Abnormality detecting method based on industrial control system network traffic
An industrial network and anomaly detection technology, which is applied in the field of information security, can solve problems such as no breakthrough progress, ineffective detection of industrial network traffic anomalies, and difficulty in meeting industrial network security needs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] Attached below figure 1 Introduce the steps of the realization method of the present invention in detail:
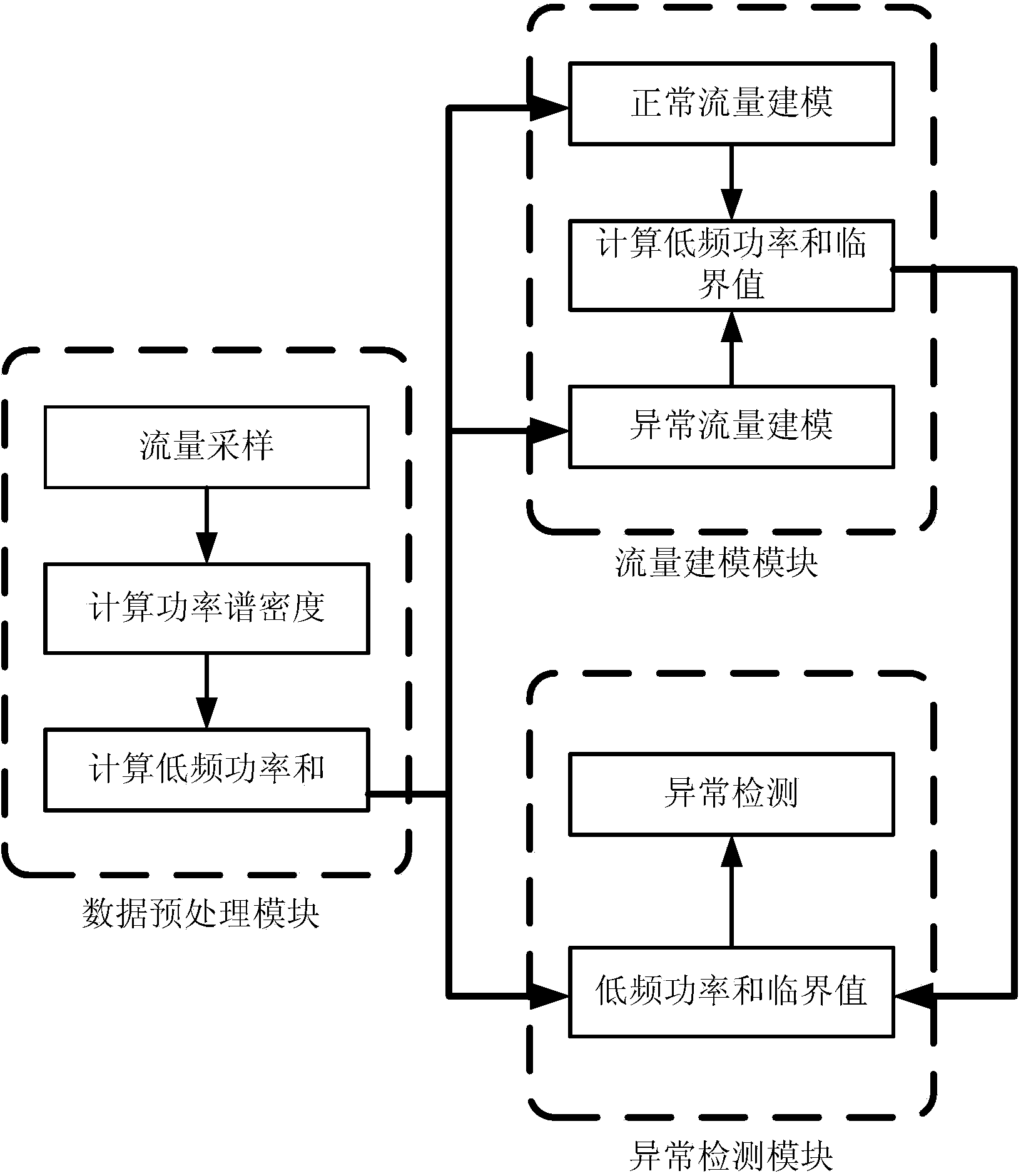
[0015] See attached figure 1 , The invention is an abnormal detection method of network traffic of an industrial control system. The detection method is divided into three modules: 1. The data preprocessing module is responsible for the processing of the data flow in the early stage; 2. The flow modeling module establishes a normal model and an abnormal model according to the low-frequency power and distribution of normal flow and abnormal flow, so as to calculate the low-frequency power and critical value; 3 anomaly detection module detects abnormality of unknown flow according to low frequency power and critical value. The specific process is as follows:
[0016] First, use the data preprocessing module to perform data preprocessing on the industrial control system network traffic.
[0017] The industrial control system experimental platform here adopts the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com