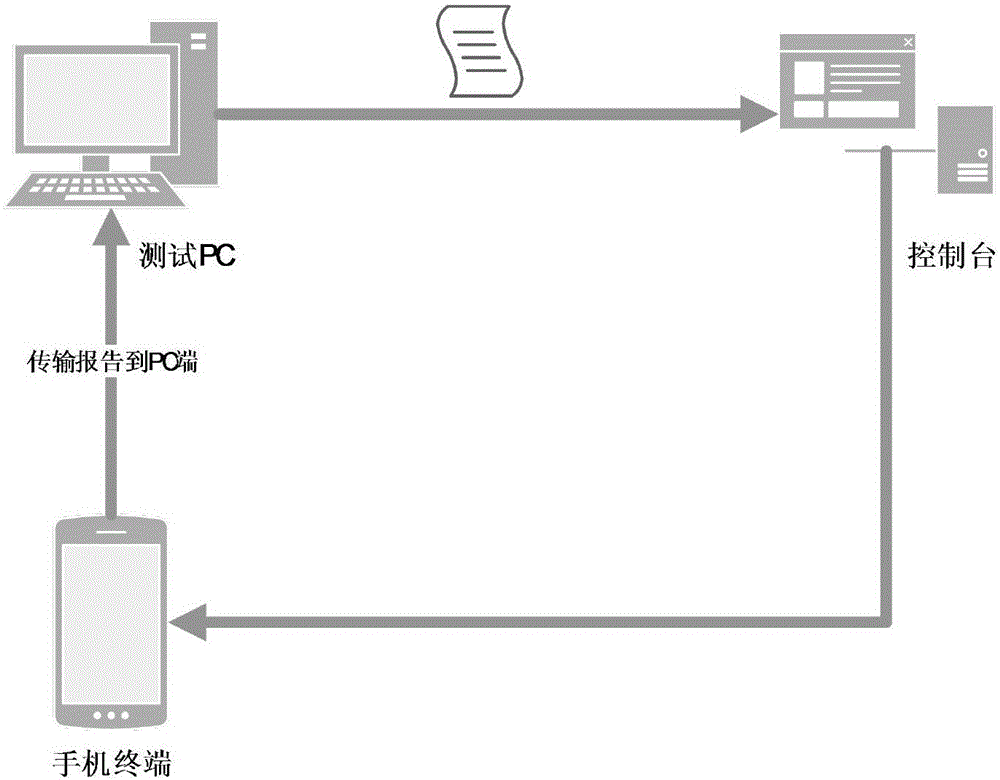
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
64 results about "Security specification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
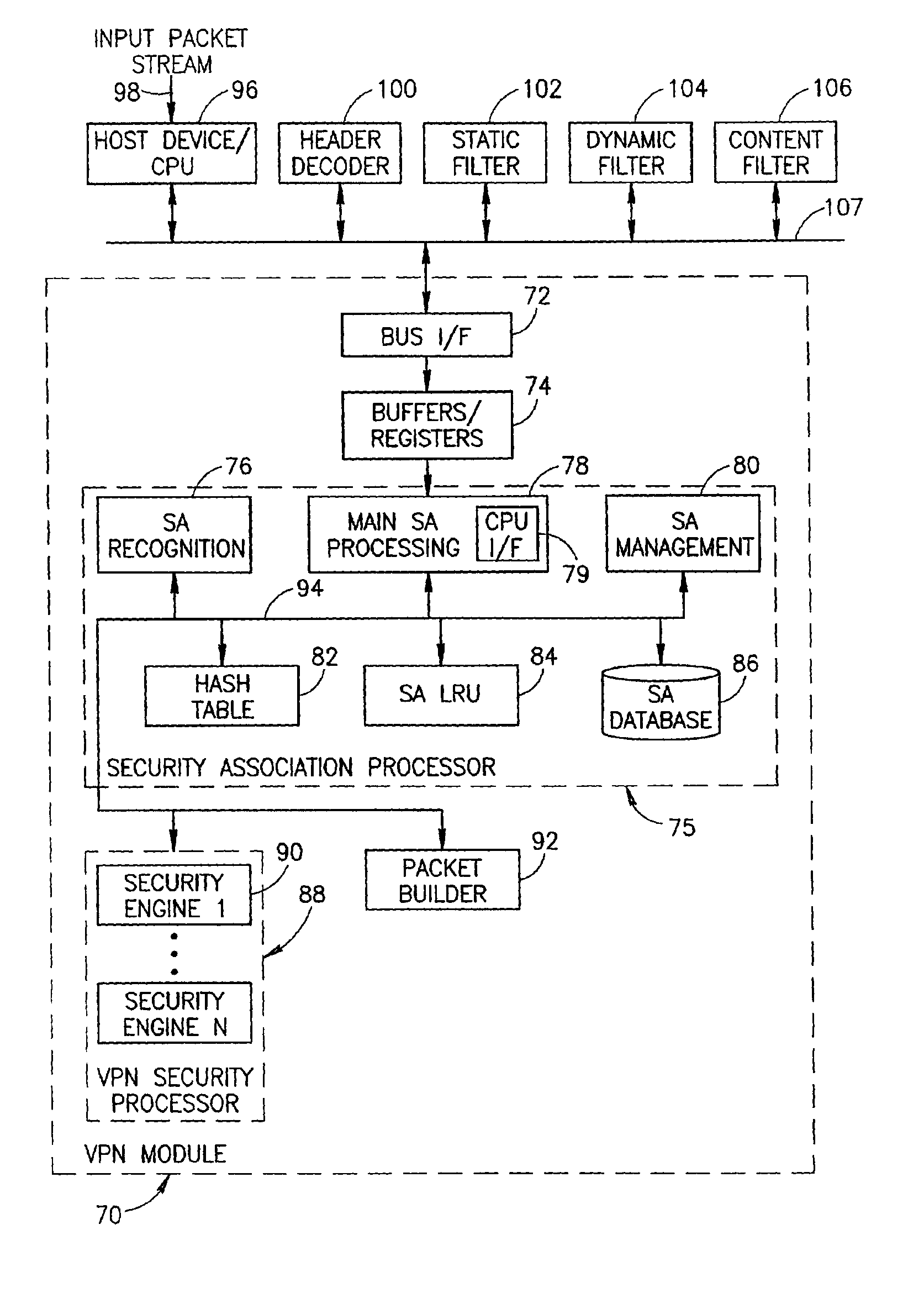
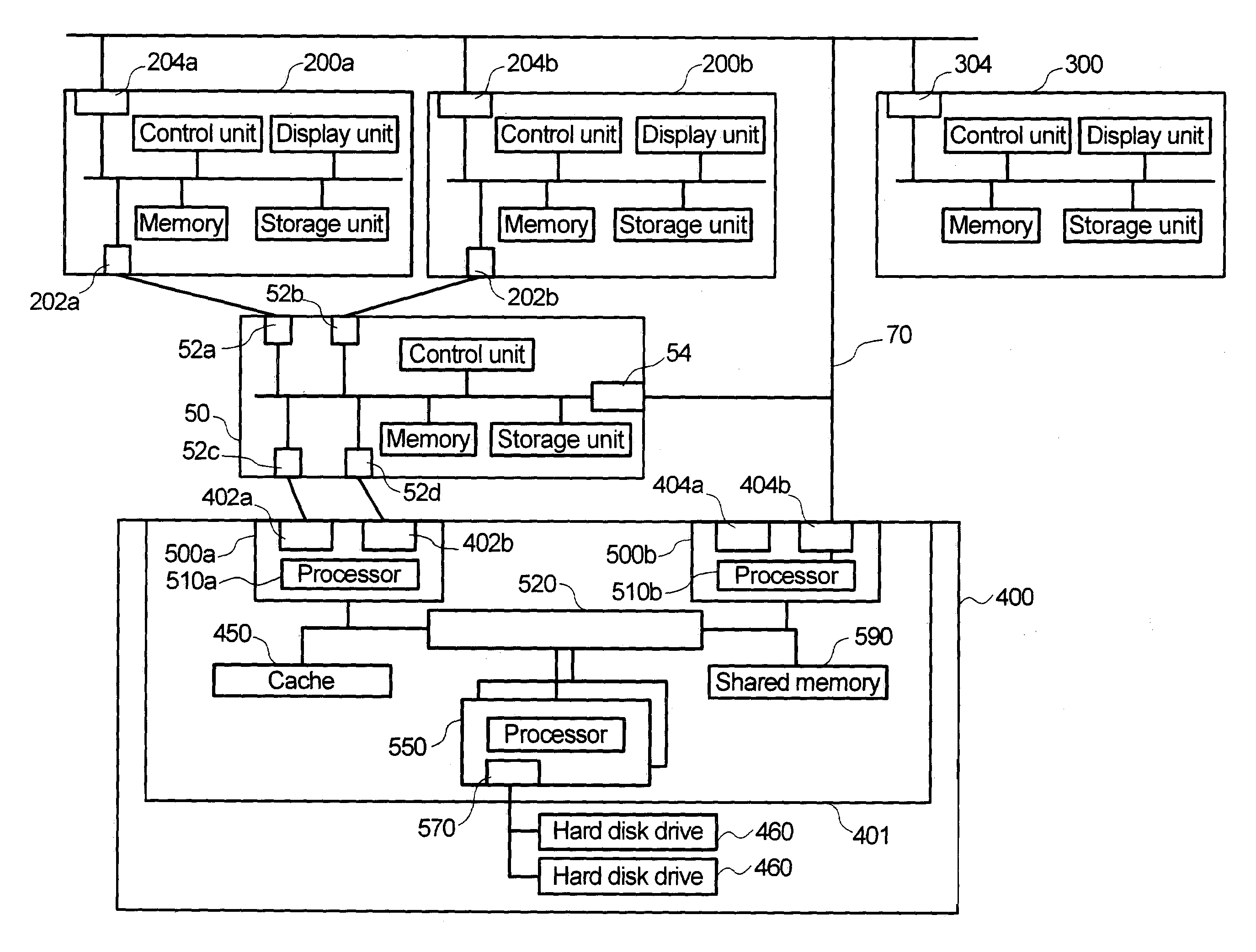
Virtual private network mechanism incorporating security association processor
ActiveUS7107464B2Low costLow-cost implementationMultiple digital computer combinationsProgram controlSecurity associationPrivate network
A novel and useful virtual private network (VPN) mechanism and related security association processor for maintaining the necessary security related parameters to perform security functions such as encryption, decryption and authentication. A security association database (SAD) and related circuitry is adapted to provide the necessary parameters to implement the IPSec group of security specifications for encryption / decryption and authentication. Each security association (SA) entry in the database comprises all the parameters that are necessary to receive and transmit VPN packets according to the IPSec specification.
Owner:TELECOM ITALIA SPA
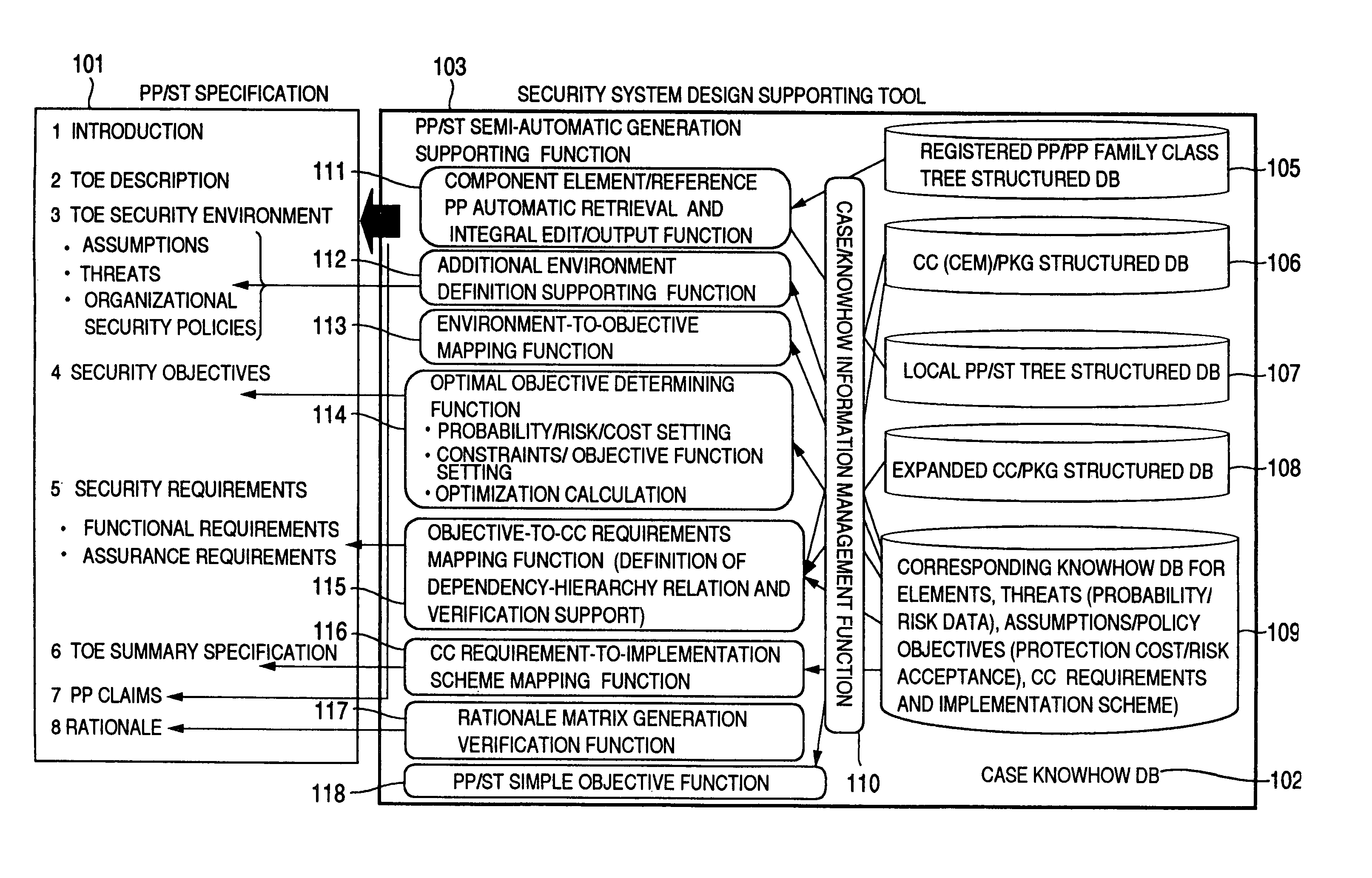
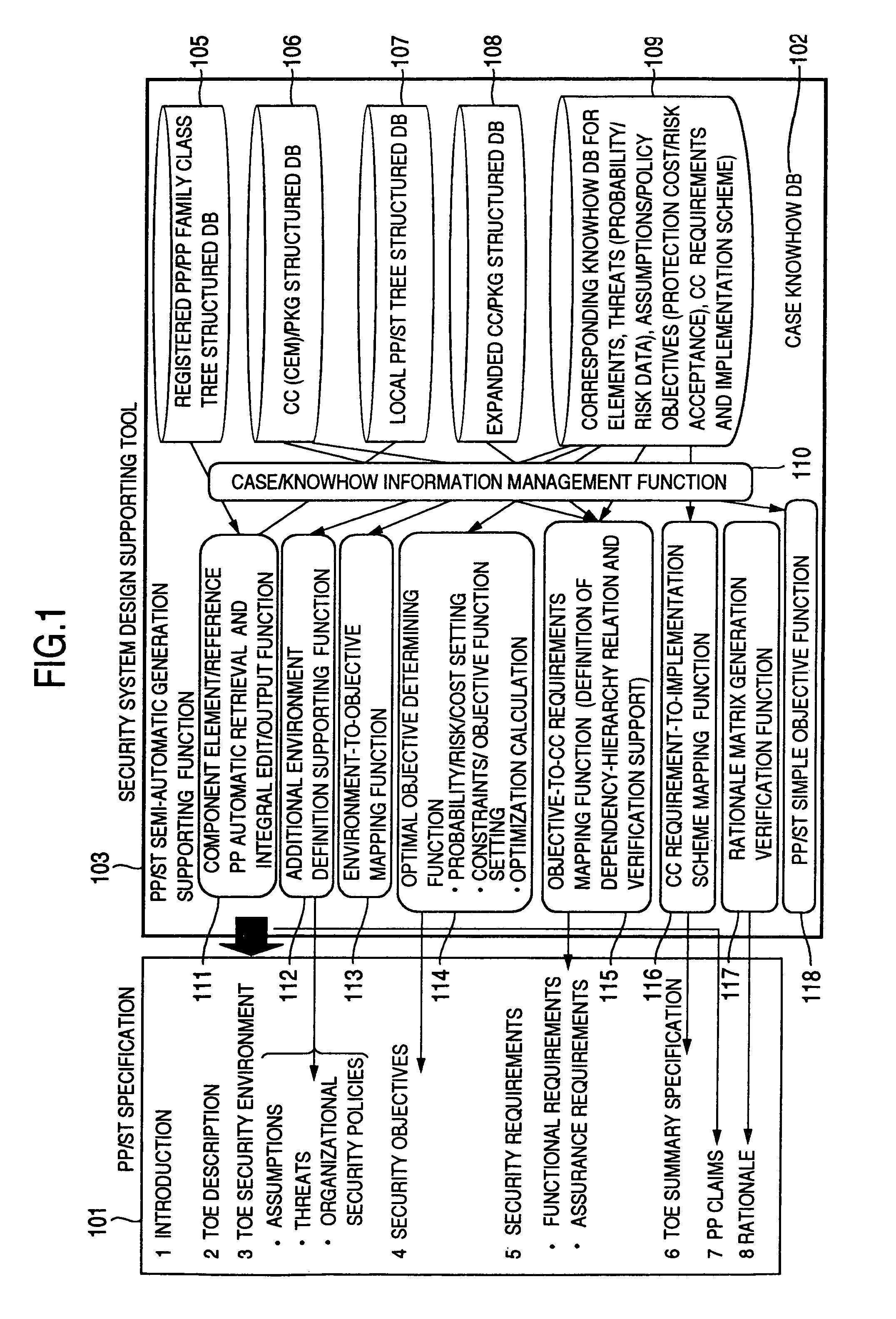
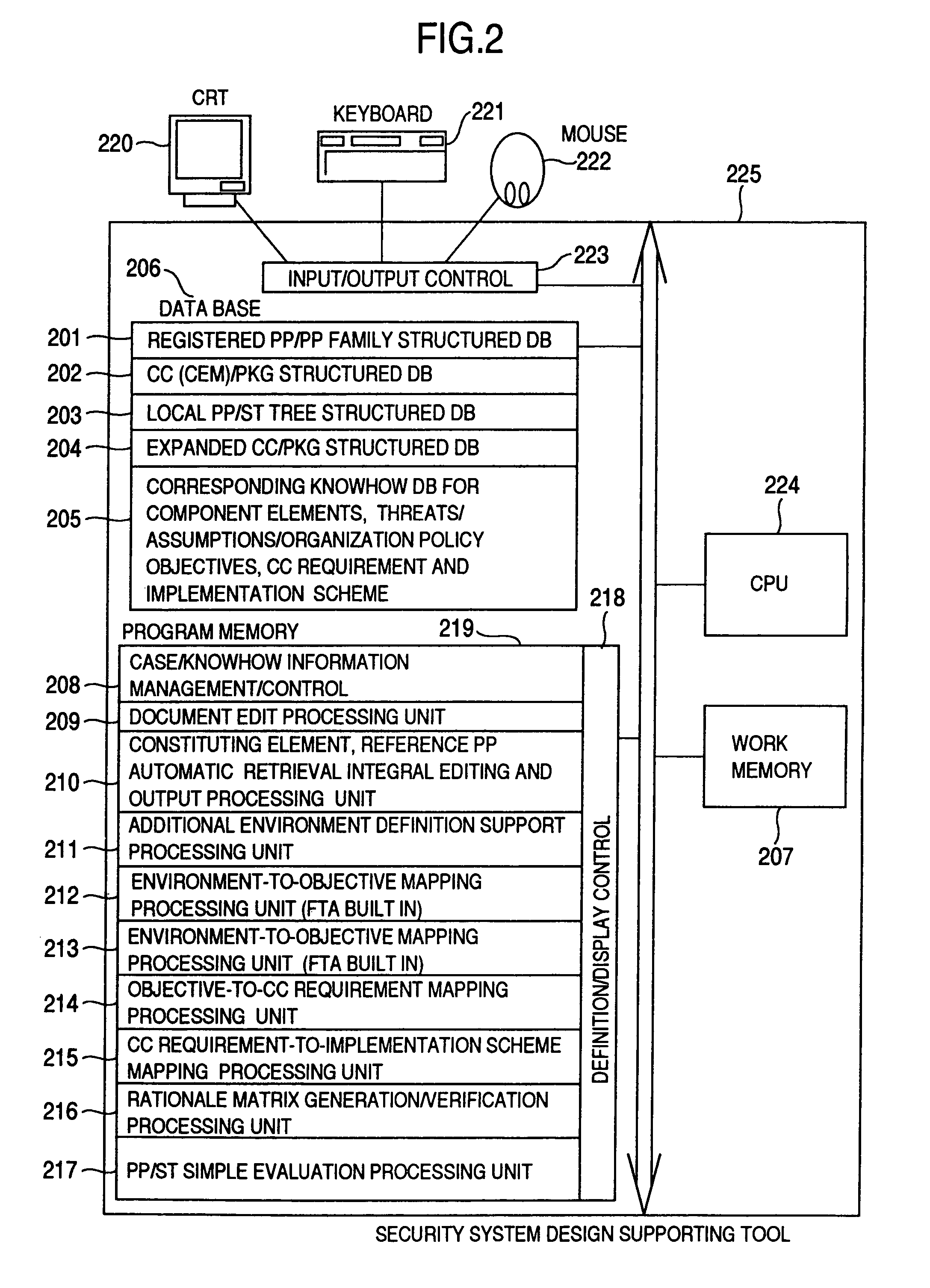
Security system design supporting method
InactiveUS7089581B1Improving efficiency of preparation stepUniform quality of preparationData processing applicationsDigital data processing detailsGeneration processSecurity specification
A security system design supporting tool and method are disclosed, in which security requirements (PP) and security specifications (ST) used for designing a product or a system (TOE) based on CC requirements can be prepared efficiently and uniformly even by ordinary designers other than specialists. In a security system design supporting method, registered PPs and past PP / ST generation cases are so structured as to reuse and / or reference as templates, a draft is automatically generated, and the draft thus generated is additionally modified or corrected by partial automatic generation utilizing a database of past generation cases and partial case accumulated in the generation process thereof.
Owner:HITACHI LTD
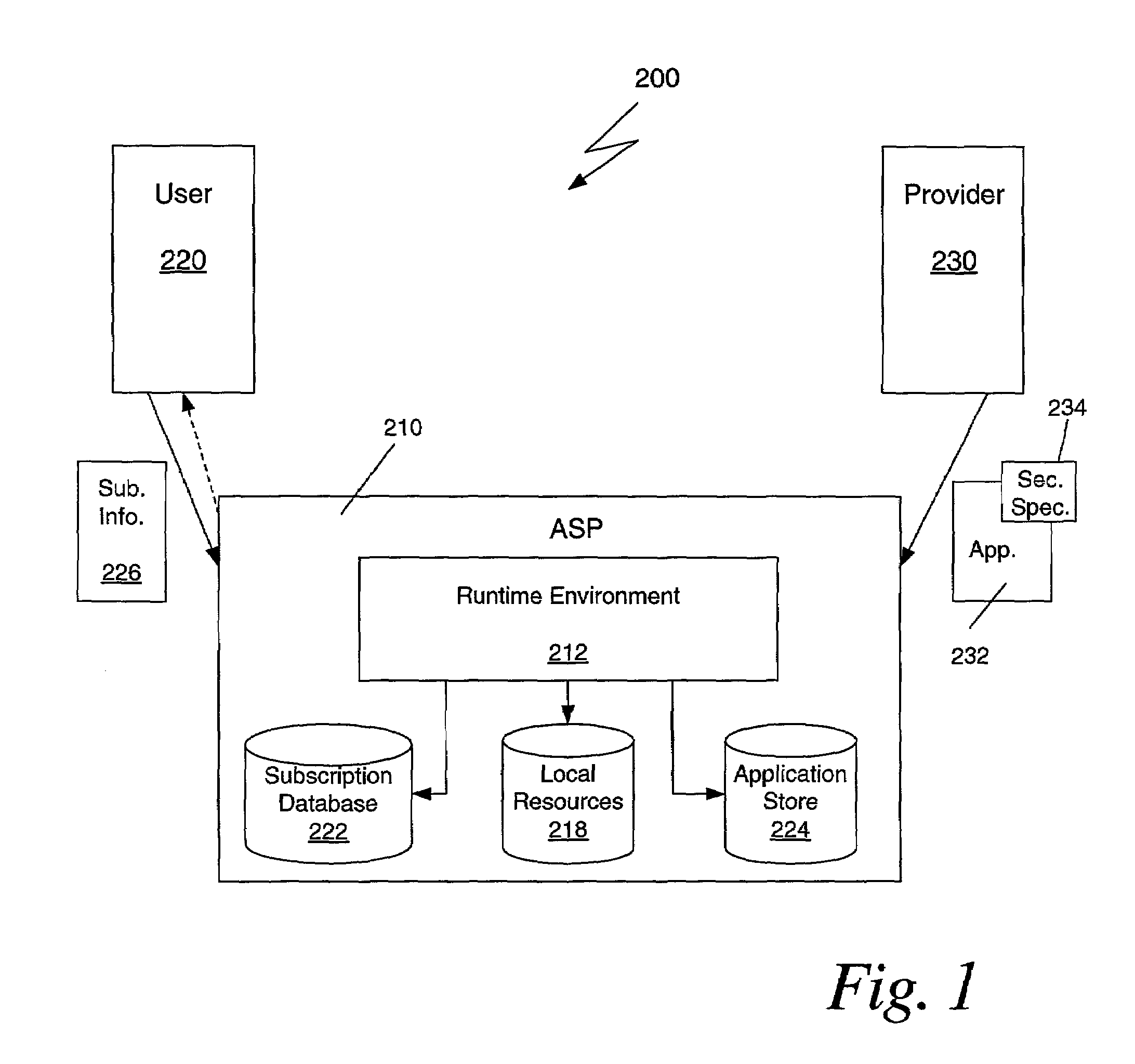
Mobile code security architecture in an application service provider environment
ActiveUS7096491B2Random number generatorsUnauthorized memory use protectionSecurity specificationResource based
A method is disclosed for providing mobile code software applications to users via an application service provider (ASP). The ASP receives a mobile code application, such as a Java application, from a provider, along with a security specification. The security specification defines access privileges requested to execute the application, including privileges to execute functions performed by the application and privileges to access local resources of the ASP. The ASP receives a subscription to the application from a user. The subscription includes subscription information granting or denying privileges, and specifying parameters for the privileges, requested in the security specification. The ASP executes the application at runtime by determining for each executable function whether the user has authorized the requested privilege. Those functions authorized by the user are executed in one embodiment. During runtime the ASP limits the application's access to local resources based on the privileges granted by the user.
Owner:ENT SERVICES DEV CORP LP
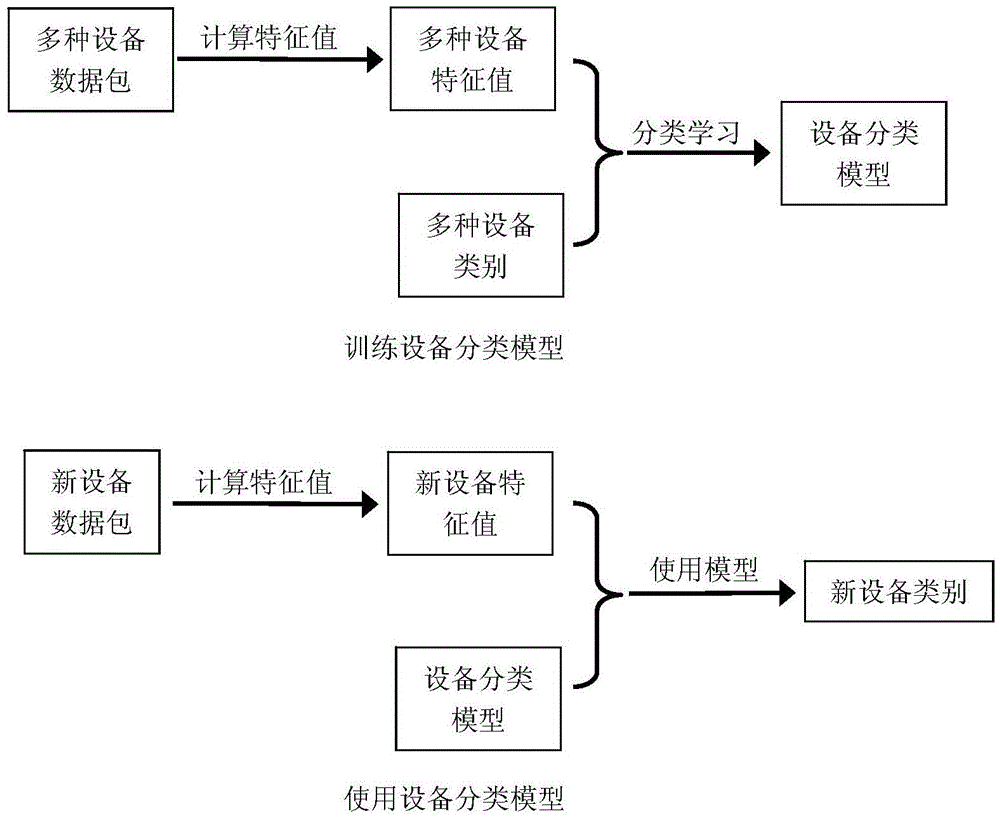
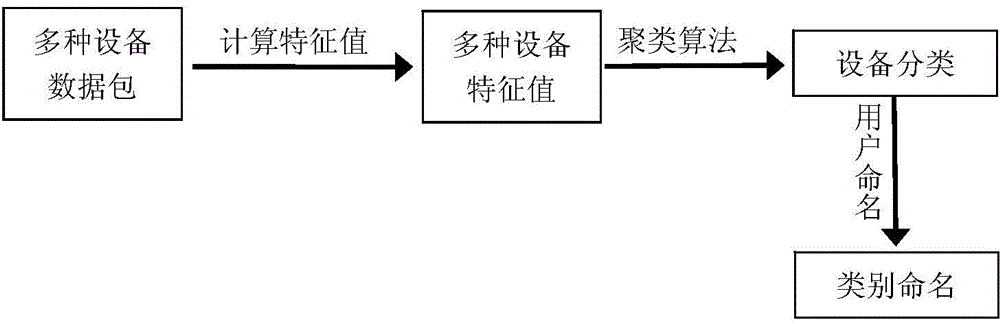
Method for classifying network equipment by utilizing machine learning
InactiveCN104883278AEasy to auditSimple safety rulesData switching networksSecurity specificationNetwork packet
The invention discloses a method for classifying network equipment by utilizing machine learning. The method establishes a classifying model for the network equipment by utilizing a supervised machine learning technology or a non-supervised machine learning technology, so as to classify known or newly added equipment in a network. The method has the technical advantages of analyzing behavior of the equipment through data packets transmitted and received by industrial control network equipment, and further classifying the equipment automatically. The understanding of types of the equipment is conducive to auditing network communication data. Unlike the traditional security specification for individual equipment, the security specification for equipment types is simpler and easy to manage, and the user can define corresponding security specifications for newly added equipment nodes easily.
Owner:BEIJING KUANGEN NETWORK TECH
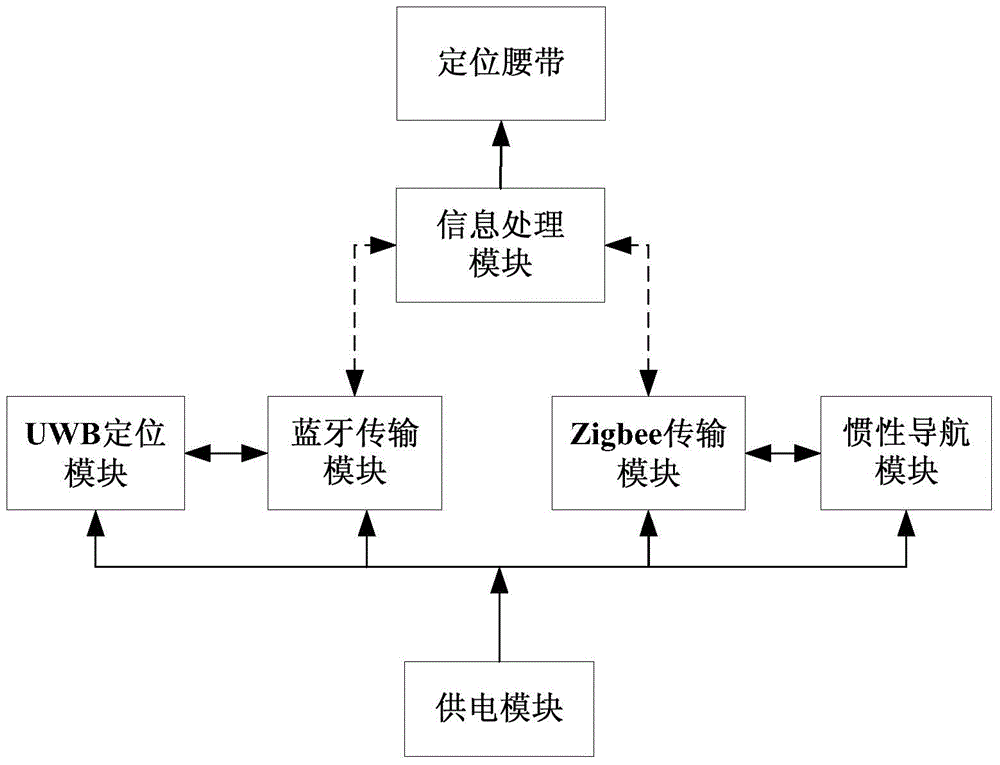
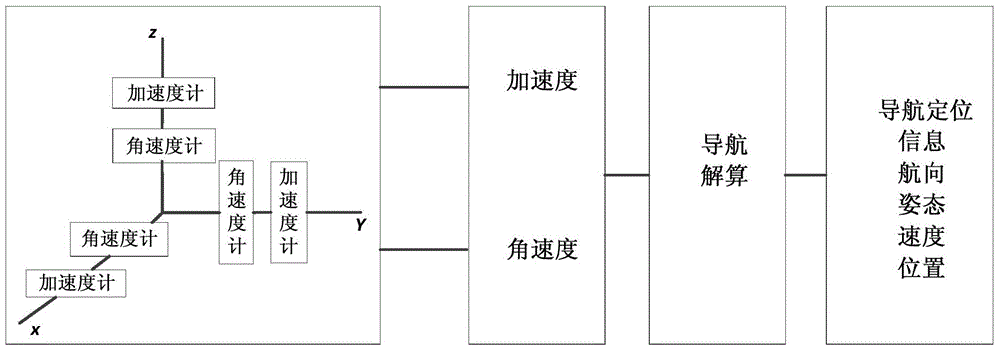
Waist type wearable indoor mobile positioning terminal
ActiveCN104661308ASolve positioningSolve the errorWireless communicationInformation processingSecurity specification
The invention provides a waist type wearable indoor mobile positioning terminal which comprises a power supply module, an ultra-wide bandwidth (UWB) locating module, a Bluetooth transmission module, a Zigbee transmission module, an inertial navigation module, an information processing module and a locating waist, wherein the UWB locating module is in two-way connection with the Bluetooth transmission module; the inertial navigation module is in two-way connection with the Zigbee transmission module; the Bluetooth transmission module and the Zigbee transmission module are respectively connected with the information processing module; the information processing module is arranged on the locating waist; the power supply module is used for supplying power for the other modules in the terminal. According to the waist type wearable indoor mobile positioning terminal, UWB locating and inertial navigation locating are fused and integrated into a special locating routing inspection waist, and a sound-light alarm signal can be sent out when the mobile positioning terminal enters a dangerous zone mistakenly; a wearable device which is in accordance with electric power security specification, is convenient to carry and is integrated with a high-accuracy wireless positioning technology is formed; after the waist type wearable indoor mobile positioning terminal is adopted, workers in the dangerous zone in a room can be conveniently and accurately located, so that the personal safety is guaranteed.
Owner:STATE GRID CORP OF CHINA +2
Computer-vision-based security detection method
InactiveCN106156765AMinor changesUnderstand the relationshipBiological neural network modelsCharacter and pattern recognitionVision basedVisual perception
The invention discloses a computer-vision-based security detection method, which is used for meeting the requirements of current security detection on persistence and high accuracy. The method comprises the following steps: performing original image gray processing on original video data, performing color space standardization on an input image, and regulating the contrast of the image to reduce the influence of a local shadow of the image and an illumination change and suppress the interference of noise; describing characteristics of a pedestrian by virtue of a gradient histogram, classifying by combining an SVM (support vector machine), analyzing a behavior of the pedestrian by virtue of deep learning after the pedestrian is found out, and sending security alarming information if the behavior of the pedestrian is inconsistent with a security specification. According to the method, existing hardware equipment can be fully utilized, so that changes in an original system are maximally reduced. Moreover, more image details can be understood by deep learning, so that a higher recognition rate is achieved. A deep learning neural network is less sensitive to the environment, light and noise, and can run in each environment after being trained once, so that high generalization capability is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
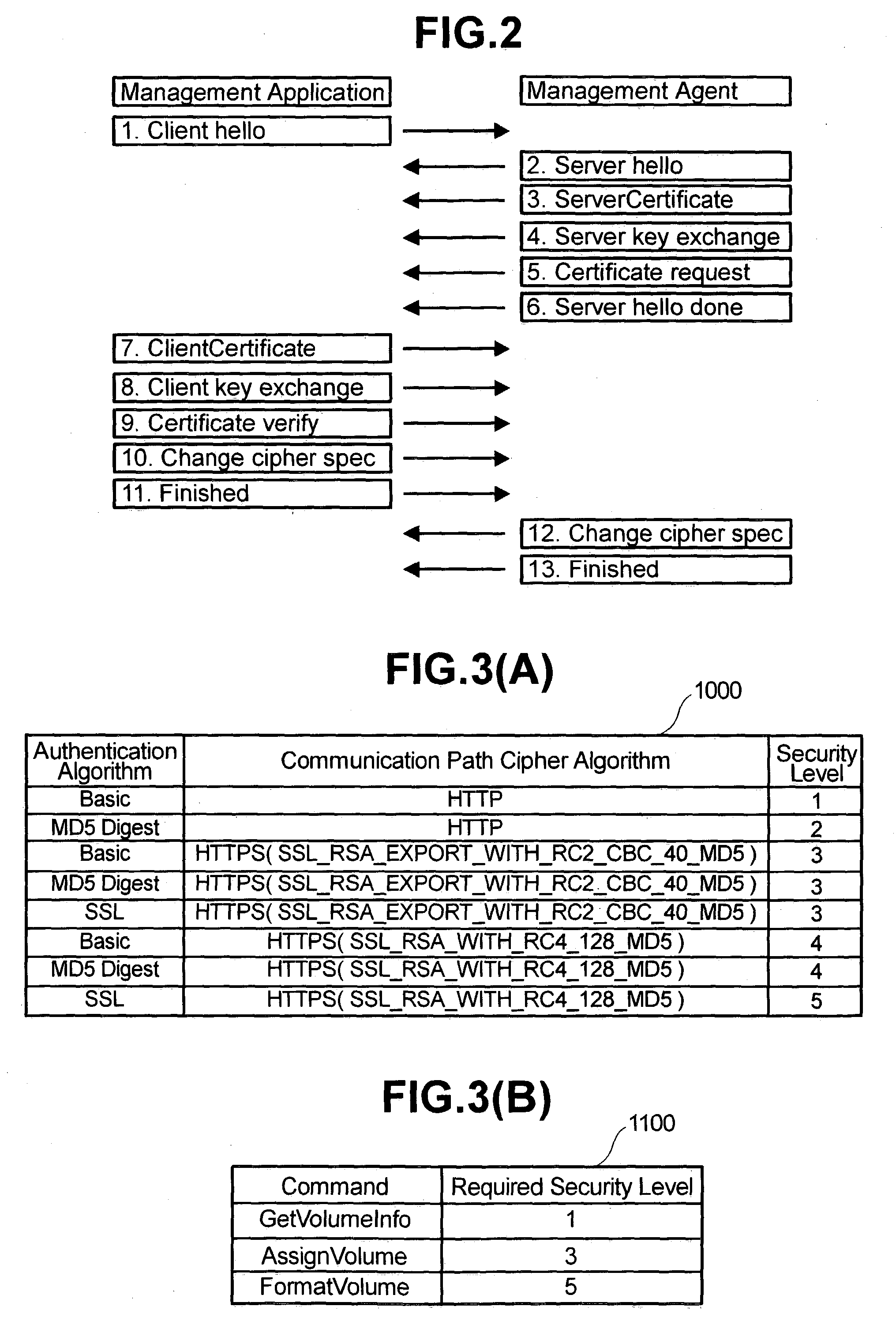
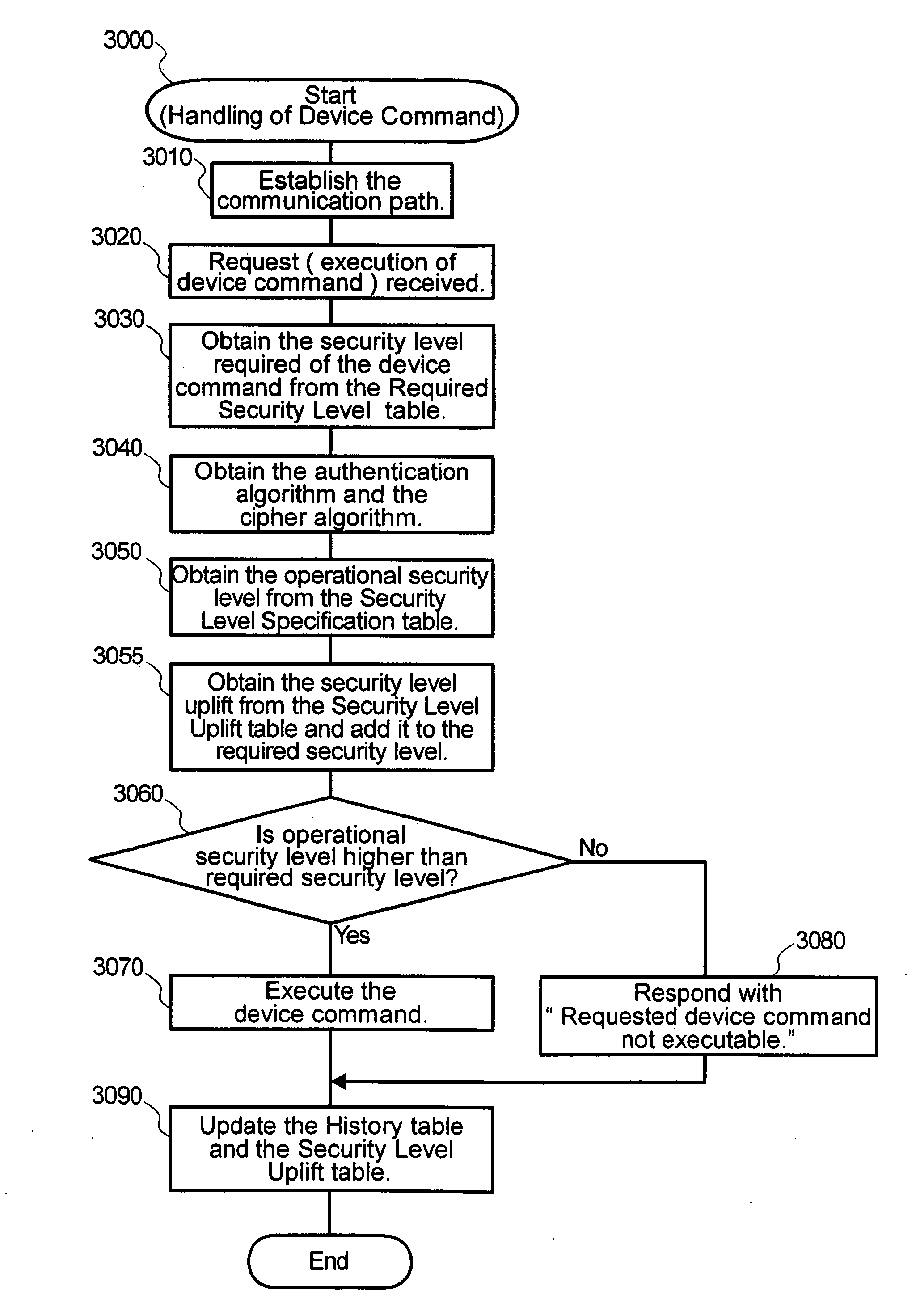
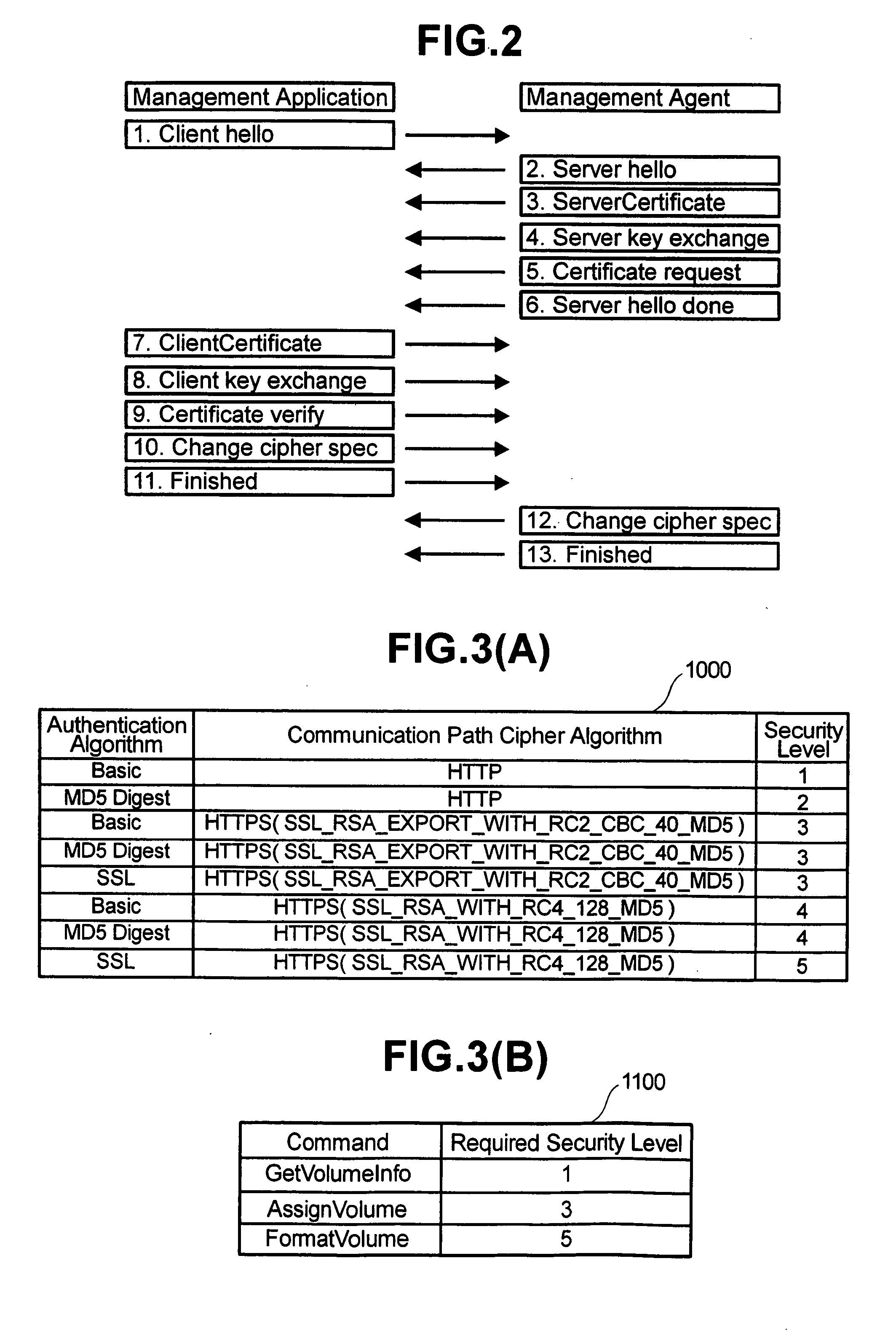
Command processing system by a management agent
InactiveUS7257843B2Improve securityPreventing executionData processing applicationsMultiple keys/algorithms usageSystems managementApplication software
In a system where a management application sends commands to a remotely-located agent over a network, the agent maintains a security specification table defining the security level for each combination of the cipher and authentication algorithms of the communication path to / from the management application and a required security level table defining the minimum security level required for the execution of each command. Upon receiving a command from the management application, the agent obtains, by referencing these tables, the operational security level of the communication path and the required security level for the command, and executes the command only if the former is greater than or equal to the latter. This mechanism ensures high security in system management by preventing a malicious intruder from executing potent commands that can cause a down of a computer system, without unreasonably limiting the use of the management application by the system administrator.
Owner:HITACHI LTD
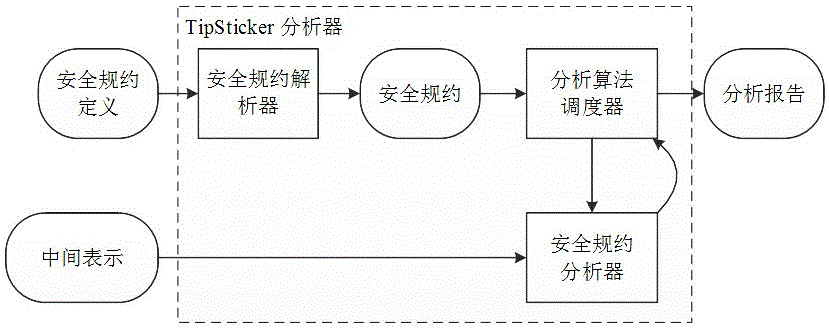
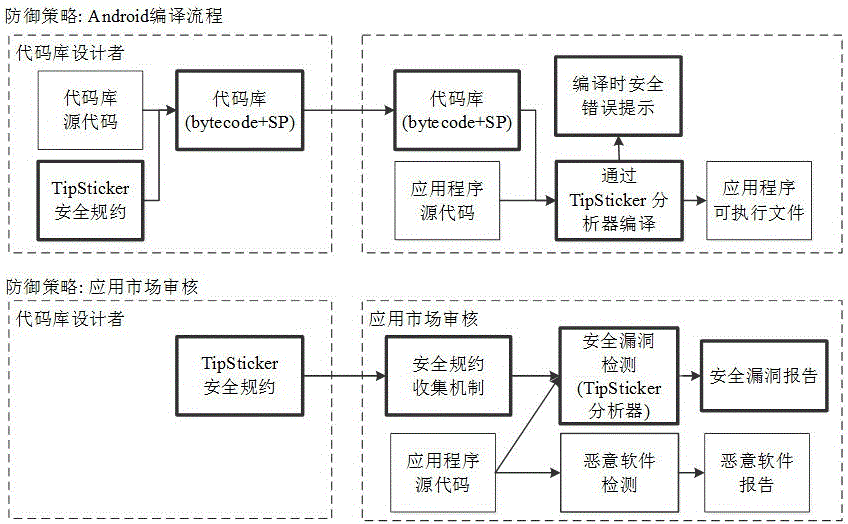
Android application used application program vulnerability detection and analysis method based on code library security specifications
ActiveCN105022958APrevent the risk of security incidentsPlatform integrity maintainanceInformation securityOperating system
The invention belongs to the technical field of program information security monitoring, and particularly relates to an Android application used application program vulnerability detection and analysis method based on code library security specifications. The method comprises the following steps: building a security specification model, i.e., describing the security specifications of the code library by using formalized rule languages; designing a static program analyzer for performing automatic verification based on the security specification model; applying the static program analyzer to two phases, i.e., compilation of application programs and examination of the application programs in an application market, and detecting security vulnerabilities. According to the detection and analysis method provided by the invention, the security risk in the program can be prevented.
Owner:FUDAN UNIV
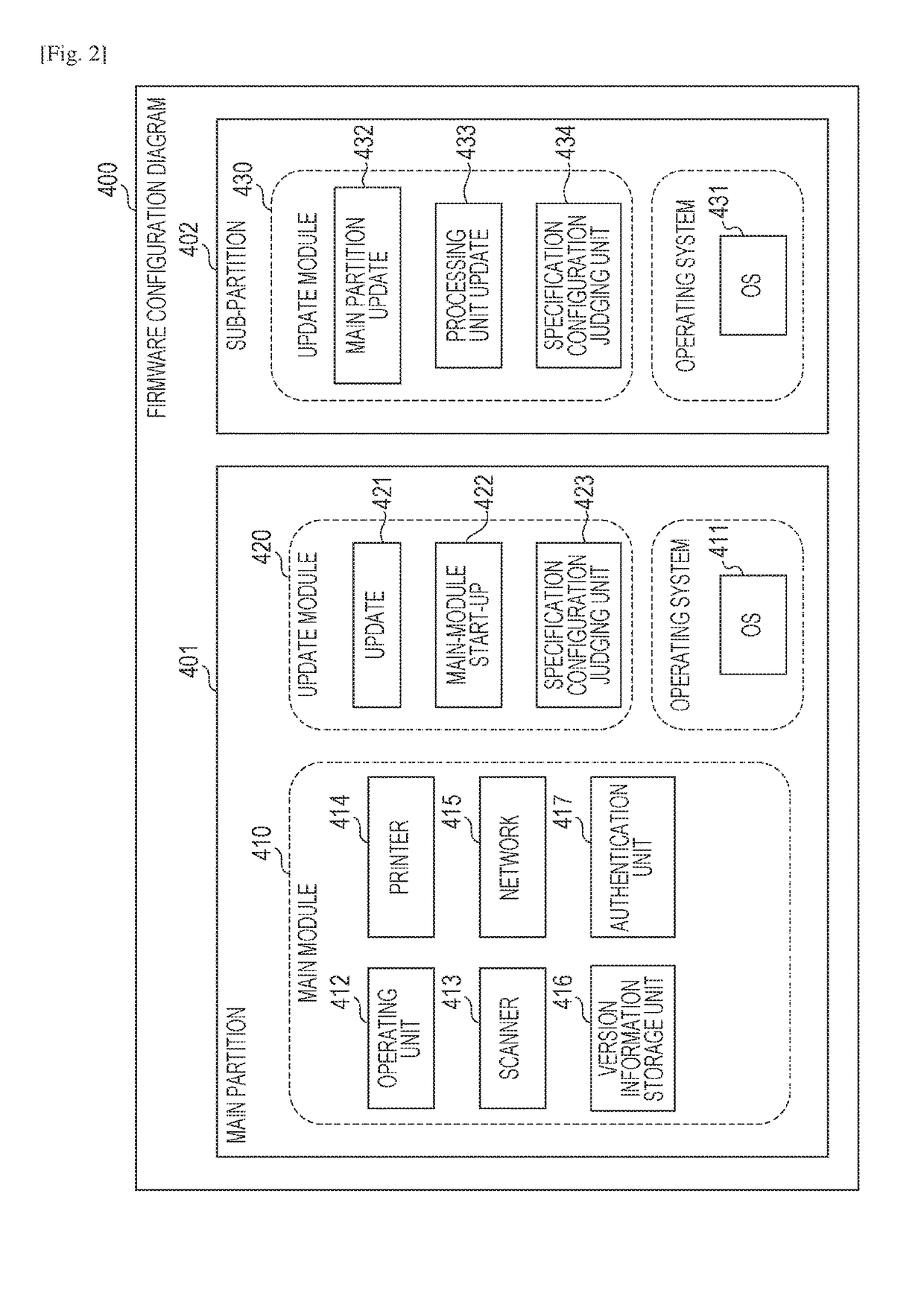
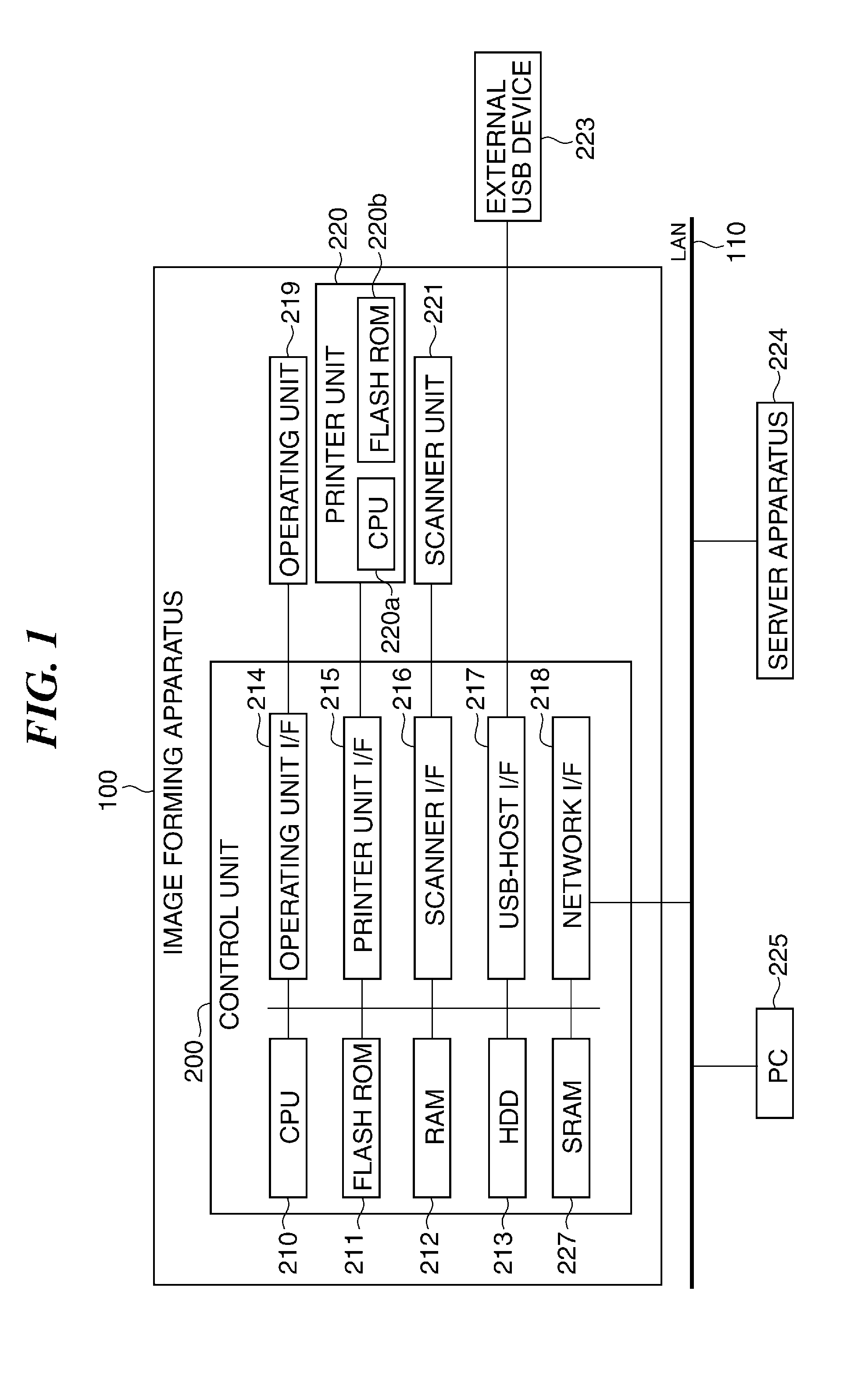
Image forming apparatus and control method for image forming apparatus
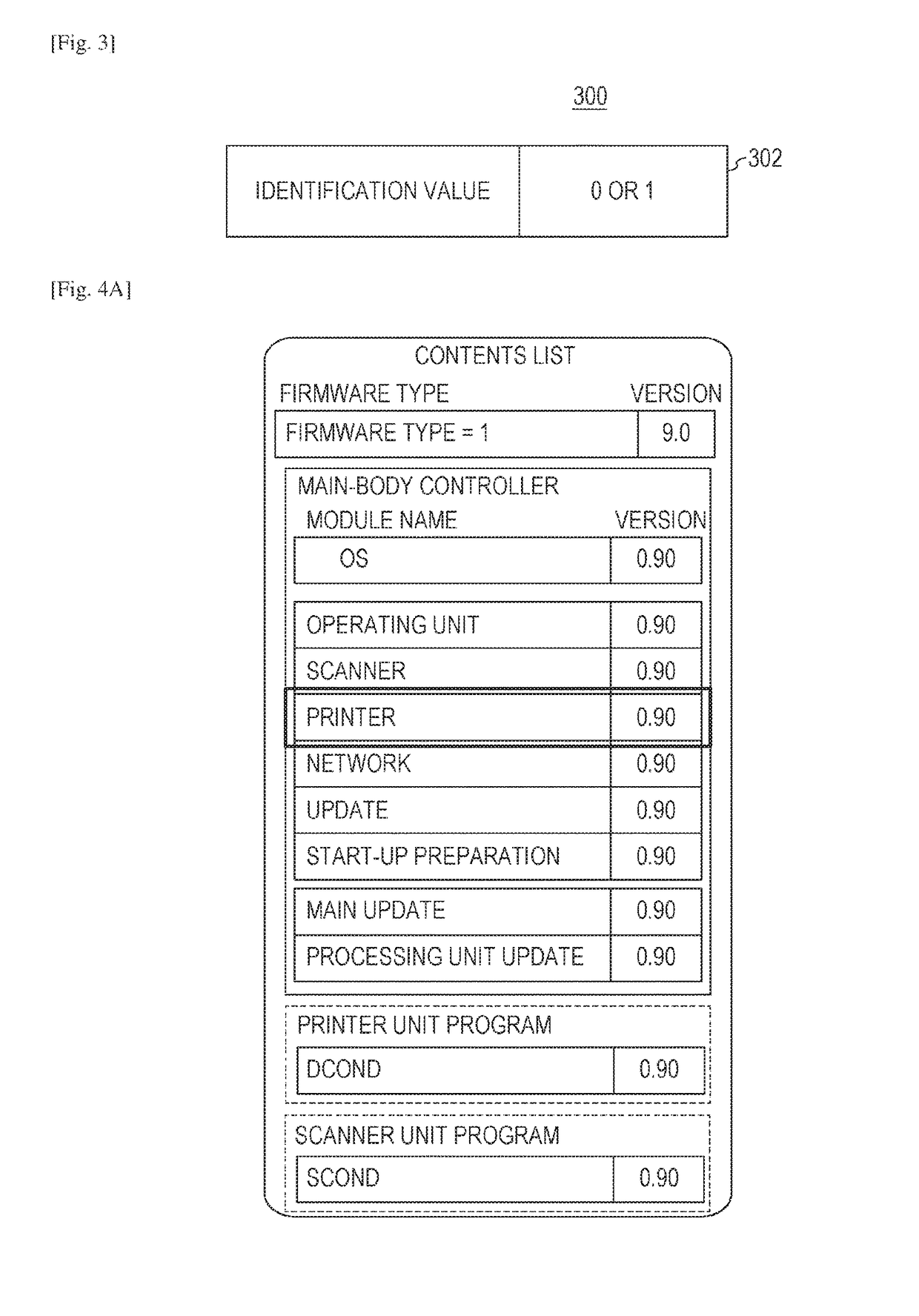
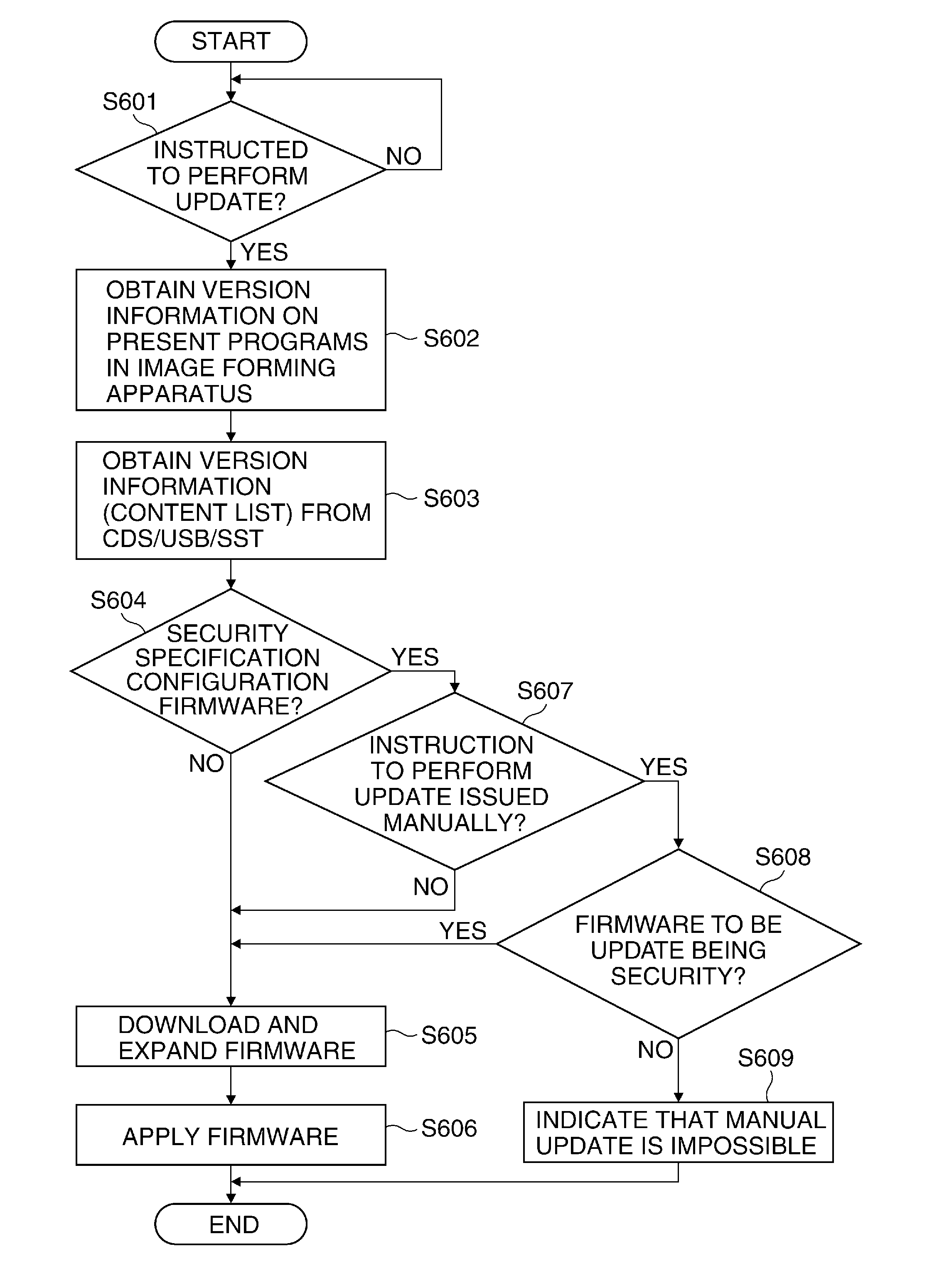
ActiveUS20160196130A1Improve securitySecurity for the image forming apparatus may be improvedComputer security arrangementsProgram loading/initiatingSecurity specificationImage formation
If firmware installed in an image forming apparatus 100 is a firmware having a security specification configuration, an operator who is permitted to instruct to update the firmware in the image forming apparatus 100 is limited to an operator having an administrator authority. This may improve the security of the image forming apparatus.
Owner:CANON KK
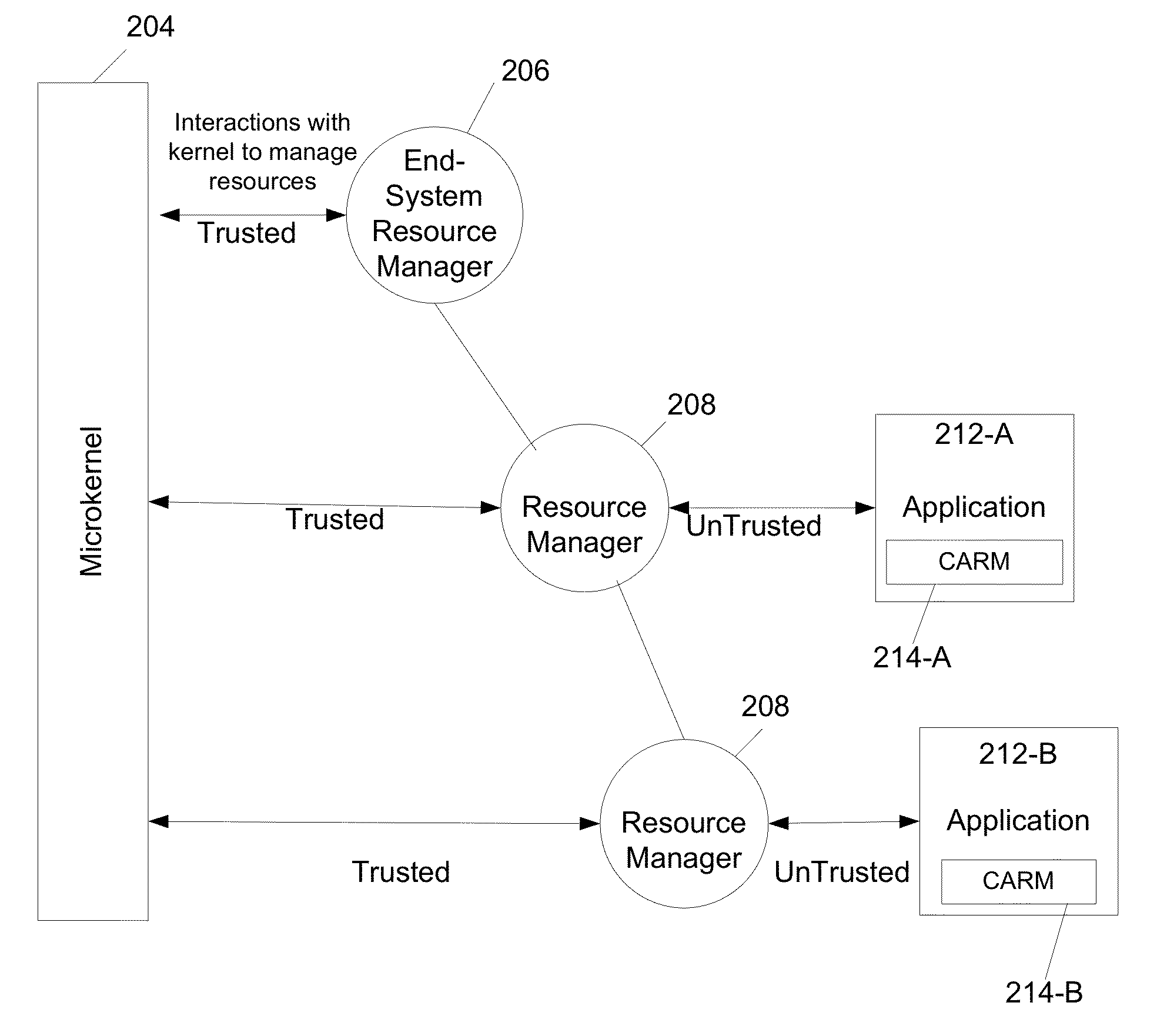
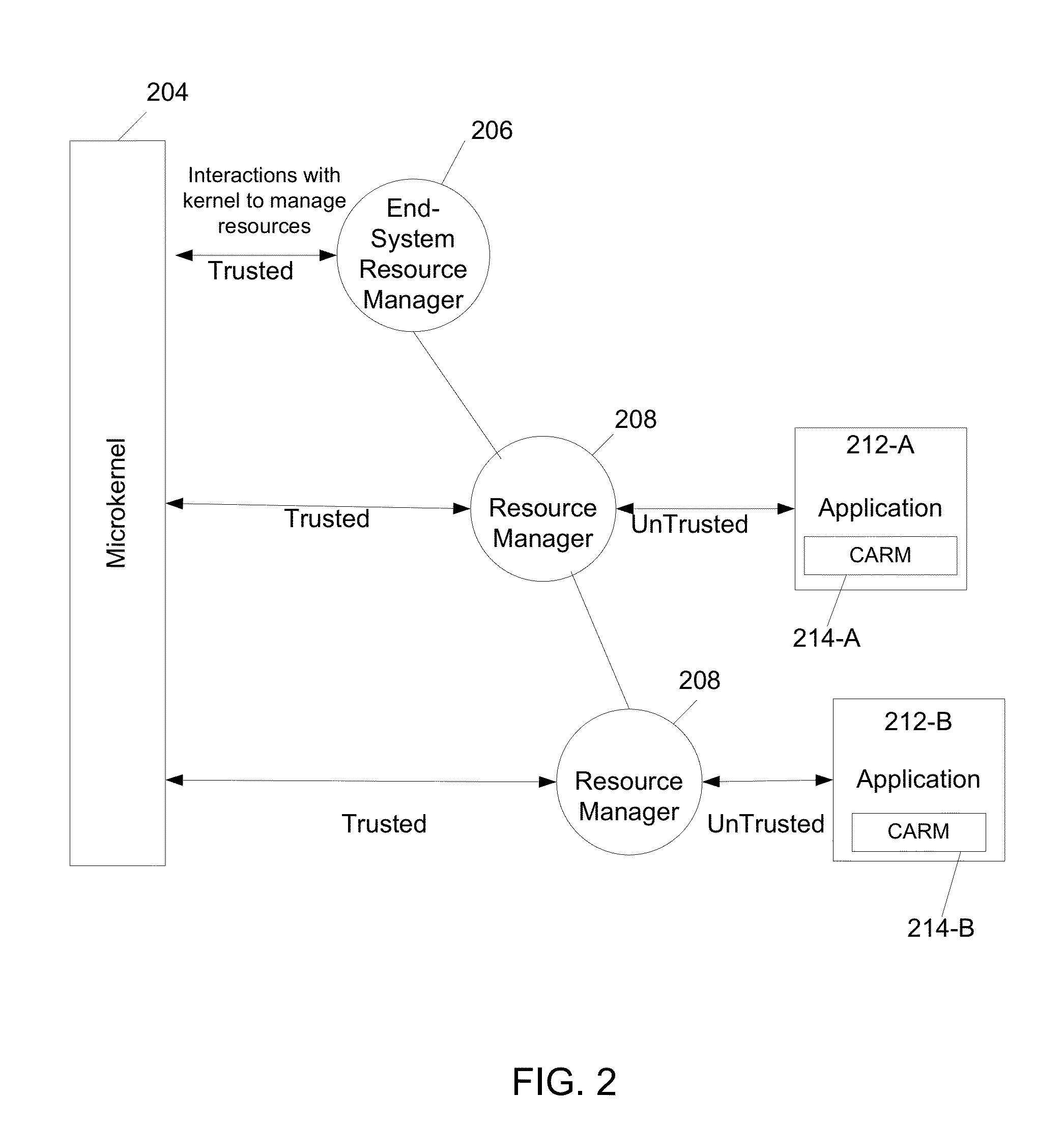
Scalable and secure application resource management and access control for multicore operating systems
InactiveUS20130283368A1Digital data processing detailsUnauthorized memory use protectionOperational systemSecurity specification
An architecture for multi-core and many-core processor systems includes a set of resource managers having a hierarchy of at least one level. The resource managers act as trusted proxies for the operating system (OS) kernel to manage resources for applications. The application may include a trusted secure specification defining resource and access privileges of the associated application.
Owner:SAMSUNG ELECTRONICS CO LTD
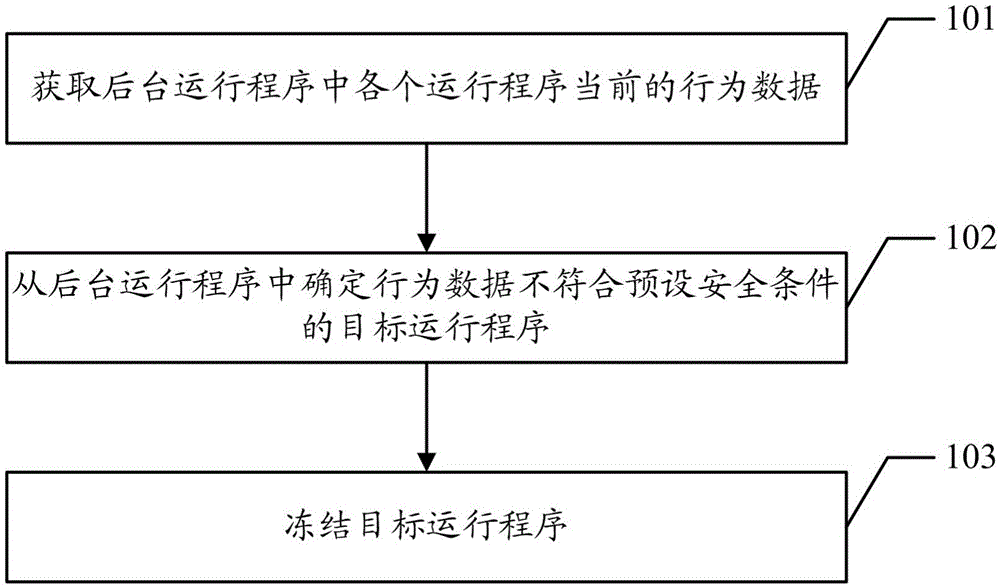
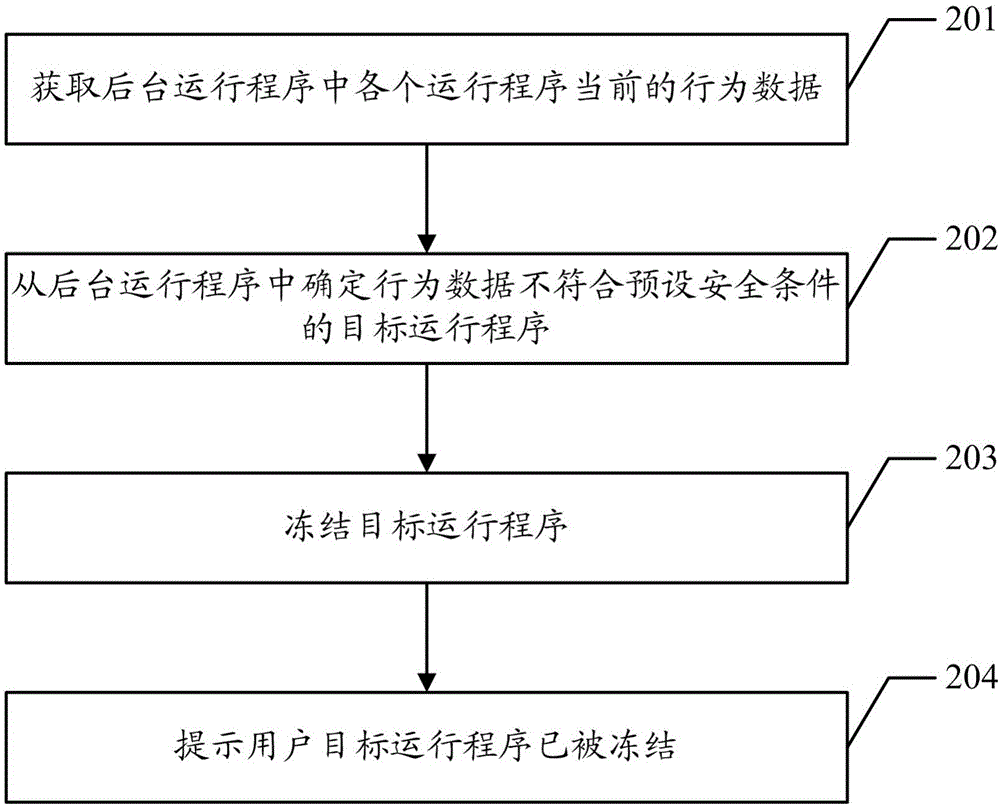
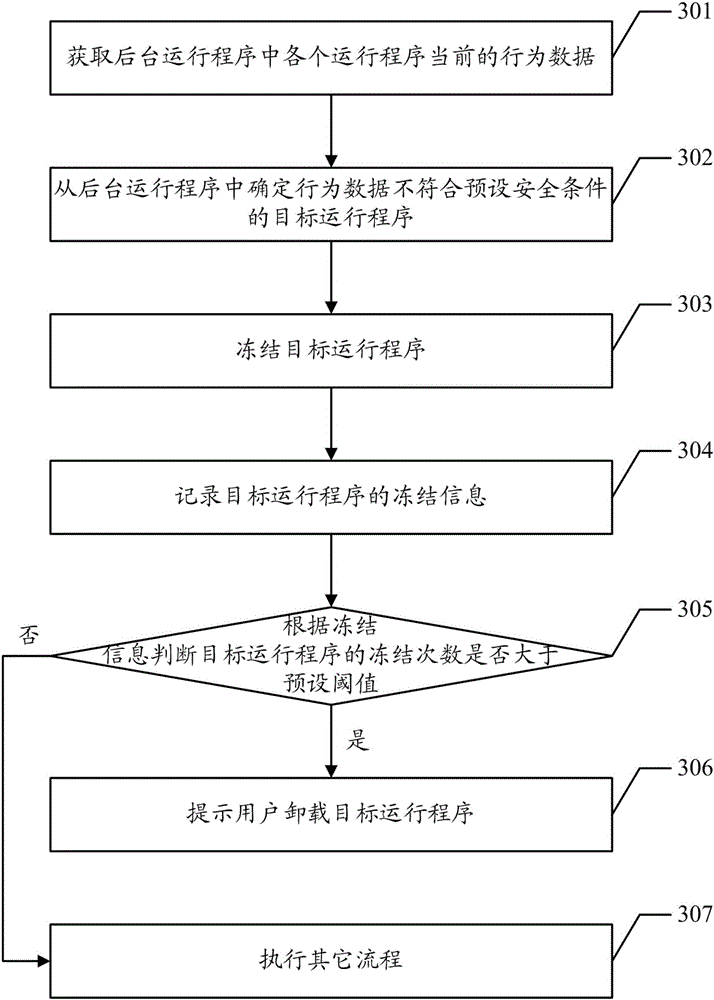
Freezing method of application program and terminal
InactiveCN106325993APrevent leakageImprove securityProgram initiation/switchingDigital data protectionSecurity specificationComputer terminal
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
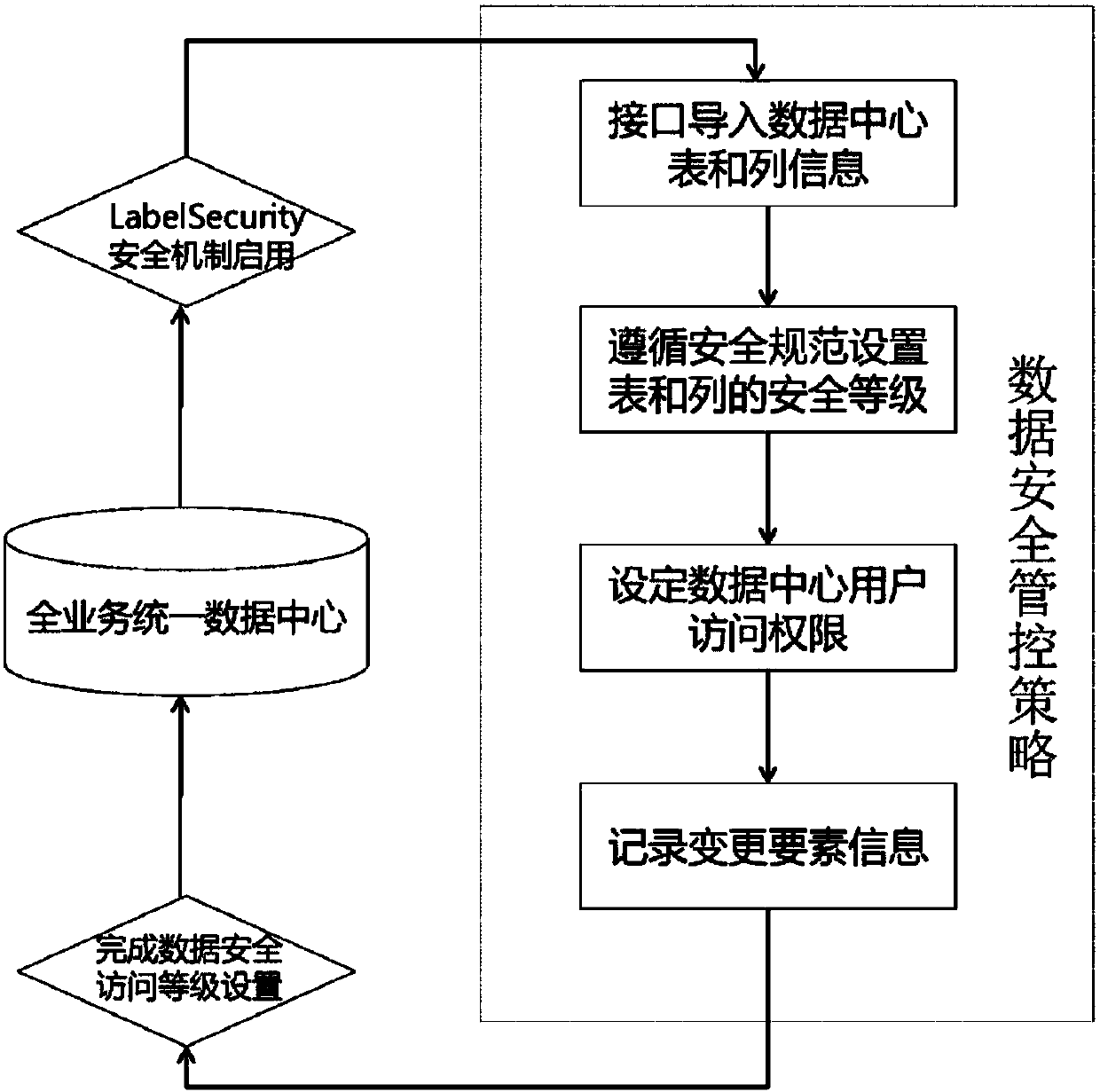
Method and system for internal security management and control of enterprise data
ActiveCN107944284AAbnormal behavior can be traced backEnsure safetyDigital data protectionOpen dataConfidentiality
The present invention discloses a method and a system for internal security management and control of enterprise data. The method disclosed by the present invention is based on a full-service unifieddata center built by an enterprise cloud platform, the full-service unified data center comprises structured data in a unified view area and in a digital warehouse area, and after carrying out actualoperating environment risk analysis on the structured data, from the perspective of the security lifecycle, the entire data protection security specification is formulated; based on the security specification, the LabelSecurity security tag mechanism is enabled on the enterprise cloud platform, and the data access levels of the enterprise cloud platform are divided into four levels of confidentiality of open data, internal data, secret data and confidential data by the security tags; and through the LabelSecurity access mechanism, different effective security control strategies are implementedfor different columns of the data in the same table. According to the method and system disclosed by the present invention, secure tracking and management and control of the service data within the life cycle is ensured; and at the same time, a friendly visual operation is ensured during the entire data management and control process.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
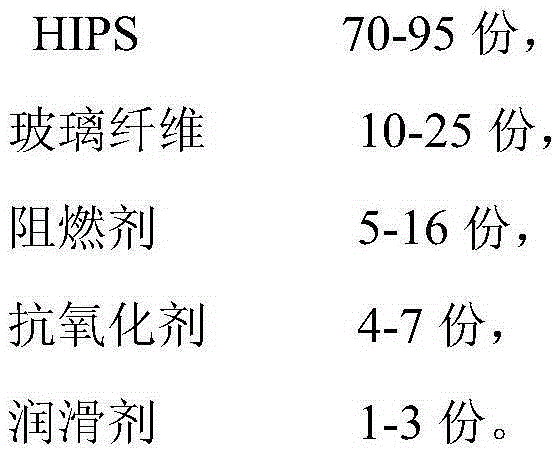
Shell material of electronic equipment and preparation method thereof
InactiveCN105295281ASmall coefficient of thermal expansionImprove flame retardant performancePolymer scienceAntioxidant
The invention discloses a shell material of electronic equipment and a preparation method thereof. The shell material comprises the following components in parts by weight: 70-95 parts of polystyrene, 10-25 parts of glass fiber, 5-16 parts of a flame retardant, 4-7 parts of an antioxidant, and 1-3 parts of a lubricant. The preparation method comprises the following steps: uniformly stirring glass fiber, polystyrene and a lubricant, sequentially adding a flame retardant and an antioxidant, and uniformly stirring the obtained mixture; transporting the obtained object to a feed hopper of a twin-screw extruder, starting the twin-screw extruder, so that a molten material is extruded; and sequentially carrying out water cooling, grain-sized dicing, sieving and drying on the molten material, so that the HIPS composite shell material disclosed by the invention is obtained. The shell material disclosed by the invention is capable of effectively improving the flame retardant rating and rigidity of shells, satisfying the requirements of information equipment on security specifications, and improving the fire prevention coefficients of electrical and electronic equipment.
Owner:HISENSE VISUAL TECH CO LTD
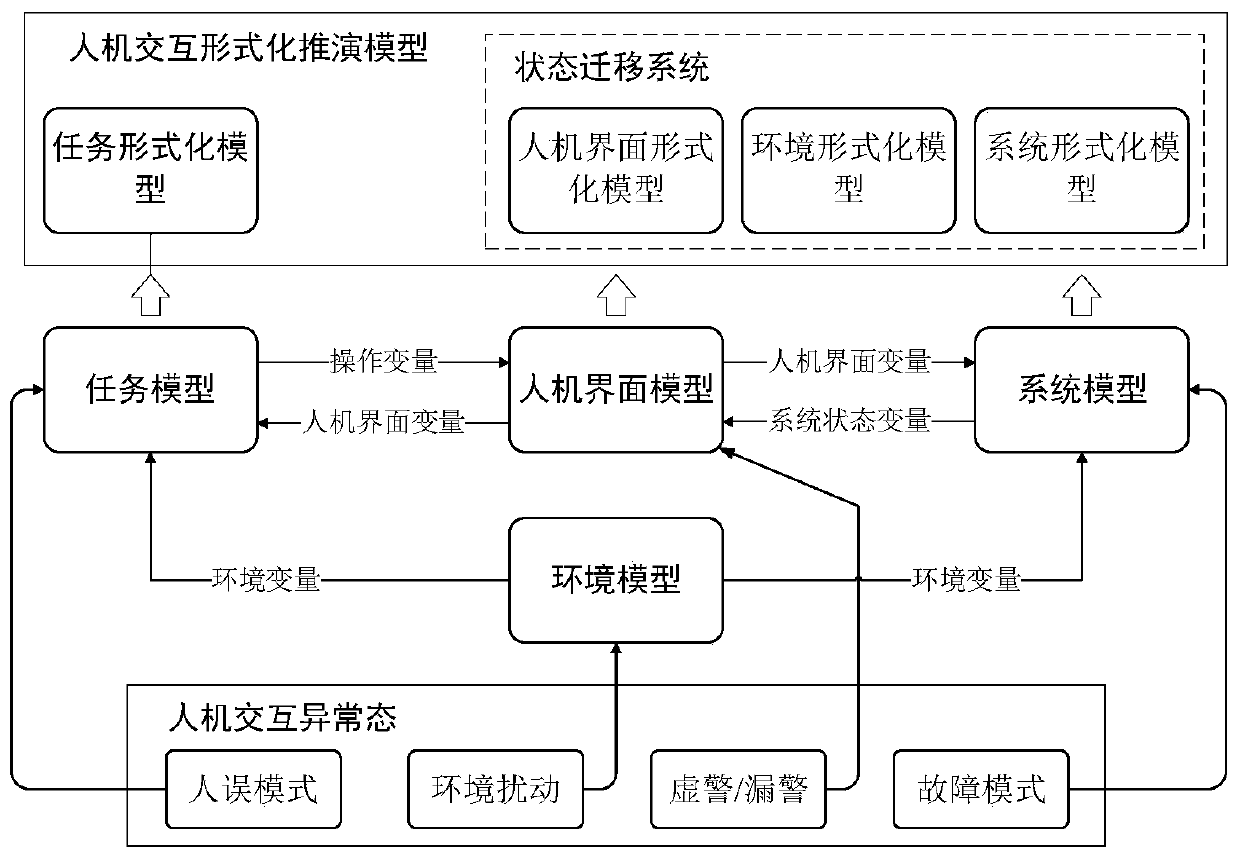
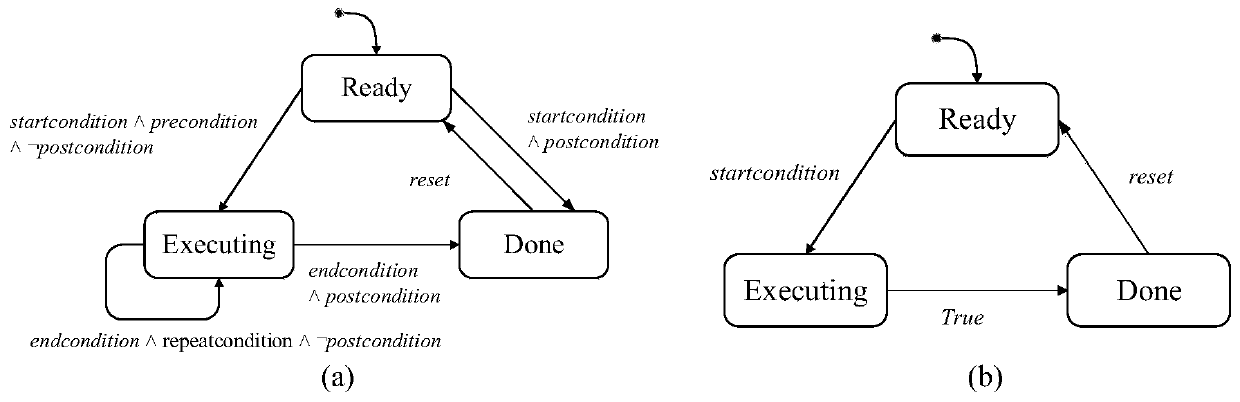
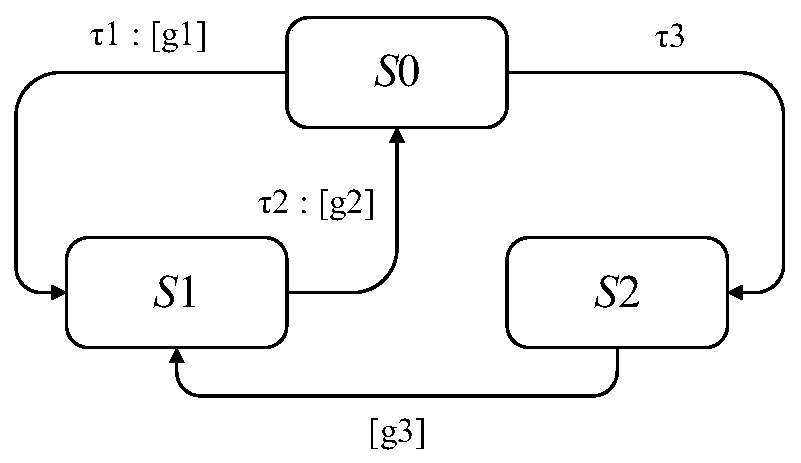
A man-machine interaction risk scene recognition method based on formal verification
ActiveCN109783870ARealize identificationSpecial data processing applicationsHuman–machine interfaceQualitative property
A man-machine interaction risk scene recognition method based on formal verification comprises the following steps that firstly, carrying out modeling on a complex man-machine interaction deduction process, and forming a universal man-machine interaction formal deduction model; 2, establishing a task formal model automatic deduction template considering human errors, and a system, a human-computerinterface and an environment formal model automatic deduction template considering abnormal states; 3, determining a man-machine system security attribute expression to obtain a man-machine system security specification; 4, completing the troubleshooting of a risk scene path by means of a model checking tool; 5, evaluating the possibility of the evolution path by adopting a qualitative comparisonmethod, and identifying a risk scene path with relatively high occurrence possibility; Through the above steps, a man-machine interaction formalization method is adopted, the problem of completenesschecking of abnormal-state interaction risk scenes of a man-machine system is solved, the effect of automatically completing complete enumeration of risk scene paths is achieved, and recognition of key risk scenes is achieved through a qualitative comparison method.
Owner:BEIHANG UNIV
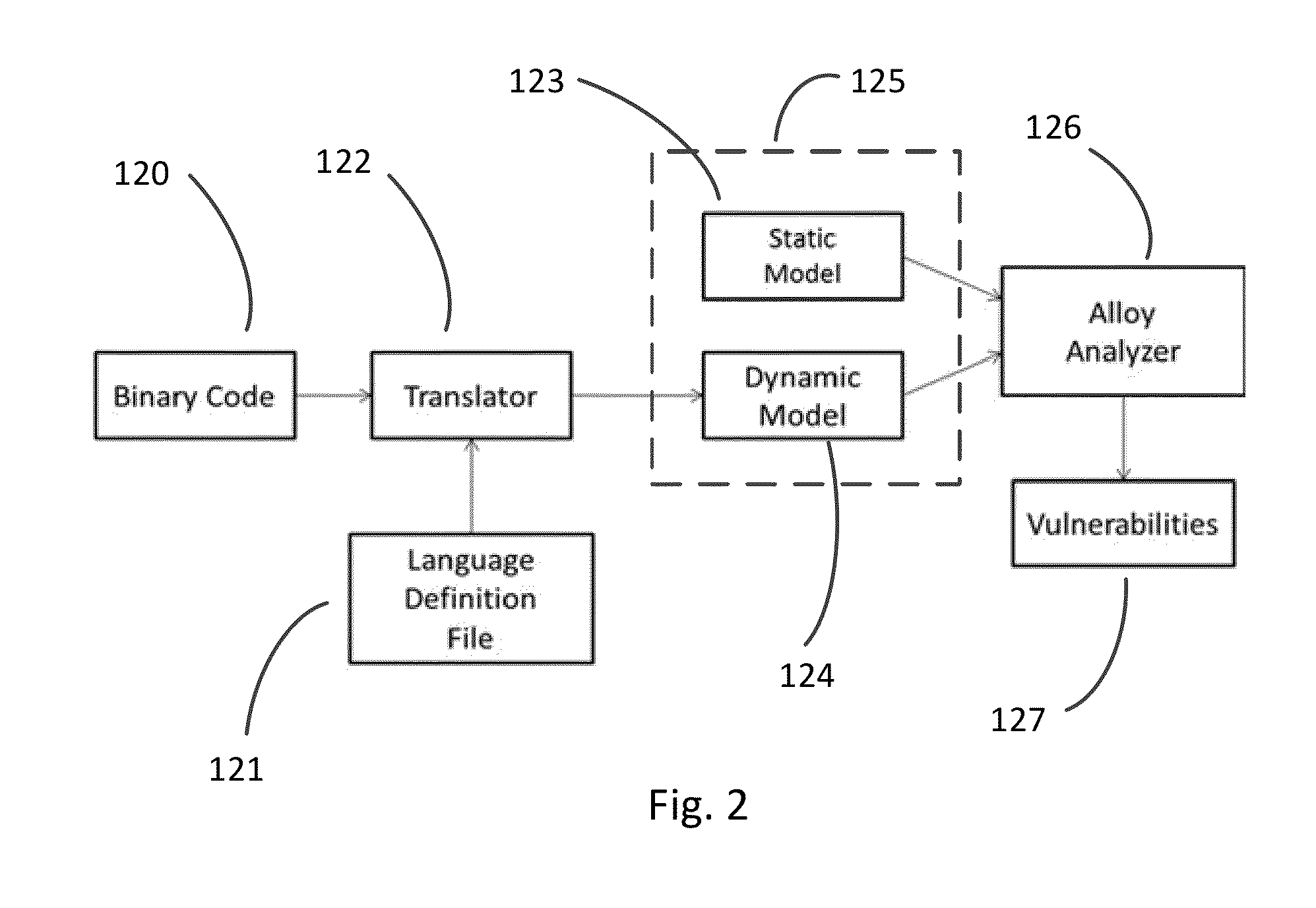
Software Inspection System
A method for software inspection analyzes a body of computer code to assess whether the body of computer code contains malware. Various embodiments extract the executable elements of the body of computer code and modify those elements using rules defining the format of instructions for the programming language in which the computer code was written, and using rules defined from the security specification of that programming language, to produce a model of the body of computer code. The method then analyzes the model using a model checking system, which determines whether any of the language rules have been violated, in which case the method flags the computer code as potentially including malware.
Owner:TRUSTEES OF BOSTON UNIV
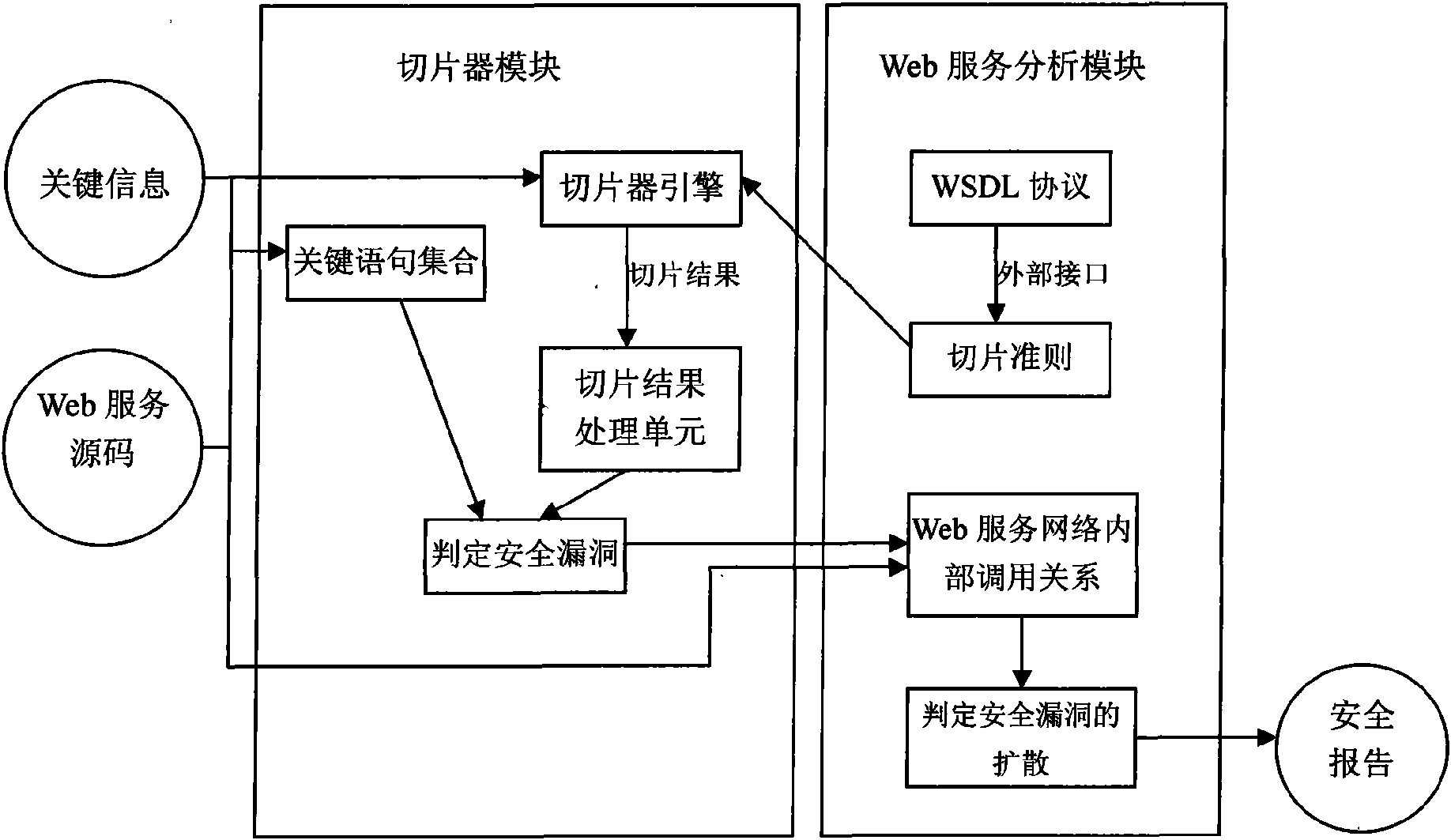
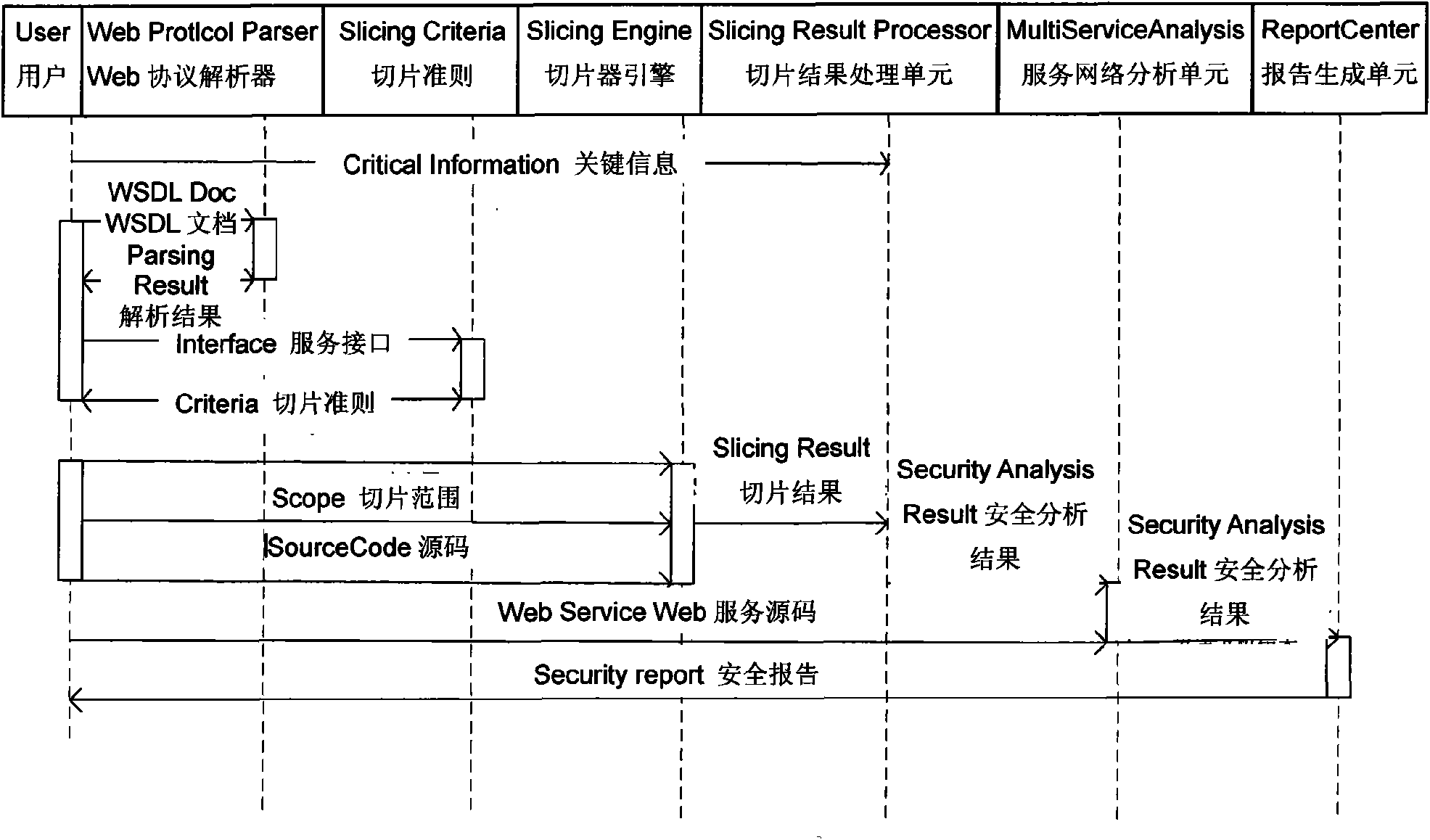
Method for estabilishing Web service security analysis model based on program slice
ActiveCN101588363AReduce security breachesQuality improvementSecuring communicationProgram slicingWeb service
The present invention relates to a software establishing technique and network security, and specifically to a method for establishing the Web service security analysis model based on the program slice. The invention provides a method for establishing Web service security analysis model based on program slice for protecting the key information and the common information in the network service from the inside and the outside and increasing the network service security. The method of the invention adopts the following technical solutions: 1) establishing a slicer module for obtaining the abstract of the information flow in the Web service realizing code; 2) establishing a network service analysis module for discovering the safety breaking state that the key information is leaked to the Internet user through the current service interface, wherein the step comprises the safety analysis of the independent network service and the safety analysis of the network service network; and 3) establishing a safety reporting module for analyzing the result based on the module, and combining the safety measures presented in the existing Web service security specification and process for generating a corresponding security report. The method of the invention is mainly used for providing the Web service security.
Owner:江苏永达电力电信安装工程有限公司
Internet-of-things-based key workshop monitoring system
InactiveCN106873491AReal-time high-definition video monitoringEnsure safe and standardized operationProgramme controlComputer controlVideo monitoringSecurity specification
The invention, which belongs to the technical field of monitoring, particularly relates to an internet-of-things-based key workshop monitoring system comprising a key equipment monitoring unit and an electronic eye. The key equipment monitoring unit is used for sending an operation state of key equipment to a monitoring management server, receiving a control instruction issued by the monitoring management server, and executing a corresponding action; and the electronic eye is used for carrying out on-line monitoring on a workshop and transmitting real-time video information to the monitoring management server. According to the internet-of-things-based key workshop monitoring system, high-definition video monitoring is carried out on internal and external import and export of a key workshop in real time; recording and on-line checking of videos of all points can be realized; security specification operations on key equipment and infrastructures at production sites can be guaranteed effectively; the workshop environment can be monitored and managed effectively and thus the environmental emergencies can be reduced; and fire-fighting equipment can be controlled remotely and the emergencies can be dealt with timely.
Owner:邹霞
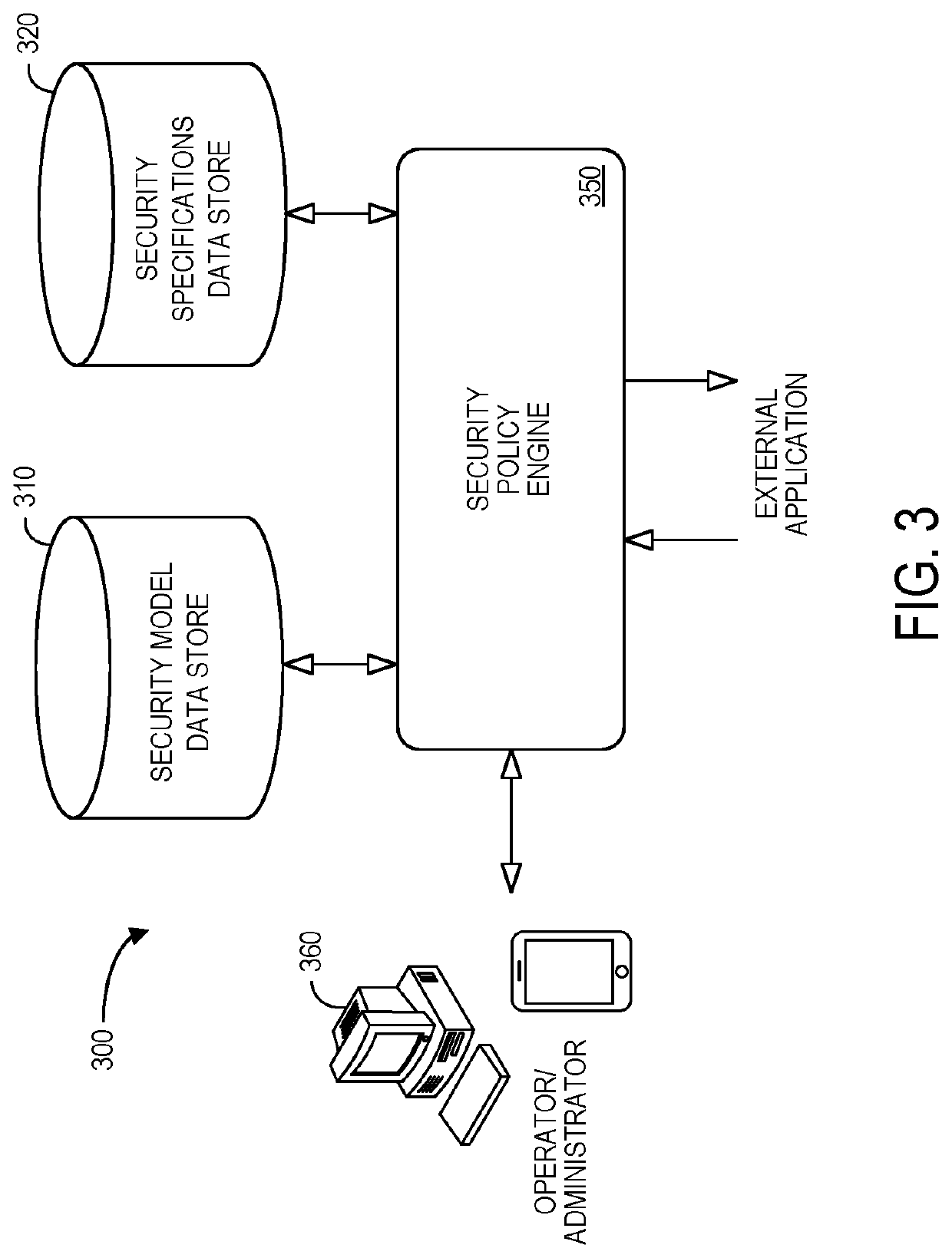
Security policy as a service
ActiveUS20200259864A1Easy to implementAccurate and efficientDigital data protectionDigital data authenticationExternal applicationInternet privacy
According to some embodiments, a security model data store may contain a plurality of potential security policies, each accessible by multiple external applications. A security specifications data store may contain a plurality of potential security specifications, each accessible by the multiple external applications. A security policy engine computer platform may receive from an external application an indication identifying a security policy package. The security policy engine may then retrieve, based on the received indication, one of the potential security models from the security policy data store. Similarly, the security policy engine may retrieve, based on the received indication, one of the potential security specifications from the security specifications data store. The security policy engine may then arrange for a security policy package to be implemented for the external application, the security policy packing being associated with the retrieved potential security model and the retrieved potential security specification.
Owner:SAP PORTALS ISRAEL
Motor employing immersion type evaporative cooling and structure optimization method thereof
ActiveCN102594026AImprove power densityReduce manufacturing costCooling/ventillation arrangementSecurity specificationNational standard
The invention discloses a structure optimization method for a motor employing immersion type evaporative cooling. The method comprises the following steps of: correspondingly reducing the thickness of a main insulating layer of a stator by 50 to 60 percent, and correspondingly improving the current density of the stator by twice to 2.5 times by taking an air-cooled motor with the same voltage grade and the same capacity as a reference; and obtaining the minimum shape data of each part structure according to combinational calculation results obtained by different values of each parameter on the basis of the thickness of the main insulating layer of the stator and the current density of the stator under conditions which are consistent with security specifications about the motor in national standard, wherein the parameters comprise air gap flux density, the number of turns of a stator winding, the internal and external diameters of the stator and a rotor, and the heights and widths of a stator slot and a rotor slot. By the method, the advantages of an immersion type evaporative cooling technology are fully utilized, the overall dimensions of the motor and each main part are greatly reduced under the same voltage grade and the same capacity, and manufacture cost is decreased. On such a basis, the invention also provides the motor employing the immersion evaporative cooling.
Owner:MCC XIANGTAN HEAVY IND EQUIP
Mobile application automation security testing platform
InactiveCN105930273AGuaranteed normal executionSoftware testing/debuggingComputer hardwareOperational system
A mobile application automation security testing platform is used for detecting security of Android applications, so as to verify whether the Android applications coincide with security standards. The platform is capable of performing component analysis on an application installed on an Android system, and by means of an exposed component, determining an attack surface, carrying out a penetration test, and mining out a vulnerability of the application in depth, wherein a coverage of the test comprises an authentication bypass test, an SQL impregnation test, insecurity of data storage and reading of a file system and the like. During a test process, acquisition of a root permission of a mobile phone terminal is not required, and it can be ensured that the mobile phone terminal interacts with other application and operating systems as a common Android application. Different from an automated scanning tool of a web field, the testing platform is an interactive security testing platform, and during a use process, the user only needs to input a command on a working state (PC terminal) of the user, and the command is transferred to a proxy program on an Android device via a connection of a port and executed, so as to complete the whole security test.
Owner:云南电网有限责任公司信息中心
Method for implementing parameter synchronization of integrated power information buses
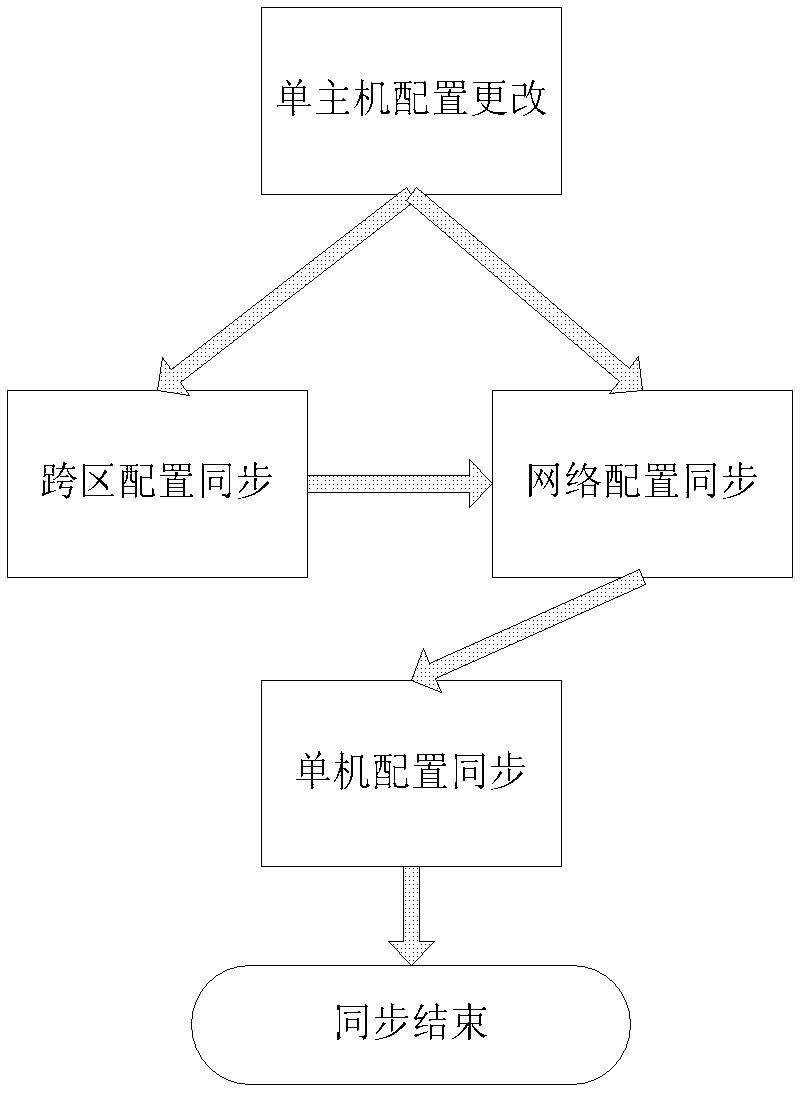
InactiveCN102662901AEnsure integrated operationMultiple digital computer combinationsElectric digital data processingComputer hardwareElectric power system
Disclosed is a method for implementing parameter synchronization of integrated power information buses. According to requirements of security specifications, software application systems in a power system need to be distributed in safety production area and a safety management area, which are isolated by a physical unit. Data exchange buses implemented by an SOA (service oriented architecture) are distributed in one safety area, a double-bus server configuration scheme is used in a practical project, and accordingly the power information data exchange buses are inevitably distributed on a virtual integrated bus formed by four buses of four bus servers by crossing the safety area, and effective and reliable synchronization of bus configuration parameters of the four bus servers is a must. By the method using the comprehensive scheme of cross-area synchronization, network synchronization and single-unit synchronization, reliable parameter synchronization of integrated power information buses is effectively achieved. The method is widely applicable to the field of integration of power software application systems in nation, networks, provinces, cities and counties of China, and also applicable to the field of software integration, except for power systems, requiring isolation and data exchange.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Command processing system by a management agent
InactiveUS20060272029A1High security in managementPreventing executionData processing applicationsDigital data processing detailsSystems managementSecurity specification
In a system where a management application sends commands to a remotely-located agent over a network, the agent maintains a security specification table defining the security level for each combination of the cipher and authentication algorithms of the communication path to / from the management application and a required security level table defining the minimum security level required for the execution of each command. Upon receiving a command from the management application, the agent obtains, by referencing these tables, the operational security level of the communication path and the required security level for the command, and executes the command only if the former is greater than or equal to the latter. This mechanism ensures high security in system management by preventing a malicious intruder from executing potent commands that can cause a down of a computer system, without unreasonably limiting the use of the management application by the system administrator.
Owner:HITACHI LTD
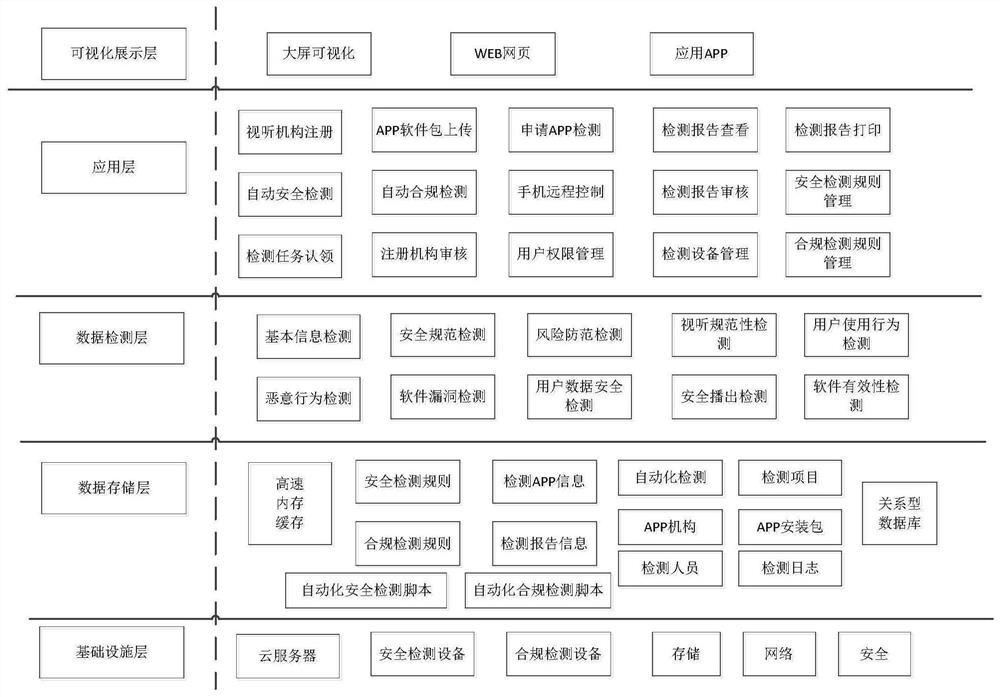
Audiovisual APP security and service compliance automatic detection system and method, and medium
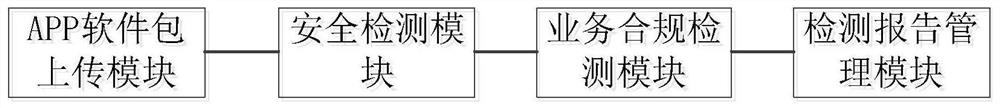
PendingCN112733138AImprove detection efficiencyDigital data protectionPlatform integrity maintainanceSecurity specificationOperating system
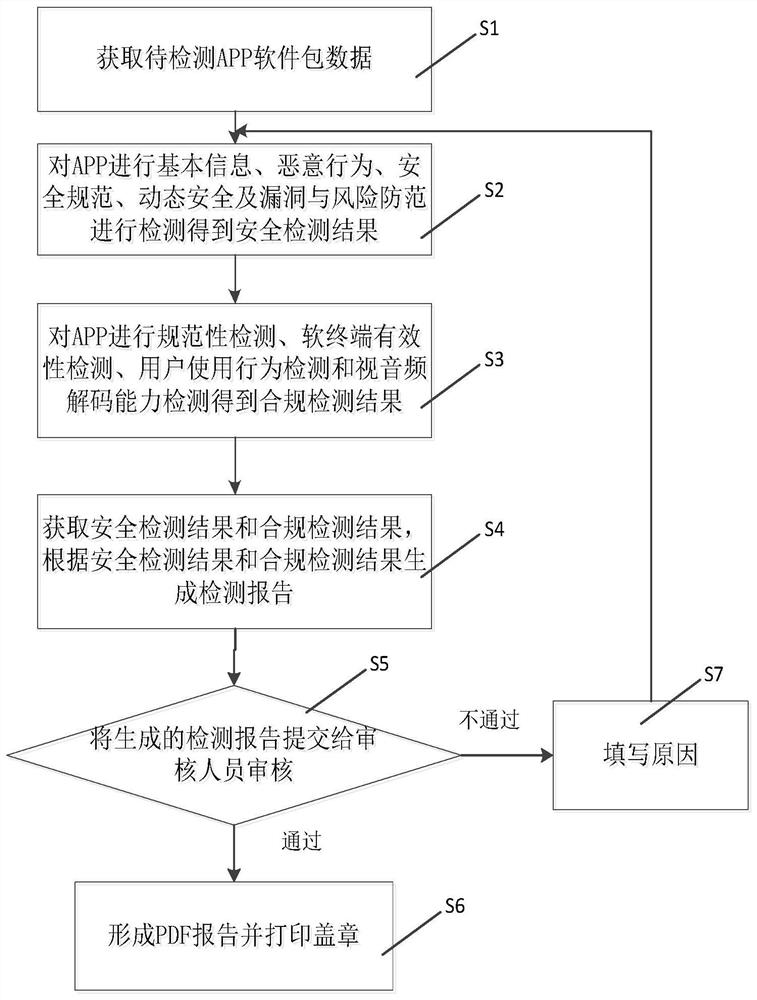
The invention discloses an audio-visual APP security and service compliance automatic detection system, which comprises an APP software package uploading module, a security detection module, a service compliance detection module and a detection report management module, and is characterized in that the APP software package uploading module is used for providing a to-be-detected APP software package uploading service; and the security detection module is used for providing an APP security detection service, and detecting basic information, malicious behaviors, security specifications, dynamic security and vulnerability and risk prevention to obtain a security detection result; the service compliance detection module is used for carrying out standardization detection, soft terminal validity detection, user use behavior detection and video and audio decoding capability detection on an APP to obtain a compliance detection result, and the detection report management module is used for generating a detection report according to the detection results of the APP security detection module and the service compliance detection module. The safety condition and the content compliance condition of the audio-visual APP are automatically detected through different dimensions, and a detection report is generated, so that the detection efficiency is improved.
Owner:北京中微云安信息科技有限公司
Image forming apparatus and control method for image forming apparatus
ActiveUS10209980B2Security for the image forming apparatus may be improvedImprove securityPlatform integrity maintainanceSpecific program execution arrangementsSecurity specificationImage formation
If firmware installed in an image forming apparatus 100 is a firmware having a security specification configuration, an operator who is permitted to instruct to update the firmware in the image forming apparatus 100 is limited to an operator having an administrator authority. This may improve the security of the image forming apparatus.
Owner:CANON KK
Hoisting system and method for hoisting high and large anaerobic jar body through low davit group
ActiveCN107140535AReduce the chance of working at heightsReduce security risksLoad-engaging elementsSecurity specificationIndustrial engineering
The invention provides a hoisting system and method for hoisting a high and large anaerobic jar body through a low davit group. The hoisting system comprises an anaerobic jar foundation, wall boards, davits, davit lugs, wall board lugs and electric chain blocks. The tops of the davits are provided with lifting lug mounting slots vertically in a cut mode. The davit lugs are inserted into the lifting lug mounting slots. The davit lugs are provided with davit lug holes. The wall board lugs are provided with wall board lug holes. The electric chain blocks and the davits are identical in number. The electric chain blocks are hung between the davits and the wall boards. One end of each electric chain block penetrates through the corresponding davit lug hole, and the other end of each electric chain block penetrates through the corresponding wall board lug hole. According to the hoisting method, an inverted hoisting manner is adopted. The hoisting system meeting the hoisting security specifications and regulations is adopted to conduct inverted construction. The hoisting system is convenient, fast and safe to use. It can be effectively guaranteed that the jar body is stably lifted up by lifting the jar body just by the height of a circle of the wall boards every time. The cost is lowered. The construction cycle is shortened. The environment is protected. Green construction and almost zero emission are realized. The construction quality is improved. Welding operations are all conducted on the ground.
Owner:BEIJING URBAN CONSTR SIXTH GRP
Security-critical software verification method and device, equipment and medium
PendingCN114385501AAvoid interferenceImprove reliabilitySoftware testing/debuggingRequirement analysisSoftware requirements specificationSecurity specification
The invention belongs to the technical field of software test verification, and provides a security-critical software verification method and device, equipment and a medium. The method comprises the following steps: expanding an FTA model based on an LTL language to obtain a formalized system security constraint condition and a corresponding software demand specification; matching the software requirement specification with a software specification symbol of the MBD according to a pre-formulated conversion rule, so that the software requirement specification is converted into a security specification model; and inputting the security protocol model and the pre-generated SCADE software design model into a model verifier to complete security verification of the software. By adopting the technical scheme of the embodiment of the invention, the security constraint condition and the software requirement specification corresponding to the security constraint condition are enabled to meet the formalized characteristics through extension of the LTL language, and meanwhile, the software requirement specification can be converted into the security specification model according to the pre-formulated conversion rule, and the security specification model is input into the model verifier for verification; the interference of human factors in a safety verification method is avoided, and the reliability is improved.
Owner:中航机载系统共性技术有限公司
System, method and apparatus for fully precise hybrid security verification of mobile applications
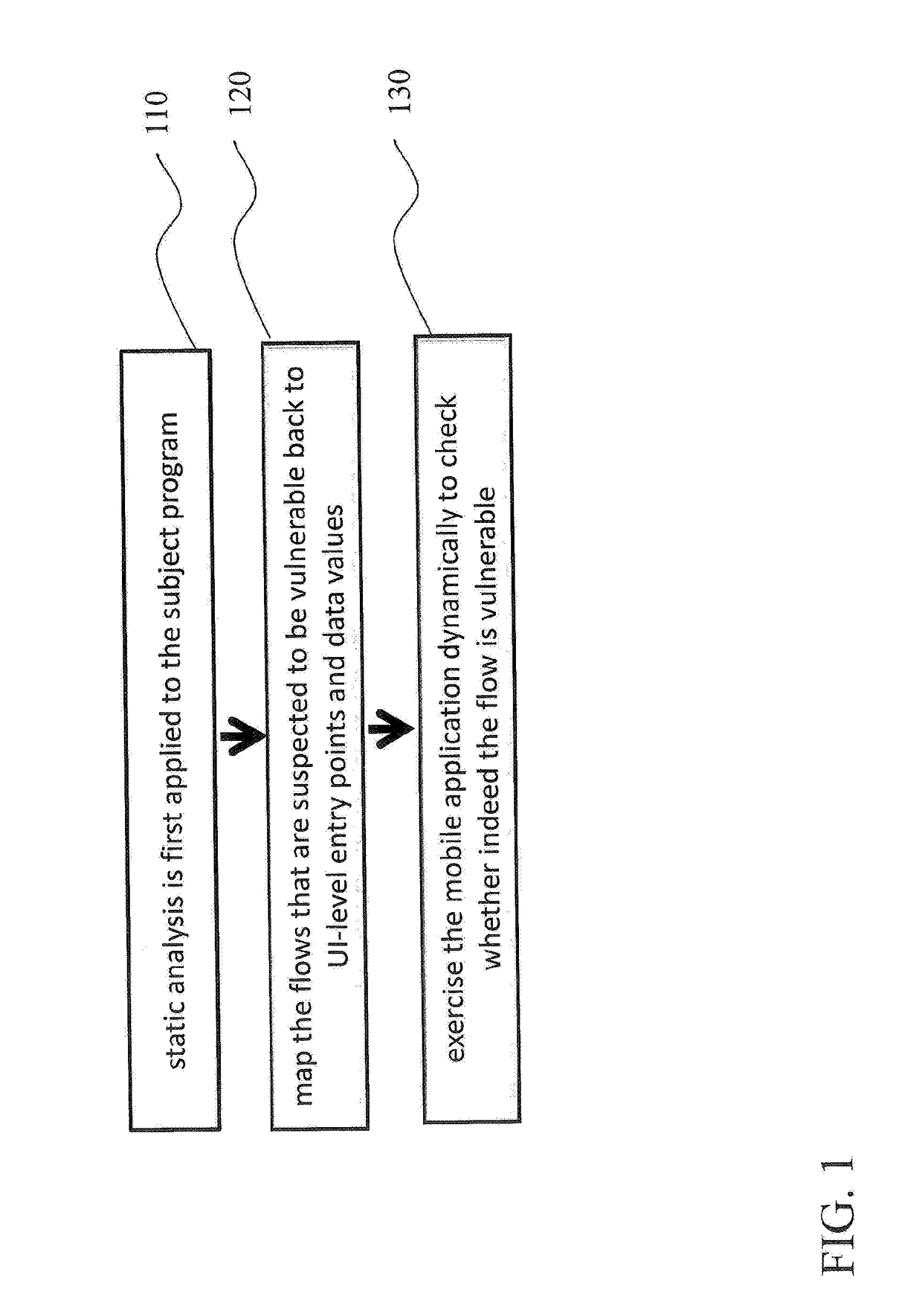
ActiveUS20170195358A1Semi-structured data mapping/conversionTransmissionSecurity specificationEntry point
A security verification system and method that includes outputting a list of potential dataflow vulnerabilities as a first output from inputting a subject program and security specification, mapping candidate vulnerabilities to a user interface (UI) entry point and payload from the output of the list of potential dataflow vulnerabilities to provide a second output, and performing directed testing of the second output.
Owner:IBM CORP
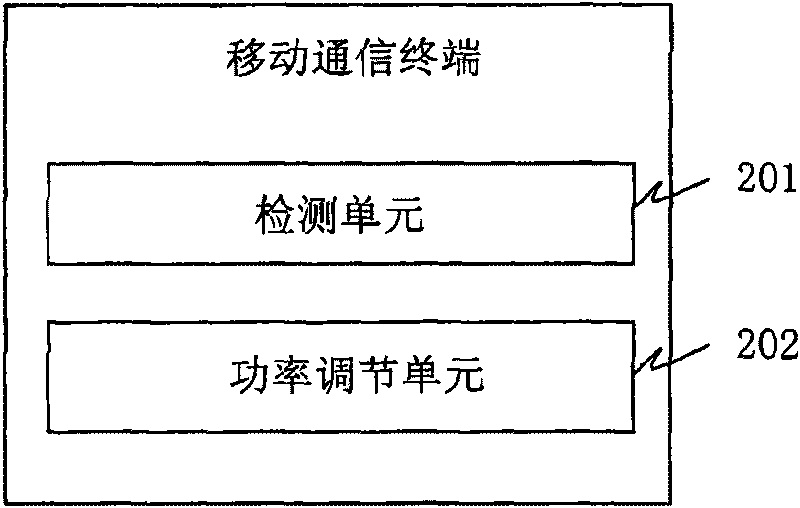
Mobile communication terminal and method thereof for adjusting power of FM/AM transmitter
ActiveCN101753158AOvercome the problem of radiation outMeet the requirements of safety regulationsPower managementTransmissionCouplingSecurity specification
Owner:HUAWEI DEVICE CO LTD
Method for detecting security of electrical equipment
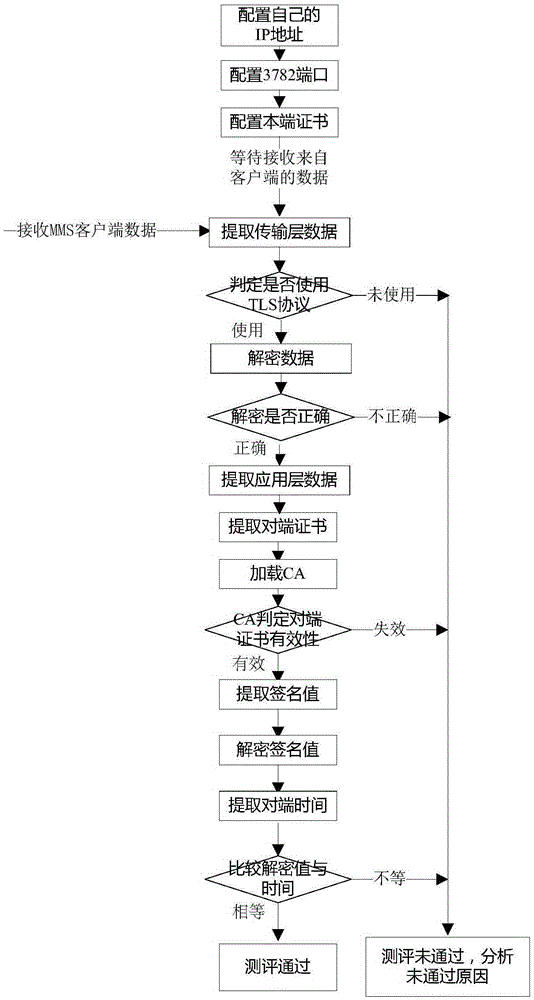
ActiveCN105306489ALow costMeet the identity authentication functionUser identity/authority verificationSecure communicationSecurity specification
The invention provides a method for detecting security of electrical equipment. The method comprises the following steps: detecting whether the electrical equipment has a specified secure communication port function; detecting whether the equipment has a TLS transport layer security function; and detecting whether the equipment has associated authentication and replay attack prevention functions of an MMS application layer. The method provided by the invention is used for detecting whether security equipment about to pull in has security specifications required by the IEC62351 standards to offer suggestions for the inbound of the equipment, and detecting the security function of the equipment after MMS protocol security reinforcement and judging whether the equipment reaches a security reinforcement effect according to the IEC62351 standards, in order to provide guidance basis for the development and inbound of the security equipment; and the cost of directly using the equipment in bound can be effectively reduced, and it is conducive to promote equipment developers to develop security equipment products satisfying the IEC62351 standards.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com