Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
152 results about "Safety rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The safety-first rule involves creating a minimum acceptable return, or threshold return. By fixing a threshold return, an investor aims to reduce the risk of not achieving the investment return. The safety-first rule, also called Roy's safety-first criterion (SFRatio), is a quantitative risk-management investment technique.
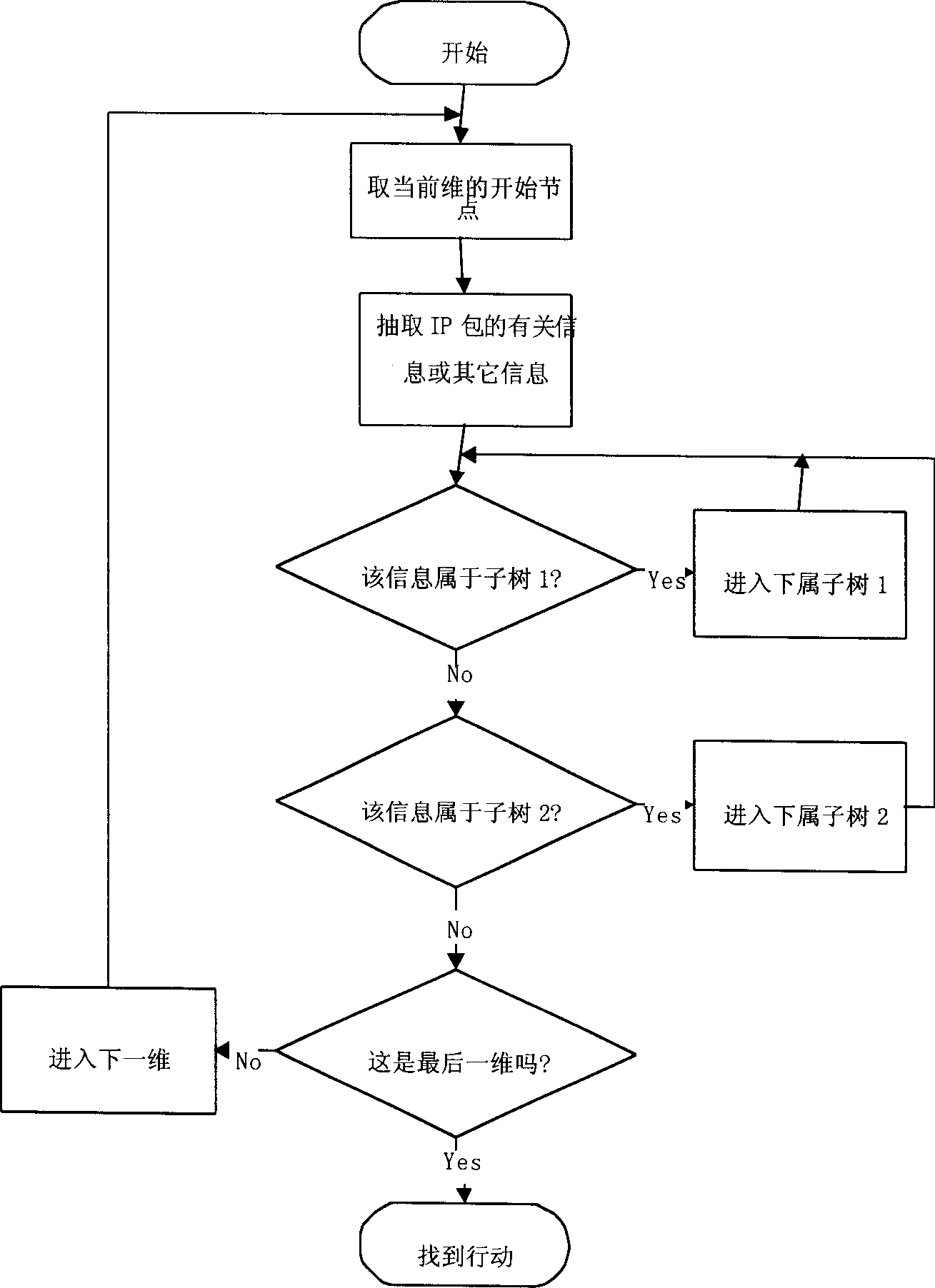
Method and apparatus for controlling a ventilator
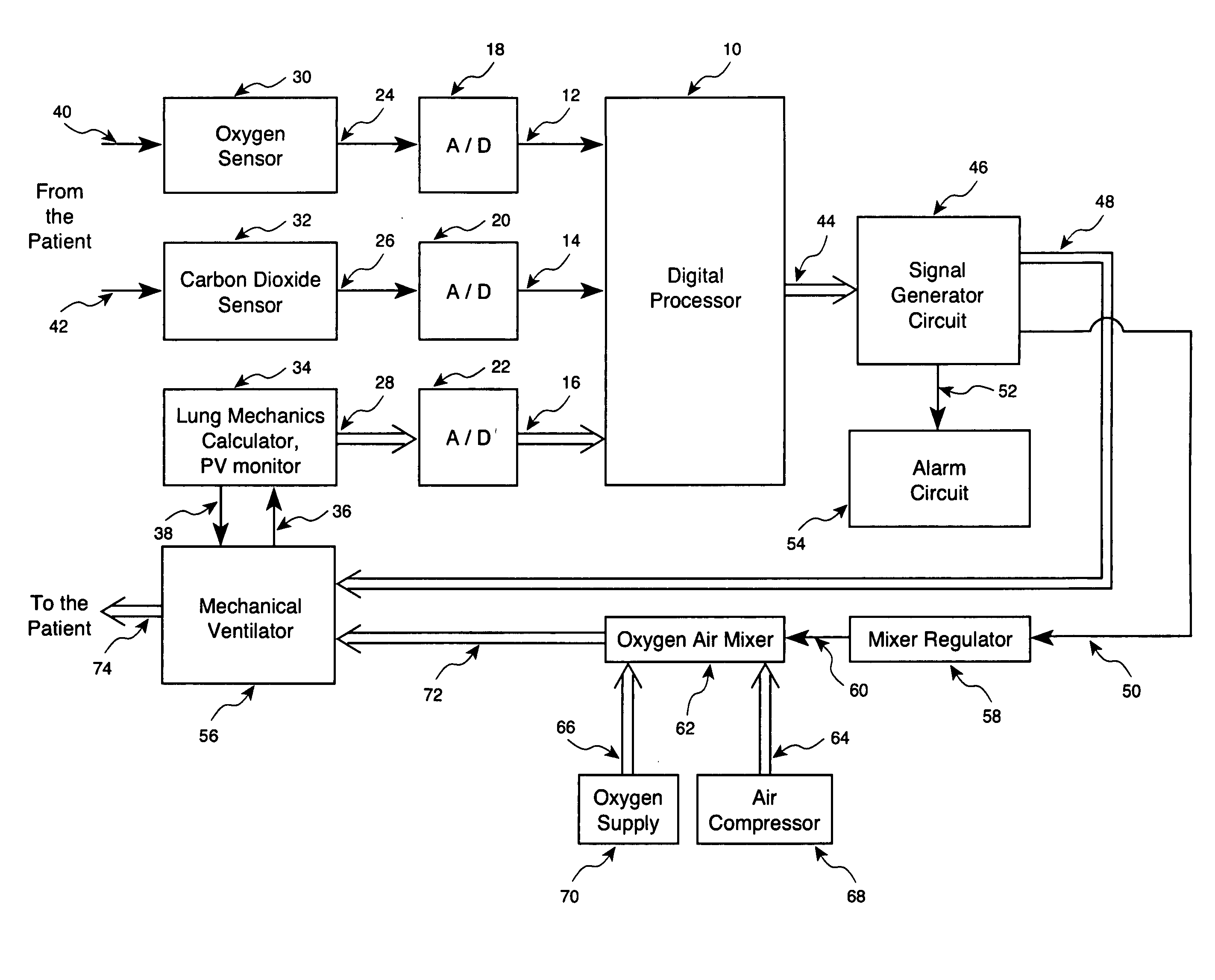
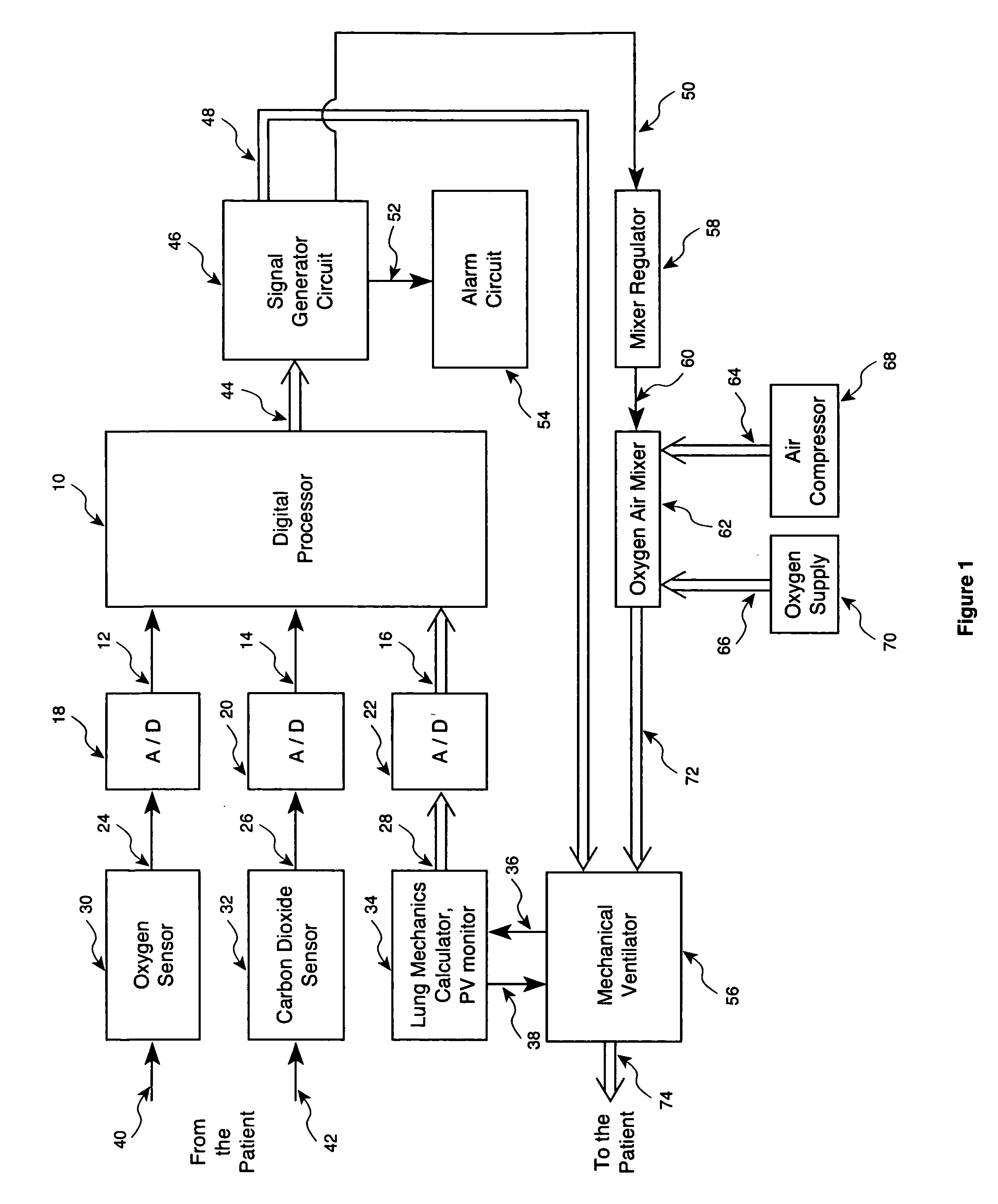
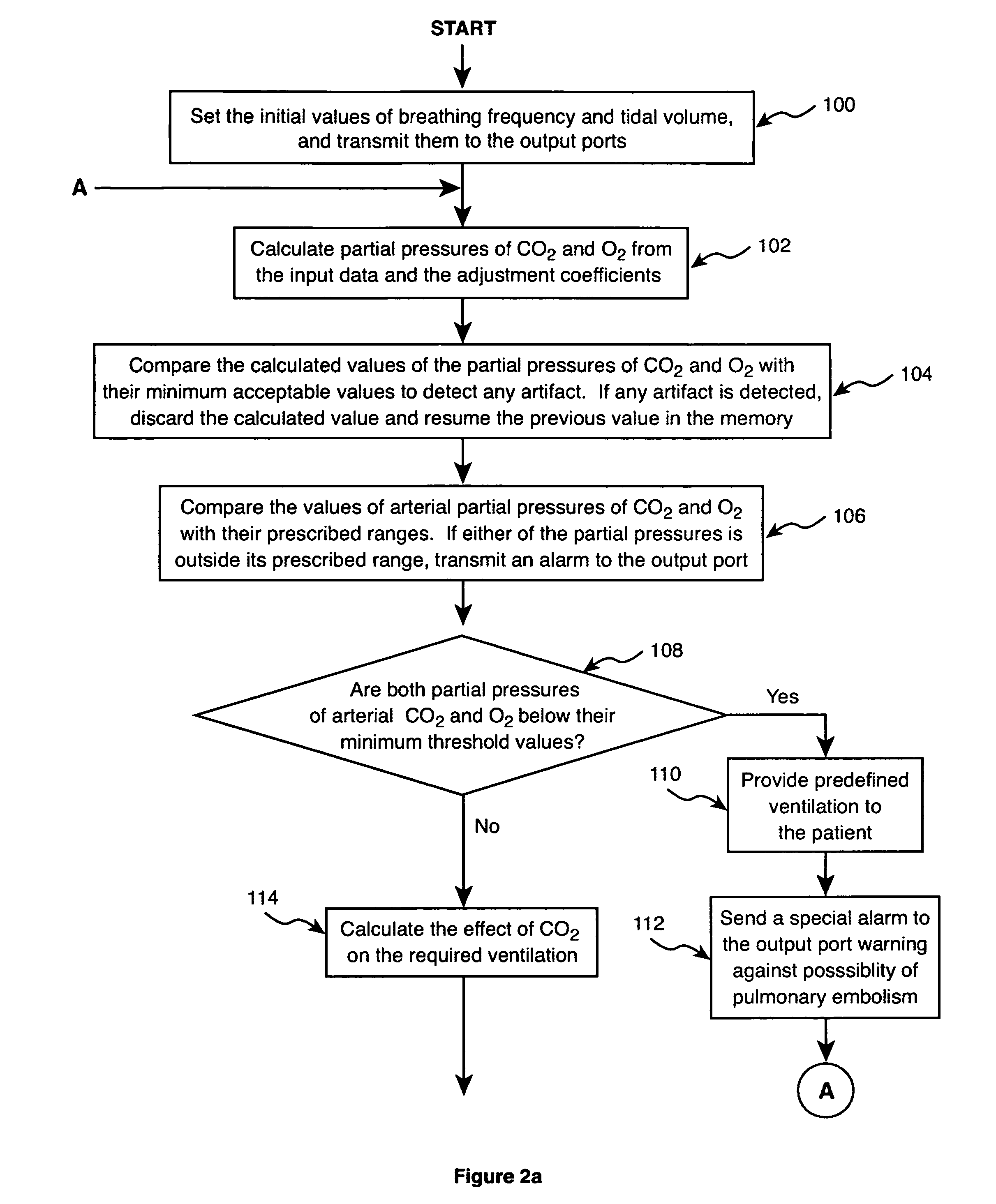
Method and apparatus for controlling a ventilator are described. The invention can be used to control mechanical ventilators as well as respiratory assist devices such as CPAP machines. The apparatus receives input data indicative of patient's oxygen level. A controller determines PEEP, or CPAP, and FIO2, on the basis of data indicative of the patient's oxygen level. In an alternative embodiment, the apparatus further receives input data indicative of patient's carbon dioxide levels, respiratory elastance and airway resistance, and barometric pressure. The controller further utilizes the said input data to determine the optimal values of tidal volume and breathing frequency for a next breath of the patient, and uses the respiratory elastance and airway resistance data to determine any necessary adjustments in the I:E ratio. The controller also applies safety rules, detects and corrects artifacts, and generates warning signals when needed.
Owner:TEHRANI FLEUR T
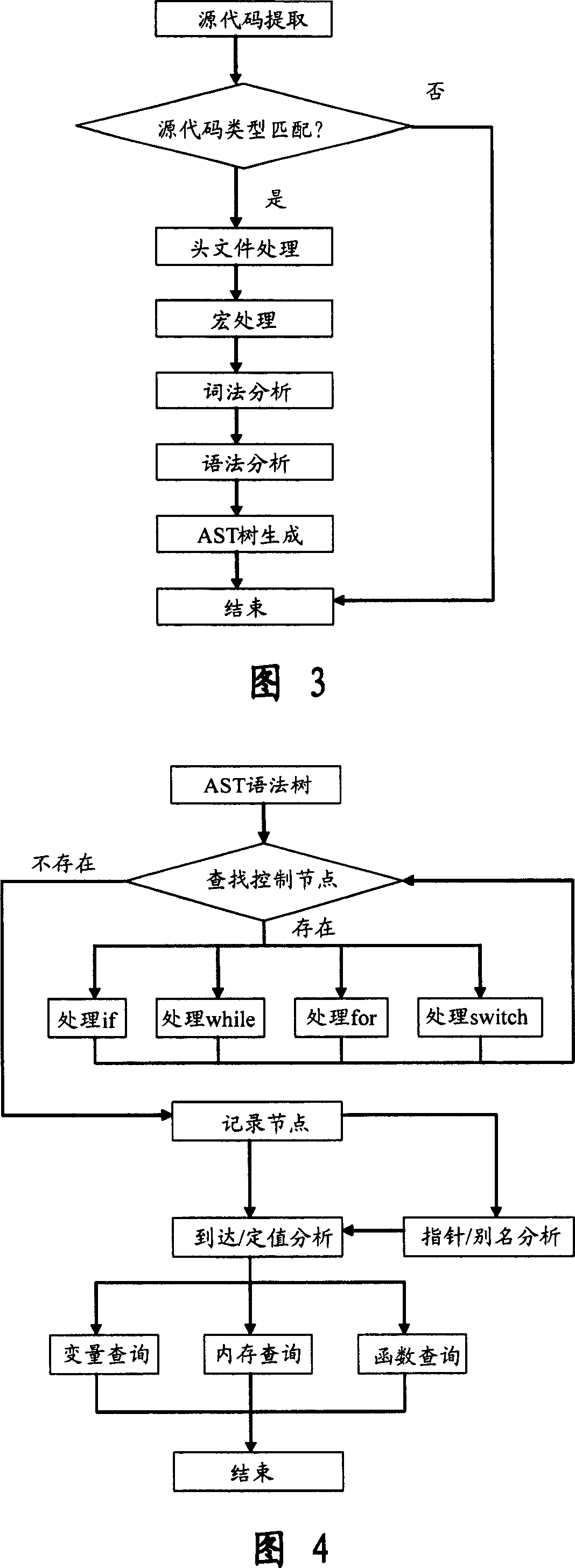
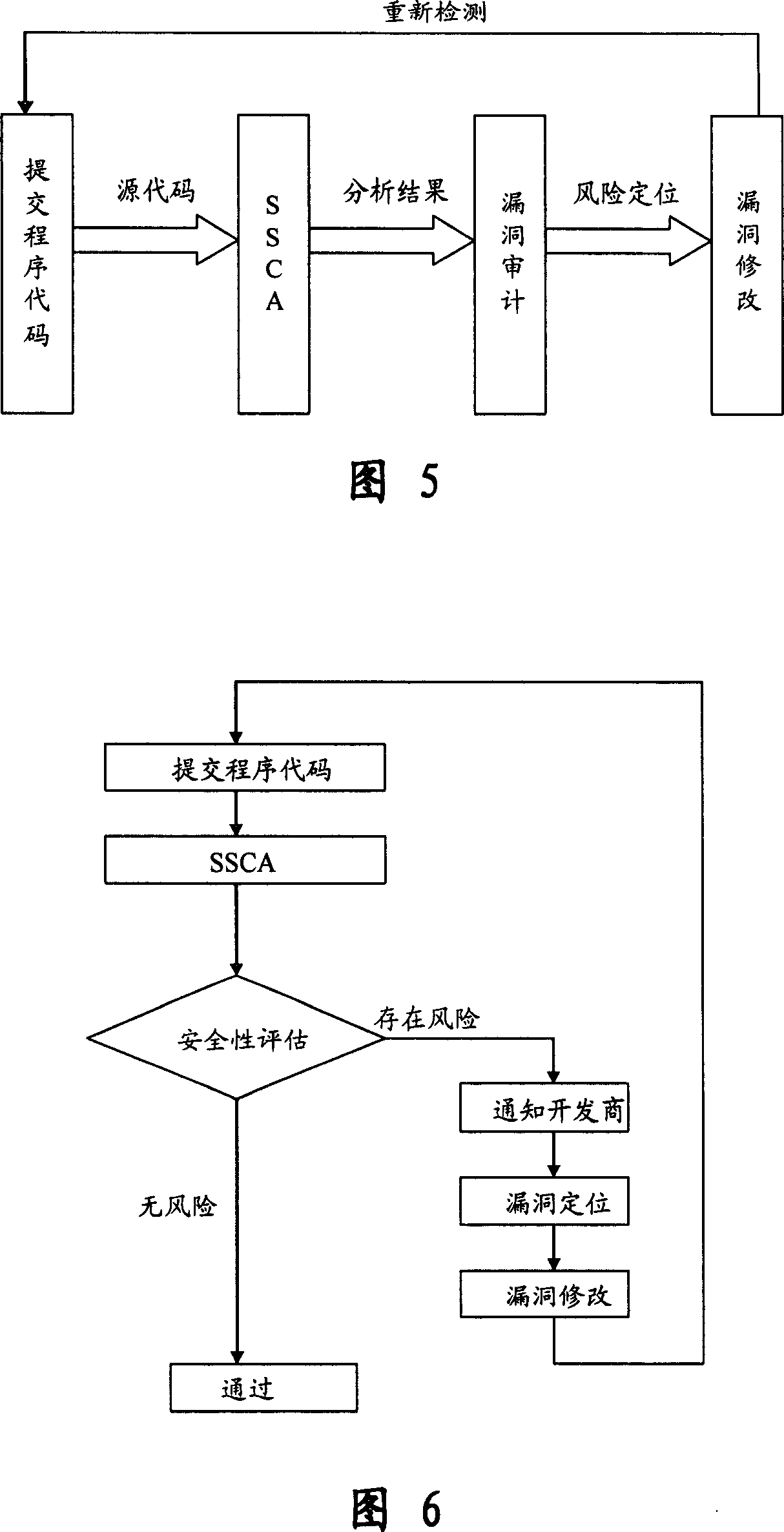
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
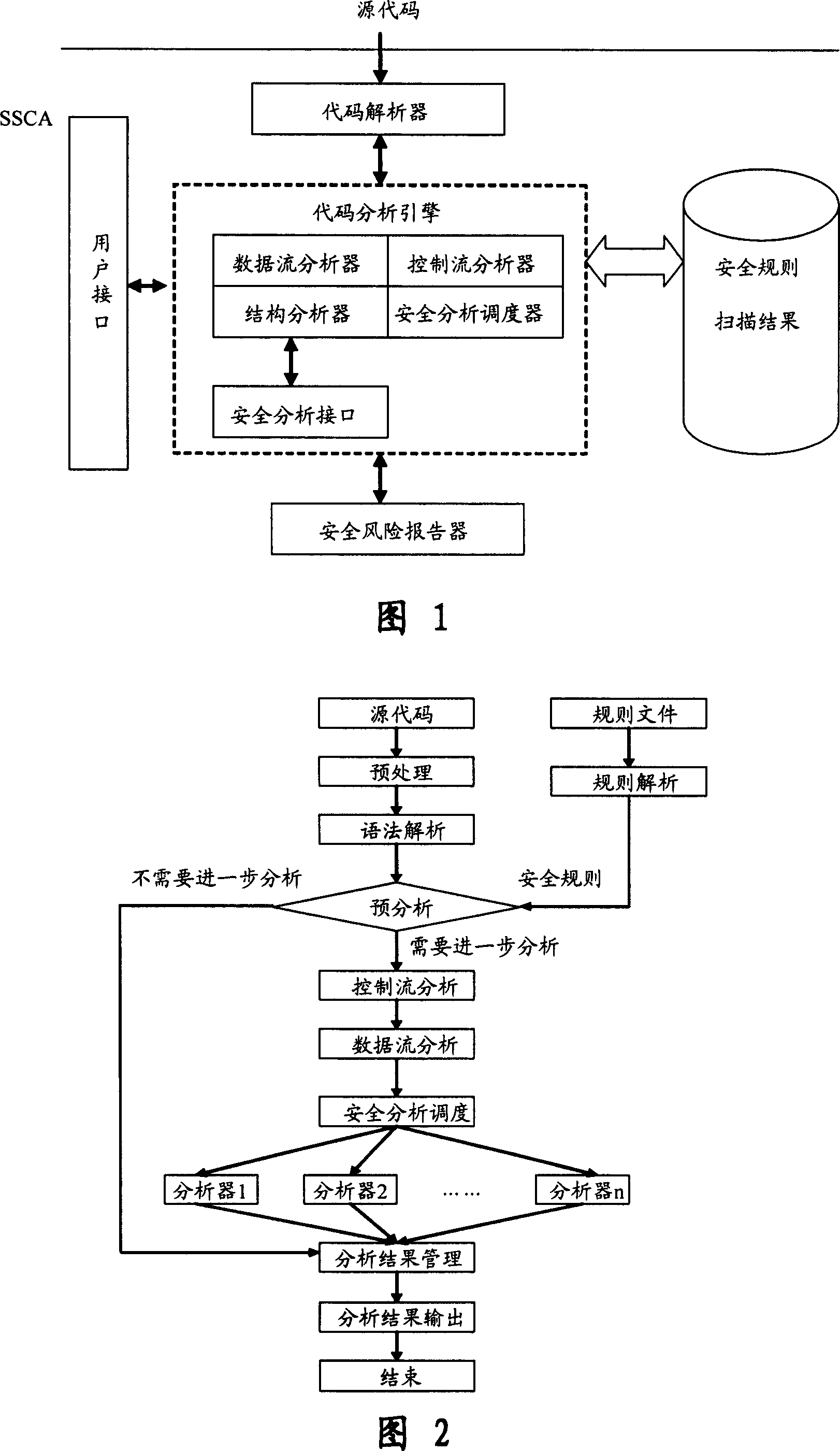
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
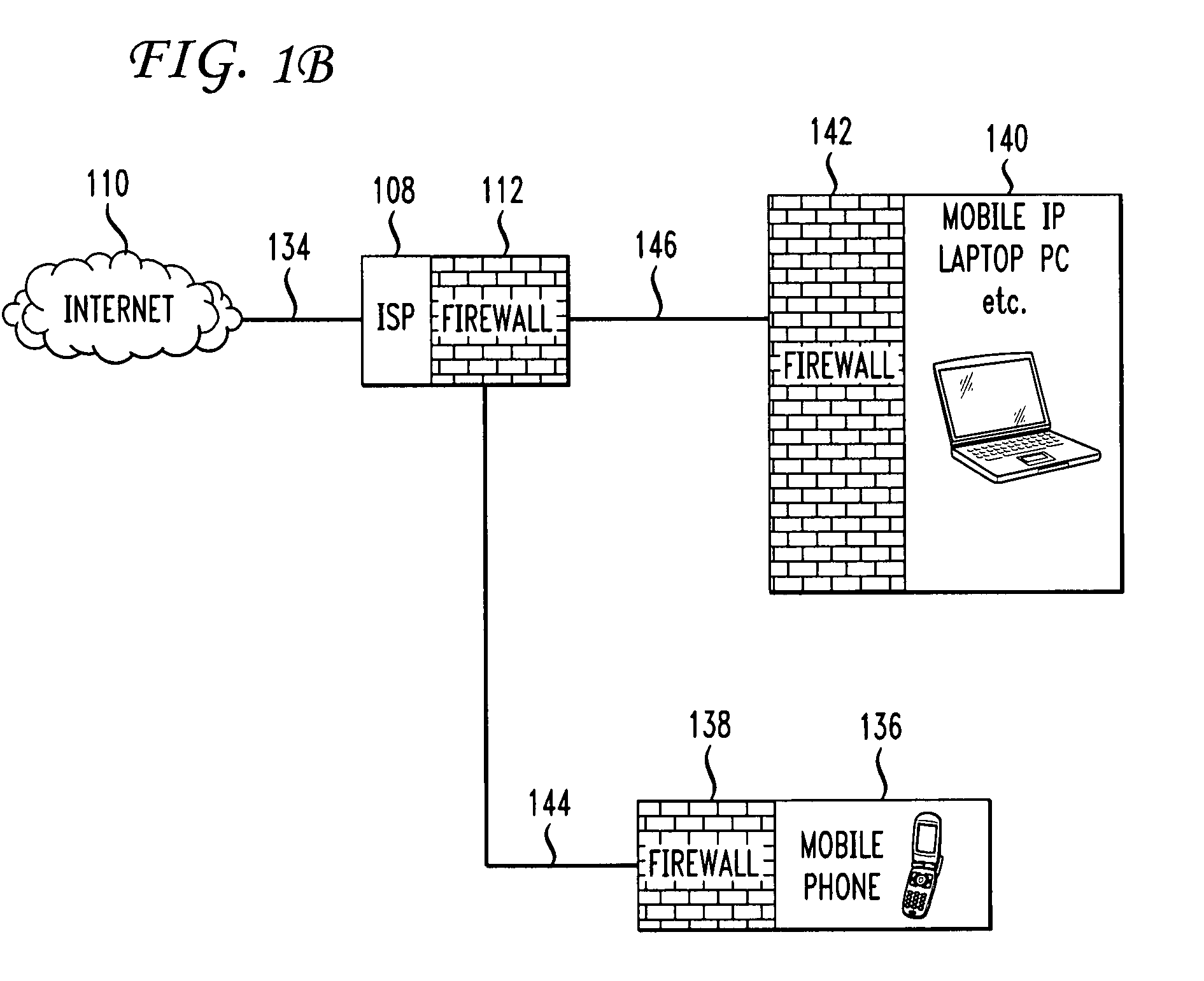
Firewall propagation
InactiveUS7853998B2Unauthorized memory use protectionHardware monitoringService provisionSecurity policy
Methods and systems for propagating data security policies and rules up a chain of network components, for example, from an end-user device having a firewall, to a network component at the “edge” of the network, from where a policy statement can be transmitted to a service provider are described. A device, such as a computer or mobile phone, has, as part of its firewall software, a policy propagation file, that communicates with pre-existing firewall software. The firewall software creates a policy statement upon detecting a triggering event, which is transmitted from the device to the next data security component up the chain, “upstream,” in the network. The firewall server may combine policy statements from numerous end-user type devices and transmit the policy statement to an external network component. The ISP or other service provider may then use the policy statement to implement data security rules for the devices in the network.
Owner:DIGICERT
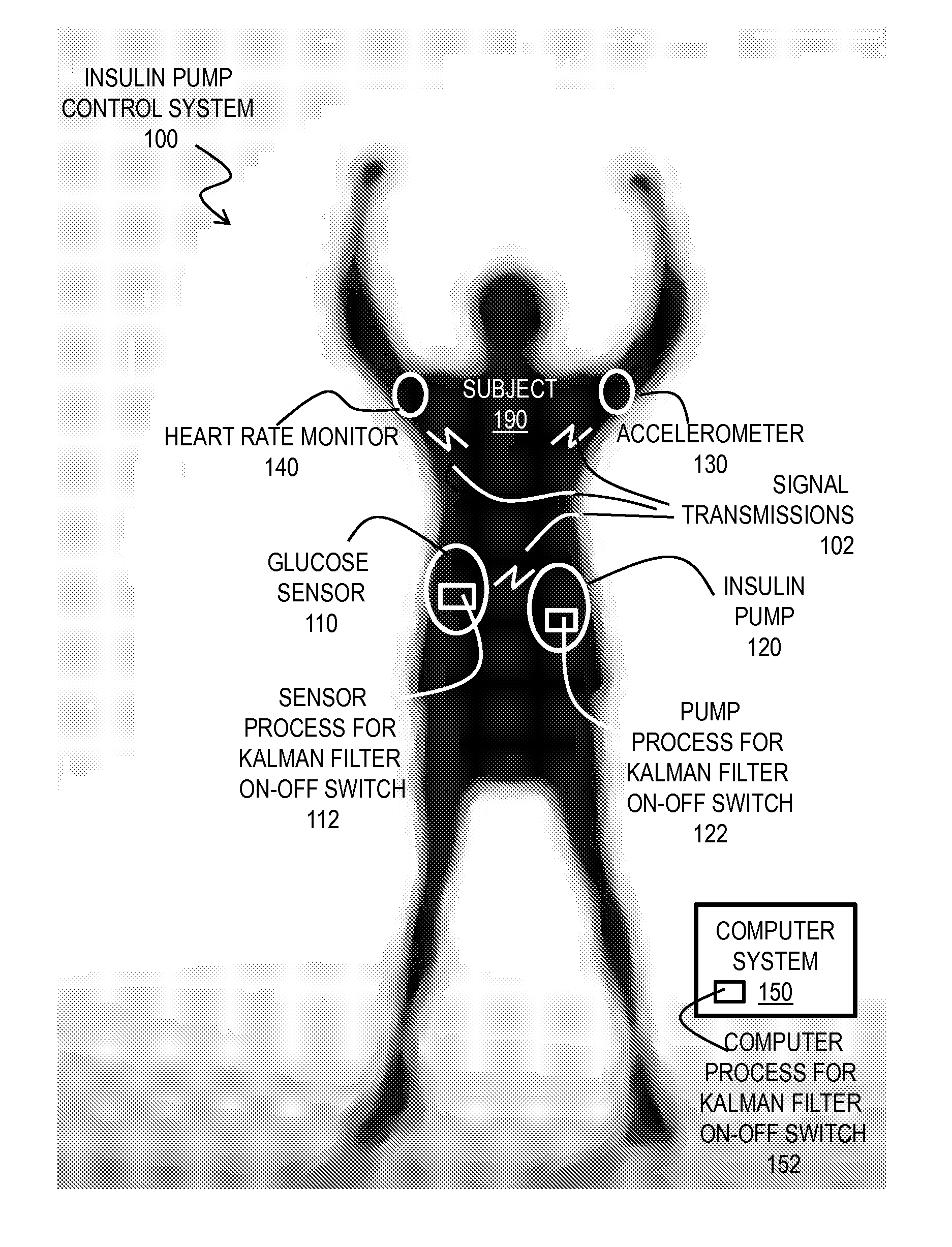
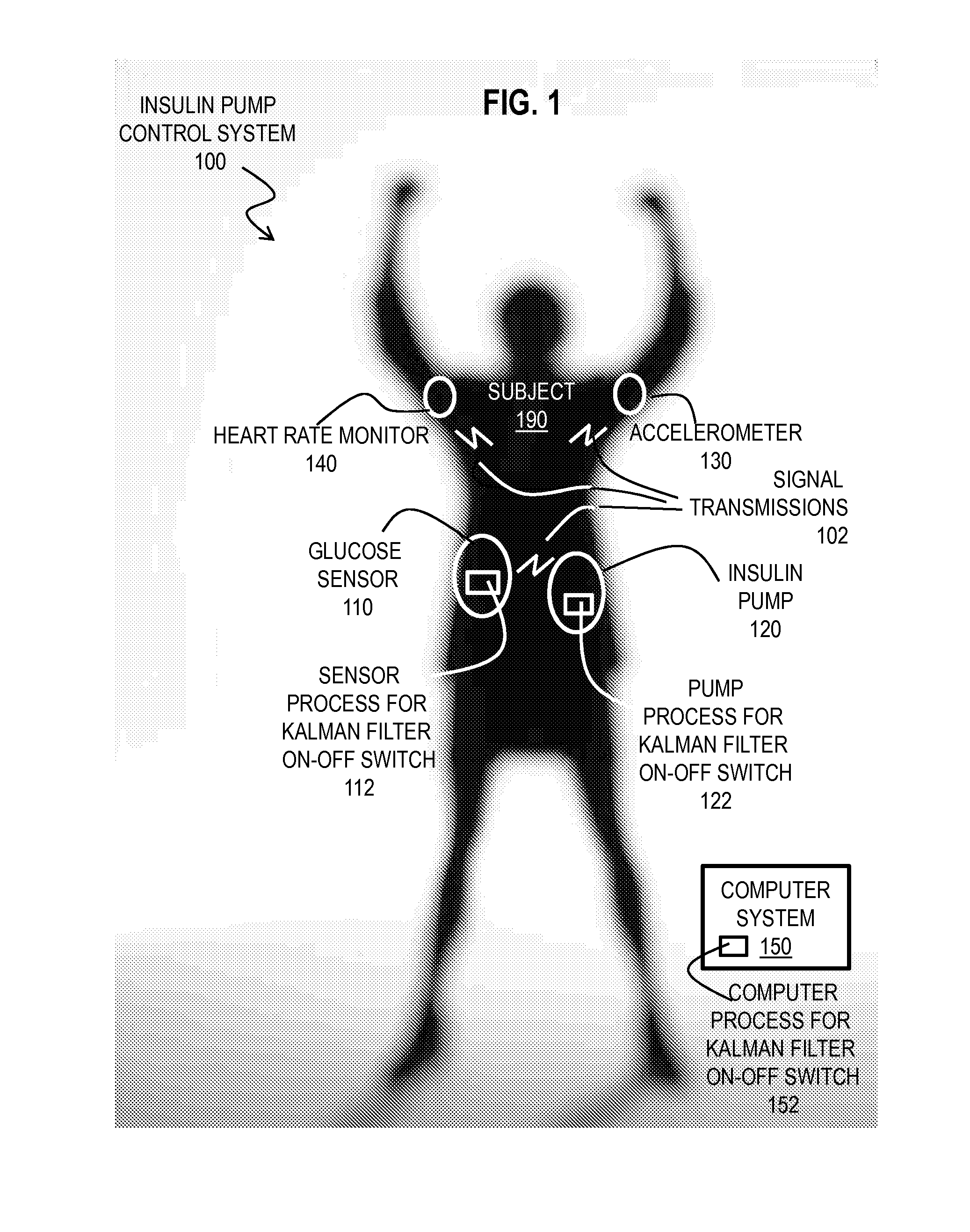
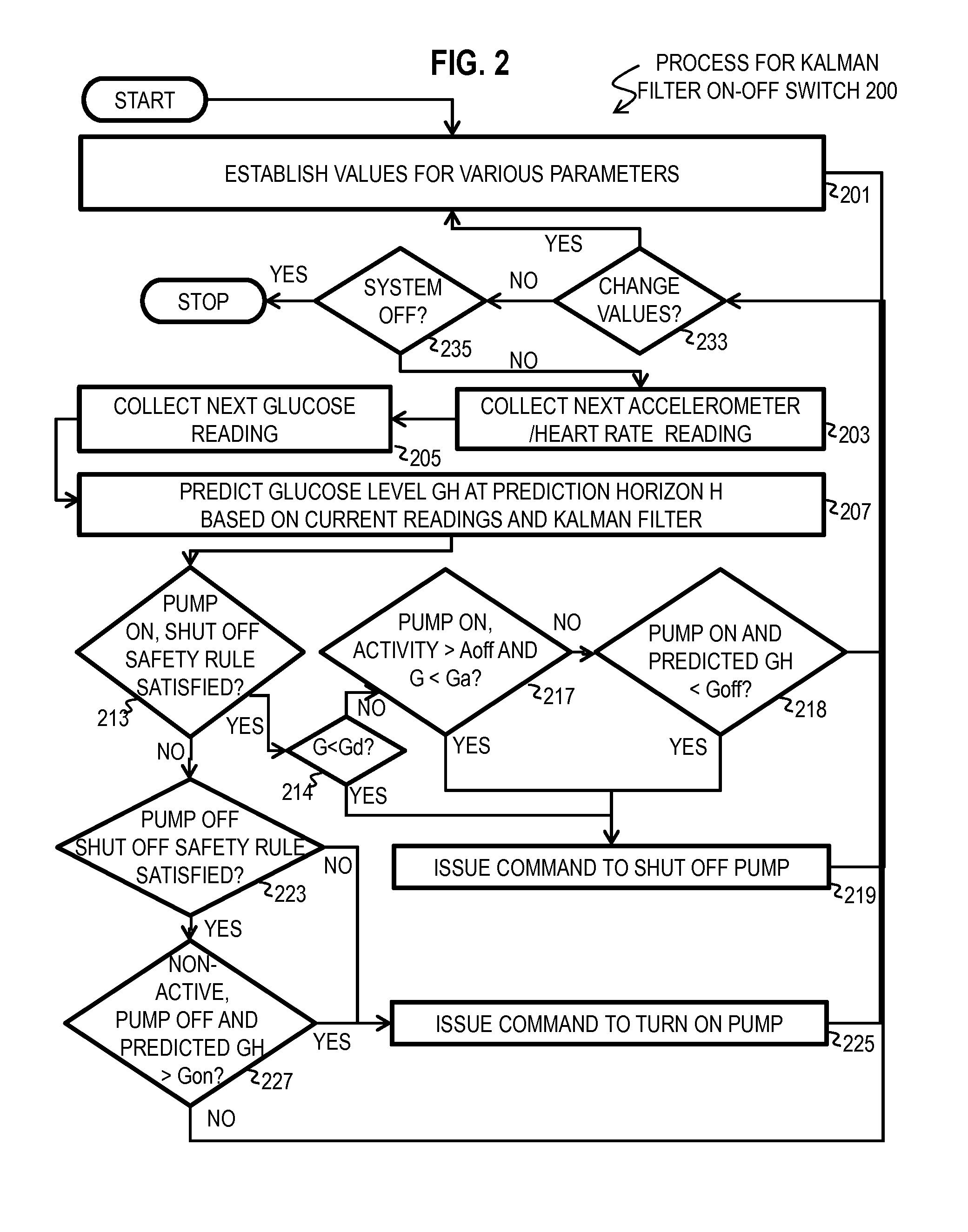
Kalman Filter Based On-Off Switch for Insulin Pump
ActiveUS20140221966A1Mitigate and prevent low blood glucose levelLower blood sugar levelsElectrocardiographyMedical devicesKaiman filterInsulin pump
Techniques for controlling an insulin pump include determining values for parameters selected from a group including a first prediction time horizon, a predicted glucose threshold (Goff) for turning the insulin pump off, a maximum shut off time within a time window, and duration of the time window. A safety rule is determined based on the maximum shut off time within the duration. Glucose readings are collected up to a current time. An expected current glucose value G and glucose temporal rate of change are determined based only on the glucose readings and a Kalman filter configured for noisy glucose readings. A glucose level (Gh1) is predicted for a future time that is the prediction time horizon after the current time. A command is issued to shut off the insulin pump if it is determined both that Gh1 is less than Goff and that the safety rule is satisfied.
Owner:UNIV OF COLORADO THE REGENTS OF +3
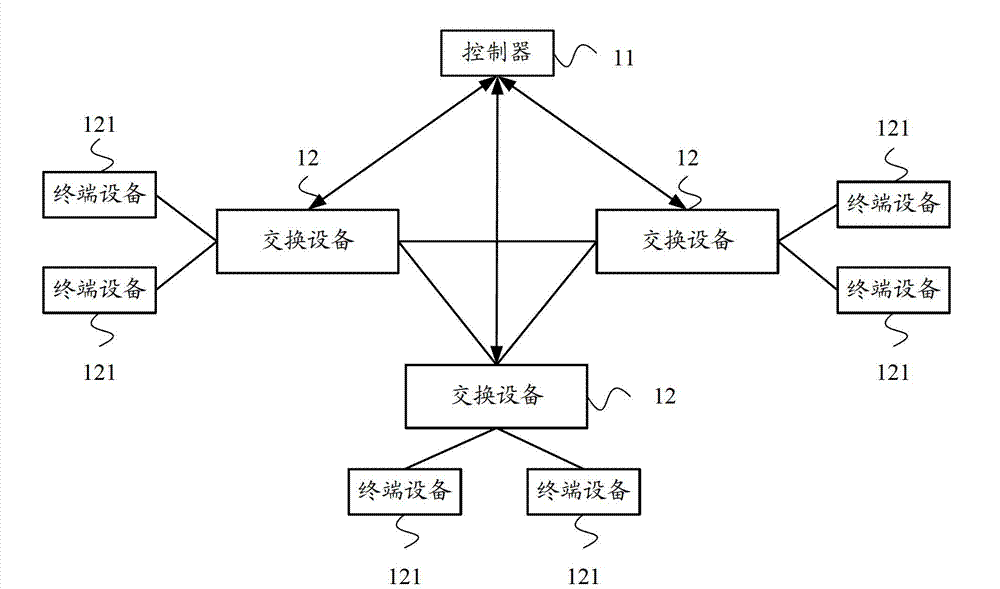
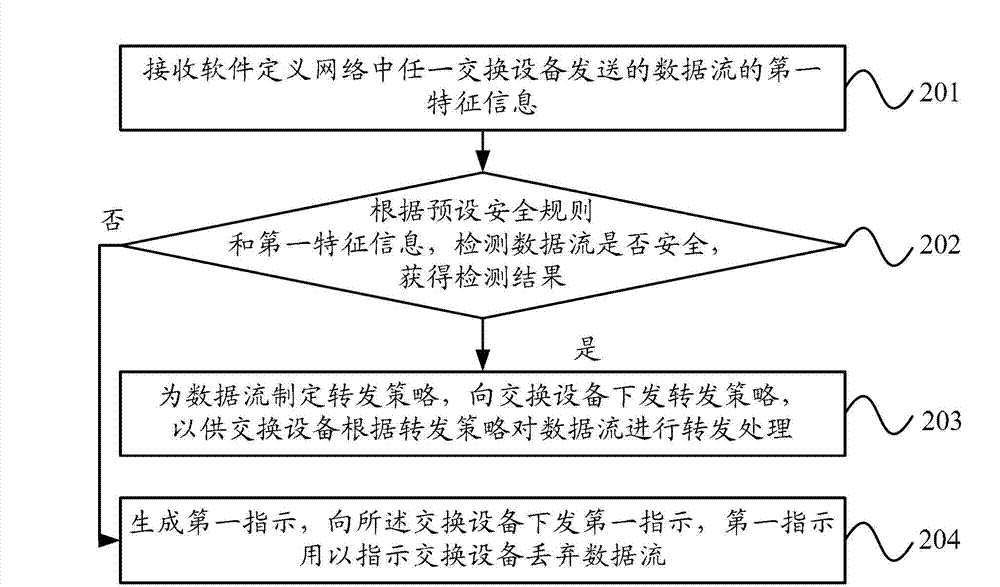
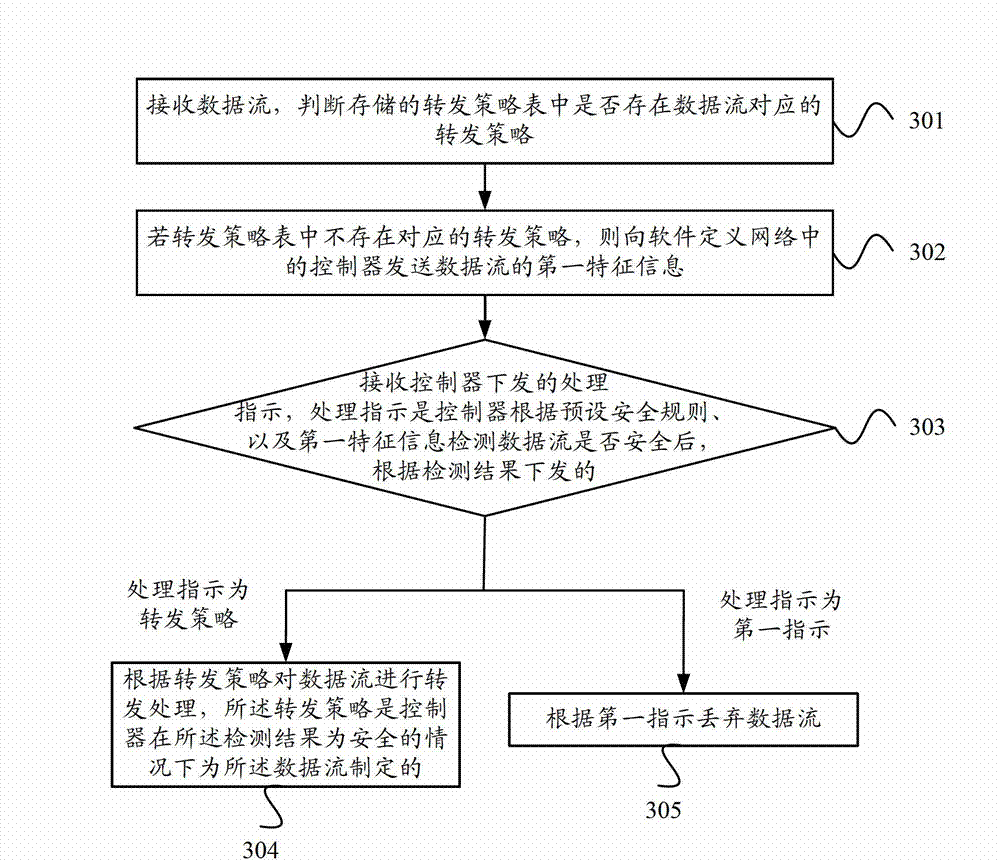
Data stream processing method and system, controller and switching equipment
ActiveCN103051557AImprove securityData switching networksData stream processingSoftware define network
The embodiment of the invention provides a data stream processing method, a data stream processing system, a controller and switching equipment. The data stream processing method comprises the following steps of: receiving the first characteristic information of a data stream transmitted by any piece of switching equipment in a software defined network (SDN), and judging whether the data stream corresponding to the first characteristic information of the data stream is safe or not according to preset safety rules to obtain a detection result; if the detection result indicates that the data stream is safe, generating a data stream forwarding strategy for the data stream, and transmitting the data stream forwarding strategy to the switching equipment, so that the switching equipment forwards the data stream according to the forwarding strategy; and if the detection result indicates that the data stream is unsafe, instructing the switching equipment to discard the data stream. According to the data stream processing method, the data stream processing system, the controller and the switching equipment, the safety of the data stream of any piece of switching equipment in the SDN can be detected.
Owner:HUAWEI TECH CO LTD
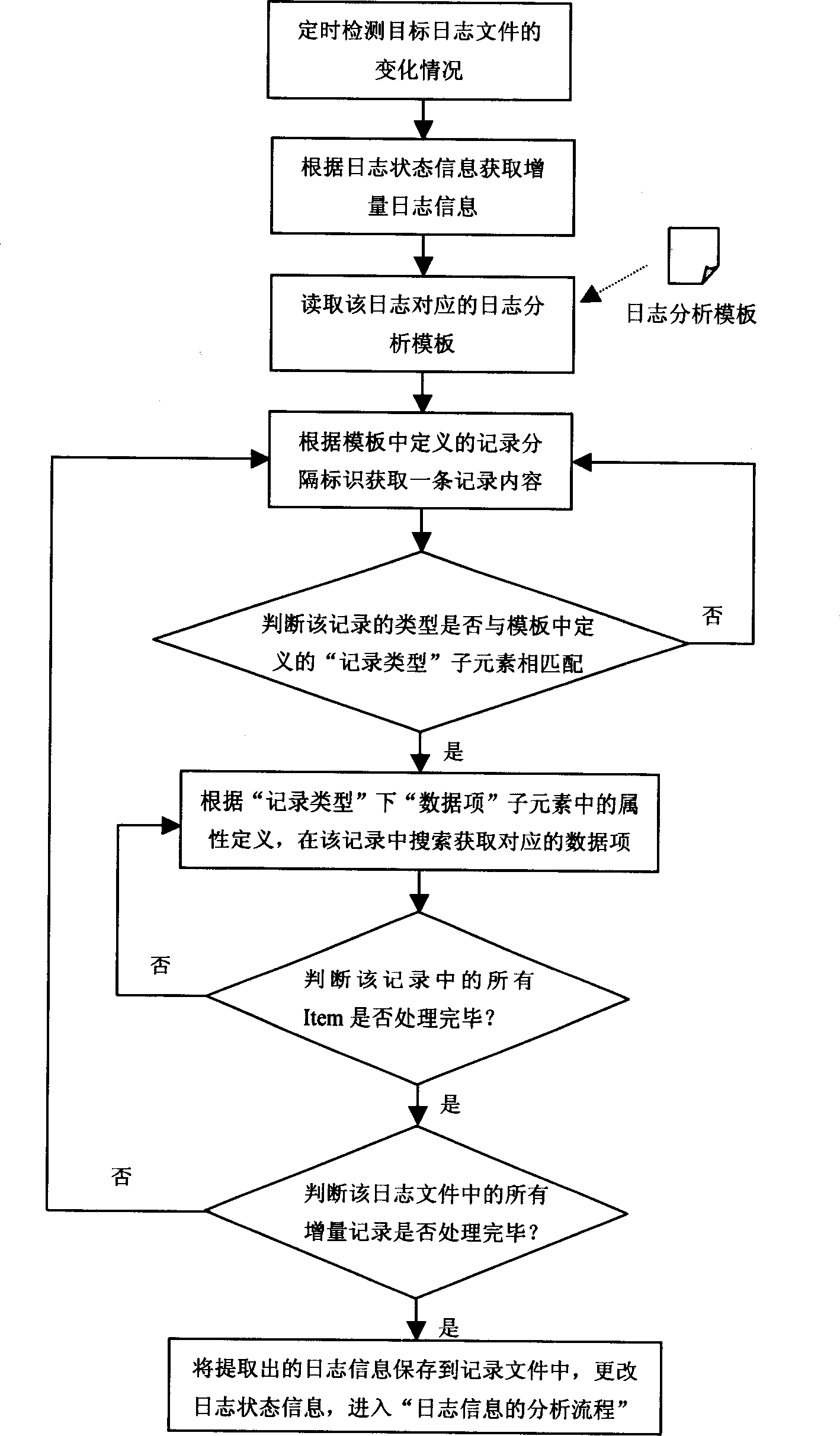
Automatic extraction and analysis for formwork based on heterogenerous logbook
InactiveCN1645336AIncrease flexibilityRealize automatic extractionRedundant operation error correctionSpecial data processing applicationsLogbookTemplate based
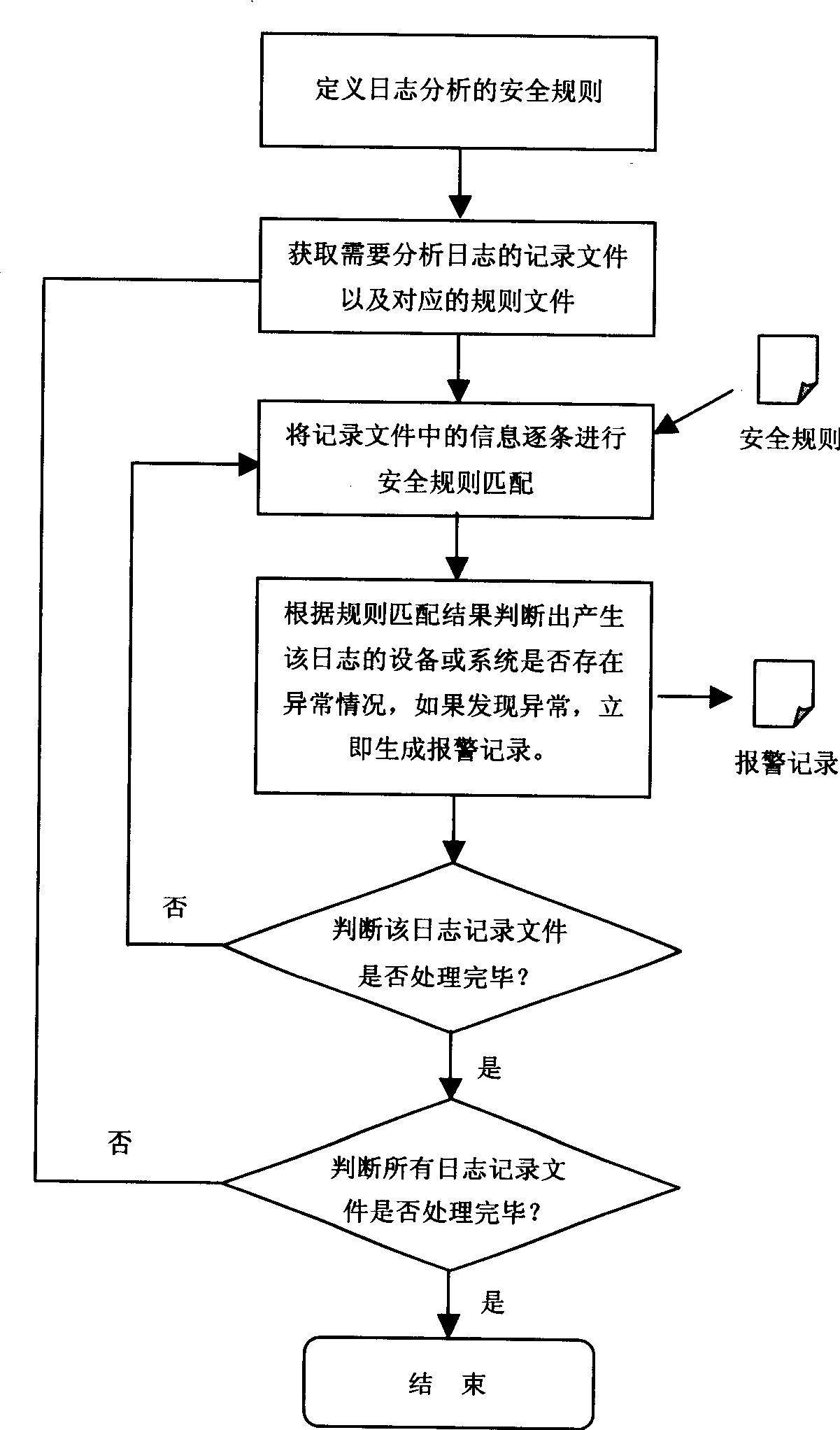
A method for picking up and analysing information automatically includes using XML daily record analysing module to enter automatic picking up procedure, compairing packed up daily record with safety rule to judge whether system operation is abnormal or not, recording biased byte value of each analysis, detecting variation of each target device or daily record file at fixed time to realize automatic analysis to increased part of daily record according to recorded state information of dialy record.
Owner:上海光华如新信息科技股份有限公司
Implementation method for safely managing intranet terminal
InactiveCN105138920APracticalEasy to managePlatform integrity maintainanceThird partyNetwork termination
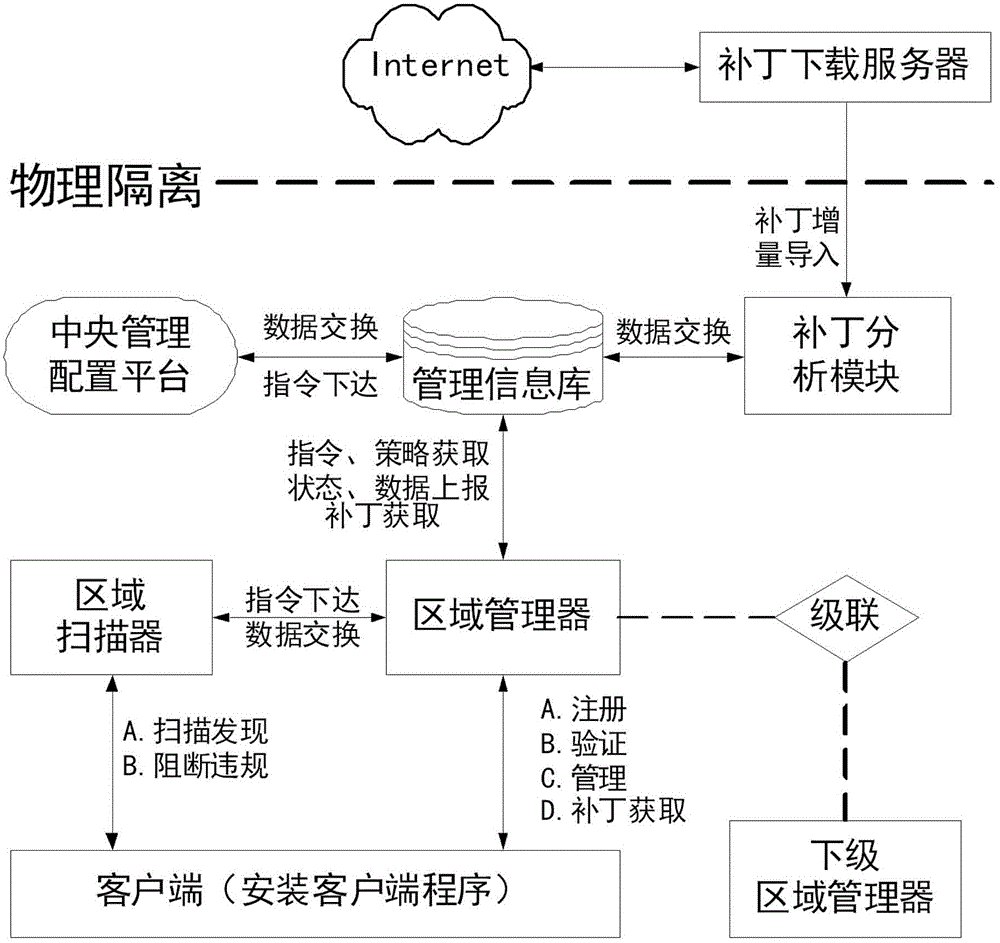
The invention discloses an implementation method for safely managing an intranet terminal. Controllable management of the internet terminal is realized through ten modules including a design terminal basic management module, an asset management module, a terminal desktop management module, a terminal safety management module, a host operation and maintenance module, a patch distribution module, a safe monitoring and auditing module, a report management module, an event alarm management module and a third-party interface management modules. Compared with the prior art, the implementation method for safely managing the intranet terminal is capable of distributing safely tested patches to network users and installing in an automatic or manual manner, setting safety rules of the terminal through unified strategy management, being safely integrated and in alarm linkage with other safe equipment, and supporting a multi-stage cascade wide area network architecture; and thus, the optimal management effect is achieved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
System and method applied to transaction platform for realizing grading safety processing of financial information
InactiveCN103745345AImprove securityDoes not compromise security by designPoint-of-sale network systemsProtocol authorisationInformation processingEmbedded security
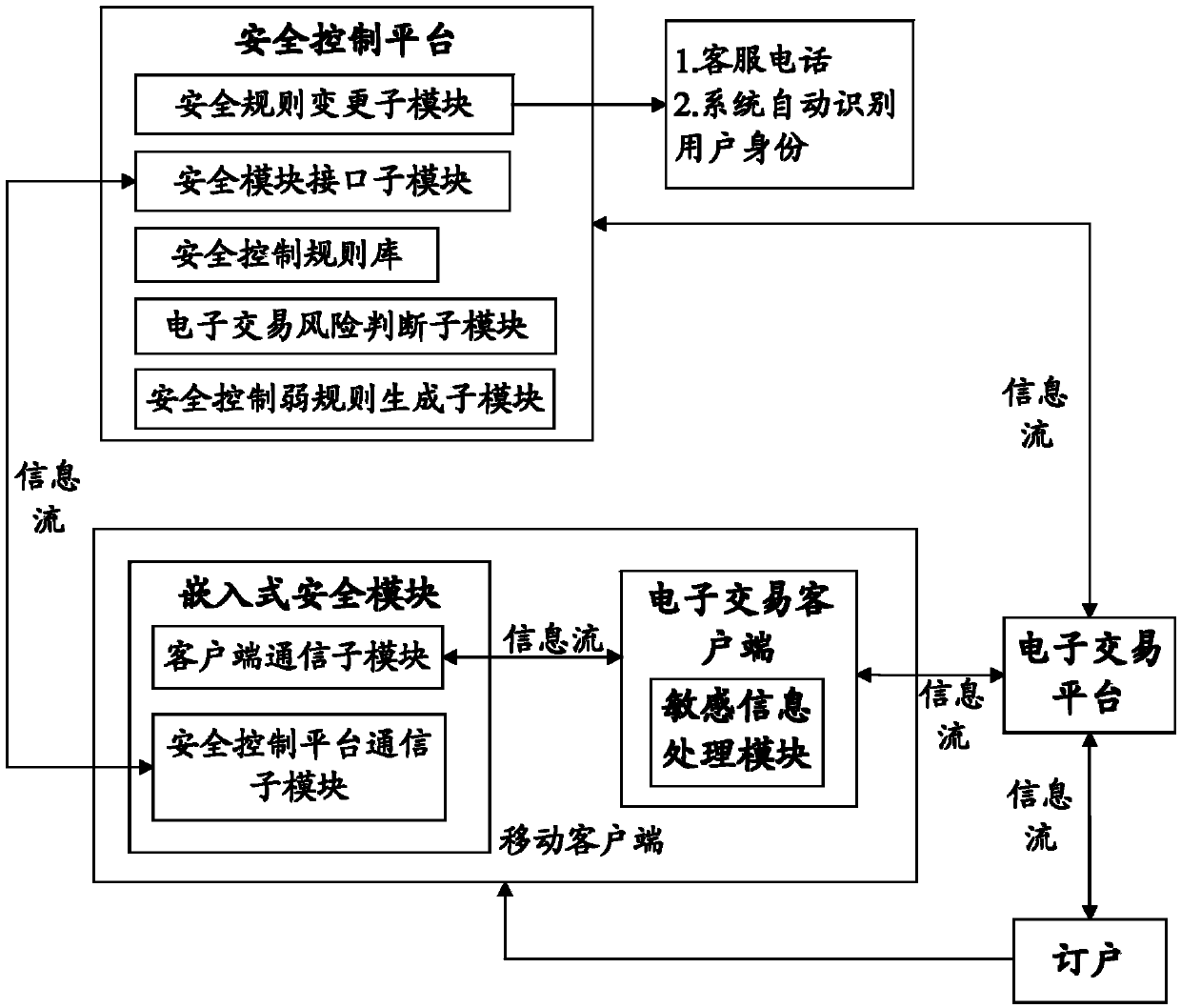
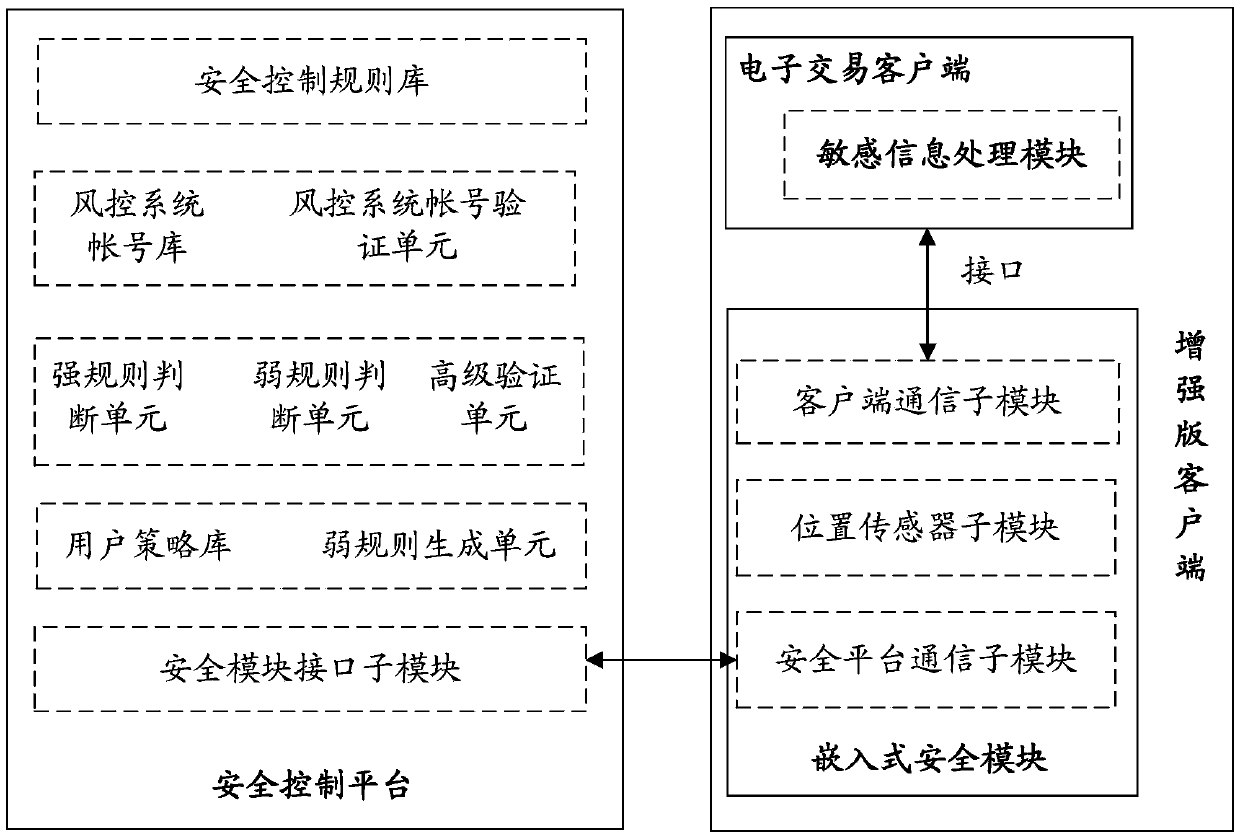
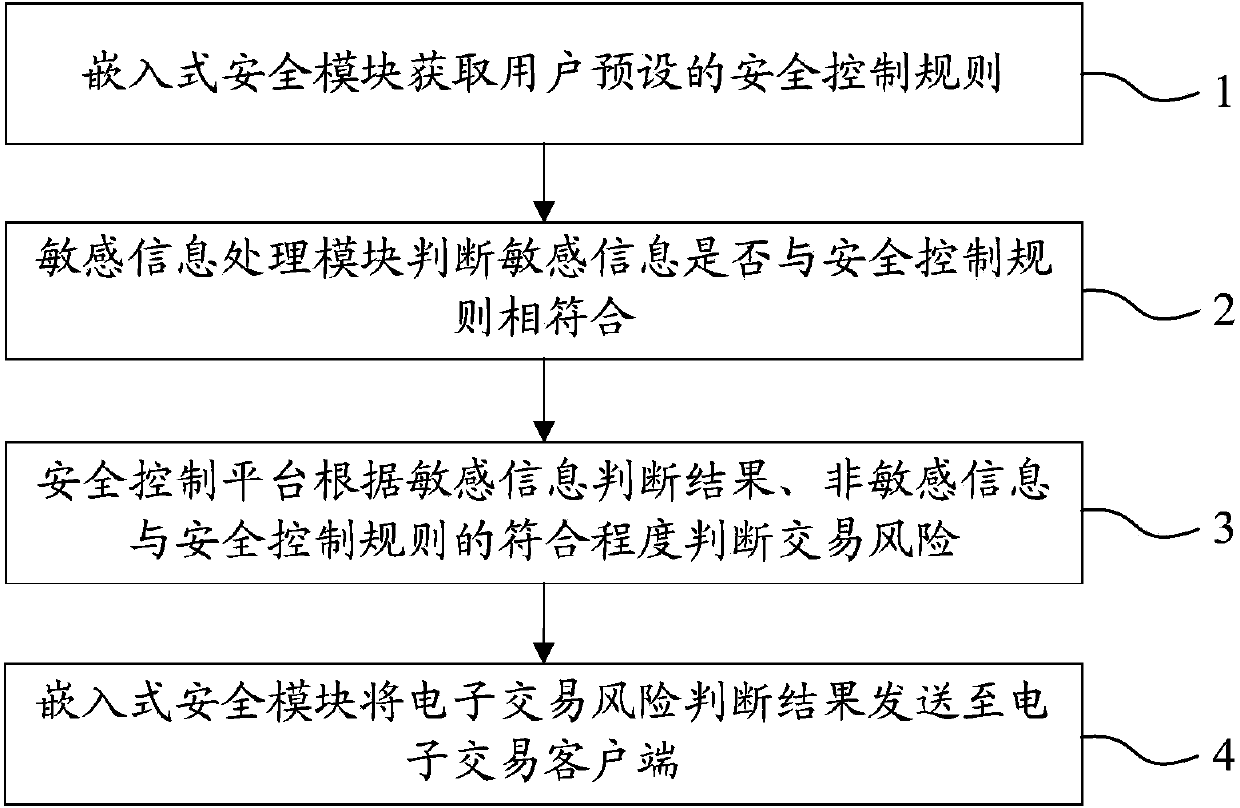
The invention relates to a system applied to a transaction platform for realizing the grading safety processing of financial information. The system comprises an embedded safety control module for acquiring a safety control rule preset by a user, a sensitive information processing module for judging the coincidence degree of the sensitive information in electronic transaction information of the user and the safety control rule and a safety control platform for judging the risk of the electronic transaction and performing identity verification on the user for which the safety rule needs to be altered. The invention also relates to a method applied to the transaction platform for realizing the grading safety processing of the financial information. According to the system, adopting such a structure, and the method applied to the transaction platform to realize grading safety processing of the financial information, the financial information of the user can be divided into the sensitive information and insensitive information, the sensitive information processing module and an electronic transaction client end are integrally packaged, the user information safety is further ensured by grading processing, loss caused by the problem of account unsafety is reduced and the system and method have a wide application range.
Owner:COEUSYS
Static analysis-based checking method of safety rules of C language
InactiveCN102012991AMake up for the lack of securityPlatform integrity maintainanceStatic timing analysisType conversion
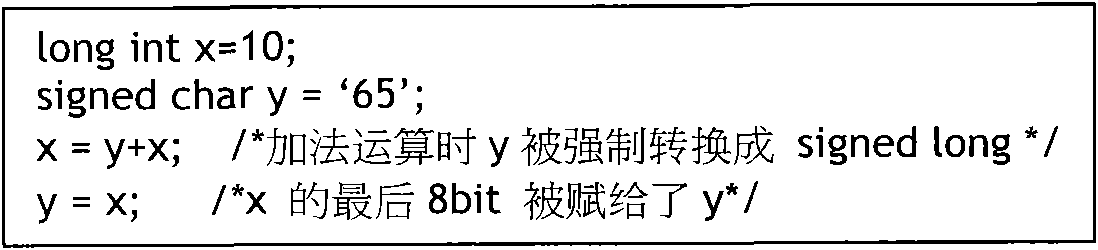
The invention relates to a static analysis-based checking method of safety rules of C language, which comprises the following steps: 1) checking the type of the C language to avoid the occurrence of compulsory type conversion and prohibiting the declaration of the type of a generic pointer; 2) stipulating that a global variable and a local variable can not be in homonymy, and the global variable and a formal parameter of a function can not be in tautonomy; 3) limiting a cyclic variable of a control flow statement; 4) strengthening the declaration and the definition of the C language; and 5) carrying out analysis of accidence, grammar and semanteme on source codes, and finding out places which do not meet the stipulation from the source codes. The method has the advantages of being capable of finding out possible loopholes on programming of the C language under the premise that the codes do not need to be executed and effectively making up for the deficiency of insufficient safety of the C language in soft engineering.
Owner:北京神舟航天软件技术股份有限公司
Method for classifying network equipment by utilizing machine learning
InactiveCN104883278AEasy to auditSimple safety rulesData switching networksSecurity specificationNetwork packet
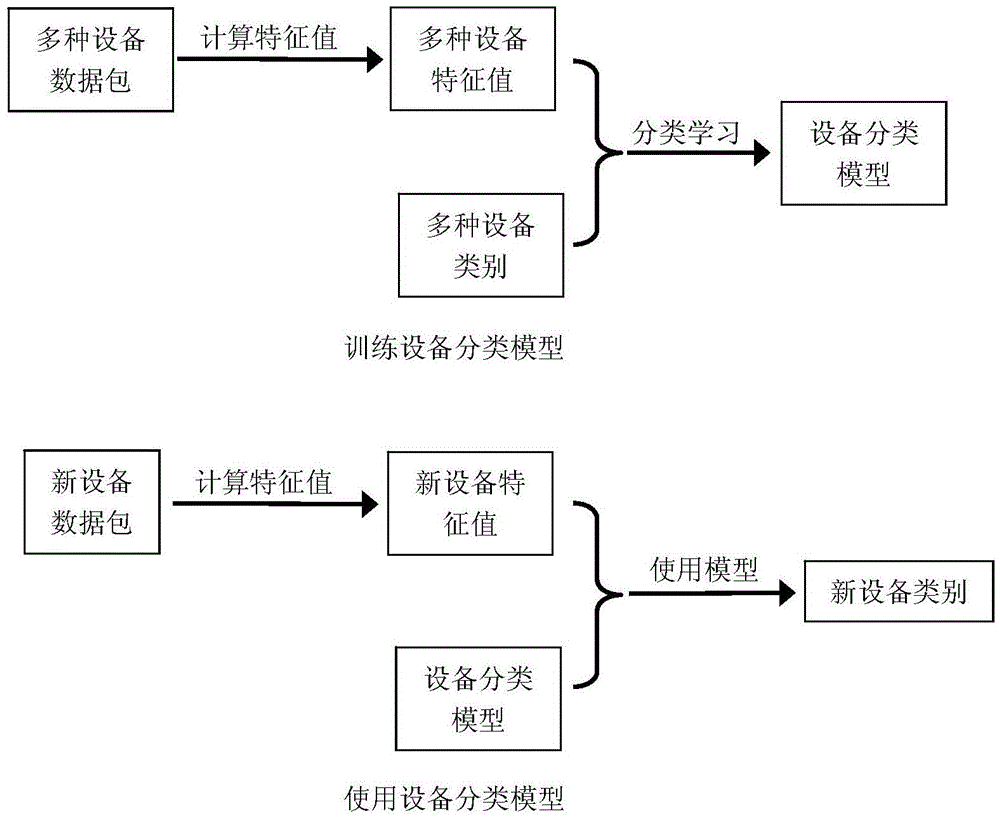
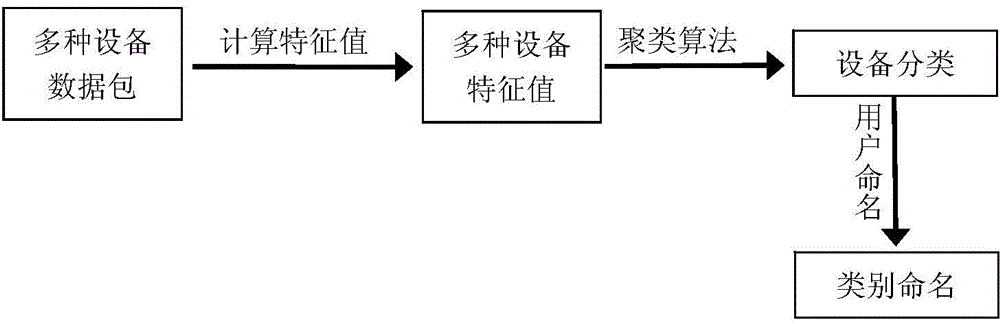
The invention discloses a method for classifying network equipment by utilizing machine learning. The method establishes a classifying model for the network equipment by utilizing a supervised machine learning technology or a non-supervised machine learning technology, so as to classify known or newly added equipment in a network. The method has the technical advantages of analyzing behavior of the equipment through data packets transmitted and received by industrial control network equipment, and further classifying the equipment automatically. The understanding of types of the equipment is conducive to auditing network communication data. Unlike the traditional security specification for individual equipment, the security specification for equipment types is simpler and easy to manage, and the user can define corresponding security specifications for newly added equipment nodes easily.
Owner:BEIJING KUANGEN NETWORK TECH
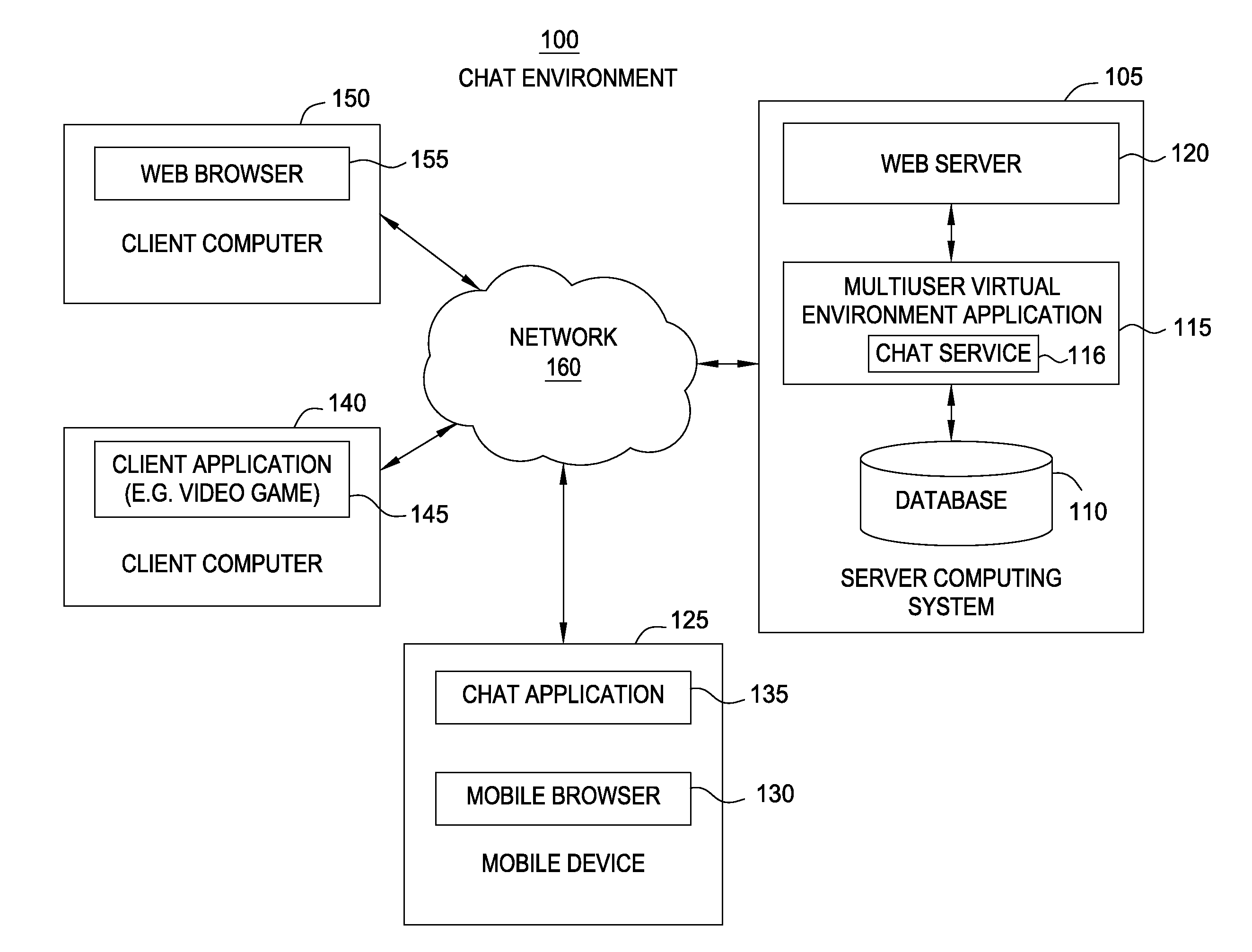
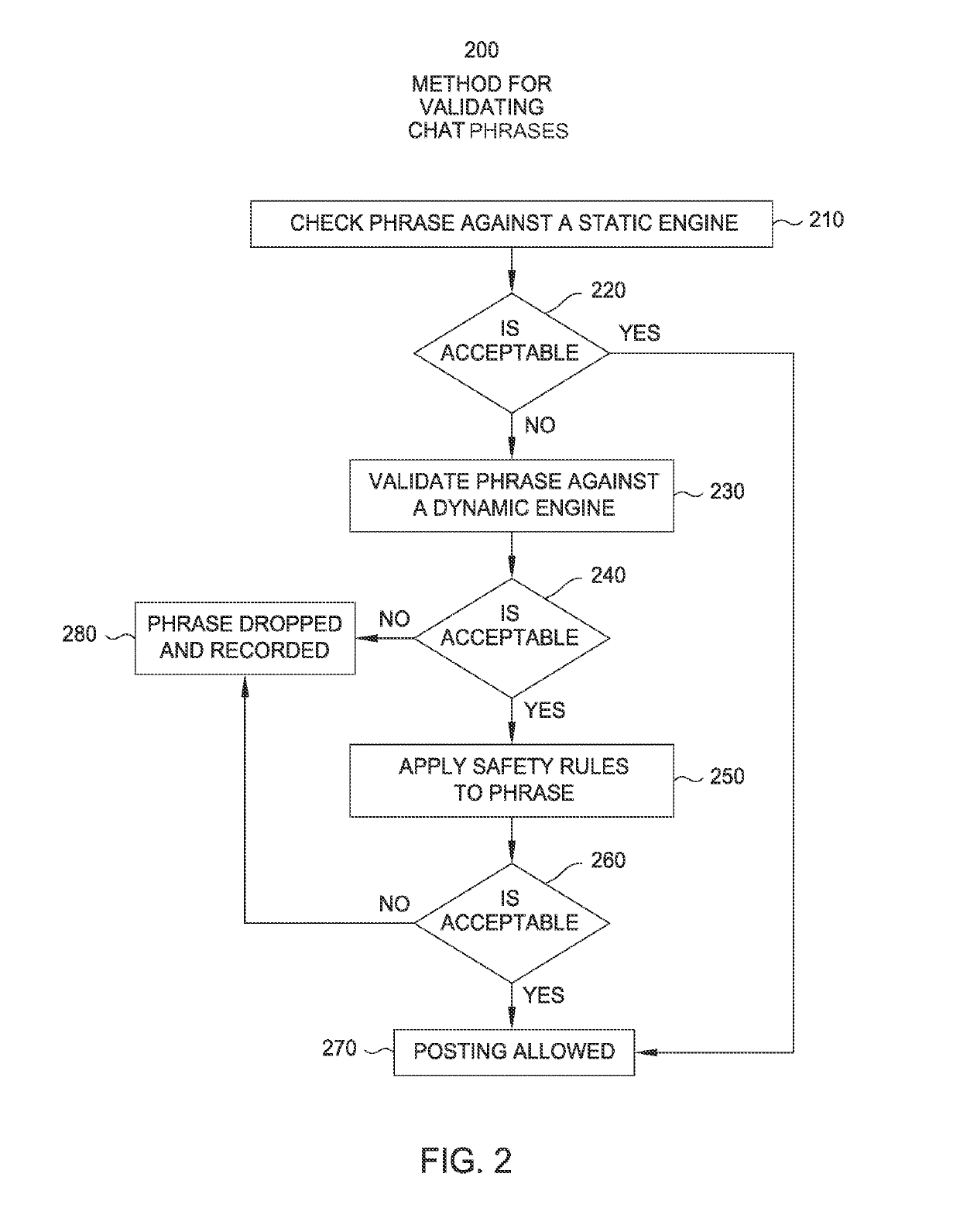
Comprehensive safety schema for ensuring appropriateness of language in online chat
ActiveUS20140278367A1Semantic analysisSpecial data processing applicationsSchema for Object-Oriented XMLHuman language
A method is disclosed for evaluating a chat message sent between users of an online environment. The method may include associating each word in the chat message with metadata. The metadata identifies a word type and usage for each word in the chat message. This method may also include identifying one or more safety rules associated with the metadata. Each safety rule identifies an ordered sequence of one or more sets of words. This method may also include applying the safety rule to the chat message to determine whether a sequence of words in the chat message present in the ordered sequence of sets of words. Upon determining a word, from each set of words in the ordered sequence of sets of words, matches a respective one of the words in the chat message, the chat message is blocked from being sent to a message recipient.
Owner:DISNEY ENTERPRISES INC
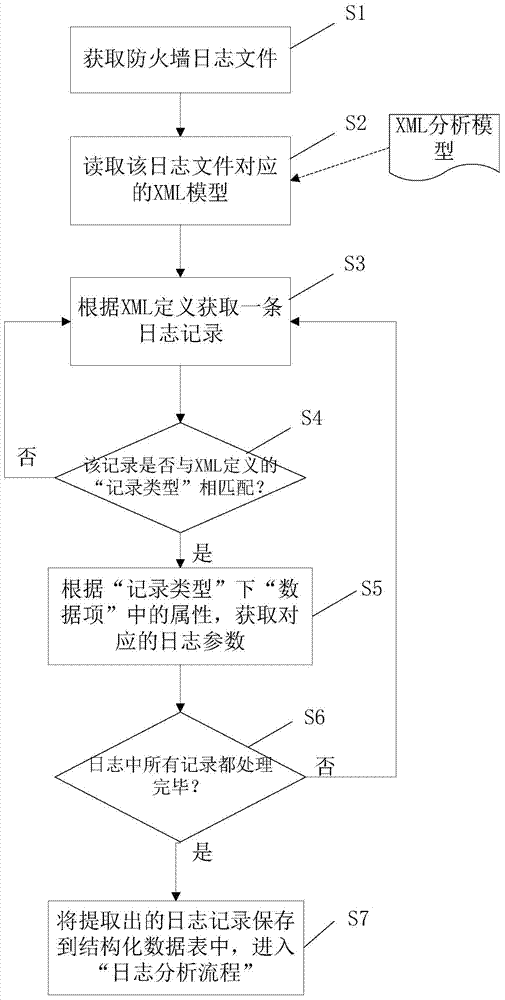
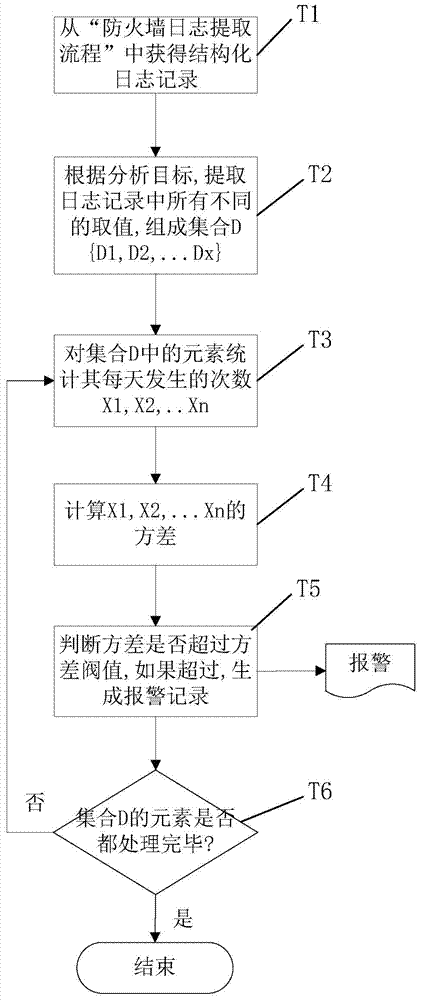
Method for automatically extracting and analyzing firewall logs based on XML rule model
The invention relates to a method for automatically extracting and analyzing firewall logs based on an XML rule model. The method includes the following steps of defining XML log analysis templates, automatically extracting the firewall logs and analyzing the firewall logs. According to the method, quintuple information of time, a source IP address, a source port, a destination IP address and a destination port contained in each log is extracted. The XML templates are formulated according to the structural features of each type of firewall log files, record type defined feature identification contained in the firewall log files is contained in the XML template, according to the identification, the firewall log files are extracted, the quintuple information in the firewall logs is automatically identified, and whether the operating state of a destination device is normal or not is automatically judged according to predefined safety rules. By the adoption of the method, a large amount of firewall log information can be automatically rapidly extracted, abnormal network access behaviors are analyzed, and a basis is provided for network safety analysis and management.
Owner:CHINA TOBACCO ZHEJIANG IND
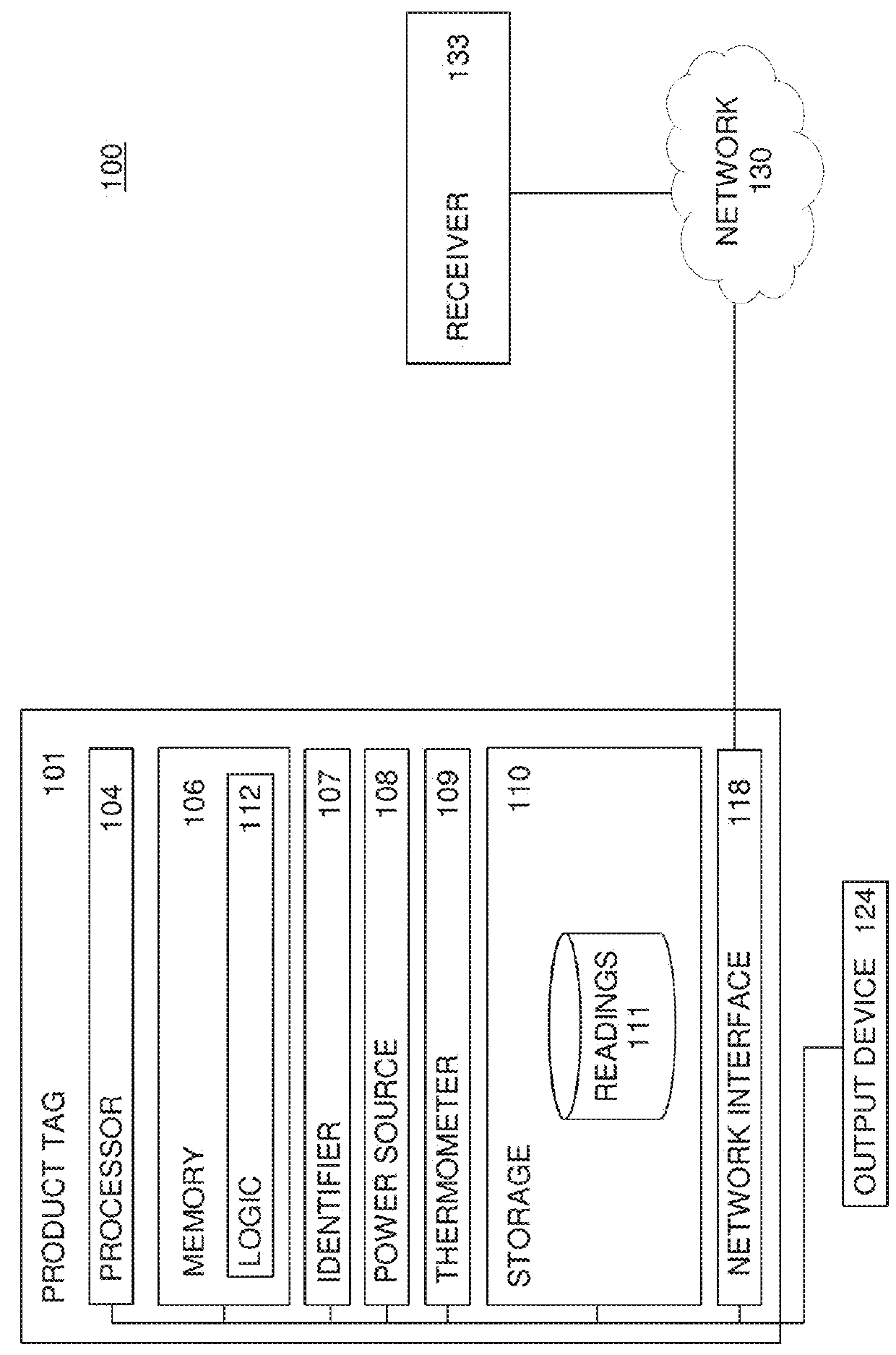
Monitoring food products
ActiveUS20160034907A1Improve food safetyThermometer detailsThermometers using mean/integrated valuesGuidelineFood safety
Systems, methods, and computer program products to improve food safety in a food and beverage supply chain. Embodiments disclosed herein utilize prepared product tags to continuously monitor food and beverage temperatures. The temperatures and other associated data may be wirelessly transmitted to centralized locations for aggregation and storage. Mobile devices may directly communicate with the product tags to receive the temperature data. A host of management applications may utilize the data in order to ensure that safety rules and guidelines are met, while also providing valuable business insight.
Owner:DISNEY ENTERPRISES INC
Access control system based on palm vein authentication and authentication method using same
InactiveCN102122402AMeet high-level security requirementsAchieve sharingIndividual entry/exit registersMedia access controlPollution
The invention discloses an access control system based on palm vein authentication and an authentication method using the same. The system comprises a plurality of palm vein terminals, a central processing unit (CPU) and a plurality of door control devices, wherein, the plurality of the palm vein terminals acquire palm vein images of a user to be authenticated, process and then send the images tothe CPU; the CPU stores rights information, safety rule information and palm vein information of a legal user, reads the palm vein images of the user to be authenticated, judges whether opening of a security door meets the safety requirements based on preset matching rules and safety rules, and sends an opening command to the corresponding door control device if opening of the security door meetsthe safety requirements; and the plurality of the door control devices respond to the opening command to control the corresponding security door to open. By utilizing the system and the authentication method using the same, the defects such as limited authentication efficiency and accuracy caused by easy theft, replication or pollution of an authentication reference object in the existing security access control authentication based on ID (identity) card and fingerprint identification are overcome, thus meeting higher safety requirements.
Owner:BEIJING TIANGONG RUIFENG TECH +2
Construction method for access control policy and system thereof
InactiveCN101778109AEasy to use and understandImprove readabilityData switching networksOperational systemSyntax
The invention relates to a method for constructing an access control policy and a system thereof which are applied to field of the safe operation system, in particular to a policy compiler for realizing the method for constructing the access control policy. Based on the analysis and the research on the classical safety model, the invention provides the method which has common and special safety rules and is used for constructing the universal access control policy, and provides the policy compiler which can realize the functions of syntax check, semantic analysis and the like, comprises a retargetable back end and is applicable to the multiple operating system environments by setting the method as the design objective of the language of the policy compiler in the system, adopting the object-oriented design concept and determining the lexical and syntax standard methods of the language. The invention has the prominent advantage that a method of the universary description on policy elements and safety rules is used to support multiple security models.
Owner:苏州国华科技有限公司
System and method for lost data destruction of electronic data stored on portable electronic devices
ActiveUS7543144B2Reduces and eliminates riskReduce riskDigital data processing detailsUnauthorized memory use protectionBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. Rules relating to encryption, as well as other security procedures, can be defined and entered by an administrator with access to the server, and then disseminated to each of a plurality of clients that access the server.
Owner:BEACHHEAD SOLUTIONS
Data detection method and device
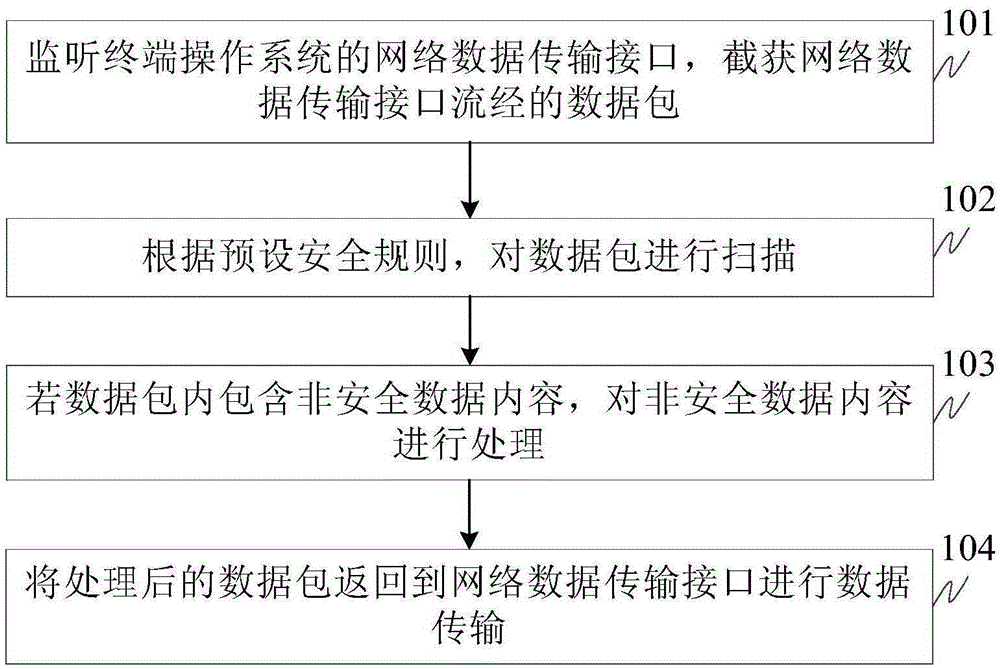
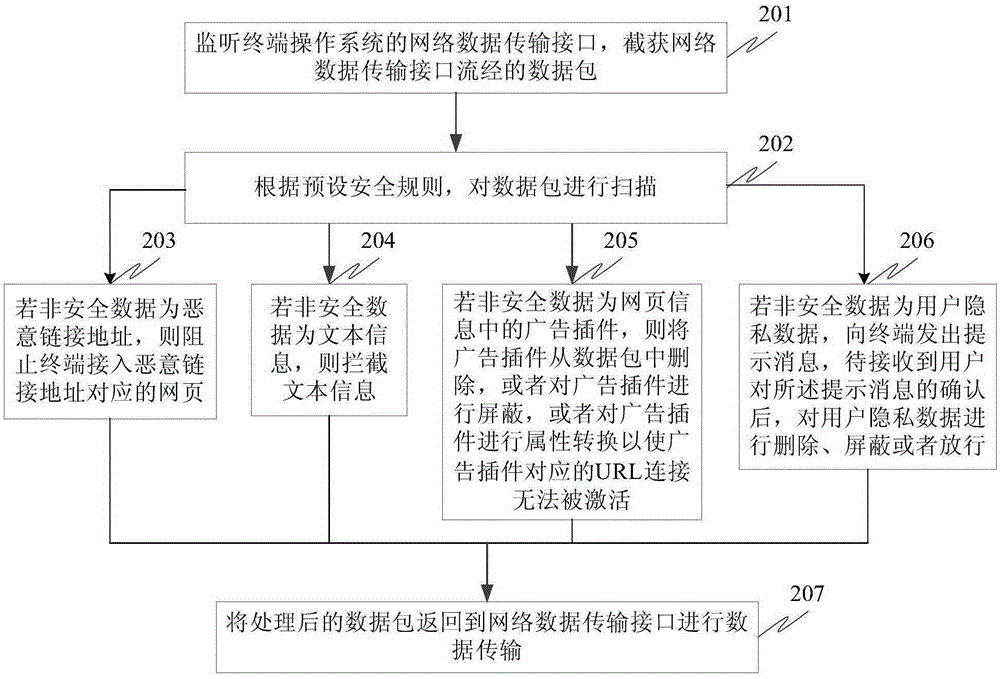
InactiveCN105323261AImplement early checksAddress threatsTransmissionOperational systemNetwork packet
The embodiment of the invention relates to a data detection method and a data detection device. The data detection method comprises the following steps: intercepting a data packet flowing through a network data transmission interface by monitoring a network data transmission interface of a terminal operating system; according to preset safety rules, scanning the data packet; if the data packet contains non-safe data content, processing the non-safe data content; and returning the processed data packet to the network data transmission interface for carrying out data transmission, so that the problems that a terminal is invaded by malicious data and a system or user data is threaten are solved, early inspection of the data packet which enters or is output from the terminal is realized, and the malicious data is timely found, so that security and reliability of data interaction in the terminal are guaranteed.
Owner:BEIJING QIHOO TECH CO LTD +1
Automatic collision avoidance system and method of port cargo ship unloader
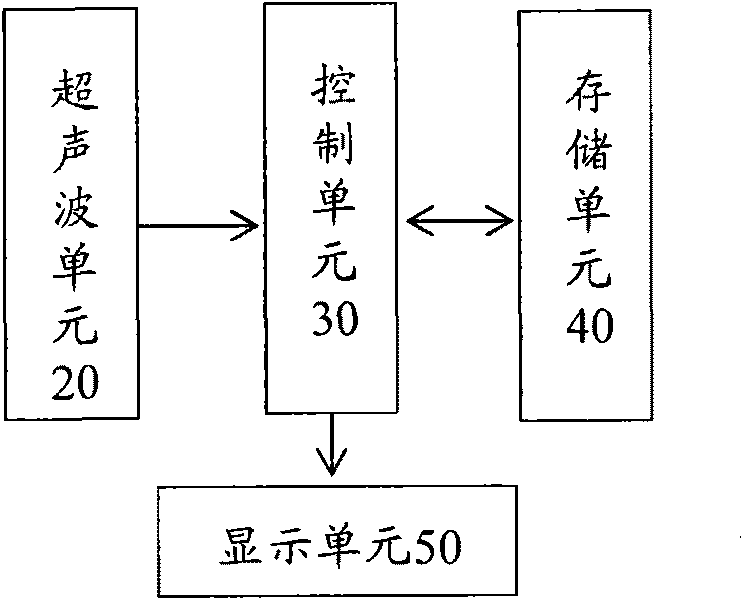
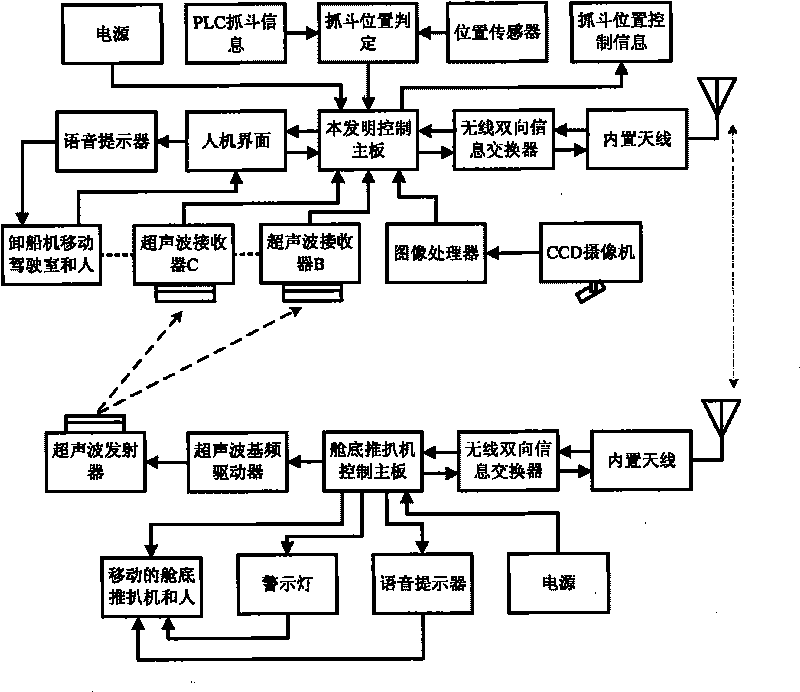
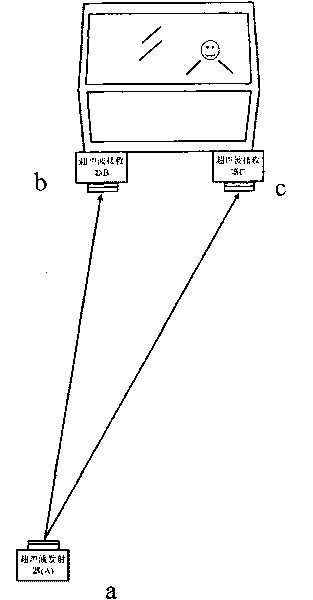
InactiveCN101723187AEfficient determinationPosition fixationLoading/unloadingControl signalCargo vessel
Owner:BAOSHAN IRON & STEEL CO LTD
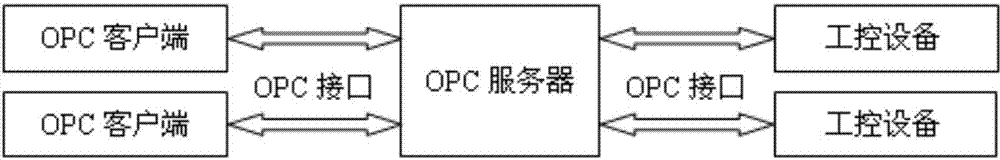
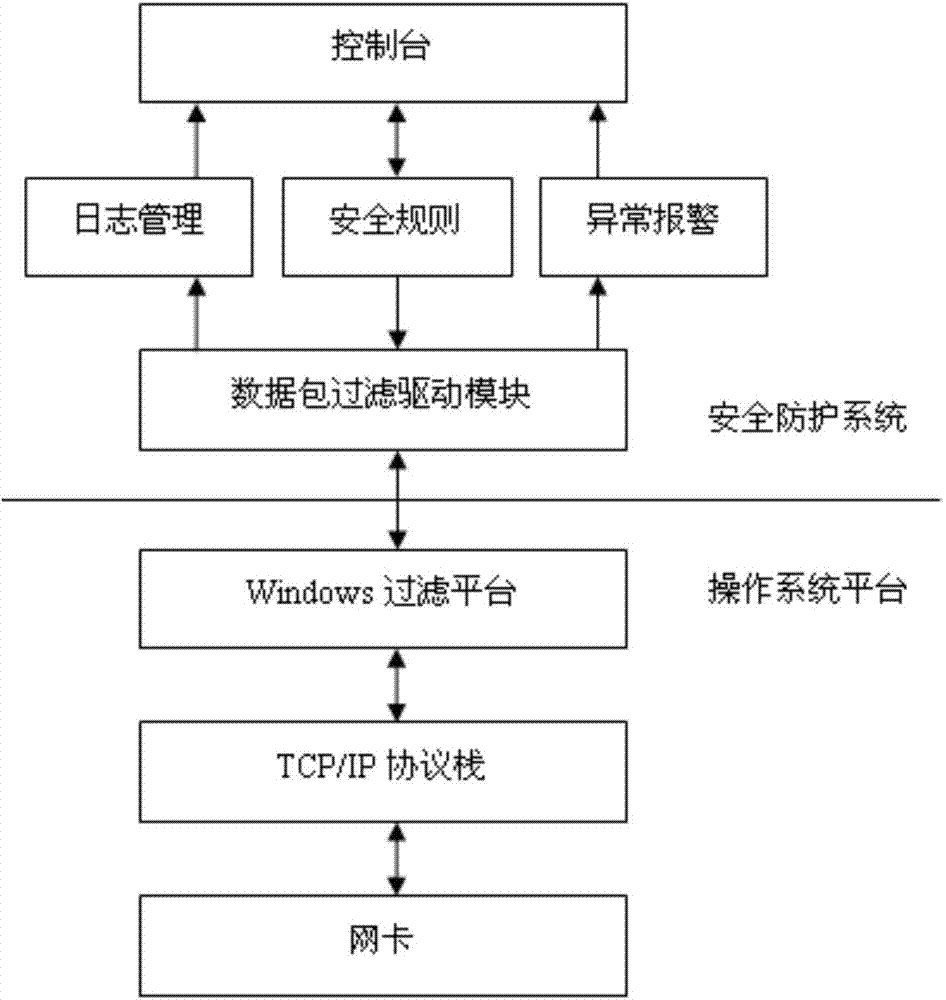
OPC server safety defending system
The invention discloses an OPC server safety defending system and aims at solving the technical problem that existing servers and industrial control systems are poor in safety. According to the technical scheme, the system comprises a safety defending system body and an operating system platform, and the safety defending system is composed of a control console and a data package filtration driving module. The operating system platform is composed of a Windows filtration platform and a network card. According to an OPC server network communication system structure, safety rules are set on a network layer, a transmission layer and an application layer of an OPC server, deep safety check and audit are conducted on data packages entering and exiting from the OPC server, vicious access behaviors and data packages are identified, filtered and removed, and the safety defending capability of the OPC server and the industrial control system is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Comprehensive safety schema for ensuring appropriateness of language in online chat
Owner:DISNEY ENTERPRISES INC
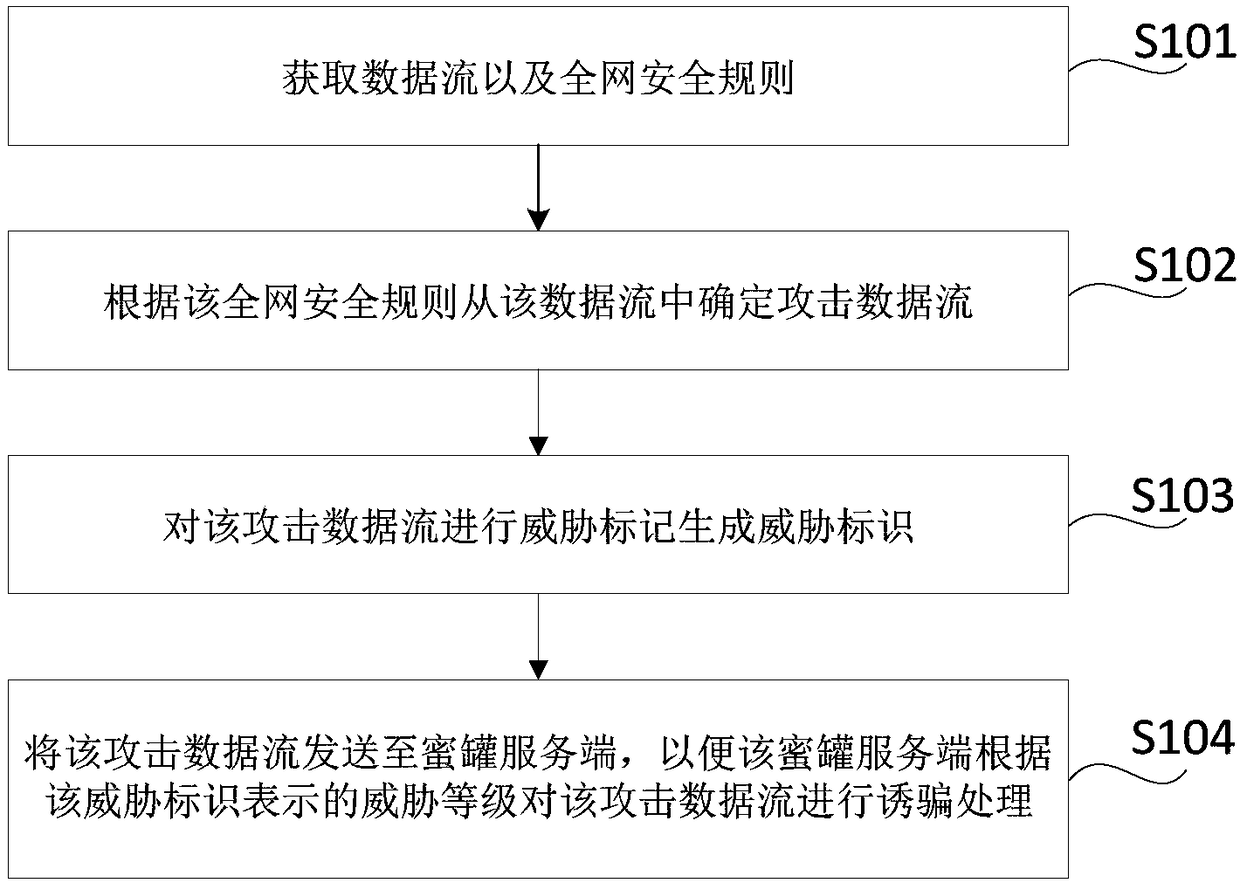
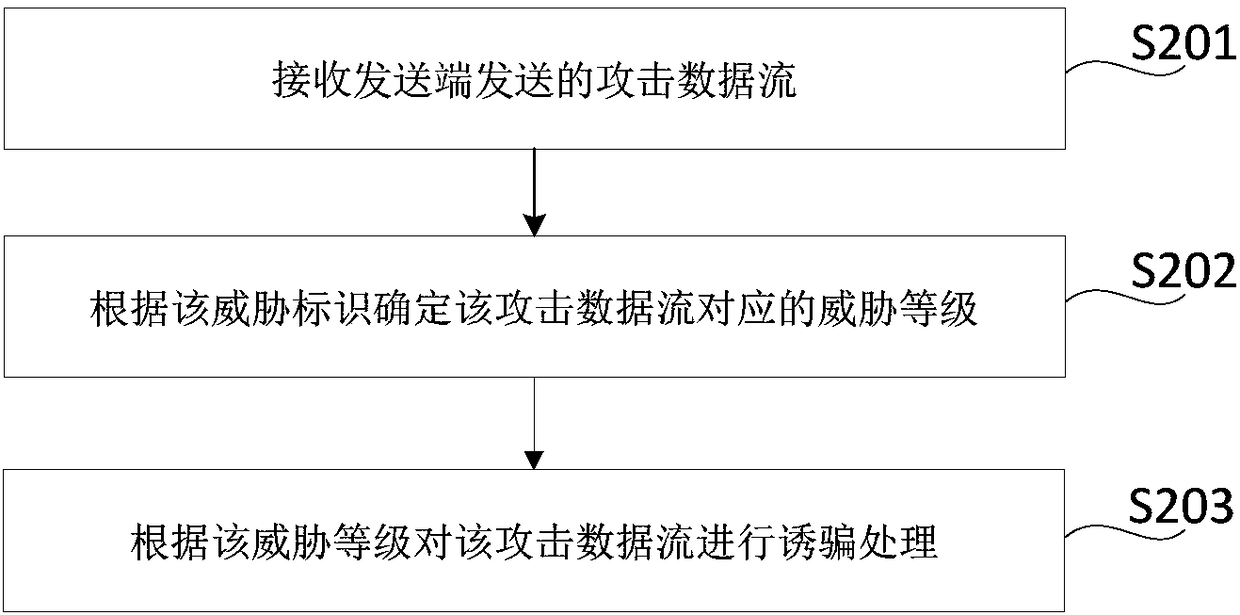
Method, device, storage medium and electronic device for defending data stream attack
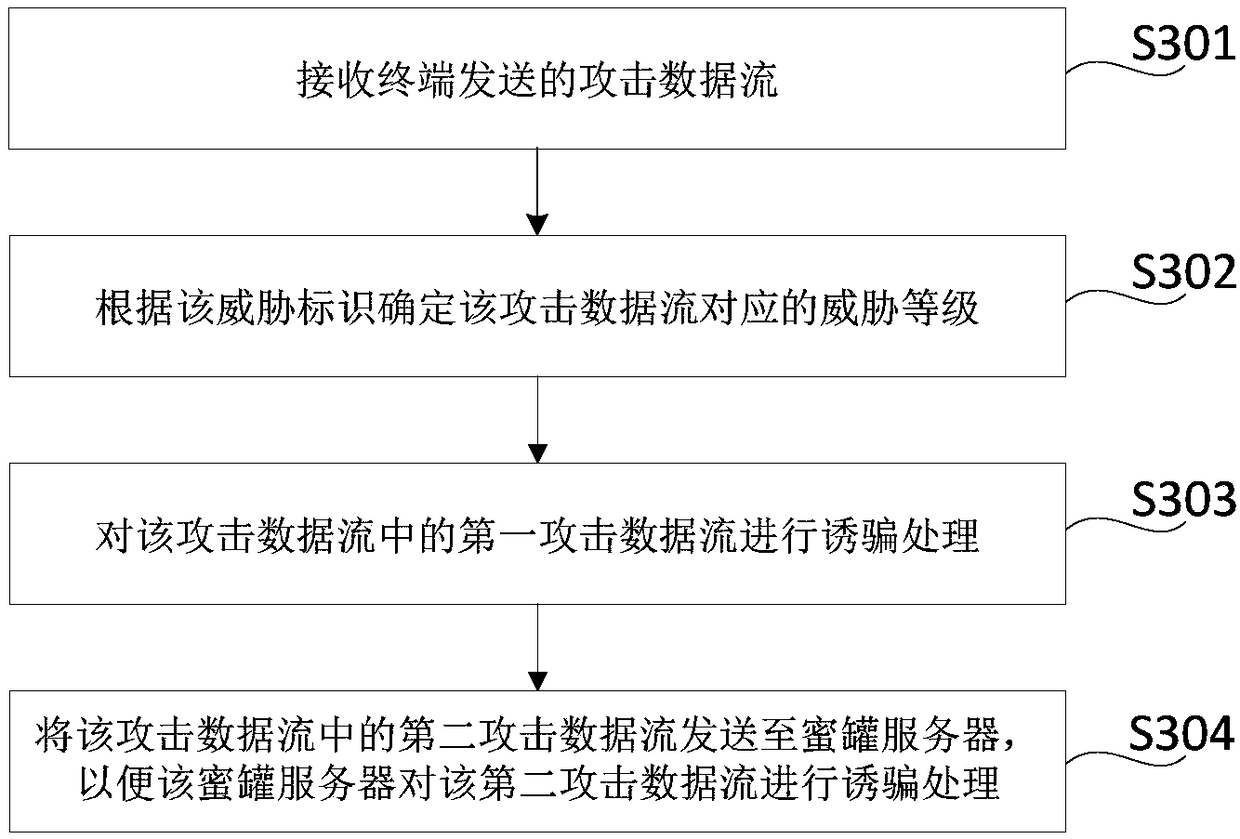
The present disclosure relates to a method, device, storage medium and electronic device for defending data stream attack; the data stream and the whole network security rules can be obtained throughthe terminal, and determine the attack data stream from the data stream according to the whole network security rules. At the same time, threat identification is performed on the attack data stream togenerate a threat identifier, the threat identifier indicates the threat level corresponding to the attack traffic; the attack traffic is sent to the honeypot server, so that the honeypot service enddecoys the attack data stream according to the threat level indicated by the threat identification, the terminal sends the attack data stream to the honeypot service end, and the honeypot service enddecoys the attack data stream, thereby reducing the occupation of the terminal resources and improving the data processing efficiency of the terminal.
Owner:NEUSOFT CORP
Electrical supply system with arc protection
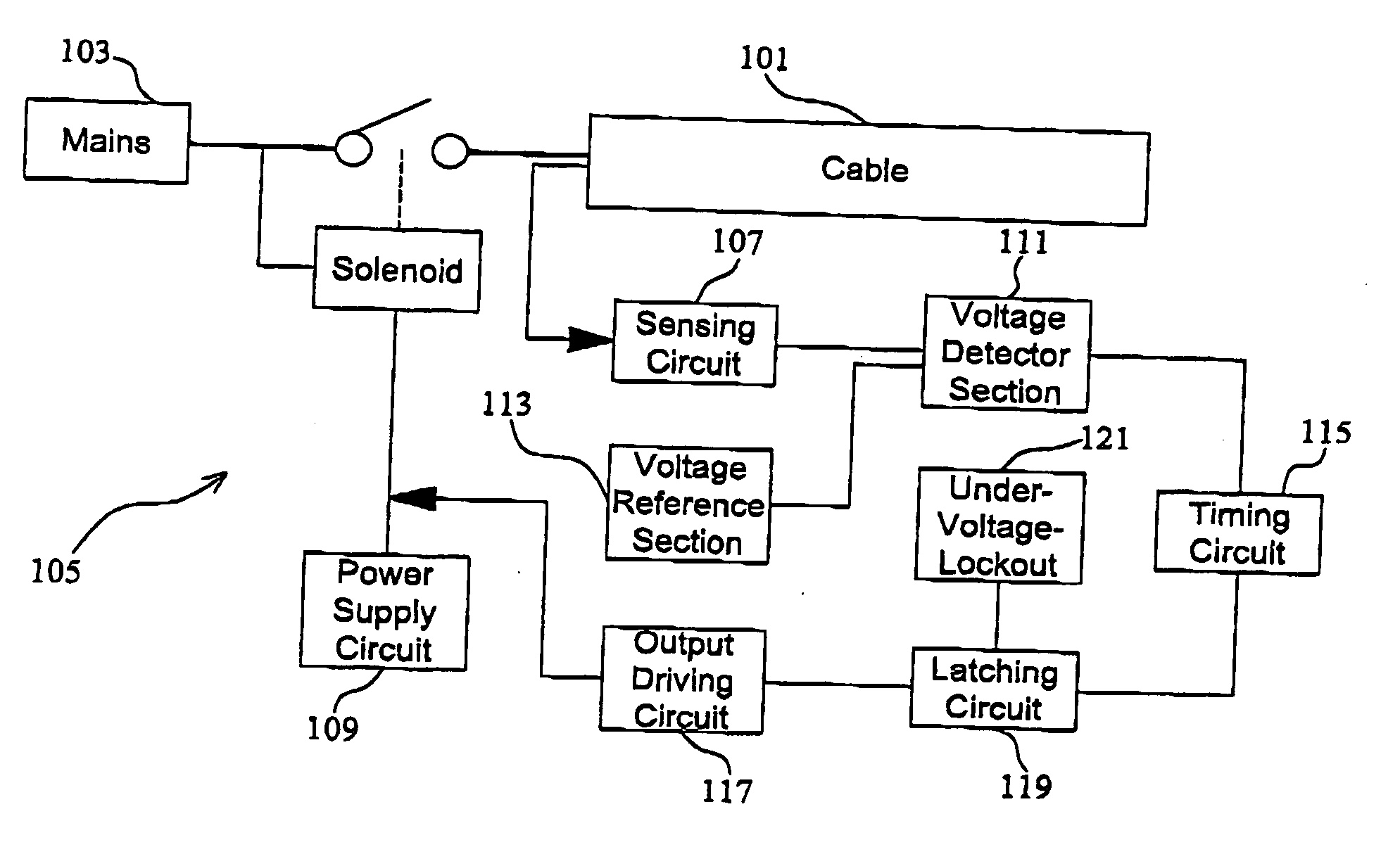
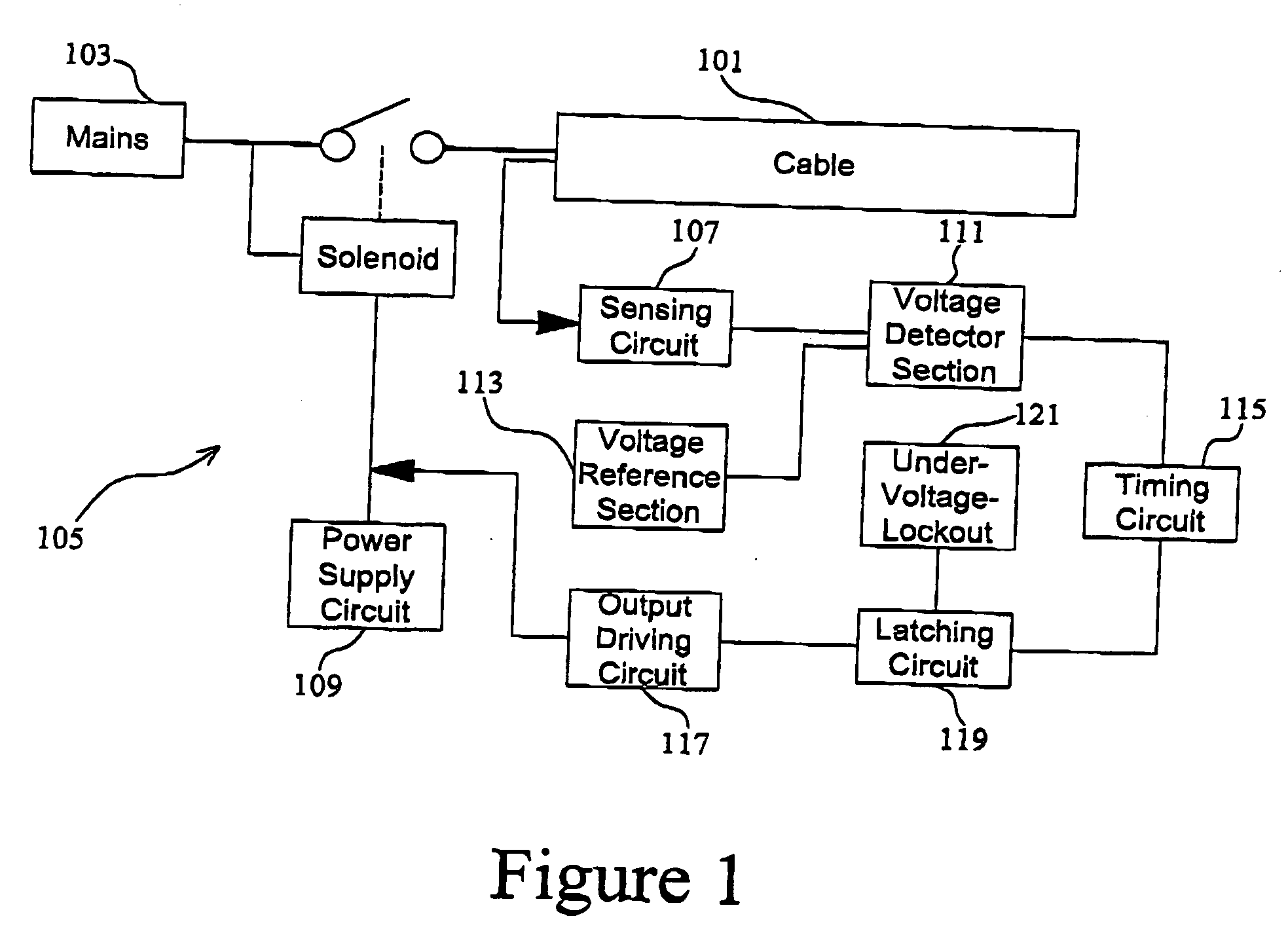
InactiveUS20060092585A1Power cables including communication wiresPower cables including electrical controlElectricityElectrical conductor
An electrical power supply system firstly includes a power cable electrically connected to a power source. The power cable has a power line and a first conductor; the first conductor is isolated from the power line and acts as a sensing line. The power cable also has a second conductor and the second conductor is isolated from the sensing line and acts as a neutral line; the power line, the sensing line and the neutral line are electrically connected to the power source. The system further includes an arc fault circuit interrupter including a sensing circuit in electrical connection with the sensing line for detecting an arc fault and a voltage source being in electrical connection with the sensing line. The voltage of the voltage source is designed to be below the hazardous voltage according to the electrical safety rules.
Owner:HONG KONG PRODUCTIVITY COUNCIL
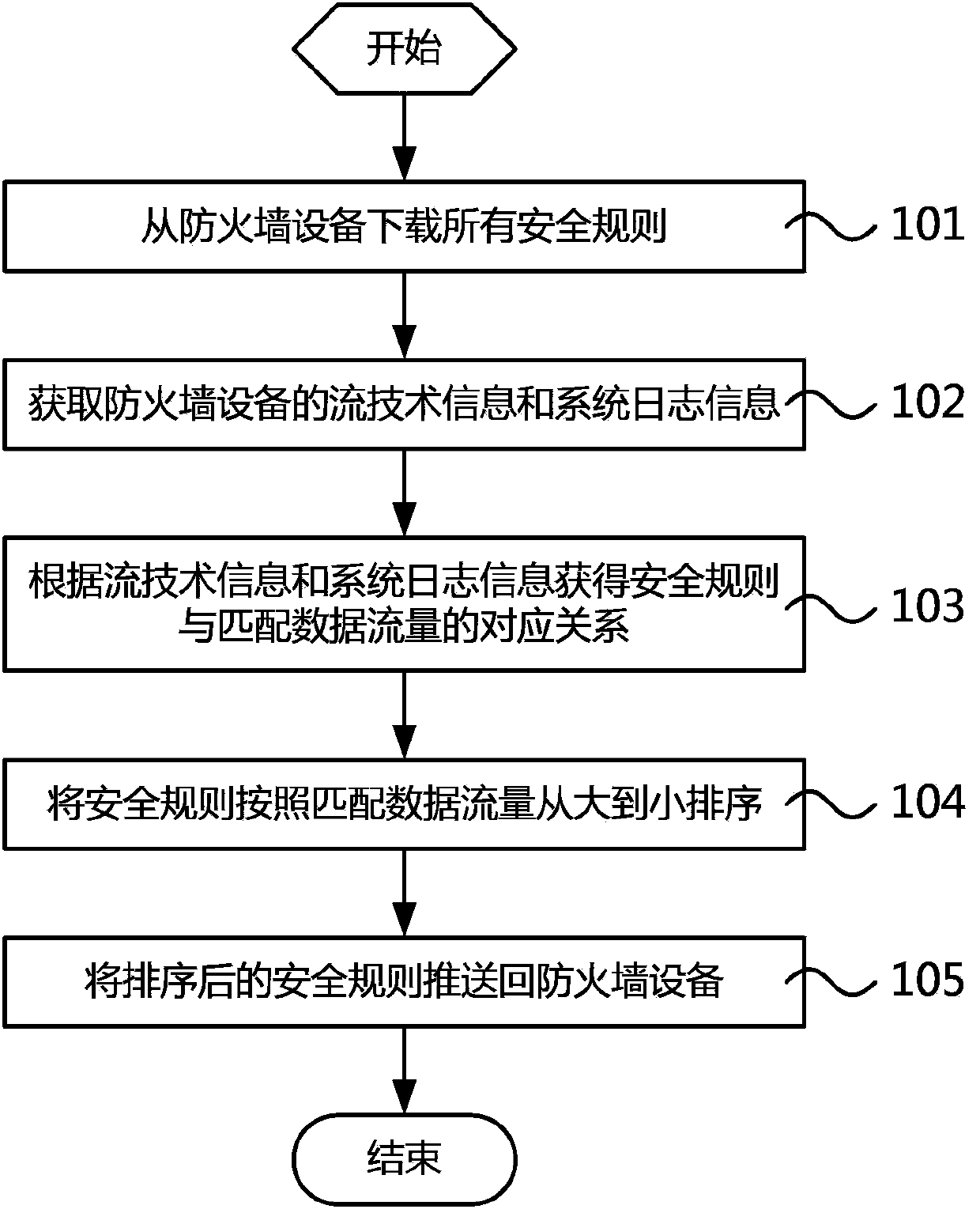
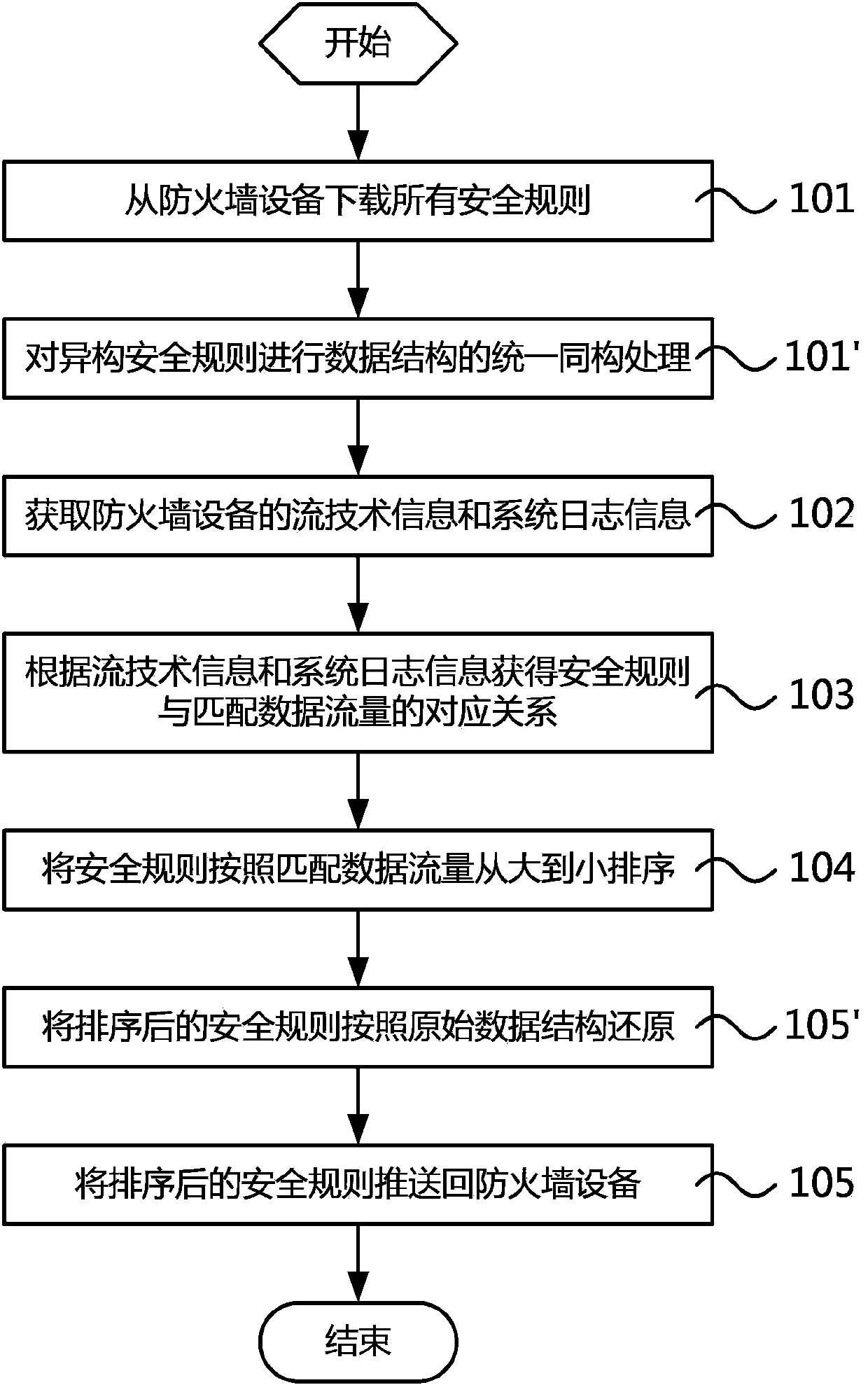
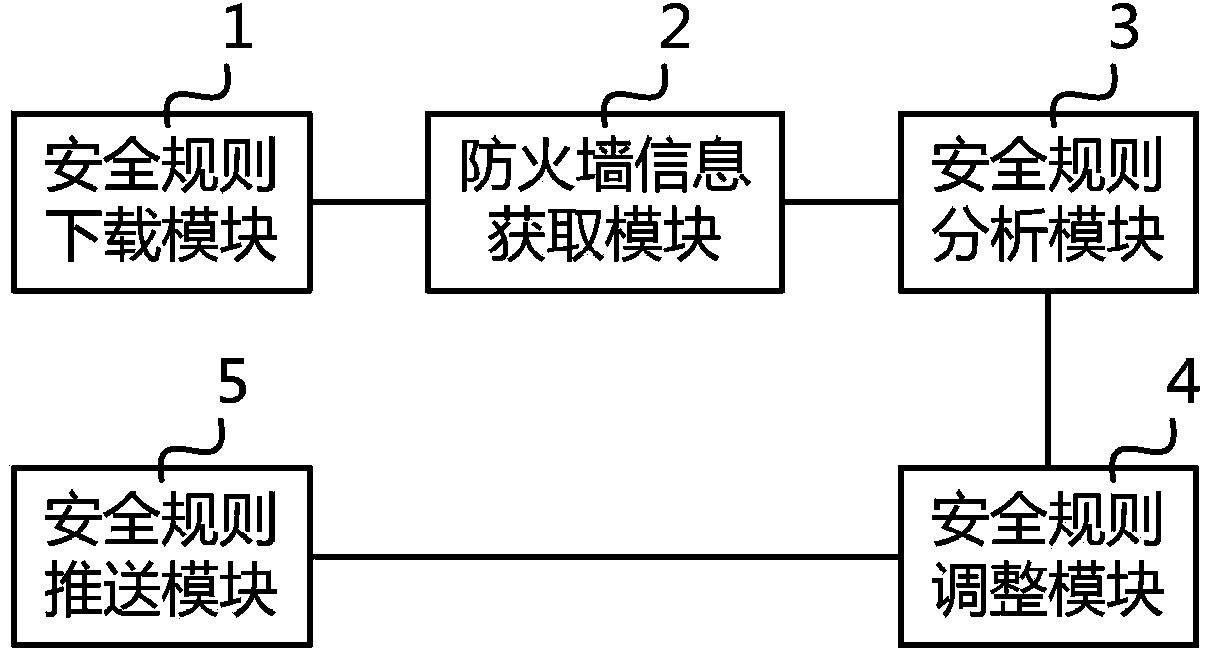
Firewall safety rule optimization method and device thereof
The invention relates to a firewall safety rule optimization method and a device thereof. The method comprises the following steps: all safety rules are downloaded from firewall equipment; a streaming technical information and system log information of the firewall equipment are obtained; correspondence between the safety rules and matched data traffic is obtained according to the streaming technical information and the system log information; and the safety rules are sorted from large to small according to the matched data traffic, and the sorted safety rules are pushed back to the firewall equipment. According to the invention, matched data traffic of each safety rule in a firewall is determined by analyzing FLOW information and SYSLOG information of the firewall, sorting operation from large to small is carried out in allusion to the data traffic, and the sorted safety rules are pushed back to the firewall. Thus, safety rules such as heavy matched traffic and high frequency are adjusted to the forefront of a safety rule list. Based on a present matching mode of the safety rule list from top to bottom, firewall rule matching efficiency is raised after the safety rule list is adjusted.
Owner:CHINA TELECOM CORP LTD
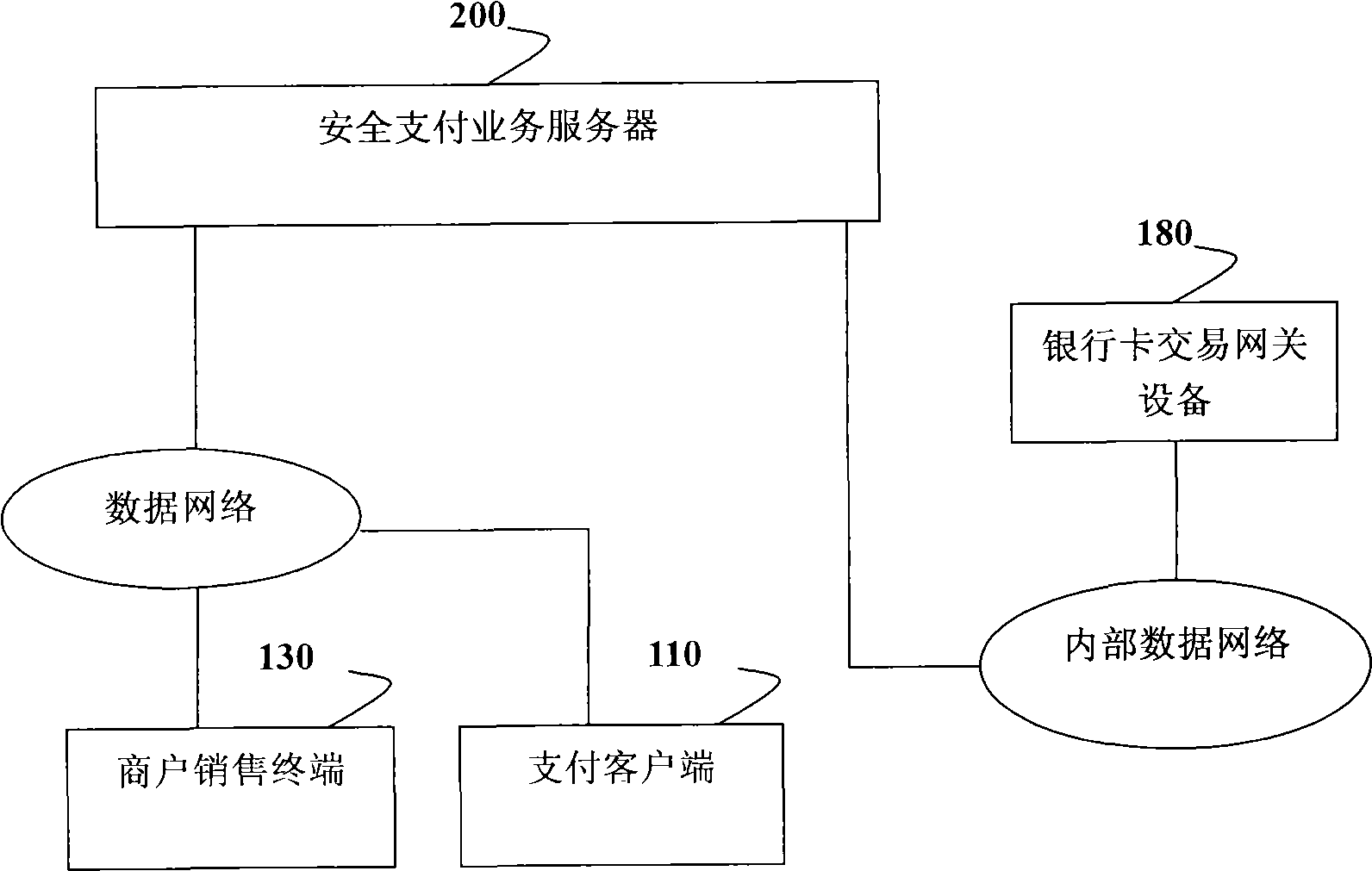
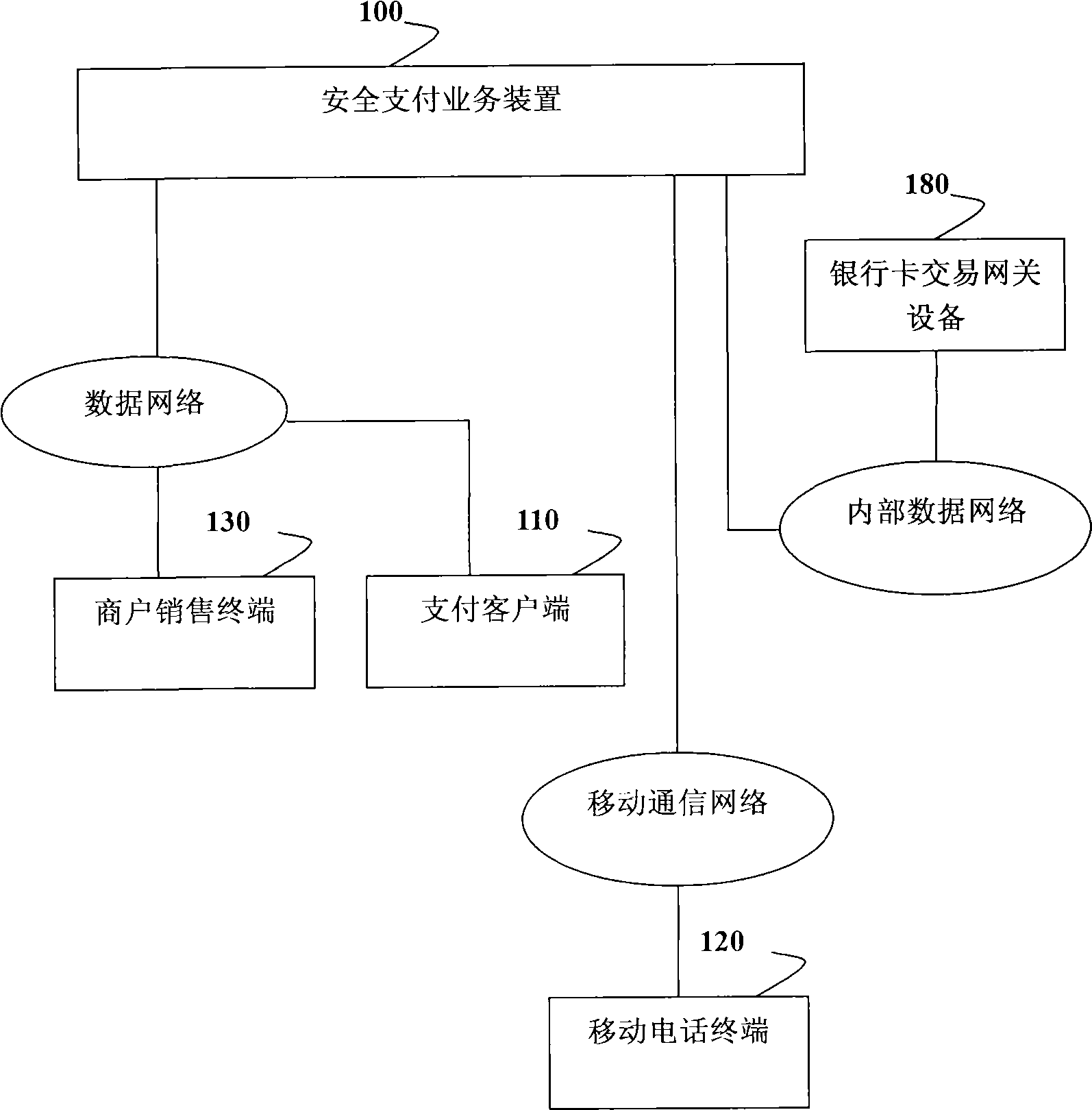
Safe payment system with separated order and payment and safe payment method
InactiveCN101533495AMeet payment needsFinancePayment architecturePayment transactionComputer terminal
The invention provides a safe payment system with separated order and payment and a safe payment method, thereby realizing the separation of order and payment and facilitating information of a bank card of a user to be confidential during the payment process or not occur at the front end of the payment, the information of the bank card of the user only occurs between a payment center and a bank card payment transaction system of a bank or the bank card payment transaction system of CUP according to safety rules of standard bank payment transactions, preferentially, the invention adopts a mode of sending an order message to a mobile phone terminal, selecting an order on the mobile phone terminal by the user and submitting the payment, thereby being capable of meeting payment needs of the user anytime and anywhere.
Owner:候万春
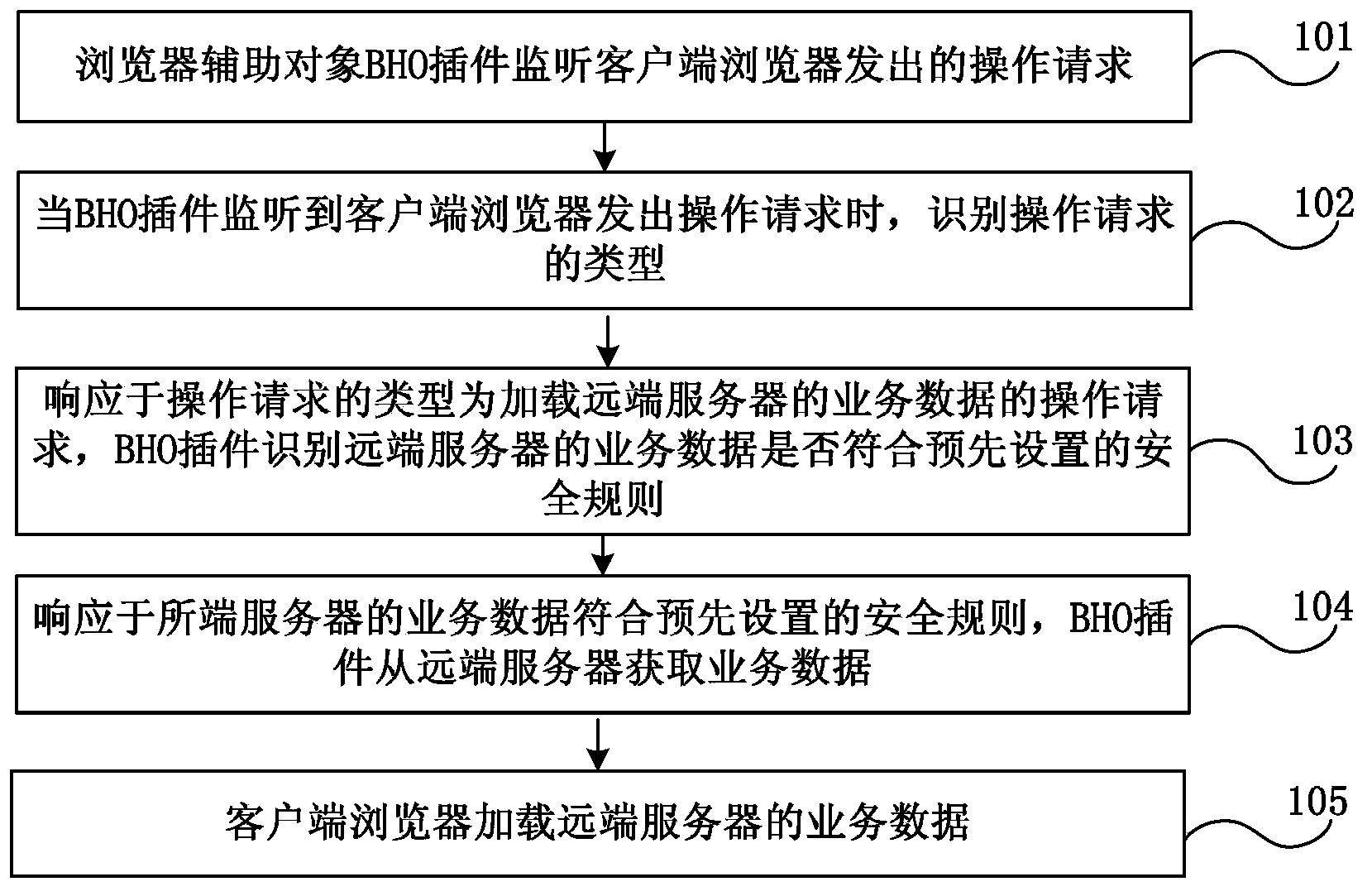
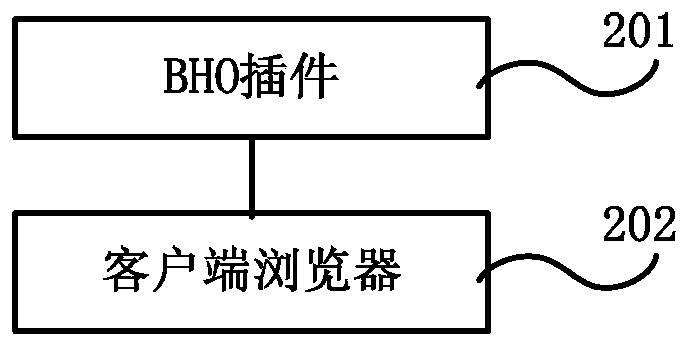
Browser service data processing method and apparatus
The invention discloses a browser service data processing method and apparatus. The method comprises: monitoring an operation request emitted by a client browser through a browser helper object (BHO) plug-in; when the BHO plug-in monitors the operation request emitted by the client browser, identifying the type of the operation request; in response to the operation request with an identification result being loading the service data of a far-end server, the BHO plug-in identifying whether the service data of the far-end server accords with a preset safety rule; in response to accordance with the preset safety rule, the BHO plug-in acquiring the service data from the far-end server; and the browser loading the service data of the far-end server. By using the browser service data processing method and apparatus, client-based cross site script vulnerability attack defense is realized.
Owner:CHINA TELECOM CORP LTD
Intrusion prevention system for vehicle-mounted information system
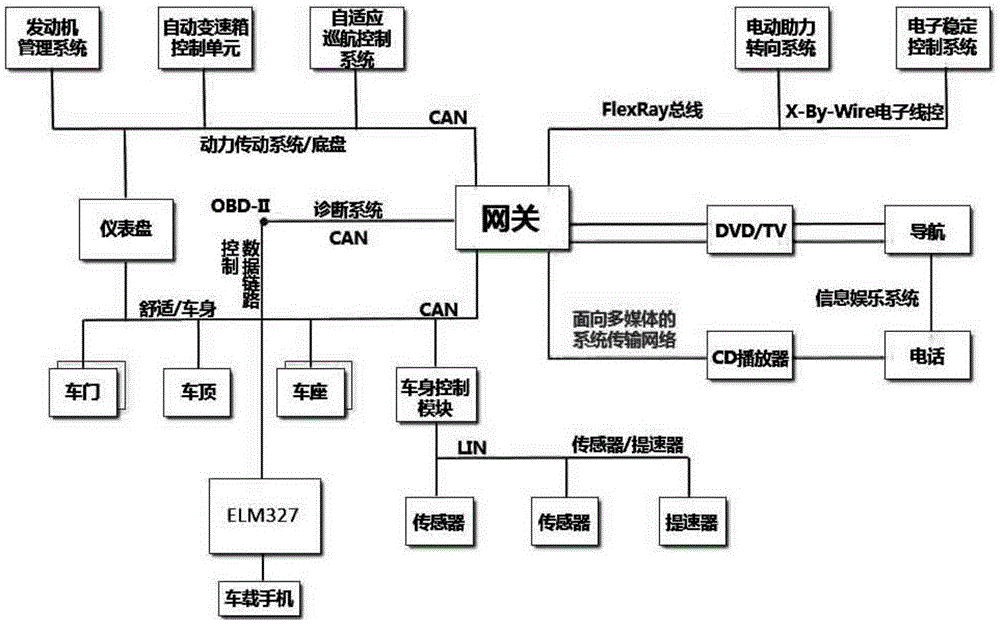
InactiveCN105083165AEnsure the safety of life and propertyElectric/fluid circuitElectric power steeringDrivetrain
The invention discloses an intrusion prevention system for a vehicle-mounted information system. The intrusion prevention system comprises a power transmission system, an electric power steering system, an electronic stability control system, an instrument panel, a diagnostic system, a vehicle body control system, a sensor, an accelerator, a multimedia system and a vehicle-mounted mobile phone. The power transmission system, the electric power steering system, the electronic stability control system, the vehicle body control system and the multimedia system are connected with the diagnostic system through a gateway, the diagnostic system is connected with the vehicle-mounted mobile phone, the instrument panel is connected with the vehicle body control system and the power transmission system, and the sensor and the accelerator are connected with the vehicle body control system. Compared with the prior art, the powerful calculation capability and storage capability of the mobile phone are utilized, the mobile phone is set as an intrusion prevention center; the formulation of safety regulations, storage of a virus reservoir, the judgment of security situation awareness and the connection with a cloud are all finished through the mobile phone, users' life and property safety is guaranteed, and the intrusion prevention system has popularization and application values.
Owner:CHENGDU UNIV OF INFORMATION TECH
Method for reinforcing and sealing coal mine and preventing gas
ActiveCN101634231AImprove physical and mechanical propertiesHigh strengthMaterial fill-upGas removalCoal mine methaneEngineering
The invention relates to the technology of coal mine gas governance, in particular to a method for reinforcing and sealing coal mine and preventing gas. The method solves the problems of air leak and gas emission caused by cracks formed by disturbing coal petrology bed during coal mining in the prior art. The method comprises the following steps: modifying and reinforcing the support of neighbor sealing tunnels; drilling and grouting at the outer side of a sealing wall; and spraying polymer material at the surface of the sealing wall to reach a target for reinforcing the sealing wall and plugging the cracks of the wall. After reinforcing and plugging the sealing wall of the tunnel, softly cracked coal rock is cemented into one body, so that the whole intensity of wall rock in a whole sealing region is greatly improved, the average sectional shrinking ratio of the wall rock of the tunnel is less than 3%, the average air leak ratio of the sealing zone of the tunnel is reduced by more than 96%, and gas emission amount meets the requirement of the safety rules of the coal mine.
Owner:SHANXI JINCHENG ANTHRACITE COAL MINING GRP CO LTD
System and method of automatically preventing and arranging processing strategy conflicts
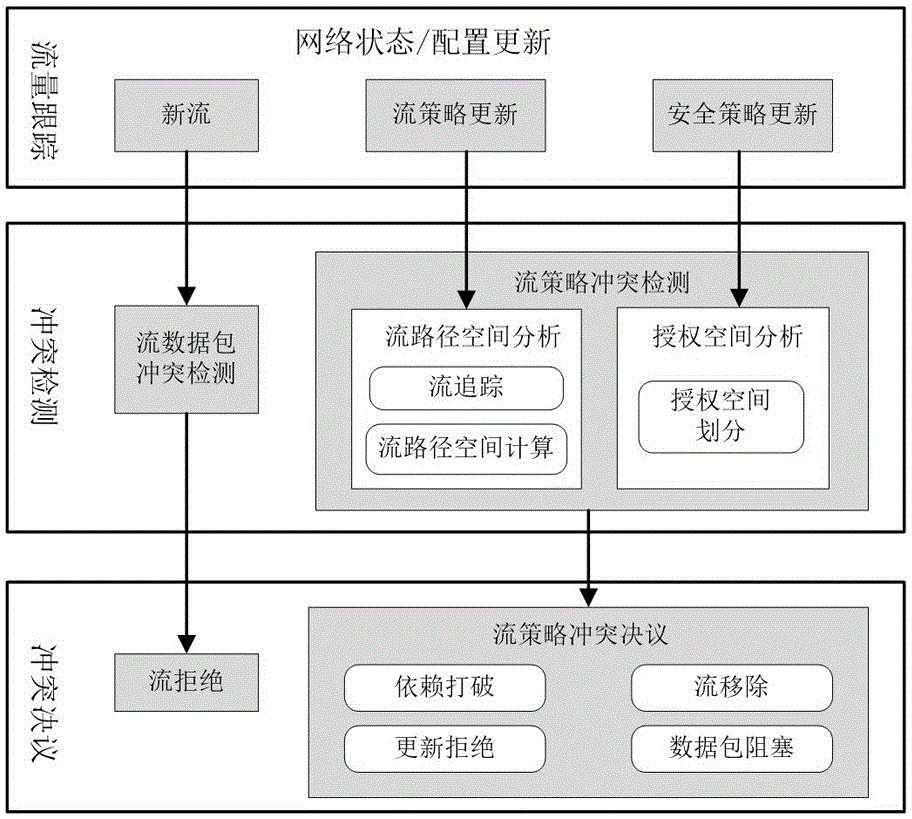
ActiveCN106817275AGuaranteed safe operationPolicy conflicts are effective and real-timeData switching networksNetwork packetComputer module
The invention discloses a system and a method of automatically preventing and arranging processing strategy conflicts. The method of solving the processing strategy conflicts comprises steps that (1) when a first packet of a new business flow is transmitted to a controller, and the security authorization module of the controller is used for the safety rule matching of the data packet, and a network entry switch is used to admit or reject the new business flow; (2) a flow path is established by acquiring network flow information; (3) the strategy conflicts are detected, and different processing methods are adopted according to the different strategy conflicts. The system and the method are used to detect the safety strategy conflicts or application strategy conflicts caused by changes of network states and flow accurately. The system is capable of effectively and timely solve the conflicts according to the concrete states of the conflicts such as partial rule conflicts or full conflicts. The system and the method are used to detect and solve the strategy conflicts actively, and therefore the safety and high-efficiency operation of the network is realized.
Owner:JIANGSU FUTURE NETWORKS INNOVATION
Method for improving fire wall performance
InactiveCN1439985AImprove processing speedImprove throughputSpecial data processing applicationsUser inputNetwork packet
A method to improve performance of fireproof wall in computer network system applies hyperspace model to create safety rules, which includes the following steps: 1) inputting safety strategic steps by the User, 2) carrying on preprocessing steps of space dividing, syntax checking and semantic analysing for the rules having been preprocessed for creating smantic structure tree of safety strategy and creation step to be down loaded into fulcrum and 4) inquring method for fireproof wall safety strategy created according to above method, of which step 4) can be operated as capturing each data packet passing through the fireproof wall by filtering module to extract information in it for obtaining access state bit in order to execute relevant action after the downloading operation.
Owner:华北计算机系统工程研究所
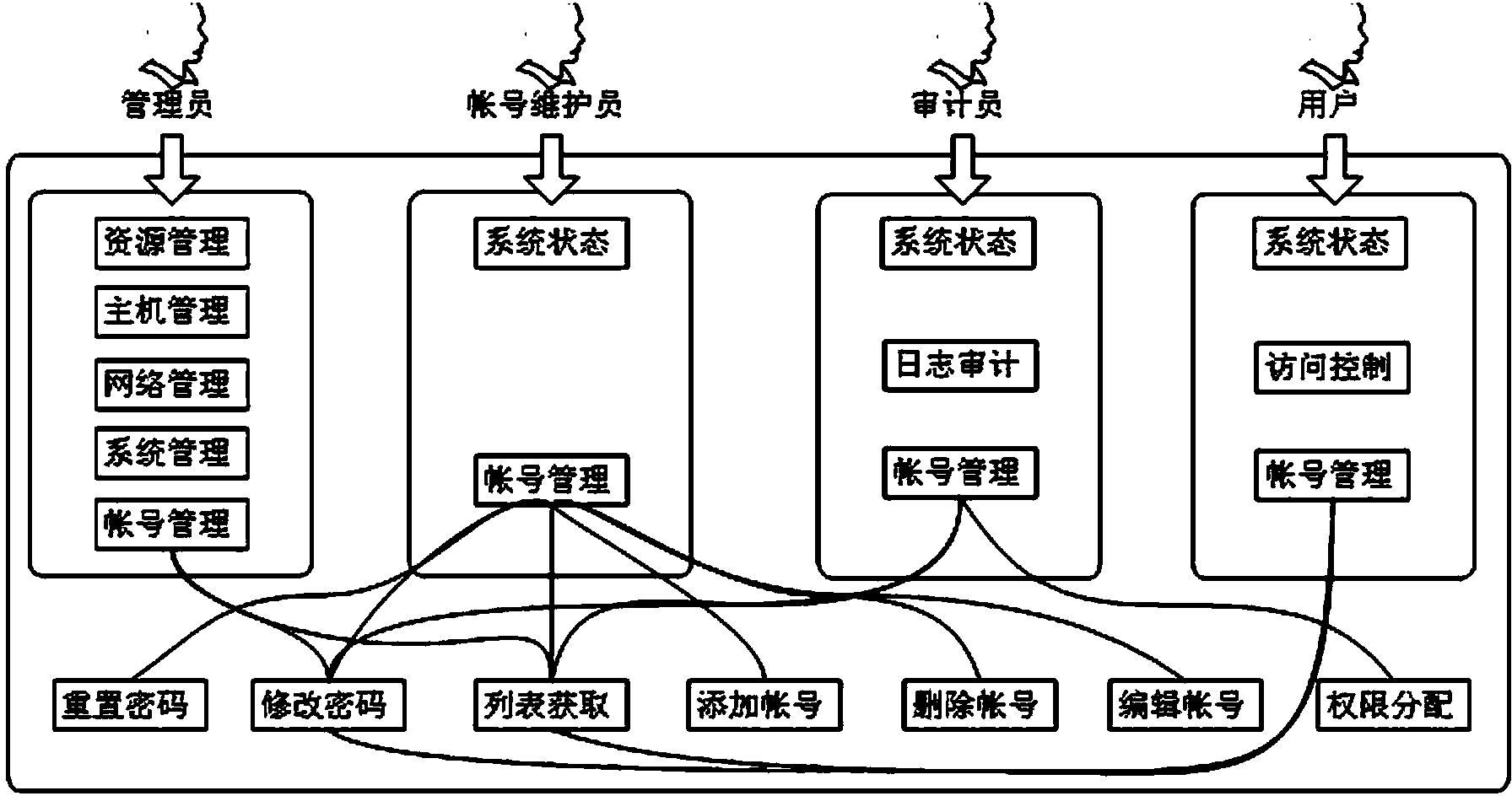
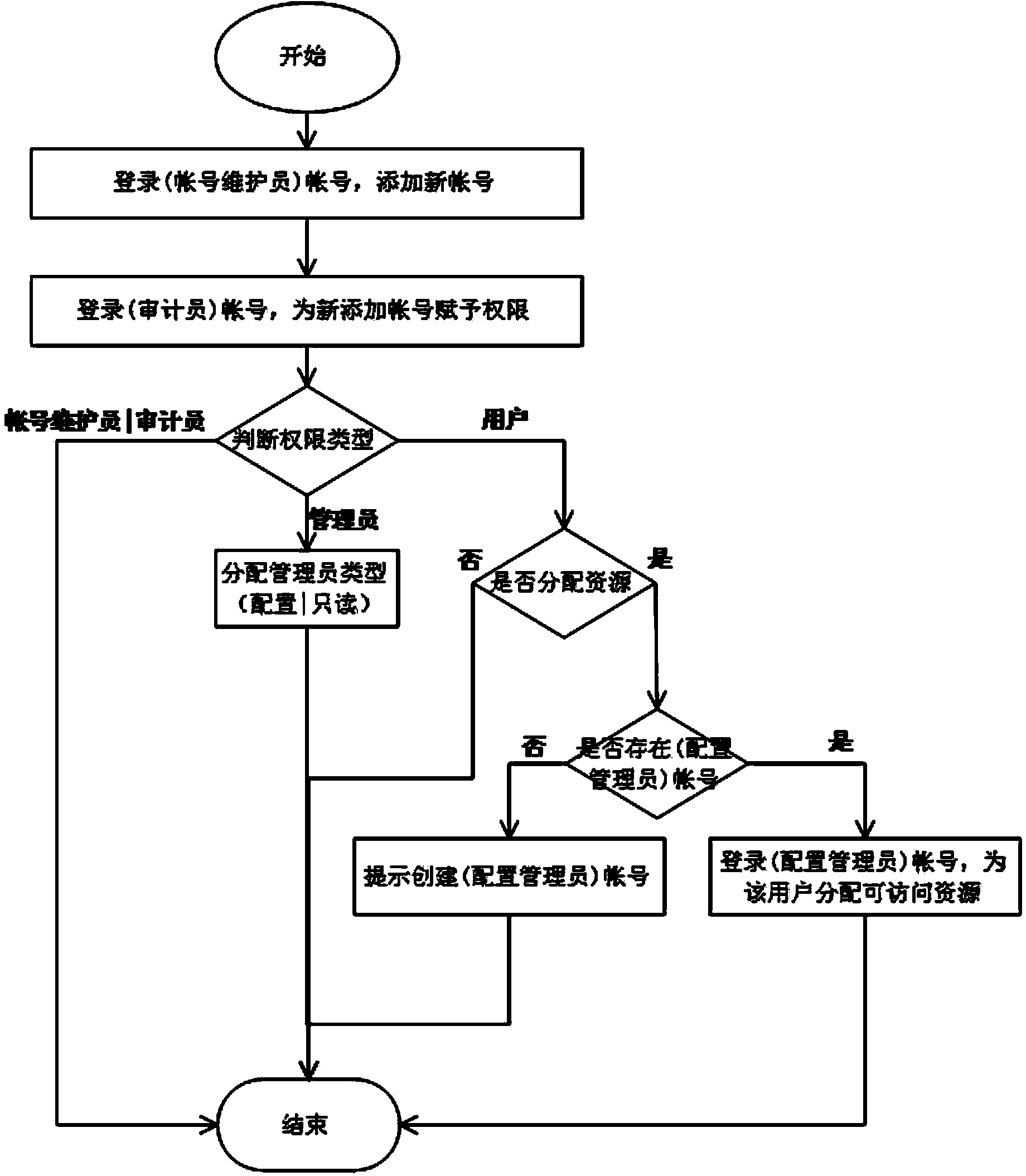
Multi-permission distribution method based on SAN storage system
ActiveCN103763369AEnable secure accessAvoid operabilityDigital data protectionInternal/peripheral component protectionDistribution methodSystems management
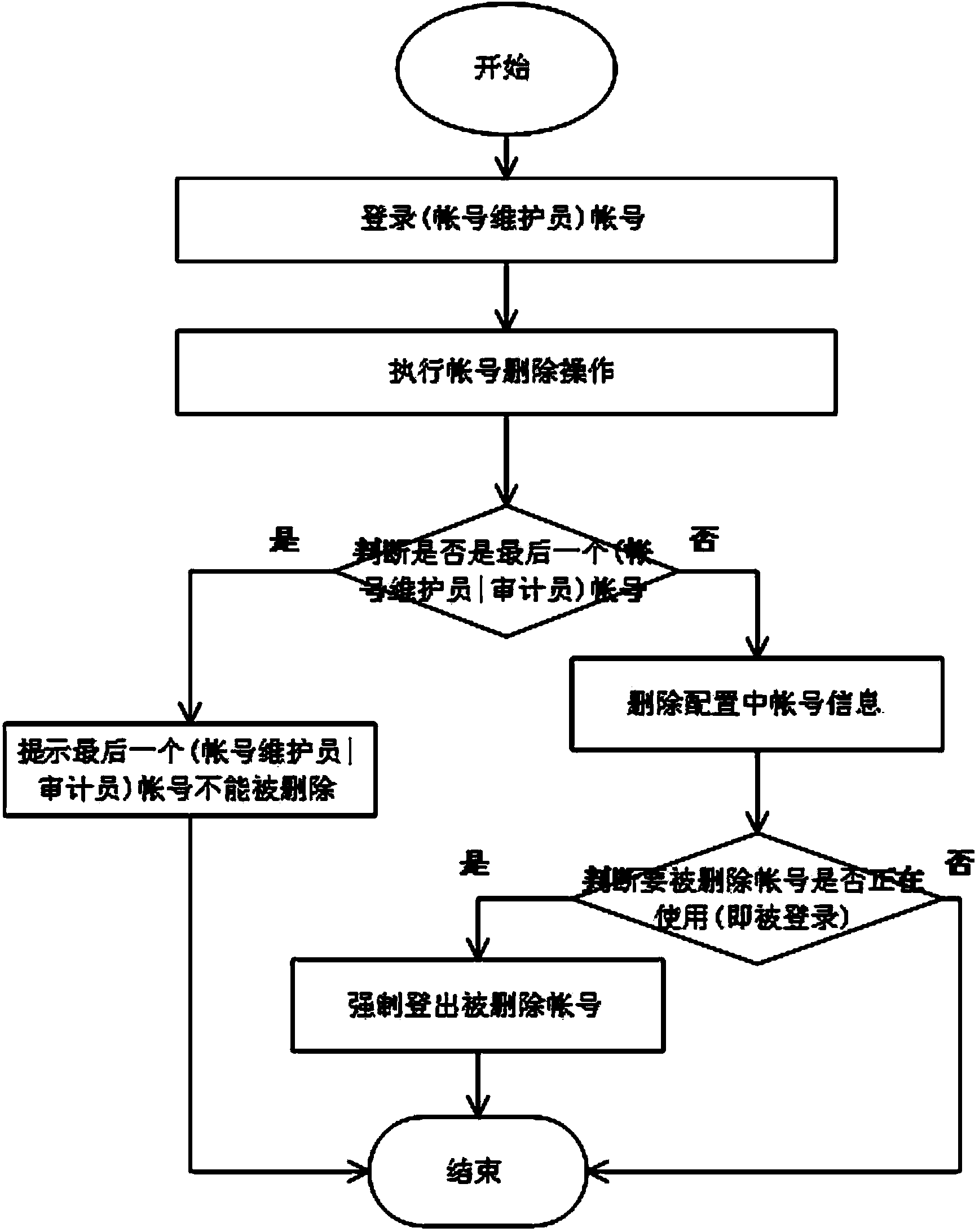
The invention provides a multi-permission distribution method based on an SAN storage system. The multi-permission distribution method specifically comprises the steps that multiple roles are distributed, namely the four roles of an account number maintainer, an auditor, an administrator and a user are set in a system management task and are endowed with corresponding permission and management ranges, the four roles restrict one another, permission of the storage system is separated according to the specific safety rule, the safety rule is the minimum privilege rule, the separated permission comprises the storage system management permission and the data visit permission, and when an attacker obtains instructions of one or two management roles, the storage system will not be completely controlled. Compared with the prior art, the multi-permission distribution method based on the SAN storage system has the advantages that specified users can have access to and control specified resources by distributing the user role resources, safety and controllability of operation on and access to the storage system are ensured, practicability is high and popularization is easy.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com