Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
196 results about "Fraudulent transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Fraudulent transactions are orders and purchases made using a credit card or bank account that does not belong to the buyer. One of the largest factors in identity fraud, these types of transactions can end up doing damage to both merchants and the identity fraud victim.
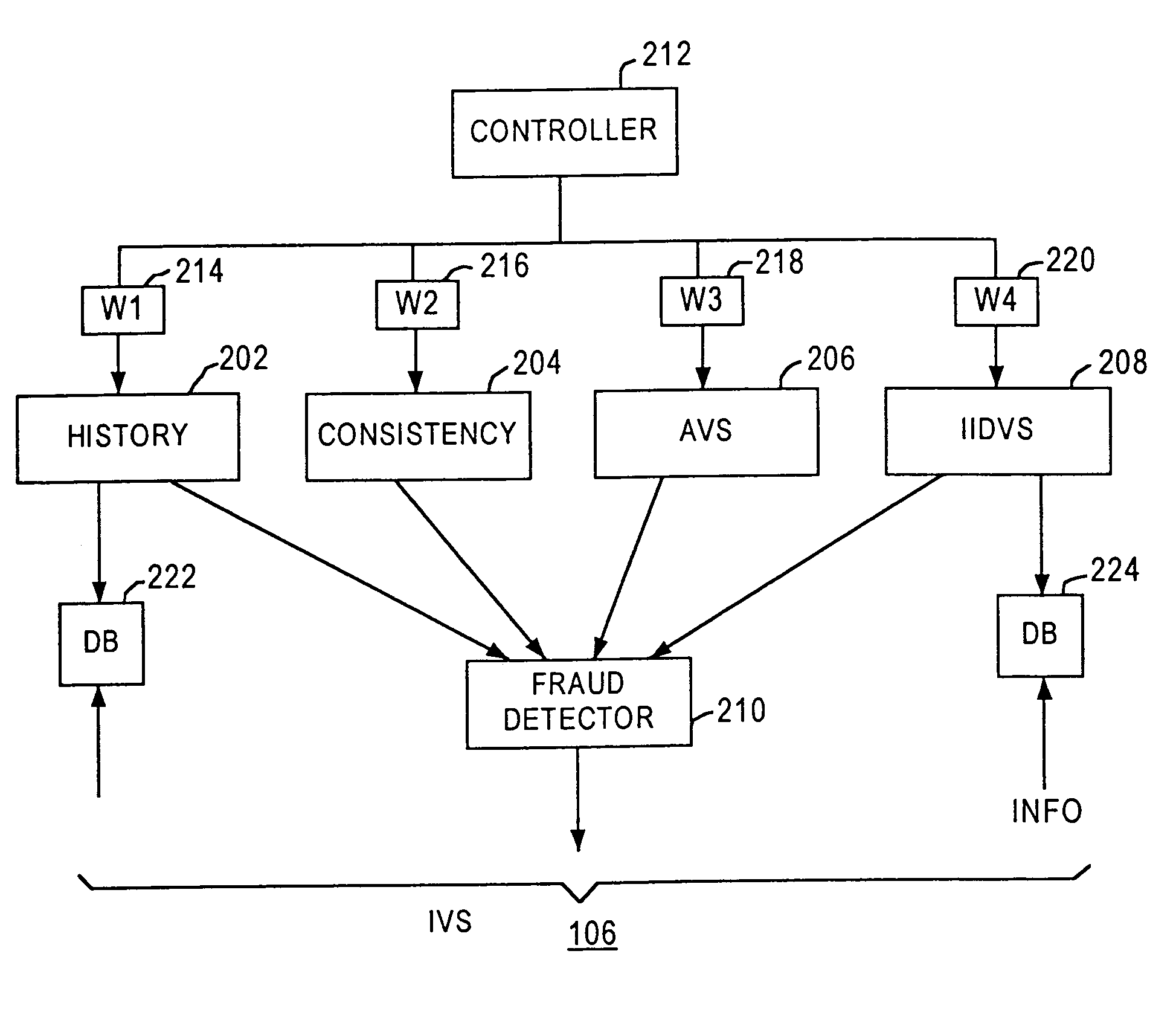
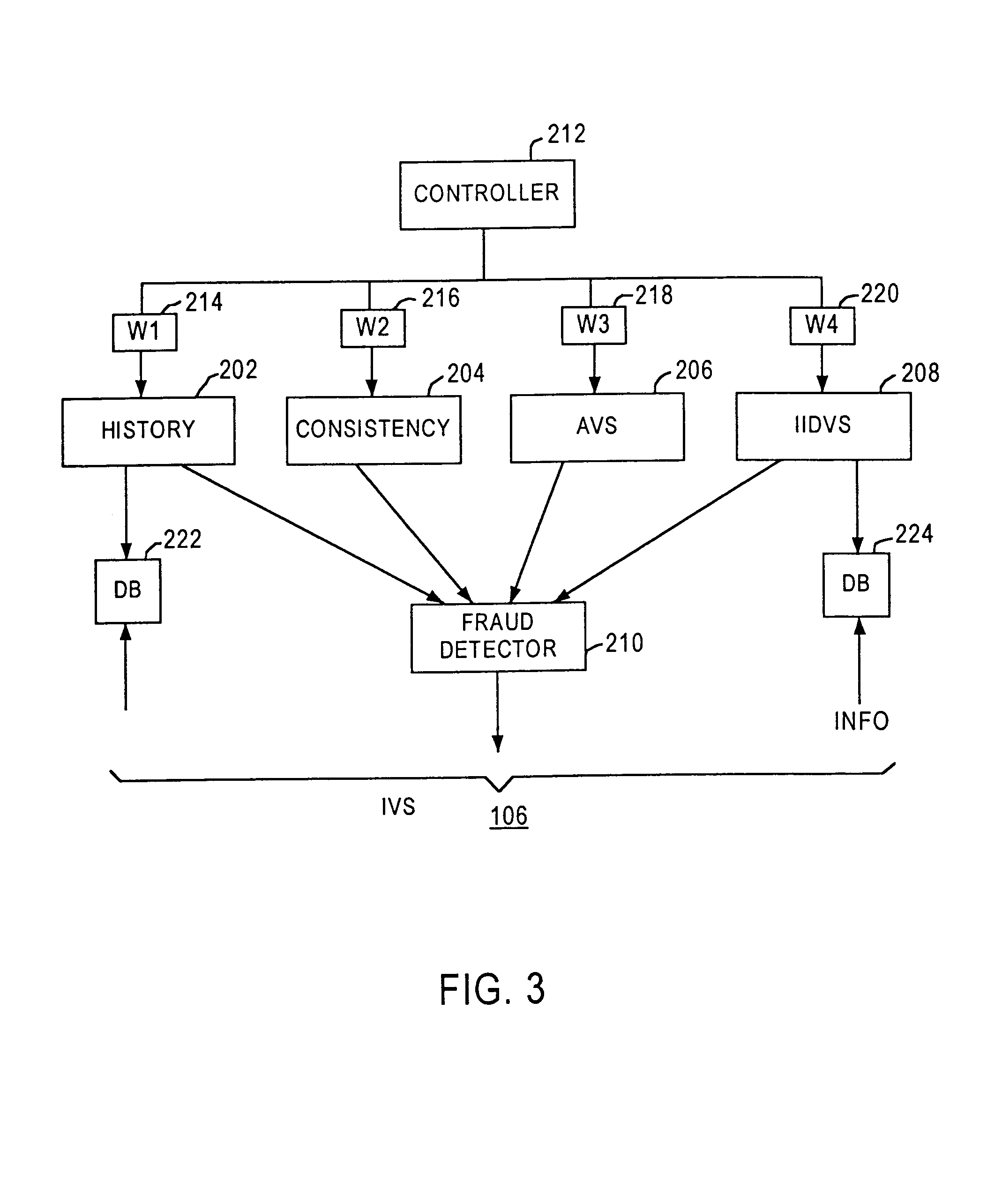
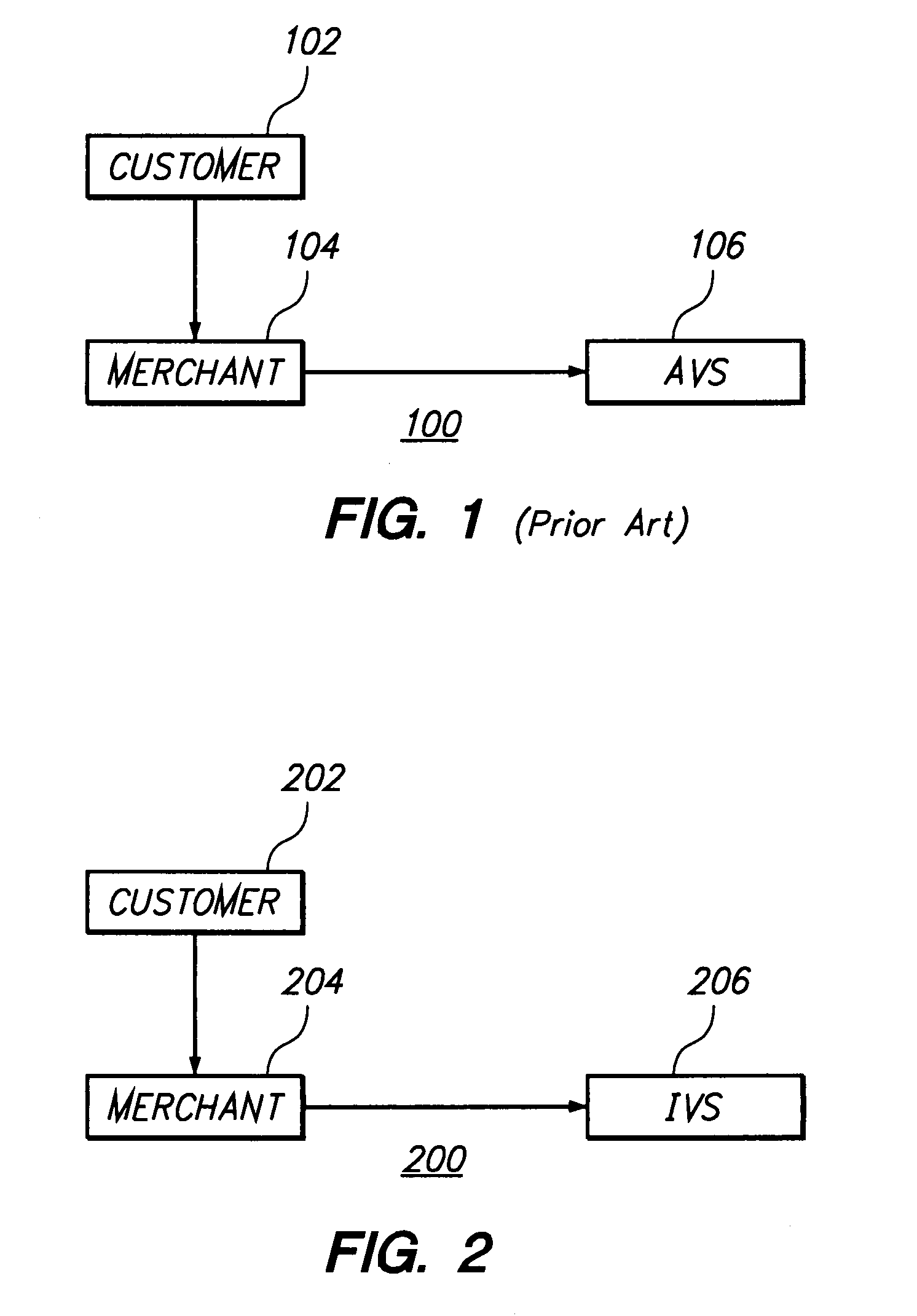
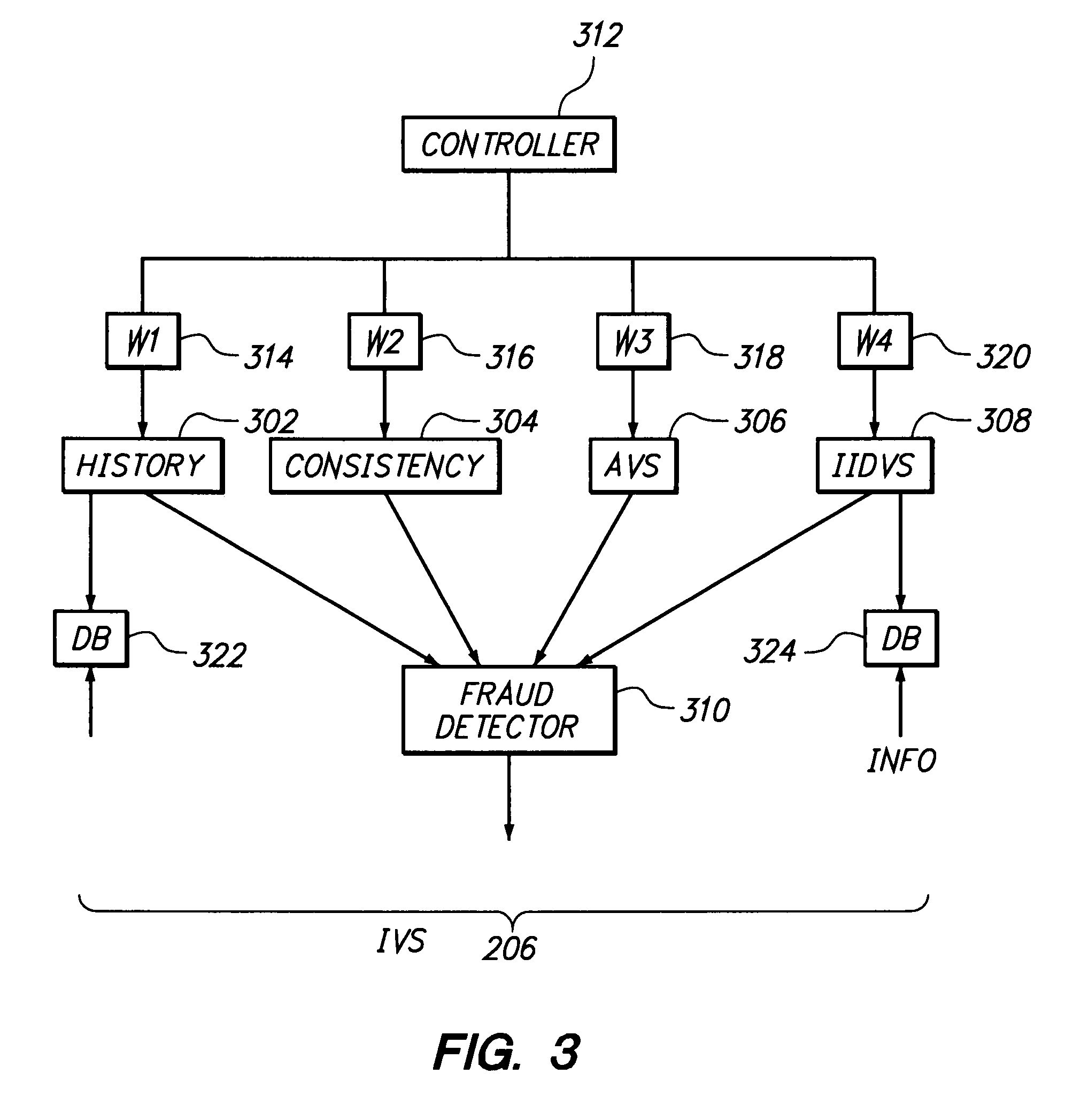
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
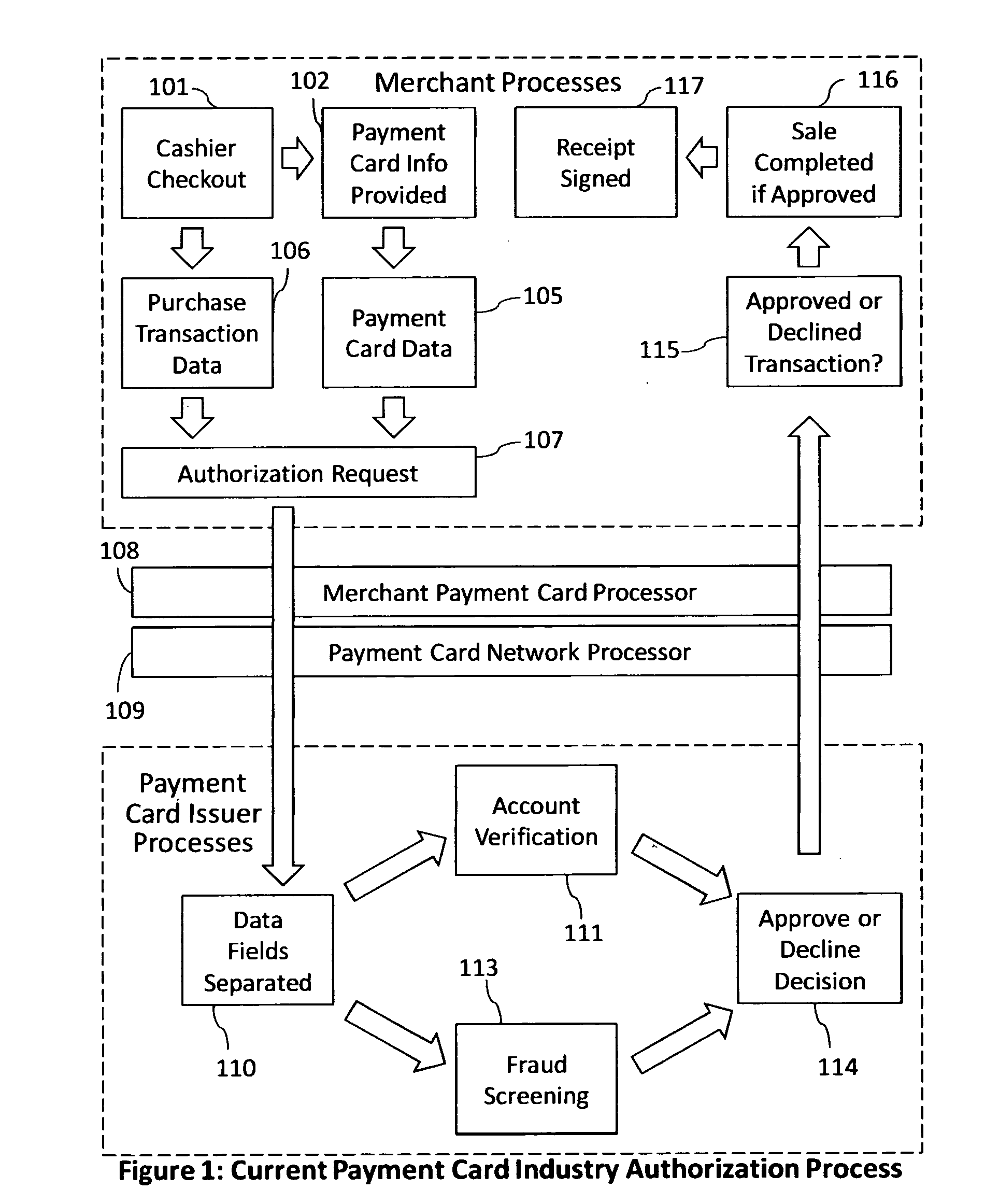
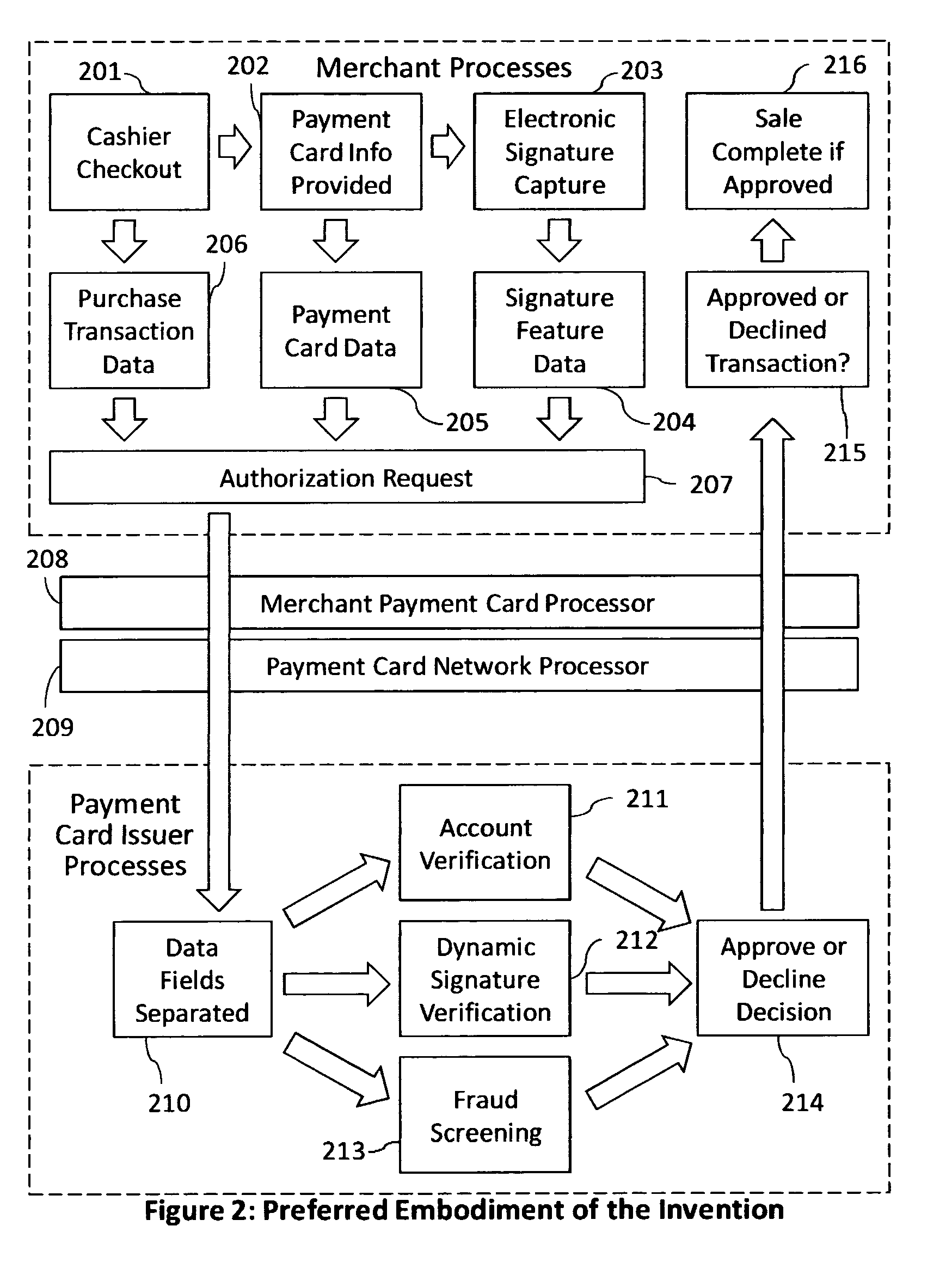
Reduction of transaction fraud through the use of automatic centralized signature/sign verification combined with credit and fraud scoring during real-time payment card authorization processes
InactiveUS20110238510A1Reduce payment card industry fraud lossReduce the amount of dataFinanceCharacter and pattern recognitionDigital signatureIdentity theft
A dynamic signature / sign biometric verification system for detecting and preventing fraudulent transactions is described. The system comprises remote digital signature / sign input devices, a means to extract spatial and temporal features from the signature, a means to transmit the signature / sign features along with customer identifier information to a centralized signature / sign verification authority, a means for combining signature / sign feature verification with other forms of fraud detection technology, and a means for transmitting the results of a signature / sign verification back to the remote location where the signature / sign was captured. The system was primarily developed for use in payment card industries (e.g. credit cards, debit cards) but has applicability to other centralized signature / sign verification applications such as Automated Teller Machine authorizations and other identity theft detection and monitoring services.
Owner:BIOCRYPT ACCESS LLC
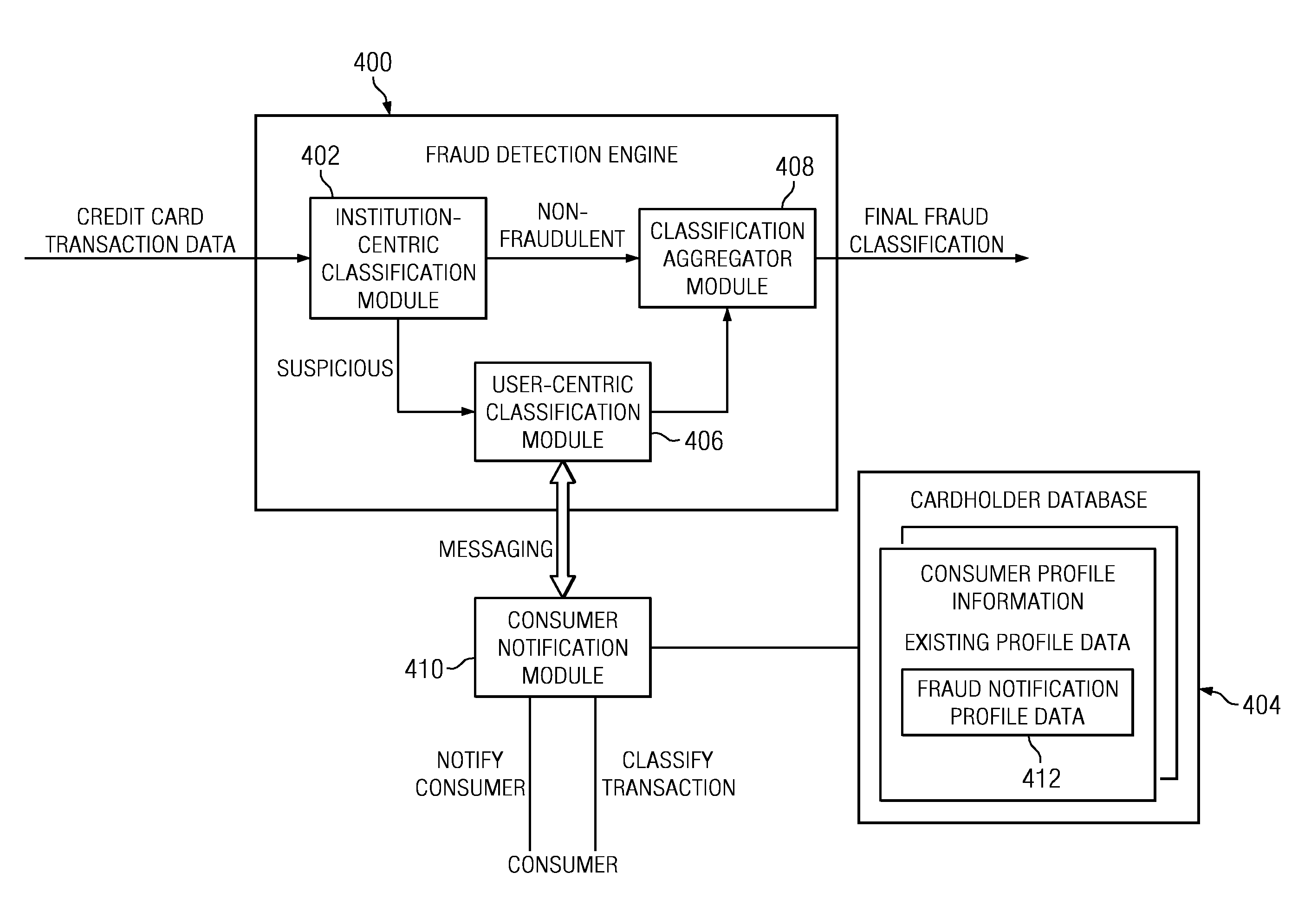
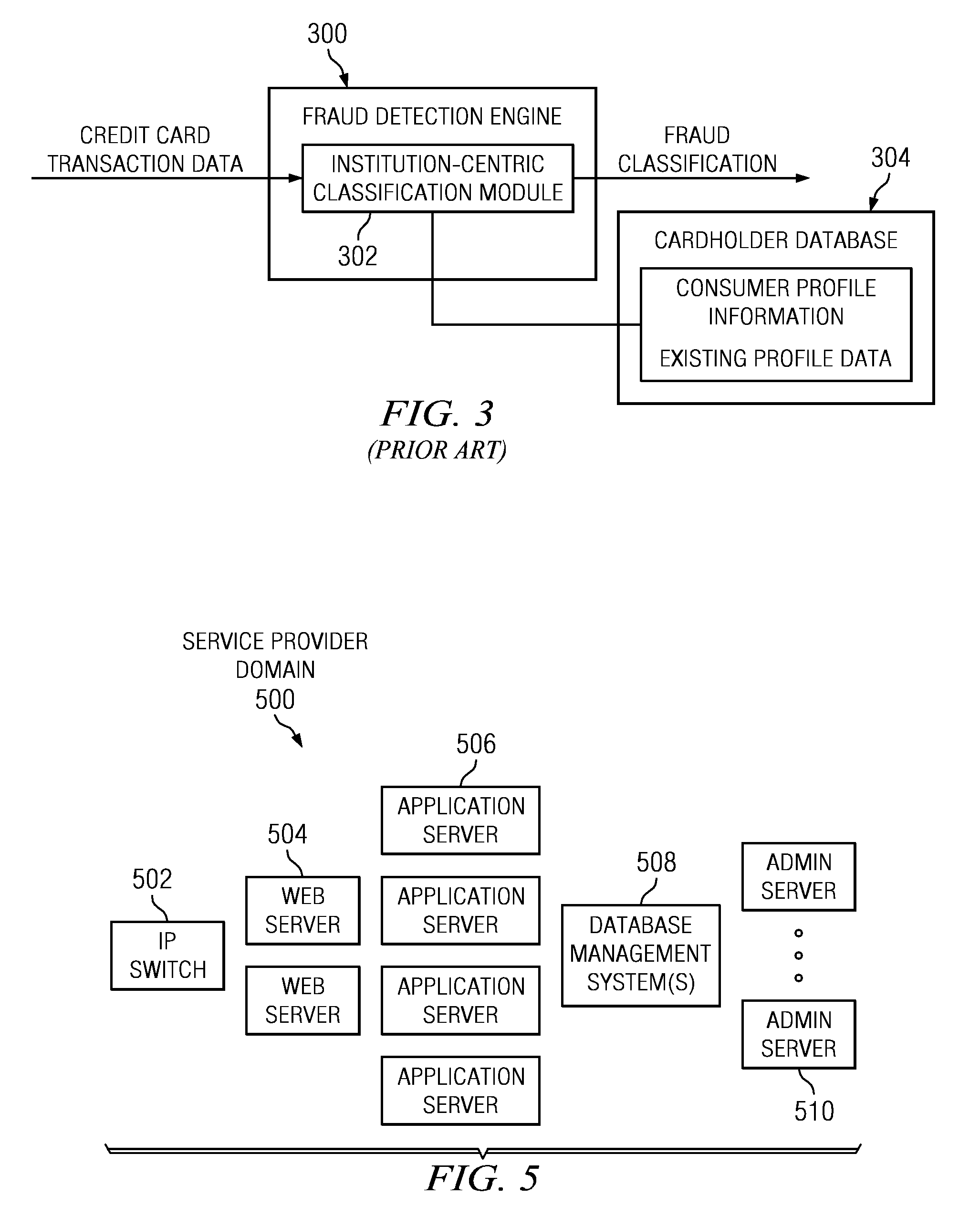
Method and System for Identification By A Cardholder of Credit Card Fraud
A method for fraud detection leverages an existing financial institution's fraud classification functionality, which produces a first level detection, with a “user-centric” classification functionality, which produces a “second” or more fine-grained detection regarding a potentially fraudulent transaction. After passing through an existing (“institution-centric”) fraud detection technique, a transaction that has been identified as potentially fraudulent is then subject to further analysis and classification at the “user” level, as it is the user is presumed to be the best source of knowledge of the legitimate credit card use. Information about the transaction is shared with the consumer, preferably via one or more near real-time mechanisms, such as SMS, email, or the like. Based on the user's response (or lack thereof, as the case may be), one or more business rules in the institution's fraud detection system can then take an appropriate action (e.g., no action, reverse the transaction if complete, deny the transaction if in-progress, or the like).
Owner:IBM CORP
Financial transactions systems and methods
InactiveUS20100106611A1Reduce percentageFinanceApparatus for meter-controlled dispensingPayment transactionService provision
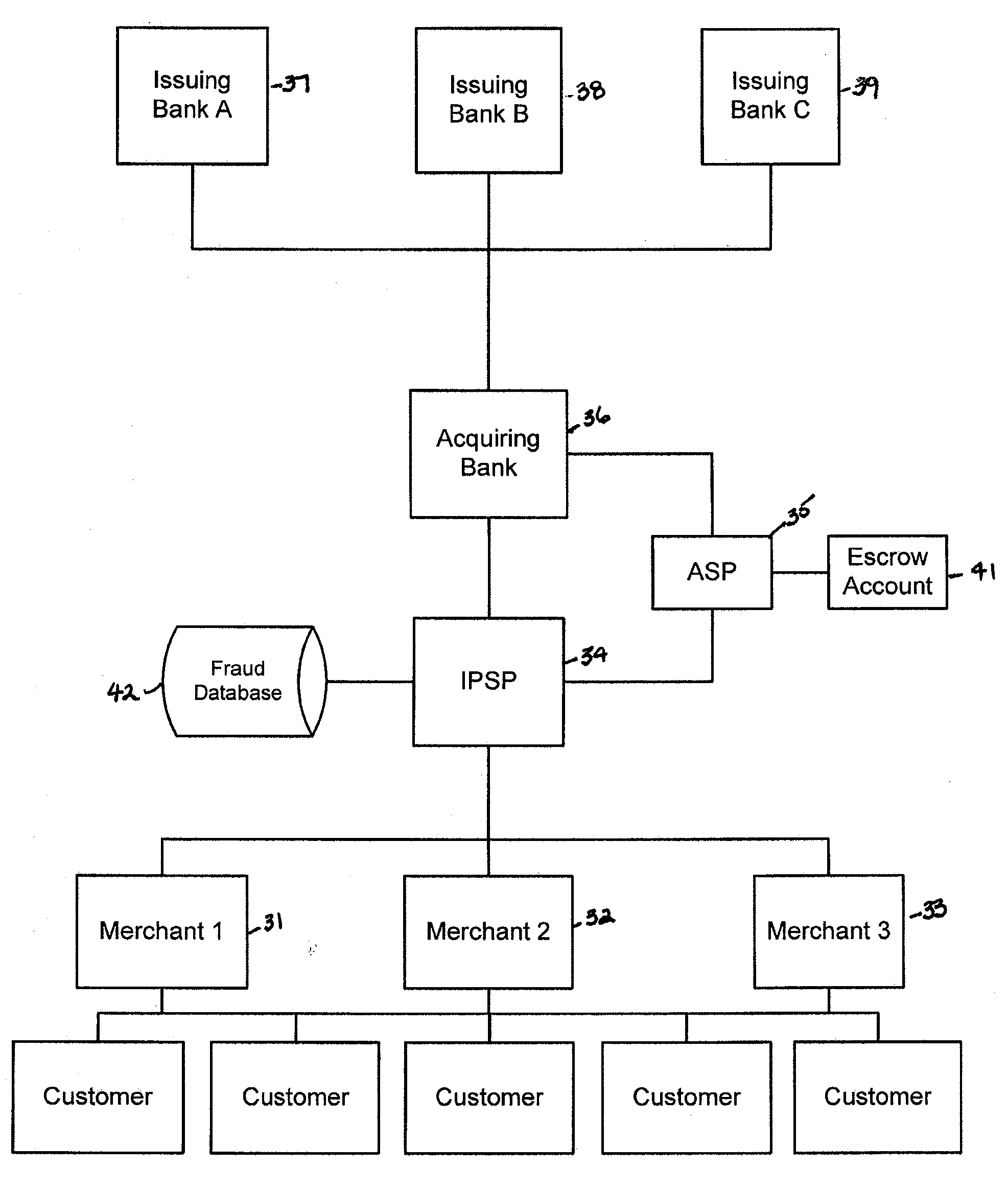
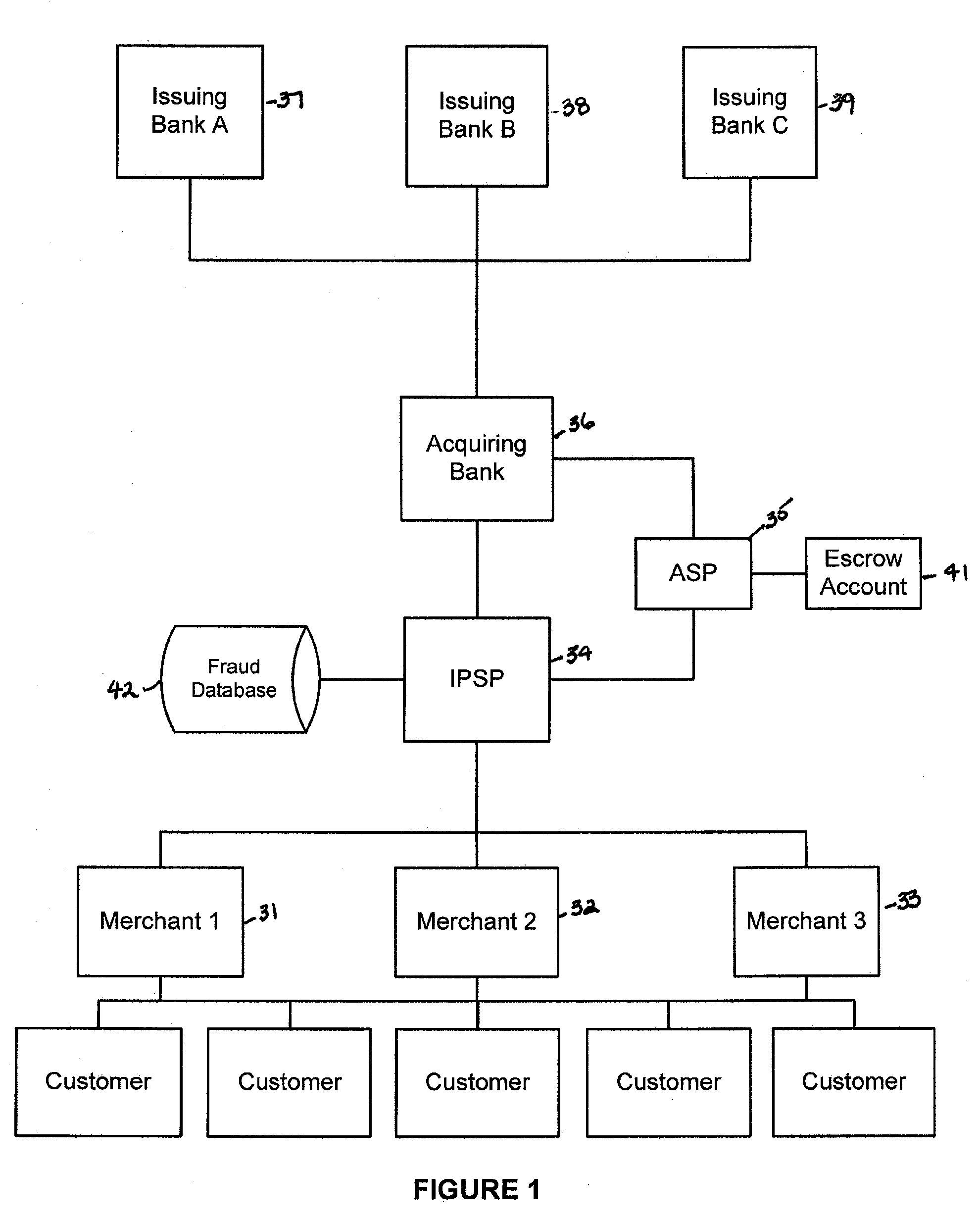
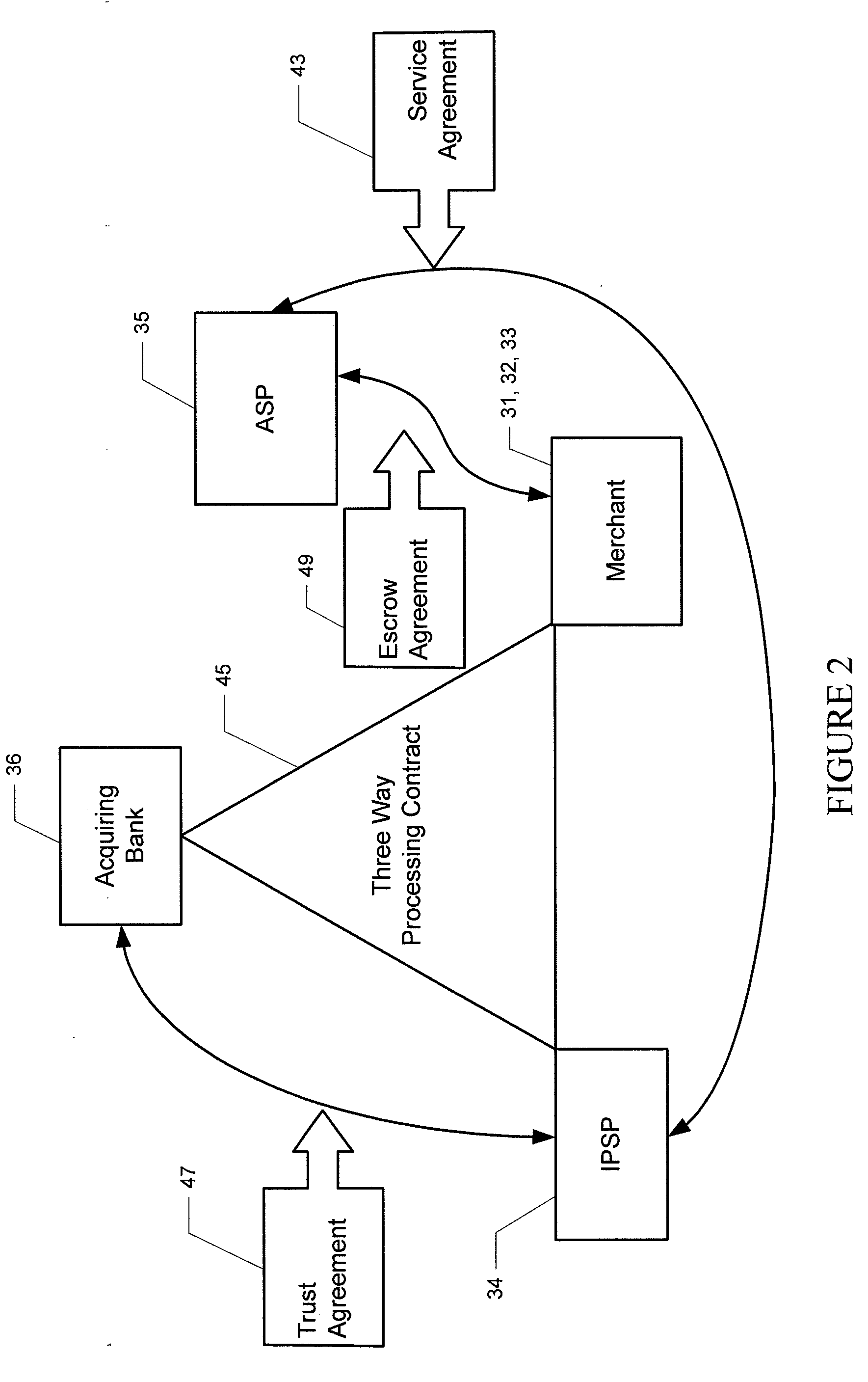
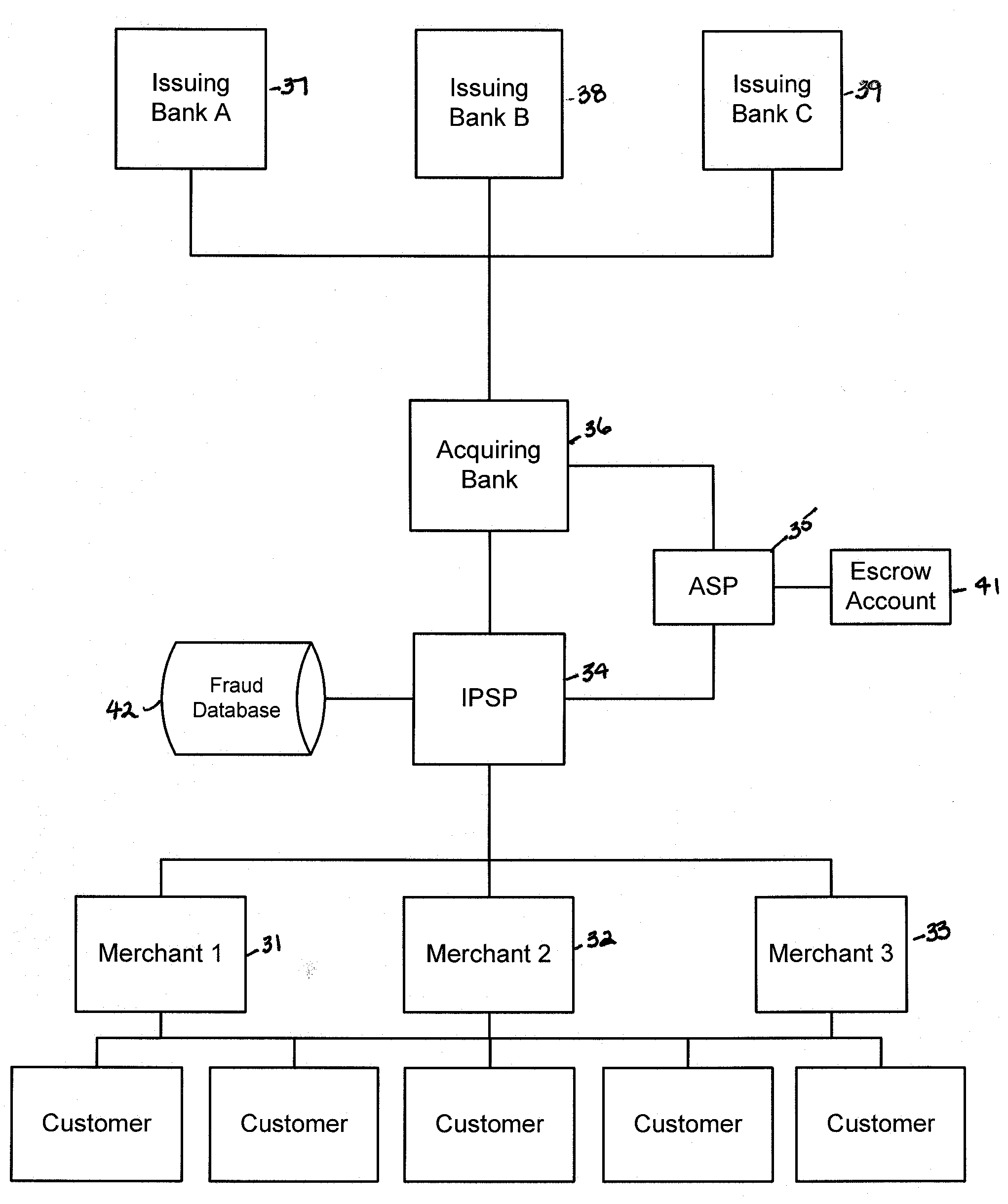
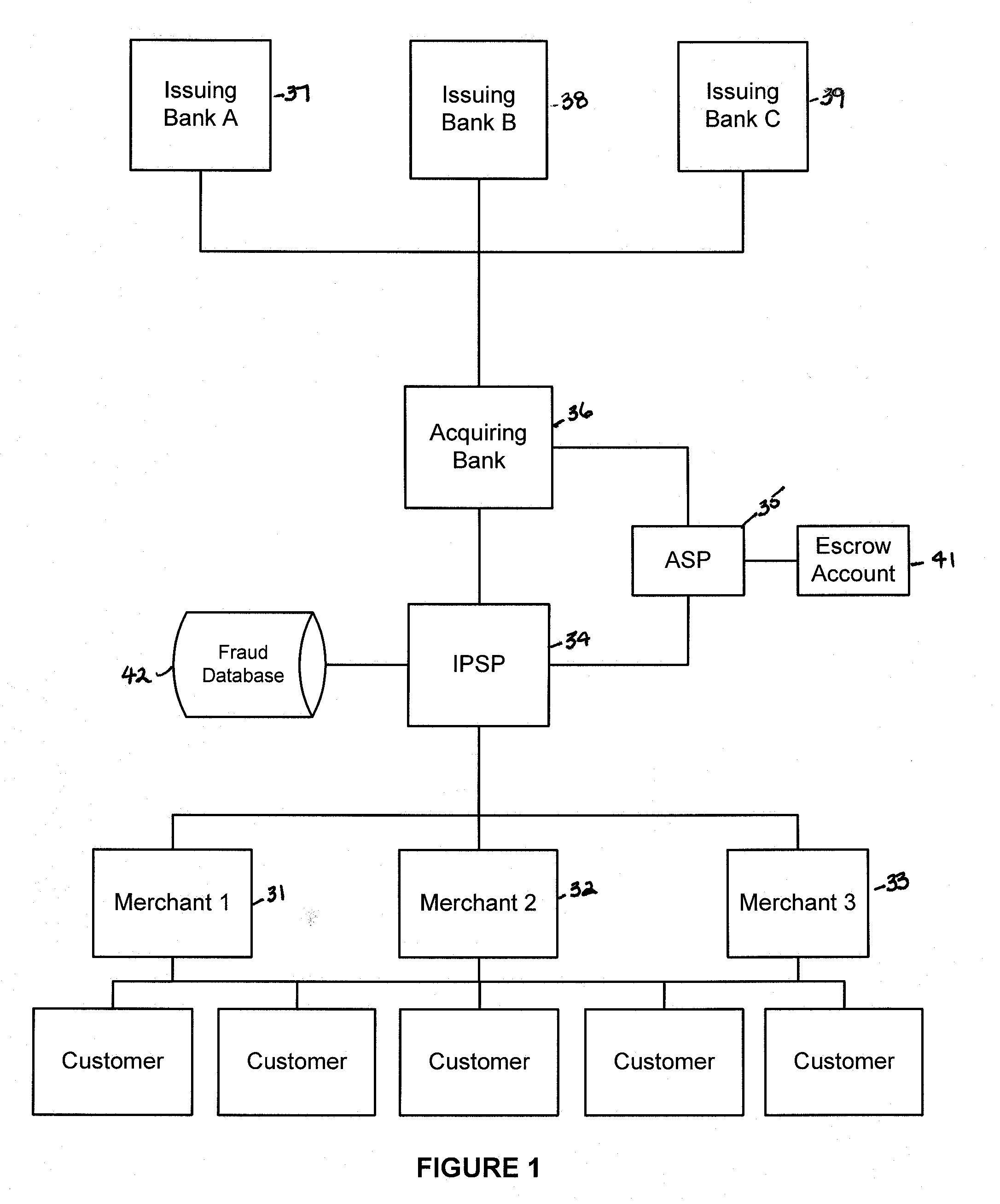
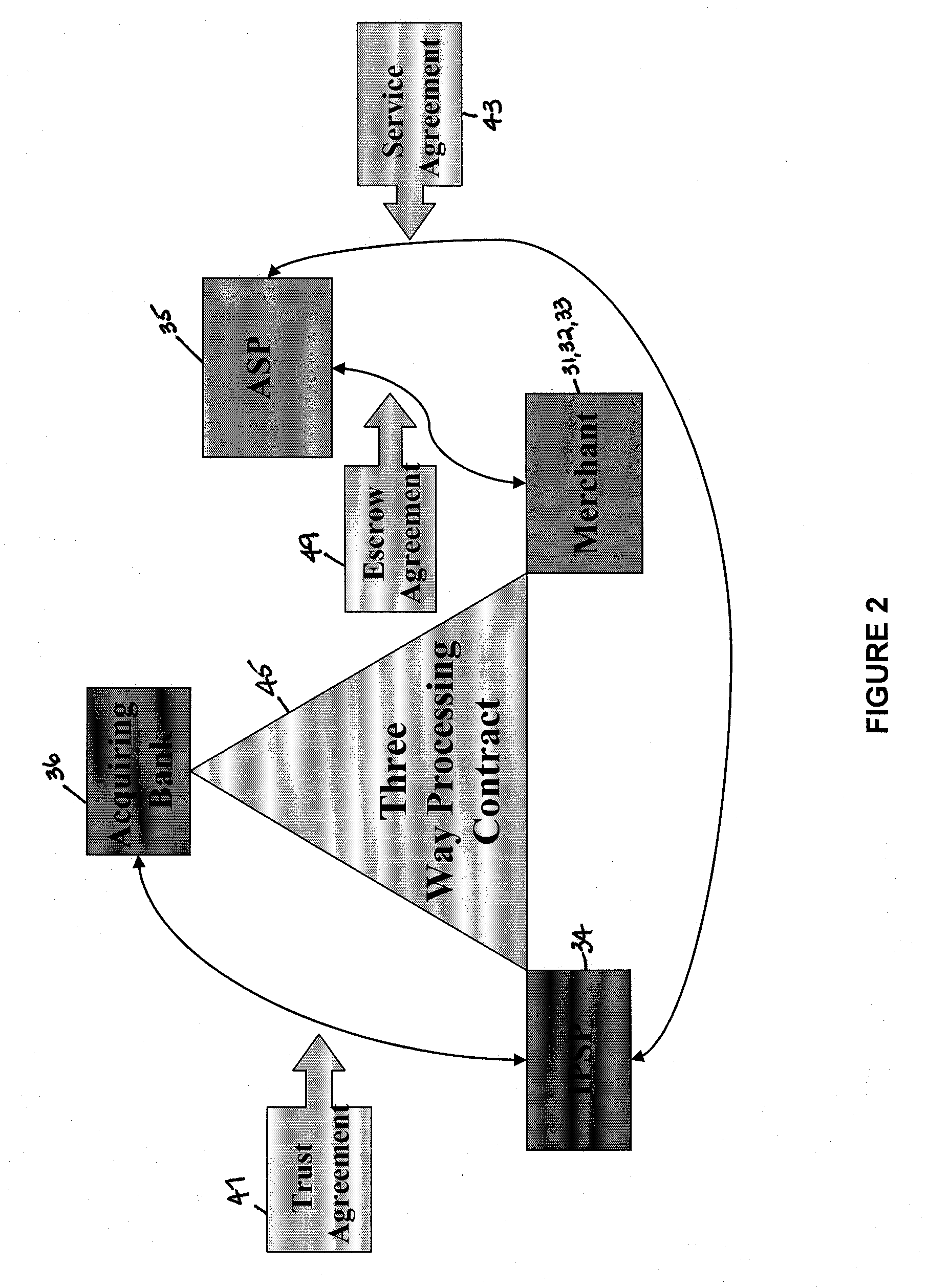
Various embodiments of the invention provide a more secure financial transaction system for e-commerce sectors that (1) more securely processes payment transactions, (2) helps to protect merchants and banks against fraudulent transactions, money laundering, and underage gambling, and (3) helps to limit other abuses in areas of e-commerce that are perceived to pose special risks, such as Internet gaming, travel, and consumer purchasing of electronic goods. To accomplish the above goals, various embodiments of the financial transaction system (1) establish operating and transaction processing protocols for merchants, Internet payment service providers, acquiring banks, and card schemes and (2) provide automated systems for monitoring and securely processing payment and financial transactions.
Owner:TRUST PAYMENTS LTD
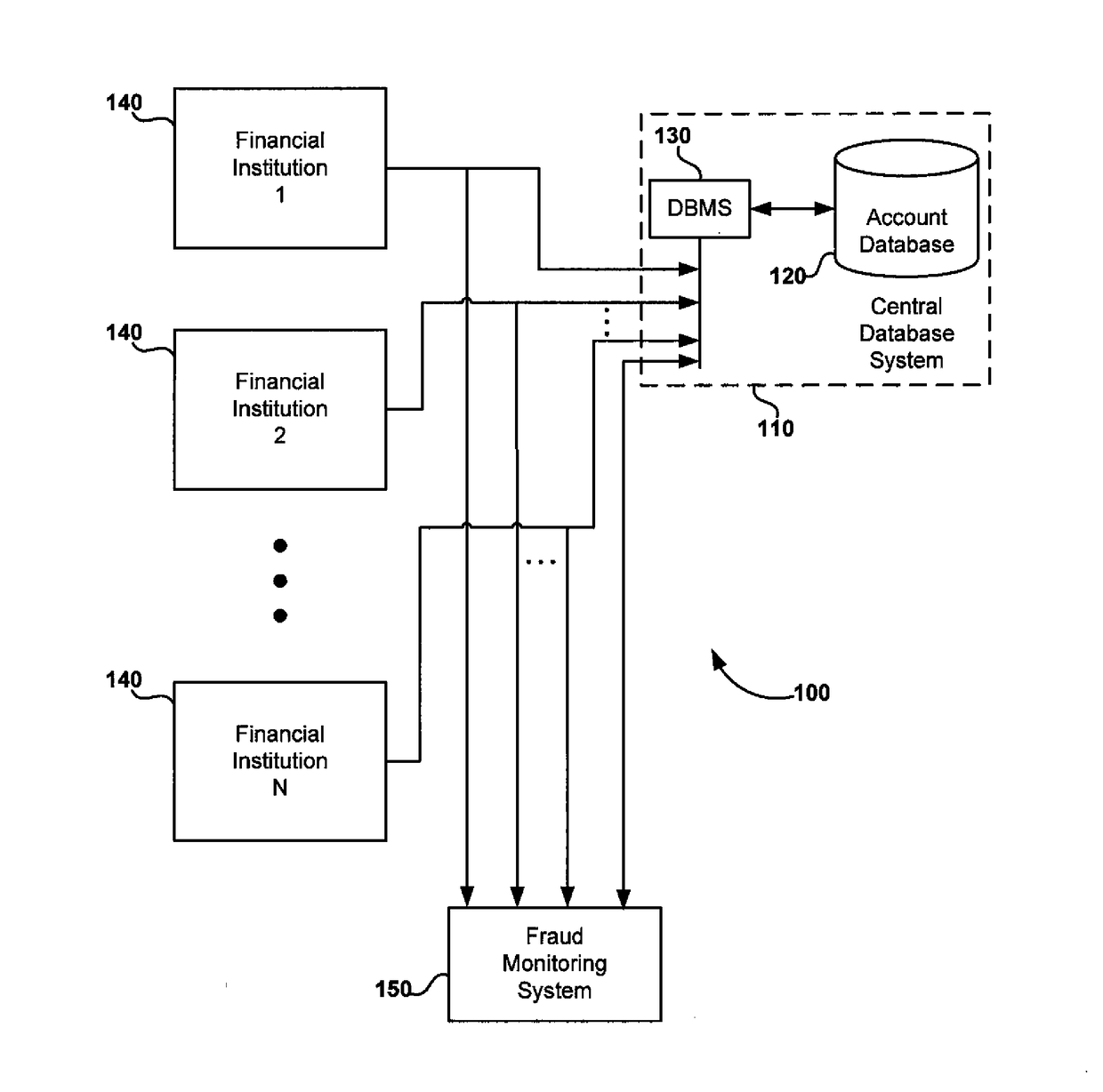
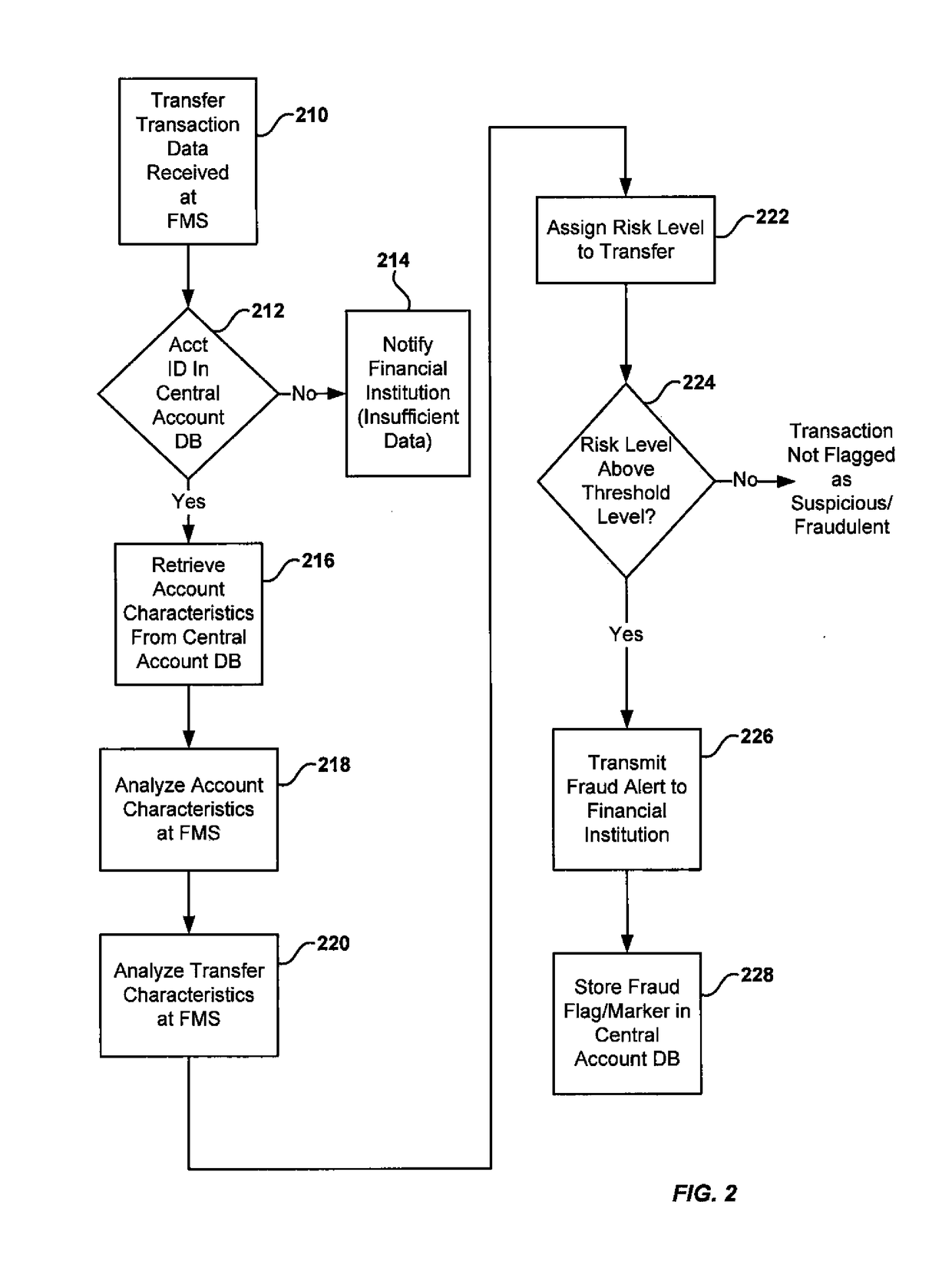
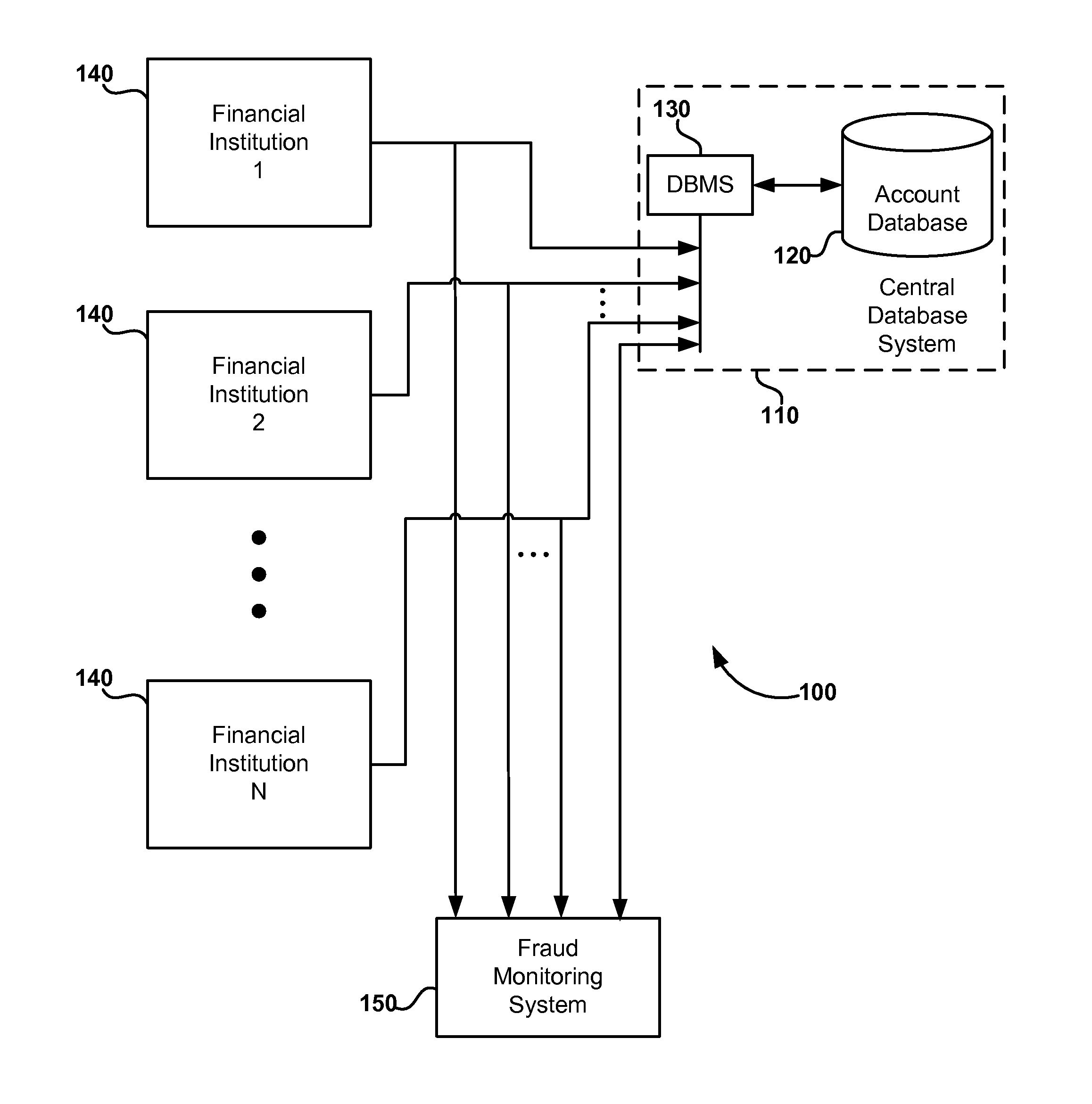
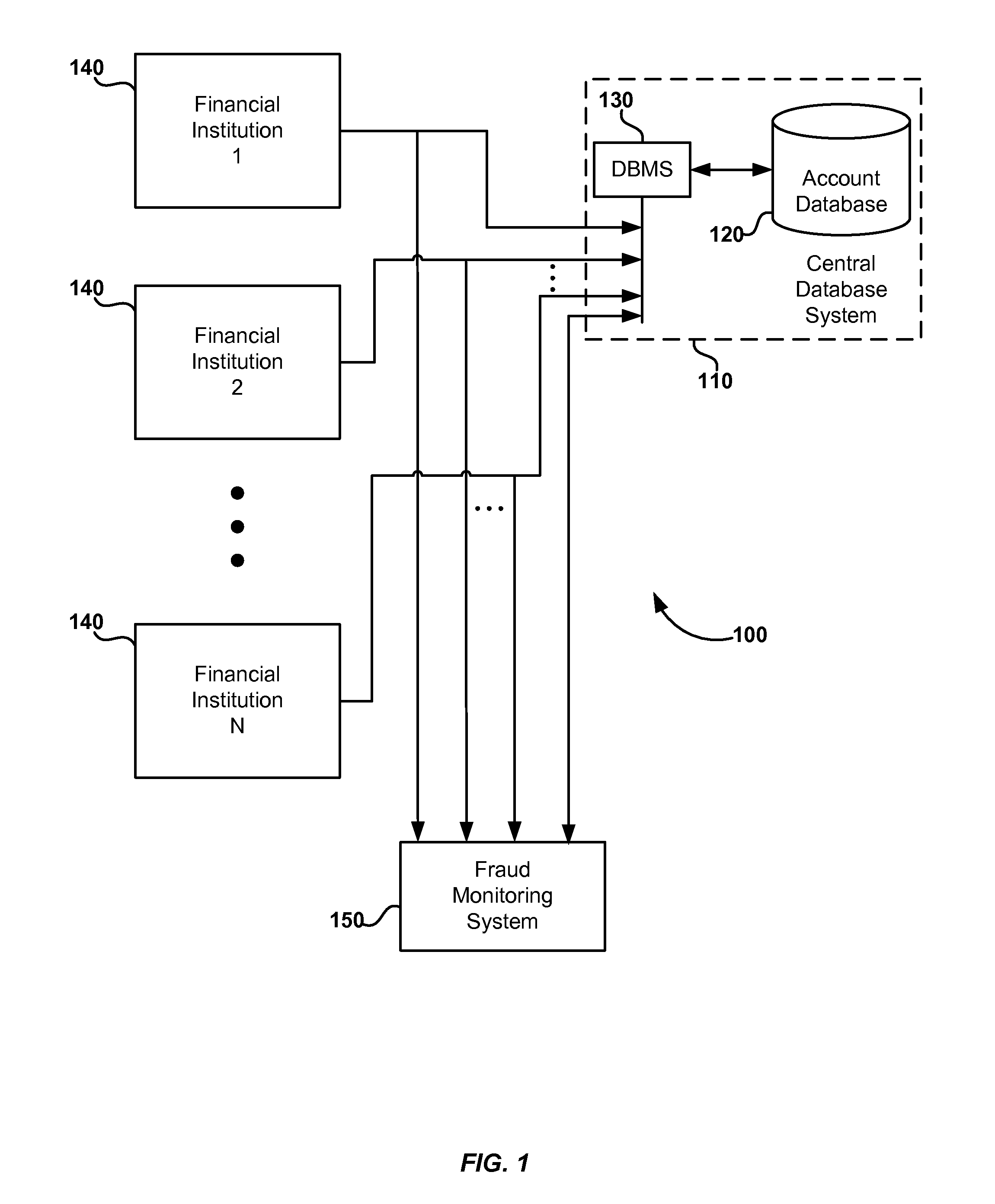
System and method for detecting fraudulent account access and transfers
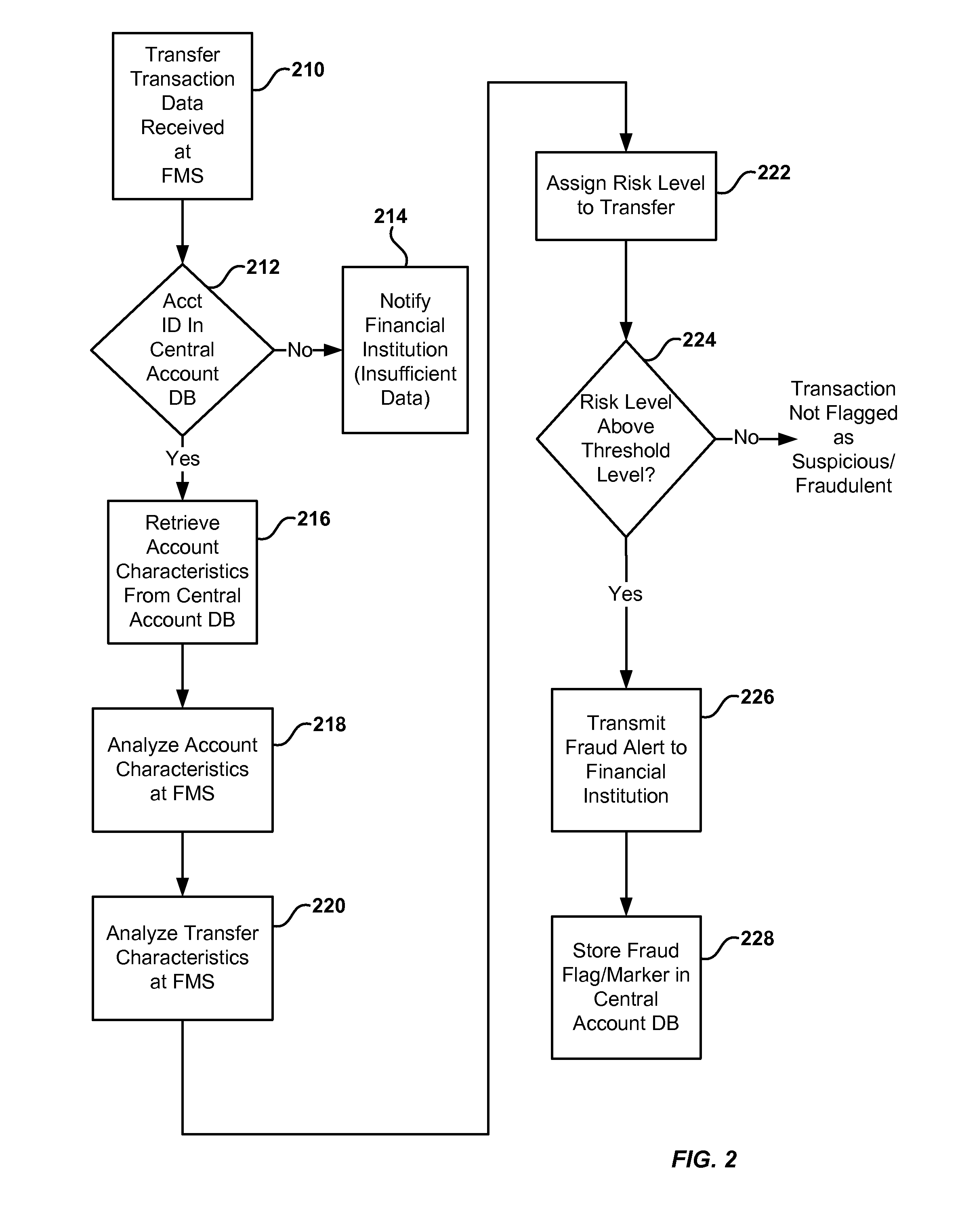
Transfers of money into a recipient account are analyzed for risk of fraud by using a fraud monitoring system to analyze characteristics of the recipient account. The recipient account characteristics are stored in a central database, which has account data (for recipient accounts) contributed from a plurality of financial institutions that maintain such accounts. When a transfer is made or attempted, the stored characteristics of the recipient account are analyzed and a risk score is assigned to the transfer based on the recipient account. If the risk score indicates a suspicious or fraudulent transaction, an alert is provided. In an alternative embodiment, the risk analysis may be supplemented by analysis of transaction data association with the transfer.
Owner:EARLY WARNING SERVICES
System and method for detecting fraudulent account access and transfers
Transfers of money into a recipient account are analyzed for risk of fraud by using a fraud monitoring system to analyze characteristics of the recipient account. The recipient account characteristics are stored in a central database, which has account data (for recipient accounts) contributed from a plurality of financial institutions that maintain such accounts. When a transfer is made or attempted, the stored characteristics of the recipient account are analyzed and a risk score is assigned to the transfer based on the recipient account. If the risk score indicates a suspicious or fraudulent transaction, an alert is provided. In an alternative embodiment, the risk analysis may be supplemented by analysis of transaction data association with the transfer.
Owner:EARLY WARNING SERVICES
System and Method for Early Detection of Fraudulent Transactions
InactiveUS20110238564A1Faster and efficient useEasy to detectFinancePayment architectureMobile deviceFraudulent transaction
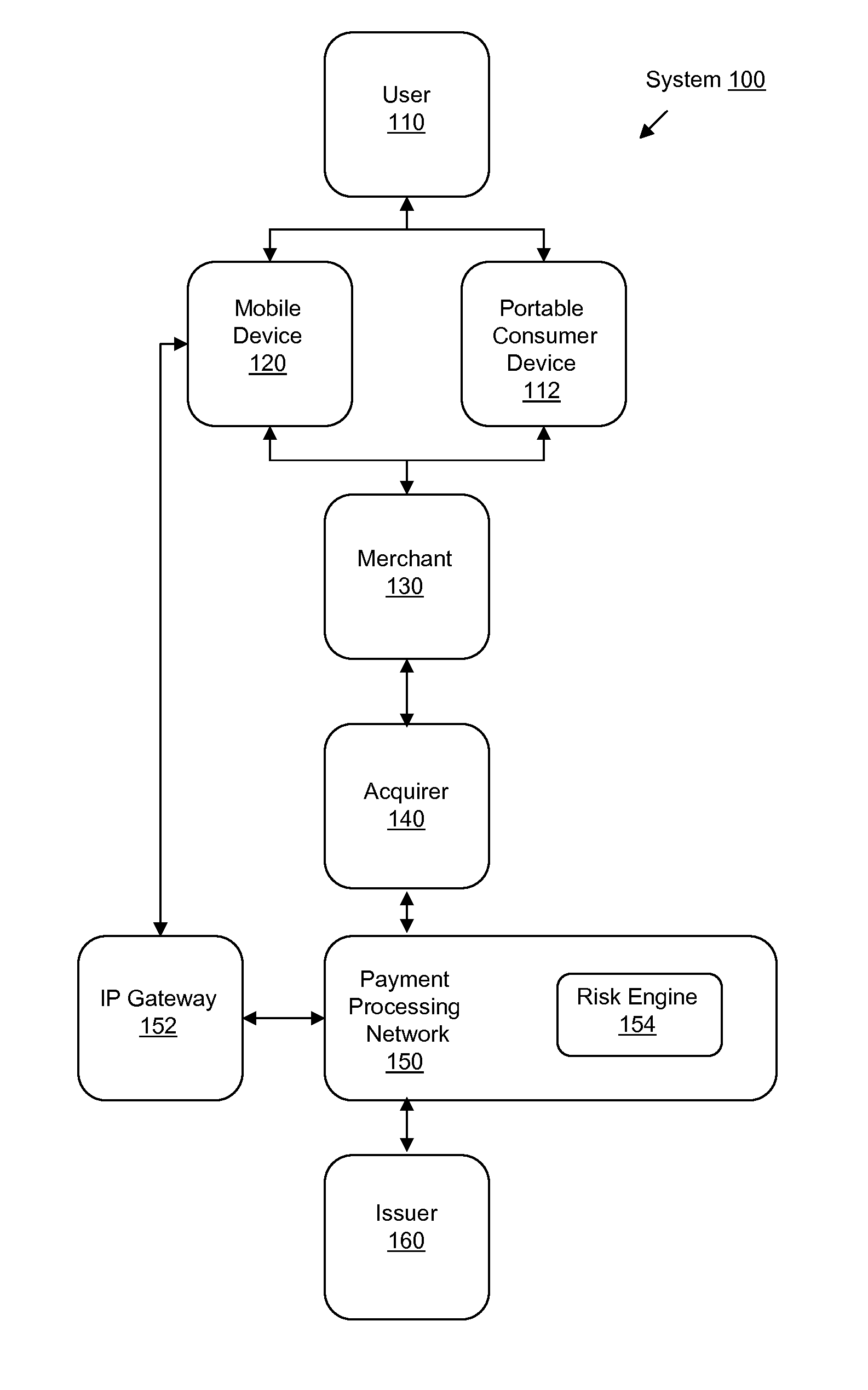
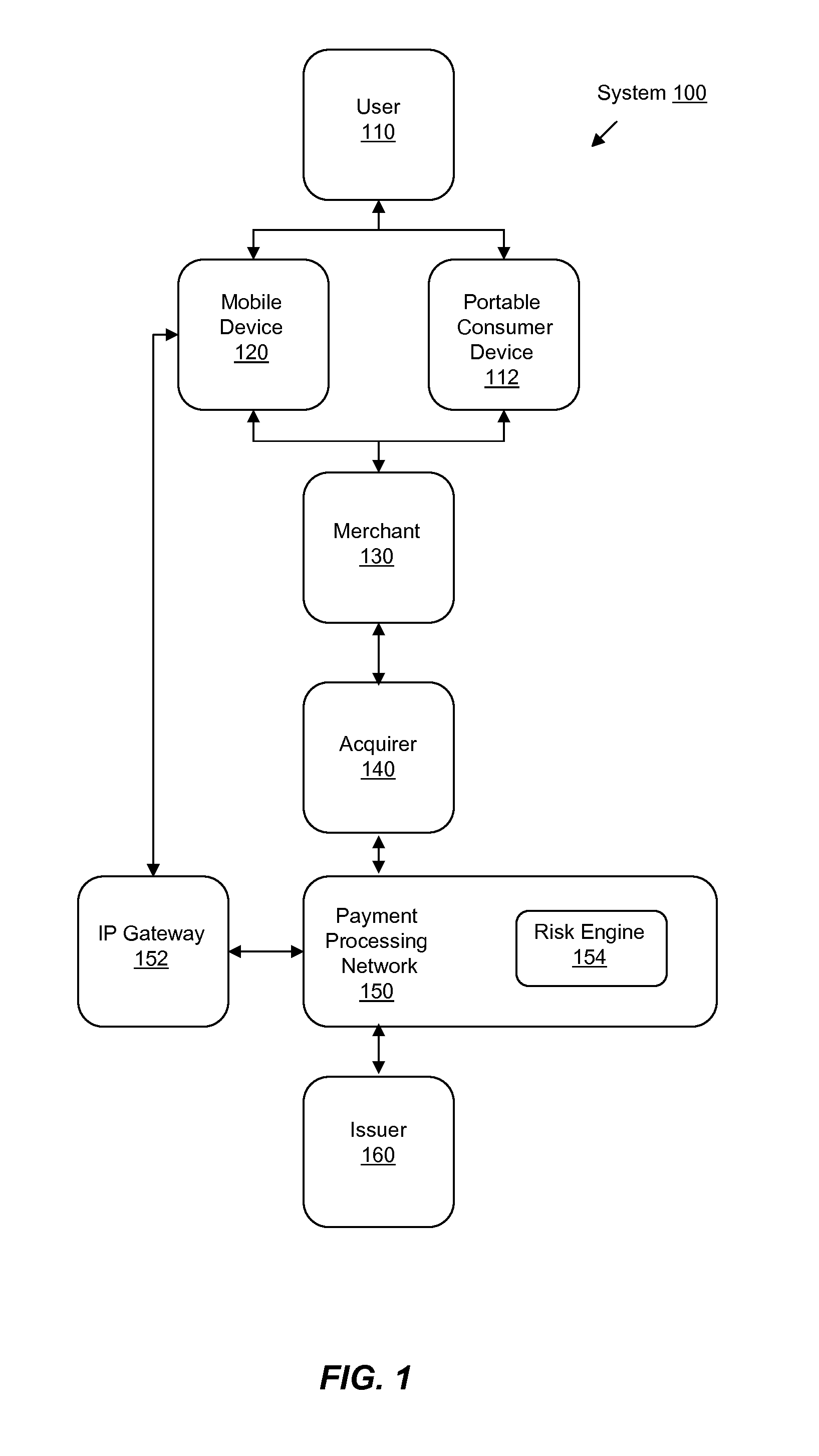
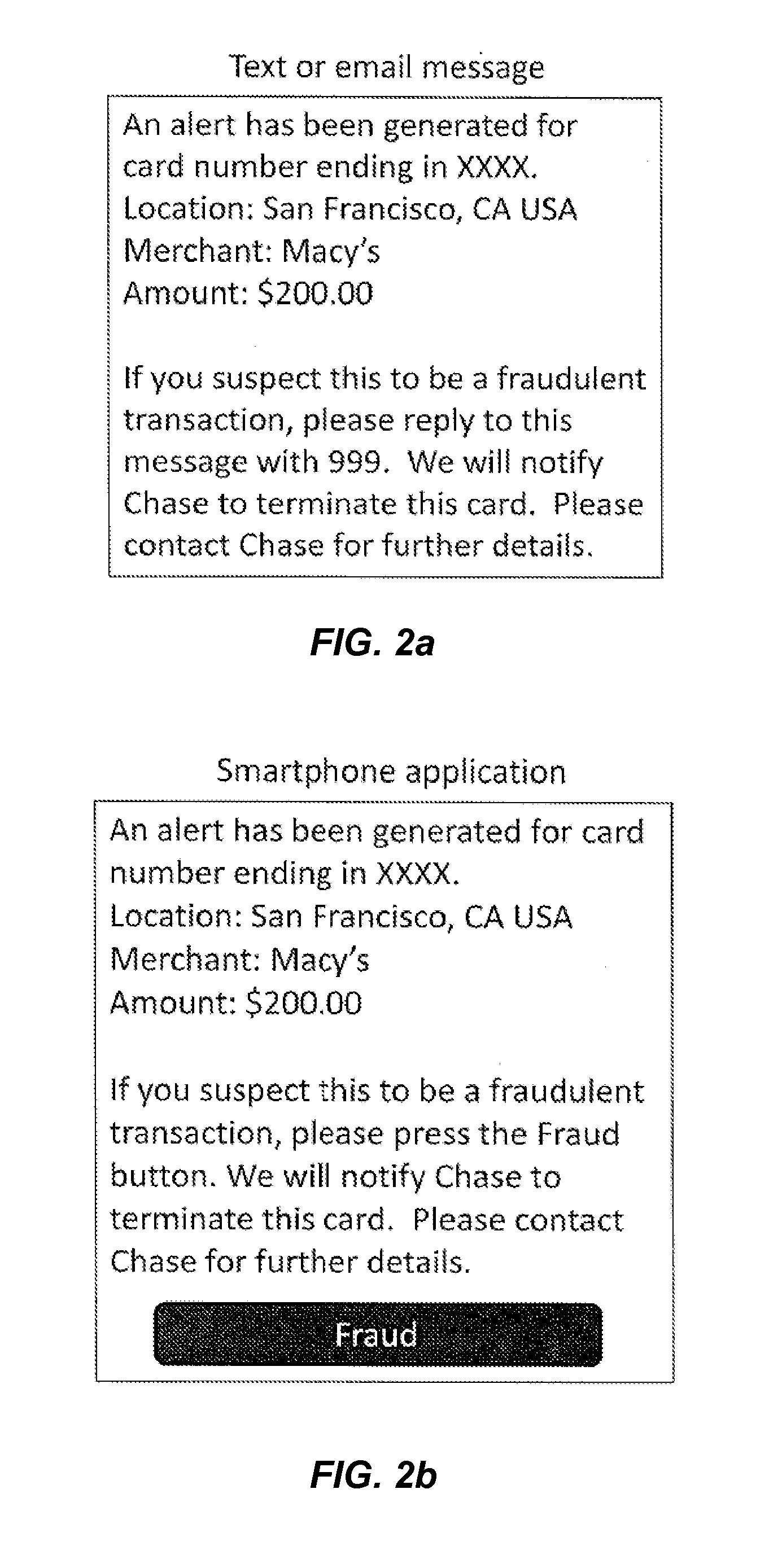
Systems, methods, and computer-readable media are disclosed for improved early detection and alerts related to fraudulent transactions. Certain embodiments involve sending an alert message to a mobile device associated with a portable consumer device. The alert includes notification of a recent transaction related to an account that is associated with the portable consumer device. A reply message is then received in response to the alert message. The response may indicate that the recent transaction is fraudulent. A risk engine is then updated with data associated with the reply message. In one potential additional embodiments, analysis and projections of potential future fraud are created or updated based on the reply message.
Owner:VISA INT SERVICE ASSOC
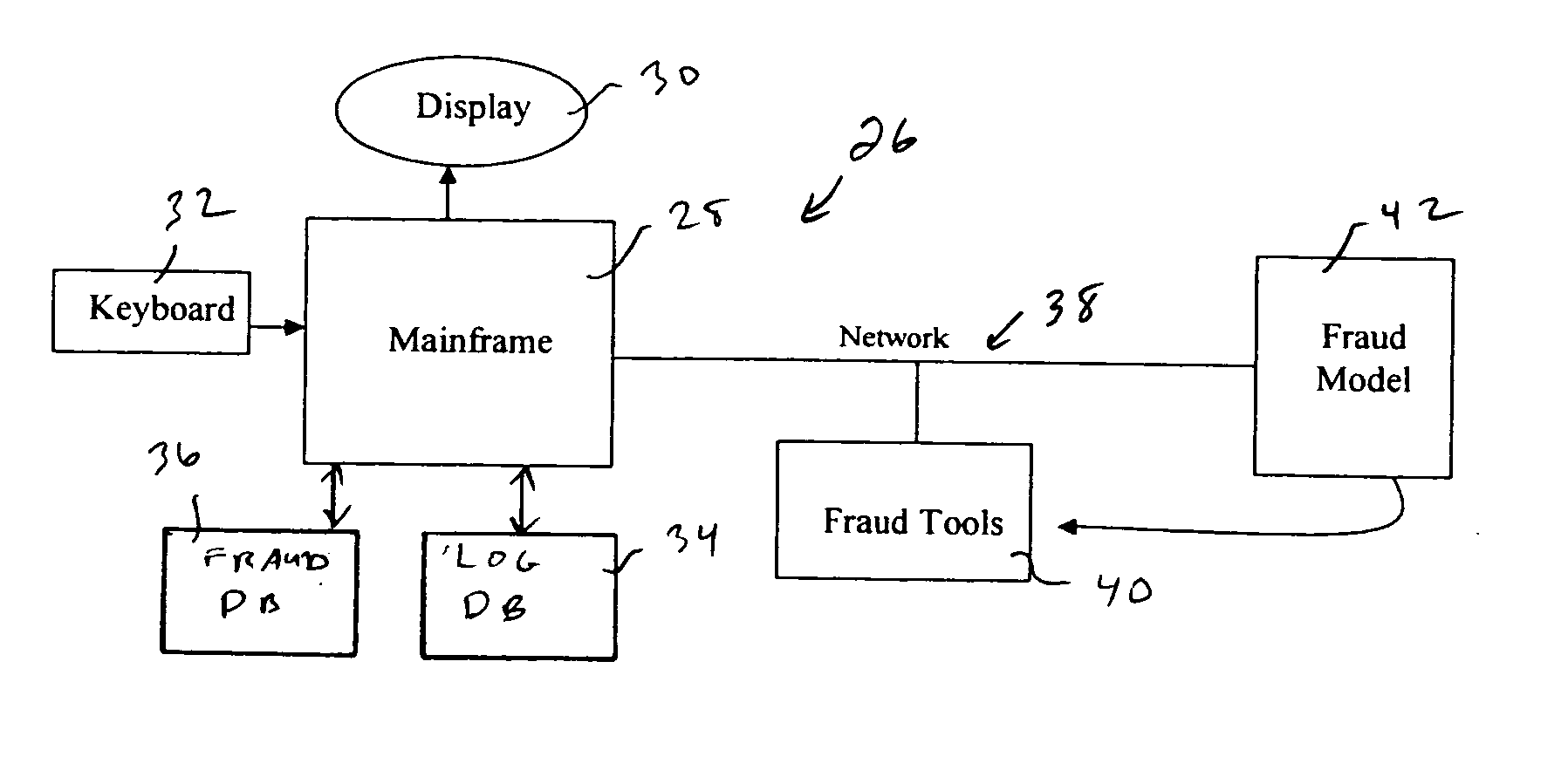
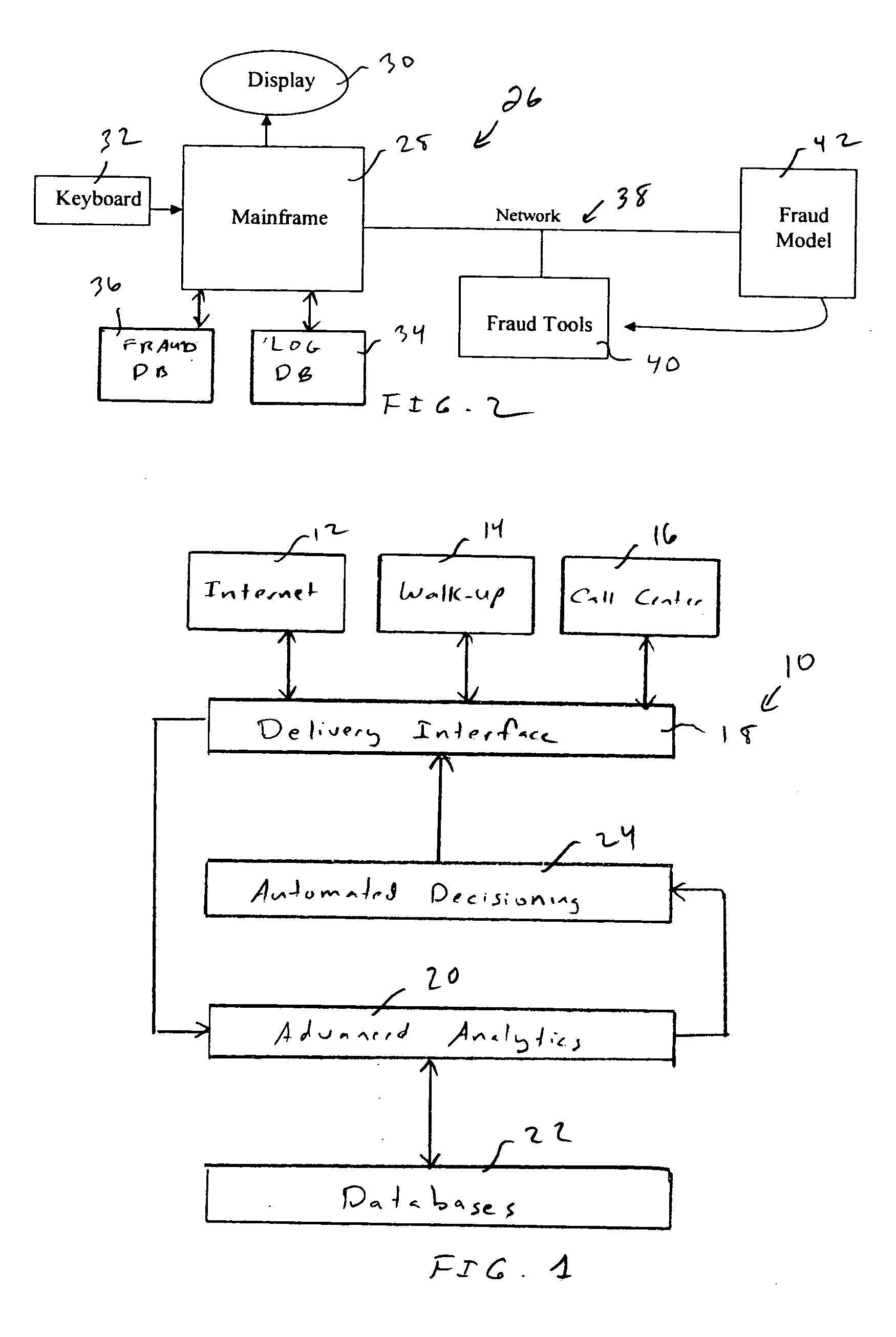
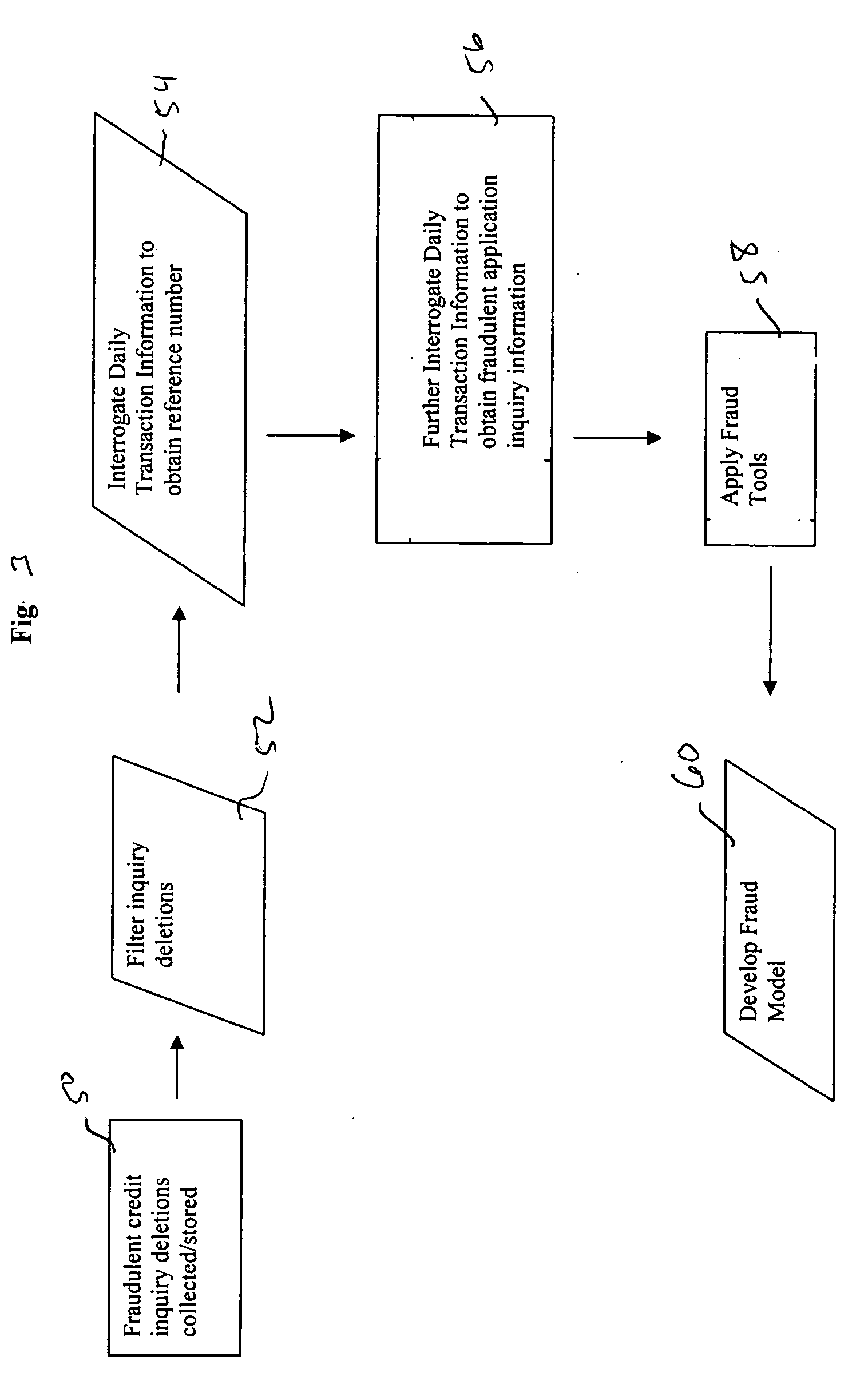
System and method for developing an analytic fraud model
A system and method is provided for developing an analytic fraud model to predict likelihood that a transaction is fraudulent comprising a first database storing a log of credit transaction information comprising requests for credit reports and including application information used by a credit requestor. A second database stores deleted credit inquiries. The deleted credit inquiries comprise fraudulent requests for credit reports. A programmed processing system is operatively associated with the first and second databases and operates in accordance with a sampling program. The sampling program filters the stored deleted credit inquiries for a select period to obtain a sample of fraudulent transactions, obtains select fraudulent credit transaction information from the log for the sample of fraudulent transactions, obtains a sample of random credit transaction information for the select period from the log, and processes the fraudulent credit transaction information and the random credit transaction information to determine characteristics of fraudulent and non-fraudulent application information used by credit requester. A predictive fraud model is developed using the determined characteristics.
Owner:TRANSUNION
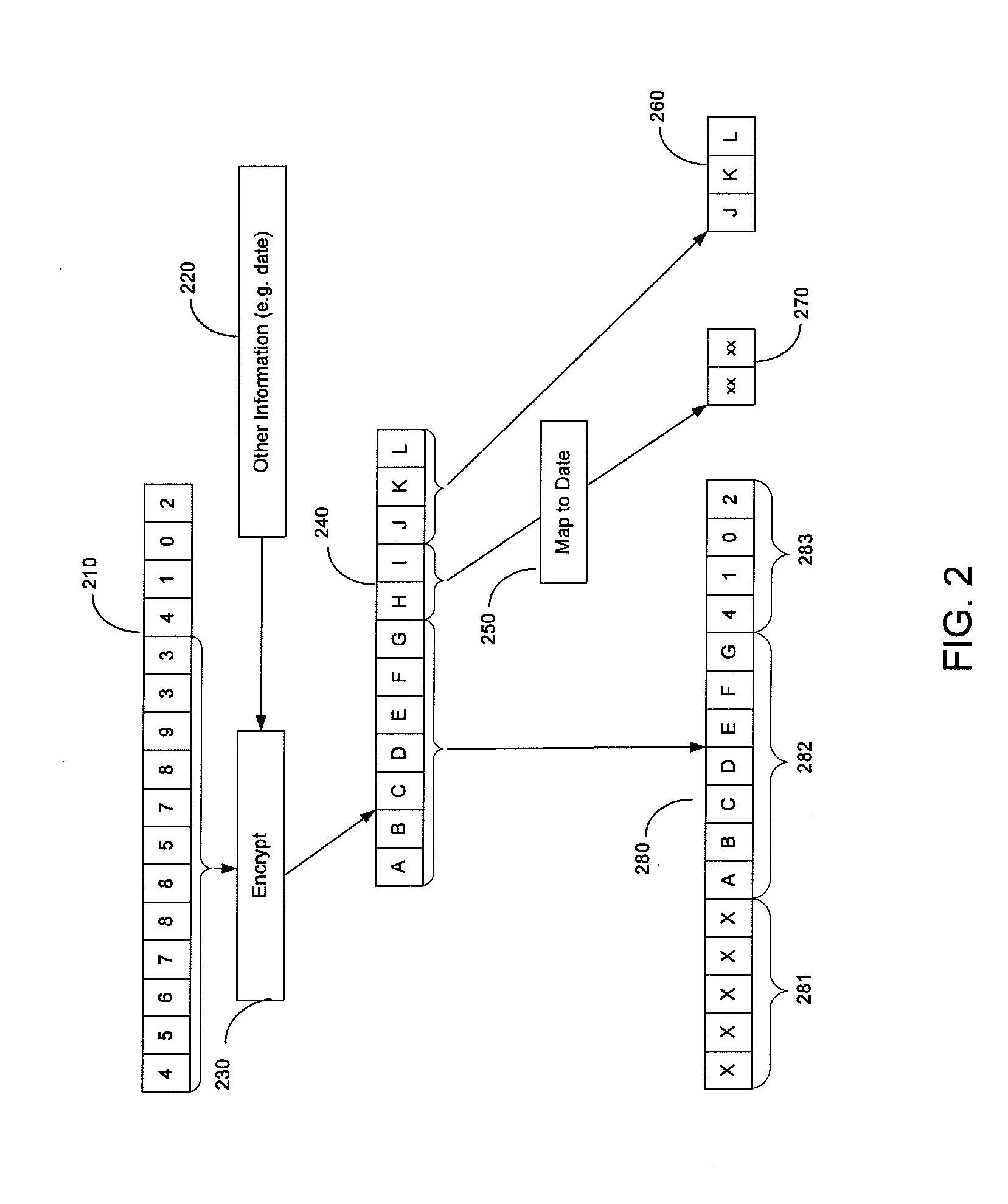
Device including encrypted data for expiration date and verification value creation
ActiveUS20100299267A1Difficult to obtainFinanceUser identity/authority verificationPayment transactionFinancial transaction
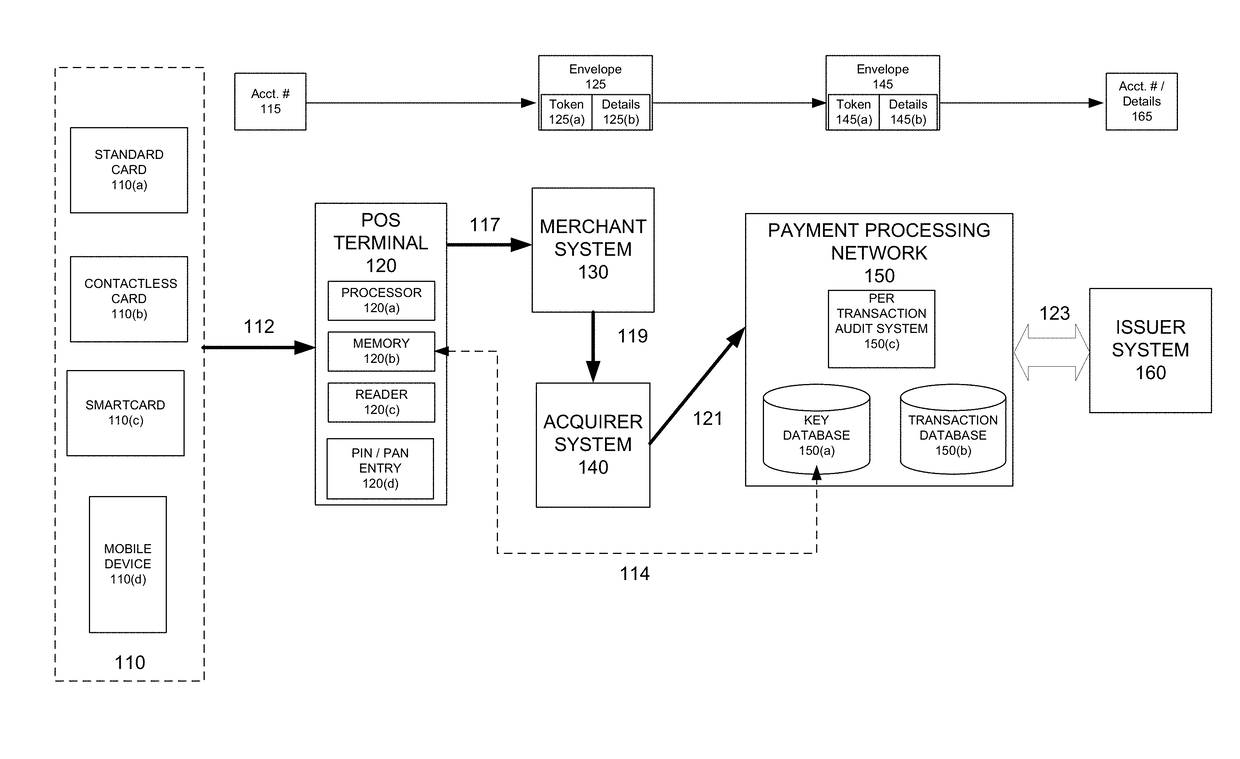
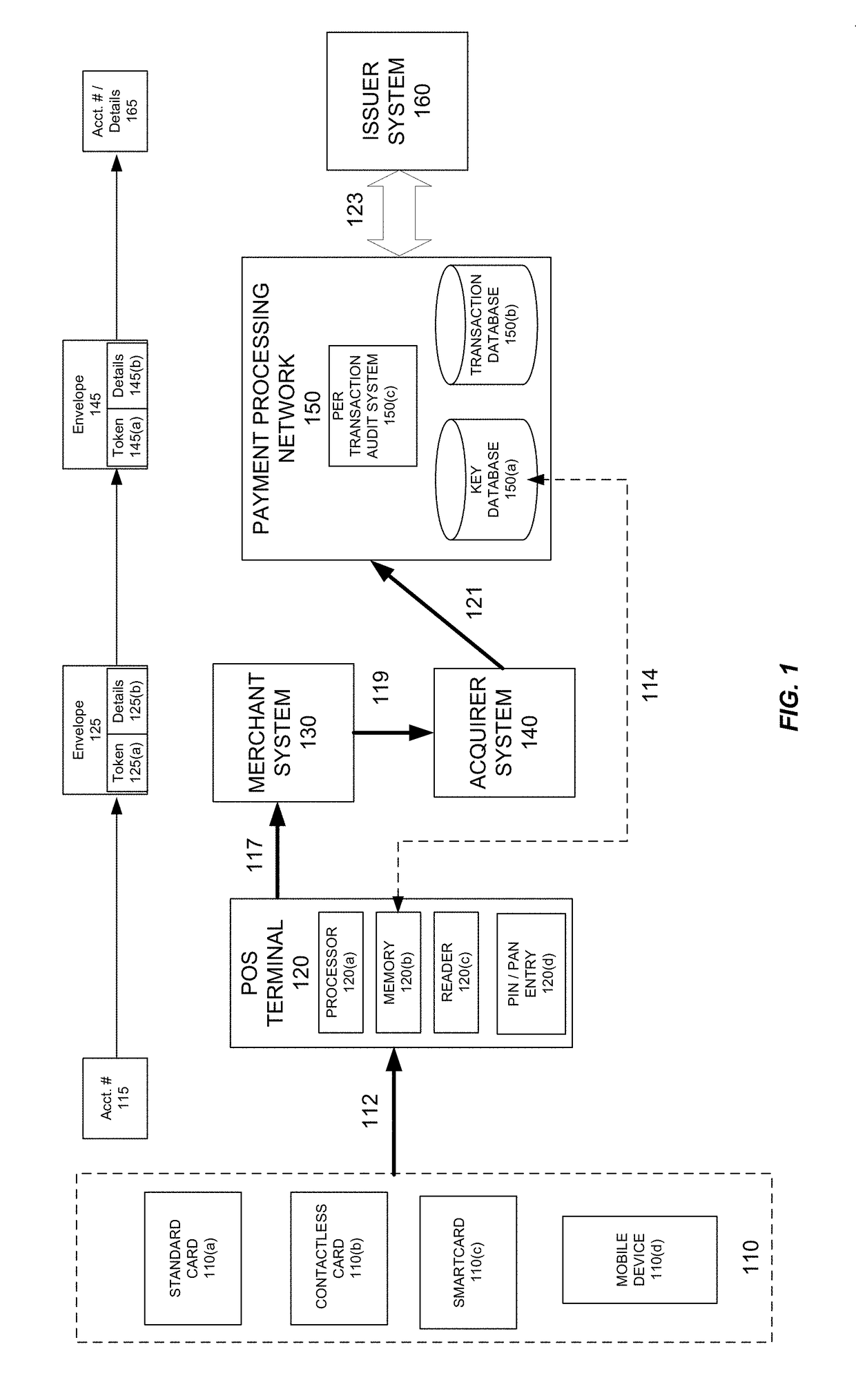
In order to make it more difficult to obtain numbers that can be used to conduct fraudulent transactions, a portion of a real account number is encrypted. The encrypted portion of the account number is used to generate a new account number, a new expiration date, and a new verification value. This information can be determined using processor that may reside in a point of sale terminal, a smart card, or a computer operated by a user. The new account number, the new expiration date, and the new verification value can be used in a payment transaction. A server computer in a central payment processing network may determine that the new account information is not the real account information, and may subsequently generate a modified authorization request message using the real account information and may send it to an issuer for approval. The transmission of data is more secure, since real account information is not sent from the merchant to the payment processing network.
Owner:VISA INT SERVICE ASSOC
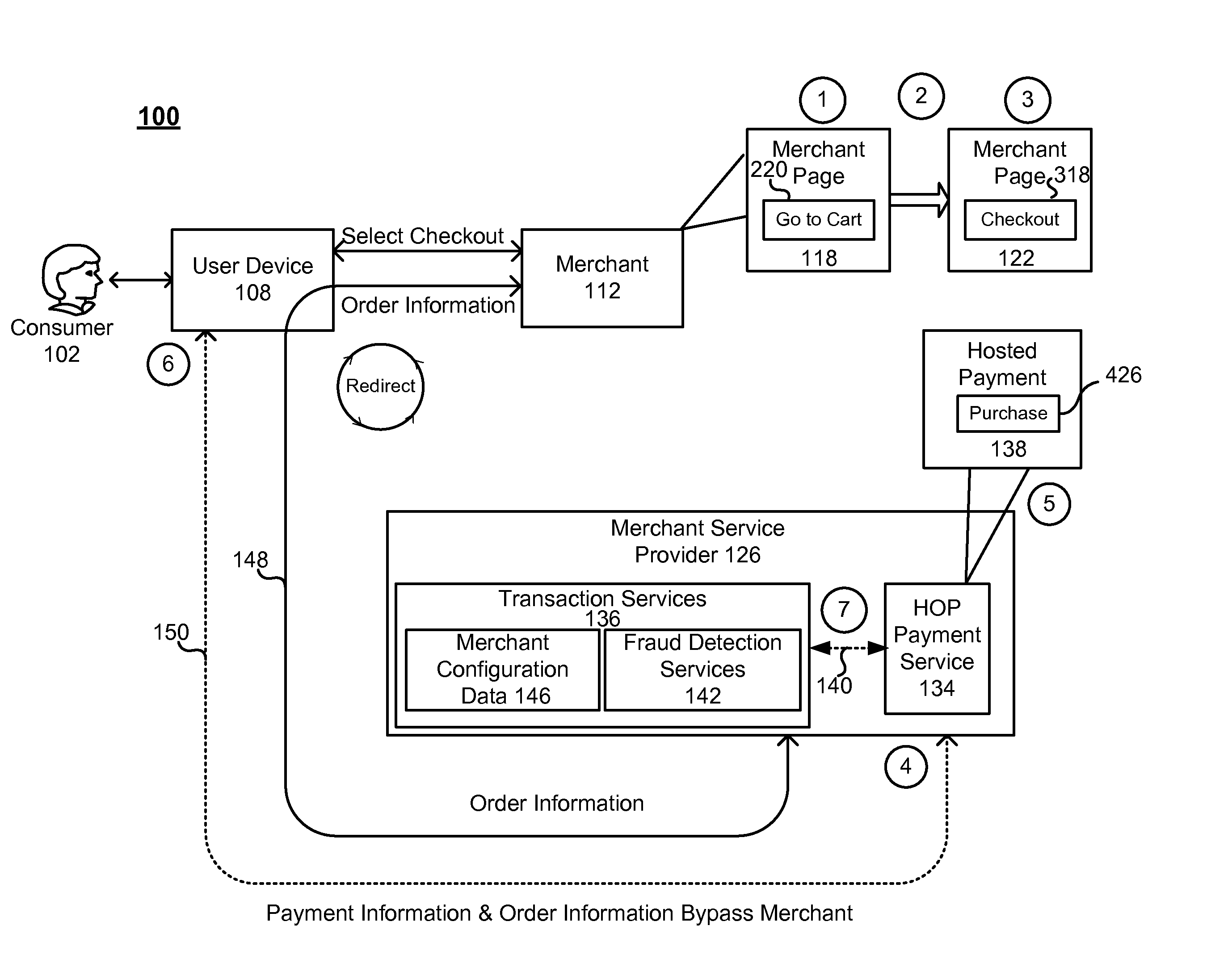
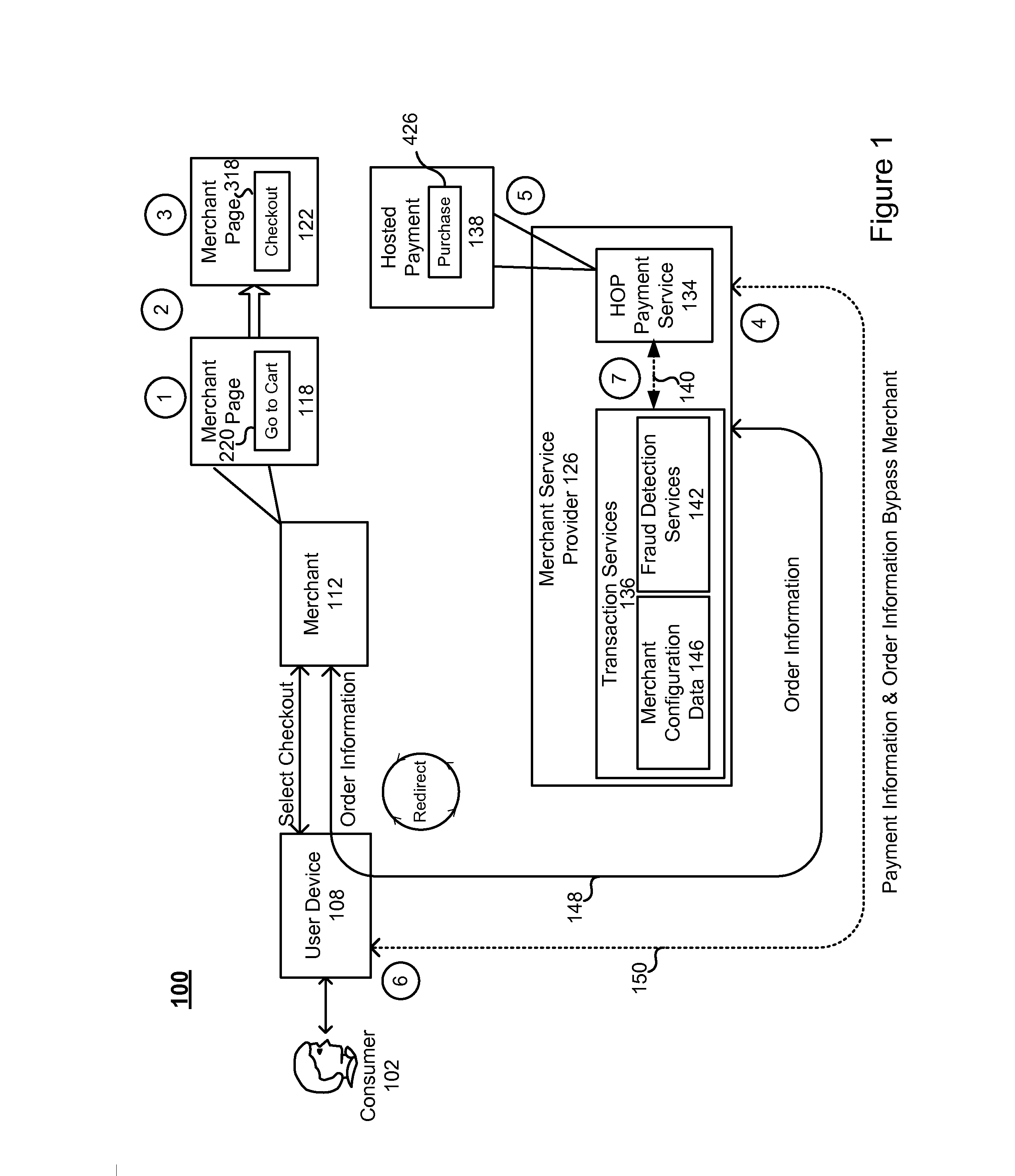
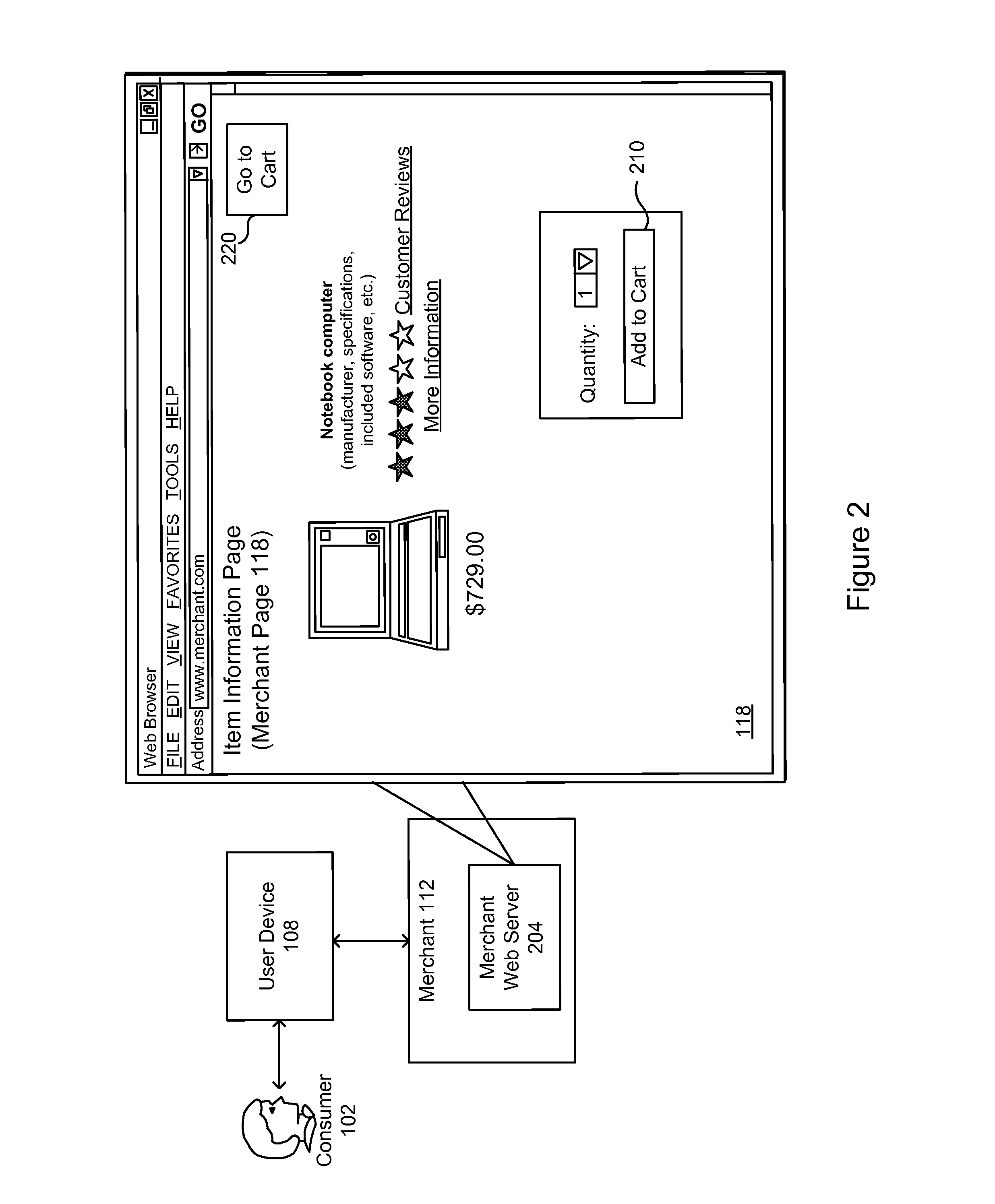
Hosted order page/silent order post plus fraud detection
ActiveUS20130018757A1Low costBuying/selling/leasing transactionsProtocol authorisationPaymentThird party
Generally, embodiments of the invention are directed to methods, computer readable medium, servers and systems for enabling merchants to use hosted order pages (HOPs) and / or silent order posts (SOPS) and thereby avoid handling payment information and the costs associated Payment Card Industry (PCI) compliance, while at the same time utilize third-party fraud detection screens and thereby avoid costs associated with fraudulent transactions.
Owner:VISA INT SERVICE ASSOC
Systems and methods for determining regulations governing financial transactions conducted over a network
Various embodiments of the invention provide a more secure financial transaction system for e-commerce sectors that (1) more securely processes payment transactions, (2) helps to protect merchants and banks against fraudulent transactions, money laundering, and underage gambling, and (3) helps to limit other abuses in areas of e-commerce that are perceived to pose special risks, such as Internet gaming, travel, and consumer purchasing of electronic goods. To accomplish the above goals, various embodiments of the financial transaction system (1) establish operating and transaction processing protocols for merchants, Internet payment service providers, acquiring banks, and card schemes and (2) provide automated systems for monitoring and securely processing payment and financial transactions.
Owner:TILLY BAKER +1
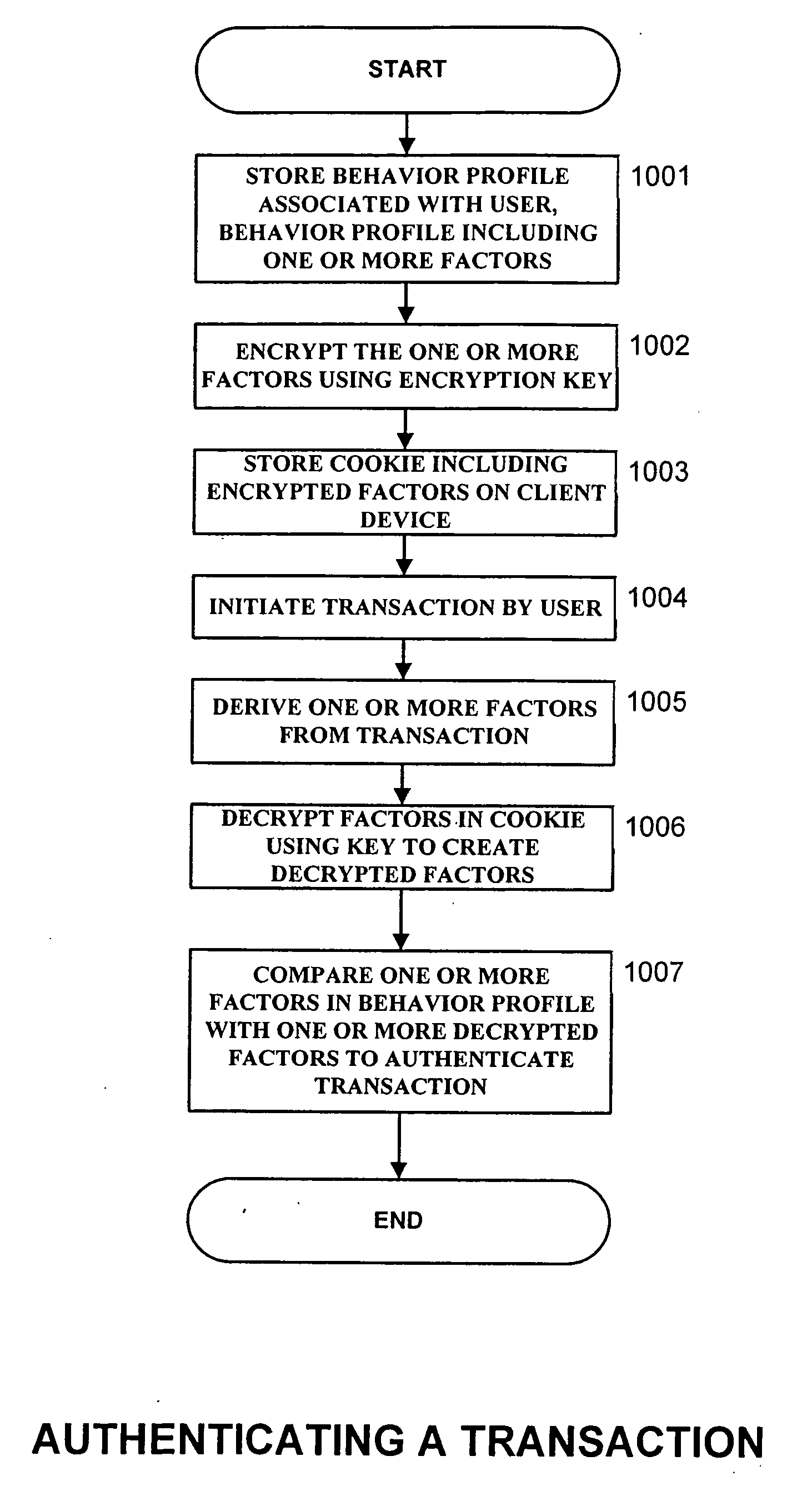
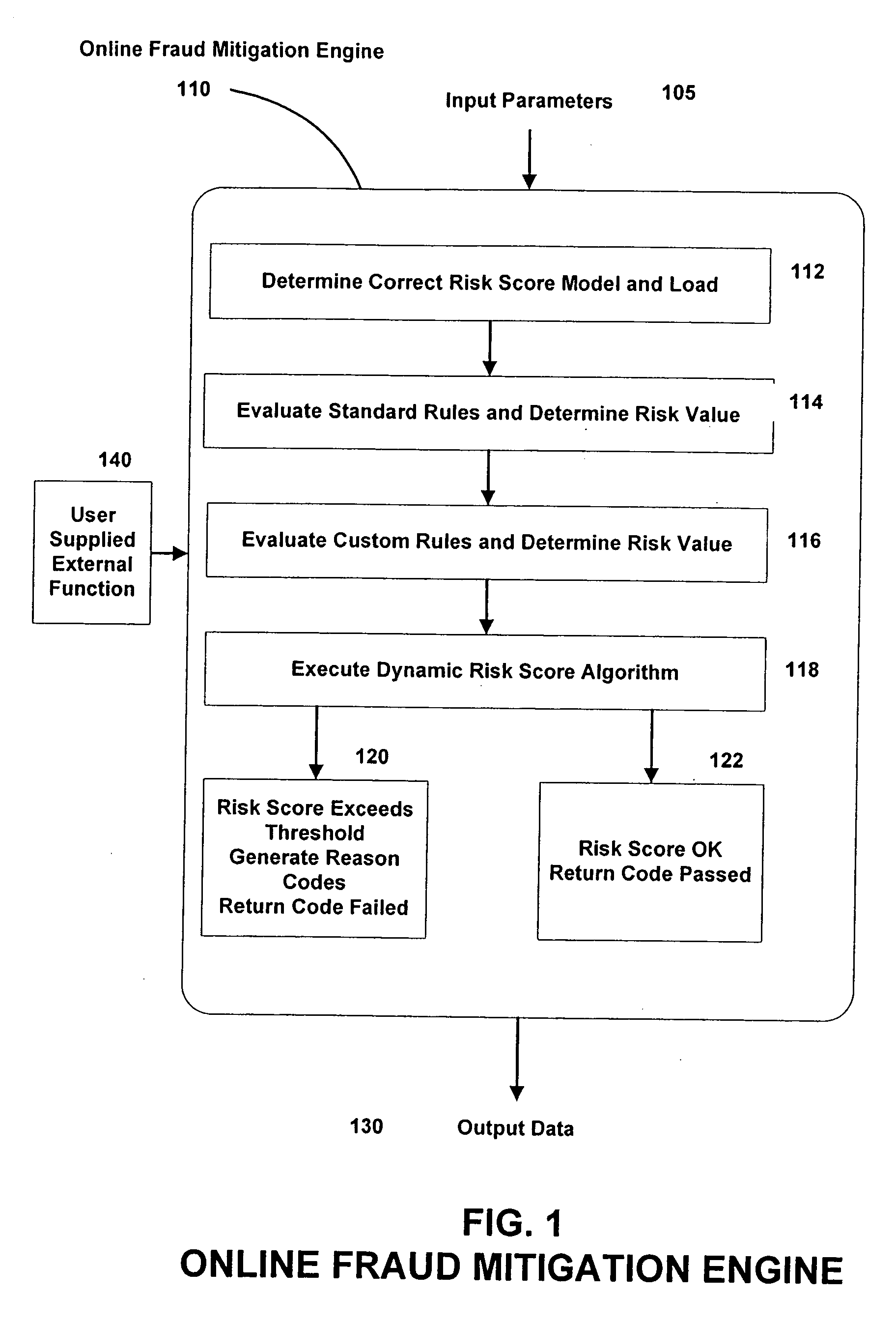
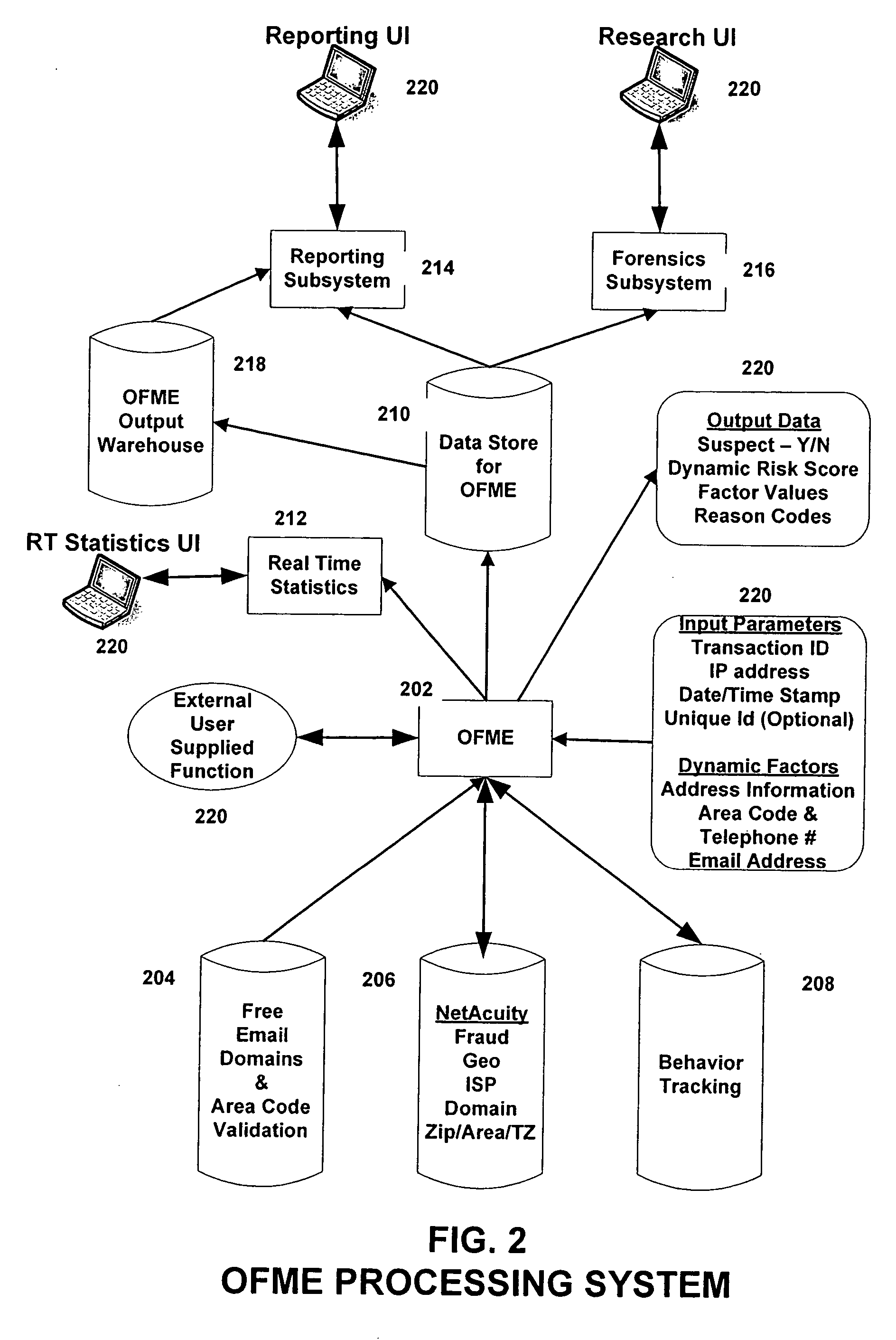
Authentication Proxy
InactiveUS20080010678A1Multiple digital computer combinationsProgram controlInternet privacyObject store
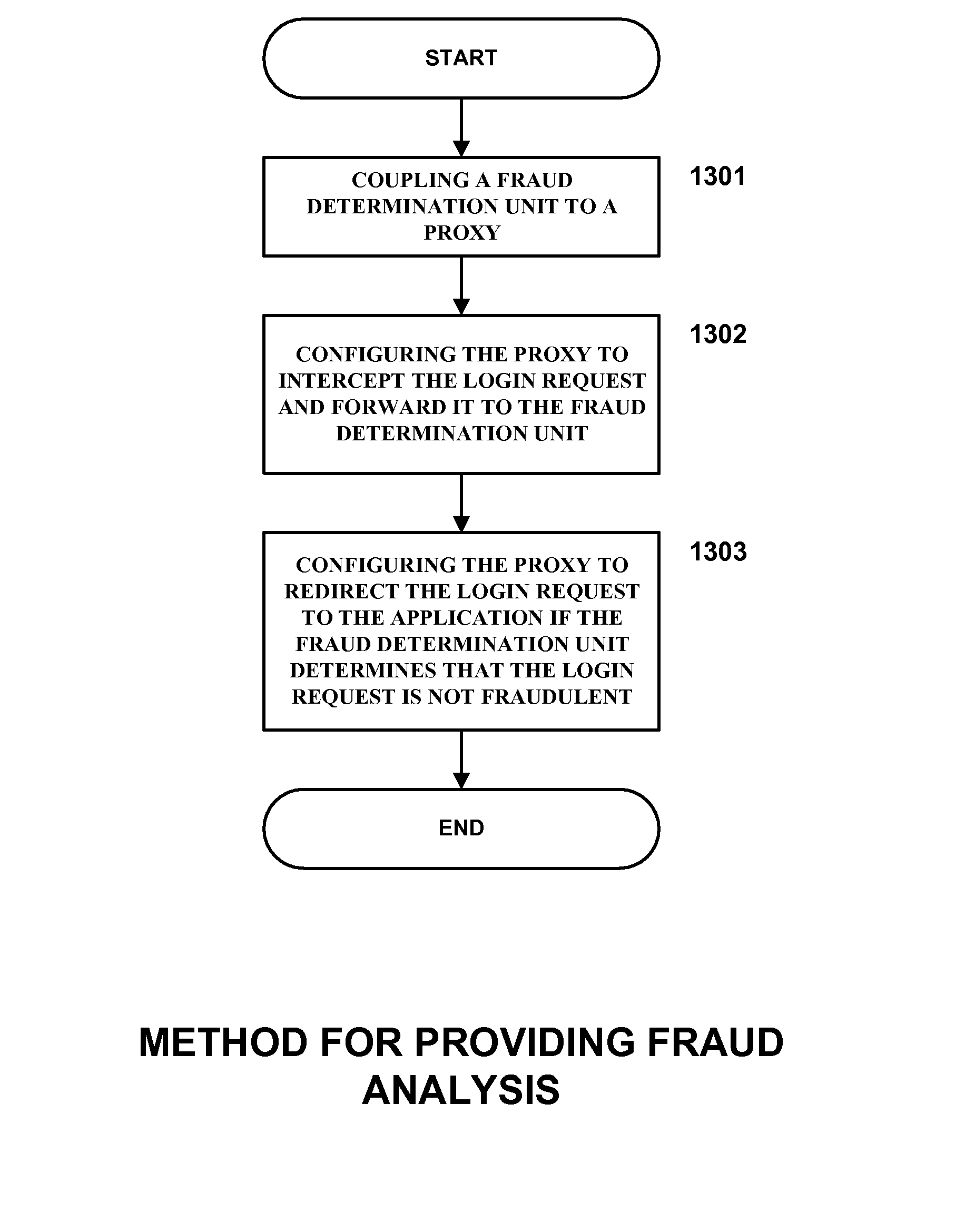
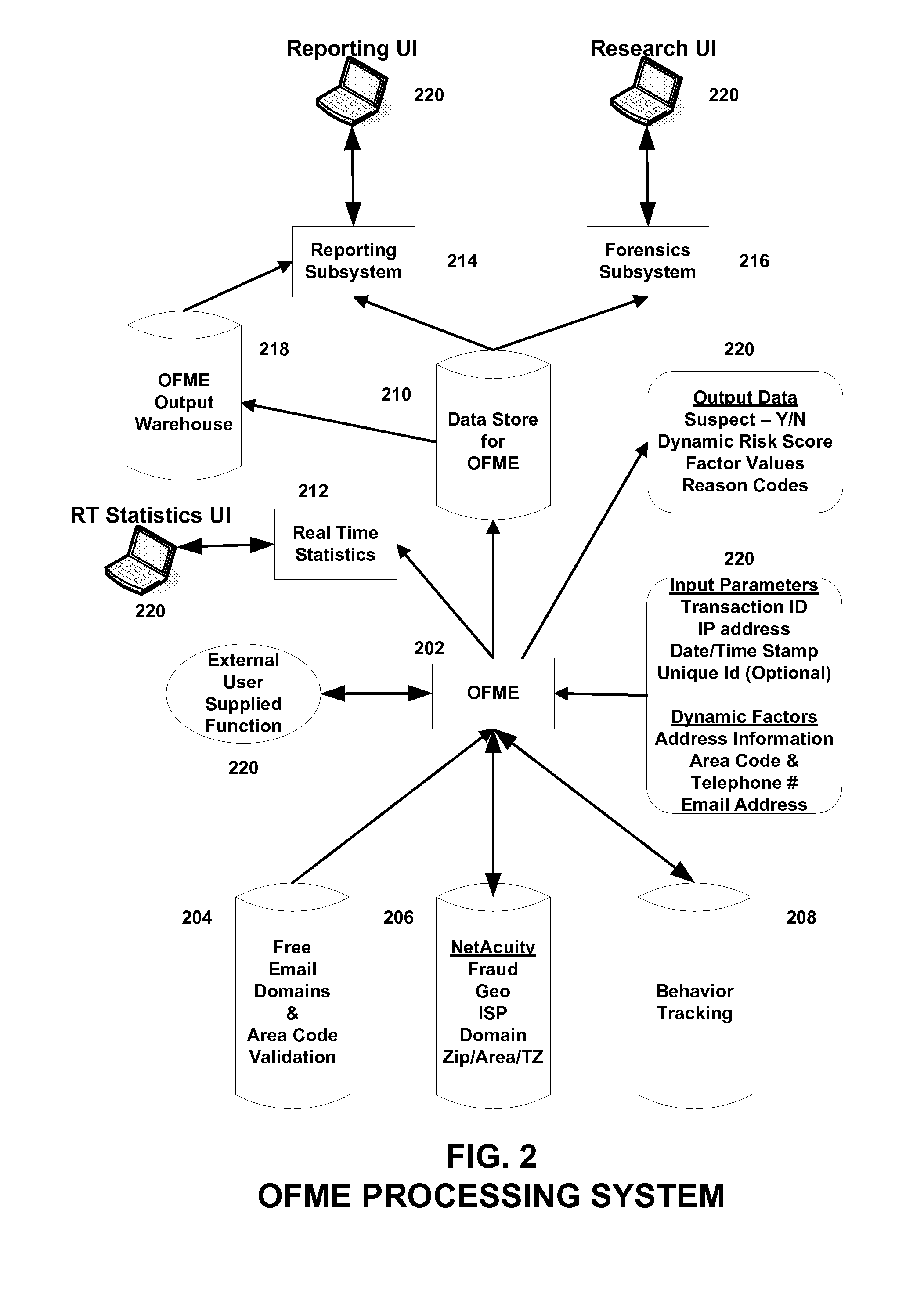
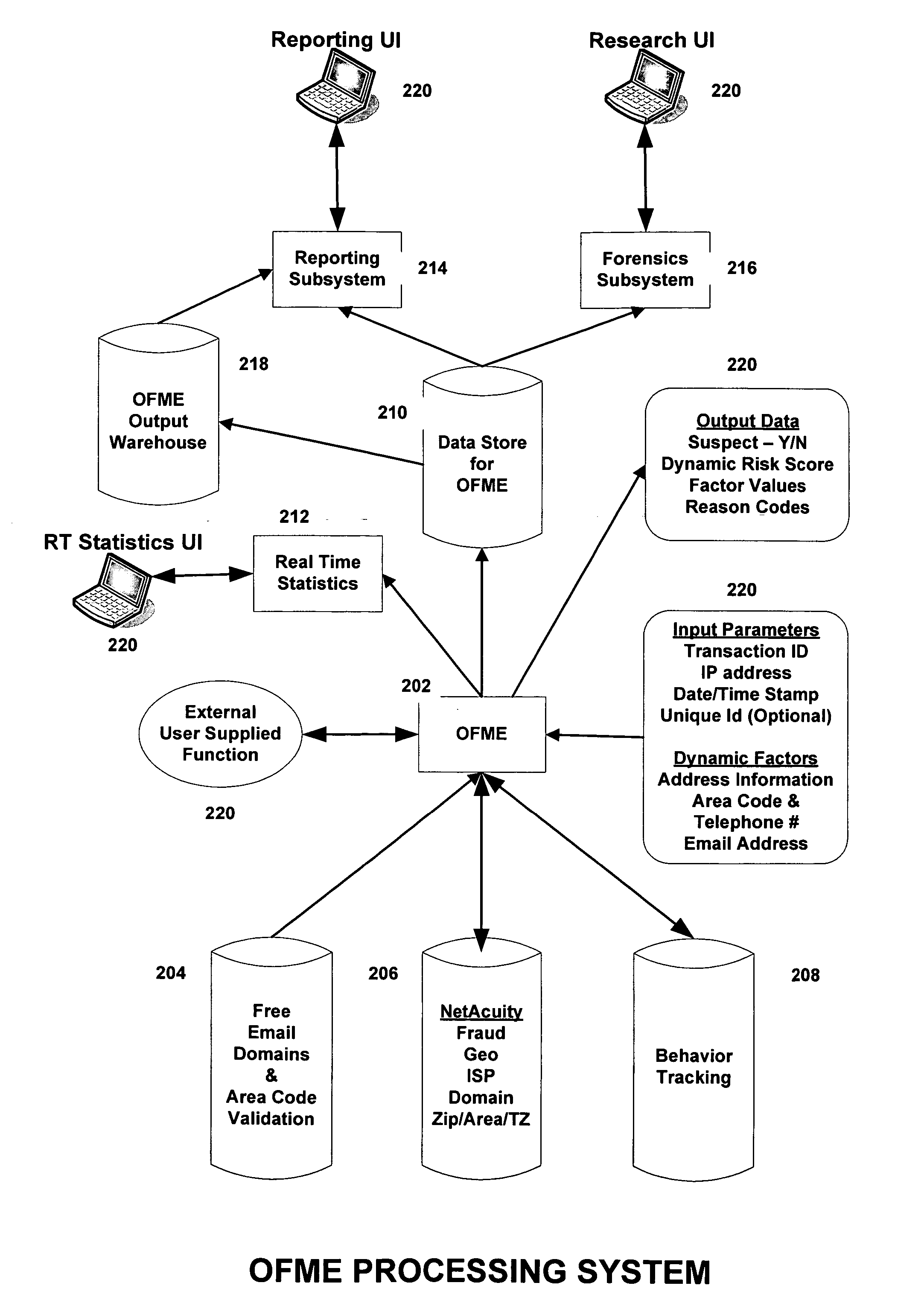
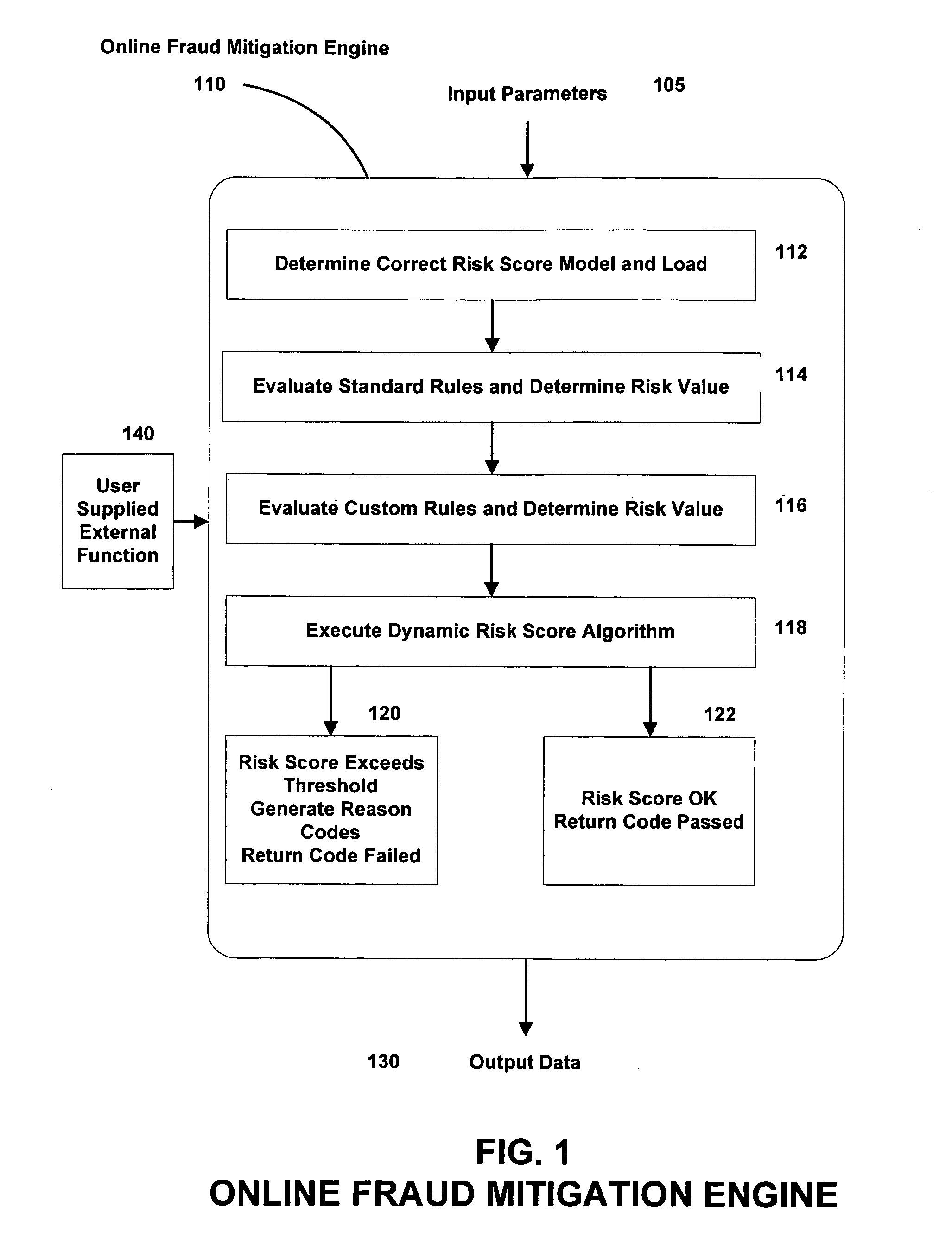
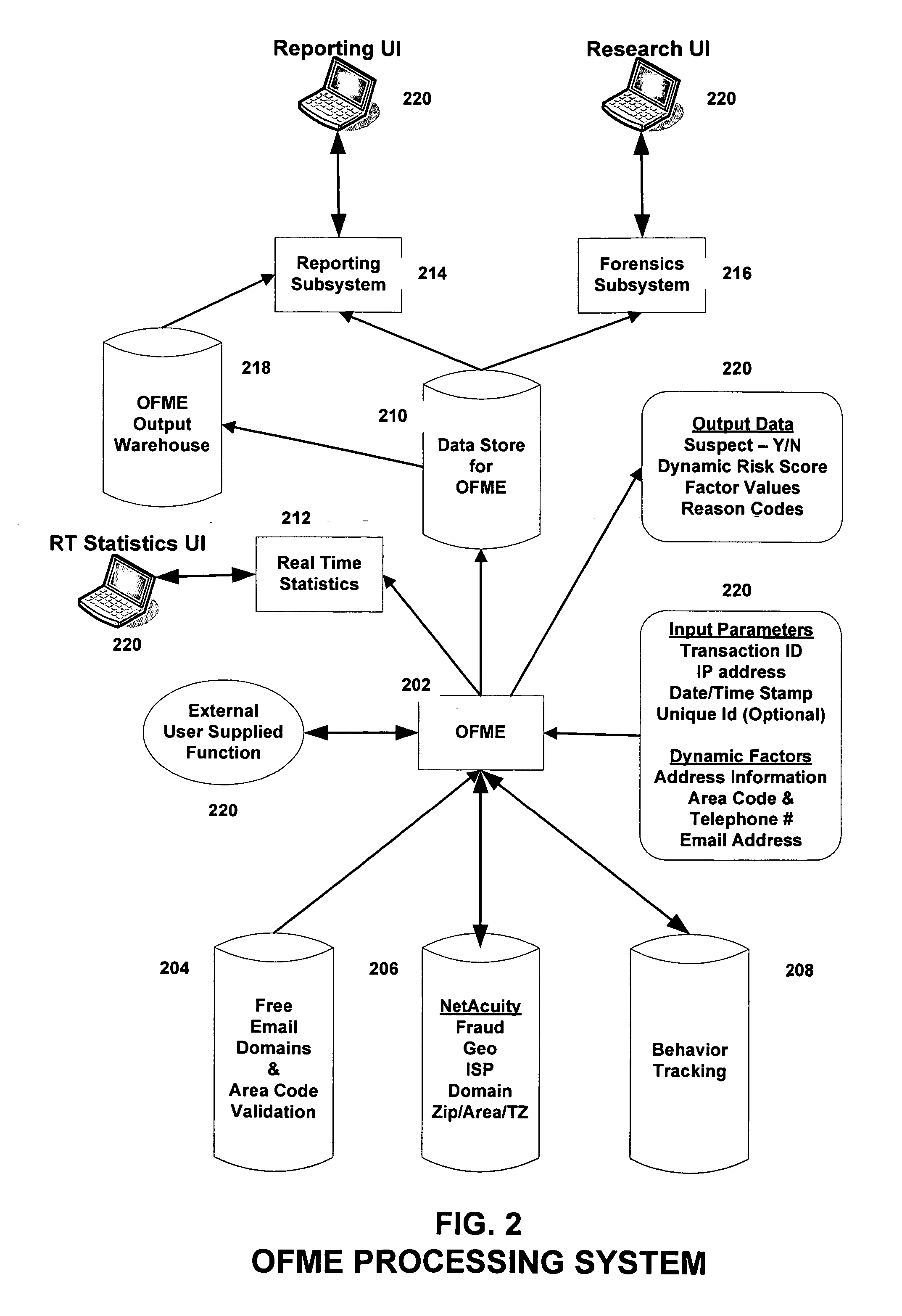
Systems, methods, and computer program products for providing fraud analysis to an application using a proxy and a fraud determination unit are provided. An Online Fraud Mitigation Engine is also provided in embodiments of the present invention for determining fraudulent transactions. Embodiments are also provided for calculating travel velocity and transaction frequency, which are useful for determining a fraudulent transaction. Further embodiments are provided for authenticating a transaction using an object stored on a client device and a behavior profile stored on a server.
Owner:DIGITAL ENVOY
Fraud prevention and replacement of credit/debit cards - lost, stolen, defective or fraudulently used
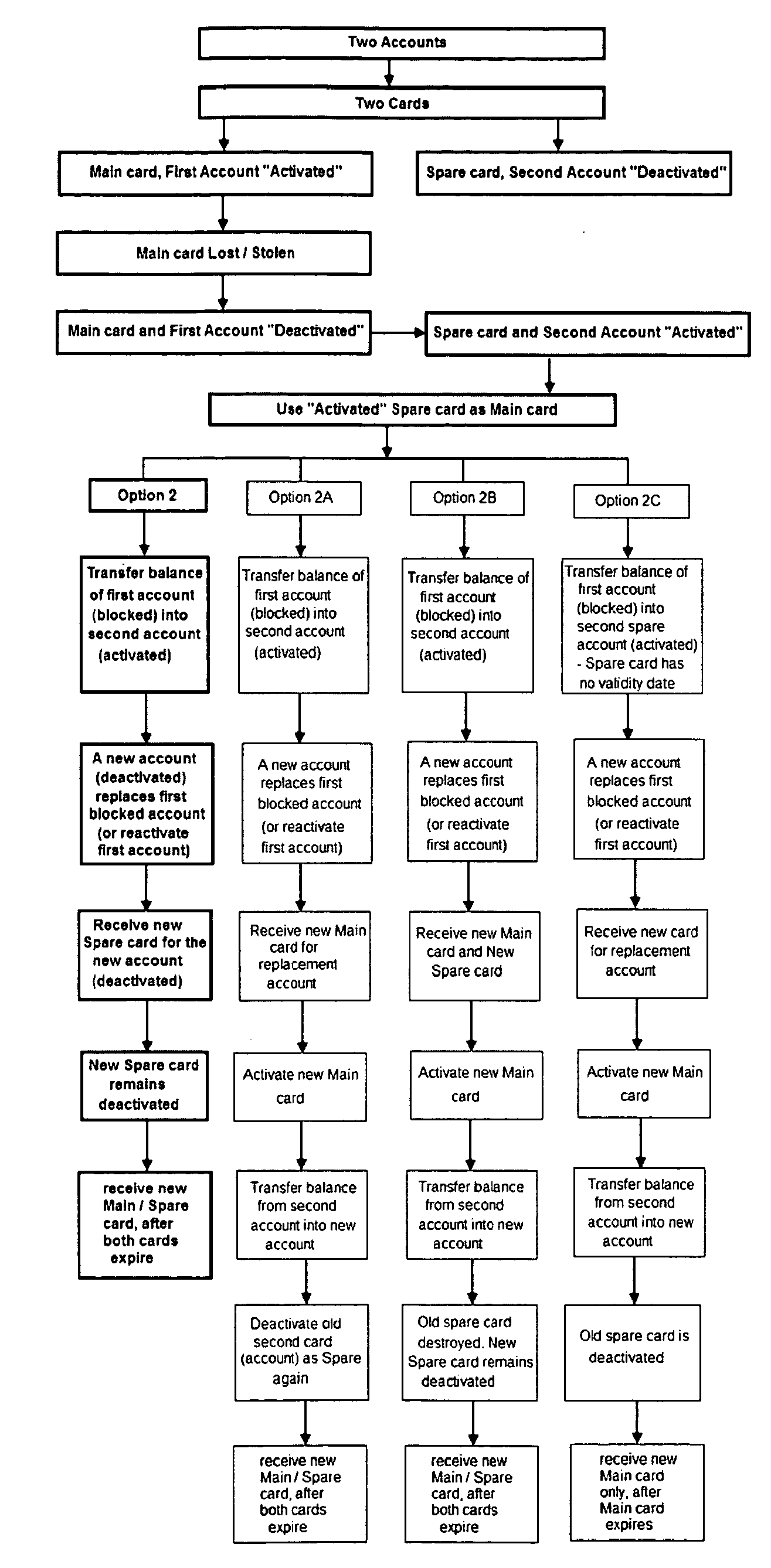
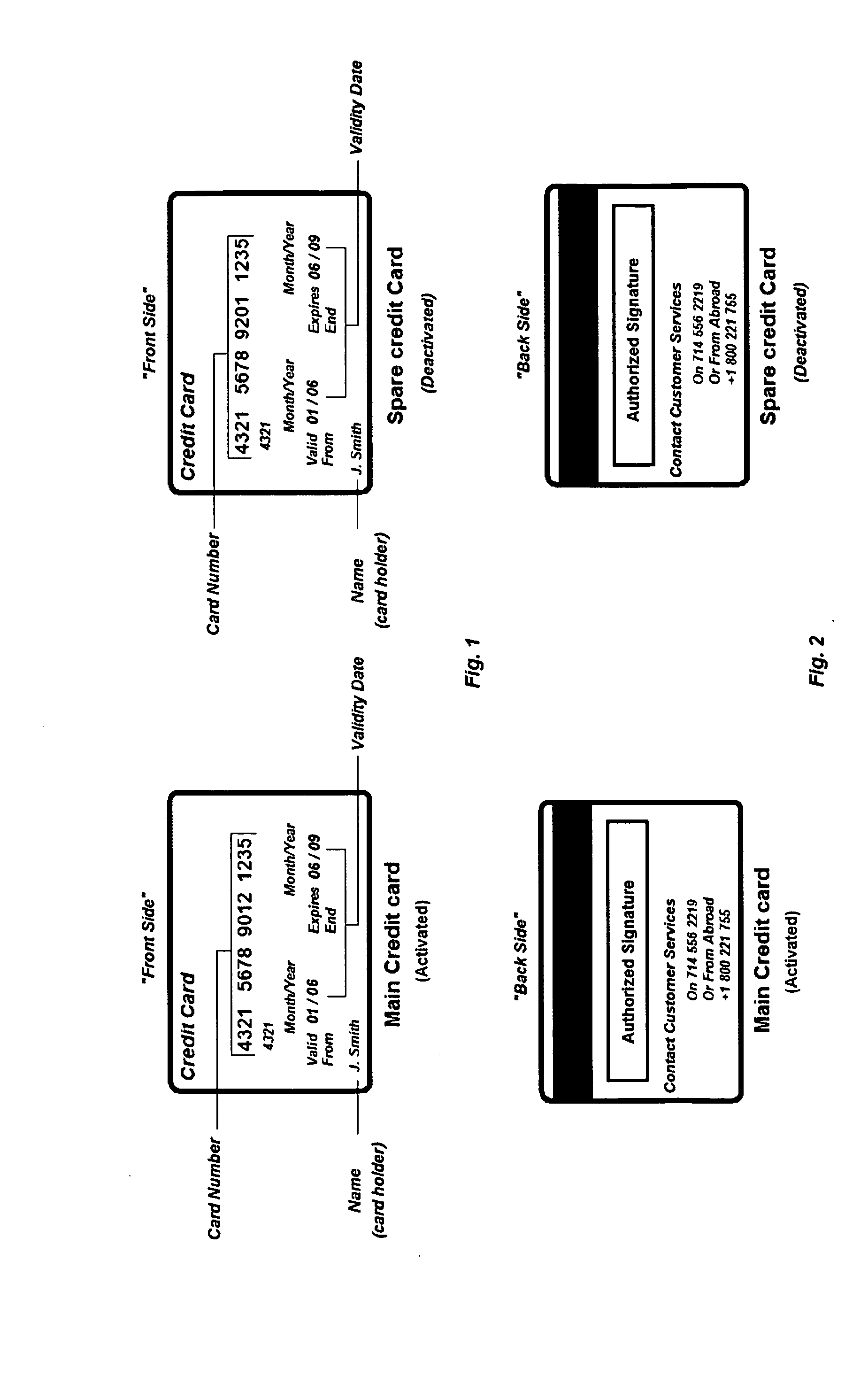
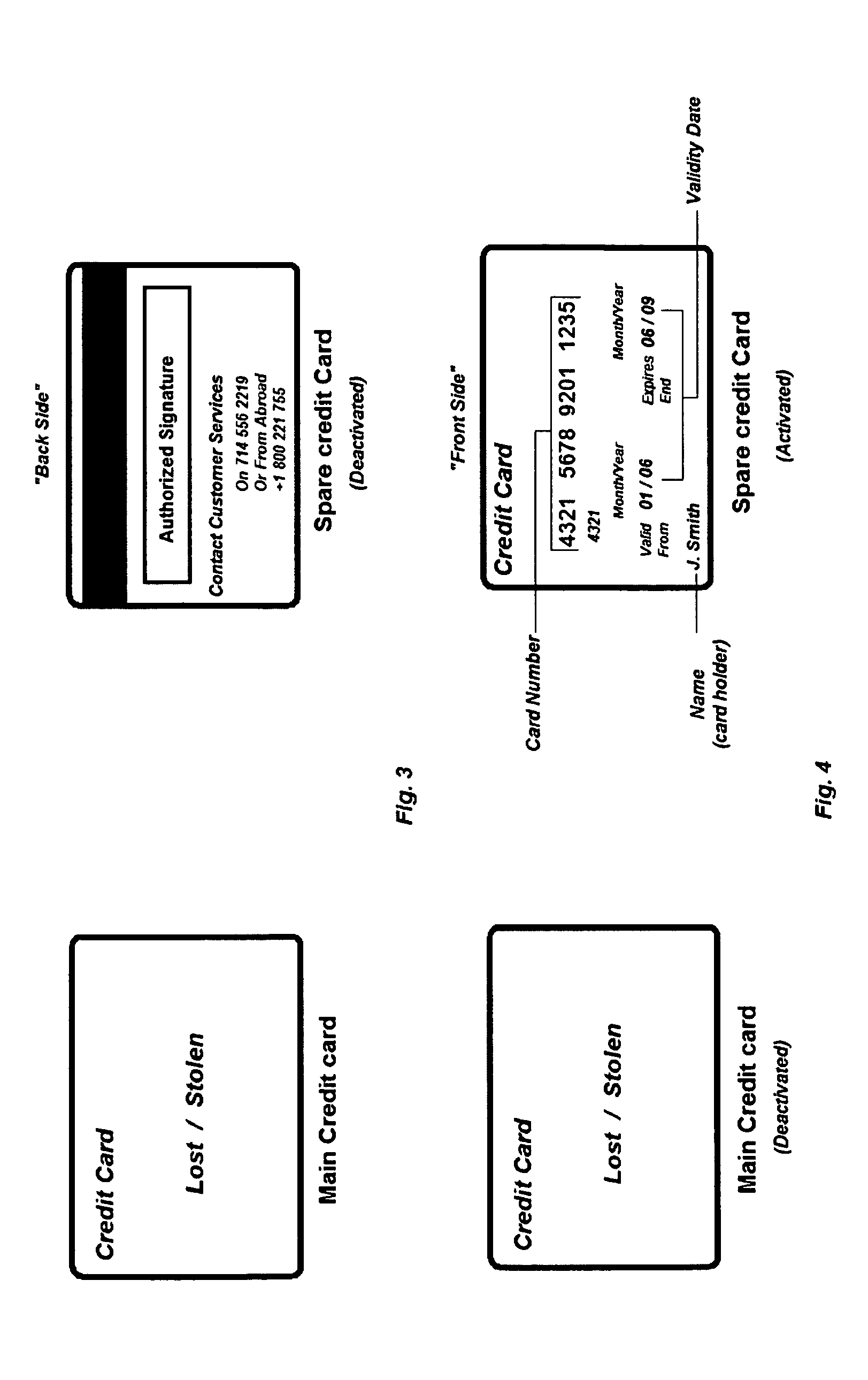
A credit card security system method for preventing fraudulent use, comprising the steps of a credit card provider opening one account with two different card numbers, with a first “main credit card” and a second credit card for a spare. The main credit card is activated by the provider and the spare credit card remains “deactivated”. On a pre-set time basis the credit card provider will automatically upon notice to the customer, deactivate the main card and activate the spare card. If any suspicious or fraudulent transaction is detected by the credit card provider, the main credit card is deactivated. If the transaction is authorized, then the main credit card is re-activated. If the transaction is not authorized, the spare credit card is activated to be used as the main credit card. The credit card provider then replaces the deactivated credit card with a new number and sends a new credit card with the new credit card remaining deactivated.
Owner:MELIK ASLANIAN STEFAN +1
Remote check deposit
InactiveUS20060242062A1Easy to optimizeConvenient truncationFinancePayment circuitsDocumentation procedureSubstitute check
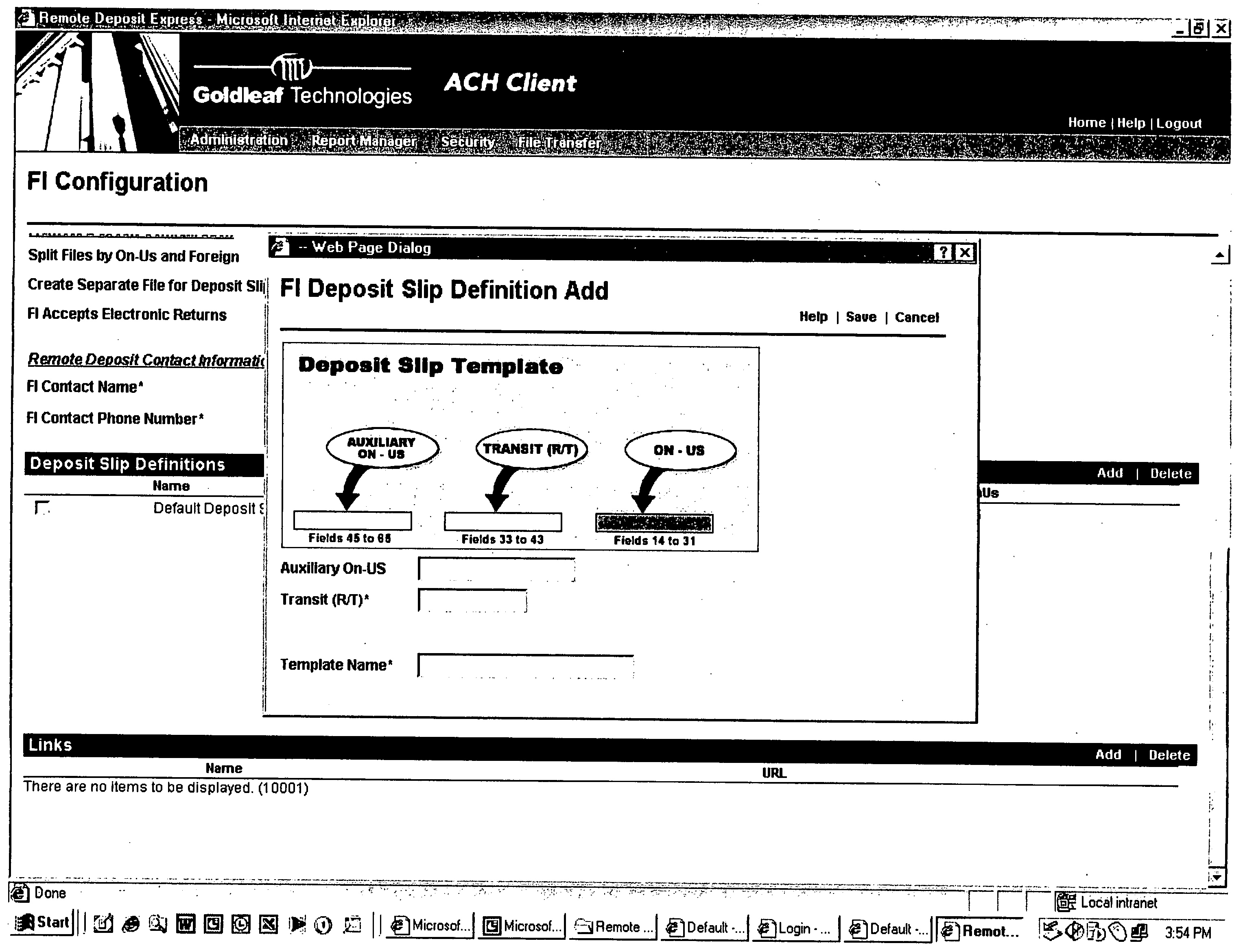
In accordance with the principles of the present invention, a system is provided for capturing a customer deposit at their place of business, converting the Magnetic Ink Character Recognition (MICR) data encoded documents into an image with an associated data file, and electronically transmit the data to a financial institution. The system allows the customer to scan each MICR encoded check that is to deposited with their financial institution, which captures financial institution routing information and customer account information. The associated image the physical check can be franked denoting the check has been electronically processed to avoid further processing. The resulting image and account data can then be processed by the financial institution. There are three options for encoding the amount: 1) the customer enters each amount after scanning the item prior to sending to the financial institution; 2) the financial institution enters the amount of each item after receiving the file from the customer; and 3) the amount field(s) are scanned and the amount is automatically entered. The system allows for both 1) online (Internet) capture of the MICR data and the associated image or 2) offline capture and the subsequent importing of the image and MICR data for transmission to the financial institution via the Internet. The financial institution can review the items captured online, and repair any item that is incorrect. The financial institution can use the system to print substitute checks that confirm to ANSI X9.90 for processing or deliver an electronic file in ANSI X9.37 format to any check processing system. The system includes secure transport over Internet connections for file transfer and dual control security to reduce fraudulent transactions from being initiated by the customer.
Owner:GOLDLEAF TECH
Method and System for Identifying Users and Detecting Fraud by Use of the Internet
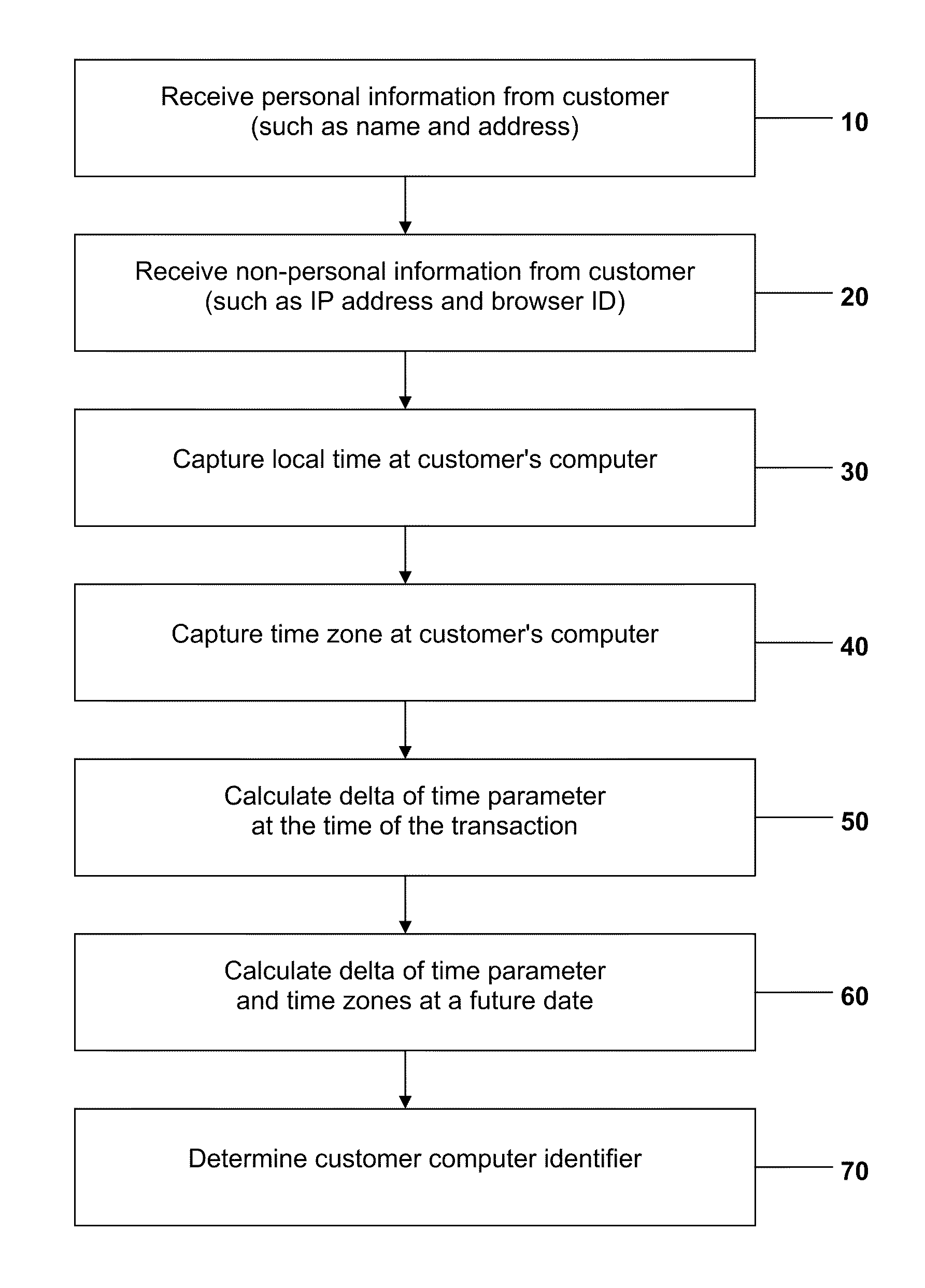
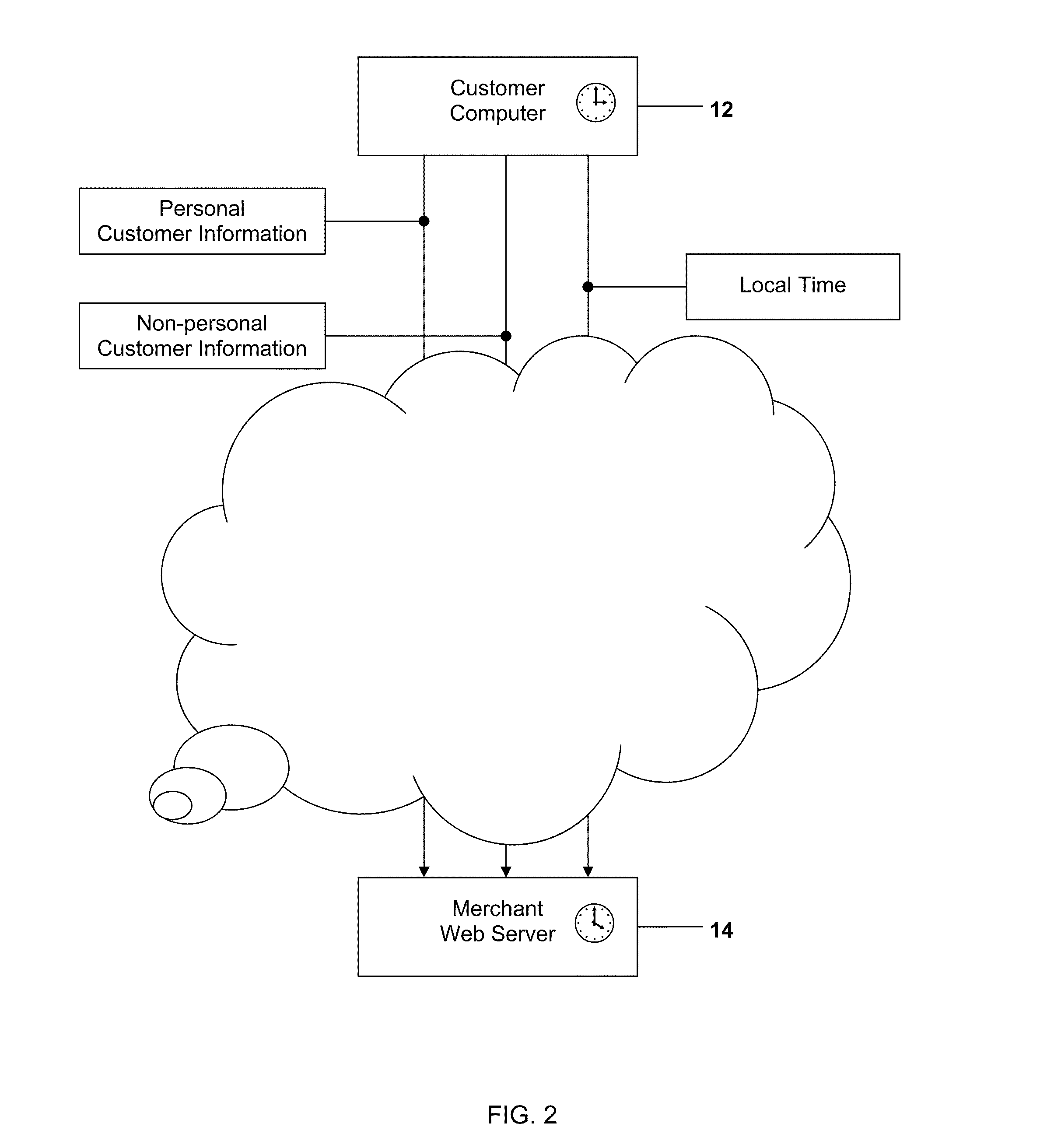
ActiveUS20110082768A1Accurate trackingAccurately and efficiently qualityTransmissionCommerceComputer usersInternet fraud
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
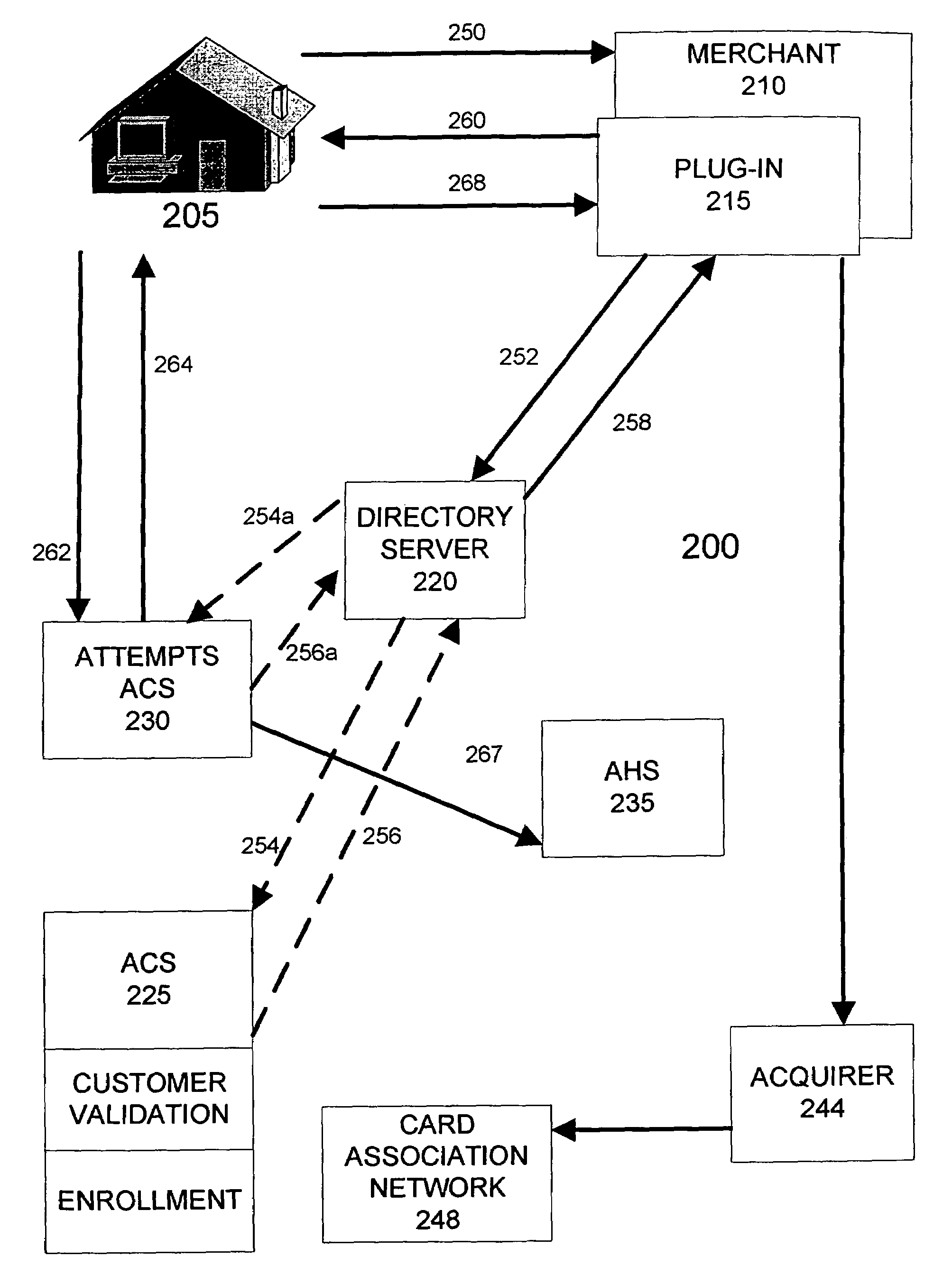
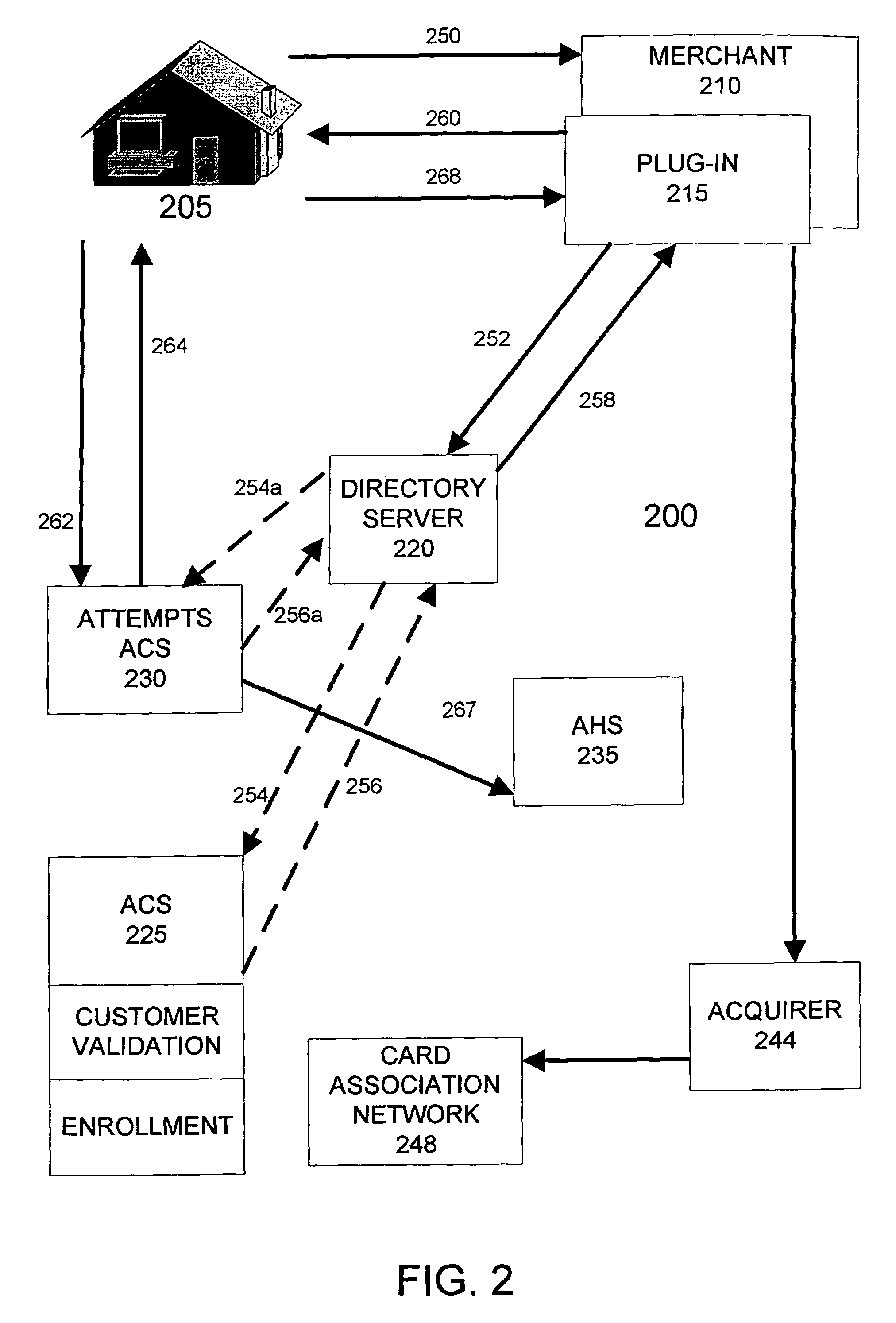
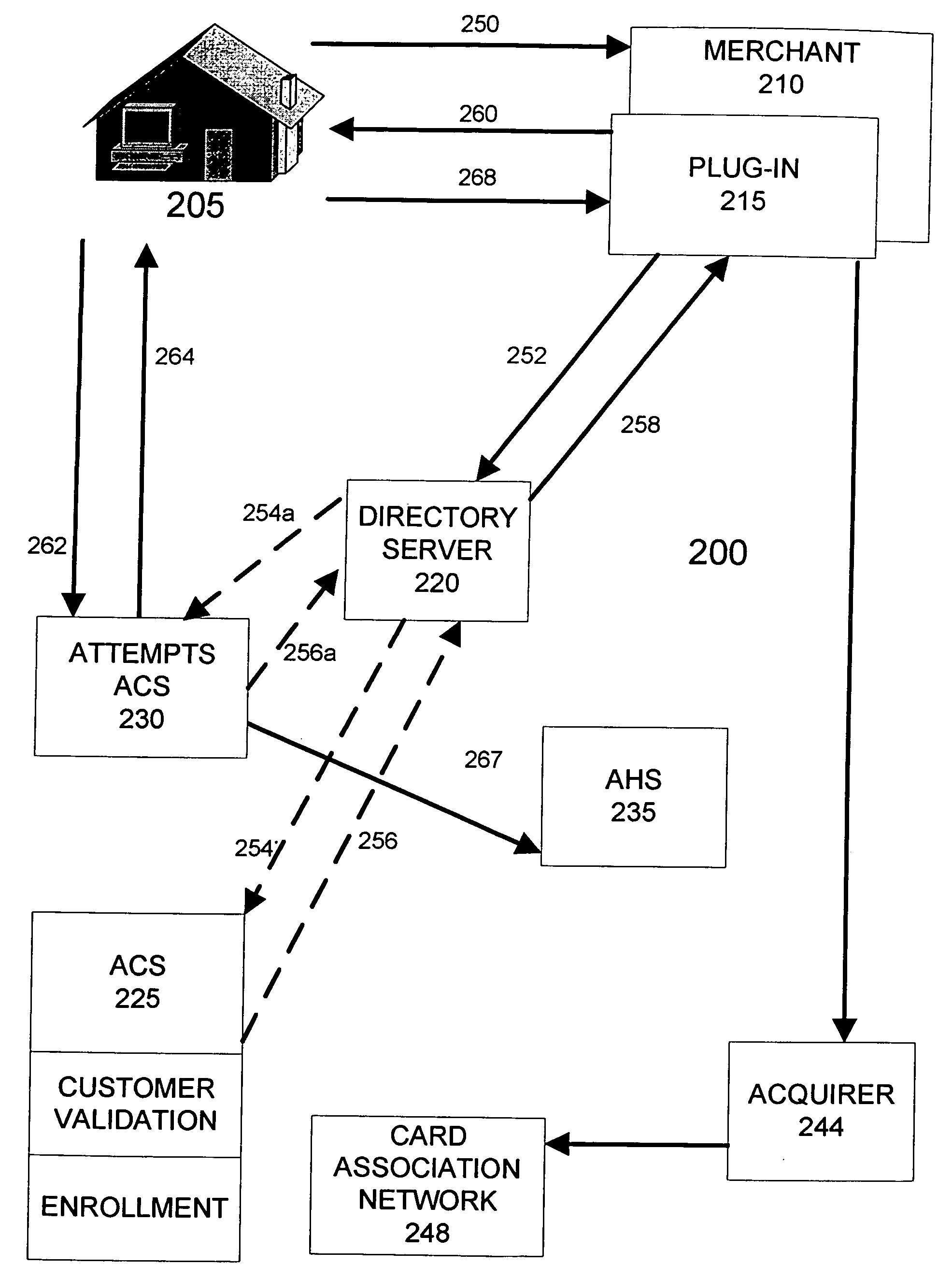
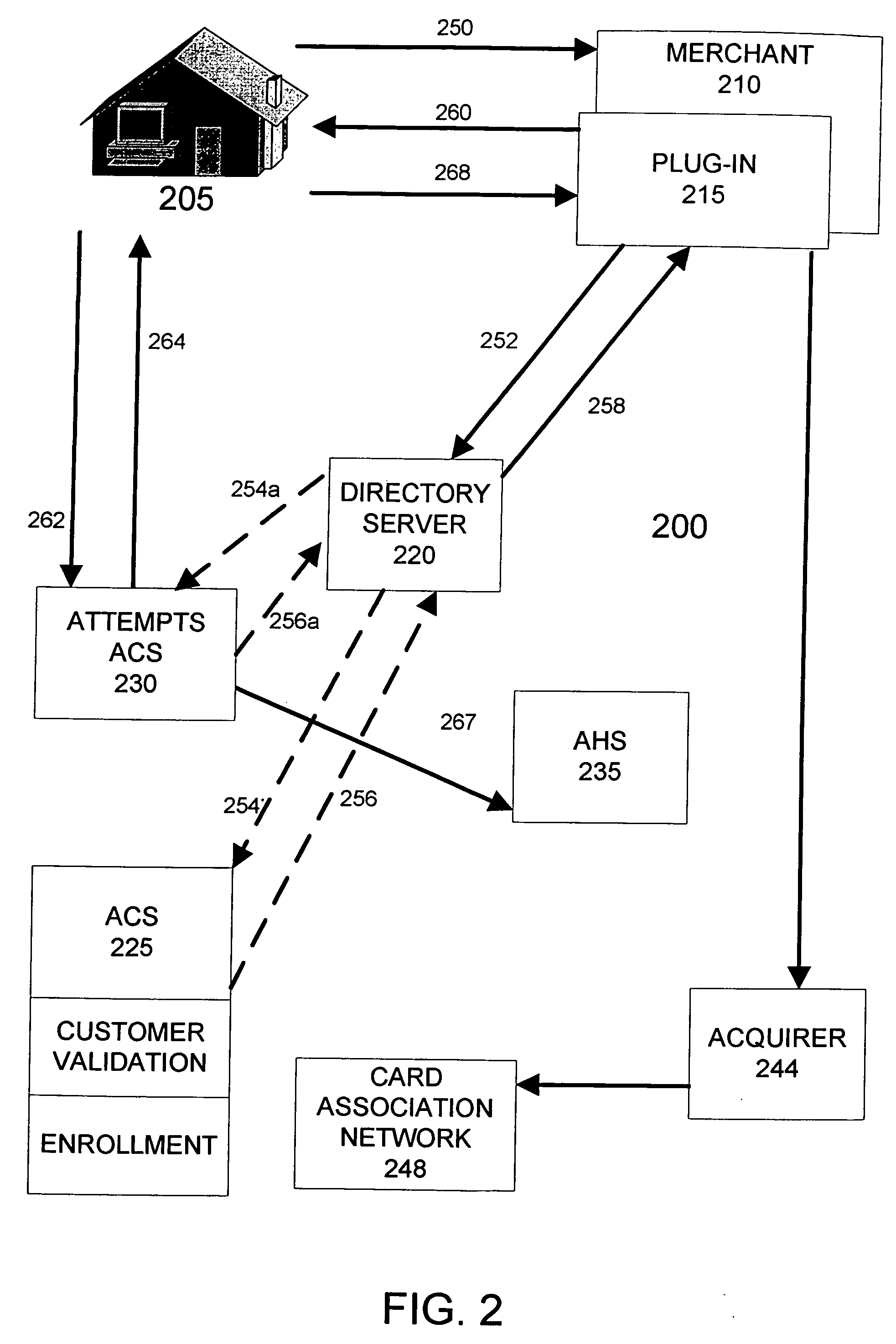
Managing attempts to initiate authentication of electronic commerce card transactions
To encourage widespread implementation of an electronic commerce card authentication system by the numerous different card issuers and merchants, the card association assigns liability for fraudulent transaction based upon a party's compliance with the authentication system. To enable this feature, an embodiment of the card processing system includes the ability to track and record attempts by merchants to initiate authentications, even in circumstances where the card issuer does not support authentication or can not authenticate the card information its receives. A directory server determines whether a card account is capable of being authenticated. If the card issuer cannot authenticate the card account, the directory server instructs the merchant system to attempt authentication with an alternate access control server. The alternate access control server is adapted to communicate an authentication response message with the merchant system indicating that the merchant system attempted an authentication.
Owner:VISA USA INC (US)
Method and system for identifying users and detecting fraud by use of the internet
ActiveUS7853533B2Accurate trackingAccurately and efficiently qualityRegistering/indicating working of machinesElectric unknown time interval measurementComputer usersInternet privacy
Owner:THE 41ST PARAMETER
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
According to one aspect, transaction information is received and applied to multiple fraud risk mathematical models that each produce a respective raw score, which are transformed with respective sigmoidal transform functions to produce optimized likelihood of fraud risk estimates to provide to a merchant. In one embodiment, the respective fraud risk estimates are combined using fusion proportions that are associated with the respective risk estimates, producing a single point risk estimate, which is transformed with a sigmoidal function to produce an optimized single point risk estimate for the transaction. The sigmoidal functions are derived to approximate a relationship between risk estimates produced by fraud risk detection models and a percentage of transactions associated with respective risk estimates, where the relationship is represented in terms of real-world distributions of fraudulent transaction and non-fraudulent transaction. One embodiment is directed to computing respective risk test penalties for multiple risk tests in one or more of the multiple fraud risk mathematical models used to estimate the likelihood of fraud, given a certain pattern of events represented by the transaction information, wherein the respective risk test penalties are computed as the inverse of the sum of one and a false positive ratio for the respective risk test.
Owner:CYBERSOURCE CORP
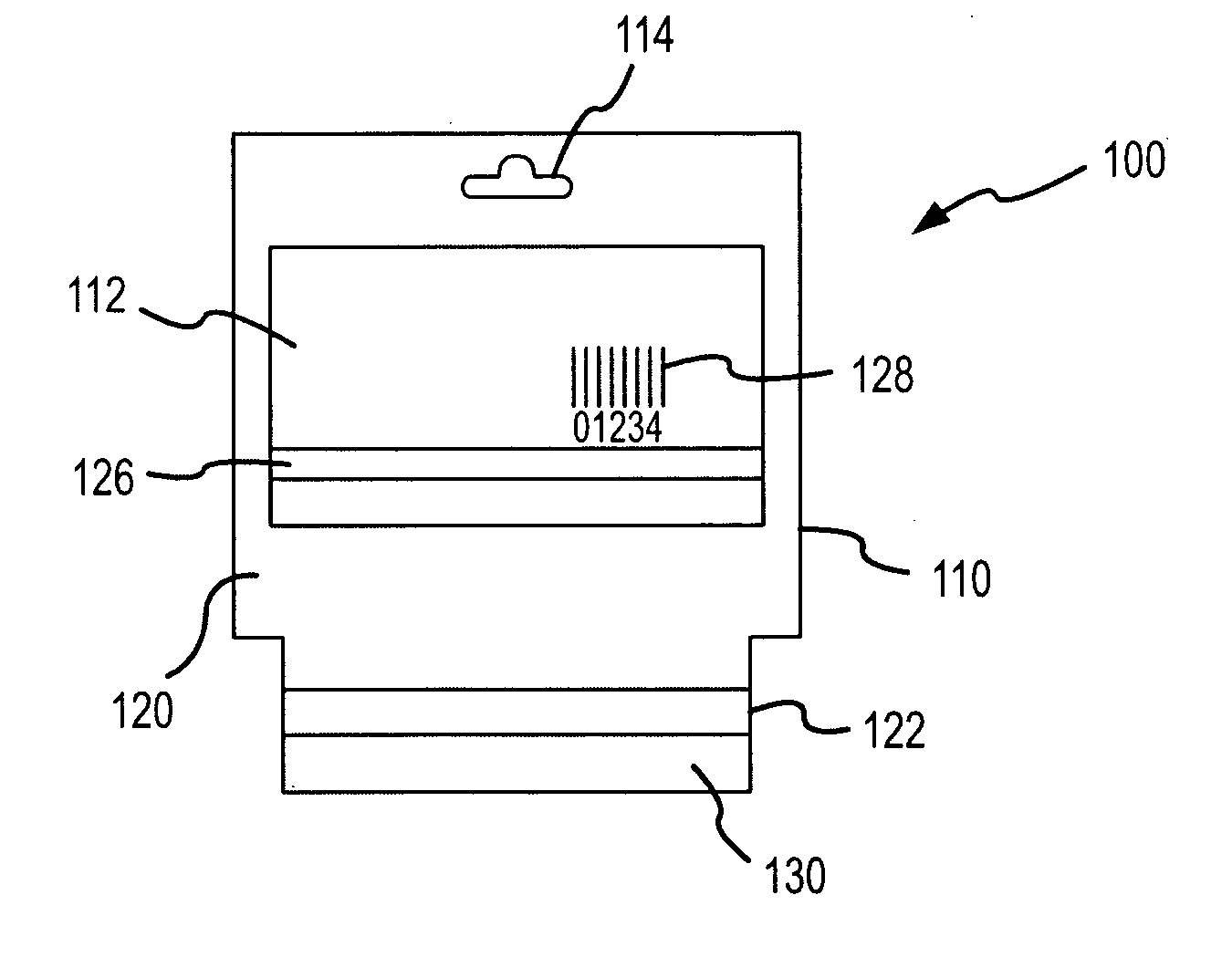
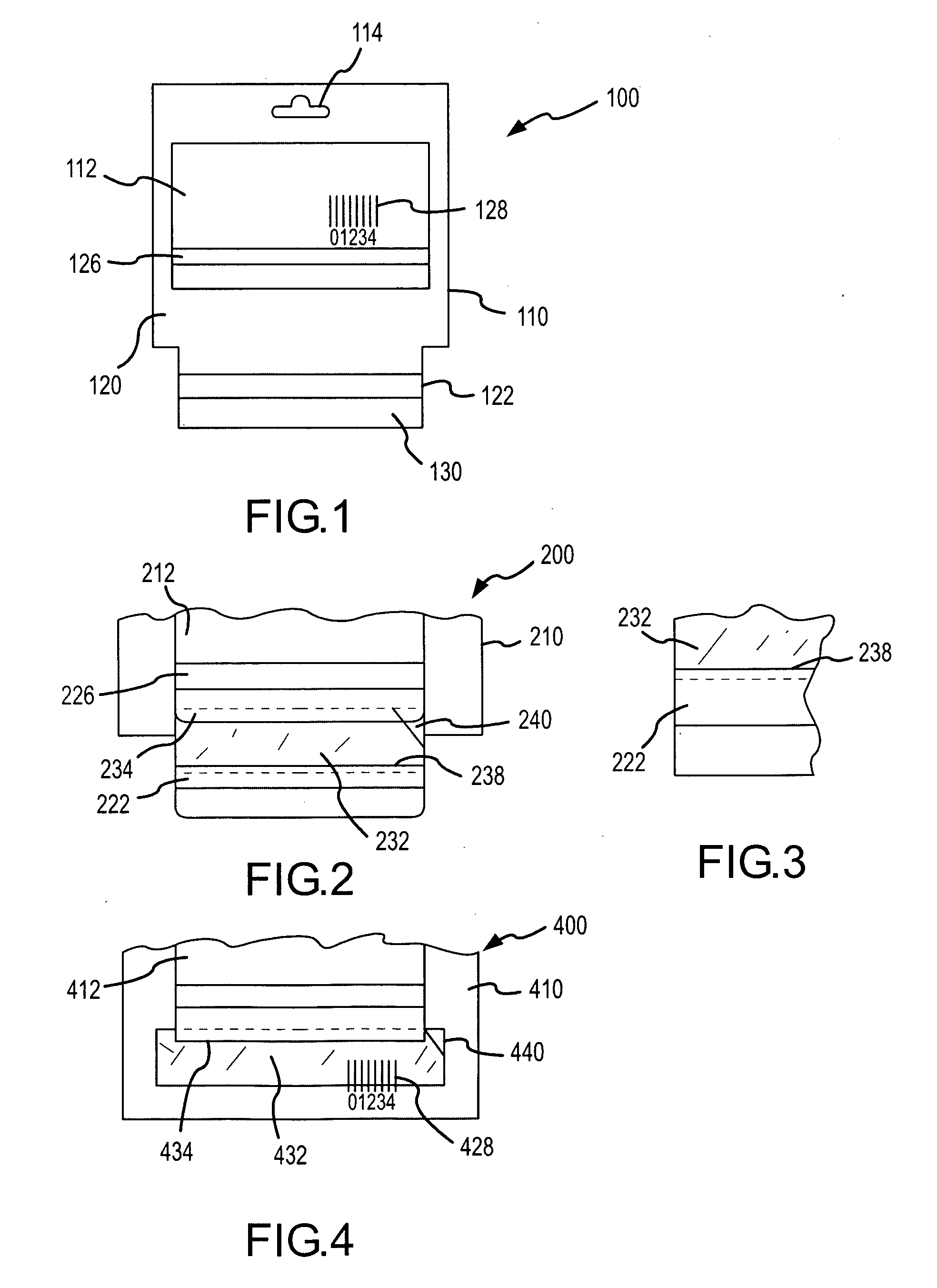
Card display system and method
A system and method for displaying a presentation instrument such as a gift card, and for establishing and maintaining an account associated with the gift card. The gift card is packaged with a card carrier for display at a retail establishment, with both the card and the card carrier each having an account identifying element, such as a magnetic stripe or bar code. The identifying element on the card may be electronically read in order to conduct transactions against the account. The identifying element on the card carrier may be electronically read to activate the account, but not conduct transactions, thereby reducing the opportunity for fraudulent transactions against the account.
Owner:FIRST DATA
Systems and methods of sharing information through a tagless device consortium
The invention provides one or more consortia of networks that identify and share information about users and / or user devices interacting with the consortia. User devices may be identified, at least in part, by a delta of time parameter between a user device used and a reference time. Other parameters may be analyzed to identify a computer user and / or device and noteworthy transactions. The invention may be used for identity-based applications such as network security, the detection of fraudulent transactions, identity theft, ratings-based communities and law enforcement.
Owner:THE 41ST PARAMETER
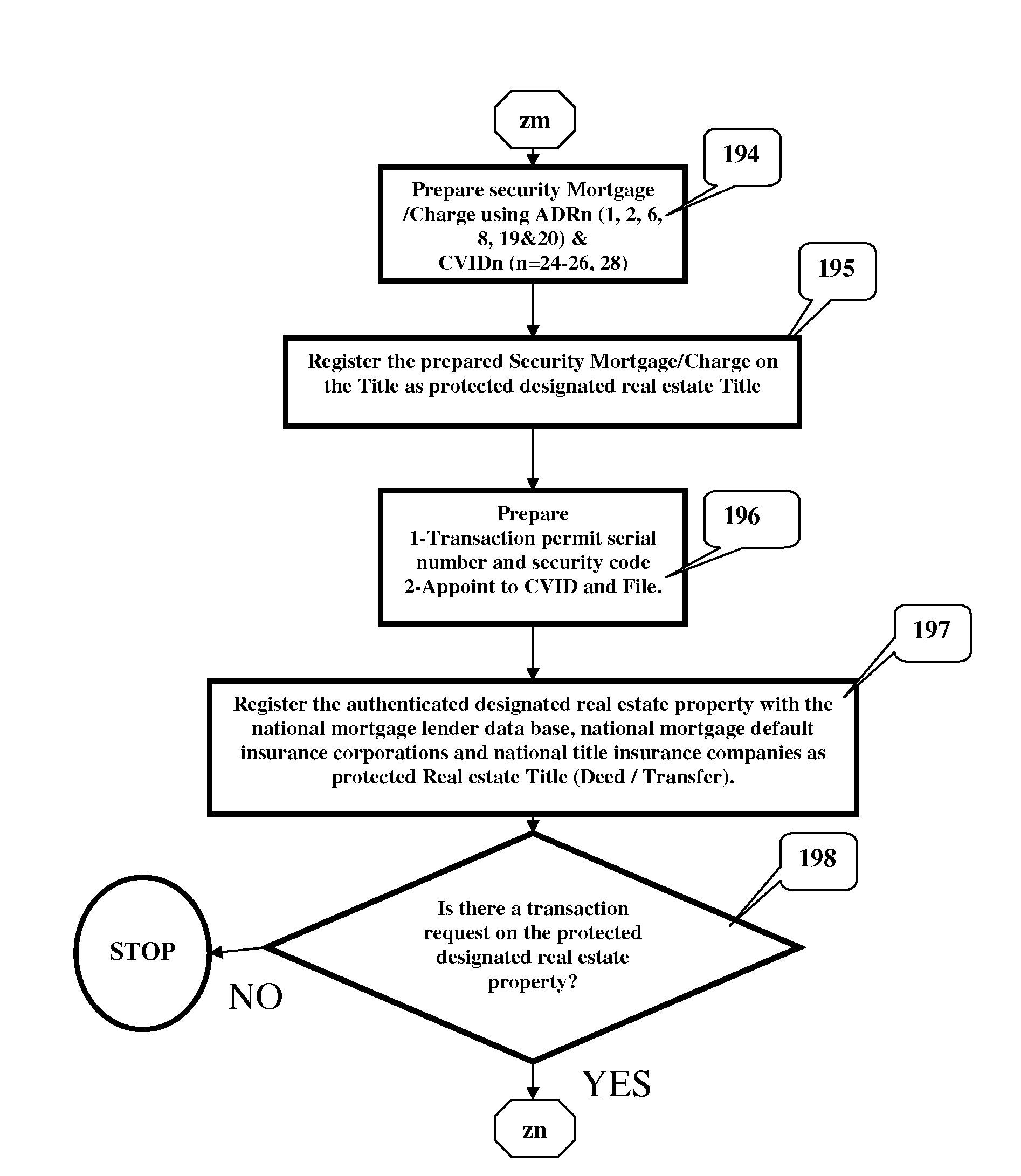
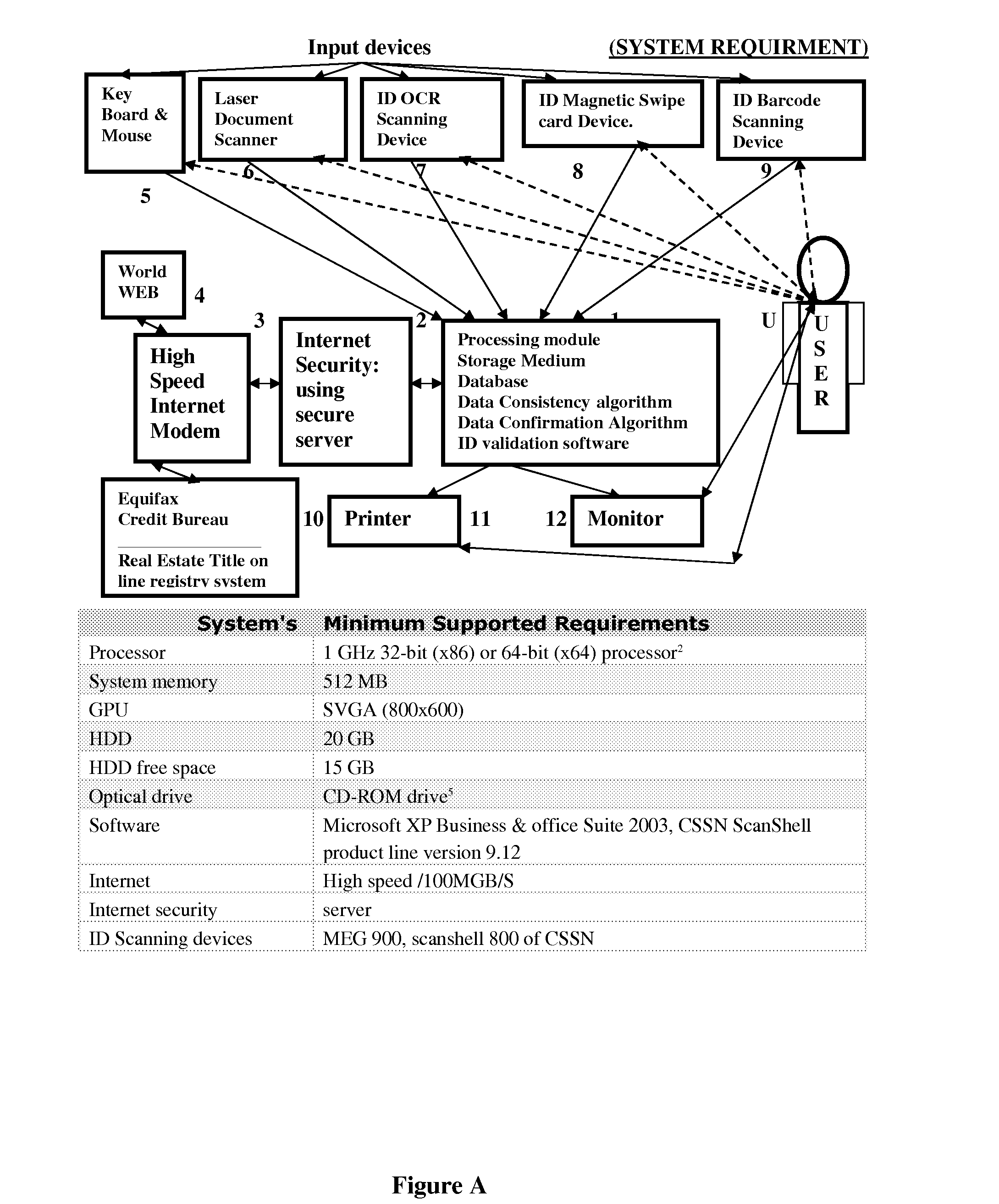
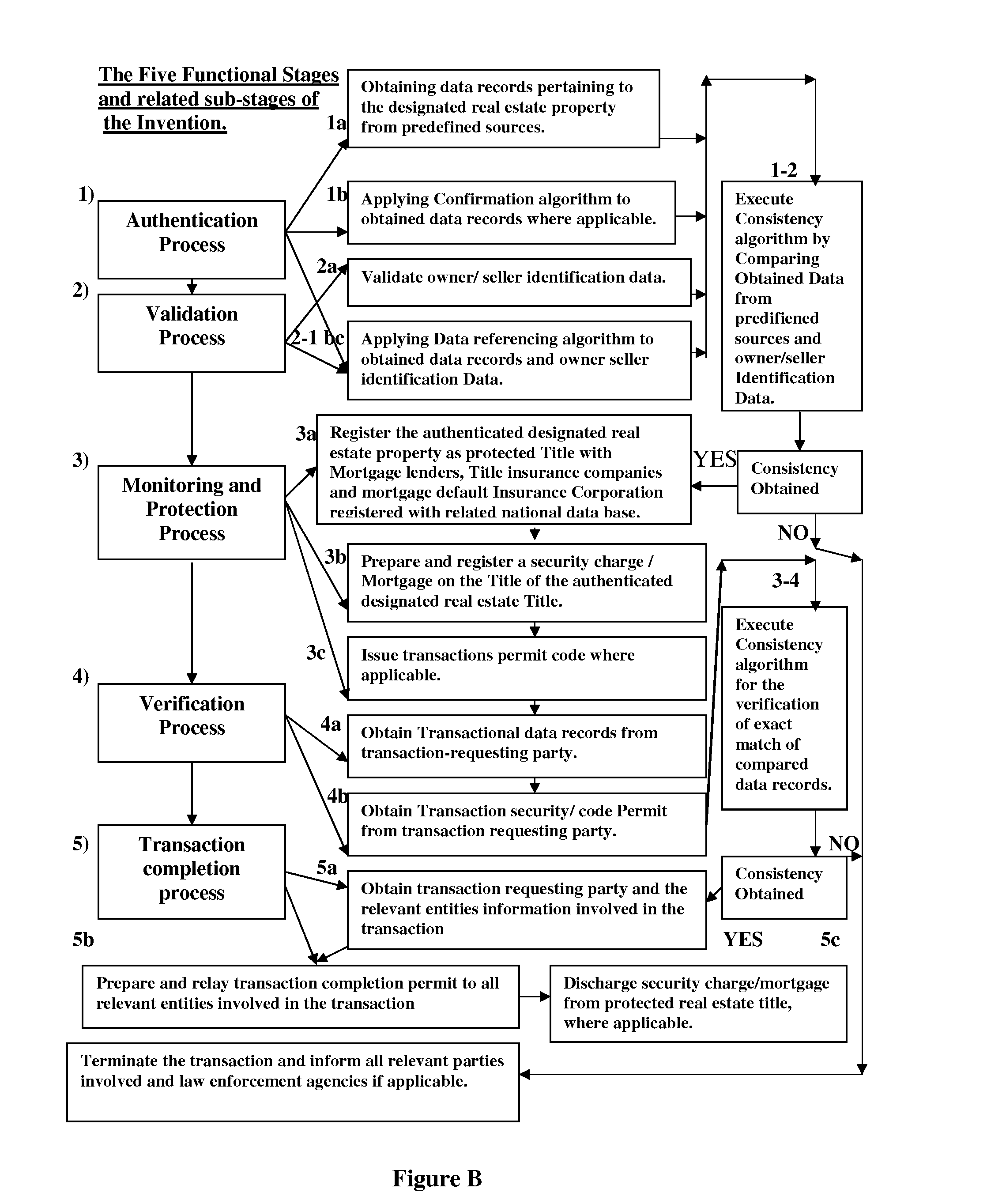
Method and System for Monitoring and Protecting Real Estate Title (Ownership) Against Fraudulent Transaction (Title Theft) and Mortgage Fraud
InactiveUS20080167883A1Prevented substantial financial losesRule out the possibilityCommerceData differencingTransaction data
A method for monitoring and protecting a designated real estate Title (Deed / Transfer) against title theft, fraudulent transaction, mortgage fraud includes process and steps of compiling selected data records associated with a designated real estate Title from plurality of predefined sources and storing the compiled data into an associated file within a computer database, number referencing stored selected data to further facilitate confirmation and authentication of the data records, execute monitoring process for an authenticated Title by preparing and registering security Charge / Mortgage on the Title, Issue transaction permit code, registering with local and national lender data base, Mortgage default insurers and Title insurance companies as protected Title, protect an authenticated Title from fraudulent transaction, mortgage fraud and illegal activity by further verifying transactional data of the requesting party with the stored authenticated data, stop transaction on detection of data discrepancies, issue transaction completion permit and discharge registered security charge by obtaining consistency in obtained data records. A system comprising of confirmation, authentication and verification algorithm and ID validation hardware components. The system further includes a computer database for storing data records, computer software to validate ID cards, reference number data records, execute confirmation, authentication and verification algorithm and issue transaction completion permit / Termination warning and security charge / discharge documents.
Owner:THAVILDAR KHAZANEH RAMIN
Fraud risk advisor
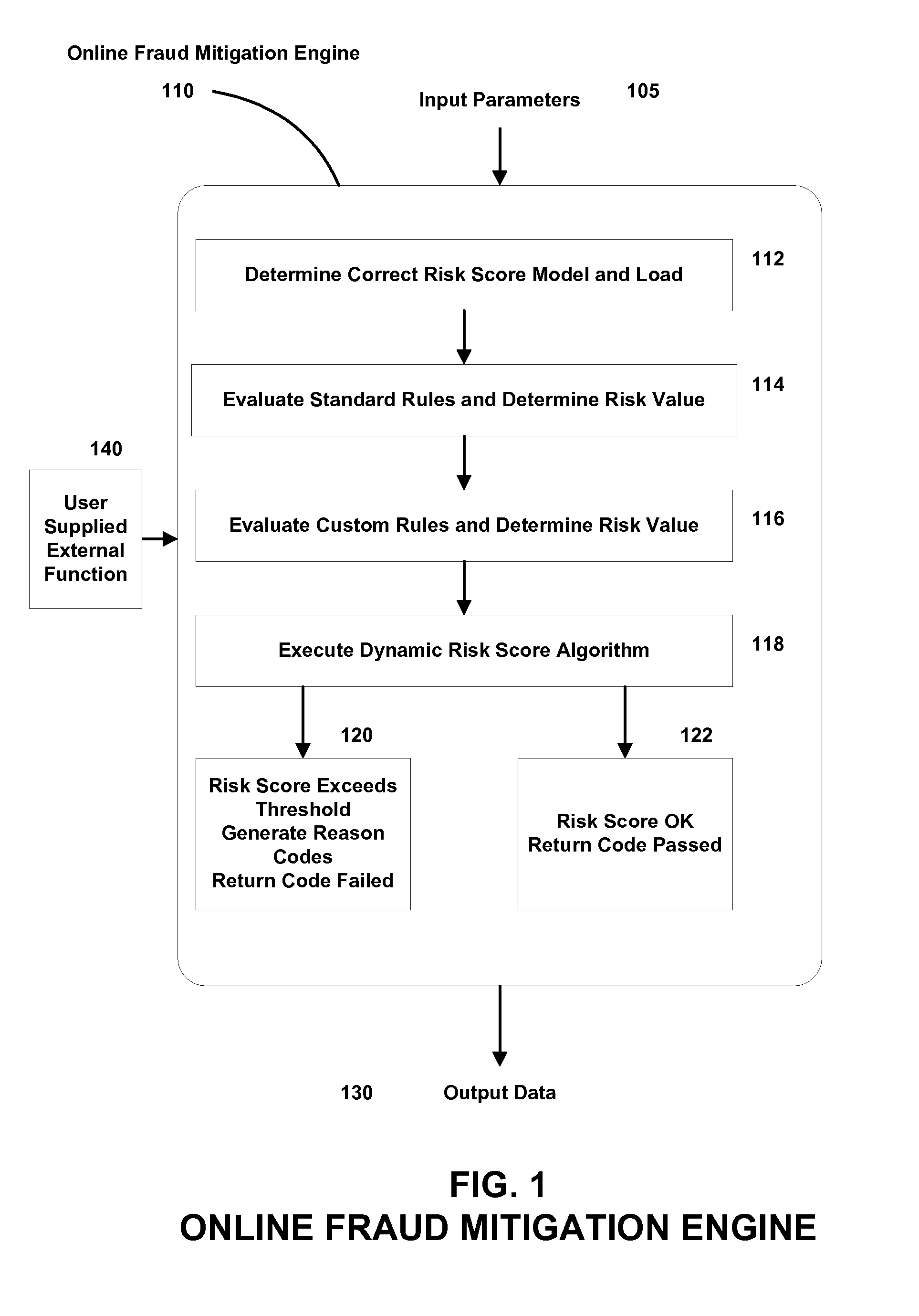
A fraudulent business transaction application (FBTA) is provided for monitoring application based fraud. When a consumer supplies account access information in order to carry out an Internet business transaction, the FBTA uses an online fraud mitigation engine to detect phishing trusions and identity theft. Methods are also provided for calculating travel velocity and transcation frequency, which are useful for determining a fraudulent transaction.
Owner:DIGITAL ENVOY
Managing attempts to initiate authentication of electronic commerce card transactions
To encourage widespread implementation of an electronic commerce card authentication system by the numerous different card issuers and merchants, the card association assigns liability for fraudulent transaction based upon a party's compliance with the authentication system. To enable this feature, an embodiment of the card processing system includes the ability to track and record attempts by merchants to initiate authentications, even in circumstances where the card issuer does not support authentication or can not authenticate the card information its receives. A directory server determines whether a card account is capable of being authenticated. If the card issuer cannot authenticate the card account, the directory server instructs the merchant system to attempt authentication with an alternate access control server. The alternate access control server is adapted to communicate an authentication response message with the merchant system indicating that the merchant system attempted an authentication.
Owner:VISA USA INC (US)
Method and system for identifying users and detecting fraud by use of the internet
InactiveUS8862514B2Accurate trackingAccurately and efficiently qualityFinanceInternal/peripheral component protectionComputer usersInternet fraud
A method and system for detecting and preventing Internet fraud in online transactions by utilizing and analyzing a number of parameters to uniquely identify a computer user and potential fraudulent transaction through predictive modeling. The method and system uses a delta of time between the clock of the computer used by the actual fraudulent use and the potentially fraudulent user and the clock of the server computer in conjunction with personal information and / or non-personal information, preferably the Browser ID.
Owner:THE 41ST PARAMETER
Encryption switch processing
InactiveUS20170186001A1Eliminate operating expenseImprove securityPoint-of-sale network systemsAnonymous user systemsFinancial transactionPoint of sale
Techniques for eliminating the need for merchants and acquirers to conduct Payment Card Industry (“PCI”) security audit procedures are provided. Merchants and acquirers can eliminate the operating expenses associated with conducting audits to ensure compliance with PCI Data Security Standards (“DSS”), while at the same time ensuring that cardholders' data remains secure, thus protecting the cardholders from fraudulent transactions. System security is further enhanced through the use of per transaction audits, with the scope of the audit being directly between the Point of Sale (POS) terminal and the payment processing network. PCI DSS compliance can thus be assured on a per transaction basis, as opposed to only ensuring compliance generally for a merchant or acquirer on a periodic basis. Per transaction PCI DSS compliance is assured, while at the same time eliminating the need for merchants or acquirers to conduct compliance audits.
Owner:REED JUDSON +2
Systems and methods of sharing information through a tagless device consortium
The invention provides one or more consortia of networks that identify and share information about users and / or user devices interacting with the consortia. User devices may be identified, at least in part, by a delta of time parameter between a user device used and a reference time. Other parameters may be analyzed to identify a computer user and / or device and noteworthy transactions. The invention may be used for identity-based applications such as network security, the detection of fraudulent transactions, identity theft, ratings-based communities and law enforcement.
Owner:THE 41ST PARAMETER
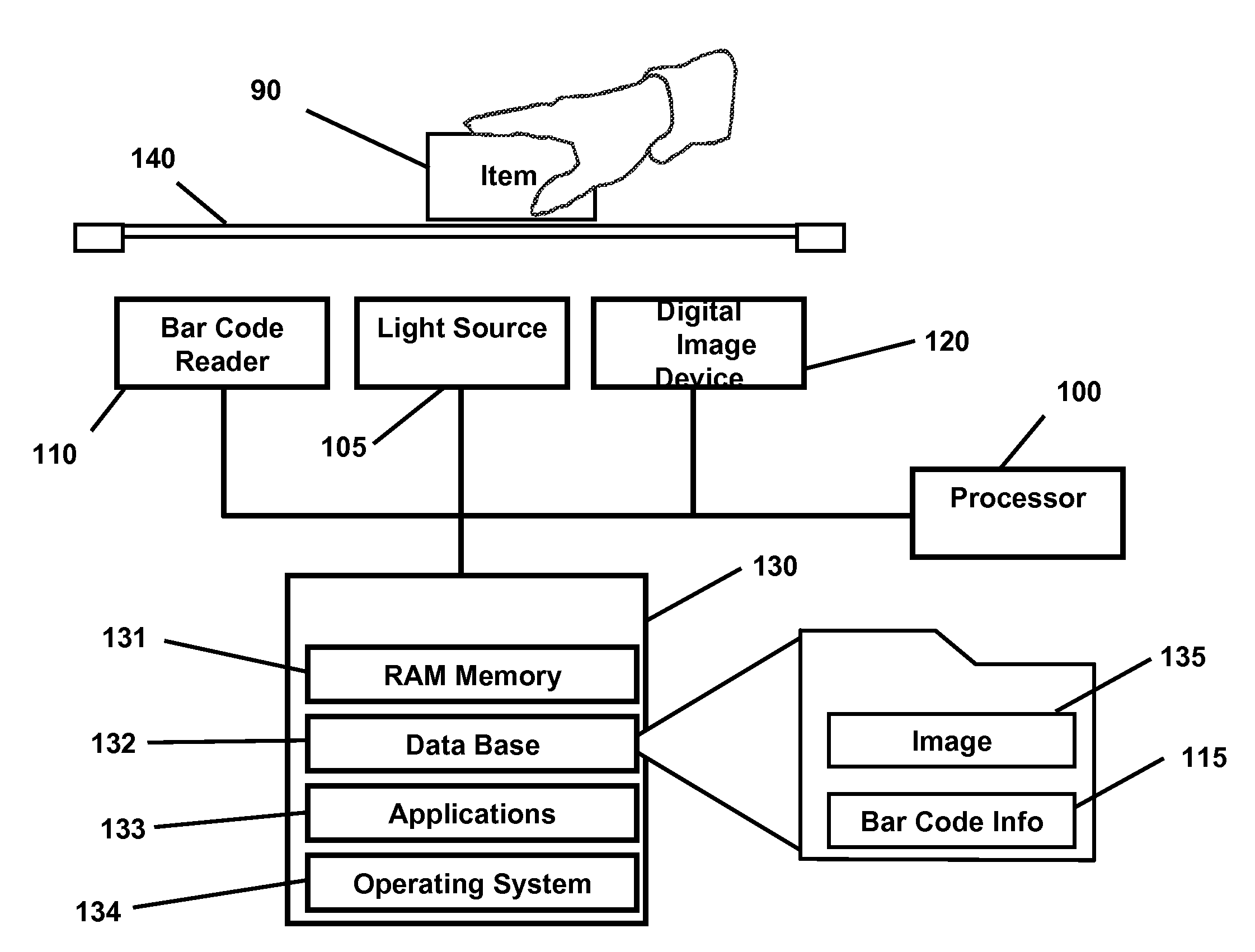
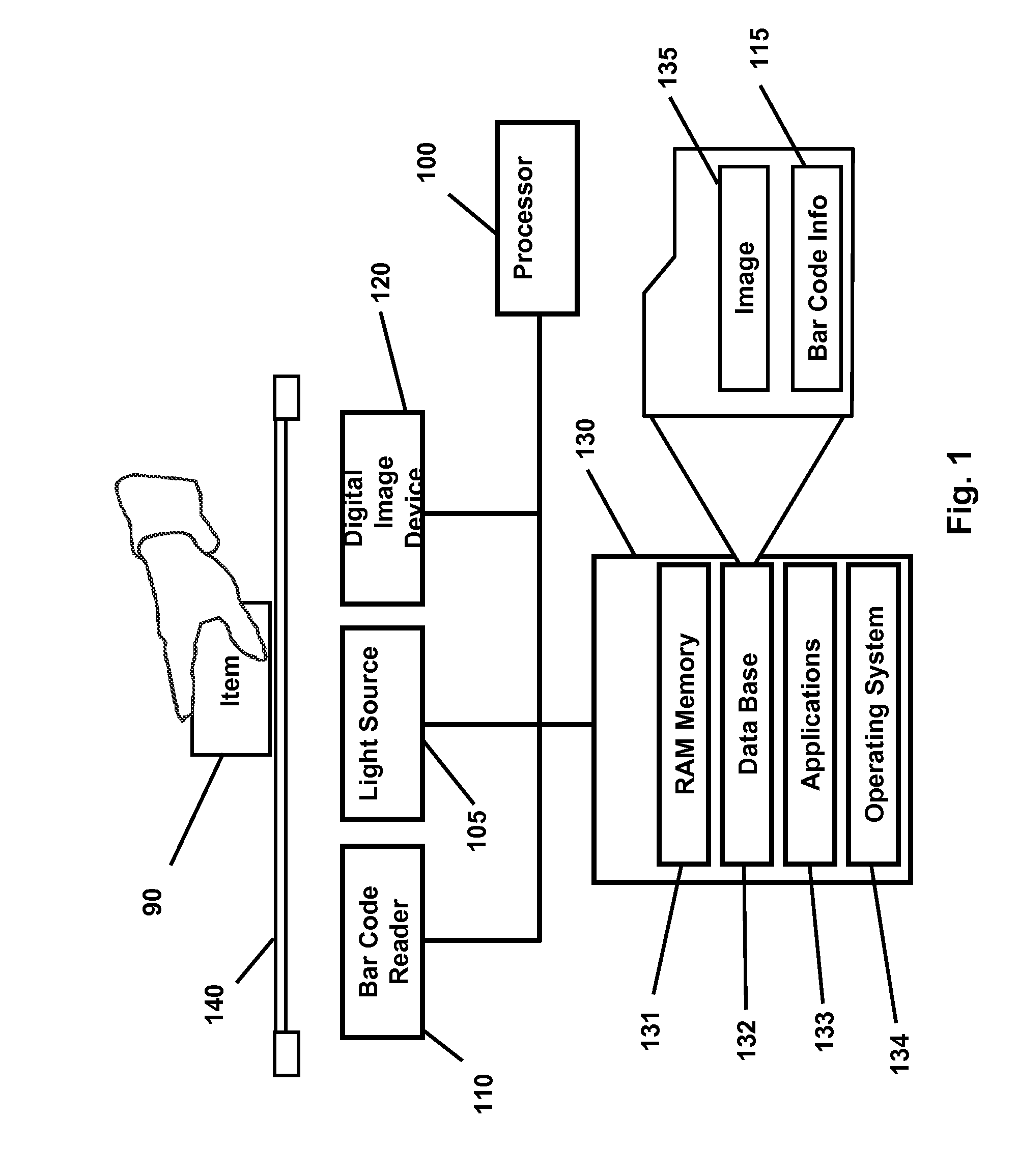
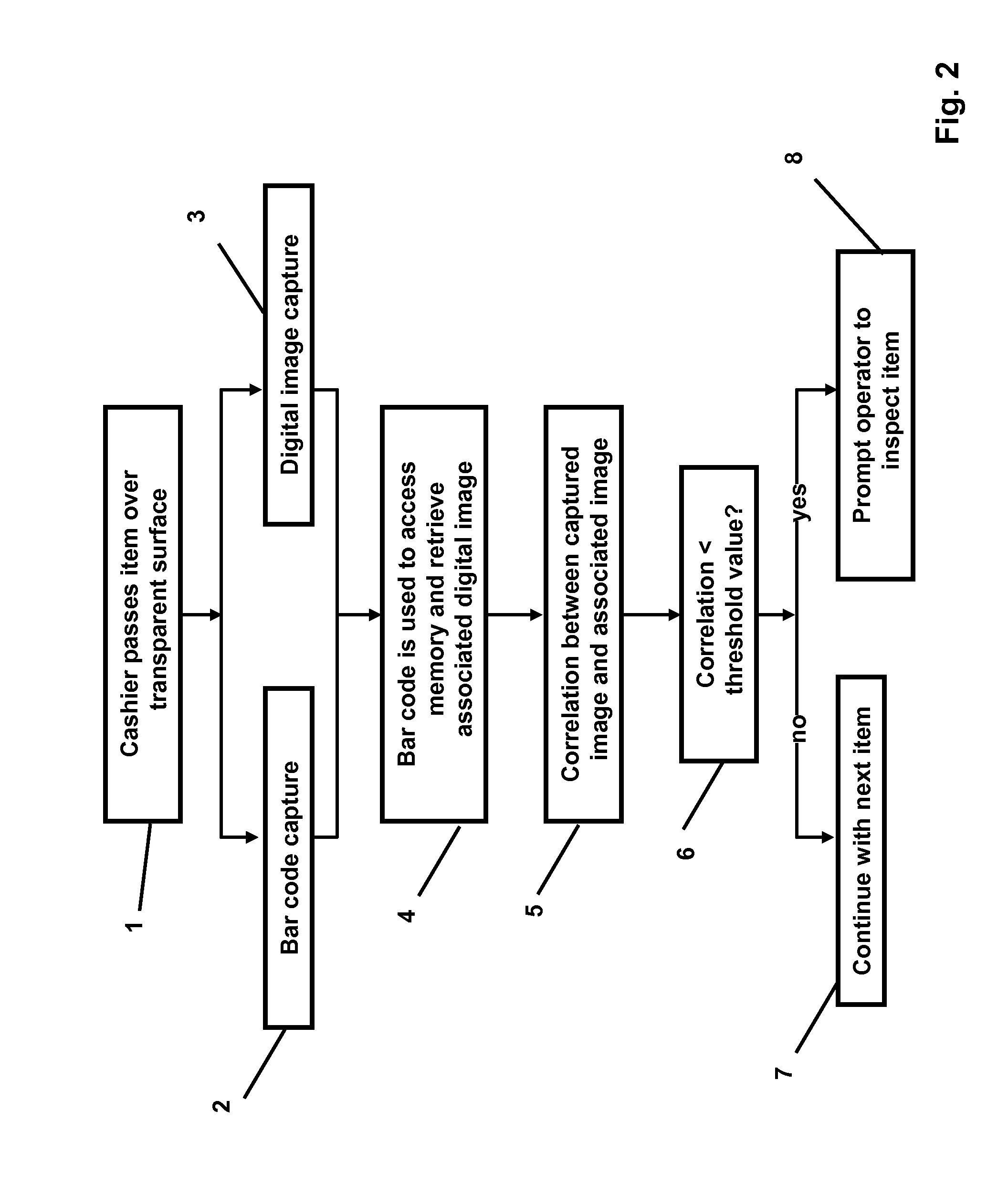
System and method for detecting fraudulent transactions of items having item-identifying indicia
InactiveUS20080149725A1Disturb efficiencyWithout any changeVisual representatino by photographic printingCharacter and pattern recognitionComputer scienceFraudulent transaction
A method of detecting a fraudulent transaction of an item having an item-identifying indicium processes the indicium to obtain item-identifying information, and captures a digital representation of a surface area of the item. The item-identifying information is used to retrieve a stored digital representation of the surface area of the item. Further, the method compares the captured digital representation with the stored digital representation to determine if the captured digital representation corresponds to the stored digital representation.
Owner:ROSENBAUM WALTER STEVEN
Location based authentication system
InactiveUS8285639B2Optimize locationFinanceBuying/selling/leasing transactionsBehaviour patternCard holder
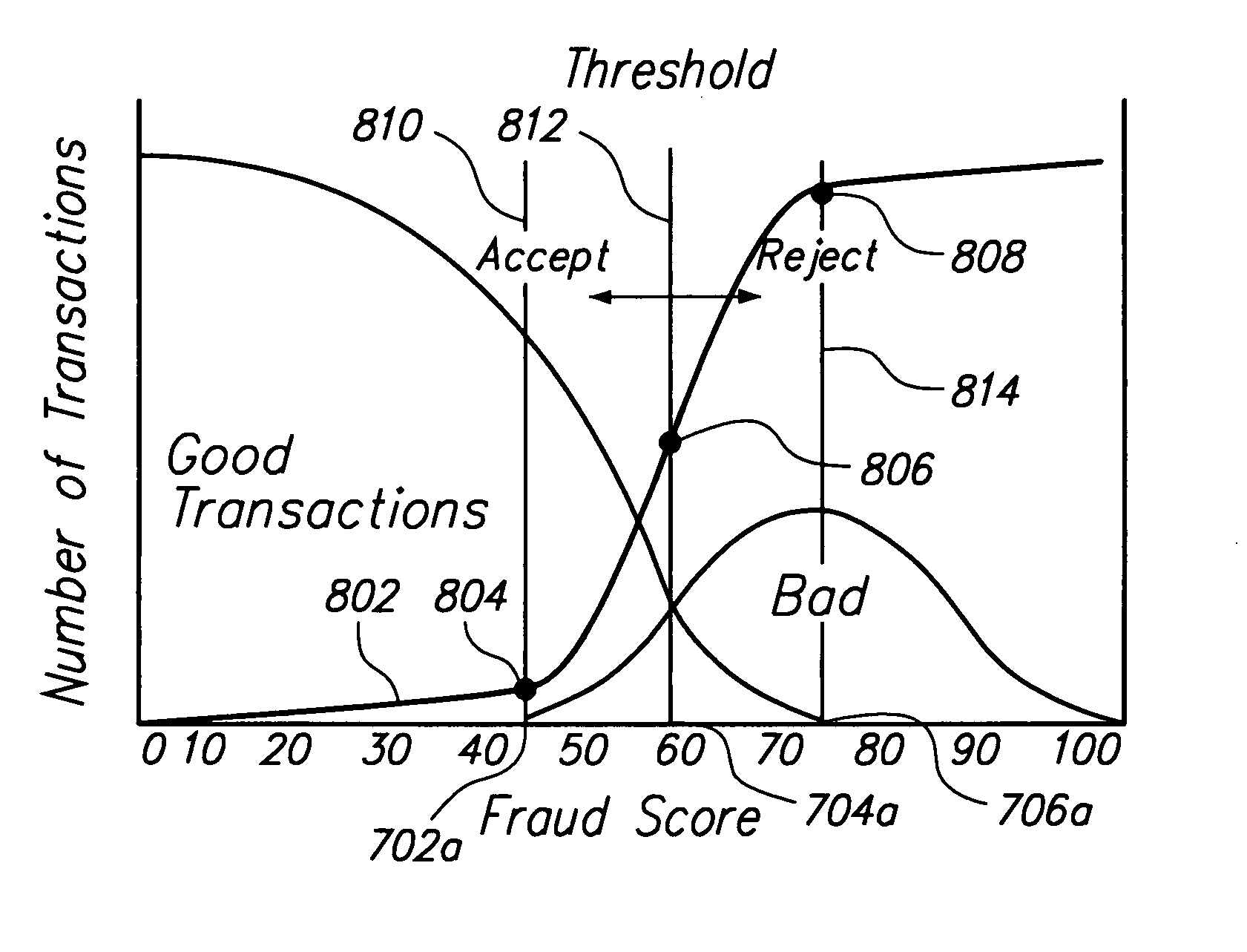
An improved location based authentication (LBA) system for detecting fraudulent transactions committed by means of misuse of payment cards is disclosed. The improved LBA system performs a series of transaction analysis and generates a fraud-score which provides an indication as whether to authorize an attempted transaction. The system is designed to increase profitability of credit card companies by reducing the accumulated losses due to fraud. In one embodiment, the system detects fraud by analyzing the behavior patterns of card holders and merchants.
Owner:MCONFIRM
Fraud analyst smart cookie
A fraudulent business transaction application (FBTA) is provided in embodiments of the present invention for monitoring fraudulent transactions. When a consumer supplies account access information in order to carry out an Internet business transaction, the FBTA uses an online fraud mitigation engine to detect phishing intrusions and identity theft. Embodiments are also provided for calculating travel velocity and transaction frequency, which are useful for determining a fraudulent transaction. Further embodiments are provided for authenticating a transaction using a cookie stored on a client device and a behavior profile stored on a server.
Owner:GREENE TODD +1
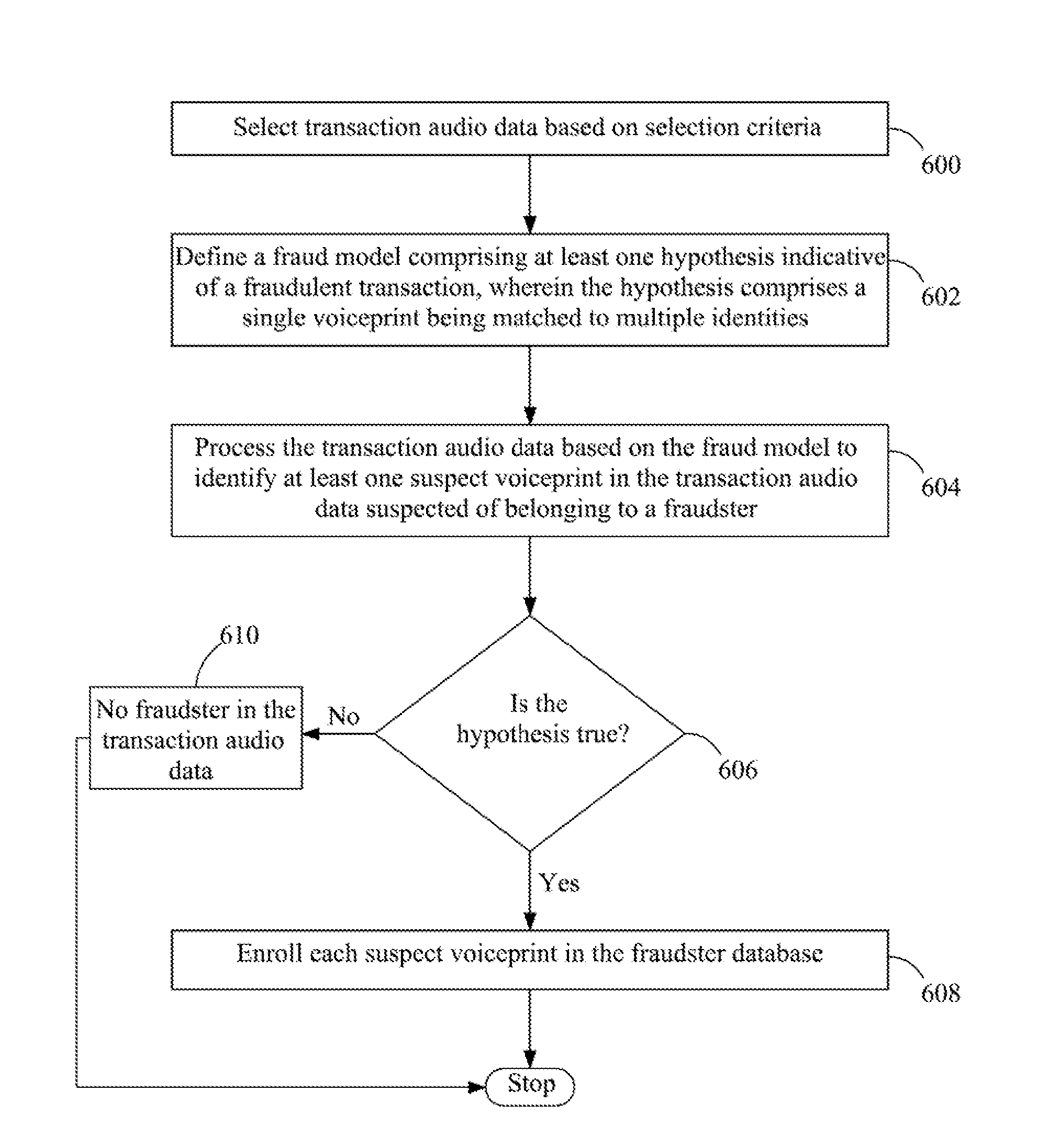
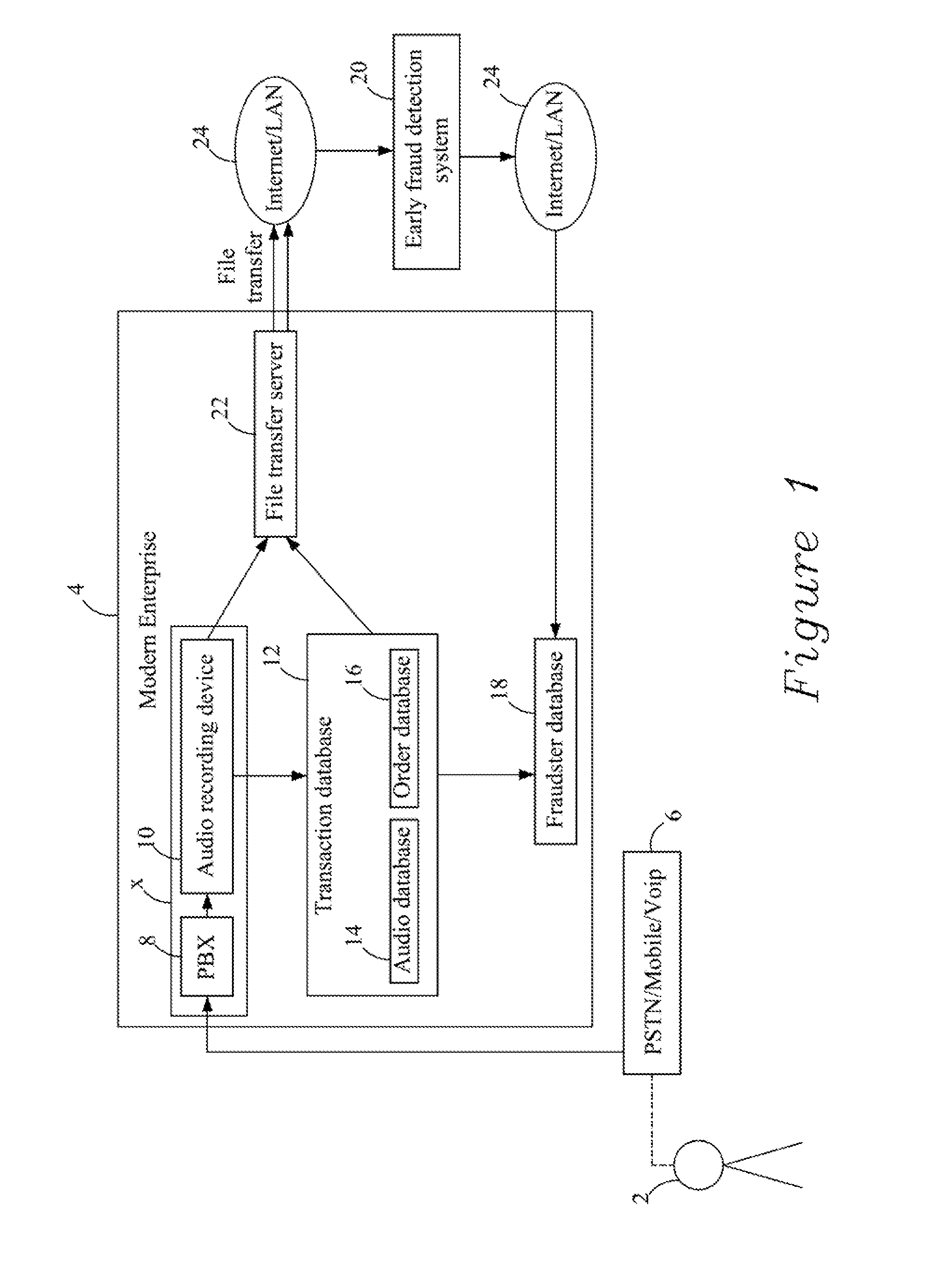
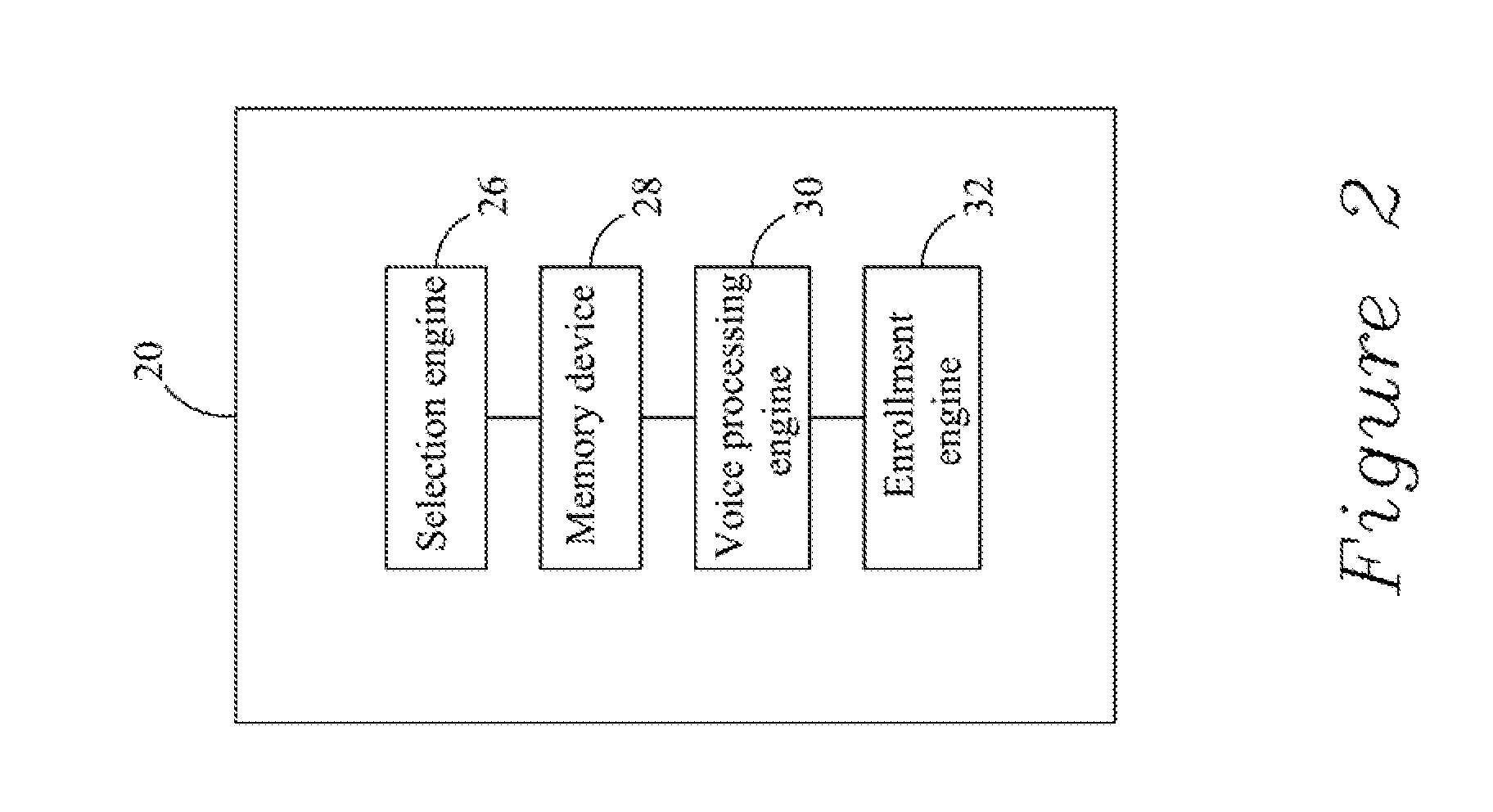
Method and system for enrolling a voiceprint in a fraudster database
Disclosed is a method for enrolling a voiceprint in a fraudster database, the method comprising: a) defining a fraud model comprising at least one hypothesis indicative of a fraudulent transaction; b) processing audio data based on the fraud model to identify at least one suspect voiceprint in the audio data suspected of belonging to a fraudster; and c) enrolling the at least one suspect voiceprint in the fraudster database.
Owner:VERINT AMERICAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com