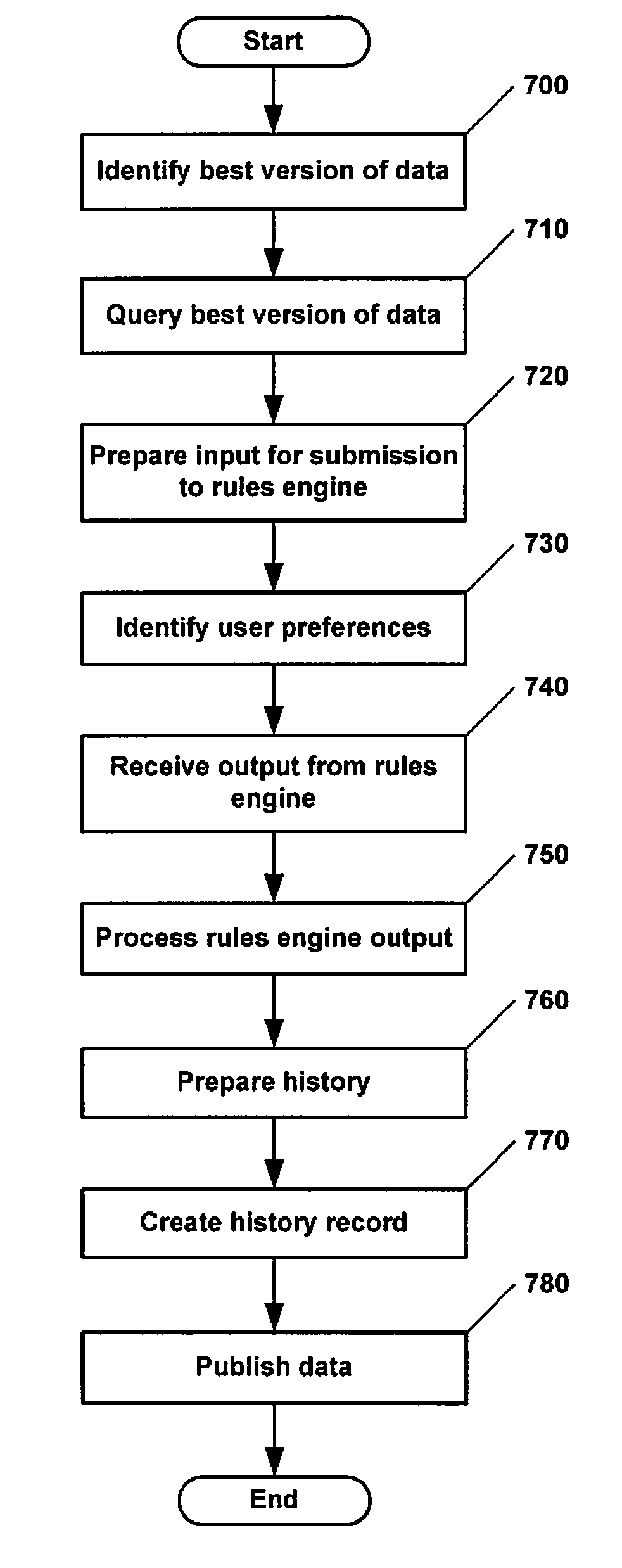
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
930 results about "Master data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Master data represents the business objects that contain the most valuable, agreed upon information shared across an organization. It can cover relatively static reference data, transactional, unstructured, analytical, hierarchical and metadata. It is the primary focus of the information technology (IT) discipline of master data management (MDM).
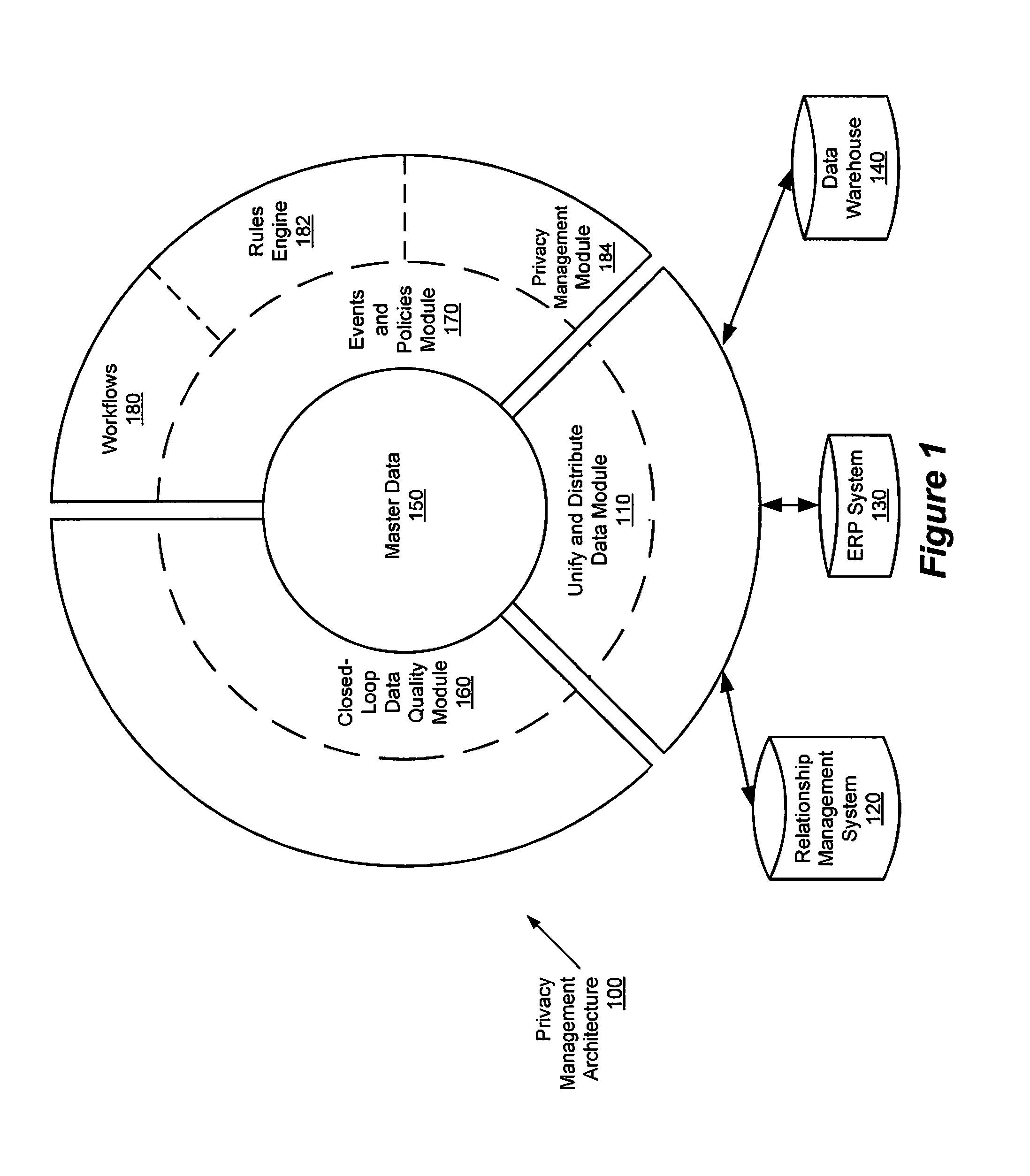
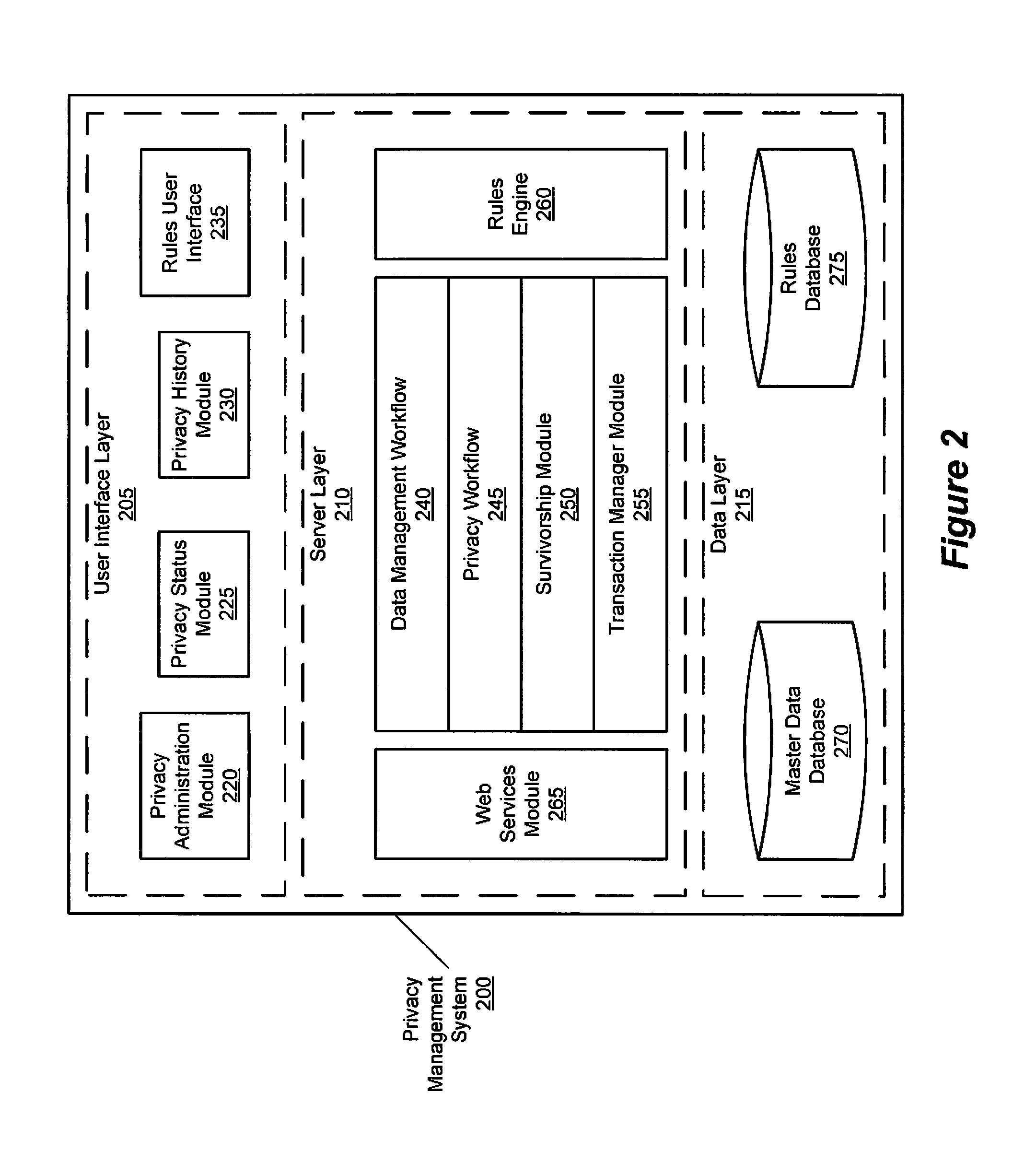
Privacy management policy hub
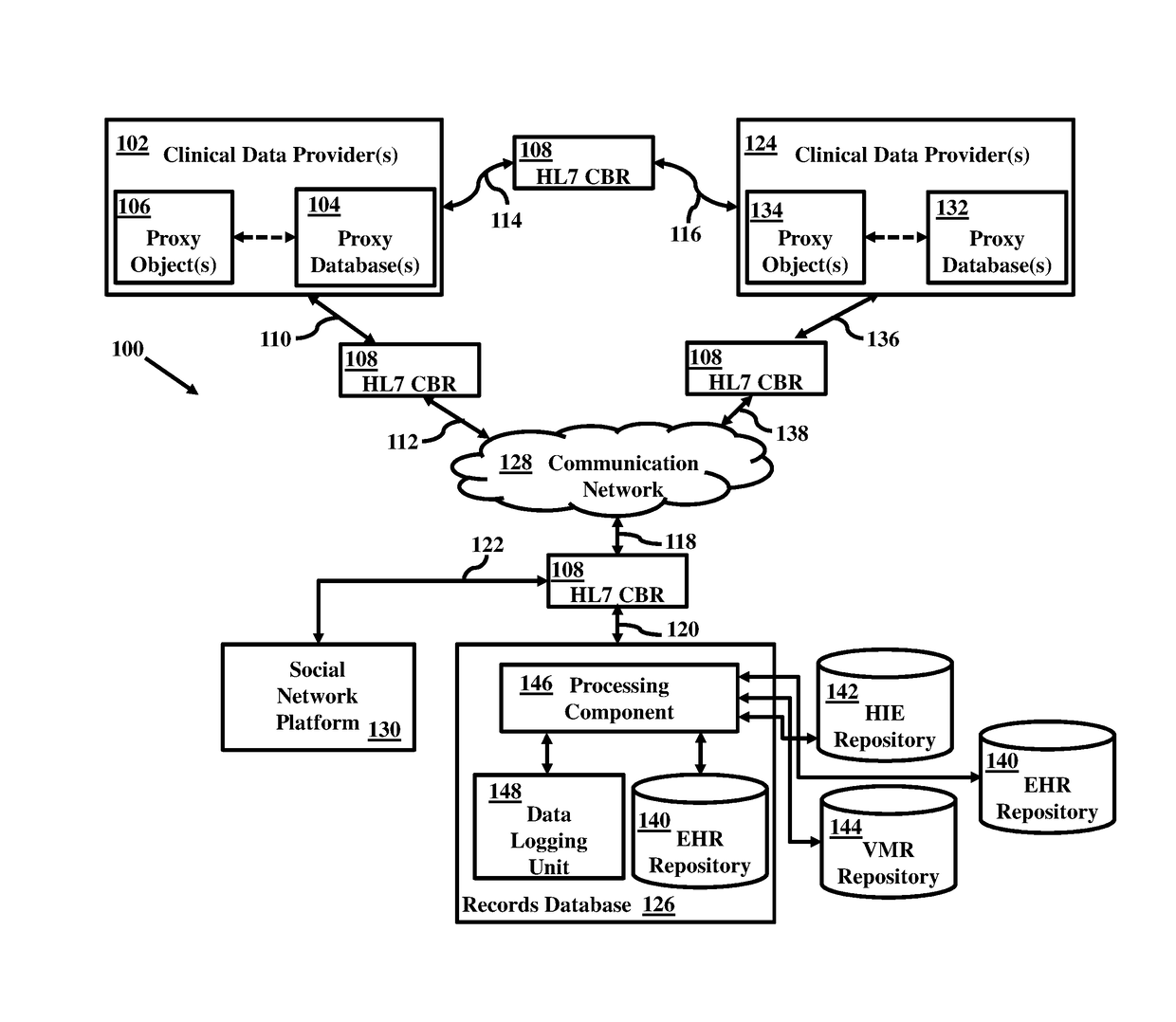
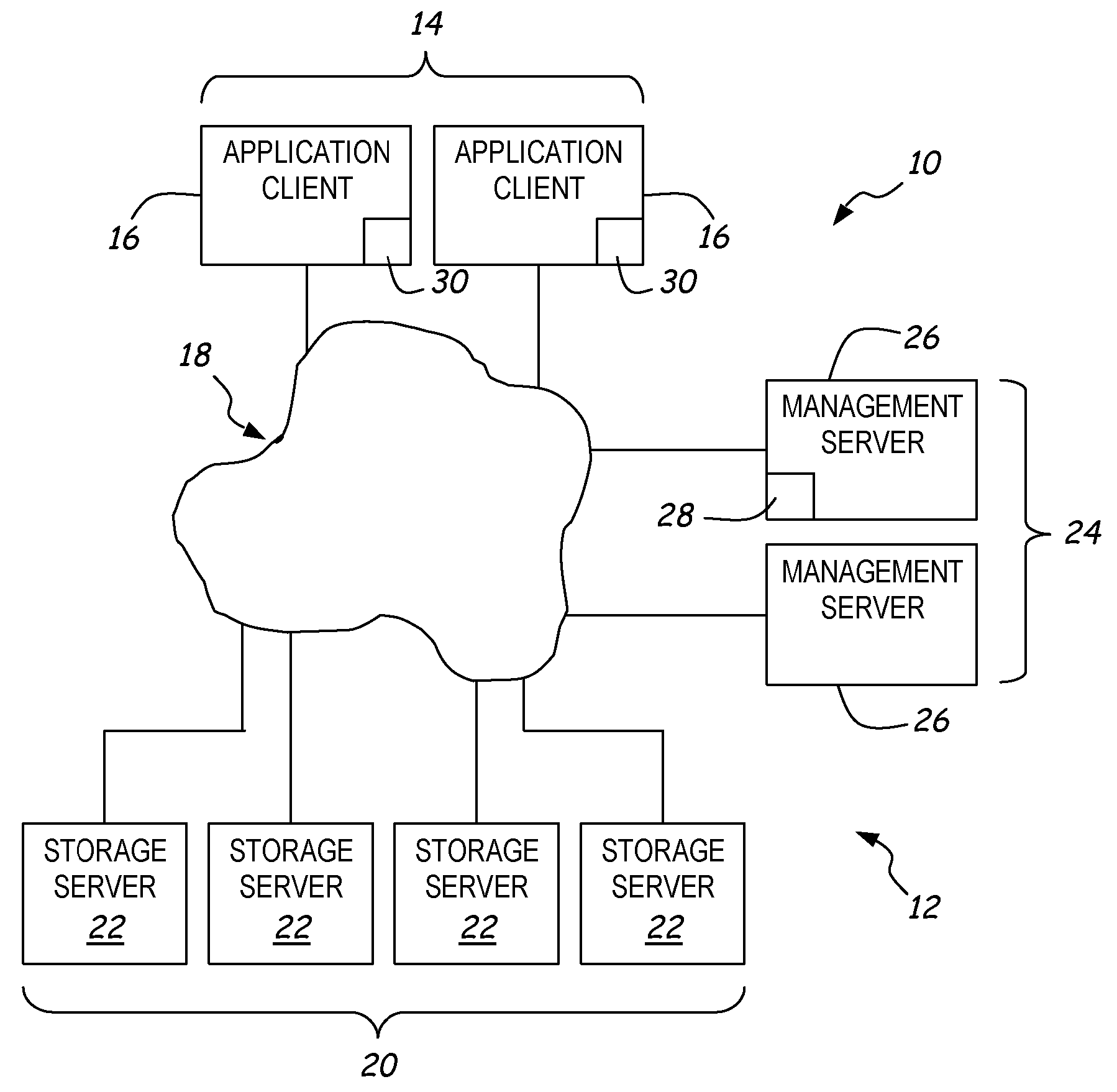
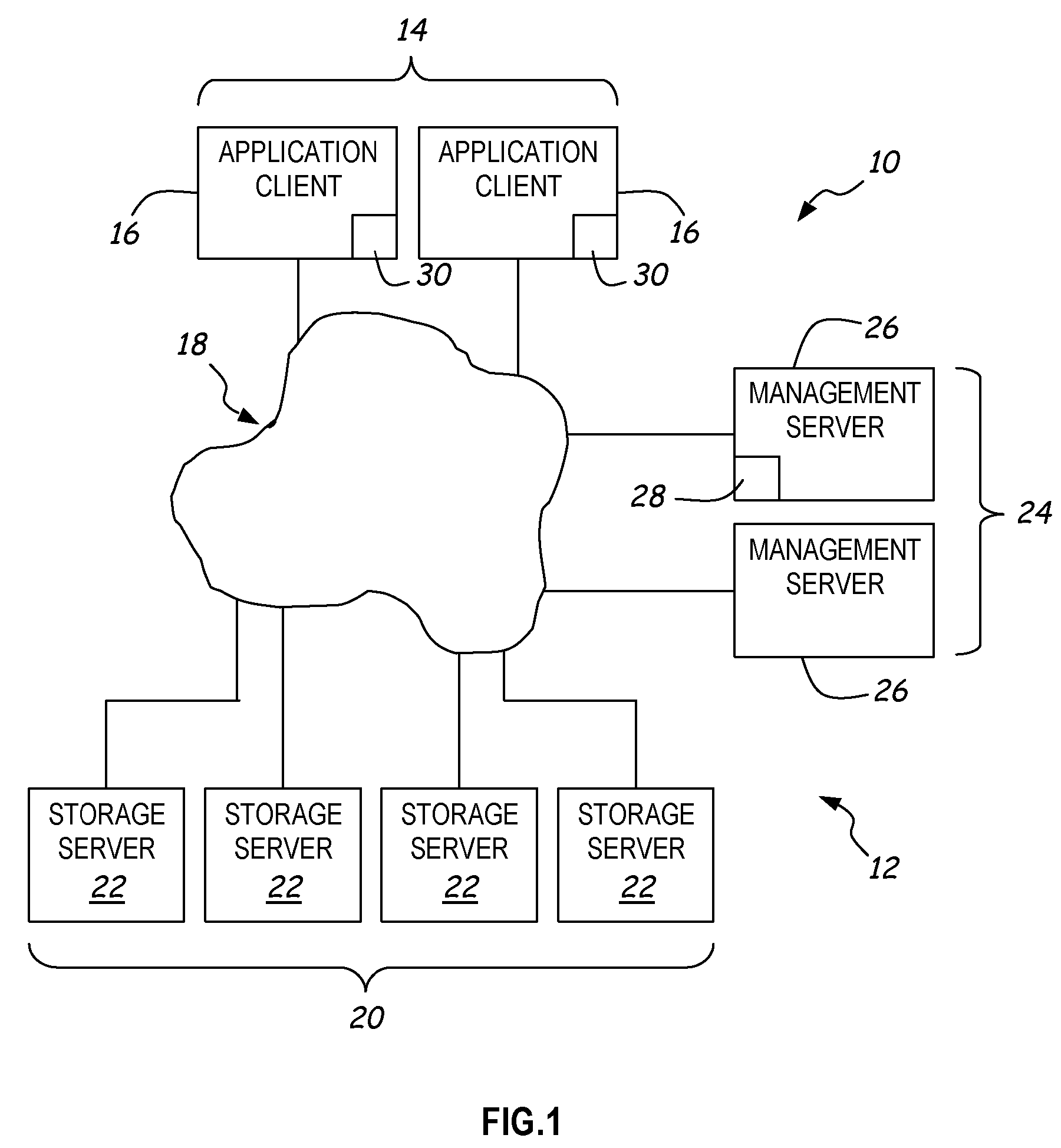
A system architecture is disclosed that includes a privacy management system. In particular, the privacy management system provides a policy hub for maintaining and managing customer privacy information. The privacy management system maintains a master data database for customer information and customer privacy preferences, and a rules database for privacy rules. The privacy management system captures, synchronizes, and stores customer privacy data. Privacy rules may be authored using a privacy management vocabulary, and can be customized for an enterprise's privacy policies.
Owner:ORACLE INT CORP
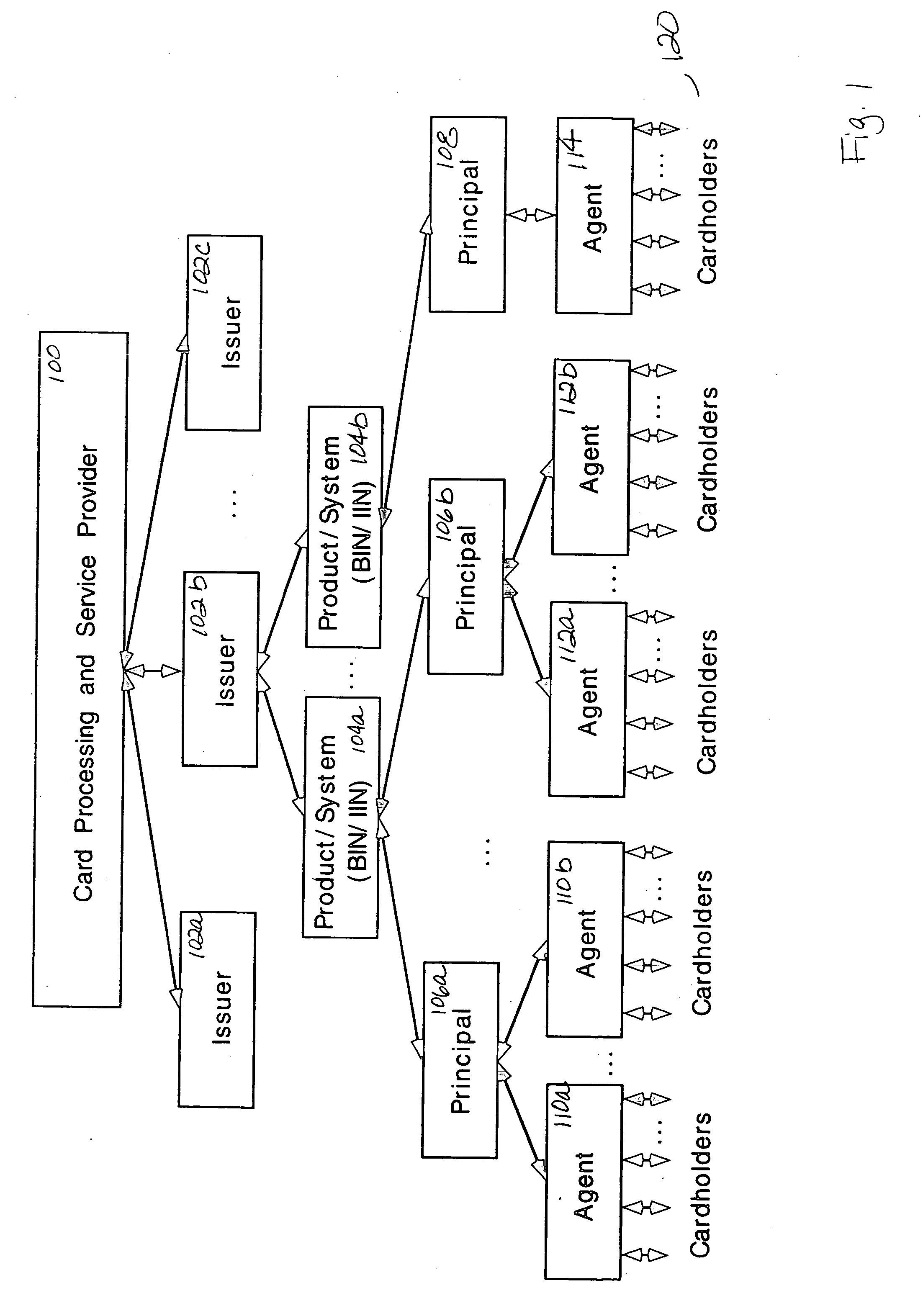
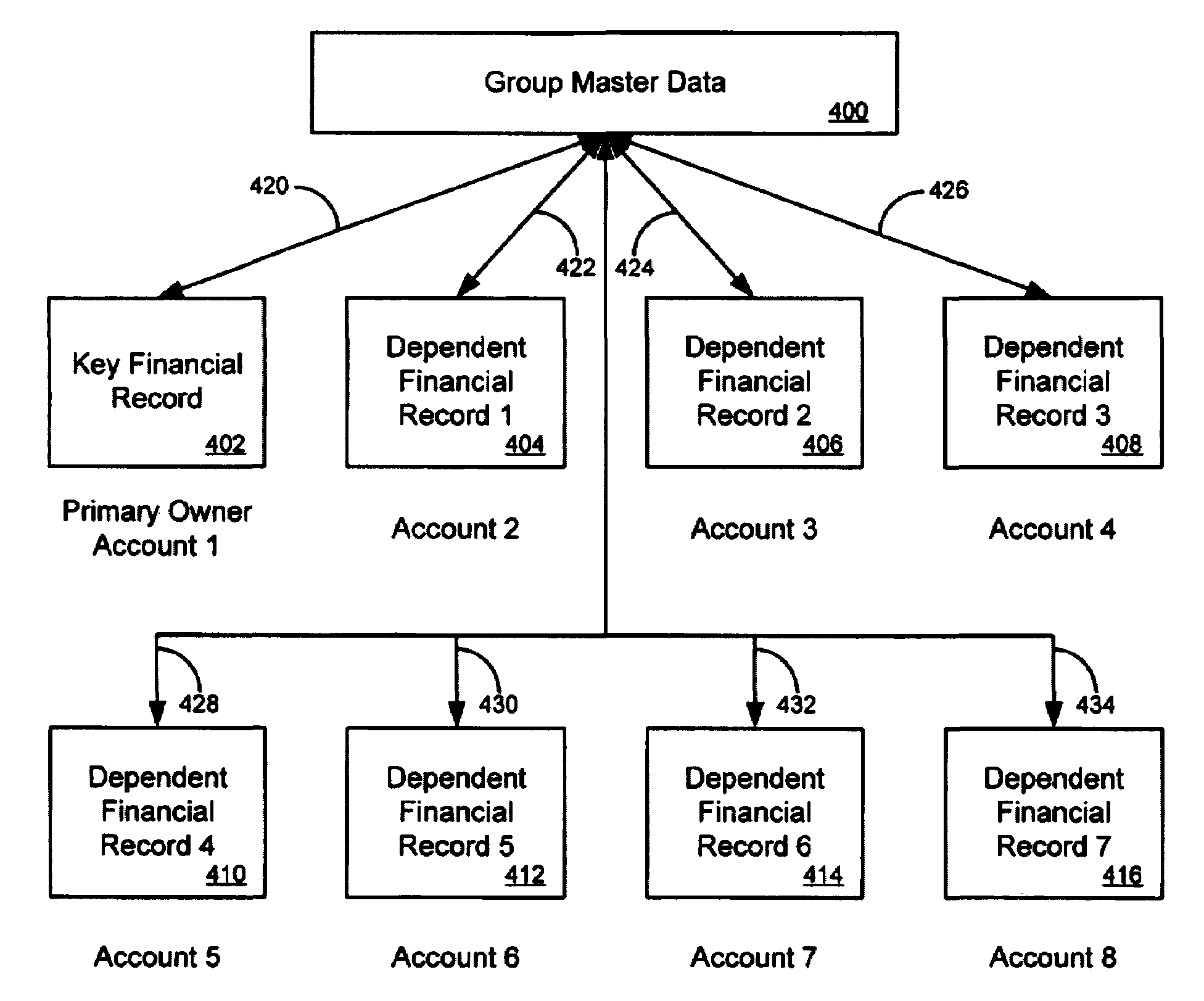
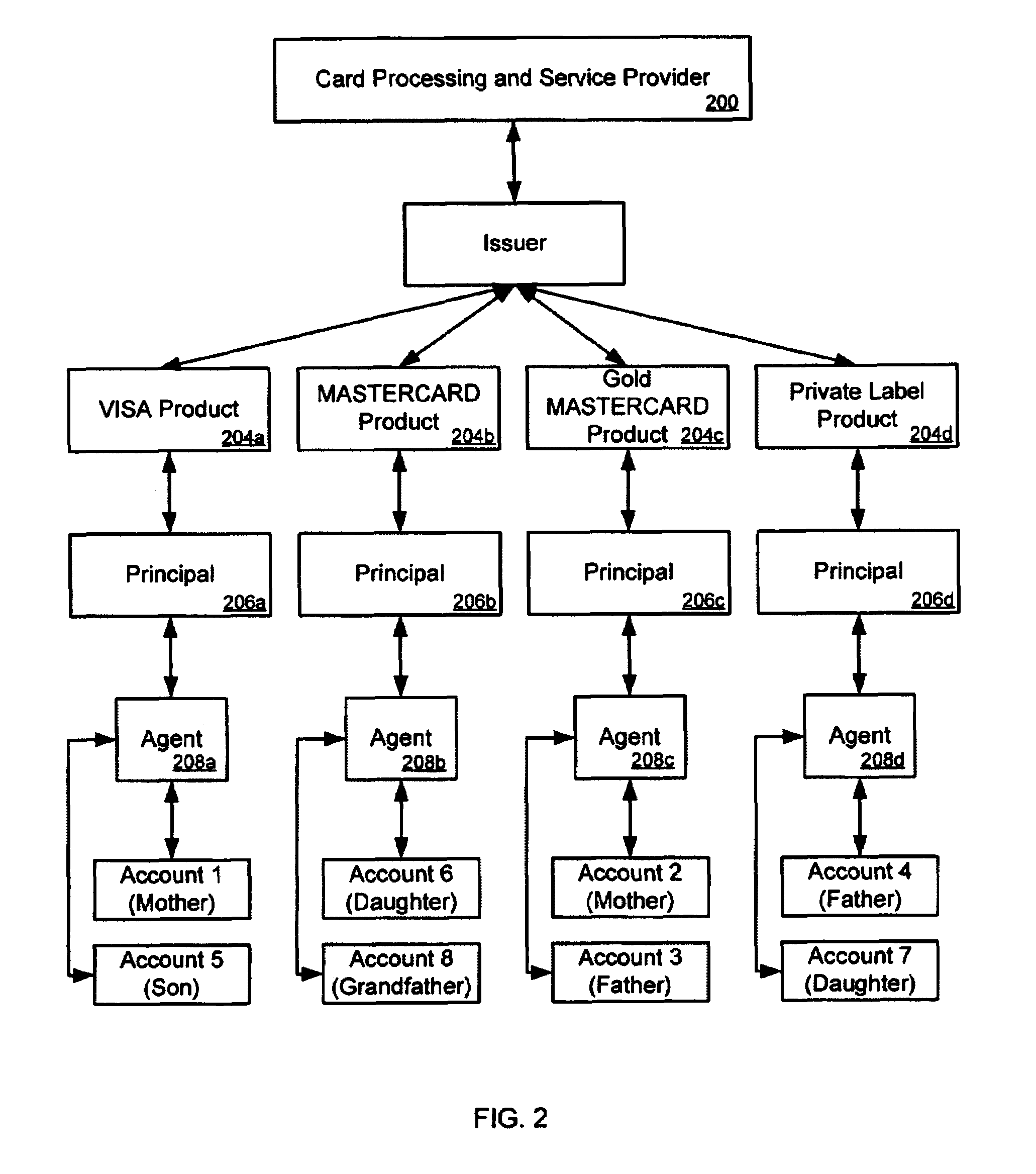
Creating groups of linked accounts
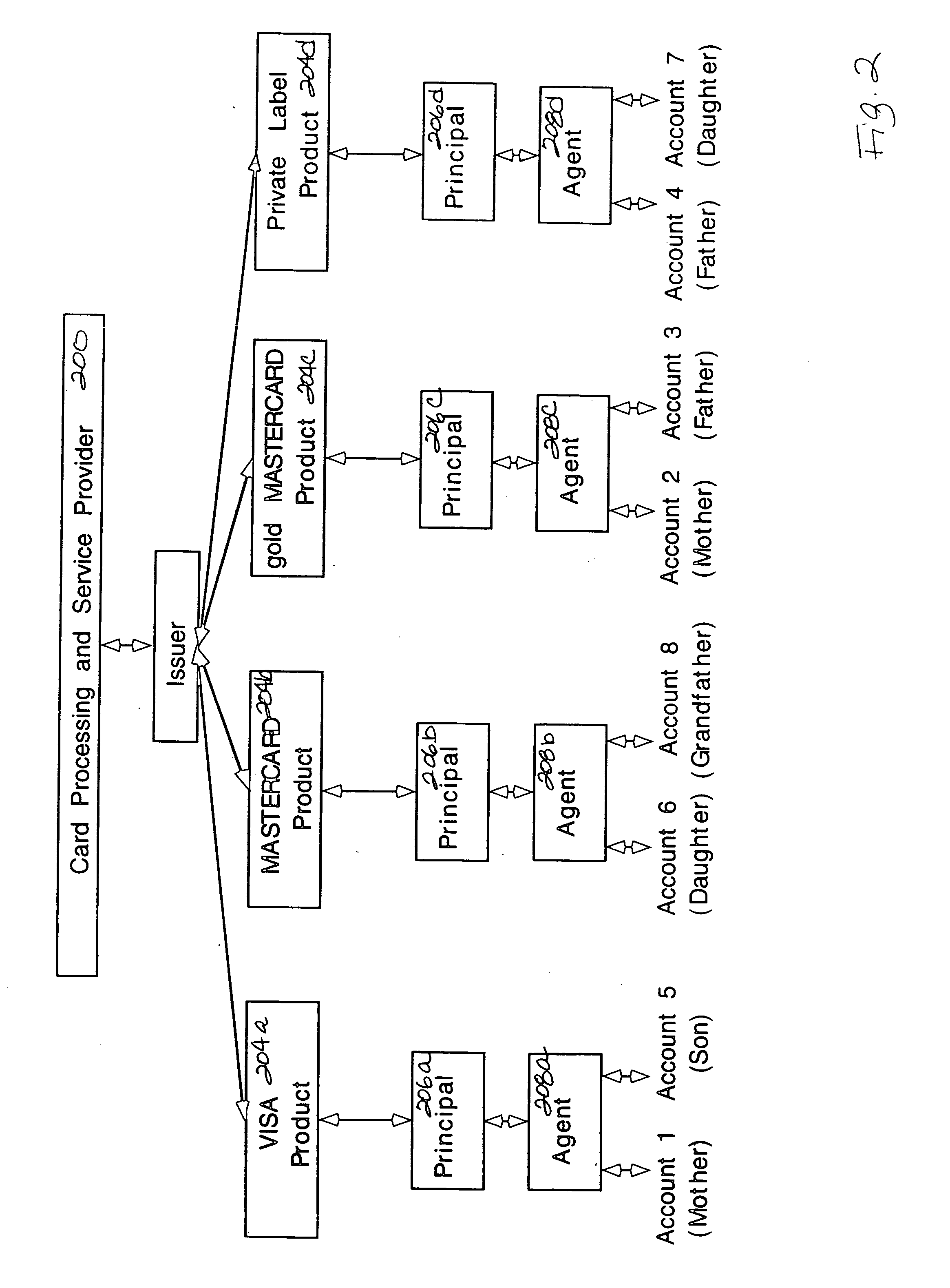
Linking accounts corresponding to different products together to create a group so that group processing can be performed at the group level while independent processing of the accounts is performed at the account level. The method links the accounts into a group by linking a financial record for each account to group master data for the group. The group master data includes information about the group, including group parameters and a group identifier. A group typically includes a key account and one or more dependent accounts. The relationship between a dependent account and the group is specified by a dependent strategy. A dependent strategy specifies group level processing options for the account. The relationships between the accounts and the group are flexible to accommodate changes in the status of the group cardholders.
Owner:FIRST DATA
Autonomous data machines and systems
ActiveUS20150205298A1Reduce negative personalReduce economic impactAcoustic signal devicesPropulsion by batteries/cellsData sourceData mining
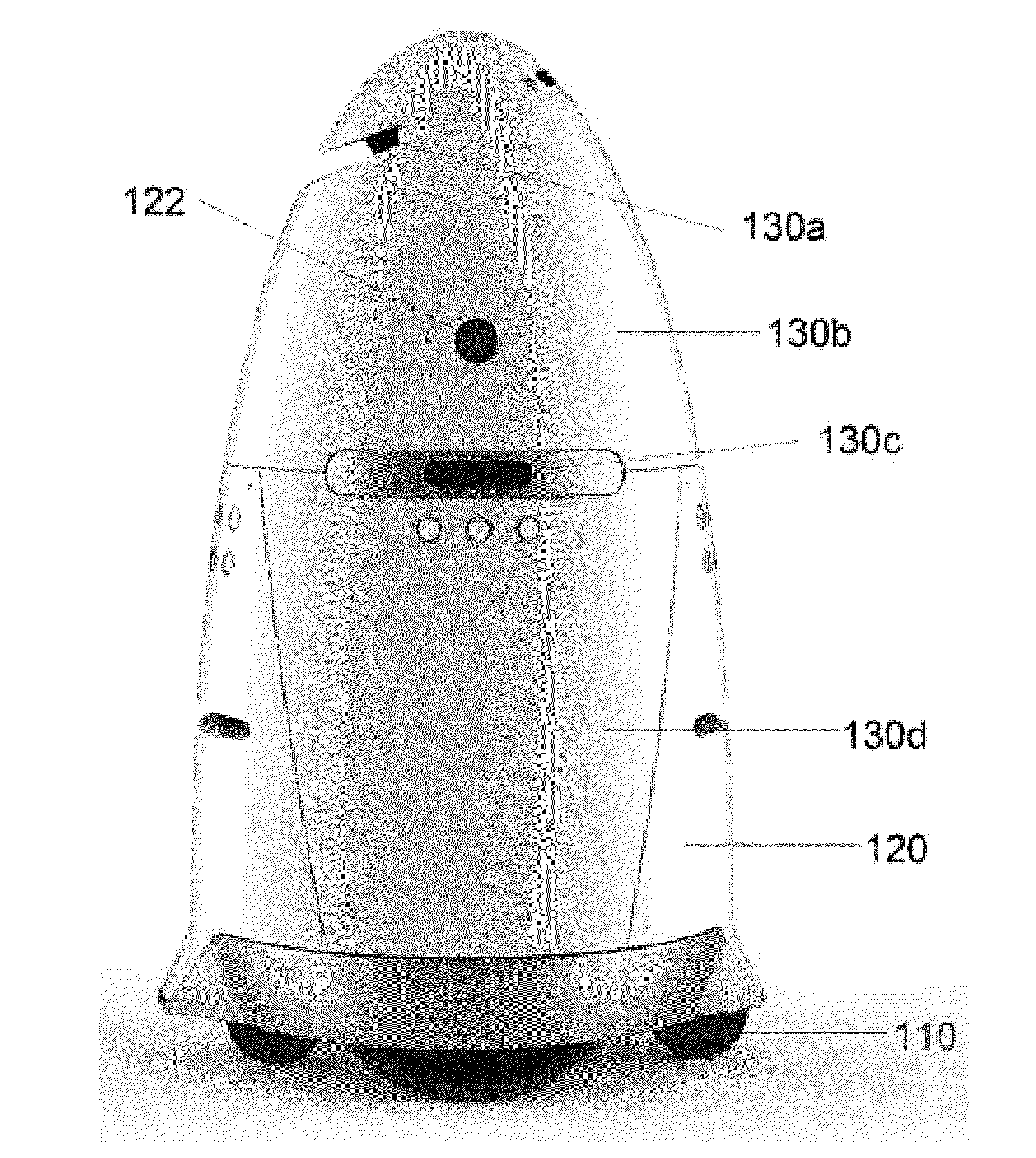
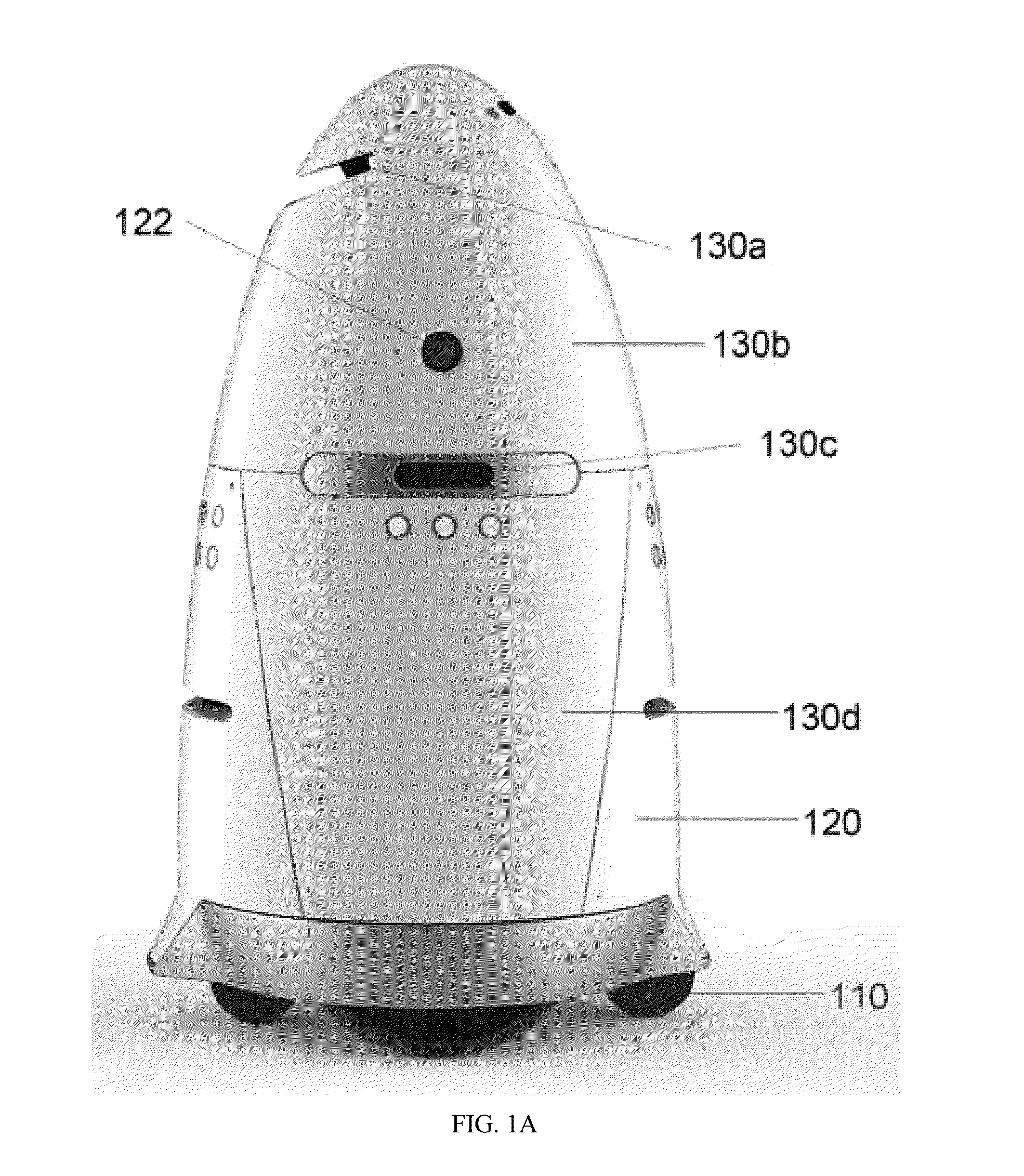
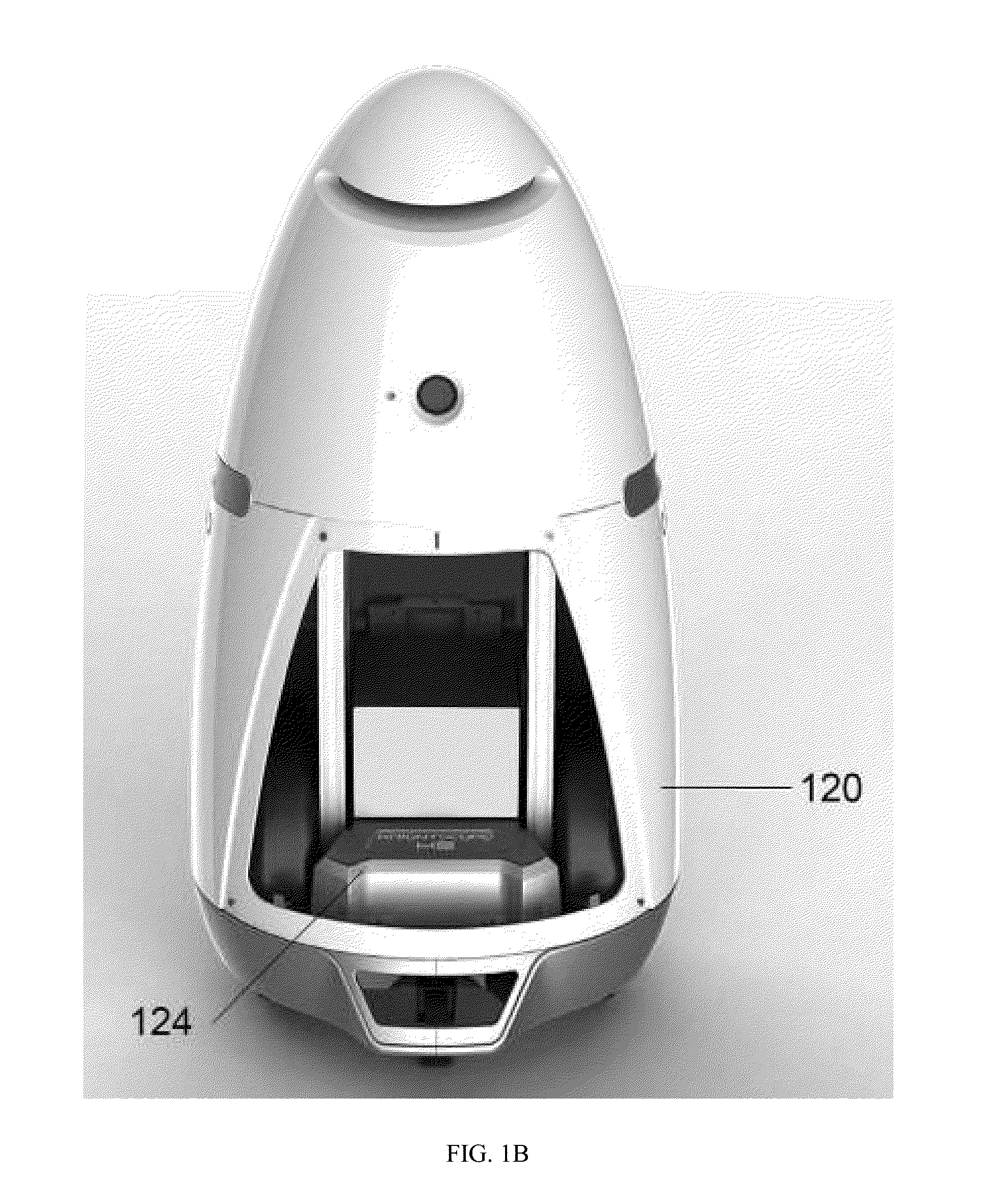
Autonomous data machines and systems may be provided, which may be deployed in an environment. The machines may roam within the environment and collect data with aid of one or more sensors. The data may be sent to a control center, which may optionally receive information from additional data sources, such as other on-site sensors, existing static data, or real-time social data. The control center may send instructions to the machines to perform one or more reaction based on the received information. The autonomous data machines may be capable of reacting autonomously to one or more detected condition. In some instances, the autonomous data machines may be employed for security or surveillance.
Owner:KNIGHTSCOPE
Blockchain system for natural language processing
ActiveUS20170103167A1Natural language translationData processing applicationsData providerData recording
A blockchain configured system includes a router and a blockchain configured record bank. The router collects data and converts it in a format in accordance with a defined standard. The blockchain configured record bank can include or be coupled to a data repository. The blockchain configured record bank can be configured to be coupled to the data provider through the router over a communication network. The blockchain configured record bank stores the data received from the data provider and can be accessible or searchable from within or outside the blockchain configured record bank. The blockchain configured record bank can be coupled to or include a data logging unit that maintains metadata associated with the data and configured to facilitate natural language processing capabilities. The router and the blockchain configured record bank may be coupled to machine learning system, metadata validation system, and master data validation system.
Owner:NETSPECTIVE COMM
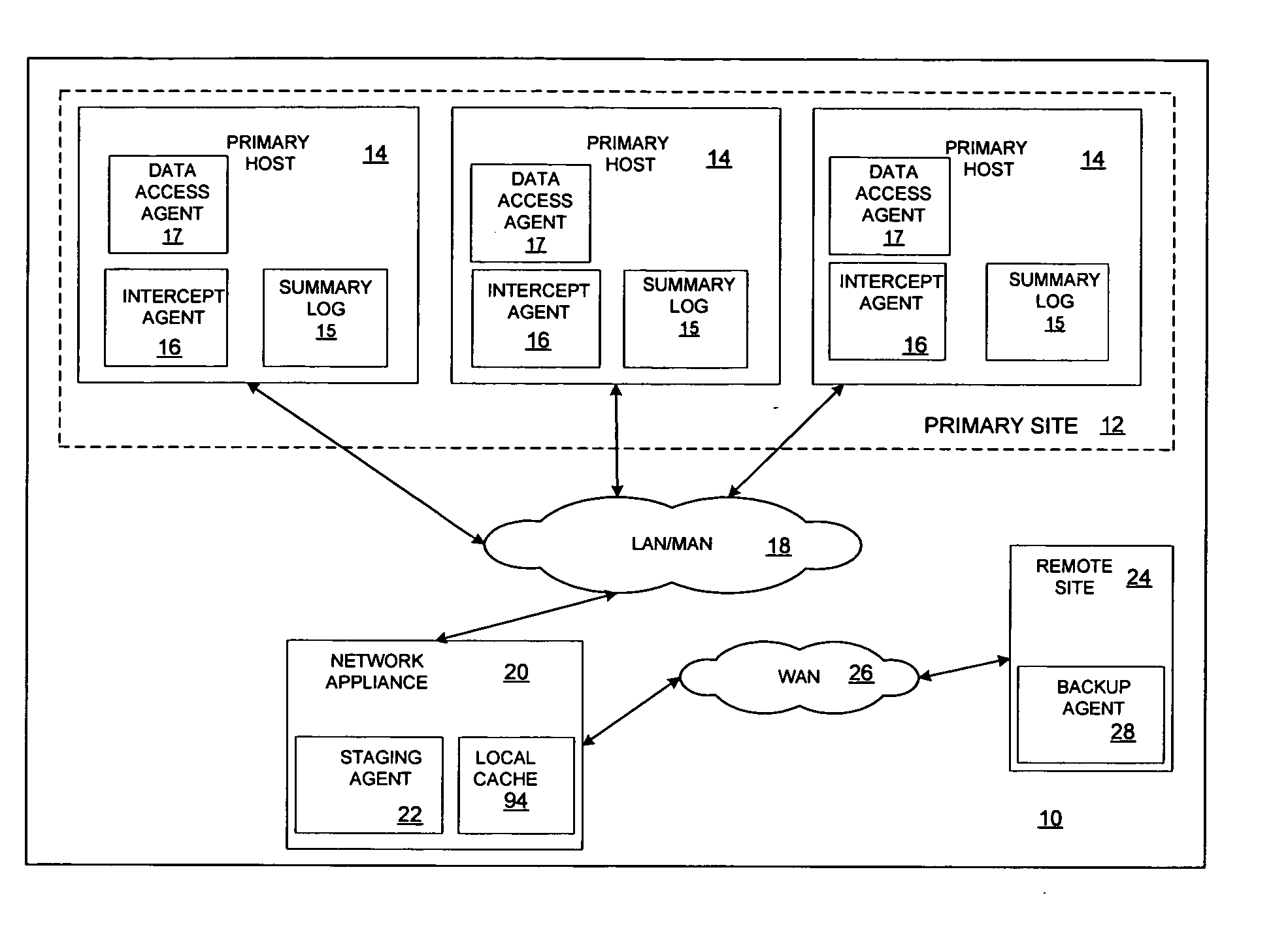
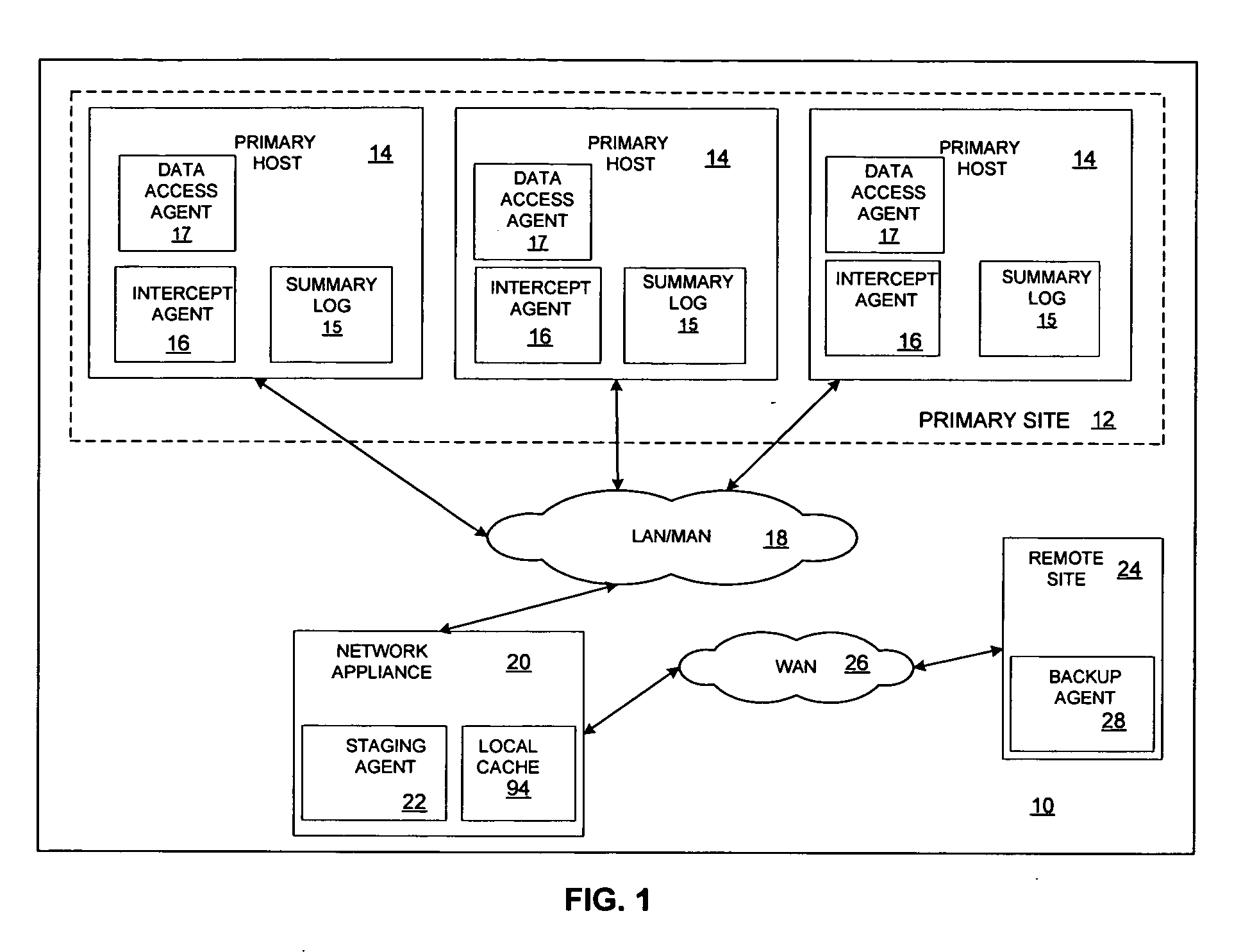
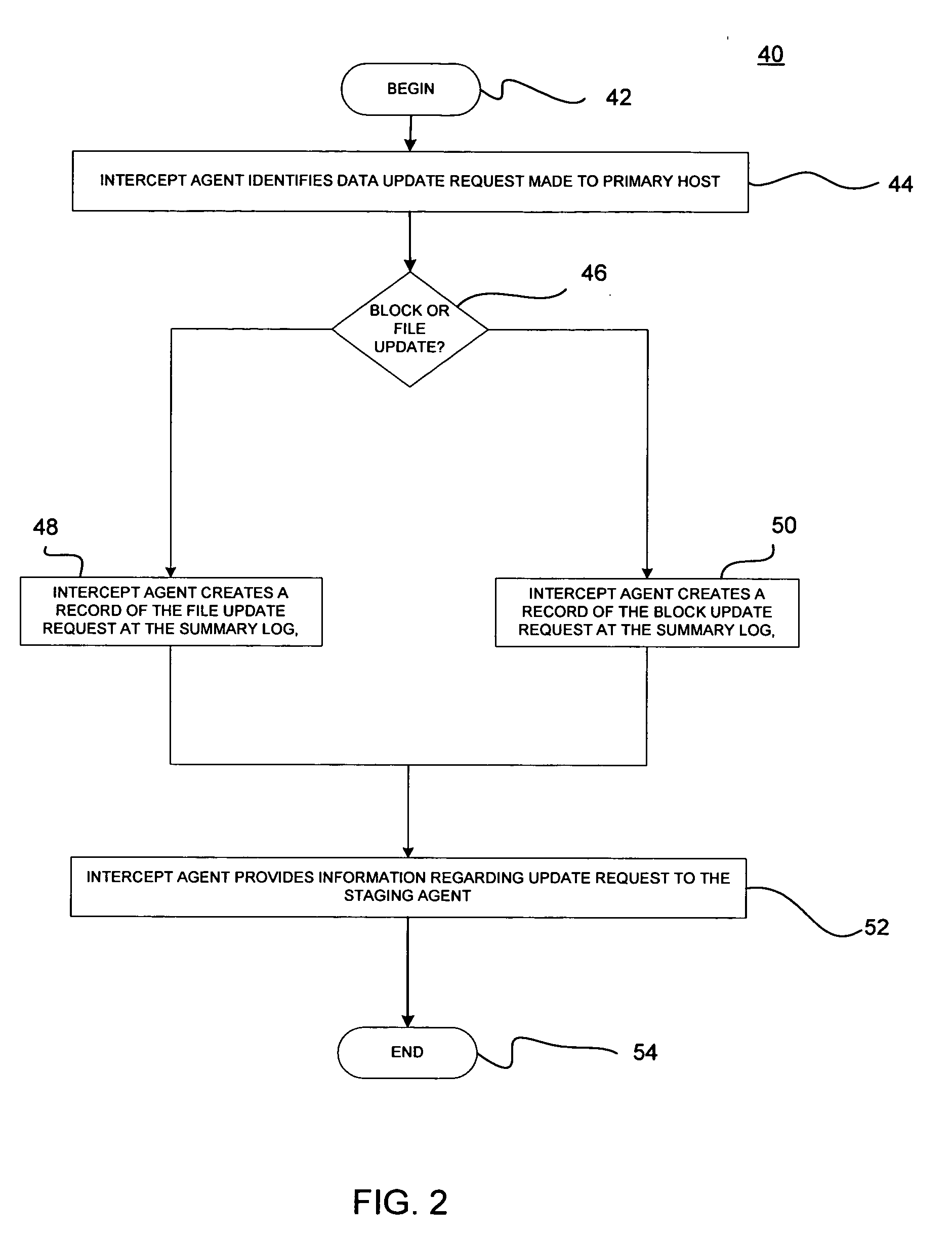
Minimizing resynchronization time after backup system failures in an appliance-based business continuance architecture
ActiveUS20050273654A1Minimize resynchronization timeMinimize timeMemory systemsRedundant hardware error correctionDowntimeSystem failure
A system for minimizing downtime in an appliance-based business continuance architecture is provided. The system includes at least one primary data storage and least one primary host machine. The system includes an intercept agent to intercept primary host machine data requests, and to collect information associated with the intercepted data requests. Moreover, at least one business continuance appliance in communication with the primary host machine and in communication with a remote backup site is provided. The appliance receives information associated with the intercepted data requests from the intercept agent. In addition, a local cache is included within the business continuance appliance. The local cache maintains copies of primary data storage according to the information received. Furthermore, the remote site is provided with the intercepted data requests via the business continuance appliance, wherein the remote site maintains a backup of the primary data storage.
Owner:LENOVO PC INT
Method for linking accounts corresponding to different products together to create a group
Linking accounts corresponding to different products together to create a group so that group processing can be performed at the group level while independent processing of the accounts is performed at the account level. The method links the accounts into a group by linking a financial record for each account to group master data for the group. The group master data includes information about the group, including group parameters and a group identifier. A group typically includes a key account and one or more dependent accounts. The relationship between a dependent account and the group is specified by a dependent strategy. A dependent strategy specifies group level processing options for the account. The relationships between the accounts and the group are flexible to accommodate changes in the status of the group cardholders.
Owner:FIRST DATA
Timeshared electronic catalog system and method
InactiveUS7103605B1Quickly and cheaply and efficiently createWithout overheadImage data processing detailsWebsite content managementData setElectronic catalog
Owner:SAP AG
Supply chain management using mobile devices
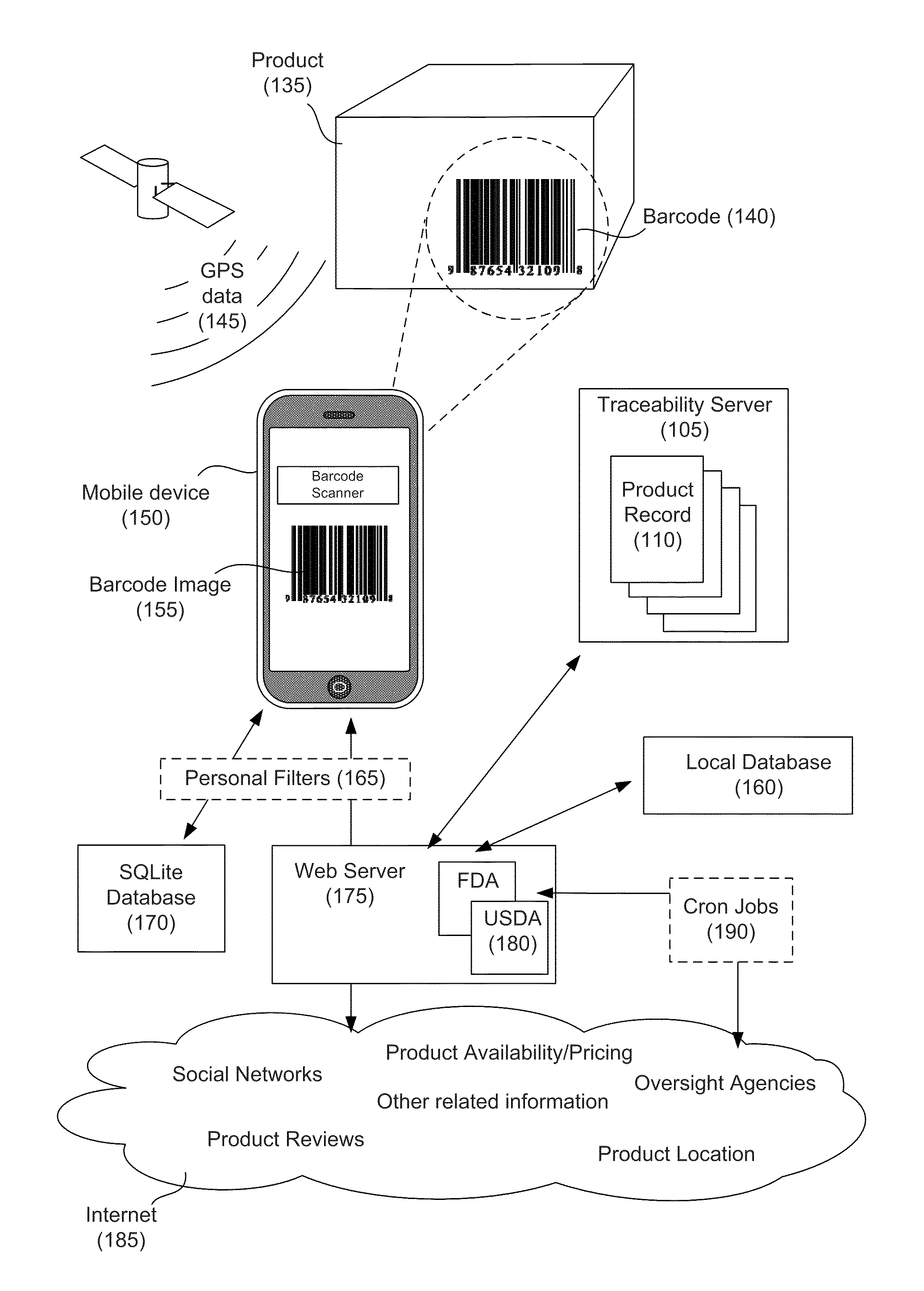
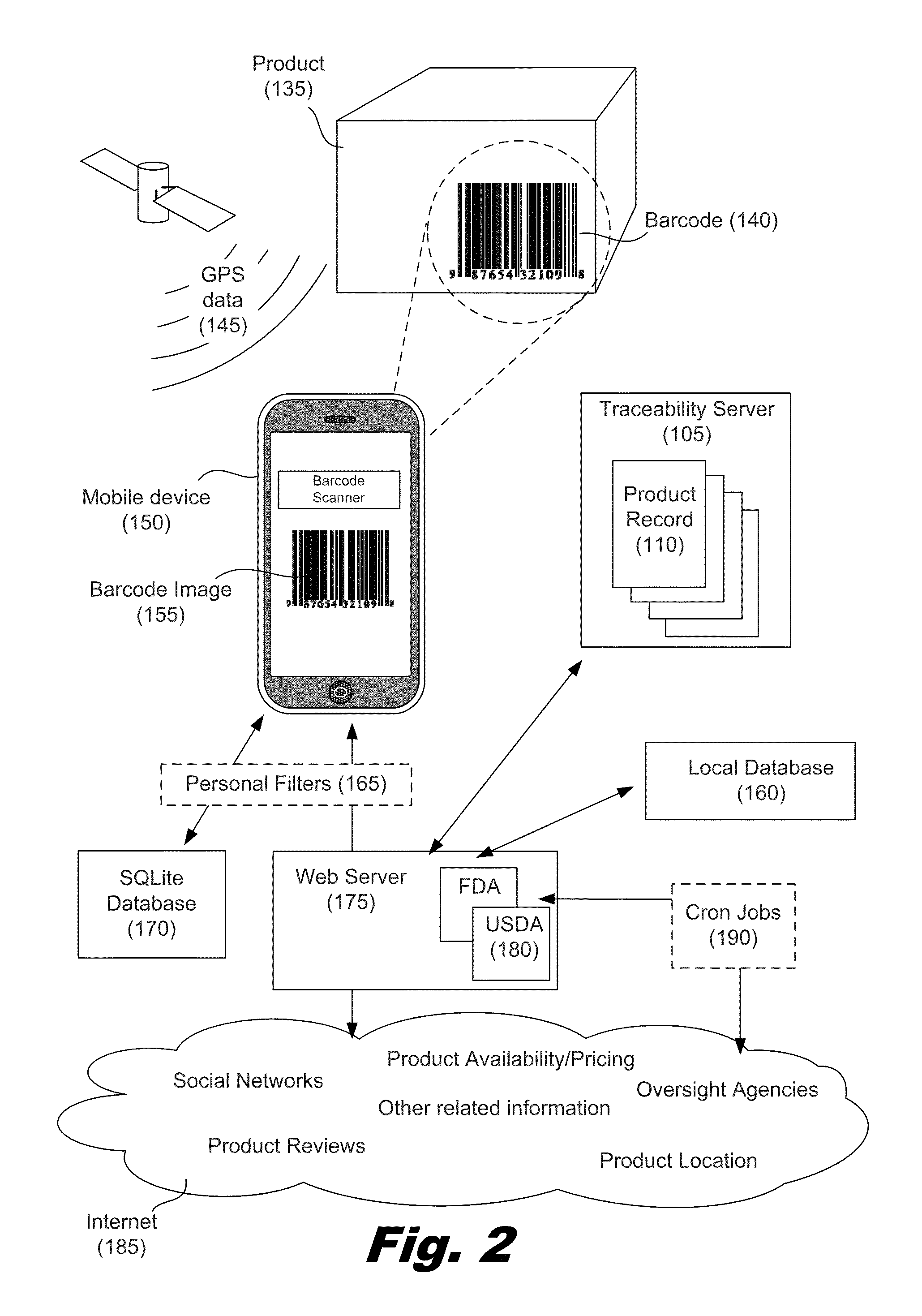
A method for supply chain management using mobile devices with a server on an electronic data network includes receiving identifying information for a product transmitted from a mobile device via the network, the server being periodically updated with product recall data. The server queries a traceability server via the network for master data and event data related to the product using the identifying information. The server processes the recall data, master data, and event data to produce product data which is output to the mobile device.
Owner:IBM CORP
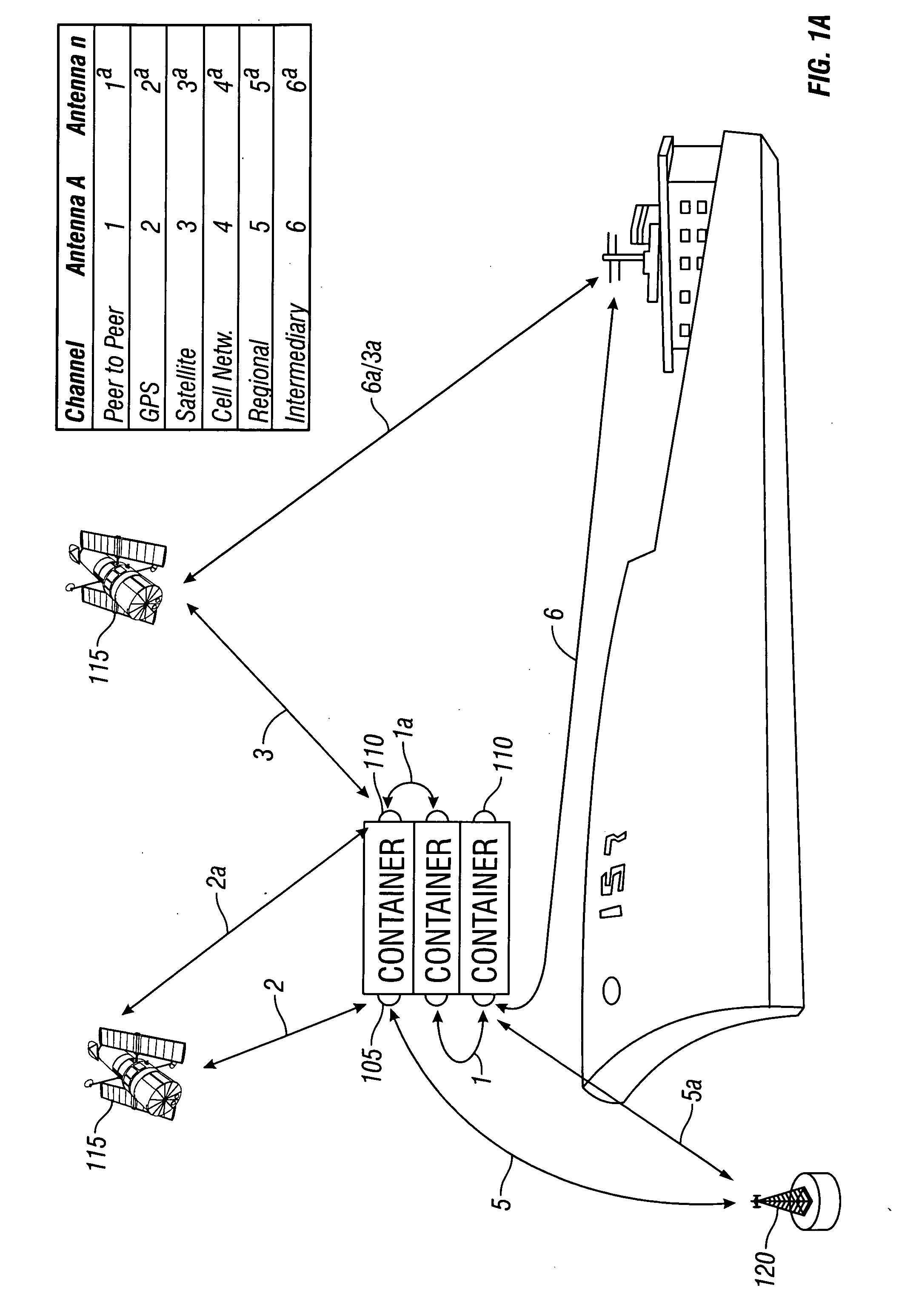
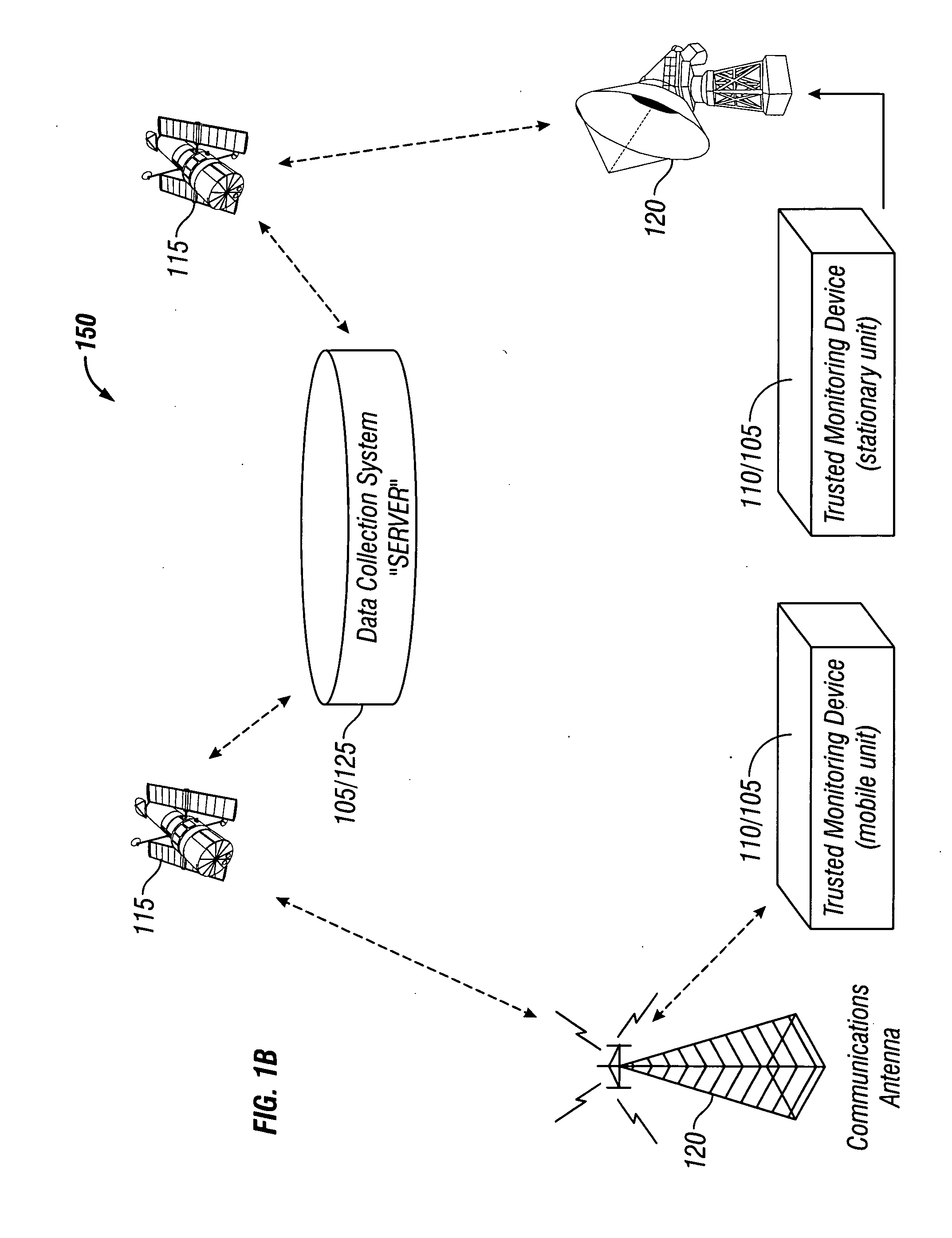
Trusted monitoring system and method
InactiveUS20060291657A1Registering/indicating working of vehiclesDigital data processing detailsMonitoring systemFixed position
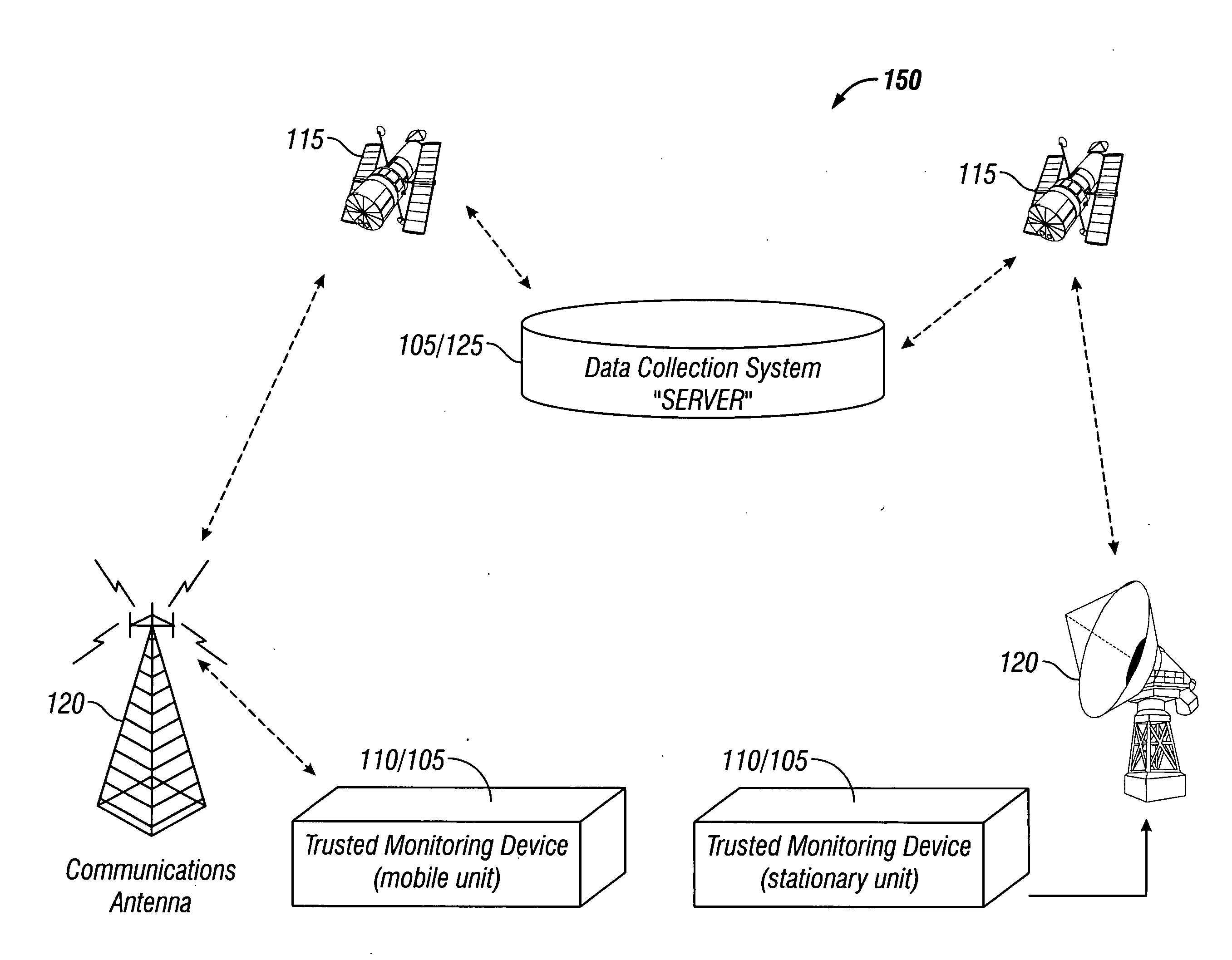
Methods and apparatus for monitoring remotely located objects with a system comprised of at least one master data collection unit, any number of remote sensor units, and a central data collection server are described. The master unit is configured to monitor any object, mobile or stationary, including monitoring multiple remote sensor units associated with the objects being monitored. The master unit may be in a fixed location, or attached to a mobile object. The master unit is configured for monitoring objects that enter and leave the area where it is located. The master unit may act as a parent controller for one or more child devices, wherein the child devices can be remote sensors or monitors of various measurable conditions including environmental conditions, substance identification, product identification and biometric identification. The master unit is able to discover new remote sensor units as they enter or leave the area where the master unit is located. The master unit can be remotely reprogrammed. The reprogramming can be accomplished with authenticated instructions.
Owner:1997 IRREVOCABLE TRUST FOR GREGORY P BENSON
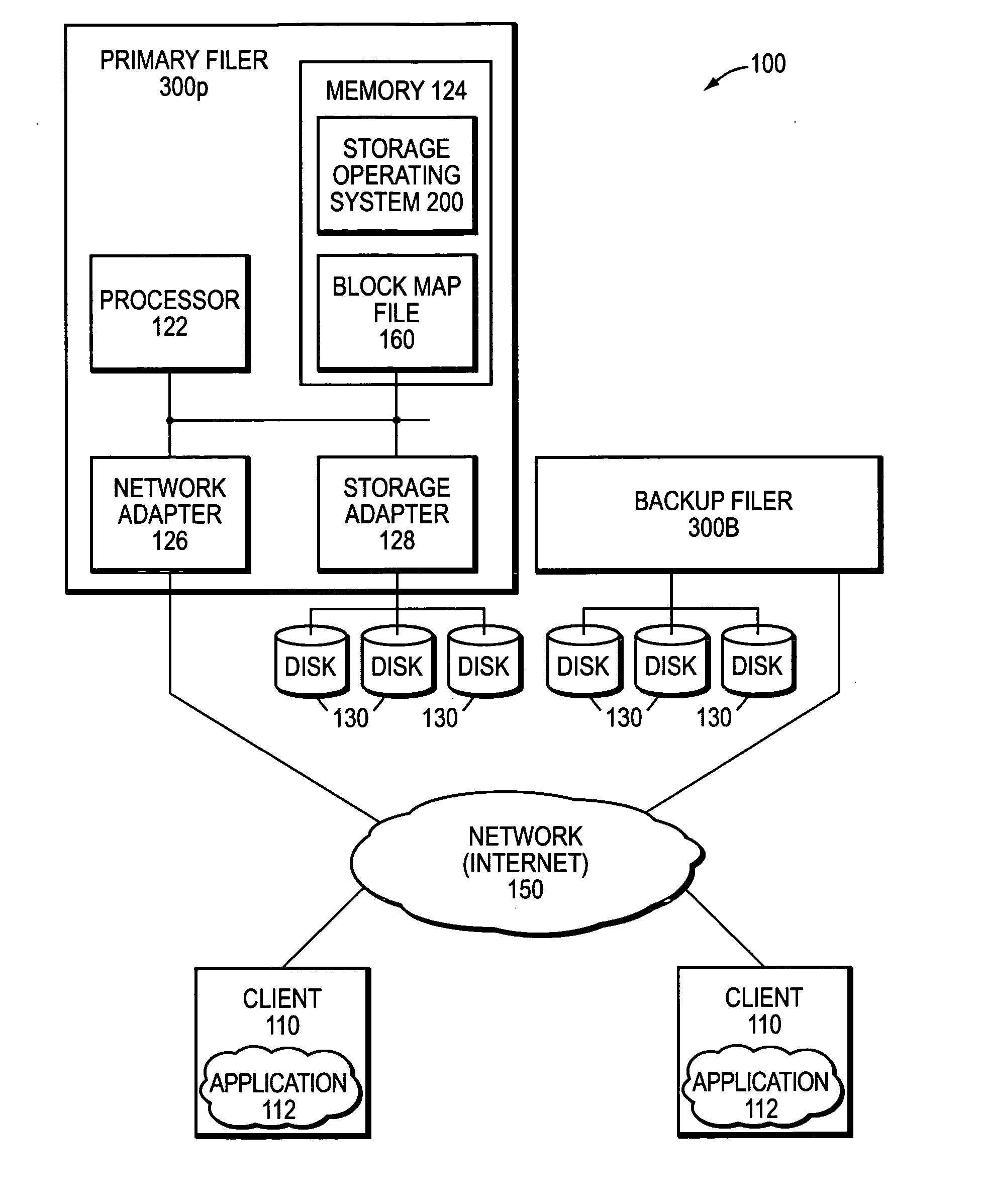
Remote disaster recovery and data migration using virtual appliance migration
InactiveUS20070038887A1Create efficientlyEfficiently servingError detection/correctionData setClient-side
A technique efficiently creates and serves a backup data set on a backup filer located at a remote site from a primary filer by essentially moving an entire operating environment of a primary data set to the backup filer. The primary filer is organized into one or more virtual filers (vfilers), one of which (the primary vfiler) is configured to serve data, such as the primary data set, for a client. In the event that the primary filer or primary vfiler becomes unavailable, the technique may be implemented as a disaster recovery or data migration sequence to enable efficient instantiation of a backup vfiler to serve the backup data set for the client.
Owner:NETWORK APPLIANCE INC
Data image management via emulation of non-volatile storage device
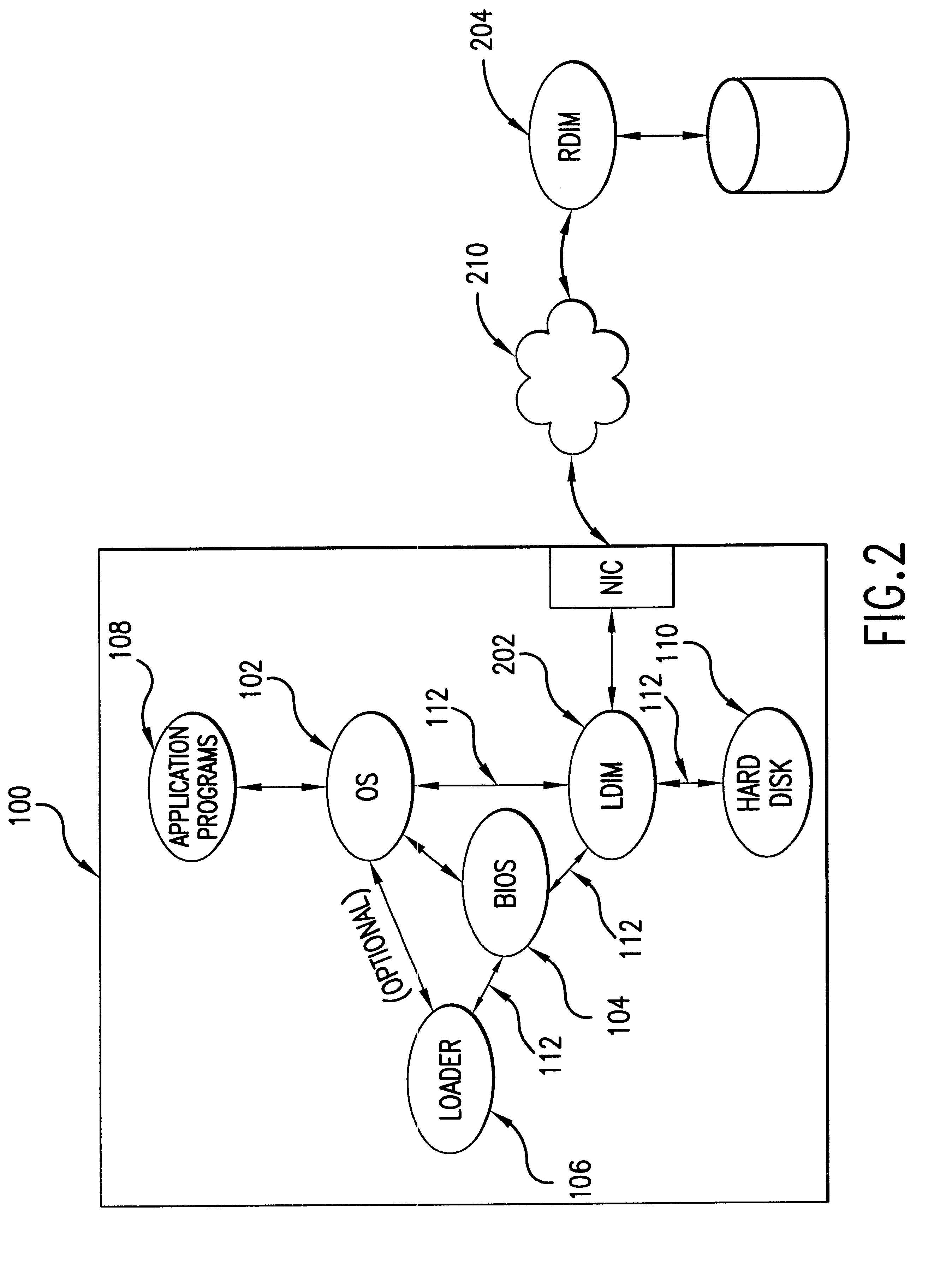
InactiveUS6477624B1Easy to integrateEliminate needDigital computer detailsBootstrappingTelecommunications linkPhoto management
A data image management system (DIMS) that includes a local data image manager (LDIM), a remote data image manager (RDIM), and a remote persistent storage device (RPSD). The LDIM communicates with the RDIM through a direct communication link or through a communication network. The RDIM can store data on and retrieve data from the RPSD. In an environment where an LDIM has been installed in a computer having a "local" persistent storage device (LPSD), the DIMS allows for the storing of the LPSD's data image on the RPSD, with the LPSD serving as a persistent, consistent cache of the data image. The data image stored on the RPSD is referred to as the "master data image" and the data image cached on the LPSD is referred to as the "local data image" or "cached data image." The LDIM functions to intercept read / write requests that are intended to be received by the LPSD. The read / write requests specify an address of the LPSD. Upon intercepting a read request, the LDIM is programmed to determine whether the portion of the cached data image that is stored at the specified address is up-to-date. If it is up-to-date, the LDIM retrieves the requested data from the LPSD and passes the data back to the component or device from which it received the request. If it is not up-to-date, the LDIM transmits the read request to the RDIM. Upon receiving the read request, the RDIM locates and reads the requested data from the master data image stored on the RPSD and then transmits the data back to the LDIM.
Owner:INTELLECTUAL VENTURES II
Methods and systems for monitoring transaction entity versions for policy compliance
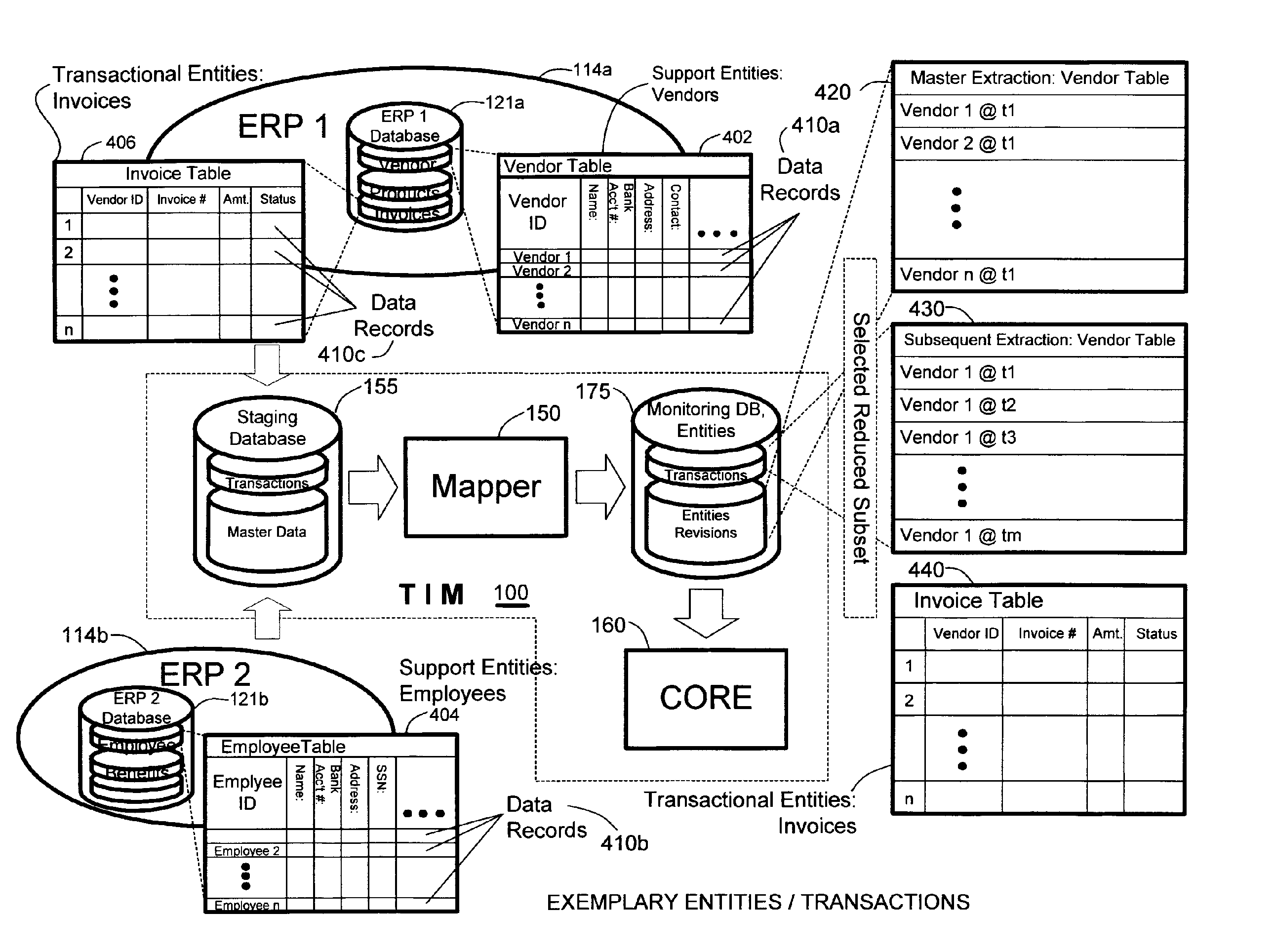
ActiveUS20060212487A1Low costQuality improvementDigital data information retrievalFinanceData ingestionData source
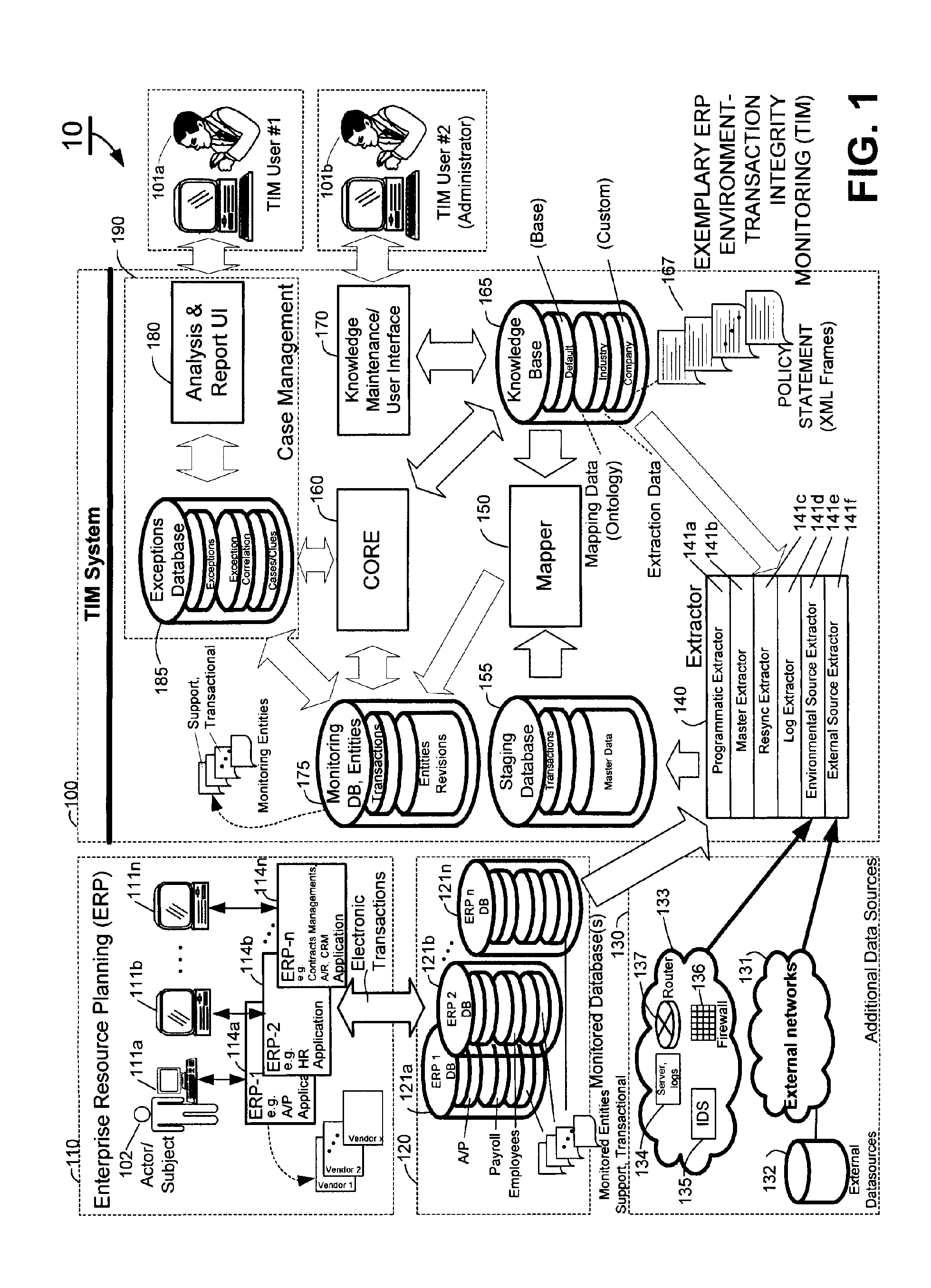
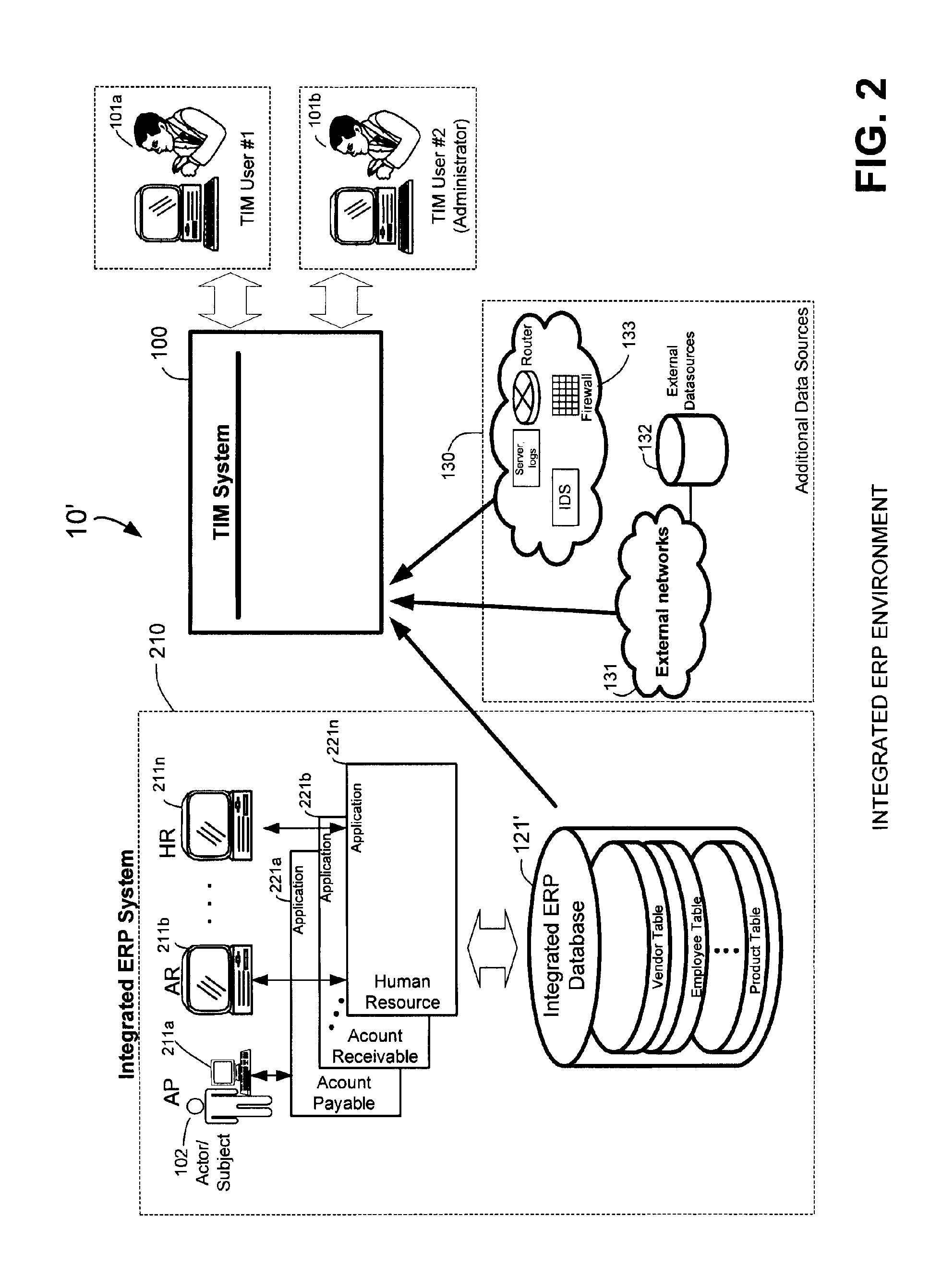
A system for determining lack of compliance of a transactional entity with an enterprise policy by maintaining an historical record of the entity as changes are made over time. The system allows establishment, codification, and maintenance of enterprise policies, monitors electronic transactions of the enterprise from various data sources, detects exceptions to established policies, reports exceptions to authorized users such as managers and auditors, and / or provides a case management system for tracking exceptions and their underlying transactions. A master data extractor establishes an initial instance of a transactional entity in a monitoring database. A changed data extractor is responsive to changed data for establishing a subsequent instance of the transactional entity in the monitoring database. A transaction analysis engine applies predetermined policy rules to data in the monitoring database to determine lack of compliance of the initial and subsequent instances of the transactional entity with enterprise policies.
Owner:OVERSIGHT SYST INC
Method and system for performing periodic replication using a log
ActiveUS7406487B1Reduce data volumeReduce the amount requiredData processing applicationsDatabase distribution/replicationData shippingExecution cycle
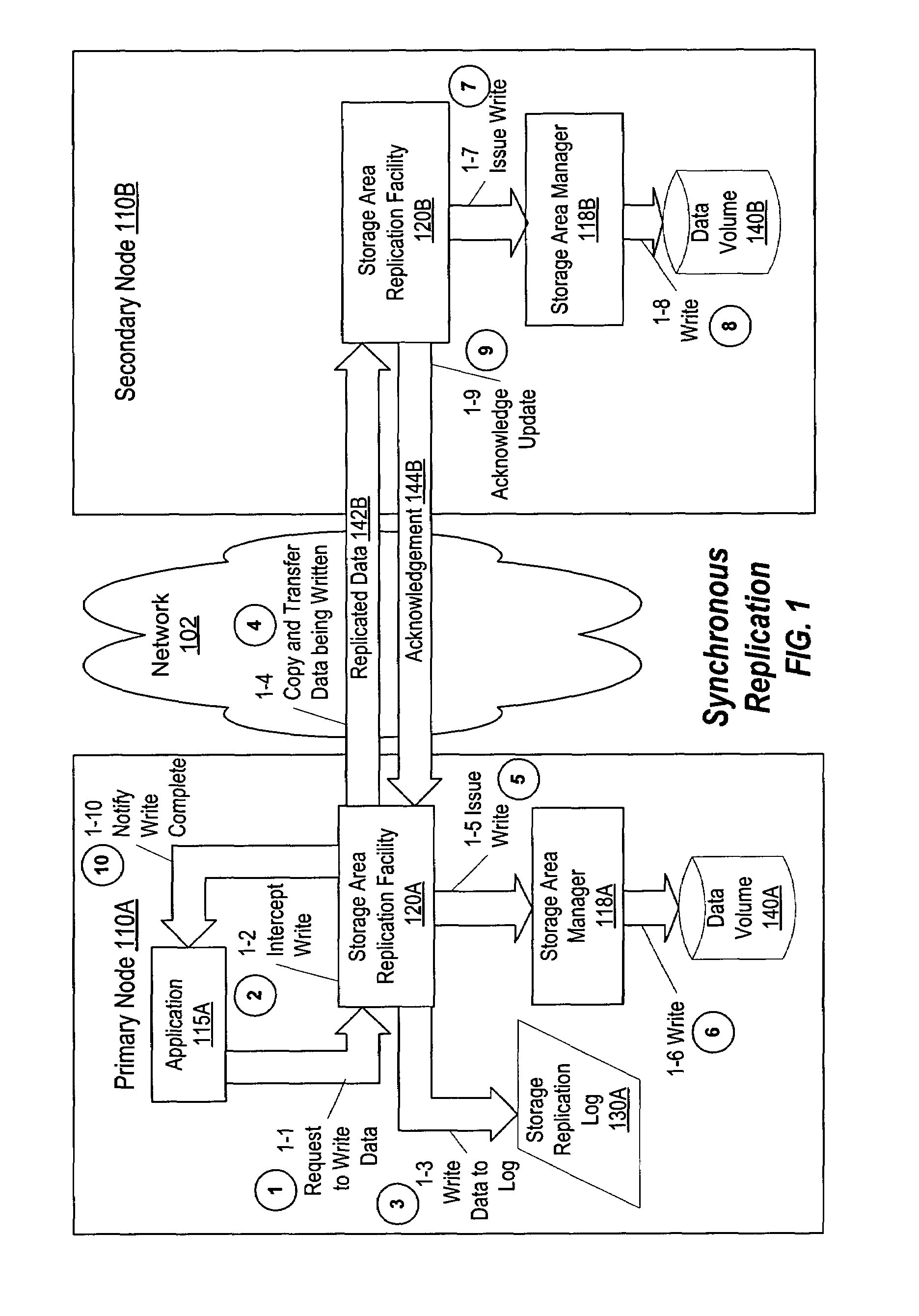
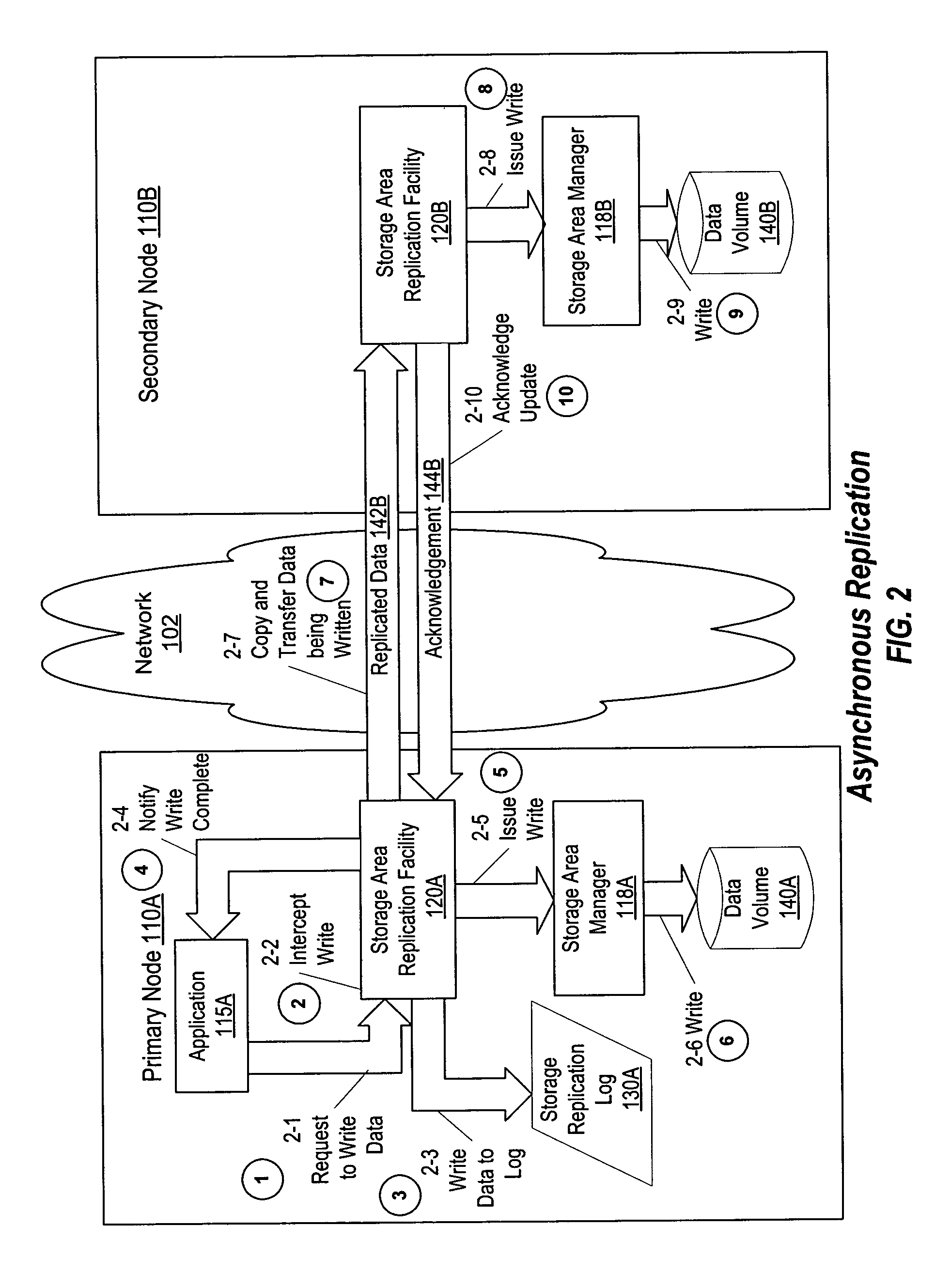
Disclosed is a method and system for performing periodic replication using a write-ordered log. According to one embodiment, a plurality of write operations to a primary data volume are tracked using a write operation log and then data associated with the plurality of write operations is replicated to a secondary data volume by coalescing the plurality of write operations utilizing the write operation log and transferring data associated with the plurality of write operations to the secondary data volume. According to another embodiment the described tracking includes storing metadata associated with the plurality of write operations within the write operation log. In another embodiment, the described coalescing includes identifying a non-overlapping portion of a first write operation and a second write operation of the plurality of write operations utilizing the metadata.
Owner:SYMANTEC OPERATING CORP
Data Synchronization Over a Computer Network
InactiveUS20060080362A1Enhanced disaster recovery optionExtended waiting timeError detection/correctionSpecial data processing applicationsData synchronizationRemote system
A method for copying data and a data storage system including a primary data storage system and a remote data storage system stores data and copies data between the primary and remote systems with enhanced performance. The primary data storage system includes a primary data storage volume, and primary snapshots comprising data stored at the primary volume since a previous primary snapshot. The remote system includes a remote volume comprising a pointer to one or more remote snapshots, the remote snapshots corresponding to the primary snapshots. In the event of a failure at the primary system, the remote volume is made into a new primary volume and data from the remote snapshots is used for read and write operations in place of the primary volume. When the primary volume recovers from the failure, the new primary volume may be resynchronized with the primary volume.
Owner:HEWLETT PACKARD DEV CO LP
Timeshared electronic catalog system and method
InactiveUS20050125310A1Quickly and cheaply and efficiently createWithout overheadImage data processing detailsWebsite content managementData setElectronic catalog
A system and method for providing a timeshared electronic catalog is disclosed. The system comprises an electronic database having a plurality of data records that comprise a master data set. The system comprises at least a first and second subset of the data records, wherein each subset comprises one or more data records selected from the master data set. The system includes a software program comprising a data record masking module for selectively providing a first view for displaying one of the subsets to a first user. Each of the plurality of data records contains a plurality of data elements, or fields, or attributes. The data record masking module is further for selecting which data elements are provided in the view. The system further includes a means for selectively providing which executable features from a plurality of executable features may be provided with each view.
Owner:SAP AG
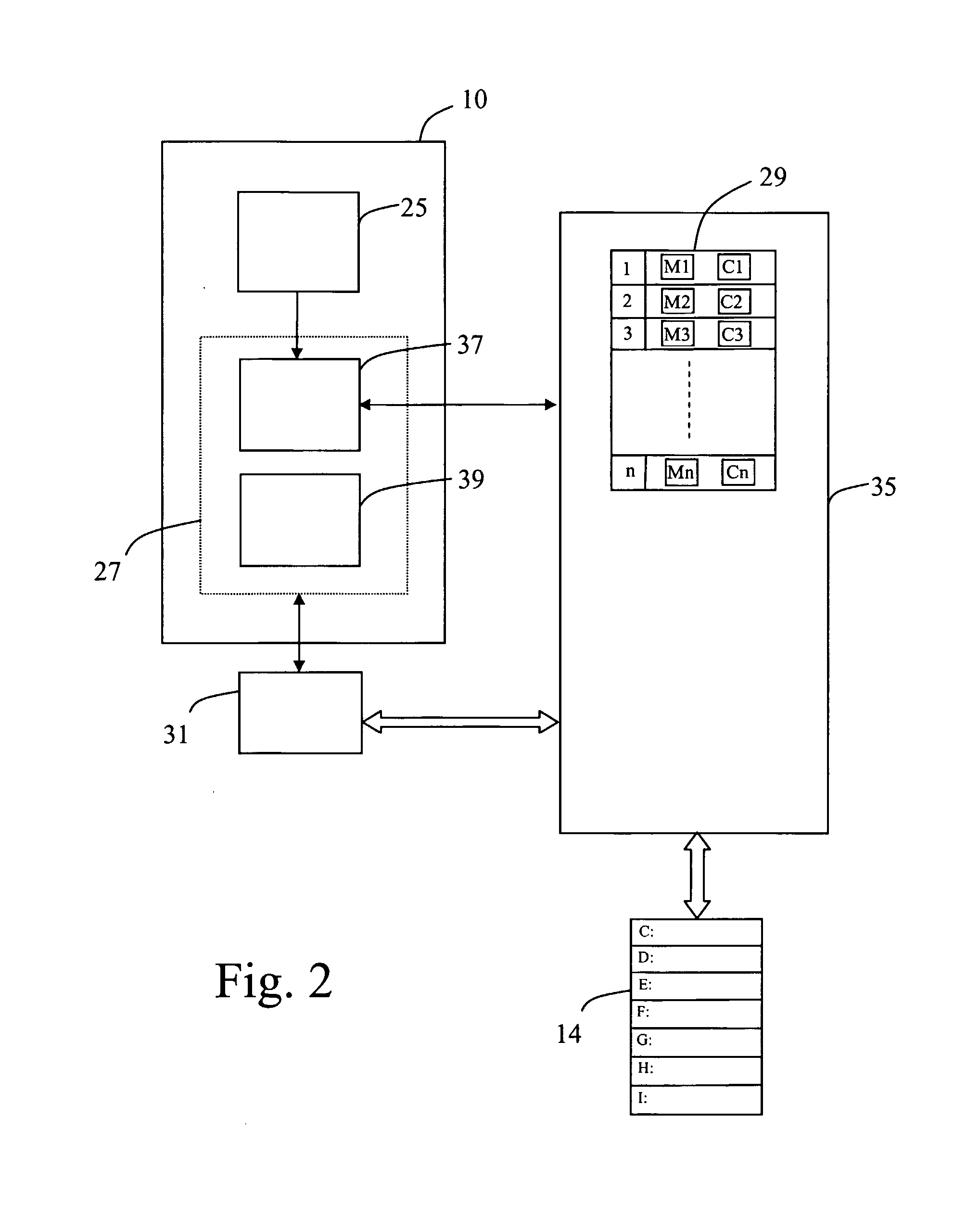
Partition Access Control System And Method For Controlling Partition Access
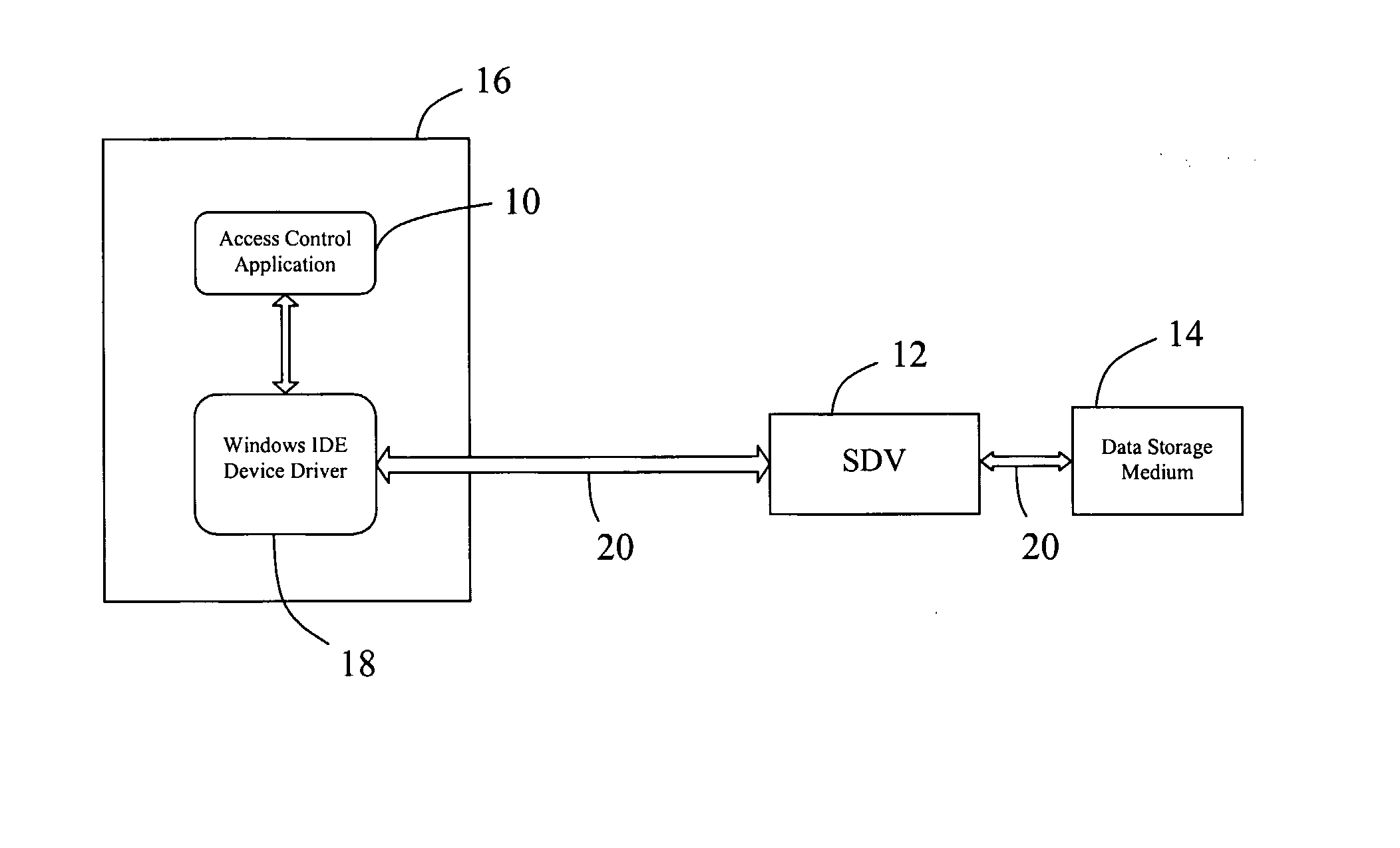
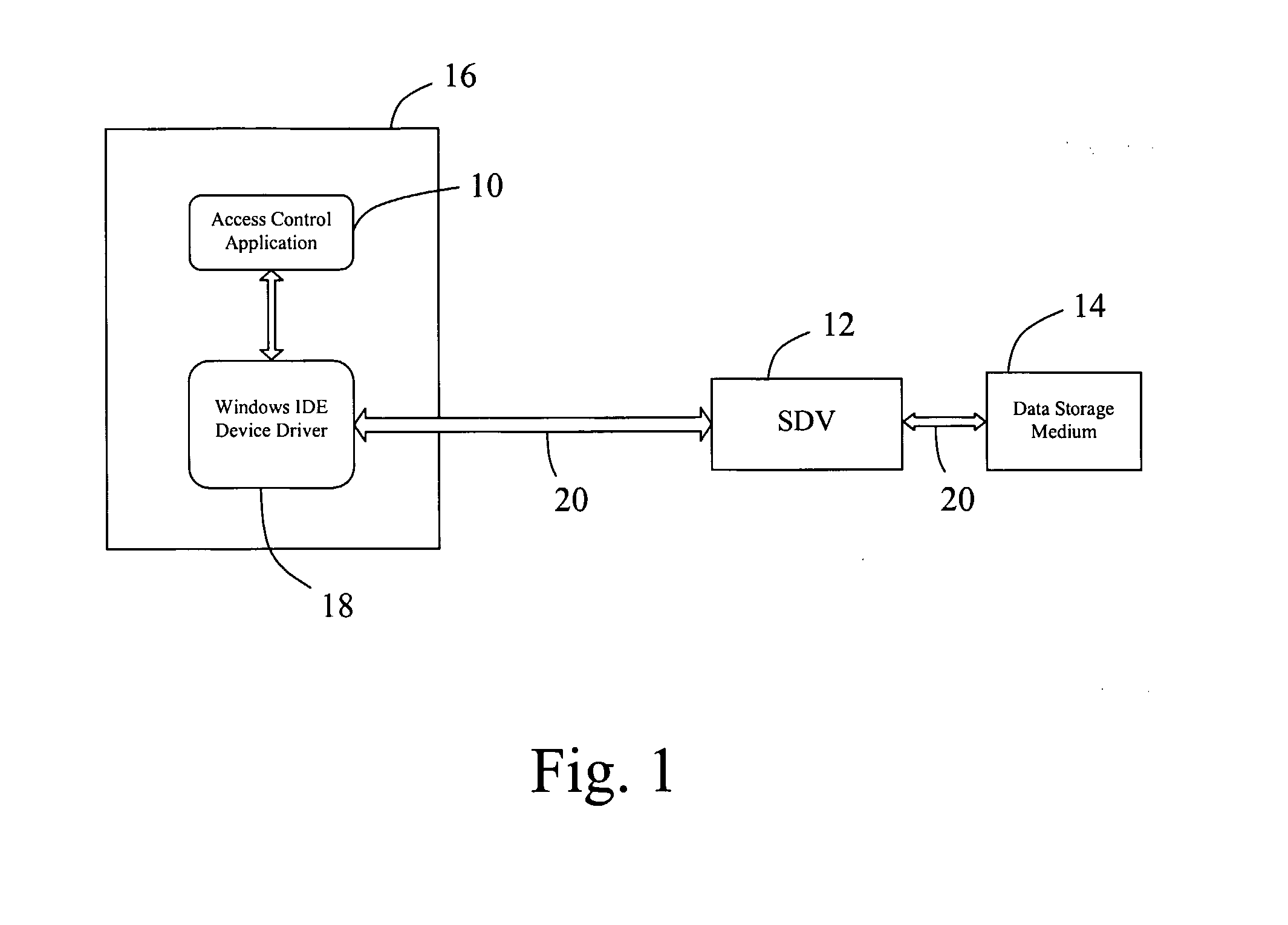
InactiveUS20070300287A1Digital data processing detailsUnauthorized memory use protectionControl systemData access
An access control system (10) is disclosed for controlling access to data stored on at least one data storage medium (14) of a computing system. The access control system (10) comprises authentication means (25) to authenticate users permitted to access data stored in the at least one data storage medium (14) and database means (29) arranged to store data access profiles. Each data access profile is associated with a user permitted to access data stored in the at least one data storage medium (14), each data access profile includes information indicative of the degree of access permitted by a user to data stored in the at least one data storage medium (14), and each data access profile includes a master data access profile (M) and a current data access profile (C). The current data access profile (C) is modifiable within parameters defined by the master data access profile (M).
Owner:SECURE SYST LTD
Autonomous data machines and systems
ActiveUS20170136631A1Reduce negative personalReduce economic impactBatteries circuit arrangementsAutonomous decision making processEngineeringCharging station
A charging system for an autonomous data machine may be provided. The system may comprise: a charging station, wherein the charging station has a low profile allowing the autonomous data machine to drive over to charge a power supply of the autonomous data machine automatically; and one or more processors of the autonomous data machine configured to make charging decisions to effect charging operations of the autonomous data machine that include charging time, charging location, and operations to be performed during charging. In some instances, the charging decision are based on at least one of the following: location of charging station, availability of charging station, mission parameters, locations of other autonomous data machines, and / or charging requirements and / or availability of charging stations
Owner:KNIGHTSCOPE
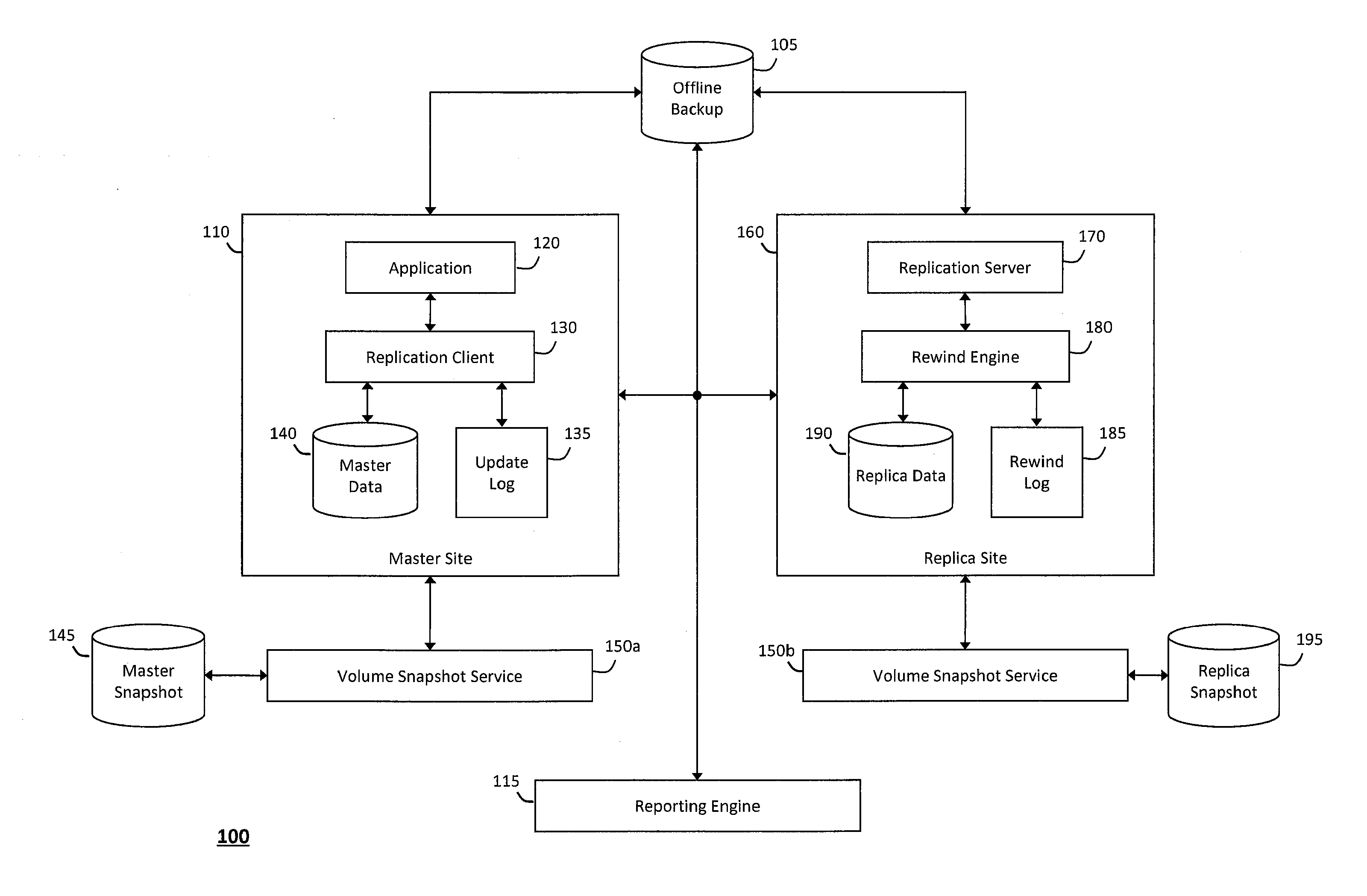
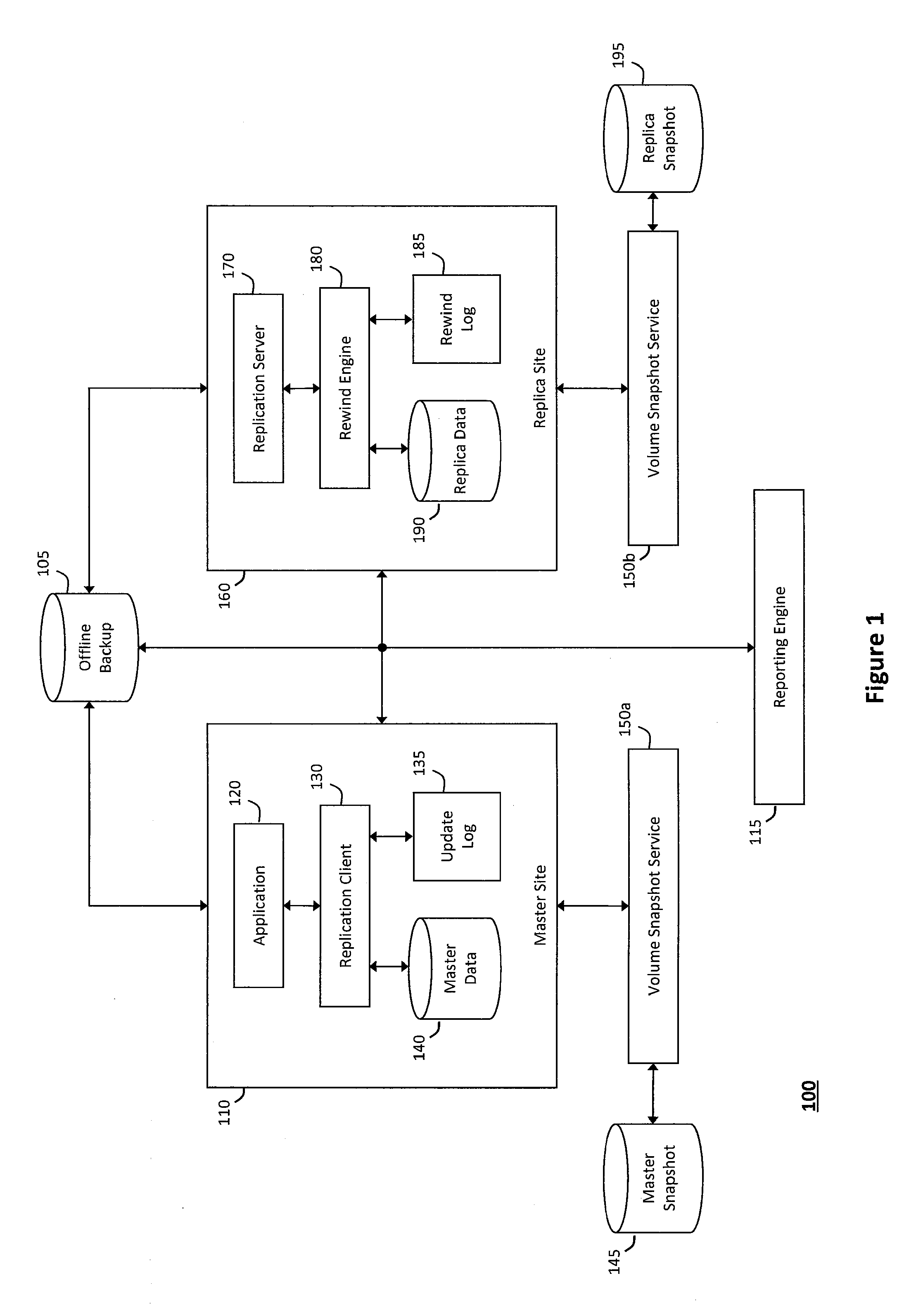
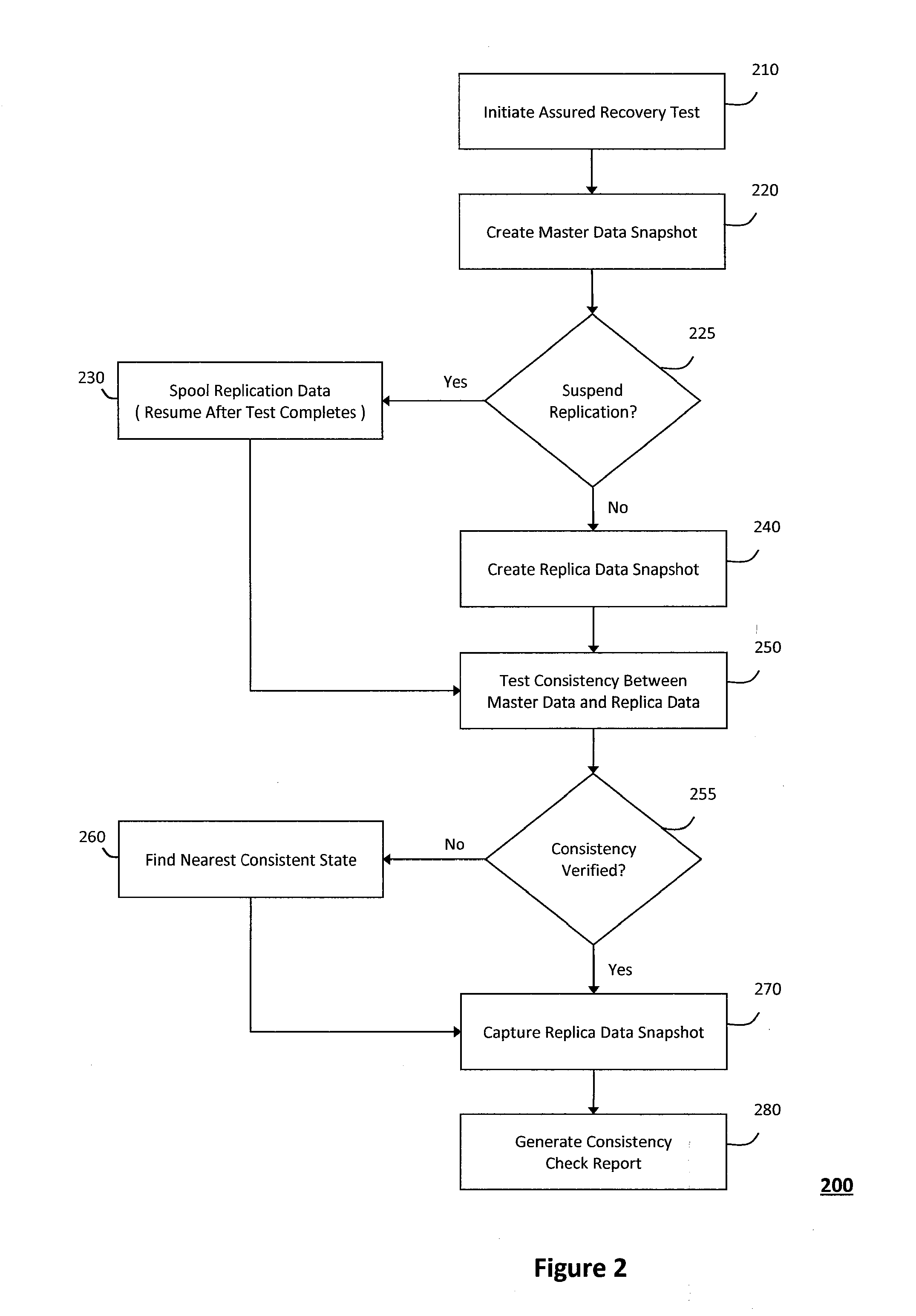
System and method for providing assured recovery and replication
ActiveUS20120233123A1Reliably utilizedDigital data processing detailsError avoidanceData sourceApplication software
The system and method for providing assured recovery and replication described herein may recover a master data source from a replica data source without impacting the master data source or the replica data source, and without having to install a standby version of an application associated with the master data source. In particular, a master snapshot may be created to copy application data stored in the master data source, wherein a replication server confirms that the replica data source can recover the master data source if the master snapshot and the replica data source are consistent. The replication server may create a replica snapshot to copy the replica data source and assign an identity associated with the master data source to the replica data source to recover the master data source. As such, replication may be resumed on a virtual machine disk file associated with the replica snapshot.
Owner:CA TECH INC
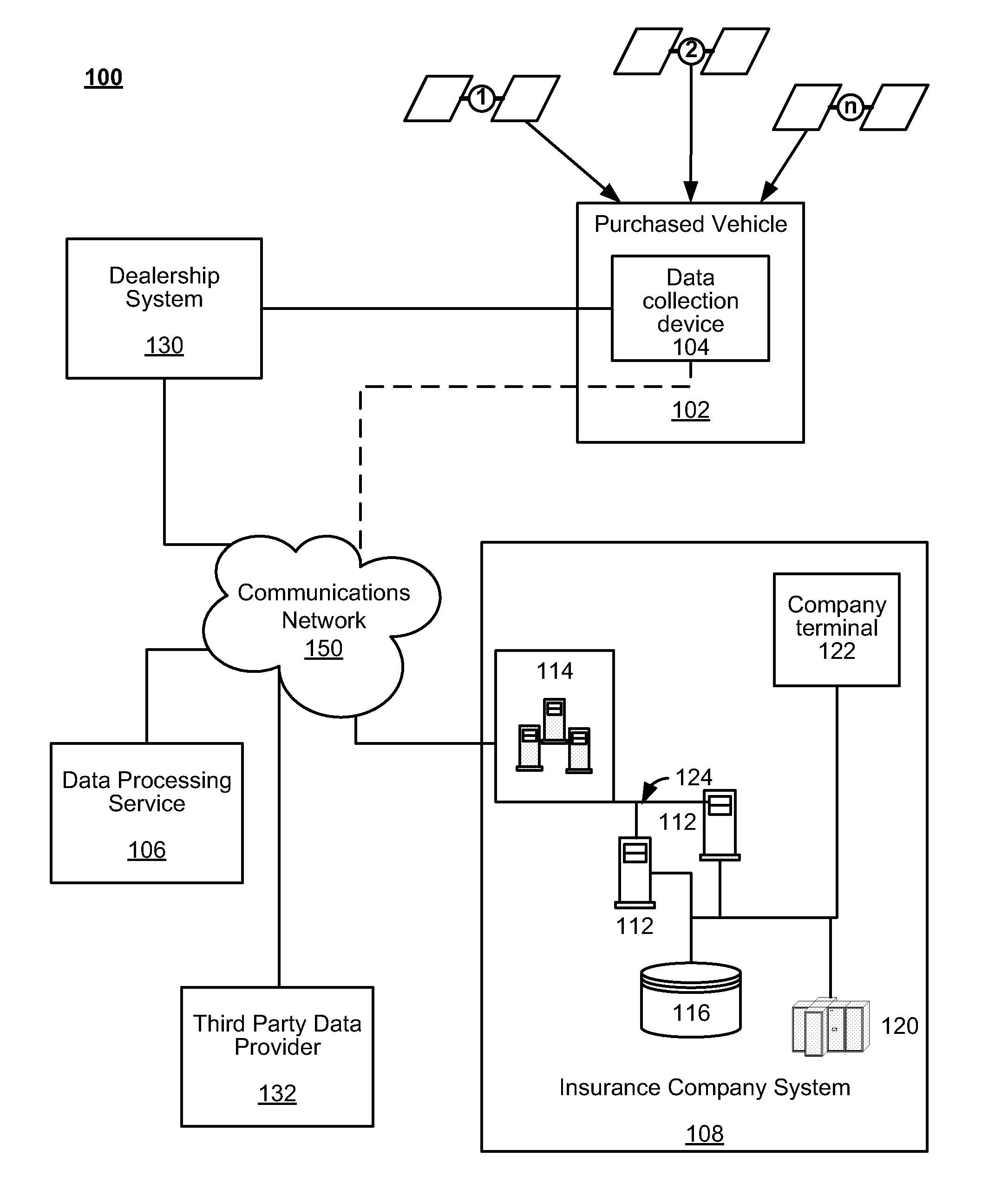
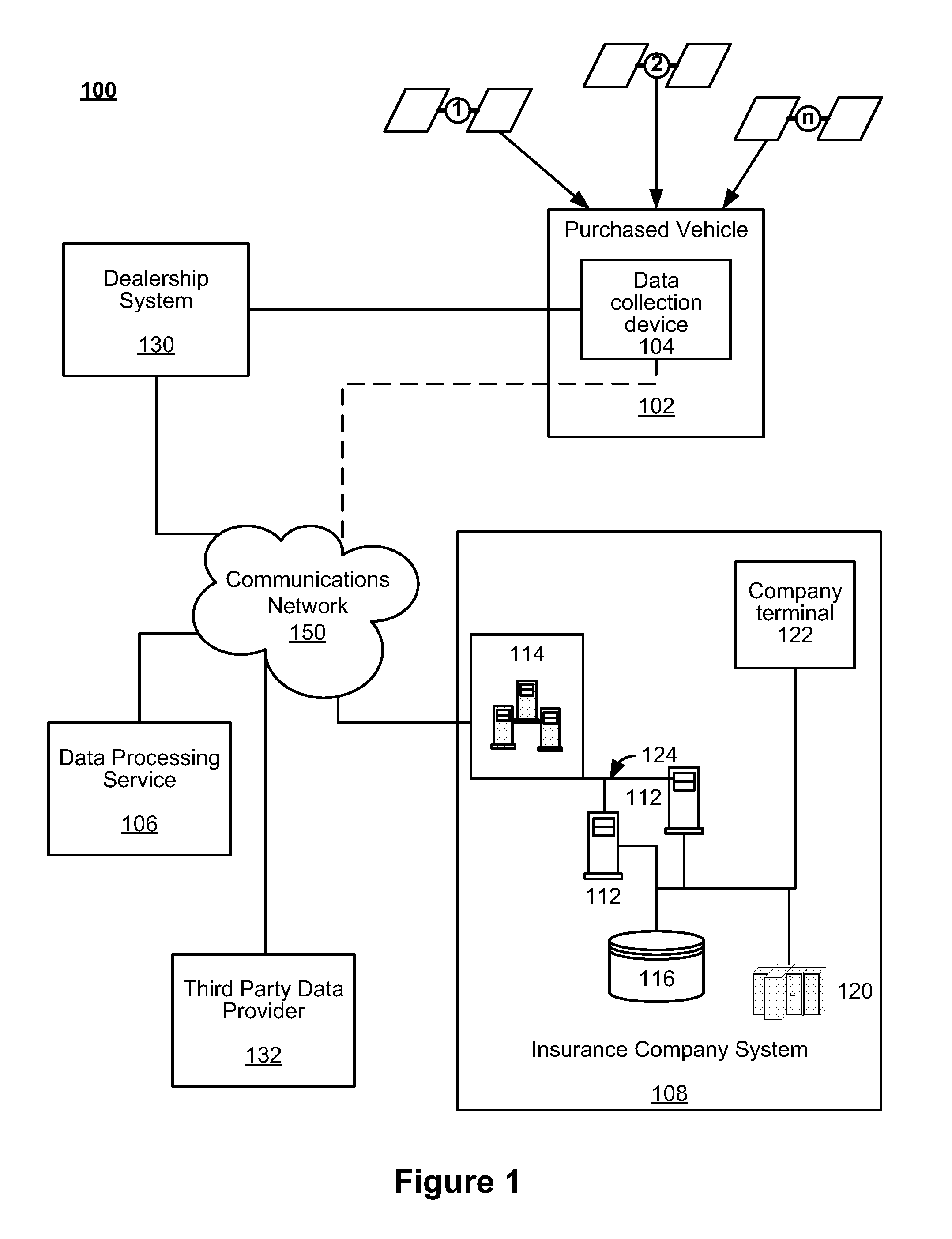
System and method for administering a telematics-enabled test drive dealer program
ActiveUS20130138460A1Strengthen incentivesFinanceBuying/selling/leasing transactionsCommunication interfaceData acquisition
Systems and methods are disclosed herein for pricing an insurance premium based on telematics data. The system includes a communications interface and a business logic processor in communications with the communications interface. The communications interface receives telematics data collected by a telematics acquisition device configured at a dealership for collecting telematics data of a vehicle sold by the dealership. The communications interface also receives vehicle data indicating the make and model of the vehicle sold and vehicle owner data related to the purchaser of the vehicle sold. The business logic processor determines an insurance quote for the purchaser based on the received telematics data, vehicle data, and vehicle owner data. The communications interface transmits the insurance quote for the purchaser of the vehicle. The business logic processor also manages a predetermined incentive that is provided to the purchaser in return for allowing the telematics data acquisition device to collect telematics data.
Owner:HARTFORD FIRE INSURANCE
Waking a main computer system to pre-fetch data for an auxiliary computing device
ActiveUS20060129855A1Reduce consumptionData efficientVolume/mass flow measurementPower supply for data processingRights managementData channel
An auxiliary computing device wakes an associated main computer system to obtain data as needed, on-demand and / or in anticipation of demand. The wakeup operation is ordinarily temporary to fetch data, whereby only a small amount of power is consumed by the main computer system. In one implementation, a control channel between the auxiliary device and the main computer system is used to signal a wakeup. A main data channel is used to obtain the data, whereby the auxiliary device has access to a larger amount of data than it can cache. Moreover, the components of the main computer system may be leveraged, such as to use the main computer system's digital rights management mechanisms. Additional data may be intelligently requested by the auxiliary device while the main computer system is powered up, e.g., to buffer media, and / or request a synchronization of calendar data, email data, and so forth.
Owner:MICROSOFT TECH LICENSING LLC
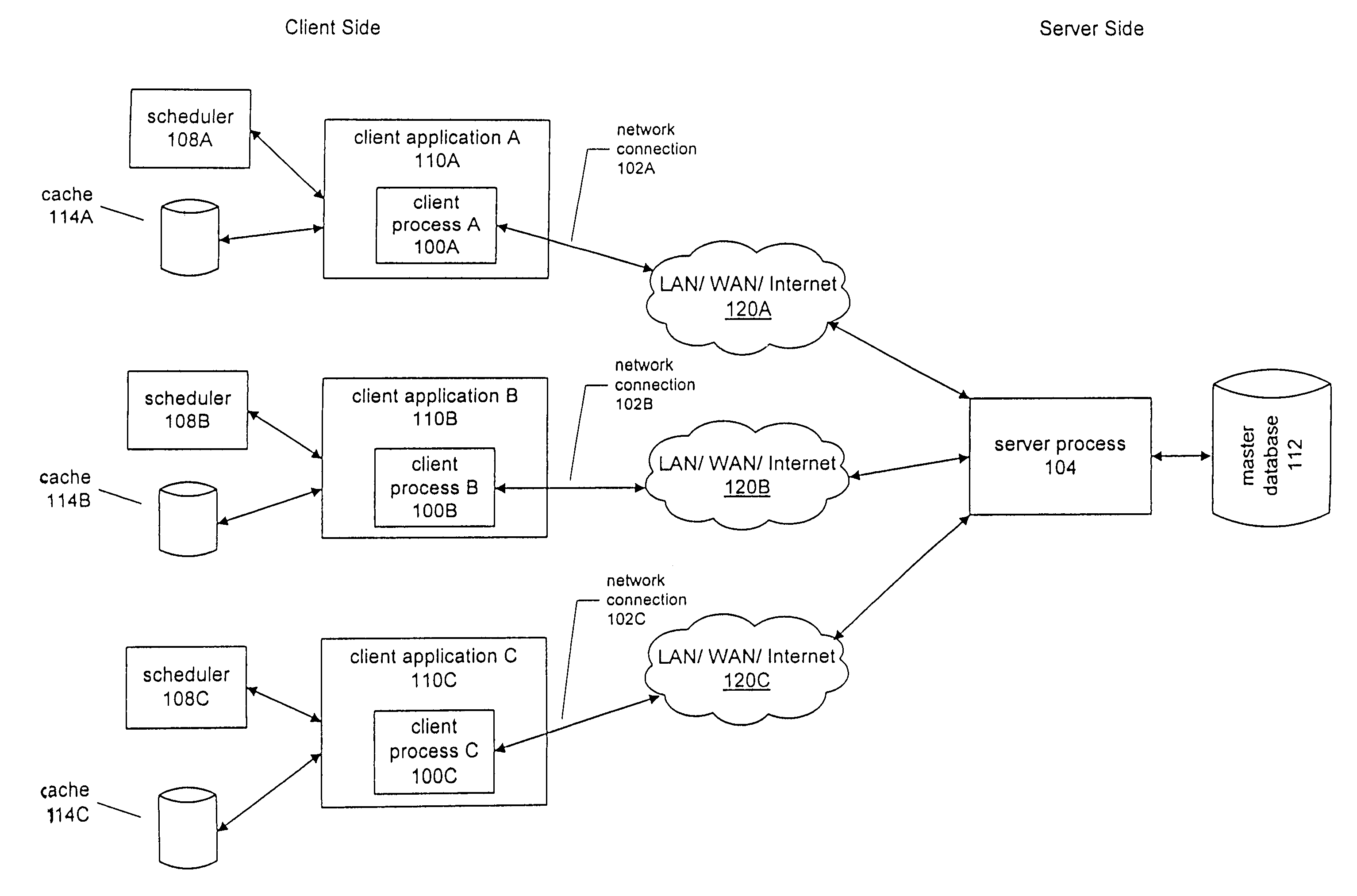
System and method for enabling a client application to operate offline from a server
ActiveUS7305475B2Multiprogramming arrangementsMultiple digital computer combinationsRecovery methodNetwork connection
One disadvantage of the client / server computing model is the client's strong dependence on the server. A system and method are disclosed for enabling a client application to operate offline from the server. For each request, the client application registers a request entry with a scheduler, informing the scheduler of an associated application callback. The scheduler then invokes this application callback when a network connection is available for use, and the client application then sends the request to the server. Error recovery methods are described for requests that are sent to the server but for which no reply is received, and for other error scenarios. Some applications may maintain client-side caches to lookup information independently of the server. Synchronization entries may be registered with the scheduler for keeping the client-side cache in sync with the server-side master data.
Owner:WEBMD HEALTH
Fixed network for an automatic utility meter reading system
ActiveUS20090102681A1Improve signal qualityElectric signal transmission systemsBroadcast information characterisationSignal qualityData collector
A fixed network for automatically reading a utility meter system has been developed. The network includes multiple meter interface units (MIUs) that each collect data from a designated utility meter. The collected data is transmitted to a primary data collector. The network includes multiple data collectors and each MIU identifies its own primary data collector based on signal quality between the collector and the MIU. The network includes a central host computer that is used to receive the collected data from the primary data collectors.
Owner:NEPTUNE TECH GROUP
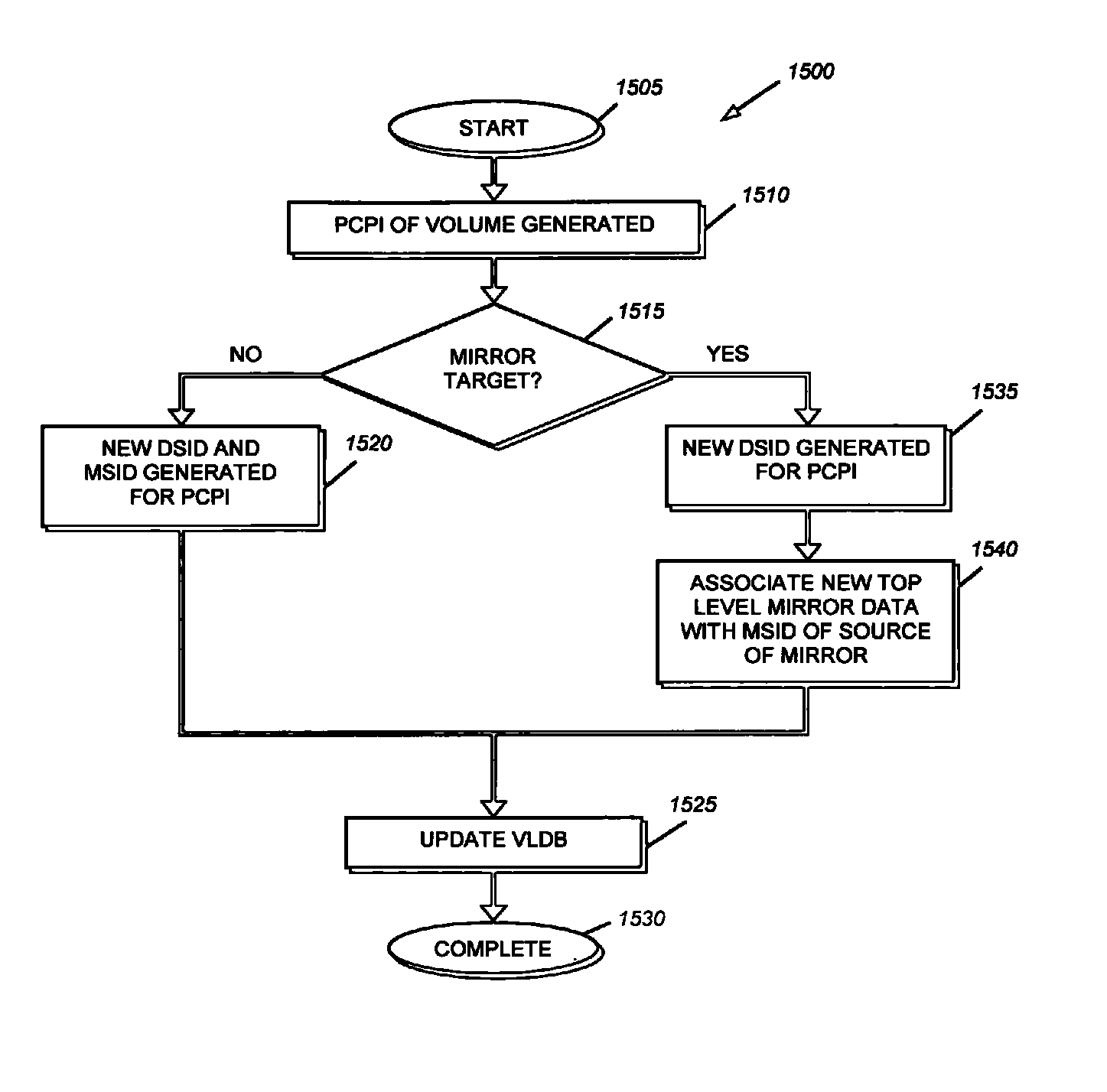
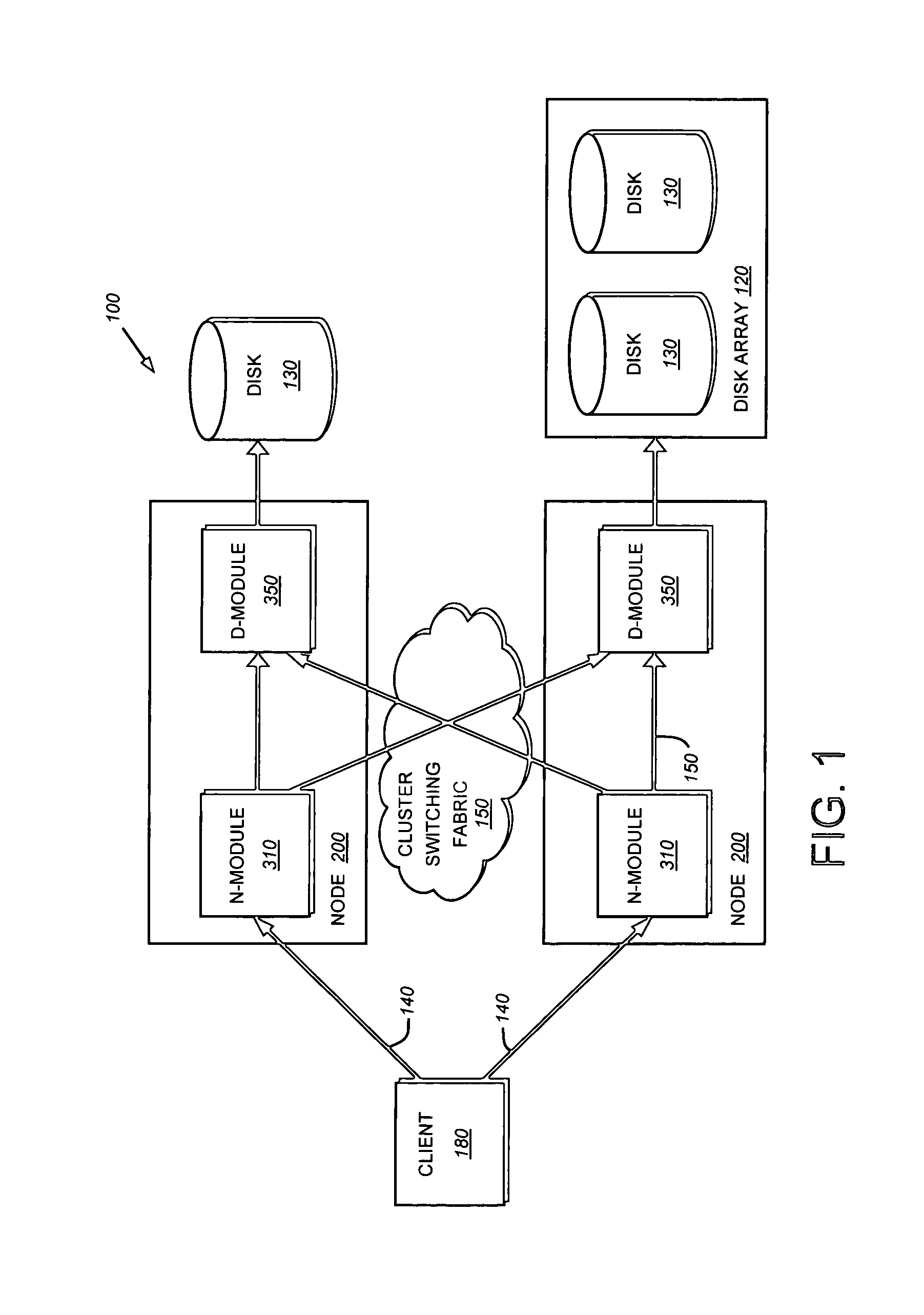
System and method for addressing data containers using data set identifiers
ActiveUS8489811B1Digital data information retrievalSpecial data processing applicationsData setData access
A system and method addresses data containers in a clustered storage system. Each instantiation of a volume, or other container set, is associated with a data set identifier (DSID). All instantiations of data that represent a single point in time are associated with a master data set identifier (MSID). A volume location database (VLDB), utilizing a replicated database among the nodes of the cluster, stores a data set data structure containing appropriate mapping information between the MSIDs and DSIDs. Clients of the clustered storage system utilize MSIDs to reference data that is desired to be accessed. When a storage system receives a data access request containing a MSID, the storage system accesses the VLDB to identify an appropriate DSID to which to forward the request. The data access request is then forwarded to the appropriate storage system for processing.
Owner:NETWORK APPLIANCE INC
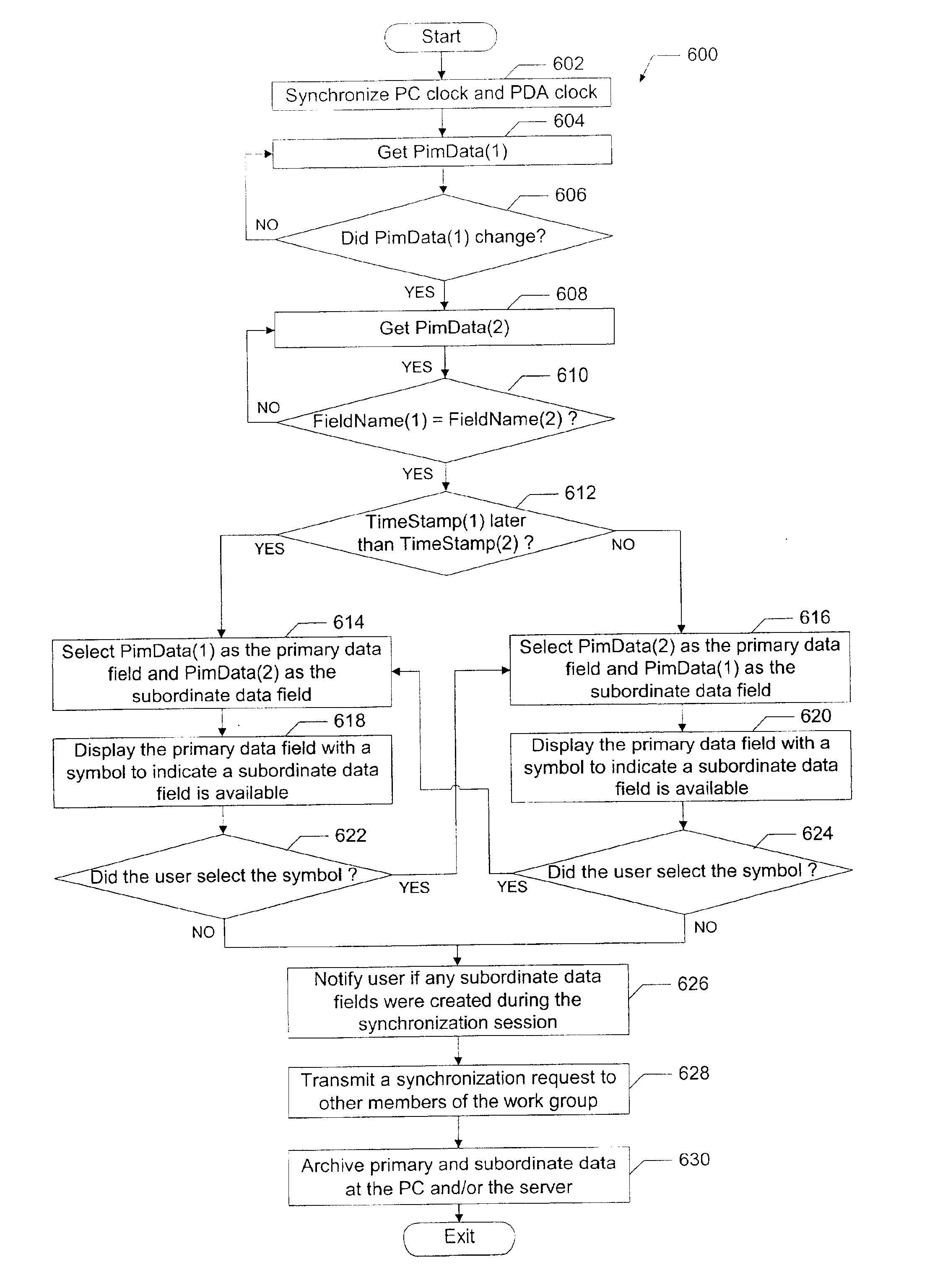
Method and apparatus for displaying personal digital assistant synchronization data using primary and subordinate data fields
InactiveUS6879996B1Multiple digital computer combinationsElectric digital data processingData displayData field
The method and apparatus described herein provides a system for displaying personal information management (PIM) data on a personal digital assistant (PDA). The PIM data may be shared by multiple users and modified at the PDA displaying the data, at another PDA, and / or at a personal computer. When the same data field is changed by more than one device, the system displays the most recent version of the data as the primary data field with a symbol to indicate a subordinate data field is available in memory. By selecting the symbol, the user may swap the primary and subordinate data fields.
Owner:PINEAPPLE34 LLC
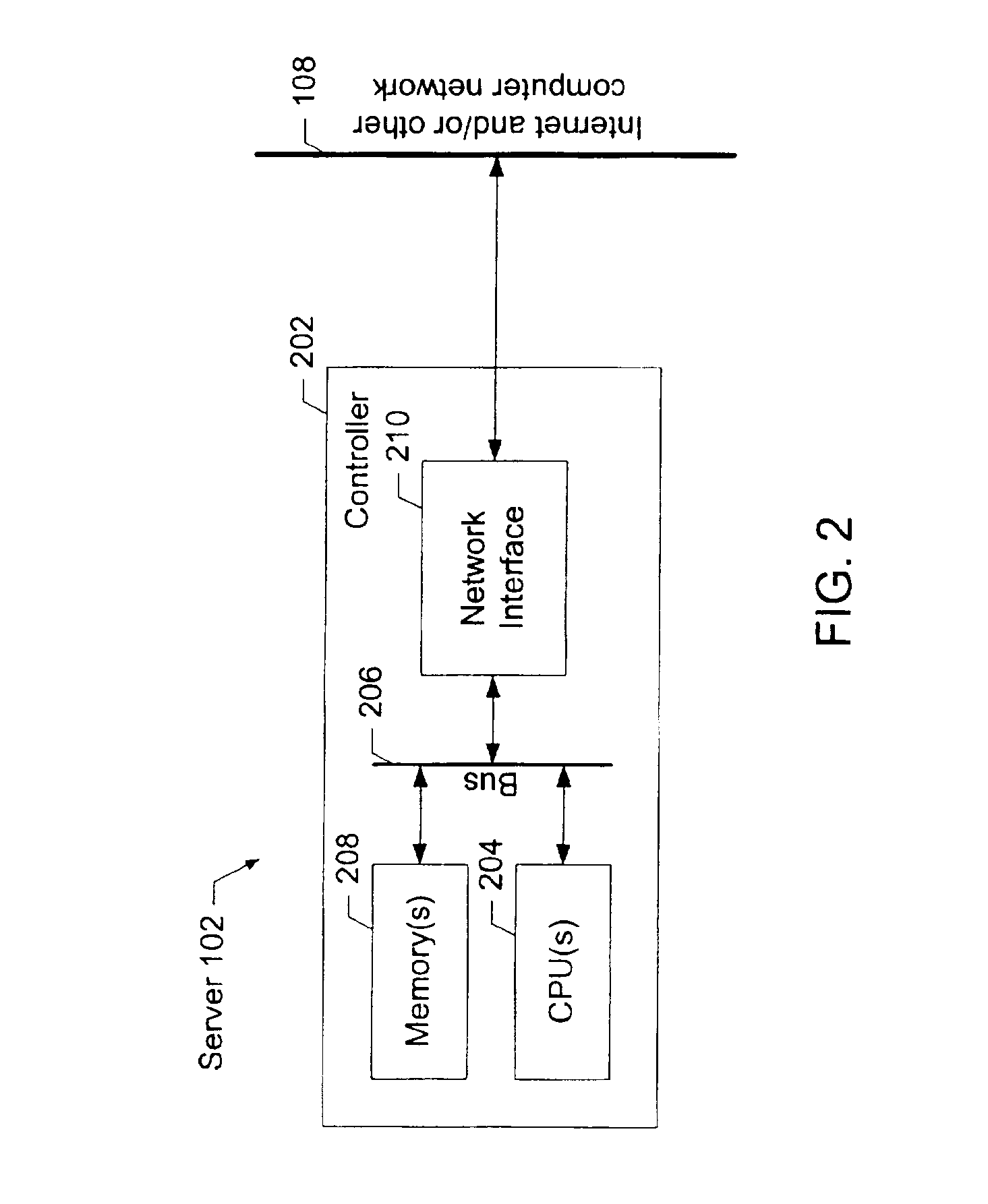
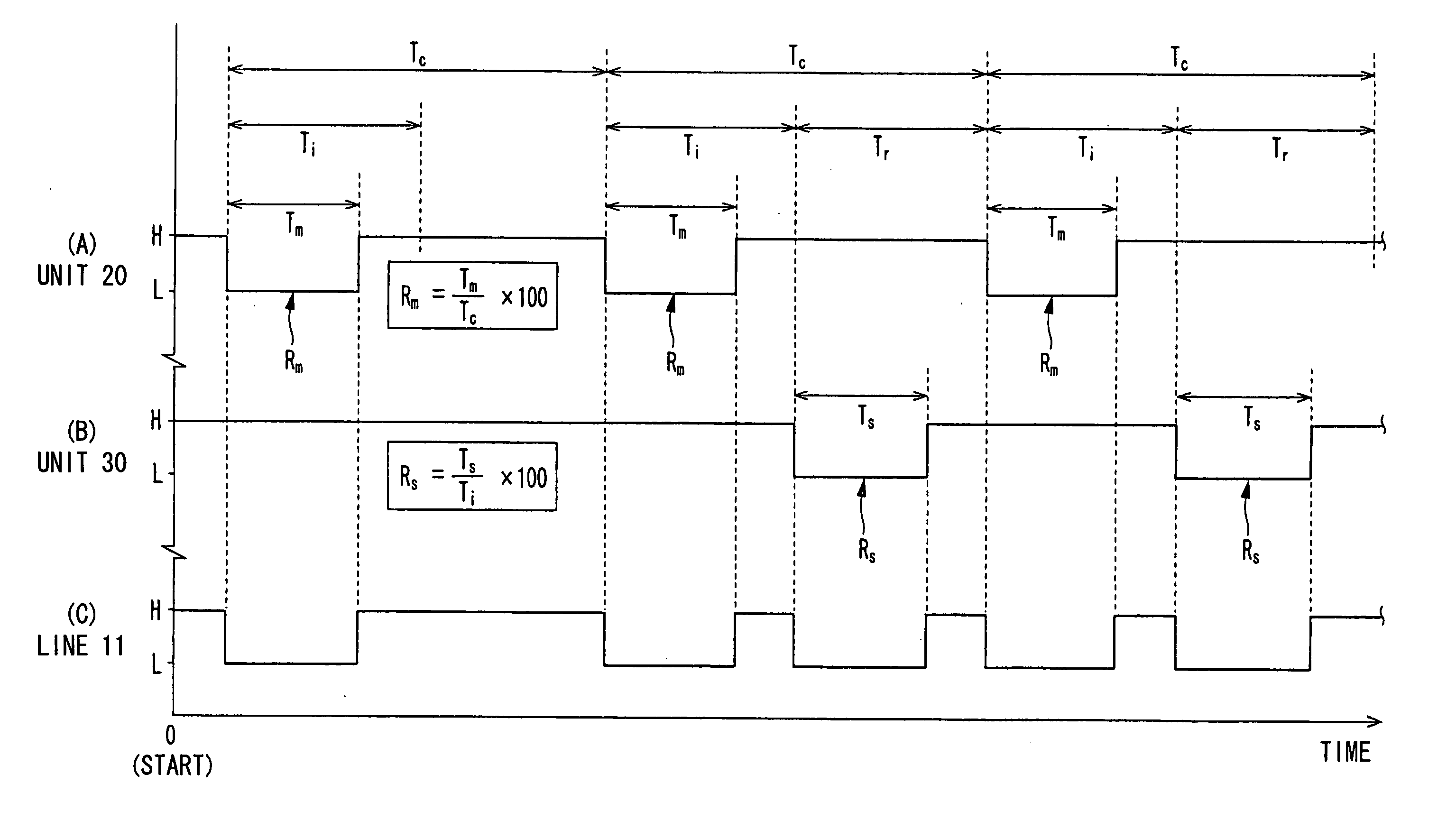
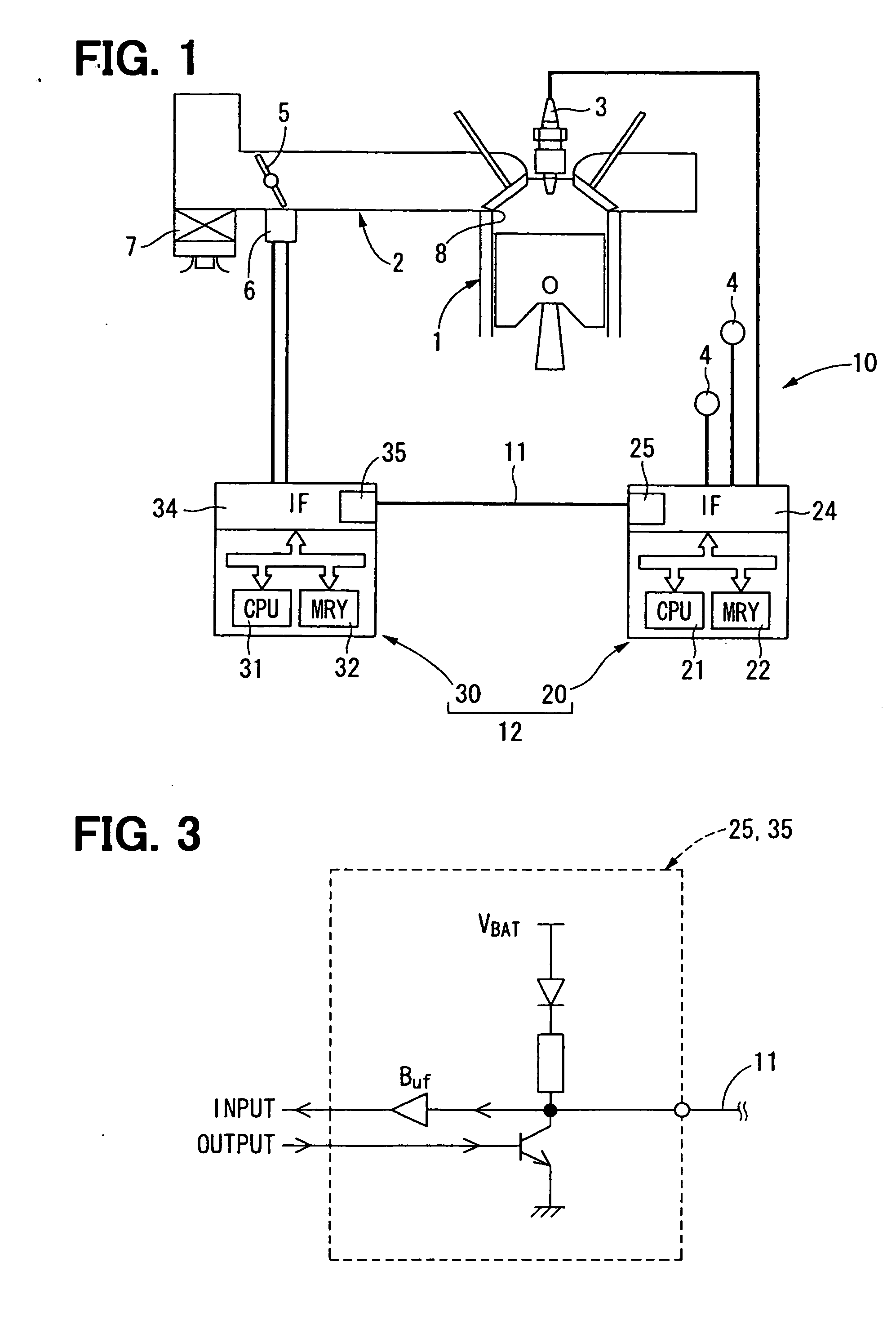
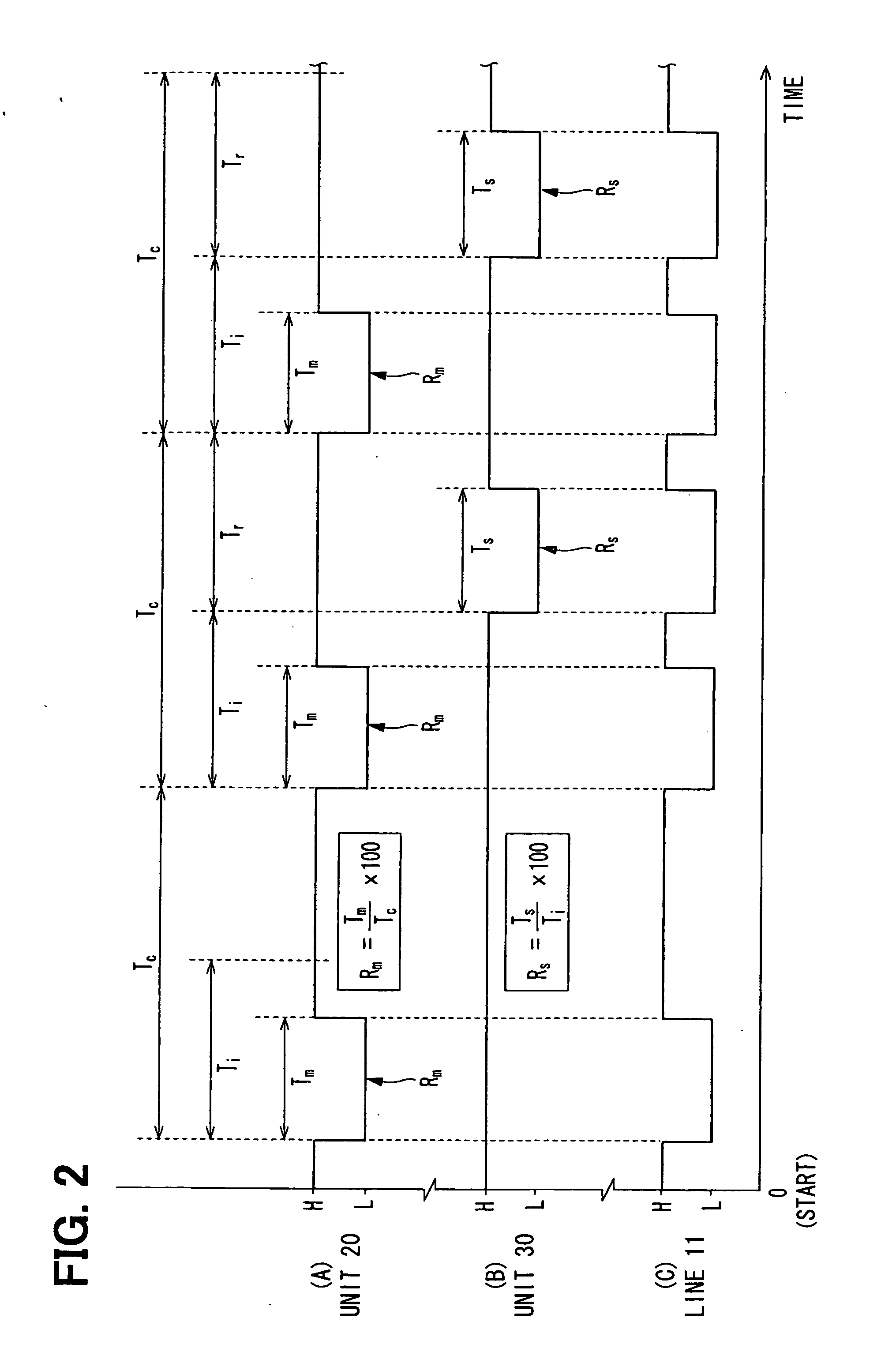
Communication system and method, and distributed control system and method
InactiveUS20070088883A1Low costAccurate communicationSuspensionsElectrical controlCommunications systemTime segment
A communication system performs bidirectional communication through a same communication path every communication cycle period between a master station and a slave station. From the start of the communication cycle period until an interval period shorter than the communication cycle period elapses, the master station transmits master data represented at a first ratio of first pulse width to the communication cycle period to the slave station. In a remaining period after the interval period in the communication cycle period, the slave station transmits slave data represented at a second ratio of second pulse width to the interval period to the master station.
Owner:DENSO CORP
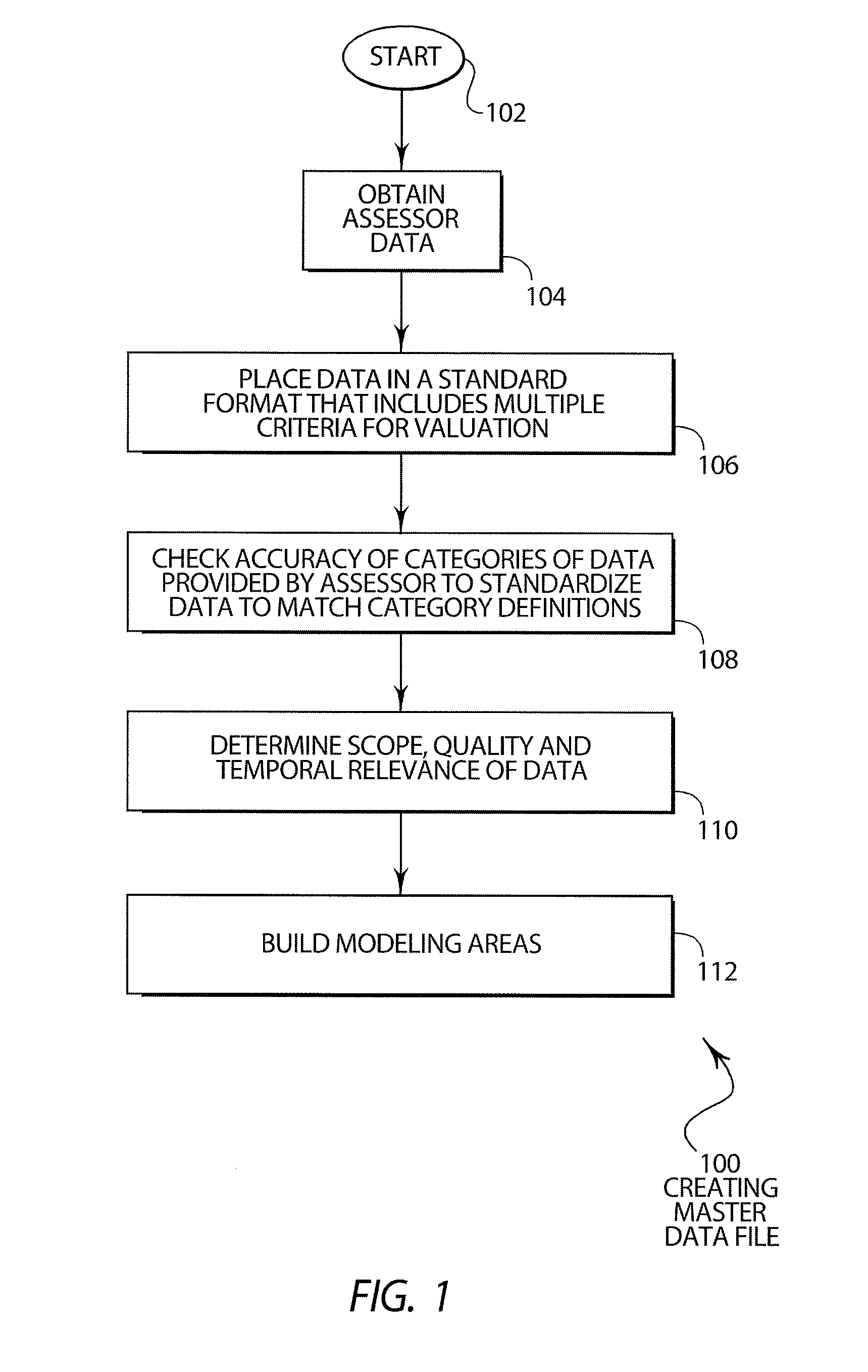
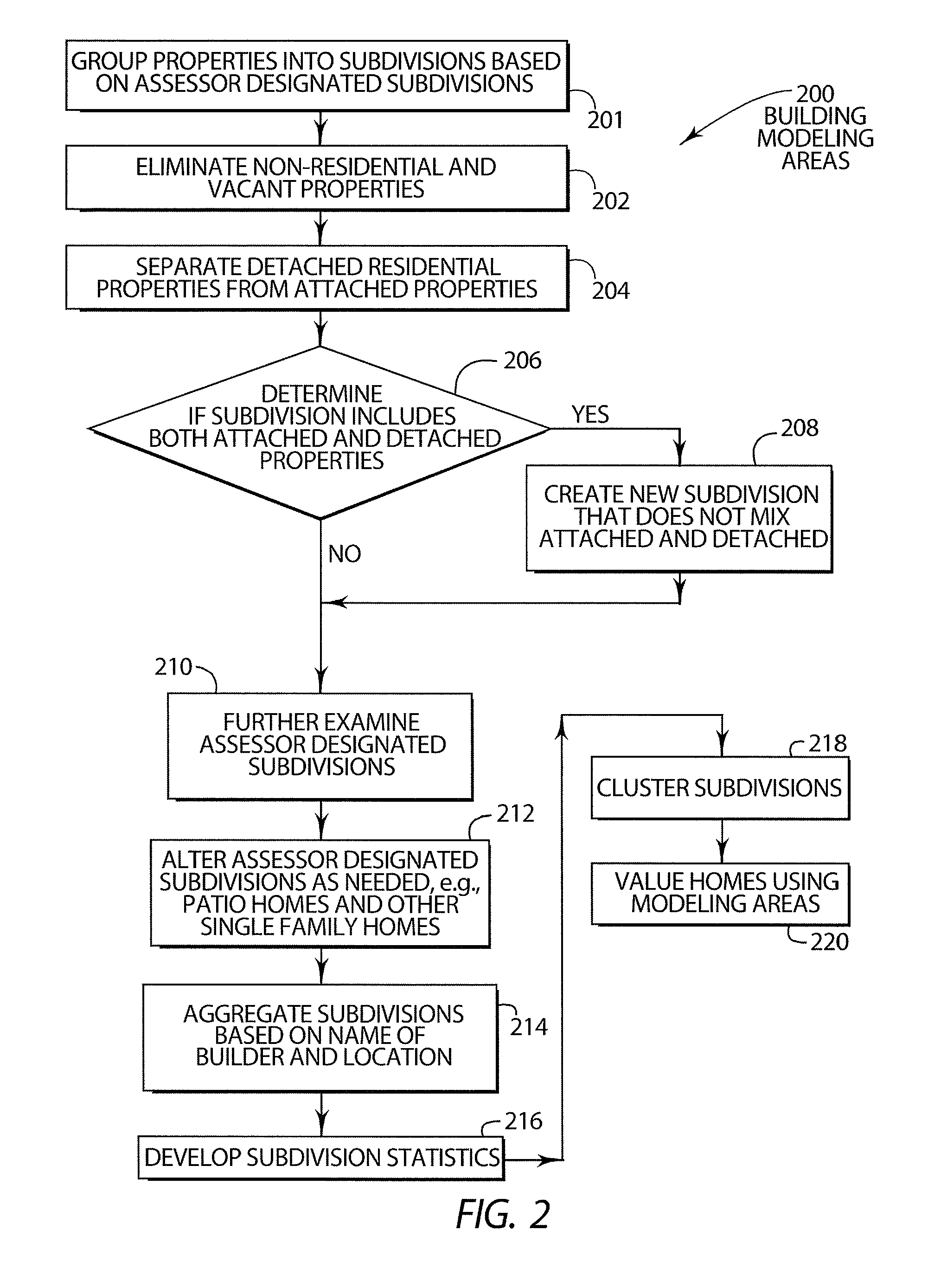
Automated valuation of a plurality of properties
Disclosed are various embodiments of a system and method for valuing a plurality of properties. Assessor data is obtained that indicates a designated subdivision and various criteria for each of the properties. Assessor data is placed into a standard format to create a master data file. Modeling techniques are then used to separate and aggregate properties into modeling areas. Modeling areas are then used to calculate a predicted value for the properties. The predicted values are compared with actual sales values to create sales ratio data. If the deviation of the sales ratio data exceeds a certain amount, the master data file data is analyzed and modified until sales ratio data is achieved that falls within an acceptable deviation.
Owner:VALUESCAPE
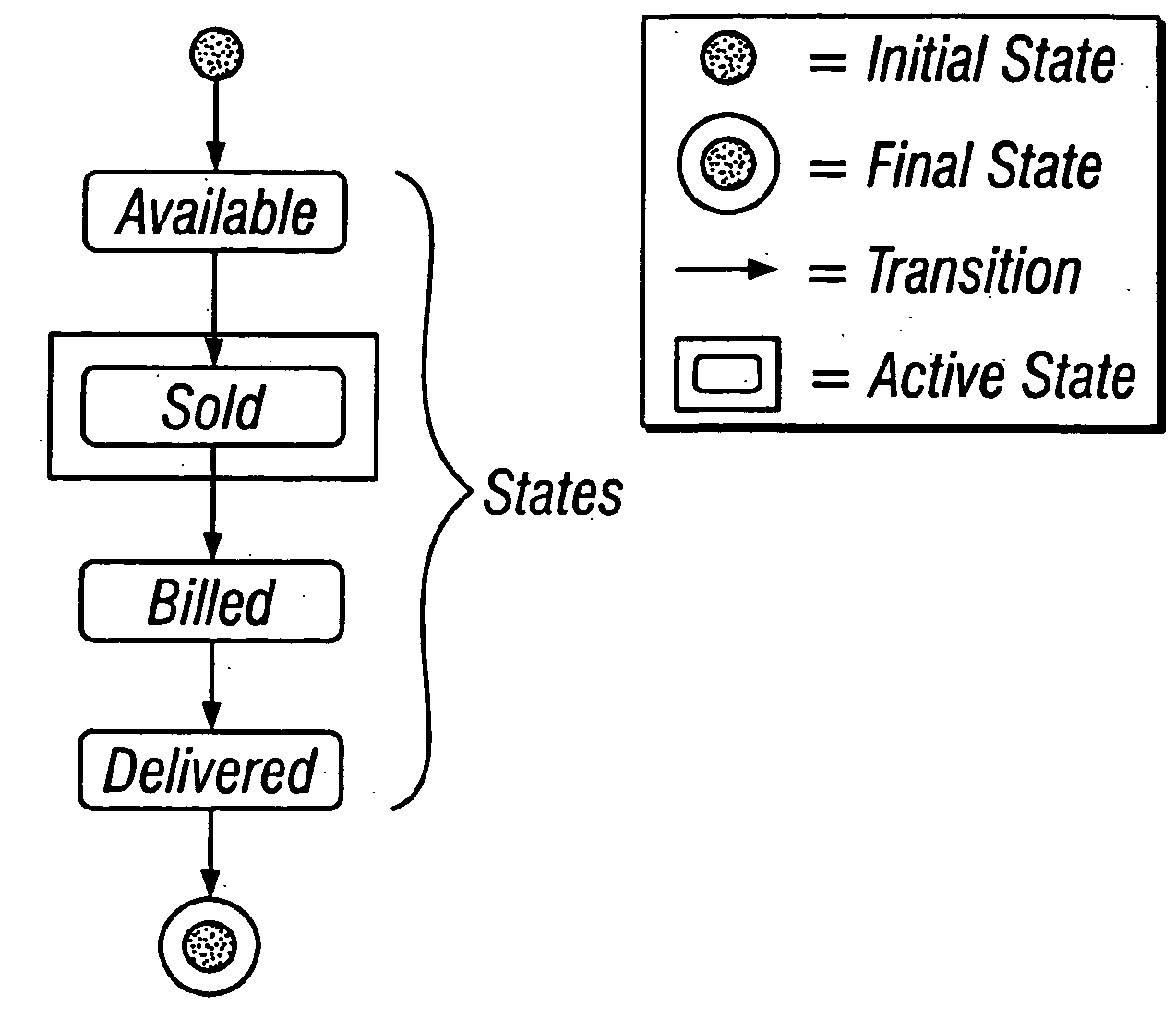
Modeling the life cycle of individual data objects
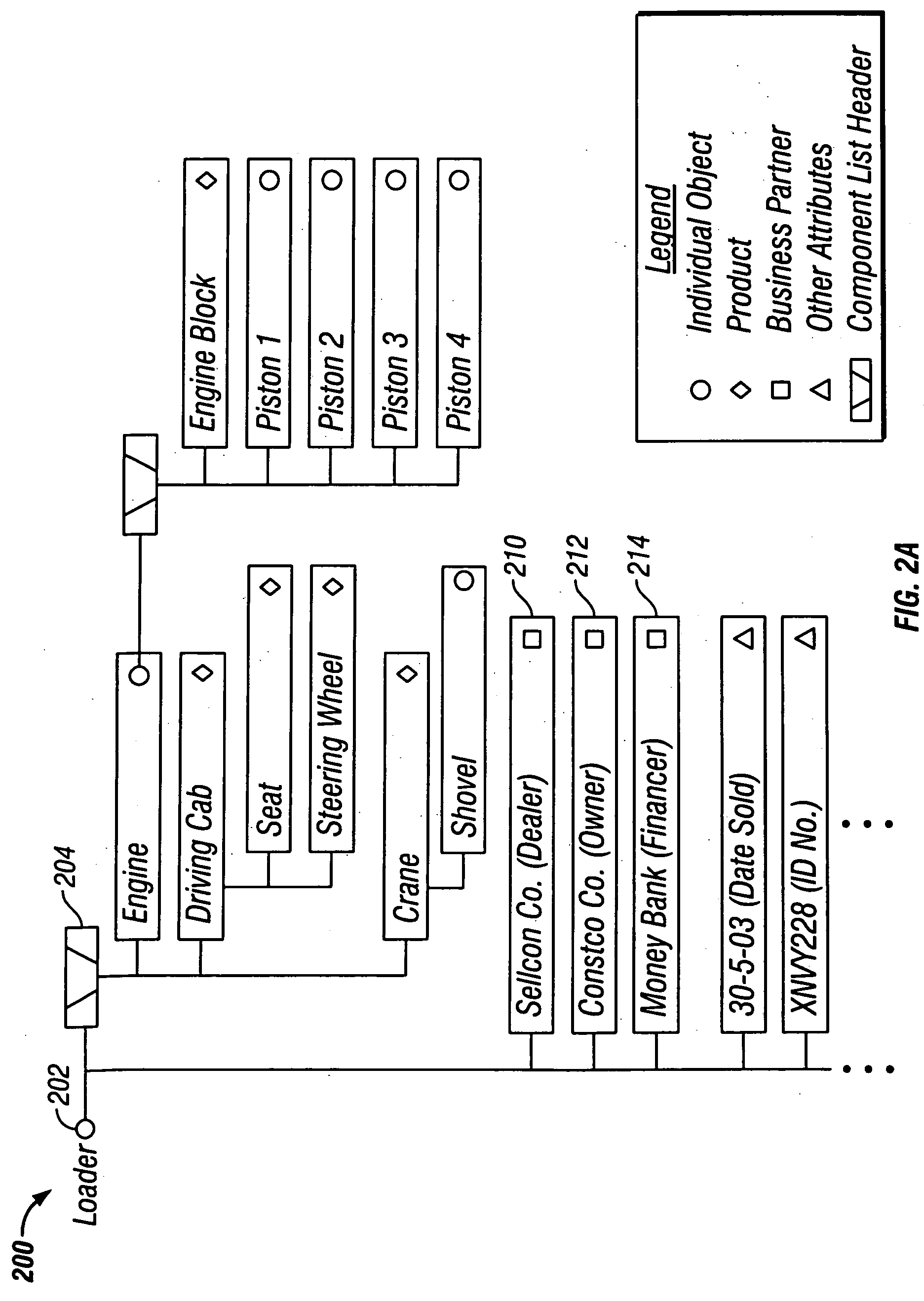
ActiveUS20050010504A1Highly configurableIncrease valueComplete banking machinesHand manipulated computer devicesEnterprise computingGeneric Product
Techniques are provided for individual data objects in an enterprise computing system, where the individual data objects represent unique assets of a family of assets. The individual data objects are used in addition to business partner master data, and also in some cases in addition to generic product master data. The individual data objects are configurable such that attributes for an individual data object change over the lifetime of the unique asset to which the individual data object pertains. Techniques for modeling the lifecycle of an individual object family are described. Techniques also are provided for an integration framework that integrates a software application with an individual object that is used or altered by the software application.
Owner:SAP AG
Methods and systems for recording to holographic storage media
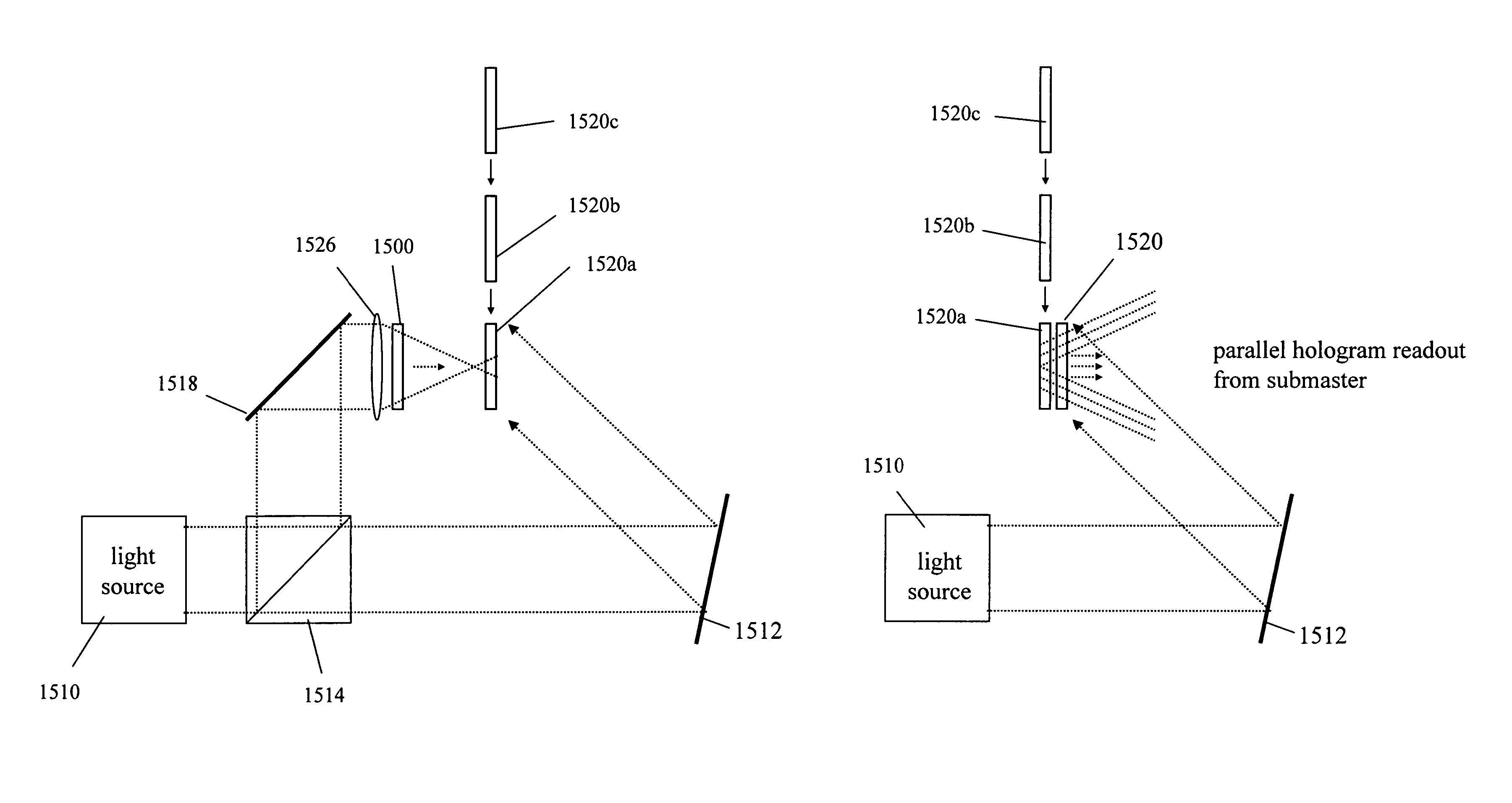
InactiveUS8786923B2Increase storage capacityOptical re-recordingInformation arrangementHolographic storageInformation layer
According to one aspect and example, a method for recording holographic media and / or holographic master data masks includes recording at least a first hologram or information layer with a first holographic medium (e.g., a “submaster”) and recording at least a second information layer with a second holographic medium (e.g., a second “submaster”). The first information layer and the second information layer from the first and second holographic media are then sequentially reconstructed and stored with a single holographic master medium (e.g., a “master”). The holographic master may then be used to record the stored first and second information layers into additional holographic media, for example, into HROM devices or the like.
Owner:AKONIA HOLOGRAPHICS
DTV transmitting system and receiving system and method of processing broadcast data
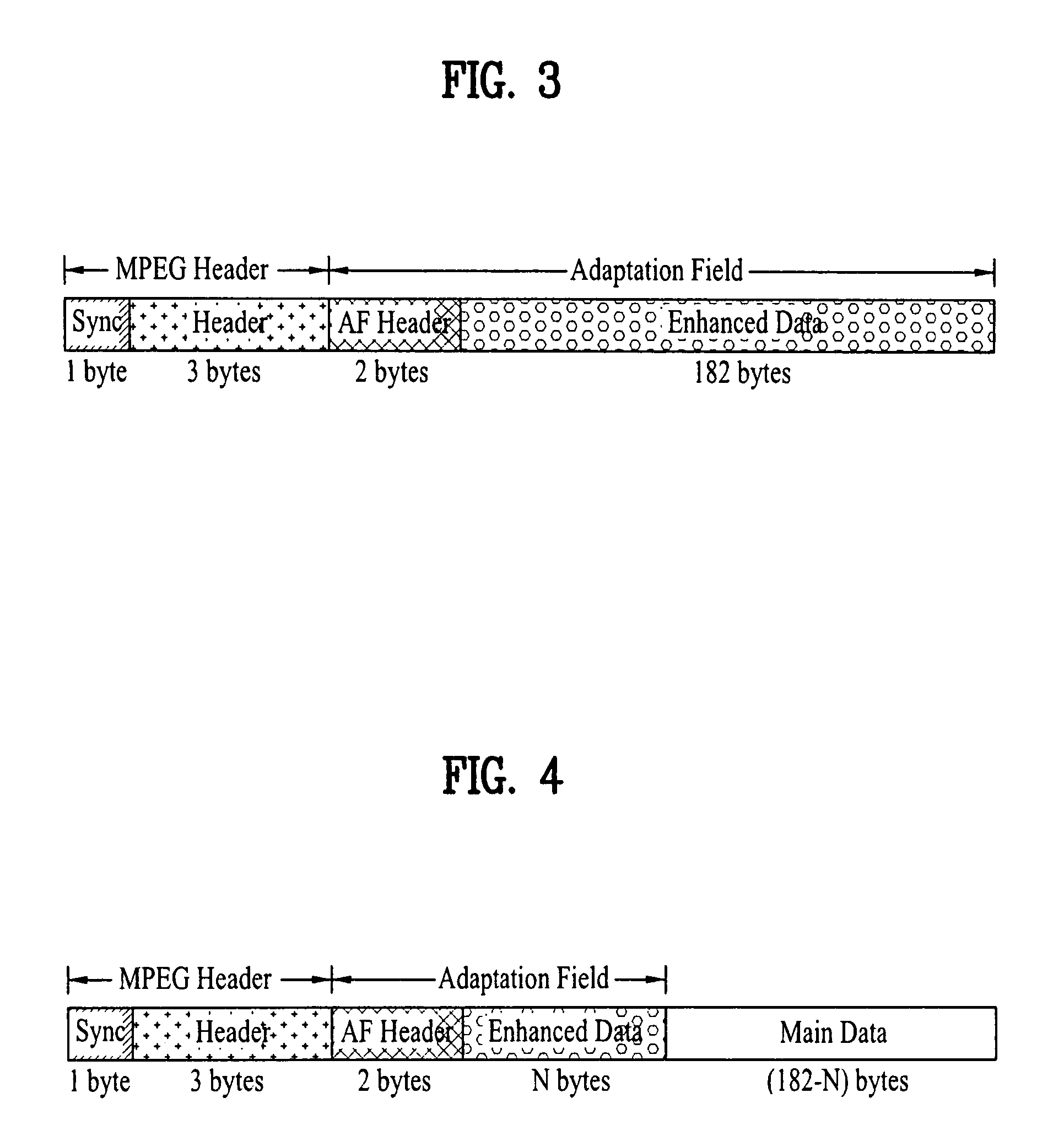
InactiveUS7779337B2Compensation DistortionTelevision system detailsData representation error detection/correctionData packPacket generator
A digital television transmitting system includes a pre-processor, a packet generator, an RS encoder, and a trellis encoder. The pre-processor pre-processes enhanced data by coding the enhanced data for first forward error correction and expanding the FEC-coded enhanced data. The packet generator generates enhanced data packets including the pre-processed enhanced data and main data packets and multiplexes the enhanced and main data packets. Each enhanced data packet includes an adaptation field in which the pre-processed enhanced data are inserted. The RS encoder performs RS encoding on the multiplexed data packets for second forward error correction, and the trellis encoder performs trellis encoding on the RS-coded data packets.
Owner:LG ELECTRONICS INC
Apparatus and method for determining battery/cell's performance, age, and health
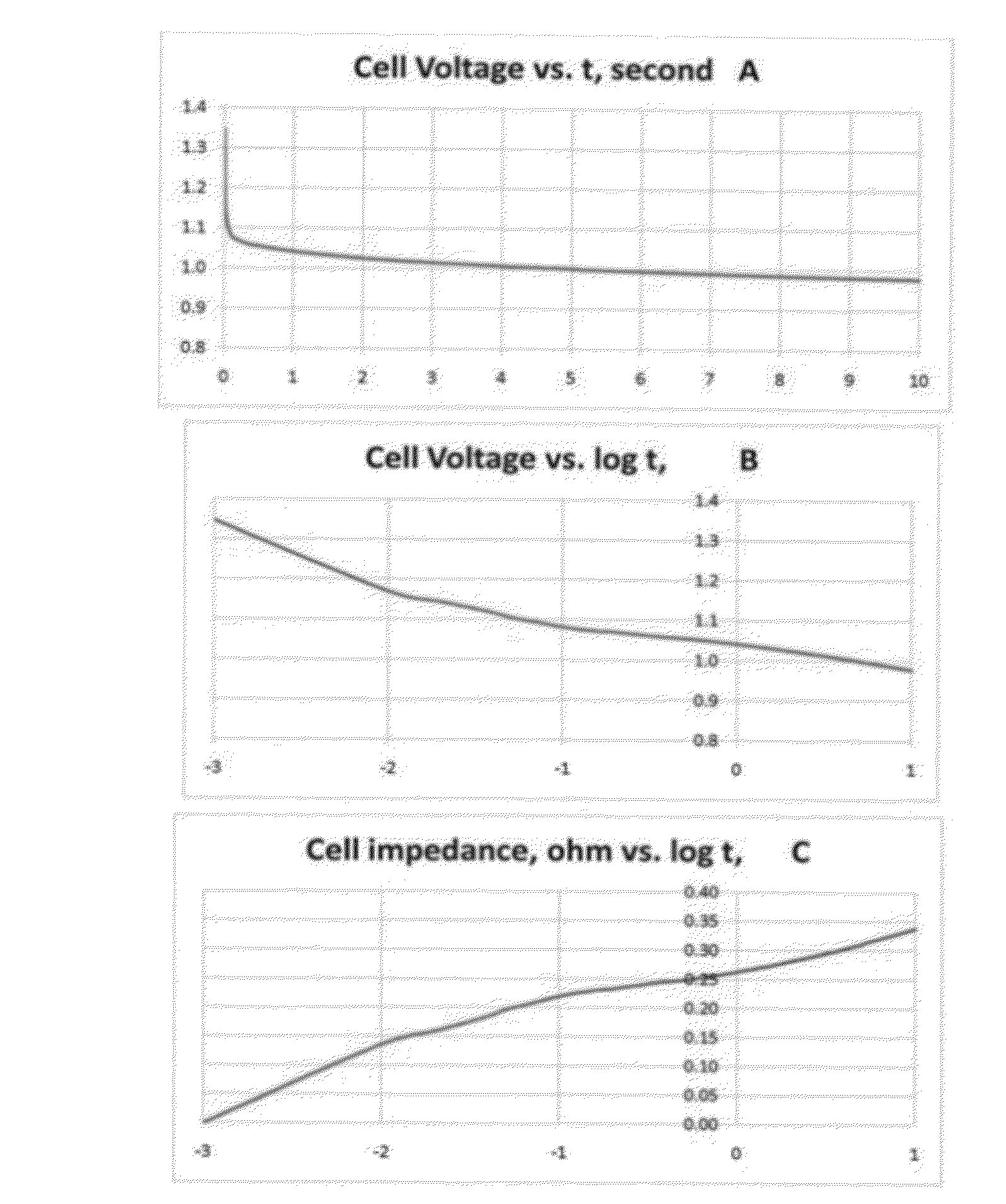
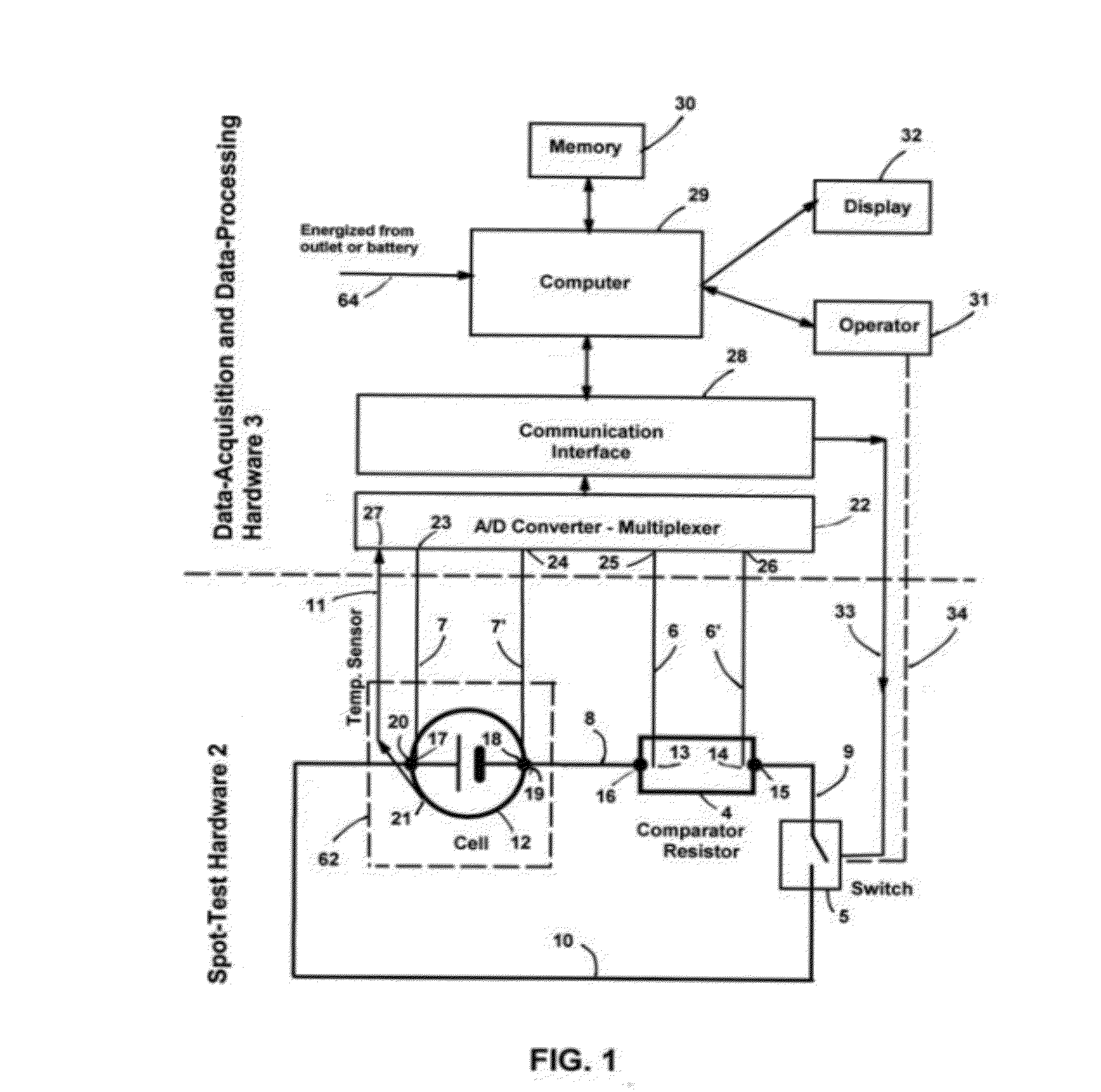
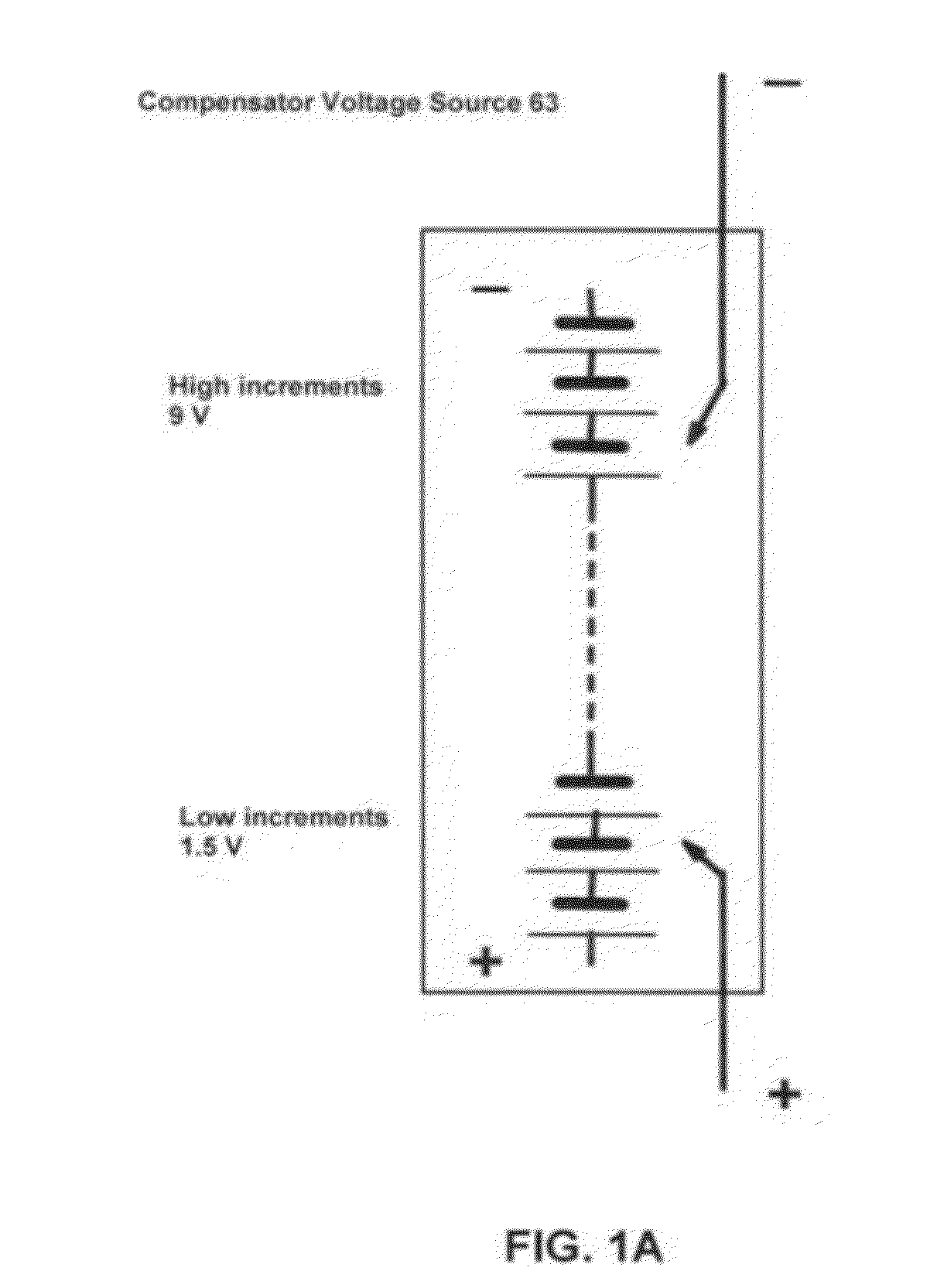
InactiveUS20120310565A1Quick and concise evaluationReliable estimateMaterial analysis by electric/magnetic meansElectrical testingTime domainVoltage response
A self-energized measuring system for determining primary and secondary battery / cell's performance, age, and health by measuring and recording battery / cell's voltage response to a specified load-changing perturbation spot-test event. The cell's voltage response is compared to a synchronously measured voltage signal of a comparator resistor. The relationship between the two voltage signals is analyzed on logarithmic time scale to determine performance parameters such as cell impedance and power and their variation in the time domain. The cell temperature is also measured for impedance and power normalization for 20 centigrade. Results are compared to a previously generated master data tabulation characteristic of a similar, new cell of perfect health condition. The time-domain performance parameters are related to the performance, age and health of the cell at any particular instant. The evaluation method can be easily adjusted to various battery chemistries, types.
Owner:REDEY LASZLO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com