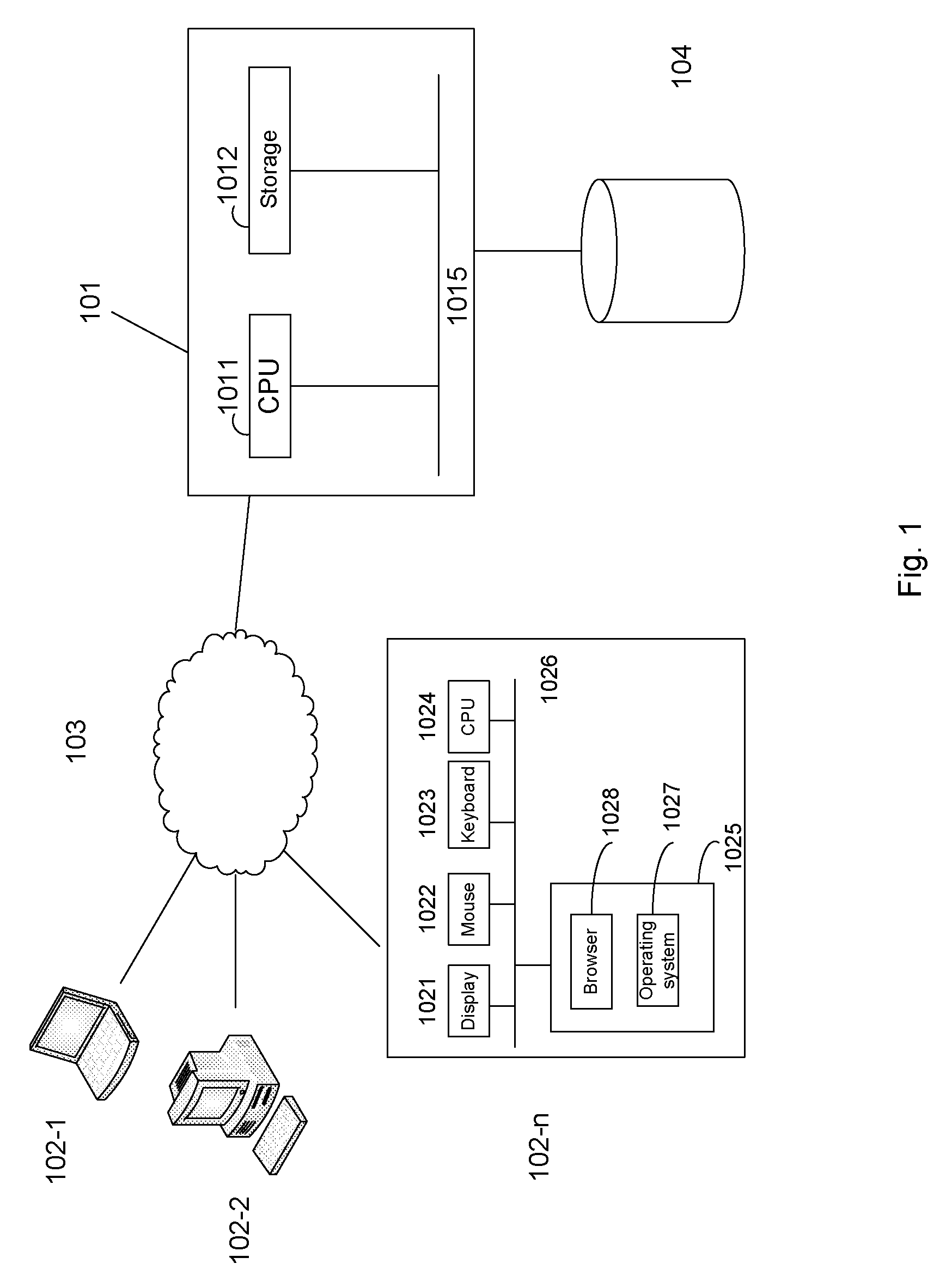
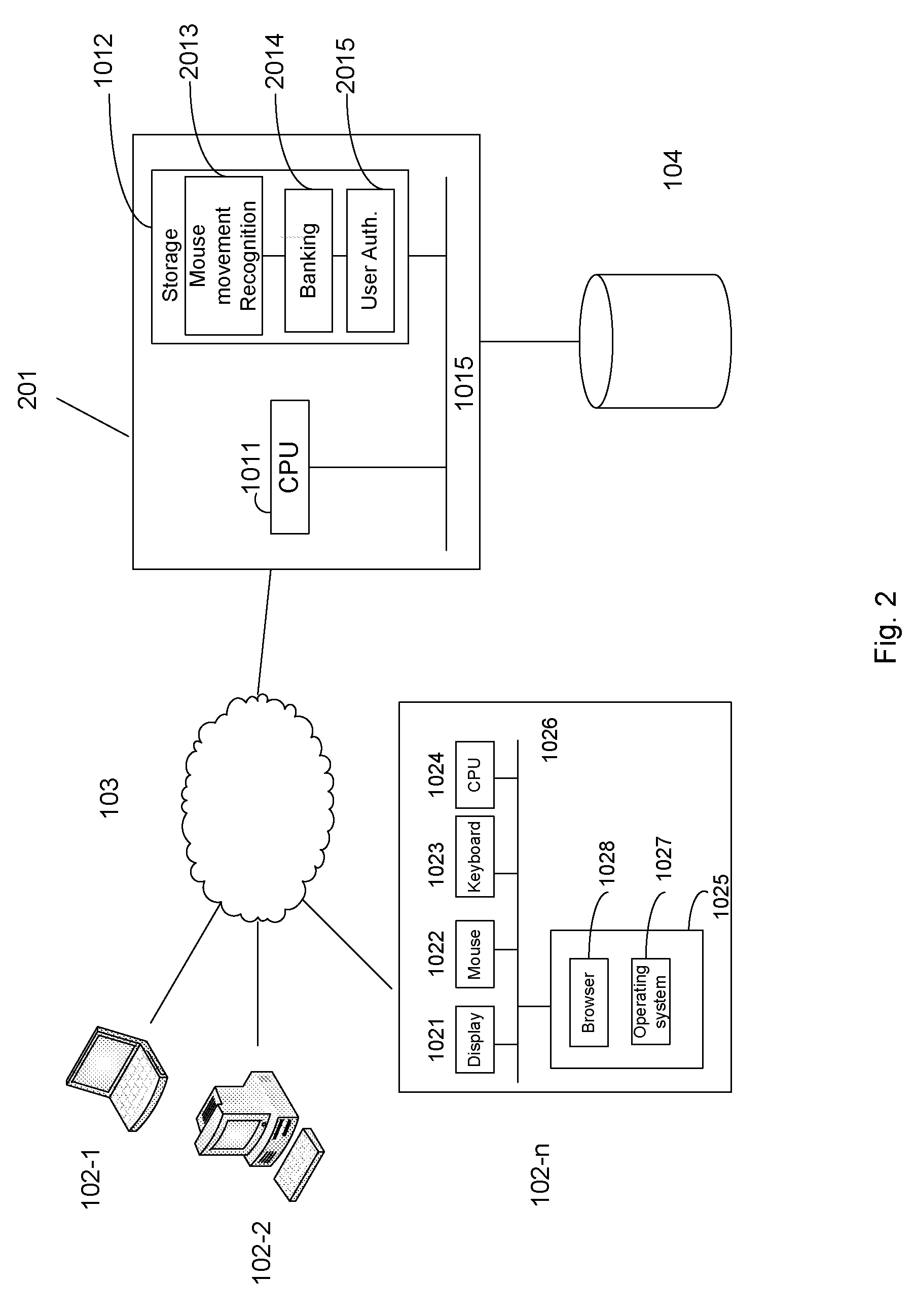
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
529 results about "Transaction security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
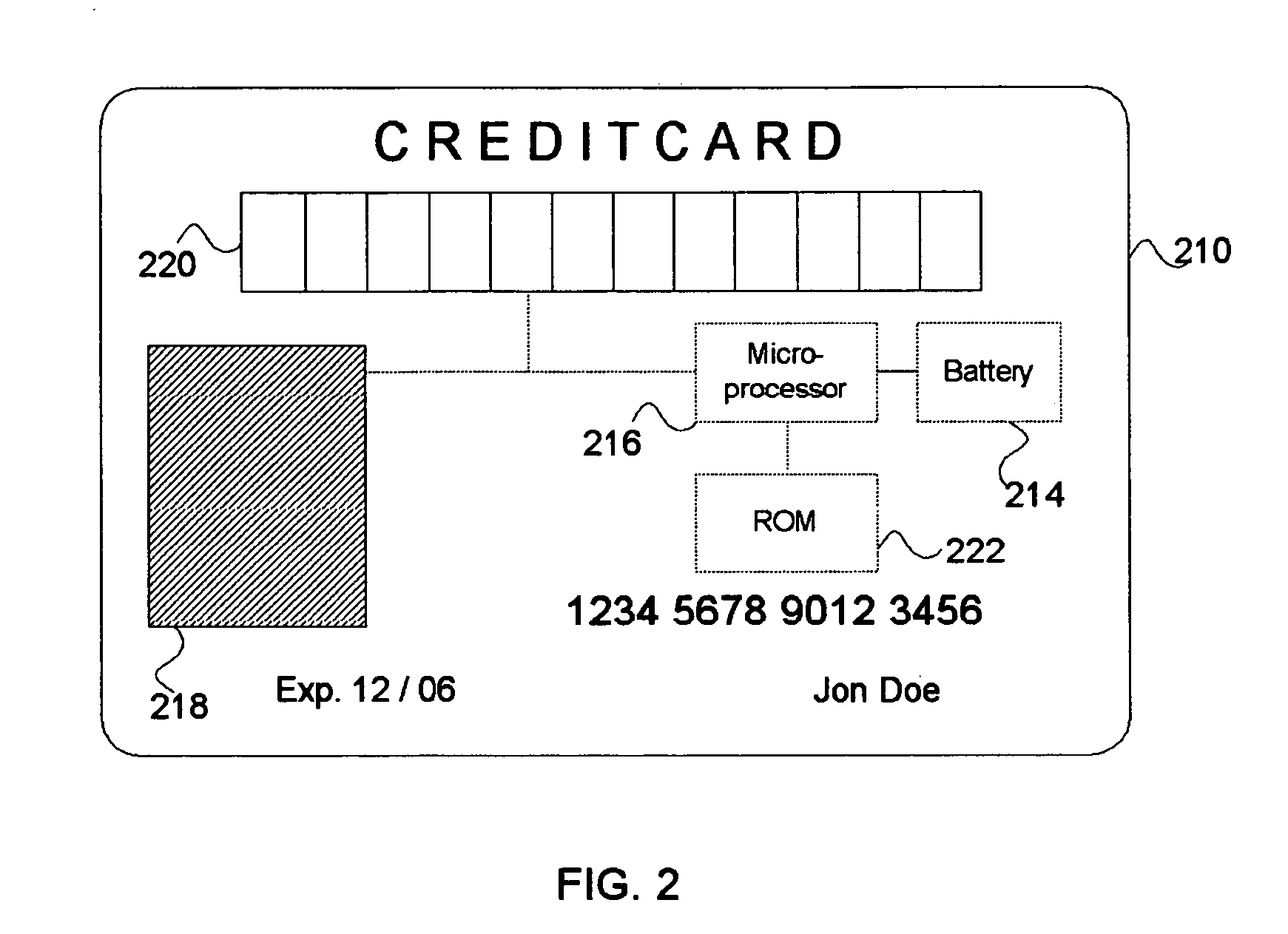
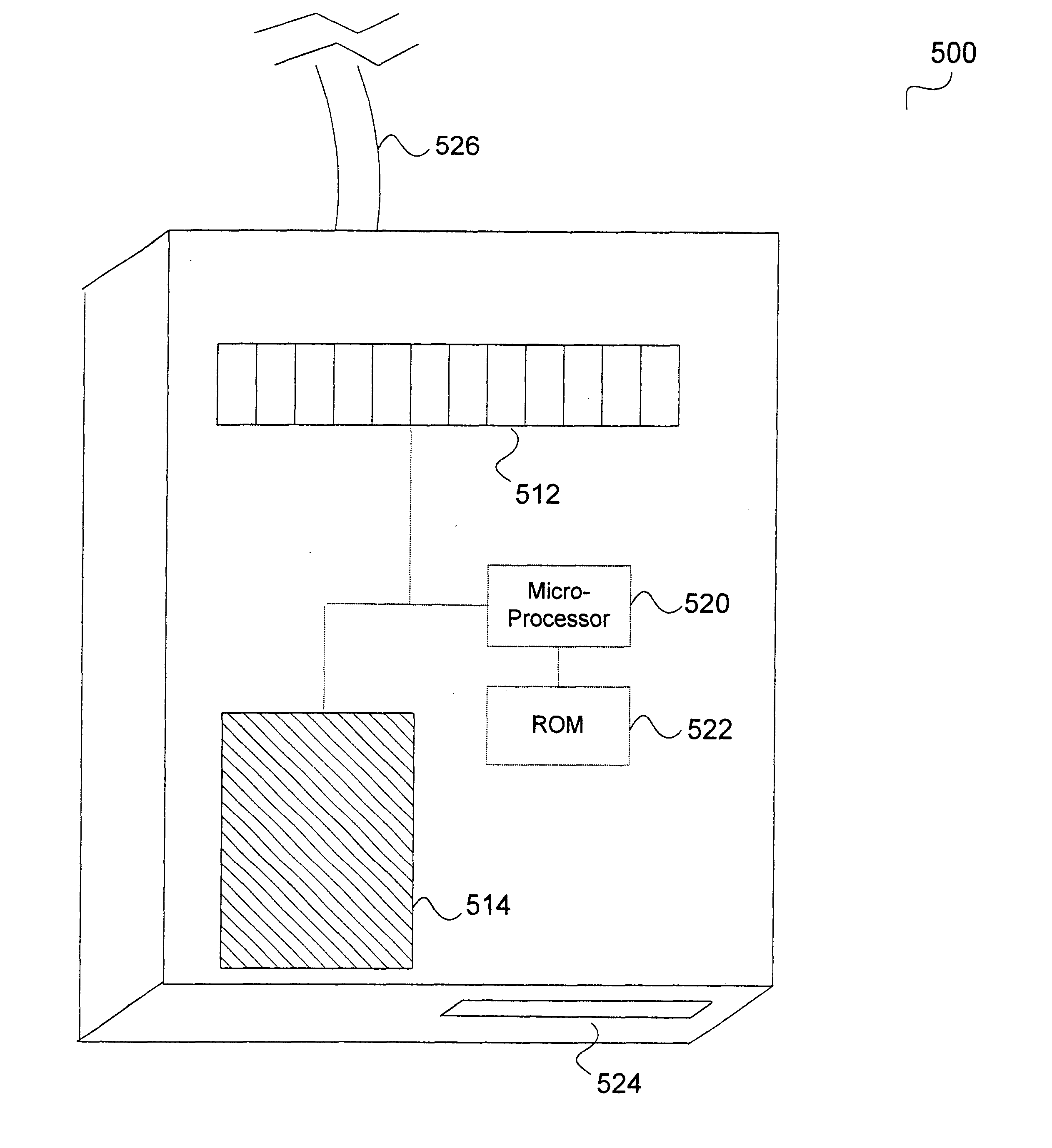
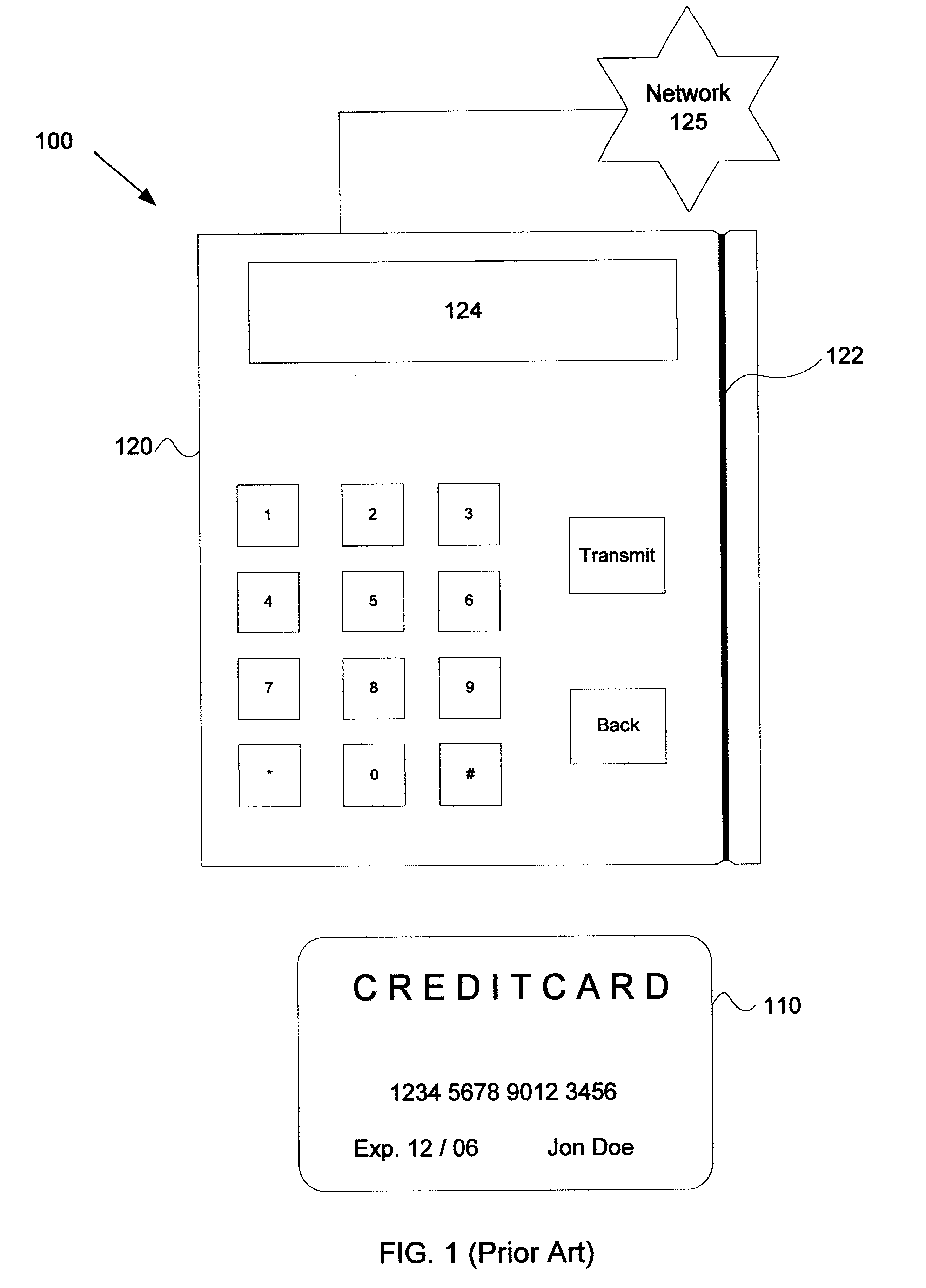
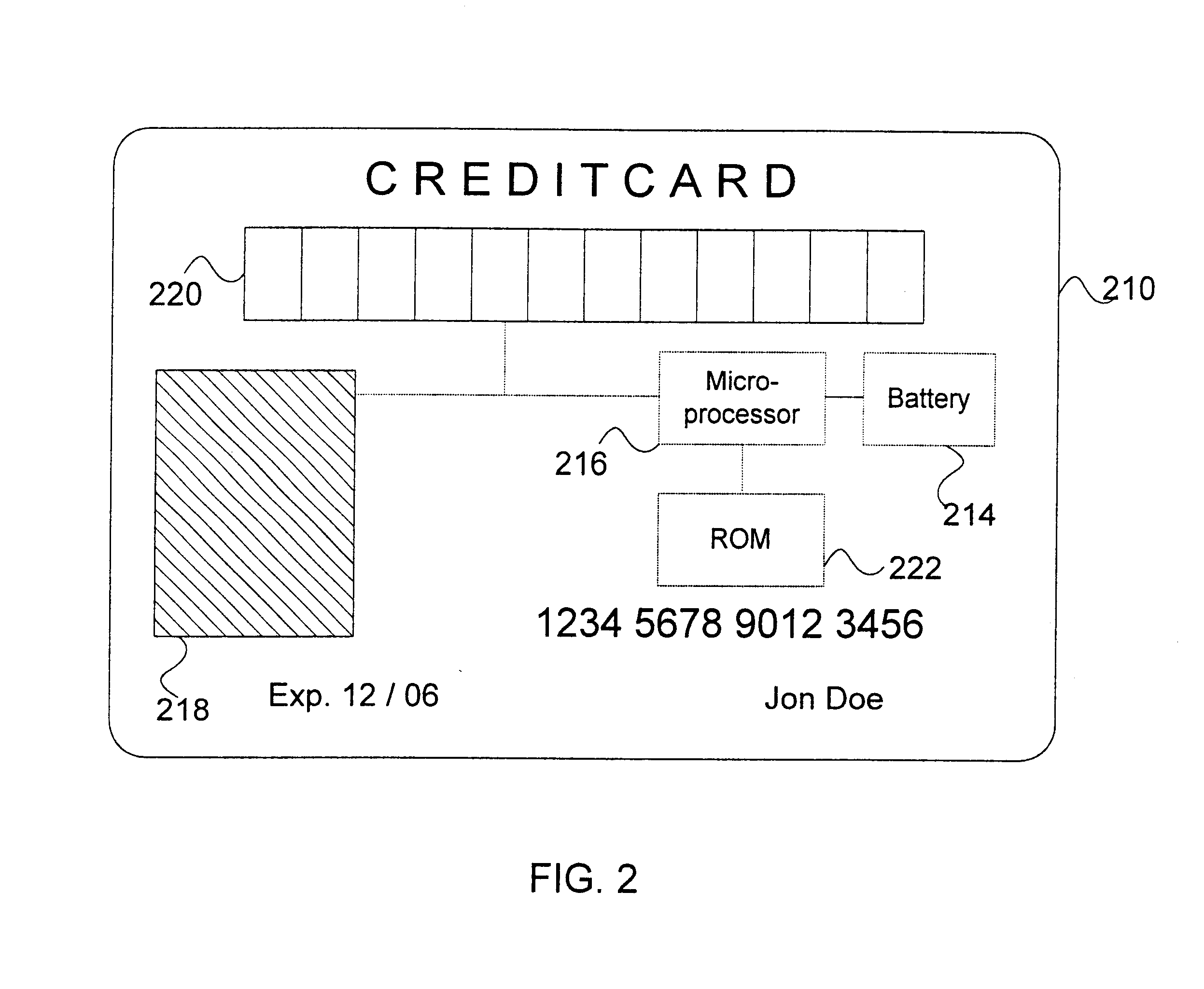
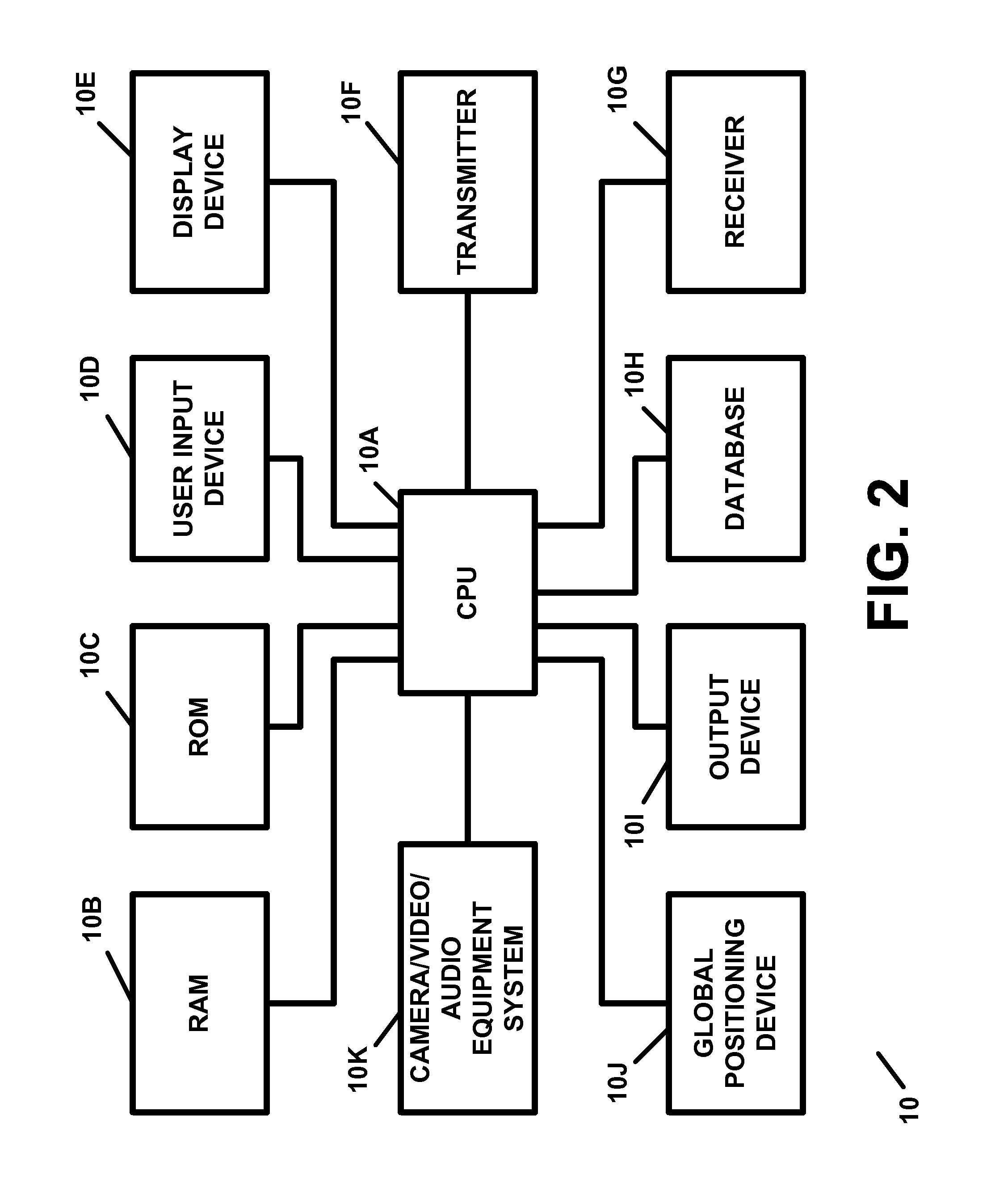
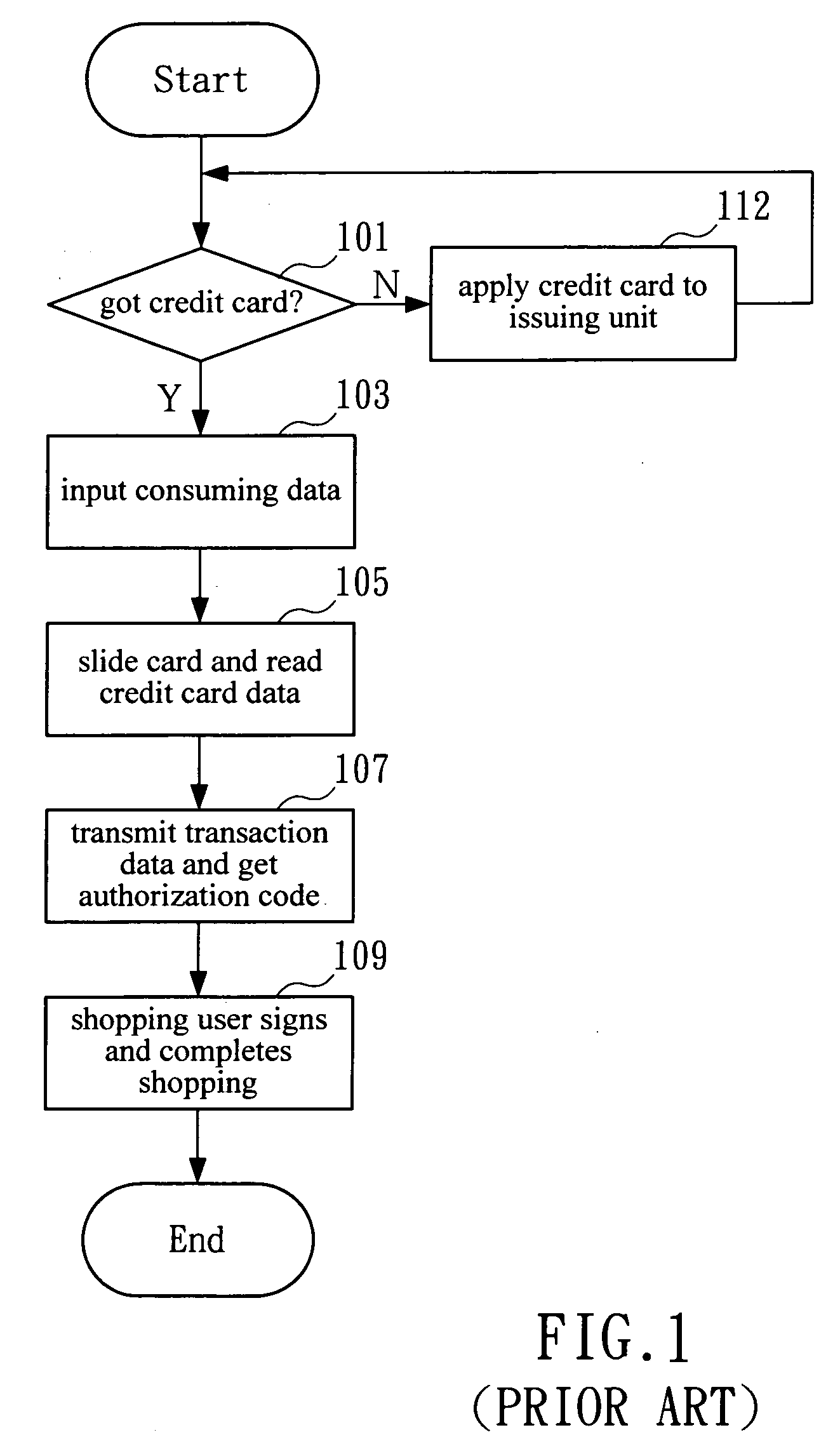
Transaction security. Transaction security (also known as attach-time security, and transaction-attach security) ensures that users that attempt to run a transaction are entitled to do so. CICS parameters controlling transaction-attach security.
Transaction security method and apparatus
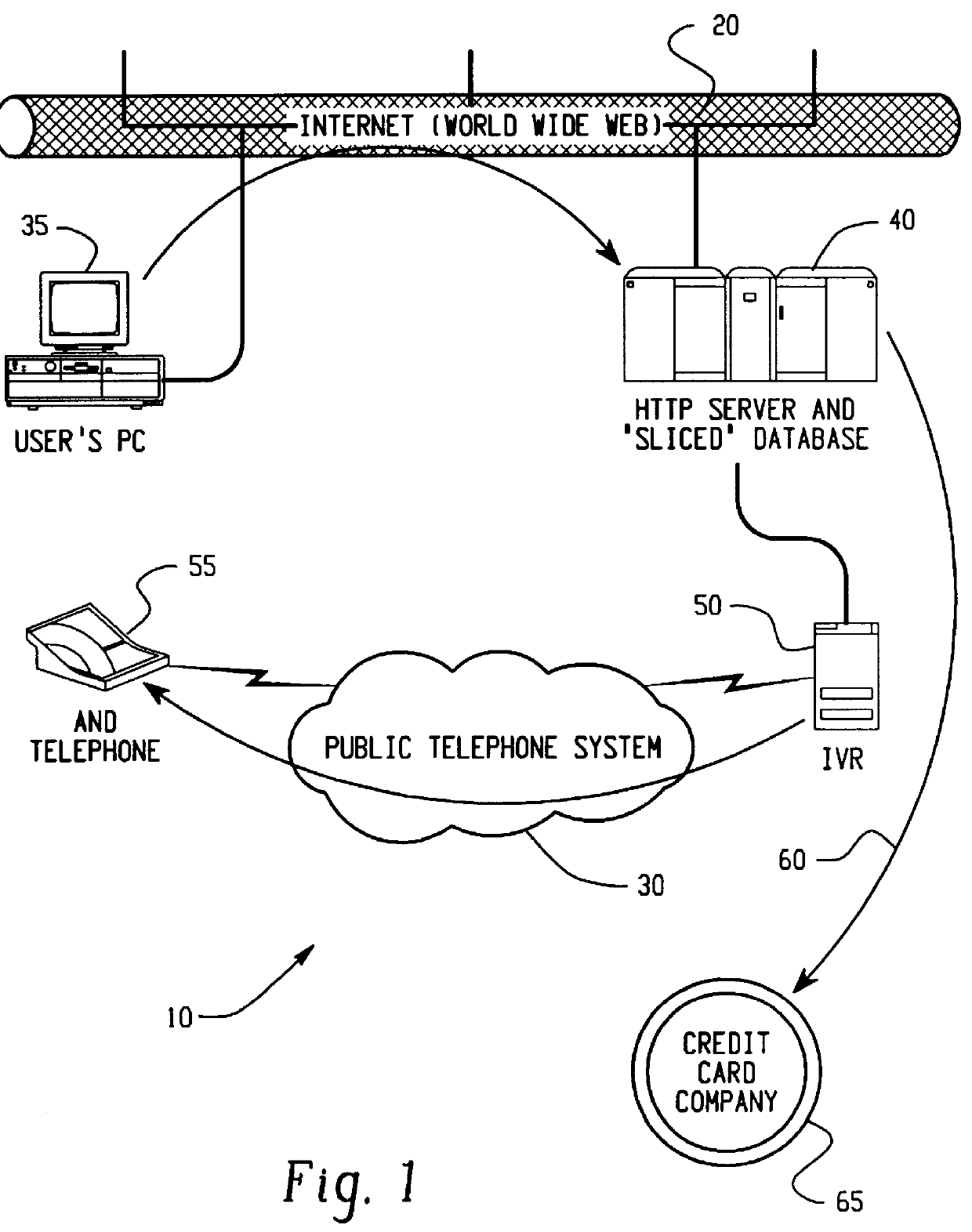
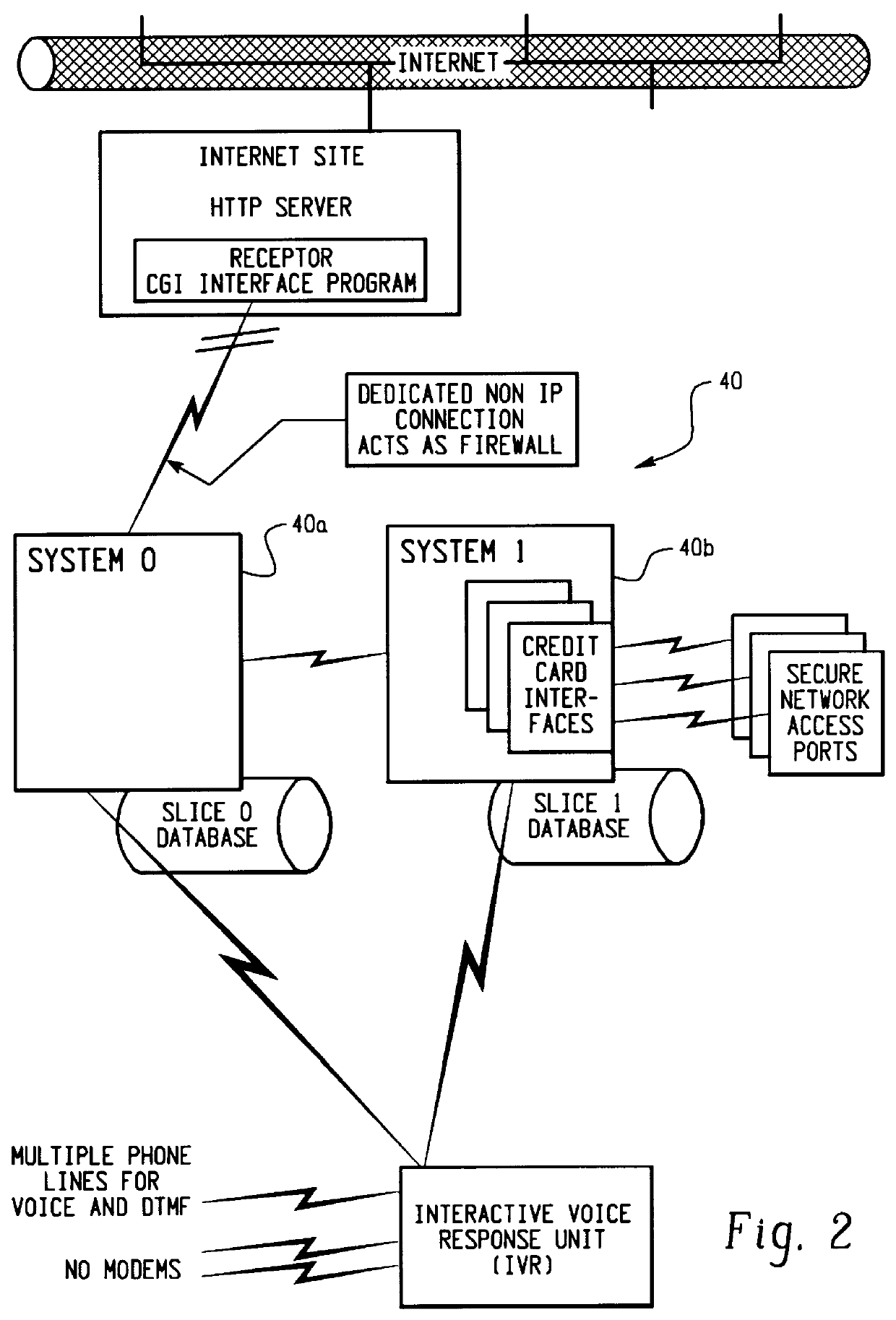
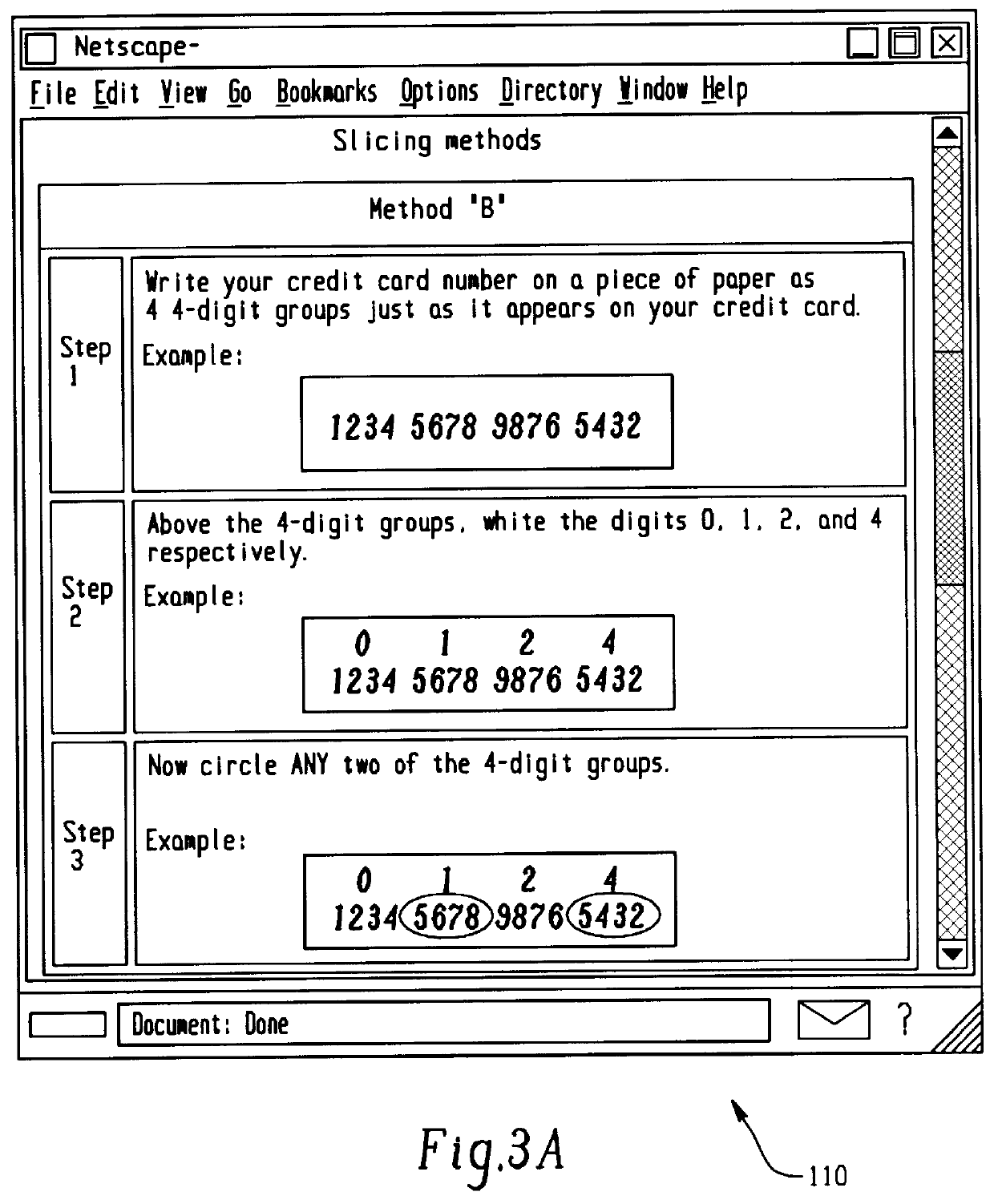
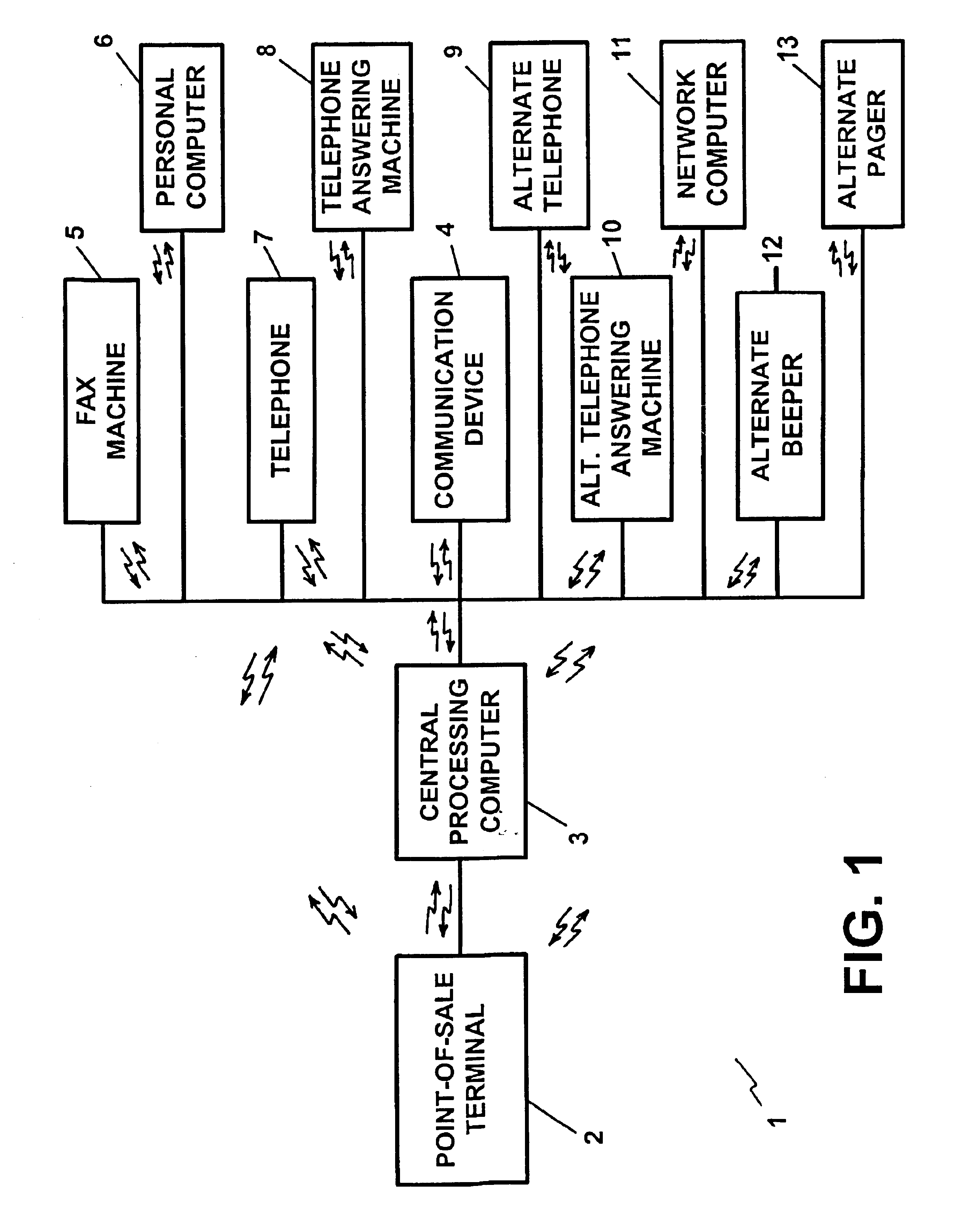
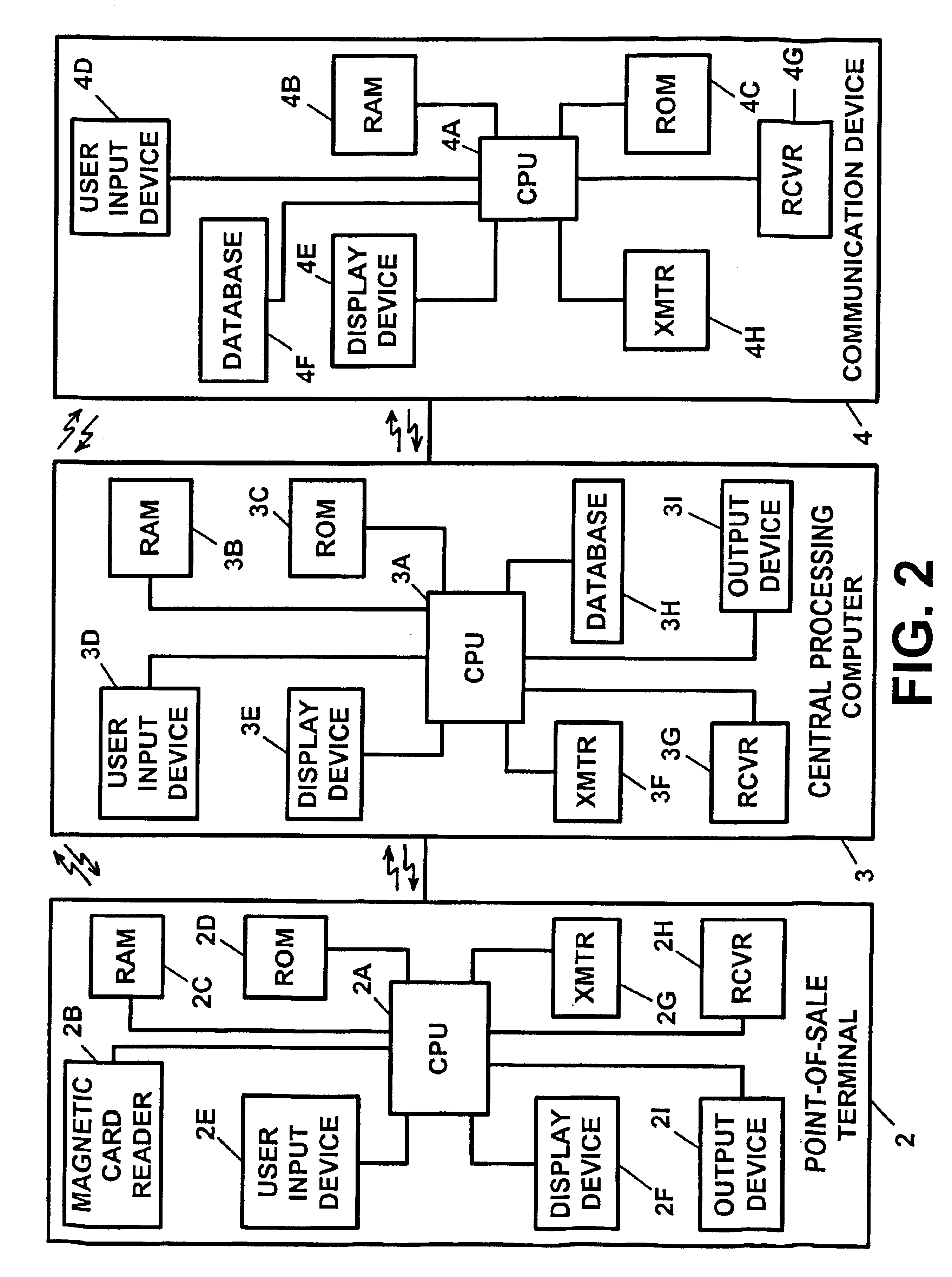
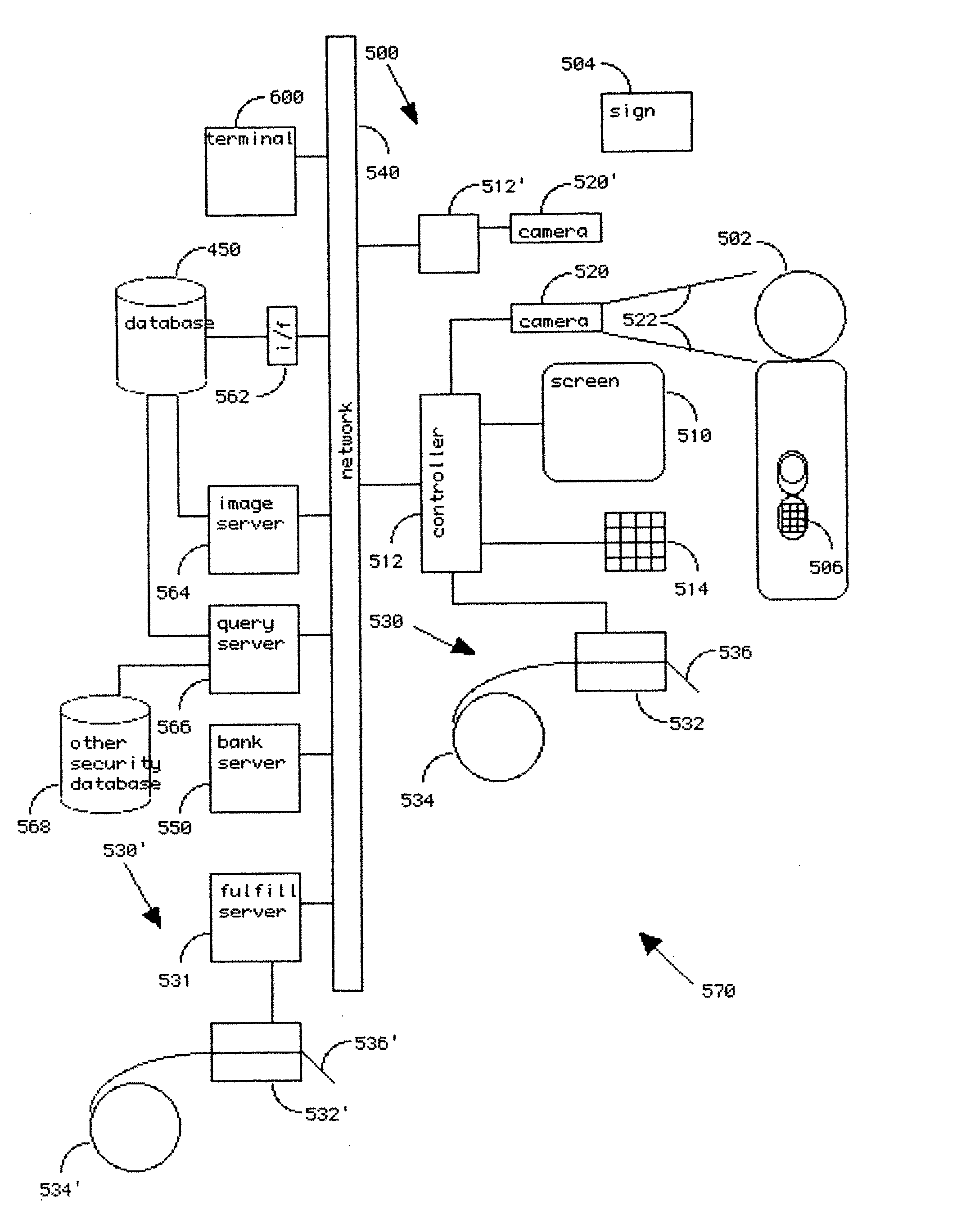
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
Transaction security apparatus
InactiveUS7096003B2Real time monitoringDigital data processing detailsPayment architectureThe InternetTransaction processing system
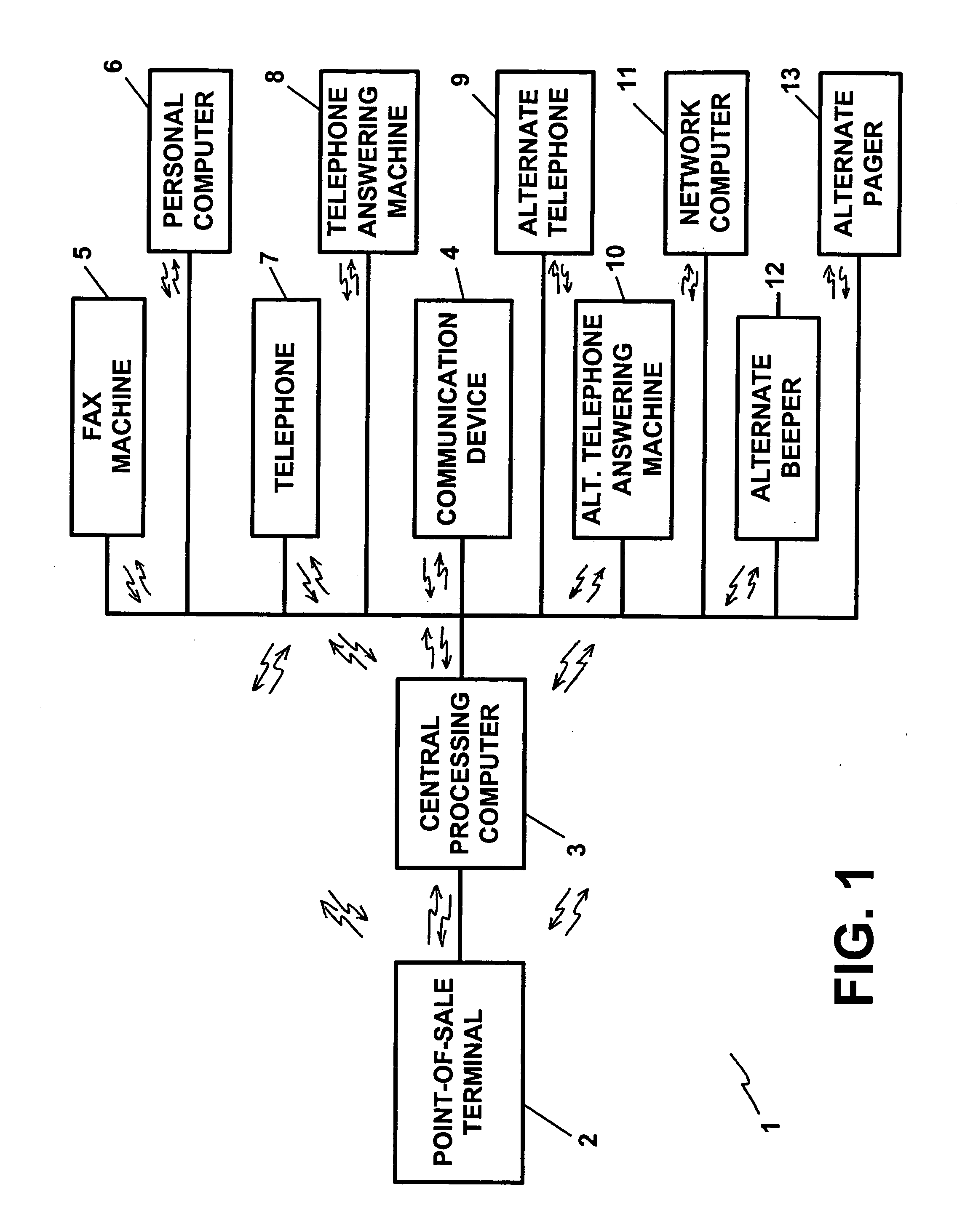
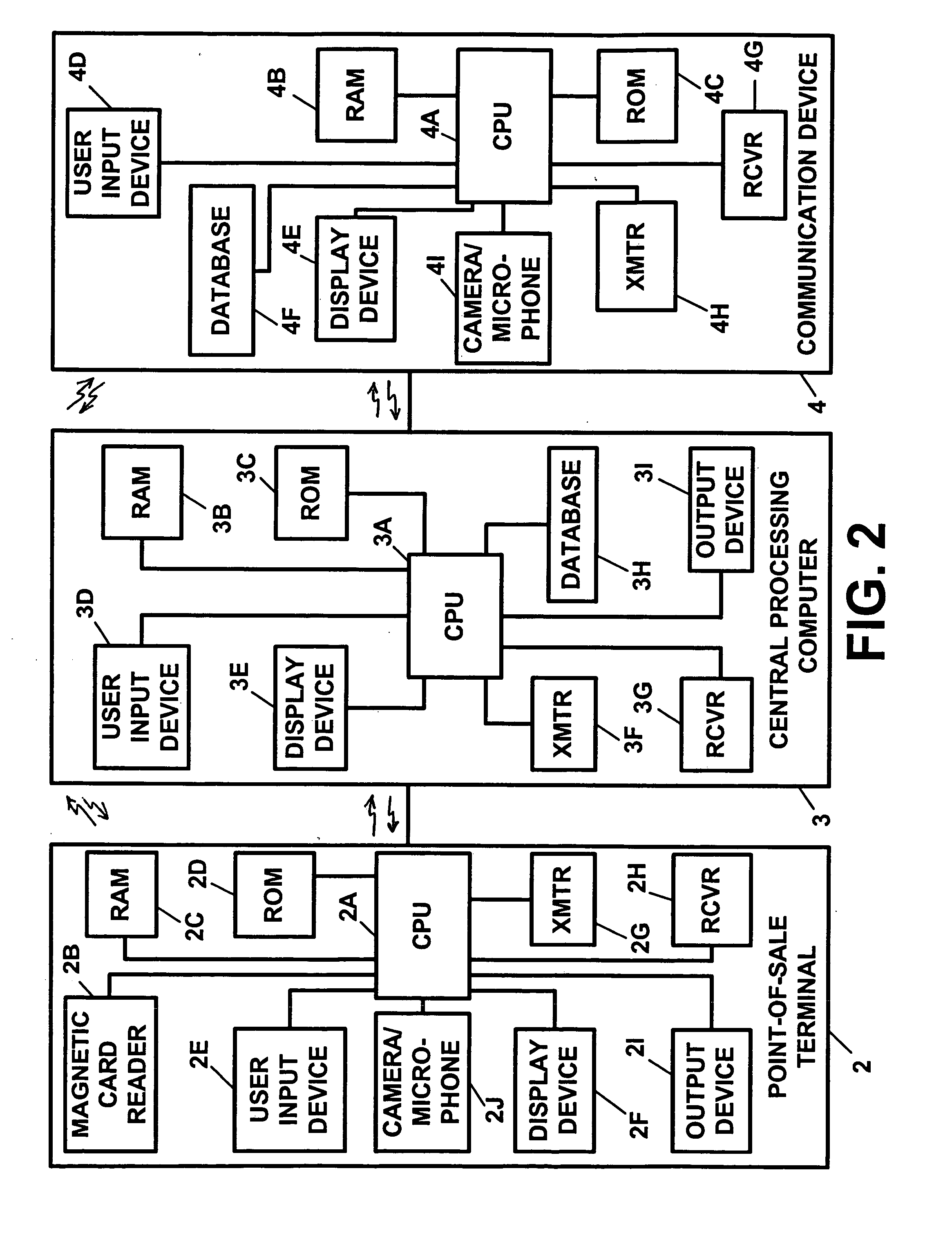
An apparatus including a memory device for storing a limitation or restriction on an account use received via the Internet and / or World Wide Web and a processing device for determining whether a transaction on the account or a use of a wireless or cellular communication device is authorized, allowed, or disallowed. An apparatus including a processing device for processing information regarding a banking transaction or use of a wireless or cellular communication device and generating a signal containing information regarding the transaction or device use and a transmitter for transmitting the signal to a communication device. An apparatus including a processing device for processing transaction information and generating a signal containing transaction information, and a transmitter for transmitting the signal to a communication device via the Internet and / or World Wide Web independently of transaction processing by a central transaction processing computer.
Owner:JOAO BOCK TRANSACTION SYST
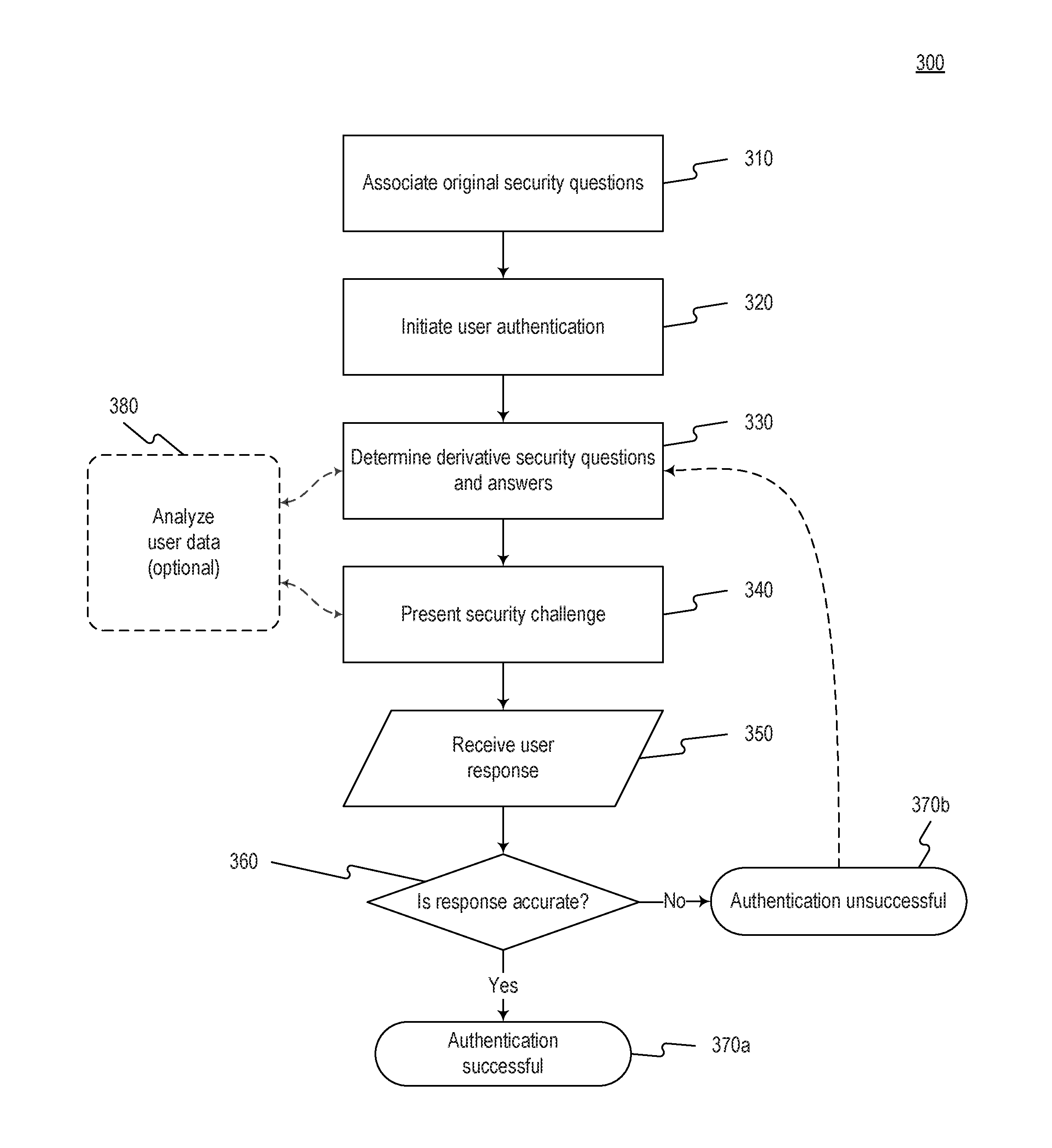
Systems and methods for derivative fraud detection challenges in mobile device transactions
InactiveUS20160381560A1Improve identification and verificationImprove experienceDigital data processing detailsMultiple digital computer combinationsInternet privacyMobile transaction
The disclosed embodiments include systems, methods, and computer-readable media configured to provide mobile device transaction security. The techniques described in the disclosed embodiments may be used to verify a mobile device user by providing derivative fraud protection challenges. Thus, the techniques may be used to improve identification and verification of users during mobile transactions. As a result, the disclosed embodiments improve mobile security and user experience as well as enhance access control.
Owner:OFFLA SELFSAFE
Cellular telephone-based transaction processing
InactiveUS7039389B2Telephonic communicationCredit schemesTelecommunications linkFinancial transaction
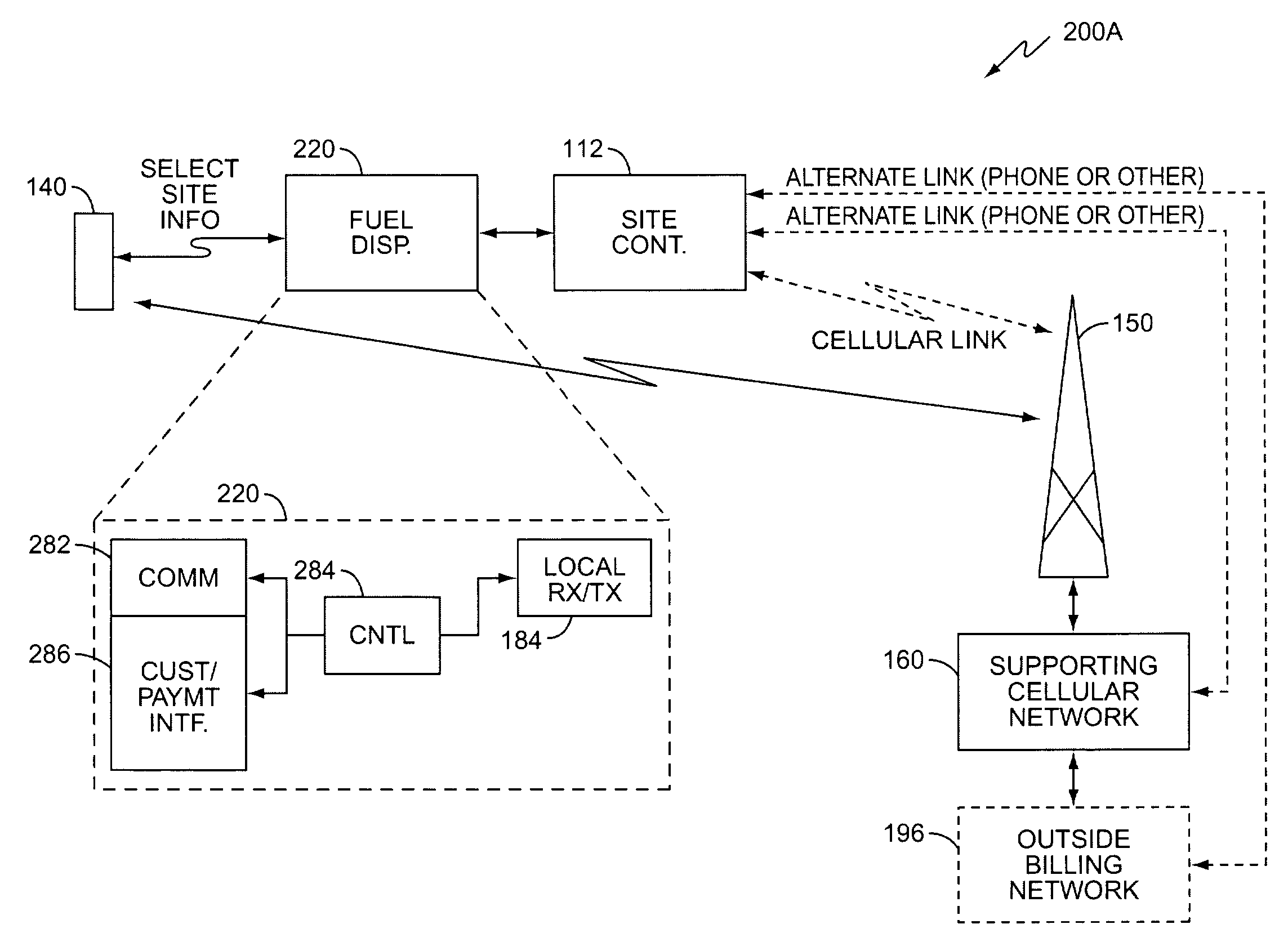
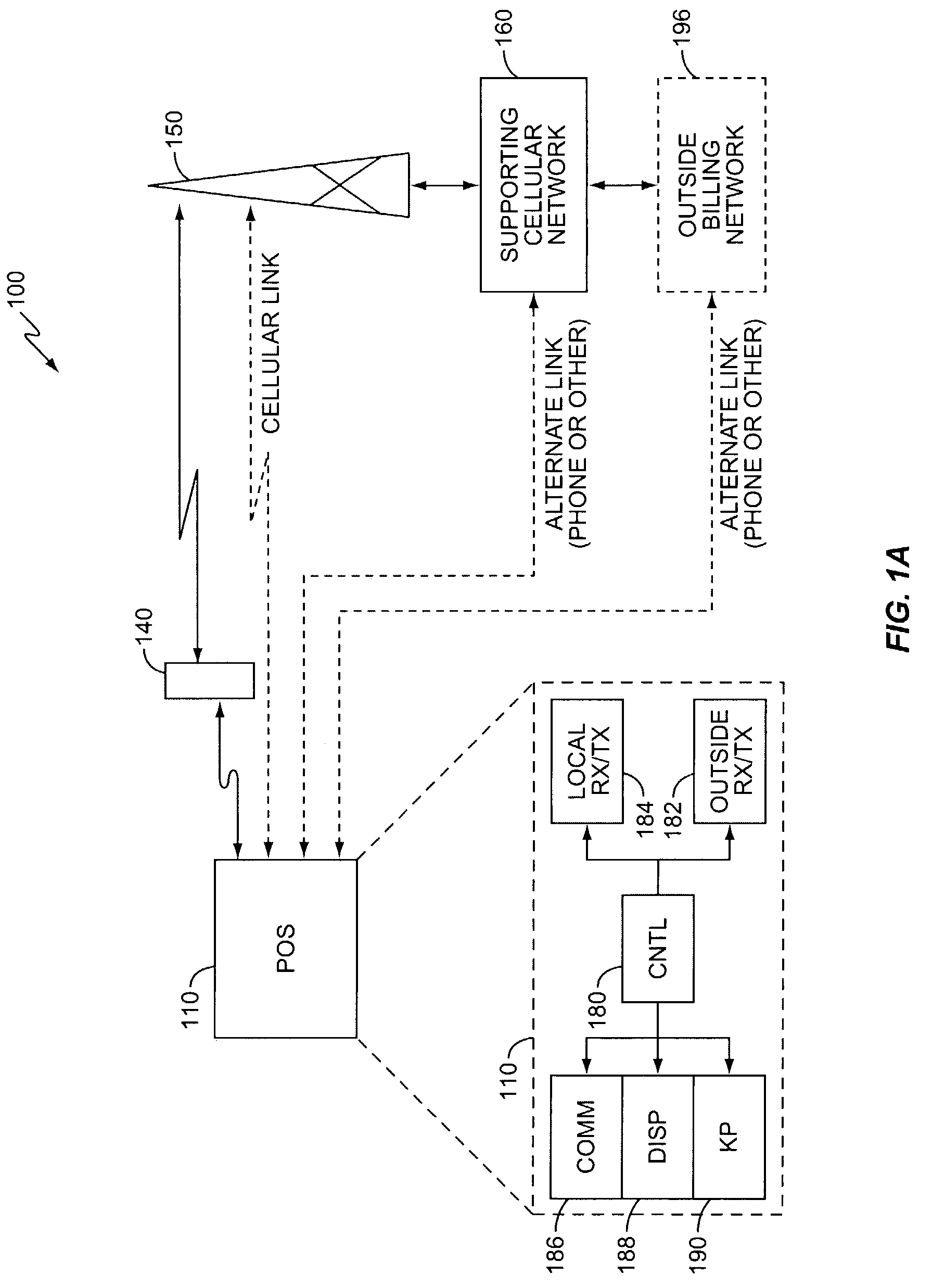
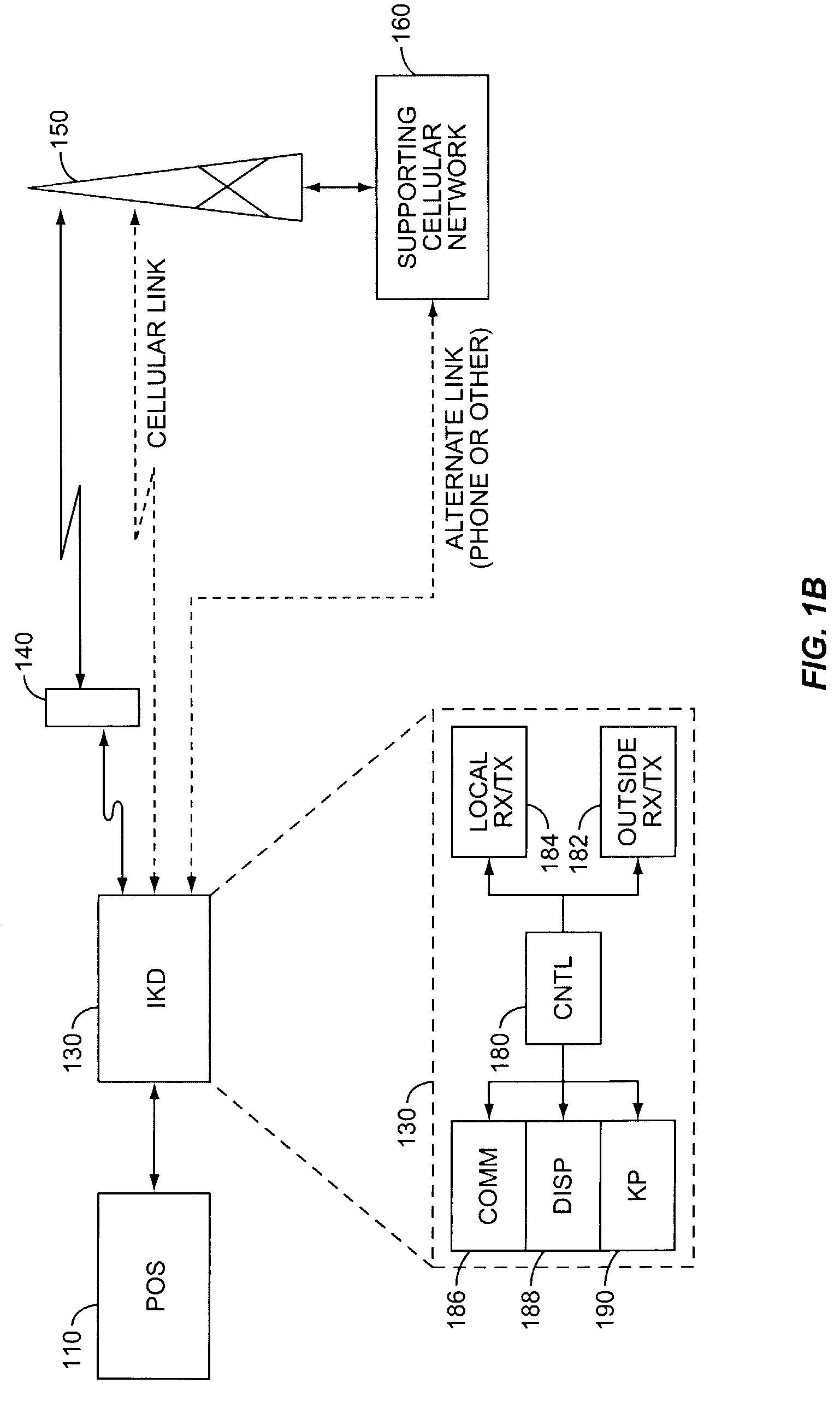
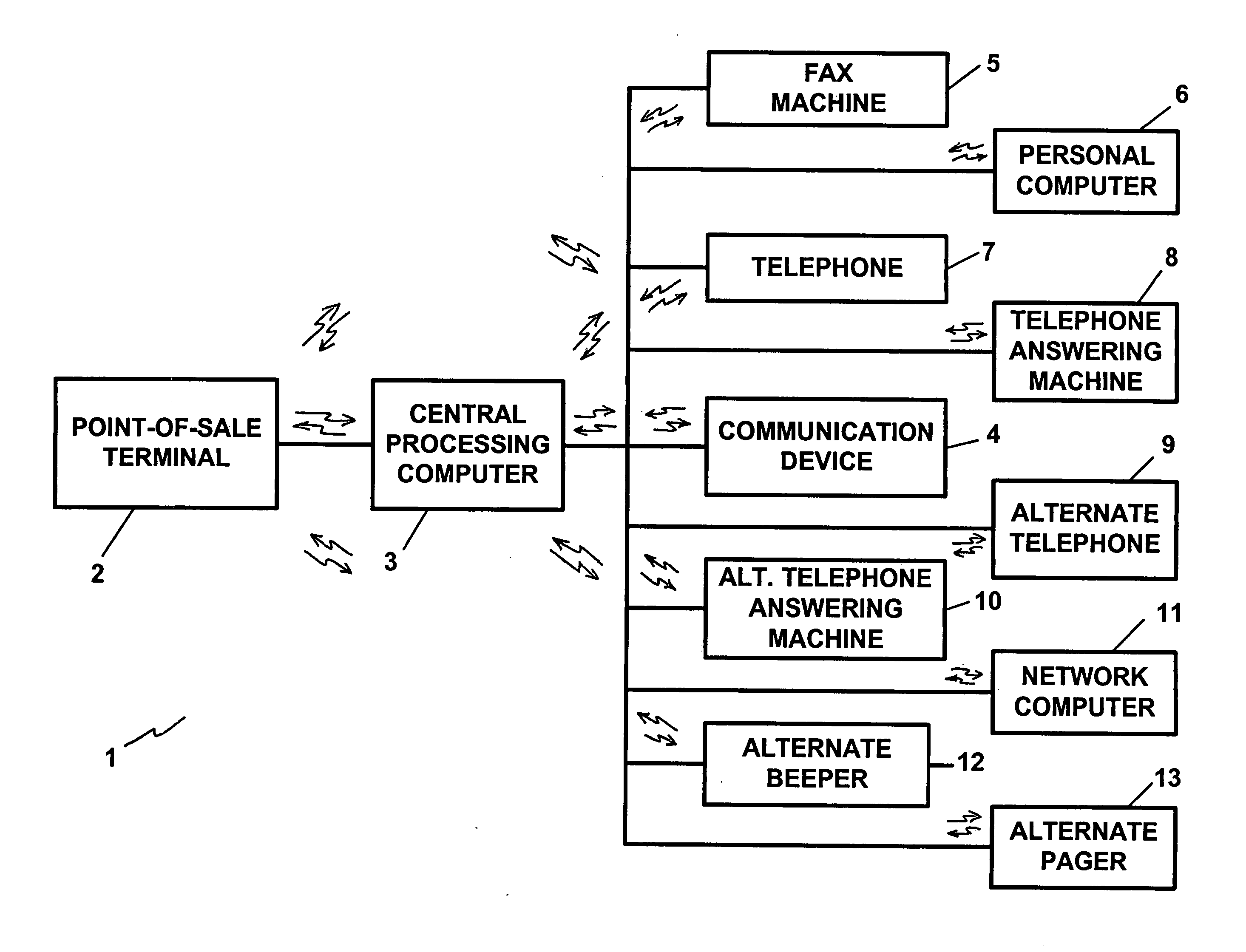
A retail transaction system provides enhanced customer convenience and increased transaction security by sending transaction information to a cellular network provider via a customer's digital cellular phone. For example, a fuel dispenser is equipped with a communications link allowing direct communications to a customer's cellular phone. When a customer desires to conduct a transaction using the fuel dispenser, the fuel dispenser transmits select information to the customer's cellular telephone using this communications link. A telephone number is included in the select information. When the customer presses send, or otherwise causes their telephone to dial the number transferred from the fuel dispenser, the select information along with any additional customer information is sent to the cellular network. This information is used by the network to authorize a purchase transaction for the customer, such authorization information returned to the fueling station at which the fuel dispenser is located via a cellular link. For enhanced security, the customer may be required to input their PIN in order to complete the transaction. Notably, the PIN and the remainder of the transaction information sent from the customer phone to the cellular network is intrinsically secure due to the digital encryption employed by the digital cellular protocol. Optionally, the system may be configured to cause the customer's cellular phone to automatically dial the number transferred by the fuel dispenser. This capability may be enabled at the customer's option. The system may be extended to other retail systems including in-store point-of-sale systems (POS).
Owner:GILBARCO
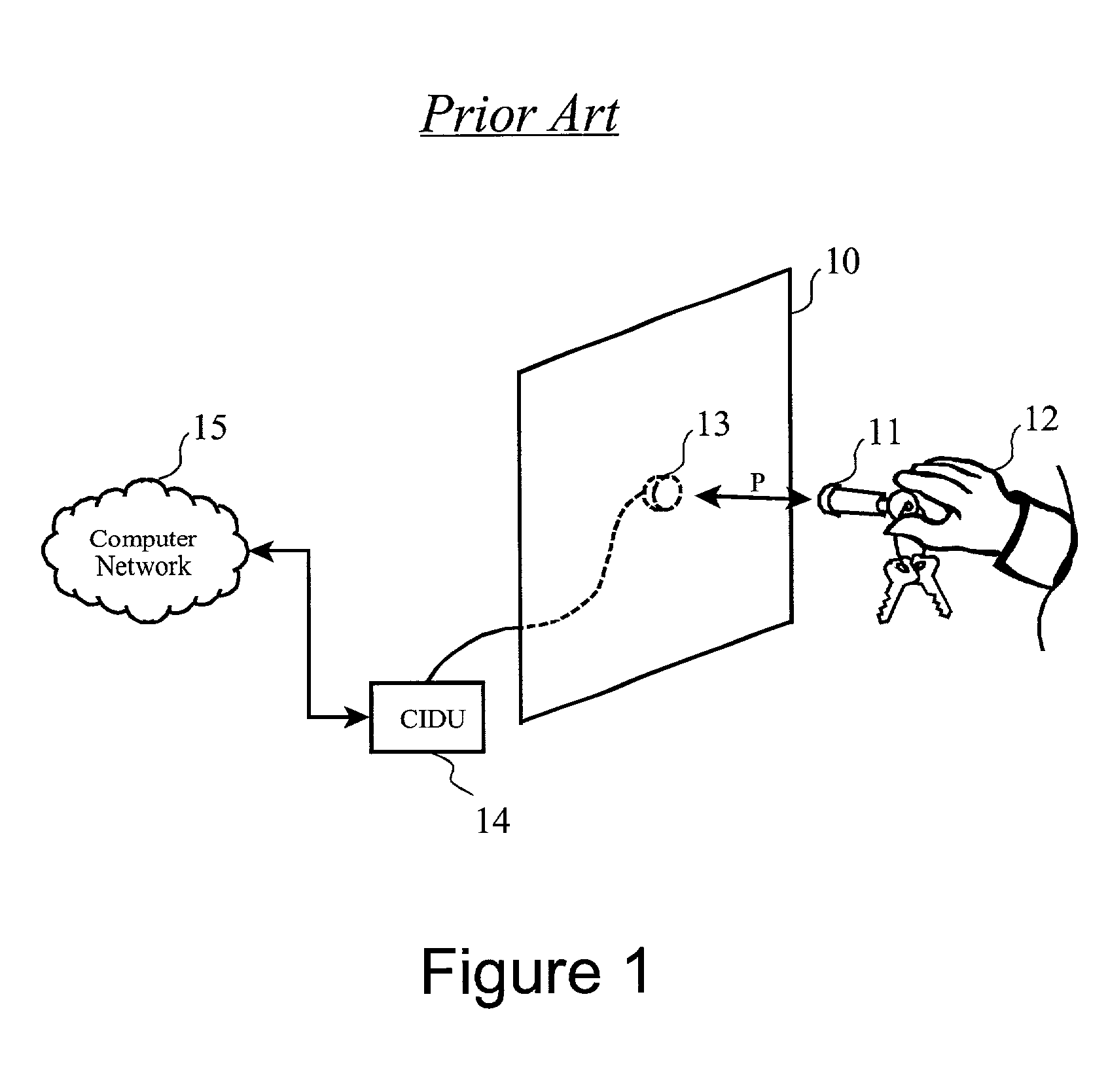
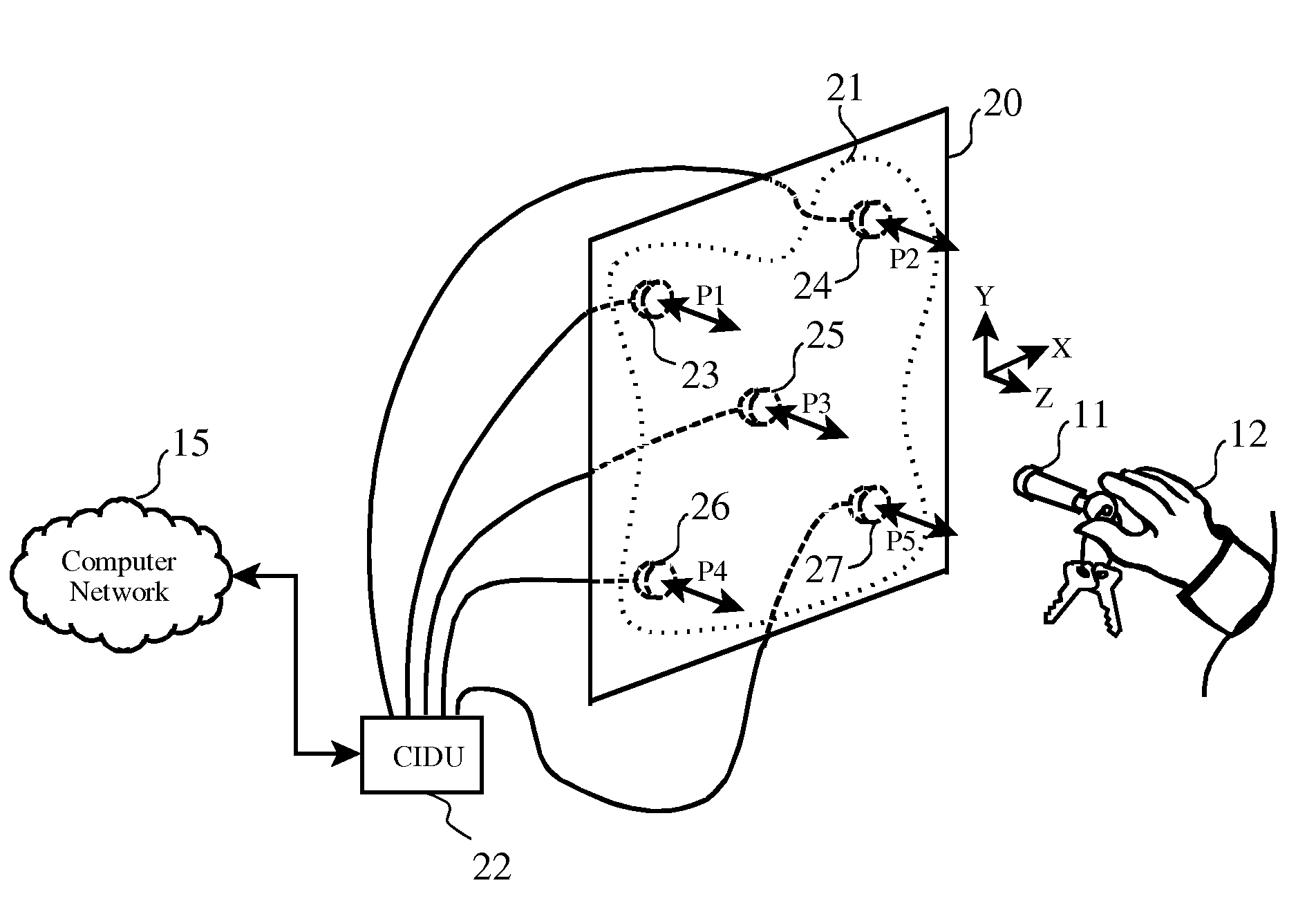
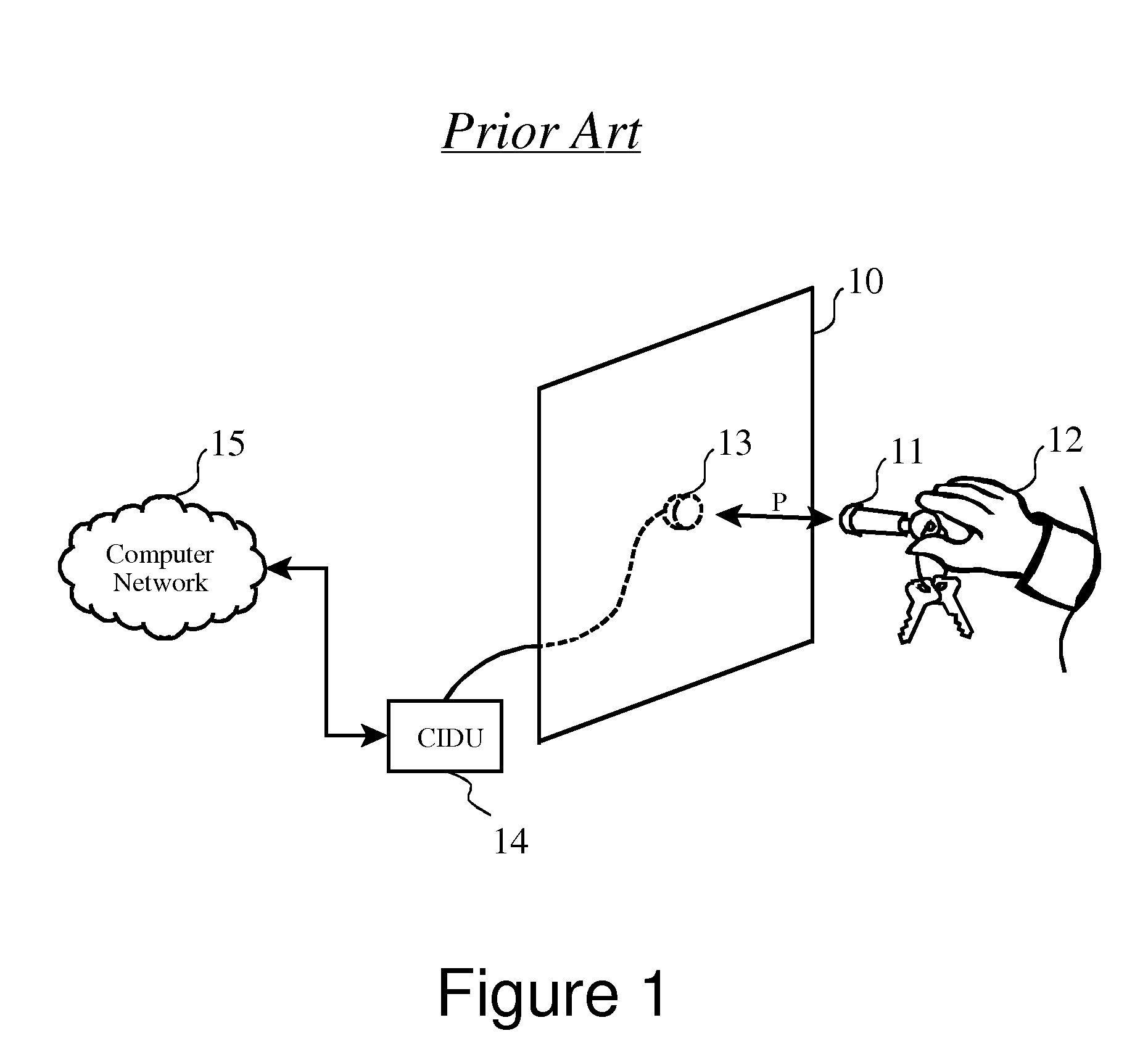
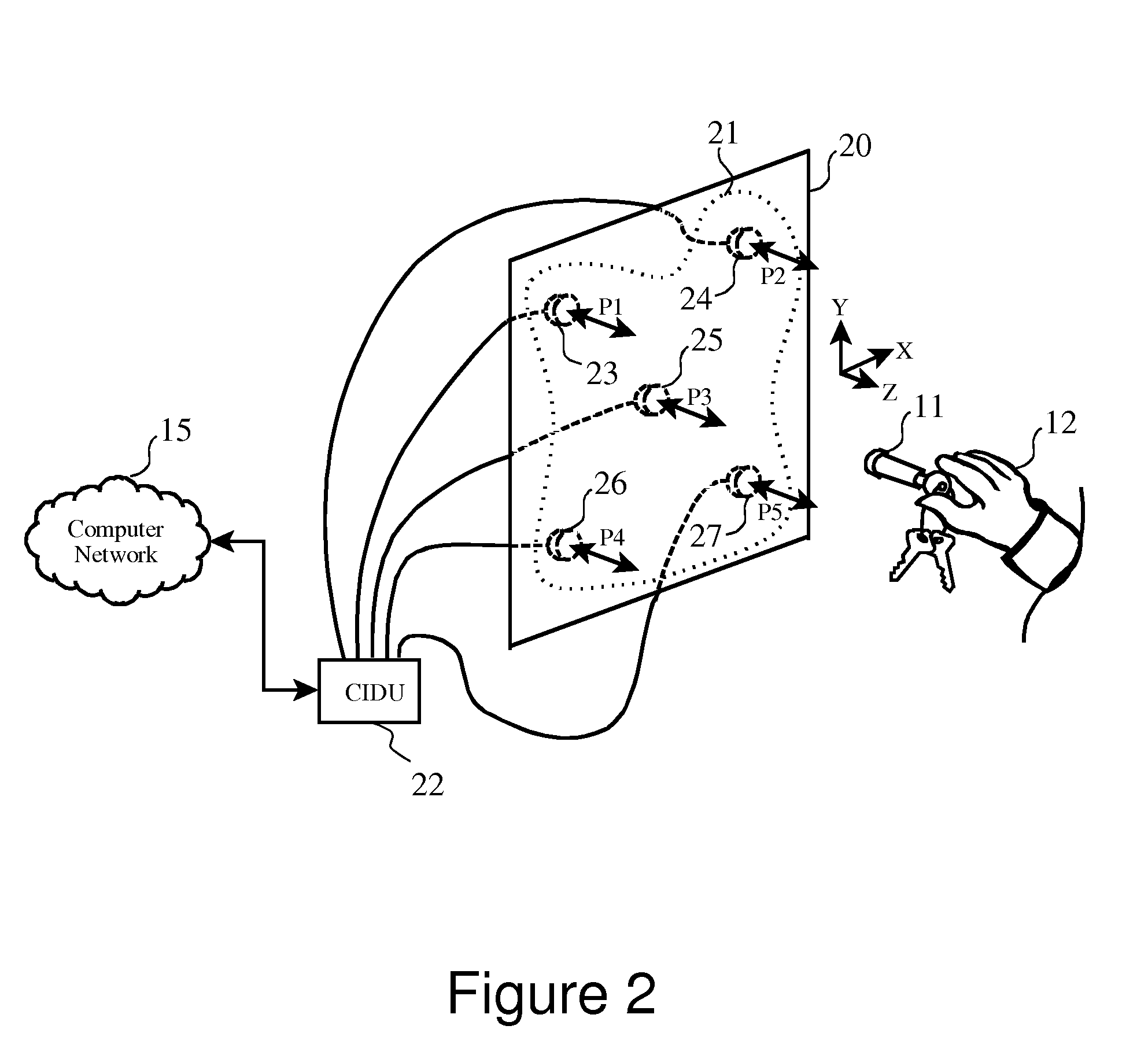
Free-space gesture recognition for transaction security and command processing
InactiveUS7394346B2Quick and efficient in handlingImprove securityInput/output for user-computer interactionElectric signal transmission systemsAuthorizationComputer science
A sensor panel having a matrix of independently decoded sensors, arranged in a two-dimensional pattern allows a consumer identification unit (CIDU) to detect a user-specific gesture made with a gesturing instrument such as an RF ID device. The CIDU monitors on a timed basis which of the sensors in the panel are receiving a signal from an RF ID device which has entered the proximity of one or more of the sensors. The user moves the sensor in a two-dimensional pattern to perform a “gesture signature” in free space near the panel, and the CIDU records the sequence of receiving sensors. This sequence can then be quickly and efficiently handled as a number to be looked up to identify and authenticate the user. Preferably, the user is allowed to define multiple signature gestures, each having the possibility of being associated with a transaction or authorization level.
Owner:SNAP INC
Mobile peer-to-peer authenticated transfers
InactiveUS20150012444A1User identity/authority verificationDigital data authenticationUser authenticationImage capture
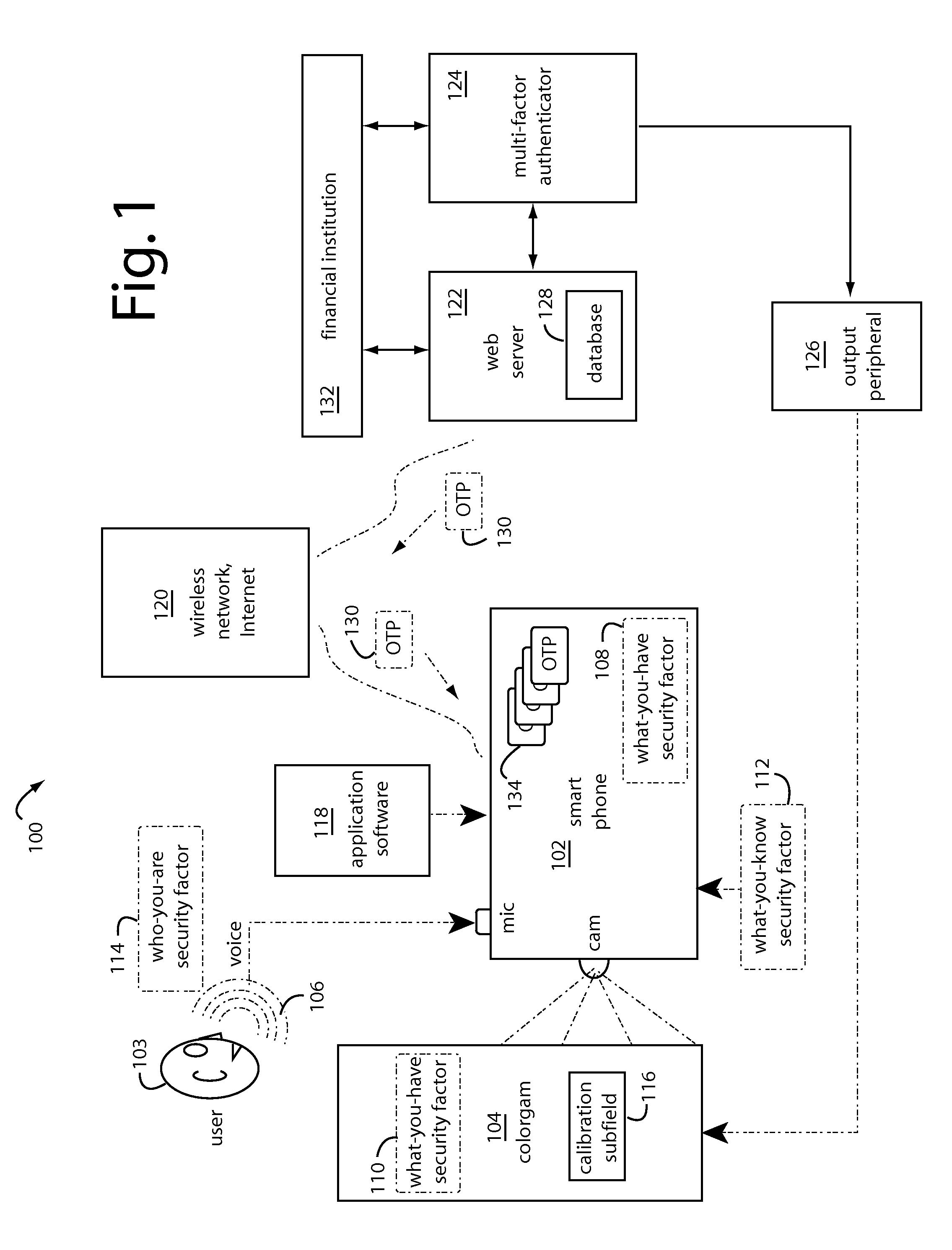
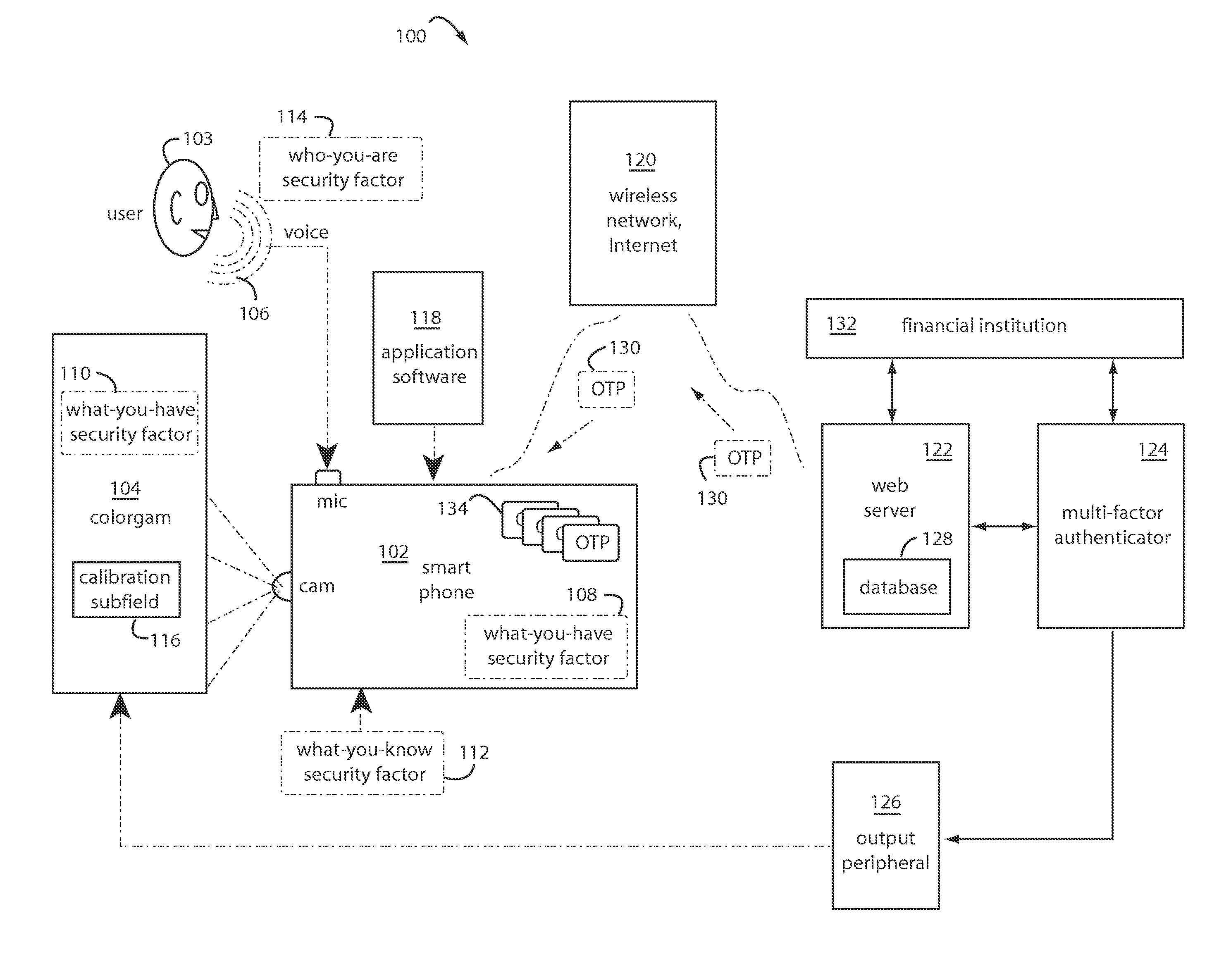
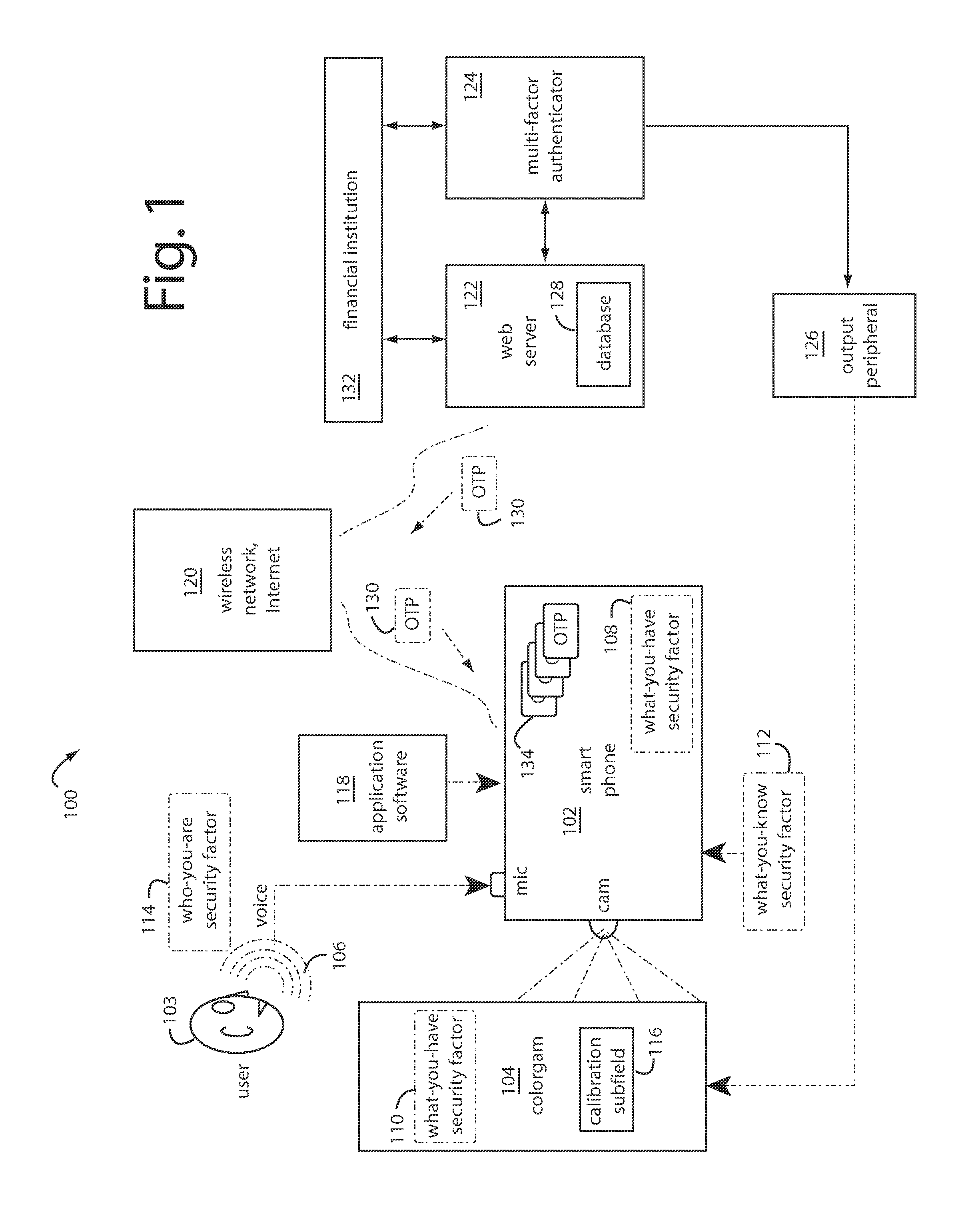
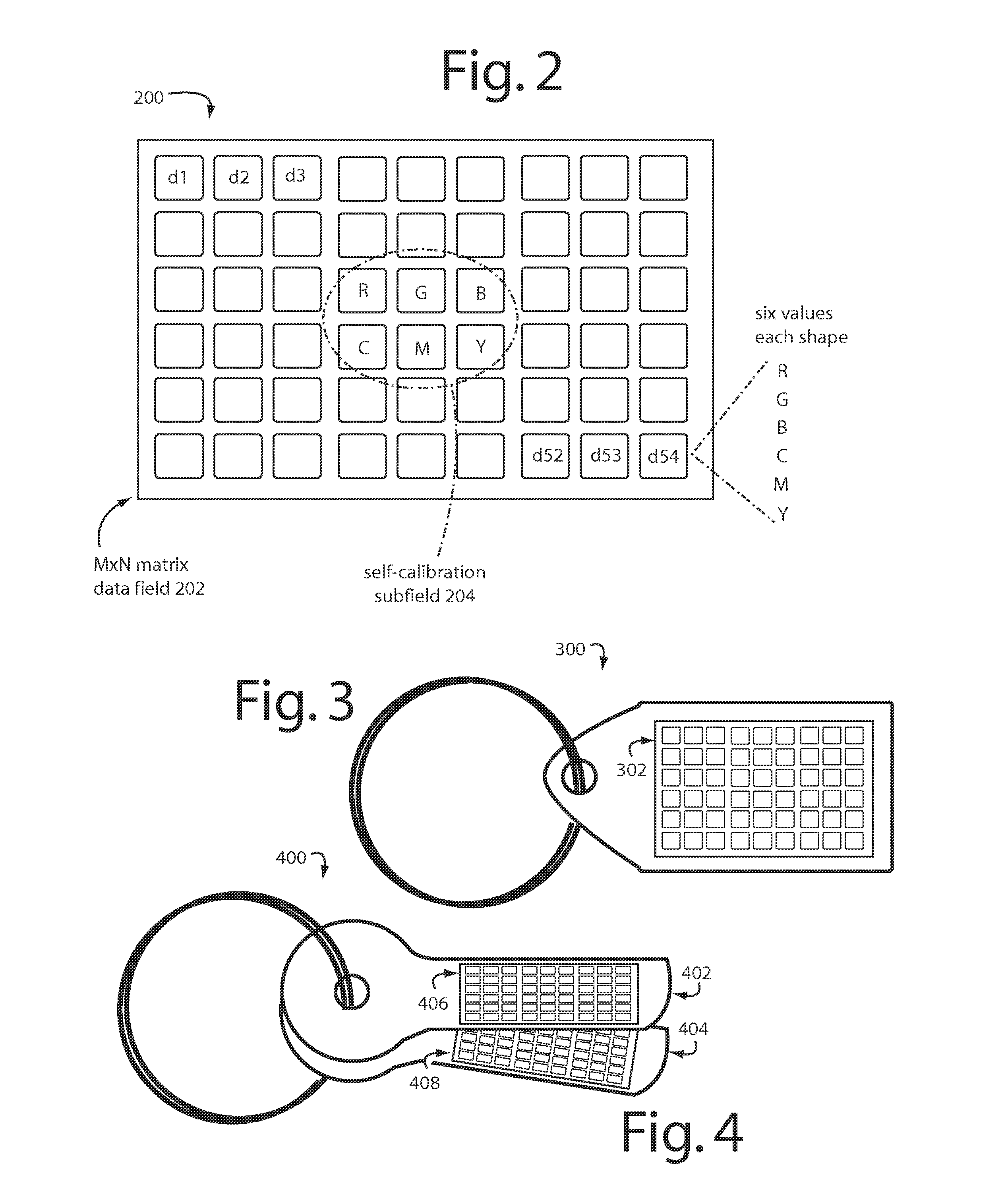
A peer-to-peer transaction security method includes authentication and identification steps for pushing an encrypted colorgram from a transaction server to a first personal trusted device. Such provides a visual key for user authentication. Persona descriptors may be included for user identification. A decryption of the colorgram is displayed on the first personal trusted device to be optically captured by a second personal trusted device. The image captured from the second personal trusted device is encrypted and uploaded to the transaction server. In some cases, the persona descriptors alone are used to build a composite rendering for identification of the first user by the second user. The second user clicks and returns an acceptance if they recognize the composite drawing as a reasonable persona of the first user.
Owner:CRYPTITE LLC
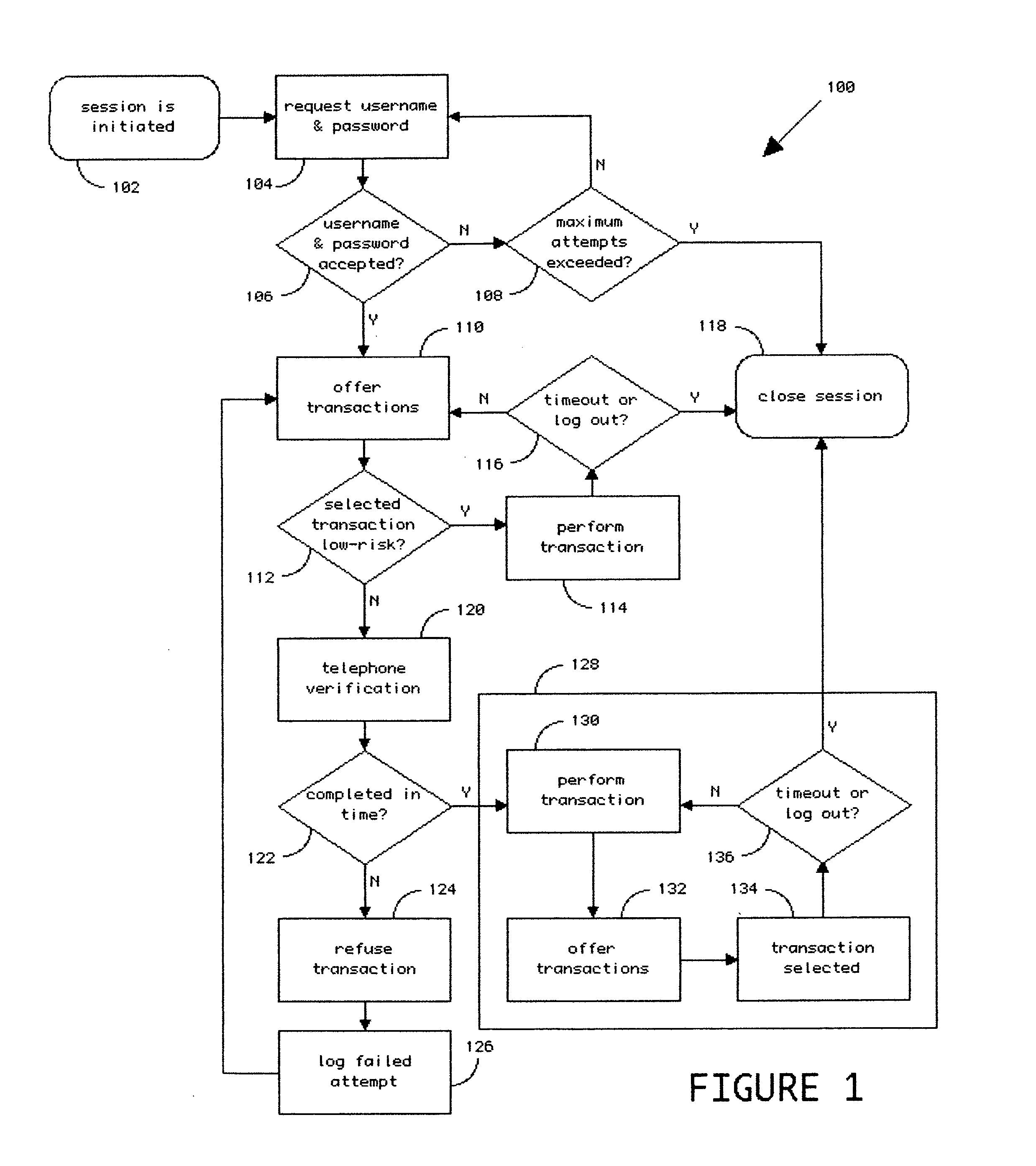
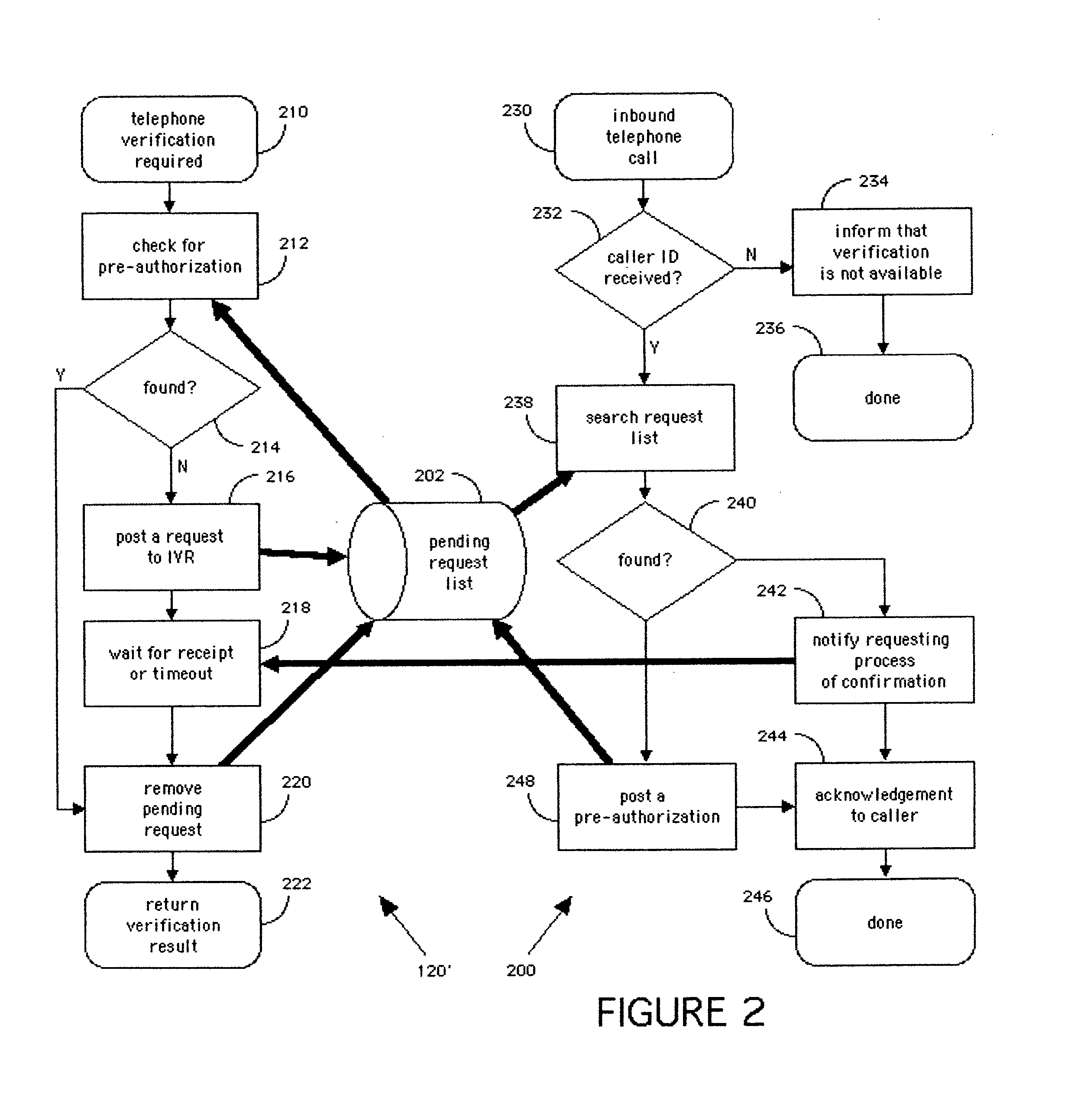
Method and apparatus for improved transaction security using a telephone as a security token
ActiveUS20070174080A1Improve securityIncreased riskFinancePayment architectureMobile Telephone NumberTransaction security
A method and apparatus are disclosed by which customers of an institution, such as a bank, may register one or more of their landline telephone or mobile telephone numbers and associate the telephone numbers with their account and thereafter in conjunction with a remote transaction, use the registered telephone to call into a bank system, or be called by a bank system, for verification, whereby the registered telephone becomes a security token that elevates the security of the transaction.
Owner:OUTWATER CHRISTOPHER SCOTT
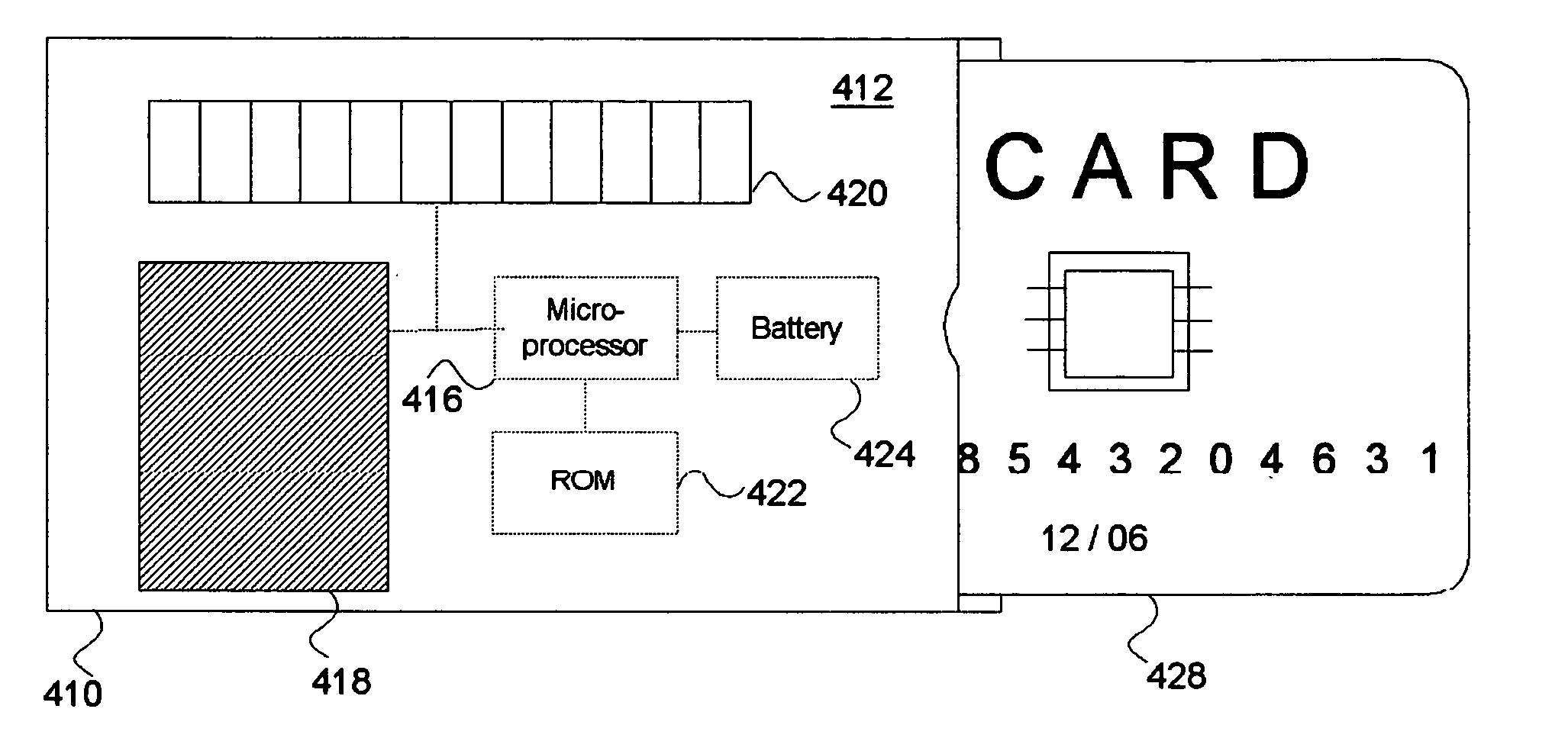
Bio-metric smart card, bio-metric smart card reader, and method of use
A system for increasing transaction security across existing infrastructure is provided. A user bio-metric sensor device is integrated into a credit or debit card. A display unit provides a key, preferably encrypted, upon successful utilization of the sensor device. Included in the key generation mechanism is an indicator of the transaction number or other sequential count indicative of card use. An authorization service decrypts the key in a manner at least partially dependent upon a second sequential count maintained in sync with the first count to determine whether the use is authorized. In one embodiment, a separate credit card reader may be configured to read conventional credit cards, smart cards, and credit cards incorporating such bio-metric sensor devices.
Owner:MCGREGOR CHRISTOPHER M +2
Bio-metric smart card, bio-metric smart card reader and method of use
InactiveUS6816058B2Improve transaction securityElectric signal transmission systemsMultiple keys/algorithms usageSmart cardAuthorization
A system for increasing transaction security across existing infrastructure is provided. A user bio-metric sensor device is integrated into a credit or debit card. A display unit provides a key, preferably encrypted, upon successful utilization of the sensor device. Included in the key generation mechanism is an indicator of the transaction number or other sequential count indicative of card use. An authorization service decrypts the key in a manner at least partially dependent upon a second sequential count maintained in sync with the first count to determine whether the use is authorized.
Owner:AUDLEM
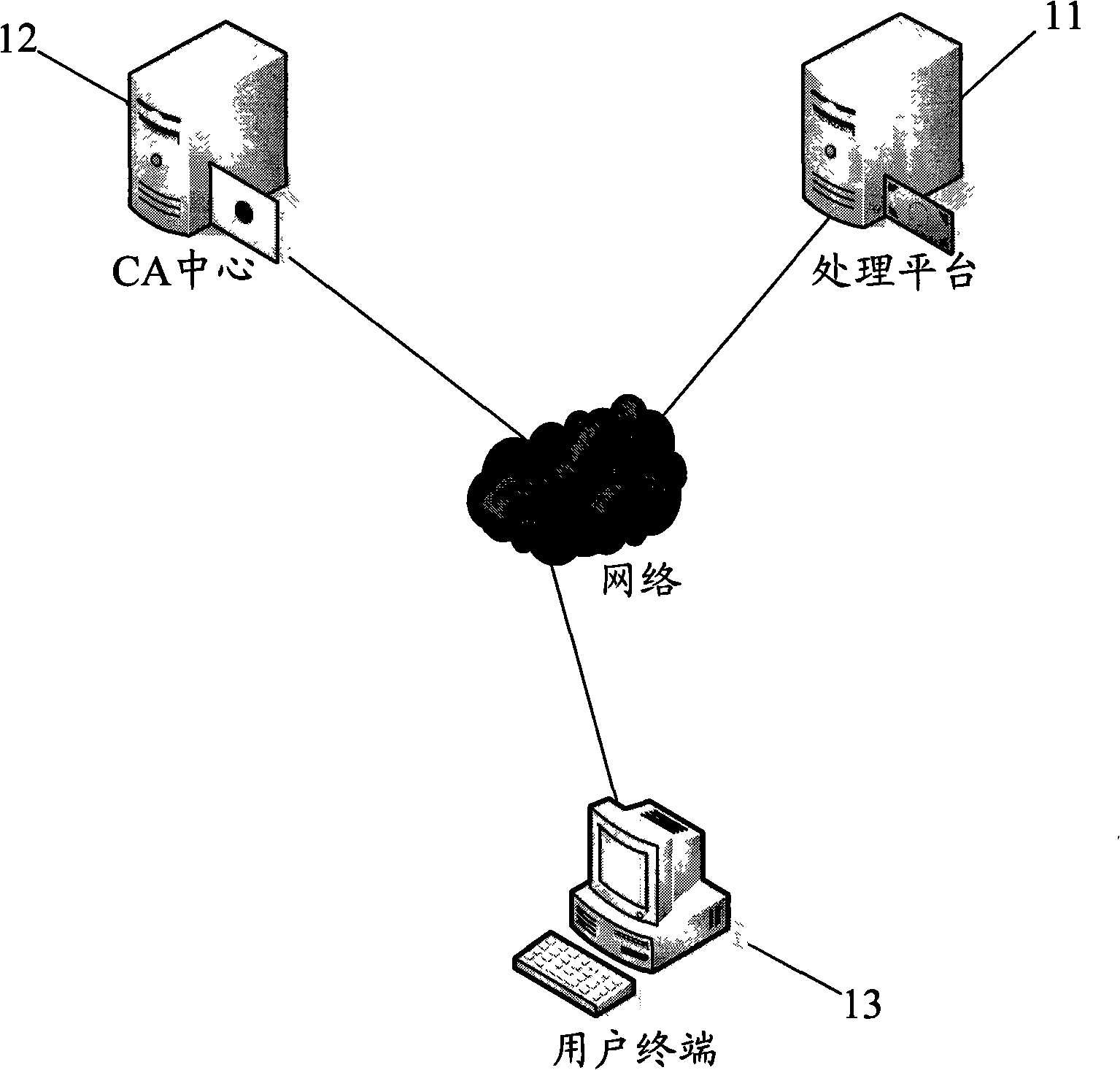
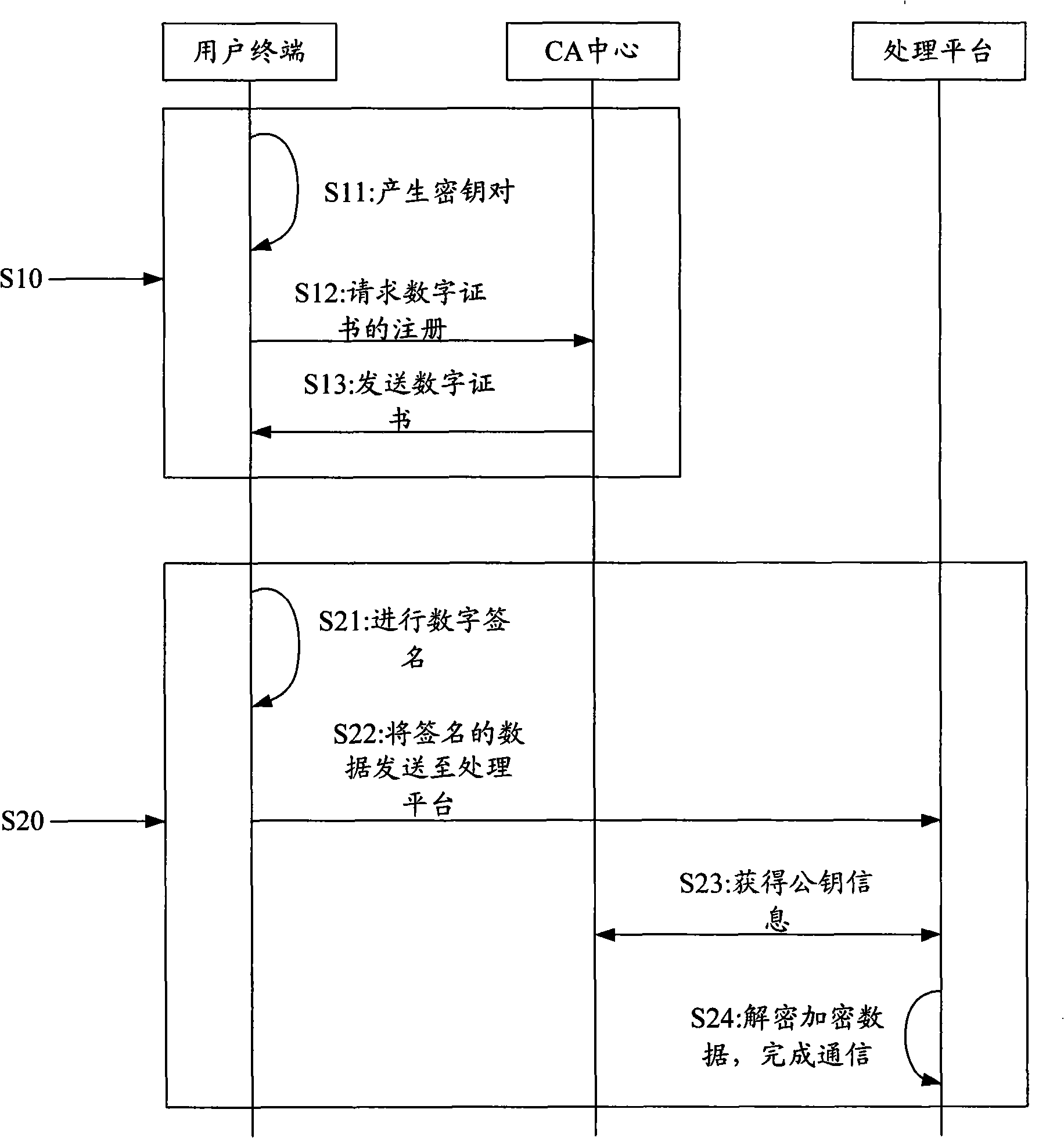
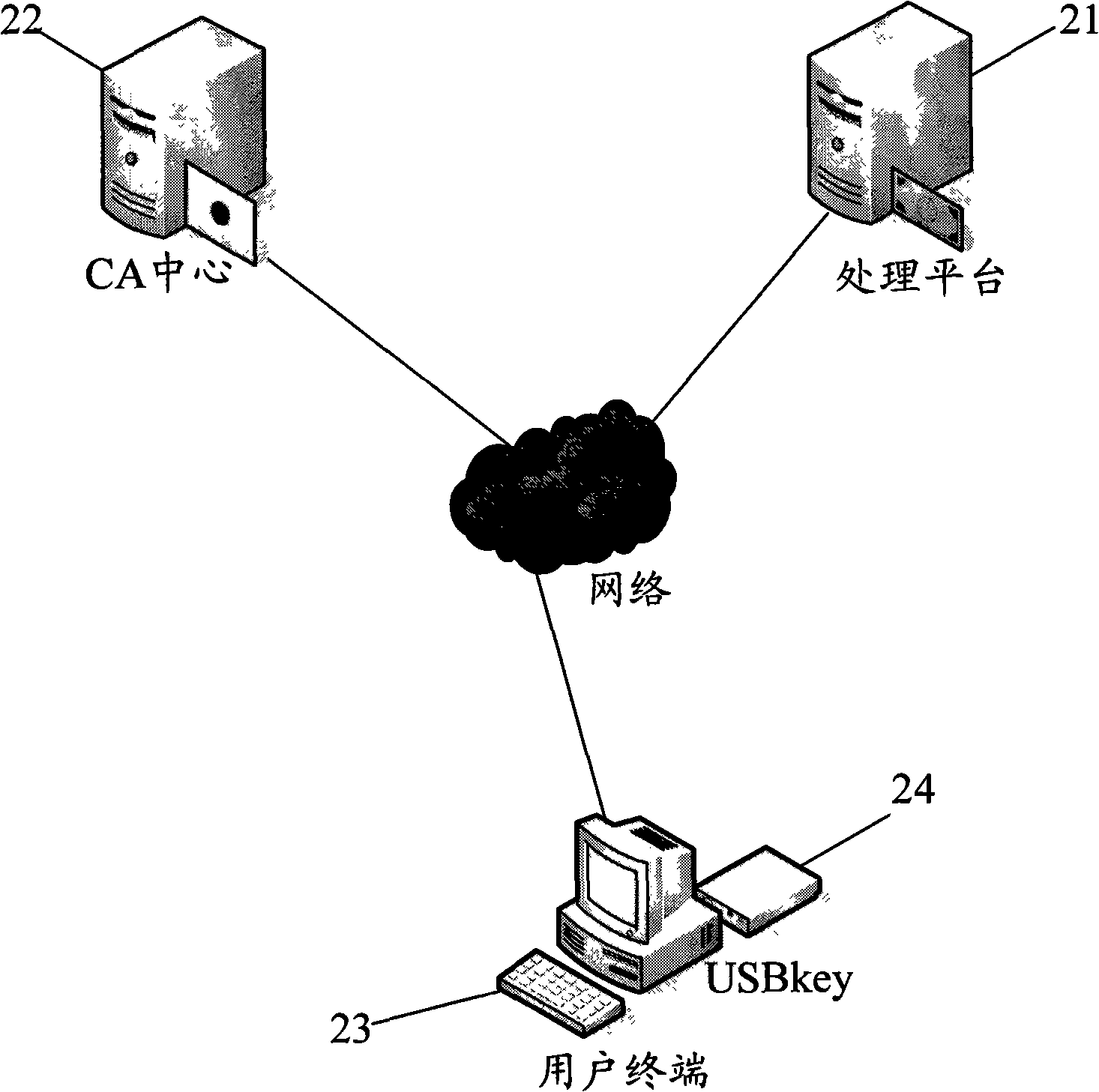
Method and system for identity authentication by finger print USBkey
InactiveCN101340285AEnsure safetyGuaranteed accuracyUser identity/authority verificationCommerceRelevant informationDigital signature
The invention discloses an identity authentication method by a fingerprint USBkey and includes the following steps: (1) the fingerprint information of users is recorded into the fingerprint USBkey and the information is saved in advance; (2) at least a digital certificate generated, which comprises the following steps: firstly, a pair of private and public keys are generated in the fingerprint USBkey; the relevant information of the public keys and the digital certificate is sent to a CA center and generating the digital certificate by the CA center; (3) each digital certificate and corresponding private keys stored and encrypted on the fingerprint USBkey; (4) when a user terminal communicates with a processing platform, the fingerprint USBkey at the user terminal firstly checks the fingerprints, digital signature is carried out on the data to be sent by the corresponding private keys and the data is transmitted to the processing platform for identity authentication. The method permits the digital signature after the fingerprints authentication succeeds; the loophole of PIN code input and transmission does not exist in the whole interactive process, which improves the transaction security to the utmost extent.
Owner:ZHEJIANG MIAXIS TECH CO LTD
Transaction security apparatus and method
InactiveUS20050170814A1Real time monitoringFinanceUnauthorised/fraudulent call preventionAuthorizationDatabase
A transaction security apparatus and method, including a receiver which receives a limitation or restriction on an account usage, wherein the limitation or restriction on an account usage is received in real-time from a communication device associated with an individual account holder, a memory device for storing the limitation or restriction on an account usage, and a processing device for processing a transaction on an account or an authorization request in conjunction with the limitation or restriction on an account usage. The processing device generates a signal, wherein the signal contains information for authorizing or disallowing the transaction.
Owner:JOAO BOCK TRANSACTION SYST
Apparatus and method for providing transaction security and/or account security
InactiveUS20150012417A1Reduce threatEasy accessFinancePayment protocolsTelecommunications linkInternet privacy
A transaction security apparatus, including a memory device for storing information regarding an account of or associated with an account holder, an input device or a receiver for inputting or for receiving transaction information regarding a transaction between the account holder and a counterparty, wherein the transaction is an in-person transaction or a face-to-face transaction, and wherein the transaction information includes information regarding the counterparty, information regarding an amount of the transaction, and information for accessing a communication device associated with the counterparty, a processing device, wherein the processing device processes the transaction information and generates a message containing information regarding the account, and further wherein the apparatus establishes a communication link with the communication device, and a transmitter, wherein the transmitter transmits the message to the communication device on, over, or via the communication link.
Owner:JOAO RAYMOND ANTHONY +1
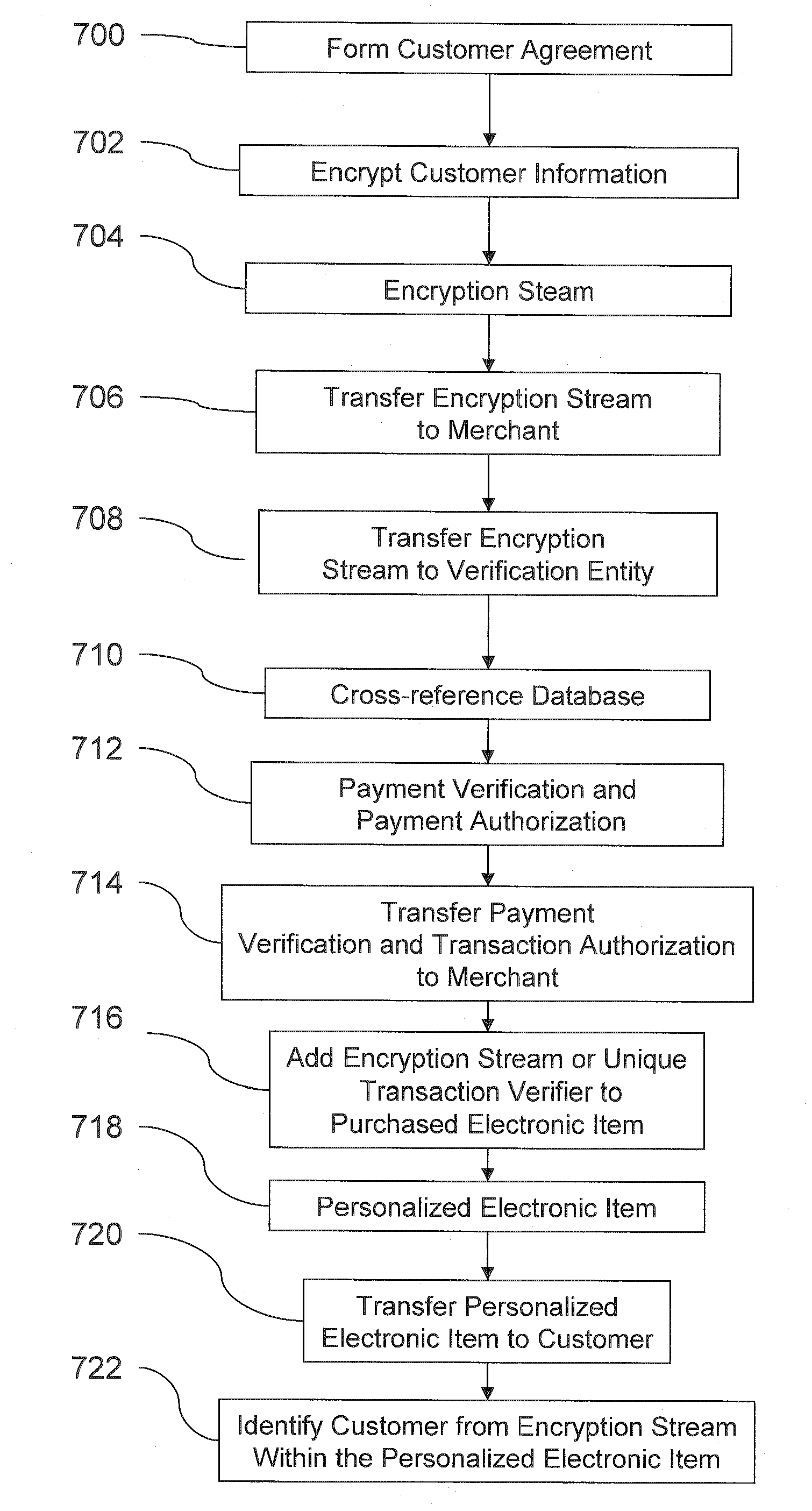
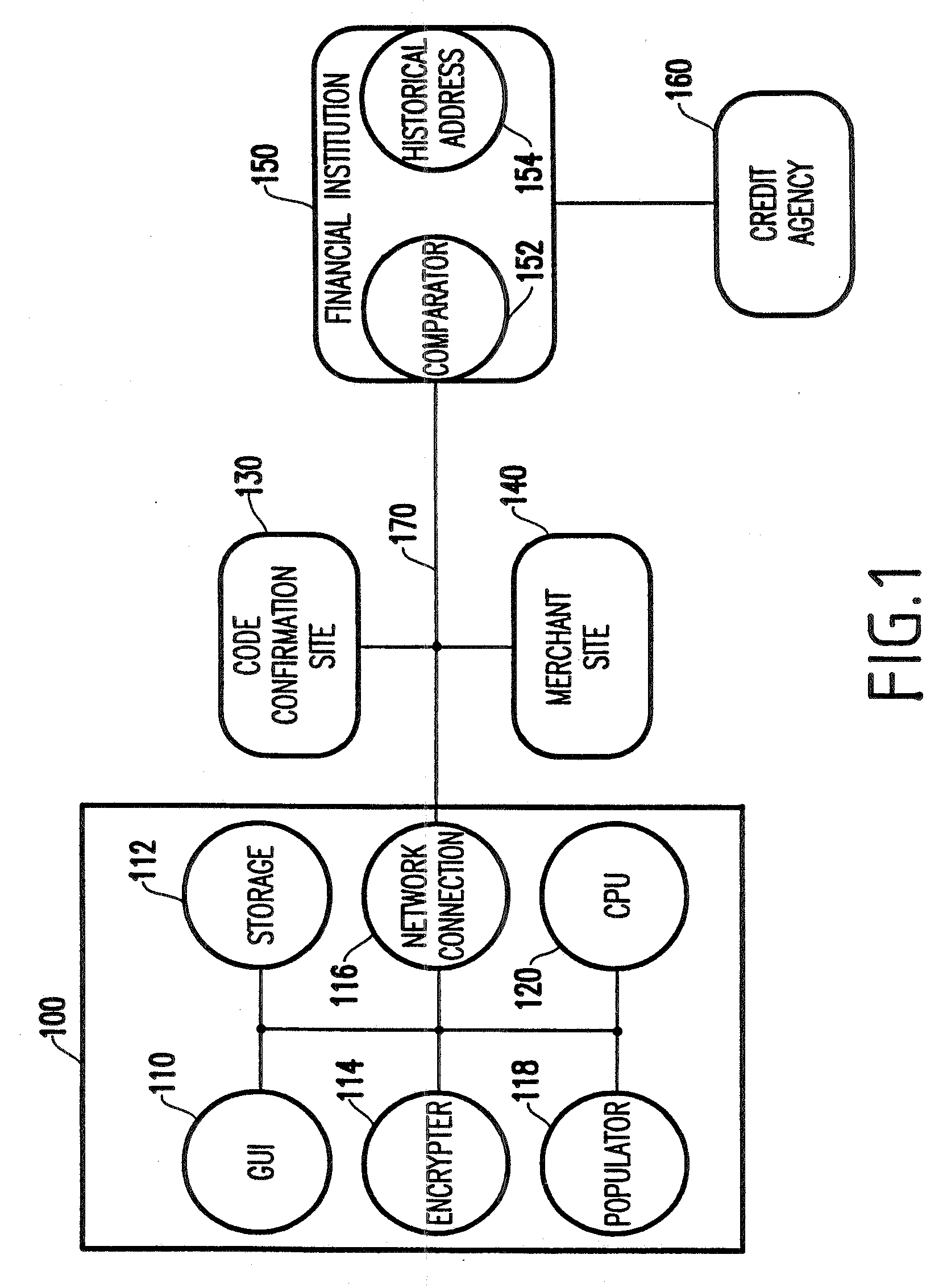
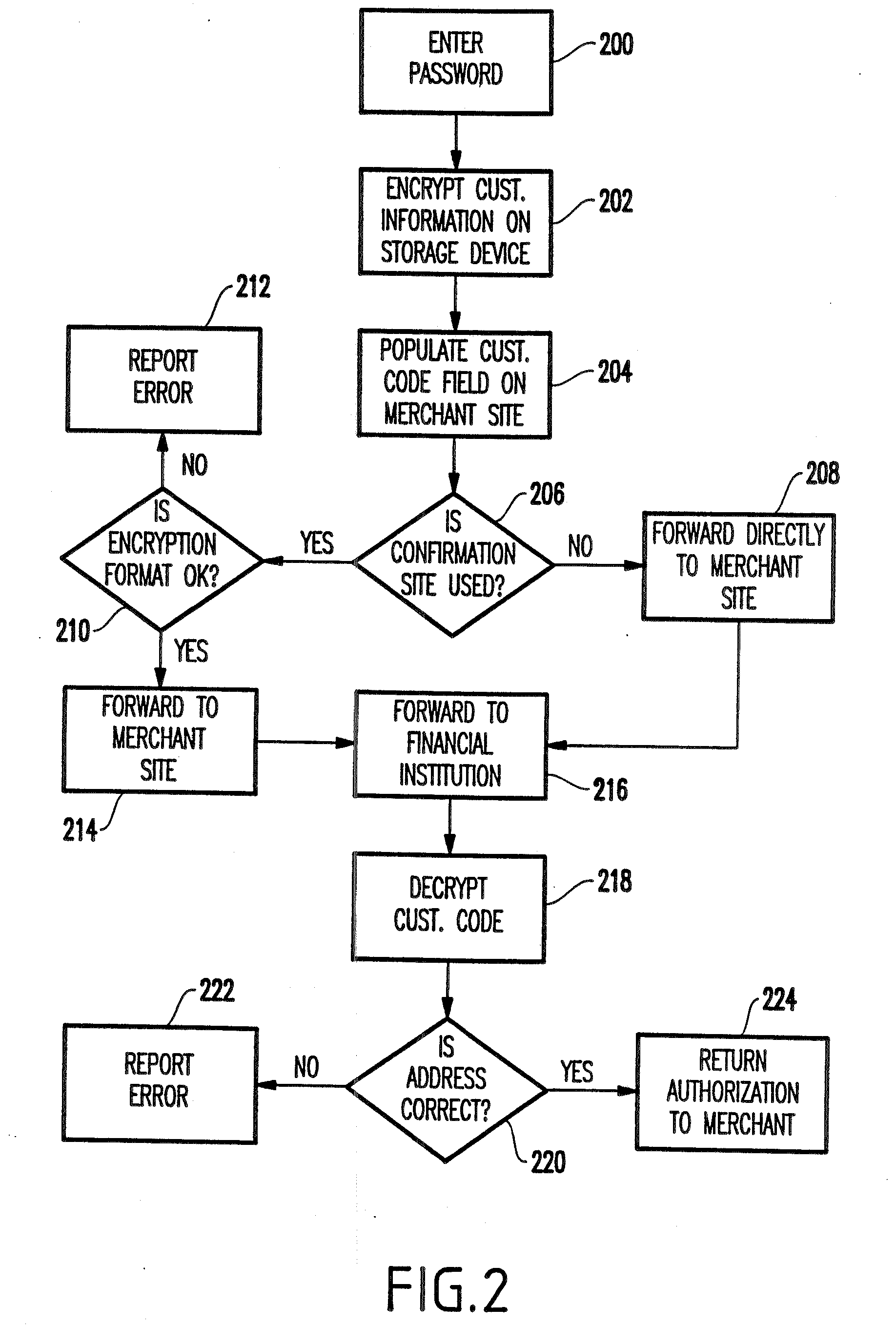
Transactional security over a network
A system and method facilitating purchase transactions over a computer network, including the purchase of electronically storable items. The embodiments herein encrypt “customer identifier string” in an encryption stream and cause the encryption stream to be transferred from the customer to a merchant in the purchase transaction. A verification entity receives the encryption stream which is sent by the merchant for identity verification and payment authorization. Then, the verification entity verifies the identifiers contained in the encryption stream and transfers an identity verification and payment authorization from the verification entity to the merchant.
Owner:BENEDORTSE
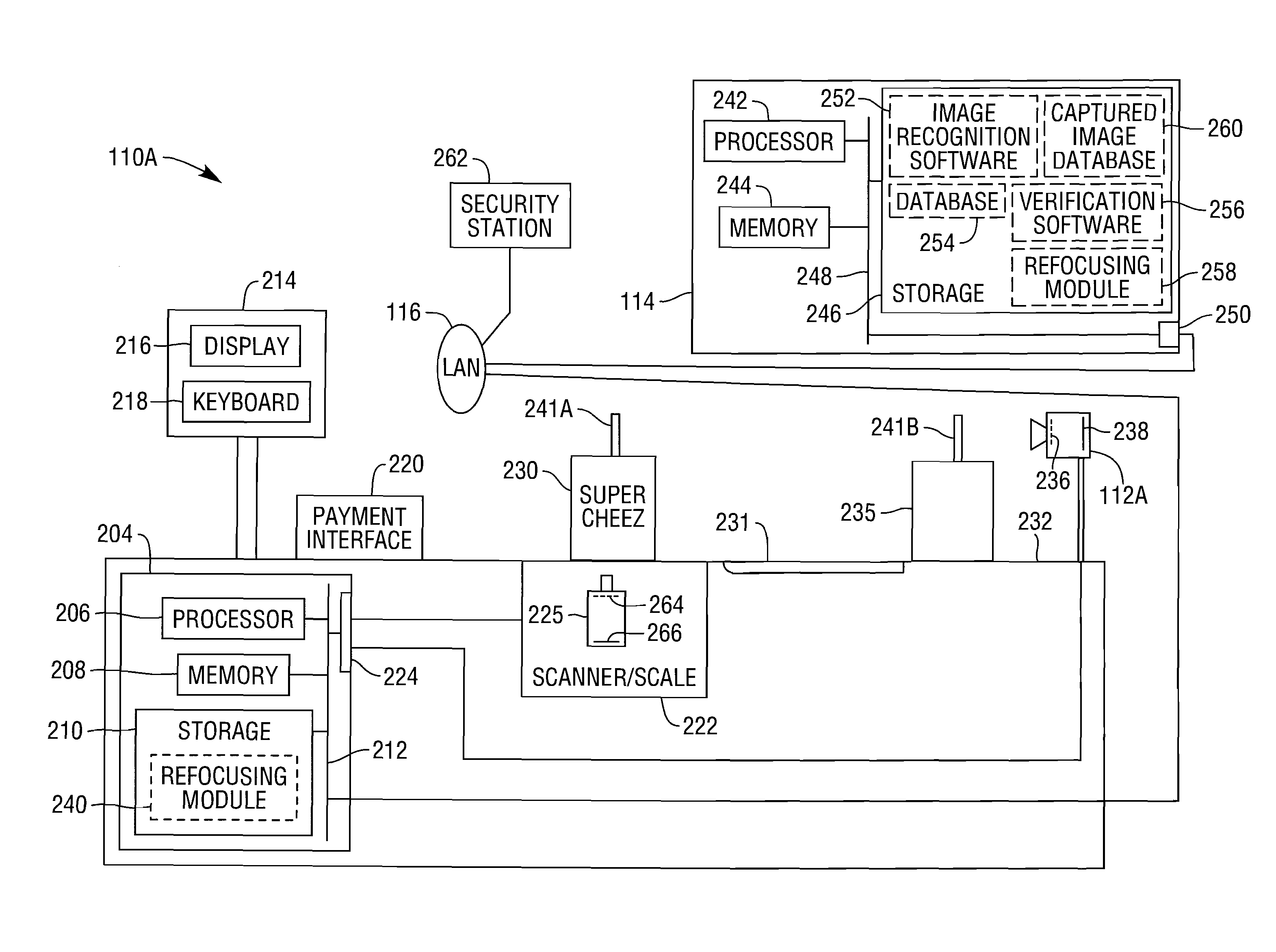
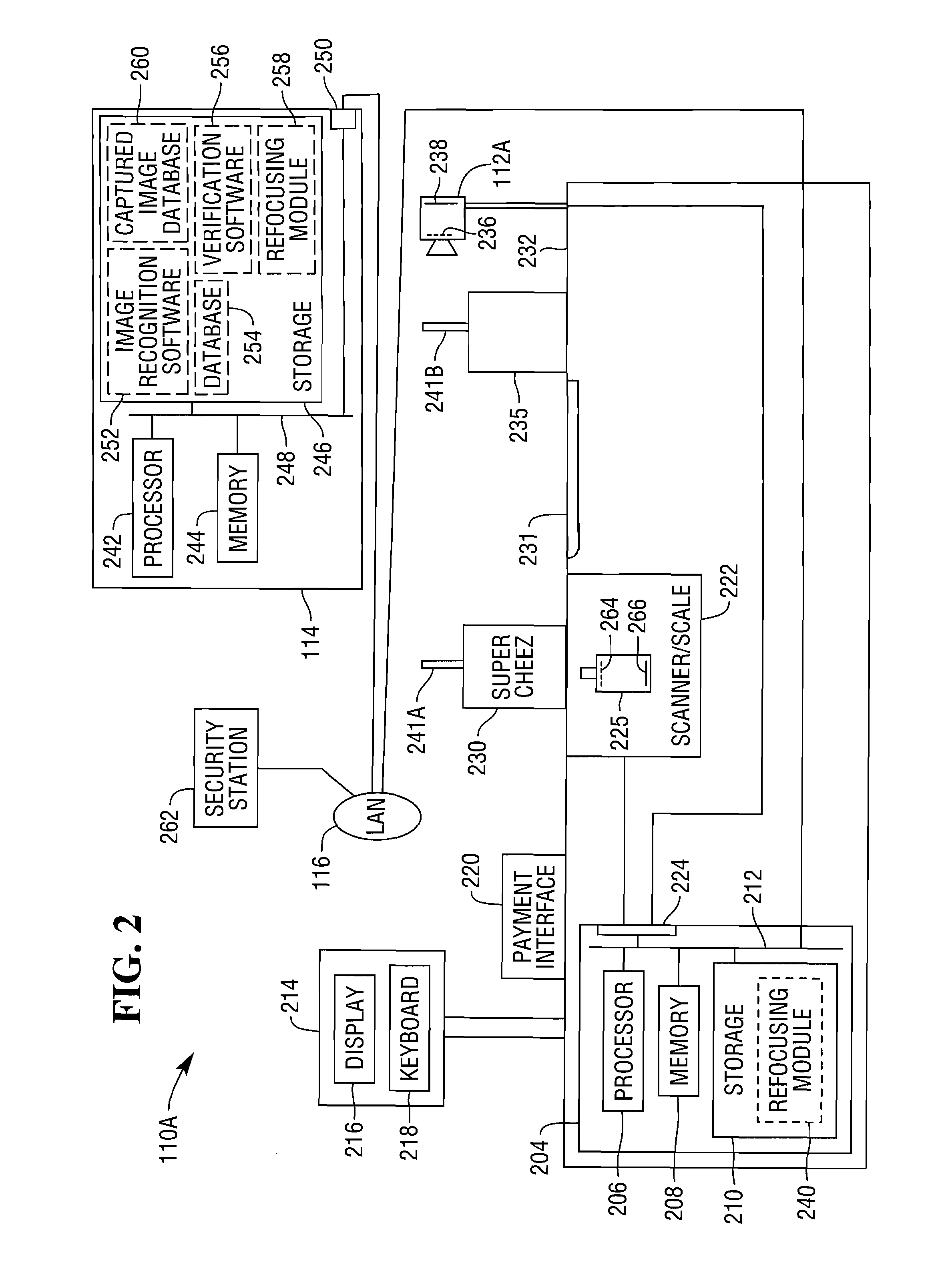
Methods and Apparatus for Improved Image Processing to Provide Retroactive Image Focusing and Improved Depth of Field in Retail Imaging Systems
InactiveUS20090160975A1Eliminate needImprove efficiencyTelevision system detailsColor television detailsImaging processingDepth of field
Systems and techniques for image capture and management in a retail environment. One or more retail cameras are directed so as to capture digital images. Each camera is configured so as to provide image information that can be used in a retroactive focusing process. Captured images are retroactively focused to provide sharp images of objects of interest, and the objects of interest are used in appropriate retail applications, such as site security, transaction security, and inventory control.
Owner:NCR CORP
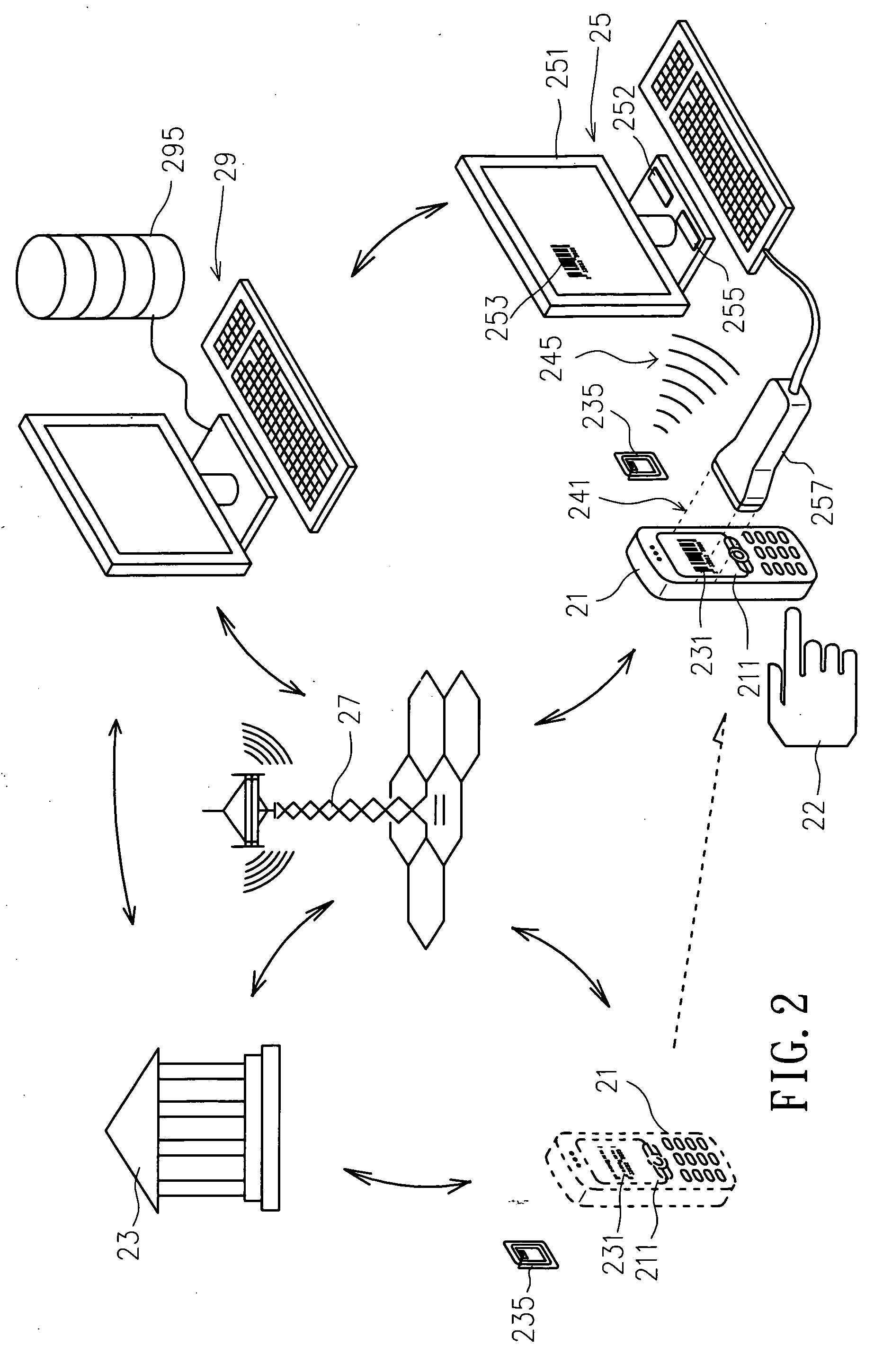
Electronic transaction system capable of improving transaction security and electronic transaction method thereof
InactiveUS20060249572A1Improve transaction securityImprove convenienceCredit schemesCoded identity card or credit card actuationManagement unitFinancial transaction
An electronic transaction system and an electronic transaction method thereof mainly comprise at least one issuing unit to generate at least one electronic certificate capable of representing the issuing unit or transaction object and at least one personal radio frequency identification capable of representing corresponding users according to the demanding application. The applying data associated with users can be stored in a certified management unit, wherein the electronic certificate can be stored in a portable electronic device owned by the user and displayed in the display screen of the portable electronic device. The personal radio frequency identification can also be kept by the user. When the user wants to proceed a shopping transaction, a sale end operation device of a sale end reads the electronic certificate and personal radio frequency identification, respectively, and connects to the certified management unit via a telecommunication device. The certified management unit determines and decides whether to permit proceeding a follow-up transaction or completing the shopping transaction according to the electronic certificate, personal radio frequency identification, and applying data. This way, not only the security and convenience in electronic transaction can be improved, but also the users have privacy.
Owner:SHOOTER DIGITAL +1
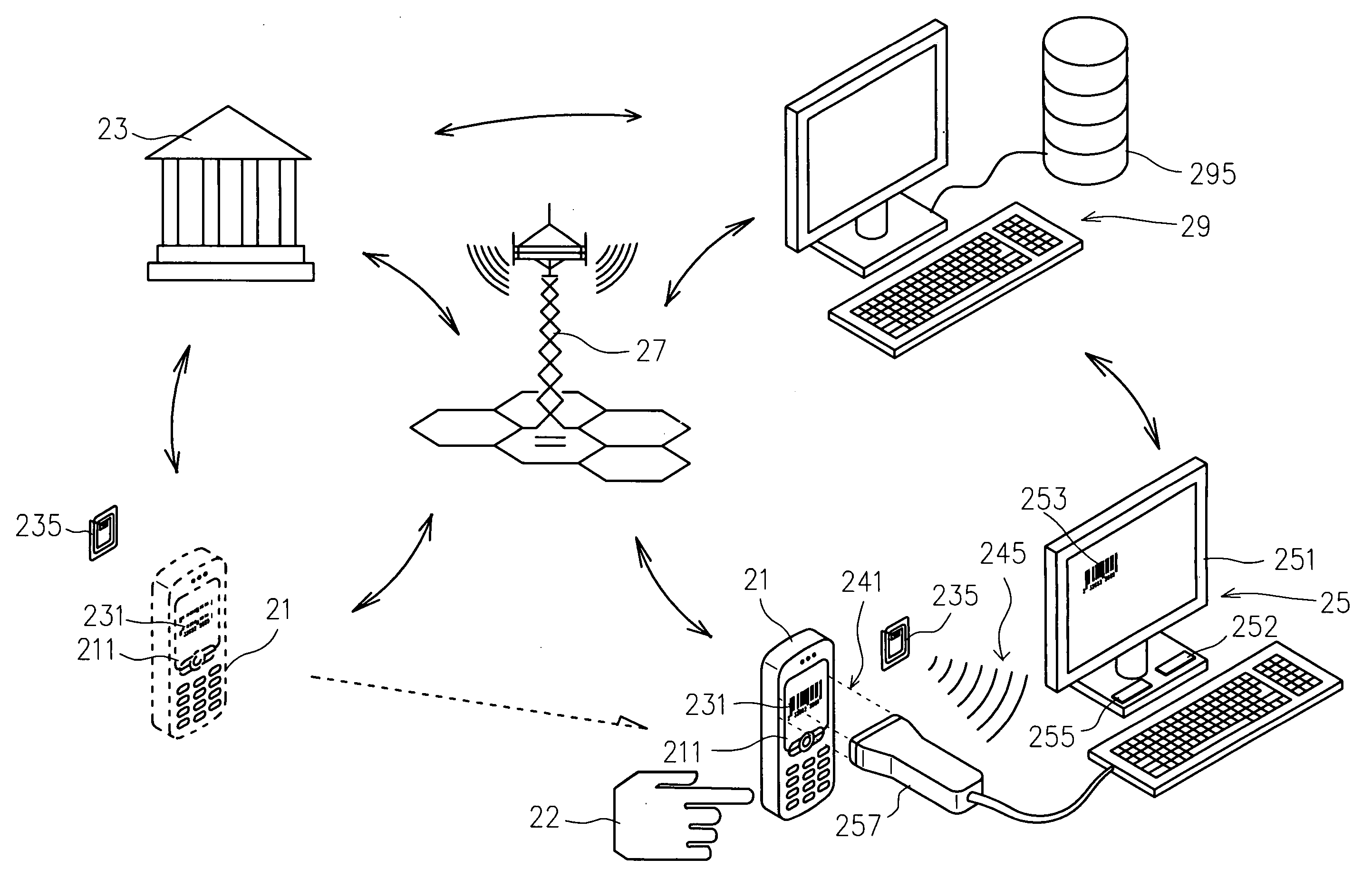
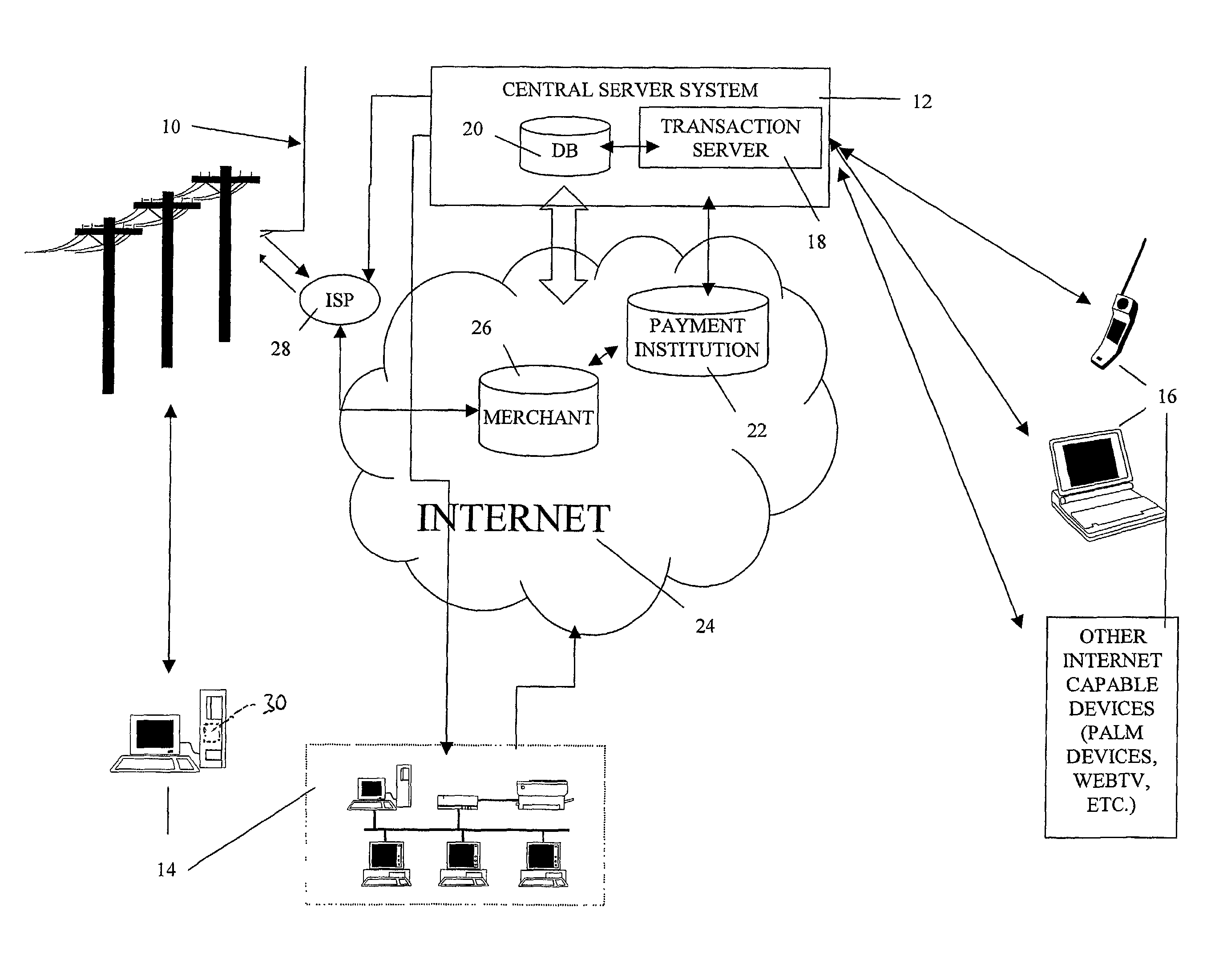
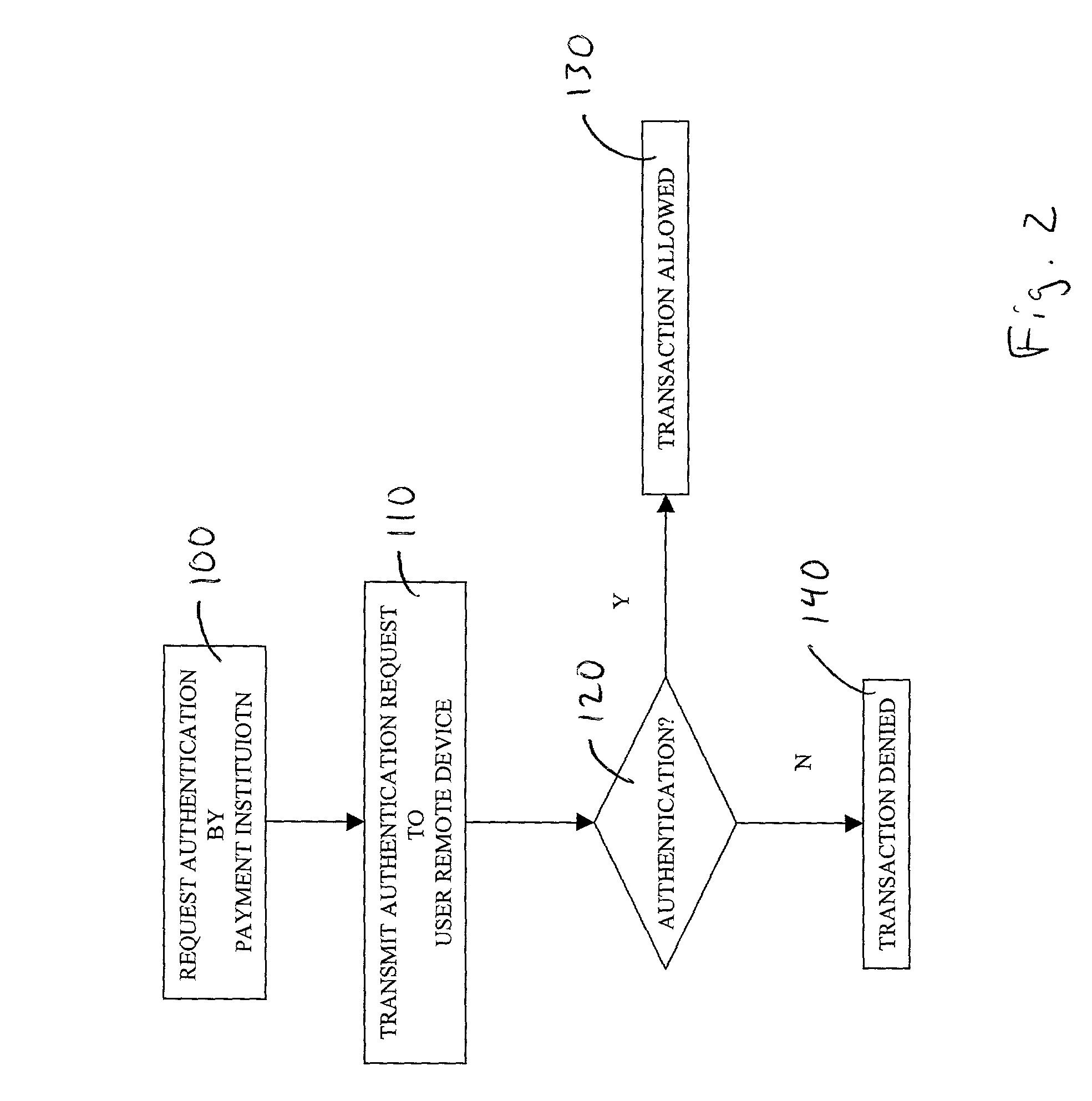
Transaction authentication system and method
A transaction security and authentication apparatus and system for electronic commerce which provides authentication of internet purchases by communication with a cardholder's base computer, or by contacting the cardholder by remote access for purchase verification. The system preferably comprises at least one central server system associated with a remote access system and configured for communication with a payment institution, and at least one internet capable device, operatively coupled for communication with the central server system, with the central server system configured to determine authentication of a cardholder electronic transaction, according to data received from the internet capable device upon a request for verification of the cardholder electronic transaction from the payment institution. The method of the invention generally comprises requesting verification of a cardholder electronic transaction, by a payment institution, from a central server system, contacting, by the central server system, at least one internet capable device associated with the cardholder, determining, by the central server system, if the cardholder electronic transaction is authorized by the cardholder, and communicating authentication information, by the central server system, to the payment institution.
Owner:IMMERSON MEDICAL INC +1
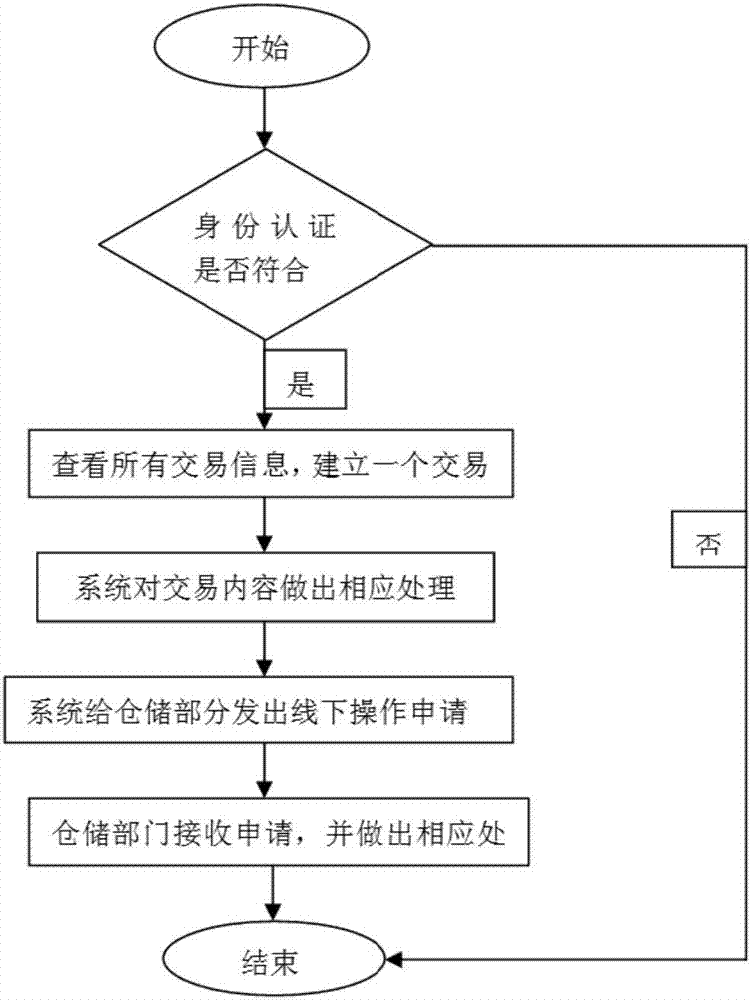
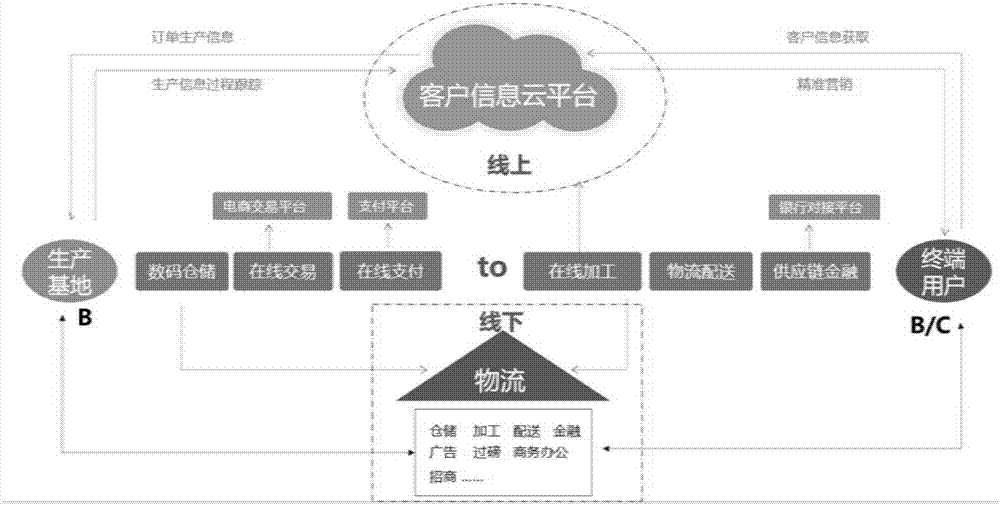
System and method for improving warehousing transaction security and operation efficiency based on block chain
InactiveCN107516180AEnsure safetyReduce manual operationsLogisticsProtocol authorisationState of artThe Internet
The invention discloses a system and a method for improving warehousing transaction security and operation efficiency based on a block chain, and aims to solve the problem of low warehousing transaction efficiency due to high difficulty in integrating operation information in warehousing information in the prior art. The whole system combines warehousing with a transaction chain and the internet, and comprises modules including a warehousing service module, a platform management module, a security reinforcement module, a related block chain interface and the like; the security reinforcement module performs bio-feature-based user identity authentication and ensures security of a goods property related interface; and a financial settlement module can manage asset conditions of all users. According to the system and the method, the warehousing is combined with the transaction chain and the internet; two characteristics of "decentralization" and "non-tampering" of the block chain are applied to business operations of warehousing, transaction and the like, so that the security in the complex warehousing and transaction processes is ensured, the manual operation is reduced, and the efficiency is improved; and the system and the method are suitable for the technical field of warehousing supervision information management systems.
Owner:MR RAY CHENGDU TECH CO LTD
Mobile Transaction Methods and Devices With Three-Dimensional Colorgram Tokens
ActiveUS20120311320A1User identity/authority verificationComputer security arrangementsUser authenticationMobile transaction
A transaction security process includes authentication and identification parts for pushing an encrypted colorgram for user authentication and persona descriptors for user identification from a transaction server to a first personal trusted device. A decryption of the colorgram is displayed on the first personal trusted device. An image is captured by a second personal trusted device. An encryption of the image captured from the second personal trusted device is uploaded to the transaction server. The persona descriptors are used to build a composite rendering for identification of the first user to the second user. The second user clicks “OK” if they recognize the composite drawing as a reasonable persona of the first user.
Owner:CRYPTITE LLC
Transaction security apparatus and method
ActiveUS20110035240A1Prevent and/or to drastically limit fraudulent and/or unauthorized useComplete banking machinesFinanceThe InternetCheque
An apparatus, including an input device or receiver for inputting or receiving transaction information regarding a transaction which includes information pertinent to the transaction and information regarding a copy, image, photograph, or picture, of a document, form, draft, check, receipt, or other entity, offered, presented, submitted, processed, involved, or used, in the transaction, a processing device for processing the information pertinent to the transaction and which generates a notification message containing information regarding the transaction and the information regarding the copy, image, photograph, or picture, and a transmitter which transmits the notification message to a communication device associated with an account holder via, on, or over, the Internet, the World Wide Web, or a wireless communication network. The notification message is transmitted to the communication device independently of any processing of the transaction by a transaction authorization processing computer.
Owner:GTJ VENTURES
Verification method and system thereof
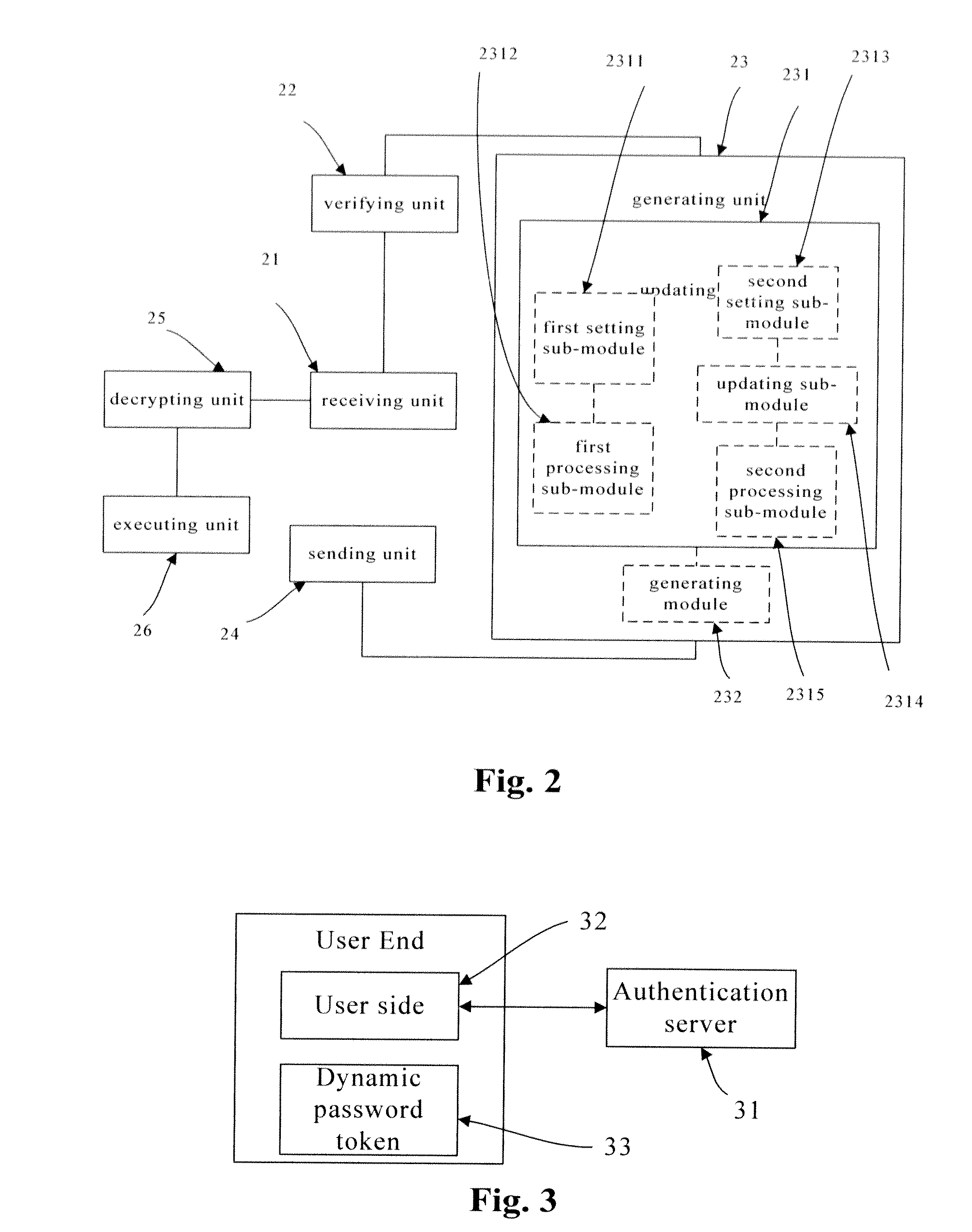
ActiveUS20120210408A1Improve securityAvoid lostMultiple keys/algorithms usageDigital data processing detailsPasswordValidation methods
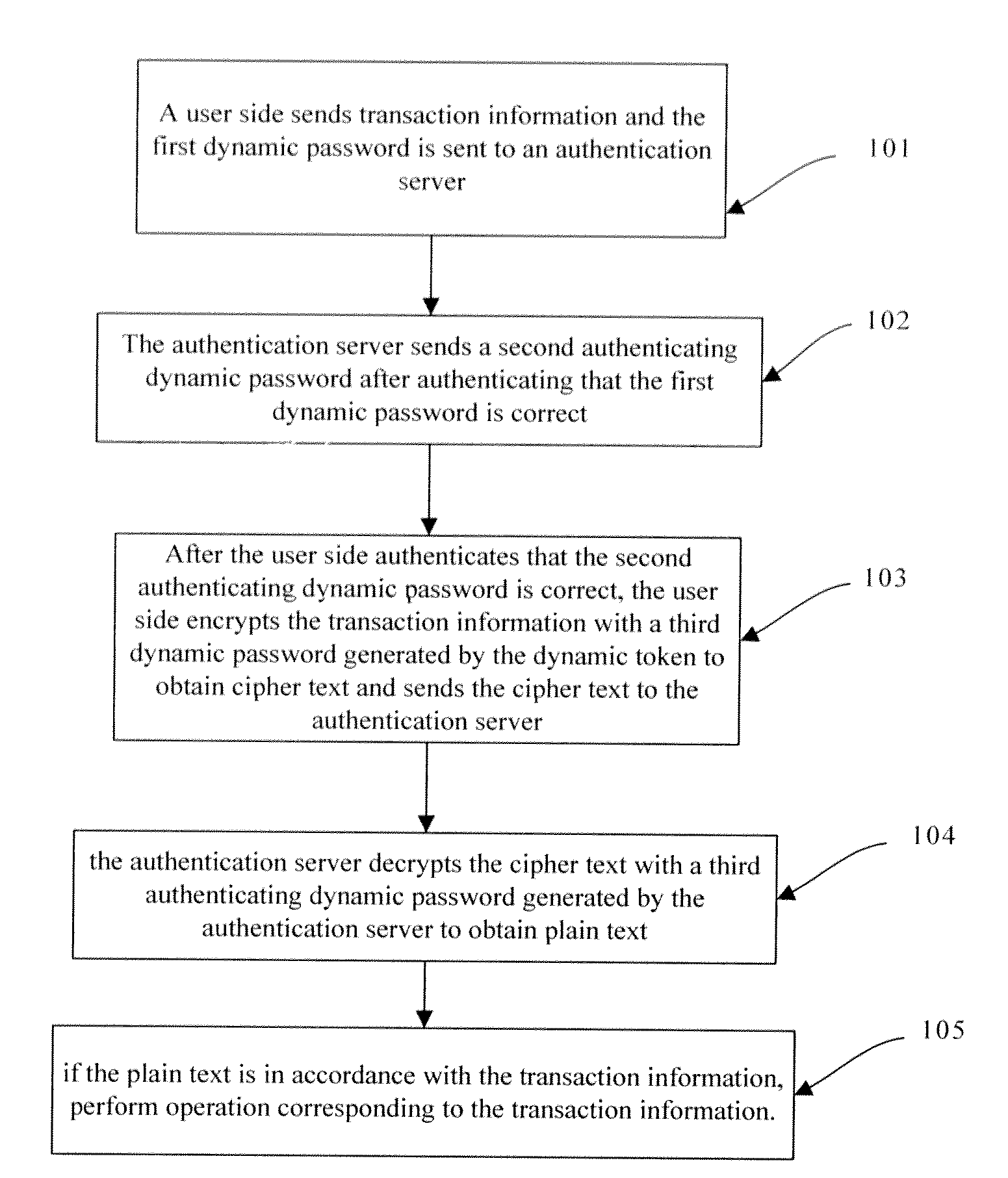
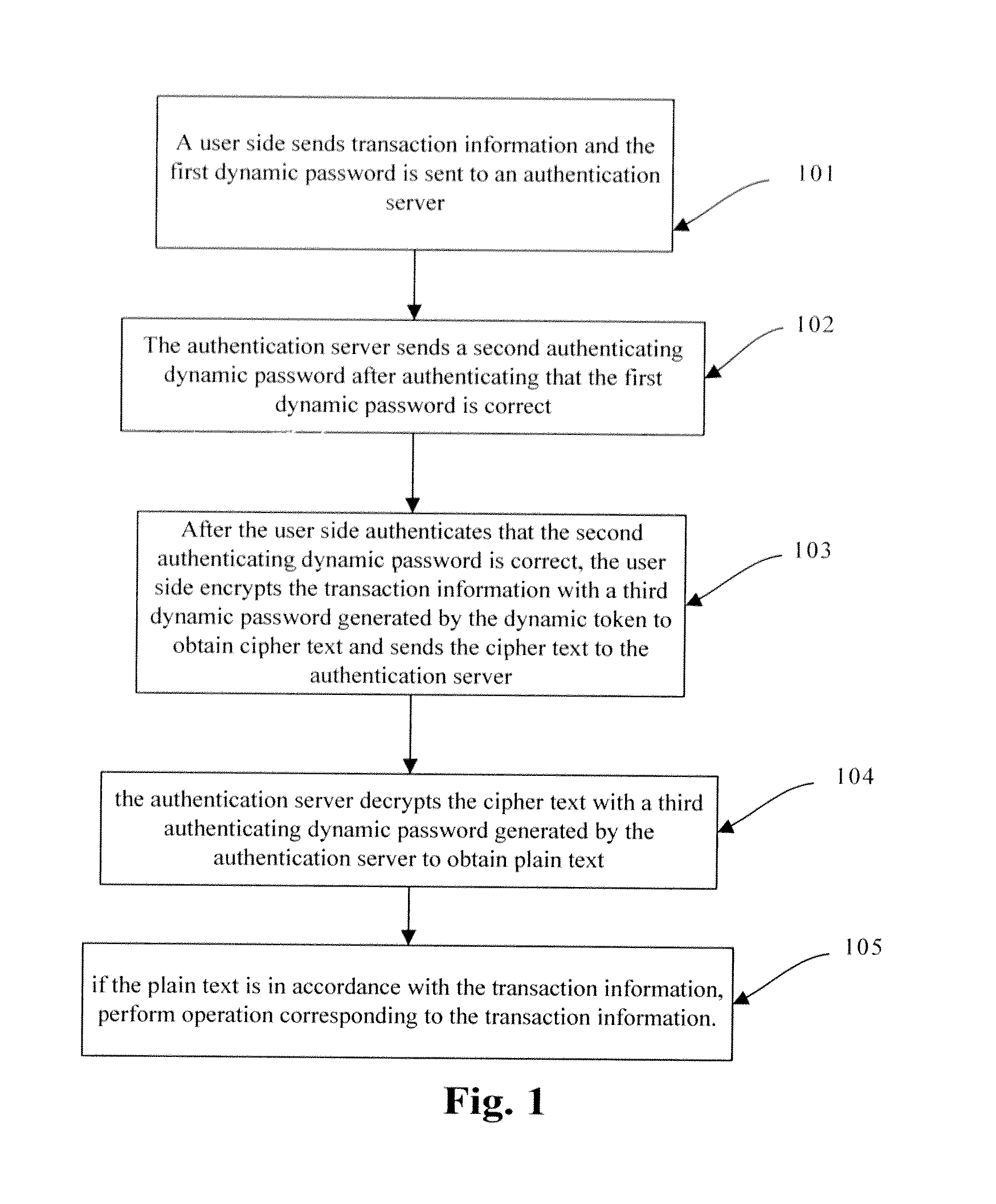
The invention discloses an authenticating method and a system thereof, which relates to information security field and solves the problem that the user information is not safe in transaction process. The embodiment of the invention comprises that the server side receives user data information and a first dynamic password sent from the user side; the server side generates the first authenticating dynamic password according to the user data information; server side verifies the first dynamic password according to the first authenticating dynamic password and generates the second authenticating dynamic password after successful verification; the server side sends the second authenticating dynamic or the first password to the user side; the server side executes the transaction data in the user data information or permits the user to log on after using a third authenticating dynamic password generated by the server side to verify the user data information or the third dynamic password sent from the user side successfully. The invention enhances the safety of transaction for the user and prevents the user from loss caused by logging on phishing website by the user.
Owner:FEITIAN TECHNOLOGIES
System and method for ensuring safety of online transactions
Online transaction security is improved by detecting a start of an online financial transaction between a user-controlled online transaction application and a remote payment service. A protected data input module, a protected environment module, and a safe data transfer module each provides a corresponding set of protection operations. A risk level of conducting the financial transaction is assessed based on a vulnerability assessment and on present condition of the local computing system. An initial degree of protection for each of the modules is set, and subsequently adjusted based on the risk level.
Owner:AO KASPERSKY LAB
Method and platform for ordering dishes on basis of mobile phone and internet
InactiveCN102081700ALower the barriers to entry for informatizationEffective budget controlTelephonic communicationTransmissionInformatizationThird party
The invention discloses a method and platform for ordering dishes on the basis of a mobile phone and the internet, relates to the field of the mobile internet and informatization of the catering industry, in particular to a method and platform for ordering dishes in the catering industry on the basis of a mobile phone, a mobile internet and cloud computing, and solves the problems of long waiting time, low service efficiency, low mutual confidence, large initial investment, insufficient resource utilization and the like in the traditional method. Under the background that the mobile internet is rapidly developed and the intelligent mobile phone is popularized acceleratively, the invention provides the method and the platform for ordering the dishes on the basis of the mobile phone and the internet so that a merchant and a customer complete the flow of ordering the dishes under the support of a third party platform, and the invention particularly supports a mode that the merchant or the customer remotely makes an appointment and orders the dishes through a cloud computing platform and a third party pays for the dishes or carries out mobile payment. The method and the platform for ordering the dishes on the basis of the mobile phone and the internet have the advantages of enhancing the convenience in consumption for consumers through informatization, networking and mobility, guaranteeing the transaction security of each party and promoting the development of the service industry.
Owner:姚武杰 +1
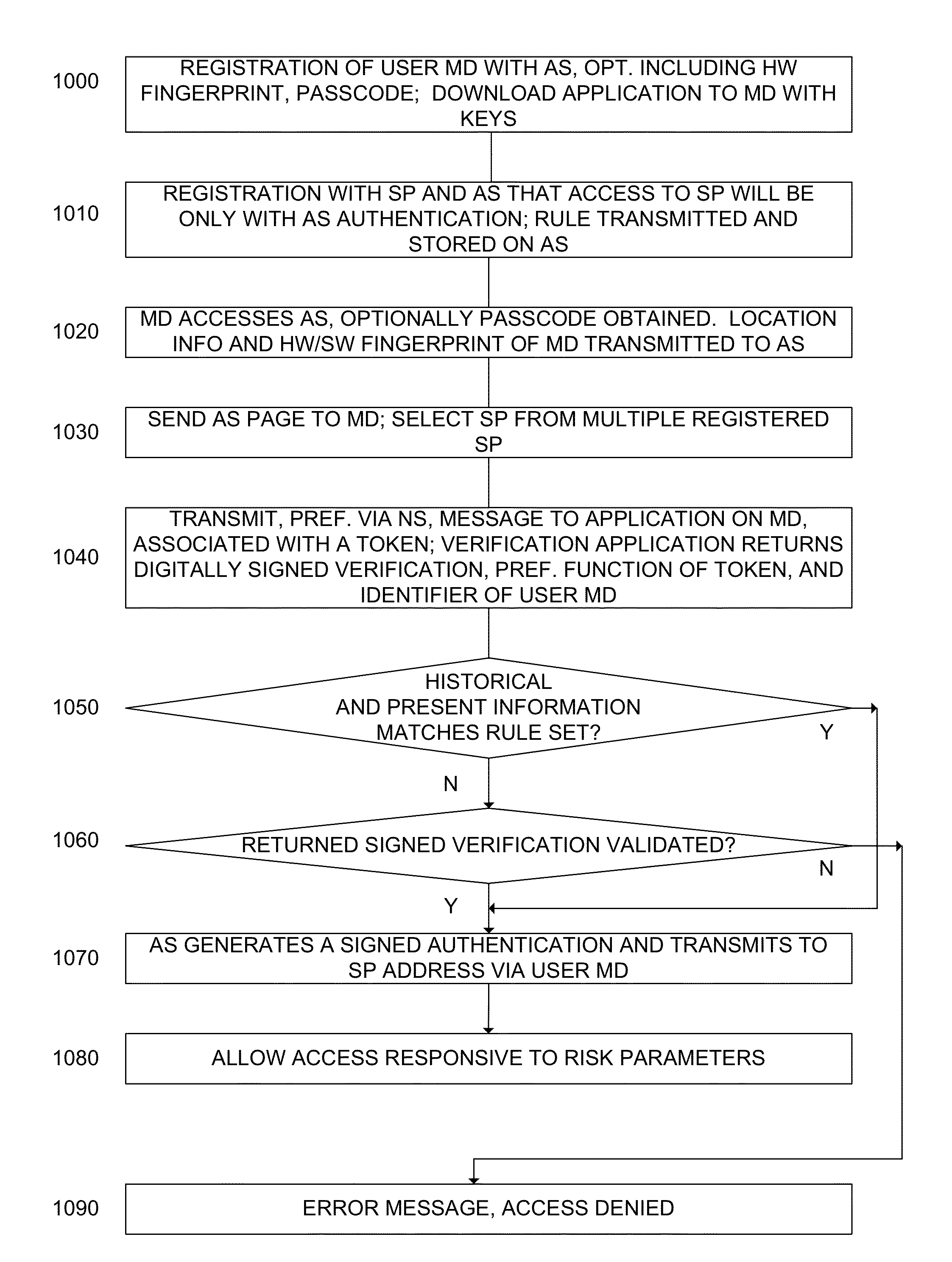
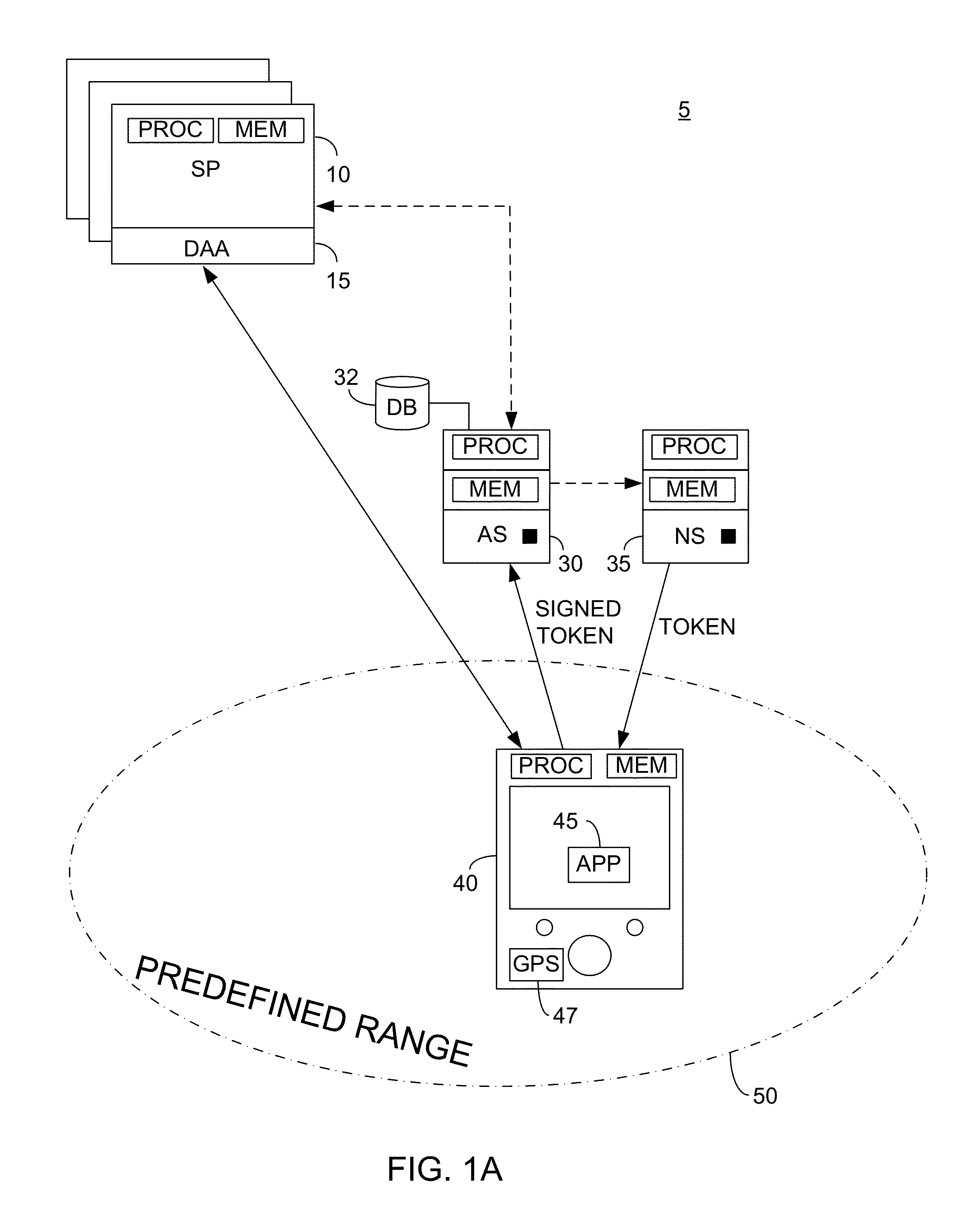
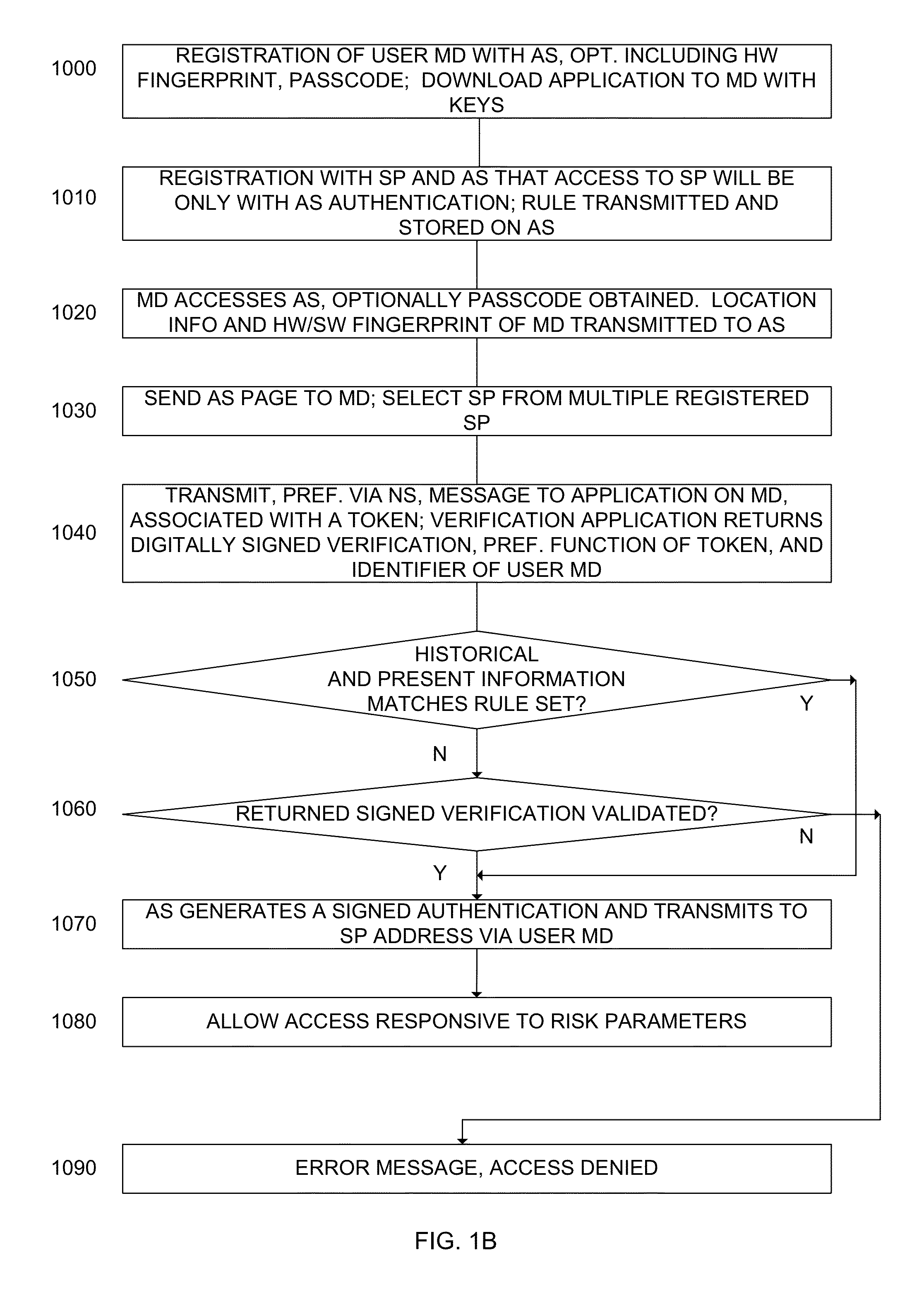
System and method for transaction security responsive to a signed authentication
ActiveUS20130023240A1Improve security levelUnauthorised/fraudulent call preventionEavesdropping prevention circuitsUser deviceAuthentication server
A system arranged to authenticate a user via its mobile device to a service provider, the system comprising: an authentication server; the user mobile device, the user mobile device provided with a verification application arranged to communicate with the authentication server; and a notification server in communication with the authentication server and arranged to transmit a notification to the user mobile device responsive to the authentication server, the authentication server arranged to provide a signed authentication to the service provider responsive to present and historical information regarding one of: the user mobile device; and an additional user device in communication with said authentication server, said signed authentication provided in accordance with a rule set determined by an authorized entity stored on said authentication server memory governing the required present and historical information attribute.
Owner:PING IDENTITY
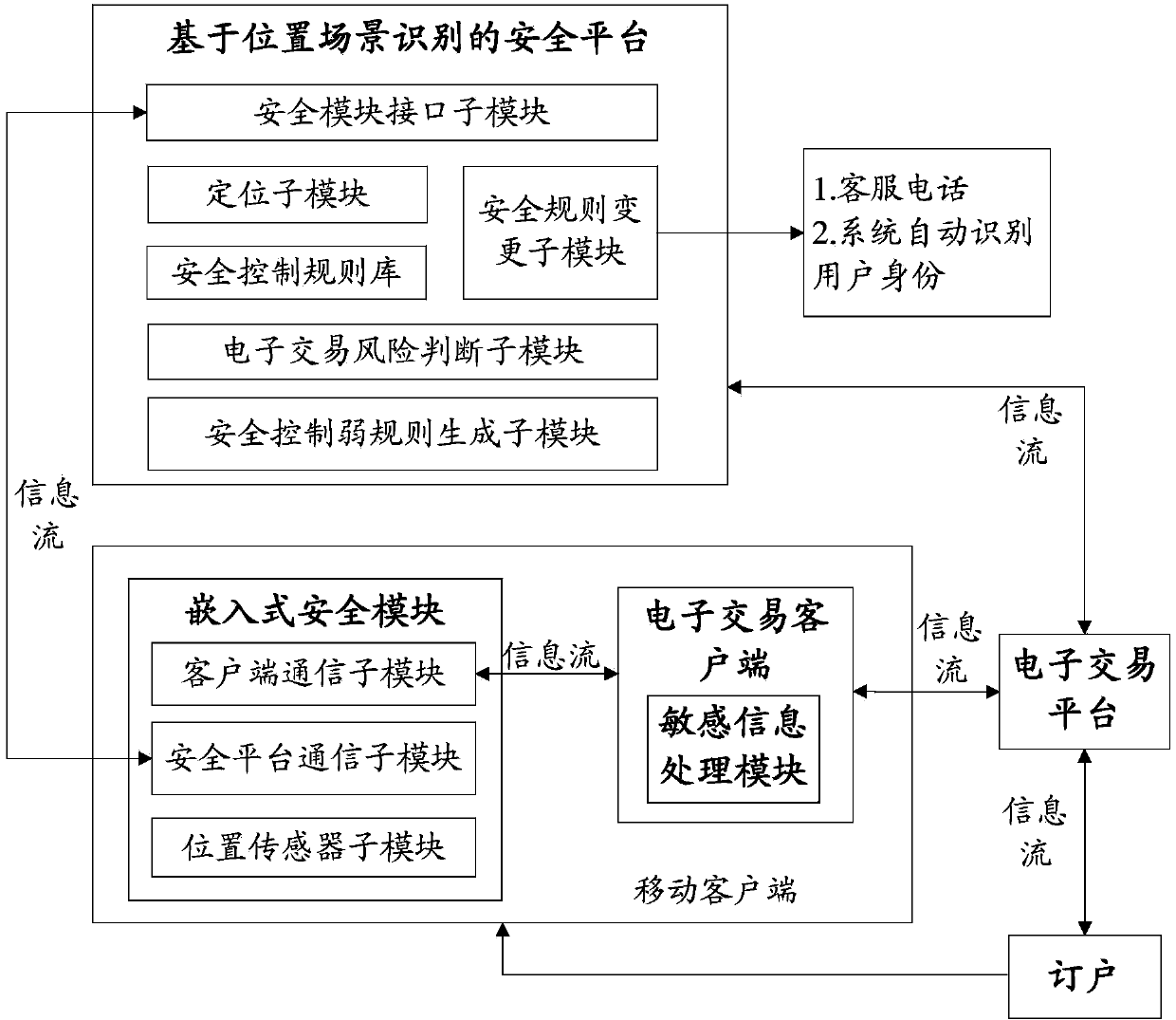
System and method for realizing electronic transaction risk control based on position scene identification
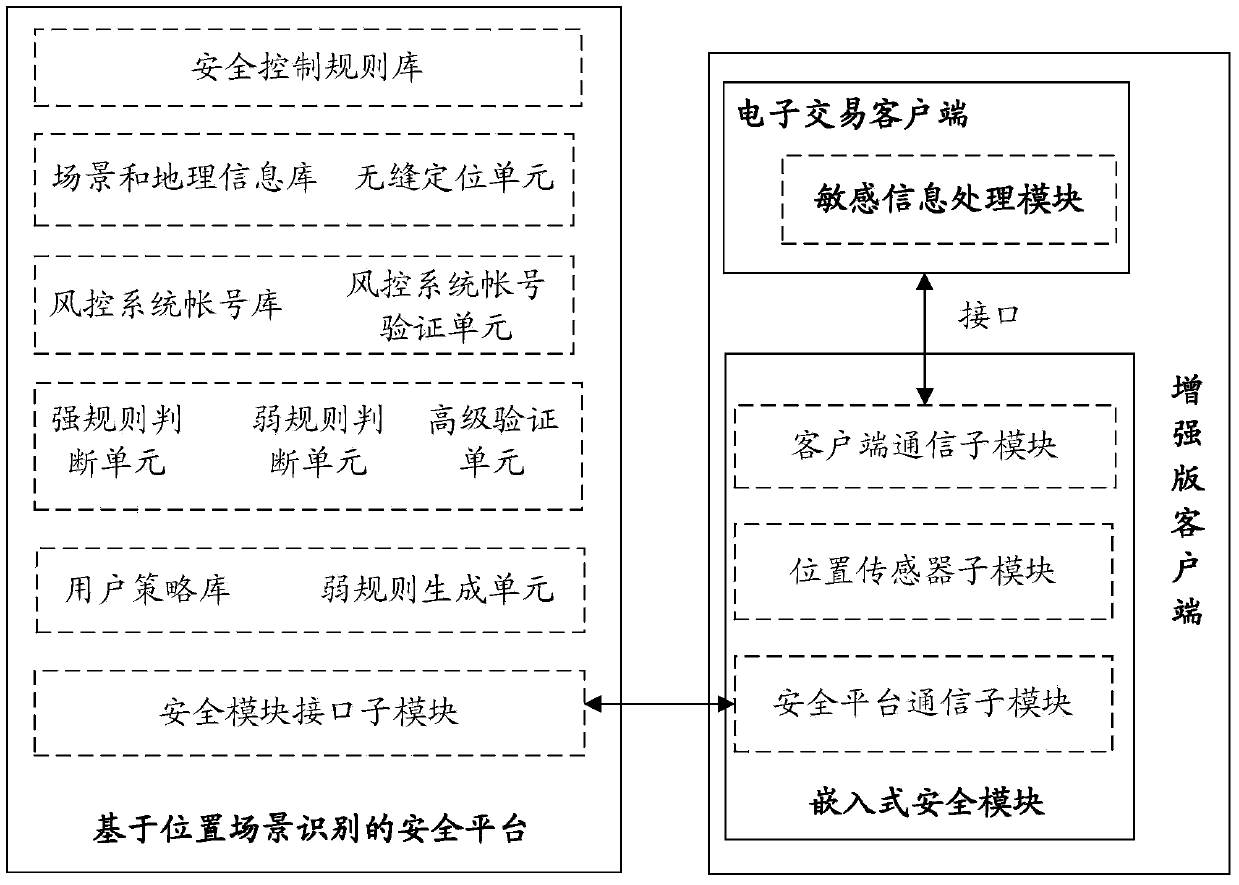
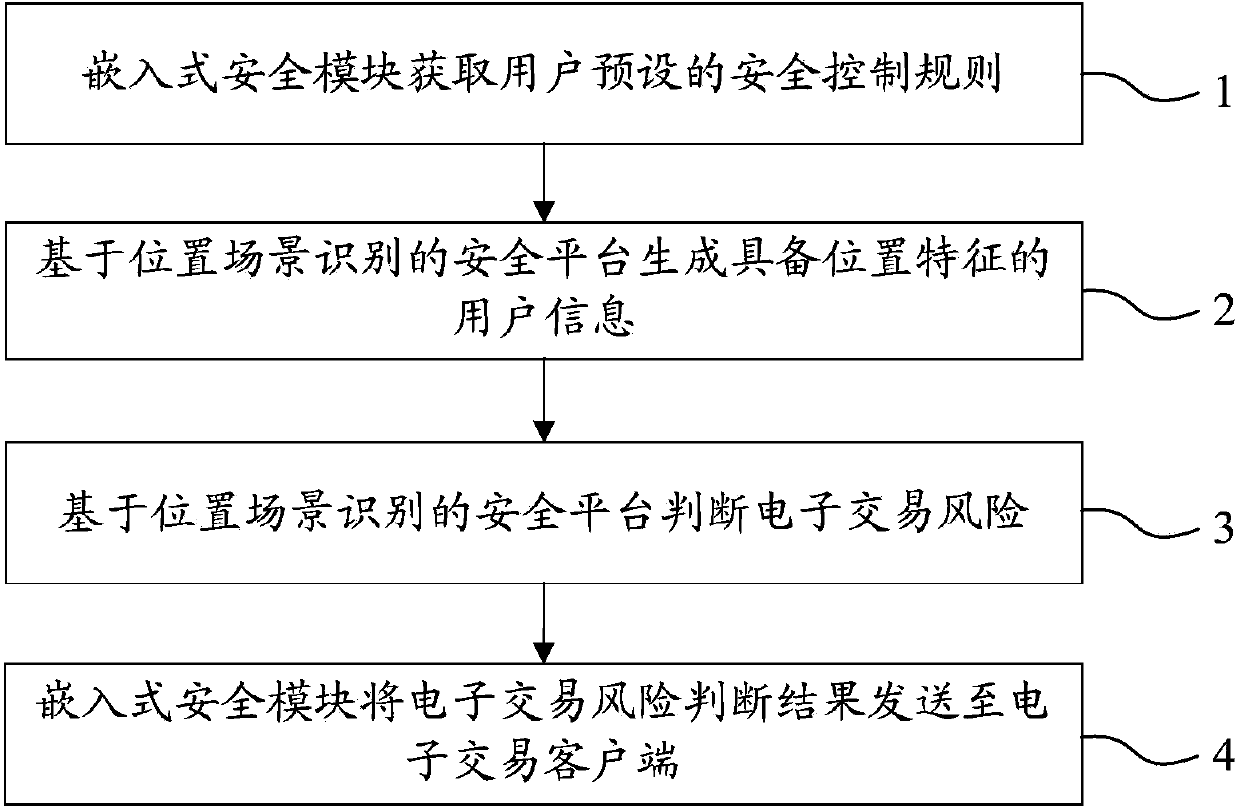
InactiveCN103745397APrevent fraudReduce personal property damageFinanceBuying/selling/leasing transactionsRisk ControlEmbedded security
The invention relates to a system for realizing electronic transaction risk control based on position scene identification. The system comprises a position scene identification-based security platform and an embedded security module, wherein the position scene identification-based security platform comprises a security interface sub-module, a positioning sub-module, a security control rule library, a security rule change sub-module, an electronic transaction risk judging sub-module and a security control weak rule generation sub-module, which are communicated with the embedded security module. The invention further relates to a method for realizing electronic transaction risk control based on position scene identification through the system. By adopting the system and the method for realizing electronic transaction risk control based on position scene identification, risk control over the electronic transactions of a user can be realized by providing positioning service and identifying a user position scene, so that the security of an electronic transaction process is enhanced, and losses caused by transaction security problems are reduced. The method is easy, convenient, and wider in application range.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
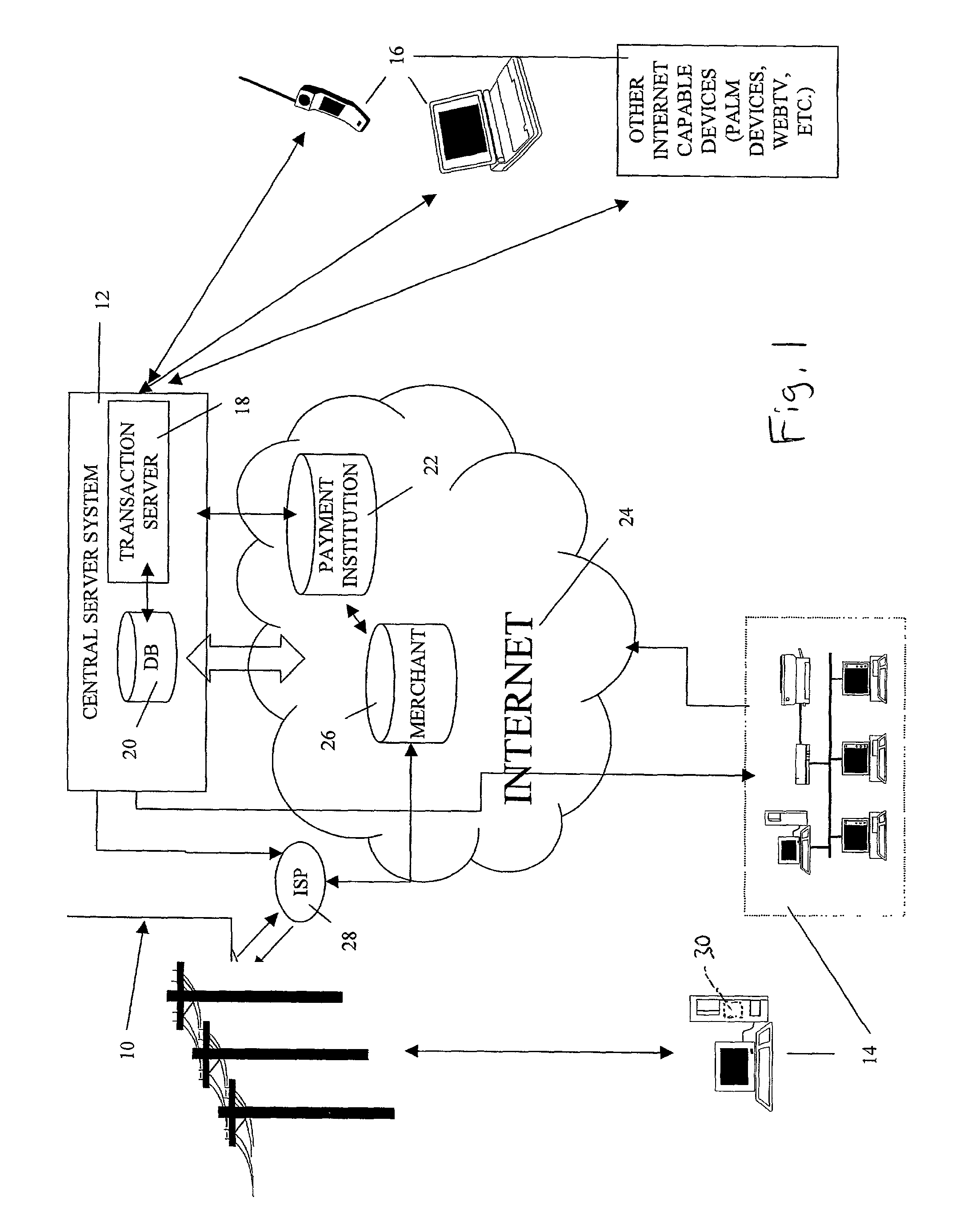
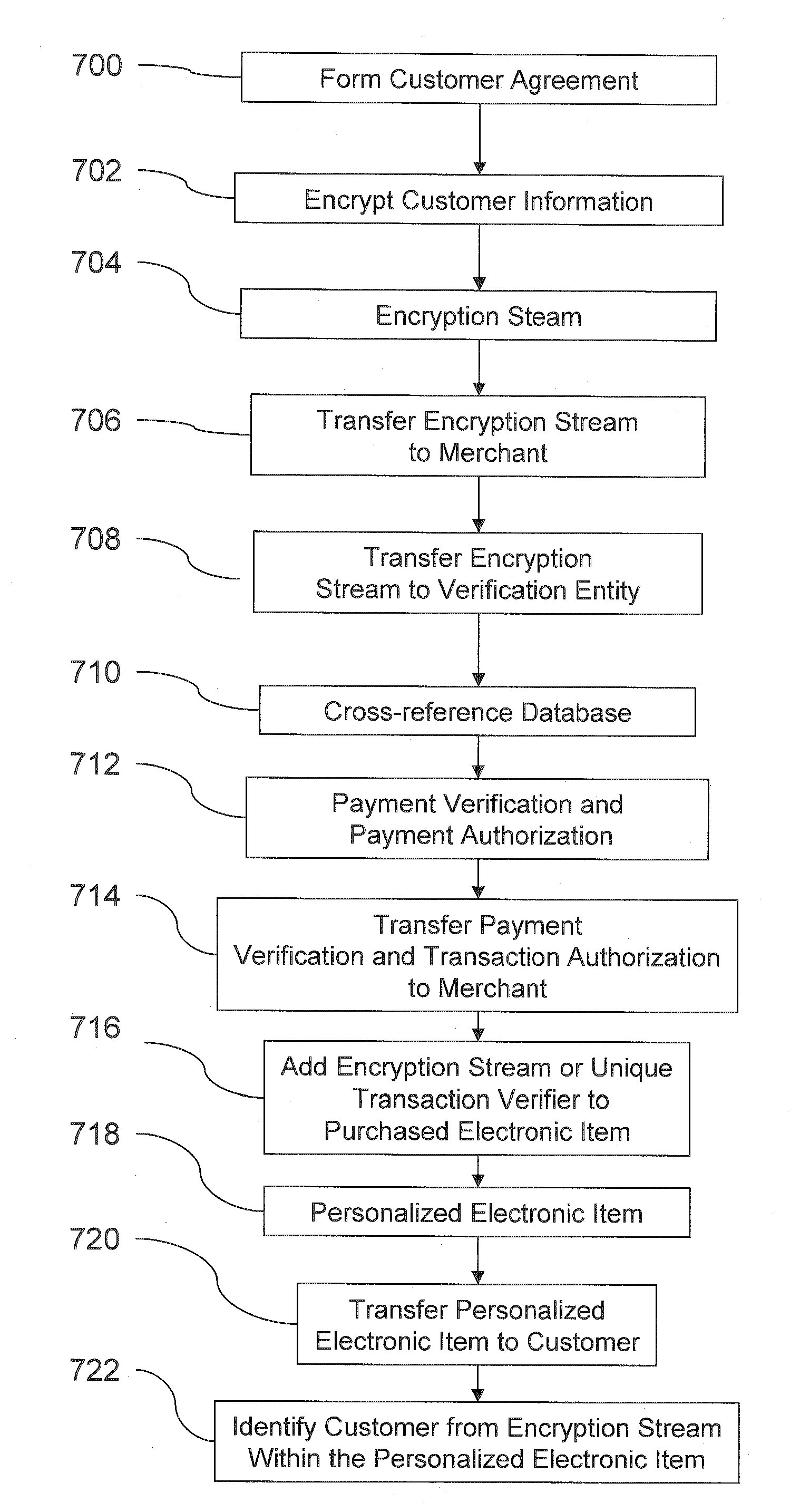
Transactional security over a network
InactiveUS20070288394A1Facilitates purchase transactionEasy to useDigital data authenticationCommercePaymentPersonalization
A system and method facilitates purchase transactions over a computer network, including the purchase of electronically storable items. The embodiments herein encrypt “customer information” in an encryption stream and cause the encryption stream to be transferred from the customer to a merchant in the purchase transaction. A verification entity receives the encryption stream which is sent by the merchant for identity verification and payment authorization. Then, the verification entity verifies the identifiers contained in the encryption stream and transfers an identity verification and payment authorization from the verification entity to the merchant. The encryption stream or unique transaction identifier can be added, by the merchant, to a purchased electronic item to create a personalized electronic item.
Owner:BENEDOR CORP
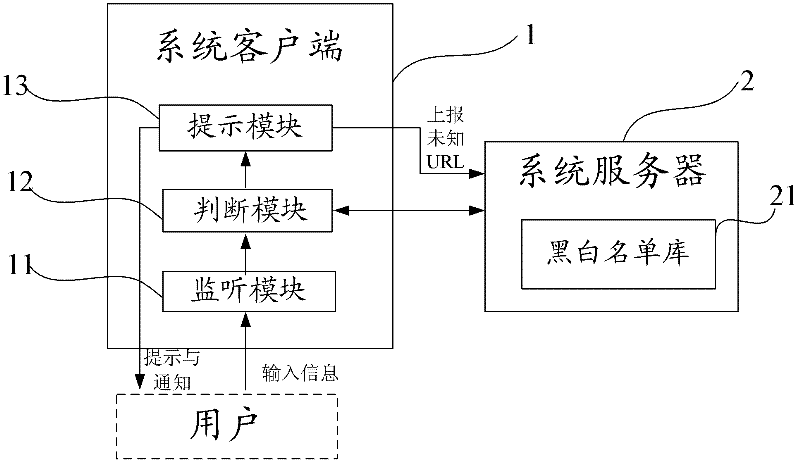
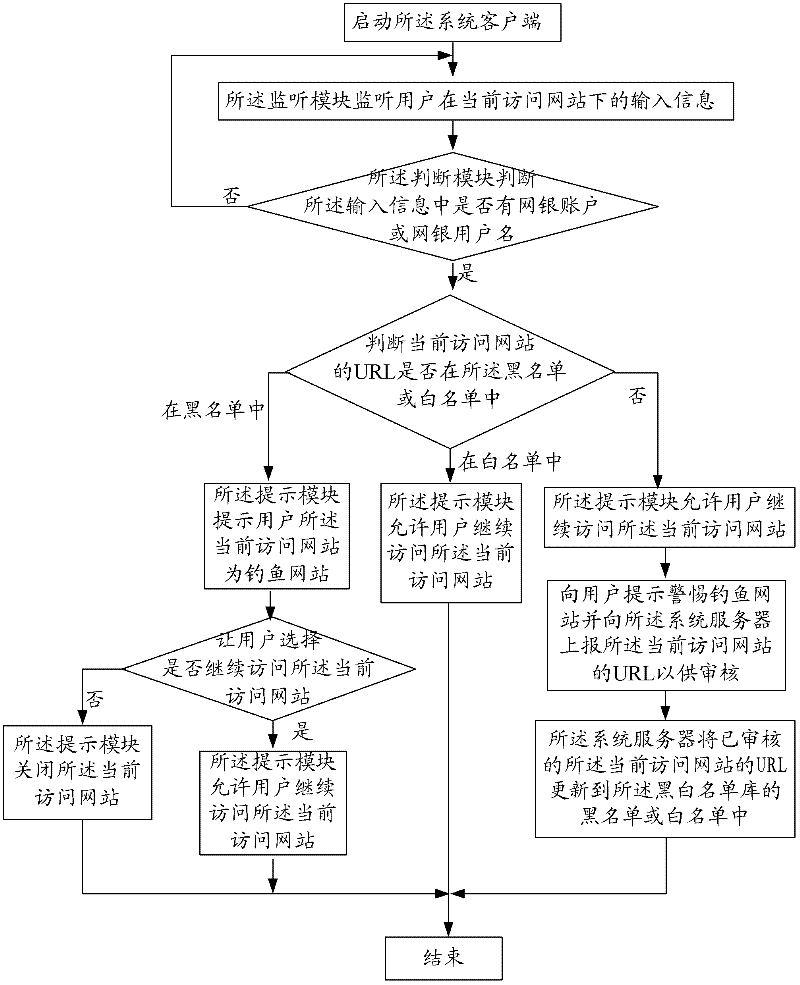
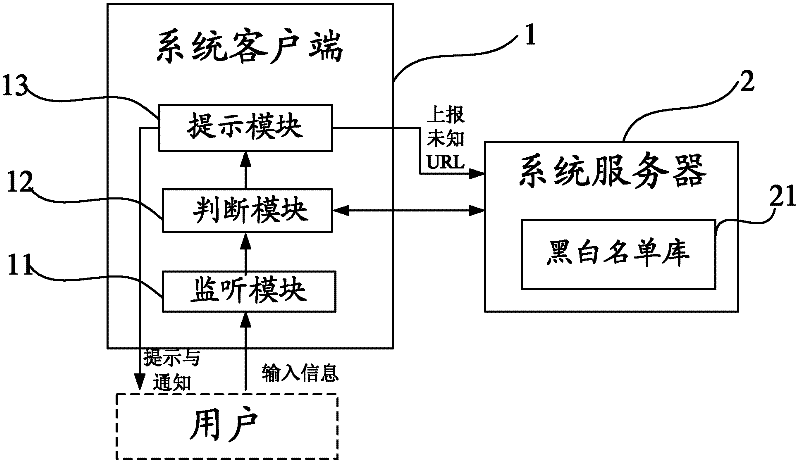
A network transaction security system and method
InactiveCN102299918AImprove accuracyImprove timelinessPayment architectureTransmissionCredit cardUser input
The present invention provides a network transaction security system and method. The monitoring module monitors user input in real time so that the judging module can judge in real time whether the currently visited website is a phishing website, and the prompt module quickly sends a vigilant prompt to the user and informs the unknown URL of the currently visited website. Report for review to update to the black and white list database, which improves the correct rate of identifying phishing websites and blocking access, and greatly reduces the probability of huge losses caused by theft of the user's online banking account. It is applicable to various bank cards, credit cards, and social security cards. Anti-phishing for online transactions such as game point cards, recharge cards, shopping cards and electronic money, with wide coverage, multiple notification methods and channels, and high timeliness.
Owner:SHENGQU INFORMATION TECH SHANGHAI
Free-space Gesture Recognition for Transaction Security and Command Processing
InactiveUS20080230598A1Quick and efficient in handlingImprove securityInput/output for user-computer interactionElectric signal transmission systemsAuthorizationComputer science
A sensor panel having a matrix of independently decoded sensors, arranged in a two-dimensional pattern allows a consumer identification unit (CIDU) to detect a user-specific gesture made with a gesturing instrument such as an RF ID device. The CIDU monitors on a timed basis which of the sensors in the panel are receiving a signal from an RF ID device which has entered the proximity of one or more of the sensors. The user moves the sensor in a two-dimensional pattern to perform a “gesture signature” in free space near the panel, and the CIDU records the sequence of receiving sensors. This sequence can then be quickly and efficiently handled as a number to be looked up to identify and authenticate the user. Preferably, the user is allowed to define multiple signature gestures, each having the possibility of being associated with a transaction or authorization level.
Owner:SNAPCHAT
Enterprise computer system
Owner:SOFTWARE AG USA
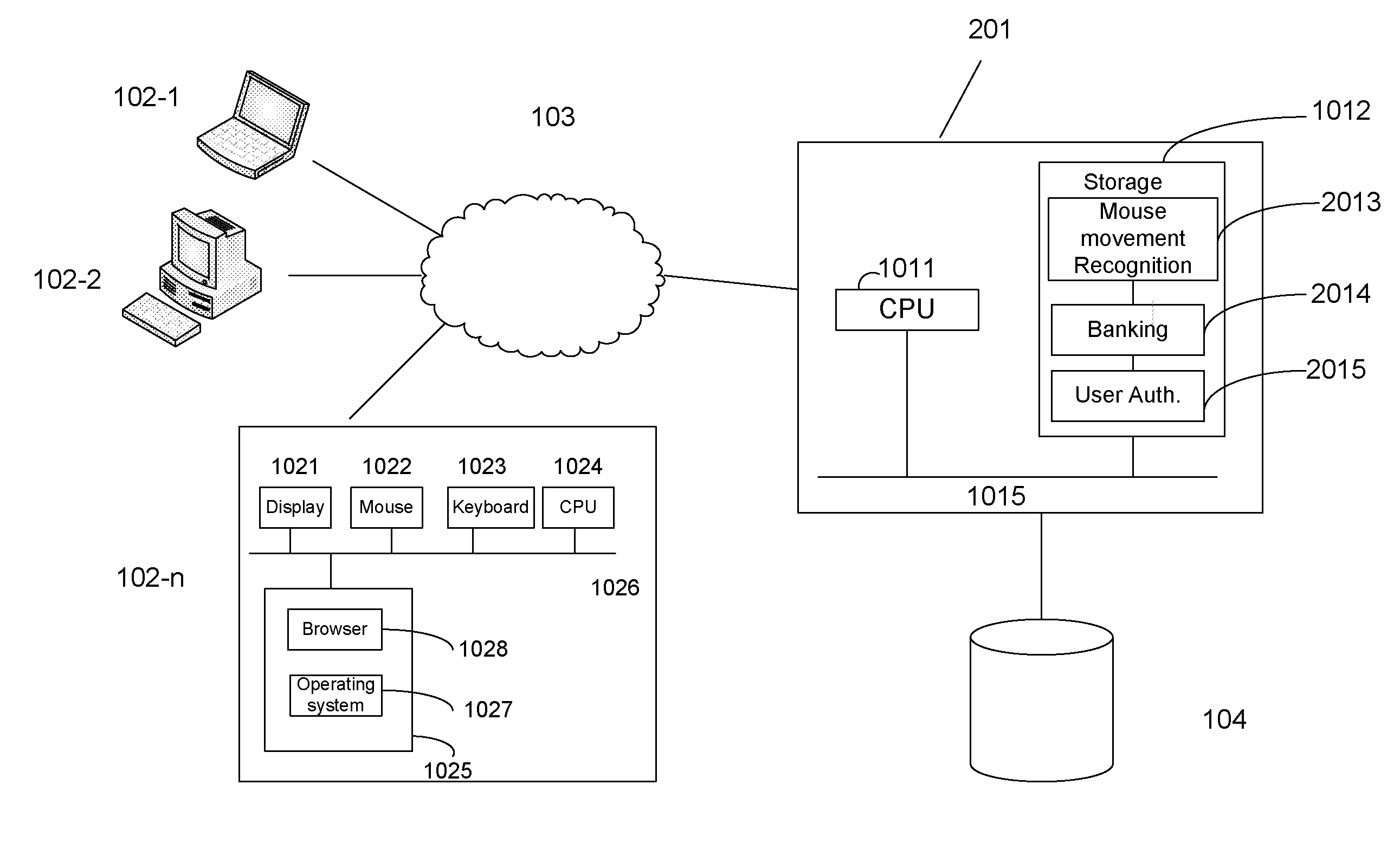
Interacting with internet servers without keyboard
ActiveUS20100269165A1Digital data processing detailsUser identity/authority verificationGraphicsPassword
A system and method which may allow users to interact with Internet servers with graphical mouse movements. The invention is especially useful to enhance online transaction security. A user may use a mouse to draw a pattern and store the pattern as his password to an online account, and draw the pattern with a mouse to log in the online account. The password may include a drawing, one or more letters, one or more numbers, or one or more characters.
Owner:SLACK TECH LLC
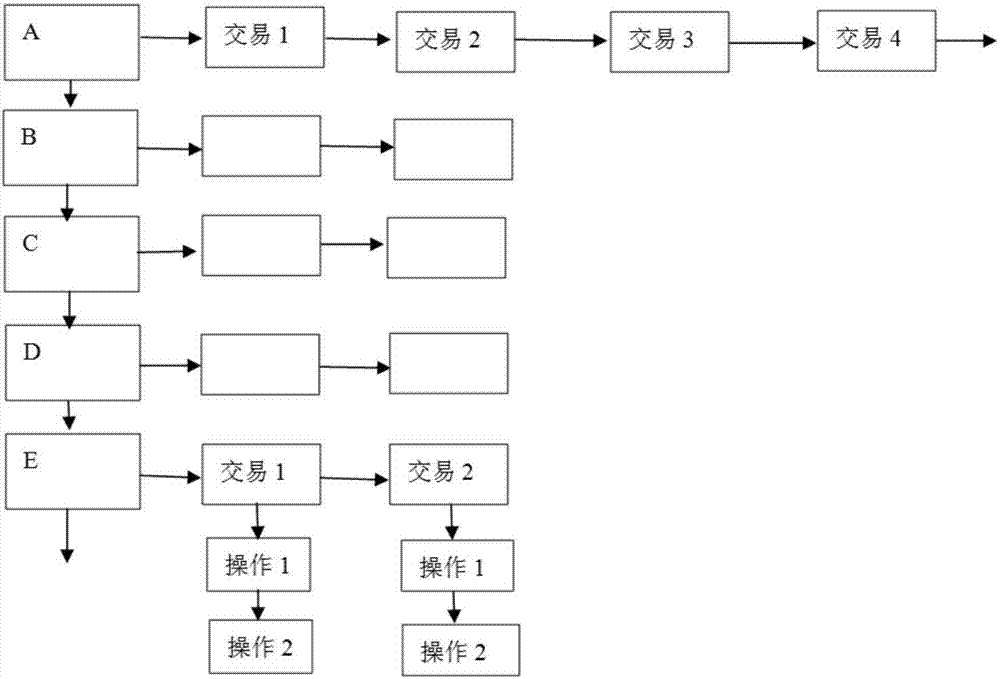
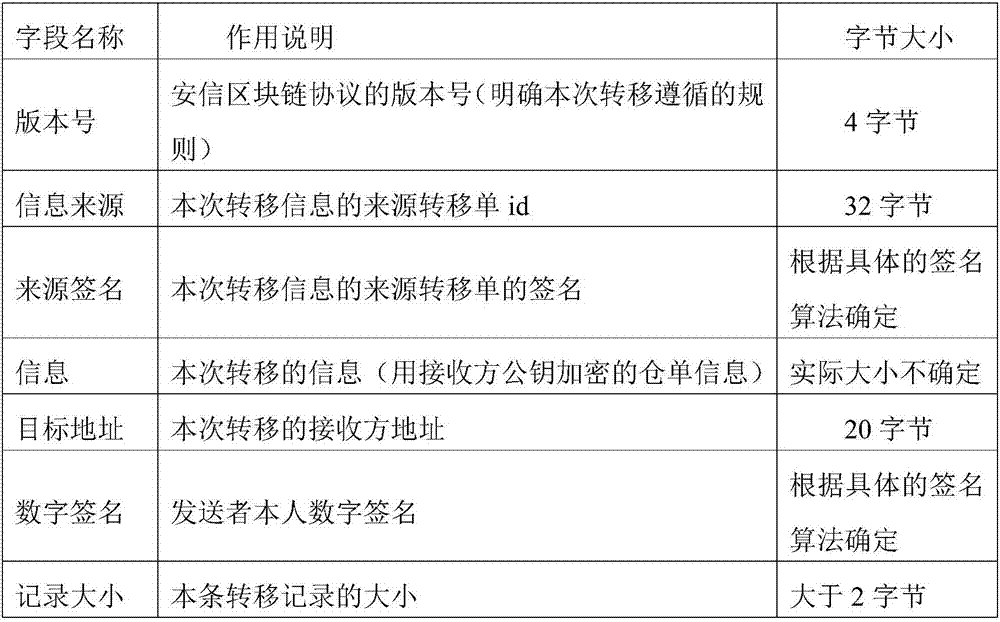
Warehouse receipt transaction security enhancing method in warehouse receipt system based on blockchain
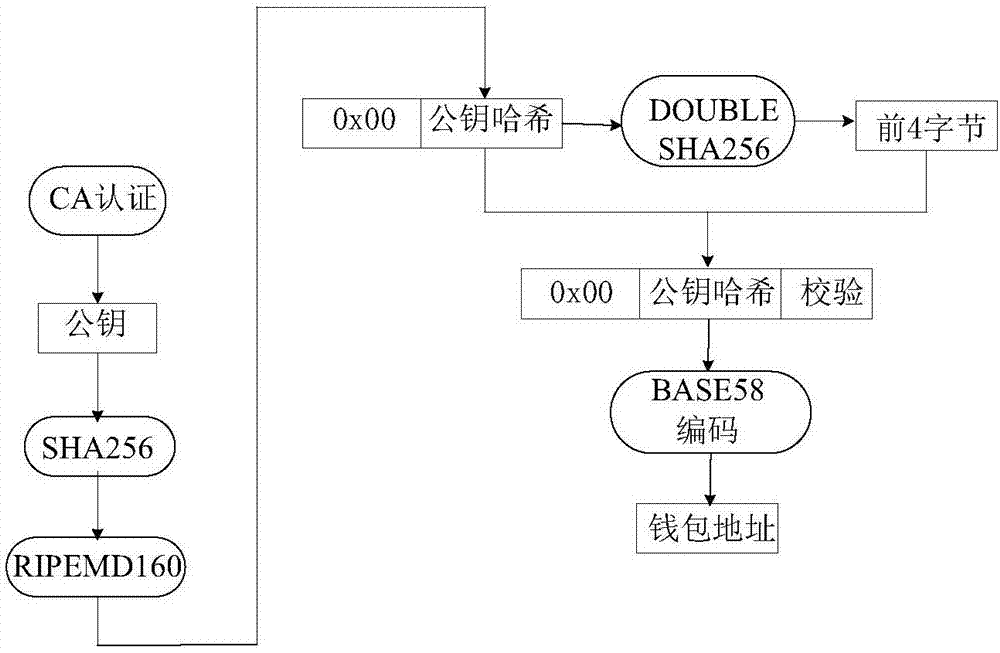
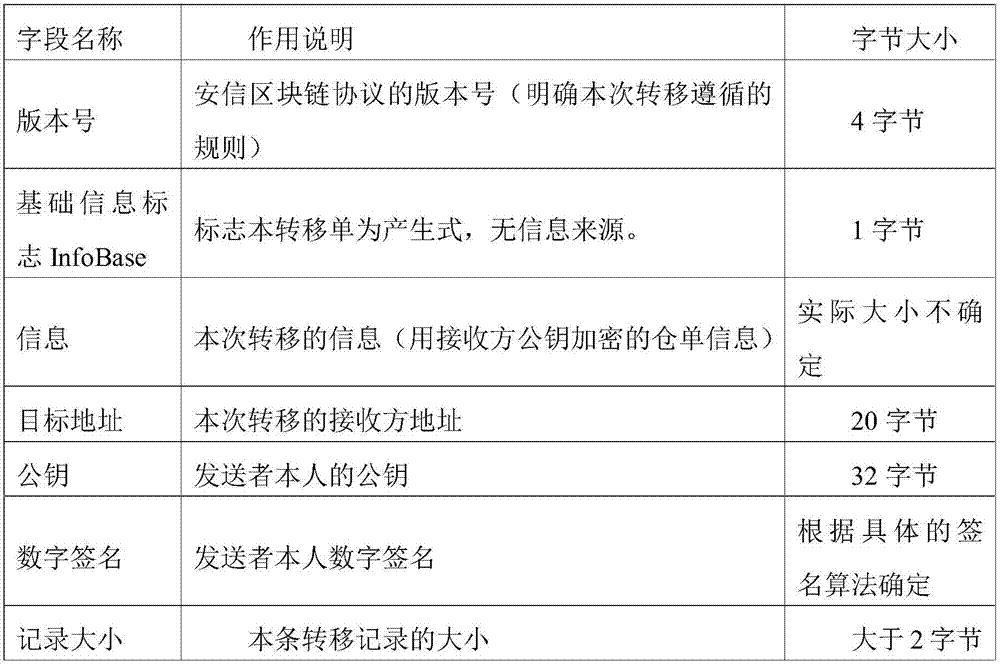
The present invention discloses a warehouse receipt transaction security enhancing method in a warehouse receipt system based on the blockchain. The method comprises that: public keys and private keys capable of verifying the identity of each node are generated by using a CA certification mechanism, wherein the warehouse receipt issuance node of the warehouse receipt system is taken as the node of a sender, a warehouse receipt is generated after the completion of warehousing, and warehouse information is encrypted by using the public key of the receiver to form a ciphertext; the ciphertext is signed by using the private key of the receiver, and a transfer order is made to be sent to the node of the receiver in the form of the broadcasting; and in each process of warehouse receipt transaction, the intermediate node and the node of the receiver use the public key of the sender to verify and sign the transfer order, and if the receiver needs to use the warehouse receipt, the private key of the receiver must be used to decrypt the warehouse receipt information on the transfer order. According to the warehouse receipt transaction security enhancing method in the warehouse receipt system based on the blockchain provided by the present invention, through the double verification mechanism of CA certification, and encryption and signature, the security of the warehouse receipt transaction and the privacy of the warehouse receipt system are improved.
Owner:深圳市华深安信科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com