Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3264 results about "Server appliance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
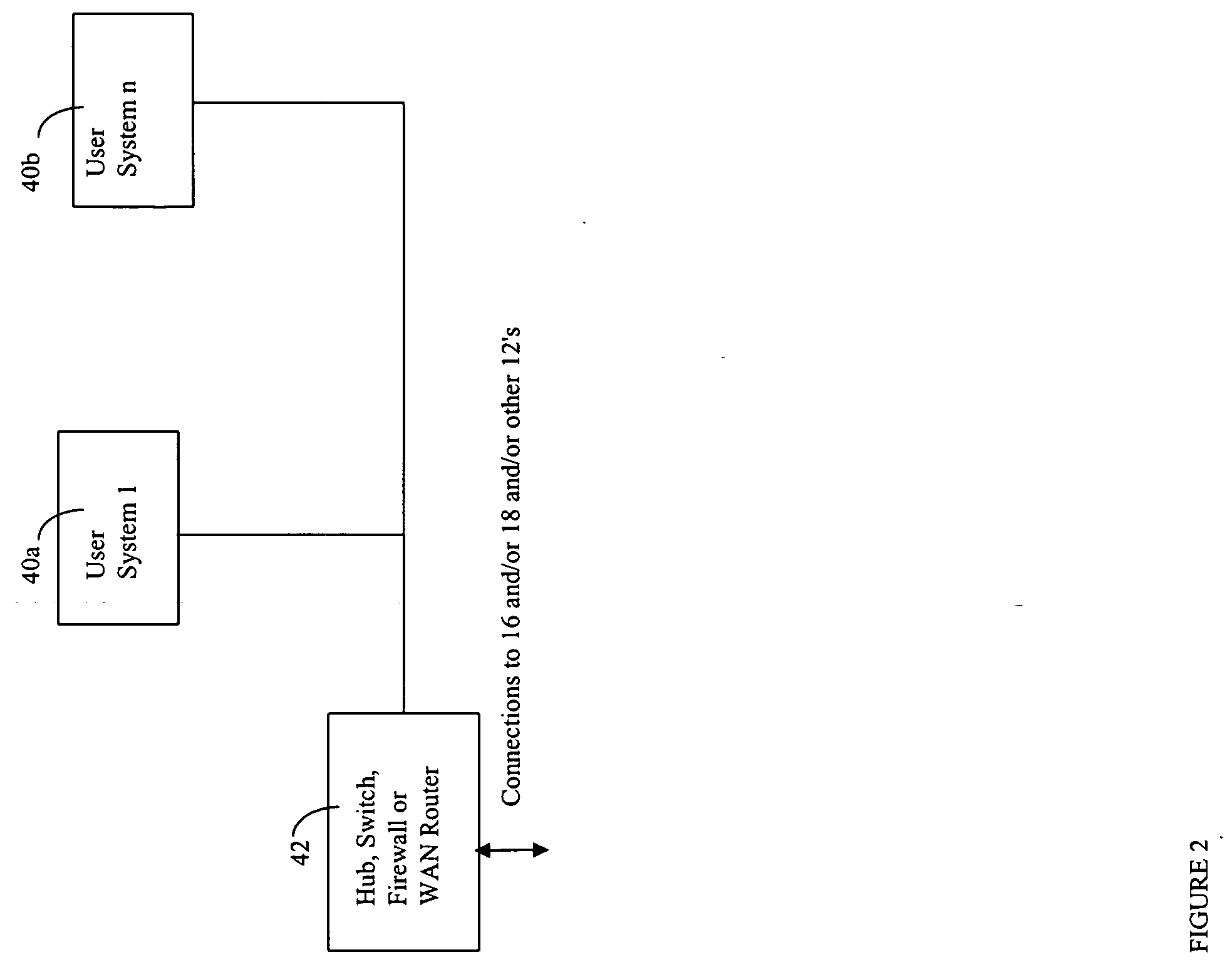
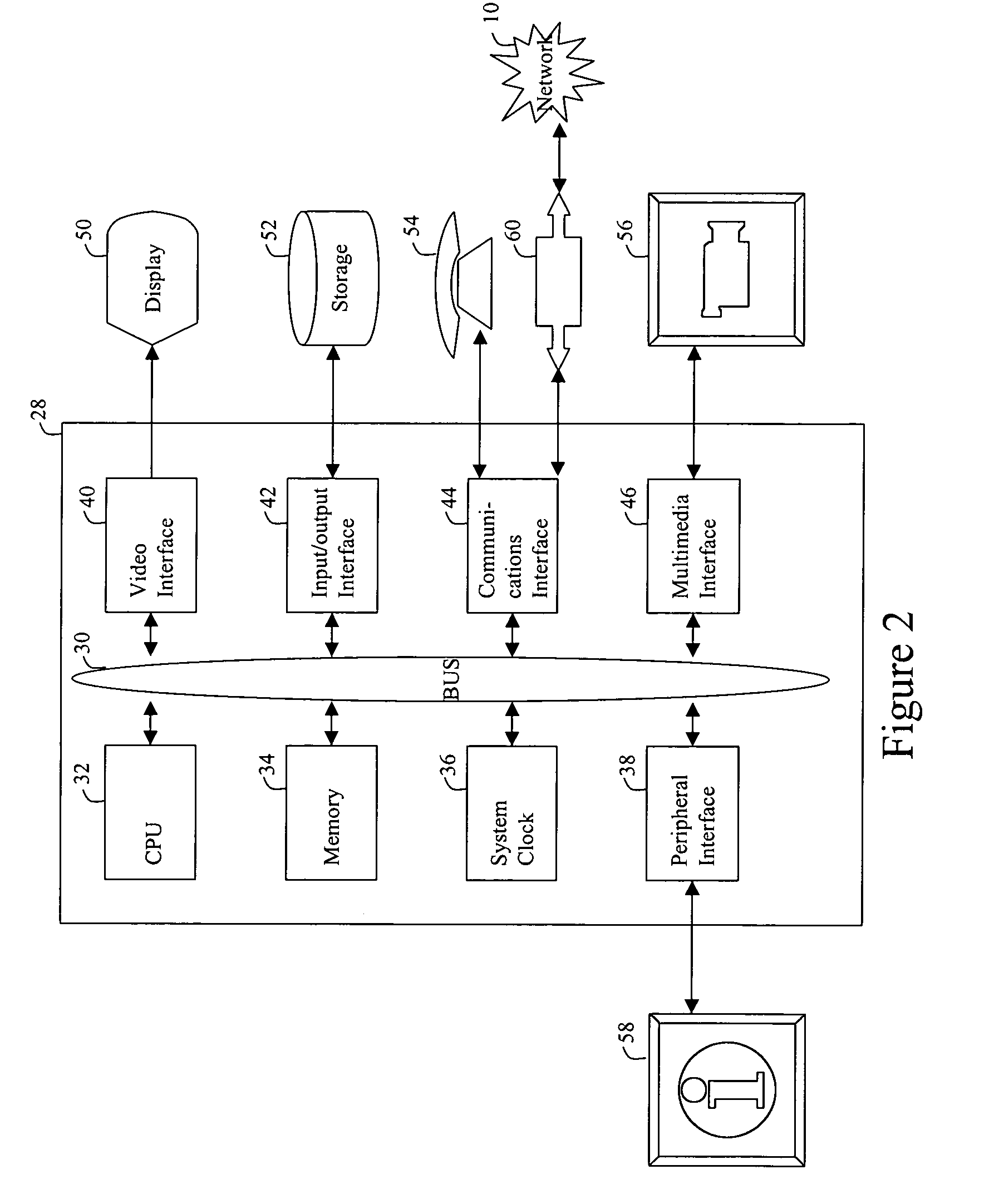
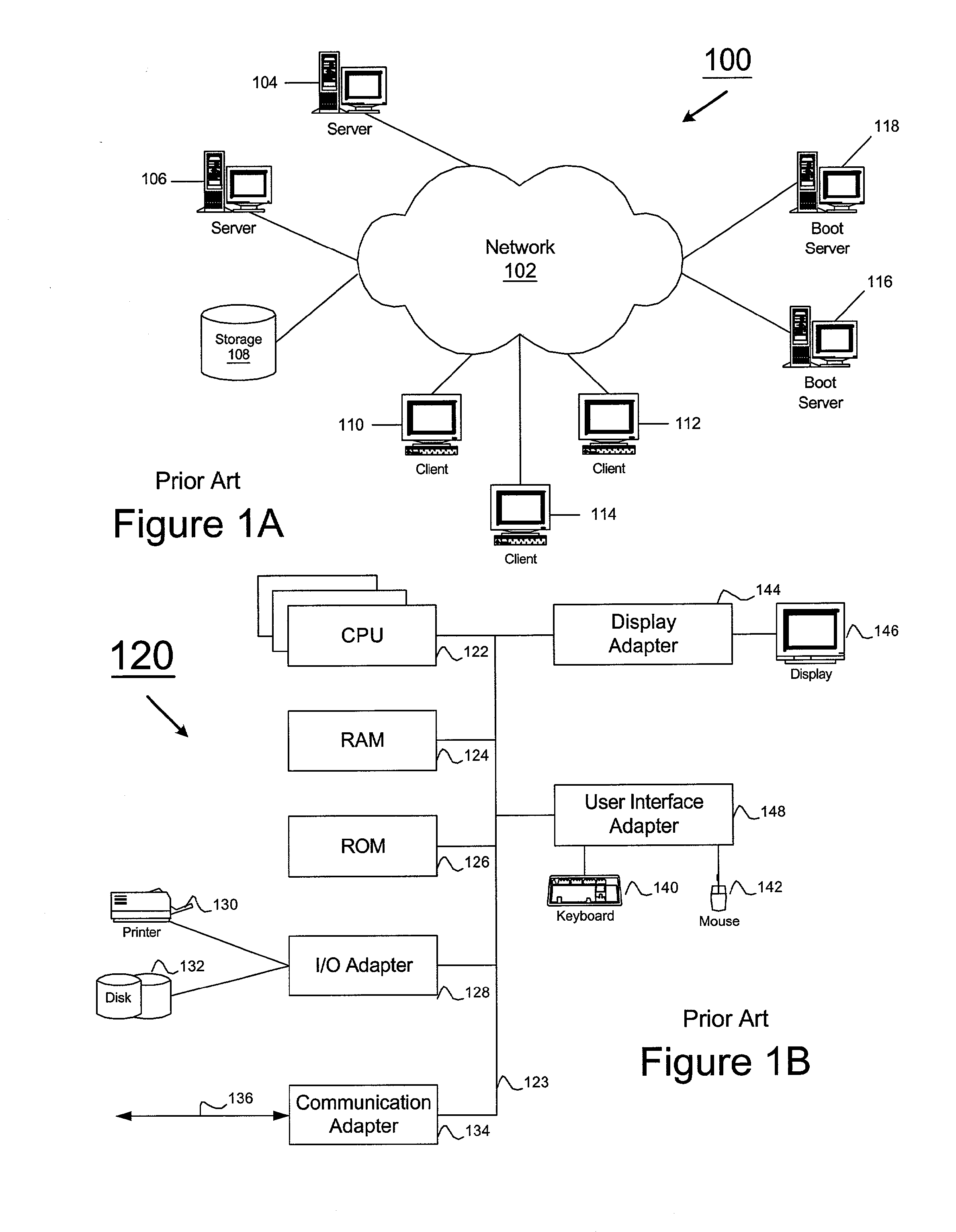
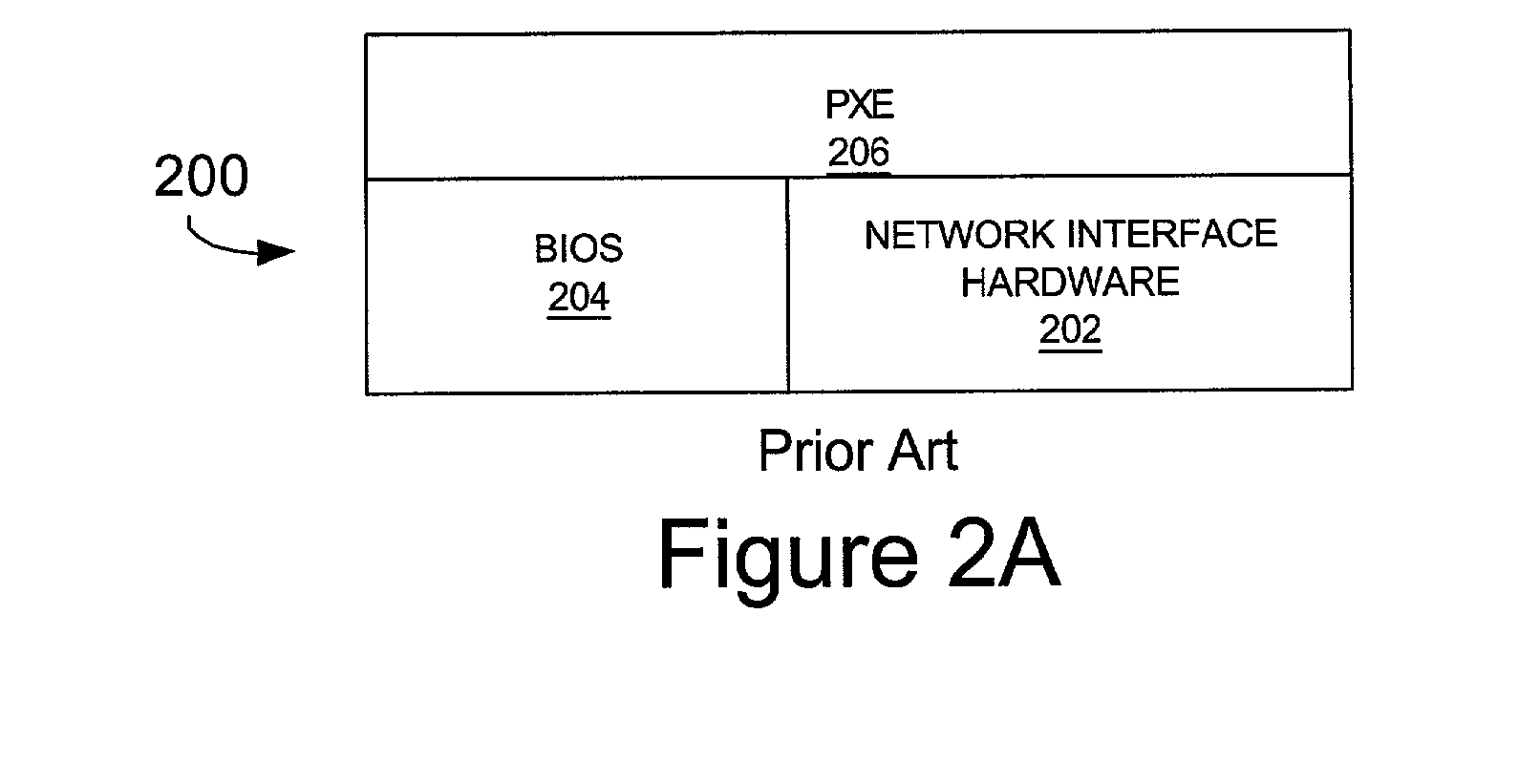
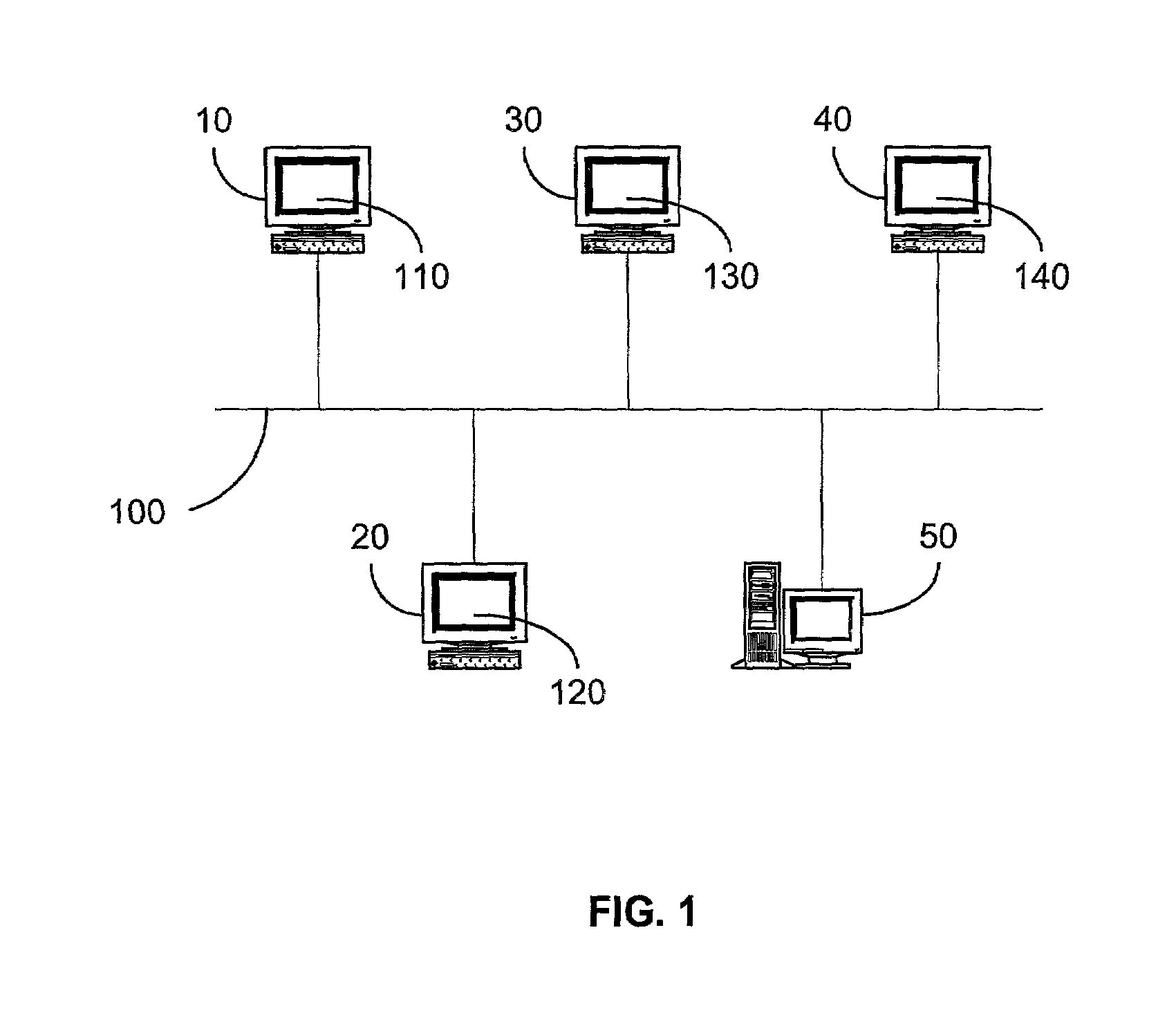
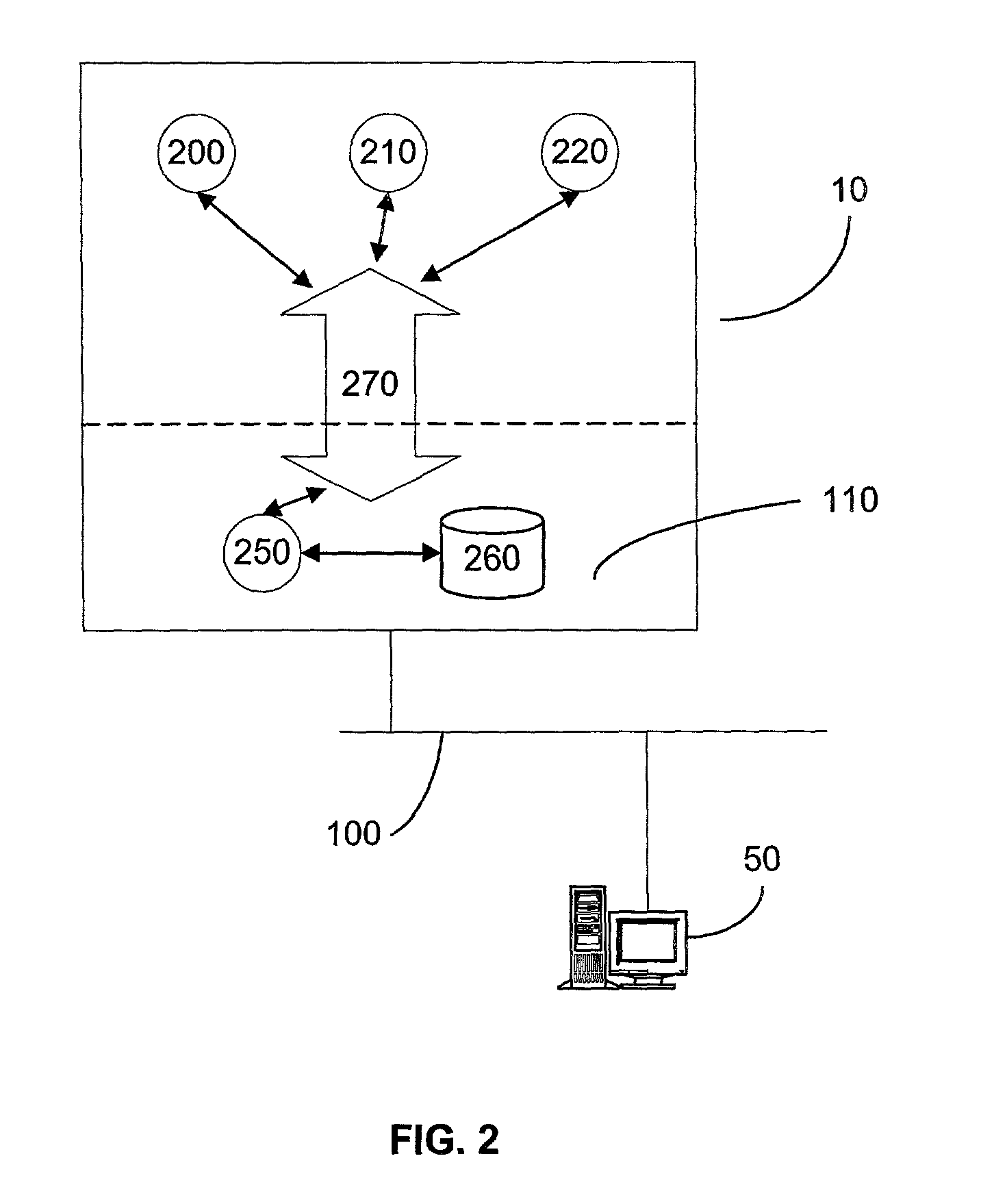
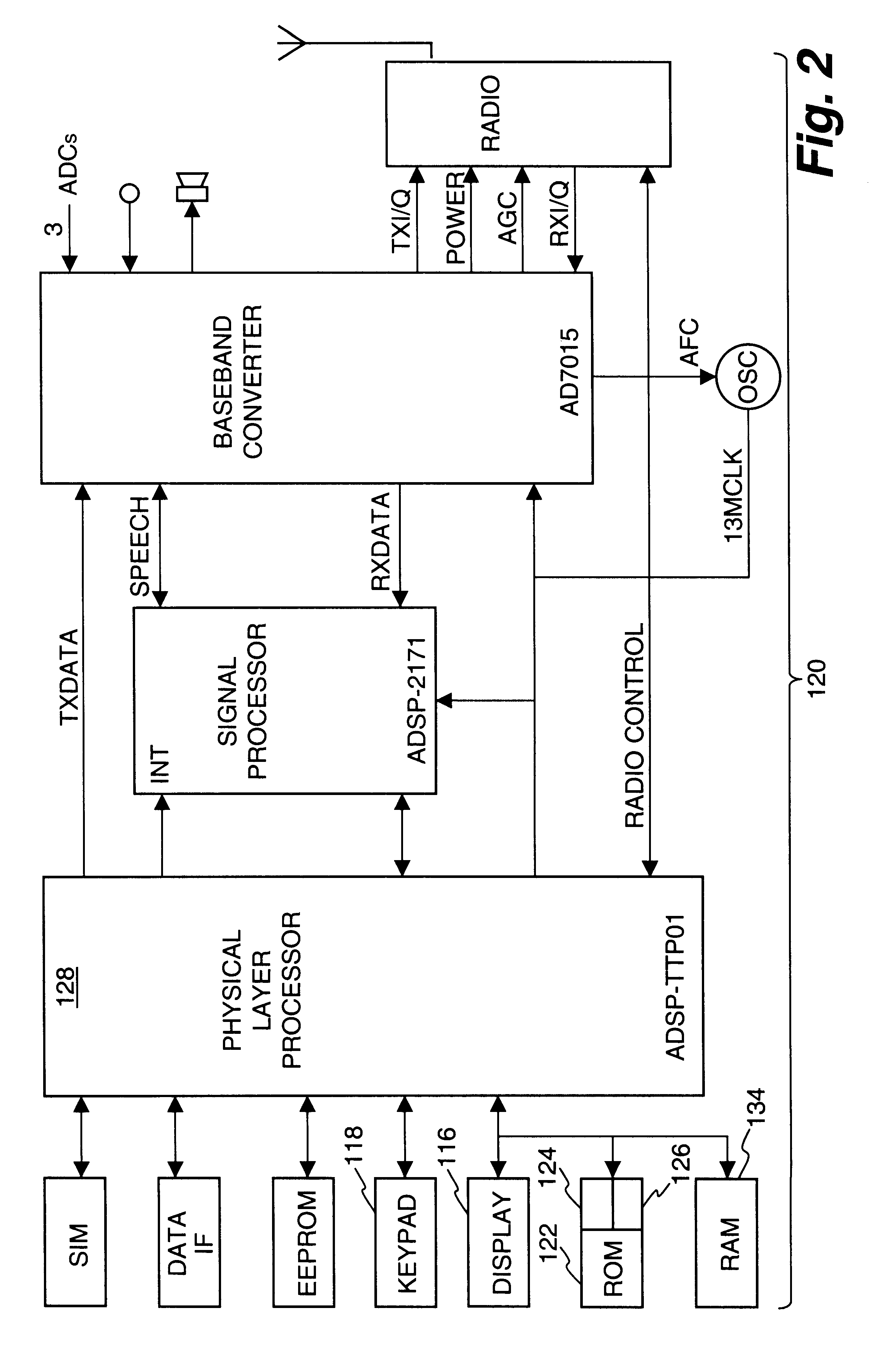
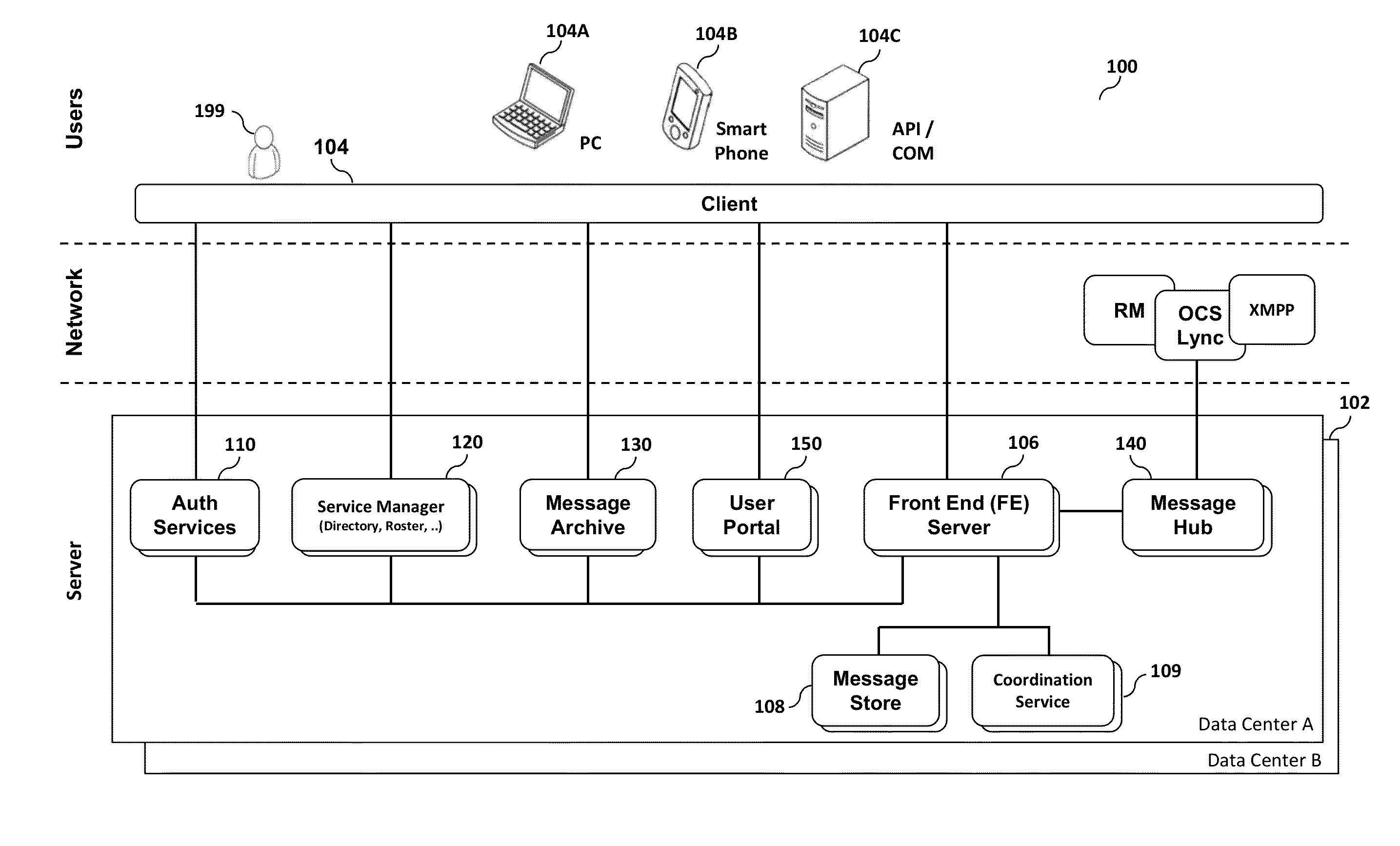
A server appliance is a computer appliance that works as a server. It is designed so that the end-user does not need to understand the details of the operating system or the commands associated with it. Server appliances have their hardware and software preconfigured by the manufacturer. The appliance is plugged into an existing network and is turned on by the end-user. The user selects the components to be active, through a simple user interface, and the appliance then boots to an active state, which is usable within minutes. Server appliances are designed to run and be controlled remotely after the initial set-up. The units are designed to be very easy to operate and provide narrow selection of network services. Examples of server appliances include the Google Search Appliance, a search appliance designed for indexing corporate websites and returning these results, as well as the ASA Firewall, a security appliance designed to protect IP networks from unwanted inbound traffic. or IBM's Lotus Foundations which is designed to offer IT infrastructure services for the small to midsize business.
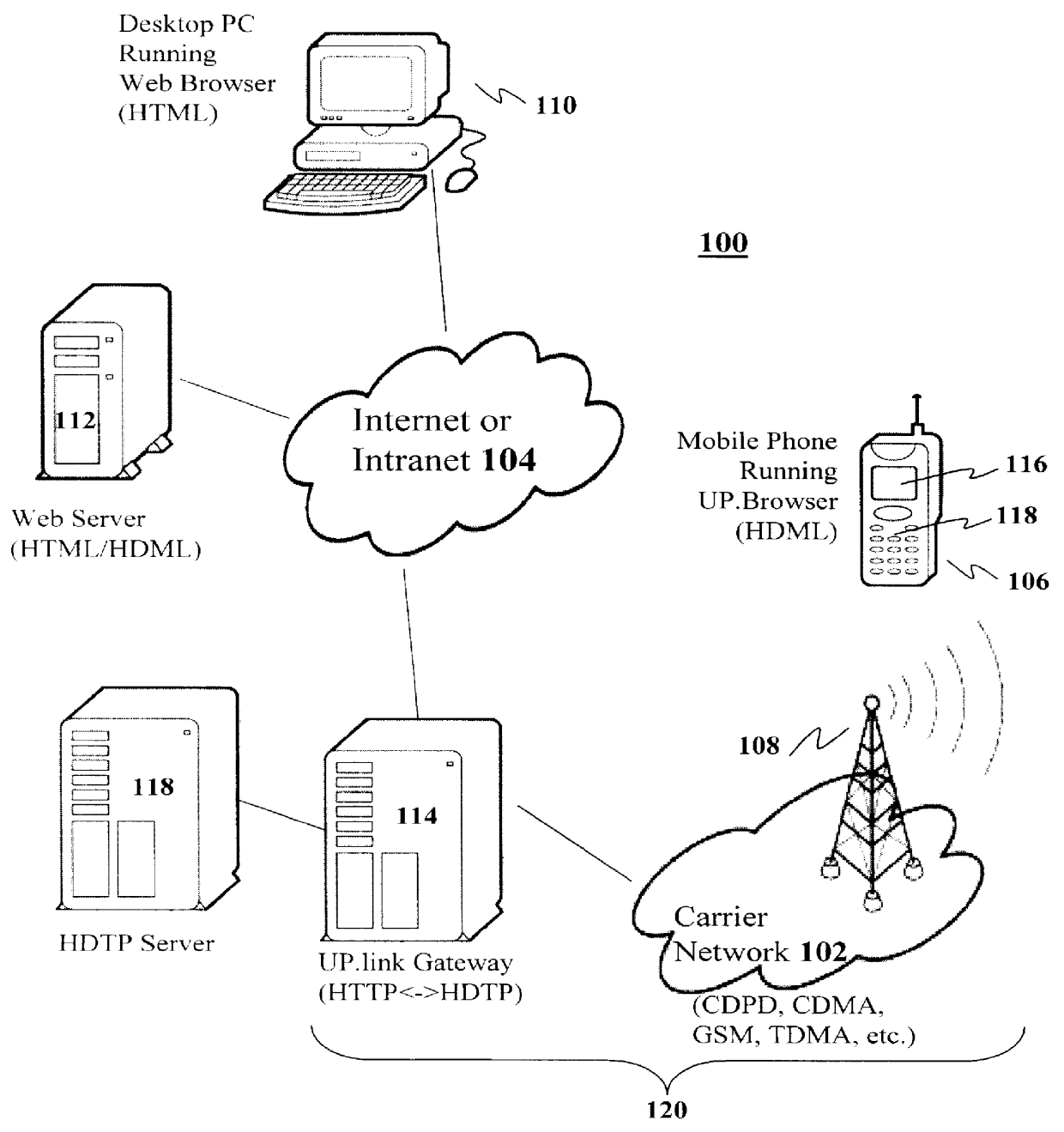
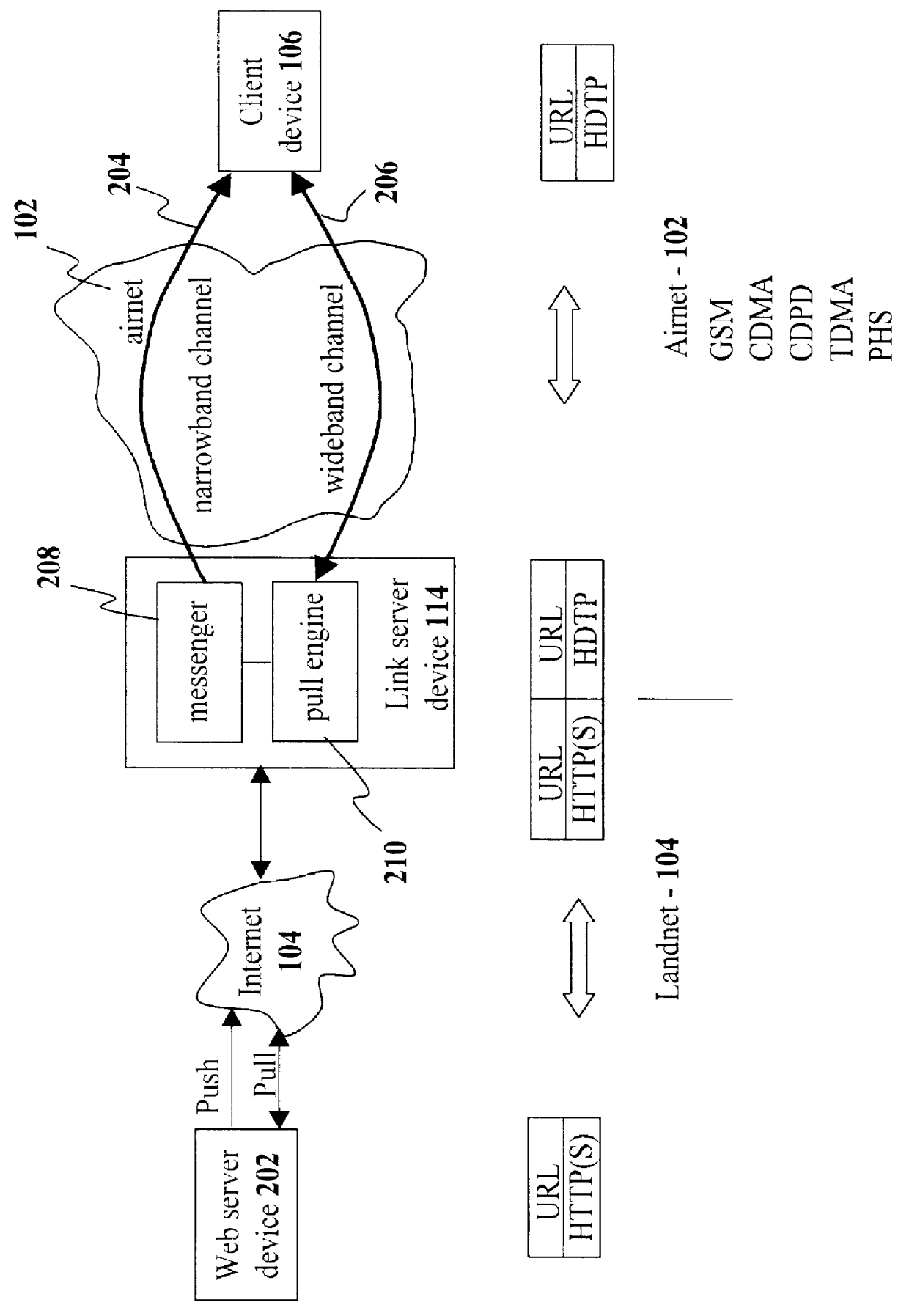
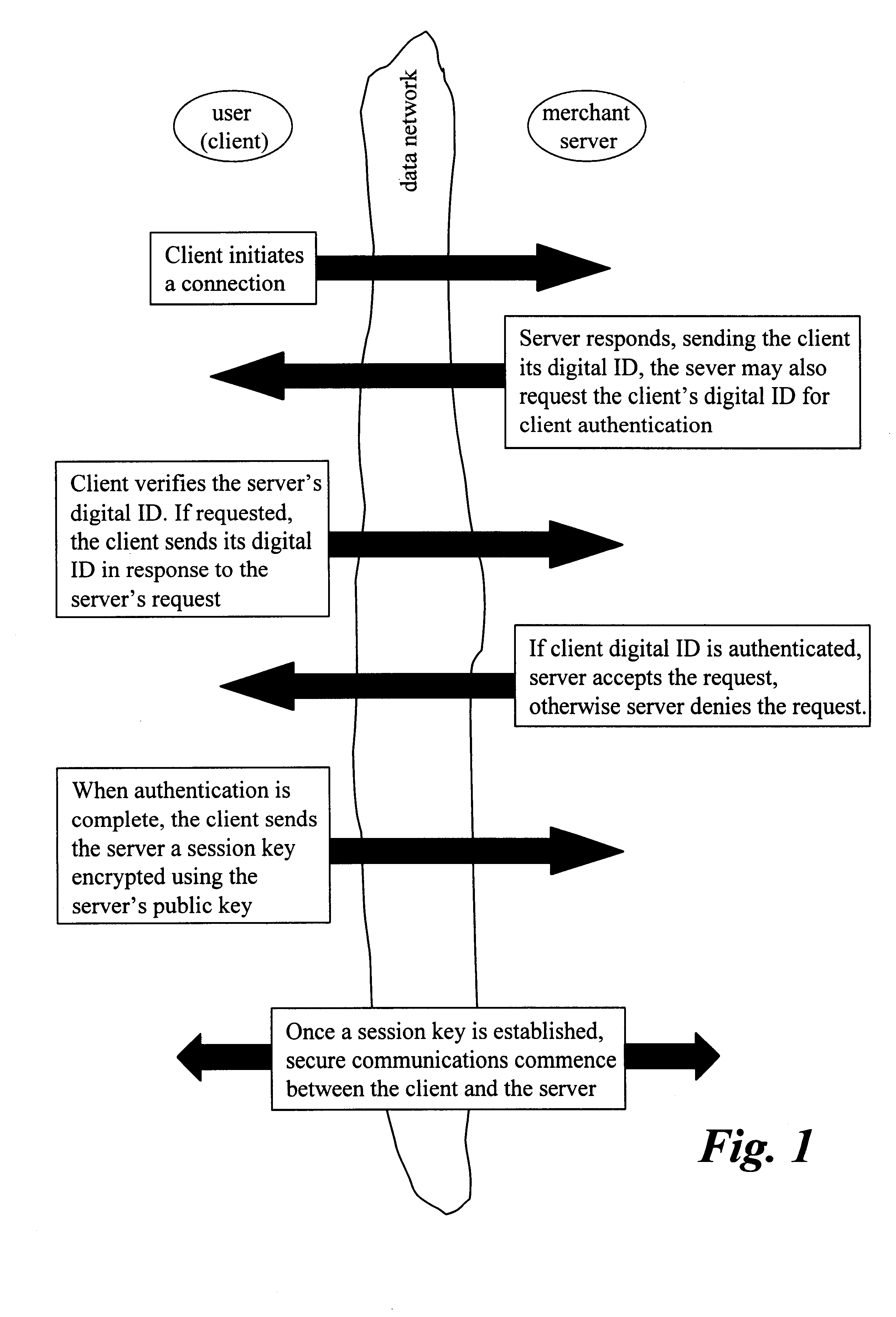
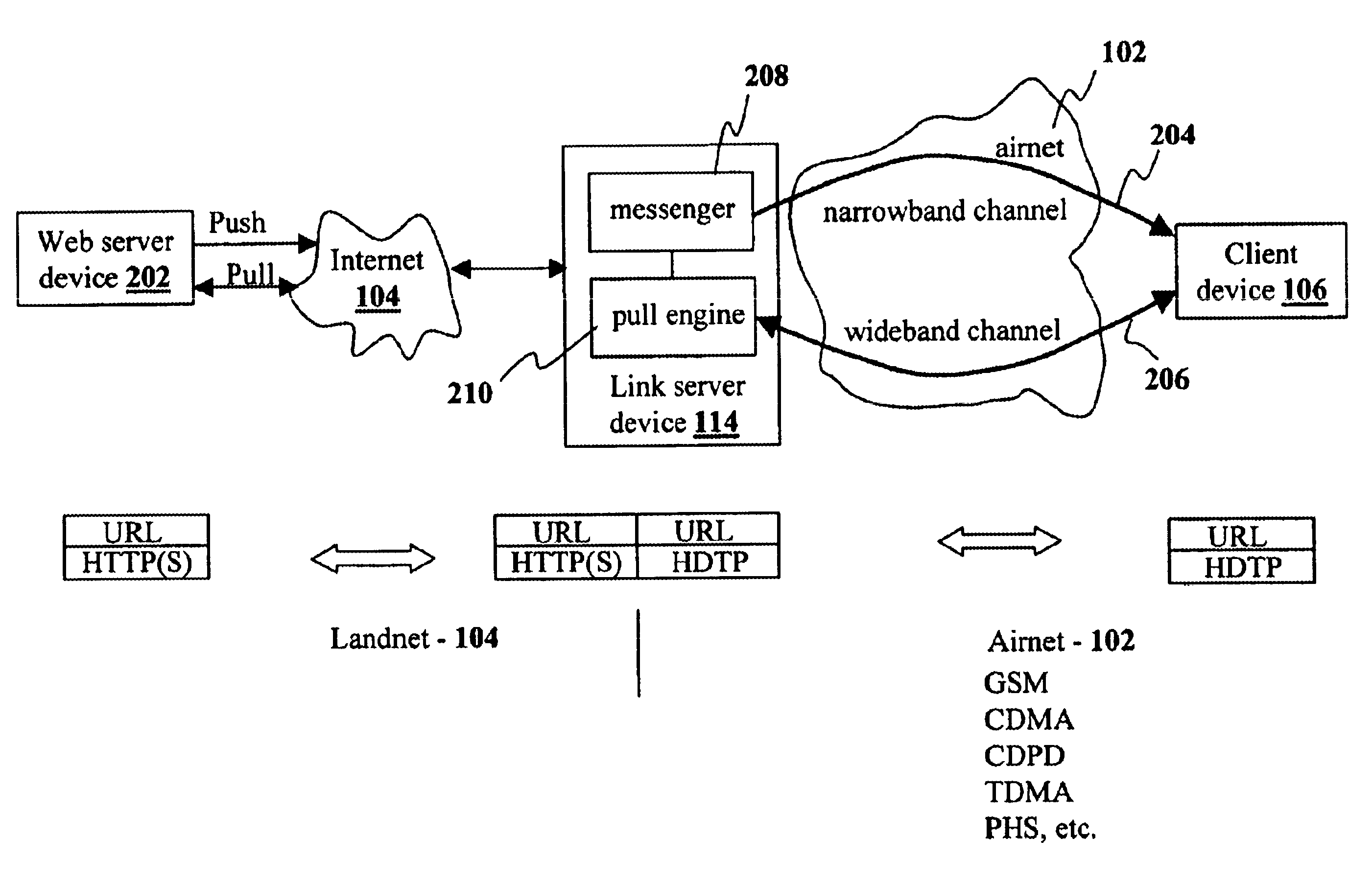
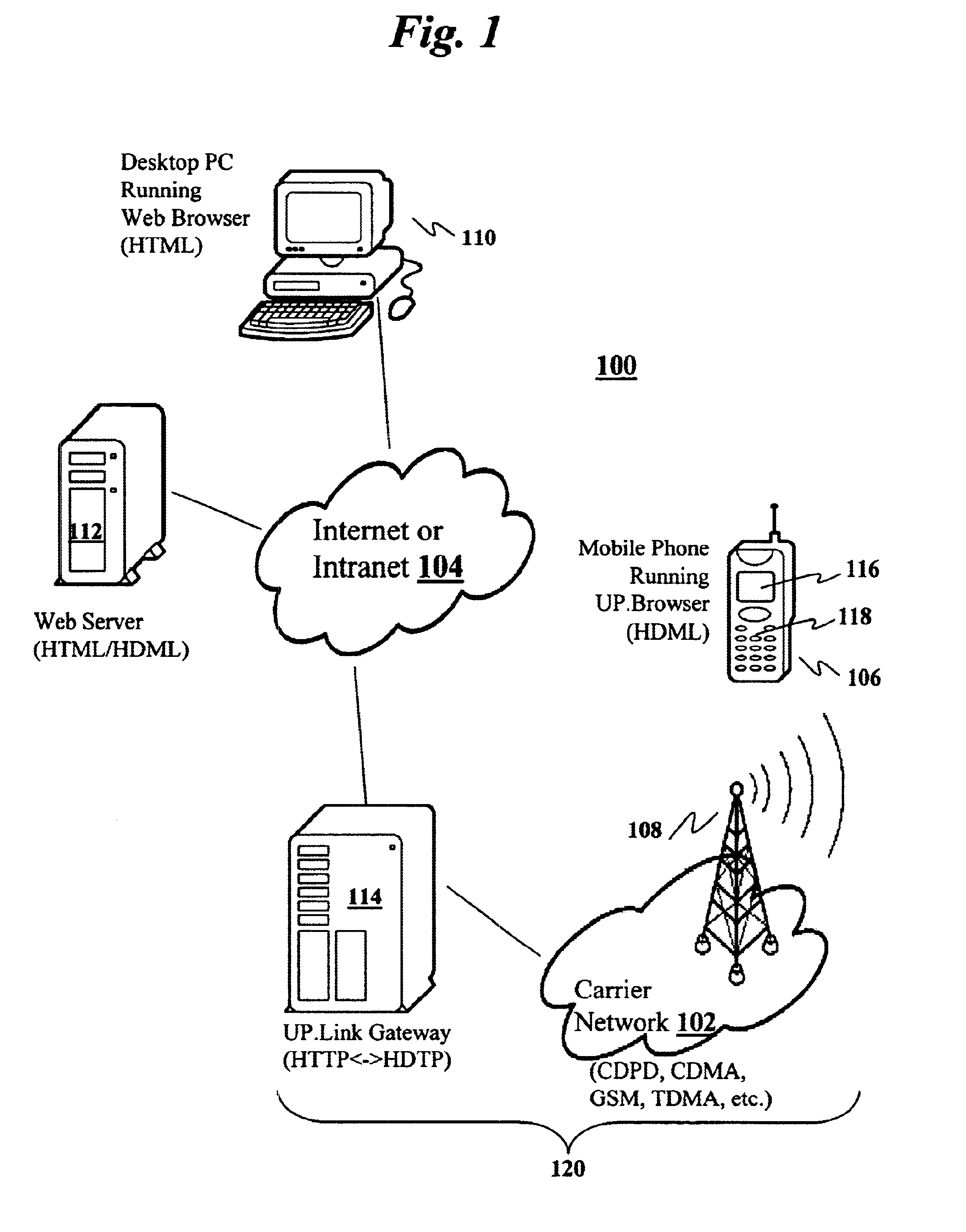
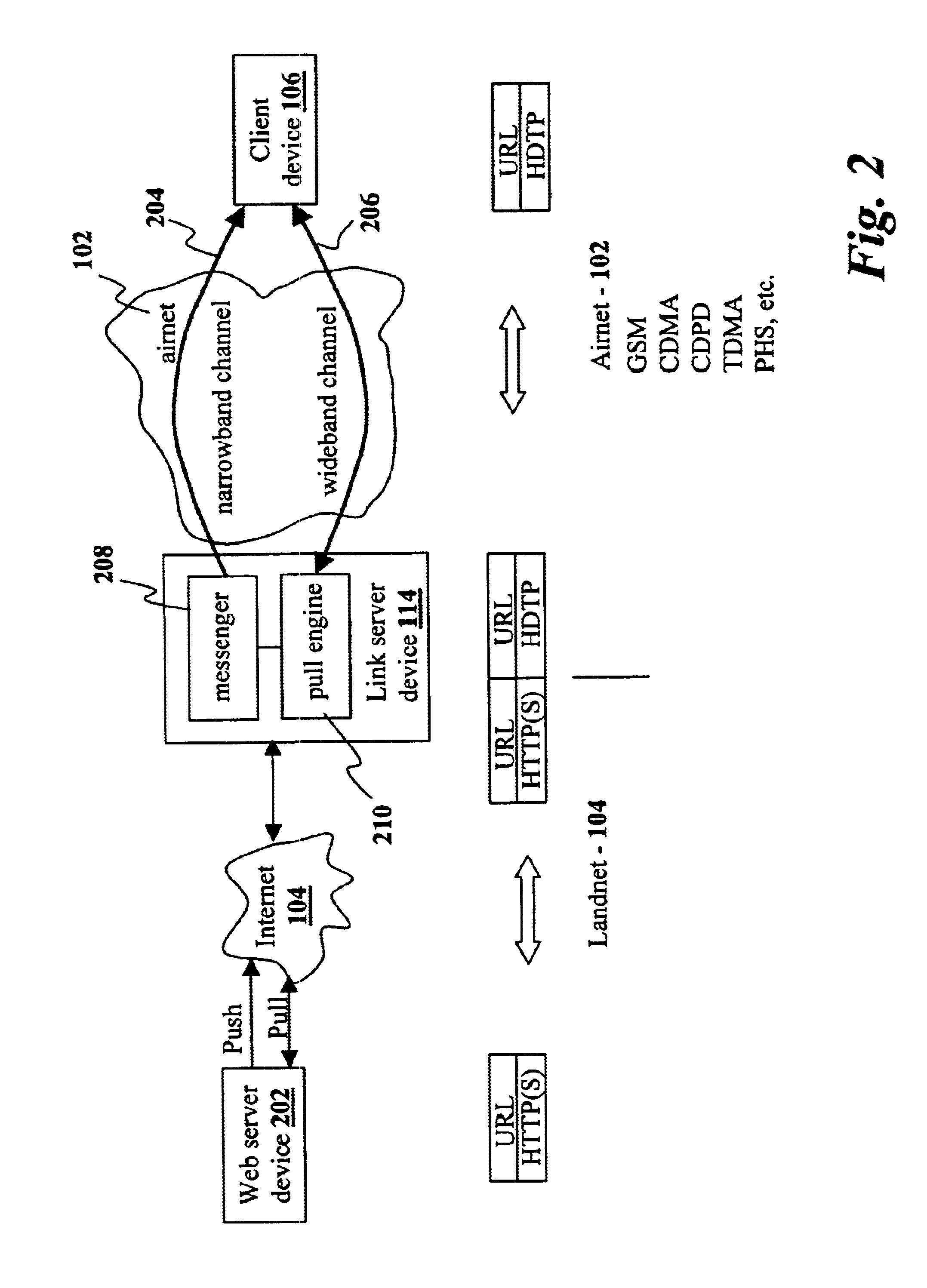
Method and system for pushing and pulling data using wideband and narrowband transport systems
InactiveUS6138158AWithout incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesTransport systemThe Internet
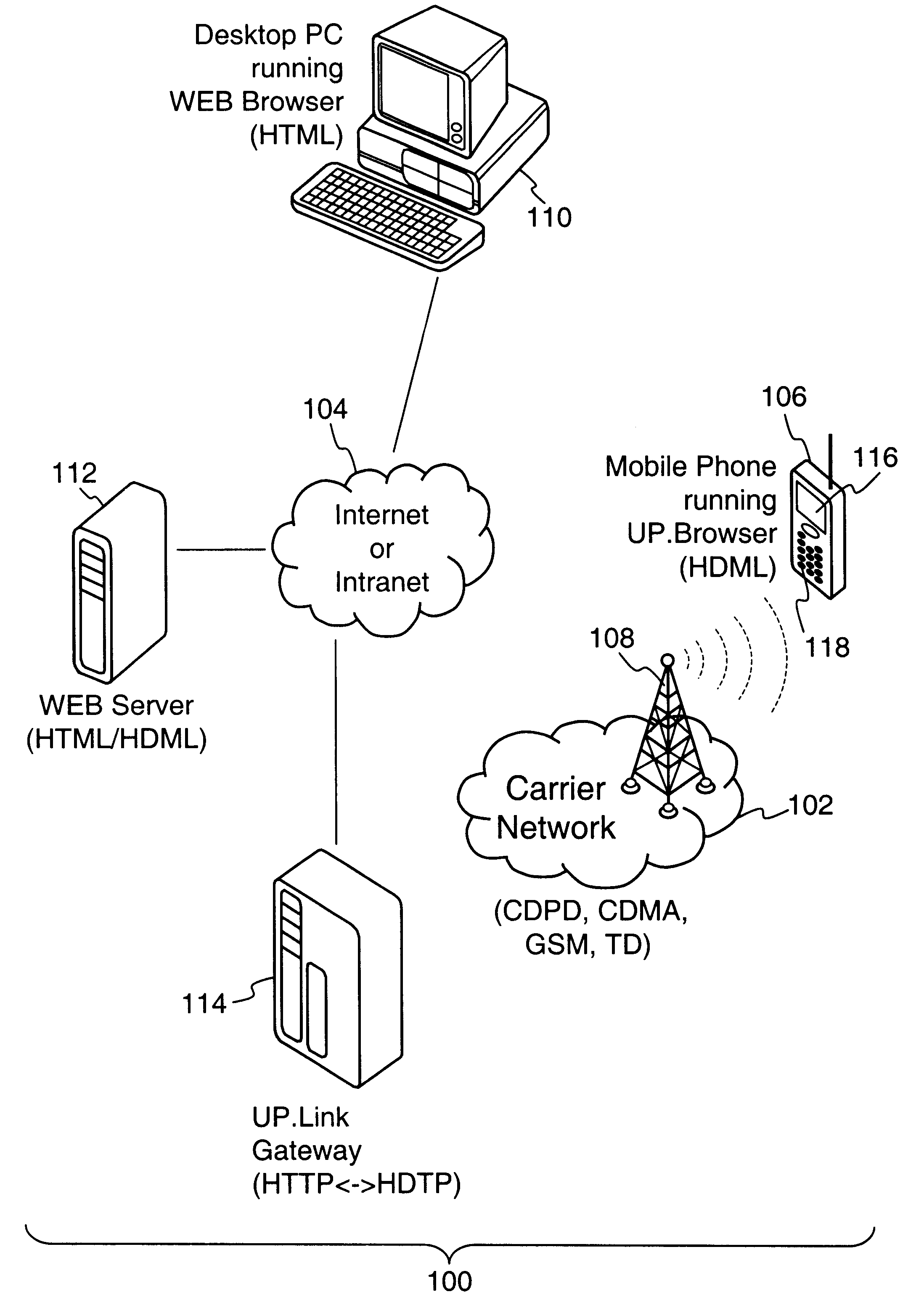
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
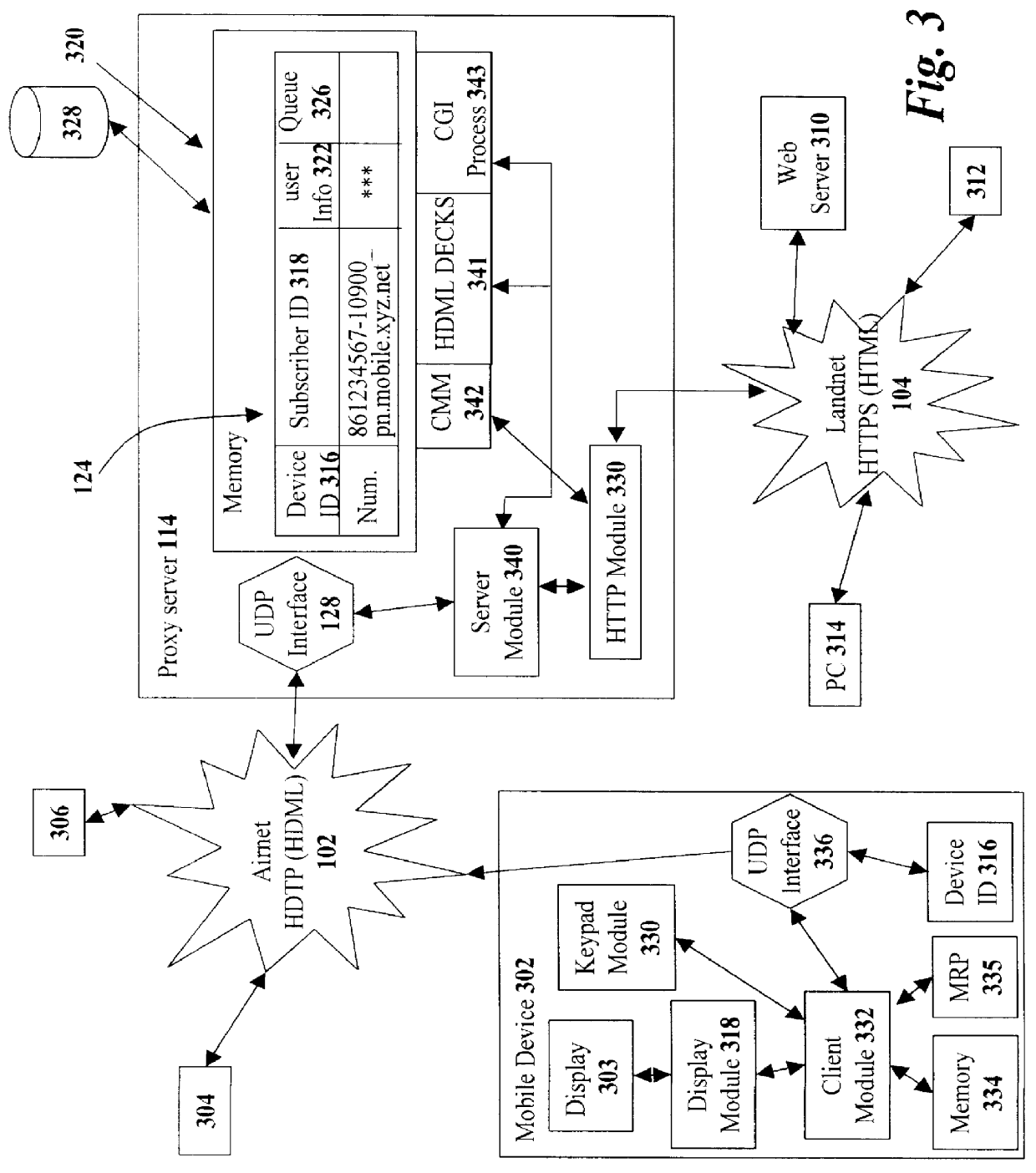
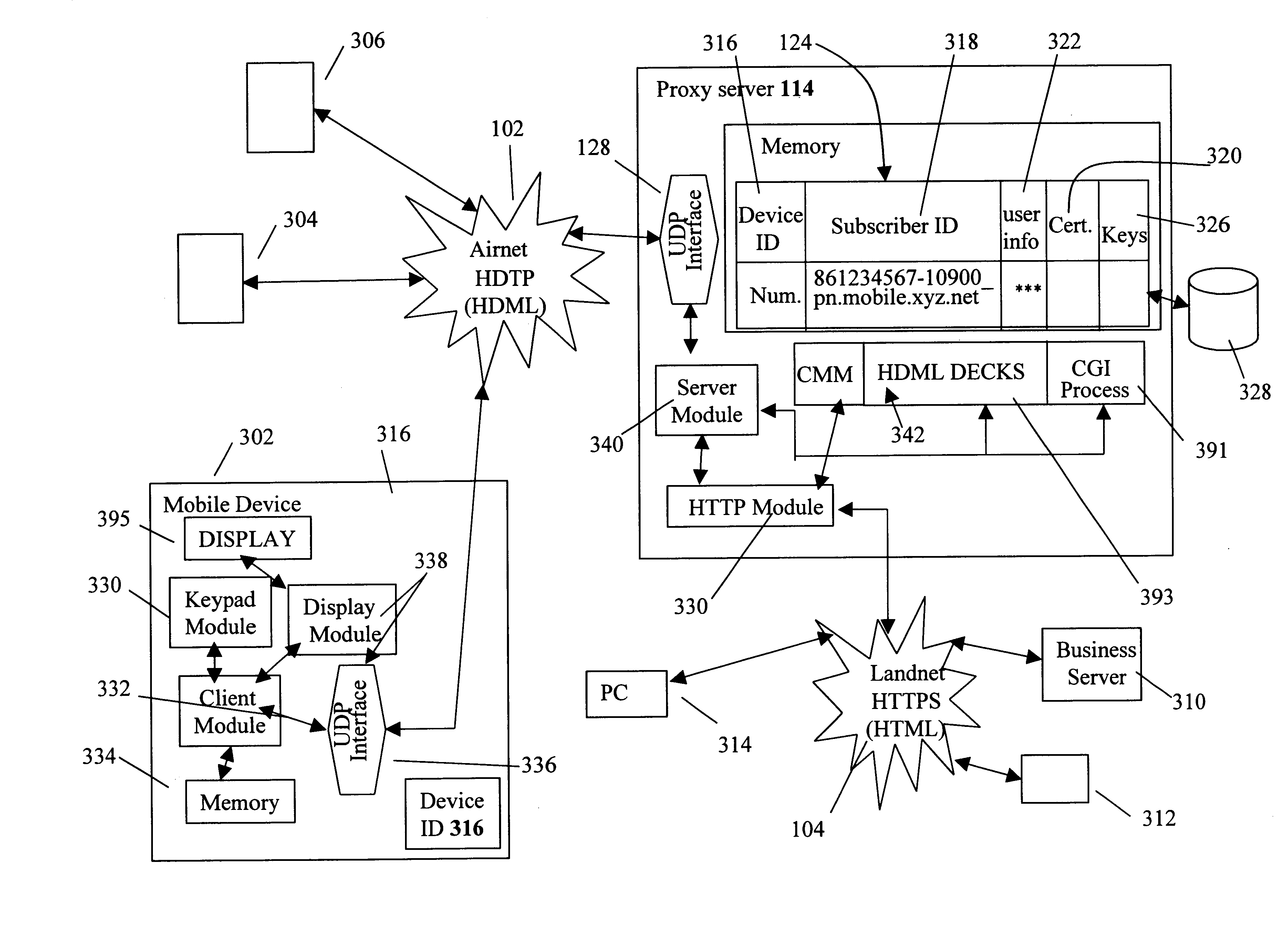
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
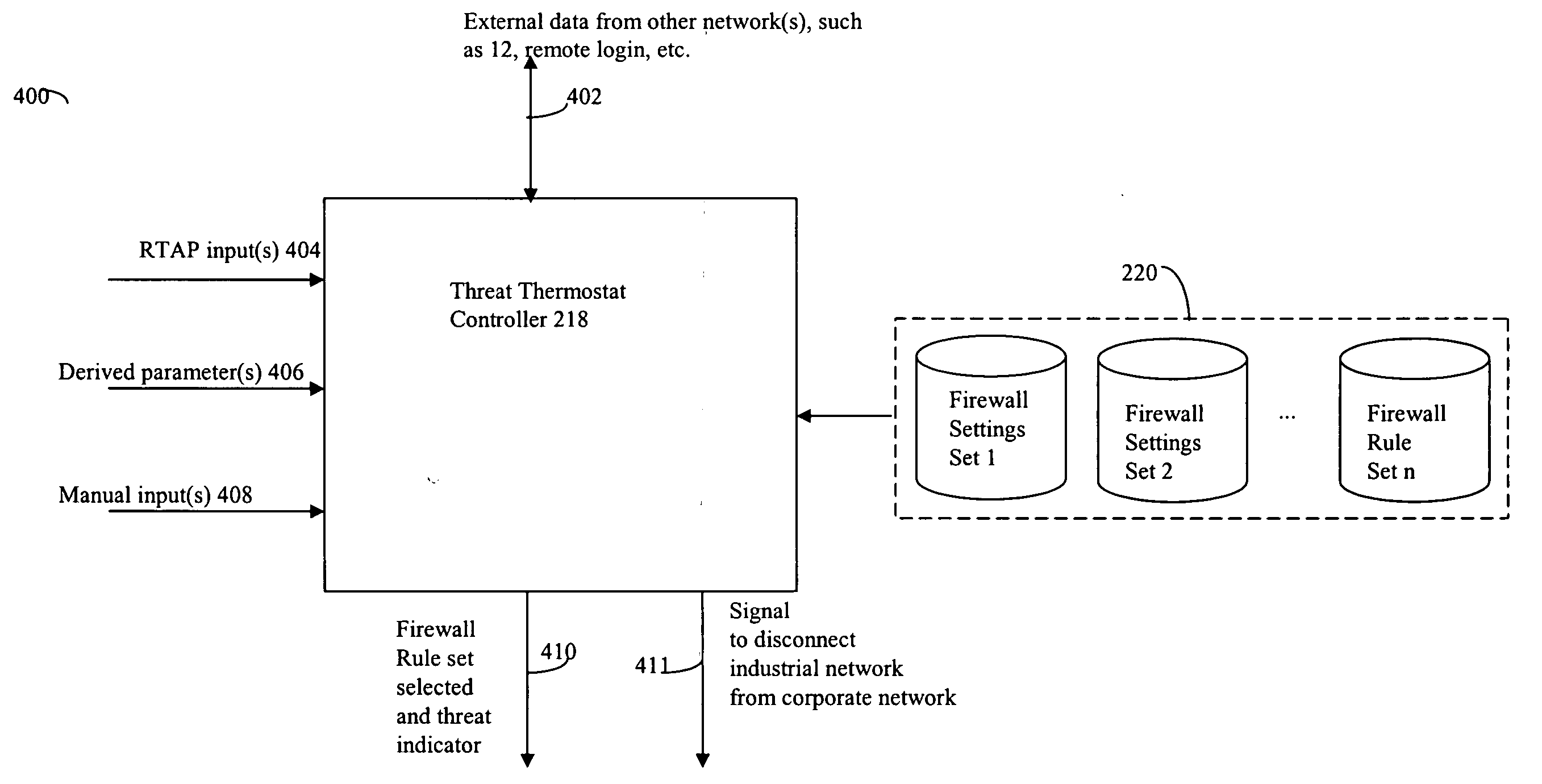
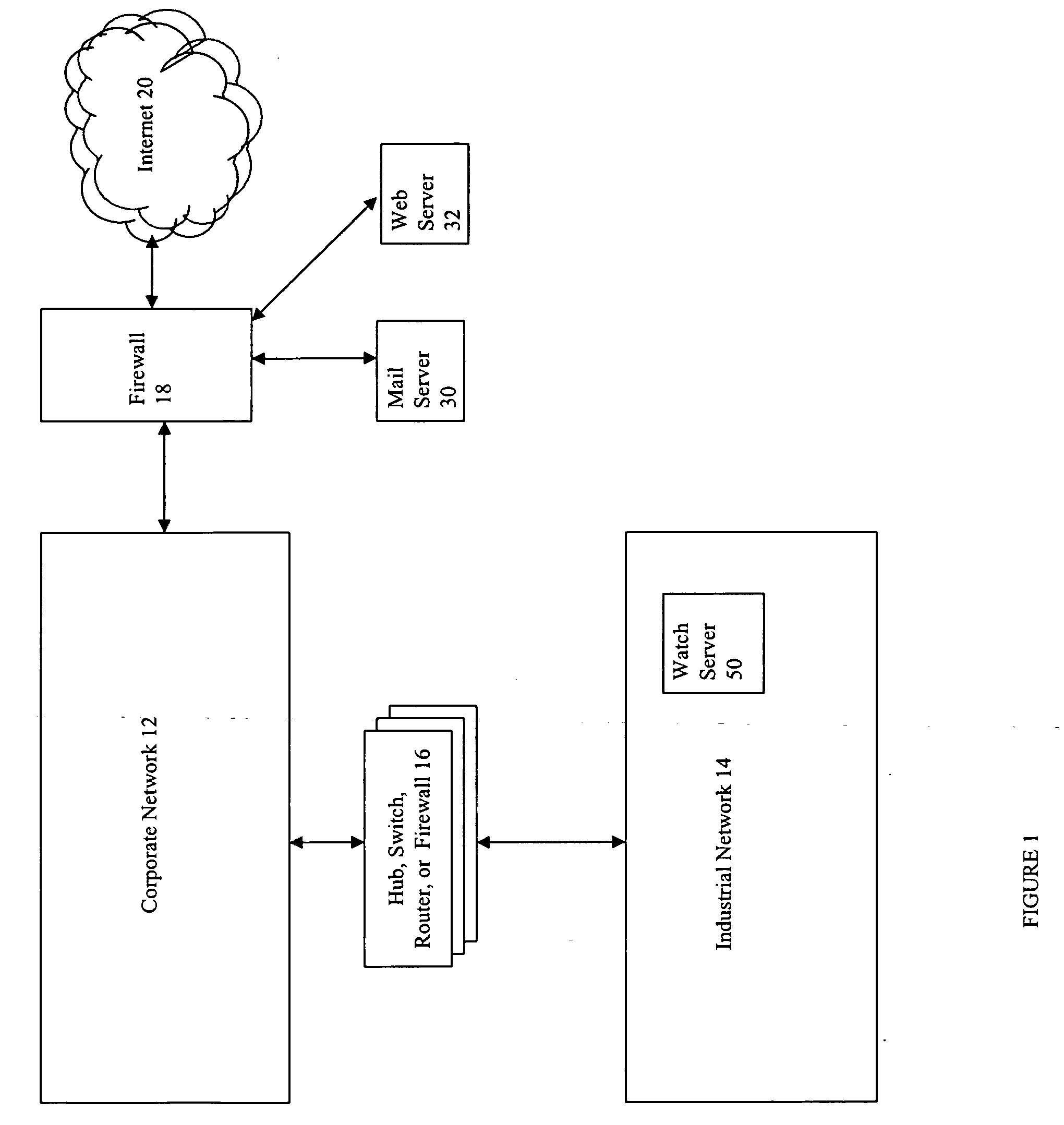
Event monitoring and management
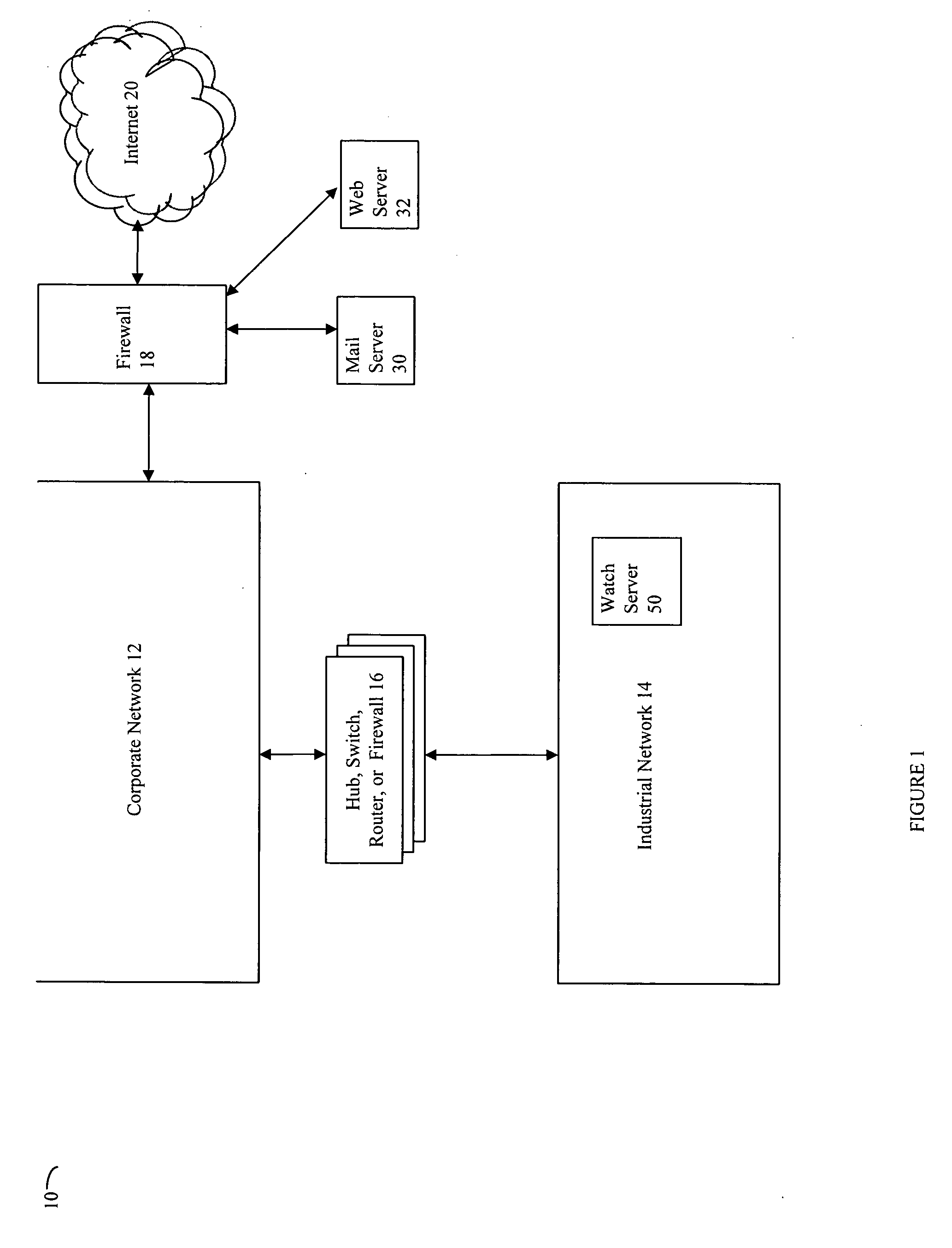
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
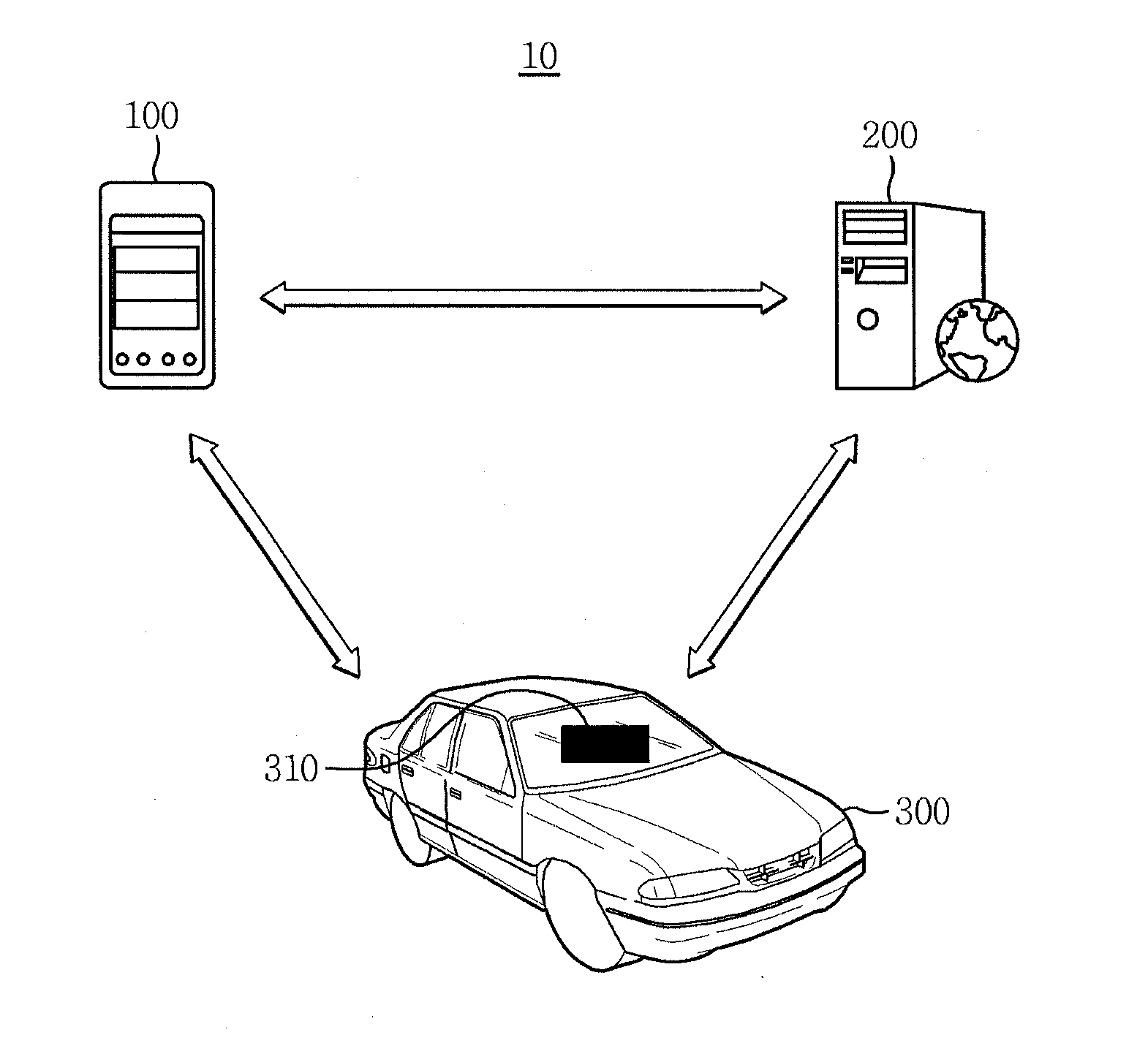
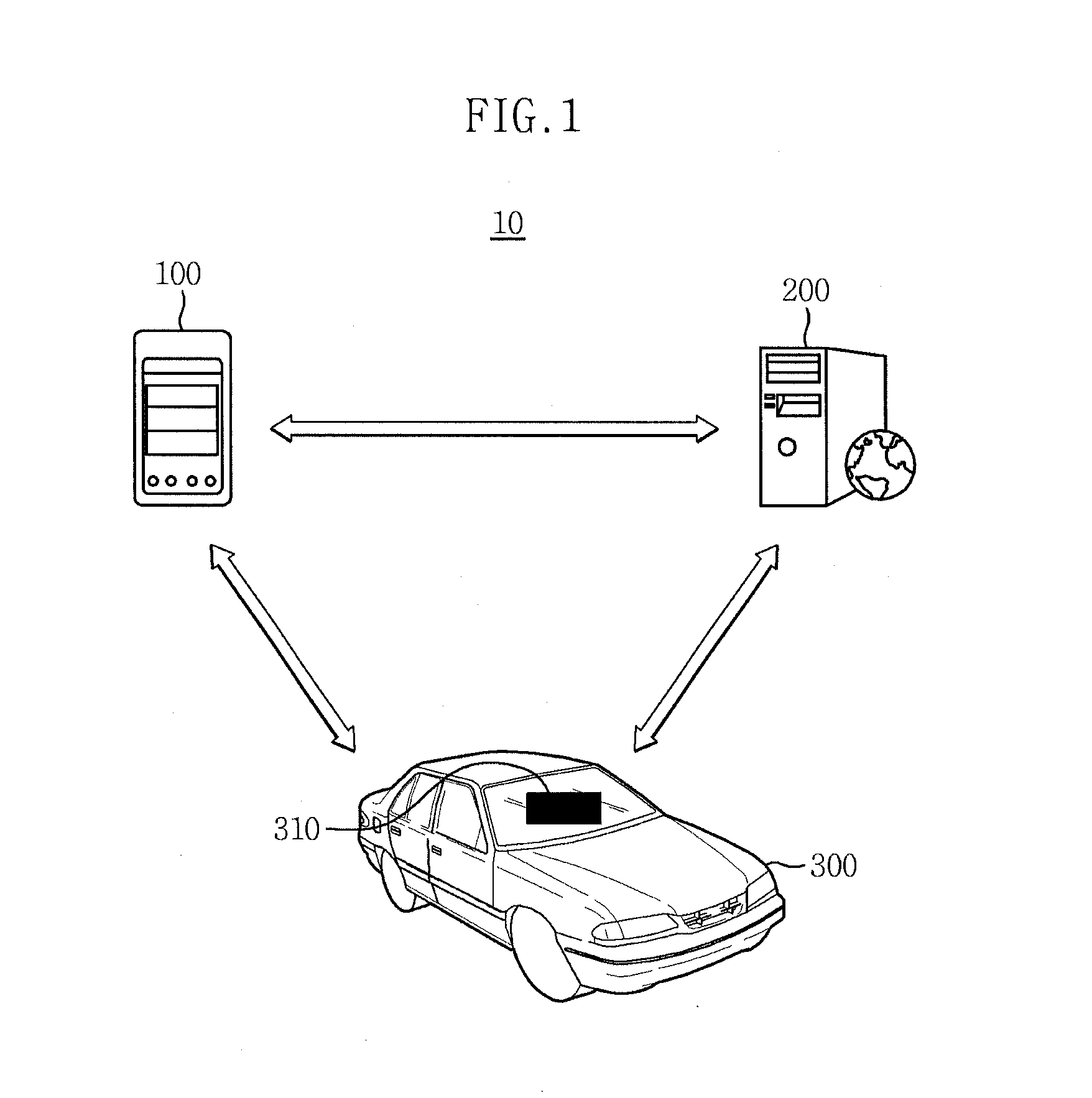
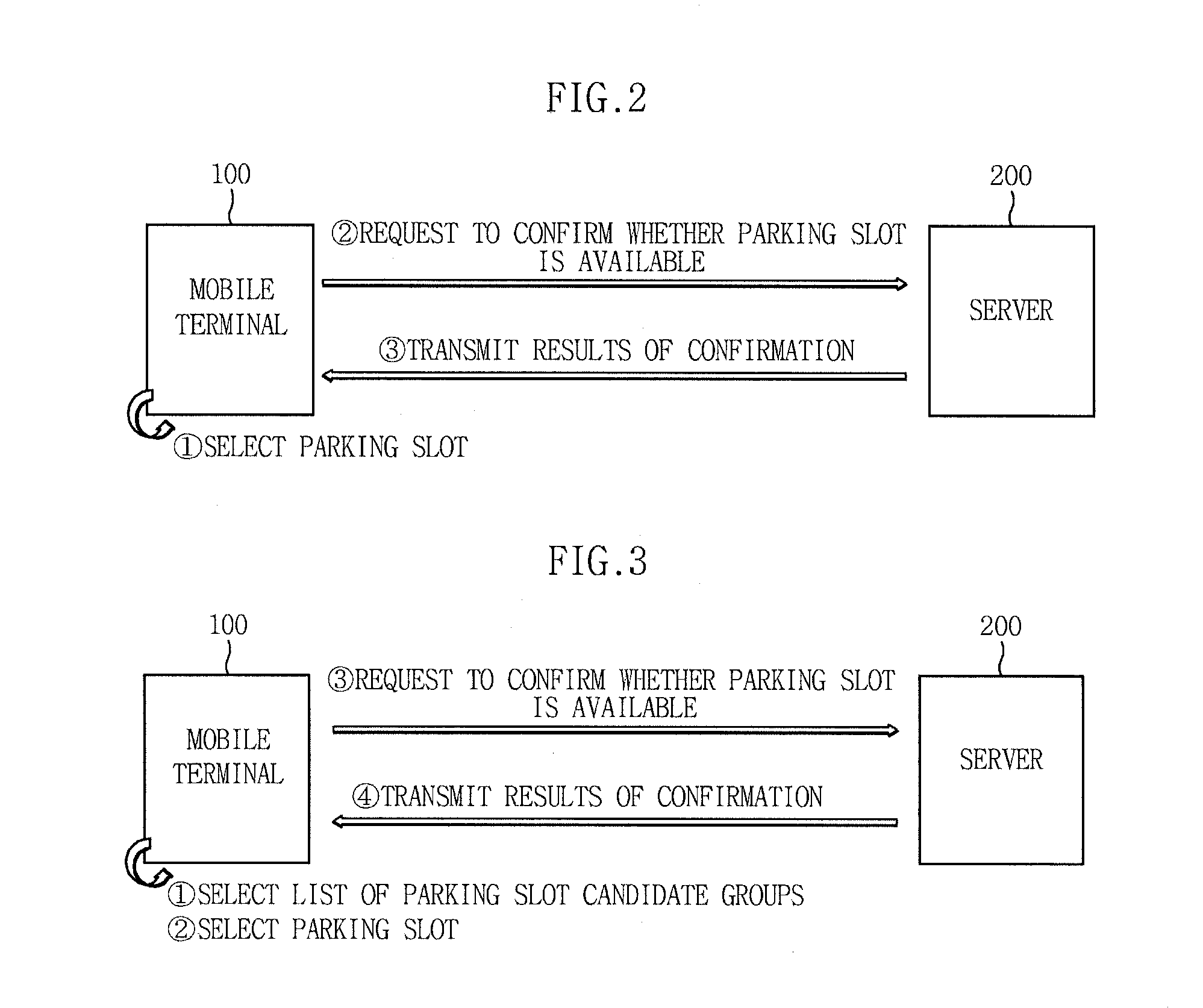
Terminal, apparatus and method for providing customized auto-valet parking service
InactiveUS20120188100A1Conveniently providedIndication of parksing free spacesSteering partsParking areaManagement unit
The present invention provides a terminal, apparatus and method for providing a customized auto-valet parking service. The server device includes a service registration management unit for receiving auto-valet parking profile information that includes information about one or more of a user, a vehicle, and a mobile terminal, and a parking map management unit for generating customized parking slots suitable for the user using the auto-valet parking profile information, and providing a parking area map, which includes information about the customized parking slots, to the mobile terminal. The parking map management unit receives information about a final slot selected by the user from among the customized parking slots via the mobile terminal, and provides a route to the final slot.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system for binding enhanced software features to a persona
InactiveUS6891953B1Preventing unchecked proliferationKey distribution for secure communicationDigital data processing detailsBiological activationUniform resource locator
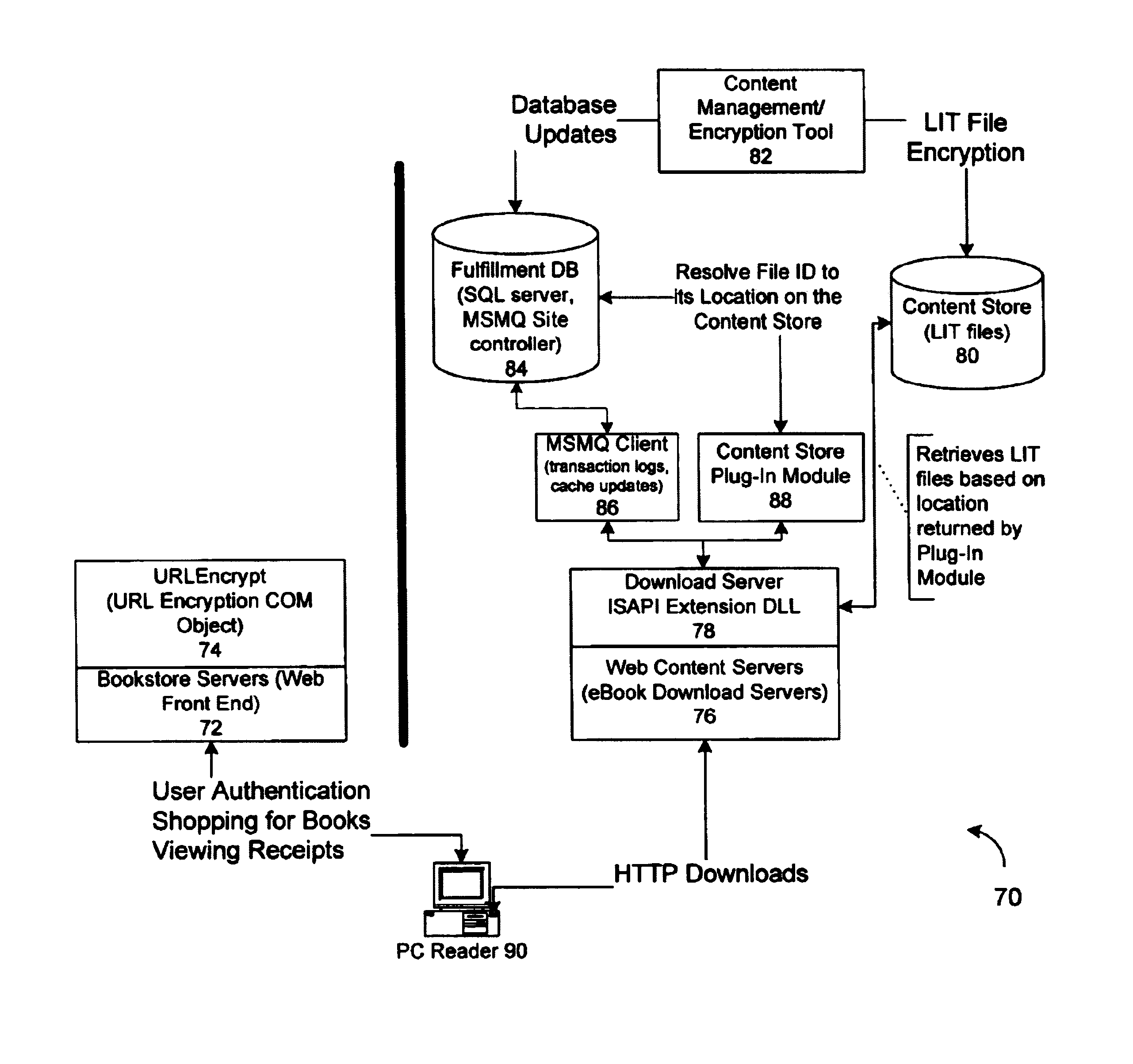
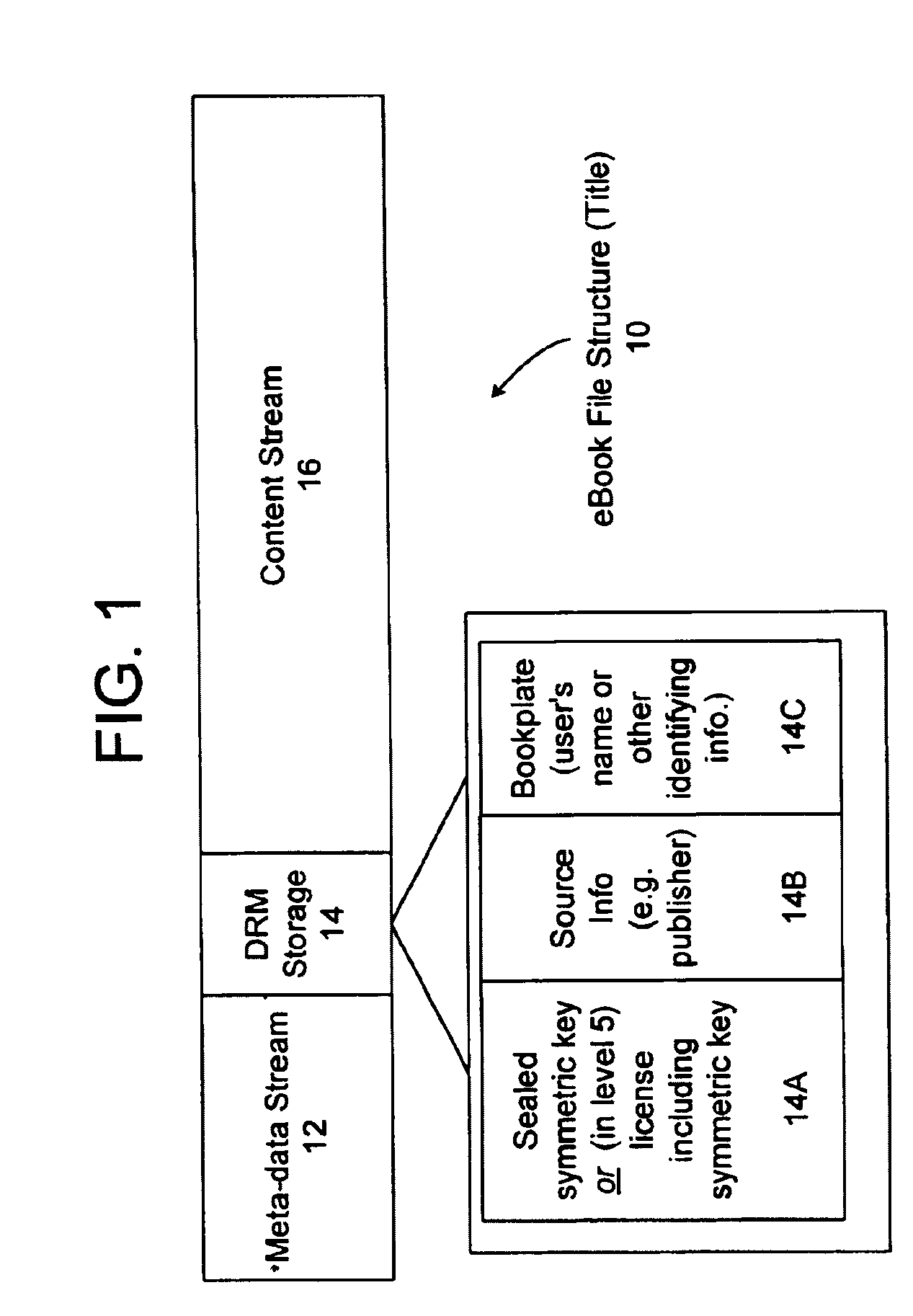
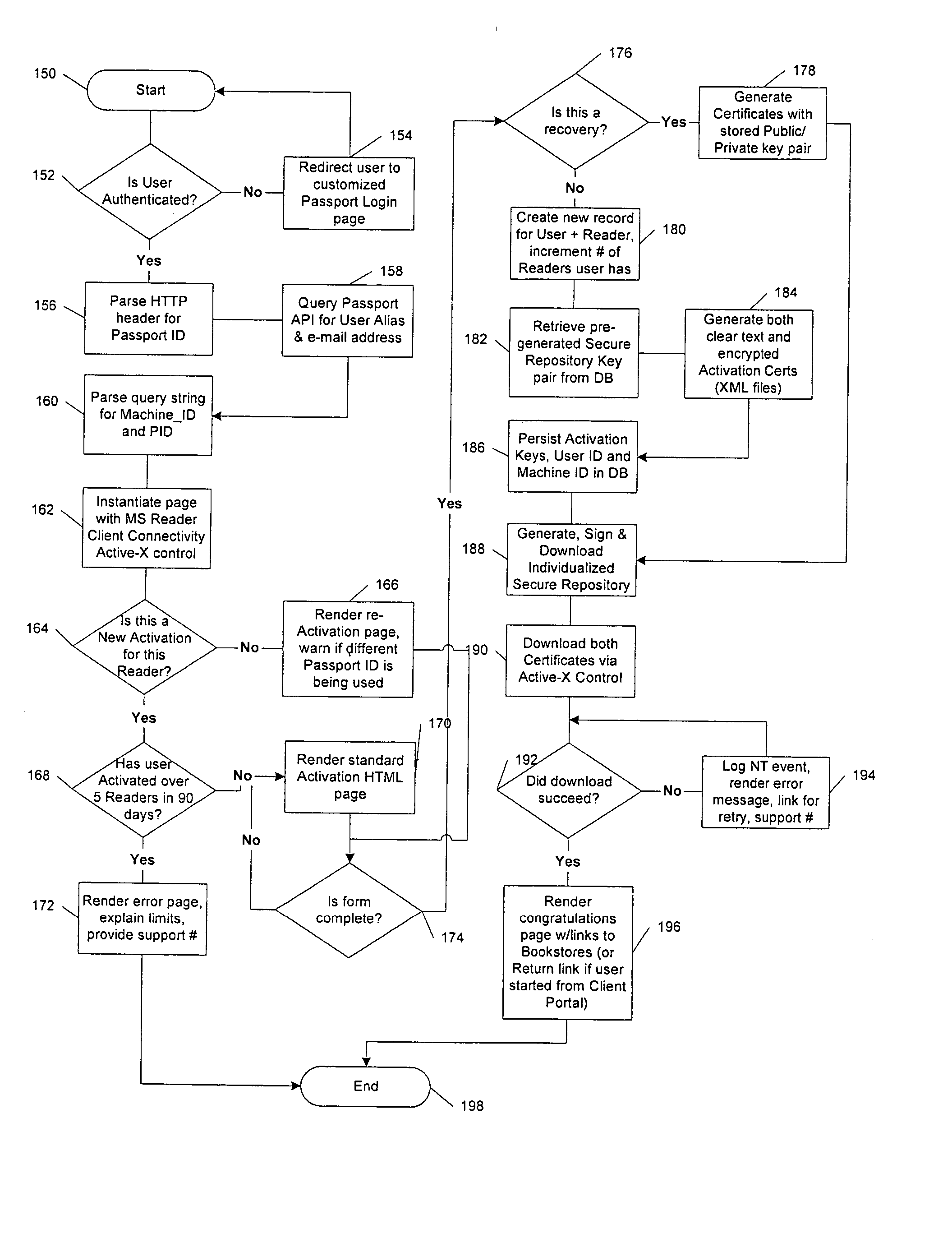
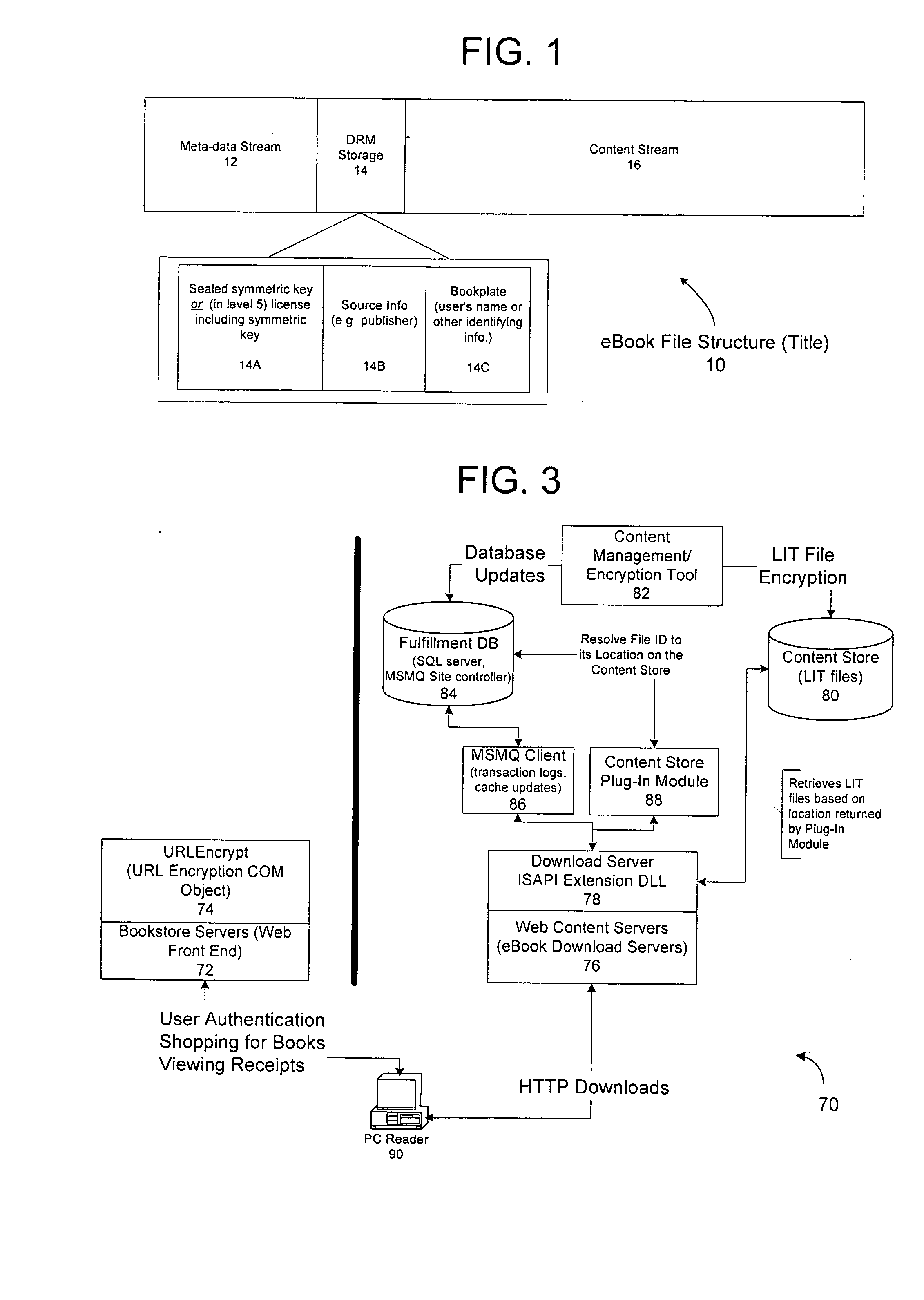
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Distributed cache for state transfer operations
ActiveUS20020138551A1Computer security arrangementsMultiple digital computer combinationsDistributed cacheClient-side
A network arrangement that employs a cache having copies distributed among a plurality of different locations. The cache stores state information for a session with any of the server devices so that it is accessible to at least one other server device. Using this arrangement, when a client device switches from a connection with a first server device to a connection with a second server device, the second server device can retrieve state information from the cache corresponding to the session between the client device and the first server device. The second server device can then use the retrieved state information to accept a session with the client device.
Owner:DELL PROD LP
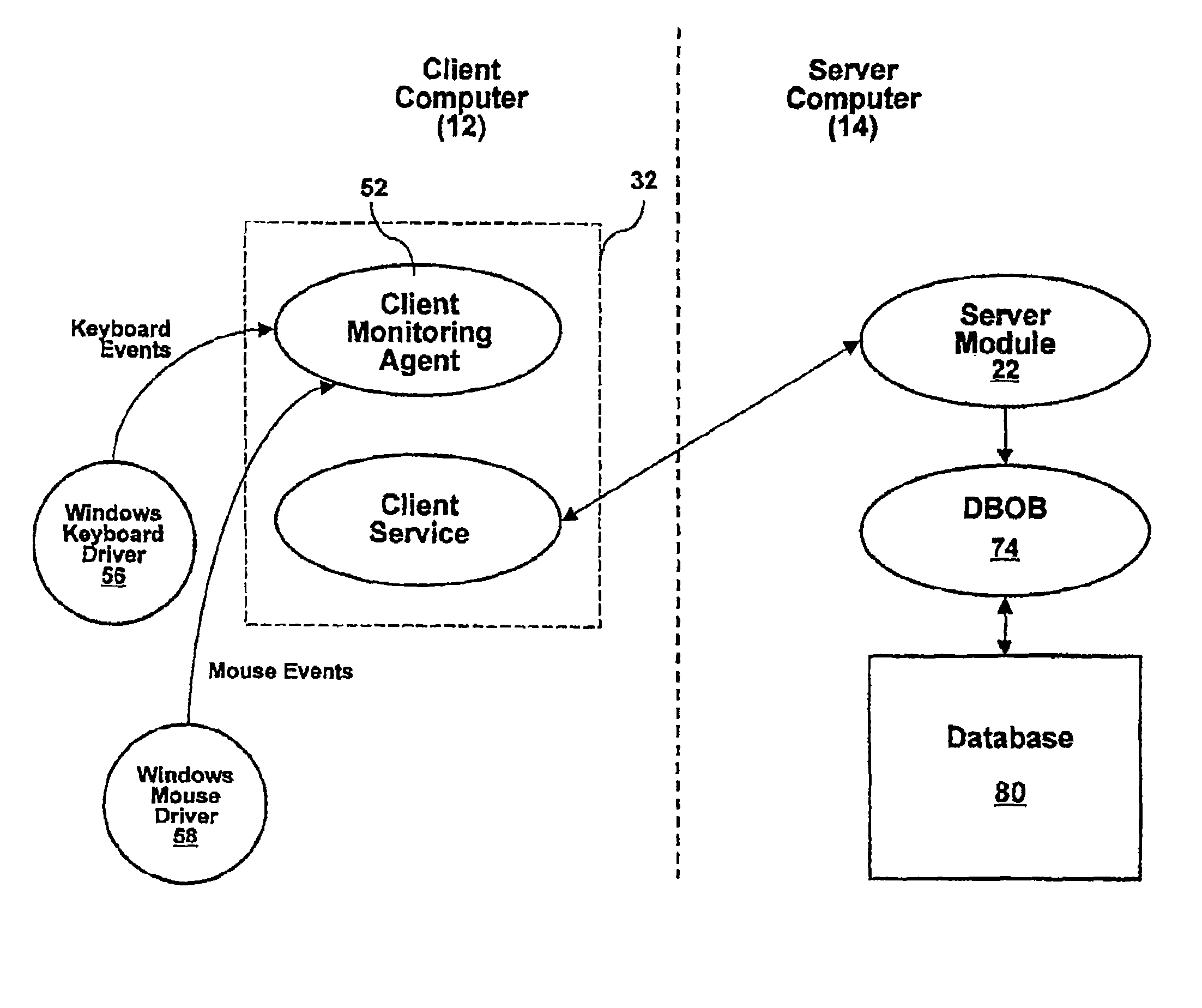
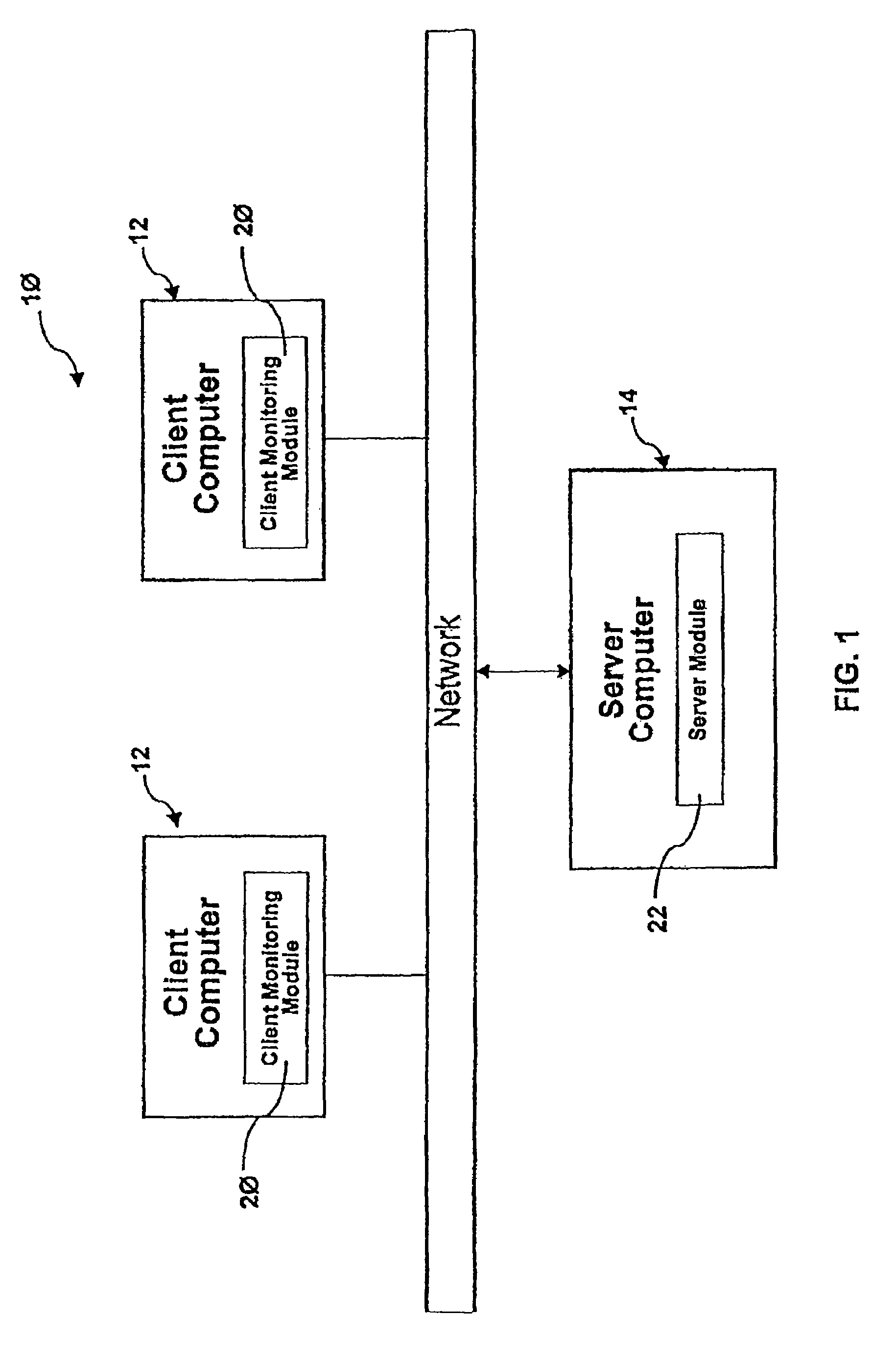
System and method for monitoring user interaction with web pages
InactiveUS20090271514A1Error detection/correctionMultiple digital computer combinationsInternet privacyClient-side
Systems and methods for monitoring usage of an electronic device are disclosed herein. A client component in stalled in a client device is operative to monitor usage of the client device in accordance with a monitoring profile, and to generate corresponding usage data. The monitoring profile typically includes information specifying which features of which application programs are to be disabled on the client device. A server component, installed on a server device in communication with the client device, provides the monitoring profile to the client device and receives the usage data from the client device.
Owner:R2 SOLUTIONS
Method and apparatus for making secure electronic payments
InactiveUS7734527B2Addressing slow performanceNo network overheadFinanceVisual presentationPaymentThe Internet
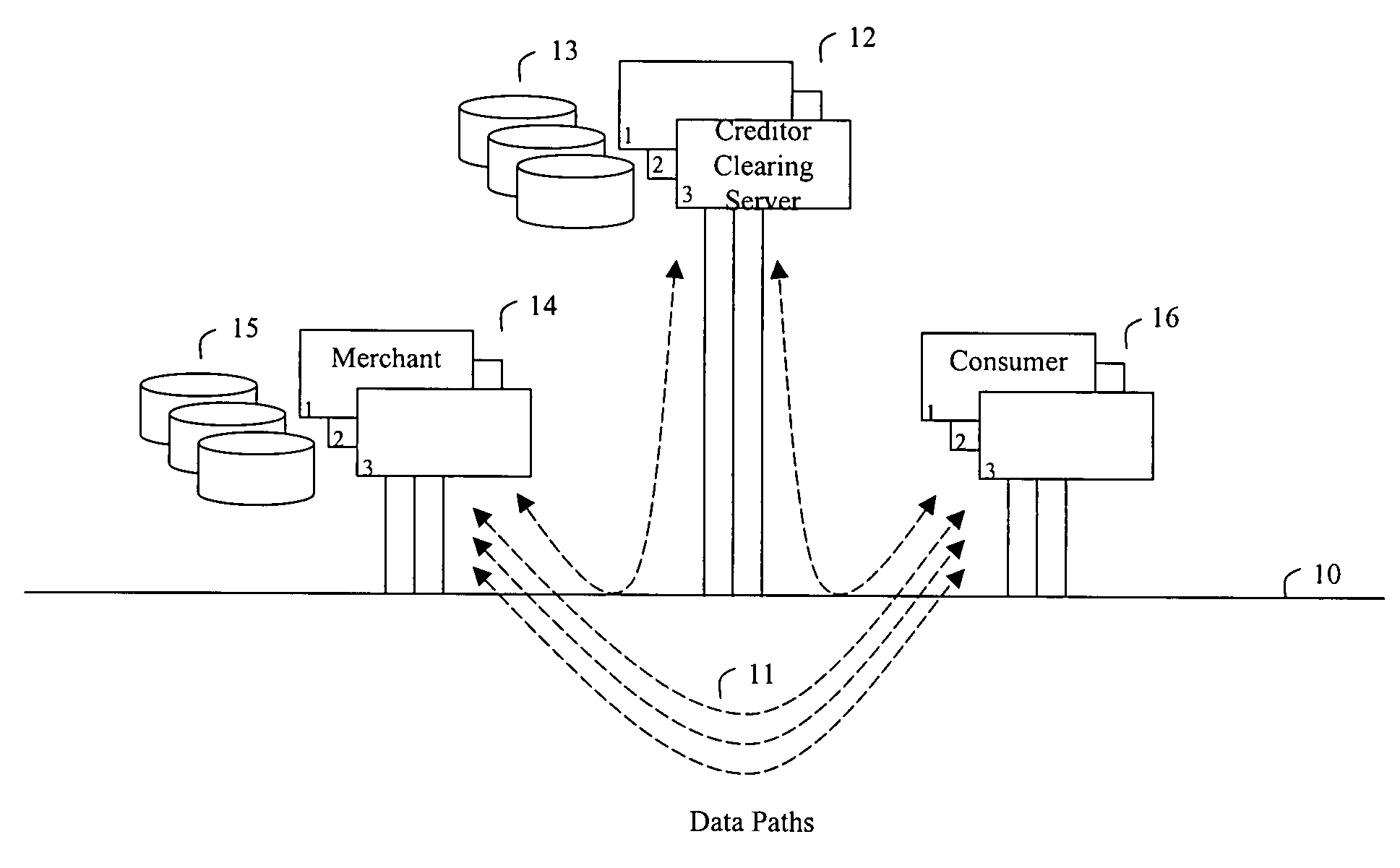
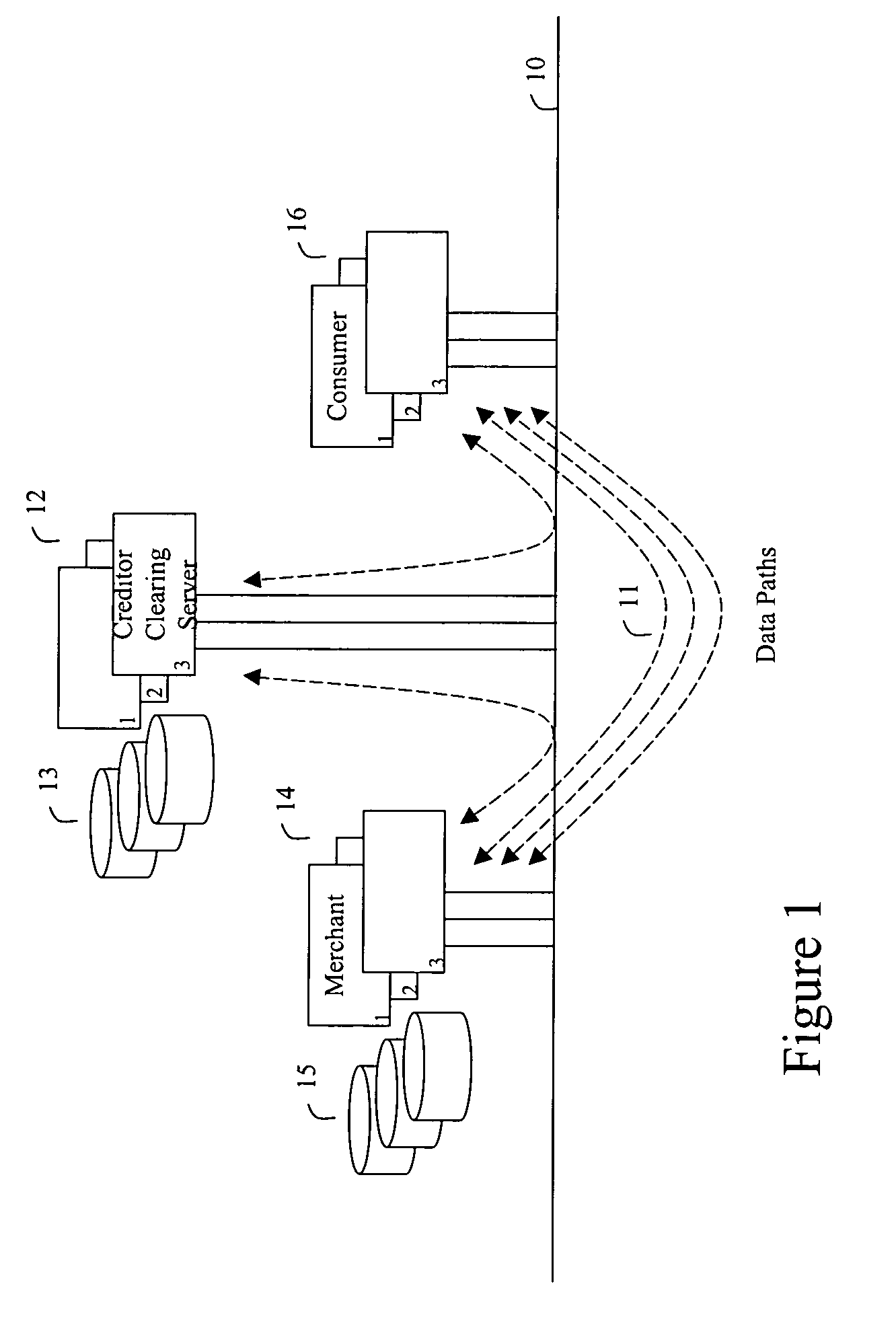
In accordance with the present invention, a consumer communicates a request for purchase of goods and services to a merchant, the goods and / or services being selected from these listed together with their price quotes on the merchant's computer or website connected to a network, such as the Internet. The merchant then communicates a request for a token and an update key to the clearing server, the token being previously purchased by the consumer and residing on a clearing server device. The update key is used as an authorization to modify the value of the token, i.e., to decrement and to increment. The merchant forwards the purchased merchandise to the consumer. When consumer discontinues making purchases at the selected merchant, the merchant returns the updated token to the clearing server. A new key is necessary to make the next purchase. This is the case even where the requesting merchant is the same as that from whom the last purchase was made. When the token is requested, if the token was used after its initial purchase, the present value of the token is made certain by receipt on the clearing server of informational downloads from the merchants.
Owner:UZO CHIJIOKE CHUKWUEMEKA
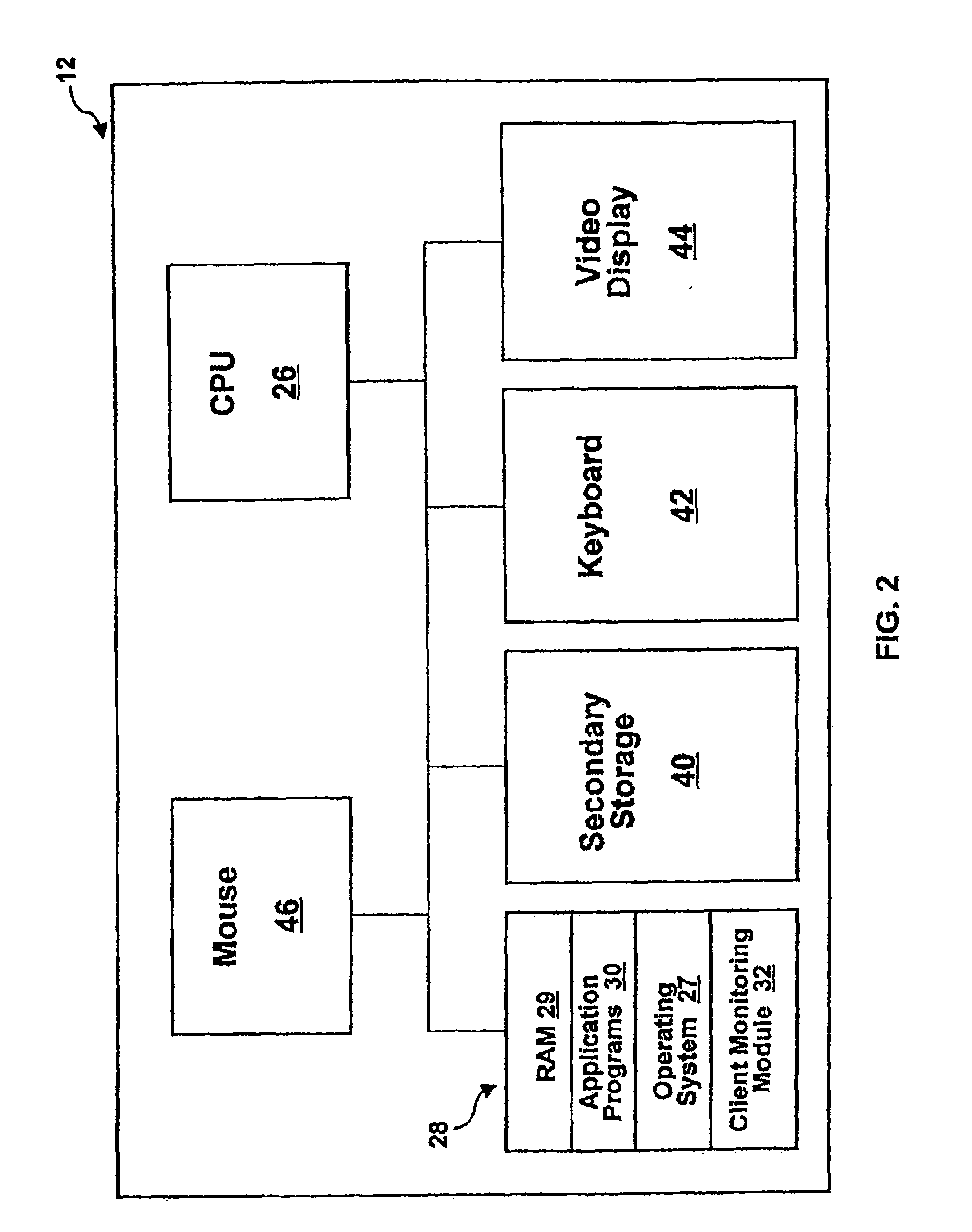
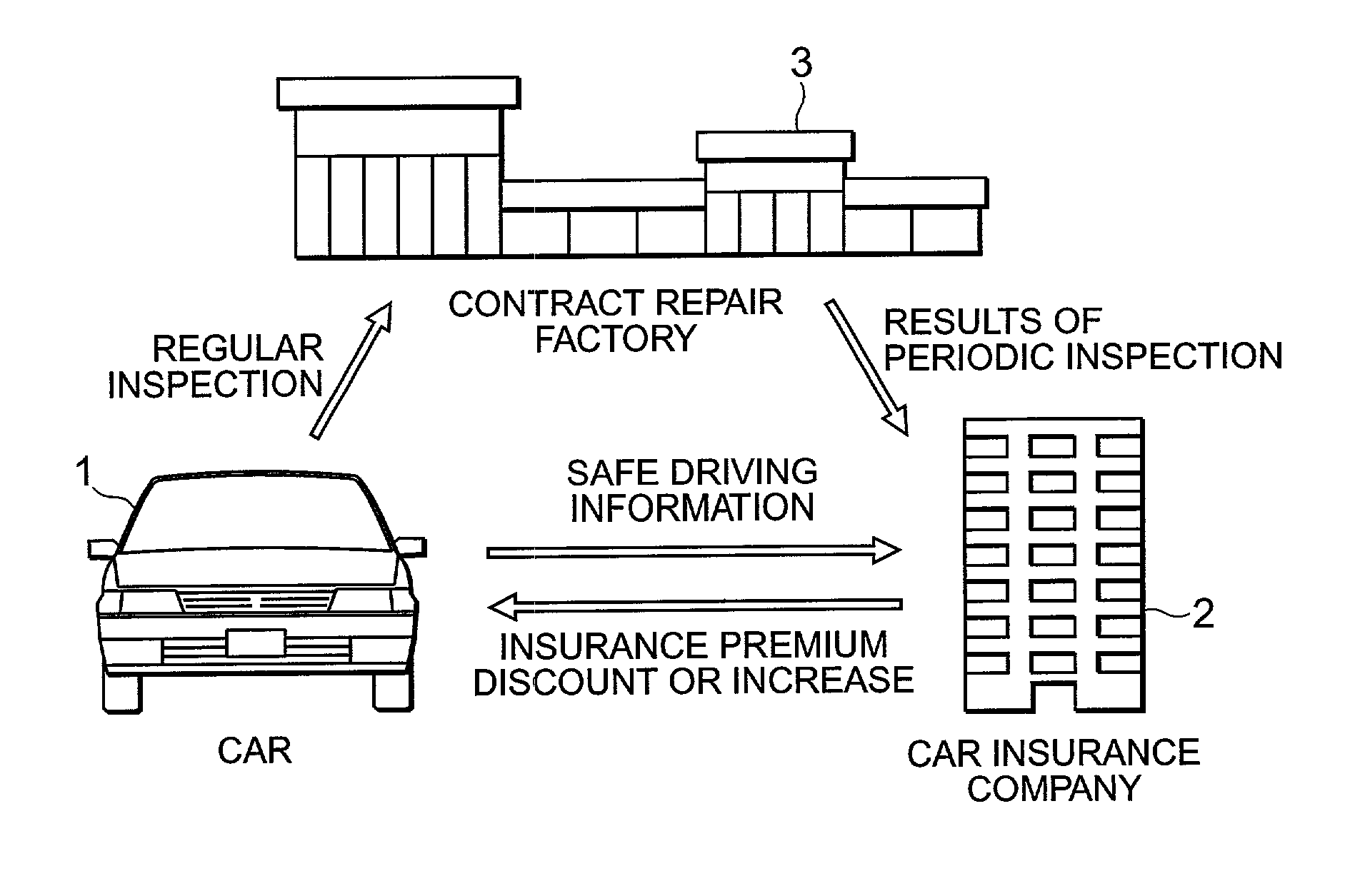
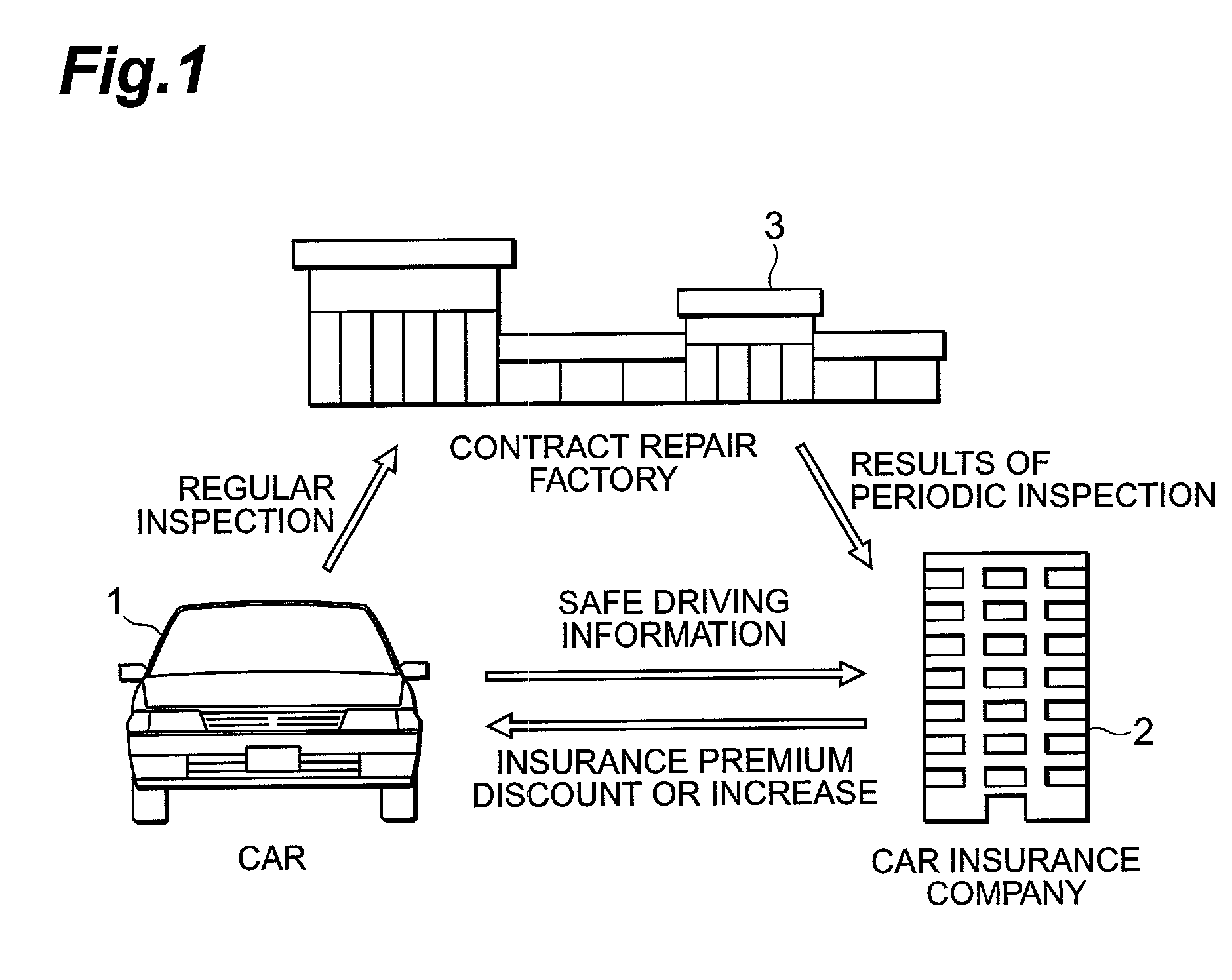
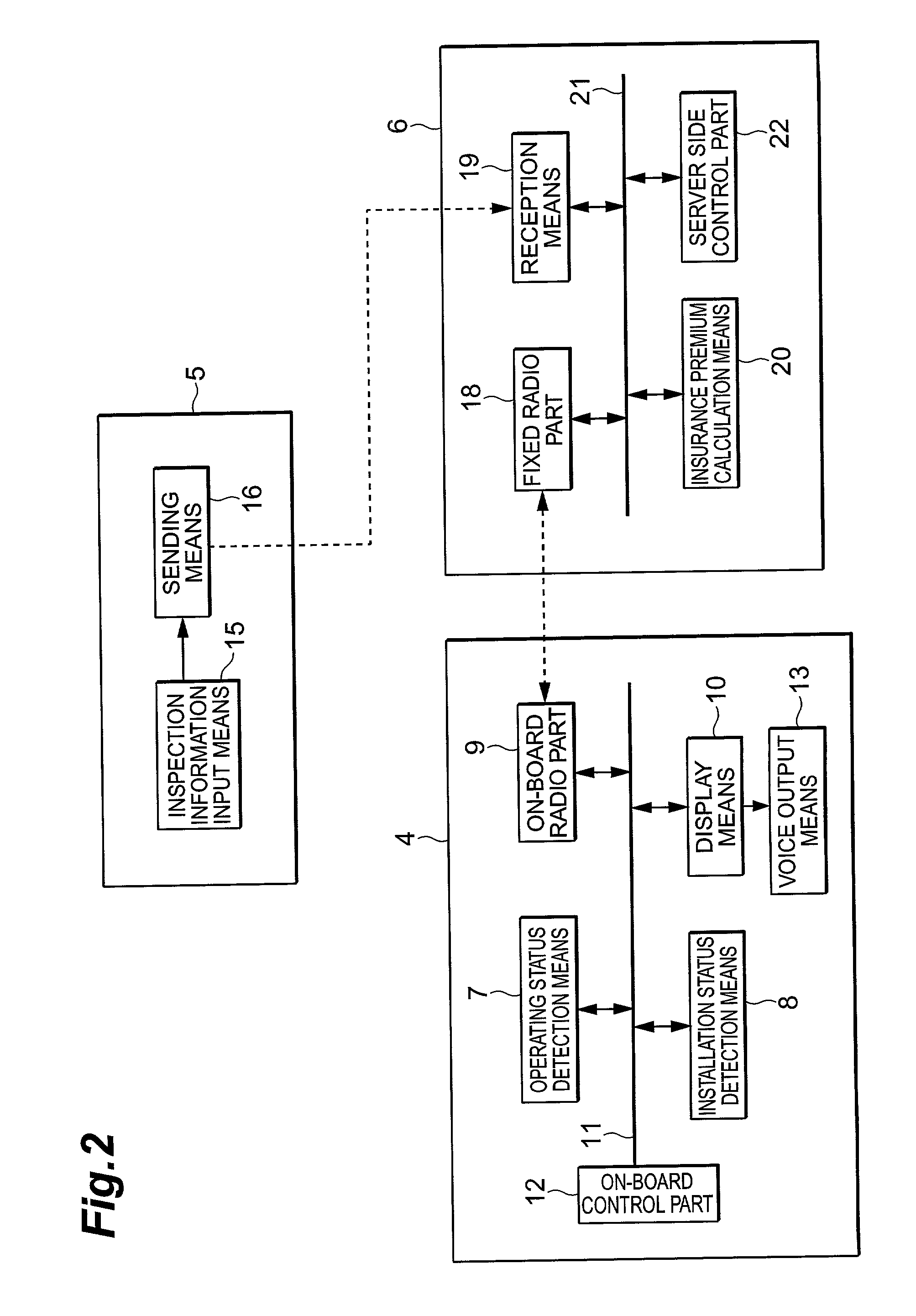
Vehicle insurance premium calculation system, on-board apparatus, and server apparatus
This system comprises a usage status detection means for detecting the usage status of a vehicle, data input means for inputting data relating to the maintenance or management of a vehicle, and insurance premium calculation means for calculating vehicle insurance premiums based on detection results and inputted data.
Owner:TOYOTA JIDOSHA KK +1
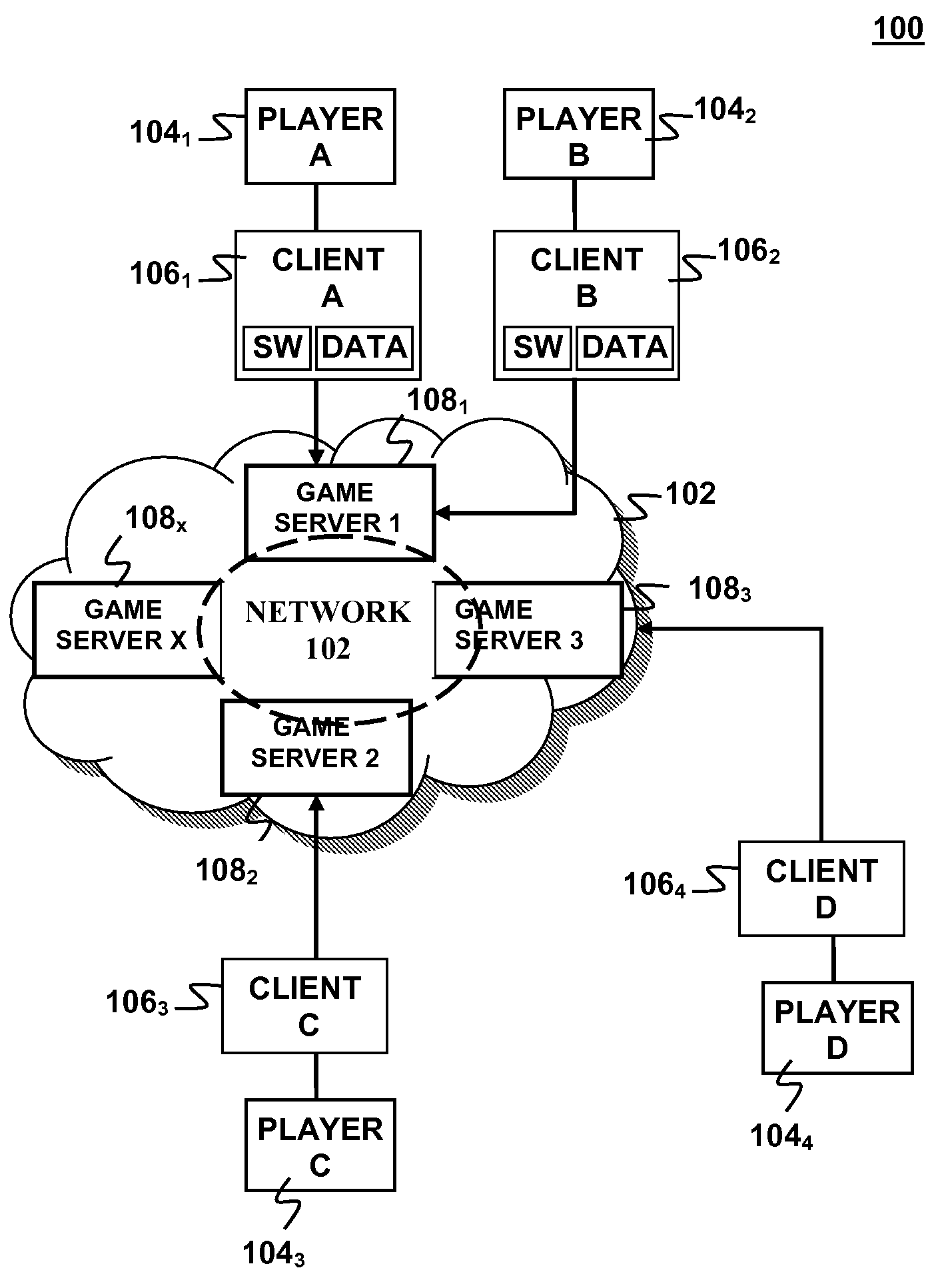
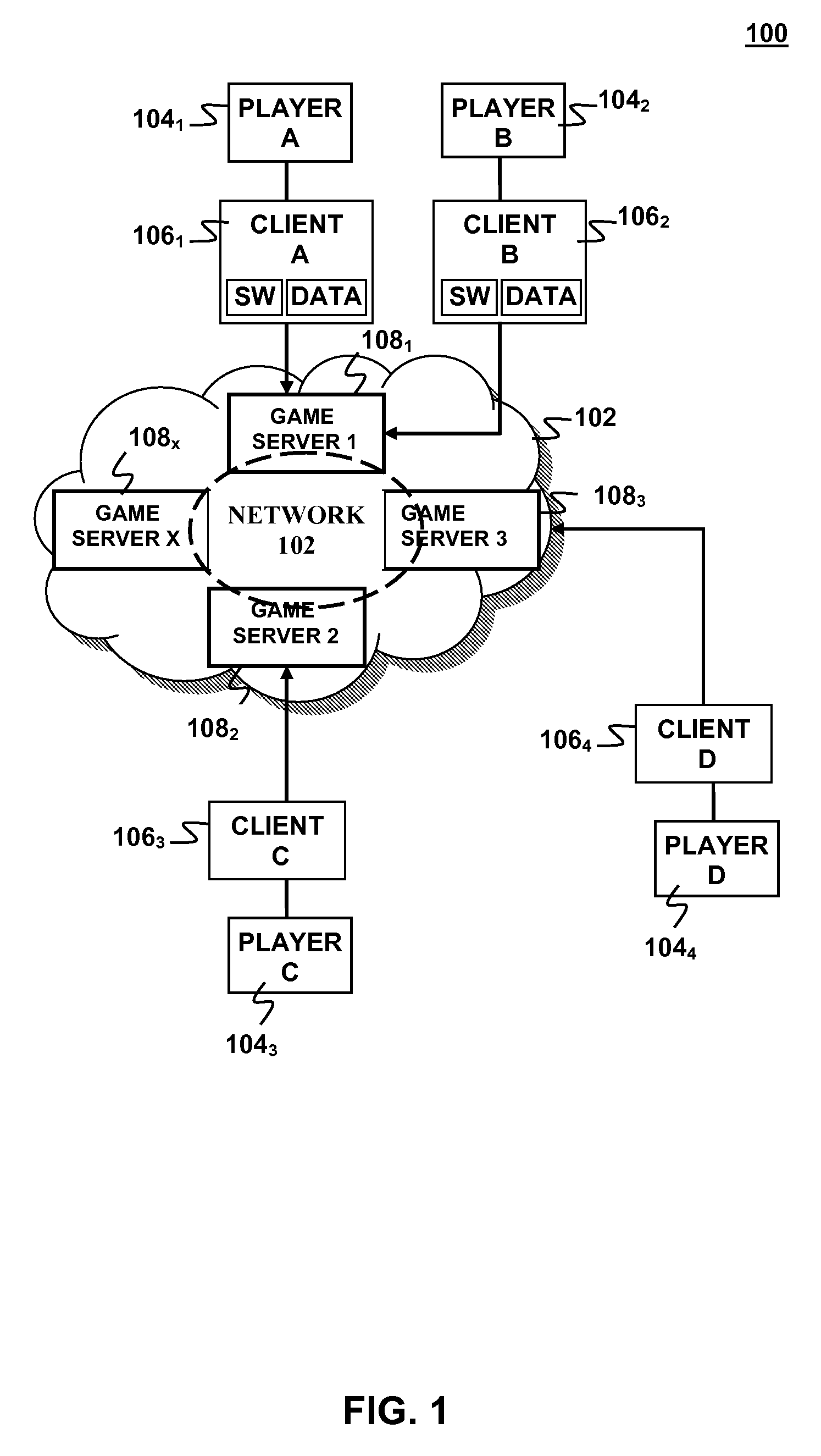
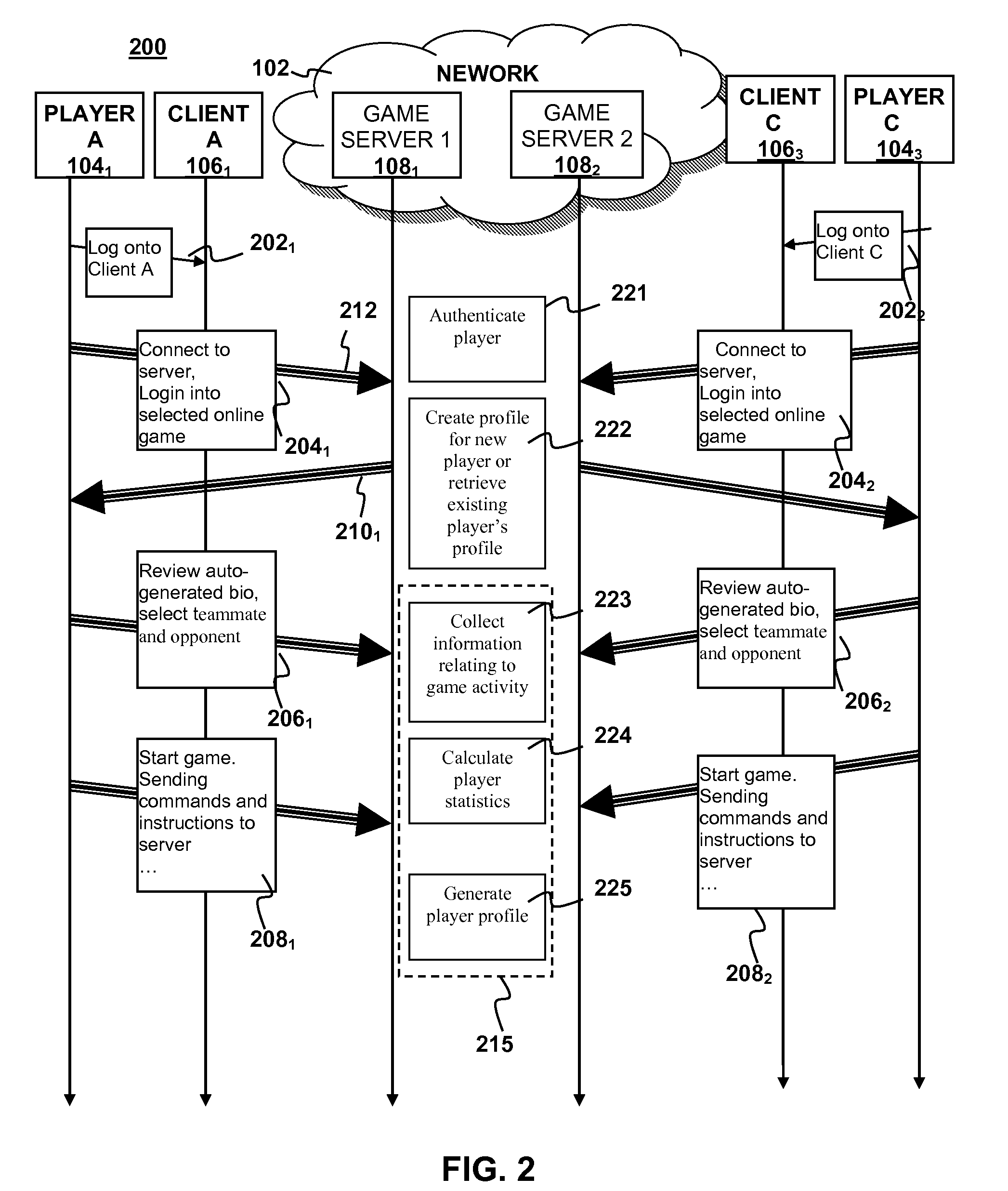
Automatic player information generation for interactive entertainment
Automatic player profile generation may be implemented for an interactive online game in which one or more players interact via one or more client devices connected to a server device via a network. Information relating to game activity may be collected for the one or more players during one or more game sessions with the server device. One or more player statistics relevant to the game activity may be calculated for each of the one or more players during the game session based on the information relating to game activity with the server device. A player profile may be generated for each of the one or more players with the server. Each player profile may include the one or more player statistics for a corresponding one of the one or more players.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
Server for an electronic distribution system and method of operating same
ActiveUS7047411B1Preventing unchecked proliferationKey distribution for secure communicationUser identity/authority verificationStore and forwardDigital rights management system
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content items, the retail site transmits to the purchase a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon the following the link, the fulfillment site downloads the ordered content to the consumer preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enable those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for making secure electronic payments
In accordance with the present invention, consumers and merchants use computing devices connected to a network, such as the Internet, through wired and wireless means, wherein the consumer connects to a clearing server device to purchase or retrieve previously purchased token, the consumer then connects to the merchant's computer or website to attain price quotes of goods and services, selects the goods and / or services to be purchased, and then communicates a request for purchase to the merchant. The merchant then communicates a request for an update key to the clearing server. The update key is used as an authorization to modify the value of the token. To debit the customer the decrement key is requested and to credit the customer an increment key is asked for. An overwrite key is another type of update key. Together with the overwrite key a replacement token is provided to the merchant who in turn forwards the new token to the customer. As an aspect of the invention, if the token was not previously used, the clearing server simply issues the update key. If, however, it is determined that the token was used, the amount paid by the consumer to a previous merchant is determined the token adjusted and the overwrite key together with the new token is returned to the merchant. The merchant then forwards the purchased merchandise, the update key, and possibly a new token to the consumer.
Owner:AMPACASH CORP
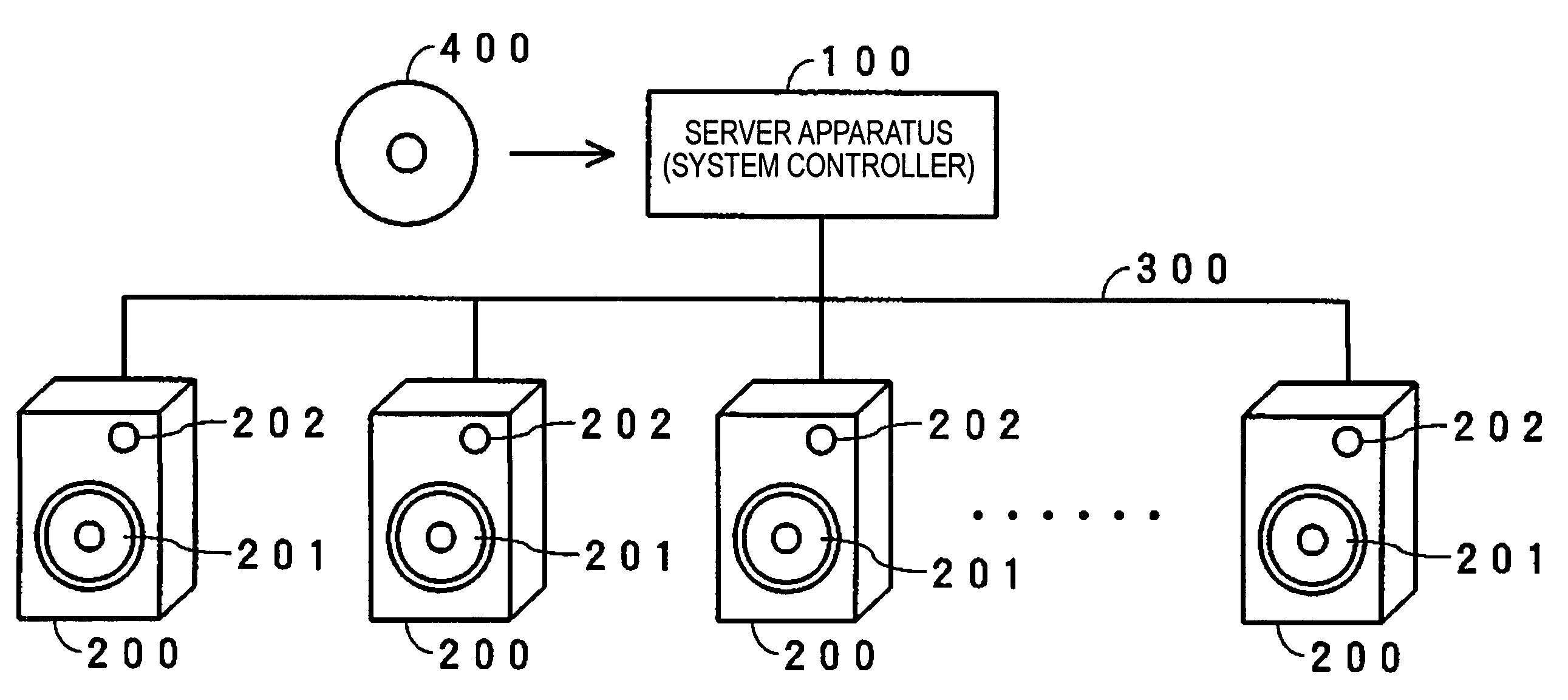
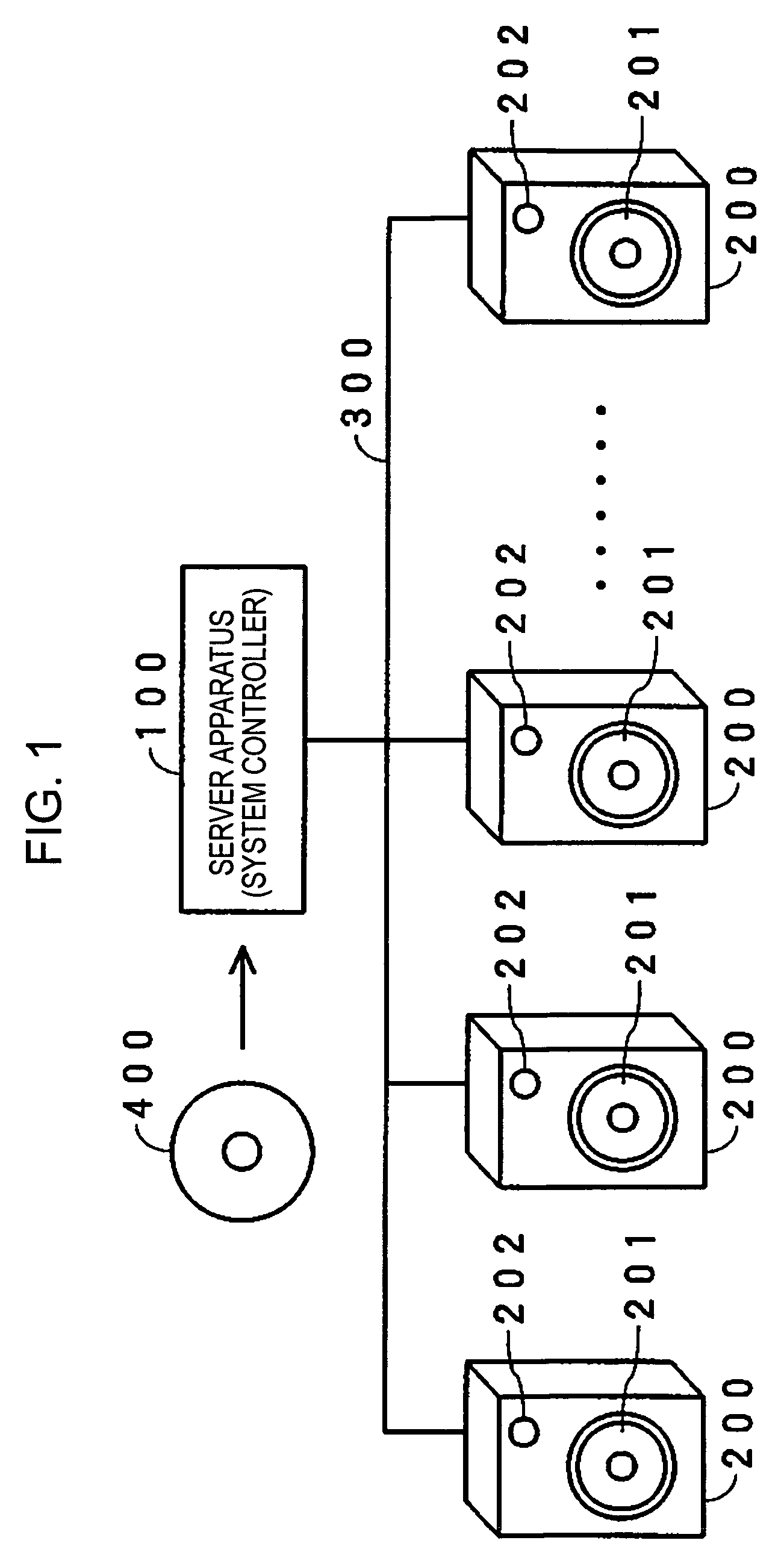
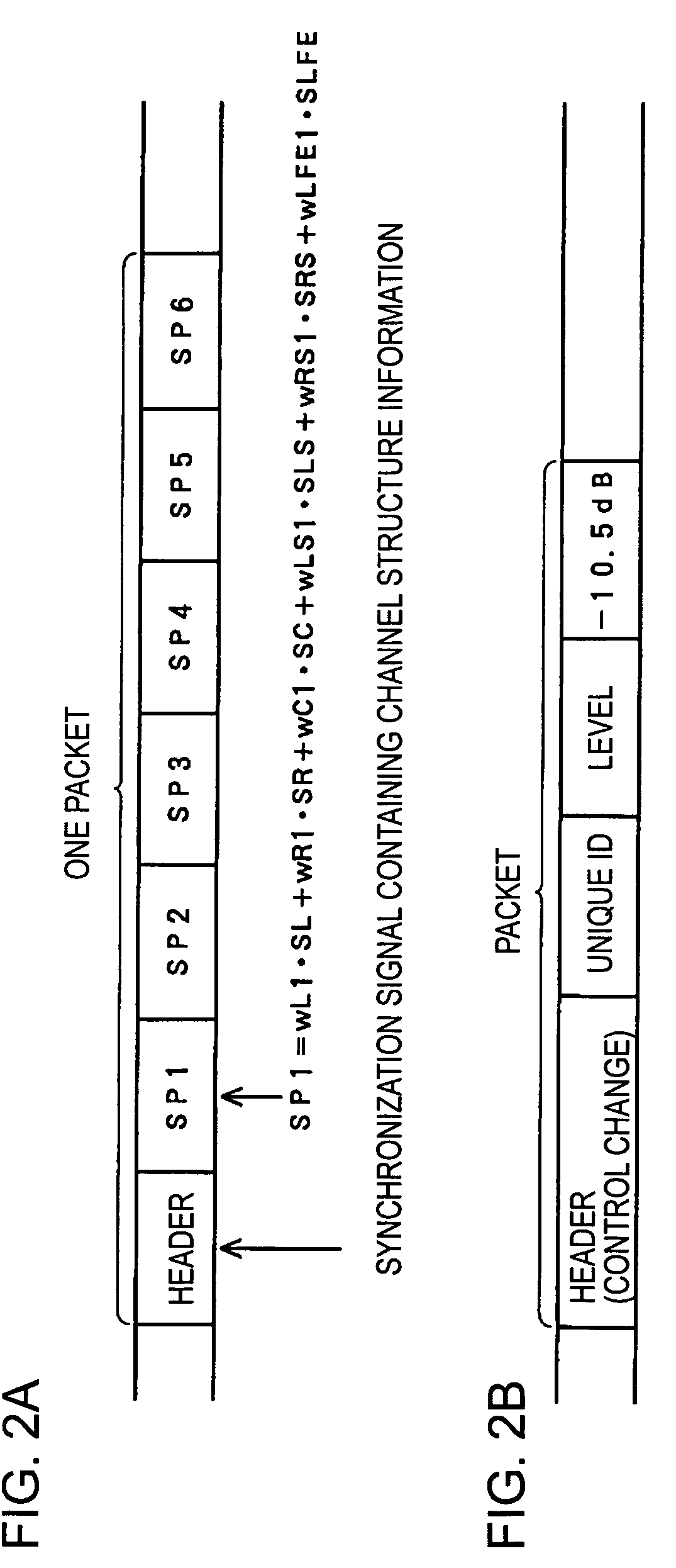
Multi-speaker audio system and automatic control method
InactiveUS7676044B2Loudspeaker enclosure positioningPseudo-stereo systemsAutomatic controlLoudspeaker
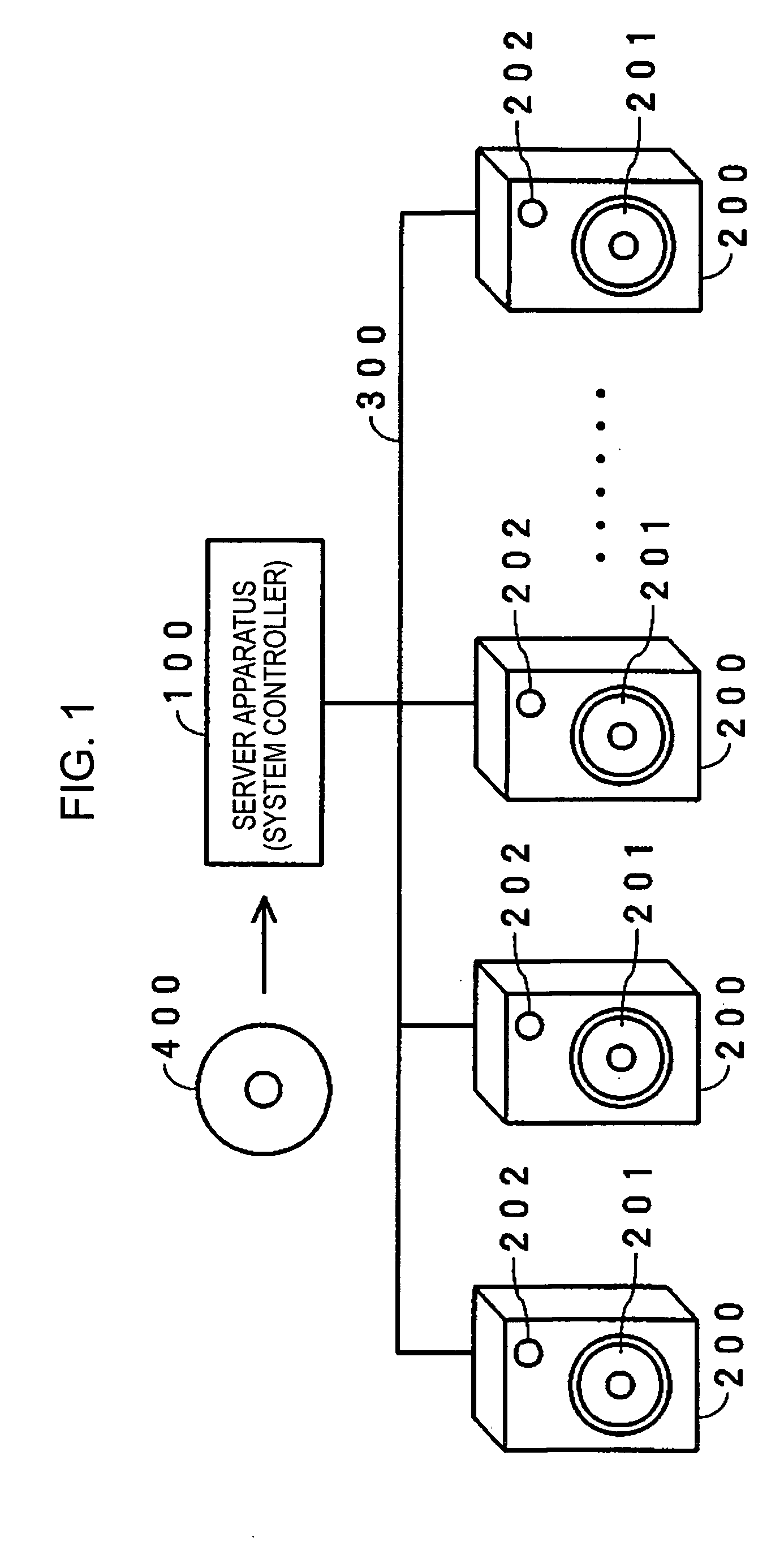
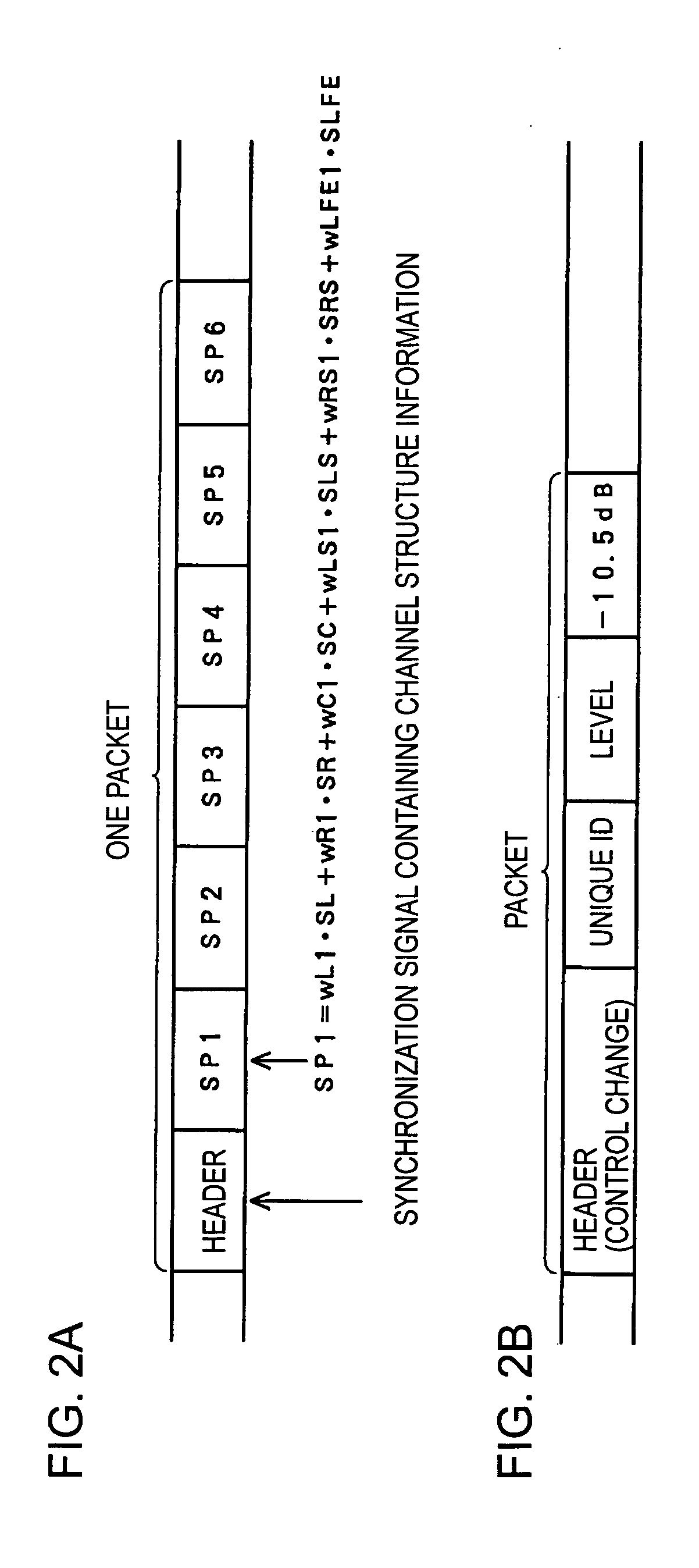
A sound produced at the location of a listener is captured by a microphone in each of a plurality of speaker devices. A sever apparatus receives an audio signal of the captured sound from all speaker devices, and calculates a distance difference between the distance of the location of the listener to the speaker device closest to the listener and the distance of the listener to each of the plurality of speaker devices. When one of the speaker devices emits a sound, the server apparatus receives an audio signal of the sound captured by and transmitted from each of the other speaker devices. The server apparatus calculates a speaker-to-speaker distance between the speaker device that has emitted the sound and each of the other speaker devices. The server apparatus calculates a layout configuration of the plurality of speaker devices based on the distance difference and the speaker-to-speaker distance.
Owner:SONY CORP
Method and system for limiting the use of user-specific software features
InactiveUS20050060266A1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationSchema for Object-Oriented XMLUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Duration of alerts and scanning of large data stores
InactiveUS20070050777A1Multiprogramming arrangementsNon-redundant fault processingThermostatEmbodied agent
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
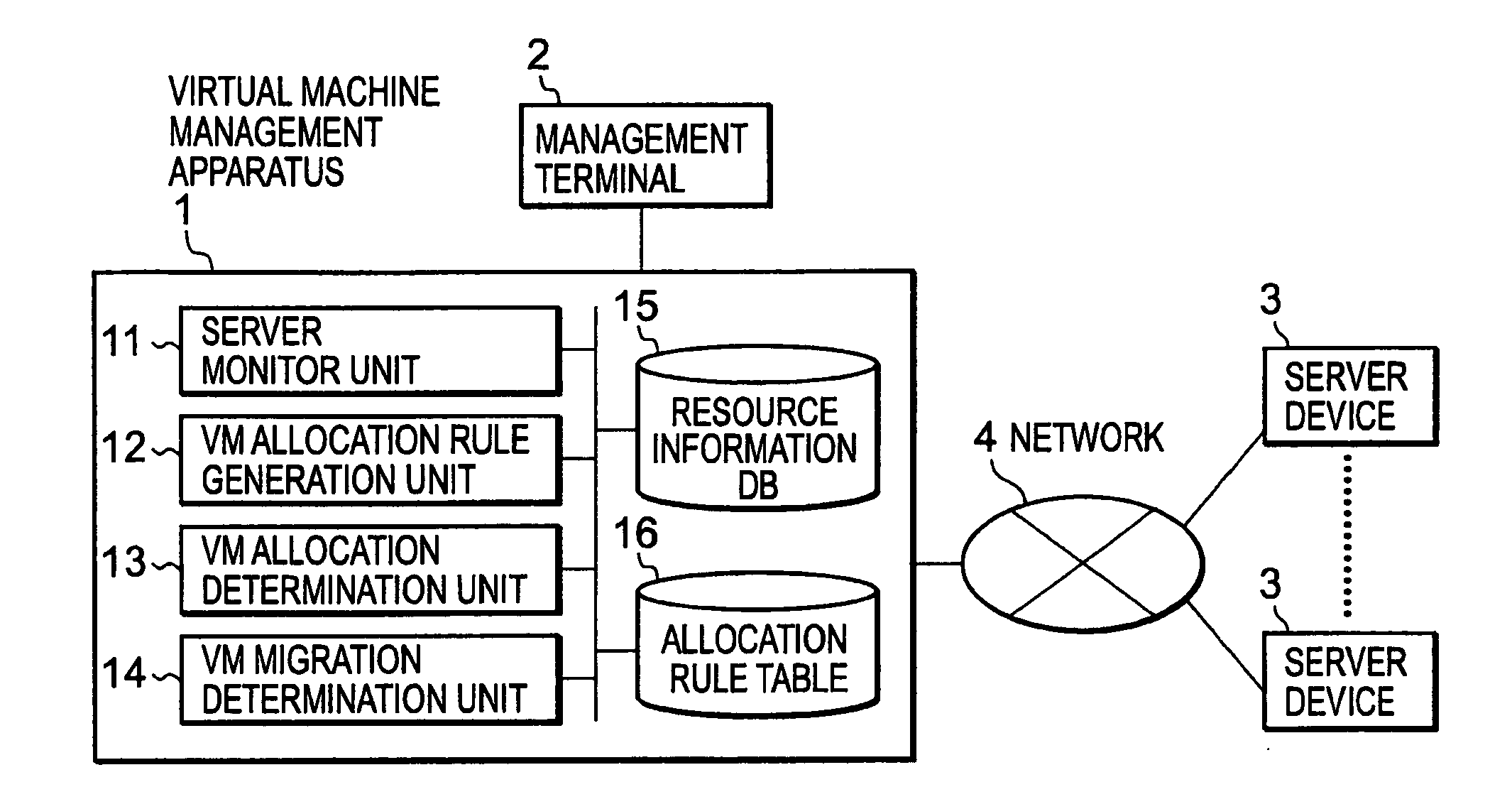
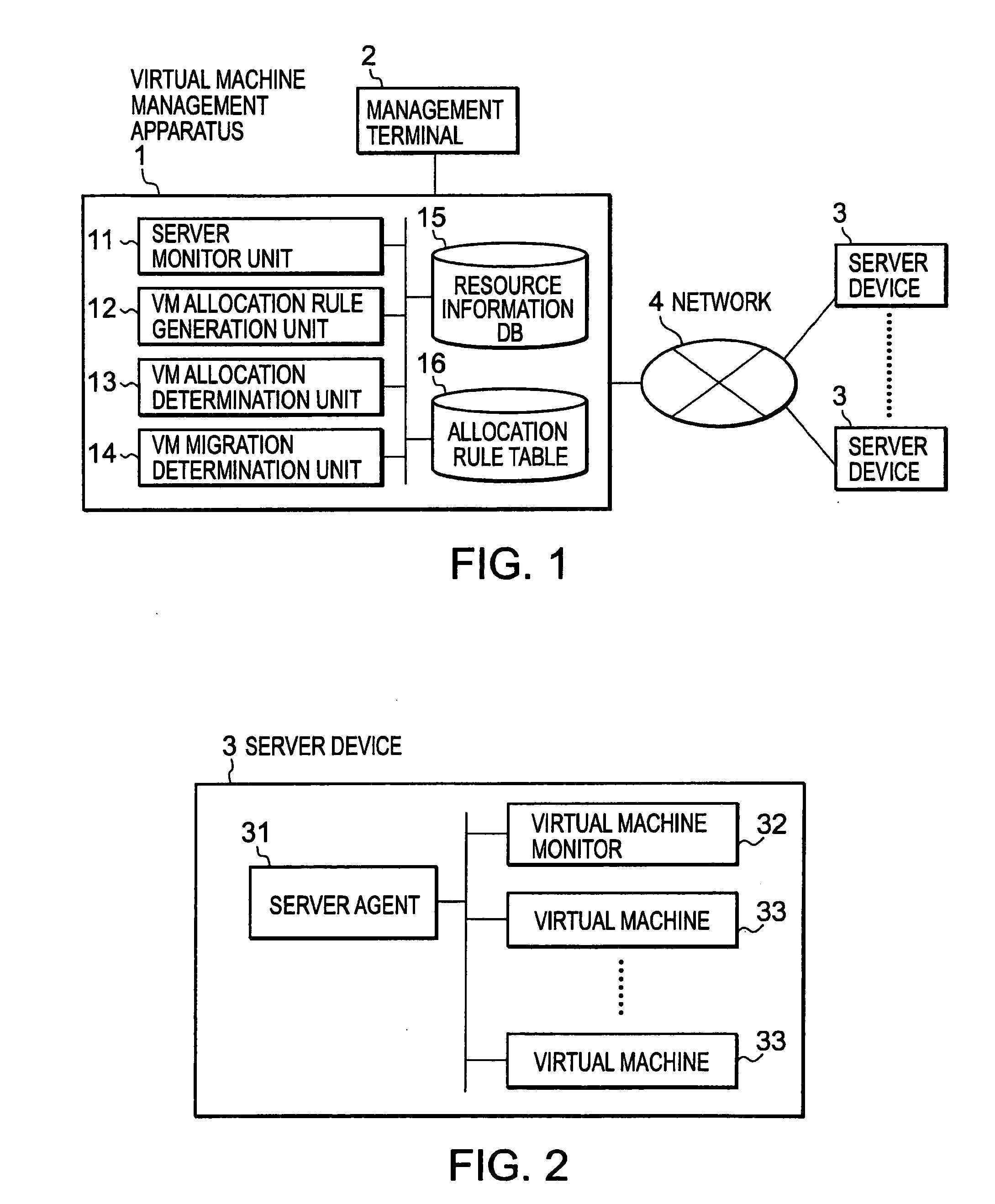
Virtual Machine Management Apparatus, and Virtual Machine Management Method and Program
ActiveUS20090210527A1Increase the likelihood of successReduce the impactDigital computer detailsSoftware simulation/interpretation/emulationNetwork connectionServer appliance
A virtual machine management apparatus connected to a plurality of server devices via a network generates a new virtual machine on a server device in accordance with a request from a management terminal. At that time, for one or more server devices to which a new virtual machine can be allocated, the virtual machine management apparatus refers to an allocation rule table for storing a score for each of combinations of types of virtual machines. The score indicates appropriateness of a condition that each combination of types of virtual machines is to be allocated to the same server device. Thus, the virtual machine management apparatus computes an index value indicative of appropriateness of a condition that the new virtual machine is to be allocated to the server device. Then the virtual machine management apparatus determines an allocation target for the new virtual machine with reference to the computed index value.
Owner:ZOOM VIDEO COMM INC
Glucose measuring device integrated into a holster for a personal area network device
A glucose meter module integrated into a holster device that can securely accommodate another device such as a portable server device or an insulin pump is described. The glucose measuring module and the health device communicate with each other by a short range wireless modality. In the case in which the accommodated device is a server, such as personal digital assistant or cell phone, the device stores data in a memory, displays data on a visual display, and can wirelessly transmit such data to other devices within a personal area network. In the case where the accommodated device is a cell phone, the phone can further transmit data to remote sites. In the case where the accommodated device is an insulin pump, wirelessly received data are stored in a memory, are available for visual display on the insulin pump, and can be incorporated into the electronic processes that regulate the performance of the pump.
Owner:THERASENSE
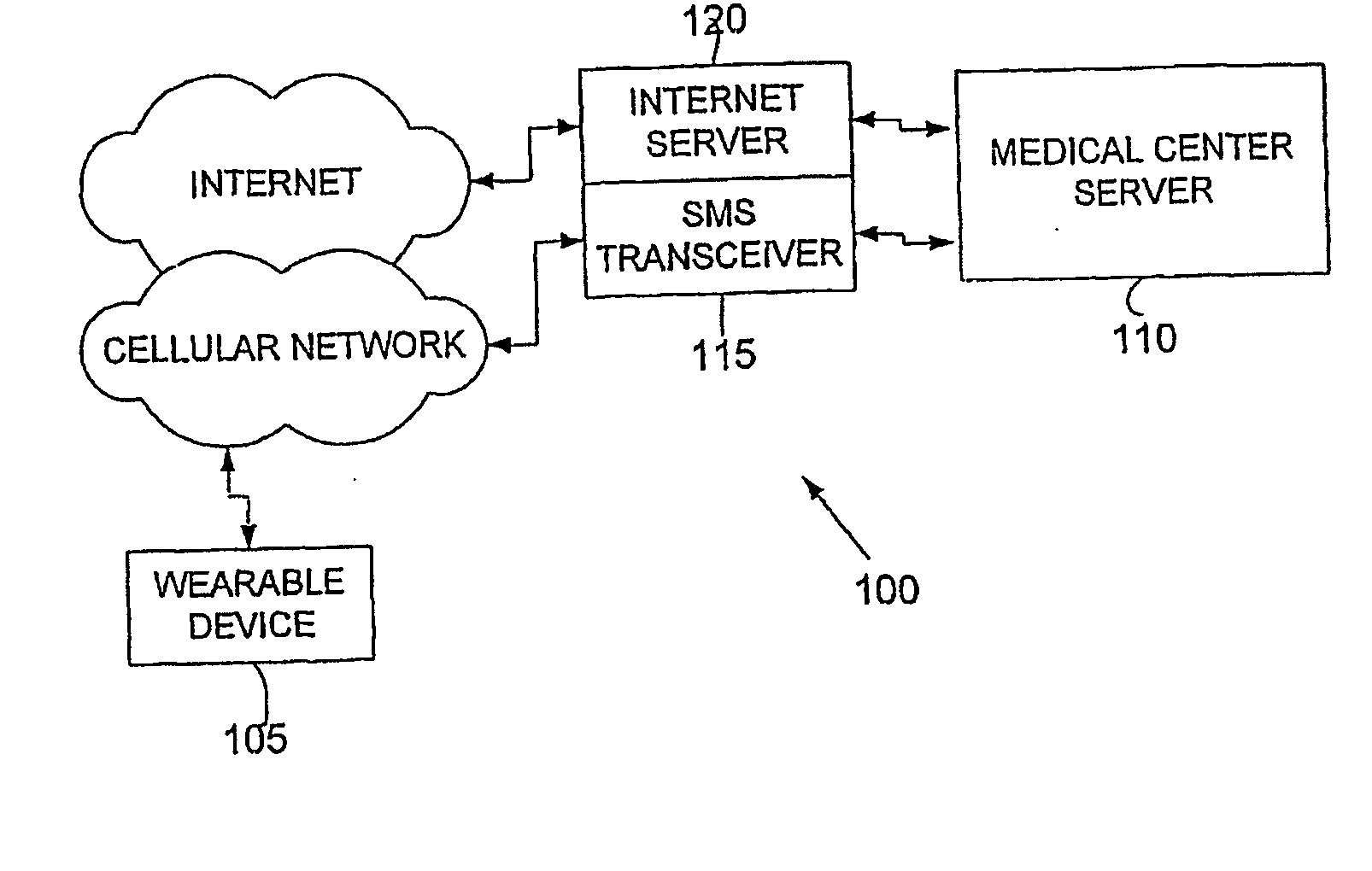
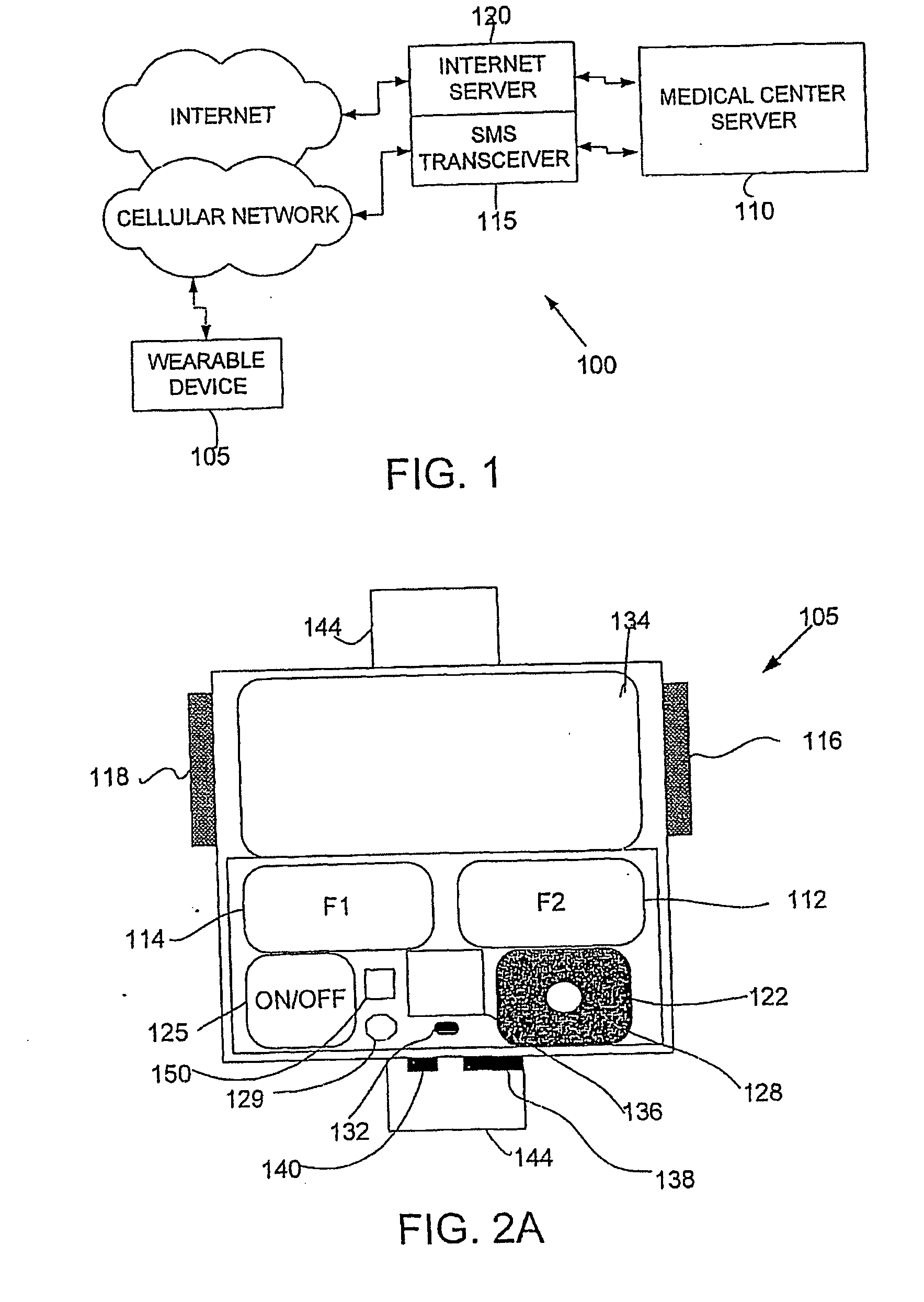
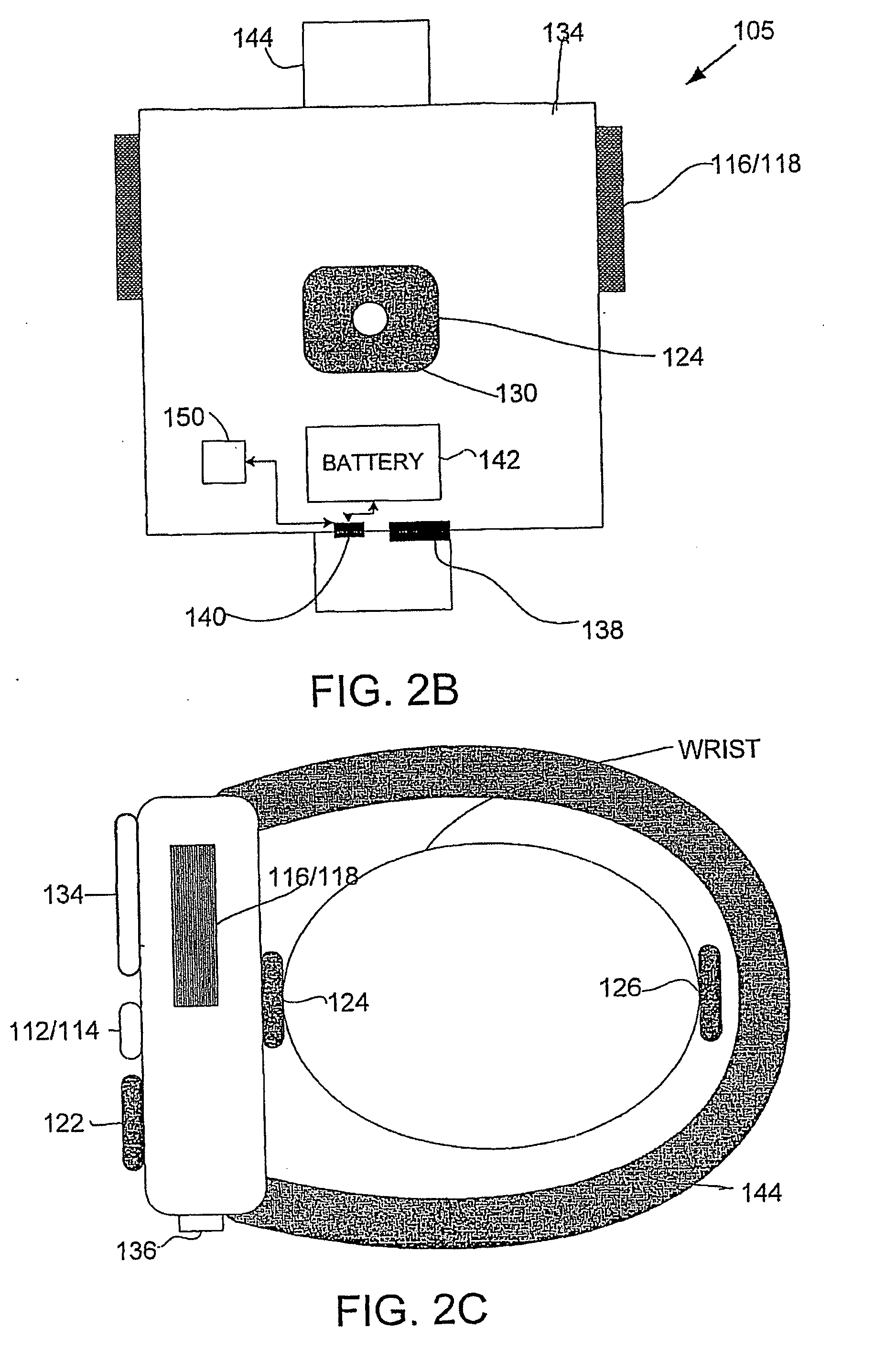
Wearable Device, System and Method for Measuring Physiological and/or Environmental Parameters
InactiveUS20080027679A1Avoid chargingDigital computer detailsNuclear monitoringSensor arrayEngineering
Systems, devices and methods are provided for monitoring parameters. The system, according to some embodiments, may include a wireless mobile monitoring device with an array of sensors and a safety module to prevent simultaneous sensing selected parameters and charging of the device, and a medical center server enabled to remotely reconfigure the functioning of the monitoring device.
Owner:SHKLARSKI DROR
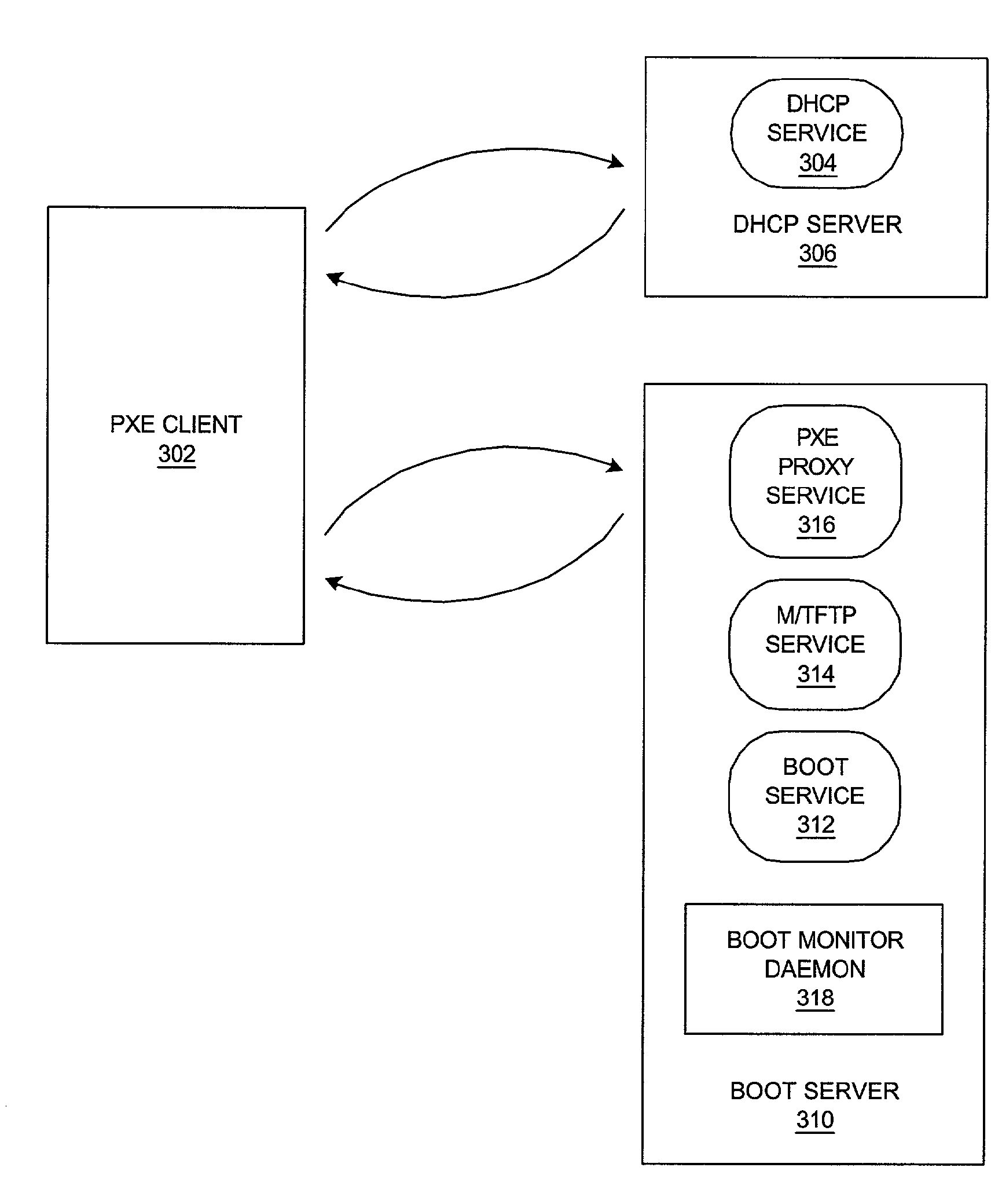
Method and System for Fault-Tolerant Remote Boot in the Presence of Boot Server Overload/Failure with Self-Throttling Boot Servers
InactiveUS20080183812A1Multiple digital computer combinationsProgram loading/initiatingQuality of serviceClient-side
Owner:INT BUSINESS MASCH CORP
Multi-speaker audio system and automatic control method
InactiveUS20050152557A1Loudspeaker enclosure positioningPseudo-stereo systemsAutomatic controlLoudspeaker
A sound produced at the location of a listener is captured by a microphone in each of a plurality of speaker devices. A sever apparatus receives an audio signal of the captured sound from all speaker devices, and calculates a distance difference between the distance of the location of the listener to the speaker device closest to the listener and the distance of the listener to each of the plurality of speaker devices. When one of the speaker devices emits a sound, the server apparatus receives an audio signal of the sound captured by and transmitted from each of the other speaker devices. The server apparatus calculates a speaker-to-speaker distance between the speaker device that has emitted the sound and each of the other speaker devices. The server apparatus calculates a layout configuration of the plurality of speaker devices based on the distance difference and the speaker-to-speaker distance.
Owner:SONY CORP
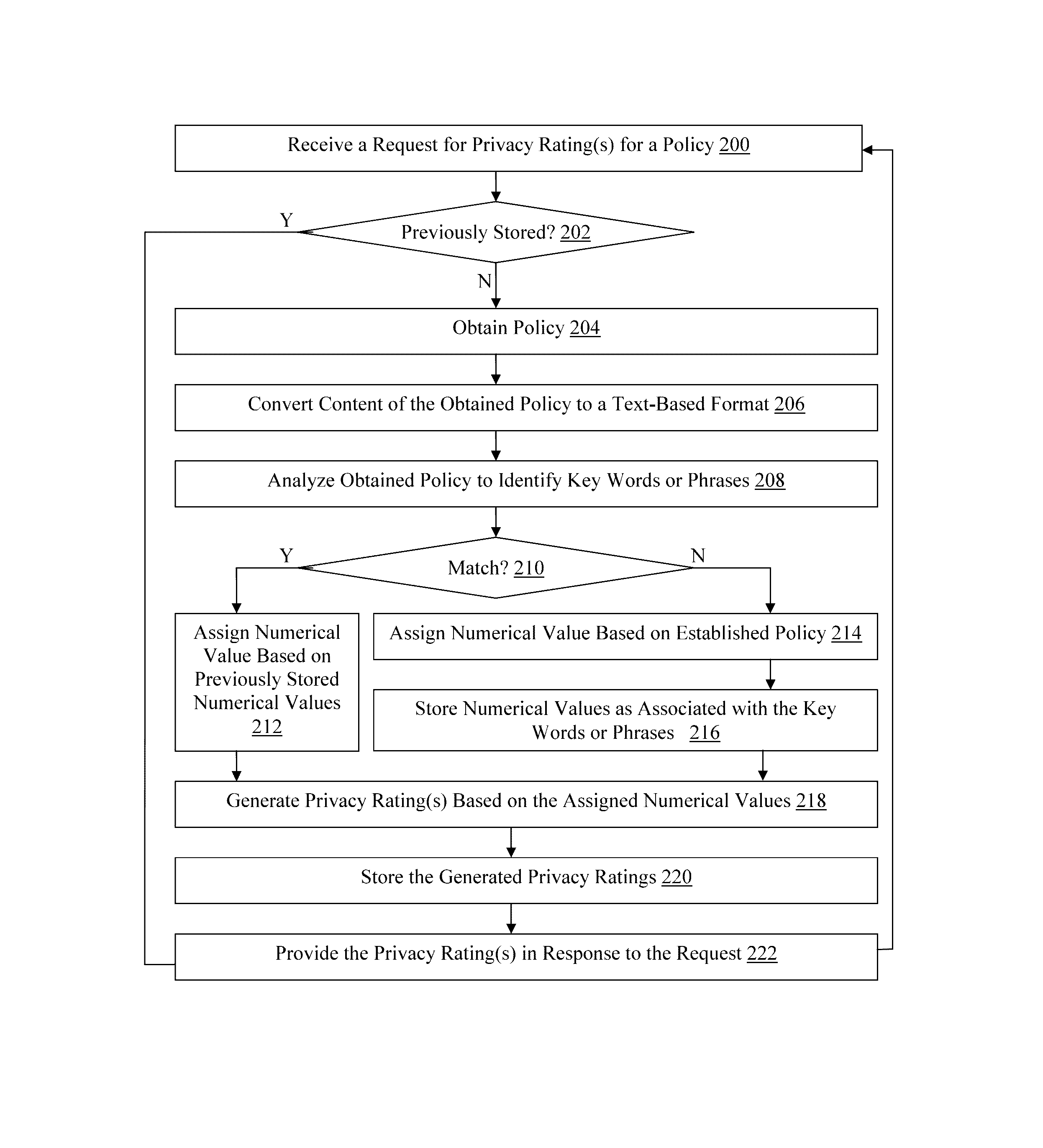
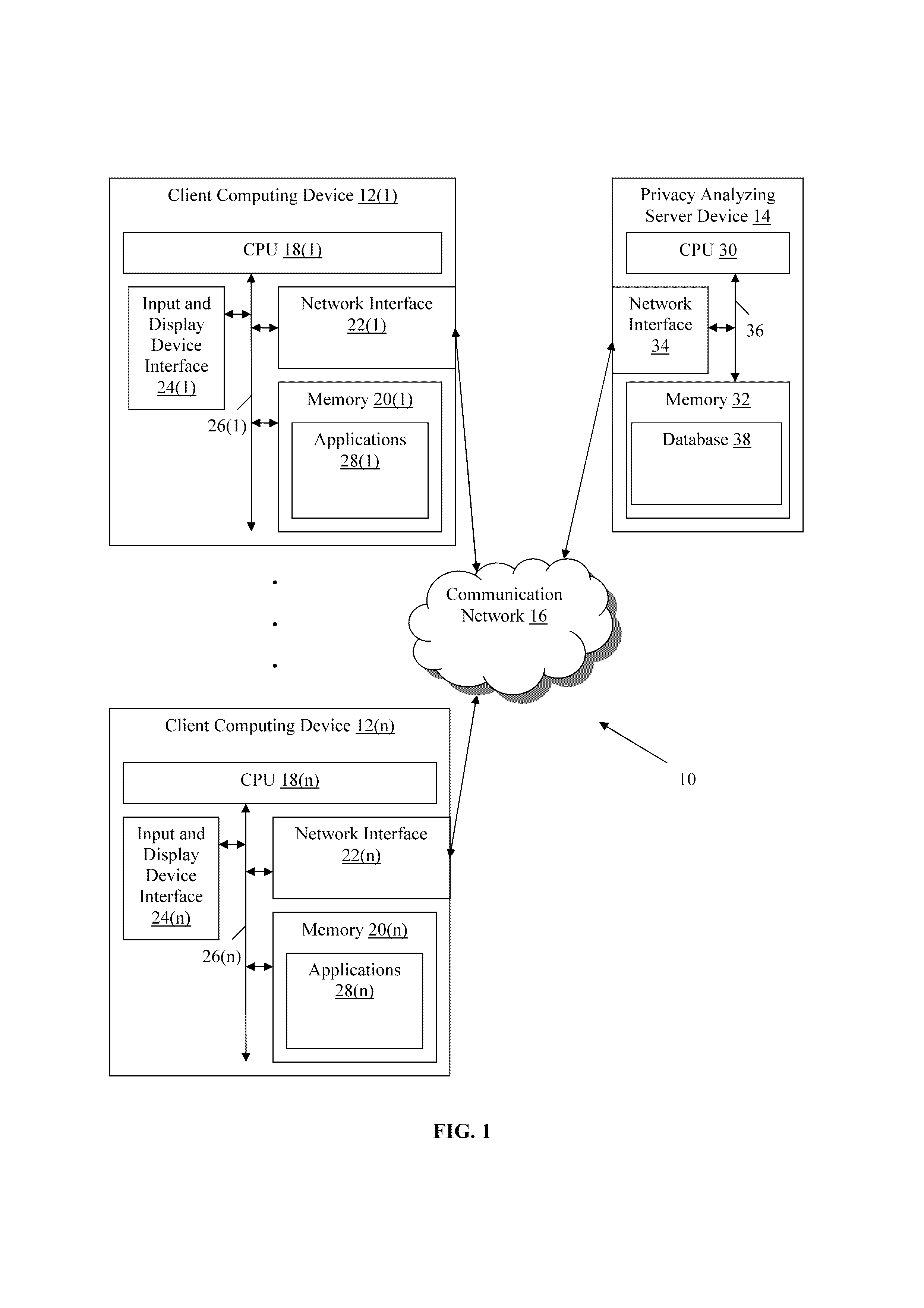
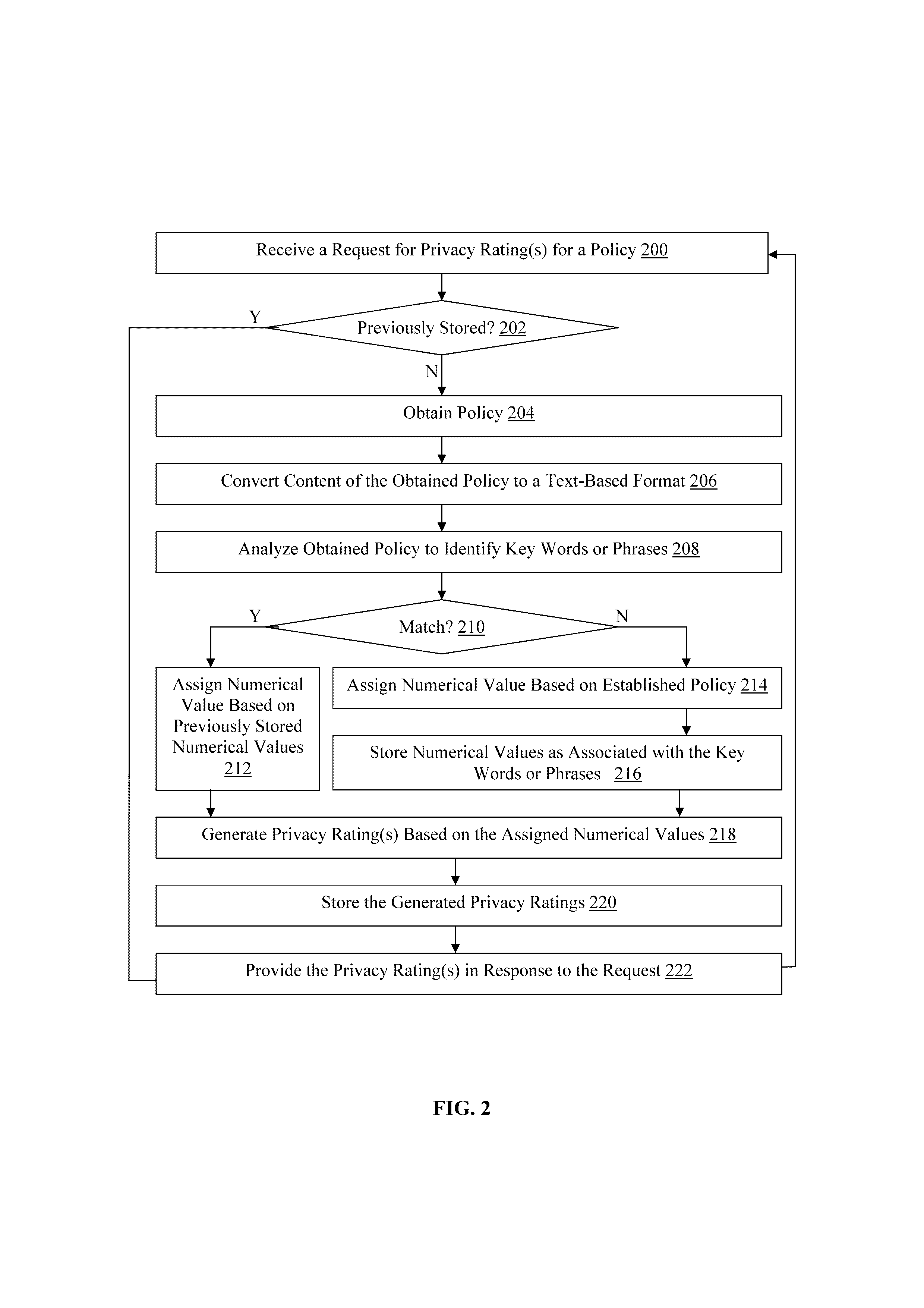
Methods and devices for analyzing user privacy based on a user's online presence
A method, non-transitory computer readable medium, and policy rating server device that receives a request from a client computing device for one or more privacy ratings. The request identifies at least one application, such as an application installed on the client computing device for example. A policy associated with the identified application is obtained. The obtained policy is analyzed to identify a plurality of key words or phrases associated with use by the at least one application of functionality of, or personal information stored on, the client computing device. One or more privacy ratings are generated based on numerical values assigned to each of the identified key words or phrases. The generated one or more privacy ratings are output to the client computing device in response to the request.
Owner:THE PRIVACY FACTOR
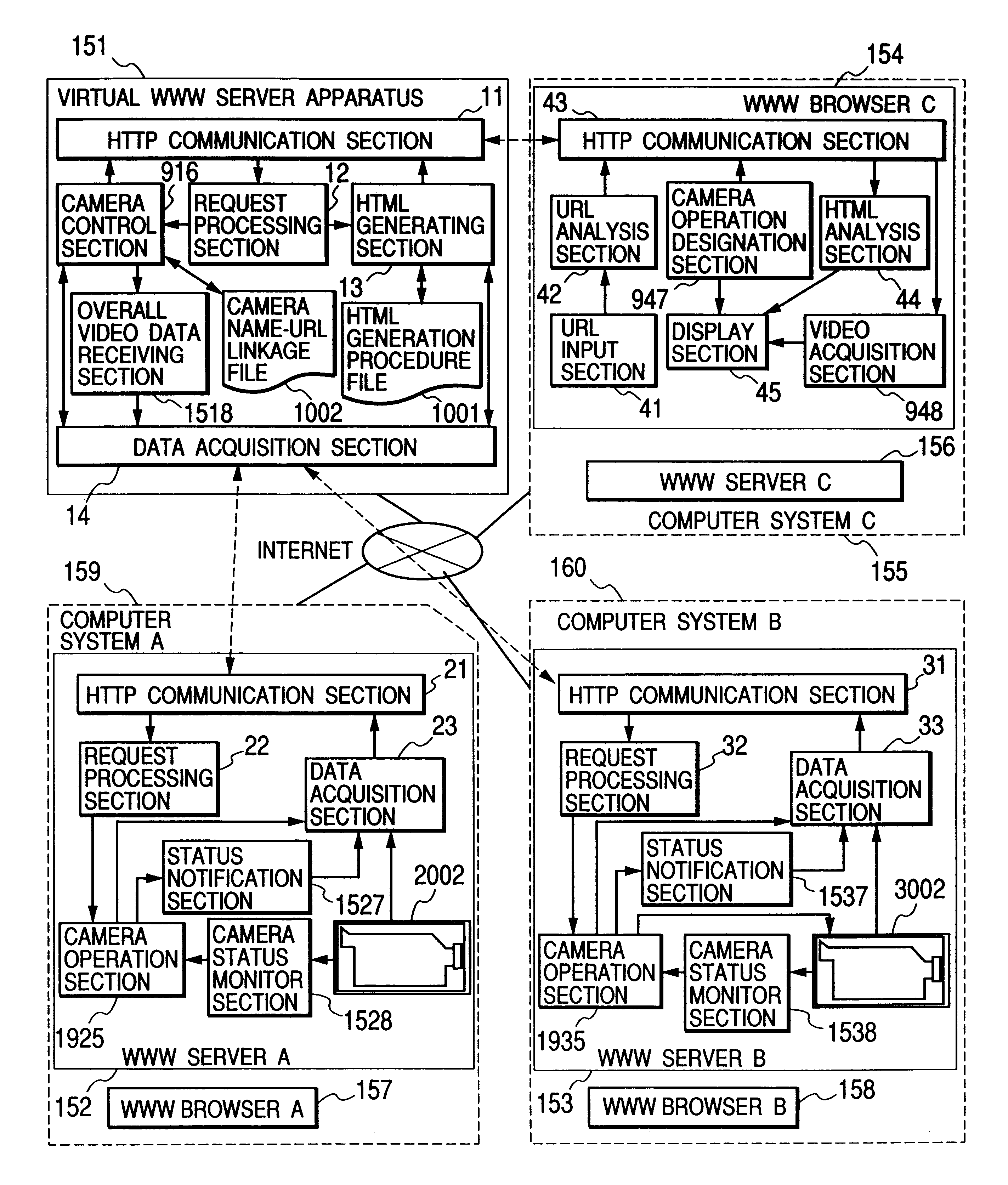
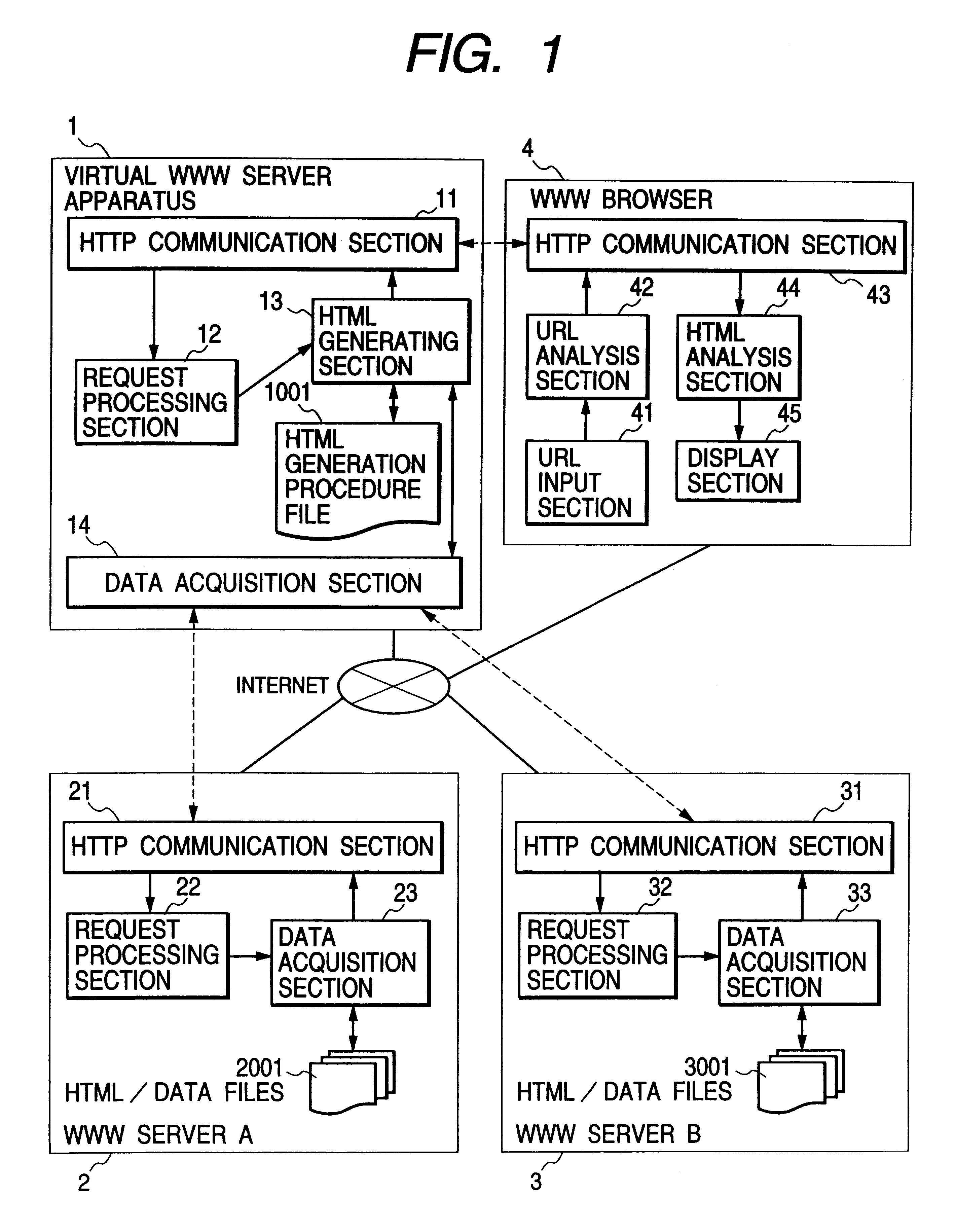
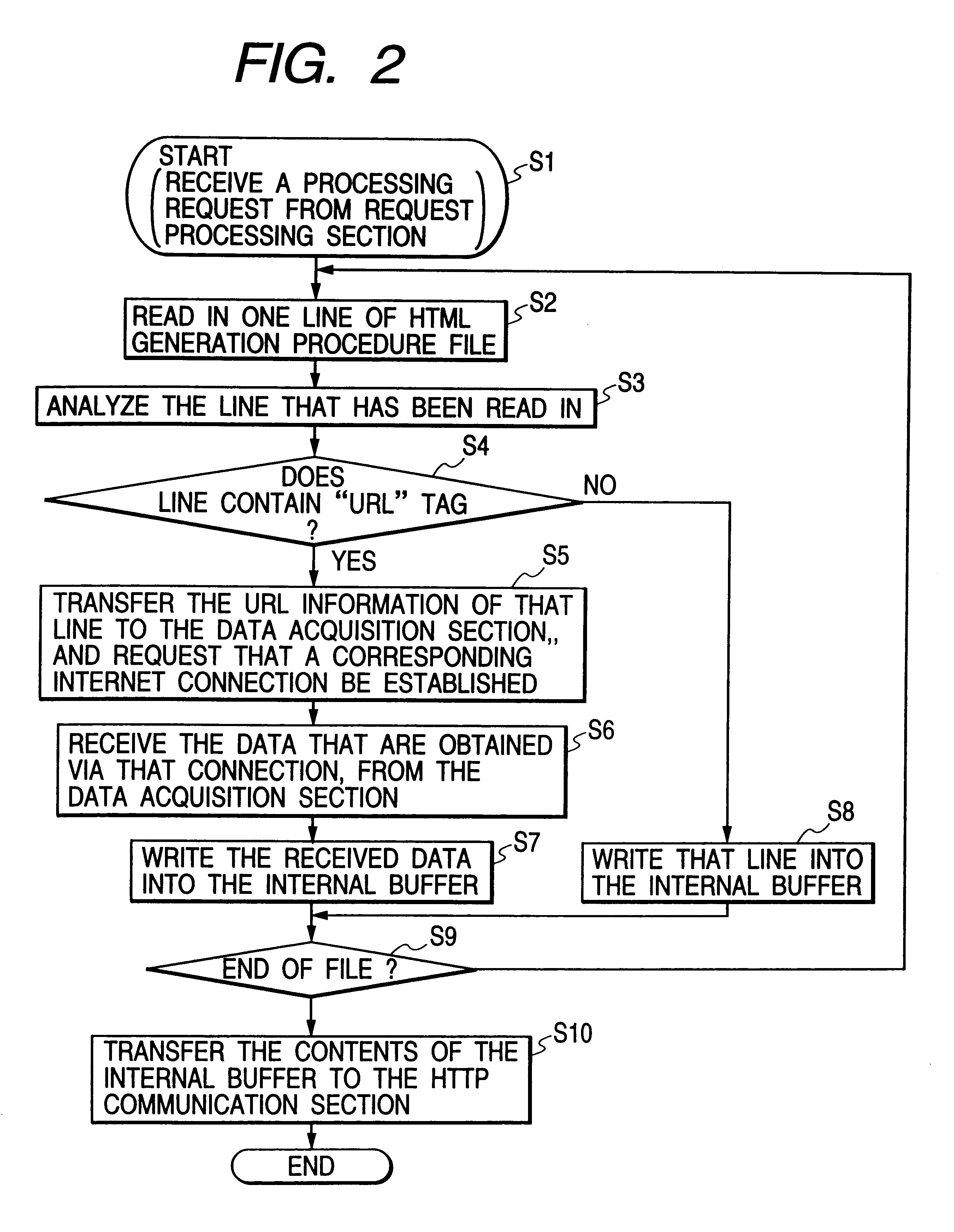
Virtual WWW server for enabling a single display screen of a browser to be utilized to concurrently display data of a plurality of files which are obtained from respective servers and to send commands to these servers
InactiveUS6182116B1Television system detailsData processing applicationsTelevision systemNetwork connection
A virtual WWW (World Wide Web) server apparatus which can obtain a plurality of predetermined HTML files and combine these into a single HTML file in response to a specific URL sent from a WWW browser, can connect to WWW servers and the browser via a network such as the Internet, to thereby enable the browser to obtain via the network the contents of a plurality of data files each of which may be HTML files, acquired from respective WWW servers through the intermediary of the virtual WWW server apparatus as a single combined file, and to thereby display the respective file contents together on a single display screen. The virtual WWW server apparatus can further include a linkage file whose contents relate respective names of video cameras controlled by various WWW servers to URLs for sending control commands for these cameras, thereby enabling commands for respective cameras, sent from a browser, to be identified by the corresponding camera names. A plurality of video images from respective cameras can be displayed embedded in respective HTML file contents on a single display screen of a browser, and hence a remote monitoring system or interactive TV system can be easily implemented.
Owner:PANASONIC CORP
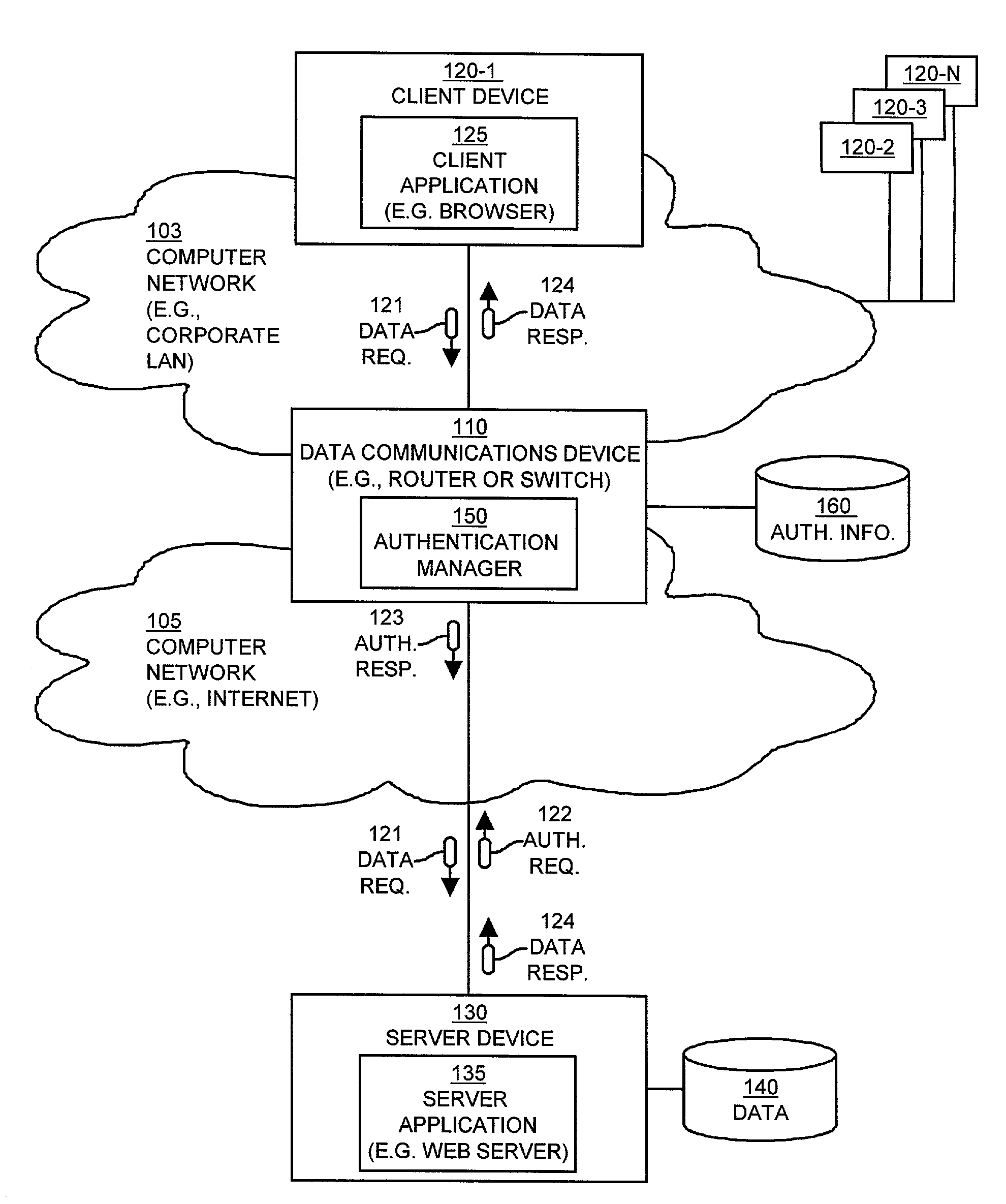
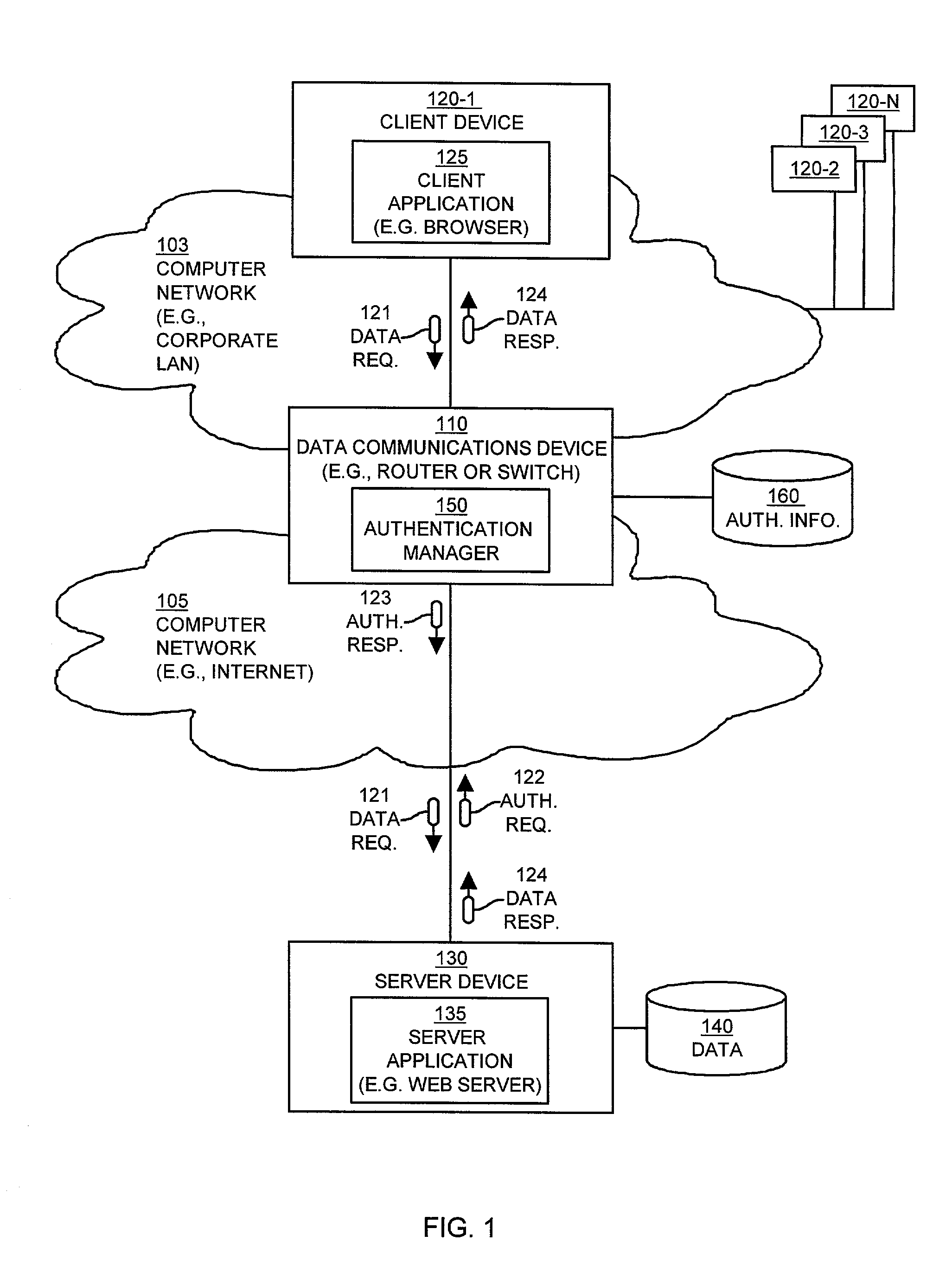
Methods and apparatus providing automatic client authentication
ActiveUS7194761B1Avoid disruptionDigital data processing detailsUser identity/authority verificationClient-sideServer appliance
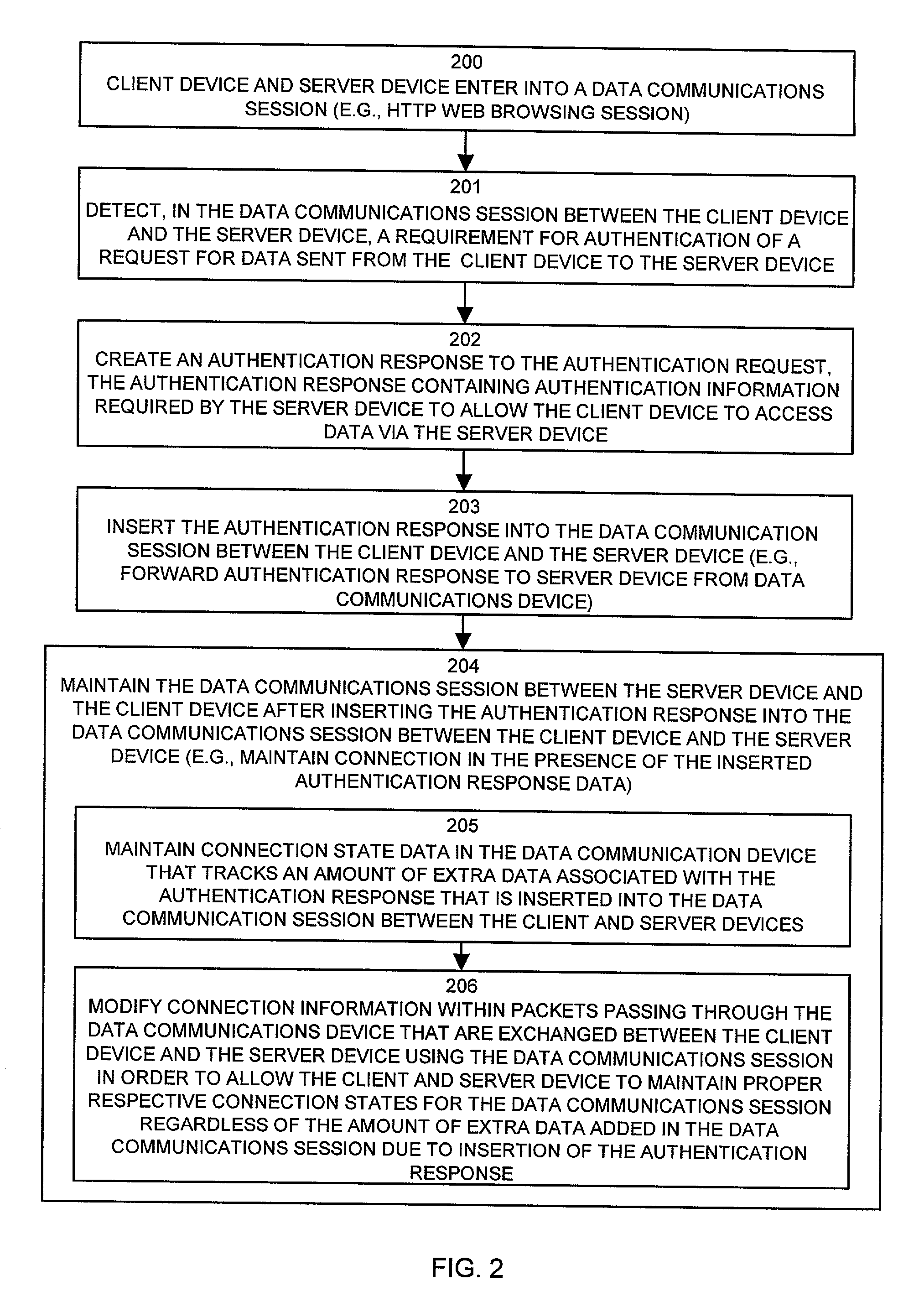
Mechanisms and techniques provide a system that operates in a data communications device to provide automatic authentication of a client device to a server device. The mechanisms and techniques (i.e., the system) operate to detect a requirement for authentication of a request for data sent from a client device to a server device. In response, the system creates an authentication response in response to detecting the requirement for authentication. The authentication response contains authentication information required by the server device to allow the client device to access data via the server device. The system then automatically inserts the authentication response into the data communications session between the client device and the server device. The authentication response authenticates, to the server device, access to the data by the client device. The system also maintains the data communications session between the server device and the client device in the presence of authentication response information inserted into the data communications session between the client device and the server device.
Owner:CISCO TECH INC
Service searching system
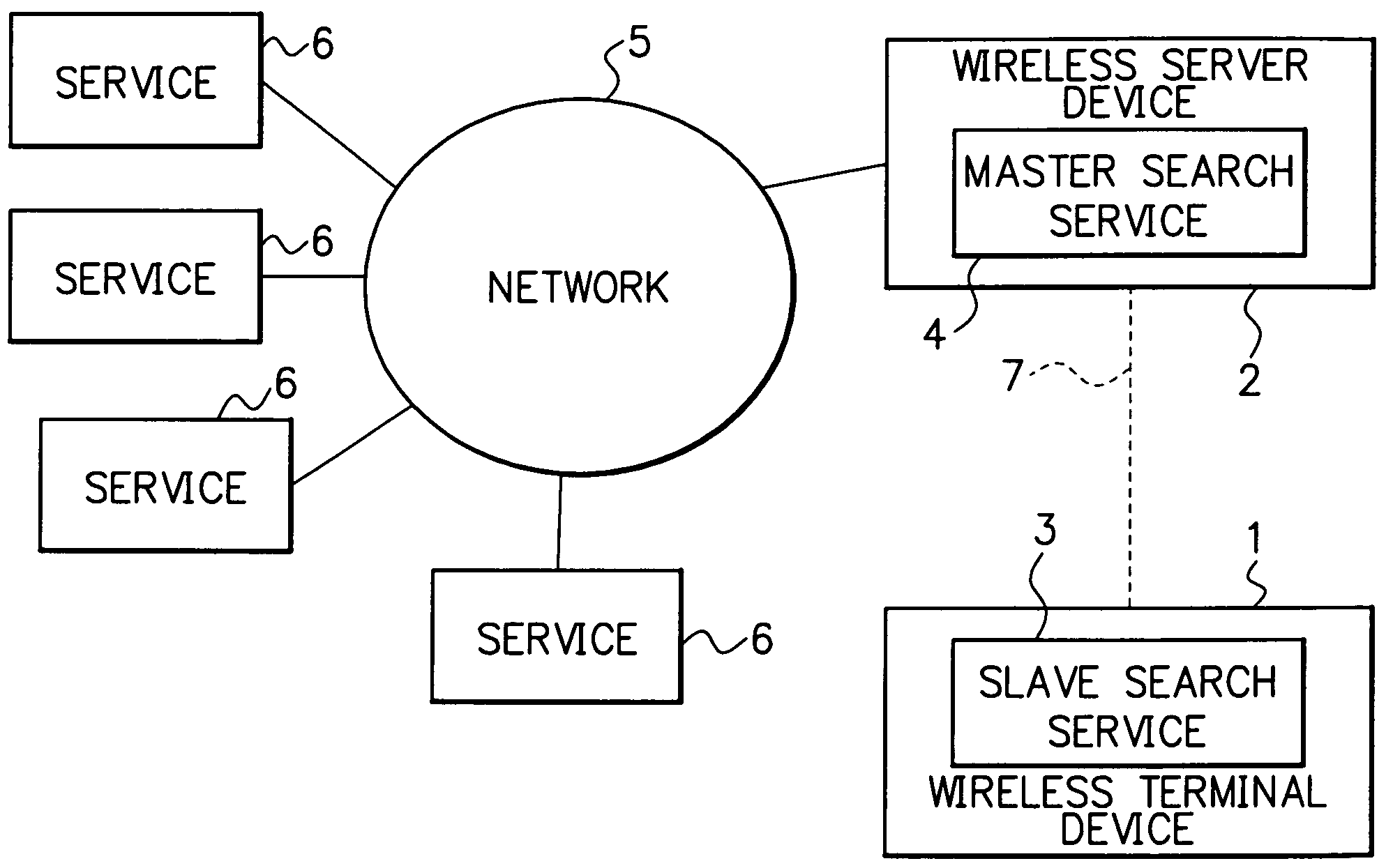
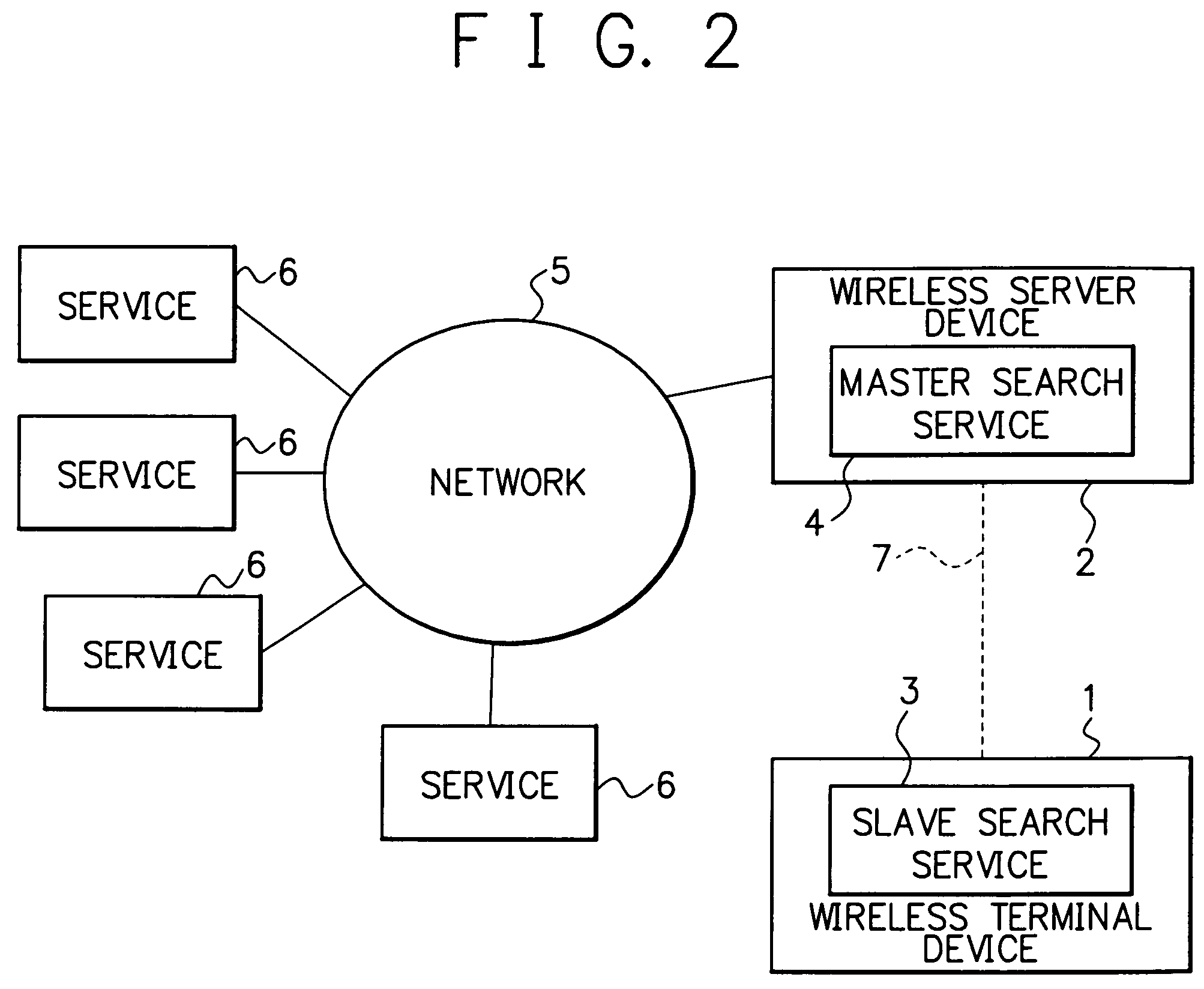
InactiveUS7139569B2Improve service rateReduce communication data volumeSpecial service for subscribersDigital computer detailsTerminal equipmentServer appliance
A service searching system for searching a service in a distributed system comprises a wireless server device and a wireless terminal device. The wireless server device is connected to a network and implements a master search service. On the other hand, the wireless terminal device implements a slave search service, and is capable of communicating with the server by wireless and utilizing the master search service. Besides, the wireless terminal device comprises a storage means that caches service objects obtained through the master search service. In addition, in searching the slave search service for a service, the wireless terminal device begins by searching the service objects cached in the storage means. In the case where the service is not detected, the wireless terminal device searches the master search service. The service objects are cached by being related to priority data. Thereby, there is provided a service searching system comprising a wireless terminal device, which is intended to search for a service in a distributed system in which a range of services are distributed in a network, wherein it is possible to cut down a service-searching time and costs, and further, it is possible to cut down communication interruptions by noise etc. in the wireless communication section compared to the conventional one.
Owner:NEC CORP
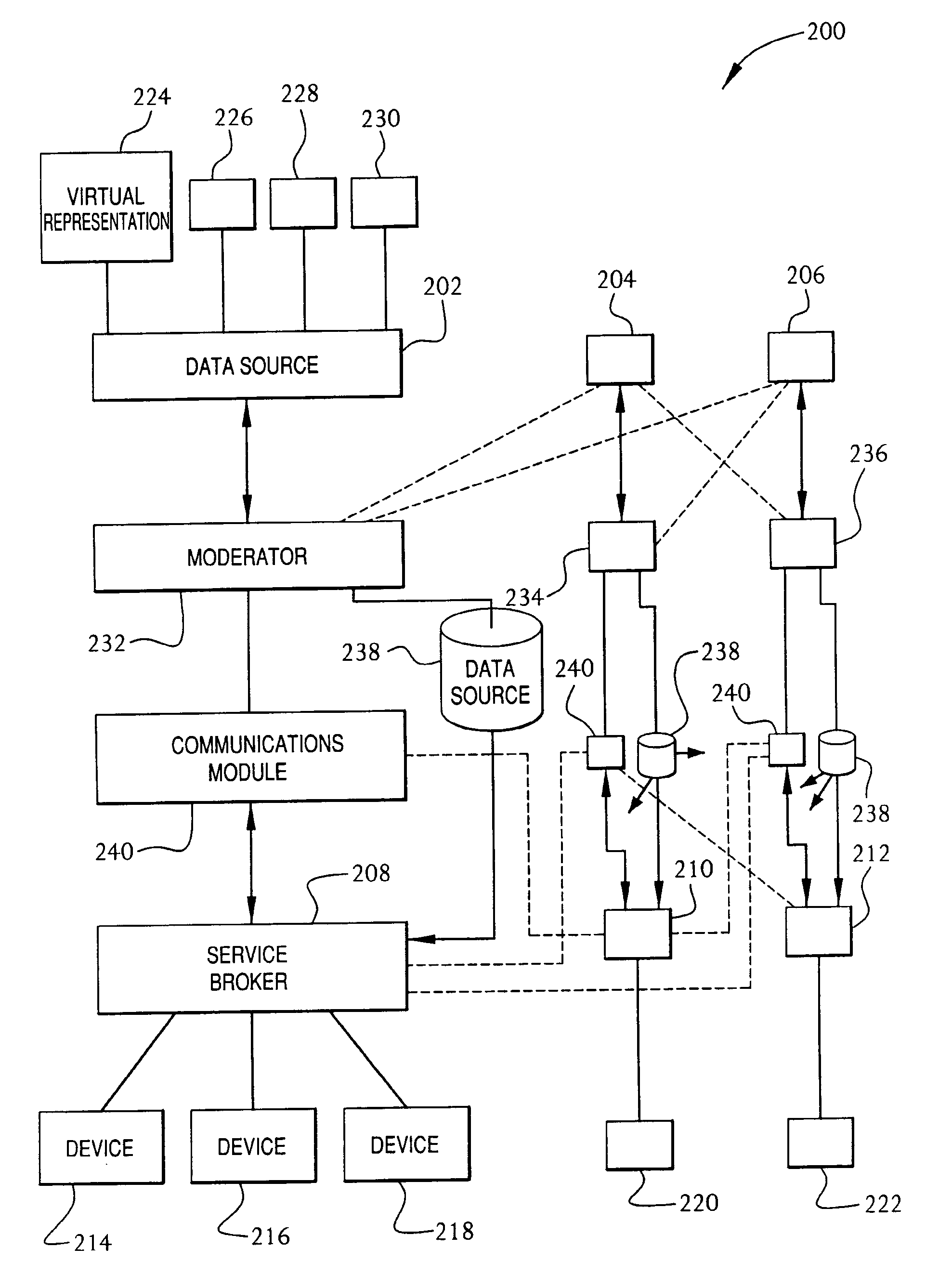
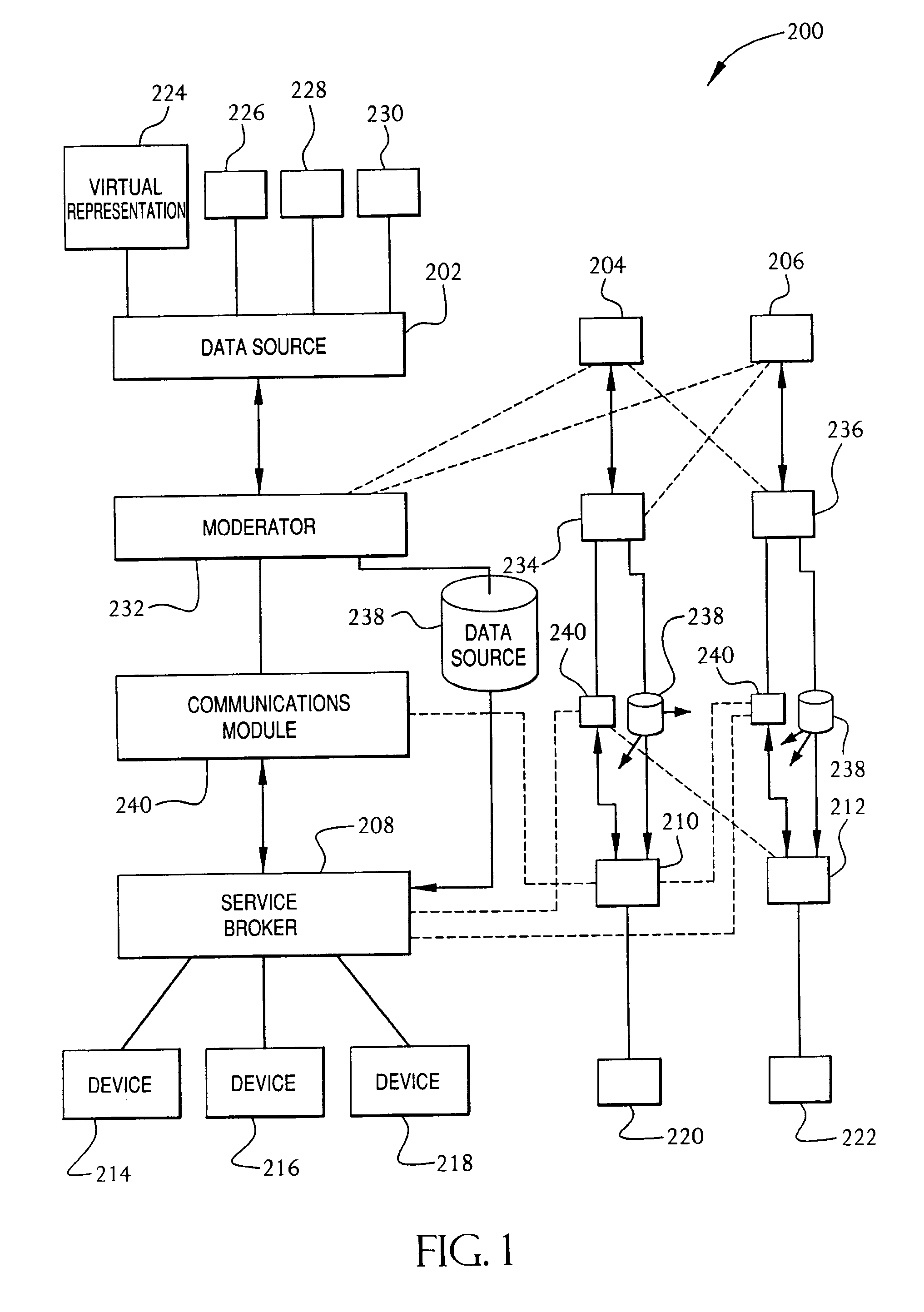
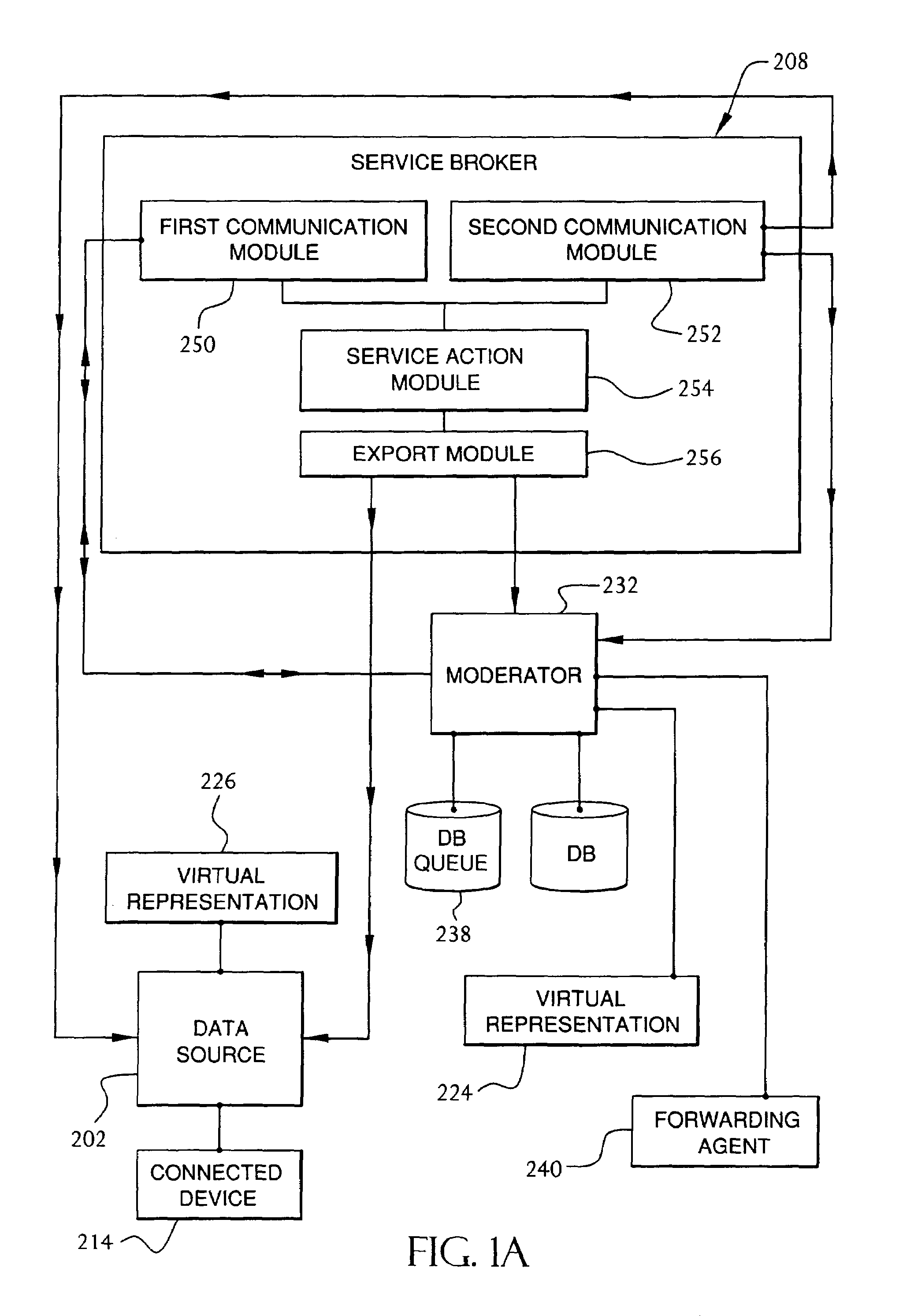
Service broker for processing data from a data network
InactiveUS7032002B1Multiple digital computer combinationsStore-and-forward switching systemsCommand languageServer appliance
A method and system for communication between server-less computing devices or clients in computers communicating over networks, such as the World Wide Web (WWW) using stateless protocols, e.g., HTTP. In this scheme, there are two classes of clients which can operate independently or can be combined in computers communicating over the network: a) clients that issue commands and request status or data, and b) clients that function as service brokers for providing services and processing commands, updating status and providing specific data—resembleing a server device but without accessible TCP / IP ports. Each service providing device is authenticated, retains a unique identity and establishes a soft state with the globally accessible server or servers. All devices and clients can compile and process a globally common command language established between all communicating network clients. The central server includes a CGI processing program and a database to retain client specific information. The server database represents a collection of queues, each having a client unique identifiable status, pending commands and / or data components. In this scheme, commands and signaling transmitted between the servers and clients utilize standard HTTP protocol semantics and HTML or standard markup language syntax. Clients encapsulate or embed information as parameters passed to HTTP CGI as a set of standard HTTP conversations. A CGI processing program converts, parses or processes each conversation and passes arguments with or without data to queues.
Owner:AT&T DIGITAL LIFE
Method and apparatus for efficient SQL processing in an n-tier architecture
ActiveUS7580971B1Efficient processingFree of ChargeDigital data information retrievalMultiple digital computer combinationsData setCache server
A method and apparatus for efficiently processing data requests in a network oriented n-tier database environment is presented. According to one embodiment of the invention, certain or all data from the tables of a database server device can be maintained in tables on the client device in a client side database cache server system. This local cache allows the network oriented n-tier database system to eliminate the expense of repetitive network transmissions to respond to duplicate queries for the same information. Additionally, the local client device may also keep track of what data is cached on peer network nodes. This allows the client to request that data from a peer database cache server and off load that burden from the database server device. Moreover, the local client may also keep statistics regarding the frequency of requested data in order to optimize the data set maintained in the local database cache server.
Owner:ORACLE INT CORP
Method and apparatus for conducting crypto-ignition processes between thin client devices and server devices over data networks
InactiveUS6263437B1Key distribution for secure communicationMultiple keys/algorithms usageTraffic capacityKey-agreement protocol
A crypto-ignition process is needed to establish an encrypted communication protocol between two devices connected by an insecure communication link. The present invention introduces a method of creating an identical secret key to two communicating parties is conducted between a thin device and a server computer over an insecure data network. The thin device generally has limited computing power and working memory and the server computer may communicate with a plurality of such thin devices. To ensure the security of the secret key on both sides and reduce traffic in the network, only a pair of public values is exchanged between the thin device and the server computer over the data network. Each side generates its own secret key from a self-generated private value along with the received counterpart's public value according to a commonly used key agreement protocol, such as the Diffie-Hellman key agreement protocol. To ensure that the generated secret keys are identical on both sides, a verification process is followed by exchanging a message encrypted by one of two generated secret keys. The secret keys are proved to be identical and secret when the encrypted message is successfully decrypted by the other secret key. To reduce network traffic, the verification process is piggybacked with a session request from the thin device to establish a secure and authentic communication session with the server computer. The present invention enables the automatic delivery of the secret keys, without requiring significant computing power and working memory, between each of the thin clients respectively with the server computer.
Owner:UNWIRED PLANET
System and method for monitoring user interaction with web pages
InactiveUS7958234B2Error detection/correctionMultiple digital computer combinationsInternet privacyApplication software
Systems and methods for monitoring usage of an electronic device are disclosed herein. A client component in stalled in a client device is operative to monitor usage of the client device in accordance with a monitoring profile, and to generate corresponding usage data. The monitoring profile typically includes information specifying which features of which application programs are to be disabled on the client device. A server component, installed on a server device in communication with the client device, provides the monitoring profile to the client device and receives the usage data from the client device.
Owner:R2 SOLUTIONS LLC
System and Method for Tracking Messages in a Messaging Service
A system, server and a method for processing messages received at a server device in a network are provided. The method comprises: for a message being transmitted from a first account associated with a client device to a second account in the network, receiving a message event associated with the message at the server; determining whether the message event is associated with an existing conversation involving the first account, and if so setting a sequence number associated with the message event to a value incremented from a current sequence number associated with the existing conversation, otherwise setting the sequence number to a value to track a new conversation; and sending the sequence number to the first user account.
Owner:GLOBAL RELAY COMM
Method and apparatus for integrating narrowband and wideband data transports
InactiveUS6665711B1Without incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesThe InternetServer appliance
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com