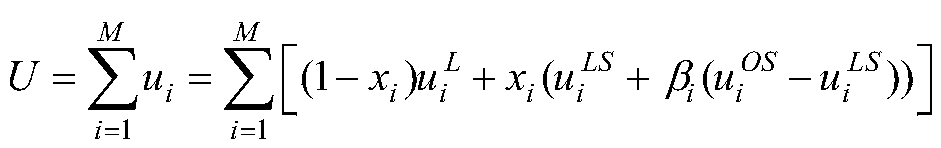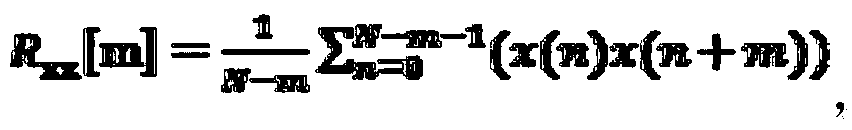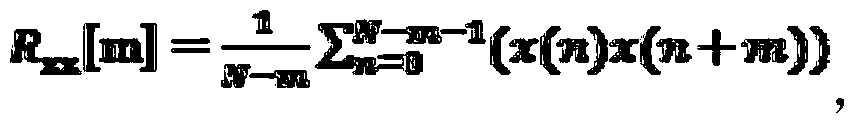Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
547 results about "Industrial network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
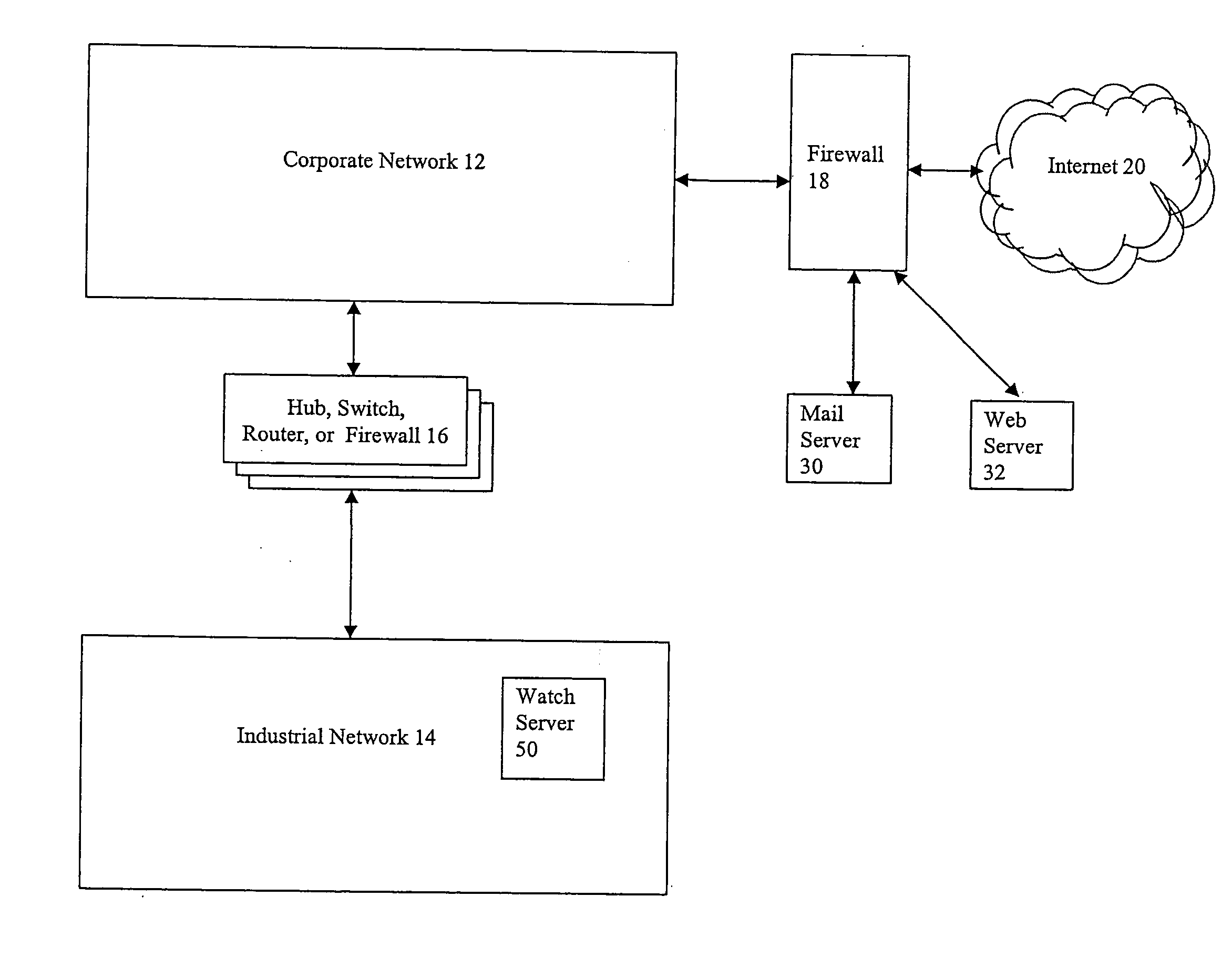
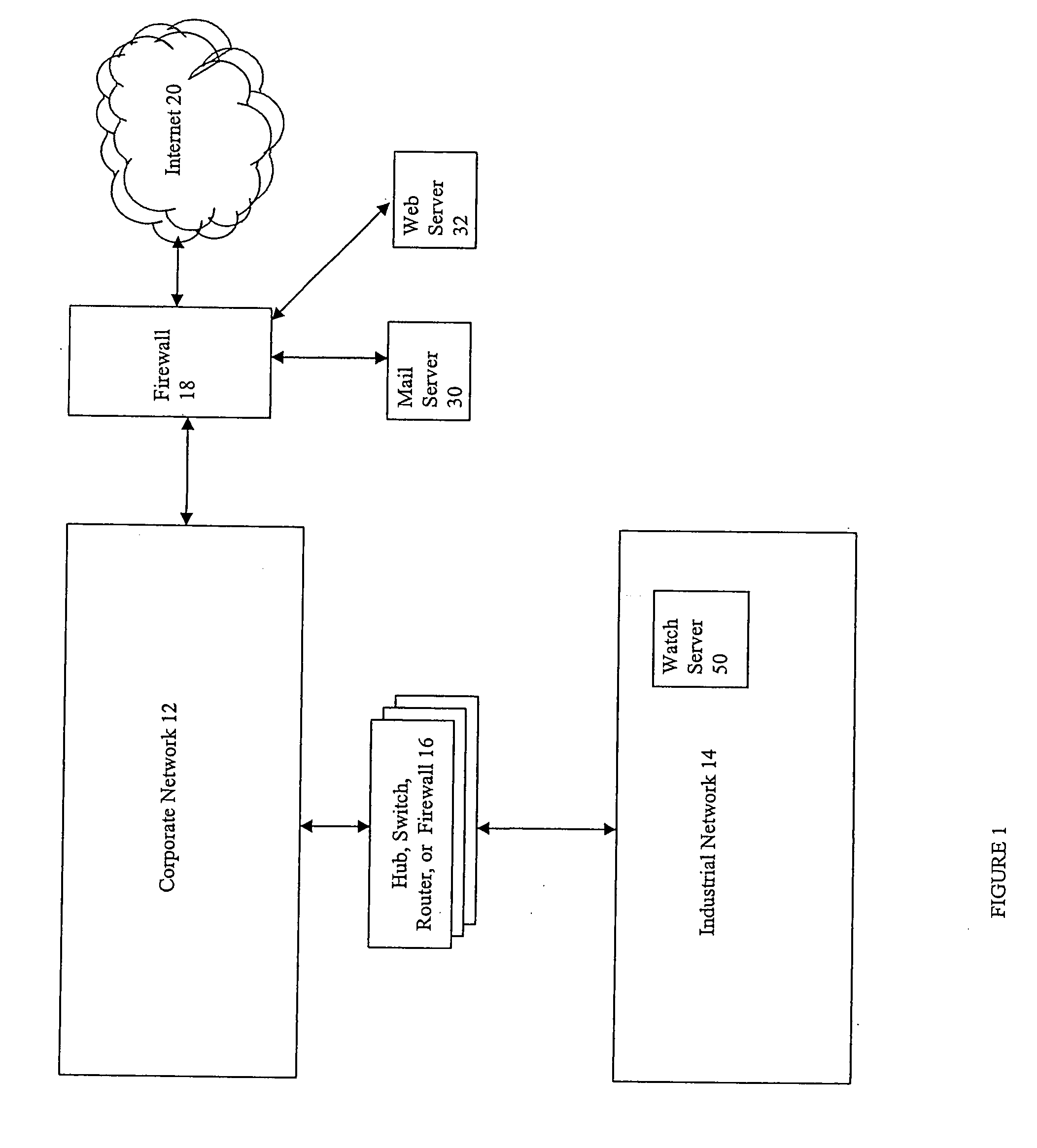
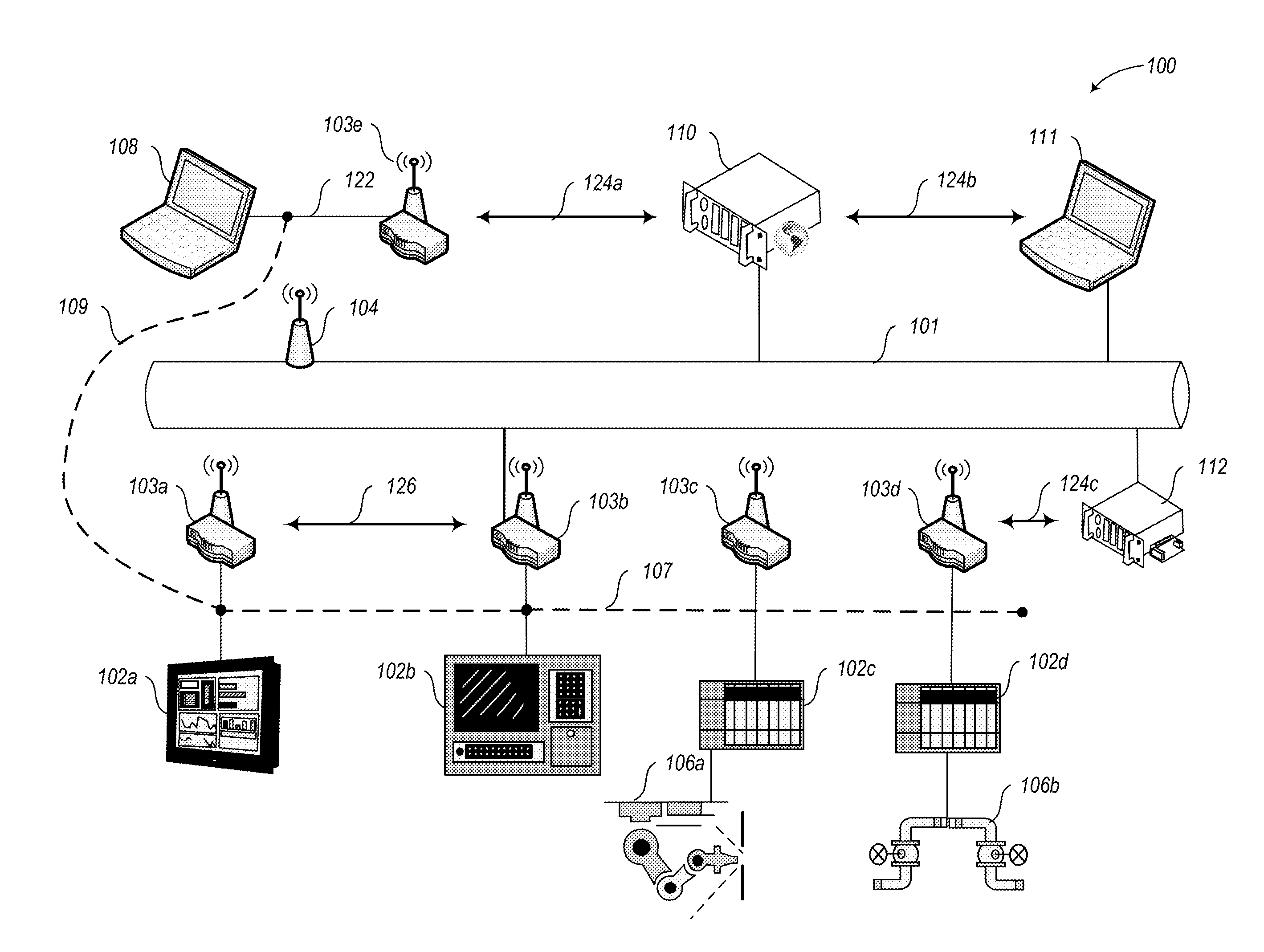
Event monitoring and management
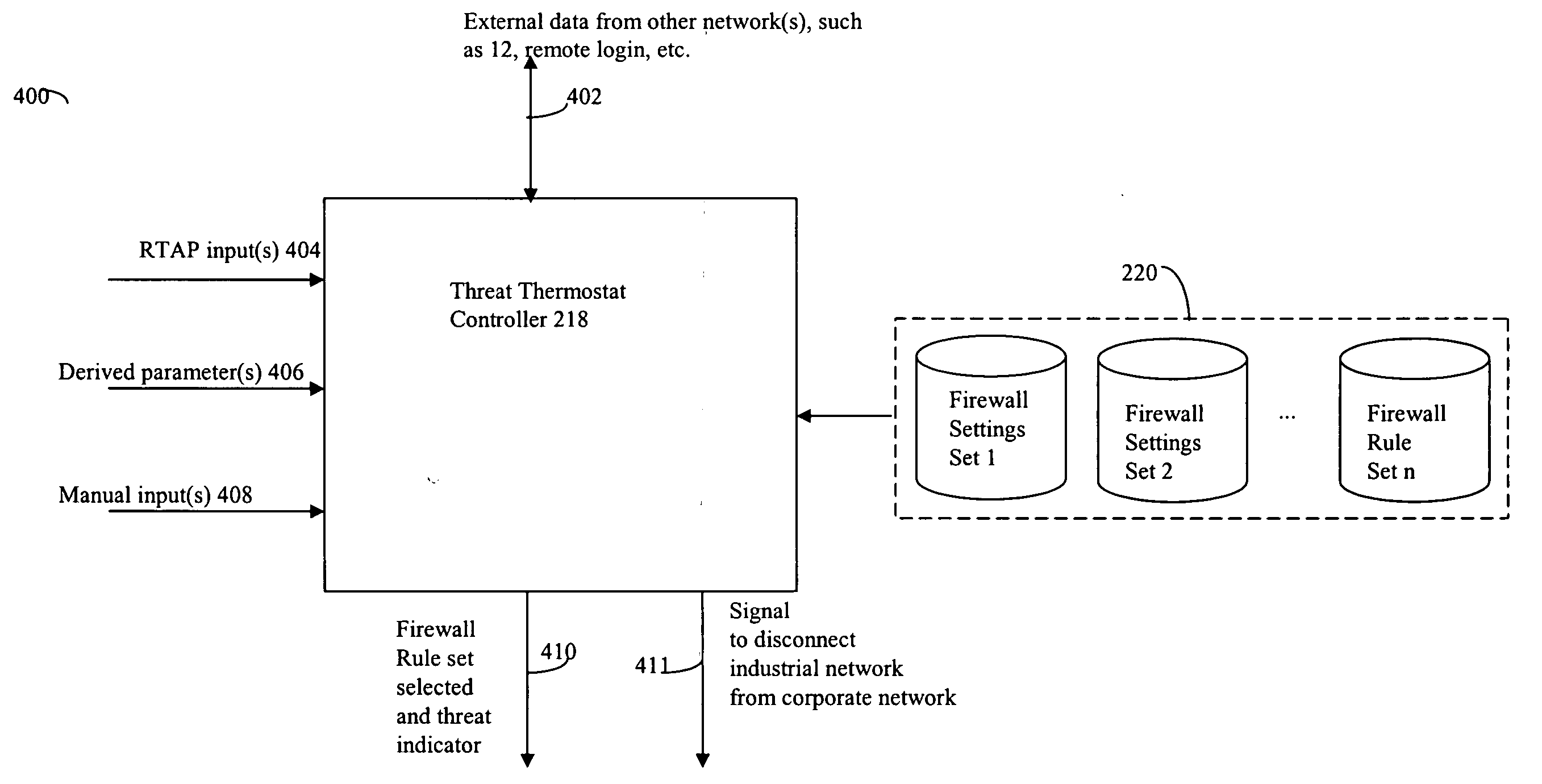
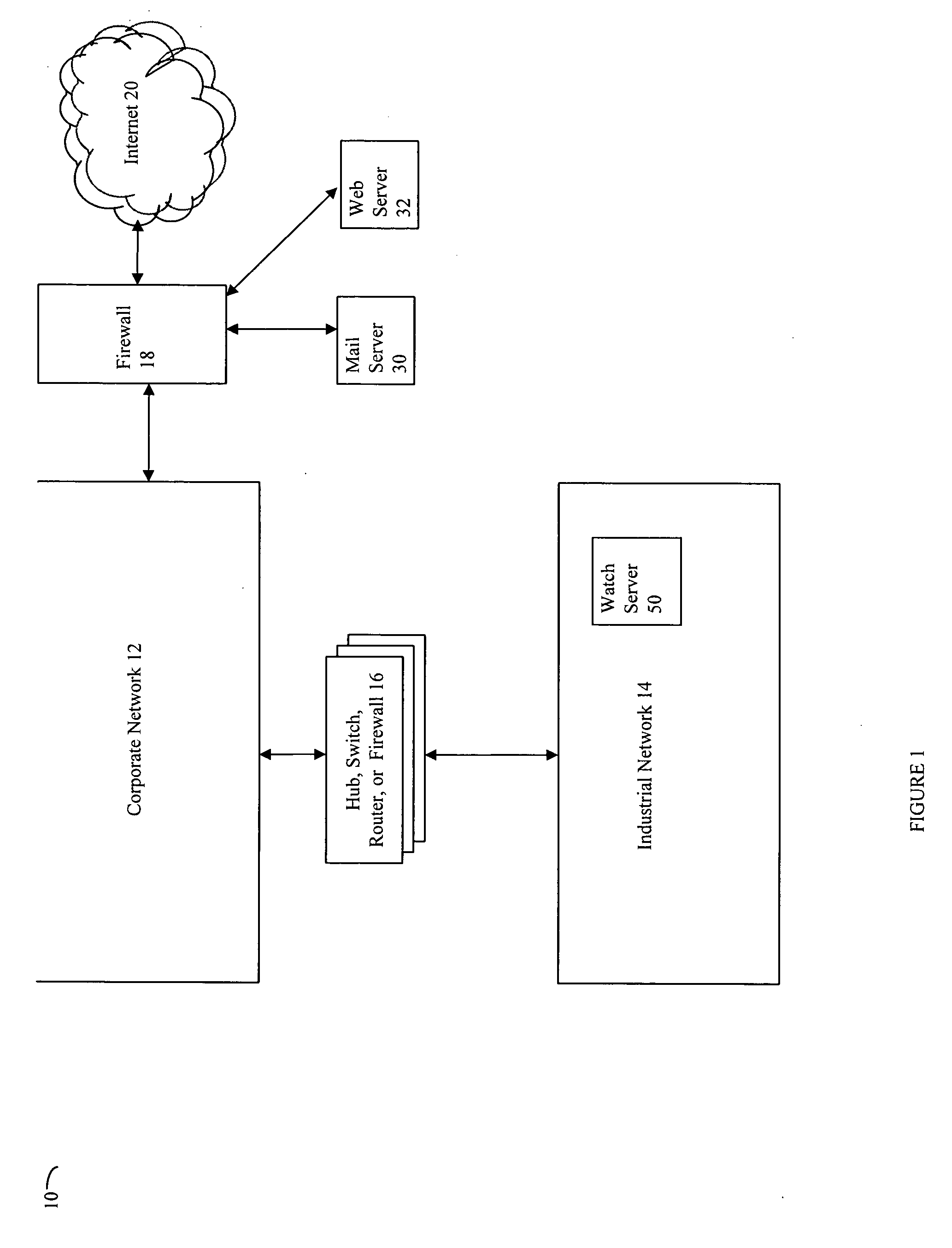
ActiveUS20050015624A1Digital data processing detailsMultiple digital computer combinationsNetwork connectionThermostat
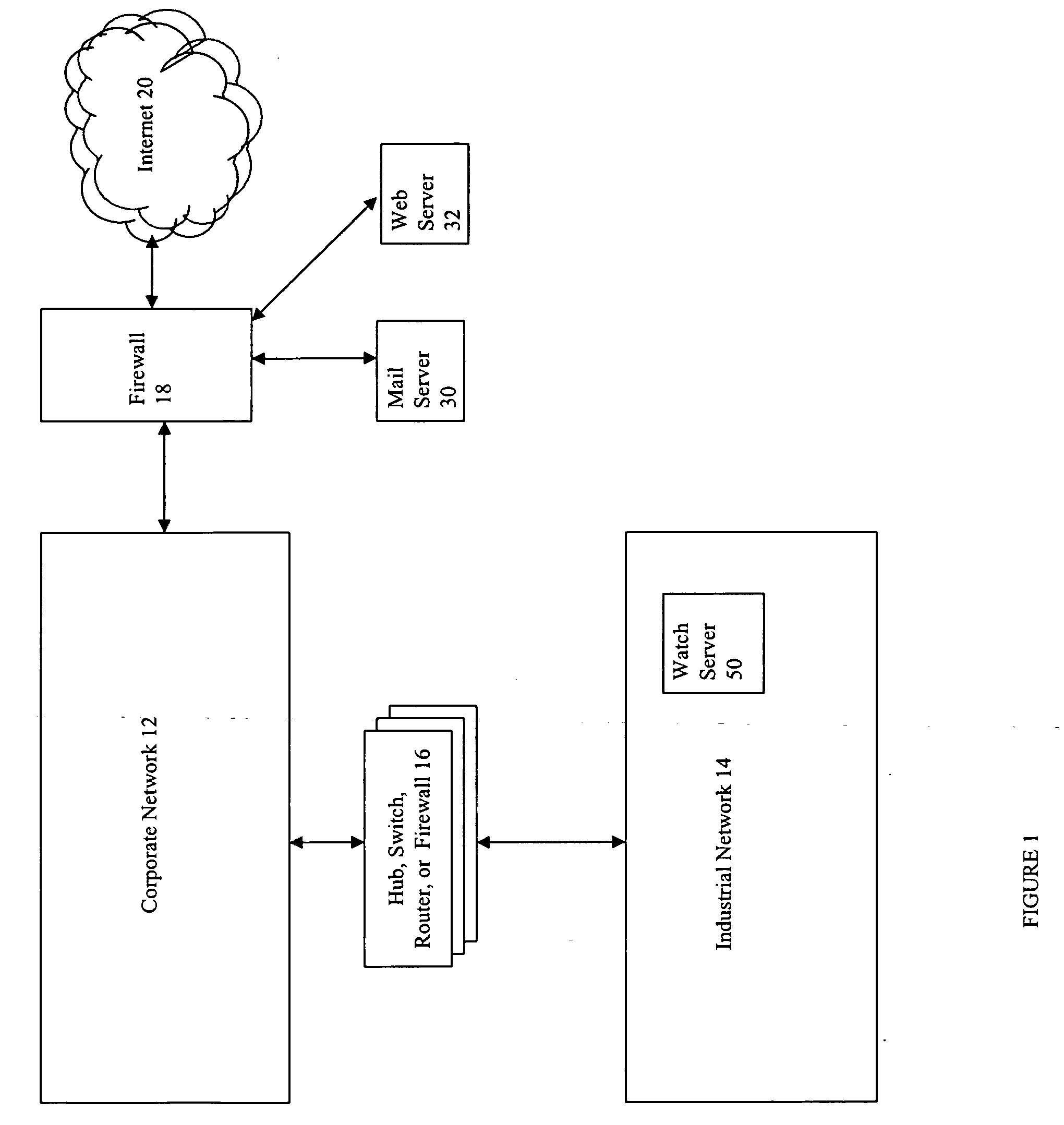
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Duration of alerts and scanning of large data stores
InactiveUS20070050777A1Multiprogramming arrangementsNon-redundant fault processingThermostatEmbodied agent
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
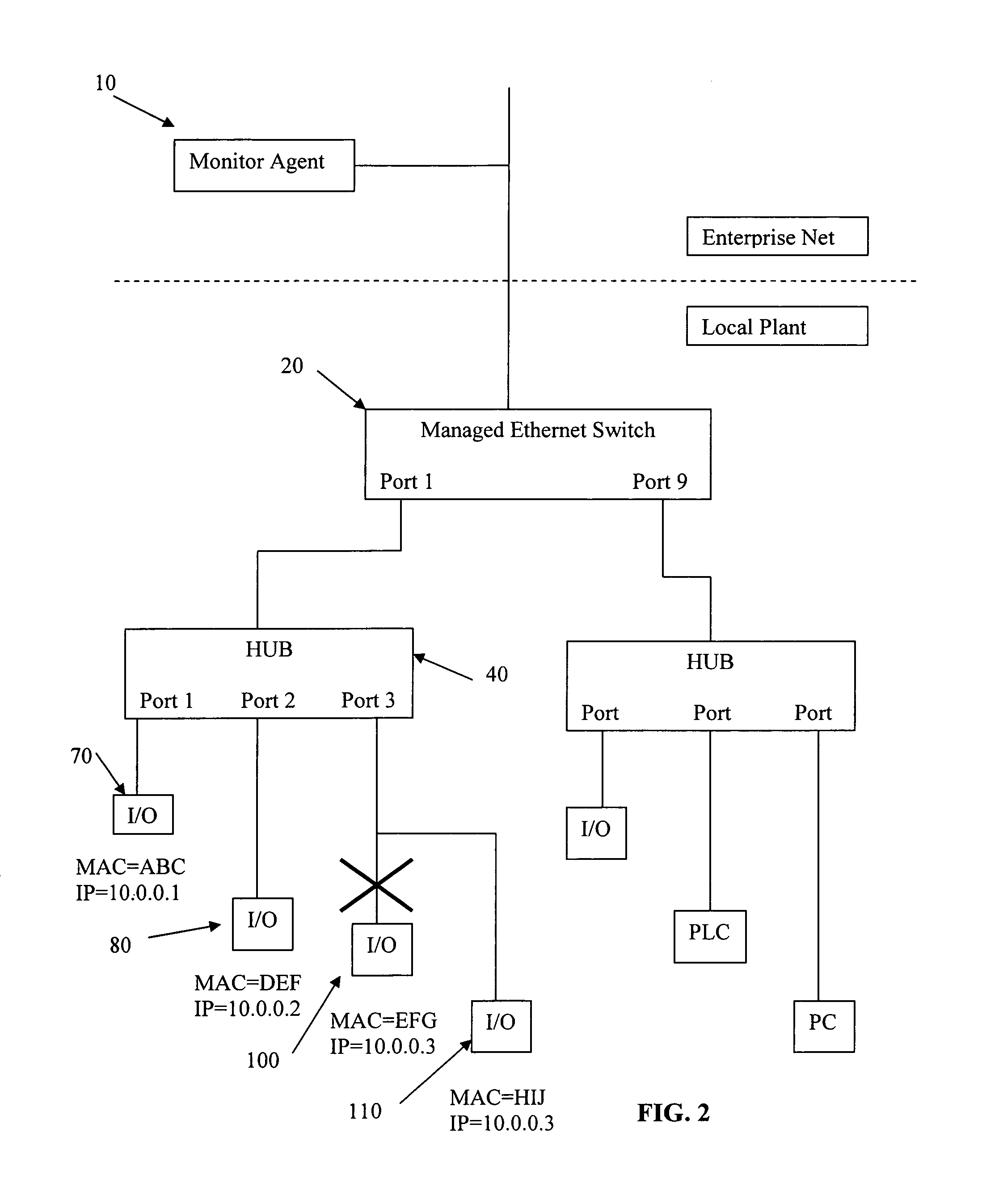
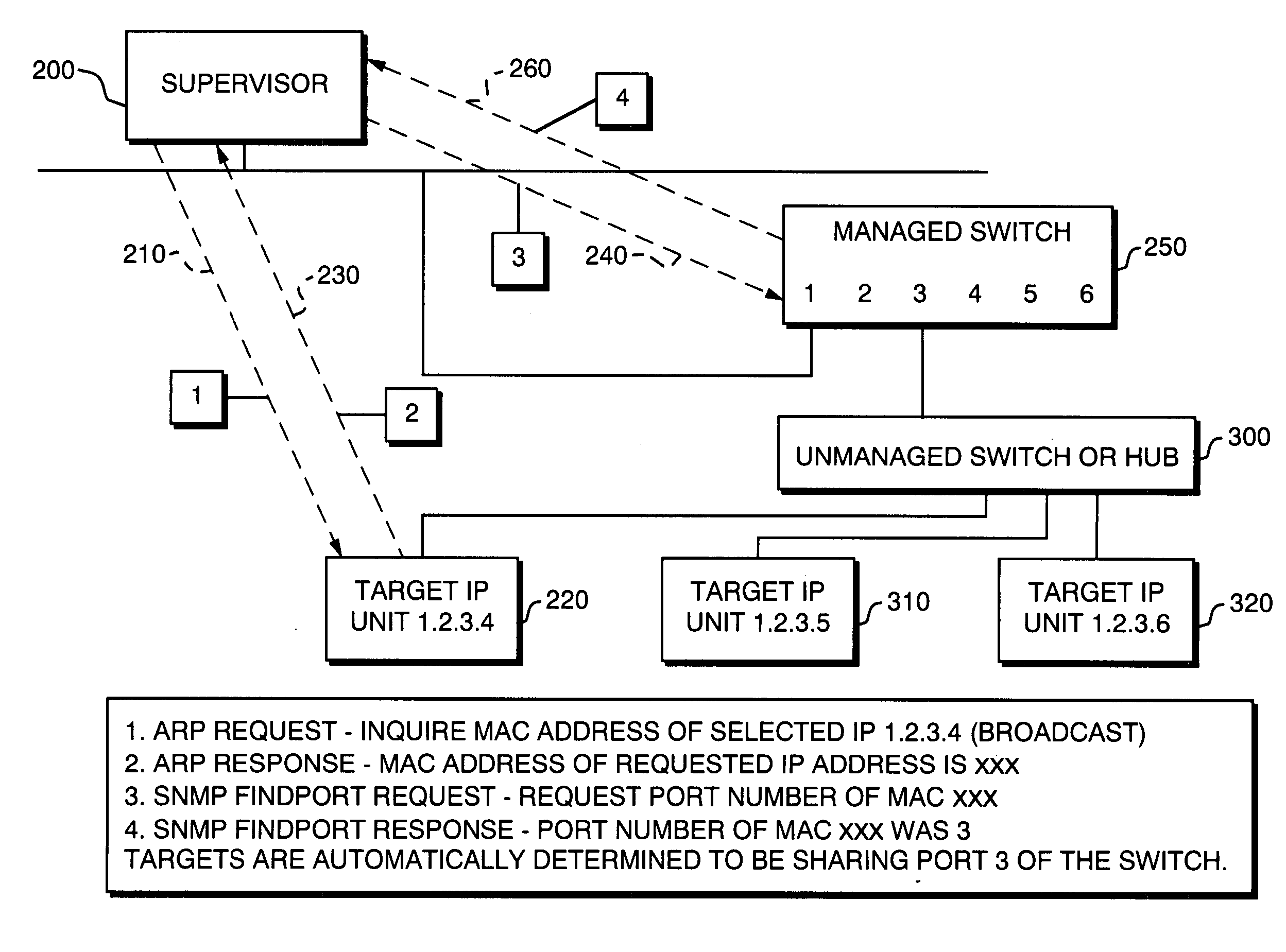
Automatic determination of correct IP address for network-connected devices
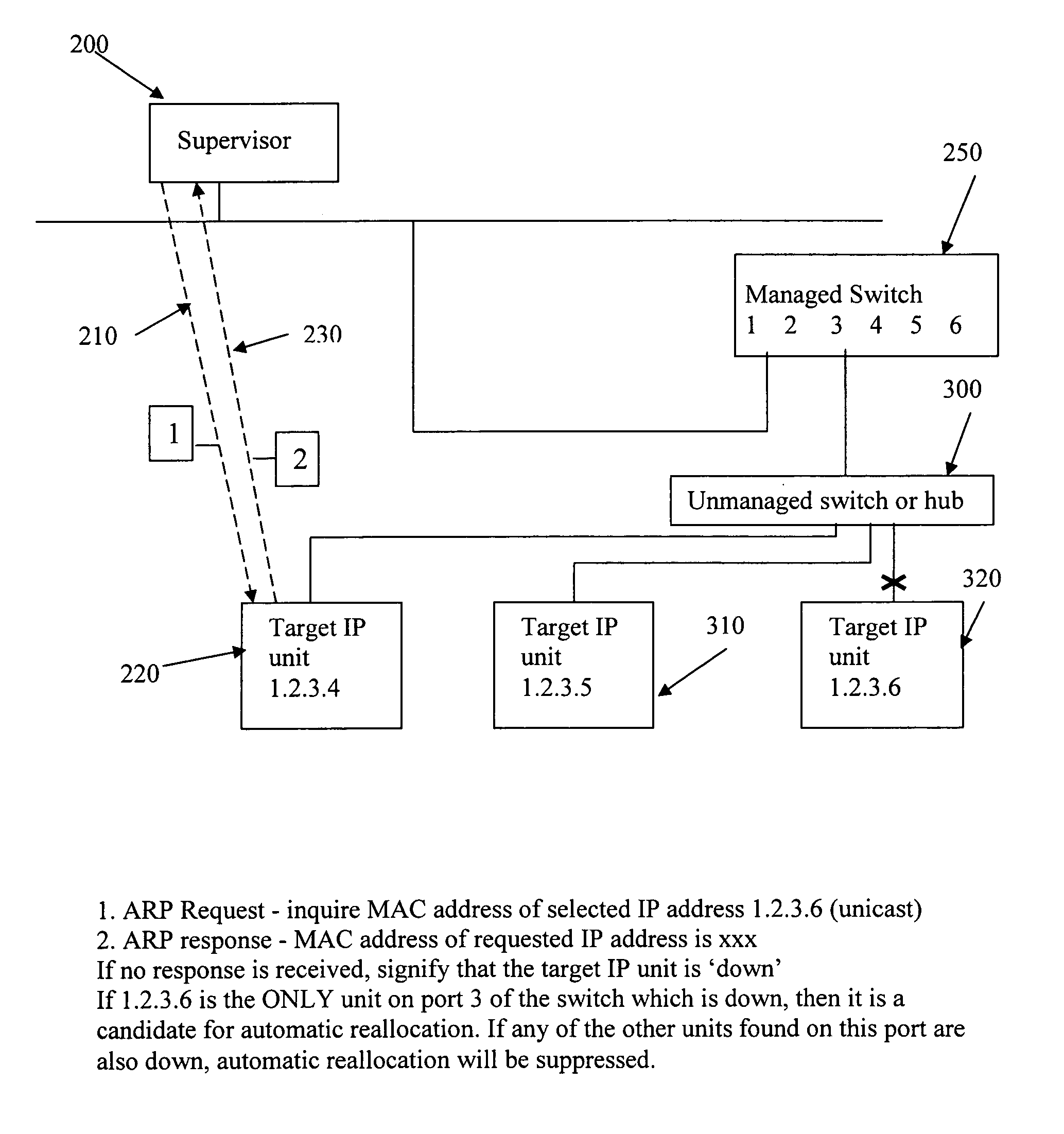
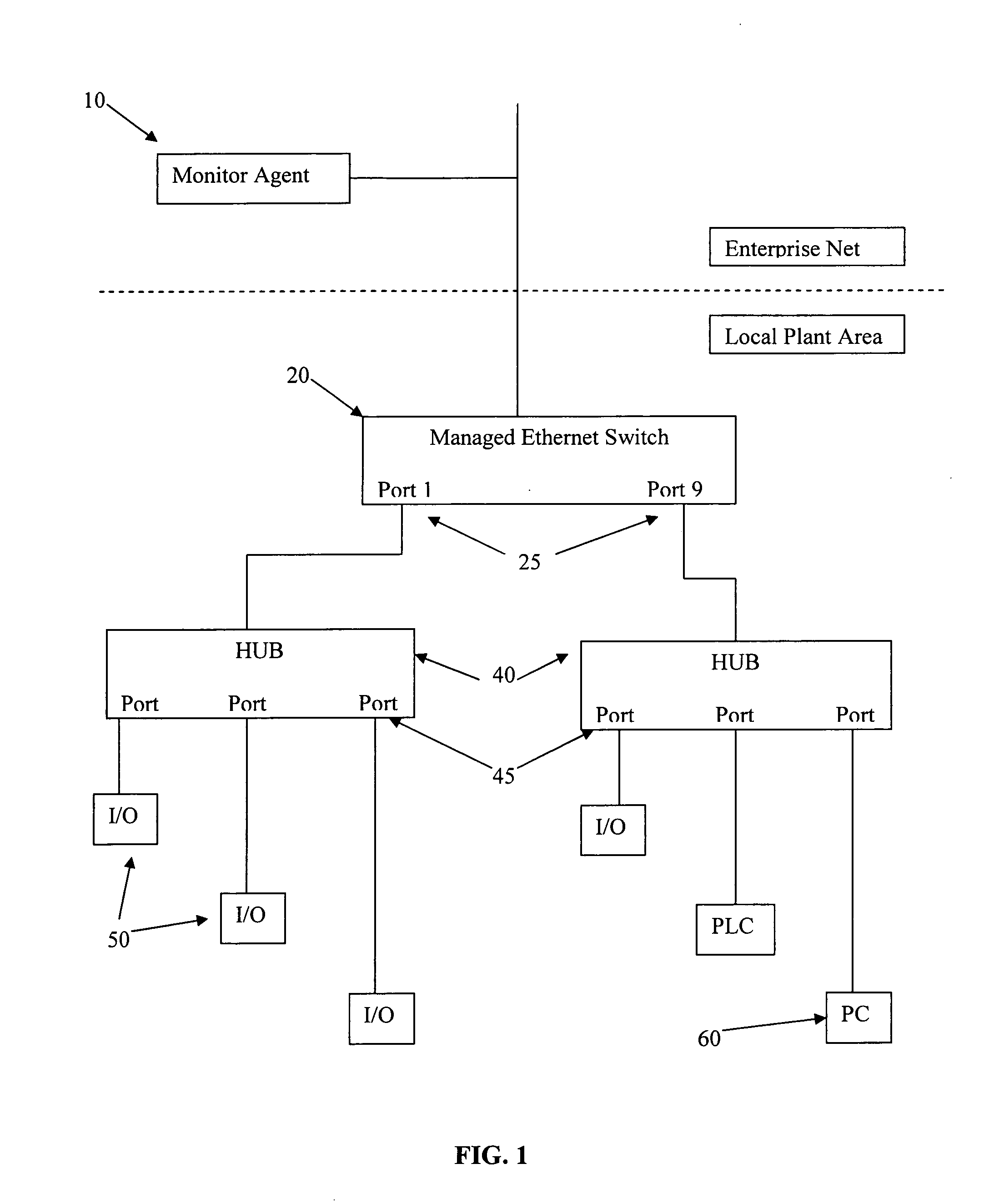
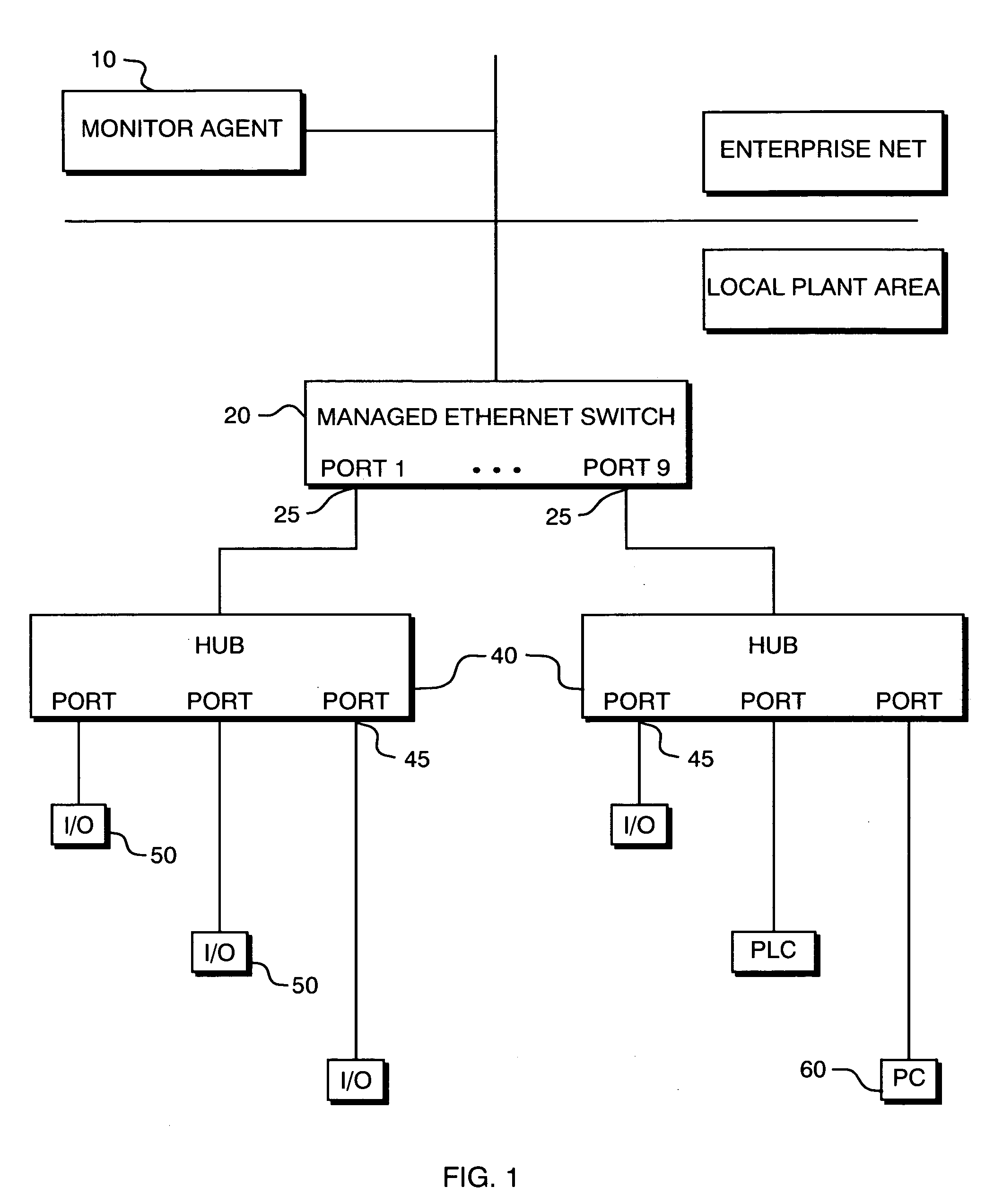
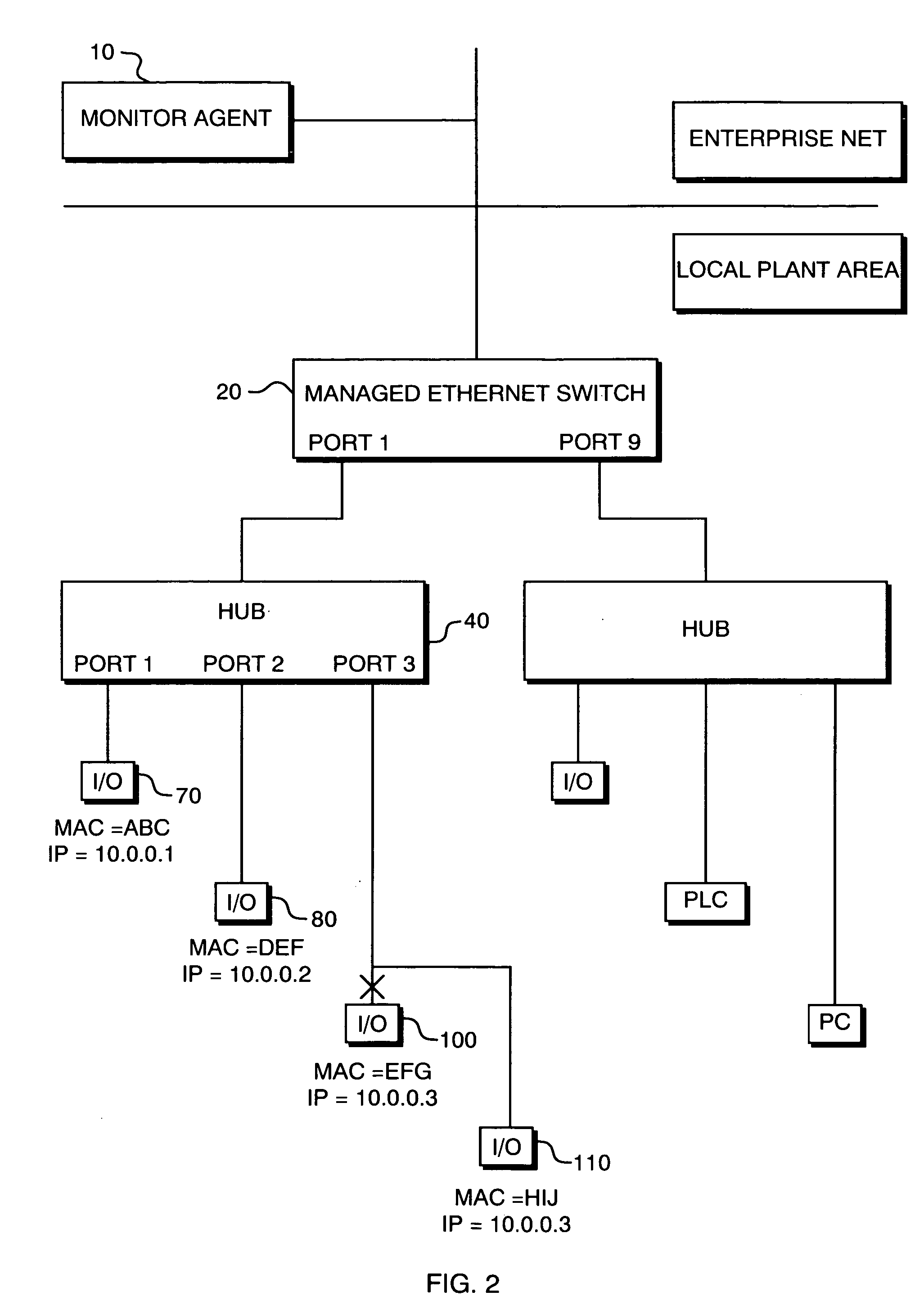
The present invention is for automatic reconfiguration of industrial networked devices. More particularly, the system described herein facilitates use of TCP / IP networks, such as Ethernet, as an alternative for industrial fieldbus or device buses by removing the need to perform significant reconfiguration of devices such as I / O modules, sensors, or transducers under field replacement situations. The present invention uses a monitor agent to track the IP and MAC addresses of networked devices as well as port information. If a device fails, maintenance personnel make an in-field replacement of the failed device and the monitor agent automatically reassigns the IP address to the replacement device.
Owner:SCORPION CONTROLS
Method and computer program product for monitoring an industrial network
ActiveUS7246156B2Digital data processing detailsMultiple digital computer combinationsEmbodied agentThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
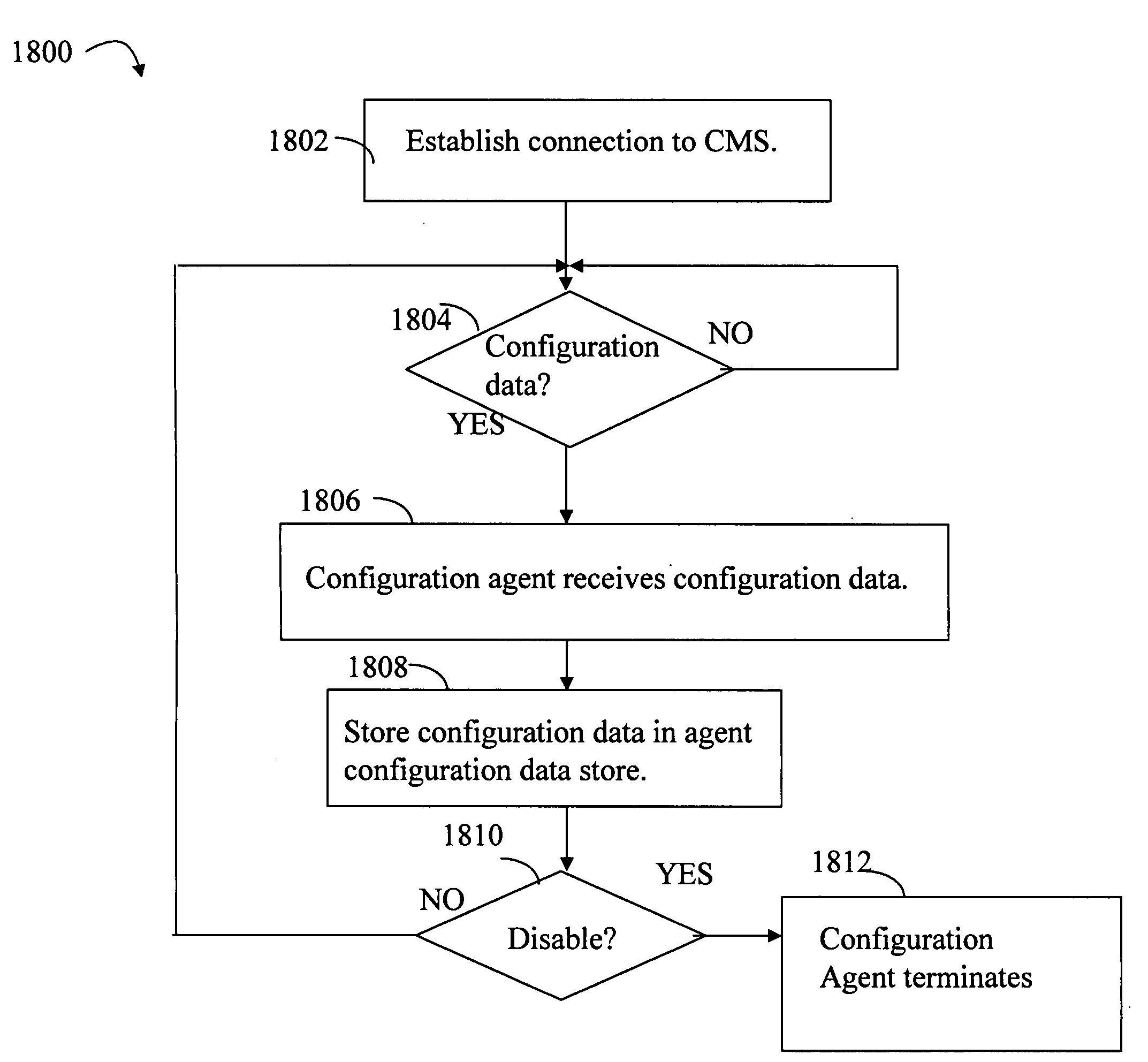
Techniques for agent configuration
InactiveUS20090271504A1Testing/monitoring control systemsDigital computer detailsNetwork applicationOperating system
Described are techniques for monitoring the performance, security and health of a system used in an industrial application. Agents on components included in the industrial network report data to an appliance or server. The agents on a component may include a configuration agent and one or more other agents. The configuration agent receives agent configuration data that may be communicated at a network application level. The agent configuration data may include information used to configure the configuration agent and other agents on the component. The configuration agent may be disabled. Once disabled, the configuration agent cannot be used to further modify agent configuration data as applied to the configuration agent and the one or more other agents until re-enabled.
Owner:IND DEFENDER
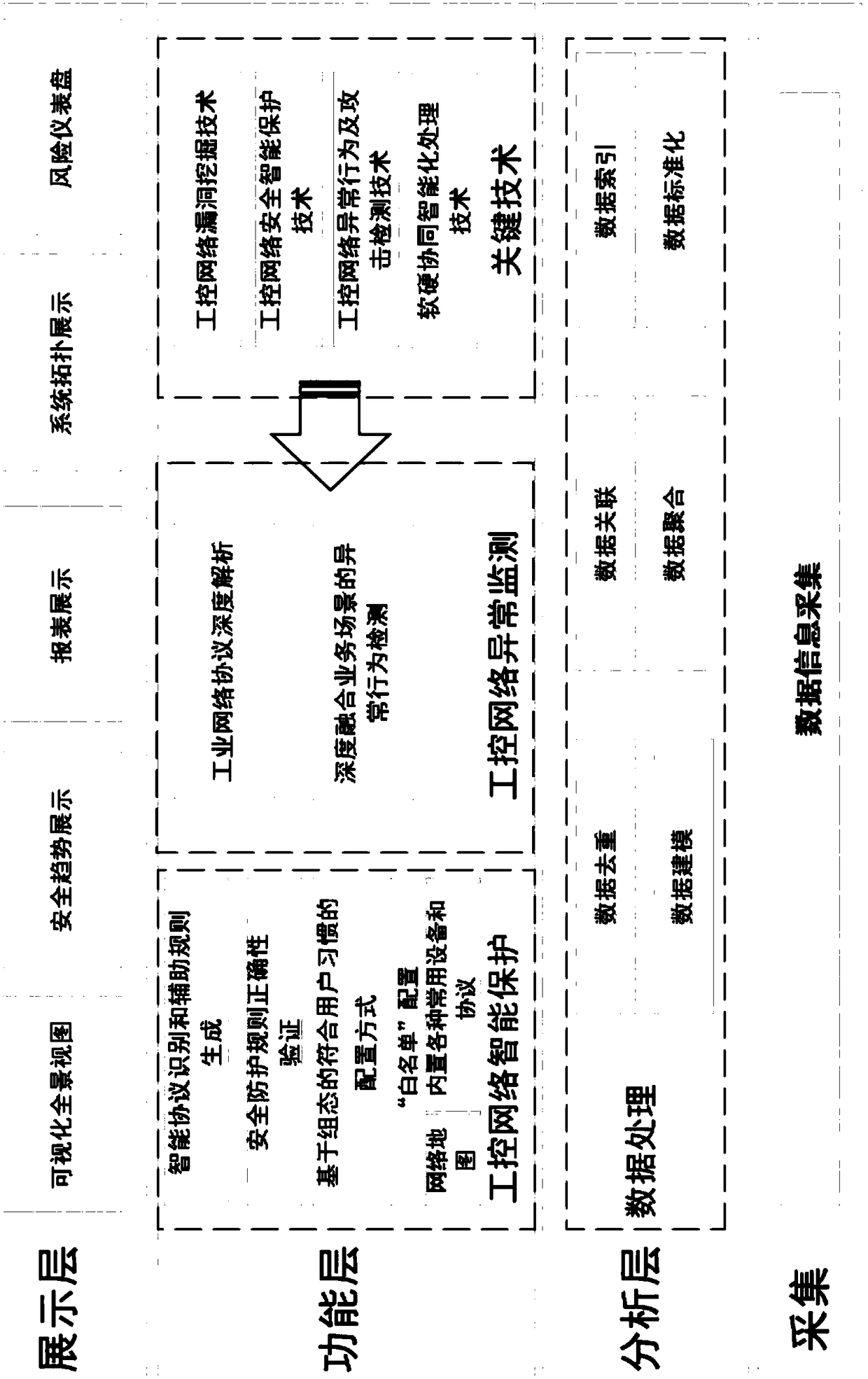
Industrial control network security protection monitoring system
InactiveCN109474607AReal-time preventionReal-time protectionTransmissionData informationData modeling
An industrial control network security protection monitoring system performs real-time prevention and protection on industrial equipment of the industrial control network, and realizes network security protection monitoring through an acquisition layer, an analysis layer, a function layer and a display layer based on an integrated application platform, wherein the display layer mainly displays security trend, system topology and industrial control panorama; the acquisition layer comprises the acquisition of network data traffic and the recording of industrial control network operations; the analysis layer mainly comprises data processing, data association, data aggregation, data modeling, and integrated interfaces of other function modules; and the function layer mainly comprises monitoring audit, intrusion prevention, vulnerability mining, and data isolation. The system provided by the invention protects and protects industrial equipment in real time through the intelligent protectiontechnology of the industrial network control system, monitors and audits the data information of the entire industrial control network through the monitoring and auditing technology to prevent the industrial control network from being attacked externally, and can also have the vulnerability mining function of the industrial control network to escort the entire industrial control network security.
Owner:中船重工信息科技有限公司
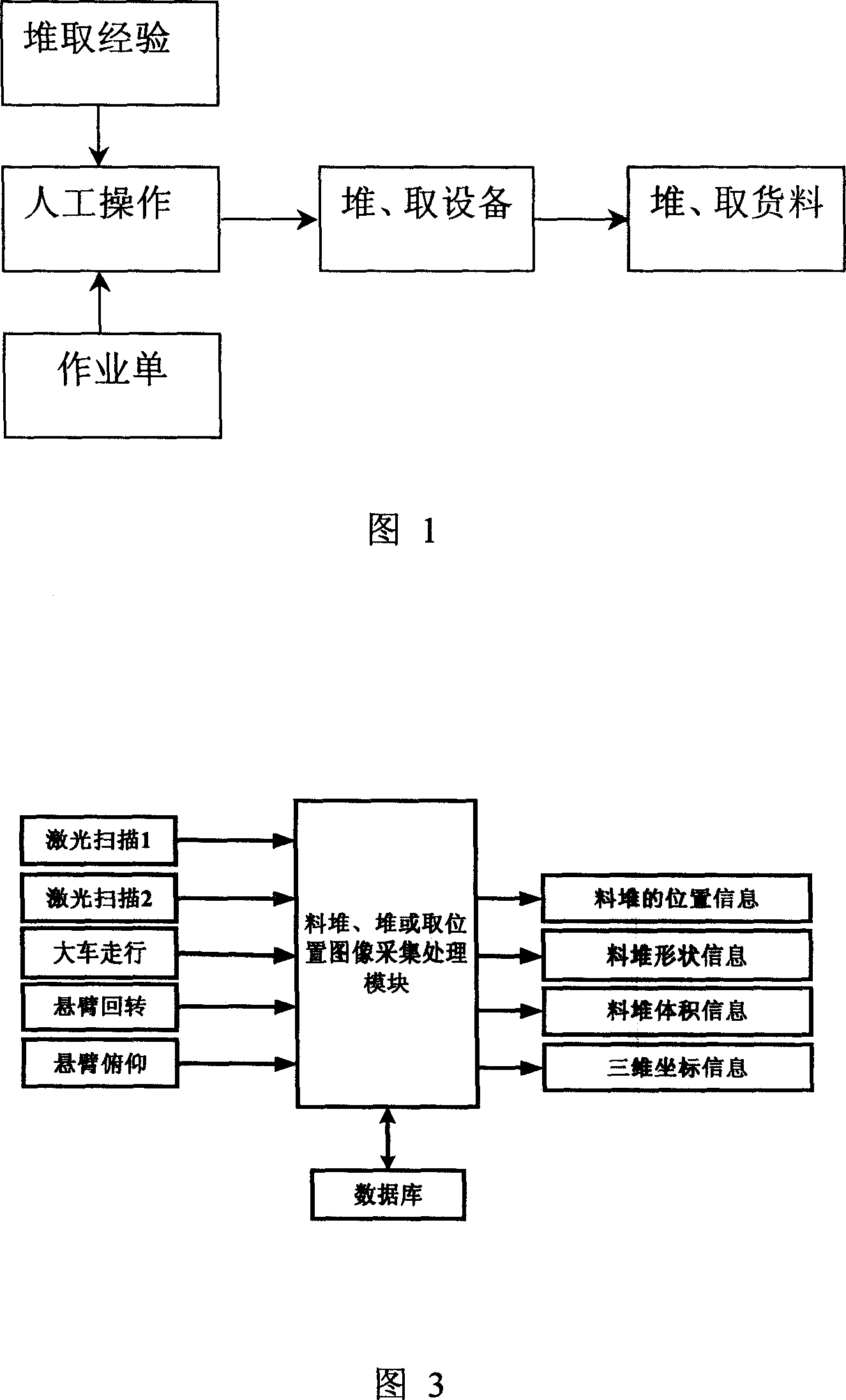
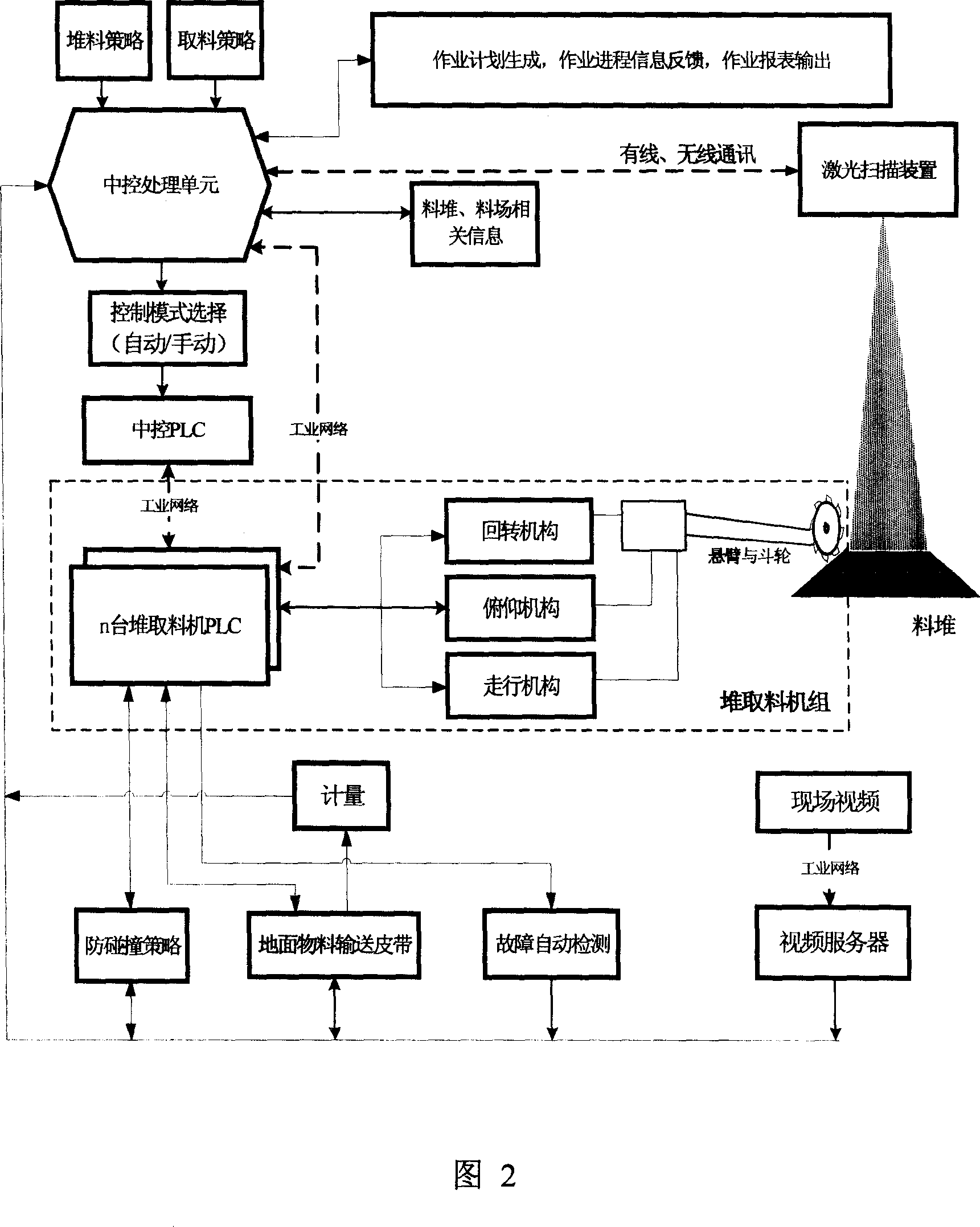
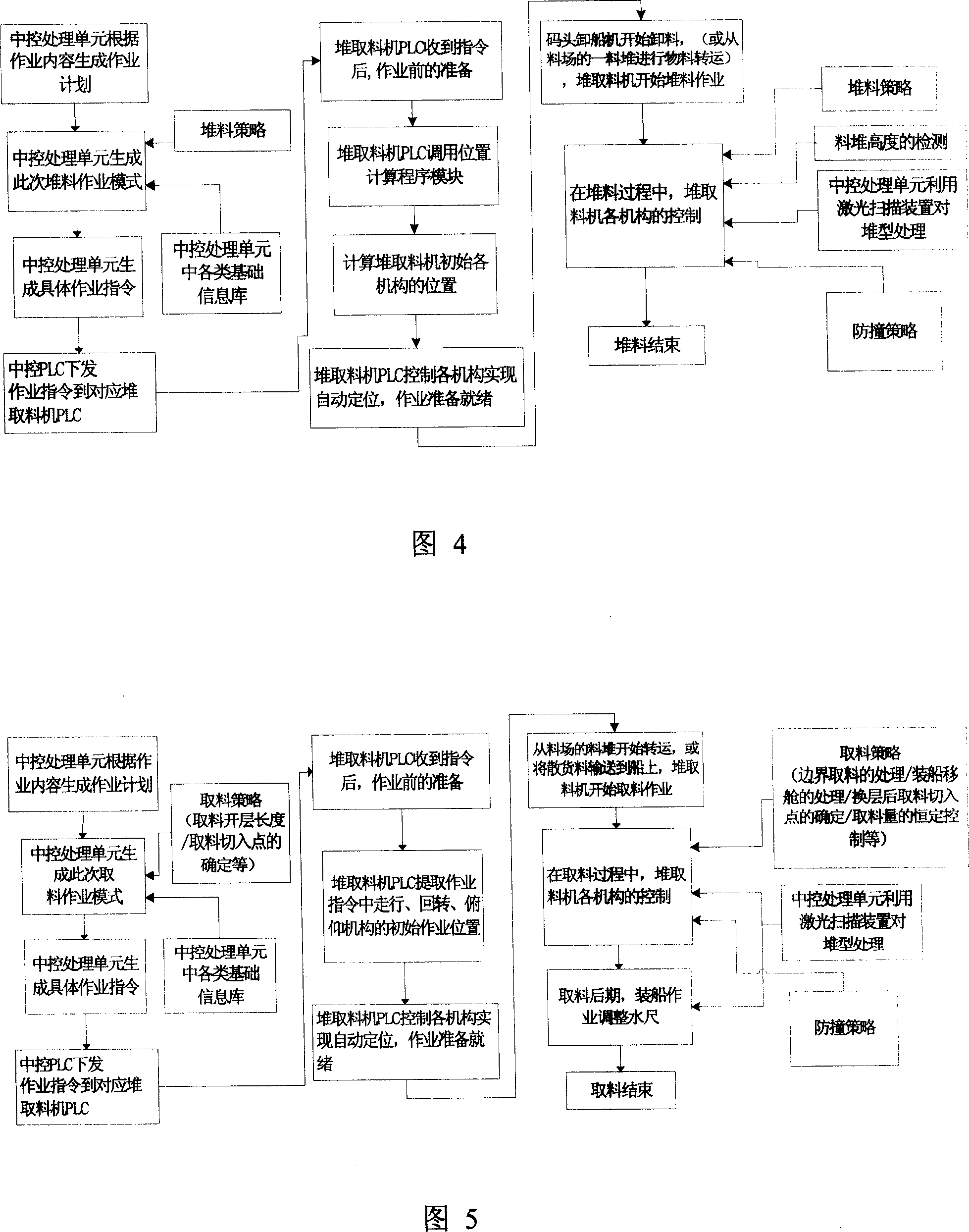
Unmanned piling and taking technique for bulk cargo stock yard
ActiveCN101104480AOvercoming automationOvercome labor intensityElectric programme controlLoading/unloadingBulk cargoLaser scanning
The invention relates to a port warehousing logistics technology, in particular to a bulk material yard unmanned stacking / reclaiming technology. Firstly, a database is established; secondly, operation instructions, automatic stacking / reclaiming operation modes and control instructions for automatic stacking / reclaiming operations are generated through input operation kinds of goods and the planning work amount; thirdly, the relevant instructions are sent to a central control PLC and then transmitted to the corresponding local stacker / reclaimer PLC through the industrial network; fourthly, the local PLC controls the operation of all components of the stacker / reclaimer to complete the local operation control. At the same time, a material stack laser scanning device is used to scan the material yard condition, and the scanned result will then be transferred to a central control processing unit through the industrial network; fifthly, the central control processing unit achieves the stack type scan data processing of the stacker / reclaimer to generate new instructions which will then be sent to the corresponding local stacker / reclaimer PLC; sixthly, a handle operating panel arranged inside a central control room can be taken as a backup means of manual operation under special circumstances. The invention can be applied to large-scale raw material yards, such as ports, wharfs, open warehouses, mine stacking yards, as well as iron and steel enterprises.
Owner:BAOSHAN IRON & STEEL CO LTD +1
Event monitoring and management
InactiveUS20070294369A1Multiple digital computer combinationsPlatform integrity maintainanceNetwork connectionThermostat
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:IND DEFENDER
Automatic determination of correct IP address for network-connected devices
InactiveUS20060031488A1Easy to useFast deliveryDigital computer detailsTransmissionIp addressTransducer
An automatic reconfiguration system for industrial networked devices. The system facilitates use of TCP / IP networks, such as Ethernet, as an alternative for industrial fieldbus or device buses by removing the need to perform significant reconfiguration of devices such as I / O modules, sensors, or transducers under field replacement situations. In one embodiment the invention uses a monitor agent to track the IP and MAC addresses of networked devices as well as port information. If a device fails, maintenance personnel make an in-field replacement of the failed device and the monitor agent automatically reassigns the correct IP address to the replacement device.
Owner:SCORPION CONTROLS
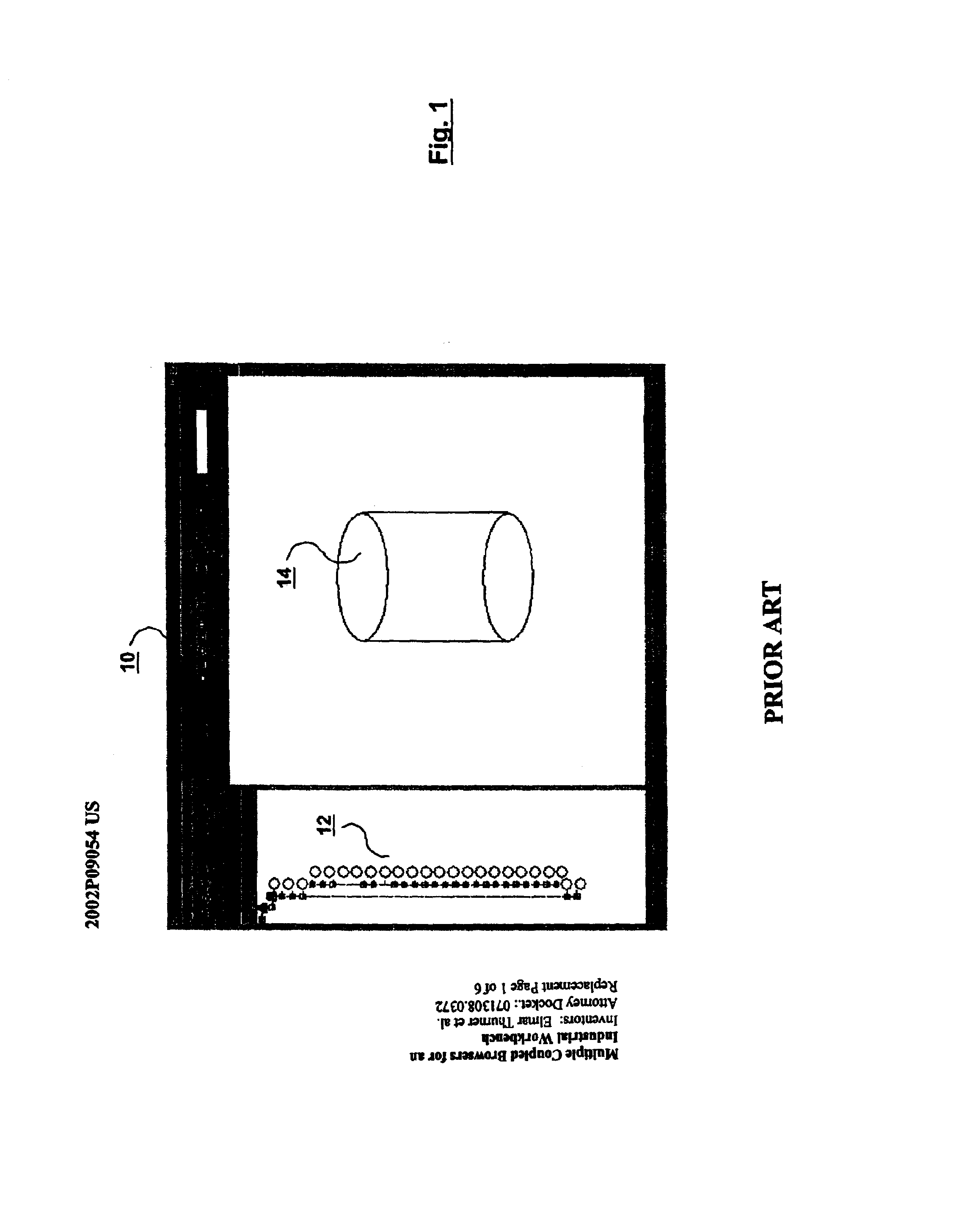
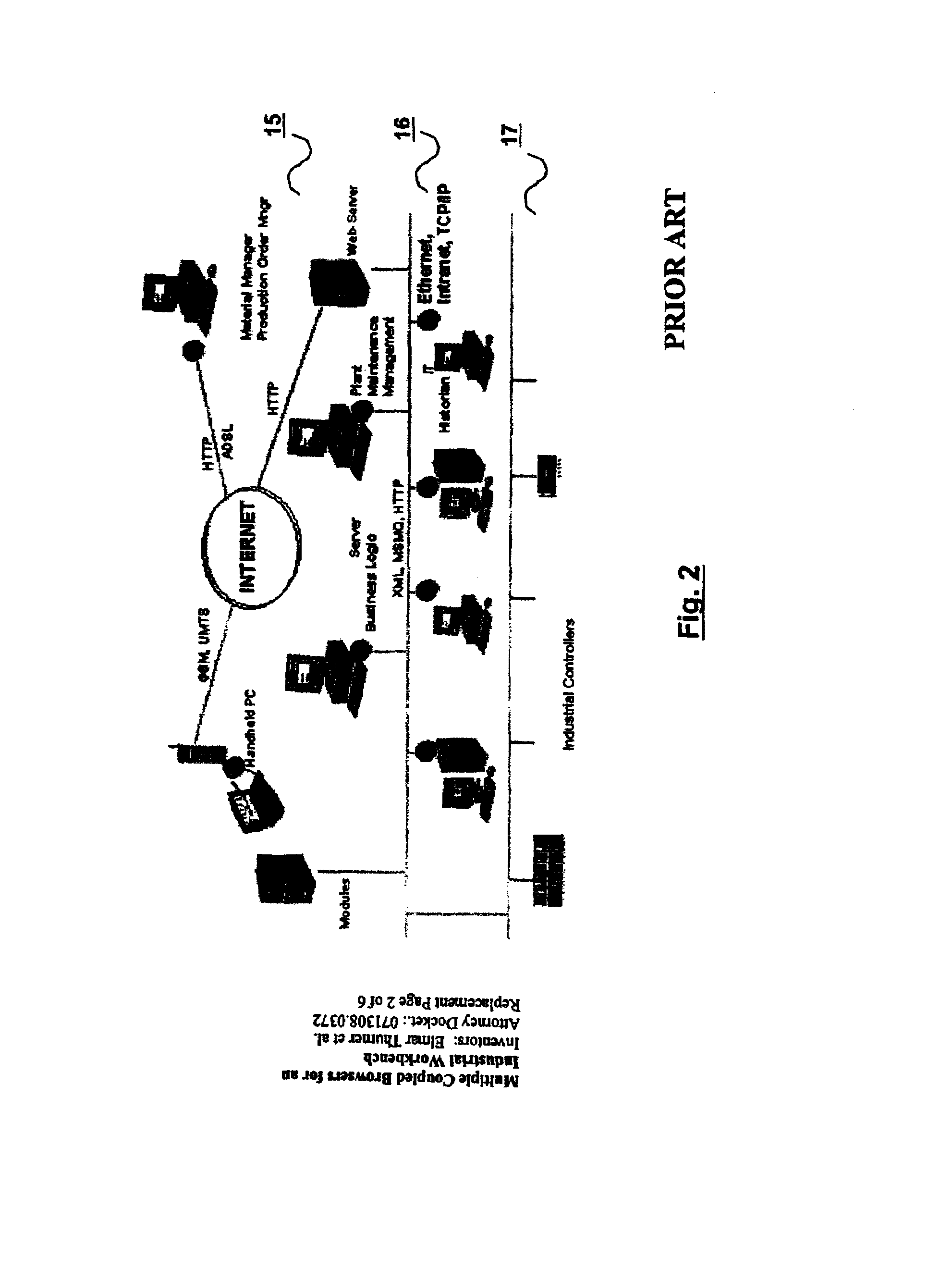
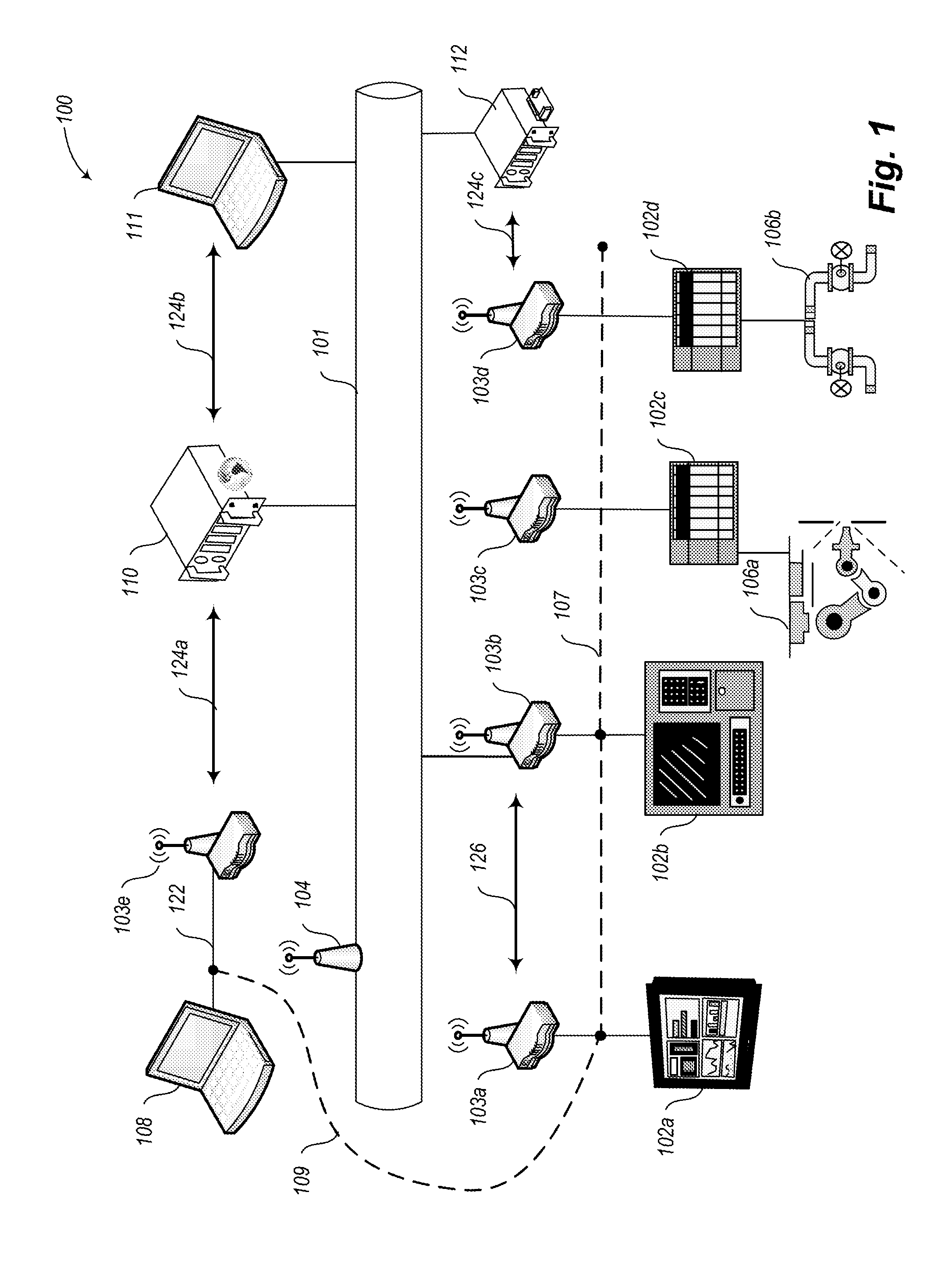
Multiple coupled browsers for an industrial workbench
Multiple Views of an Industrial Plant are graphically displayed and viewed. A graphical user interface displays the views in corresponding panes or windows of the graphical user interface. The views, being graphical representations of systems of the Industrial Plant, are coupled by a coupler according to a predetermined relationship between the underlying systems of the Industrial Plant represented by the coupled views. The coupler automatically refocuses the panes to display different views of the Industrial Plant based on a selection of an object in any of the panes or on a manual refocus of one view and on the predetermined relationship for coupling the views. The Coupled views represent different domains of the Industrial Plant or Industrial Network e.g. real-time monitoring and operation, configuration, debugging, maintenance, scheduling, asset management, documentation, training, simulation, physical construction, material flow monitoring, programming, interconnecting function blocks, performance analysis. The analysis may be provided at different points in time (now, past, predicted future) and with a different spatial focus (parts, whole). Coupling different views greatly reduces handling effort for building and operating Industrial Plants.
Owner:SIEMENS AG
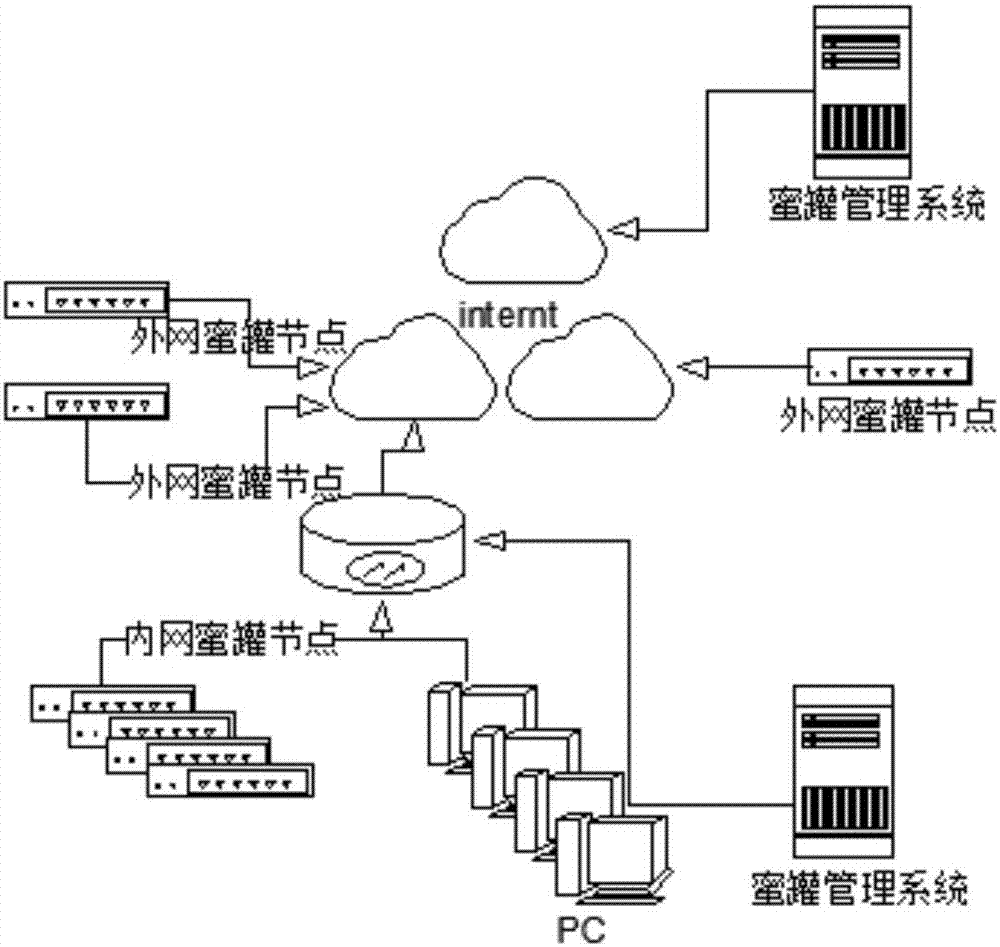
Industrial control network honeypot system
The invention discloses an industrial control network honeypot system, which comprises an external network honeypot node, an internal network honeypot node, a honeypot management system, Internt and a PC. The beneficial effects of the present invention are: the external network honeypot node can help users set up a disguised "business system" around the IP address of the core server, and induce attackers by constructing a real industry business SCADA template, thereby protecting the real business system, honeypot The management system can simulate SCADA and PLC system services, and can switch to different business types according to the multi-service templates preset in the system, making it impossible for attackers to distinguish the real attack target. The industrial control protocol simulation module creates a real industrial control system for attackers. The operating environment of the service, any operation and scanning attack behavior of the attacker will be recorded by the data analysis function of the honeypot system.
Owner:CHINA ELECTRONICS STANDARDIZATION INST +1
Event monitoring and management
InactiveCN1820262AElectric digital data processingInformation technology support systemThermostatThreat level
Described are techniques used in monitoring the performance, security and health of a system used in an industrial application. Agents included in the industrial network report data to an appliance or server. The appliance stores the data and determines when an alarm condition has occurred. Notifications are sent upon detecting an alarm condition. The alarm thresholds may be user defined. A threat thermostat controller determines a threat level used to control the connectivity of a network used in the industrial application.
Owner:工业守护者公司
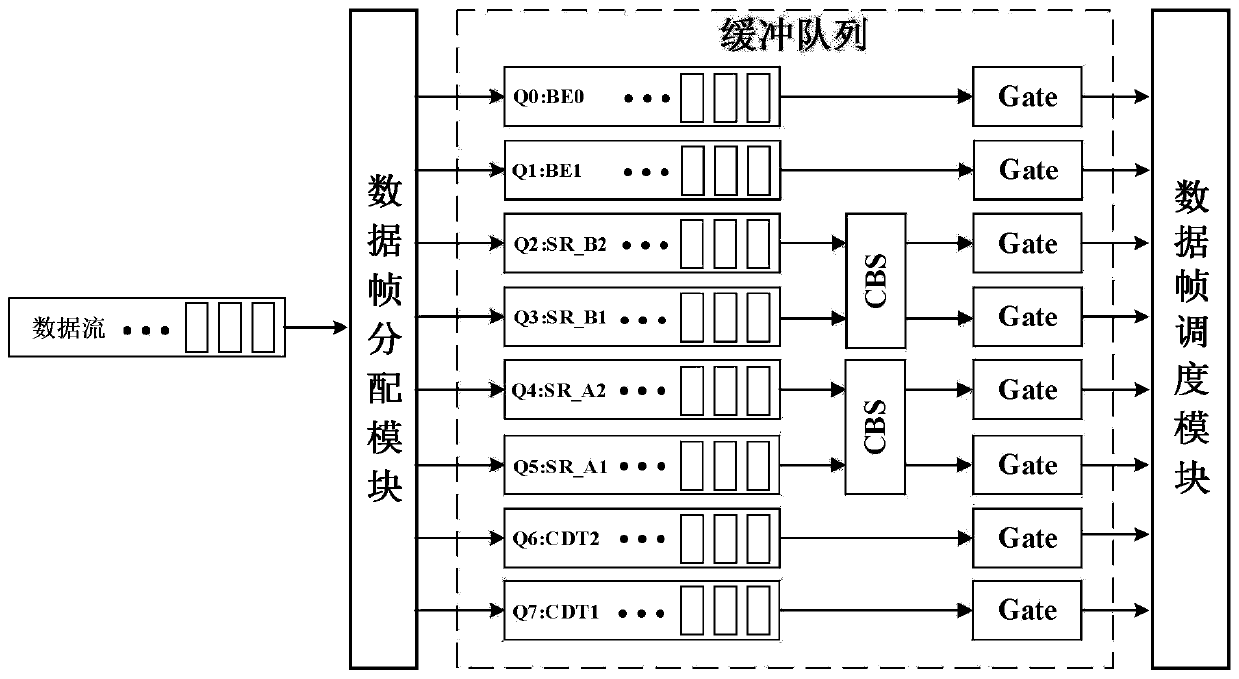
Industrial time-sensitive network data deterministic scheduling method
PendingCN111327540AGuaranteed normal transmissionImprove connectivityData switching networksIndustrial EthernetNetwork data
The invention relates to an industrial time-sensitive network data deterministic scheduling method, which belongs to the technical field of industrial networks and comprises the following steps that:S1: a TSN management network allocates priorities to data frames sent by industrial Ethernet equipment; S2, defining industrial data characteristics according to the data frame characteristic parameters; S3, establishing a data scheduling model at an output port of the industrial TSN switch, wherein the data scheduling model is composed of a data frame distribution module, a buffer queue and a data frame scheduling module; the data frame distribution module divides the buffer queue into eight scheduling queues according to the frame characteristic parameters; S4, distributing the data frames into different scheduling queues; S5, different shaping mechanisms are adopted for all the scheduling queues according to different determinacy and real-time requirements of the data frames; and S6, the data frame scheduling module performs output scheduling on the data frames. According to the method, the determinacy and the real-time performance of industrial CDT type data transmission are ensured, the jitter of SR type data can be effectively reduced, and meanwhile, the transmission of BE type data is allowed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
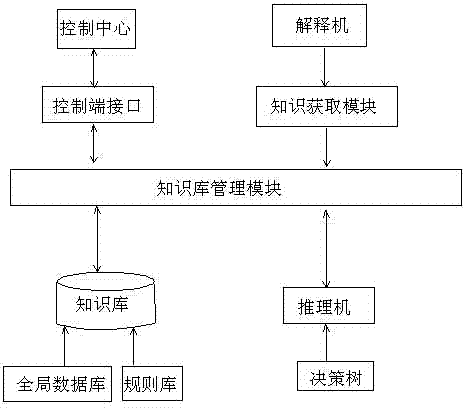
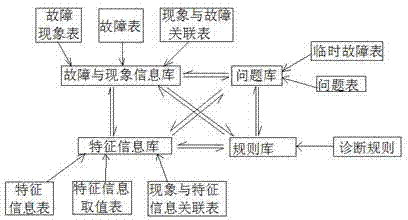
Fault diagnosis expert system based on decision tree for industrial Ethernet network
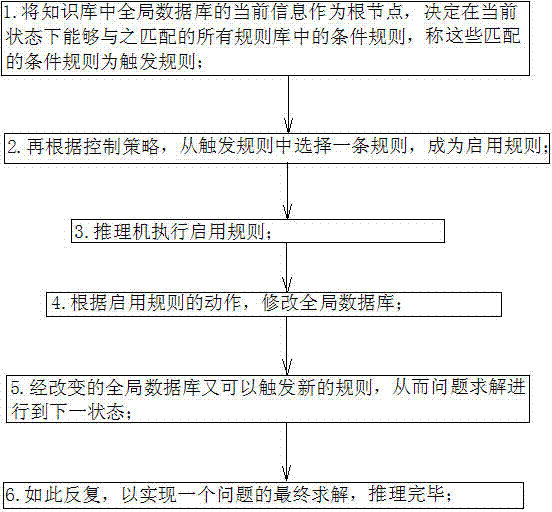
The invention discloses a fault diagnosis expert system based on a decision tree for an industrial Ethernet network. Firstly, an expert system comprising a knowledge base, an inference engine, a knowledge base management module, a knowledge acquisition module, an explanation facility and a control center is established; secondly, the knowledge base is utilized to contact the inference engine and the control center to obtain data required by the modules for storing a diagnosis rule, various pieces of data of the system and an intermediate result generated during the system diagnosis period; thirdly, comparison, commonly called as matching, is carried out between a condition part of a rule base and a content of a global data base through the inference engine, if matching is successful, a conclusion part is displayed, the global data base is modified according to an action part of an enable rule, the changed global data base can trigger a new rule, so that problem solving proceeds to the next state, and so forth, one problem is finally solved; and lastly, post processing is carried out through the inference engine, a new knowledge base is updated by the control center, so that the expert system is gradually improved.
Owner:CHINA TOBACCO HENAN IND
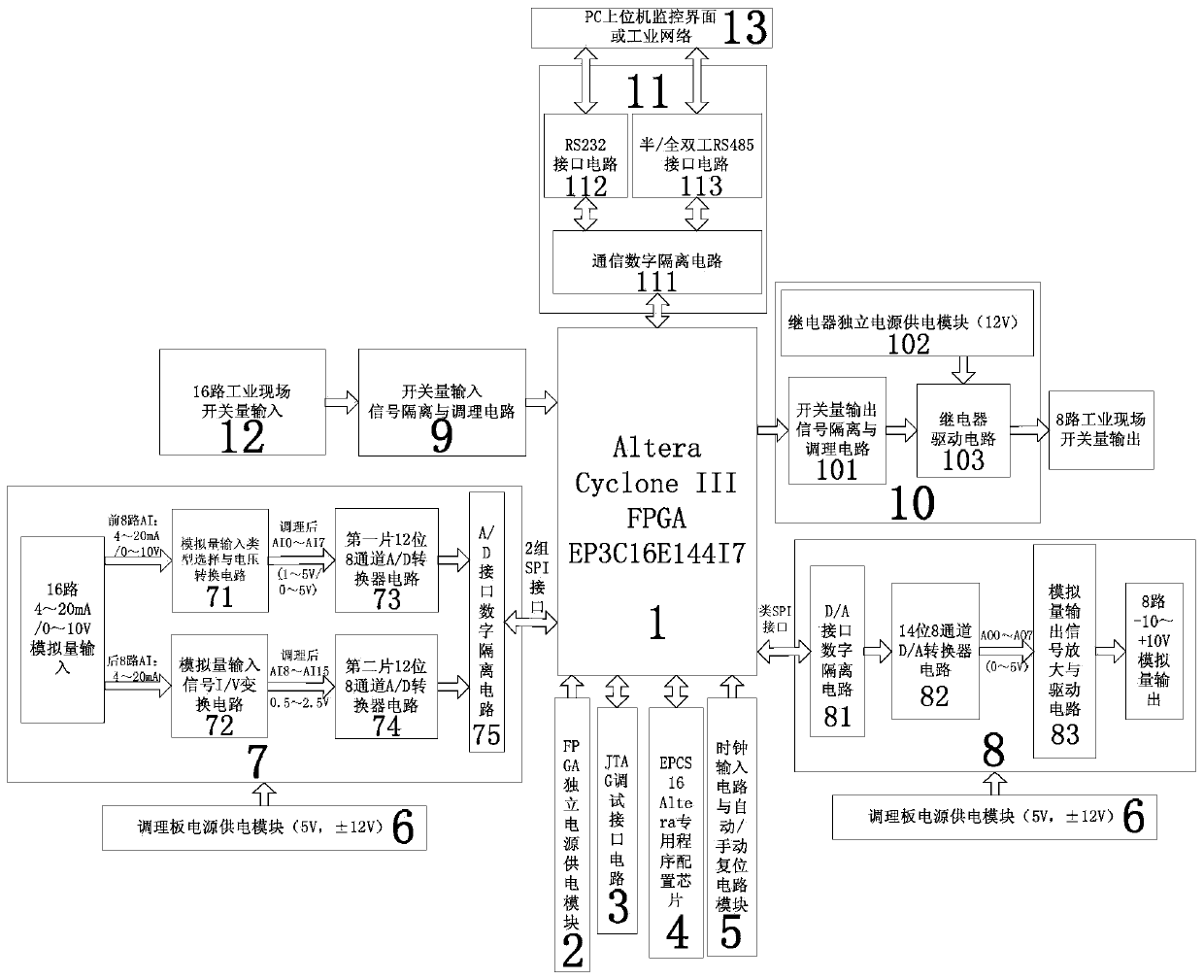
FPGA-based ultrahigh-speed industrial controller
InactiveCN103631176AImprove reliabilityLow costProgramme controlComputer controlControl cellHemt circuits
An FPGA-based ultrahigh-speed industrial controller comprises a main control unit, an FPGA independent power supply unit, a JTAG debugging interface circuit, an EPCS16 program configuration circuit, a clock input and automatic / manual reset circuit unit, a conditioning board power supply unit, a 16-path analog quantity input A / D conversion unit, an eight-path analog quantity output D / A conversion unit, a switch quantity input signal isolation and conditioning unit, a switch quantity output signal isolation and drive unit, an RS232 / half / full-duplex RS485 / RS422 bus communication unit, 16 paths of industrial site switch quantity input, an upper computer or an access industrial network. According to the FPGA-based ultrahigh-speed industrial controller, only one FPGA is used as a main control chip to complete analog quantity and switch quantity acquisition and control of an industrial control system. The FPGA-based ultrahigh-speed industrial controller has the most prominent features of high speed and ultrahigh speed and has the advantages of low cost, good versatility, high stability, good reliability, field programmability and strong expansion capability and the like.
Owner:TIANJIN UNIV
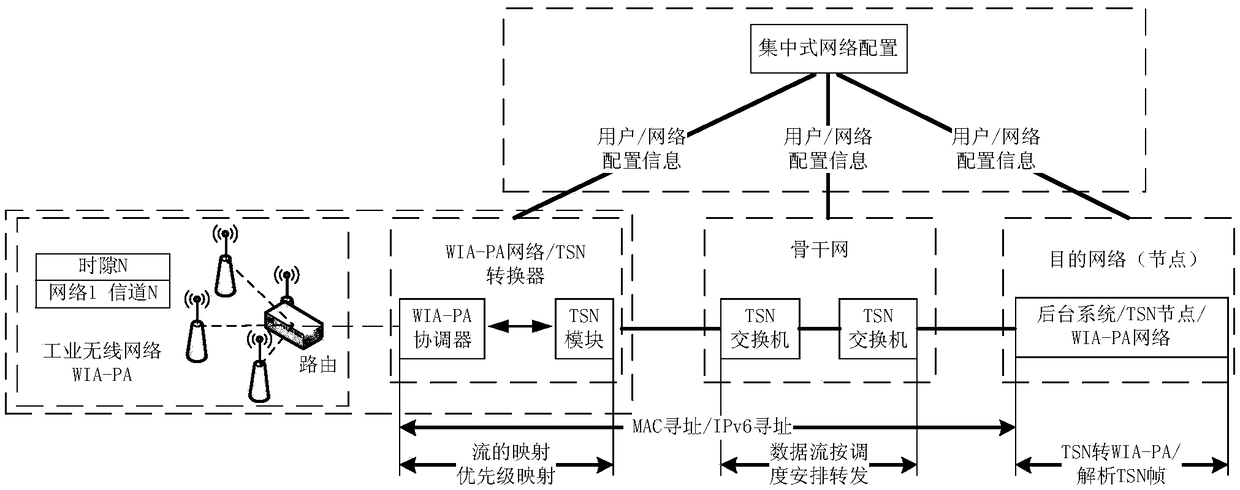
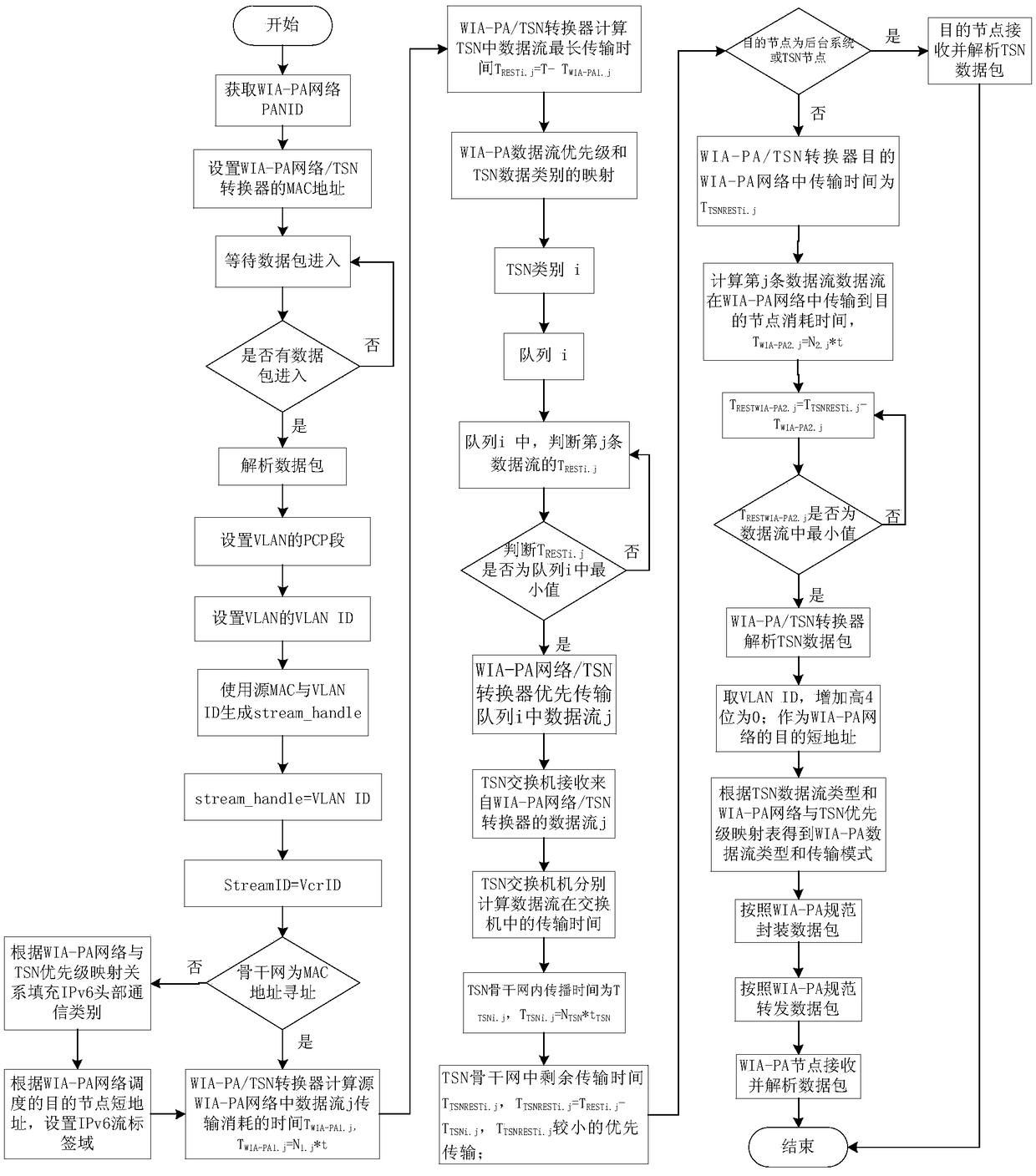
Industrial wireless WIA-PA network and time sensitive network conversion method and apparatus
ActiveCN108965171AGuaranteed priorityRealize interconnectionData switching networksData streamField device
The invention relates to an industrial wireless WIA-PA network and time sensitive network conversion method and apparatus, and belongs to the technical field of industrial networks. The apparatus consists of a TSN switch, a WIA-PA / TSN converter, a WIA-PA router and a WIA-PA field device. In the method, the WIA-PA / TSN converter is designed, two manners of MAC address addressing and IPv6 address addressing are supported, the mapping between a WIA-PA data stream and a TSN data stream is completed, the support of a data transmission priority is maintained, and the protocol conversion and interconnection between WIA-PA and TSN are effectively achieved; and furthermore, the invention further provides a transmission delay guarantee method between the WIA-PA and the TSN, the data can arrive withina specified deadline by allocating communication resources such as transmission time slots and the like, so that the instantaneity and certainty of the transmission of the data between the WIA-PA / TSNis ensured.
Owner:INST OF IND INTERNET CHONGQING UNIV OF POSTS & TELECOMM
Message tunneling in an industrial network
A networking system is discussed. The system may be used for industrial networks where access to field device data is valuable. Commands, such as read or write requests to particular field device data, may be encapsulated within application layer protocol messages, such as MODBUS messages. Responses to the commands may also be encapsulated within MODBUS messages. The encapsulated commands and responses may be transmitted between various devices of an industrial network, including a controller and a gateway device, such as a multiplexer, of the industrial network. Encapsulating the commands and responses may provide a tunneling mechanism allowing a controller complete access to the data of the field devices in communication with the gateway device.
Owner:SCHNEIDER ELECTRIC IND SAS
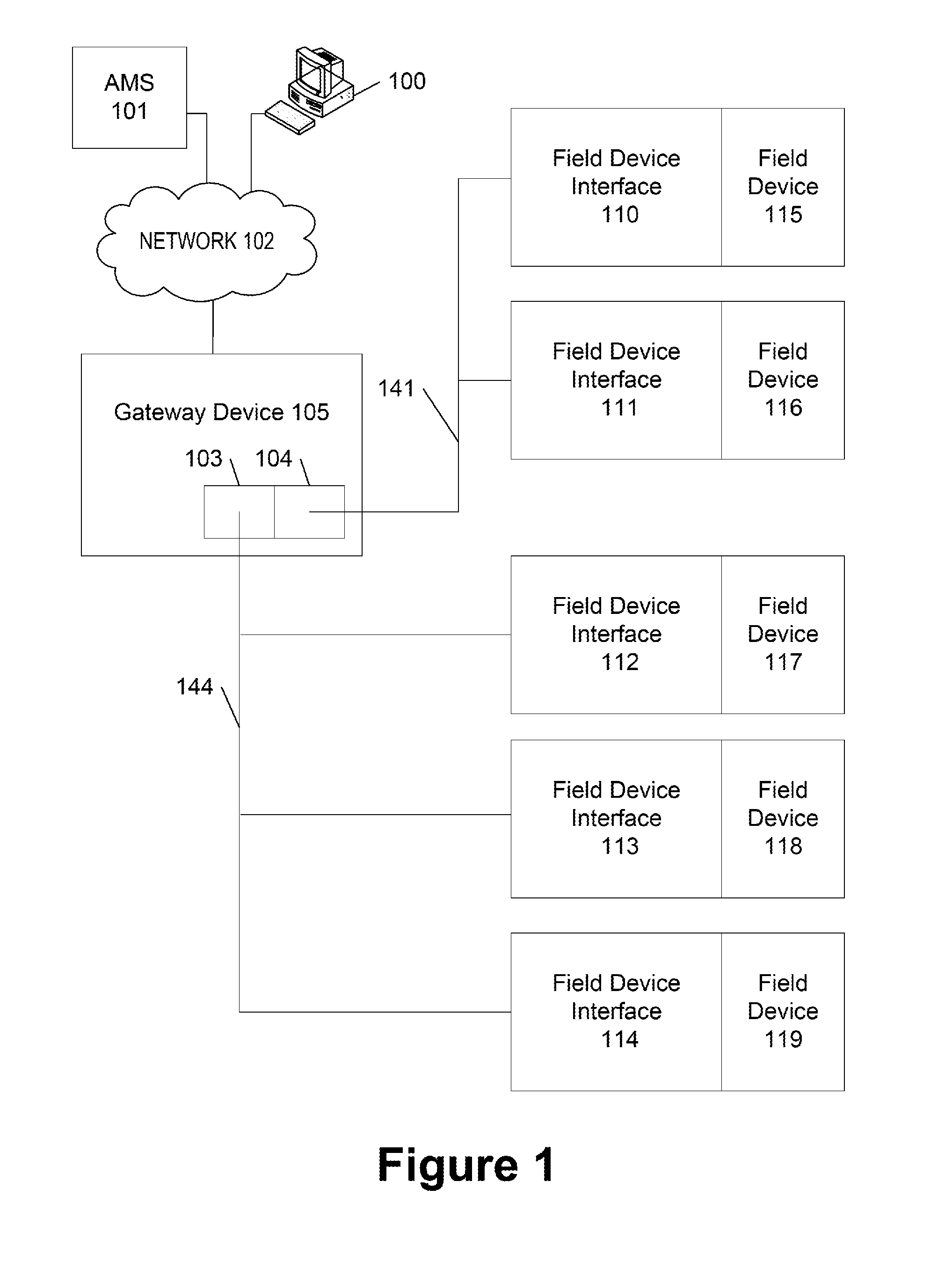
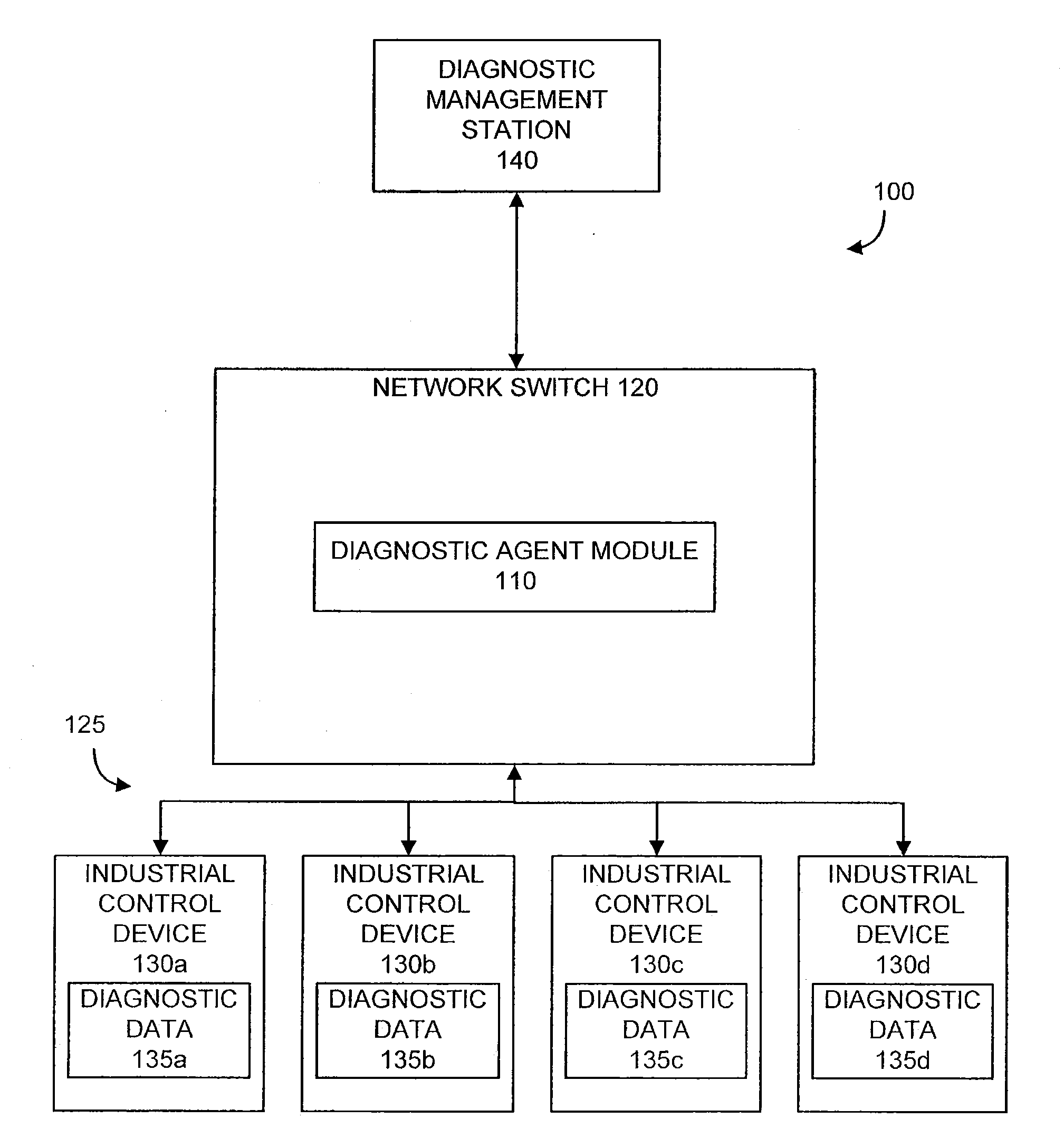
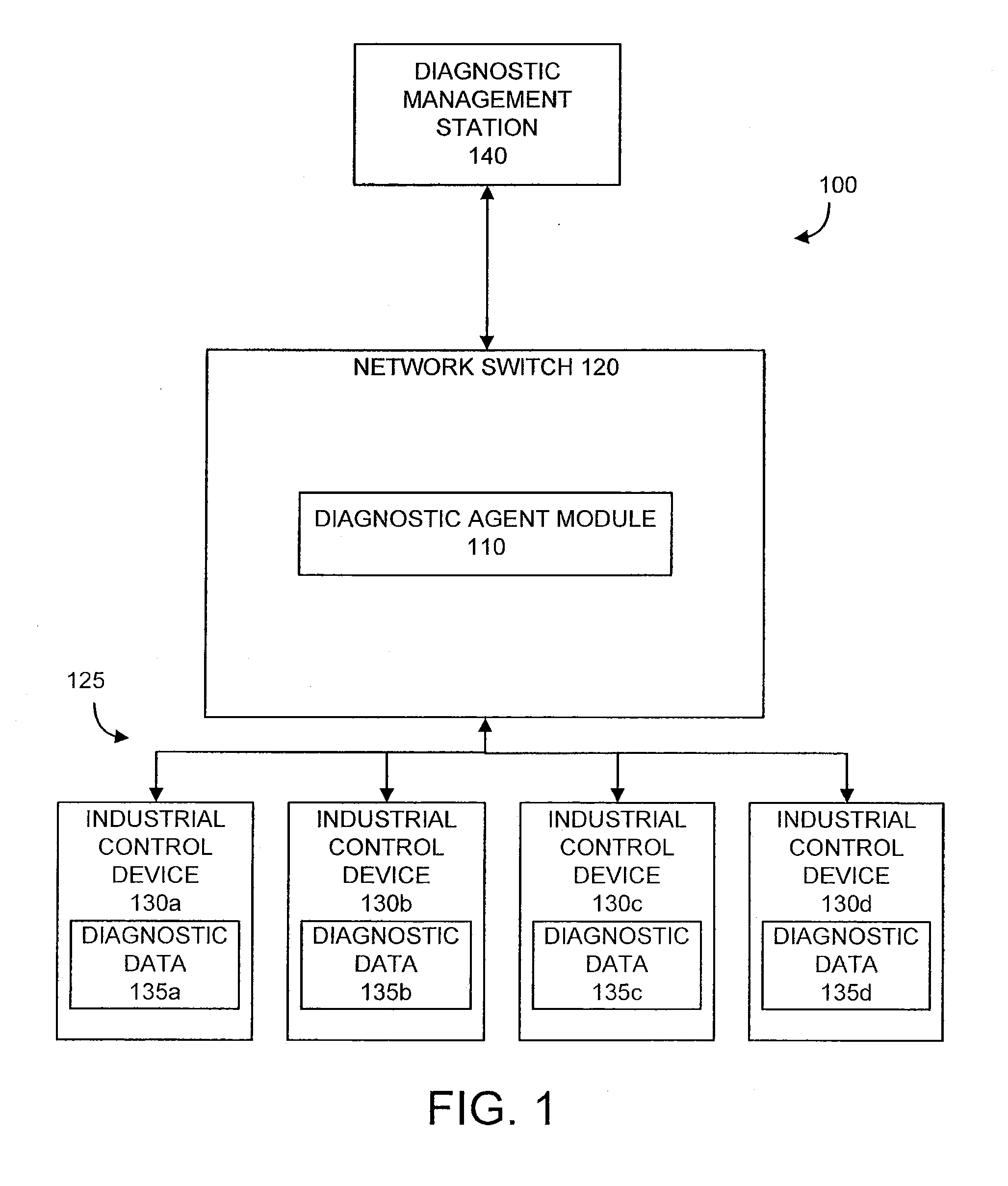
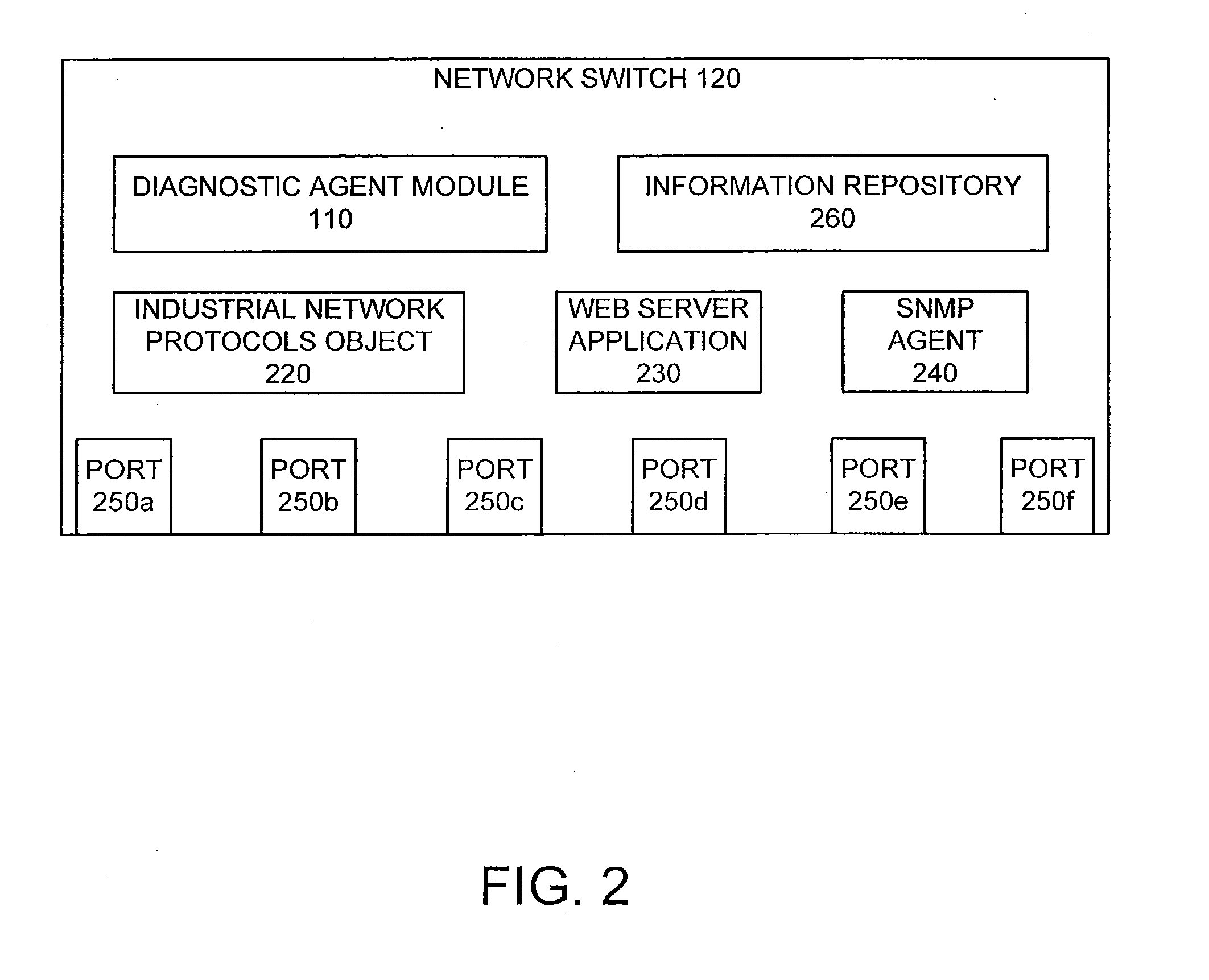
Diagnostic Module For Distributed Industrial Network Including Industrial Control Devices
InactiveUS20110060427A1Easy to processProgramme controlSafety arrangmentsComputer moduleDiagnostic information
A network component for an industrial automation system. The component includes a network switch processor configured to implement a networking switching function, at least one communication port configured to provide a communication channel between the network switch processor and at least one industrial control device over a network, and a diagnostic module configured to be implemented by the network switch processor and configured to retrieve diagnostic information from the at least one industrial control device.
Owner:ROCKWELL AUTOMATION TECH
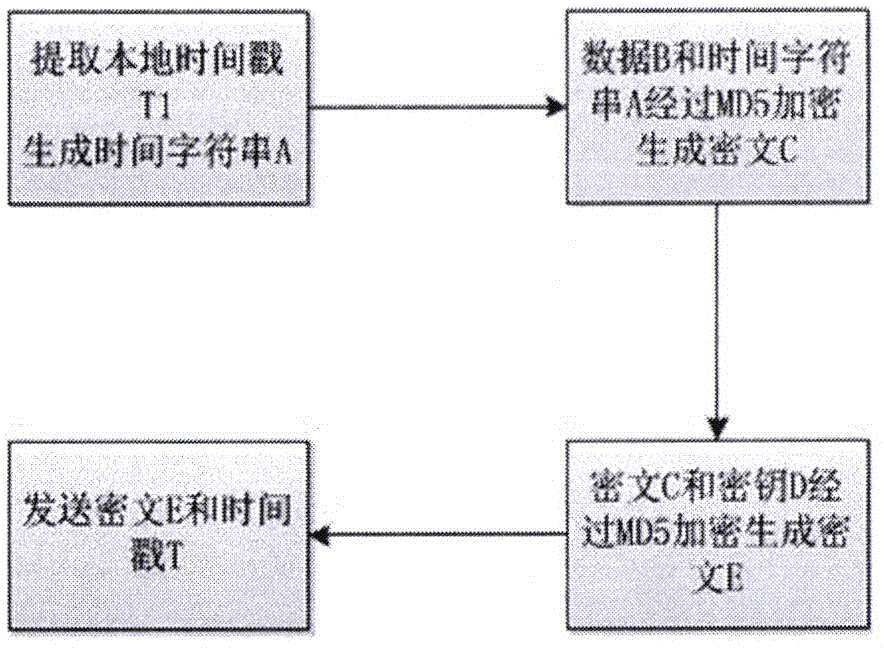
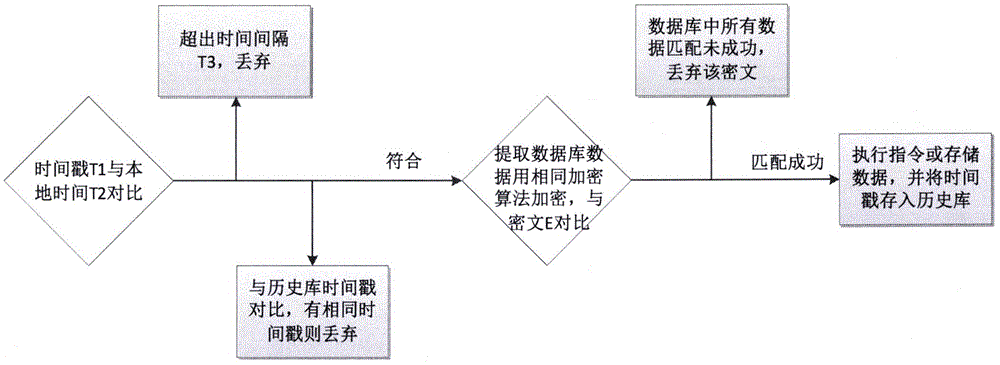
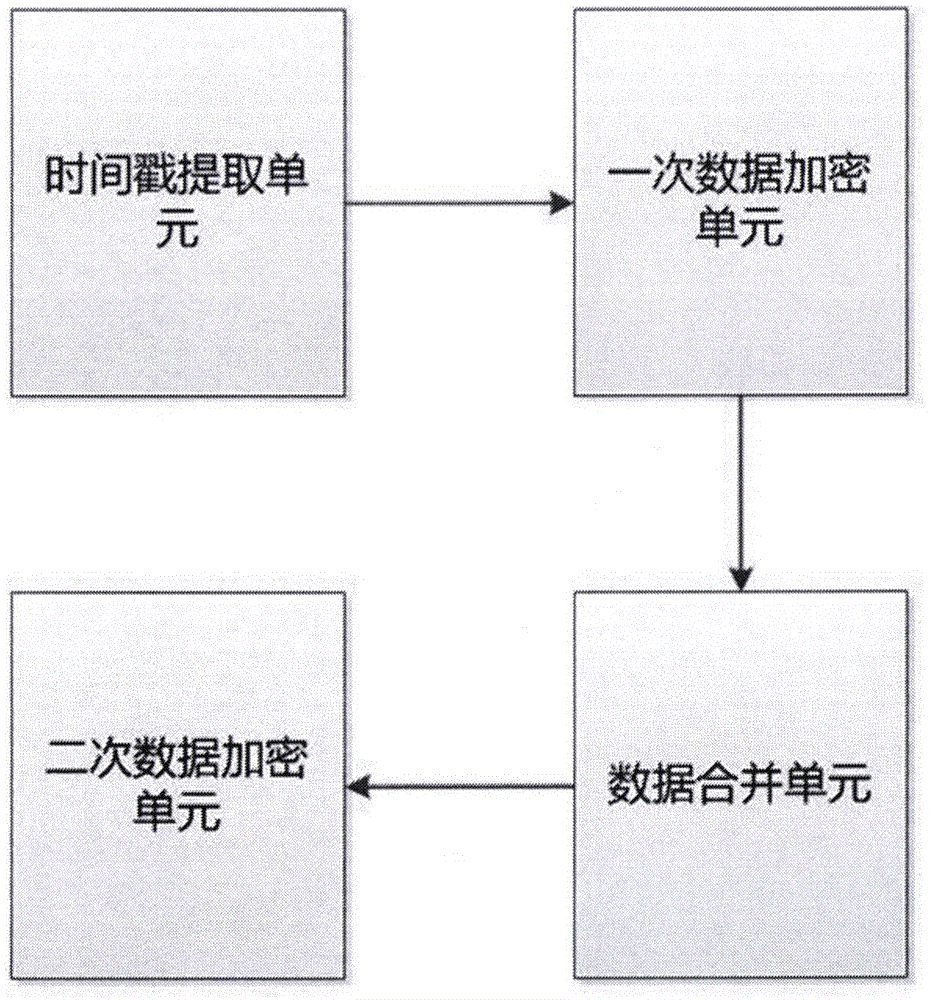
Timestamp technique-based industrial network security transmission method
InactiveCN105827408APrevent cheatingCannot be reusedUser identity/authority verificationTimestampSecure transmission
The invention relates to a timestamp technique-based industrial network security transmission method and belongs to the technical field of security transmission. The method comprises the steps of encrypting at a transmitting end and decrypting at a receiving end. During the encrypting process, the local time is extracted to generate a time character string, and then to-be-sent data or instructions are added into the time character string. After that, the time character string is encrypted according to an encryption algorithm to generate a ciphertext, and the ciphertext is encrypted for a second time through introducing a user key to generate a final ciphertext. Finally, the time character string and the final ciphertext are transmitted together. During the decrypting process, the received ciphertext and a received timestamp are verified to be whether outmoded / forged or not. On the condition that the ciphertext and the timestamp are verified to be outmoded / forged, the ciphertext and the timestamp are discarded. Otherwise, all possible instructions / data are matched in the same encryption mode with the transmitting end. If the matching result is successful, the decryption is successful. If the matching is not successful, the operation is continued till no data or instruction is matched successfully. After that, the data / instructions are discarded. According to the technical scheme of the invention, the deceit through maliciously counterfeiting data can be prevented, so that real data obtained through sniffing cannot be reused. Moreover, the method is simple, practical, efficient, and low in requirement on hardware.
Owner:CHINA AEROSPACE SYST ENG
Task unloading method based on power control and resource allocation
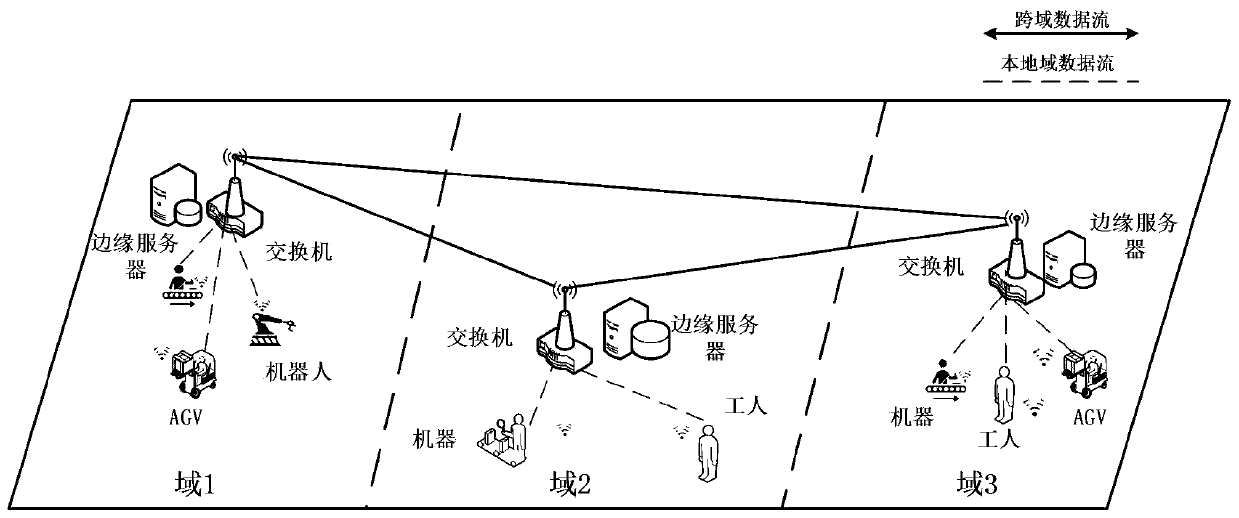
ActiveCN111245651AReduce offload overheadReduce time complexityData switching networksQuality of serviceOptimal decision
The invention discloses a task unloading method based on power control and resource allocation, and relates to the field of industrial Internet of Things. The method comprises the steps: establishinga cross-domain network model of an industrial field; constructing a calculation model of an equipment task; according to the model, constructing a mixed integer nonlinear programming model for communication power control, resource allocation and calculation unloading problems; decomposing a problem into three sub-problems; solving an optimal communication power and a resource allocation strategy by utilizing convex optimization knowledge, a Lagrange multiplier method and a KKT (Karush-Kuhn-Tucker) condition; after substituting an original target function, solving an optimal decision of a taskcalculation position by utilizing a deep reinforcement learning algorithm, and obtaining an optimal strategy of communication power, resource allocation and the calculation position of task unloading.The method can obtain the optimal strategy in industrial network task unloading, and has the technical effects of reducing the task delay, reducing the equipment energy consumption and ensuring the service quality.
Owner:SHANGHAI JIAO TONG UNIV
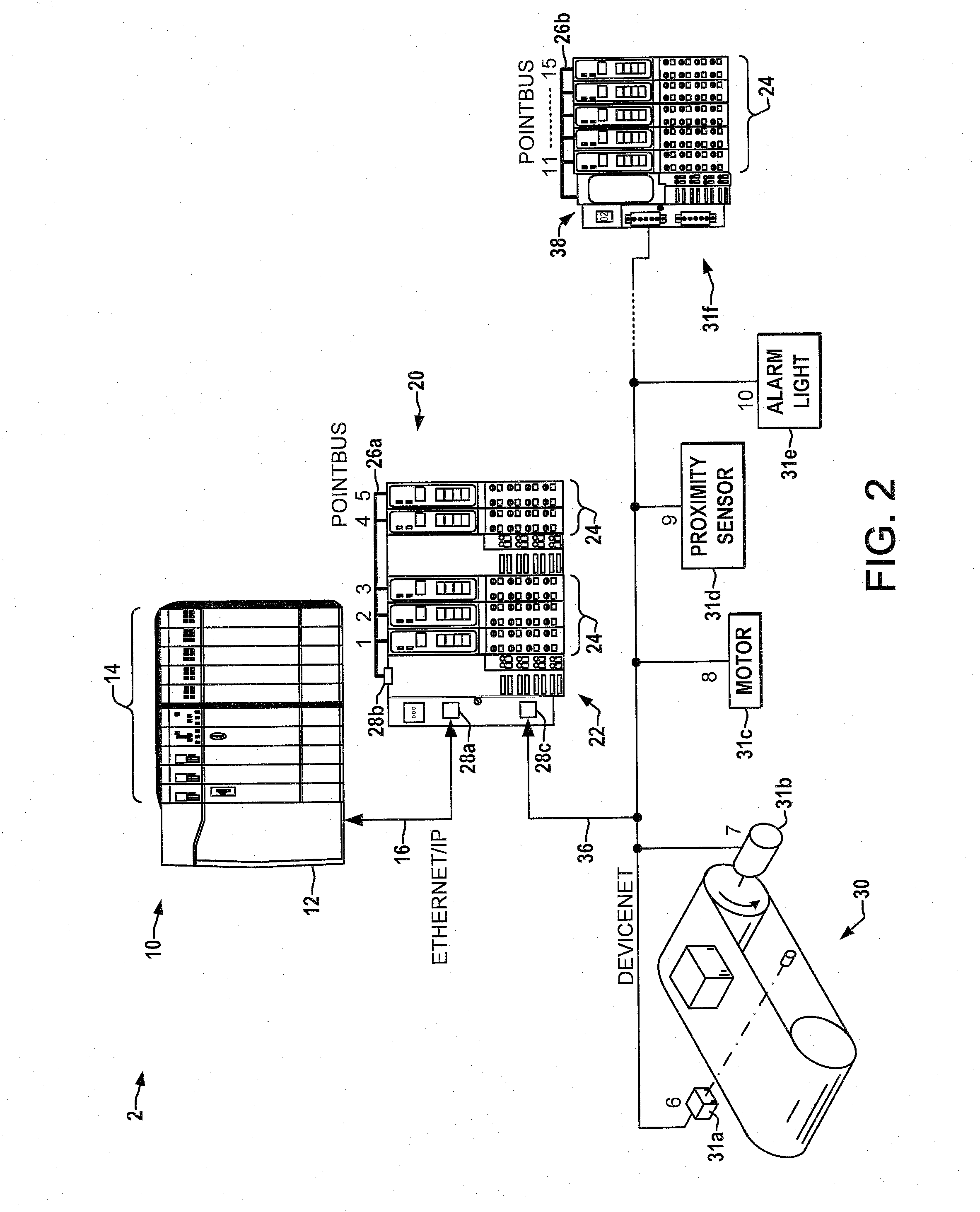
Industrial ethernet communications adapter
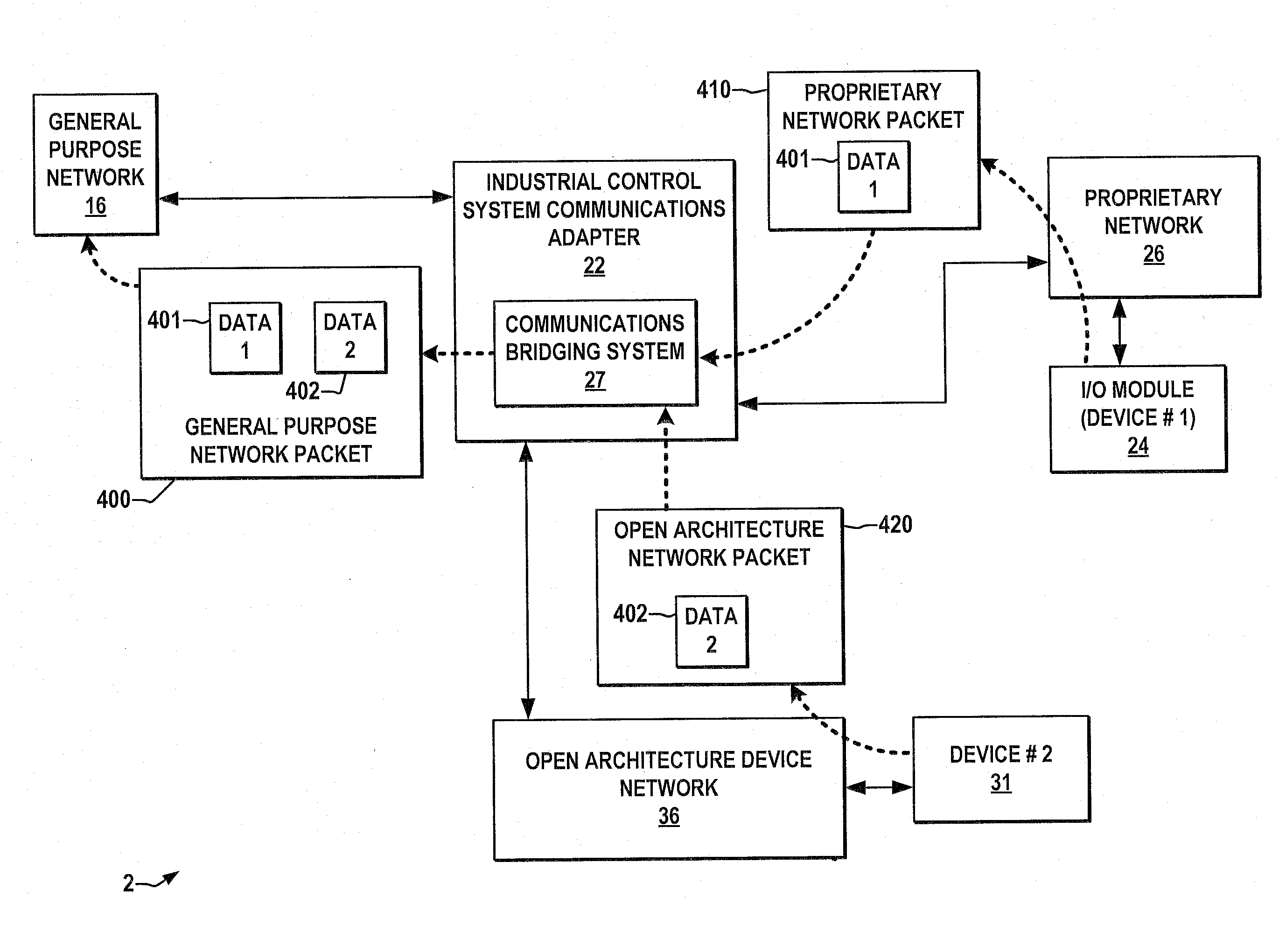
ActiveUS20080080521A1Facilitates cost-effective enterprise-wide communication integrationEasy to understandError preventionTransmission systemsGeneral purposeEtherNet/IP
Communications adapters and methods are provided for interfacing communications for an EtherNet / Ip or other general purpose industrial network, a Fieldbus or other open protocol device network, and a PointBus or other proprietary network. The adapter may be integrated in a module of a backplane system with connections to the general purpose, proprietary, and open protocol device networks, and provides a bridging for communications across the networks to make devices on the proprietary and open protocol networks accessible as if they were on a single device network and with sequential addressing capabilities.
Owner:ROCKWELL AUTOMATION TECH
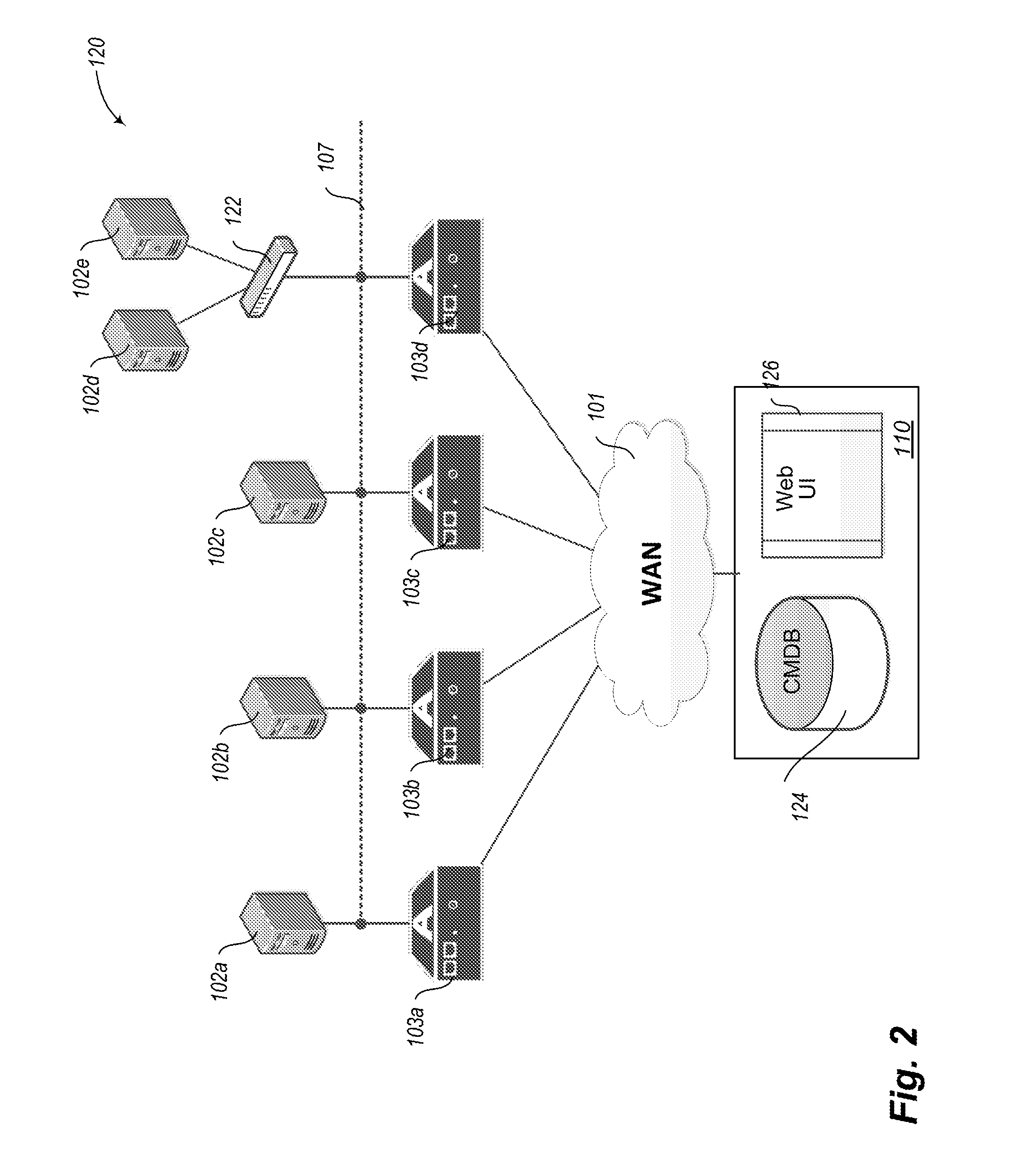
Remote industrial network monitoring method and system based on S-Link and VLAN (Virtual Local Area Network) technique
ActiveCN102096405AAchieve securityImprove integrityTransmissionProgramme total factory controlFrequency changerPlaintext
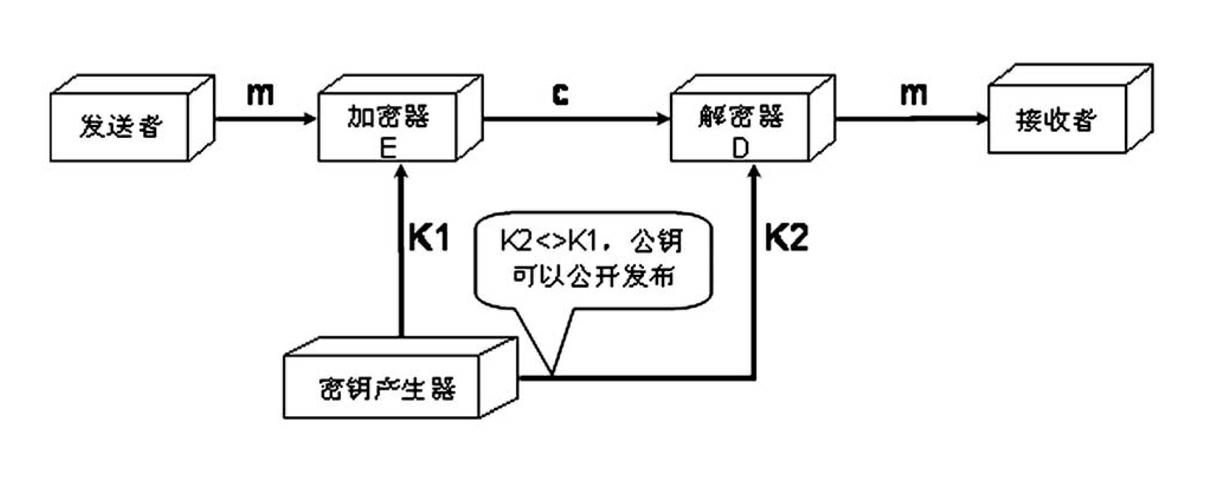
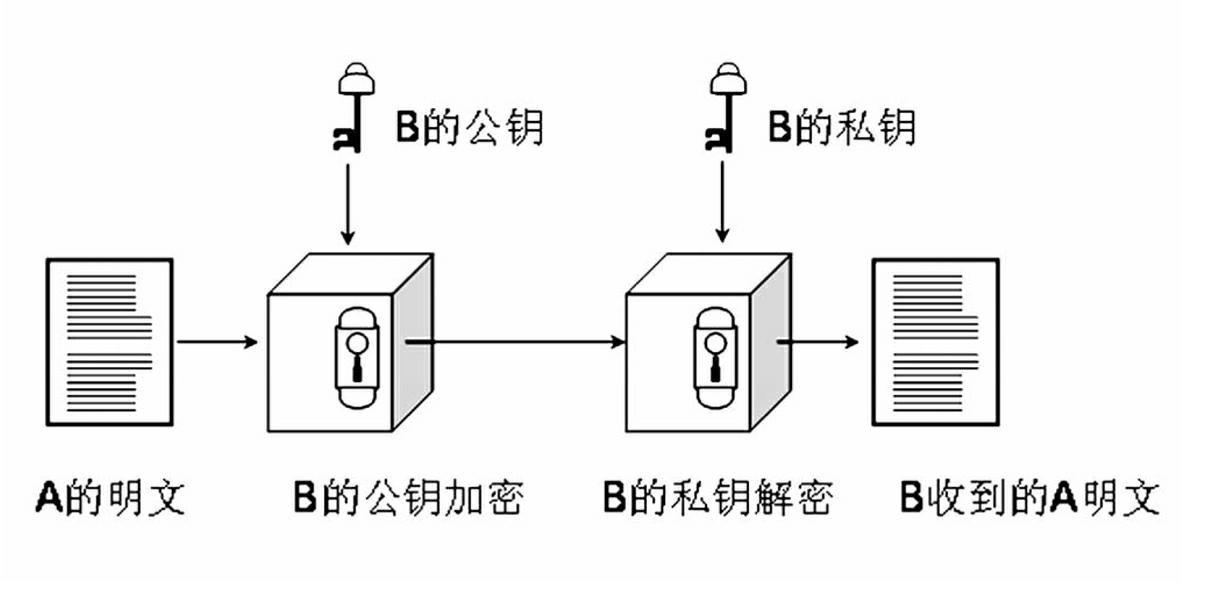
The invention relates to a remote industrial network monitoring method and system based on an S-Link and VLAN (Virtual Local Area Network) technique. An S-Link protocol and a VLAN are comprised in the method, wherein if A wants to send a plaintext to B through a double-key encrypting technique, and B has a pair of public key and private key, an encrypting and decrypting process is carried out as follows: B sends the public key to A; A uses the public key of B for encrypting information of A and then sends the encrypted information to B; B uses the private key to decrypte the information of A;conversely, if B wants to send the plaintext to A, the process is carried out as follows: A receives the plaintext of B; the private key of A is used for decryption; the public key of A is used for encryption; and B receives the plaintext of A. The system comprises a management computer, a server, a remote safety communication module, a 3G communication module, a PLC (Programmable Logic Controller) main station, a PLC auxiliary station, a camera, a frequency changer, a multifunctional panel HMI (Human Machine Interface) and an Internet.
Owner:SHENZHEN FUTURELOOKS AUTOMATION SYST
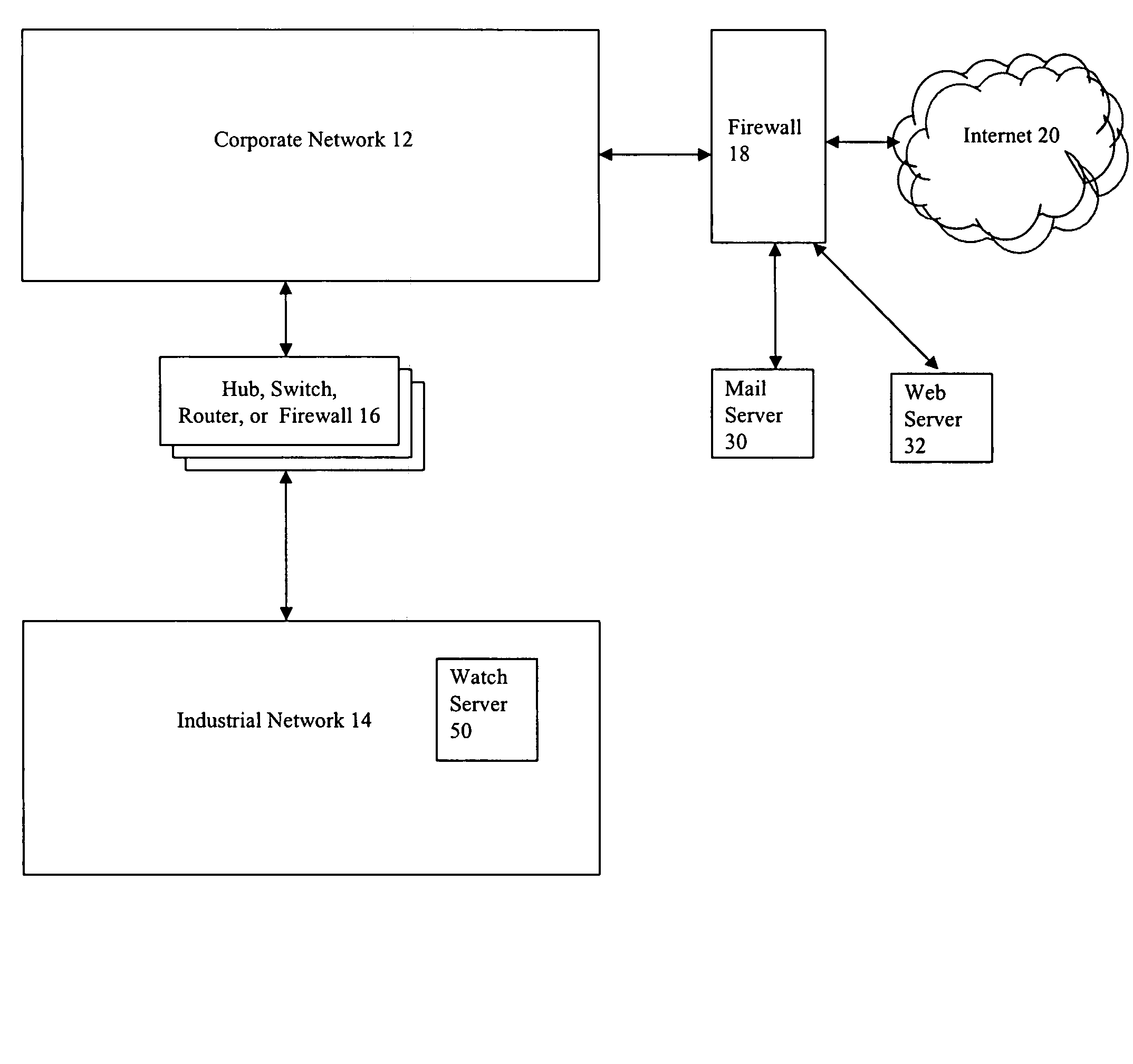
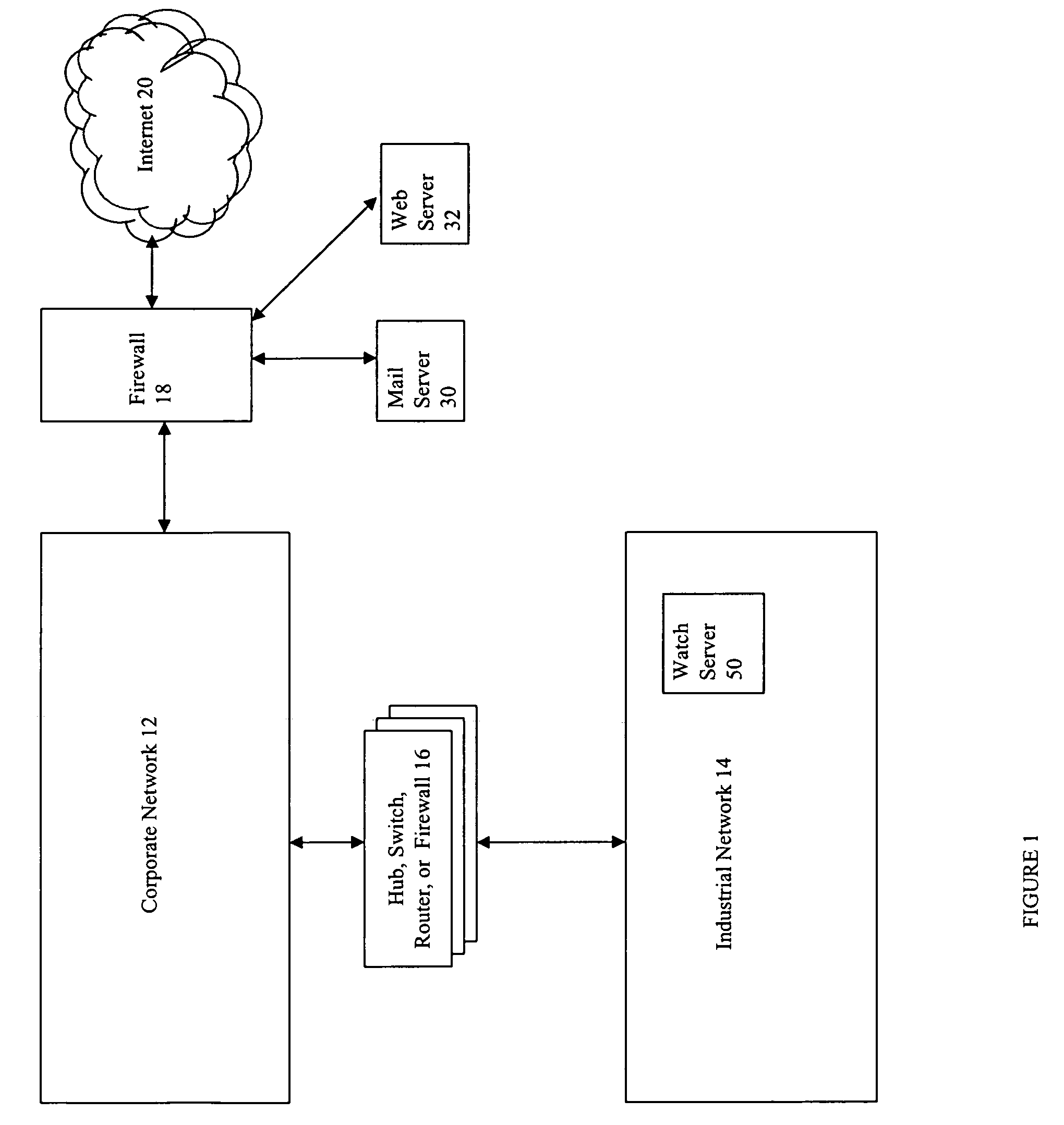
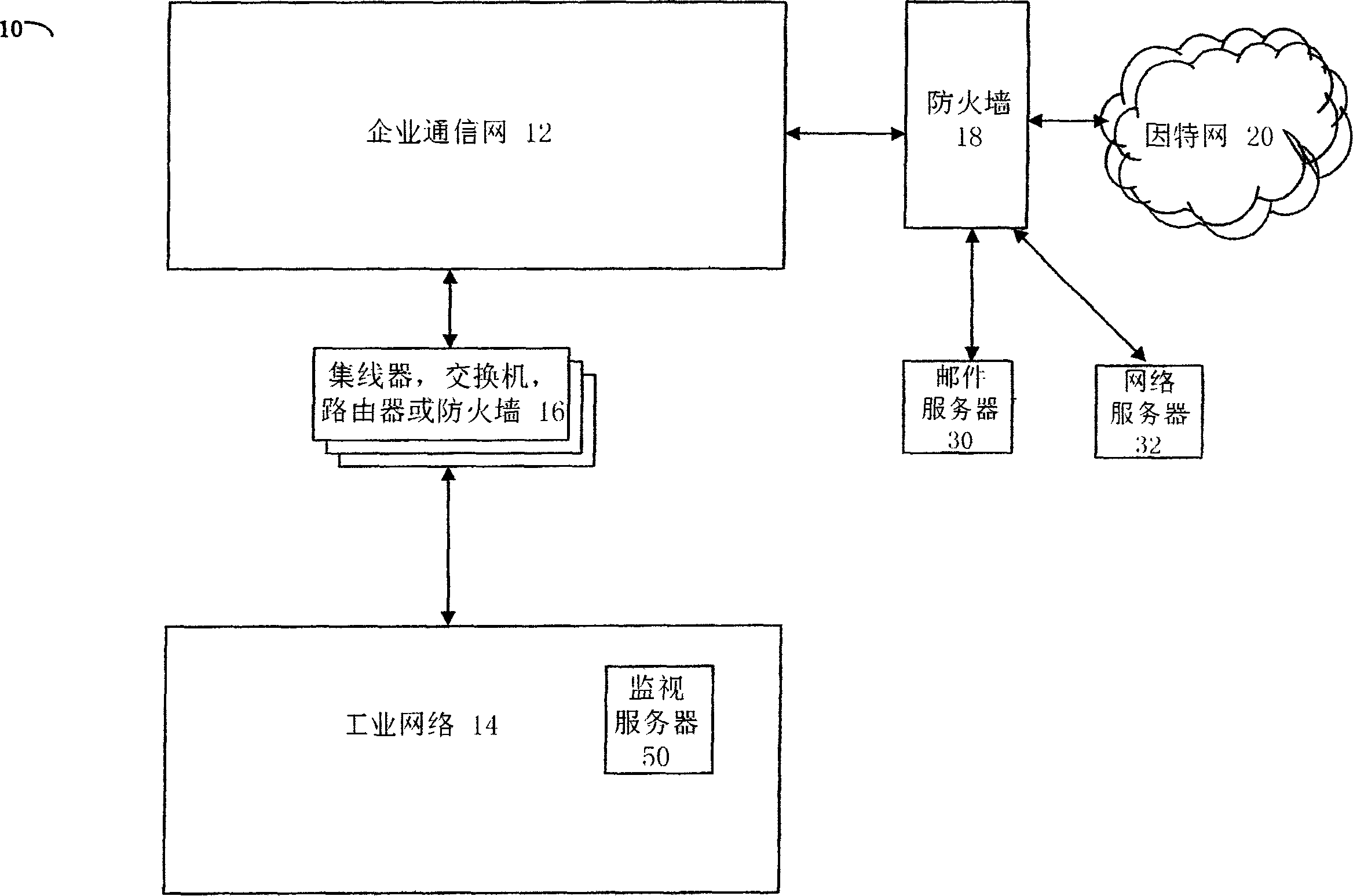
Industrial network security
ActiveUS20140282850A1Facilitate communicationImprove network securityTransmissionSpecial data processing applicationsIndustrial safety systemNetwork link
A private overlay network is introduced into an existing core network infrastructure to control information flow between private secure environments. Such a scheme can be used to connect a factory automation network linking operations devices to a corporate network linking various business units, with enhanced network security. Such a connection can be facilitated by introducing into the existing infrastructure a set of industrial security appliances (ISAs) that work together to create an encrypted tunnel between the two networks. The set of ISAs can be scalable to overlay differently sized core networks, to create the private overlay network. Connections to the private overlay network can be managed by the ISAs in a distributed fashion, implementing a peer-to-peer dynamic mesh policy. The industrial security system disclosed may be particularly advantageous in environments such as public utility systems, medical facilities, and energy delivery systems.
Owner:TEMPERED NETWORKS
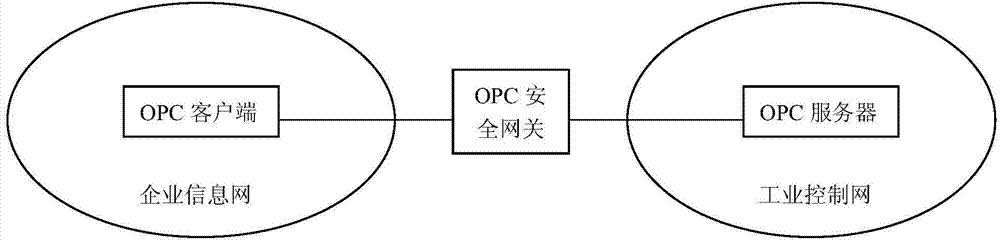
OPC security gateway system
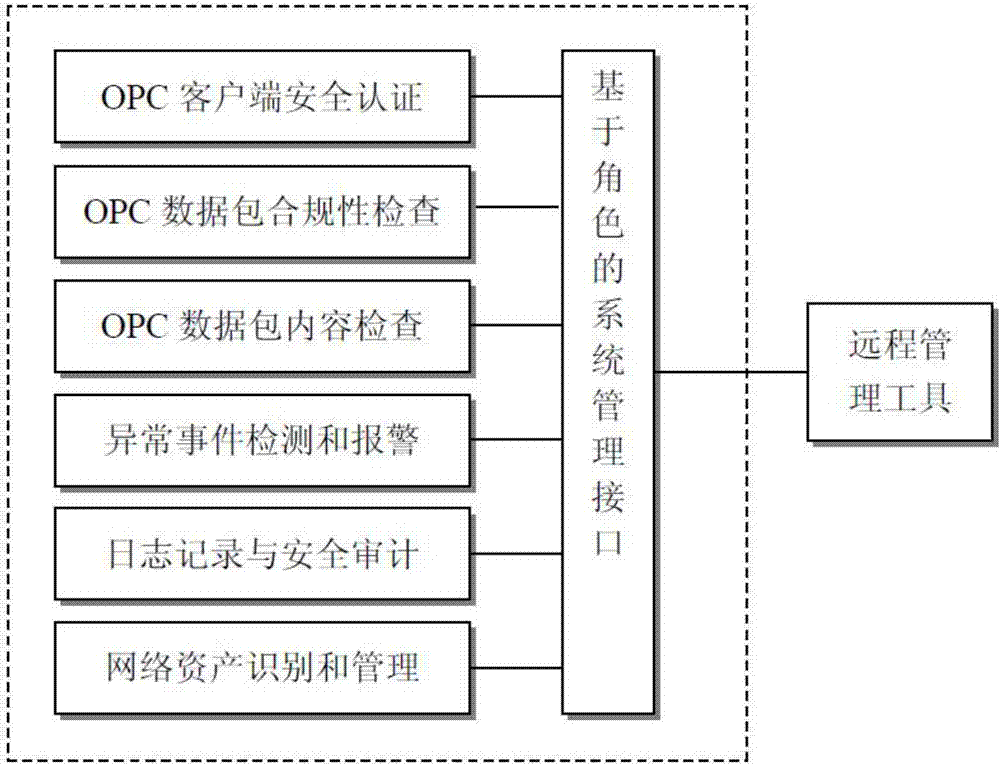
InactiveCN104753936AAvoid attackAvoid destructionNetwork connectionsNetwork packetSystems management
The invention discloses an OPC security gateway system, and aims at solving the technical problems of poor security in interconnection of the existing enterprise information network and industrial control network. According to the technical scheme, the system comprises an OPC client security authorization module, an OPC data packet validity inspection module, an OPC data packet content inspection module, an abnormal event detection and alarming module, a log recording and security auditing module, a network assets recognizing and managing module, a system management interface module and a remote management tool. According to the system, the information of the enterprise information network enters the industrial control network through the OPC security gateway system, the OPC security gateway system performs security authorization for the communication behavior and inspects the validity and content of a data packet as well as recognizing and filtering malevolence communication behavior and an OPC data packet, so as to prevent invasion of illegal users, preventing from being attacked by abnormal or deformed OPC data packet as well as preventing the industrial network control from being attacked; the security in interconnection of the enterprise information network and the industrial control network can be improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Method for detecting and alleviating DDoS attack of industrial SDN network
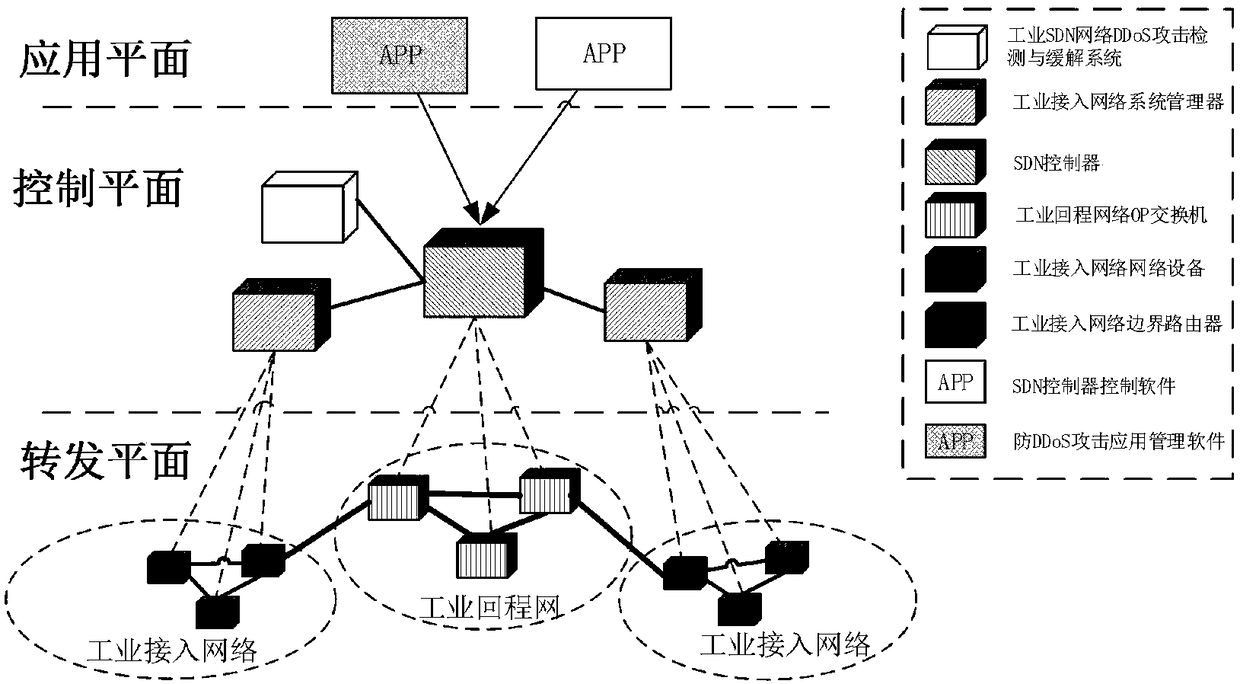
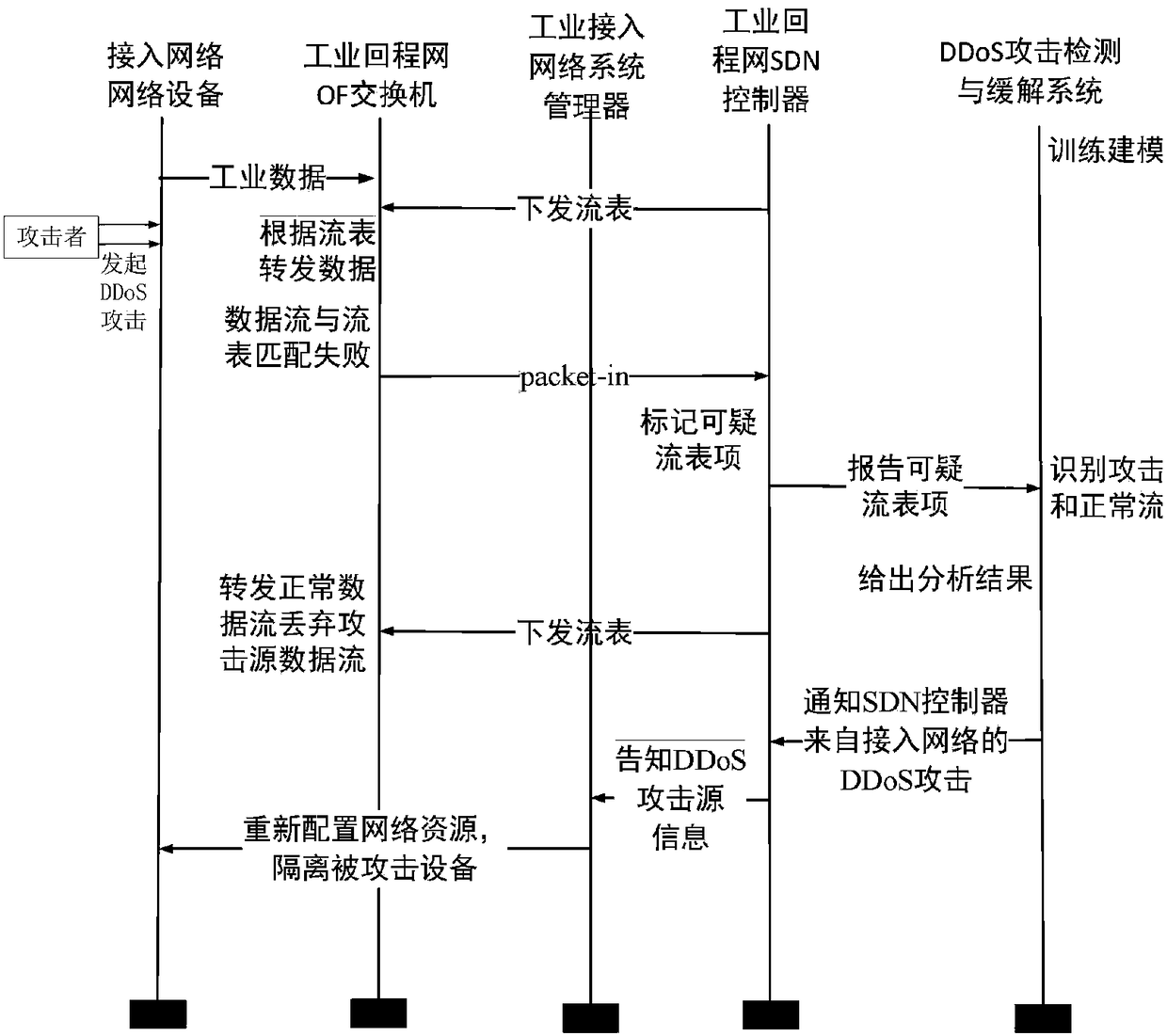
ActiveCN108289104AHighly Reliable Data TransmissionGuaranteed real-timeNetwork topologiesData switching networksAccess networkData stream
The invention relates to a method for detecting and alleviating DDoS attack of an industrial SDN network, wherein the method belongs to the field of network safety. According to the method of the invention, by means of cooperative function between an east-and-west direction interface of an SDN controller in an industrial backhaul network and a system manager of an industrial access network, according to the characteristics of the industrial backhaul network and an industrial access network data packet, an OpenFlow switch flow item matching domain is expanded, and a flow table 0 is set to an elevate DDoS attack specialized flow table for resisting an attack data flow in time. the SDN controller and the DDoS attack detecting and alleviating system of the industrial backhaul network are utilized, thereby identifying an attacking data flow and finding out a DDoS attack source, and applying a DDoS attack alleviating strategy through scheduling an industrial access network system manager. The method ensures normal flow of the industrial backhaul network and the industrial access network and overcomes threat of DDoS attack to safety of the industrial network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Light-weight authentication key negotiation method based on implicit certificate
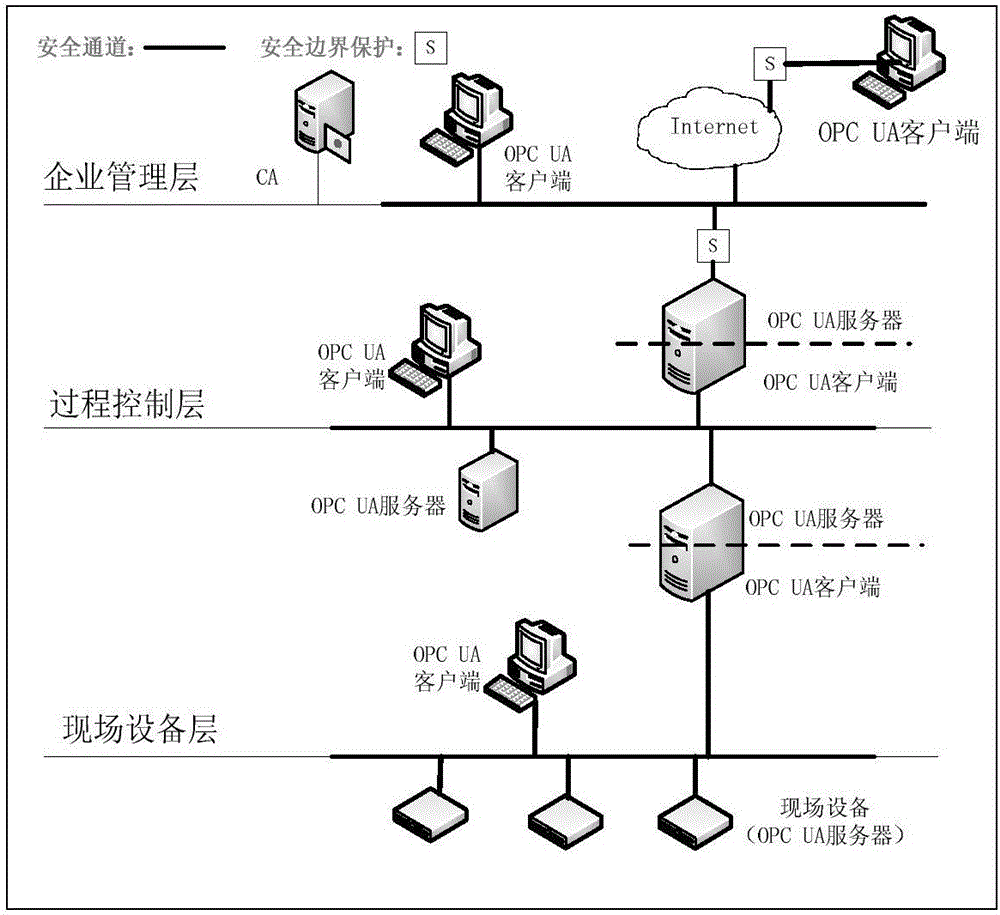
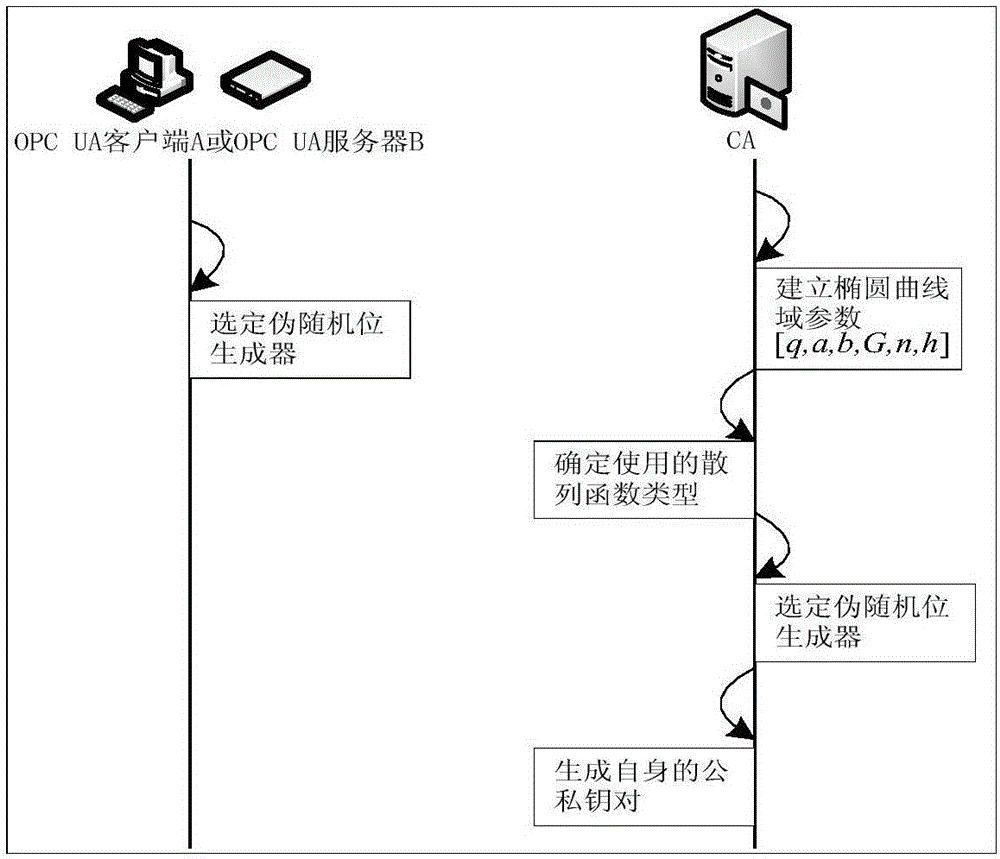
ActiveCN106411528ACalculation speedReduce the probability of collisionKey distribution for secure communicationPublic key for secure communicationClient-sideSecure channel
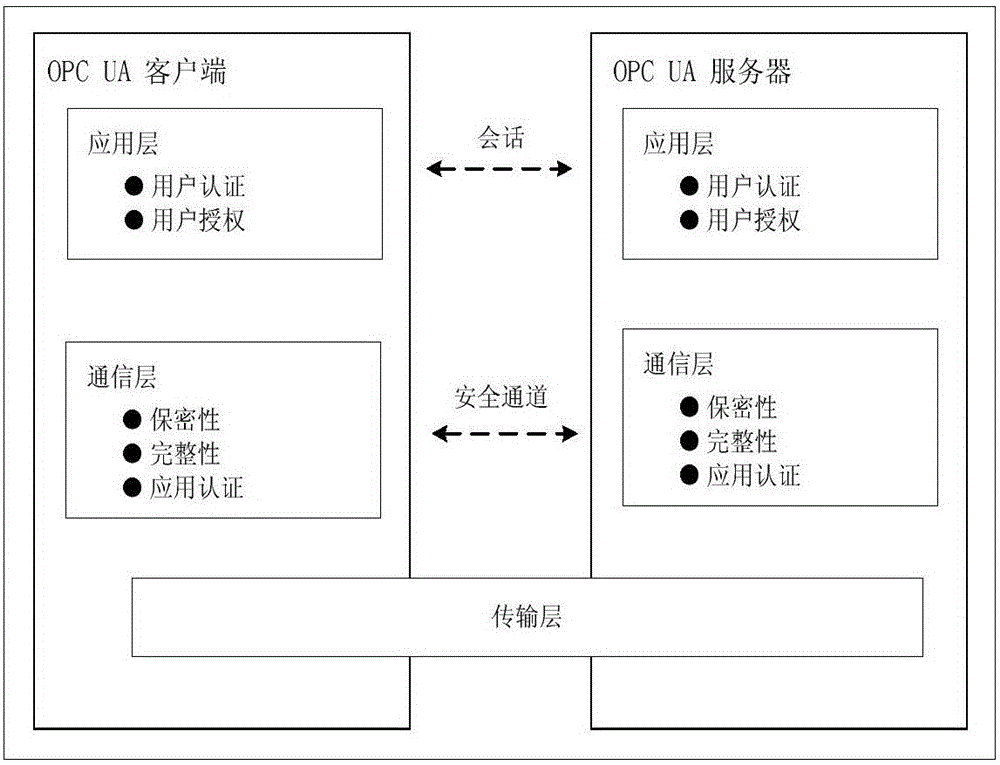
The invention relates to a light-weight authentication key negotiation method based on an implicit certificate, and belongs to the technical field of identity authentication. The method is used for establishing a secure channel between an OPC UA server and an OPC UA client and generating of a session key. Three entities, a credible certification authority (CA), the OPC UA client A and the OPC UA server B, are involved in an authentication key negotiation process. The OPC UA server B and the OPC UA client A acquire the own implicit certificates after the CA completes identity registration. Then the OPC UA server B and the OPC UA client A complete bidirectional authentication and key negotiation between the entities by using a light-weight algorithm. According to the method provided by the invention, the light-weight authentication key negotiation method based on the implicit certificate is provided aiming at the problem that an existing OPC UA security mechanism is not applicable to a resource-constrained communication environment. The method provided by the invention can be efficiently and safely applicable to an industrial network with a large amount of resource-constrained embedded OPC UA equipment.
Owner:KYLAND TECH CO LTD
Information safe transmission control method between inside network and outside network and gateway thereof
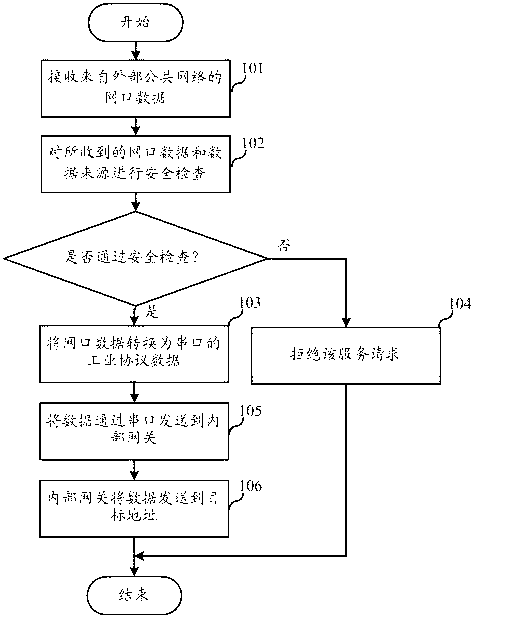
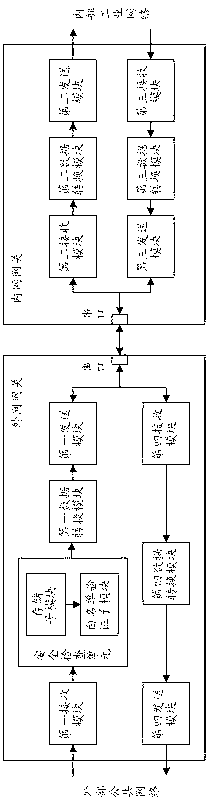
The invention discloses an information safe transmission control method between an inside network and an outside network and a gateway thereof. An inside network gateway and an outside network gateway are respectively arranged between an inside industrial network and an outside public network. The inside industrial network is connected with the inside network gateway; the outside public network is connected with the outside network gateway through a network interface; and the inside network gateway and the outside network gateway are connected through a serial port. When the outside network gateway receives the data of the network interface from the outside public network, safety check is carried out to the received data of the network interface and the data source, and the data of the network interface passing the safety check is converted as the industrial protocol data of the serial port and sent to the inside network gateway through the serial port; and the data is sent to a targeted address through the inside network gateway. The gateway transmission manner realizes the double isolation of the hardware interface and the software protocol between the inside network and the outside network so as to effectively prevent the inside network from being attacked by outside adverse programs and ensure the security of the inside network.
Owner:ASAT CHINA TECH
Industrial control protocol fuzzy test method based on flow replay
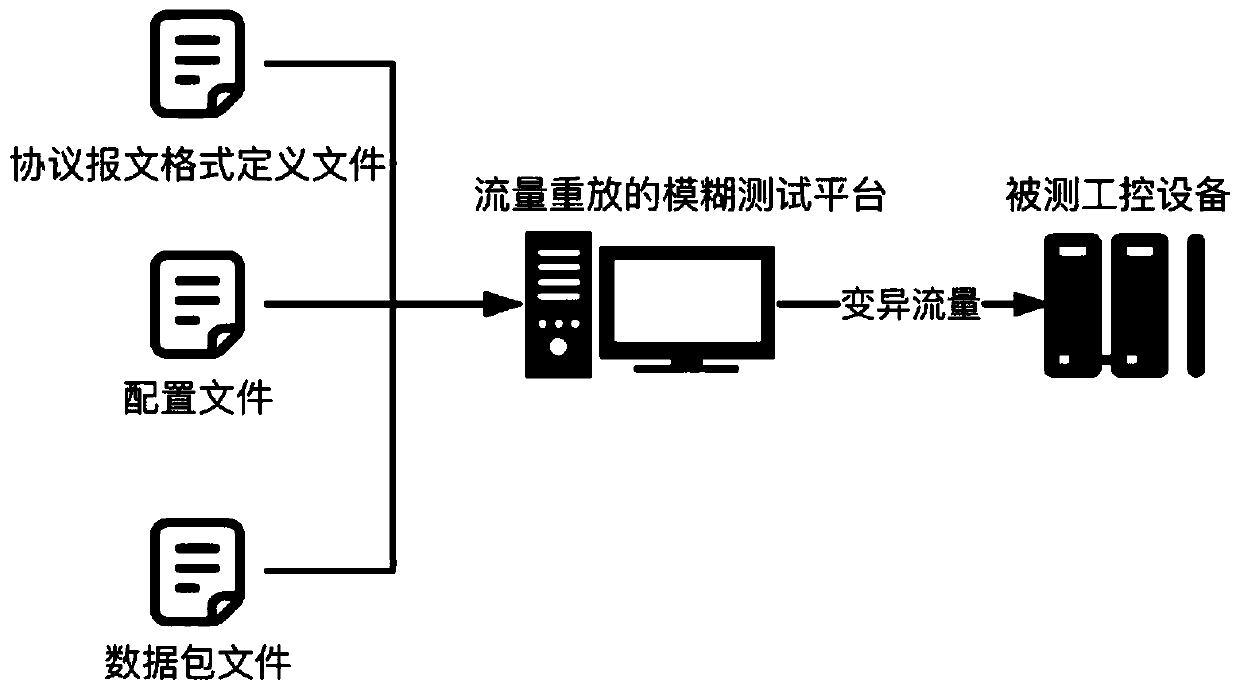
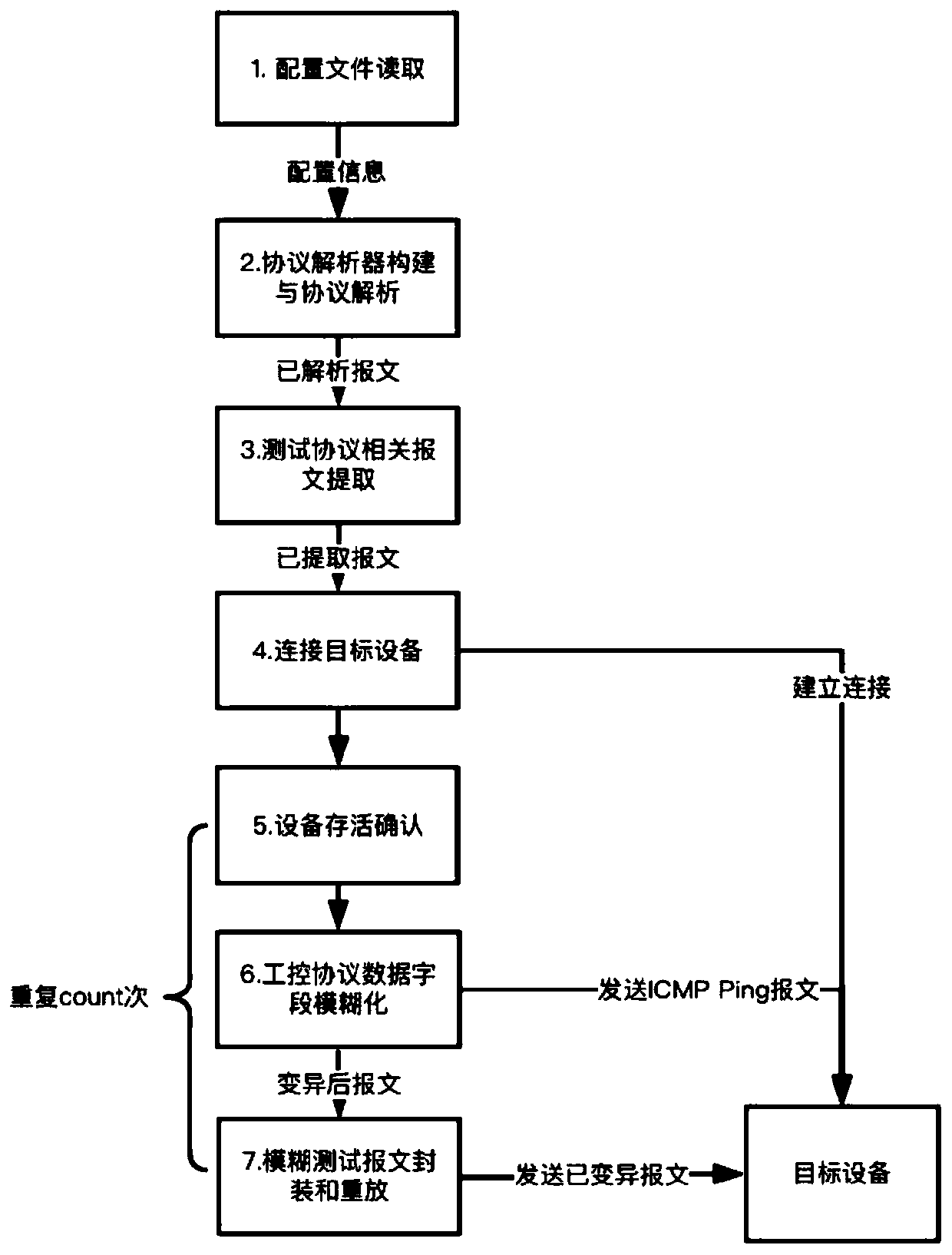
ActiveCN110505111AShorten the test preparation phaseData switching networksTraffic capacityProtocol Application
The invention relates to the field of industrial network security, in particular to an industrial control protocol fuzzy test method based on flow replay. The invention aims to provide an industrial control protocol fuzzy test method based on flow replay. Real protocol flow data of an operation environment of industrial control equipment is taken as a basis. A format is defined through a simple configuration file format and an industrial control protocol message. A corresponding protocol analyzer is constructed. An device protocol state message is extracted to fuzzify an industrial control protocol field specified by a user. Message application layer data is extracted. The message application layer data is packaged and replayed. An industrial control protocol fuzzy test is quickly and efficiently carried out on the premise of ensuring effective input and complete establishment of a protocol session. The invention is suitable for automatic testing of existing industrial control protocolvulnerability mining and industrial control protocol research and development and the like.
Owner:HANGZHOU DIANZI UNIV
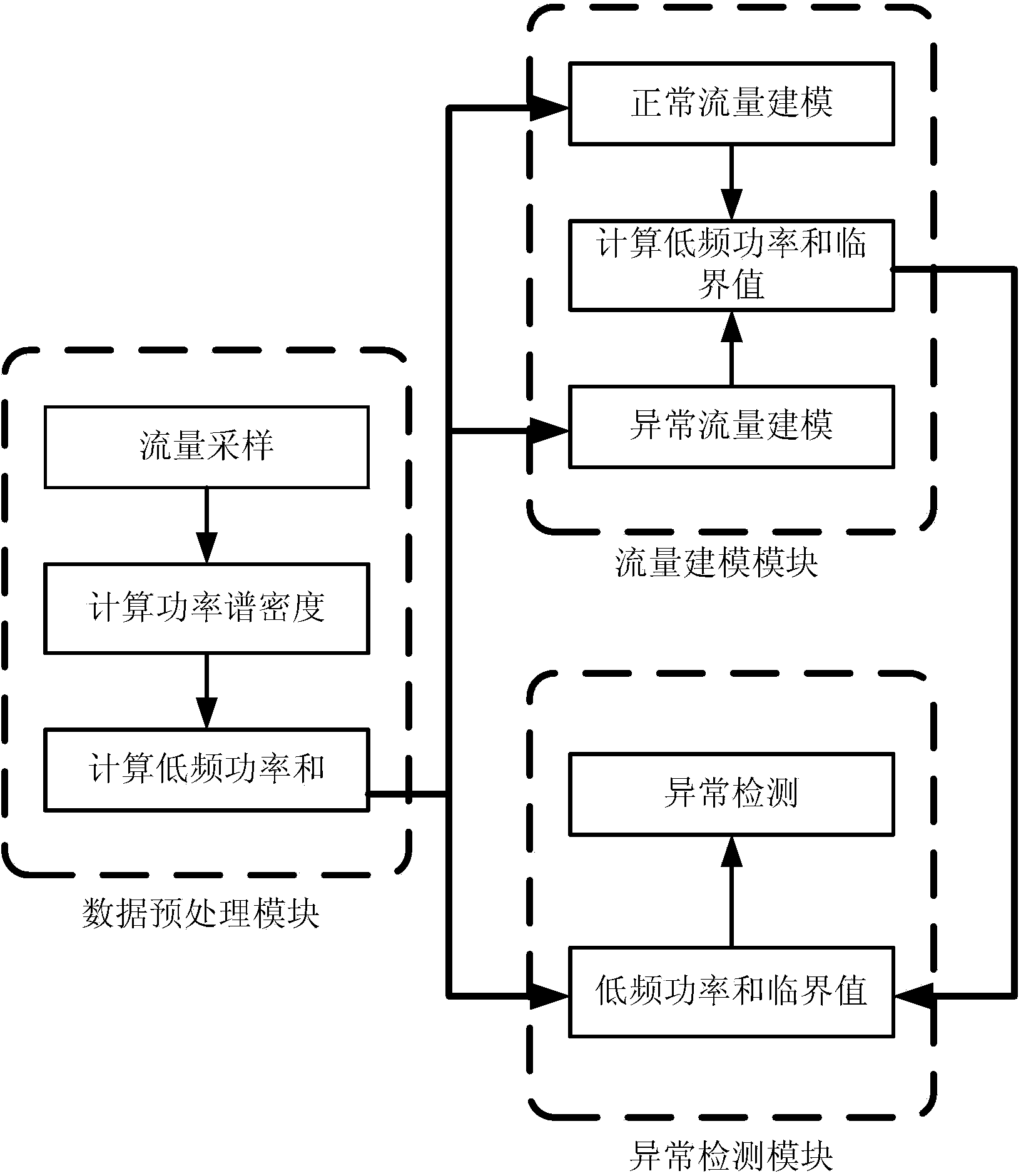
Abnormality detecting method based on industrial control system network traffic
The invention relates to an abnormality detecting method based on industrial control system network traffic and belongs to the field of information security. The industrial control system network traffic is collected, by analyzing the traffic features, the fact that normal traffic and abnormal traffic samples are evidently different in terms of power spectral density is discovered when a digital signal processing method is used to convert traffic signals from a time domain to a frequency domain, a low-frequency power sum critical value is found by analyzing the difference features in a large amount of historical data, if the low-frequency power of a to-be-detected sample is larger than the critical value, the sample traffic is taken as the abnormal traffic. The method includes a data preprocessing module, a traffic modeling module and an abnormality detecting module, wherein the data preprocessing module is used for processing early data traffic, the traffic modeling module is used for building normal models and abnormal models according toe low-frequency power and distribution of normal traffic and abnormal traffic, and the low-frequency power sum critical valve can be calculated. The abnormality detecting module is used for detecting abnormality. The false alarm rate of the method is 6.1% and the alarm missing rate of the method is 9.3%.
Owner:BEIJING UNIV OF TECH
Motor vehicle exhaust smoke video identification system
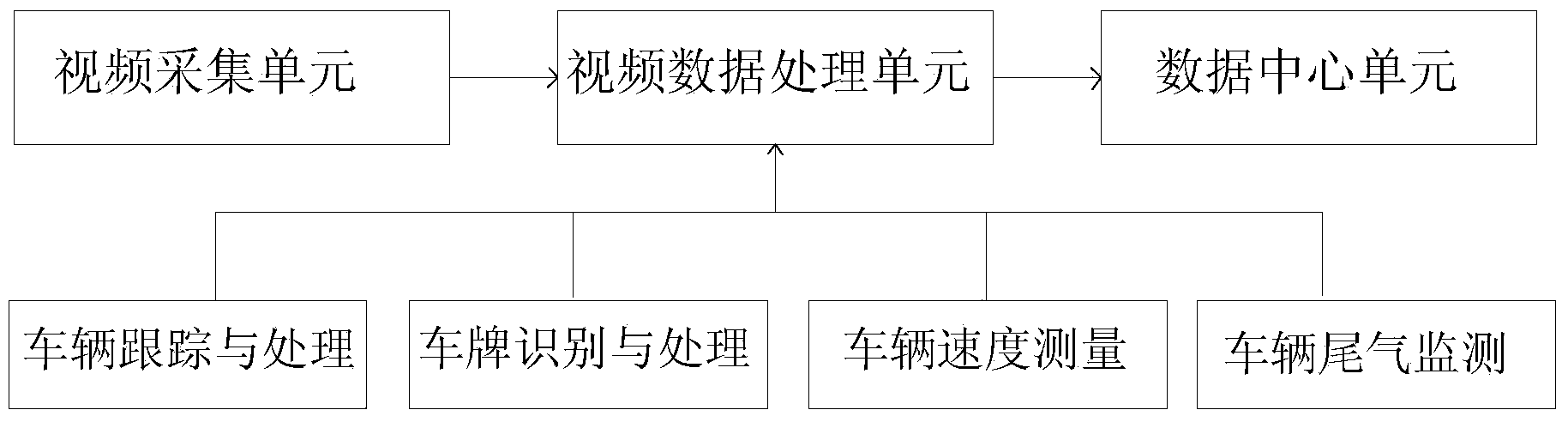
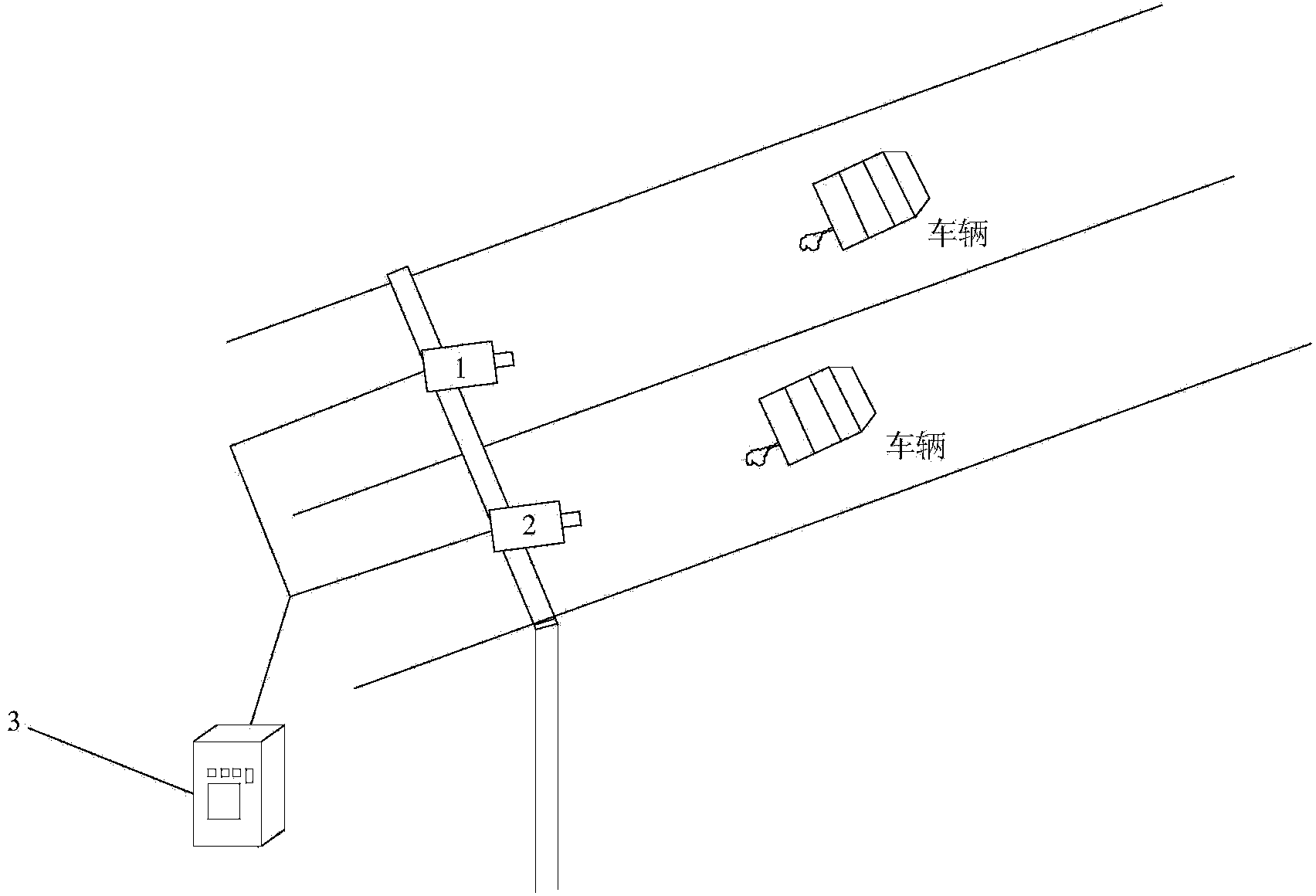
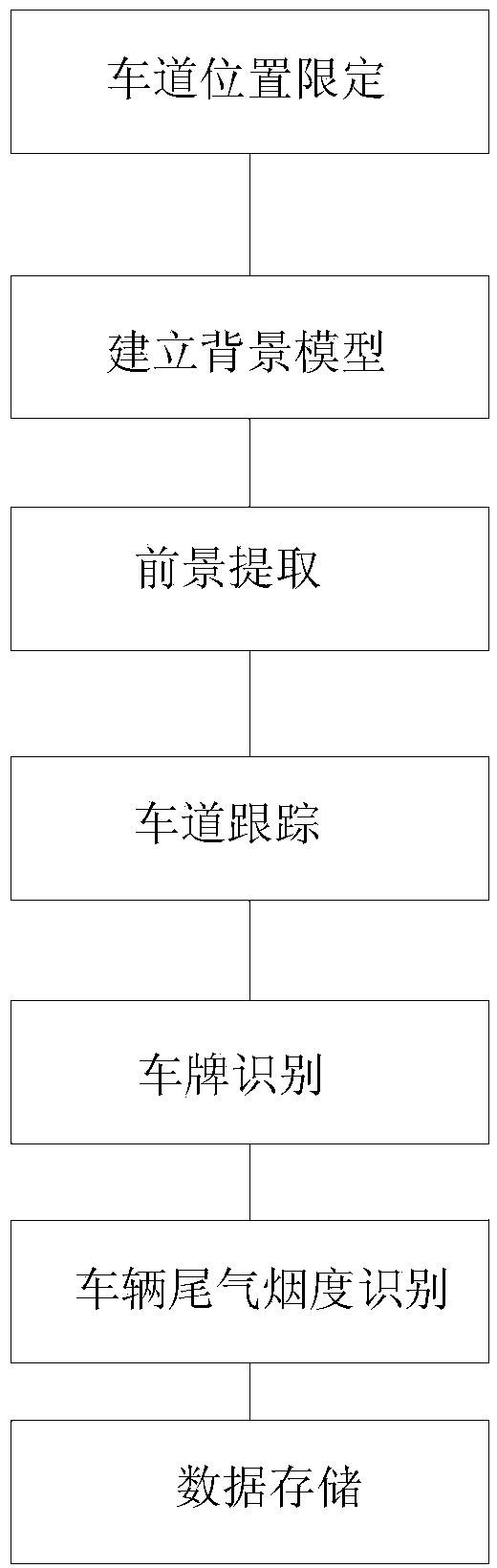
ActiveCN103714363AEasy to installSimple structureCo-operative working arrangementsMotor vehicle partData center
The invention discloses a motor vehicle exhaust smoke video identification system. The motor vehicle exhaust smoke video identification system comprises a video acquisition unit, a video data processing unit and a data center unit, wherein the video acquisition unit comprises an industrial network camera, the video data processing unit comprises an industrial control computer, and the industrial control computer comprises a vehicle tracking and processing module, a license plate identification and processing module, a vehicle speed measuring module and a vehicle exhaust monitoring module. The motor vehicle exhaust smoke video identification system has properties of simple structure, good robustness and no linkage equipment and has no equipment linkage coupling problem. Multi-lane monitoring, excessive vehicle discharge monitoring and license plate recording can be accomplished at one step, position recording is intelligible, and video recording is more persuasive. According to the motor vehicle exhaust smoke video identification system, the industrial network camera and the industrial control computer are only needed to realize processing on the lanes such as vehicle exhaust monitoring, license plate identification, smoke detection, vehicle velocity measurement, cost for equipment and mounting is greatly saved, and smoke detection efficiency is improved.
Owner:NANJING NEWVISION INTELLIGENT TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com