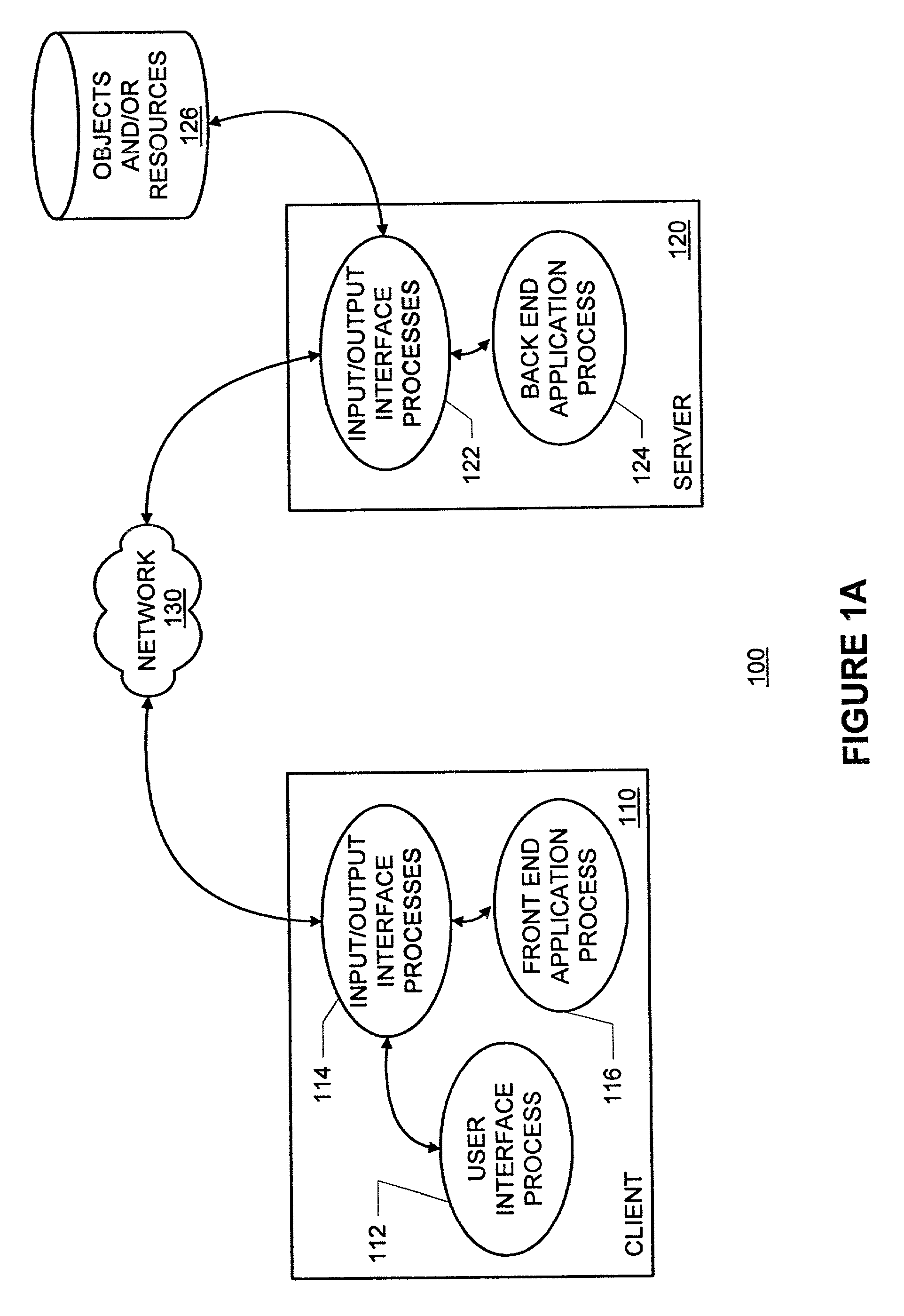
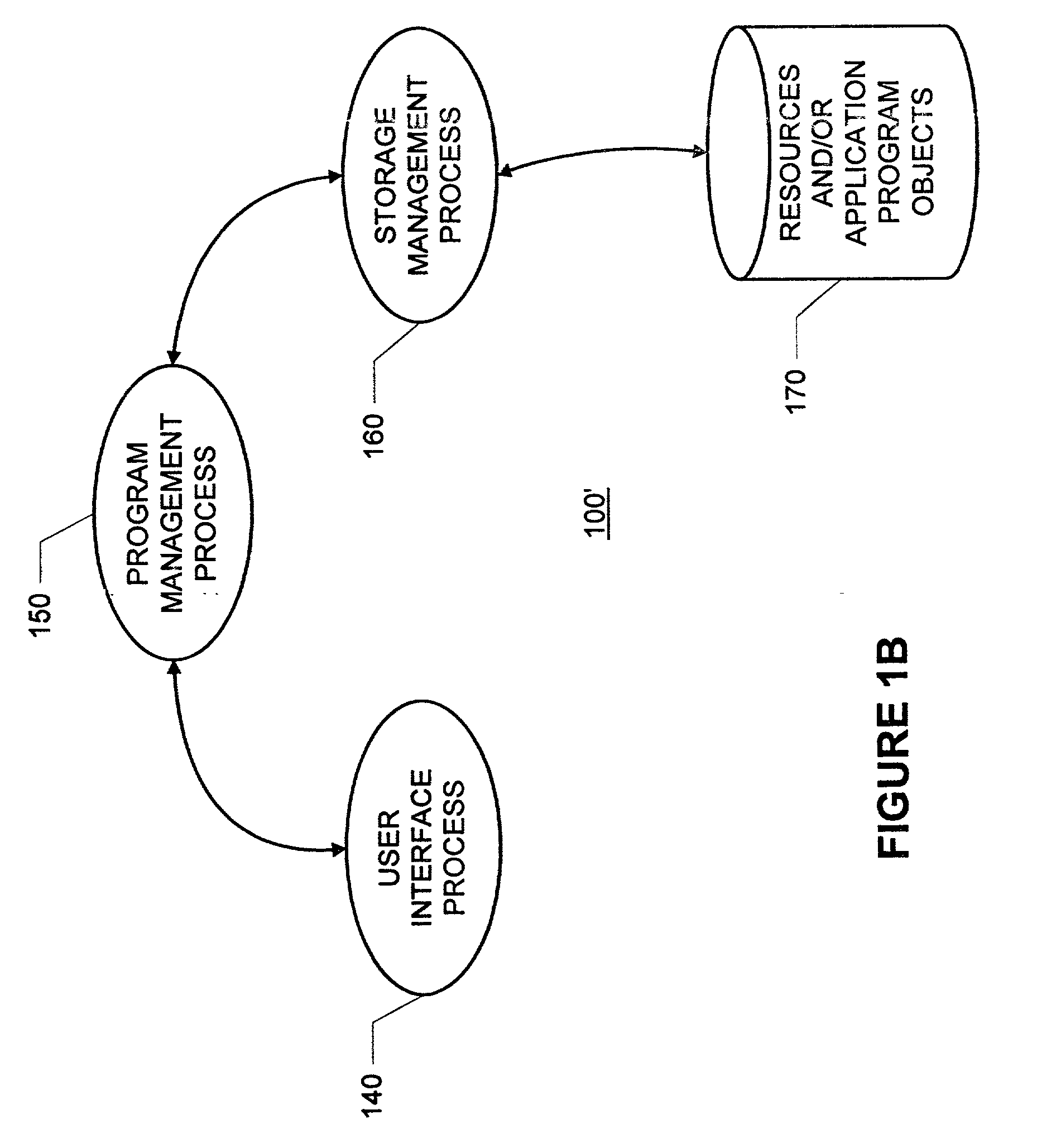
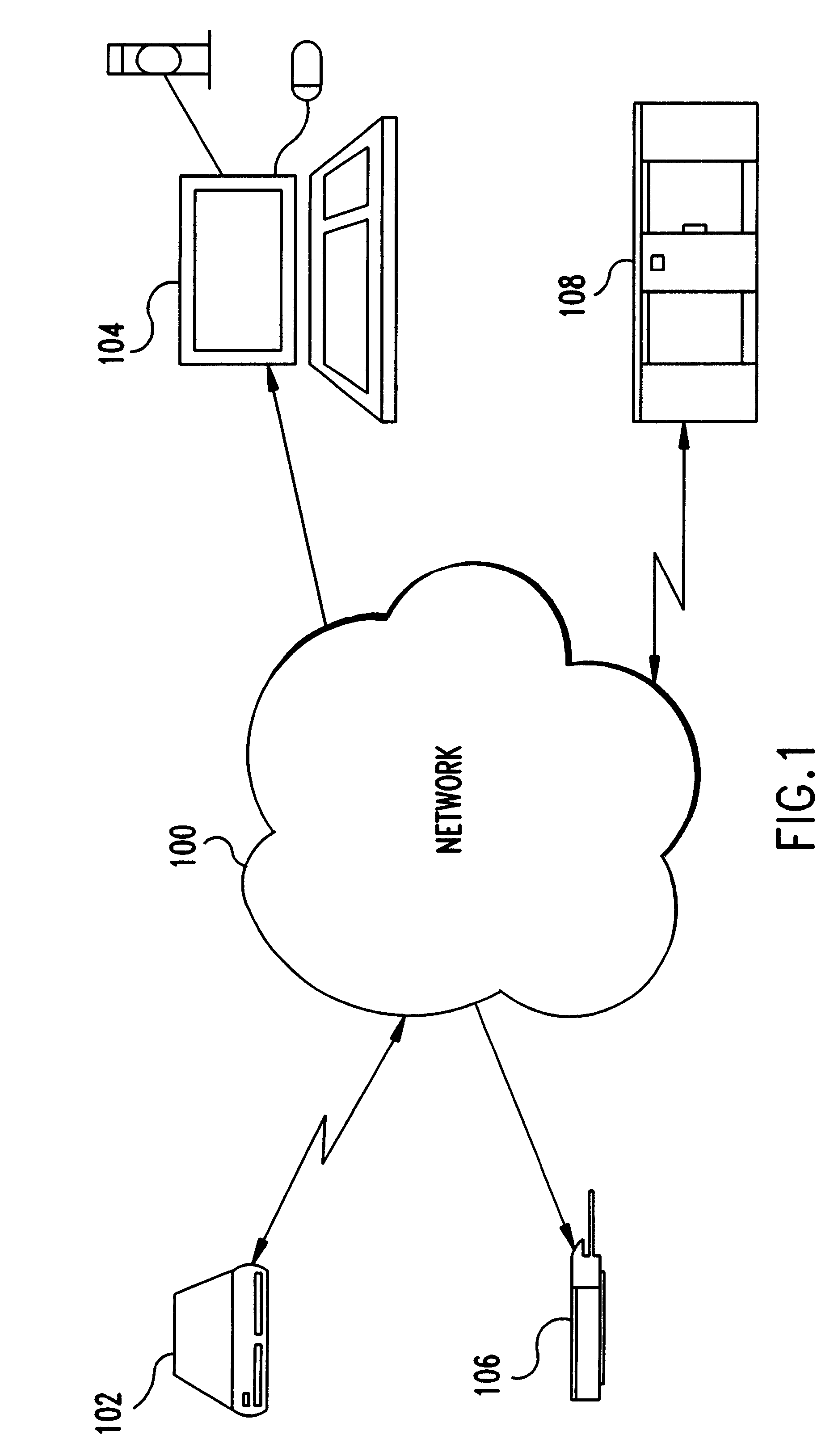
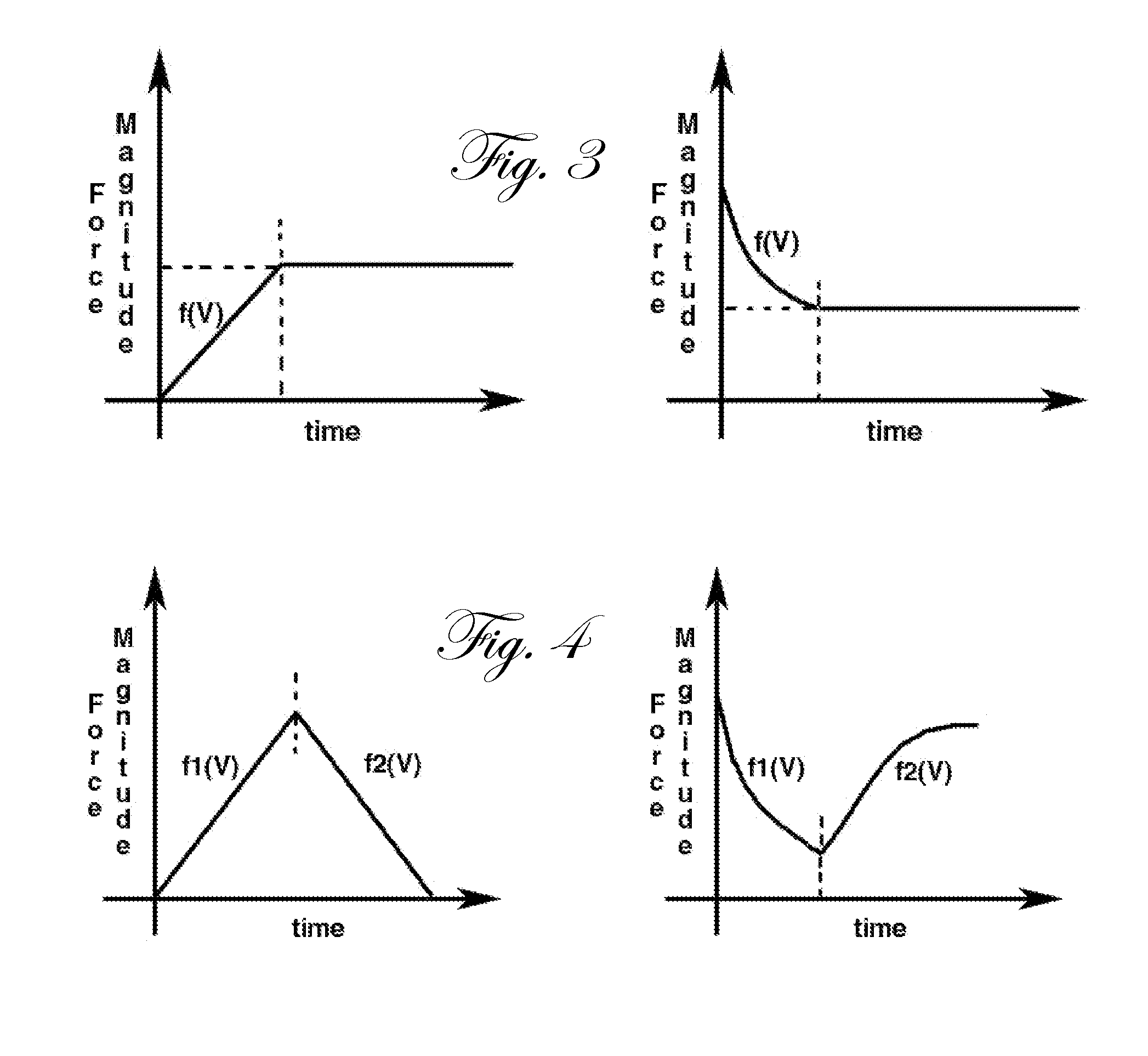Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
916 results about "Computer users" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A user is a person who utilizes a computer or network service. Users of computer systems and software products generally lack the technical expertise required to fully understand how they work. Power users use advanced features of programs, though they are not necessarily capable of computer programming...
Automatic, personalized online information and product services
InactiveUS6981040B1Improve performanceManage efficiently enormousDigital data information retrievalMultiple digital computer combinationsLearning machinePersonalized search
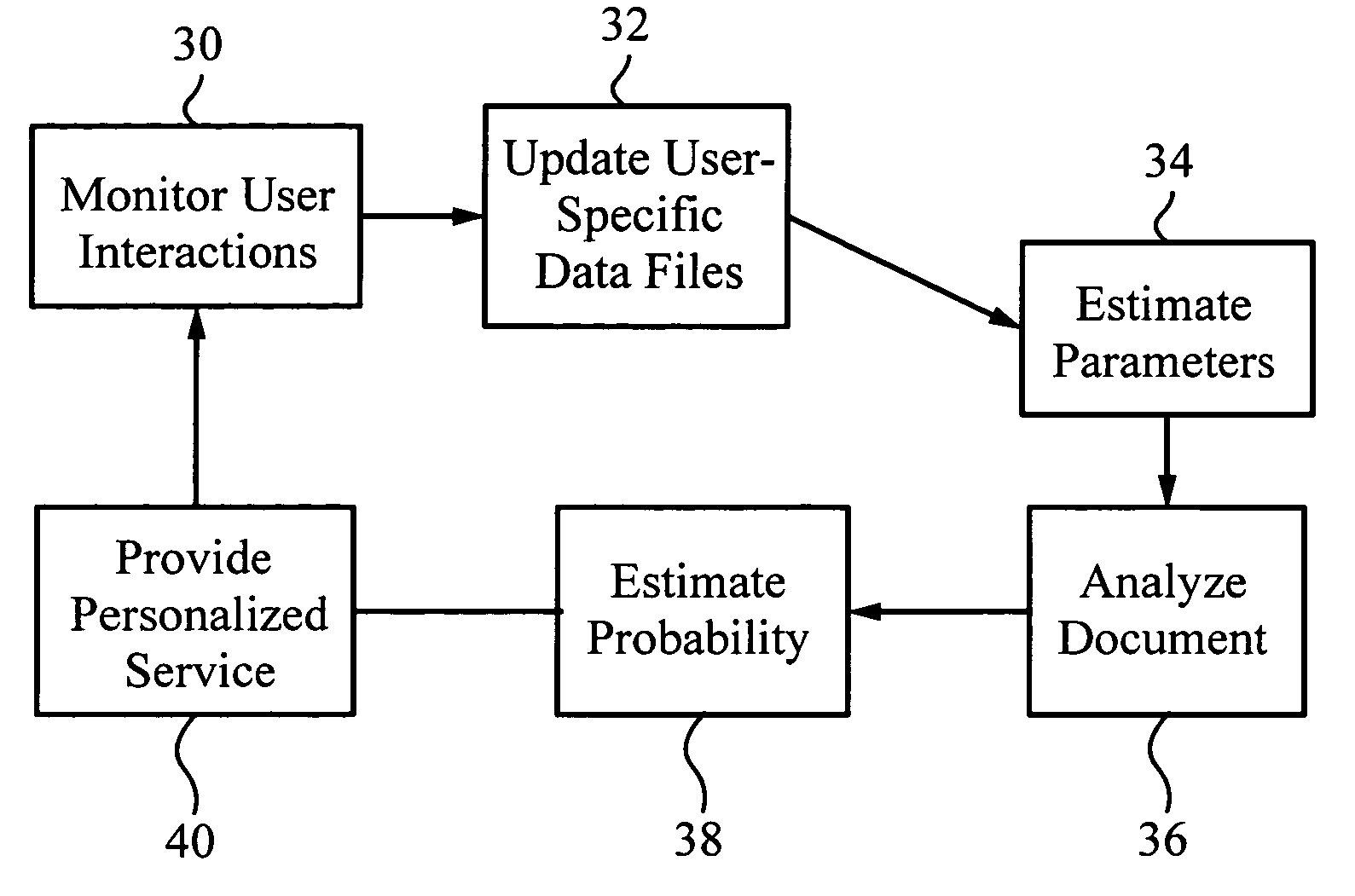
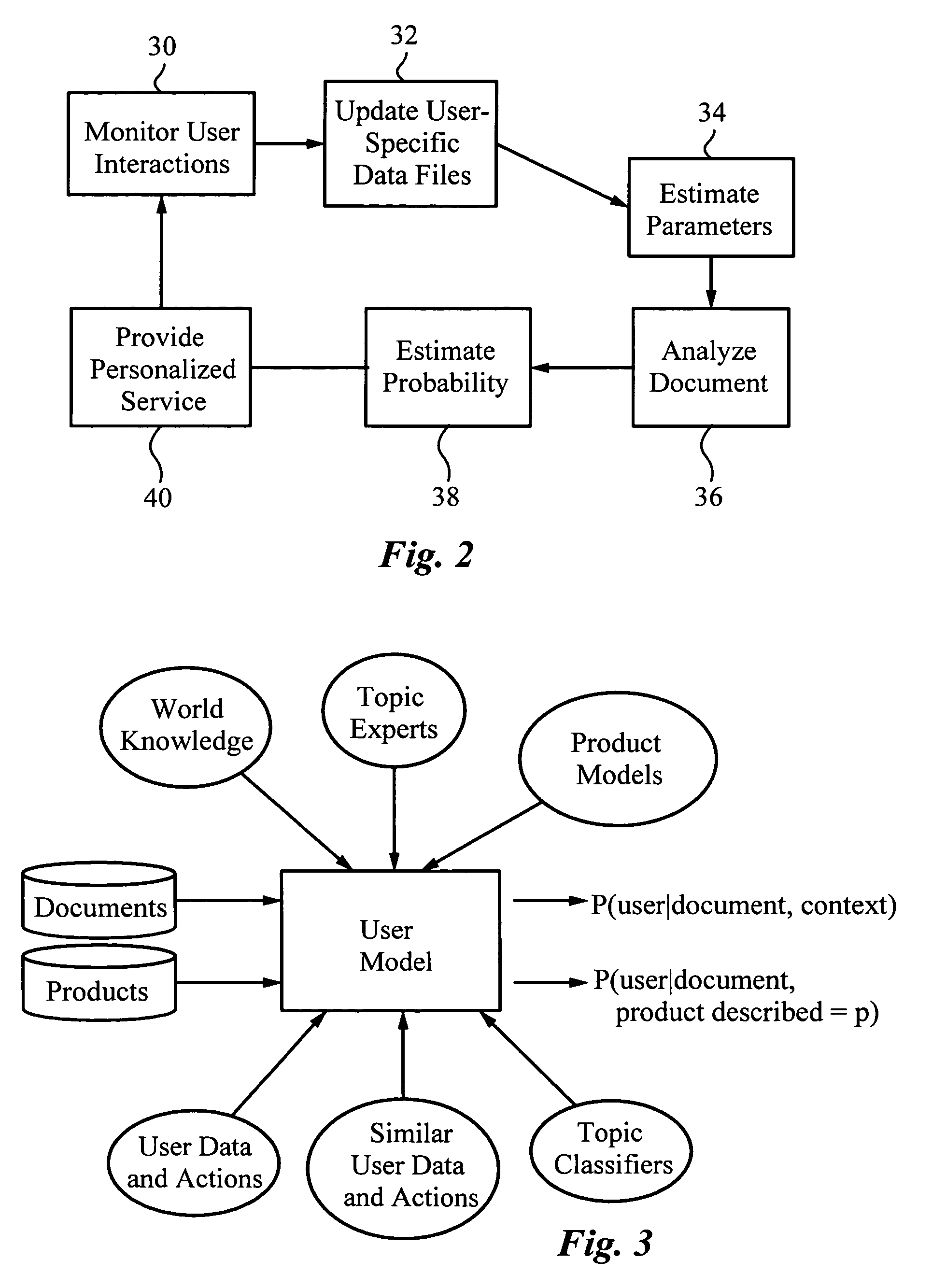
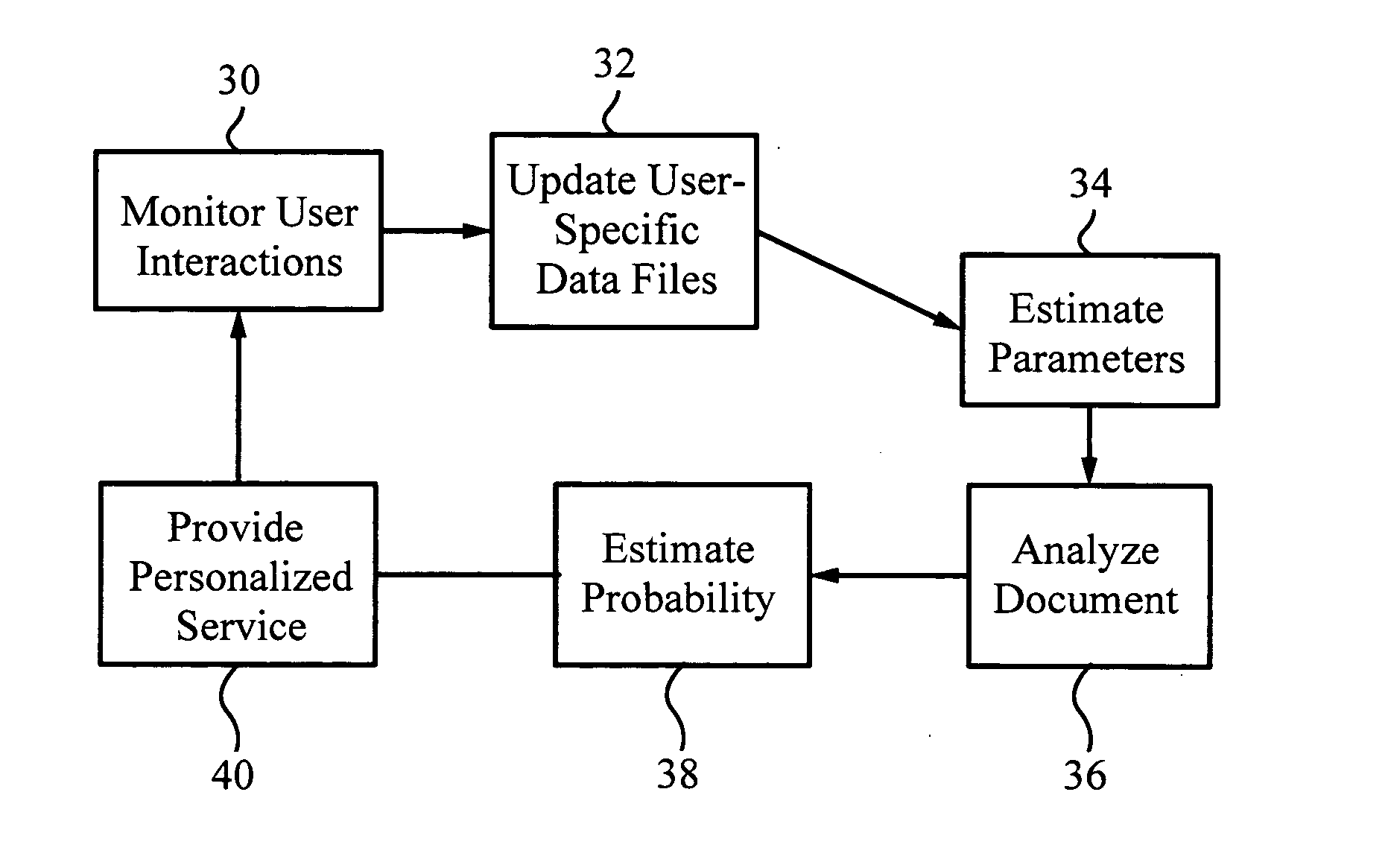
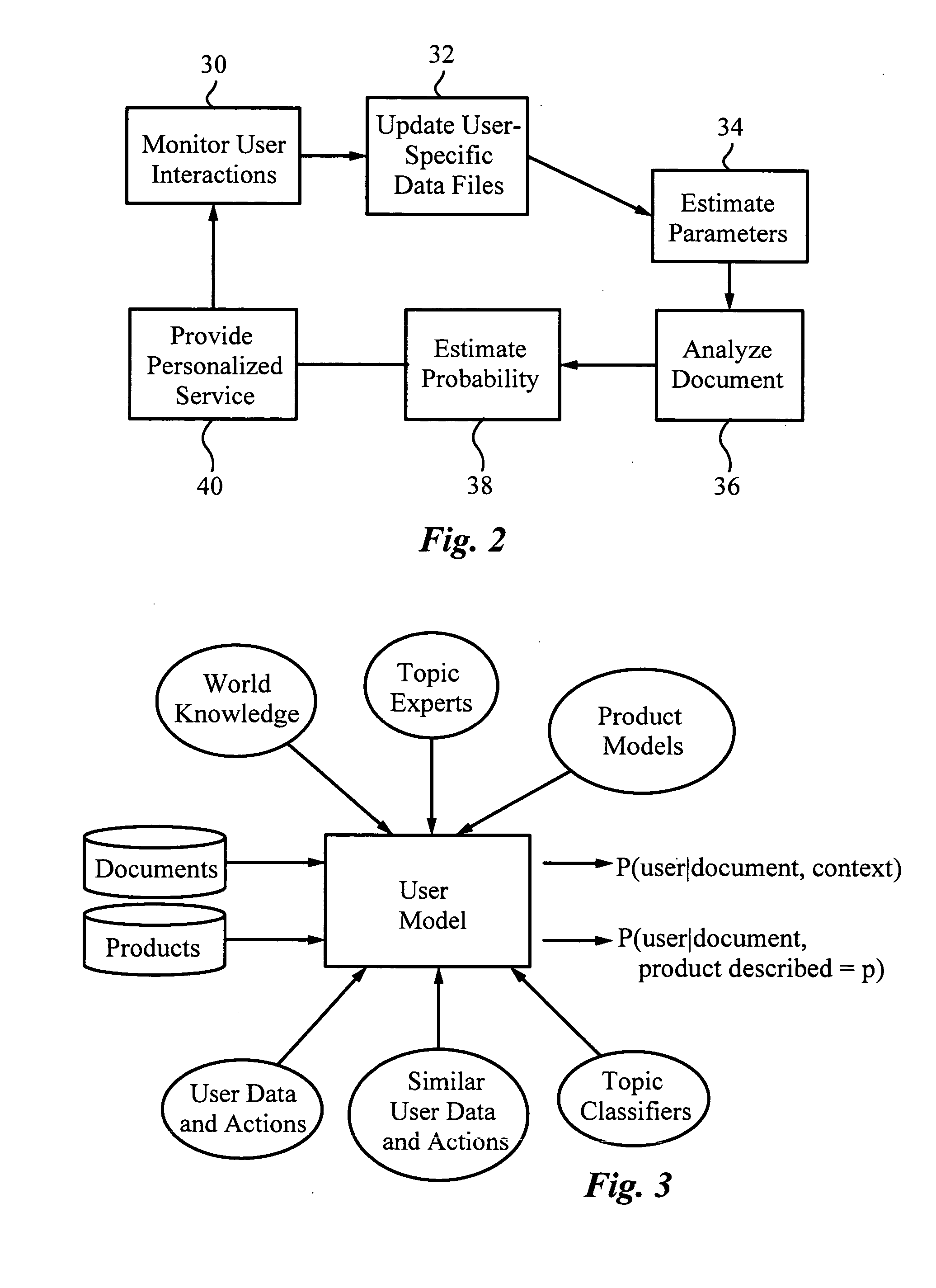
A method for providing automatic, personalized information services to a computer user includes the following steps: transparently monitoring user interactions with data during normal use of the computer; updating user-specific data files including a set of user-related documents; estimating parameters of a learning machine that define a User Model specific to the user, using the user-specific data files; analyzing a document to identify its properties; estimating the probability that the user is interested in the document by applying the document properties to the parameters of the User Model; and providing personalized services based on the estimated probability. Personalized services include personalized searches that return only documents of interest to the user, personalized crawling for maintaining an index of documents of interest to the user; personalized navigation that recommends interesting documents that are hyperlinked to documents currently being viewed; and personalized news, in which a third party server customized its interaction with the user. The User Model includes continually-updated measures of user interest in words or phrases, web sites, topics, products, and product features. The measures are updated based on both positive examples, such as documents the user bookmarks, and negative examples, such as search results that the user does not follow. Users are clustered into groups of similar users by calculating the distance between User Models.
Owner:PERSONALIZED USER MODEL PUM
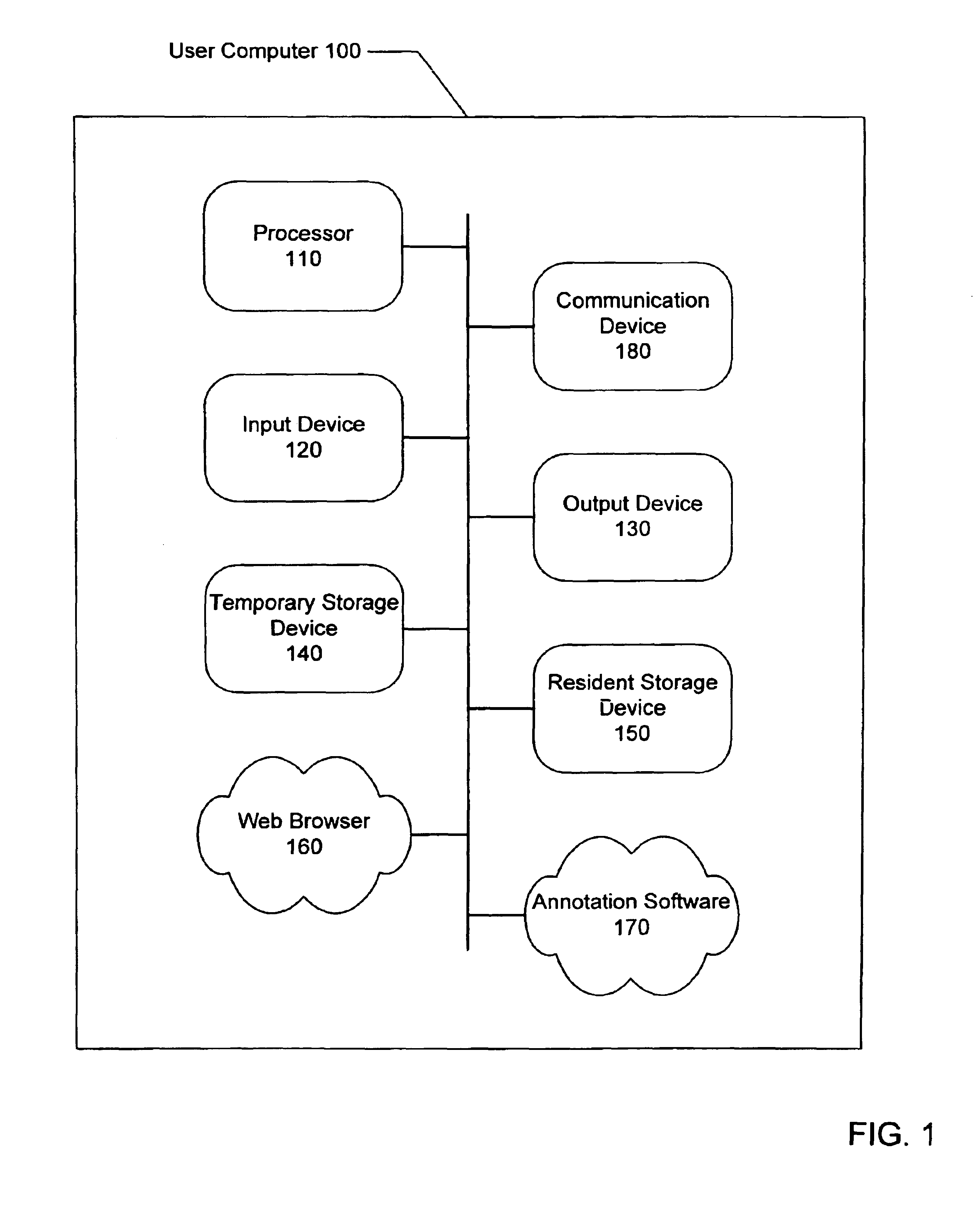
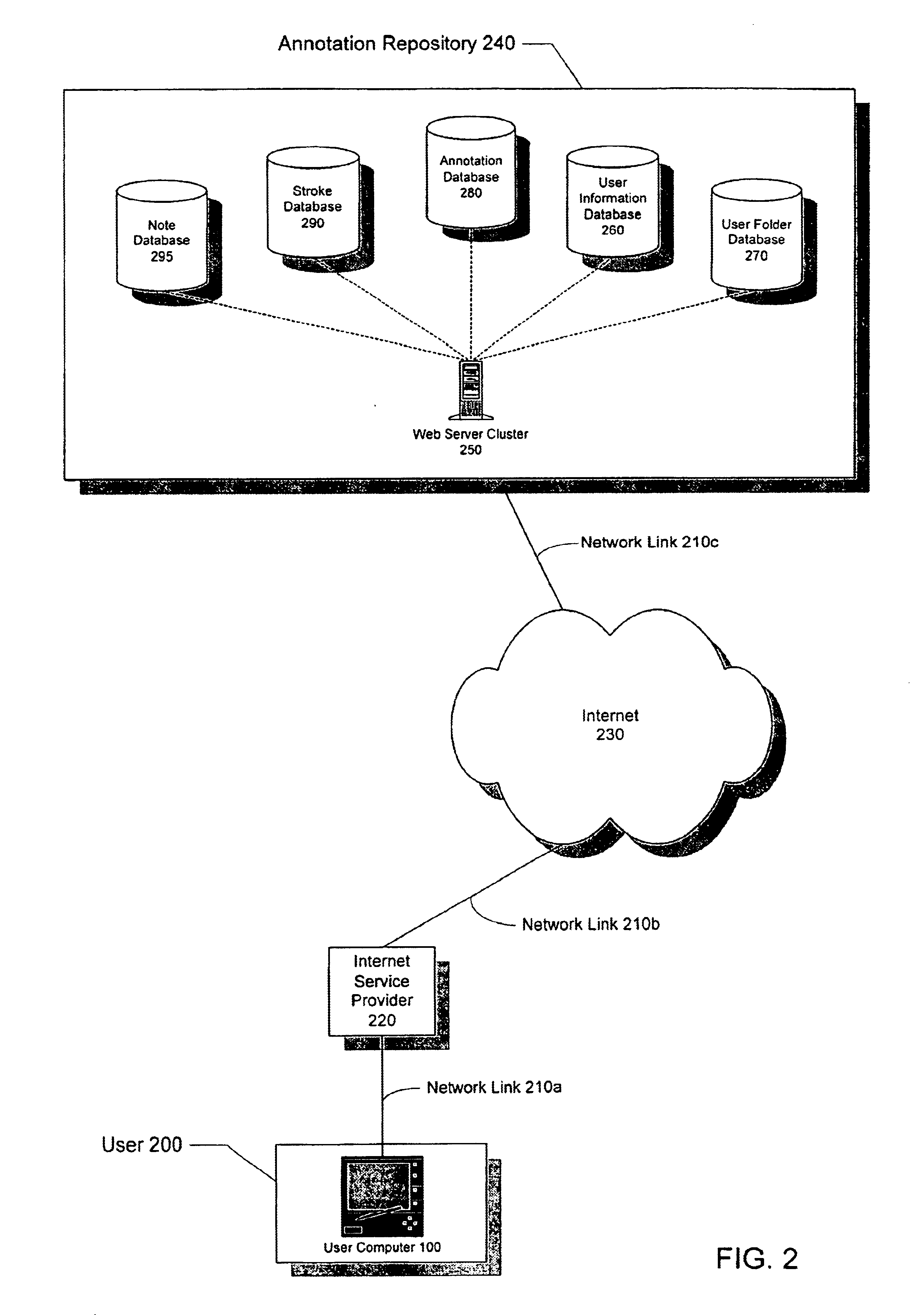
System and method for annotating web-based documents
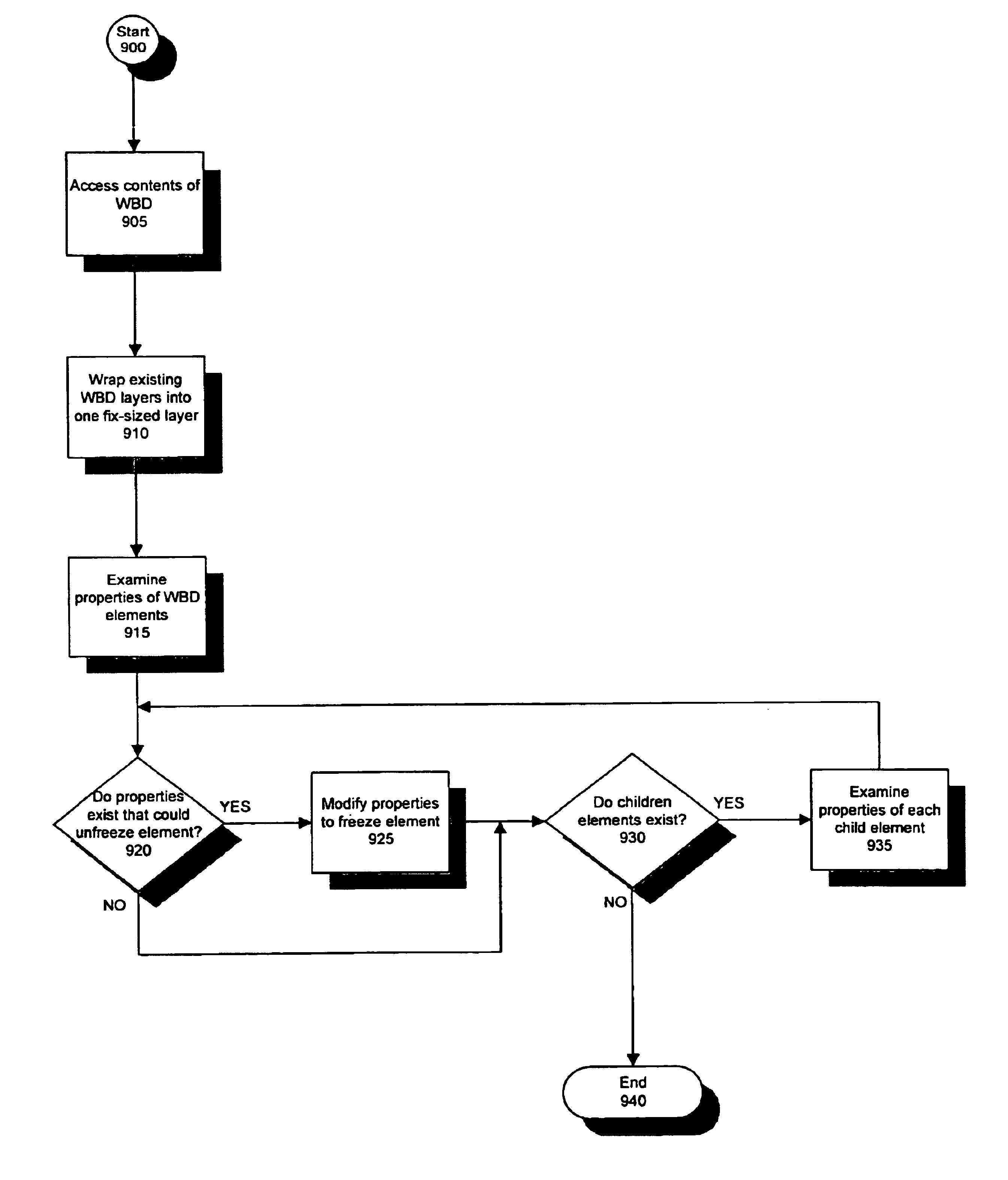
InactiveUS6859909B1Simple interfaceEffectively converting their Web browsersDrawing from basic elementsDigital computer detailsPersonalizationComputer users
The present invention allows computer users to integrate any annotation, including ink, highlighter, text-based notes and audio, directly into a Web-based document (WBD) displayed by a Web browser. This integration enables others to view the personalized annotated WBD, which retains its original active links and properties, over the Internet without the need for specialized software. Annotations are integrated into WBDs by freezing the WBD, overlaying an image file containing the annotations onto the WBD, and enabling browser events to pass through the image layer. Annotations may also be integrated into WBDs by using component object technology. The present invention collects and organizes annotated WBDs, and provides users with an intuitive Web-based interface for accessing, viewing and searching the annotated WBDs. Users may annotate blank WBDs, effectively converting their Web browsers into online notebooks / scrapbooks. The present invention also provides users with many novel interface techniques, such as dog-ears and its associated navigation tools, splitting pages, turning pages, selecting and copying various portions of a WBD (including shaking out a copy), and marking menus suited for right-handed or left-handed users.
Owner:MICROSOFT CORP
Human-computer user interaction
ActiveUS20100261526A1Input/output for user-computer interactionElectronic switchingHuman interactionComputer users
Methods of and apparatuses for providing human interaction with a computer, including human control of three dimensional input devices, force feedback, and force input.
Owner:META PLATFORMS INC
Proximity detection of valid computer user
InactiveUS6189105B1Digital data processing detailsUser identity/authority verificationOperational systemComputer users
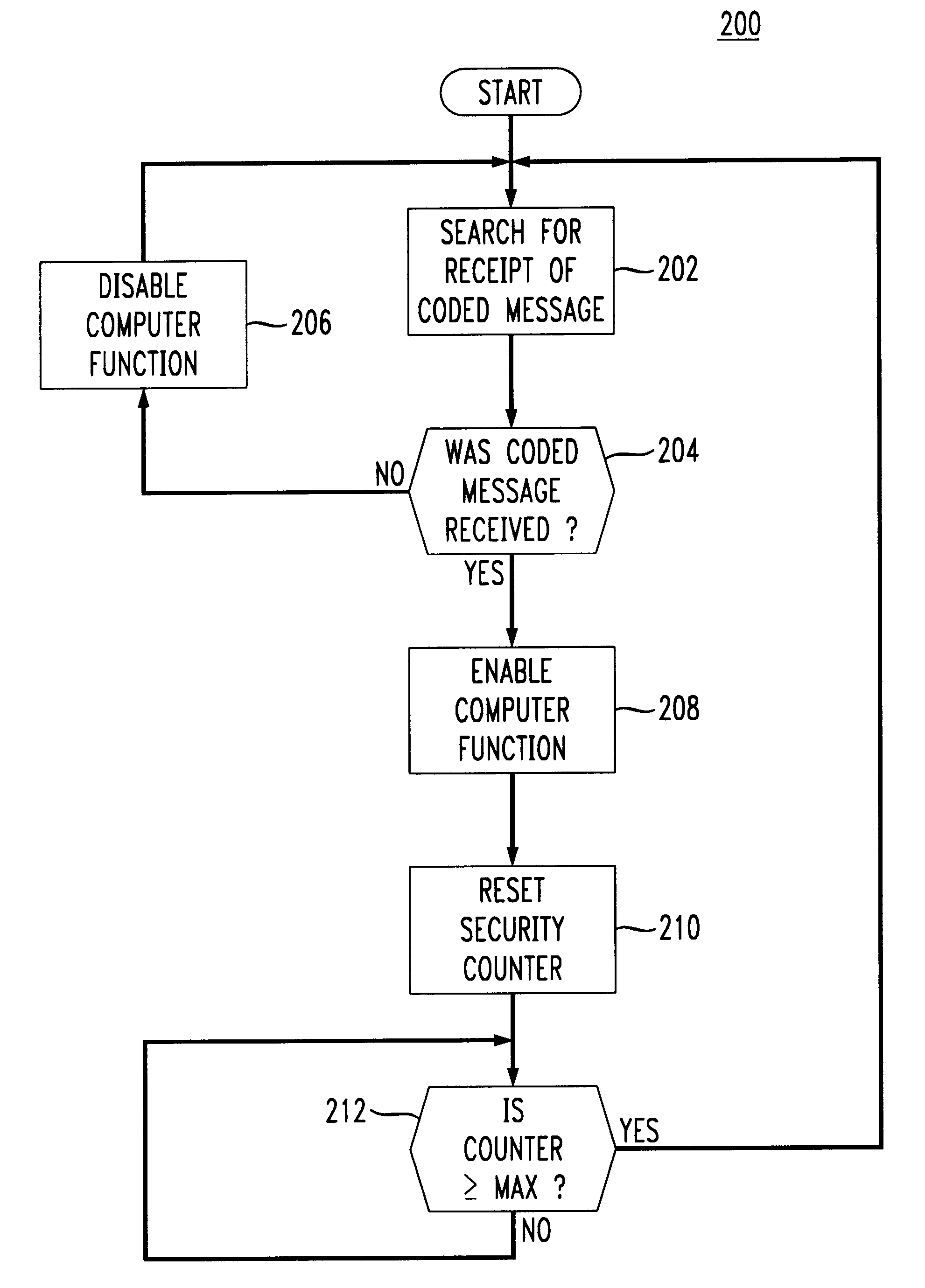
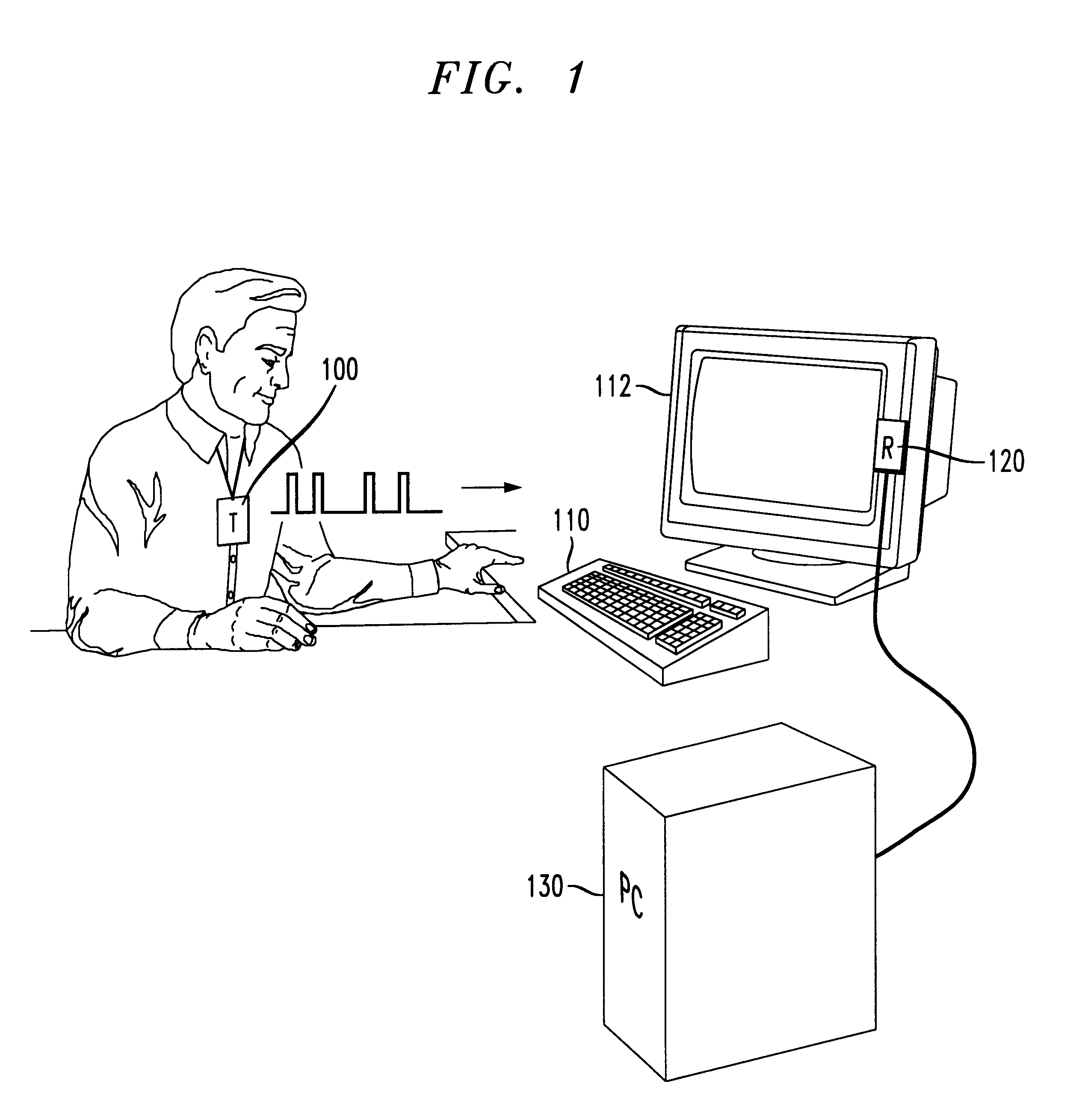
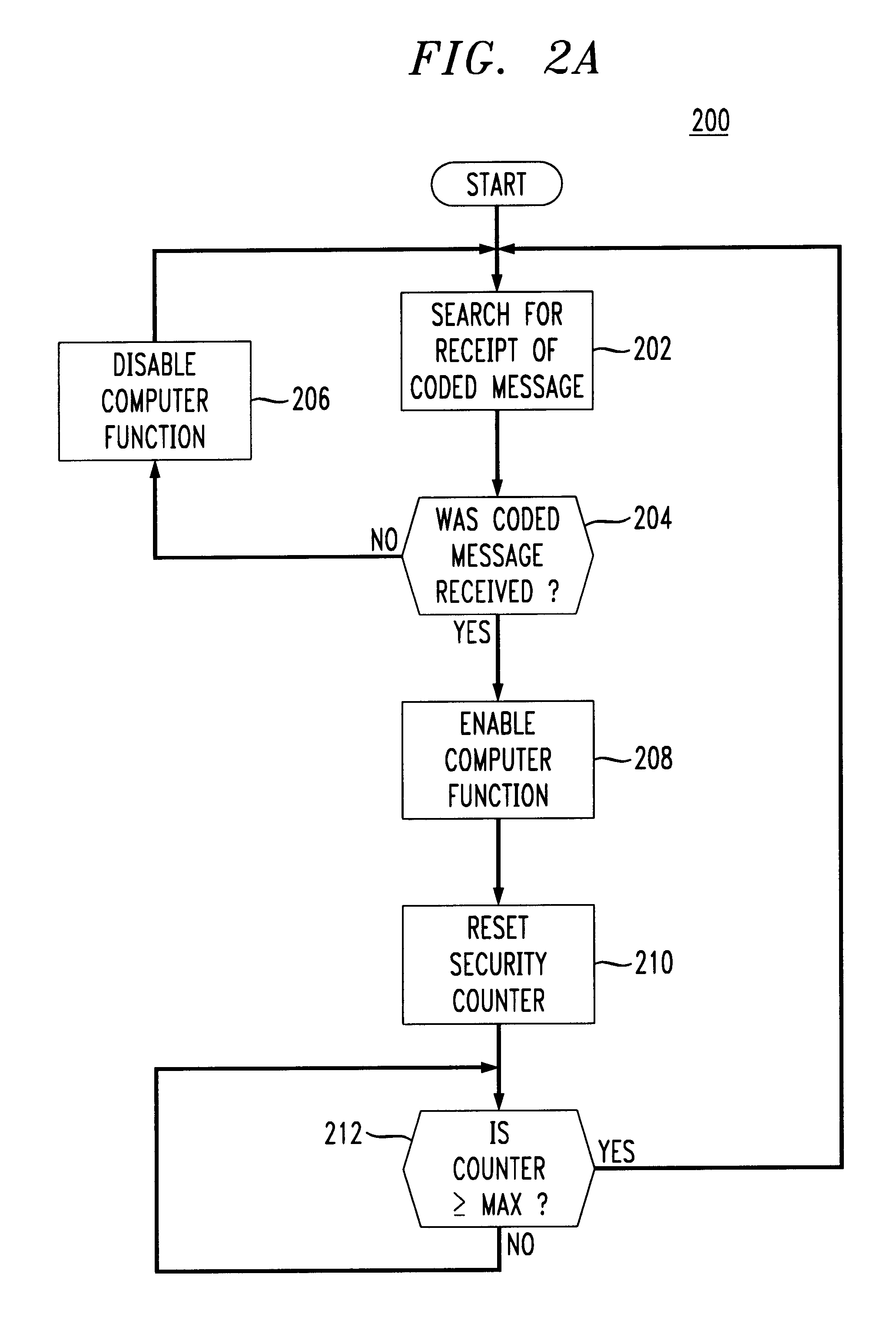
A method and apparatus for continuously authorizing a computer for use. A proximity detection system provides a coded message from a badge on an authorized user to a proximity reader in communication with the computer. The computer contains a process either in its kernel, operating system, and / or application program to repeatedly and continuously detect the presence of an authorized user within a desired proximity of the computer. If an authorizing code is received from an authorized user, the computer continues to allow full use of the computer. If an authorizing code is not received, a desired feature of the computer (e.g., the display, the keyboard, the mode of the processor) is disabled until the authorized user again enters the proximity zone of the computer.
Owner:WSOU INVESTMENTS LLC +1
Semantic user interface
InactiveUS6438545B1Easy to learnEasy to operateData processing applicationsSpecial data processing applicationsOperational systemComputer users
A system and method that allows a user to use their everyday language or user defined words to operate a computer in a highly efficient way. In short, every word, letter, control character and symbol is potentially actionable. A computer user's productivity is dramatically increased by making available those functions that enable a user to produce most of his work through simple, language-based commands. The present invention provides an intuitive interface, referred to as a semantic user interface (SUI), that enhances the operation of the current standard window-based interface in a manner that is simple, richer and natural. By leveraging all of the richness and power inherent in a user's language, the present invention provides an important tool that allows the personal computer to operate in a manner that is much closer to our natural way of interacting. A user is allowed to enter "commands" in his everyday natural language in order to control the operations of the computer. All commands are language-based and user-defined. These commands can be entered from any context of the user's computer (e.g., any application or operating system workspace). The commands allows a user to launch applications and navigate within applications by using language rather than clicks from a pointing device such as a mouse. It also allows the replacement of keystrokes with stored words or keystrokes. The system also keeps a complete archive record of all the text content the user provides as input, regardless of which application program or operating system window the user is operating in at the time. The combined set of all user defined commands and the memory of all the input text that is stored in the archive constitutes the personality profile and is transportable from one computer to another.
Owner:ACTIVEWORD SYST
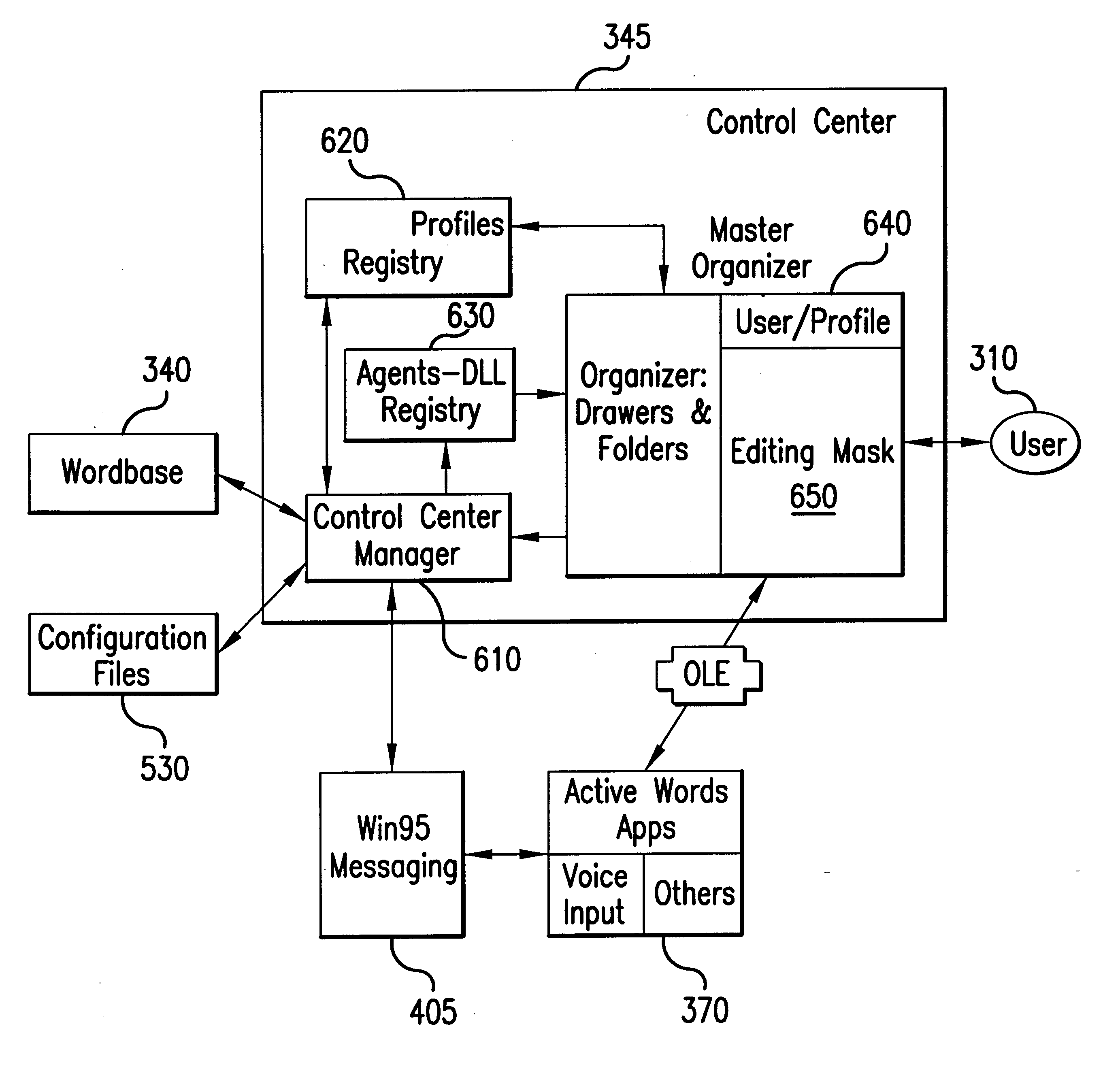
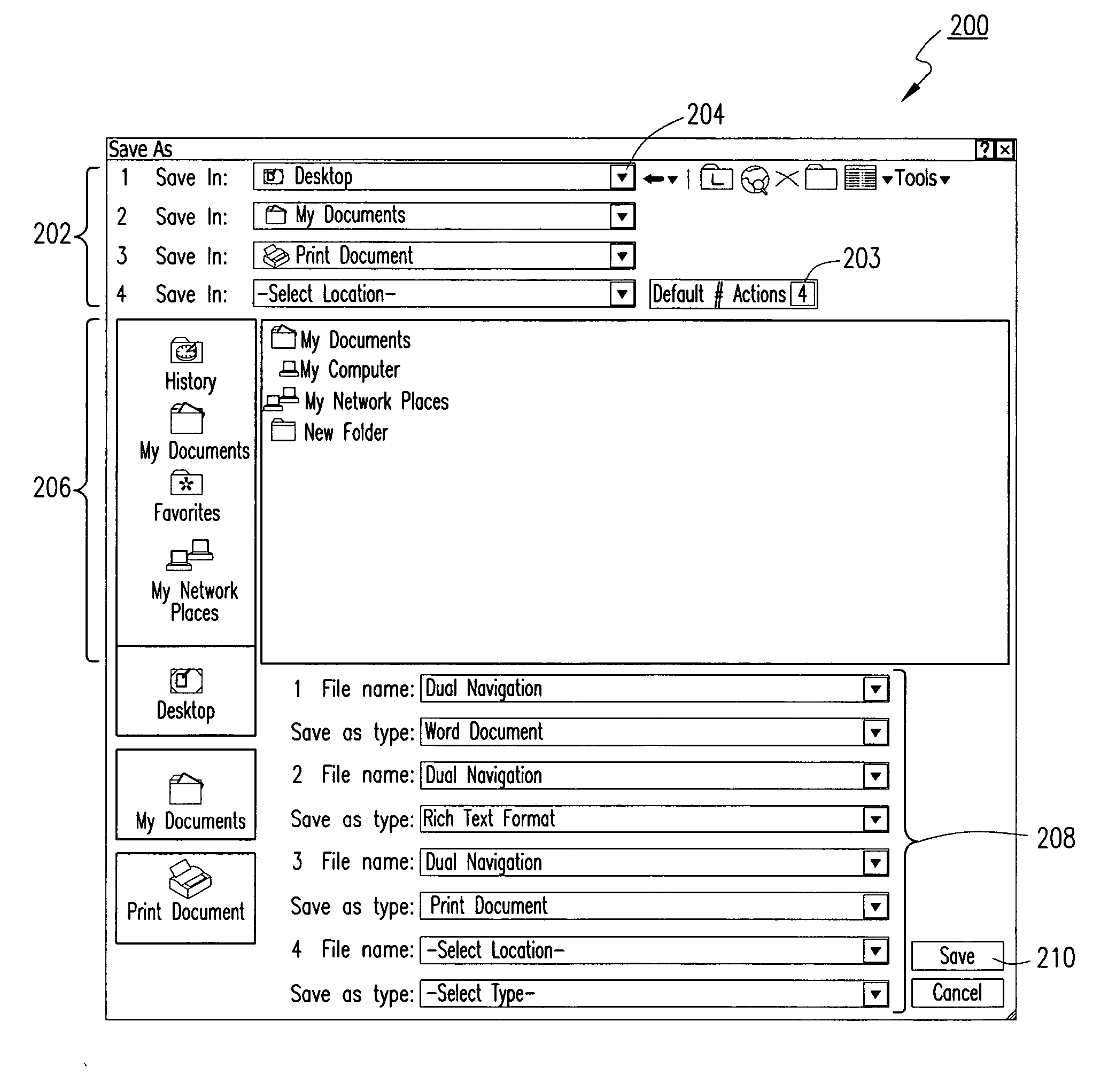
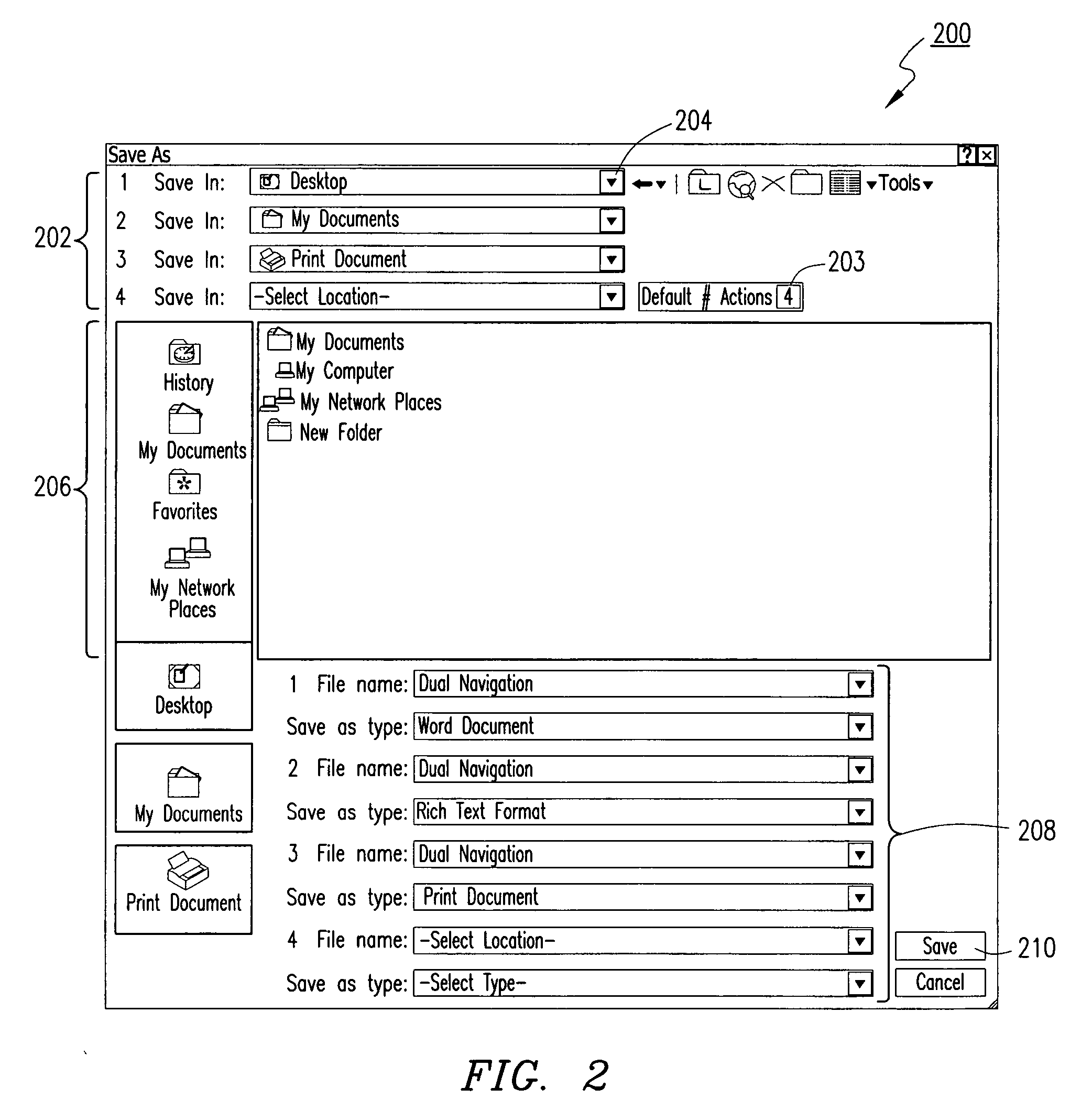
Method and graphic interface for storing, moving, sending or printing electronic data to two or more locations, in two or more formats with a single save function
InactiveUS20060129746A1Shorten the timeProgram loading/initiatingExecution for user interfacesGraphicsComputer users
A single graphic user interface enabling a computer user to store, print, back up or send an electronic file to multiple locations. The electronic file can be sent on multiple paths to multiple devices in multiple formats.
Owner:ITHINK
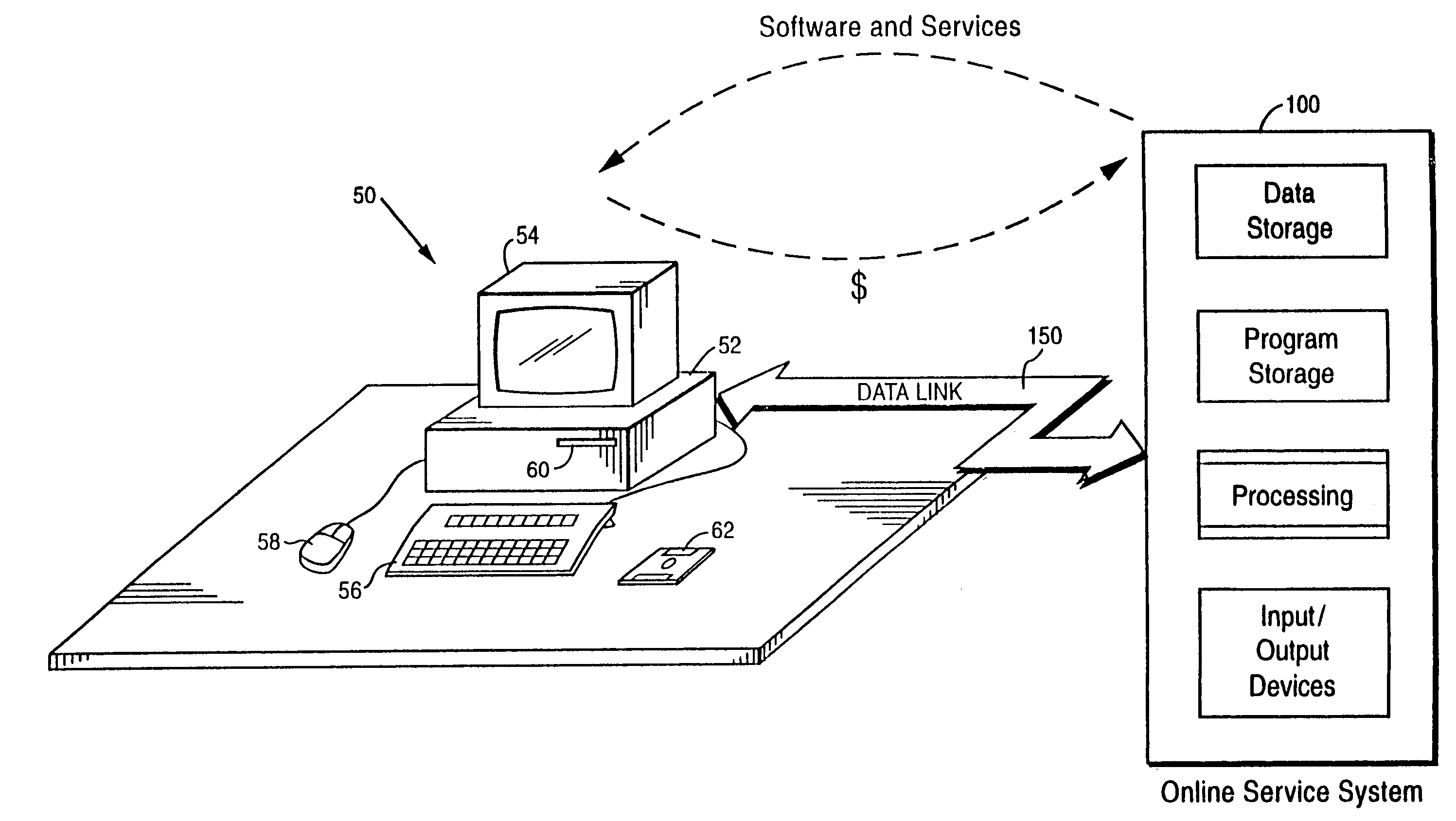
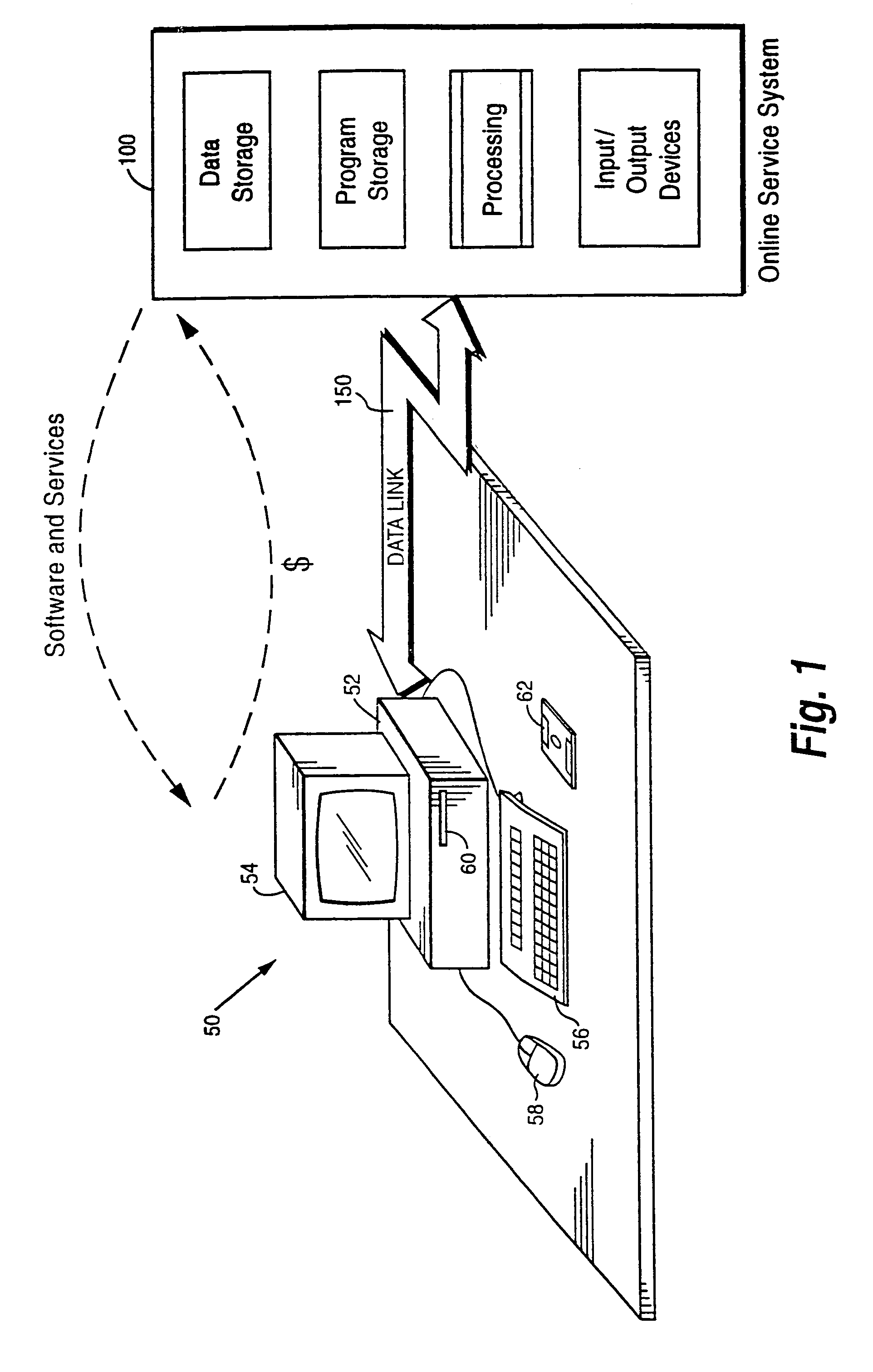
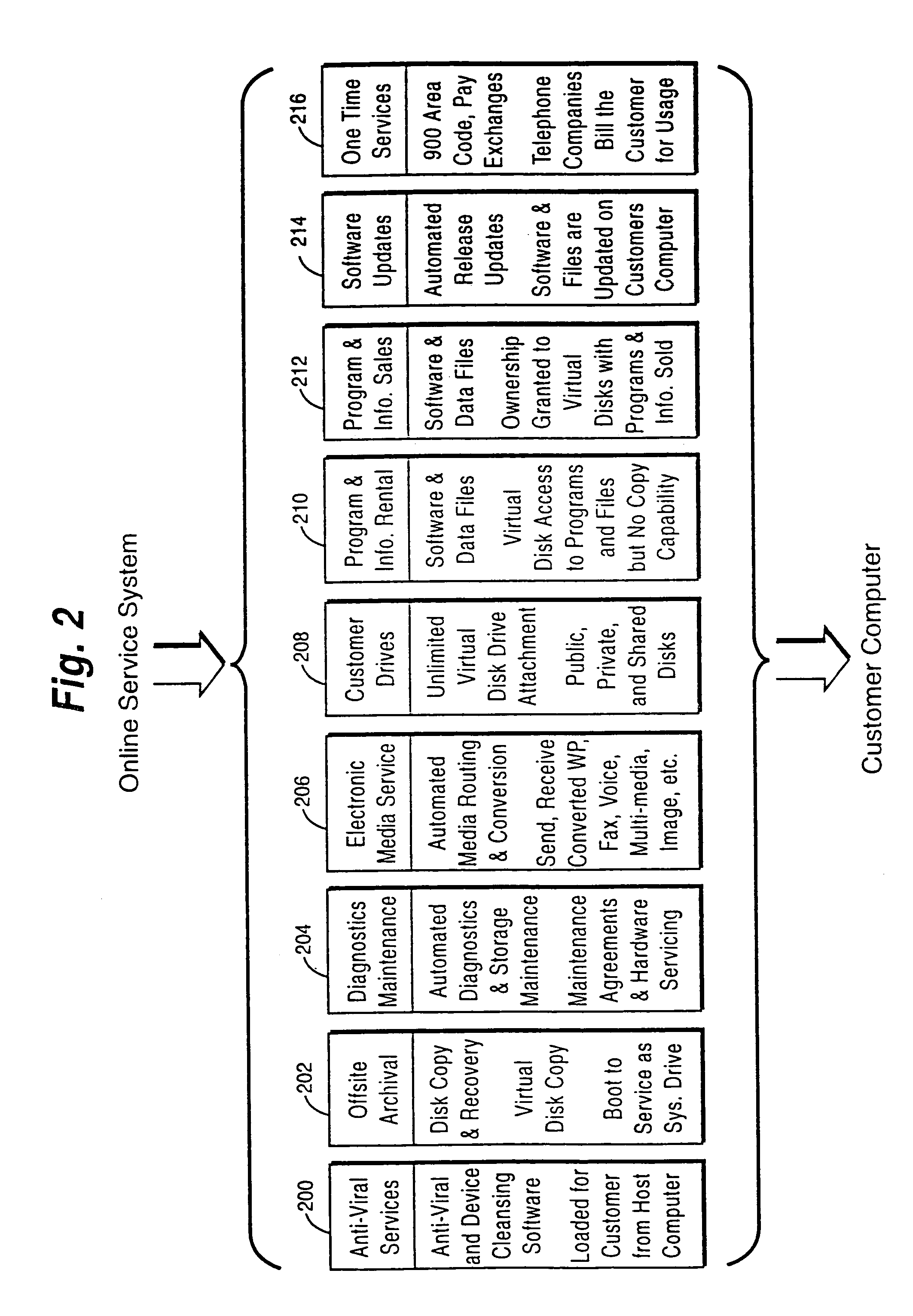
Internet download systems and methods providing software to internet computer users for local execution
A customer computer connects to an online service provider by phone, Internet, or other telecommunications link. The link gives the customer access to additional processing and storage resources such as virtual storage, processing power and / or additional software or data through interaction between the customer computer and an online service provider computer over the link. The additional resources made available to the customer computer enhance the customers' local needs through access to virtual storage, a more powerful processor of similar type for program execution, and / or online support services such as software rental, software sales, release update services, anti-viral services, data backup and recovery services, diagnostic services and / or repair services.
Owner:OASIS RES +6
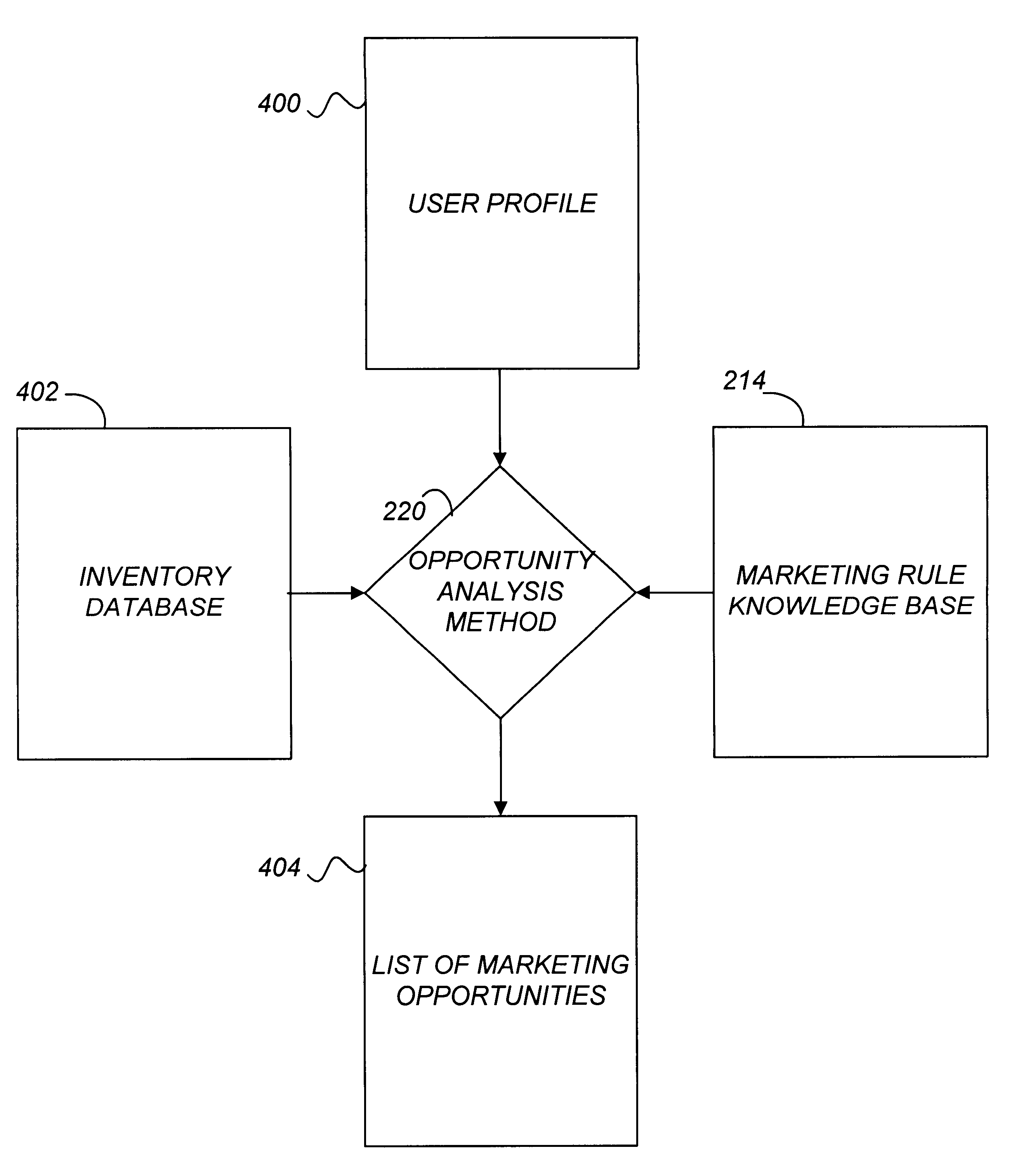
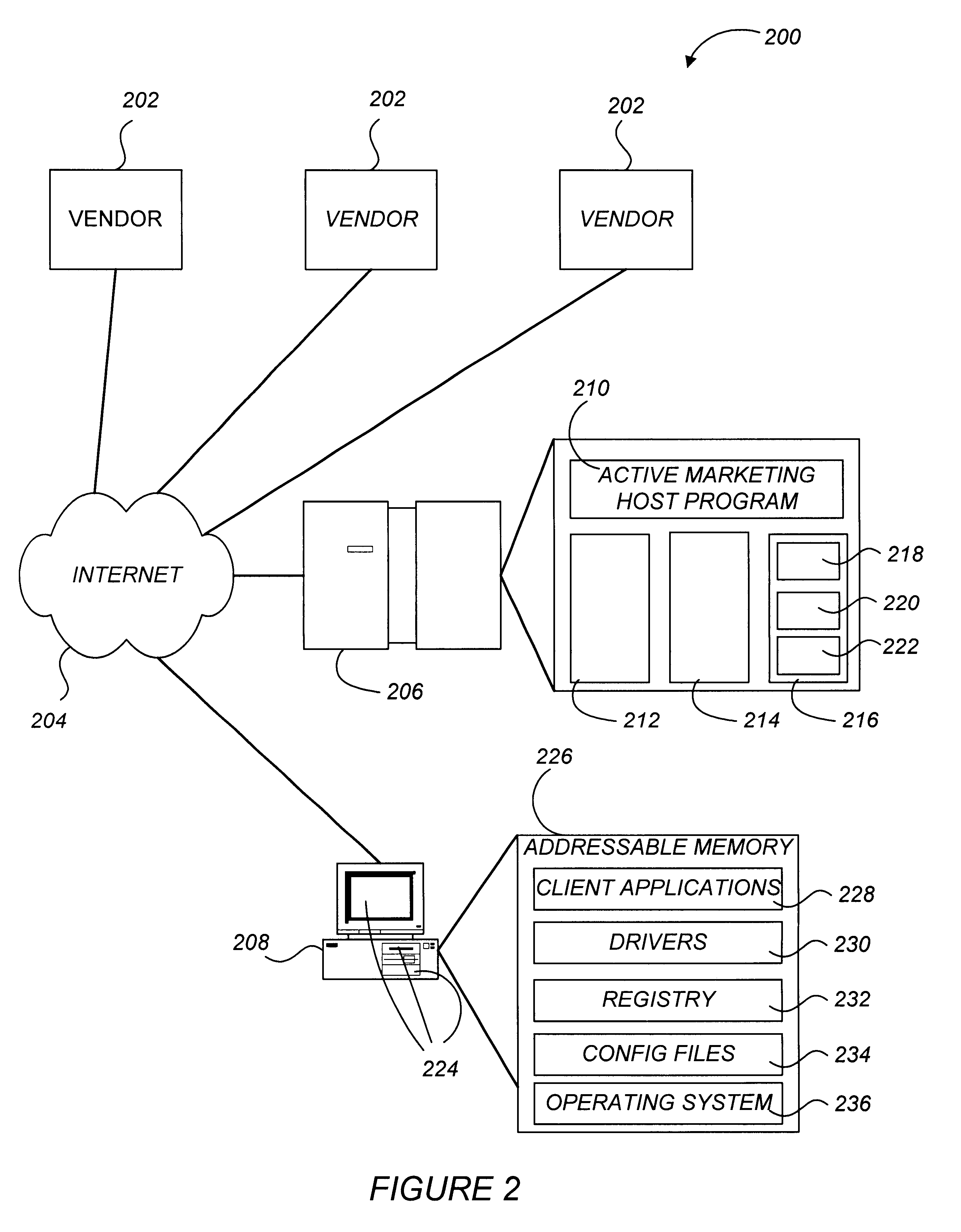
Active marketing based on client computer configurations
A system and method for actively marketing products and services to a user of a client computer such as over a network are disclosed. A product information database comprising product summary files that facilitate determination of presence or absence of products associated with the client computer, a marketing rule knowledge base comprising opportunity rule files governing marketing opportunities, and an opportunity detection object for determination of marketing opportunities are utilized to determine active marketing opportunities and may be downloaded to the client computer from a service provider computer system. The opportunity detection object may comprise a scan engine, an opportunity analysis engine, and a presentation engine which collectively determine and present marketing information to the client computer user. The scan engine compares the client computer against the product information database to determine the configurations of the client computer and to generate a client computer inventory database. The opportunity analysis engine analyzes the client computer inventory database against the marketing rule knowledge base and generates a list of marketing opportunities for the client computer. The presentation engine analyzes the list of marketing opportunities and provides marketing and / or other information regarding marketed products to the user.
Owner:MCAFEE LLC
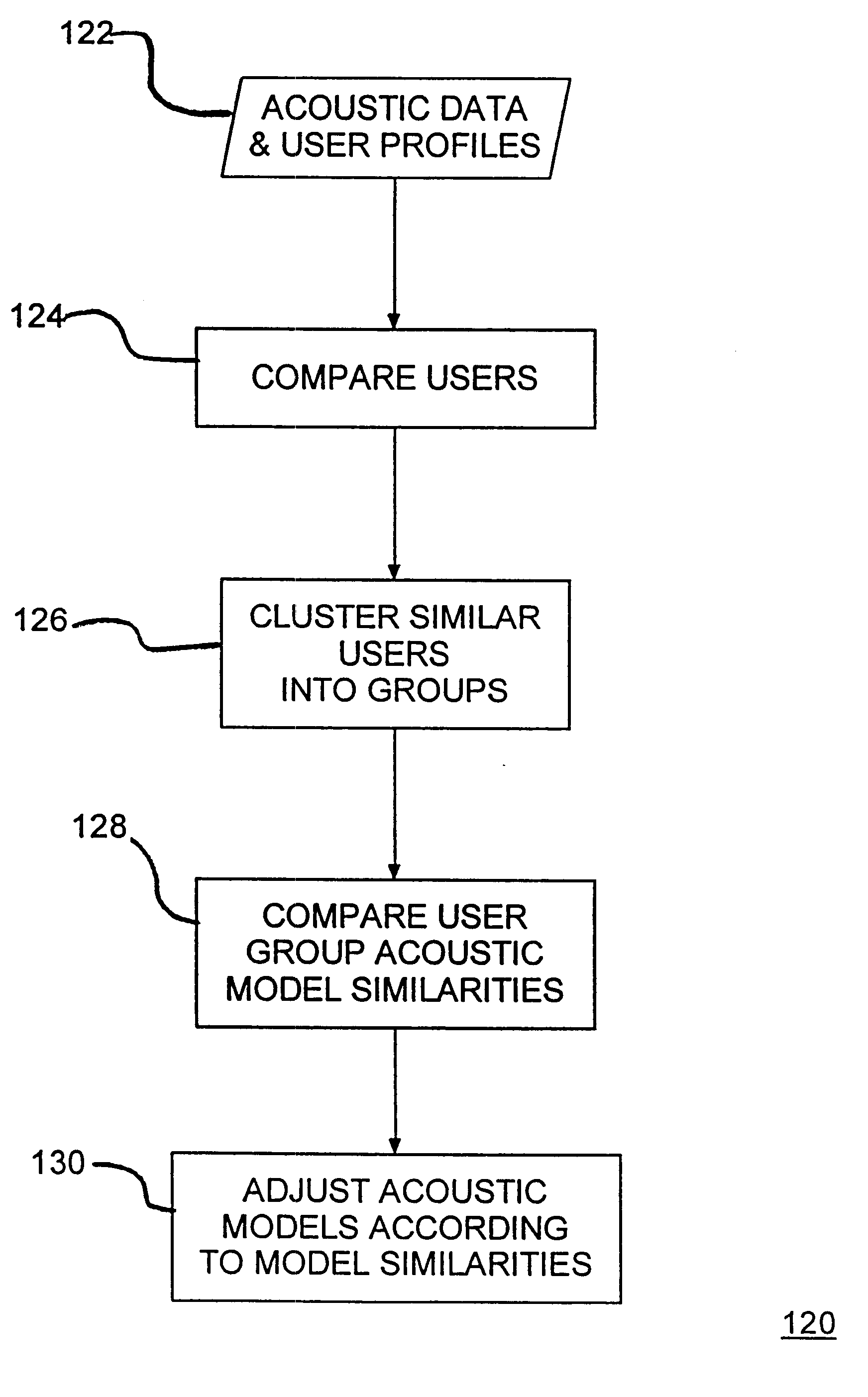
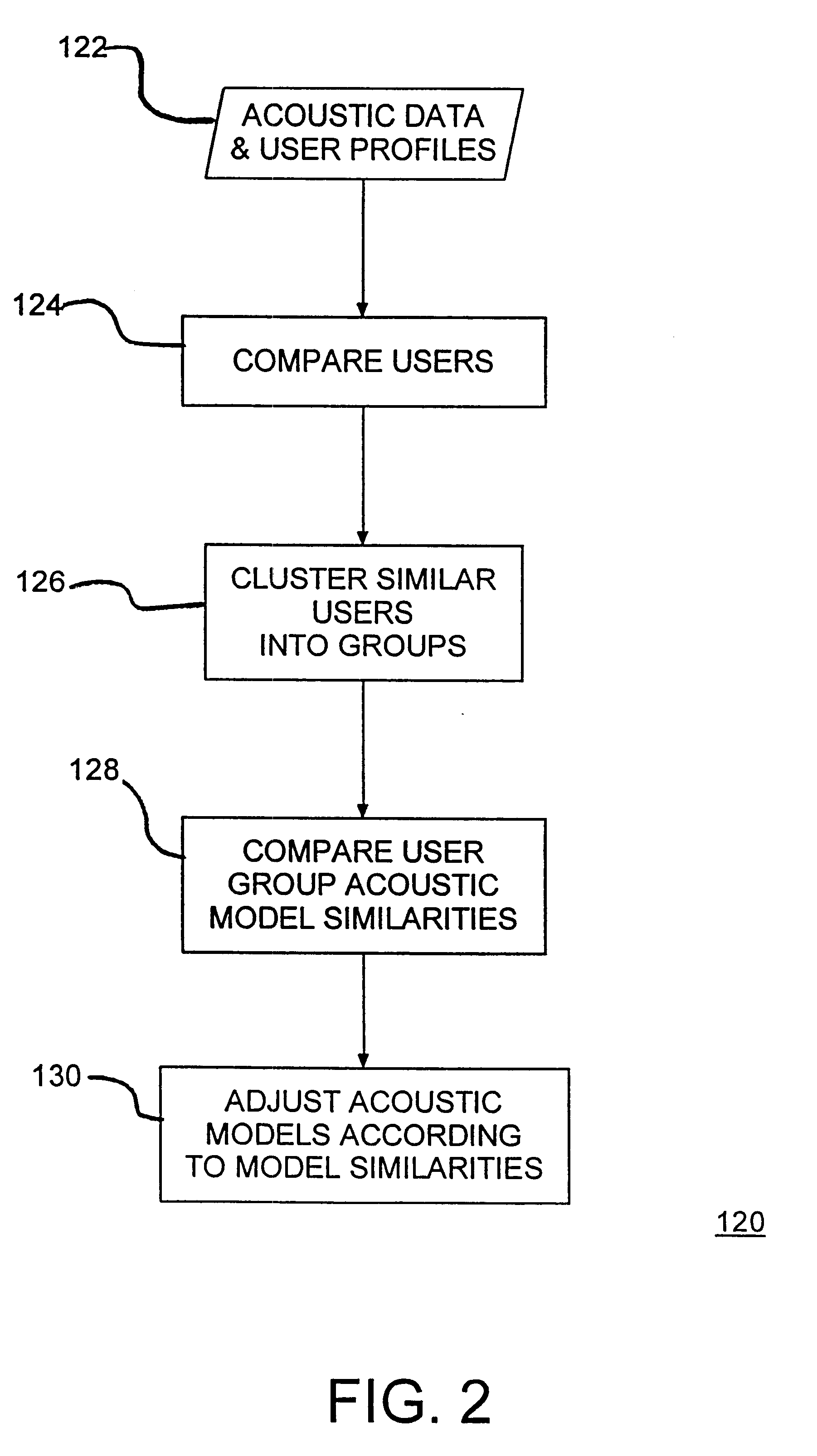
Speaker model adaptation via network of similar users
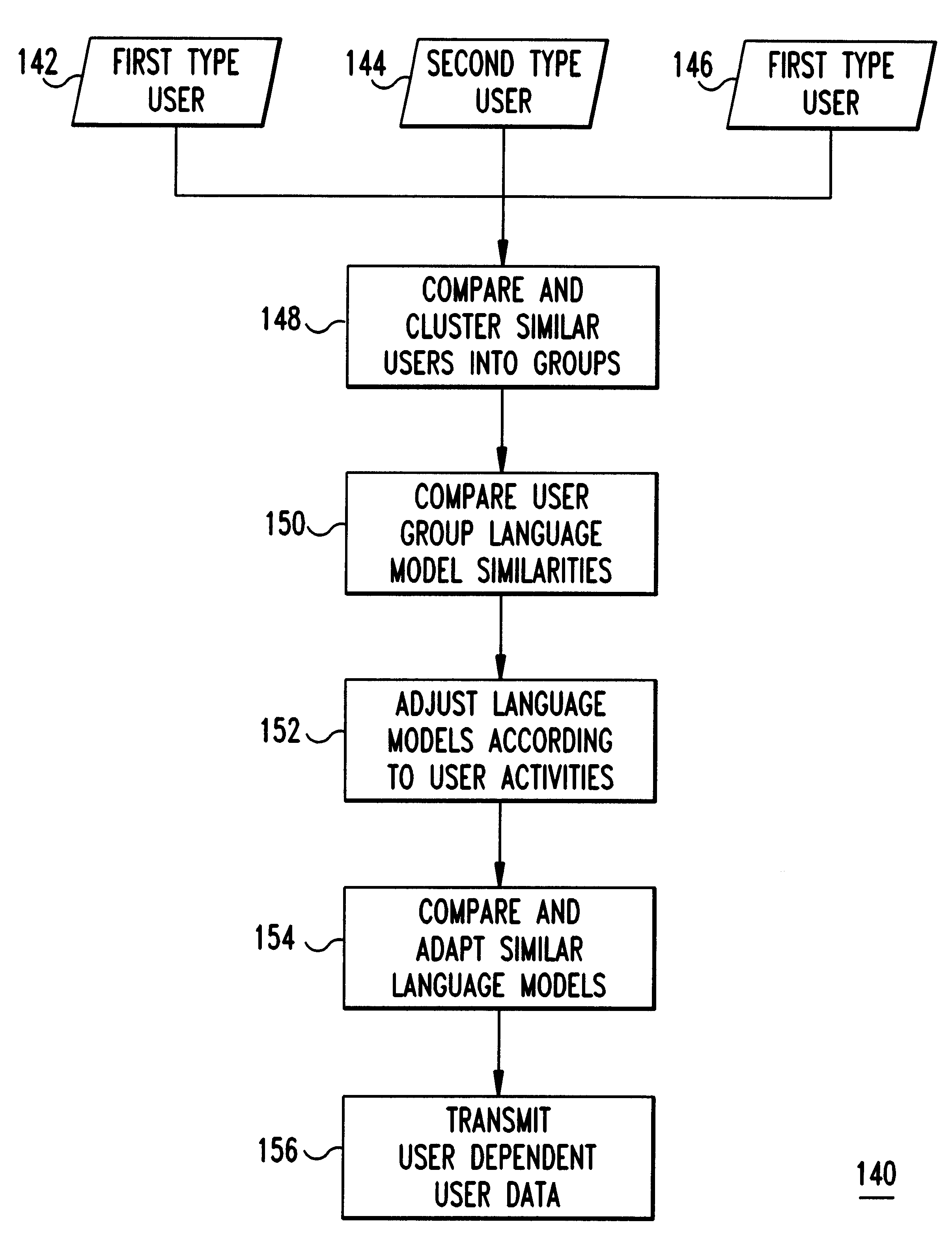
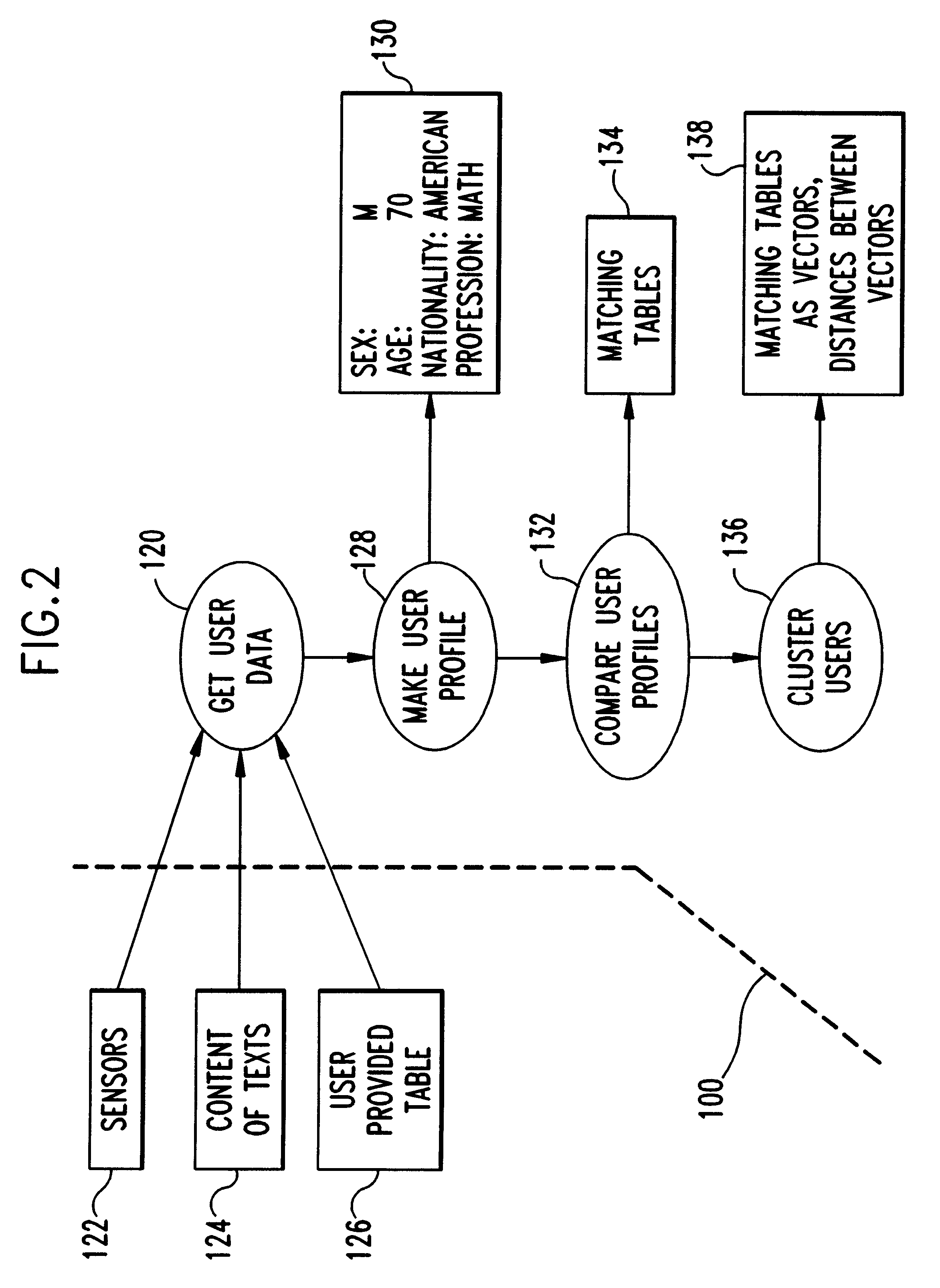
A speech recognition system, method and program product for recognizing speech input from computer users connected together over a network of computers. Speech recognition computer users on the network are clustered into classes of similar users according their similarities, including characteristics nationality, profession, sex, age, etc. Each computer in the speech recognition network includes at least one user based acoustic model trained for a particular user. The acoustic models include an acoustic model domain, with similar acoustic models being clustered according to an identified domain. User characteristics are collected from databases over the network and from users using the speech recognition system and then, distributed over the network during or after user activities. Existing acoustic models are modified in response to user production activities. As recognition progresses, similar language models among similar users are identified on the network. Update information, including information about user activities and user acoustic model data, is transmitted over the network and identified similar language models are updated. Acoustic models improve for users that are connected over the network as similar users use their respective speech recognition system.
Owner:NUANCE COMM INC
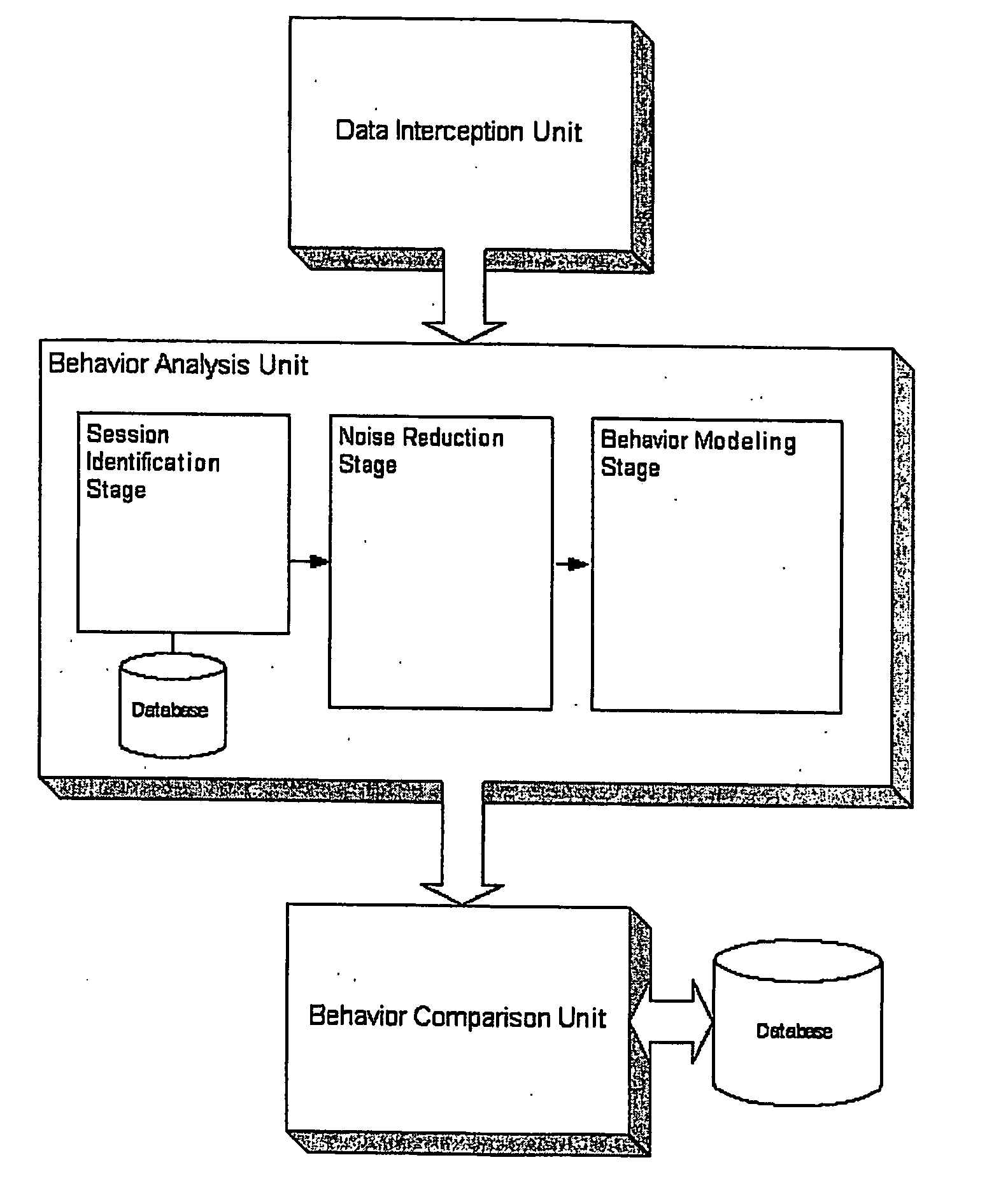
System and method for determining a computer user profile from a motion-based input device
ActiveUS20060224898A1Reduce noiseDigital data authenticationSecret communicationComputer usersBiometrics
The present invention provides a system and methods for computer user profiling based on behavioral biometrics. The approach consists of establishing distinctive profiles for computer users based on how they use a motion-based input device such as, but not limited to, a mouse and / or a keyboard. The profiles computed in the present invention are more accurate than those obtained through the traditional statistical profiling techniques, since they are based on distinctive biological characteristics of users.
Owner:PLURILOCK SECURITY SOLUTIONS INC
Systems and methods for producing, managing, delivering, retrieving, and/or tracking permission based communications
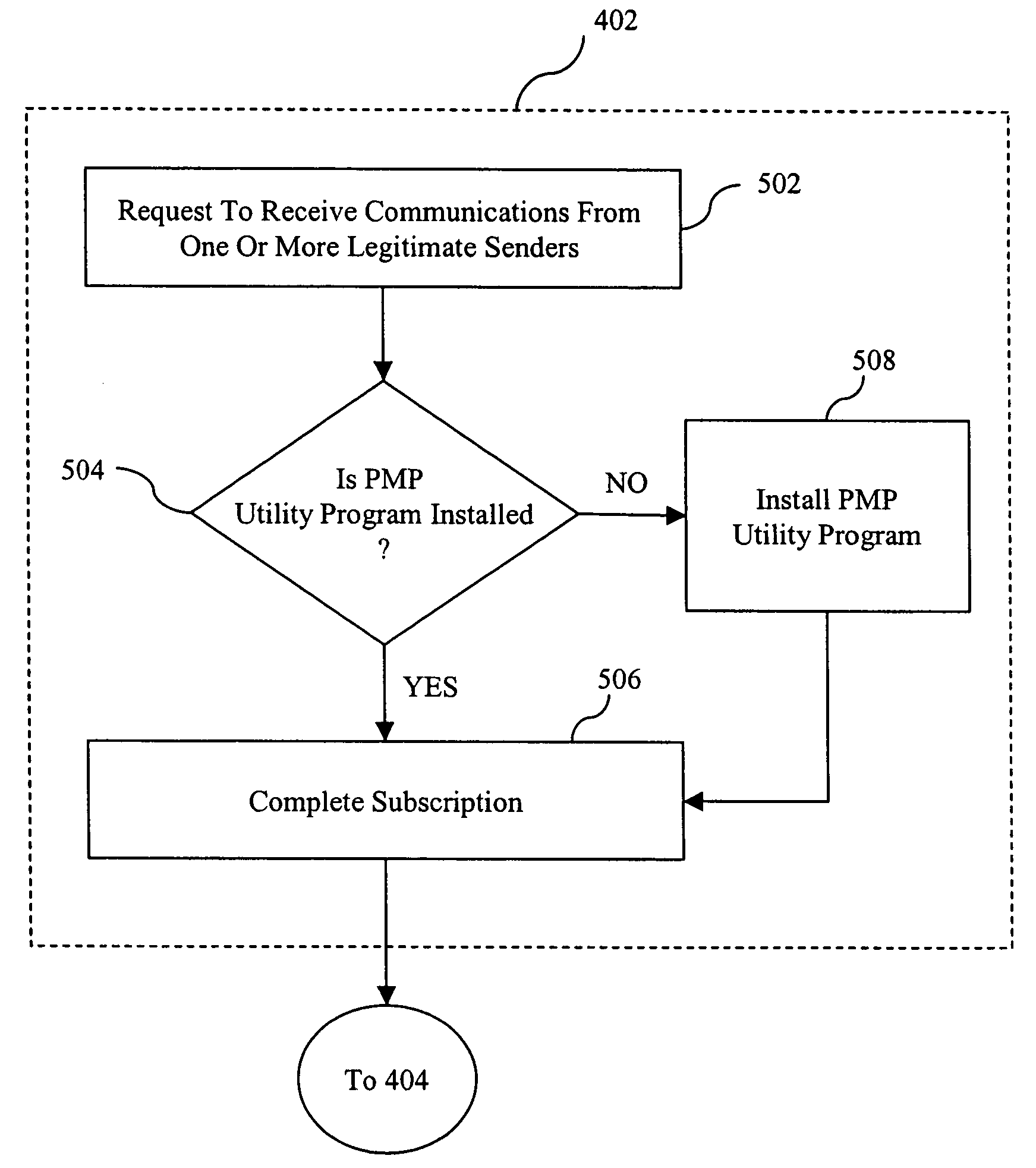
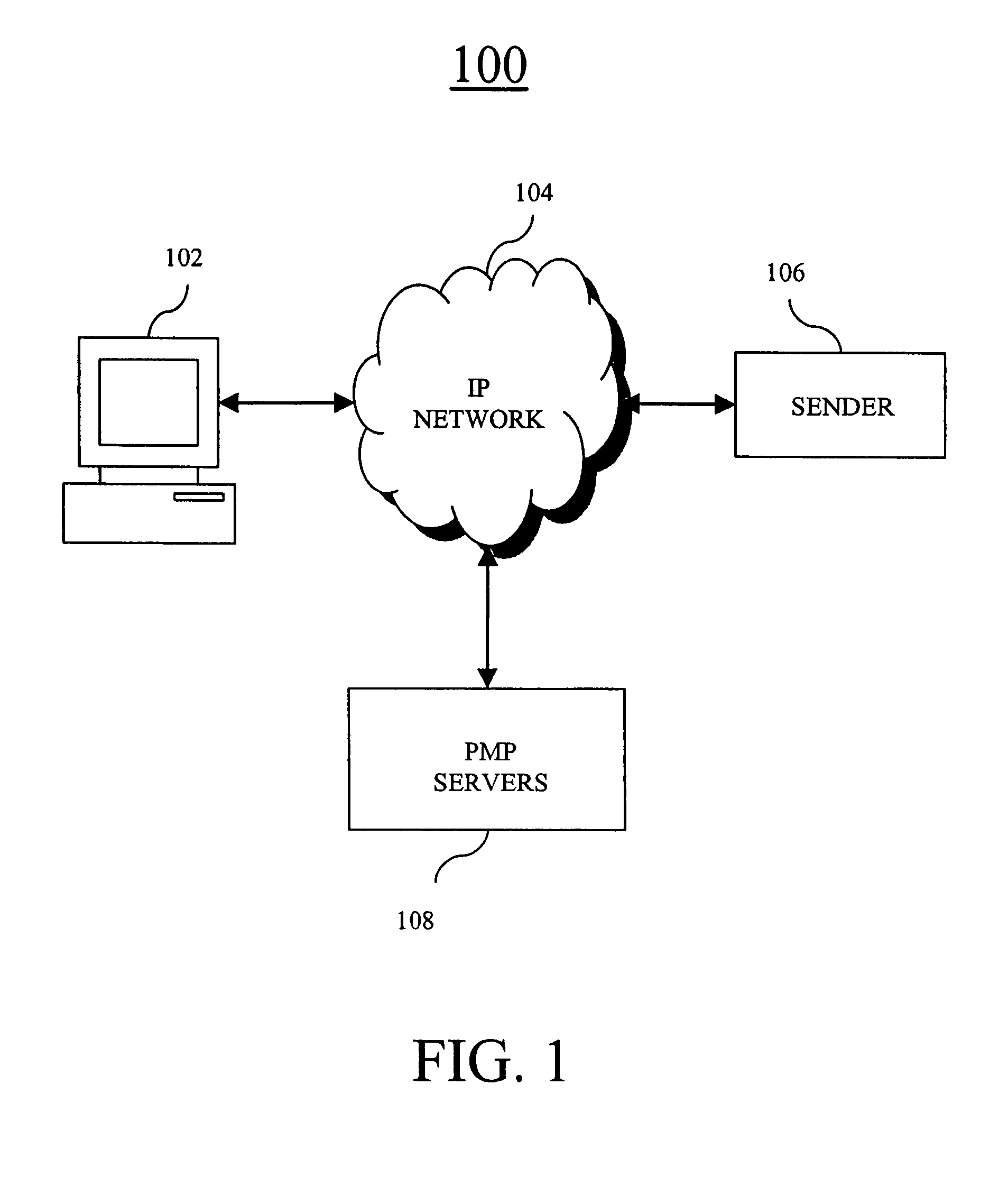
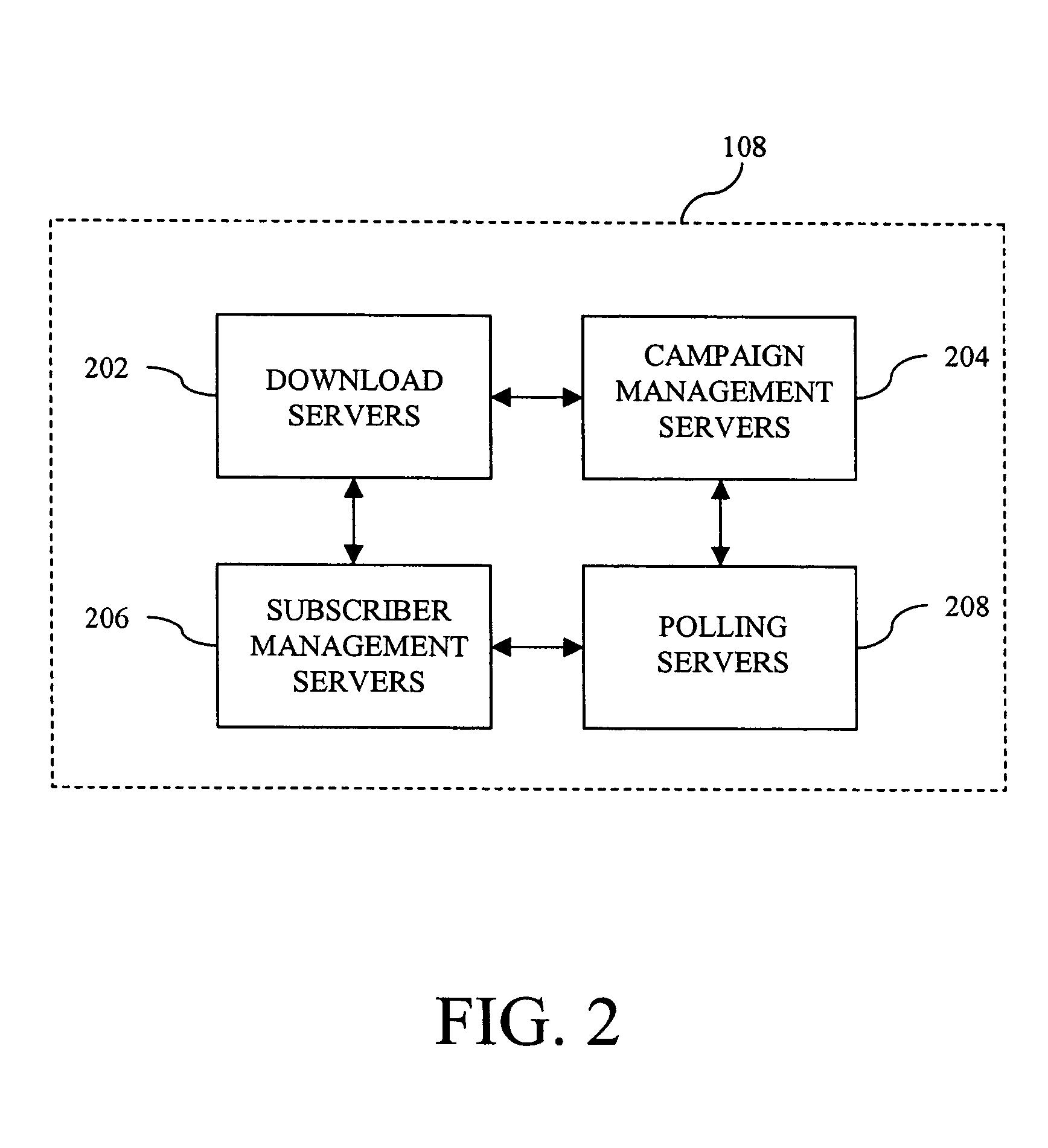
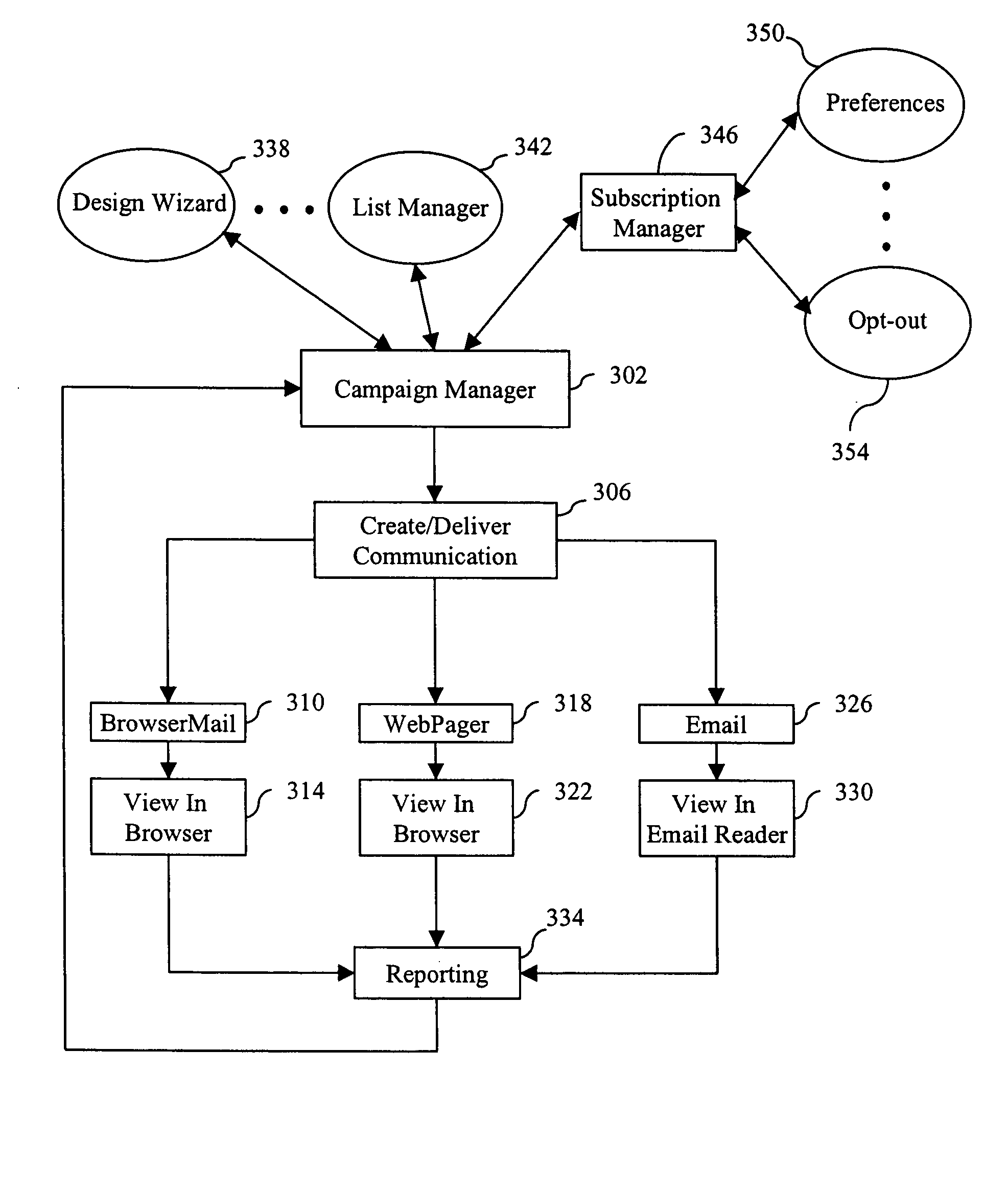
ActiveUS7640322B2Easy to processReporting is web-centricMultiple digital computer combinationsData switching networksComputer usersWeb browser
New and improved methods and systems are provided for producing, managing, delivering, retrieving, and / or tracking permission communications that alleviate several of the existing problems commonly associated with existing permission communications. According to the invention, computer users can request to receive direct communications from one or more senders. When a new communication is detected, an alert is provided to the recipients, who can use the alert to view the communication in their Web browser. Similar alerts may also be provided to one or more recipients when particular Web pages are updated. Various alternative embodiments are also disclosed.
Owner:TRUEFIRE LLC
Systems and methods for producing, managing, delivering, retrieving, and/or tracking permission based communications
ActiveUS20050228899A1Avoid inbox clutterAvoid blockageMultiple digital computer combinationsData switching networksComputer usersWeb browser
New and improved methods and systems are provided for producing, managing, delivering, retrieving, and / or tracking permission communications that alleviate several of the existing problems commonly associated with existing permission communications. According to the invention, computer users can request to receive direct communications from one or more senders. When a new communication is detected, an alert is provided to the recipients, who can use the alert to view the communication in their Web browser. Similar alerts may also be provided to one or more recipients when particular Web pages are updated. Various alternative embodiments are also disclosed.
Owner:TRUEFIRE LLC
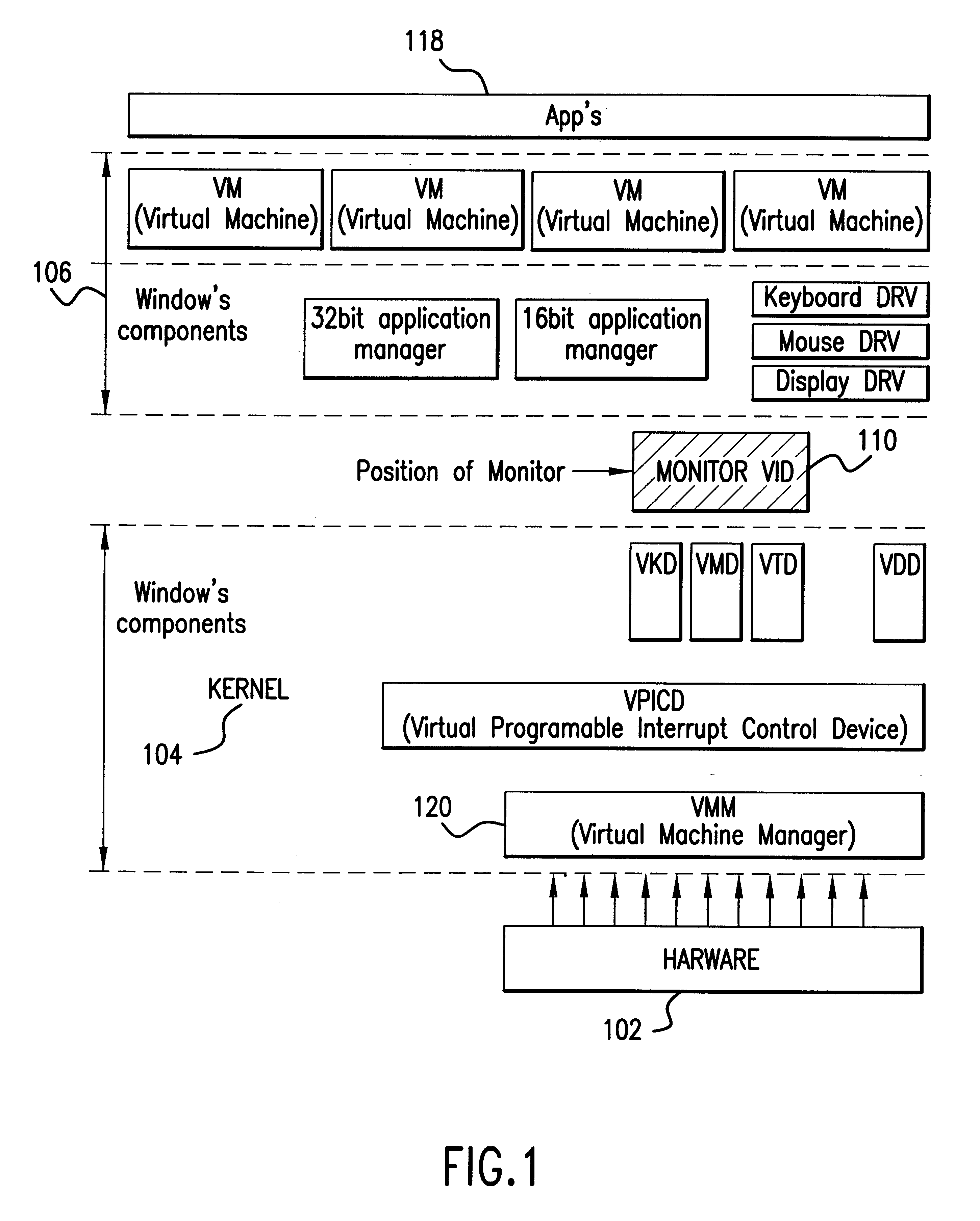
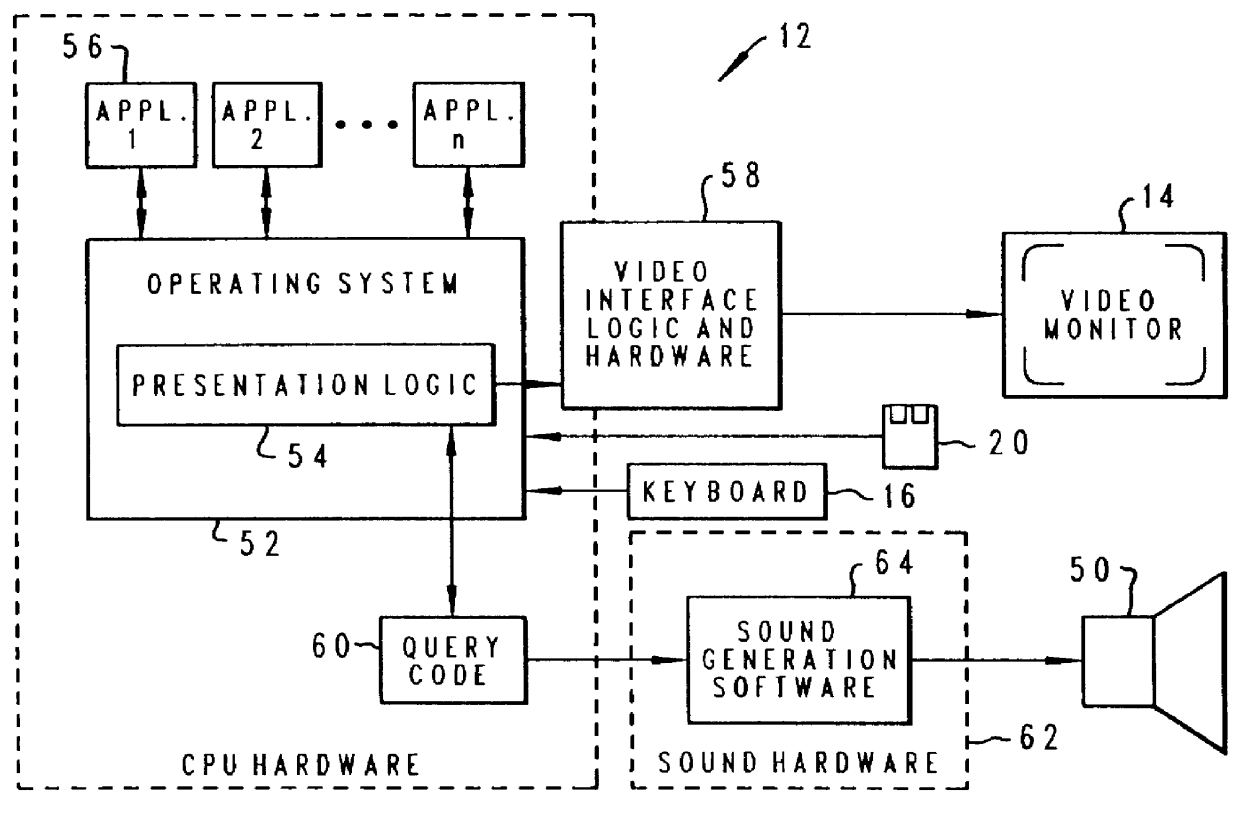
Method and apparatus for presenting two and three-dimensional computer applications within a 3D meta-visualization
InactiveUS6597358B2Cathode-ray tube indicatorsInput/output processes for data processingGraphicsData set
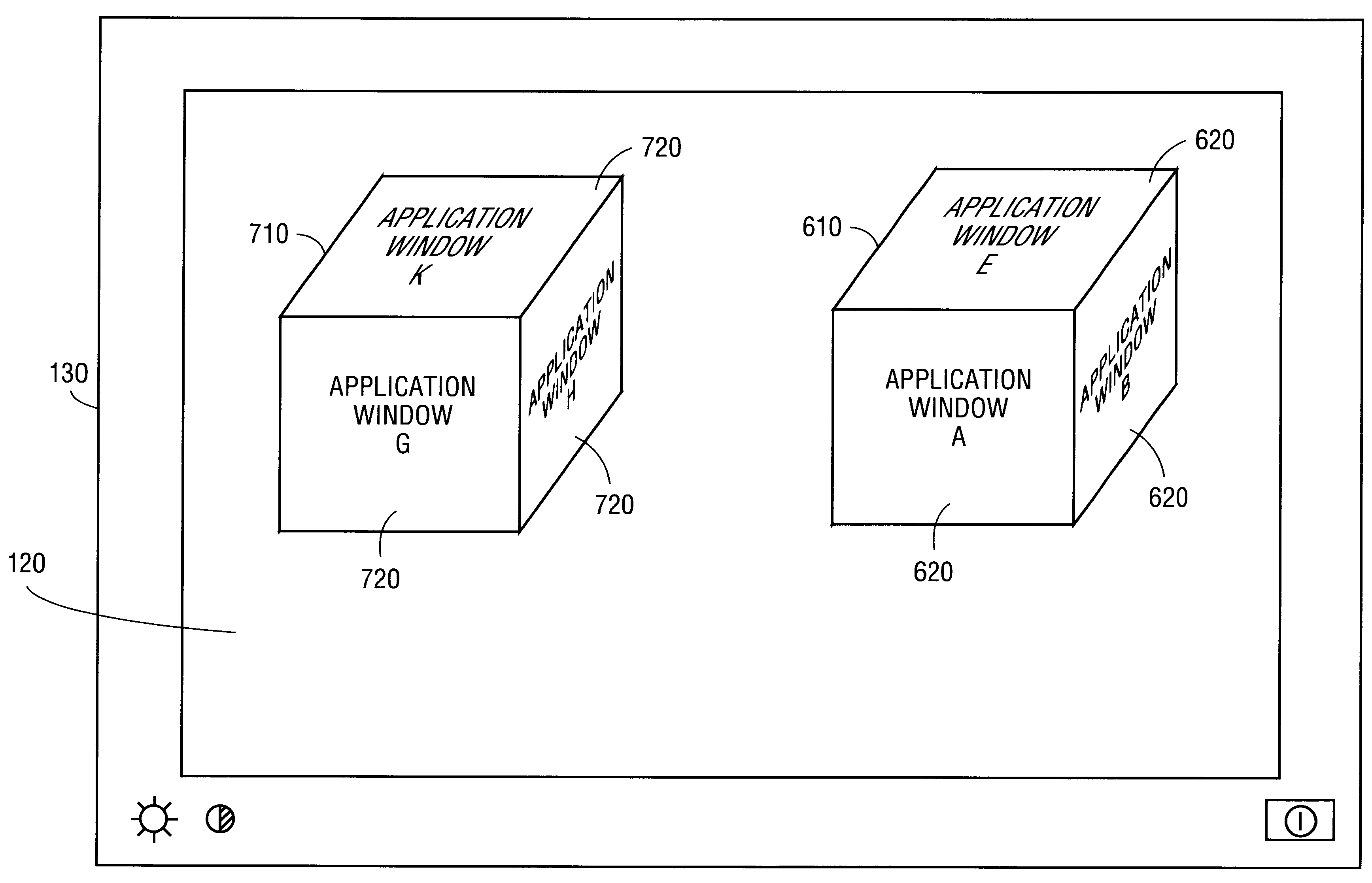
A method and apparatus for organizing two and / or three-dimensional computer applications on a display in a three-dimensional viewing perspective. A two-dimensional bitmap is created for each respective computer application and applied to a three-dimensional geometry (i.e., primitive). In one embodiment, the three-dimensional geometry is a cube and each respective computer application is mapped onto a respective surface of the cube. The computer user has the ability to manipulate the orientation of the cube, via a computer mouse, for example, to view the different surfaces, and, thus, different computer applications mapped thereon. The user is further given the capability to manipulate or interact with each computer application on each respective surface of the cube. In another embodiment, two or more cubes could be employed for displaying the various computer applications running on the computer's processor. The user could also allocate a particular group or category of applications to each respective cube to accomplish different tasks.
Owner:INTEL CORP
Computer user interfaces that are generated as needed
InactiveUS7039875B2Maximal functionalitySpecific program execution arrangementsInput/output processes for data processingGraphicsComputer users
A computer user interface generation system and method is disclosed, wherein computer user interfaces can be generated dynamically during activation of the computer application for which the generated user interface provides user access to the functional features of the application. The generated user interface may be a graphical user interface (GUI) that uses instances of various user interaction techniques. A user interface specification is provided in a configuration database for generating the user interface, and by changing the user interface specification in the configuration database, the user interface for the computer application can be changed during activation of the application.
Owner:ALCATEL-LUCENT USA INC
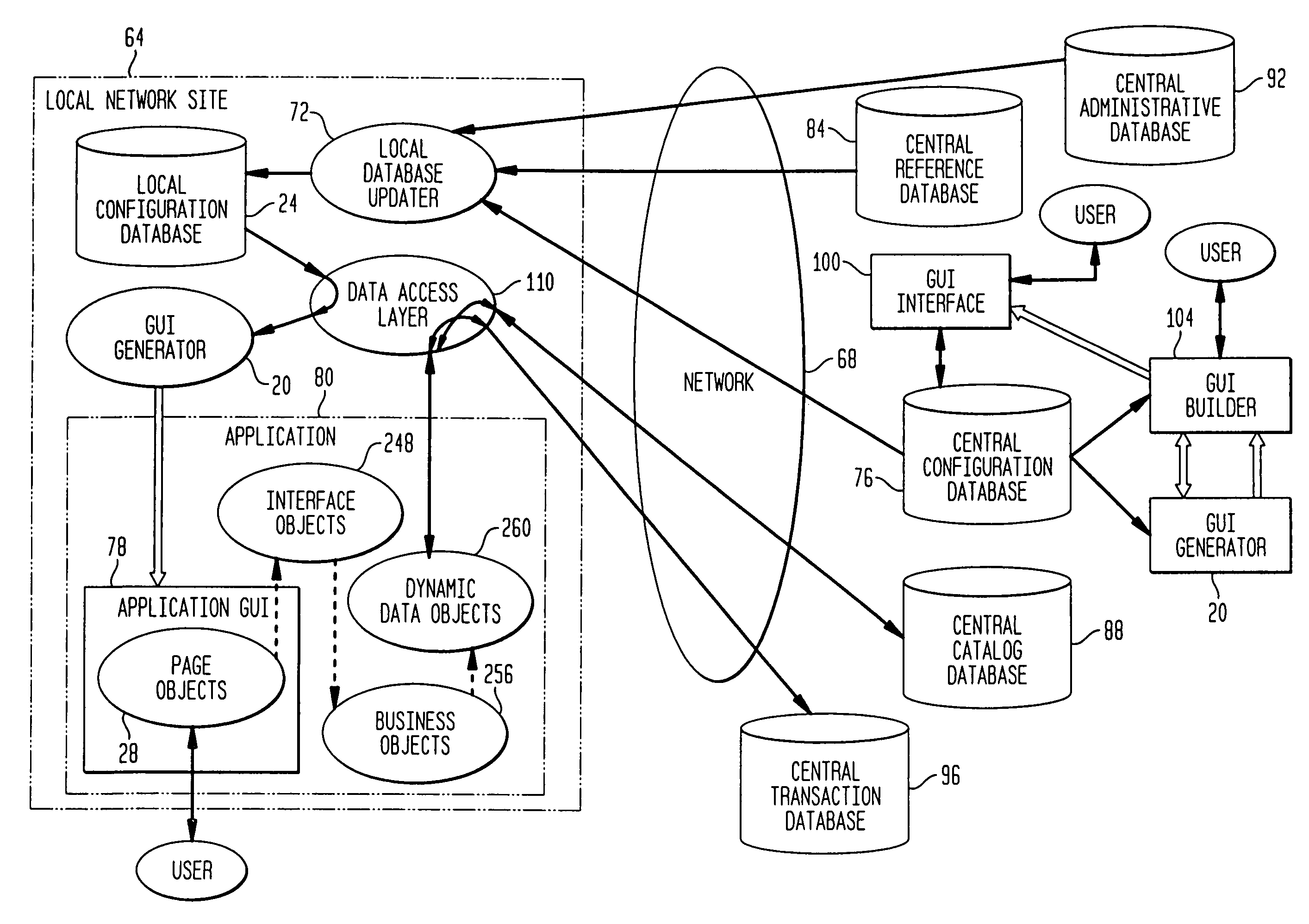
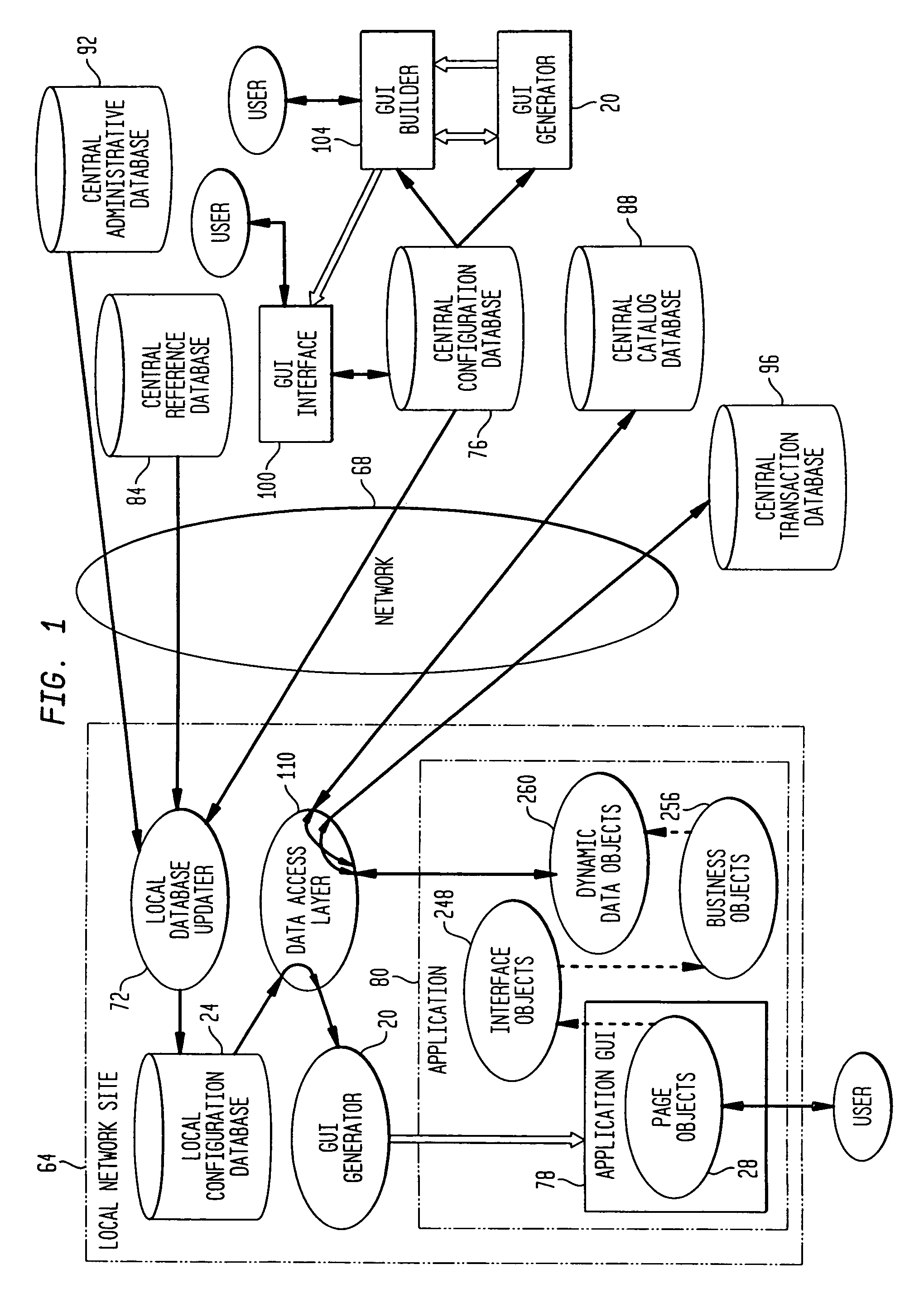
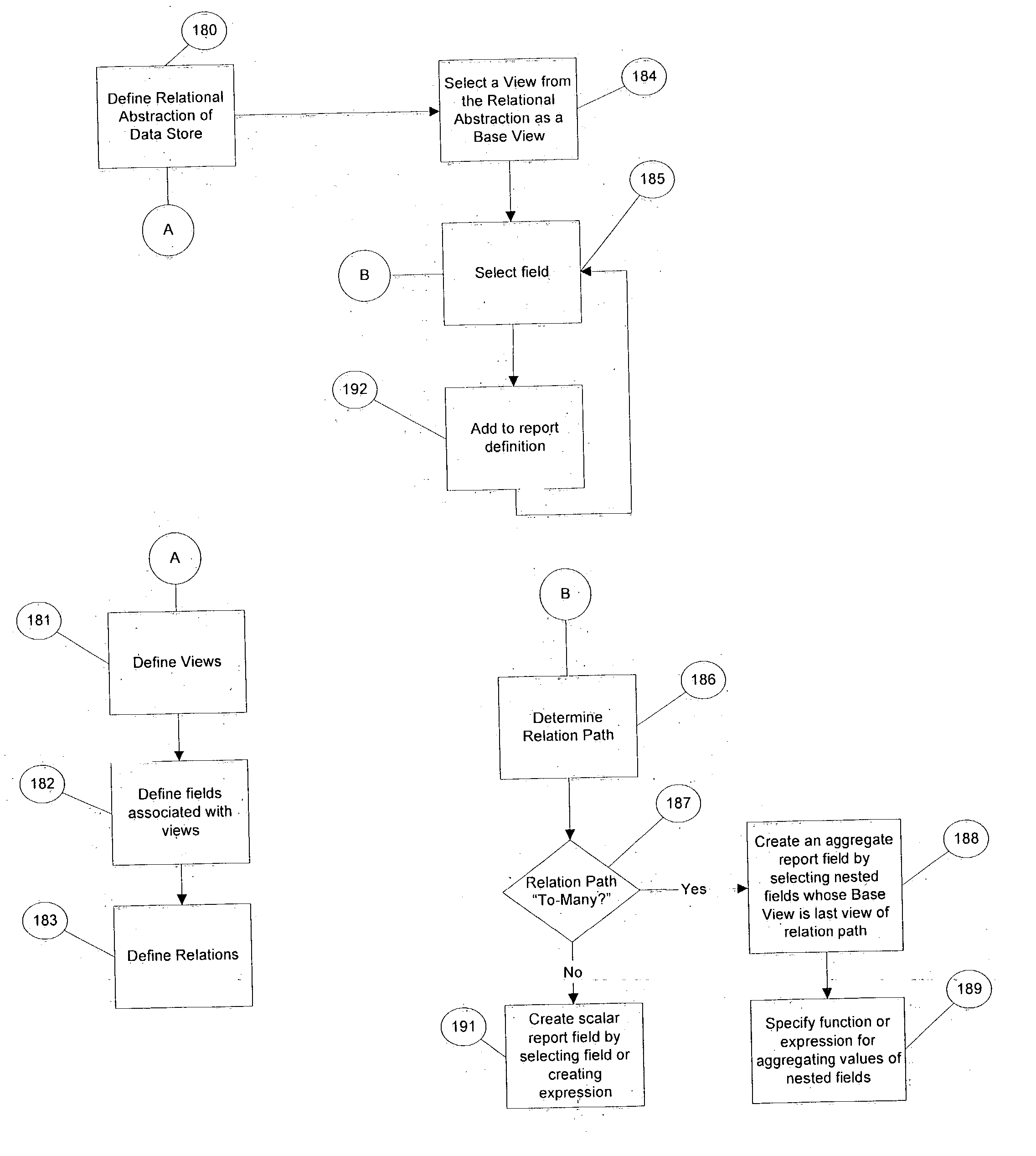
Method and system for building a report for execution against a data store
ActiveUS20050039033A1Minimizes learning curveQuickly and easily understandDigital data processing detailsUnauthorized memory use protectionComputer usersData access
A data query and reporting method and system are provided. The method and system allow non-technical computer users to build and execute complex database queries. The method and system accommodate the need for a simple, easy-to-understand interactive and iterative means for generating and validating database queries. The method and system reduce the complexity and costs associated with retrieving useful information for organizations of all sizes, especially smaller businesses. The method and system support a robust security model, enabling organizations to protect sensitive data while providing broad data access.
Owner:MICROSOFT TECH LICENSING LLC
Automatic, personalized online information and product services
InactiveUS20060136589A1Digital data information retrievalDigital computer detailsLearning machineComputer users
Owner:PERSONALIZED USER MODEL PUM
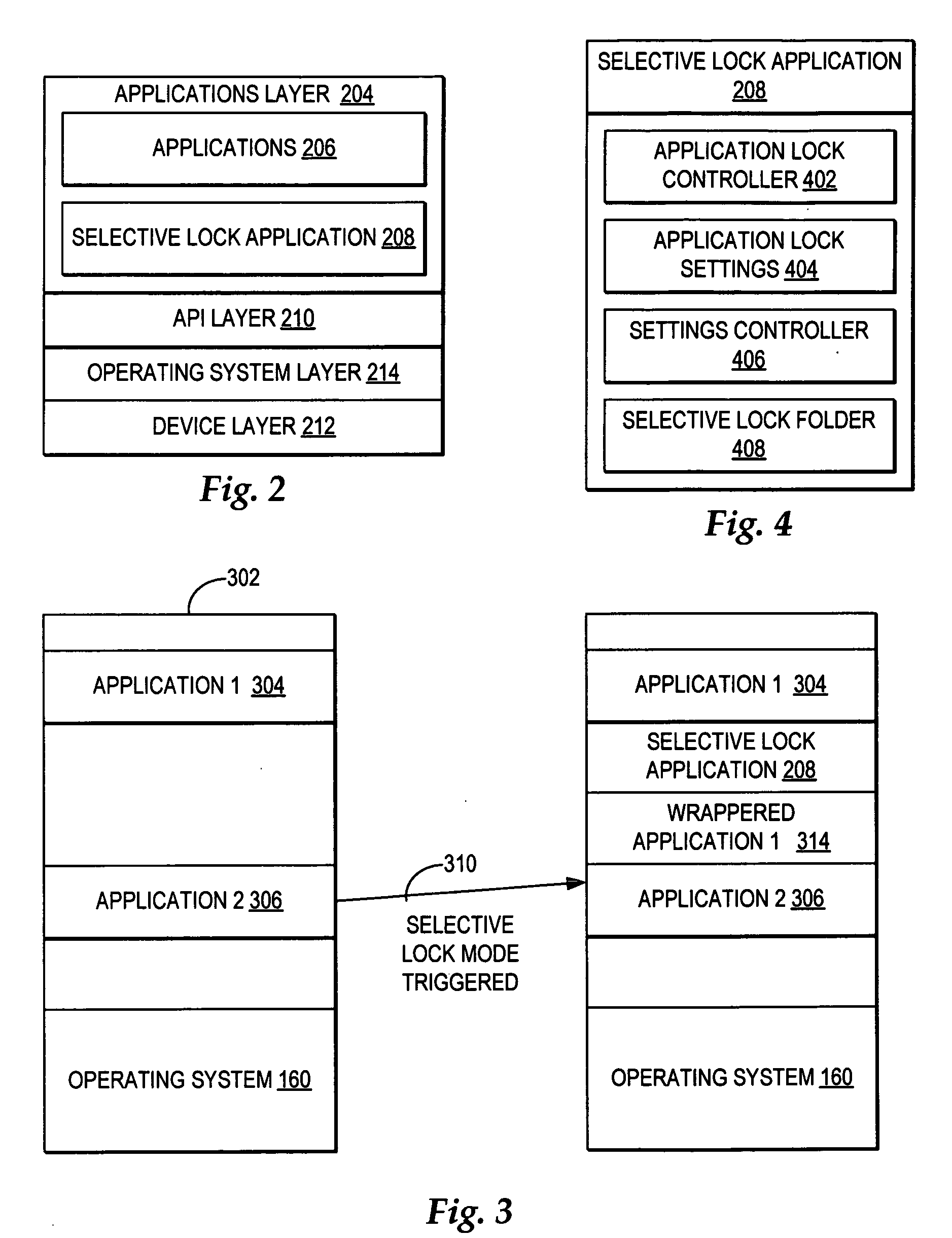
Allowing any computer users access to use only a selection of the available applications
InactiveUS20070016958A1Reduce usageDigital data processing detailsUser identity/authority verificationComputer usersUser input
A computer system operates in normal mode where all applications and files are accessible to an authorized user, where an authorized user enters a required log in to access all applications. When a trigger to change the control access from normal mode to selective lock mode is detected, access to the applications and files is blocked and the content within the user interface is cleared to initiate the selective lock mode. Next, content is added to the user interface including a folder with only a selection of the applications each accessible through a separate selectable link, where the selectable links are designated in the particular folder by an authorized user during normal mode. During selective lock mode, any user may only select to open one of the selection of applications by selecting a displayed selectable link for the application. Responsive to a selection of a selectable link, a wrapper function is called that opens the application, wherein any user is enabled to fully access only the wrappered application and the wrapper blocks access to the remainder of the computer system, such that during selective lock mode any user is presented with access, without first logging in, to a fully functioning version of each of the selection of applications designated by the authorized user in the particular folder.
Owner:IBM CORP
Method and system in a graphical user interface for facilitating cursor object movement for physically challenged computer users
InactiveUS6031531ASimple interfaceEfficient use ofCathode-ray tube indicatorsInput/output processes for data processingGraphicsComputer users
A method and system for assisting physically challenged users in positioning cursor objects at desired icons displayed within a graphic interface of a computer system. Icons are displayed within the graphic interface, such that an icon, when graphically selected by a user, facilitates a particular application function. Icon domains are established about each icon, wherein each icon domain is larger than the icon itself. The cursor object may thereafter be automatically positioned at the center of a particular icon, in response to moving the cursor object into an icon domain associated with that particular icon, thereby assisting physically challenged users in efficiently positioning the cursor object at the icon in order to graphically select a particular function associated with the icon. According to this method and system, the icons are thereby graphically magnetized, such that a cursor object is immediately snapped toward a desired icon when entering a graphically magnetized domain surrounding the desired icon, eliminating the need for positioning the cursor object precisely on the icon or other graphical object to be selected.
Owner:IBM CORP
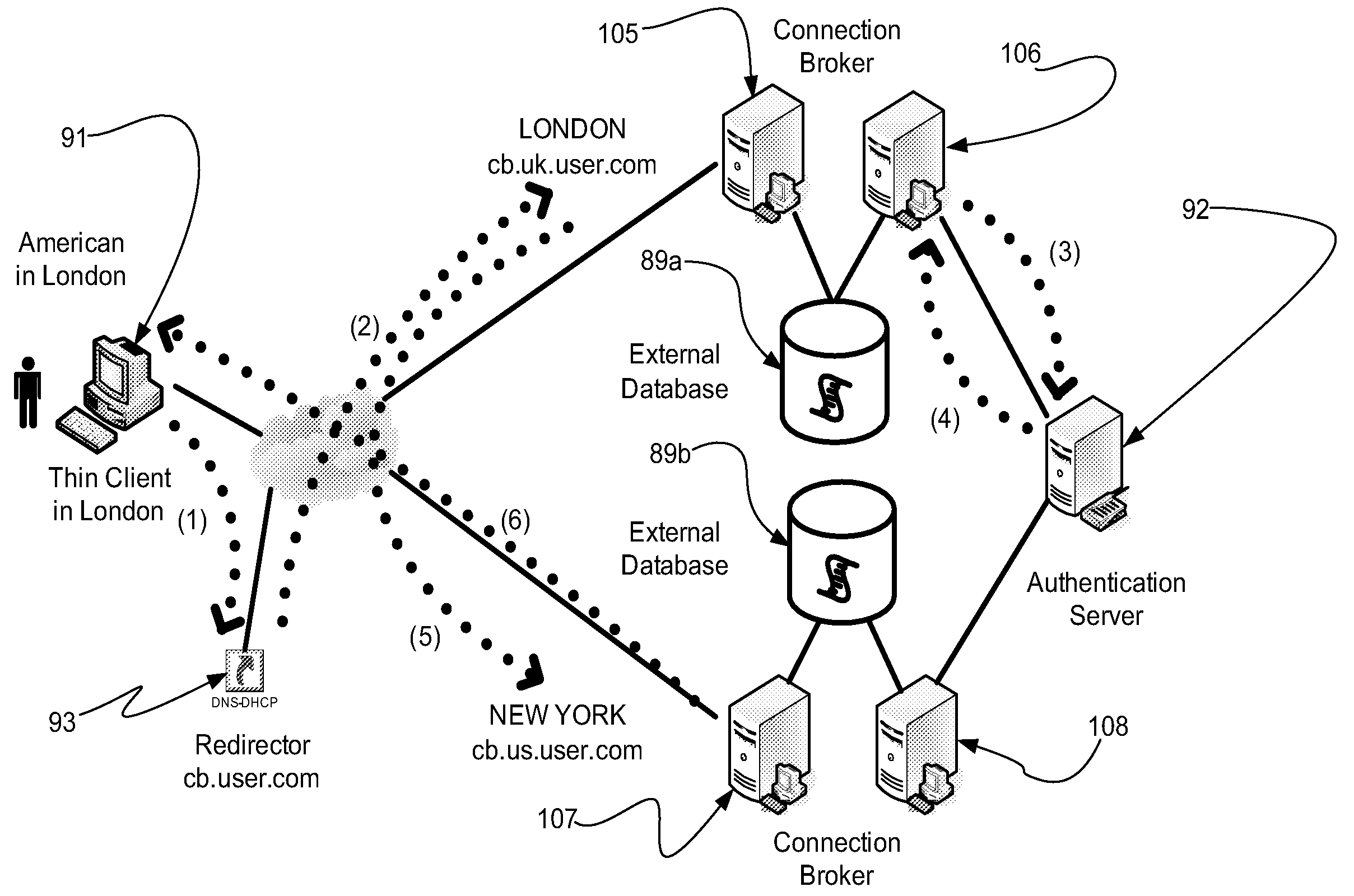
Management layer method and apparatus for dynamic assignment of users to computer resources
InactiveUS20080235361A1Increasing mobile contemporary workforceDigital computer detailsProgram controlComputer resourcesComputer users
A management layer method and apparatus for dynamically assigning computer users to remote computer resources according to predetermined rules and irrespective of remote viewer protocol utilized by the user. The method and apparatus is capable of managing hundreds of thousands of users across multiple physical sites and is operable with a wide variety of network, Internet, and application solutions. The method and apparatus is useful for an increasing mobile contemporary workforce in a world where the need for around the clock coverage coexists with the ever present possibility of catastrophic network failure.
Owner:LEOSTREAM
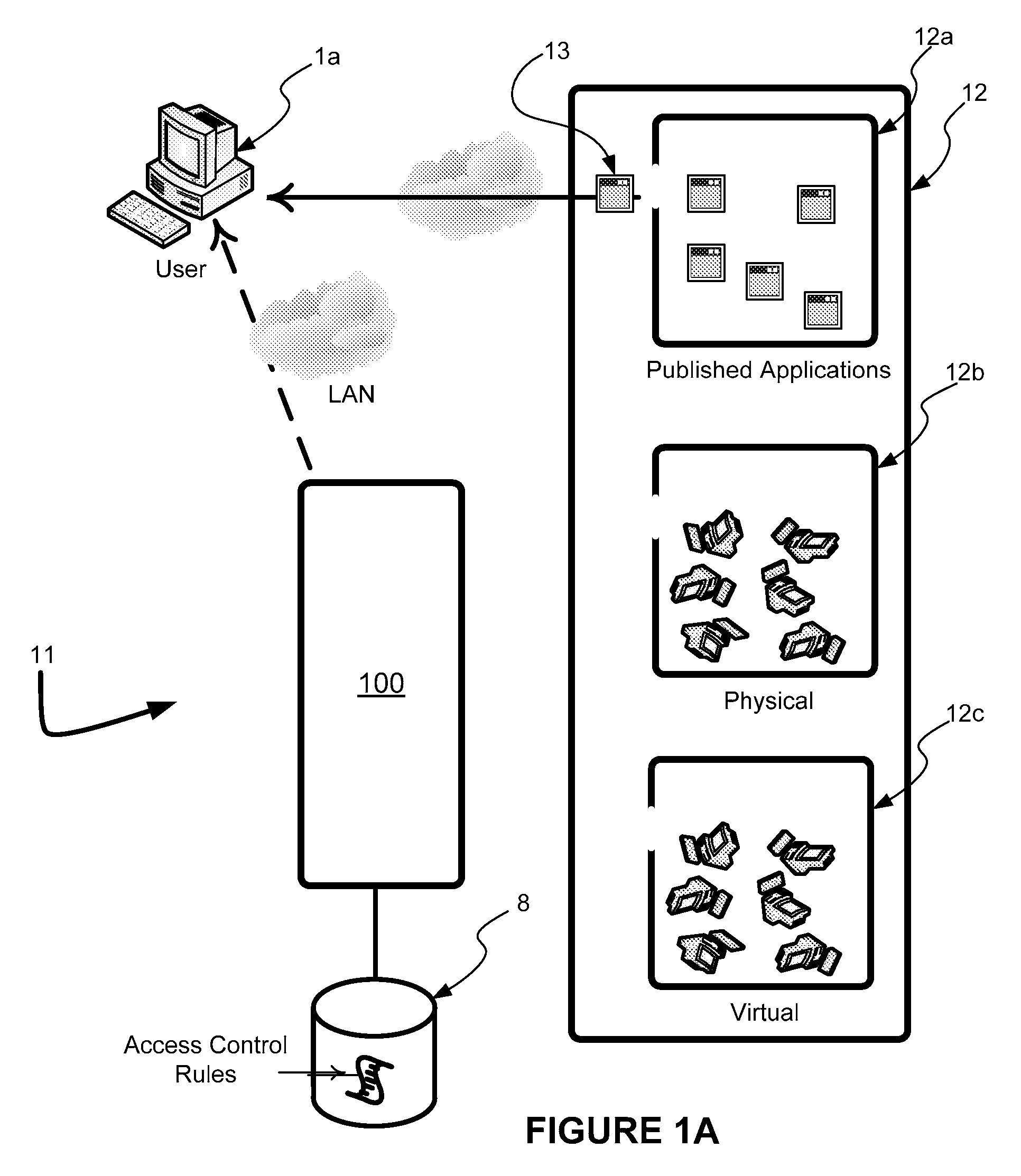
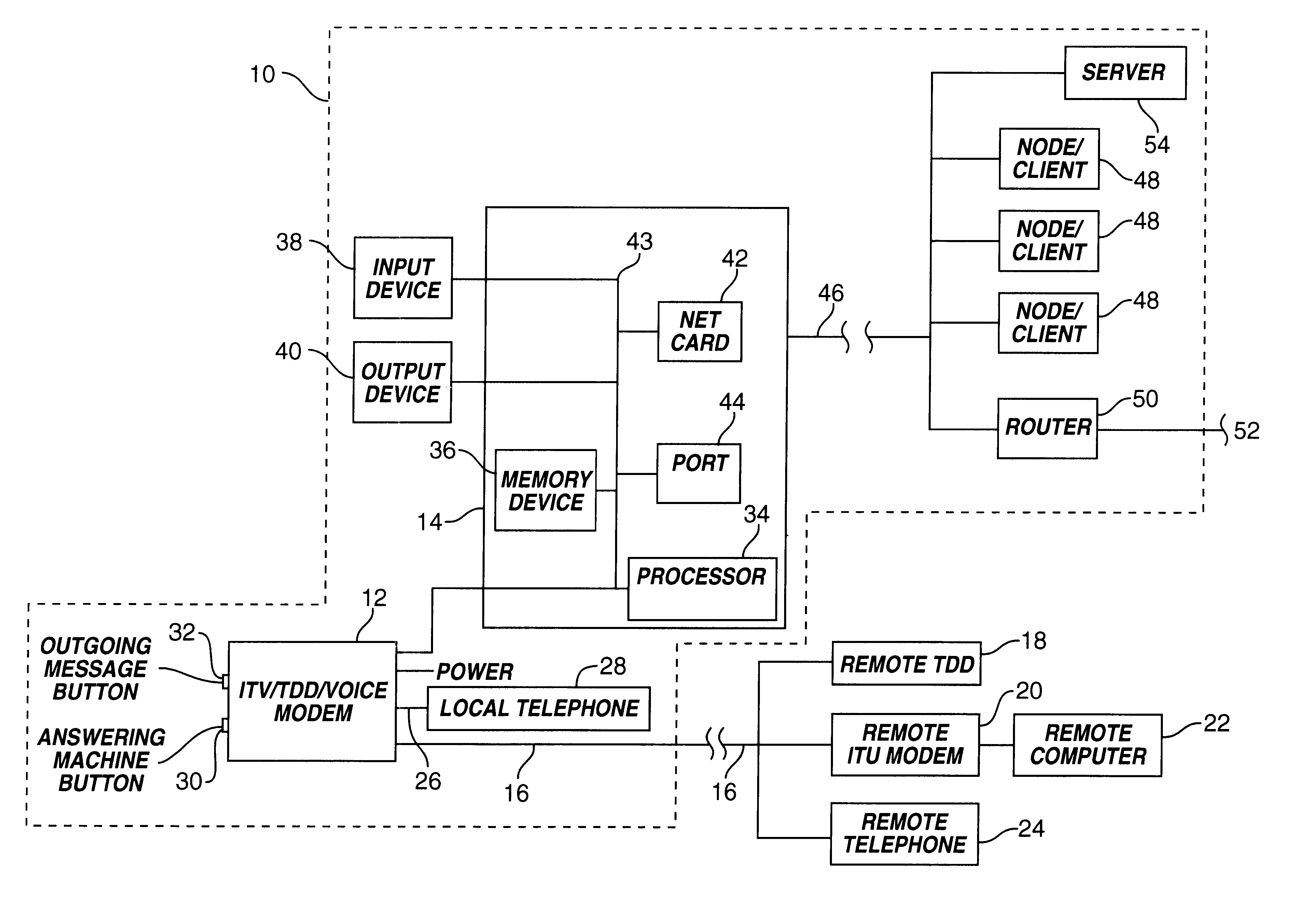
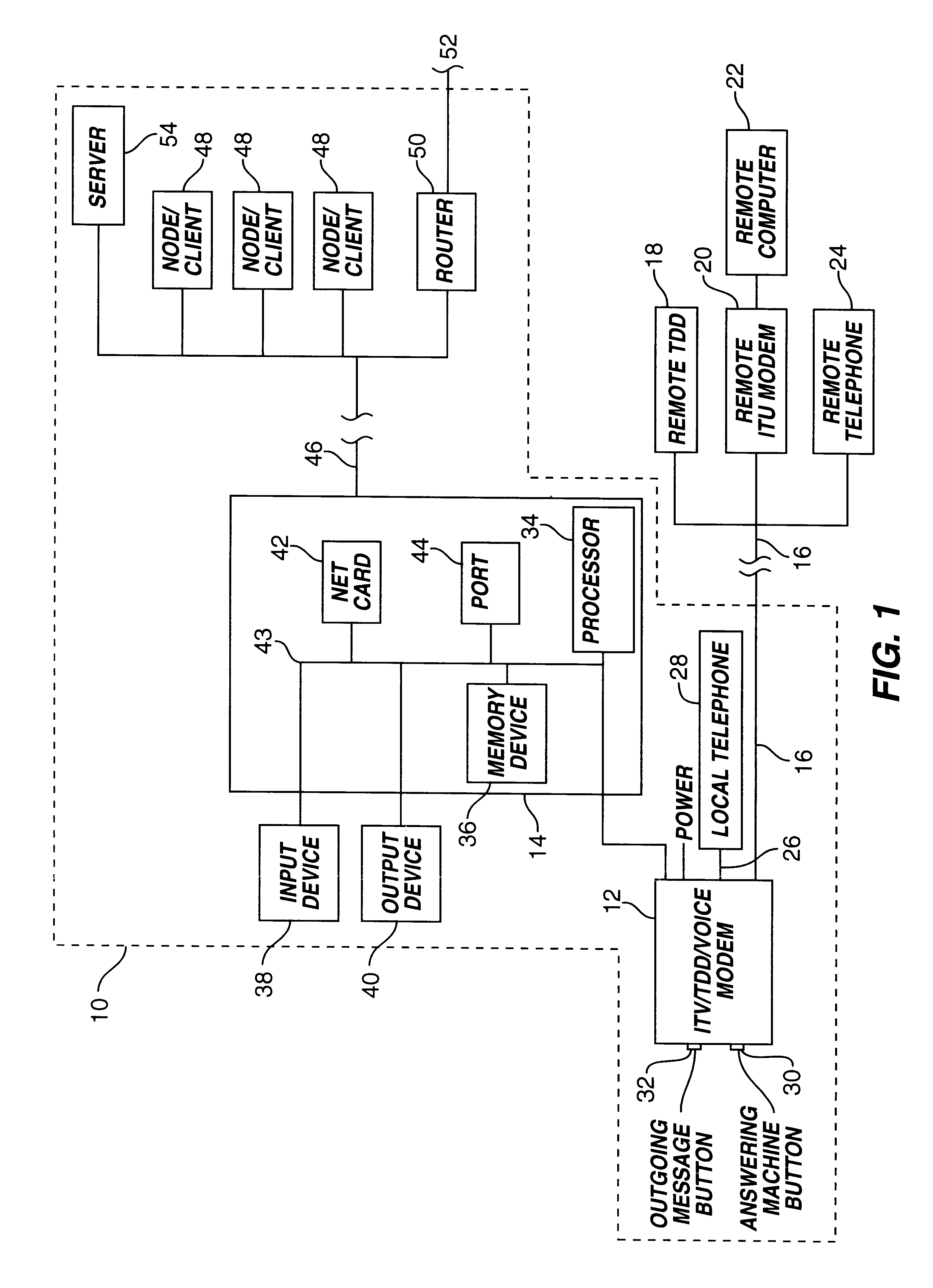
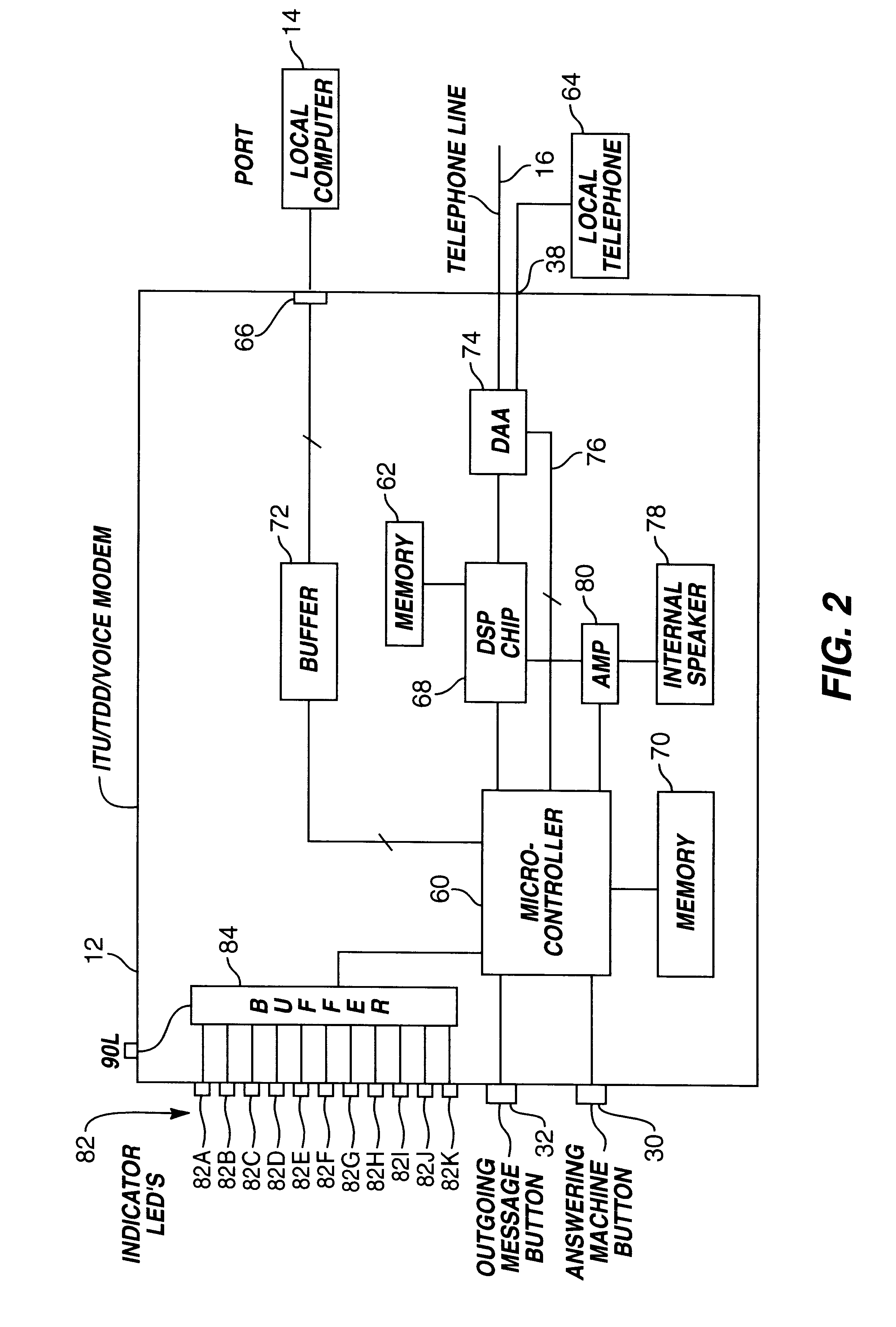
Network communication system
InactiveUS6181736B1Interconnection arrangementsSubstation equipmentCommunications systemComputer users
A network communications system containing one or more nodes includes an ITU / TDD / VOICE modem in electrical communication with a local computer. A remote device connecting to the ITU / TDD / VOICE modem is able to converse in real time using textual characters with the local computer user. Once connected to the ITU / TDD / VOICE modem, the remote device is recognized by the network as an additional node. If the remote device wishes to textually communicate with a node on the network, the local computer formats the data into a network compatible format for transmission to the node. The local computer transmits the data to the node while communication between the ITU / TDD / VOICE modem and the remote device is maintained. Once the remote device is connected to the network, the network may treat the remote device as an additional node. Thus, the remote device may be privileged to some or all of the network services. Furthermore, the remote device may be allowed to utilize a network modem for connection to a second remote device.
Owner:MCLAUGHLIN THOMAS J +1
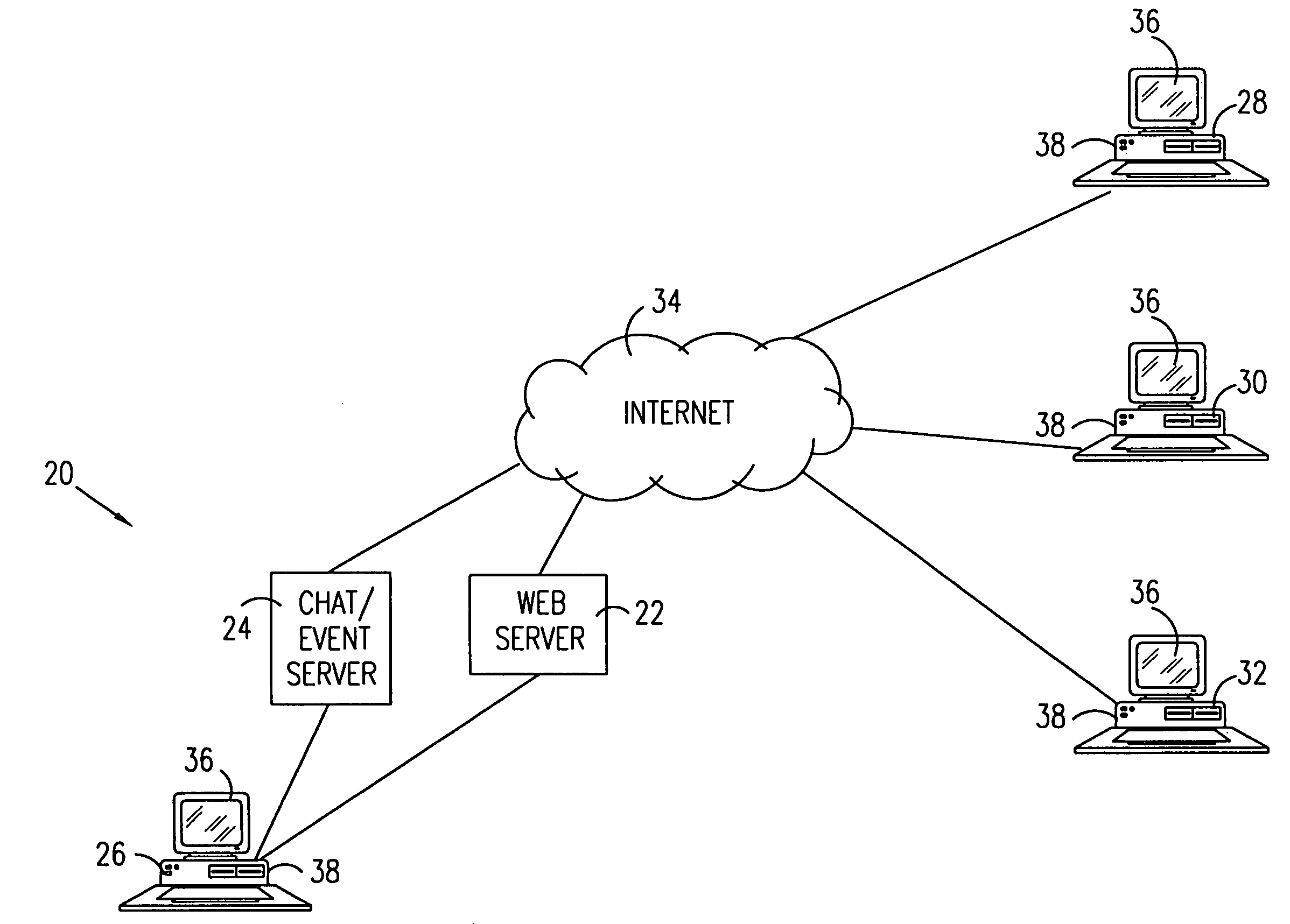
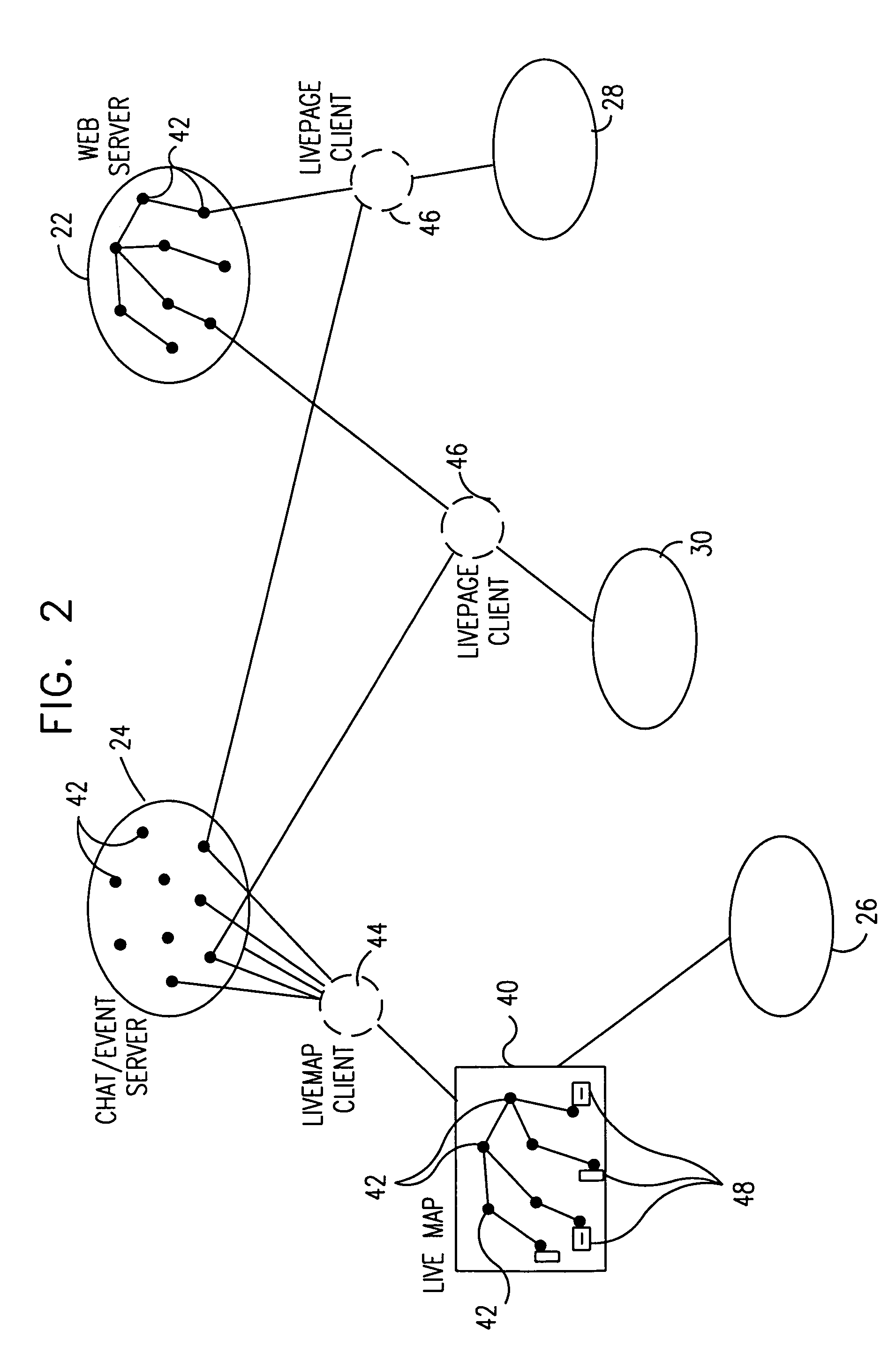
Real-time monitoring of web activities
InactiveUS7035926B1Increase awarenessEnhanced interactionMultiple digital computer combinationsWebsite content managementComputer usersWorld Wide Web
A method for monitoring activity on a computer network includes providing a map of a group of resources, which are accessible via the computer network, and tracking access of the resources in the group by computer users, so as to identify one or more of the users with respective resources that they are accessing. An identification of the one or more users and their respectively-accessed resources is registered with the map.
Owner:ADOBE SYST INC
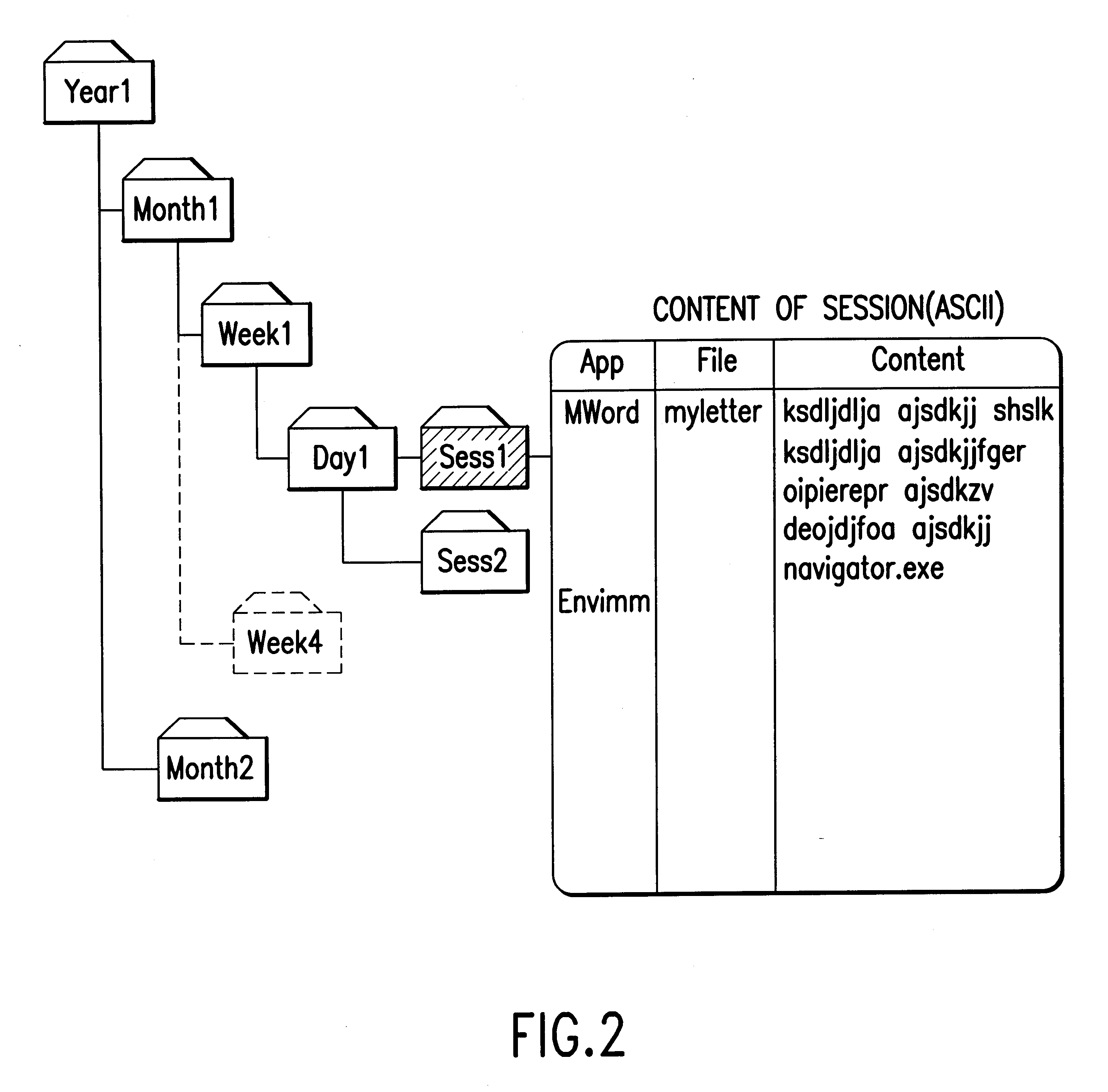
Methods, apparatus and data structures for providing a uniform representation of various types of information
InactiveUS20030014421A1Complete efficientlyDigital data information retrievalDigital data processing detailsTask analysisComputer users
Methods and apparatus for analyzing tasks performed by computer users by (i) gathering usage data, (ii) converting logged usage data into a uniform format, (iii) determining or defining task boundaries, and (iv) determining a task analysis model by "clustering" similar tasks together. The task analysis model may be used to (i) help users complete a task (such help, for example, may be in the form of a gratuitous help function), and / or (ii) to target marketing information to users based on user inputs and the task analysis model. The present invention also provides a uniform semantic network for representing different types of objects in a uniform way.
Owner:MICROSOFT TECH LICENSING LLC
Language model adaptation via network of similar users
A language recognition system, method and program product for recognizing language based input from computer users on a network of connected computers. Each computer includes at least one user based language model trained for a corresponding user for automatic speech recognition, handwriting recognition, machine translation, gesture recognition or other similar actions that require interpretation of user activities. Network computer users are clustered into classes of similar users according to user similarities such as, nationality, profession, sex, age, etc. User characteristics are collected by sensors and from databases and, then, distributed over the network during user activities. Language models with similarities among similar users on the network are identified. The language models include a language model domain, with similar language models being clustered according to their domains. Language models identified as similar are modified in response to user production activities. After modification of one language model, other identified similar language models are compared and adapted. Also, user data, including information about user activities and language model data, is transmitted over the network to other similar users. Language models are adapted only in response to similar user activities, when these activities are recorded and transmitted over the network. Language models are given a global context based on similar users that are connected together over the network.
Owner:NUANCE COMM INC
Systems and methods for providing and installing software
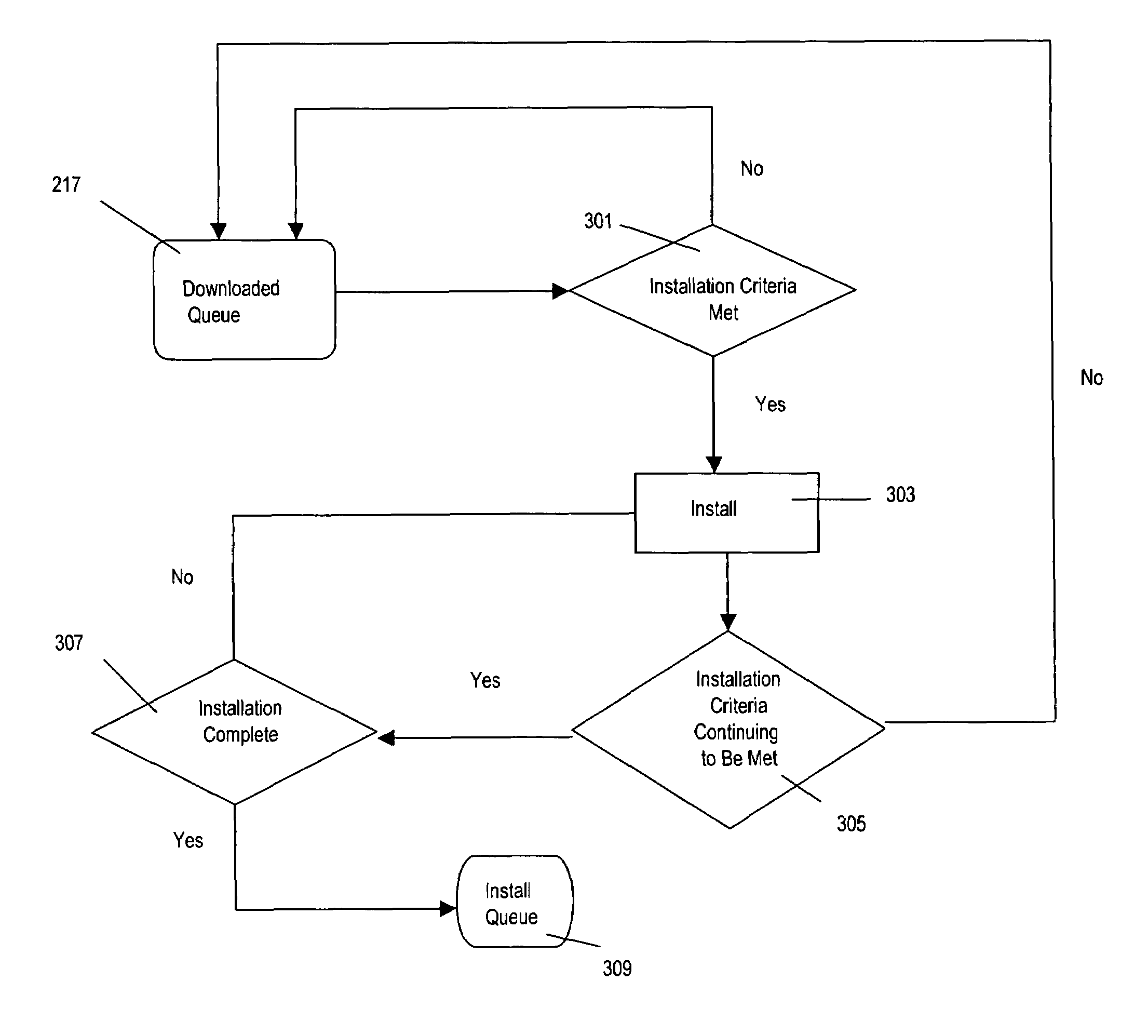
ActiveUS7707573B1Limited bandwidthSufficient processor shareDigital computer detailsProgram loading/initiatingComputer usersNetwork connection
The present invention comprises systems and methods, and computer readable media comprising the methods, for installing software components. A user's need for a software component may be determined prior to installation. The systems and methods of the present invention provide automation and flexibility to the installation process. In an embodiment, processor usage and network usage are monitored and software installation are initiated and / or continued during periods where processor and / or network usage are low. The installation process may be halted when the processor and / or network connection are called upon for other uses. Processor and / or network usage may also be throttled, for example limiting the bandwidth available for the installation to maintain sufficient processor share and / or bandwidth for other tasks. Adverse impact on a computer user is minimized.
Owner:GOOGLE LLC
Method and system for enabling blind or visually impaired computer users to graphically select displayed elements
InactiveUS6046722AInput/output for user-computer interactionCathode-ray tube indicatorsVisually impairedGraphics
The method and system of the present invention may be utilized to enable a blind or visually impaired computer user to graphically select a displayed graphic element within a computer system display. A unique identifiable audible signal is associated with each displayed graphic element. A movable cursor element or pointer is displayed within the computer system display and a composite audible signal is periodically generated in response to the position of the movable cursor element. The composite audible signal preferably includes elements of each identifiable audible signal associated with each displayed graphic element within a predetermined radius of the location of the movable cursor element. In one embodiment of the present invention, each displayed graphic element comprises multiple picture elements and the composite audible signal includes elements of each identifiable audible signal associated with each displayed graphic element having picture elements within a rotatable sector of a circle having its origin at the movable cursor element and a radius equal to the predetermined radius.
Owner:IBM CORP
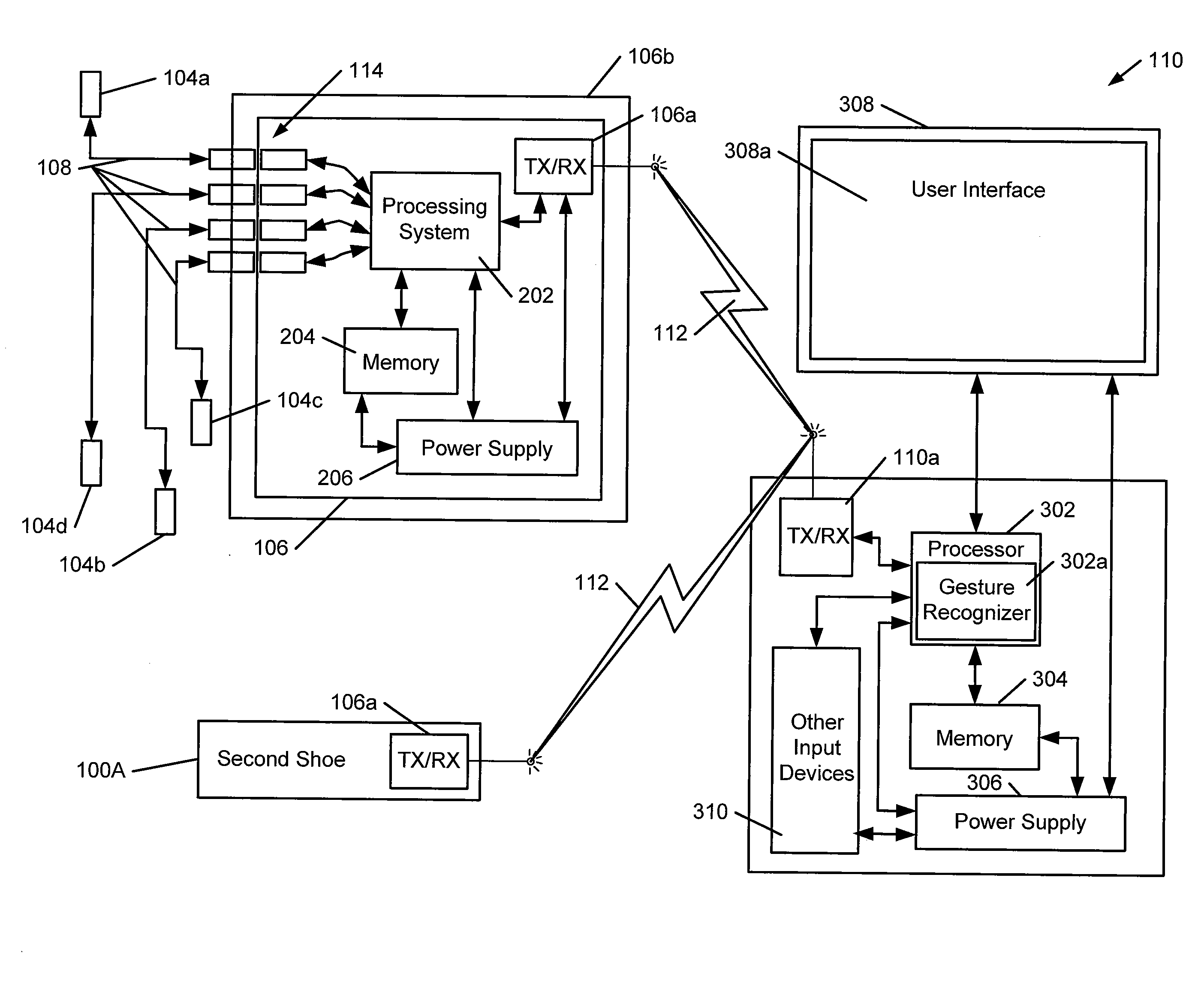
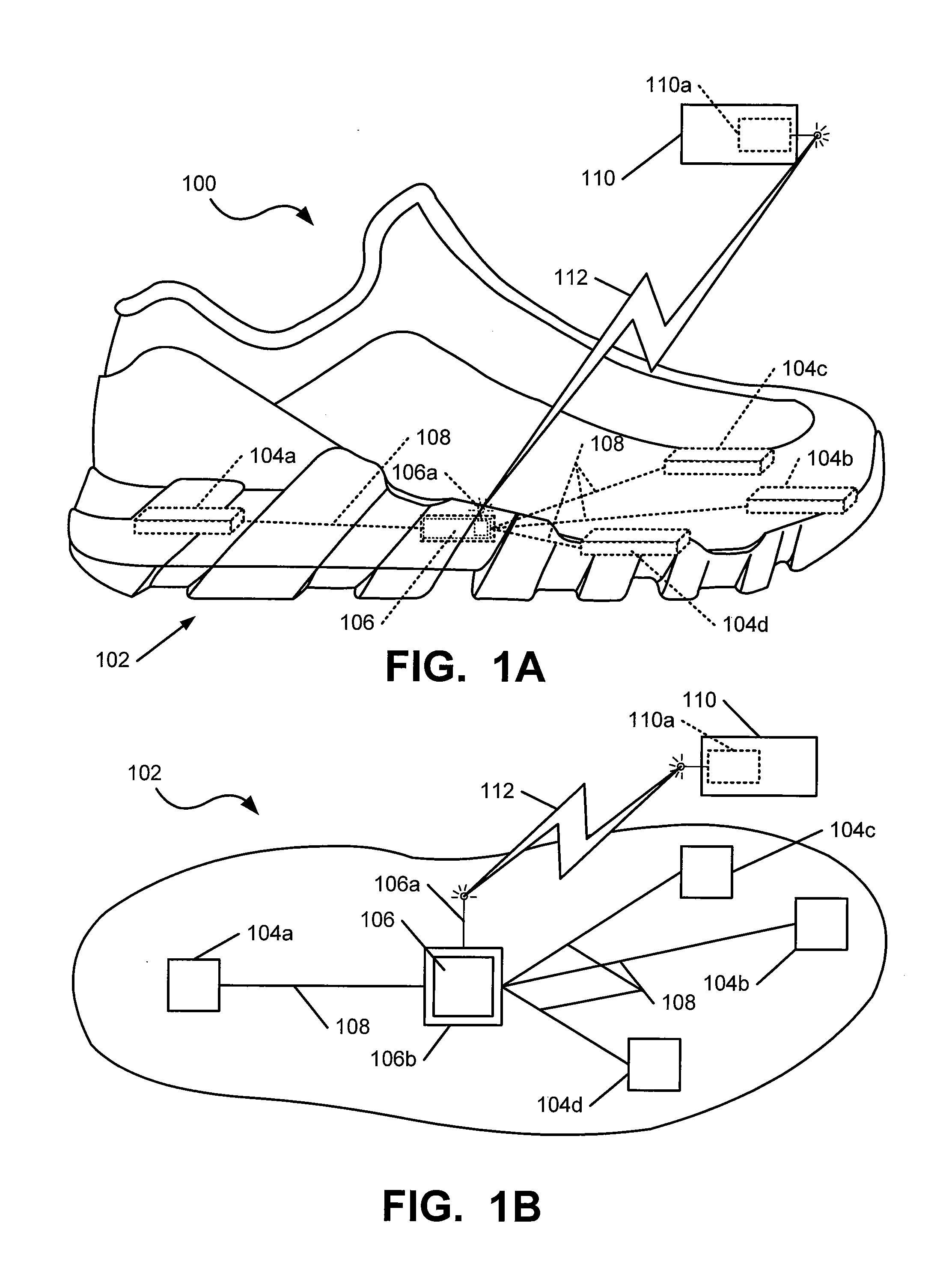
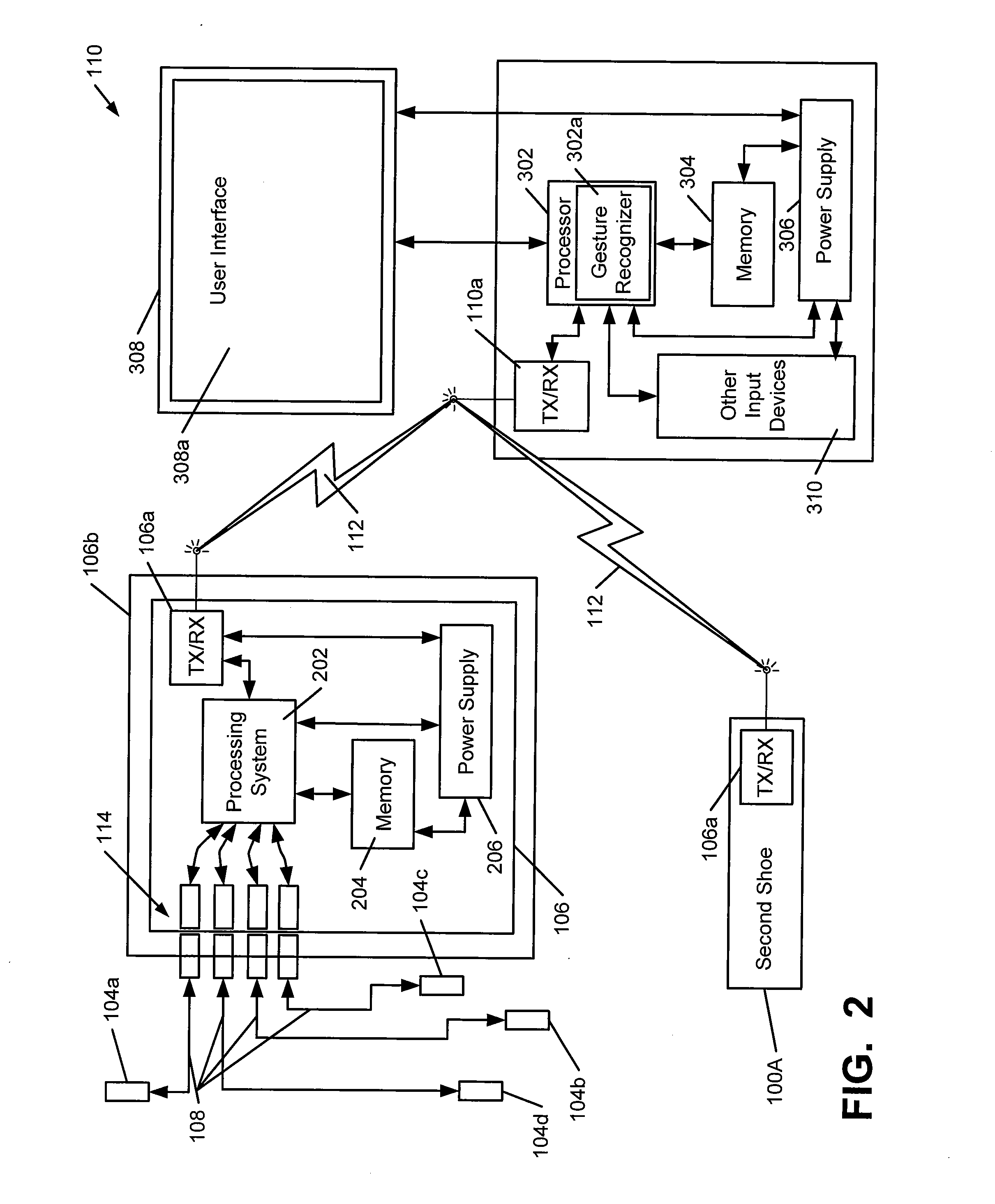
Foot Gestures for Computer Input and Interface Control
Non-video game computer user interfaces utilize human foot action to generate input for controlling the interface (e.g., a graphical user interface). Computer systems that use such input may include: (a) at least one input system including one or more sensing devices for sensing action by one or more feet; (b) a data transmission system for transmitting the sensed foot action to (c) a processing system that utilizes the foot action input to provide control data input for a user interface; and (d) an output device for producing a non-video game computer output based, at least in part, on data provided by the processing system. The control data relating to the foot action is used, at least in part, for controlling a user interface associated with the computer output.
Owner:NIKE INC
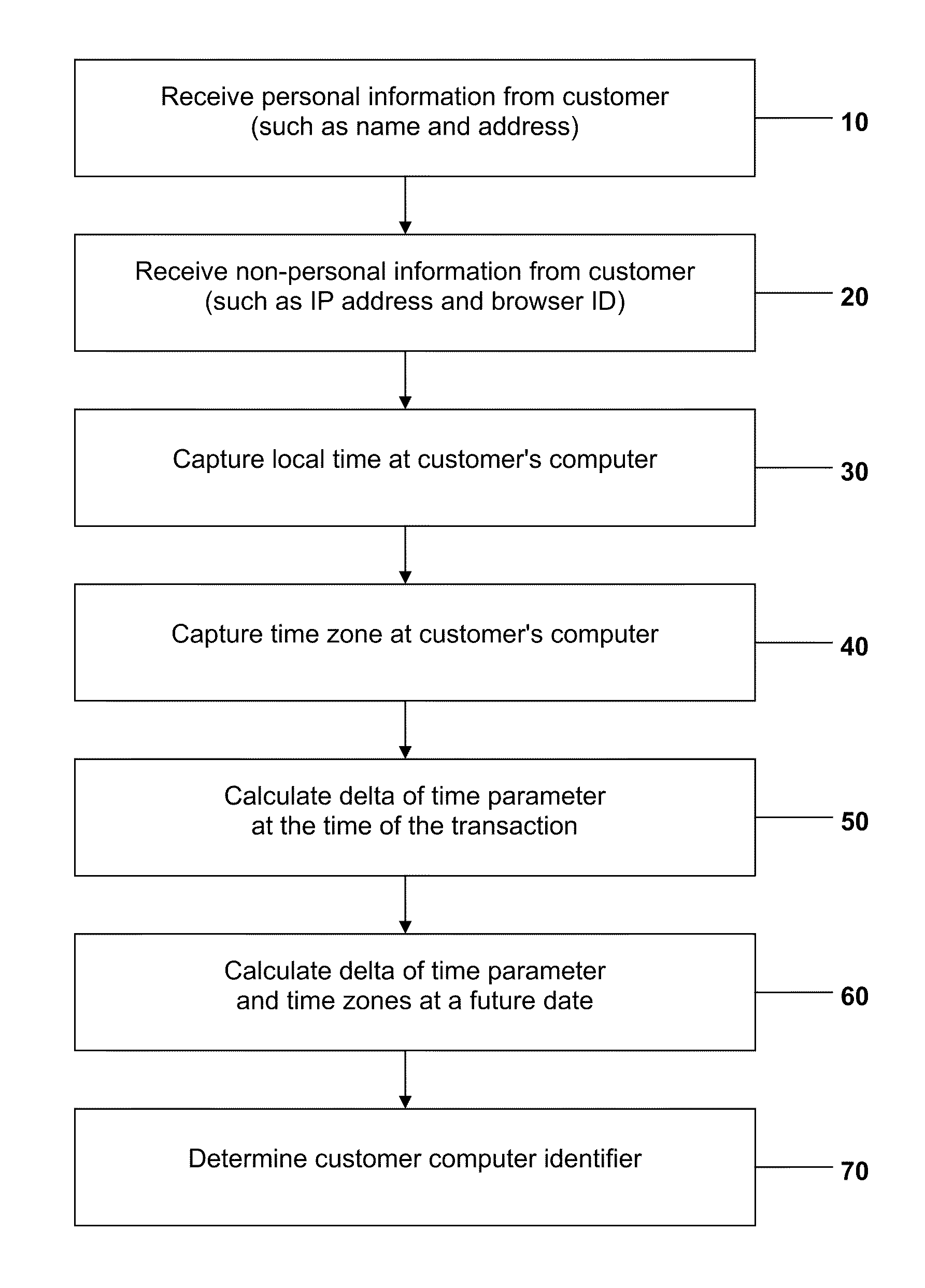
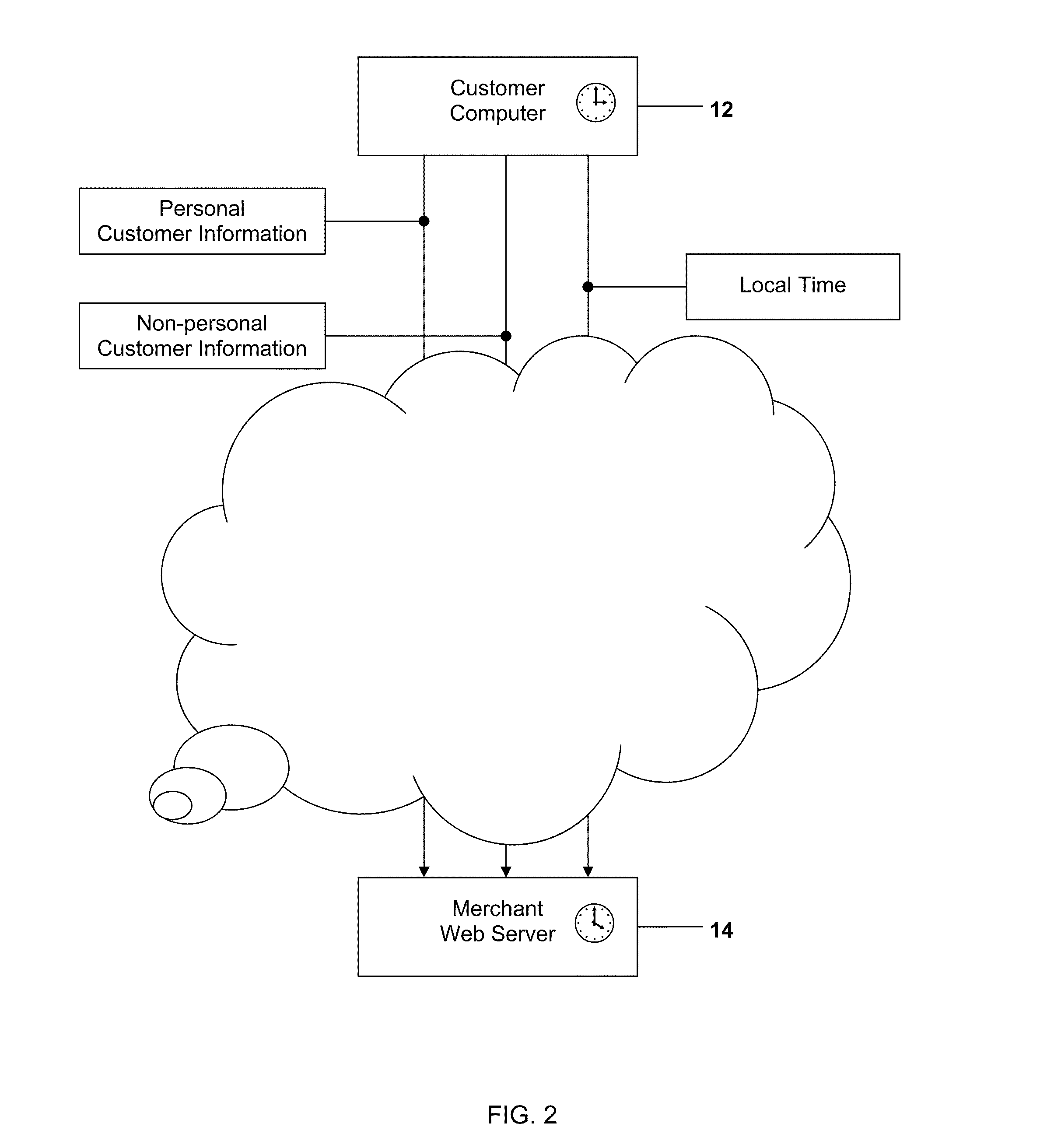
Method and System for Identifying Users and Detecting Fraud by Use of the Internet
ActiveUS20110082768A1Accurate trackingAccurately and efficiently qualityTransmissionCommerceComputer usersInternet fraud
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Method and system for sensing and reporting detailed activity information regarding current and recent instant messaging sessions of remote users
ActiveUS20050165893A1Error detection/correctionMultiple digital computer combinationsComputer usersActivity level
Owner:RAKUTEN GRP INC
Methods and apparatus using task models for targeting marketing information to computer users based on a task being performed
InactiveUS6330554B1Complete efficientlyDigital computer detailsDigital dataTask analysisComputer users
Methods and apparatus for analyzing tasks performed by computer users by (i) gathering usage data, (ii) converting logged usage data into a uniform format, (iii) determining or defining task boundaries, and (iv) determining a task analysis model by "clustering" similar tasks together. The task analysis model may be used to (i) help users complete a task (such help, for example, may be in the form of a gratuitous help function), and / or (ii) to target marketing information to users based on user inputs and the task analysis model. The present invention also provides a uniform semantic network for representing different types of objects in a uniform way.
Owner:MICROSOFT TECH LICENSING LLC
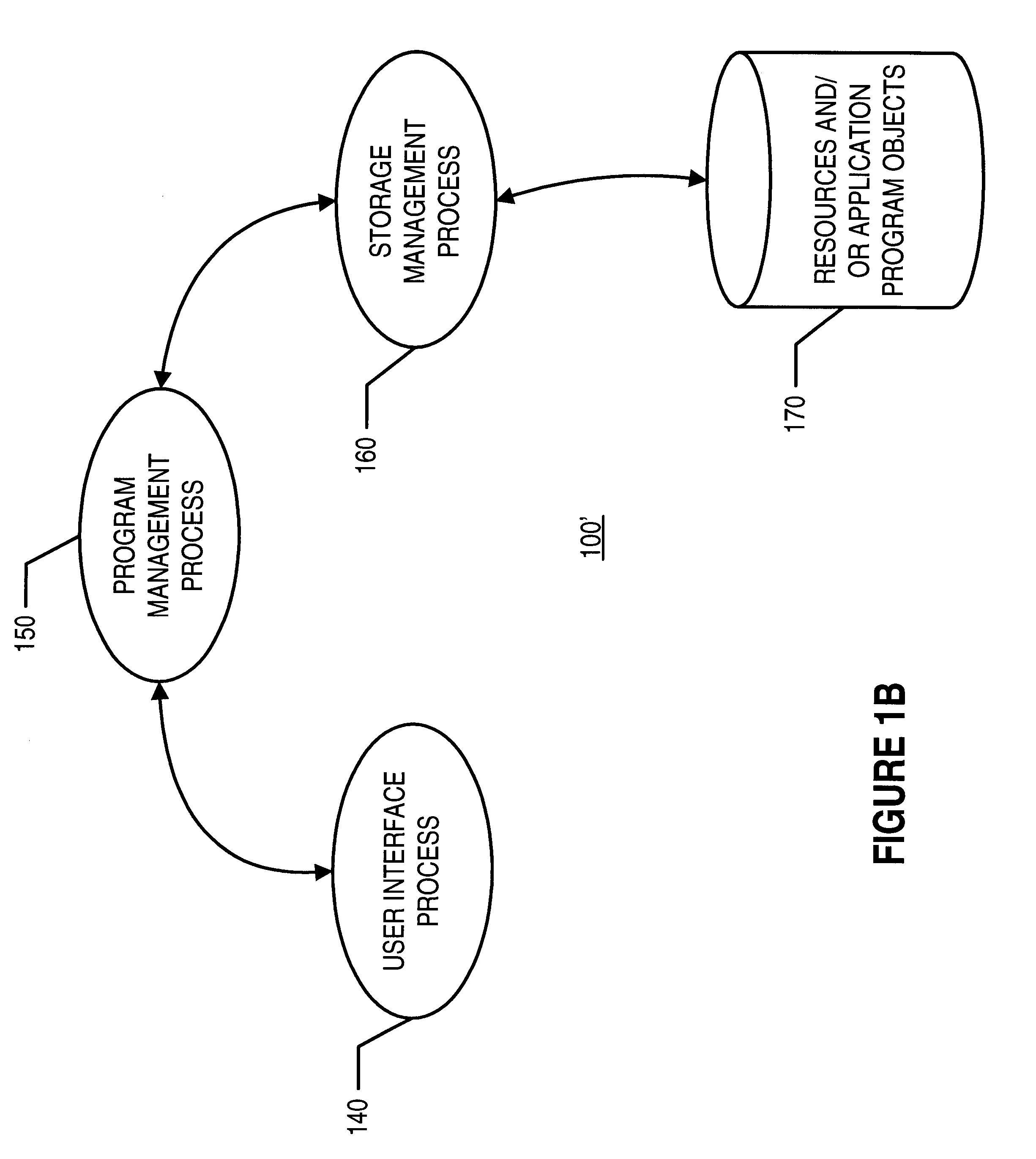
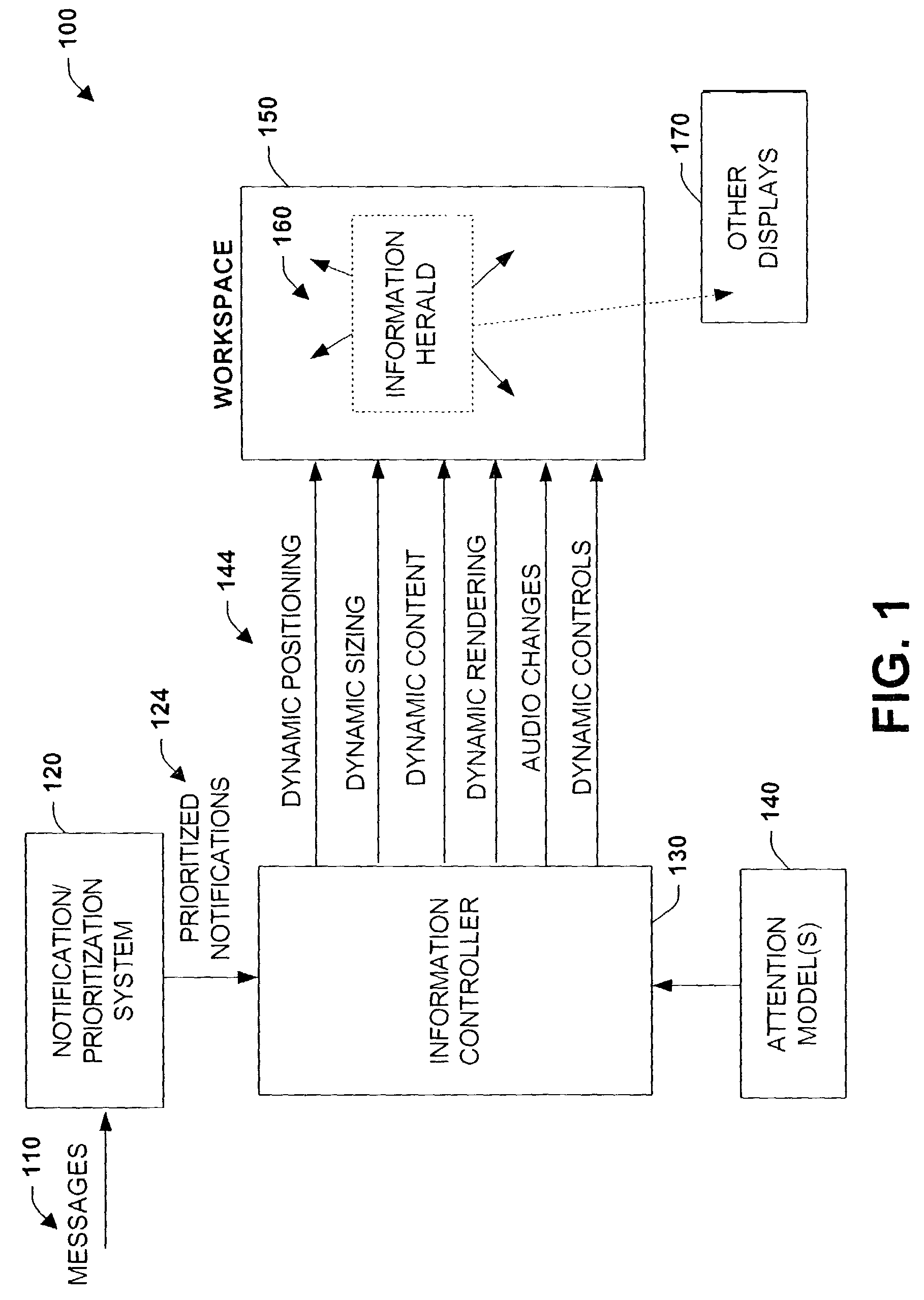
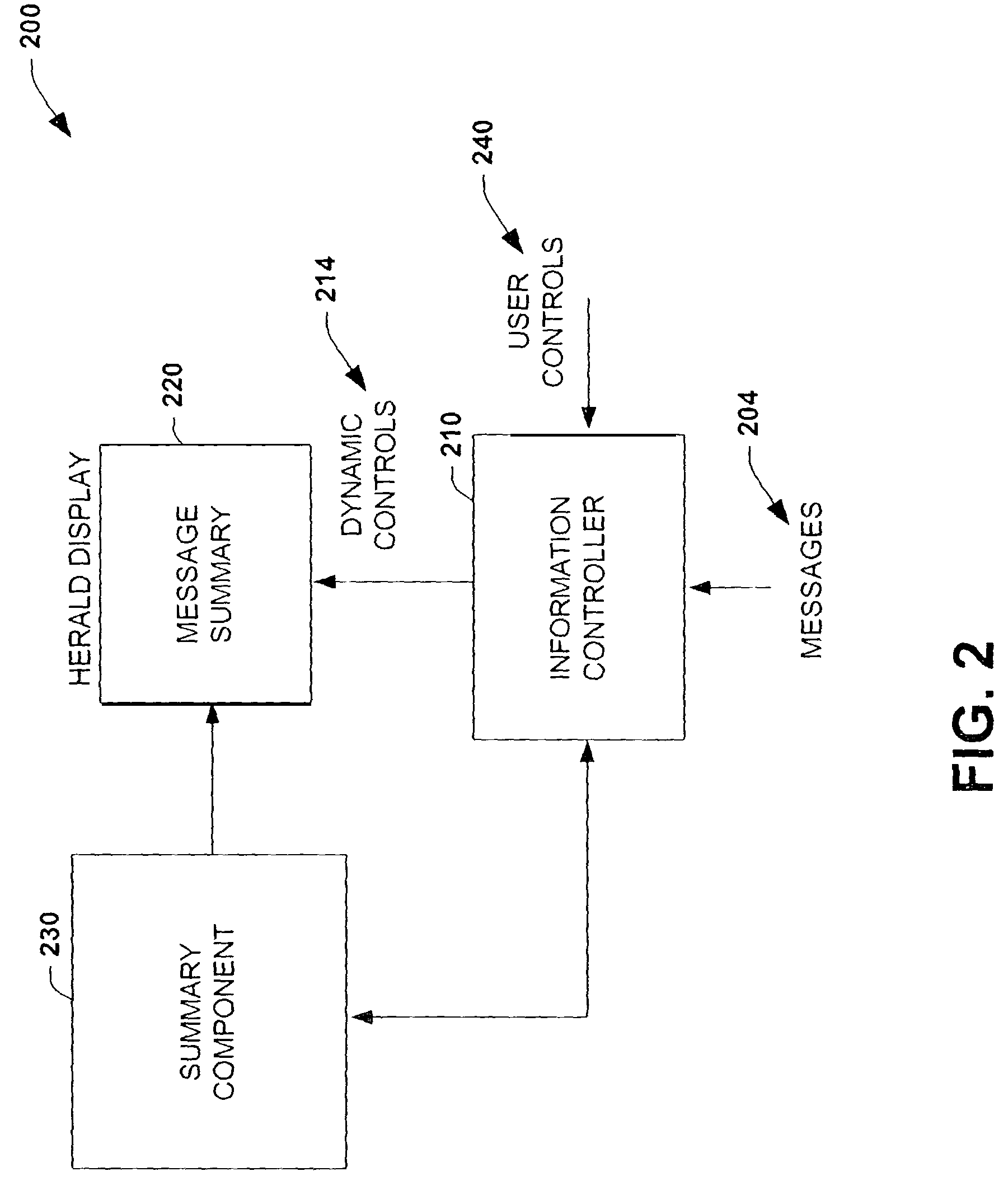
Positioning and rendering notification heralds based on user's focus of attention and activity
ActiveUS7743340B2Minimal cognitive loadUse in some applicationProgramme controlComputer controlComputer usersNotification system
The present invention relates to a system and method to facilitate providing computer users with efficient access to electronic notifications while minimizing disruption in the context of ongoing tasks. A notification system provides visual information heralds that provide summarizations of notifications to users. An information controller considers the importance or urgency of content and a user's current and / or recent activities in decisions about the rendering and positioning of the information herald on a display screen or screens in order to facilitate user processing of the summarized notifications with minimal disruption to ongoing tasks.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com