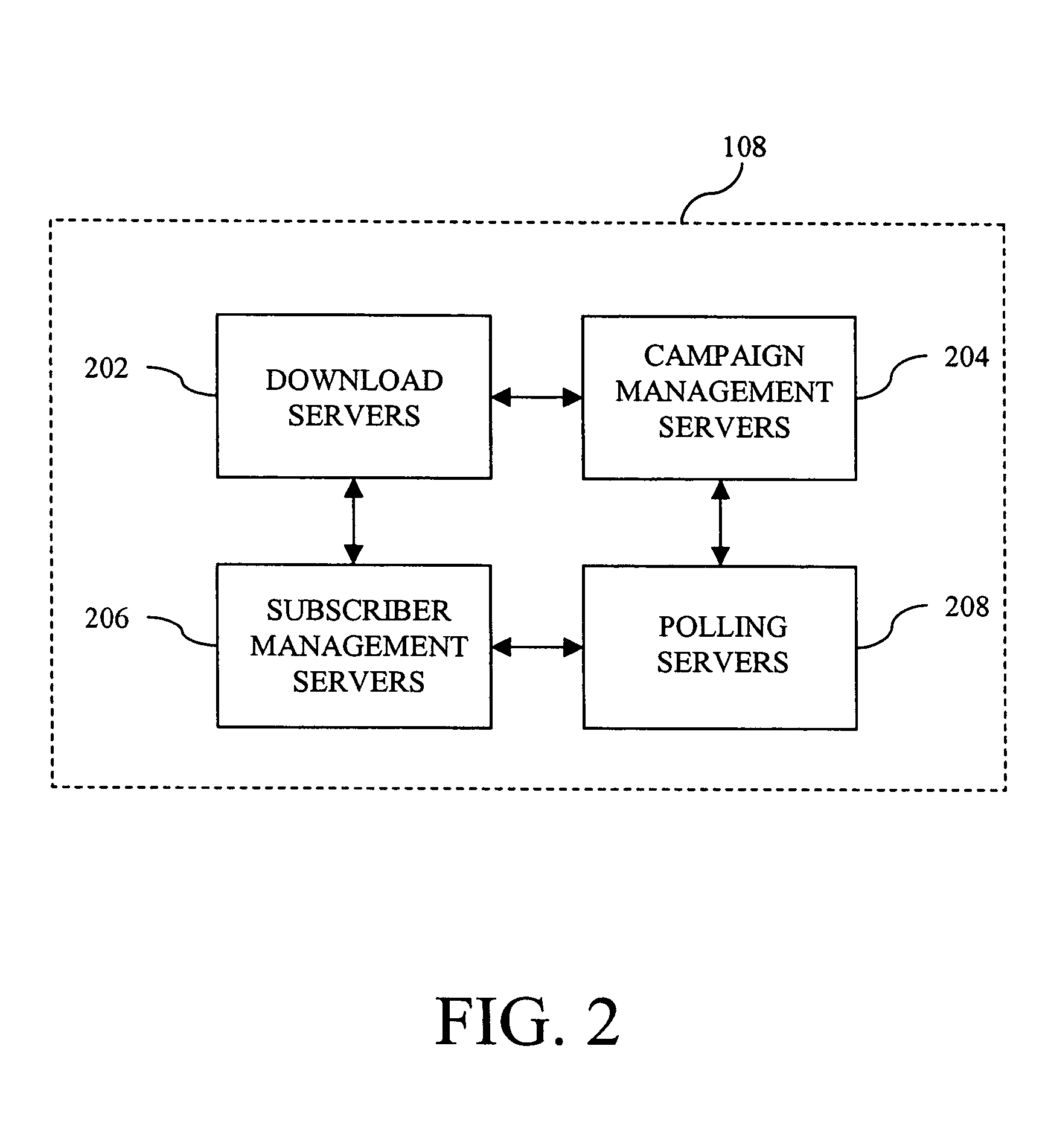
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2388 results about "Direct communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Direct Communication. Direct communication involves saying what a person thinks and feels, and it is marked by active listening and effective feedback. It is clear, straightforward, and involves the two-way, free-flowing sharing of thoughts, feelings, and ideas.
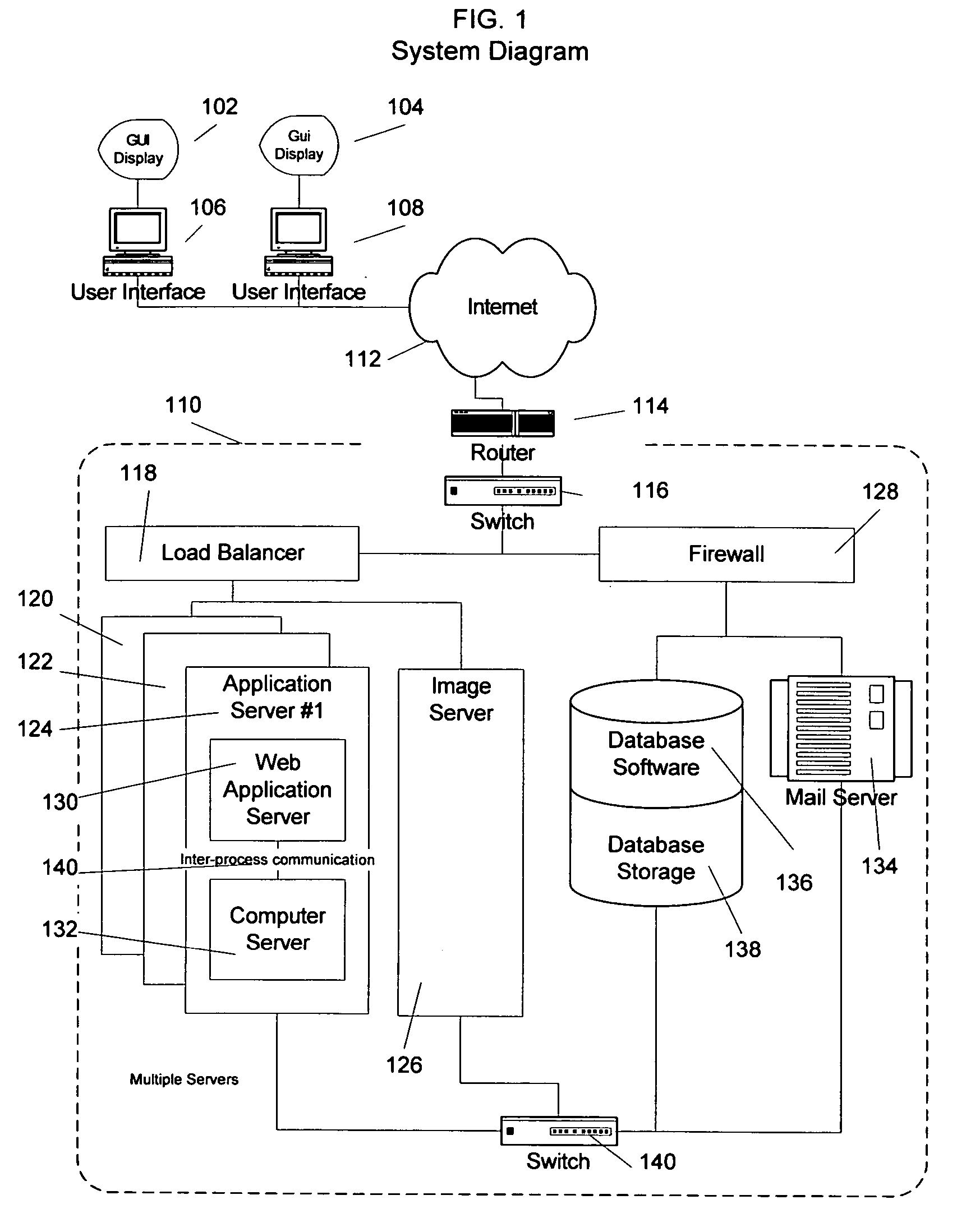
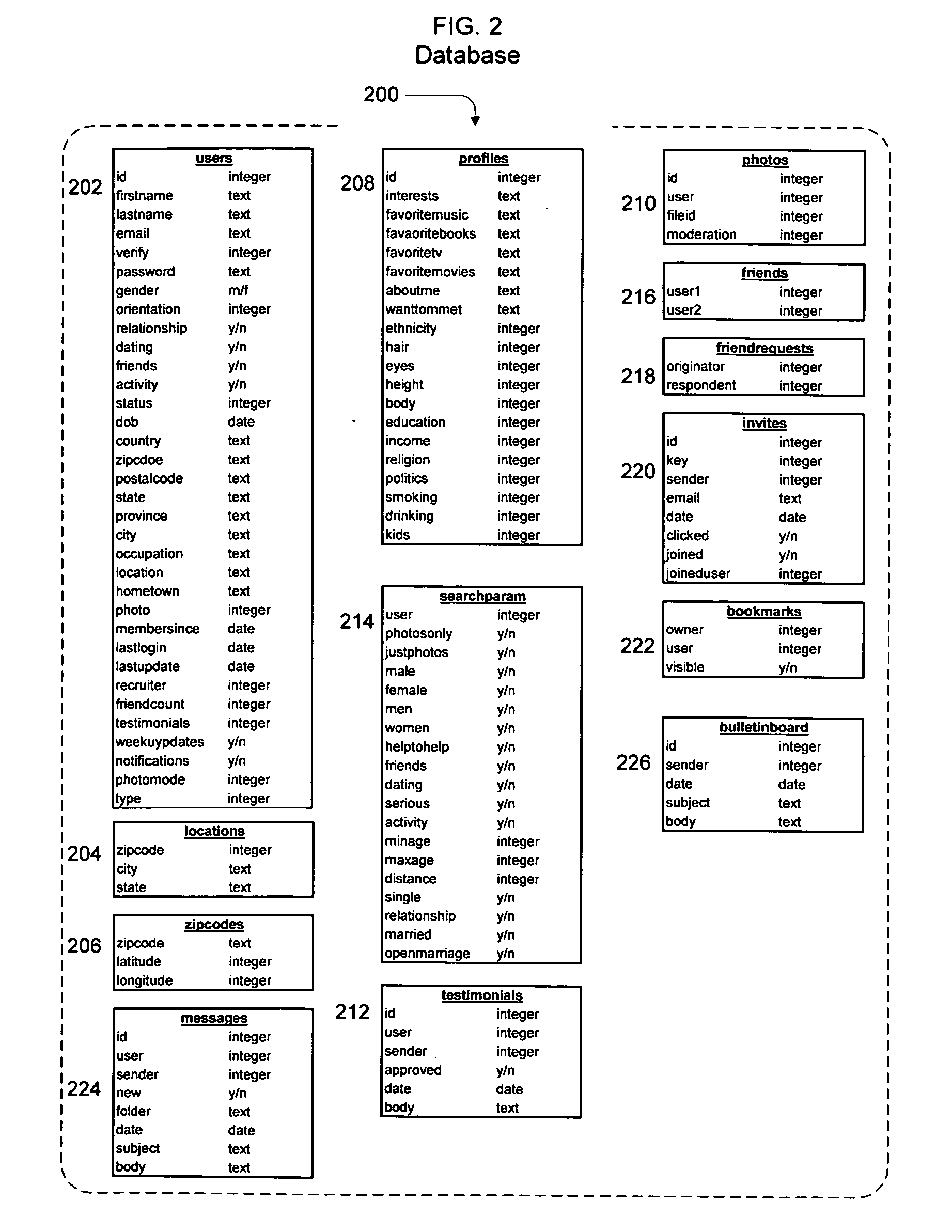
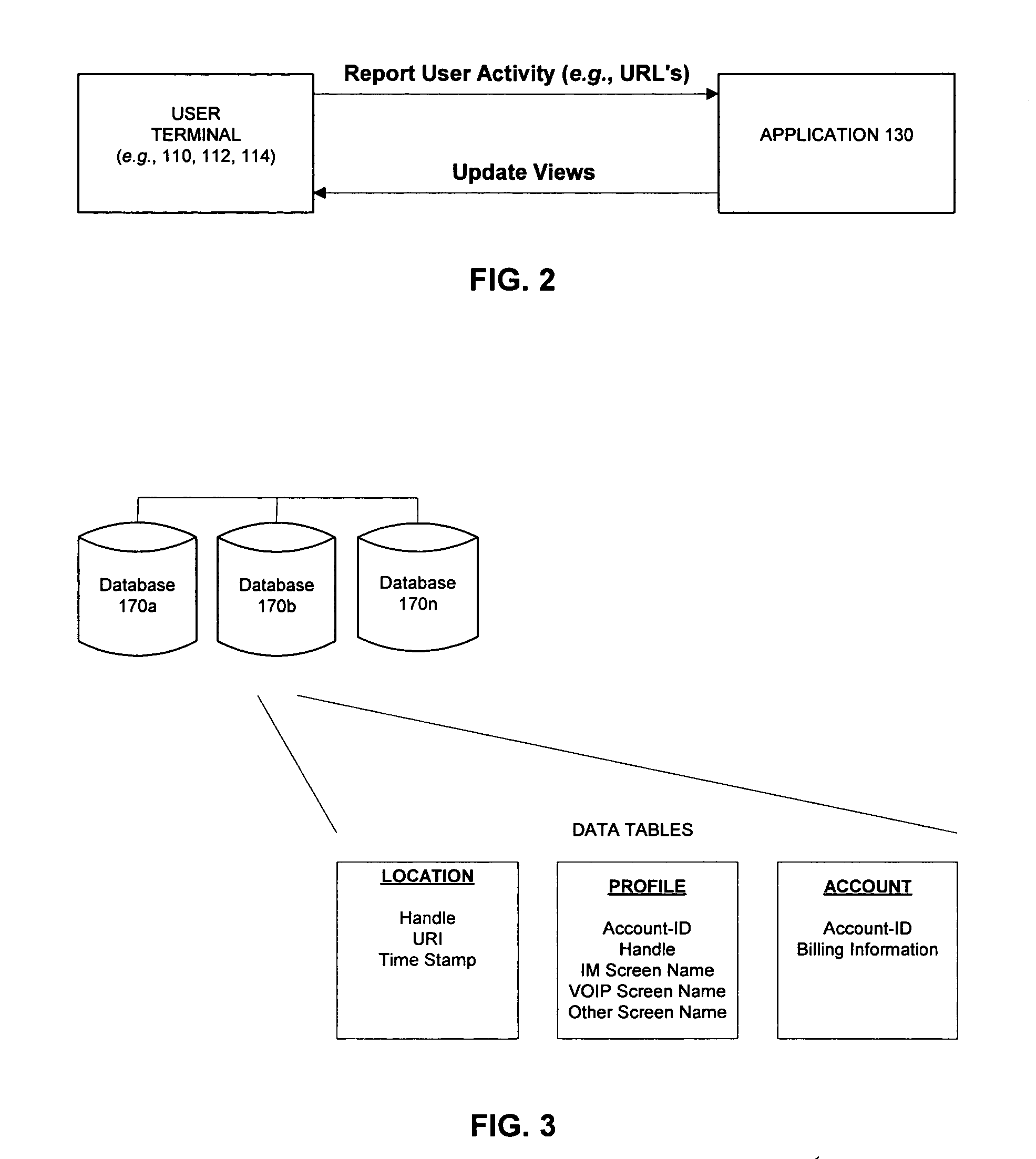
System, method and apparatus for connecting users in an online computer system based on their relationships within social networks
InactiveUS7069308B2Enhanced interactionIncrease valueMultiple digital computer combinationsOffice automationComputerized systemSocial network
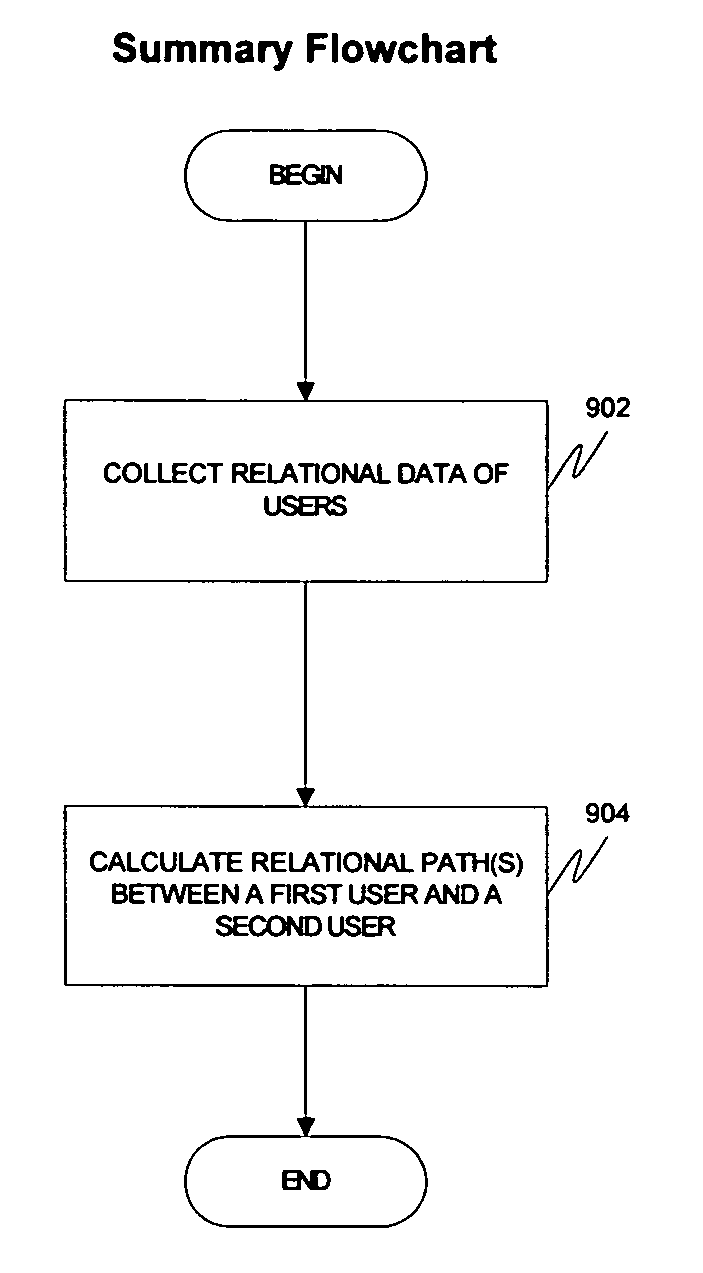
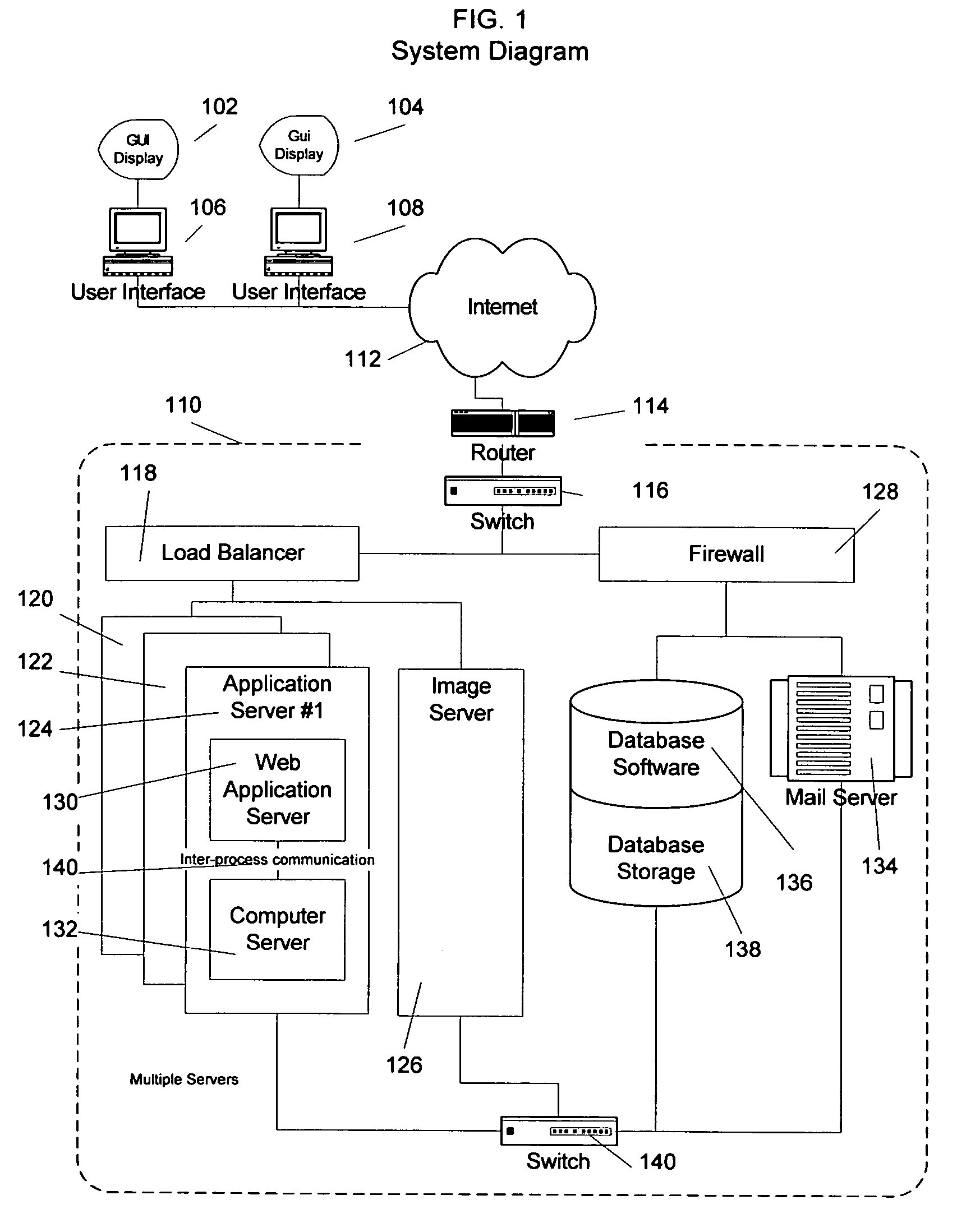
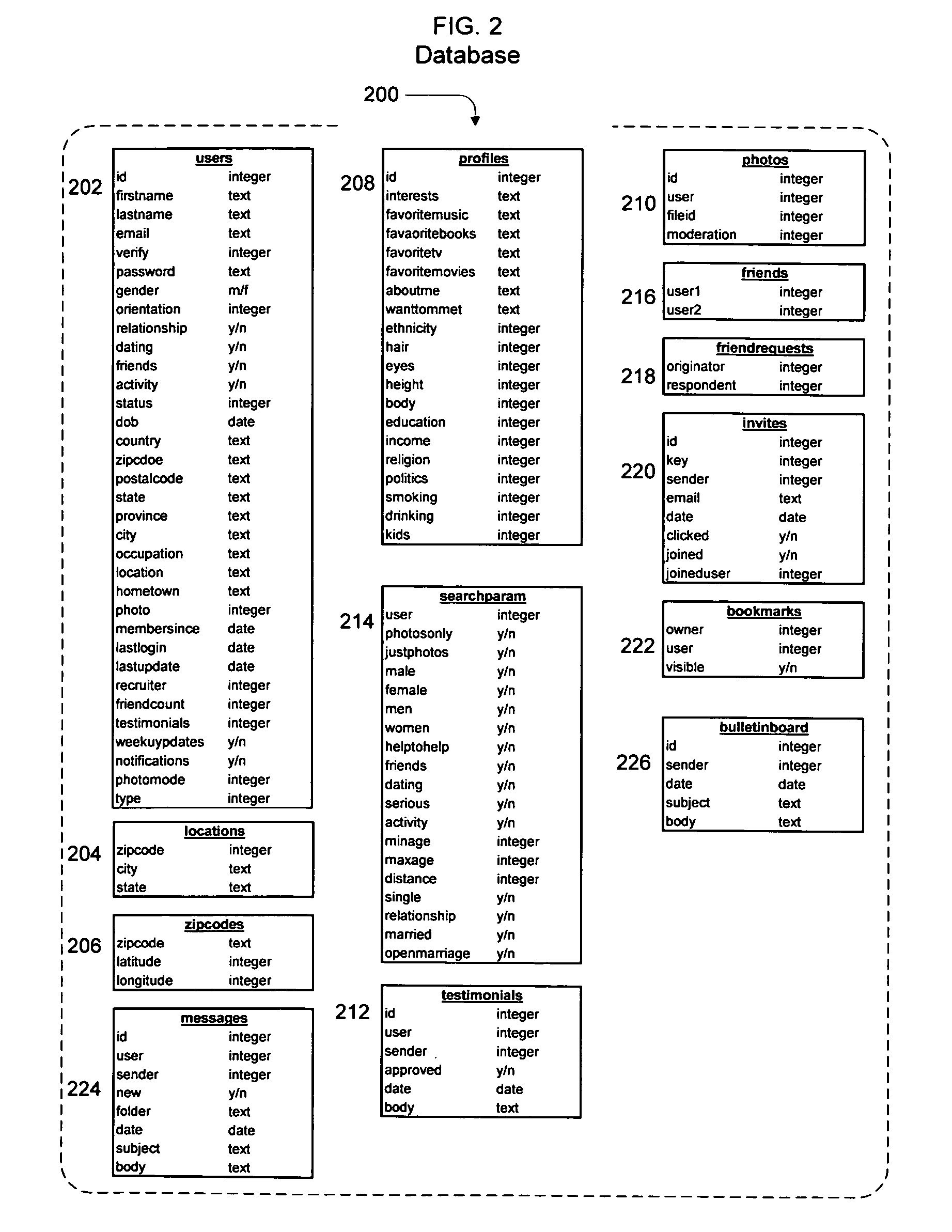
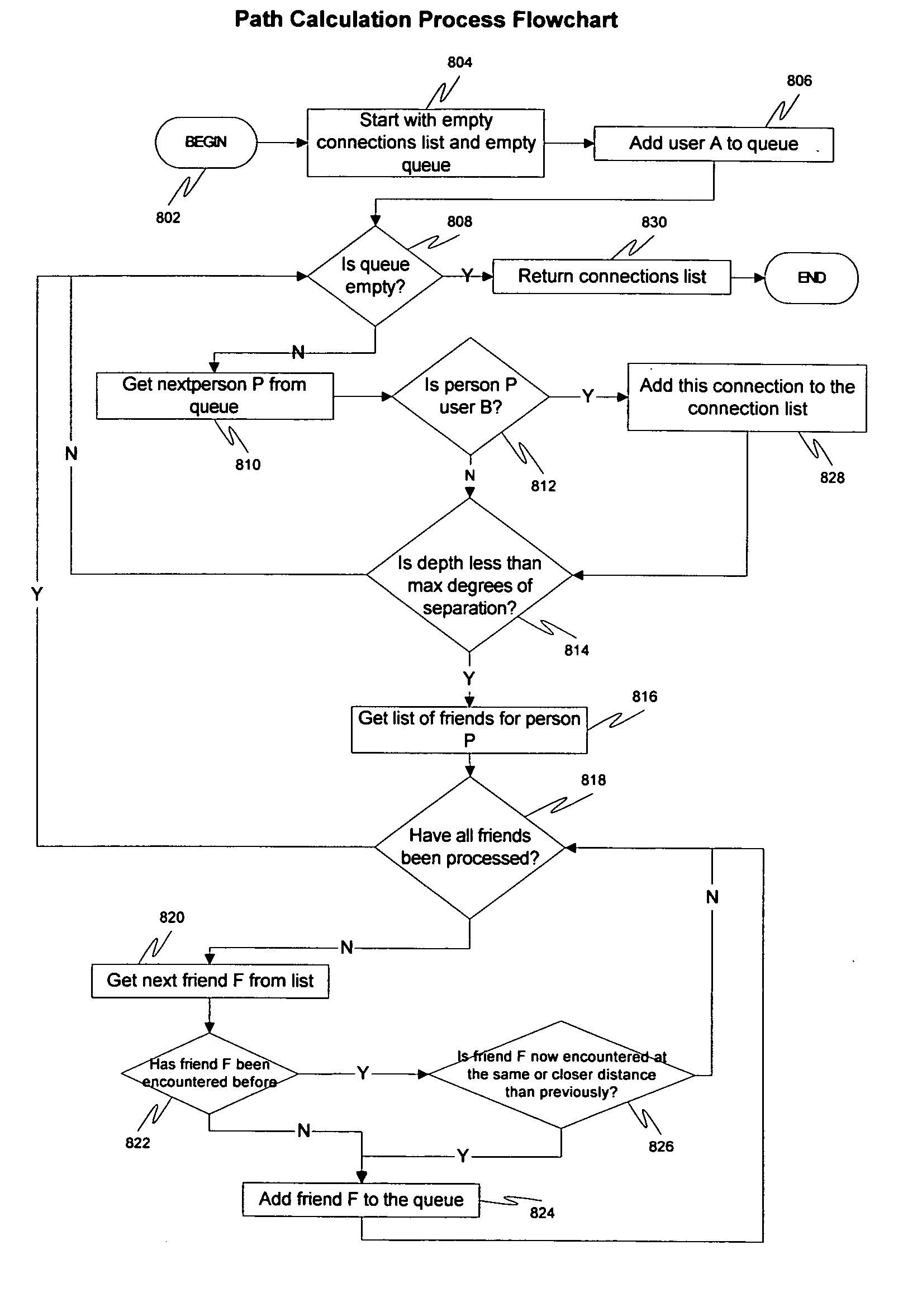
A method and apparatus for calculating, displaying and acting upon relationships in a social network is described. A computer system collects descriptive data about various individuals and allows those individuals to indicate other individuals with whom they have a personal relationship. The descriptive data and the relationship data are integrated and processed to reveal the series of social relationships connecting any two individuals within a social network. The pathways connecting any two individuals can be displayed. Further, the social network itself can be displayed to any number of degrees of separation. A user of the system can determine the optimal relationship path (i.e., contact pathway) to reach desired individuals. A communications tool allows individuals in the system to be introduced (or introduce themselves) and initiate direct communication.
Owner:META PLATFORMS INC
System, method and apparatus for connecting users in an online computer system based on their relationships within social networks
ActiveUS20050021750A1Enhanced interactionIncrease valueMultiple digital computer combinationsOffice automationDirect communicationSocial internet of things
A method and apparatus for calculating, displaying and acting upon relationships in a social network is described. A computer system collects descriptive data about various individuals and allows those individuals to indicate other individuals with whom they have a personal relationship. The descriptive data and the relationship data are integrated and processed to reveal the series of social relationships connecting any two individuals within a social network. The pathways connecting any two individuals can be displayed. Further, the social network itself can be displayed to any number of degrees of separation. A user of the system can determine the optimal relationship path (i.e., contact pathway) to reach desired individuals. A communications tool allows individuals in the system to be introduced (or introduce themselves) and initiate direct communication.
Owner:META PLATFORMS INC
Method and system for efficient communication
InactiveUS20140071818A1Error preventionFrequency-division multiplex detailsTelecommunicationsNetwork on
Owner:INNOVATION SCI LLC
Method and apparatus for remotely monitoring a site
InactiveUS6972676B1Easy to distinguishAccurate locationElectric testing/monitoringElectric/electromagnetic visible signallingTime informationOperating energy
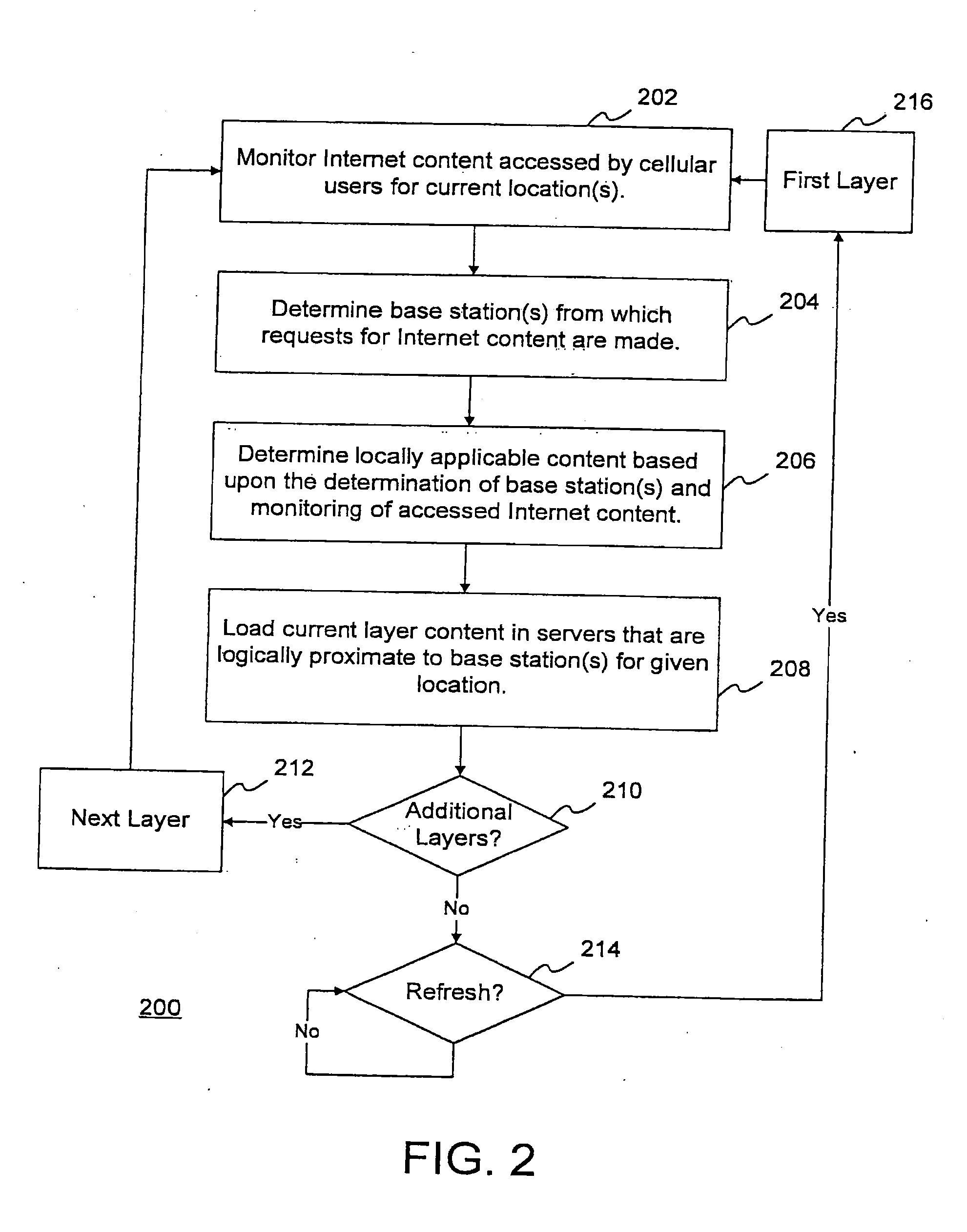
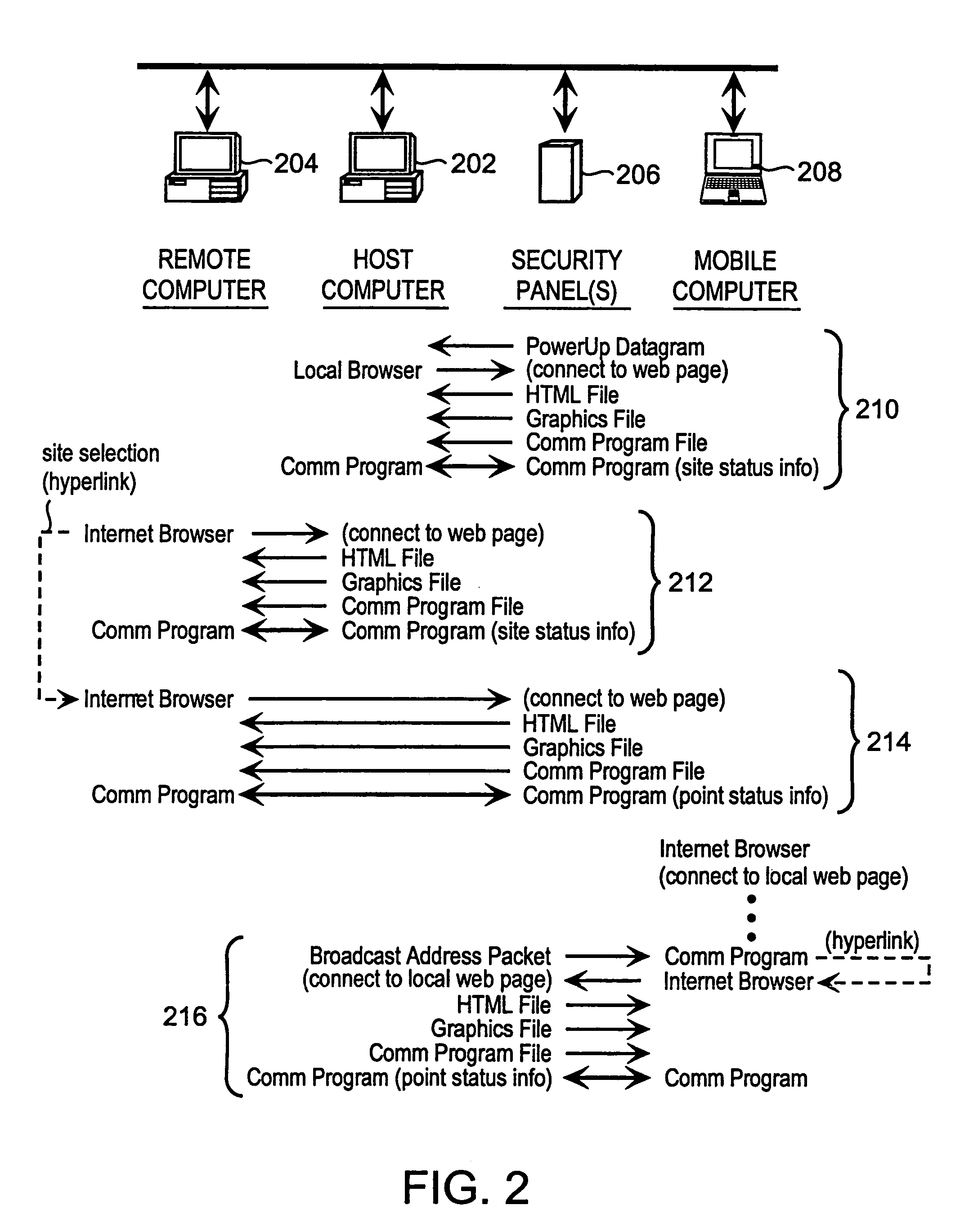
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real time information which can readily permit false alarms to be distinguished, and which can identify and track the precise location of an alarm. In exemplary embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in a novel interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in real-time over preexisting communication networks, such as the Internet. A wireless network can also be established using browser encapsulated communication programs (for example, active X control, Java applets, and so forth) to transmit data packets which comply with any standard wireless local area network protocol. Communications can thereby be established between a web server embedded in a centrally located host monitoring station and a separate security panel deployed in each of the buildings to be remotely monitored. In exemplary embodiments, communications can be handed off from the centrally located host monitoring station to a mobile monitoring station (for example, to a laptop computer in a responding vehicle, such as a police or fire vehicle). The handoff can be such that direct communications are established between a security panel site being monitored and the laptop, or over, for example, a cellular network or indirect communications can be established via the host monitoring station.
Owner:NETTALON SECURITY SYST
Method and system for radio link establishment and maintenance with p2p communication in wireless communication
InactiveUS20060168343A1Adaptable to changeSmooth switchingPower managementNetwork traffic/resource managementCommunications systemTelecommunications link
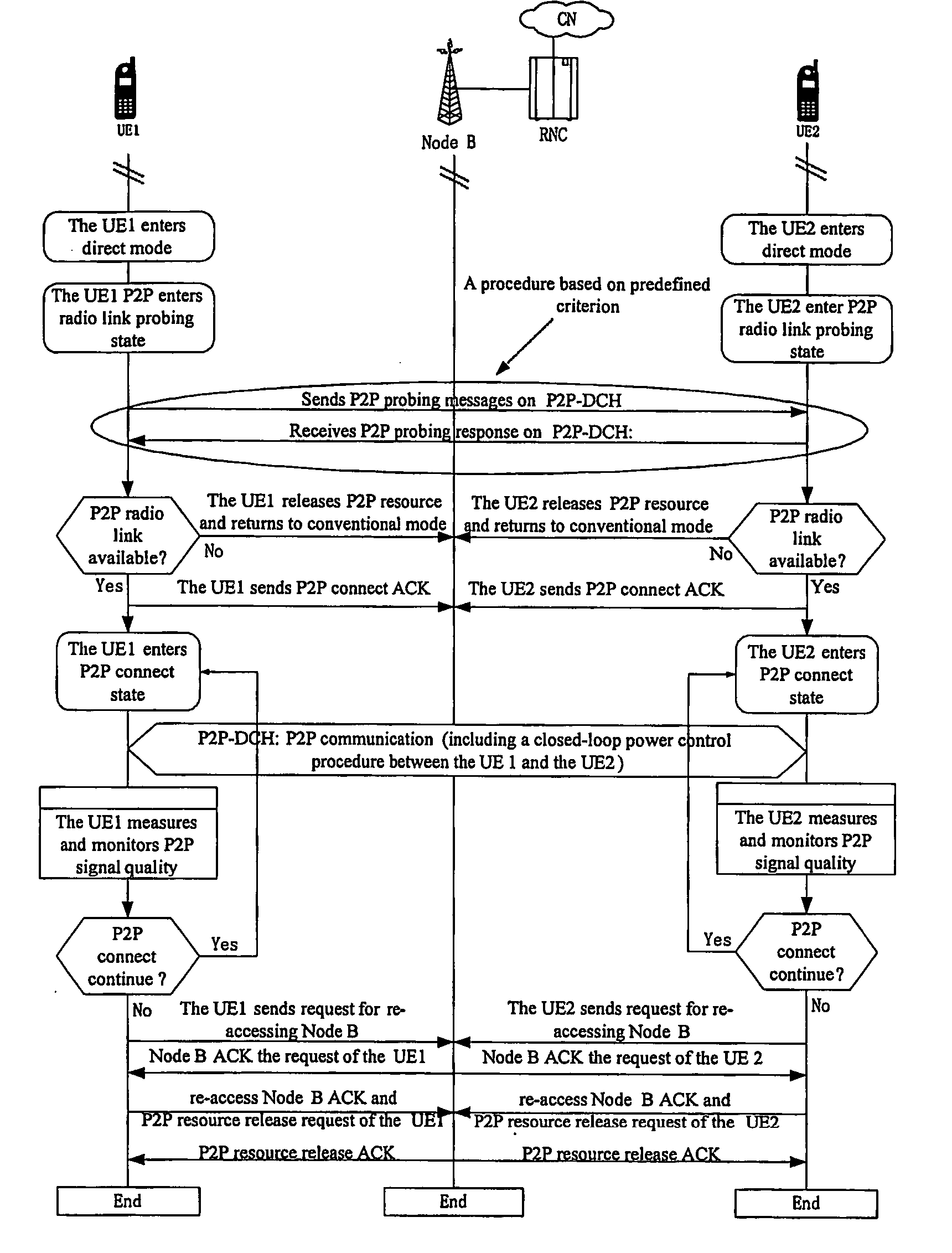
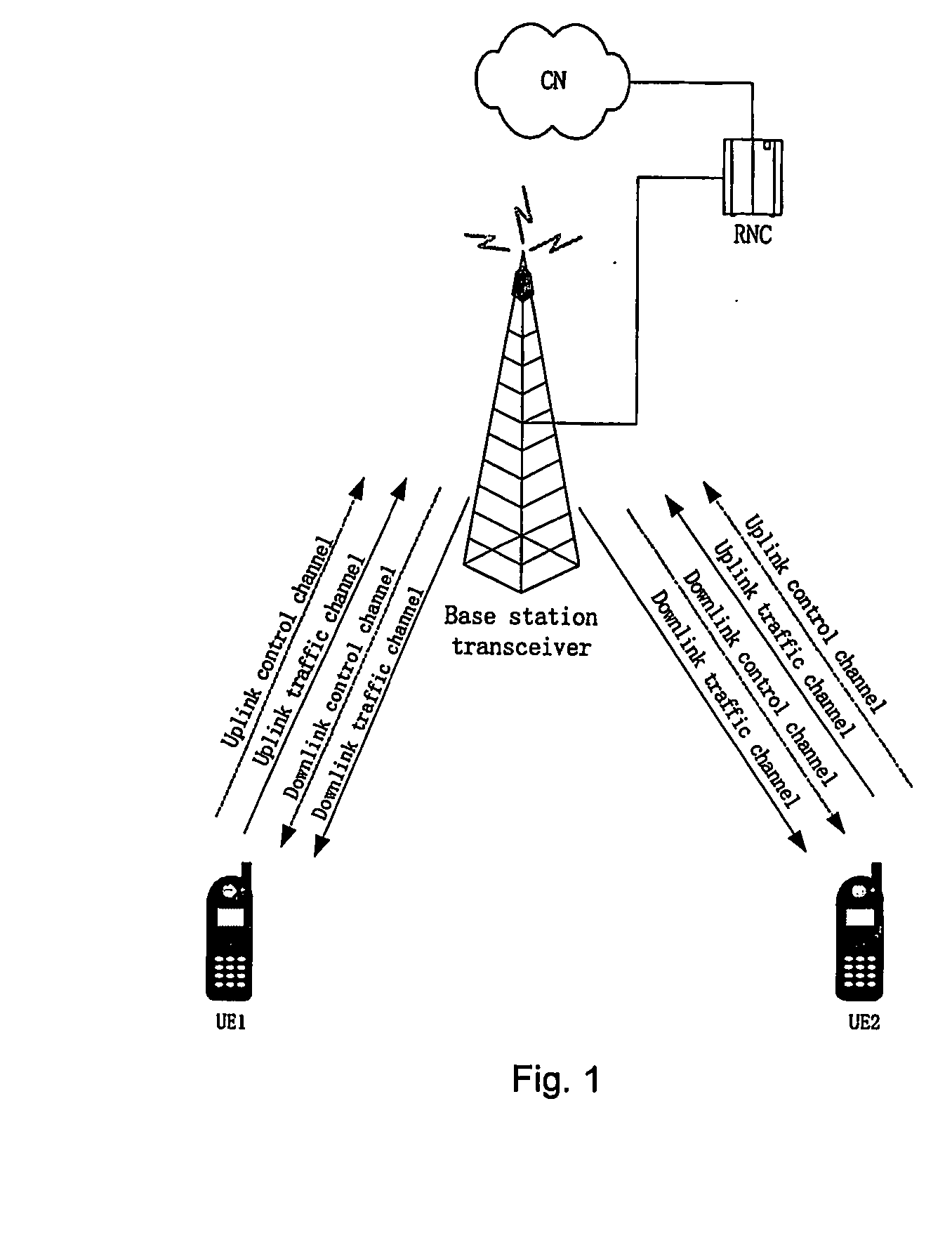
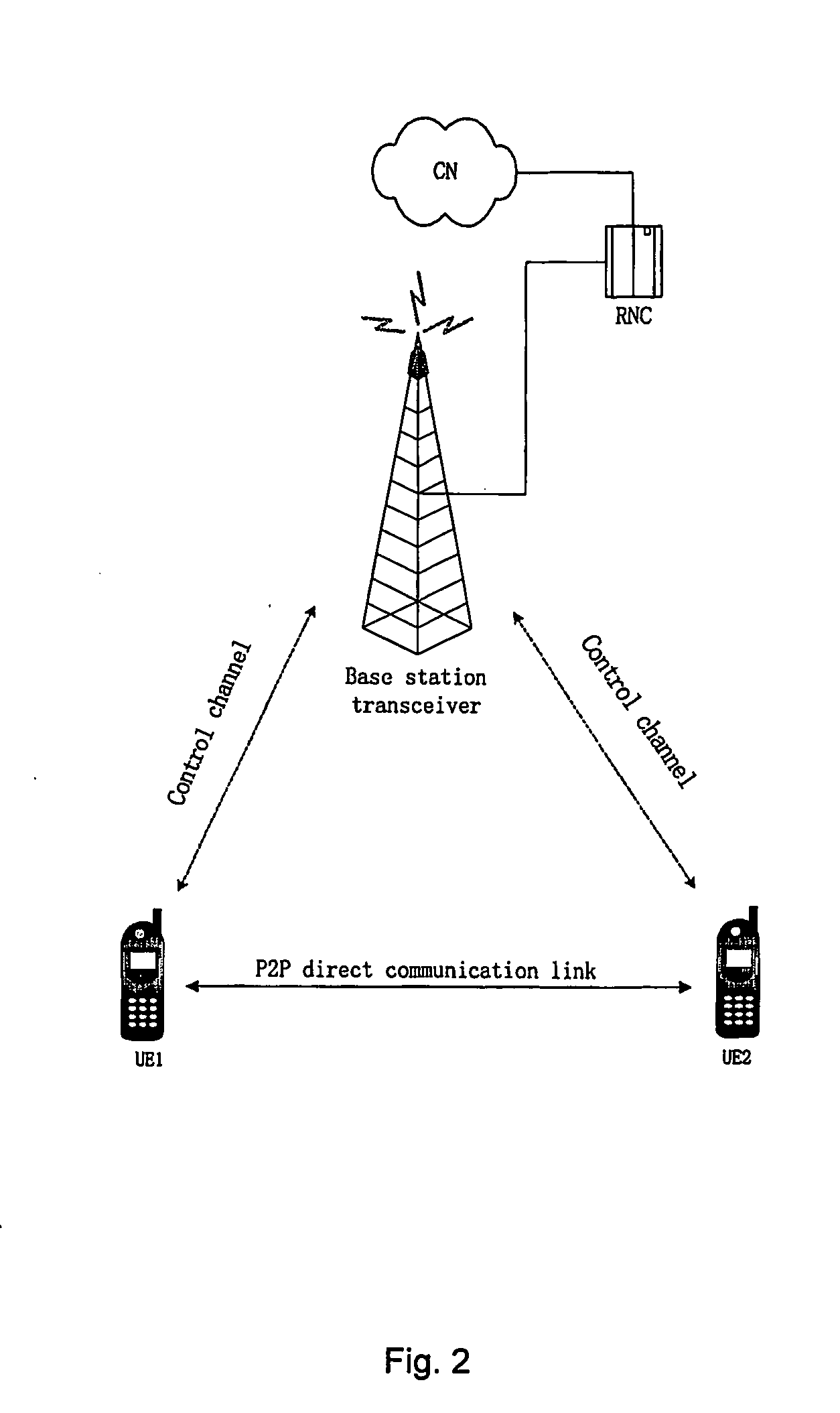
A method is provided for establishing P2P radio connection in wireless communication networks, comprising: the user equipment, as the link probing originator, transmits link probing signals via the allocated direct communication link to another user equipment as the link probing responder, according to the initial probing power provided by the wireless communication system; said another user equipment transmits the ACK message to the link probing originator via the direct communication link when receiving the link probing signals and said link probing signals meet the basic requirement for direct communication; the user equipment, as the link probing originator, monitors the direct communication link, and communicates directly with the link probing responder via the direct communication link after detecting the ACK message from the link probing responder. This method effectively guarantees the procedure of establishing P2P communication between the user equipments in P2P communication course, by utilizing the link probing process of transmitting link probing signals.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
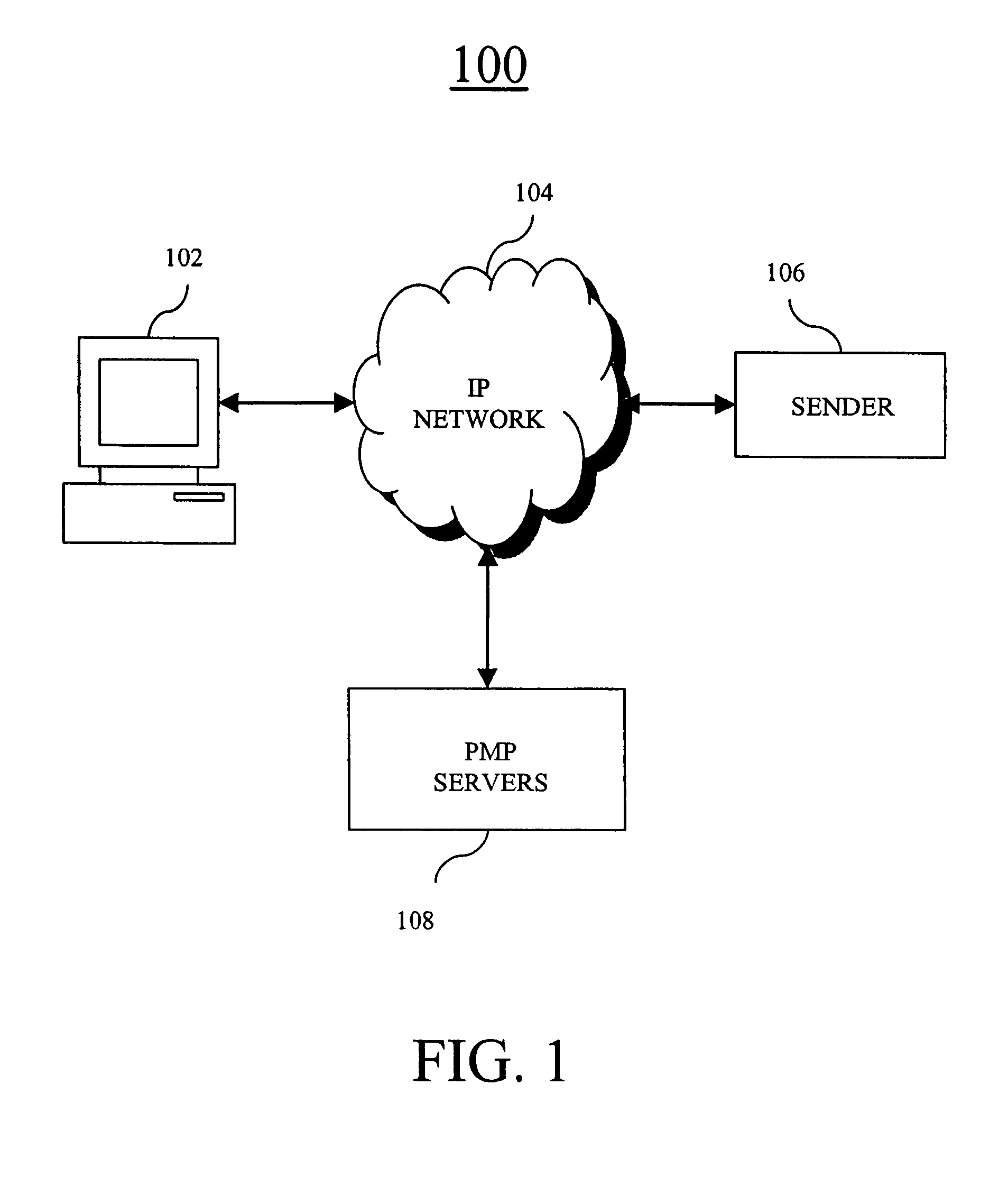
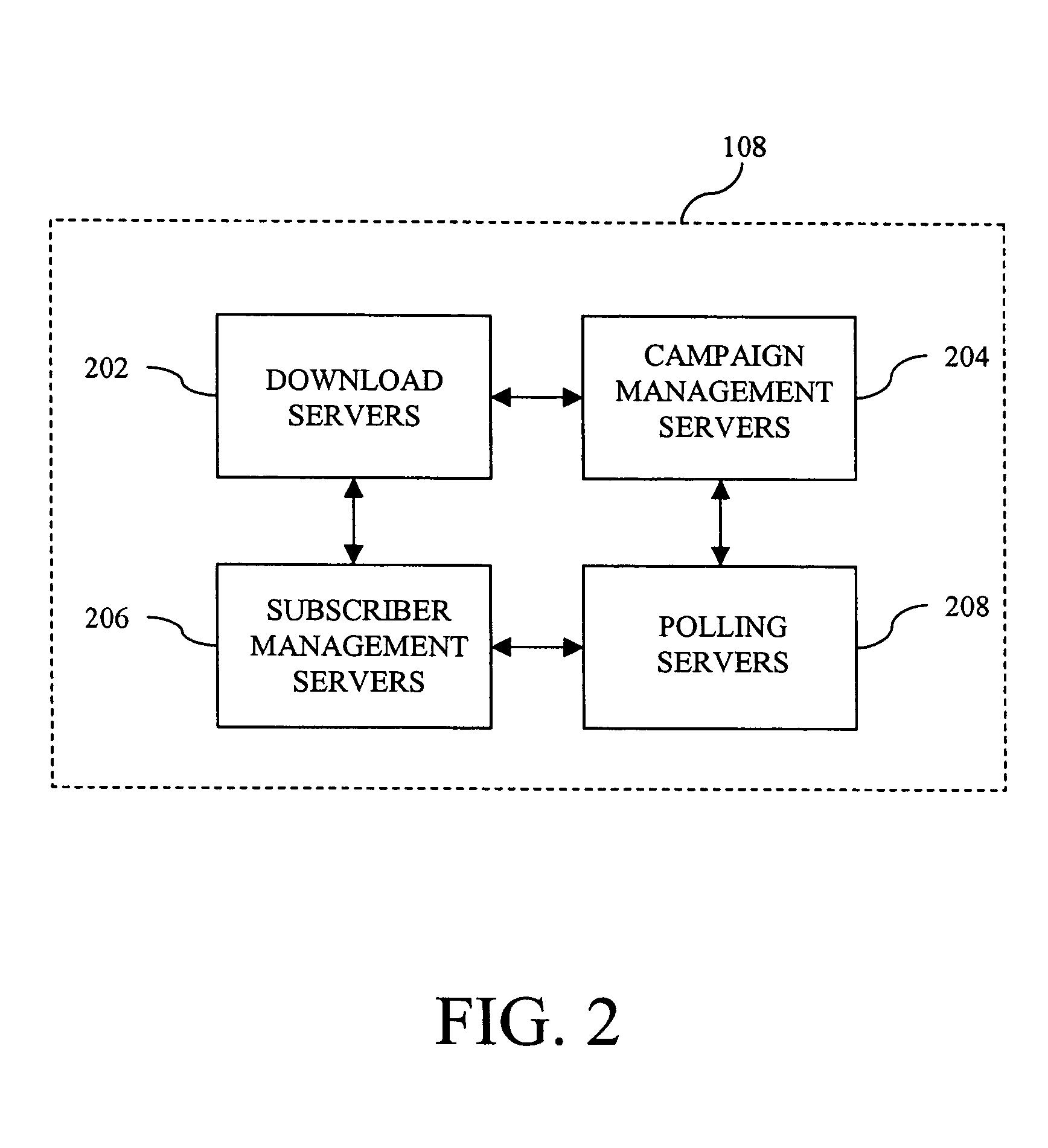
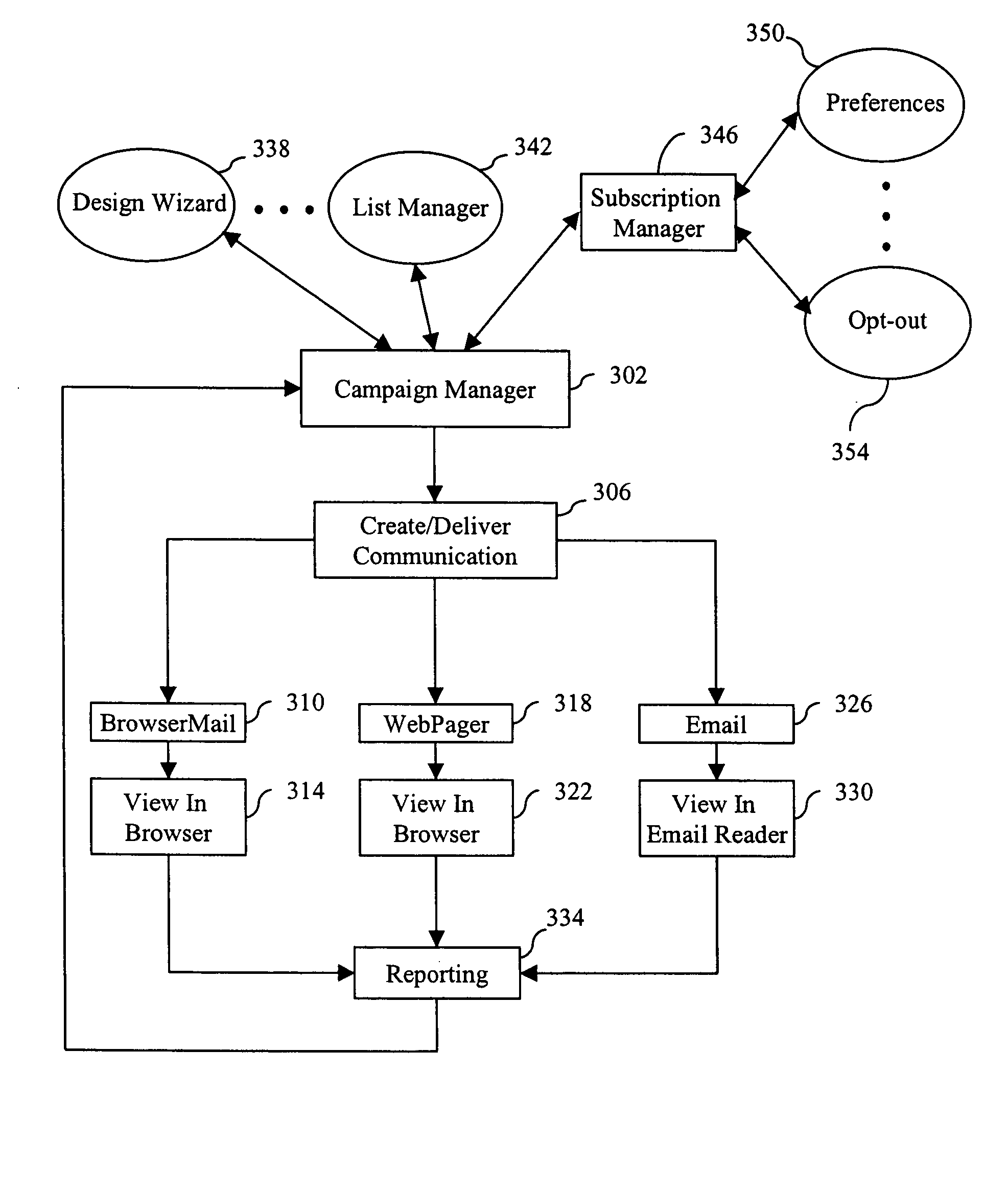
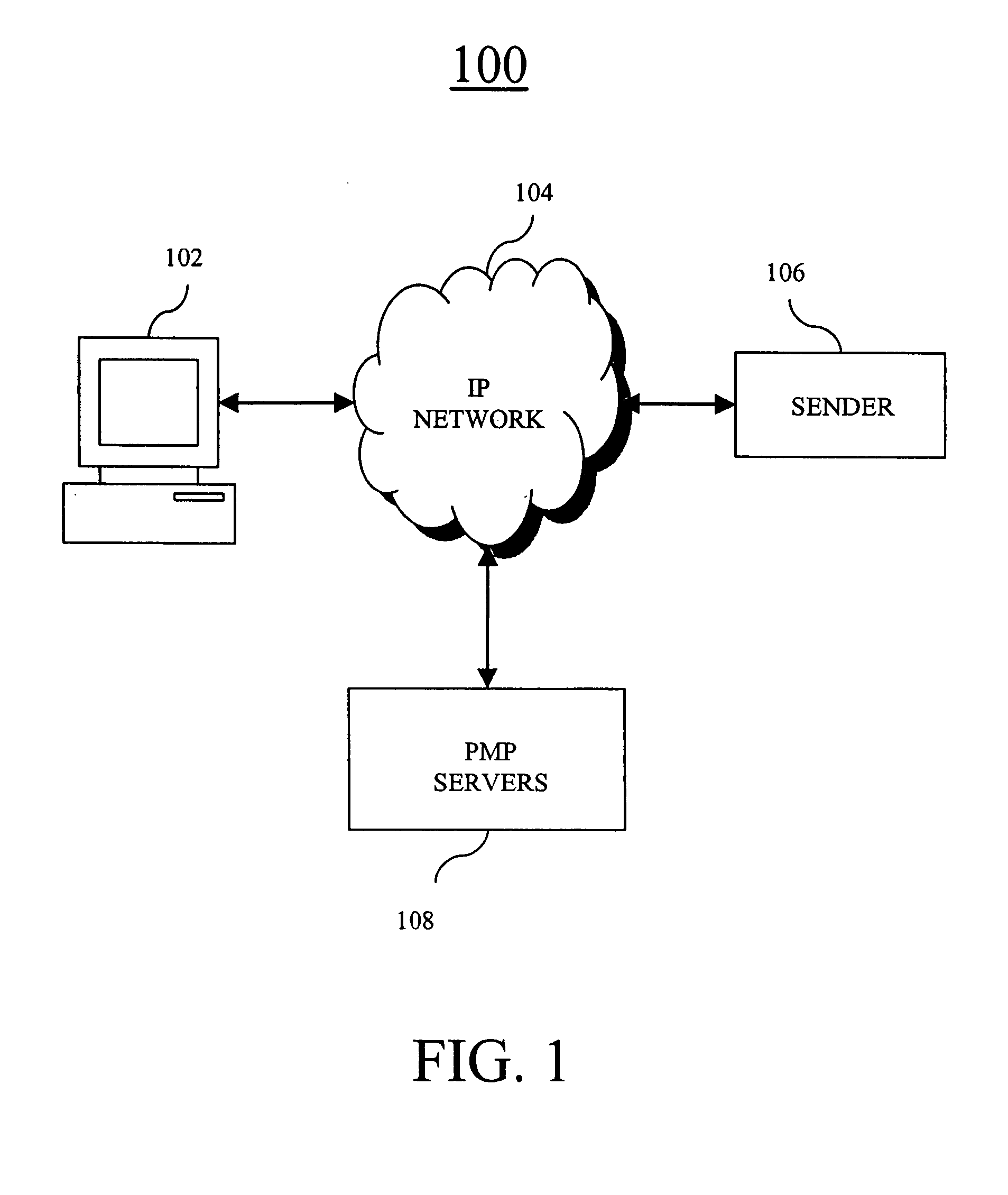
Systems and methods for producing, managing, delivering, retrieving, and/or tracking permission based communications
ActiveUS7640322B2Easy to processReporting is web-centricMultiple digital computer combinationsData switching networksComputer usersWeb browser
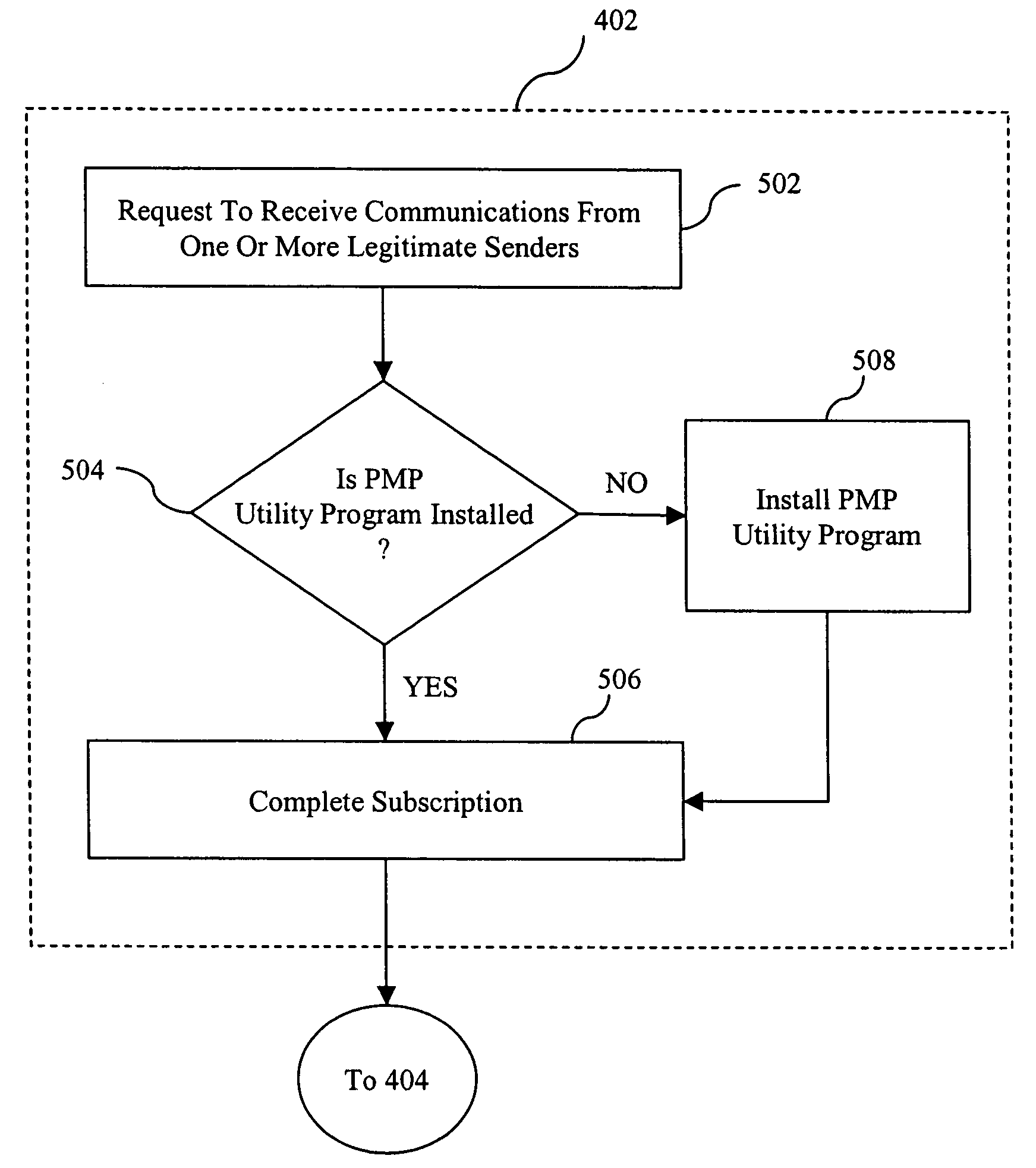
New and improved methods and systems are provided for producing, managing, delivering, retrieving, and / or tracking permission communications that alleviate several of the existing problems commonly associated with existing permission communications. According to the invention, computer users can request to receive direct communications from one or more senders. When a new communication is detected, an alert is provided to the recipients, who can use the alert to view the communication in their Web browser. Similar alerts may also be provided to one or more recipients when particular Web pages are updated. Various alternative embodiments are also disclosed.
Owner:TRUEFIRE LLC
Systems and methods for producing, managing, delivering, retrieving, and/or tracking permission based communications
ActiveUS20050228899A1Avoid inbox clutterAvoid blockageMultiple digital computer combinationsData switching networksComputer usersWeb browser
New and improved methods and systems are provided for producing, managing, delivering, retrieving, and / or tracking permission communications that alleviate several of the existing problems commonly associated with existing permission communications. According to the invention, computer users can request to receive direct communications from one or more senders. When a new communication is detected, an alert is provided to the recipients, who can use the alert to view the communication in their Web browser. Similar alerts may also be provided to one or more recipients when particular Web pages are updated. Various alternative embodiments are also disclosed.
Owner:TRUEFIRE LLC
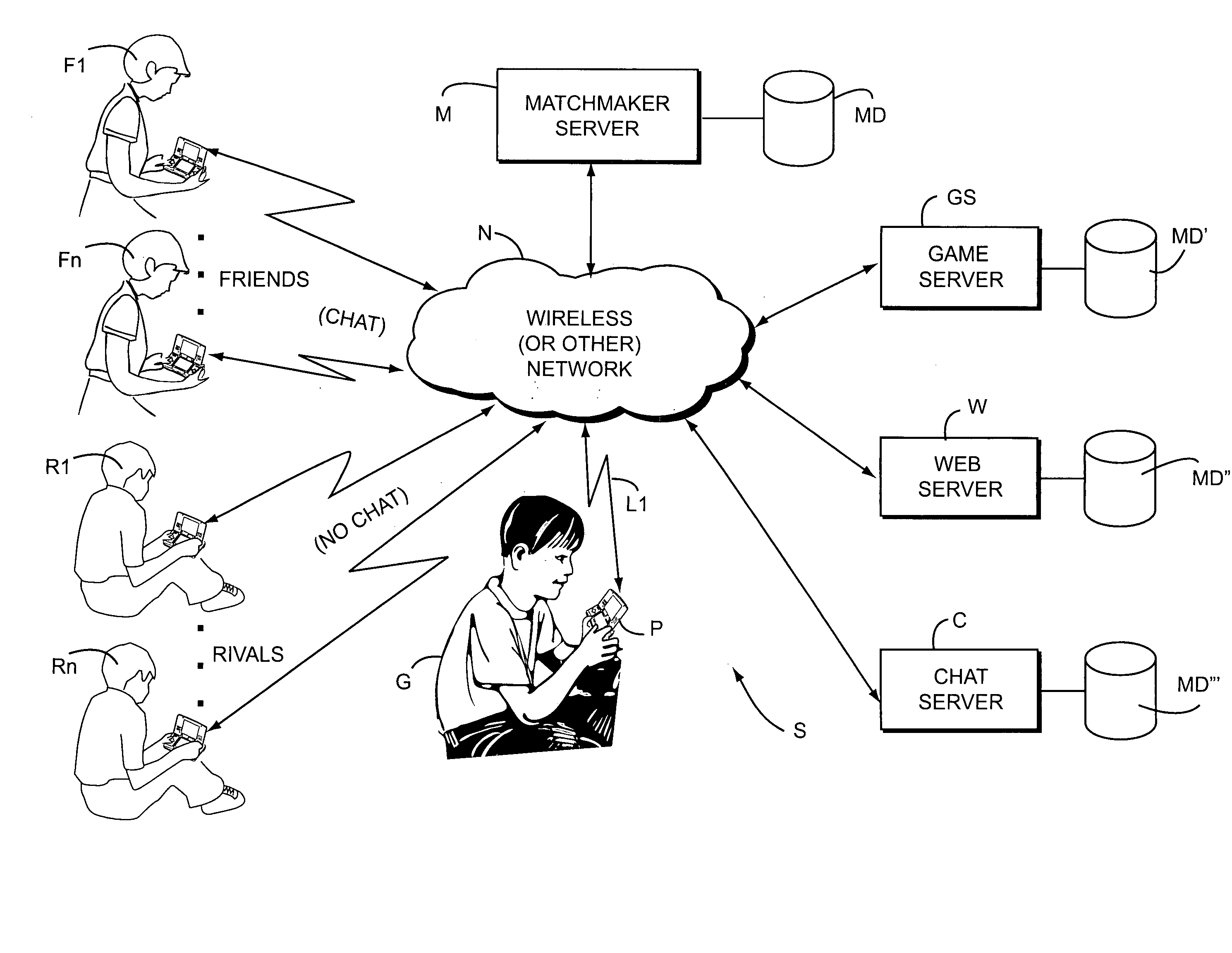
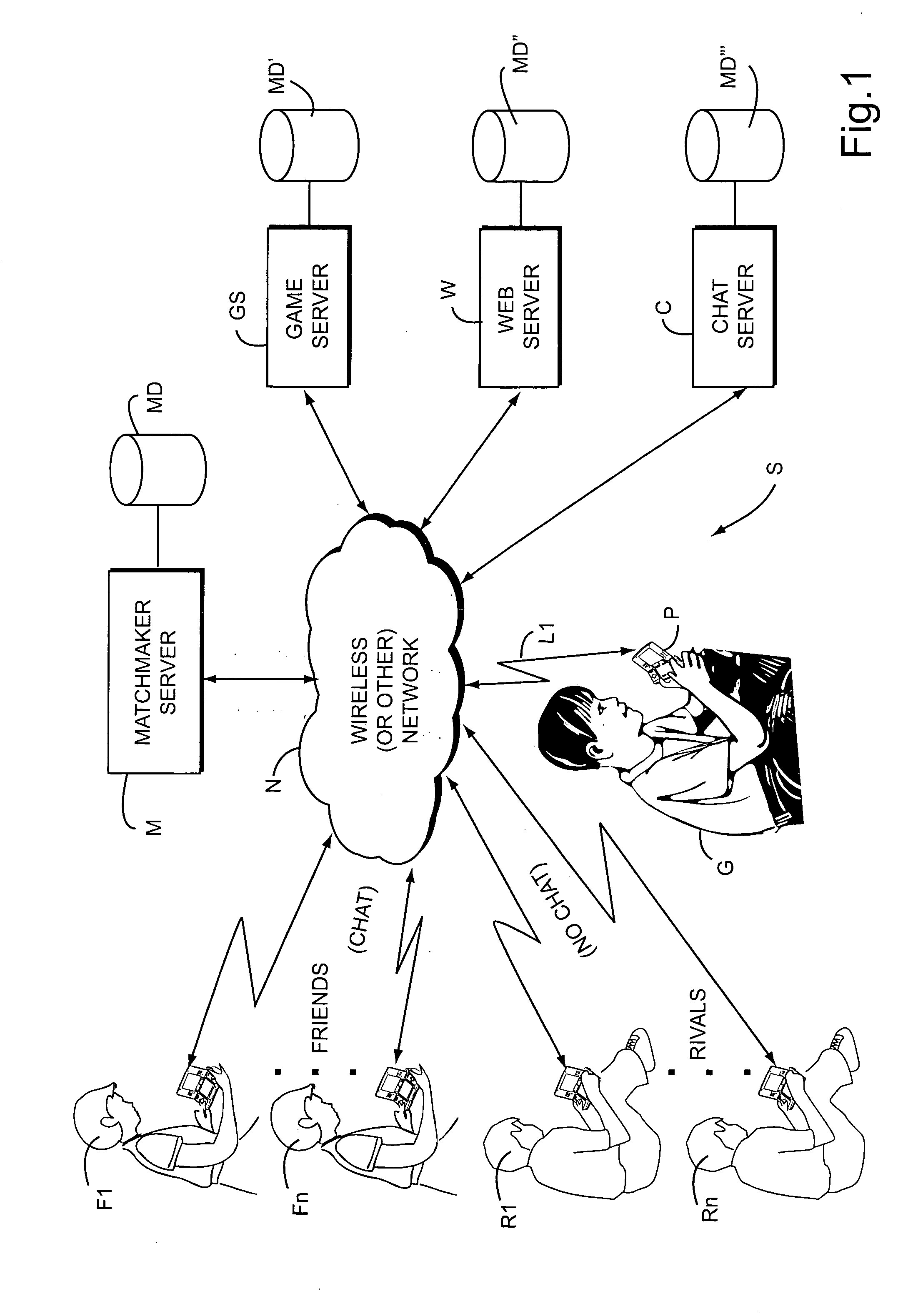
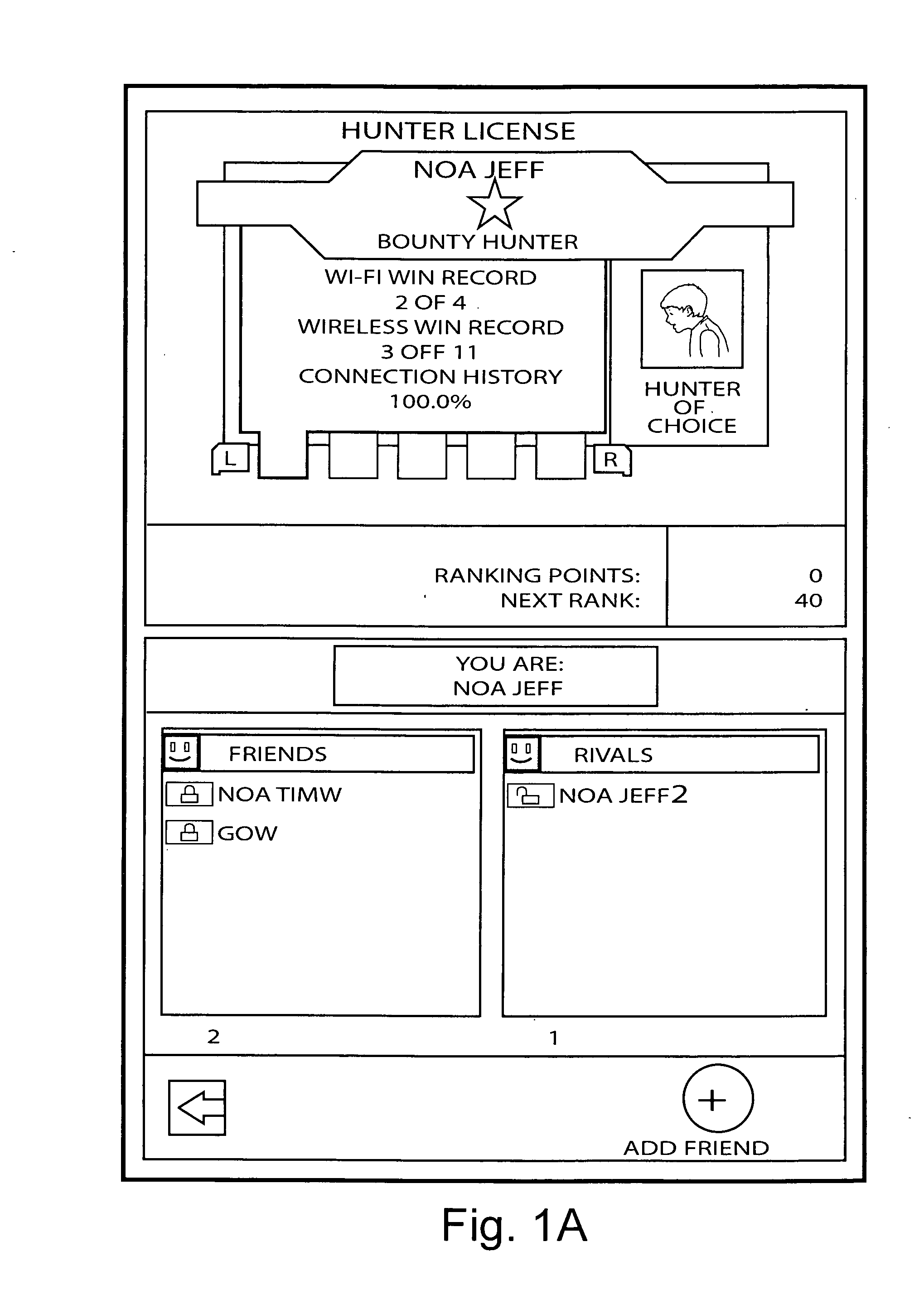
Systems, methods and techniques for safely and effectively coordinating video game play and other activities among multiple remote networked friends and rivals
ActiveUS20070218997A1Meet the selection requirementsEnsuring privacyVideo gamesSpecial data processing applicationsGame playerDirect communication
Real time interactive networked gaming is provided with two different classes of bookmarked online game players: “Friends” and “Rivals.”“Friends” are game players that are known personally. “Rivals” are game players who are not known personally but whom one has played against in the past in an online gaming scenario. Game software may allow chatting or other direct communication with “Friends” but not with “Rivals.” Rivals may be tracked to a limited degree so that for example it is possible to play against the Rival when he or she is online. Rivals may for example be players who you wish to track or keep track of, but in a manner that is safe for both you and the “rival.” When a player goes online again, he or she can see whether his or her Rivals are online and invite them to play another game. Inviting Rivals to play may be selectable, so an online player can invite Friends, Rivals or both to play.
Owner:NINTENDO CO LTD
Method and apparatus for providing wideband services using medium and low earth orbit satellites
InactiveUS6678520B1Interference minimizationMinimize interferenceActive radio relay systemsRadio/inductive link selection arrangementsHigh elevationLow earth orbit
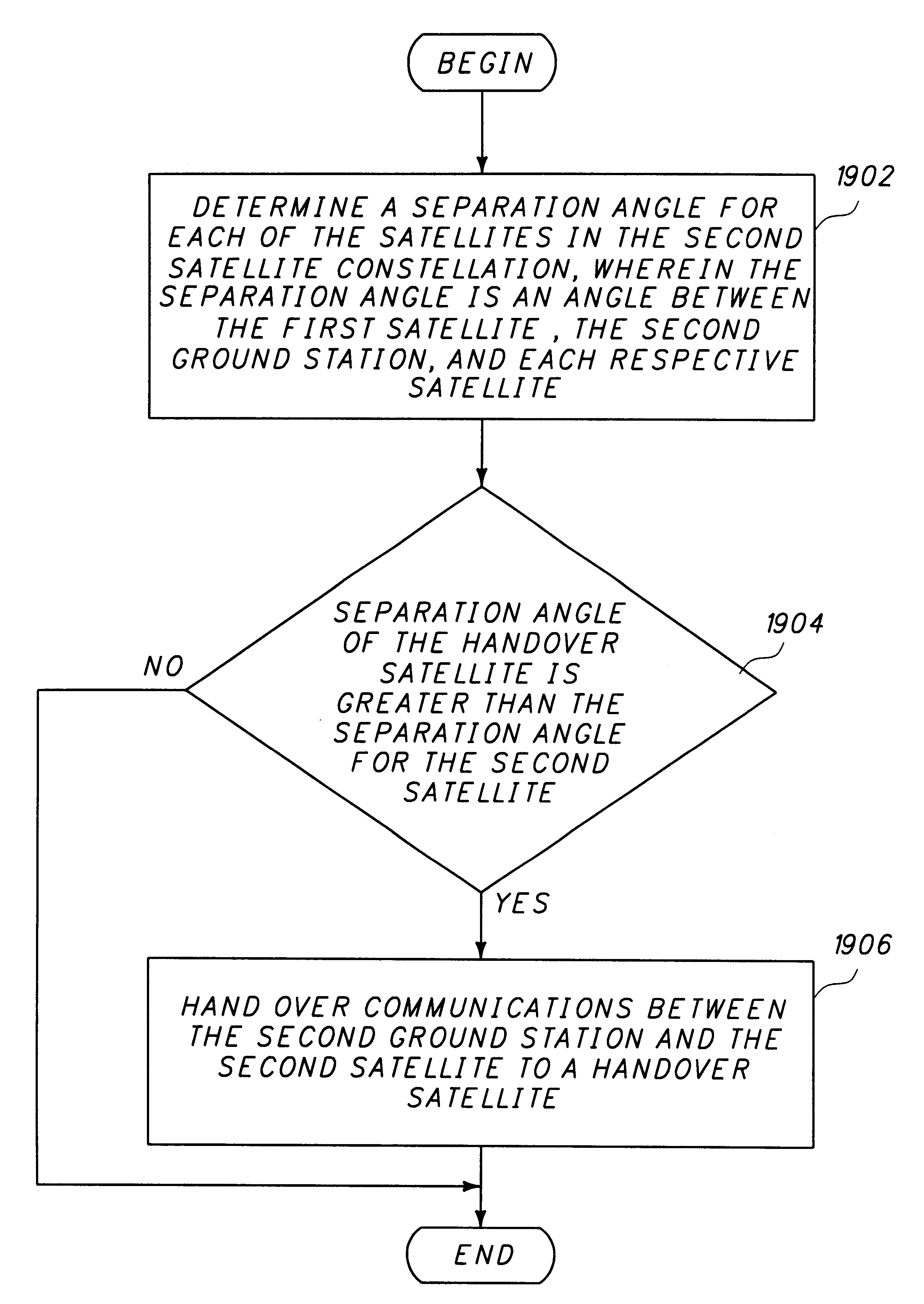
A method and apparatus for mitigating communications interference between satellite communications systems in different orbits is disclosed. The method comprises the steps of evaluating a geometrical relationship between a second ground station and the satellites in the second satellite constellation, and directing communications between the second ground station and the second satellite according to the evaluated geometrical relationship. In one embodiment communications are handed over from a first satellite to another satellite when the first satellite is no longer at the highest elevation angle of visible satellites. In another embodiment, handover occurs when the first satellite drops below a minimum elevation angle.
Owner:HUGHES ELECTRONICS
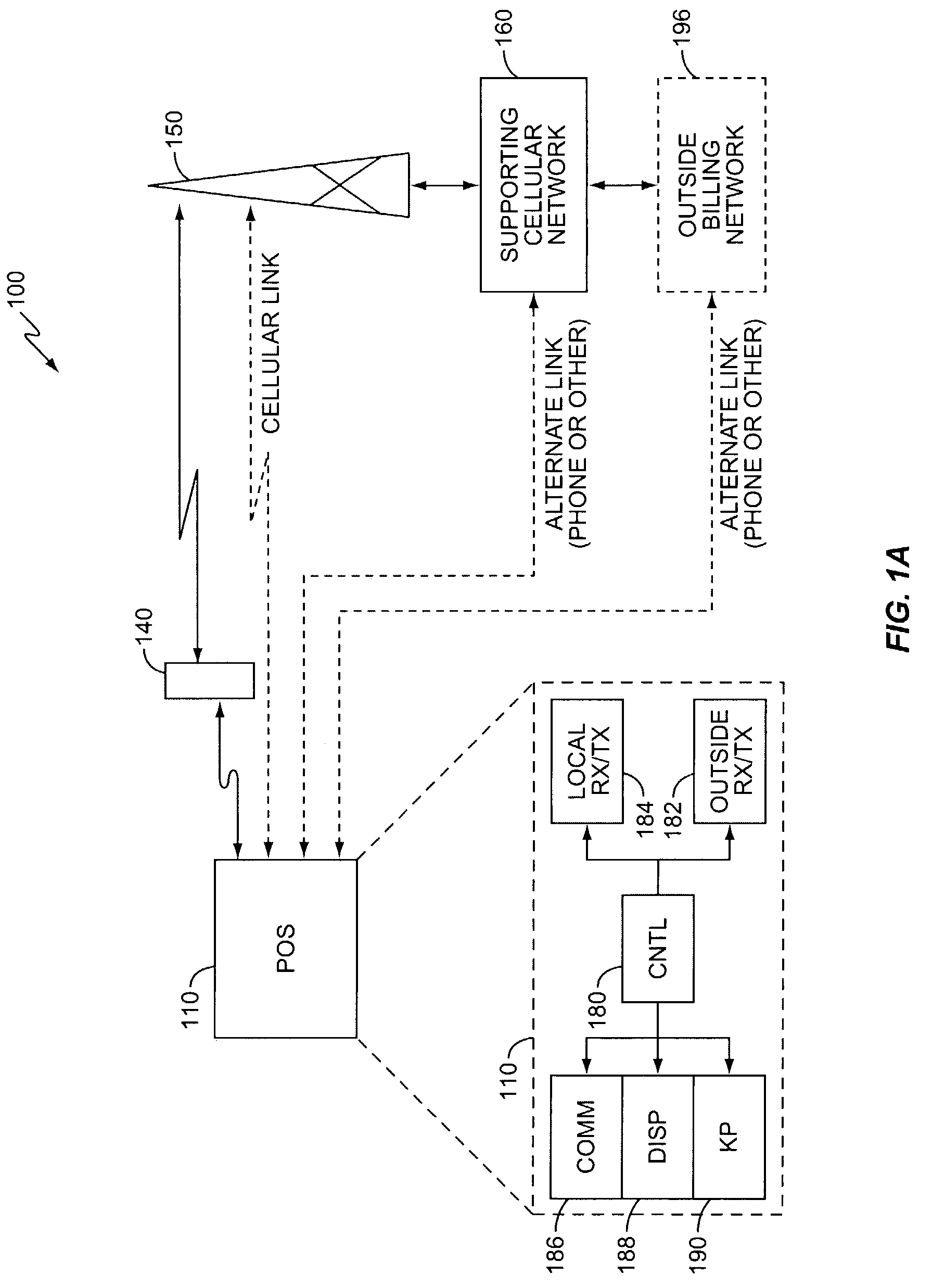
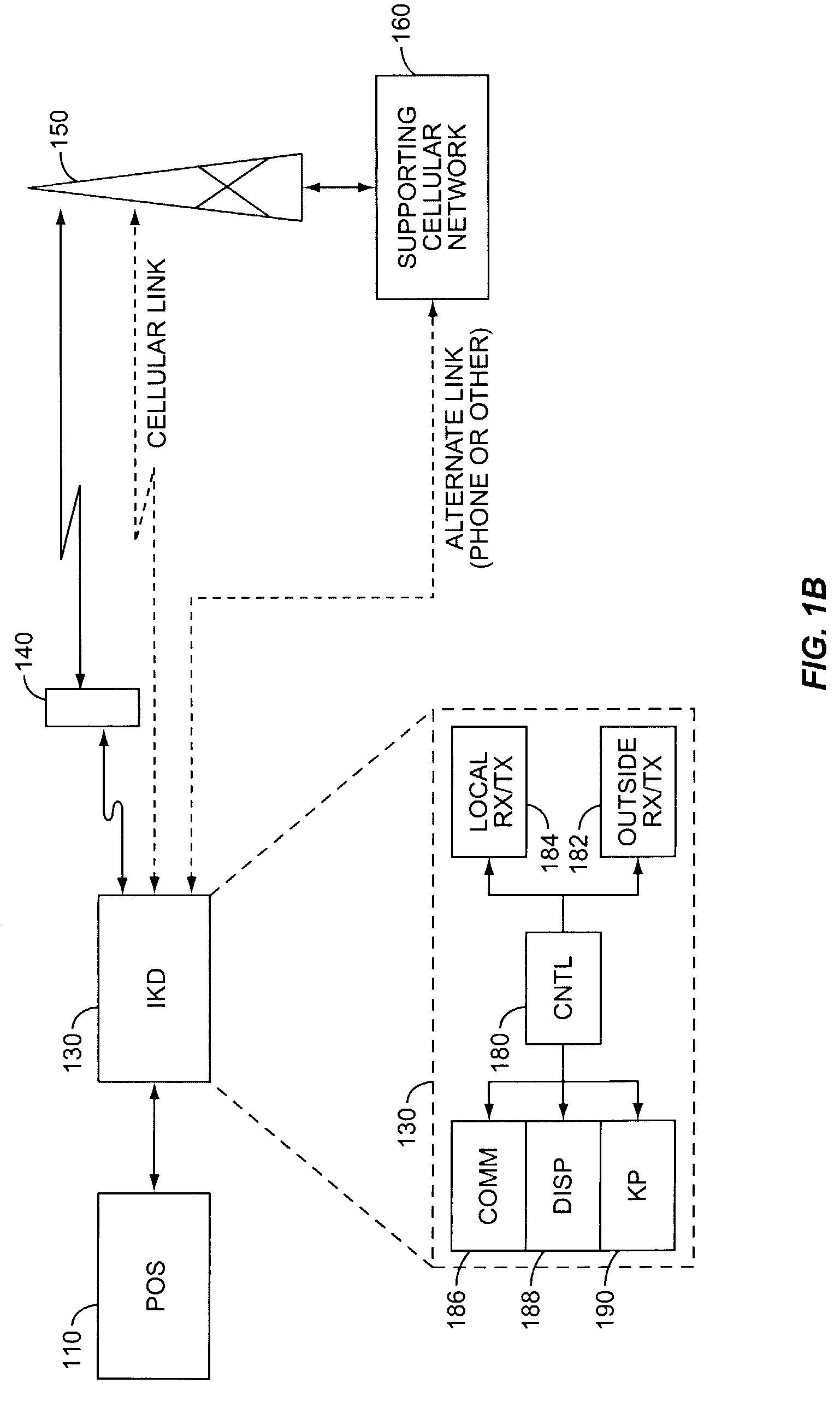
Cellular telephone-based transaction processing
InactiveUS7039389B2Telephonic communicationCredit schemesTelecommunications linkFinancial transaction
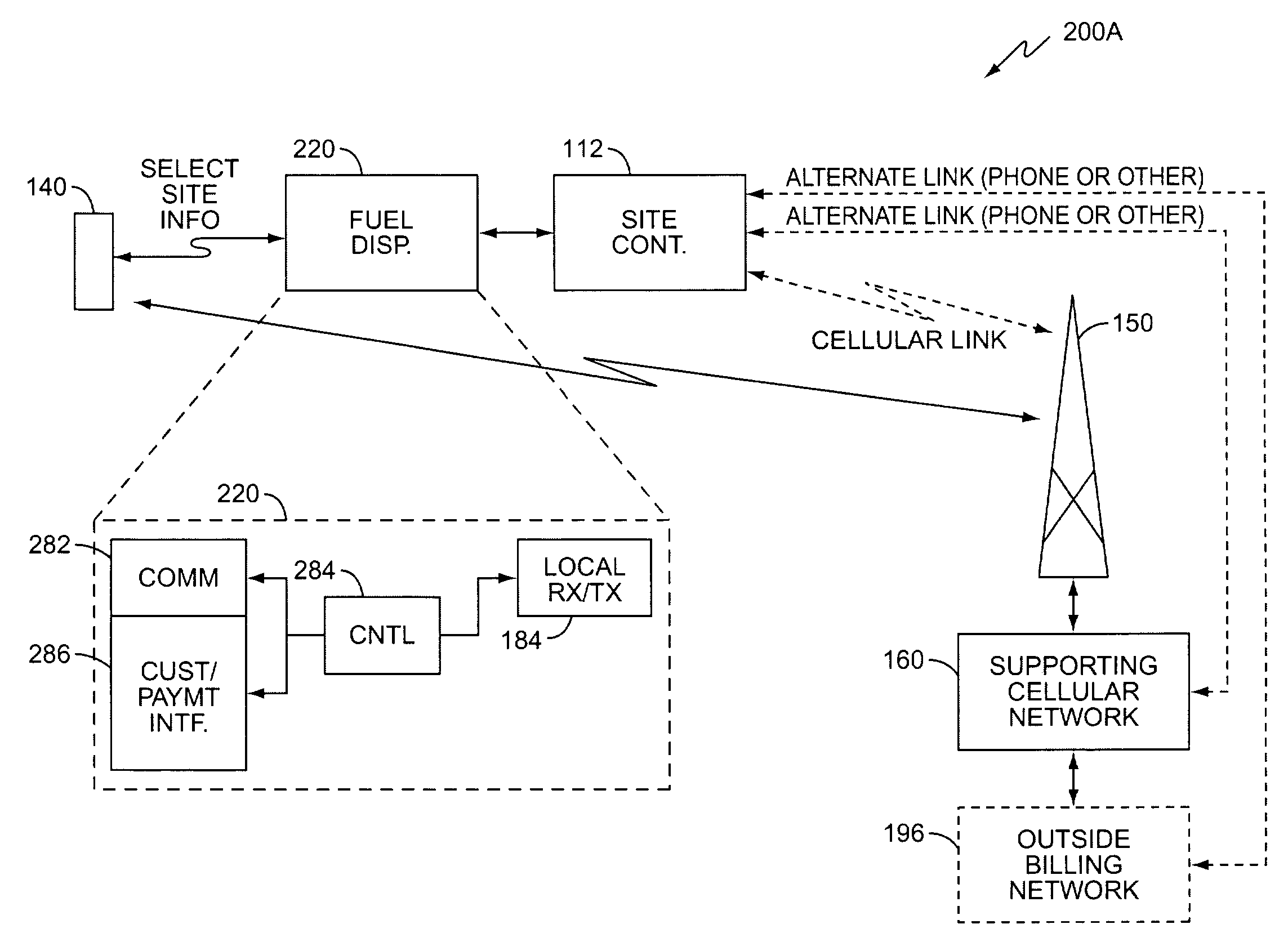
A retail transaction system provides enhanced customer convenience and increased transaction security by sending transaction information to a cellular network provider via a customer's digital cellular phone. For example, a fuel dispenser is equipped with a communications link allowing direct communications to a customer's cellular phone. When a customer desires to conduct a transaction using the fuel dispenser, the fuel dispenser transmits select information to the customer's cellular telephone using this communications link. A telephone number is included in the select information. When the customer presses send, or otherwise causes their telephone to dial the number transferred from the fuel dispenser, the select information along with any additional customer information is sent to the cellular network. This information is used by the network to authorize a purchase transaction for the customer, such authorization information returned to the fueling station at which the fuel dispenser is located via a cellular link. For enhanced security, the customer may be required to input their PIN in order to complete the transaction. Notably, the PIN and the remainder of the transaction information sent from the customer phone to the cellular network is intrinsically secure due to the digital encryption employed by the digital cellular protocol. Optionally, the system may be configured to cause the customer's cellular phone to automatically dial the number transferred by the fuel dispenser. This capability may be enabled at the customer's option. The system may be extended to other retail systems including in-store point-of-sale systems (POS).
Owner:GILBARCO
Real-time collaboration and communication in a peer-to-peer networking infrastructure
ActiveUS20050216556A1ReliablyMultiple digital computer combinationsTransmissionGraphicsDirect communication
Methods that enable real-time communication and collaboration in a peer-to-peer (P2P) network are provided. More specifically, methods for the creation and access of an underlying graph and / or group structure to pass collaboration / real-time communication data and other functions such as the retrieval of node / member and graph / group information, the addition, modification, deletion and management of records (data), the direct communication between graph / group nodes / members, the registering for event notifications, and other functions are used to pass real-time communication / collaboration data between nodes in a graph or members of a group.
Owner:MICROSOFT TECH LICENSING LLC
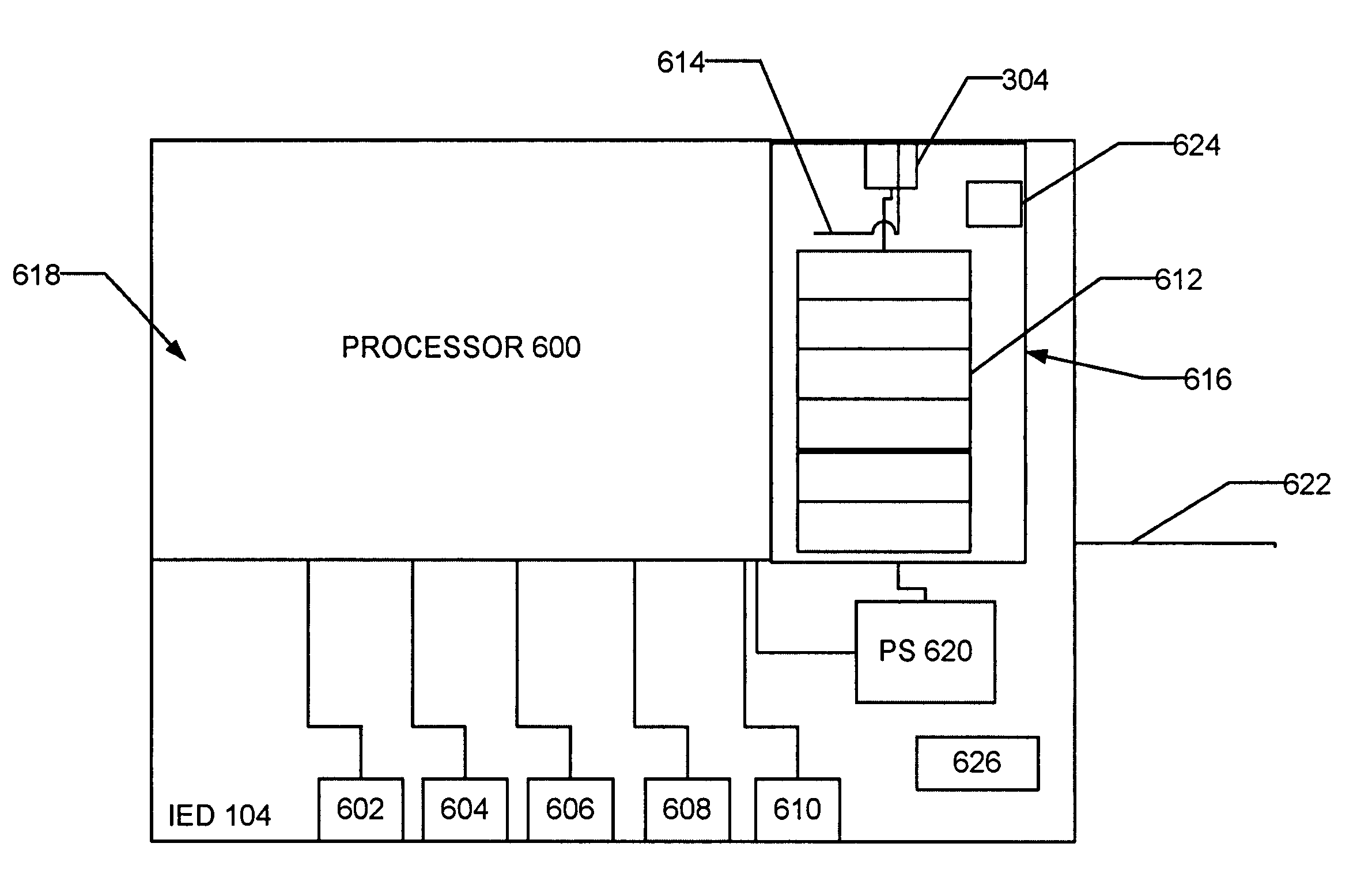
Intelligent electronic device with embedded multi-port data packet controller
ActiveUS8730834B2Improve reliabilityImprove noise immunityTime-division multiplexData switching by path configurationNetwork packetEngineering
An intelligent electronic device (IED) configured to supervise a process having a state has at least one of a current, voltage or resistive input configured to monitor the state of the process, a binary status input configured to monitor the state of the process, a binary status input configured to receive a digitally encoded serial communication package for monitoring the state of the process, a control output configured to output a signal to control process protection, control, or automation, or a combination thereof, or a control output configured to output a digitally encoded serial communication package to control protection, control, or automation, or a combination thereof. The IED is also configured to facilitate digital communication between at least two compatible devices by directing communication packets from ports connected to an originating compatible device to ports connected to a destination compatible device.
Owner:GE INFRASTRUCTURE TECH INT LLC
Systems and methods for non-traditional payment using biometric data
InactiveUS20070052517A1Convenient transactionFacilitate payment transactionElectric signal transmission systemsMultiple keys/algorithms usageComputer hardwareBiometric data
Facilitating transactions using non-traditional devices and biometric data to activate a transaction device is disclosed. A transaction request is formed at a non-traditional device, and communicated to a reader, wherein the non-traditional device may be configured with an RFID device. The RFID device is not operable until a biometric voice analysis has been executed to verify that the carrier of the RFID equipped non-traditional device is the true owner of account information stored thereon. The non-traditional device provides a conduit between a user and a verification system to perform biometric voice analysis of the user. When the verification system has determined that the user is the true owner of one or more accounts stored at the verification system, a purchase transaction is facilitated between the verification system. Transactions may further be carried out through a non-RF device such as a cellular telephone in direct communication with an acquirer / issuer or payment processor
Owner:LIBERTY PEAK VENTURES LLC
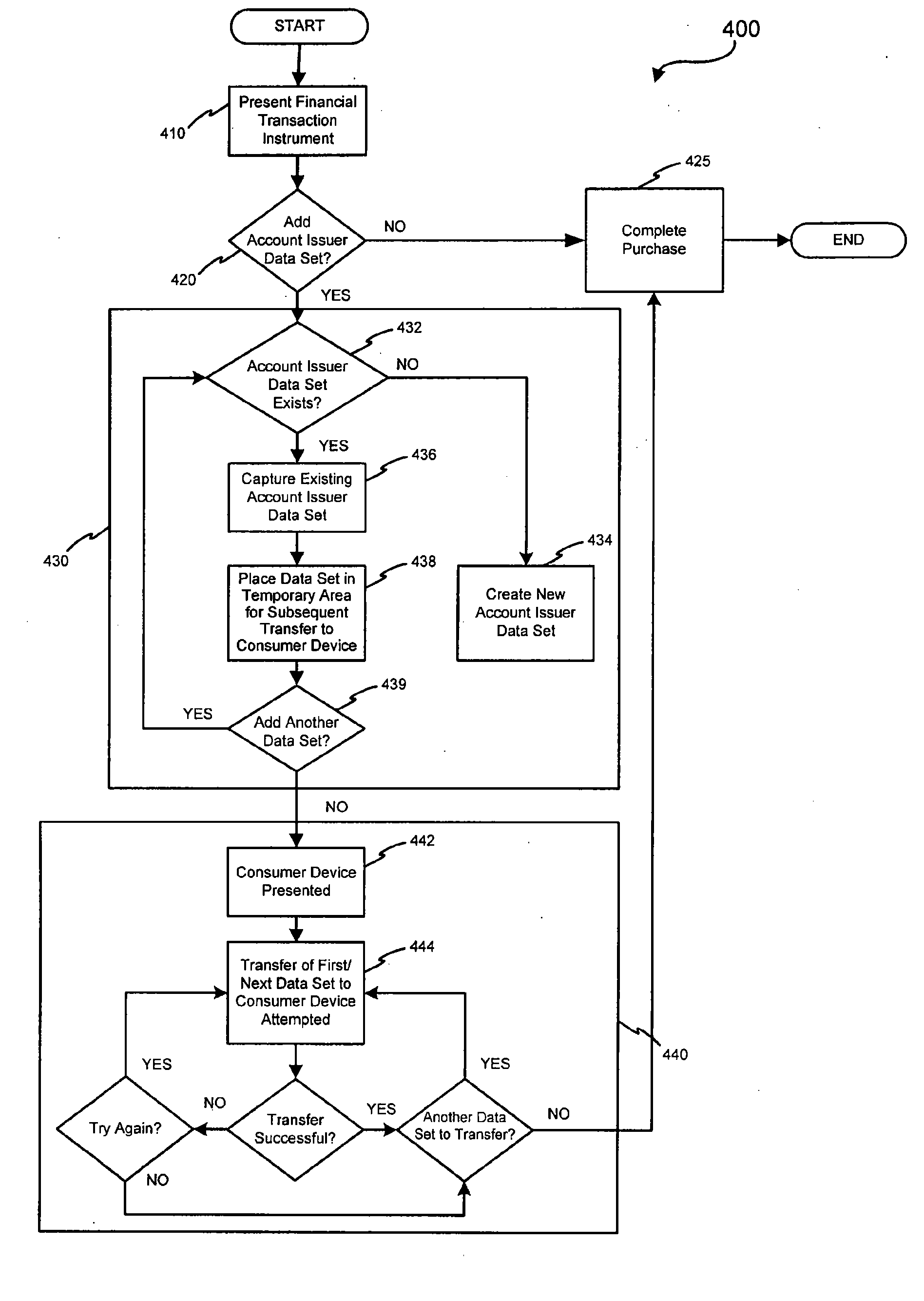
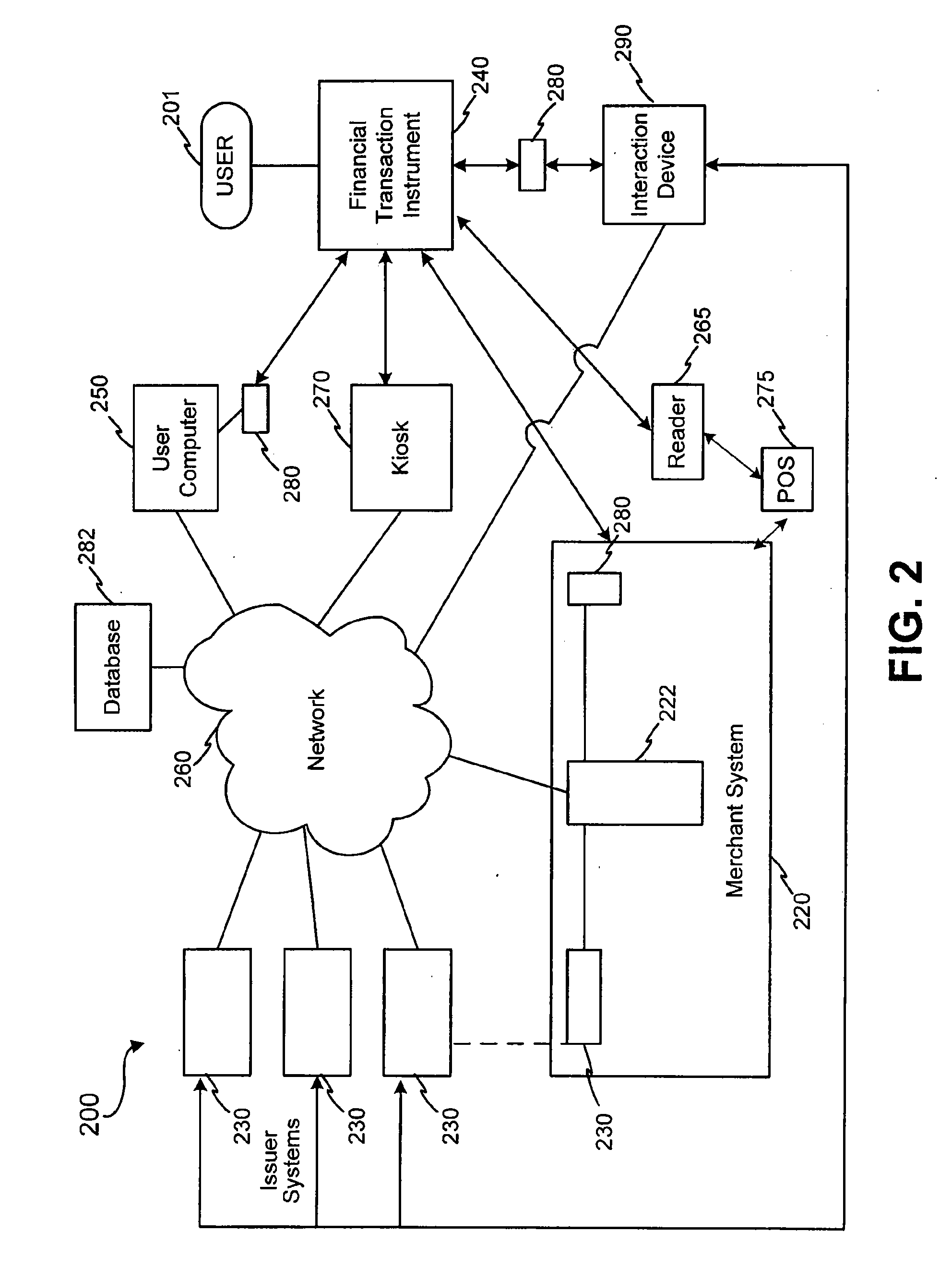
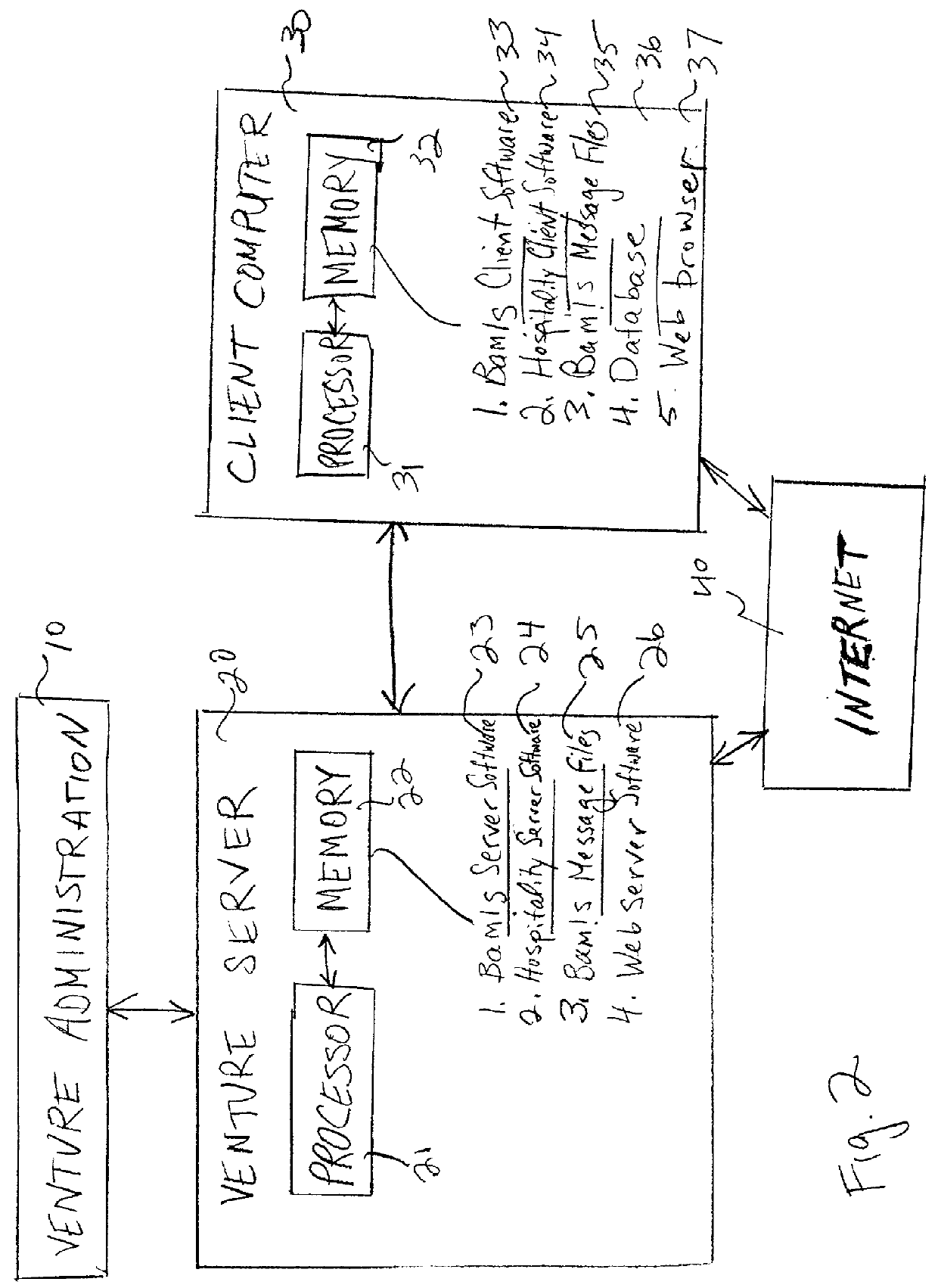
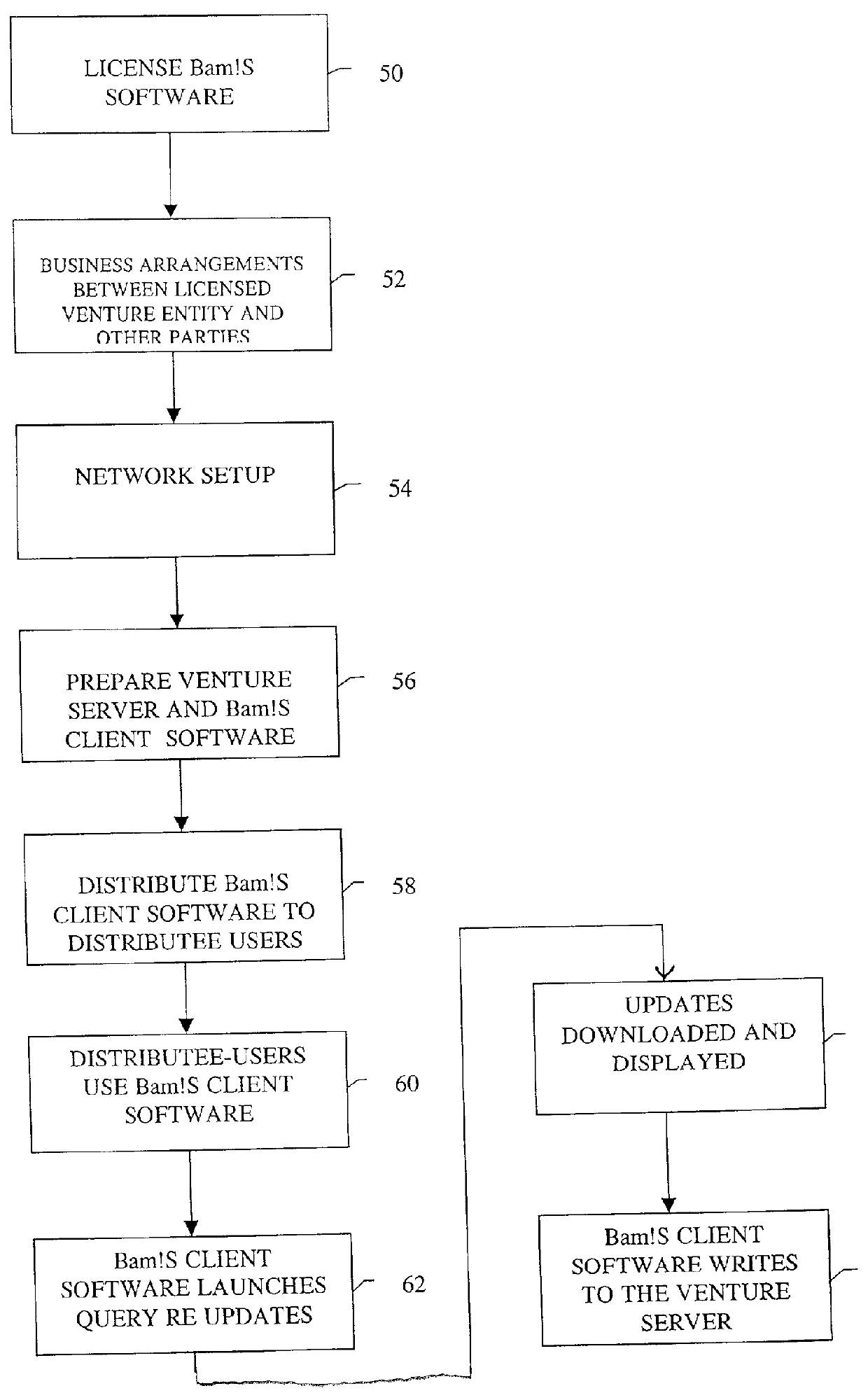
Method of direct communication between a business and its customers
A business model, system, and method for a business entity to distribute branding, advertising, marketing, and service (BAMS) data to consumer-users is described. The business entity establishes and maintains a venture server that transmits BAMS data to client applications installed on the electronic devices of consumer-users and controls usage and display of the BAMS data at the electronic devices. The client application, which is prepared and assigned a unique identifier by the business entity, performs a useful function that requires a graphical user interface (GUI) to be displayed in the display of the user's electronic device. After receiving the BAMS data, the client application stores it, and displays it in the GUI. The client application can be written so that no user information is transmitted from the electronic device to the venture server.
Owner:INTEL CORP
Methods for controlling shared access to wireless transmission systems and increasing throughput of the same
InactiveUS6795407B2Reduce loadReduce overheadError prevention/detection by using return channelPower managementCommunications systemWireless transmission
A wireless communication system implements a calibration mode by which individual nodes in the system can determine which other nodes in the system are physically close to them and therefore can be reached with less than full transmitting power. Nodes which can communicate with one another via low power can form a low power constellation (a subset of the complete network) whose nodes can communicate directly with one another using this low power arrangement. The direct communication mode may additionally be used by itself. In another mode, the nodes in the system can communicate amongst themselves via bridges-other, non-access point nodes-to lessen the load on the access point or to accommodate environmental or other conditions. Various ones of these modes may be combined into a predetermined cycle of communication modes to help the physical layer accommodate various types of data handled by the network using beacons or another coordinating technique. Overhead in the form of packet retransmission may be reduced by interpolating to recover lost packets rather than retransmitting them.
Owner:QUALCOMM INC
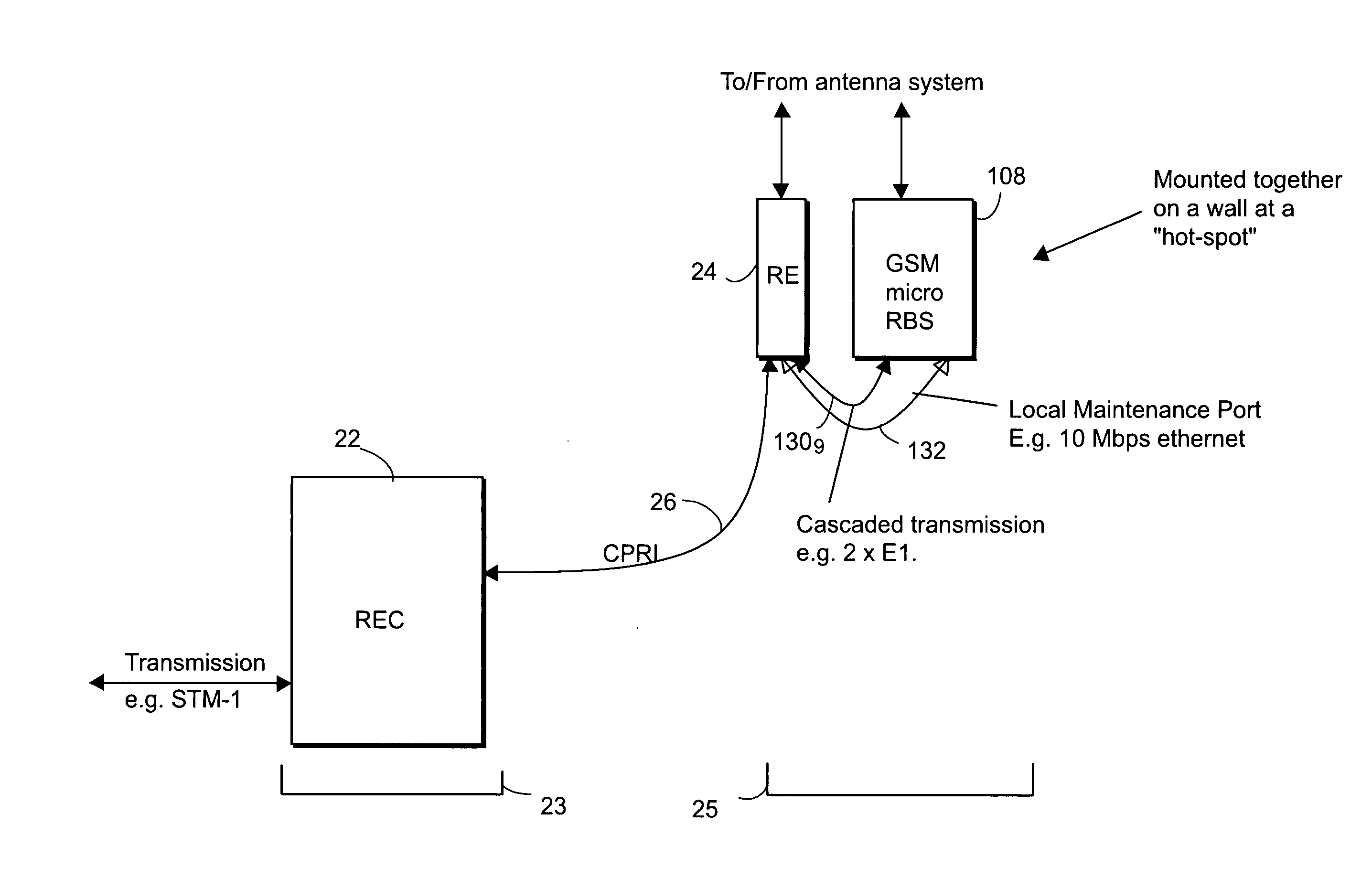
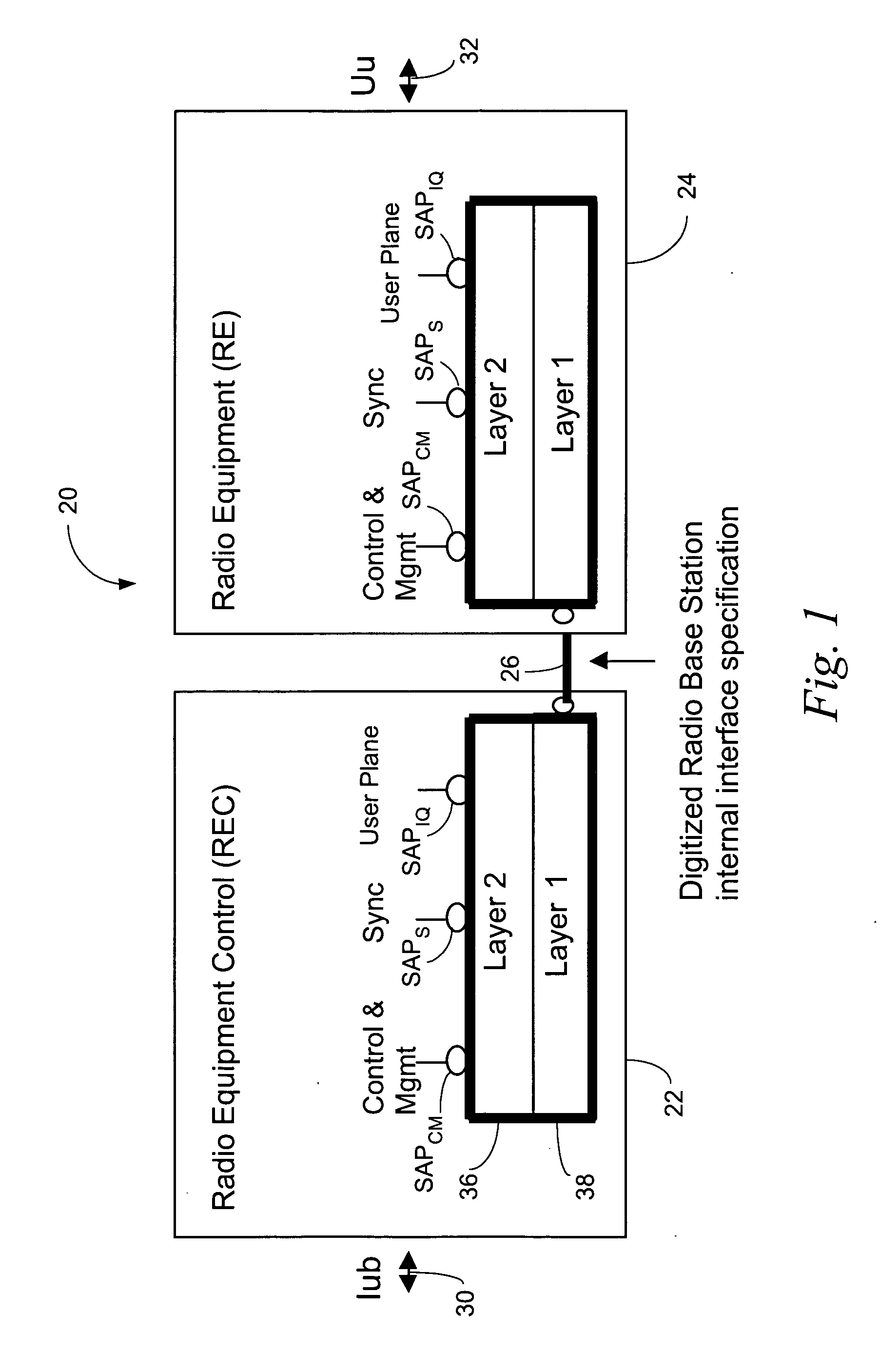
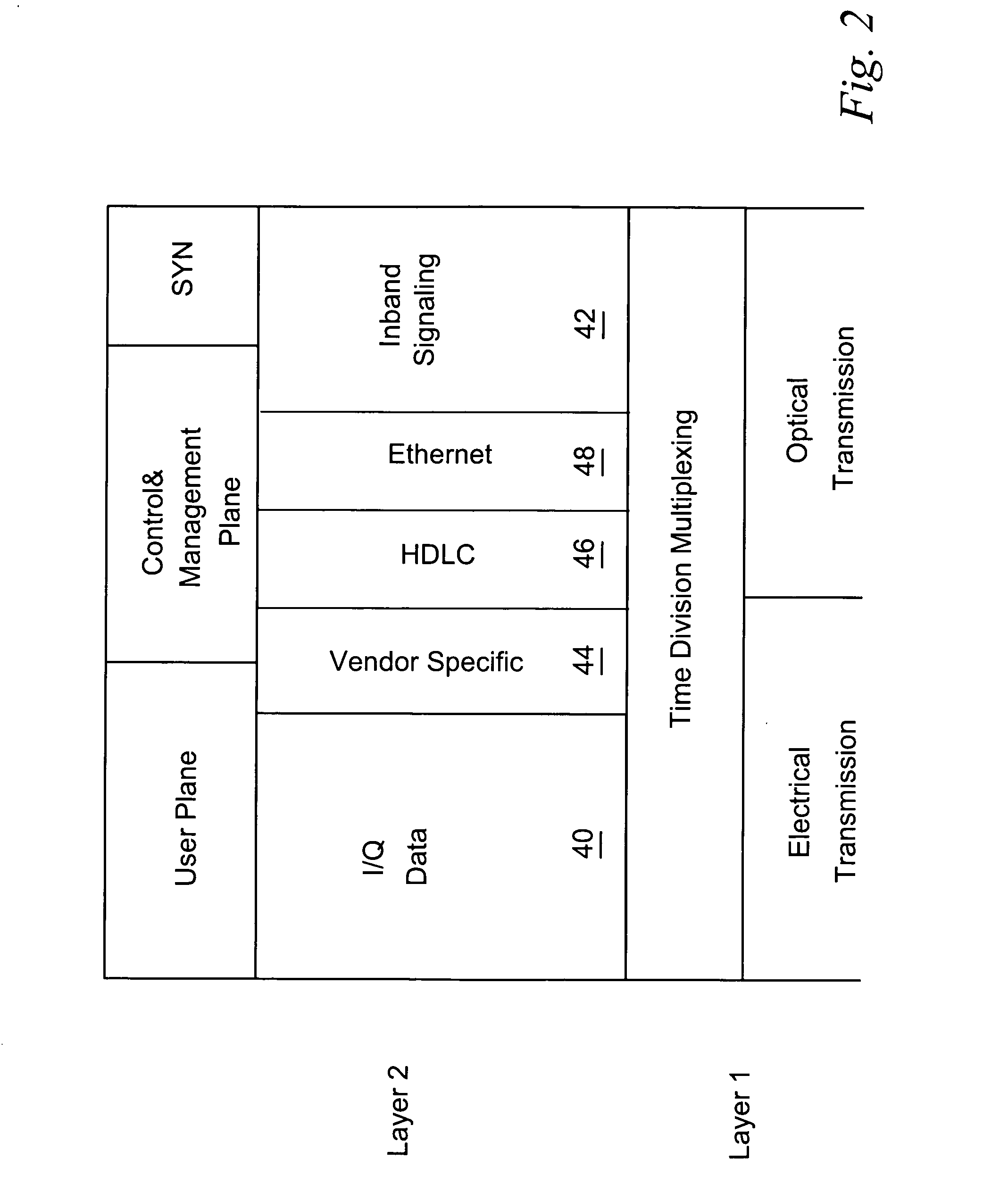
Encapsulation of independent transmissions over internal interface of distributed radio base station
ActiveUS20050105552A1Network traffic/resource managementTime-division multiplexRadio equipmentEngineering
A distributed radio base station (20) comprises a radio equipment controller (REC) (22) situated at a main site (23) and a radio equipment (RE) (24) situated at a remote site (25). A remote unit (102, 104, 106, 108, 110, 124) configured to engage in direct communications with the radio equipment controller (REC) is also situated at the remote site (25). An internal interface (26) connects the radio equipment controller (REC) and the radio equipment (RE). Advantageously, the internal interface (26) also encapsulates the direct communications between the radio equipment controller (REC) (22) and the remote unit, thereby obviating a separate physical link between the radio equipment controller (REC) and the remote unit. A new physical link (130) transmits, between the radio equipment (RE) and the remote unit, the direct communications between the radio equipment controller (REC) and the remote unit which are encapsulated over the internal interface (26). The remote unit can take various differing forms, including that of an antenna (102) with remote electrical tilt control; a tower mounted amplifier (TMA) (104); a Transmission network unit (106); a separate radio base station (108) which is co-located at the remote site; a proprietary equipment unit (110); or even one or more cascaded radio equipments (RE) (124).
Owner:TELEFON AB LM ERICSSON (PUBL)
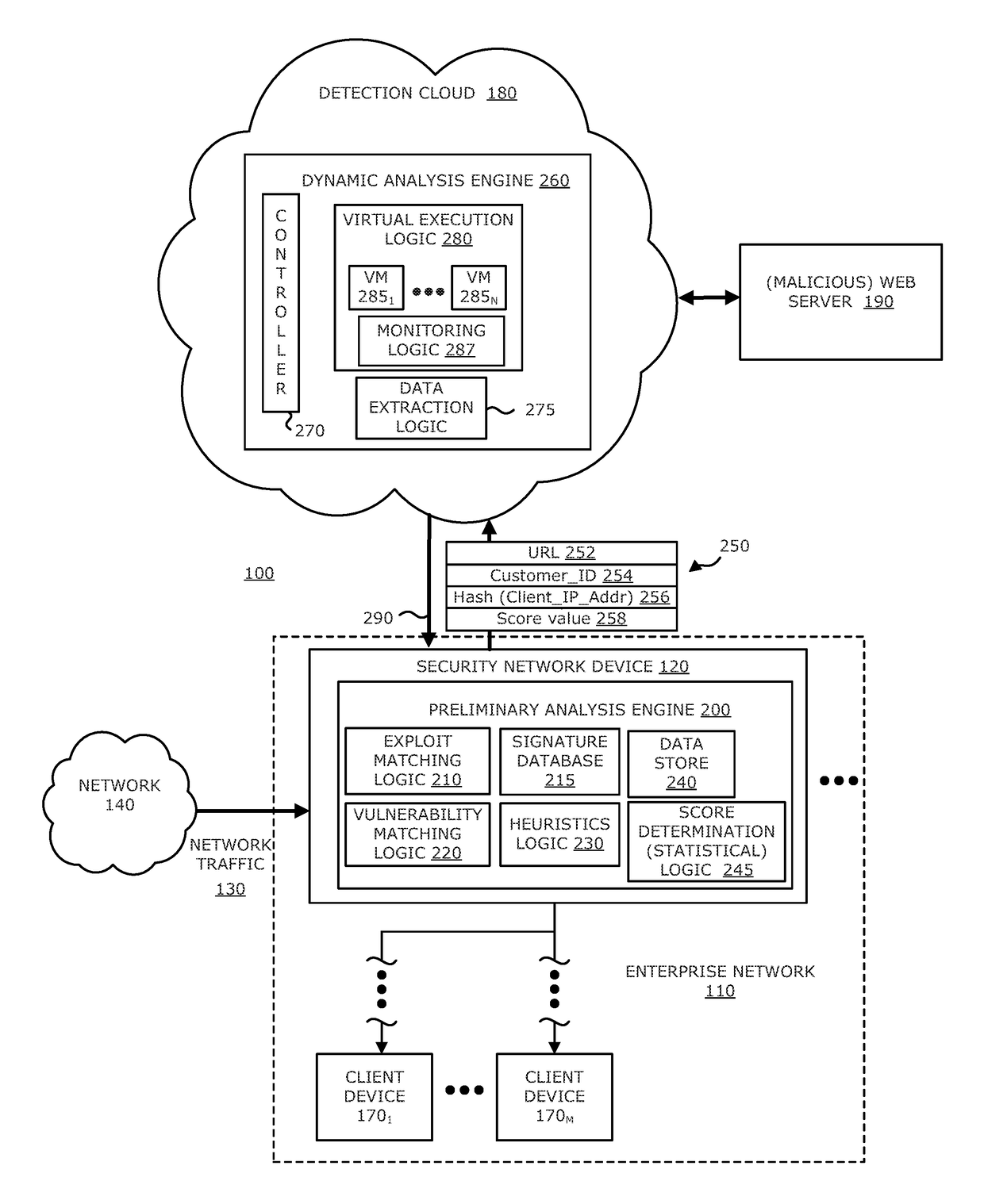
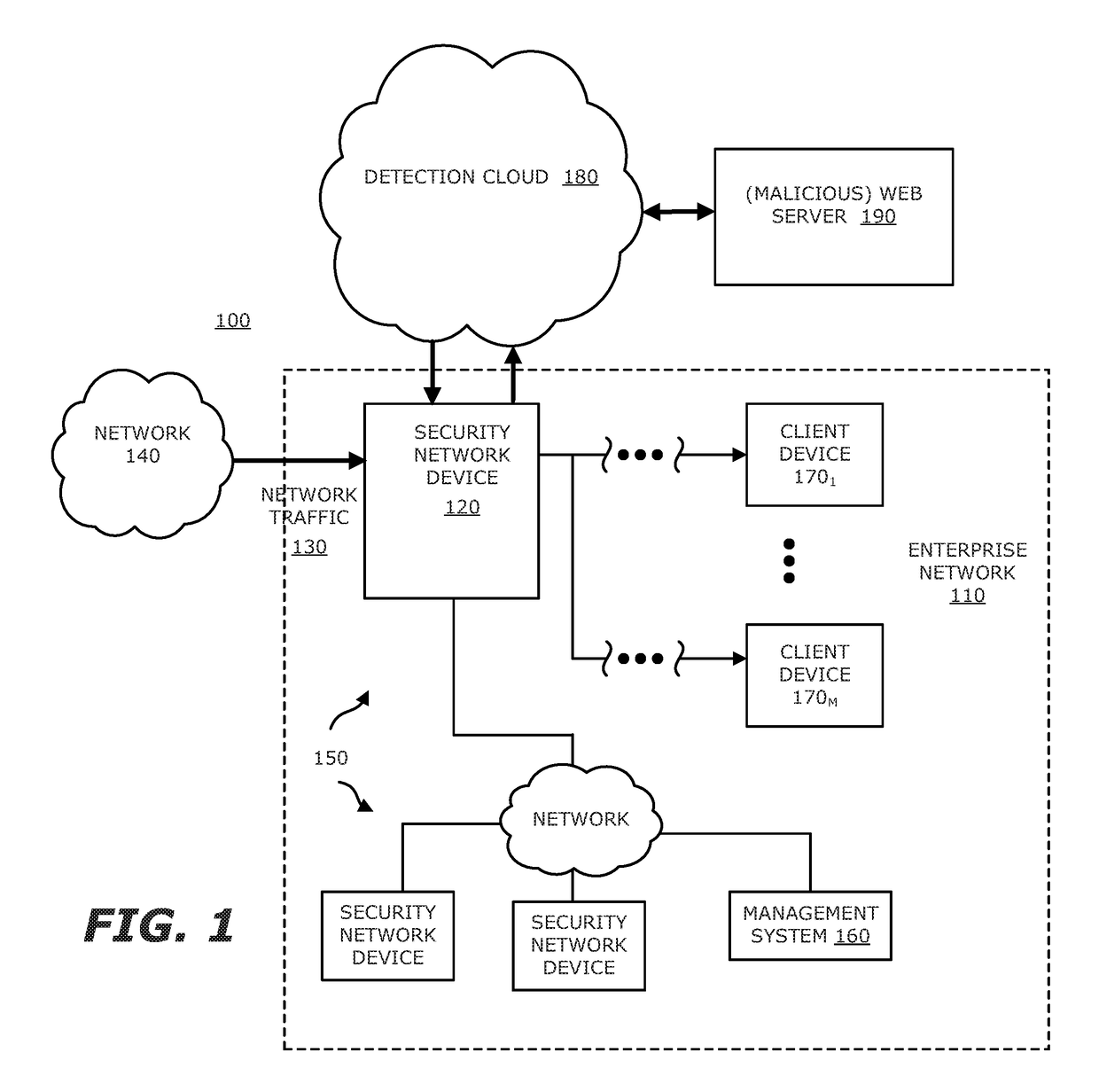
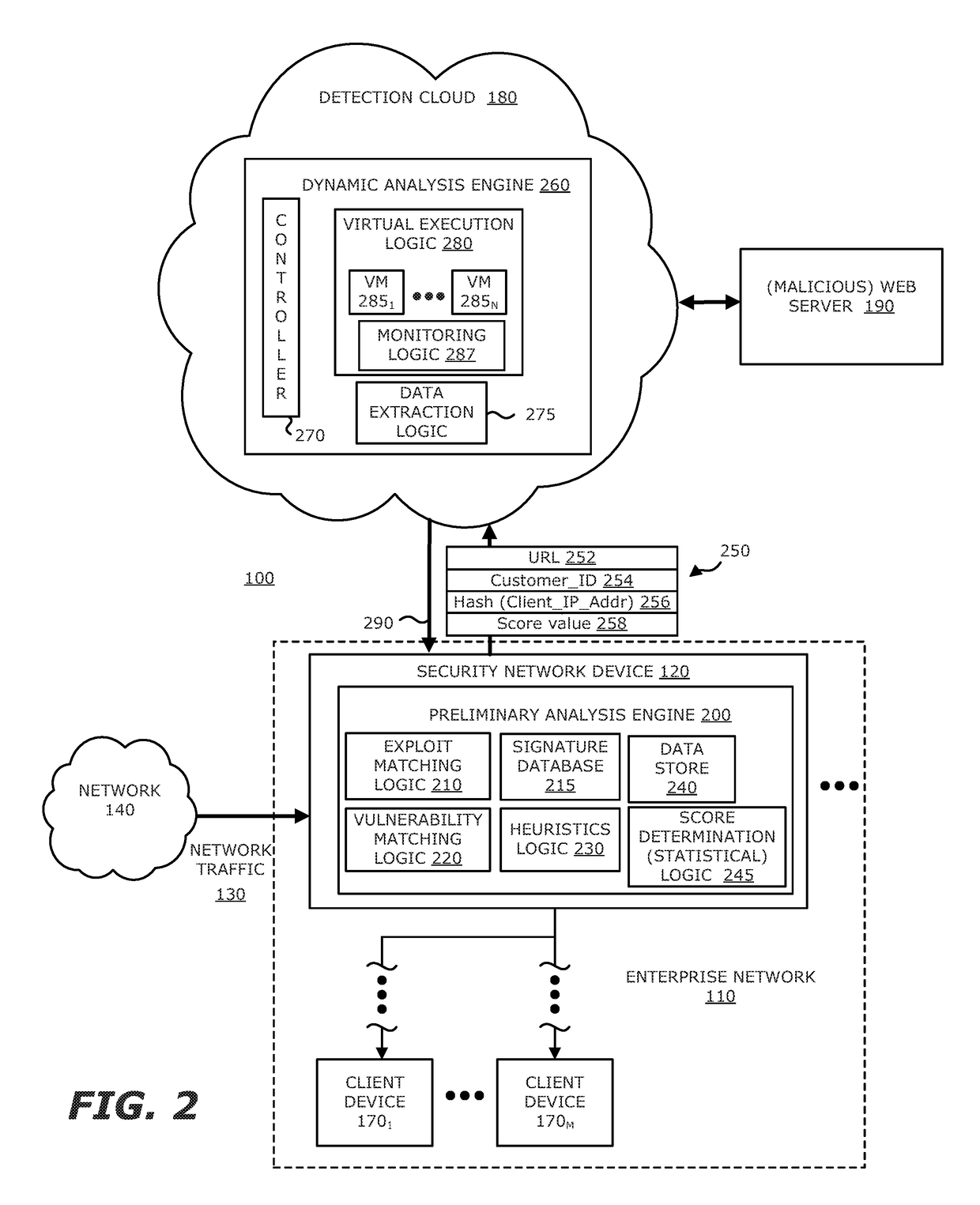
System, device and method for detecting a malicious attack based on direct communications between remotely hosted virtual machines and malicious web servers
ActiveUS9838408B1TransmissionSoftware simulation/interpretation/emulationTraffic capacityWeb service
In an embodiment, a system, device and method for detecting a malicious attack is described. Herein, the system includes a security network device that conducts an analysis on received network traffic to detect a suspicious object associated with the network traffic and determine an identifier associated with a source of the suspicious object. Information associated with the suspicious object and / or ancillary data, including information that identifies a return path for analysis results to a customer, are uploaded to a detection cloud. The detection cloud includes provisioning logic and one or more virtual machines that are provisioned by the provisioning logic in accordance with at least a portion of the ancillary data. The provisioning logic to customize functionality of the detection cloud for a specific customer.
Owner:FIREEYE SECURITY HLDG US LLC +1
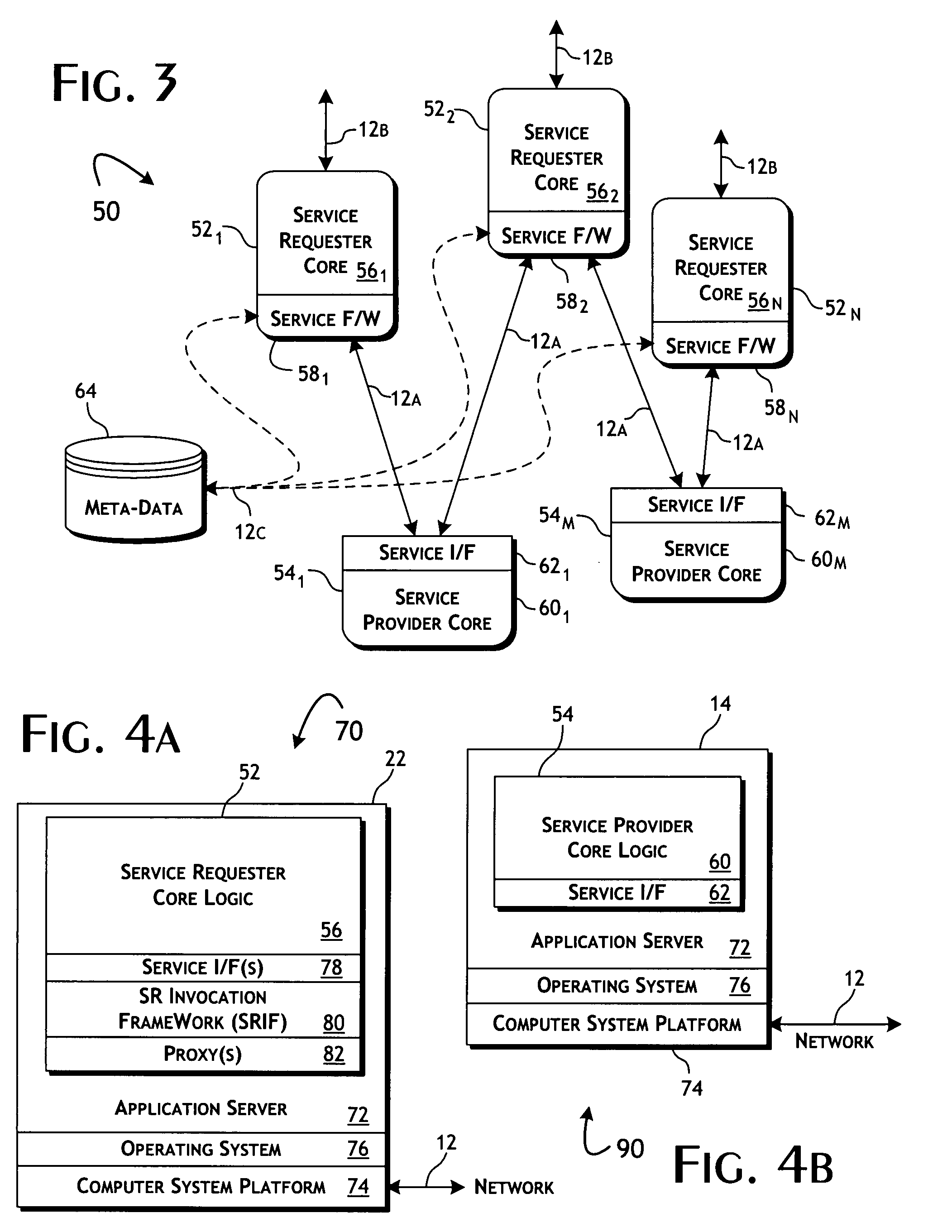
Service-oriented architecture and methods for direct invocation of services utilizing a service requestor invocation framework
InactiveUS20080140857A1Effective guidanceEfficient use ofData processing applicationsMultiple digital computer combinationsData processing systemDirect communication
A data processing system implementing a service-oriented architecture that efficiently provides for self-directed communications between service requesters and service providers. Service providers, operative to implement a predefined computing functions, are responsive to first service requests and operative to provide a first service responses. Service requesters executed remote from service providers are operative to provide second service requests and receive second service responses. A service invocation framework local to each service requester functions to convert between first and second service requests and first and second service responses and to establish direct invocation communications connection with a selected service provider for the exchange of first service requests responses. A service invocation manager provides configuration meta-data, upon dynamic request by a service invocation framework, to define the conversions and communications connection to be implemented by the service invocation framework with respect to a service provider.
Owner:PRIMITIVE LOGIC
Method, apparatus and computer program product for allocating resources in wireless communication network
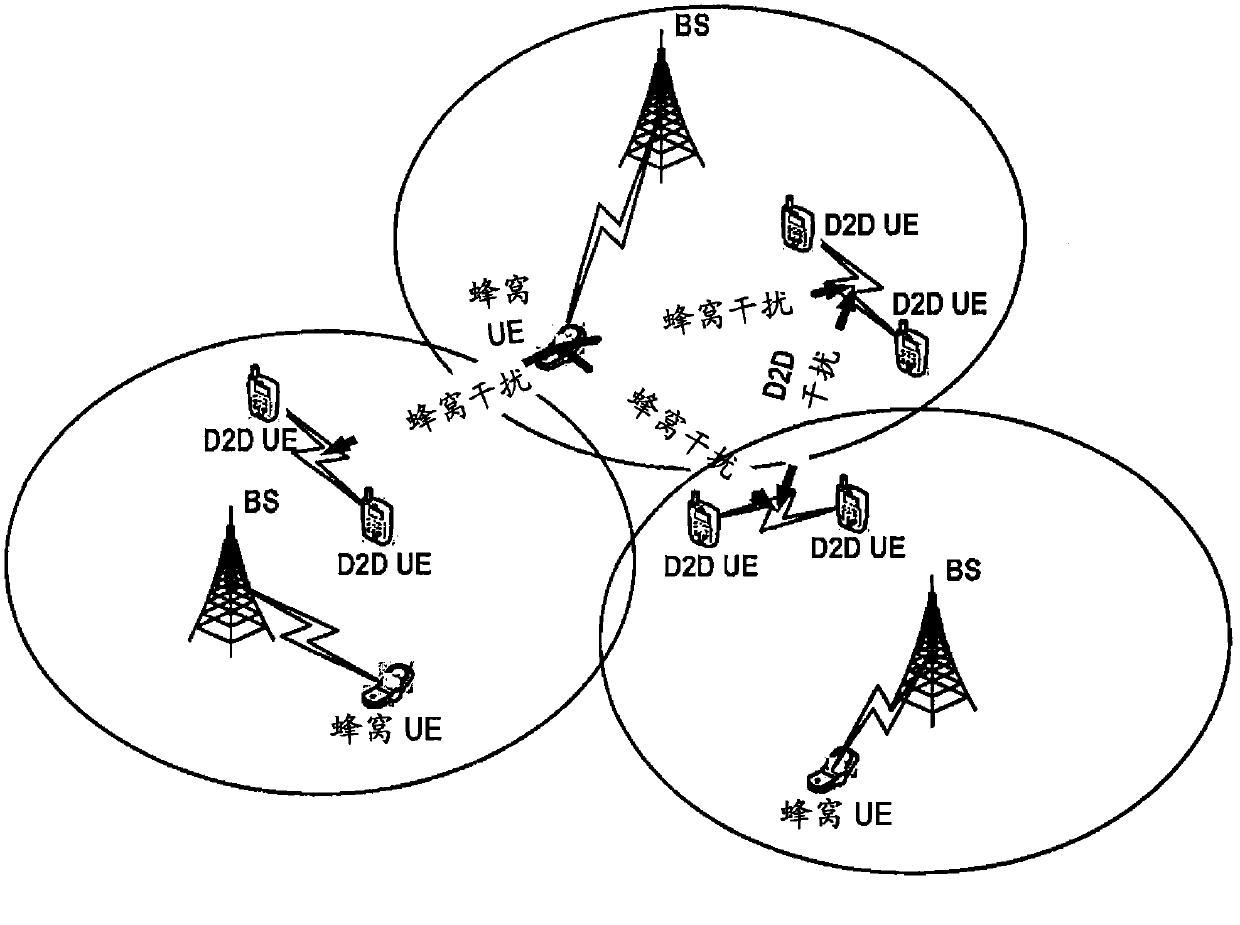
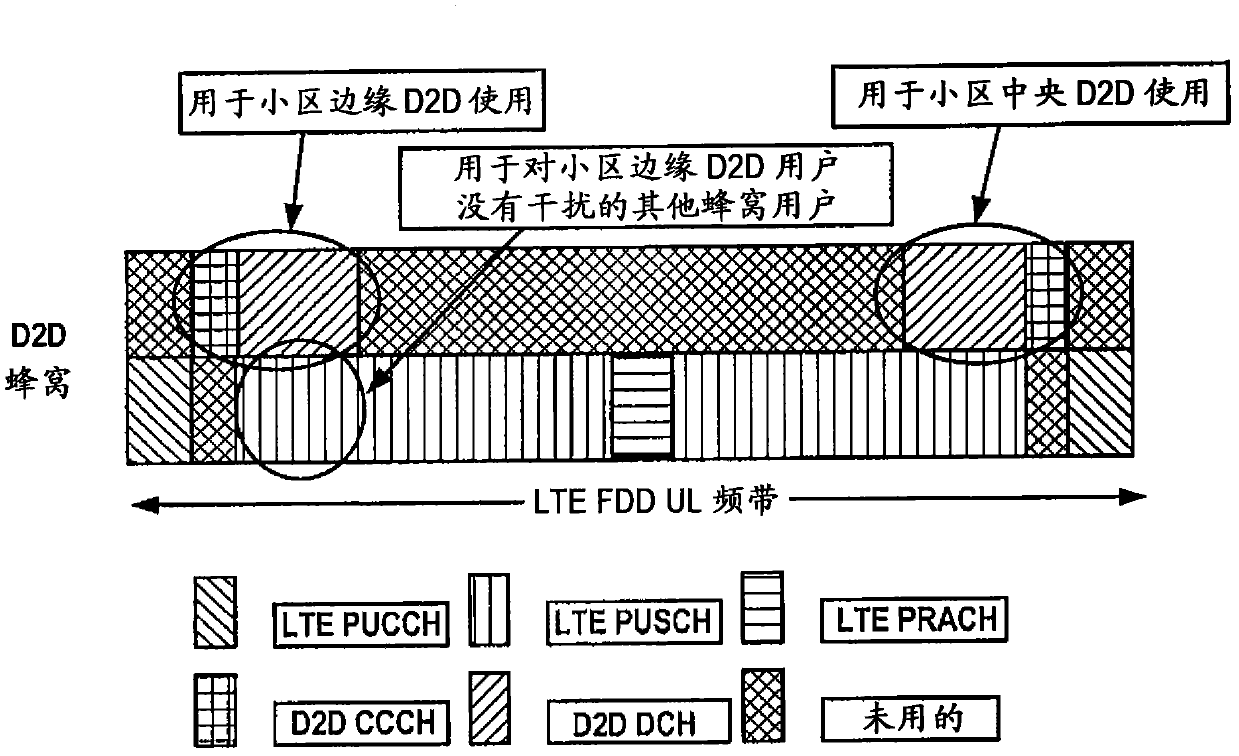
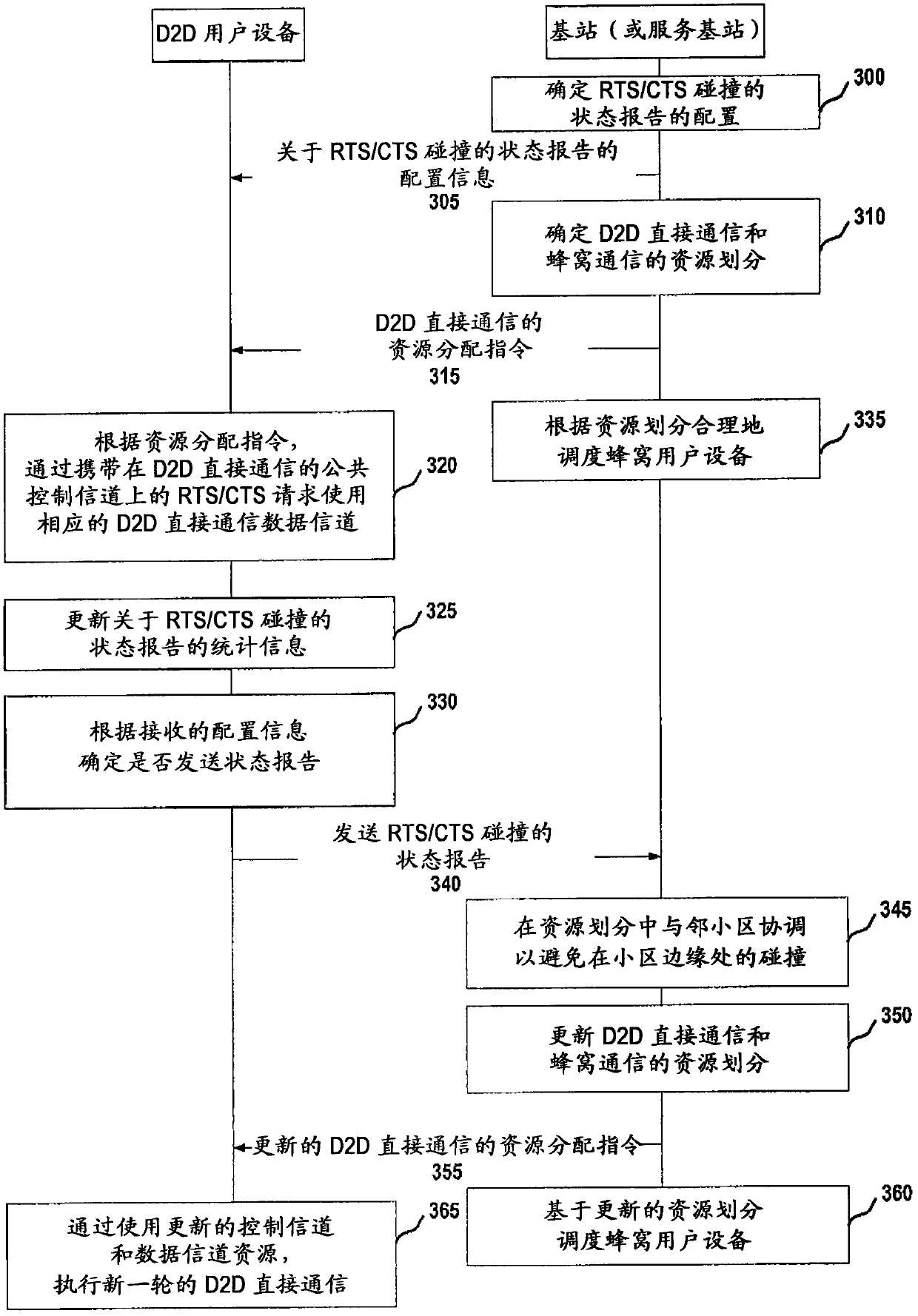
InactiveCN102792745AEasy to useImprove spectral efficiencyPower managementNetwork topologiesDirect communicationResource allocation
The present application discloses a method, an apparatus and a computer program product for allocating resources for a Device-to-Device (D2D) direct communication user equipment in a wireless communication network, wherein the method comprises: transmitting a communication channel status report regarding Device-to-Device direct communication to a base station; receiving resource allocation instructions generated by the base station based on the communication channel status report; and performing Device-to-Device direct communication between user equipments on the allocated resources; the disclosed apparatus comprises transmitting means for transmitting a communication channel status report regarding Device-to-Device direct communication to a base station; receiving means for receiving resource allocation instructions generated by the base station based on the communication channel status report; and performing means for performing Device-to-Device direct communication between user equipments on the allocated resources. By using the method, apparatus and computer program product disclosed in the present application, resource sharing / allocation collision between the D2D user equipment and cellular user equipment can be effectively reduced and use rate of resources can be improved.
Owner:NOKIA TECHNOLOGLES OY
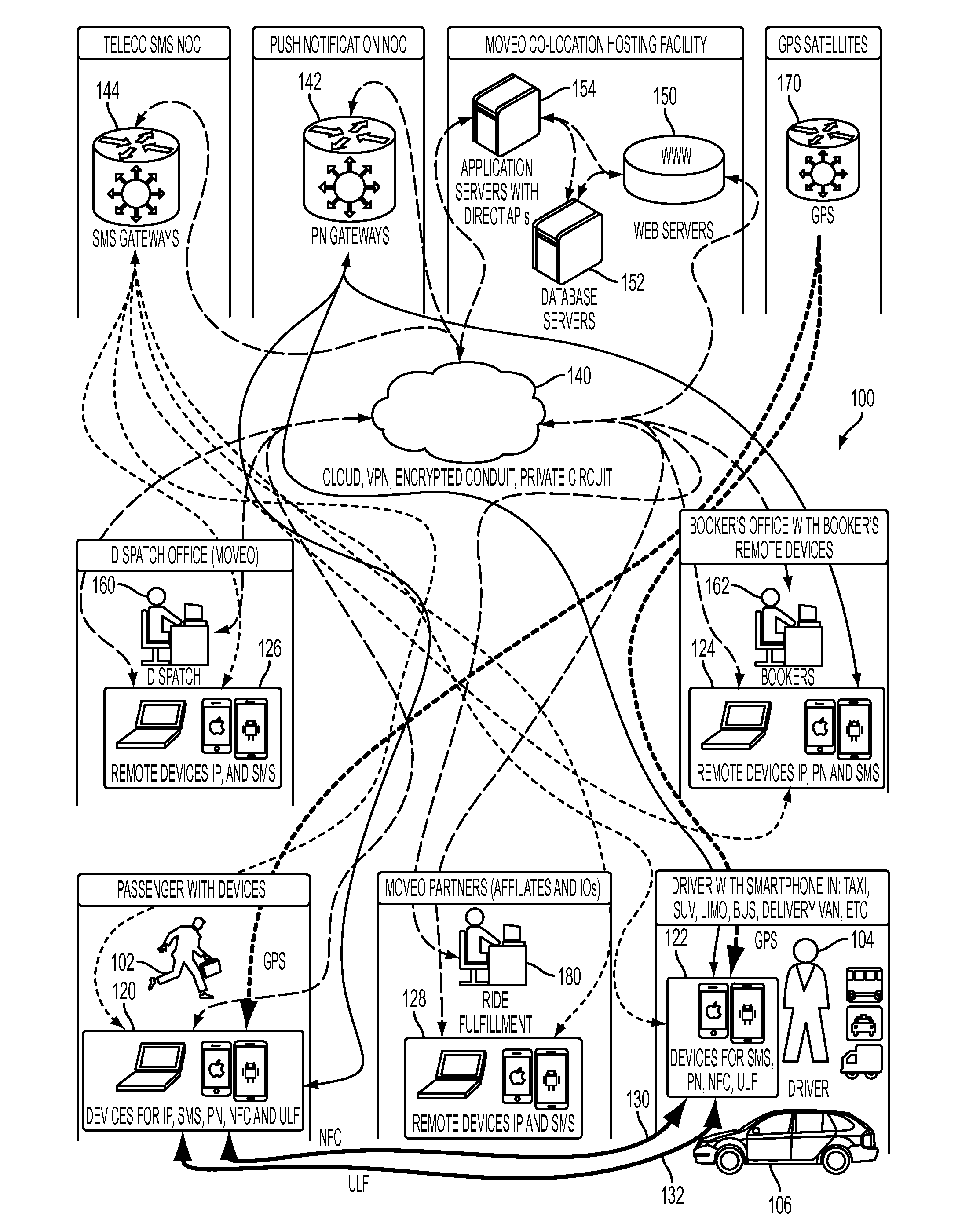
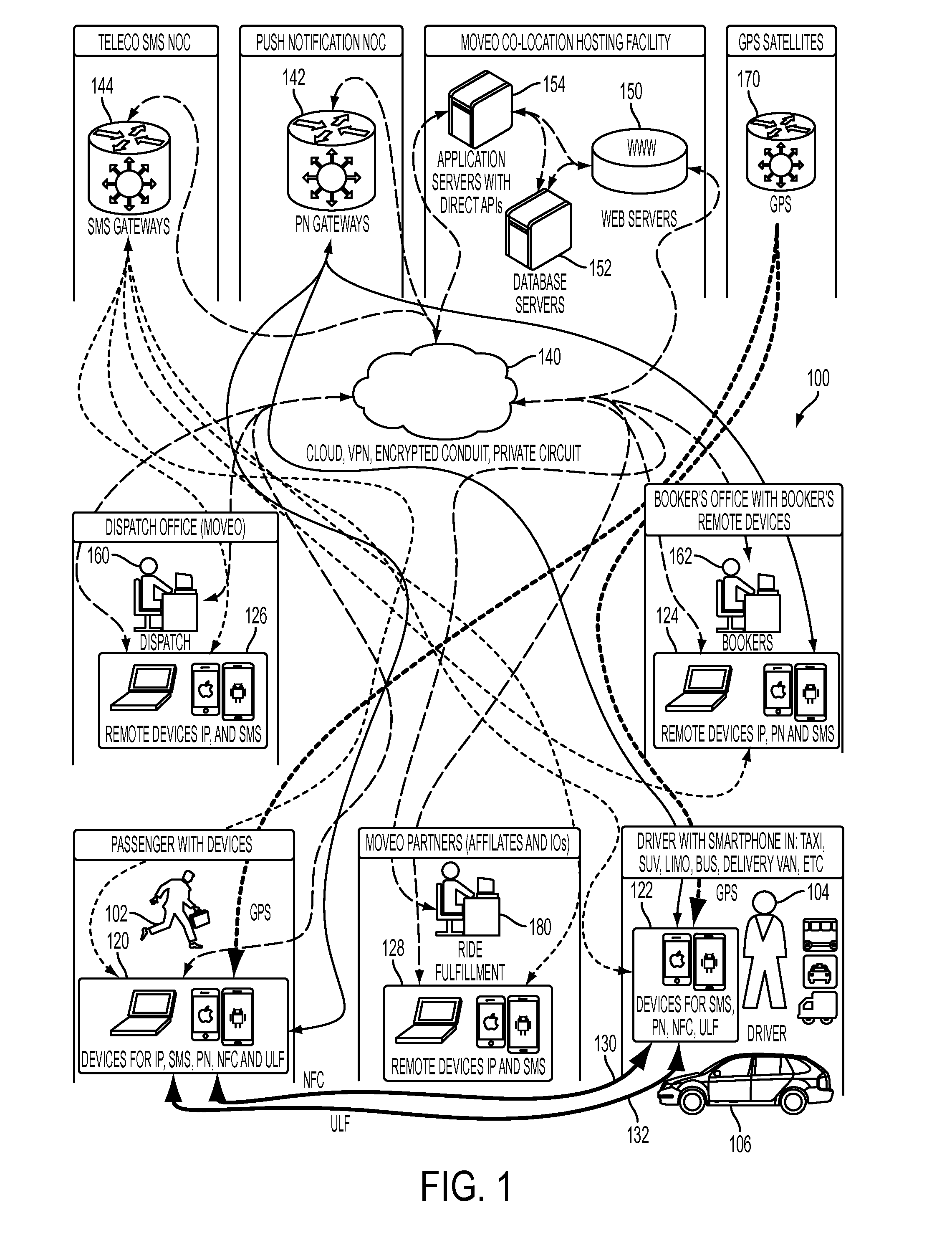
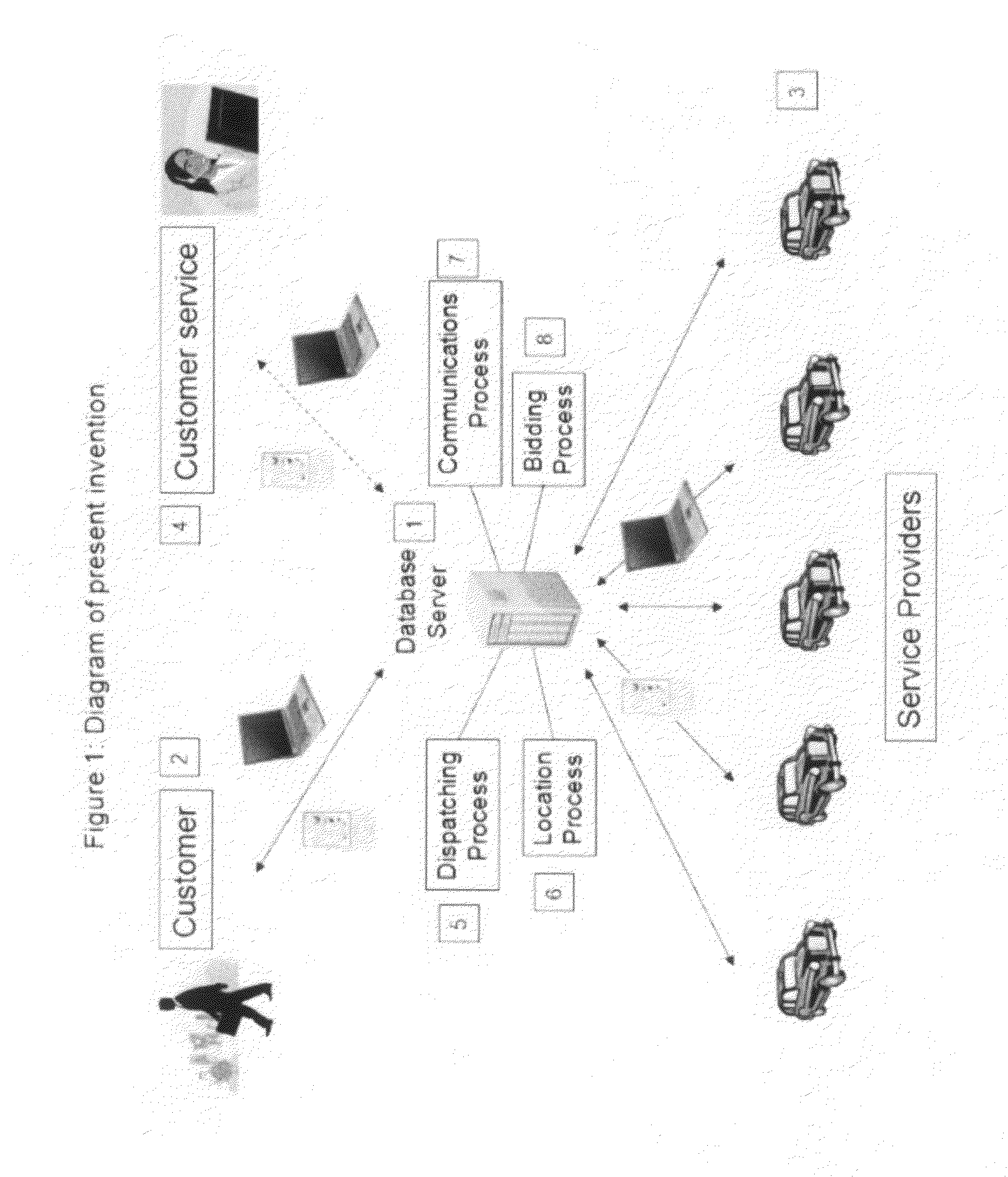
Dispatch system and method of dispatching vehicles
InactiveUS20160042303A1Eliminate needInstruments for road network navigationParticular environment based servicesEngineeringDirect communication
Provided are a fully automated dispatch system and method of dispatching vehicles that requires no direct communication between a dispatch person and the driver or passenger.
Owner:MOVEO TECH CORP
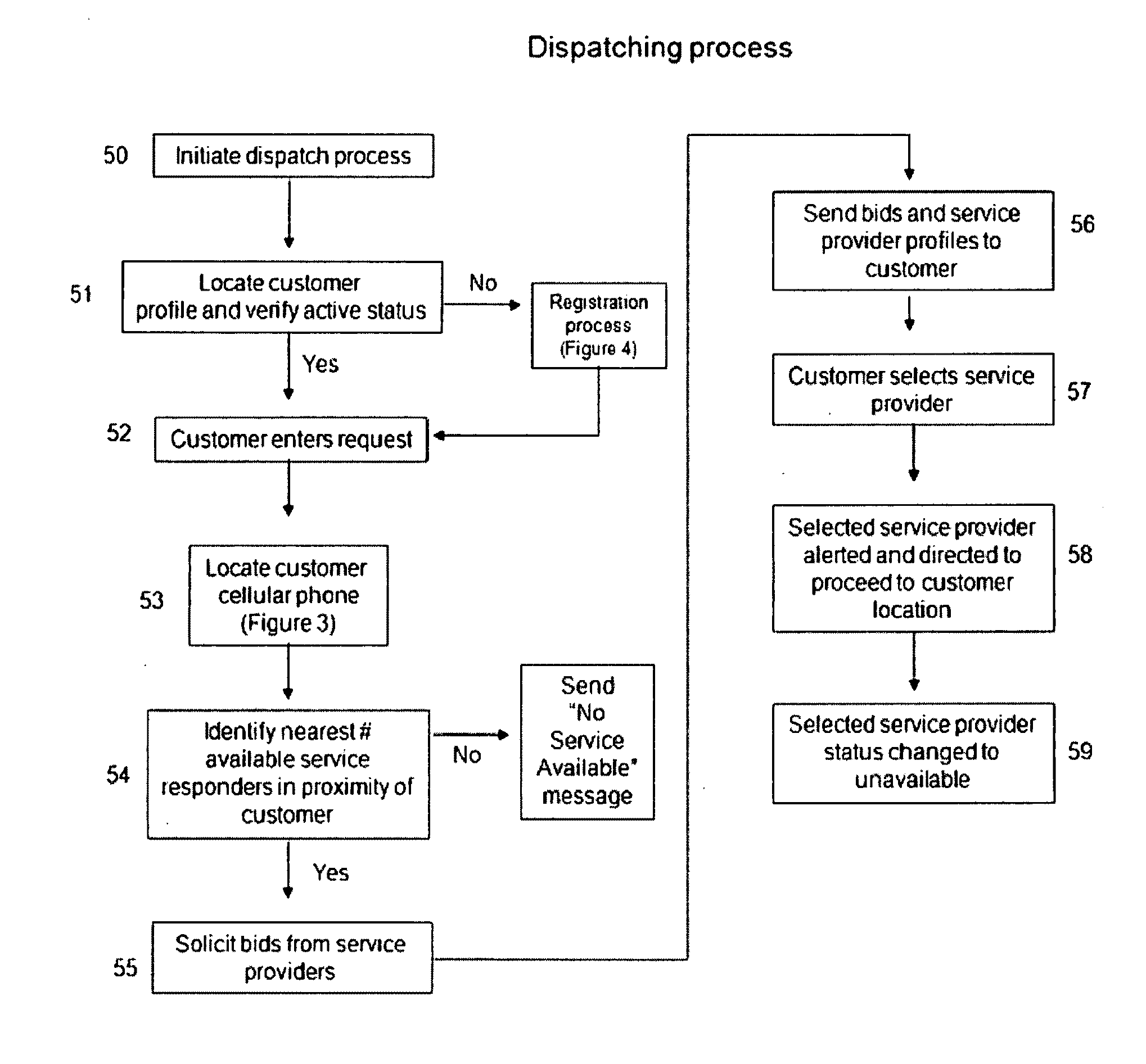
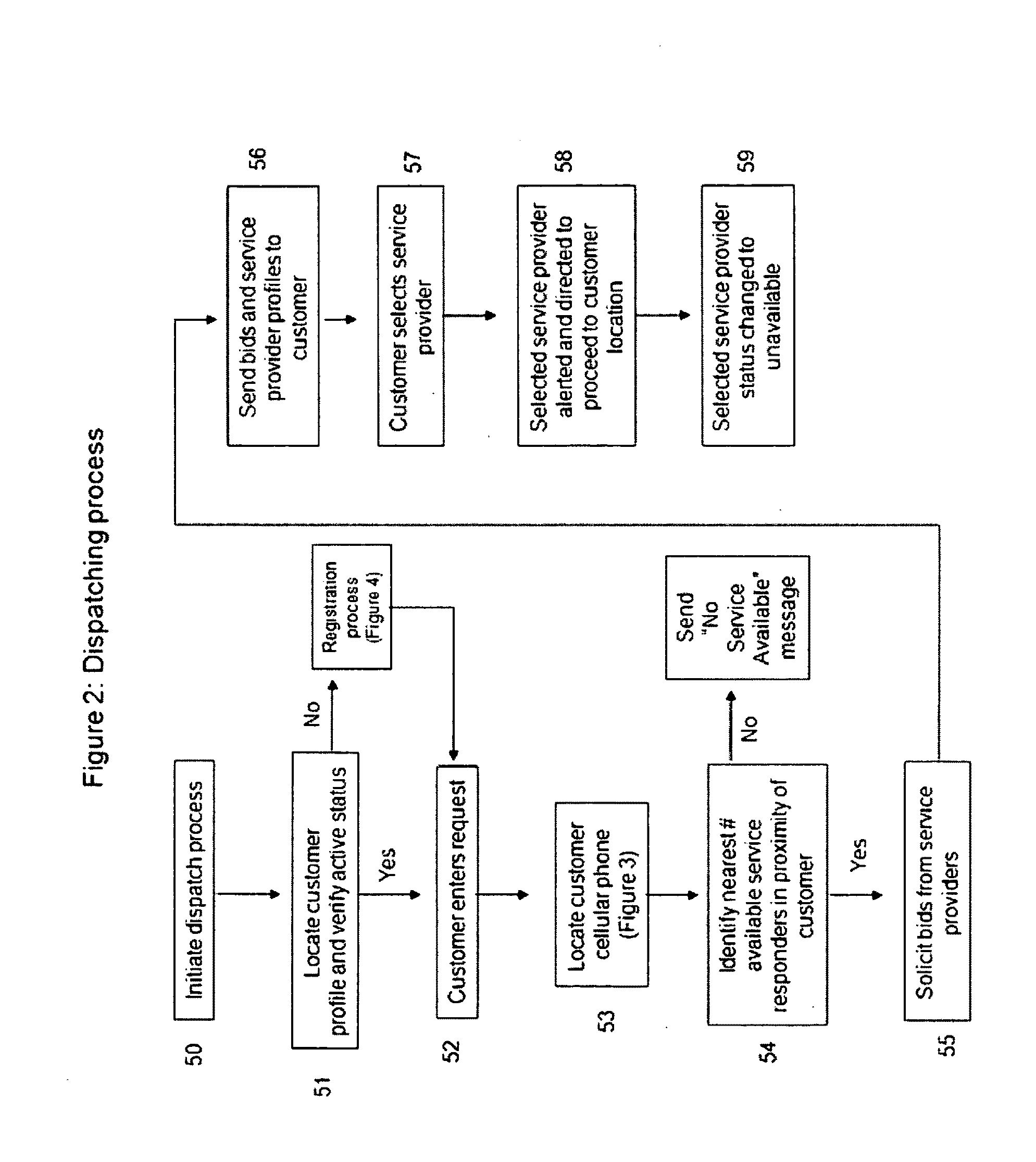
Consumer initiated, service provider direct dispatching system
InactiveUS20090313077A1Convenience to workIncrease in costInstruments for road network navigationTemperatue controlPersonal detailsDirect communication
A customer originated and directed dispatching system to provide direct coordination of requested service to service providers without the need for intermediary dispatching assistance. A database stores records each documenting needed services and customer and service provider profiles. Processing circuitry (which may be one or several networked computers) performs a dispatching process which reviews these records, locates records indicating a need for immediate service, locates the customer, identifies potential service responders, carries out an auction for the requested service and collects a list of potential service provides with their bids and profiles. The processing circuitry also performs a monitoring process which monitors service provider's activities by reviewing the records, and automatically obtained service provider's activity information, and records customer and service provider performance ratings to the database. Communications circuitry enables direct communication between the service provider and the customer as well as updates of the service provider's activity and review customer and service provider performance records.
Owner:WHEELER IV GEORGE Y
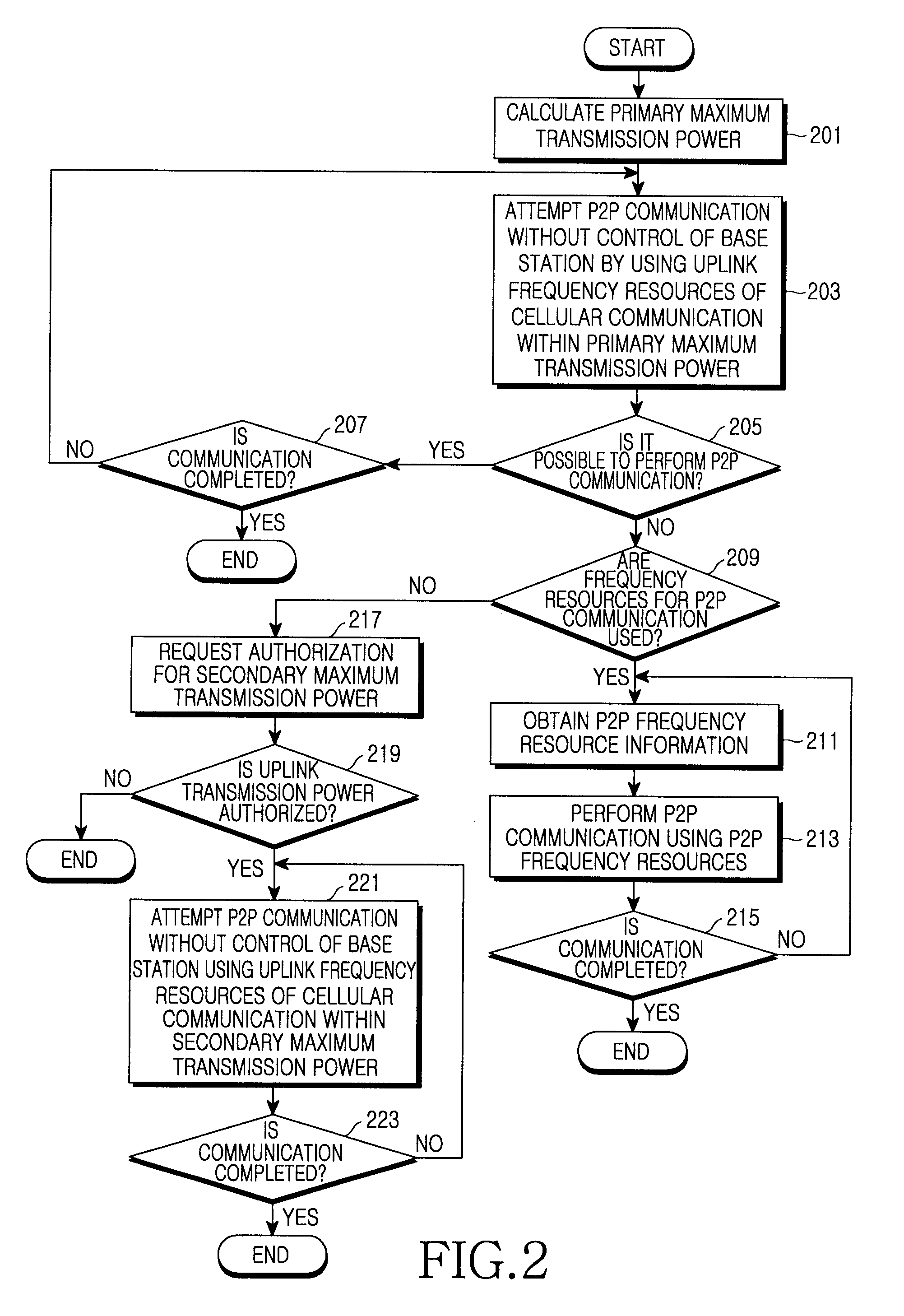
Apparatus and method for determining resources for peer to peer communication in communication system
ActiveUS20090011770A1Reduce resource consumptionWithout reducing capacityEnergy efficient ICTTransmission path divisionCommunications systemCellular communication systems
A method and apparatus for allocating frequency resources for peer to peer (P2P) communication between terminals without a base station are provided. The method determines resources used for a direct communication between two terminals in a communication system. The method includes determining uplink frequency resources of a cellular communication system for use in the direct communication between the two terminals, determining a primary maximum transmission power to minimize interference caused by the direct communication on the cellular communication system and performing the direct communication between the two terminals by using the uplink frequency resources and a transmission power less than the determined primary maximum transmission power.
Owner:SAMSUNG ELECTRONICS CO LTD
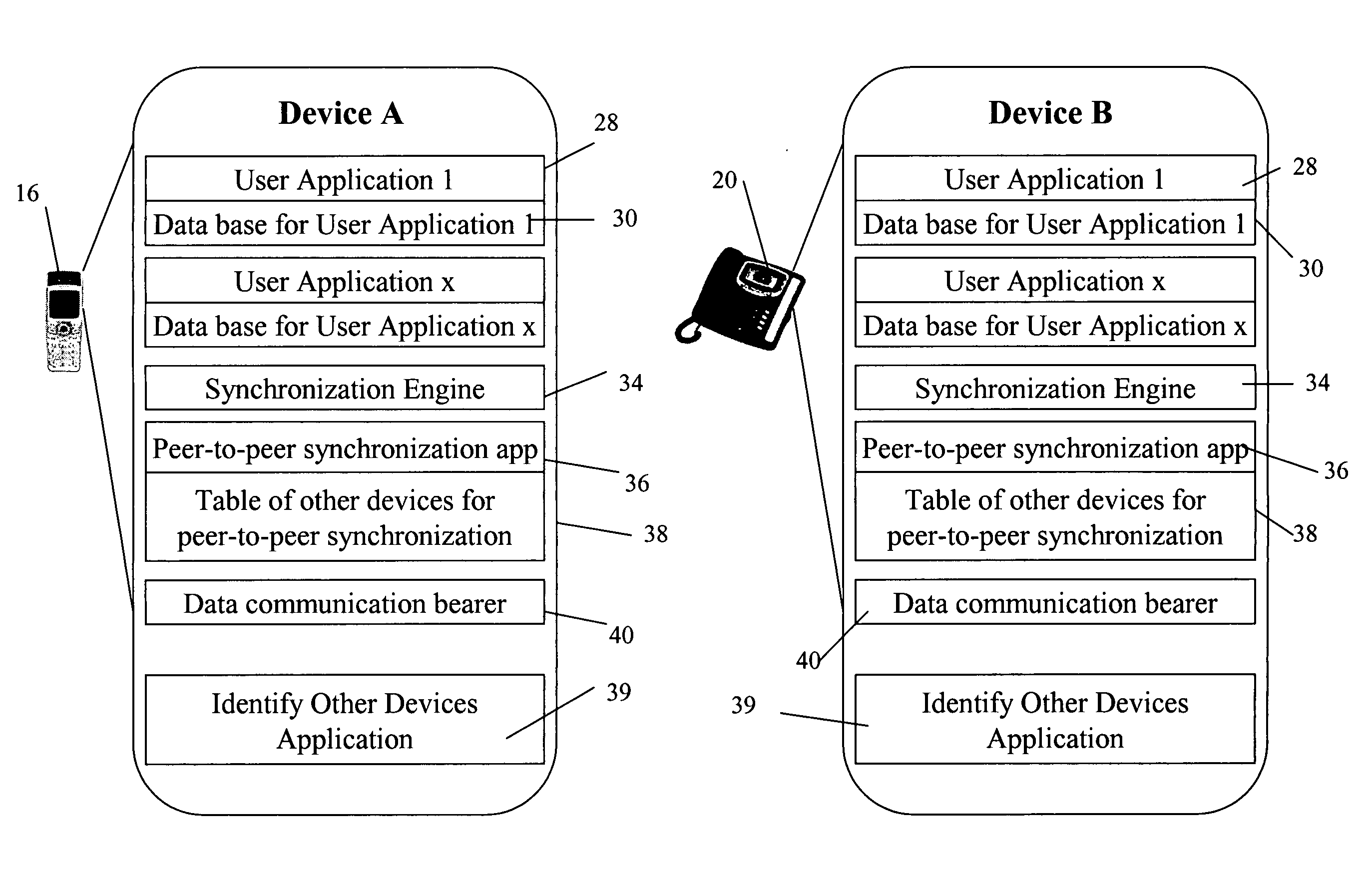
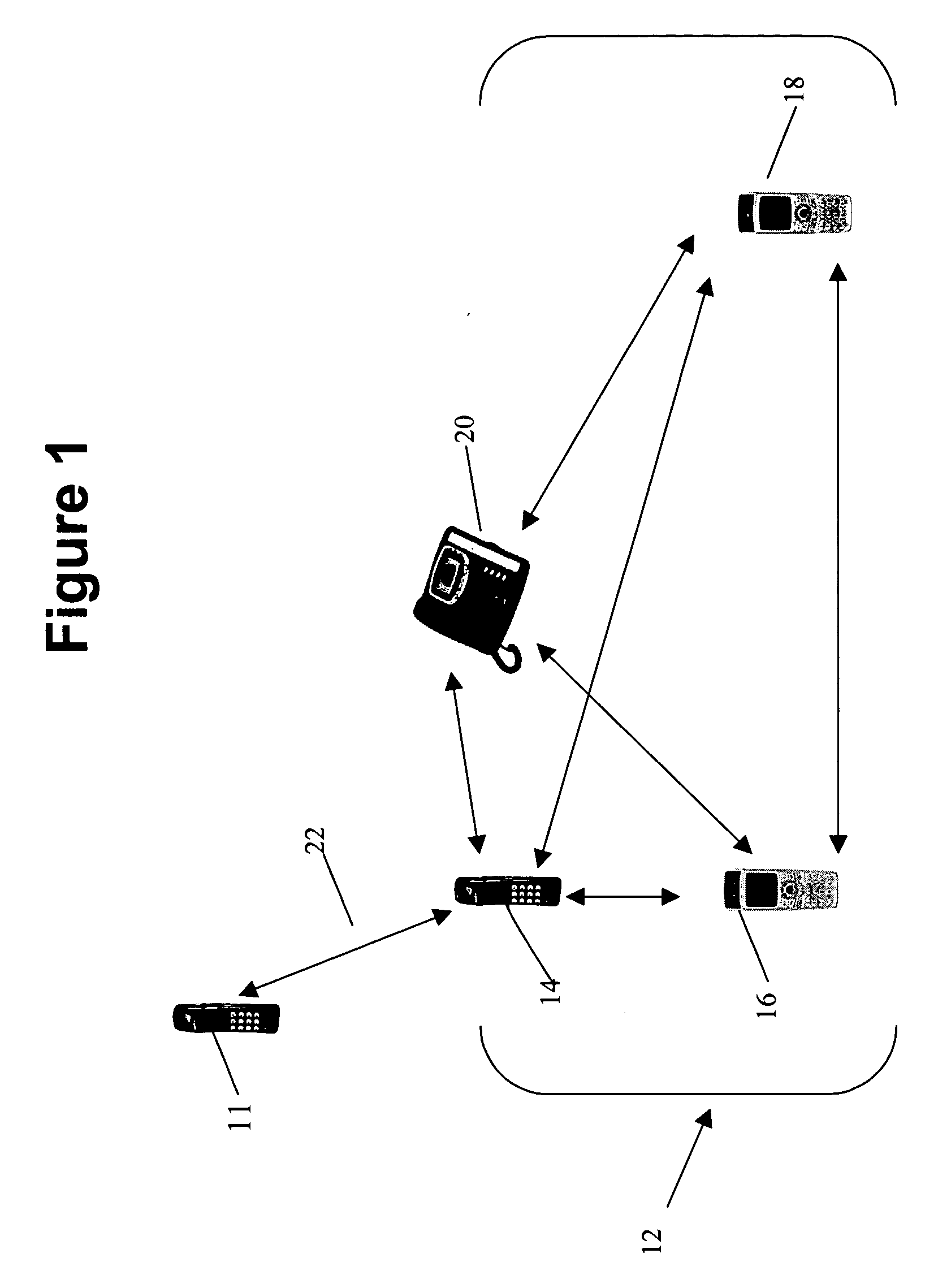
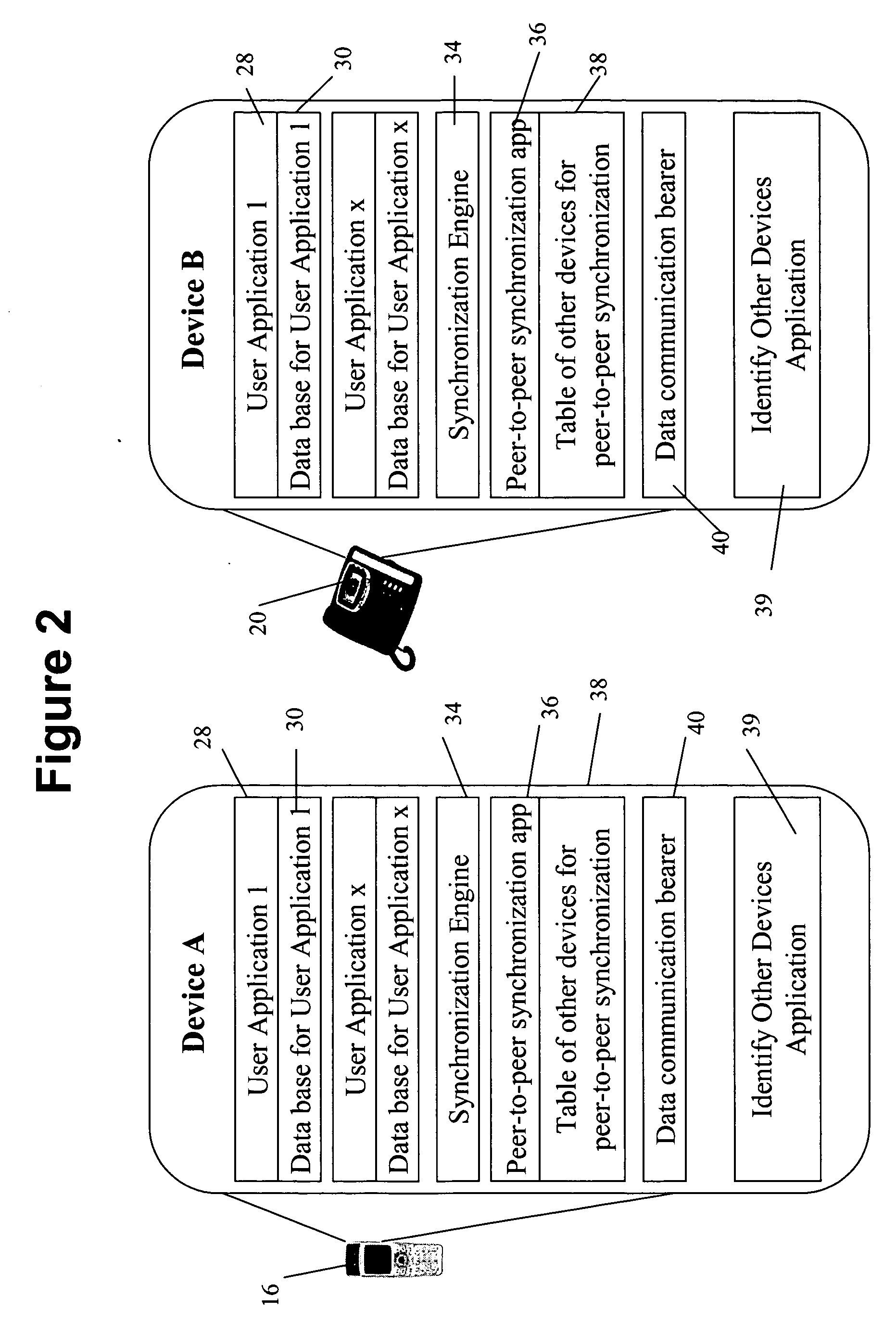
Peer-to-peer synchronization of data between devices
ActiveUS20070014314A1Time-division multiplexData switching by path configurationUser deviceDirect communication
An automatic synchronization method and apparatus that synchronizes data on a peer-to-peer basis across multiple devices. Automatic synchronization occurs on one or more similar user devices from one device to another and does not require synchronization with a central server. No single device acts as a central synchronization server, but all devices on which the application resides and that have the data to be synchronized can communicate with each other directly, or indirectly through other devices that have direct communication with the device on which data is changed.
Owner:BELLSOUTH INTPROP COR
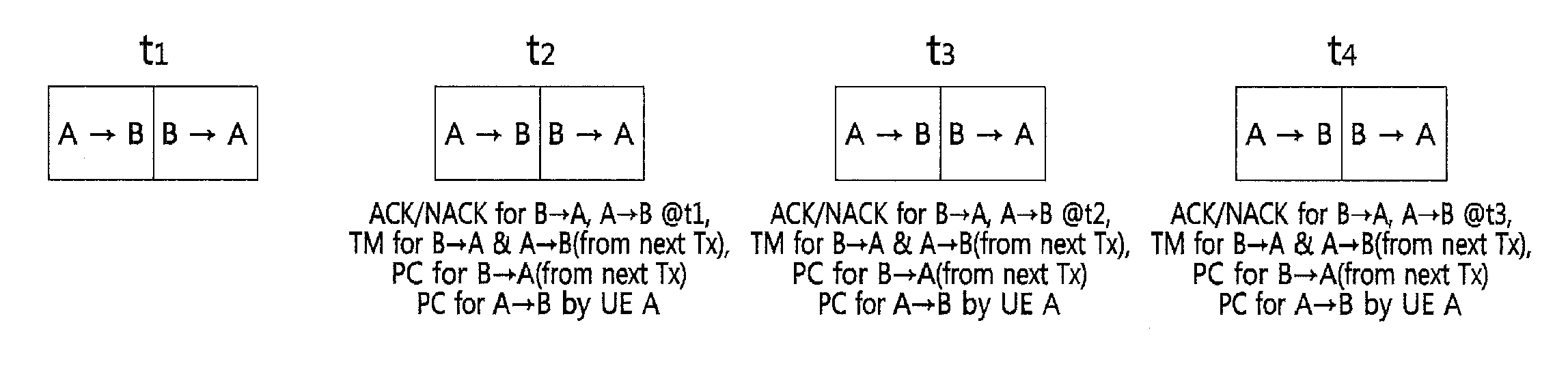
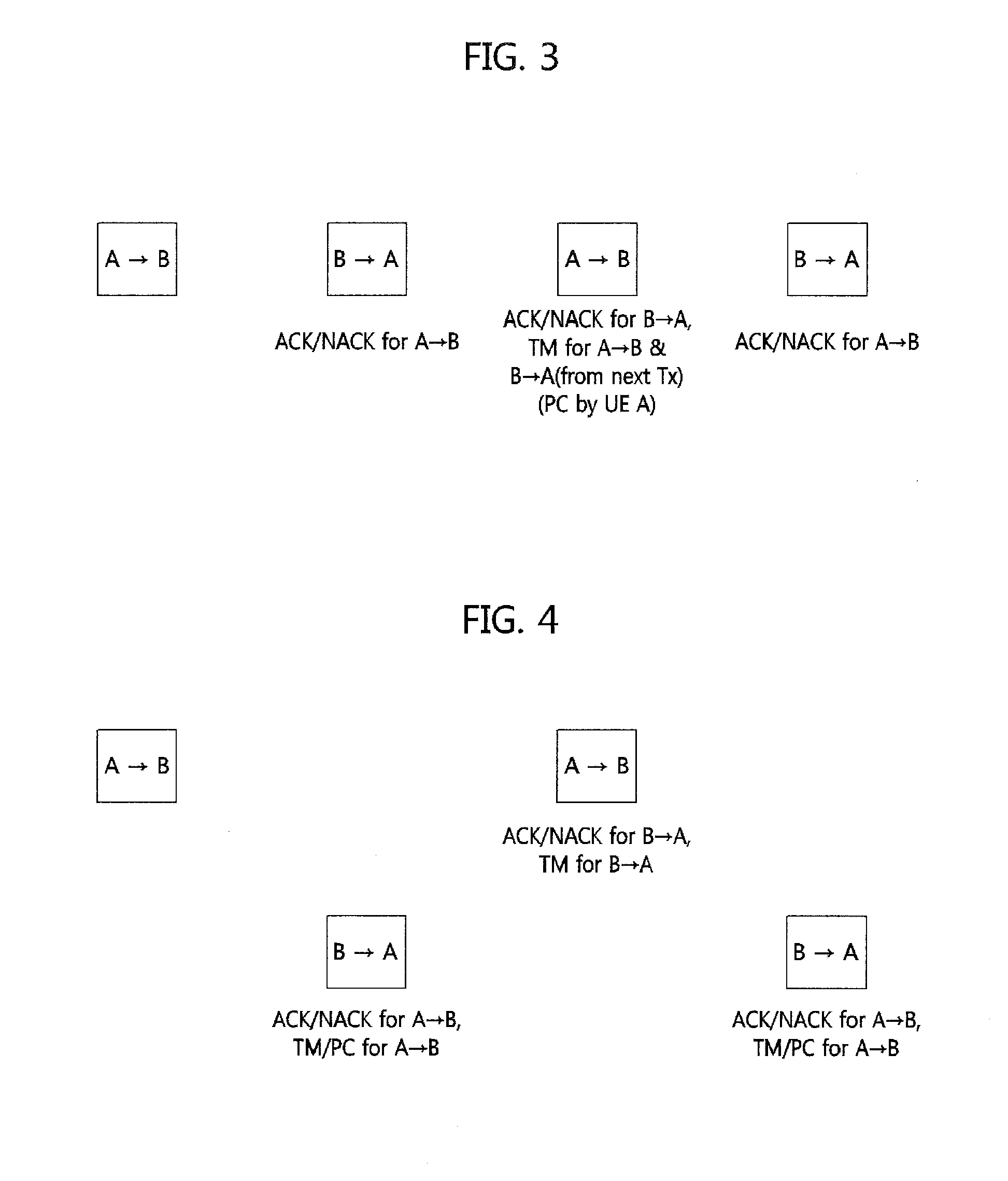
Method for HARQ and link adaptation of device to device link in direct communication between user equipments and relaying by user equipment
Provided is a method of processing hybrid automatic repeat request (HARQ) and adaptive transmission of a device-to-device (D2D) link. In the method, an operation method of user equipment (UE) includes (a) receiving an initial transmission mode (TM) and transmission power for the D2D link from a base station, and performing data transmission through the D2D link, (b) determining, at the UE, a TM and transmission power of a succeeding subframe, or receiving a TM control value and a transmission power control value from counterpart UE of the D2D link and determining the TM and the transmission power of the succeeding subframe, and (c) performing the data transmission to the counterpart UE using the determined TM and transmission power. Here, (b) and (c) are repeated.
Owner:ELECTRONICS & TELECOMM RES INST
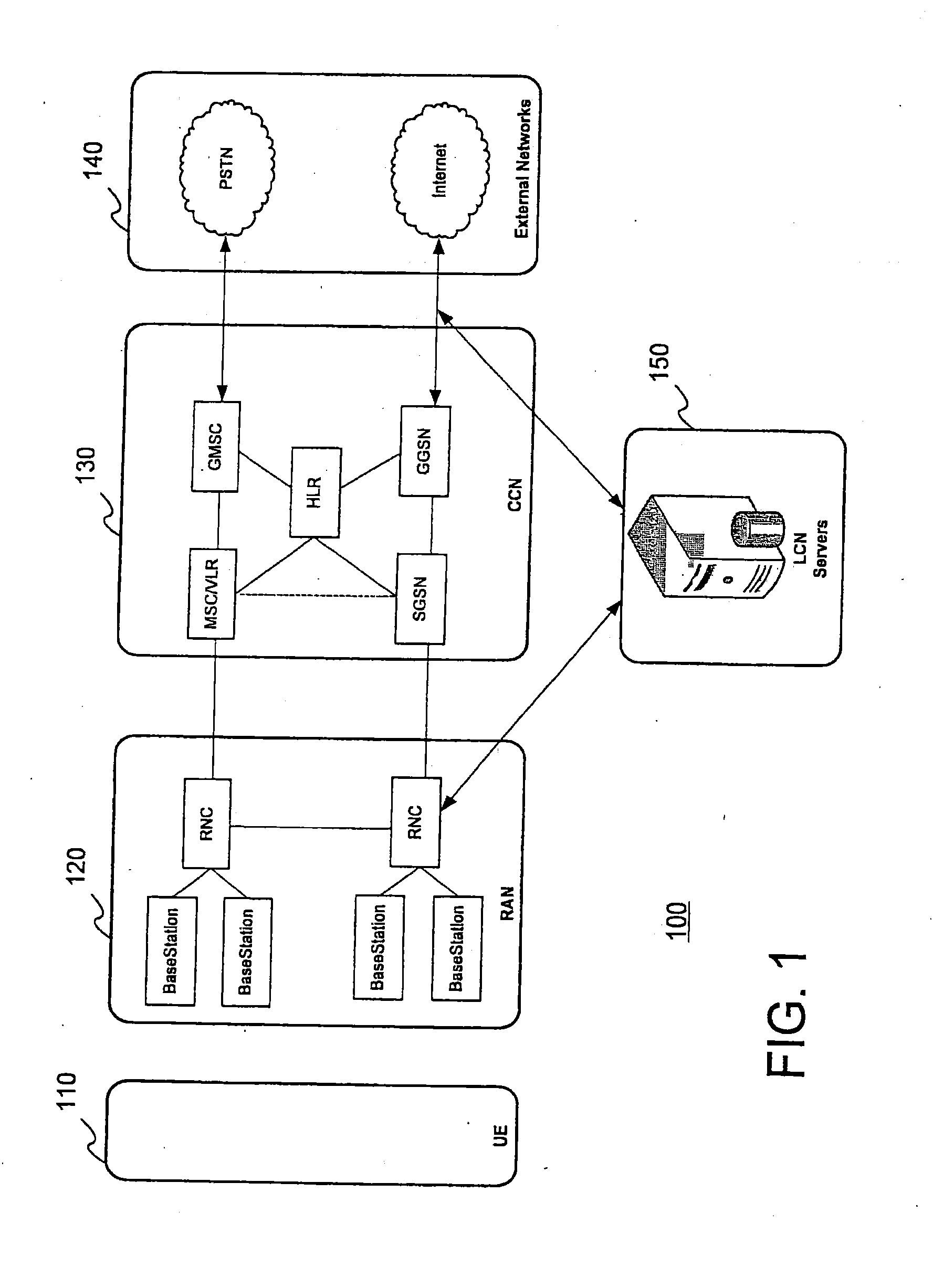
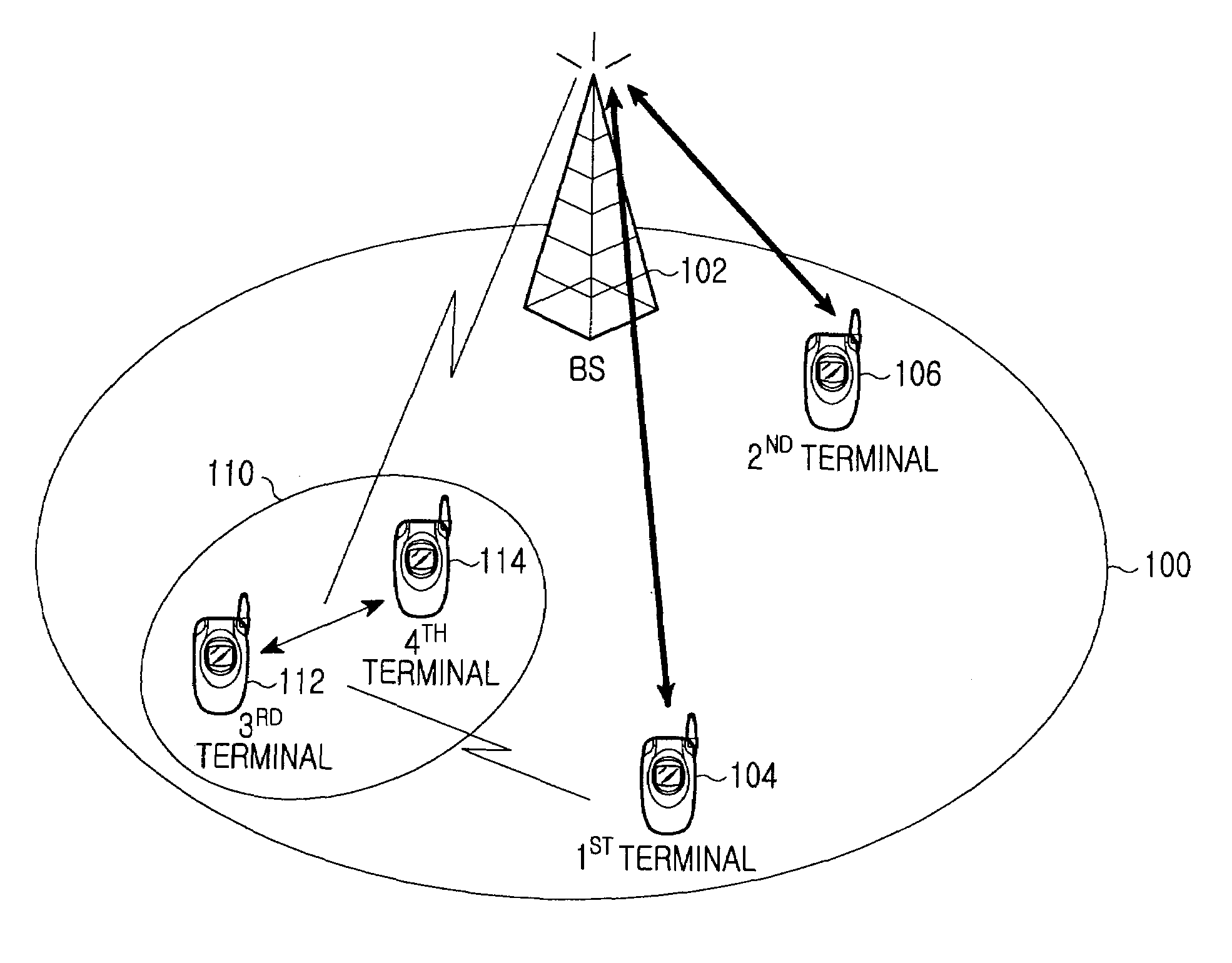
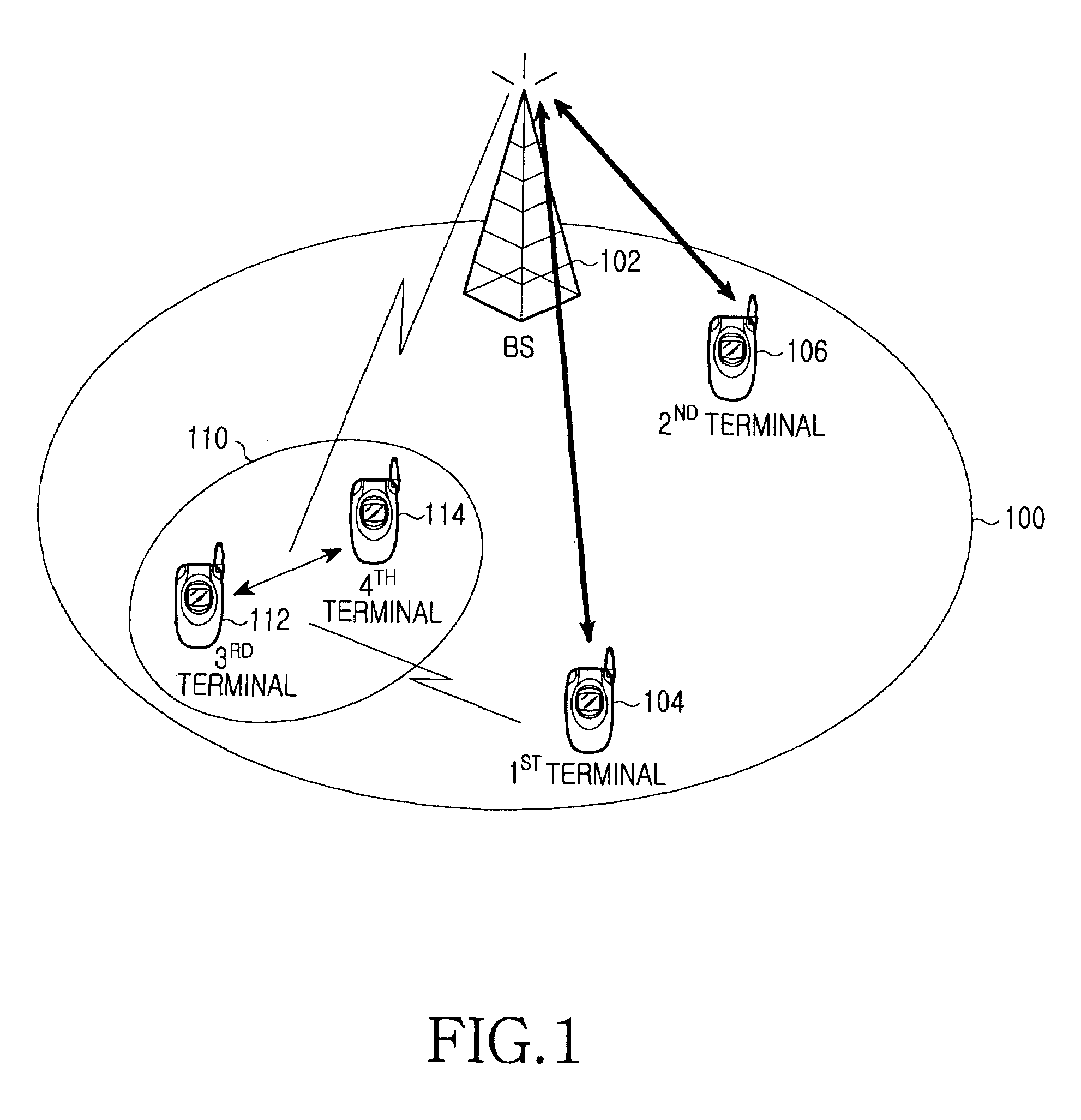
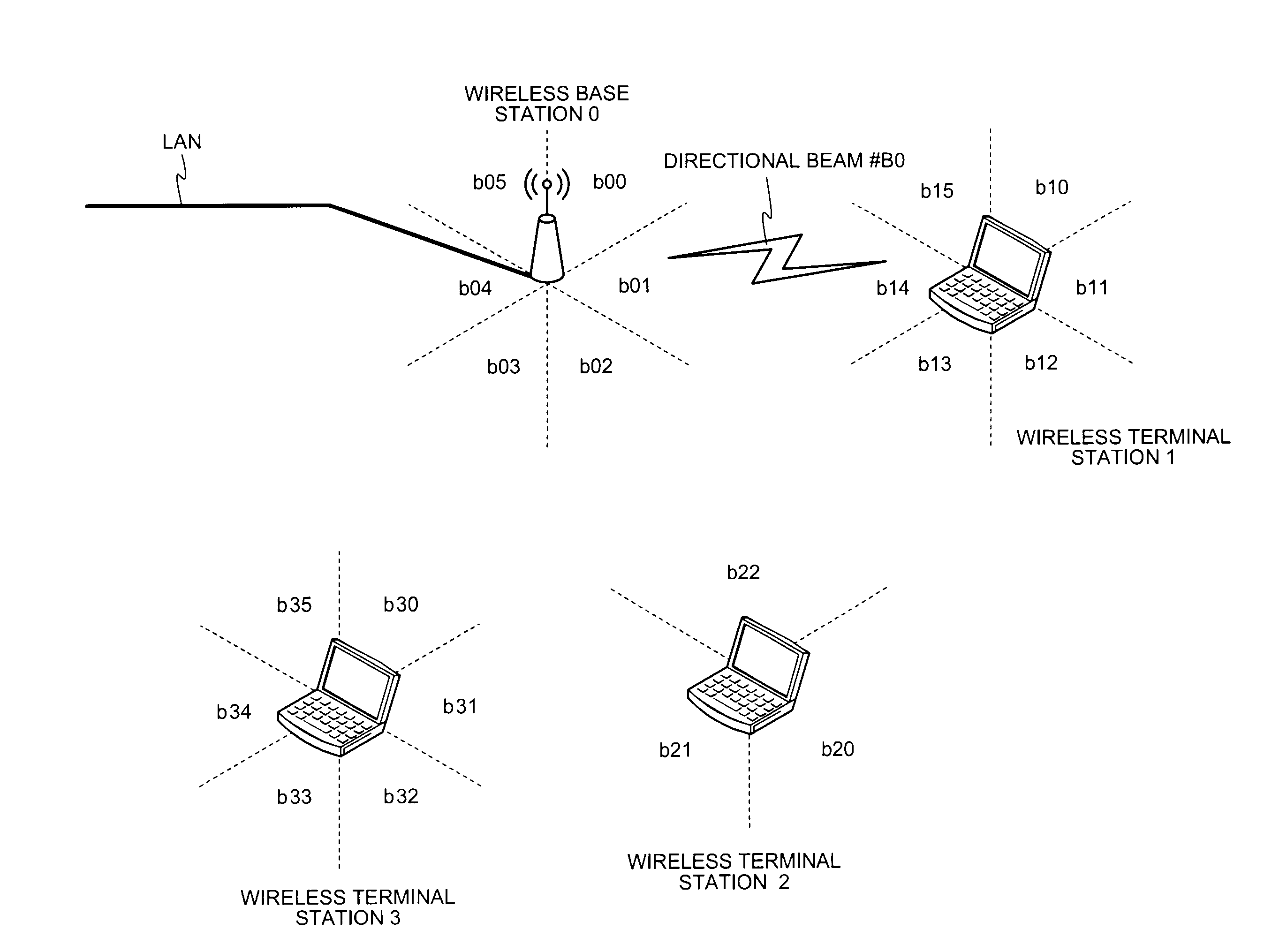
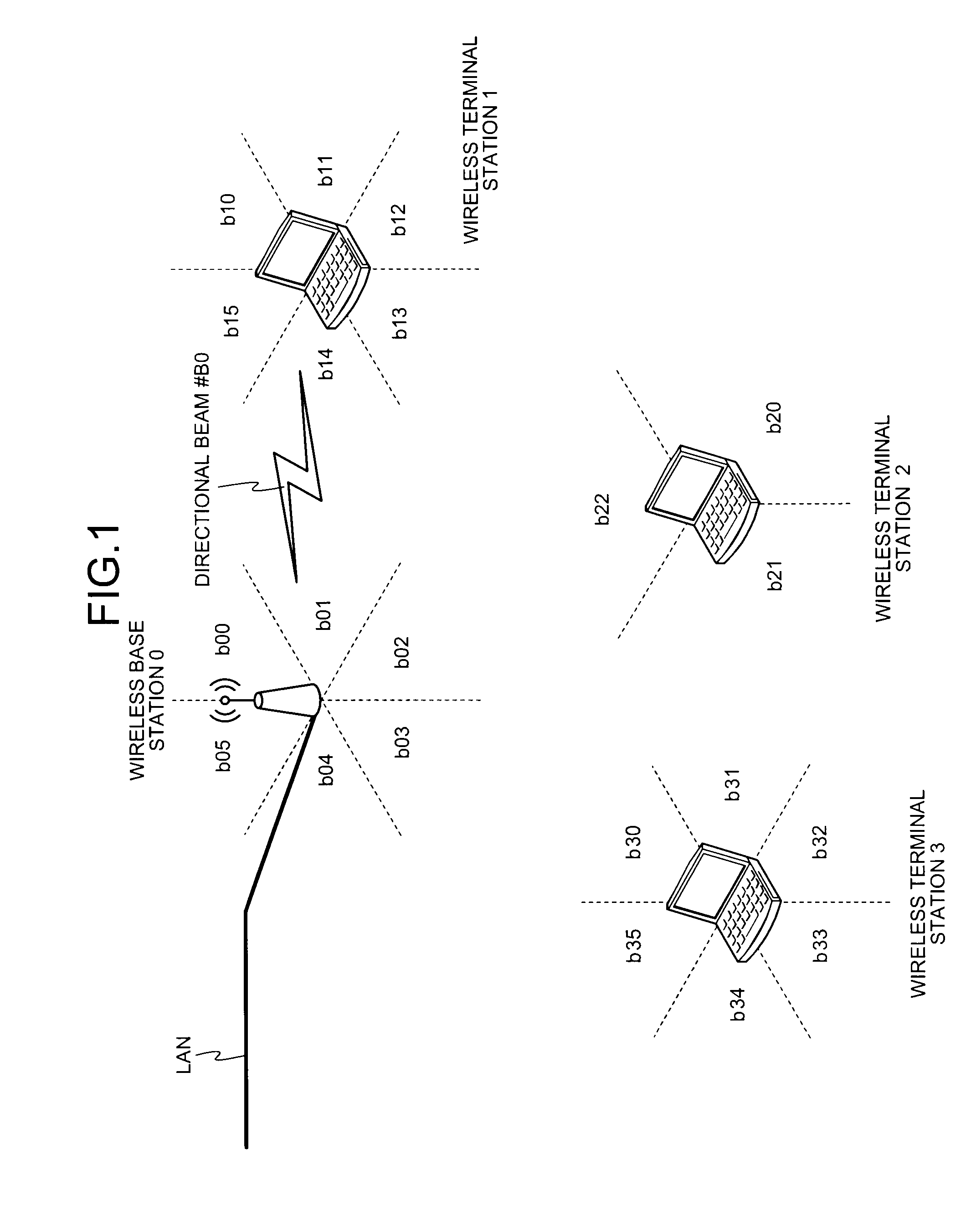
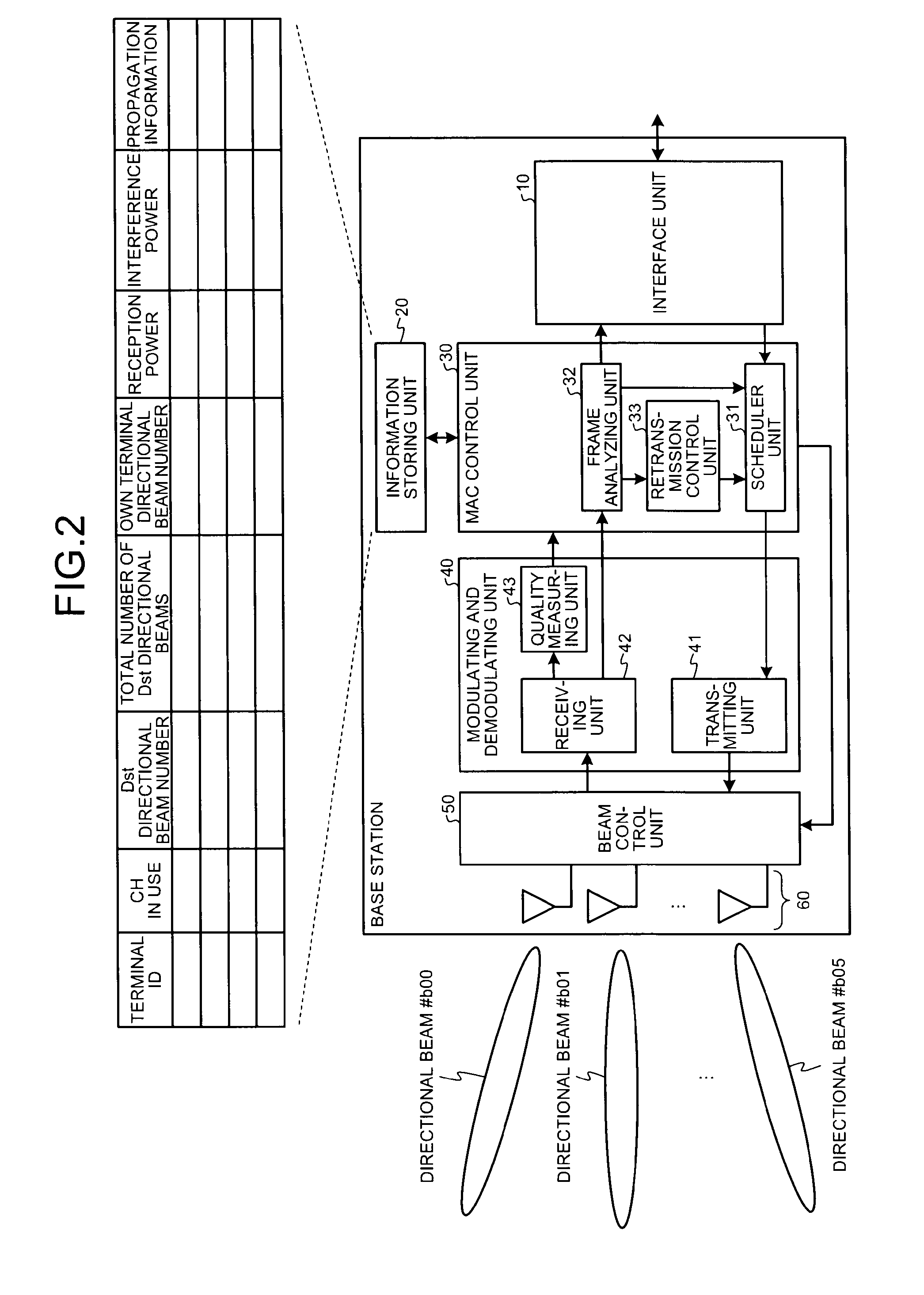
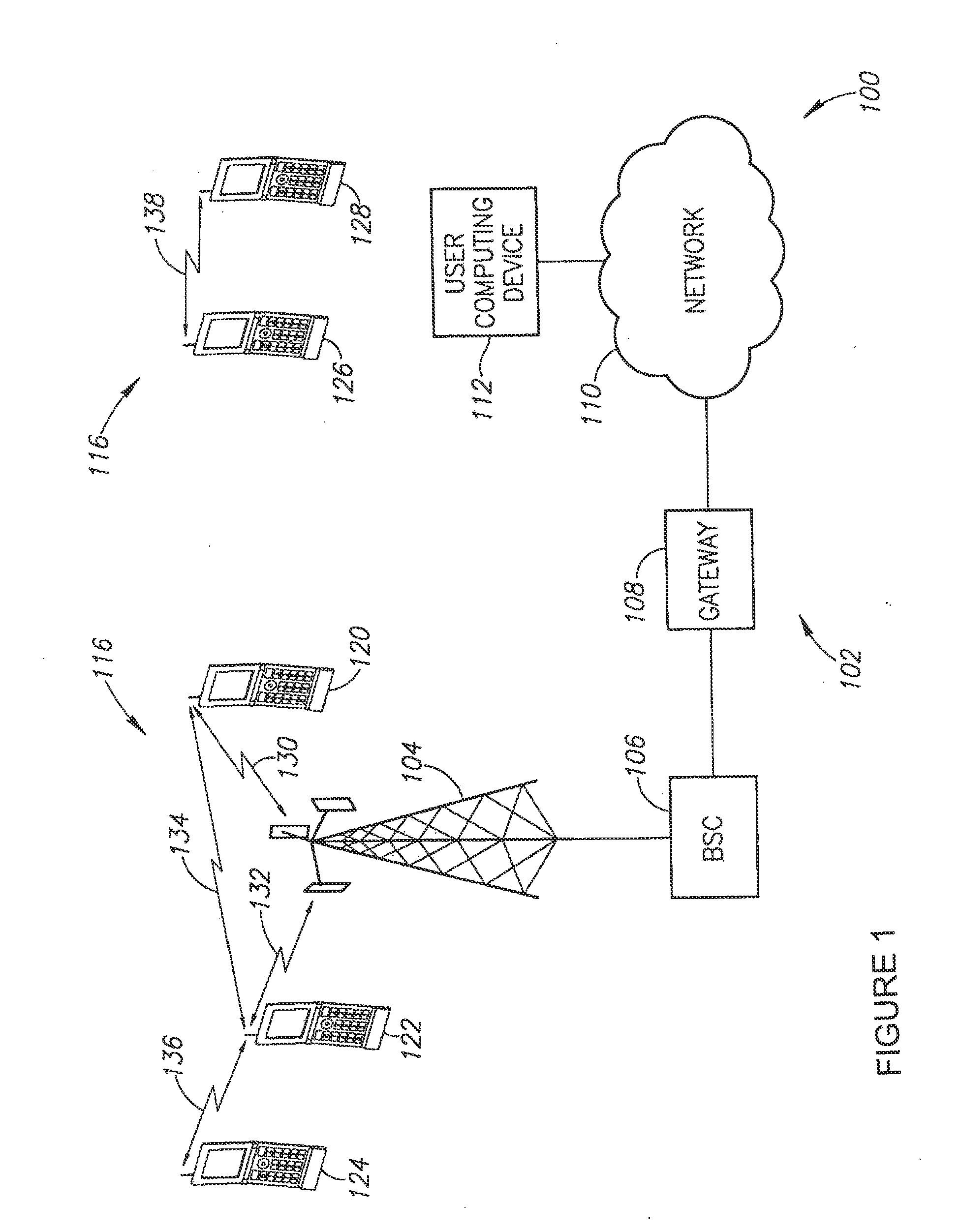
Wireless communication system, wireless terminal station, wireless base station, and wireless communication method
ActiveUS20100014463A1Easy to useNetwork traffic/resource managementConnection managementCommunications systemEngineering
A first wireless terminal station transmits beam transmission direction identification information in all directions. A second wireless terminal station receives the transmission direction identification information, combines reception direction identification information and the transmission direction identification information, and transmits directivity direction combination information to a wireless base station. The first and the second wireless terminal stations form directional beams in directions indicated by the directivity direction combination information to thereby perform a direct communication.
Owner:MITSUBISHI ELECTRIC CORP
Multi tier wireless communication system
InactiveUS7027416B1Limited rangeNeed not be optimized for longer transmission distancesEnergy efficient ICTPower managementMotion detectorTransceiver
A monitoring system is provided with a two tier communication network. Multiple first tier nodes comprising wireless or RF sensors are each equipped with transceivers operating at a first, low power level. Multiple second tier nodes are spaced to communicate with selected sensors at the lower bandwidth level, and also communicate with each other at a higher power level and higher bandwidth, to route sensor communications to a central controller. The sensors comprise standard home and small business sensors such as motion detectors, glass breakage, pressure, temperature, humidity and carbon monoxide sensors to name a few, each equipped with a transceiver. The sensors are placed throughout a structure to be protected or monitored. Since such structures can be quite large, several second tier routers are provided such that at least one is within range of each sensor to receive its low power signals. A routing table is dynamically generated to direct communications between routers and the controller
Owner:HONEYWELL INC
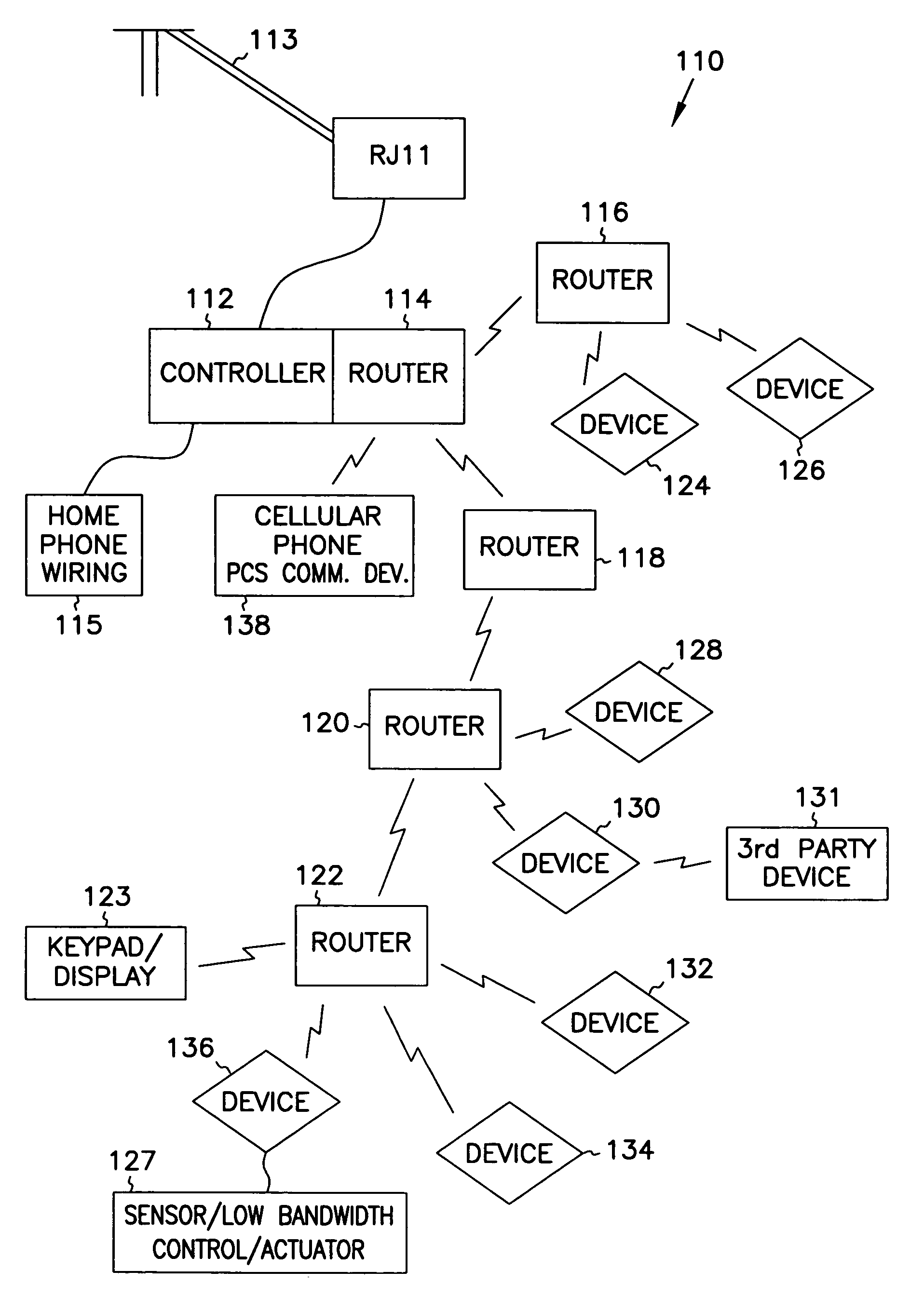
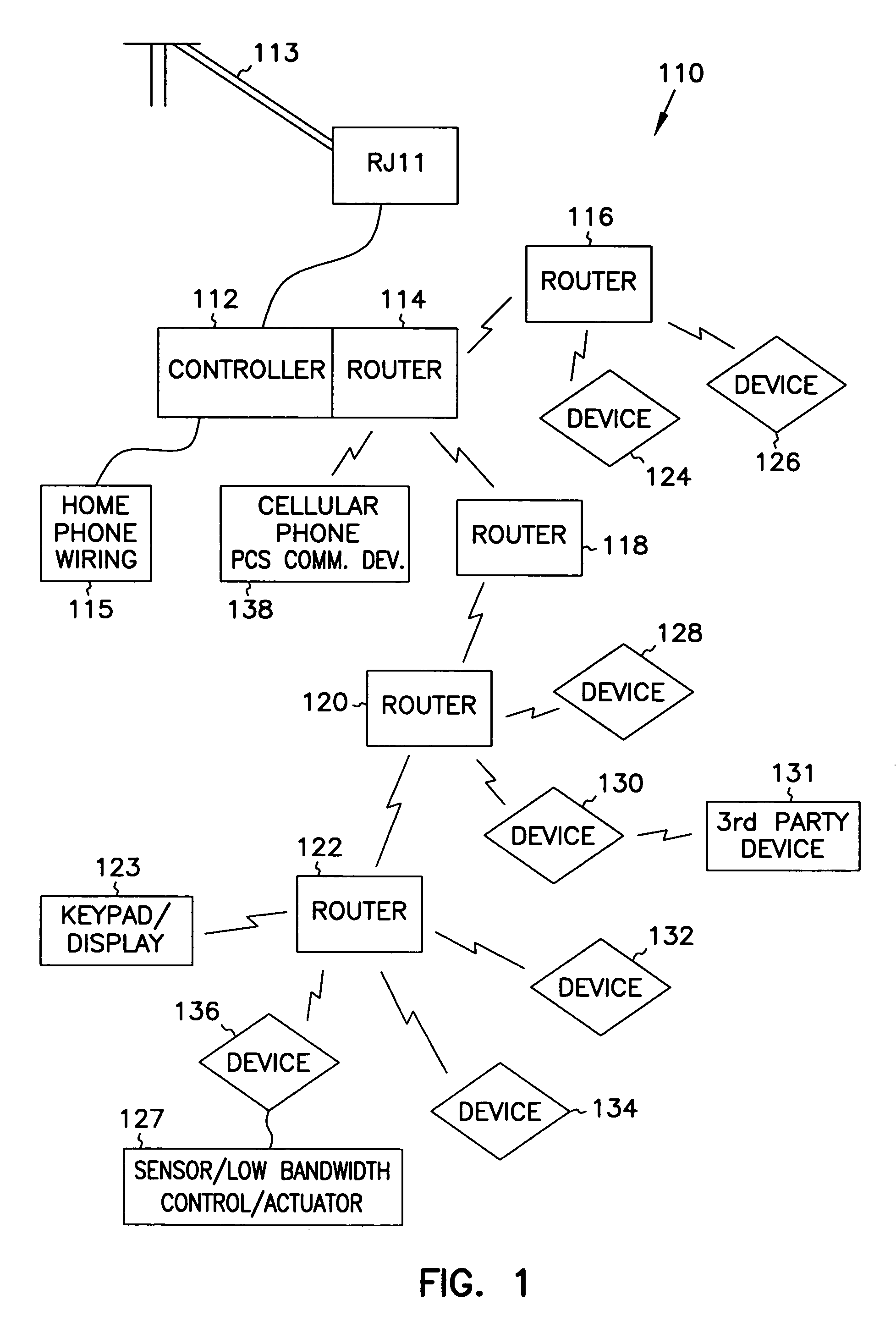
Intelligent Reconfigurable Locker System
InactiveUS20140330603A1OptimizationQuick and simple setupComputer controlResourcesModularityE-commerce
This invention involves the configuration of locker sizes during installation that can be reconfigured periodically to conform to the packages that arrive at the locker location. Locker control software can enable the efficient selection of locker size so that the locker bank can be optimized to the size of the packages that are delivered to the locker location. The reconfigurable lockers also may include a modular locker control module that can assist in the easy facilitation of changing the locker size. Also, the locker software can be flexible enough so that customers can have a direct communication link to the locker software that would allow the customer's mobile device to input authentication and access codes that would open up locker door(s). The locker software could also be enabled on the cloud providing an e-commerce goods seller, shipper or locker operator with information about goods that are shipped to locker locations and when customers stop by to pick up their goods or to return their goods to the e-commerce seller.
Owner:AIRLOCKER INC
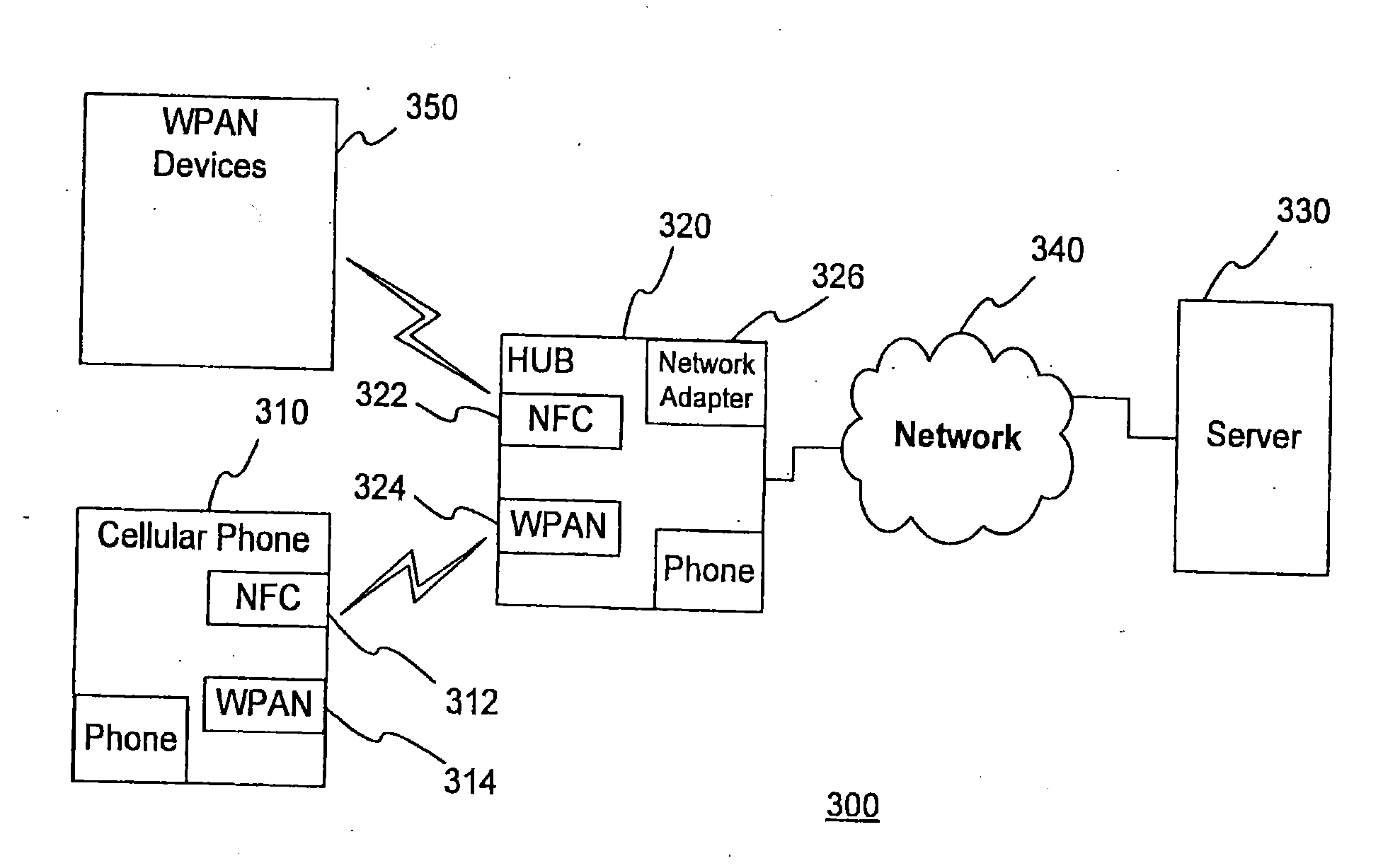
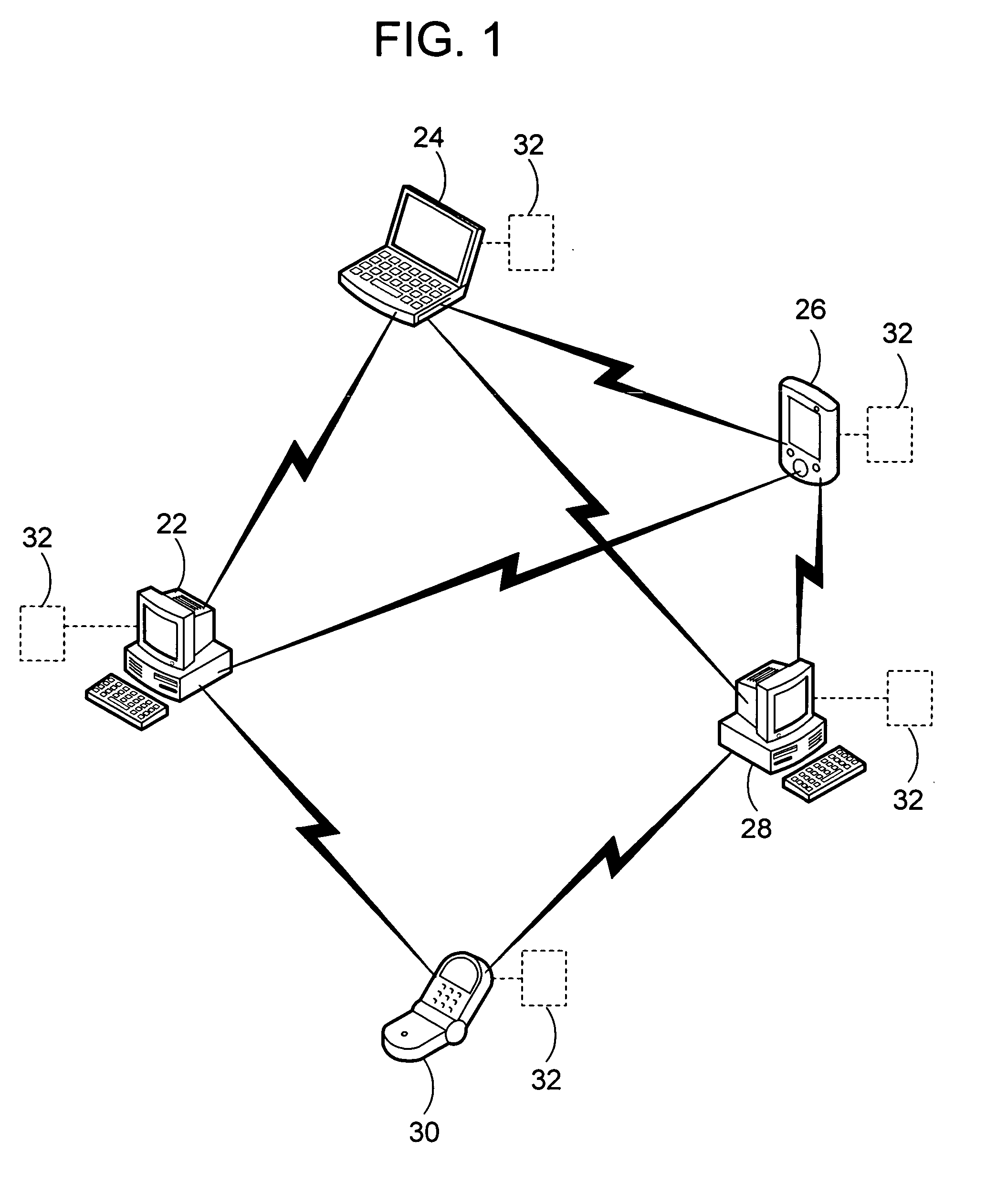
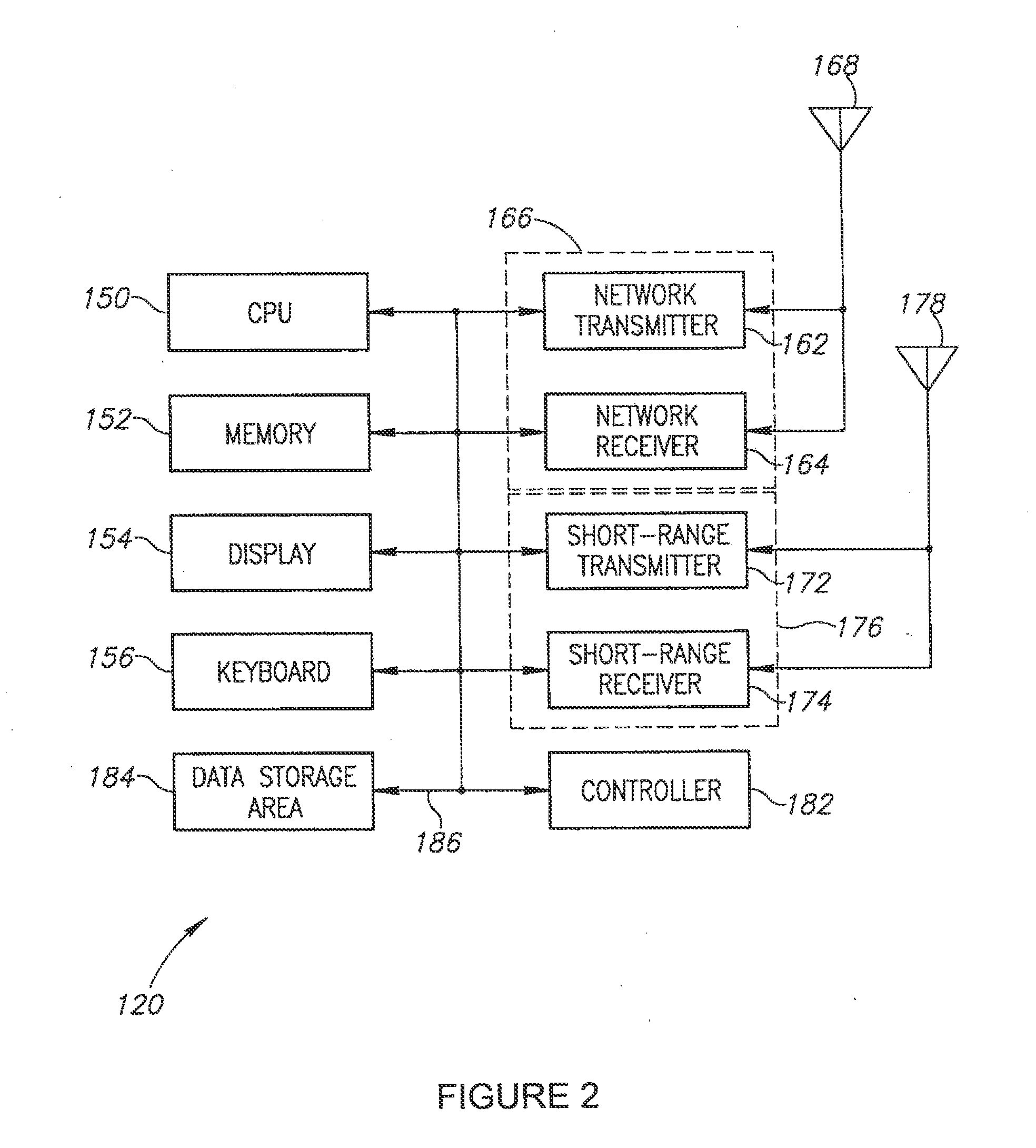
System and method for management of a dynamic network using wireless communication devices
A short-range wireless communication network may be established by direct communication between two or more wireless communication devices. A conventional cellular telephone includes an integrated short-range transceiver. The short-range transceivers of multiple wireless communication devices can be coupled together to form a short-range communication network without utilizing any wireless communication network supported by wireless service providers. The short-range communication network may be extended as additional devices come within range or consolidated as wireless communication devices leave the communication range. The short-range communication network is built upon the proximity of wireless communication devices with each other. Data is disseminated between the wireless communication devices using a data message synchronization process. Messages may also be carried from one wireless network to another as the communication devices are carried by individuals.
Owner:IP INVESTEMENT HOLDINGS LLC
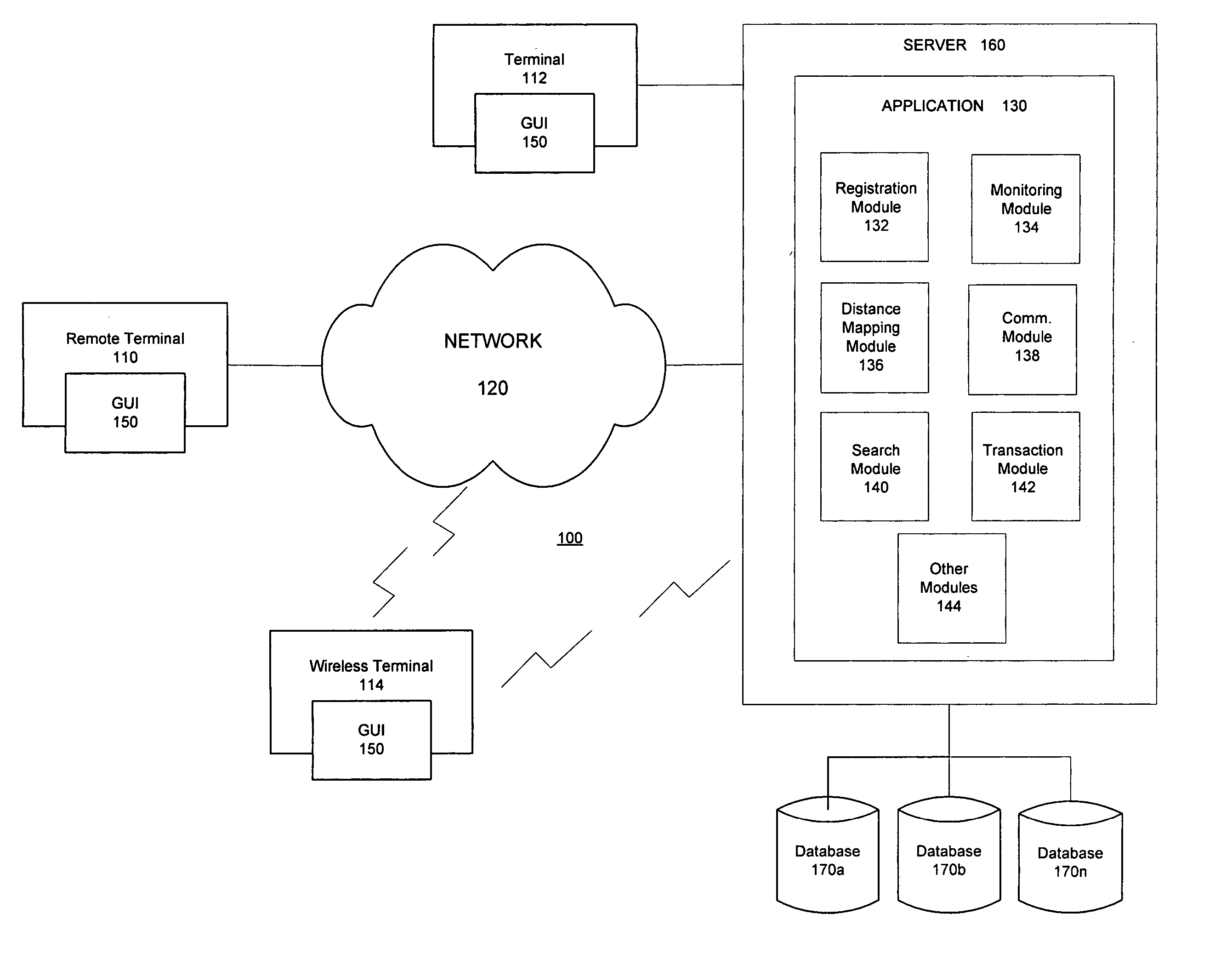
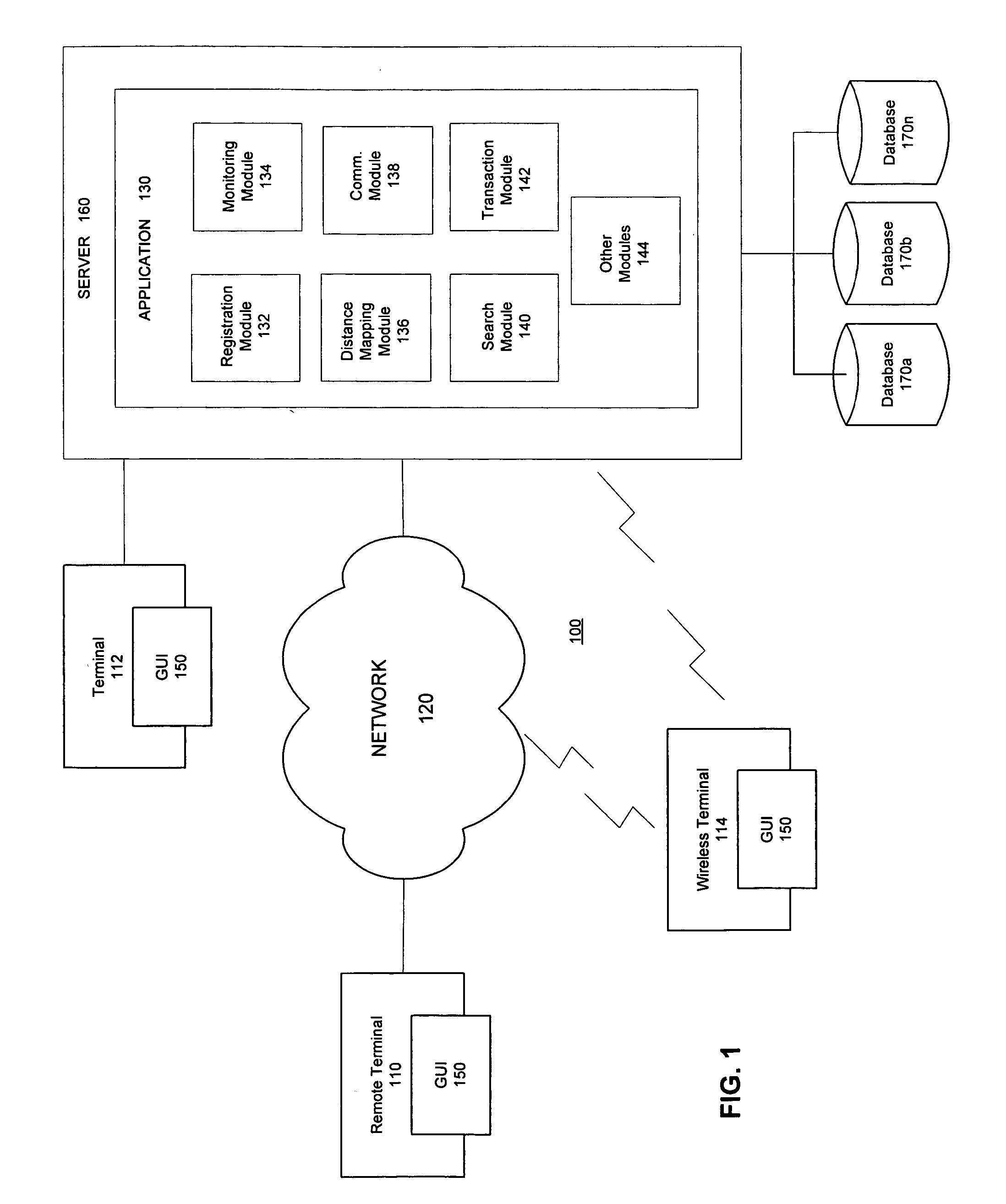
System and method for enabling identification of network users having similar interests and facilitating communication between them
InactiveUS20050210102A1Easy to identifyFacilitate direct communicationMultiple digital computer combinationsTransmissionWeb siteDirect communication
A system and method is provided for enabling identification of network users having similar interests and for facilitating communication between them. An Internet-based (or “on-line”) application is provided that: 1) facilitates the identification of users having similar interests using web-browsing behavior; 2) determines the virtual distance between web sites; and 3) utilizes profiling techniques and user-supplied descriptive information to facilitate direct communication between users who need not have had prior contact, and without requiring the participation of the visited web sites.
Owner:JOHNSON AARON Q
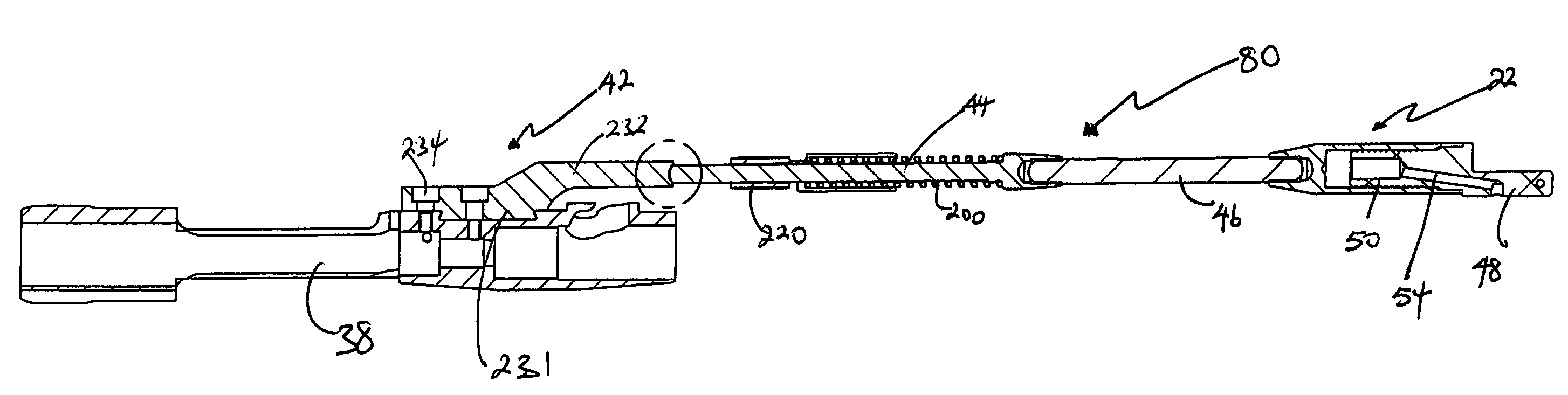
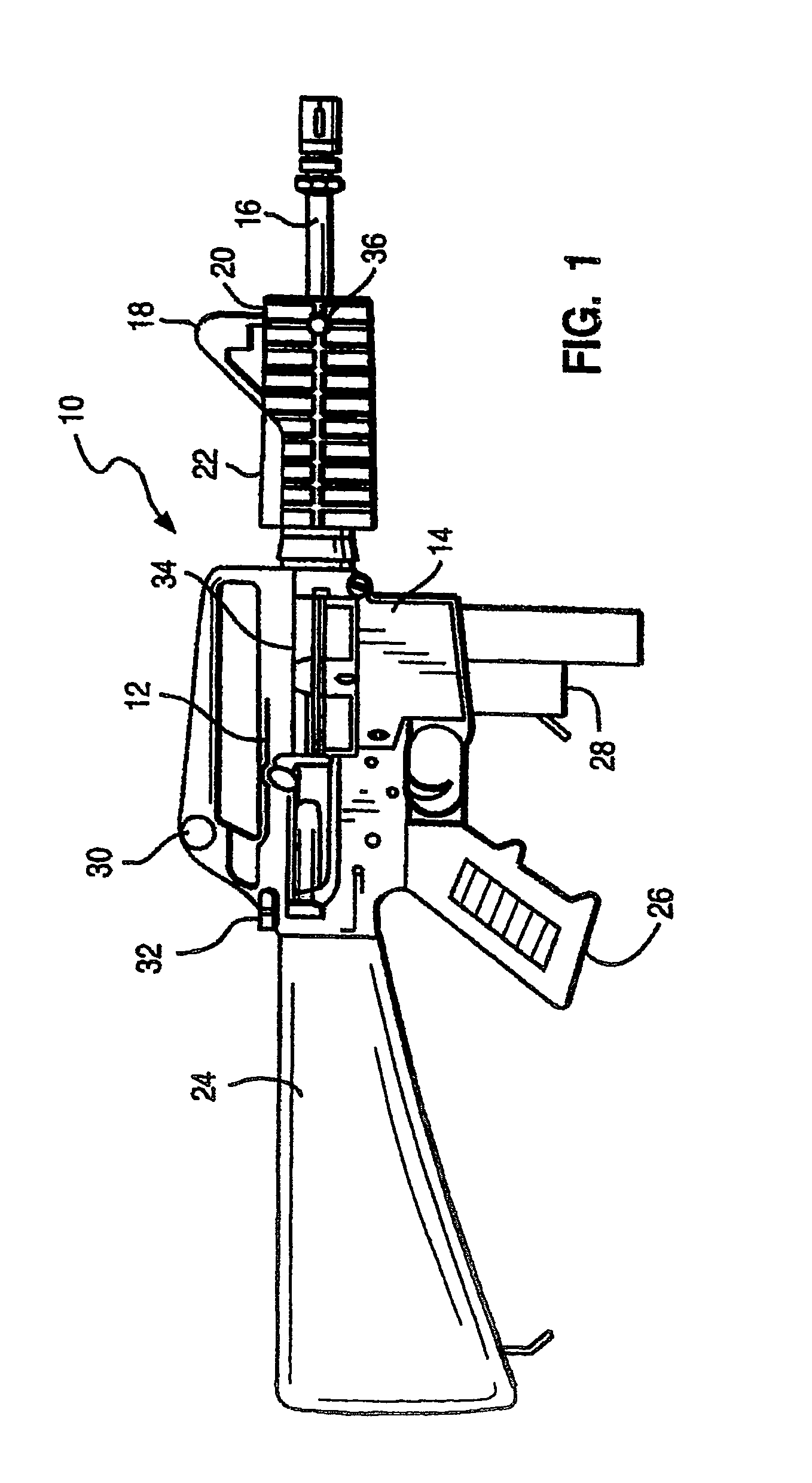
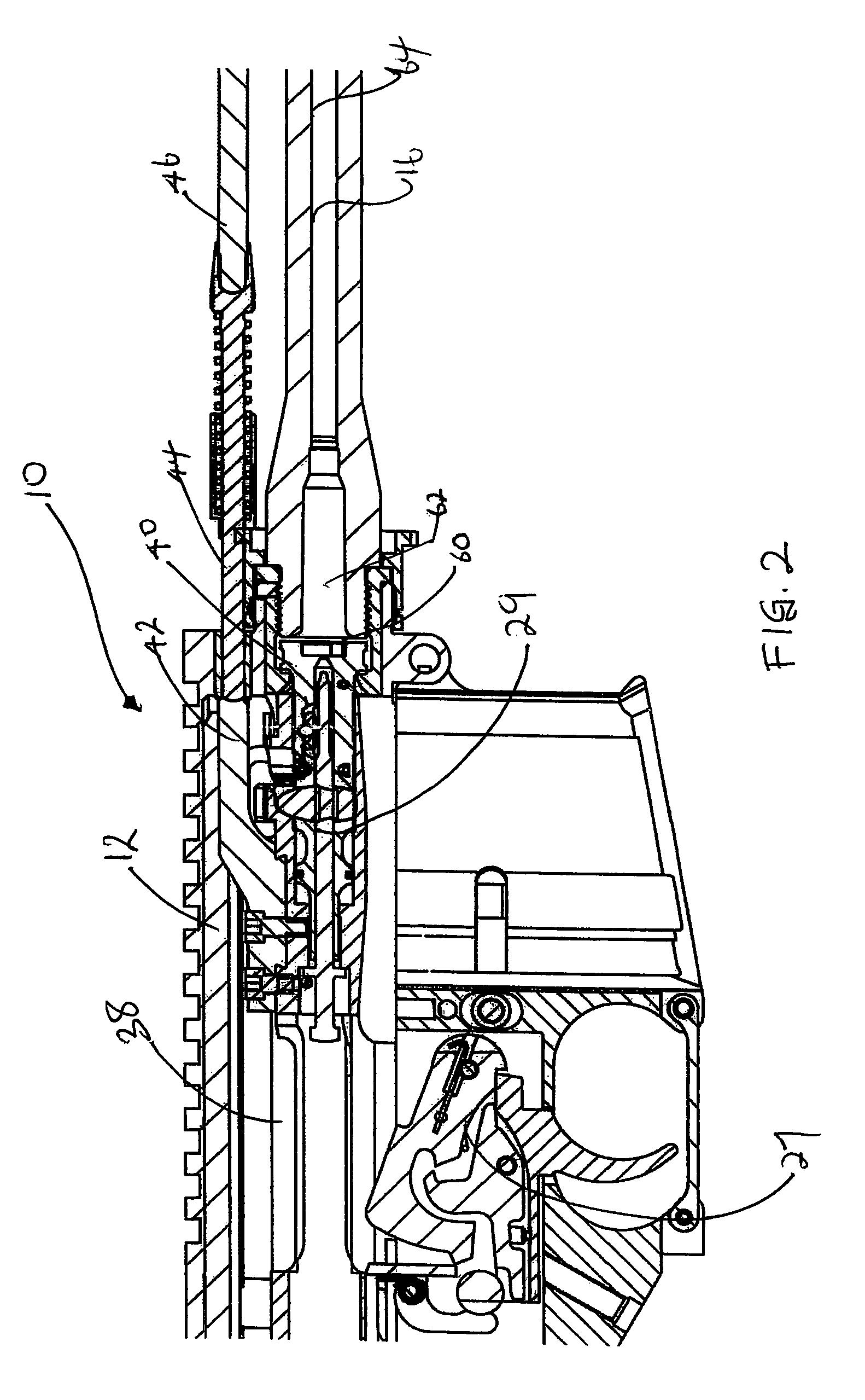
Self-cleaning gas operating system for a firearm
Owner:LWRC INTERNATIONAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com