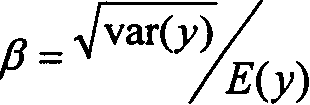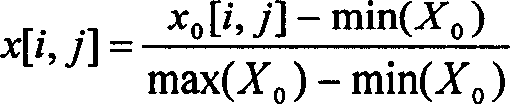Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
114 results about "Target signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Target signature. (*) 1. The characteristic pattern of a target displayed by detection and identification equipment. 2. In naval mine warfare, the variation in the influence field produced by the passage of a ship or sweep. (US DoD)
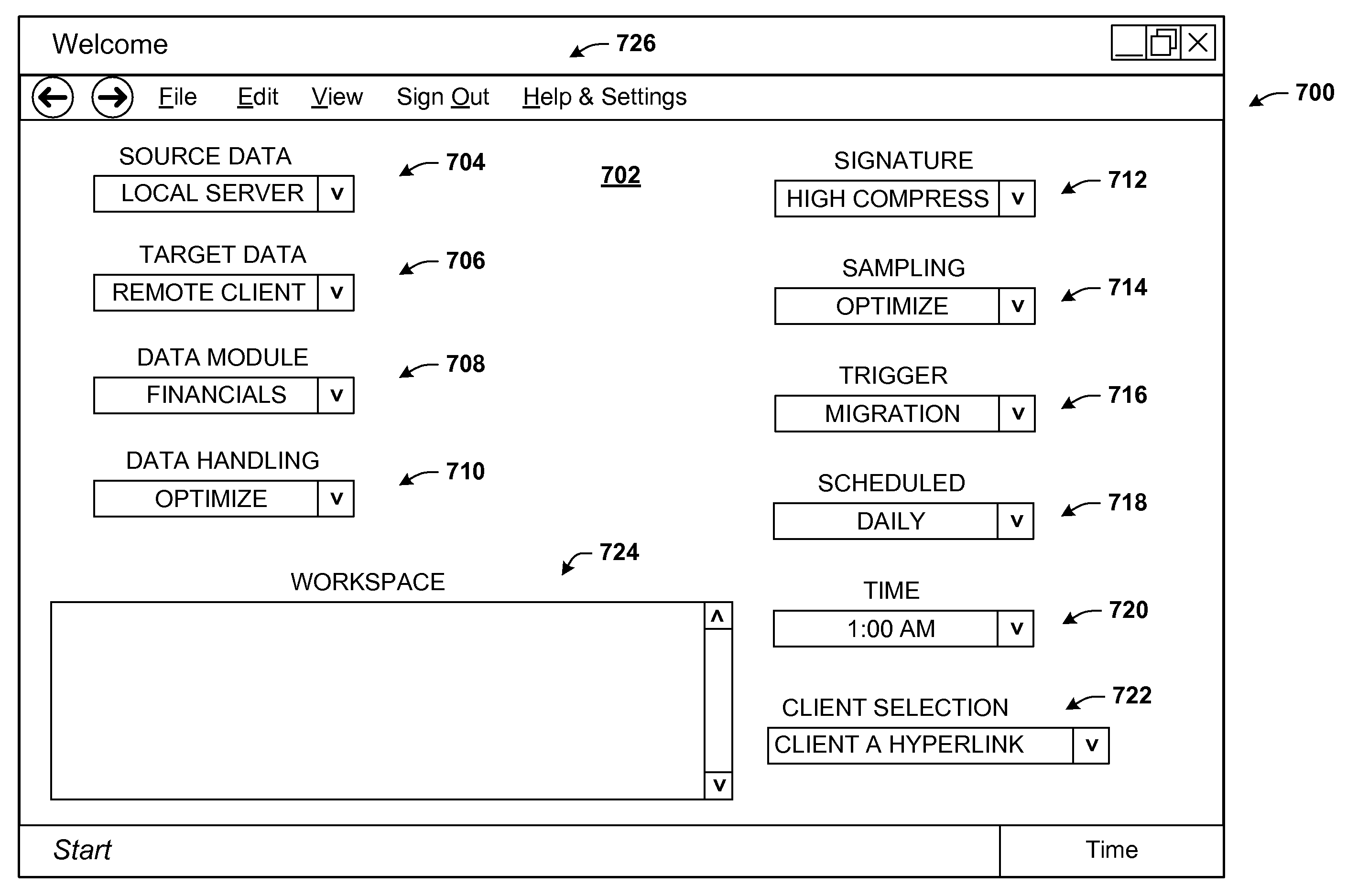
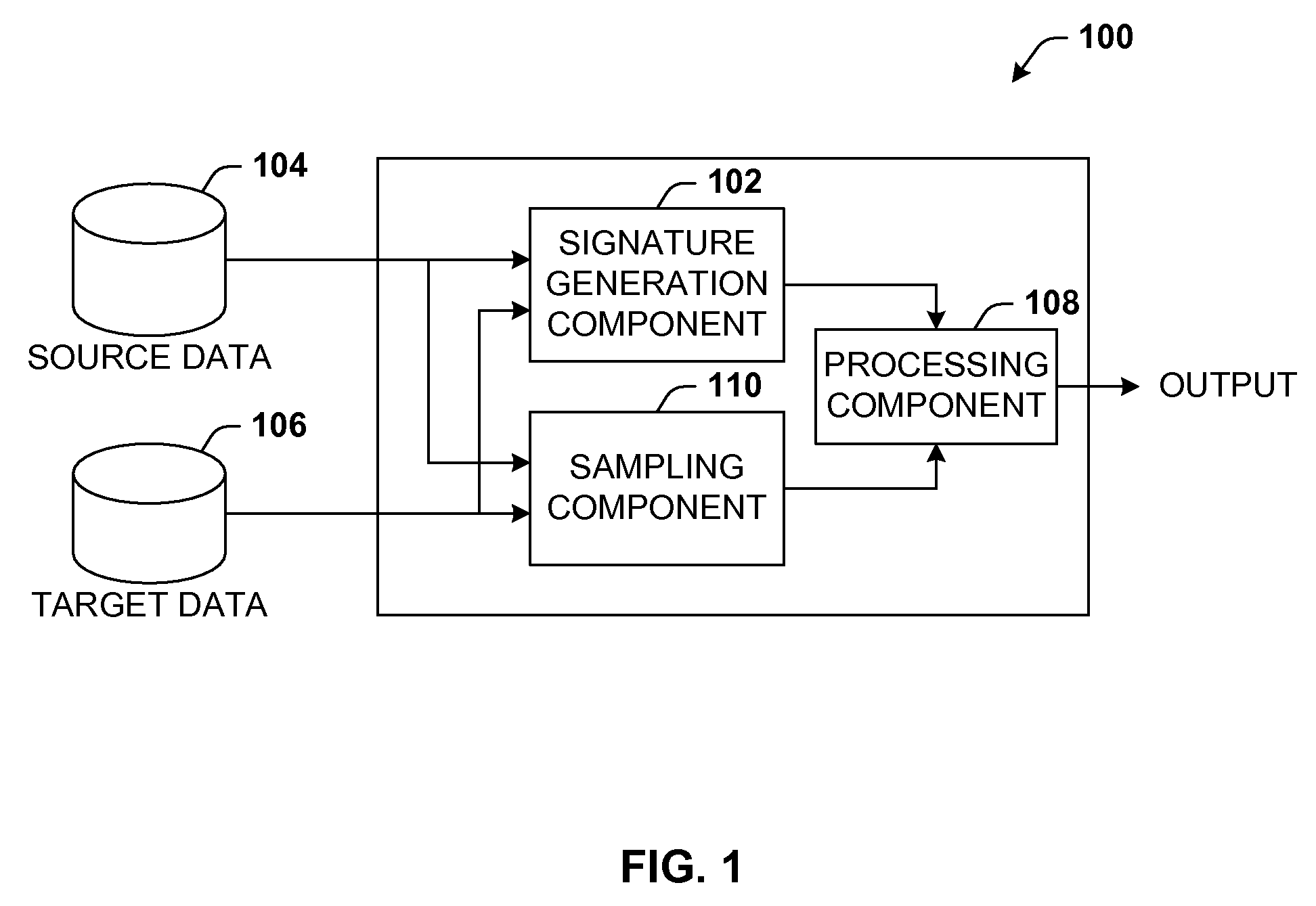
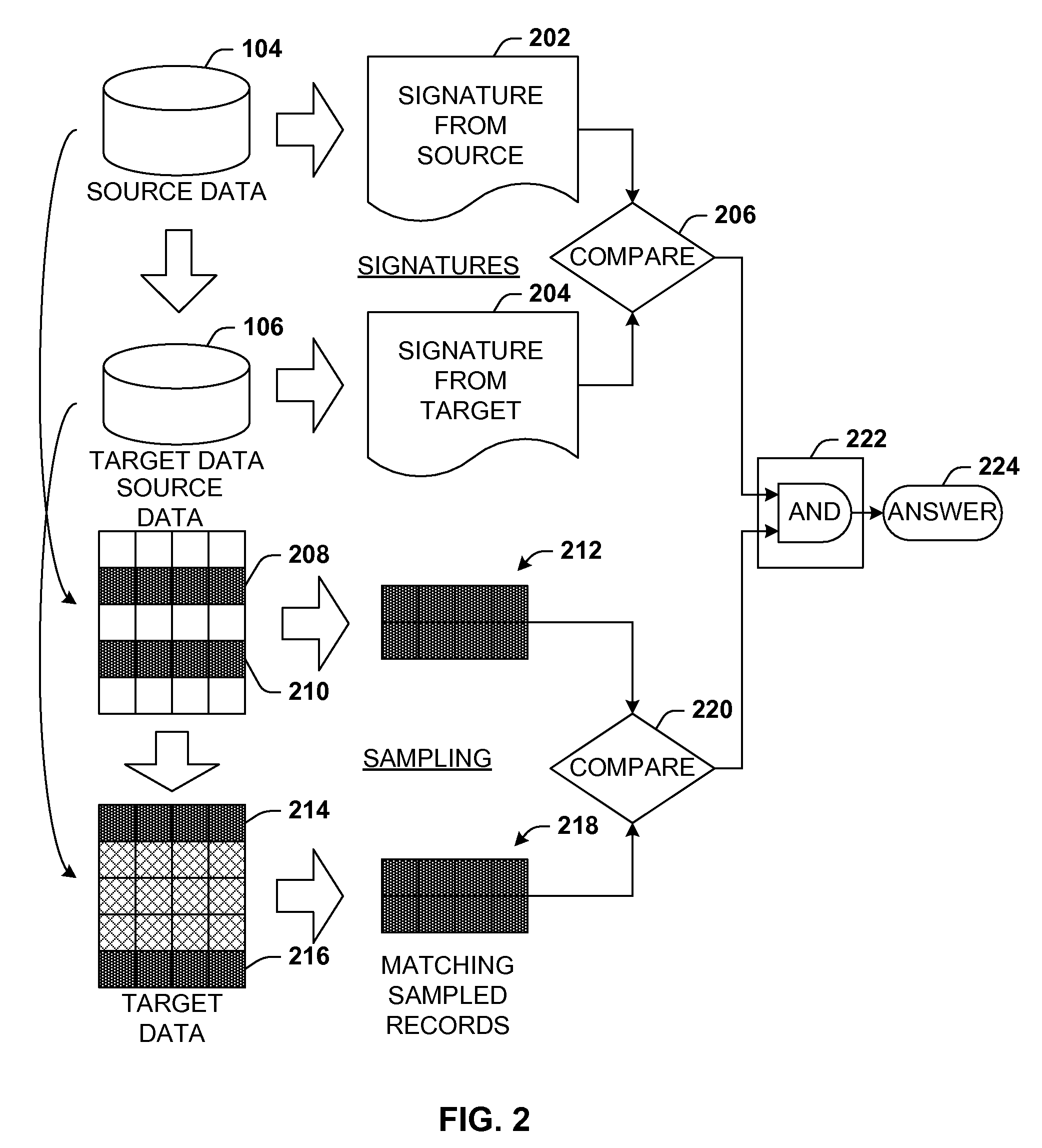
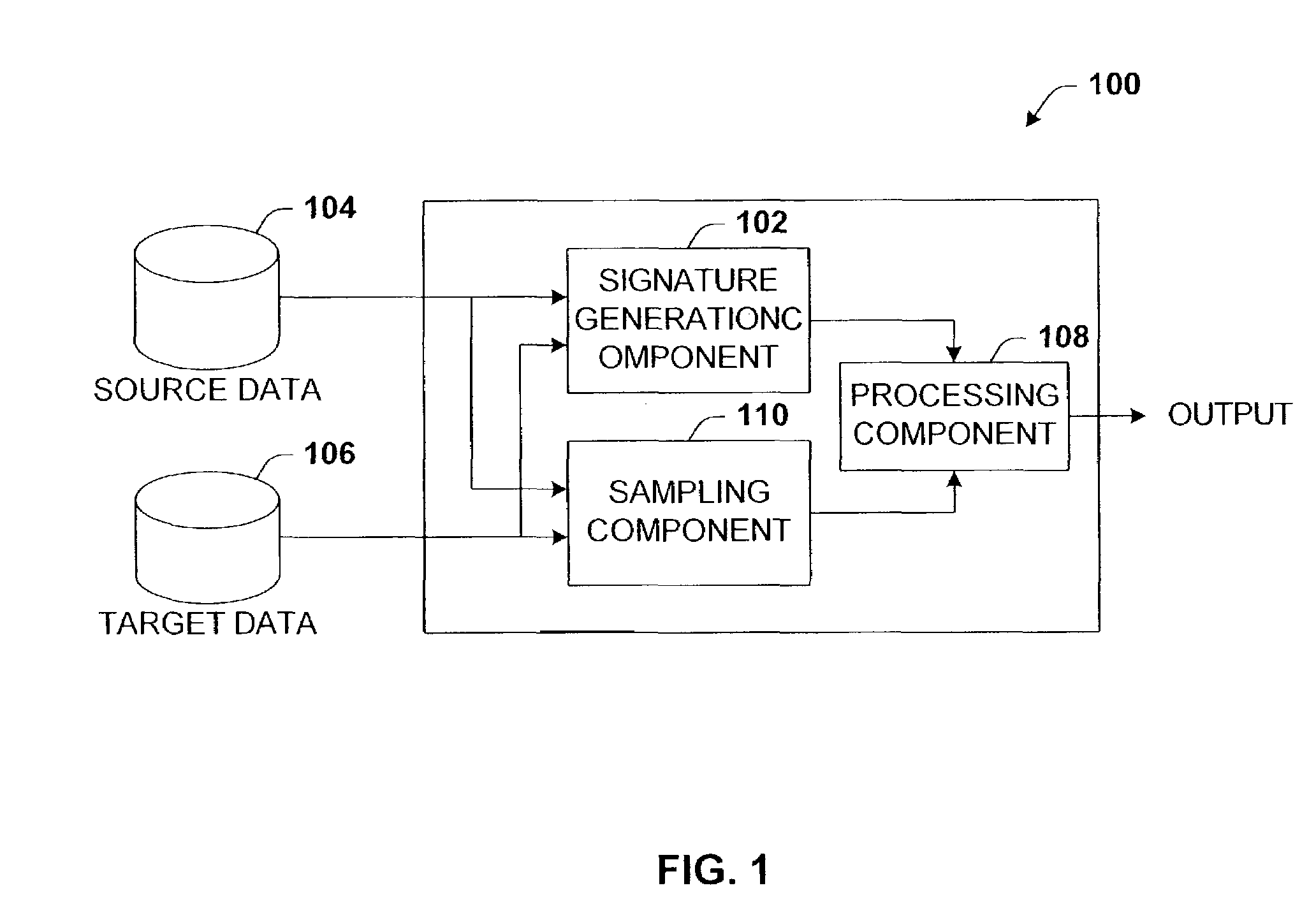
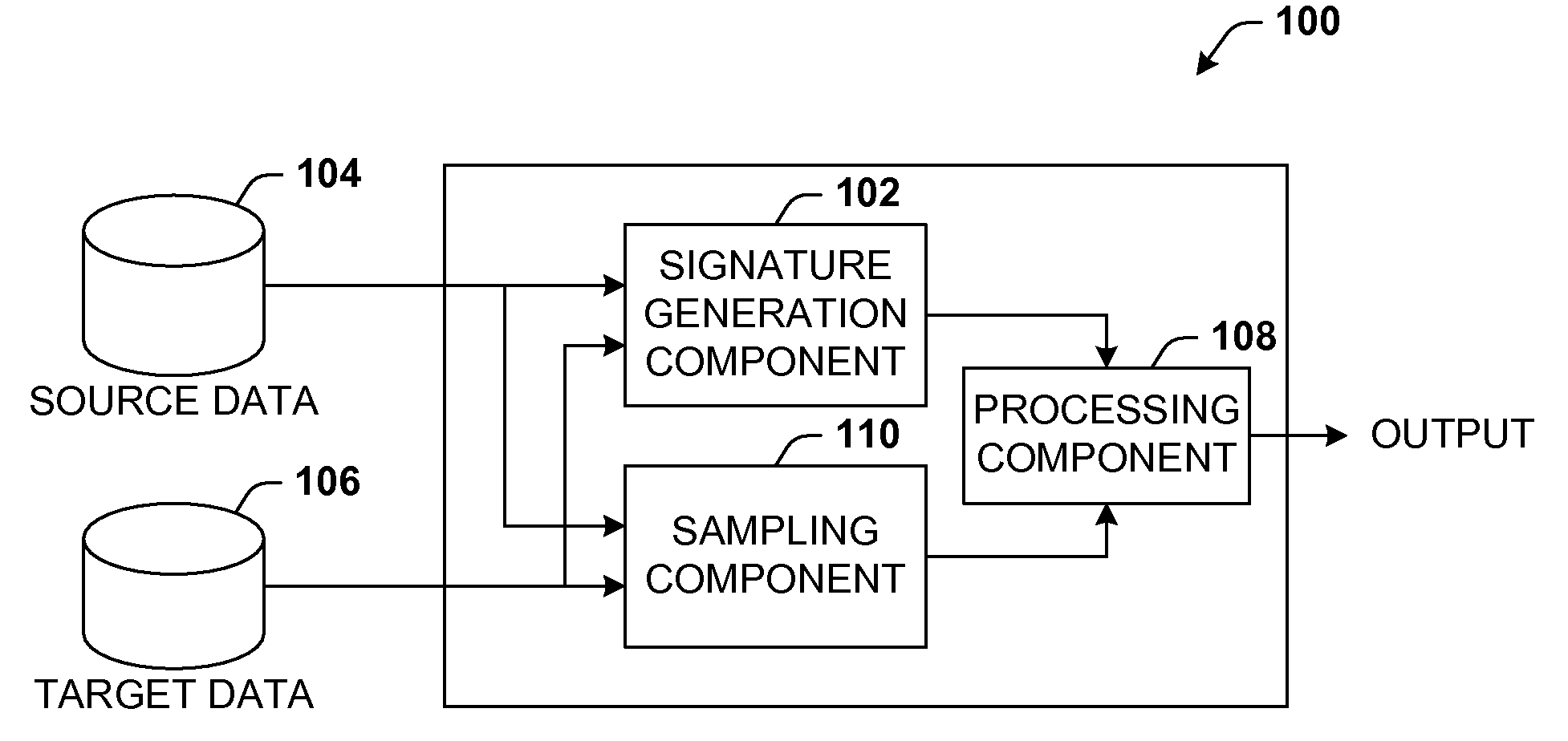
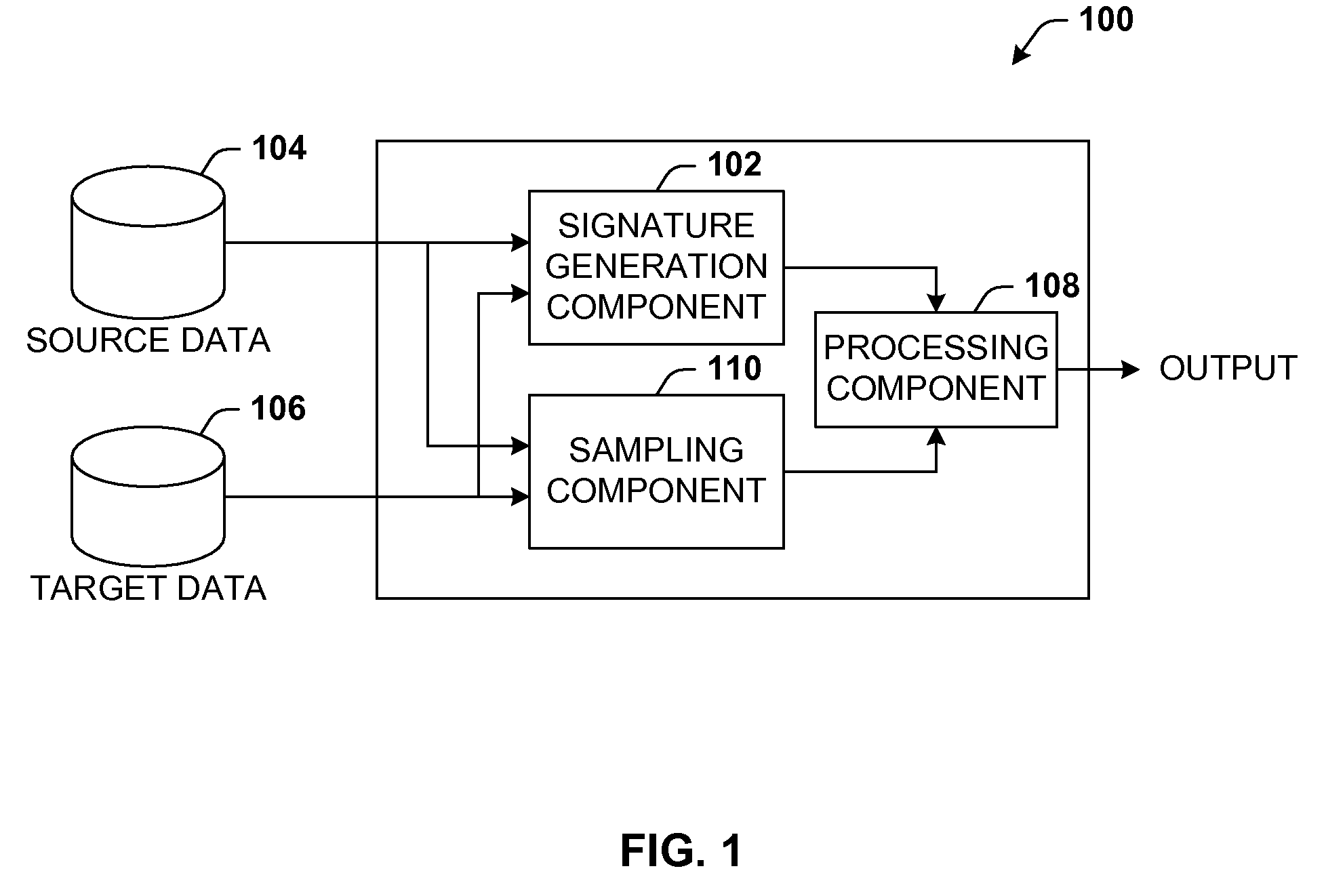
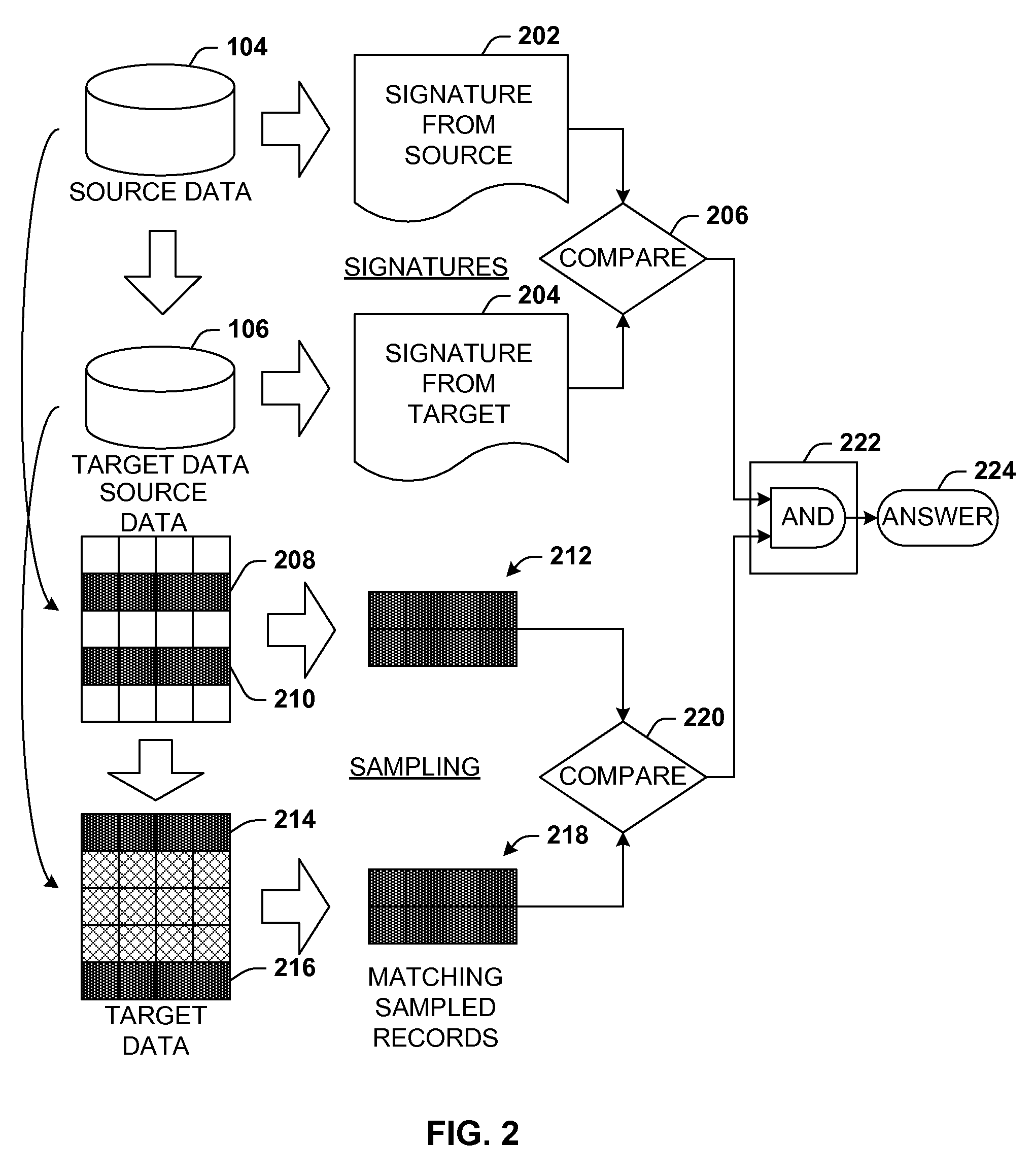
Data validation using signatures and sampling
InactiveUS20090132955A1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
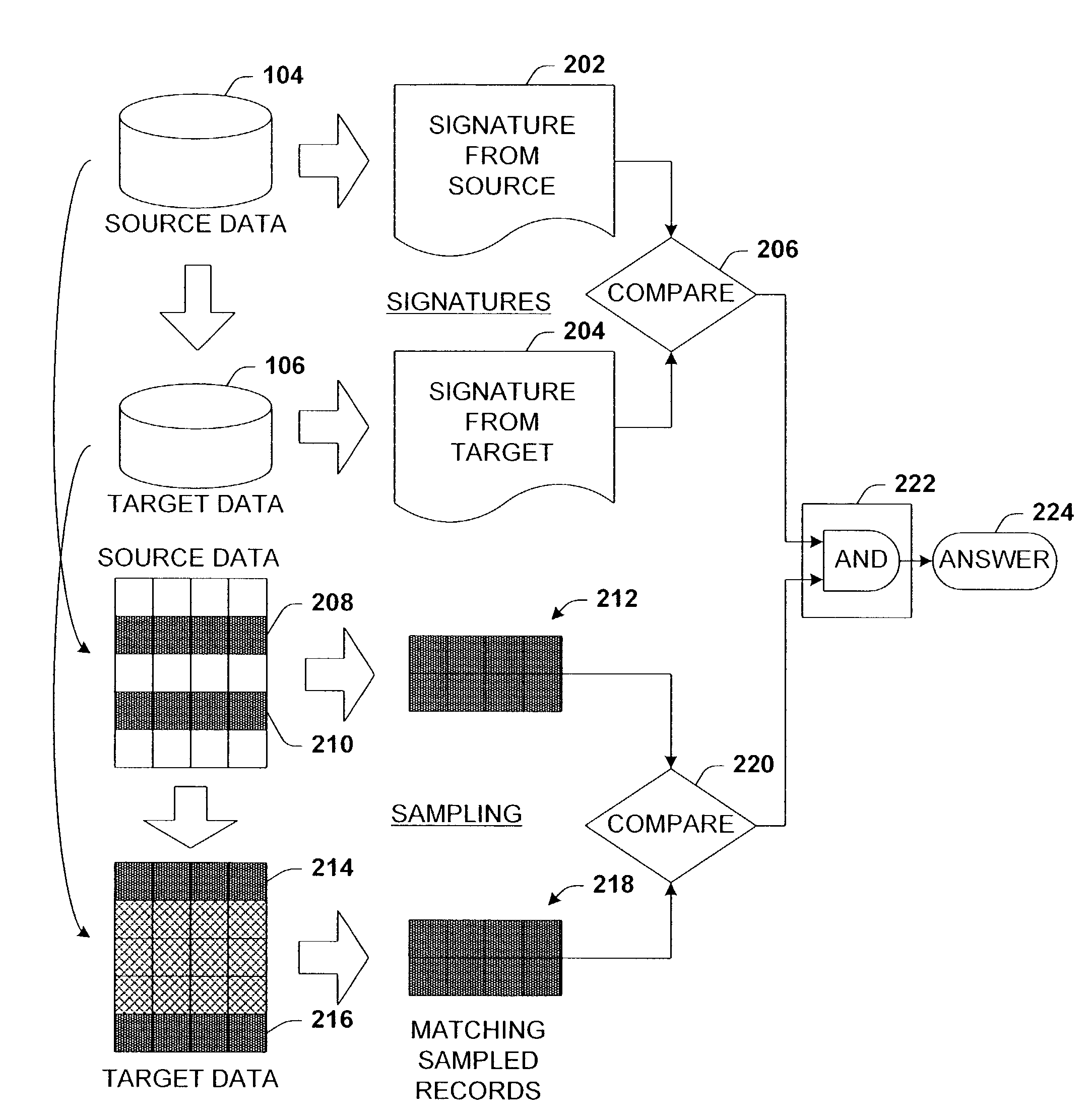
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
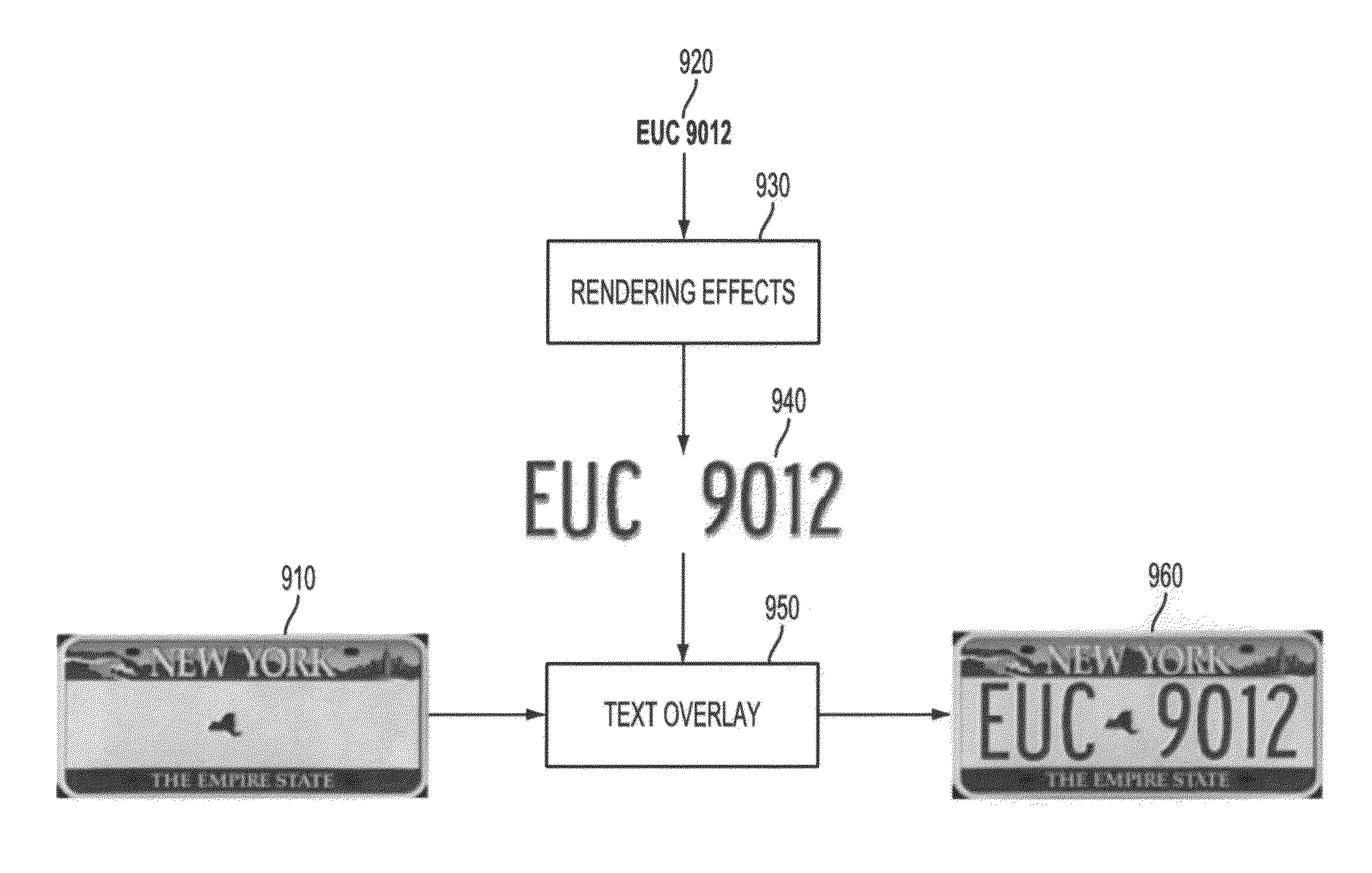
Methods and systems for improving yield in wanted vehicle searches
In response to determining that a target vehicle is at large, identification information associated with the target vehicle's license plate may be retrieved and used to generate one or more synthetic license plate images. The synthetic license plate images may be subjected to one or more transformation to cause them to resemble authentic license plate image captures and / or to mimic authentic license plate image captures from existing and operational ALPR system cameras. Target signatures may then be calculated from the synthetic license plate images. Upon capturing an authentic license plate image using an ALPR system camera, a signature of the authentic license plate image may be calculated. If a match is found between the signature of the authentic license plate image and a target signature, law enforcement may be alerted that the target vehicle was detected at the location of the ALPR system camera.
Owner:CONDUENT BUSINESS SERVICES LLC
Hyperspectral remote sensing systems and methods using covariance equalization
InactiveUS7194111B1Reduce decreaseEasy to detectTelevision system detailsOptical detectionAlgorithmCovariance
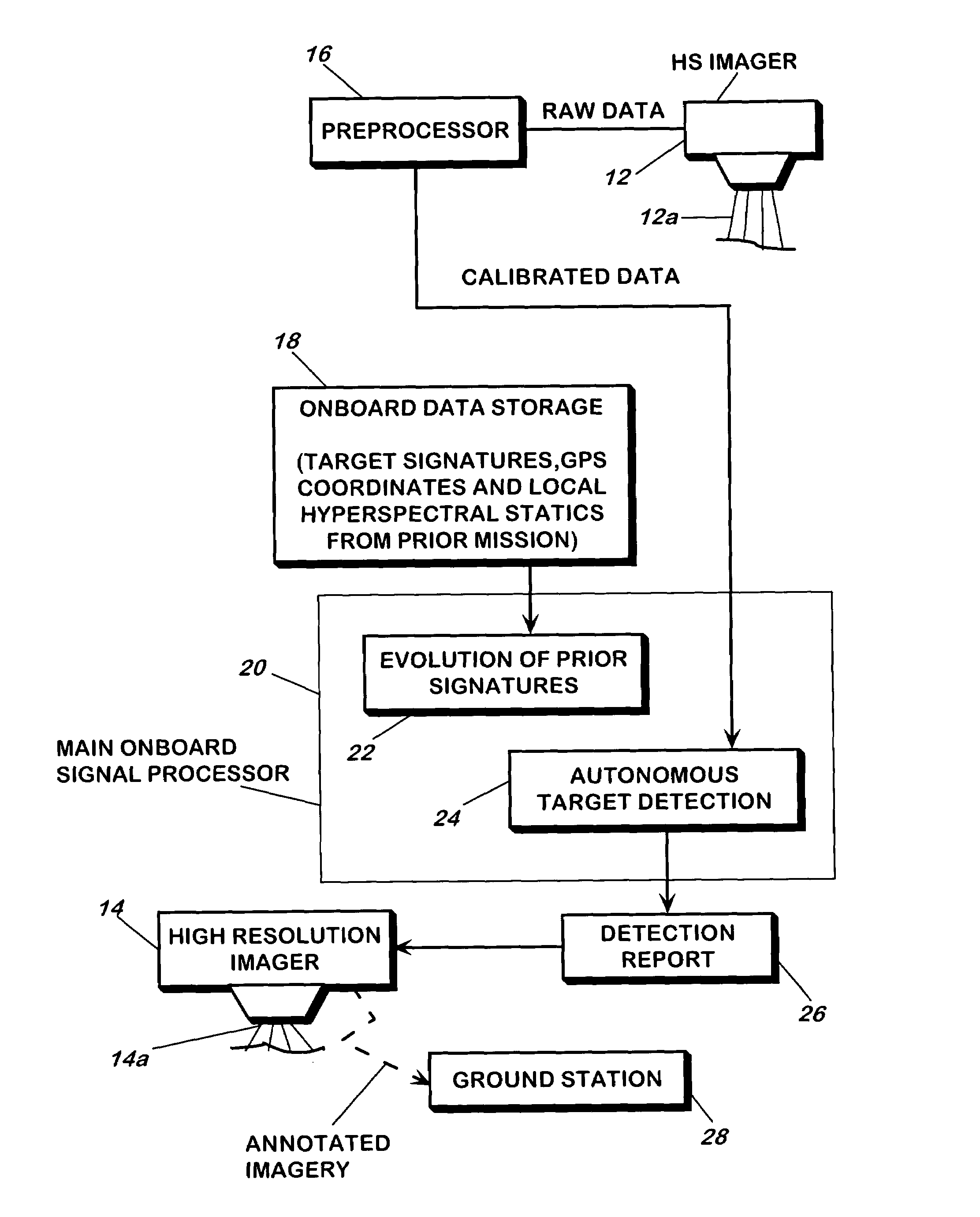
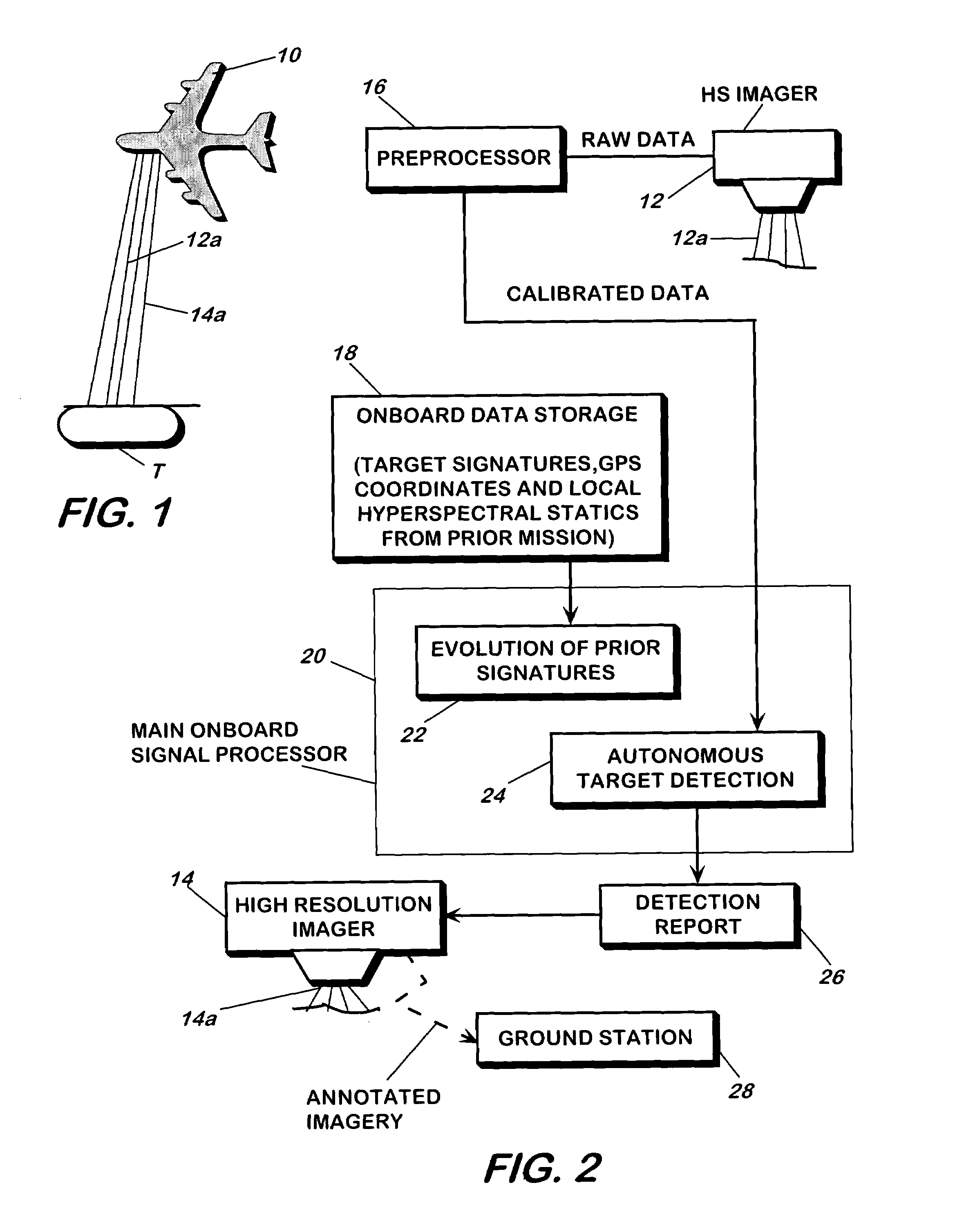
A method and apparatus for detecting a target or targets in a surrounding background locale based on target signatures obtained by a hyperspectral imaging sensor used the hyperspectral imaging sensor to collect raw target signature data and background locale data during a first data collection mission. The data is processed to generate a database including a plurality of target signatures and background data relating to the background locale. The hyperspectral imaging sensor is later used to collect further background data during a further, current data collecting mission so as to provide continuously updated background data, in real time. A covariance equalization algorithm is implemented with respect to the background data contained in the database and the updated background data collected during the current mission to effect transformation of each target signature of the database into a transformed target signature. A detection algorithm which employs the resultant transformed target signature is used to produce detection information related to the target or targets.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Data validation using signatures and sampling
InactiveUS7484096B1User identity/authority verificationCharacter and pattern recognitionData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
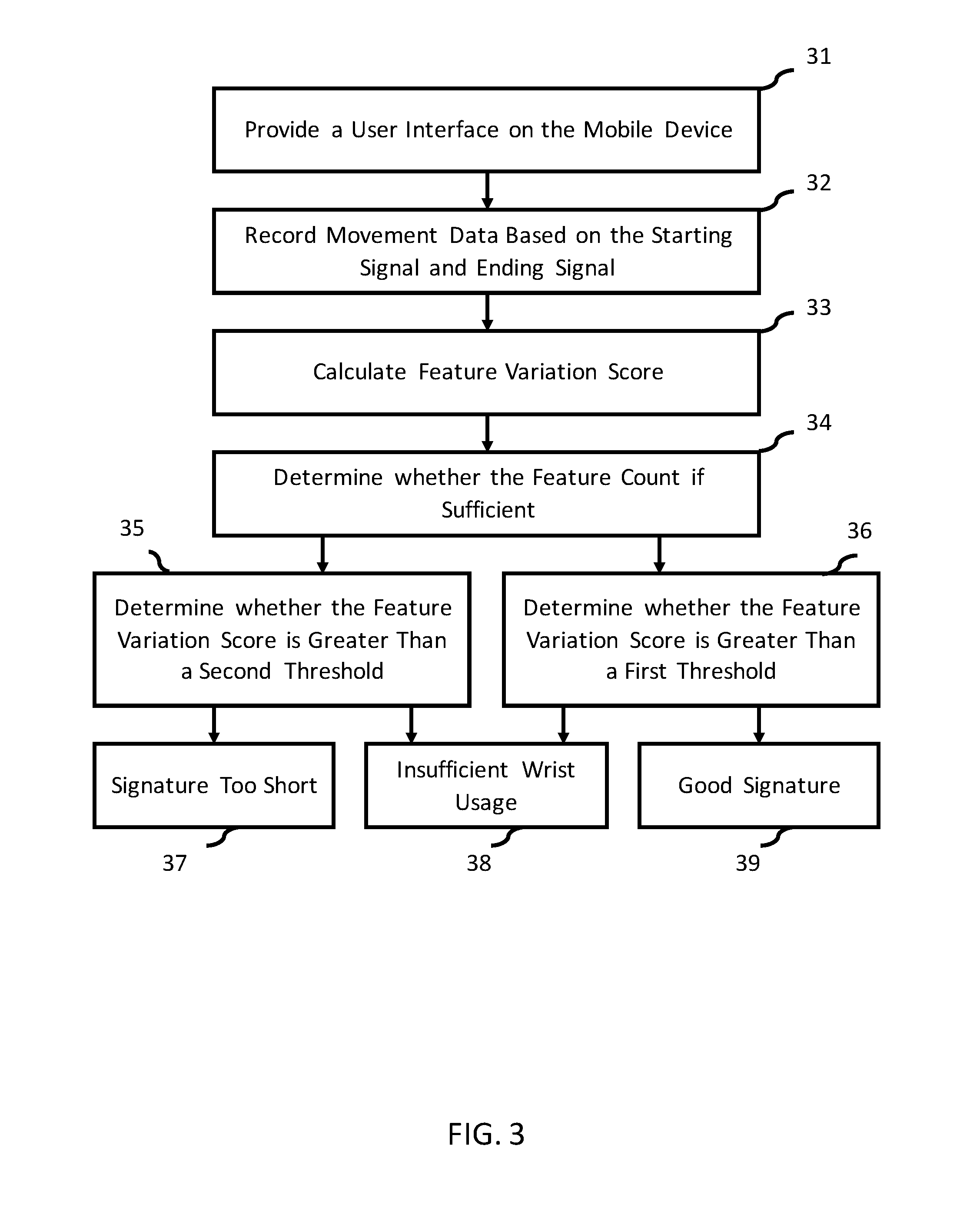
Motion based authentication systems and methods
InactiveUS20160226865A1Fast and secure and low-cost of authenticationCryptography processingDigital data authenticationUser inputTarget signature
A motion-based authentication method of authenticating a user with a mobile device is provided. A pre-training routine is conducted to detect an orientation characteristic and a duration characteristic associated with a user input. A training routine is conducted to capture a set of base signatures and to compute the consistency level associated with the signatures. A verification routine is conducted to compare the target signature with the set of base signatures. Authorization is granted if the target signature has reached the similarity threshold with respect to the base signatures.
Owner:CHEN PO KAI
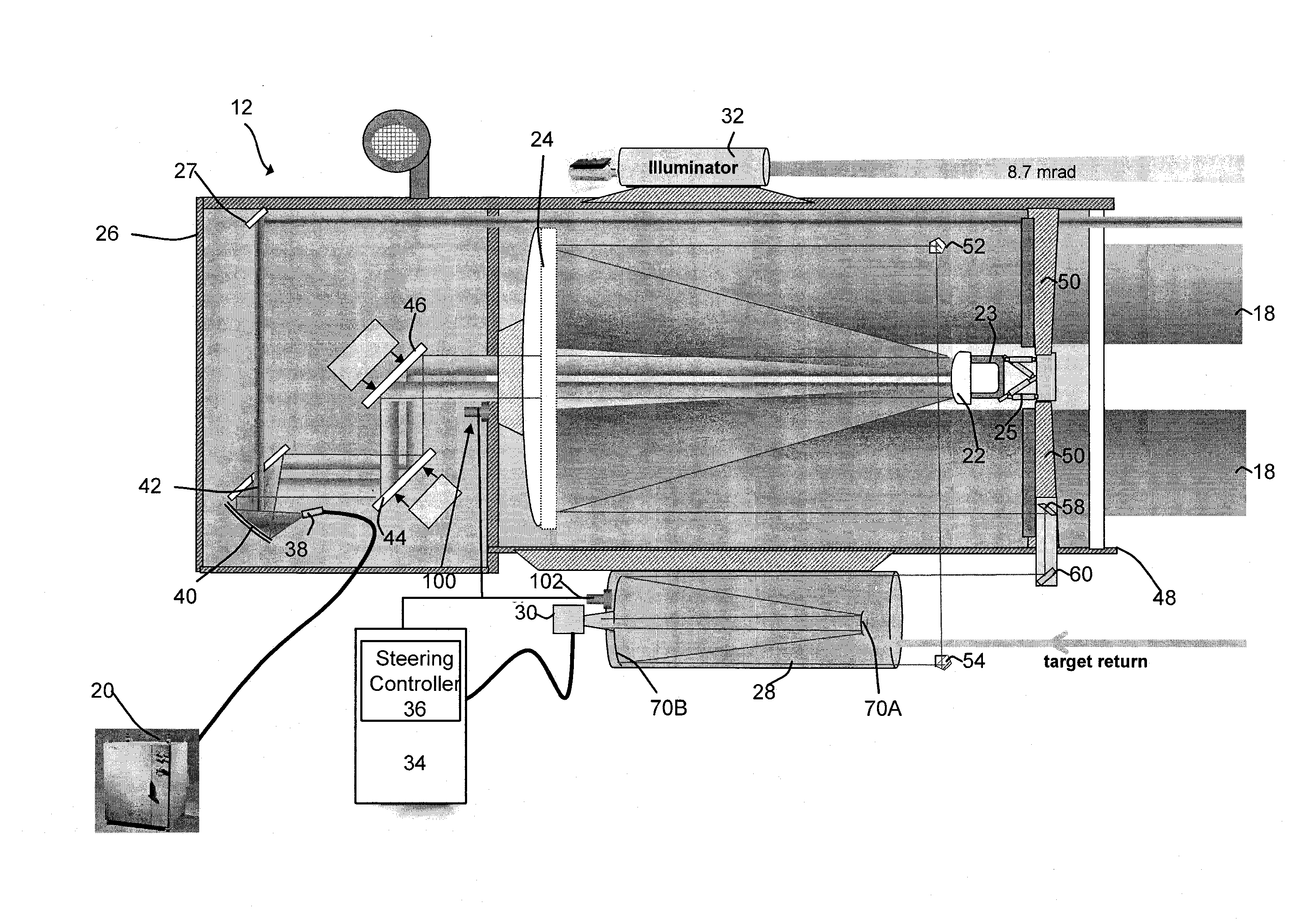
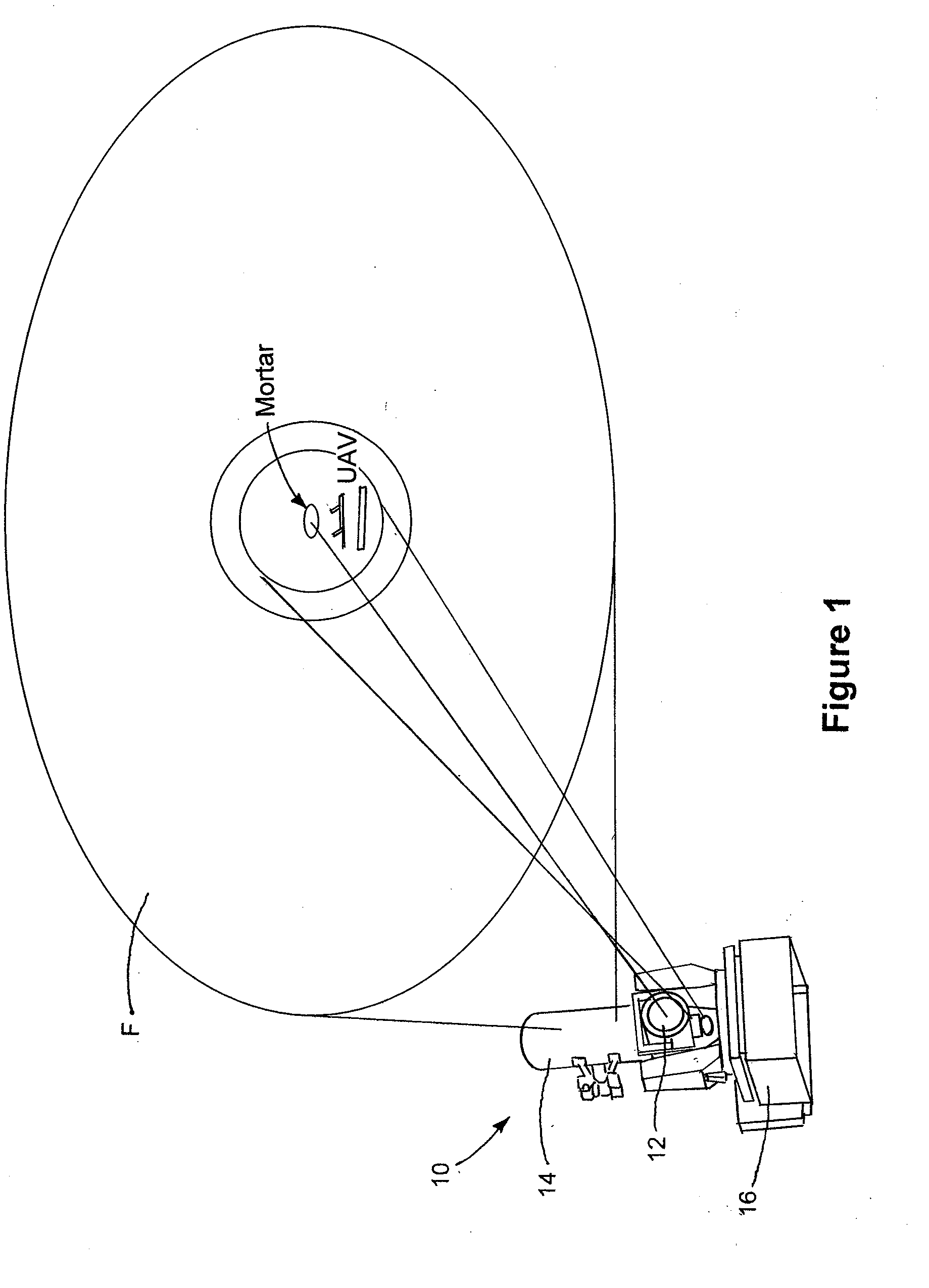
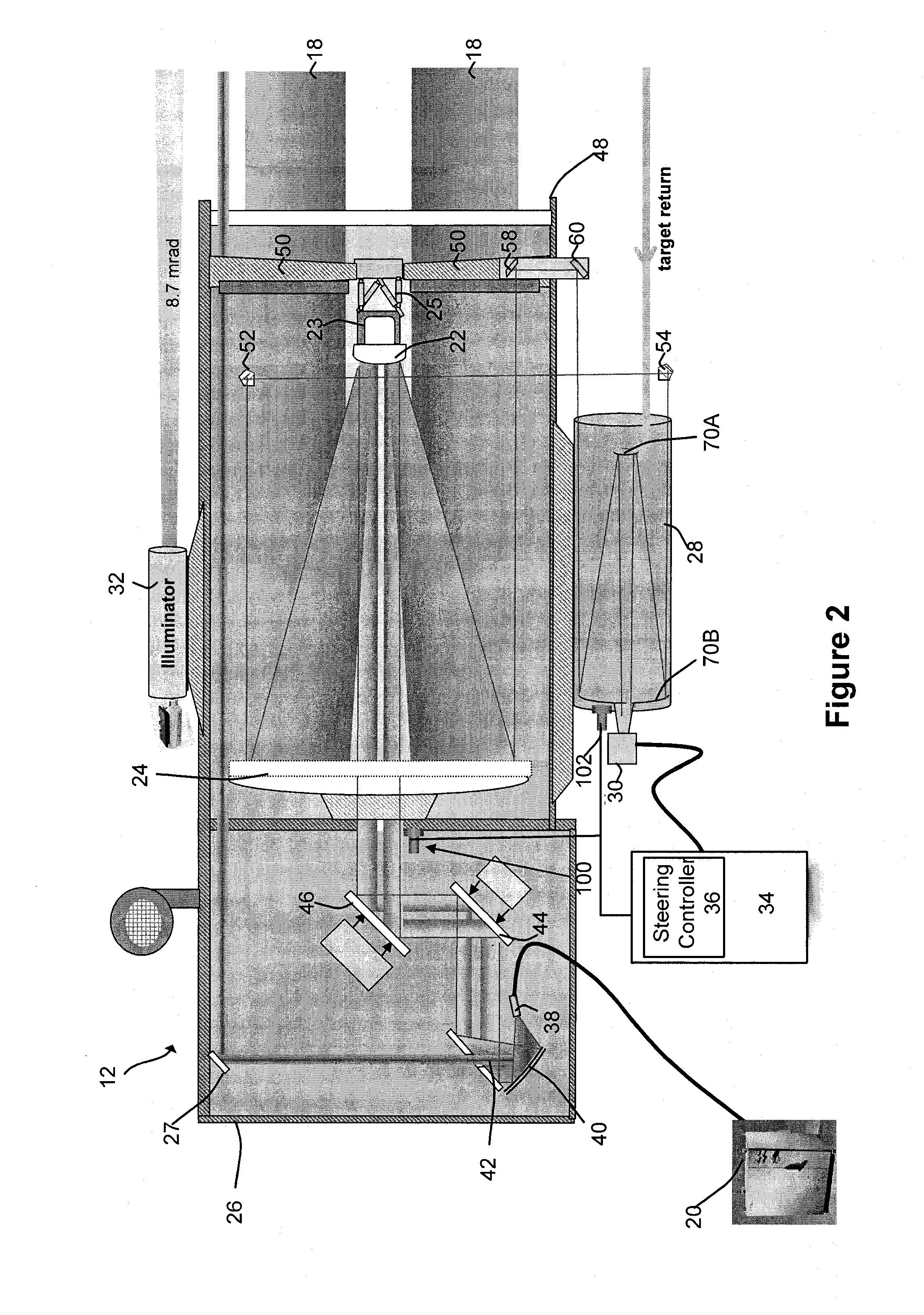
Semi-active optical tracking system
A system and method for tracking an airborne target including an illumination source (e.g., a diode laser array) is used to enhance a target signature and a detector (e.g., a passive high-speed camera) is used to detect to electromagnetic radiation (e.g., infrared radiation) reflected off the target. The received electromagnetic radiation may be processed by a digital computer and passed through a spatial filter that implements a band limited edge detection operation in the frequency domain. The filter may remove low spatial frequencies that attenuate soft edged clutter such as clouds and smoke as well as filter out artifacts and attenuated medium to high spatial frequencies to inhibit speckle noise from the detector as well as speckle from the laser return off the target.
Owner:RAYTHEON CO
Tracing method for video movement objective self-adapting window
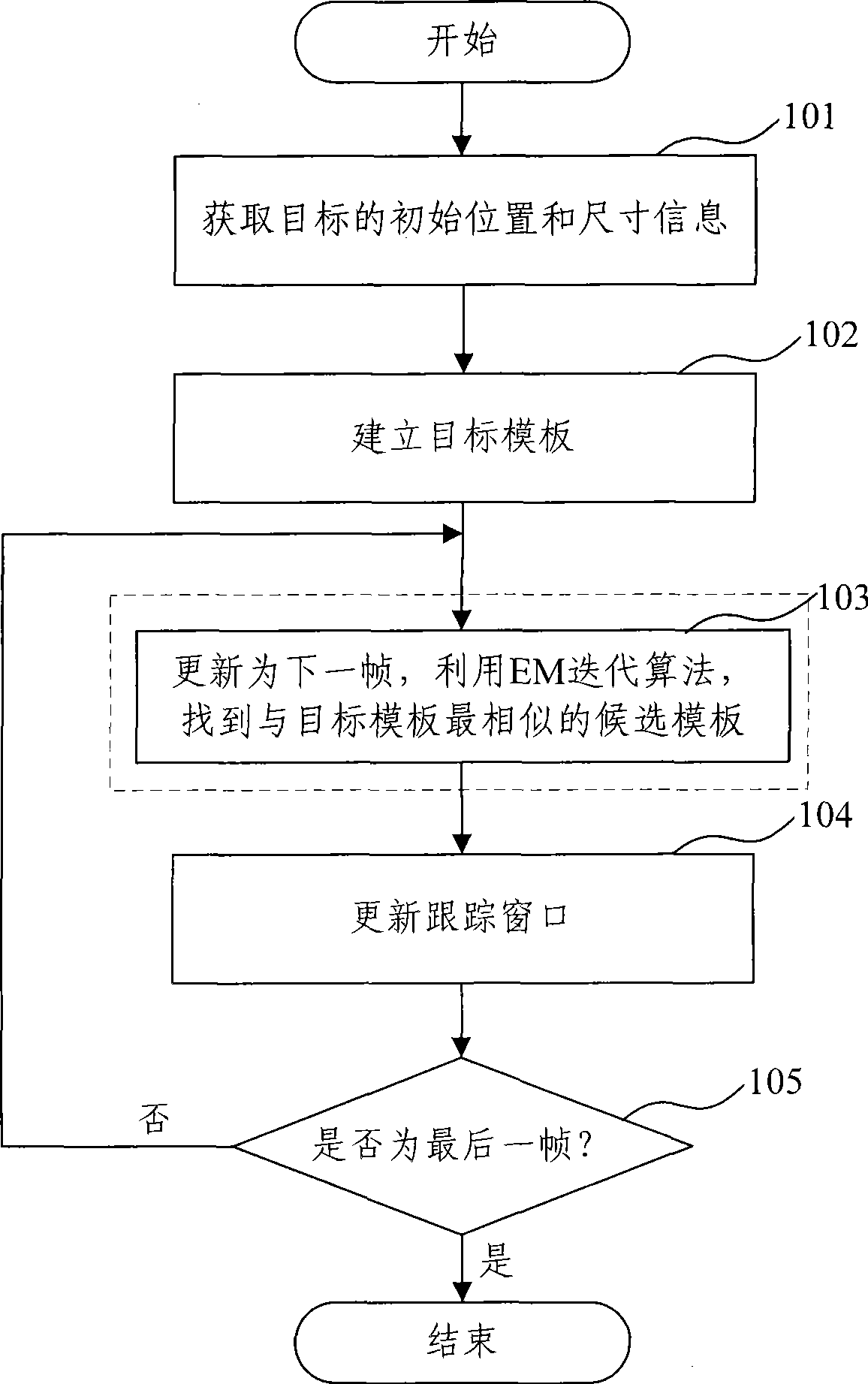
InactiveCN101369346AAccurate descriptionImprove reliabilityImage analysisVideo sequenceModel parameters
The invention discloses a tracking method of a video frequency moving object target self-adapting window, relating to machine vision and pattern recognition technique. A frame image of a video frequency sequence is read into a postpositional memory zone, and staring position and size information of a tracked object is obtained in the frame, then distribution statistical information of a target signature is extracted to build a gauss mixed model as an object template, a mean vector and a covariance matrix in gauss mixed distribution are used to describe the position and the size of the object, then the next frame image of the video frequency sequence is read into the postpositional memory zone. In a new frame video frequency image, a parameter estimation method is used to obtain object gauss mized model parameters in the current frame in iterative computation and find candidate template similar to the object template, and the final model parameters obtained in iteration are used to update the tracking window for realizing self-adaption of the tracked window. According to the tracking method of the video frequency moving object target self-adapting window, tracking reliability is greatly increased, which is widely applied in the fields of robot technology, vision navigation, automatic supervision, traffic control and the like.
Owner:BEIHANG UNIV
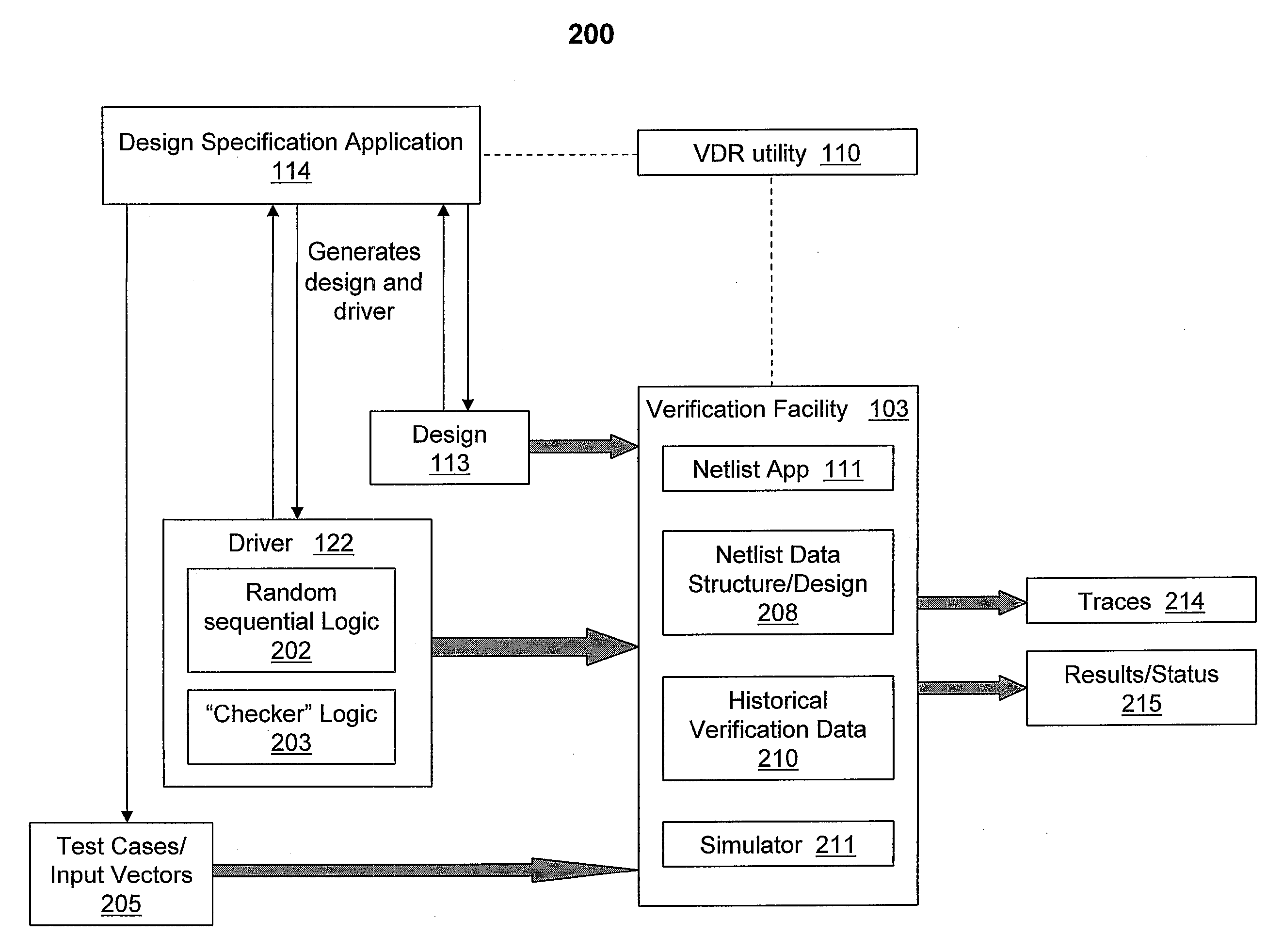
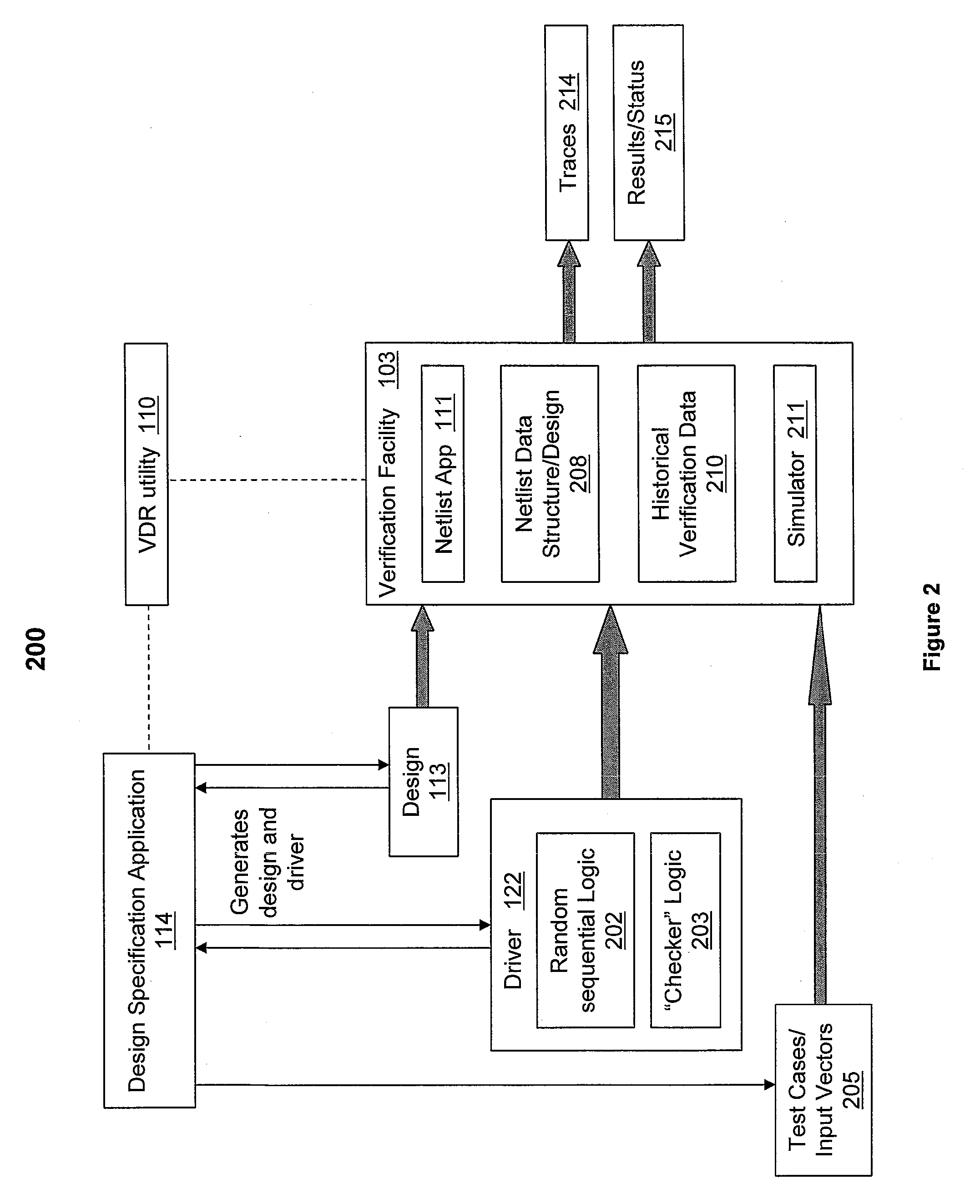
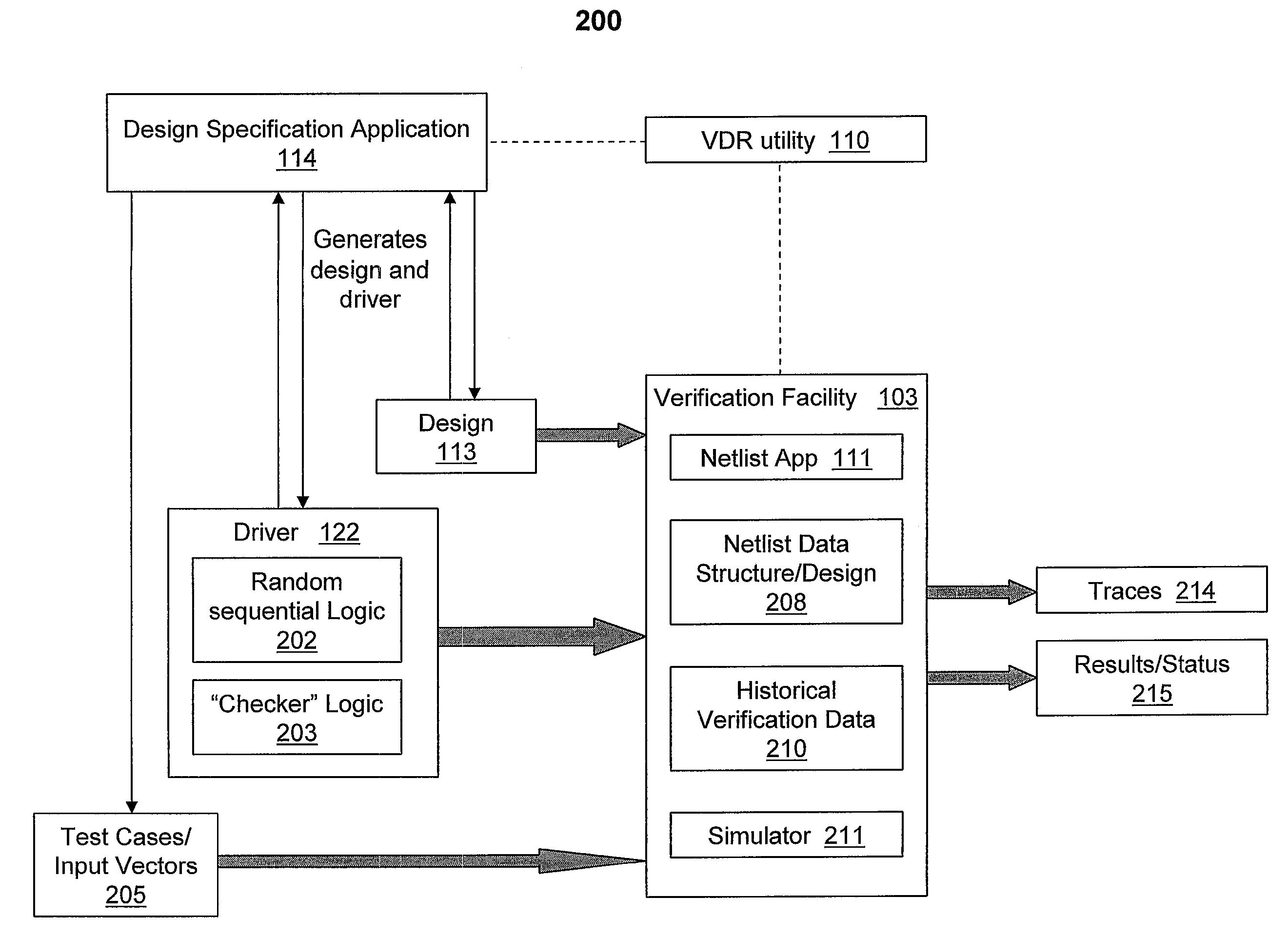
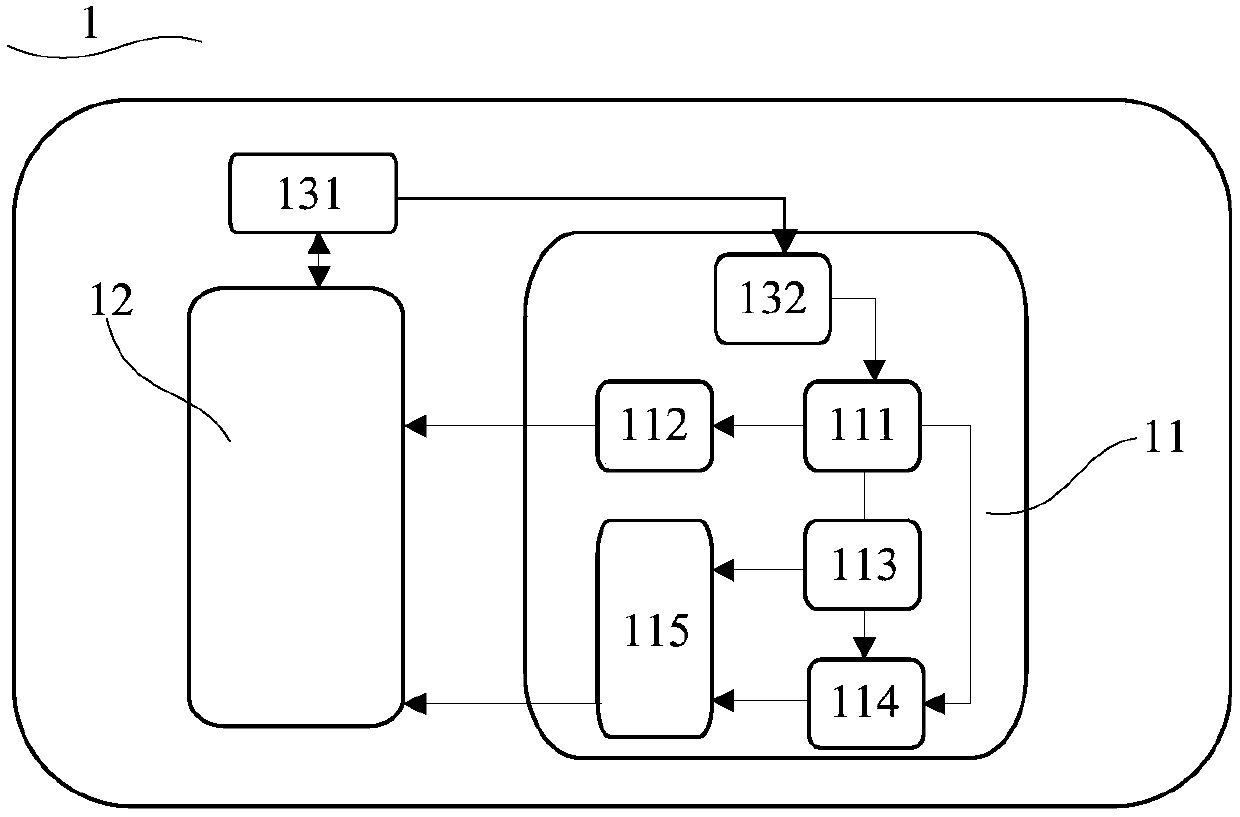
Enhancing Formal Design Verification By Reusing Previous Results
InactiveUS20100257494A1Computer aided designSoftware simulation/interpretation/emulationSoftware engineeringTarget signature
A method, a system and a computer program product for re-using verification results associated with a circuit design to eliminate a formal verification re-run associated with a subsequent verification of the circuit design. A Verification Data Re-use (VDR) utility initiates the creation of a first netlist data structure and a first set of target signatures for the circuit design. The VDR utility initiates an initial functional verification run of the circuit design and stores the results of the verification run. When a subsequent verification of the initial design is initiated, the VDR utility compares the first set of target signatures with a second set of target signatures for the subsequent verification run. A match of target signatures indicates that corresponding design targets have an identical functionality and the VDR utility re-uses verification results from the initial verification run to eliminate an extensive formal verification
Owner:MENTOR GRAPHICS CORP
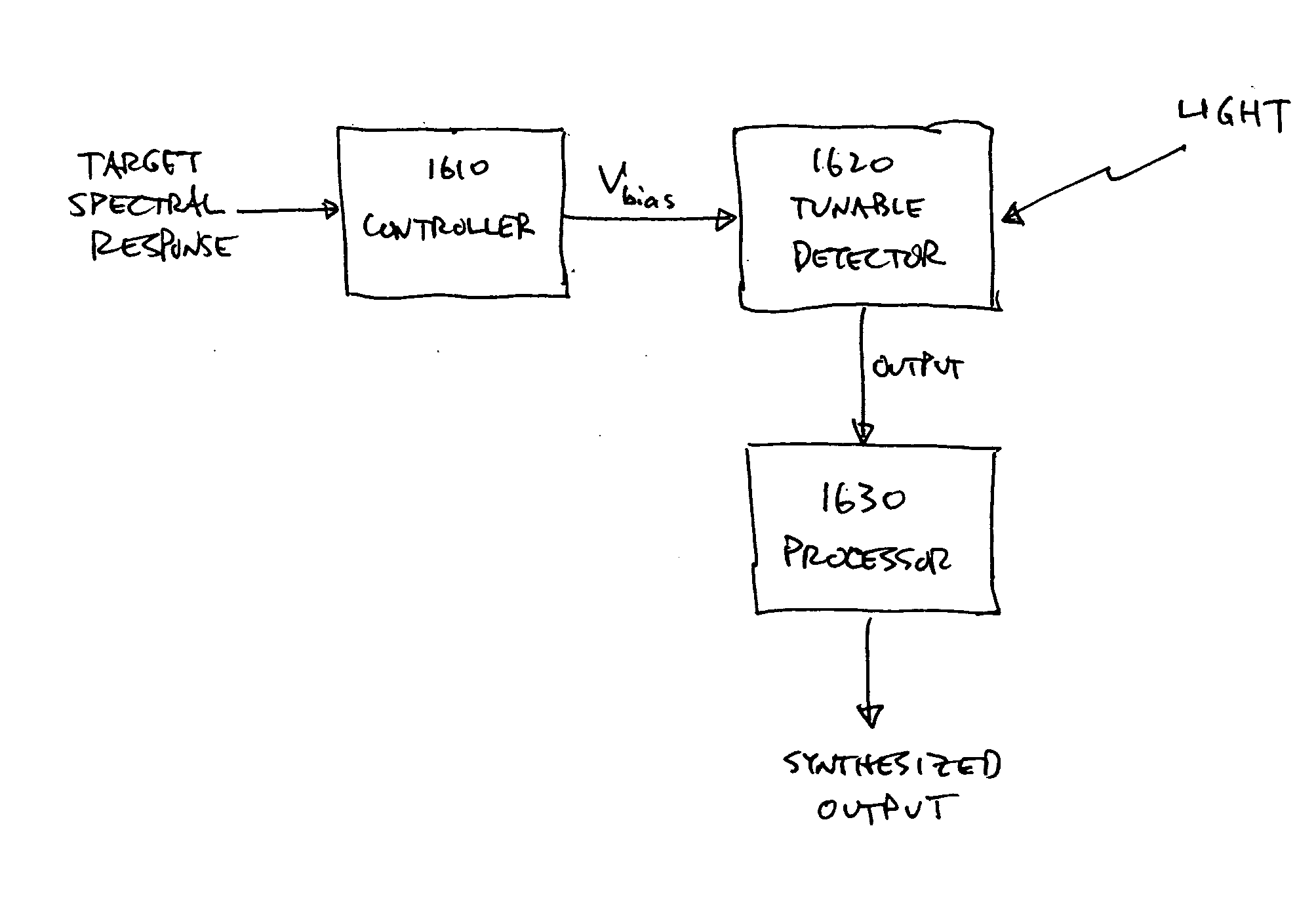
Detector with tunable spectral response
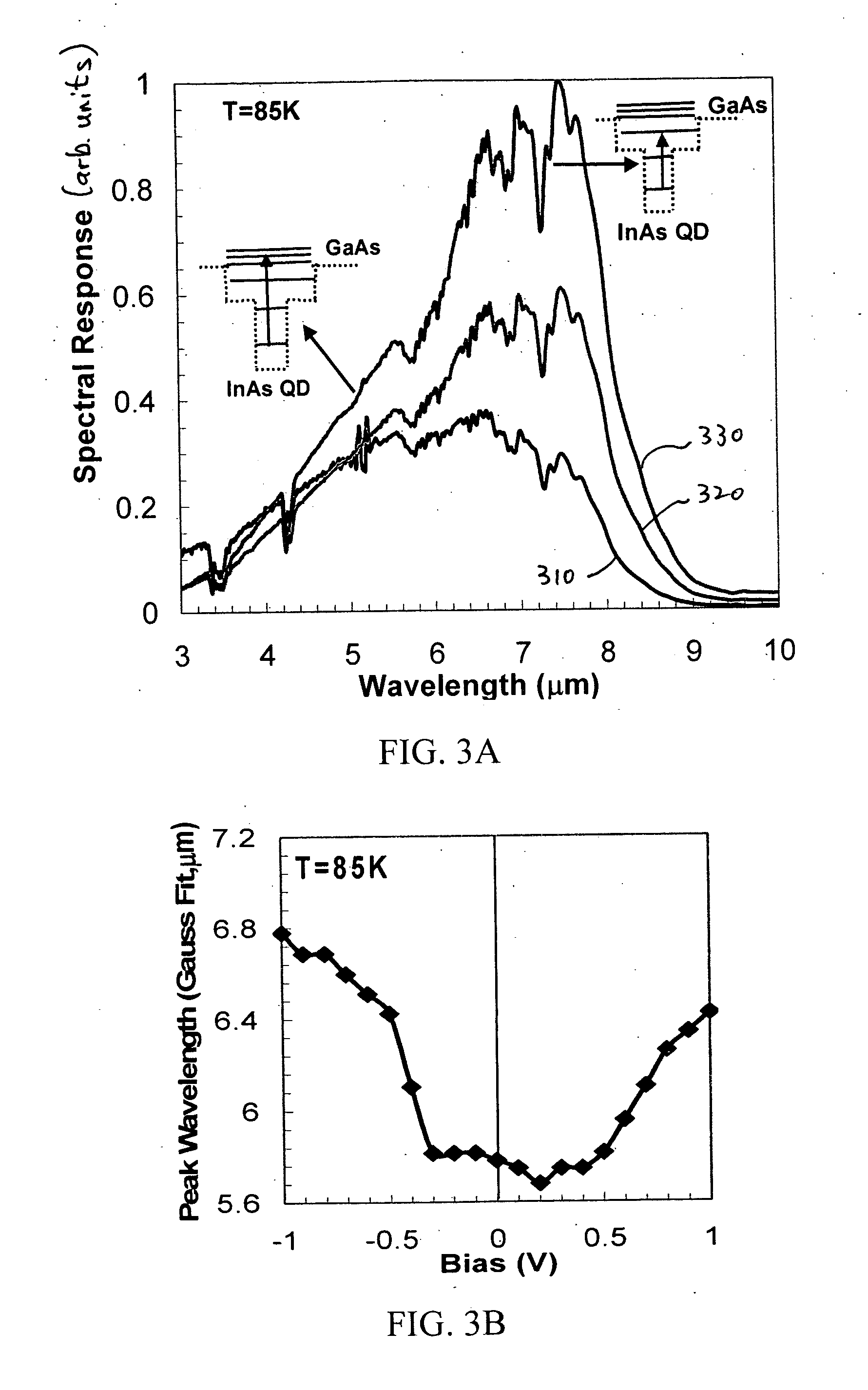
ActiveUS20050211873A1Low costReduce complexitySpectrum investigationNanoinformaticsSpectral responseTarget signature
A semiconductor detector has a tunable spectral response. These detectors may be used with processing techniques that permit the creation of “synthetic” sensors that have spectral responses that are beyond the spectral responses attainable by the underlying detectors. For example, the processing techniques may permit continuous and independent tuning of both the center wavelength and the spectral resolution of the synthesized spectral response. Other processing techniques can also generate responses that are matched to specific target signatures.
Owner:STC UNM
Request authentication method and system
The invention discloses a request authentication method. The method comprises the steps of obtaining preset token information contained in a request when the request initiated by a target client is received; obtaining an encryption key in a configuration file, and decrypting and decoding the preset token information according to the encryption key, thereby obtaining signature information; judgingwhether the signature information is the same as preset target signature information or not; authenticating the request successfully if the signature information is the same as the preset target signature information; and authenticating the request unsuccessfully if the signature information is different from the preset target signature information. According to the authentication method, the authentication is carried out through utilization of the preset token information of the client, and the information does not need to be stored by a server. The problem that each time when the request isinitiated, session storage request information needs to be established at the server, when more and more clients initiate the requests, the cost of the memory of the server is continuously increased,and an authentication process also can be congested is avoided.
Owner:BEIJING CHINA POWER INFORMATION TECH +2
Signature method and system for block chain
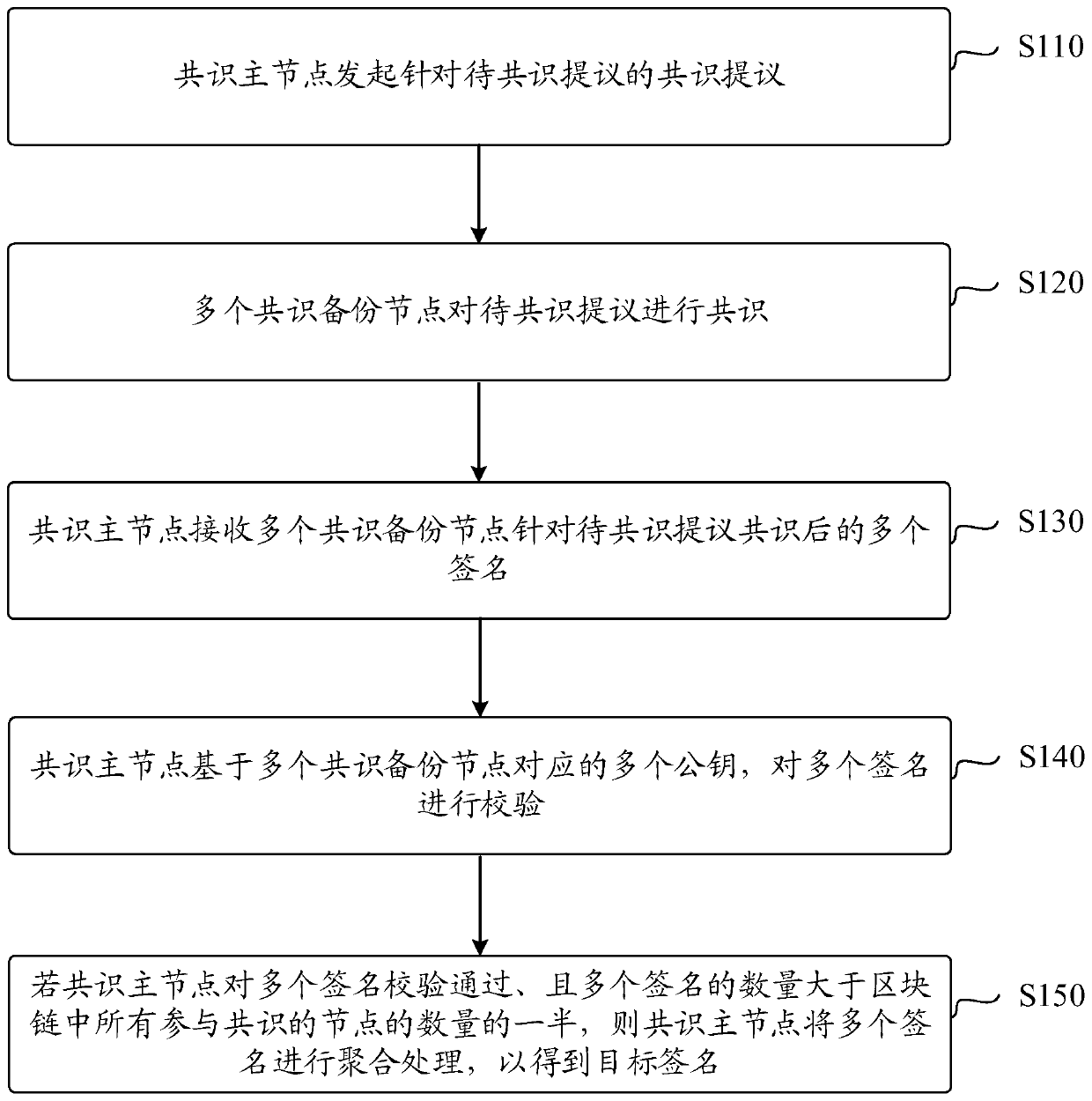
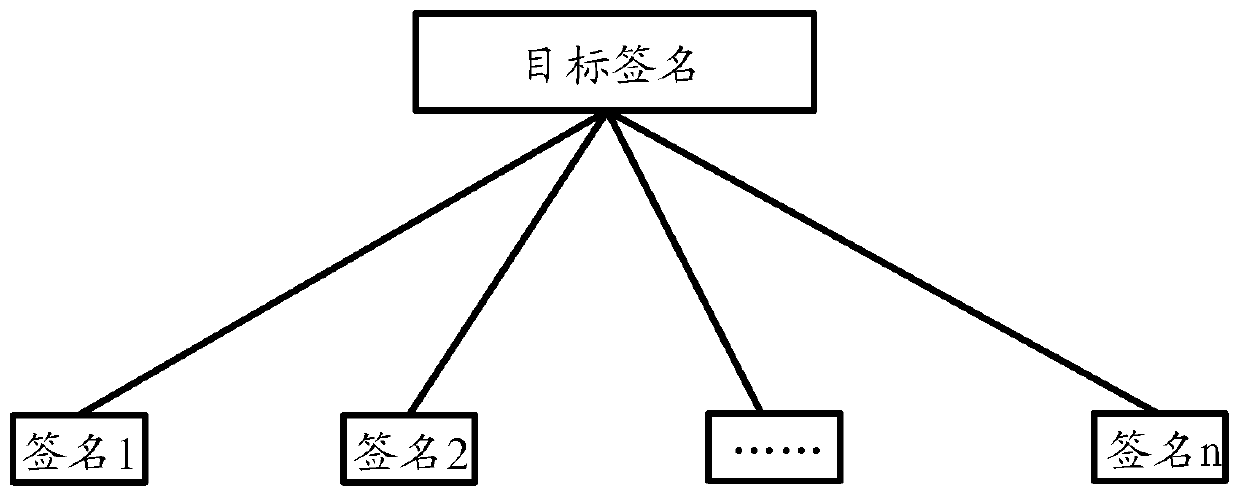
InactiveCN110798308ASave storage spaceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkEngineering
The invention discloses a signature method and system for a block chain. The method comprises the steps that a consensus main node initiates a consensus proposal for a to-be-consensus proposal; a plurality of consensus backup nodes perform consensus on the to-be-consensus proposal; the consensus main node receives a plurality of signatures after the plurality of consensus backup nodes propose consensus for the to-be-consensus; the consensus master node verifies the plurality of signatures based on a plurality of public keys corresponding to the plurality of consensus backup nodes; and if the consensus main node verifies the plurality of signatures successfully and the number of the plurality of signatures is greater than twice of the number of failure nodes in all consensus backup nodes inthe blockchain, the consensus main node aggregates the plurality of signatures to obtain a target signature.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
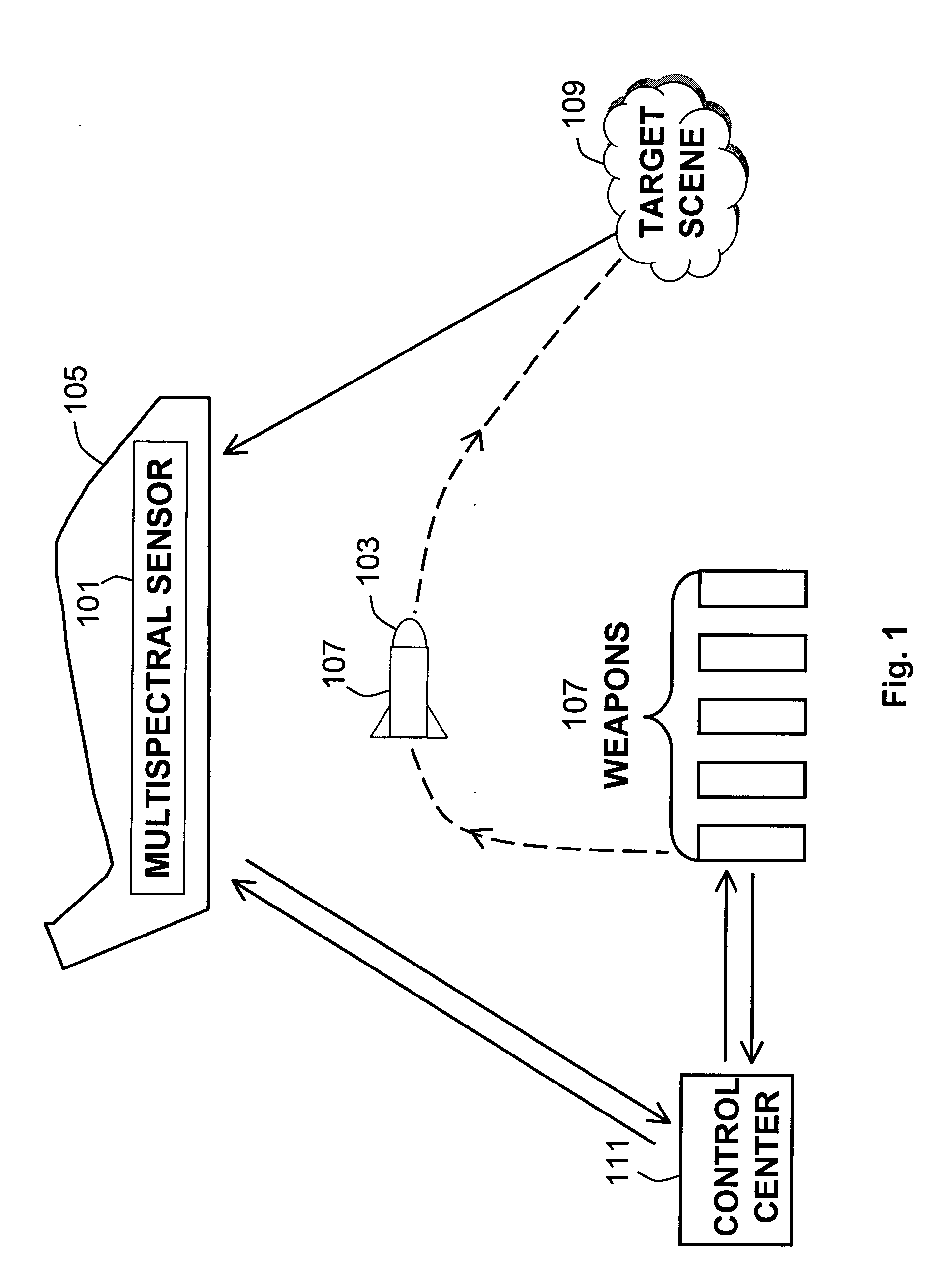
Weather-agile reconfigurable automatic target recognition system
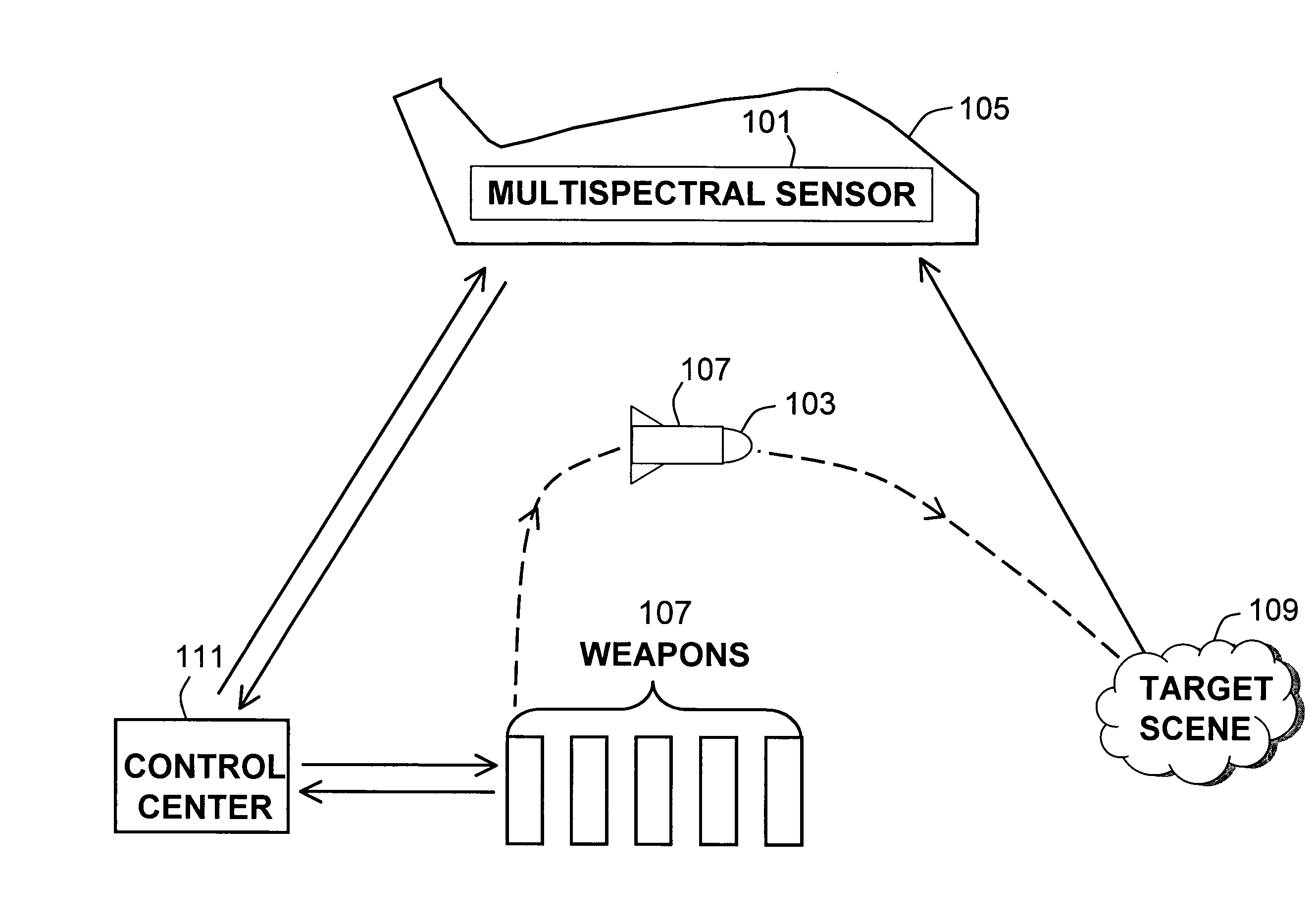
InactiveUS7040570B2Direction controllersCharacter and pattern recognitionEngineeringTarget signature
Applicants' ATR system is weather-agile because it is comprised of a primary target sensing means that is capable of surveilling the target scene in foul or fair weather, and a secondary target sensing means that is also capable of sensing targets in various weather. The primary and secondary sensing means communicate through a control center so that ultimately, among several weapons available, the most strategically located and equipped weapon is activated for the destruction of a selected target, given the weather. The control center accomplishes the communication by receiving the sensed target signature from the primary sensing means, processing the signature using database already resident in the center and transmitting the processed target signature to the weapon possessing the greatest potential for successfully destroying the target.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
Hyperspectral remote sensing systems and methods using covariance equalization
InactiveUS20070076955A1Reduces performance-degrading effectEasy to detectOptical detectionScene recognitionCovarianceTarget signature
A method and apparatus for detecting a target or targets in a surrounding background locale based on target signatures obtained by a hyperspectral imaging sensor used the hyperspectral imaging sensor to collect raw target signature data and background locale data during a first data collection mission. The data is processed to generate a database including a plurality of target signatures and background data relating to the background locale. The hyperspectral imaging sensor is later used to collect further background data during a further, current data collecting mission so as to provide continuously updated background data, in real time. A covariance equalization algorithm is implemented with respect to the background data contained in the database and the updated background data collected during the current mission to effect transformation of each target signature of the database into a transformed target signature. A detection algorithm which employs the resultant transformed target signature is used to produce detection information related to the target or targets.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Data validation using signatures and sampling
InactiveUS20090125623A1User identity/authority verificationDigital computer detailsData validationSource Data Verification
Architecture that facilitates validation of a data mapping of data from a data source to a data target. There is included a signature generation component that generates a source signature of all or a portion of the data source and a target signature of all or a corresponding portion of the data target, and a sampling component that obtains a sample of the source data a corresponding sample of the target data. The data signatures and data samples are compared respectively and processed with a processing component to determine the status of the validation process.
Owner:MICROSOFT TECH LICENSING LLC
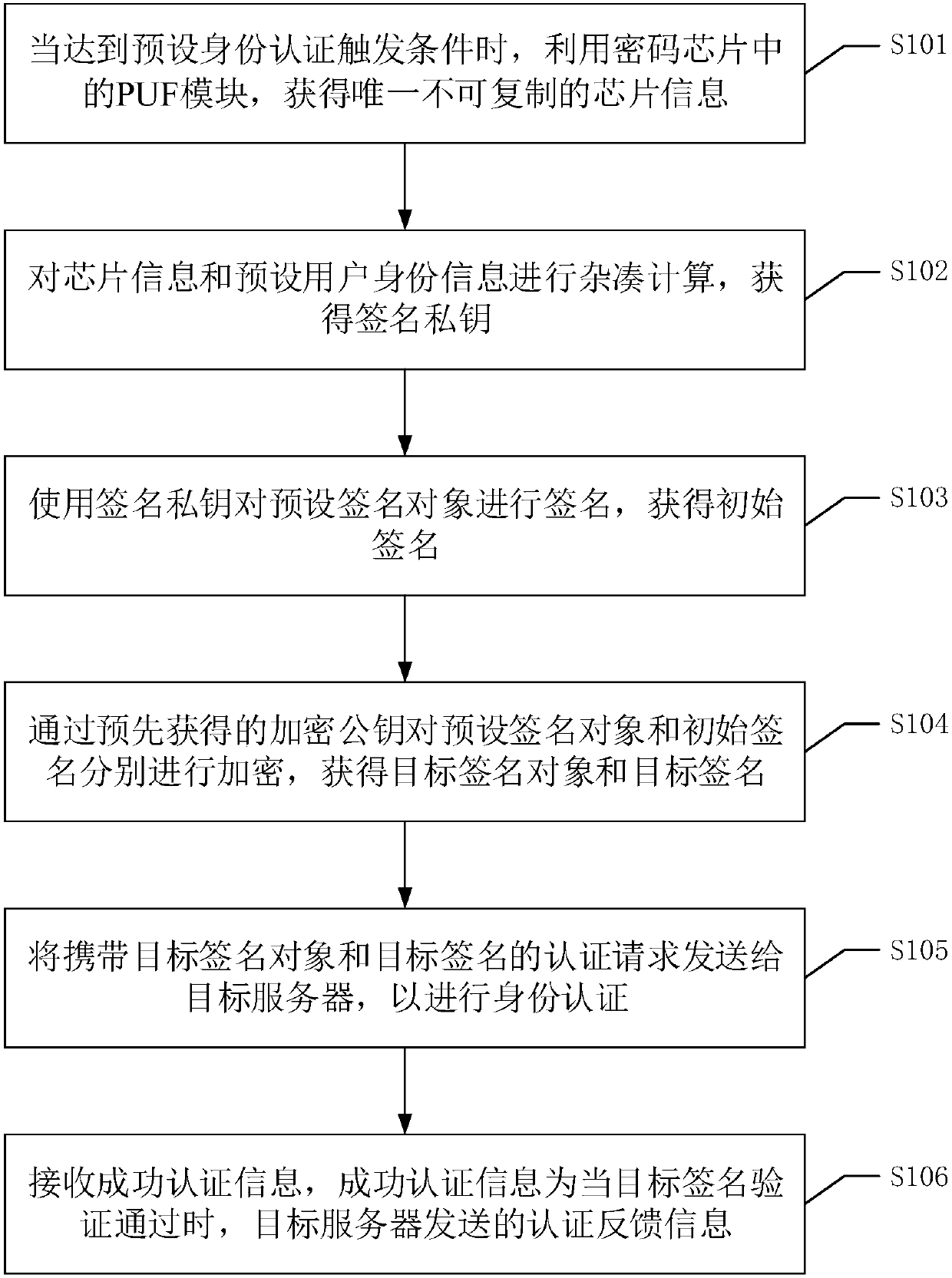
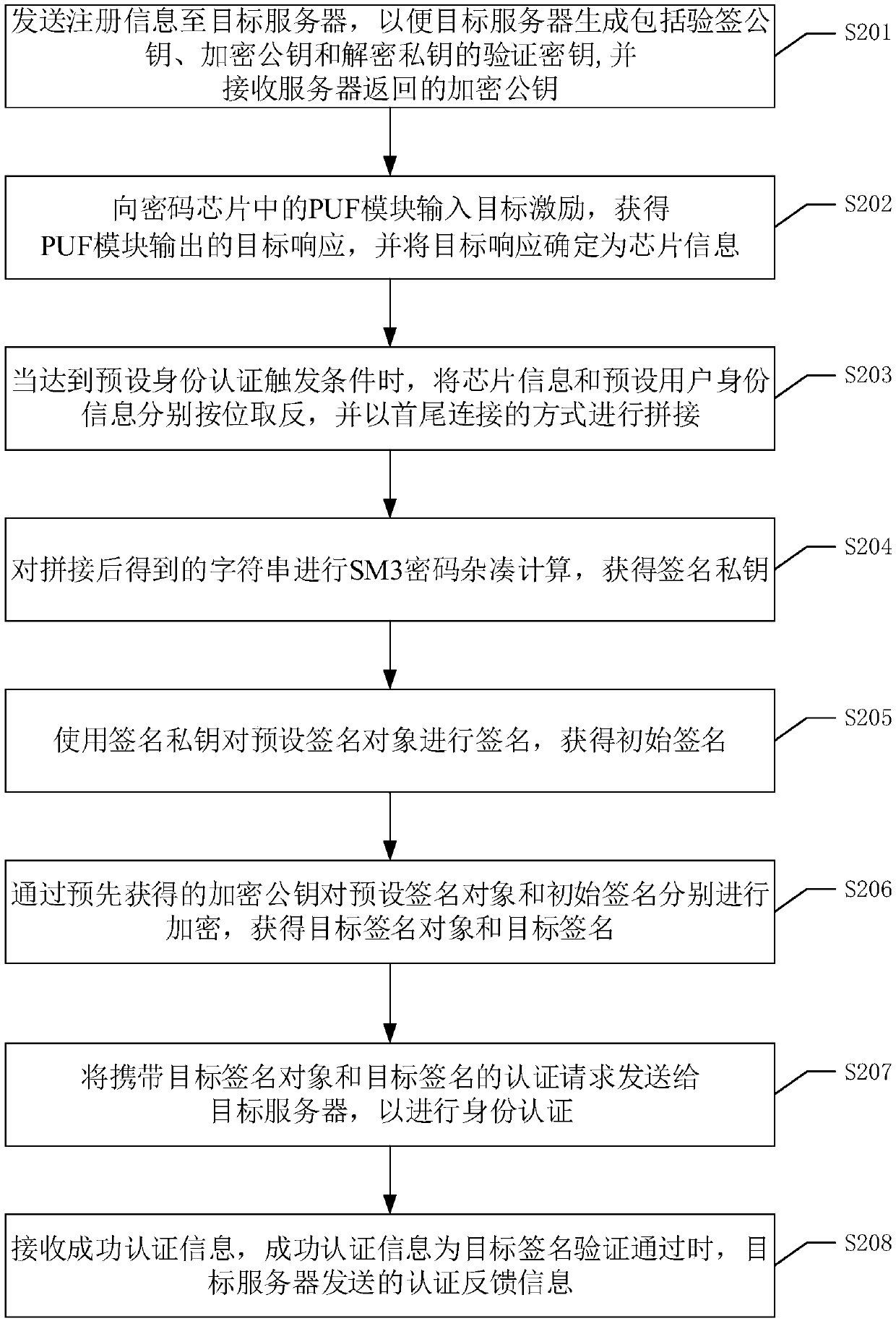
Identity authentication method, device, equipment and system and readable storage medium
The invention discloses an identity authentication method, which comprises the following steps: when a preset identity authentication triggering condition is reached, obtaining unique chip informationwhich cannot be copied by using a PUF module in a cryptographic chip; performing hash calculation on the chip information and preset user identity information to obtain a signature private key; signing a preset signature object by using the signature private key to obtain an initial signature; encrypting the preset signature object and the initial signature through a pre-obtained encryption public key to obtain a target signature object and a target signature; sending the authentication request to a target server; receiving success authentication information. Because the chip information is unique and cannot be copied, the security of the signature key can be enhanced, the security of the identity authentication process is ensured, and the security of information, property and the like ofa legal user is further protected. The invention further discloses an identity authentication device, equipment, a system and a readable storage medium, which have corresponding technical effects.
Owner:GUANGDONG UNIV OF TECH
Detector with tunable spectral response
ActiveUS7217951B2Enhance and diversify tunabilityEfficient synthesisSpectrum investigationNanoinformaticsSpectral responseTarget signature
A semiconductor detector has a tunable spectral response. These detectors may be used with processing techniques that permit the creation of “synthetic” sensors that have spectral responses that are beyond the spectral responses attainable by the underlying detectors. For example, the processing techniques may permit continuous and independent tuning of both the center wavelength and the spectral resolution of the synthesized spectral response. Other processing techniques can also generate responses that are matched to specific target signatures.
Owner:STC UNM
Super-resolution based on frequency domain interferometric processing of sparse multi-sensor measurements
ActiveUS7242342B2Reduce in quantityReduce bandwidth requirementsElectromagnetic wave reradiationRadio wave reradiation/reflectionTransceiverTarget signature
A system for obtaining frequency domain interferometric super-resolution of a target scatterer, having a first and a second coherent transceivers, a mutual coherent sub-system and an estimation system. The first and second coherent transceivers are operative to produce a plurality of first and second sampling signals separated from each other by a predetermined frequency difference within the first and second sub-band, respectively. The mutual coherent sub-system is coupled to the first and second coherent transceivers to receive phase and amplitude of the first and second sampling signals, so as to evaluate an ambiguous range estimate from a pair of the first and second sampling signals and an unambiguous range estimate from a pair of the first and / or second sampling signals. The estimation system follows the mutual coherent sub-system to reconcile the ambiguous and unambiguous range estimates so as to obtain a target signature with a super-resolution defined by a frequency offset between the first and second sub-bands.
Owner:PARSONS GOVERNMENT SERVICES
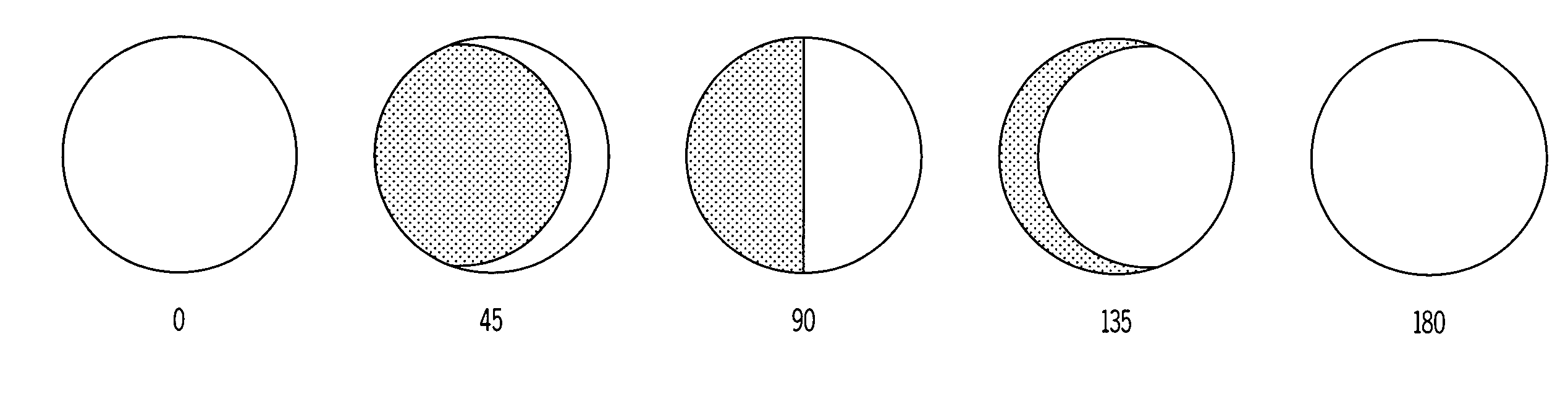
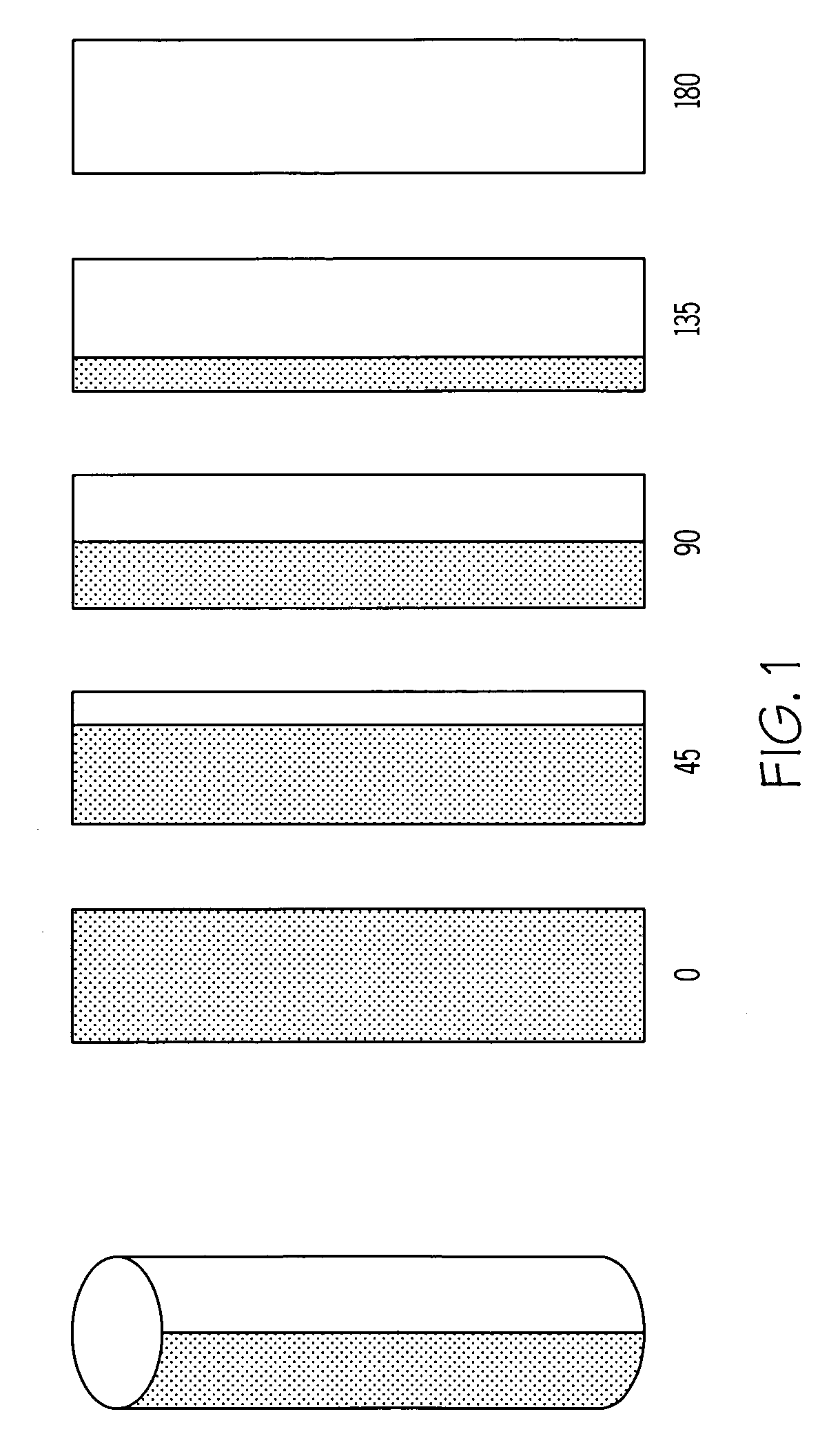
Variable emittance surfaces
Designs for constructing a surface with variable emittance are described. This is achieved by making a surface where the emissivity varies on a scale smaller than the resolution of a thermal imager viewing the surface. One design utilizes many cylindrical surfaces with their axis parallel and their surfaces nearly in contact. Individual cylinders have the property that when rotated to zero degrees they show a surface with an emissivity of one and when rotated to 180 degrees display a surface with an emissivity of zero. At intermediate angles of rotation a sensor that could resolve individual cylinders would see alternate lines with high and low emittance but a sensor unable to resolve individual cylinders sees a surface with an emittance that depends on the angle the cylinders are rotated. Variable emittance surfaces are expected to be useful for controlling target signature and for making spectral reflectivity measurements using a hyper-spectral radiometer.
Owner:ARMY UNITED STATES OF AMERICA AS REPRESENTED BY DEPT OF THE
Enhancing formal design verification by reusing previous results
InactiveUS8042078B2Software simulation/interpretation/emulationSpecial data processing applicationsSoftware engineeringTarget signature
A method, a system and a computer program product for re-using verification results associated with a circuit design to eliminate a formal verification re-run associated with a subsequent verification of the circuit design. A Verification Data Re-use (VDR) utility initiates the creation of a first netlist data structure and a first set of target signatures for the circuit design. The VDR utility initiates an initial functional verification run of the circuit design and stores the results of the verification run. When a subsequent verification of the initial design is initiated, the VDR utility compares the first set of target signatures with a second set of target signatures for the subsequent verification run. A match of target signatures indicates that corresponding design targets have an identical functionality and the VDR utility re-uses verification results from the initial verification run to eliminate an extensive formal verification re-run for the circuit design.
Owner:MENTOR GRAPHICS CORP
Super-resolution based on frequency domain interferometric processing of sparse multi-sensor measurements
ActiveUS20060077091A1Reduce in quantityReduce bandwidth requirementsElectromagnetic wave reradiationRadio wave reradiation/reflectionTransceiverTarget signature
A system for obtaining frequency domain interferometric super-resolution of a target scatterer, having a first and a second coherent transceivers, a mutual coherent sub-system and an estimation system. The first and second coherent transceivers are operative to produce a plurality of first and second sampling signals separated from each other by a predetermined frequency difference within the first and second sub-band, respectively. The mutual coherent sub-system is coupled to the first and second coherent transceivers to receive phase and amplitude of the first and second sampling signals, so as to evaluate an ambiguous range estimate from a pair of the first and second sampling signals and an unambiguous range estimate from a pair of the first and / or second sampling signals. The estimation system follows the mutual coherent sub-system to reconcile the ambiguous and unambiguous range estimates so as to obtain a target signature with a super-resolution defined by a frequency offset between the first and second sub-bands.
Owner:PARSONS GOVERNMENT SERVICES
Weather-agile reconfigurable automatic target recognition system
InactiveUS20050087649A1Direction controllersCharacter and pattern recognitionTarget signatureEngineering
Applicants' ATR system is weather-agile because it is comprised of a primary target sensing means that is capable of surveilling the target scene in foul or fair weather, and a secondary target sensing means that is also capable of sensing targets in various weather. The primary and secondary sensing means communicate through a control center so that ultimately, among several weapons available, the most strategically located and equipped weapon is activated for the destruction of a selected target, given the weather. The control center accomplishes the communication by receiving the sensed target signature from the primary sensing means, processing the signature using database already resident in the center and transmitting the processed target signature to the weapon possessing the greatest potential for successfully destroying the target.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
Data processing method and device, computer equipment and medium
PendingCN111489159AImprove securityImprove reliabilityPayment protocolsComputer networkTransaction data
The embodiment of the invention discloses a data processing method and device, computer equipment and a medium, and the method comprises the steps: obtaining target signature information related to business data, and enabling an agent node and a client to carry out the cooperative signature of the business data to obtain the target signature information; obtaining a client certificate of a clientand a node certificate of a proxy node, wherein the node certificate and the client certificate contain the same shared public key, and the shared public key is used for verifying the validity of thetarget signature information; adopting the business data, the target signature information, the node certificate and the client certificate to generate transaction data; and broadcasting the transaction data to a consensus node in the blockchain network so that the consensus node performs consensus on the transaction data, and adding the transaction data to a blockchain of the blockchain network after the transaction data passes the consensus. By adopting the embodiment of the invention, the reliability and safety of data uploading can be effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
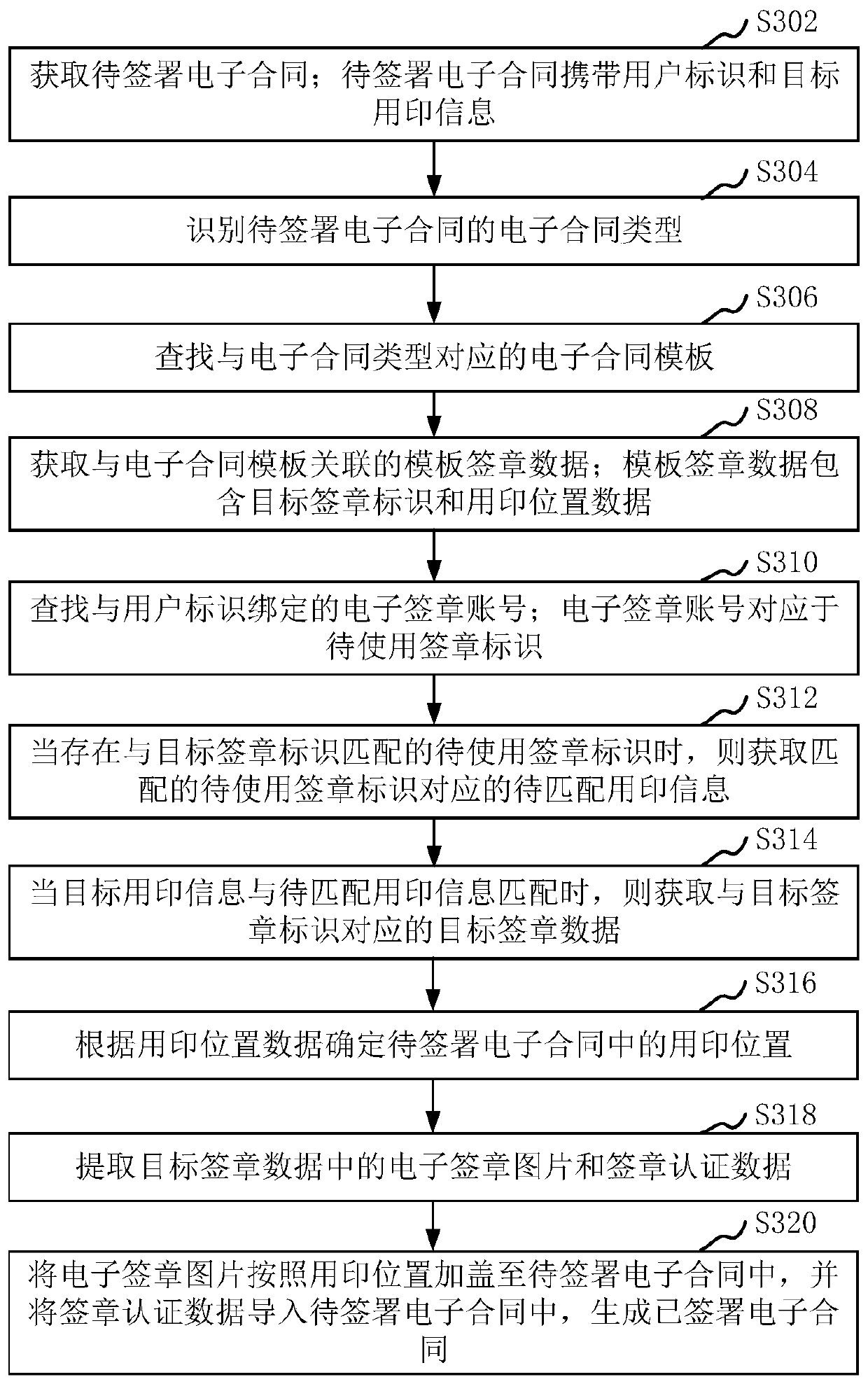
Electronic contract signing method and device, computer device and storage medium
The invention relates to an electronic contract signing method and device, a computer device and a storage medium. The method comprises the steps of obtaining a to-be-signed electronic contract; wherein the to-be-signed electronic contract carries a user identifier and target stamping information; obtaining a target signature identifier corresponding to the to-be-signed electronic contract; searching an electronic signature account bound with the user identifier; wherein the electronic signature account corresponds to a signature identifier to be used; when the to-be-used signature identifiermatched with the target signature identifier exists, obtaining to-be-matched seal use information corresponding to the matched to-be-used signature identifier; when the target seal use information ismatched with the to-be-matched seal use information, obtaining target signature data corresponding to the target signature identifier; and synthesizing the target signature data into the to-be-signedelectronic contract to generate a signed electronic contract. By adopting the method, the electronic contract signing business process is optimized, and the electronic signature can be correctly called.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
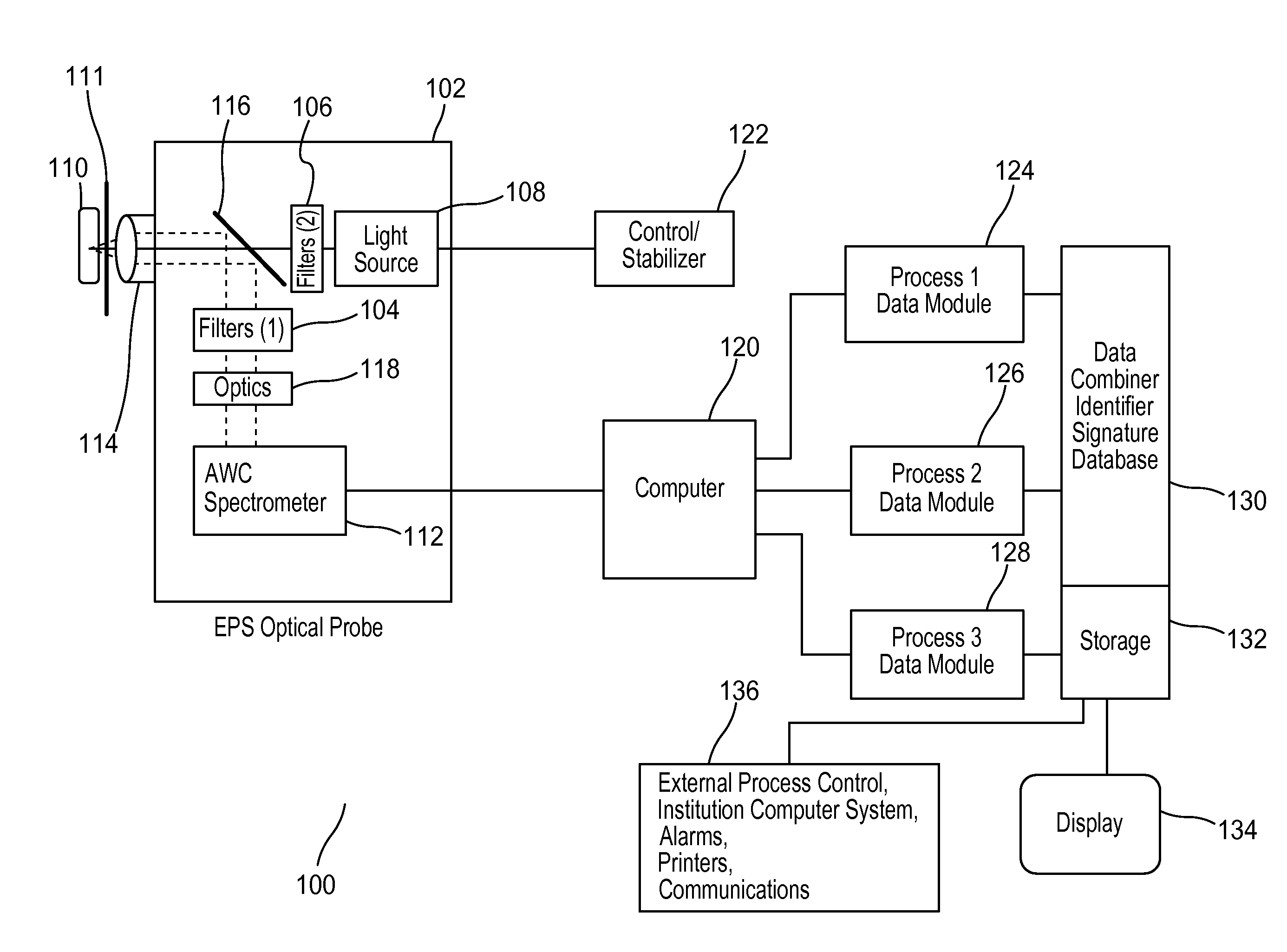
Chemical and molecular identification and quantification system utilizing enhanced photoemission spectroscopy
ActiveUS20150009490A1Scattering properties measurementsRaman scatteringMolecular identificationInverse photoemission spectroscopy
An enhanced photoemission spectroscopy (EPS) system uses at least three photoelectric detection processes to identify a substance or substances in a target. The target can be in a container, and the EPS system accounts for this in the identification process. The photoelectric detection processes include Raman scattering, fluorescence and spectral reflection. The EPS system uses all three processes to generate spectral data that is then combined to derive a target signature. The target signature is then compared to stored signature data to determine the substance or substances in the target.
Owner:CDEX
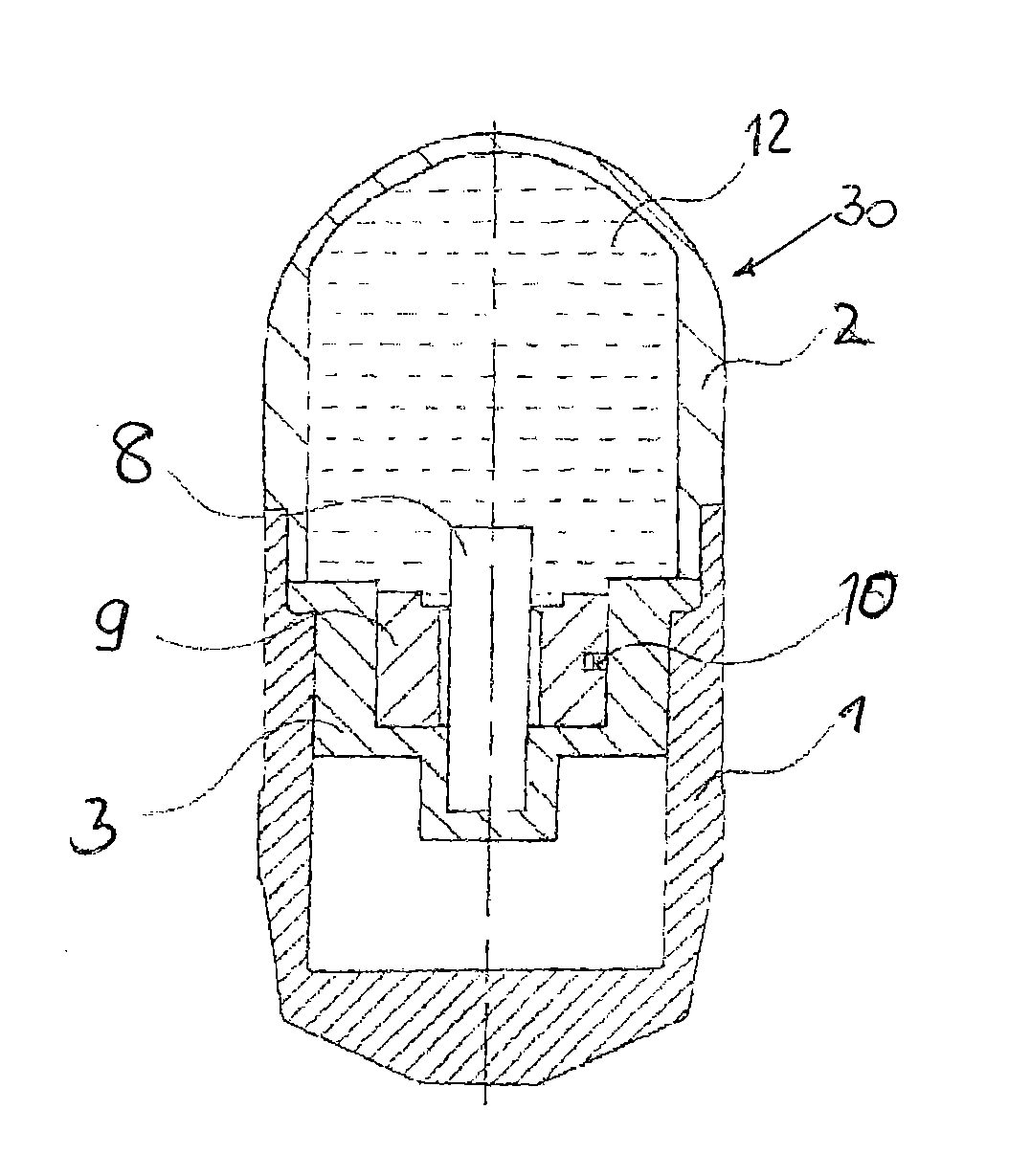
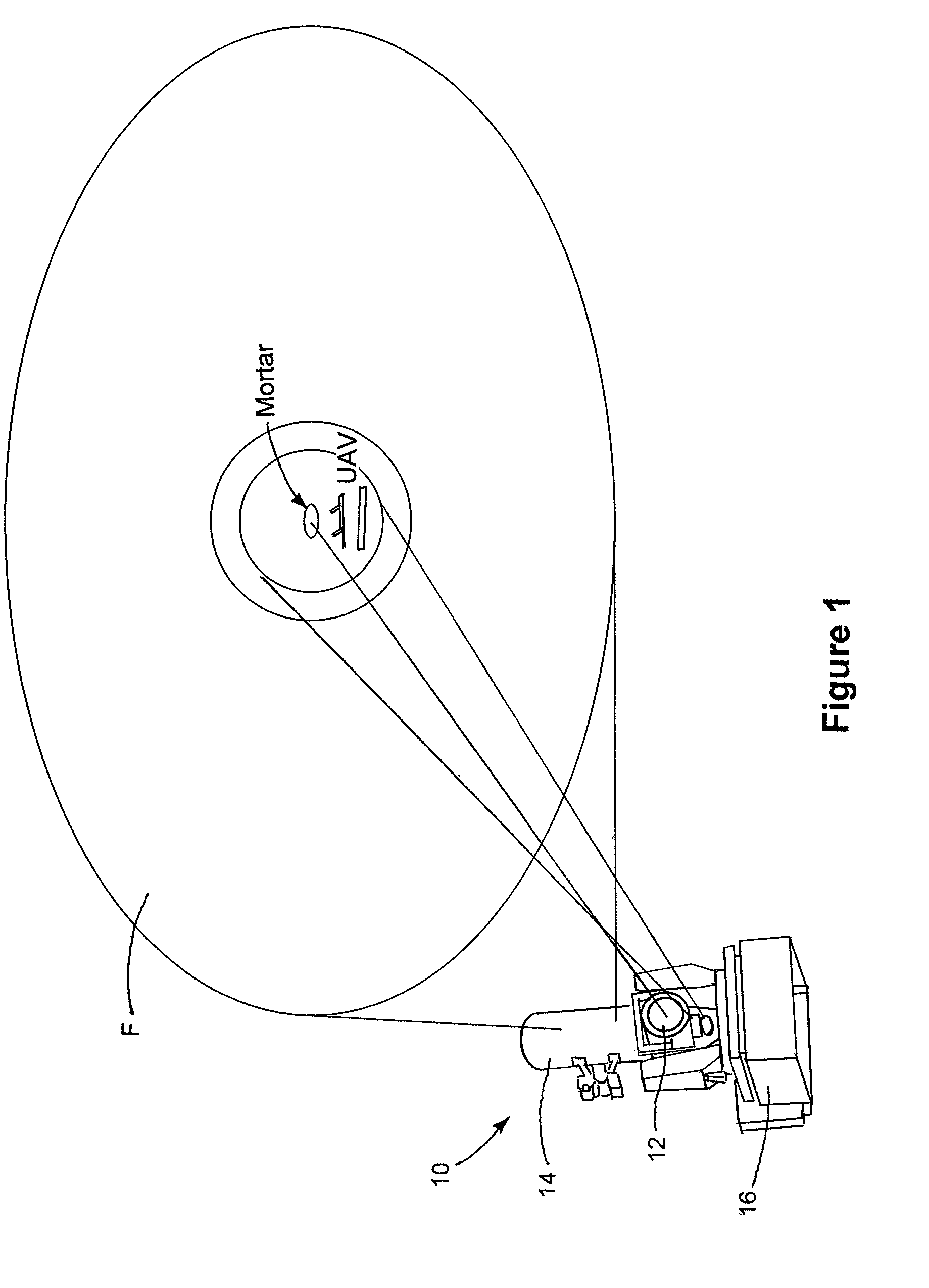
Amunition with projectile containing no explosive material in order to create a multi-spectral target signature
ActiveUS20140305328A1Effective rangeA large amountAmmunition projectilesImpact fuzesNight visionEngineering
An ammunition is proposed with an explosive-free missile that releases, upon dismantling at the target a fuel or fuel mixture as flammable air-fuel mixture, being caused to spontaneously react by at least one, by impact dismantling triggered, explosive-free, spark-generating ignition mechanism. The thus produced optical and thermal target signature can be detected with the naked eye, as well as with rifle scopes or other optical target detection systems, as well as with night-vision and thermal imaging devices.
Owner:RHEINMETALL WAFFE MUNITION GMBH
Application-based service security system and method
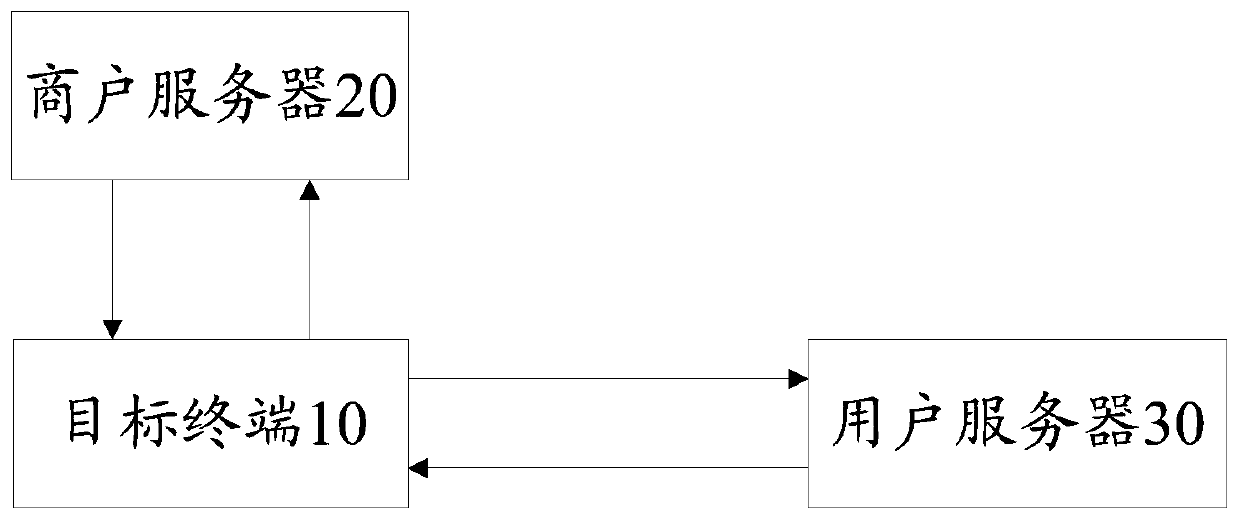
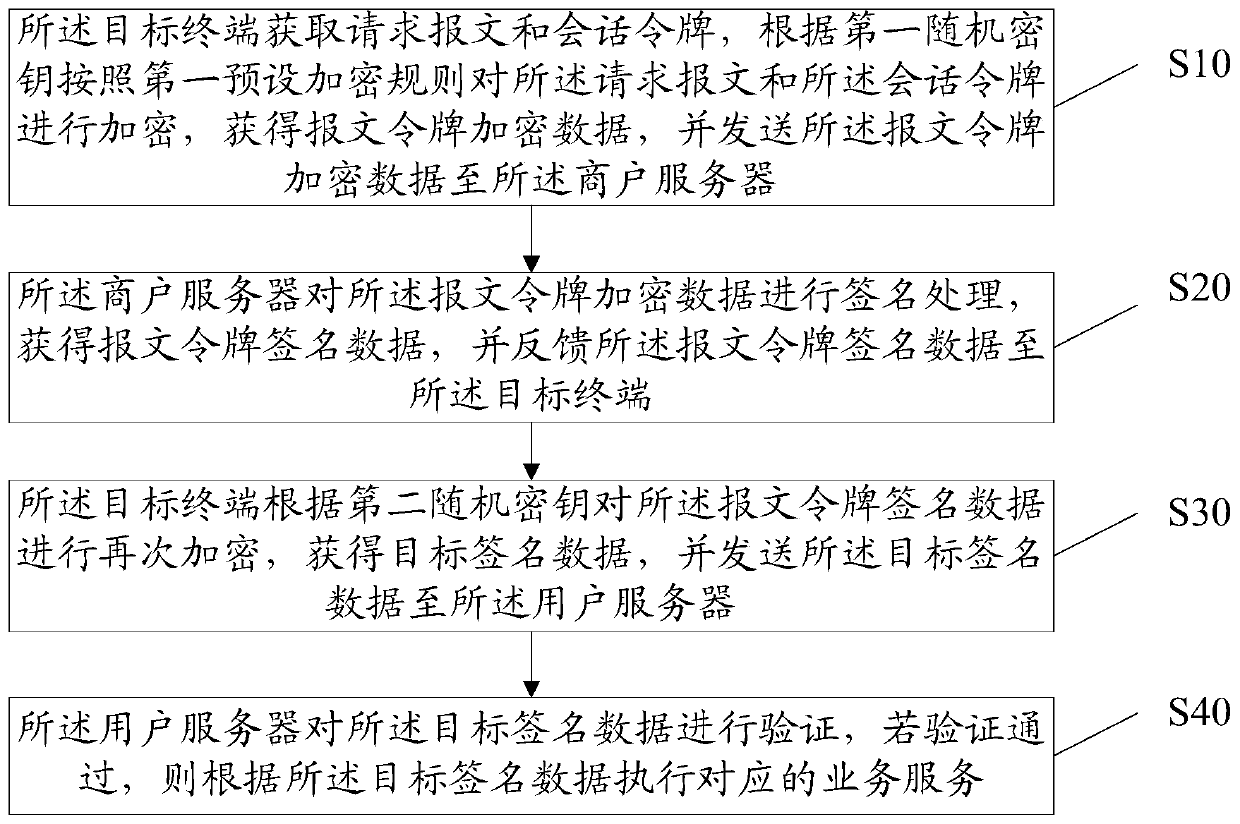
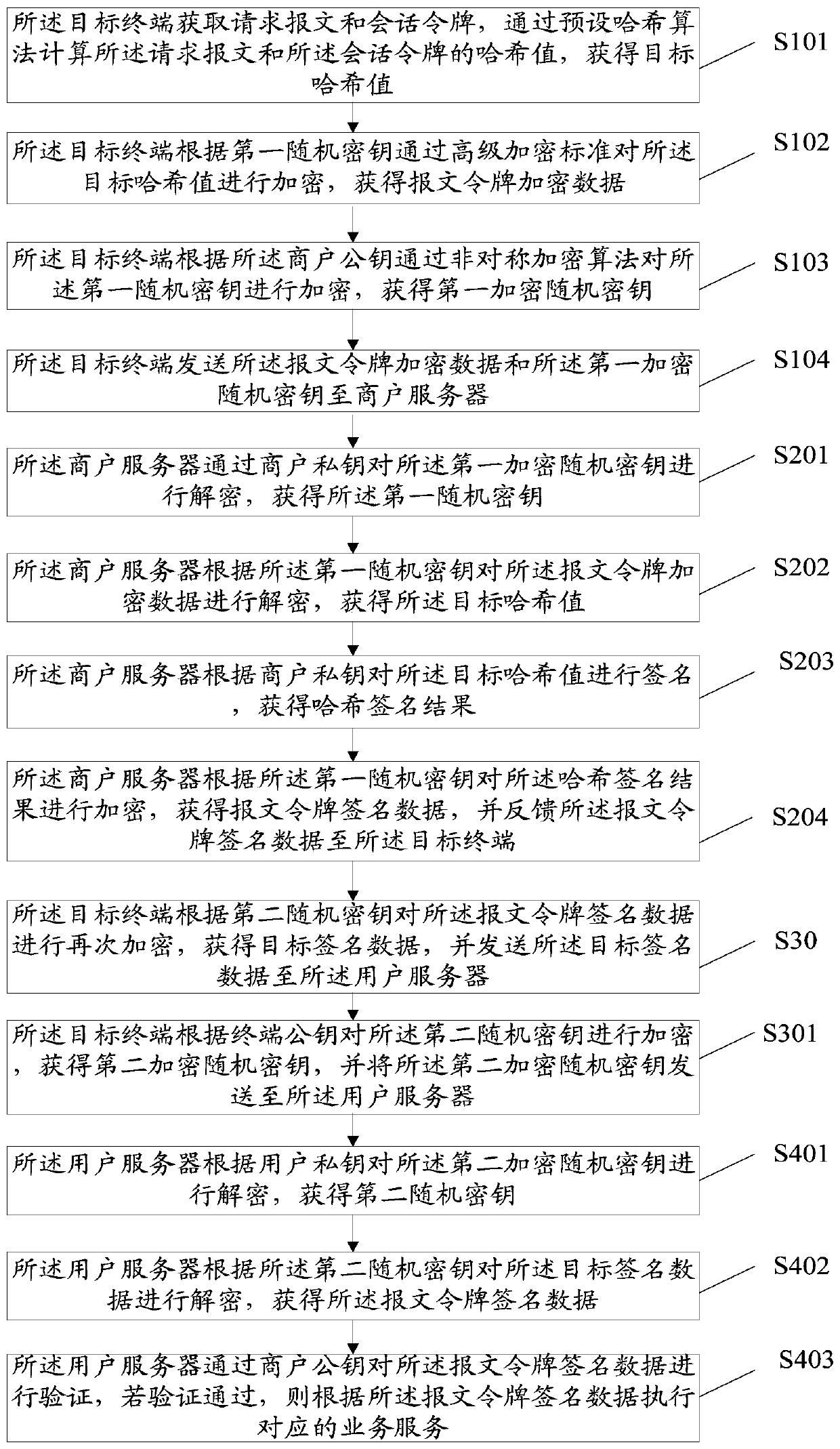
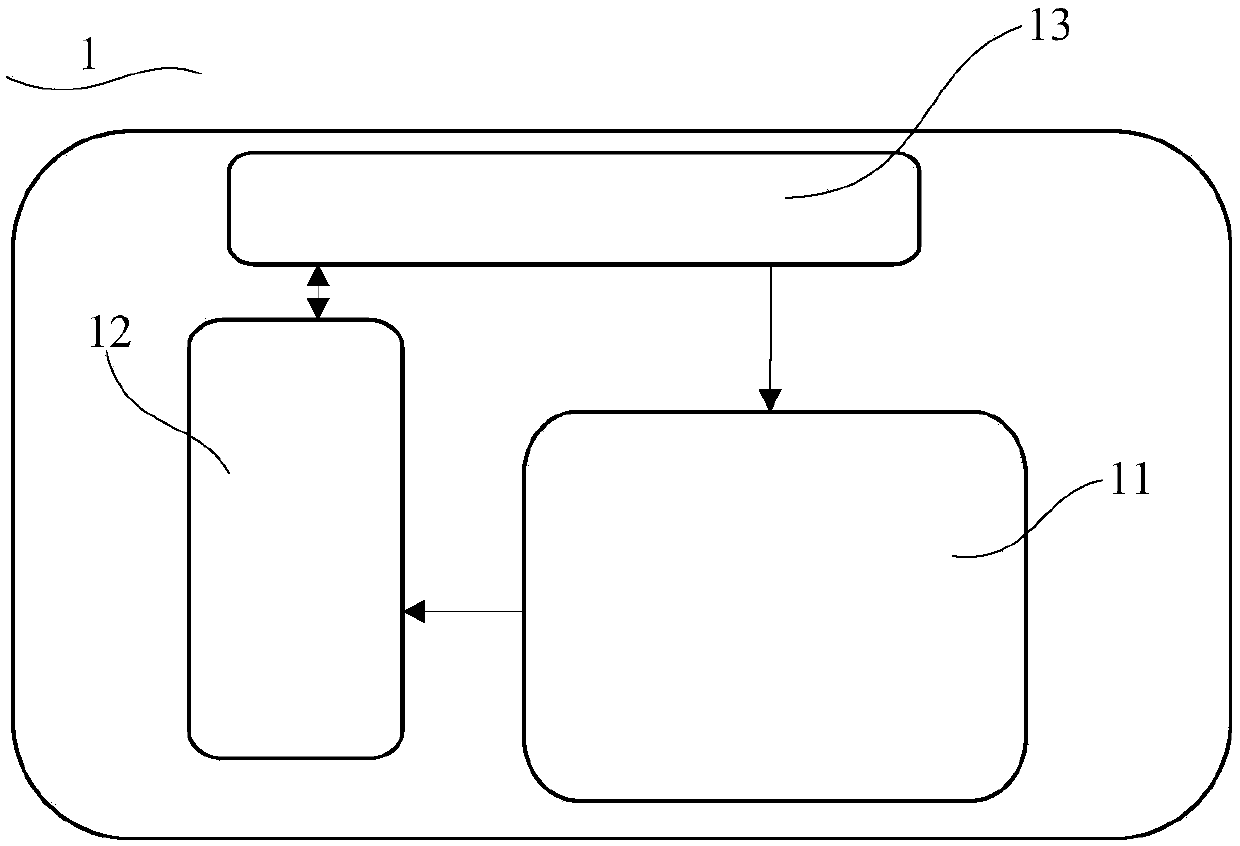
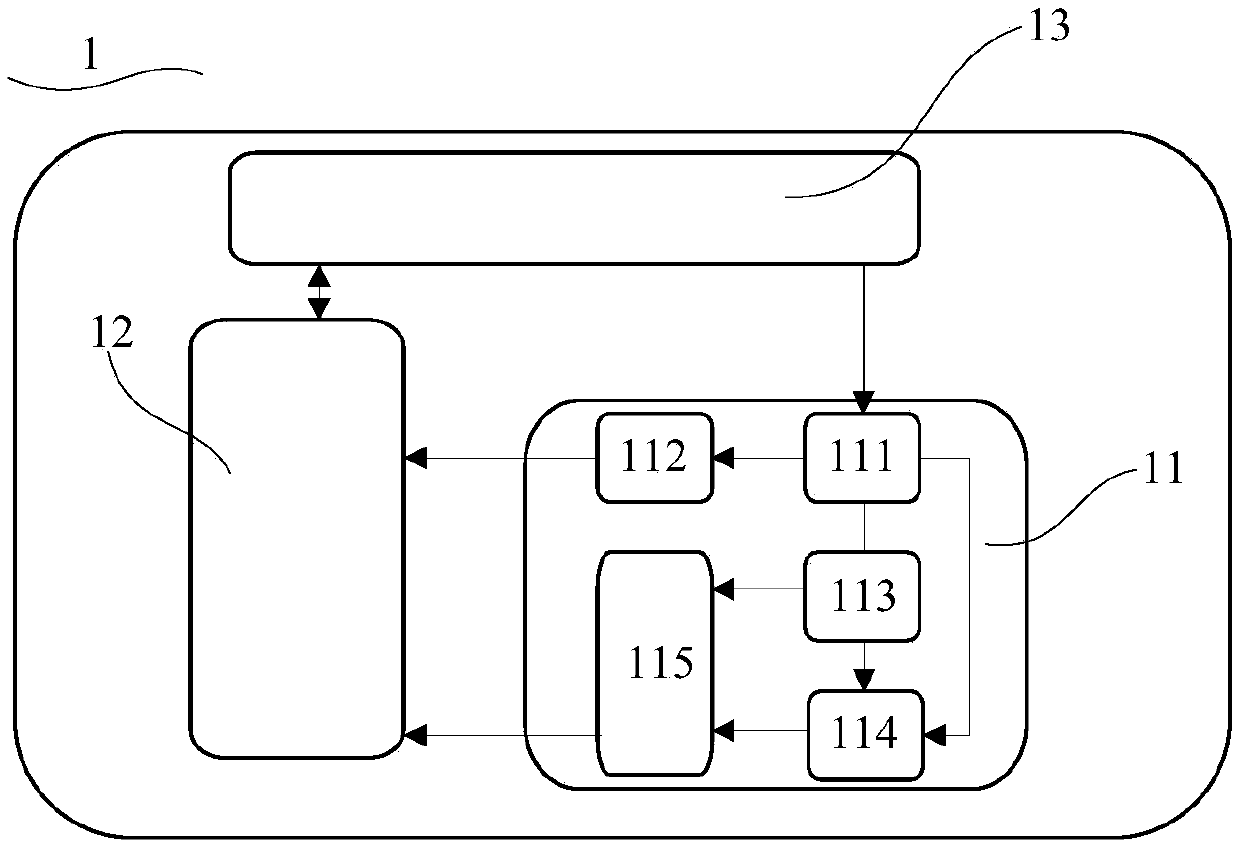
InactiveCN110290102AReduce risk of leakageReduce theftUser identity/authority verificationComputer terminalTarget signature
The invention discloses an application-based service security system and method. In the system, a target terminal is used for acquiring a request message and a session token, encrypting the request message and the session token according to a first random key and a first preset encryption rule to obtain message token encrypted data, and sending the message token encrypted data to a merchant server; a merchant server is used for carrying out signature processing on the message token encrypted data, obtaining message token signature data and feeding back the message token signature data to the target terminal; a target terminal is also used for encrypting the message token signature data again according to the second random key to obtain target signature data and sending the target signature data to the user server; and a user server is used for verifying the target signature data, and executing the corresponding business service according to the target signature data if the verification is passed. Based on the information security, the data interaction security is improved by encrypting the message, authenticating the identity and signing the data.
Owner:武汉众邦银行股份有限公司
EID film card, mobile terminal device and eID authentication system
ActiveCN109525392ASecure and fast loginPrevent leakageUser identity/authority verificationSignature CodeTerminal equipment
The invention provides an eID film card, a mobile terminal device and an eID authentication system. The eID film card comprises: an eID application module for storing eID information and a target signature code corresponding to the eID information. The eID application module prompts the input of a signature code to be verified when receiving a signature instruction, compares the input signature code to be verified with the target signature code, and assembles the signature according to the eID information when the input signature code to be verified matches the target signature code. The eID film card also comprises a communication protocol module electrically connected to the eID application module for information interaction between the eID application module and an external device structure. The eID film card provided by the invention stores the eID information in the eID film card, and the eID film card can be installed in the mobile terminal after being seamlessly attached to theSIM card. When a user performs identity authentication on the mobile terminal, the eID information can be used for authentication, and the user information such as ID number or mobile phone number isnot involved, which can effectively prevent the leakage of user information.
Owner:上海方付通科技服务股份有限公司
Semi-active optical tracking system
A system and method for tracking an airborne target including an illumination source (e.g., a diode laser array) is used to enhance a target signature and a detector (e.g., a passive high-speed camera) is used to detect to electromagnetic radiation (e.g., infrared radiation) reflected off the target. The received electromagnetic radiation may be processed by a digital computer and passed through a spatial filter that implements a band limited edge detection operation in the frequency domain. The filter may remove low spatial frequencies that attenuate soft edged clutter such as clouds and smoke as well as filter out artifacts and attenuated medium to high spatial frequencies to inhibit speckle noise from the detector as well as speckle from the laser return off the target.
Owner:RAYTHEON CO
Tech, for inhibiting radar imaging coherent spot
InactiveCN1786735AReduce speckle noiseImprove image qualityRadio wave reradiation/reflectionRadar imagingImaging quality
The invention offers radar image coherent macula restraining technique. It starts from statistical characterization that radar image and coherent macula noise are independent each other, and uses analysis method to separate coherent macula form radar image to realize radar image coherent macula restraining. The method can reduce coherent macula noise, improve image quality, keep higher effect at target signature, and solves the contradiction between coherent macula noise restraining and image edge characteristic keep. And the invention has the feature of simple structure and fast convergence rate.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Threshold group signature method based on public verification of block chain
InactiveCN110401540ASimplify the management processAvoid Privacy LeakageKey distribution for secure communicationUser identity/authority verificationThird partyUser privacy
The invention discloses a threshold group signature method based on public verification of a block chain, a trusted center and a threshold group signature system. The scheme comprises the following steps: determining a to-be-signed target message; generating a share signature corresponding to the target message by using the signature member; synthesizing the share signatures of the signature members with the threshold number to obtain a target signature; and storing the target signature, the share signature of the signature member and the identity information of the signature member subjectedto secondary blinding processing into a block chain. Visibly, the scheme can trace back the user identity according to the signature information. In addition, the user identity is subjected to blind processing, so that the user privacy is effectively prevented from being leaked. Finally, the signature information and the blinded user identity information are stored on the block chain, and the block chain has non-revocable and non-tamperable capabilities, so that the third party can be prevented from maliciously tampering the contents, but other participants are allowed to open and verify the information.
Owner:ZHENGZHOU NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com