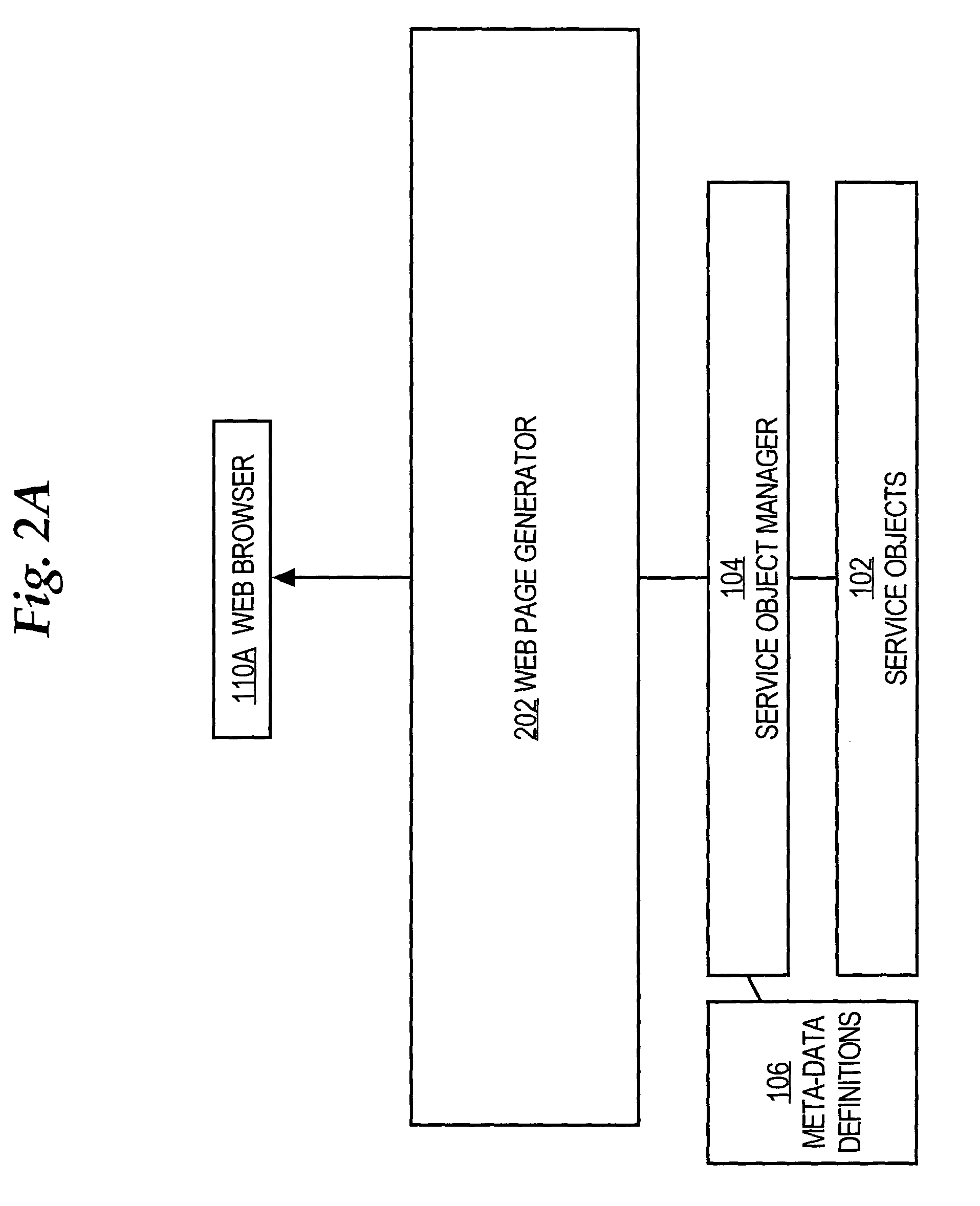
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3076 results about "Source Data Verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data verification is a process in which different types of data are checked for accuracy and inconsistencies after data migration is done. It helps to determine whether data was accurately translated when data is transferred from one source to another, is complete, and supports processes in the new system.
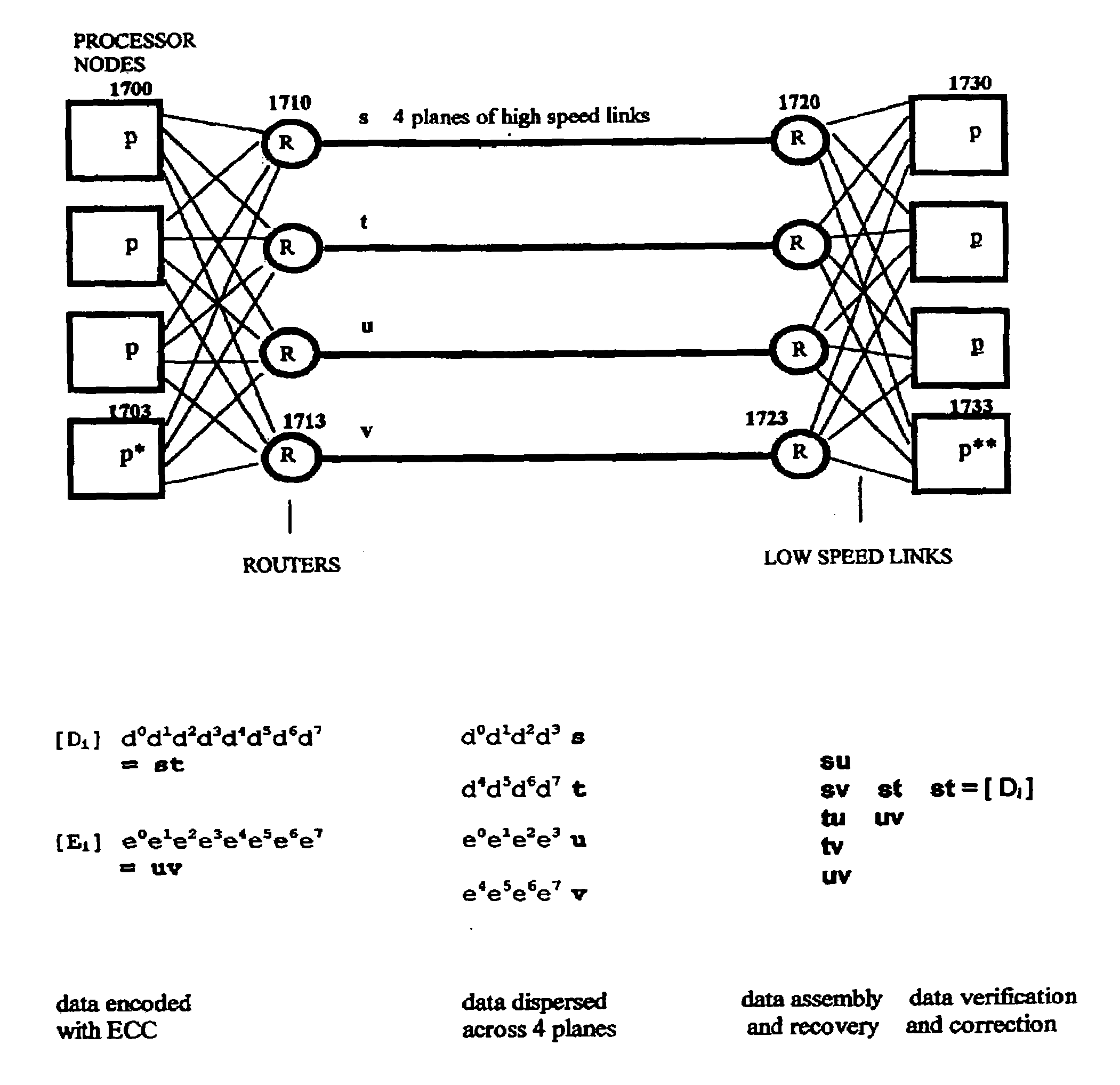
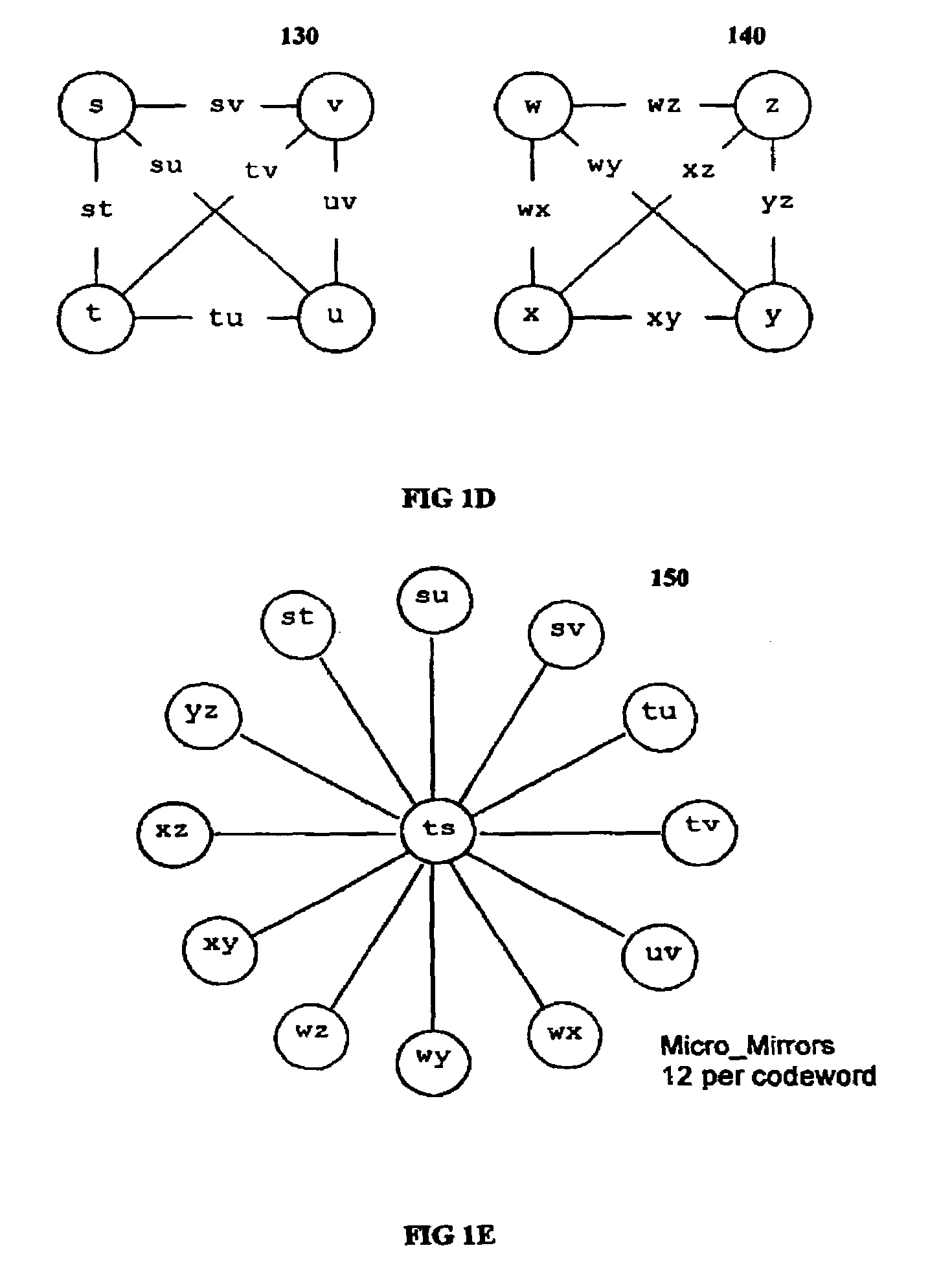
Multi-dimensional data protection and mirroring method for micro level data
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
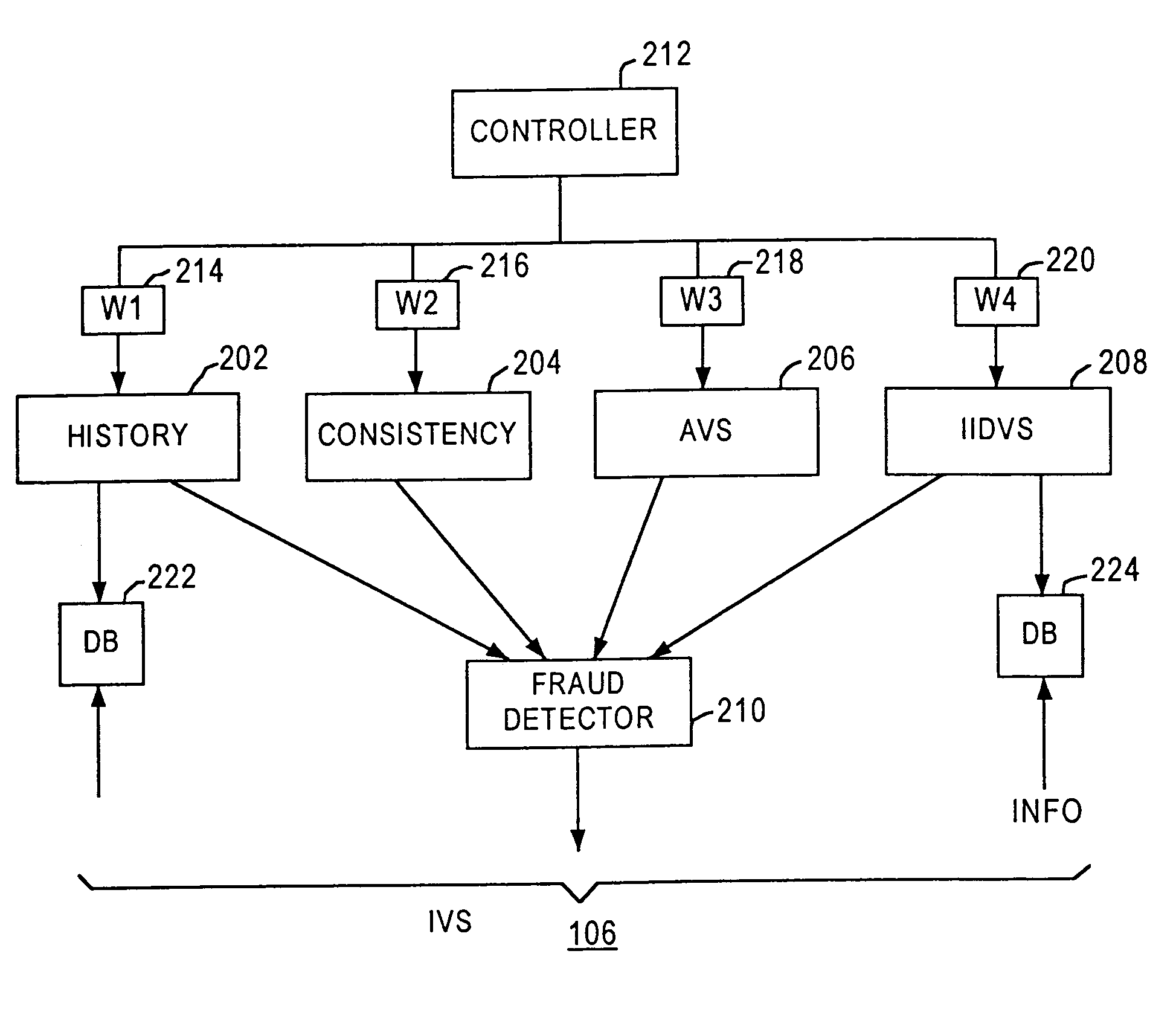
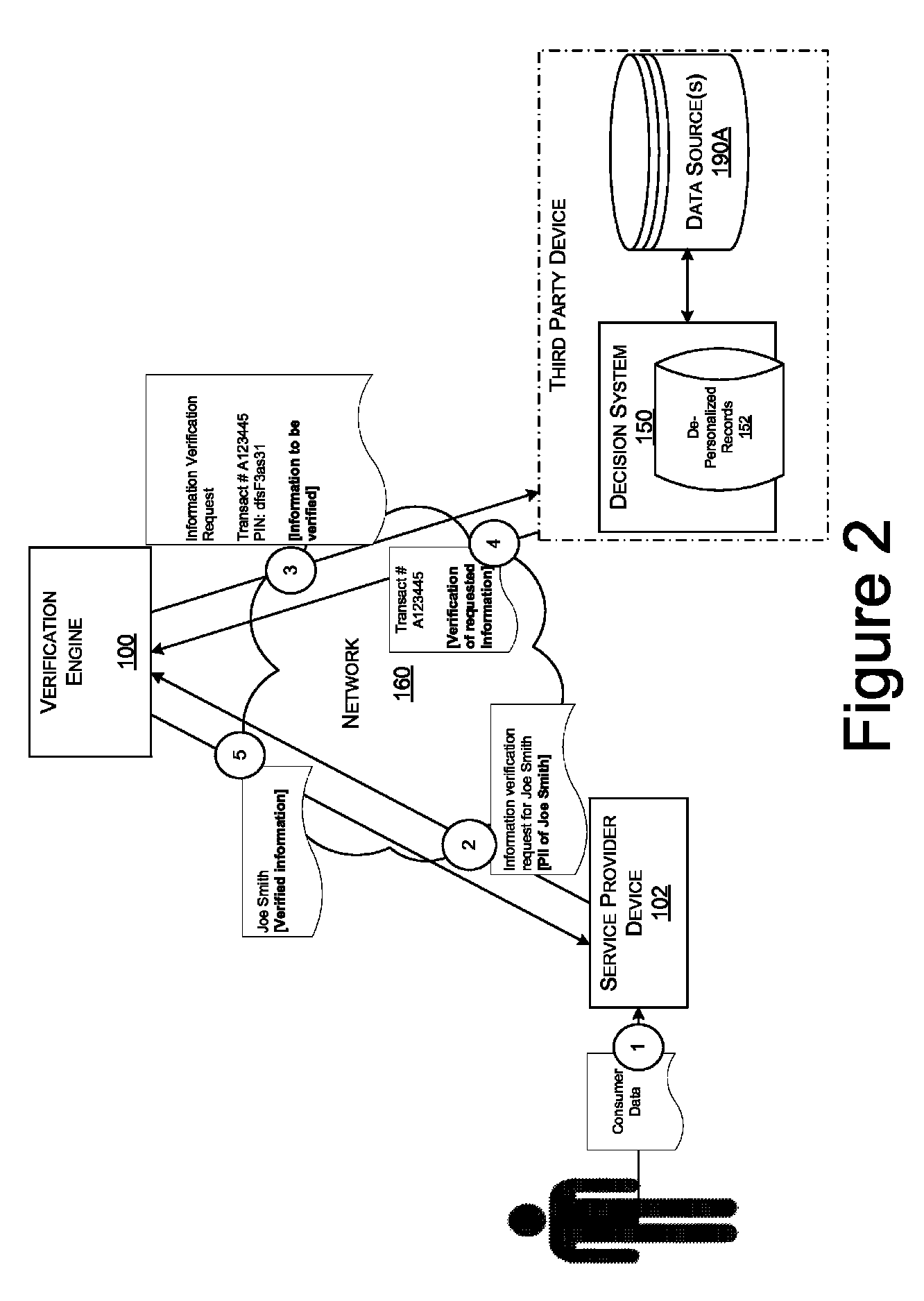
Method and apparatus for evaluating fraud risk in an electronic commerce transaction
A technique for evaluating fraud risk in e-commerce transactions between consumer and a merchant is disclosed. The merchant requests service from the system using a secure, open messaging protocol. An e-commerce transaction or electronic purchase order is received from the merchant, the level of risk associated with each order is measured, and a risk score is returned. In one embodiment, data validation, highly predictive artificial intelligence pattern matching, network data aggregation and negative file checks are used. The system performs analysis including data integrity checks and correlation analyses based on characteristics of the transaction. Other analysis includes comparison of the current transaction against known fraudulent transactions, and a search of a transaction history database to identify abnormal patterns, name and address changes, and defrauders. In one alternative, scoring algorithms are refined through use of a closed-loop risk modeling process enabling the service to adapt to new or changing fraud patterns.
Owner:CYBERSOURCE CORP
Method, system, and computer program product for customer-level data verification
ActiveUS20070284433A1Improve accuracyReduce error rateComplete banking machinesFinanceData validationSource Data Verification
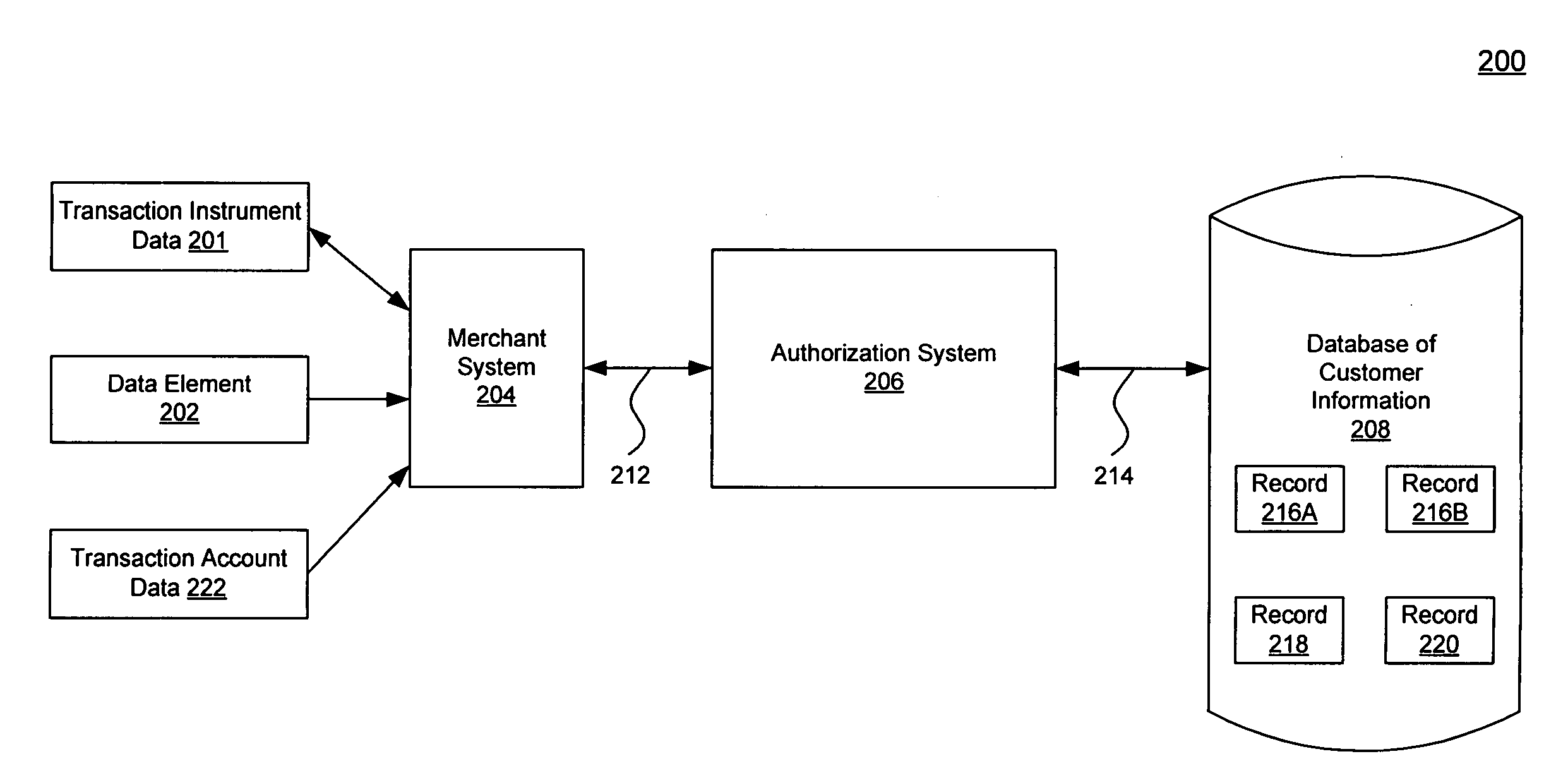
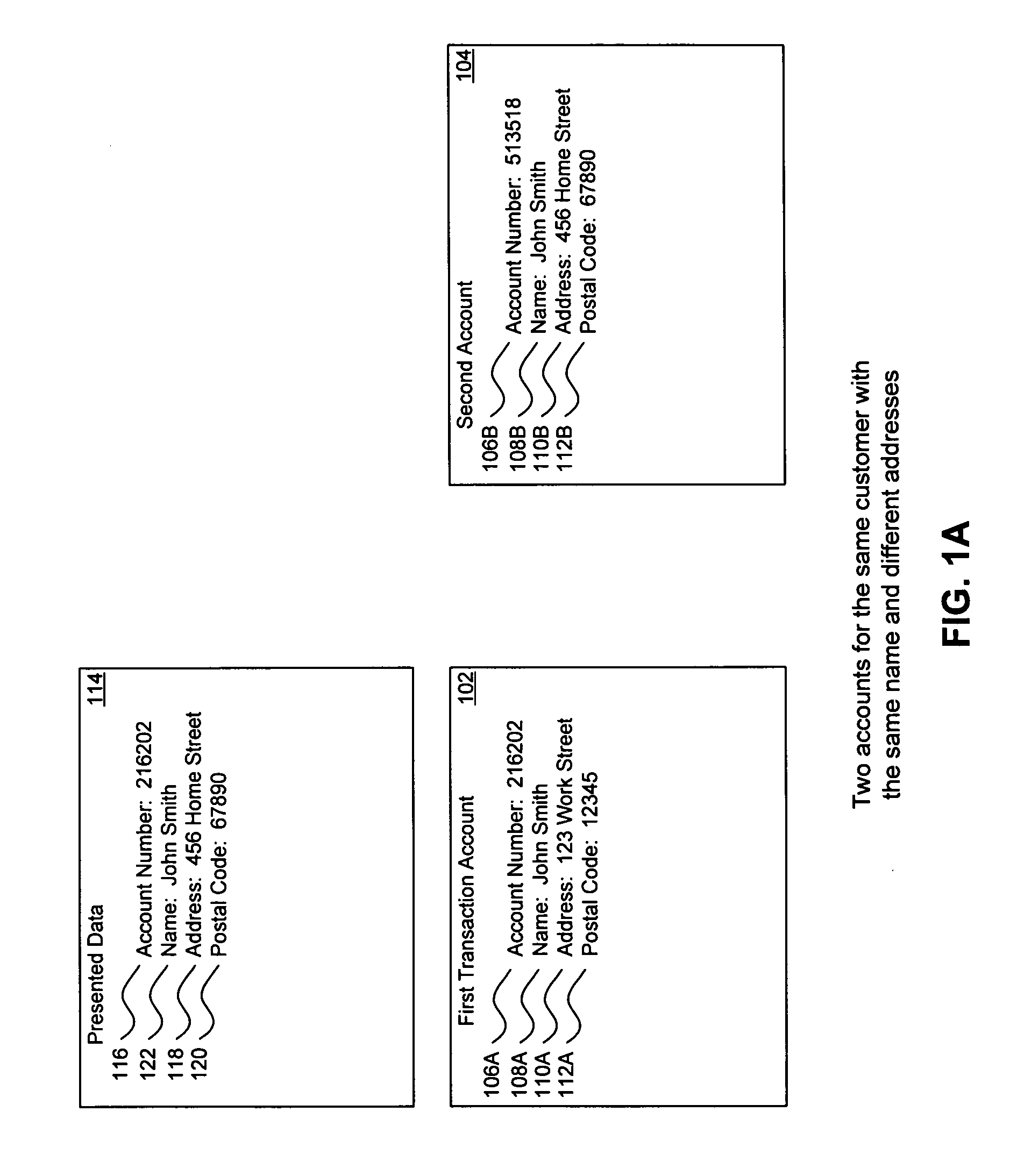
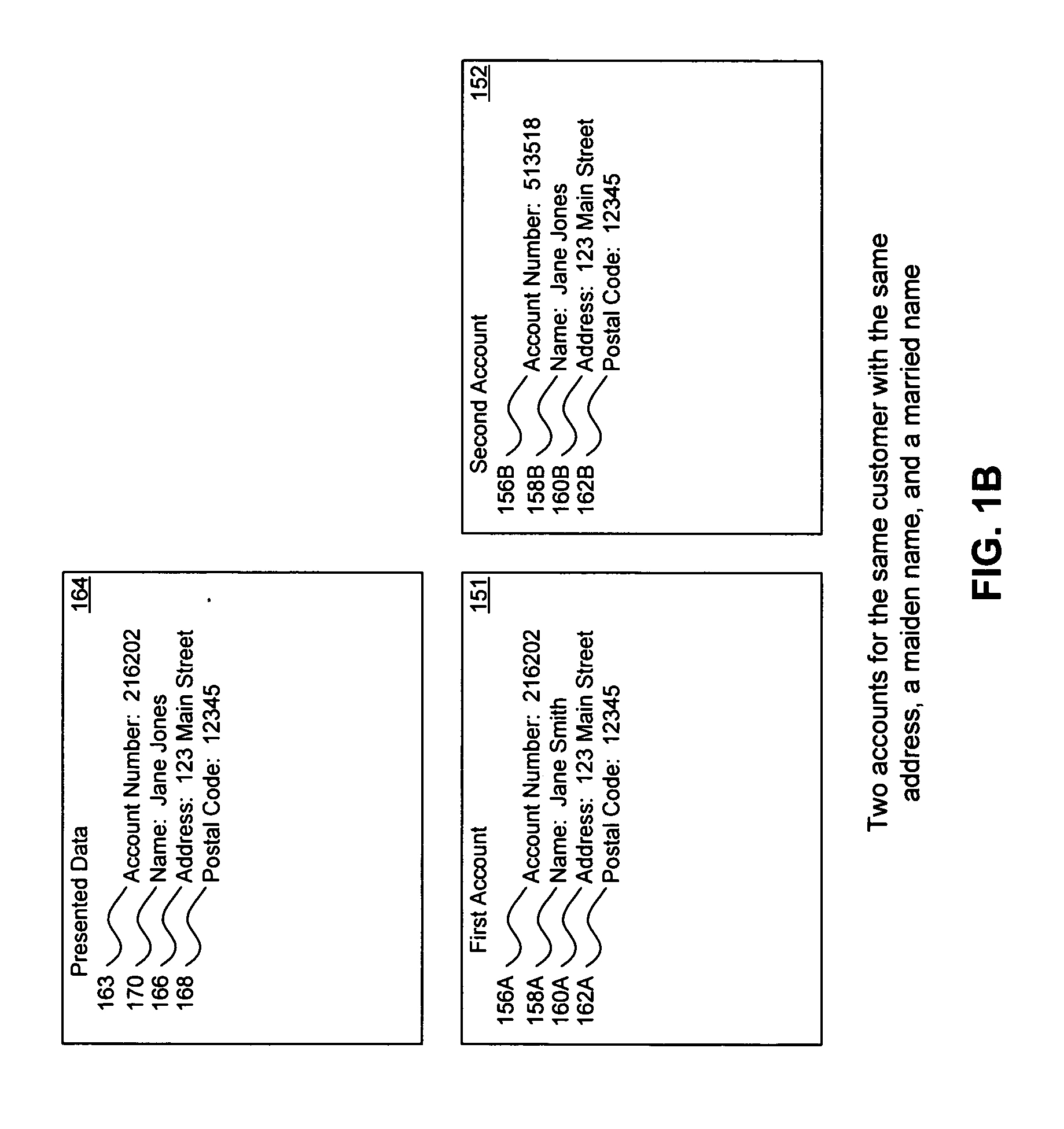
A system, method, and computer program to reduce incorrectly declined transactions and improve risk calculation accuracy by reducing error probability during fraud detection. The tool first receives at least one data element as well as transaction account data and / or financial transaction instrument data. Then a customer is determined from a first record associated with the transaction account data and / or financial transaction instrument data. A record search is performed to identify at least one additional record associated with the customer. Finally, the data element is compared to the information contained in the additional record to create a comparison result that verifies a customer address. The comparison result may be used as an input to transaction risk calculations. The comparison result may also be provided to a merchant system and / or merchant for use in a decision-making process, for example, to verify customer identity.
Owner:LIBERTY PEAK VENTURES LLC
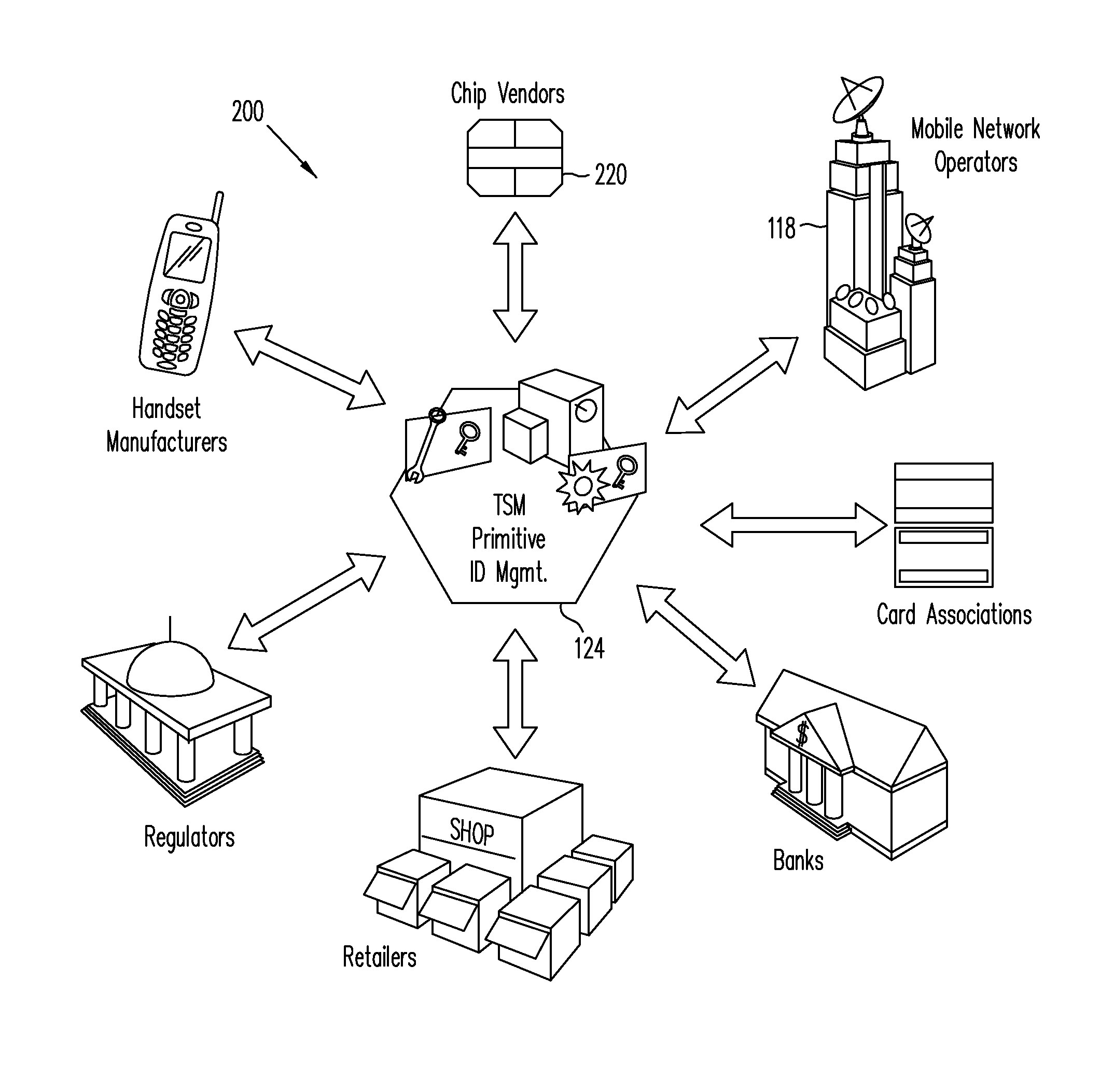
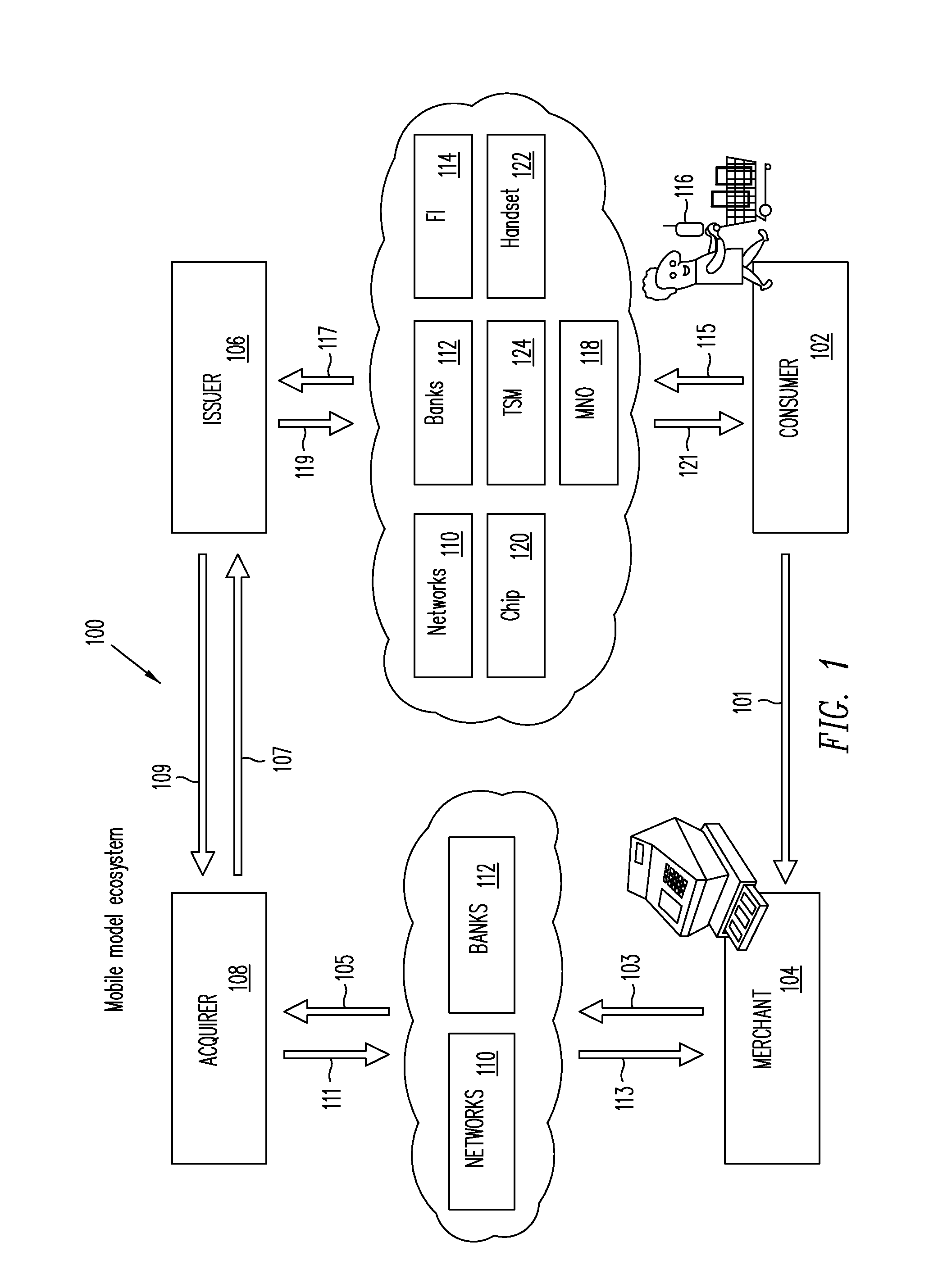
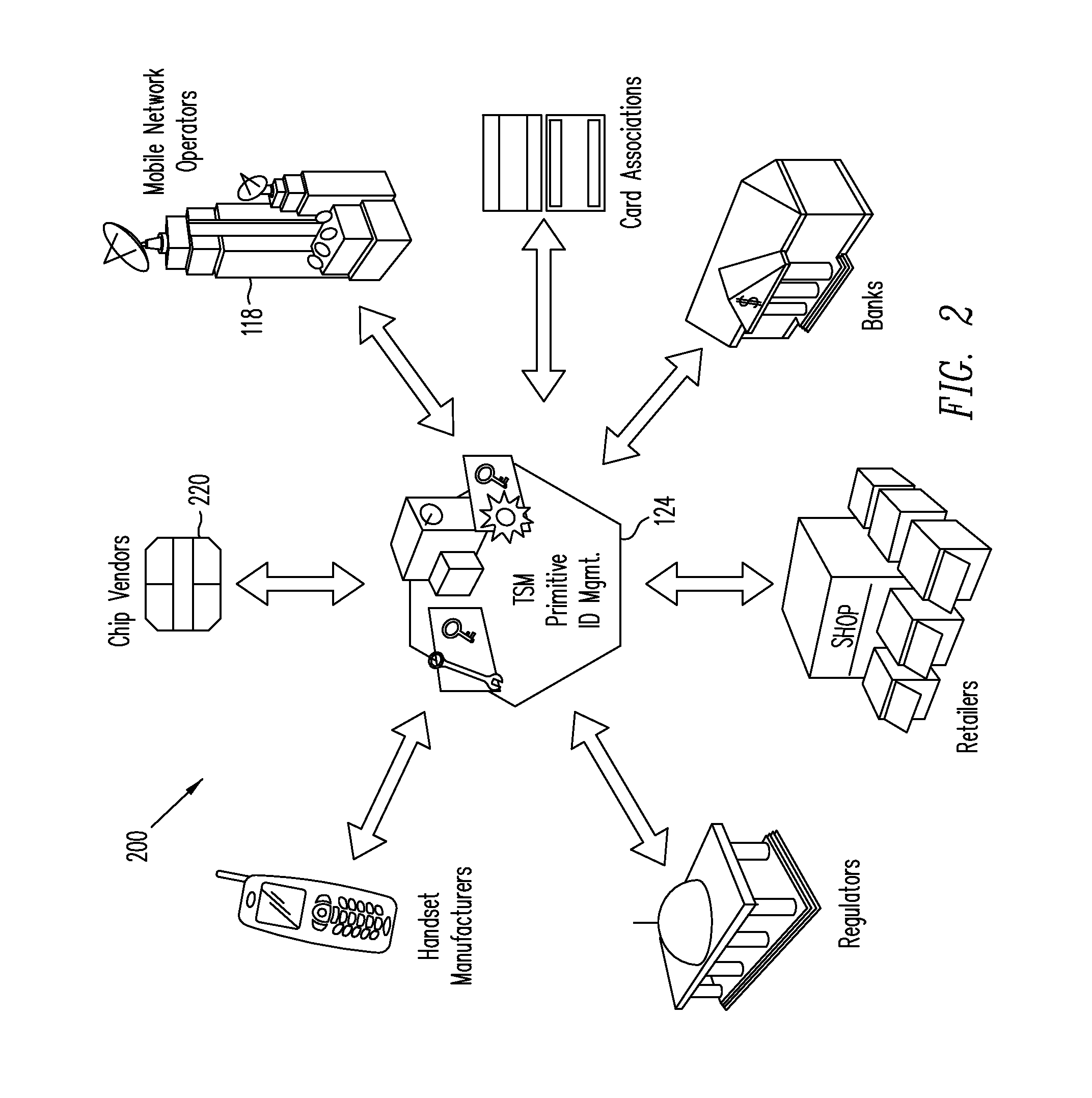
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
System and method for integrating and validating genotypic, phenotypic and medical information into a database according to a standardized ontology
InactiveUS20070178501A1Safest and most effective treatmentGood decisionData processing applicationsMicrobiological testing/measurementData validationMedical record
The system described herein enables clinicians and researchers to use aggregated genetic and phenotypic data from clinical trials and medical records to make the safest, most effective treatment decisions for each patient. This involves (i) the creation of a standardized ontology for genetic, phenotypic, clinical, pharmacokinetic, pharmacodynamic and other data sets, (ii) the creation of a translation engine to integrate heterogeneous data sets into a database using the standardized ontology, and (iii) the development of statistical methods to perform data validation and outcome prediction with the integrated data. The system is designed to interface with patient electronic medical records (EMRs) in hospitals and laboratories to extract a particular patient's relevant data. The system may also be used in the context of generating phenotypic predictions and enhanced medical laboratory reports for treating clinicians. The system may also be used in the context of leveraging the huge amount of data created in medical and pharmaceutical clinical trials. The ontology and validation rules are designed to be flexible so as to accommodate a disparate set of clients. The system is also designed to be flexible so that it can change to accommodate scientific progress and remain optimally configured.
Owner:NATERA
Systems and methods for client-based web crawling
InactiveUS20050071766A1The process is fast and accurateReducing server-client communication trafficData processing applicationsWeb data indexingData validationSource Data Verification
The present invention provides systems and methods for obtaining information from a networked system utilizing a distributed web crawler. The distributed nature of clients of a server is leveraged to provide fast and accurate web crawling data. Information gathered by a server's web crawler is compared to data retrieved by clients of the server to update the crawler's data. In one instance of the present invention, data comparison is achieved by utilizing information disseminated via a search engine results page. In another instance of the present invention, data validation is accomplished by client dictionaries, emanating from a server, that summarize web crawler data. The present invention also facilitates data analysis by providing a means to resist spoofing of a web crawler to increase data accuracy.
Owner:MICROSOFT TECH LICENSING LLC
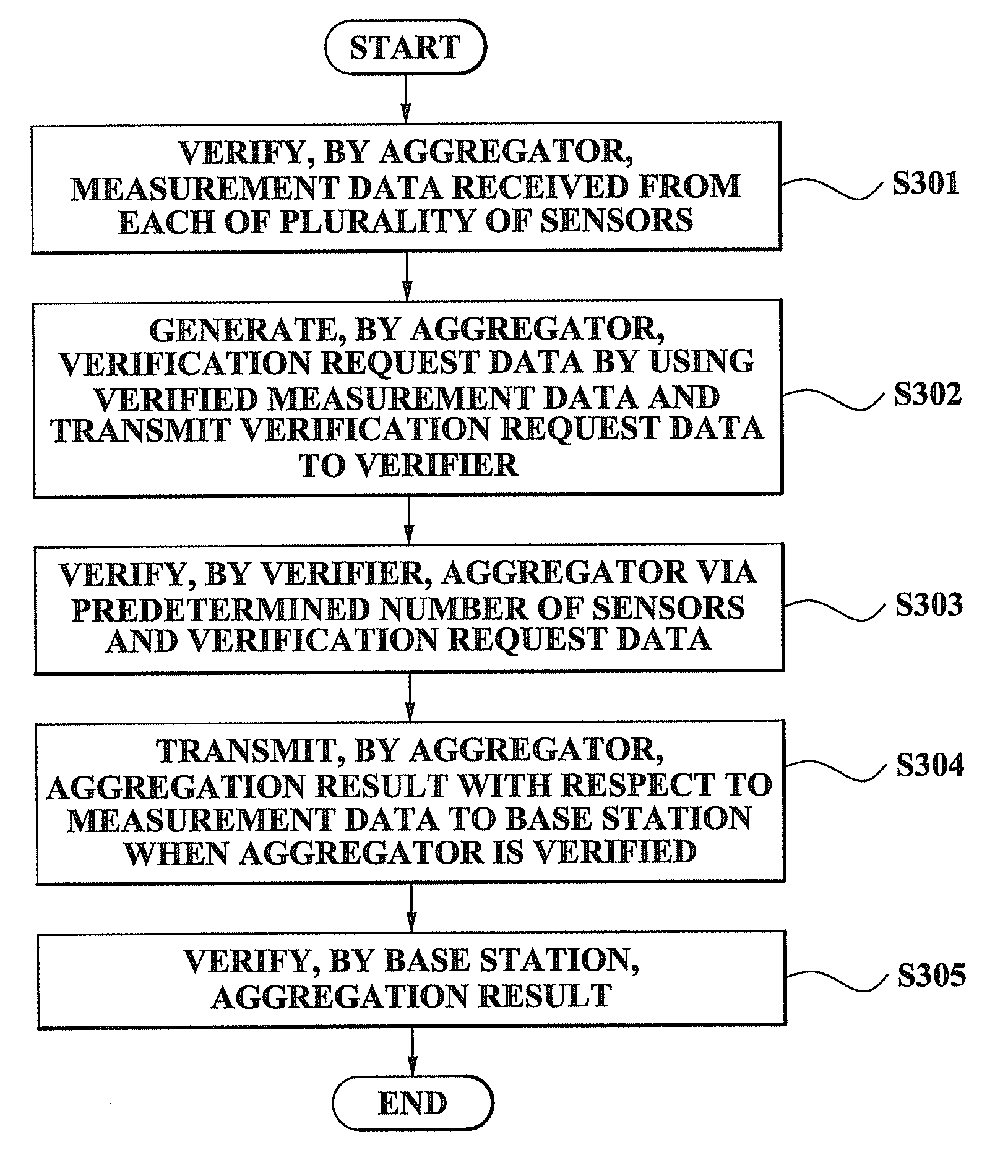
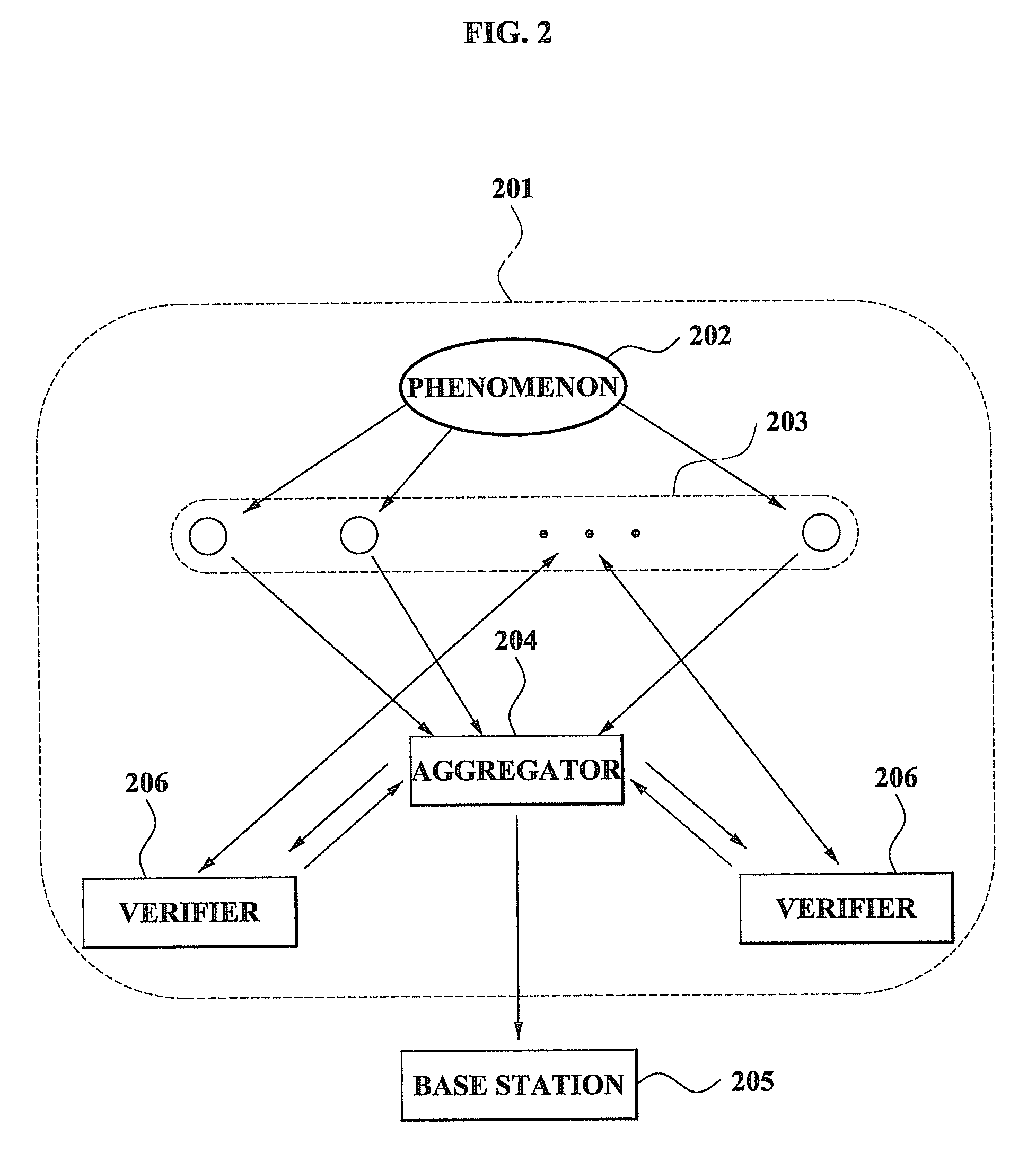
Method and system for performing distributed verification with respect to measurement data in sensor network
ActiveUS20080262798A1Efficient managementImprove securityAmplifier modifications to reduce noise influenceDigital data processing detailsData validationSource Data Verification
A method and system for performing a distributed verification with respect to measurement data in a sensor network. The method of performing the distributed verification with respect to measurement data in a sensor network includes: verifying, by an aggregator, the measurement data received from each of a plurality of sensors; generating, by the aggregator, verification request data by using the verified measurement data; transmitting the verification request data to a verifier; and verifying, by the verifier, the aggregator via a predetermined number of sensors of the plurality of sensors and the verification request data. The method of performing a distributed verification with respect to measurement data in a sensor network further includes transmitting, by the aggregator, an aggregation result with respect to the measurement data to a base station when the aggregator is verified; and verifying, by the base station, the aggregation result.
Owner:SAMSUNG ELECTRONICS CO LTD
Data certification and verification system having a multiple-user-controlled data interface
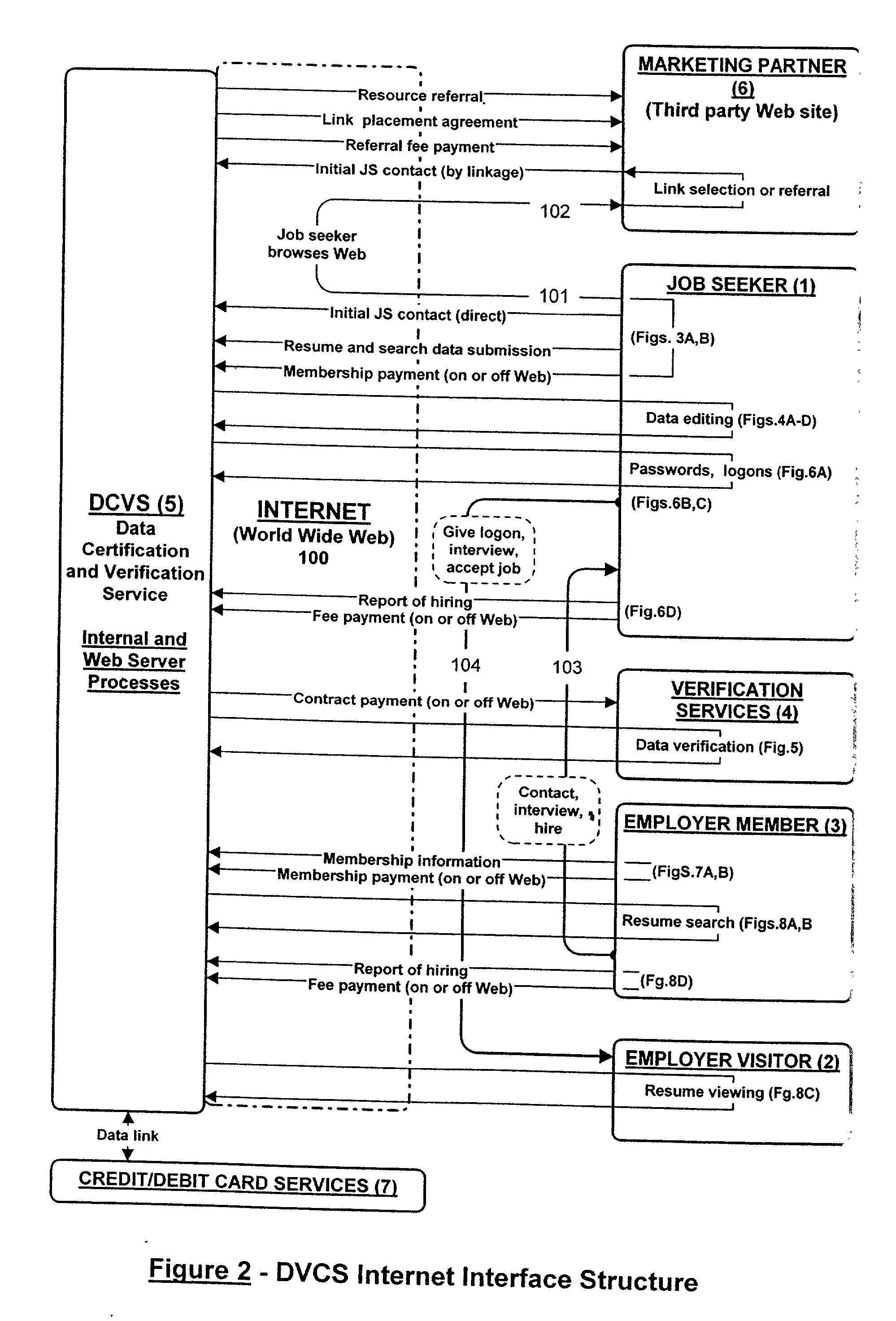
InactiveUS6658400B2Preserve valueFast and cost-effective operationComputer security arrangementsOffice automationData validationSource Data Verification
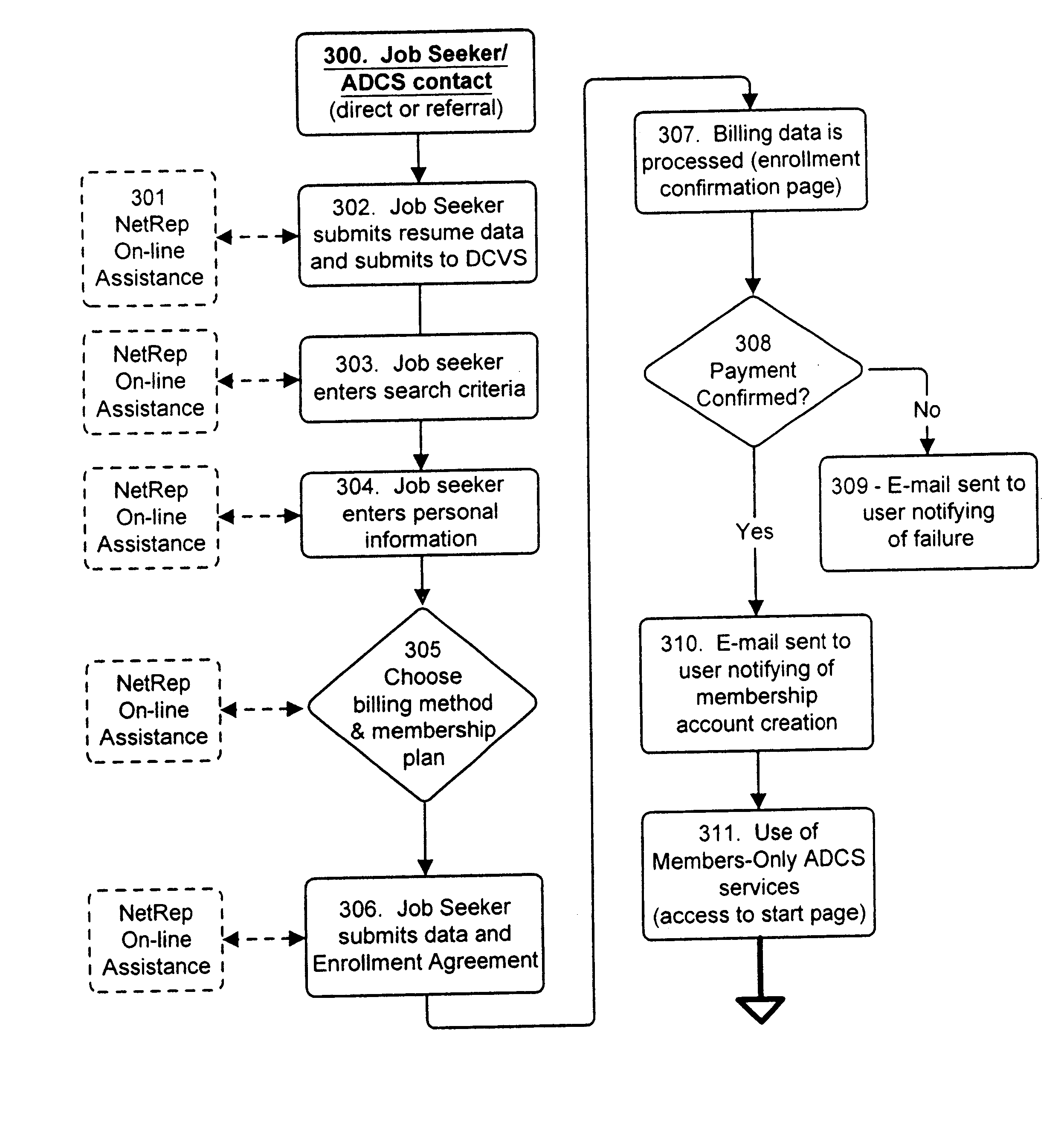
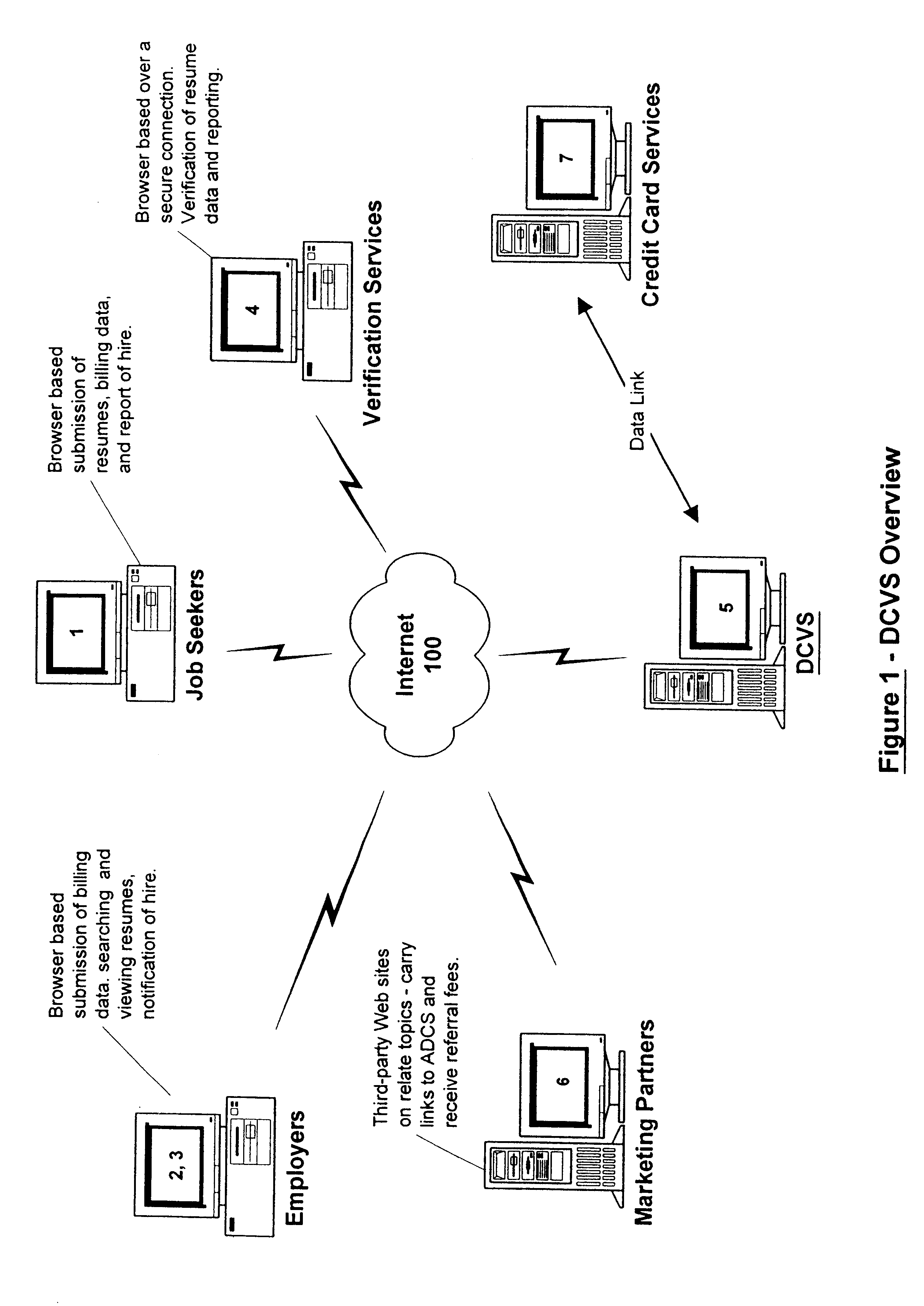
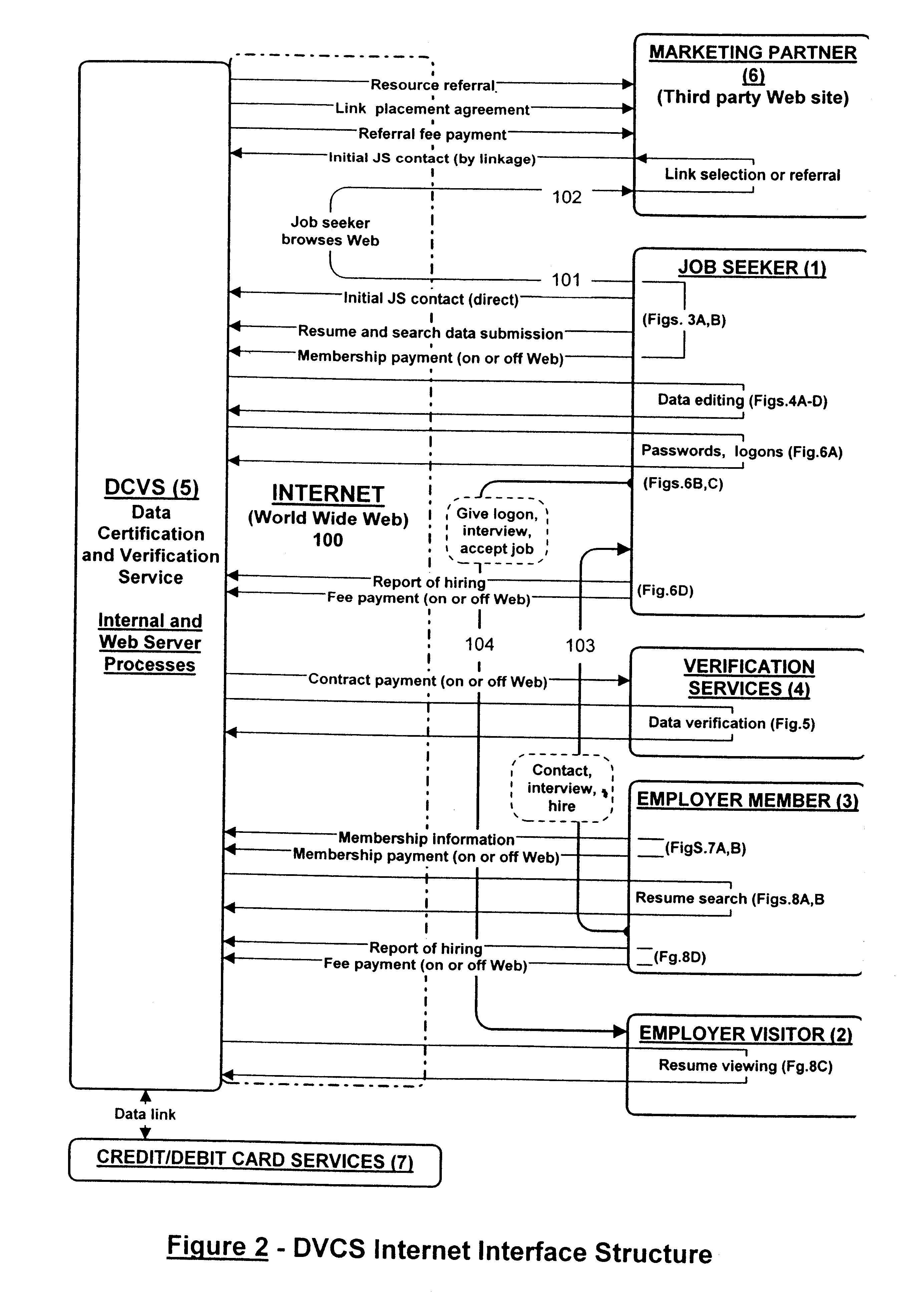
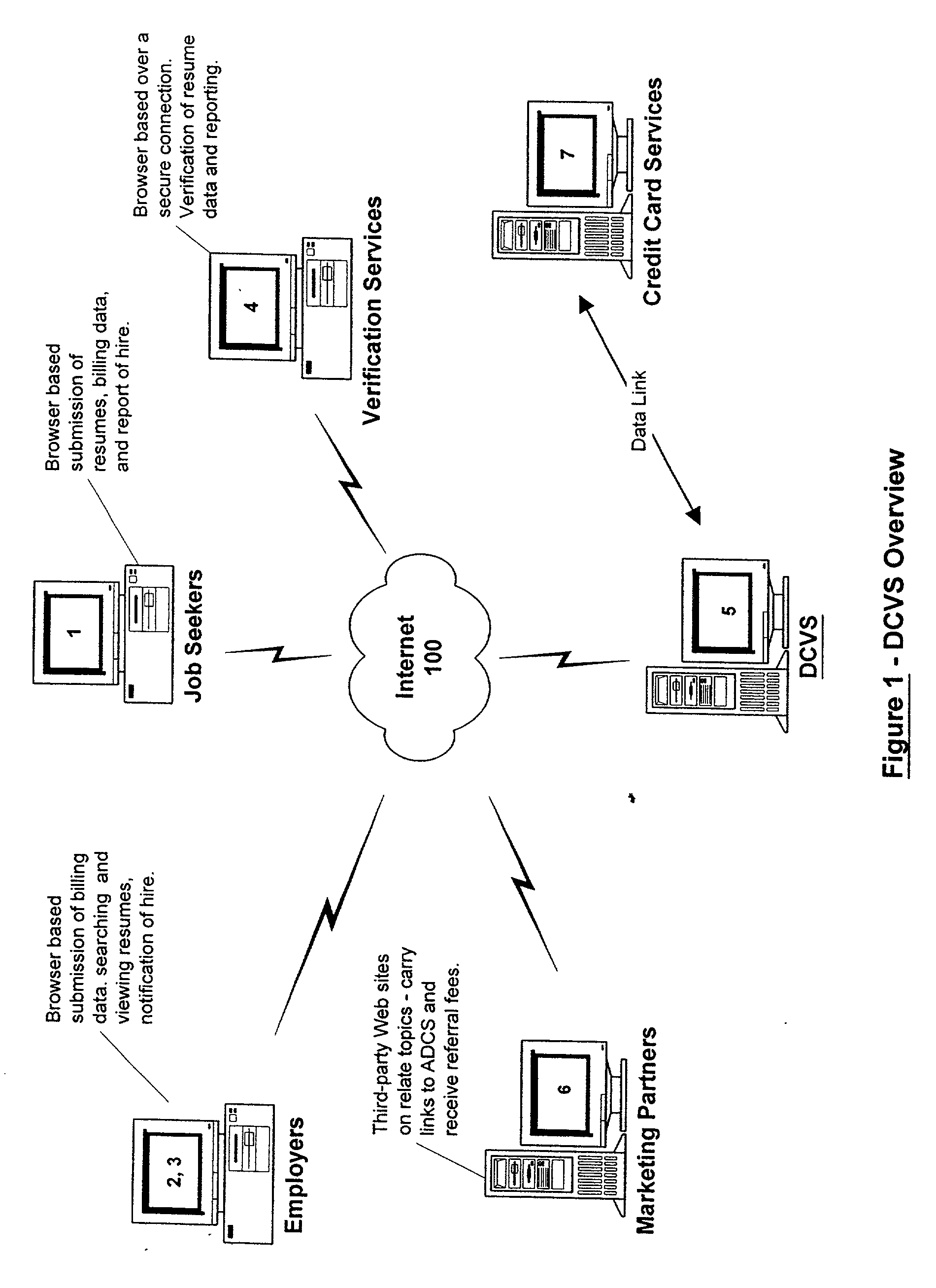
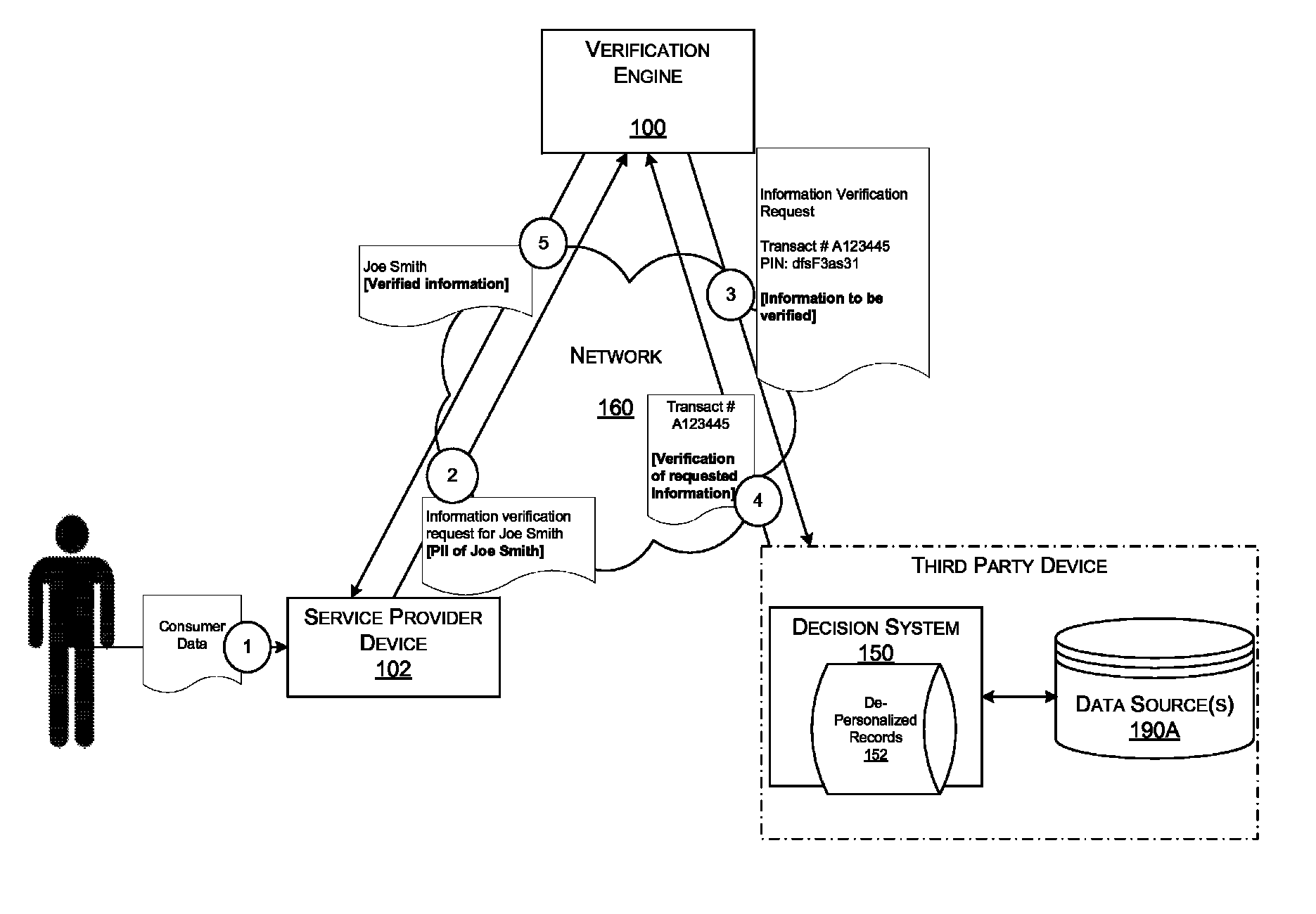
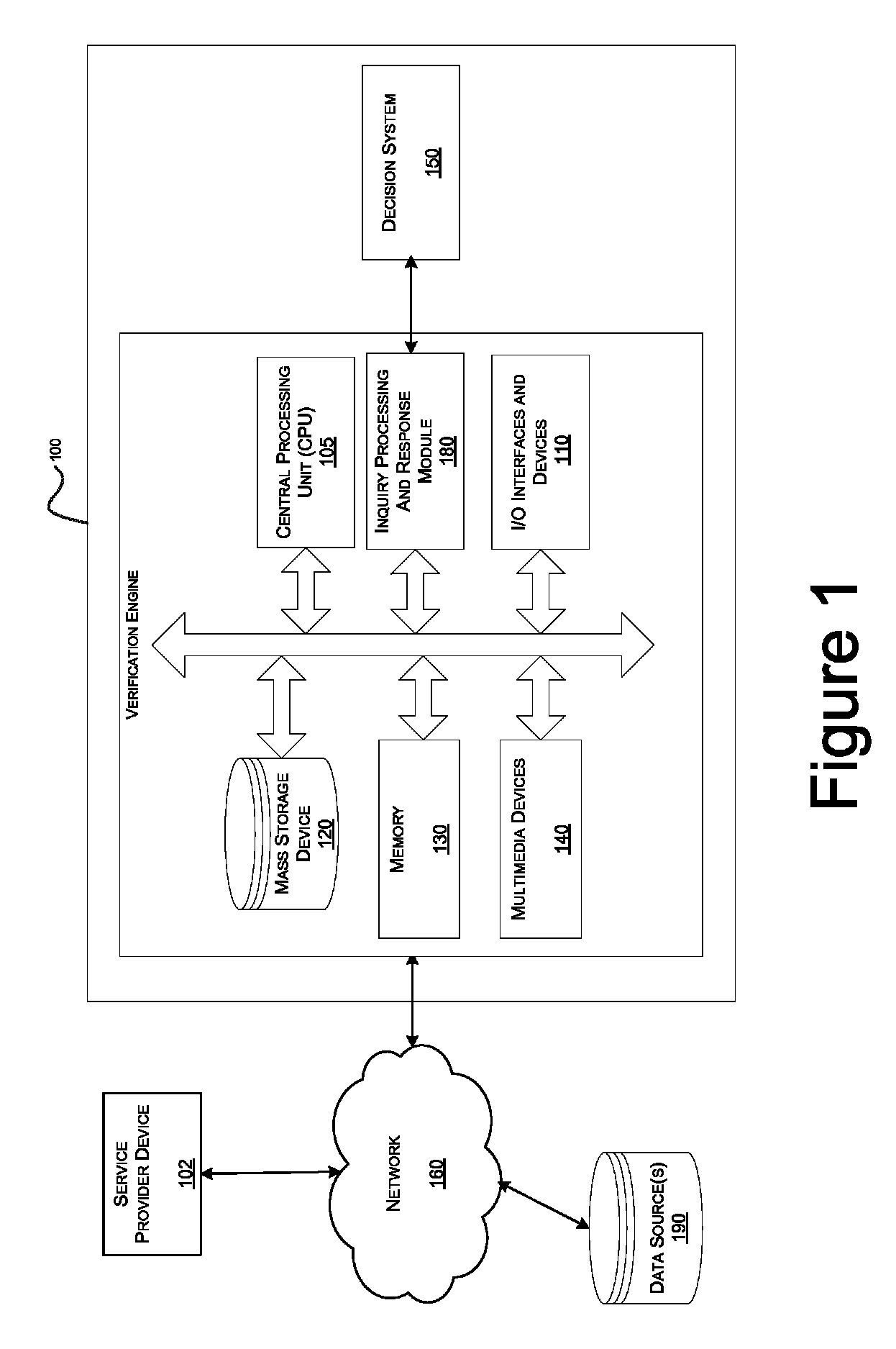
A method and apparatus is described for multiple-party data attribute management system and interface structure which permits different categories of users to contribute and control different types of source data, while adding informational value to data contributed by other users. The system provides a secure repository for verified and authenticated data, and provides a system of controlled access to the repository. The preferred embodiment of the invention comprises a data verification and certification system which in a principal embodiment is useful to create a data bank to match job seekers with potential employers based on verified resume data and employer specified search criteria. The interface structure The system of the invention preferably includes computer databases and interactive Internet based server systems.
Owner:VERIFIED HIRING
Data certification and verification system having a multiple- user-controlled data interface
InactiveUS20010047347A1Fast and cost-effective operationAvoid effortComputer security arrangementsMultiple digital computer combinationsData validationSource Data Verification
Owner:VERIFIED HIRING
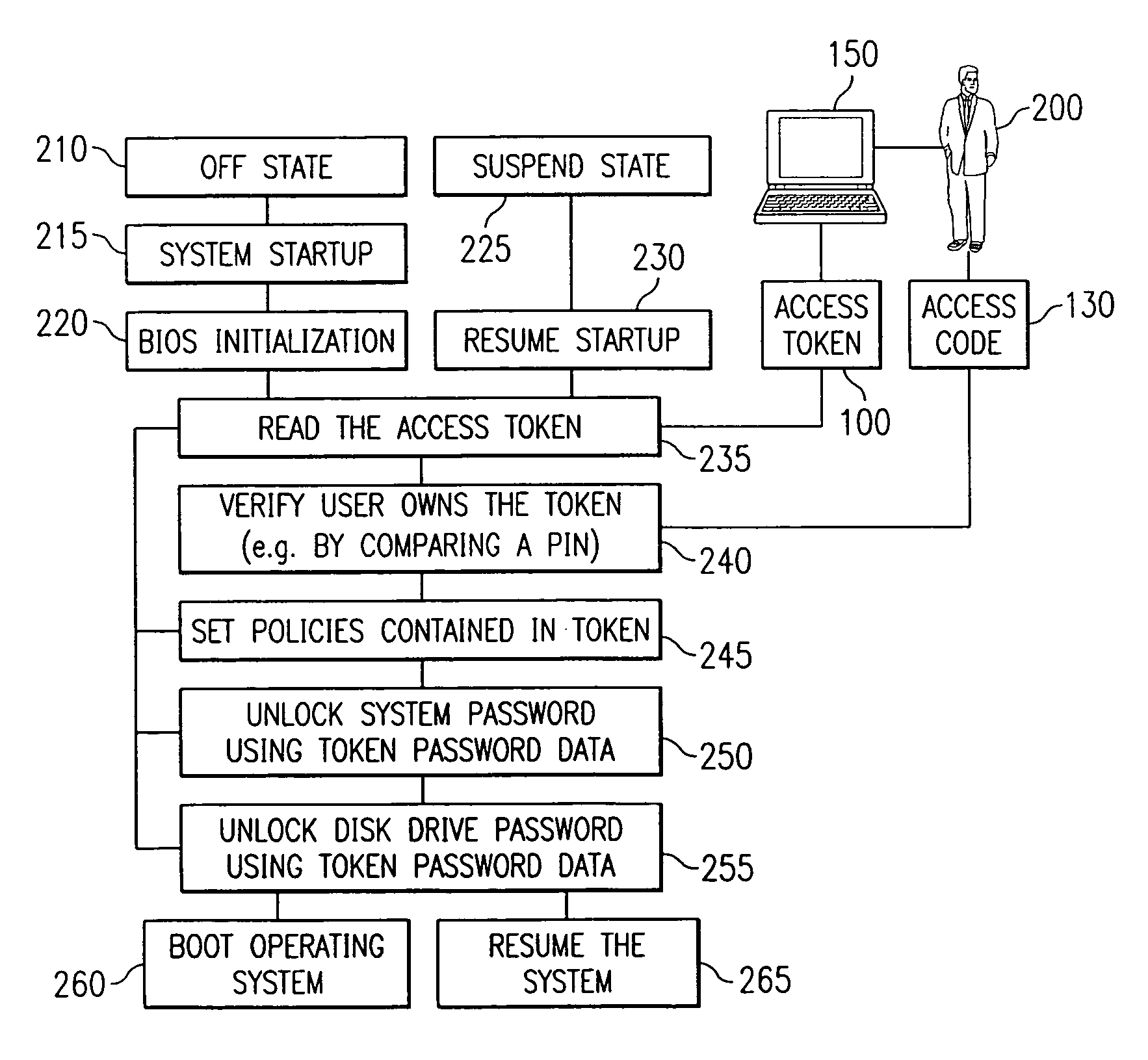
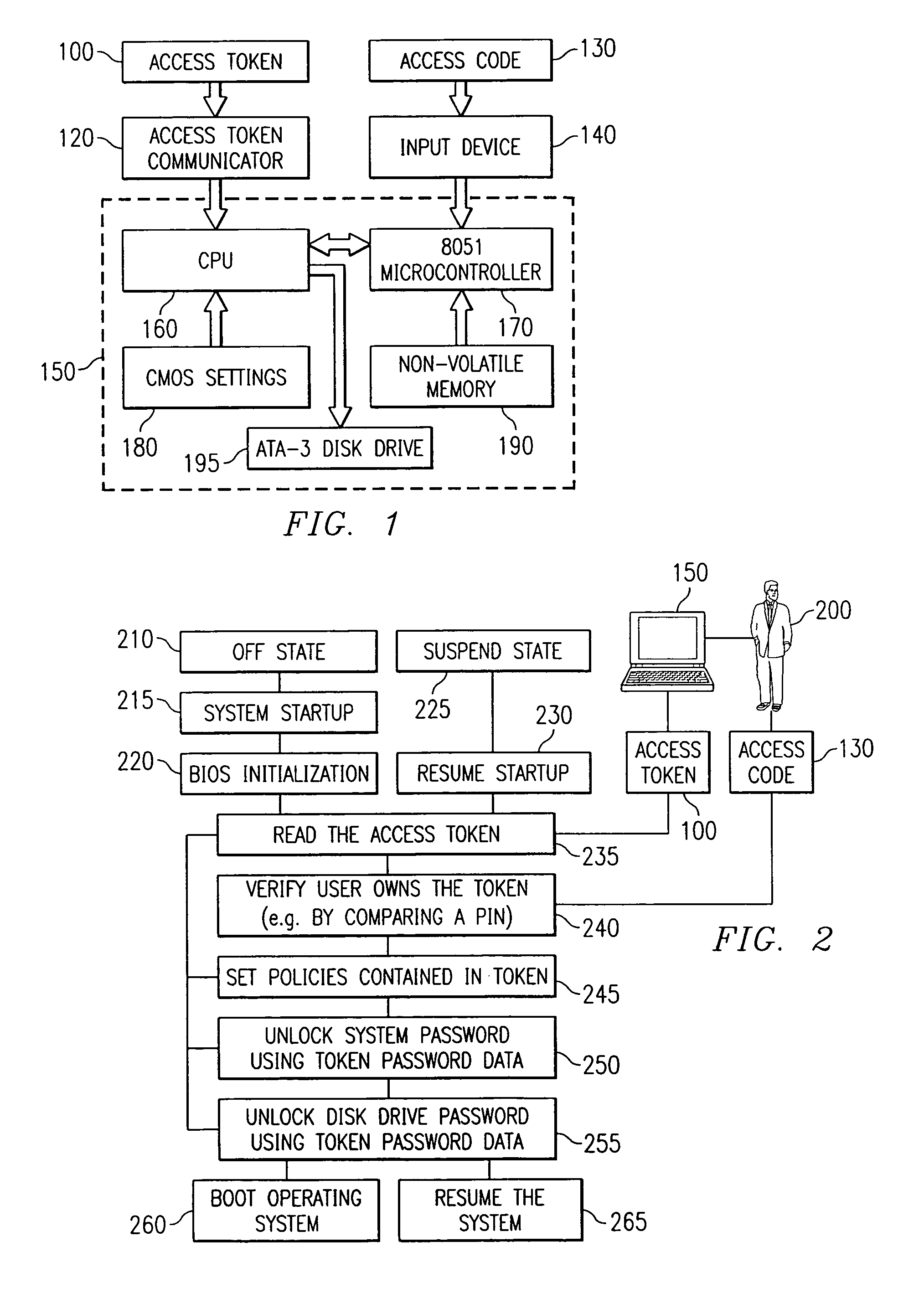
Portable computer system with hierarchical and token-based security policies
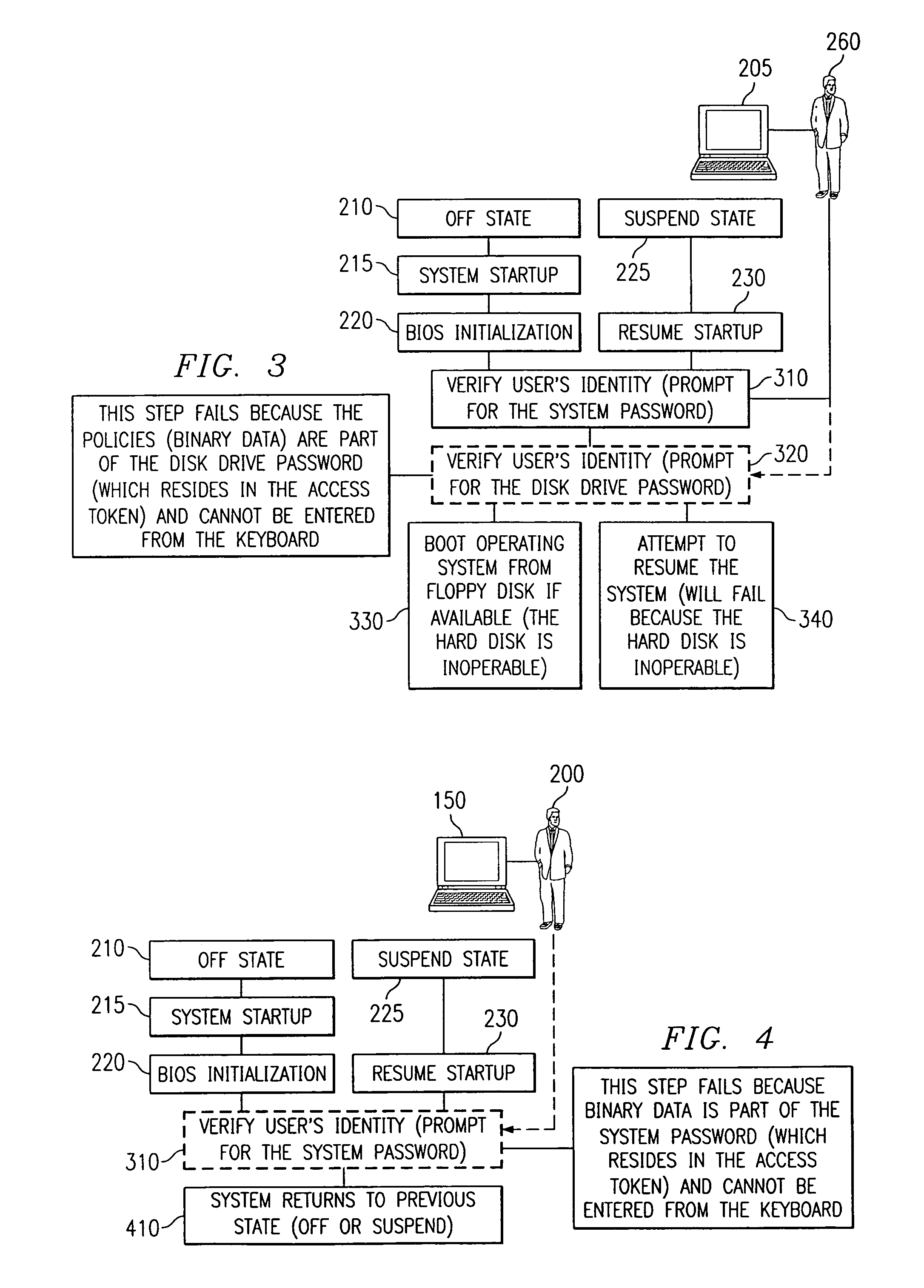
InactiveUS7111321B1Reduce the possibilityError detection/correctionVolume/mass flow measurementSource Data VerificationComputerized system
A computer system including a processor, an access token communicator capable of being coupled to the processor and adapted to read an access token, an input device coupled to the processor that is able to receive verification data that confirms authorized access of the access token, and software executable on the processor that includes instructions to control access to the processor and including code to access the access token and the verification data, code to verify the validity of the access token using the verification data, code to set security policies in the processor, and code to control access to resources in the processor based on the security policies. In addition, a method for reading an access token, verifying the validity of the access token, setting security policies in a computer system, and unlocking a computer system and a nonvolatile storage device attached to the computer system.
Owner:DELL PROD LP
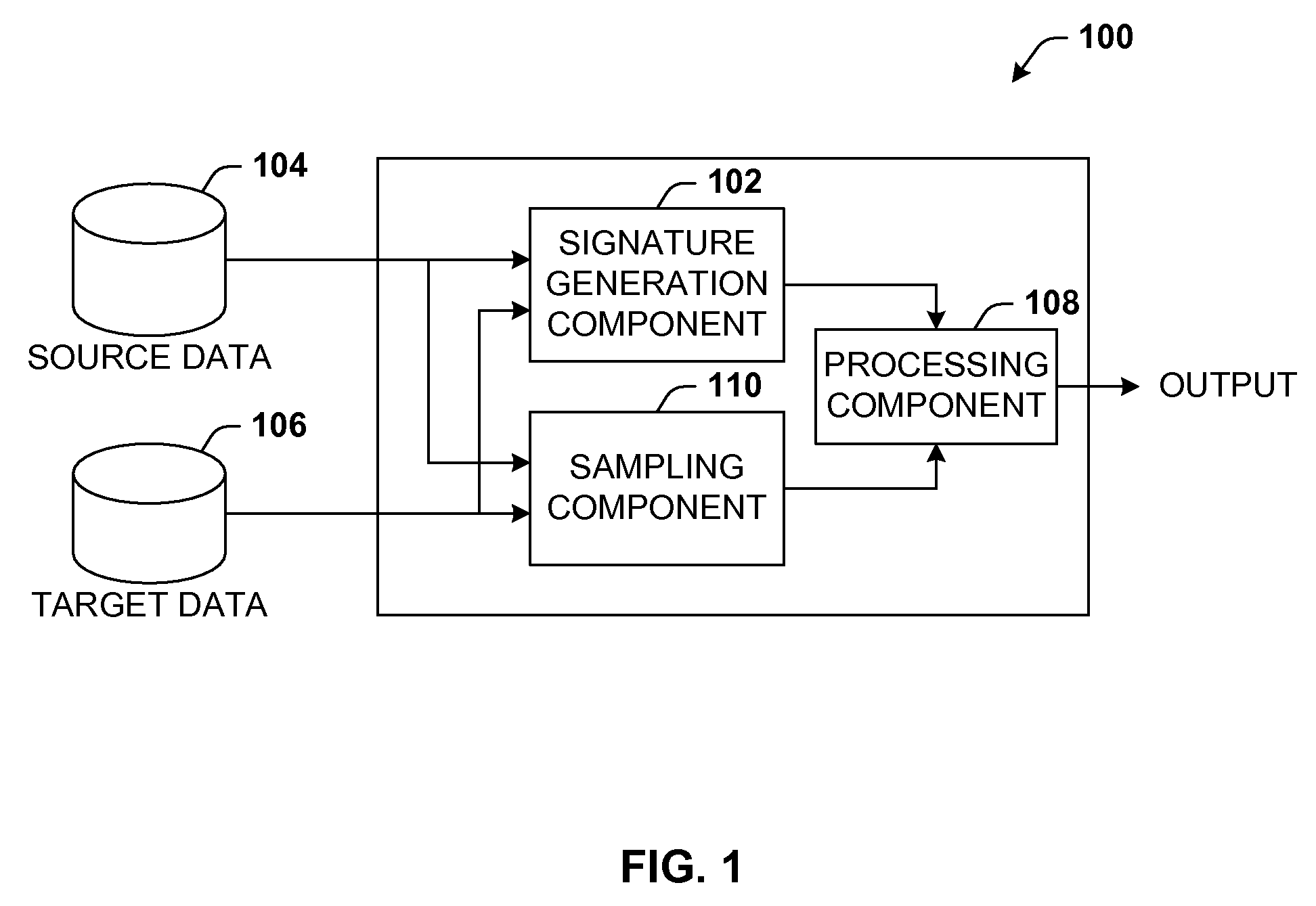
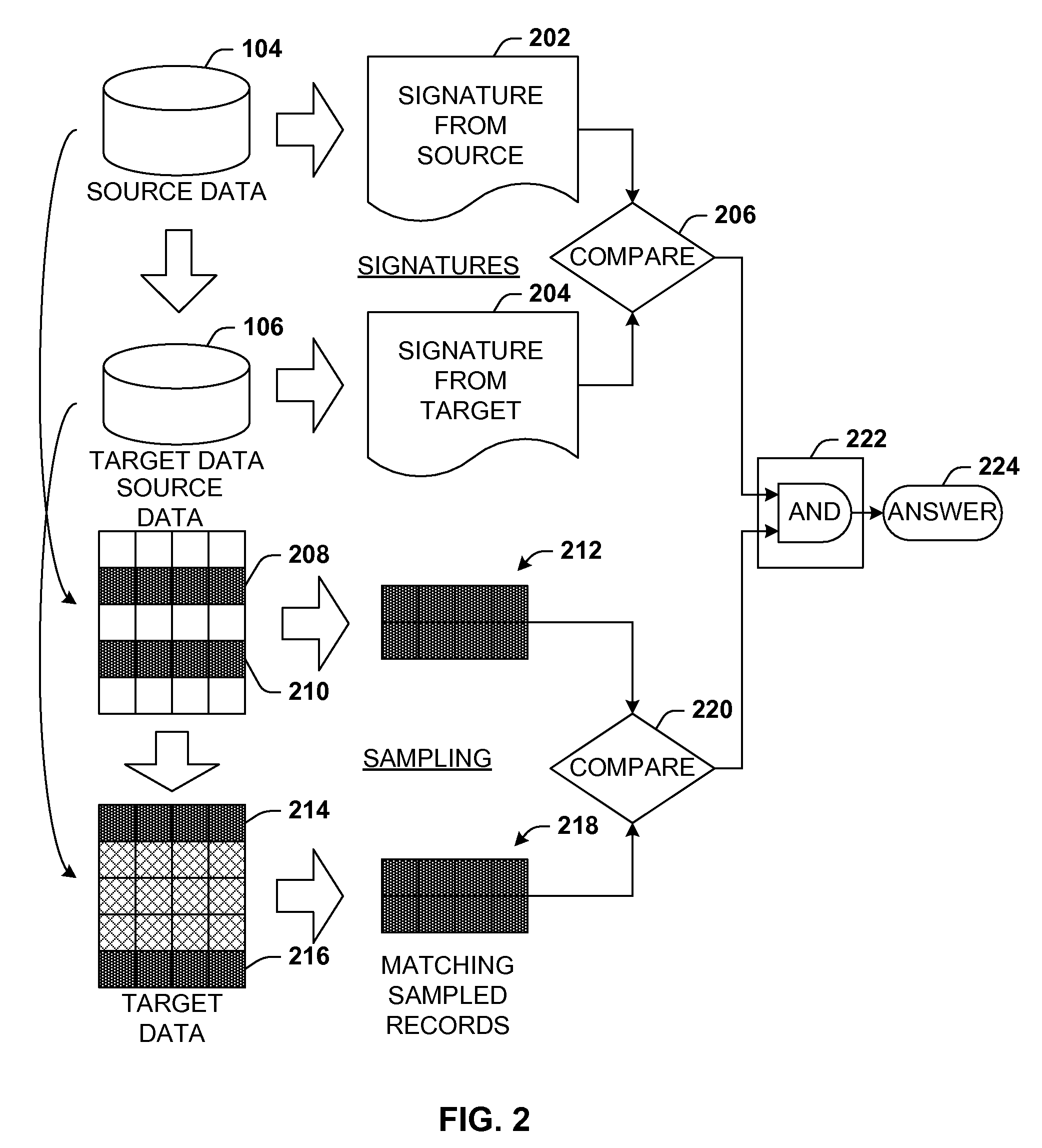
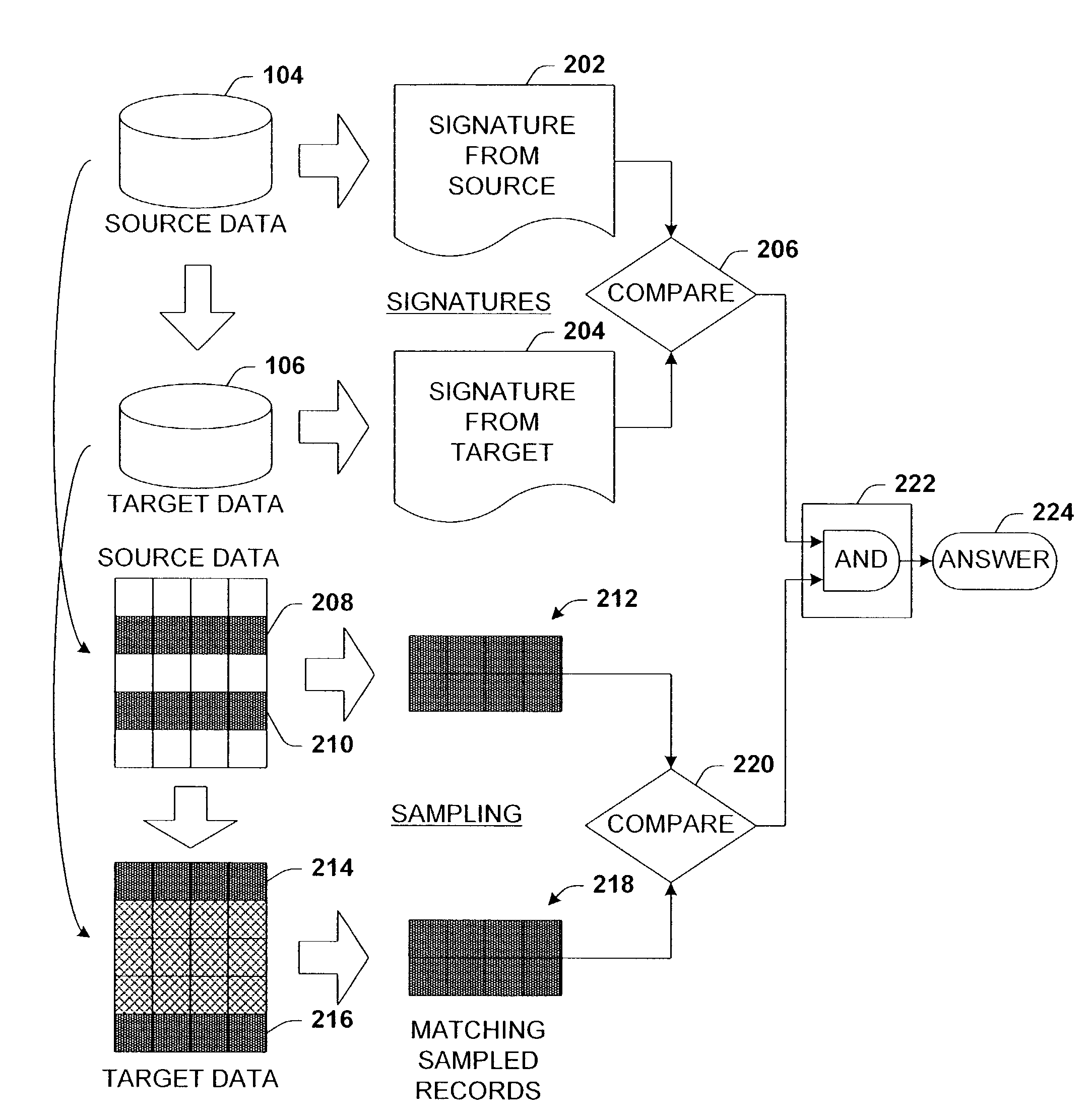
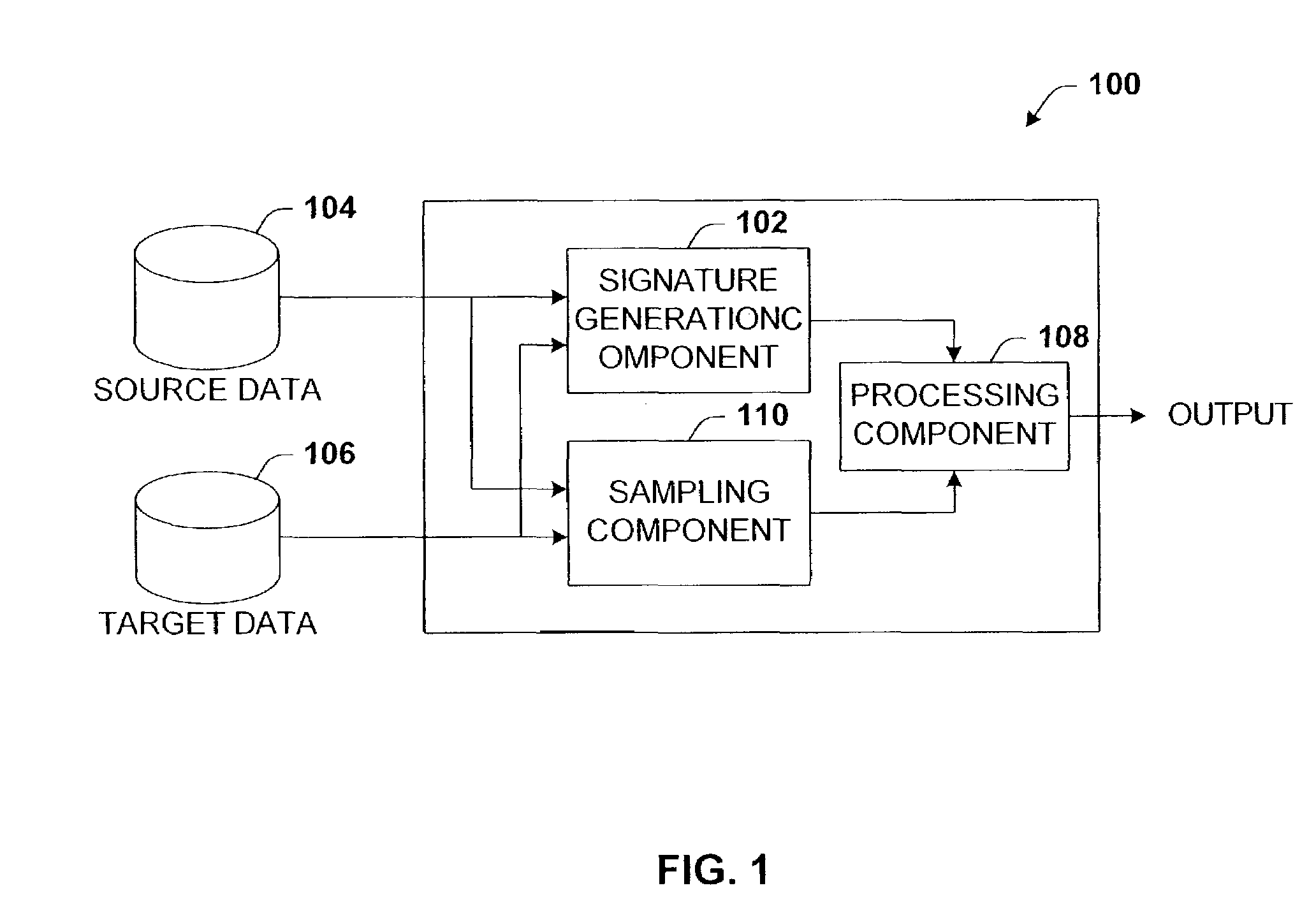
Data validation using signatures and sampling
InactiveUS20090132955A1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
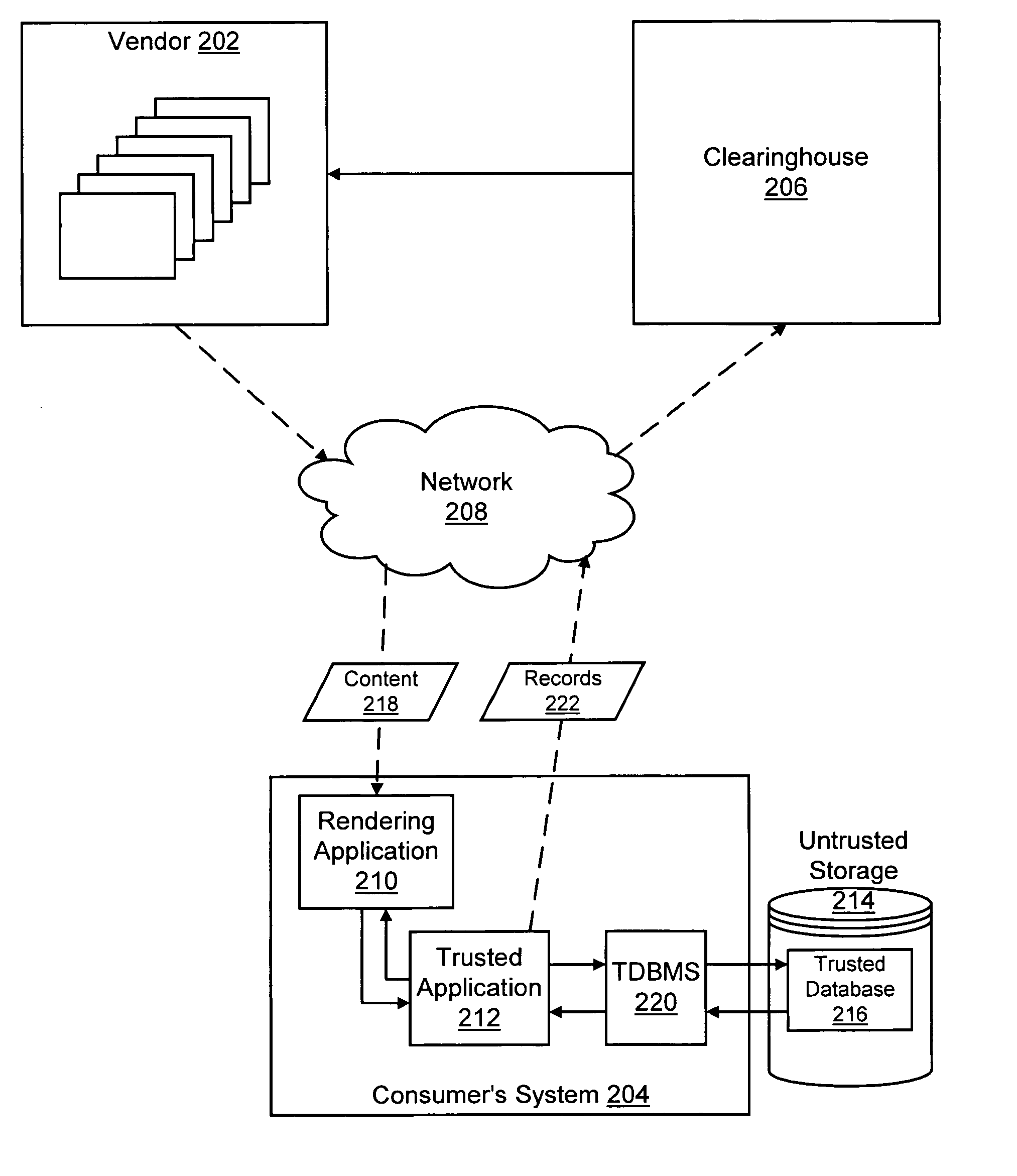
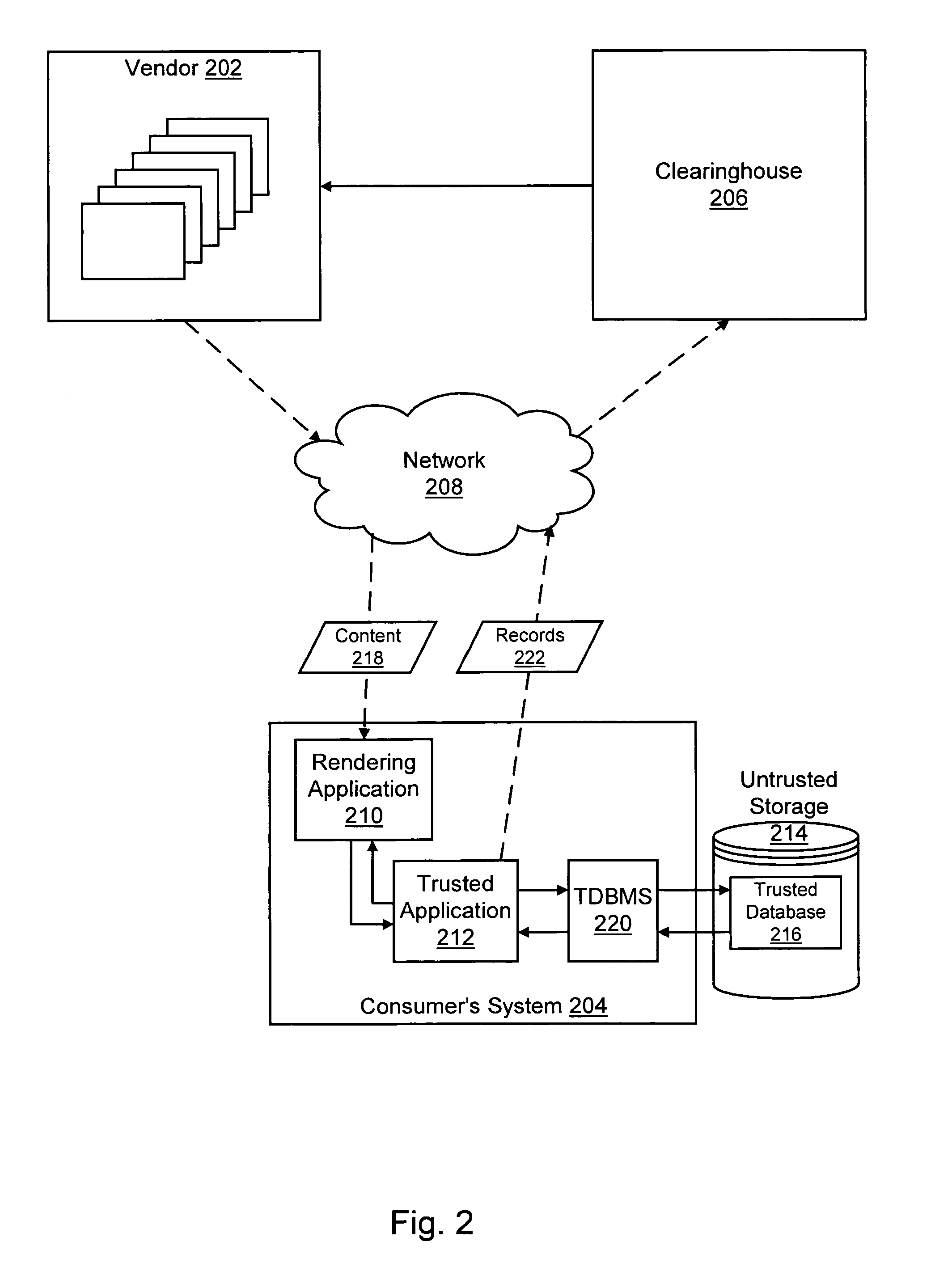
Trusted storage systems and methods
InactiveUS7152165B1Reduces predictabilityEasy to implementDigital data processing detailsUser identity/authority verificationData validationSource Data Verification
Systems and methods are disclosed for providing a trusted database system that leverages a small amount of trusted storage to secure a larger amount of untrusted storage. Data are encrypted and validated to prevent unauthorized modification or access. Encryption and hashing are integrated with a low-level data model in which data and meta-data are secured uniformly. Synergies between data validation and log-structured storage are exploited.
Owner:INTERTRUST TECH CORP
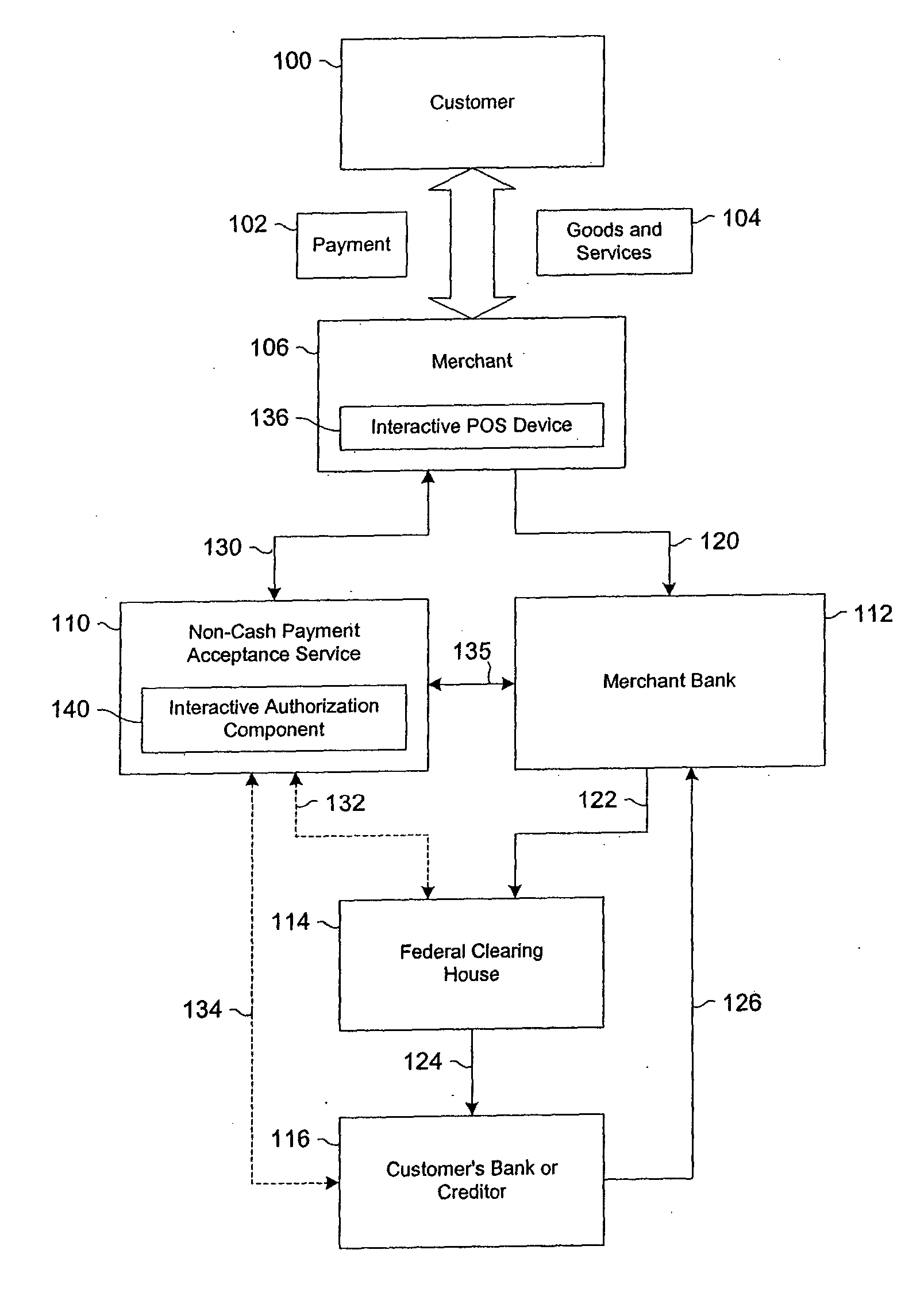
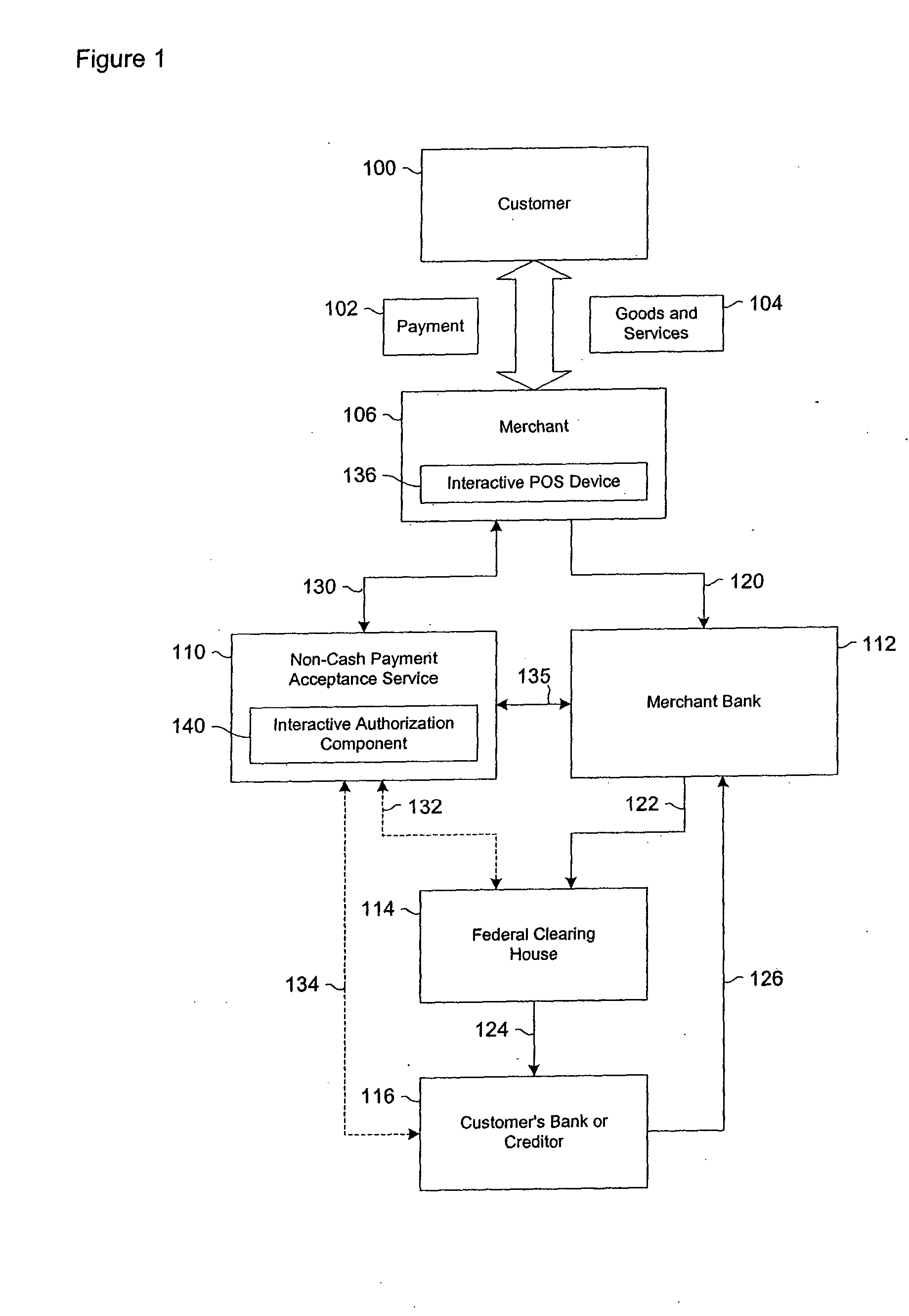
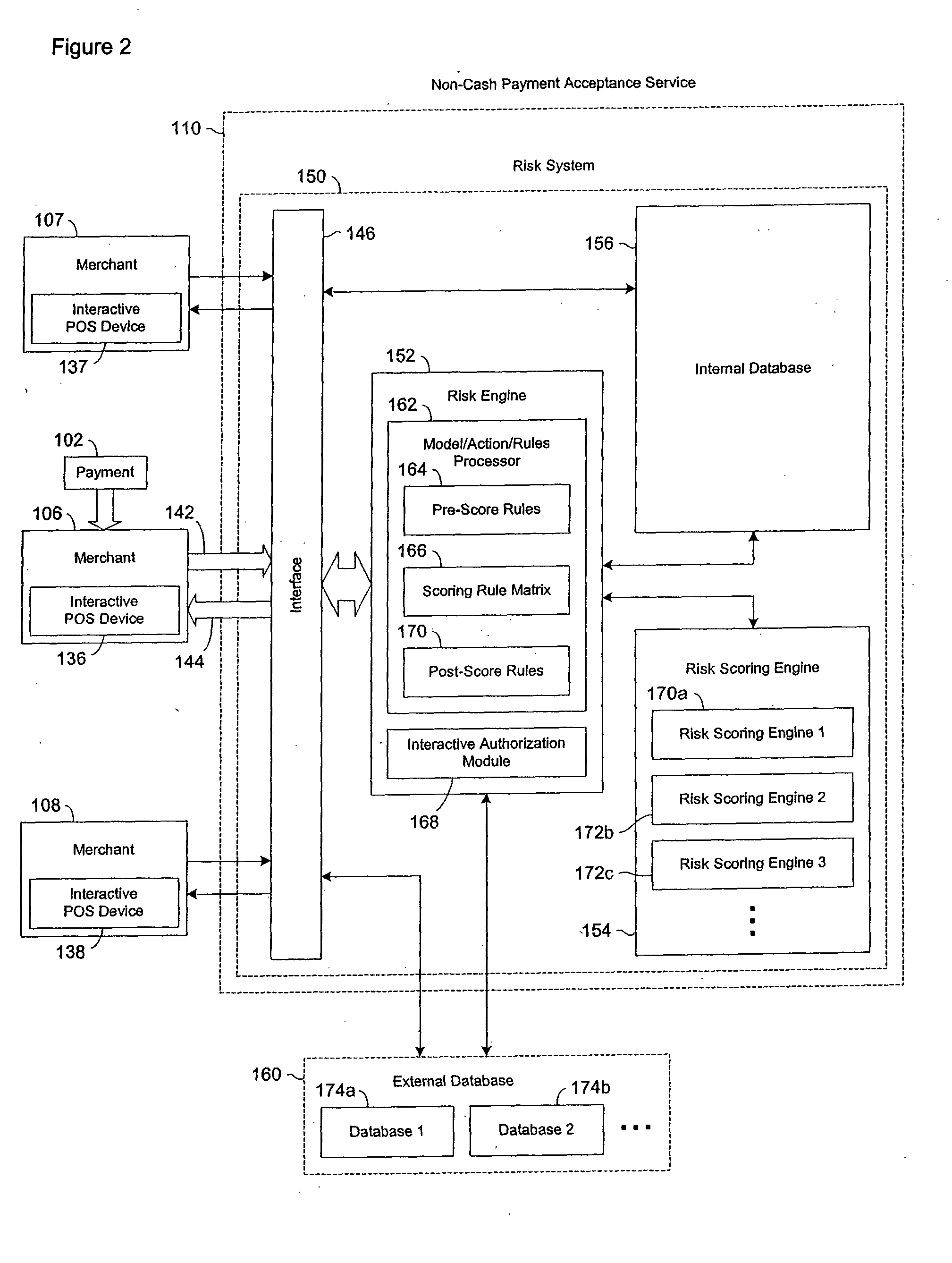
Data validation systems and methods for use in financial transactions
A risk system that performs a risk assessment of a financial transaction to obtain a risk score. Based on the risk score, the risk system may request additional transaction information from a customer and / or a merchant. The request is based at least in part on financial transactions that are of moderate risk to thereby provide a non-cash payment acceptance service with more information to further evaluate the financial transaction risks. Thus, moderately risky financial transactions, that are likely to benefit the non-cash payment acceptance service and the merchant that subscribes to the non-cash payment acceptance service, are authorized for increased profitability and customer satisfaction. Furthermore, the risk system may approve or authorize financial transactions that generally fail standard risk assessments that use a cut-off risk score to divide the financial transactions into either approved or declined groups. As a result, the risk system is capable of re-evaluating some of the moderate risk cases for the purpose of securing beneficial financial transactions.
Owner:FIRST DATA
Systems and methods for data verification
Systems and methods for verifying data including income and employment, assets, healthcare claims, clinical data, and other types of data subject to various regulatory and / or privacy restrictions.
Owner:EXPERIAN INFORMATION SOLUTIONS
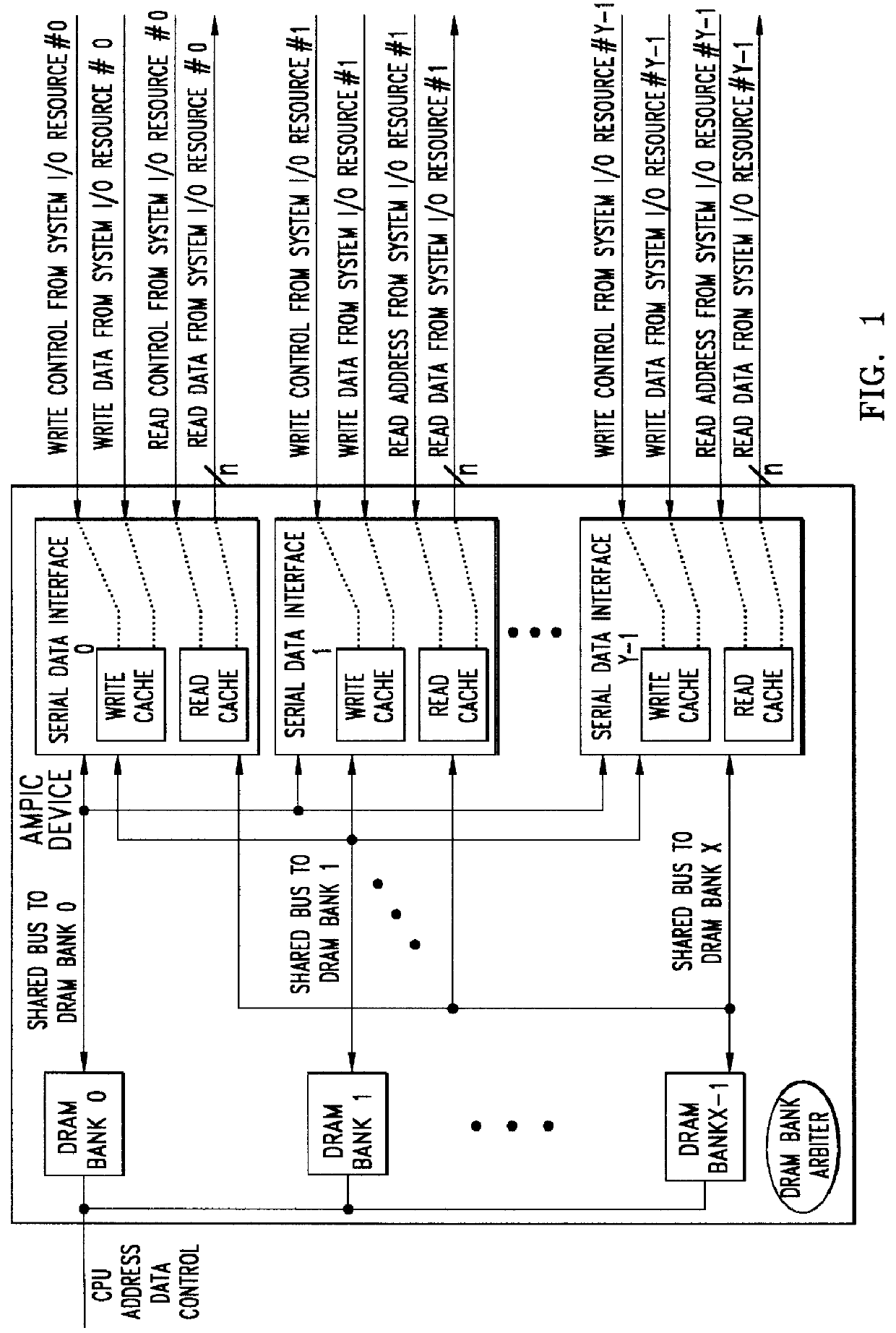
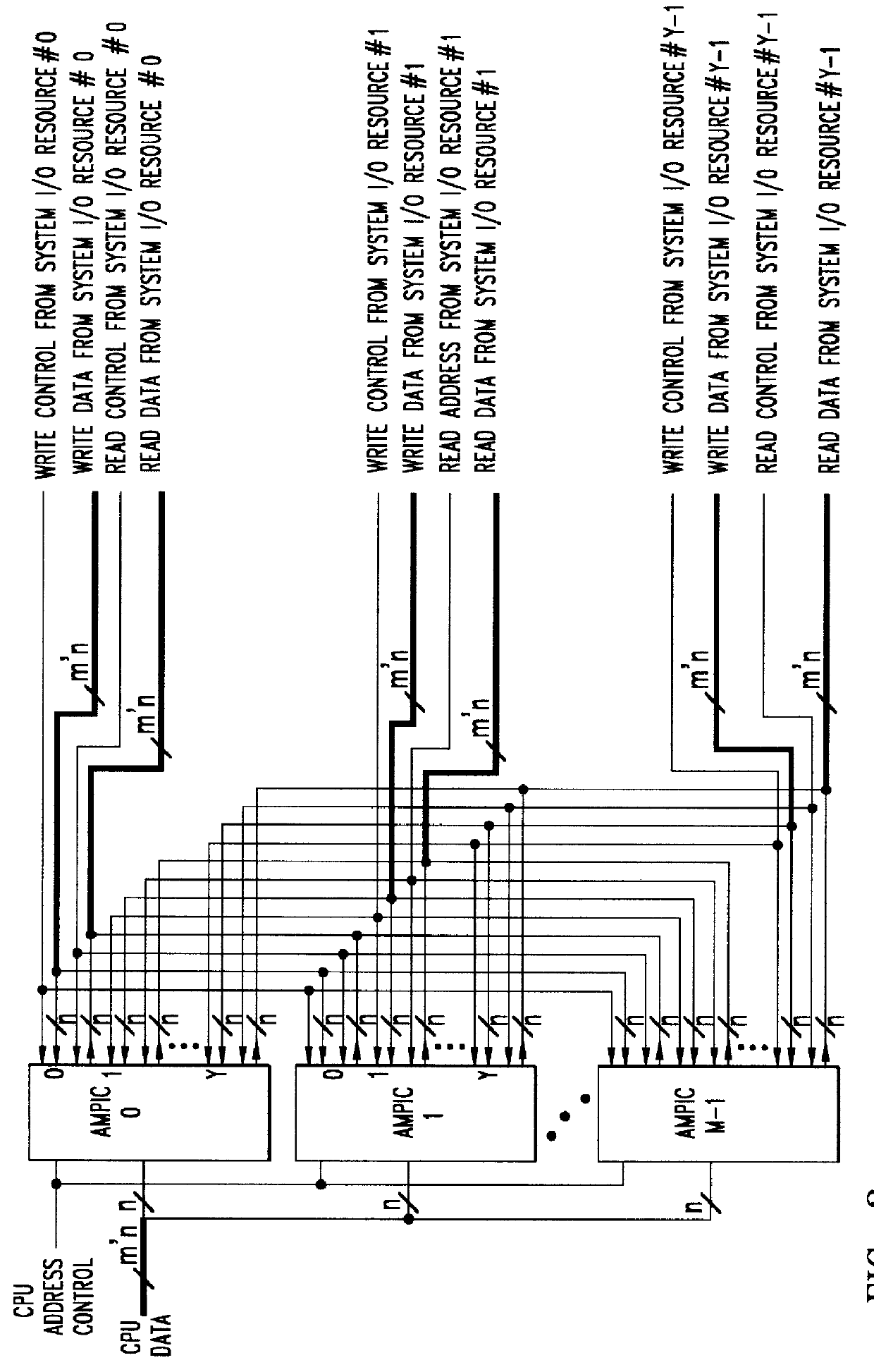
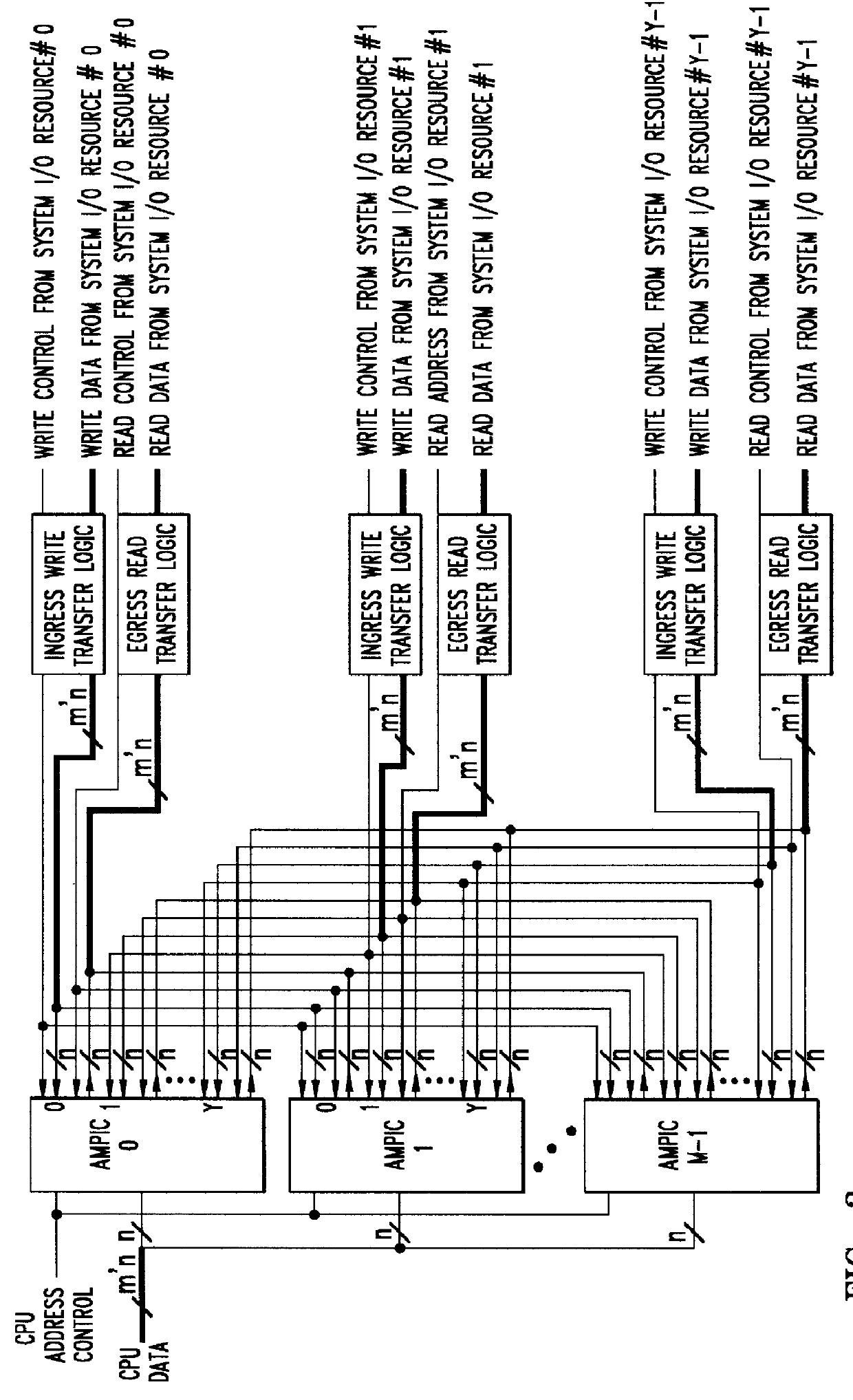
Method of and apparatus for validating data read out of a multi port internally cached dynamic random access memory (AMPIC DRAM)
InactiveUS6085290AEliminates race conditionMemory architecture accessing/allocationMemory adressing/allocation/relocationData validationStatic random-access memory
An apparatus for and method of enhancing the performance of a multi-port internal cached DRAM (AMPIC DRAM) by providing an internal method of data validation within the AMPIC memories themselves to guarantee that only valid requested data is returned from them, or properly marked invalid data. A modified technique for identifying bad data that has been read out of AMPIC memory devices in the system.
Owner:NEXABIT NETWORKS +1
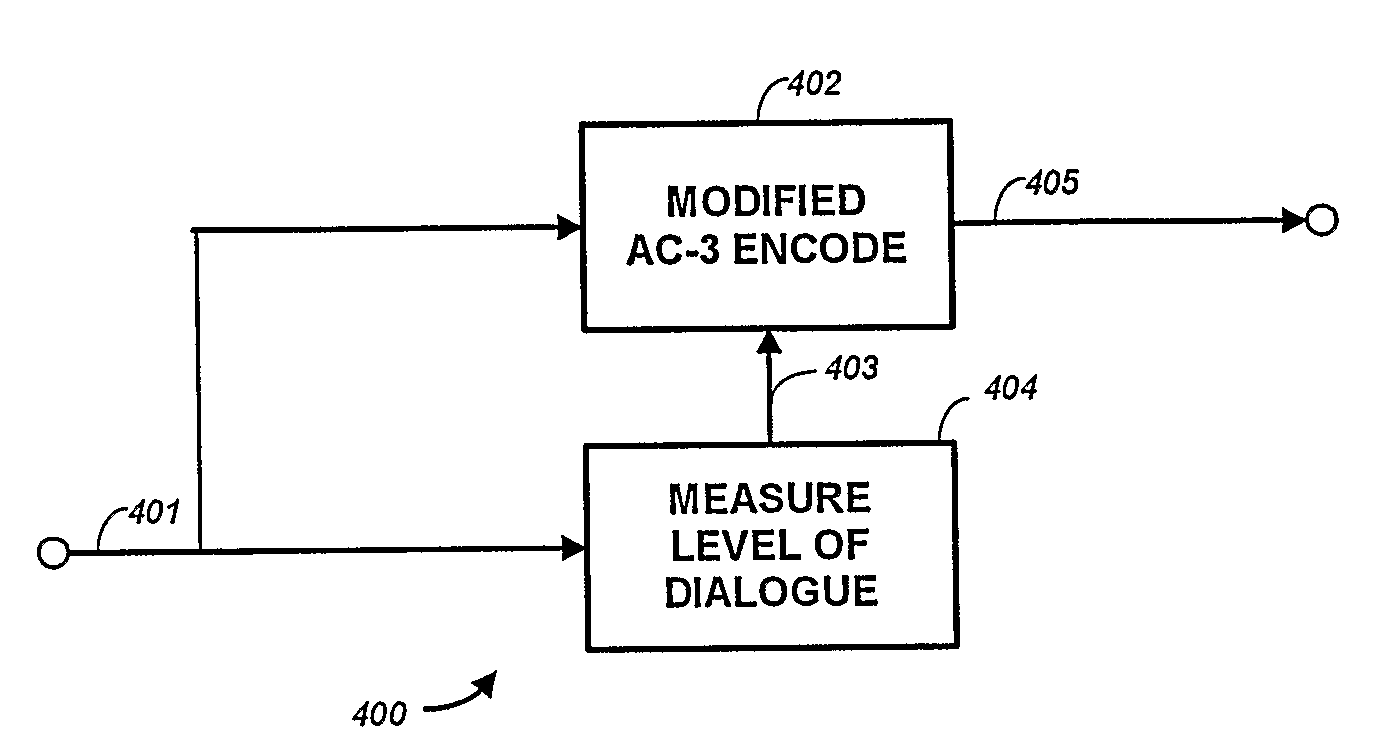
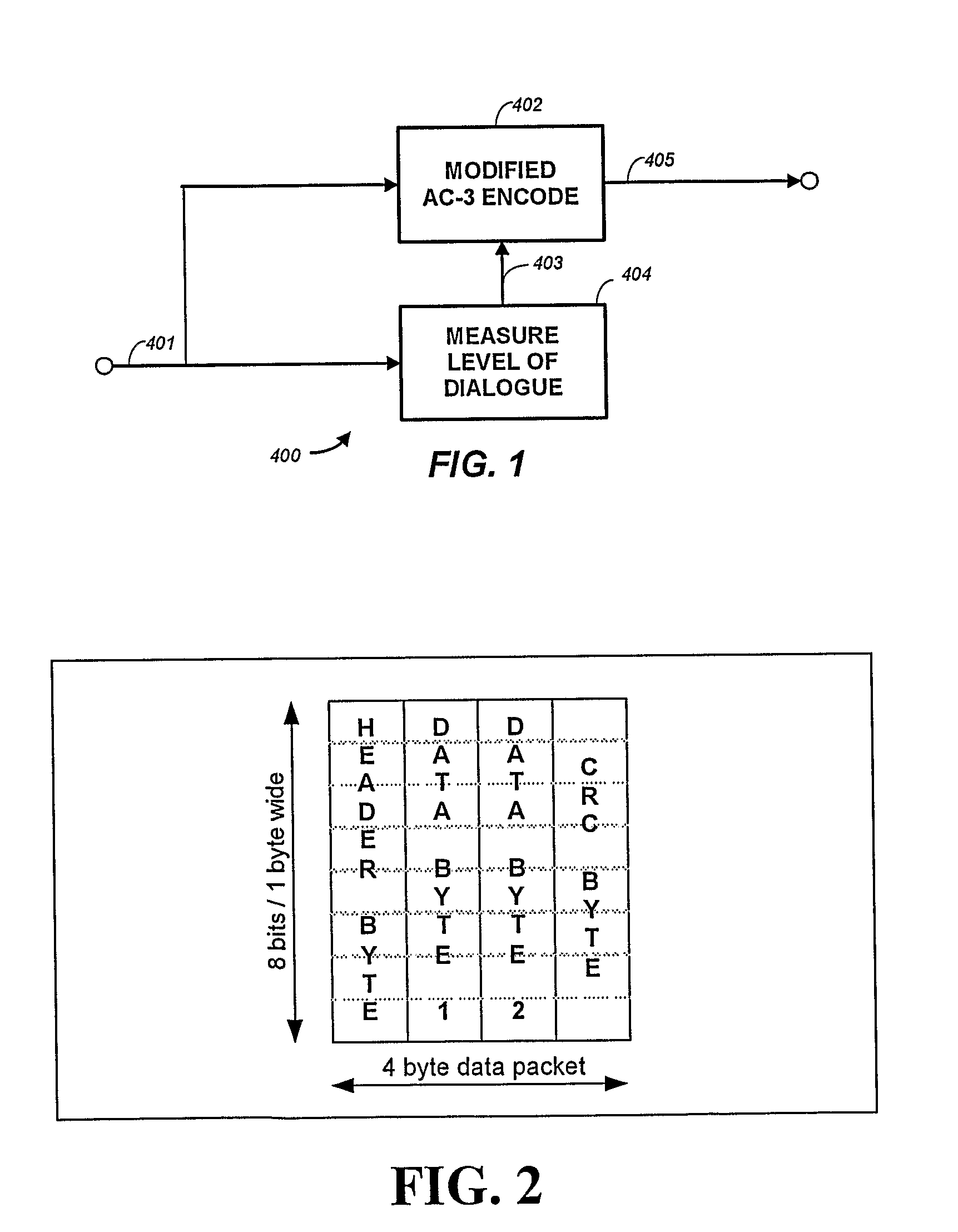
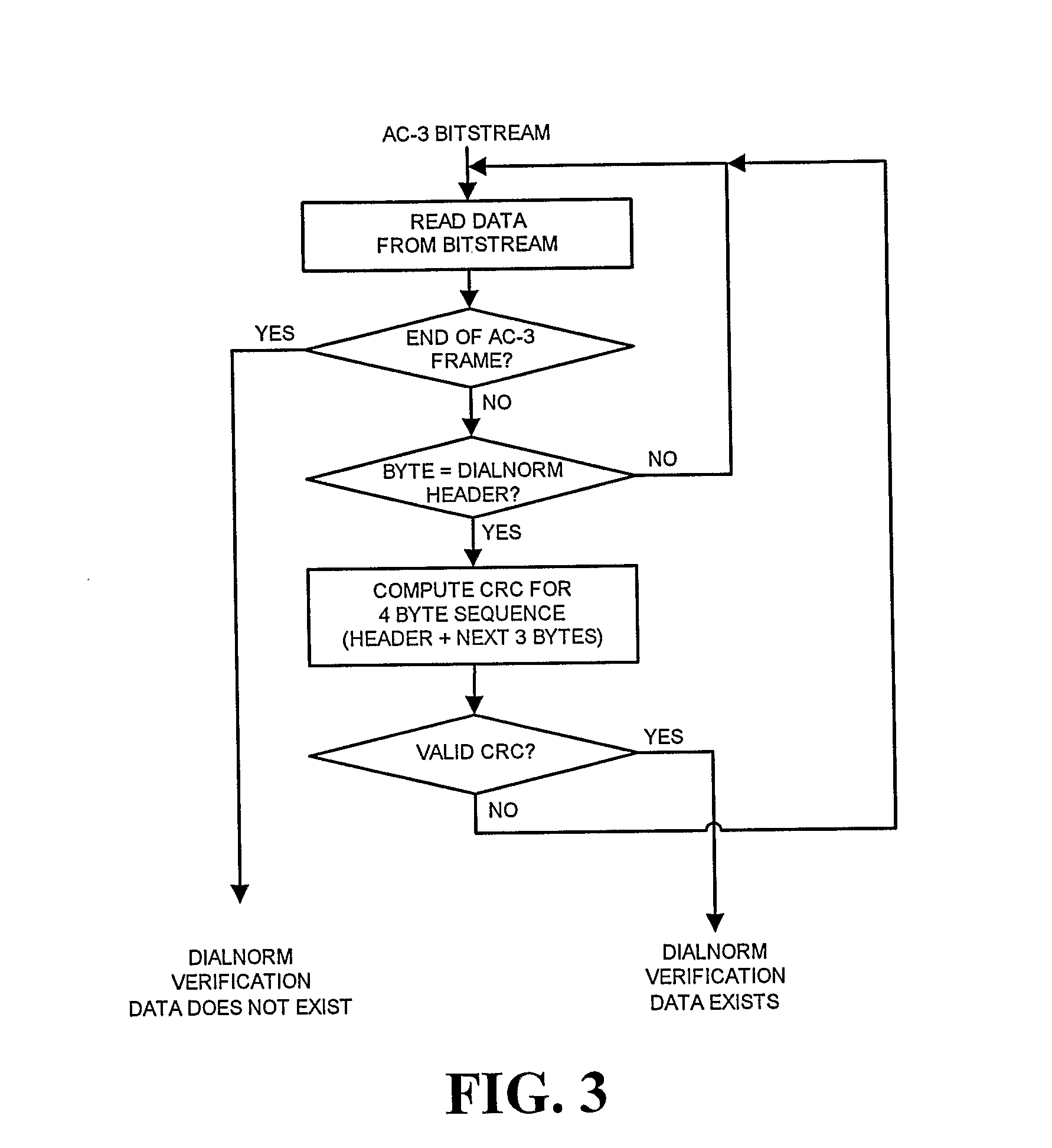
Audio Metadata Verification
InactiveUS20090063159A1Preserve backward compatibilityData bit may become shortenedElectronic editing digitised analogue information signalsSpeech analysisData validationData compression
A digital bitstream, comprising data bits representing audio, metadata intended to be correct for the audio, and metadata verification information, wherein all or part of the metadata may not be correct for the audio. The metadata verification information is usable to detect whether or not metadata is correct for the audio and, if not correct, to change it so that it is correct. The metadata verification information usable to detect and change metadata may include a copy, or a data-compressed copy, of a correct version of the metadata.
Owner:DOLBY LAB LICENSING CORP
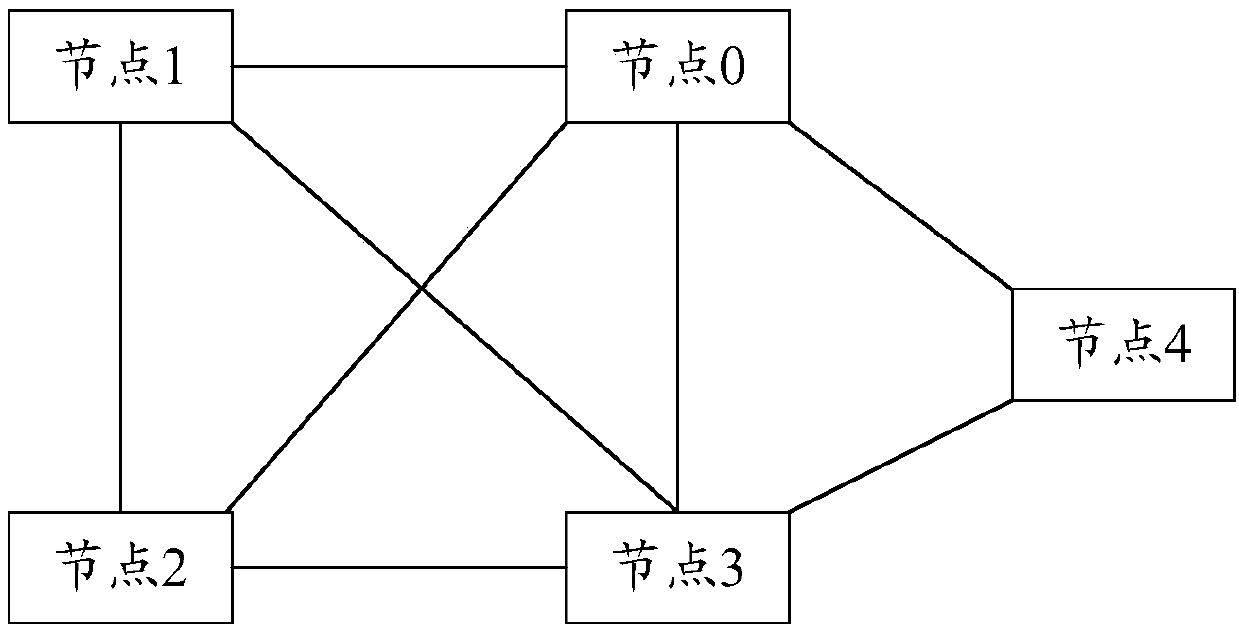
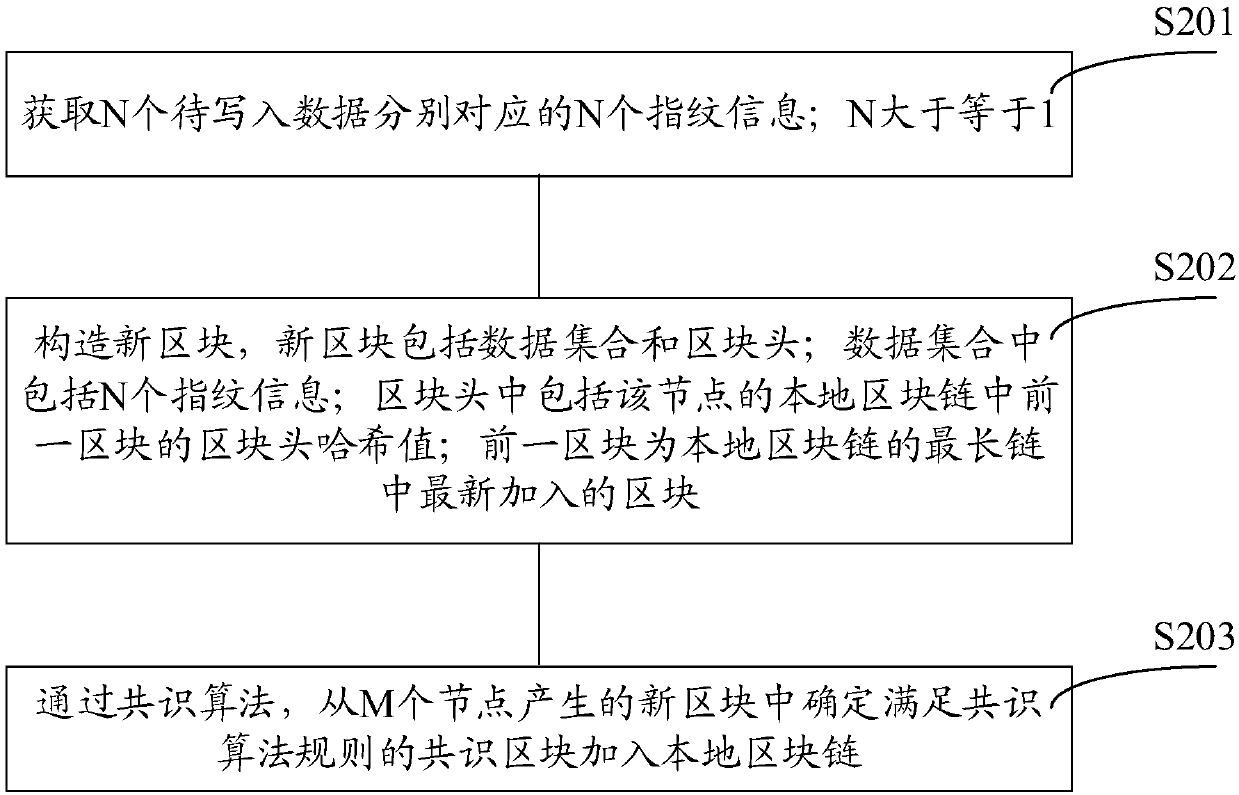
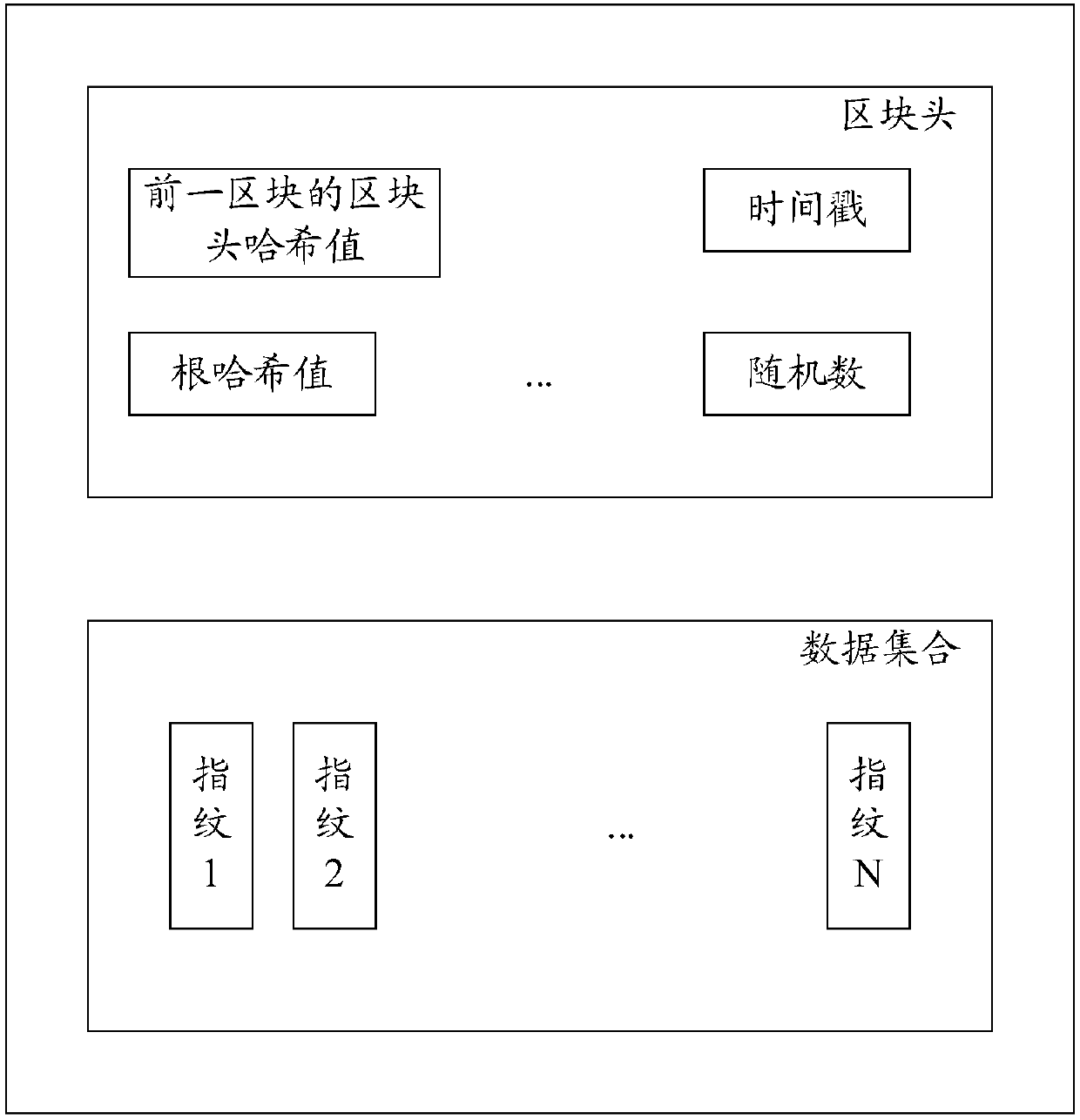
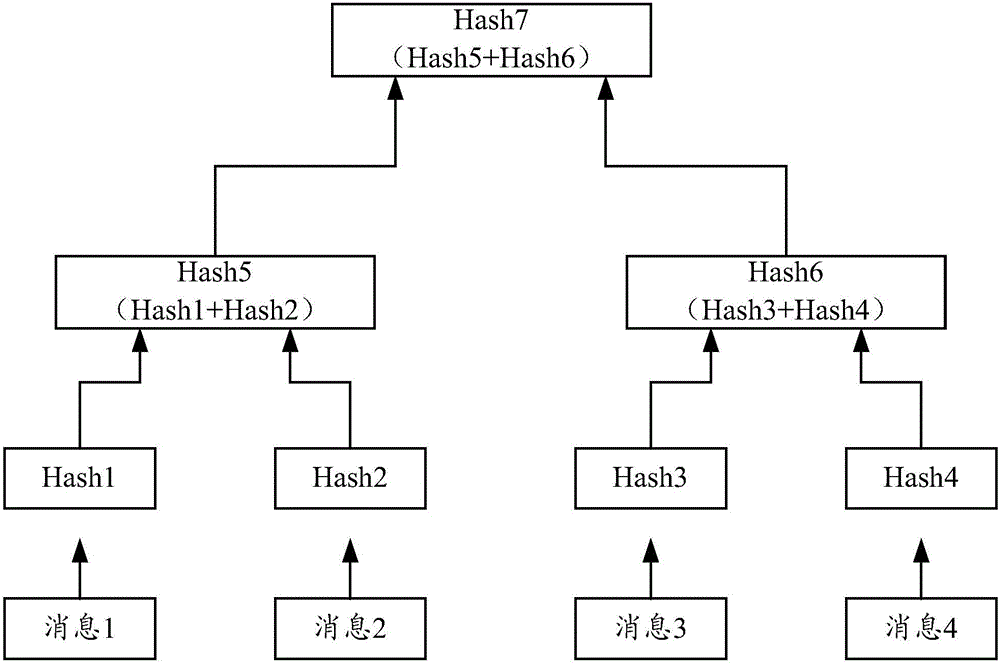
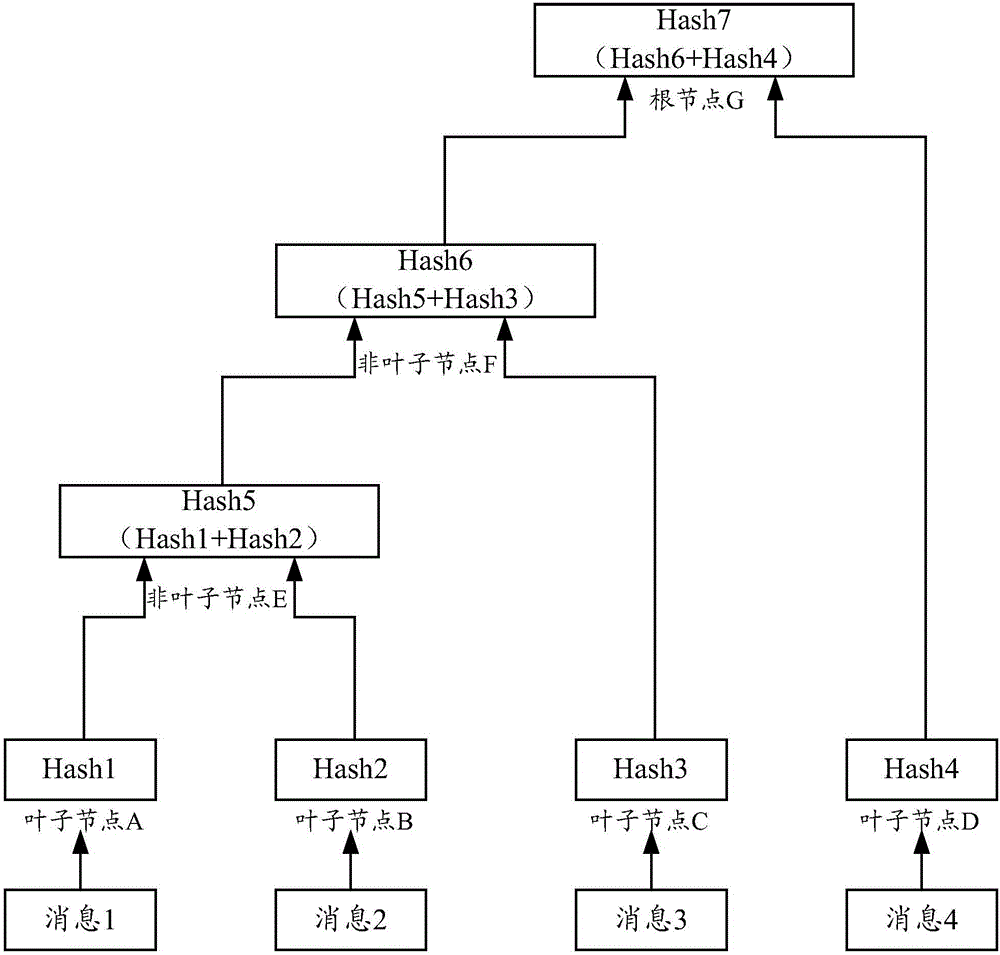
Block chain generation method, data verification method, nodes and system
ActiveCN107807951AReduce occupancyIncrease profitUser identity/authority verificationDigital data protectionData validationData set
The invention discloses a block chain generation method, a data verification method, nodes and a system. The block chain generation method is used for increasing the utilization rate of a storage space and is applied to a block chain system containing M nodes. According to each of the M nodes, the block chain generation method comprises the steps that N pieces of fingerprint information corresponding to N pieces of to-be-written data are acquired, wherein N is greater than or equal to 1; a new block is constructed, wherein the new block comprises a data set and a block head; the data set comprises N pieces of fingerprint information; the block head comprises a Hash value of a block head of a previous block in a local block chain of the node, wherein the previous block is a newly added block in a longest chain of the local block chain; and through a consensus algorithm, a consensus block is determined from new blocks generated by M nodes and is added into the local block chain. In thisway, the storage space occupied by other information of non-to-be-written data in transaction information is saved, and therefore the utilization rate of the storage space and is increased.
Owner:UNION MOBILE PAY
Pluggable semantic verification and validation of configuration data
ActiveUS20040019670A1Digital computer detailsData switching networksData validationSource Data Verification
A pluggable semantic verification and syntactic validation mechanism for server configuration information. In one embodiment, the data verification and validation mechanism may be implemented as modules that may be plugged into a framework. In one embodiment, the mechanism may include a generic test case framework that may call test cases to verify and validate changes to configuration information. In one embodiment, each test case may implement an interface through which the framework calls a test case. The test case may return results, e.g. whether the test passed or failed, and may return additional information, e.g. why the test failed. If the change is valid, then the change may be made to the configuration information. If the change is not valid, the change is not made or alternatively is made with a warning. If the change is made, one or more other servers may be notified of the change.
Owner:ORACLE INT CORP
One-way data transfer system with built-in data verification mechanism
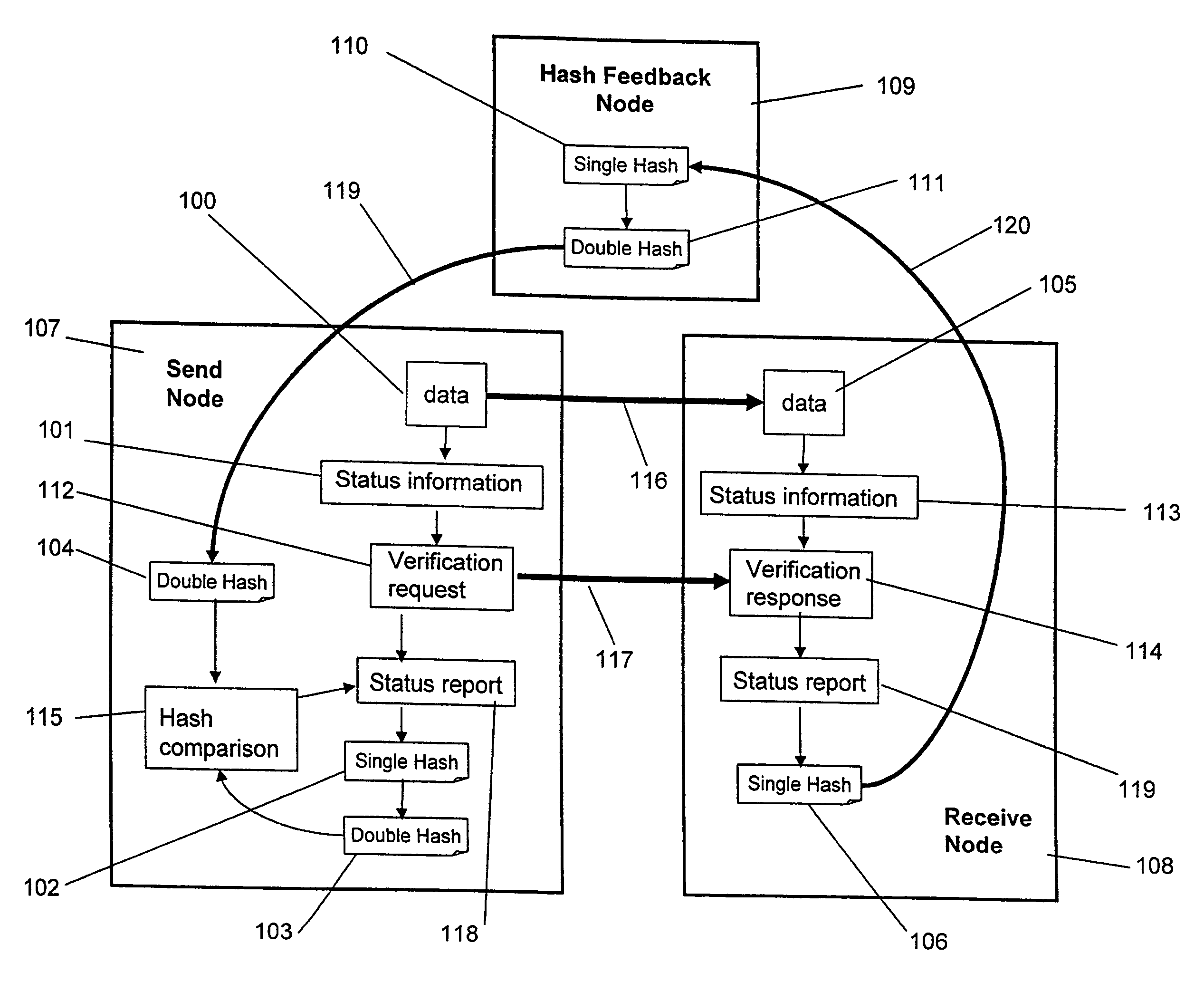
Embodiments of the present invention are directed to a one-way data transfer system with built-in data verification mechanism, comprising three nodes (Send Node, Receive Node, and Feedback Node) wherein (1) the three nodes are interconnected with each other by a one-way data link, and (2) the Feedback Node is designed solely for processing and relaying data verification information from the Receive Node to the Send Node. In these embodiments, the Send Node is capable of verifying the status of data it transferred to the Receive Node over a one-way data link without sacrificing the unidirectionality of data flow in the system and thereby compromising the level of security provided by use of one-way data links.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
Device and method for authenticating user's access rights to resources
InactiveUS20010009026A1Program control using stored programsData taking preventionData validationSource Data Verification
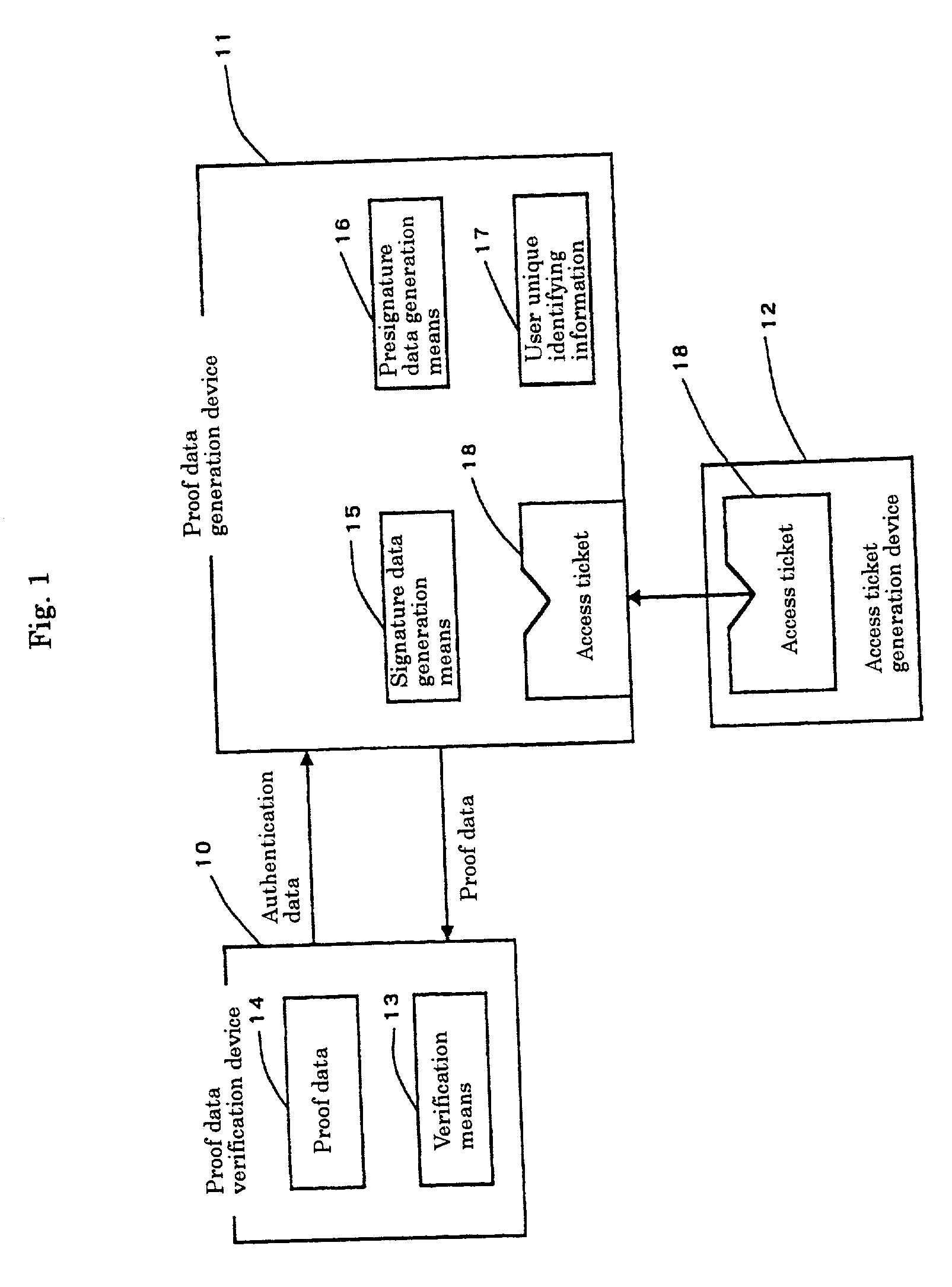
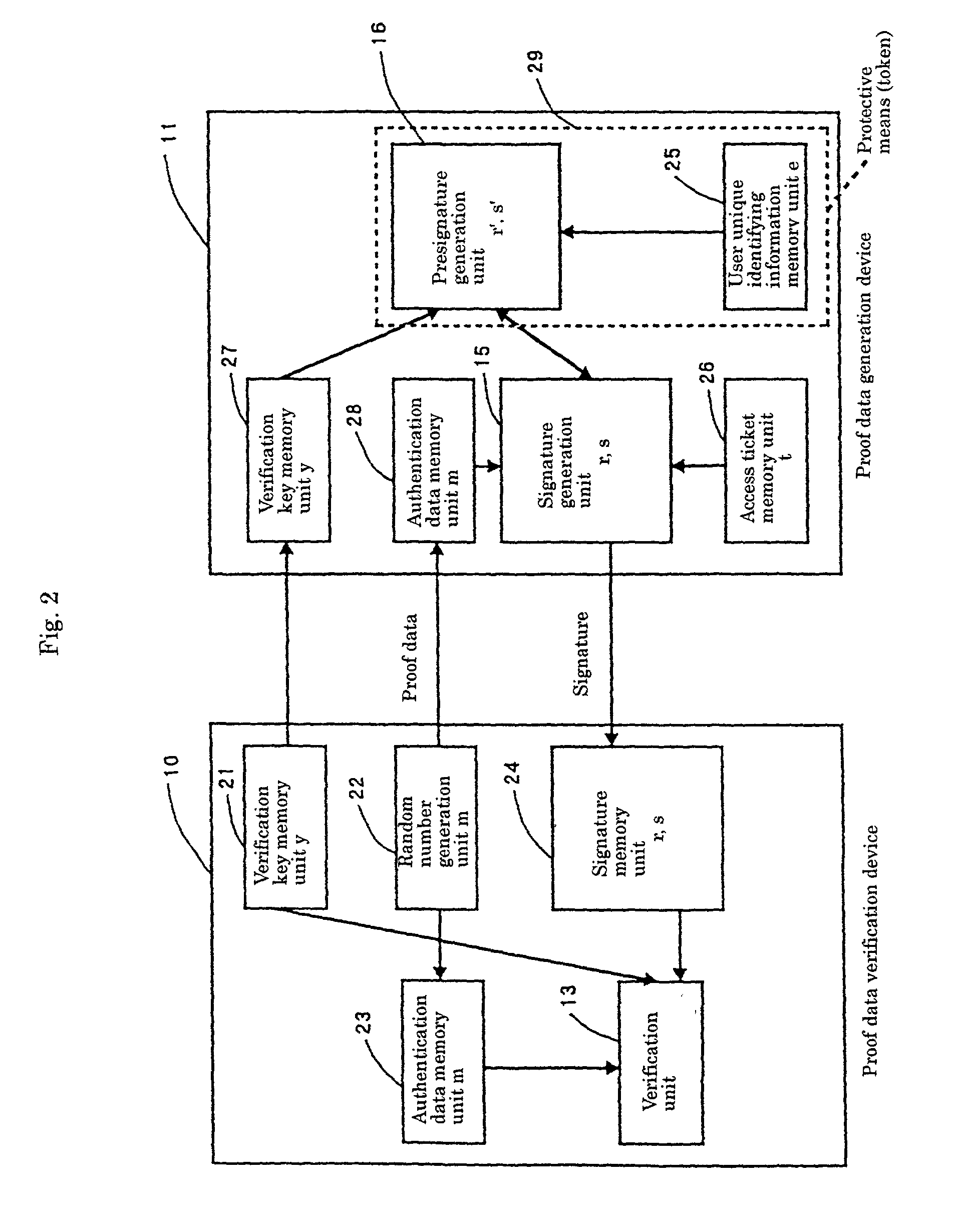
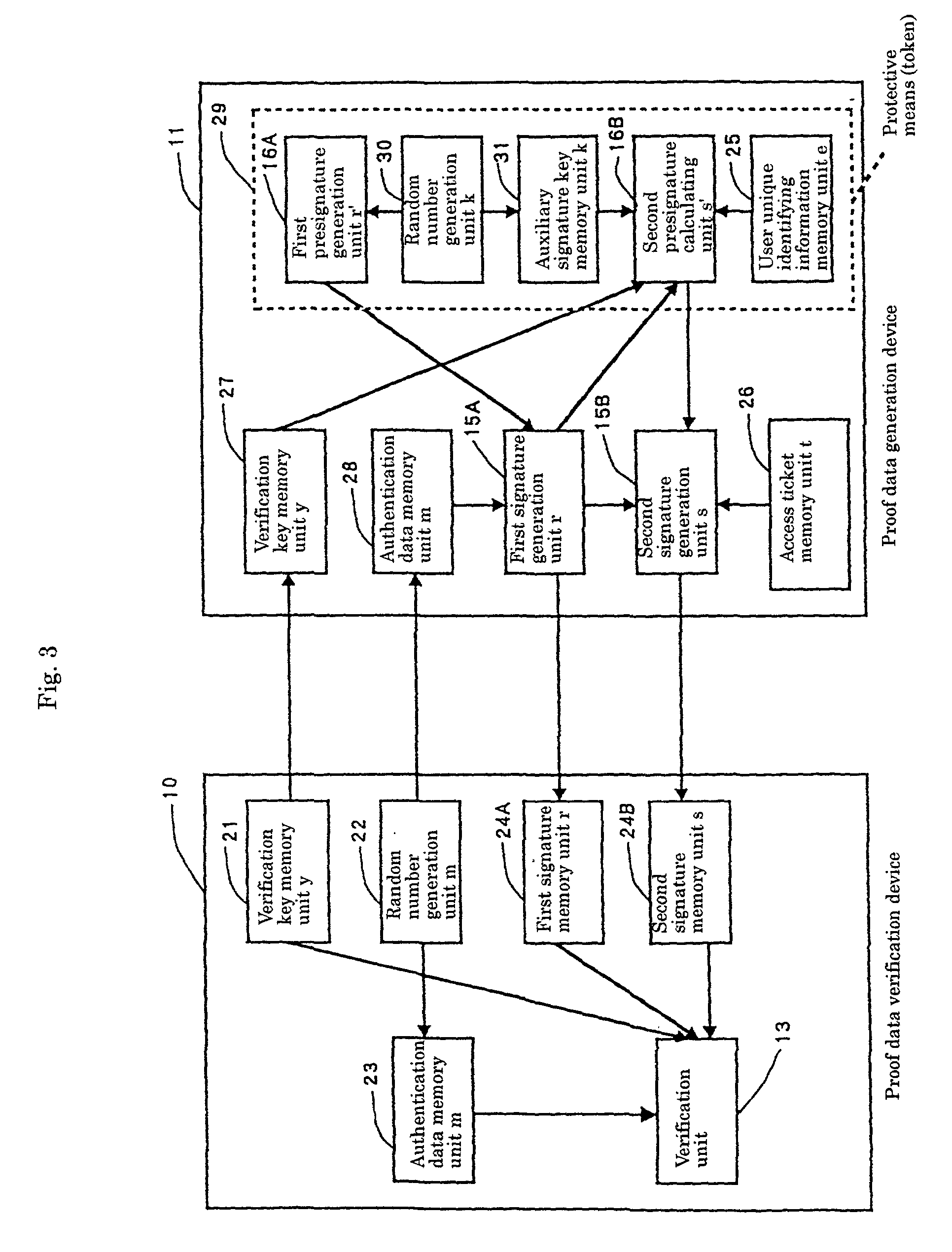
A burden caused by handling a large number of unique identifying information pieces such as authentication keys is to be lightened from both the user side and the protector side such as application creators. A proof data verification device sends authentication data to a proof data generation device. Signature data generation means and presignature data generation means in the proof data generation device cooperate with each other to generate proof data (a signature based on a discrete logarithm problem) from the received authentication data as well as held user unique identifying information and an access ticket, and send the proof data back to the proof data verification device. Verification means in the proof data verification device verify the signature, and if the verification is successful, the execution of program is allowed.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Universal forms engine
InactiveUS7376891B2Simple methodSpeed up the processData processing applicationsNatural language data processingData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant.The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
Data retention and verification method and device
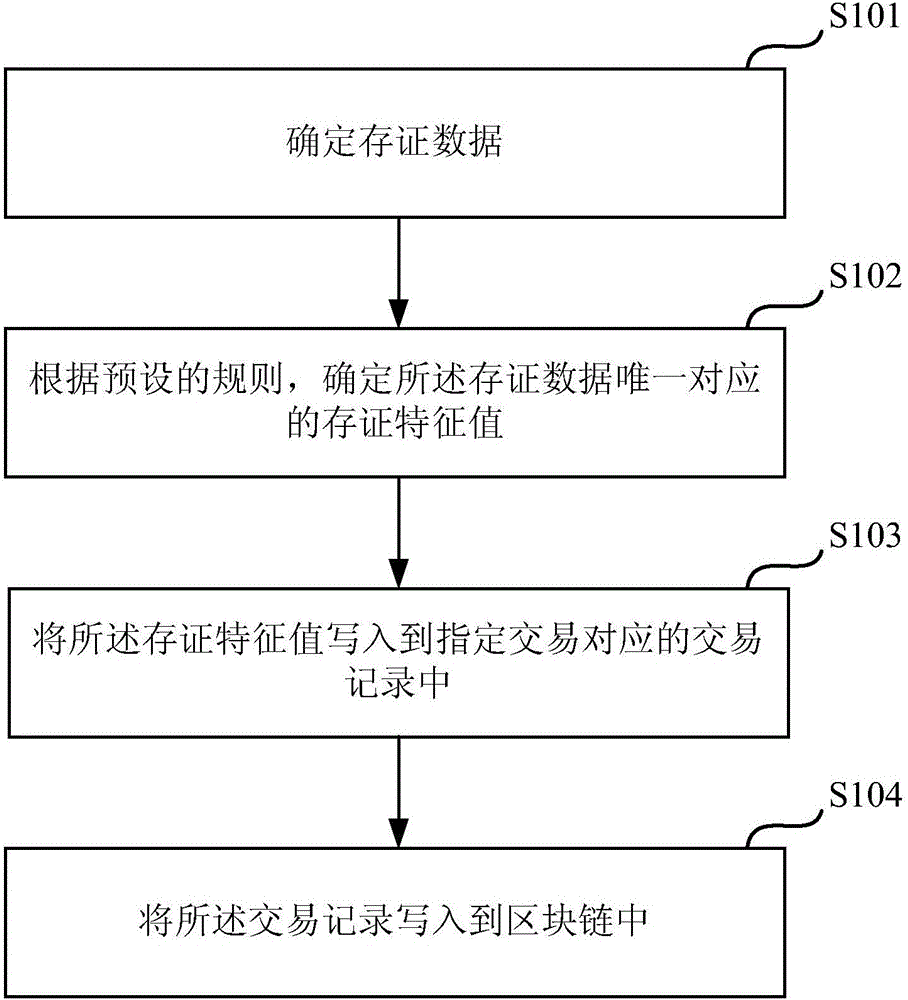
InactiveCN106548091AGuaranteed reliabilityRealization of certificate depositDigital data protectionIndividual entry/exit registersData validationSource Data Verification
Embodiments of the invention provide a data retention and verification method and device. The method comprises the following steps of: determining a retention characteristic value uniquely corresponding to retention data by a server according to a preset rule, writing the retention characteristic value into a transaction record of an appointed transaction, and writing the transaction record into a block chain to be stored; when the server verifies verification data, determining a to-be-verified characteristic value uniquely corresponding to the verification data according to the previously adopted manner, and comparing the to-be-verified characteristic value with the retention characteristic value stored in the transaction record of the block chain so as to verify the verification data. Through the method, the data stored in the block chain is unchangeable, and the server can attach the retention characteristic value uniquely corresponding to the retention data into the transaction record to be stored in the block chain, so that the reliability of the retention characteristic value is ensured, and the reliability of carrying out data verification on the verification data by the server through the retention characteristic value is further ensured.
Owner:北京爱接力科技发展有限公司
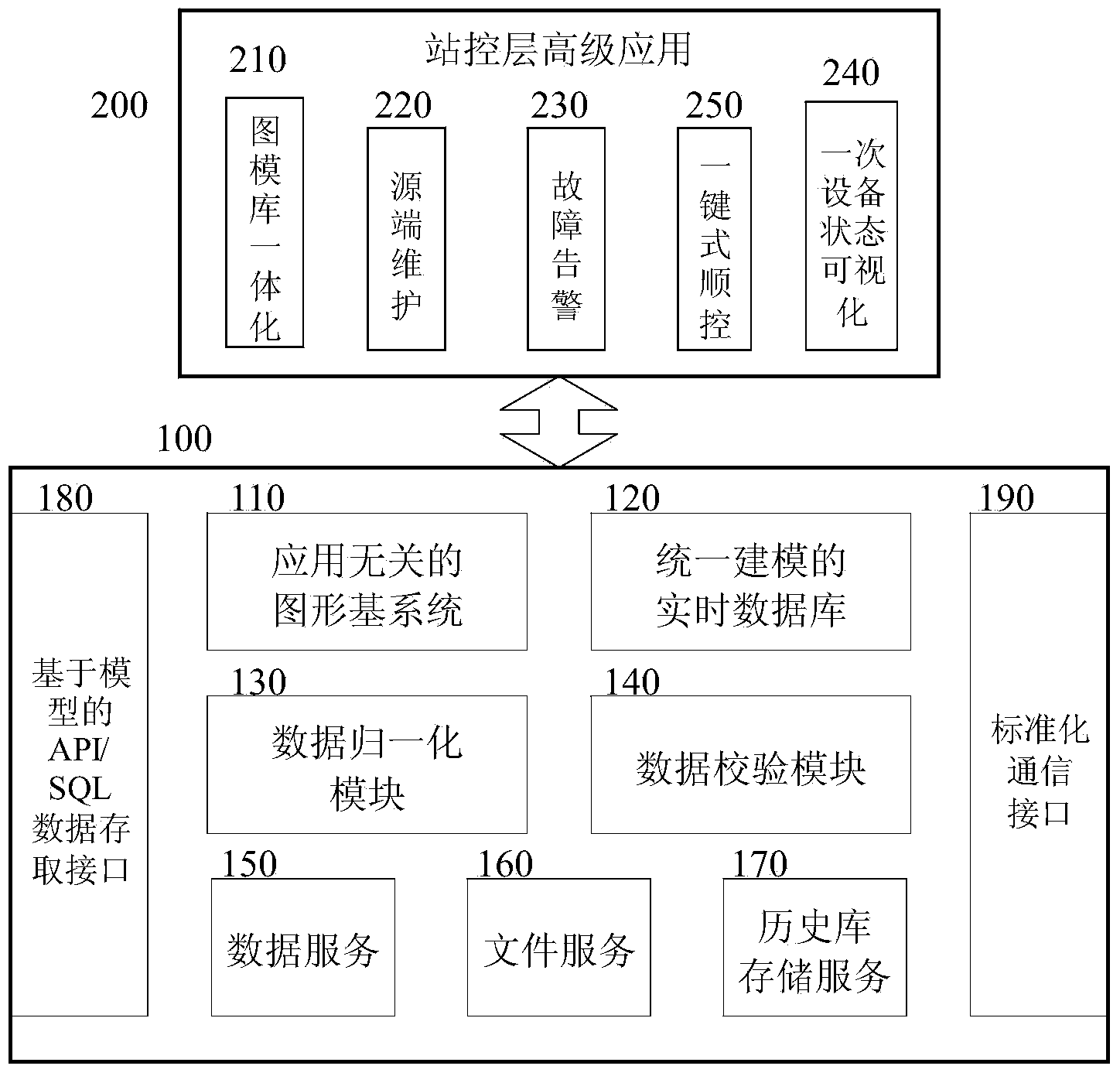
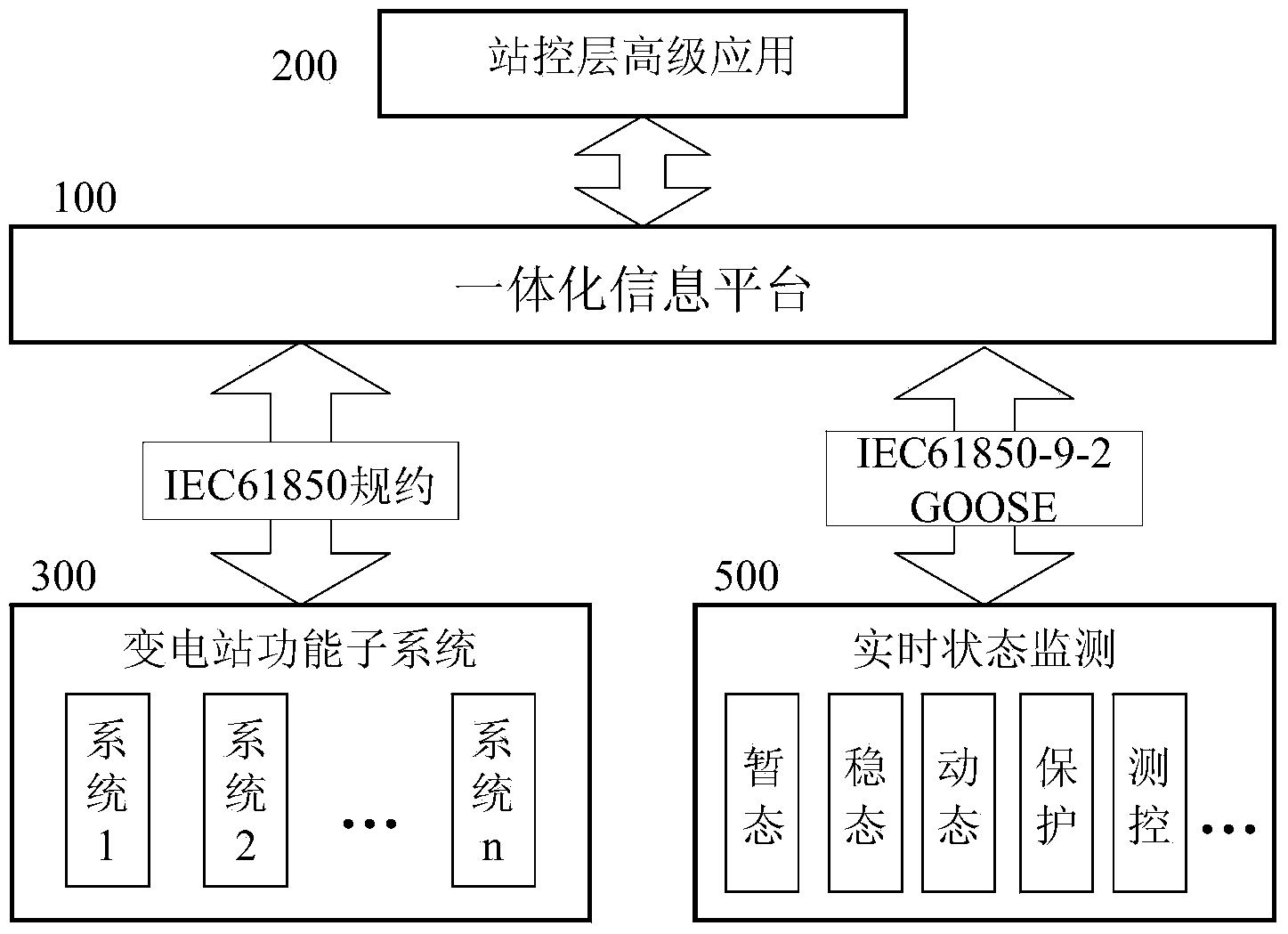
Integrated monitoring system information platform for transformer substation
InactiveCN103441571AEasy accessImprove data utilizationCircuit arrangementsInformation technology support systemSource Data VerificationTransformer
The invention relates to a circuit device used for providing distant indication for conditions of a distribution network and carrying out distant control on a switching device in the distribution network, in particular to an integrated monitoring system information platform for a transformer substation. The integrated monitoring system information platform comprises an integrated information platform body and a station level advanced application module. The integrated information platform body comprises an application-independent graphic base system, a real-time database based on the unified modeling technology, a data normalization module, a data verification module, a data service module, a file service module and a historical library storage service module. The station level advanced application module comprises a graphic, model and library integrated module, a source side maintenance module, a primary equipment status visualization module and a one-button sequential control module. According to the integrated monitoring system information platform, by arranging and integrating functions of various subsystems and carrying out data structure reconstitution on the unified platform, the use ratio and interactivity of data are improved, the reliability, integration and maintainability of the system are improved, and new functional subsystems can have access to the transformer substation conveniently.
Owner:STATE GRID CORP OF CHINA +3
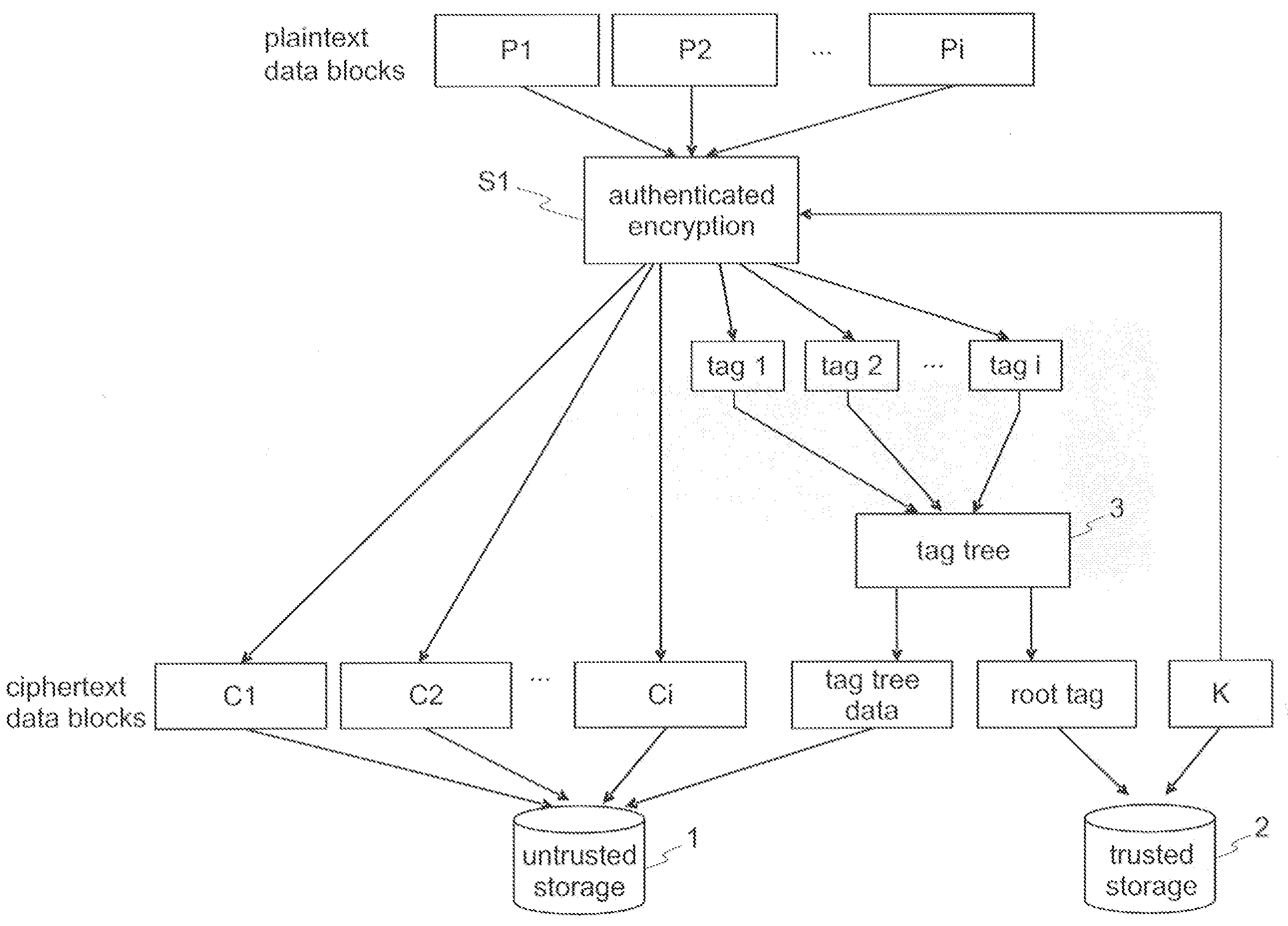
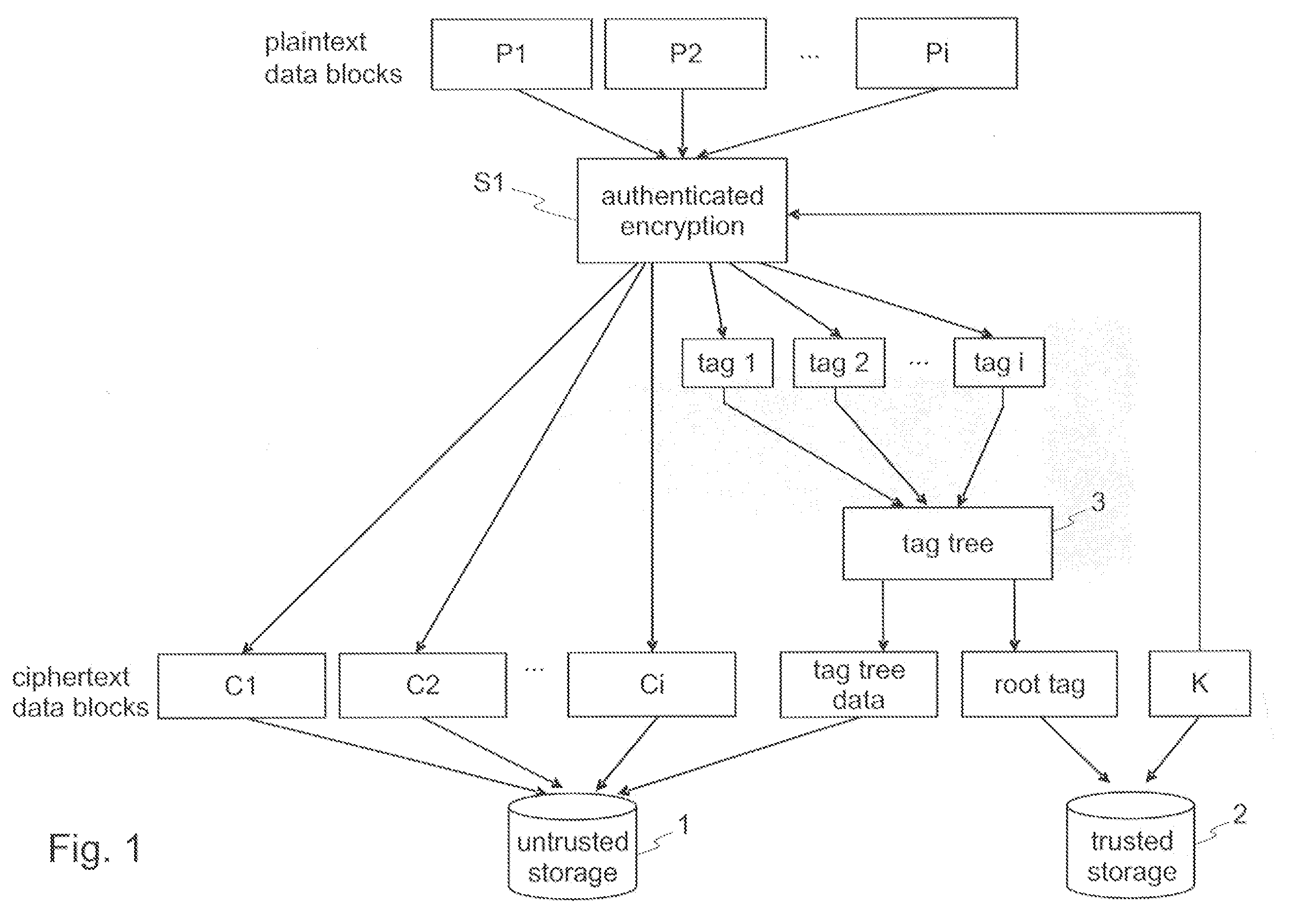
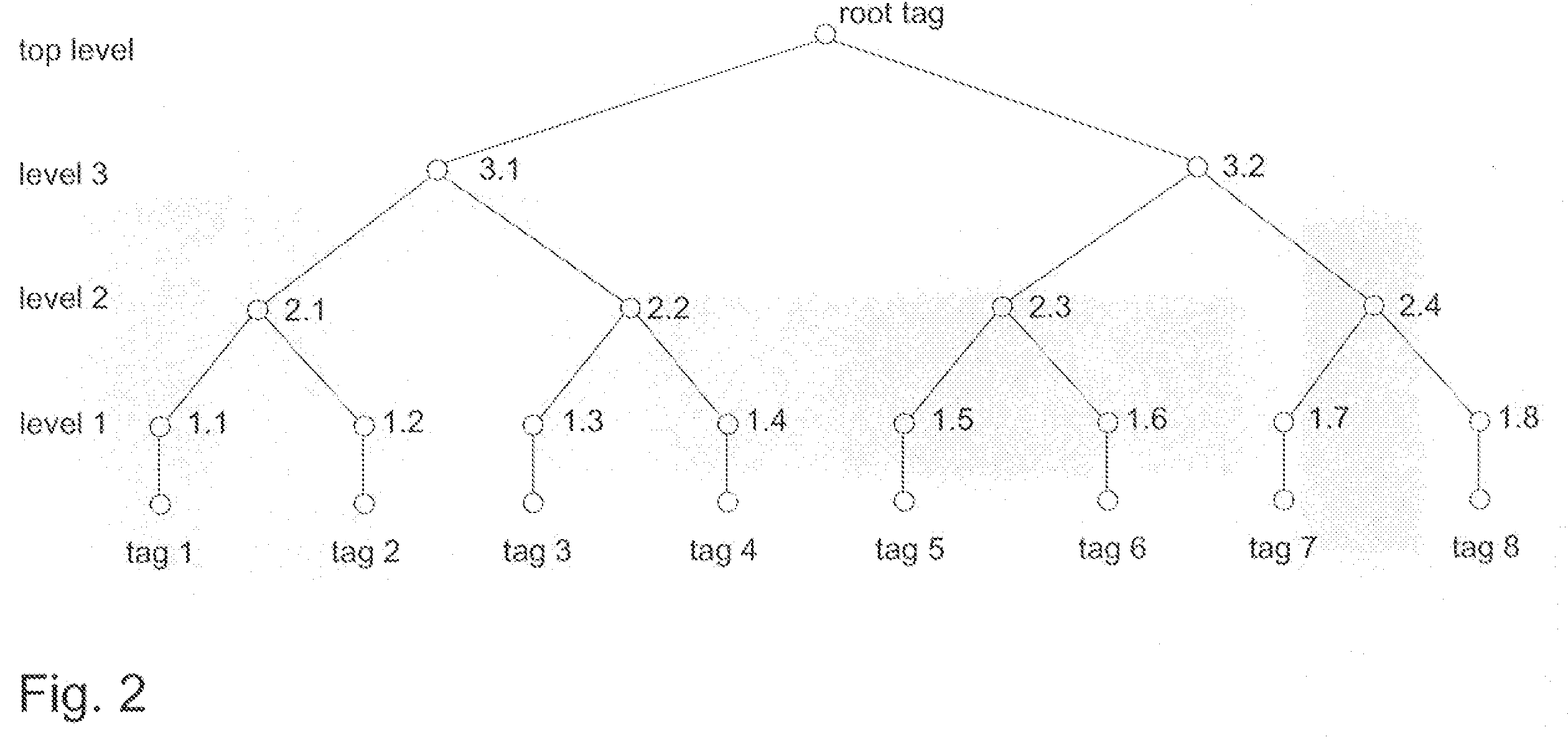
Encryption and authentication of data and for decryption and verification of authenticity of data
InactiveUS20080172562A1Effective timeEasy to implementUnauthorized memory use protectionHardware monitoringPlaintextComputer hardware
Techniques for encryption and authentication of data. One or more plaintext data blocks ciphertext data blocks and corresponding authentication tags are generated by means of authenticated encryption. A tag tree is generated by means of the authentication tags. The ciphertext data blocks and the tag tree data of the tag tree are stored in an untrusted storage, and the root tag of the tag tree is stored in a trusted storage.
Owner:IBM CORP
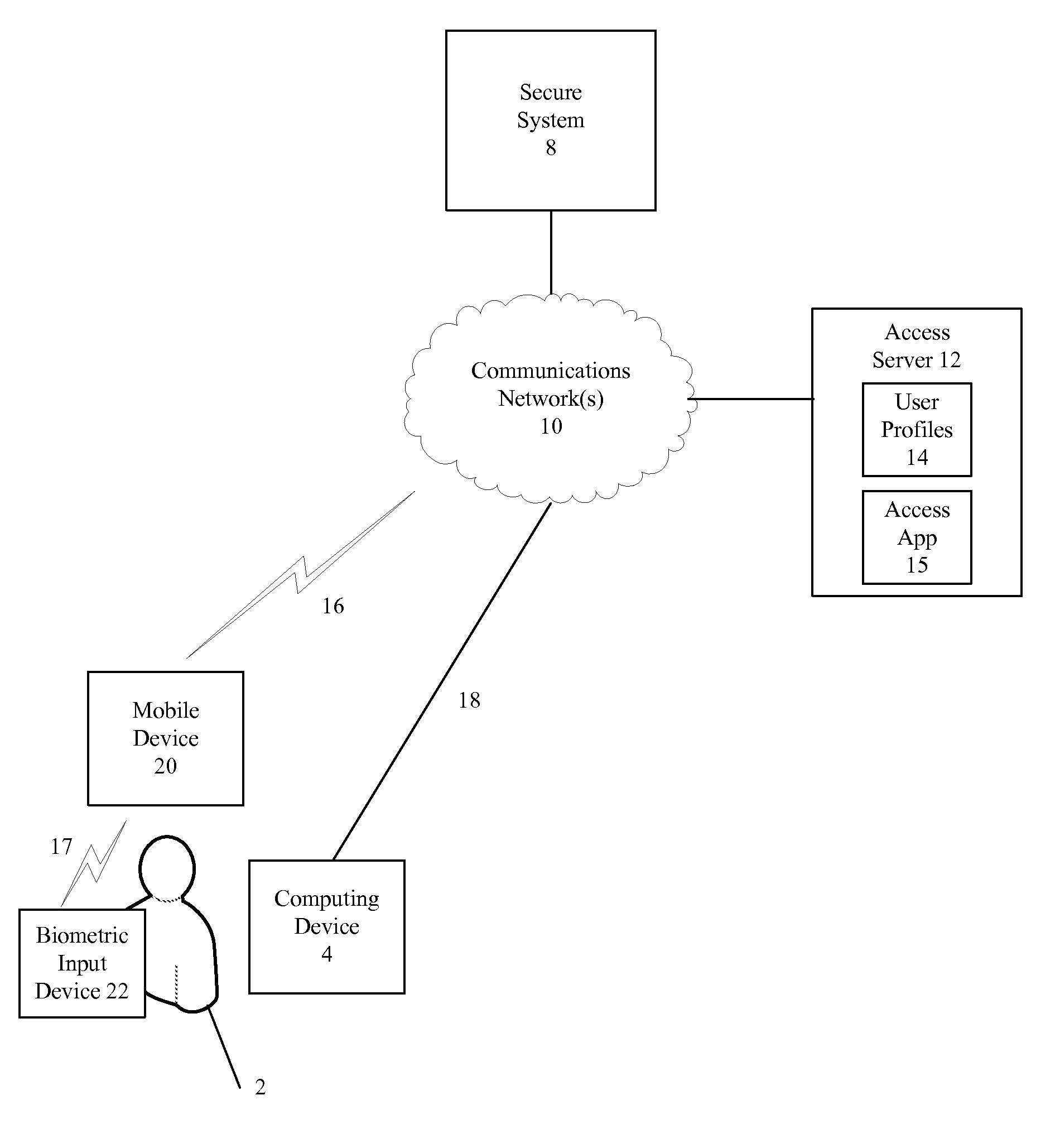
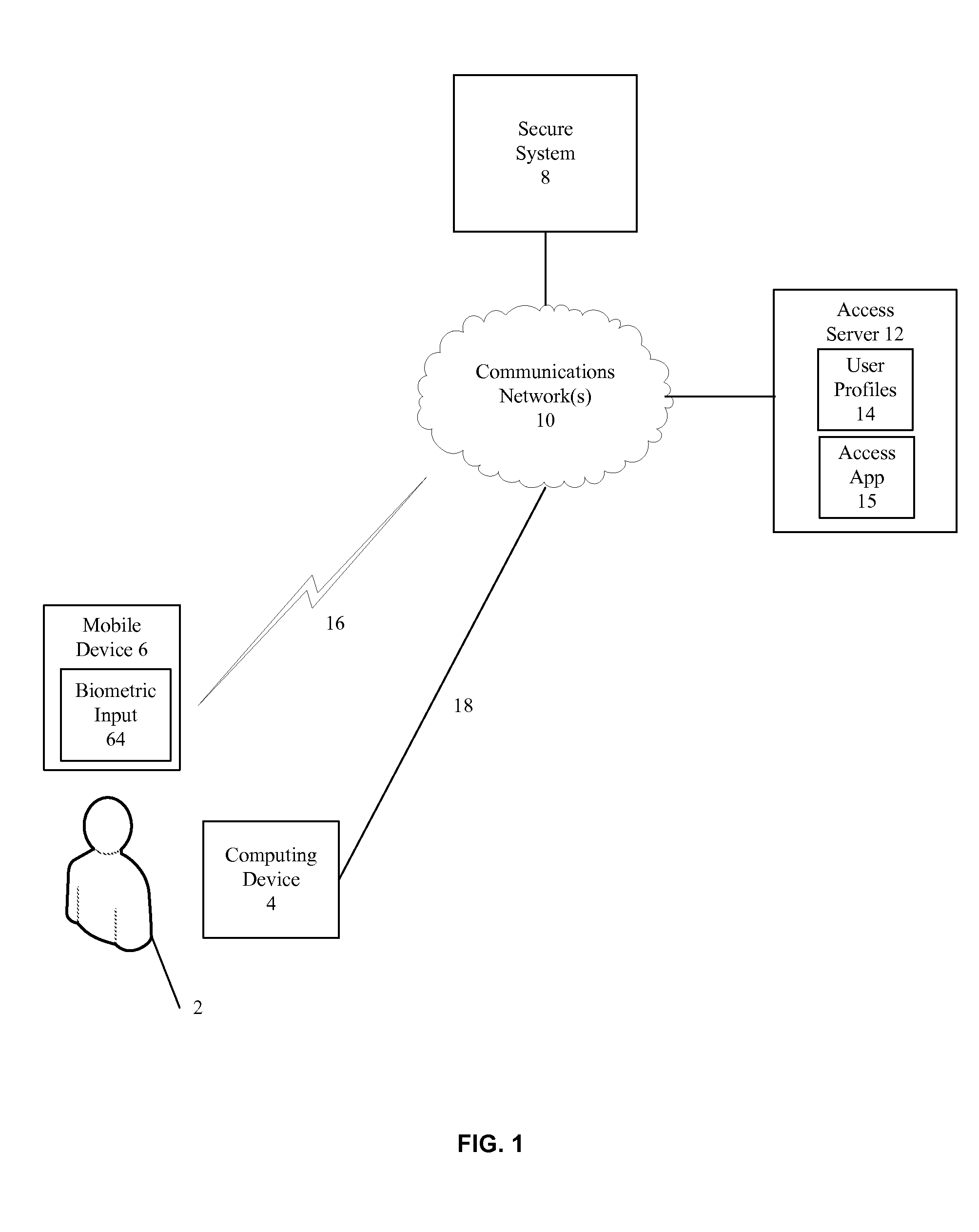
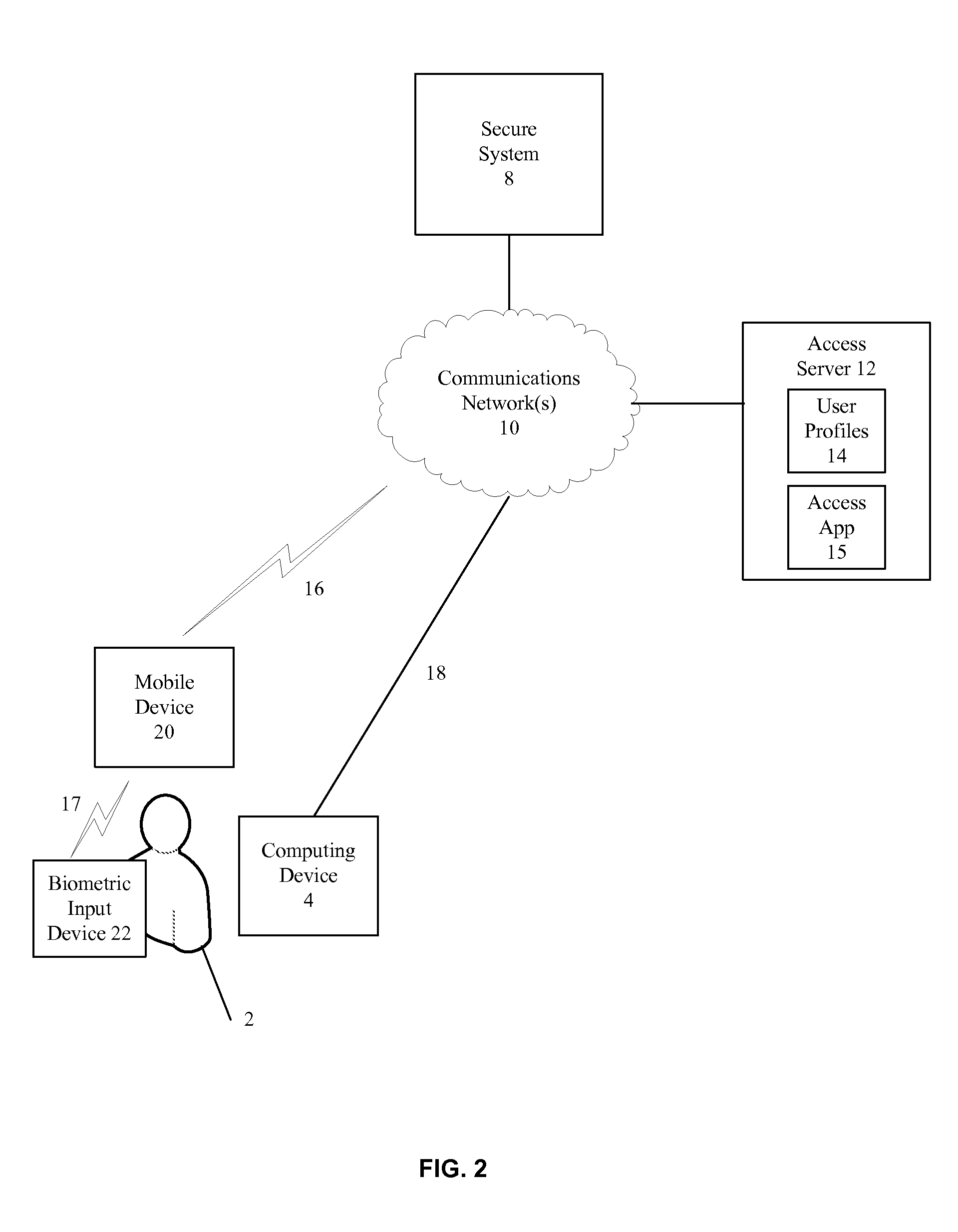
Secure System Access Using Mobile Biometric Devices
InactiveUS20140090039A1Digital data processing detailsMultiple digital computer combinationsData validationBiometric data
Methods and apparatuses for secure system access are disclosed. In one example, a user request to access a secure system is received. A biometric user authentication request is transmitted to a user mobile device, and biometric data is obtained from the user. The user identity is authenticated utilizing the biometric data, and a response is transmitted from the mobile device to the secure system indicating the user identity is authenticated.
Owner:PLANTRONICS
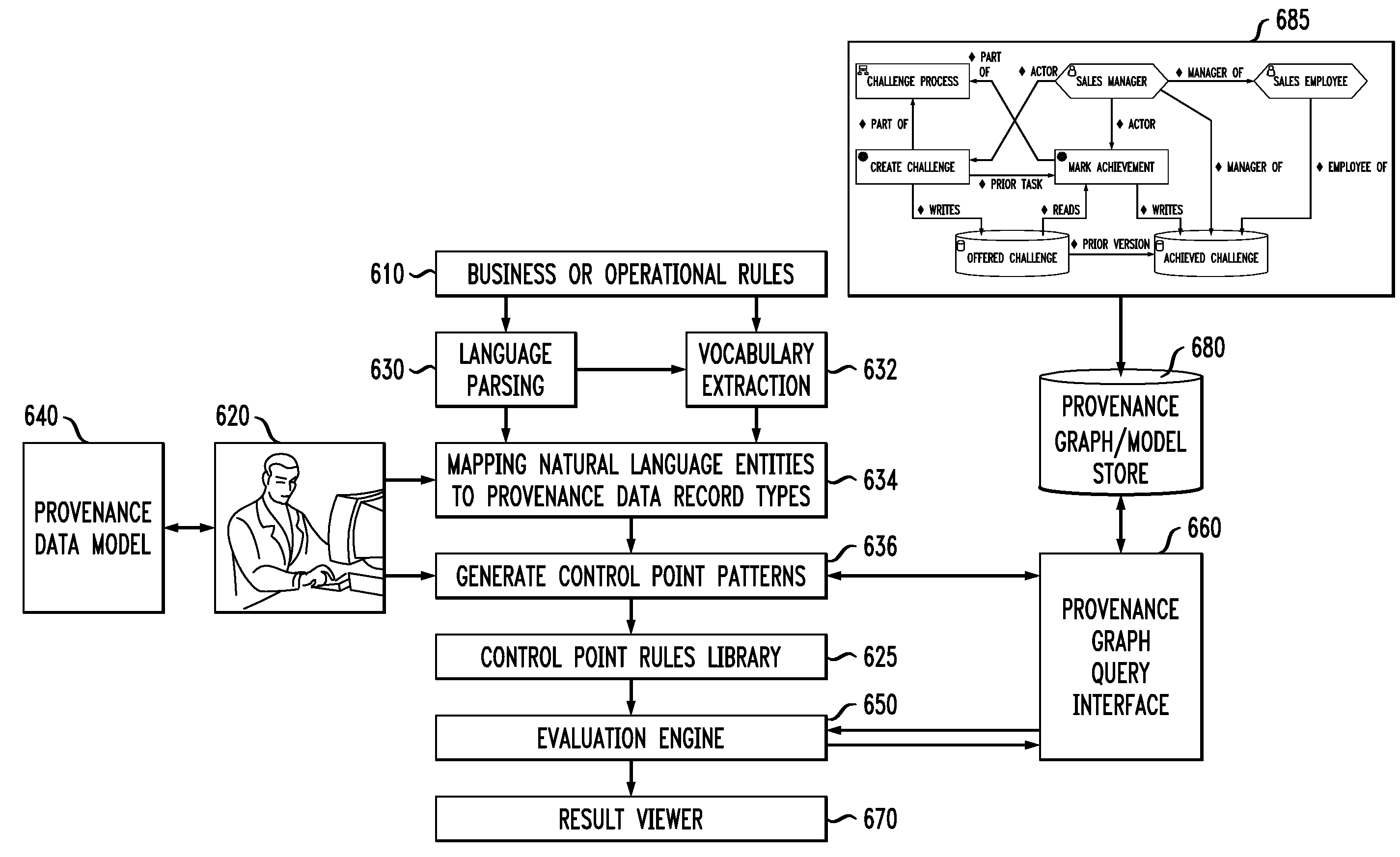
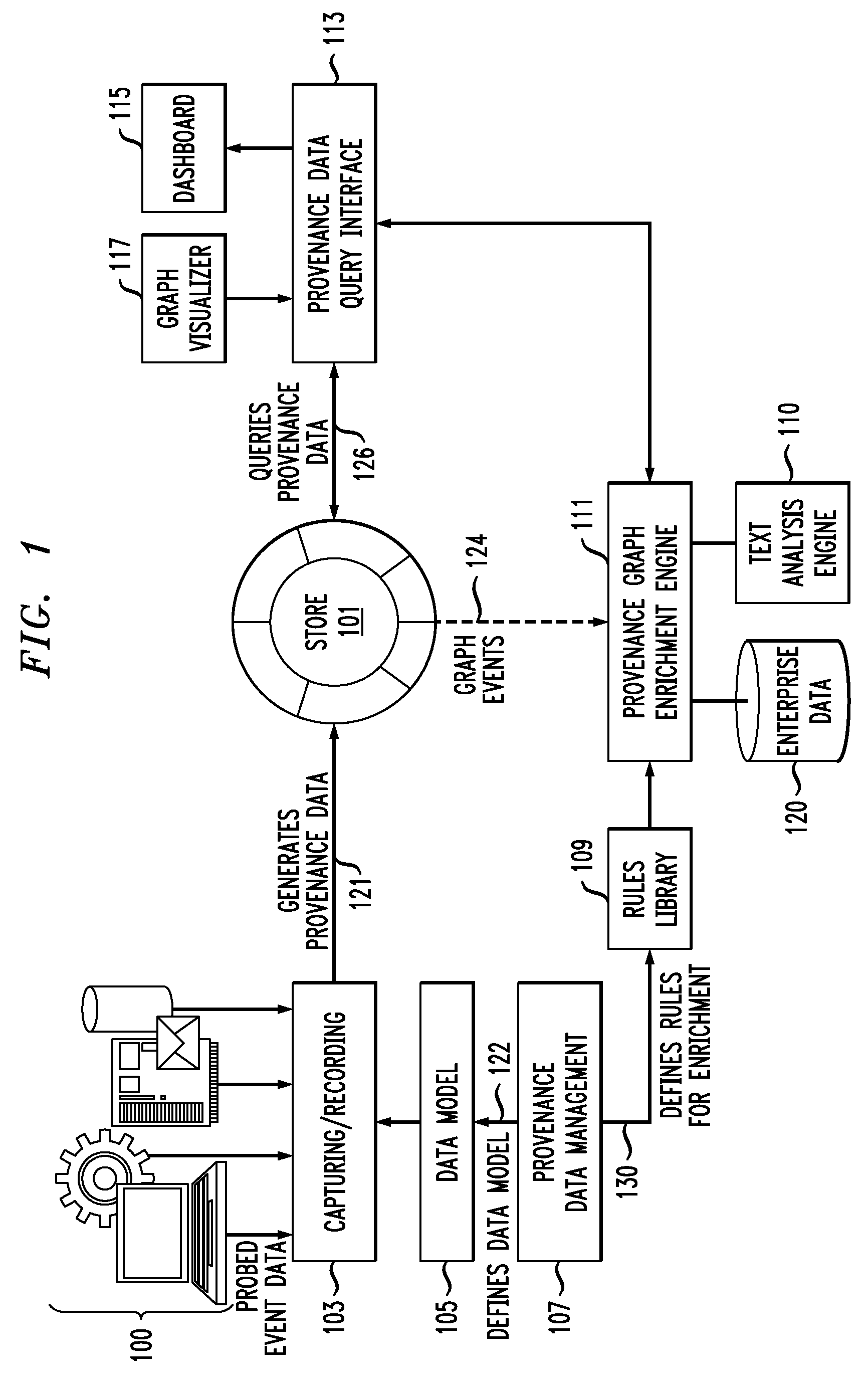
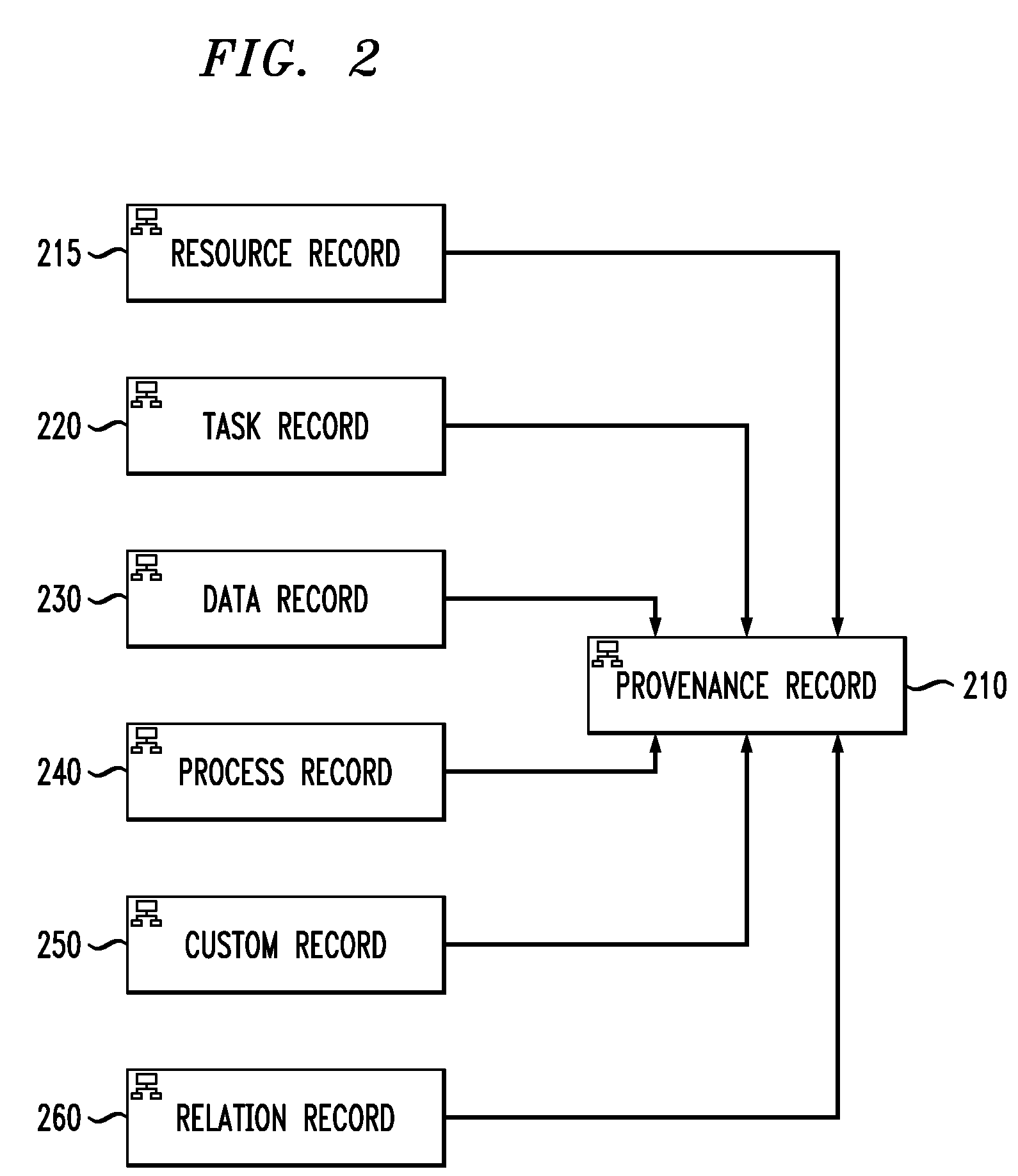
Validating Compliance in Enterprise Operations Based on Provenance Data
InactiveUS20100114628A1Low costDrawing from basic elementsDigital data processing detailsData validationEnterprise process
Techniques are disclosed for validating compliance with enterprise operations based on provenance data. For example, a computer-implemented method for validating that an enterprise process is in compliance with a rule comprises the following steps. Provenance data is generated, wherein the provenance data is based on collected data associated with an actual end-to-end execution of the enterprise process and is indicative of a lineage of one or more data items. A provenance graph is generated that provides a visual representation of the generated provenance data, wherein nodes of the graph represent records associated with the collected data and edges of the graph represent relations between the records. A correlation is generated between one or more entities in the rule and one or more record types in the provenance data. One or more control points are generated in accordance with the generated correlation. A validation is performed as to whether the enterprise process is in compliance with the rule using the one or more control points.
Owner:IBM CORP
Method and device for verifying identity of user
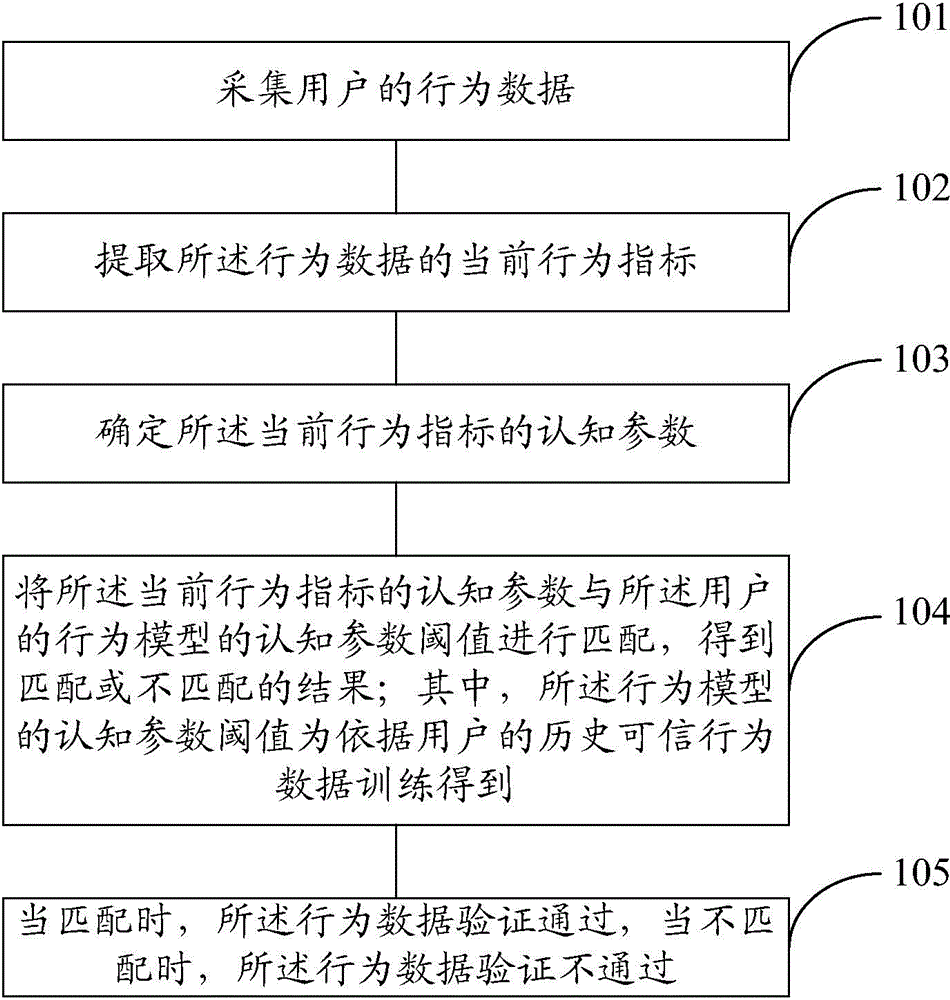
ActiveCN104318138AEnsure safetyEnable persistent authenticationInput/output for user-computer interactionDigital data authenticationData validationSource Data Verification
The embodiment of the invention provides a method and a device for verifying the identity of a user. The method specifically comprises the following steps of acquiring behavior data of the user; extracting the current behavior index of the behavior data; determining the cognitive parameters of the current behavior index; matching the cognitive parameters of the current behavior index with the cognitive parameter threshold value of the behavior model of the user to obtain a matched result or an unmatched result; wherein the cognitive parameter threshold value of the behavior model is obtained through training according to the historical dependable behavior data of the user; when the match result is obtained, the behavior data pass the verification, and when the unmatched result is obtained, the behavior data do not pass the verification. According to the method and the device, the continuous verification on the identity of the user can be realized.
Owner:TONGDUN HLDG CO LTD
Method and apparatus for generating consistent user interfaces
InactiveUS7873908B1Software engineeringInput/output processes for data processingData validationSource Data Verification
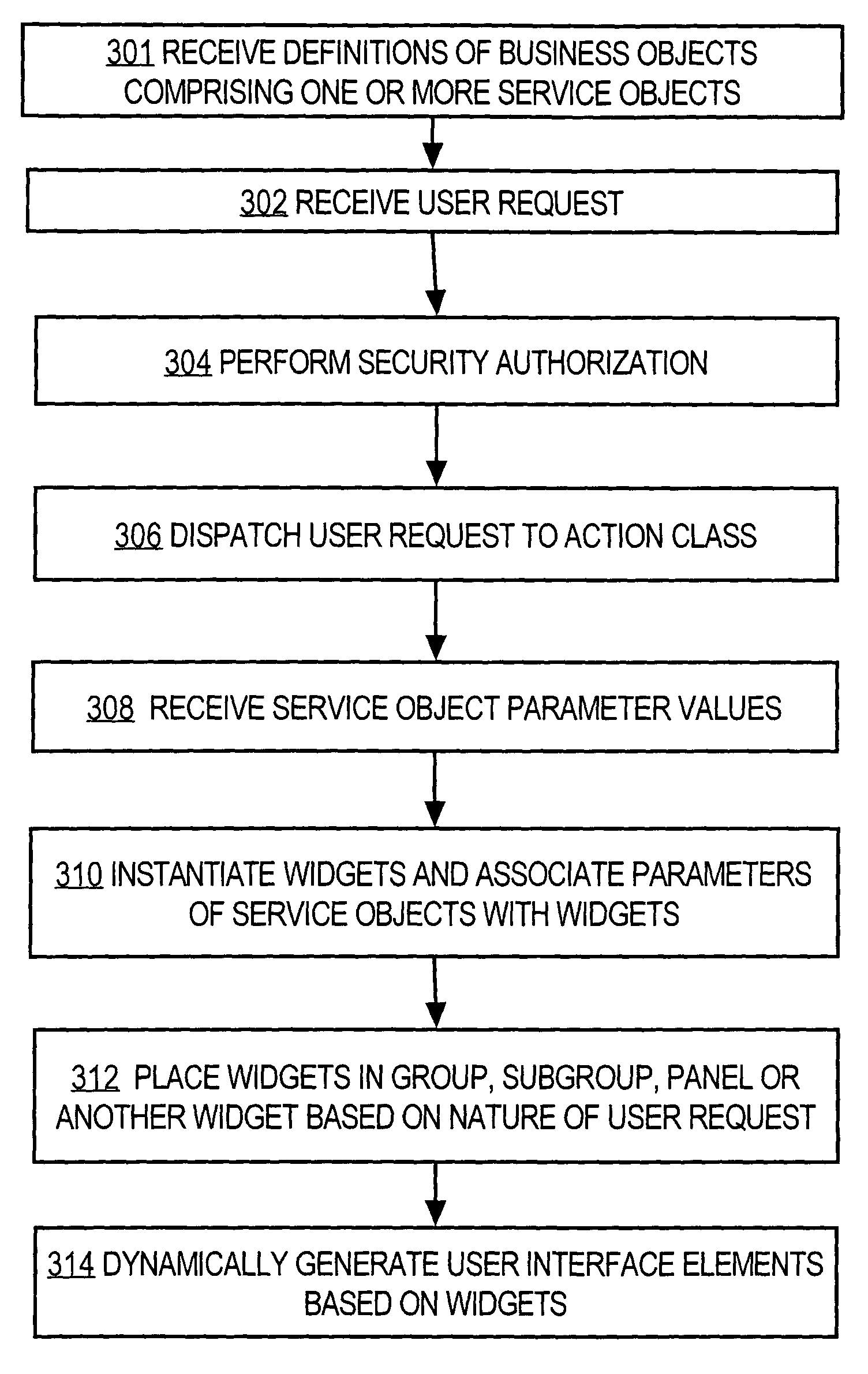
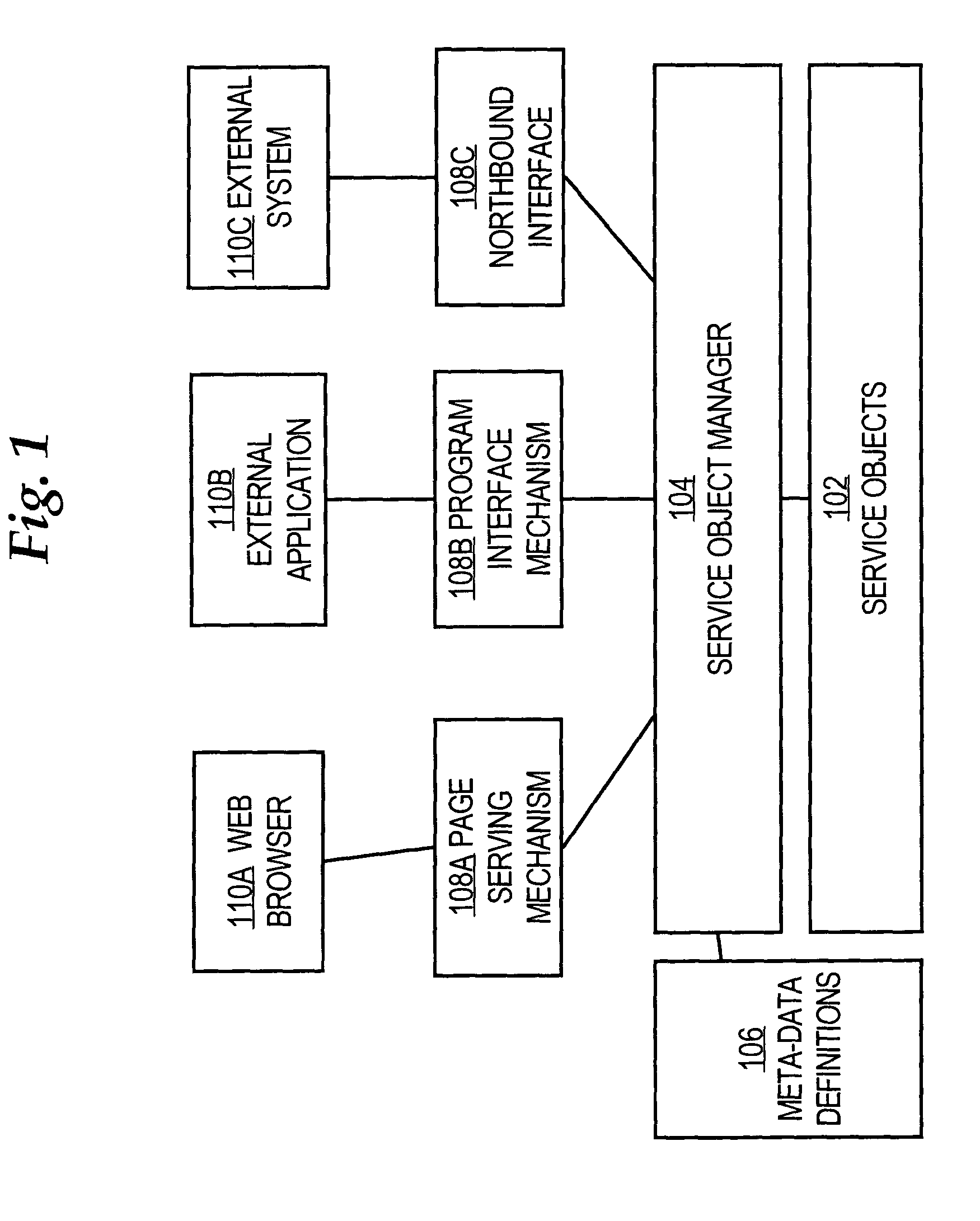
A method is disclosed for generating a consistent user interface for an HTML-based application program, without extensive coding of Java Server Pages and other elements. In one approach, business objects each define a user action for the application program, and metadata elements defining parameters for the user actions of the business object. A controller is communicatively coupled to one or more actions, widgets, and panels. A user request is received from a browser and dispatched to one or the actions. Using the actions, one or more parameter values are obtained from the business objects. The business object parameter values are associated with a widget selected from among the one or more widgets. The selected widget is associated with a panel selected from the one or more panels. An HTML user interface page that includes the selected panel is generated. The widgets represent properties of the business objects as HTML elements, automatically generate client-side executable code for performing data validation, and convert values received in users requests into programmatic objects of appropriate data types for use by the application program.
Owner:CISCO TECH INC
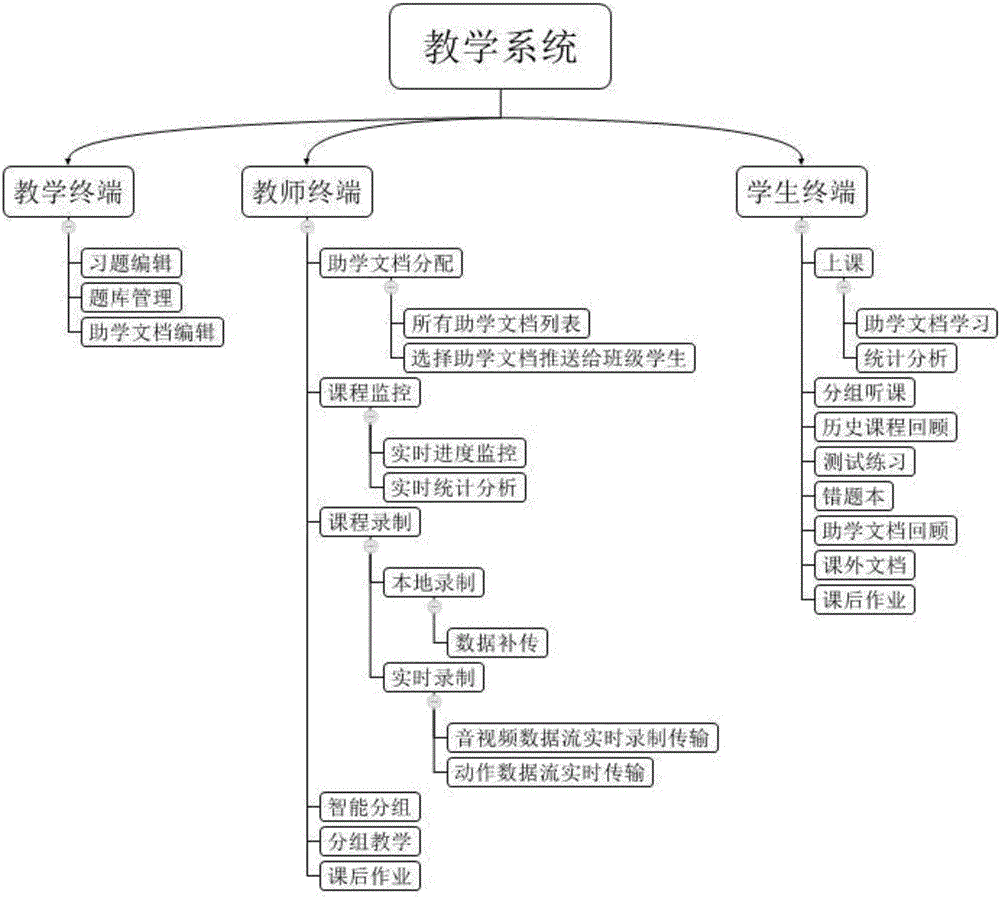
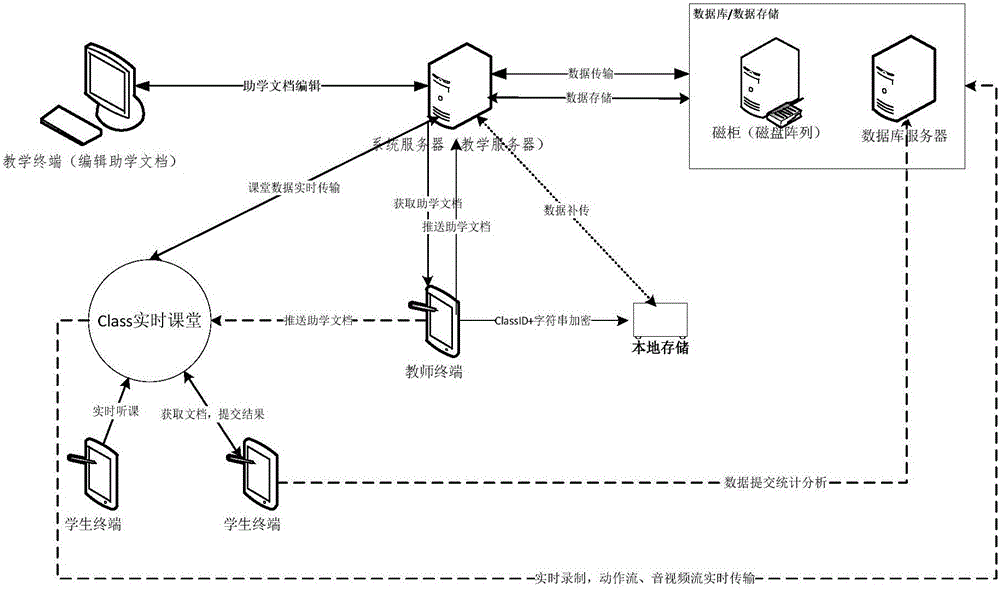
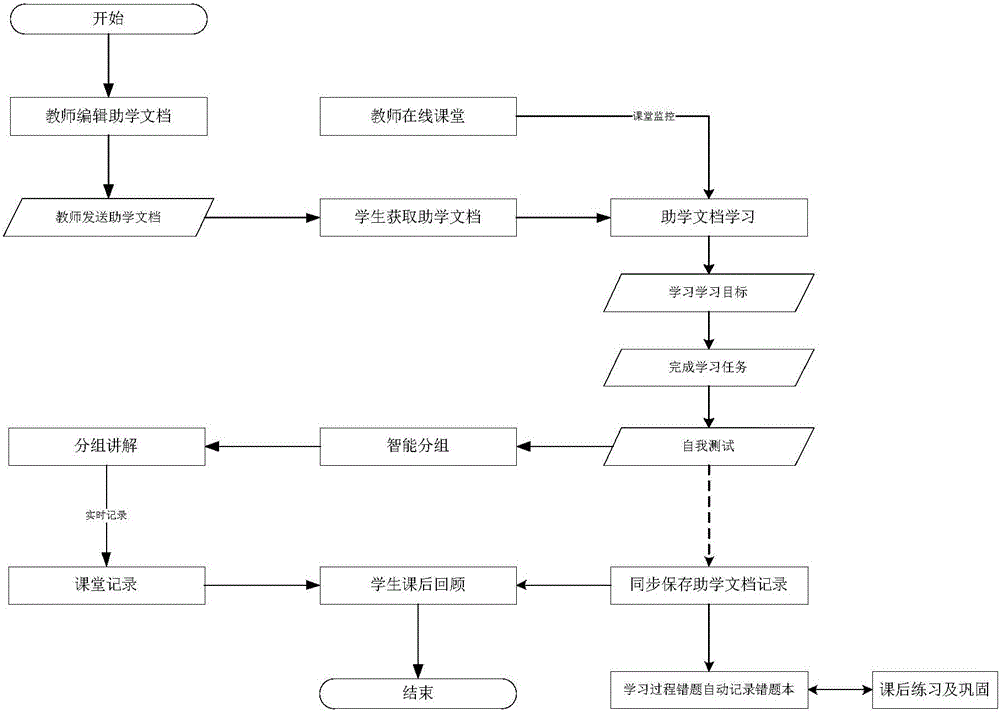
Internet teaching method and system
ActiveCN105869091AImprove learning efficiencyImprove learning effectData processing applicationsElectrical appliancesTimestampSource Data Verification
The invention provides an Internet teaching method and system for developing teaching activities through the Internet including a wireless communication network, and particularly discloses a method and system capable of recording the Internet teaching process in real time and accurately and efficiently storing the Internet teaching process in a cloud side. The method includes the step of evaluating educational document learning results by students to learn and distinguish learning situations of students of different levels, thereby achieving targeted differential teaching, tutoring, homework doing, exercising and the like and easily improving the learning efficiency and learning effect, especially continuously improving the students at different learning progresses. Furthermore, by means of a data return gateway, a data verification mechanism, a timestamp verification mechanism, an audio and video flow verification mechanism, a data complementary transmitting mechanism, a local fragmentation encrypting, storing and uploading mechanism and other means, recorded data is stored in the cloud side efficiently and accurately.
Owner:鹰硕(韶关)信息产业集团有限公司
Data validation using signatures and sampling
InactiveUS7484096B1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com