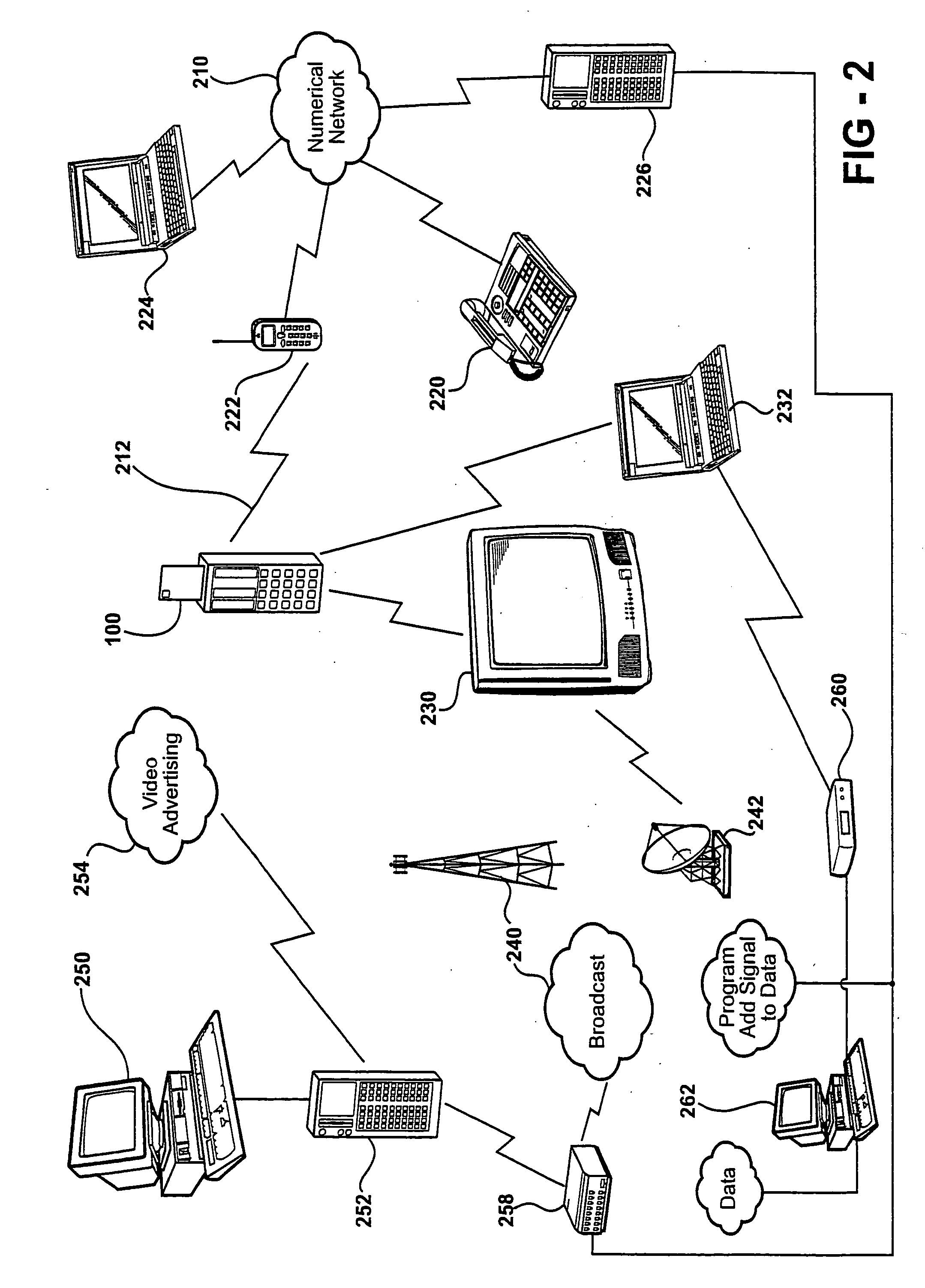
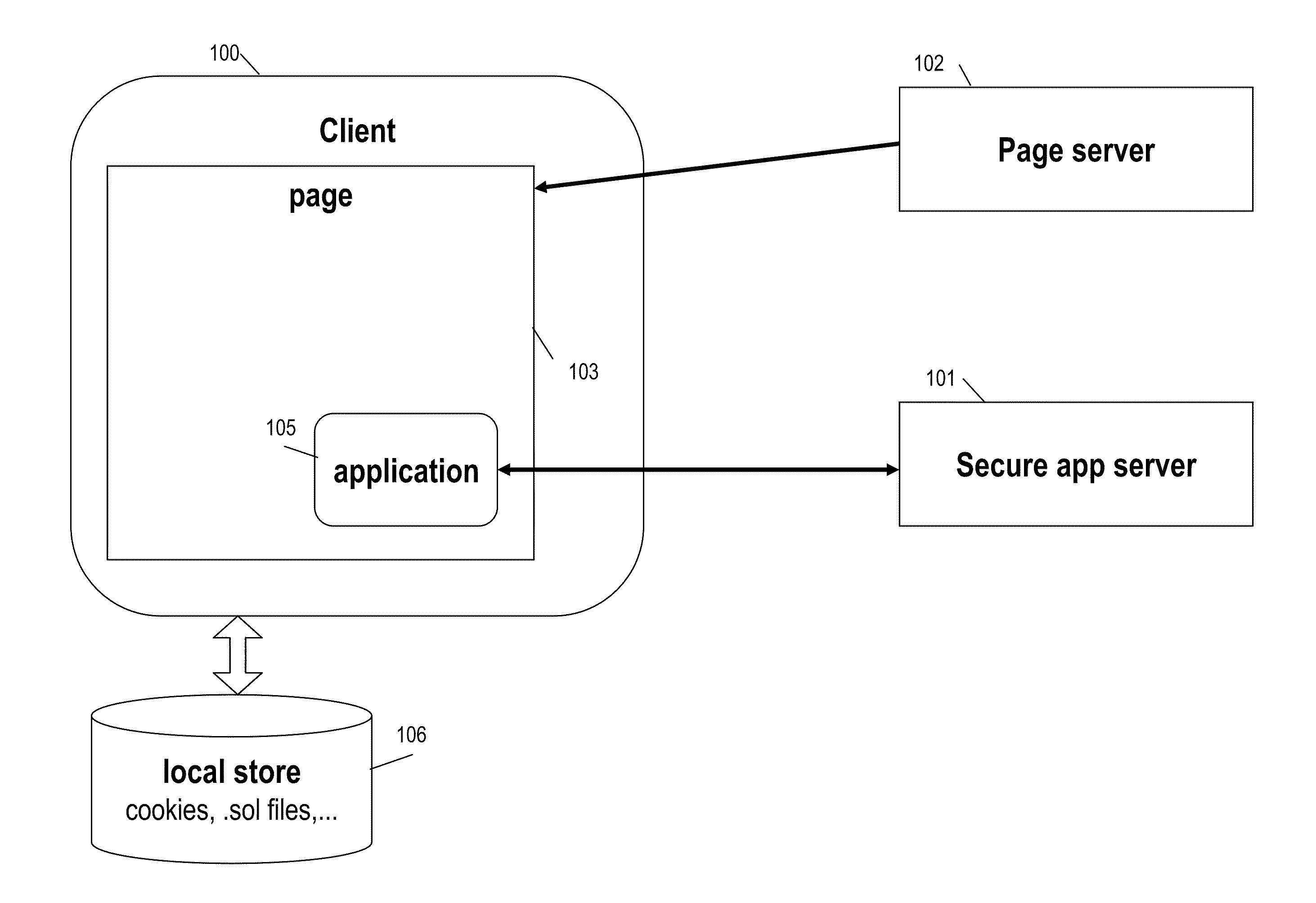
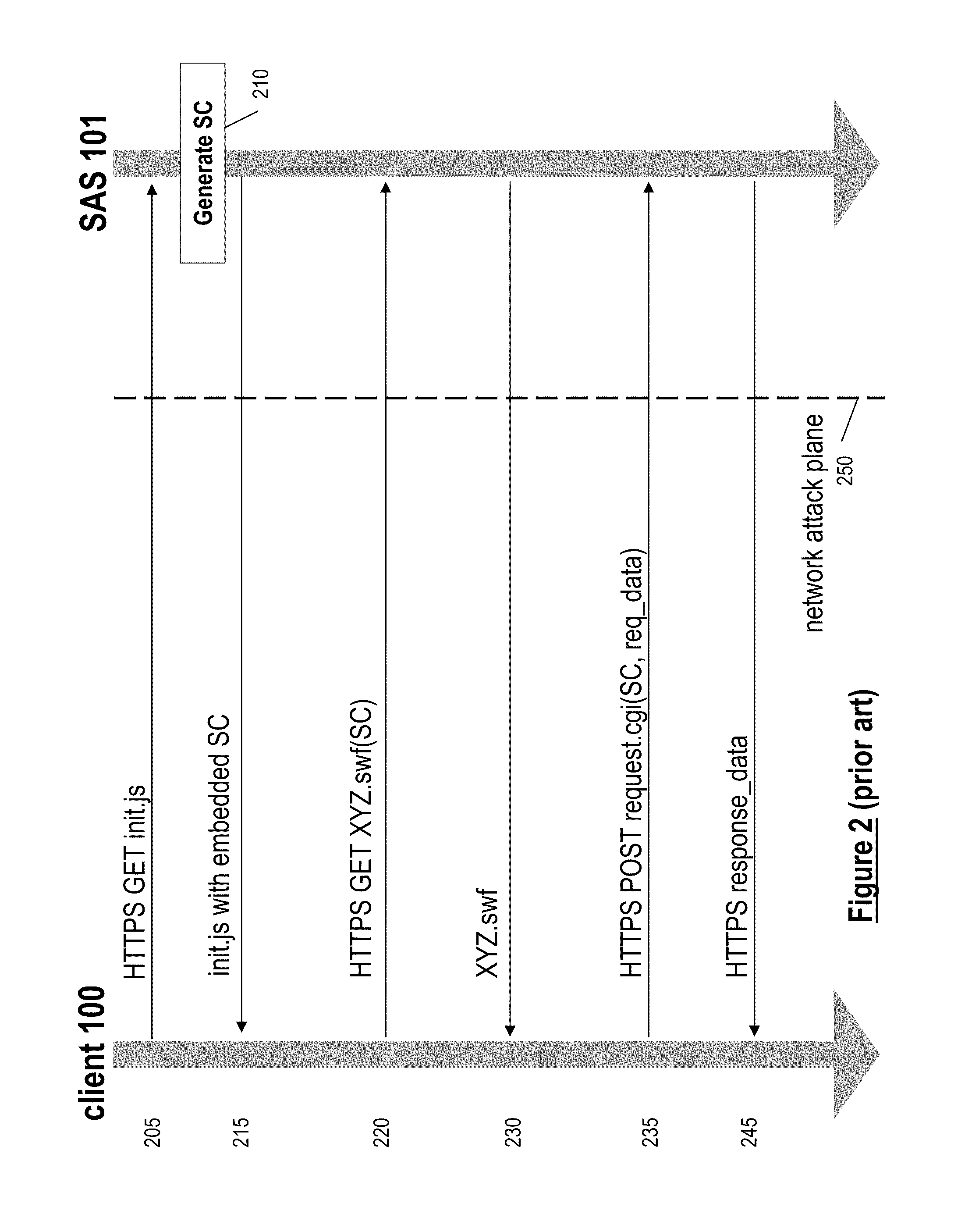
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
234 results about "Embedded security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Embedded system security is a strategic approach to protecting software running on embedded systems from attack. An embedded system is a programmable hardware component with a minimal operating system and software. New Trend in IoT: Digital Twin Tech.
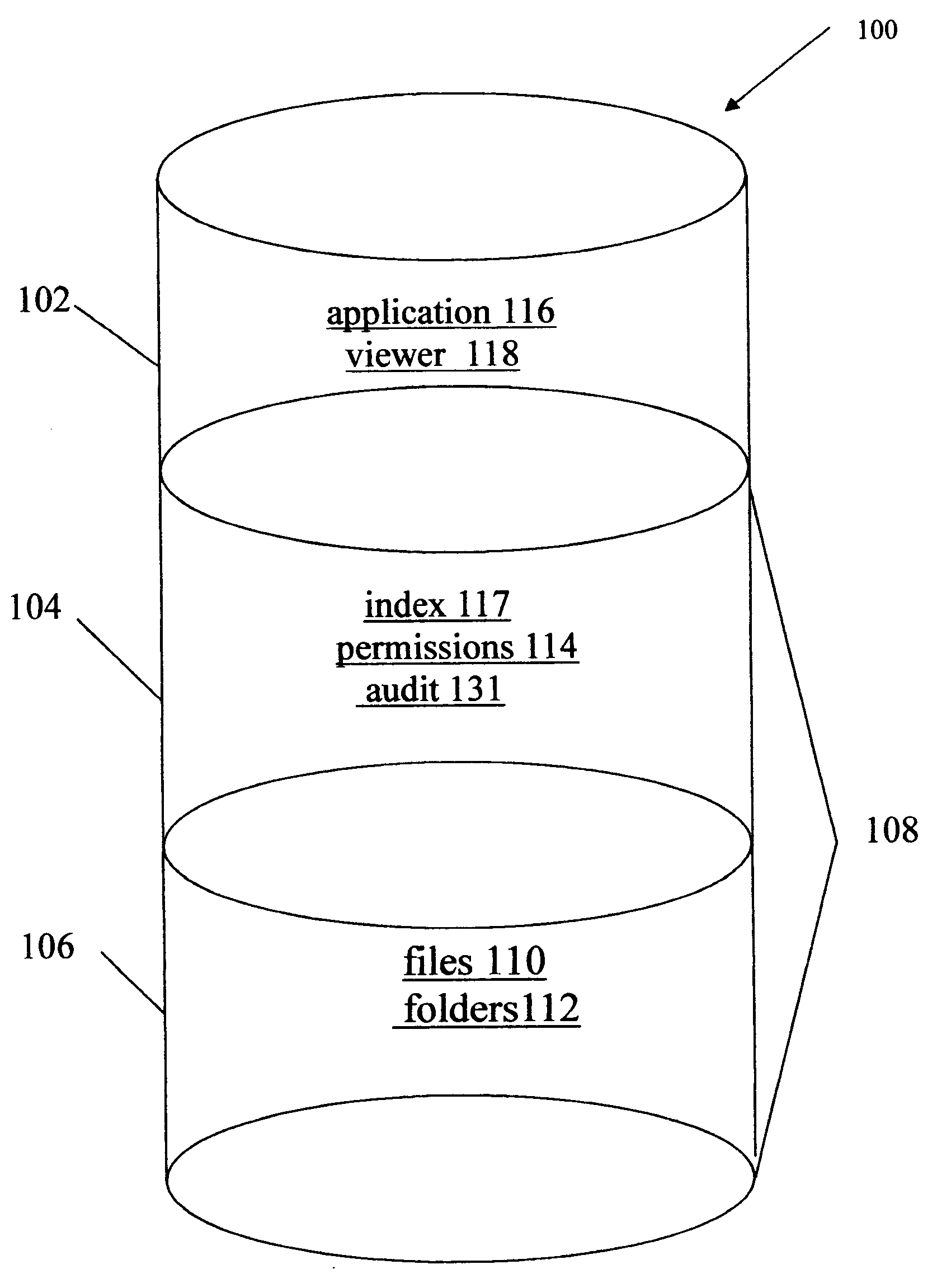
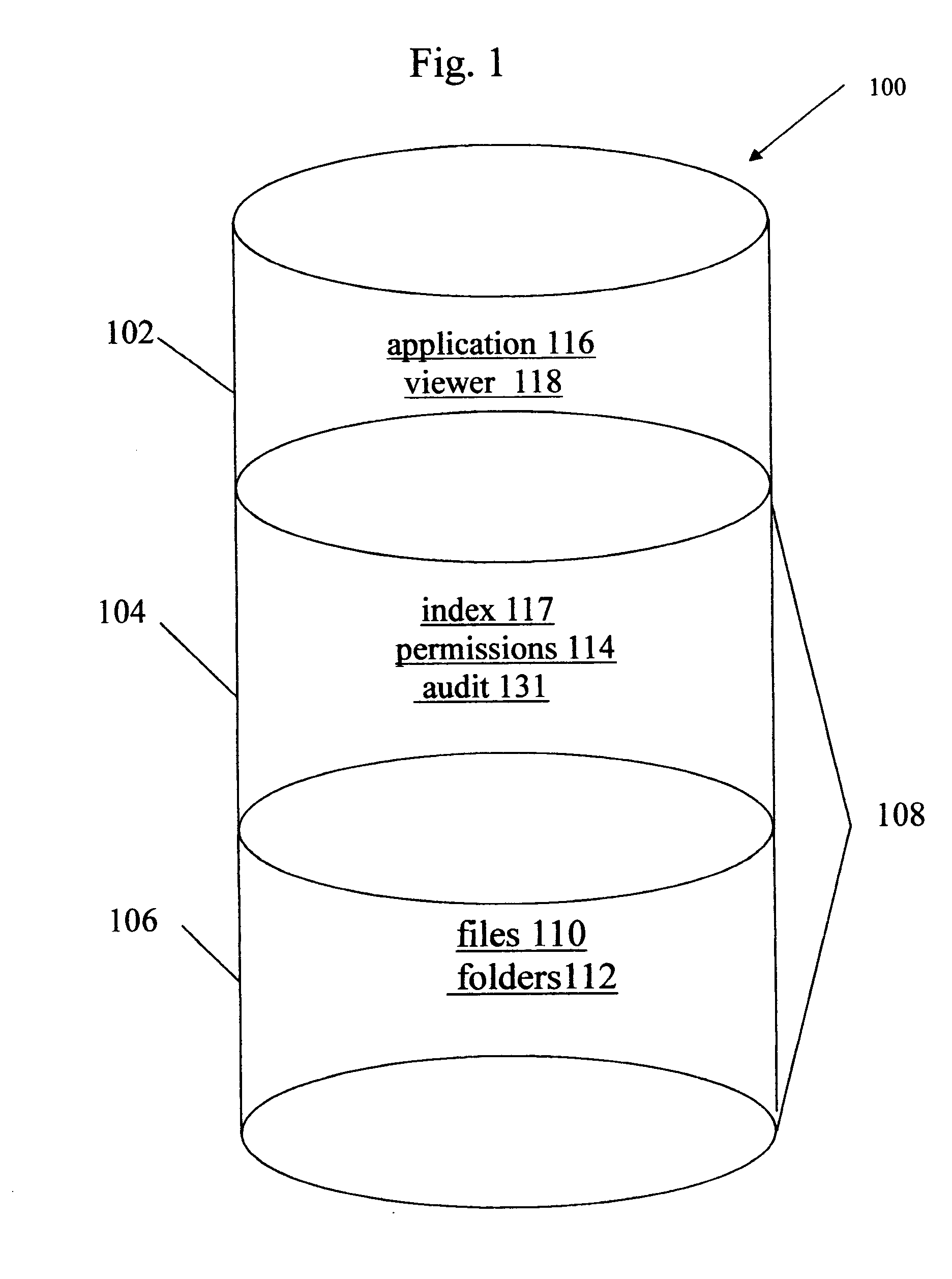
Data rights management of digital information in a portable software permission wrapper
InactiveUS20050114672A1Minimize impactImprove protectionSecret communicationProgram/content distribution protectionEmbedded securityTransaction management
The present invention provides systems and methods for secure transaction management and electronic rights protection. The invention is a software permission control wrapper that is used to encrypt and encapsulate digital information for the purpose of enforcing discretionary access control rights to the data contained in the wrapper. The permission control wrapper enforces rules associated with users, and their rights to access the data. Those rights are based on deterministic security behavior of the permission wrapper based on embedded security policies and rules contained therein and that are based, in part, on the user type, network connectivity state, and the user environment in which the data is accessed.
Owner:ENCRYPTX CORP
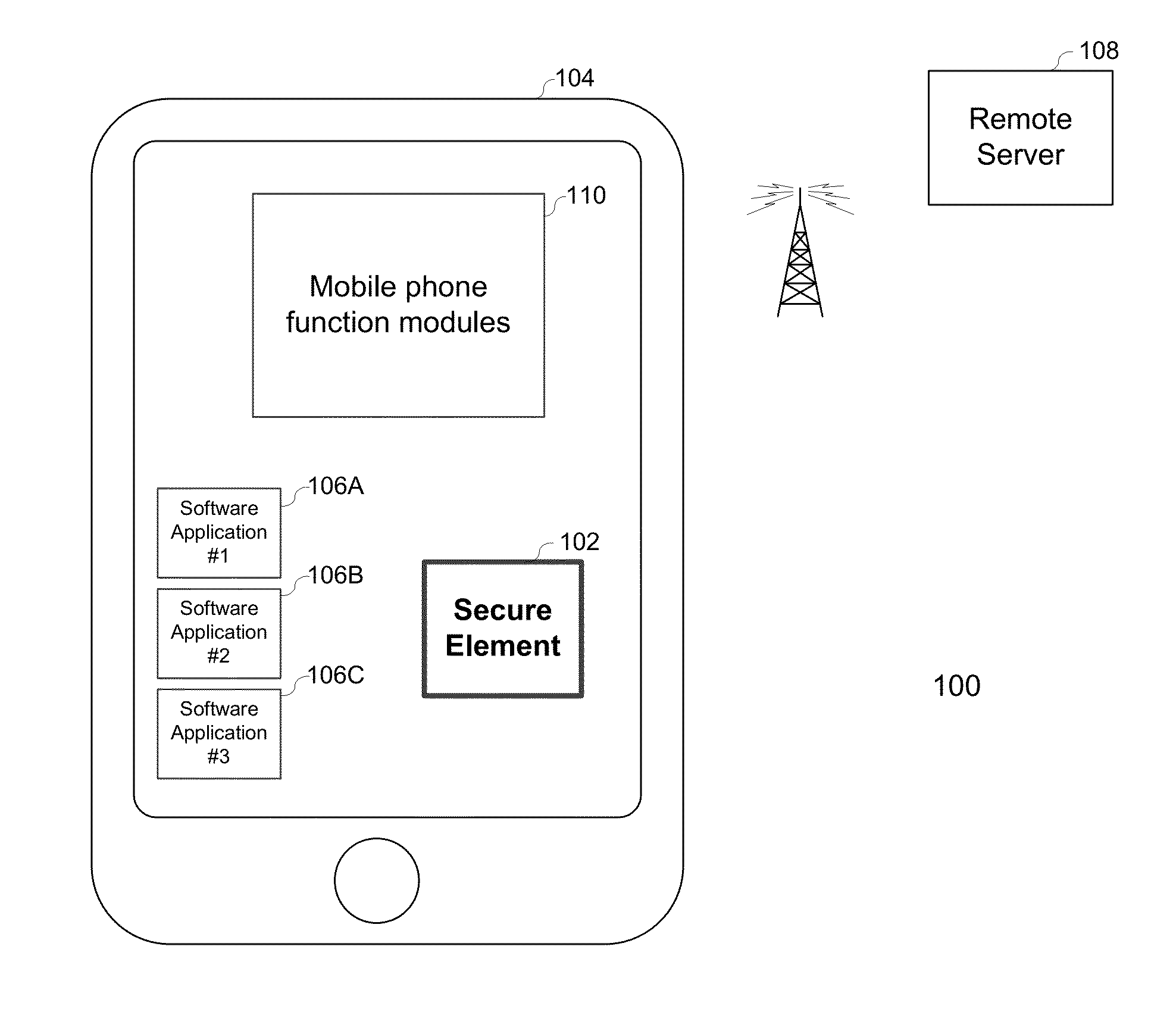
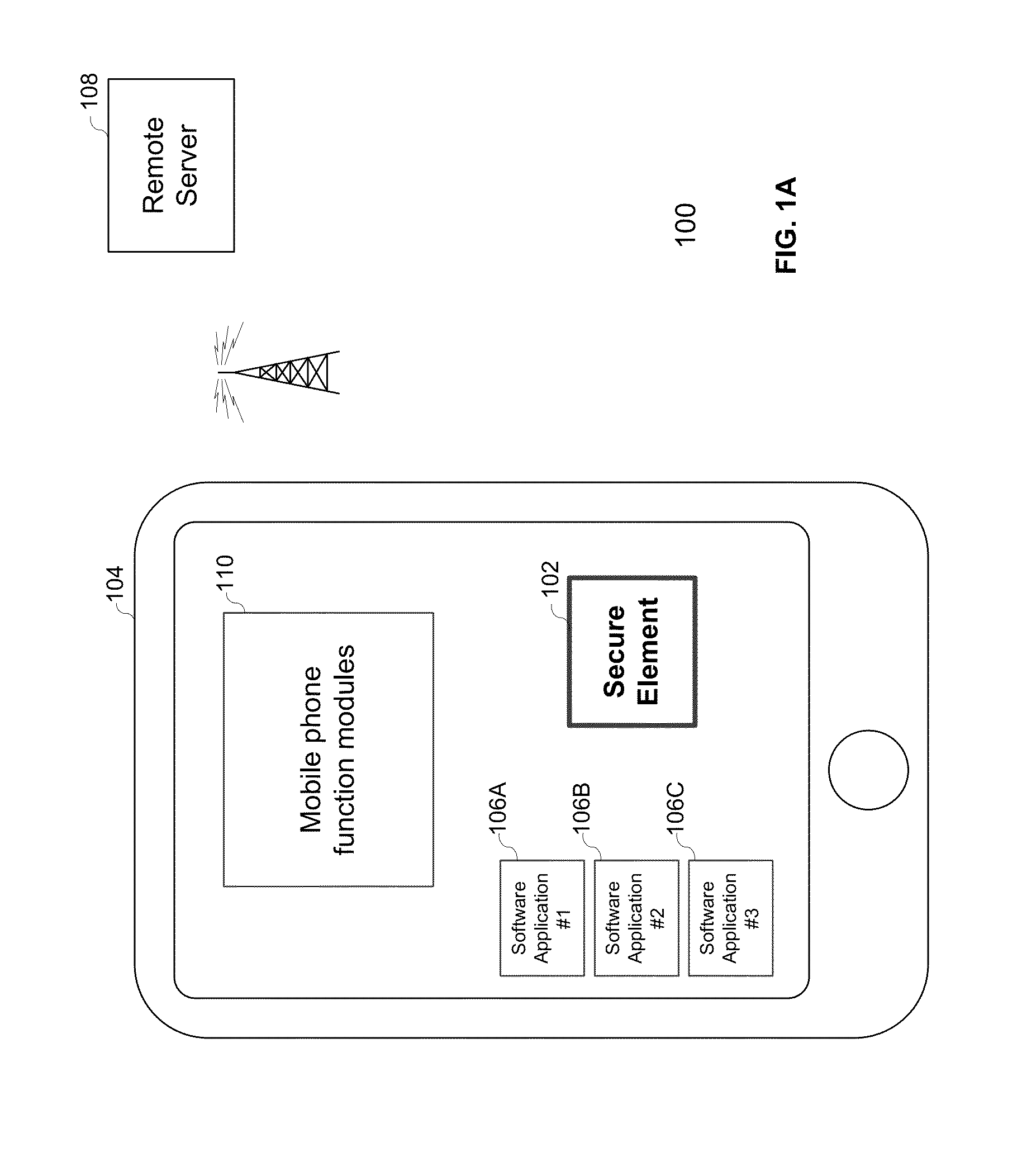
Embedded secure element for authentication, storage and transaction within a mobile terminal
ActiveUS20140013406A1Improve security levelImprove securityNear-field transmissionDigital data processing detailsEmbedded securityApplication software
Various embodiments of the present invention relate to incorporating an embedded secure element into a mobile device, and more particularly, to systems, devices and methods of incorporating the embedded secure element into a mobile device for identity authentication, data storage and processing in trusted transactions. These trusted transactions require a high security level to protect sensitive data or programs in bank account management, purchasing orders, contactless payment, passport verification, and many other high-security applications. The secure element will provide a root of trust such that that applications running on the mobile device are executed in a controlled and trusted environment. In addition to conventional password or encryption protection, alternative security features are introduced from both software and hardware levels based on the embedded secure element. Therefore, the security level of the mobile device is not only enhanced, but also may potentially exceed that of the conventional POS terminals.
Owner:MAXIM INTEGRATED PROD INC
Authentication methods and apparatus for vehicle rentals and other applications
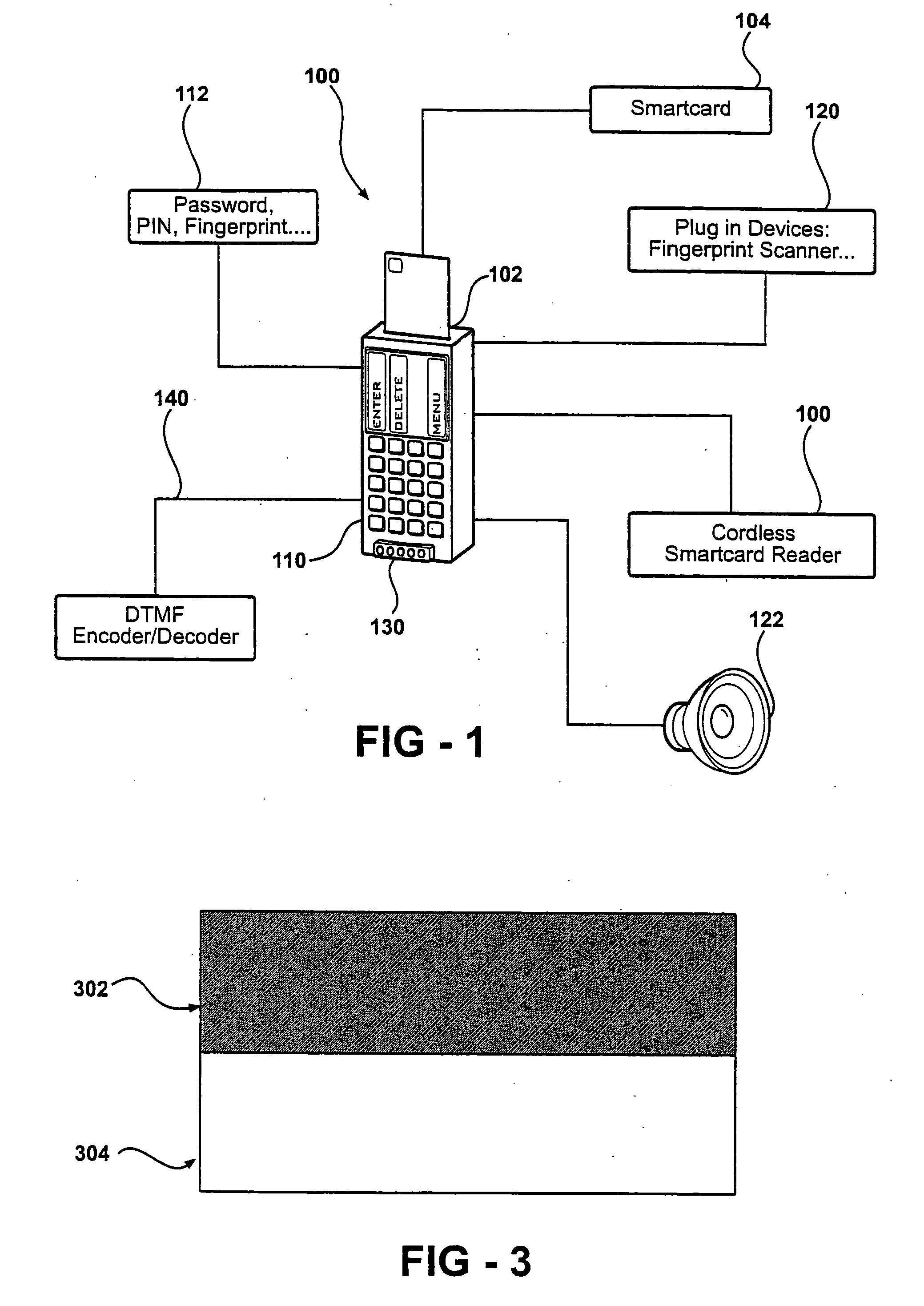
InactiveUS20050001028A1Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. The invention finds utility in a wide range of applications, including commercial transactions and security, including the generation of prepaid credit / debit card numbers, vehicle rental, and other uses.
Owner:BRITE SMART
Method for enhancing network application security
InactiveUS8302170B2Improve securityDigital data processing detailsUser identity/authority verificationSecure communicationEmbedded security
Owner:RICHEMONT INT
Code Download and Firewall for Embedded Secure Application
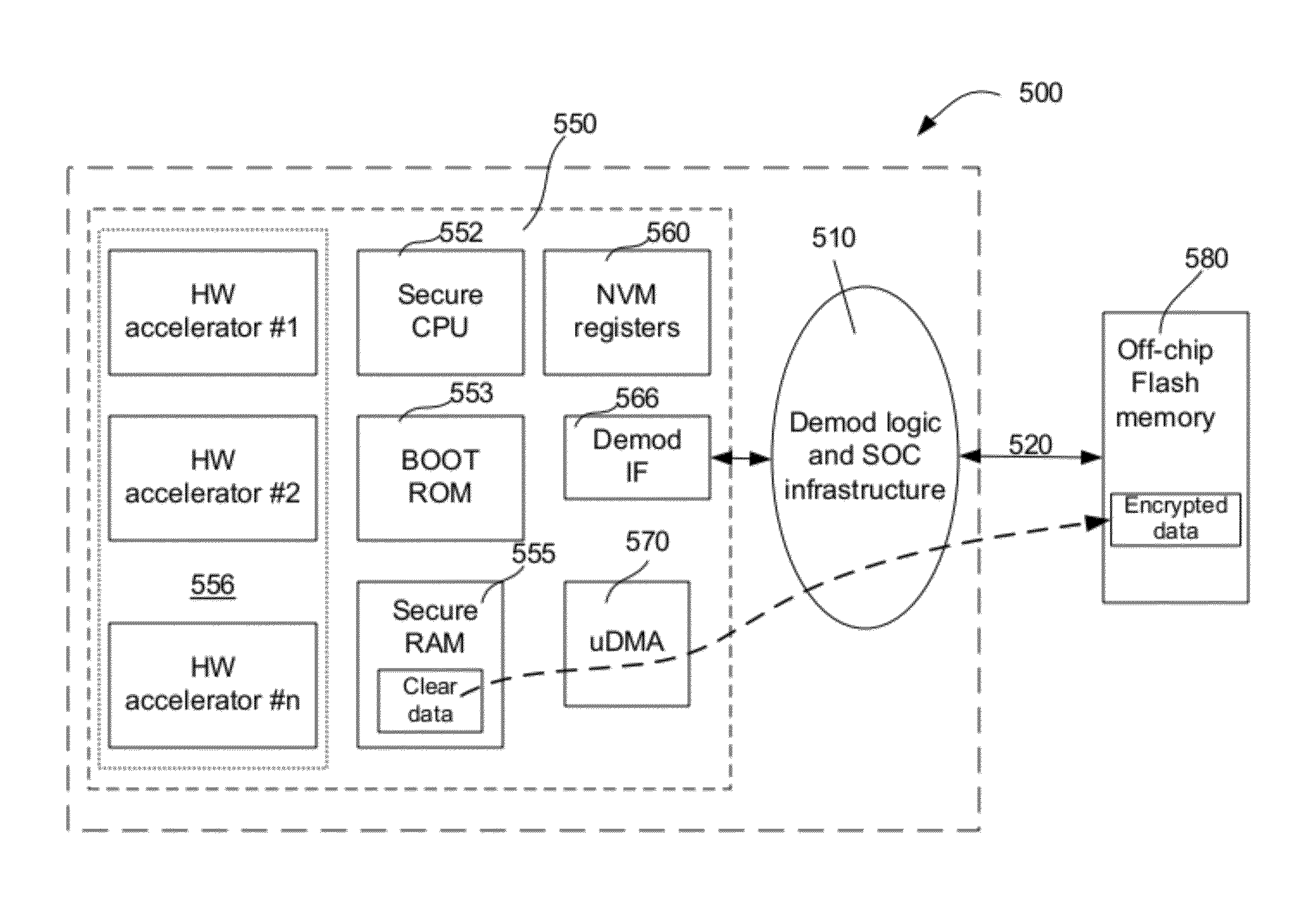
InactiveUS20120060039A1Unauthorized memory use protectionHardware monitoringEmbedded securityExternal storage
A device includes a demodulator for receiving an encrypted content, an interface unit communicatively coupled to an external memory, and a hardware unit coupled to the demodulator and configured to enable the demodulator to decrypt the received content. The hardware unit includes a processing unit, a ROM having a boot code causing the device to fetch data from the external memory, a RAM for storing the fetched data, multiple non-volatile memory registers or fuse banks, and a mechanism configured to write the stored data to an external storage device in response to a backup event. The data may be encrypted using an encryption key prior to being written to the external storage device. The interface unit may include a wired or wireless communication link. The boot code includes executable instructions performing a series of validations. The device disables the executable instructions in the event of a validation failure.
Owner:RADIOXIO LLC
Apparatus and method for encrypting and decrypting data recorded on portable cryptographic tokens
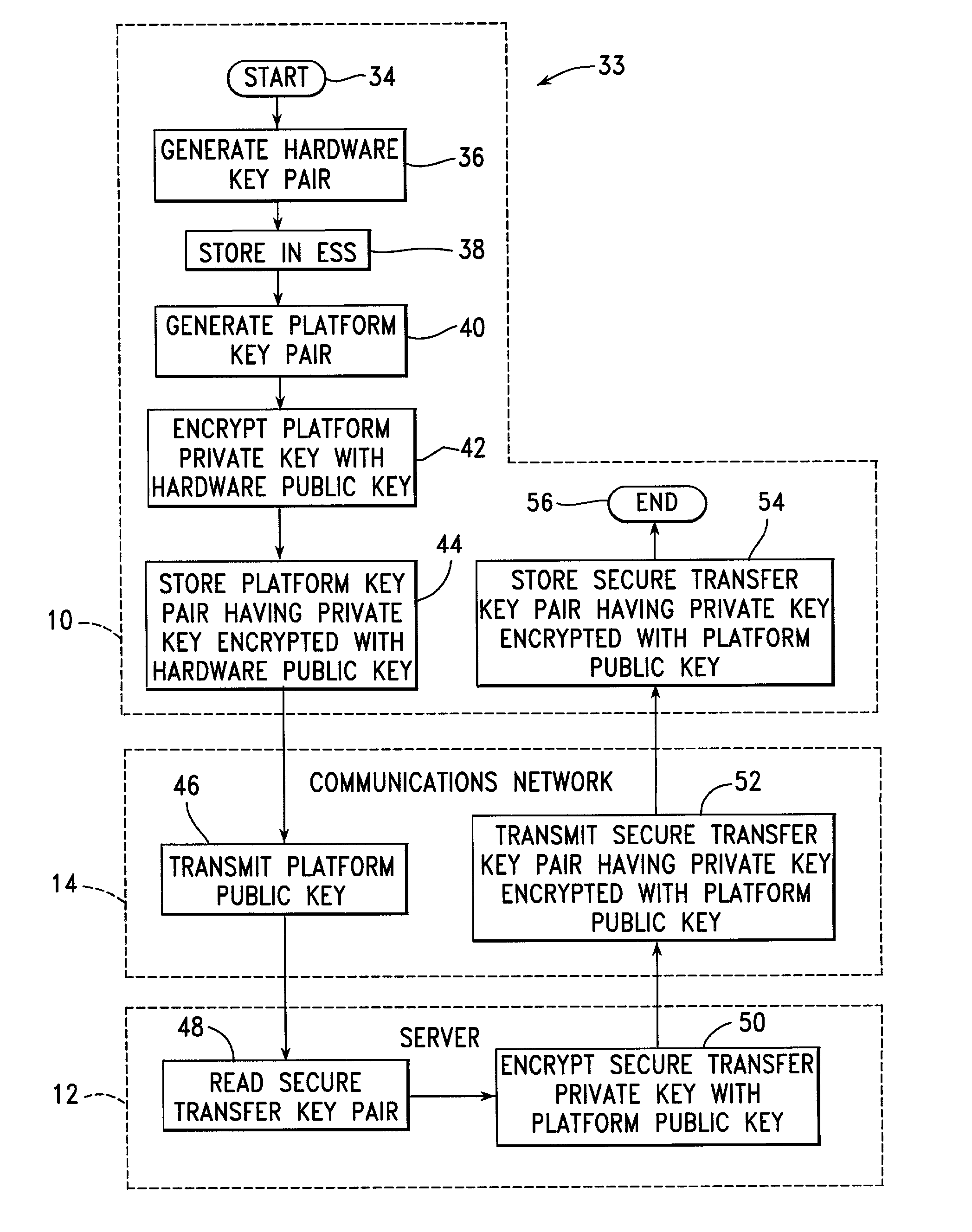
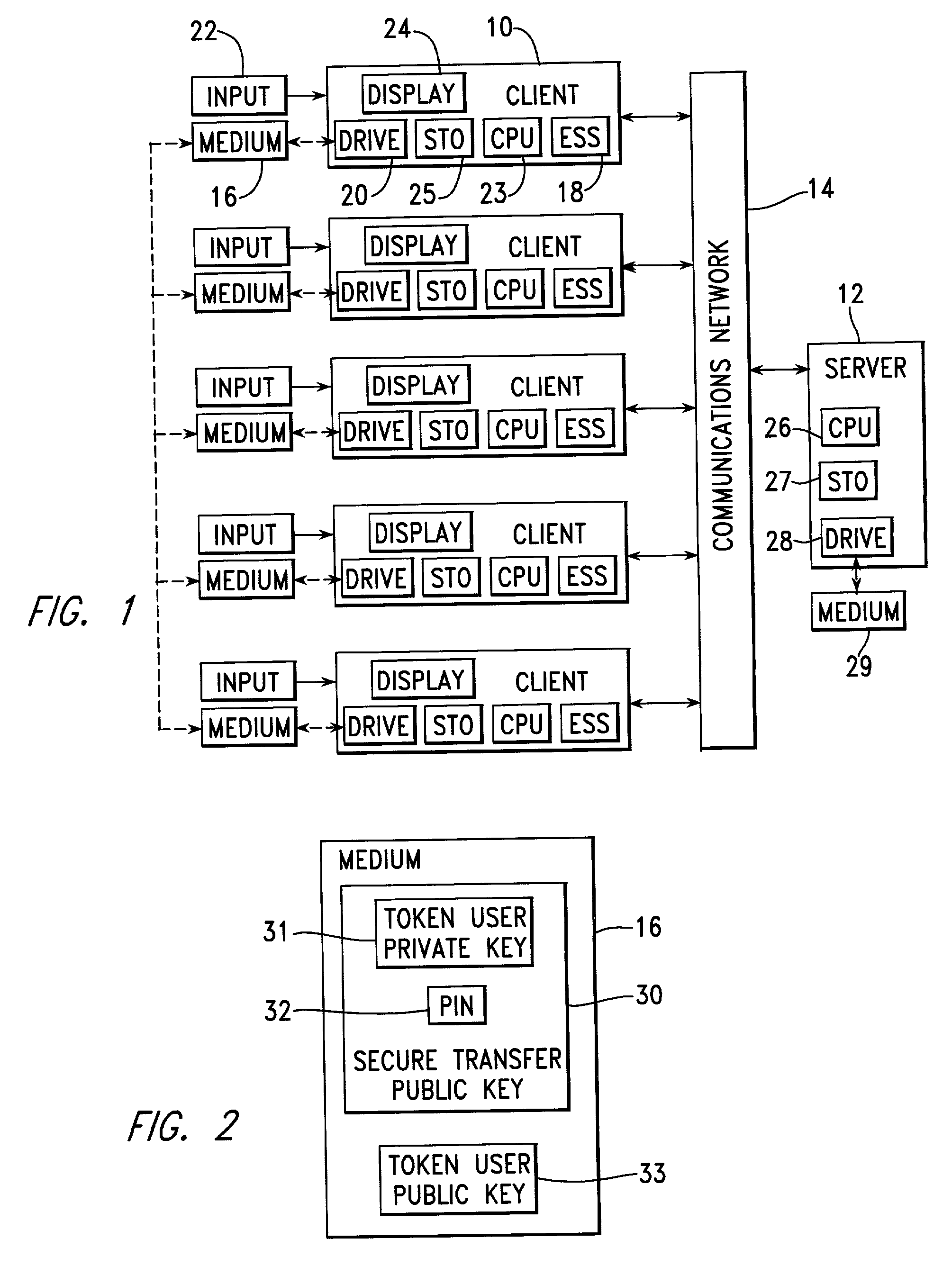
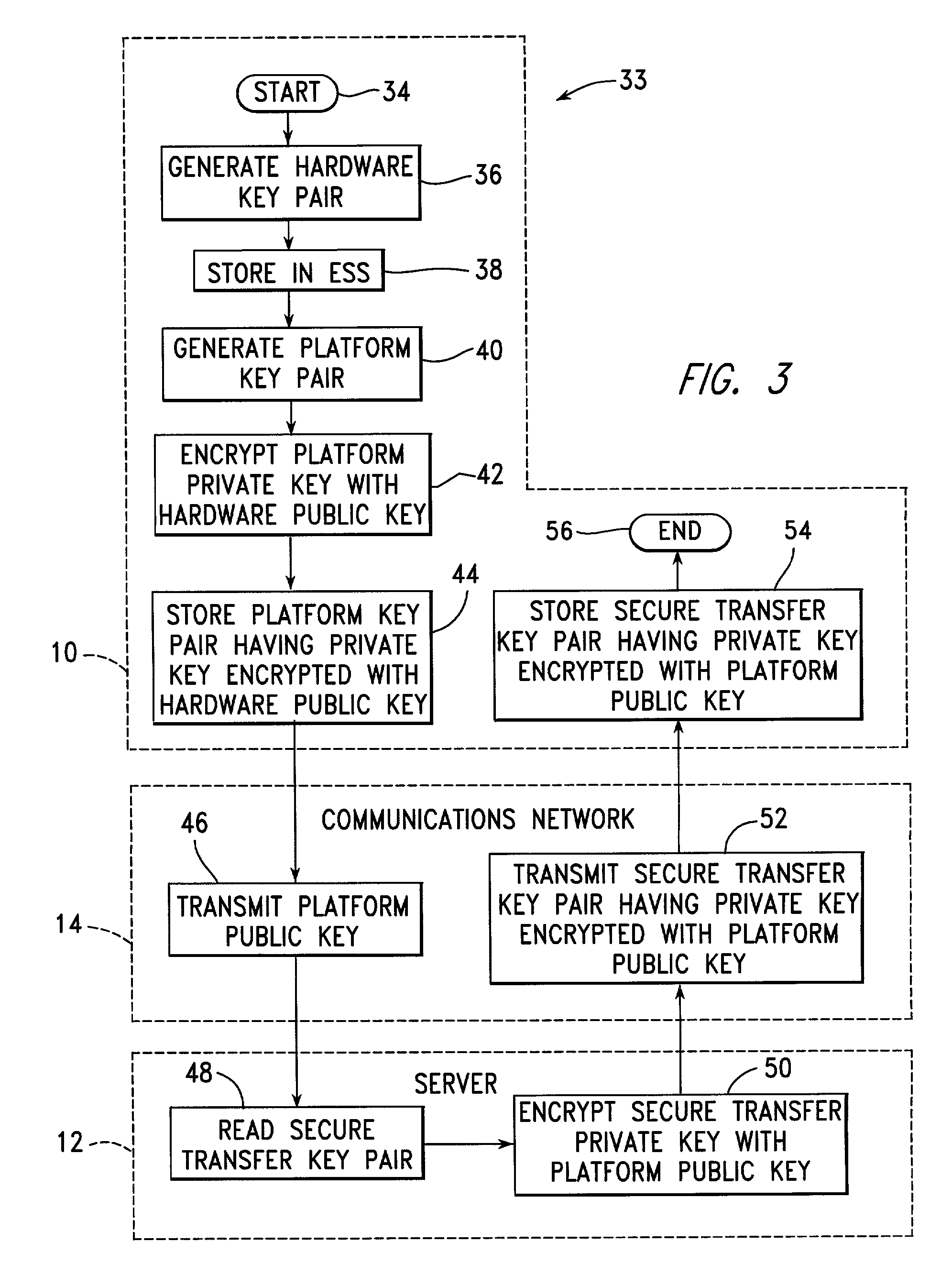
InactiveUS20020129261A1Provide securitySecure transmissionKey distribution for secure communicationPublic key for secure communicationEmbedded securitySecure transmission
A number of client systems receive a common secure transfer key pair from a server during initialization. The secure transfer private key is encrypted in the server with a platform public key sent to the server from the client system. Each client system is then able to encrypt data, using a secure transfer public key, to be recorded on a computer readable medium, and subsequently to decrypt such data using a secure transfer private key. Preferably, each client system includes an embedded security subsystem (ESS) performing cryptographic processes and providing secure key storage. Then, the secure transfer private key is stored as encrypted, and is decrypted using a private key within the ESS. Preferably, the platform private key is also stored encrypted, to be decrypted within the ESS using a hardware private key.
Owner:IBM CORP
Method and apparatus for authenticating a shipping transaction
InactiveUS6991174B2Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. In essence, the device is a closed box with only two communication ports. The emulation of the device is therefore extremely complex due to the fact that it involves PKI and or identity-based encryption (IBE), key pair, elliptic curves encryption scheme, hardware serialization for communication and software implementation, in conjunction with a specific hardware embodiment and service usage infrastructure component that returns a response necessary for each unique transaction.
Owner:BRITE SMART
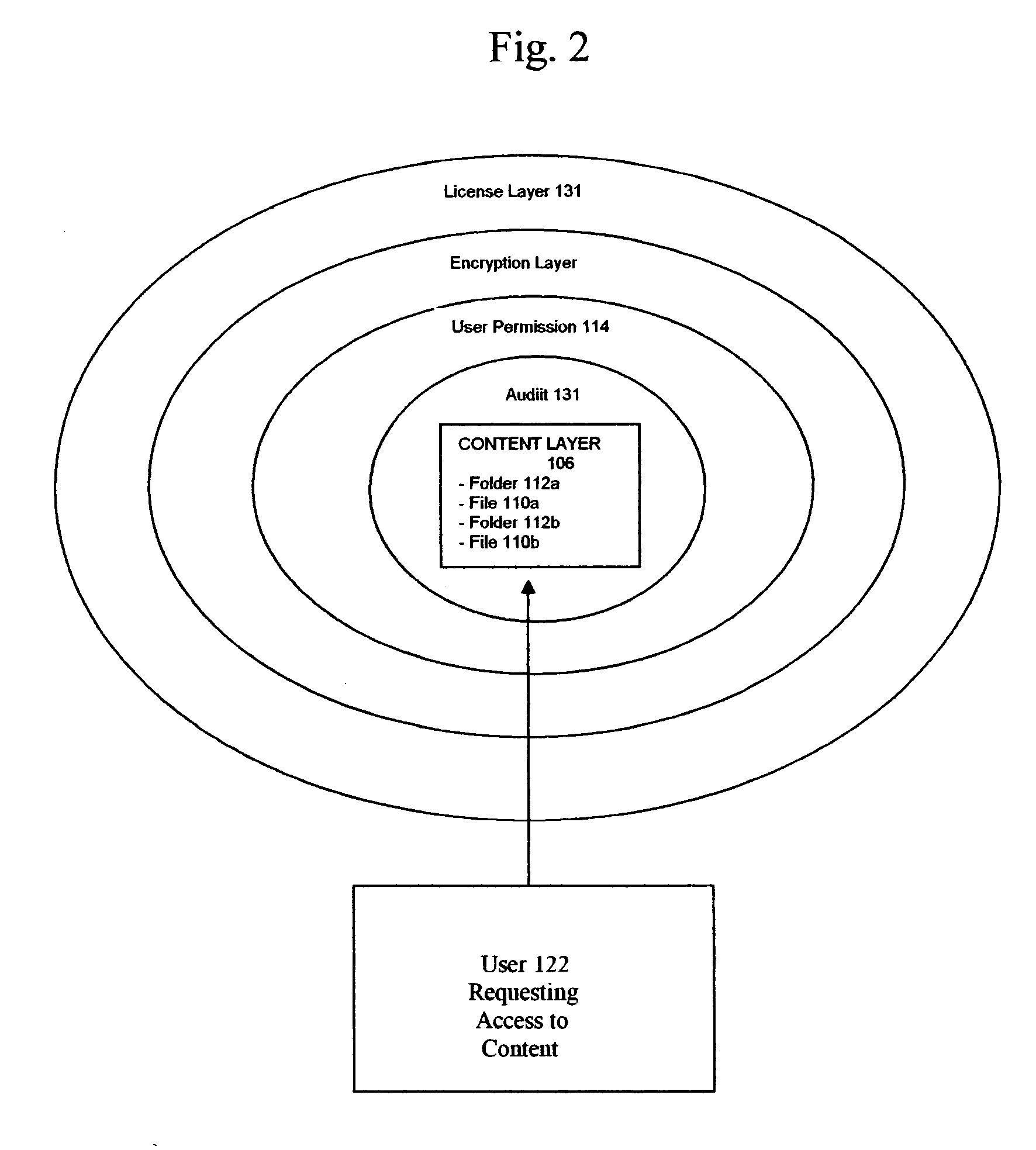
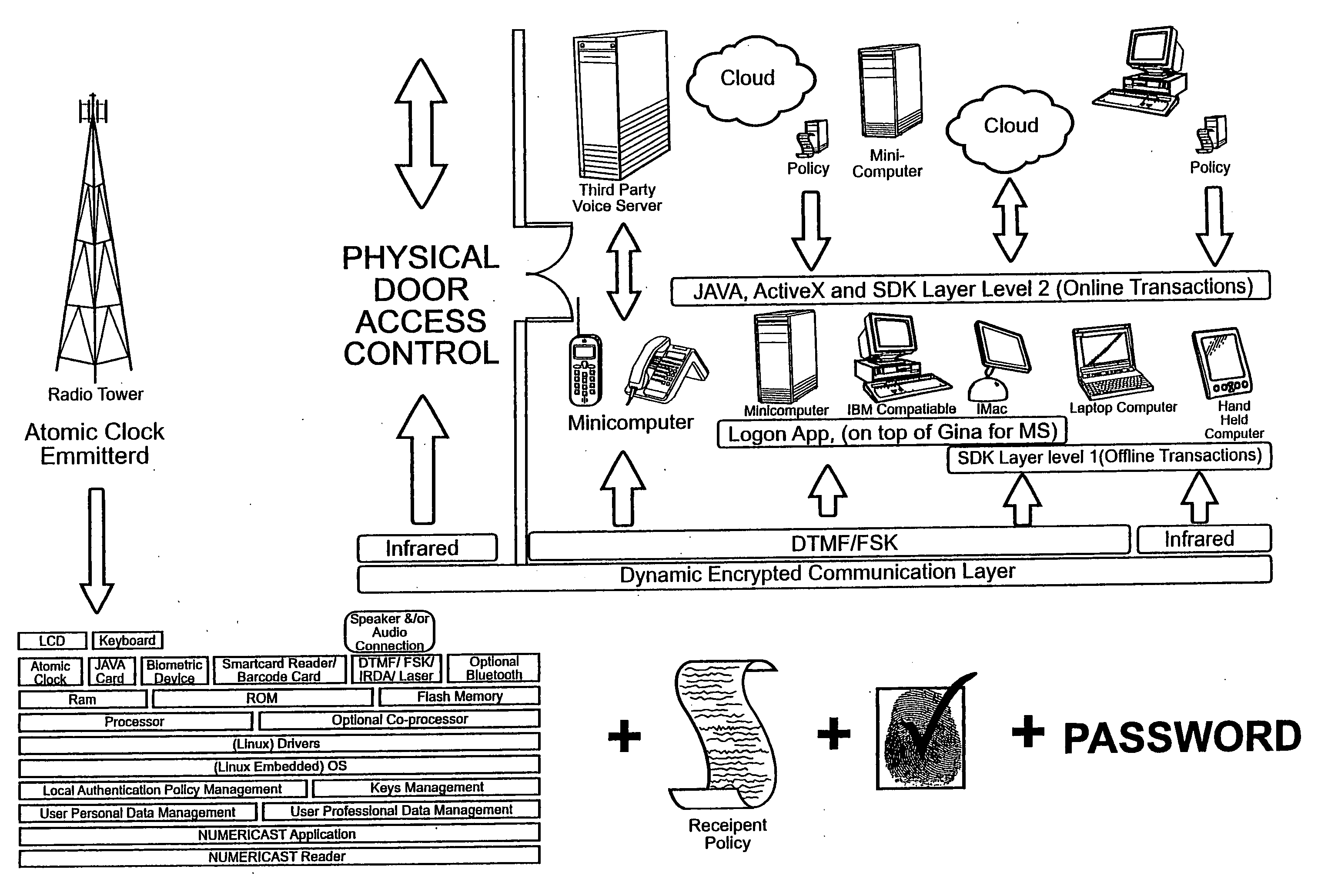
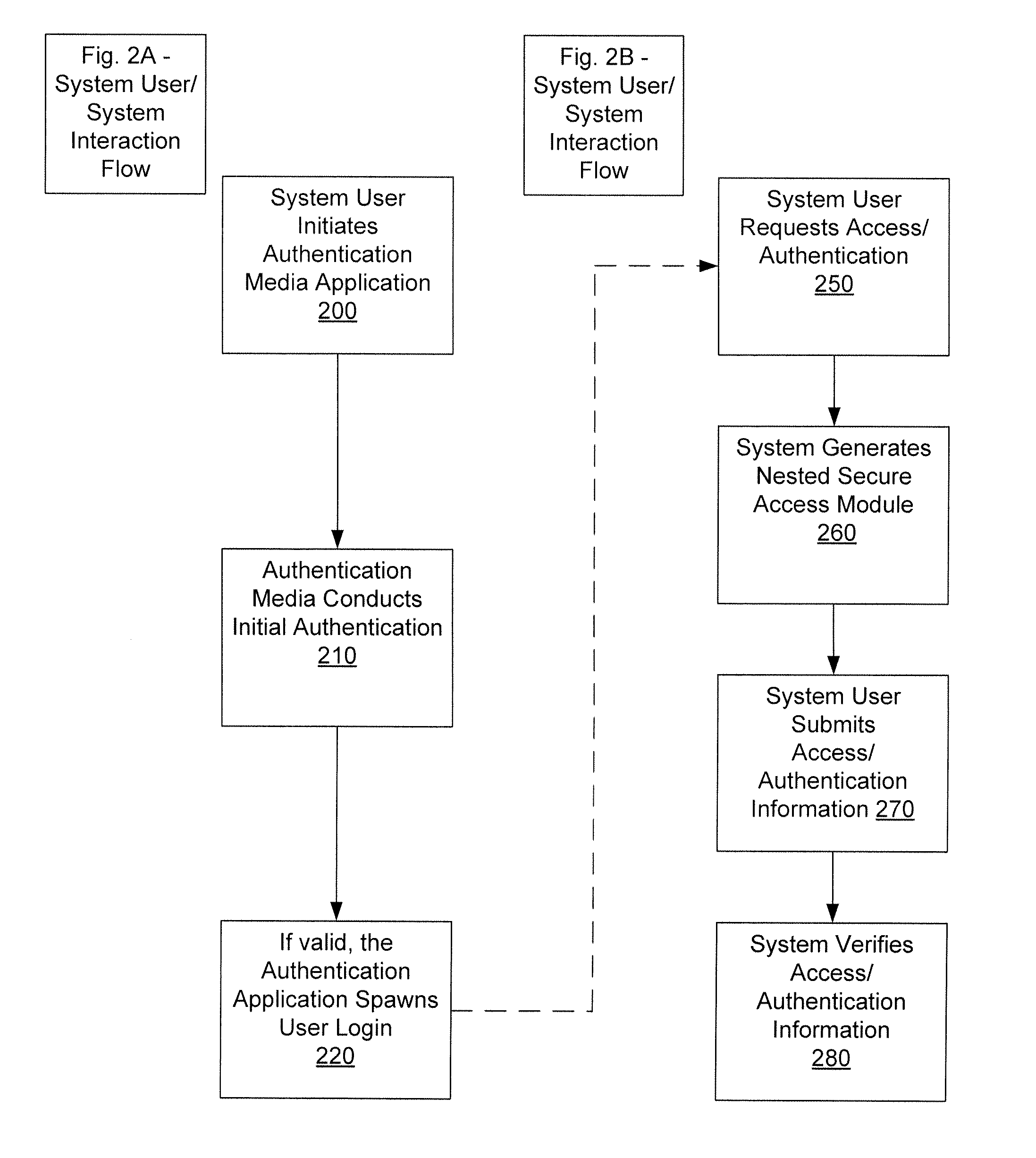
Method, System, And Apparatus For Nested Security Access/Authentication With Media Initiation
InactiveUS20080222417A1Digital data processing detailsUser identity/authority verificationEmbedded securityPassword
The disclosure details a nested security access system that manages access points / verification requests to create a series of layered security applications for securing access / user identification data. The NSA system works in coordination with an access point / verification module to generate a series of instructions as a login / verification module that may be executed locally. The login / verification module is executed by the access point / verification module to create a system user access / verification data entry form. Depending on the implementation, the access point / verification module may be configured to accept typed text or clicked image access / verification data, token access / verification data or selected image sequence access / verification data. The process of selected image sequence access involves the system user selecting a series of images that represent individual elements of a password without having to type the information into a data entry form.
Owner:IMX SOLUTIONS
Method for enhancing network application security
InactiveUS20100077216A1Improve securityDetection valueDigital data processing detailsUser identity/authority verificationSecure communicationEmbedded security
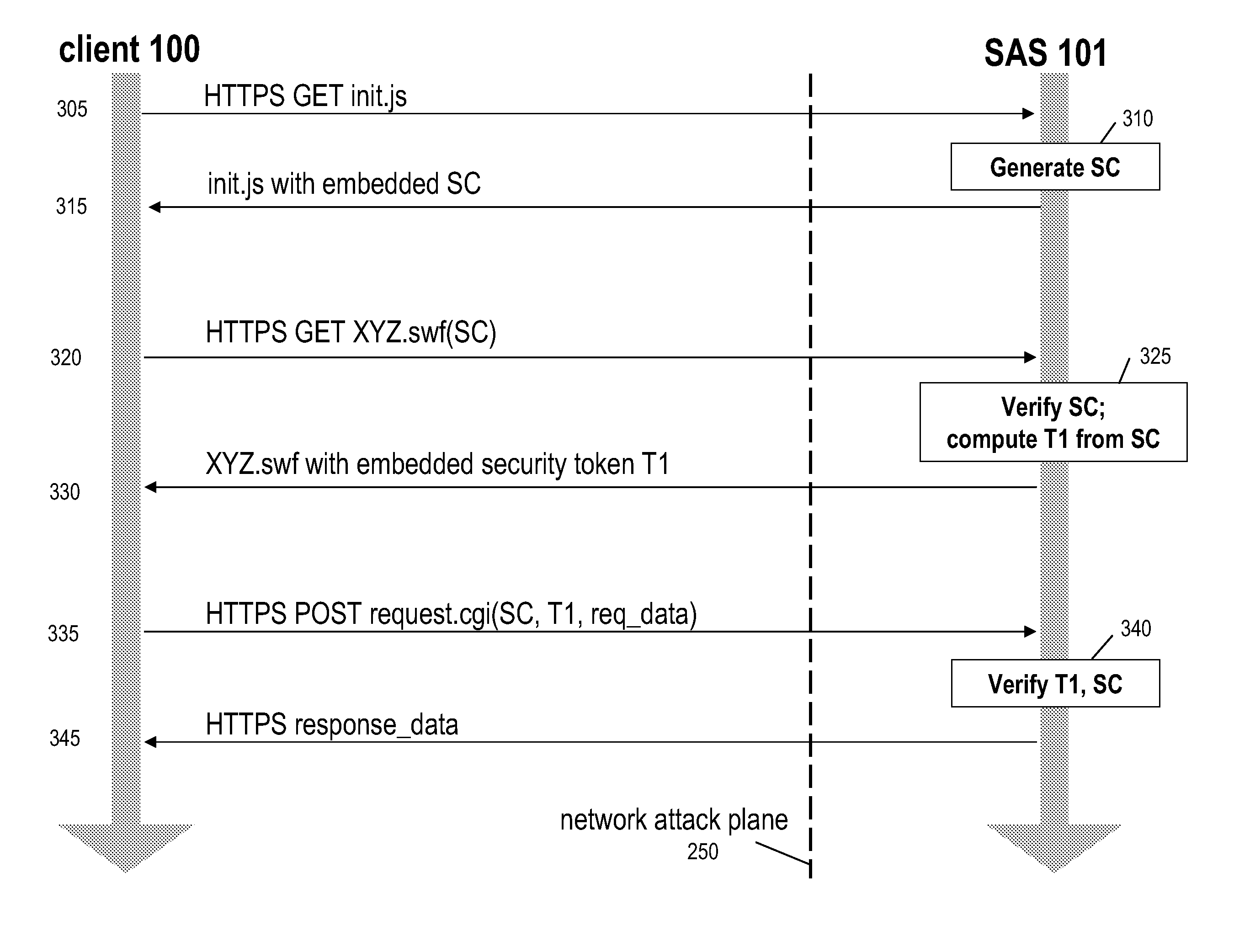
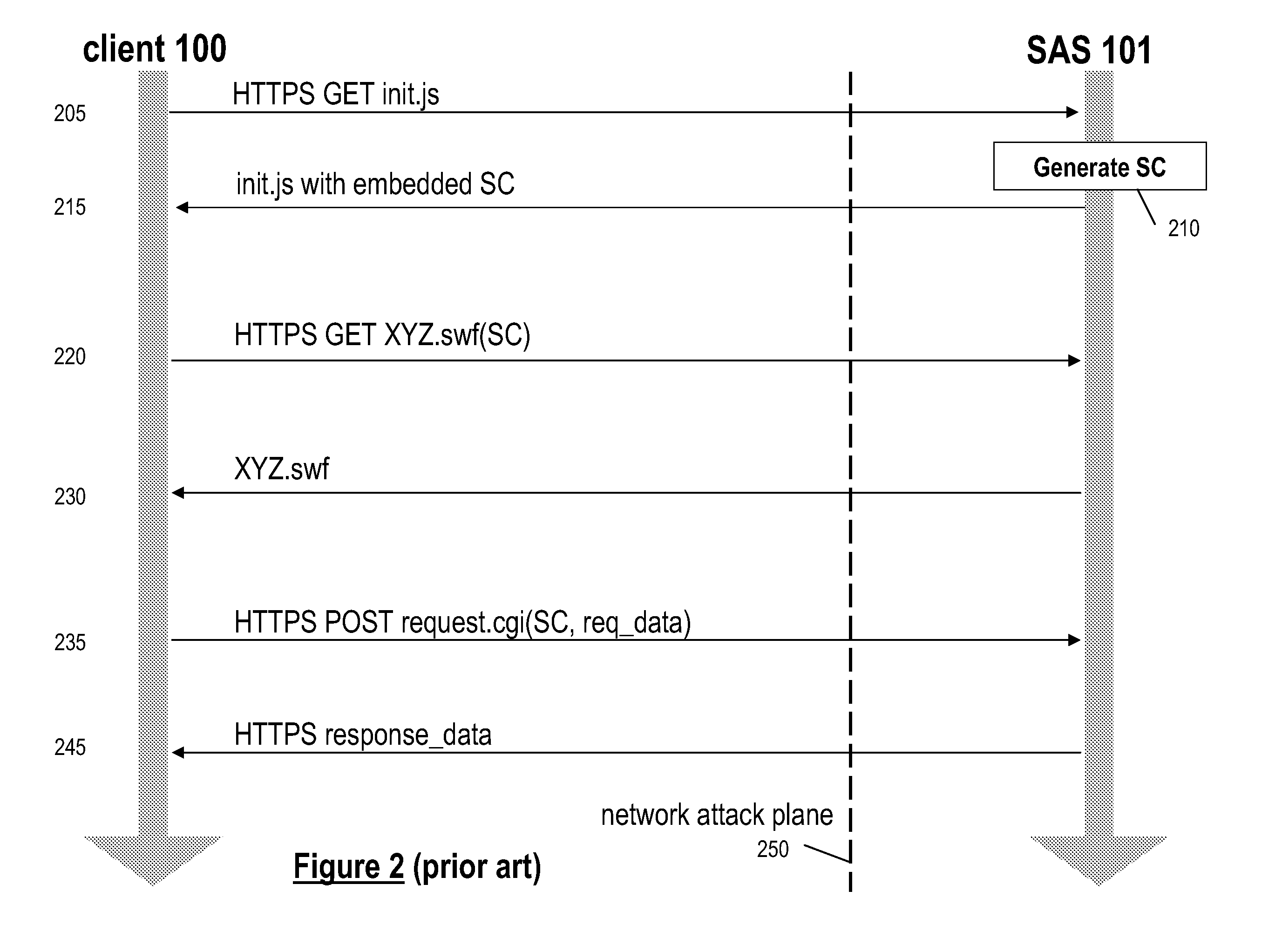
A method for securing communications between a server and an application downloaded over a network onto a client of the server is disclosed. A first request is received from the client, and in response a session credential security token is generated and sent to the client. A second request is received from the client to download the application and includes the value of the session credential security token. The server verifies that the value of the session credential security token is valid and, if so, generates a second security token that is tied to the session credential security token. The second token is embedded in application code and then the application code is sent to the client. A subsequent request for data from the application running on the client includes the value of the session credential security token and the value of the embedded security token. Verification of validity of the values of the session credential security token and the second security token received with the data request then occurs at least in part by determining that the values are cryptographically tied to one another. Upon verification, the requested data is sent to the client.
Owner:RICHEMONT INT
Process control system with an embedded safety system
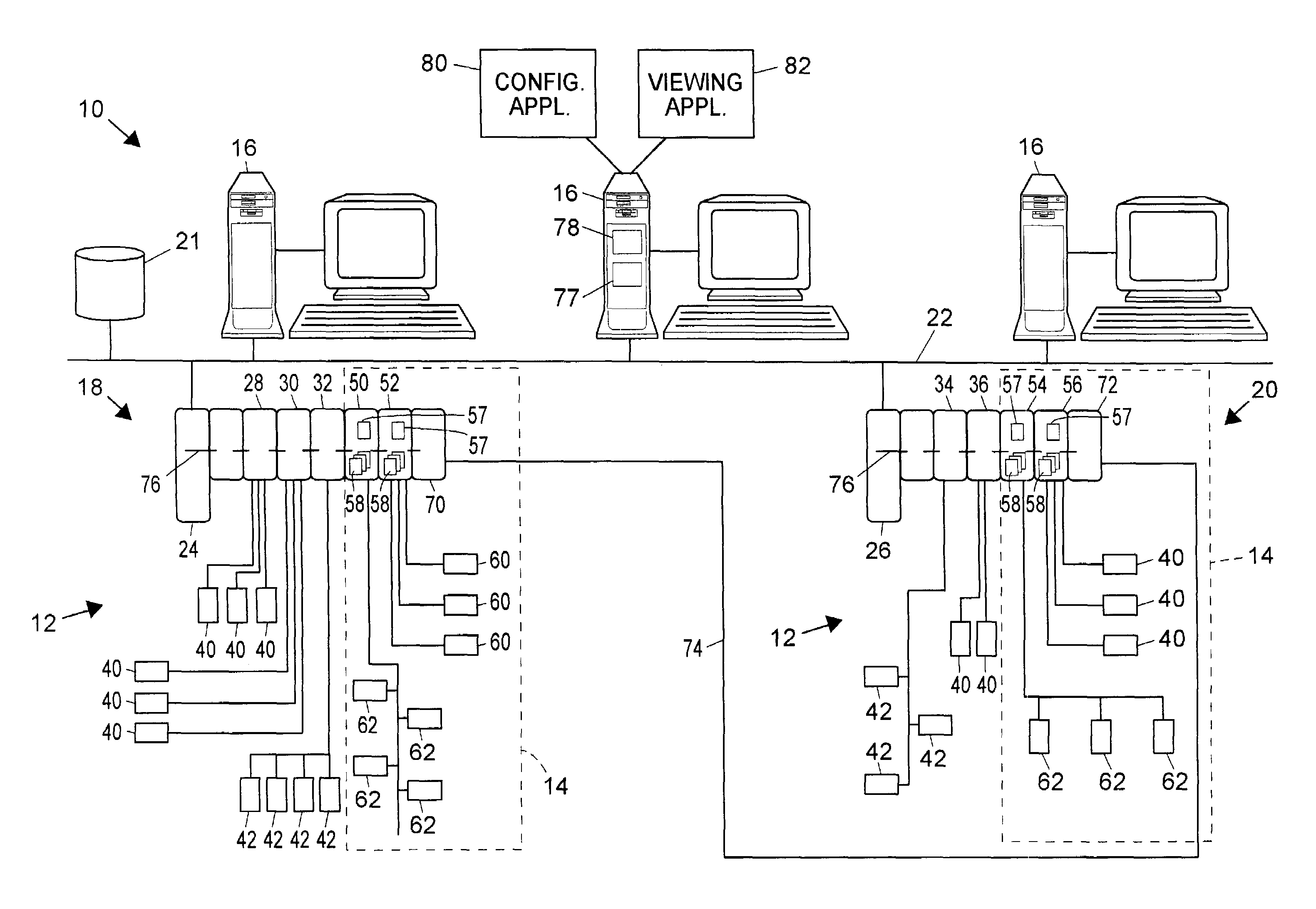
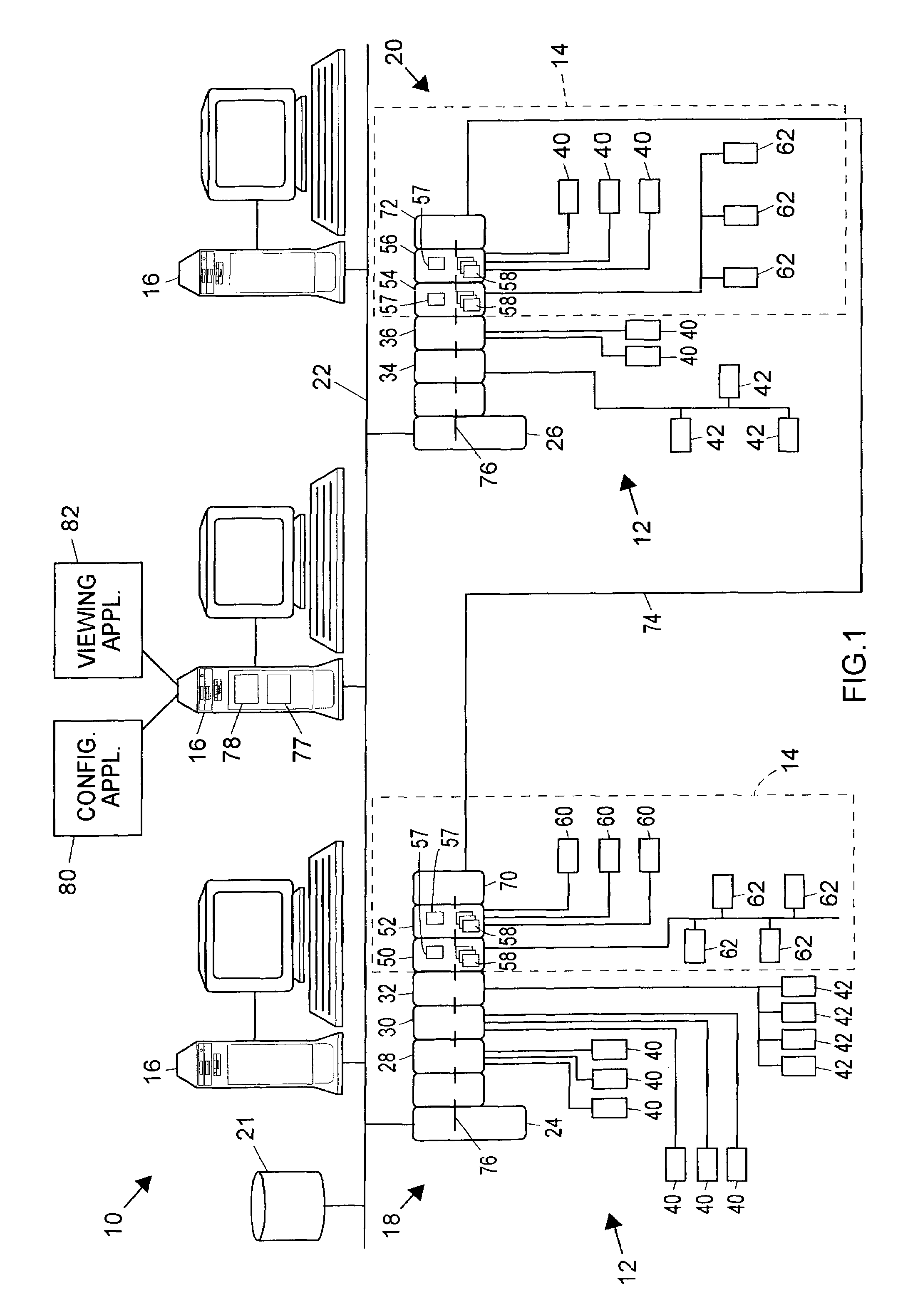
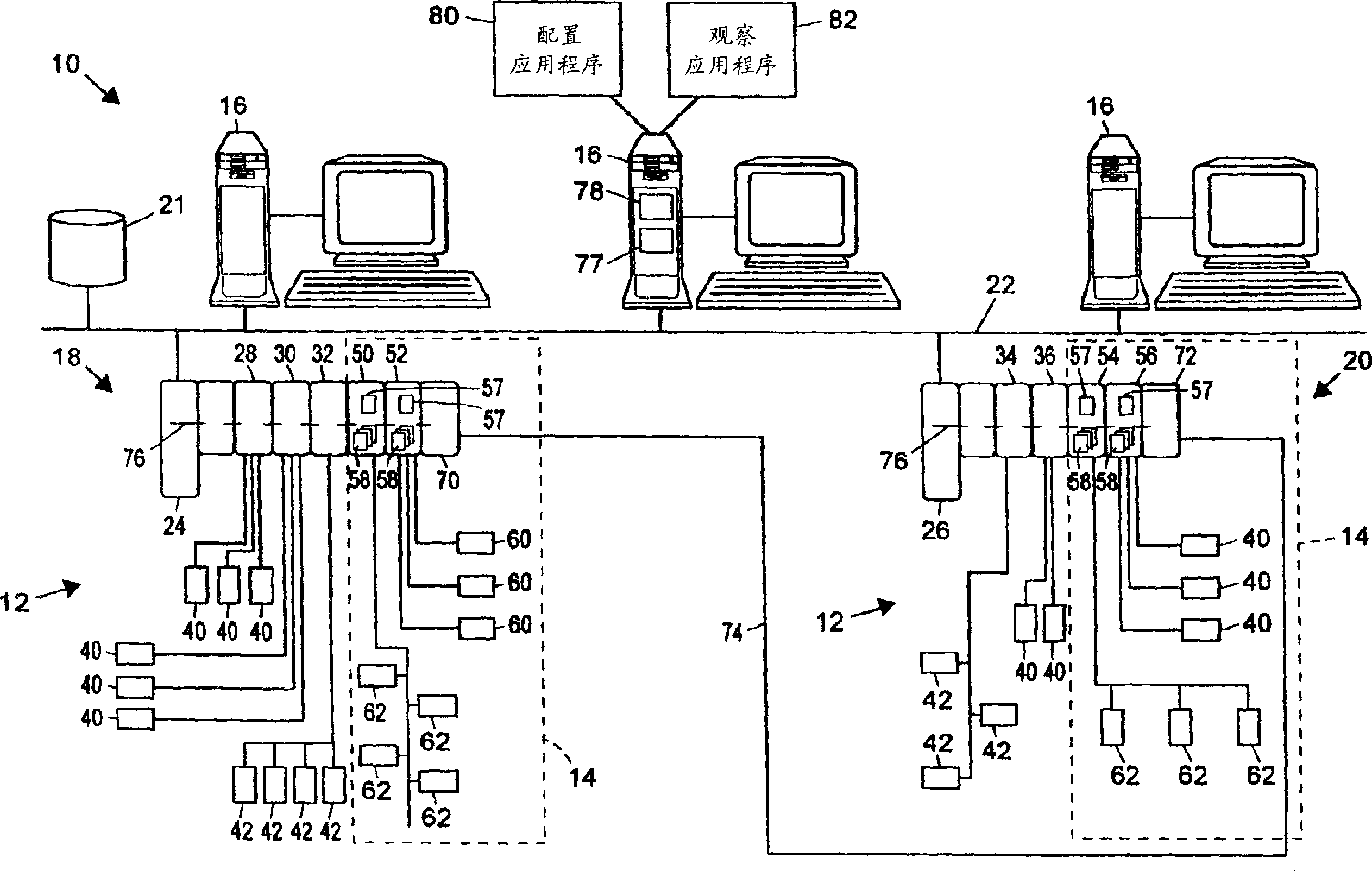
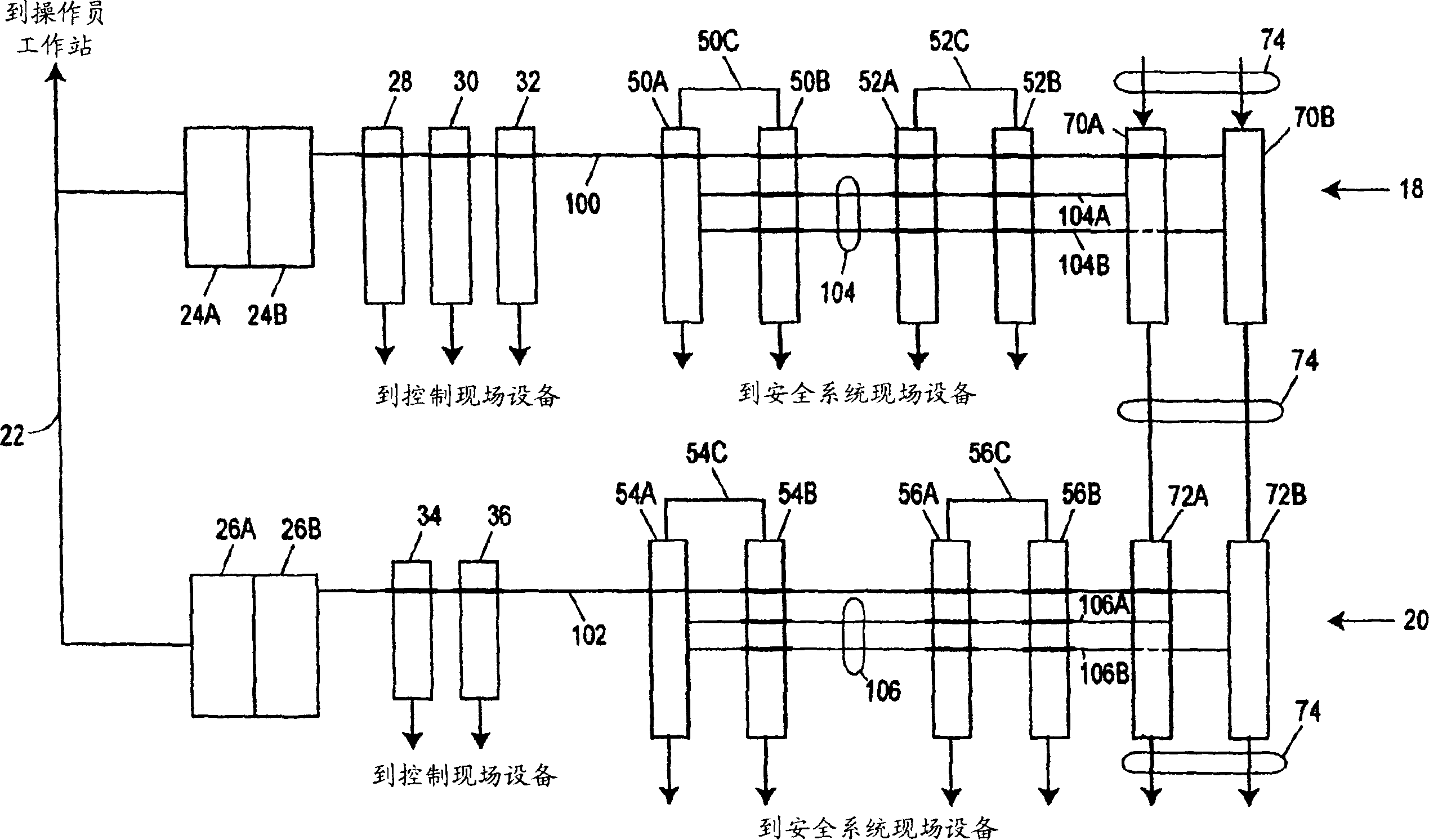
ActiveUS7289861B2Eliminate needSafety arrangmentsDigital data processing detailsEmbedded securityControl system
A process plant includes a process control system having a safety system embedded therein. The integrated process control and safety system includes a host computer arranged to send and receive process level messages and safety level messages, a controller operatively connected to the host computer by a first communication network, at least one first input / output device adapted for operative communication with at least one process control field device, and at least one second input / output device adapted for operative communication with at least one safety-related field device. The first and second input / output devices are operatively connected to the controller via a second communication bus. The second input / output device includes a processor programmed to monitor both the process level messages and the safety level messages, to distinguish the process level messages from safety level messages, to select the safety level messages and to communicate with the safety-related field device based on the safety level messages.
Owner:FISHER-ROSEMOUNT SYST INC
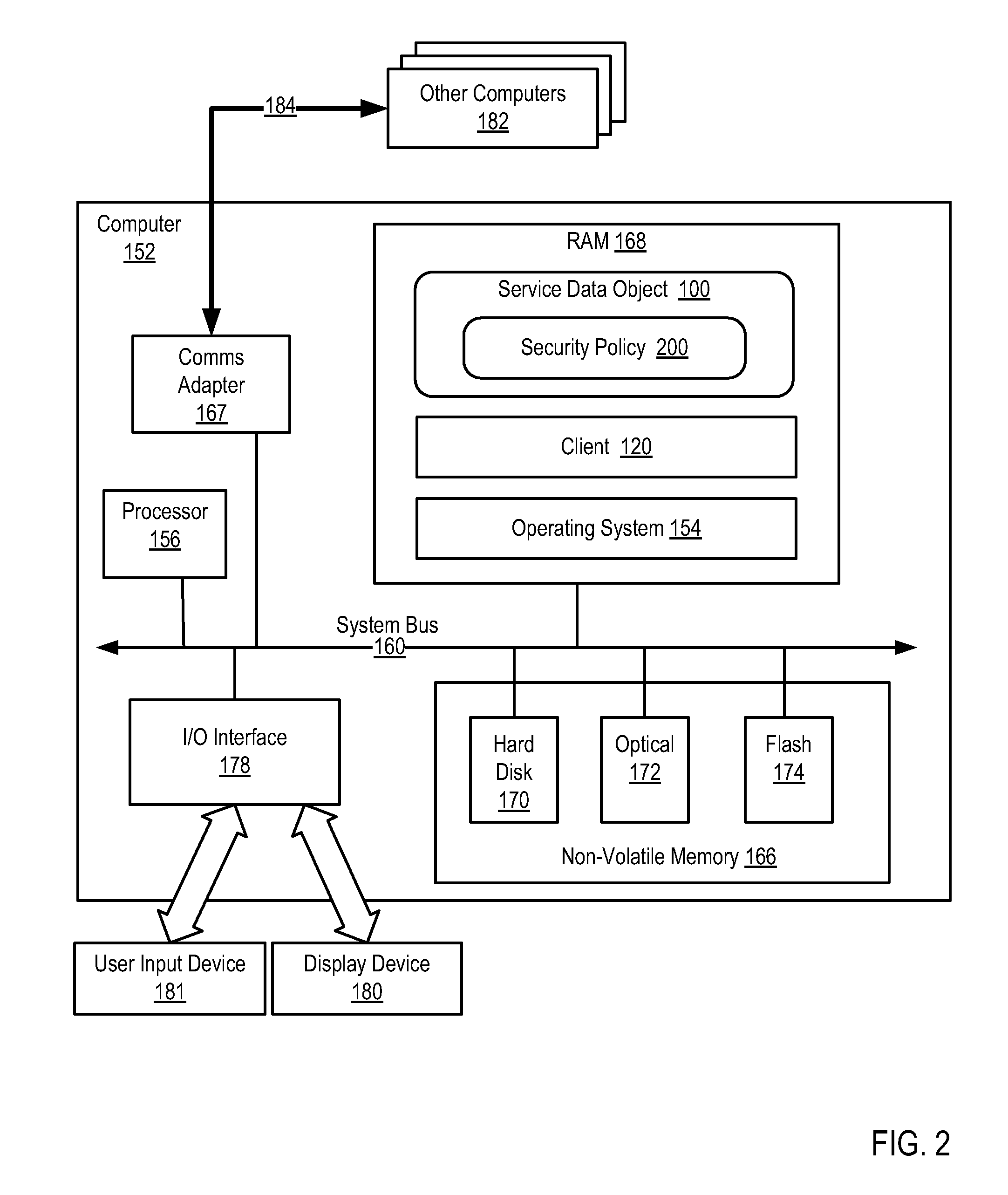
Securing access to a service data object
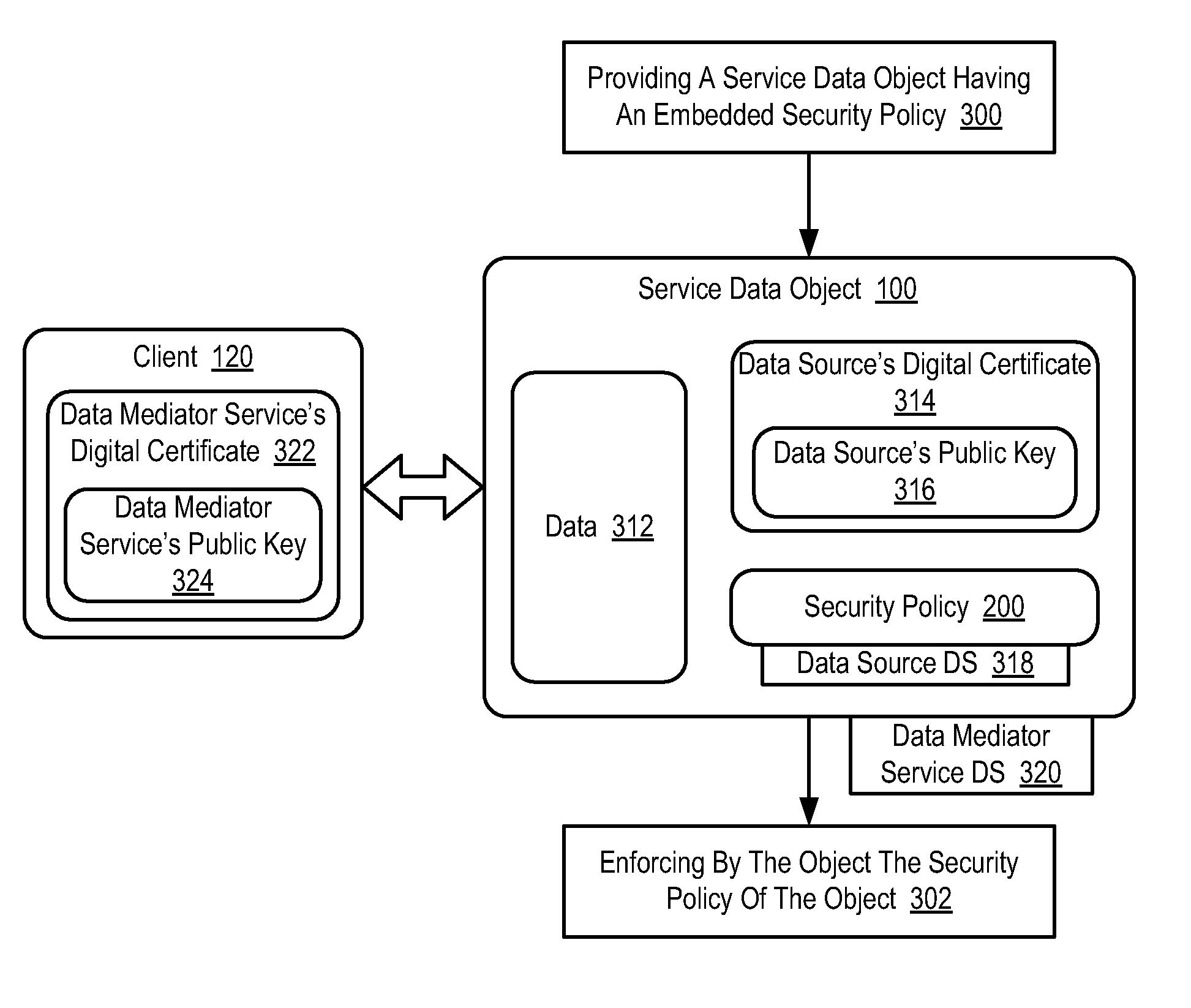
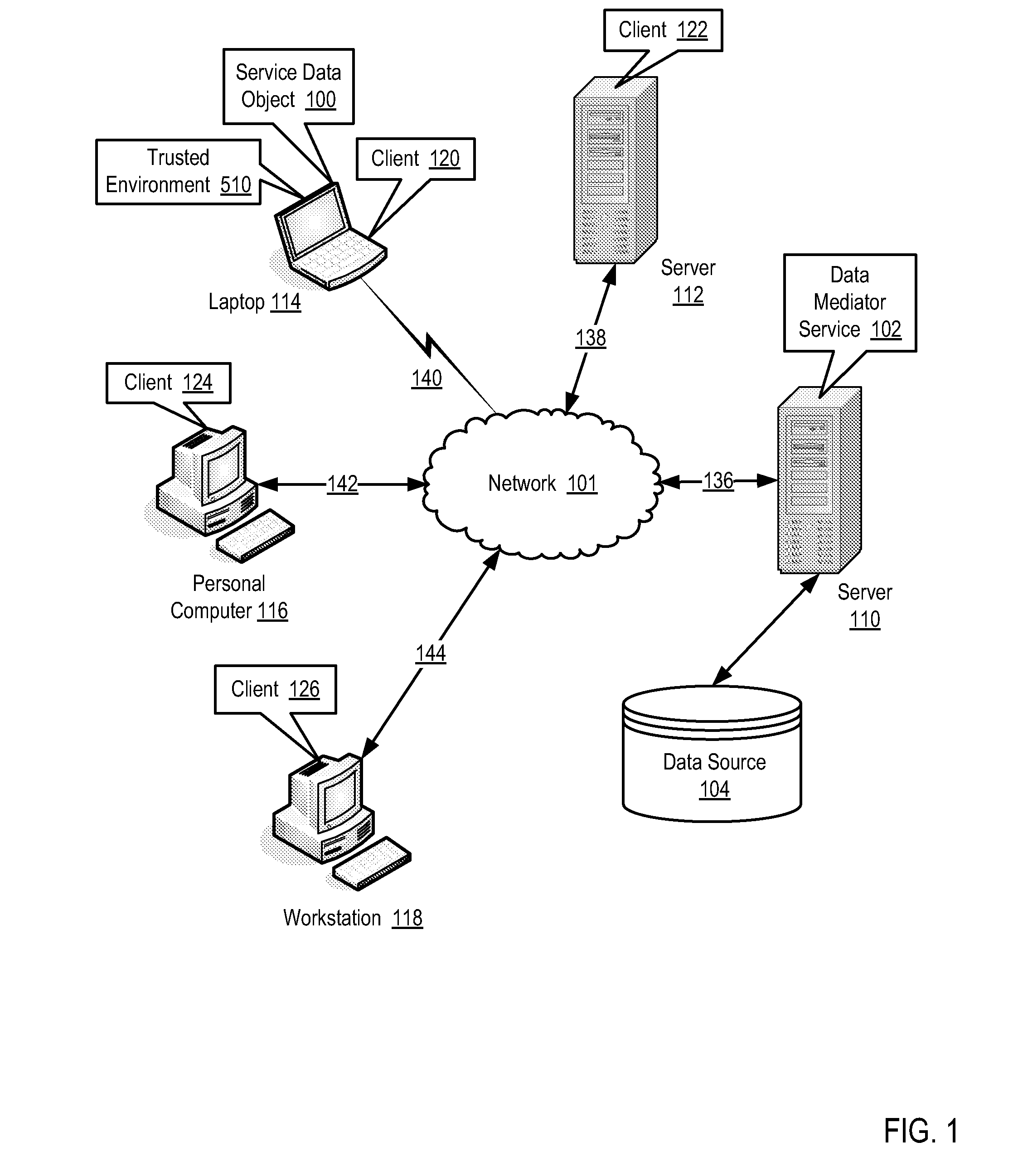
InactiveUS20070271618A1Digital data processing detailsUser identity/authority verificationEmbedded securityTrust relationship
Methods, systems, and computer program products are disclosed for securing access to a service data object that include providing a service data object having an embedded security policy, and enforcing by the object the security policy of the object. Securing access to a service data object may include establishing a trust relationship with a trusted environment, transmitting the object to the trusted environment, and enforcing by the object the security policy of the object in the trusted environment. Securing access to a service data object may include exposing an interface to provide access to the object in dependence upon an authorization policy of the security policy for an authenticated user. Securing access to a service data object may include exposing attributes of the object in dependence upon an authorization policy of the security policy for an authenticated user.
Owner:IBM CORP
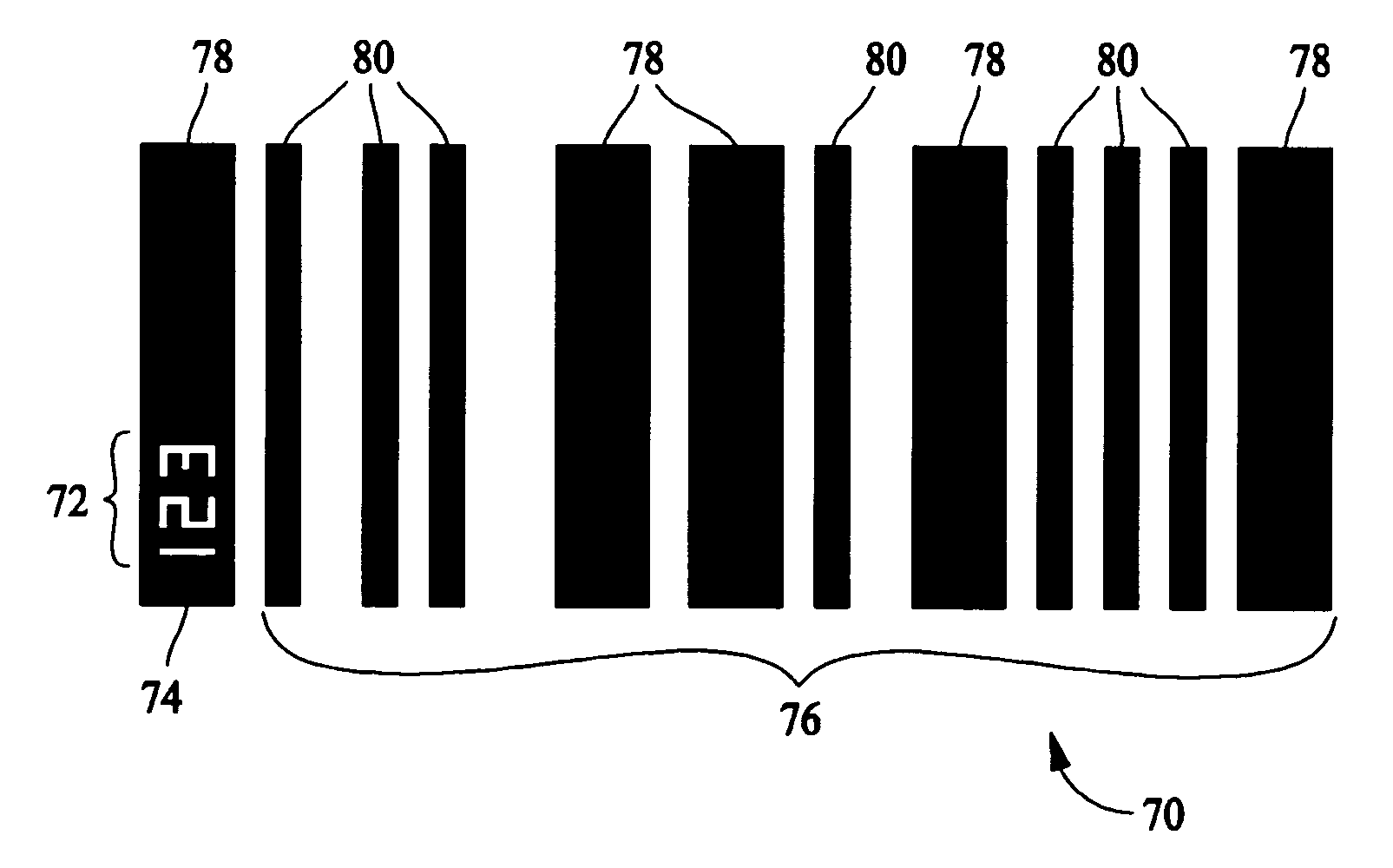
Barcodes including embedded security features and space saving interleaved text
InactiveUS7025269B2Character and pattern recognitionRecord carriers used with machinesEmbedded securityPattern recognition
A method for adding authentication features to a barcode is described. The barcode includes a plurality of printed parallel bars and the method includes embedding printed security features within the printed barcode. The parallel bars of the bar code are of varying width and at least one of the parallel bars has security features printed within that are printed in a color that is different than a color of the parallel bars.
Owner:WATSON LABEL PRODS CORP
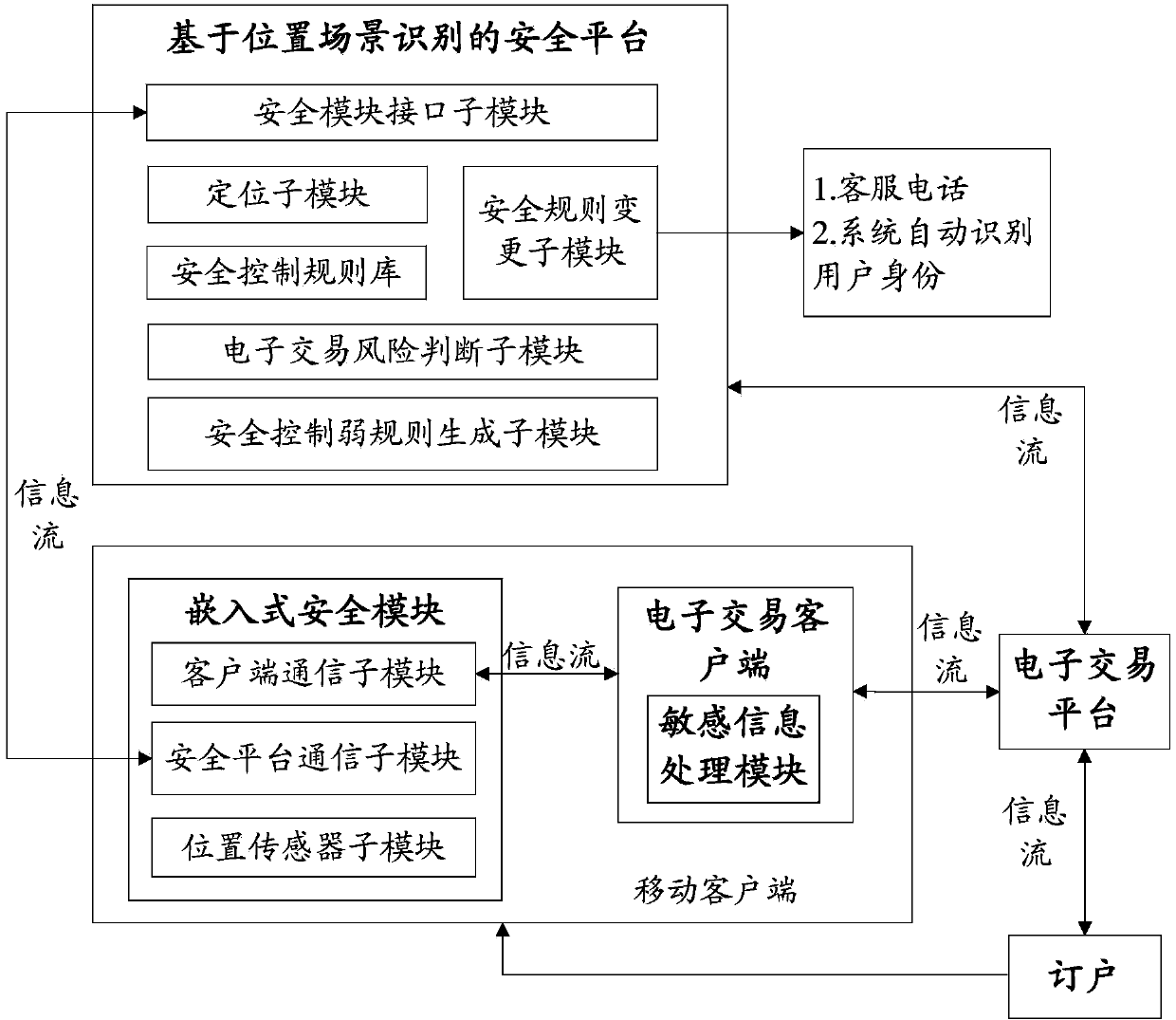
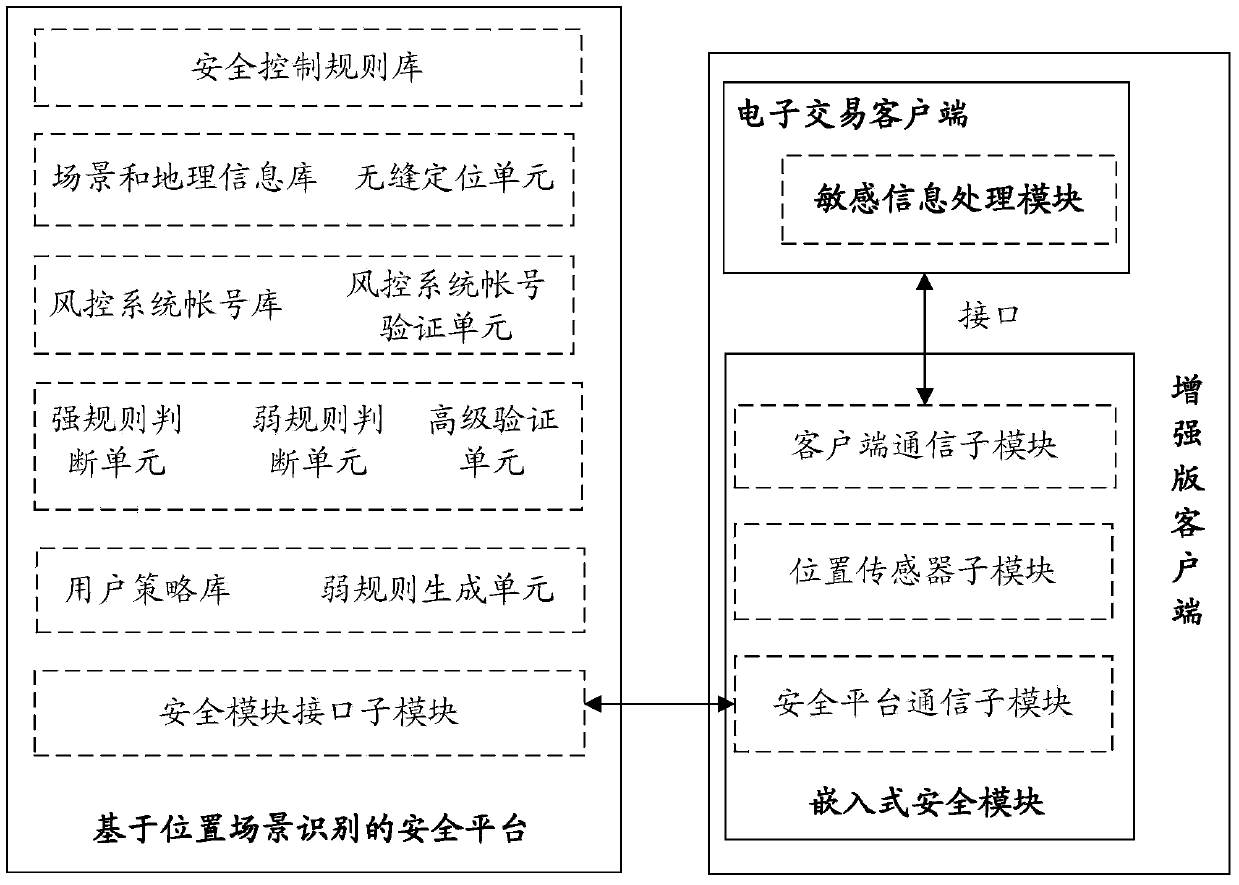
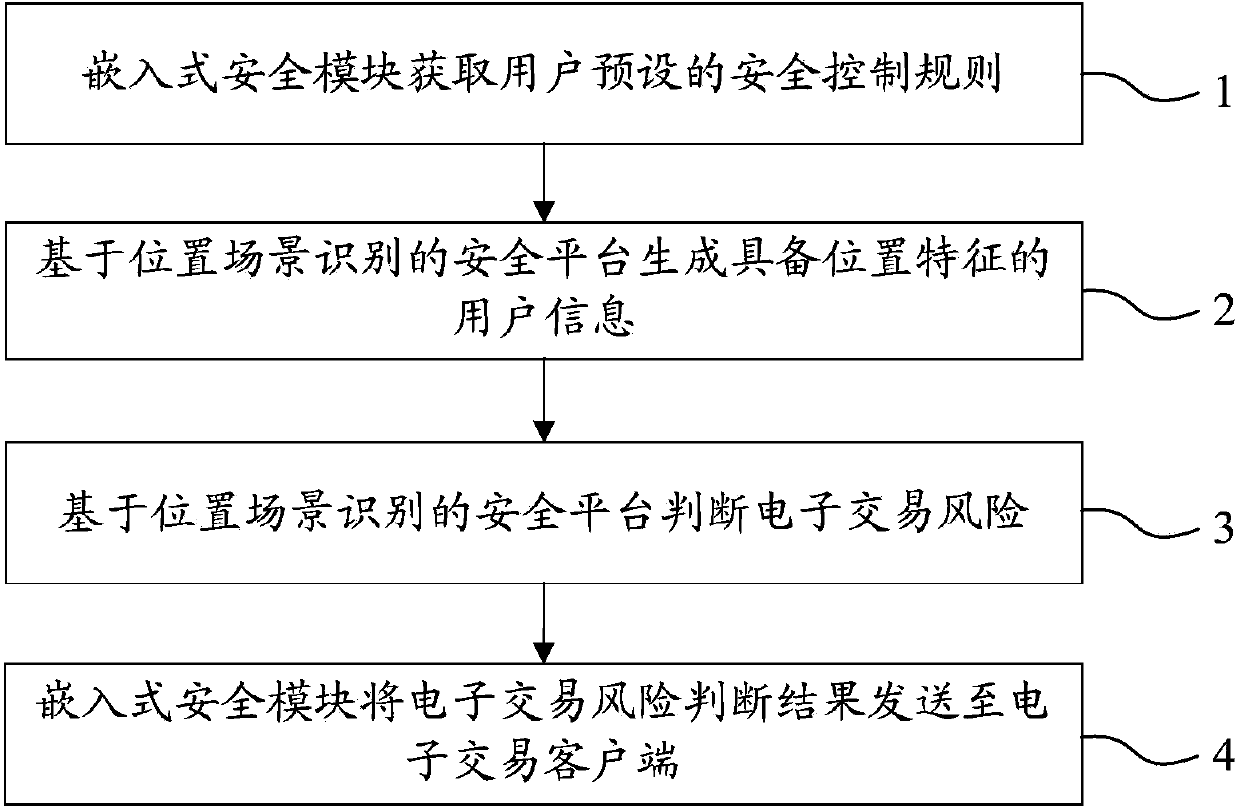
System and method for realizing electronic transaction risk control based on position scene identification
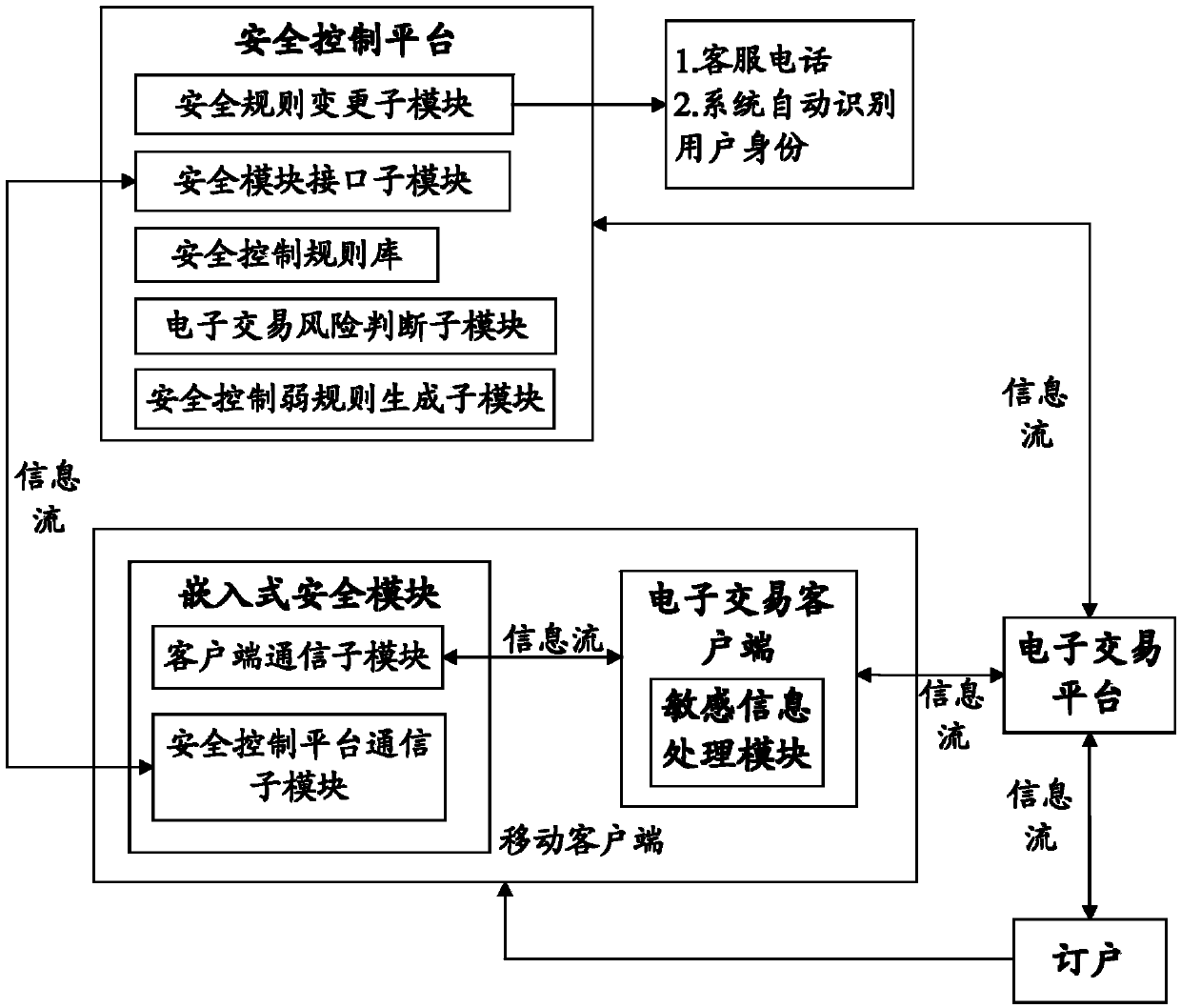
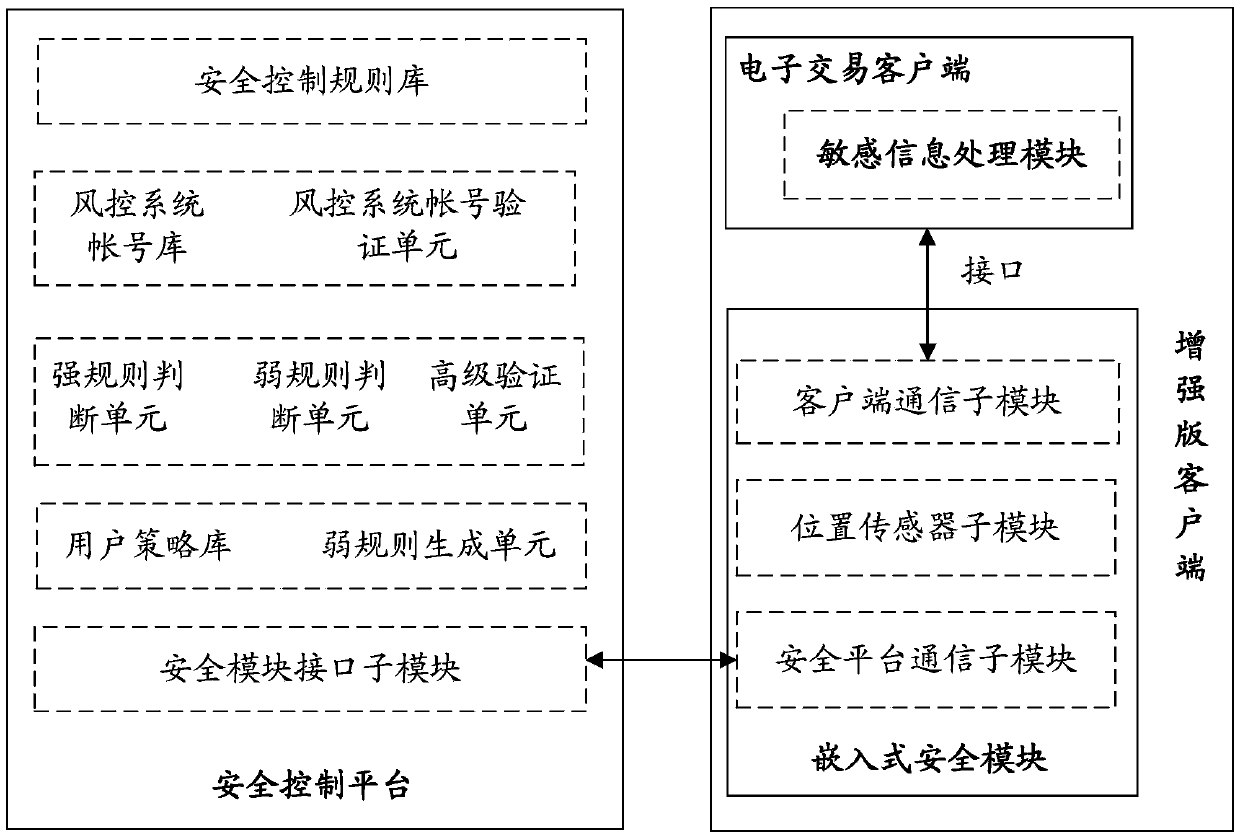
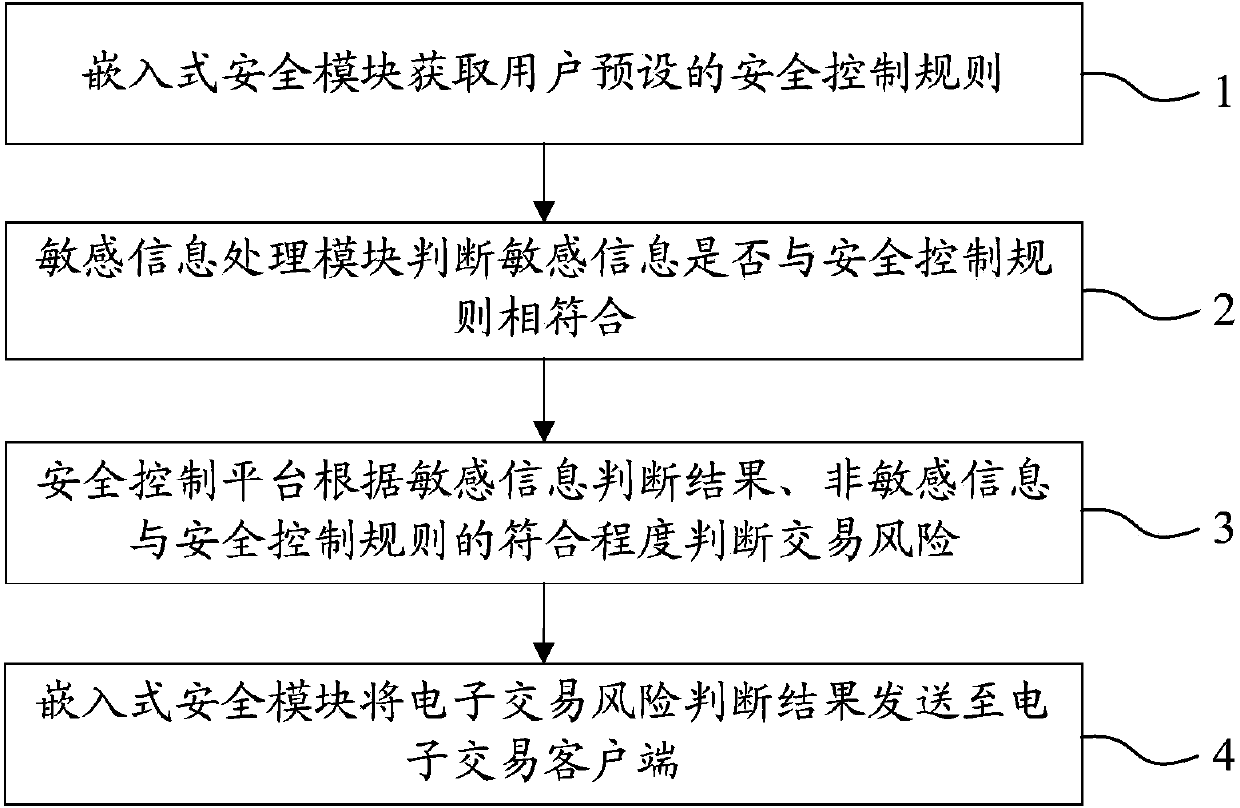
InactiveCN103745397APrevent fraudReduce personal property damageFinanceBuying/selling/leasing transactionsRisk ControlEmbedded security
The invention relates to a system for realizing electronic transaction risk control based on position scene identification. The system comprises a position scene identification-based security platform and an embedded security module, wherein the position scene identification-based security platform comprises a security interface sub-module, a positioning sub-module, a security control rule library, a security rule change sub-module, an electronic transaction risk judging sub-module and a security control weak rule generation sub-module, which are communicated with the embedded security module. The invention further relates to a method for realizing electronic transaction risk control based on position scene identification through the system. By adopting the system and the method for realizing electronic transaction risk control based on position scene identification, risk control over the electronic transactions of a user can be realized by providing positioning service and identifying a user position scene, so that the security of an electronic transaction process is enhanced, and losses caused by transaction security problems are reduced. The method is easy, convenient, and wider in application range.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
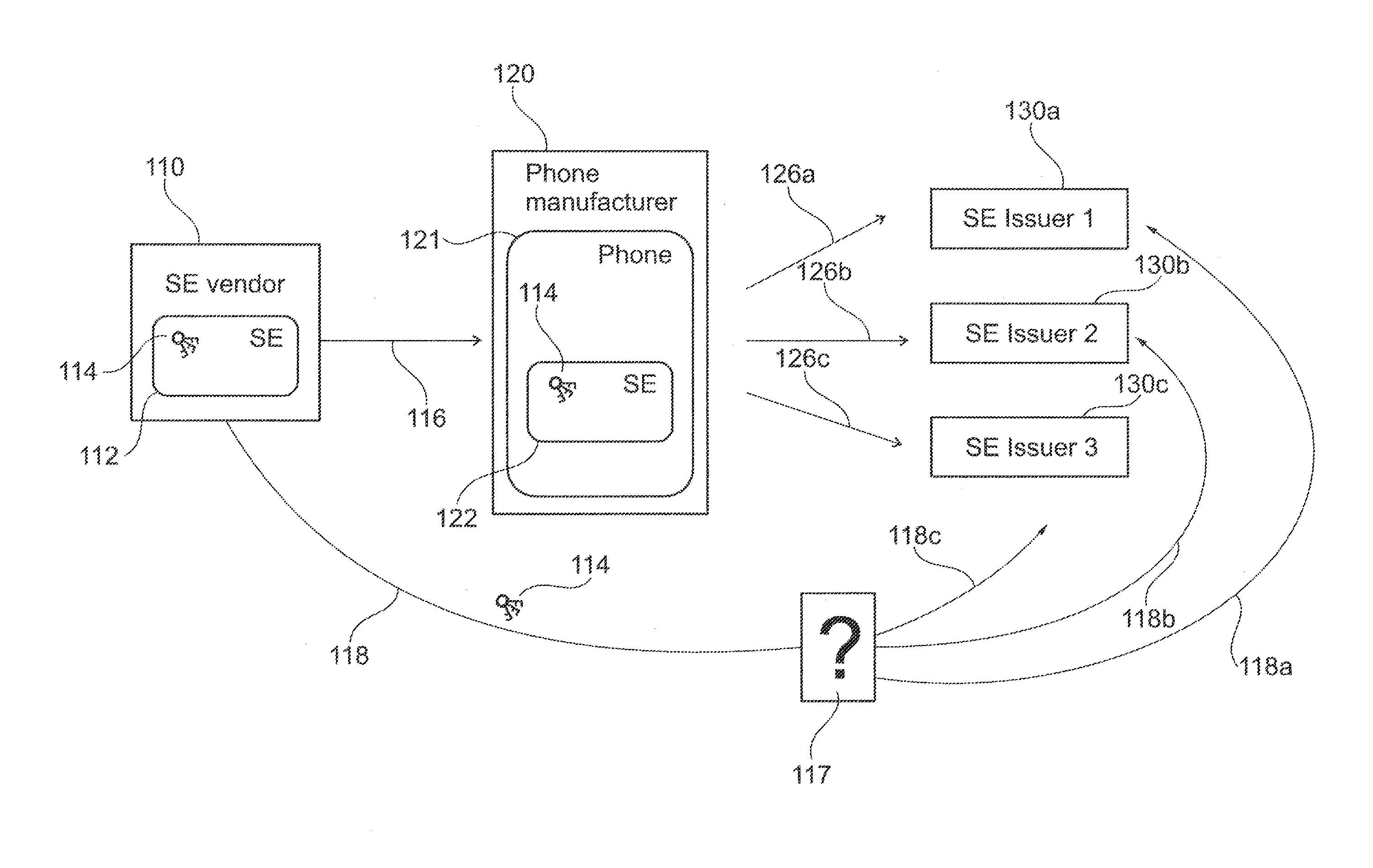
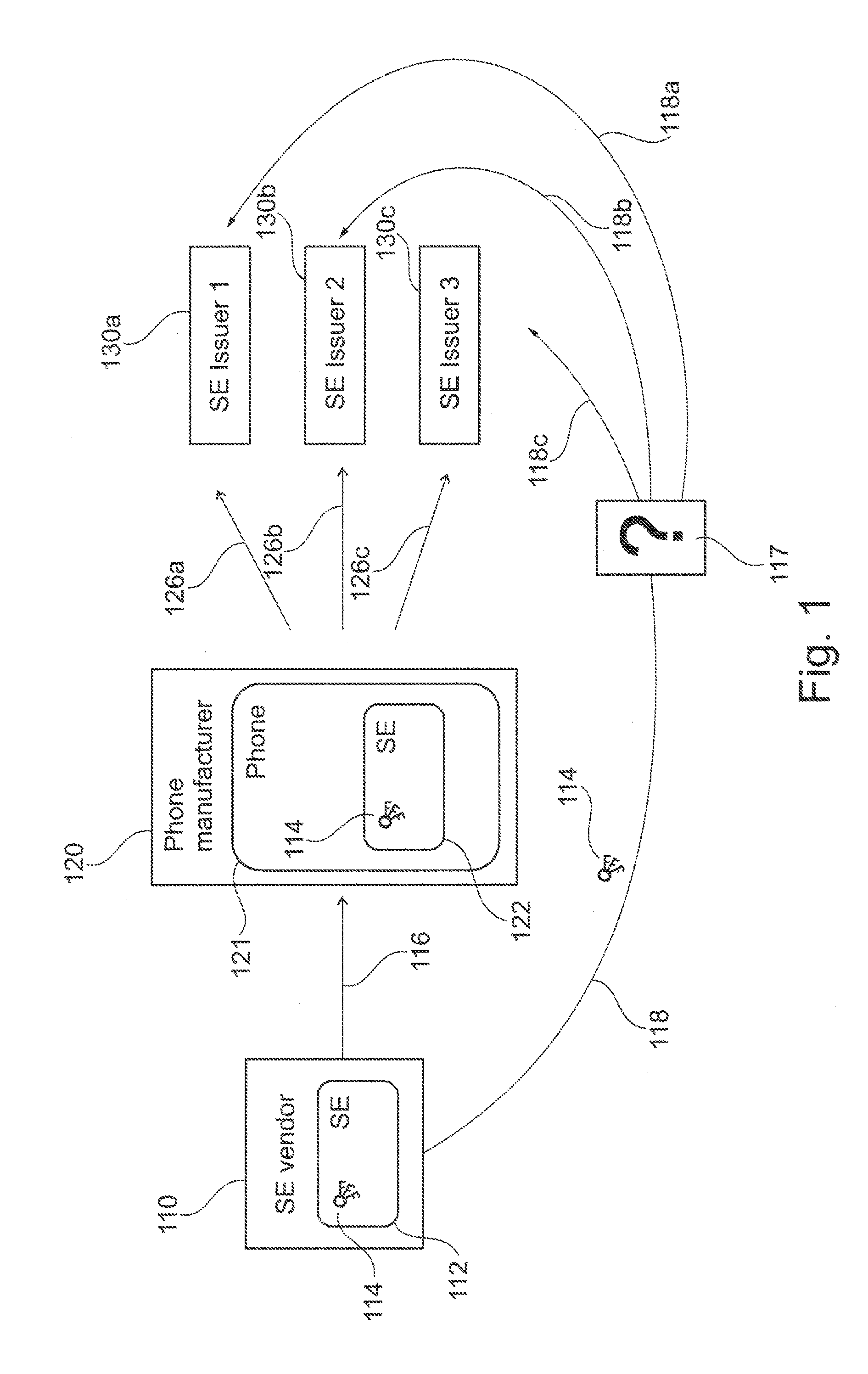
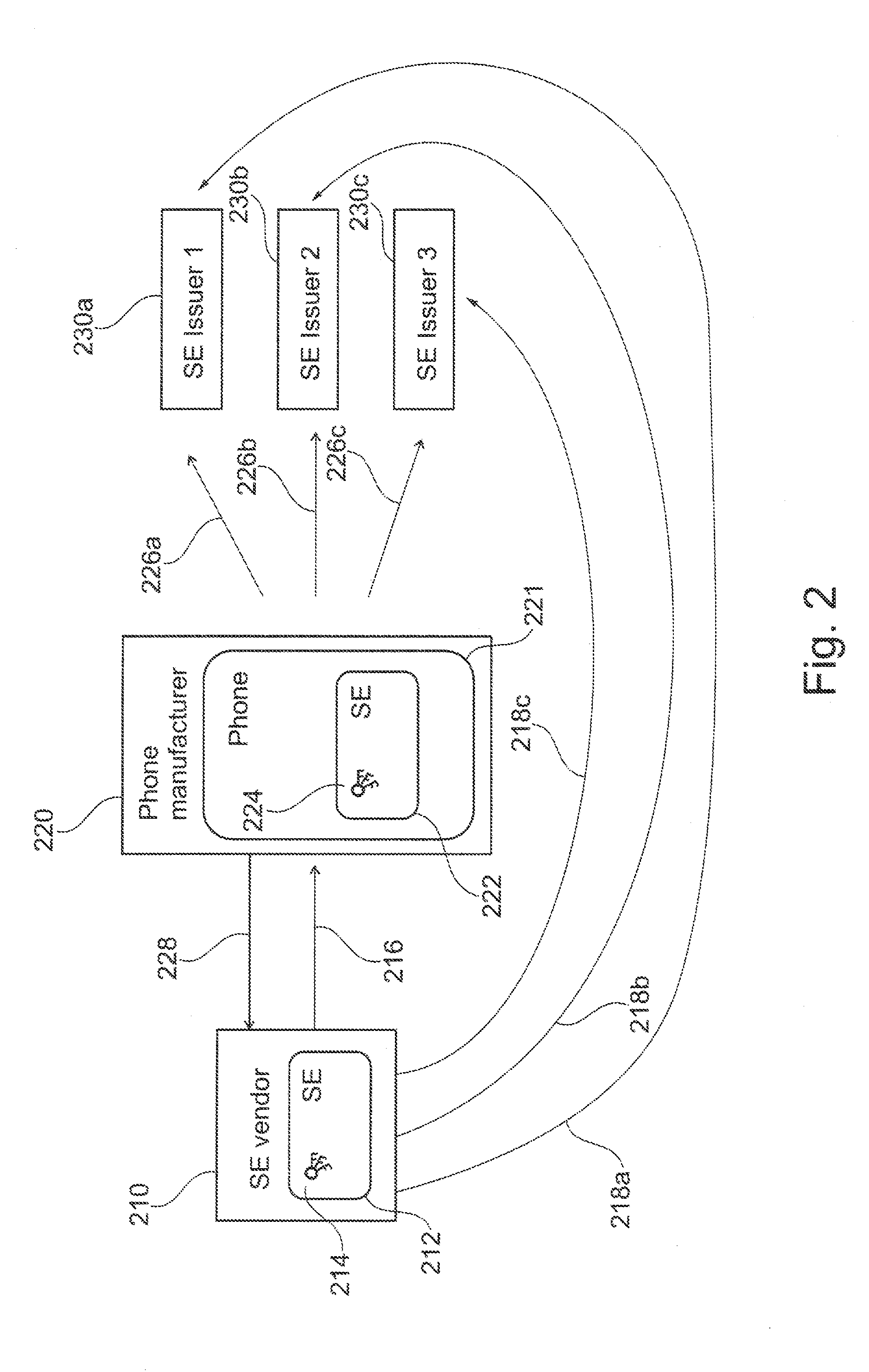
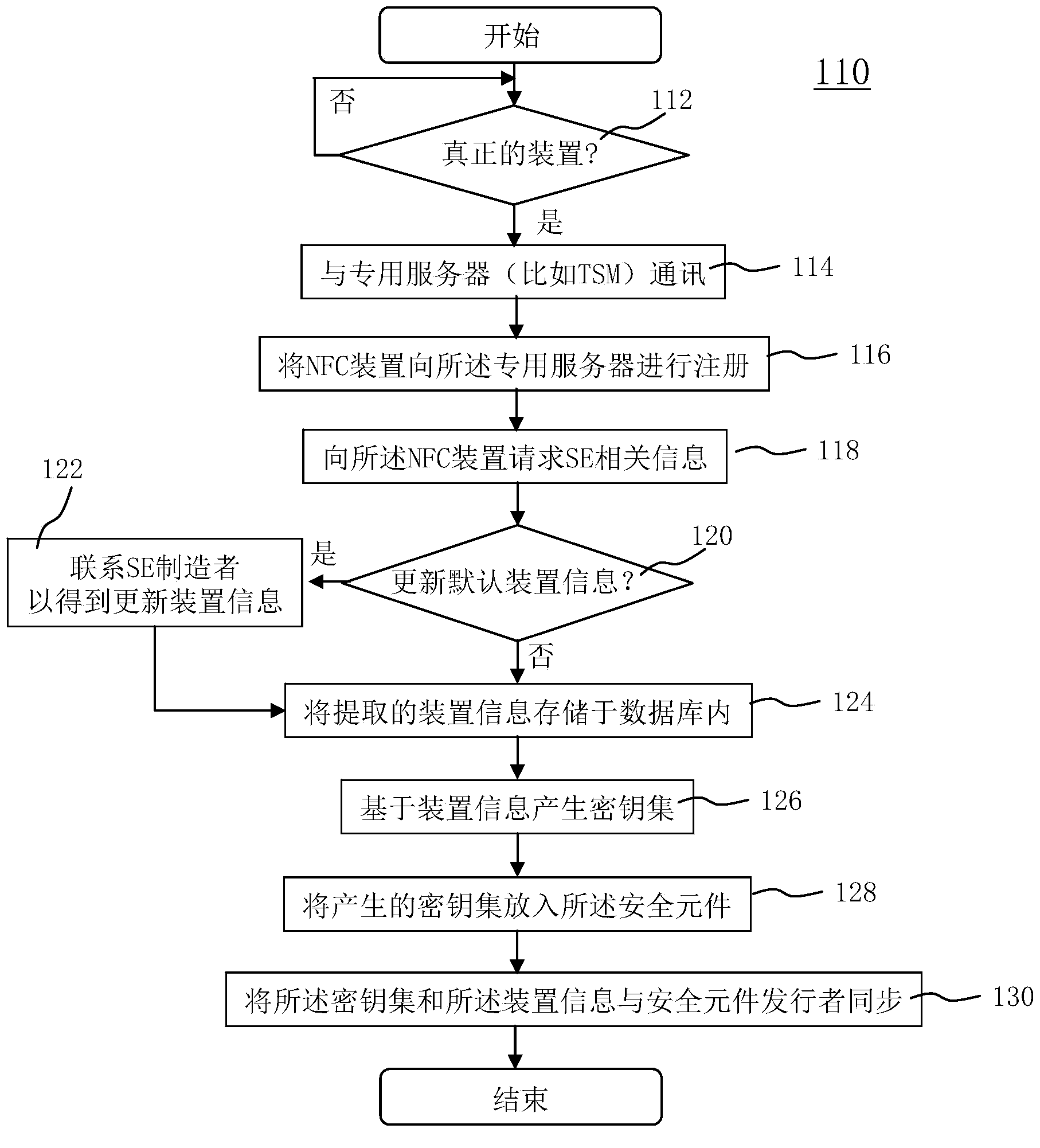
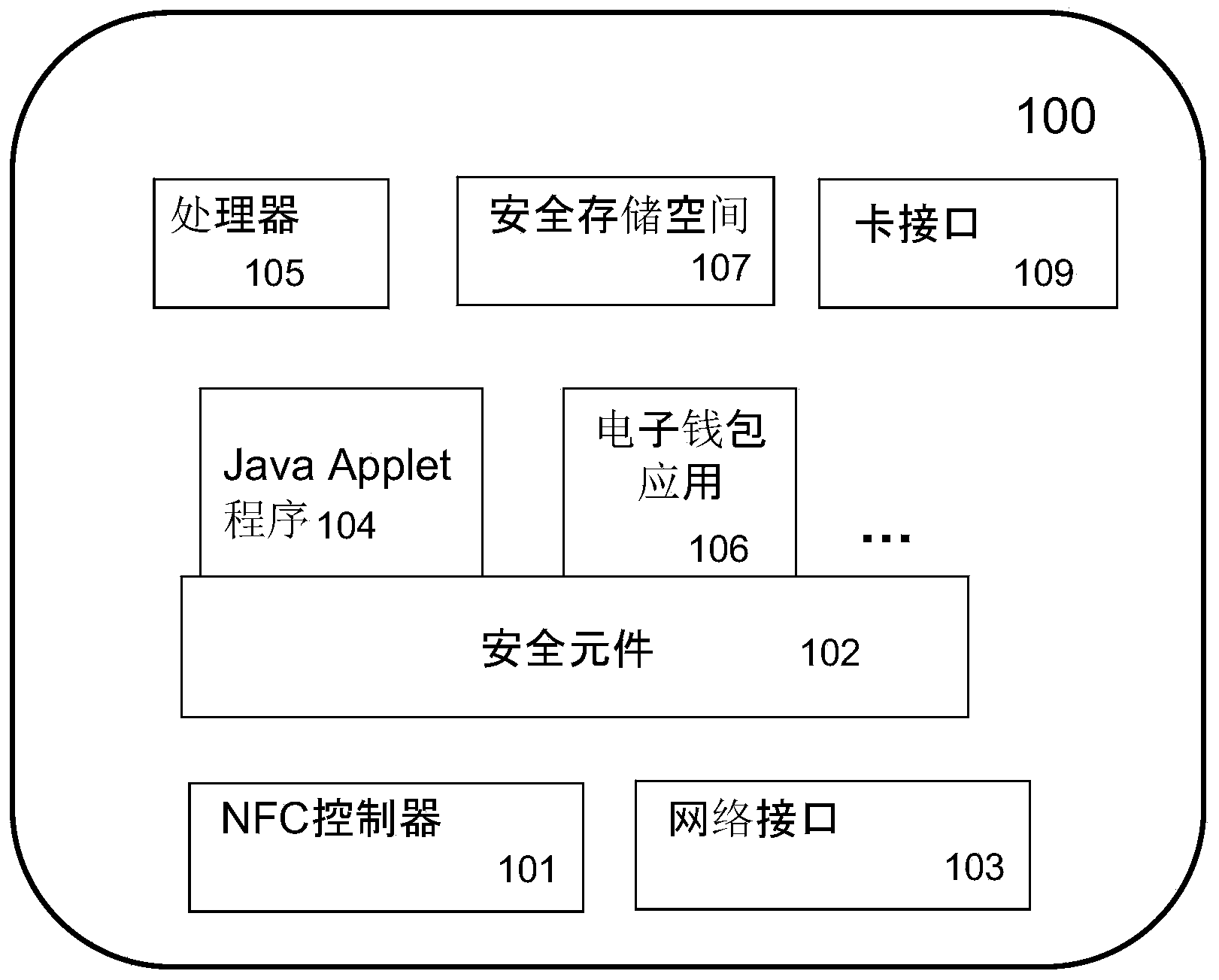
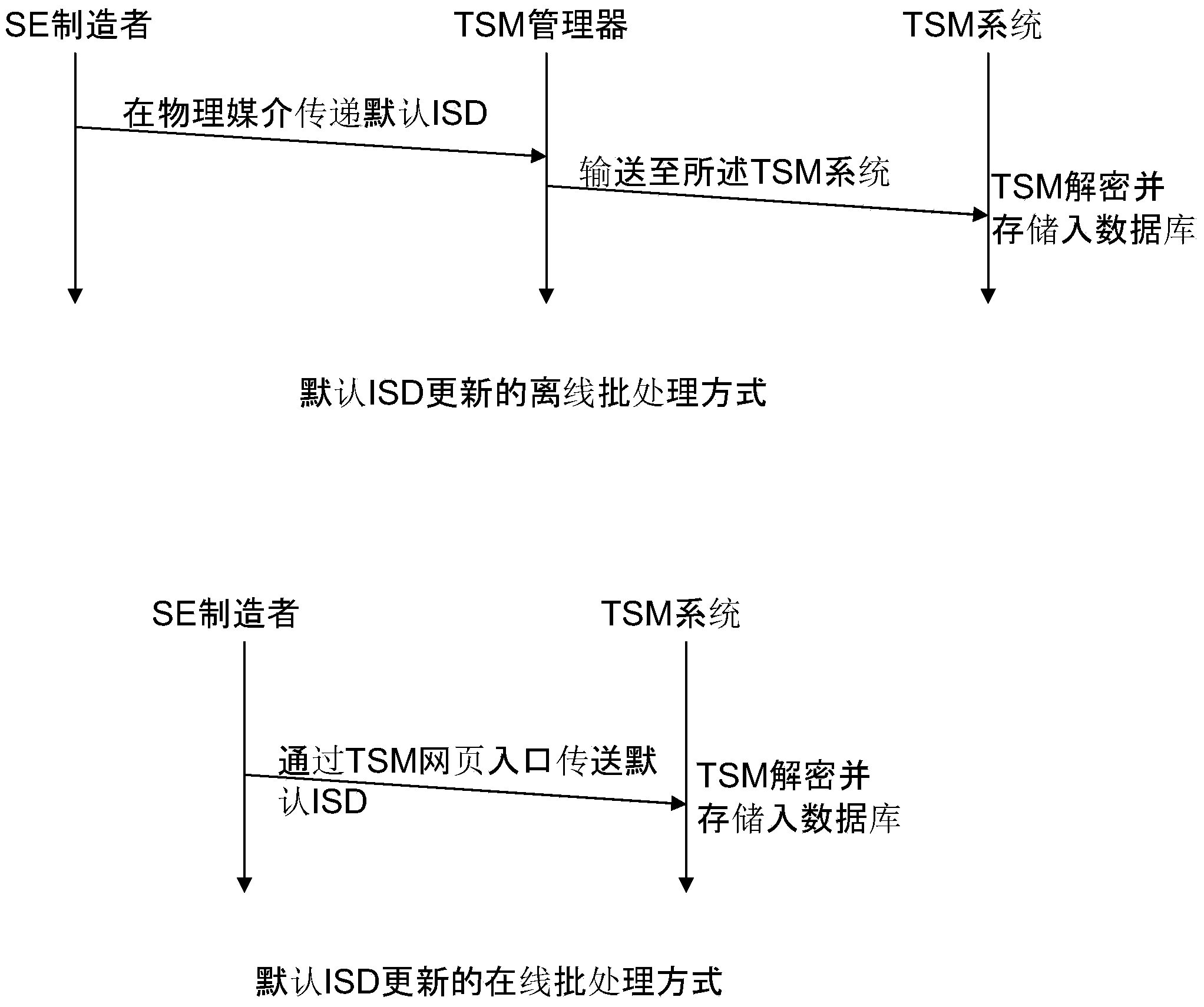
Initialization of embedded secure elements
There is described a method for initializing a secure element (112, 122, 212, 222) for use with a host unit (121, 221), the method comprising (a) storing a set of initial keys and a master key in a memory of a secure element (112, 122, 212, 222), (b) providing an identifier of a host (121, 221) unit associated with the secure element, (c) generating a modified set of keys based on the initial set of keys, the master key and the identifier of the host unit, and (d) storing the modified set of keys in the memory of the secure element. There is also described a secure element (112, 122, 212, 222) adapted for being embedded into a host unit (121, 221). Furthermore, there is described a system for initializing a secure element, a computer program and a computer program product.
Owner:NXP BV
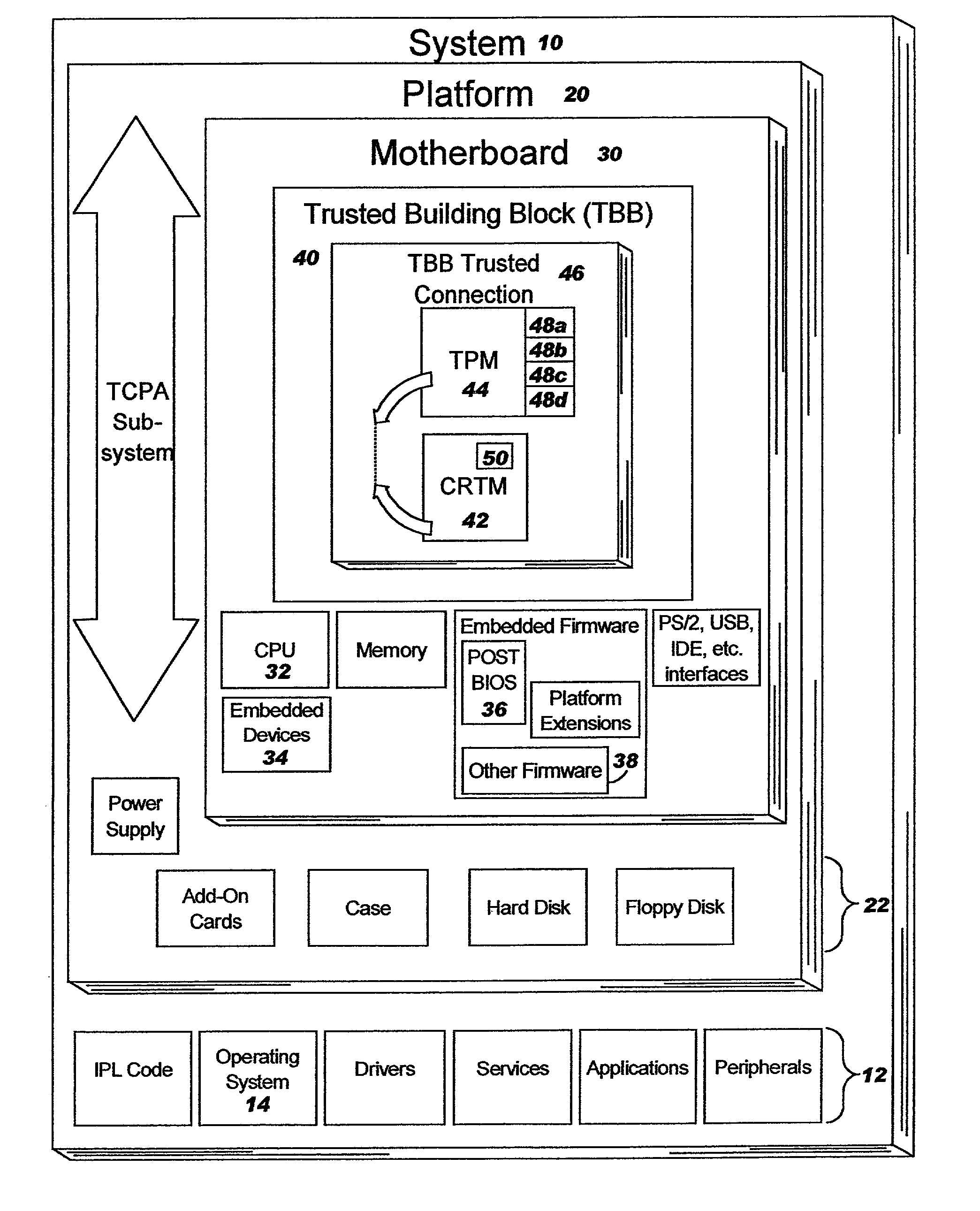
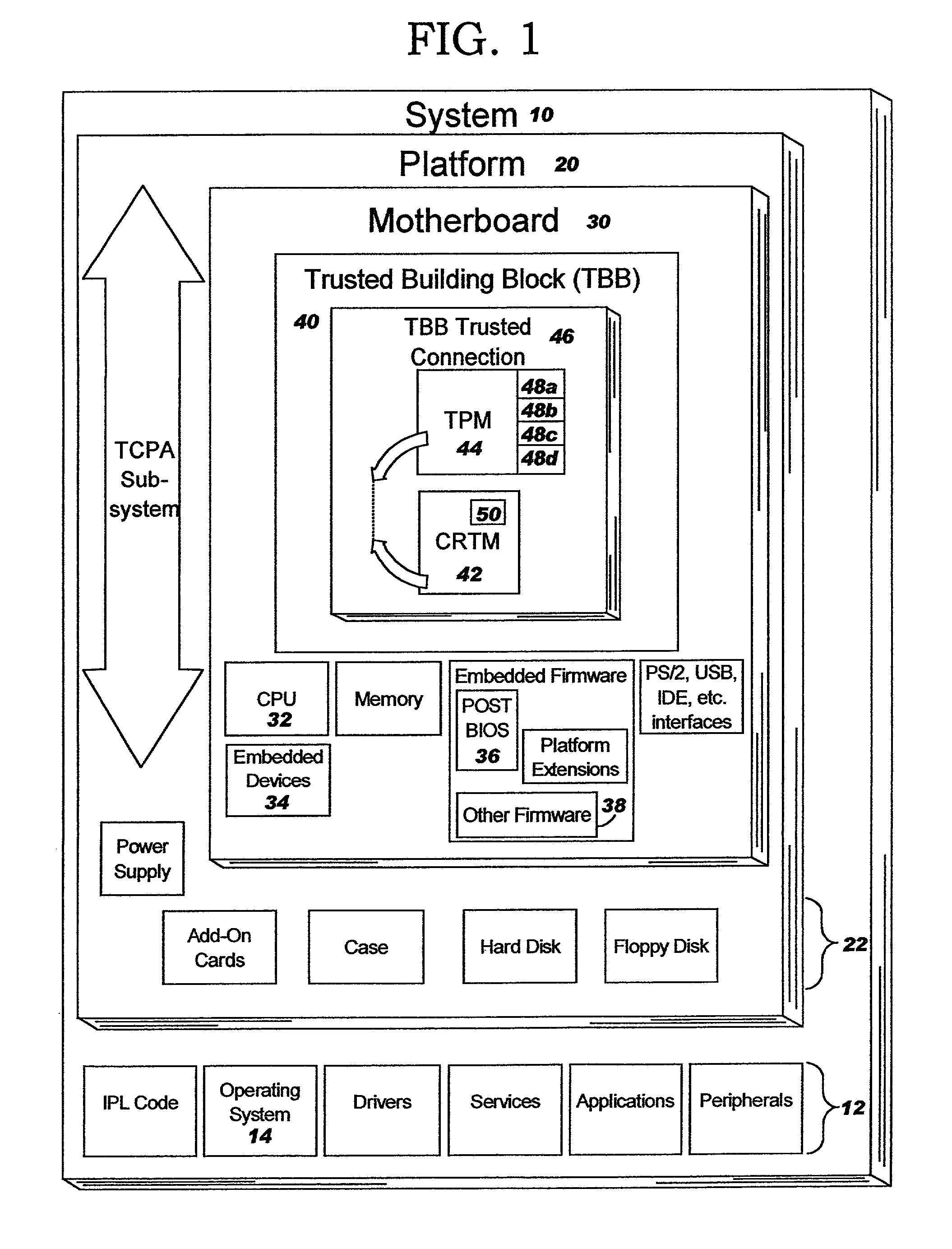
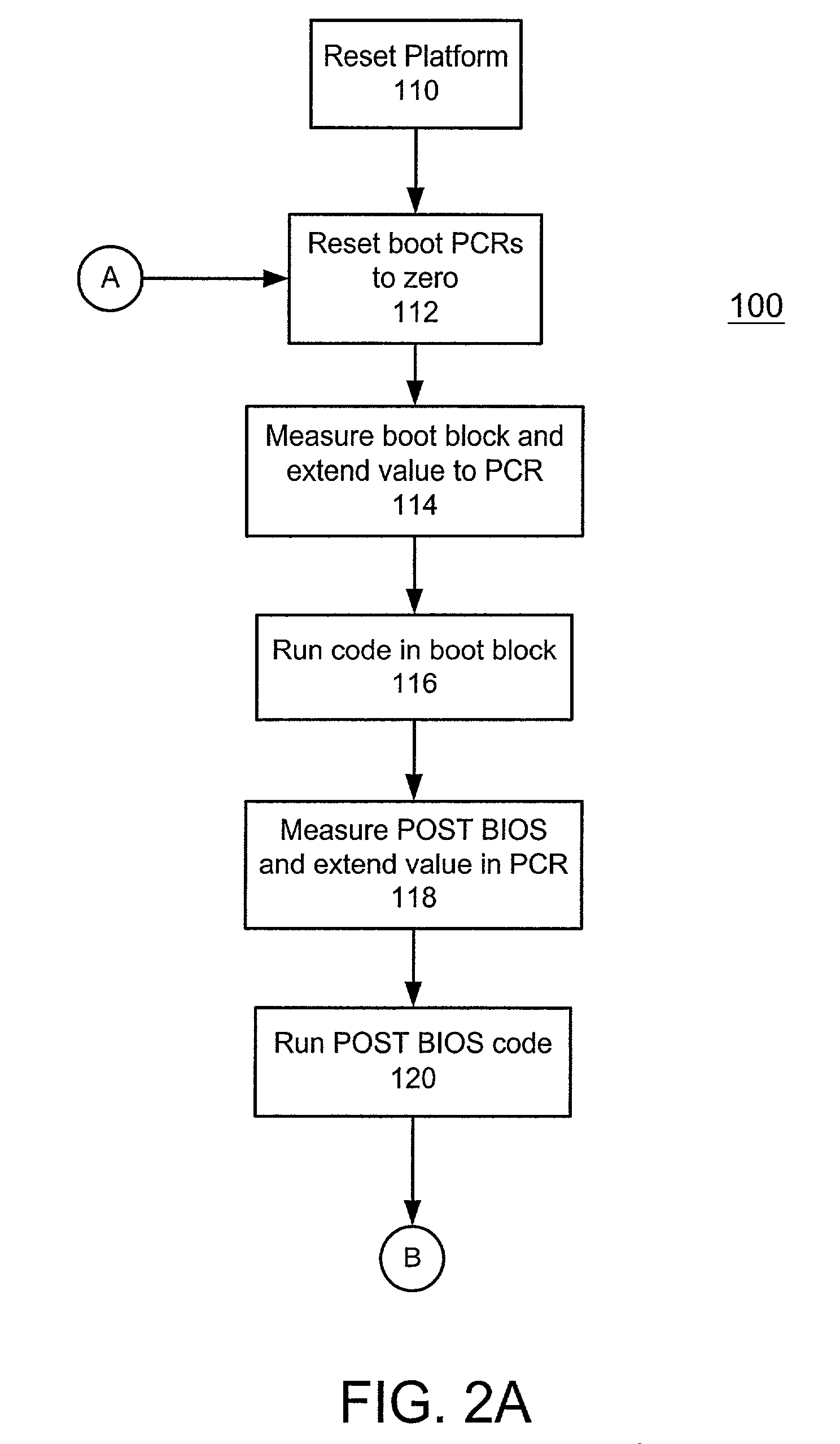
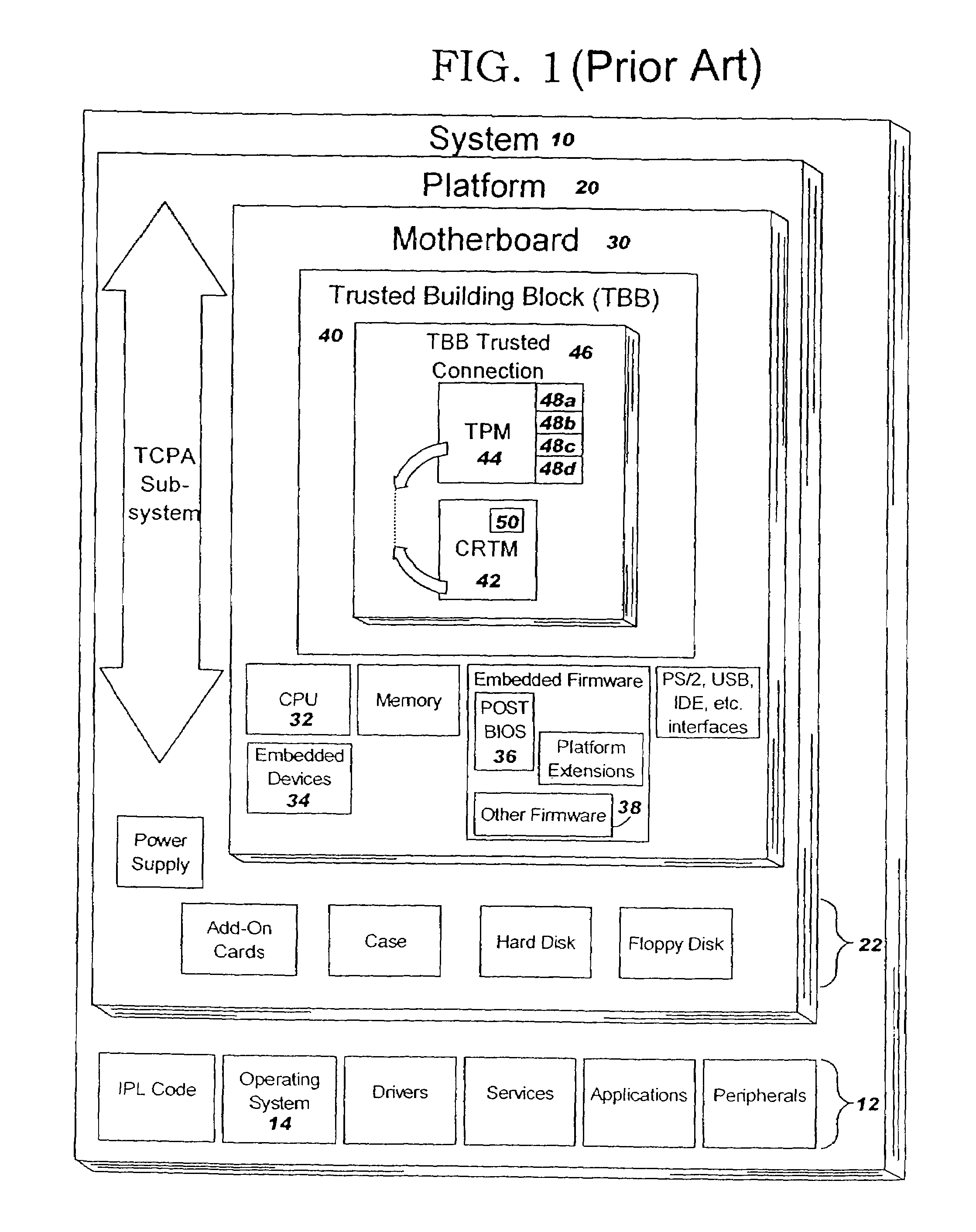
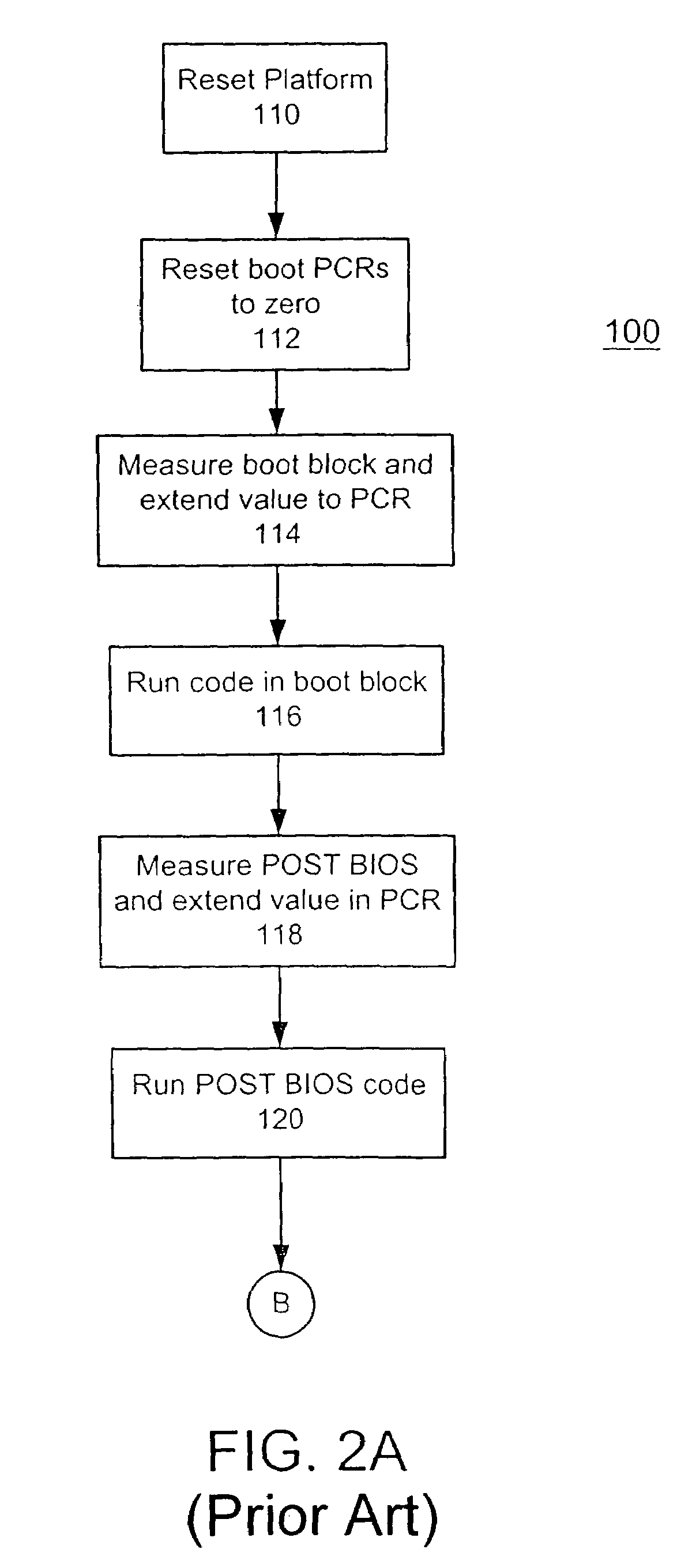
Method and system for tracking a secure boot in a trusted computing environment
ActiveUS7191464B2Digital data processing detailsUser identity/authority verificationEmbedded securityTrusted Computing
A method, system and computer readable medium containing programming instructions for tracking a secure boot in a computer system having a plurality of devices is disclosed. The method, system and computer readable medium include providing an embedded security system (ESS) in the computer system, wherein the ESS includes at least one boot platform configuration register (PCR) and a shadow PCR for each of the at least one boot PCRs, initiating a platform reset to boot the computer system via BIOS, and, for a device booted, generating a measurement value for the device and extending that value to one of the at least one boot PCRs and its corresponding shadow PCR. The system, method and computer readable medium of the present invention also includes comparing the measurement values of the boot PCRs to their corresponding shadow PCRs, whereby the computer system is trusted if the measurement values match.
Owner:LENOVO PC INT
Method and system for providing controllable trusted service manager
ActiveCN103530775AControl personalization/configurationEasy to deployPayment architectureTransmissionEmbedded securitySecurity domain
Techniques for realizing or providing controllable trusted service management are disclosed. The techniques are related to empowering a service provider with application provisioning and applet and secure element (SE) management capabilities. A service management module, herein referred to as Controllable TSM or CTSM, is provided to a service provider to provision certain applications distributed through the service provider. A system or platform contemplated in this invention allows a service provider to operate under a supplementary security domain (SSD) installed by an SE issuer or an updated SSD key set exclusively known to the service provider. Such a platform is designed to support embedded SE (eSE) and can be extended to support UICC-based SE. With the CTSM, a service provider can use the SSD to personalize applets installed on each SE securely and independently.
Owner:深圳市可秉资产管理合伙企业(有限合伙)
Multi-service provider authentication
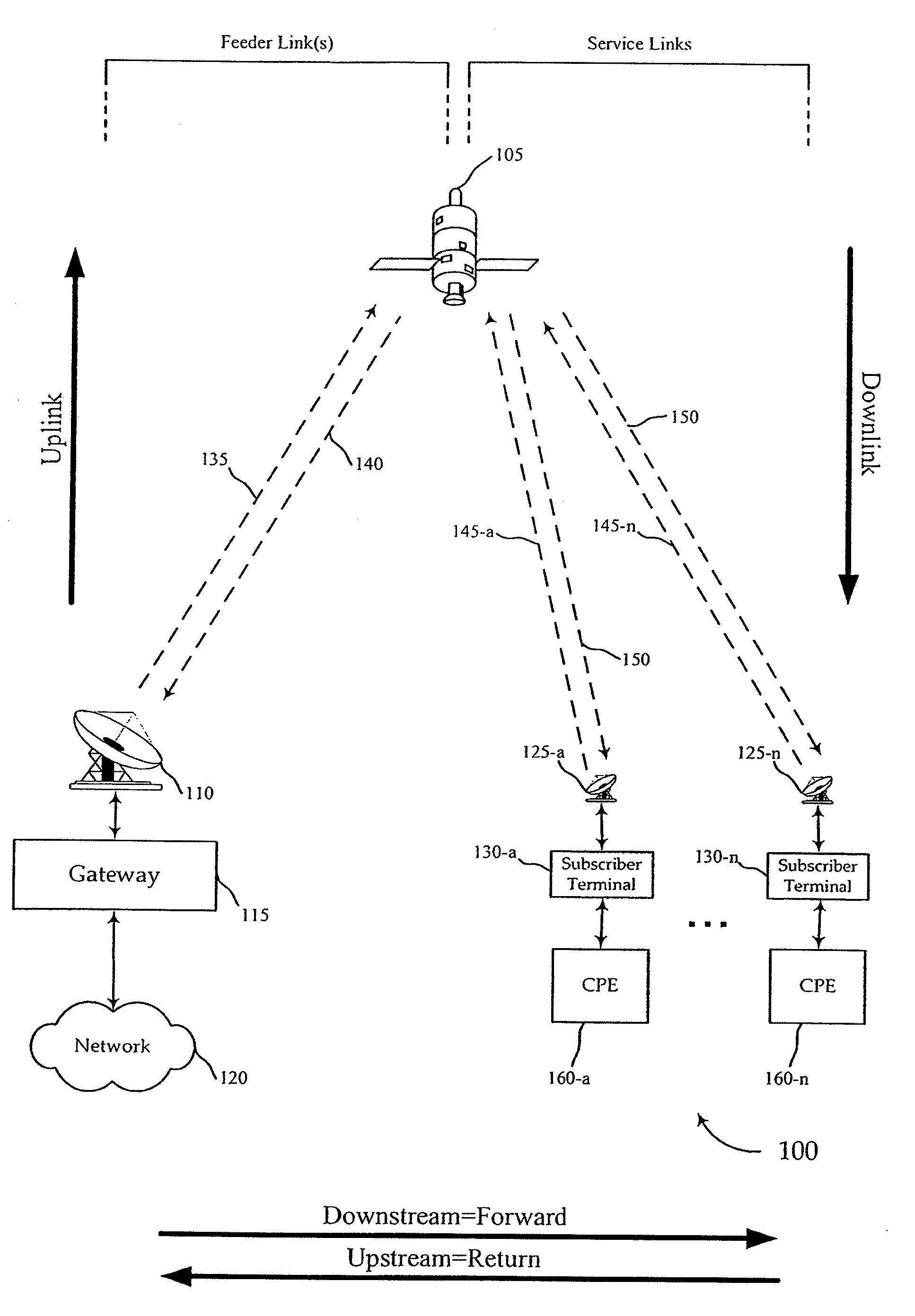
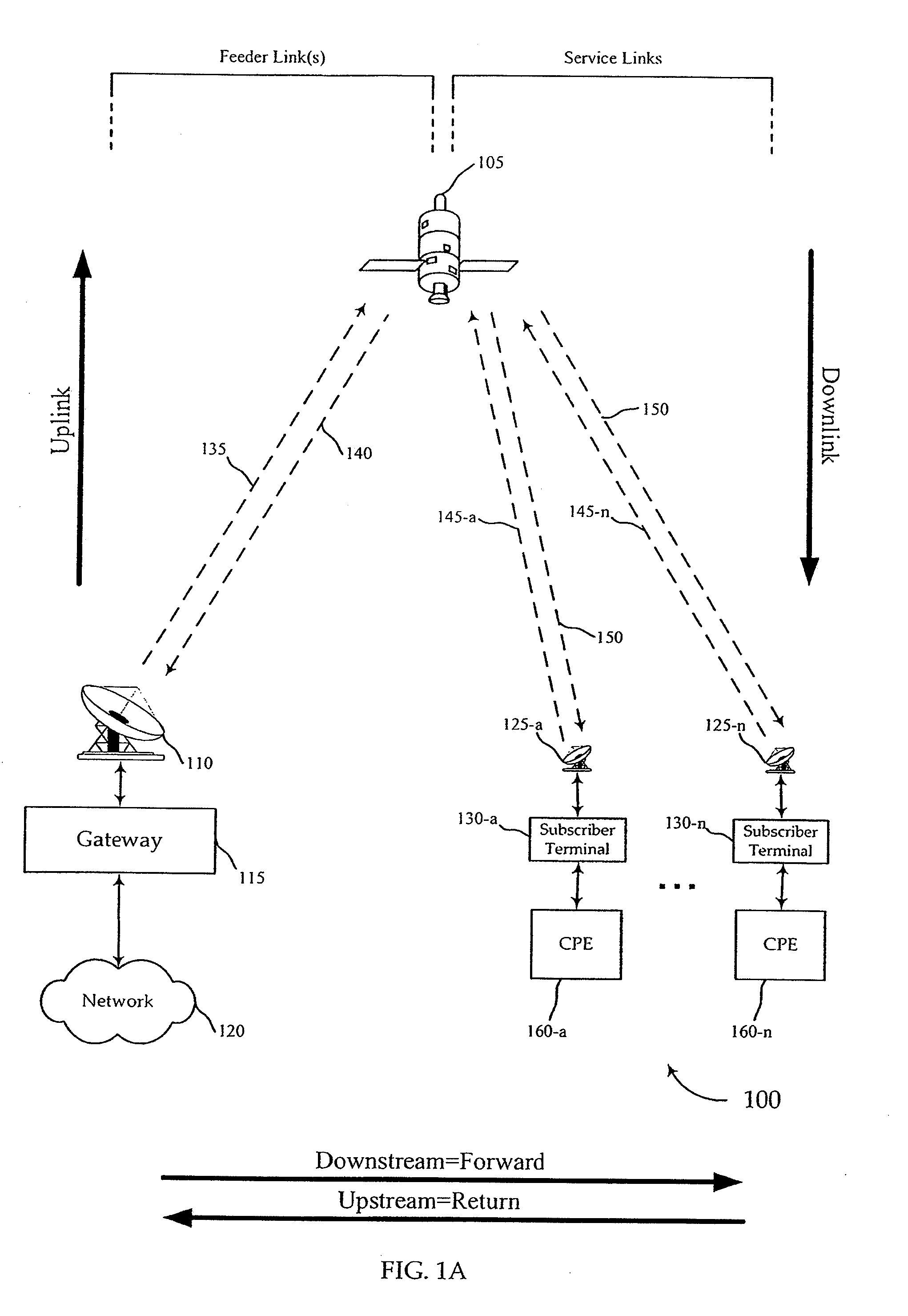
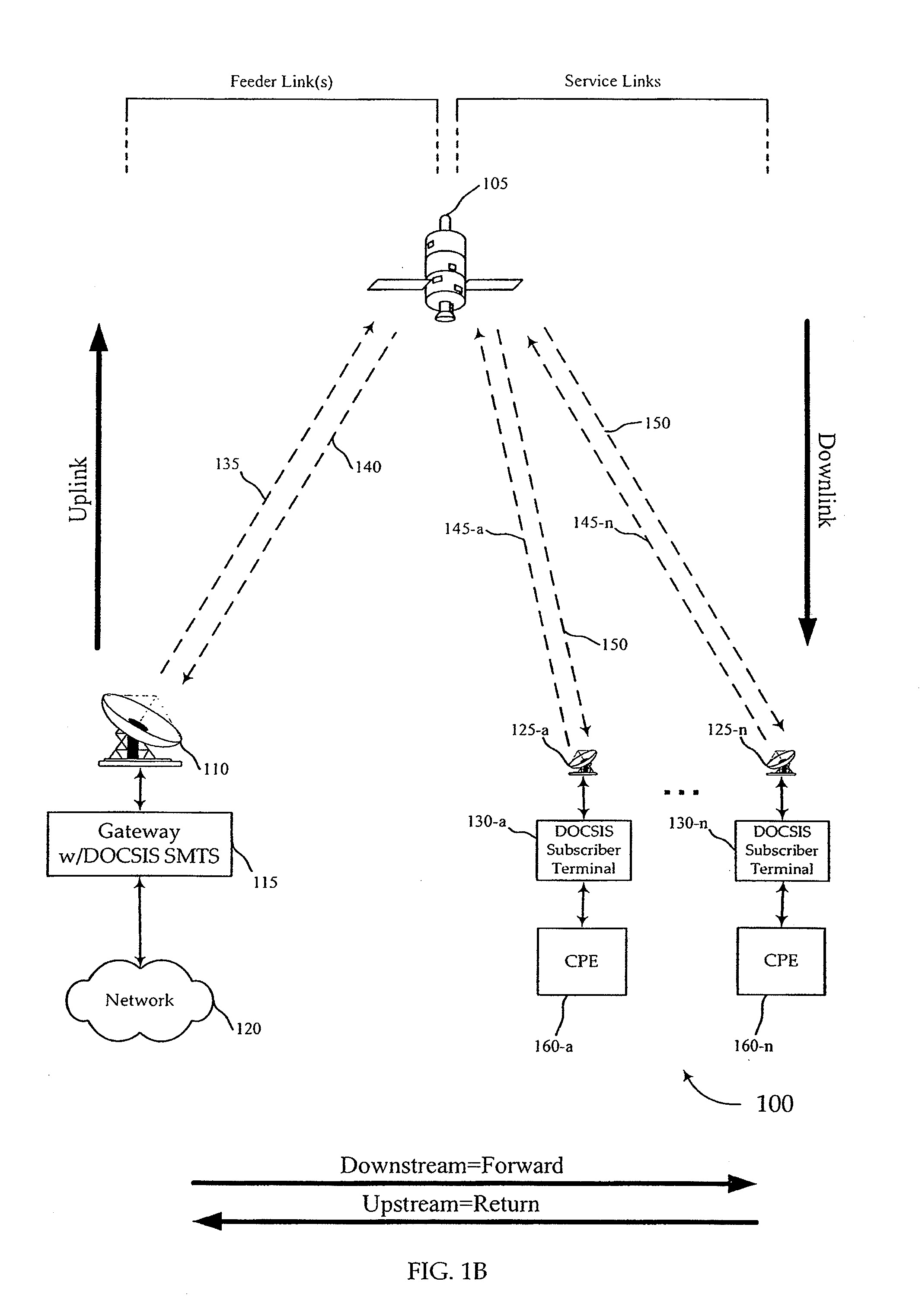
InactiveUS20100037308A1Accurate identityUser identity/authority verificationMultiple digital computer combinationsEmbedded securityModem device
Network access providers implement interactive procedures and subscriber terminals employ embedded secure authentication structures and procedures to ensure that a satellite modem at the subscriber terminal accurately verifies the identity of a satellite modem terminal system at the location of the network access provider gateway facility during the satellite modem initialization process so that the satellite modem will only attempt to acquire satellite resource from the appropriate (authenticated and authorized) satellite modem termination system. In a virtual downstream channel environment, diverse downstream channel feeds are distinguished by authentication procedures. The present invention differs from standard theft of service prevention because theft of subscriber prevention is in a virtual channel environment, where subscriber terminals have access to a plurality of virtual channels by the nature of the signal.
Owner:VIASAT INC
System and method applied to transaction platform for realizing grading safety processing of financial information
InactiveCN103745345AImprove securityDoes not compromise security by designPoint-of-sale network systemsProtocol authorisationInformation processingEmbedded security
The invention relates to a system applied to a transaction platform for realizing the grading safety processing of financial information. The system comprises an embedded safety control module for acquiring a safety control rule preset by a user, a sensitive information processing module for judging the coincidence degree of the sensitive information in electronic transaction information of the user and the safety control rule and a safety control platform for judging the risk of the electronic transaction and performing identity verification on the user for which the safety rule needs to be altered. The invention also relates to a method applied to the transaction platform for realizing the grading safety processing of the financial information. According to the system, adopting such a structure, and the method applied to the transaction platform to realize grading safety processing of the financial information, the financial information of the user can be divided into the sensitive information and insensitive information, the sensitive information processing module and an electronic transaction client end are integrally packaged, the user information safety is further ensured by grading processing, loss caused by the problem of account unsafety is reduced and the system and method have a wide application range.
Owner:COEUSYS
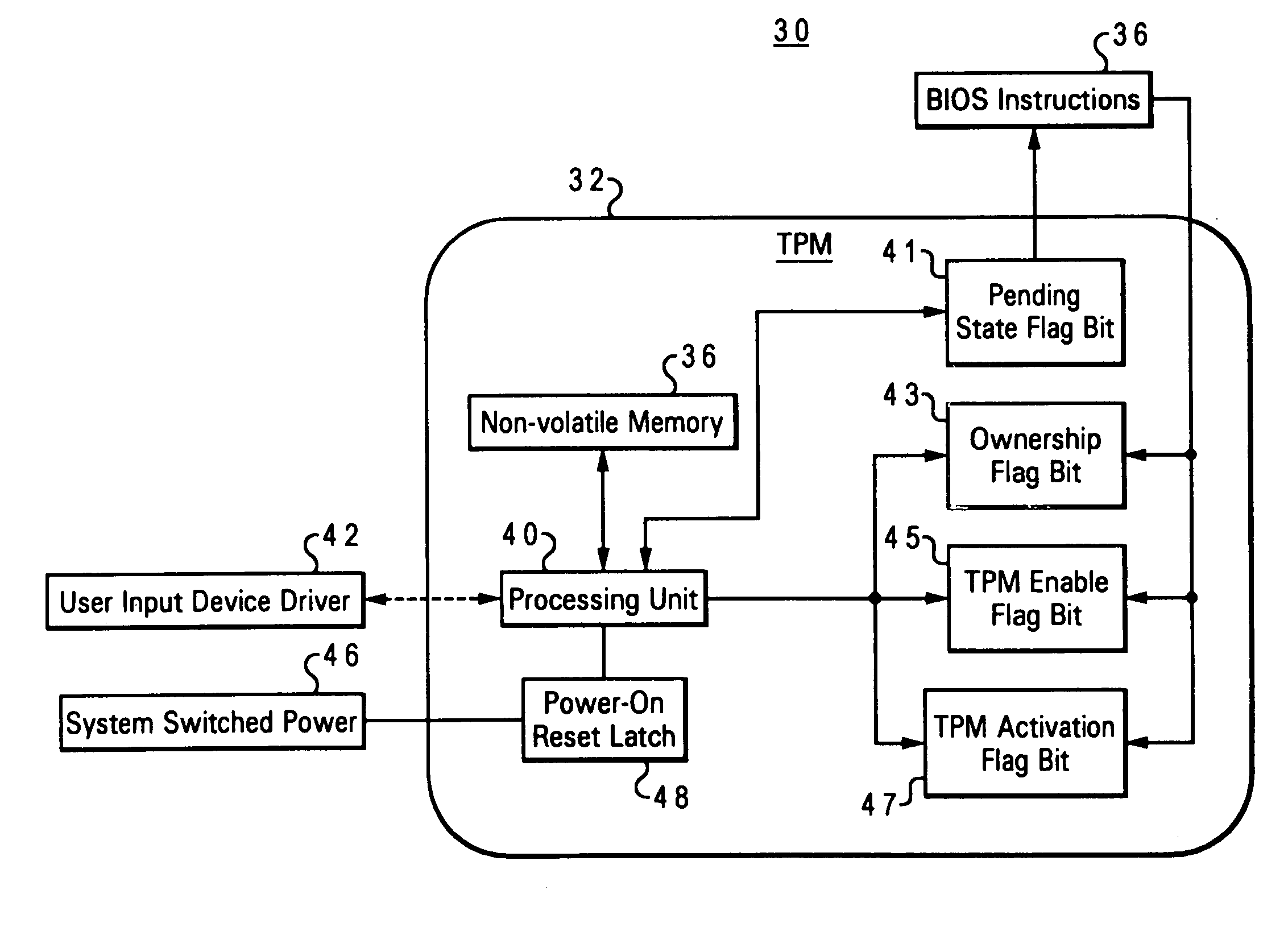
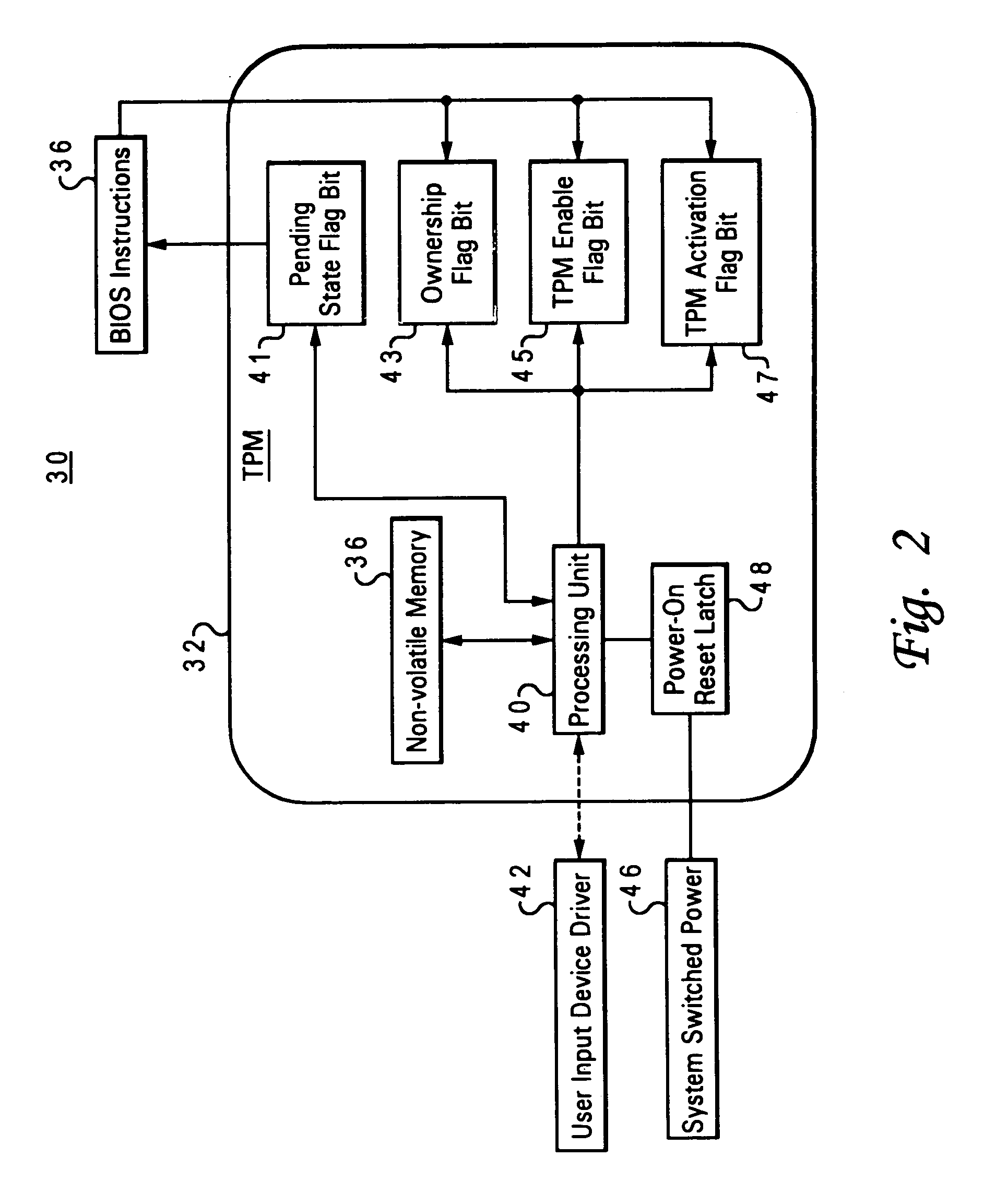
Method and system for securing enablement access to a data security device
ActiveUS7107460B2Digital data processing detailsUnauthorized memory use protectionData processing systemPower-on reset
An embedded security subsystem, and method for implementing the same, which provide secure controllability of a data security device within a data processing system. The embedded security subsystem of the present invention includes a persistent enable flag for providing control access to the data security device, wherein the persistent enable flag is accessible only in response to a power-on reset cycle of the data processing system. The persistent enable flag is read-only accessible to runtime program instructions. A pending state change flag that is write accessible by runtime program instructions is utilized for setting an intended next state of the persistent enable flag such that control access to the data security device is enabled only during a subsequent power-on reset of said data processing system.
Owner:MICROSOFT TECH LICENSING LLC
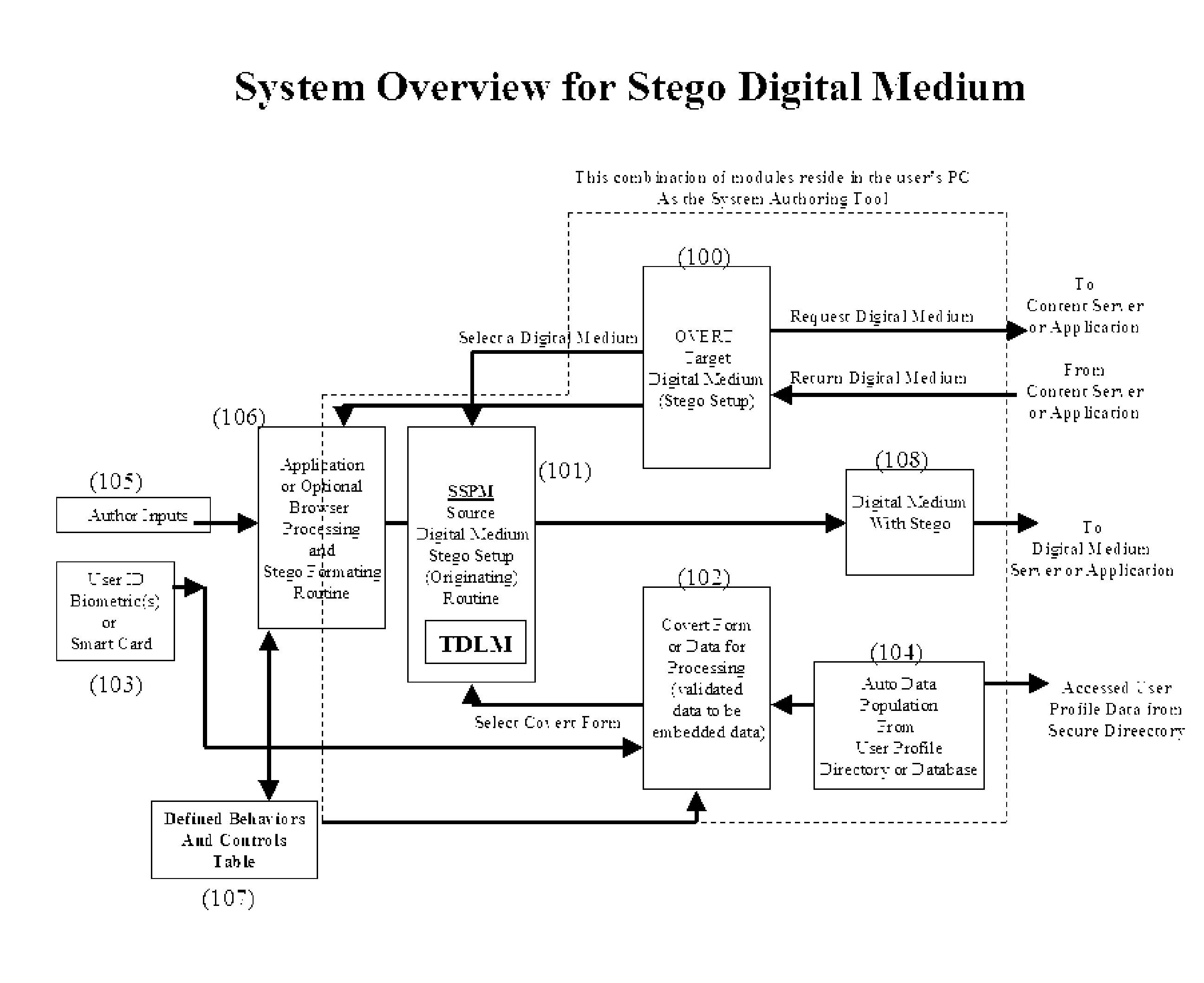
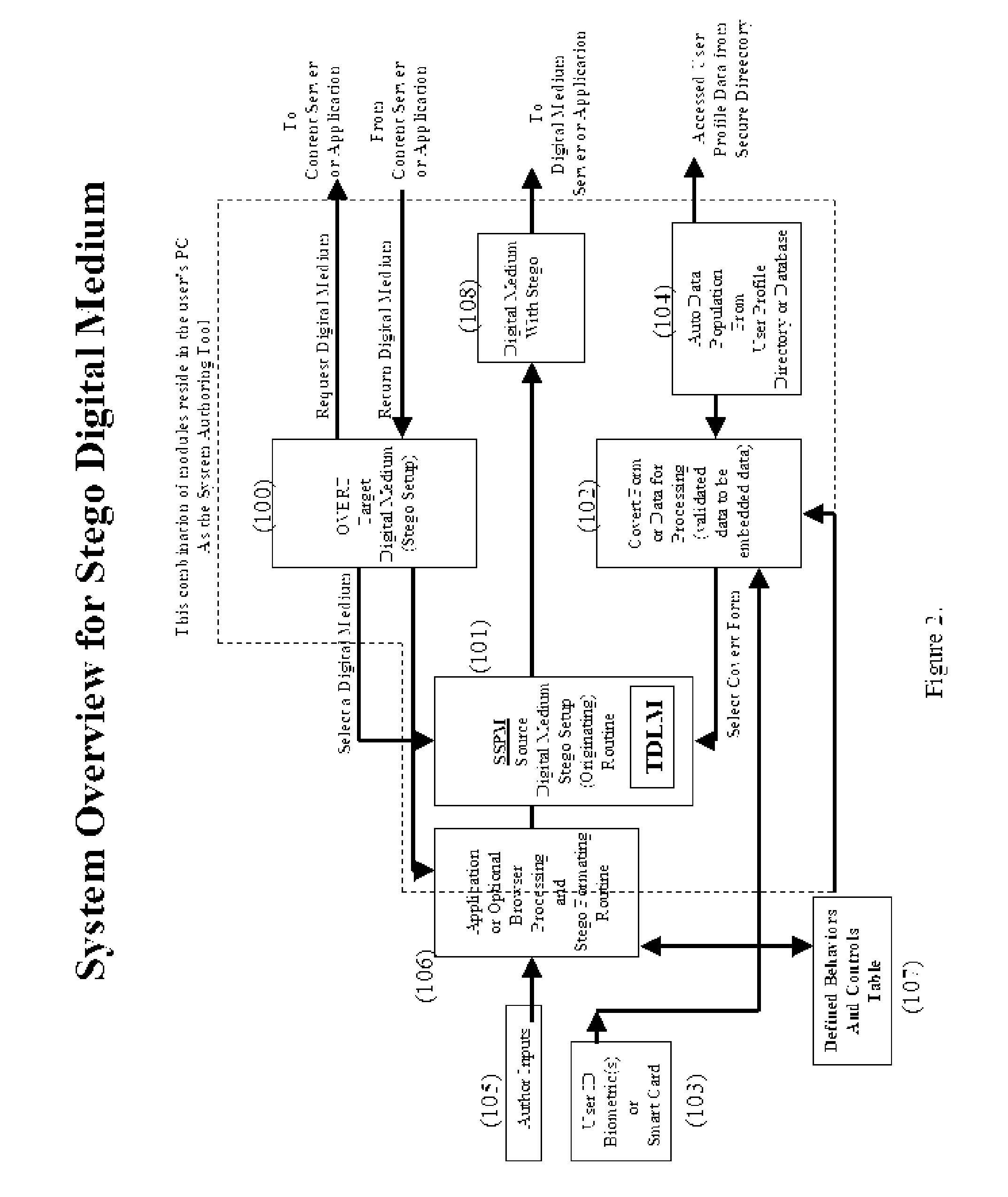
A system for embedding, extracting, and executing self-governing behavior and use controls within digital medium content
InactiveUS20060177094A1Improve securityCharacter and pattern recognitionOffice automationEmbedded securityBehavior control
Steganography is the art of hiding information within information. The hidden information is called “covert” and the carrier information is called “overt.” In the digital world, steganography as a security technique differs considerably from encryption, watermarking, or placing data within digital envelopes. This invention uses steganographic techniques to embedded hidden behaviors, controls, and security within content creating self-governance of the content itself. The hidden behaviors include who, what, when, where, and how content is to be used. The hidden controls govern what can be done with the content such as copied, stored, deleted, and archived. The hidden embedded security includes authentication of author, source, and user of the content. In effect, the content becomes “smart content” and does not require network-centric security controls allowing ubiquitous exchanges across enterprises. This invention renders content counterfeit resistant, one-of-a-kind and includes self-editing schema for multimedia applications.
Owner:SMITH MR ROBERT E +1
Process control system with an embedded safety system
ActiveCN1525271AEliminate structureSafety arrangmentsComputer controlEmbedded securityControl system
A process plant includes a safety system that is physically and logically integrated with a process control system such that the safety system and the process control system can use common communication, diagnostic and display hardware and software within the process plant while still providing functional isolation between the safety system controllers and the process control system controllers. This integrated process control and safety system uses a common data communication structure for both the safety system and the process control system so that applications can send data to and receive data from devices in either system in the same manner, e.g., using the same communication hardware and software. However, the common data communication structure is set up to distinguish process control system devices from safety system devices using tags, addresses or other fields within the messages sent to or received from the devices, which enables data associated with the process control system to be distinguishable from data associated with the safety system, thereby enabling a diagnostic application within a user interface to automatically treat this data differently depending on the source (or destination) of the data.
Owner:FISHER-ROSEMOUNT SYST INC
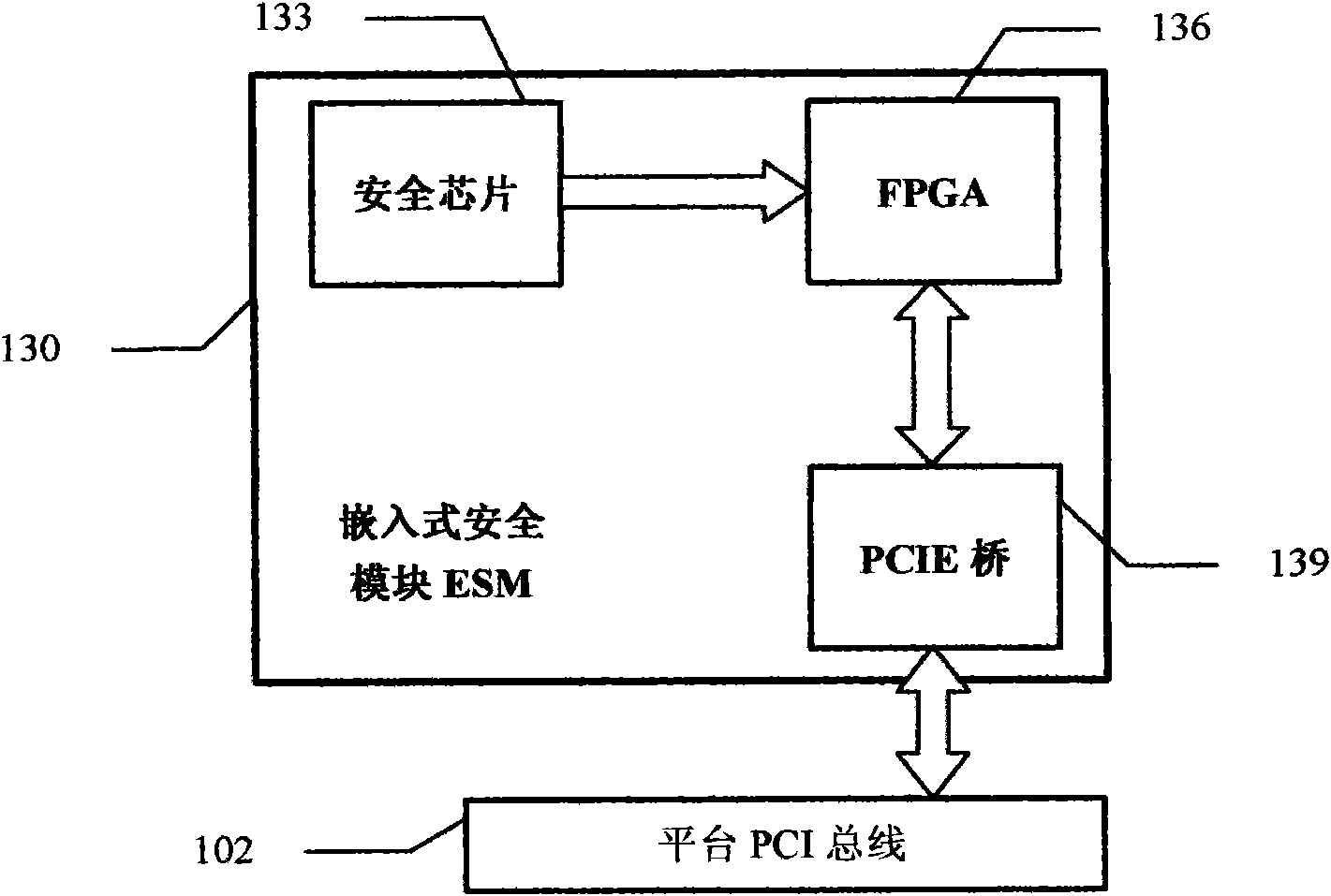
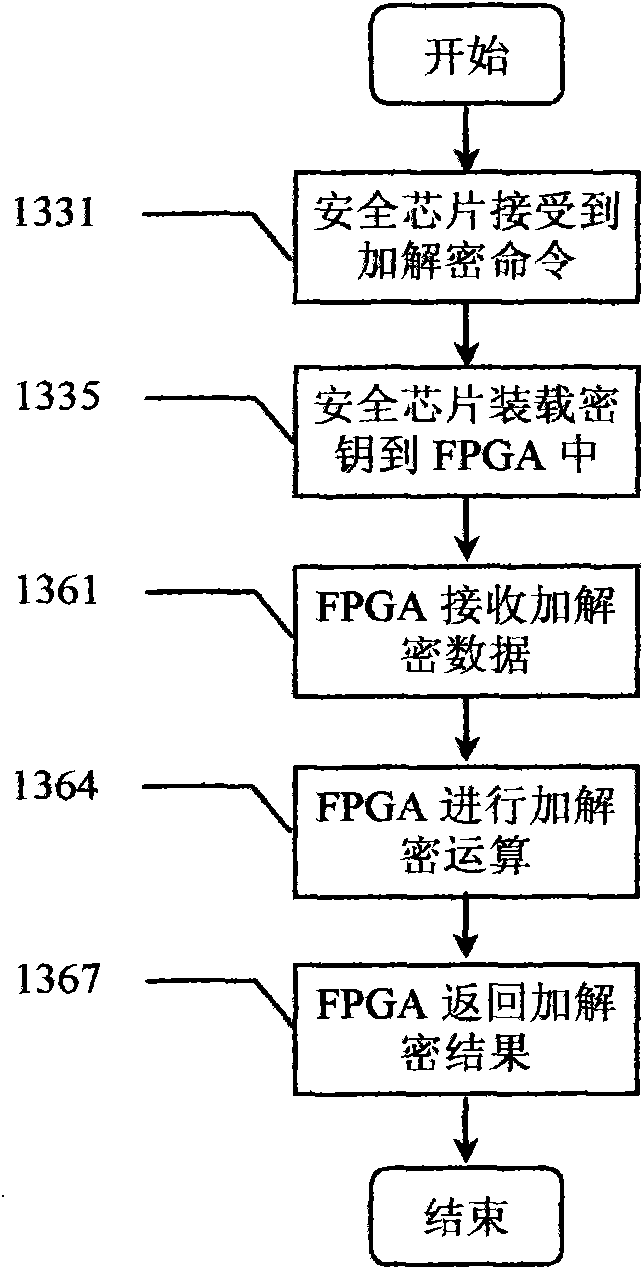
Creditable calculation password platform and realization method thereof
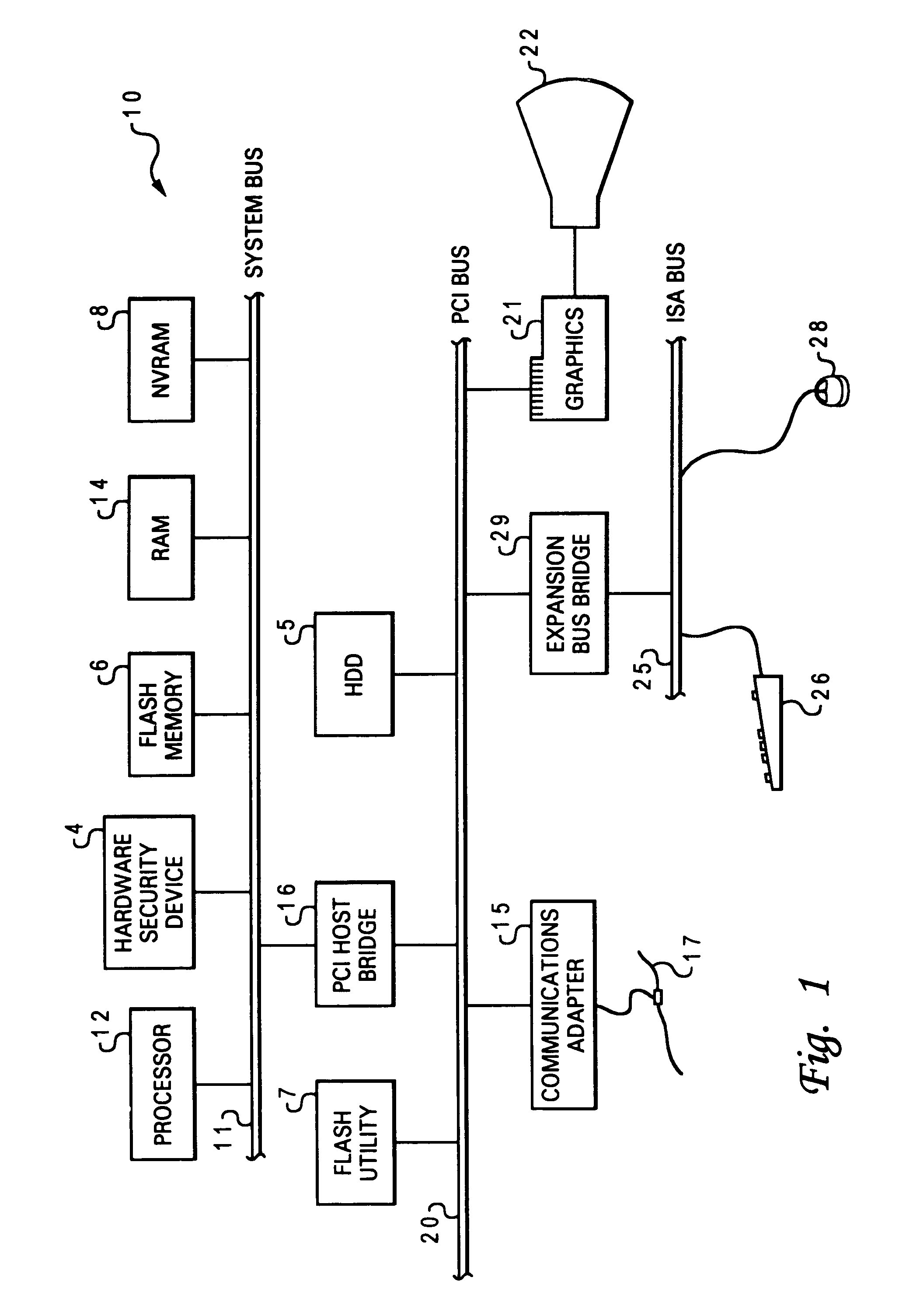
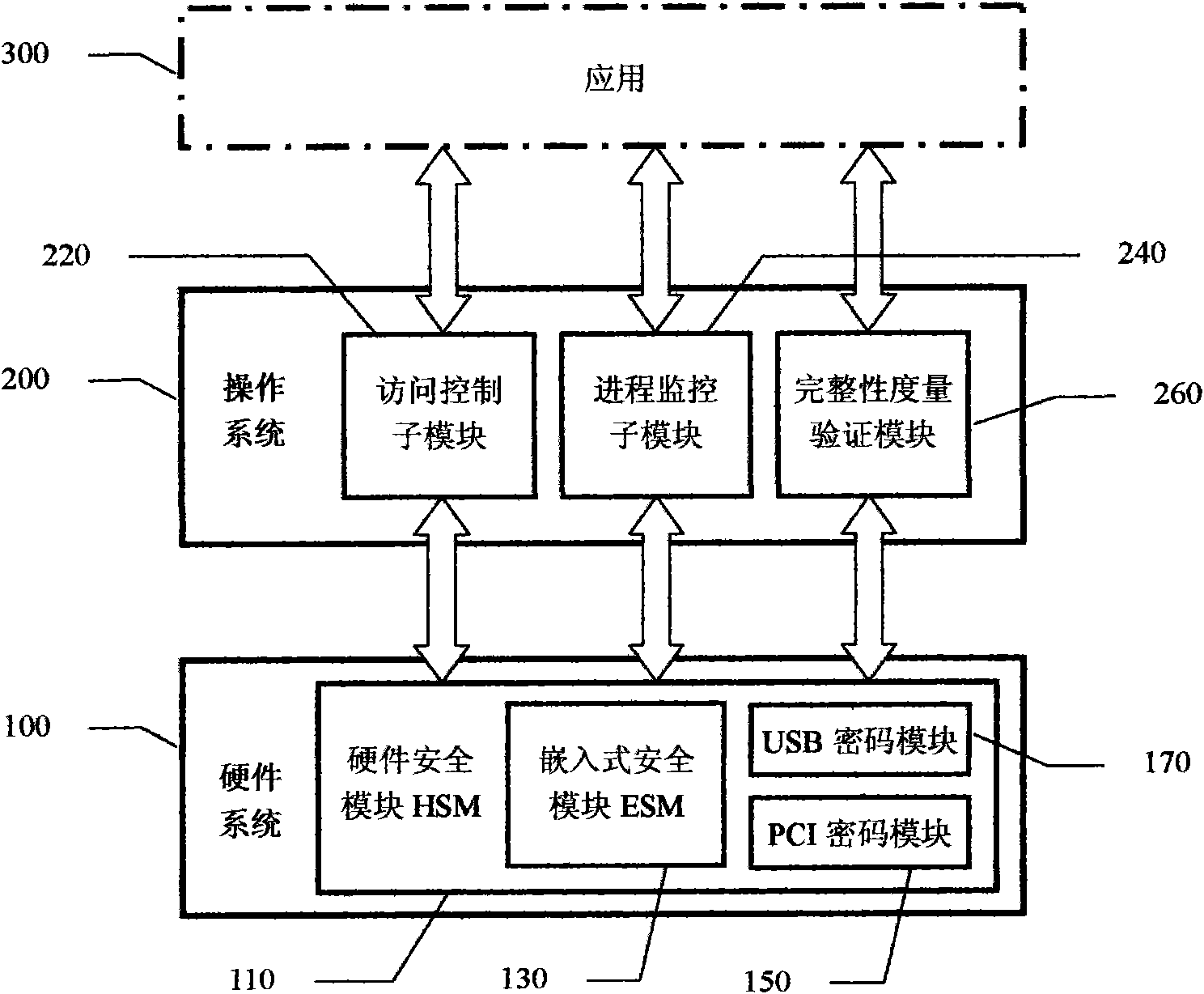
InactiveCN101650764AImprove securityImprove security strengthDigital data protectionEmbedded securityOperational system
The invention relates to a creditable calculation password platform and a realization method thereof, which belong to the technical field of computer safety. The creditable calculation password platform comprises a hardware system and an operation system, wherein the hardware system is connected with the operation system; the hardware system comprises a hardware safety module (HSM); the HSM is bound with the platform and the realization method thereof and comprises an embedded safety module (ESM) or / and an inserted and pulled USB / PCI password module which is connected to a main plate; and theoperation system is provided with an operation system safety module comprising a forced access control submodule, a progress monitoring submodule and an application program integrality measurement identification module. The invention has the advantages of increasing the application range of the creditable calculation password platform and the technique of the realization method thereof, increasingthe self attack resisting degree of the forced access control submodule, the progress monitoring submodule and the integrality measurement identification module, measuring the integrality of the whole platform and the realization method thereof, establishing the creditable environment of the whole platform and the realization method thereof and fully ensuring the benefit of a user of the platformand the realization method thereof.
Owner:瑞达信息安全产业股份有限公司
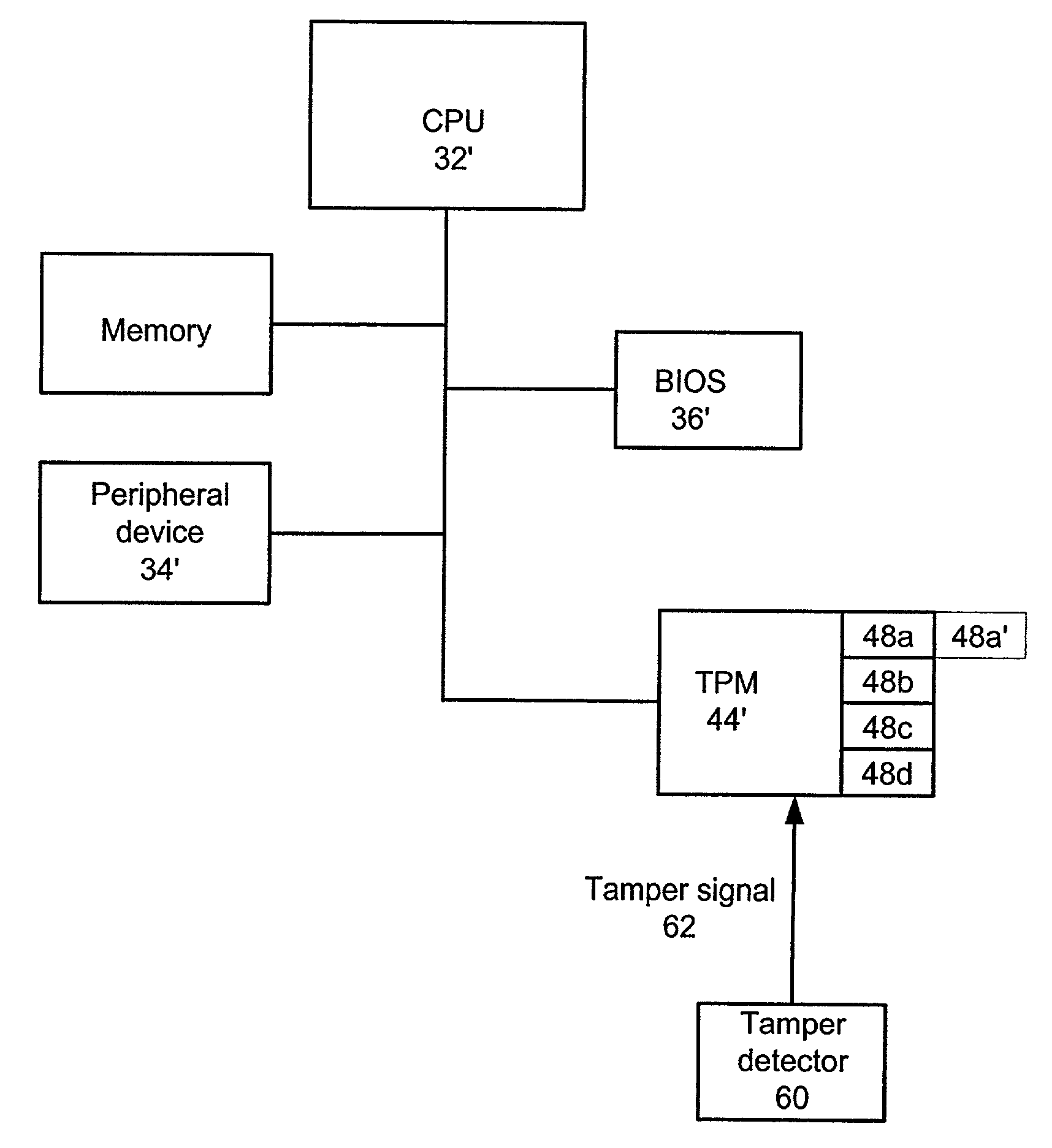
Method and system for detecting a tamper event in a trusted computing environment
InactiveUS7490250B2Capable of detectUser identity/authority verificationUnauthorized memory use protectionEmbedded securityOperational system
A method, system and computer readable medium containing programming instructions for detecting a tamper event in a computer system having an embedded security system (ESS), a trusted operating system, and a plurality of devices is disclosed. The method, system and computer readable medium of the present invention provide for receiving a tamper signal in the ESS, and locking the tamper signal in the ESS. According to the method, system and computer readable medium of the present invention, the trusted operating system is capable of detecting the tamper signal in the ESS.
Owner:LENOVO PC INT
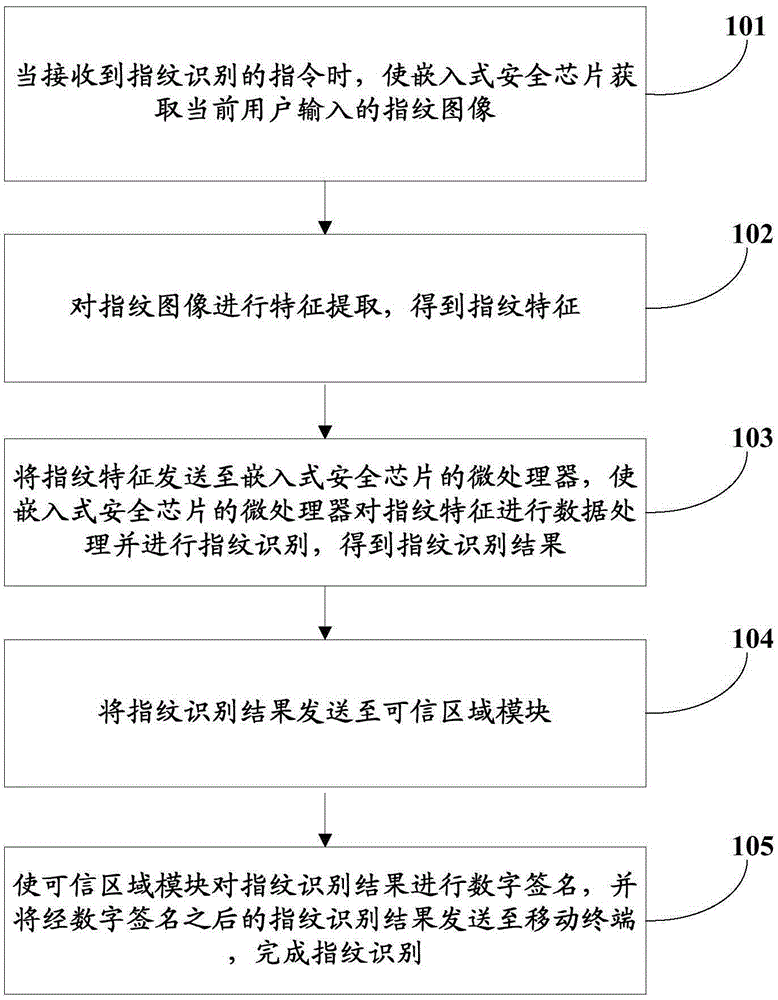
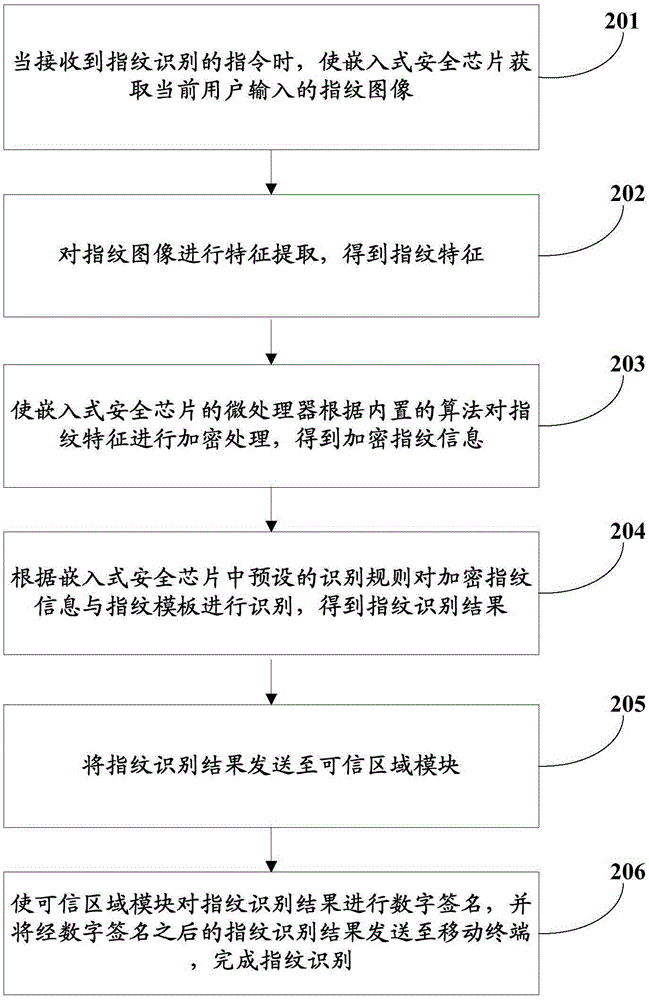
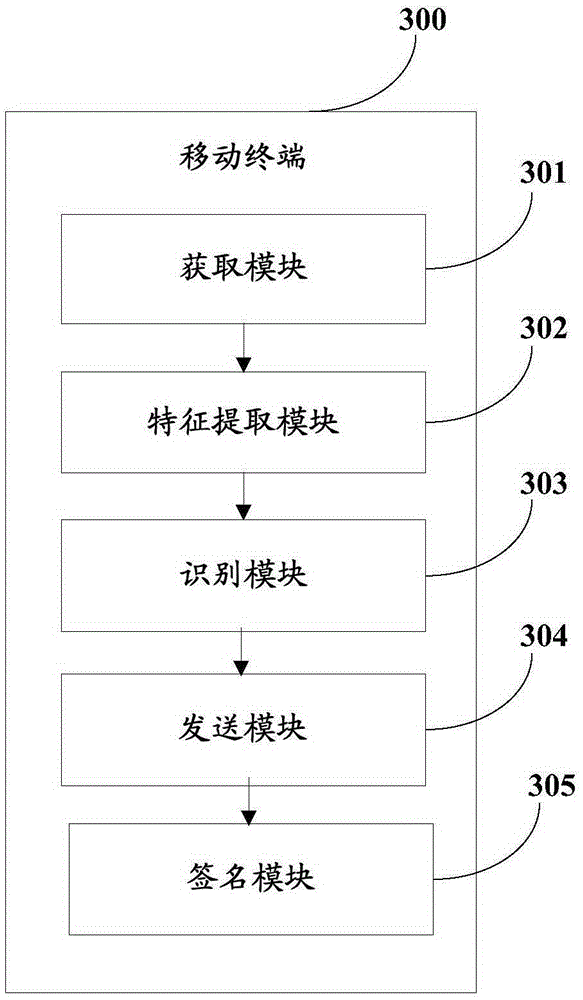
Fingerprint recognition method and mobile terminal
ActiveCN105354466ADo not reduce experienceImprove securityInternal/peripheral component protectionDigital data authenticationEmbedded securityFeature extraction
The invention provides a fingerprint recognition method and a mobile terminal. The method is applied to the mobile terminal which is provided with an embedded security chip and a confidence region module. The method comprises the following steps of: enabling the embedded security chip to acquire a fingerprint image input by a current user when receiving a fingerprint recognition instruction; performing feature extraction on the fingerprint image so as to obtain fingerprint features; sending the fingerprint features to a microprocessor of the embedded security chip and enabling the microprocessor of the embedded security chip to perform data processing and fingerprint recognition on the fingerprint features, so as to obtain a fingerprint recognition result; enabling the embedded security chip to send the fingerprint recognition result to the confidence region module; and enabling the confidence region module to perform digital signature on the fingerprint recognition result, then sending the fingerprint recognition result subjected to digital signature to the mobile terminal, thereby finishing fingerprint recognition. According to the fingerprint recognition method and the mobile terminal, a fingerprint recognition process is maliciously tampered.
Owner:维沃移动通信(深圳)有限公司
POS (Point Of Sale) system based on cloud middleware
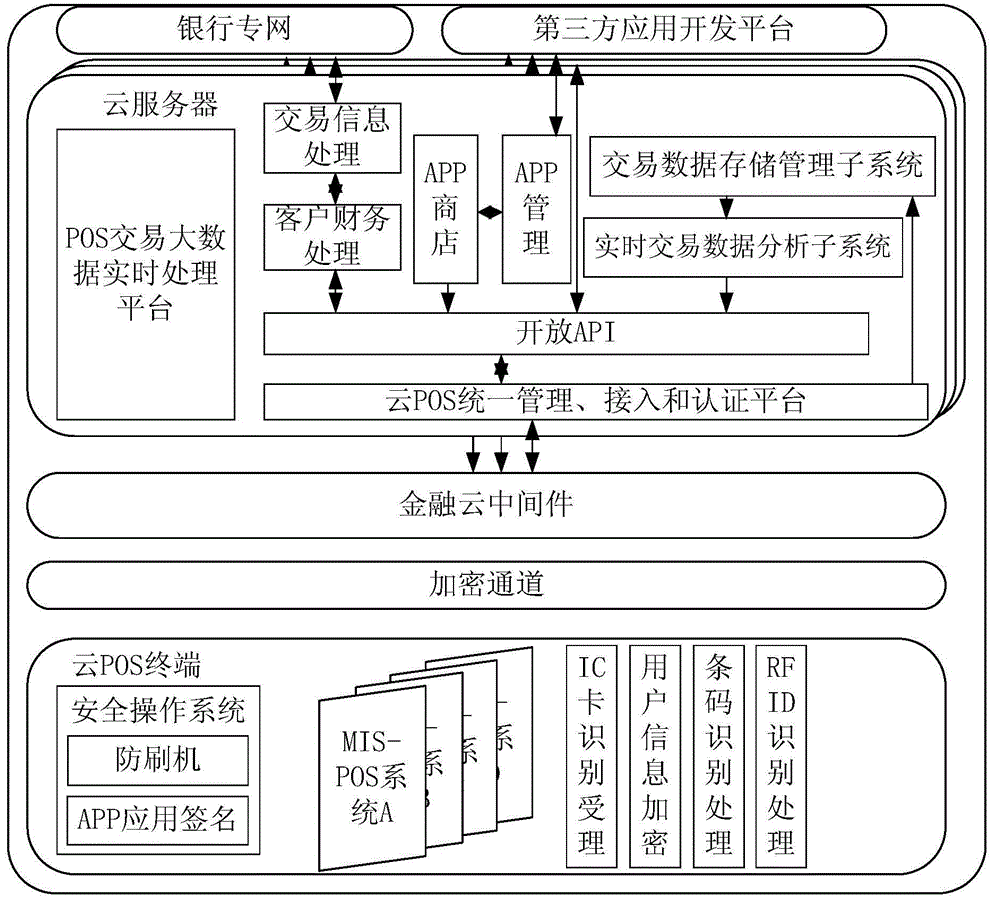
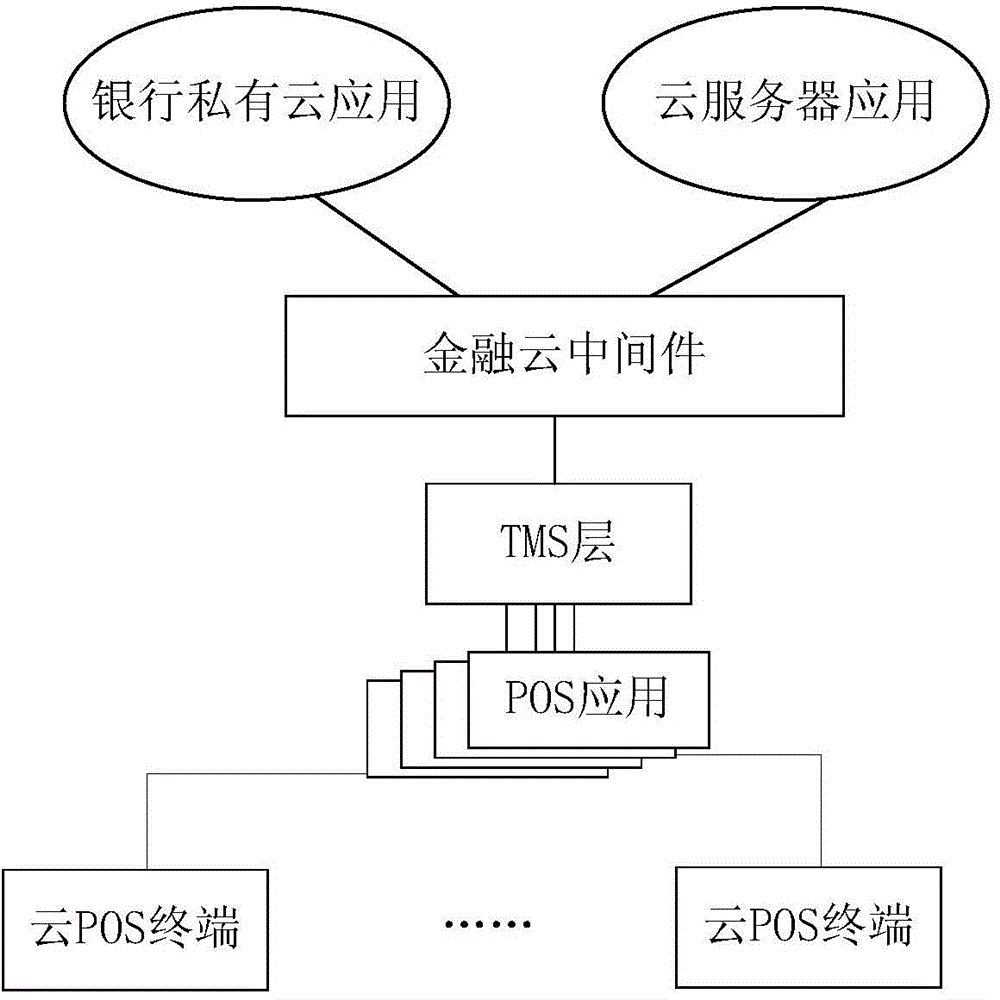
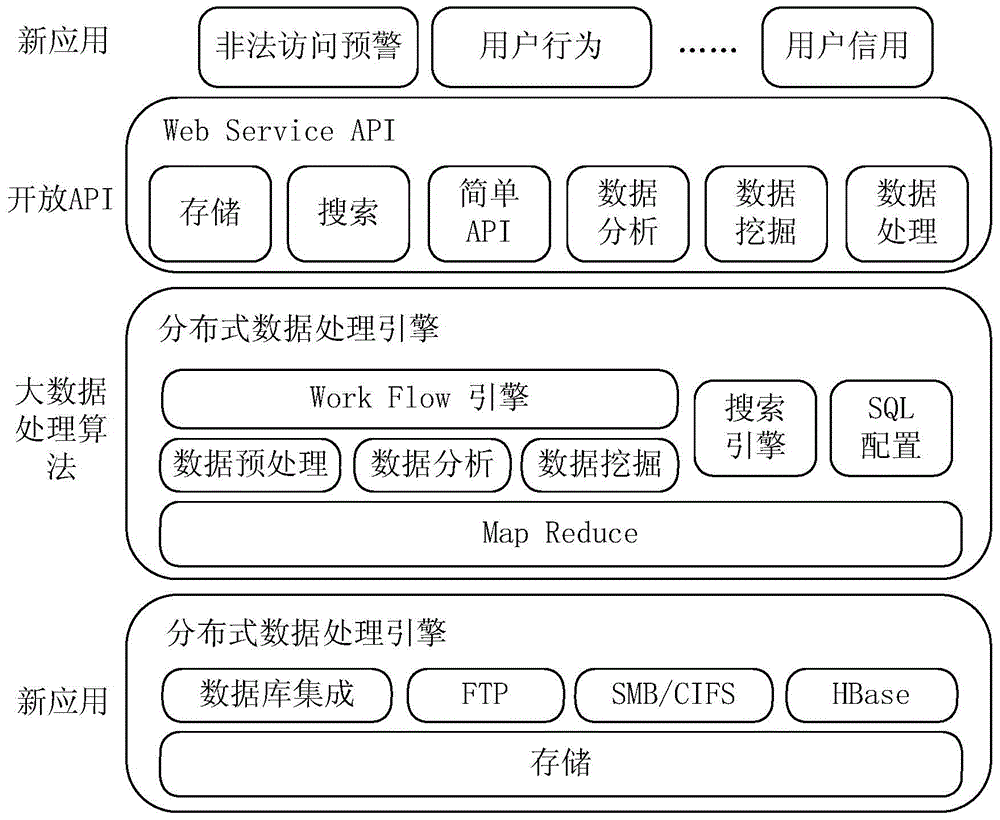
ActiveCN104158882AImprove function extensionVersatileTransmissionPoint-of-sale network systemsEmbedded securityData acquisition
The invention discloses a POS (Point Of Sale) system based on a cloud middleware. The POS system comprises a cloud POS terminal, an encrypted tunnel, a financial cloud middleware and a cloud server, wherein the cloud POS terminal is provided with an embedded safety operation system for configuring user account information, and inputting and displaying user consumption information; the cloud POS terminal is provided with a third-party application; the encrypted tunnel is used for encrypting the data; the financial cloud middleware is used for implementing data exchange between the cloud server and the cloud POS terminal through protocol conversion and standard conversion; the cloud server is provided with a POS transaction big data real-time processing platform for carrying out data acquisition sharing, data integration, distributed retrieval, load balancing and data management on the data received by the cloud server; a data processing result of the POS transaction big data real-time processing platform is transmitted to the cloud POS through the third-party application. According to the POS system, function extension of the POS terminal is improved to provide more complete functions for financial service.
Owner:SUNYARD SYST ENG CO LTD
Solid-color embedded security feature
ActiveUS20070248364A1Revealing the latent imageRecording apparatusPaper-money testing devicesEmbedded securityLatent image
A latent image is incorporated into an apparent solid-color background for representing a desired solid-color background having a target color. An underlying solid-color background is printed on a print medium using a first color composition that differs from the target color. Line-screen patterns embedding a latent image in a visually integrated setting are printed over the solid-color background using a second color composition that differs from both the first color composition and the target color. The visual characteristics of the line-screen patterns forming the latent image and the visually integrated setting are matched for rendering the latent image practically indistinguishable from the visually integrated setting without a visual aid. The print densities of the line-screen patterns and the first and second color compositions are interrelated so that the line-screen patterns in combination with the underlying solid-color background produce the apparent solid-color background in the target color.
Owner:PROOF AUTHENTICATION CORP
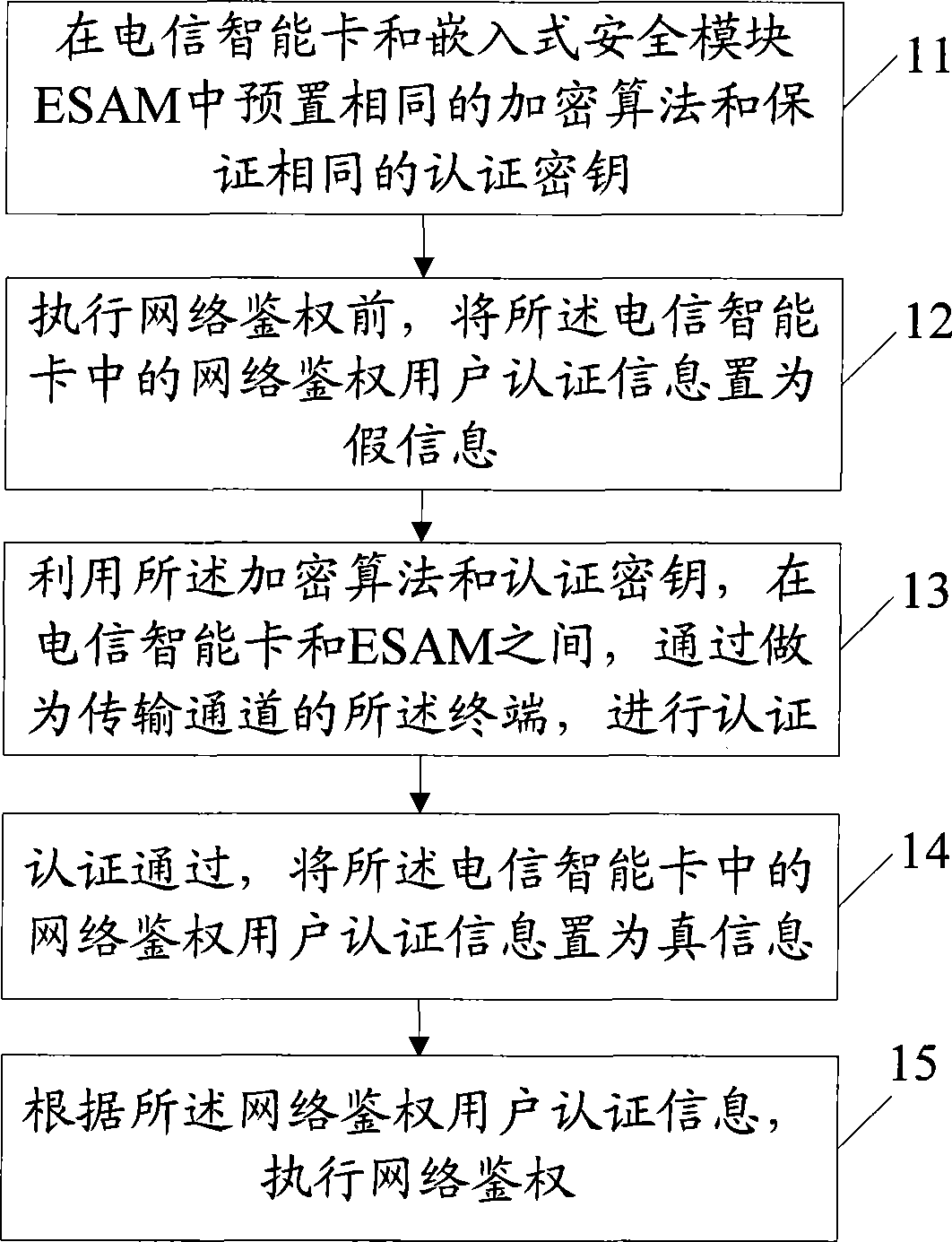
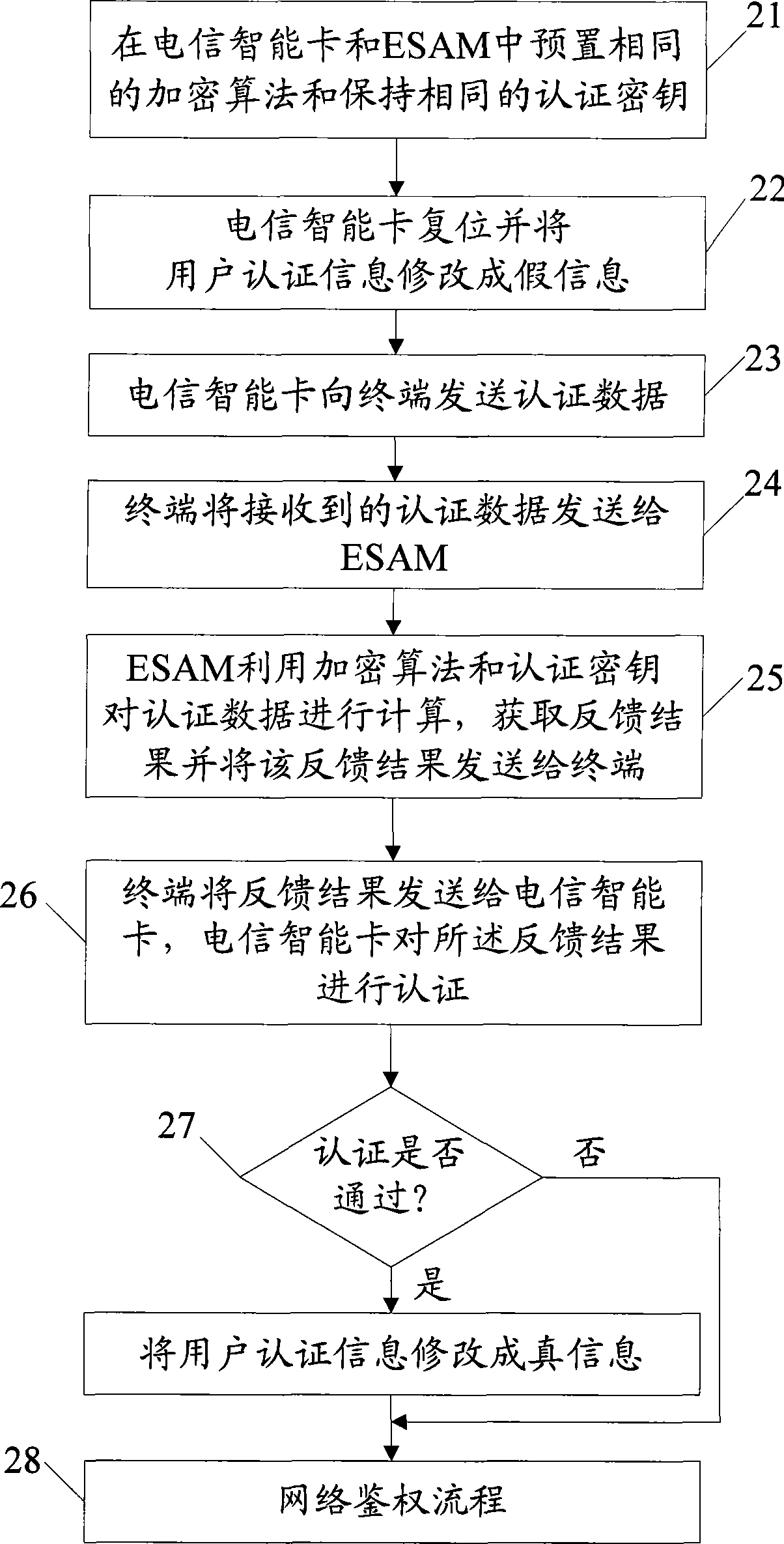
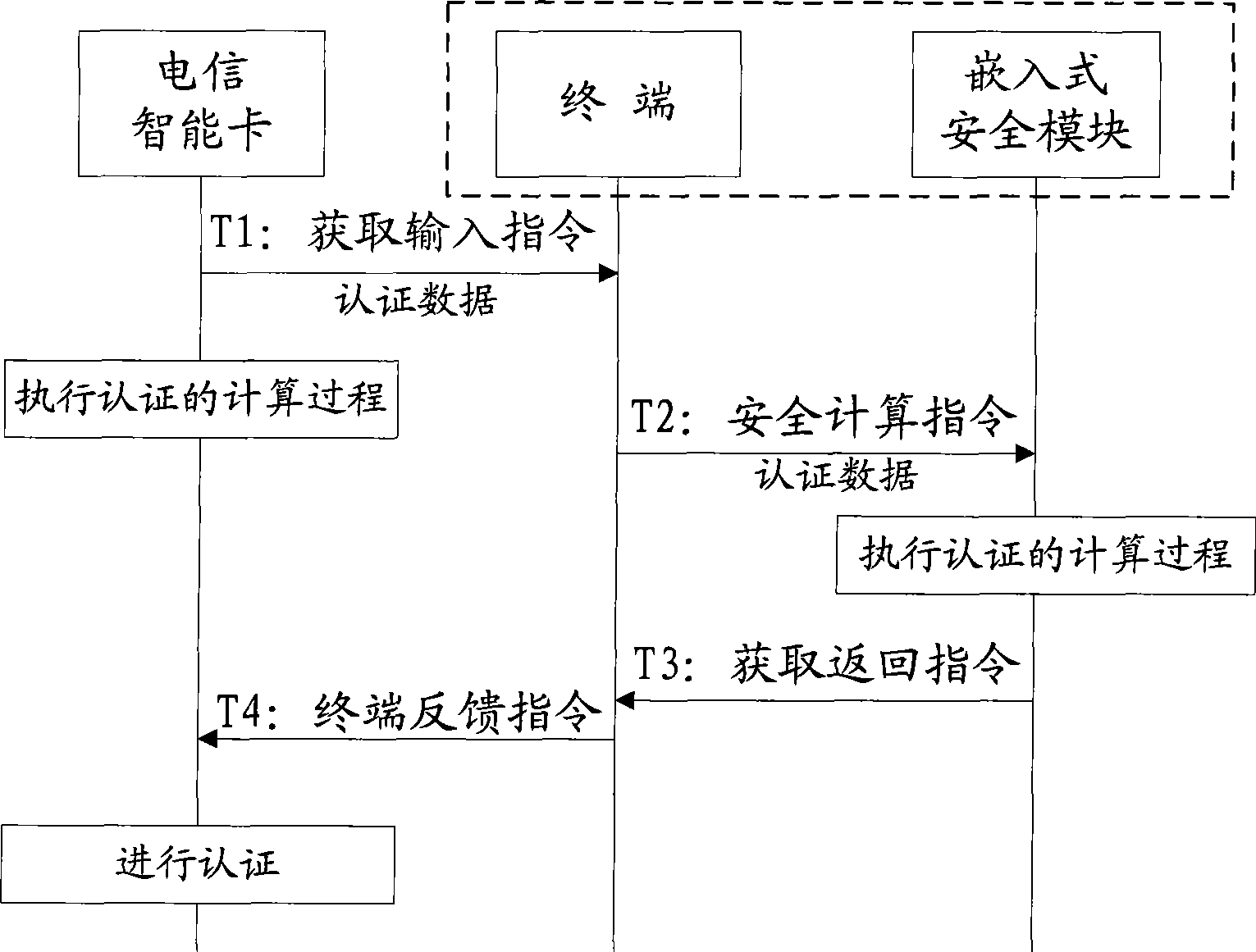
Authentication method and terminal for telecom smart card
The invention discloses an authentication method of a telecommunication intelligent card and a terminal thereof which relate to the data security field. The method and the terminal can prevent a wireless business phone and the telecommunication card of a wireless public phone from embezzling by the unwarranted terminal, and avoid telephone expenses running off. The method includes steps as follows: preplacing a same encryption arithmetic and an authentication key ensuring same on the telecommunication intelligent card and an embedded type safe module ESAM, the embedded type safe module locates in the terminal; placing the network authentication user authentication information as a false information before executing the network authentication; processing authentication through the terminal as a transmitting channel between the telecommunication intelligent card and ESAM by using the encrypting arithmetic and the authentication key; if passing through authentication, placing the network authentication user authentication information as a true information of the telecommunication intelligent card; executing network authentication according with the network authentication user authentication information.
Owner:BEIJING WATCH DATA SYST
Method utilizing embedded safety element to realize safety protection for SIM card data
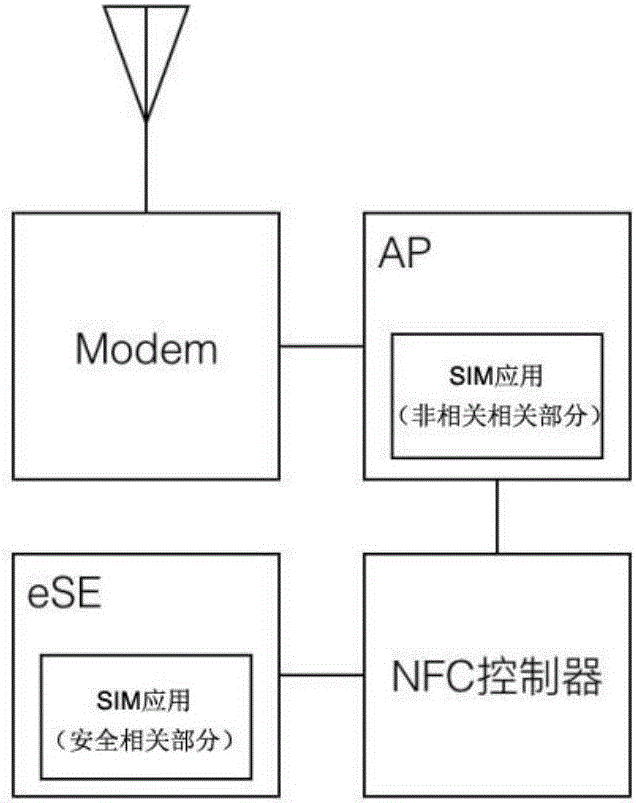
ActiveCN106658474ARealize security protectionImprove performanceKey distribution for secure communicationSecurity arrangementEmbedded securityModem device
The invention provides a method utilizing an embedded safety element to realize safety protection for SIM card data. According to the method, an SIM application is divided through employing the embedded safety element into a safety related portion and a non-safety related portion to realize an virtual SIM card; the virtual SIM card is utilized by a modem according to an instruction of an application processor to interact with a network side through an air interface; an instruction supposed to be sent to a physical SIM card is sent to the application processor; safety protection processing and non-safety protection processing are carried out by the application processor according to safety attributes of the instruction. The method is advantaged in that the embedded safety element (eSE) is taken as a storage and calculation entity of a safety function, on one hand, safety protection for the SIM card data is realized, on the other hand, functions of the non-safety related portion can be processed through utilizing application processor software, and performance and flexibility are relatively improved.
Owner:上海优咔网络科技有限公司
User interface enhanced storage sled handle with embedded security features
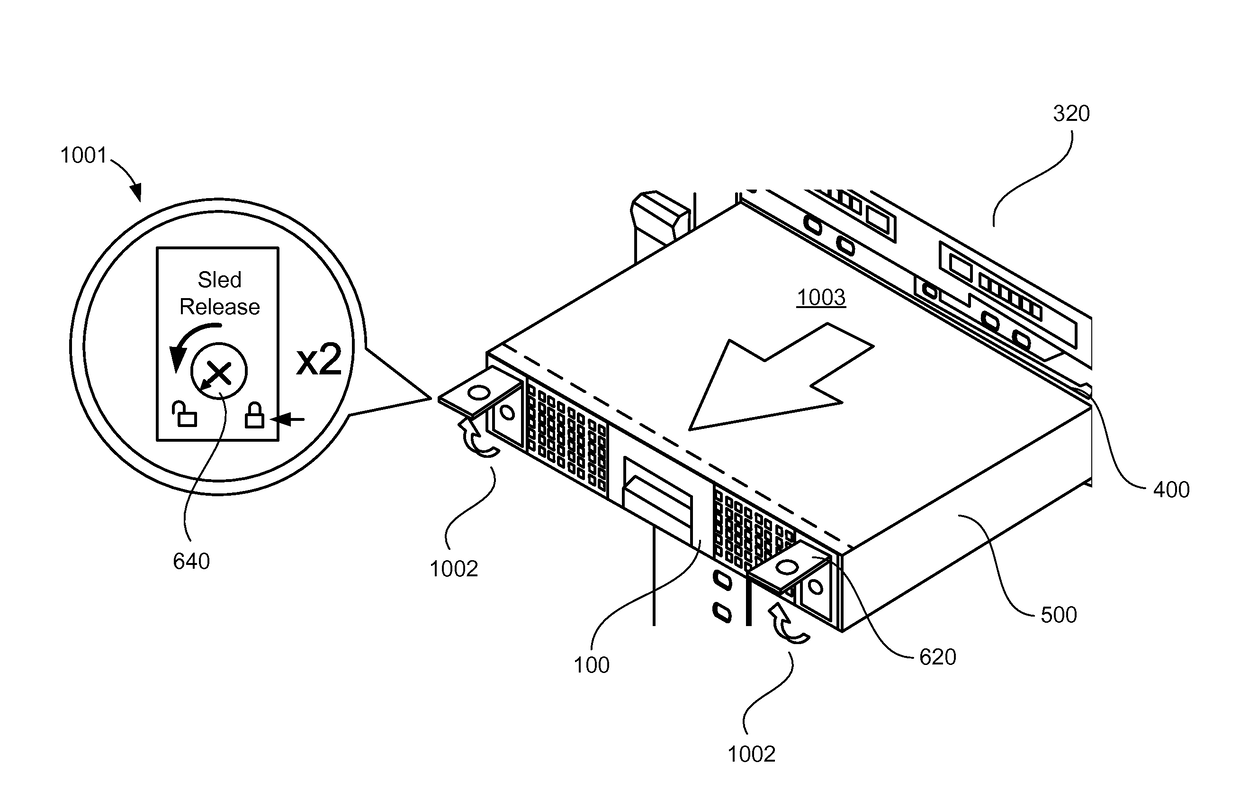
A latch for securing a compute sled into a chassis is provided. The latch includes a body with a user manipulable control, the body configured for mounting to a drawer of the compute sled, the user manipulable control configured for causing a slider to one of engage and disengage a deadbolt with a complimentary slot of a sleeve for containing the drawer, the latch further configured for engaging a retention element of the chassis.
Owner:DELL PROD LP
Short-distance wireless communication node and wireless communication method
InactiveCN102685740APrevent unauthorized accessStrengthen the basic conditionsKey distribution for secure communicationSecurity arrangementEmbedded securityData stream
The invention discloses a short-distance wireless communication node and a wireless communication method. The short-distance wireless communication node acquires a plurality of types of sensing information or accesses a universal bus to form a self-organization communication network with security identification and encryption functions. The short-distance wireless communication node is mainly characterized in that an embedded security algorithm coprocessor is installed on hardware to allow wireless node equipment to have low-power-consumption and high-speed encryption and decryption calculation capacities of performing a complicated algorithm such as Rivest-Shamir-Adleman (RSA), error checking and correcting (ECC) and advanced encryption standard (AES), thereby improving wireless network access identification and data stream encryption and decryption, and improving the information security of a network is through hardware enhancement. According to the functions of a wireless network, the short-distance wireless communication node can serve as front-end acquisition equipment as well as routing equipment and gathering equipment; and as being externally provided with a plurality of universal bus interfaces, the short-distance wireless communication node can be conveniently connected with the conventional security protection sensor or network, so that the security and the credibility of the conventional system during wireless communication expansion are improved to adapt to applications with relatively high security level demands. The short-distance wireless communication node can be applied to the security protection fields of fire prevention, theft prevention, intelligent monitoring and the like.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com