Patents
Literature
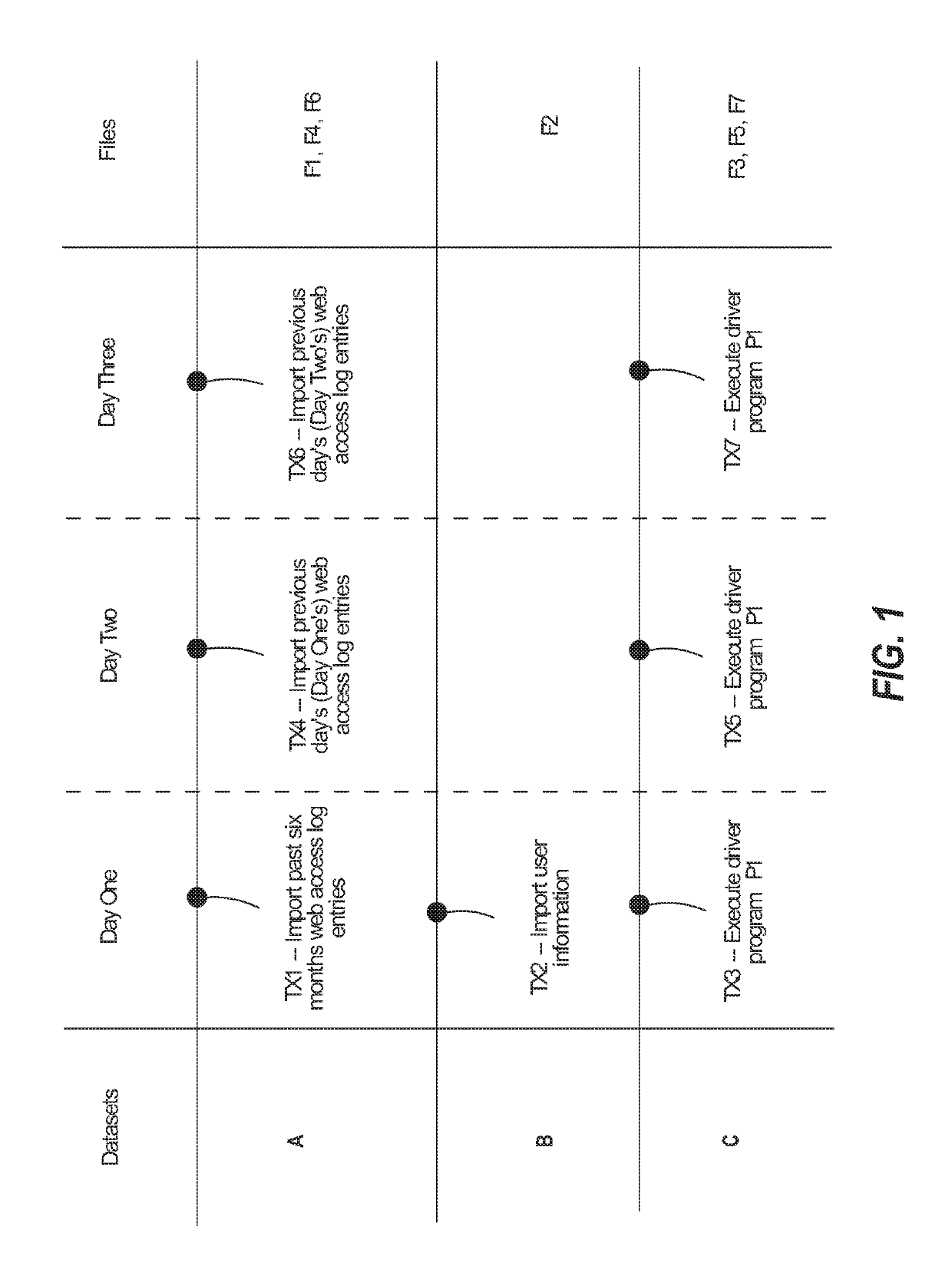
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
141 results about "JAR" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
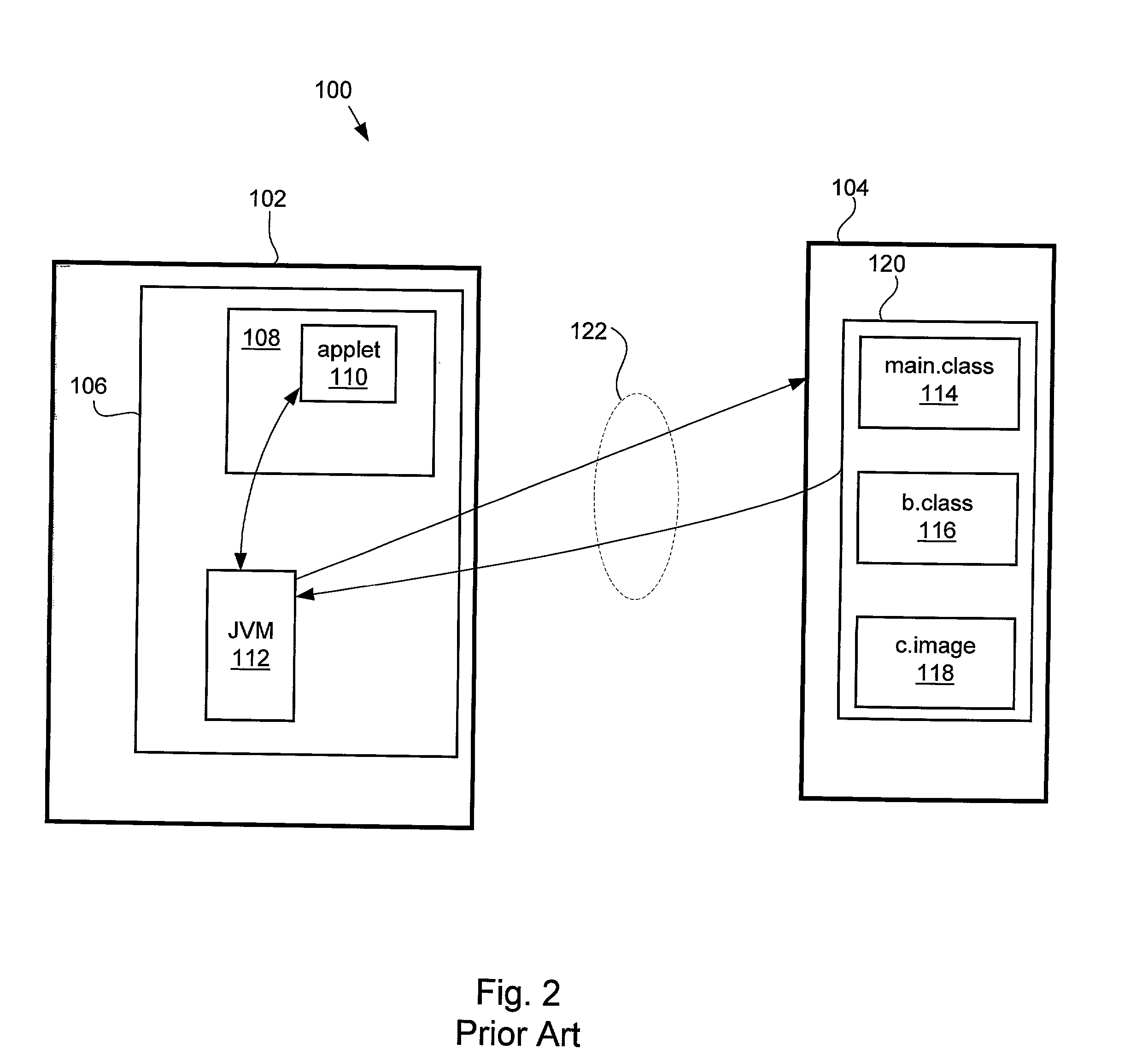
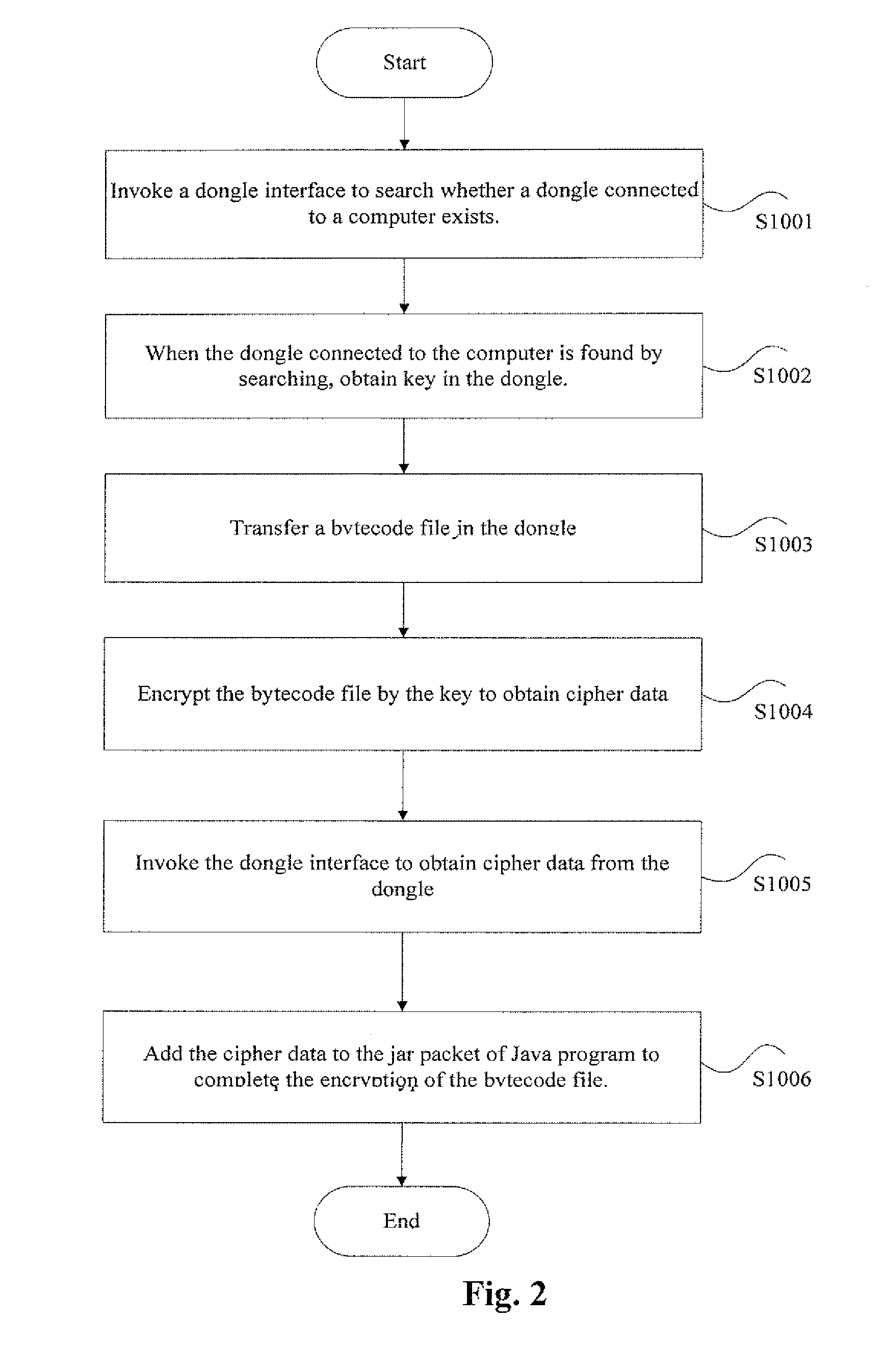
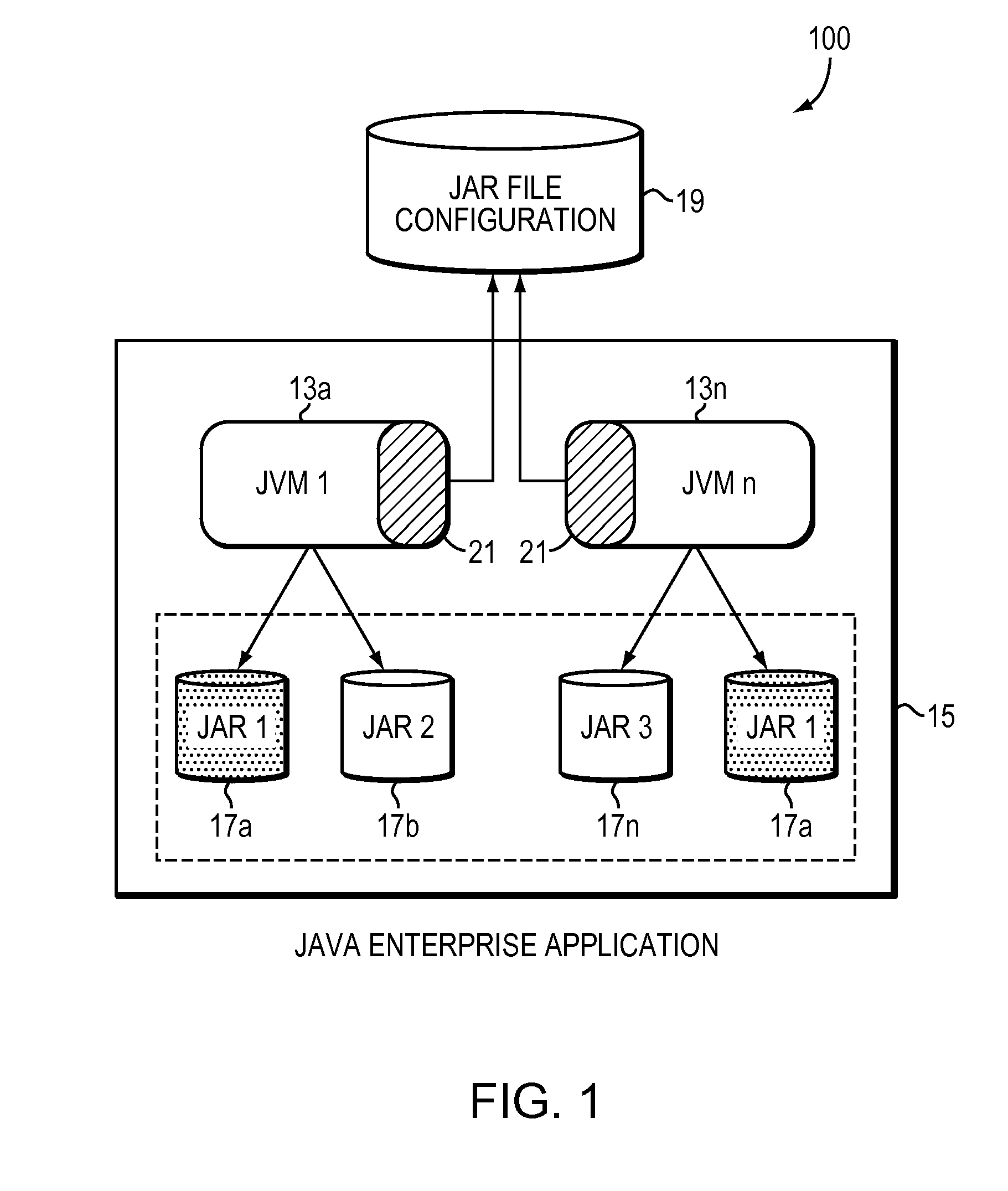
A JAR (Java ARchive) is a package file format typically used to aggregate many Java class files and associated metadata and resources (text, images, etc.) into one file for distribution. It is used to store classes of java created by the user in order to help the runnable and inference concepts embedded within the language.
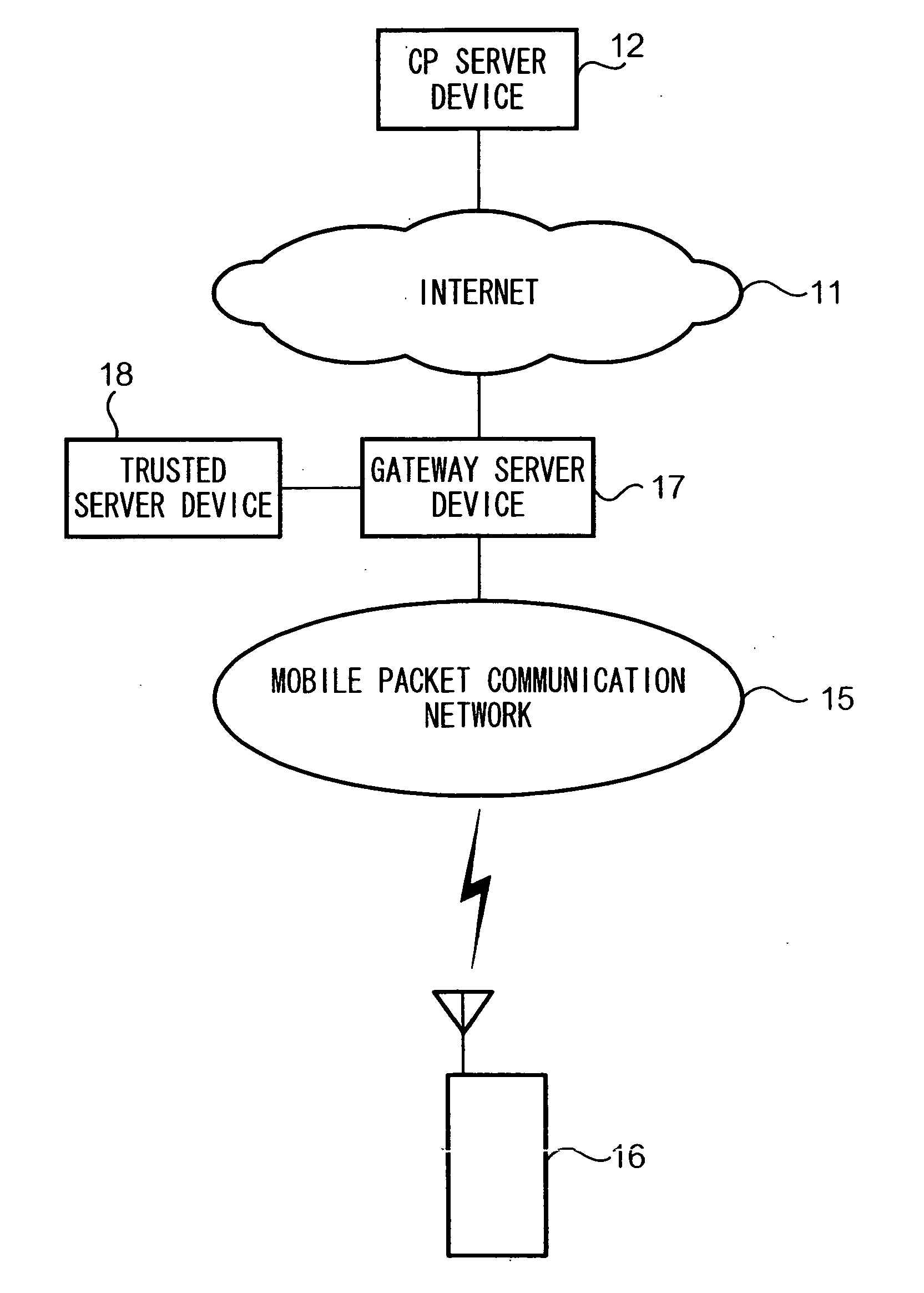
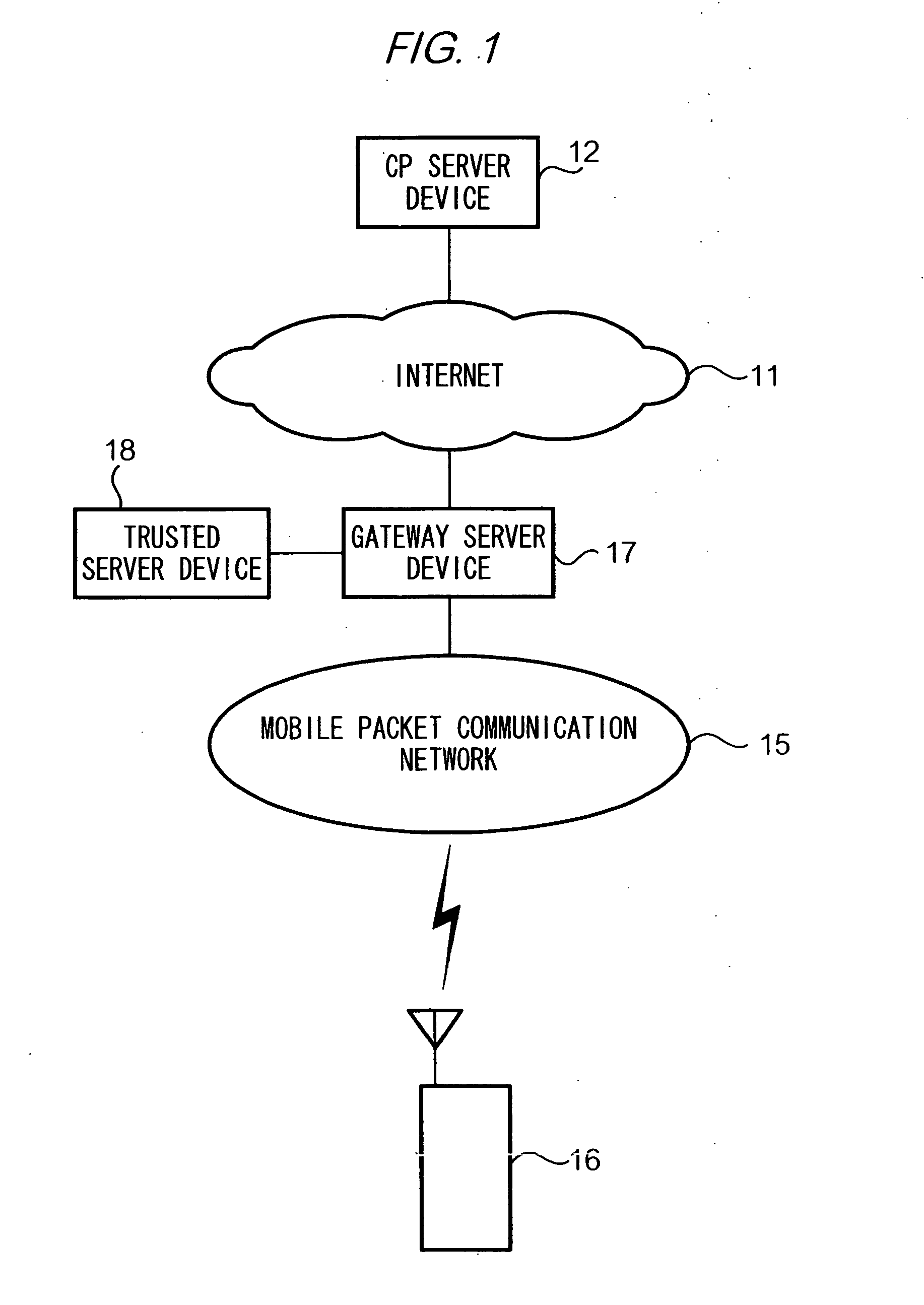
Communication device and program
InactiveUS20050005099A1Confirm their validityUnauthorized memory use protectionDigital data protectionMobile stationServer appliance
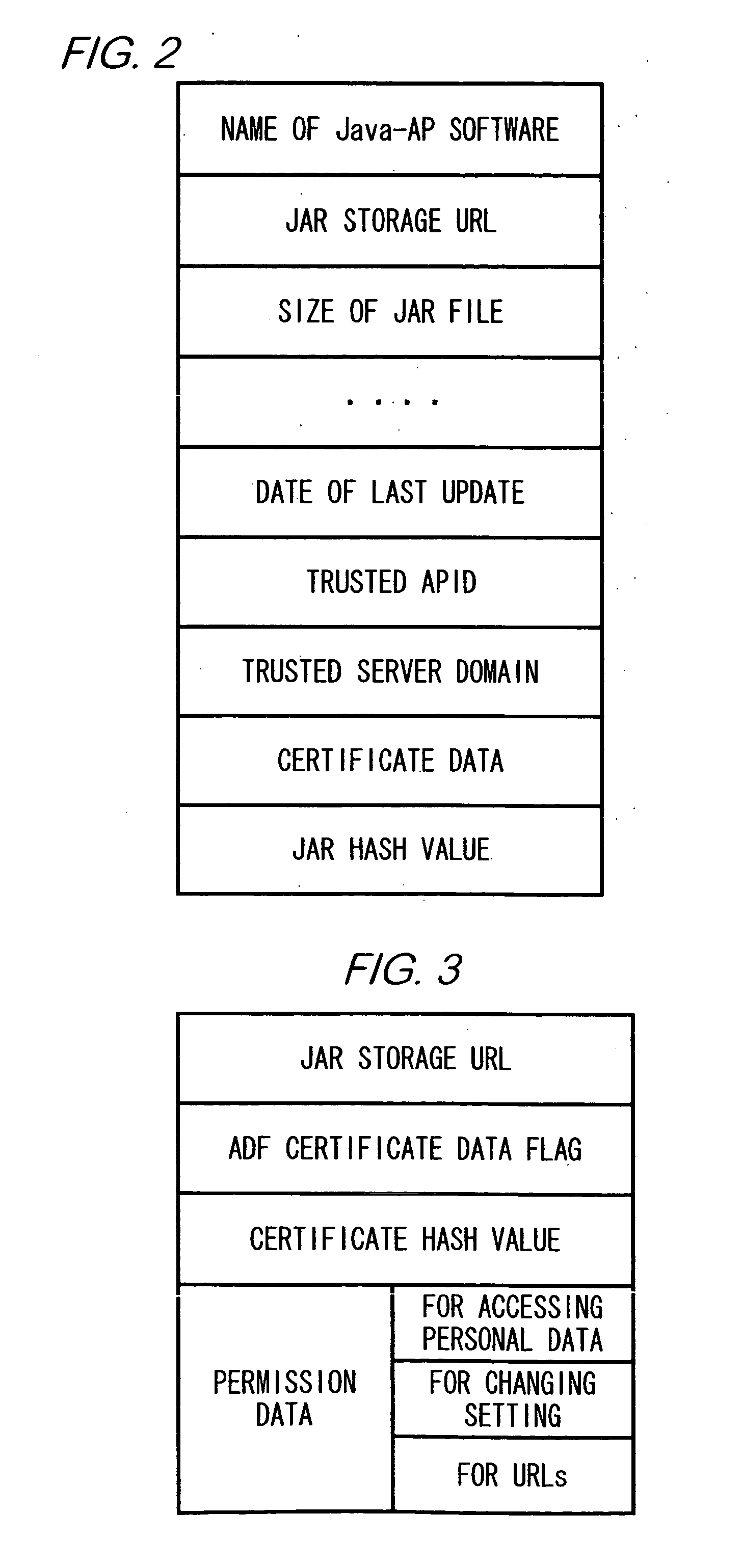
The present invention provides a means for determining authenticity of a combination of files which are downloaded to a mobile station, and which are related to one another. To achieve the stated object, in a system according to the present invention, mobile station 16, which is capable of running a Java-APP, receives an ADF from CP server device 12. Then mobile station 16 receives a SDF from trusted server device 18, which is identified by data contained in the ADF. Mobile station 16 calculates a hash value of certificate data contained in the ADF, and verifies whether the calculated hash value of the certificate data and a hash value of the certificate data which is contained in the SDF are identical to each other. Next, mobile station 16 receives a JAR file from CP server device 12. Mobile station 16 calculates a hash value of the JAR file, and verifies whether the calculated hash value of the JAR file and a hash value of the JAR file contained in the ADF are identical to each other.
Owner:NTT DOCOMO INC
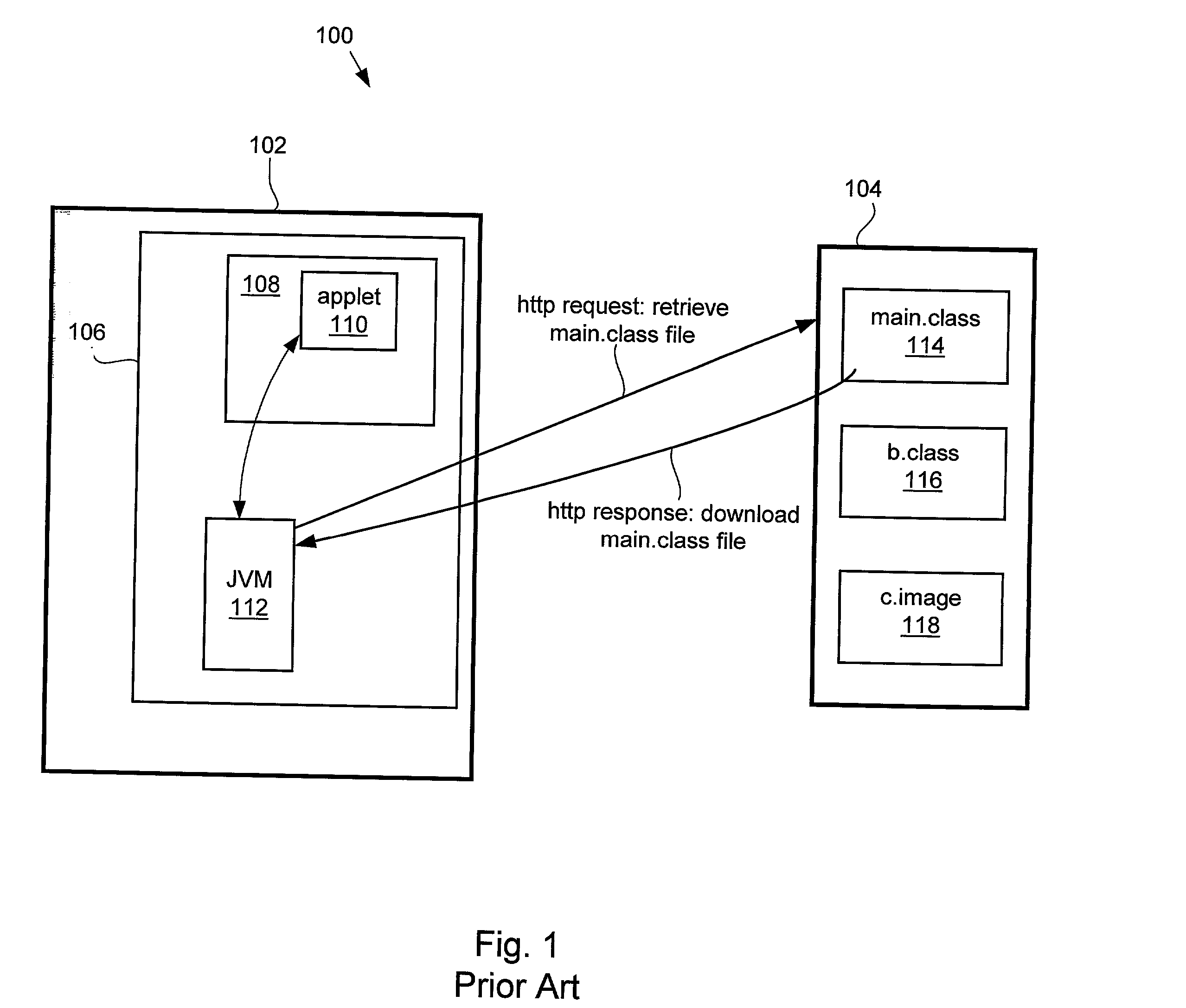
Method and apparatus for expedited file downloads in an applet environment
InactiveUS20030105888A1Multiple digital computer combinationsProgram loading/initiatingHash tableVirtual machine
Methods and apparatus for executing an applet are disclosed. A virtual machine that includes a class loader generates a file download request in the form of an http request to a particular server computer that contains appropriate applet component files. The class loader queries a root JAR file having an index file associated with applet. The class loader creates a HASH table based upon the contents of the index file that provides a mapping of all packages and all corresponding JAR files required to execute the applet by the virtual machine. During virtual machine runtime the class loader queries the HASH table in order to directly access the appropriate applet component file to be downloaded and executed by the virtual machine.
Owner:ORACLE INT CORP
Modular development method for Android
ActiveCN102722370AImprove reusabilityReduce complexitySpecific program execution arrangementsSoftware engineeringJAR
The invention discloses a modular development method for Android, comprising a module export step, a module import step, and a module removal step, wherein the import operation and the removal operation are realized by a modules folder used for monitoring items; if a new file is added in the folder and ended by.jar, the new file is defaulted to be a module file, and an import process is started; if a file is removed from the folder and ended by the.jar, a removal process is started; and if a file needs to be replaced, the removal process and the import process are sequentially started respectively. According to the method, a mode that an Android program module is independently compiled to be a jar package based on plug-in features of Eclipse and ADT plug-in characteristics of the Android, other Android programs can be used for analyzing the jar package, and the function of the module is added in a new Android program. And moreover, the function of a certain assembly can be removed by removing the jar package.
Owner:南京华设科技股份有限公司
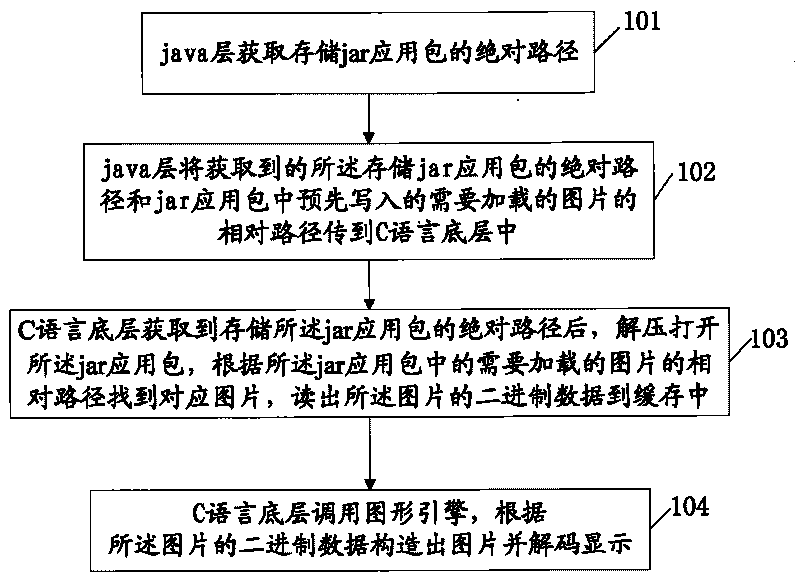
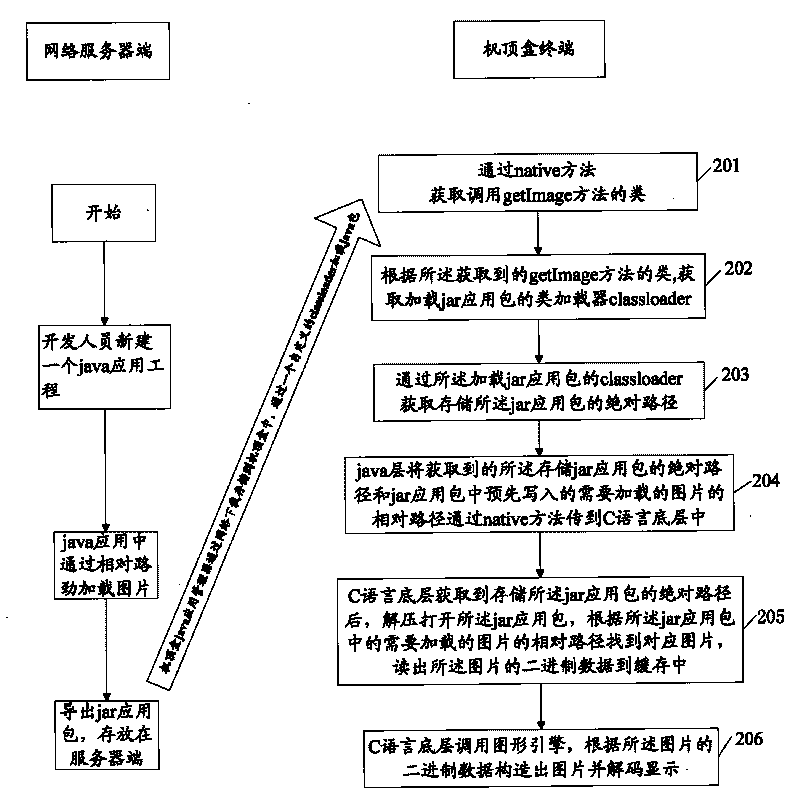
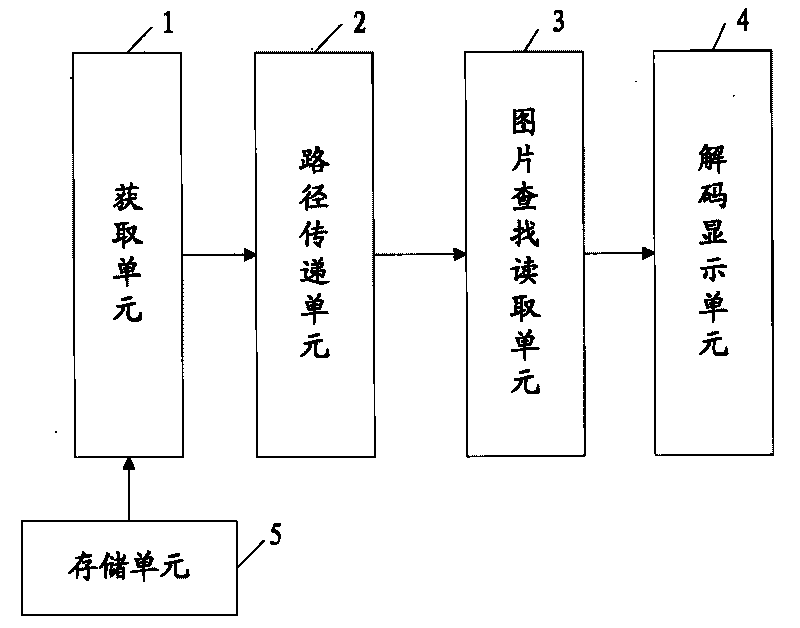
Method and device for loading pictures during java application
InactiveCN101729753AEfficient loadingWork lessTelevision system detailsColor television detailsGraphicsWorkload
The invention provides a method for loading pictures during java application. The method comprises the following steps that: a java layer acquires an absolute path storing a jar application packet; the java layer transmits the acquired absolute path storing the jar application packet and a pre-written-in relative path for the pictures needing loading in the jar application packet into a C-language bottom layer; after acquiring the absolute path storing the jar application packet, the C-language bottom layer decompresses and unpacks the jar application packet, finds corresponding pictures according to the relative path for the pictures needing loading in the jar application packet and reads out binary data of the pictures in a cache; and the C-language bottom layer calls an graphics engine, constructs the pictures according to the binary data of the pictures and decodes the pictures for displaying. Correspondingly, the invention also provides a device for loading the pictures during the java application so as to realize efficient picture loading and improve the efficiency while lightening the workload of personnel developing set-top box application.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
Targeted runtime compilation
ActiveUS20050193373A1Software engineeringSpecific program execution arrangementsProgramming languageLinkage concept
Owner:COMCAST CABLE COMM MANAGEMENT LLC
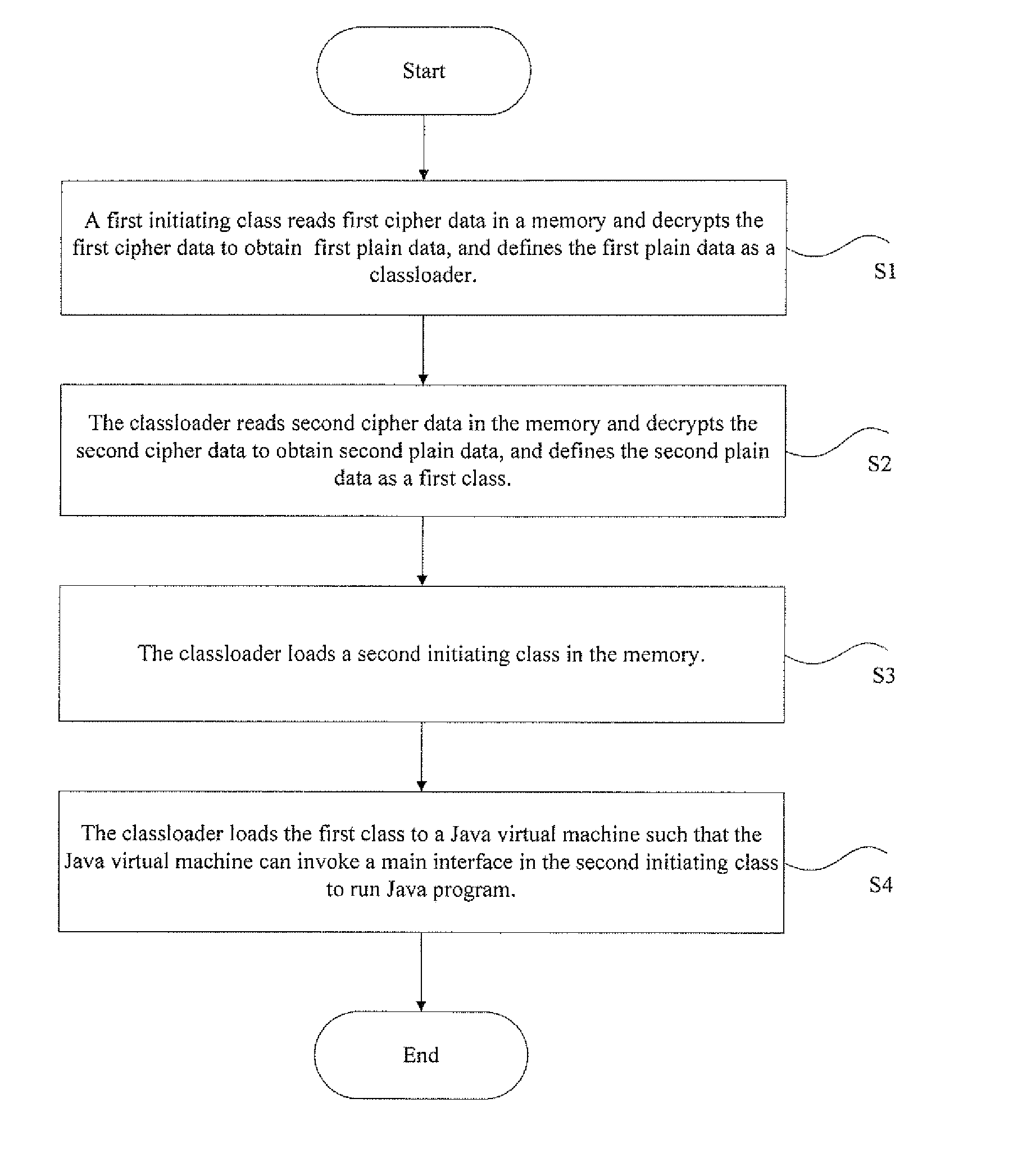
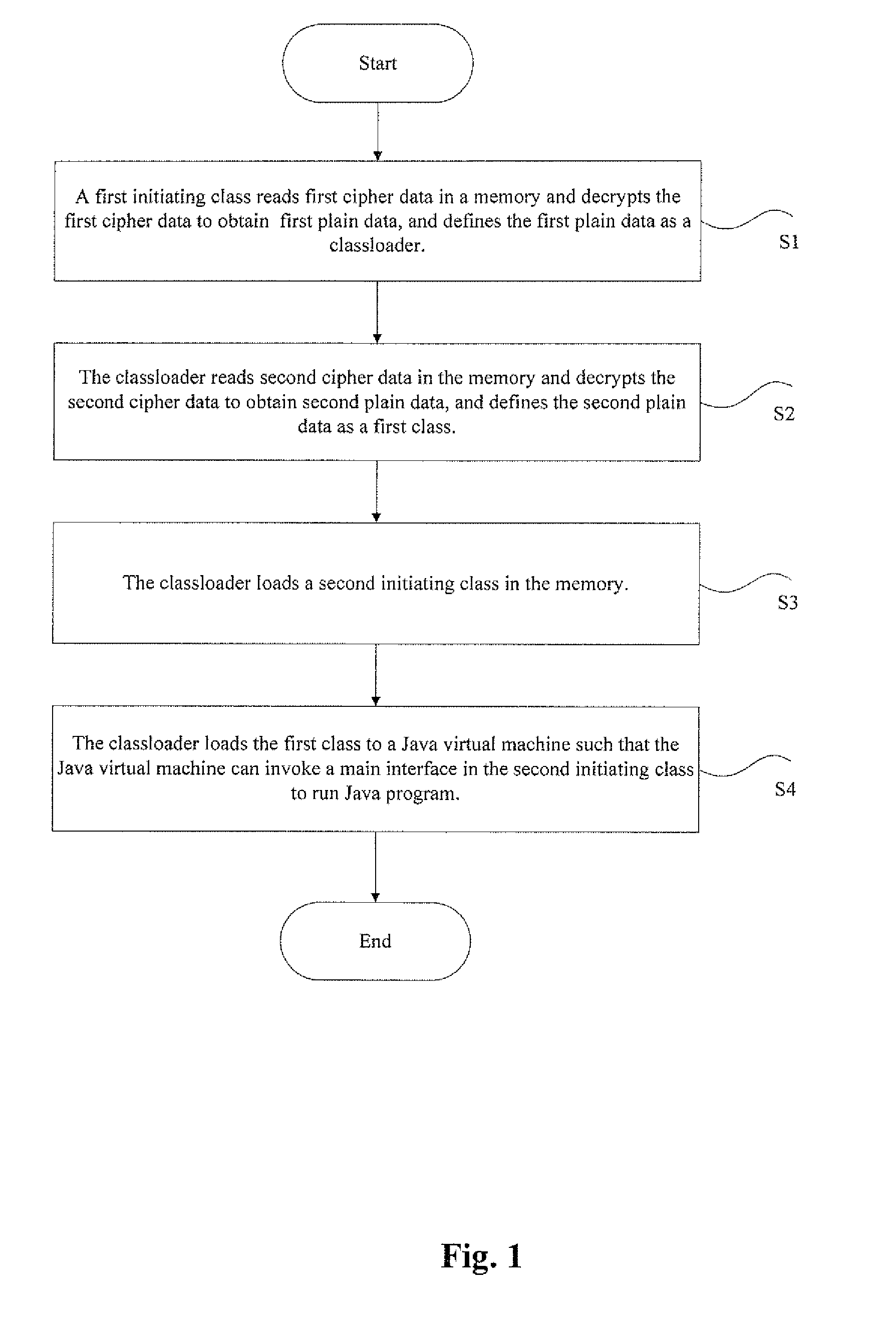
Protecting method and system of JAVA source code
ActiveUS20140195824A1Easily decompiledUnauthorized memory use protectionHardware monitoringCiphertextSoftware engineering
The present disclosure discloses a protecting method and system of Java source code. When a first initiating class is invoked, the method comprises following steps, wherein the first initiating class is an initiating class of Java program: the first initiating class decrypts first cipher data to obtain a class loader; the class loader reads second cipher data to the memory and decrypts the second cipher data to obtain a first class, wherein the first class is a class run by a Java virtual machine, and the suffix of the first class is .class; the class loader loads a second initiating class to the memory; wherein the second initiating class is an original class in jar packet of the Java program; and the class loader loads the first class to the Java virtual machine so that the Java virtual machine can invoke a main interface in the second initiating class to run the Java program. The present disclosure can protect Java source code and make it difficult to decompile the Java source code.
Owner:FEITIAN TECHNOLOGIES
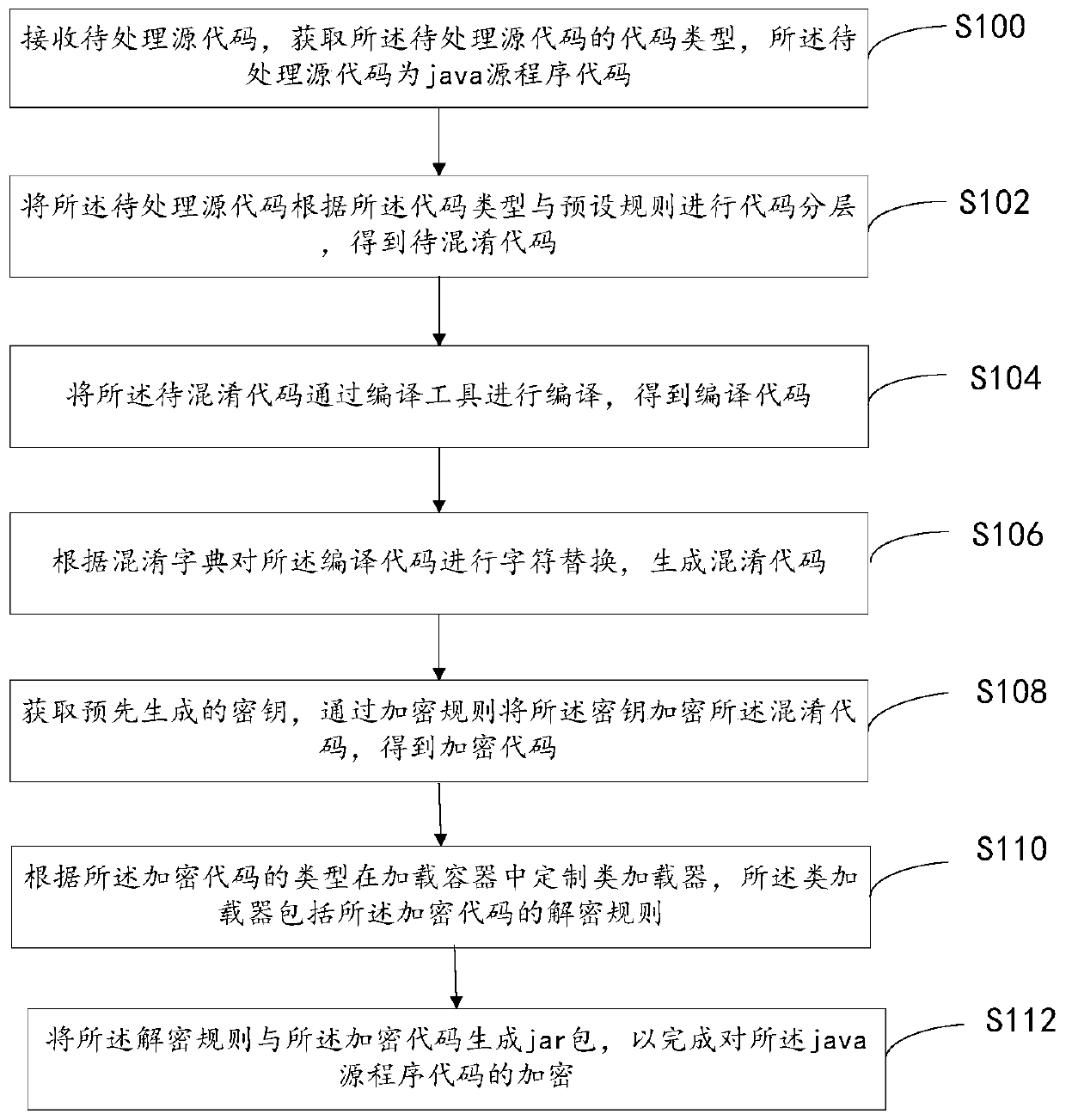
Java code encasing method and system
InactiveCN111552931ALess invasiveReduce the risk of decompilation and crackingProgram/content distribution protectionCode generationTheoretical computer science
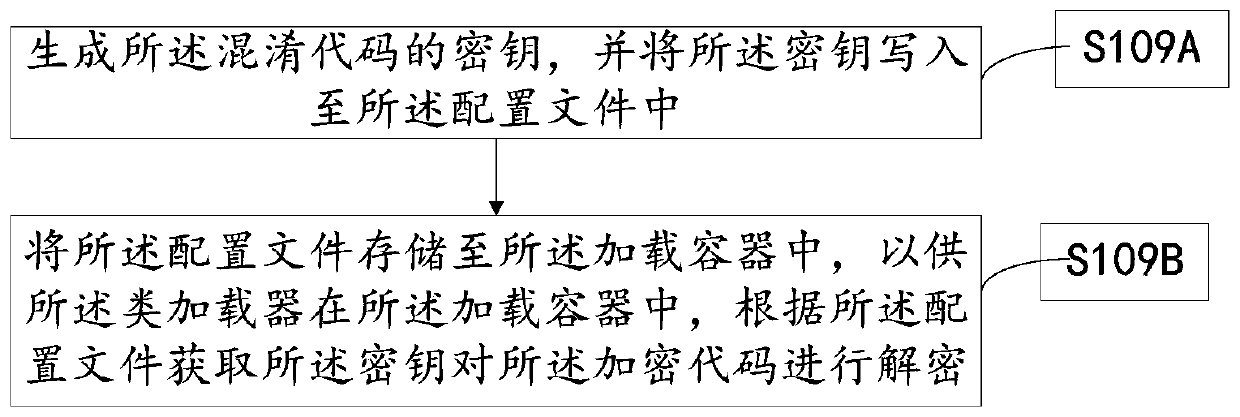
The invention discloses a java code encasing method, which comprises the steps of performing code layering on a to-be-processed source code according to a code type and a preset rule to obtain a to-be-obfuscated code; compiling the to-be-obfuscated code through a compiling tool to obtain a compiled code; performing character replacement on the compiled code according to an obfuscation dictionary to generate an obfuscation code; obtaining a pre-generated secret key, and encrypting the obfuscated code by the secret key through an encryption rule to obtain an encrypted code; customizing a class loader in a loading container according to the type of the encrypted code, wherein the class loader comprises a decryption rule of the encrypted code; and generating a jar package by using the decryption rule and the encrypted code to complete encryption of the java source program code. The method has the beneficial effect that the security of the code is improved. In addition, the invention also relates to a block chain technology, and the decryption rule can be stored in the block chain node.
Owner:PING AN TECH (SHENZHEN) CO LTD
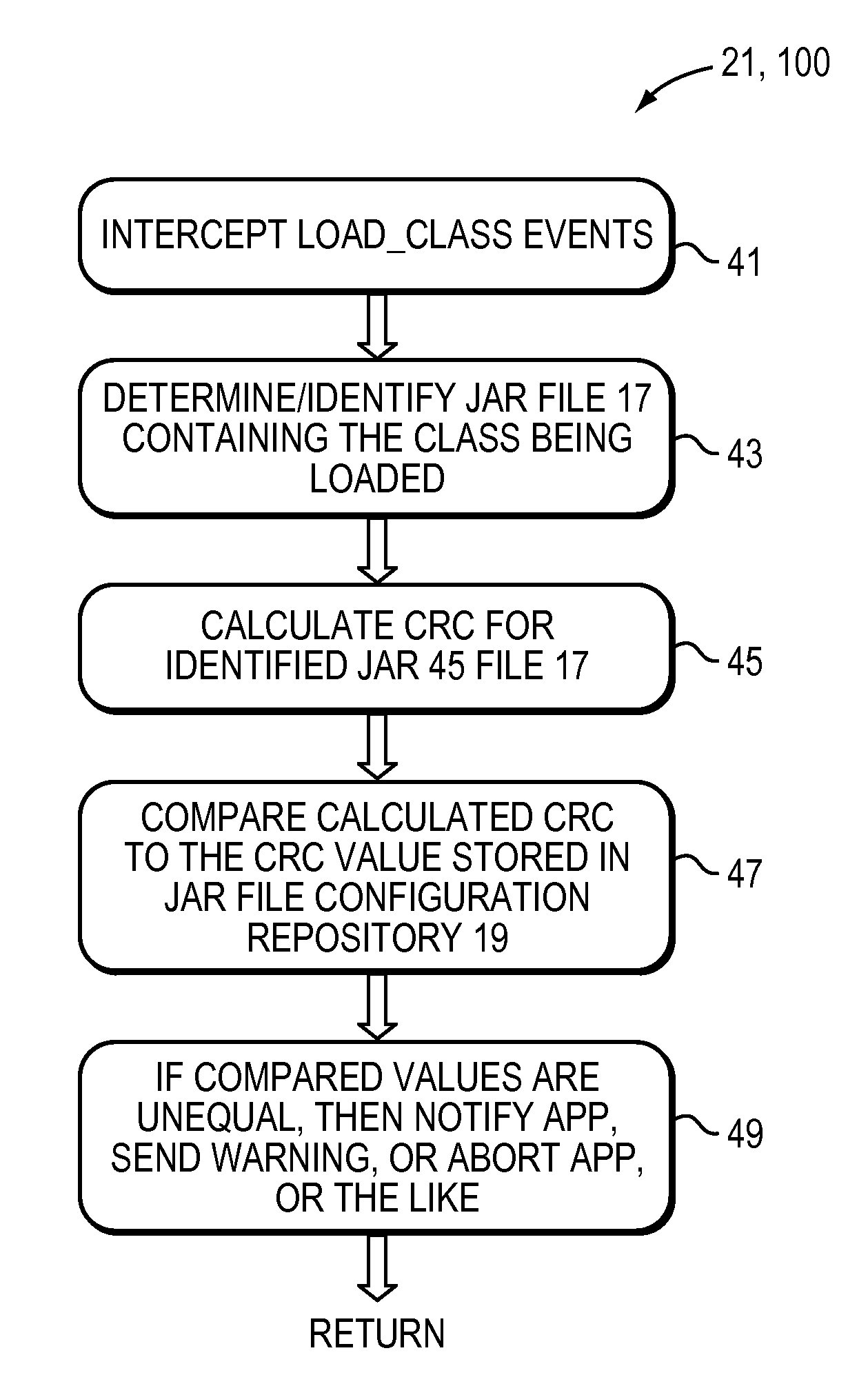
Method and system for checking the consistency of application jar files
InactiveUS20120317563A1Provide consistencyEnsure consistencyError detection/correctionSpecific program execution arrangementsMultiple copyApplication software
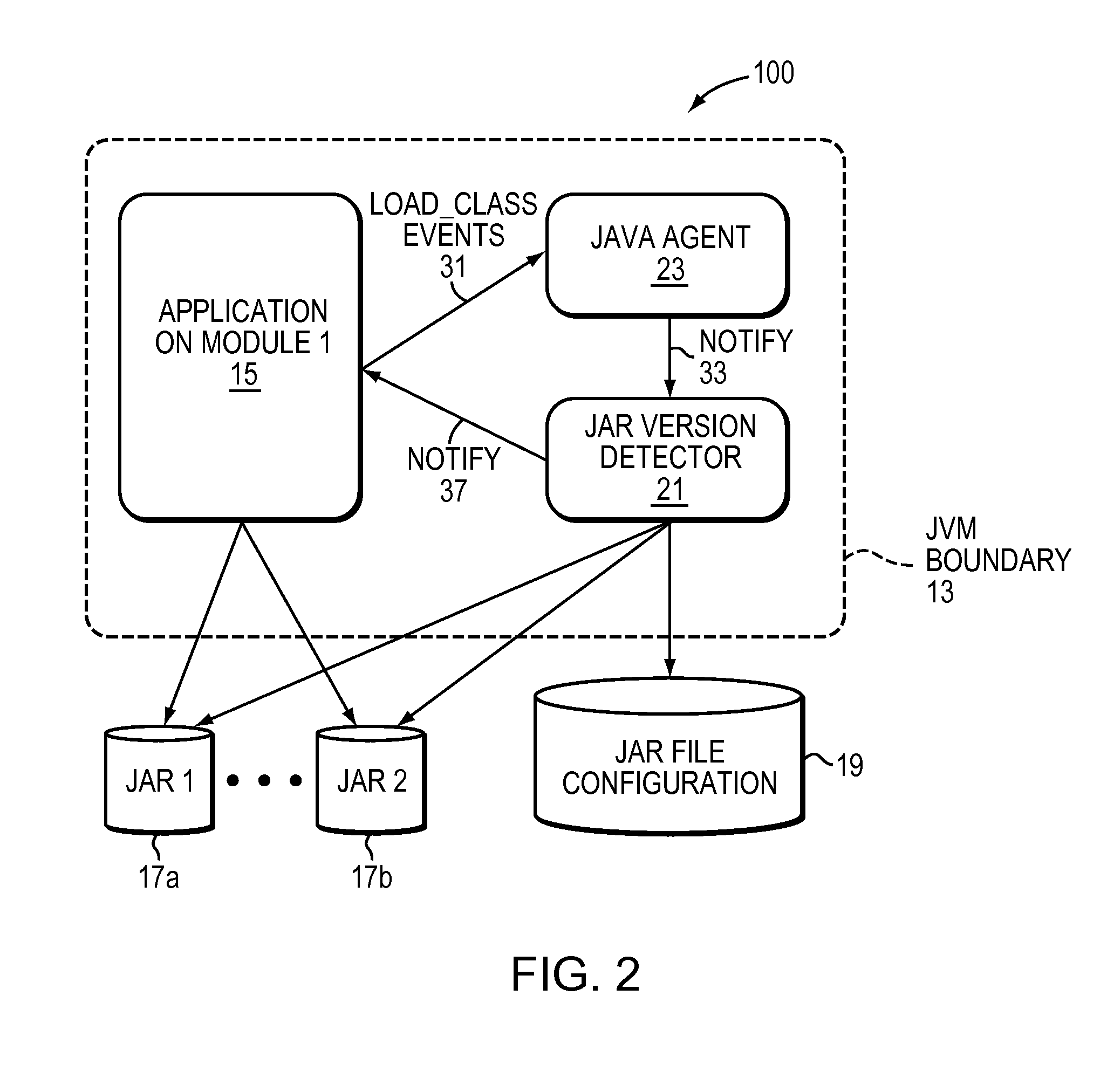
A computer method and system dynamically provide consistency of Java application files. A processor executed routine is configured (e.g., instrumented as an agent) to intercept each class that is loaded into a subject Java application or JVM. The system computes a cyclic redundancy check (CRC) of the respective JAR file surrounding the loaded class. The system compares the computed CRC value to a CRC value of at least one other copy of the respective JAR file. Based on results of the comparison, the system determines consistency (e.g., same version) of the multiple copies of the respective JAR file used by the subject Java application. If the multiple copies of the respective JAR file are determined to be inconsistent, the system alerts the user and / or enables the application to abort. The comparative CRC value may be stored in a repository; and the step of comparing looks up the stored CRC value in the repository.
Owner:IBM CORP
Method and device for detecting robustness of JAVA application program
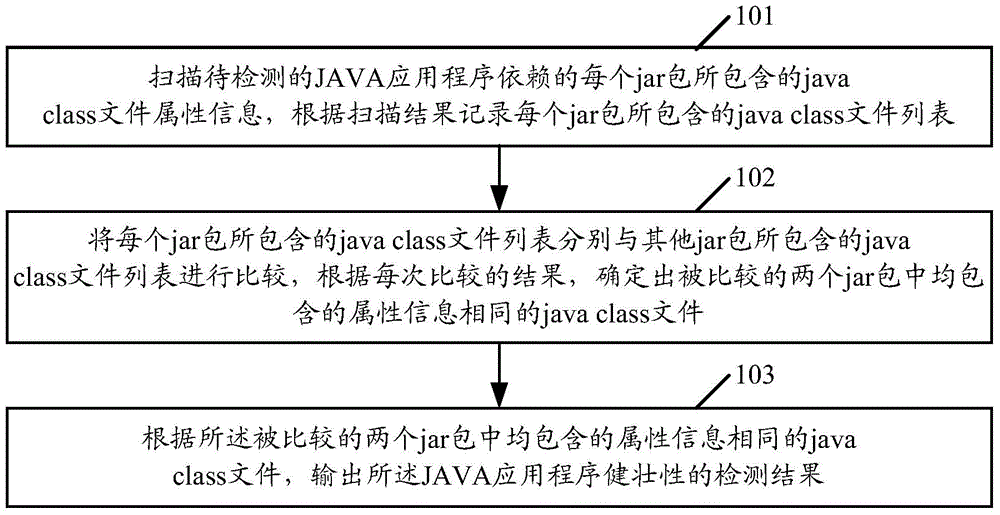
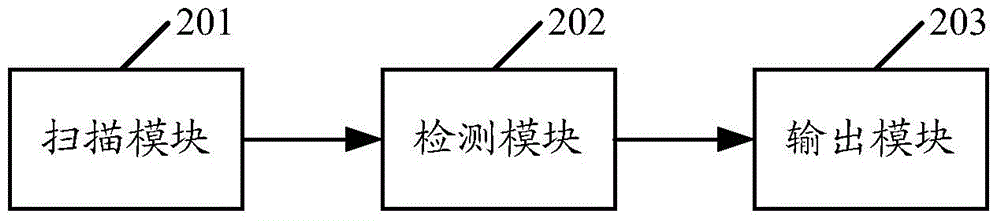
ActiveCN103559132AImprove robustnessImprove stabilitySoftware testing/debuggingProgramming languageJava class file
The embodiment of the invention discloses a method and a device for detecting robustness of a JAVA application program. The method comprises the following steps of scanning java class file attribute information contained in each jar packet on which a to-be-detected JAVA application program depends, and recording the java class file list of each jar packet; respectively comparing the java class file list of each jar packet with java class file lists of other jar packets to determine java class files of which the attribute information contained in two compared jar packets is same; outputting a robustness detection result according to the java class files of which the attribute information is same. By applying the method and the detection disclosed by the invention, the robustness of the JAVA application program can be detected before actual operation, and therefore, the robustness of the JAVA application program and the stability of a system based on the JAVA application program can be helped to be improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
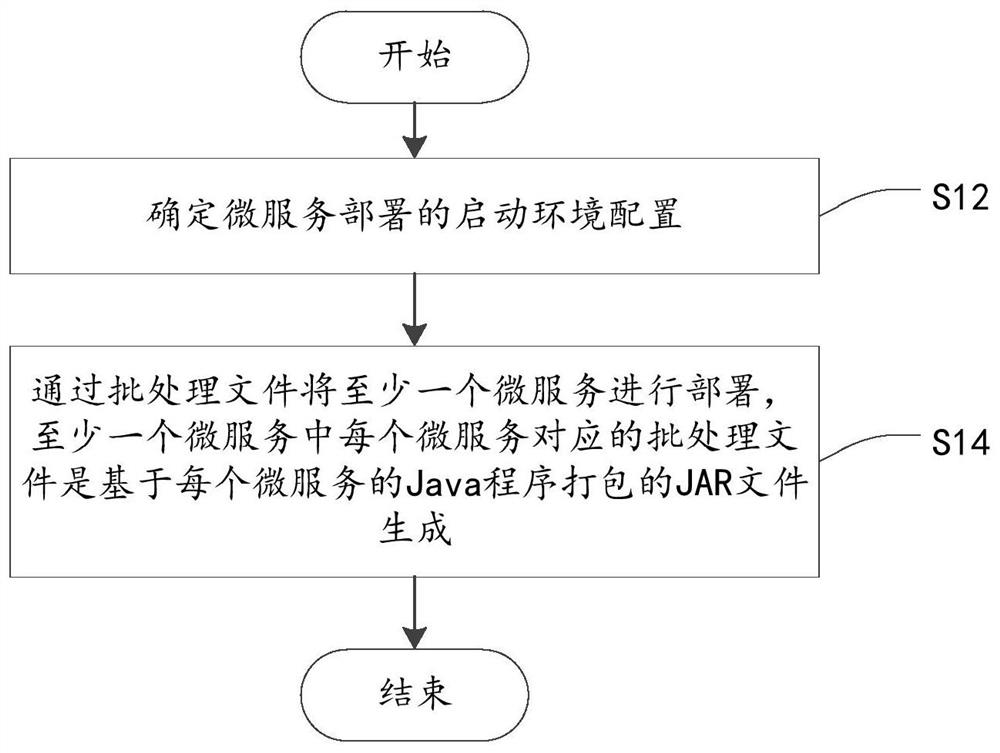
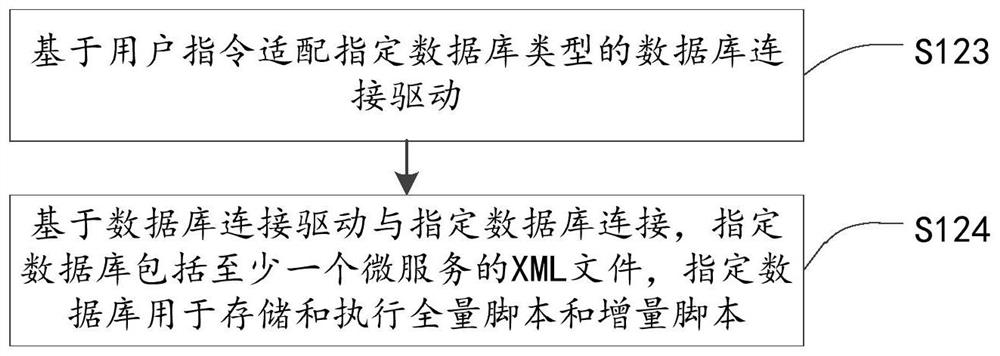
Micro-service deployment method and device, electronic equipment and storage medium
The invention provides a micro-service deployment method and device, electronic equipment and a storage medium, and relates to the technical field of micro-services. The method comprises the followingsteps: determining starting environment configuration of micro-service deployment; and deploying at least one micro-service through the batch processing file, wherein the batch processing file corresponding to each micro-service in the at least one micro-service is generated based on a JAR file packaged by a Java program of each micro-service. According to the method, script execution is carriedout on the JAR file packaged by the Java program of the micro-service through the batch processing file, so that batch automatic deployment of the micro-service is realized, and the micro-service deployment efficiency is improved.
Owner:宏桥高科技集团有限公司
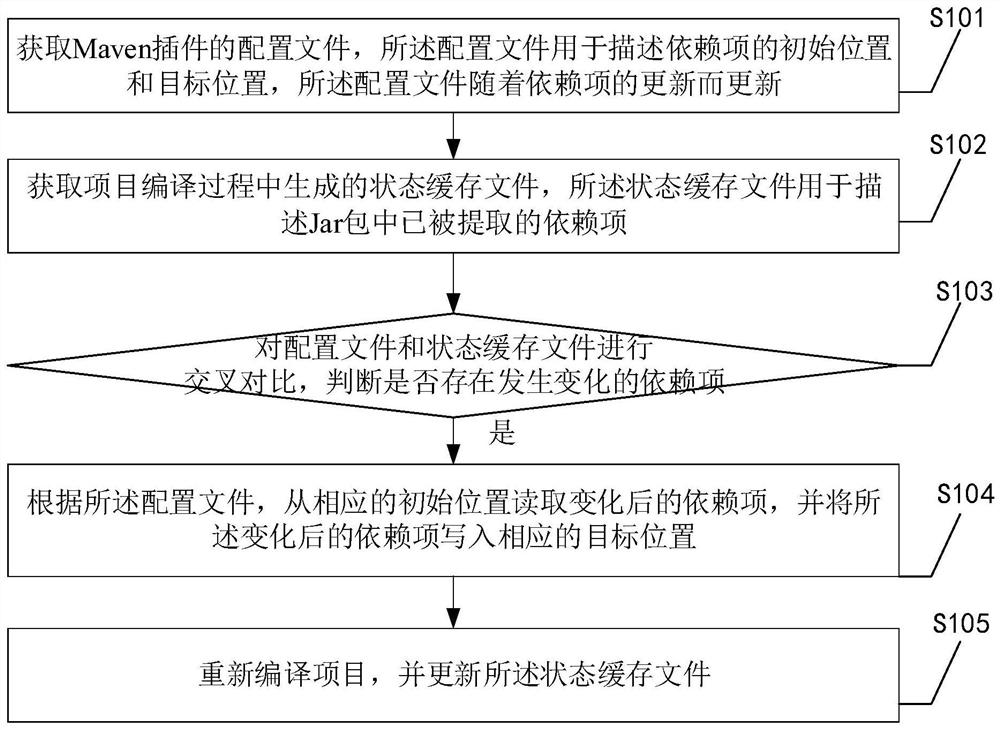
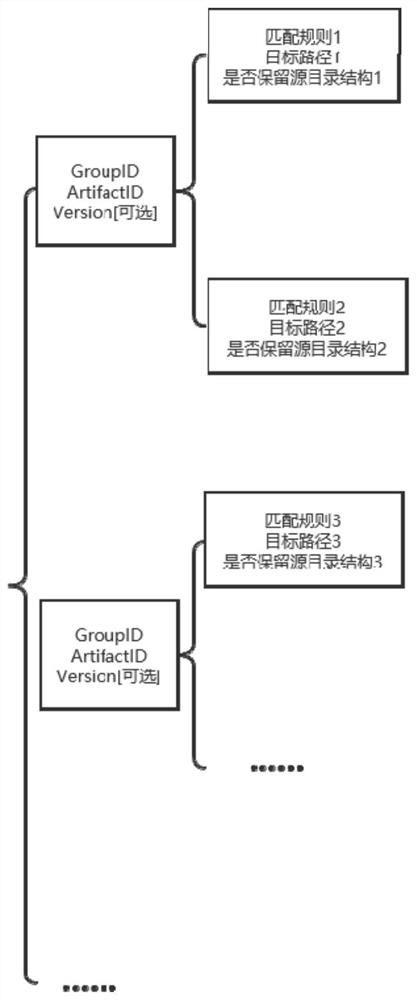
Multi-dependency-item file extraction method and device based on Maven plug-in
PendingCN111897570AReduce complexityReduce maintenance workloadVersion controlCode compilationThird partyConfigfs
The invention discloses a multi-dependency-item file extraction method and device based on a Maven plug-in, which is implemented on the basis of the Maven plug-in, sets a source position and a targetposition of a dependent item through a self-defined configuration file, and provides a function of extracting dependent item files from a specified Jar packet to the target position in batches. A third-party server or a folder and the like do not need to be introduced, so that the system complexity is reduced. The extraction process is finished based on a Maven insert. As the Maven only depends ona cross-platform operation environment of JDK, the method is not related to the platform or a version. There is no need to require additional script or system to support. In addition, the invention provides a Maven plug-in-based multi-dependent-item file extraction device and apparatus and a readable storage medium, and the technical effect of the Maven plug-in-based multi-dependent-item file extraction device and equipment corresponds to the technical effect of the method.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
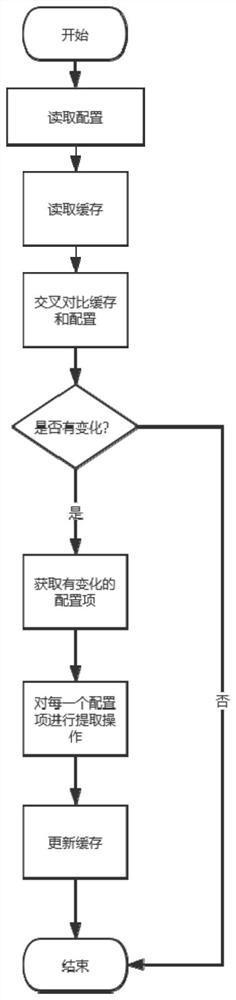
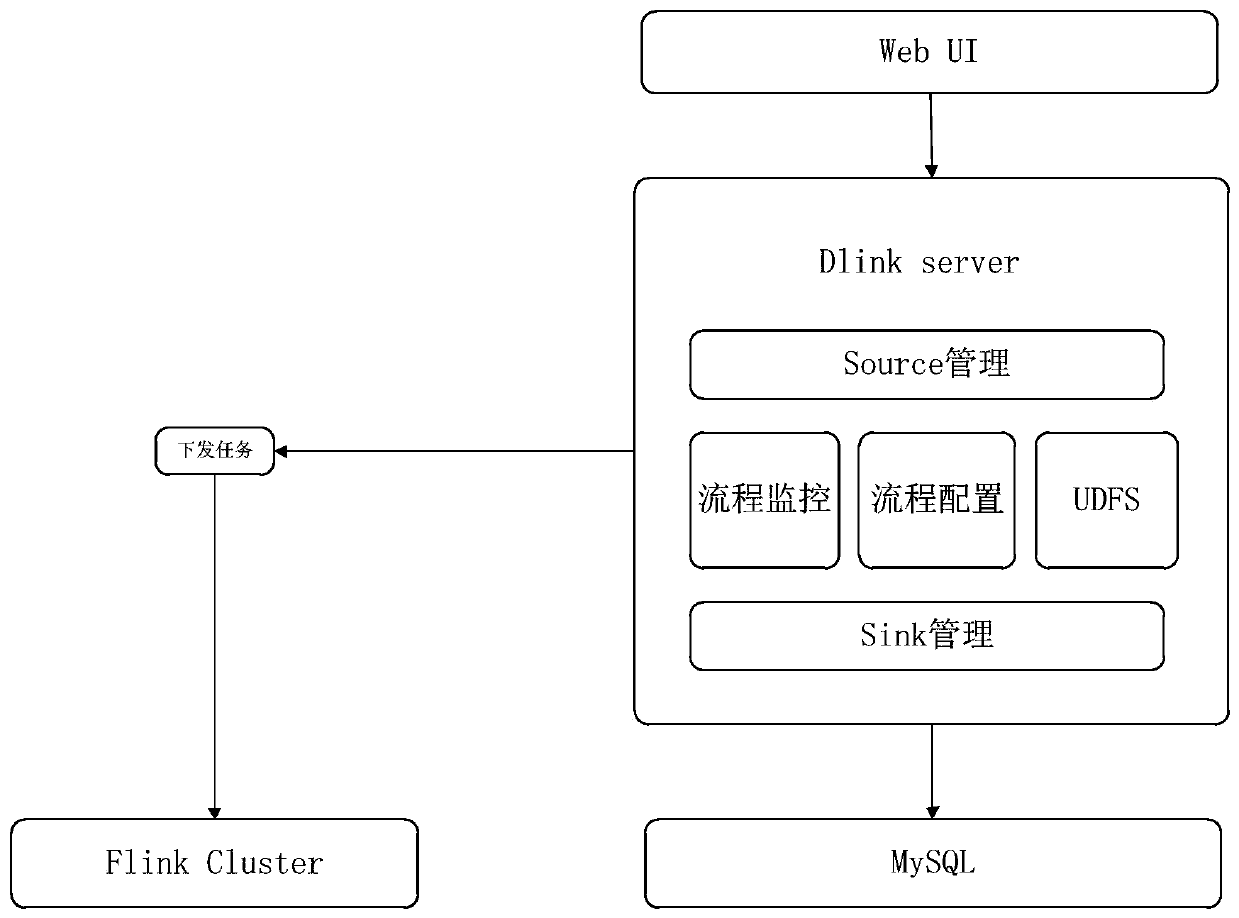
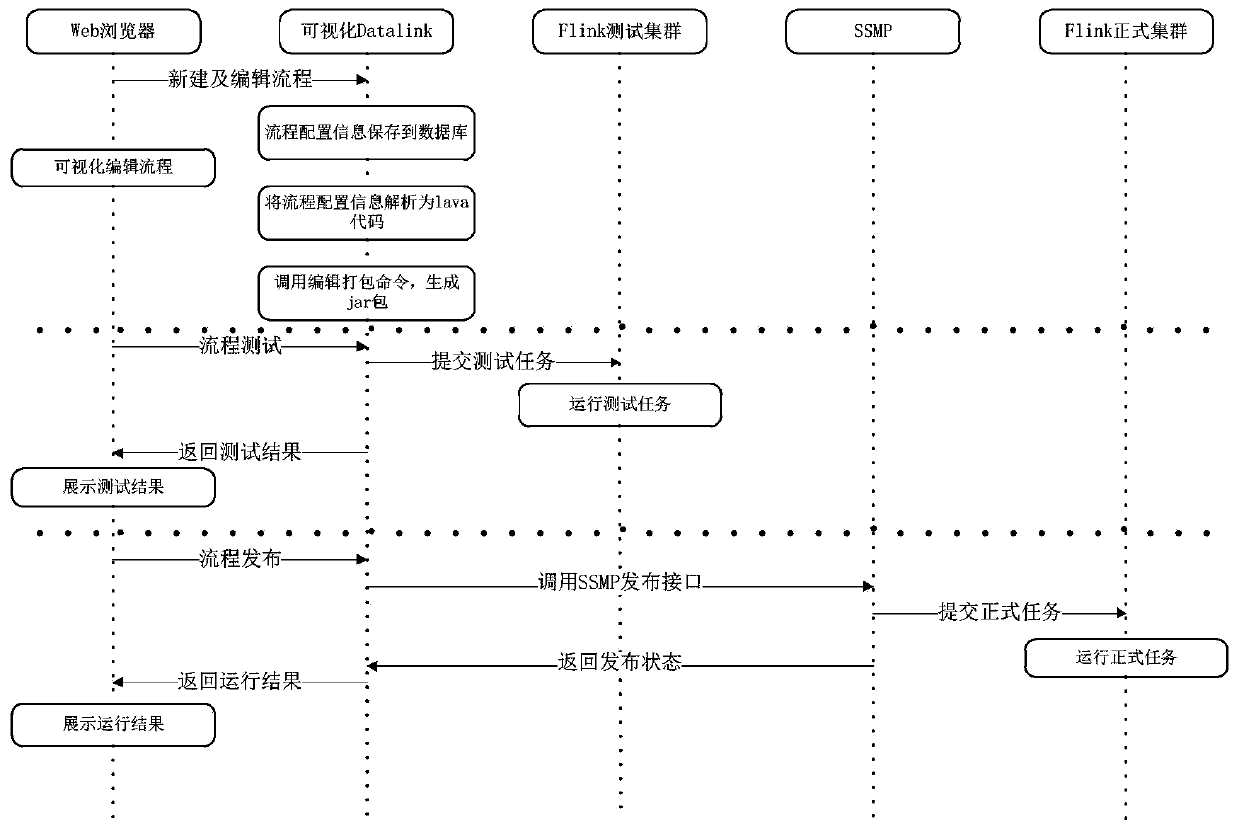
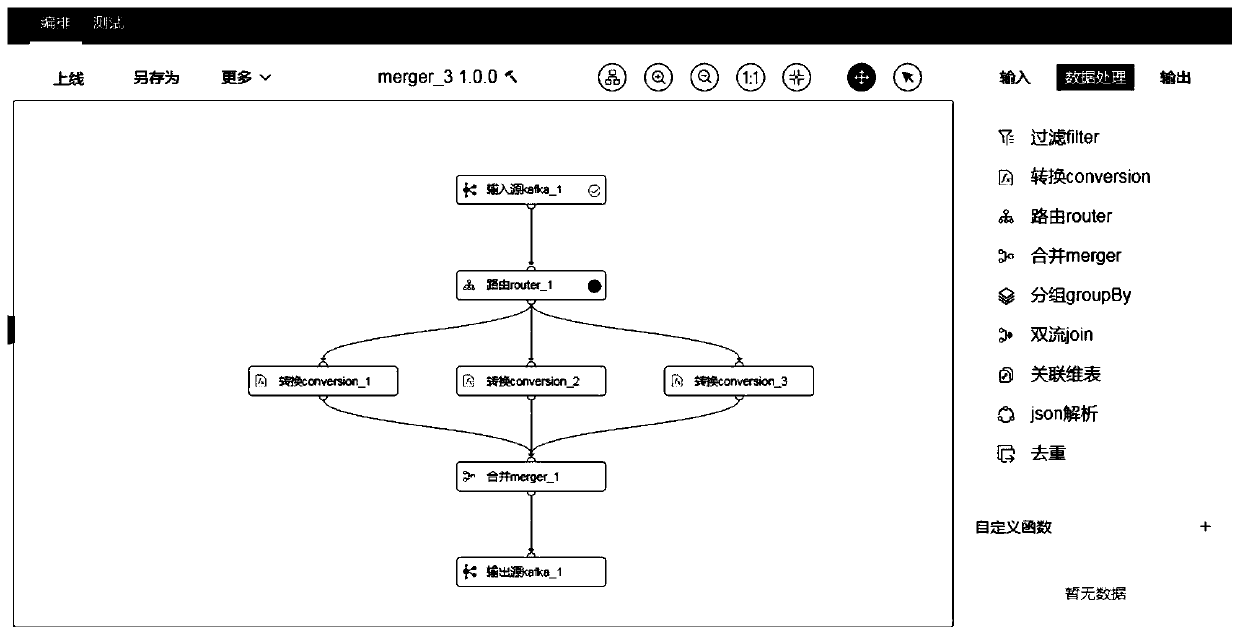
Real-time computing visual development system and application method thereof
PendingCN111352616ASimple processAvoid calling scenesVisual/graphical programmingData classSoftware engineering
The invention discloses a real-time computing visual development system and an application method thereof. The method comprises steps of selecting a corresponding component according to the data typeof the service scene; on a process configuration interface, connecting the components in a dragging manner to form a complete process, and performing visual business process configuration; and assembling the configured process information into a Table & SQL API code which can be executed by the Flink, calling a compiling and packaging command, generating a task jar package of the Flink, and issuing the task jar package to the Flink cluster for running. Through a visual development mode, the code process is simplified, more scenes which are not supported by SQL development are supported, the calling scene of a black box in the development process is avoided, the real-time task development threshold is reduced, operation and maintenance personnel and business personnel can also develop real-time tasks, and the development efficiency is improved.
Owner:SUNING CLOUD COMPUTING CO LTD
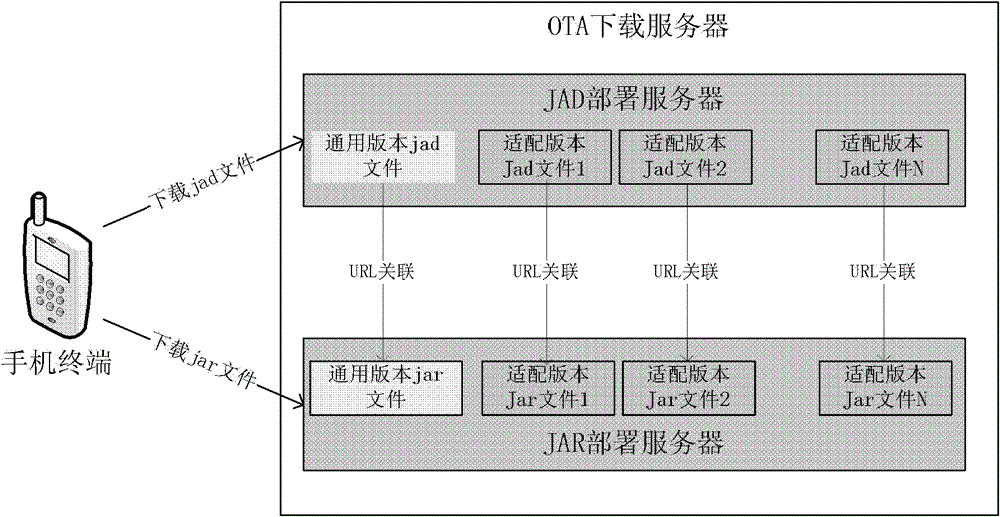
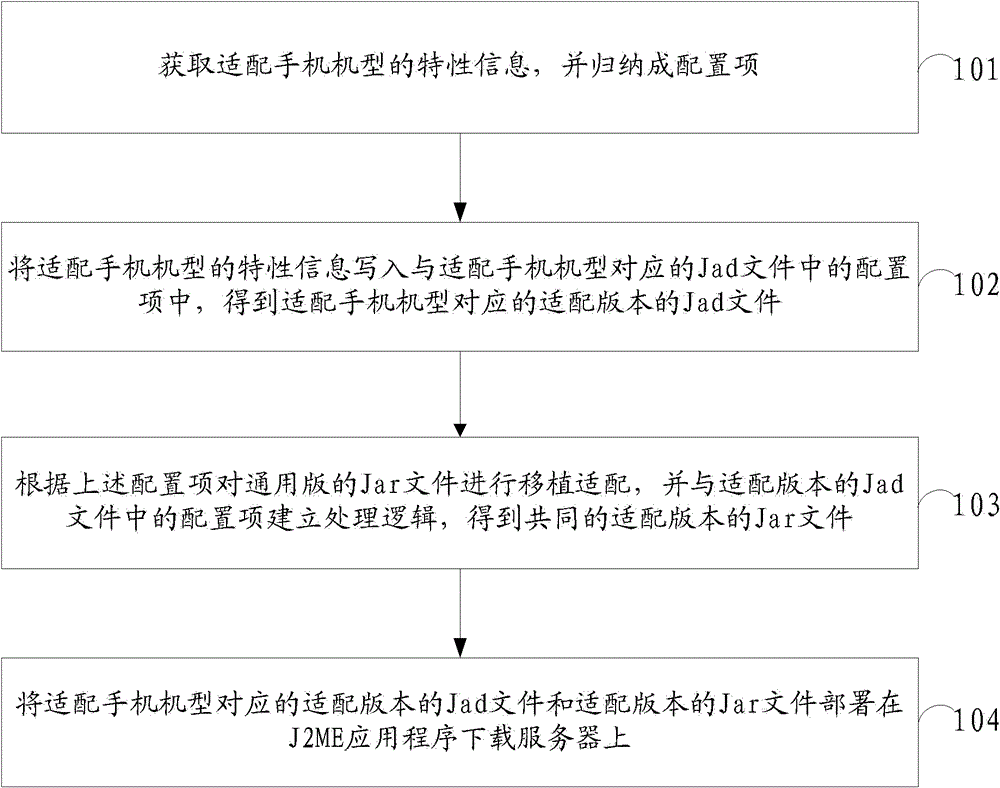
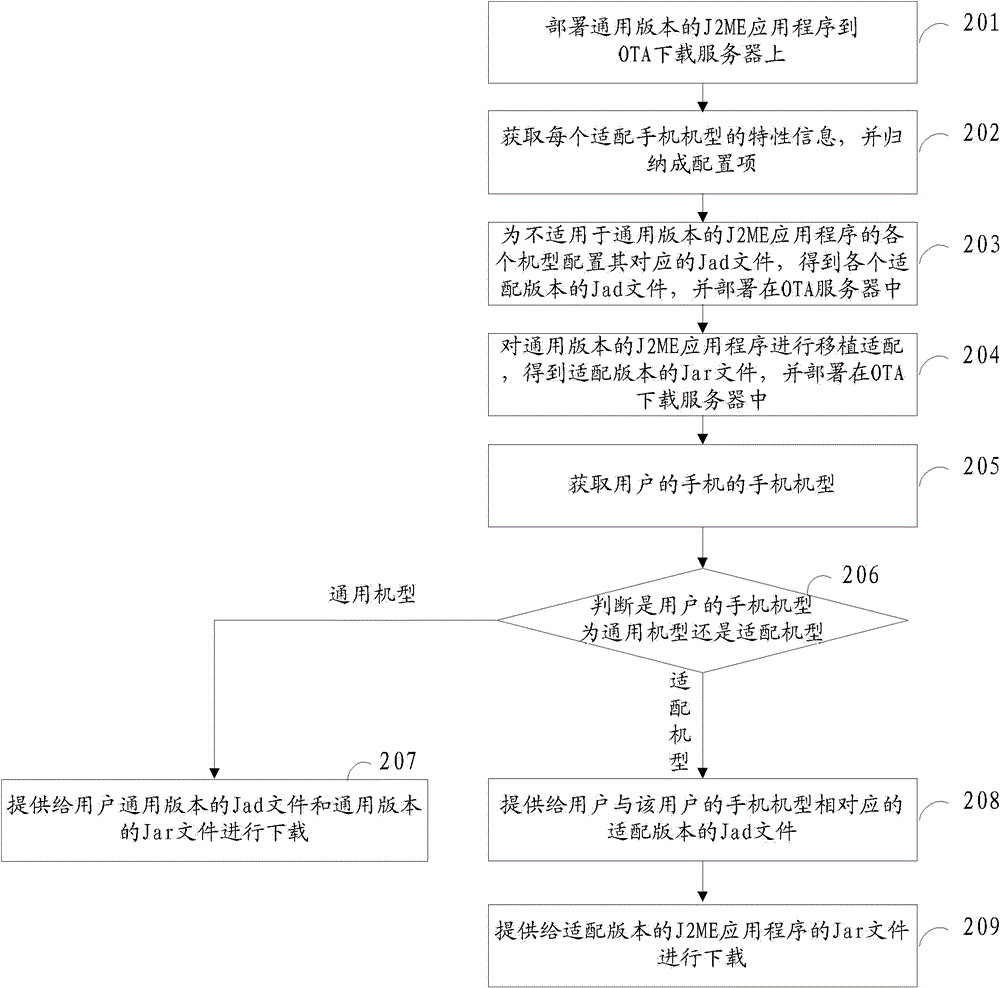
Method and device for deploying J2ME (Java 2 Micro Edition) application programs
ActiveCN102801749AWork lessRealize transplant adaptation releaseTransmissionConfiguration itemWorkload
The invention provides a method and device for deploying J2ME (Java 2 Micro Edition) application programs, and belongs to the field of computers. The method comprises the following steps: acquiring characteristic information of the type of an adapted mobile phone, inducing into a configuration item, writing the characteristic information into a configuration item in a Jad file corresponding to the type of the adapted mobile phone, respectively obtaining the Jad file of an adaptation version, performing transplanting adaptation on a Jar file of a general version according to the characteristic information of the type of the adapted mobile phone, establishing a processing logic with the configuration item in the Jad file of the adaptation version to obtain a Jar file of the common adaptation version, and deploying the Jad file and the Jar file of the adaptation version to a downloading server. Therefore, the number of transplanted adaptation versions can be greatly reduced, and mobile phone type transplanting adaptation and publication can be implemented quickly; and when a mobile phone type is added, only the added Jad file is configured, so that the version test work is reduced, the publication workload and the version operation workload are reduced, and the maintenance work of code branches is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Software project testing method and device, equipment and storage medium
The embodiment of the invention discloses a software project test method and device, equipment and a storage medium. The method comprises the steps of obtaining a Dubbo test Jar packet; establishing atest management thread group according to the thread group configuration information; calling the Dubbo test Jar packet through the test management thread group so as to trigger a performance test and / or an interface test; and correspondingly storing the test results of the performance test and / or the interface test according to result tree configuration information. According to the technical scheme, the obtained Dubbo test Jar packet is called through the Jmeter, the Dubbo test class is executed, the interface test and / or the performance test of the Dubbo service are / is realized, and the test result obtained through the result tree configuration information already comprises detailed test data, so that the analysis of the output log is avoided, the test process is simplified, the consumption of test resources is reduced, and the test efficiency is improved.
Owner:ZHUHAI SUIBIAN TECH CO LTD
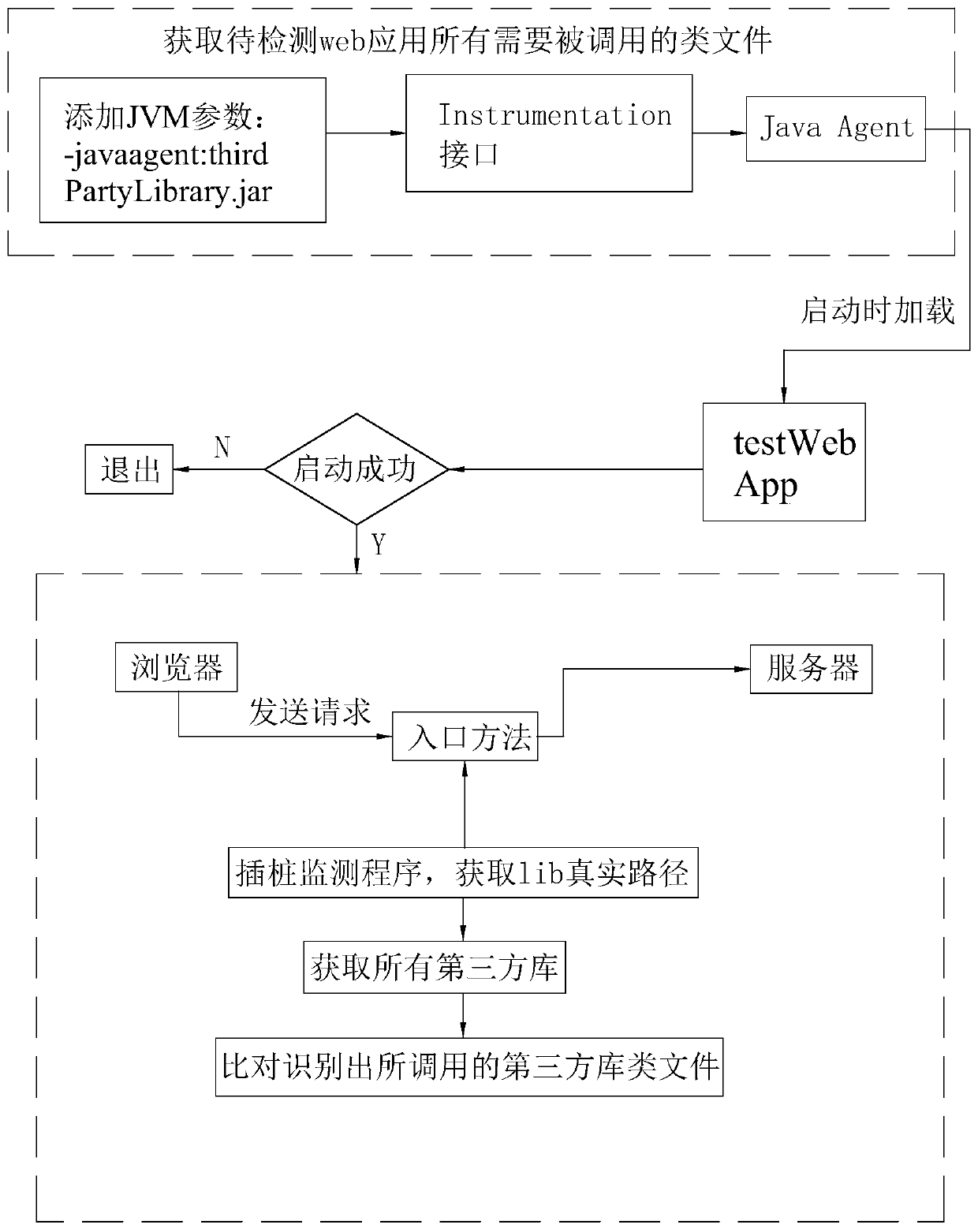
Method and system for detecting third-party code calling of web application
PendingCN110941534AGuaranteed accuracyIncrease flexibilityHardware monitoringThird partyWeb application
The invention discloses a method and system for detecting calling of a third-party code of a web application. The method comprises the steps: 1), generating an agent package based on a Javagent structure, and enabling the agent package to comprise a class file recognition program and a monitoring program; 2) before the web application is started, adding the agent program package into the JVM parameters, and inserting the monitoring program into an entry method of a web server processing request; 3) starting the web application, and acquiring all class files required to be called by the web application through an Instrumentation interface on the JVM by the class file recognition program; 4) obtaining a third-party library of the web application; (5) comparing all the called class files obtained in the step (3) with the jar files in the third-party library obtained in the step (4) so as to identify third-party class files called by the web application; all the class file data needing tobe called of the web application obtained through the detection method are based on the web application, and therefore the accuracy of the data is effectively guaranteed.
Owner:SECZONE TECH CO LTD
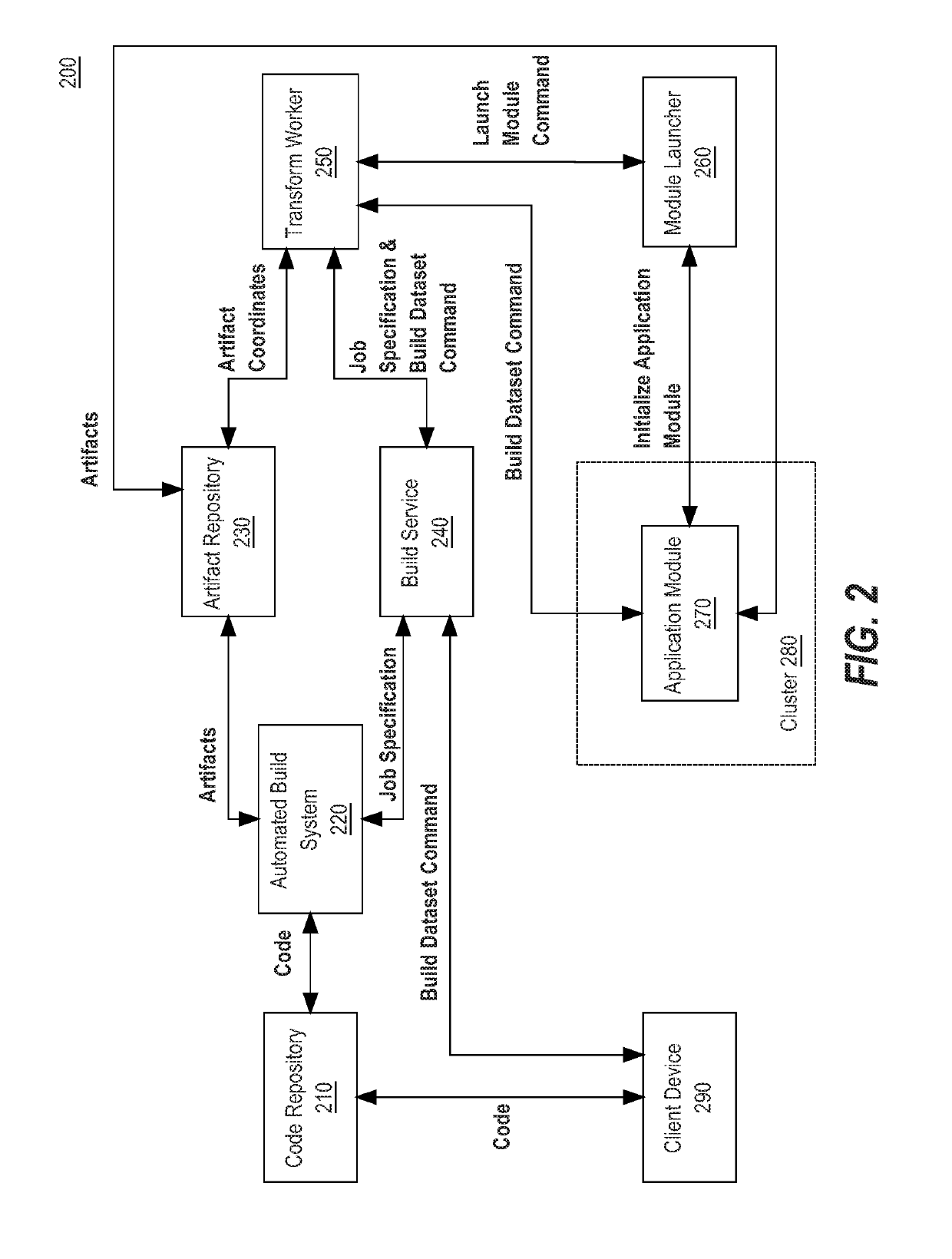
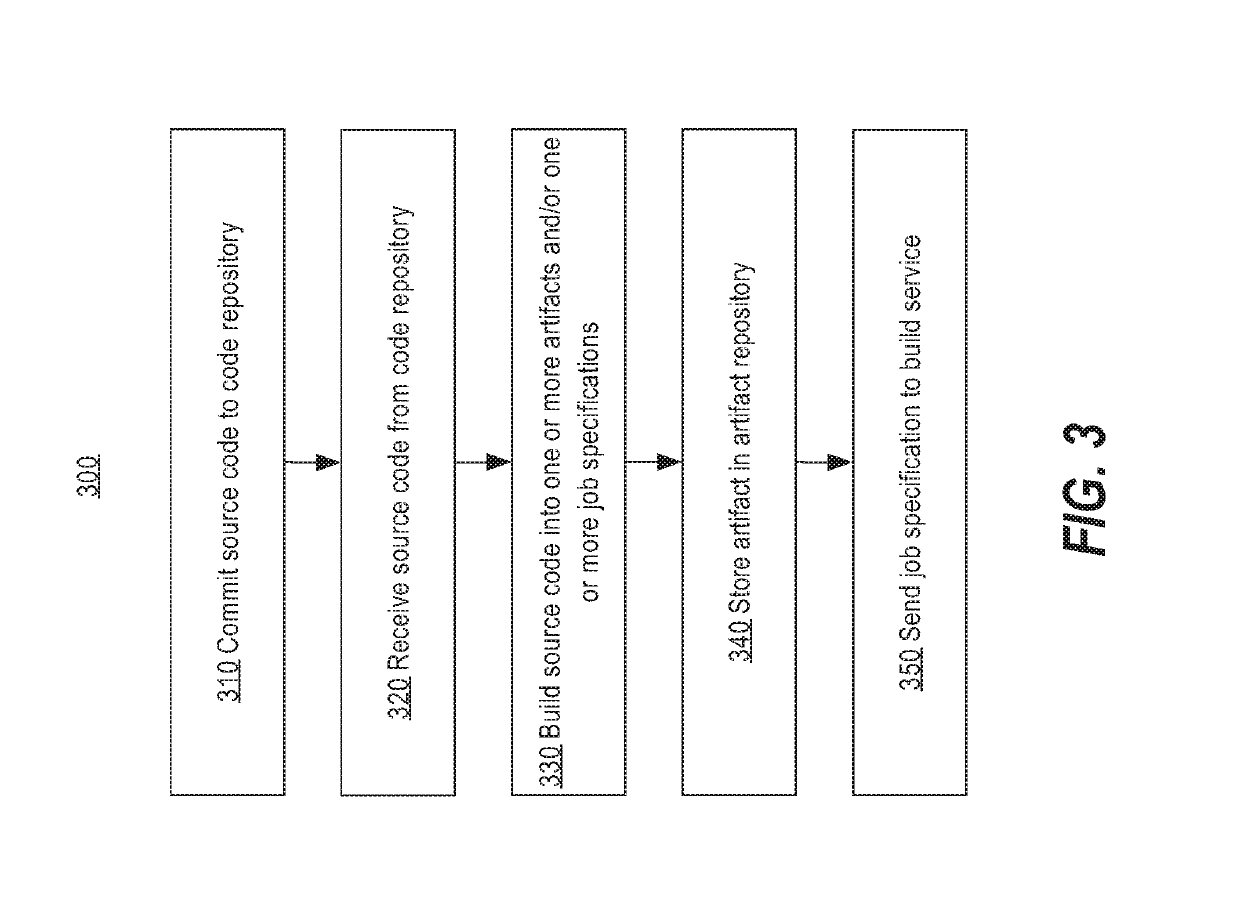
Extensible data transformation authoring and validation system
Data transformation in a distributed system of applications and data repositories is described. The subsystems for the overall framework are distributed, thereby allowing for customization to require only isolated changes to one or more subsystems. In one embodiment, a source code repository is used to receive and store source code. A build subsystem can retrieve source code from the source code repository and build it, using one or more criteria. By building the source code, the build subsystem can generate an artifact, which is executable code, such as a JAR or SQL file. Likewise, by building the source code, the build subsystem can generate one or more job specifications for executing the executable code. In one embodiment, the artifact and job specification may be used to launch an application server in a cluster. The application server can then receive data transformation instructions and execute the data transformation instructions.
Owner:PALANTIR TECHNOLOGIES
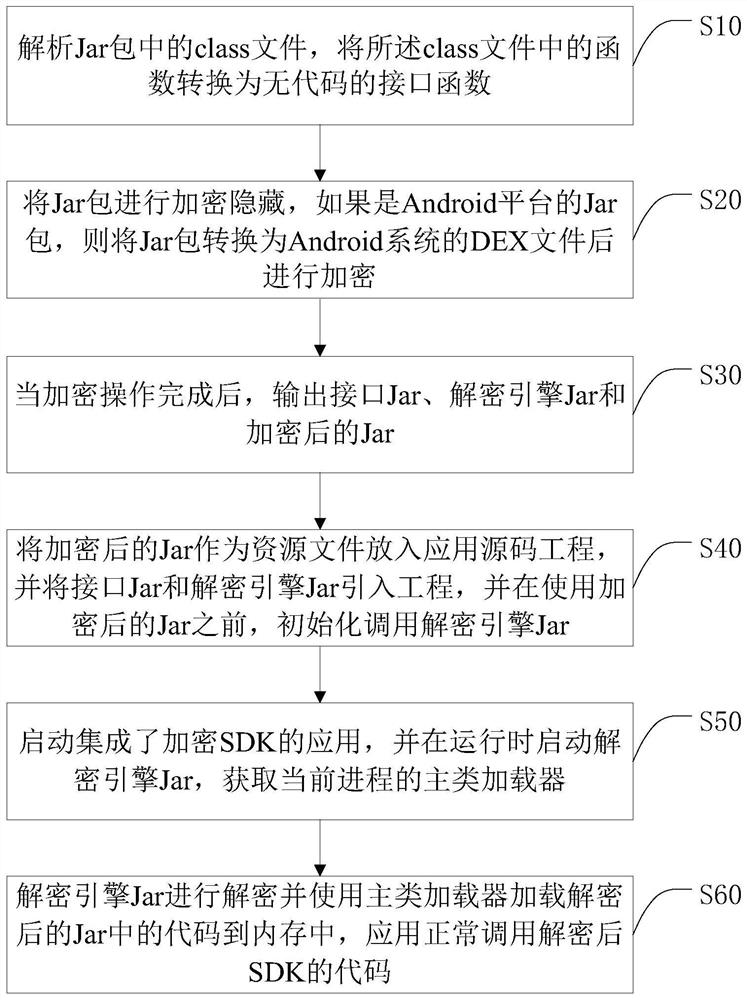
Java SDK code encryption and decryption method based on dynamic loading and terminal
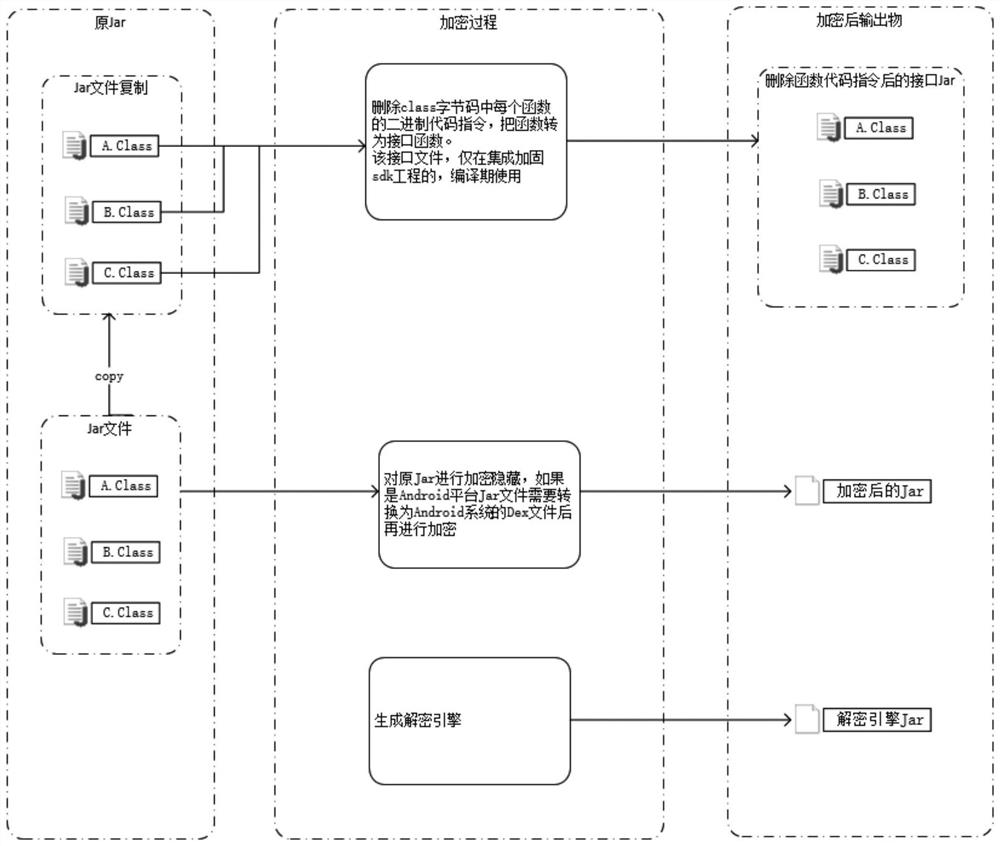
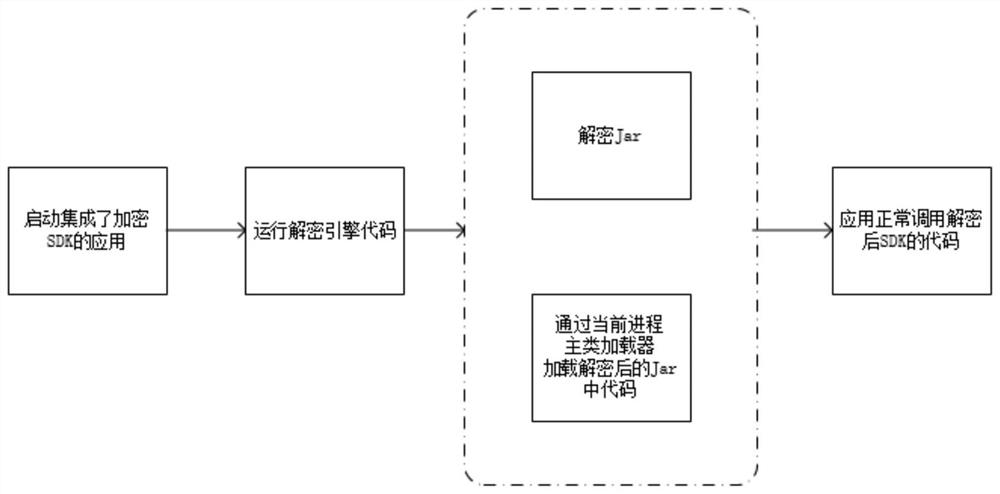
The invention discloses a Java SDK code encryption and decryption method based on dynamic loading and a terminal, and the method comprises the steps: analyzing a class file in a Jar package, and converting a function into a code-free interface function; encrypting and hiding the Jar packet; after the encryption operation is completed, outputting an interface Jar, a decryption engine Jar and the encrypted Jar; putting the encrypted Jar as a resource file into an application source code project, introducing an interface Jar and a decryption engine Jar into the project, and initializing and calling the decryption engine Jar before the encrypted Jar is used; starting an application integrated with the encrypted SDK, and starting a decryption engine Jar during running to obtain a main class loader of the current process; using the decryption engine Jar and enabling the main class loader to load the decrypted code in the Jar into the memory, and enabling the application to normally call thedecrypted code of the SDK, so that the code security of the SDK is effectively protected.
Owner:北京智游网安科技有限公司
Cross-platform workflow implementation method and system based on Java
PendingCN110969414AEasy to displayEasy to searchObject oriented databasesOffice automationJavaFunctional modeling
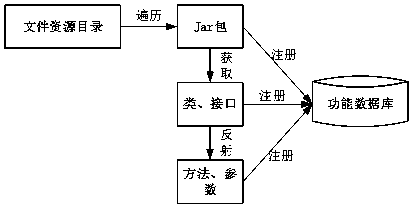
The invention relates to the technical field of workflows, in particular to a Java-based cross-platform workflow implementation method and system. The Java-based cross-platform workflow implementationmethod is characterized by comprising the following steps: S1, function registration: obtaining classes, interfaces, methods and parameters from a Jar packet, and selectively registering the functionmethods into a function database to facilitate function display, search and function modeling; s2, building a functional process; s3, function process management and service release: performing unified management on the function process templates, providing import, export, edit and delete functions of the function process templates, and realizing process management and release; s4, functional process service operation testing; and S5, function process service calling: calling through a function library web interface. According to the invention, the service process can be flexibly defined, andthe cross-platform establishment of the workflow is supported.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN) +1
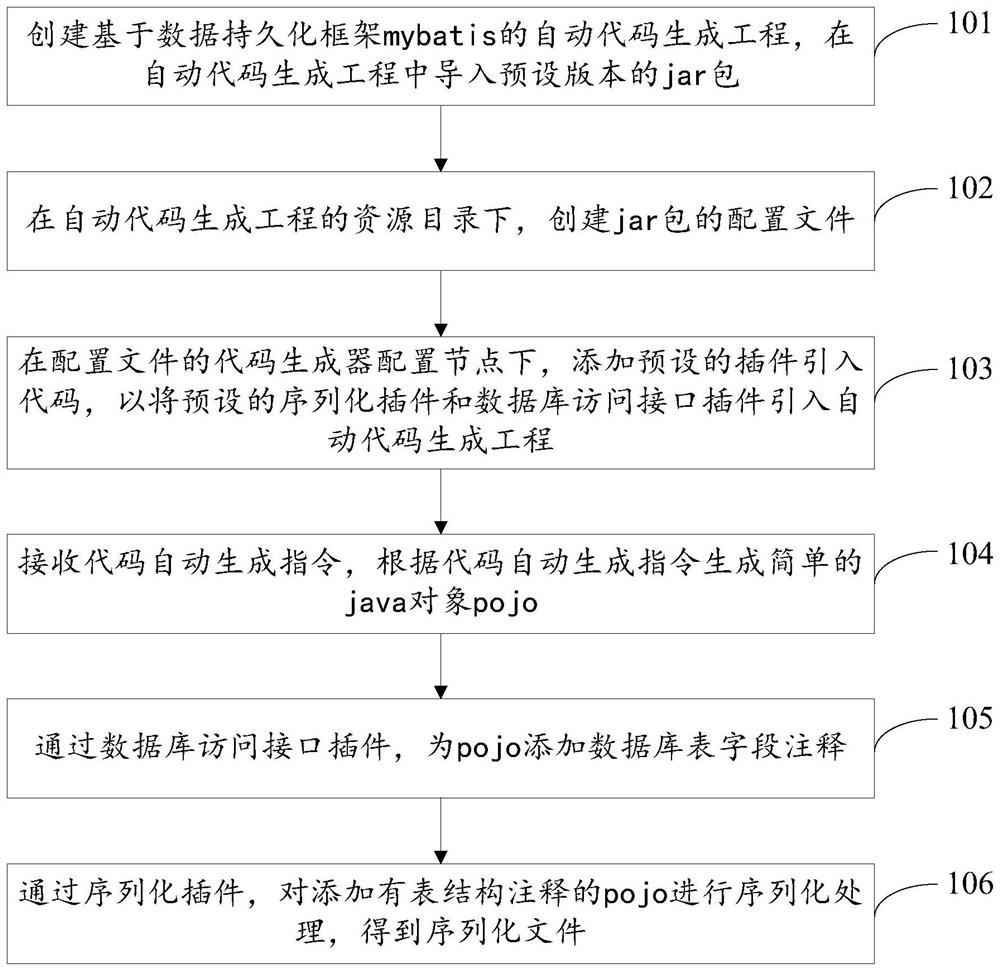
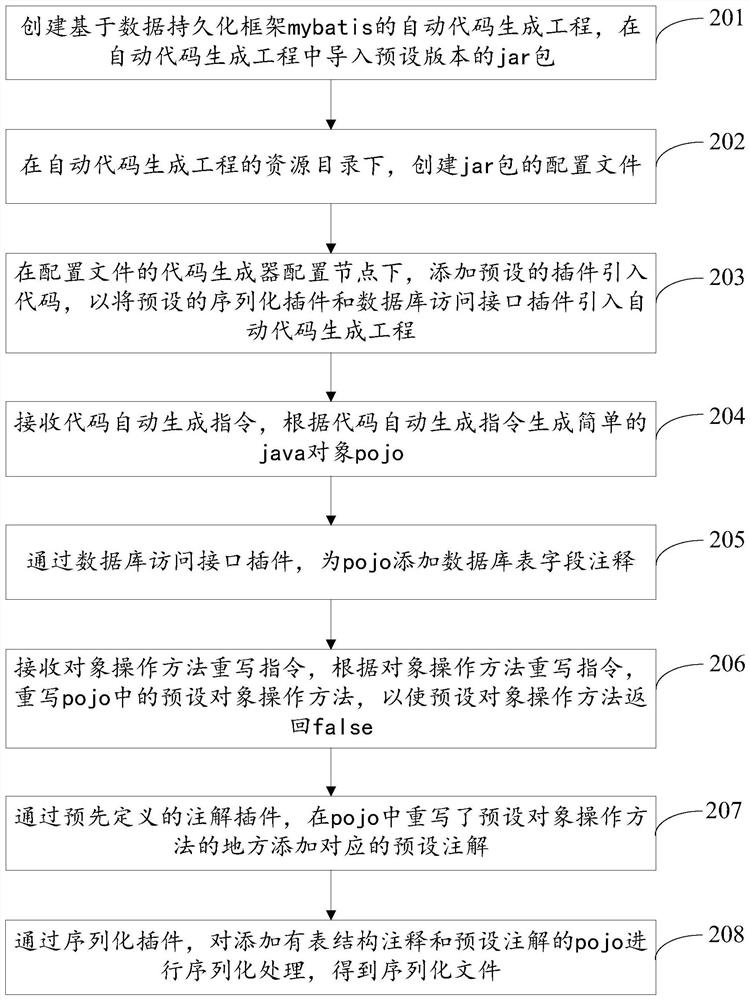
Automatic code generation method, device and equipment and storage medium
PendingCN112000320AImprove development efficiencyVersion controlProgram documentationTable (database)Code generation
The invention relates to the field of development assistance, discloses an automatic code generation method, device and equipment and a storage medium, and the method, the device and the equipment areused for improving the code development efficiency based on a mybatis framework. The method comprises the steps of creating an automatic code generation project based on a data persistence frameworkmybatis, and importing a jar package of a preset version into the automatic code generation project; under a resource directory of the automatic code generation project, creating a configuration fileof the jar package; under a code generator configuration node of the configuration file, adding a preset plug-in introduction code so as to introduce a preset serialized plug-in and a database accessinterface plug-in into an automatic code generation project; receiving an automatic code generation instruction, and generating a simple java object pojo according to the automatic code generation instruction; adding database table field annotations to the pojo through a database access interface plug-in; and performing serialization processing on the pojo added with the table structure annotationthrough a serialization plug-in to obtain a serialized file.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
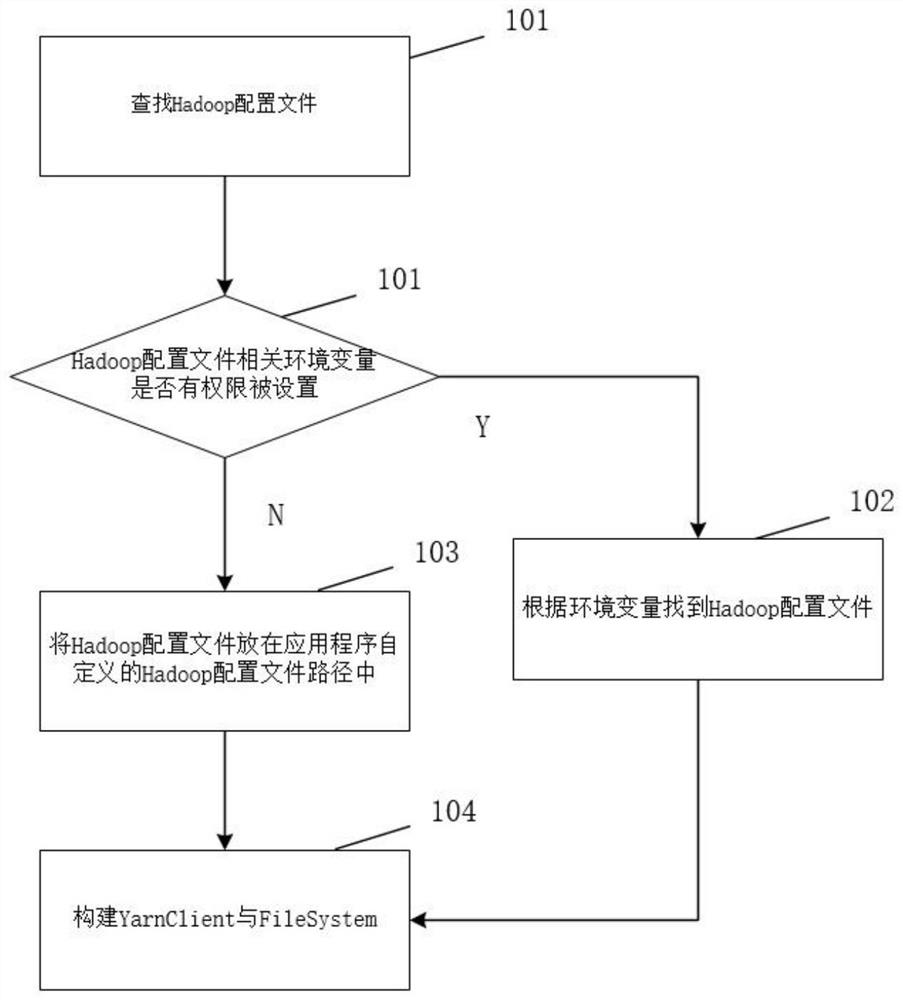
Implementation method and device for submitting flink job to yarn cluster in application program
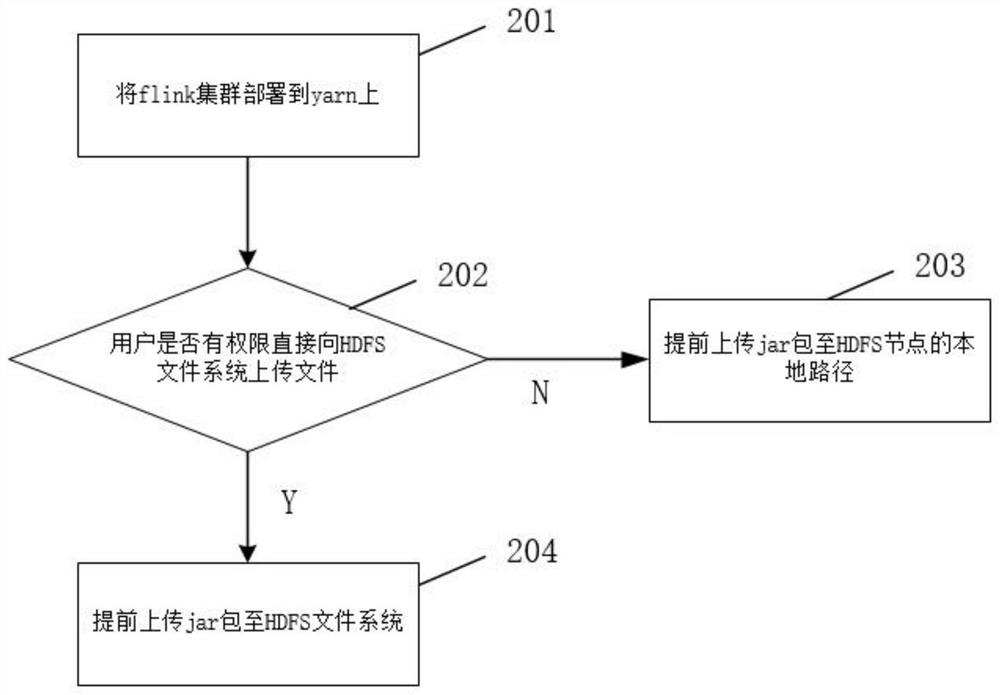
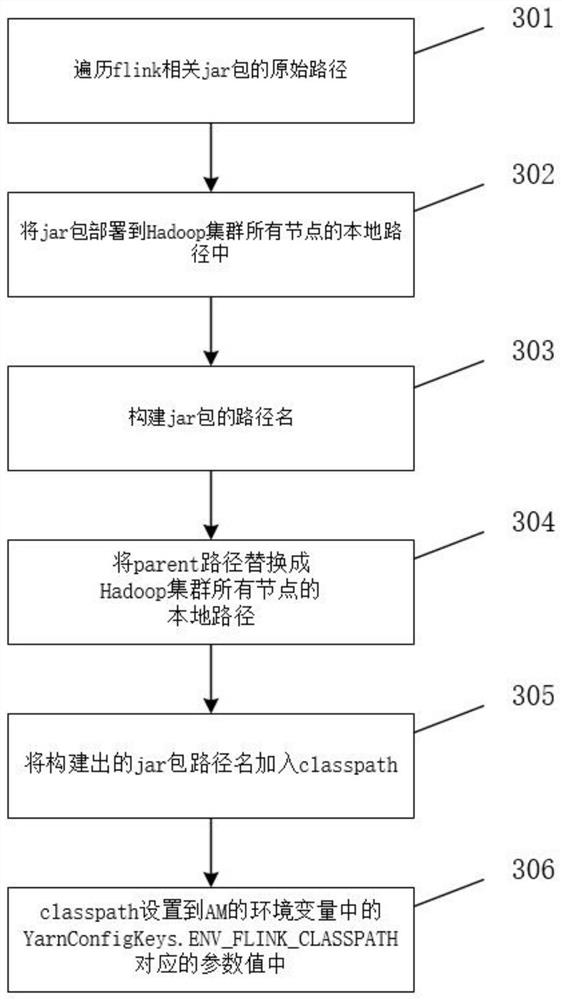
ActiveCN114489833AImprove deployment flexibilityImprove convenienceDigital data information retrievalVersion controlThird partyYarn
The invention relates to the technical field of big data computing, discloses an implementation method and device for submitting an flink job to a Yarn cluster in an application program, solves the deployment problem of a Hadoop configuration file and a third-party dependent jar package, and realizes self-defined deployment of the Hadoop configuration file and the third-party dependent jar package by rewriting a part of functions in an flink system class. The deployment flexibility, convenience and operation efficiency of the application programs are improved, the degree of dependence on the environment is reduced, and mutual interference possibly existing between different application programs is avoided.
Owner:WUHAN DAMENG DATABASE
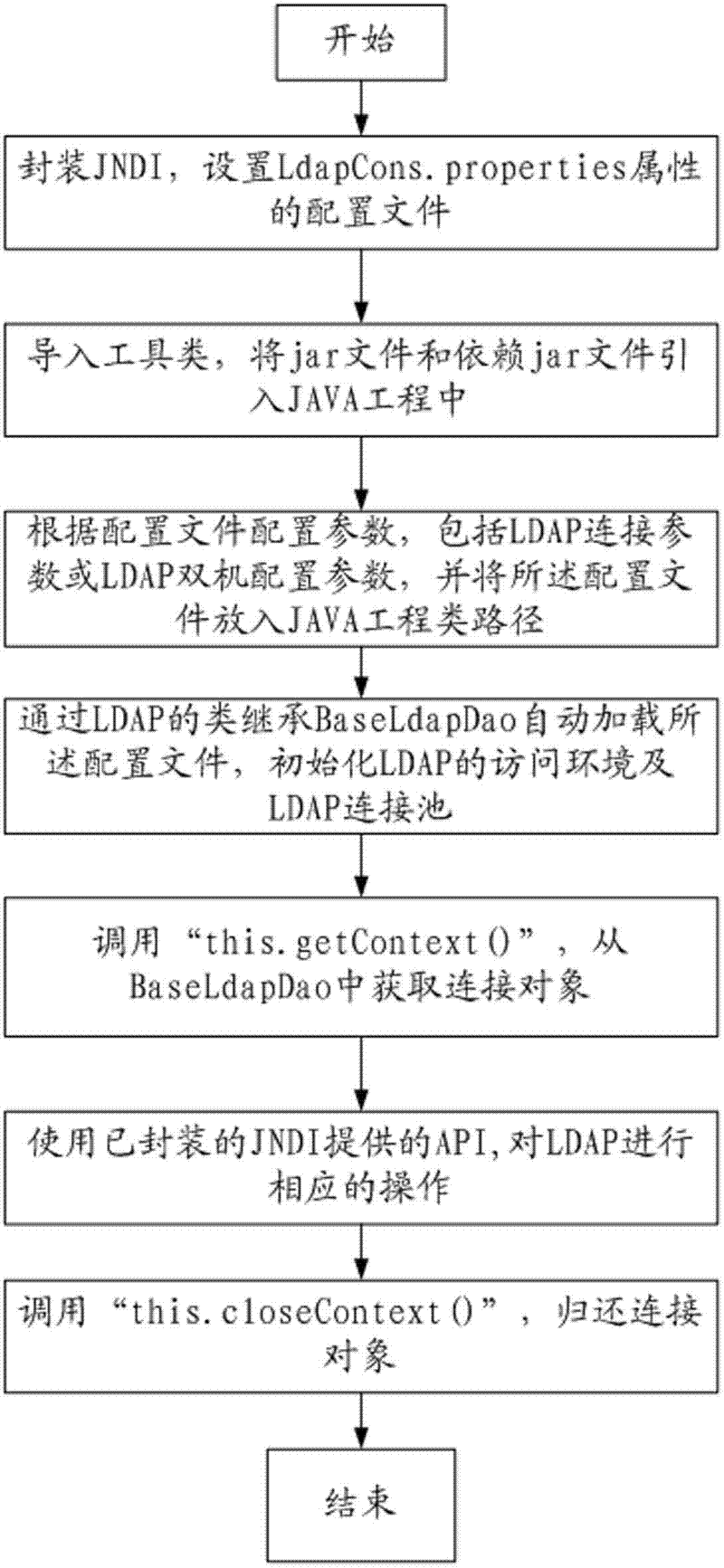
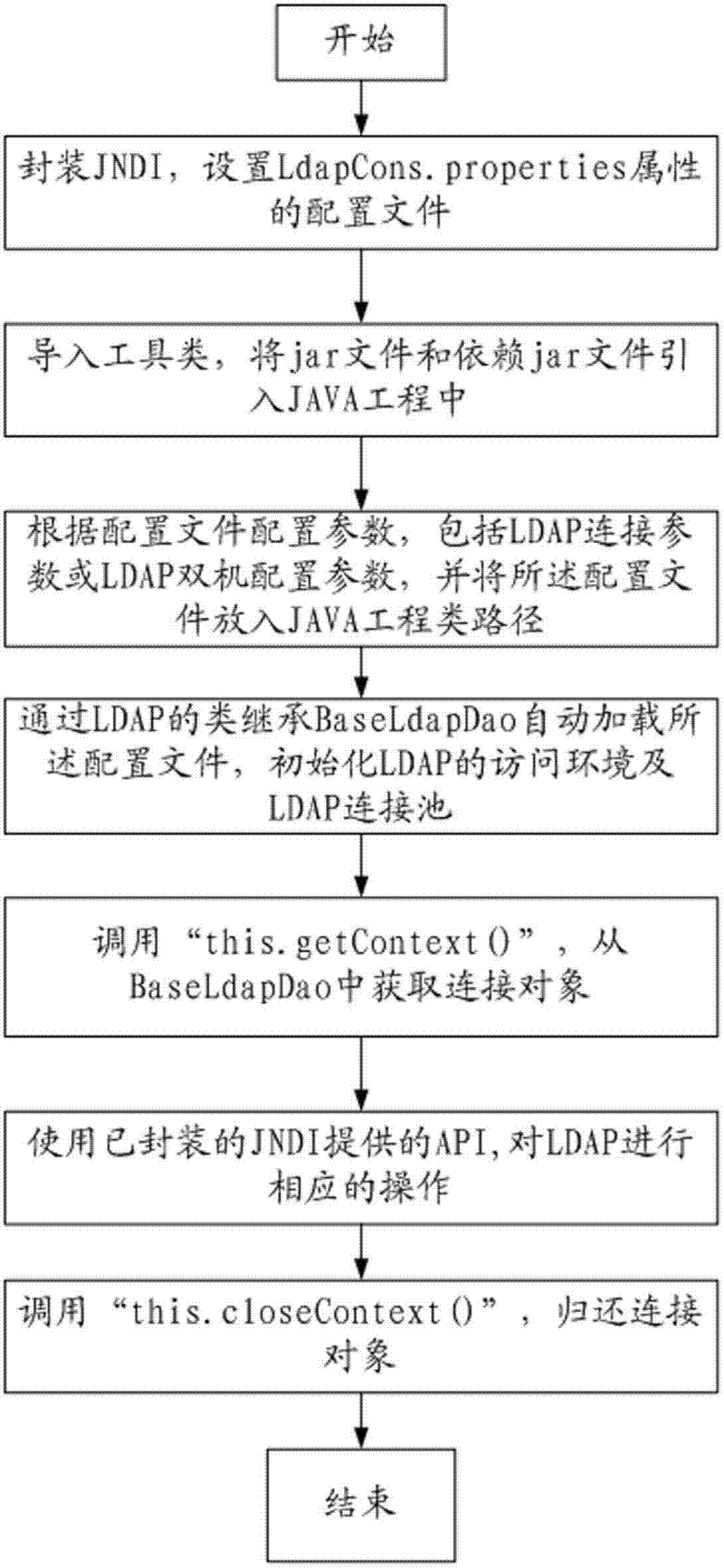
Method and system for accessing and operating light weight directory access protocol (LDAP) by JAVA language
InactiveCN102306147AFlexible configurationImprove efficiencySpecial data processing applicationsDirectory Access ProtocolLightweight Directory Access Protocol
The invention relates to a method for accessing and operating a light weight directory access protocol (LDAP) by a JAVA language. The method comprises the following steps of: 1, encapsulating a JAVA naming and directory interface (JNDI) and setting a configuration file with LdapCons.properties; 2, importing a tool type and introducing a jar file and a dependent jar file into a JAVA project; 3, placing the configuration file into a JAVA project route according to configuration parameters, namely an LDAP connection parameter or an LDAP double-engine configuration parameter, of the configuration file; 4, automatically loading the configuration file and initializing accessing environment of the LDAP and an LDAP connection pool through similar succession BaseLdapDao of the LDAP; 5, acquiring connection from the connection pool so as to acquire a connection object in a similar succession configuration file of the LDAP corresponding to the connection, and accessing and operating the LDAP; 6, correspondingly operating the LDAP by using an application programming interface (API) provided by the encapsulated JNDI; and 7, after the access and the operation for the LDAP are finished, returning the connection object. The method has the advantage of improving the efficiency and reliability of accessing and operating LDAP by a JAVA program.
Owner:北京思特奇信息技术股份有限公司
Data processing method, device, equipment and system based on byte code
PendingCN111782340ASolve the need to modify the application codeSolve the problem of application landing difficultiesExecution paradigmsSoftware simulation/interpretation/emulationParallel computingJAR
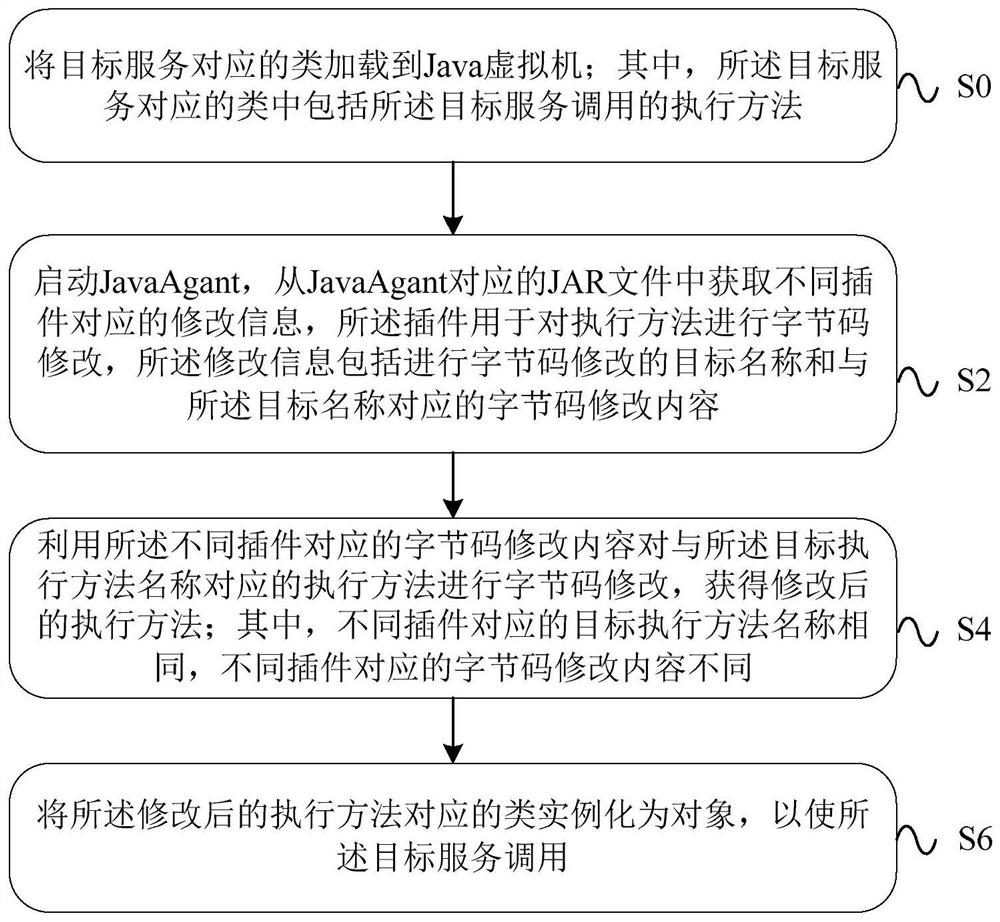
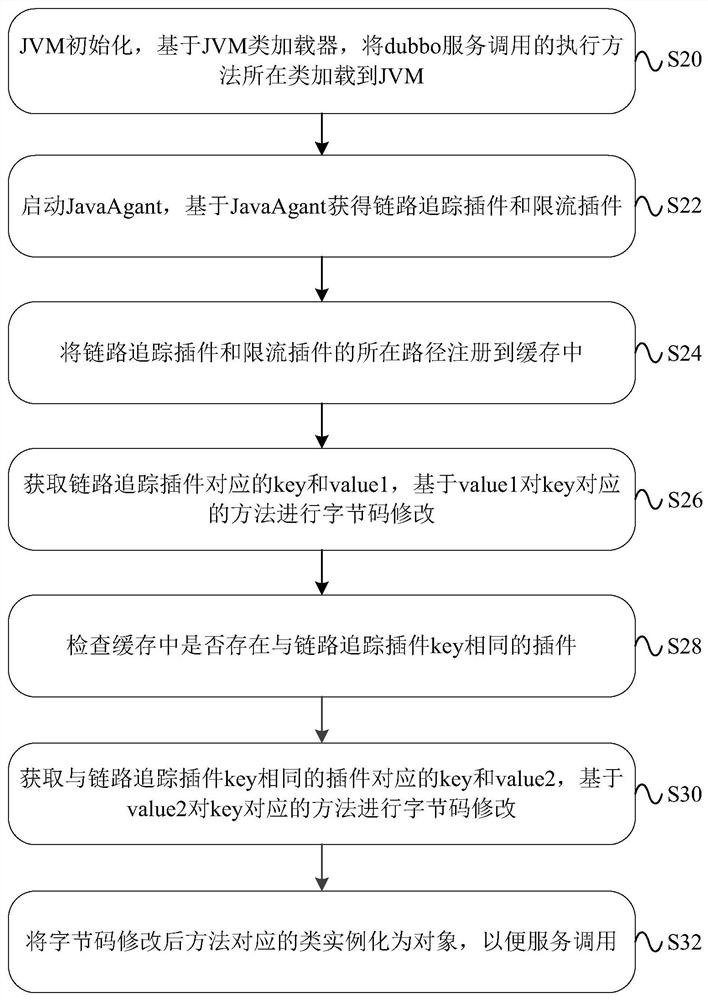
The invention provides a data processing method, device, equipment and system based on a byte code. The method comprises the steps that a class corresponding to a target service is loaded to a Java virtual machine; JavaAgant is started, modification information corresponding to different plug-ins is obtained from a JAR file corresponding to the JavaAgant, and the modification information comprisesa target name for byte code modification and byte code modification content corresponding to the target name; byte code modification is performed on an execution method corresponding to the target name by utilizing the byte code modification contents corresponding to the different plug-ins to obtain a modified execution method, wherein the target names corresponding to the different plug-ins arethe same, and the byte code modification contents corresponding to the different plug-ins are different; and the class corresponding to the modified execution method is instantiated as an object, so that the target service is called. By utilizing the embodiment of the invention, byte code modification can be realized in a non-invasive manner for the application, so that the workload is reduced.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
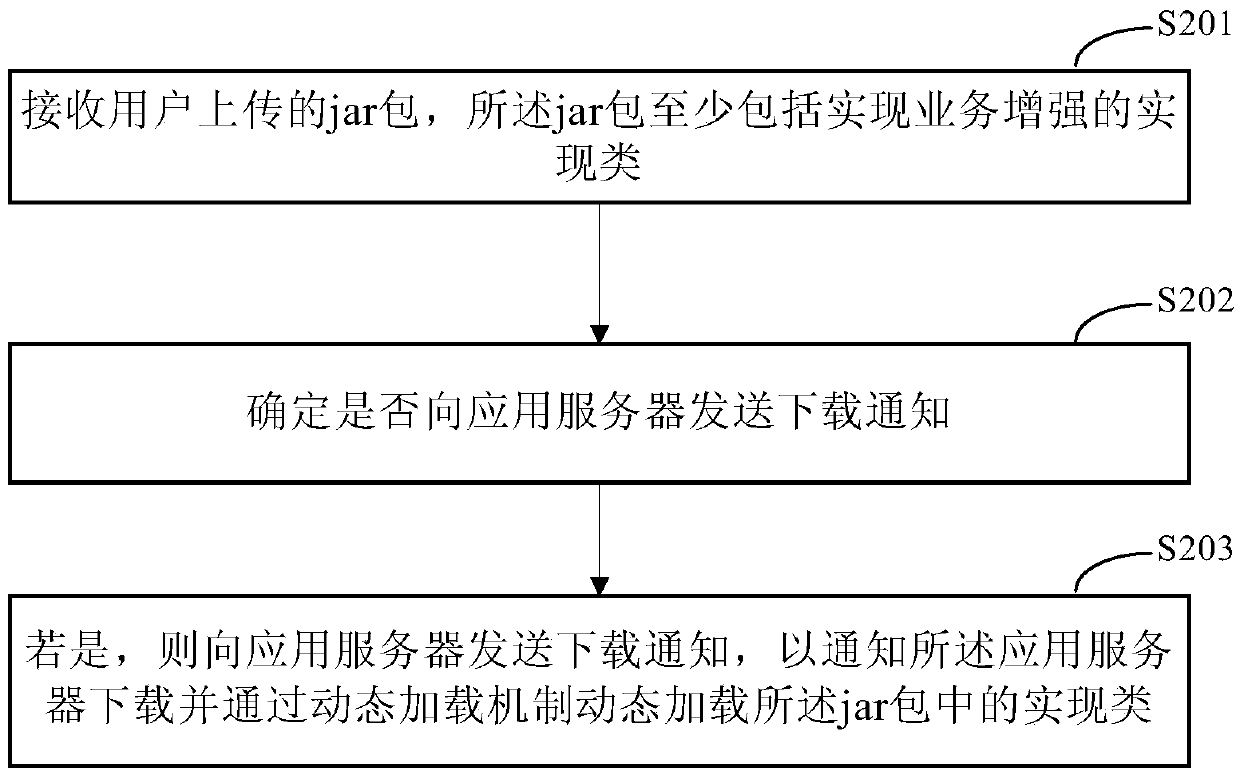
Method and device for realizing service enhancement
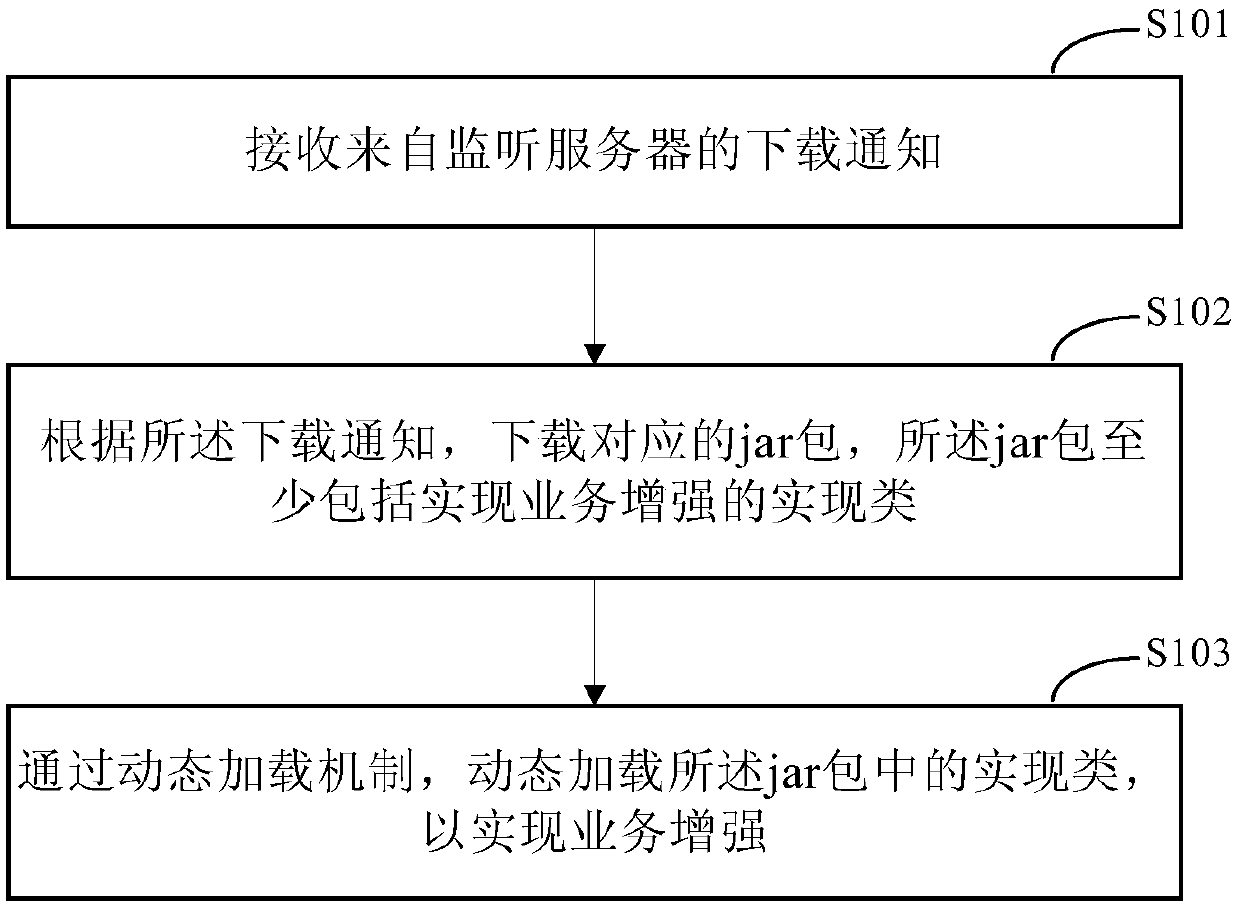
PendingCN110895468AReach enhancementsReduce the risk of human errorSoftware engineeringProgram loading/initiatingJAREngineering
The invention discloses a method and a device for realizing service enhancement, and relates to the technical field of computers. A specific embodiment of the method comprises the following steps: receiving a download notification from a monitoring server; downloading a corresponding jar packet according to the downloading notification, the jar packet at least comprising an implementation class for implementing service enhancement; and dynamically loading the implementation class in the jar packet through a dynamic loading mechanism so as to realize service enhancement. According to the method, the execution code can be dynamically replaced to achieve a service enhancement function. According to the implementation mode, logic operation of the execution process is replaced under the condition of not interrupting or stopping service, the method can be used for input and output check or other function enhancement of online abnormal execution, the risk of human errors caused by manual codemodification is reduced, and tedious operation of repeatedly publishing service codes is avoided.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Method for mapping xml service logic to java service logic
ActiveCN111104122AEasy to manageEasy maintenanceNatural language data processingEnergy efficient computingJavaSoftware engineering
The invention discloses a method for mapping xml service logic to java service logic, and belongs to the technical field of big data. The method comprises the following steps: establishing a service database and a system center server, wherein the service database is used for storing xml service logic data, and the service database communicates with the system center server through the Internet; and establishing a workflow module, an actuator module and a variable action domain module in a system center server. The technical problem of realizing separation of business logic and a system in order to cope with a tedious online process in development is solved, the system is very simple to build on a small scale and can be realized only by loading a plurality of jar packets, and the service realizes interface management, is easy to maintain and test and is easy to manage and maintain.
Owner:联通(江苏)产业互联网有限公司
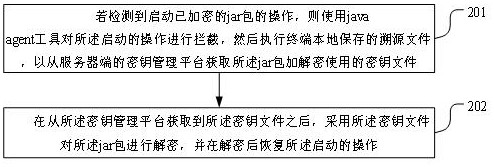
Jar packet encryption and decryption method and device, terminal equipment and storage medium
InactiveCN111737718AEasy to manageImprove securityKey distribution for secure communicationDigital data protectionJavaTerminal equipment
The invention is applicable to the technical field of information security, and provides a jar packet encryption and decryption method and device, terminal equipment and a storage medium. In the application, the key file used for encryption and decryption of the jar package is stored in the key management platform of the server after being generated, and the terminal can locally adopt the java agent tool to send the request to the key management platform, so that the key file is acquired and the encryption operation of the jar package is completed. Besides, the traceability file of the key file is generated and stored locally at the terminal, and then the key file can be found from the key management platform through the traceability file when the jar package needs to be decrypted. Therefore, in the encryption and decryption process of the jar package, the secret key file used for encryption and decryption can be conveniently managed, and the safety of the secret key file is improved.
Owner:PINGAN INT SMART CITY TECH CO LTD
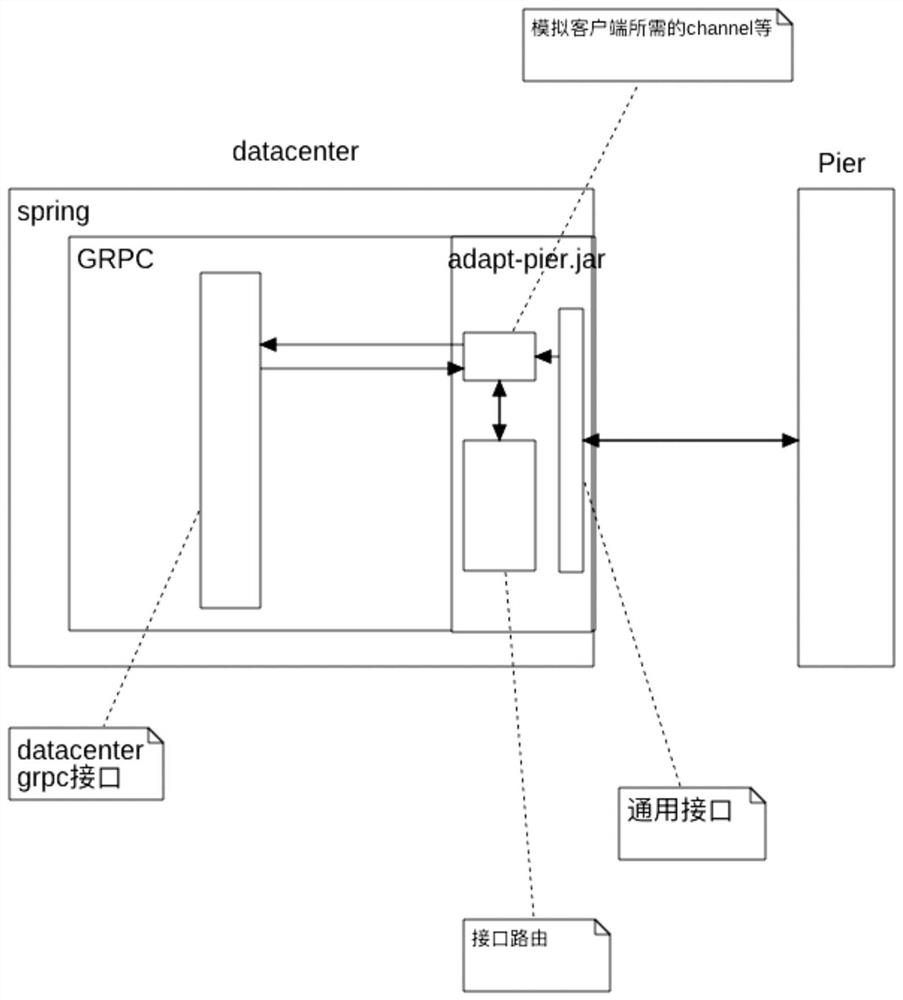
Method for dynamically calling server side by client side through GRPC
ActiveCN113515319AResolve synchronizationSimplify the development processData processing applicationsProgram loading/initiatingJavaSoftware engineering
The invention discloses a method for a client to dynamically call a server through a GRPC, and the method comprises the steps: the server configures a preset adaptive jar package, the adaptive jar package comprises a java item, a grpc module and a grpc interface, supports the bidirectional flow of the GRPC and upgrades a core class to a springboot-starter mode, and the grpc interface is an entry which can be dynamically called by the server on the premise that the code of the server is not invasive; and the client side sends a calling request to the server side and receives response data sent by the server side, and the method that the client side dynamically calls the server side through the GRPC is completed. According to the method, the cost of maintaining the protocol file by both the client and the server can be saved, the calling of the client and the server can be realized on the premise of not introducing a grpc interface packet, the working cost of personnel is reduced, and bugs generated by synchronizing the protocol file are reduced.
Owner:BEIJING KEDONG ELECTRIC POWER CONTROL SYST
Interceptor-based data processing method and apparatus, and computer device
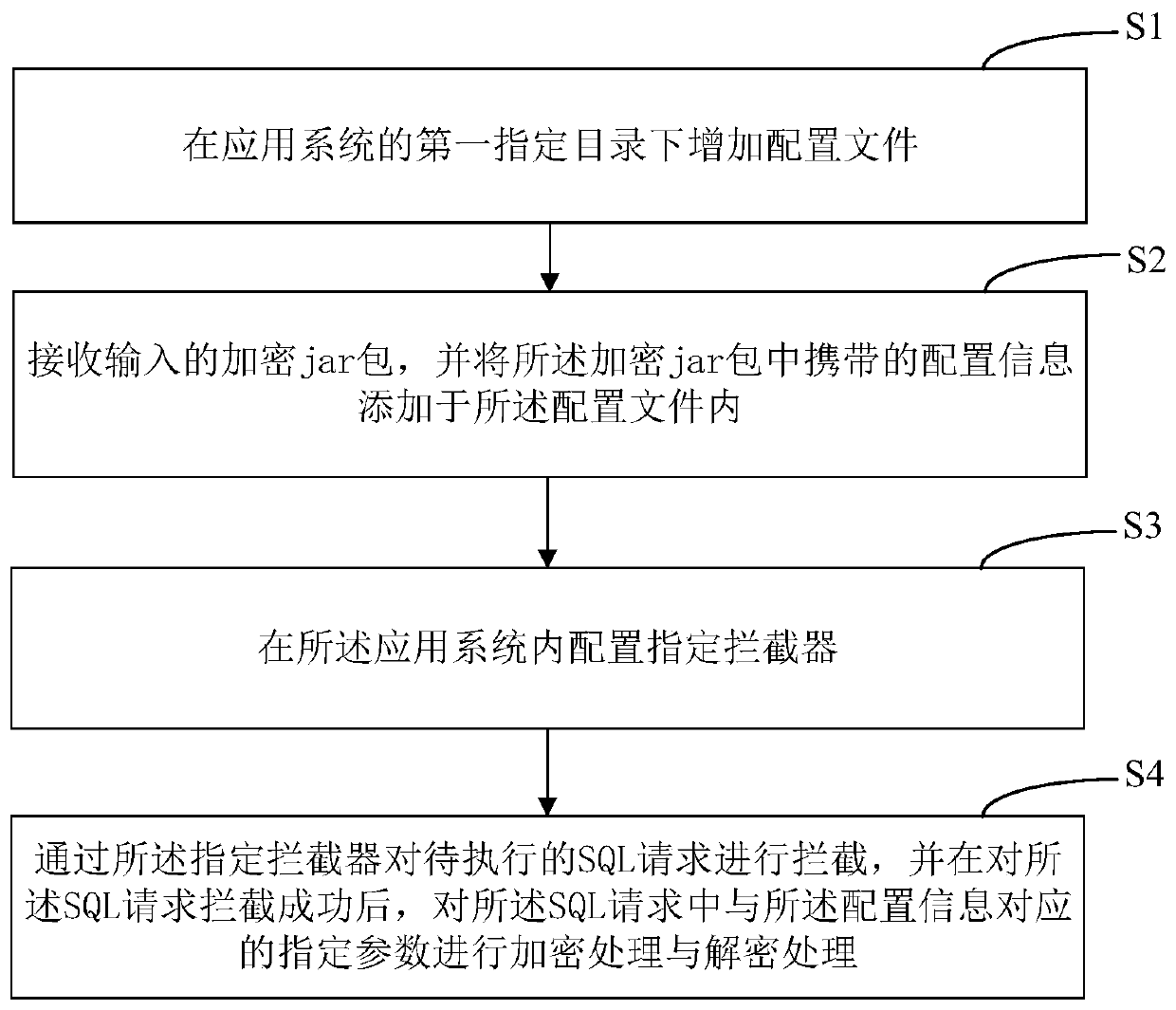
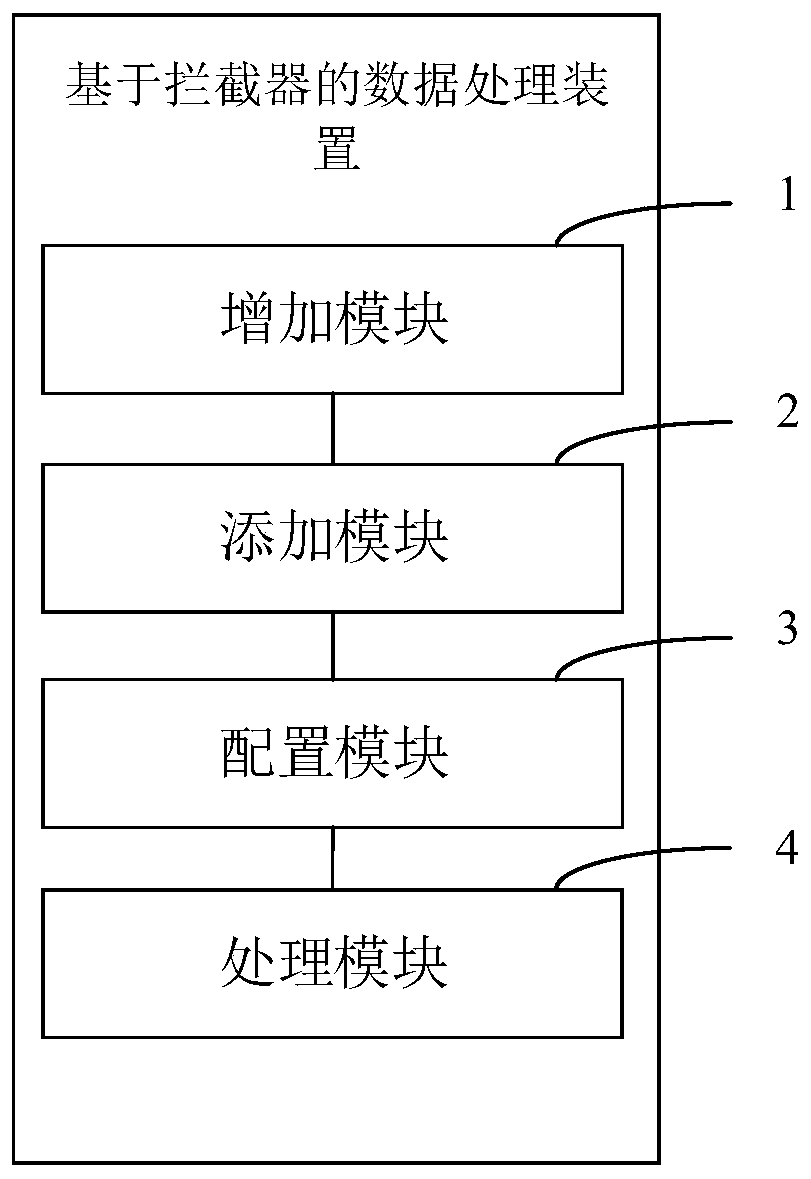
PendingCN111475524ALow retrofit costImprove the success rate of transformationDigital data information retrievalDigital data protectionComputer hardwareJAR
The invention discloses an interceptor-based data processing method and apparatus, and a computer device. The method comprises the steps of adding a configuration file under a first specified directory of an application system; receiving an input encrypted jar packet, and adding configuration information carried in the encrypted jar packet into the configuration file; configuring a specified interceptor in the application system; and intercepting a to-be-executed SQL request through the specified interceptor, and after the SQL request is successfully intercepted, performing encryption processing and decryption processing on specified parameters corresponding to the configuration information in the SQL request. According to the embodiment of the invention, an existing mode of carrying out security transformation on the data of the application system based on the application code is abandoned; the specified interceptor is innovatively configured and used in the application system to quickly and conveniently execute encryption processing and decryption processing on the specified parameter corresponding to the configuration information, so that the transformation cost of the application system is effectively reduced, and the transformation efficiency of the specified parameter is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Code generation method and device
ActiveCN111324343ARealize generationImprove development efficiencyProgramming languages/paradigmsModel driven codeCode generationSoftware engineering
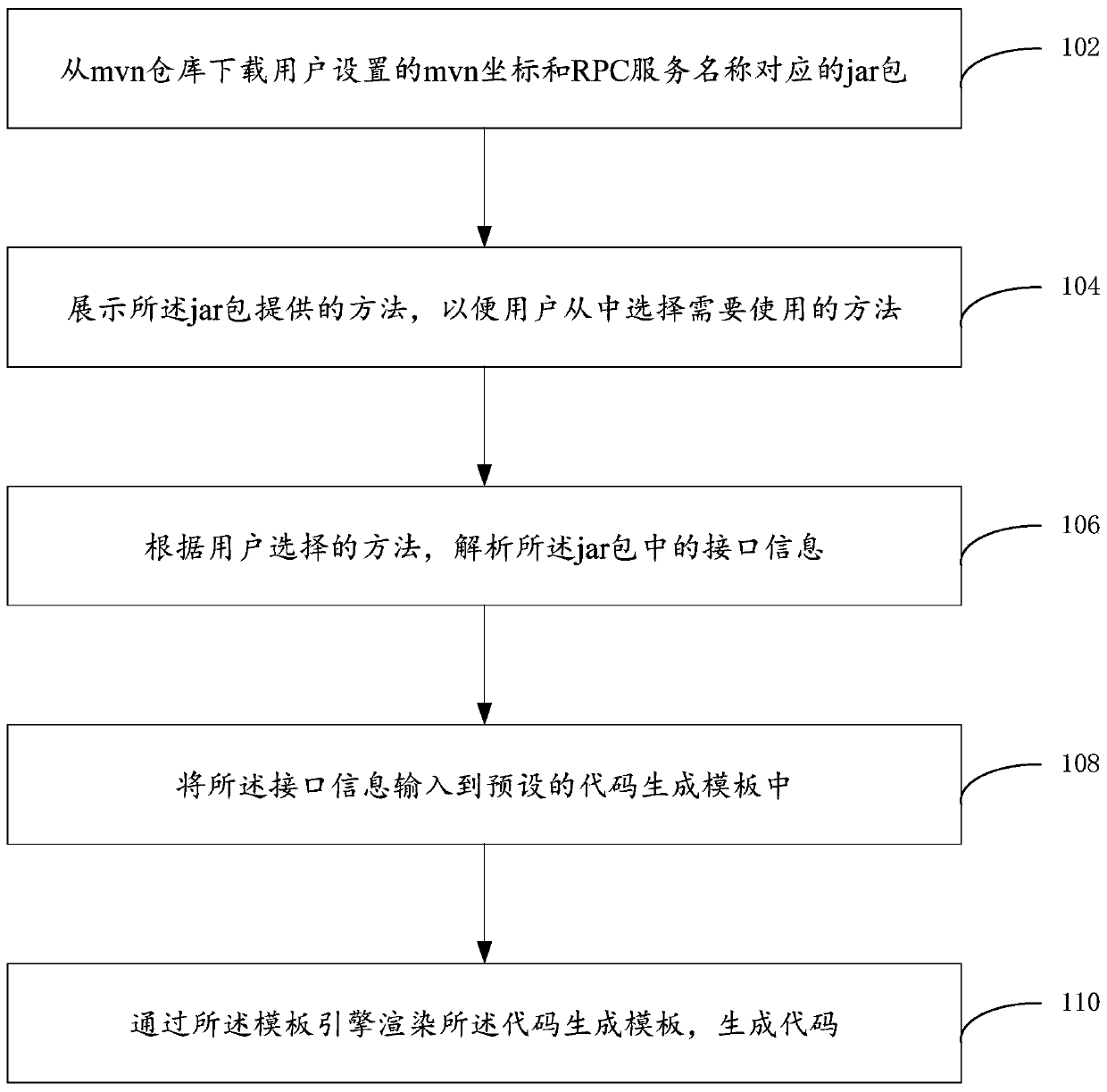
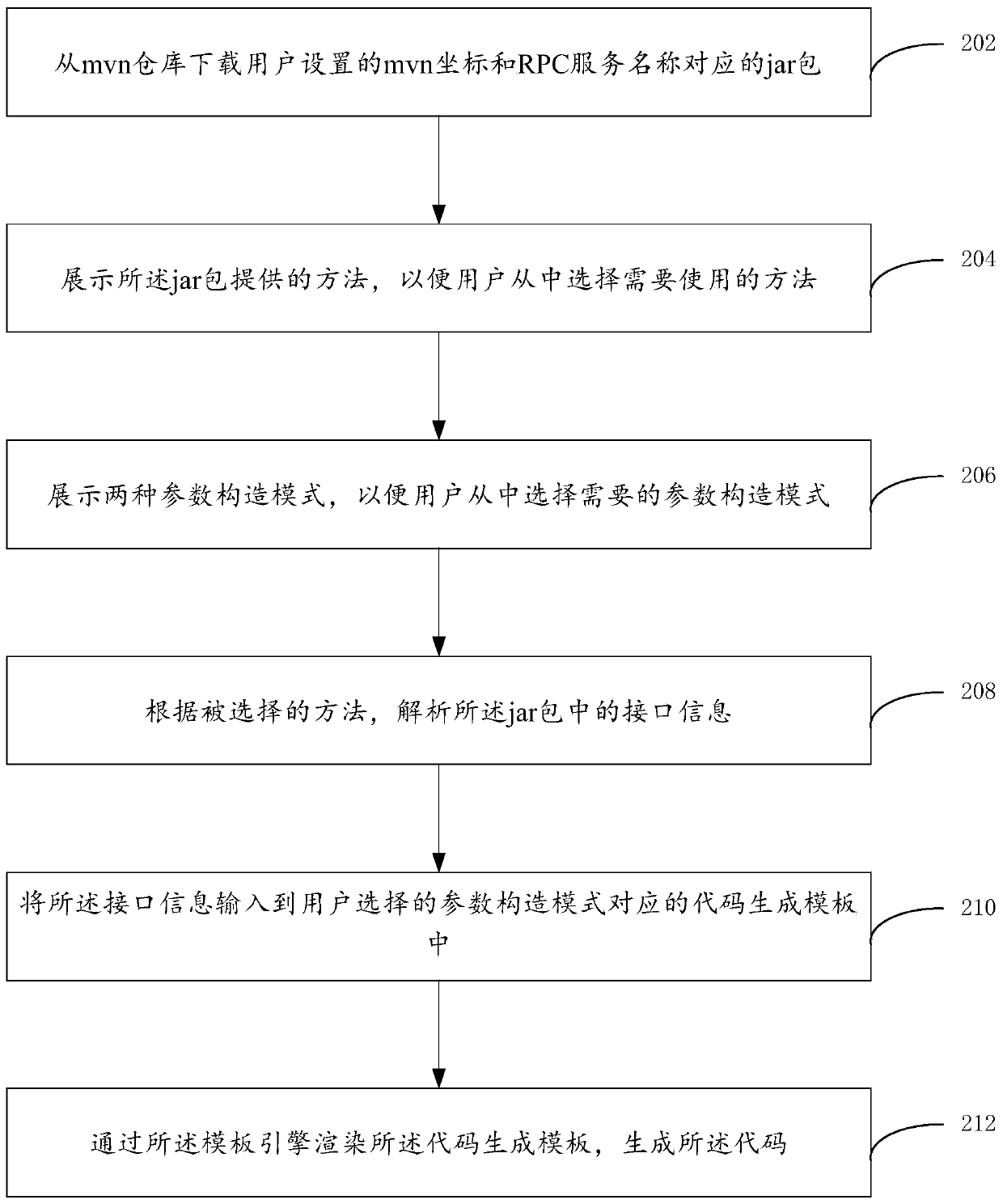
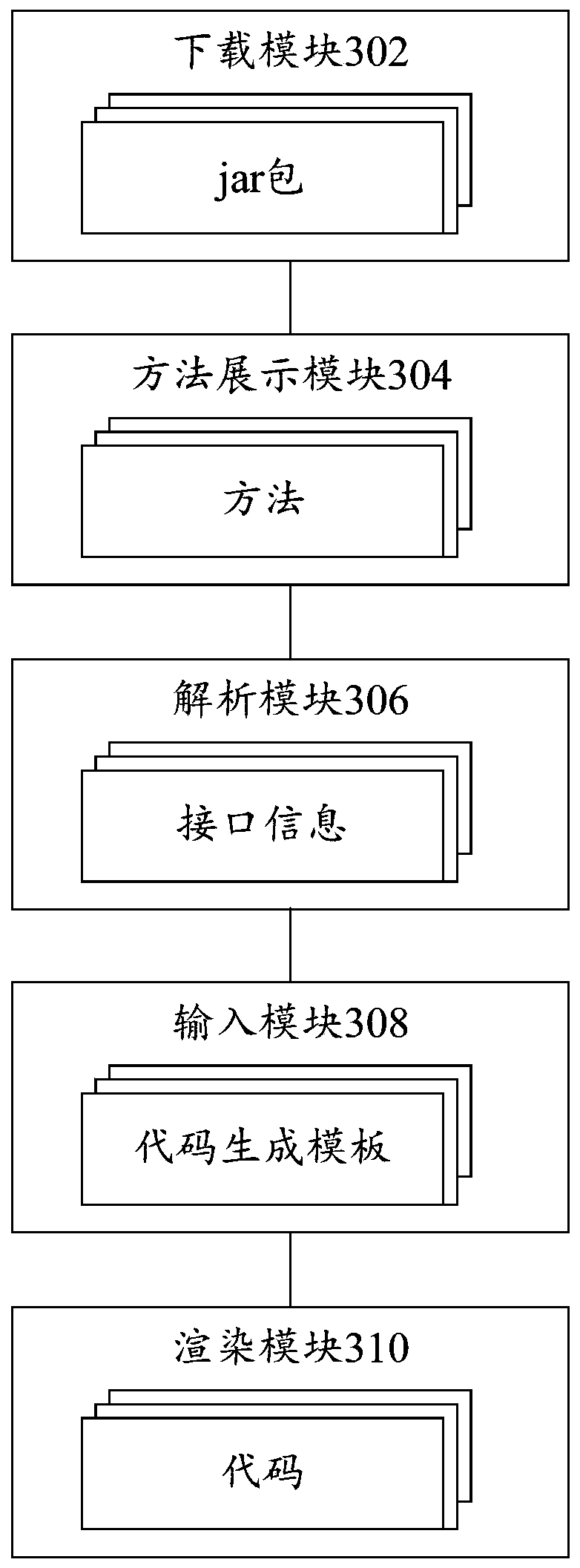
The embodiment of the invention provides a code generation method and device. The code generation method comprises the steps that mvn coordinates set by a user and a jar package corresponding to an RPC service name are downloaded from an mvn warehouse; the method provided by the jar package is displayed, so that a user can select a method needing to be used from the jar package; analyzing interface information in the jar packet according to the selected method; the interface information is input into a preset code generation template, a template language allowed by a template engine in the code generation template describes codes generated according to the interface information, and the codes are used for calling the selected method; and rendering the code generation template through the template engine to generate the code.
Owner:ANT WEALTH (SHANGHAI) FINANCIAL INFORMATION SERVICES CO LTD
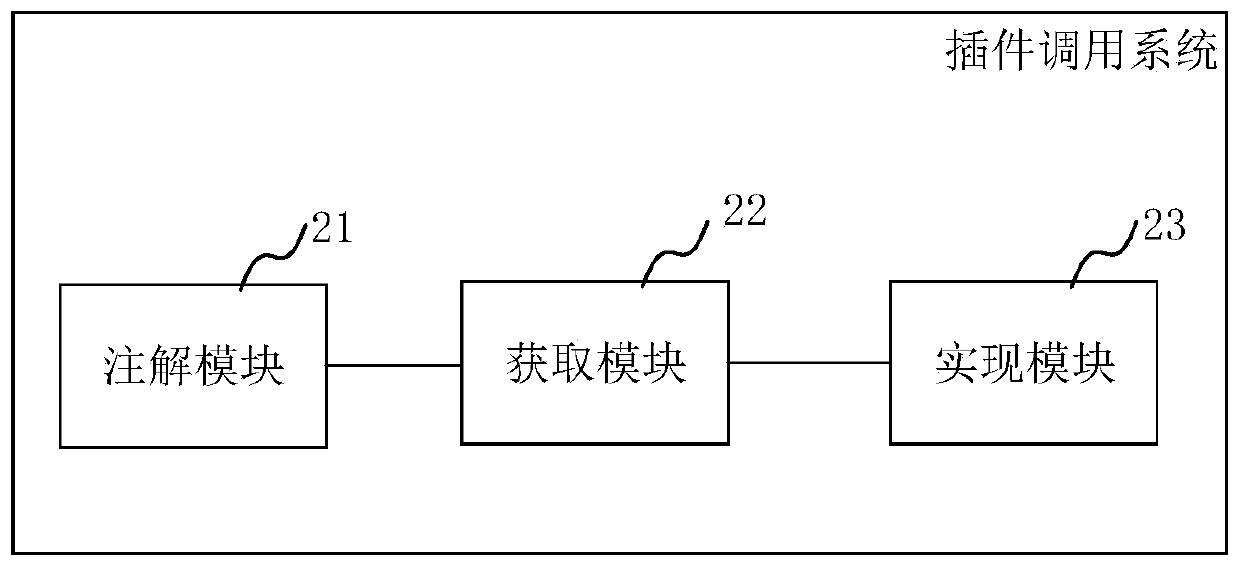
Plug-in calling method, system and device, and medium
ActiveCN110673890APromote research and developmentEasy maintenanceVersion controlProgram documentationSpecific functionSoftware engineering
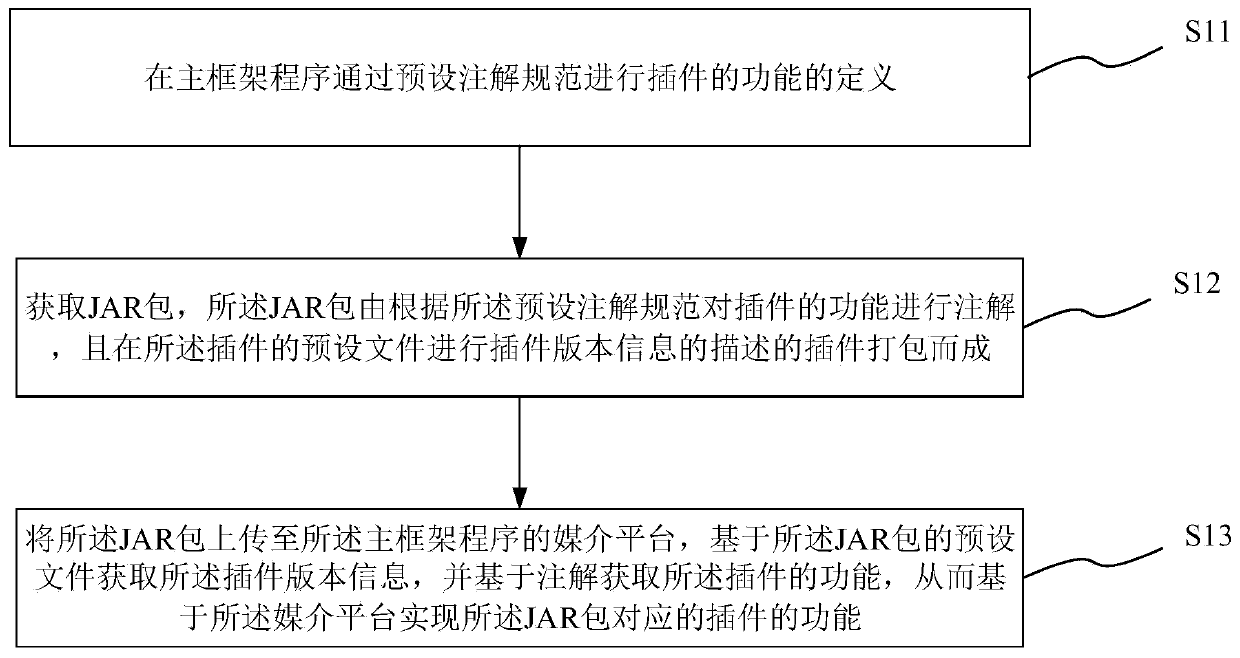
The invention provides a plug-in calling method, system and device, and a medium. The plug-in calling method comprises the following steps: defining functions of a plug-in in a main framework programthrough a preset annotation specification; obtaining a JAR package, wherein the JAR package is formed by packaging plug-ins which annotate functions of the plug-ins according to the preset annotationspecifications and describe plug-in version information in preset files of the plug-ins; and uploading the JAR package to a medium platform of the main frame program, obtaining the plug-in version information based on a preset file of the JAR package, and obtaining the function of the plug-in based on annotation, thereby realizing the function of the plug-in corresponding to the JAR package basedon the medium platform. The plug-in calling method is used for defining the function of the plug-in through an annotation method while a specific function interface is not needed, is good in the expandability of the function, and provides convenience for research, development and maintenance of a main framework program.
Owner:TIANYI ELECTRONICS COMMERCE
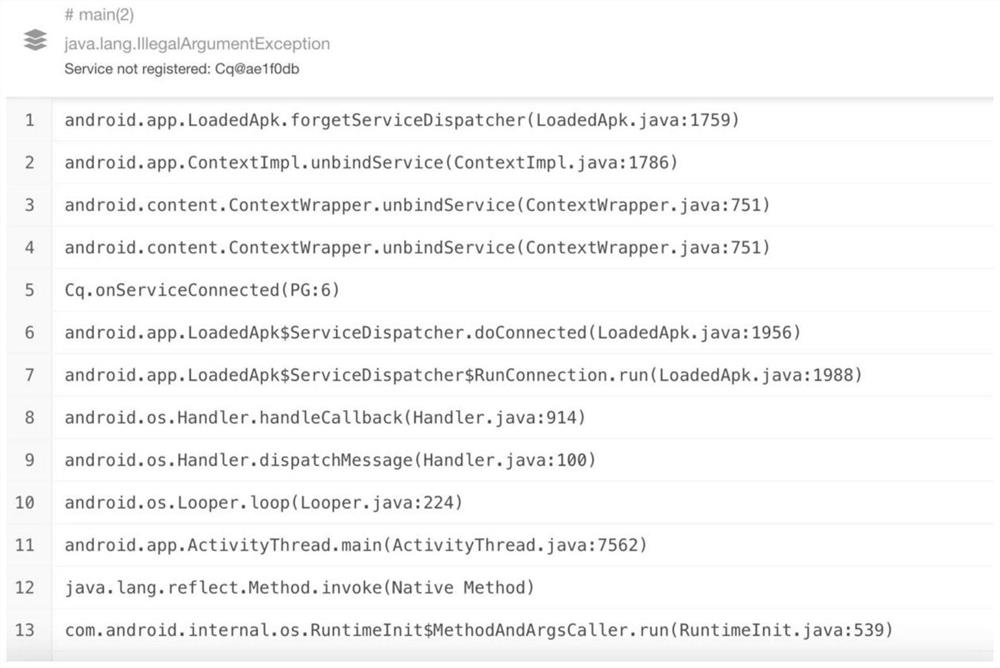
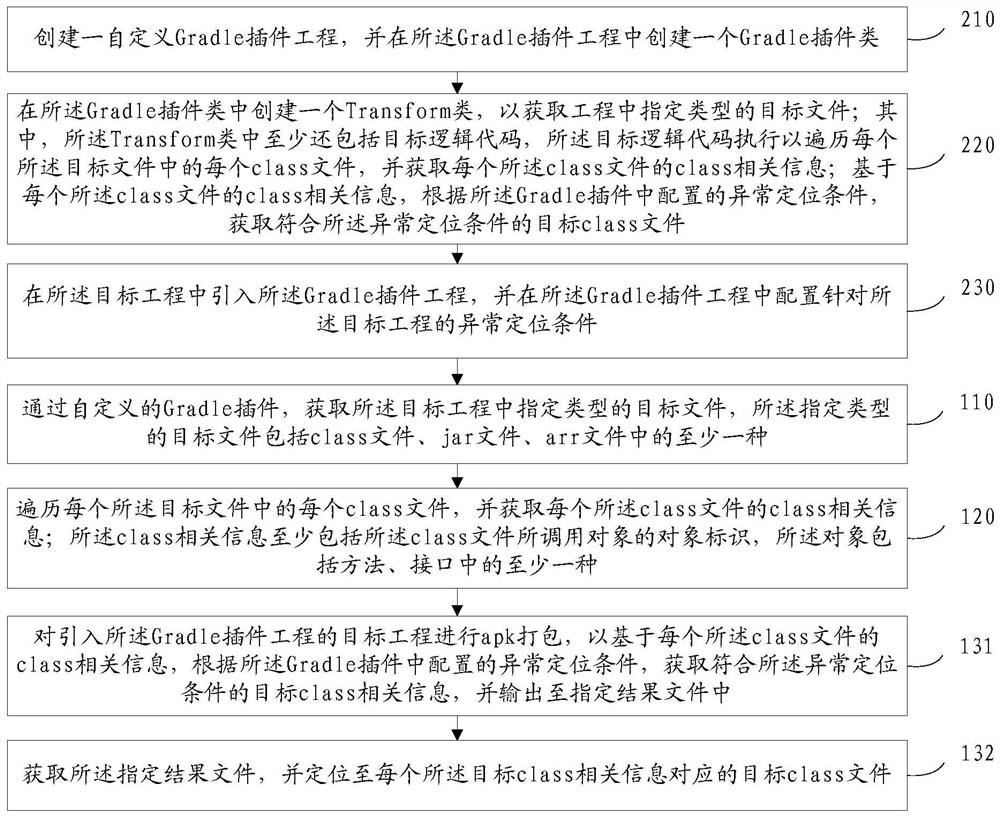
Abnormal positioning processing method and device, electronic equipment and storage medium
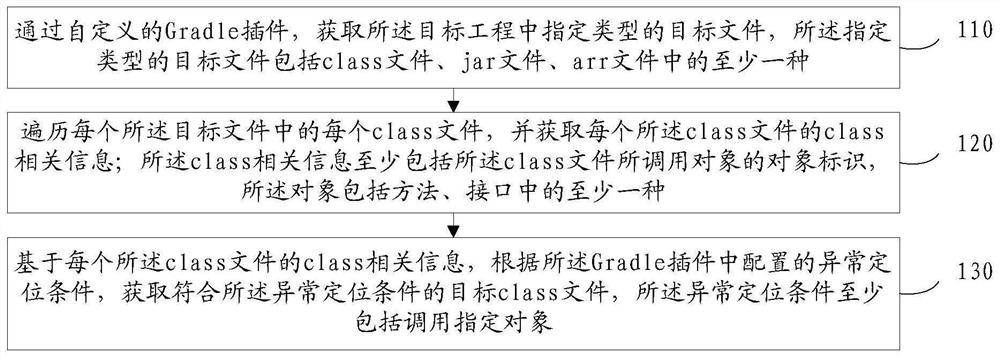
PendingCN113791966ARapid positioningSoftware testing/debuggingNon-redundant fault processingComputer hardwareJAR
The invention provides an abnormal positioning processing method and device, electronic equipment and a storage medium. The method comprises the steps that: target files of a specified type in a target project are obtained through a self-defined Gradle plug-in, wherein each target file of the specified type comprises at least one of a class file, a jar file and an arr file; each class file in each target file is traversed, and class related information of each class file is obtained, wherein the class related information at least comprises an object identifier of an object called by the class file, wherein the object comprises at least one of a method and an interface; and on the basis of the class related information of each class file, according to an abnormal positioning condition configured in the Gradle plug-in, a target class file meeting the abnormal positioning condition is obtained, wherein the abnormal positioning condition at least comprises calling of a specified object.
Owner:WUBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com