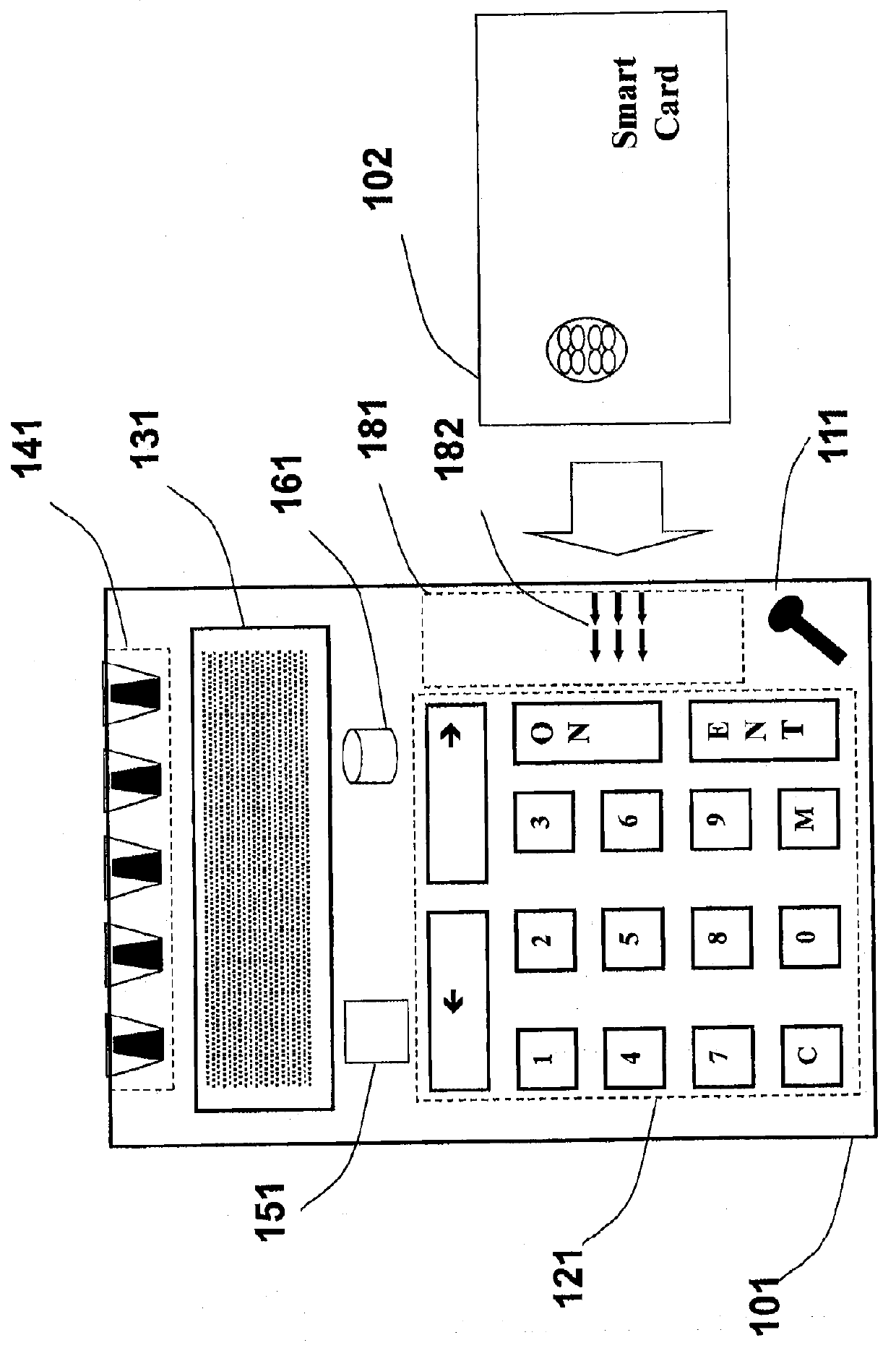
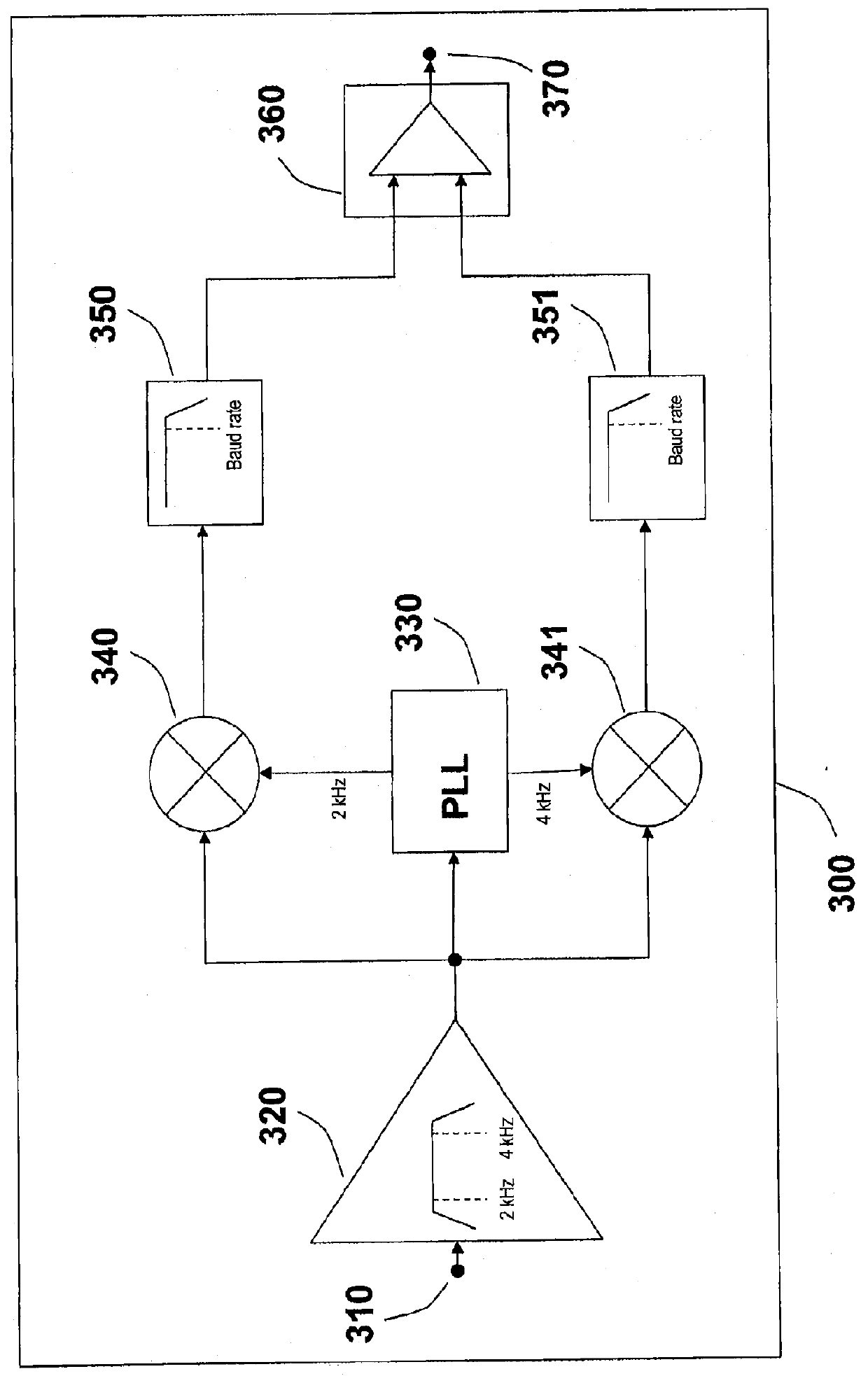
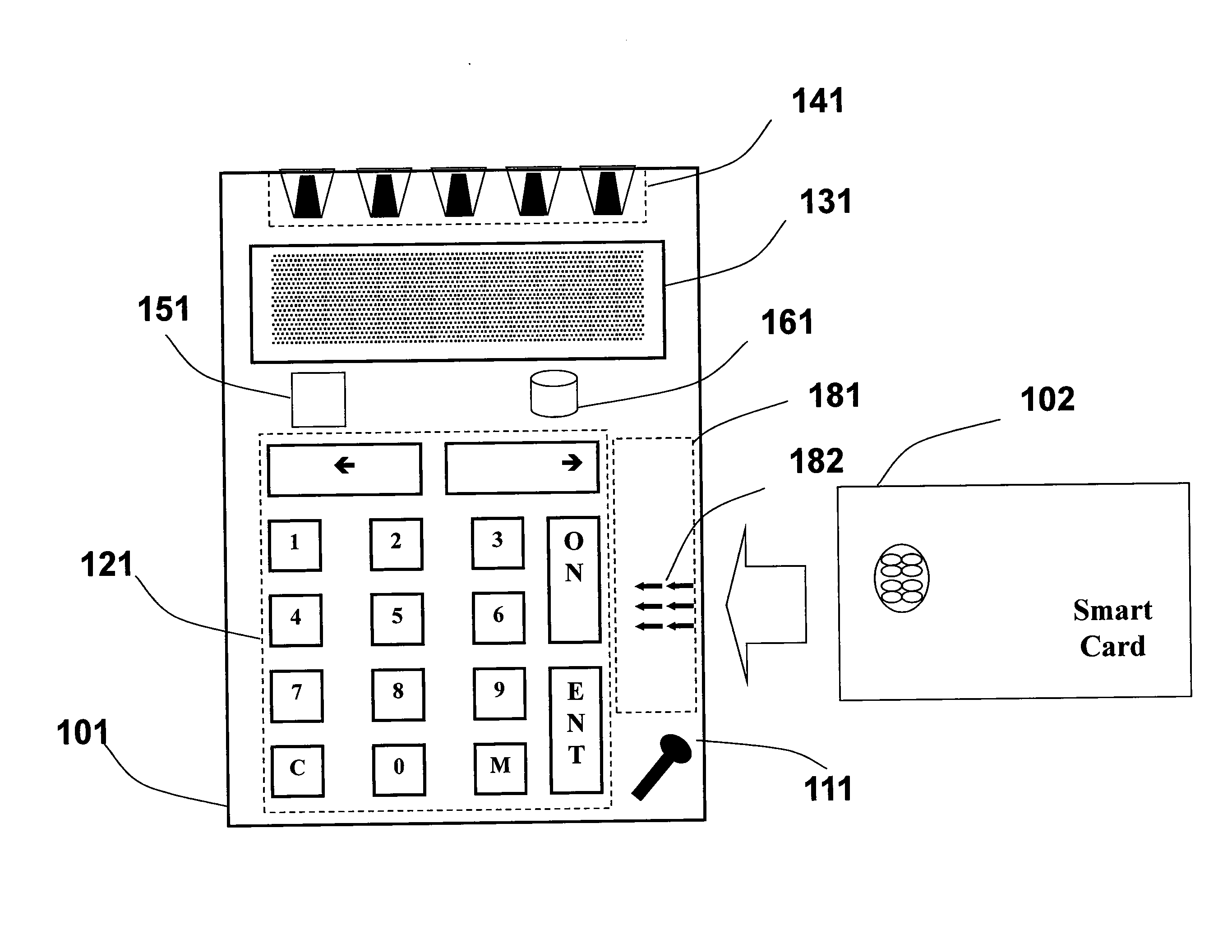
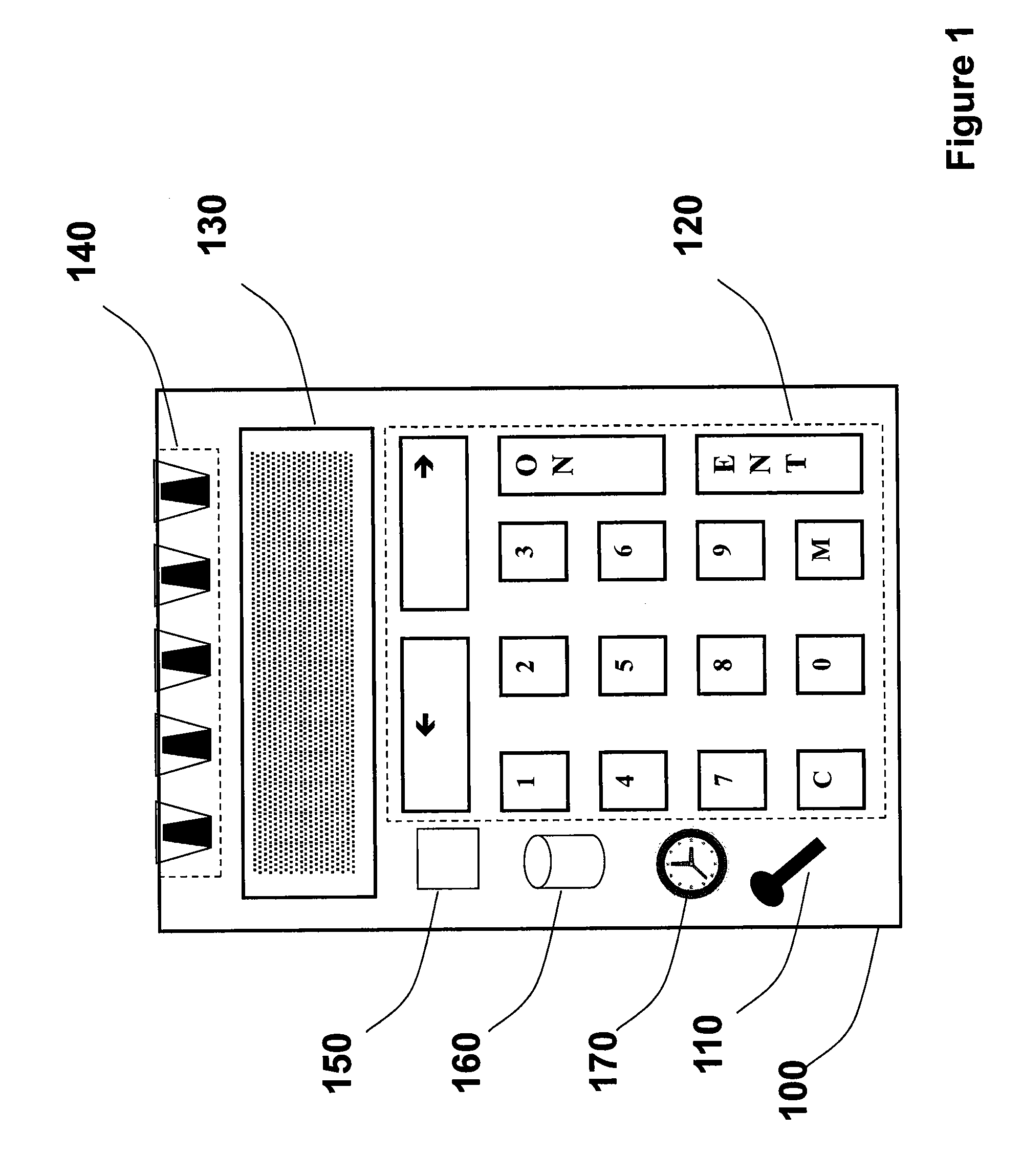
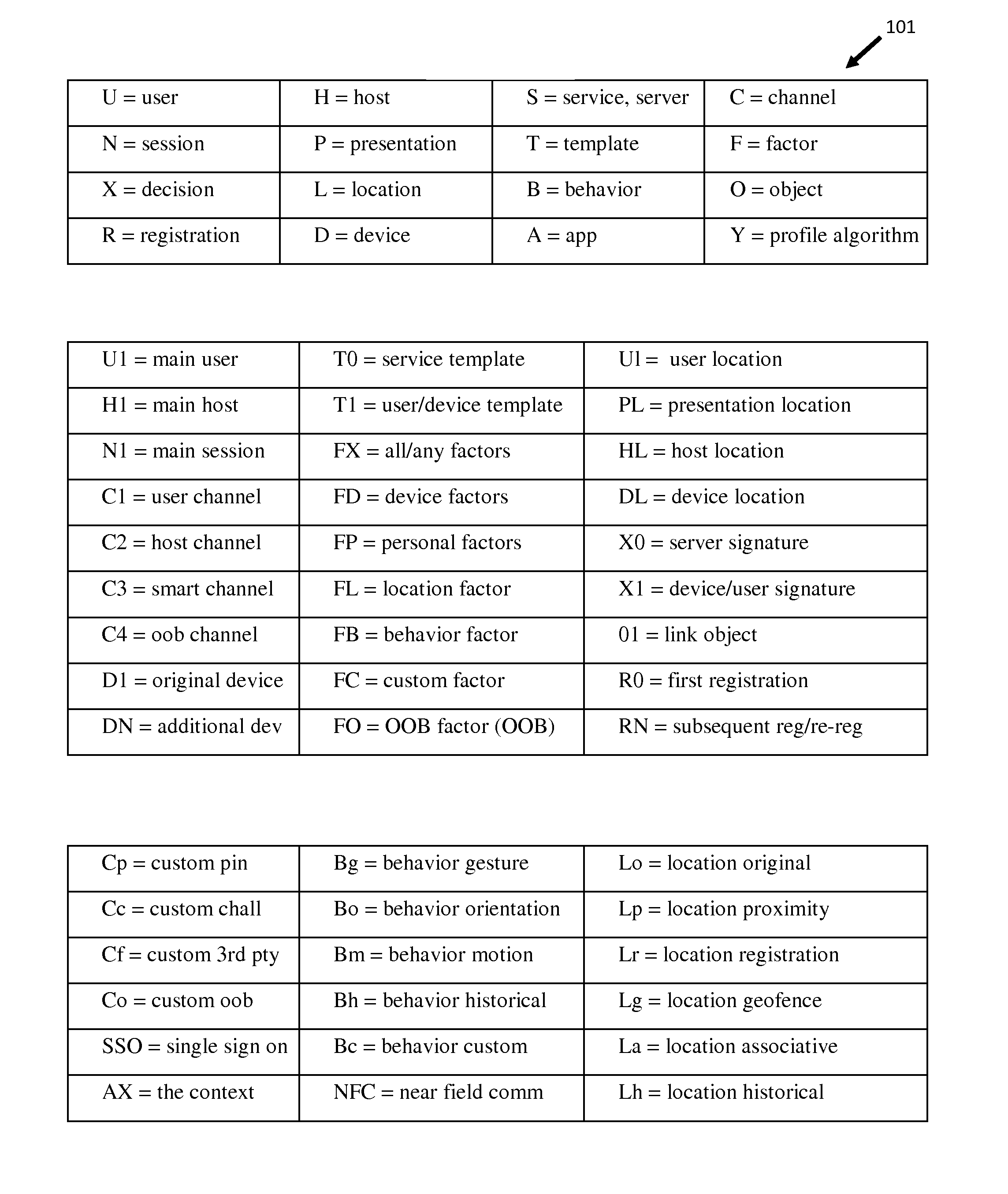
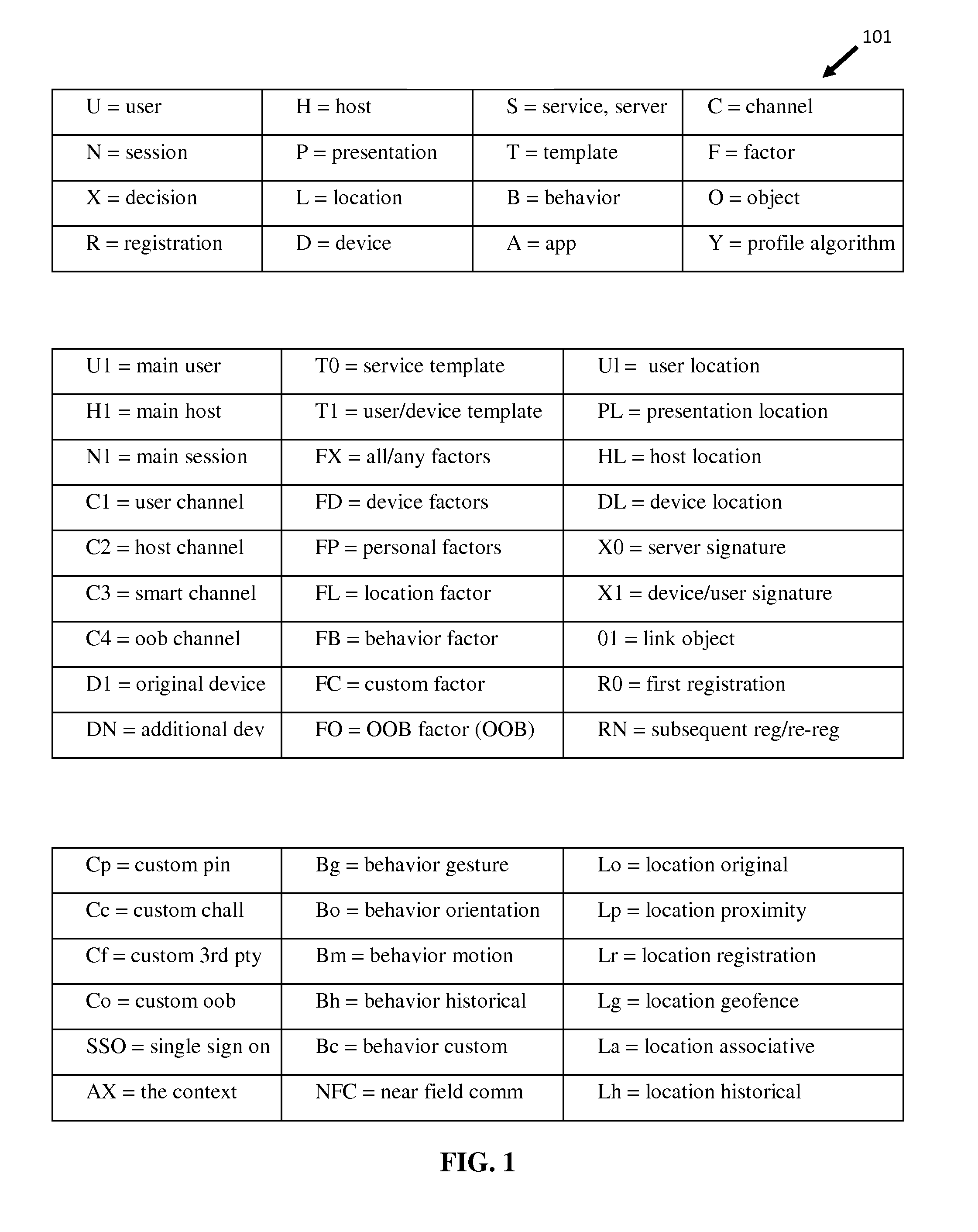
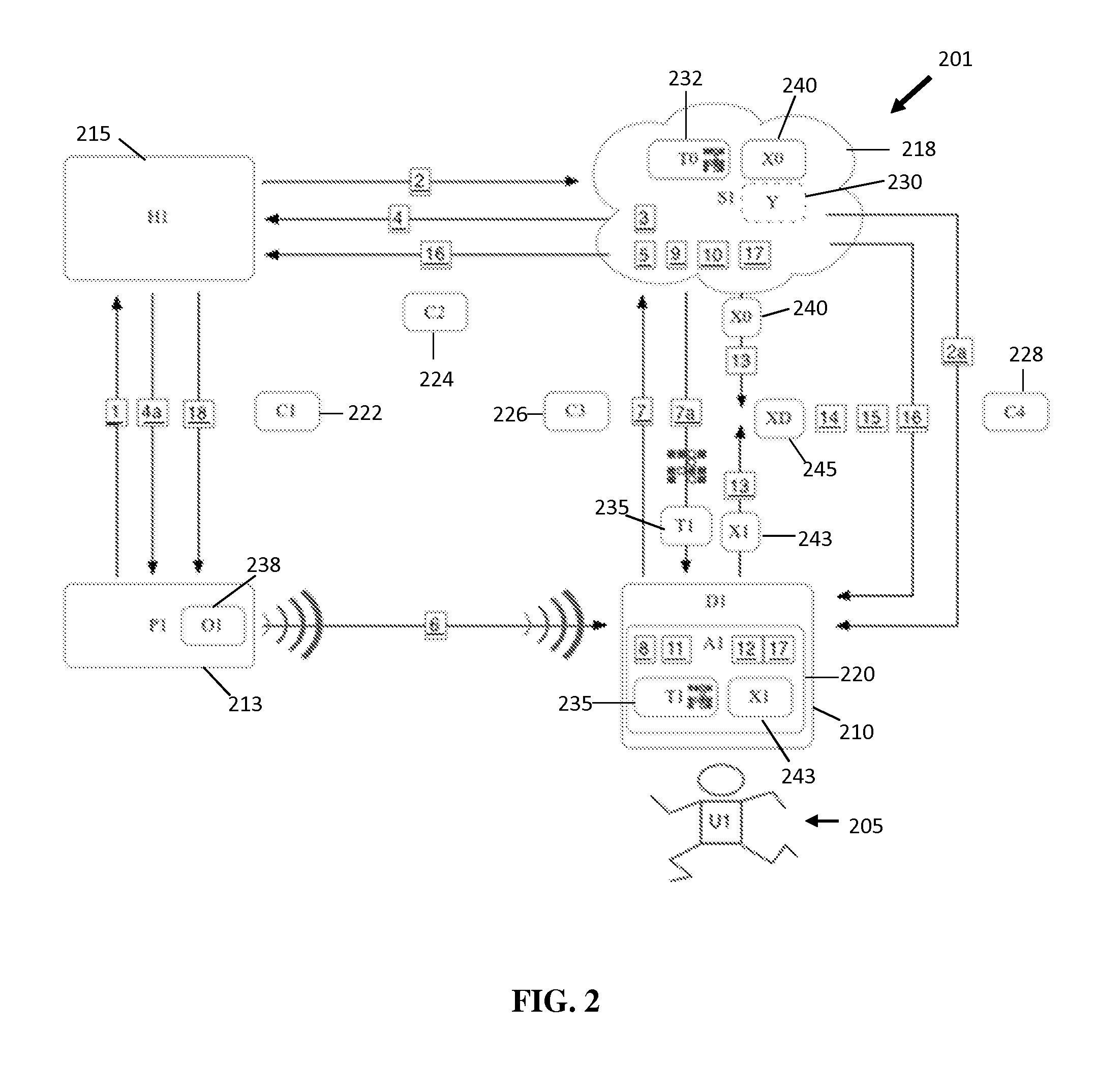
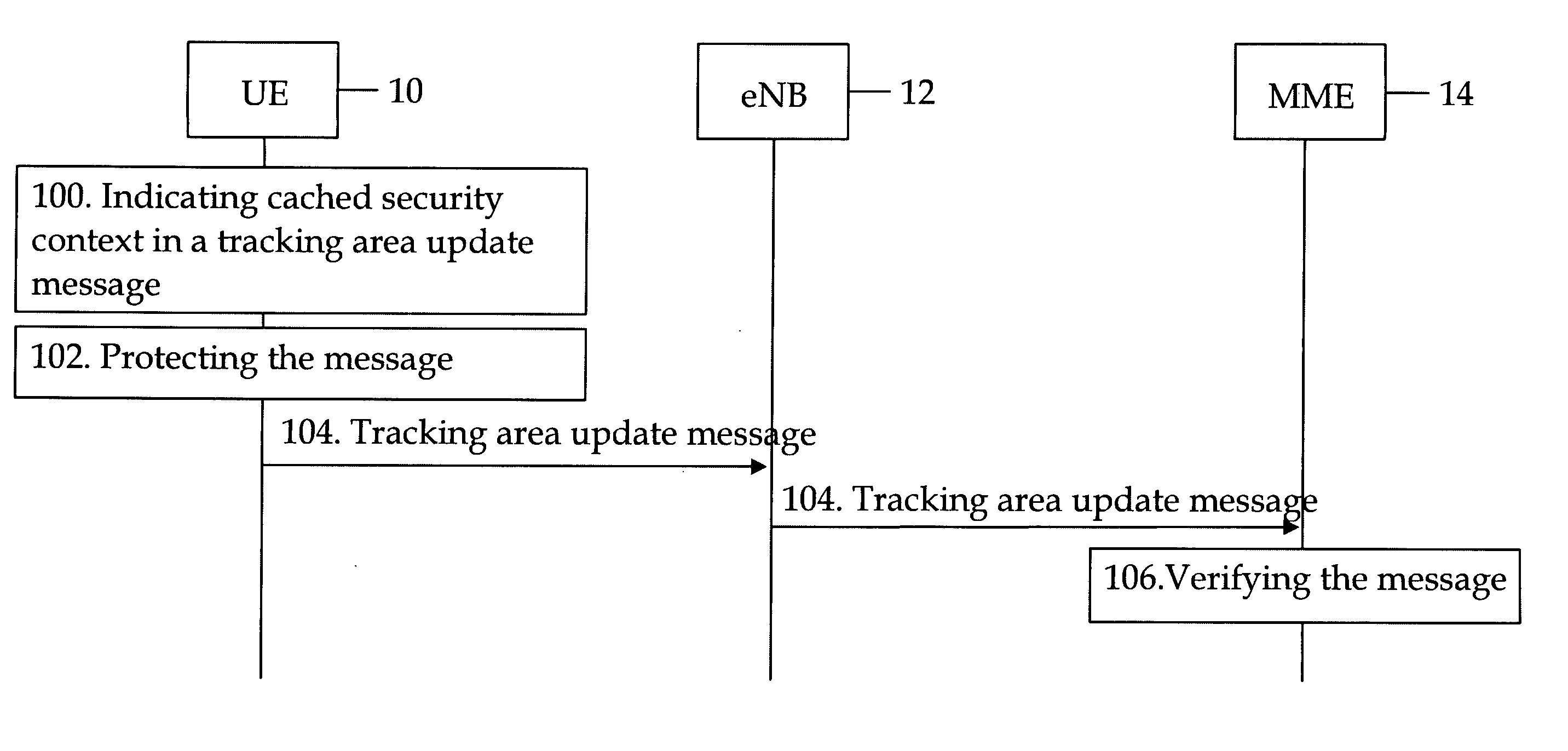
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
273 results about "Mobile security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
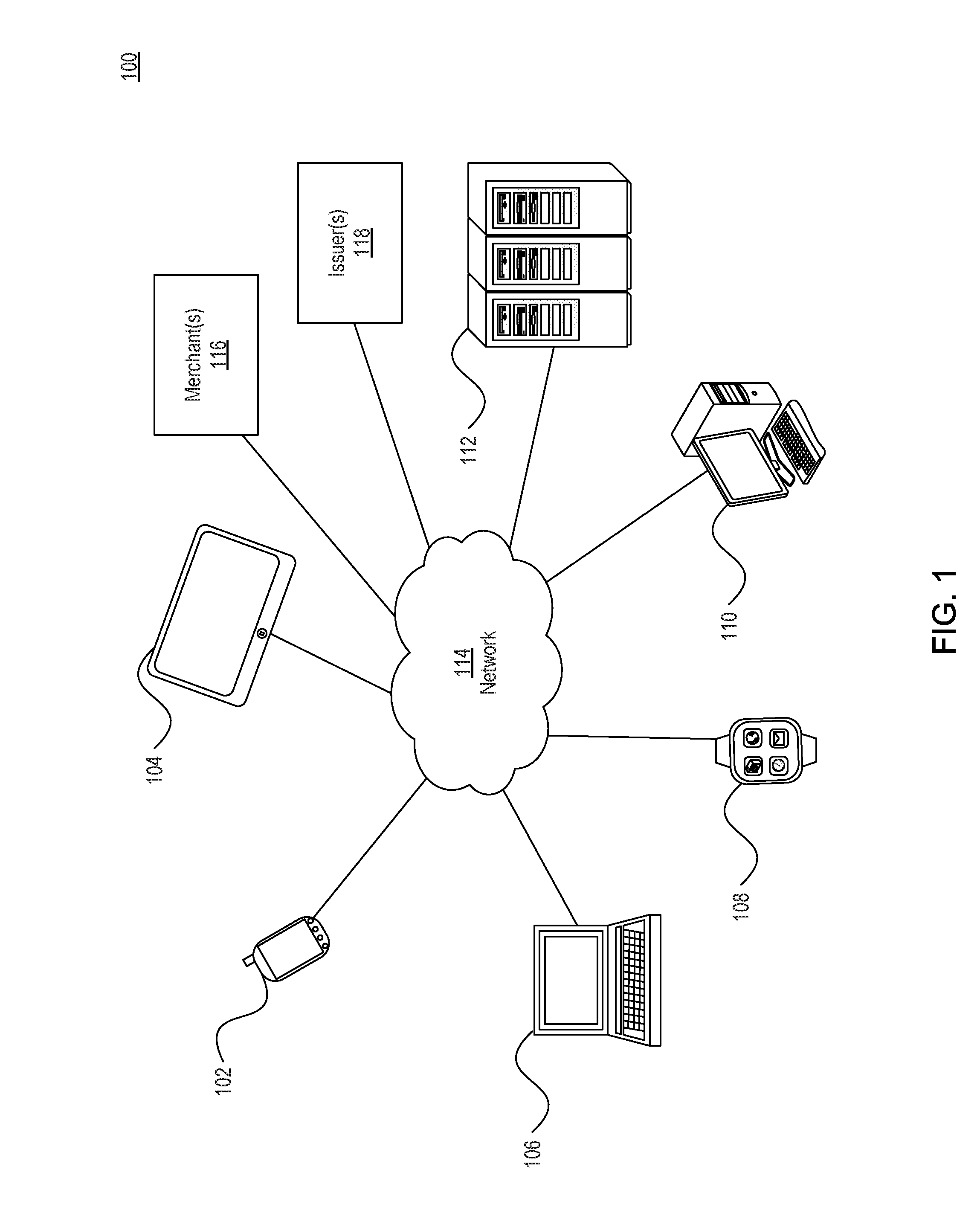
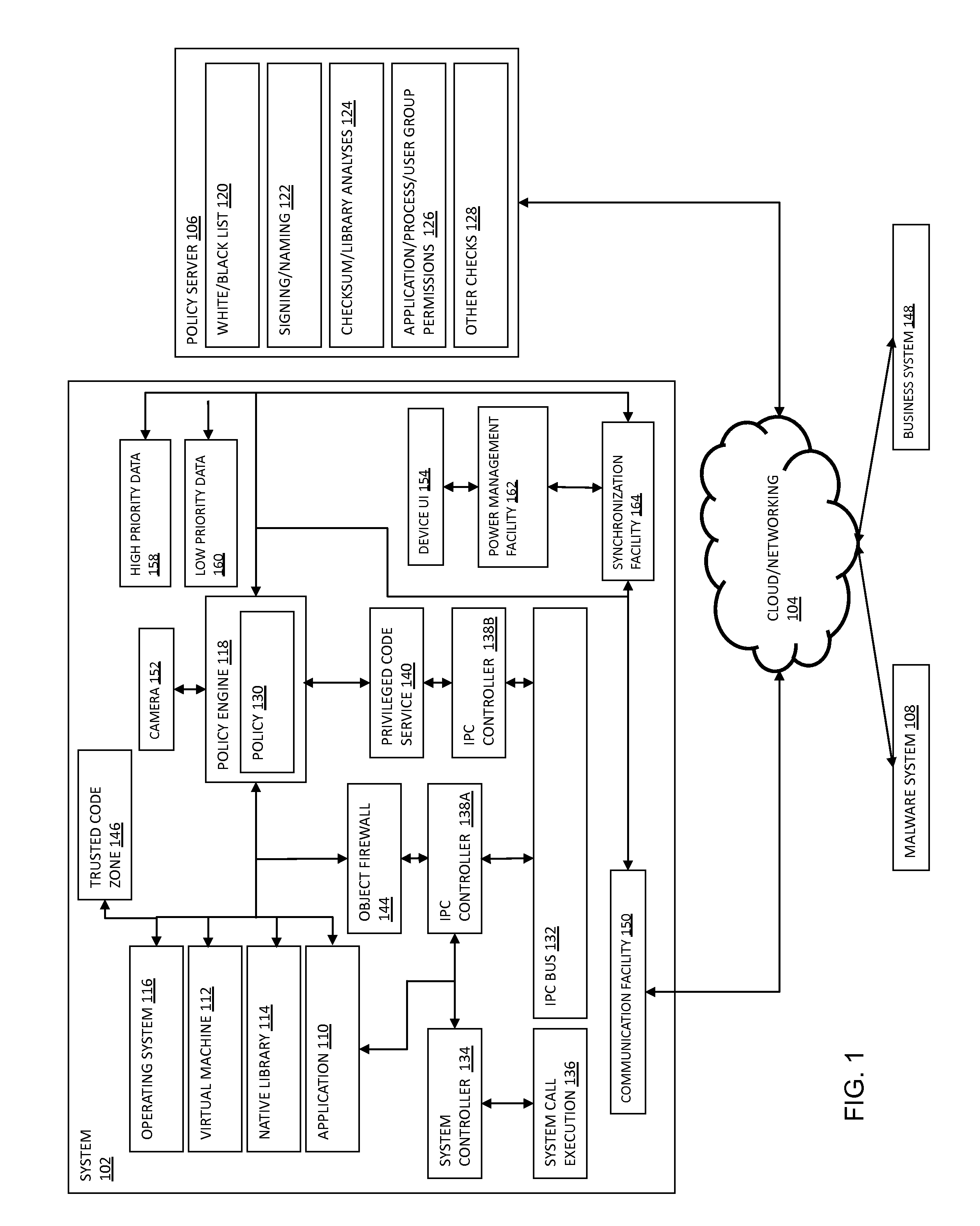
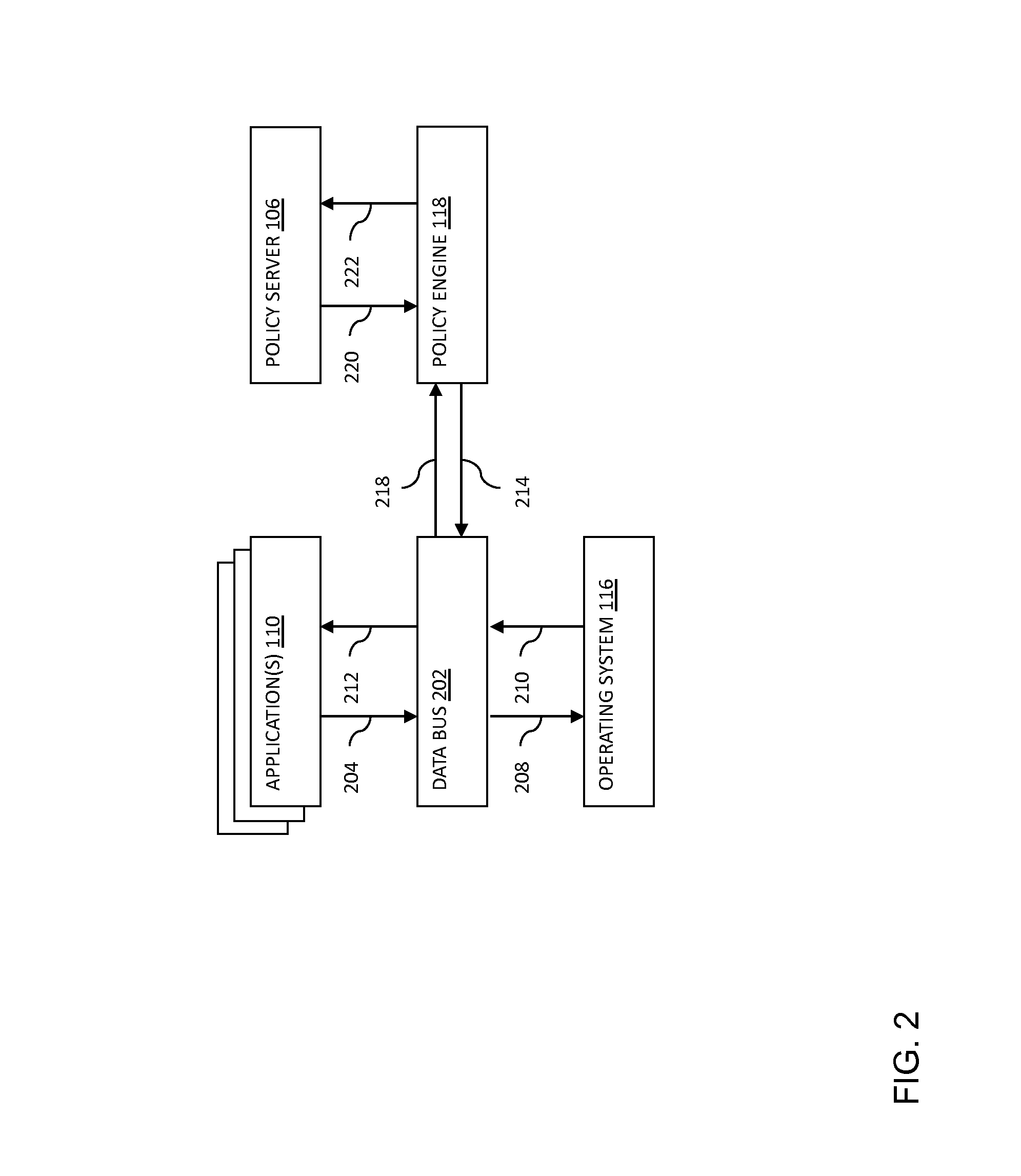
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
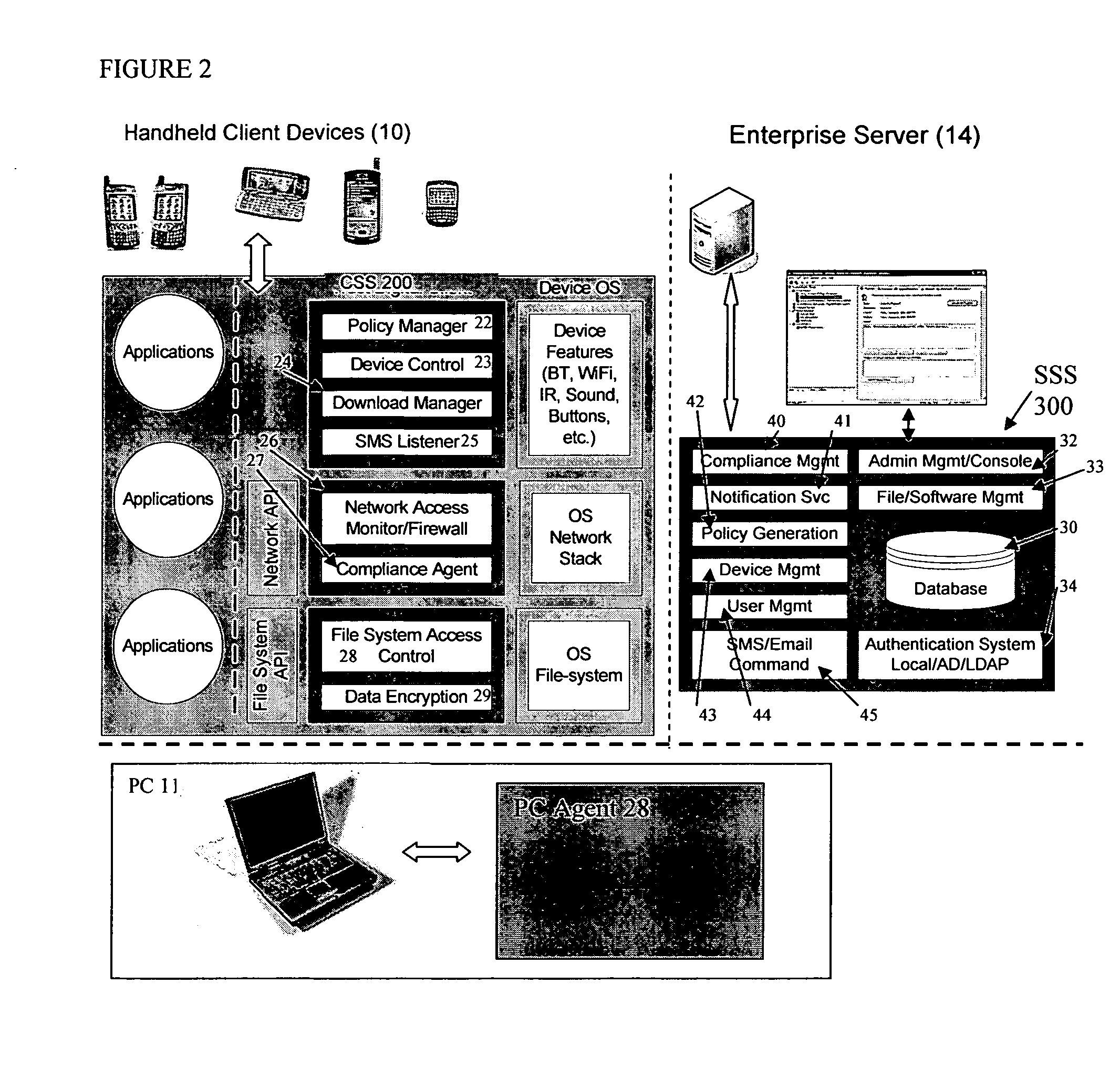
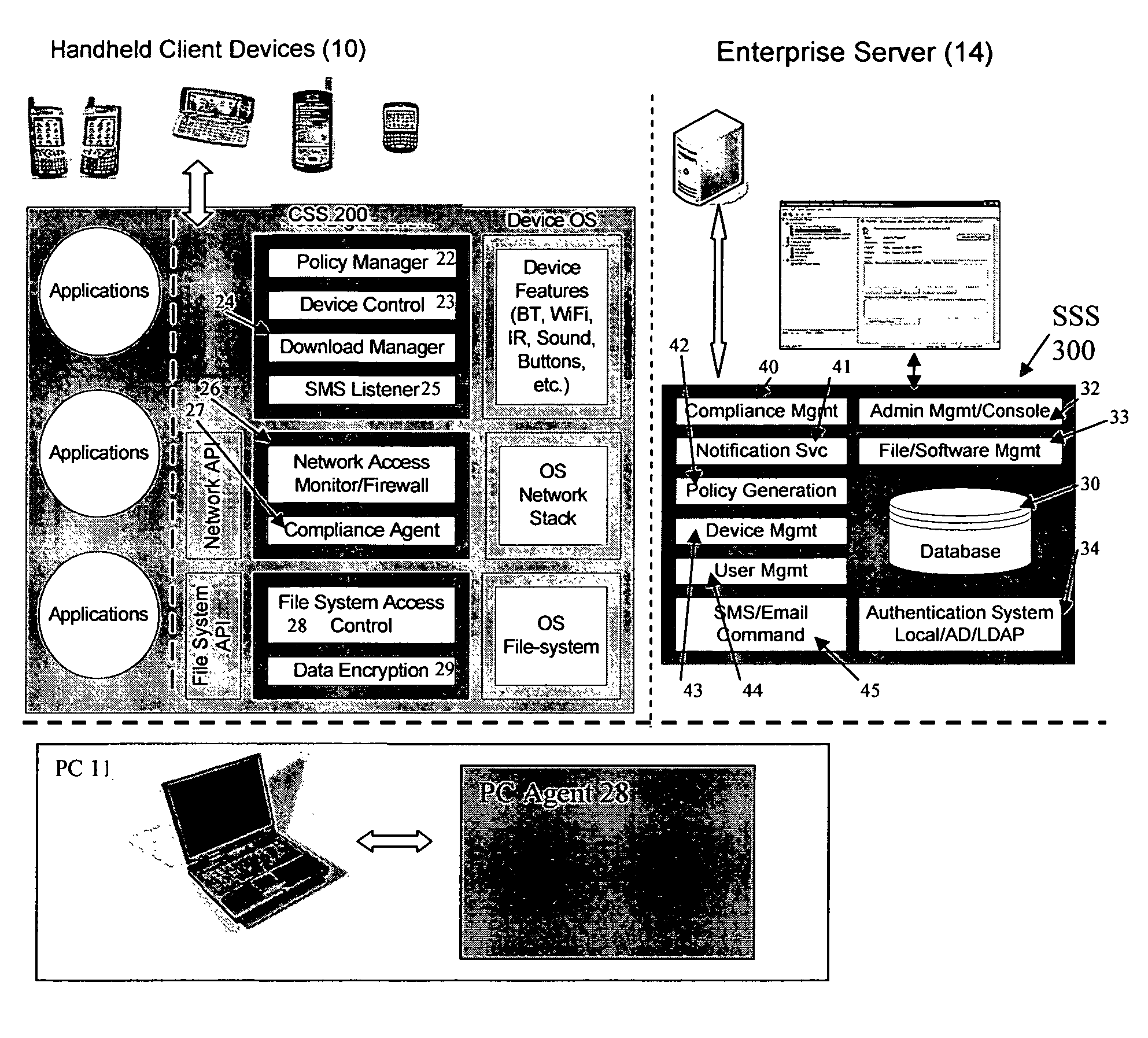
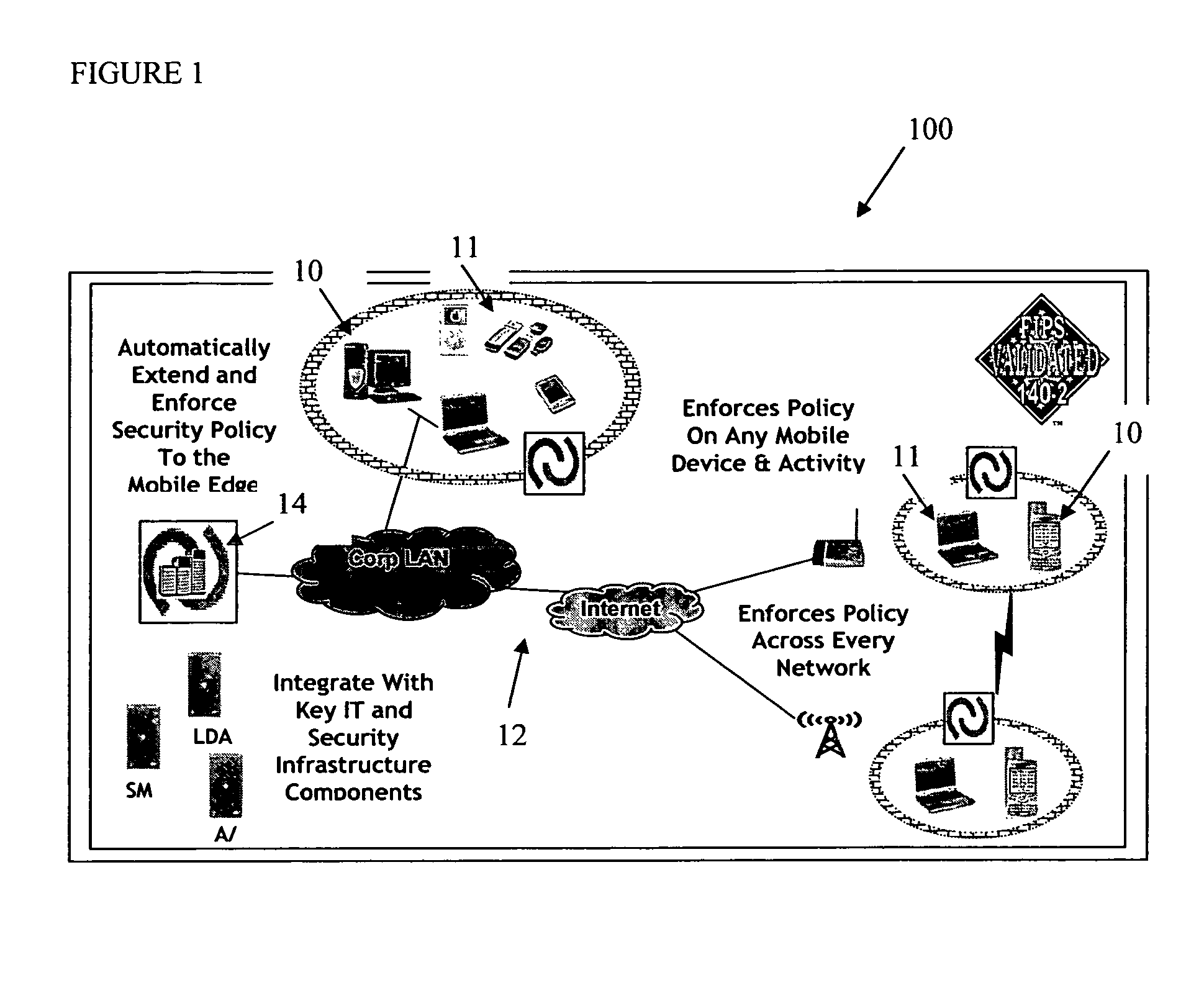
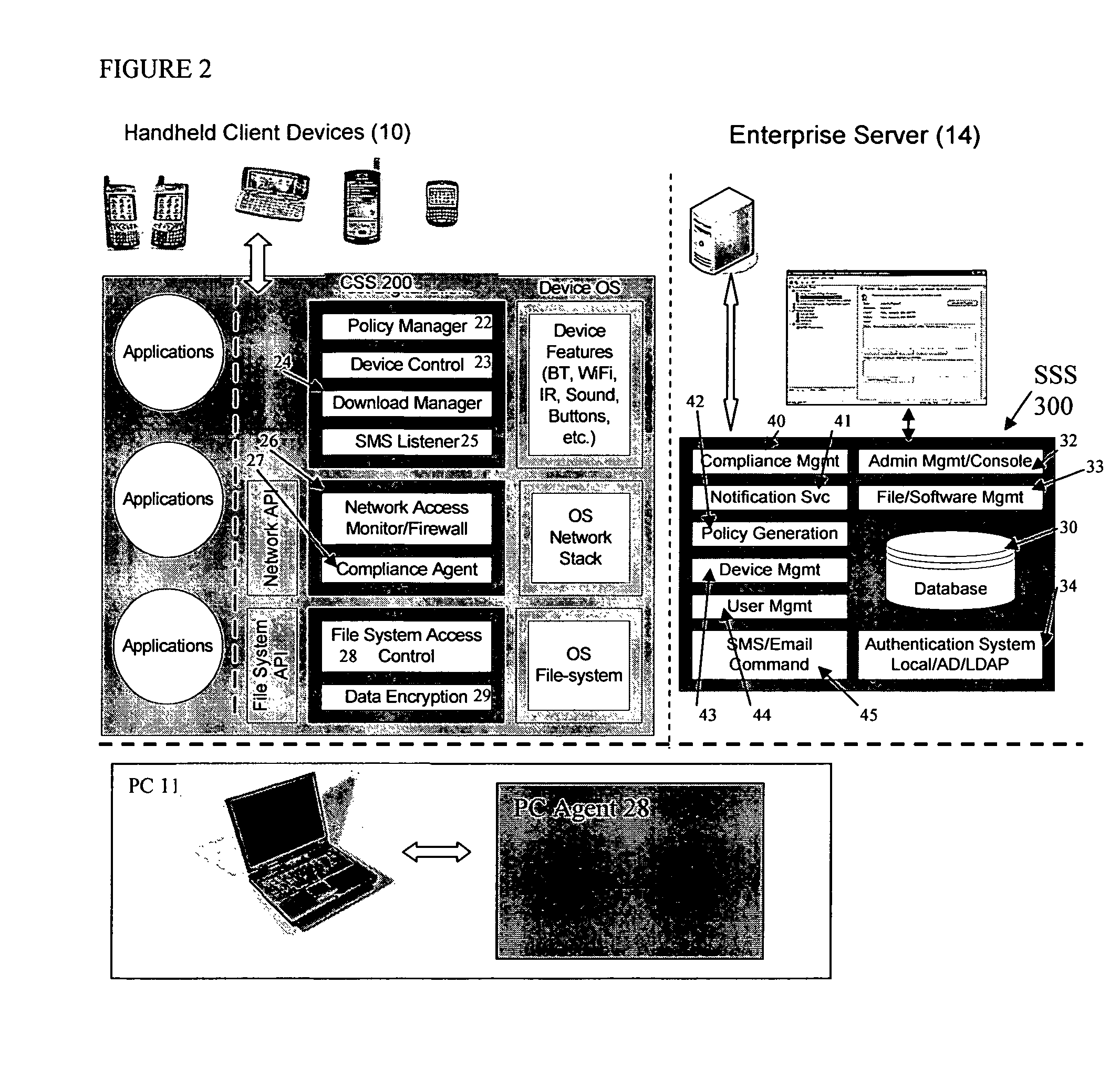
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
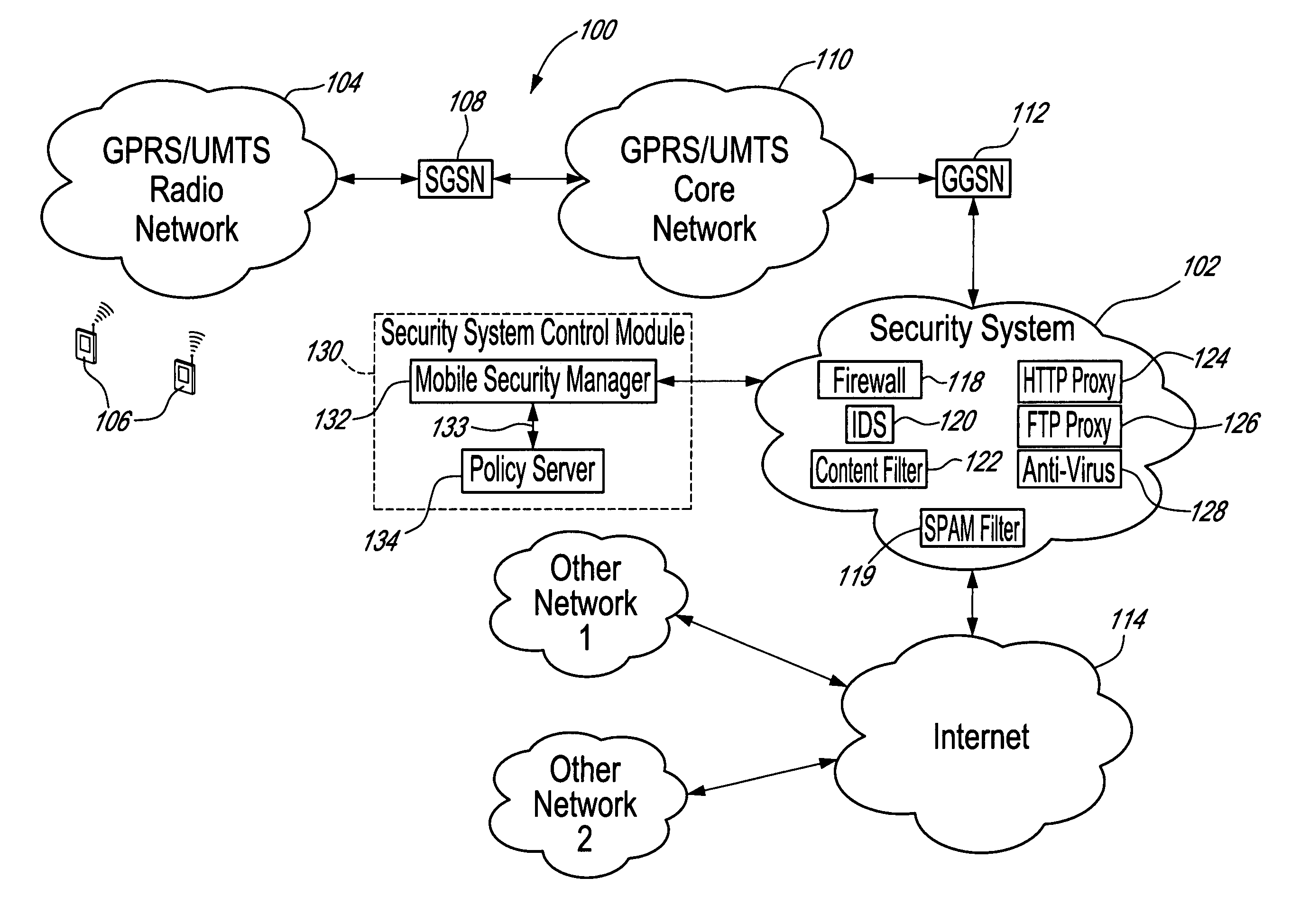
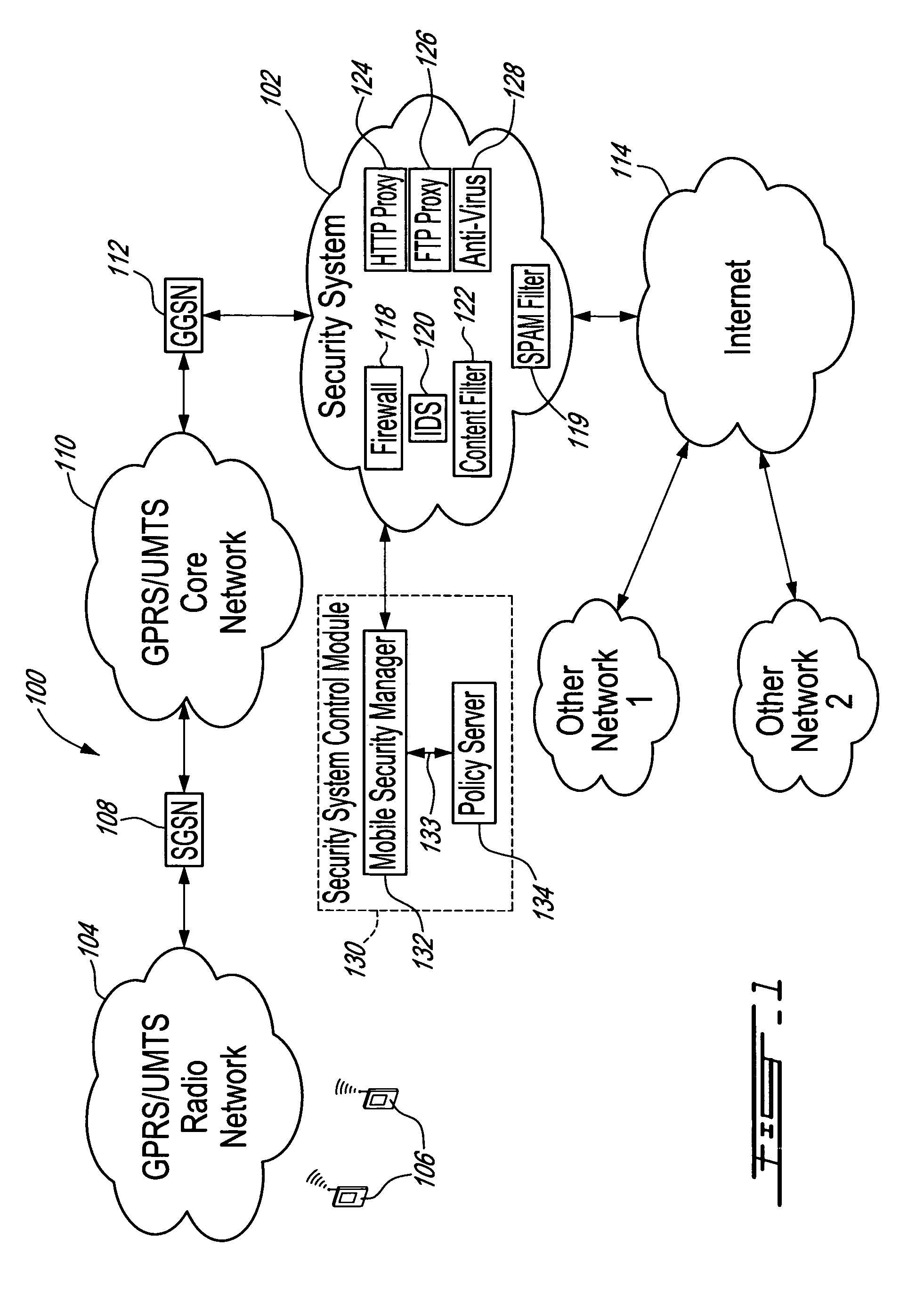
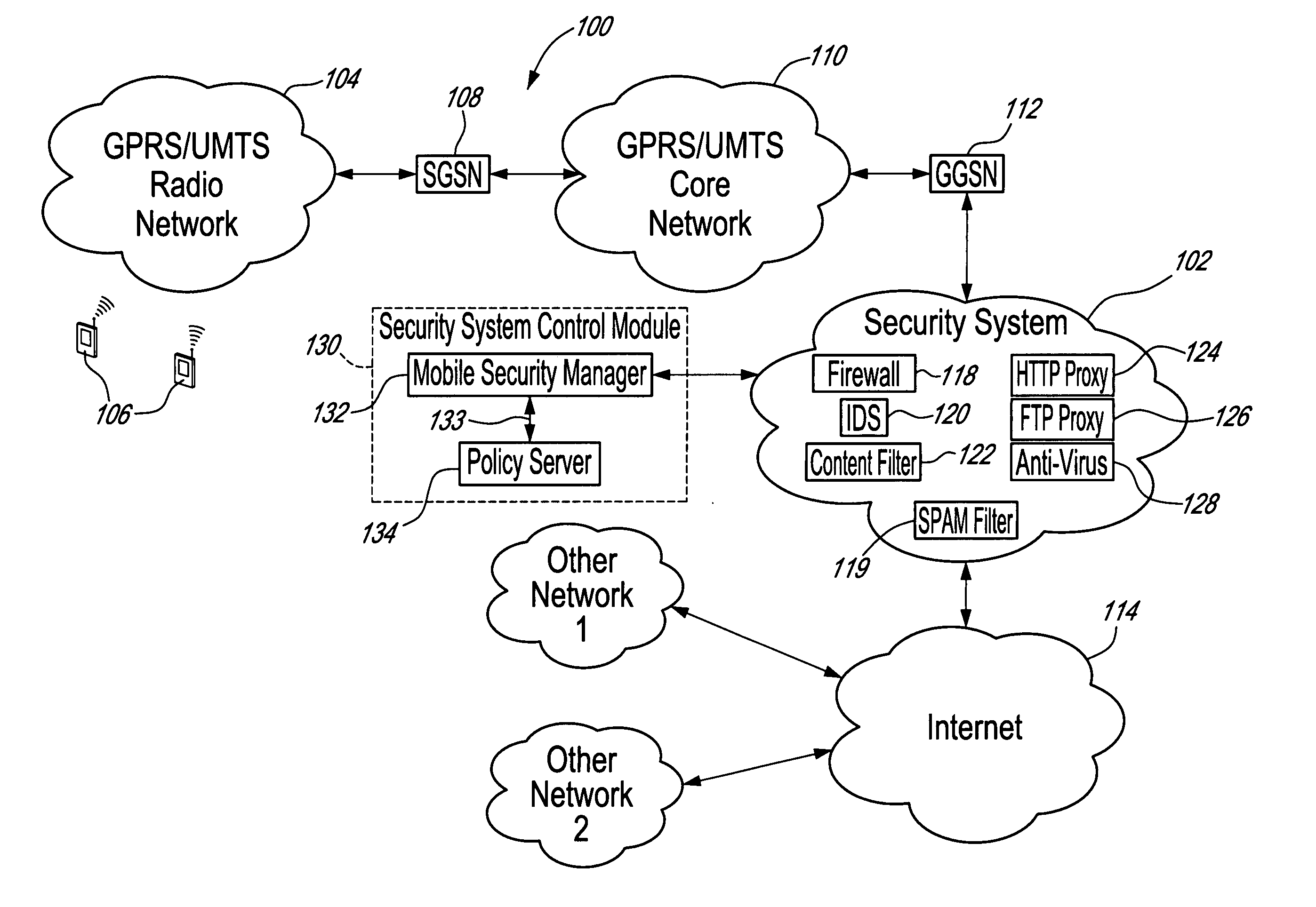
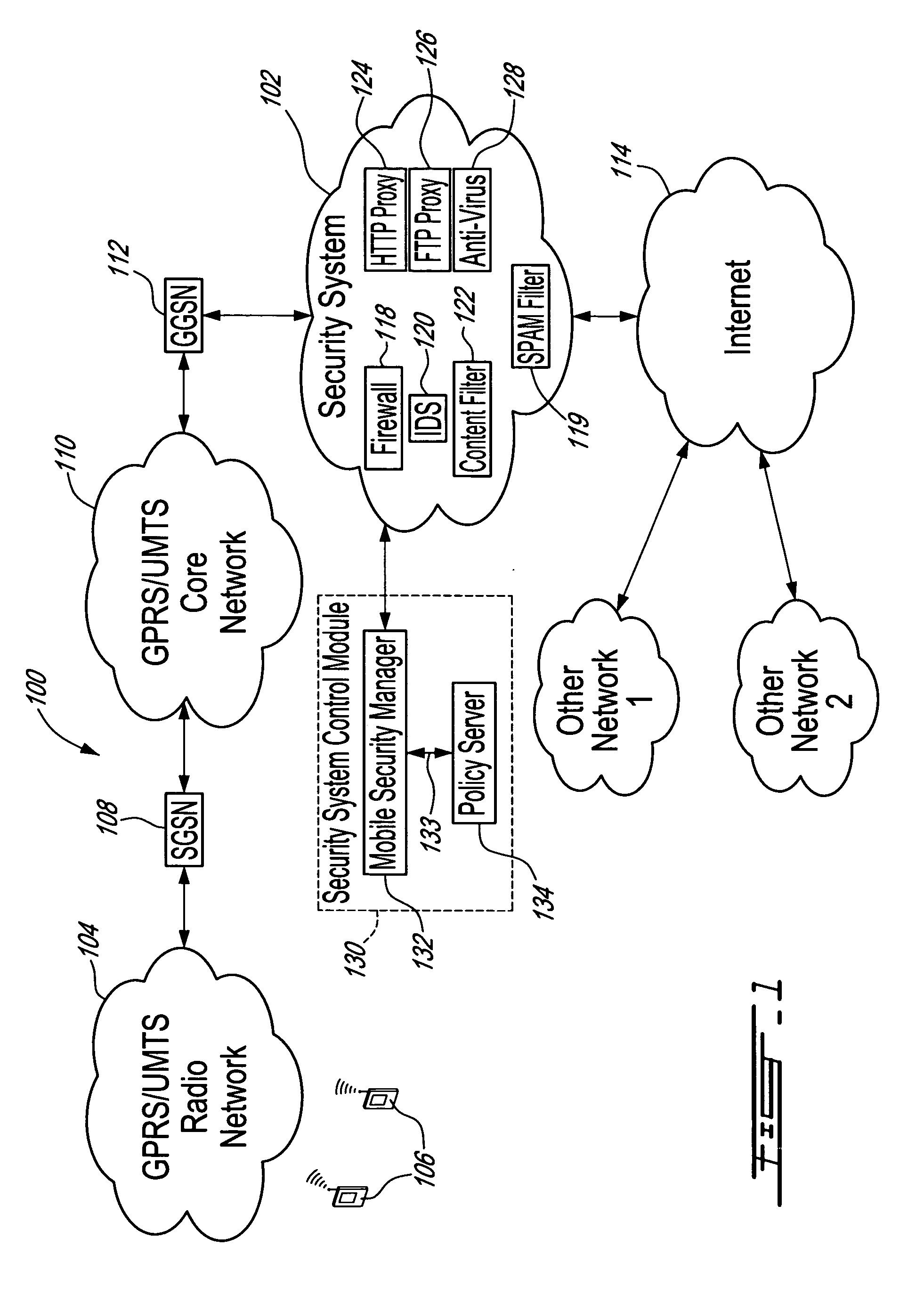
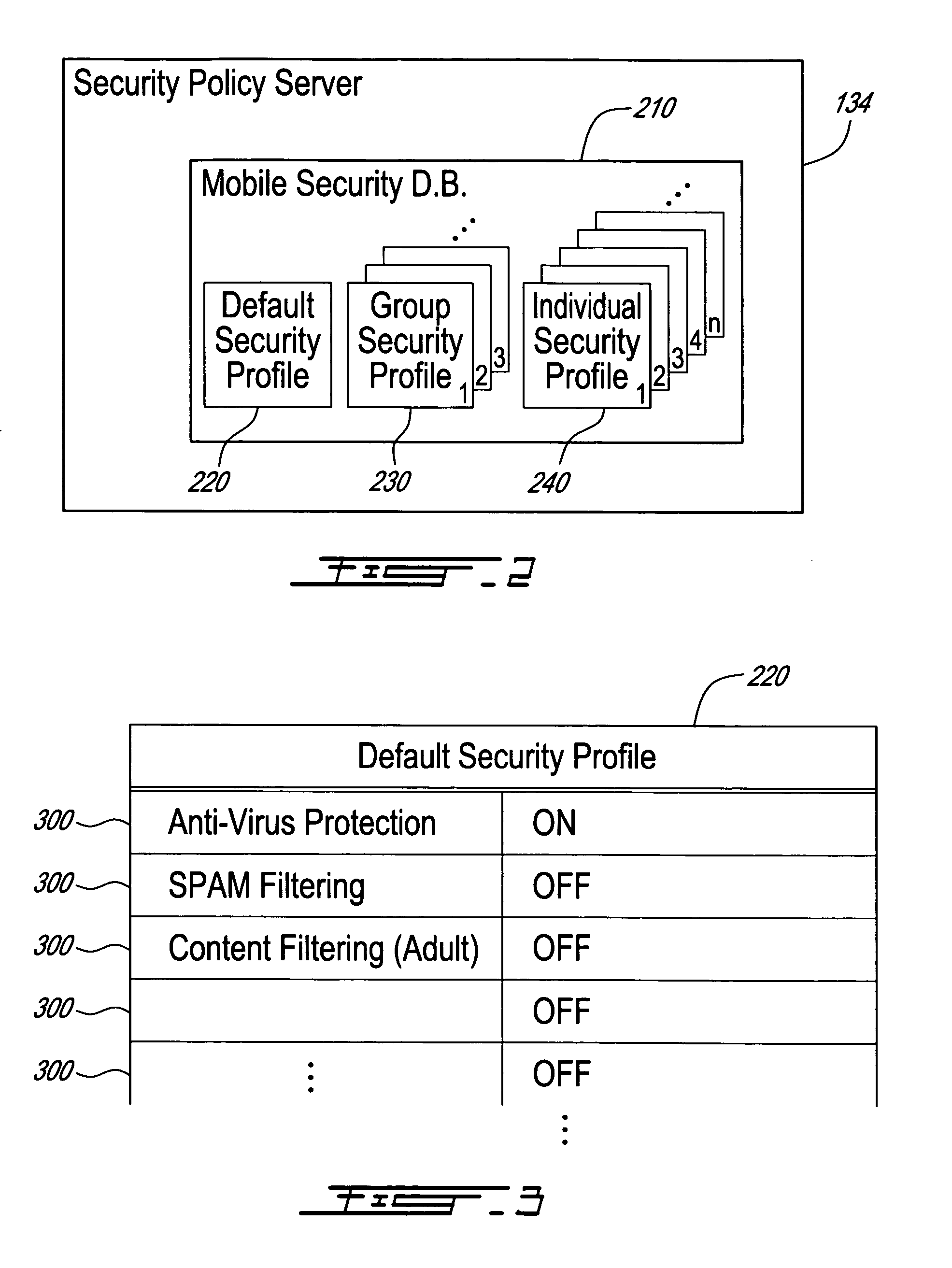
Method, security system control module and policy server for providing security in a packet-switched telecommunications system
ActiveUS7418253B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile station
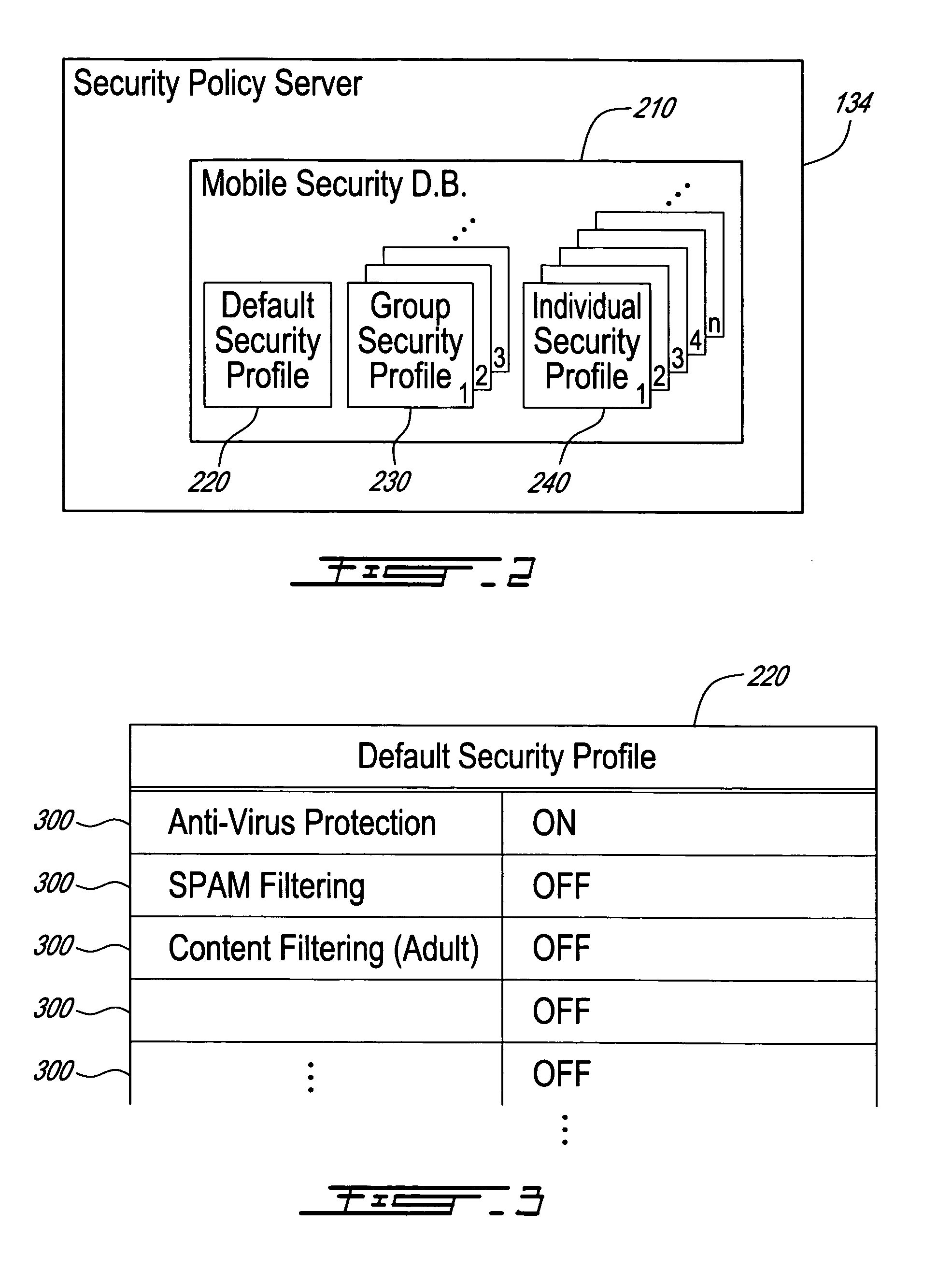
A method, security system control module and policy server for providing security for Mobile Stations (MSs) in a Packet-Switched Telecommunications System. When an MS accesses the system, its identity is sent to a security system control module that retrieves a security profile associated with the MS. A policy server of the security system control module stores individual security profiles, default security profiles and group security profiles for registered subscribers. Security settings associated with the MS security profile are returned from the policy server to a mobile security manager of the control module, which then determines if they should be propagated in the system. When no previous network access was made in a given time period by an MS having similar security settings, i.e. belongs to the same group security profile, the settings are propagated in the system in order to be enforced, for providing security protection for the MS.
Owner:TELEFON AB LM ERICSSON (PUBL)
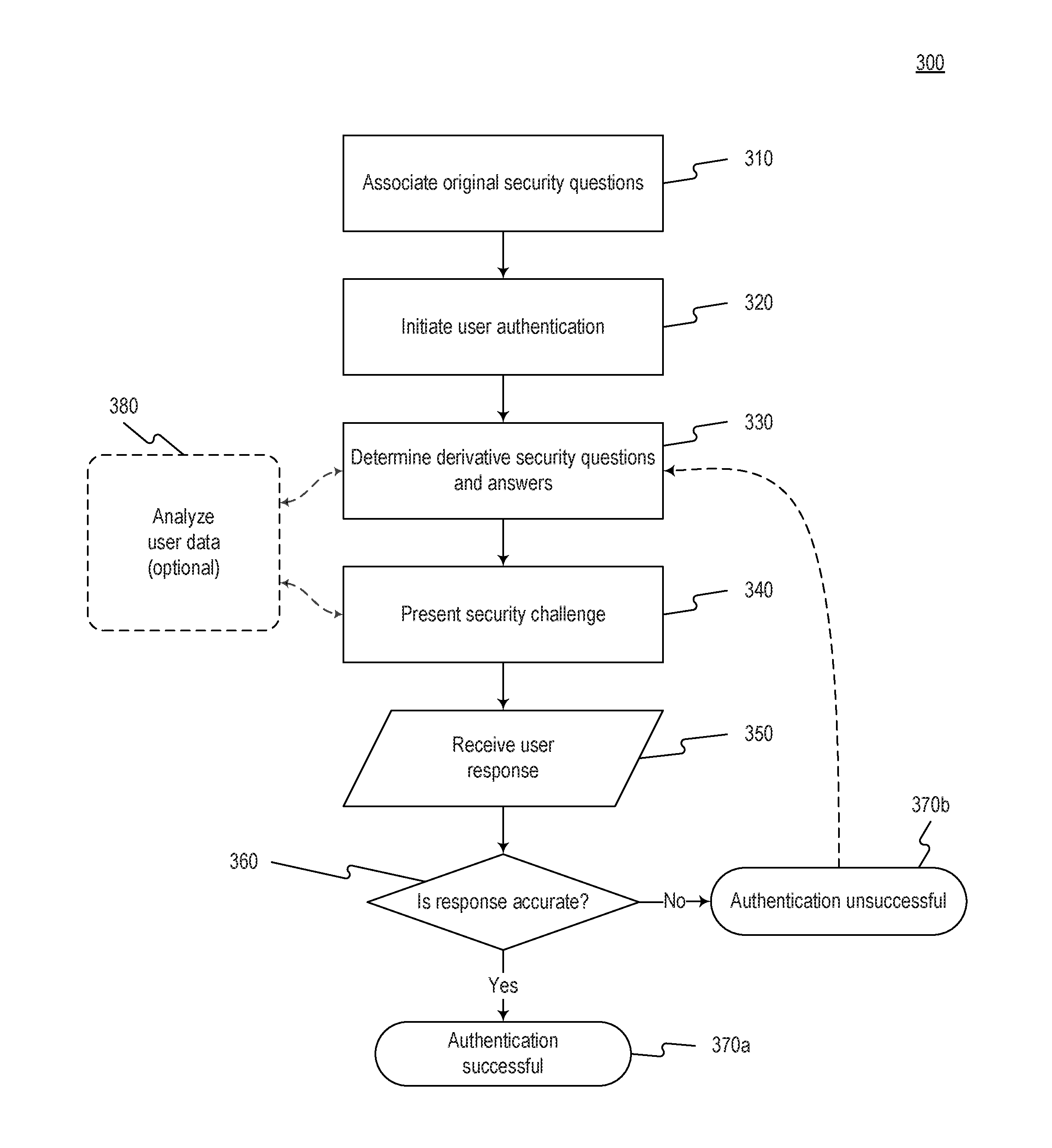
Systems and methods for derivative fraud detection challenges in mobile device transactions
InactiveUS20160381560A1Improve identification and verificationImprove experienceDigital data processing detailsMultiple digital computer combinationsInternet privacyMobile transaction
The disclosed embodiments include systems, methods, and computer-readable media configured to provide mobile device transaction security. The techniques described in the disclosed embodiments may be used to verify a mobile device user by providing derivative fraud protection challenges. Thus, the techniques may be used to improve identification and verification of users during mobile transactions. As a result, the disclosed embodiments improve mobile security and user experience as well as enhance access control.
Owner:OFFLA SELFSAFE
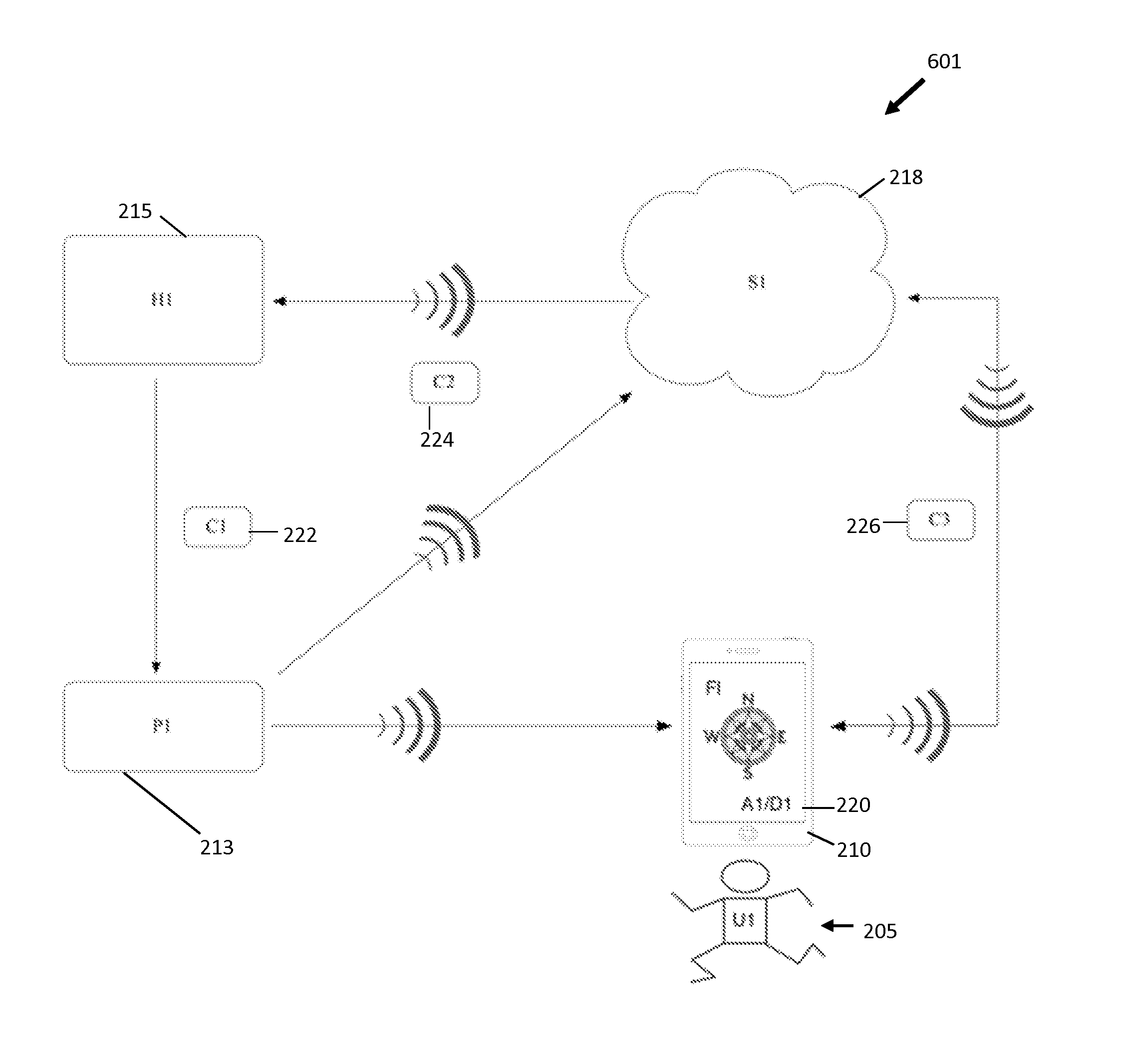
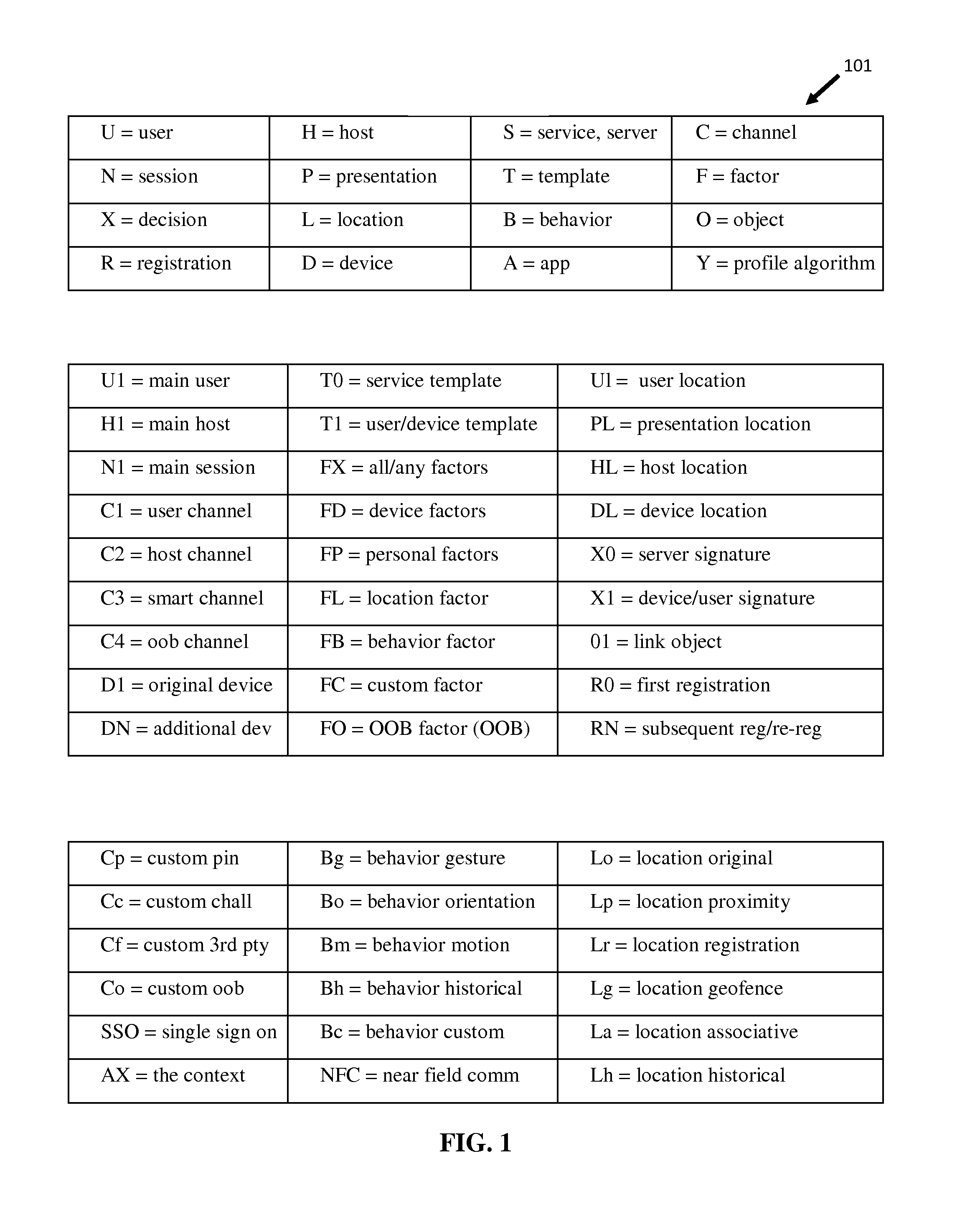
Method for mobile security context authentication
ActiveUS20140096215A1Easy to solveDigital data processing detailsMultiple digital computer combinationsMobile securityMobile electronics
The present invention is a system and a method for improving the authentication security across a network from a mobile electronic computing device in the context of one or more users, devices, sites / sessions, servers, locations, proximity, motion and / or behavioral attributes within a defined session lifecycle. The authentication method and system utilizes a strong, elegant, private, definitive and real-time, triangulated verification, which requires mutual authentication between the parties.
Owner:LIVE ENSURE LTD
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
Systems and methods for providing mobile security based on dynamic attestation
ActiveUS20130298242A1Memory loss protectionError detection/correctionMobile securityApplication software
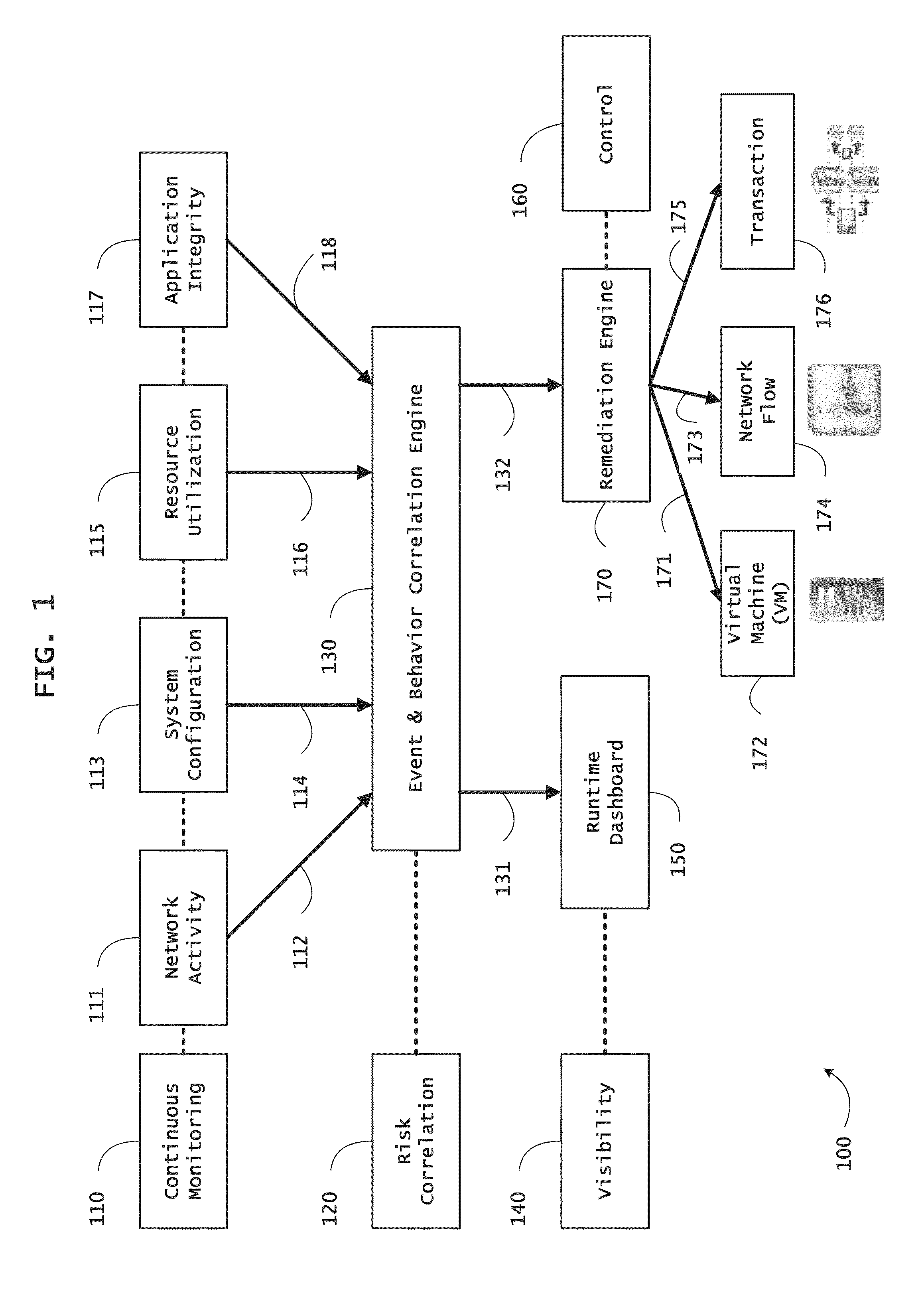
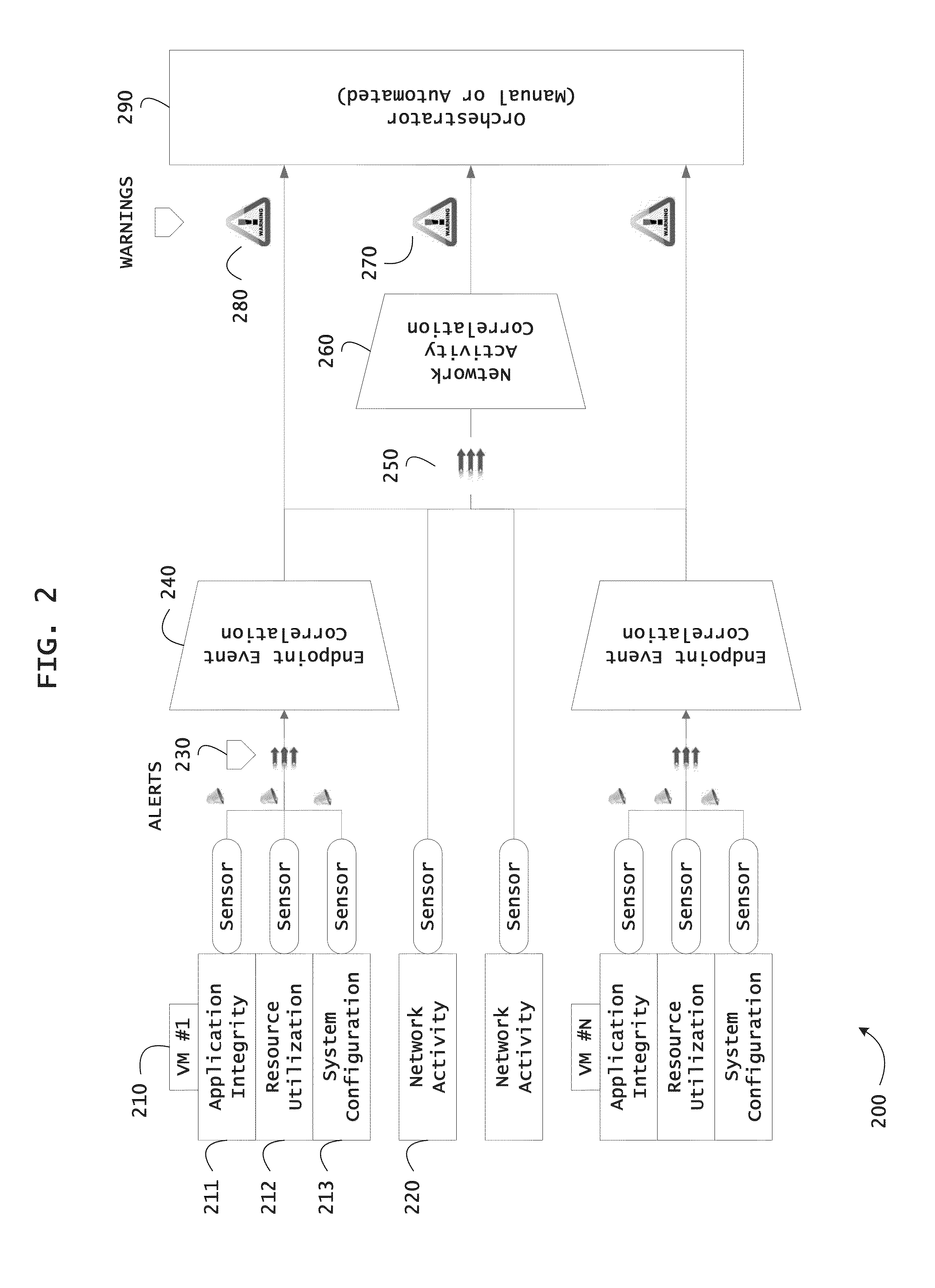
Instrumented networks, machines and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects (including mobile devices) and applications on the instrumented target platform. Methods and systems are disclosed for dynamic attestation of mobile device integrity based upon subject reputation scores. In an embodiment, a method scores trustworthiness of a mobile device based on reputation scores for users associated with the device and / or a device reputation score. The method generates runtime integrity alerts regarding execution anomalies for applications executing on the device, calculates risks based on a ruleset, and determines a calculus of risk for the device. The method sends endpoint events comprising data and content of the integrity warnings to a trust orchestrator, which generates an integrity profile based on the endpoint events.
Owner:TAASERA LICENSING LLC
System for mobile security
InactiveUS20130298208A1High correlationModulated-carrier systemsDigital data processing detailsMobile securityData security
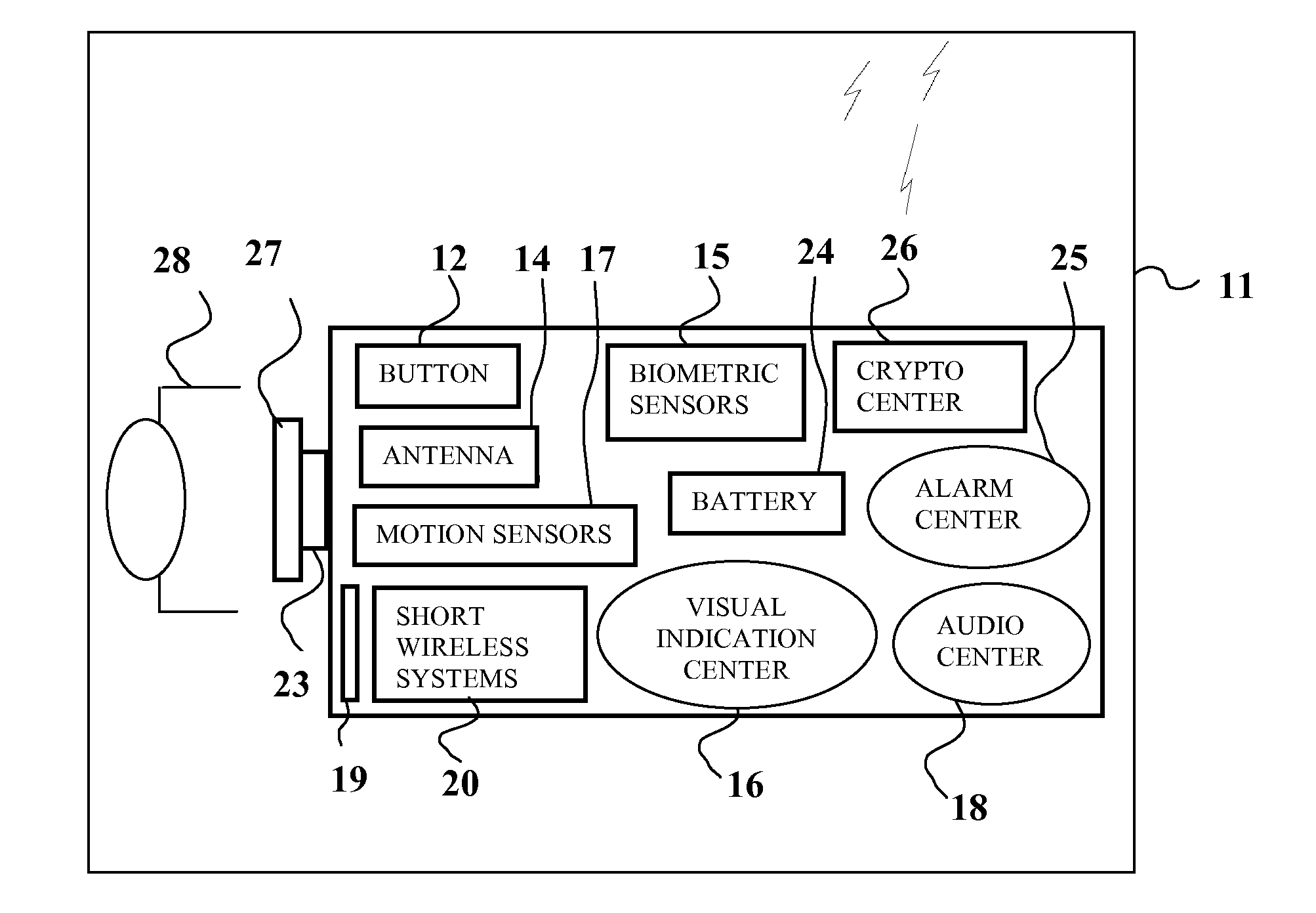
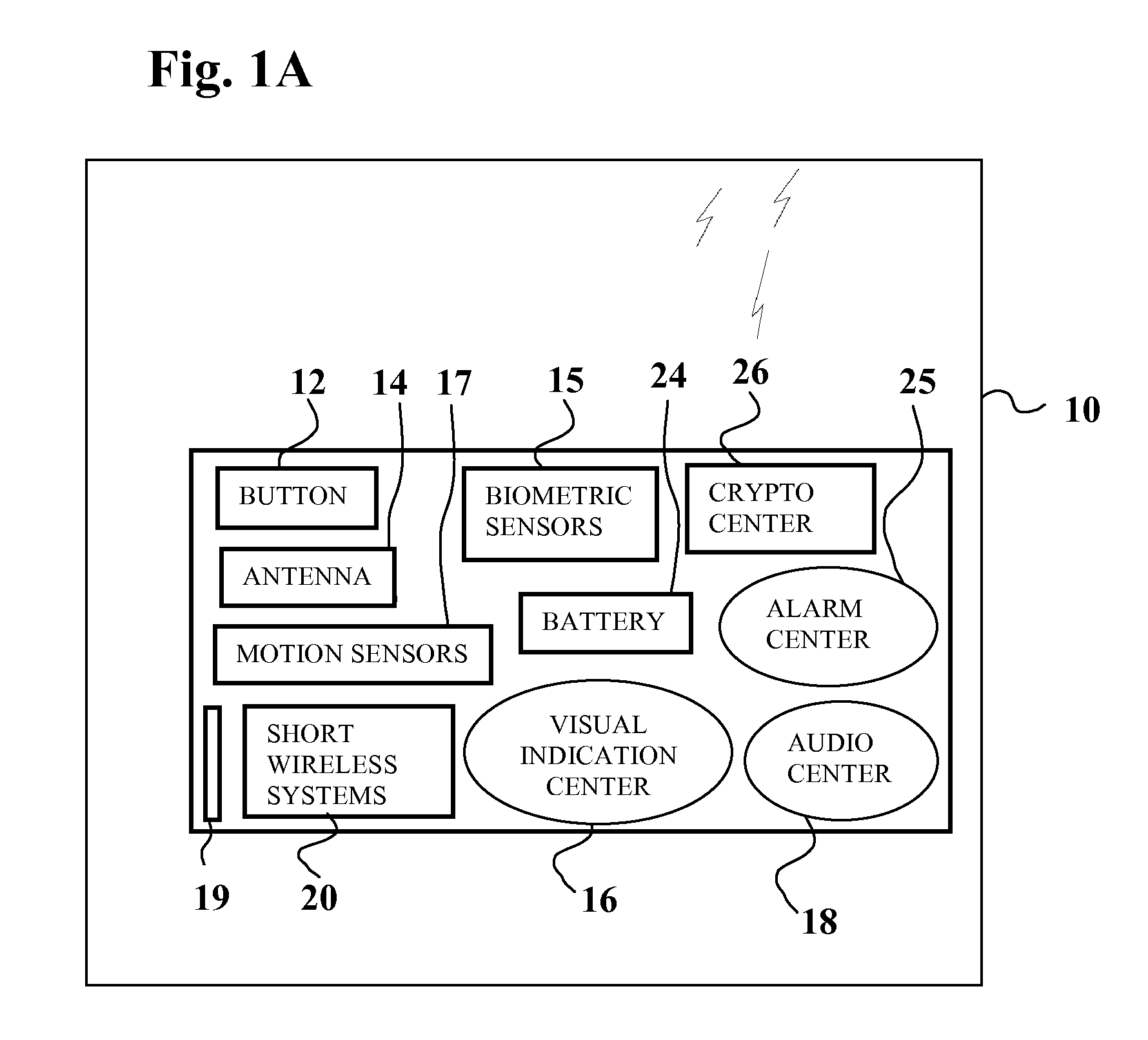
A method and apparatus for mobile security using a short wireless device. The method and device increases mobile device security and data security and reduces false alerts.
Owner:AYED MOURAD BEN
Distributed, multi-tenant virtual private network cloud systems and methods for mobile security and policy enforcement
ActiveUS8464335B1Computer security arrangementsMultiple digital computer combinationsCloud systemsPrivate network
The present disclosure provides distributed, multi-tenant Virtual Private Network (VPN) cloud systems and methods for mobile security and user based policy enforcement. In an exemplary embodiment, plural mobile devices are configured to connect to one or more enforcement or processing nodes over VPN connections. The enforcement or processing nodes are configured to perform content filtering, policy enforcement, and the like on some or all of the traffic from the mobile devices. The present invention is described as multi-tenant as it can connect to plural clients across different companies with different policies in a single distributed system. Advantageously, the present invention allows smartphone and tablet users to protect themselves from mobile malware, without requiring a security applications on the device. It allows administrators to seamless enforce policy for a user regardless of the device or network they are connecting to, as well as get granular visibility into the user's network behavior.
Owner:ZSCALER INC
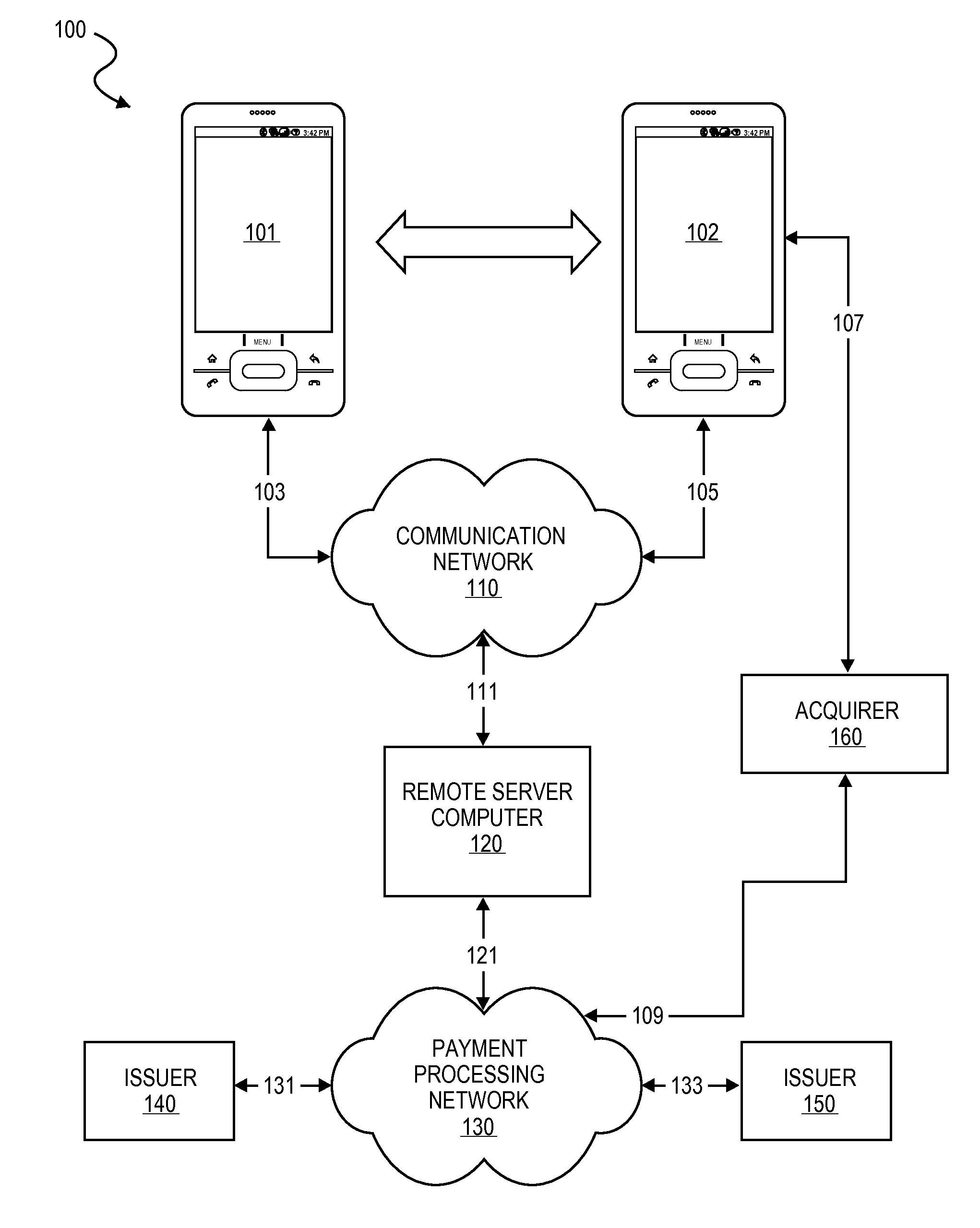
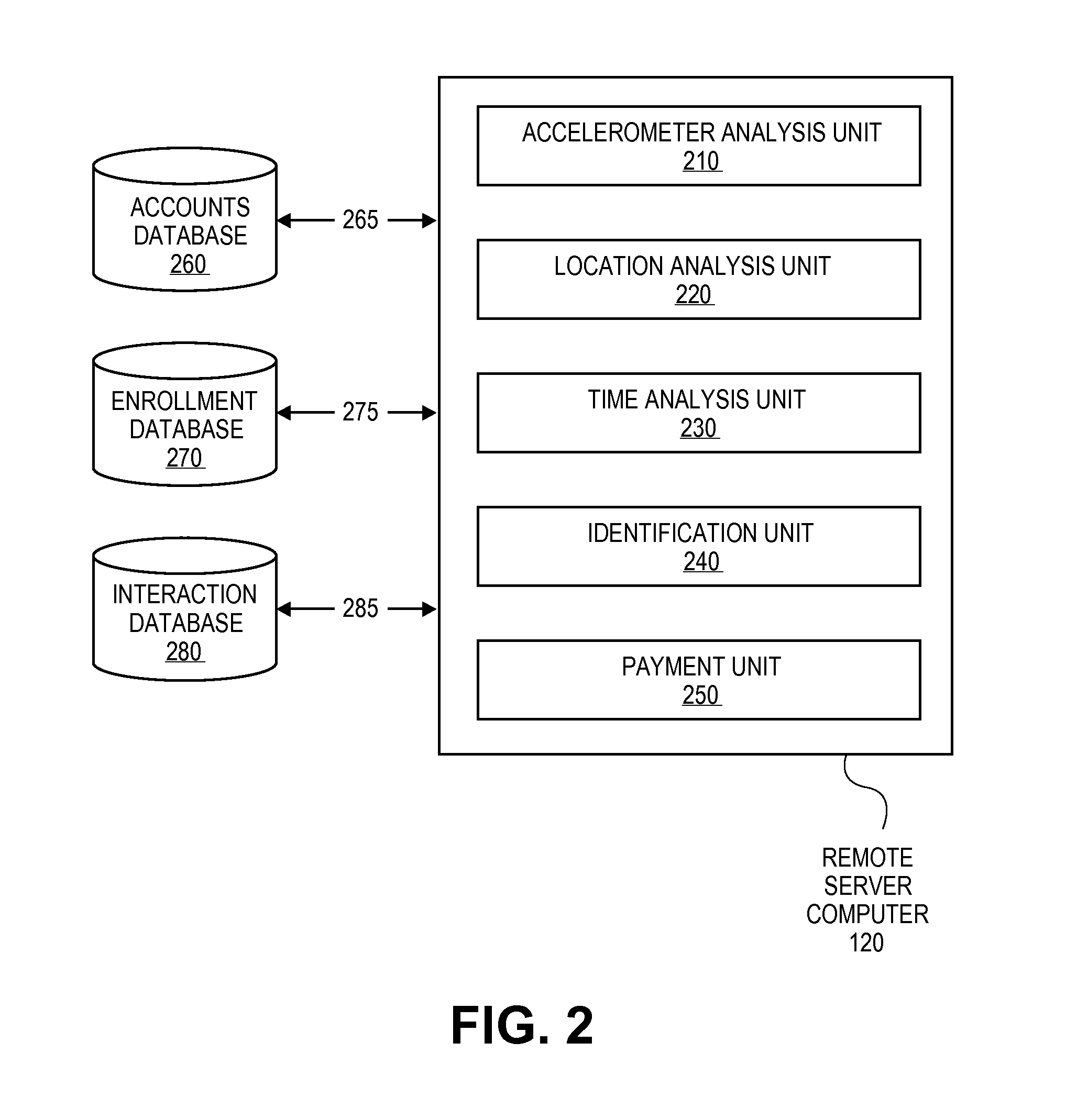
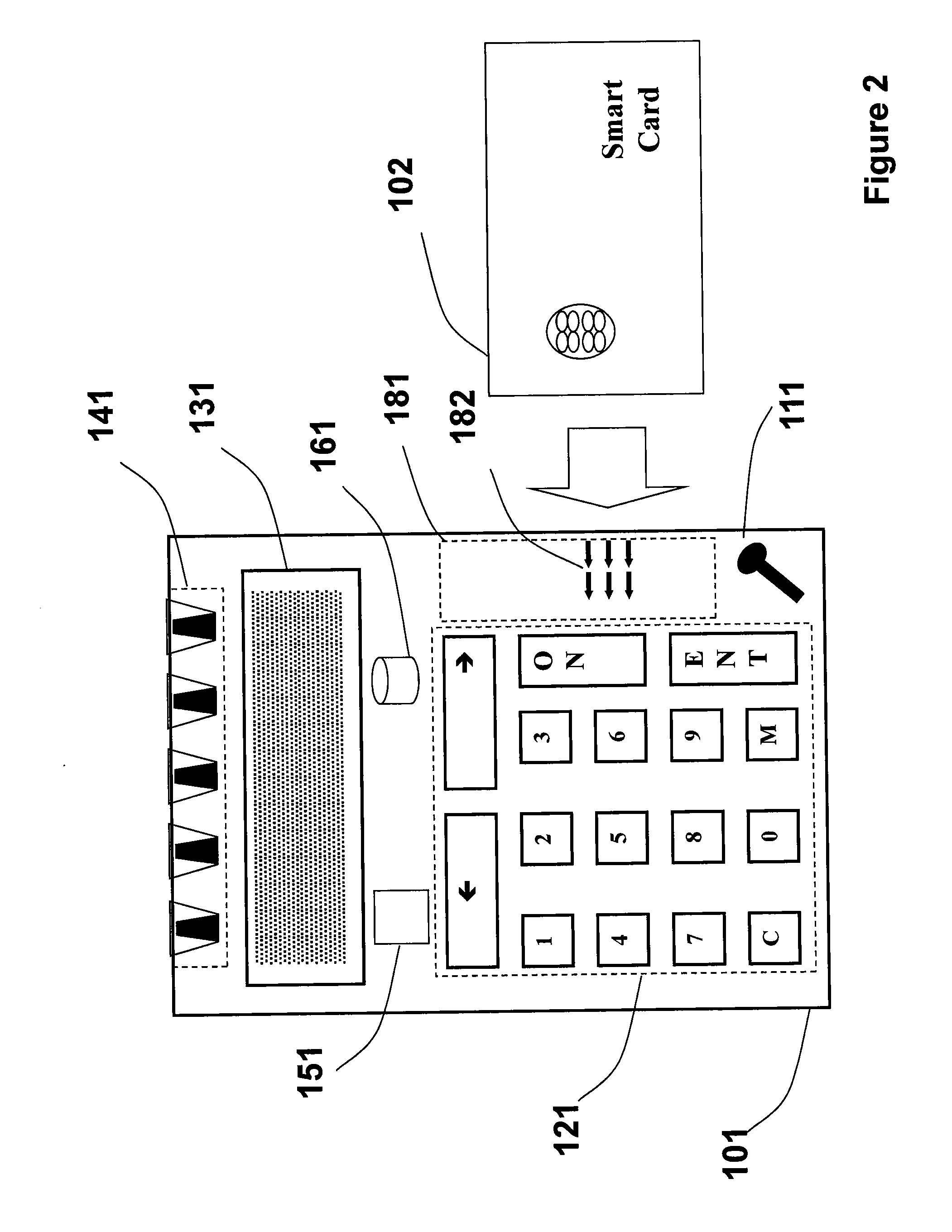
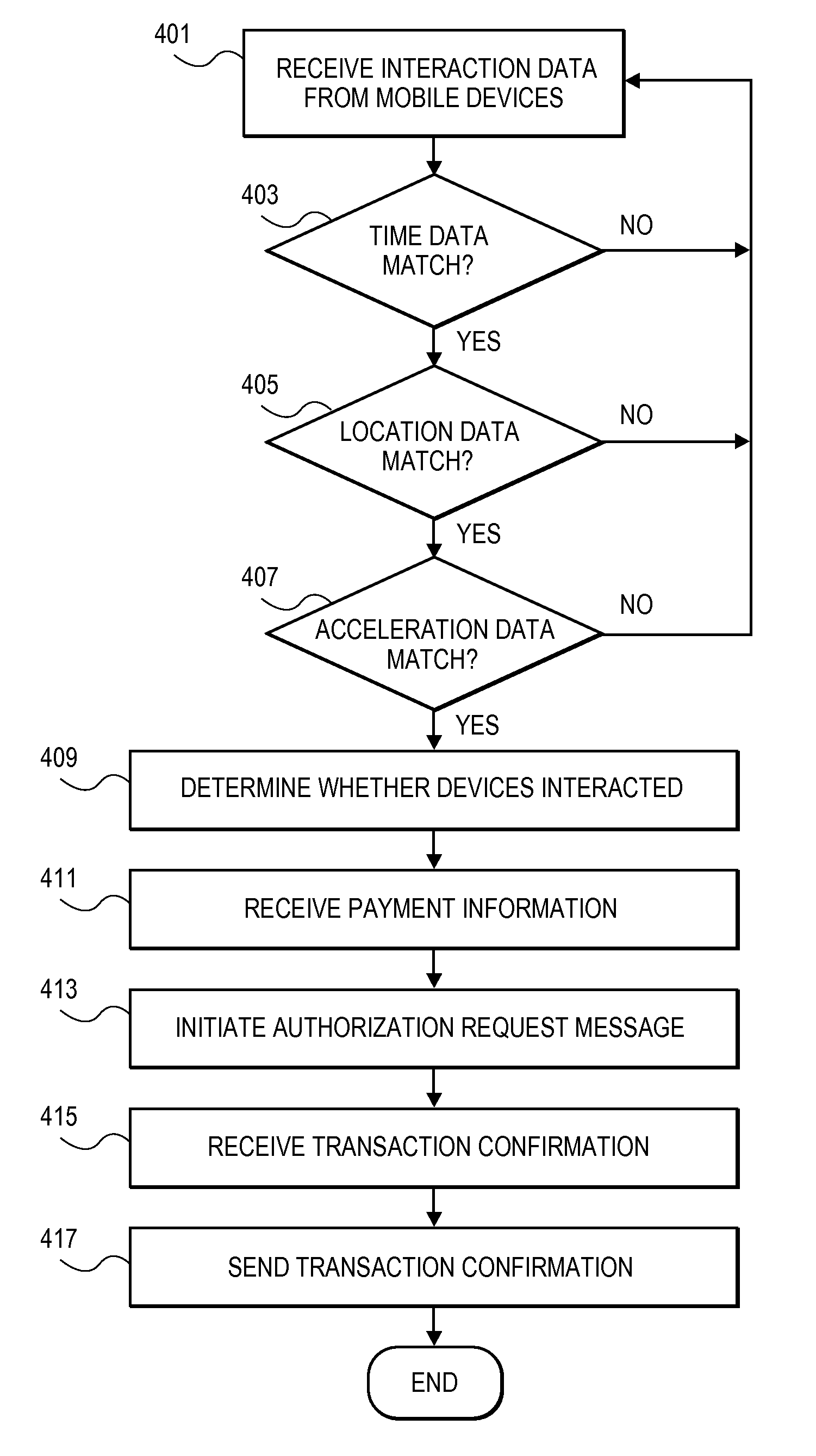
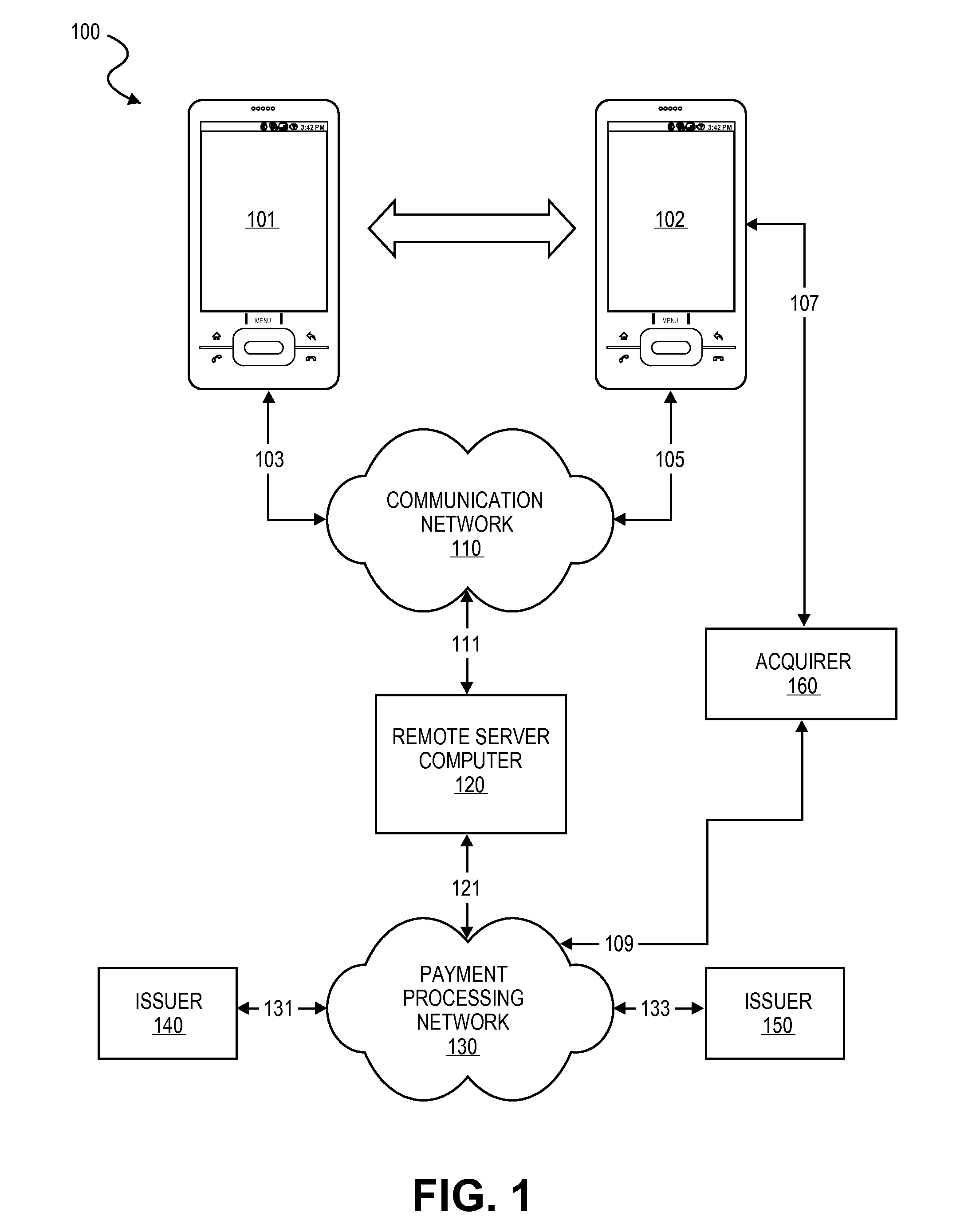
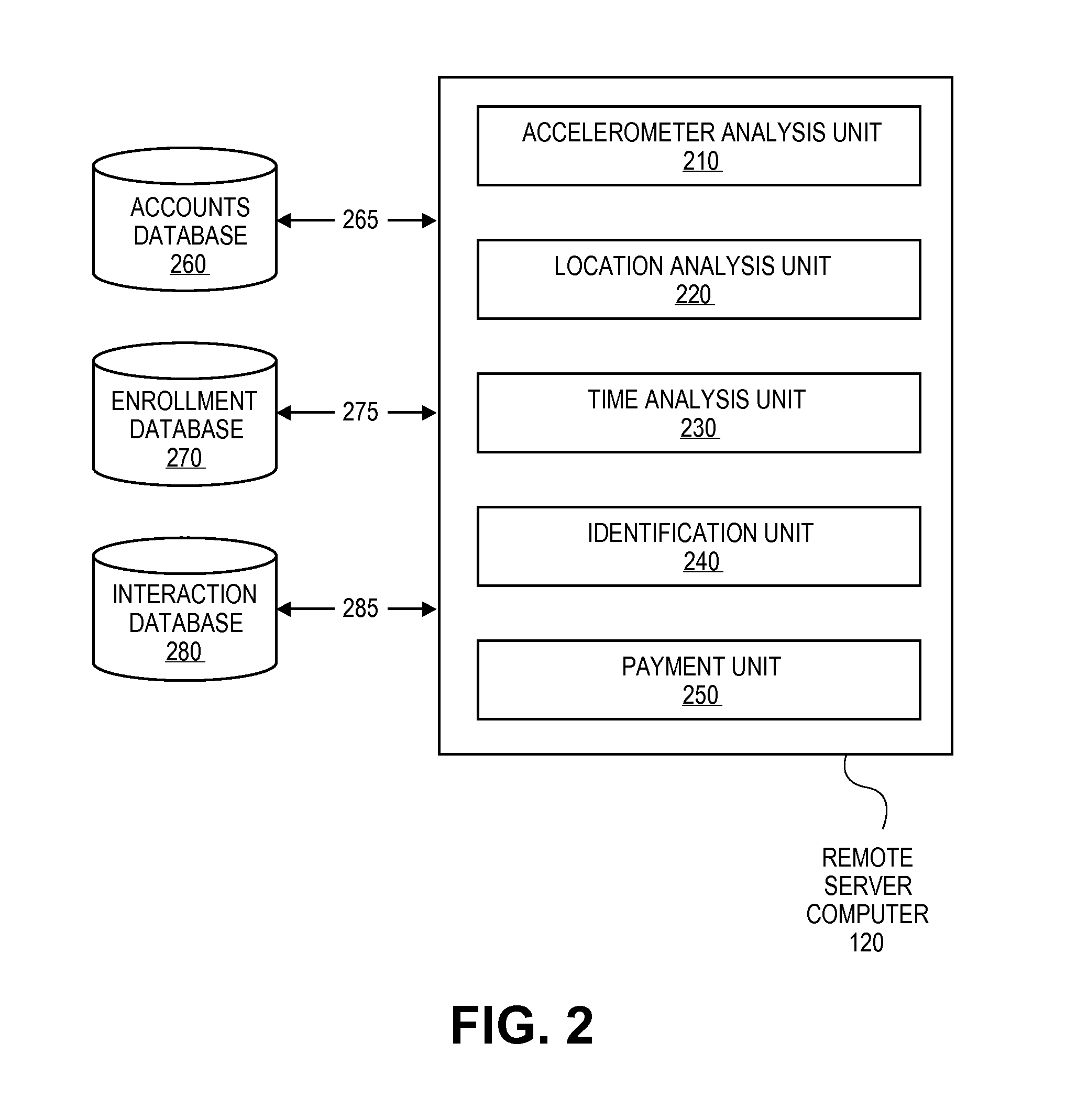
Transaction Using A Mobile Device With An Accelerometer
Embodiments of the invention may use a first accelerometer to measure first acceleration data of a first device. Other interaction data, including time data and geographic location data, generated by the first device may also be recorded. First acceleration data is compared by a remote server computer to second acceleration data generated by a second accelerometer in a second device. If the first and second accelerometer data are substantially equal, it can be determined that the devices have interacted and communications can be initiated. After communications are initiated, a financial transaction is conducted. Accelerometer data may be stored and / or used as part of the authentication process in a payment processing network. Other embodiments of the invention use the accelerometer to generate movement security data to make financial transaction more secure. Accelerometer data is used for authentication, security, encryption, session keys, non-repudiation, or fraud protection.
Owner:VISA INT SERVICE ASSOC
Method, security system control module and policy server for providing security in a packet-switched telecommunications system
ActiveUS20060013191A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile station
A method, security system control module and policy server for providing security for Mobile Stations (MSs) in a Packet-Switched Telecommunications System. When an MS accesses the system, its identity is sent to a security system control module that retrieves a security profile associated with the MS. A policy server of the security system control module stores individual security profiles, default security profiles and group security profiles for registered subscribers. Security settings associated with the MS security profile are returned from the policy server to a mobile security manager of the control module, which then determines if they should be propagated in the system. When no previous network access was made in a given time period by an MS having similar security settings, i.e. belongs to the same group security profile, the settings are propagated in the system in order to be enforced, for providing security protection for the MS.
Owner:TELEFON AB LM ERICSSON (PUBL)
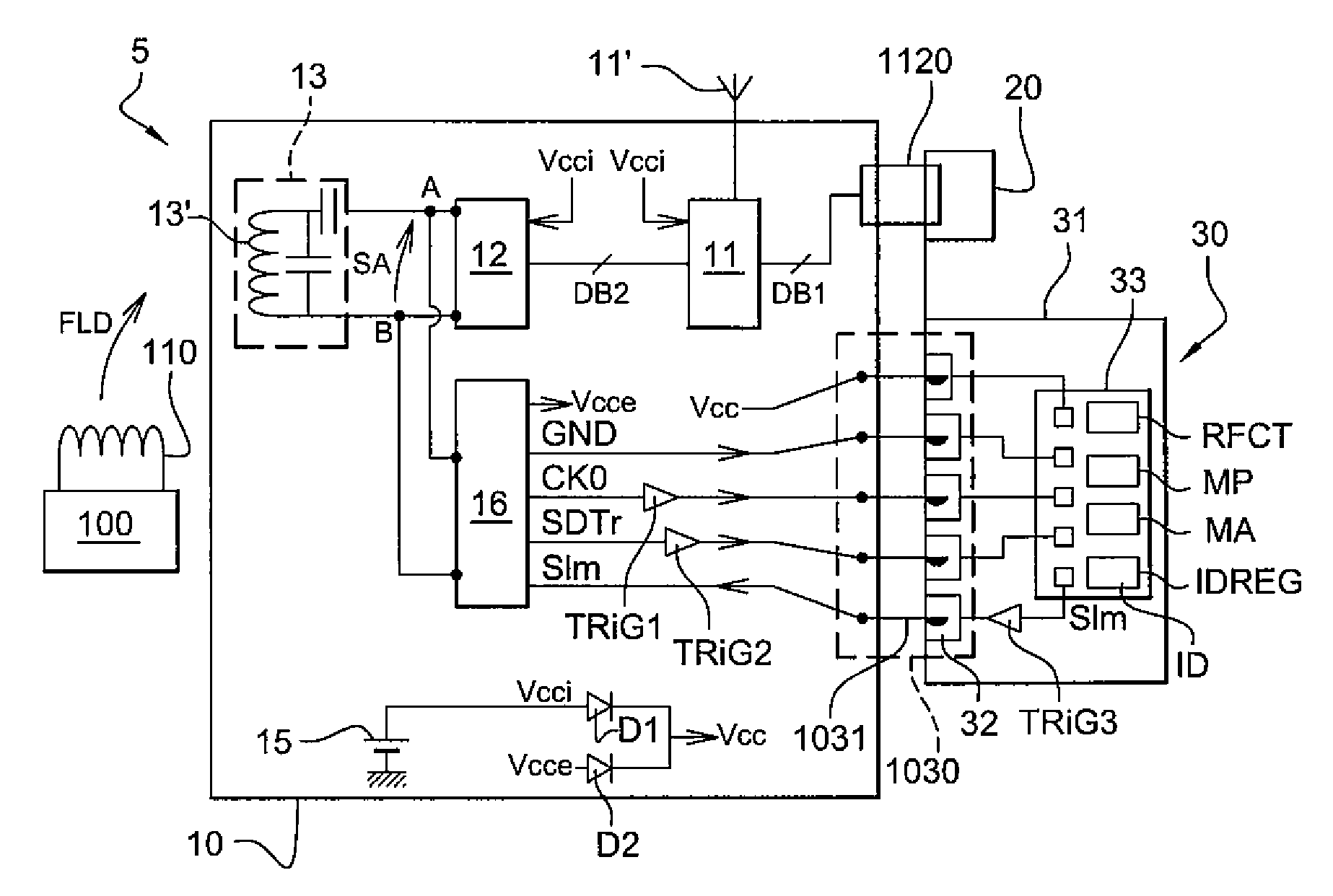
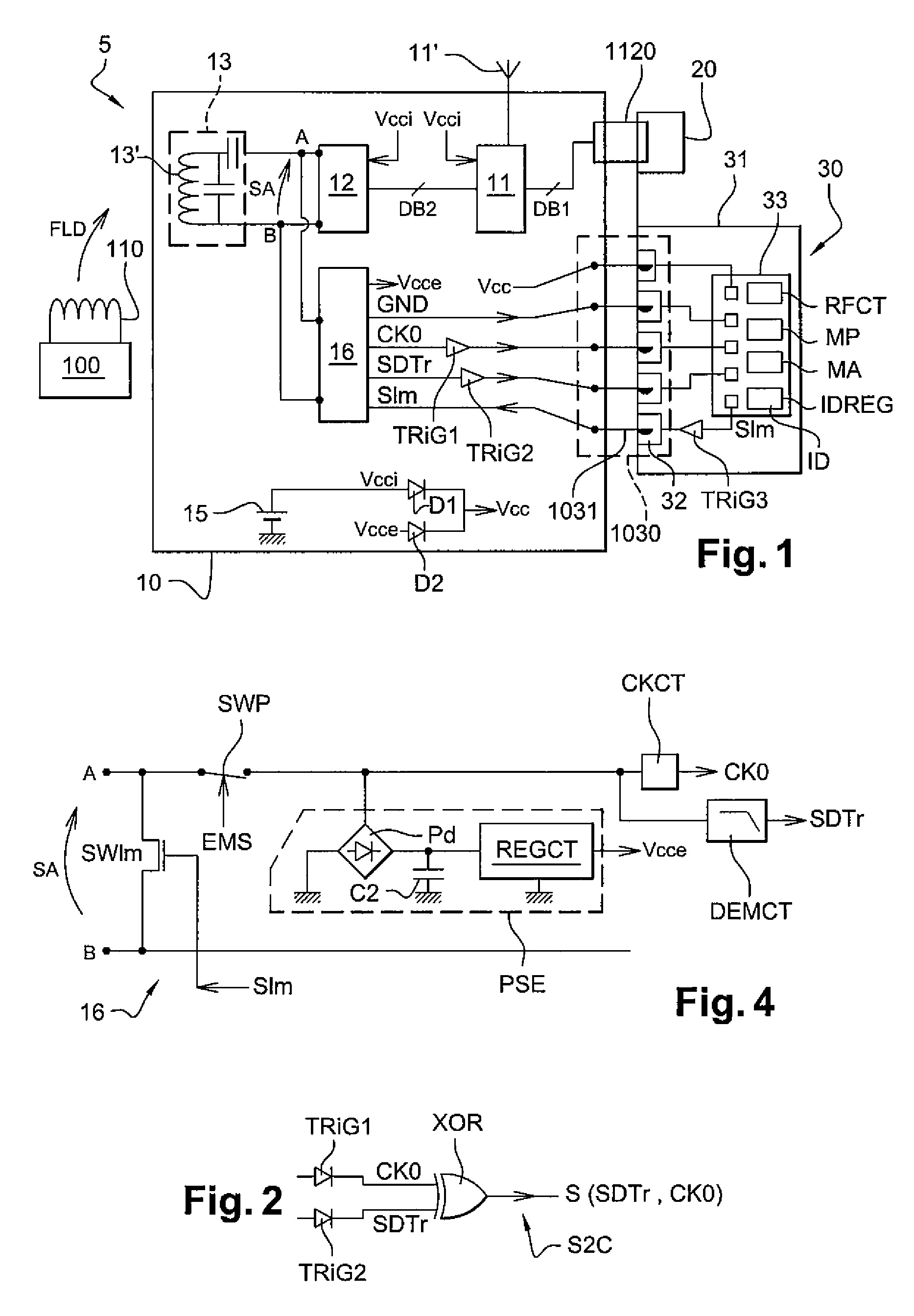
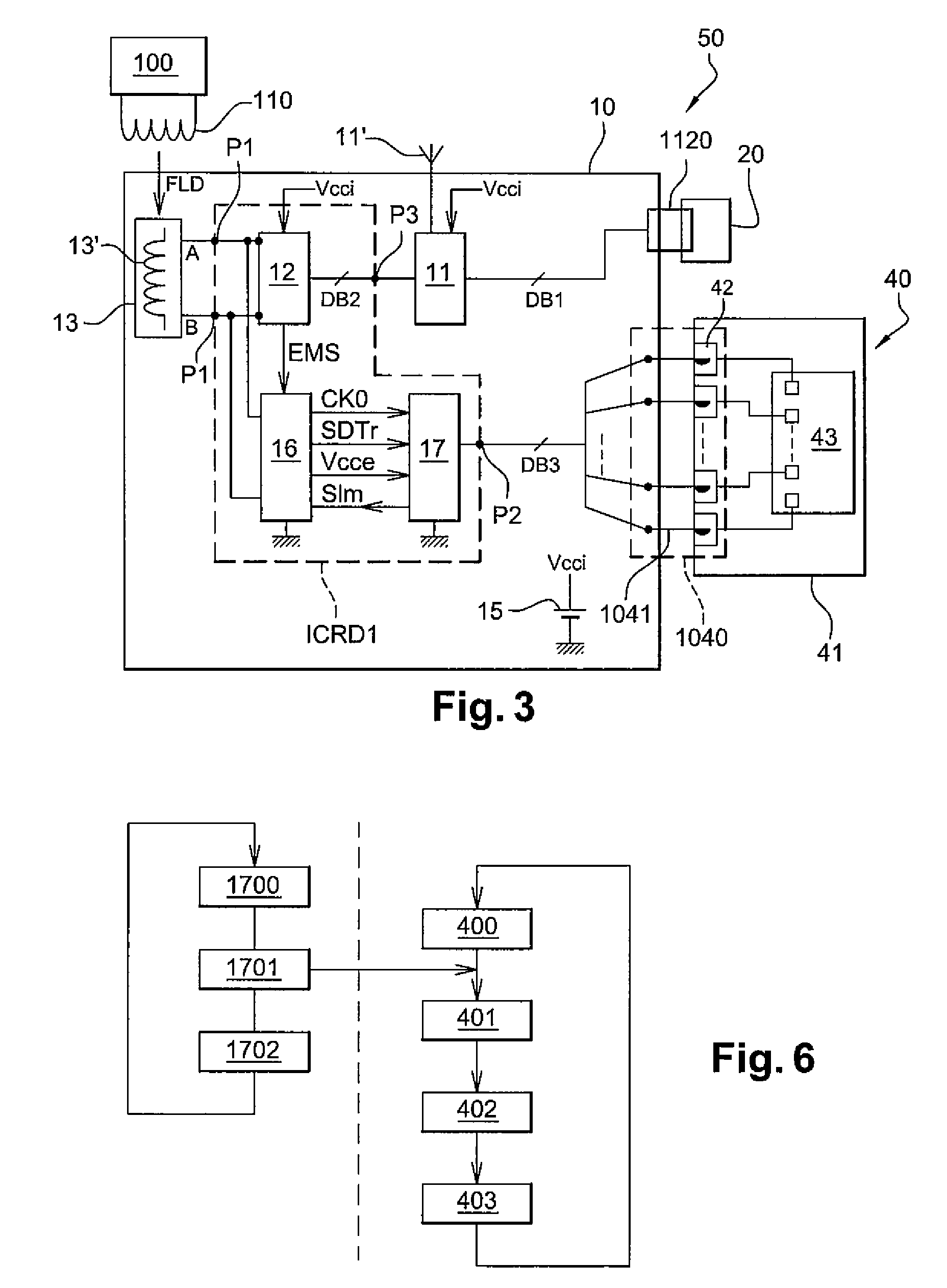
NFC reader having a passive operating mode with low electrical consumption
InactiveUS20090101716A1Reduce power consumptionSatisfactory communication distanceMemory record carrier reading problemsNear-field for read/write/interrrogation/identification systemsElectricityData signal
An inductive coupling reader includes a passive interface circuit for modulating the impedance of an antenna circuit and extracting from the antenna circuit a data signal and a RF clock signal, and circuitry for coupling the reader to a removable security module. The reader includes an emulation circuit for opening a RF transmission channel with another reader, a non-removable electrical link linking the emulation circuit to the passive interface circuit, by which the data signal and the RF clock signal are supplied to the emulation circuit, and a data bus clocked by a bus clock signal having a frequency inferior to the frequency of the RF clock signal, for linking the emulation circuit to the removable security module. The reader has low electrical consumption.
Owner:STMICROELECTRONICS SRL
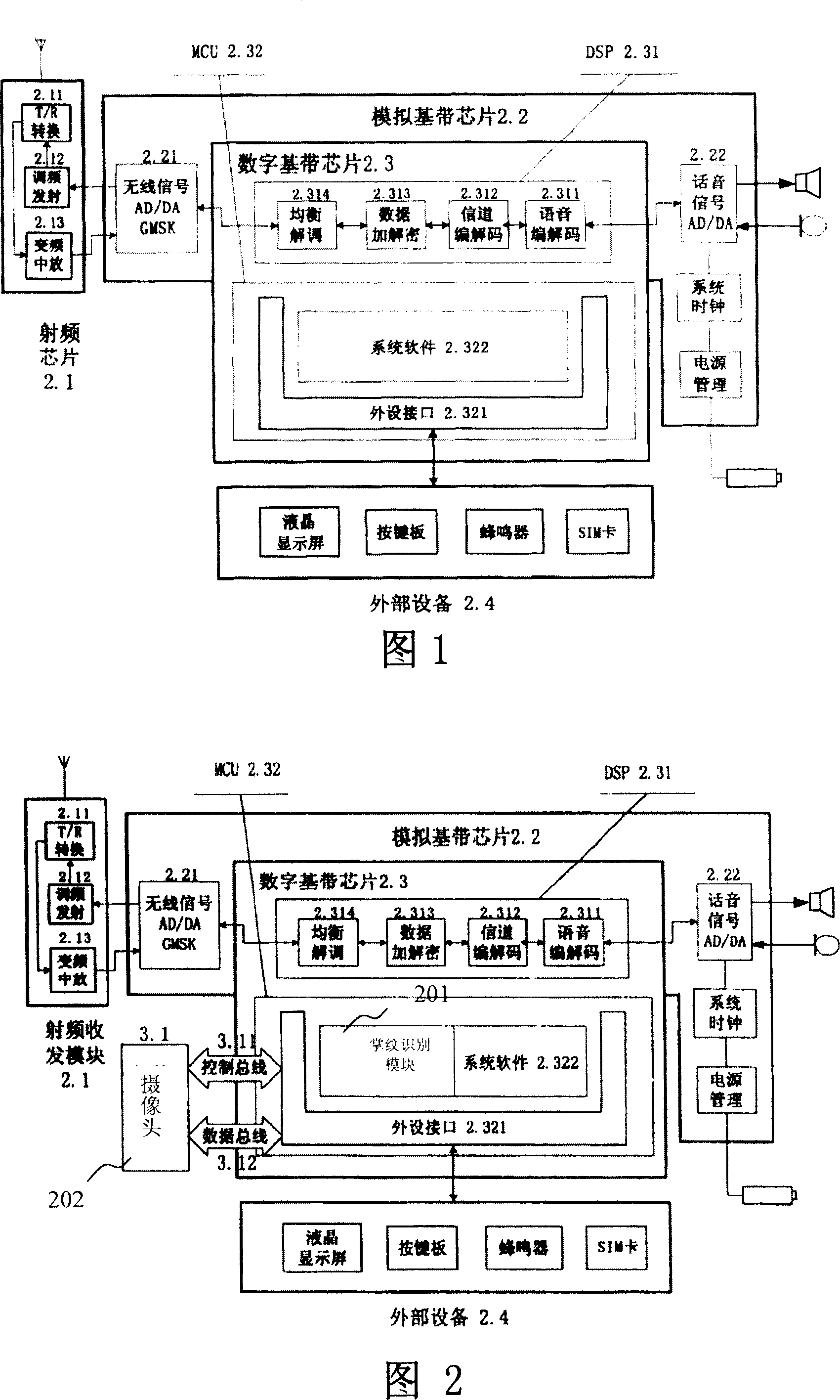
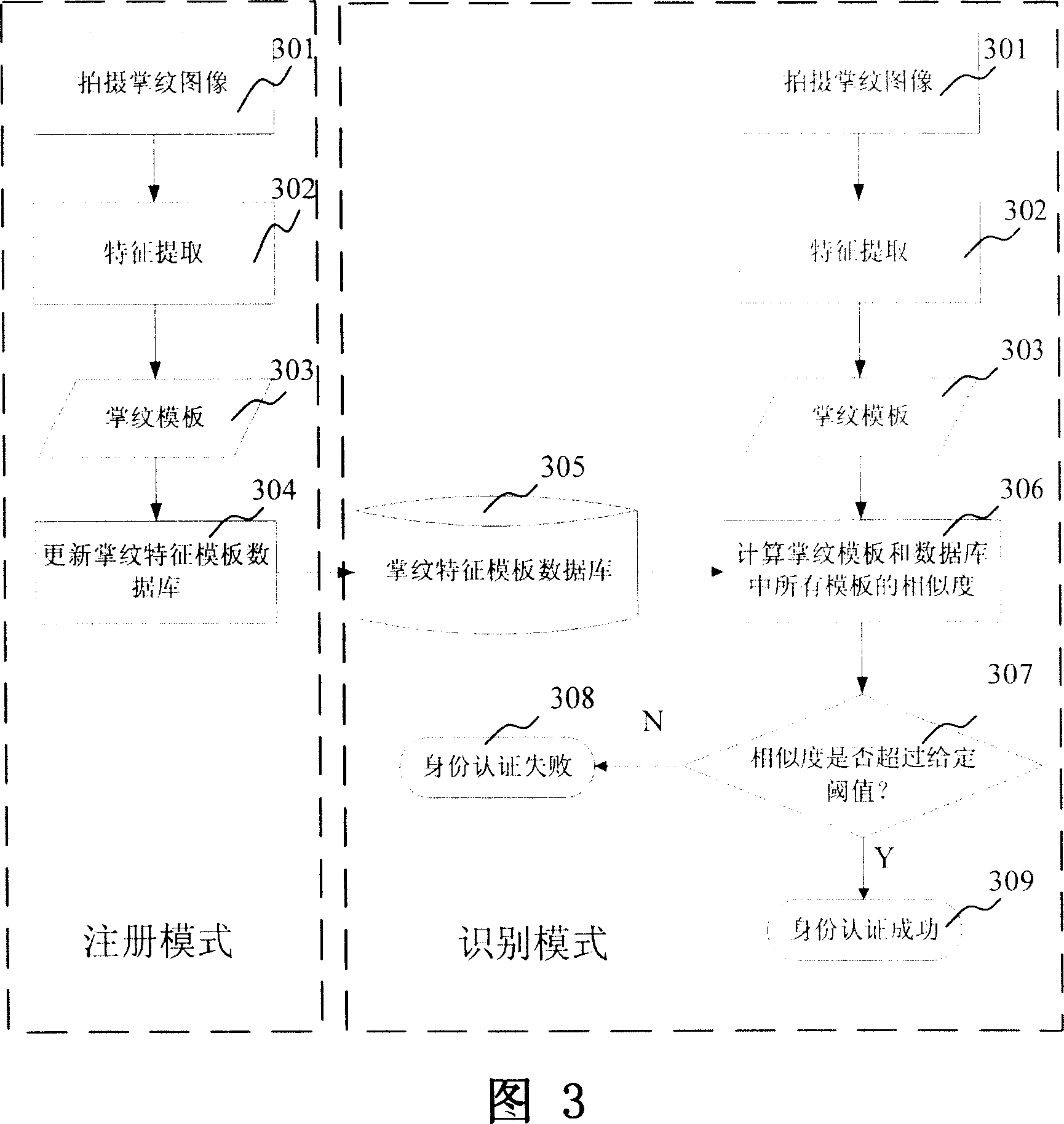
A mobile identity authentication system and its authentication method
InactiveCN1972186ABuild securityEasy to buildUser identity/authority verificationTelephonic communicationPattern recognitionComputer terminal
This invention relates to digital image process, mode identification and wireless communication technique field and to one mobile id system and method, which uses palm image identification to test id on cell phone or PDA and comprises the following steps: getting palm images; extracting palm characteristics and computing similarity; identifying user; mobile device cameral head is image forming device to extract image characteristics to select local mobile terminal or remote servo.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Method and apparatus for encoding and decoding data transmitted to an authentication token
ActiveUS20120221860A1Increase chanceSimilar costDigital data processing detailsUser identity/authority verificationCommunication interfaceSmart card
Methods and apparatus for encoding and decoding data transmitted acoustically and / or optically to strong authentication tokens to generate dynamic security values are disclosed. The tokens may also include a selection mechanism to select either an acoustical or an optical input interface to receive data. A communication interface may be provided to communicate with a removable security device such as a smart card and the token may be adapted to generate dynamic security values in cooperation with the removable security device.
Owner:ONESPAN NORTH AMERICA INC
Strong authentication token with acoustic data input
InactiveUS20120221859A1Increase chanceSimilar costDigital data processing detailsUser identity/authority verificationCommon baseCommunication interface
Strong authentication tokens for generating dynamic security values having an acoustical input interface for acoustically receiving input data are disclosed. The tokens may also include an optical interface for receiving input data and may have a selection mechanism to select either the acoustical or the optical input interface to receive data. A communication interface may be provided to communicate with a removable security device such as a smart card and the token may be adapted to generate dynamic security values in cooperation with the removable security device. The acoustic signal received by the token may be modulated using a frequency shift keying modulation scheme using a plurality of coding frequencies to code the acoustical signal where each coding frequency may be an integer multiple of a common base frequency.
Owner:ONESPAN NORTH AMERICA INC
Transaction using a mobile device with an accelerometer
Embodiments of the invention may use a first accelerometer to measure first acceleration data of a first device. Other interaction data, including time data and geographic location data, generated by the first device may also be recorded. First acceleration data is compared by a remote server computer to second acceleration data generated by a second accelerometer in a second device. If the first and second accelerometer data are substantially equal, it can be determined that the devices have interacted and communications can be initiated. After communications are initiated, a financial transaction is conducted. Accelerometer data may be stored and / or used as part of the authentication process in a payment processing network. Other embodiments of the invention use the accelerometer to generate movement security data to make financial transaction more secure. Accelerometer data is used for authentication, security, encryption, session keys, non-repudiation, or fraud protection.
Owner:VISA INT SERVICE ASSOC
Method for mobile security via multi-factor context authentication
ActiveUS8935769B2Easy to solveDigital data processing detailsUser identity/authority verificationMobile securityMobile electronics
Owner:LIVE ENSURE LTD
Intersystem mobility security context handling between different radio access networks
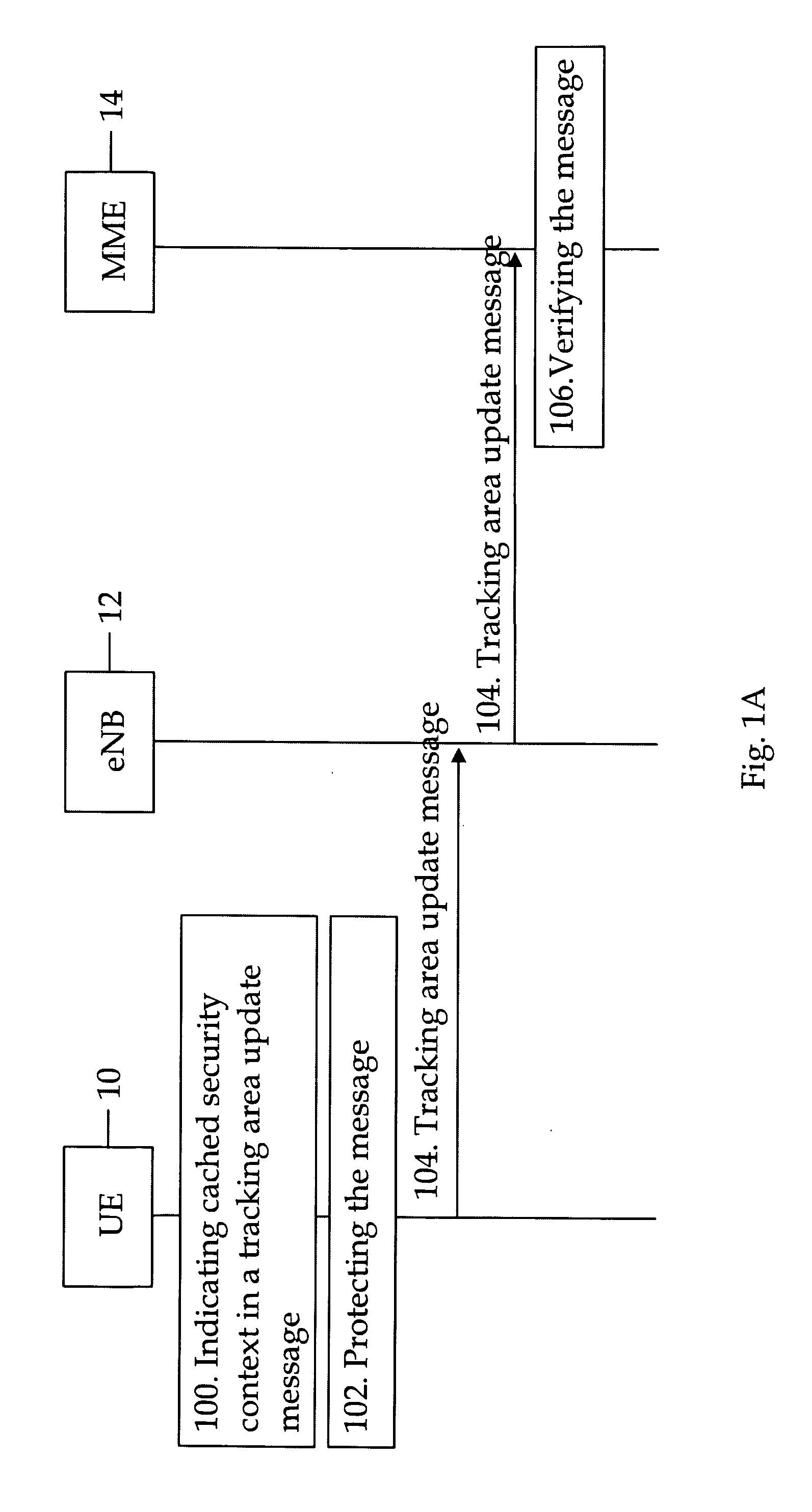
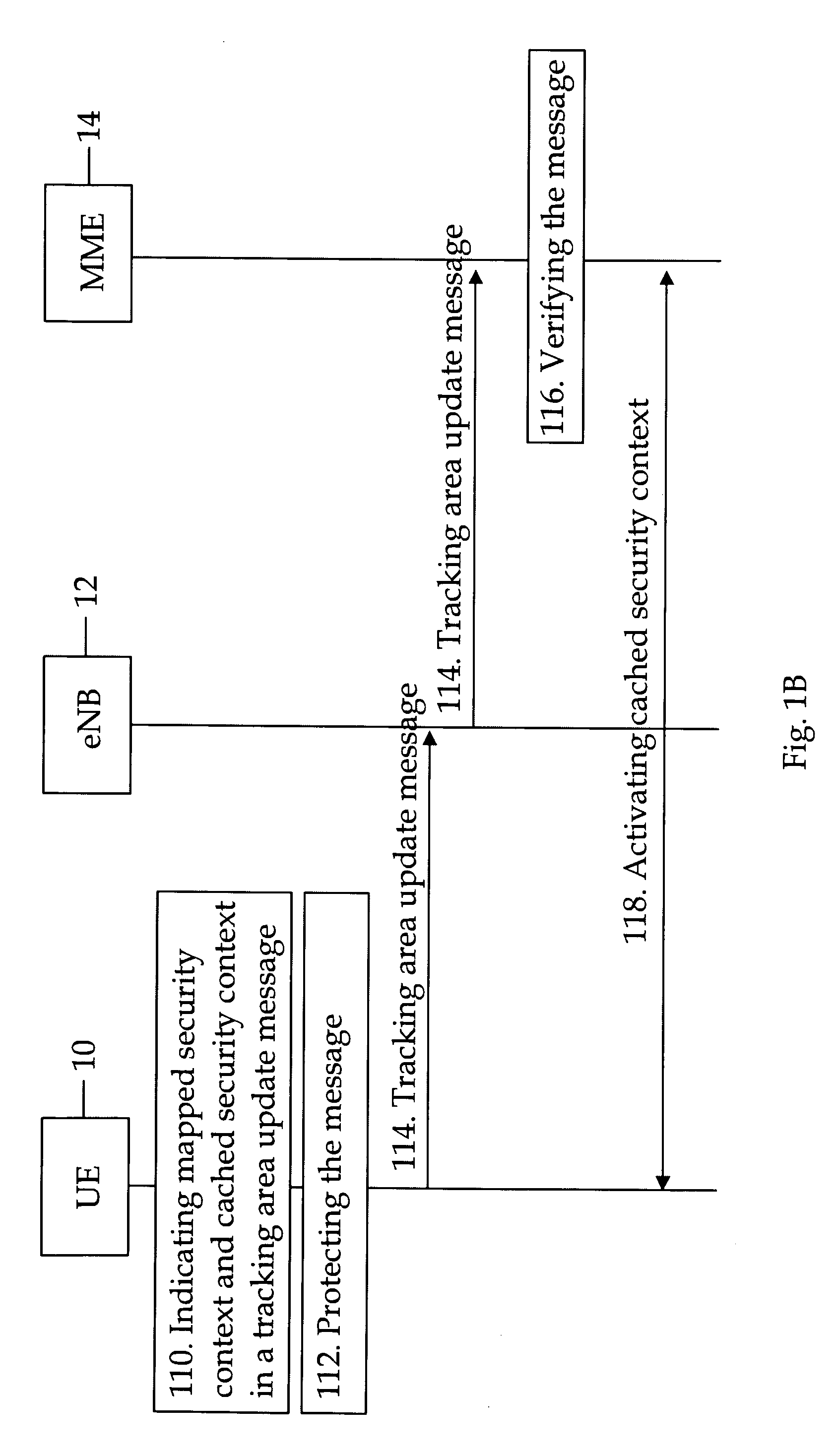
ActiveUS20090271623A1User identity/authority verificationSecurity arrangementRadio access networkMobile security
A method and apparatus for intersystem mobility security context handling between different radio access networks which can include a receiver configured to receive a tracking area update message from a user terminal. The message can include a first key identifier configured to identify a mapped security context and a second key identifier configured to identify a cached security context. A verifier can be configured to verify the tracking area update message with a key identified by the first or second key identifier.
Owner:NOKIA TECHNOLOGLES OY
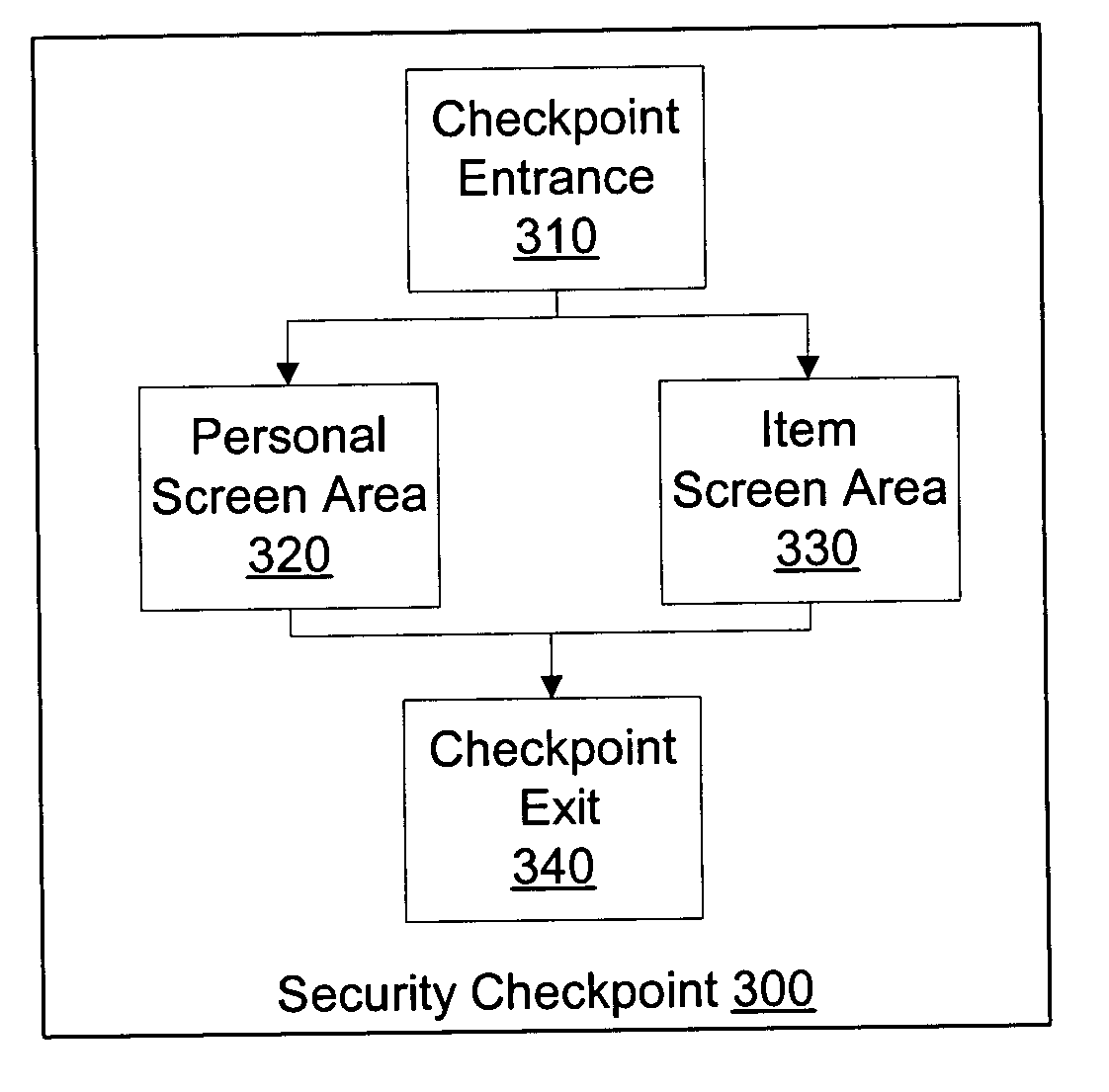
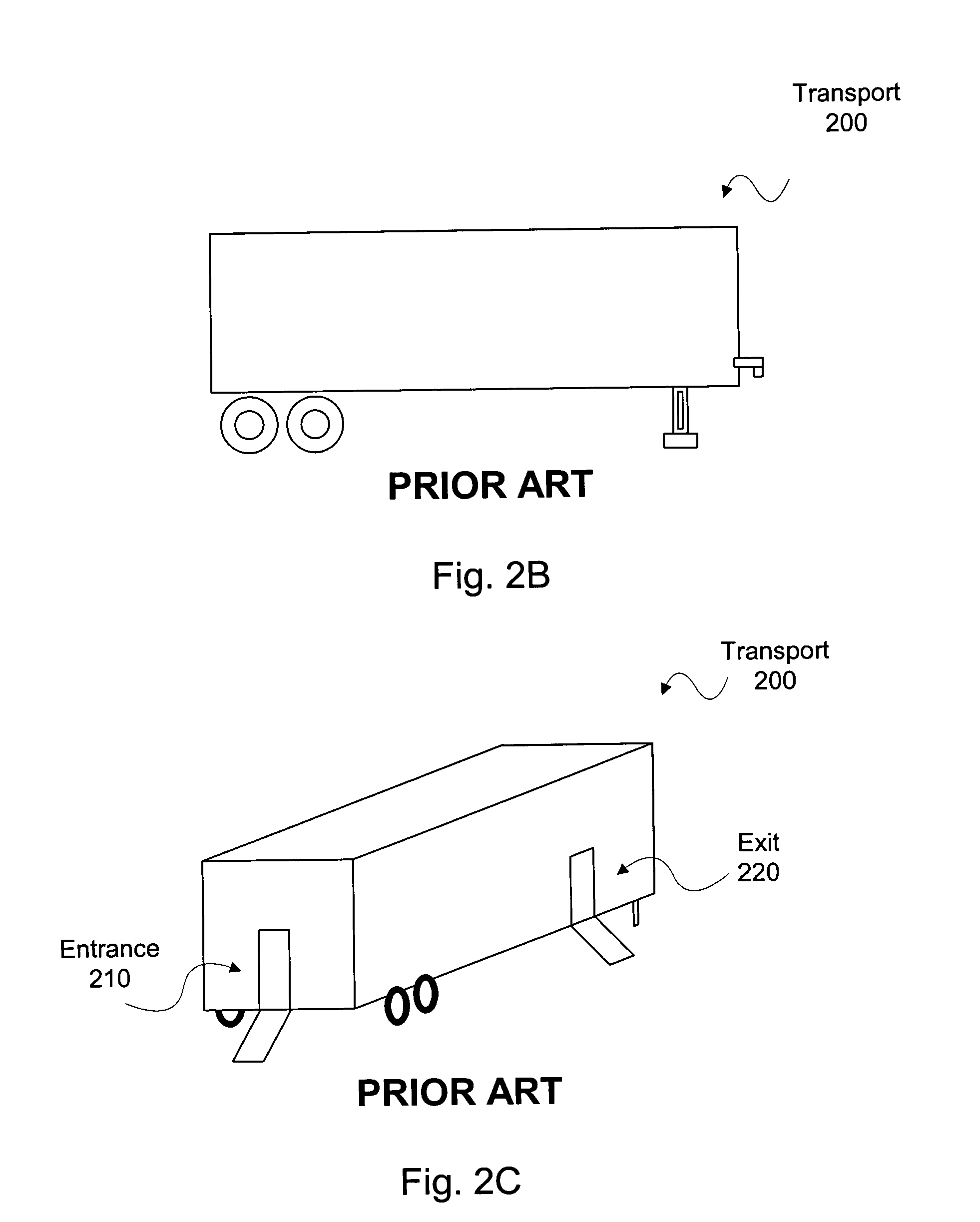
Mobile security unit
ActiveUS20050074086A1Minimize frequencyImprove throughputMaterial analysis using wave/particle radiationRadiation/particle handlingTelecommunicationsMobile security
A Mobile Security Unit (MSU) has a security checkpoint and a transport. The security checkpoint has an item screening area and a personal screening area. The checkpoint is configured as needed to fit within the transport. The MSU may further separate certain individuals into a secure, enclosed wanding station for additional security screening. The wanding station may be constructed using glass (or other strong, visually transparent substance) and metallic (such as aluminum or steel) posts so that people may be securely enclosed in the wanding station but still have a direct line of sight to personal items being screened at another location. The MSU is configured so that most people pass straight through the checkpoint, and people leaving the wanding station can easily obtain their items without delaying others.
Owner:ACCENTURE GLOBAL SERVICES LTD
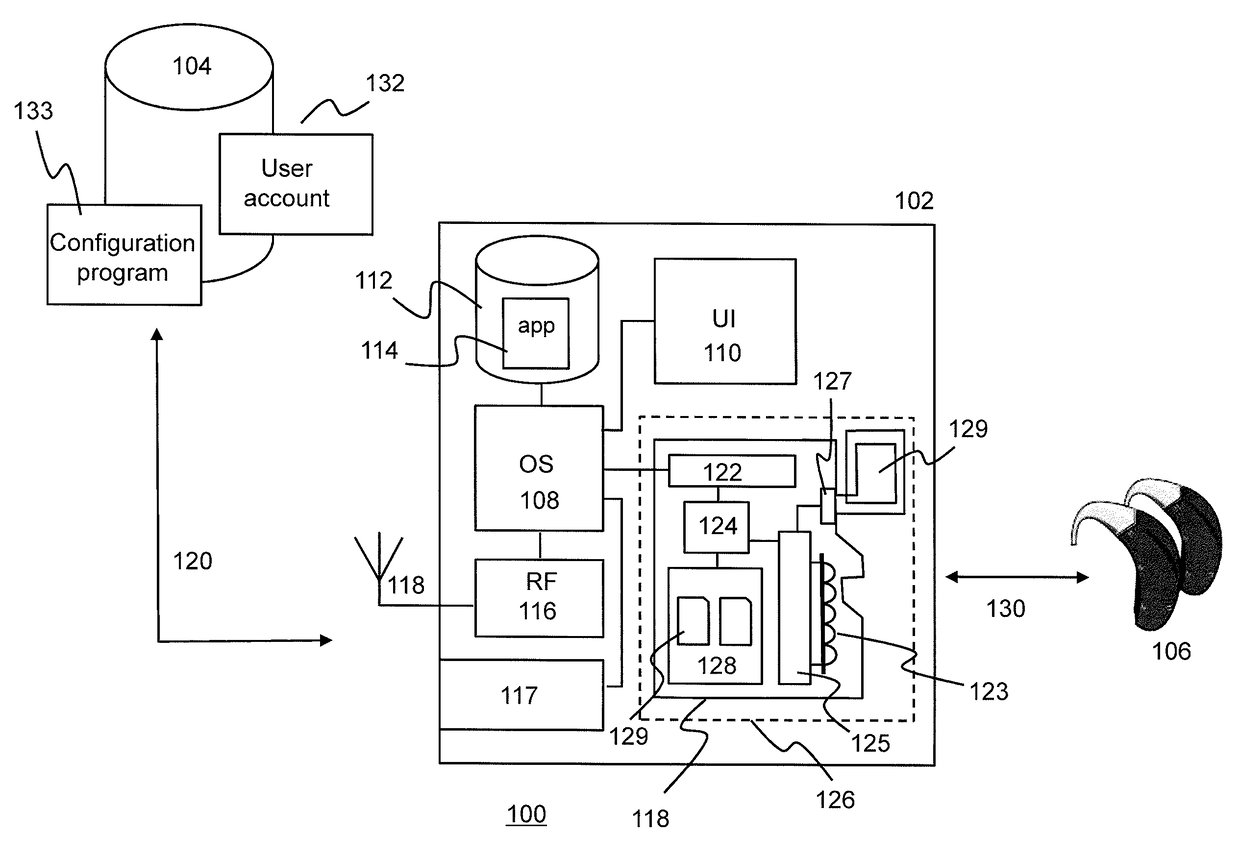
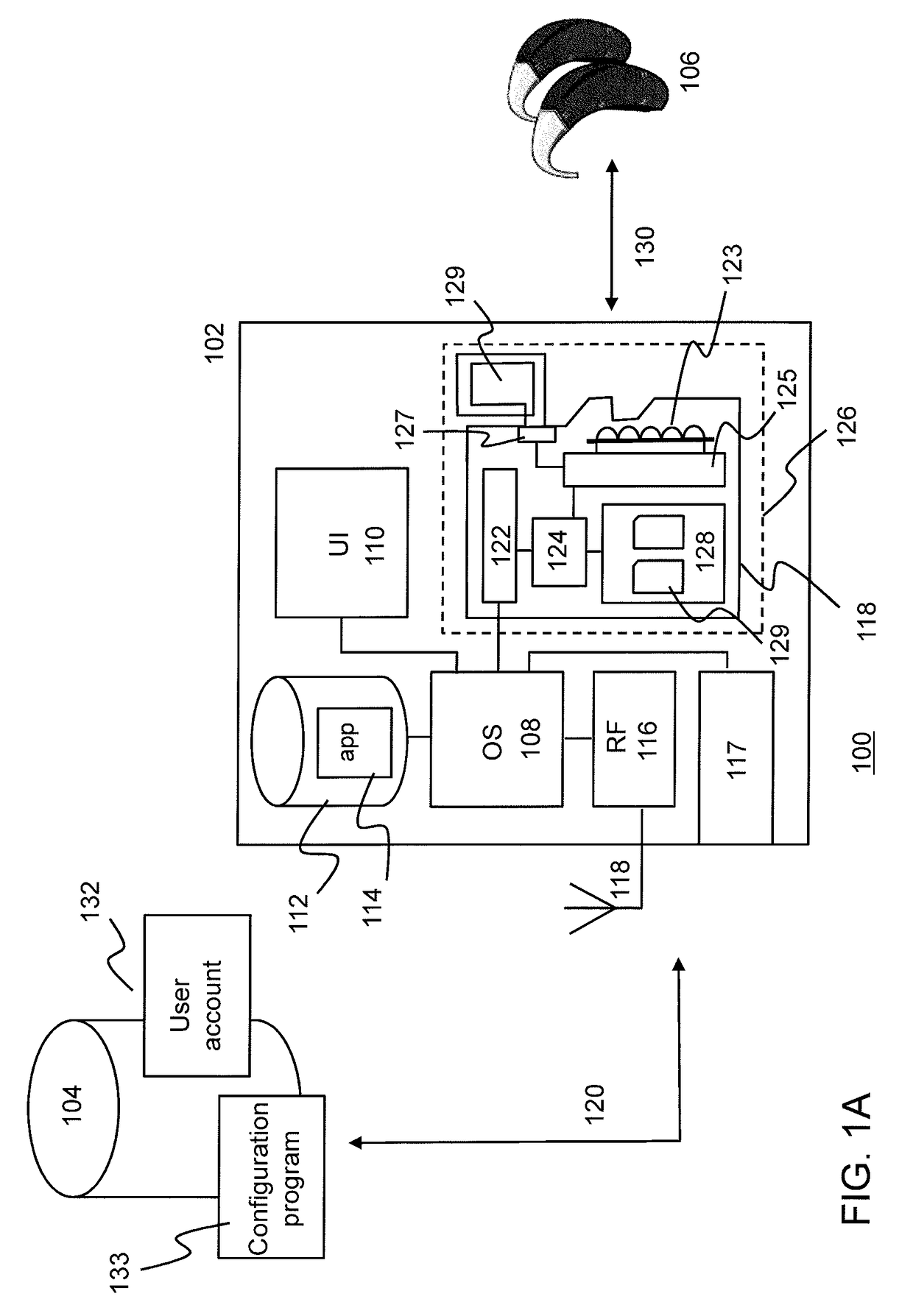
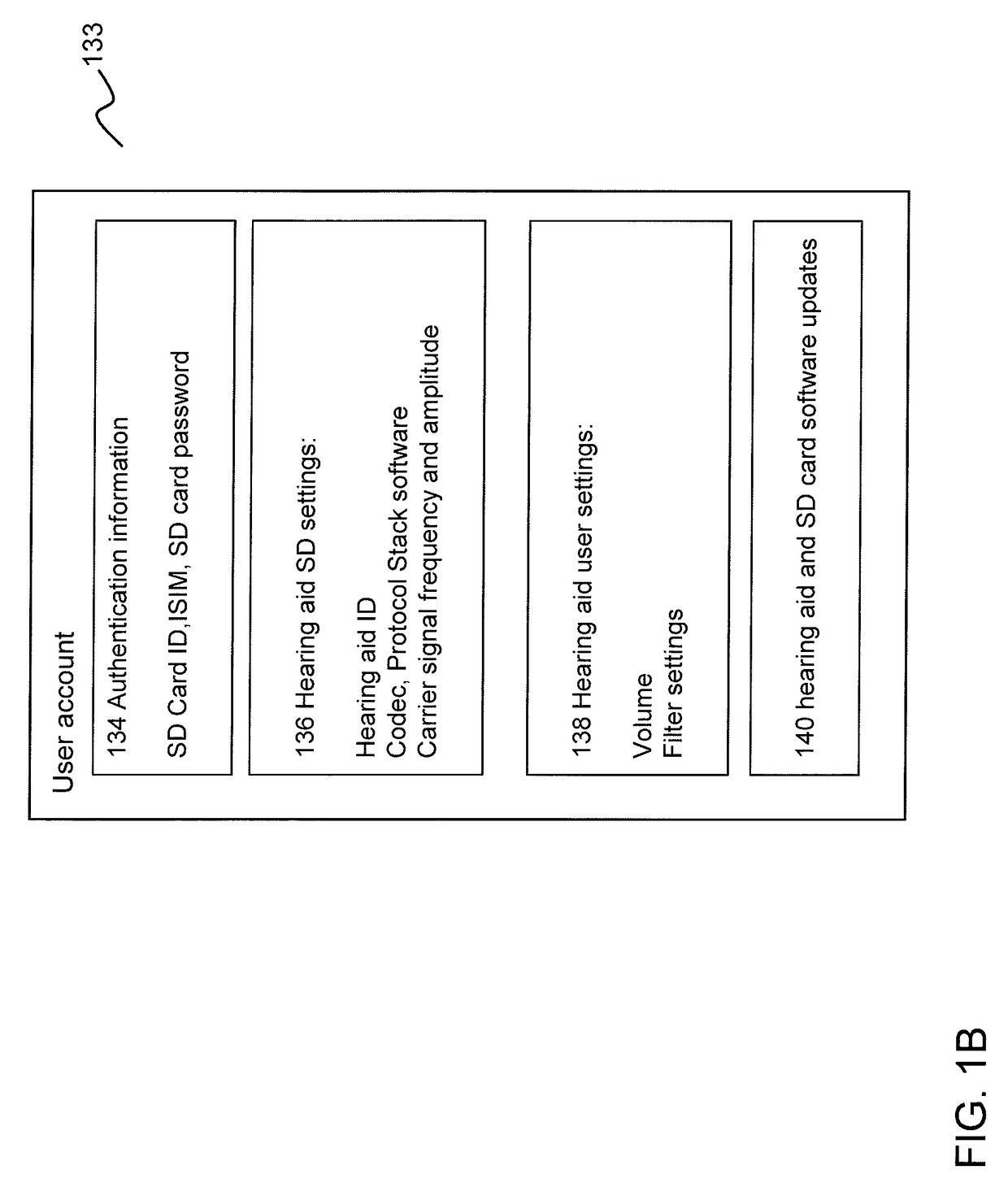
Mobile wireless controller for a hearing aid
ActiveUS20170180886A1Easily interchangeableEasily connected to communication moduleDigital data authenticationTransmissionUser deviceComputer module
The invention relates to a method for configuring a mobile user device as a remote controller for a hearing aid, said mobile user device, comprising a removable secure digital (SD) card, comprising a radio interface and an antenna controller for configuring said radio interface for wireless communication with said hearing aid; and, a computer-readable memory for storing a software application for remotely controlling said hearing aid via said communication module; said method comprising: requesting a communication module identifier, from said communication module; sending a request for hearing aid setting information associated with said hearing aid to a server, said request comprising said communication module identifier; receiving at least part of said hearing aid setting information if said server determines on the basis of said communication module identifier that access to said hearing aid setting information by said mobile user device is allowed; and, configuring the radio interface of said communication module on the basis of said hearing aid setting information.
Owner:AN DIRECT BV
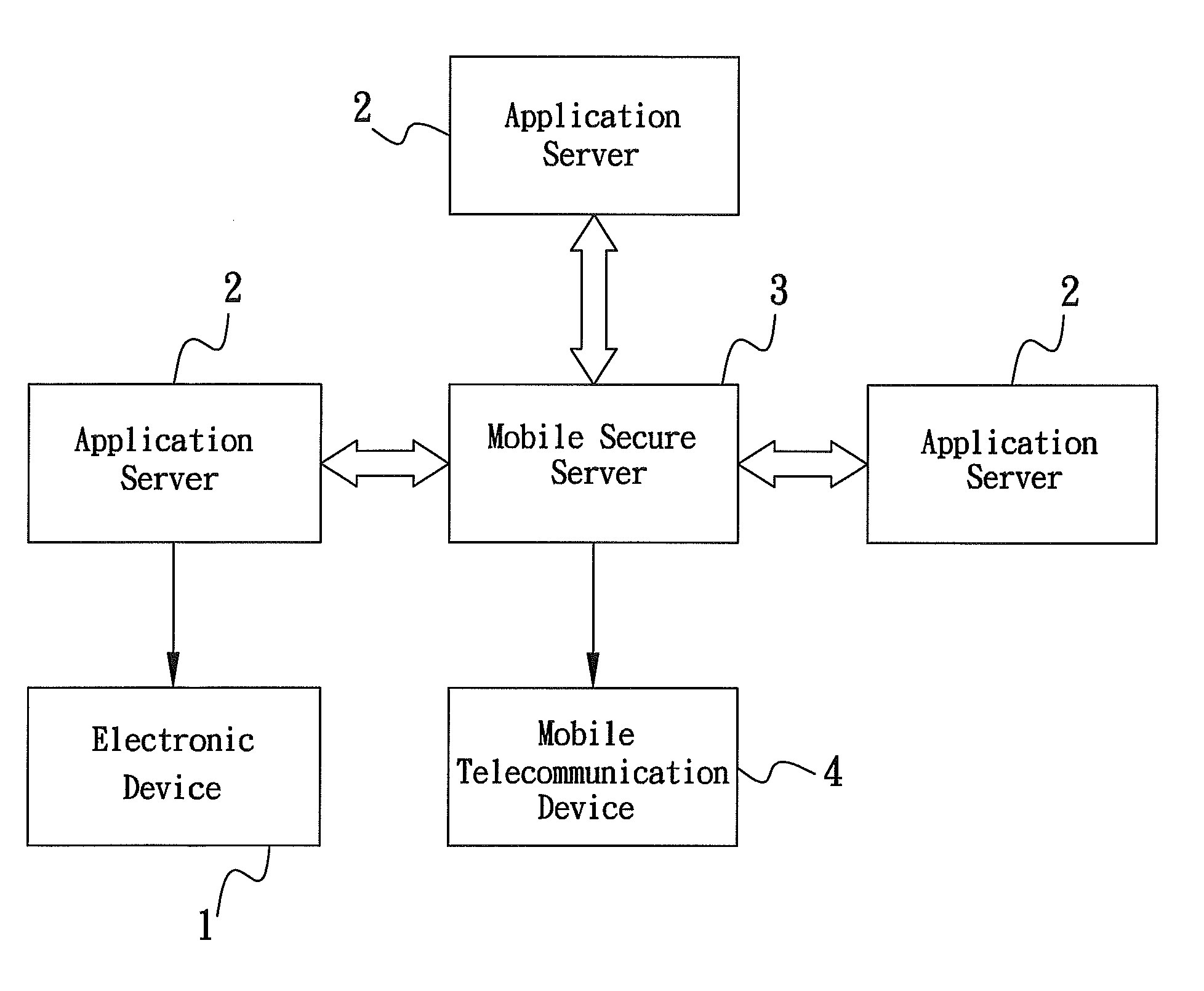
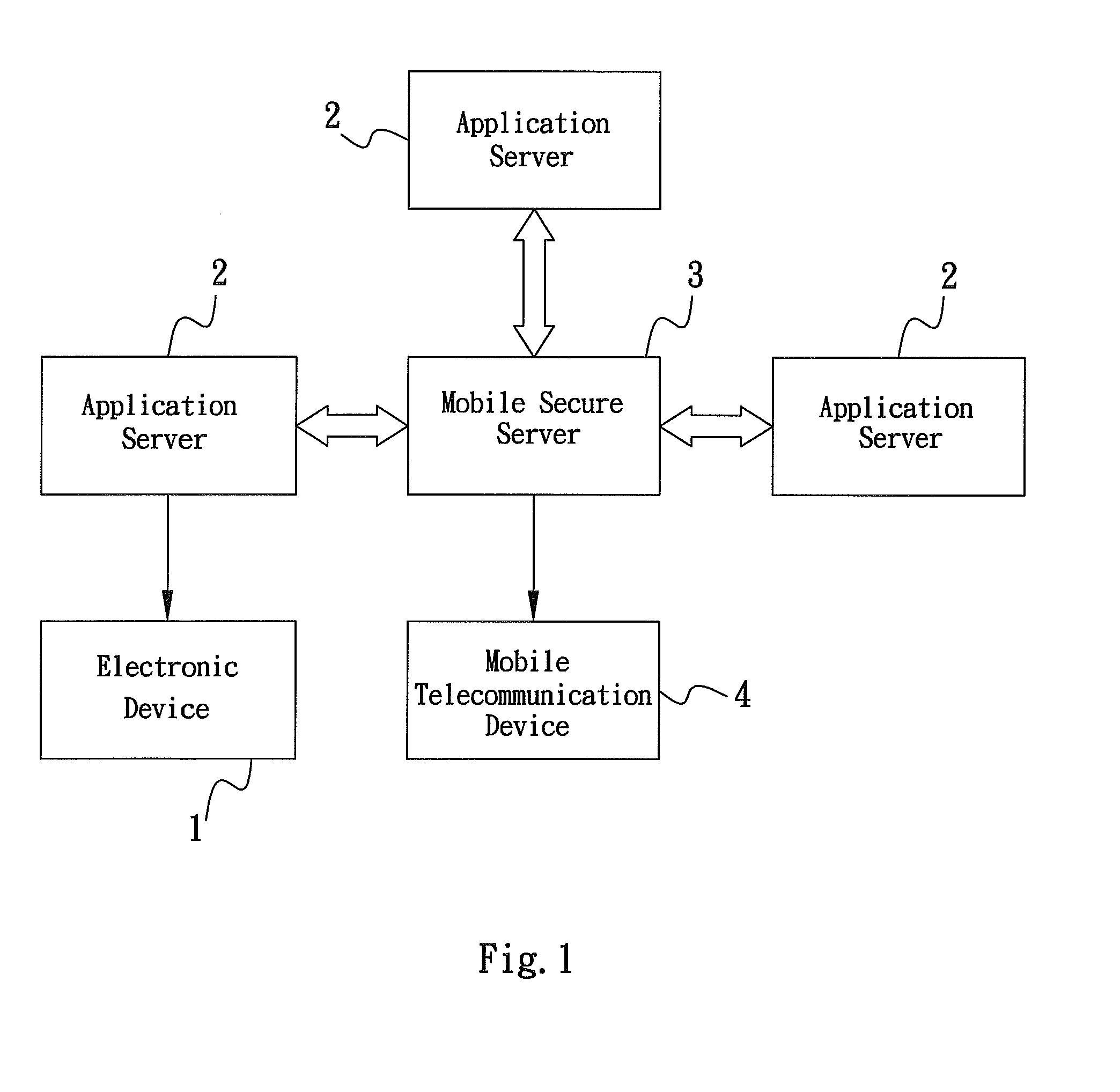
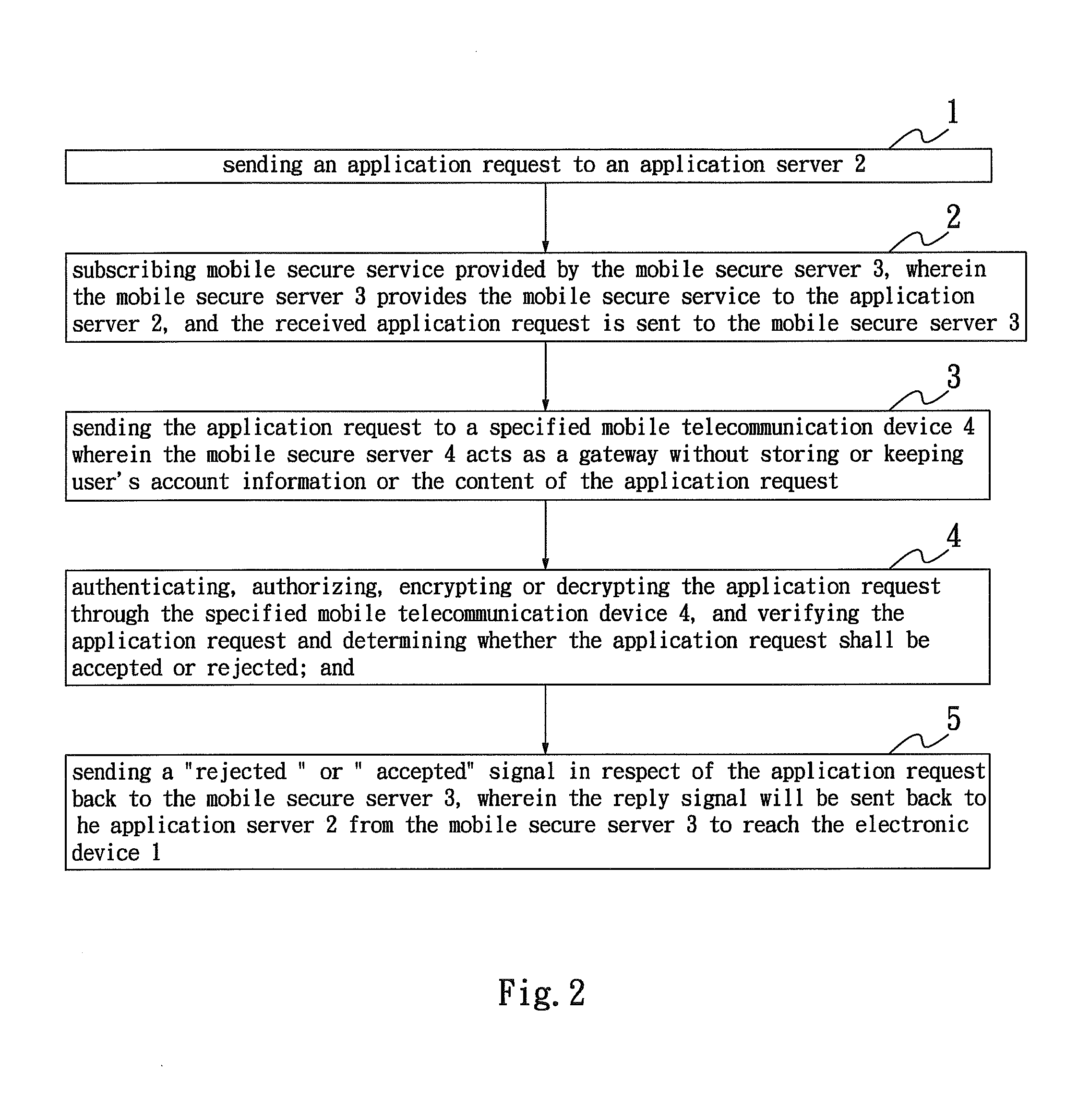
Method of authenticating, authorizing, encrypting and decrypting via mobile service
InactiveUS20090187980A1Digital data processing detailsUser identity/authority verificationApplication serverMobile security
The present invention provides a method of authenticating, authorizing, encrypting and decrypting an application by utilizing a mobile secure server as the platform that can allow the subscriber to authenticate, authorize, encrypt or decrypt a document or an application through the mobile secure server. The account user can register and activate the service to have a secure banking transaction, such as online payment. A request message is submitted via an electronic device to an application server, which performs specific operations in accordance with the instruction of the request message, and sends the request message to the mobile secure server, wherein the mobile secure server will forward the request message to the account mobile telecommunication device that hosts the digital ID and certificates to be sued to authenticate, authorize, encrypt or decrypt the request message and then sends back a reply message to electronic device via the account mobile telecommunication device, application server and mobile secure server.
Owner:TUNG TIEN CHUN
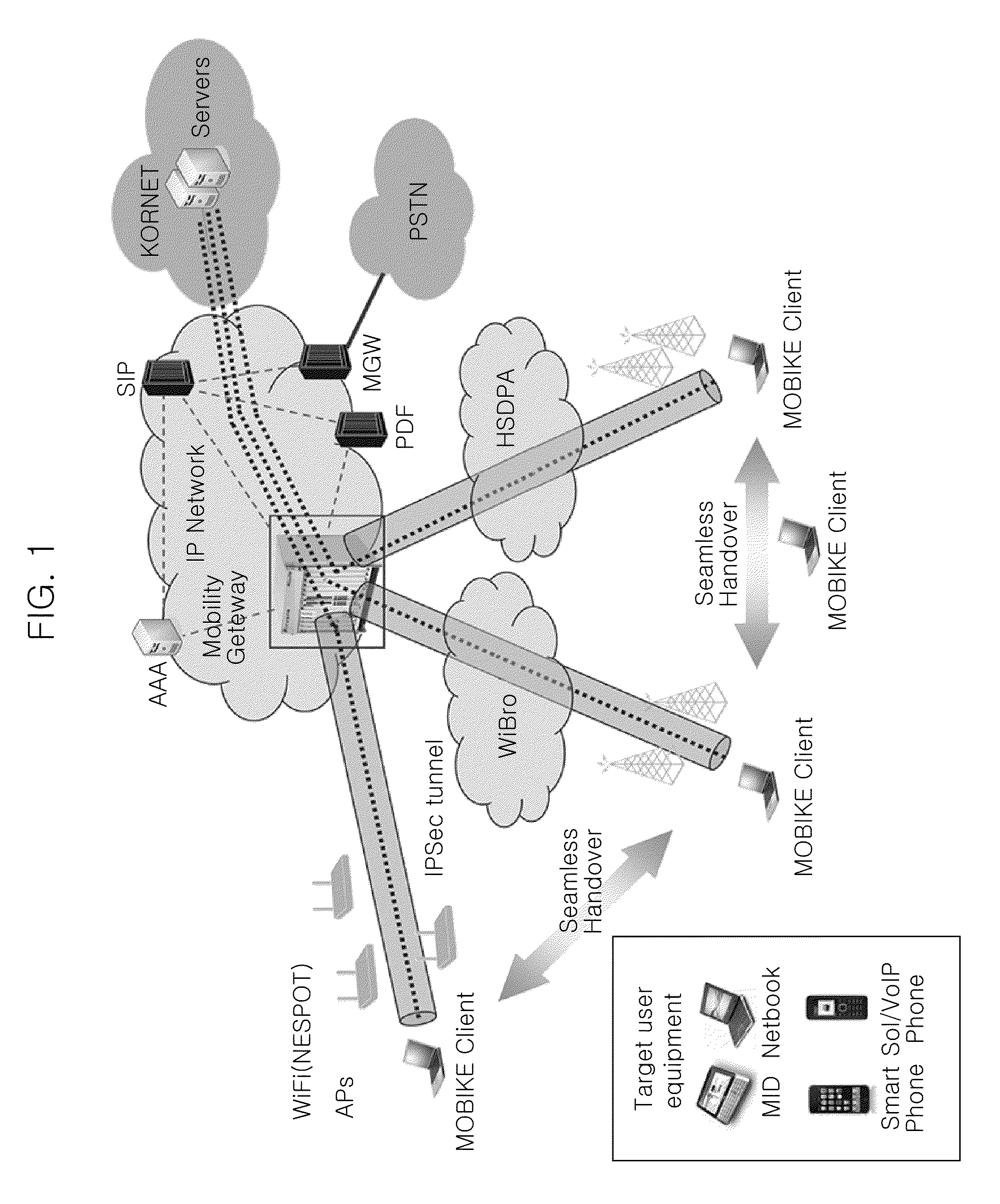
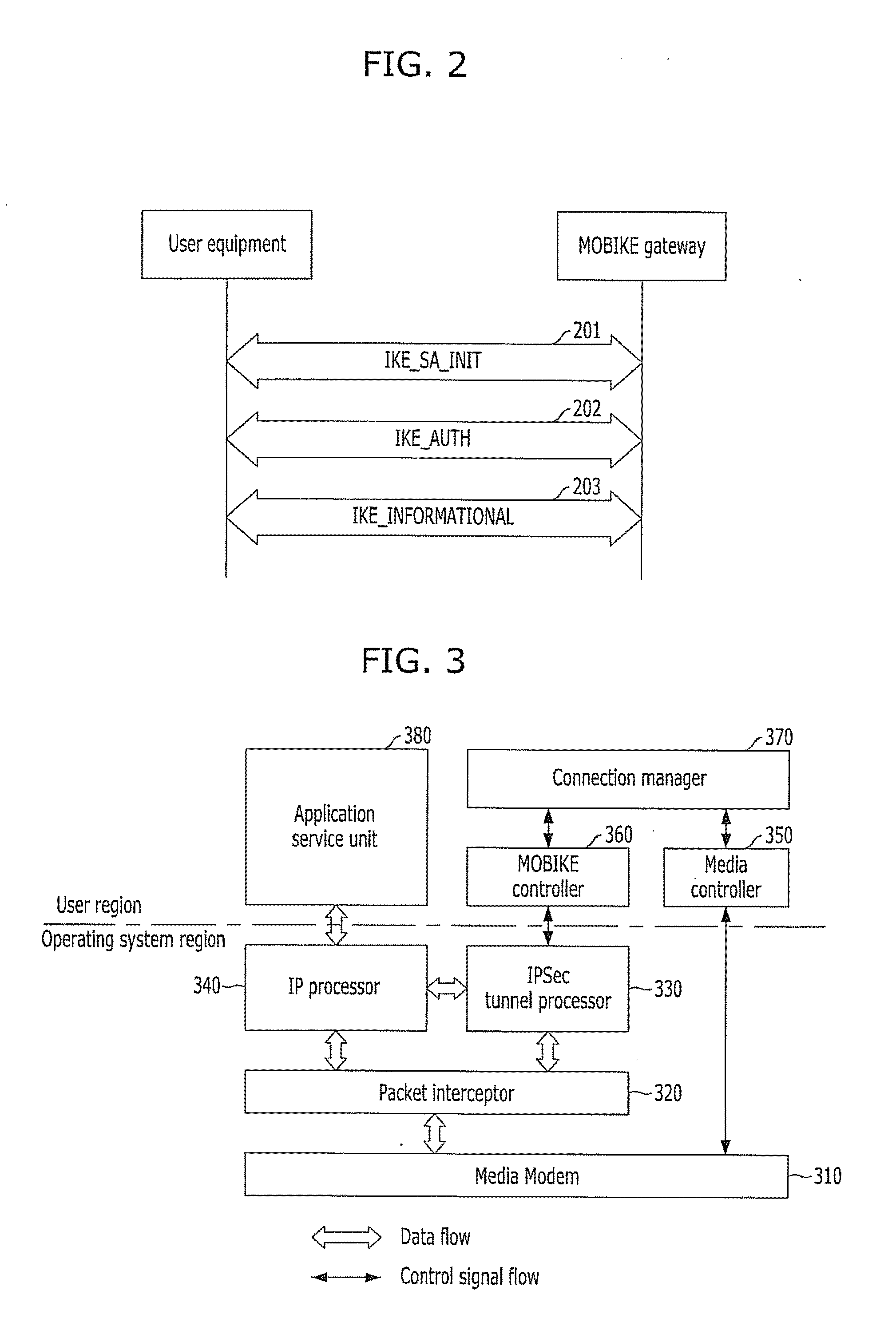
Client apparatus for supporting mobility and security between heterogeneous networks using mobike protocol
InactiveUS20110002466A1Digital data processing detailsComputer security arrangementsHeterogeneous networkConnection manager
A client apparatus includes a wireless network access unit configured to access wireless networks, a packet analysis unit configured to analyze uplink and downlink data packets, a security tunnel processor configured to establish a mobile security tunnel and to maintain the established mobile security tunnel when handover is performed in heterogeneous networks, a wireless network controller configured to control a wireless network accessing process and a connection releasing process of the wireless network access unit, a mobile security tunnel controller configured to perform a MOBIKE protocol and to control a process of establishing and maintaining a mobile security tunnel of the security tunnel processor, and a wireless network connection manager configured to request the mobile security tunnel controller to perform a MOBIKE protocol by managing MOBIKE information and to control handover by setting up and managing a wireless network access policy.
Owner:KT CORP
Counterfeit proof labels having an optically concealed progressive shifting security safety symbol for quick visual identification utilizing a mobile phone for online verification
The prevention of counterfeiting labels for various products is addressed by introducing counterfeit proof labels having an optically concealed, invisible progressive shifting security safety symbols for quick identification. The label is printed on a high-resolution micro-optic photo chromogenic material. A multiple number of images of an optically compressed security safety symbol are printed on the focal plane along the linear optical center of each micro-lenticule across the entire area or a small portion of the label. Due to the optical effect of the micro-optic, the complete security safety symbol is not clearly visible at normal viewing distance. When viewing the label directly or using the camera of a mobile phone at a close-up distance or slightly bending the label, each micro-lenticule within the viewing angle projects and magnifies a small section of the compressed security safety symbol on the surface of the micro-lenticules to reassemble the complete original image of the security safety symbol for identification.The image elements that compose the compressed security safety symbols under each micro-lenticules are printed at the approximately same location on the focal plane of each micro-lenticule in relation to the linear optical center of the micro-lenticule. Therefore the same and complete reassembled image of the security safety symbol can be seen from any location of the label for quick identification. The complete reassembled image of the security safety symbol is progressive shifting following a moving viewpoint for quick and accurate identification.The color photo of the reassembled security safety symbol can be sent by a mobile phone installed with a related software to an Anti-Counterfeiting Control Center for computer matching and verification and the consumer will be advised of the result in a matter of seconds
Owner:LO ALLEN K
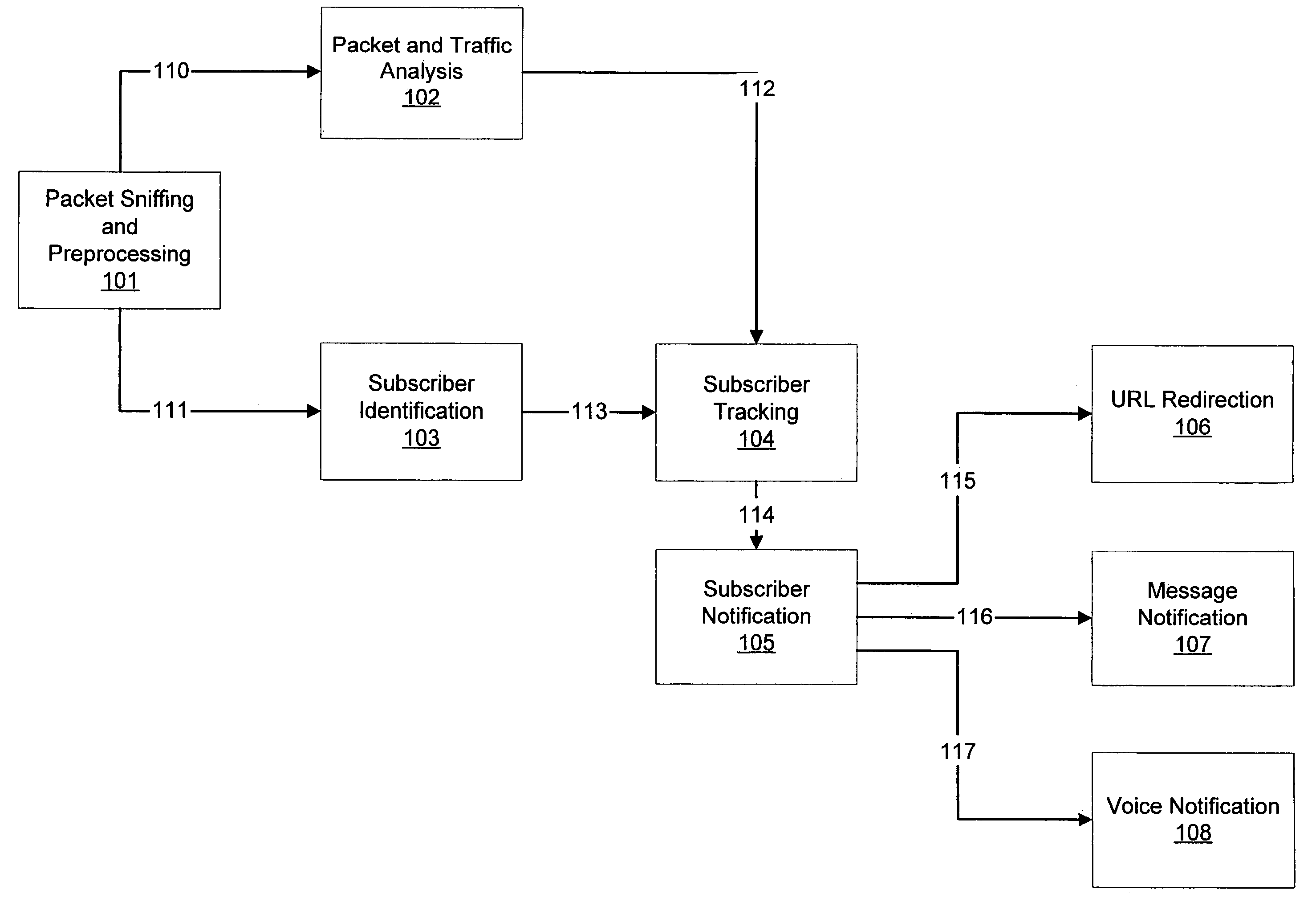
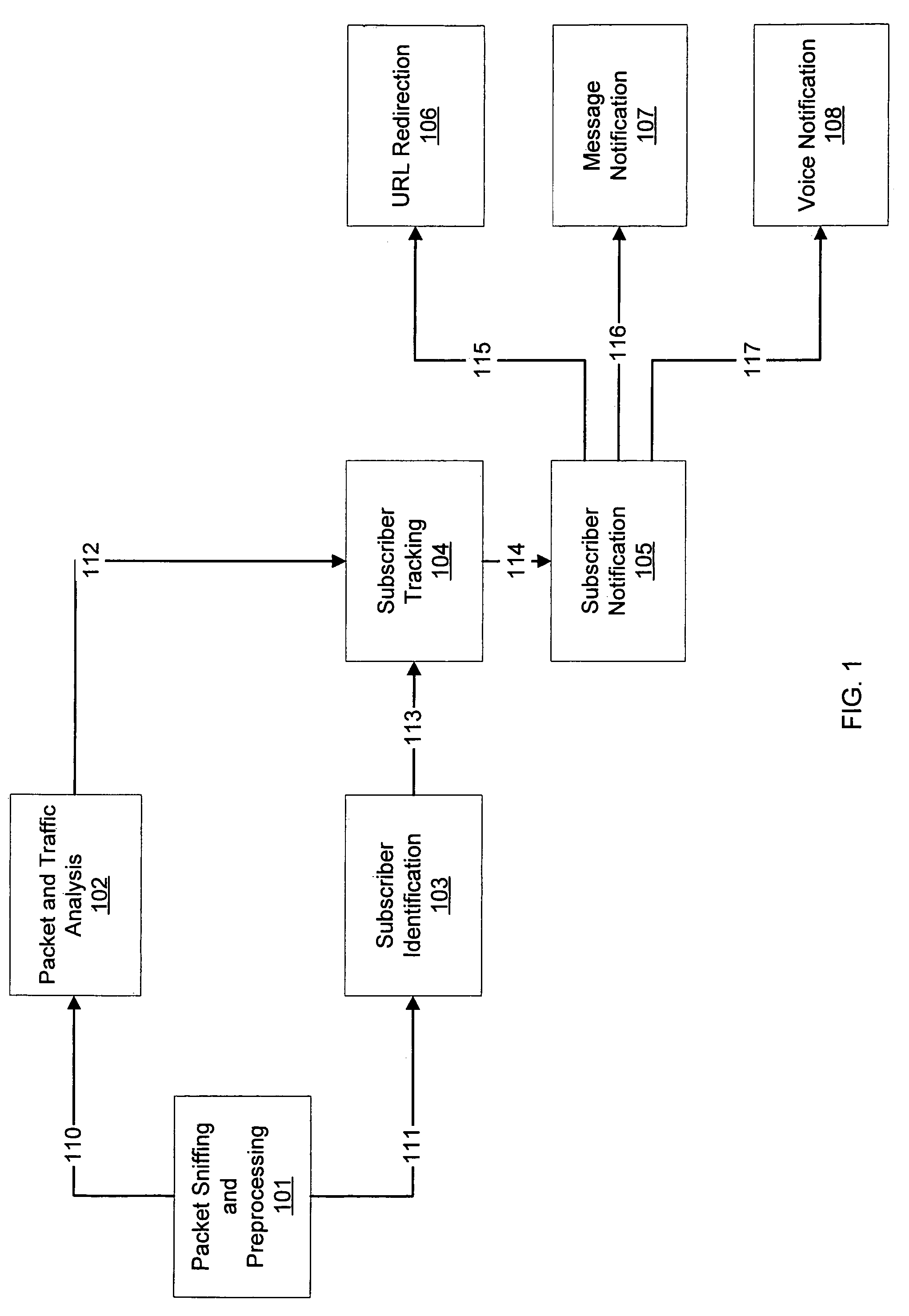
Method for malicious traffic recognition in IP networks with subscriber identification and notification
InactiveUS7676217B2Unauthorised/fraudulent call preventionMemory loss protectionUnique identifierMobile security
A technique for recognizing malicious traffic in IP networks coupled with an identification and notification of a mobile subscriber generating or receiving malicious traffic is provided. An embodiment of the present invention may include intrusively or non-intrusively monitoring in real-time the mobile subscriber's data traffic for malicious traffic as well as mobile security intrusion attempts. Another embodiment of the present invention may report the identification of those mobile subscribers generating or receive malicious traffic to an operator. By knowing the identity of the mobile subscriber, an embodiment of the present invention may block the mobile subscriber's subscription or alert the mobile subscriber in question about the malicious traffic. One embodiment of the present invention may be applied to mobile networks where the mobile subscriber's identity is known by an unique identifier (e.g., an IMSI or a phone number) and where a notification system may be implemented using a messaging service e.g., SMS, MMS, IM, email, or voice.
Owner:THETA NETWORKS
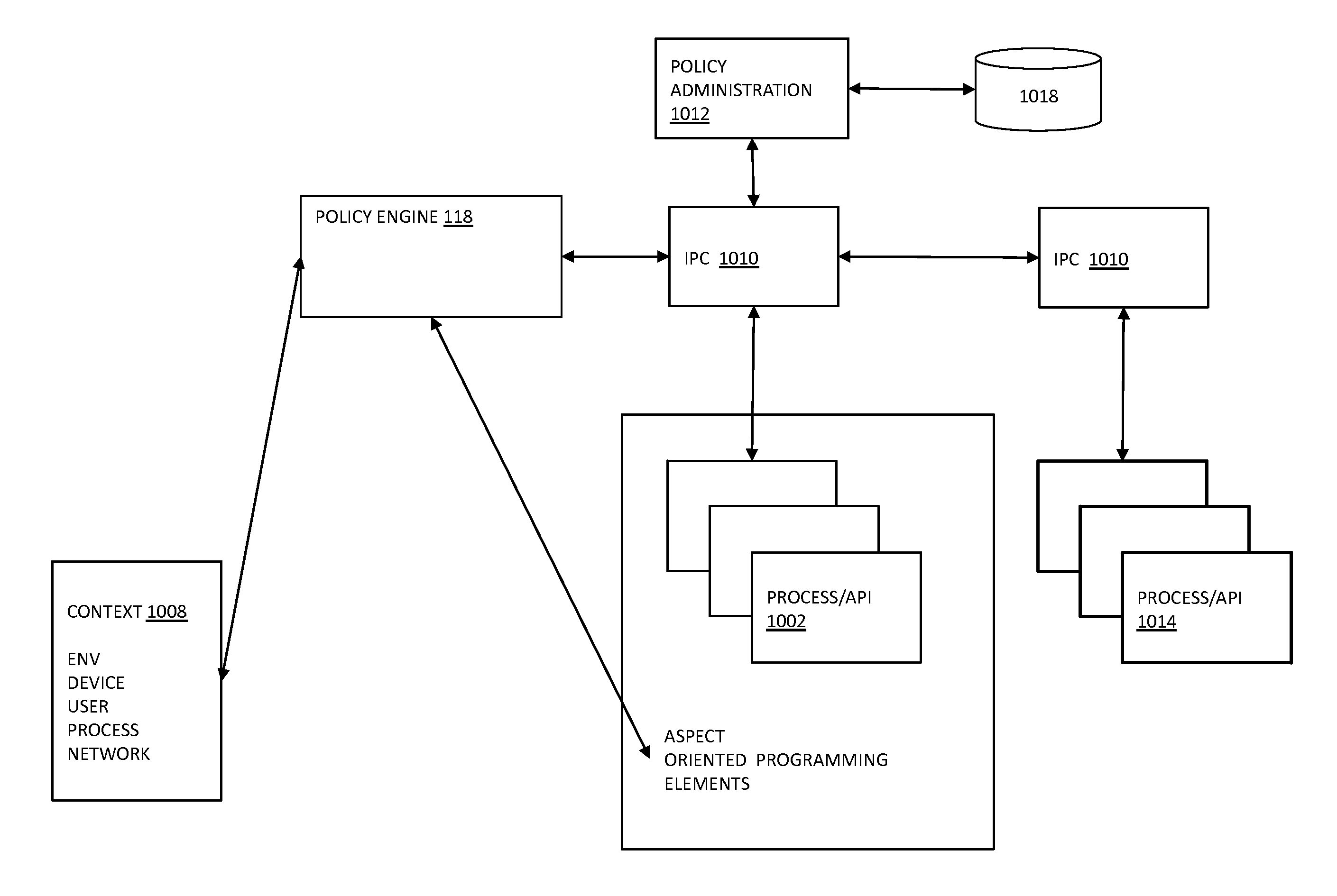
Systems and methods for enhancing mobile security via aspect oriented programming
InactiveUS20130312058A1Improve securityPlatform integrity maintainanceTransmissionMobile securitySecurity policy
Methods and systems described herein relate to enhancing security on a mobile device. A method for enhancing mobile device security includes applying a security policy to process code by an aspect-oriented program.
Owner:OPTIO LABS
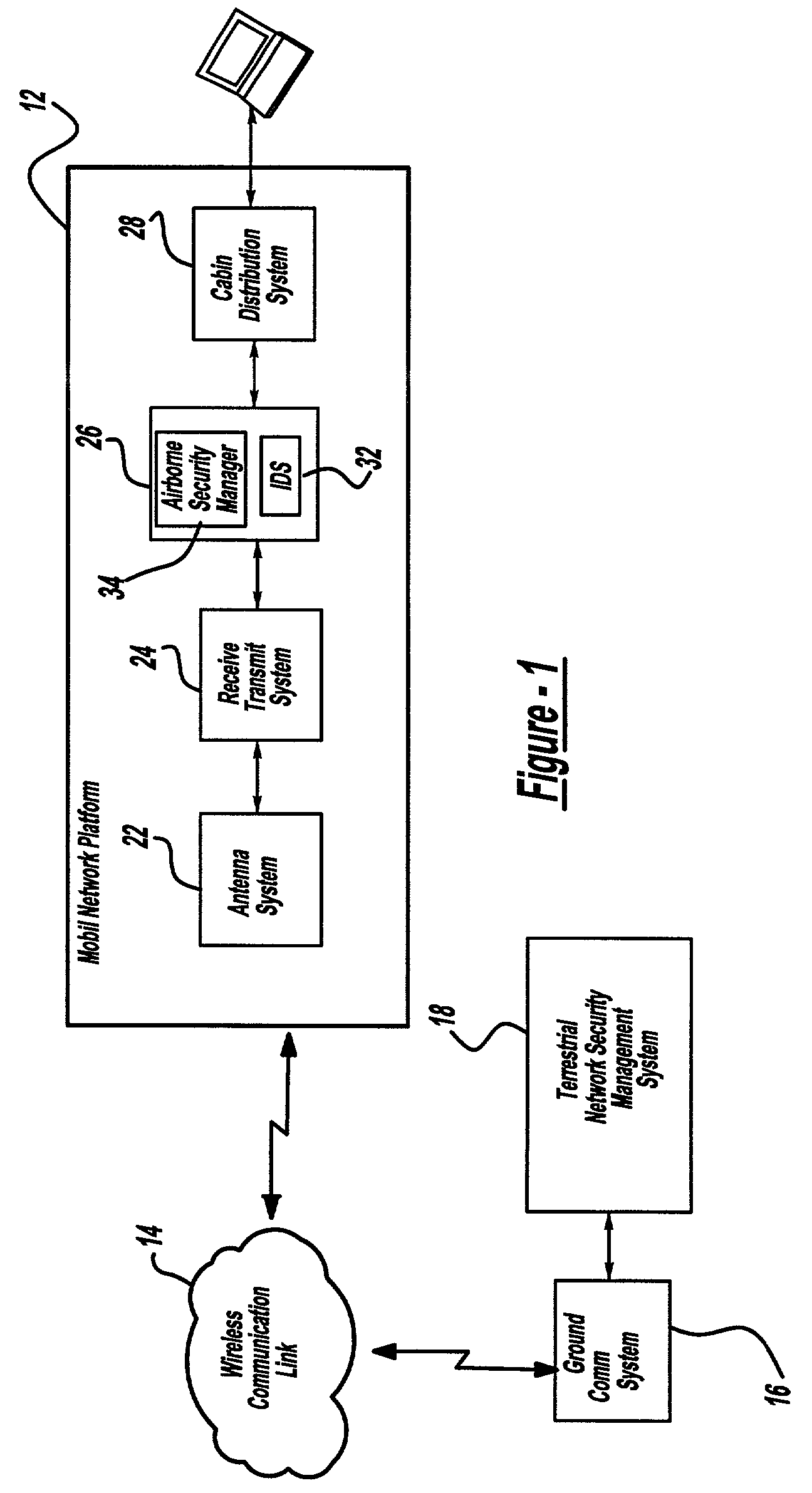
Airborne security manager
InactiveUS7715819B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkSafety management systems
An airborne security management system is provided for monitoring security activities in a mobile network platform. This system includes a mobile network that is interconnected via an unreliable communication link to a terrestrial-based network security management system; an intrusion detection system connected to the mobile network and operable to detect a security intrusion event whose origination is associated with the mobile network; and a mobile security manager adapted to receive the security intrusion events from the intrusion detection system. The mobile security manager is operable to transmit a message indicative of the security intrusion event to the network security management system and to perform security response activities in response to security commands received from the network security management system. The mobile security manager is further operable to command security response activities on the mobile network platform, when the mobile network platform is not connected with network security management system.
Owner:THE BOEING CO
Mobile Security Monitoring Method and System and an Alarm Security Node In the System
InactiveUS20090231122A1Ease in possibilityMinimized cost levelTelephonic communicationElectric testing/monitoringVideo monitoringUser device
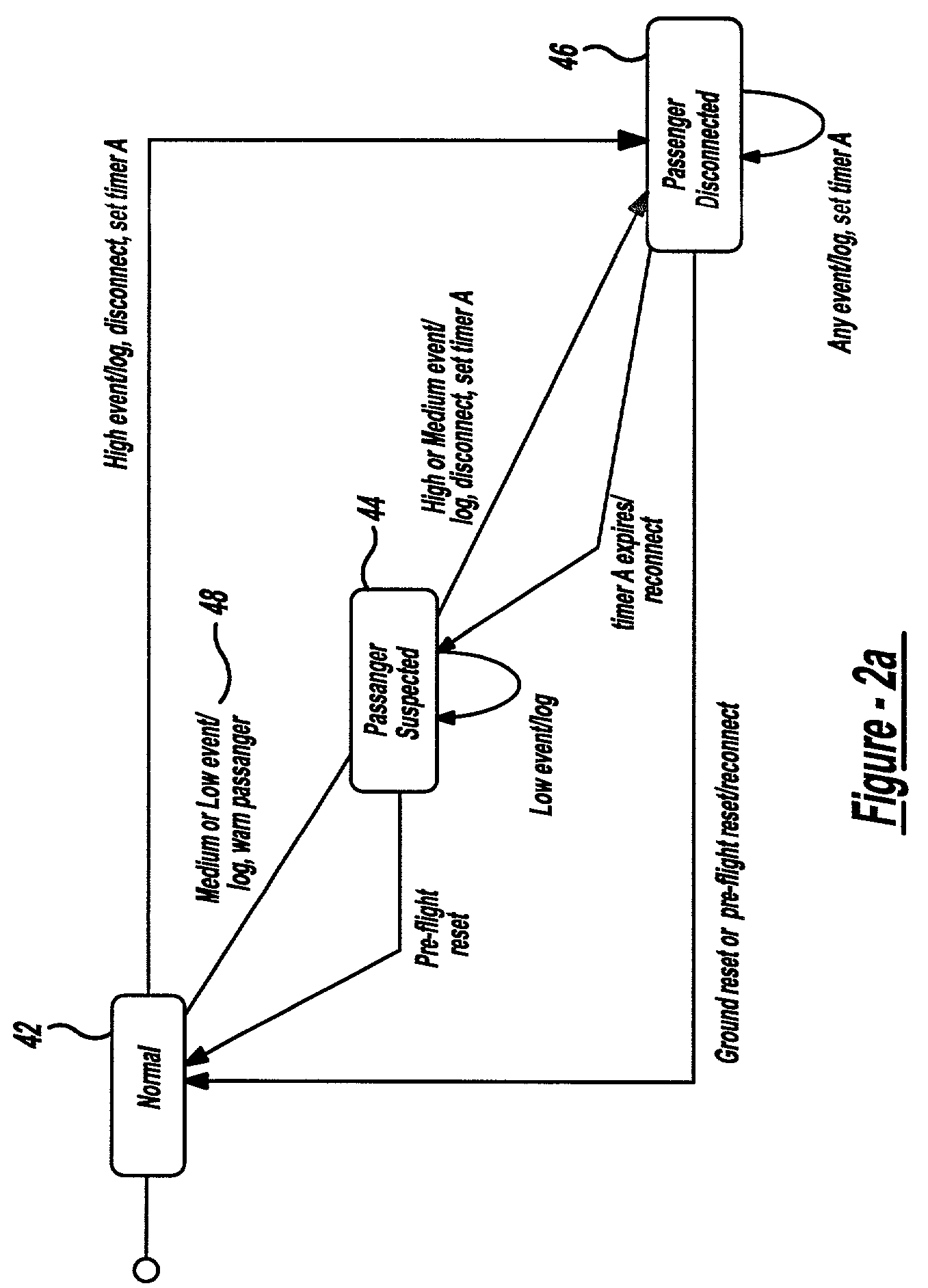
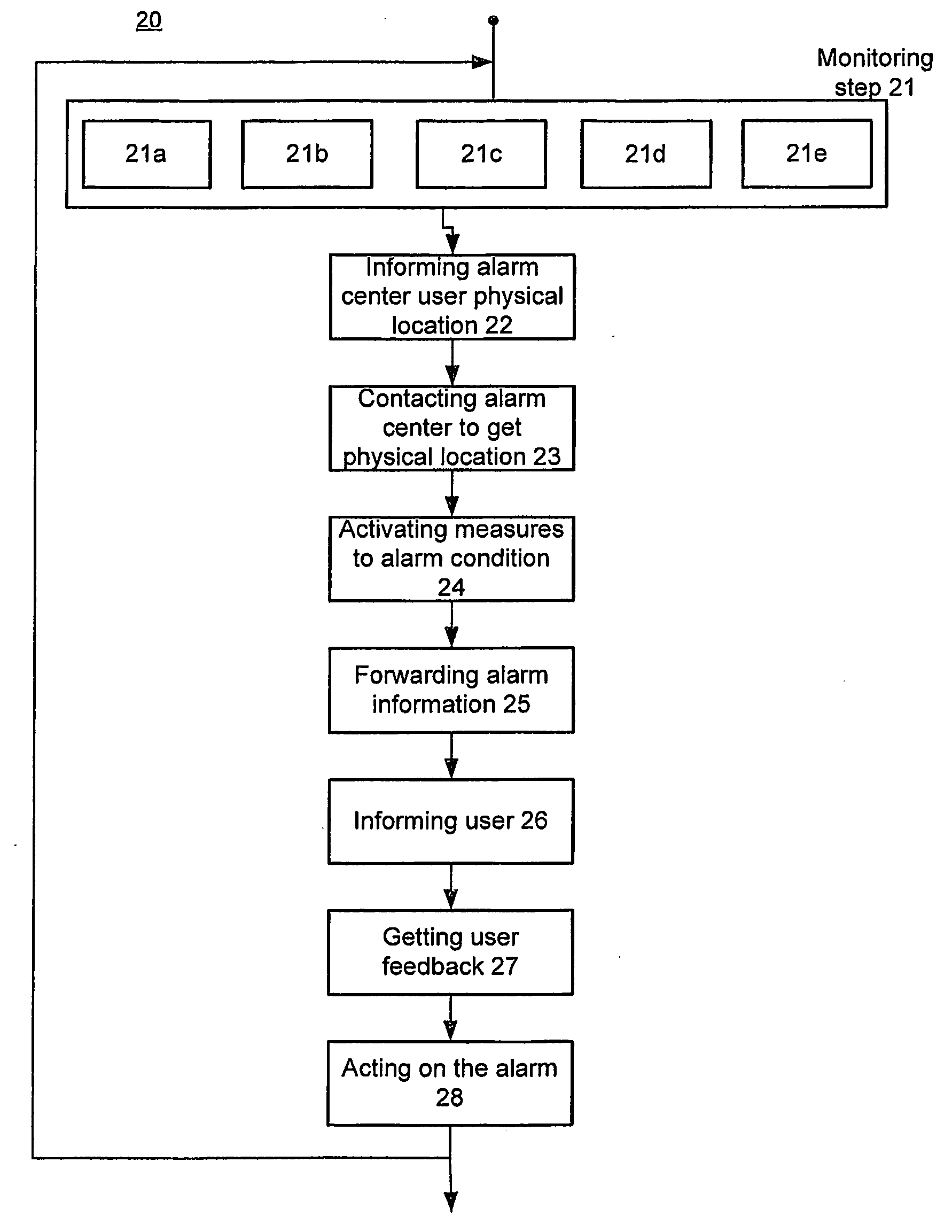
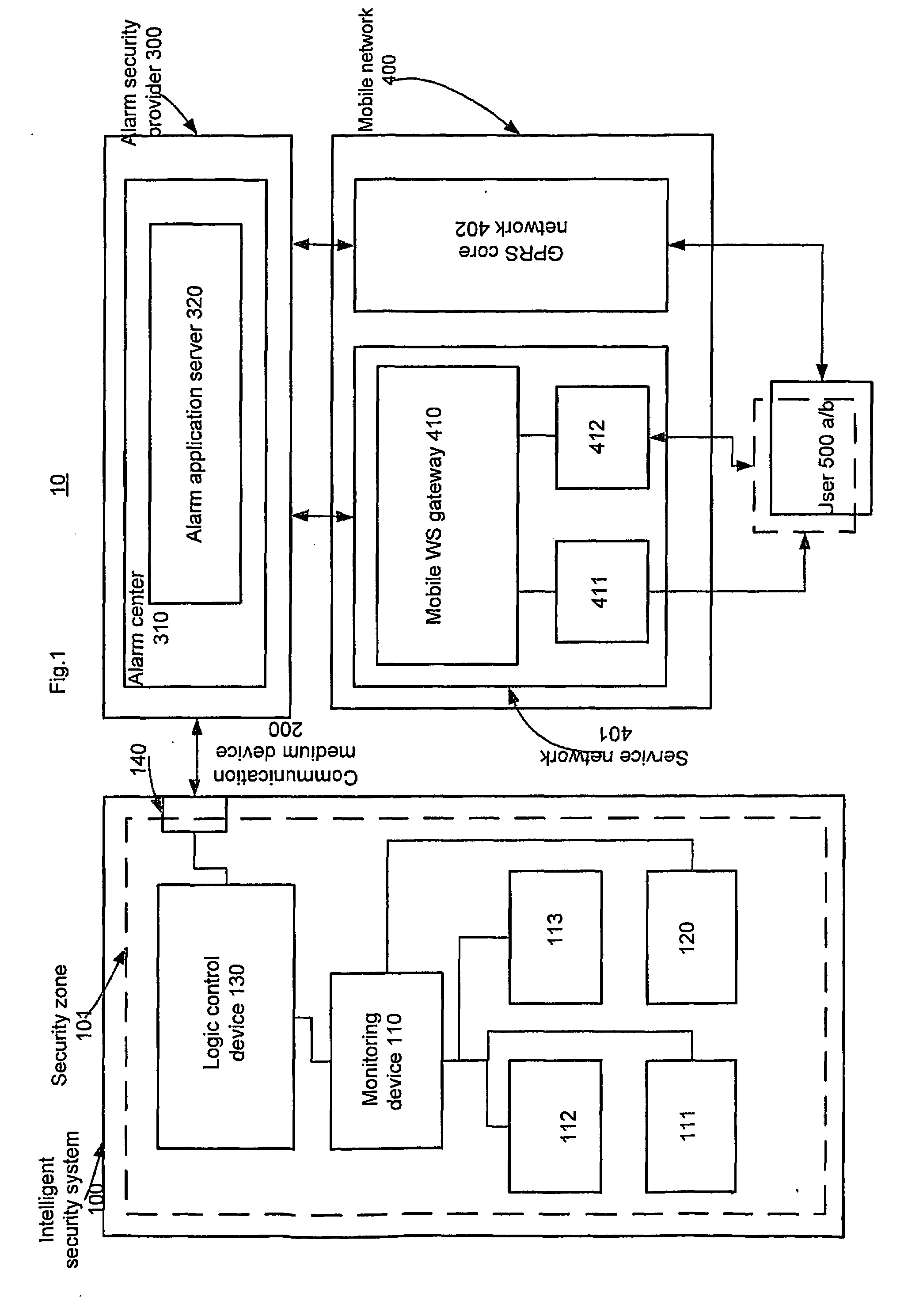
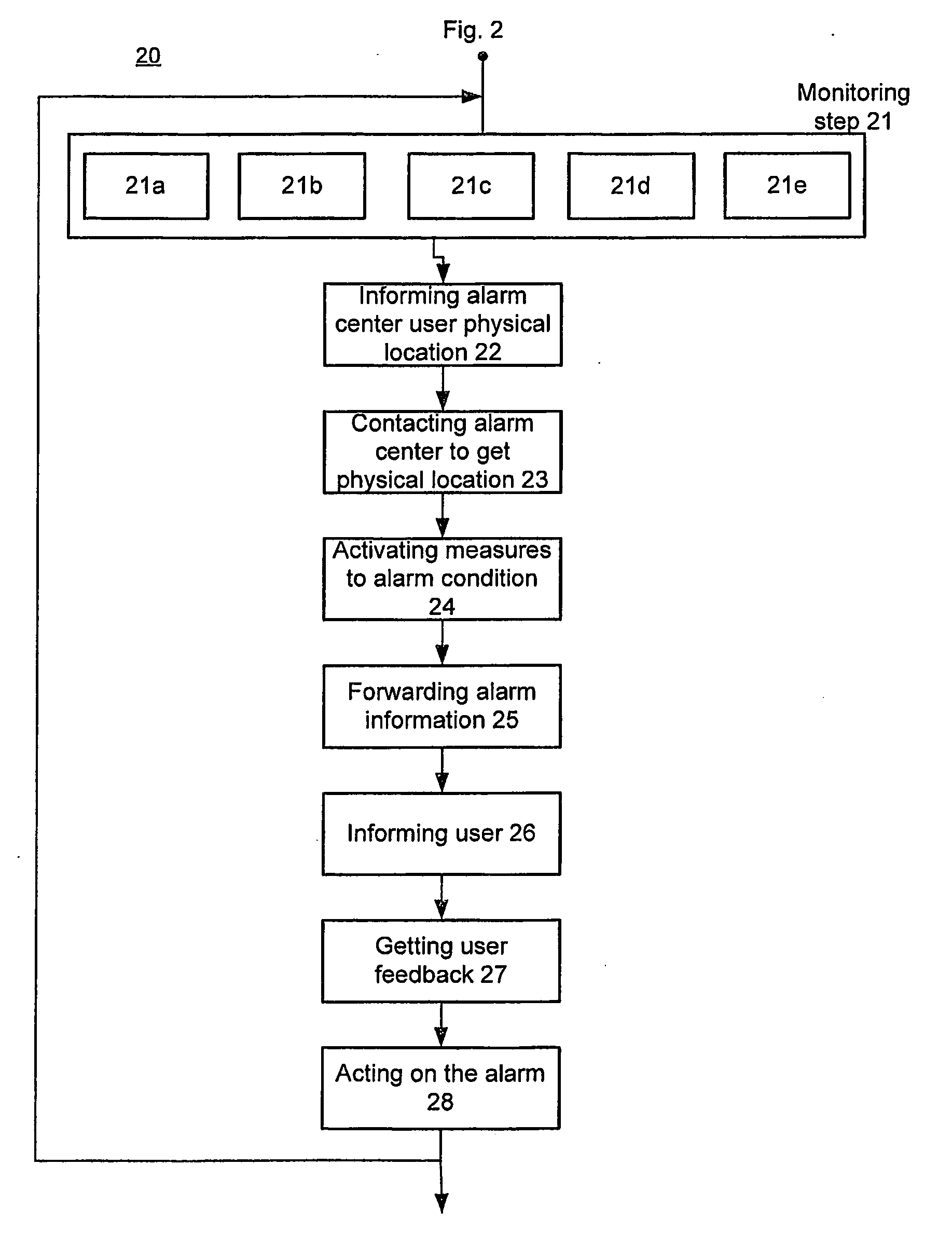
A mobile security monitoring method and system and an alarm security node in the system for intelligent security system, where said intelligent security system is activated by a breach in a security zone. This breach will start a video monitoring / recording sequence that is sent out via the broadband to an alarm center. The alarm center forwards this alarm information to a user as SMS / MMS information through a mobile network. The user can view and evaluate what is going on at the security zone and can decide what action to initiate. This will minimize a false alarm generation and thus cut down the costs of follow thru of the false alarm (s) by i.e. an alarm security provider. For security and cost reason, the intelligent security system is the only client of the server-side alarm center. The concept is to use existing IT infrastructure at the security zone for user like W-LAN, broadband, GPRS and mobile devices. A mobile phone can be used for activation and deactivation of intelligent security system based on manual push of a button on the user device. Another aspect is to make the activation / deactivation step dependent on mobile location like GPS or mobile positioning system based on mobile network 400 infrastructures that use the spatial trigger.
Owner:OPTIS WIRELESS TECH LLC
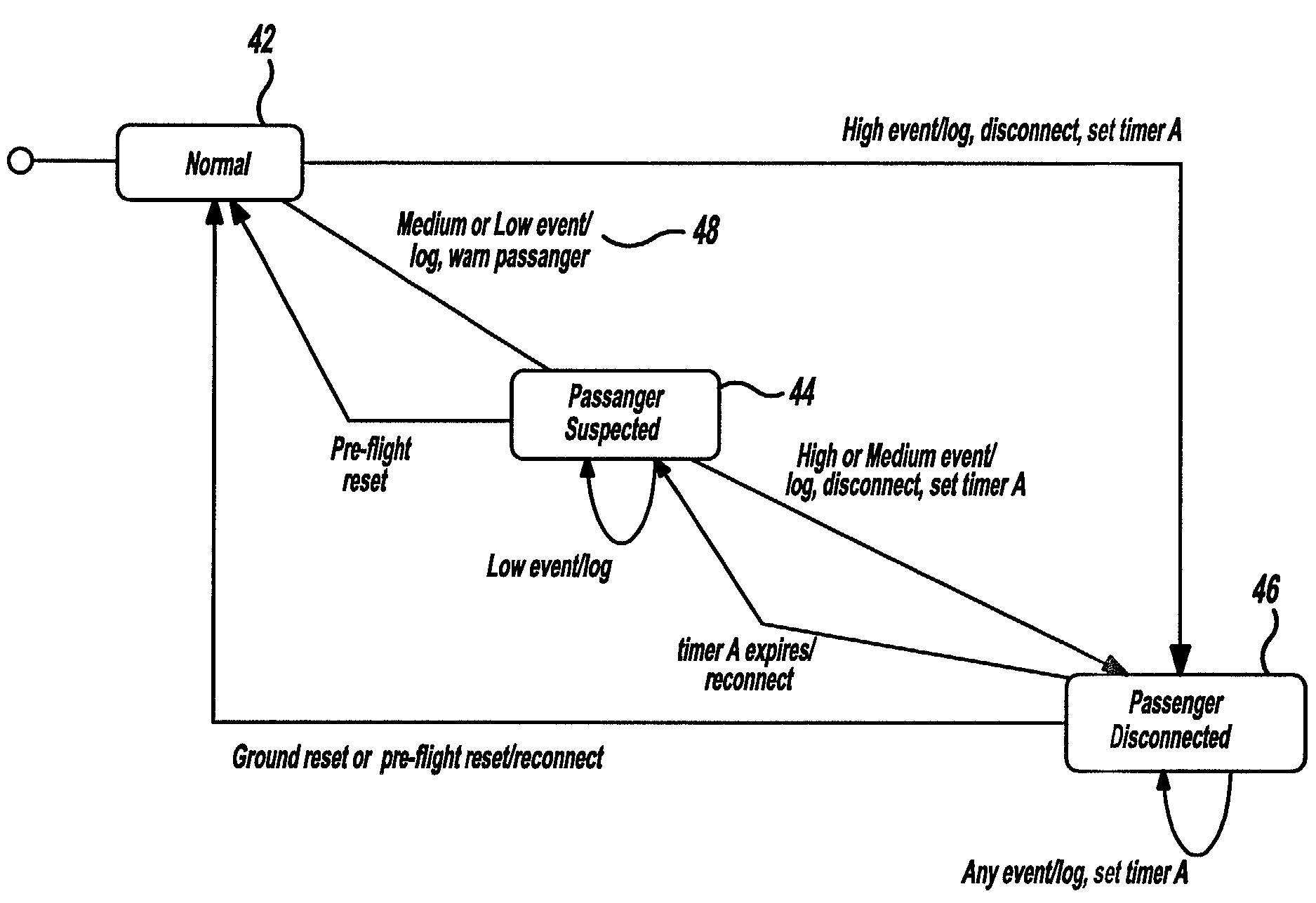
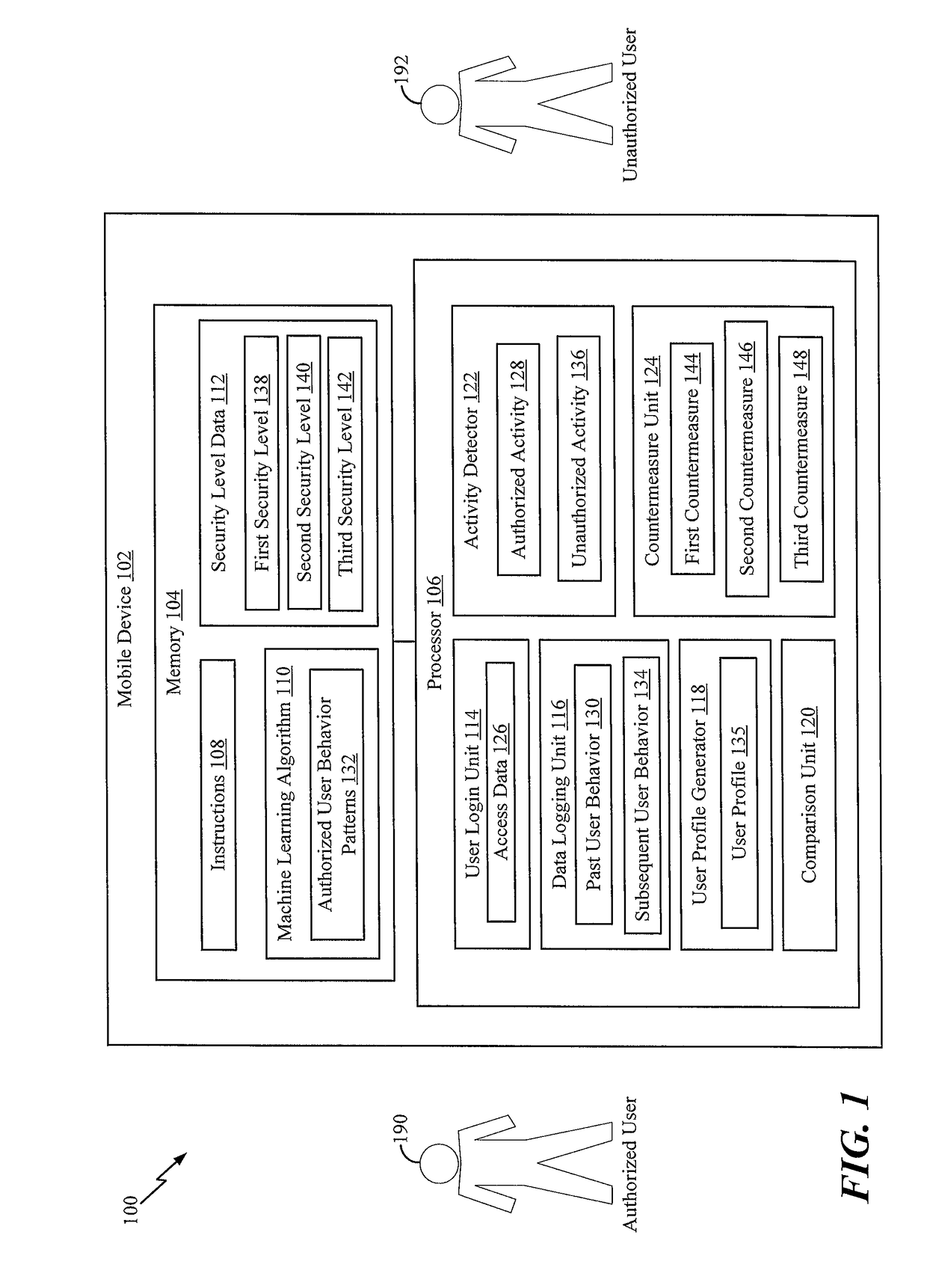
Mobile security countermeasures
ActiveUS20190020676A1Preventing access to their dataAvoid dataSpeech analysisDigital data authenticationCountermeasureInternet privacy
A method includes generating a user profile for an authorized user of a mobile device based on behavior patterns associated with the authorized user. The method also includes detecting subsequent user behavior of a particular user during an attempt by the particular user to access the mobile device. The method also includes comparing the subsequent user behavior to the behavior patterns of the user profile to determine whether the particular user is authorized or unauthorized. In response to determining that the particular user is an unauthorized user, the method includes detecting activity by the unauthorized user and performing a countermeasure of a plurality of countermeasures in response to detecting the activity. Each countermeasure of the plurality of countermeasures has a different security level and corresponds to a degree of the activity.
Owner:THE BOEING CO
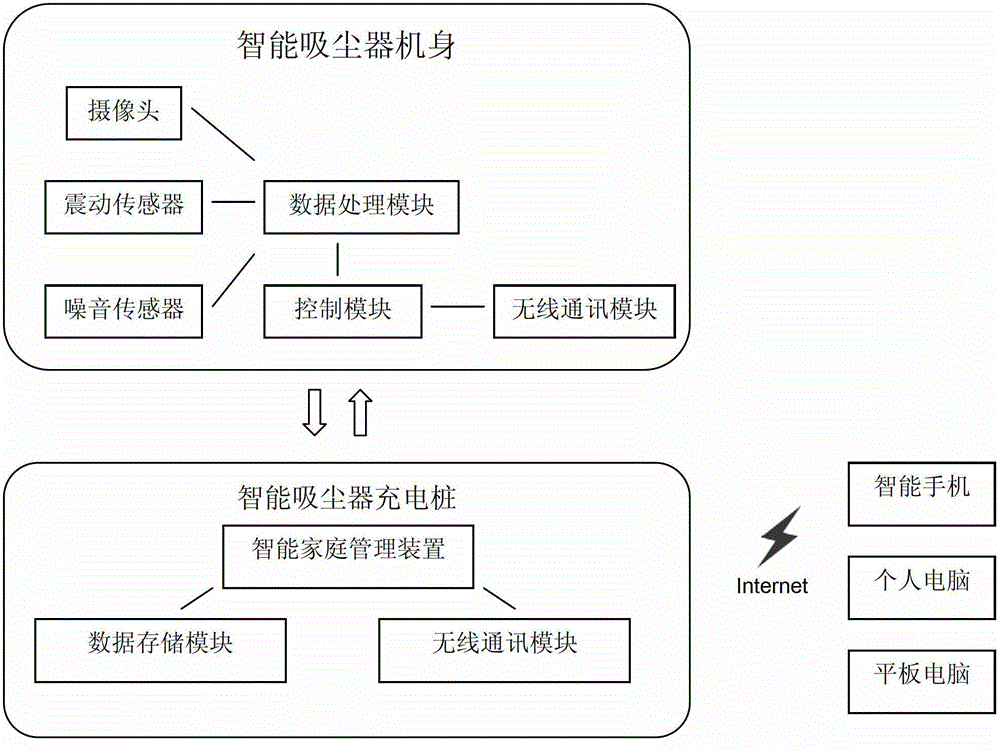
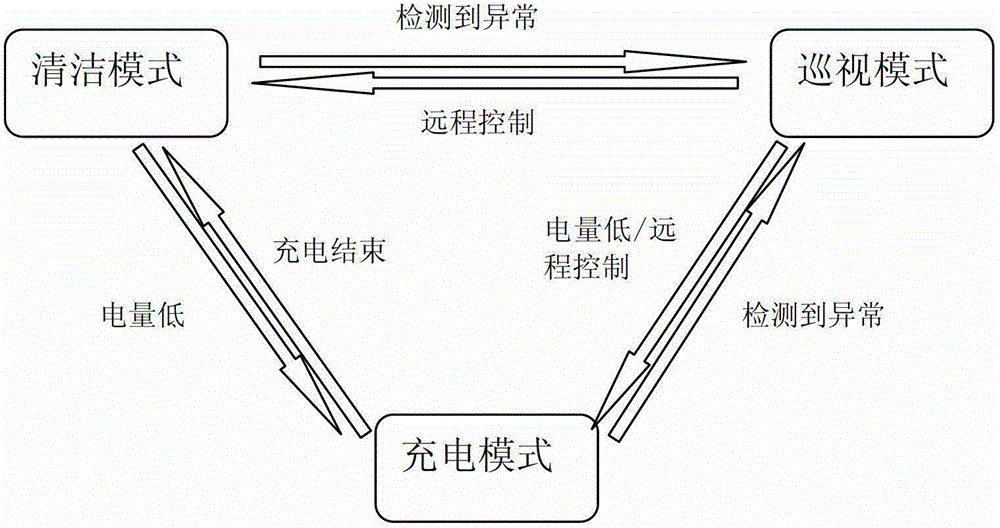
Smart vacuum cleaner with mobile security monitoring function
InactiveCN103142188ASafe Home MonitoringAutomatic obstacle detectionTravelling automatic controlThe InternetData memory
The invention provides a smart vacuum cleaner with a mobile security monitoring function. The smart vacuum cleaner comprises a cleaner body and a charging post thereof, wherein the cleaner body comprises a camera, a vibration sensor, a noise sensor, a first wireless network module and a control module; if the control module detects abnormal vibration, abnormal noise or abnormal movement under a deployment state, the first wireless module sends an alarm to the charging post; the command which is sent by the charging post is switched to an inspection mode, and shot monitoring images are sent to the charging post; the charging post comprises a data memory module for storing the monitoring images which is wirelessly sent by the cleaner body, a second wireless network module and a management device; and the management device receives the alarm command which is sent out by the cleaner body through the second wireless network module, so that the cleaner body is switched to the inspection mode, accesses an internet through a wireless network to transmit alarm information to a remote user terminal and transmits the monitoring images to a remote user. The vacuum cleaner can provide safer household monitoring for the users.
Owner:LG ELECTRONICS CHINA RANDD CENT SHANGHAI CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com