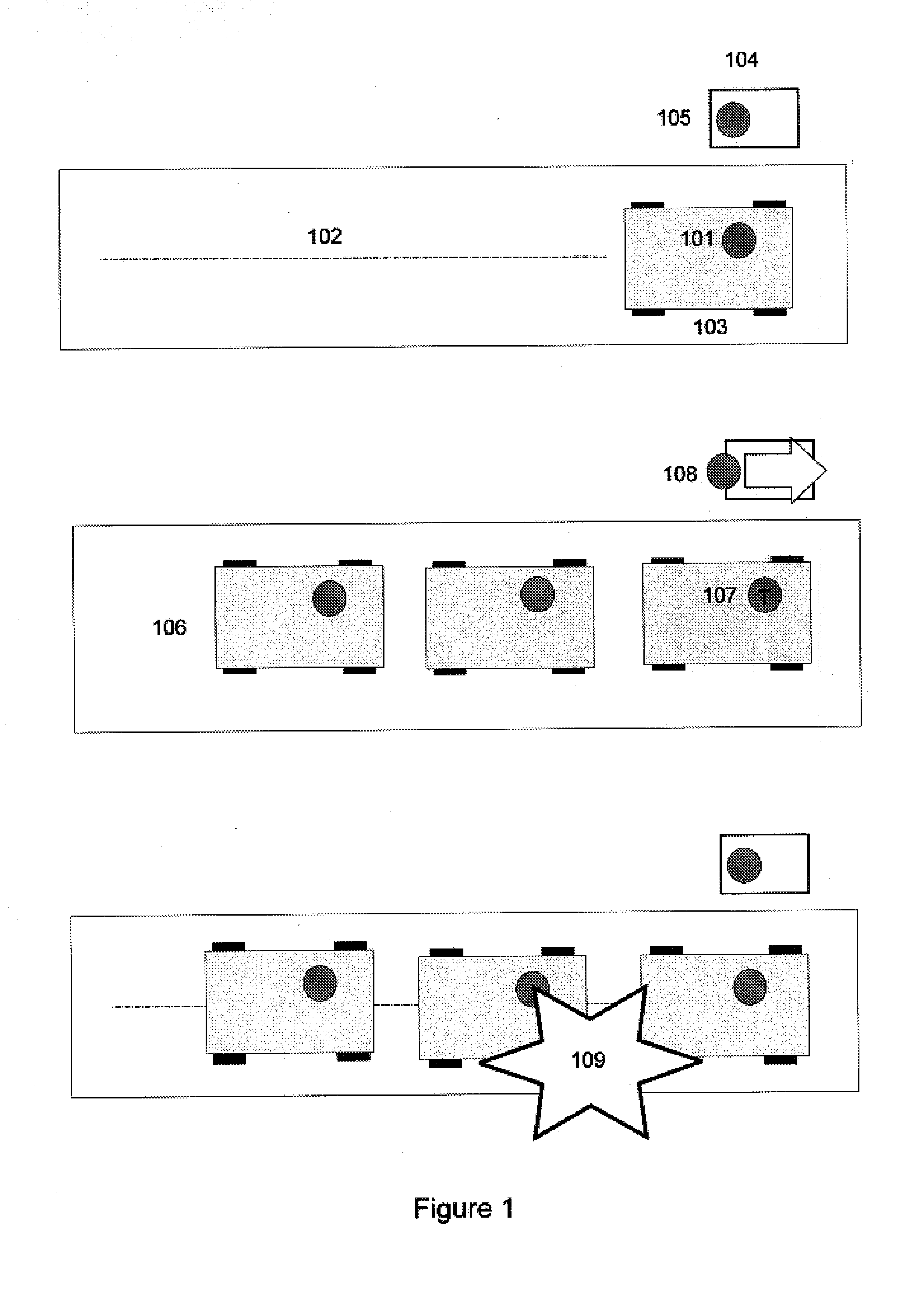
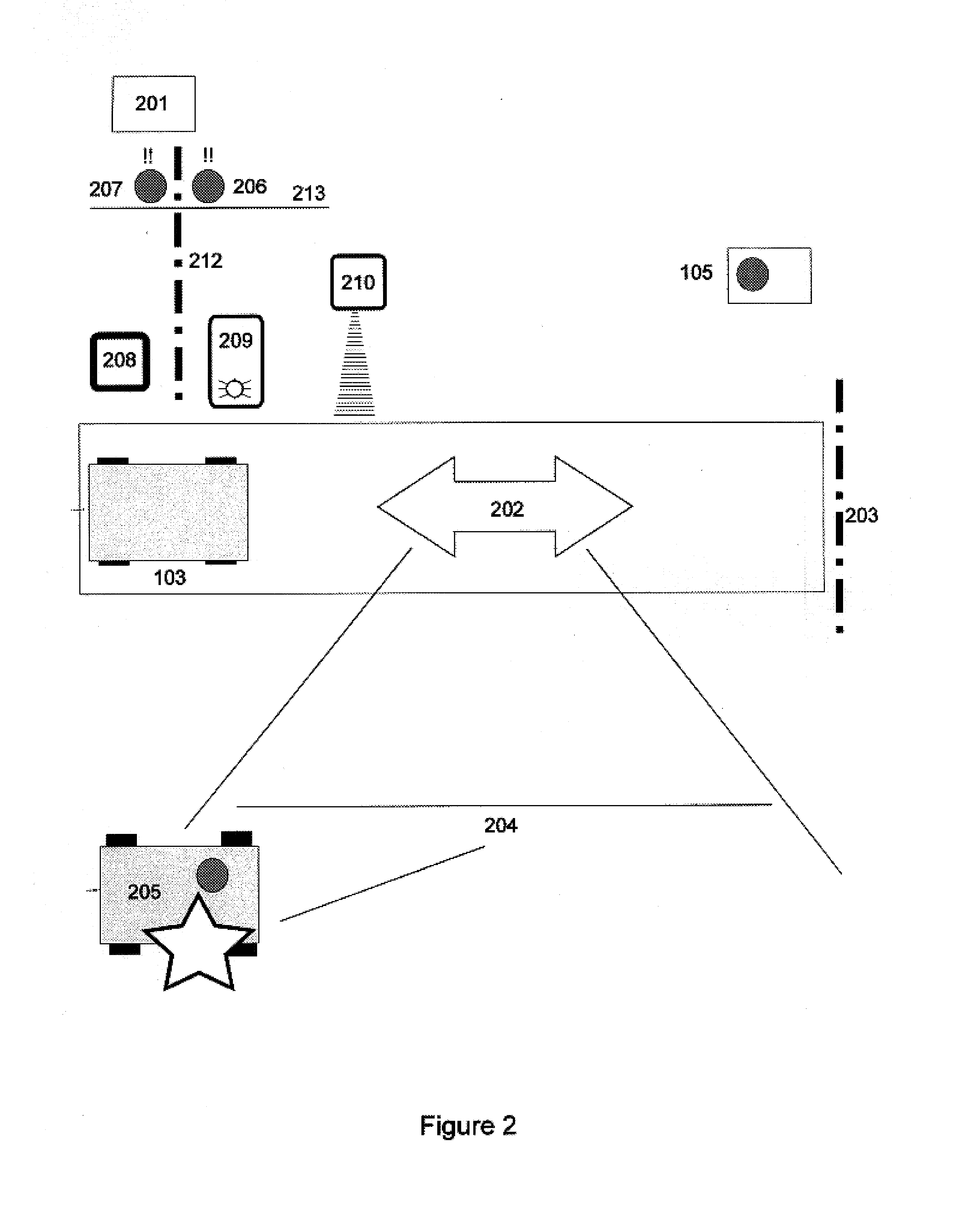
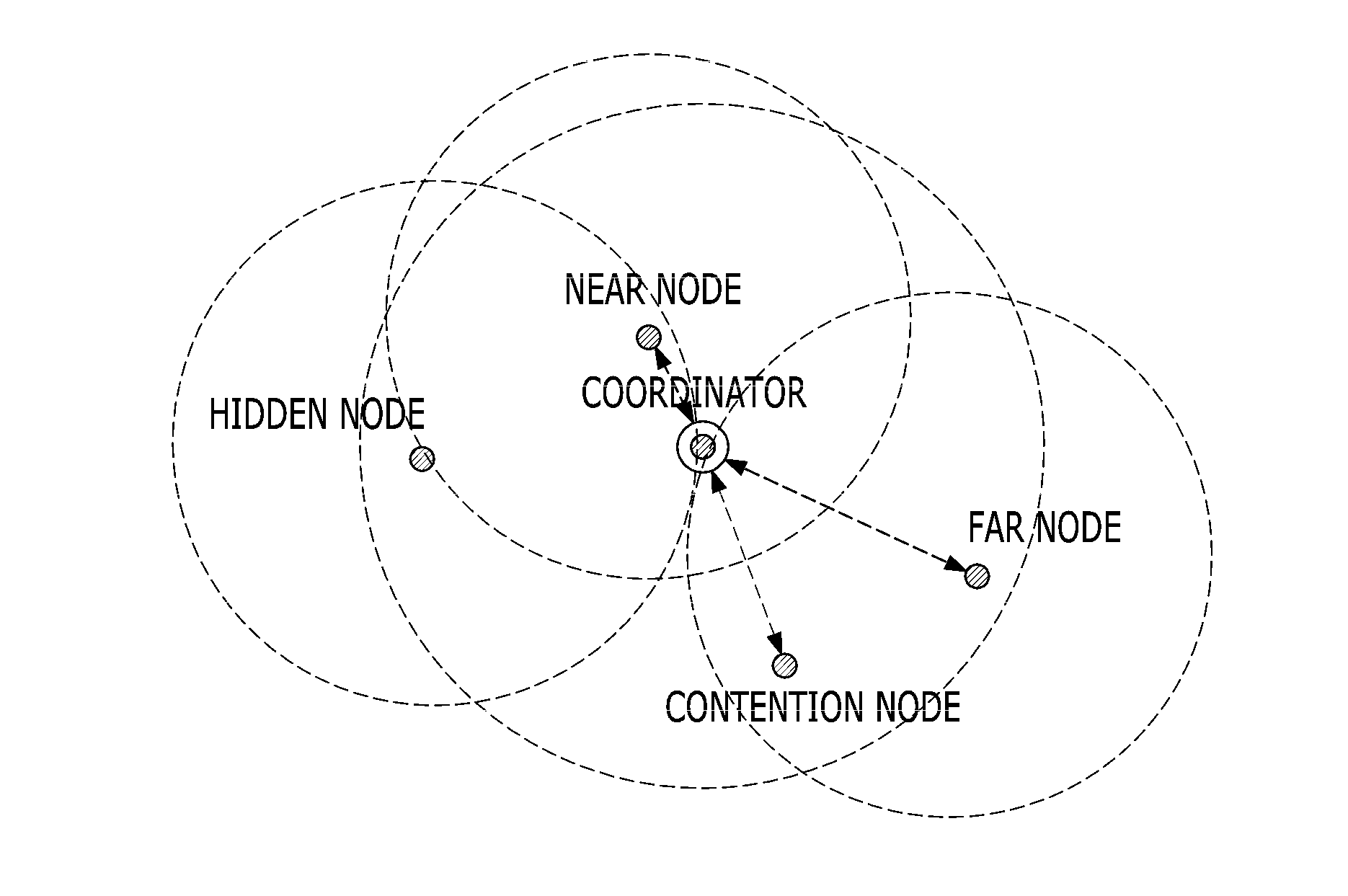
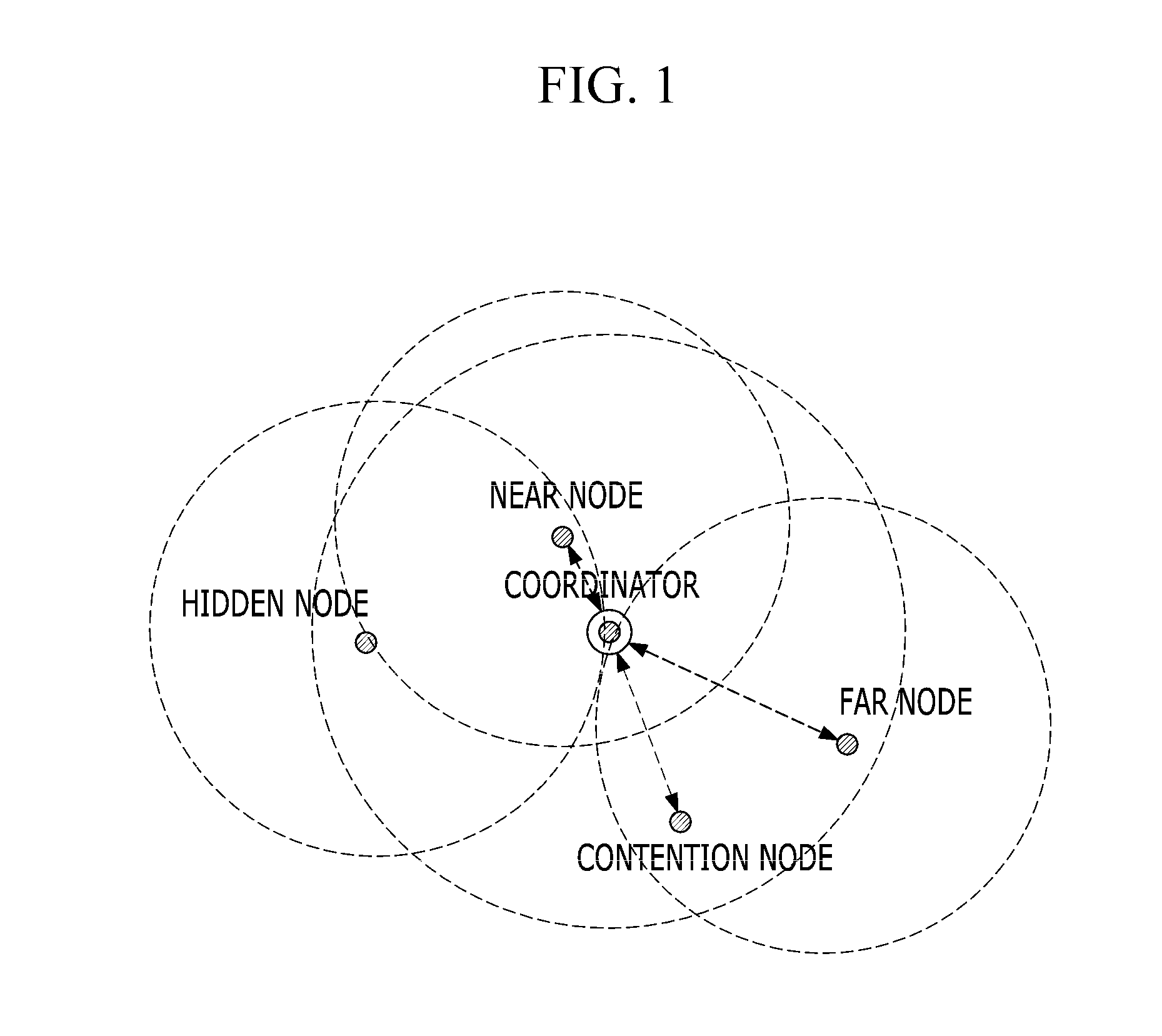
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
69 results about "Critical infrastructure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
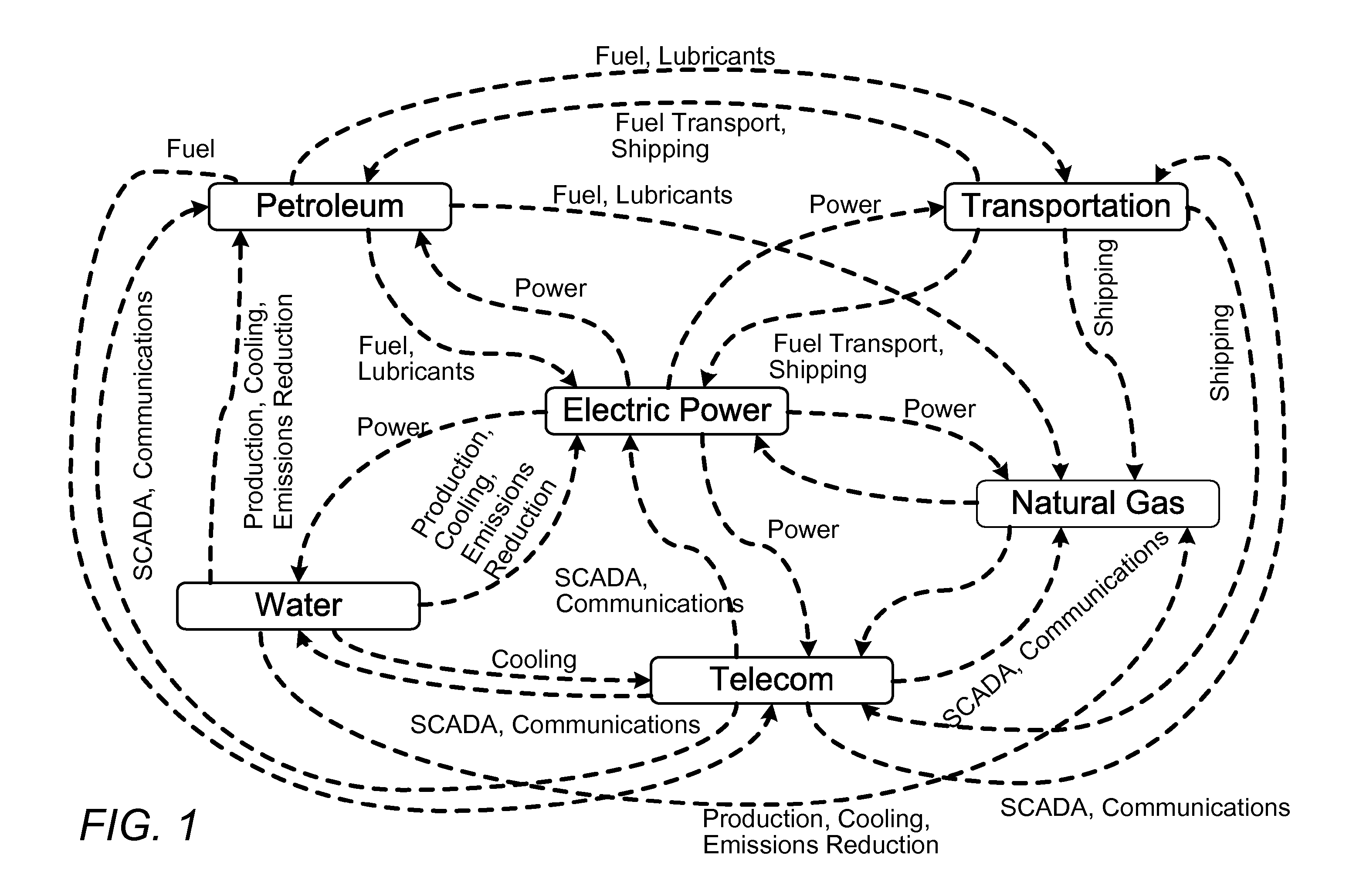
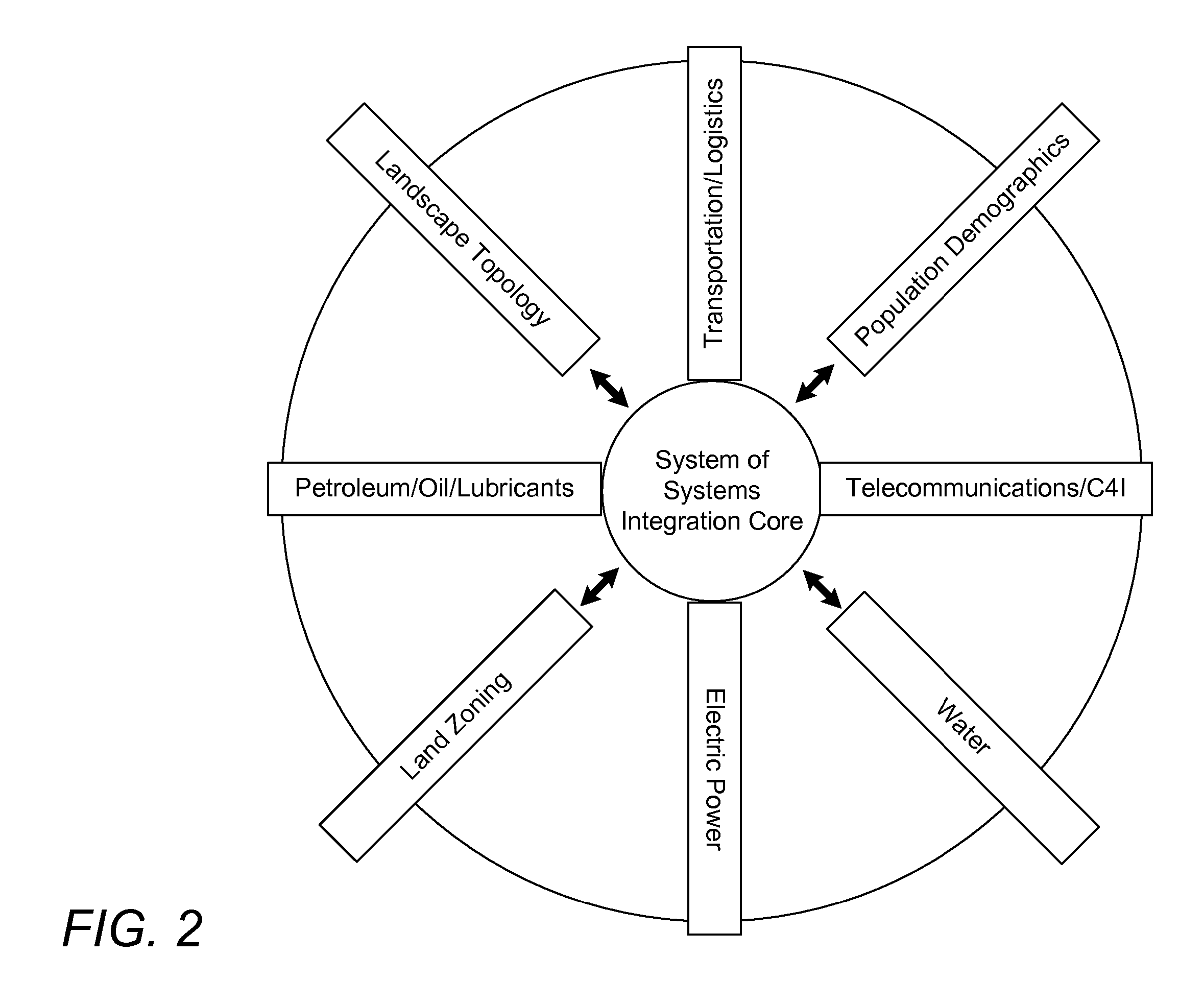
Critical infrastructure (or critical national infrastructure (CNI) in the UK) is a term used by governments to describe assets that are essential for the functioning of a society and economy – the infrastructure.
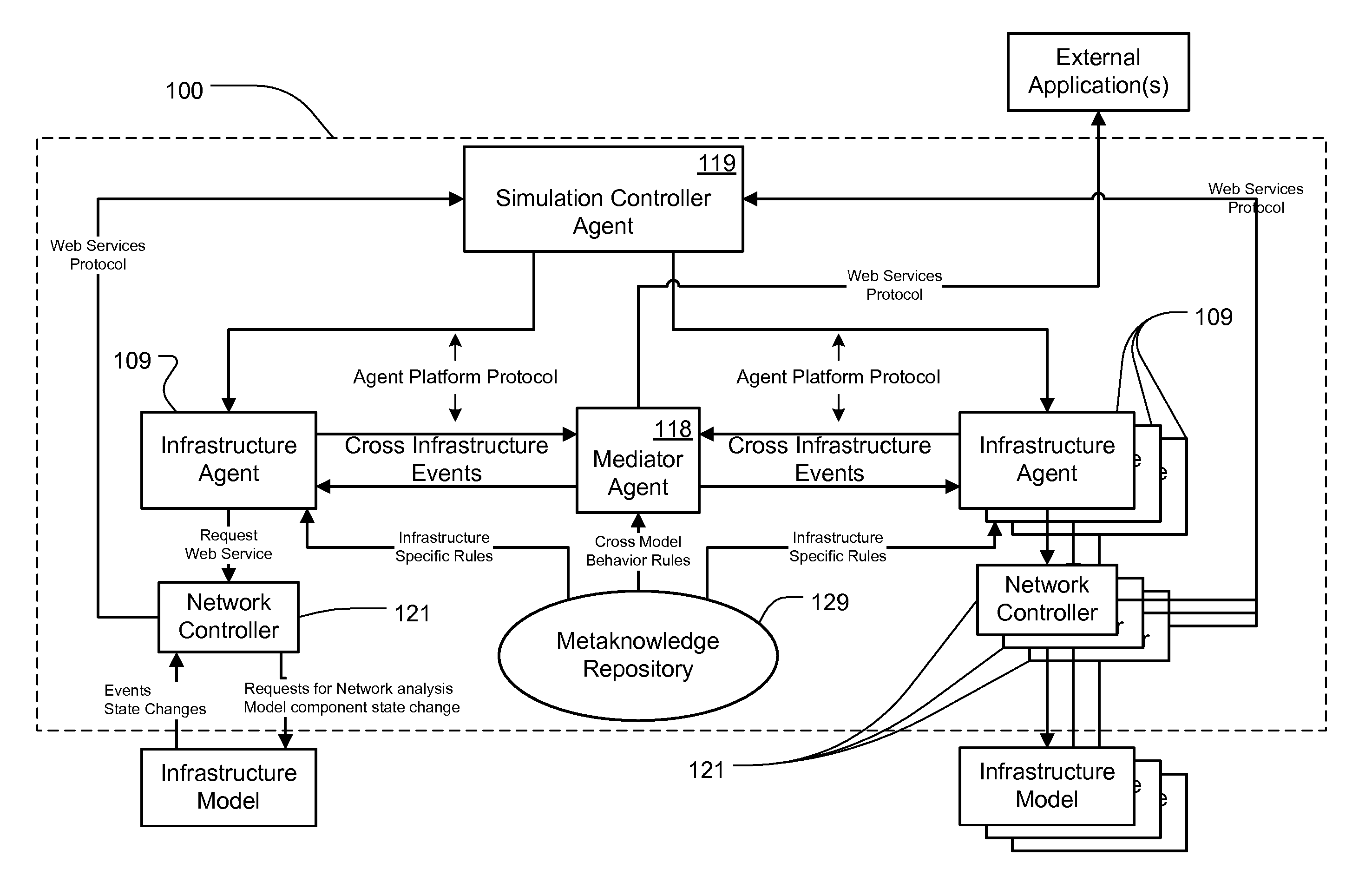
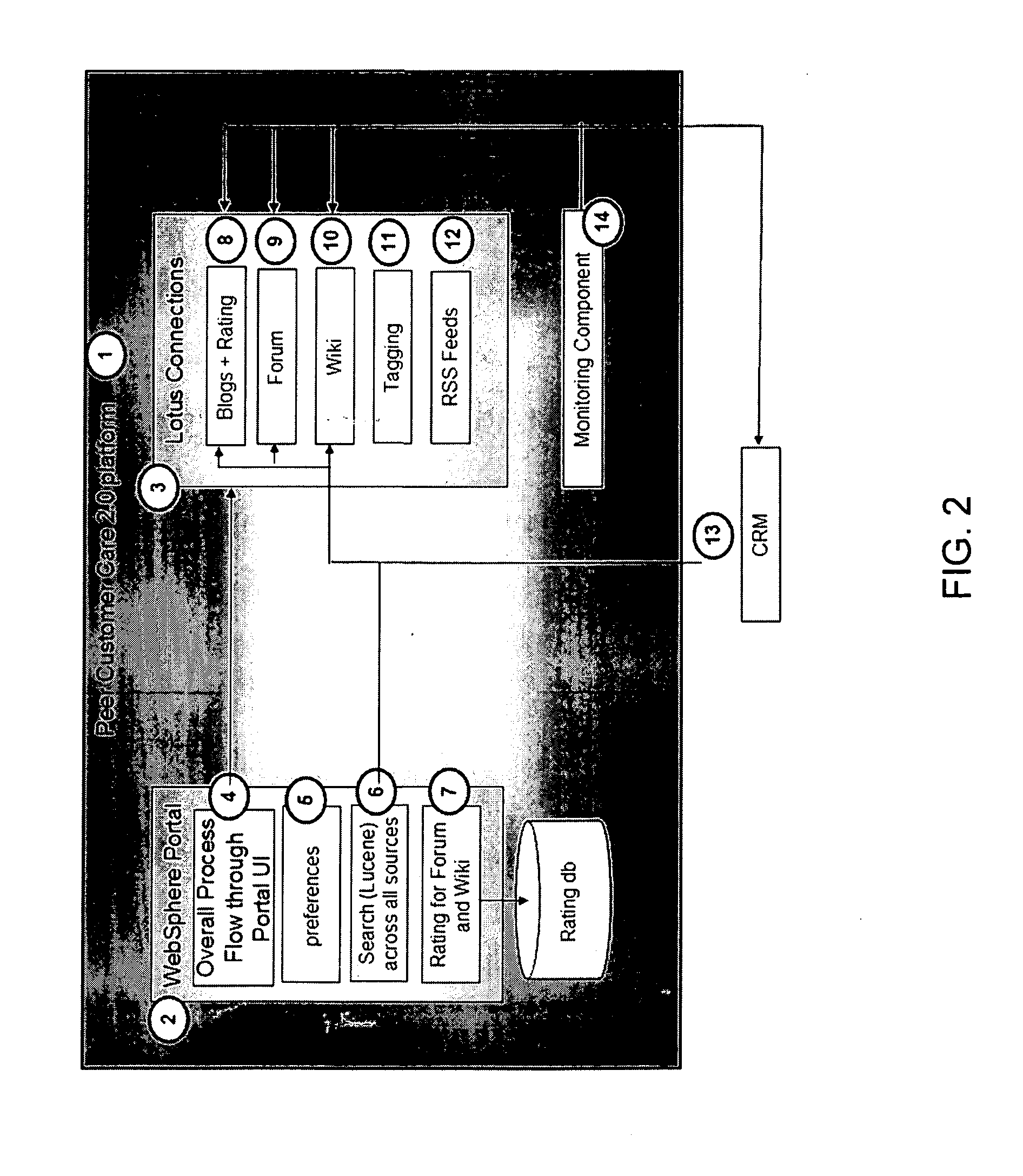
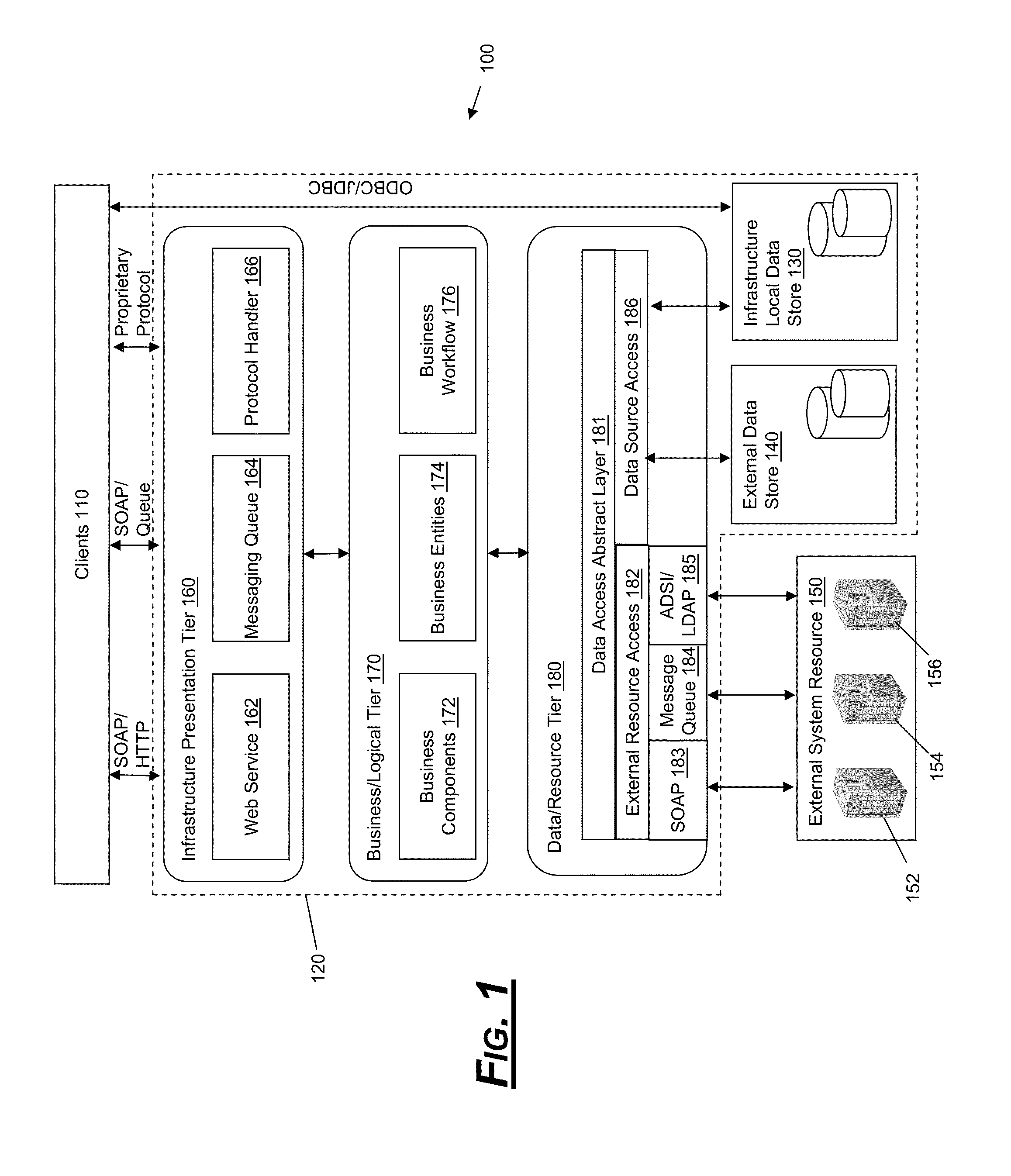
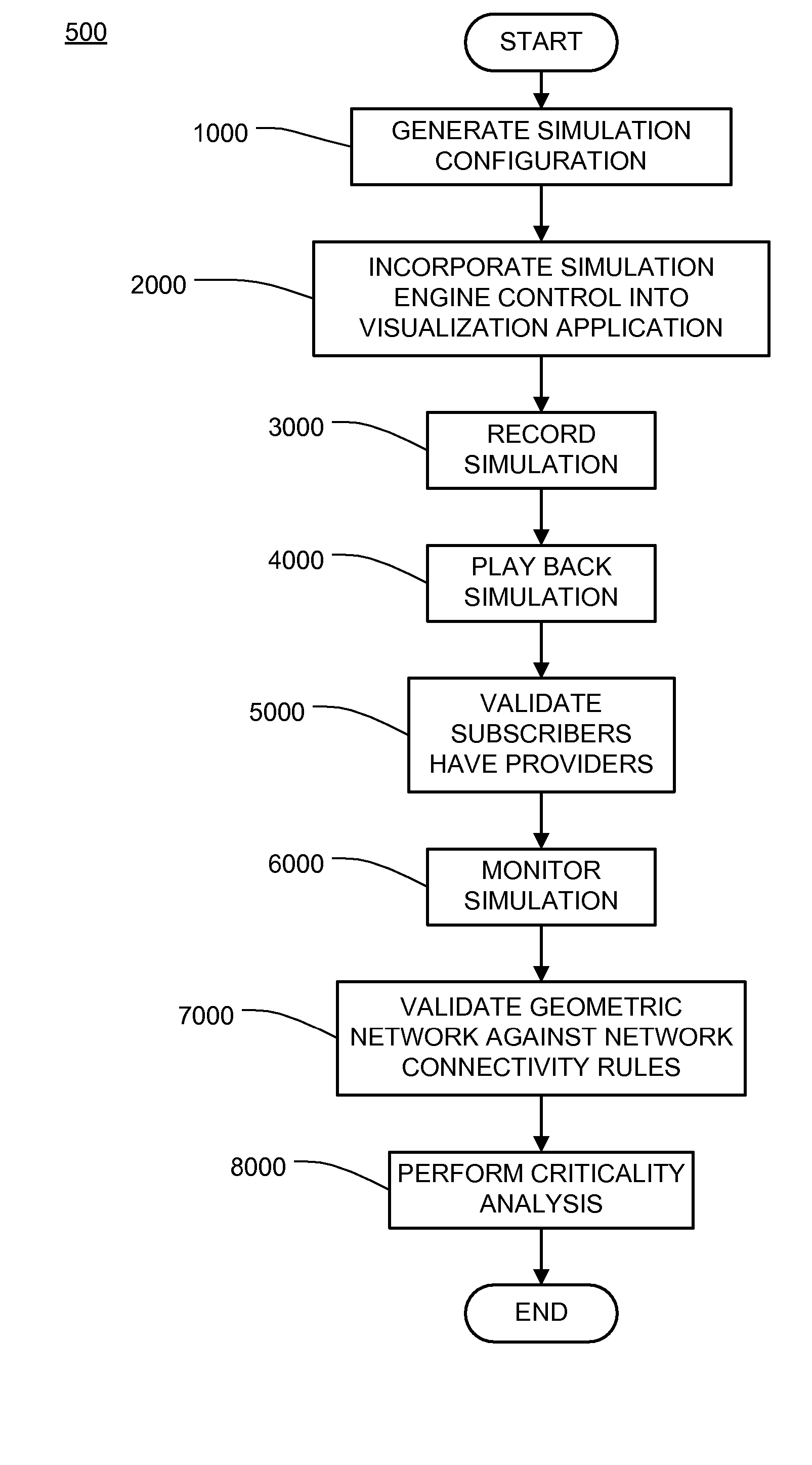
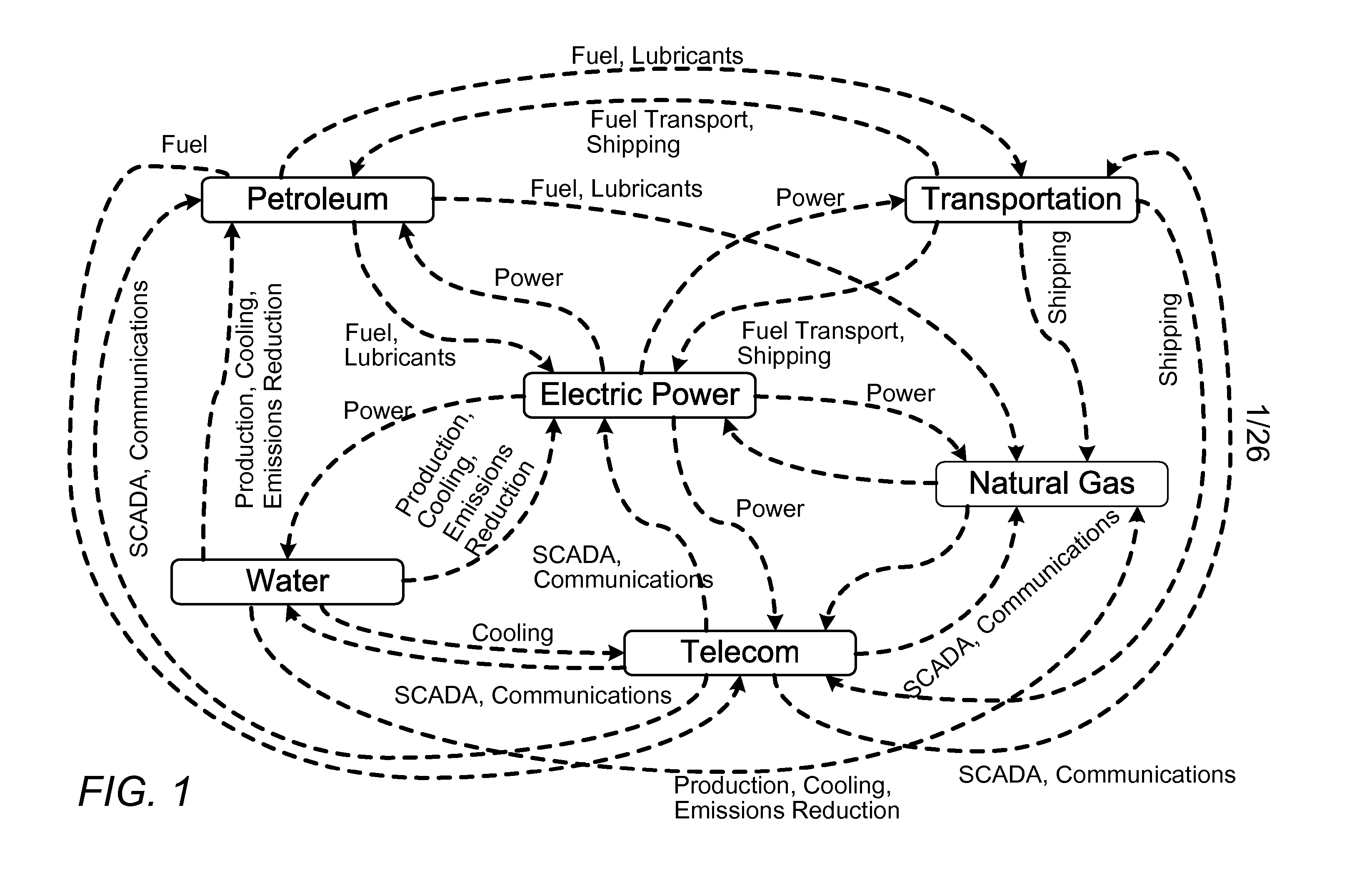
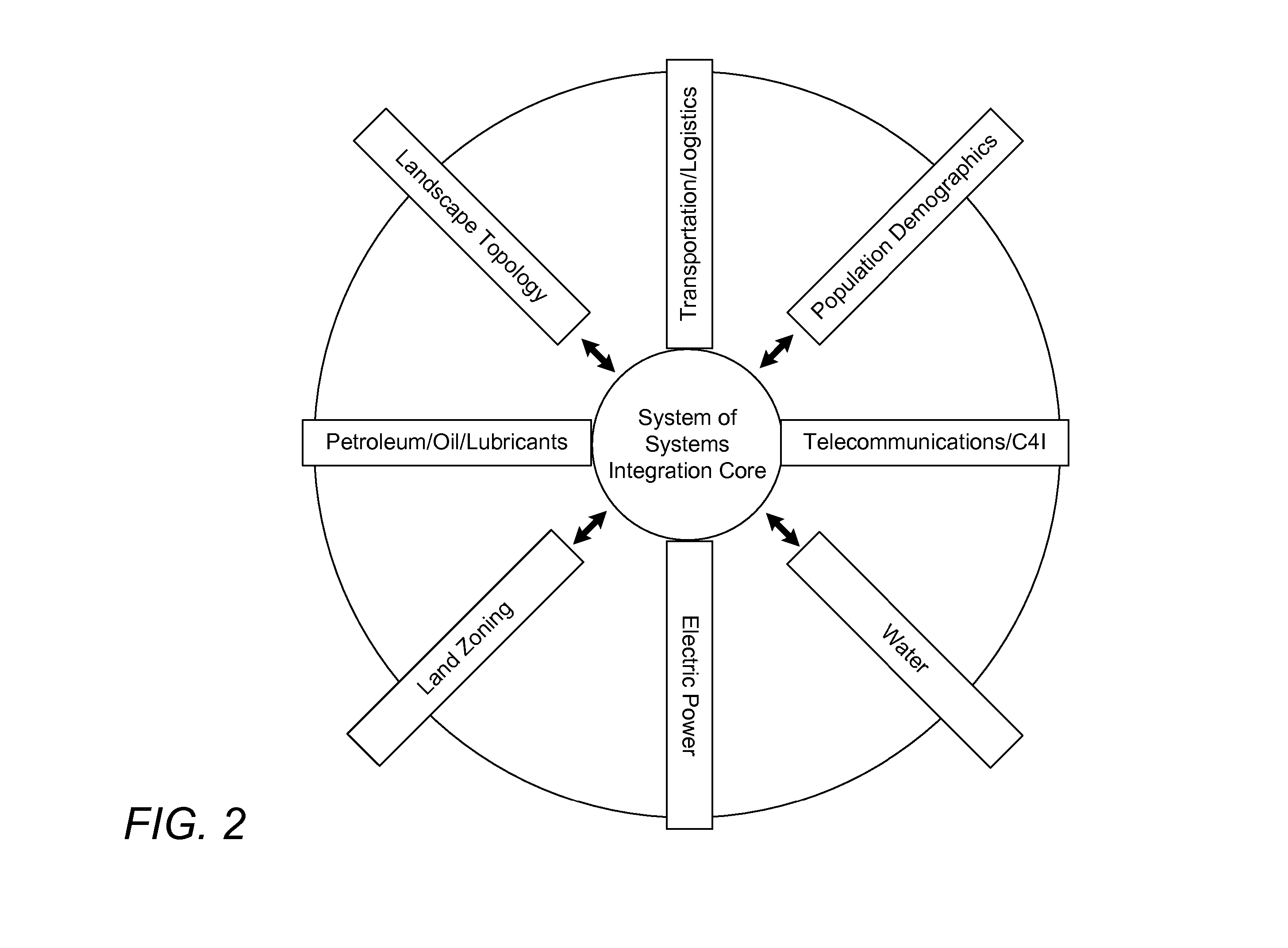
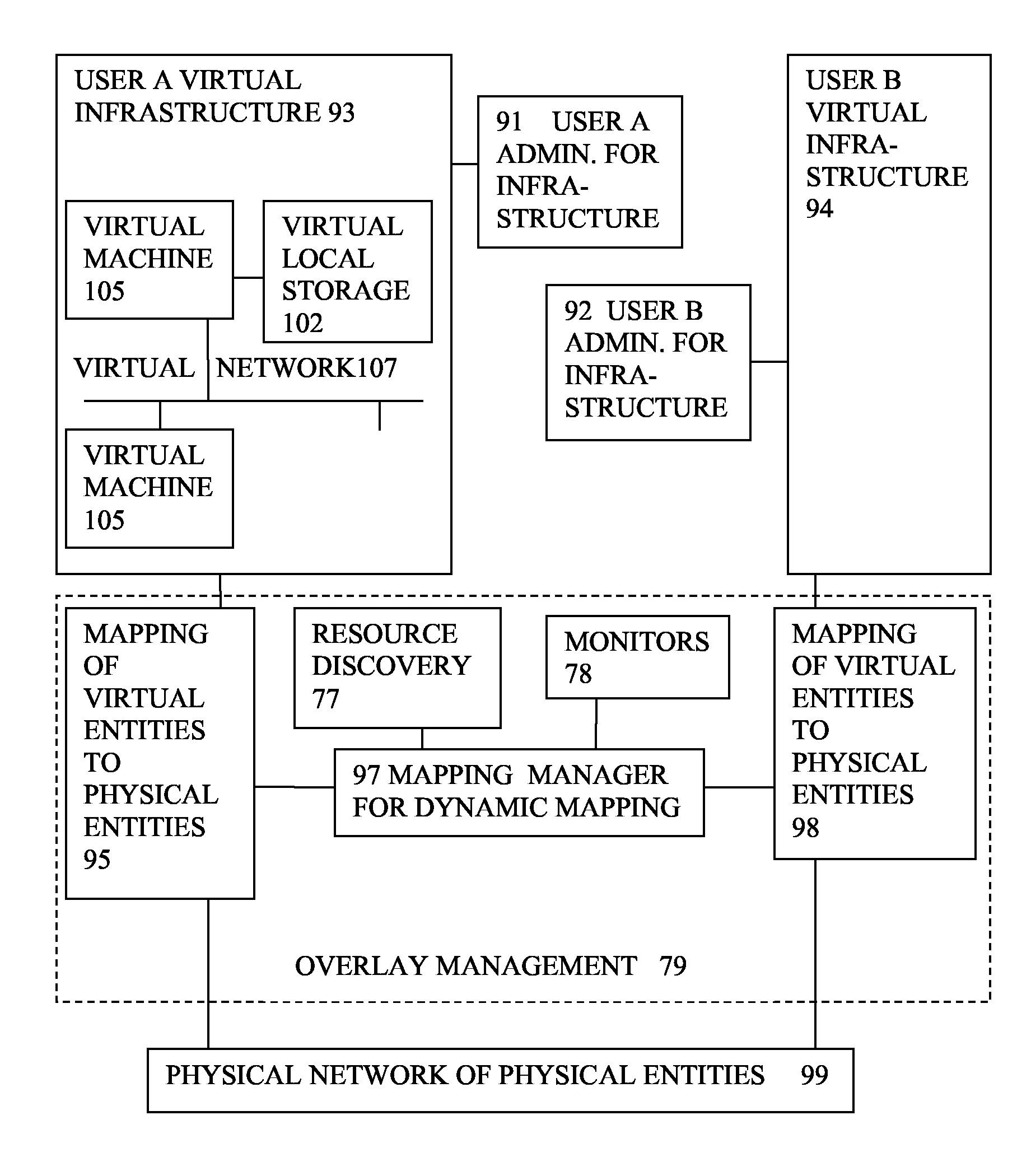
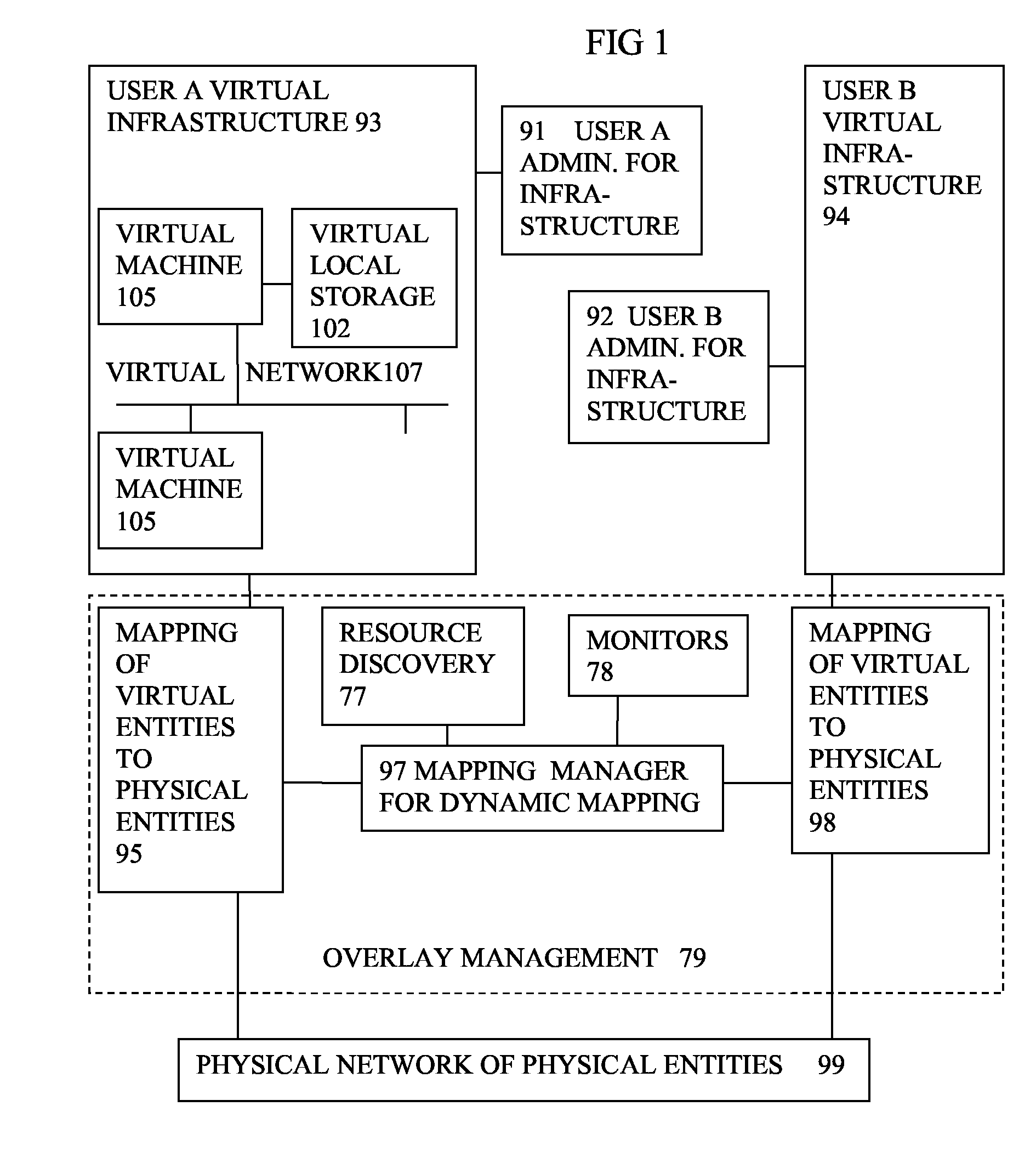
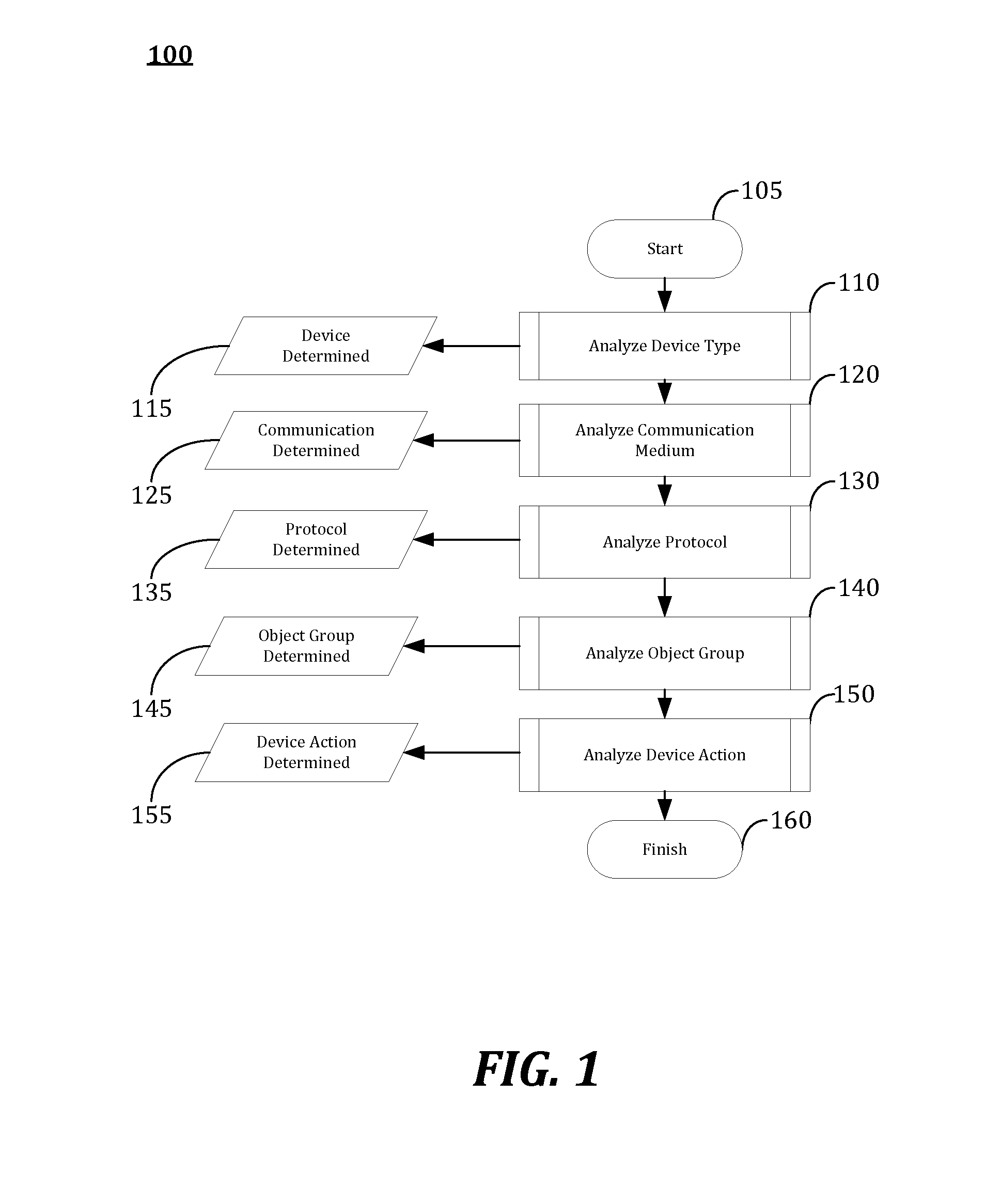
Multi-infrastructure modeling system
ActiveUS7657406B2Geometric CADComputation using non-denominational number representationSoftware agentComputer science
A system for simulating interdependencies between a plurality of infrastructure models includes a first infrastructure data model that models a first infrastructure, a second infrastructure data model that models a second infrastructure, a simulation engine including a society of software agents and adapted to automatically produce, in response to a first change in the infrastructure data model, a second change in the infrastructure data model, and a user interface permitting a user to interact with the simulation engine. The system is adapted to simulate interdependencies between different critical infrastructure models as well as interdependencies between an infrastructure of one infrastructure category and an infrastructure of a different infrastructure category. Infrastructure categories include behavioral infrastructures, relational infrastructures, and physical infrastructures.
Owner:INTEPOINT
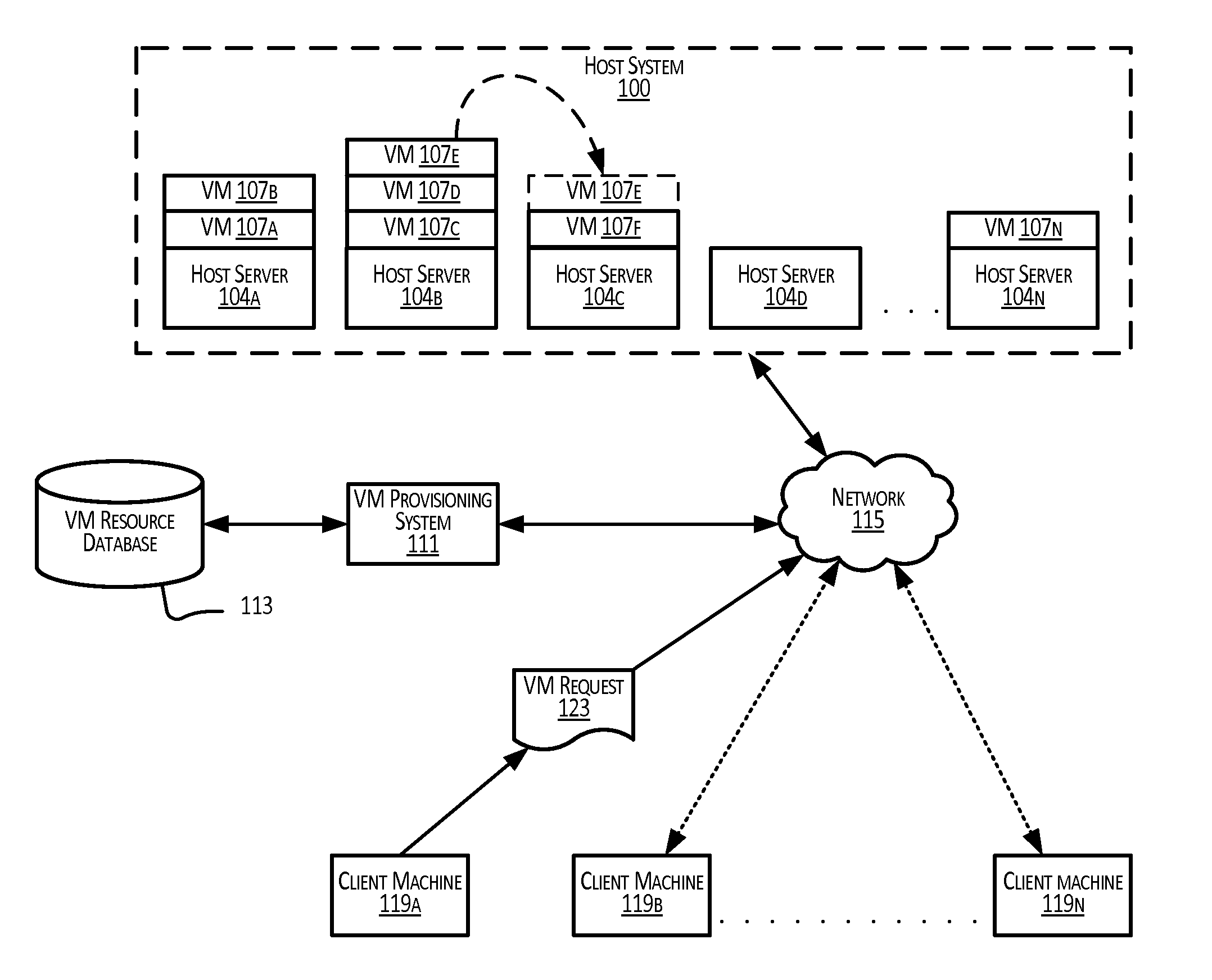
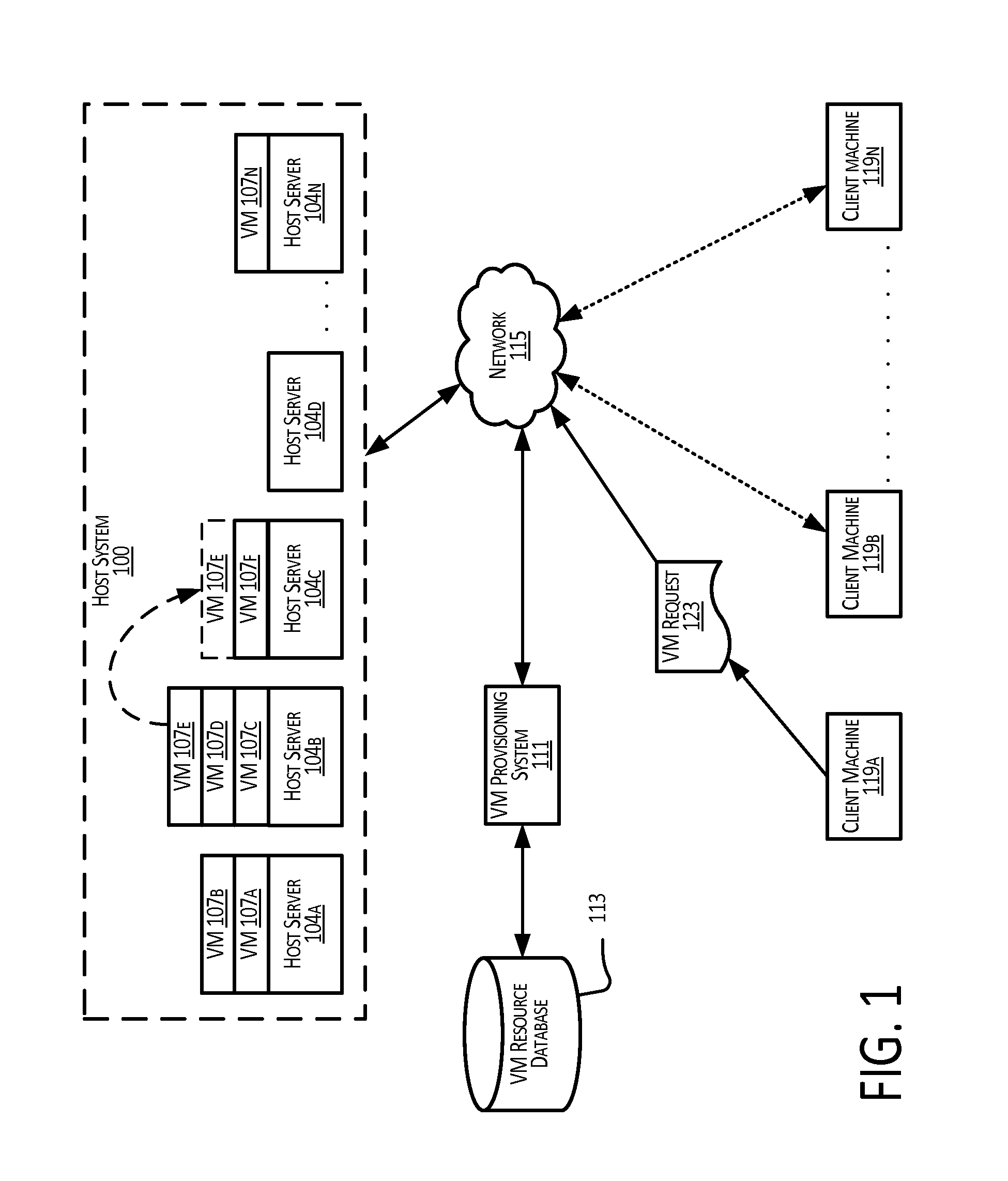
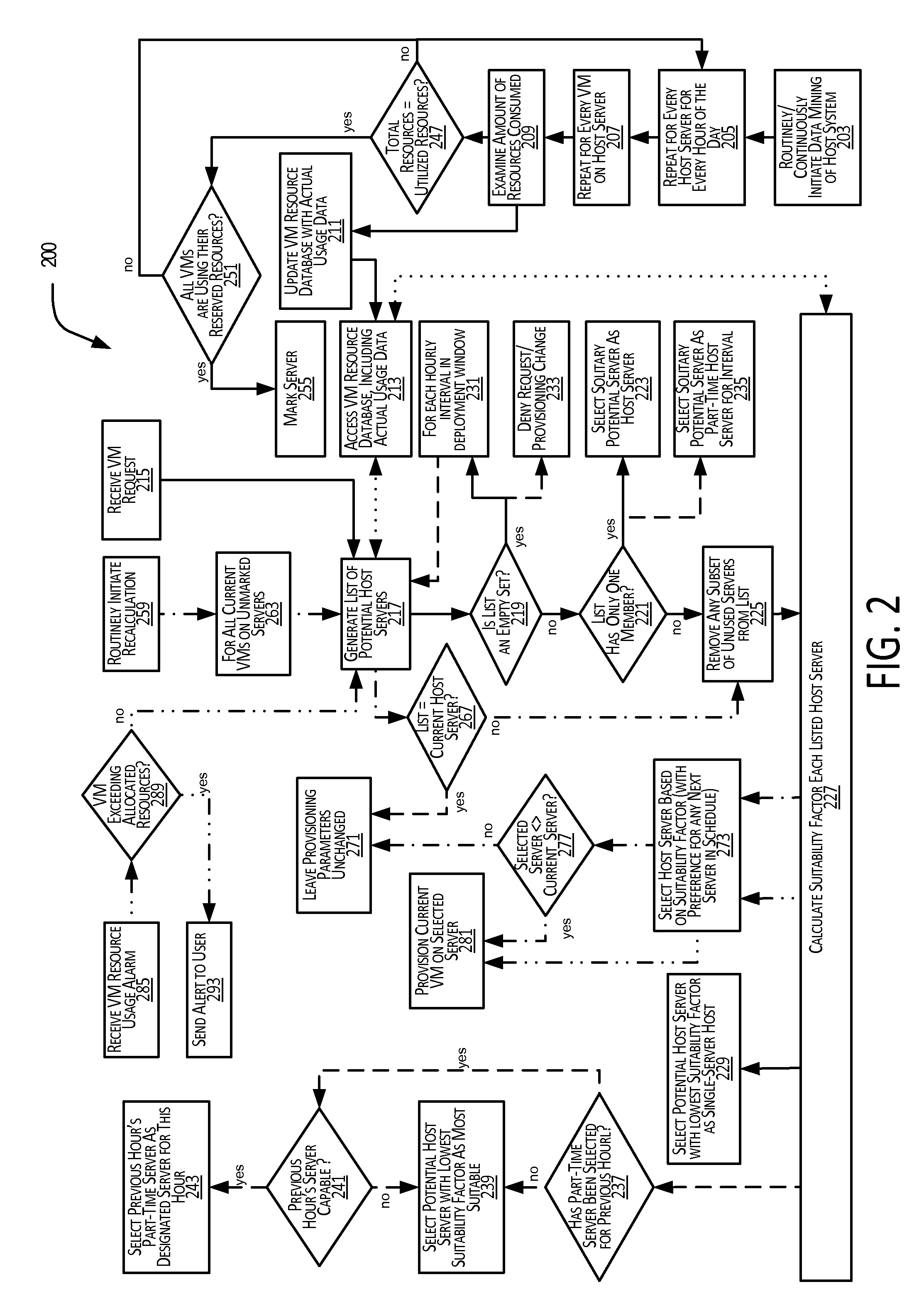
Provisioning virtual machines on a physical infrastructure
InactiveUS20140282520A1Software simulation/interpretation/emulationMemory systemsComputer scienceVirtual machine
Example methods and systems provide for the provisioning of virtual machines on a physical infrastructure based on actual past resource usage of a plurality of virtual machines currently deployed on the physical infrastructure. Upon receiving a request for a new virtual machine based on specified resource requirements, actual usage data that indicate past resource usage of the plurality of current virtual machines are accessed, and provisioning parameters for the new virtual machine are calculated based at least in part on the actual usage data and the specified resource requirements.
Owner:HCL AMERICA INC
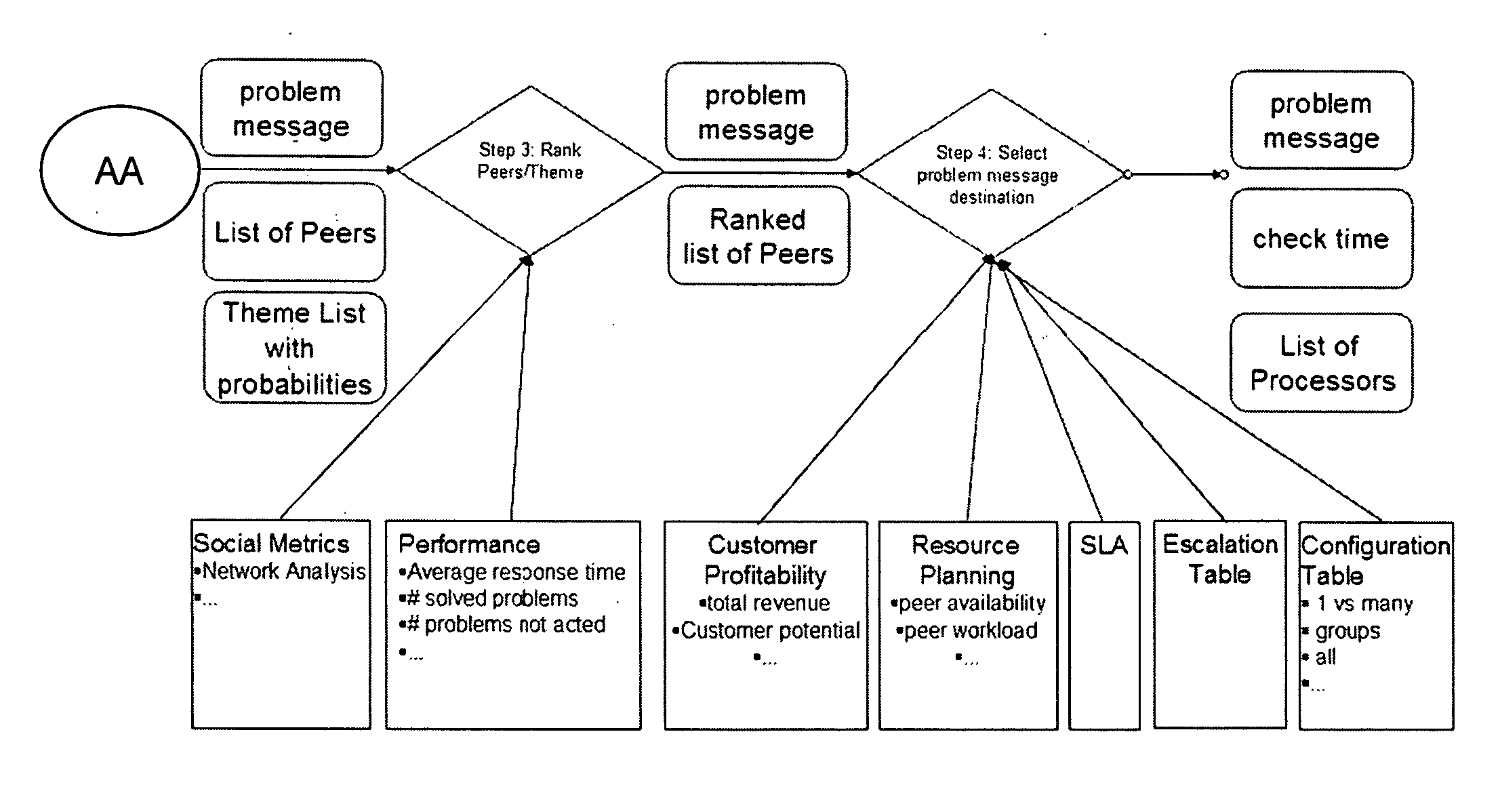
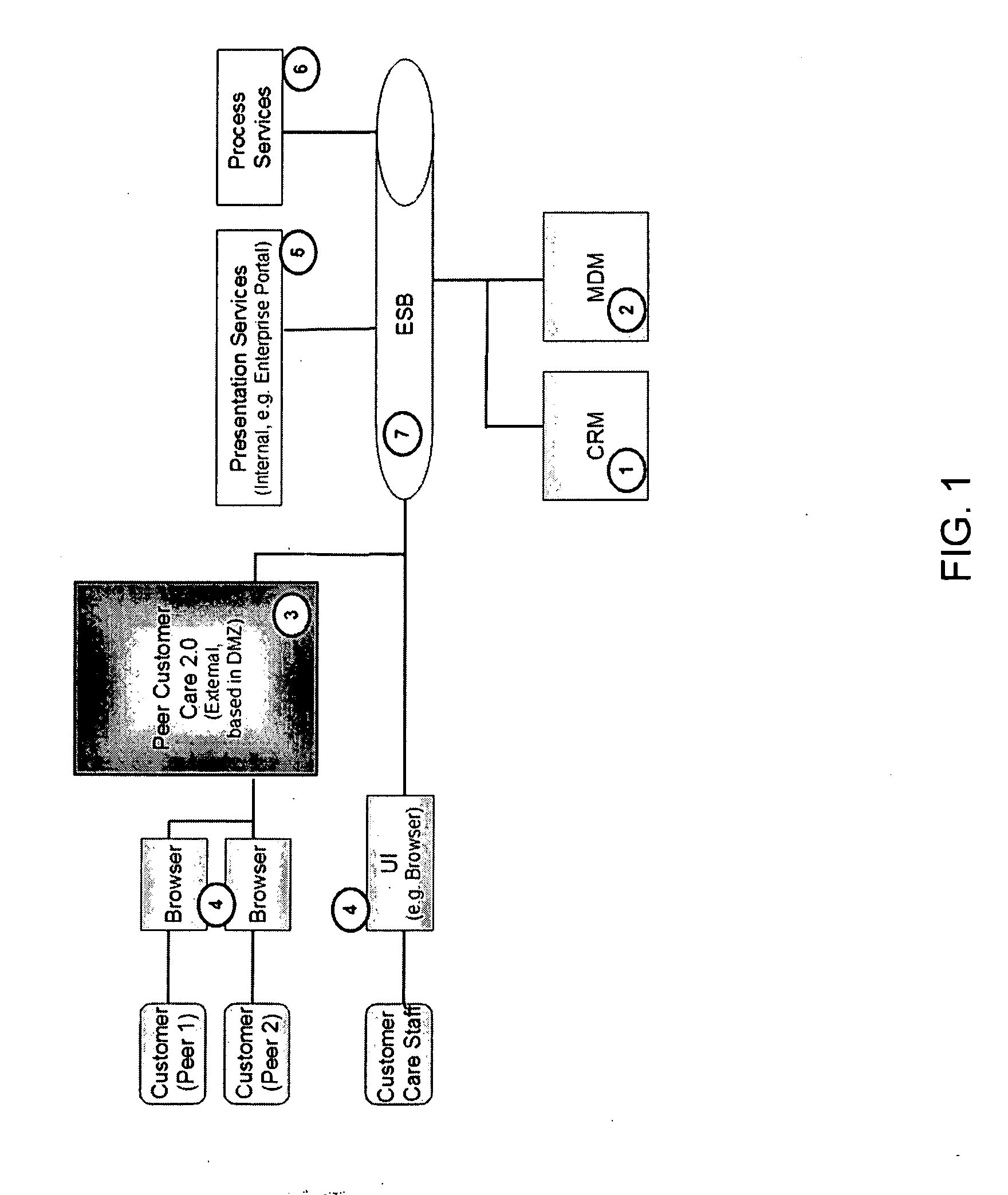
Interaction solutions for customer support
InactiveUS20100169148A1Digital data processing detailsResourcesUrban infrastructureCustomer engagement
The present invention provides a system, architecture and process to support new interaction paradigms in customer support. Specifically, the approach of the present invention will unify through a new process and innovative system architecture the two basic methods of in house support and online support. To accomplish this unification, the present invention enables customers to work together as peers in problem resolution by exploiting the customer expertise (they work with the products on a daily basis and often have deep understanding what works / does not work). Among other things, the present invention provides: incentives for customers to participate in this new support; a rating infrastructure in which multiple good ratings helps to become “THE EXPERT” by increasing the score; incentives upon receipt of good ratings and or certain score levels; a problem routing mechanism; Master Data Management (MDM) for insights in customers and products.
Owner:IBM CORP
Risk modeling system
InactiveUS20160379326A1Improve accuracyData processing applicationsTransmissionDashboardSocial media
The system provides early warning intelligence feeds which analyze risks of potential human caused threats and naturally caused hazards. It includes data mining functions that autonomously search and categorize threats / hazards from worldwide open source data on a continuing basis. Data comes from many news feeds, social media feeds, government databases, etc. Key word analyses allow potential threats / hazards to be sorted into categories traditionally used by government agencies. Physical and cybersecurity vulnerabilities are analyzed and measured with threats to disclose potential impacts to people, properties, processes, special events, and related critical infrastructures and industries. Overall risk scores are instantly displayed as color coded icons on a worldwide electronic map / dashboard at any geolocation. Daily Intelligence reports and certain immediate alerts are also produced.
Owner:CHAN GOVE MARIE N +1
Corporate infrastructure management system
ActiveUS8706692B1Reduce expensesEliminate disparate infrastructure applications and systemsDigital data processing detailsDatabase distribution/replicationApplication softwareDisparate system
CIMS can provide users with essential resources; provide a mechanism for instantly creating, modifying, and delivering infrastructure data that used to take hours or days; improve the efficiency of systems interfacing with it while reducing costly infrastructure; ensure audit and regulatory requirements are satisfied by automatically creating and recording a history of all application transactions; eliminate the cost overhead and human error associated with manual, time-consuming work currently performed by many systems administrators on each disparate system; and be transparent to end users, thereby defraying the costs of time off the job normally incurred with retraining CIMS offers the functionality of the disparate applications and consistently interfaces with the underlying infrastructure. As a result, infrastructure providers do not have to communicate directly with a vast array of business applications. Instead, infrastructure service providers and client applications can focus on being more productive in the development lifecycle.
Owner:CITIBANK
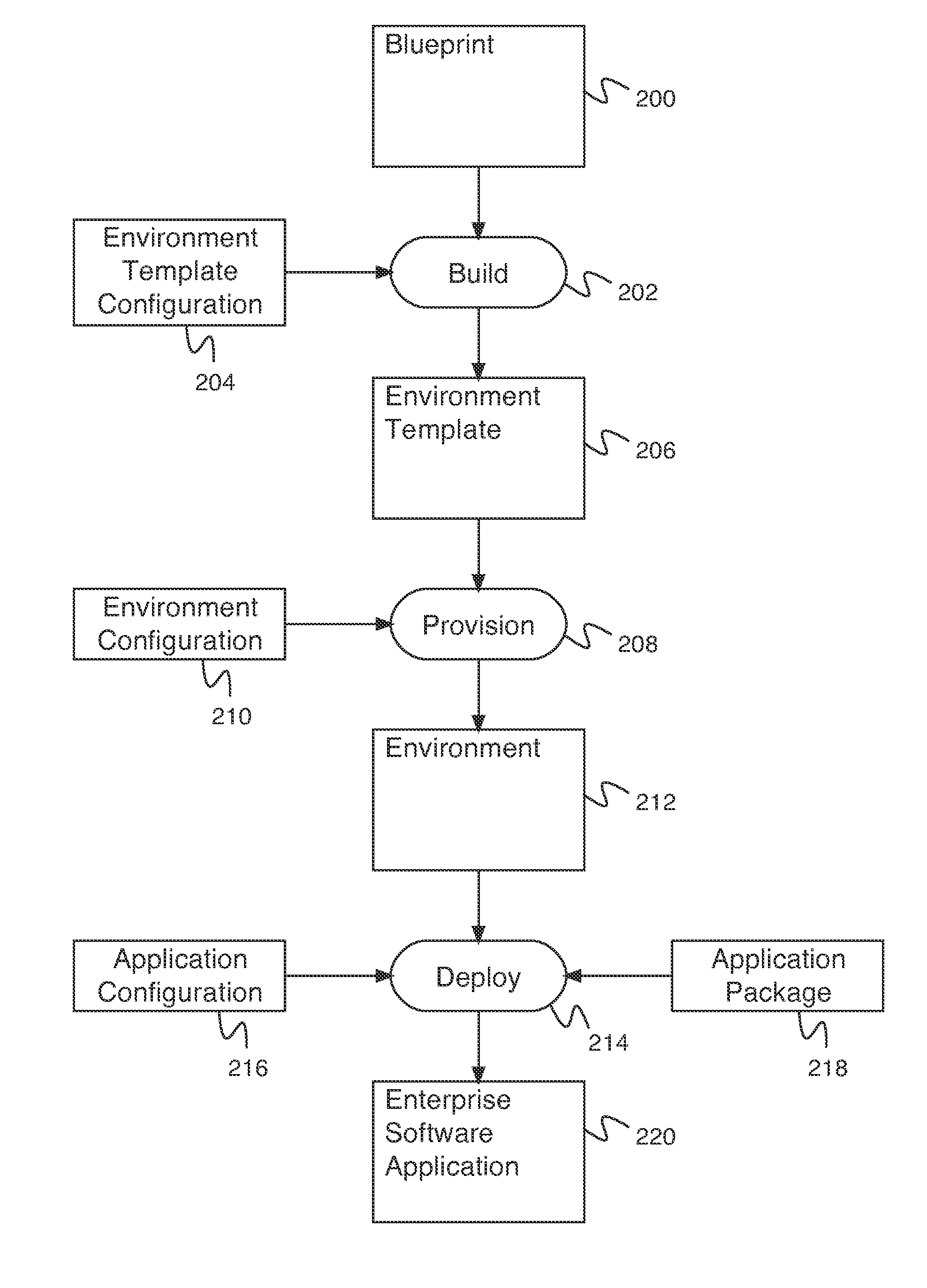
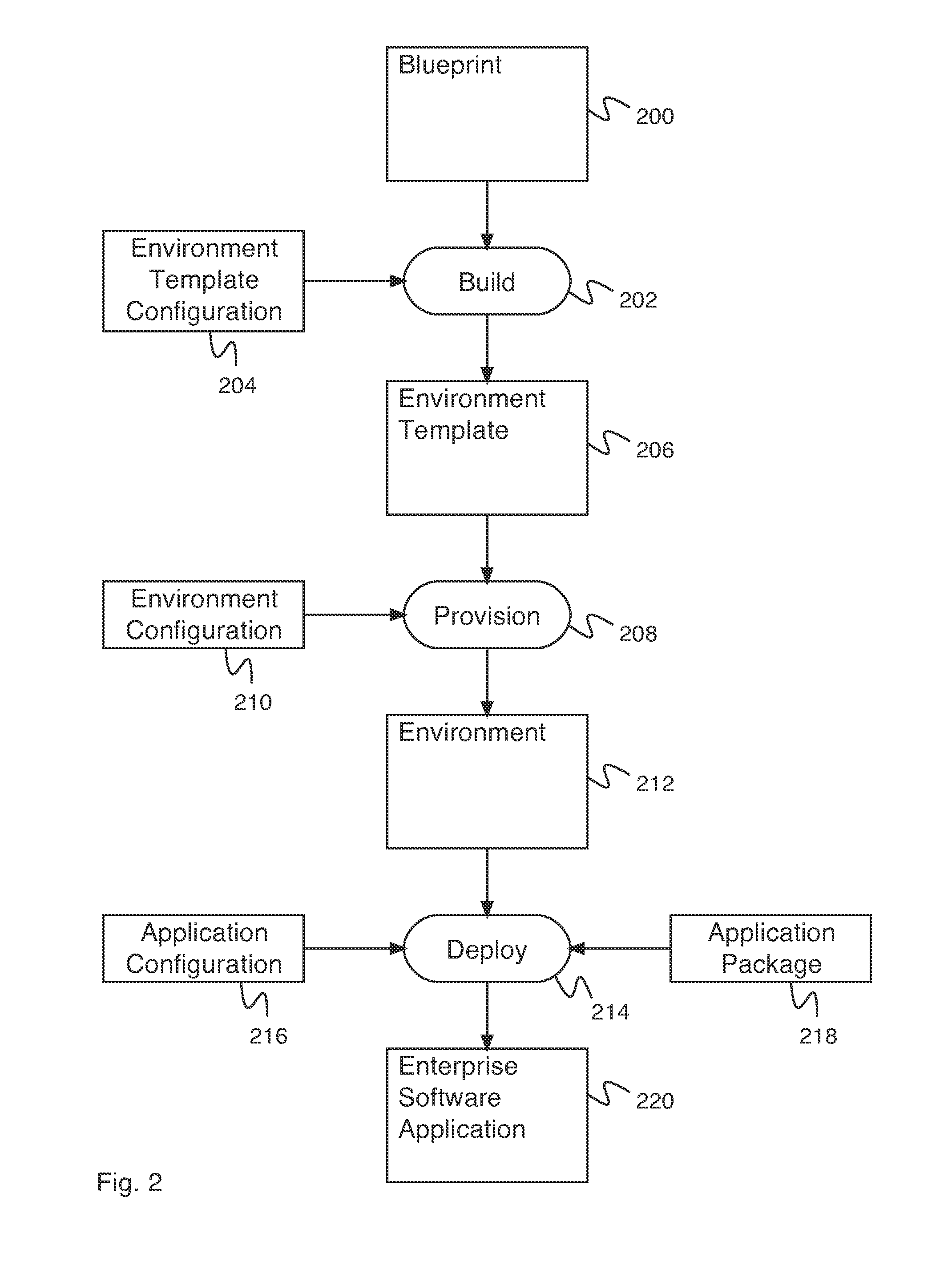
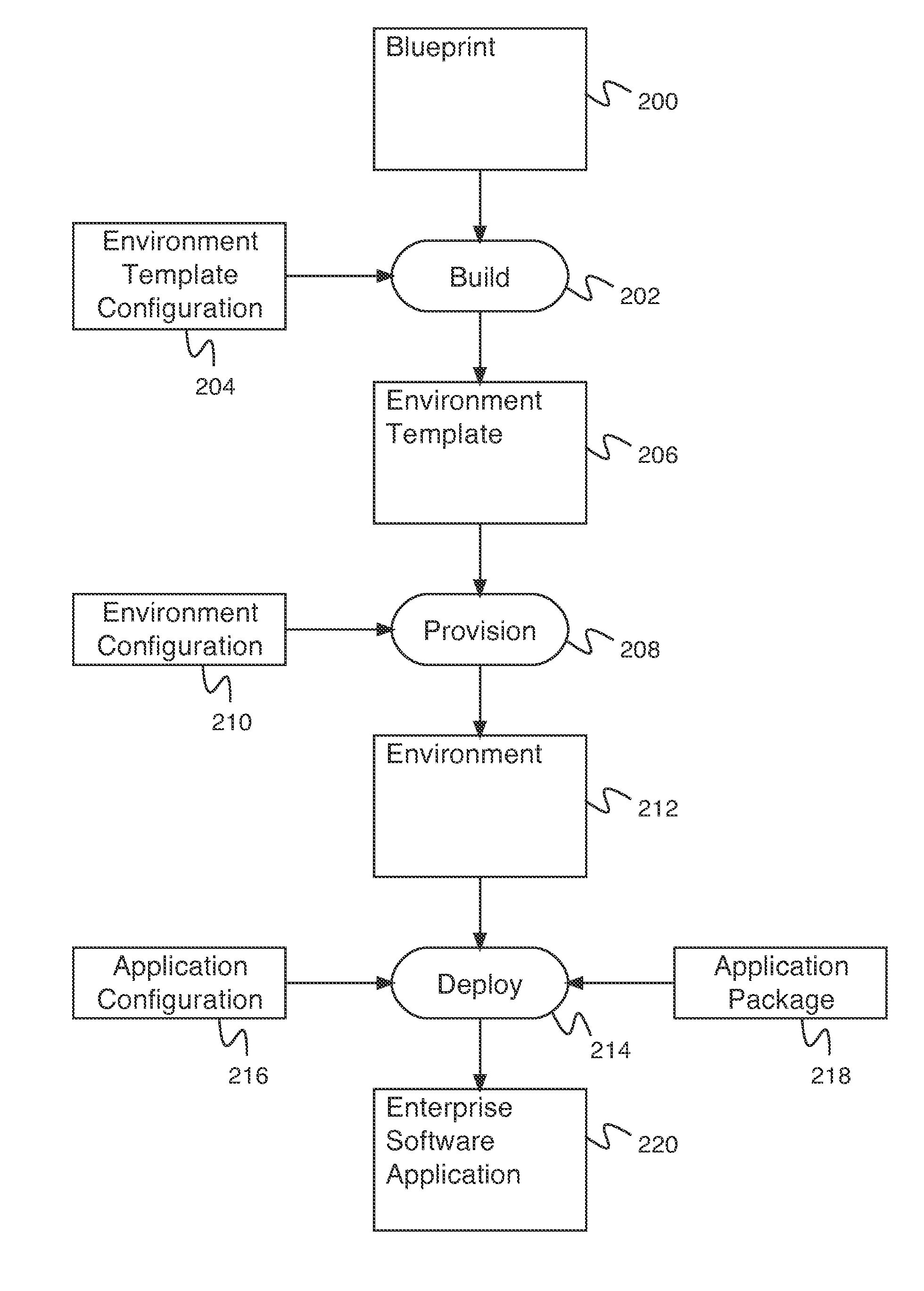
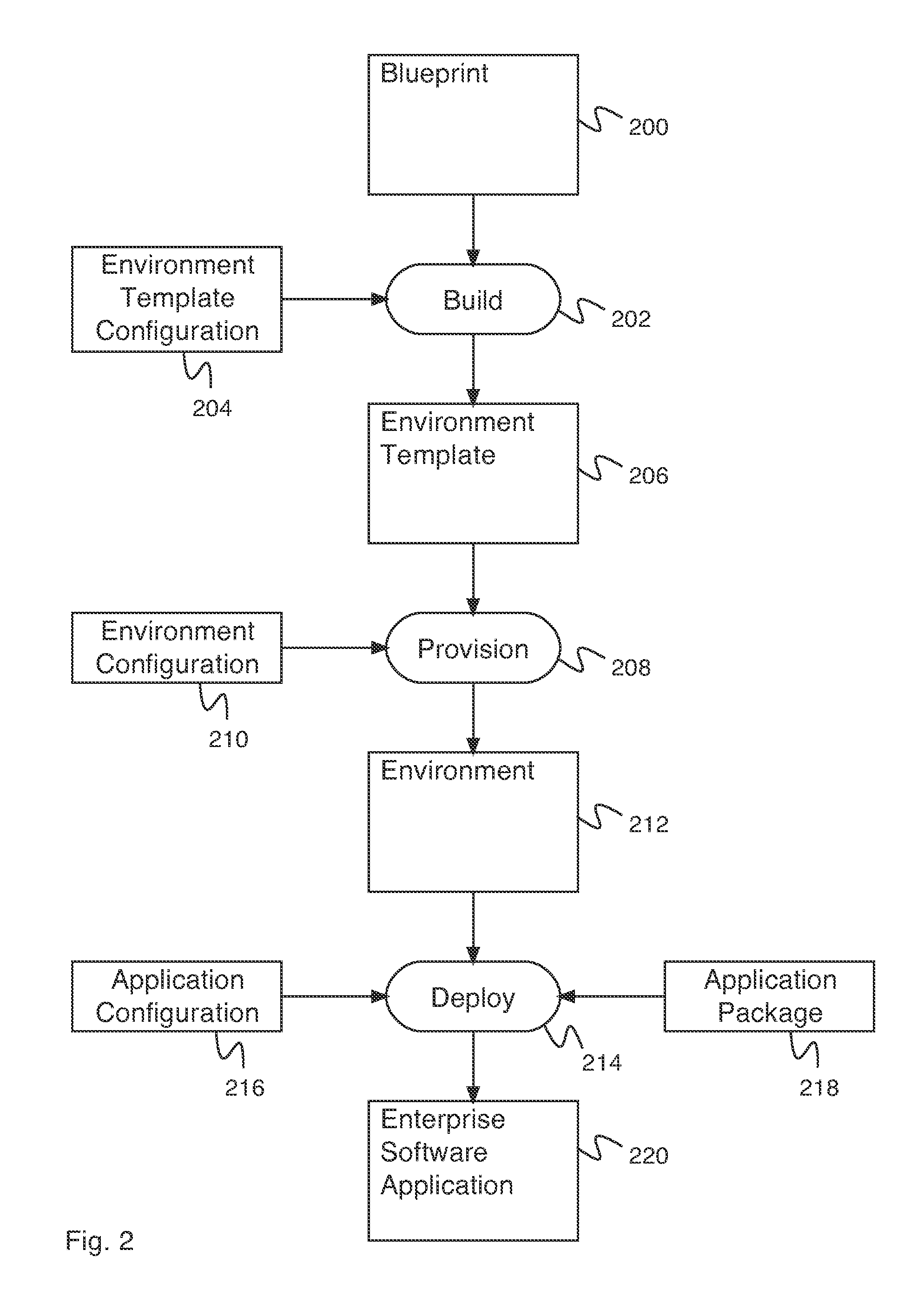
Environment-driven application deployment in a virtual infrastructure
A system for recipe and blueprint-driven automated application deployment comprises a processor and a memory. The processor is configured to receive an environment, receive an application configuration, and deploy an application using the environment and the application configuration. The environment is provisioned using an environment template, and wherein the environment template is built using a blueprint. The application configuration comprises one or more application endpoints. The memory is coupled to the processor and is configured to provide the processor with instructions.
Owner:EMC CORP
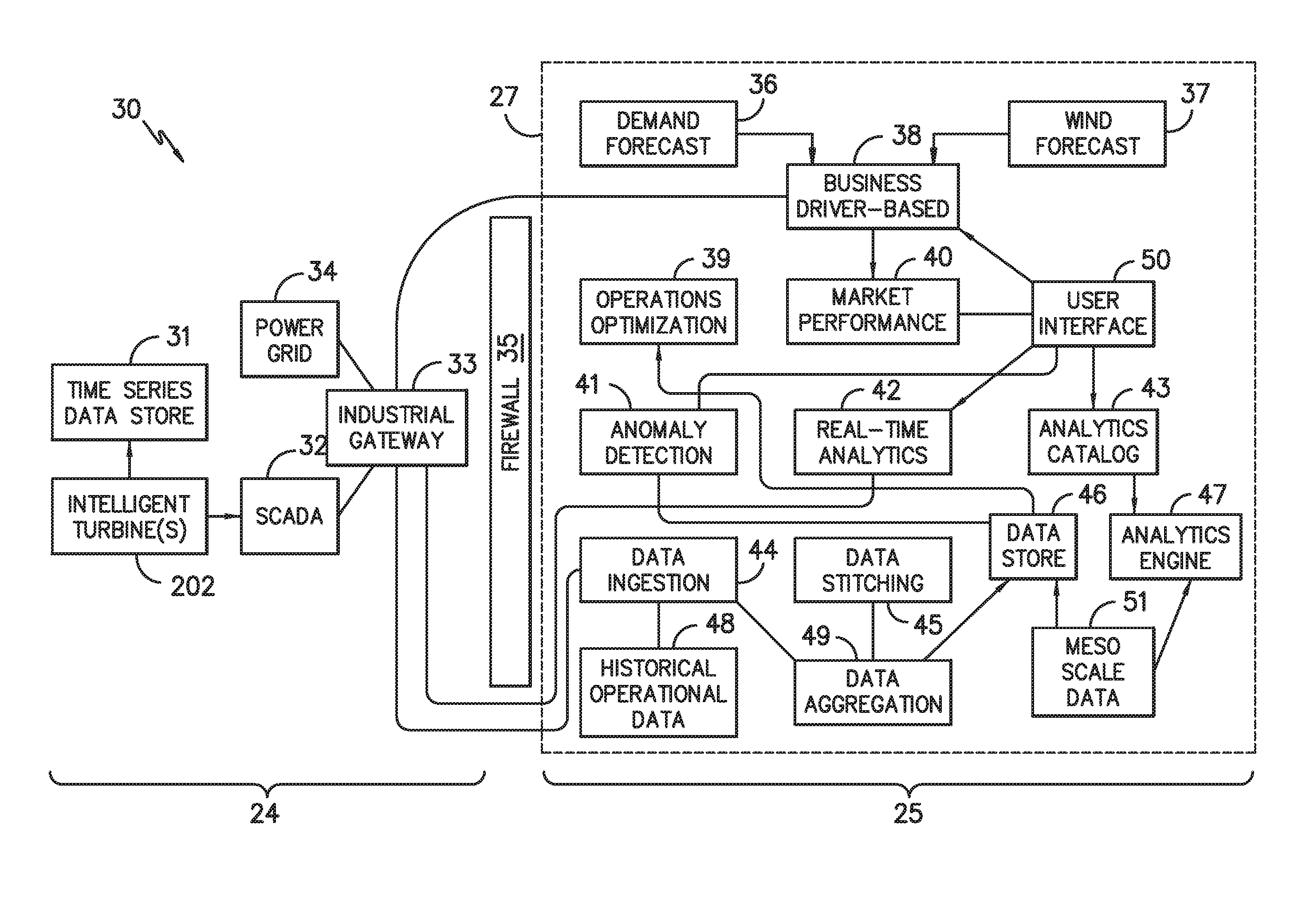
Digital wind farm system
The present disclosure is directed to a digital system for managing a wind farm having a plurality of wind turbines electrically coupled to a power grid. The system includes a farm-based first communication network having one or more individual wind turbine control systems communicatively coupled to the one or more wind turbines and an overall wind farm control system. The system also includes a cloud-based second communication network communicatively coupled to the first communication network via an industrial gateway. The second communication network includes a digital infrastructure having a plurality of digital models of the one or more wind turbines, wherein the plurality of digital models of the one or more wind turbines are continuously updated during operation of the wind farm via data supplied by the farm-based first communication network.
Owner:GENERAL ELECTRIC CO
Multi-infrastructure modeling system
ActiveUS20070021955A1Geometric CADComputation using non-denominational number representationPhysical infrastructureSoftware agent
A system for simulating interdependencies between a plurality of infrastructure models includes a first infrastructure data model that models a first infrastructure, a second infrastructure data model that models a second infrastructure, a simulation engine including a society of software agents and adapted to automatically produce, in response to a first change in the infrastructure data model, a second change in the infrastructure data model, and a user interface permitting a user to interact with the simulation engine. The system is adapted to simulate interdependencies between different critical infrastructure models as well as interdependencies between an infrastructure of one infrastructure category and an infrastructure of a different infrastructure category. Infrastructure categories include behavioral infrastructures, relational infrastructures, and physical infrastructures.
Owner:INTEPOINT
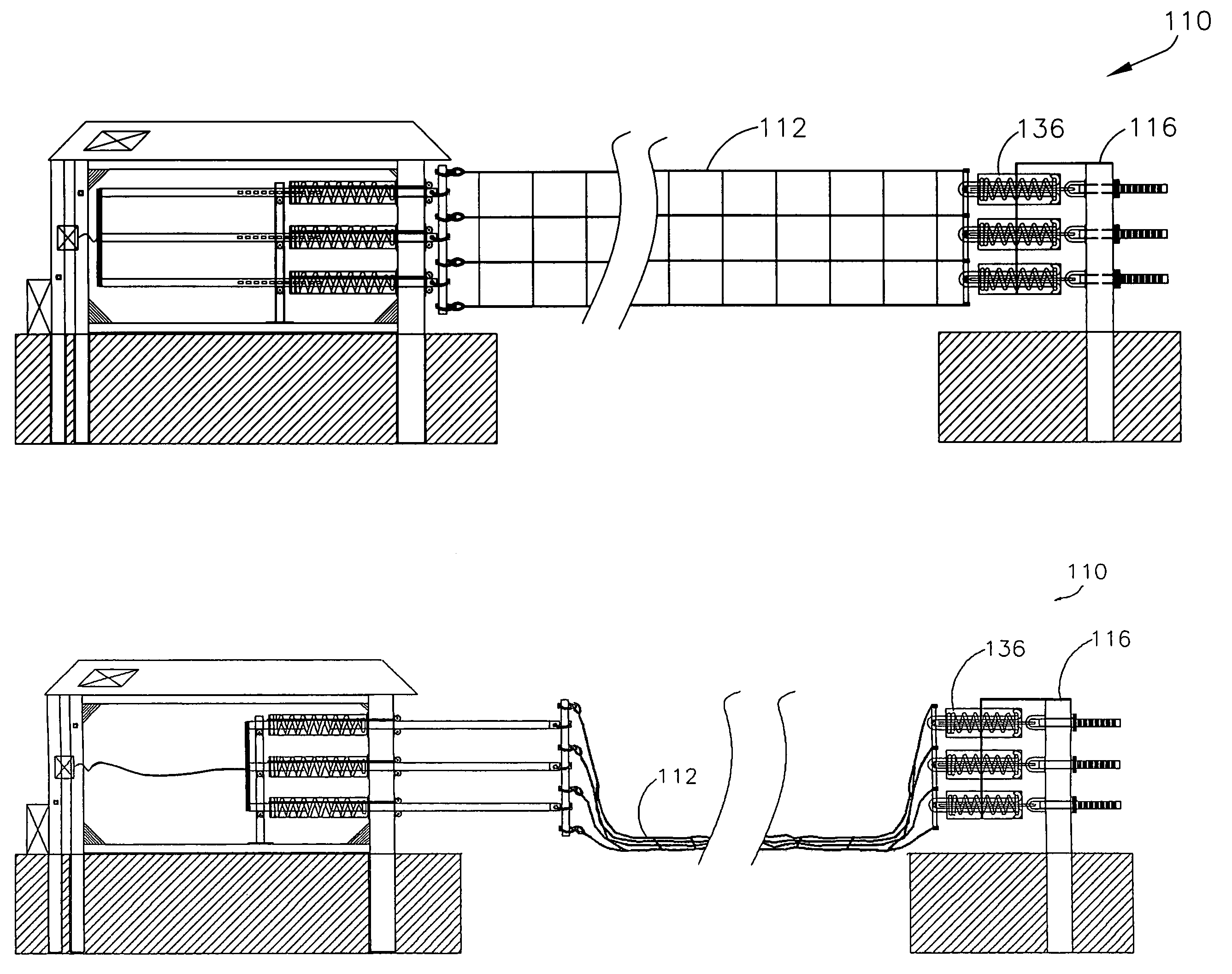
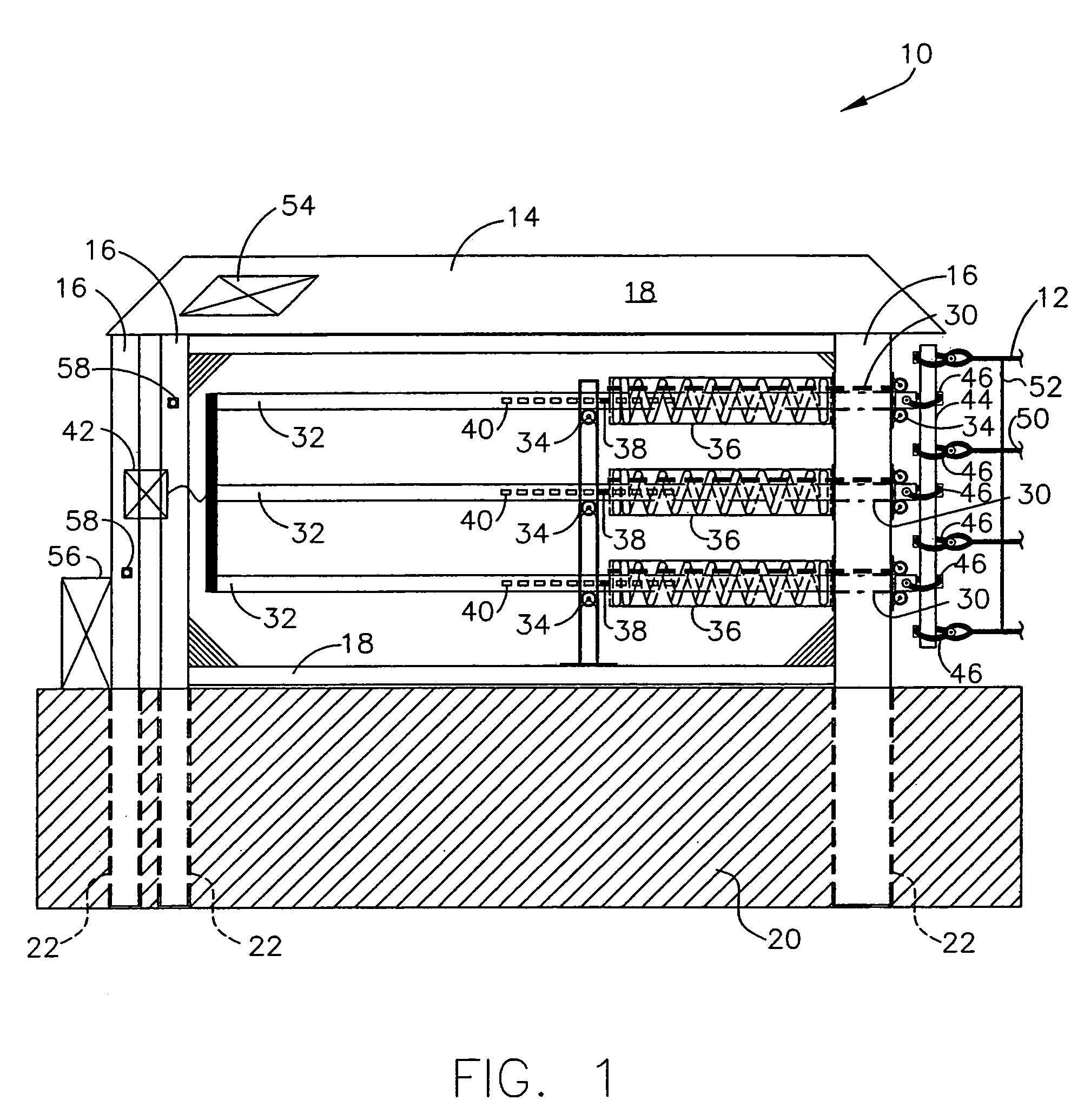
Retractable wide-span vehicle barrier system
ActiveUS7083357B2Easy to deployEliminate requirementsTraffic restrictionsRoadway safety arrangementsModularityEqualization
A vehicle barrier system that stops unwanted vehicle intrusion, controls vehicle access, and protects assets and critical infrastructure. The vehicle barrier system, which can span up to 250 feet without requiring fixed intermediate supports, will stop a 15,000 lb vehicle traveling at impact speed of 50 mph. The barrier net is attached to vertical steel end supports anchored in concrete, and include energy absorbers, pivoting connections, and force equalization bars. The barrier net can remain in the “up” or “down” position, and can be raised or lowered using a winch powered by common 12 volt battery with solar power recharge. The barrier net and system components are modular, and can be easily installed or removed.
Owner:BARRIER1 SYST LLC
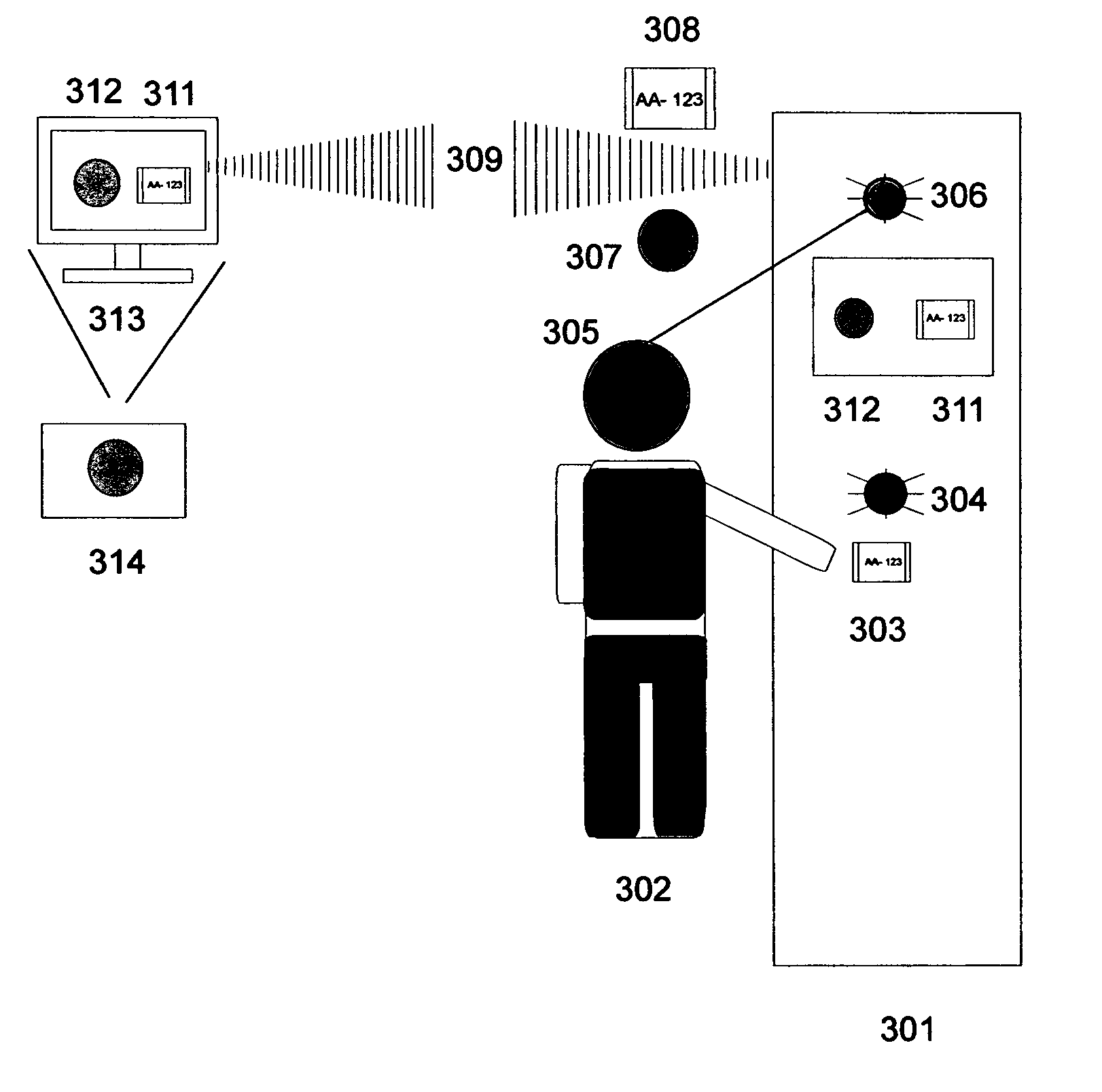
Standoff security and real-time vendor verification system and apparatus
InactiveUS20050219359A1The process is convenient and fastStrong and more organizedElectric signal transmission systemsMultiple keys/algorithms usageOperational systemEngineering
A stand-off security checkpoint system and apparatus that enables security officers entrusted with protecting our nations' critical infrastructure or other high risk locations, a means of verifying in real-time, the identity of entrants to a facility. Via a communications system and apparatus that is positioned a safe, stand-off distance away from the entrance to a facility, a person entering a facility exits his vehicle or walks up to a machine housing which is equipped with cameras and sensor equipment. A close up view of the persons' identification as well a picture of the person himself is captured and readied for real-time transmission to security personnel well away from the entrants location at the machine. Via wireless transmitter and receiver equipment, and computer hardware and software arrangements incorporated into the system, the entrant and his identification card can be viewed and verified, from a safe standoff distance by on-site, as well as off-site security screening personnel. The utilization of wireless networks and internet communications networks, along with the machines' physical features and use, creates multiple opportunities to detect suspicious behavior by entrants to facility well before they reach an unsafe distance to the entrance. While in operation, and with the person a safe distance away from the entrance, the system further equipped with sensors to detect metal, chemical and biological substances can also send special alerts to the detection of harmful substances, well before the entrant reaches the entrance to the facility or security checkpoint. By design, the system and apparatus creates a new and effective means of deterring terrorists who may be trying to effect a terrorist infiltration by disguising themselves as officials or vendors. Additionally, the system is designed to be laid out so as to prompt a direct separation of a would-be suicide or truck bomber from his vehicle. This can greatly deter his desire to effect an attack at that location, as the chances for nullification and or the detection of suspicious activity by security officers operating the system, well before he reaches his location are greatly in odds against him.
Owner:TRELA RICHARD STEVEN
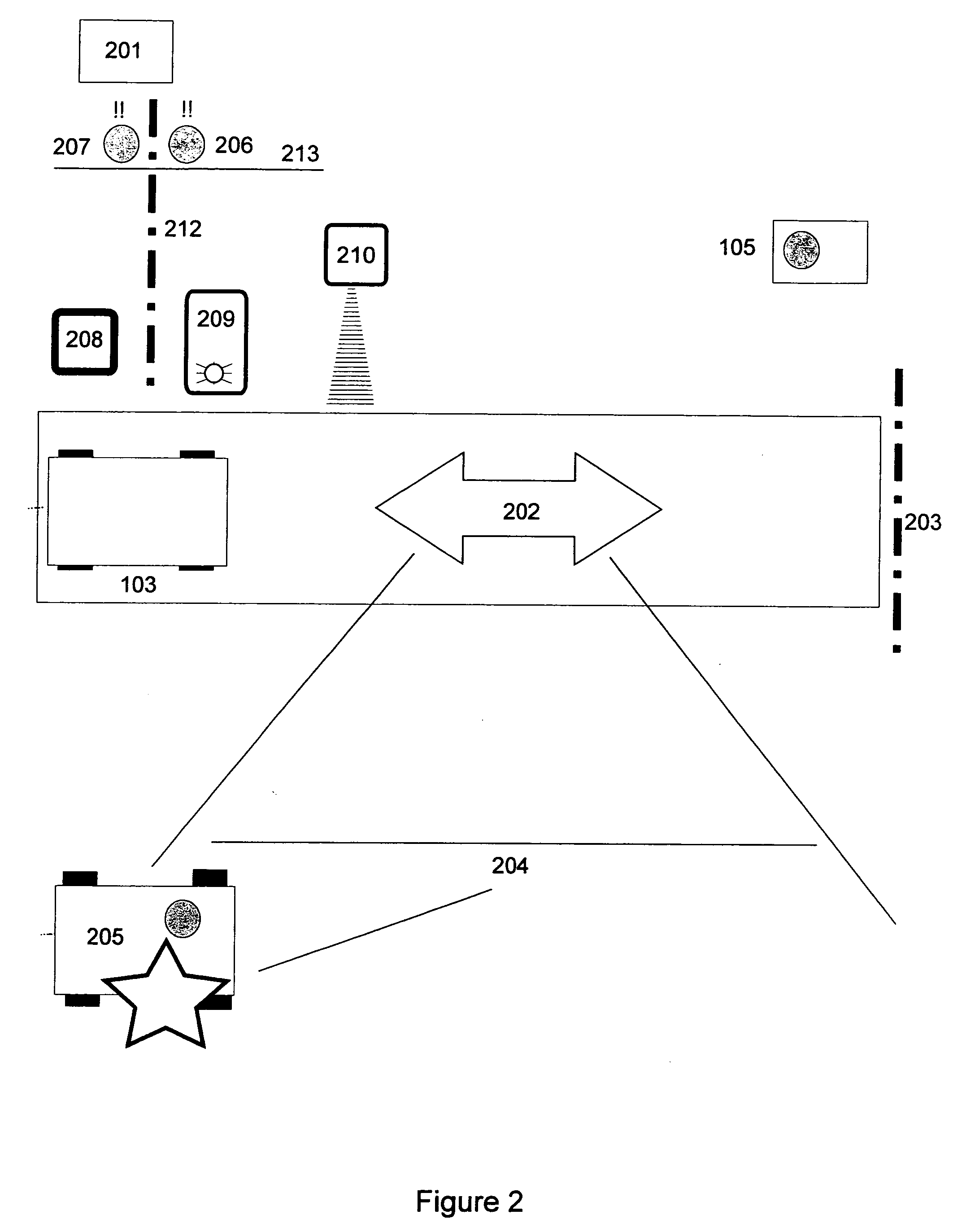
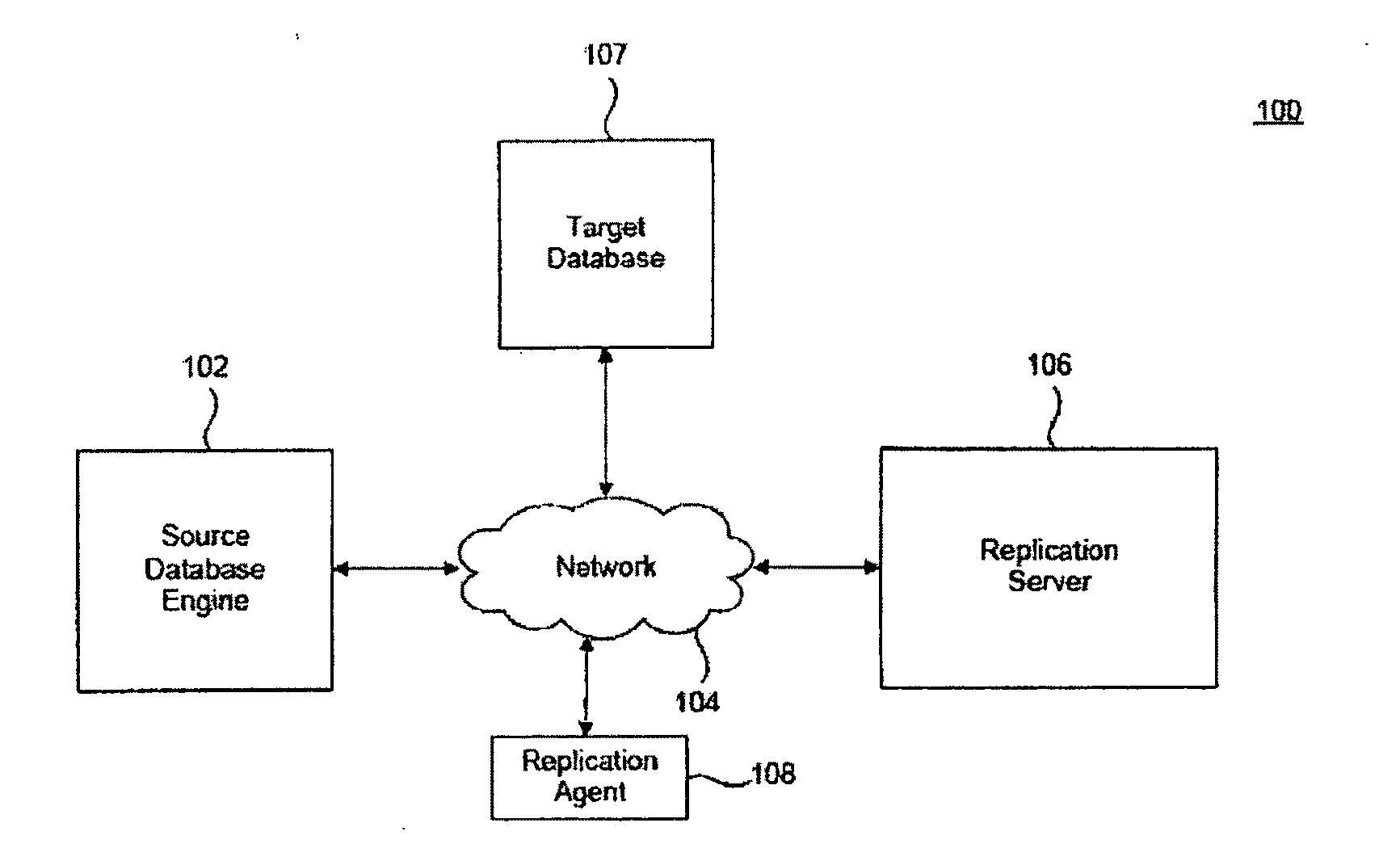
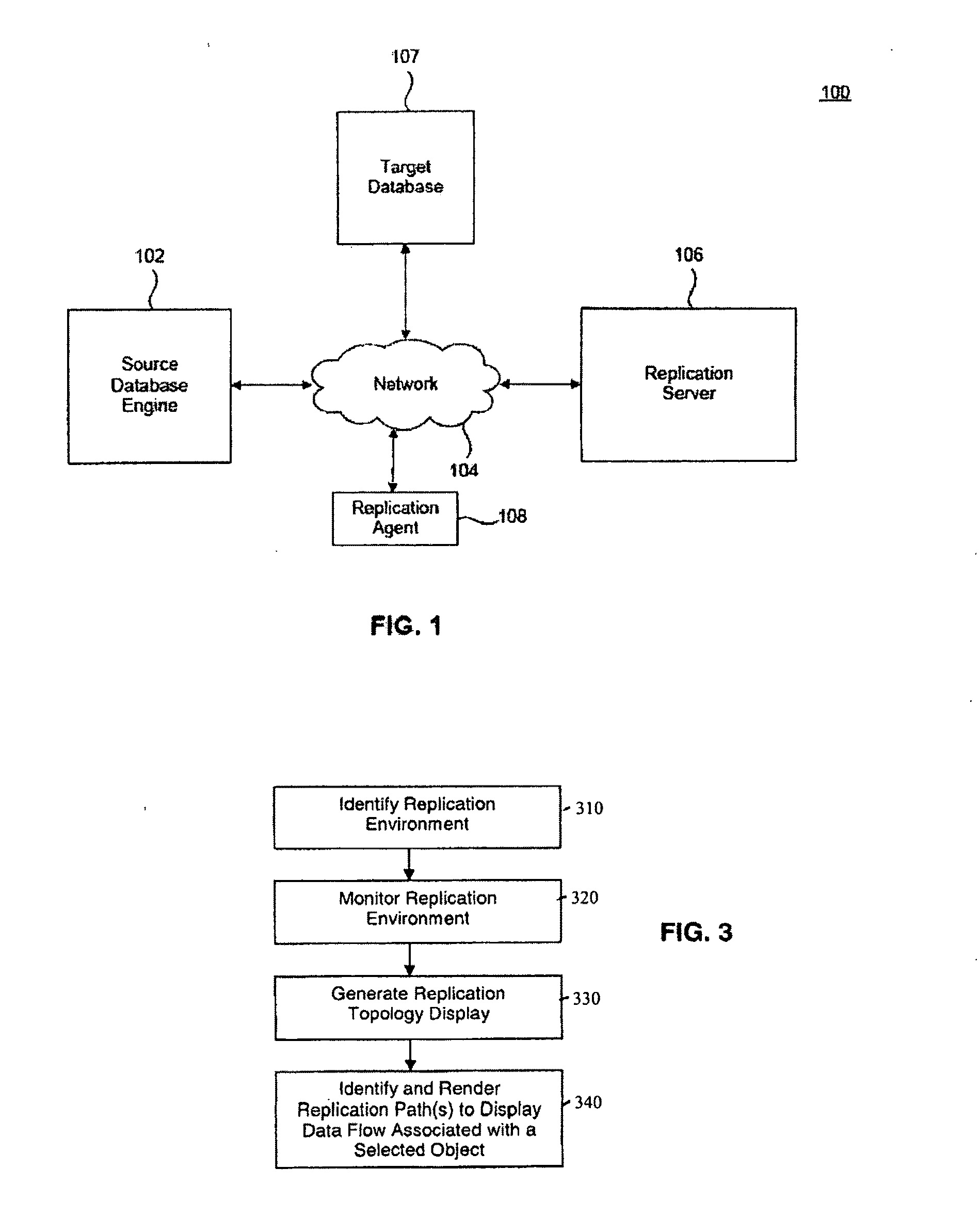
Data replication tracing
ActiveUS20110252124A1Multiple digital computer combinationsTransmissionData streamUrban infrastructure
System, method, computer program product embodiments and combinations and sub-combinations thereof for data replication tracing are provided. In an embodiment, the data replication tracing includes identifying a replication environment within a multi-tier infrastructure of an enterprise data processing network, and monitoring operational performance within the replication environment. A path is rendered on a topology to display data flow for the replication environment based upon a configuration of the replication environment. The data flow may be represented relative to a target data node, relative to a source data node, and / or relative to a replication server.
Owner:SYBASE INC
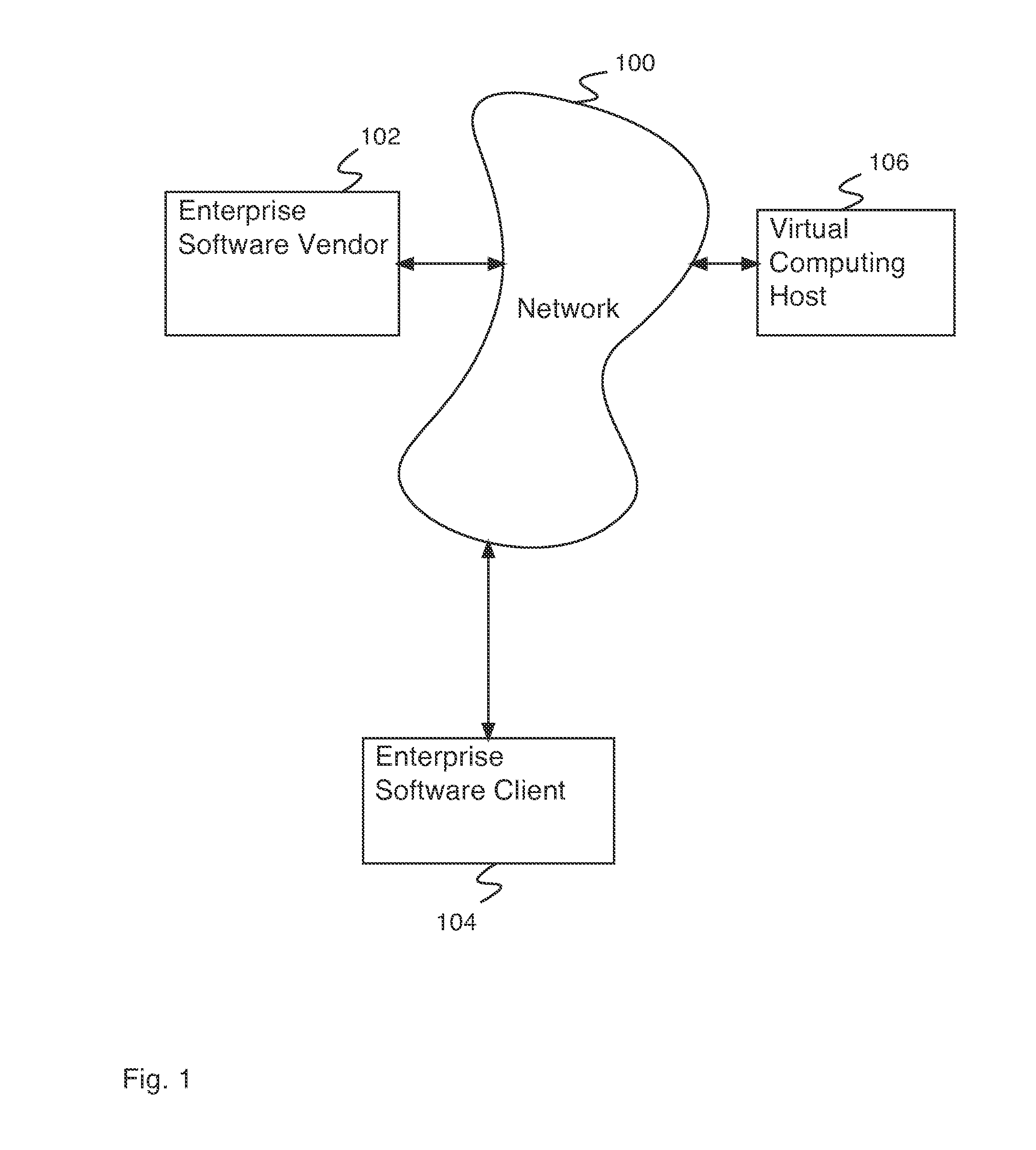
Virtual computing infrastructure
ActiveUS8719914B2Overcome disadvantagesAssist in debugging and testingResource allocationMultiple digital computer combinationsNetwork communicationApplication software
Owner:RED HAT +1
Industrial Control System Emulator for Malware Analysis
InactiveUS20150205966A1Improve defenseDisrupt operationMemory loss protectionError detection/correctionMalware analysisOil and natural gas
Embodiments of the present invention may provide an Industrial Control System (ICS) Emulator for Malware Analysis. The ICS Emulator may be embodied in a software. The software may be developed by testing and operating thousands of ICS devices that are used every day in critical infrastructure from power to oil & gas. Then, based on the tests and operations, the software may be configured to identify if, when, and how malware may be attacking various industrial control systems.
Owner:MALCRAWLER
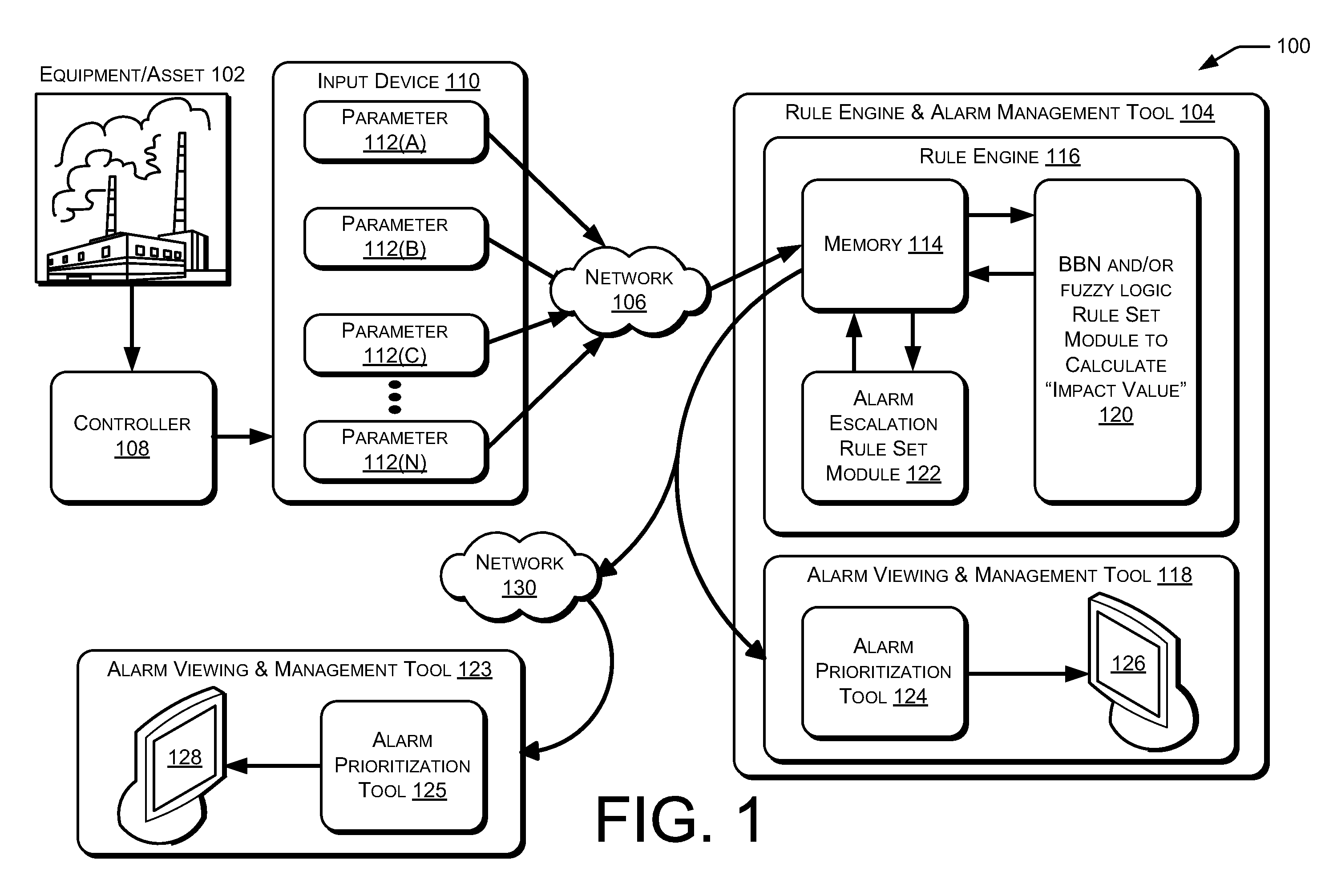
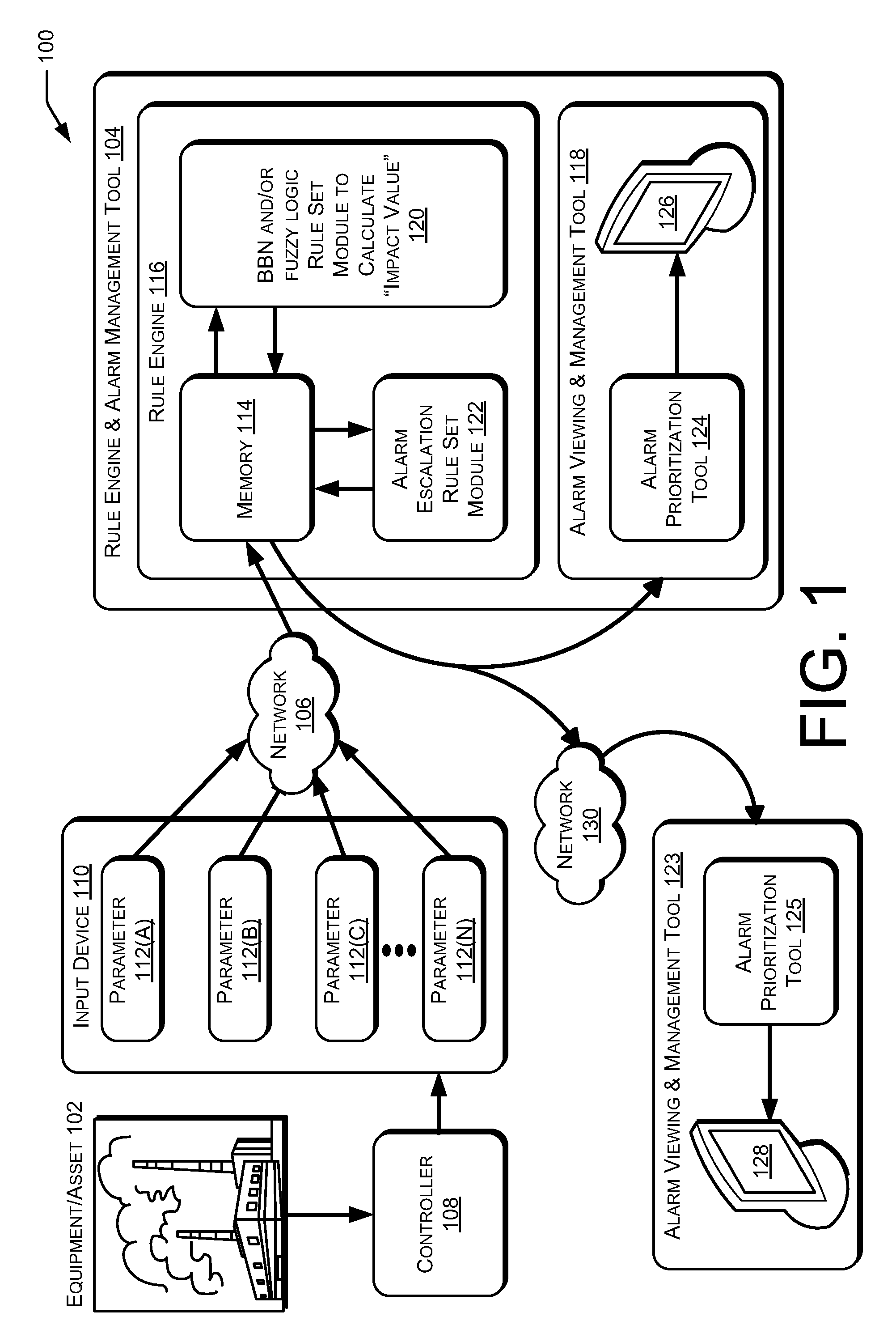
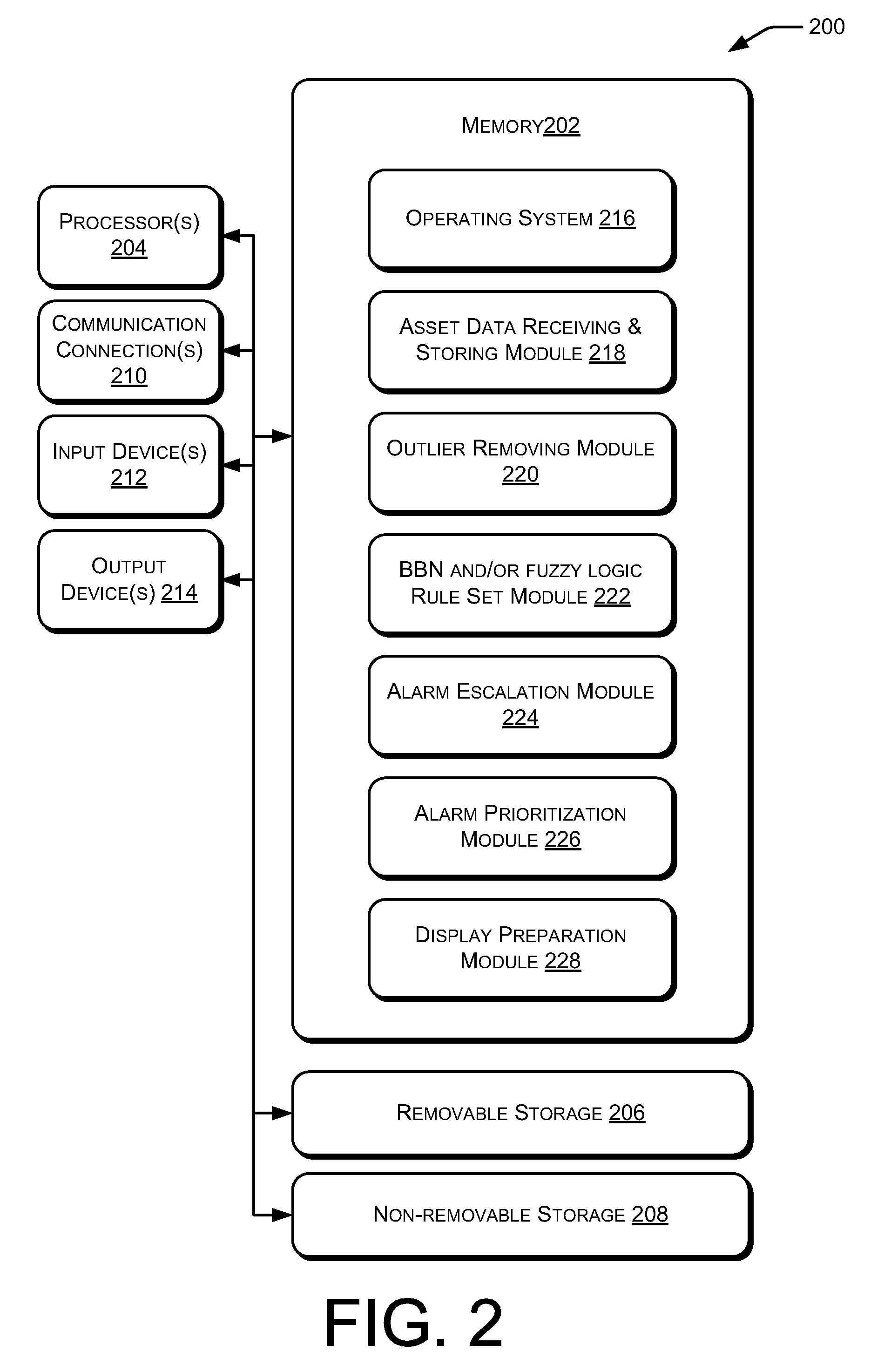
Alarm Management
ActiveUS20130015967A1Programme controlTesting/monitoring control systemsCommunications systemWeb service
Systems and methods for two-way secure data communication within critical infrastructures are usable to protect critical infrastructure information while allowing real-time monitoring and remote access. Such communication systems and methods can be used to protect critical data by, for example, providing a single point of access via unidirectional, serial, non-routable connections. Additionally, data flow may be controlled by a Web server that is not directly connected, and does not have direct access to, the critical information.
Owner:GENERAL ELECTRIC CO
Ticket-holder security checkpoint system for deterring terrorist attacks
InactiveUS20100033572A1Fast trainingGood for observationProgramme controlElectric signal transmission systemsCommunications systemThe Internet
A security checkpoint system and apparatus that provides security officers entrusted with protecting our nations' critical infrastructure or other high risk locations, a means of isolating and tracking suspicious persons who enter large public events or public transportation systems. Via a machine, communications system and components that are positioned at entrance points such as stadium section entrances, train station platform entrances, etc., a suspicious person entering the system is processed through a series of onsite as well as off-site follow-up investigations upon first being noticed as suspicious. The machine and it's overt security checkpoint system is designed to induce a suspicious reaction in persons with a guilty mind. As the person registers upon entrance to a facility, a close up view of the persons' face, as well as his seat assignment, is captured by the machine in digital image format. It is then sent by real-time transmission to security personnel in proximity to the location of the machine. A security officer positioned to spot persons manifesting suspicious behavior upon having to register at the machine, highlights the suspicious entrant electronically and sends an e-mail alert along with the digital images of both the suspicious entrant and his ticket, that also displays his seat number or destination, to on-site, as well as offsite law enforcement personnel for further review and investigation as necessary. As the system ties directly into the internet and can be sent to various law enforcement agencies for review, the resulting effect of such broad coverage of review of suspicious persons by law enforcement, makes this invention one of the most effective means of deterring terrorists and criminals in society today.
Owner:LG DISPLAY CO LTD
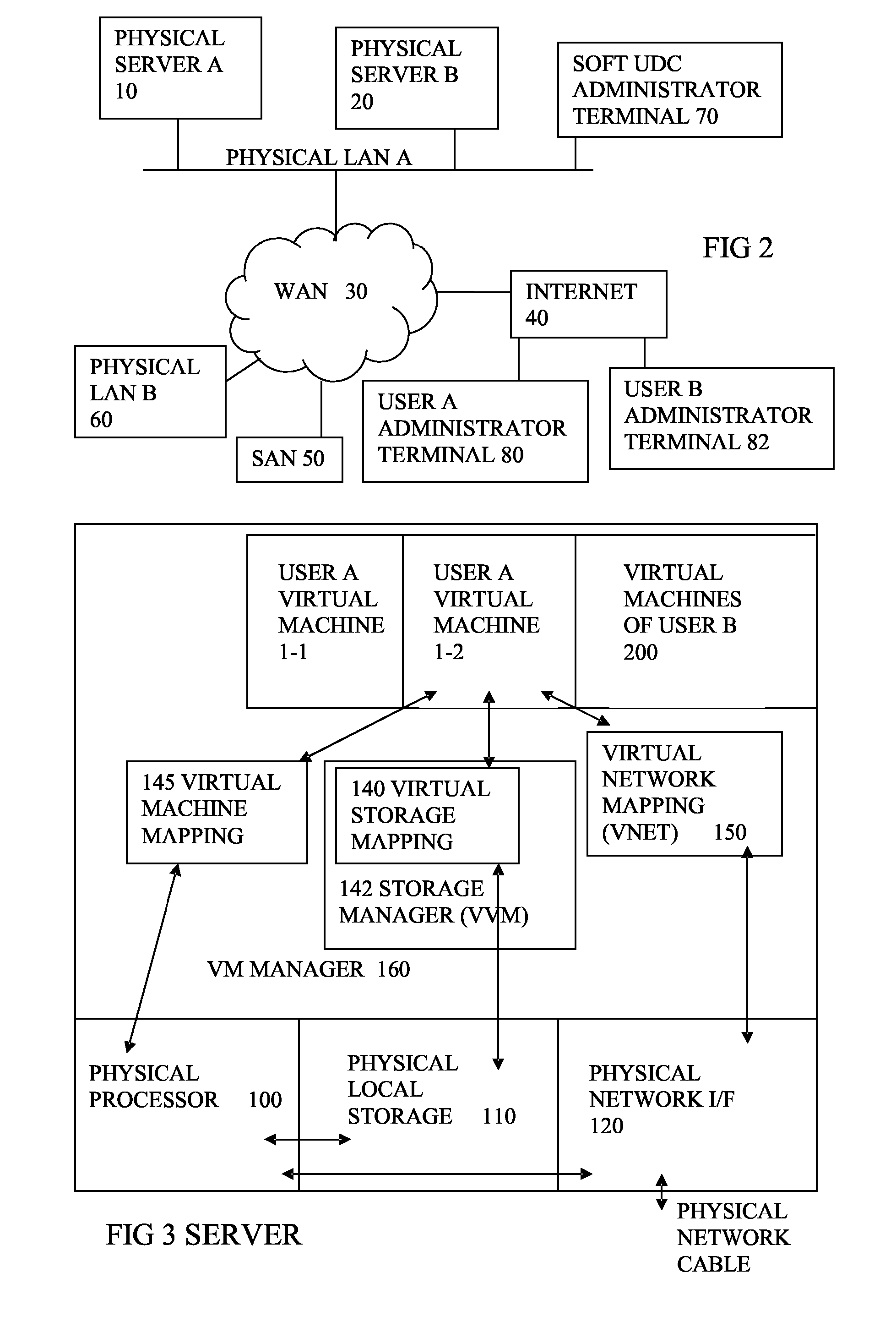
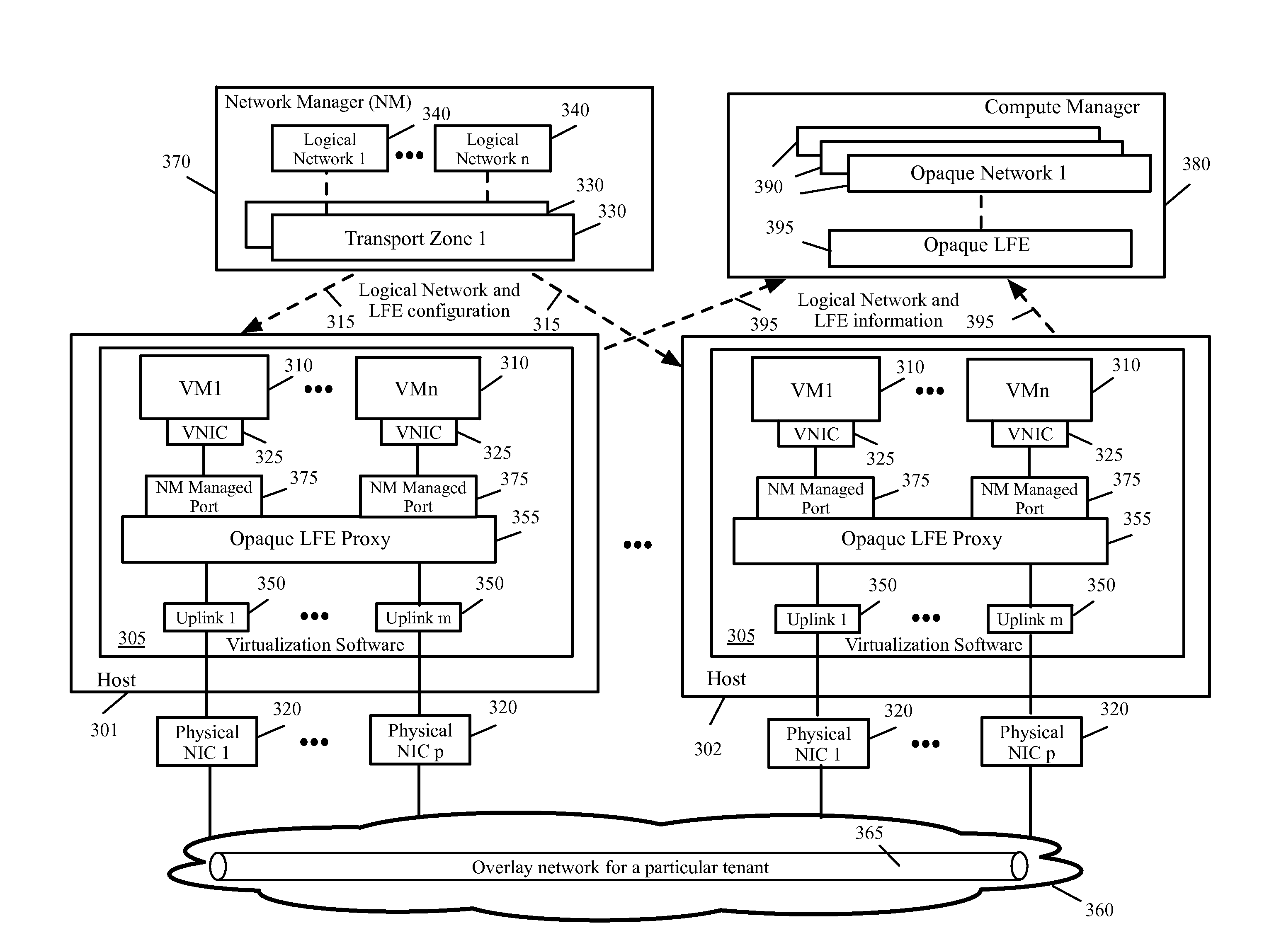
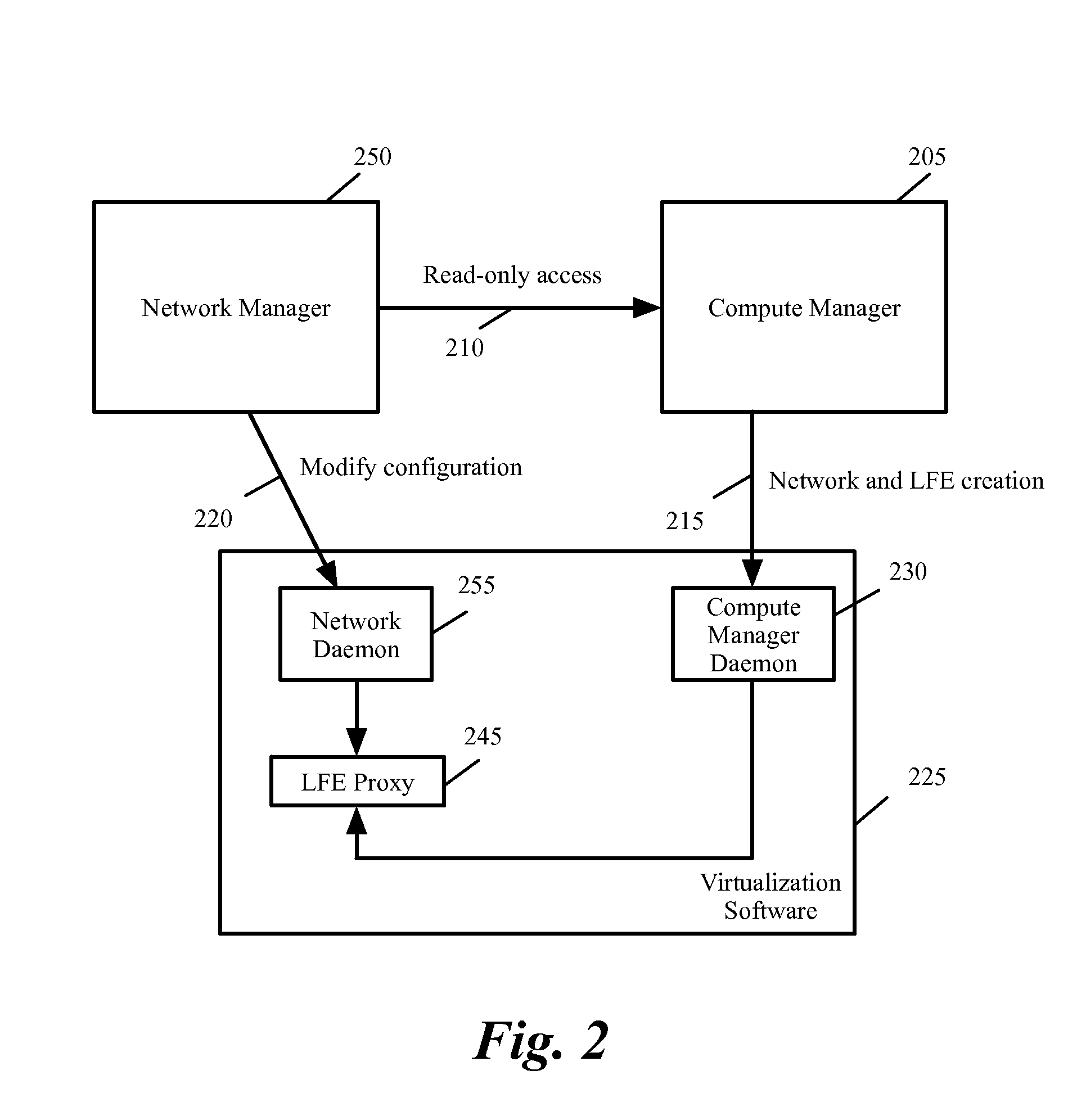
Method and system for migrating virtual machines in virtual infrastructure
A method of migrating a data compute node (DCN) in a datacenter comprising a plurality of host physical computing devices, a compute manager, and a network manager is provided. The method by the network manager configures a plurality of logical networks and provides a read-only configuration construct of at least one of the plurality of logical networks to the virtualization software of each host. The construct of each logical network includes a unique identification of the logical network. The method by the compute manager obtains the unique identification of one or more of the logical networks, determining that a particular logical network is available on first and second hosts based on the unique identification of the particular logical network, and configures a first DCN to move from the first host to the second host based on the determination that the first and second hosts are on the particular logical network.
Owner:NICIRA
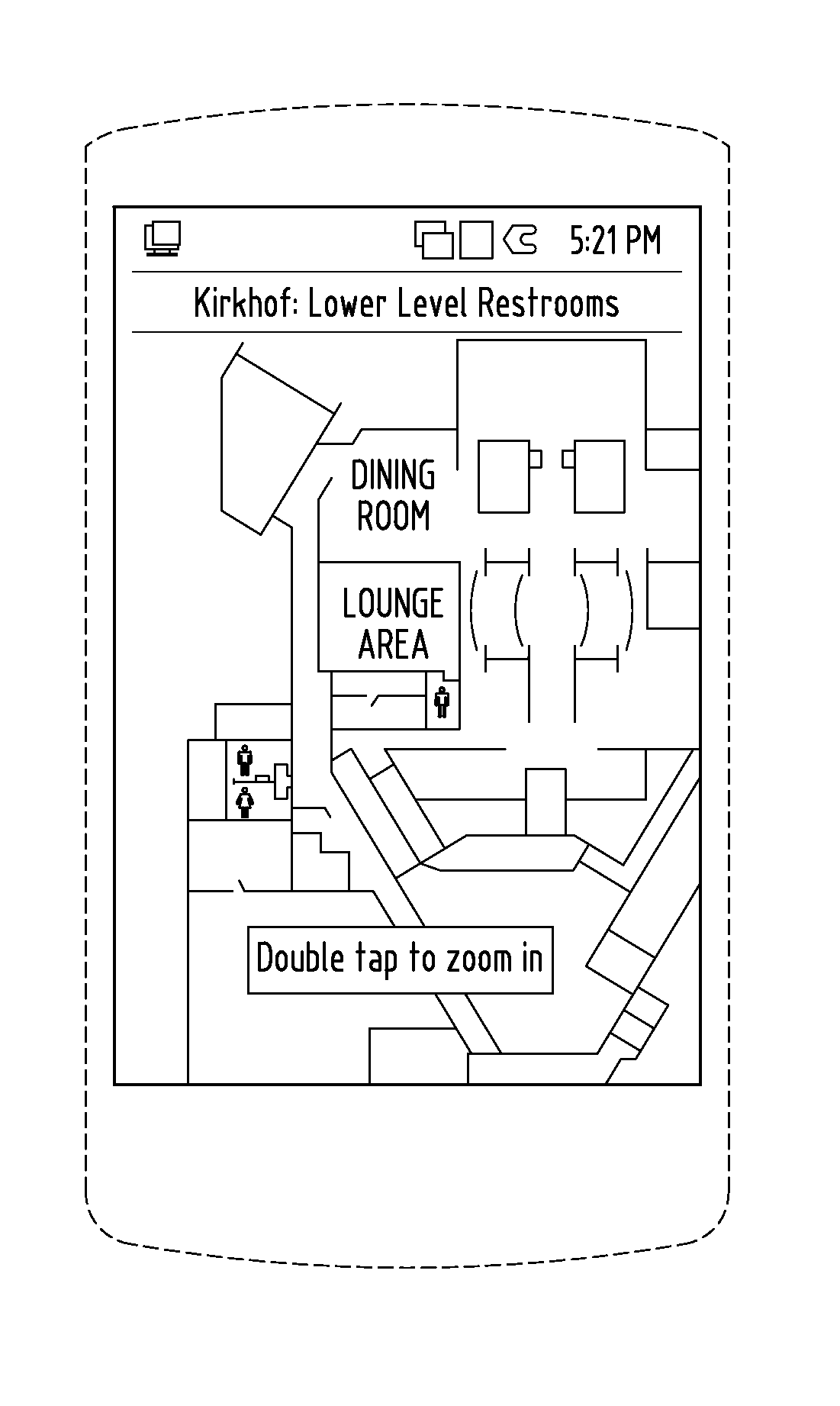
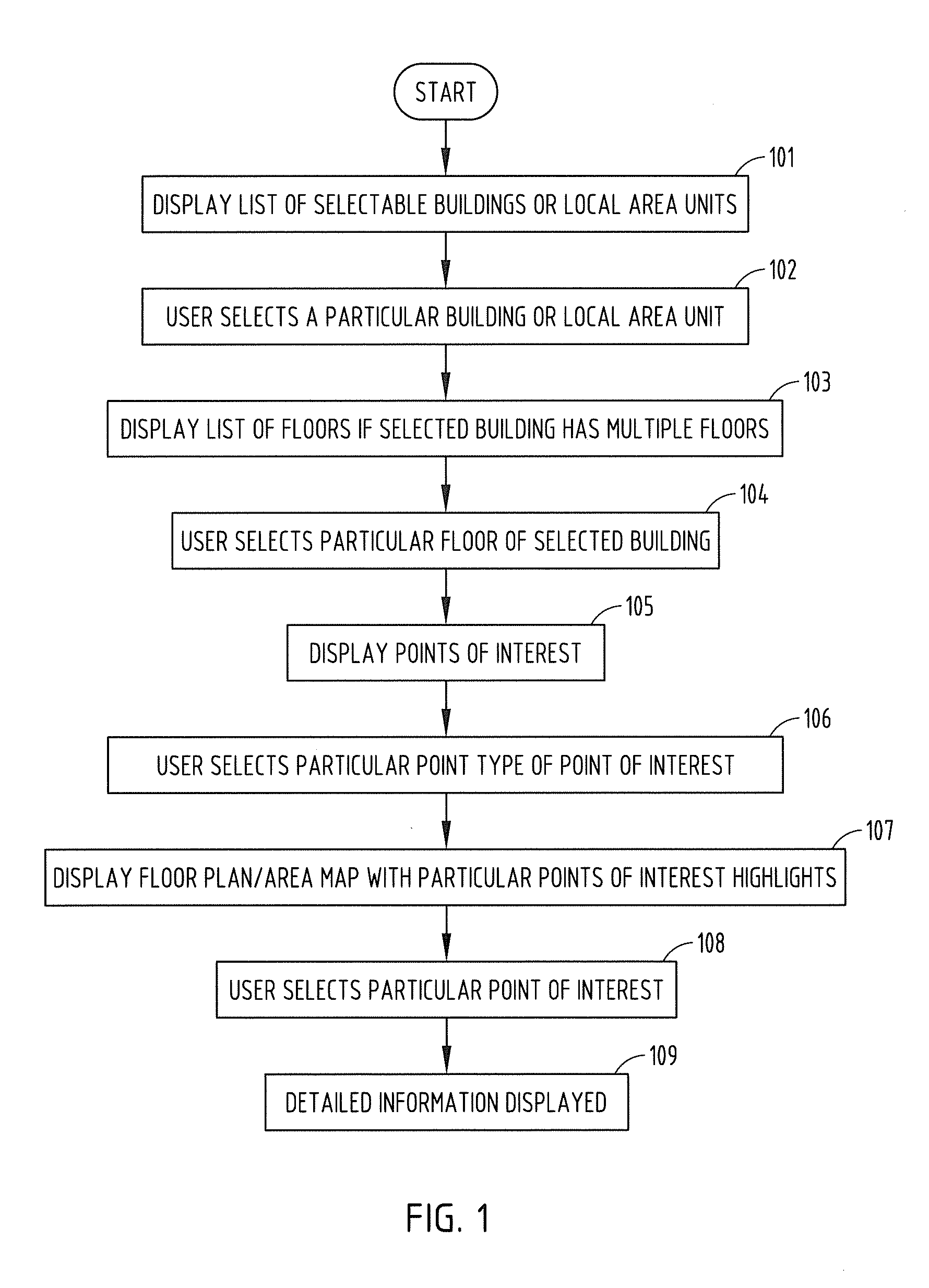
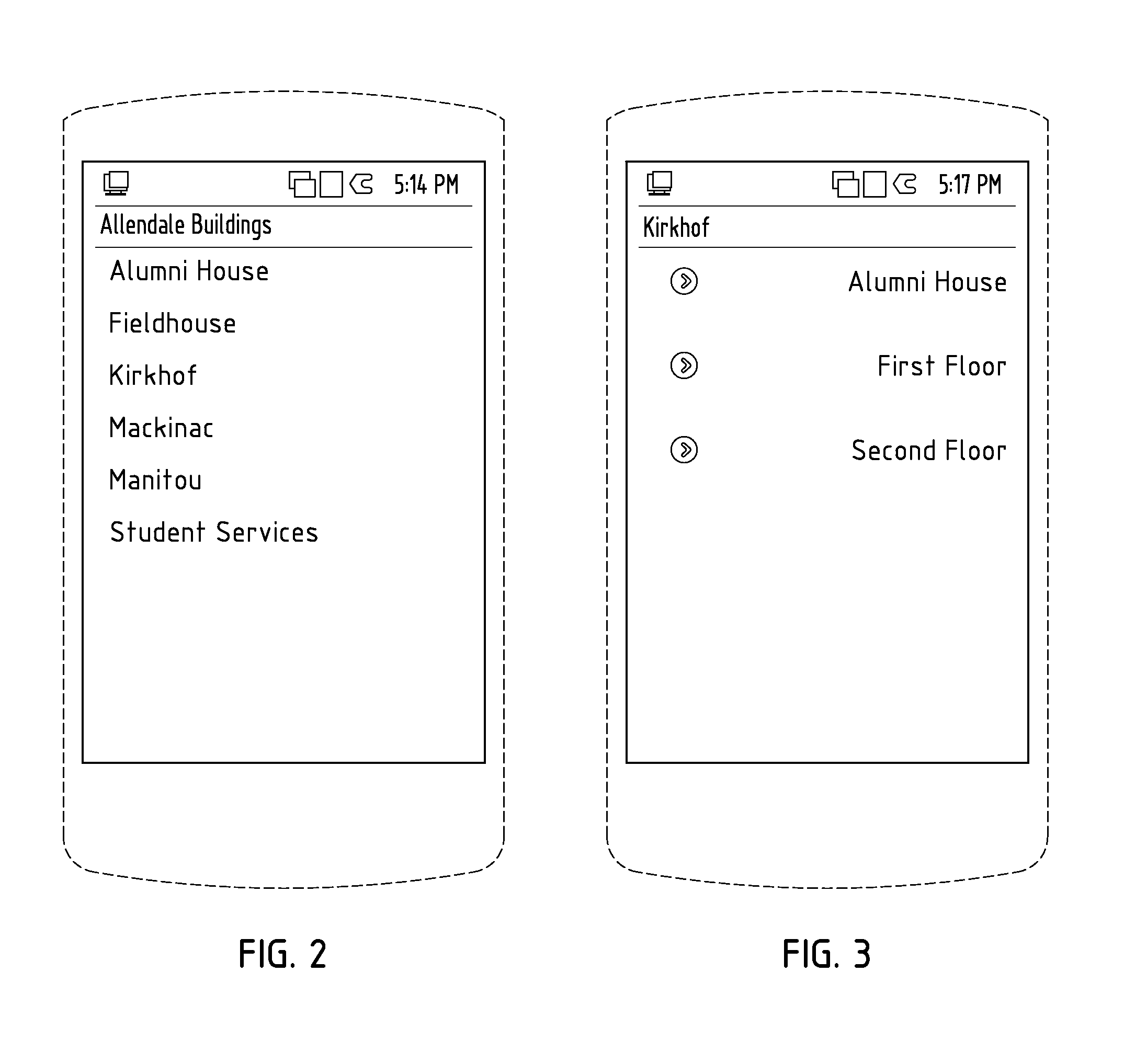
Systems and methods for providing information pertaining to physical infrastructure of a building or property
A computer implemented system and method for displaying information pertaining to physical infrastructure in a building or on a property via a mobile software application operating or a mobile device are provided. The mobile software application includes steps of (a) optionally displaying a list of selectable buildings and / or areas at a property, (b) optionally displaying a list of selectable floors if a building having multiple floors is selected, (c) displaying a list of points of interest for the selected floor, building or area, and (d) displaying a floor plan or area map with selected points of interest highlighted.
Owner:ALBRIGHT HLDG
Environment-driven application deployment in a virtual infrastructure
InactiveUS20150261517A1Version controlProgram loading/initiatingApplication softwareMultiple applications
A system for recipe and blueprint-driven automated application deployment comprises a processor and a memory. The processor is configured to receive an environment, receive an application configuration, and deploy an application using the environment and the application configuration. The environment is provisioned using an environment template, and wherein the environment template is built using a blueprint. The application configuration comprises one or more application endpoints. The memory is coupled to the processor and is configured to provide the processor with instructions.
Owner:EMC CORP
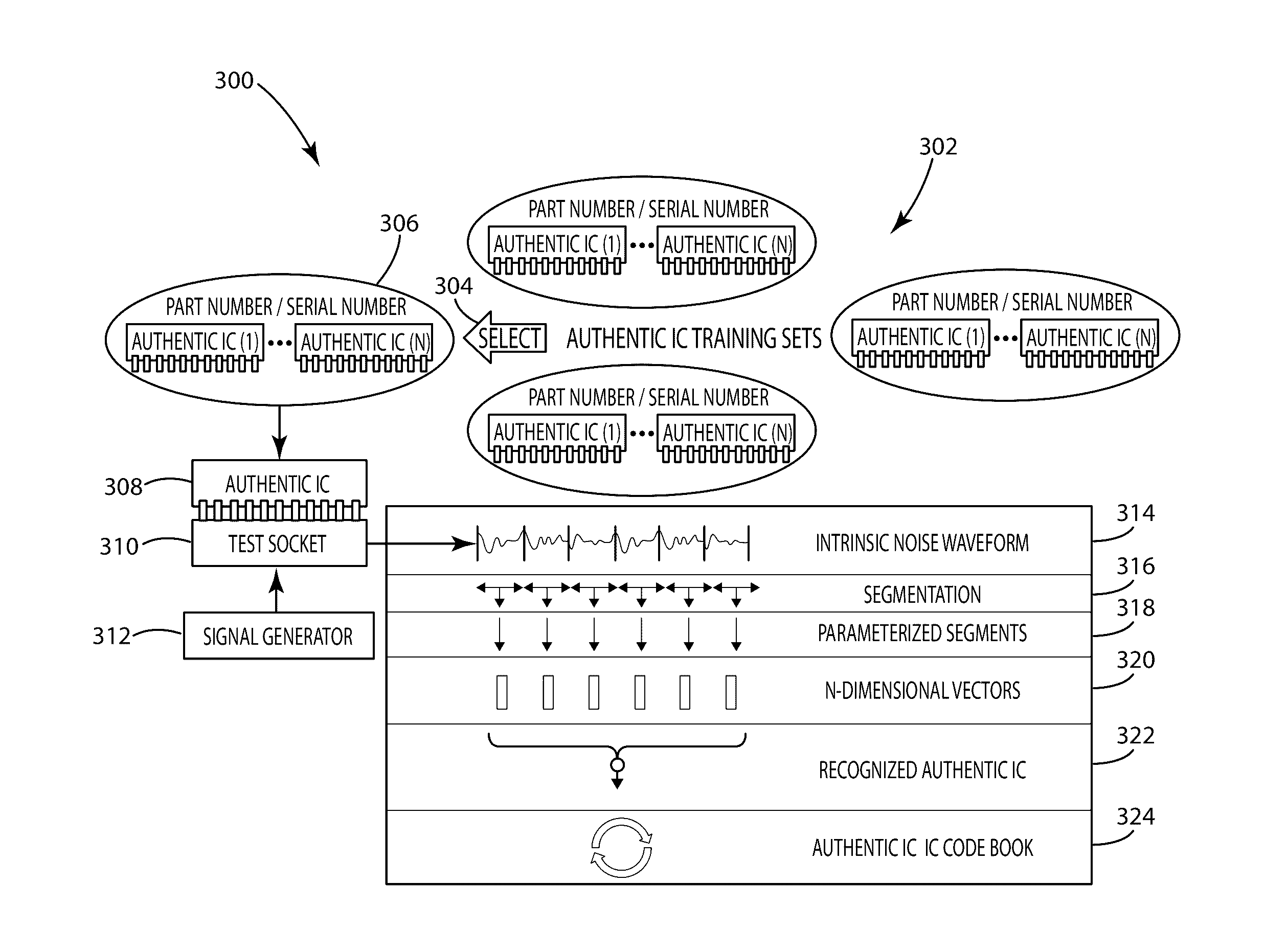
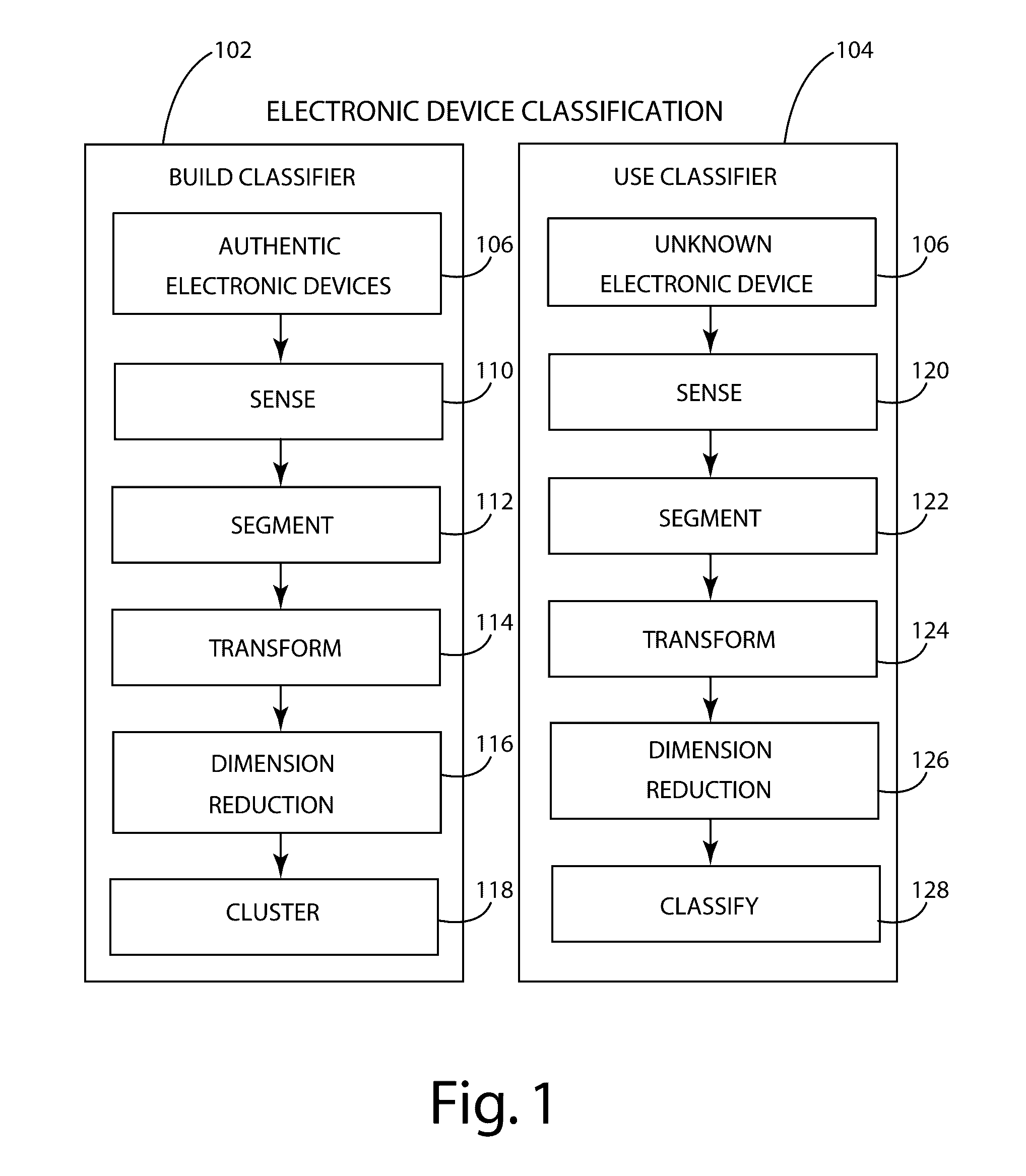
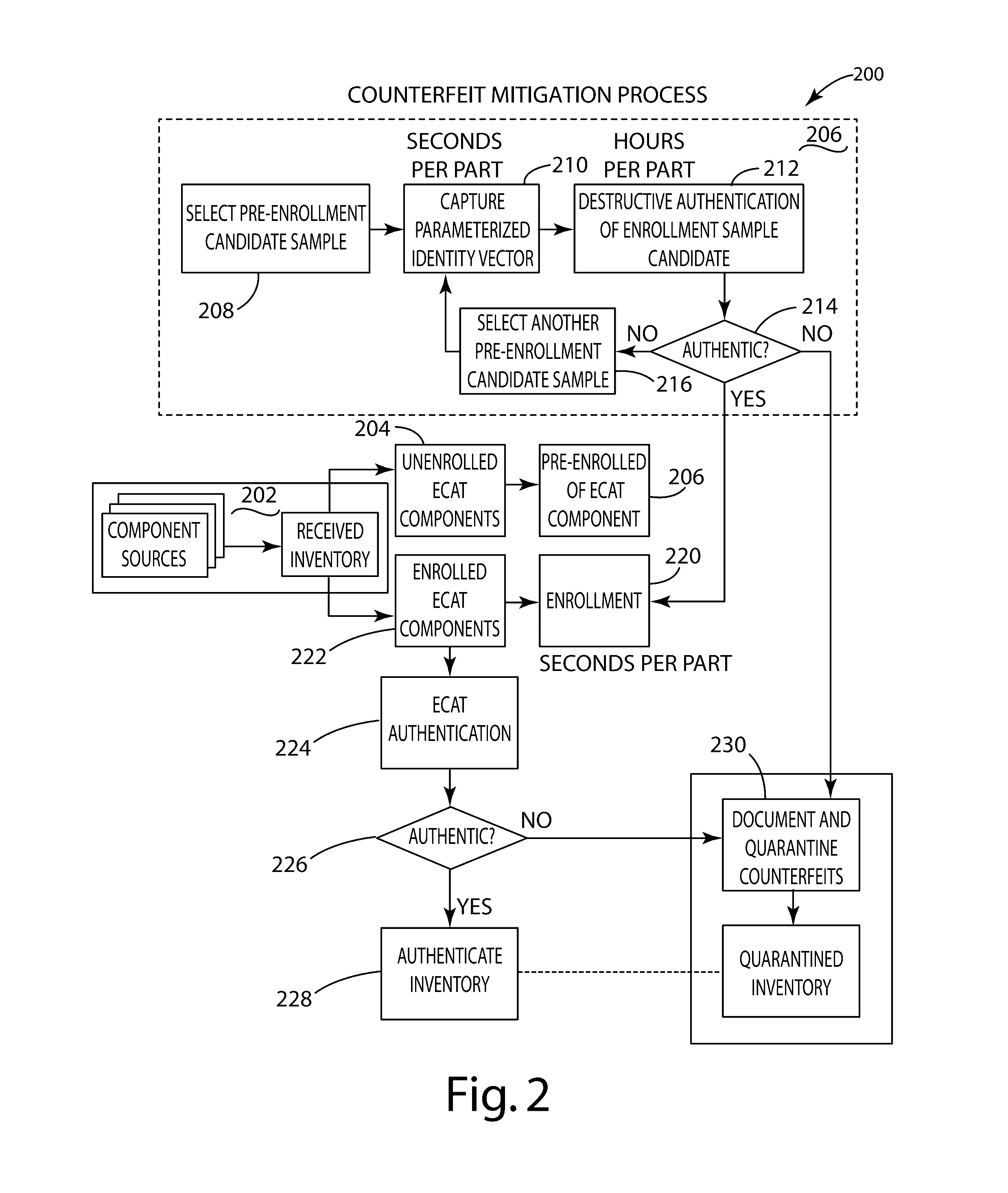
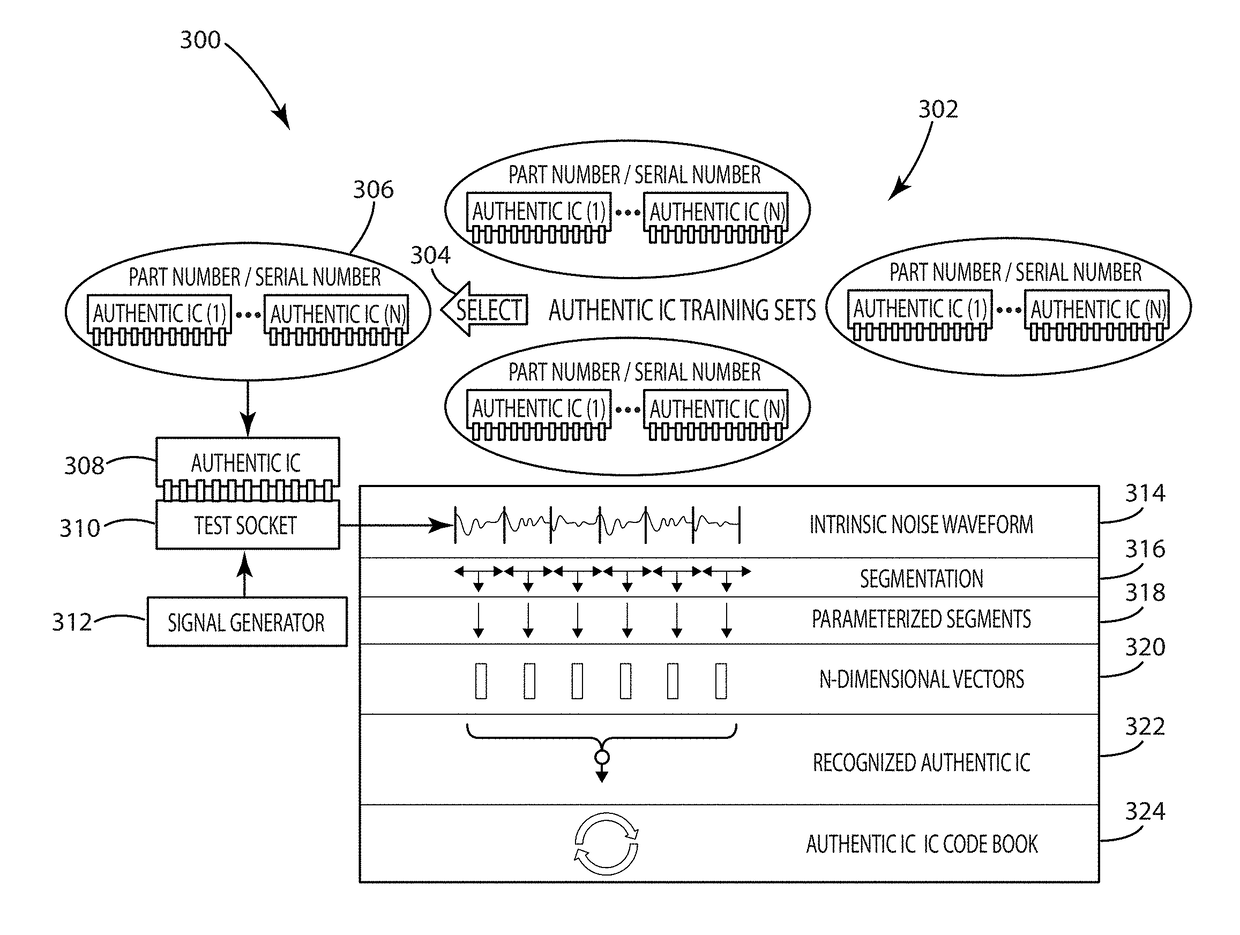
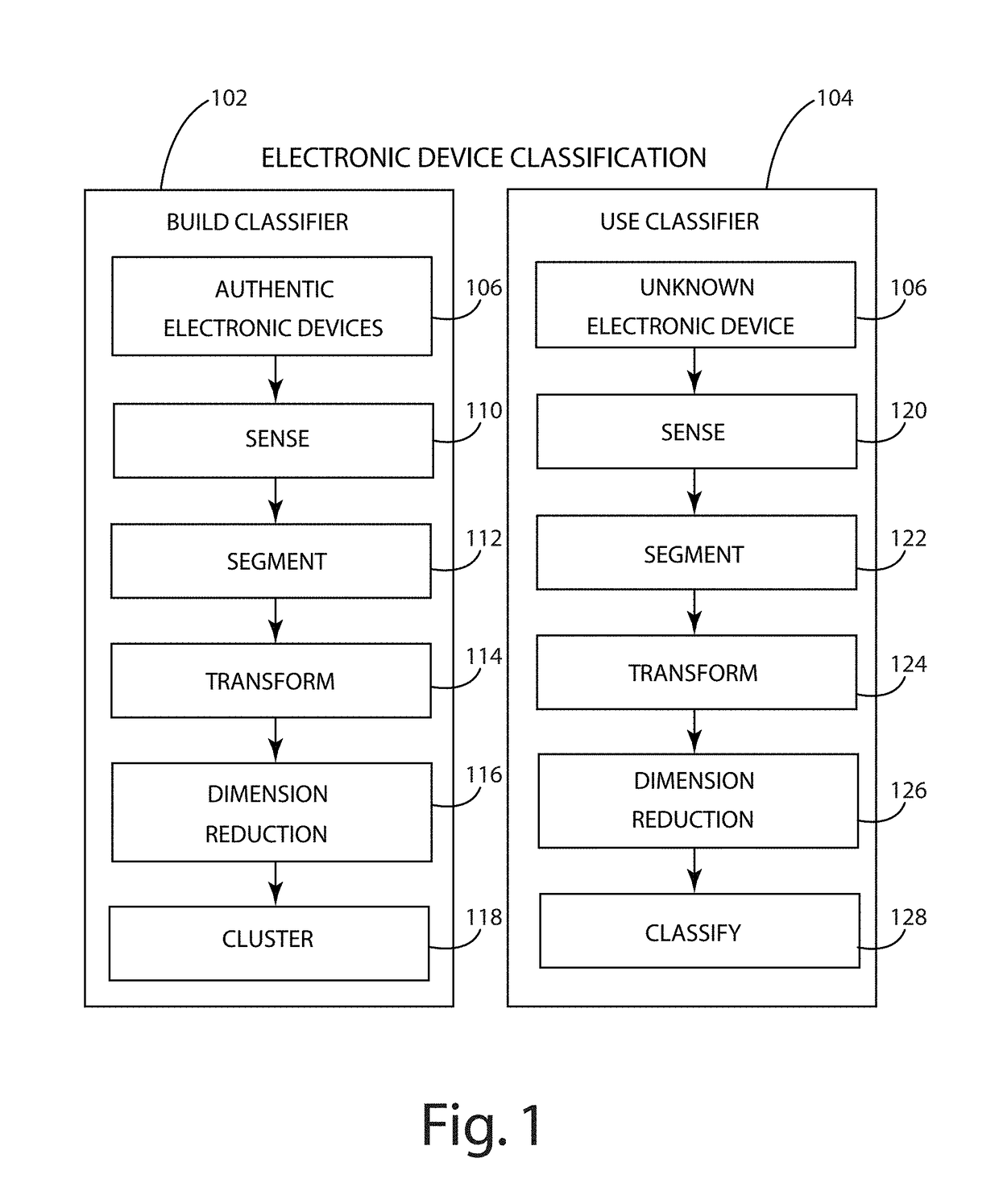
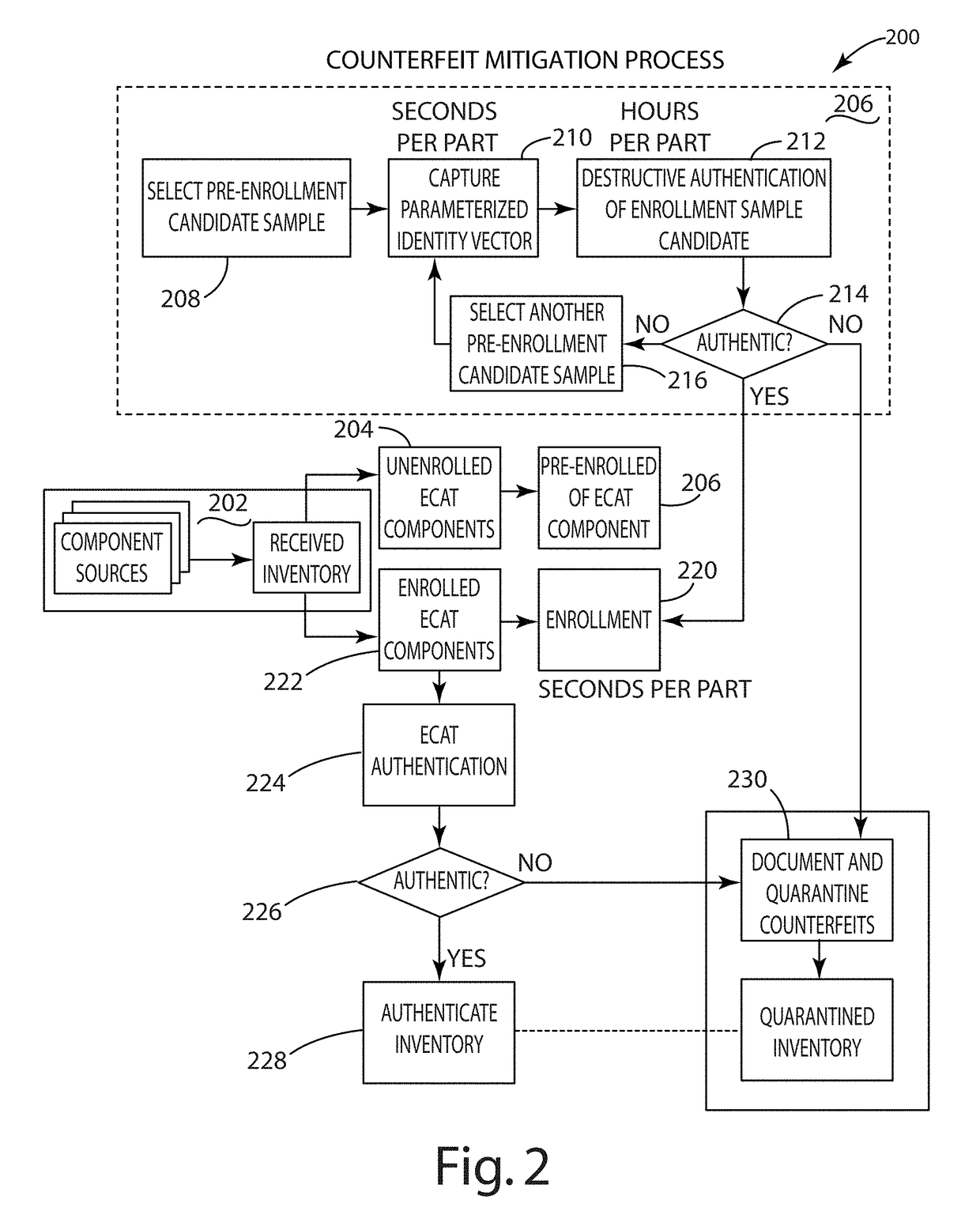
Electronic component classification
ActiveUS20160282394A1Low costNoise figure or signal-to-noise ratio measurementCharacter and pattern recognitionAviationClassification methods
A system and method of electronic component authentication or component classification can reduce the vulnerability of systems (e.g., satellites, weapons, critical infrastructure, aerospace, automotive, medical systems) to counterfeits. Intrinsic deterministically random property data can be obtained from a set of authentic electronic components, processed, and clustered to create a classifier that can distinguish whether an unknown electronic component is authentic or counterfeit.
Owner:BATTELLE MEMORIAL INST
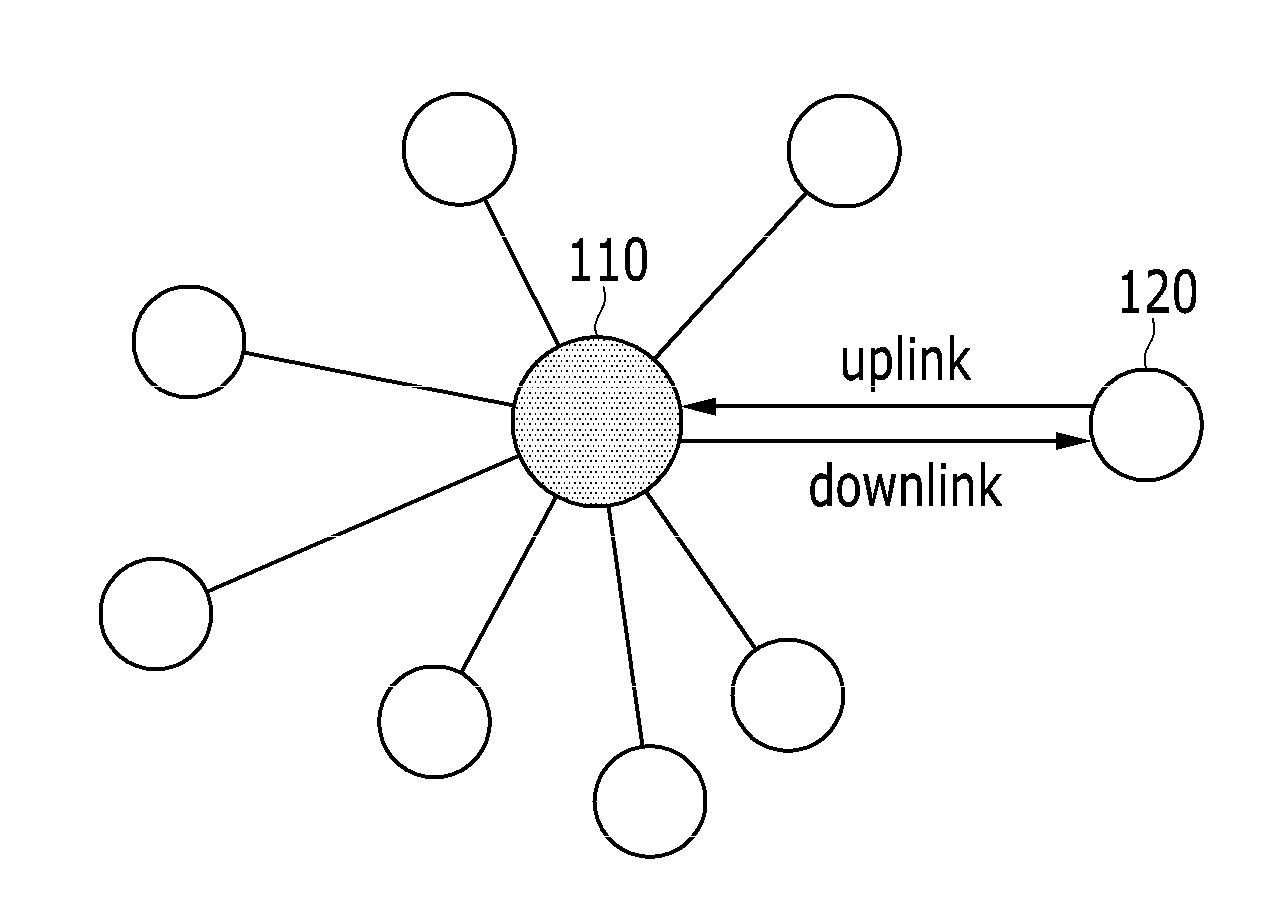
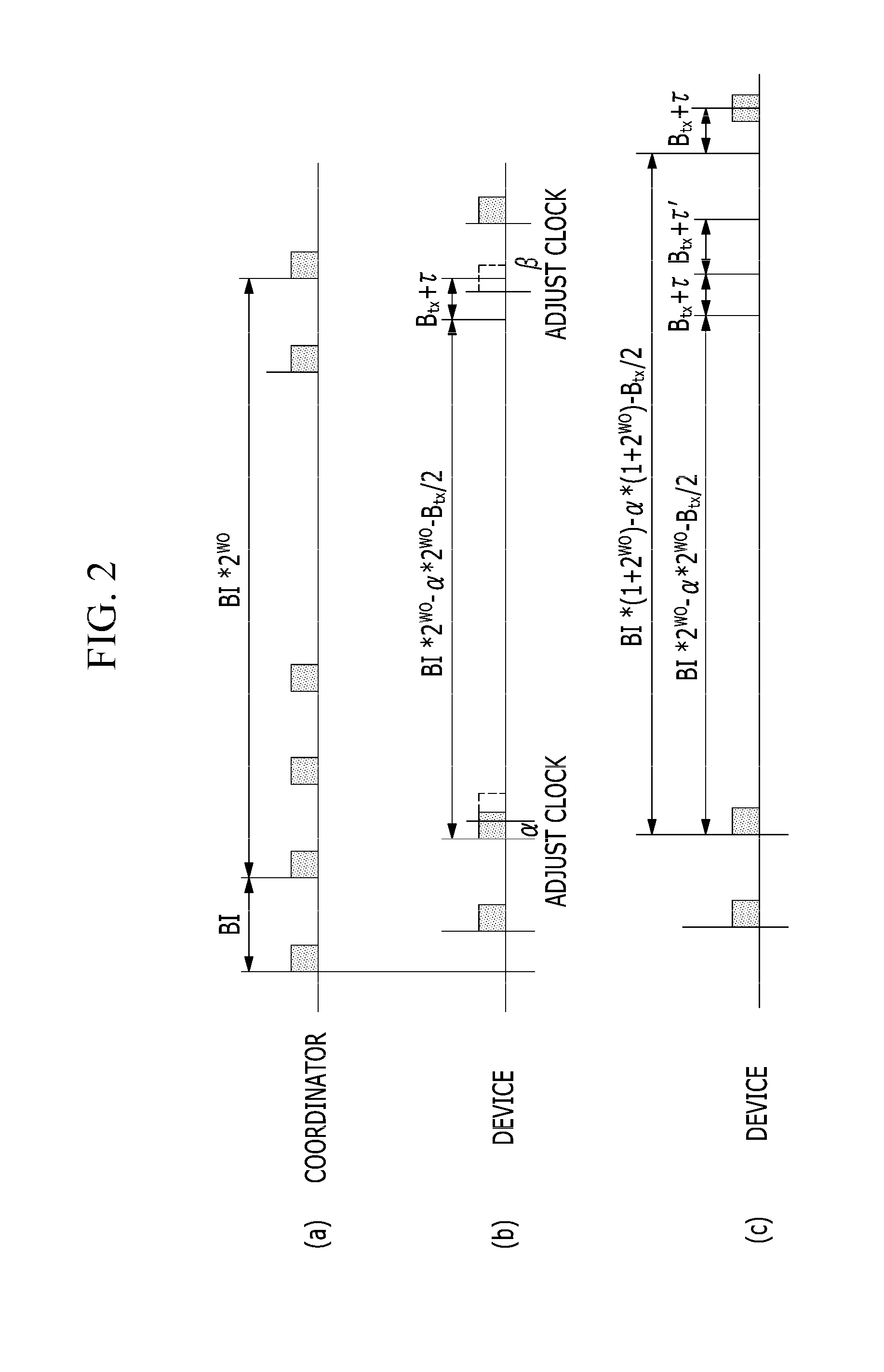
Method of generating and receiving packets in low energy critical infrastructure monitoring system
ActiveUS20130058360A1Low powerLarge communicationTime-division multiplexAngle modulationComputer hardwarePhysical layer
A method of generating a packet for low energy critical infrastructure monitoring (LECIM) wireless communication is provided. The method includes steps of generating a first bit string by multiplexing a physical layer header (PHR) bit and a physical layer service data unit (PSDU) bit; convolution encoding the first bit string; interleaving the convolution-encoded first bit string; generating a second bit string by multiplexing the interleaved first bit string with a synchronization header (SHR) bit; and modulating the second bit string with a frequency shift keying (FSK) method and a position-based FSK method.
Owner:ELECTRONICS & TELECOMM RES INST
Retractable wide-span vehicle barrier system
ActiveUS20060140717A1Easy to deployEliminate requirementsTraffic restrictionsRoadway safety arrangementsCritical infrastructureModularity
A vehicle barrier system that stops unwanted vehicle intrusion, controls vehicle access, and protects assets and critical infrastructure. The vehicle barrier system, which can span up to 250 feet without requiring fixed intermediate supports, will stop a 15,000 lb vehicle traveling at impact speed of 50 mph. The barrier net is attached to vertical steel end supports anchored in concrete, and include energy absorbers, pivoting connections, and force equalization bars. The barrier net can remain in the “up” or “down” position, and can be raised or lowered using a winch powered by common 12 volt battery with solar power recharge. The barrier net and system components are modular, and can be easily installed or removed.
Owner:BARRIER1 SYST LLC
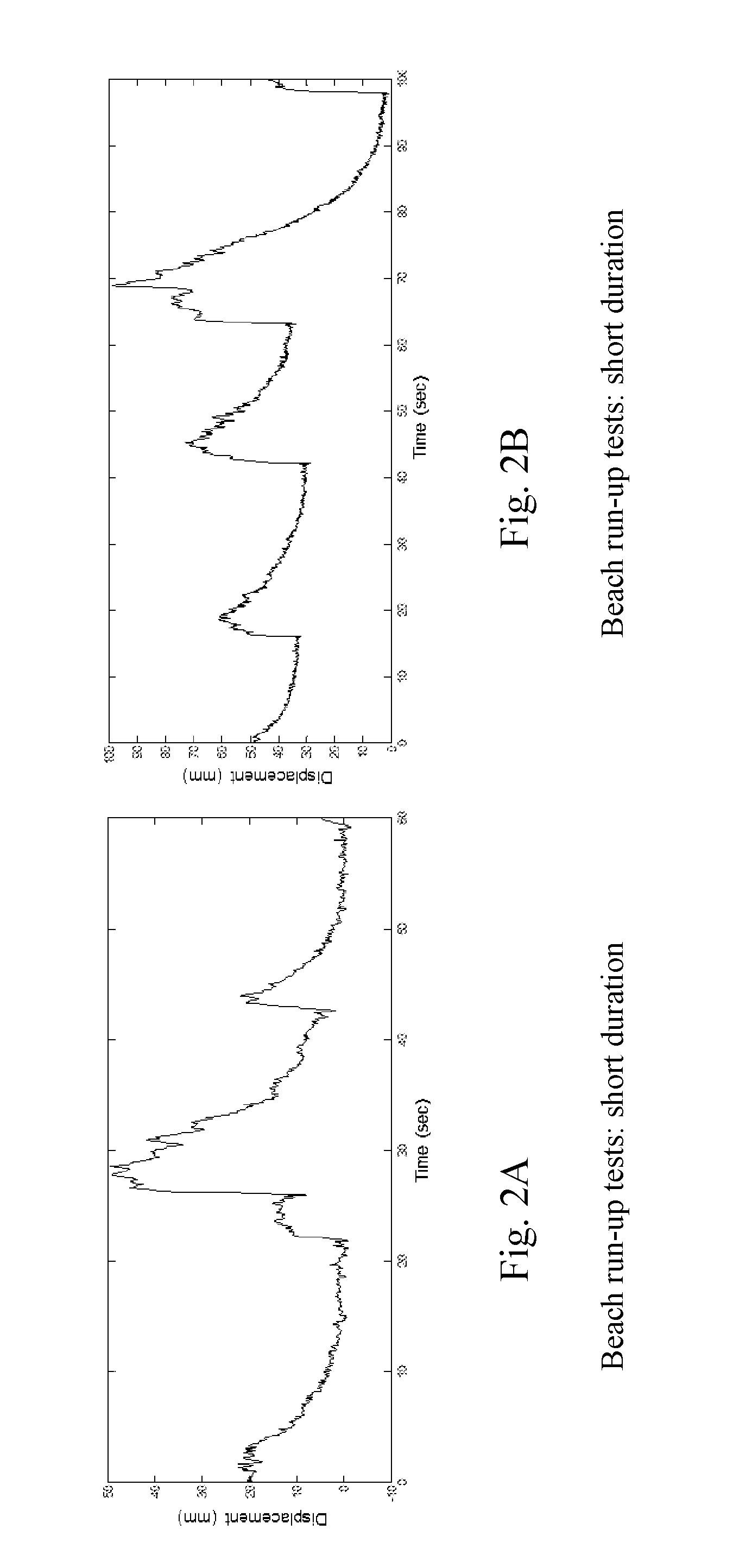
Interferometric Doppler Radar and Method for Wave and Water Level Measurement
ActiveUS20160209260A1Maximizing measurement accuracyMaximizing resolutionMachines/enginesLevel indicatorsMeasurement deviceData stream
Devices, methods and systems for wave and water level measurement using a single DC (direct current)-coupled CW (continuous wave) Doppler radar for detecting water elevation changes in time when installed up to several meters from the water surface. The radar is wireless and can stream continuous data to a local PC (personal computer) or base station in range of its radio. The radar can sample up to 40 Hz and can run on batteries for continuous sampling. The radars can include multiple radar configurations of 1, 2 and 4 radar configurations. Applications for this radar can include the measurement of beach run-up, free surface elevation in tidal zones, and storm surge elevations near bridges and critical infrastructure during storm events.
Owner:UNIV OF FLORIDA RES FOUNDATION INC +1
Industrial Control System Emulator for Malware Analysis
InactiveUS20170177865A1Improve defenseDisrupt operationPlatform integrity maintainanceTransmissionMalware analysisOil and natural gas
Embodiments of the present invention may provide an Industrial Control System (ICS) Emulator for Malware Analysis. The ICS Emulator may be embodied in a software. The software may be developed by testing and operating thousands of ICS devices that are used every day in critical infrastructure from power to oil & gas. Then, based on the tests and operations, the software may be configured to identify if, when, and how malware may be attacking various industrial control systems.
Owner:MALCRAWLER
Tidal lane driving direction dynamic control method
ActiveCN105279981ASolve the hysteresisUniversalControlling traffic signalsUrban infrastructureResource utilization
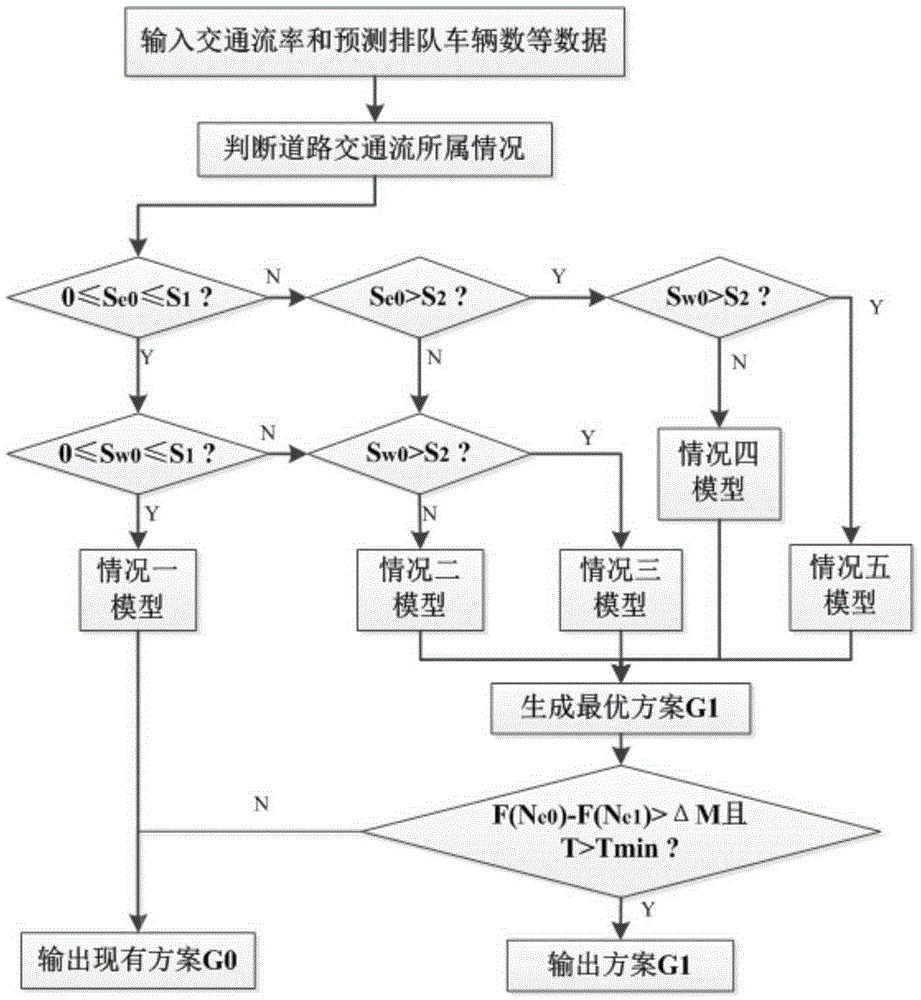
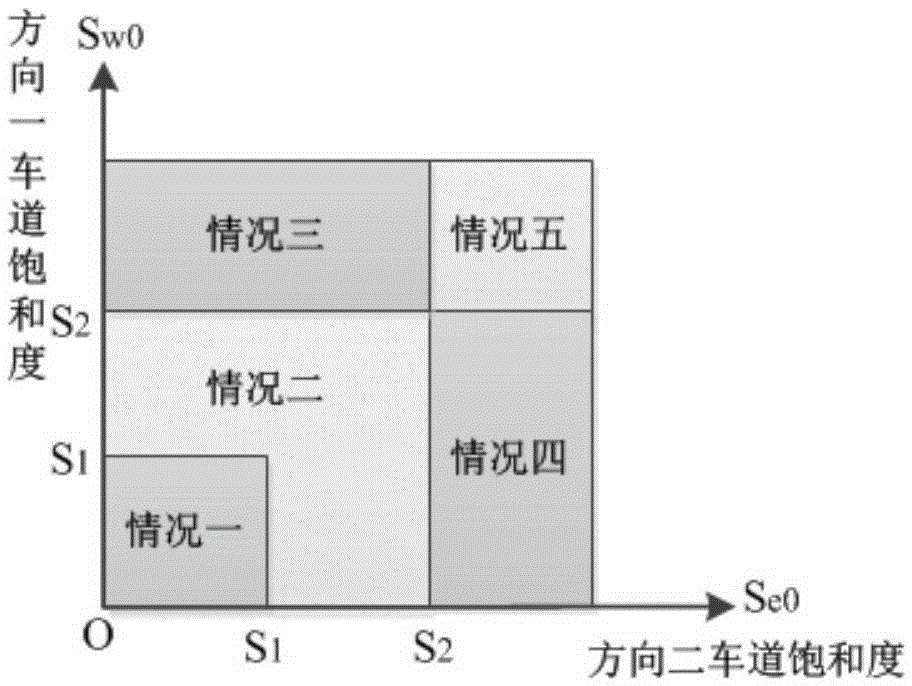
The invention discloses a tidal lane driving direction dynamic control method. The method comprises the steps that road basic data, real-time traffic flow rate and predicted number of queue vehicles are input; according to saturation in two directions, road traffic conditions are divided into five modes; according to a corresponding condition, a corresponding control model is called to solve an optimal control scheme; whether the optimal control scheme meets an optimization condition is determined; and if the optimal control scheme meets the optimization condition, the optimal scheme is output to road infrastructure and is carried out, otherwise the existing scheme is output. According to the invention, a model which dynamically changes the driving direction of a lane according to the real-time traffic flow rate and the predicted number of queue vehicles is provided for the first time; the method is suitable for a variable-lane road with more than 2 lanes; and the method has the advantages of high road resource utilization, good economic benefit, being universal and the like.
Owner:SOUTH CHINA UNIV OF TECH
Method in a communication network
ActiveUS20160173352A1Convenient verificationSufficient informationError preventionTransmission systemsWide areaCyber-attack
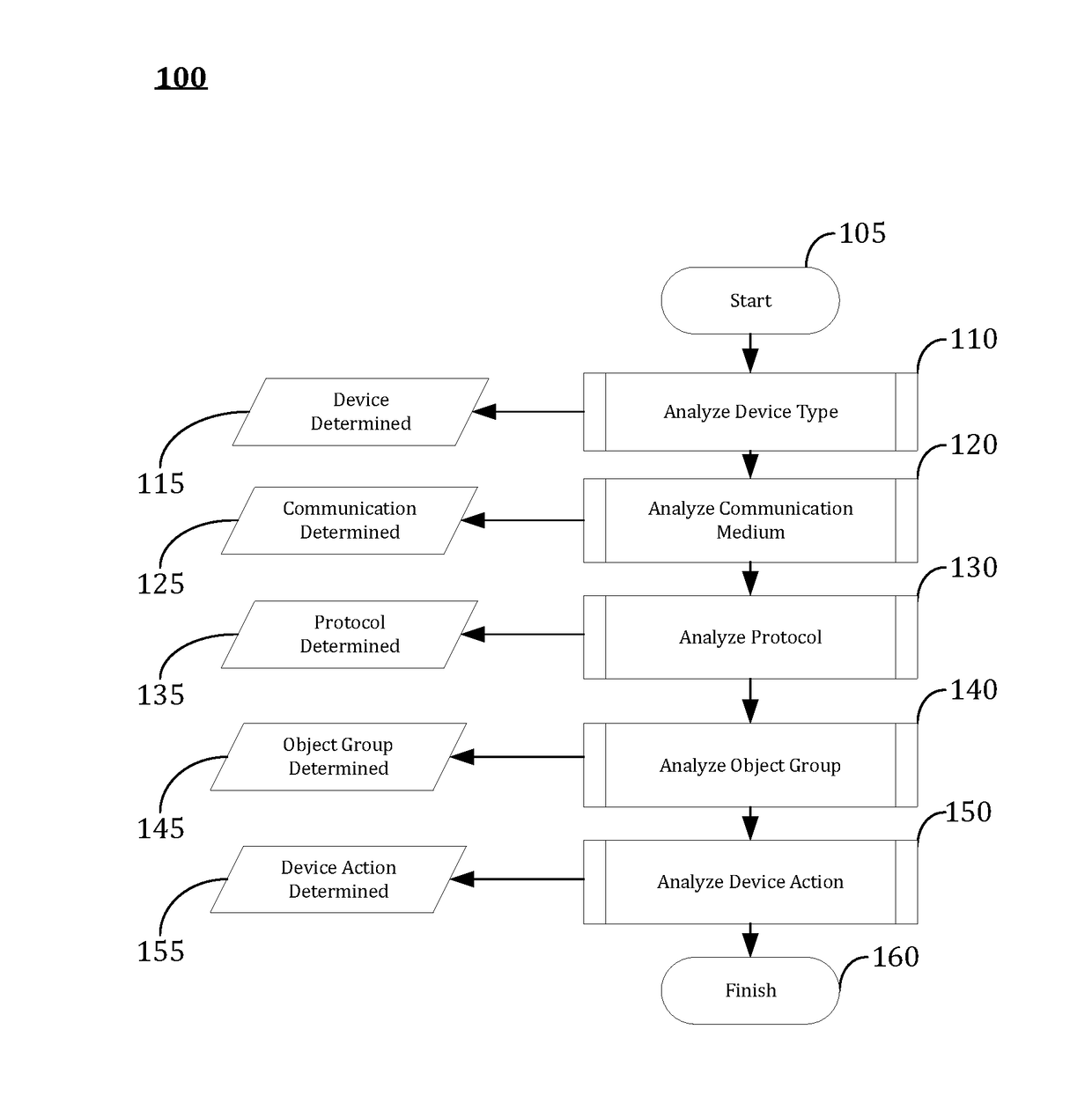
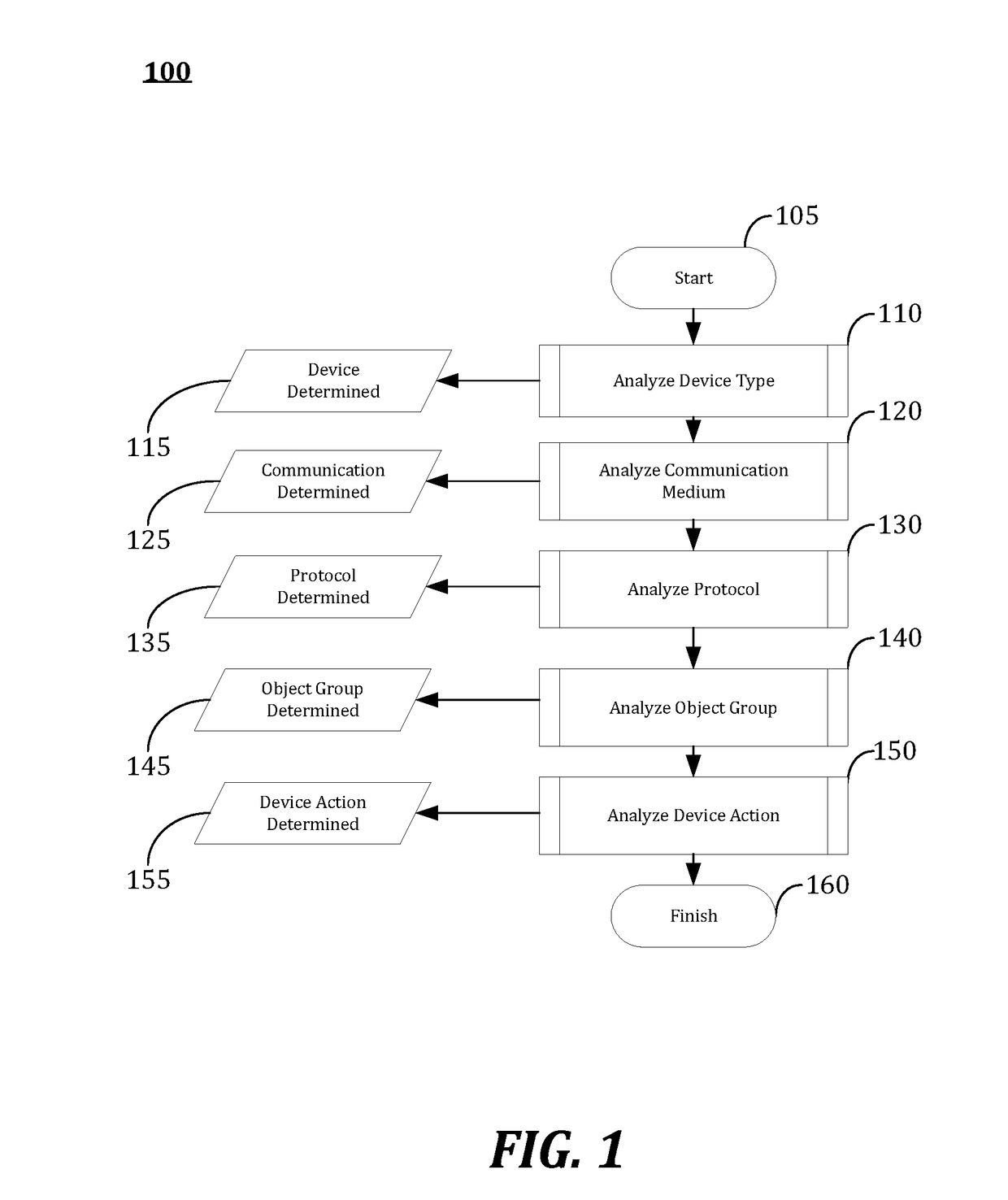
A method to provide a cyber attack resistant and fault tolerant precision clocking scheme for wide area critical infrastructure networks through what is called Distributed Time Source Validation, DTSV, is provided, which is a distributed algorithm and signaling mechanism for a network to detect a compromised time source or sources in a multiple master clock system. The method includes providing a local clock signal, receiving in a node R1 an external clock signal from an external source, C or S1, estimating based on the local clock signal and the external clock signal timing parameters associated with the first node and the external source, comparing the timing parameters to detect any Mutual Clock Discrepancy (MCD) between the first node and the external source, and distributing any detected MCD in the network.
Owner:NET INSIGHT
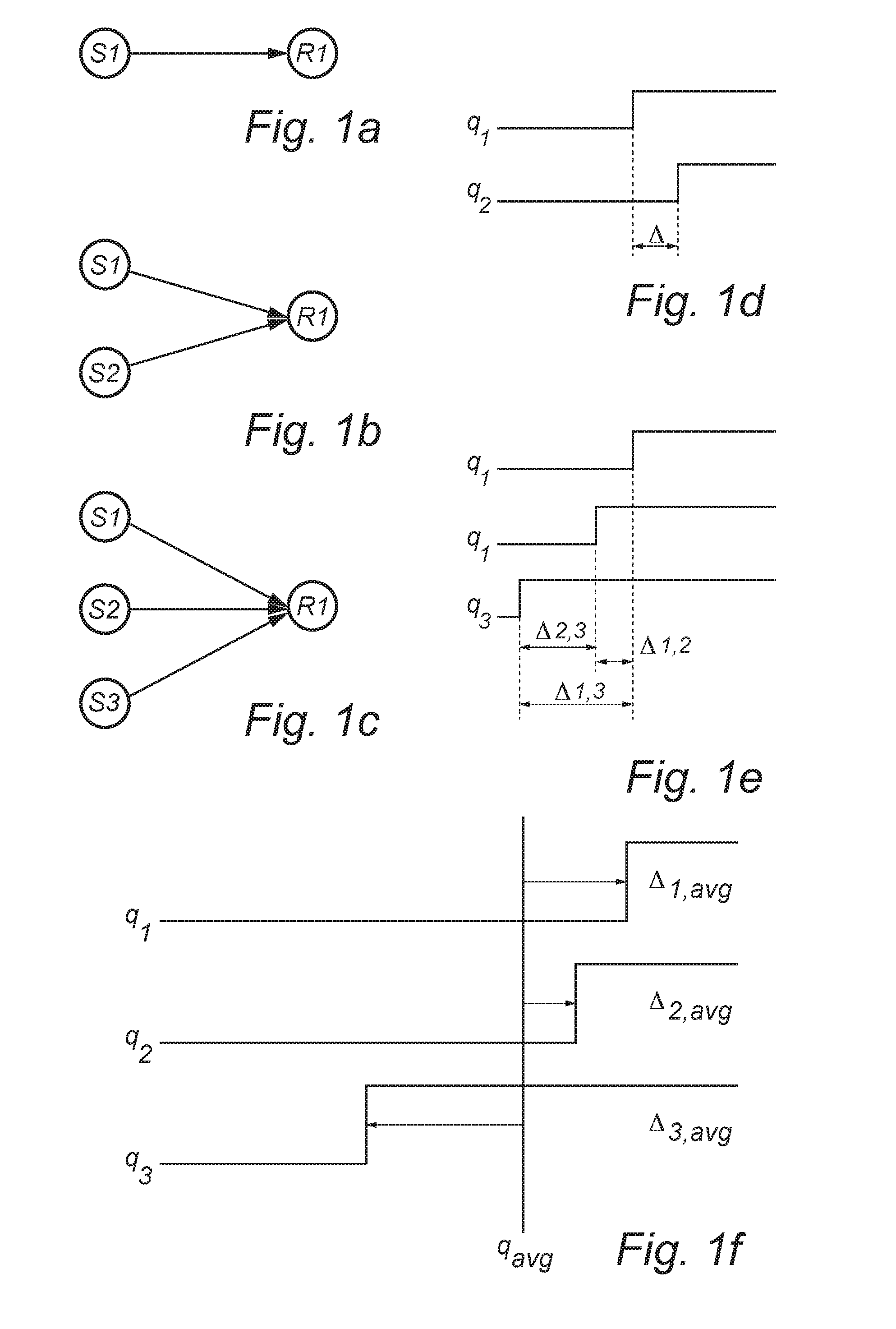
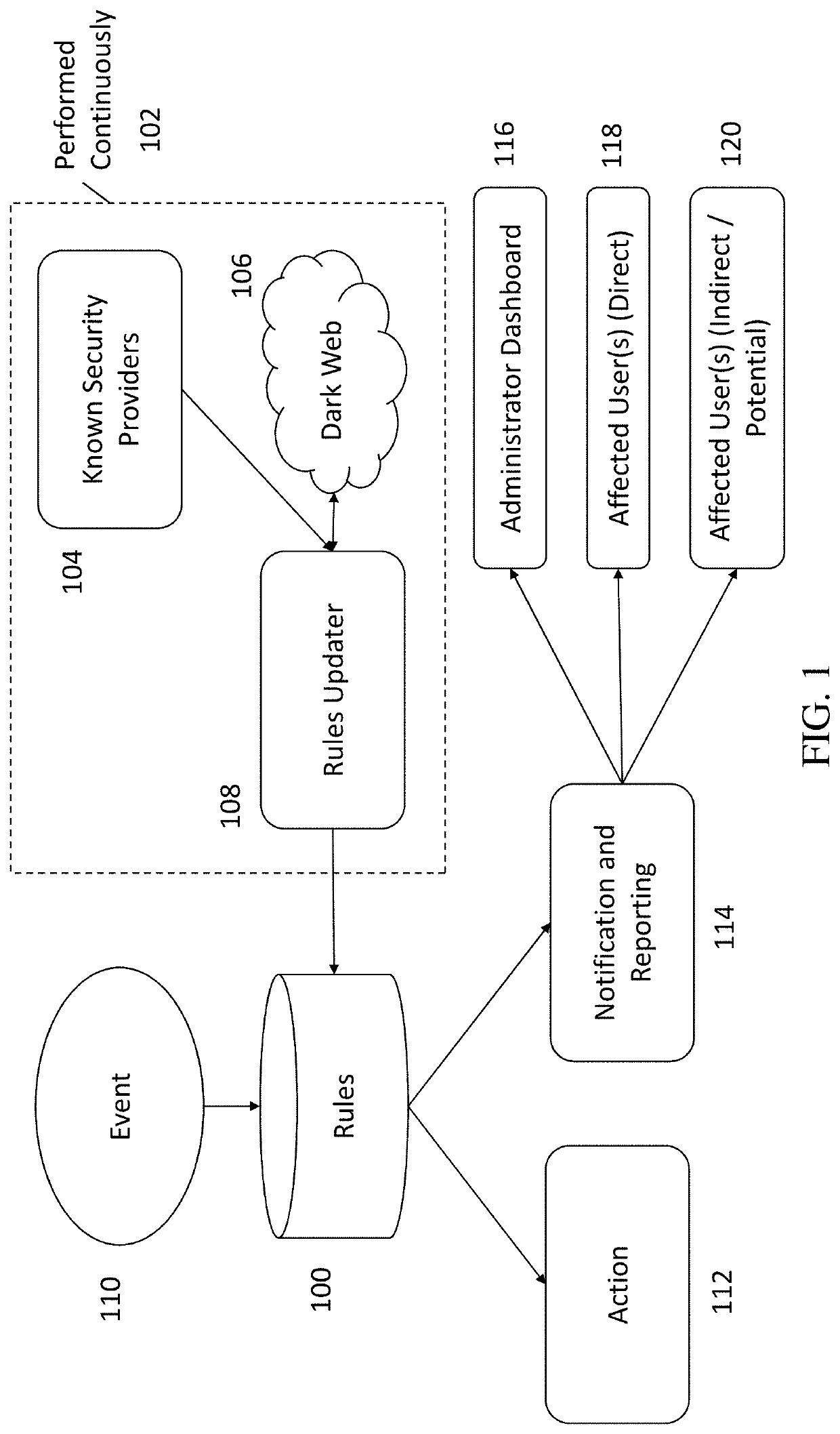
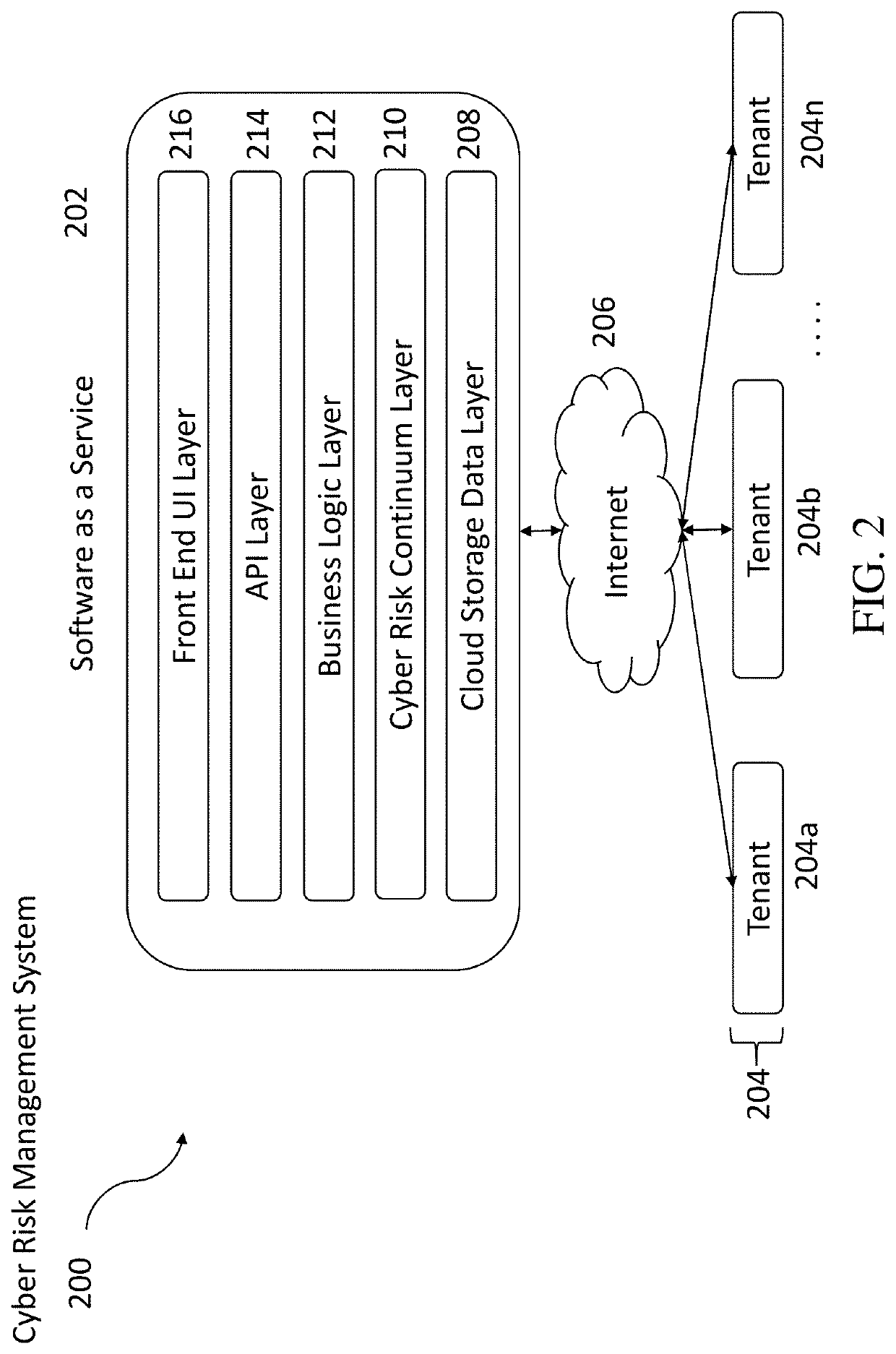
Methods, systems, and computer program products for continuous cyber risk monitoring
The subject matter described herein includes methods, systems, and computer program products for a software as a service (SaaS) system for continuous cyber risk management and monitoring. The method includes storing, maintaining, and updating one or more rules that associates a cyber risk, threat, or vulnerability with an action for one or more assets. The one or more assets includes at least one of: information systems, critical infrastructure, tangible objects, persons, data, and metadata. When an event is detected, it is determined whether a rule applies to the event by searching and matching information associated with the event with the one or more rules. If a rule applies, an action may be performed and various users notified. The action performed includes a corrective, remedial, or mitigating action as specified by the applicable rule. The method for continuous cyber risk management and monitoring described herein are performed automatically and continuously.
Owner:OLYMPUS INFOTECH LLC
Anti-terrorist system
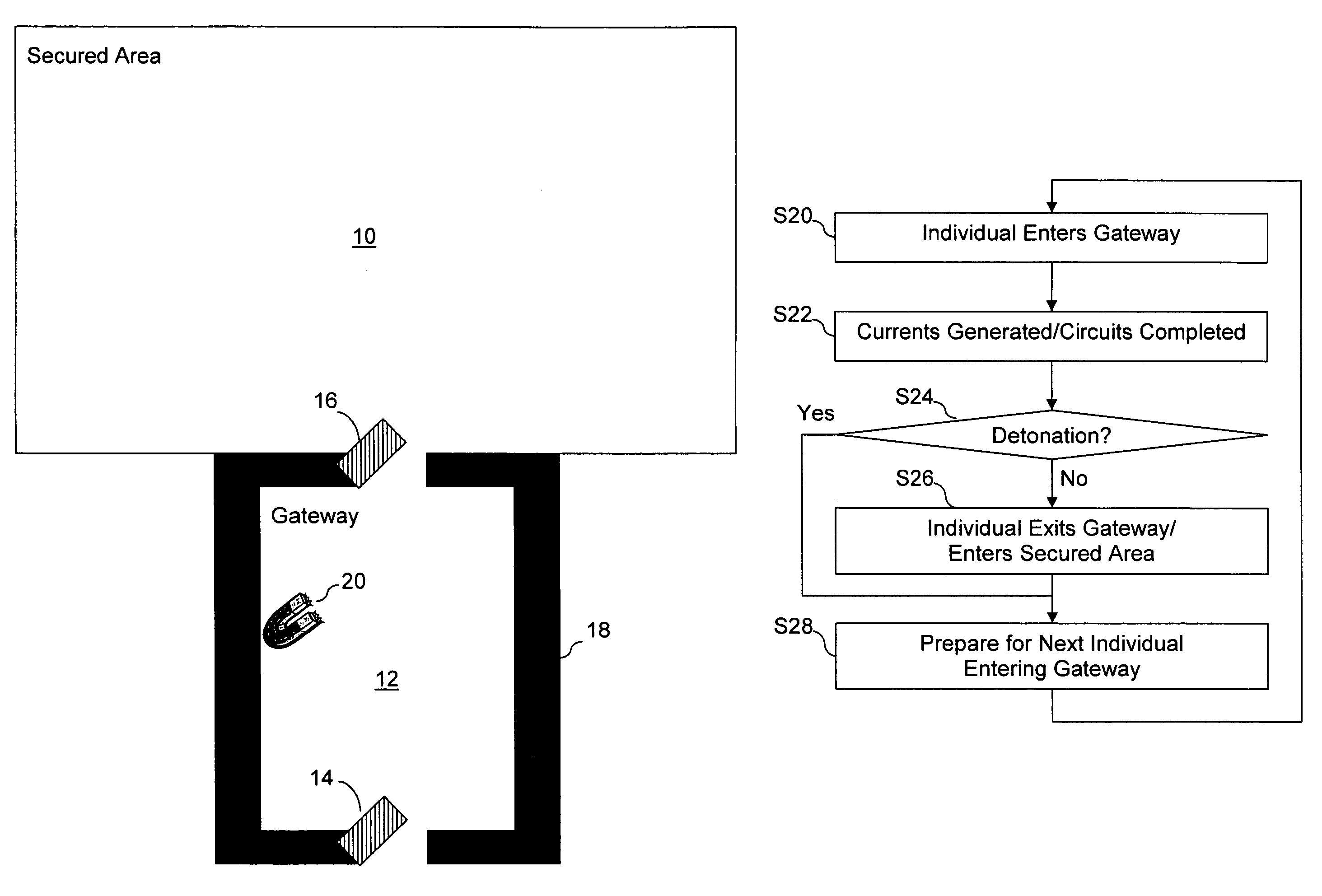
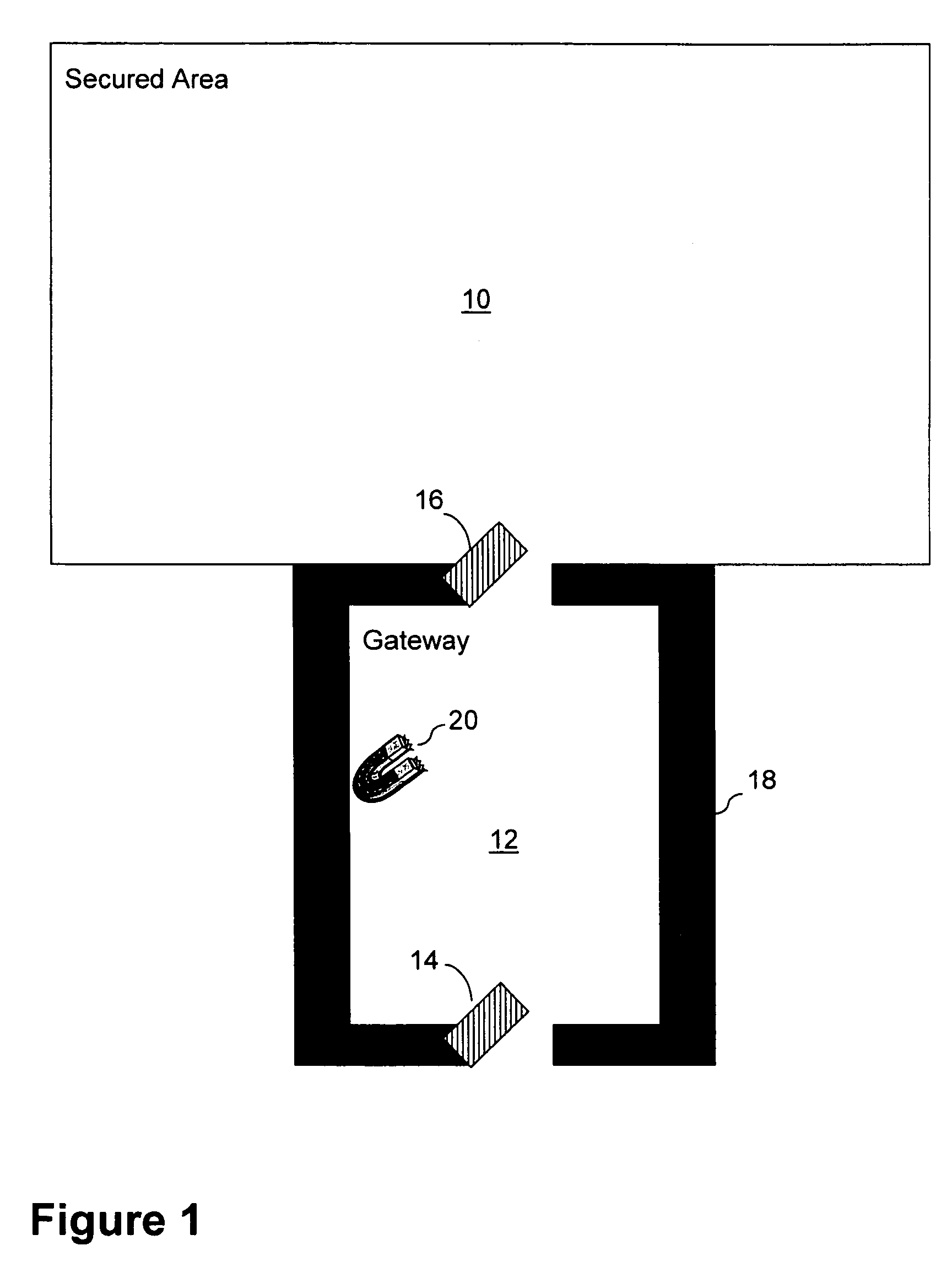
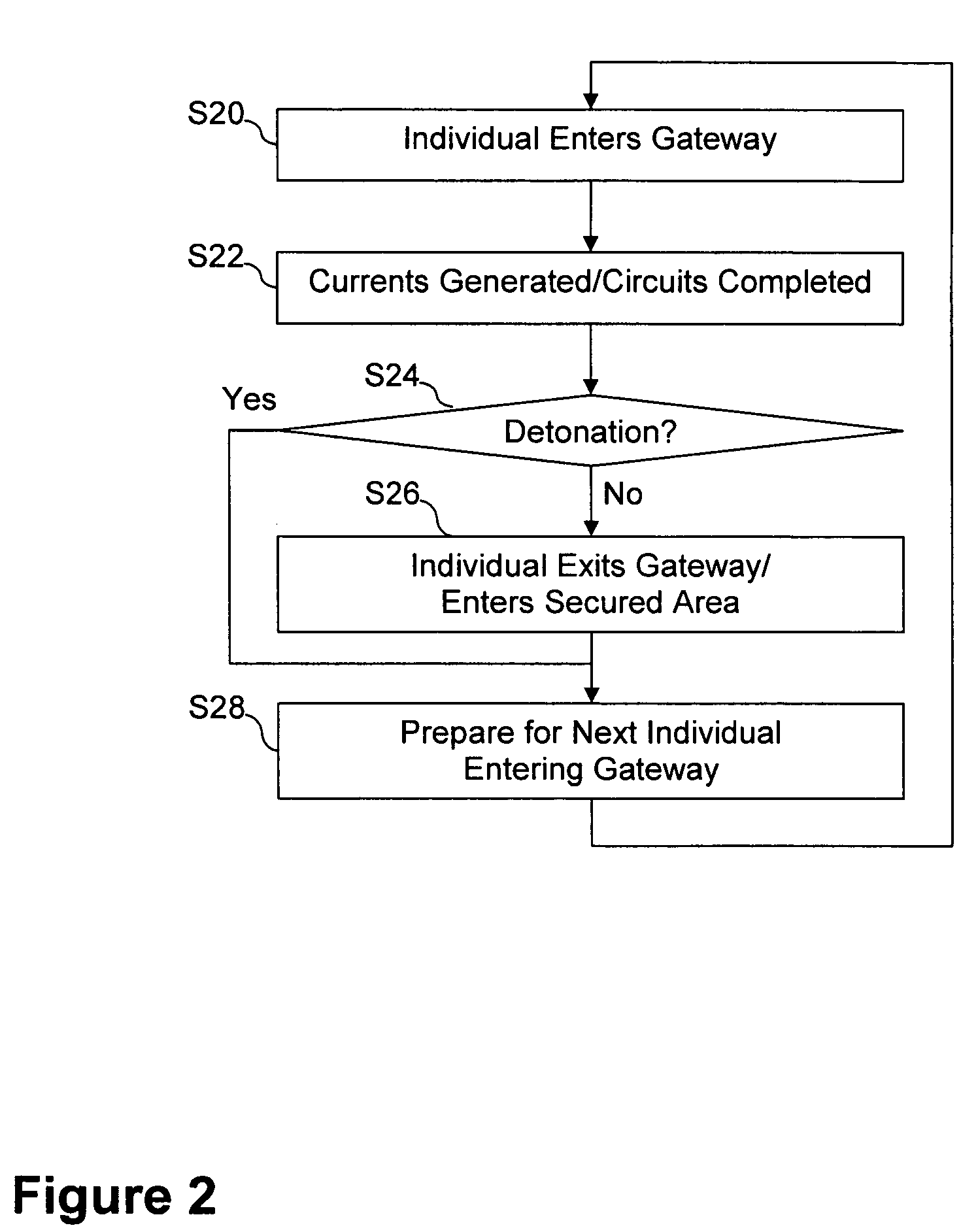
InactiveUS7784389B2Minimize damageDefence devicesElectric signal transmission systemsTelecommunicationsExplosive Agents
Owner:IO LLLP +3
Electronic component classification
ActiveUS9759757B2Low costNoise figure or signal-to-noise ratio measurementCharacter and pattern recognitionAviationIntrinsics
A system and method of electronic component authentication or component classification can reduce the vulnerability of systems (e.g., satellites, weapons, critical infrastructure, aerospace, automotive, medical systems) to counterfeits. Intrinsic deterministically random property data can be obtained from a set of authentic electronic components, processed, and clustered to create a classifier that can distinguish whether an unknown electronic component is authentic or counterfeit.
Owner:BATTELLE MEMORIAL INST
Standoff security and real-time vendor verification system and apparatus
InactiveUS7280042B2Fast trainingReduce riskElectric signal transmission systemsMultiple keys/algorithms usageOperational systemEngineering
A stand-off security checkpoint system and apparatus that enables security officers entrusted with protecting our nations' critical infrastructure or other high risk locations, a means of verifying in real-time, the identity of entrants to a facility. Via a communications system and apparatus that is positioned a safe, stand-off distance away from the entrance to a facility, a person entering a facility exits his vehicle or walks up to a machine housing which is equipped with cameras and sensor equipment. A close up view of the persons' identification as well a picture of the person himself is captured and readied for real-time transmission to security personnel well away from the entrants location at the machine. Via wireless transmitter and receiver equipment, and computer hardware and software arrangements incorporated into the system, the entrant and his identification card can be viewed and verified, from a safe standoff distance by on-site, as well as off-site security screening personnel. The utilization of wireless networks and internet communications networks, along with the machines' physical features and use, creates multiple opportunities to detect suspicious behavior by entrants to facility well before they reach an unsafe distance to the entrance. While in operation, and with the person a safe distance away from the entrance, the system further equipped with sensors to detect metal, chemical and biological substances can also send special alerts to the detection of harmful substances, well before the entrant reaches the entrance to the facility or security checkpoint. By design, the system and apparatus creates a new and effective means of deterring terrorists who may be trying to effect a terrorist infiltration by disguising themselves as officials or vendors. Additionally, the system is designed to be laid out so as to prompt a direct separation of a would-be suicide or truck bomber from his vehicle. This can greatly deter his desire to effect an attack at that location, as the chances for nullification and or the detection of suspicious activity by security officers operating the system, well before he reaches his location are greatly in odds against him.
Owner:TRELA RICHARD STEVEN
Method of synchronization and link access for low energy critical infrastructure monitoring network
ActiveUS20130070582A1Prompt and efficiency time synchronizationMinimize contentionPower managementError prevention/detection by using return channelAccess methodStructure of Management Information
The present invention provides a time synchronization method in a low energy critical infrastructure monitoring network and a coordinate access method using a superframe. According to the exemplary embodiments of the present invention, time synchronization can be promptly and efficiently performed in the low energy critical infrastructure monitoring network, a link access method with three grades of link access can be provided, and a frame structure and a process for link generation, link management, and extended connection are provided.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com