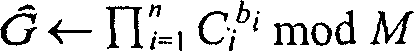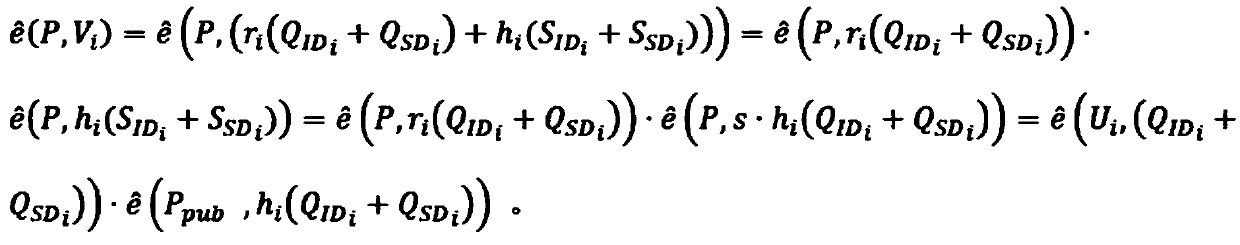Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
78 results about "Signature Code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Signature Panel Code is the last three digits that appear on the back of your card, on the signature panel. It is used as an extra security measure to make sure you are in the possession of the card you are registering.
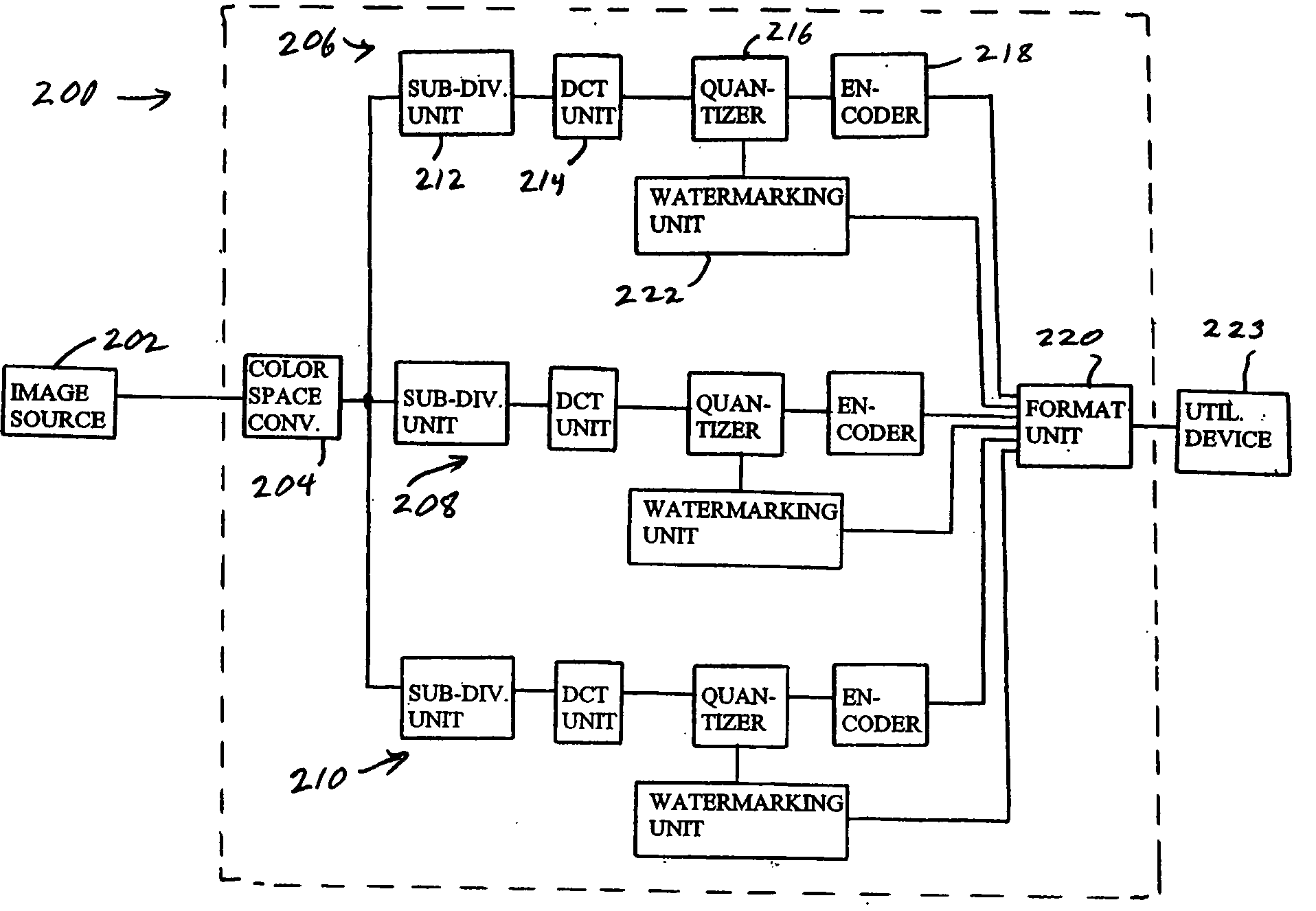
Proximity measuring apparatus
InactiveUS6614387B1Reduced risk of collisionAnti-collision systemsCode division multiplexMeasurement deviceSignature Code
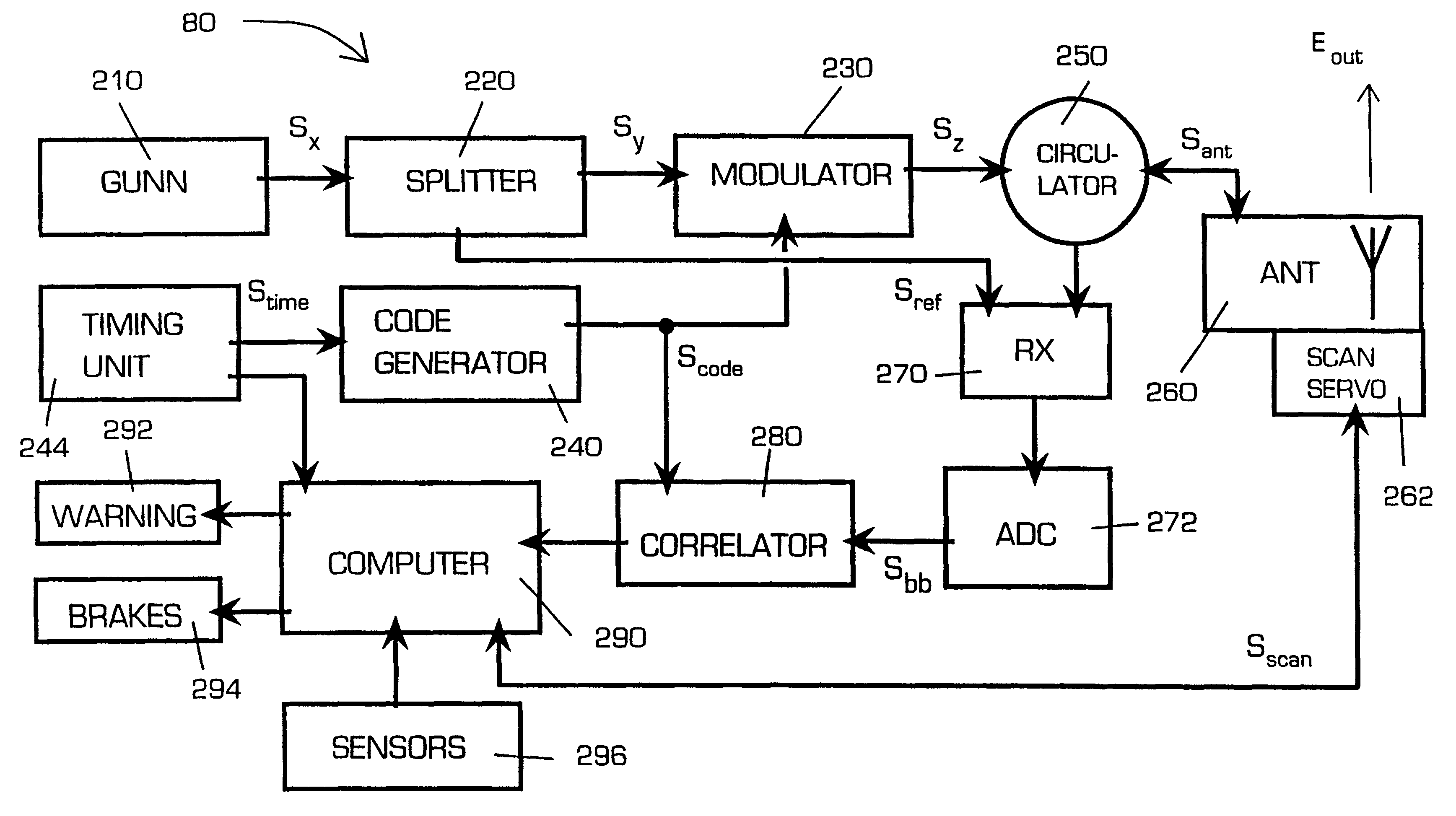
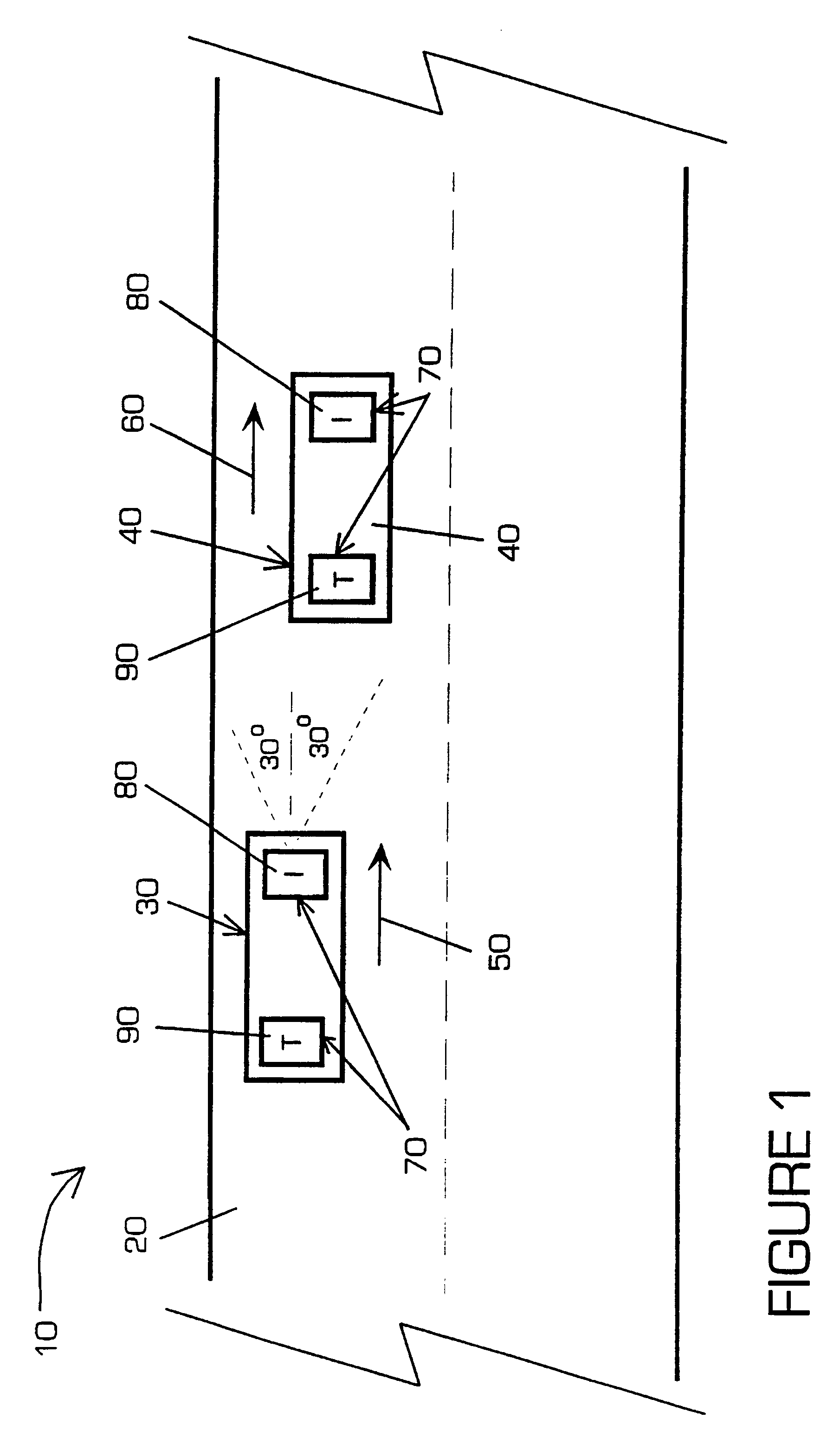
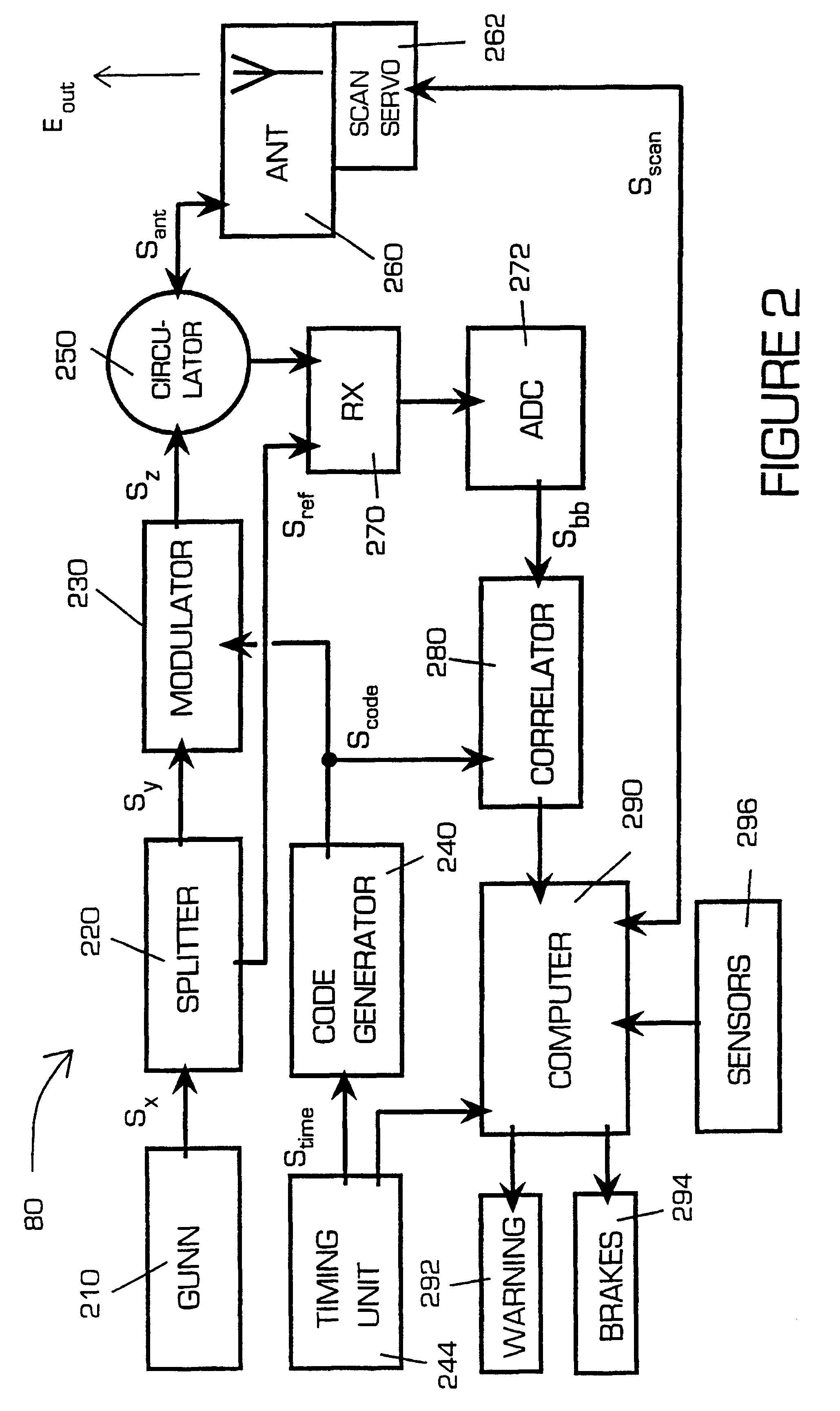
A proximity measuring apparatus (70) comprises an interrogator (80) for generating an interrogation signal encoded with a reference signature code comprising concatenated codes and emitting it as interrogating radiation. It also incorporates a transponder (90) for receiving the interrogating radiation, demodulating it to extract its signature code and then remodulating it after a delay period to provide a signal for reemission as return radiation therefrom. The interrogator (80) receives return radiation at its antenna (260) and demodulates it to extract its signature code and then correlates the code with the reference code to determine mutual correlation thereof. The interrogator (80) incorporates a computer (290) for controlling a scan direction of the antenna (260) and for measuring time delay between emission of the interrogating radiation therefrom and receipt of corresponding return radiation. The computer (290) computes distance and relative bearing of a transponder (90) providing the return radiation from the scan direction and the time delay. The apparatus (70) may be used for improving road vehicle safety.
Owner:QINETIQ LTD
Closed loop feedback system for improved down link performance
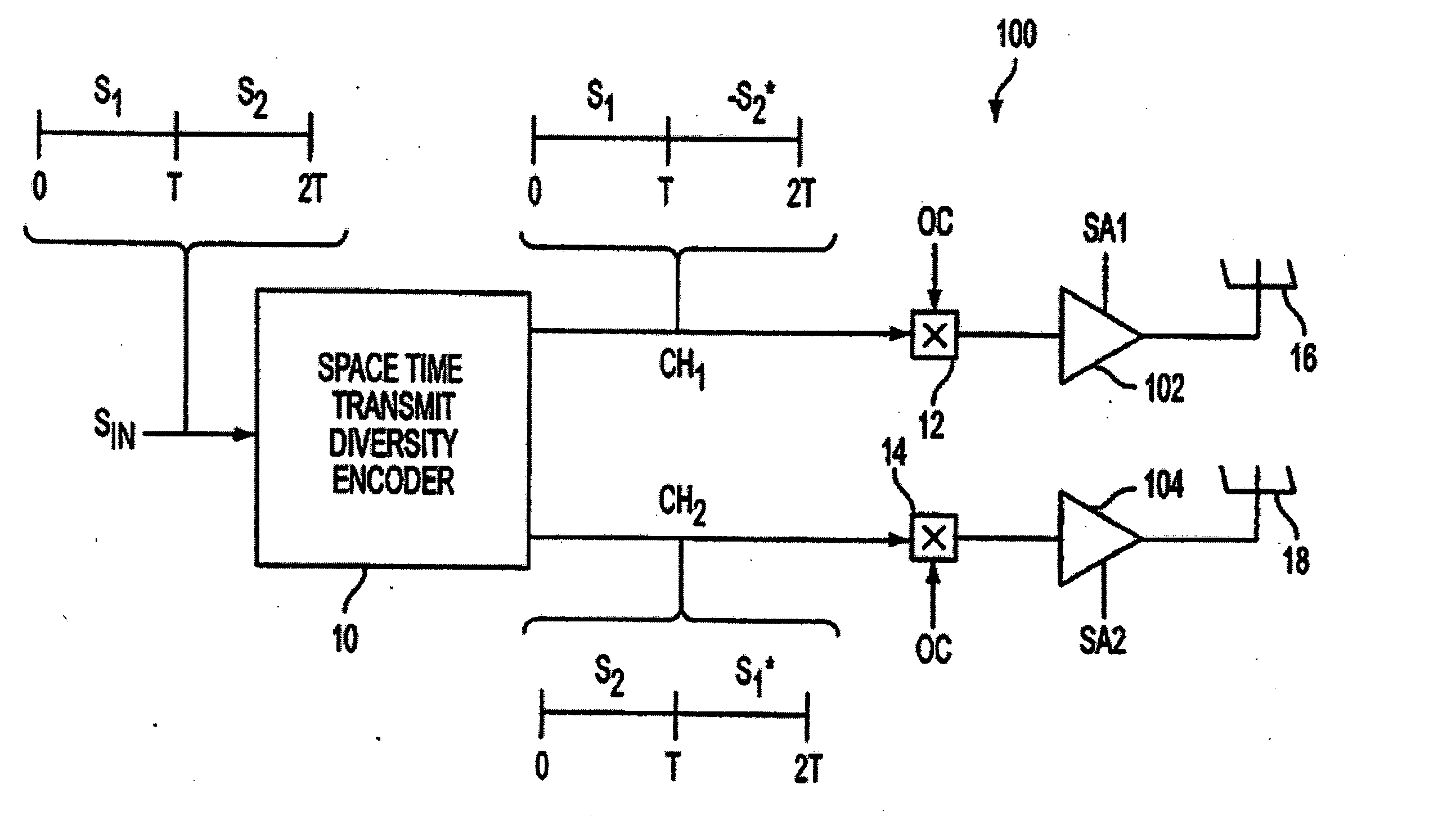
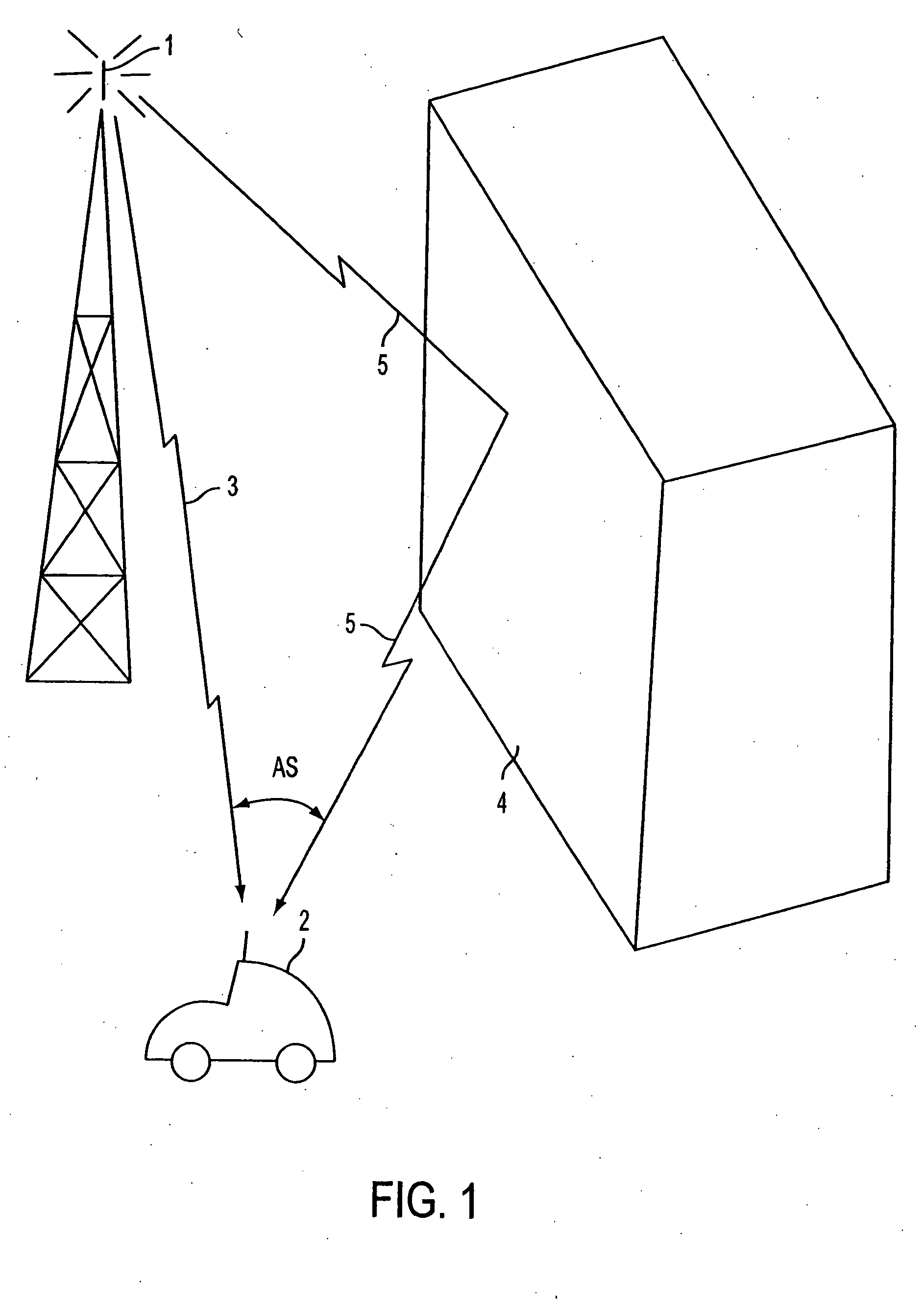
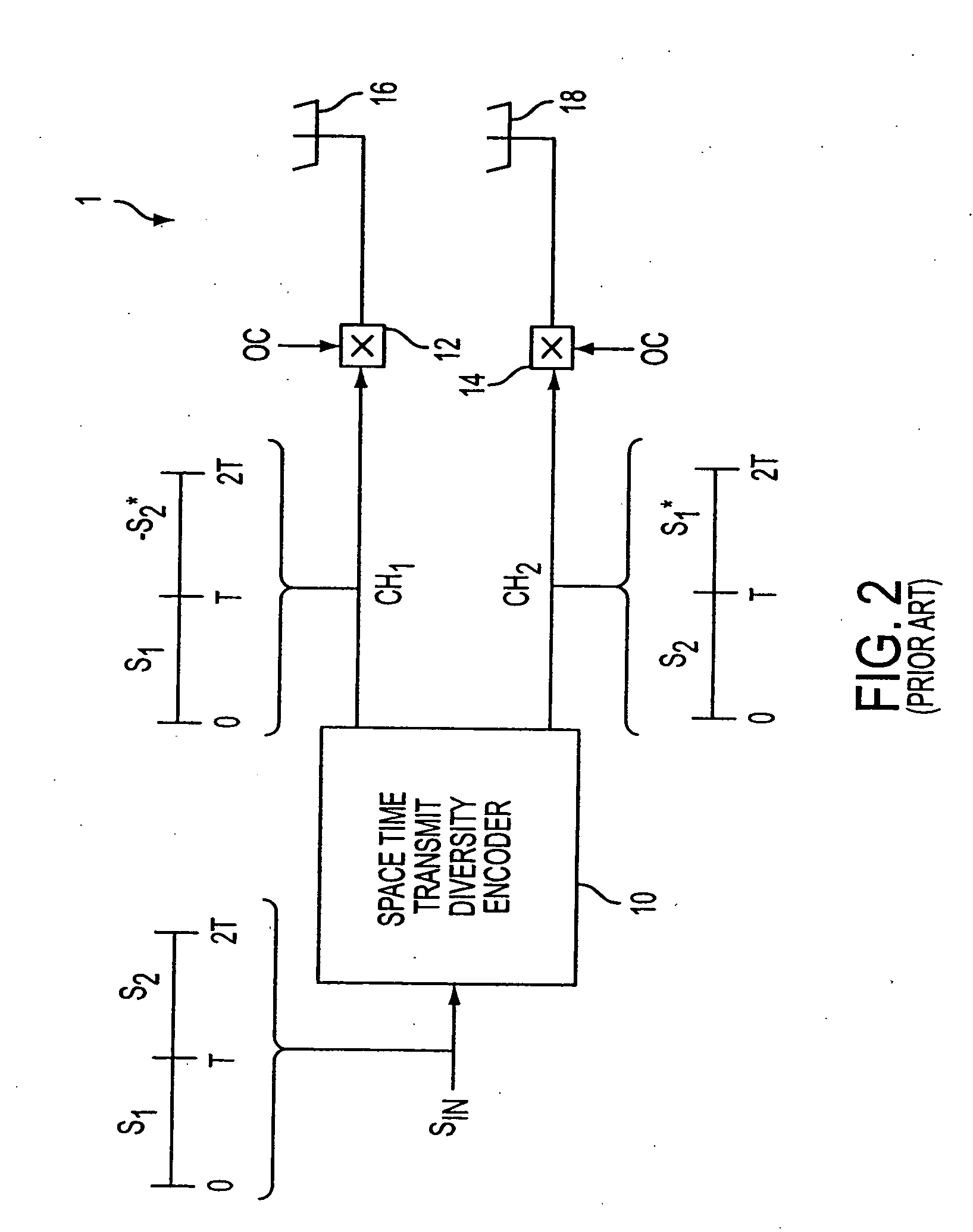
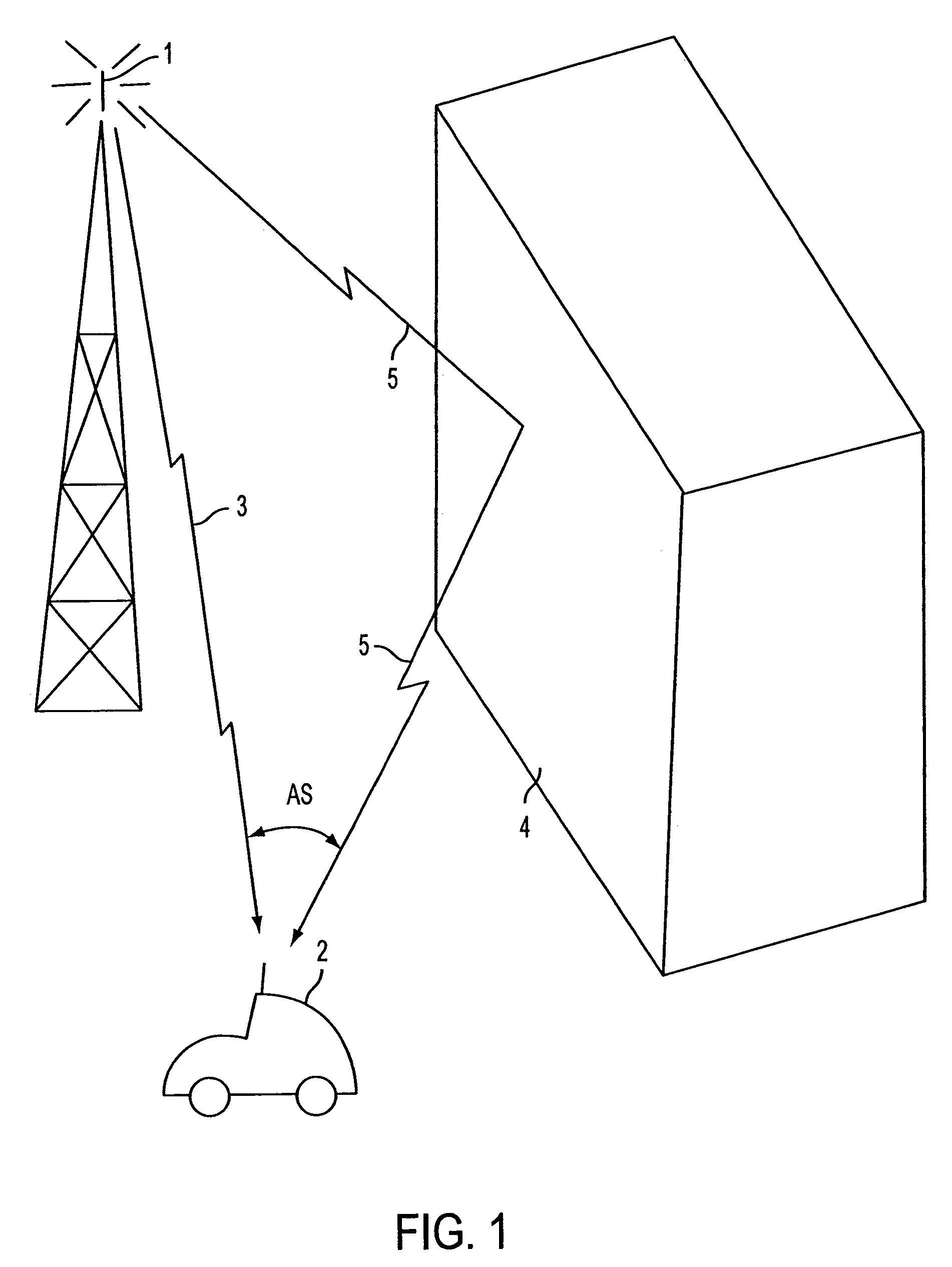
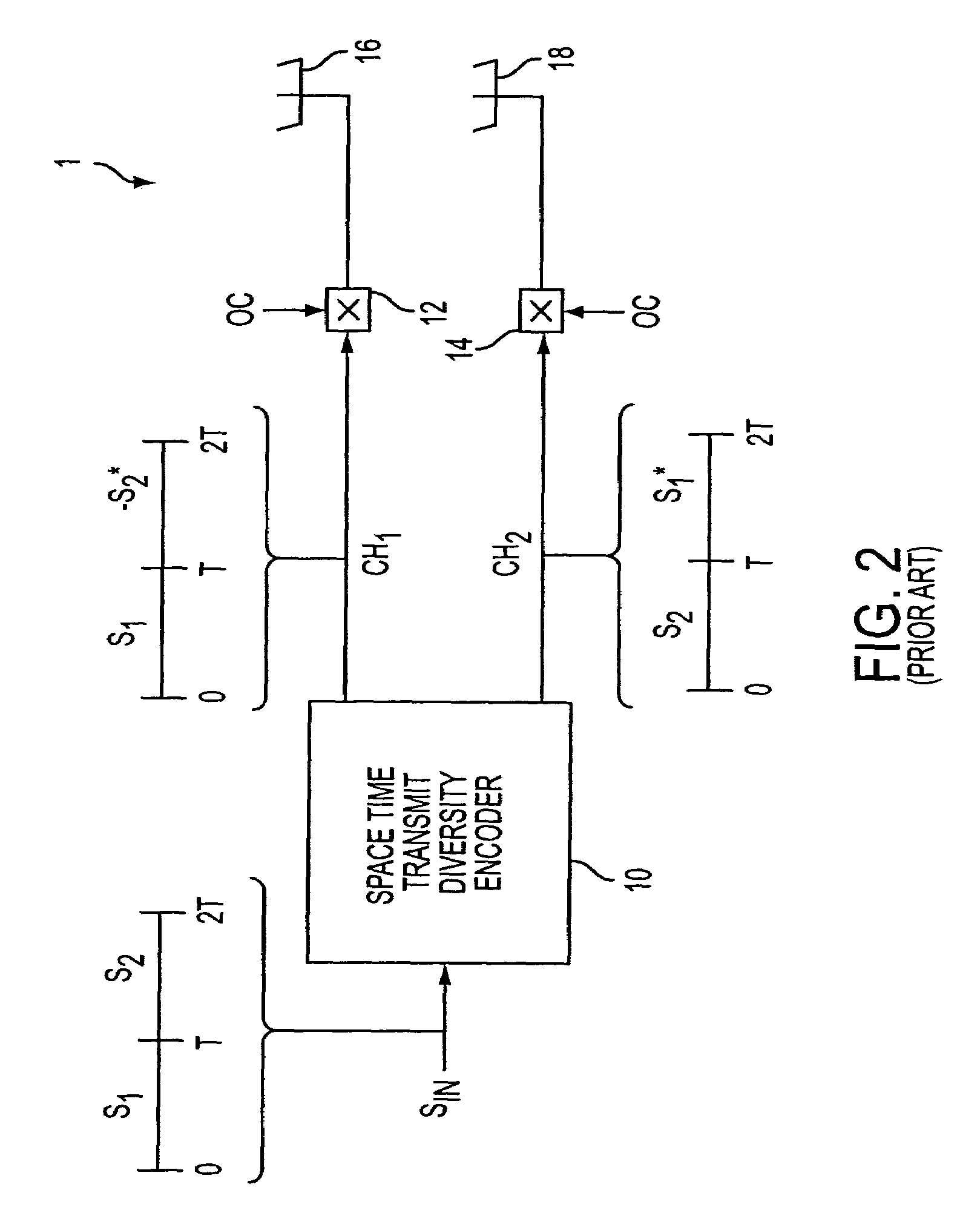
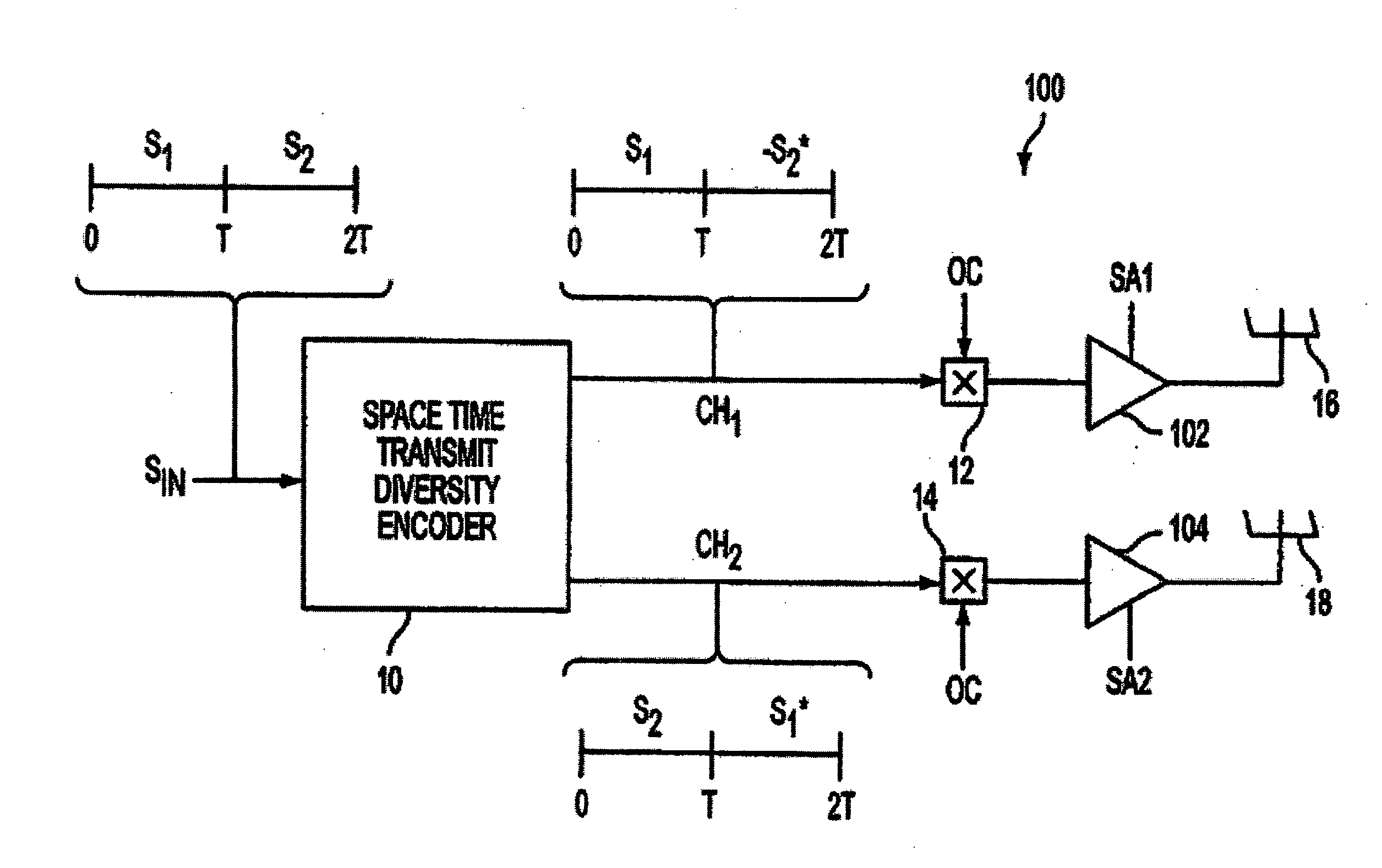
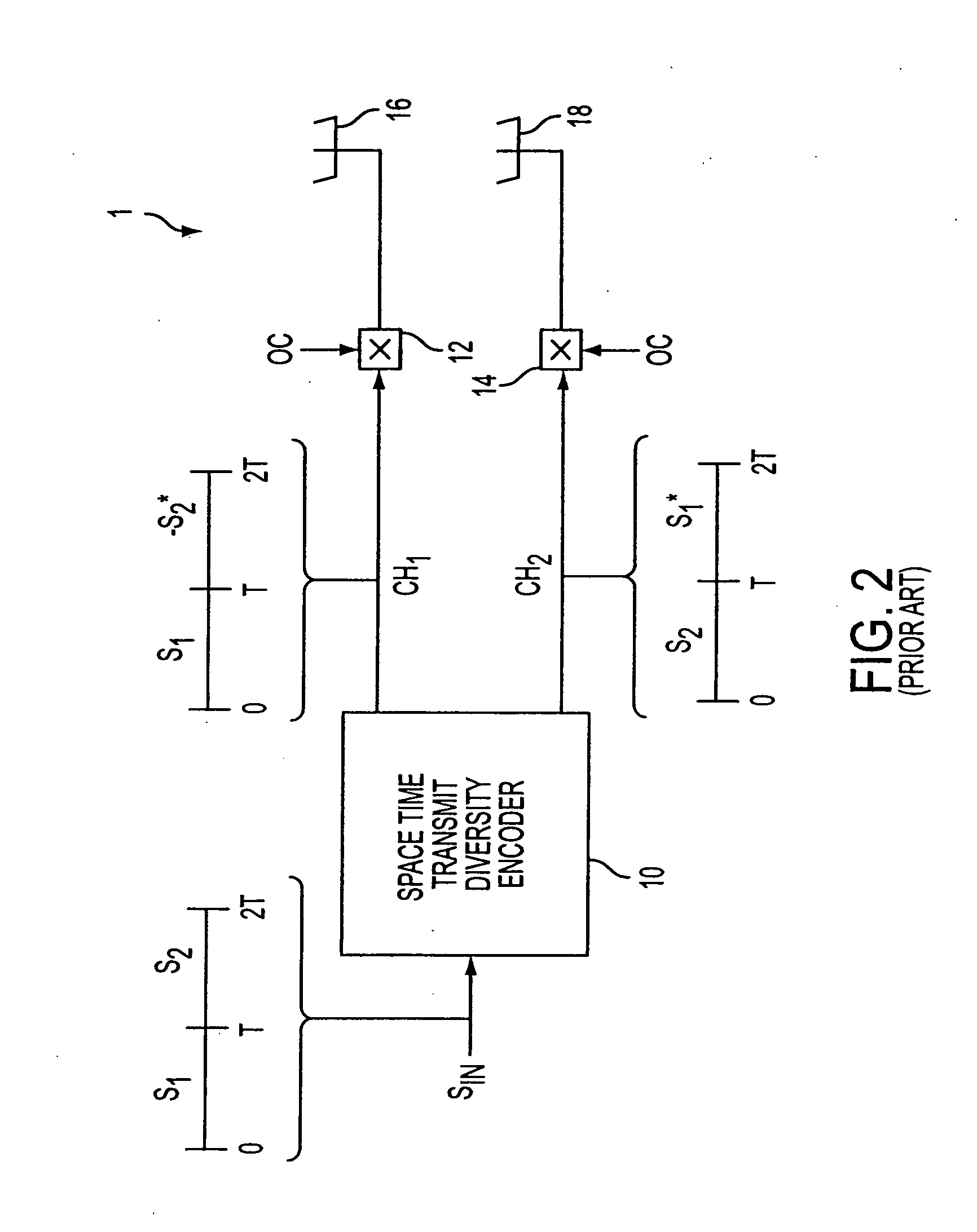
ActiveUS20050157683A1Improve downlink performanceMinimize undesired effect of fadingPower managementSpatial transmit diversityChannel state informationChannel impulse response
A method includes receiving at least two space-time coded signals from an antenna system associated with a first station, determining complex channel state information based on the received space-time coded signals, and sending the complex channel state information to the first station. In an alternative embodiment, a method includes transmitting at least two space-time coded signals in respective beams of a multi-beam antenna array, measuring a channel impulse response for each space-time coded signal at a second station, and sending an indicia of a selected set of least attenuated signals from the second station to the first station. The multi-beam antenna array is associated with a first station. The beams transmit a signature code embedded in each respective space-time coded signal, and the signature codes are orthogonal so that the second station can separate and measure the channel impulse response corresponding to each space-time coded signal.
Owner:INTELLECTUAL VENTURES I LLC
Closed loop feedback system for improved down link performance
InactiveUS7139324B1Improve downlink performanceMinimize undesired effect of fadingPower managementSpatial transmit diversityChannel state informationFinite impulse response
Owner:INTELLECTUAL VENTURES I LLC
Closed loop feedback system for improved down link performance
ActiveUS20050157684A1Improve downlink performanceMinimize undesired effect of fadingSpatial transmit diversityModulated-carrier systemsChannel state informationChannel impulse response
Owner:INTELLECTUAL VENTURES I LLC
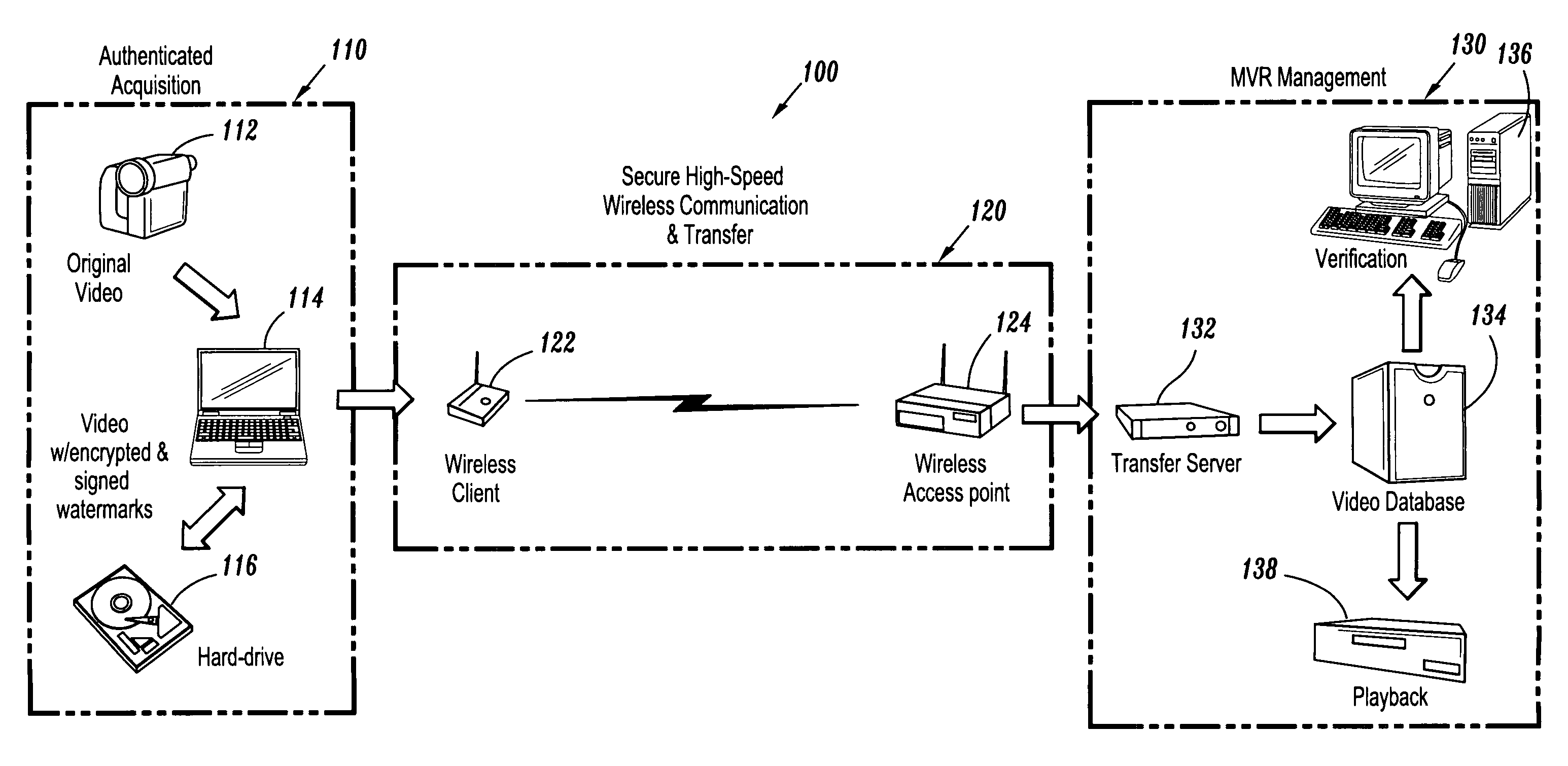
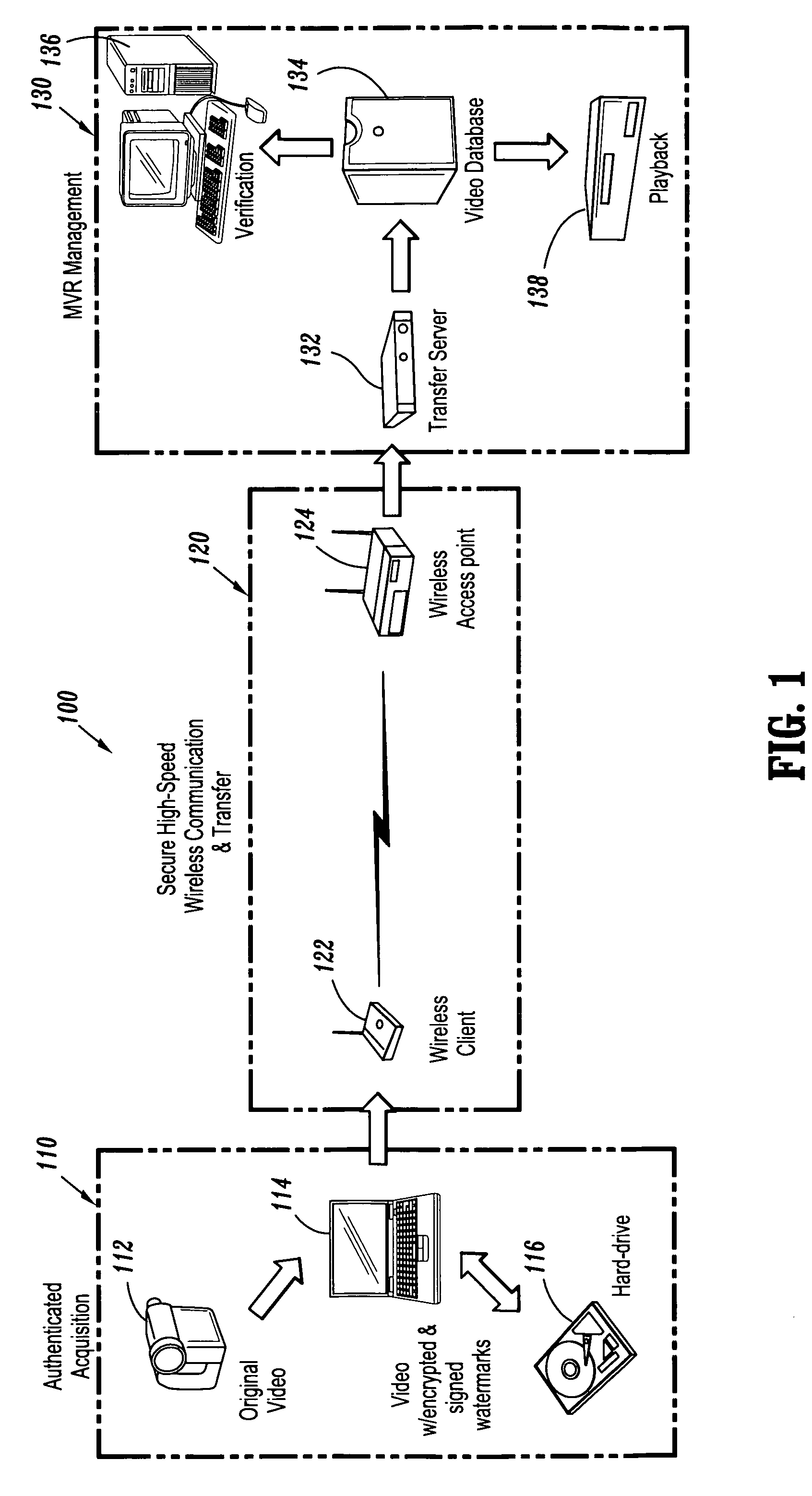
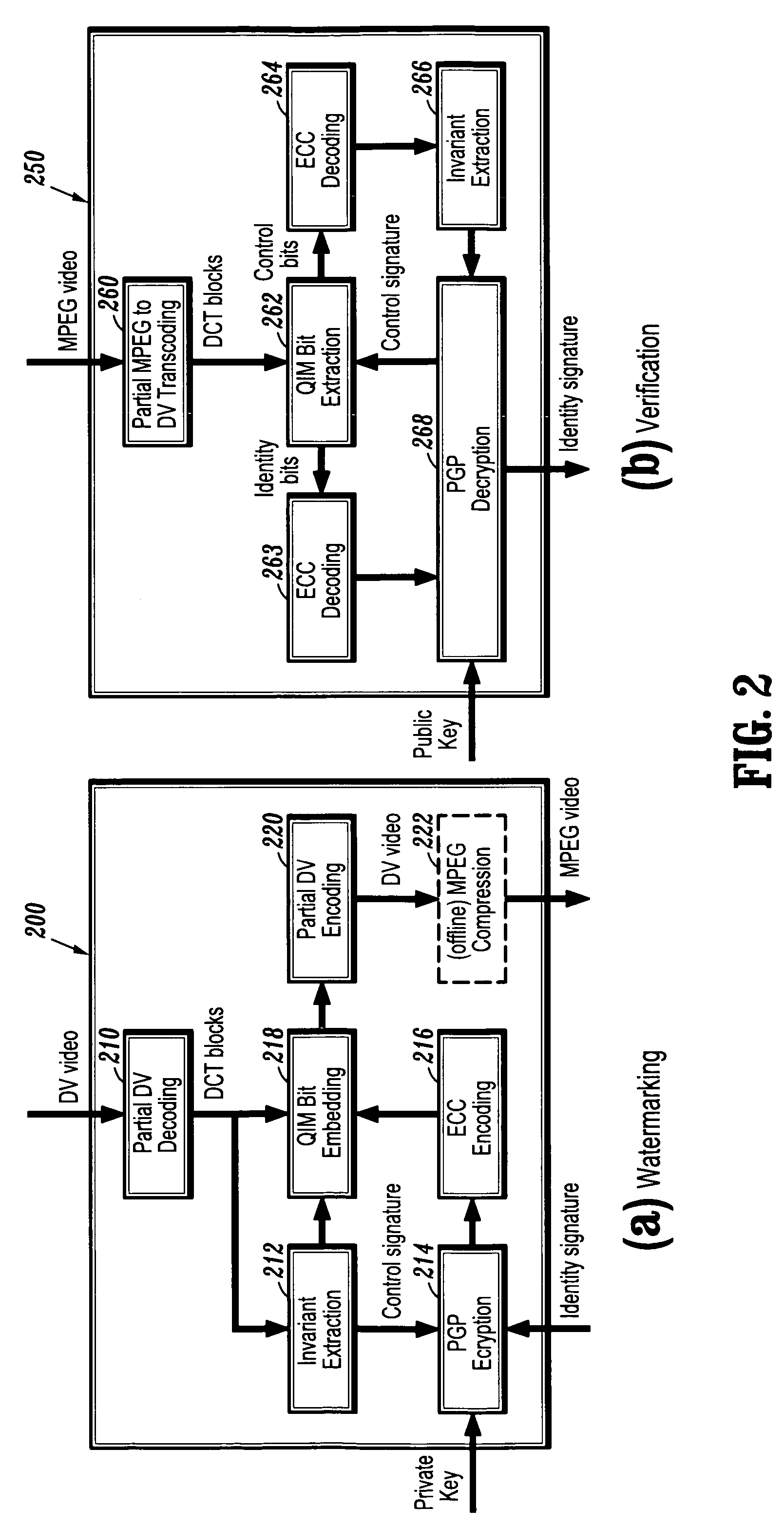
Hybrid digital watermarking for video authentication
InactiveUS7409556B2Varying robustnessTelevision system detailsUser identity/authority verificationSignature CodeRate distortion
A hybrid digital watermarking system for video authentication includes an authenticated acquisition subsystem for digitally watermarking video data and a video management subsystem in signal communication with the authenticated acquisition subsystem for verifying the digitally watermarked video data, where the authenticated acquisition subsystem may include a watermarking device for applying each of an identity signature and a control signature to the video data within a hybrid digital watermark, and the hybrid digital watermark may achieve progressively varying robustness by means of error-correcting signature coding and / or rate-distortion guided bit embedding.
Owner:MY EZ COMM
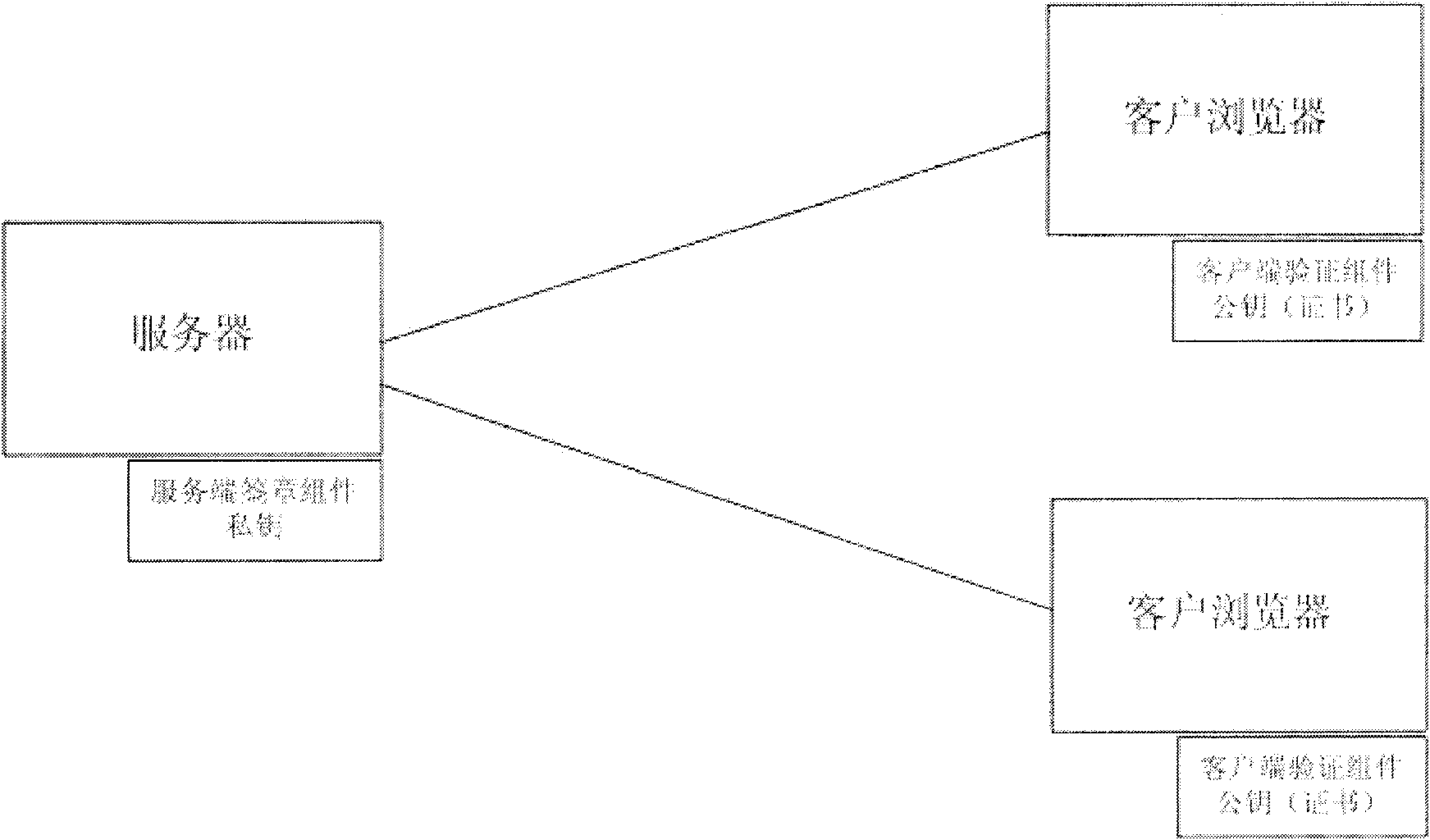
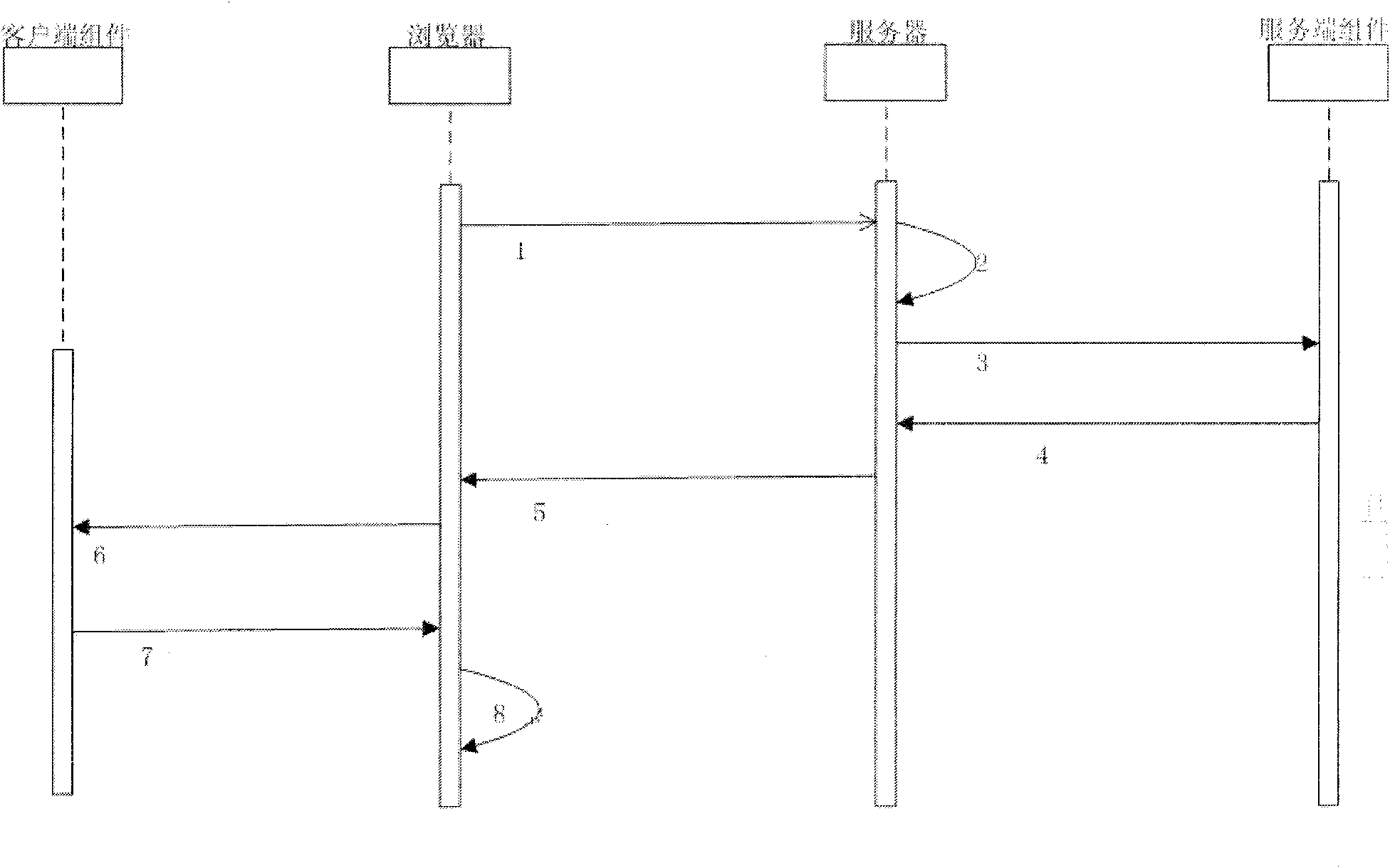
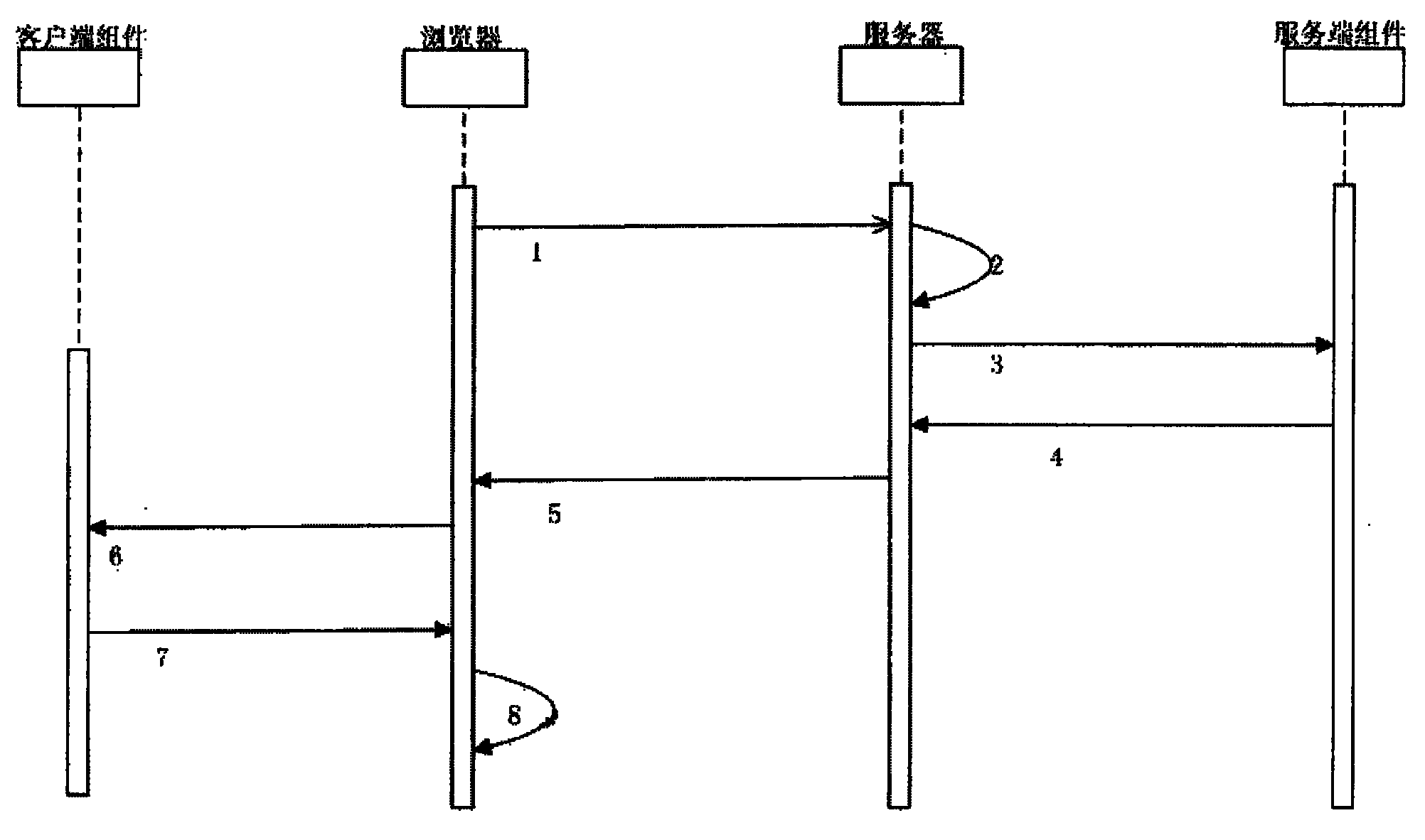
Static webpage anti-tampering system and method based on digital signatures
ActiveCN101795276AImprove protectionSolve the protection functionTransmissionPlaintextSignature Code
The invention relates to static webpage anti-tampering system and method based on digital signatures. The system comprises a server side and a client side, wherein the server side comprises a server and a server side signing assembly, and the client side comprises a browser and a client verifying assembly. The server side signing assembly realizes the full page signature of a webpage code sent out by the server side and transmits a signature code obtained by signing together with the webpage code to the browser of the client side, and when the webpage code is downloaded to the client side, the client verifying assembly is activated and extracts a webpage plain text and the signature code of the server side for verification. The static webpage anti-tampering system and method based on digital signatures can solve the problems that the present webpage can not be effectively utilized and may be illegally tampered, and can be matched with a client side digital signing assembly to realize a protection function on the transmission from the server side to the client side and from the client side to the server side.
Owner:北京江南博仁科技有限公司
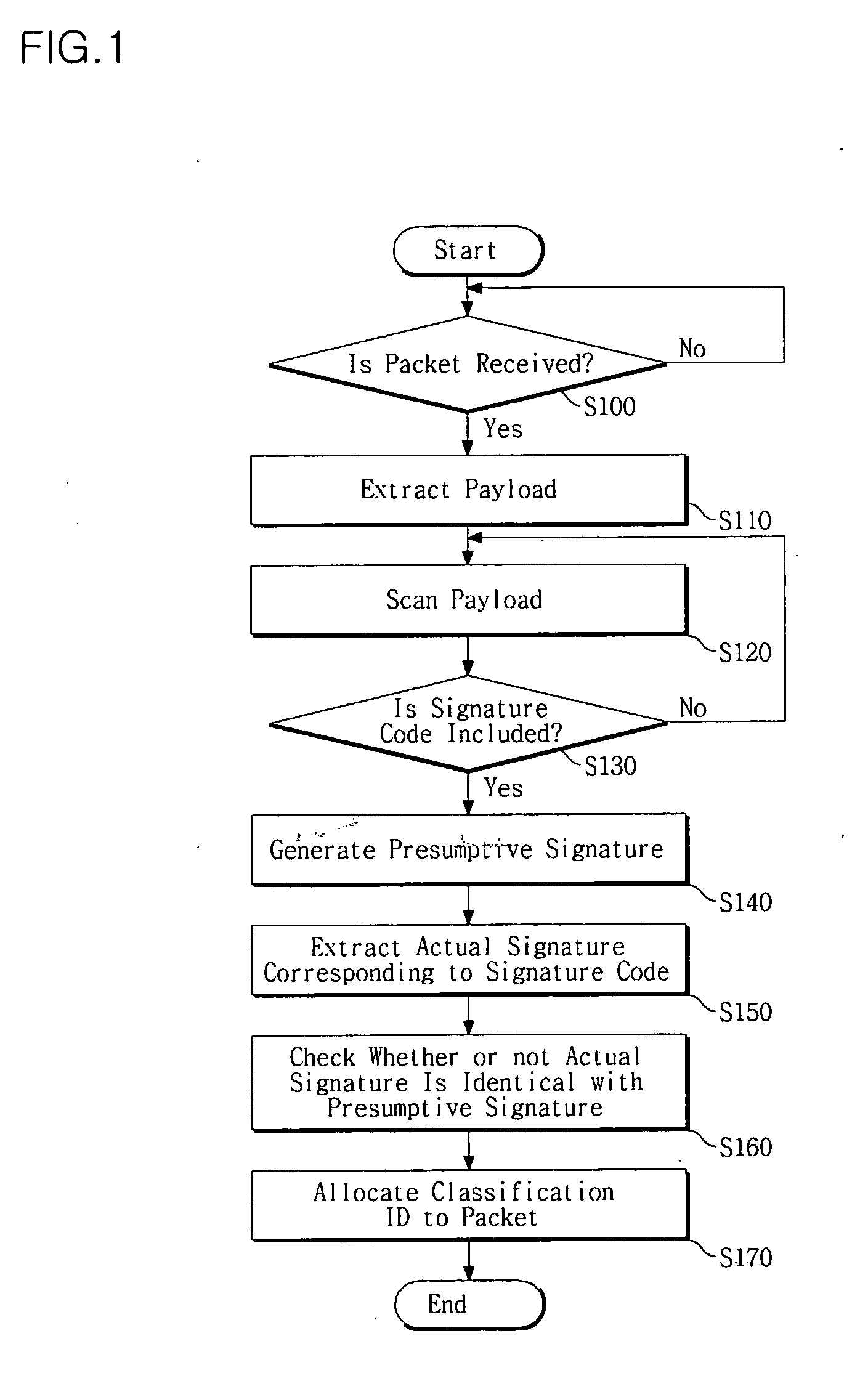
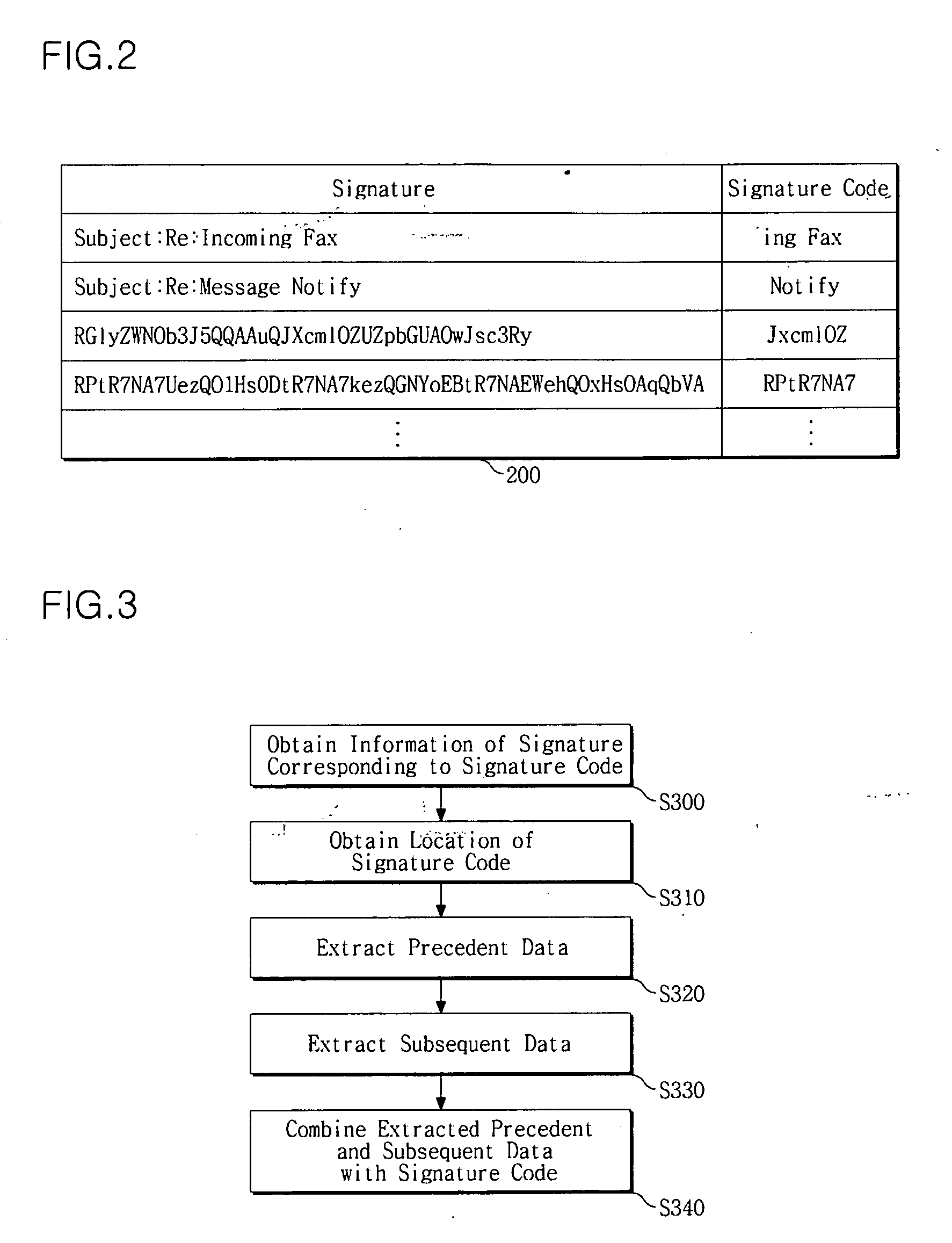
Method and apparatus for classifying harmful packet
A network apparatus and method of classifying received packets based on a predetermined standard are disclosed. The method of classifying received packets in a security system, the method comprises parsing a received packet and extracting a payload from the parsed packet; scanning the payload to check whether or not a predetermined signature code is included in the payload; if it is determined from the result of the scanning that the predetermined signature code is included in the payload, generating a presumptive signature based on information included in the predetermined signature code; and determining whether or not the generated presumptive signature is identical with a signature corresponding to the predetermined signature code, and allocating an classification identifier (ID) to the received packet according to the result of the determination, thereby classifying the received packet according to the classification ID, wherein the predetermined signature code is formed by a part of the signature corresponding to the signature code. Accordingly, possible harmful packets such as attack packets can be classified at high speed, and thereby being blocked immediately.
Owner:SYSMATE
Offline payment method based on NFC
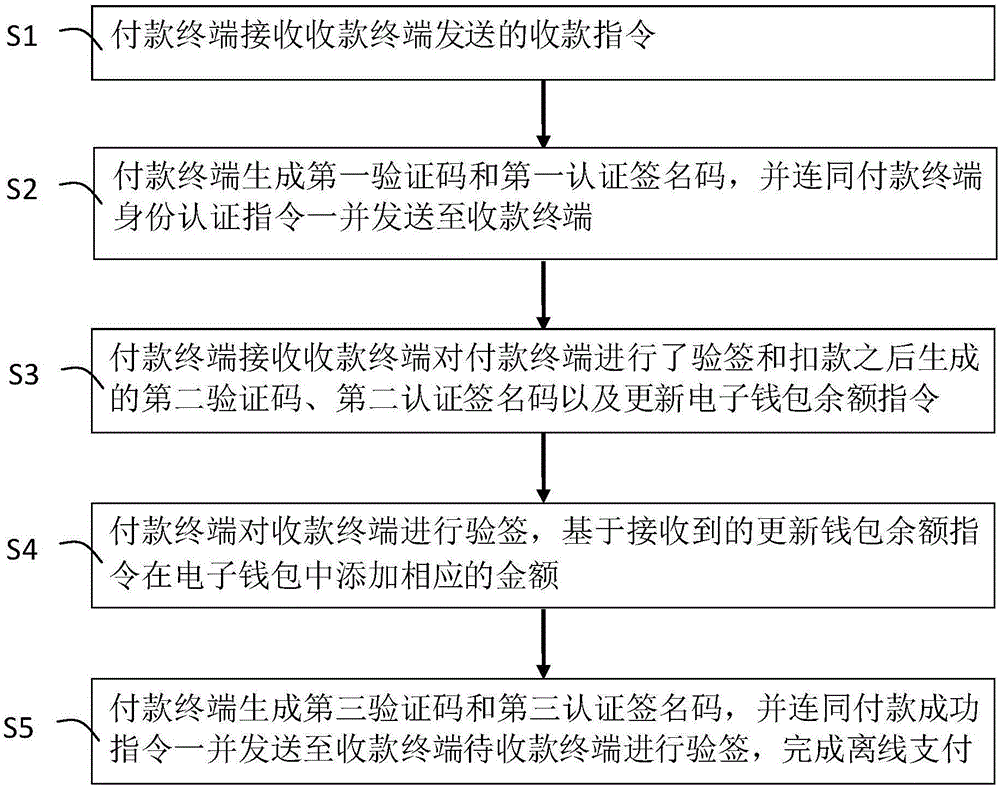
InactiveCN106327186ARealize non-network paymentRealize data exchangePoint-of-sale network systemsProtocol authorisationSignature CodeComputer terminal
The invention belongs to the technical field of mobile payment, and discloses an offline payment method based on NFC. The method includes steps: S1, a payment terminal receives a collection instruction sent by a collection terminal; S2, the payment terminal generates a first verification code and a first authentication signature code, and sends the first verification code, the first authentication signature code and a payment terminal identity authentication instruction to the collection terminal; S3, the payment terminal receives a second verification code, a second authentication signature code, and an update electronic wallet balance instruction which are generated after signature verification and deduction of the payment terminal by the collection terminal; S4, the payment terminal performs signature verification on the collection terminal, and the corresponding amount is added to an electronic wallet based on the received update wallet balance instruction; and S5, the payment terminal generates a third verification code and a third authentication signature code, and sends the third verification code, the third authentication signature code, and a payment success instruction to the collection terminal so that the collection terminal can perform signature verification. According to the method, non-network payment and data exchange between two terminals can be realized.
Owner:CHINA SMARTCITY TECH
Random access collision back-off method
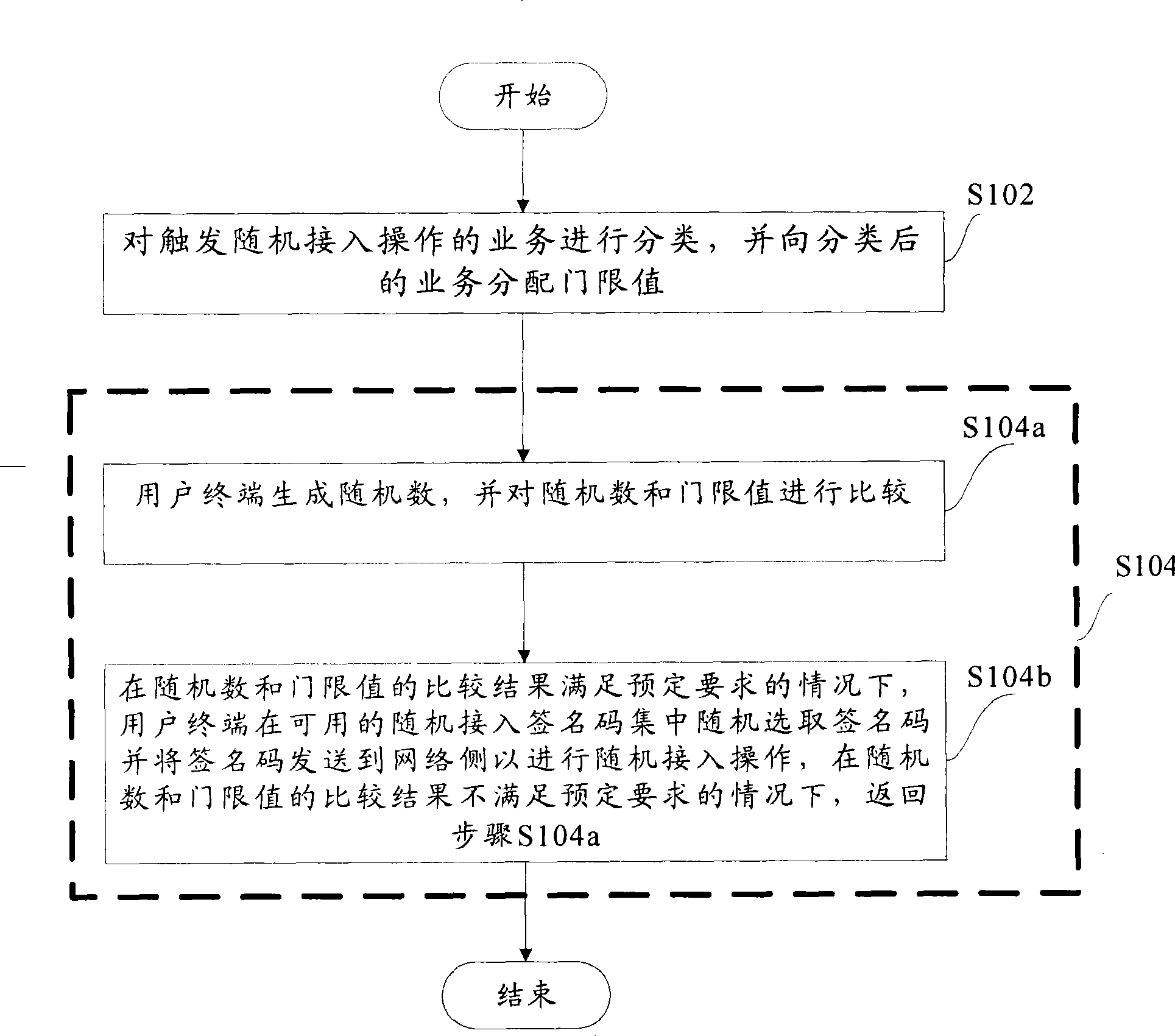
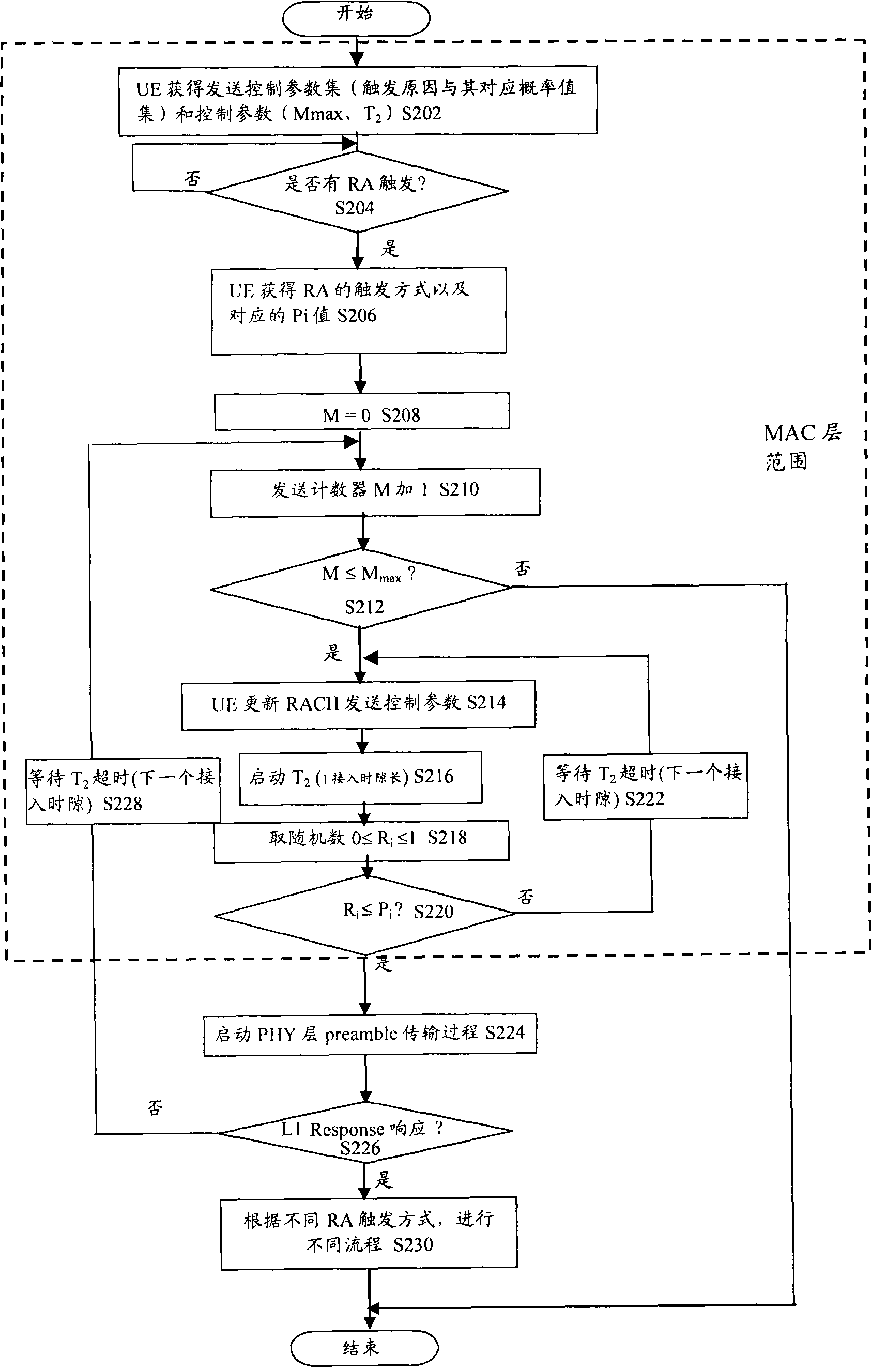
InactiveCN101400145AReduce the number of retriesEasy accessWireless communicationSignature CodeComputer science
The invention provides a random access collision retreat method, comprising: the step S102, classifying service of triggering the random access operation, and distributing threshold values to the classified service, performing random access operation according to the threshold values by user terminals, wherein the step S104 comprises: the step S104a, the user terminals generates random number, and compares the random number with the threshold values, and the step S104b, the user terminals randomly select a signature code from available random access signature code aggregate and transmit to the network side to perform random access operation, when the comparing result of the random number and the threshold values satisfies the scheduled requirement; when the comparing result of the random number and the threshold values does not satisfy the scheduled requirement, returning to the step S104a.
Owner:ZTE CORP
Certificate false proof method based on light weight digital signature scheme
InactiveCN101388767AEnsure safetyEasy to useFinanceUser identity/authority verificationSignature CodeDigital Signature Algorithm
The invention relates to a method for proofing false certificates based on a lightweight level digital signature scheme, which belongs to the cryptography and the computer field, the method enables the unforgeability of the certificates to be corresponding to the safety of a public key digital signature scheme and comprises the three parts of a key generating part of certificate forgery, a digital signature part and an identification checking part, wherein the key generating part is used for generating a pair of a private key and a public key of a license-issuing authority, the digital signature part is used for generating signature codes to the Hash abstract of key information of the certificates for the license-issuing authority, the identification checking part is used for identifying authenticity of the certificates for a user end inquiry unit, the method is safe and has low cost, can prevent insiders of the license-issuing authority commit a crime, can replace official seals of companies and can widely used in distributing business of various certificates.
Owner:苏盛辉 +2
Method and system for watermarking an electronically depicted image
InactiveUS20050123167A1Small error rateCharacter and pattern recognitionImage watermarkingSignature CodeFalse alarm
A system for watermarking an image file selects coefficients using a selection procedure that is kept secret, and assigns the selected coefficients to coefficient pairs. The difference between the coefficients of the pairs is then used to generate multi-bit raw signature values that characterize the authentic image at different locations. To detect an unauthorized alteration after the image file has been watermarked, coefficient pairs are selected using the same secret procedure that was originally used to generate the raw signature values. The difference between the coefficients of the pairs is then checked against the raw signature values derived from the original image file. The raw signature values derived from the authentic image file may be placed in the header of the file or in a separate file. Alternatively, they may be embedded in host coefficients that are selected in accordance with a procedure that is kept secret. To reduce the risk of false alarms, more than one raw signature value may be accepted for certain difference ranges of the difference between coefficients of the pairs. Furthermore, the raw signature values may be grouped into sets, which are mapped onto shortened signature codes having a reduced number of bits. The assignment of sets of raw signature values to the shortened signature codes may be based on the probability of the sets of raw signature values.
Owner:MAENO KURATO +3
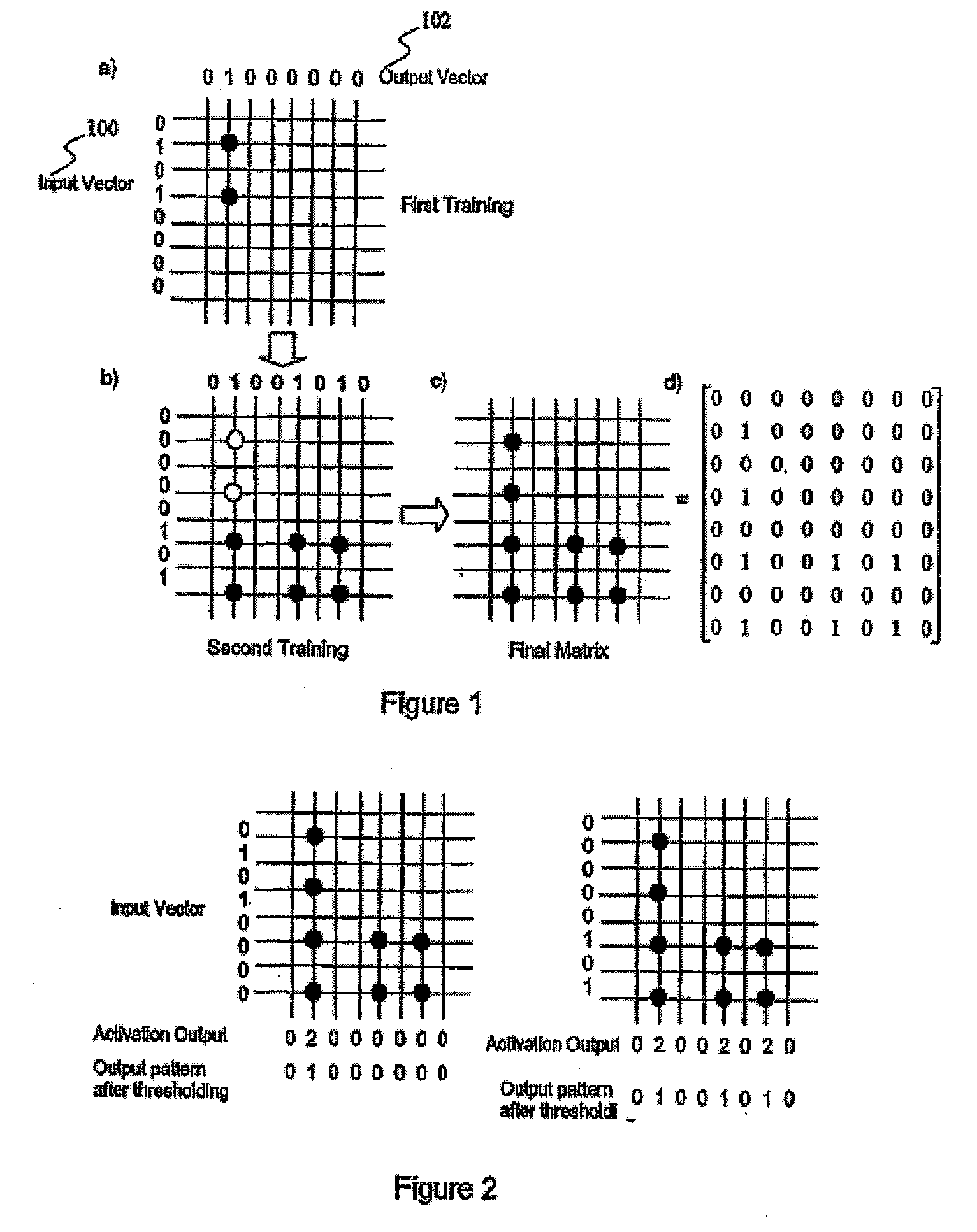
Method and System for Identification of Audio Input
InactiveUS20090138108A1Character and pattern recognitionSpecial data processing applicationsSignature CodeAudio frequency
A method for use in identifying an audio input, comprising the steps of: deriving a signature code from the audio input; subjecting the signature code to Correlation Matrix Memory (CMM) processing; and identifying the audio input based on an output of the CMM processing.
Owner:PANASONIC CORP
Method for establishing a communication channel between a host device and a memory device, associated memory device and controller thereof, and associated host device and host device application
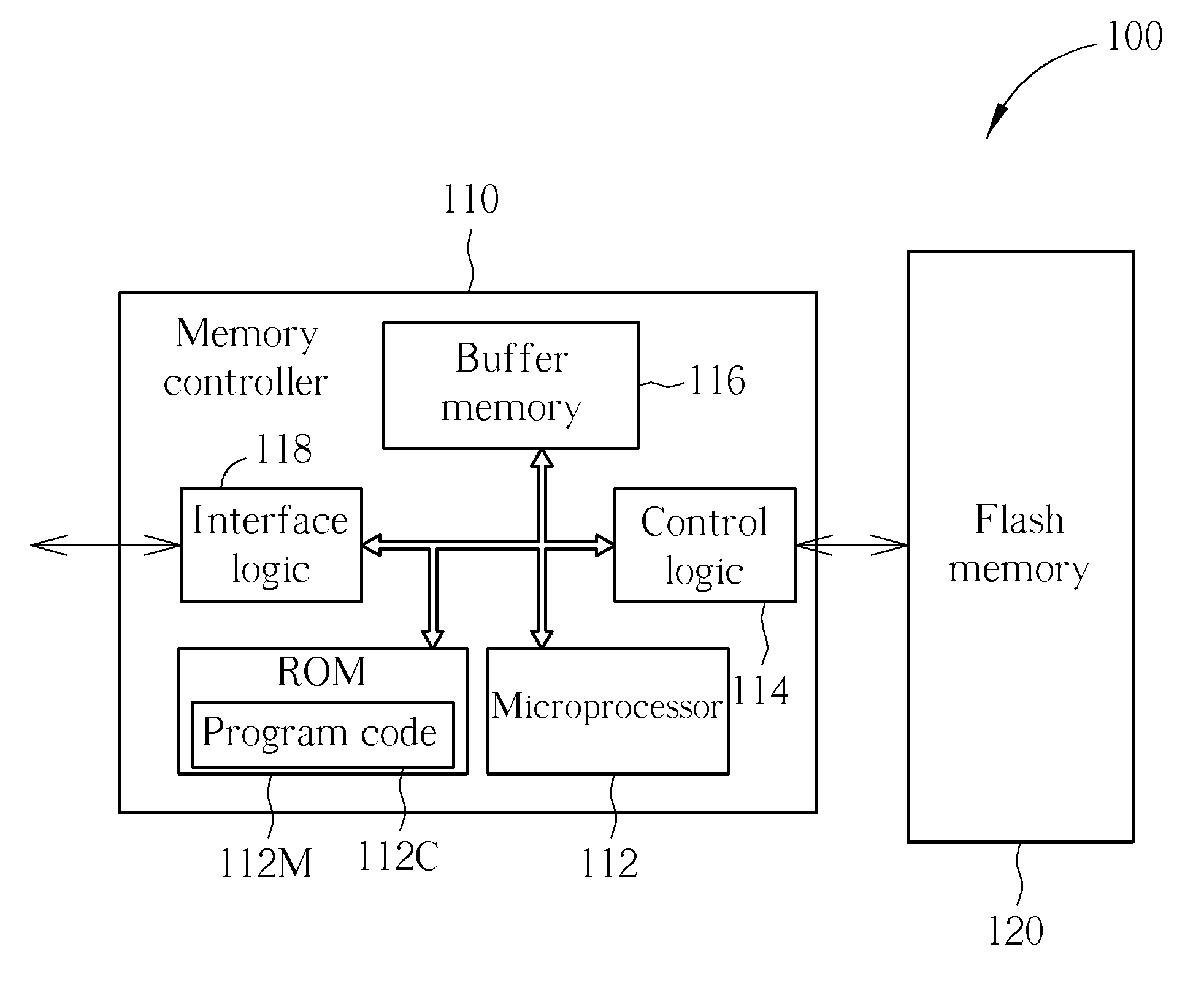
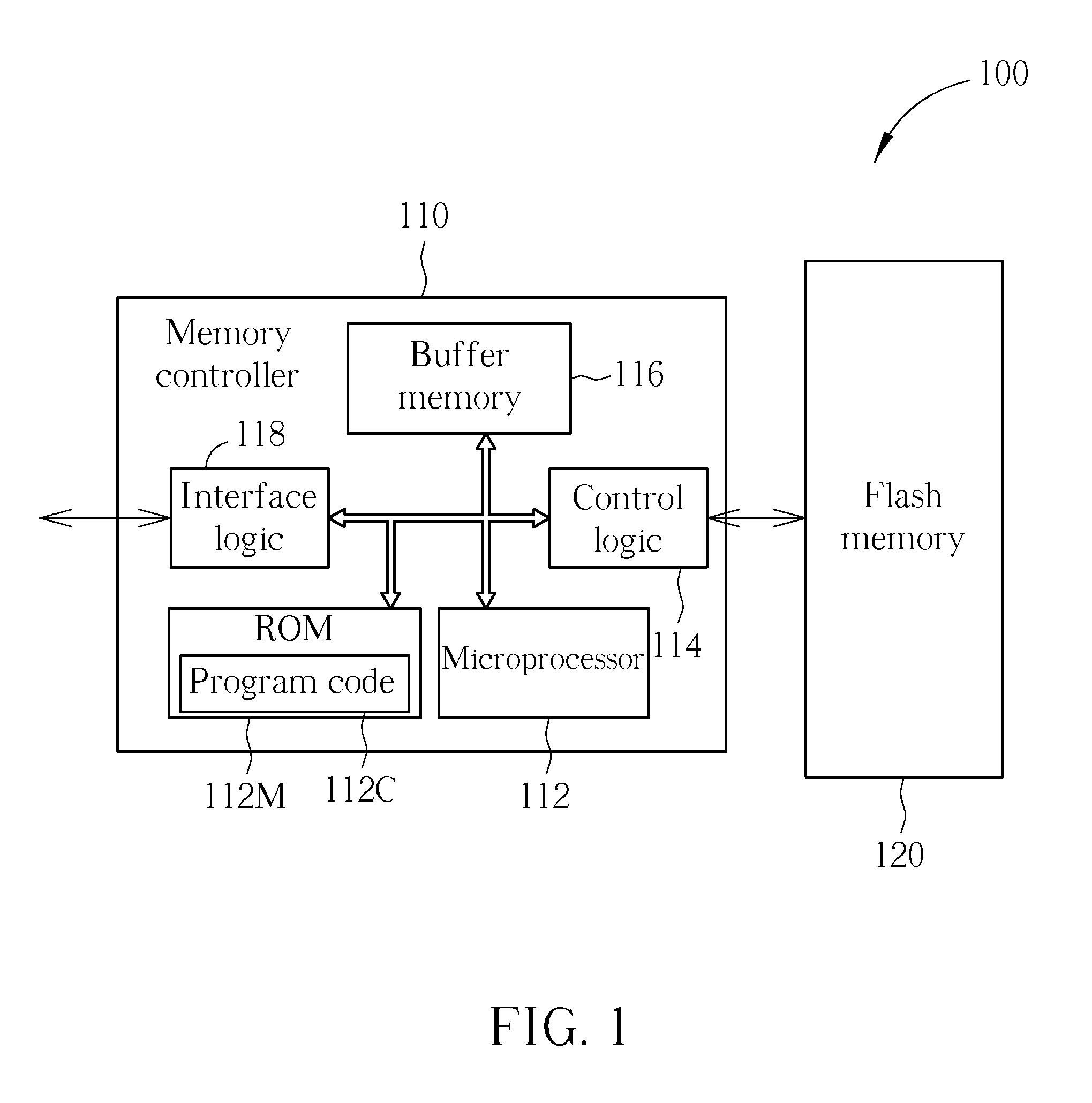
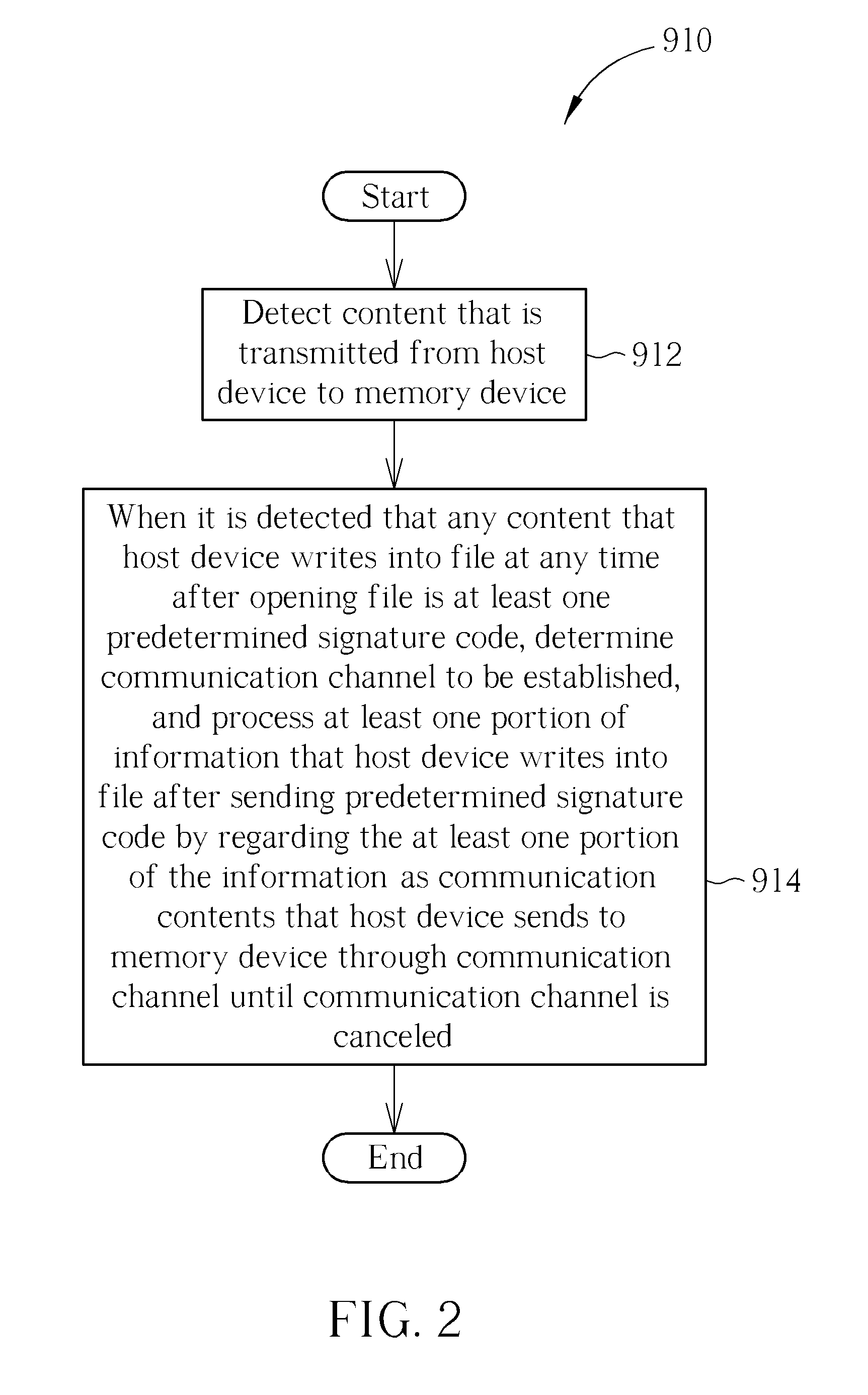
InactiveUS20110055430A1Memory adressing/allocation/relocationInput/output processes for data processingSignature CodeFlash memory
A method for establishing a communication channel between a host device and a memory device including a Flash memory includes: detecting at least one content that is transmitted from the host device to the memory device; and when it is detected that any content that the host device writes into a file after opening the file is at least one predetermined signature code, determining the communication channel to be established, and processing at least one portion of information that the host device writes into the file after sending the predetermined signature code by regarding the at least one portion of the information as communication contents that the host device sends to the memory device through the communication channel until the communication channel is canceled. An associated memory device and a controller thereof, and an associated host device and an associated host device application are also provided.
Owner:SILICON MOTION INC (TW)
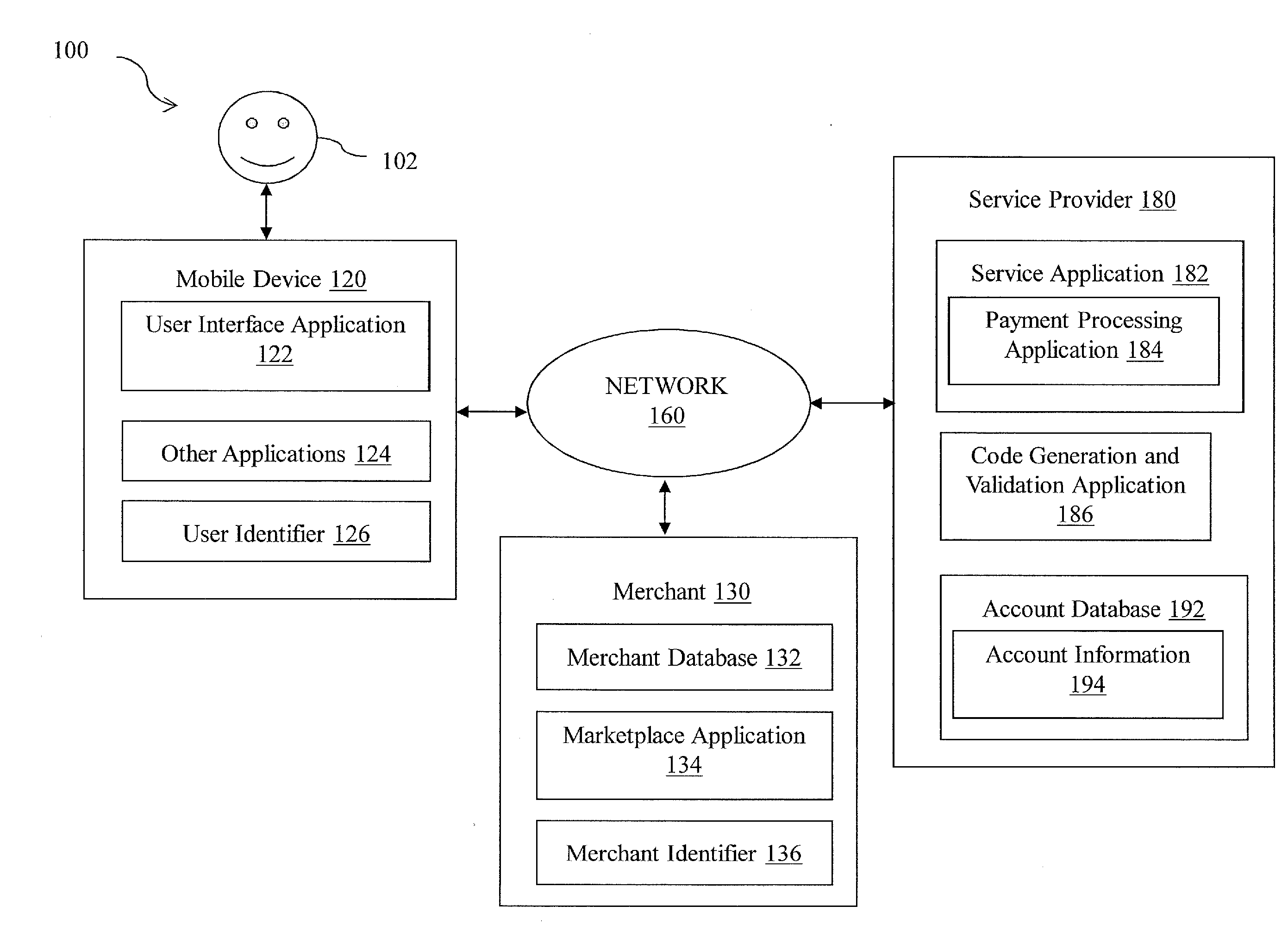
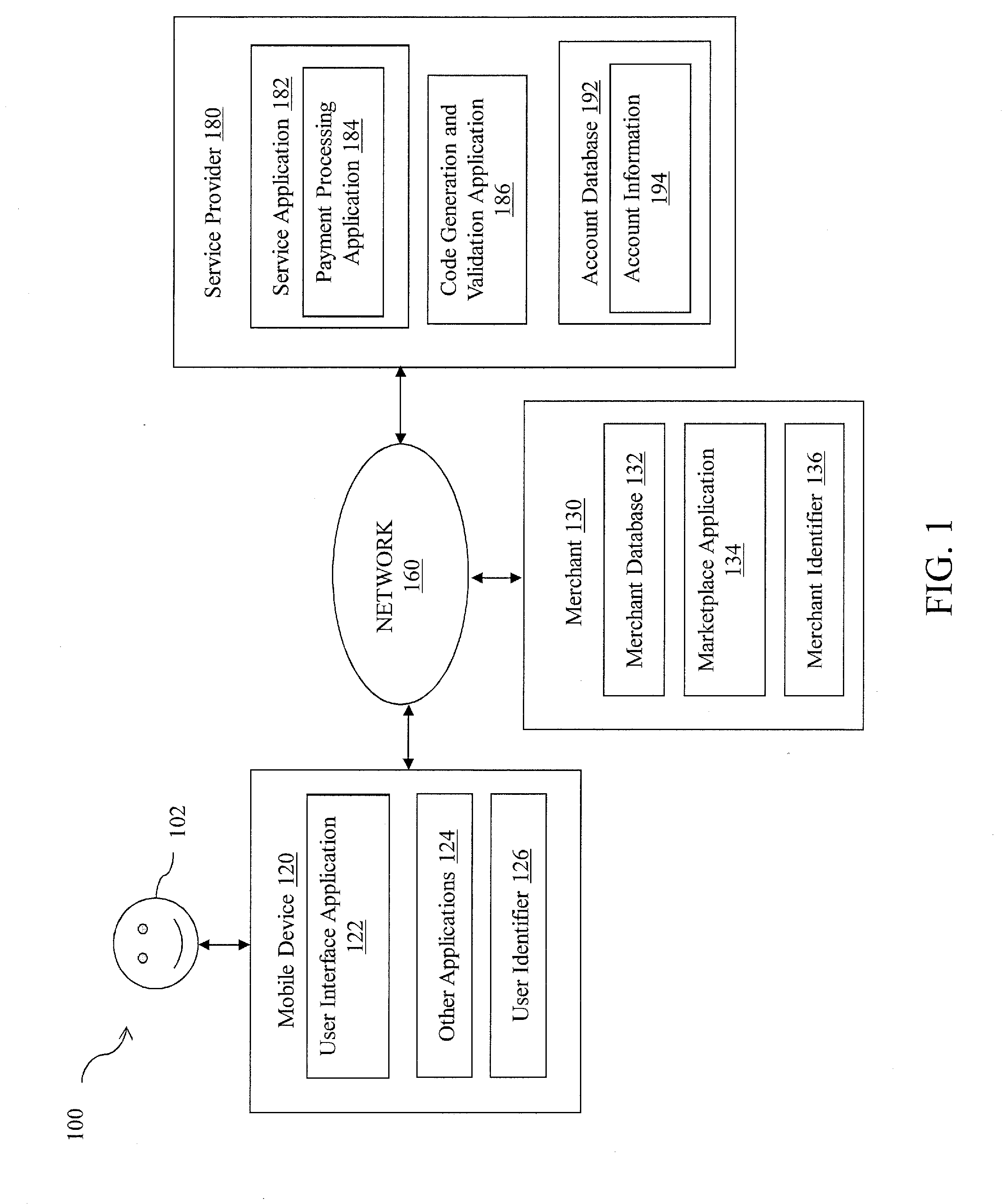
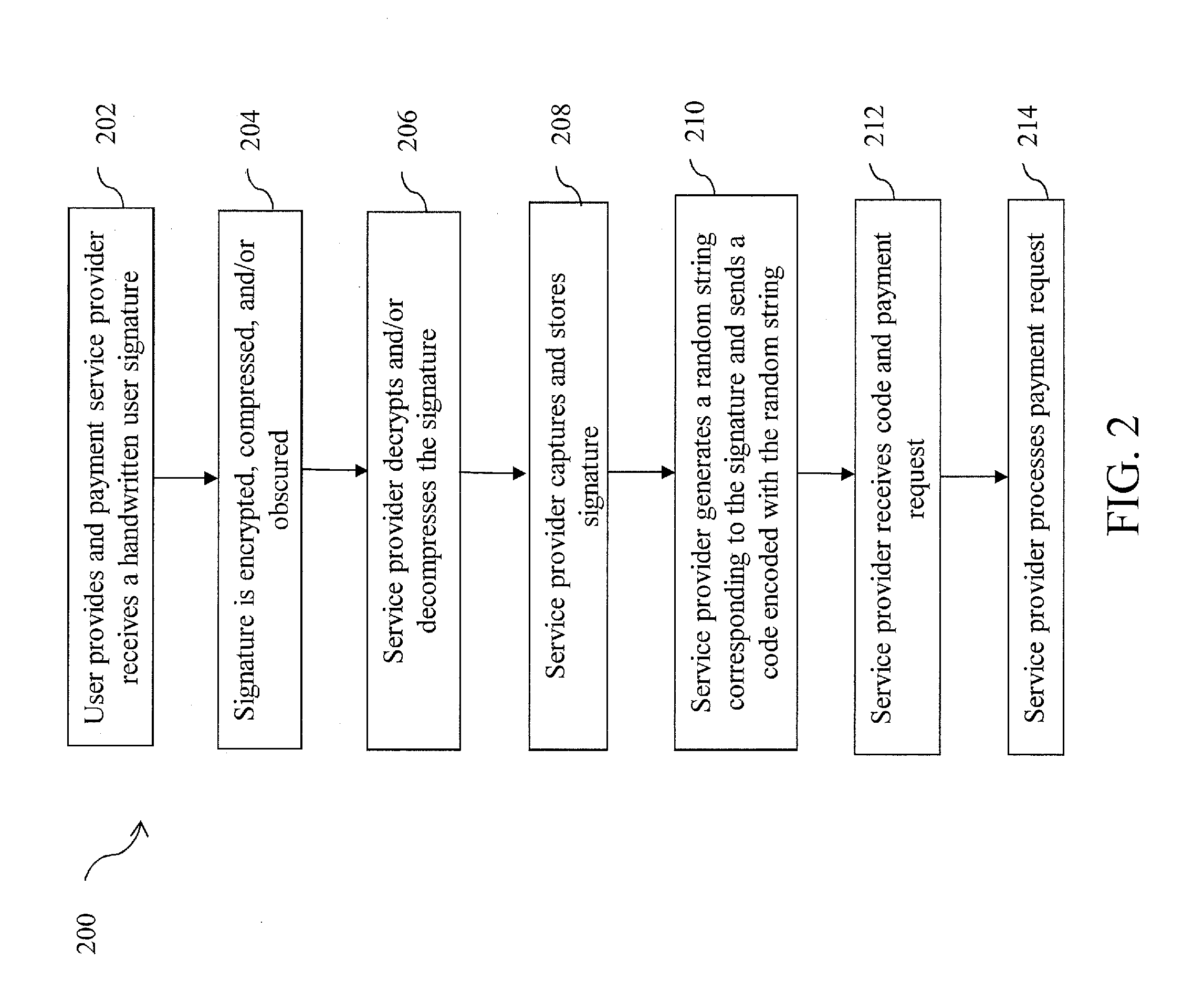
Touchless signature
Methods and systems for facilitating secure payments are described. A user signature is shared with a merchant without providing an actual signature to the merchant. A signature code encoded with a user's handwritten signature is generated and presented to a merchant upon request for signature. The signature code is scanned by the merchant, and data in the signature code is transmitted to a service provider. The service provider receives the data and retrieves the signature. The signature code can be used at a retail location during checkout, during delivery of merchandise, or for acknowledgement of mail delivery.
Owner:PAYPAL INC
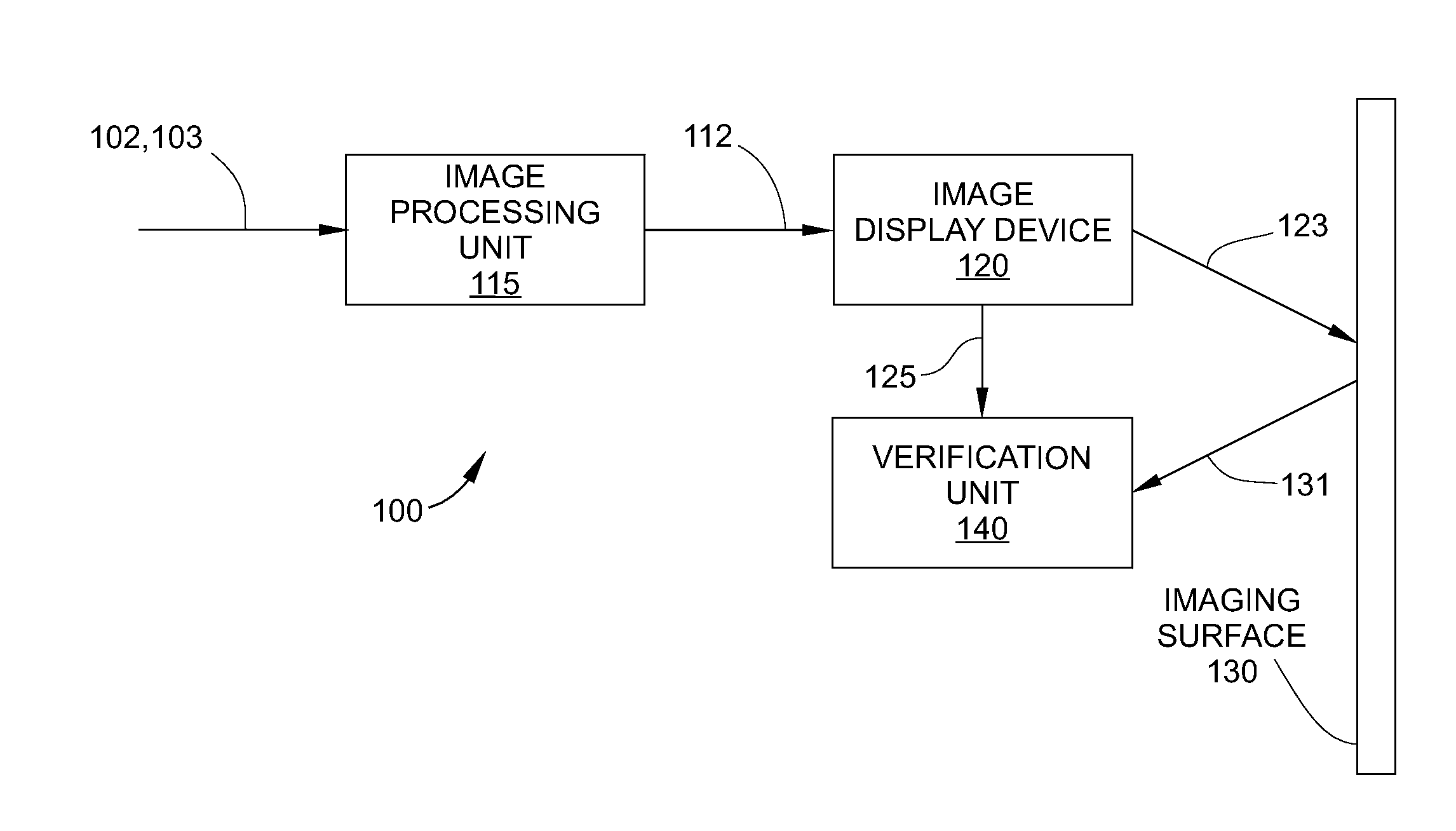
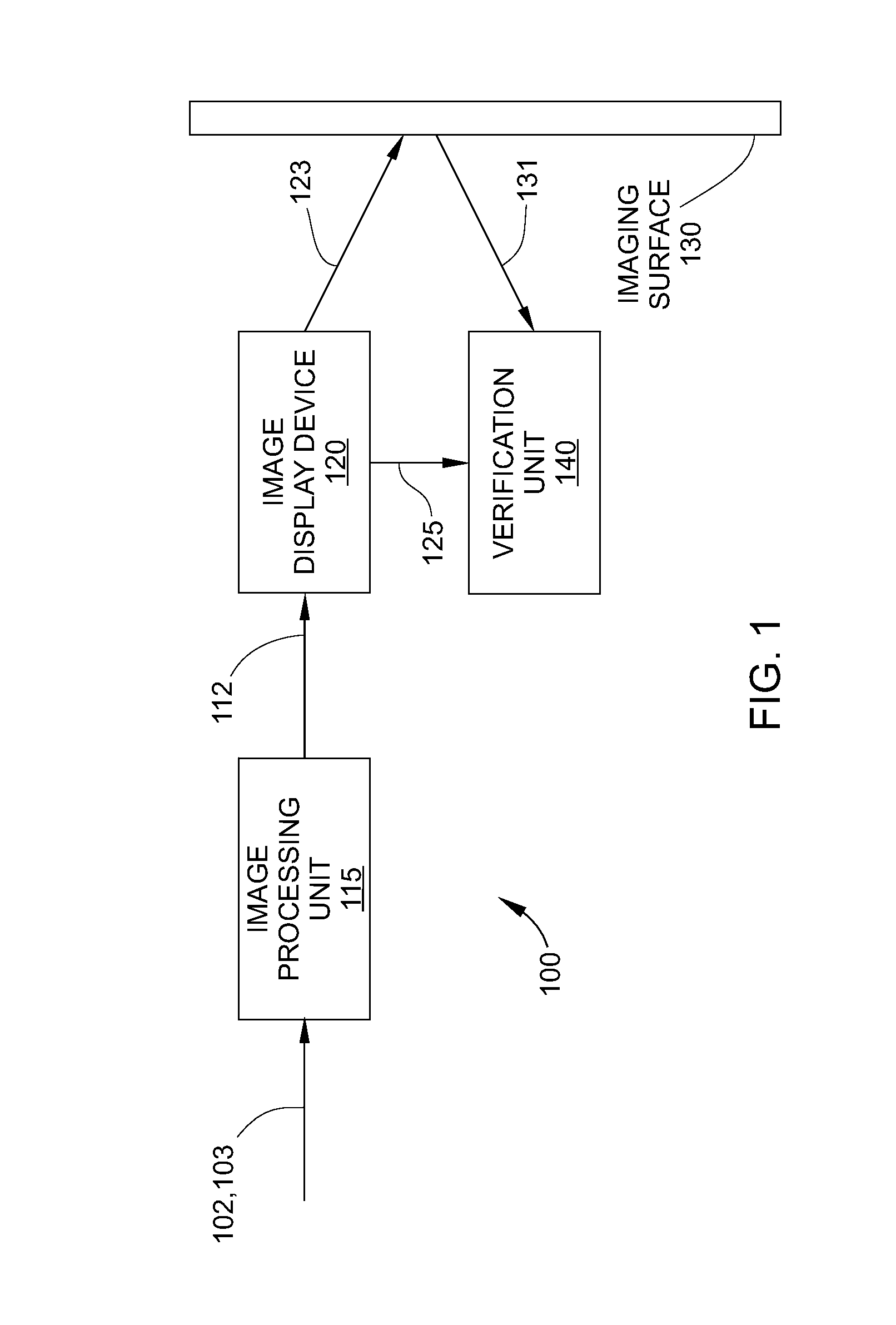
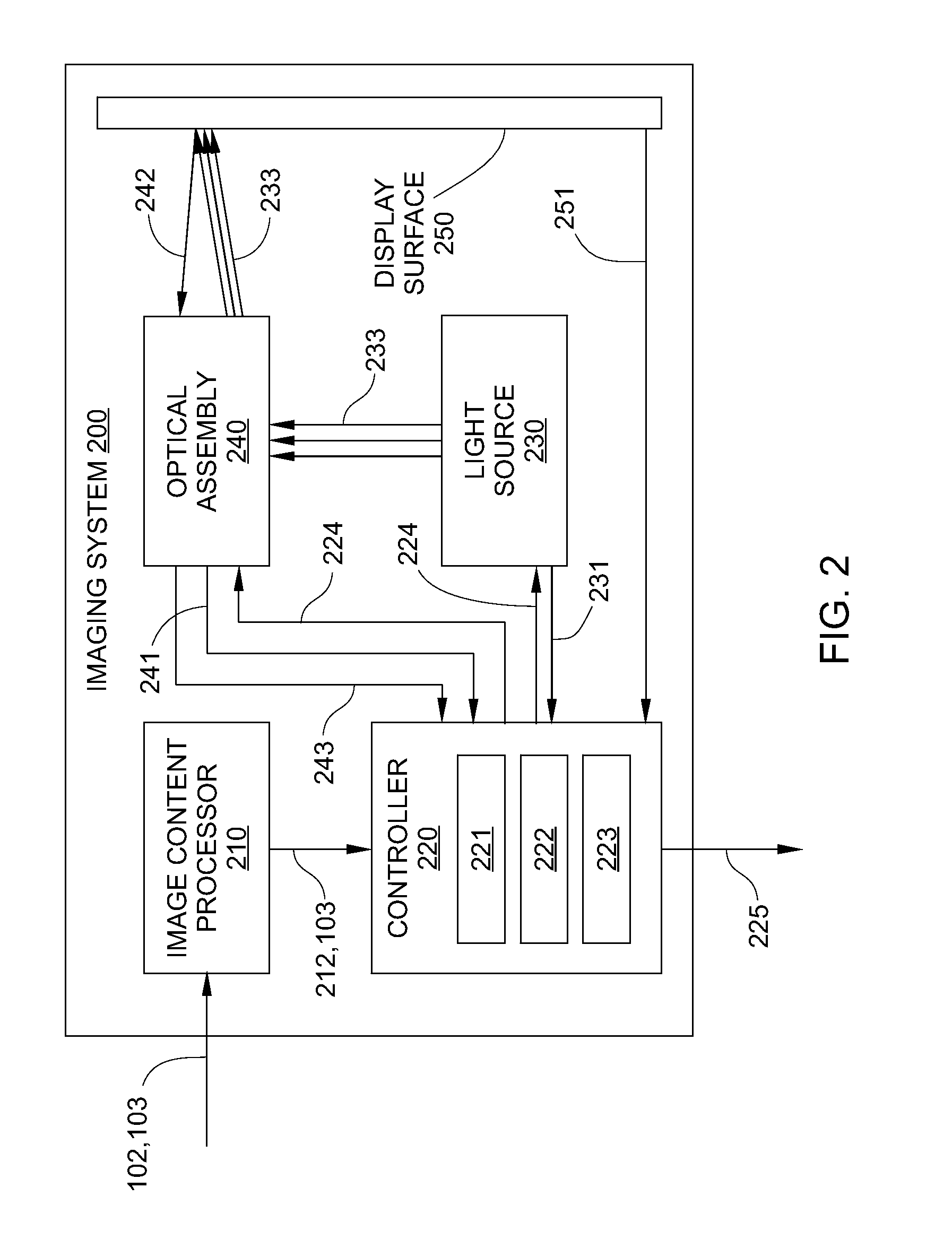
Closed loop verification of rendered content
An electronic display device provides closed-loop verification that specific content has been displayed by the display device. When desired digital image content is rendered as an image or video by the electronic display device, a confirmation signal is generated by one or more components of the display device to verify that the image content has been successfully displayed. The confirmation signal may include performance measurements of the one or more components of the display device and / or a signature output that is associated with a signature code embedded in the image content. The signature output uniquely identifies the digital image content.
Owner:PRYSM SYST INC
Method for verifying contents on basis of digital signature codes
InactiveCN104376252AEasy to confirmDigital data authenticationProgram/content distribution protectionSignature CodeDigital content
Owner:陈杰
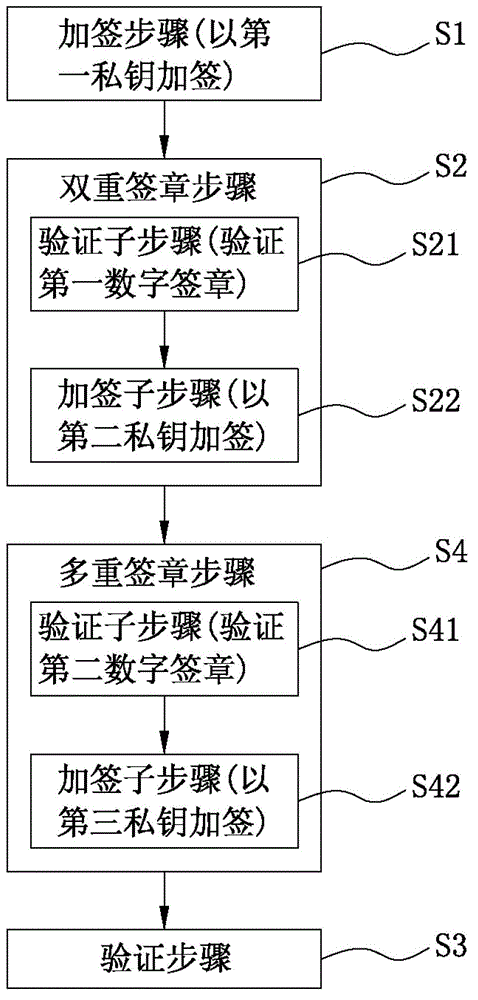
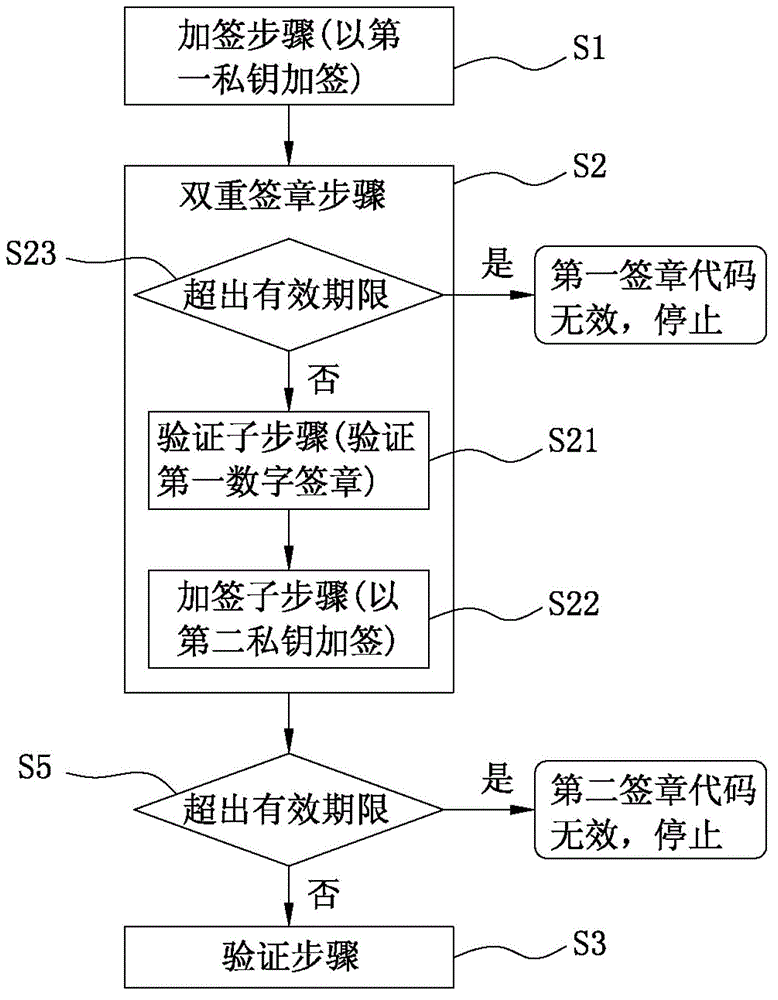
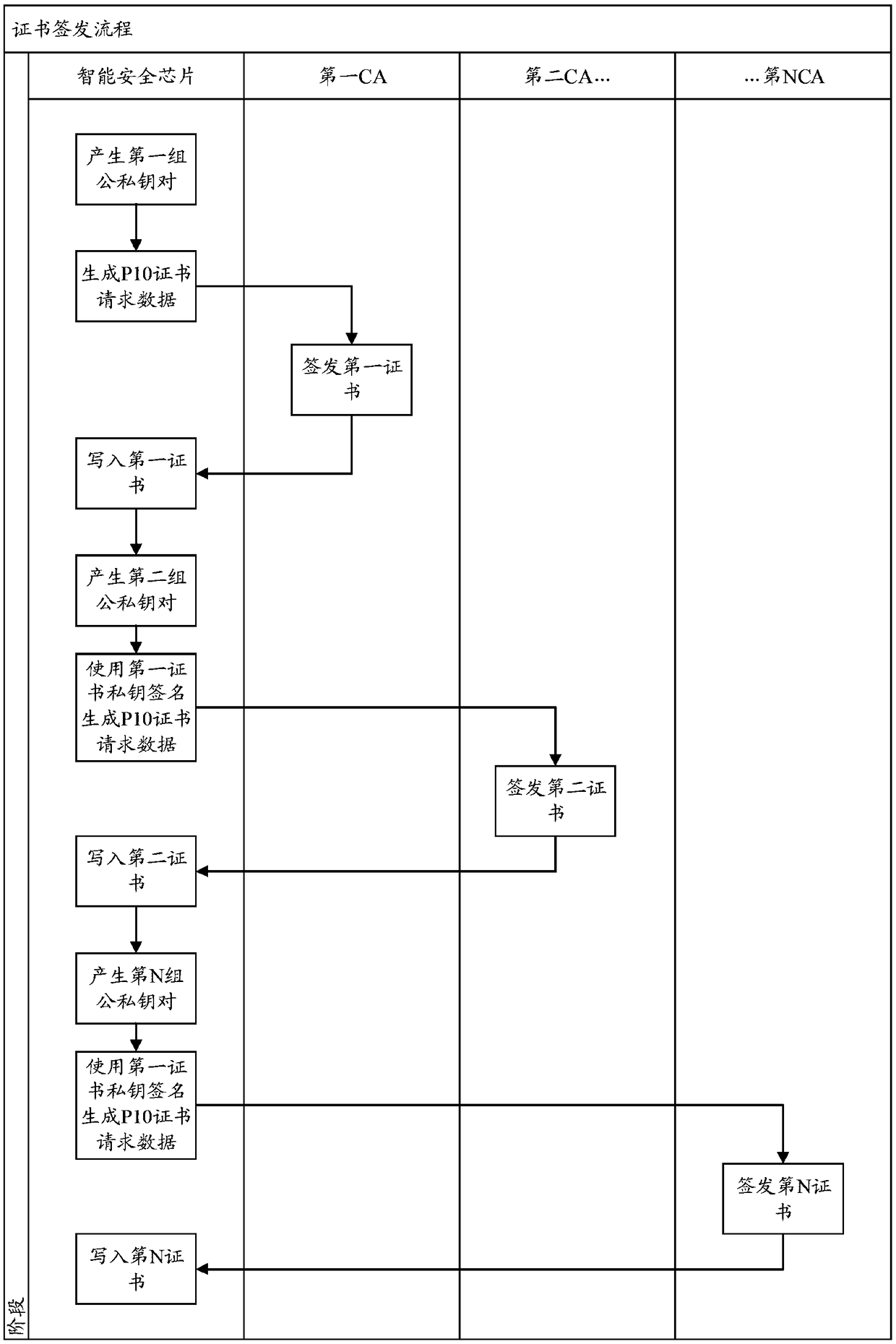
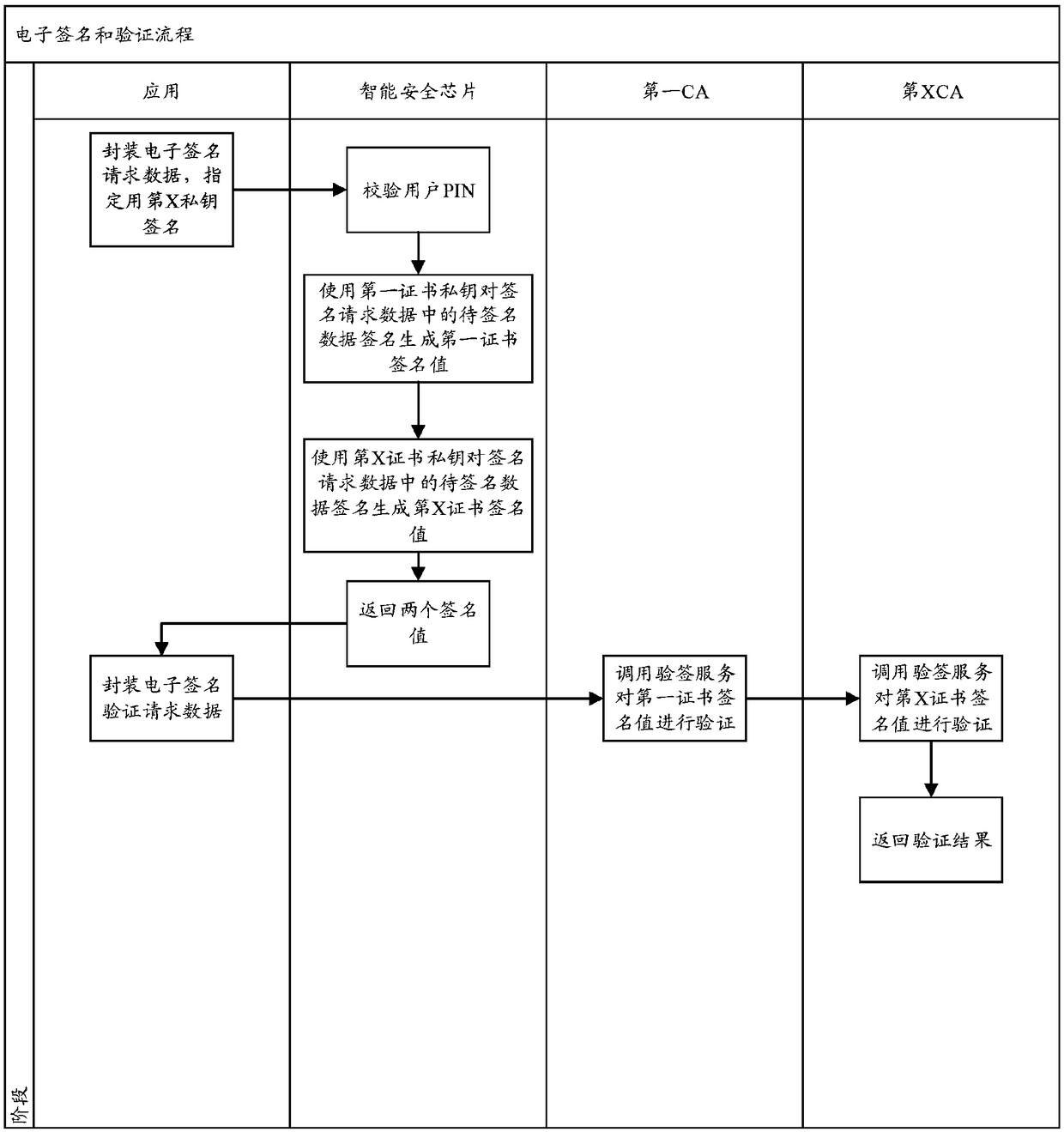
Multi-certificate issuing and verifying method based on intelligent security chip
ActiveCN108900305AAvoid inconvenienceUser identity/authority verificationSignature CodeBusiness data
The invention relates to a multi-certificate issuing and verifying method based on an intelligent security chip, can use a single smart security chip carrier to apply to multiple CAs for certificatesand store the certificates, wherein only one CA (hereinafter referred to as the first CA) needs to perform strict identity checking for certificate issuing and a unique signature PIN code is set, andwhen applying to other CAs for certificates, an applicant only needs to use the certificate issued by the first CA to prove user identity to complete online certificate application. By adoption of themulti-certificate issuing and verifying method based on an intelligent security chip, the problem of previous inconvenience of applying to multiple CAs for certificates and electronic signatures by auser is solved, strict identity checking needs to be performed only once, then the user can apply to multiple CAs for digital certificates, the certificate applied through strict identity checking isused for identity authentication, other certificates can be used for electronic signatures of business systems, and during signature verification, the first certificate is utilized to complete identity authentication first and then a designated certificate is utilized to perform electronic signature verification of business data.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Digital signature method based on multivariable array problem and super logarithm problem
InactiveCN101753310AImprove securityPublic key for secure communicationUser identity/authority verificationSignature CodeDigital signature
A digital signature method based on multivariable array problem and super logarithm problem belongs to encryption and computer technical field; the method includes three parts, namely key generation, digital signature and authentication; the user has two keys, namely a private key and a public key, and the private key cannot be derived by the public key; the private key of the sender is used for generating a file or the signature code of a message, the public key of the sender is used by the receiver to verify the corresponding file or the signature code of the message; the method can effectively defend the attacks employing analysis approaches, has the characteristics of small modulus, high computation speed and public technology, is applicable to the signature and verification of any file and data of mobile phones, computers and communication networks, and is also applicable to the authentication and content acknowledgment of e-government affairs and e-business.
Owner:苏盛辉 +3
EID film card, mobile terminal device and eID authentication system
ActiveCN109525392ASecure and fast loginPrevent leakageUser identity/authority verificationSignature CodeTerminal equipment
The invention provides an eID film card, a mobile terminal device and an eID authentication system. The eID film card comprises: an eID application module for storing eID information and a target signature code corresponding to the eID information. The eID application module prompts the input of a signature code to be verified when receiving a signature instruction, compares the input signature code to be verified with the target signature code, and assembles the signature according to the eID information when the input signature code to be verified matches the target signature code. The eID film card also comprises a communication protocol module electrically connected to the eID application module for information interaction between the eID application module and an external device structure. The eID film card provided by the invention stores the eID information in the eID film card, and the eID film card can be installed in the mobile terminal after being seamlessly attached to theSIM card. When a user performs identity authentication on the mobile terminal, the eID information can be used for authentication, and the user information such as ID number or mobile phone number isnot involved, which can effectively prevent the leakage of user information.
Owner:上海方付通科技服务股份有限公司
Digital signature method based on super logarithm difficult problem, and dual coresidual theorem
InactiveCN1960257AImprove securityFinanceUser identity/authority verificationSignature CodeDigital signature
The method utilizes the level function, super logarithm aporia, twin coresidual theorem to design a public secret key digital signature method. The method consists of key generation, digit signature and ID verification. The user holds two keys, i.e. a private key and a public key. There is no way to derive the private key from the public key. The private key is used to generate the signature code of the document or the message. The public key is used to verify the signature code of the document or the message. This method can prevent attack from existed analysis means effectively. The method can be used for any signature and verification of document and data in computer and comm. network and for ID appraisal or content validation in the electronic government affairs and the electronic business.
Owner:苏盛辉
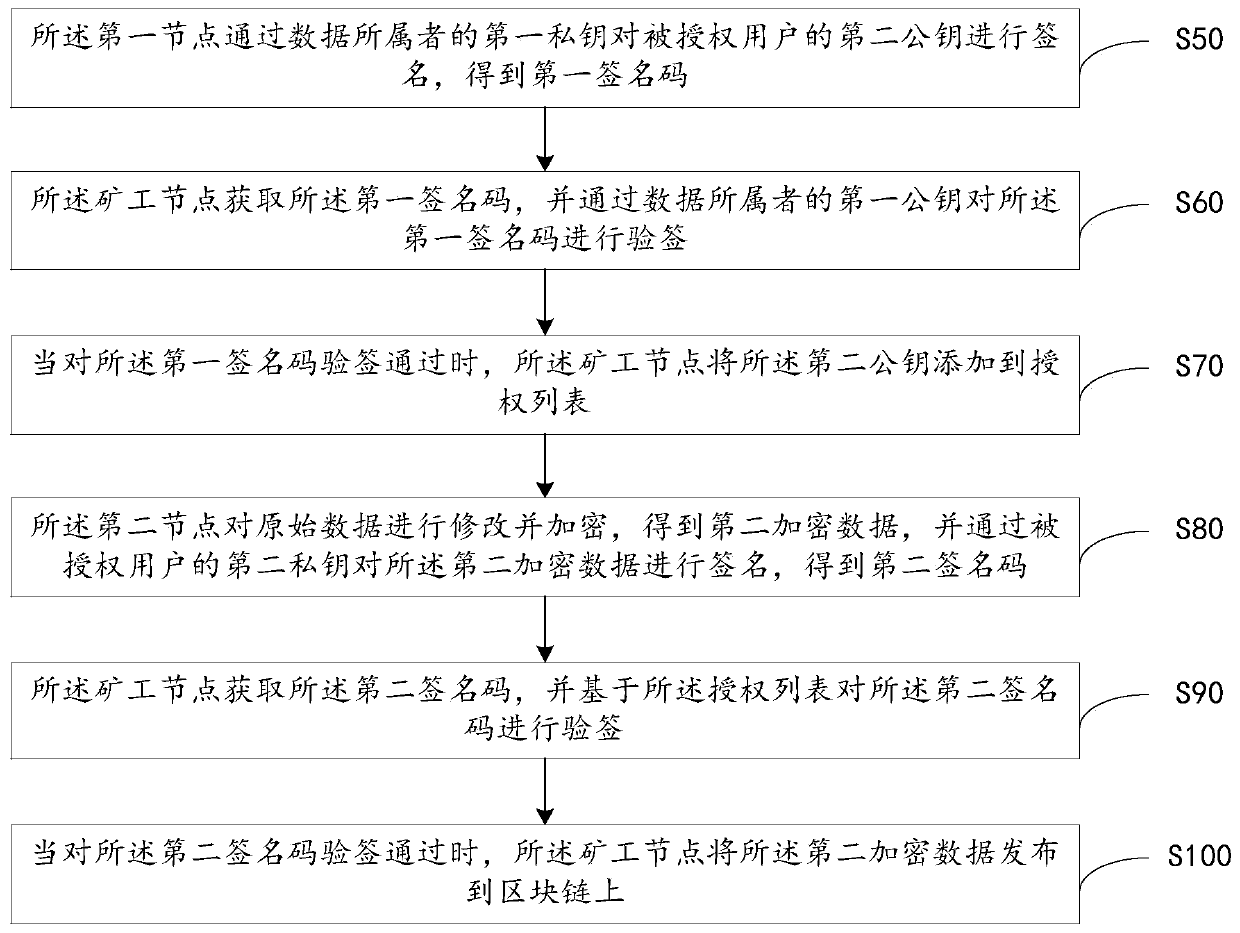
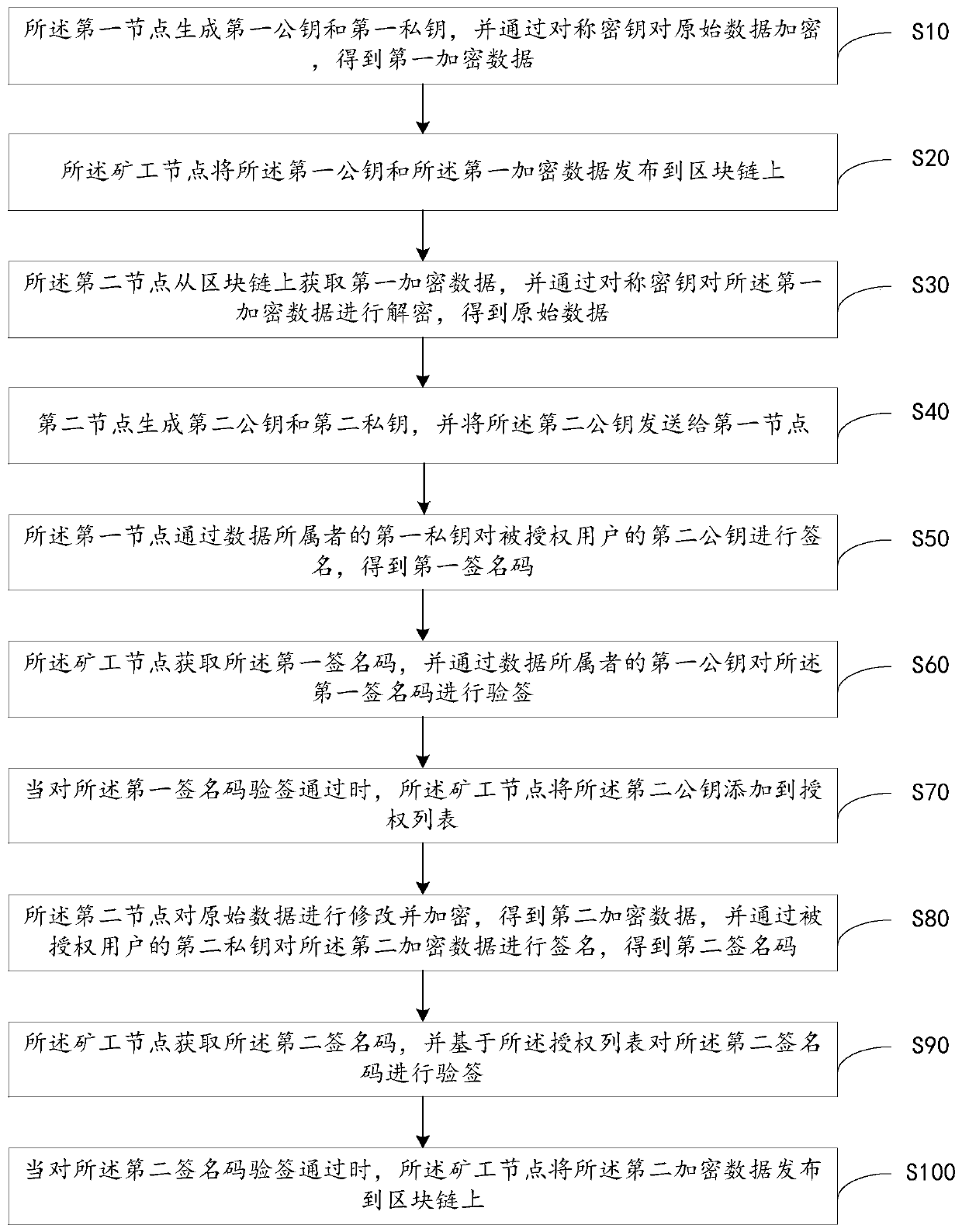
Authorization management method and system and equipment and computer readable storage medium
The invention relates to the technical field of block chains, and discloses an authorization management method and system, equipment and a computer readable storage medium. The authorization management method comprises the steps that a first node signs a second public key through a first private key to obtain a first signature code, then the first signature code is subjected to signature verification through the first public key, and when the signature verification is passed, the second public key is added to an authorization list; and the second node signs the second encrypted data through asecond private key to obtain a second signature code, then the second signature code is verified based on the authorization list, and when the second signature code passes the signature verification,the second encrypted data is released to the block chain. Through the method and the device, the owner of the data grants the authority of modifying the data to the authorized party on the basis thatthe owner of the data does not provide the private key to the authorized party, so that the owner of the data always keeps the absolute control authority of the data, and the data security is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Roaming authentication method for a GSM system
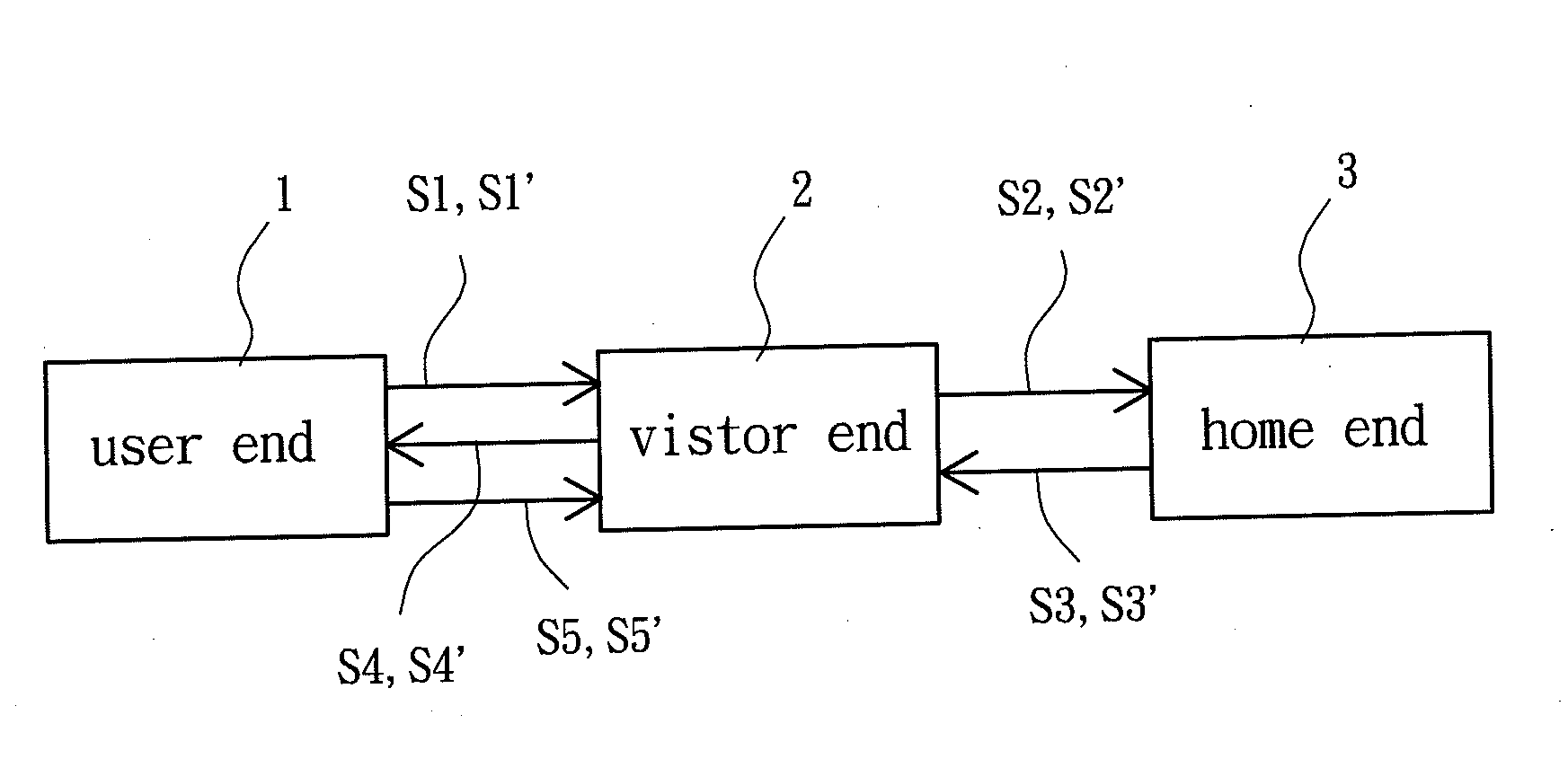
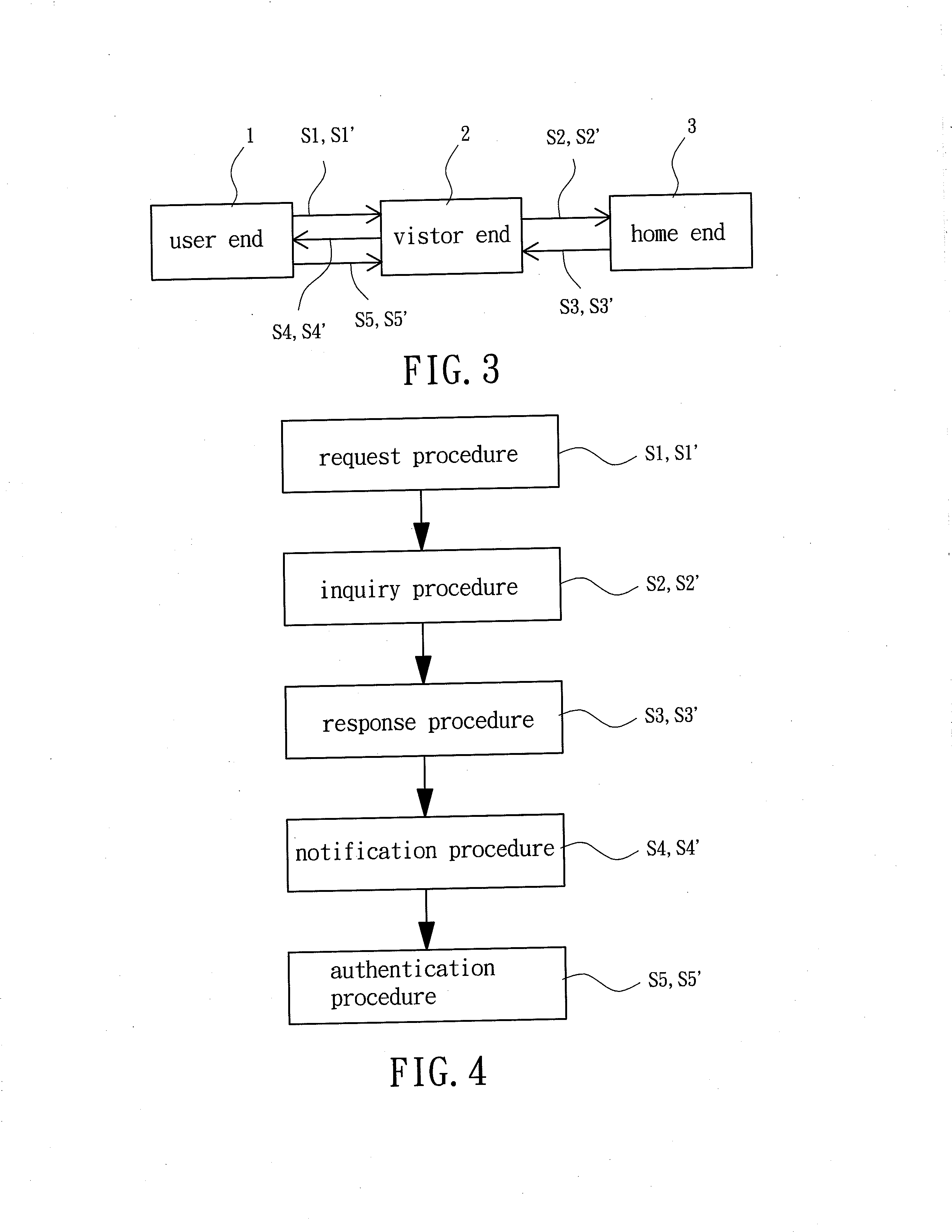
InactiveUS20130178191A1Provide mechanismUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSignature CodeGSM
A roaming authentication method for a GSM system is disclosed. The method sends an IMSI of a user end to a visitor end, generates a challenge code, and sends the IMSI and the challenge code to a home end. The method further generates a random code, a signature code and a communication key and combines them into an authentication data. The method further generates and sends a response code to the visitor end. The user end generates and sends the authentication signature code to the visitor end for authentication purposes. In another embodiment, the visitor end sends one more challenge code to the home end. The home end generates an authentication key that is stored in the visitor end and used to generate an authentication code. The authentication code is sent to the use end which generates and sends an authentication signature code to the visitor end for authentication purposes.
Owner:NAT CHENG KUNG UNIV
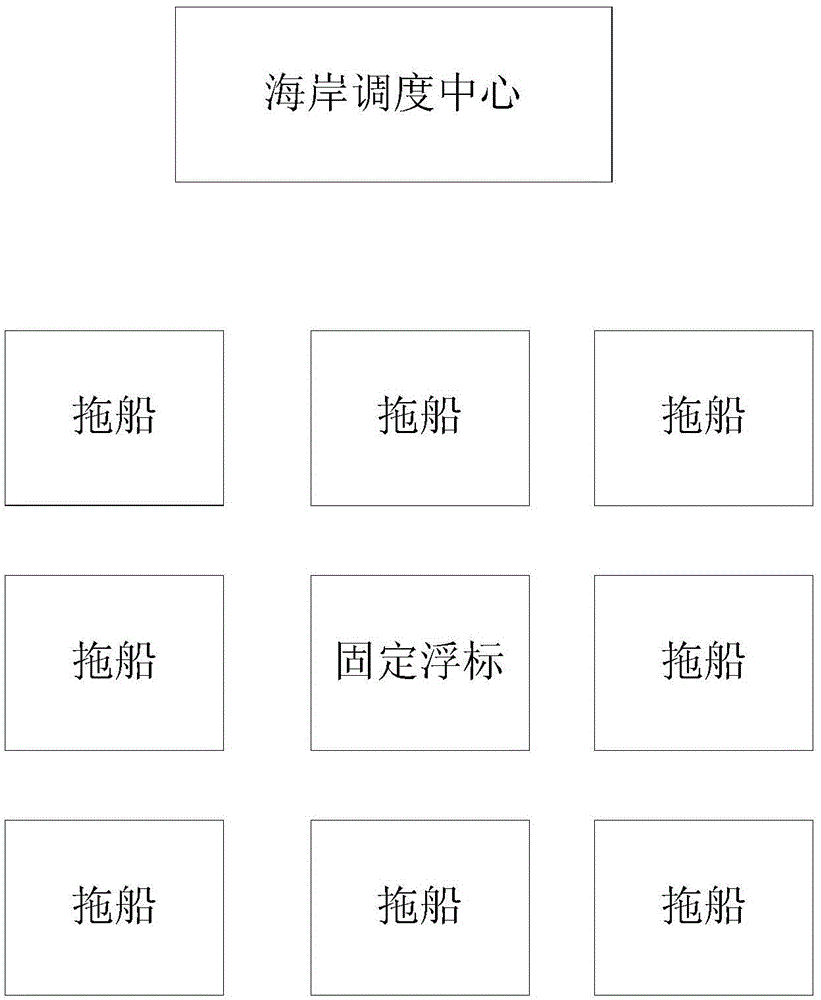
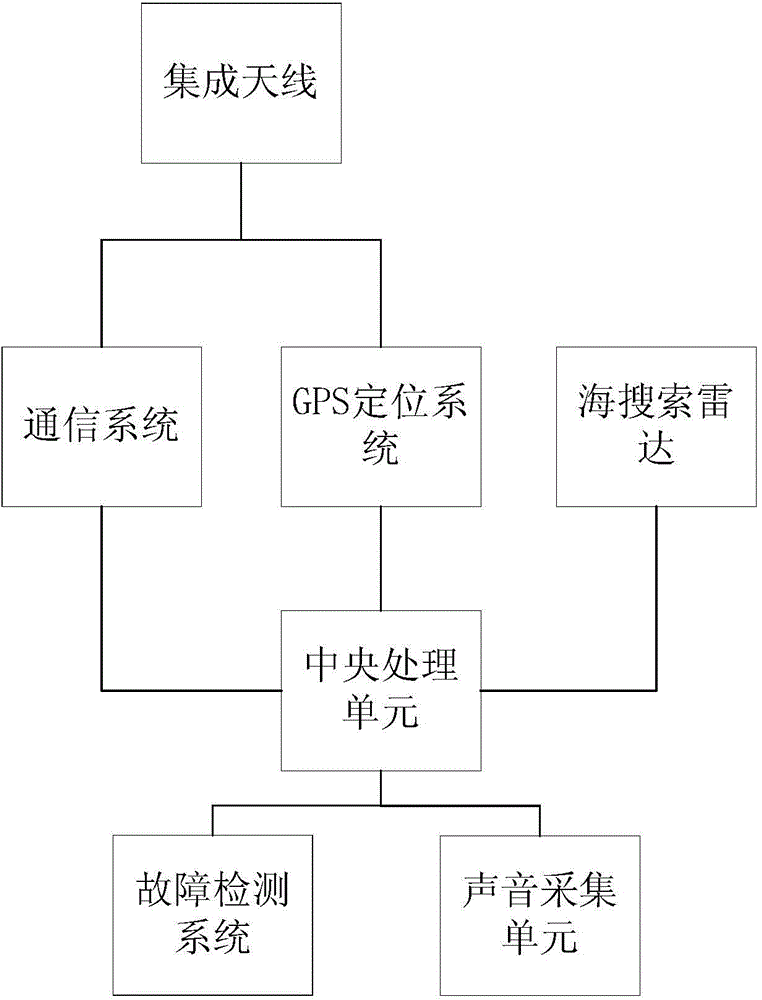
Remote towboat fault diagnosis system
InactiveCN104677488AReal-time effective masteryImprove accuracyTransmission systemsSubsonic/sonic/ultrasonic wave measurementSignature CodeRadar
The invention discloses a remote towboat fault diagnosis system, which comprises an integrated antenna with a satellite signal receiving function, a GPS (Global Position System) for acquiring a current towboat position, a fixed buoy arranged on an operation sea area of a towboat and provided with a radar responder, an airborne-radar for sea search arranged on the towboat, a central processing unit, a fault detection system in communication connection with a ship bus, a fault detection unit communicated with the bus, and a sound acquisition unit for acquiring sound characteristics of engine operation, wherein the airborne-radar for sea search is used for transmitting a radar wave, receiving a back wave of the radar responder and acquiring an own position; the central processing unit is used for receiving current towboat position information acquired by the GPS and a return position signal of the airborne-radar for sea search and calculating the current towboat position; the fault detection system is used for acquiring a fault signature code of the current ship through the bus; meanwhile, through the fault detection unit and the sound acquisition unit, a remote center can master the operation state of the towboat in real time. The adopted technology is mature and reliable, so that the remote towboat fault diagnosis system is very applicable to be popularized and applied in large area.
Owner:DALIAN JUNFANG TECH
Digital signature method based on non-homogeneous ultra-increasing sequence
InactiveCN101369888AImprove securityKey distribution for secure communicationPublic key for secure communicationSignature CodeDigital signature
The invention belongs to the cryptography and the computer science. A public key digital signature method is worked out based on a non-uniform super increasing sequence and super logarithm puzzles comprising a key generation part, a digital signature part and an authentication part; the user has two keys, that is a private key and a public key, and the private key is not calculated from the public key; the private key is used for generating a signature code of a file or a message, the public key is used for authenticating the signature code of the file or the message. The method of the invention can effectively defend against the attack of the prior analysis means and be suitable for the signature and the authentication of any files in the computer and communication network, the personal identification and the content confirmation in the e-government and the e-commerce and the authentication and the anti-counterfeiting of the finance bills and relative certificates in the real world.
Owner:苏盛辉 +2
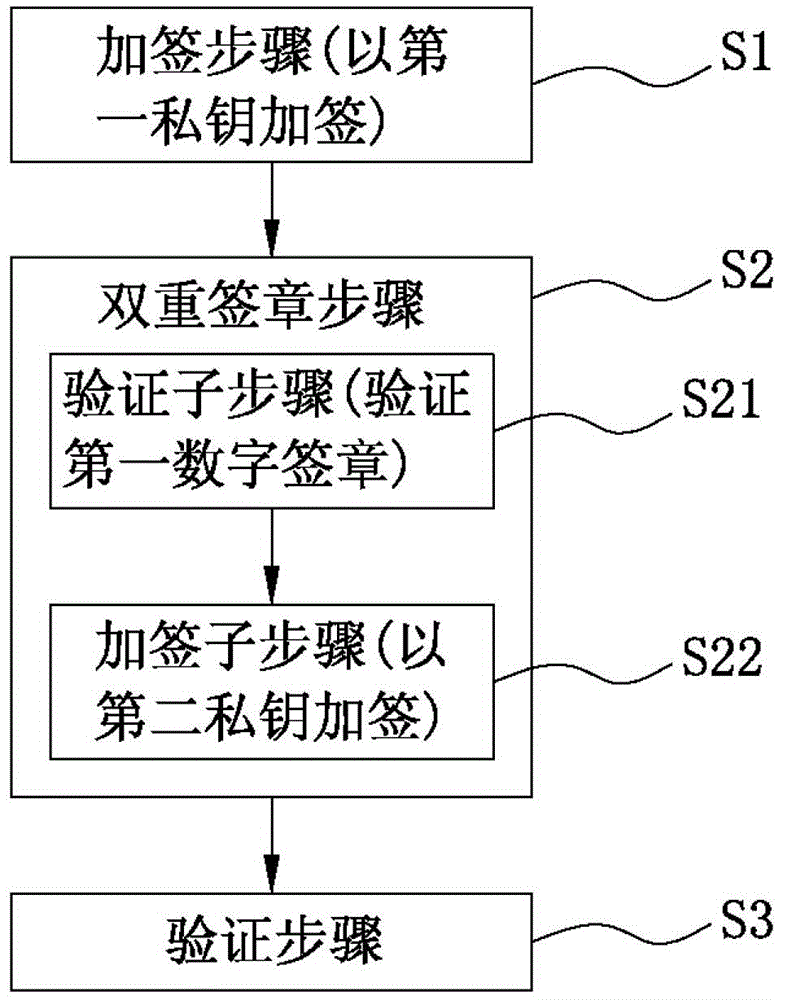
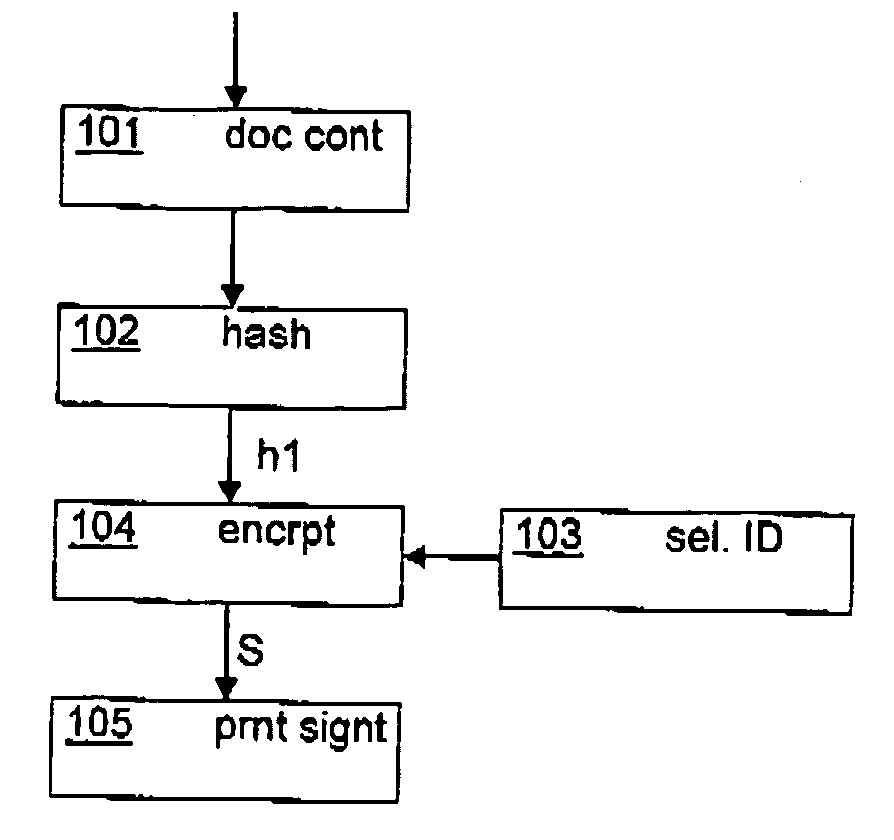
Methods and systems for signing physical documents and for authenticating signatures on physical documents
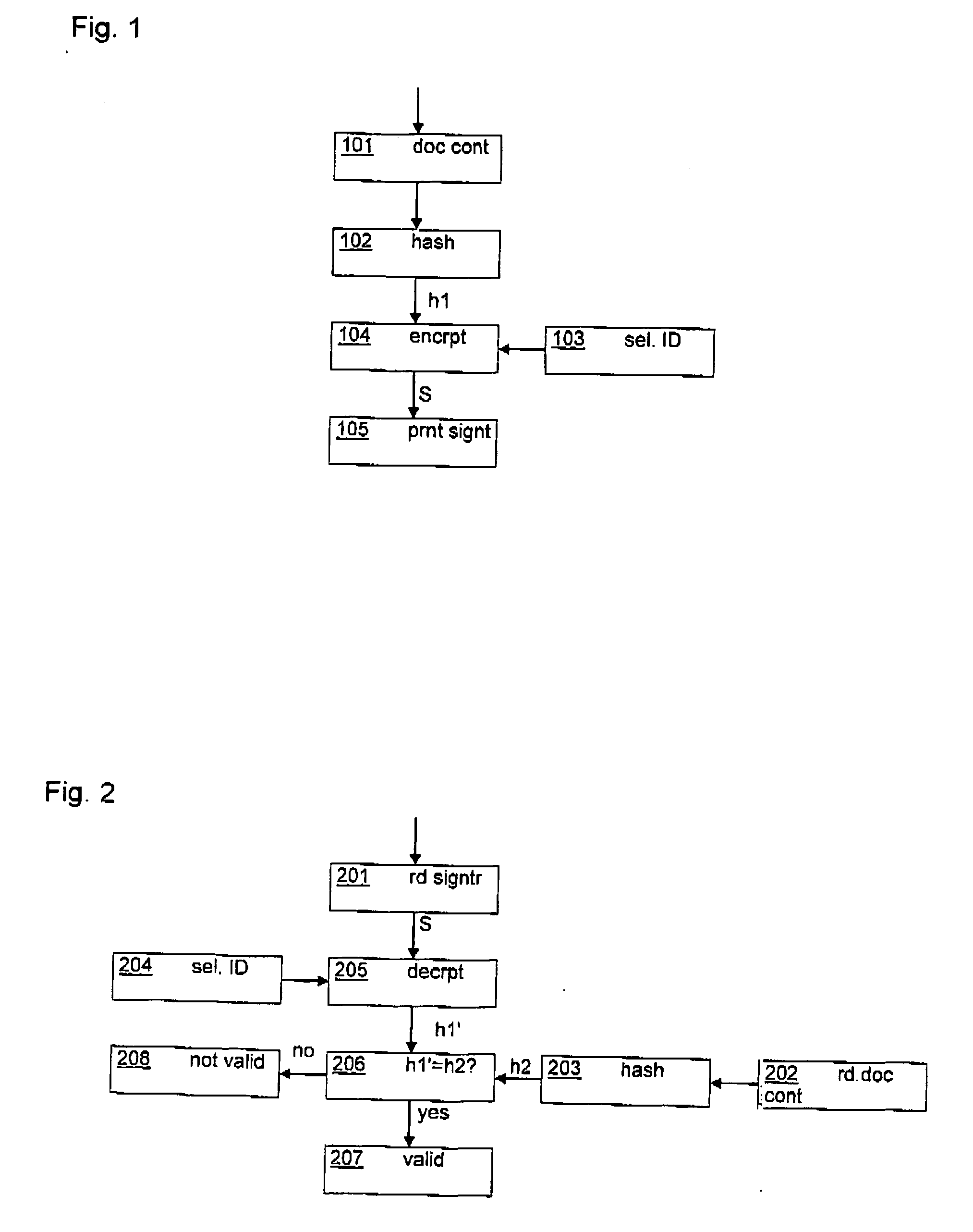
InactiveUS20070016789A1User identity/authority verificationPayment architectureSignature CodePaper document
In a method for providing physical documents with a signature, a document code is derived from at least a part of a content of the physical document. A signature code is derived at least from the document code and from an identification code of a signing party. The physical document is provided with a signature marking representing the signature code. Optionally, the physical document is provided with a document marking representing the document code. A signature provided on a physical document may be authenticated. During authentication, a signature marking provided on the physical document is detected. The signature marking represents a signature code. Then, the signature code is derived from the detected signature marking. Content data representing at least a part of the content of the physical document is received and a first document code is derived from the content data. Then, a relationship between the signature code, an identification code of a signing party and the first document code is determined. The signature is validated in case the relationship satisfies a validation criterion.
Owner:NEOPOST
Crosscorrelation interference mitigating position estimation systems and methods therefor
ActiveUS8548106B2Reduce time and processing powerReduce complexityError preventionLine-faulsts/interference reductionSignature CodeSelf adaptive
Provided is a method that includes dynamically adjusting a GPS signature code to minimize the interference (e.g., the cross-correlation interference) experienced due to one or more other GPS signals. Further provided is a method that includes adjusting the complexity of an adaptive solution to reduce the time and processing power associated with tracking a GPS signal.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Document circulation monitoring method and system
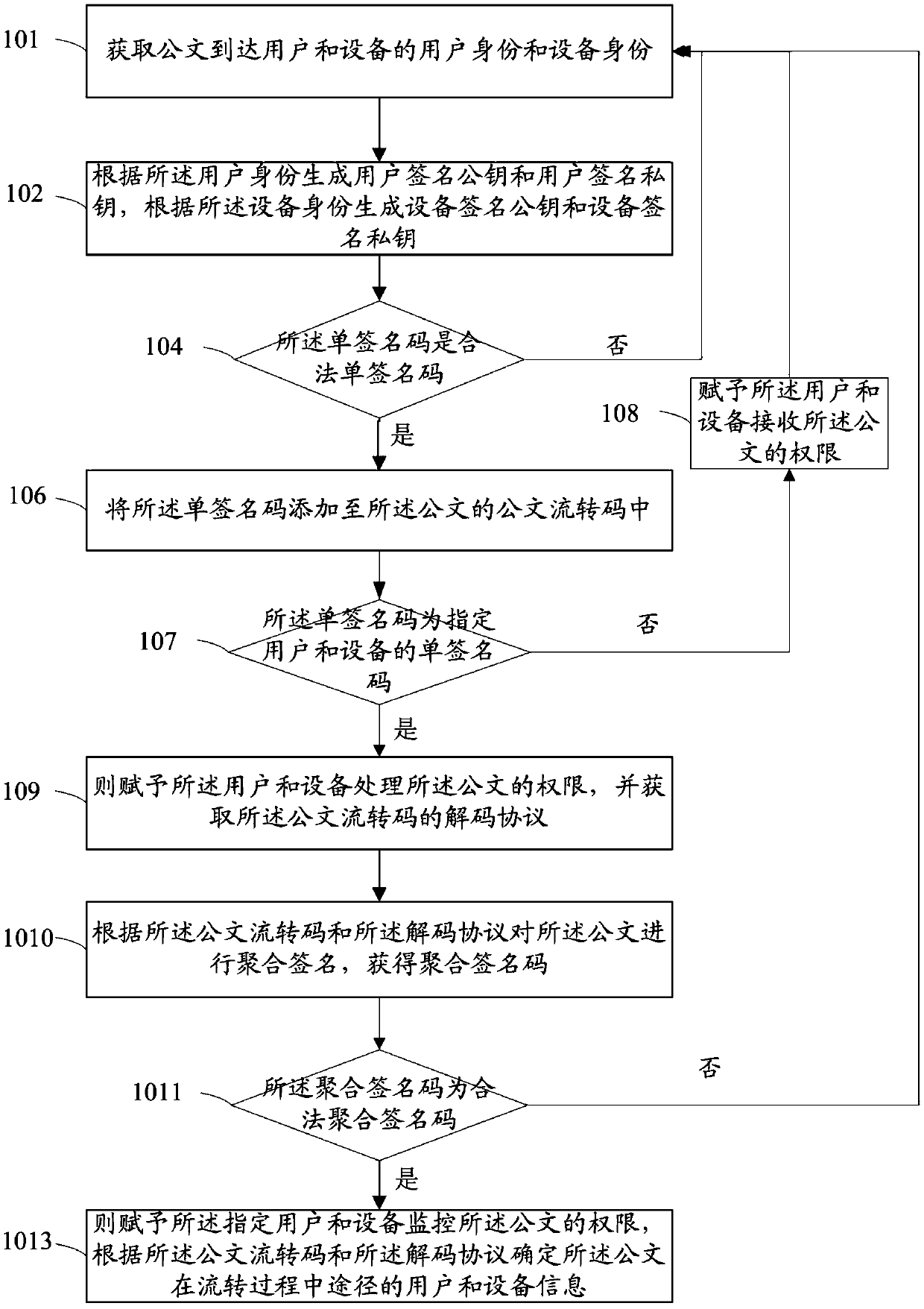
InactiveCN109658048AIntegrity guaranteedRealize monitoringOffice automationSignature CodeComputer science
The invention discloses a document circulation monitoring method and system. The monitoring method comprises: respectively signing for an intermediate user and a device during the flow of the document, generating a single signature code related to the user and the device, and generating a single signature code, adding a respective signiature code into the flow transcoding process of the document,performing aggregation signature according to the document flow transcoding and decoding protocol by a receiver of the flow process, adopting an aggregation signature mode so that a user and a deviceof the receiver acquires the authority of monitoring the document and determining user and device information in the process of document flow and sending user and device information in the process ofdocument flow into the user and the device of the receiver. The single-signature process and the aggregated signature of the present invention not only restrict the users of the document circulation process, but also constrain the device using the official document to ensure that the designated user can operate the official document on the designated device, thereby realizing the process of document circulation. The users and devices in the middle channel are monitored.
Owner:王亚萍
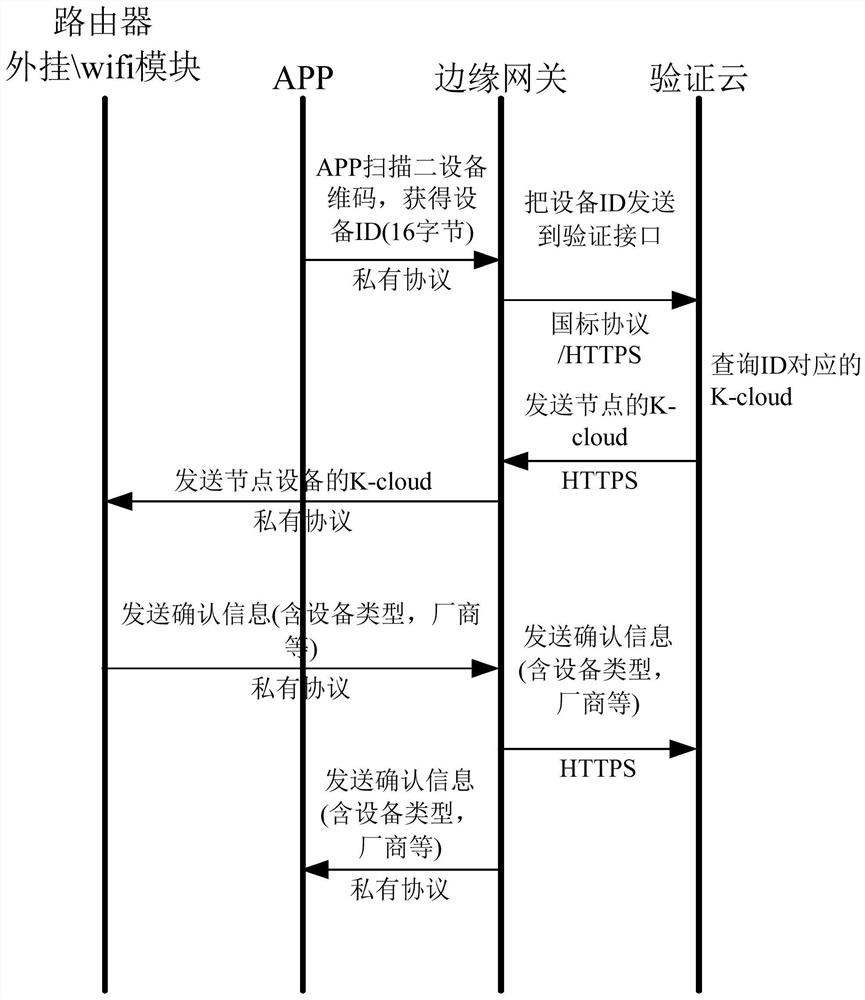
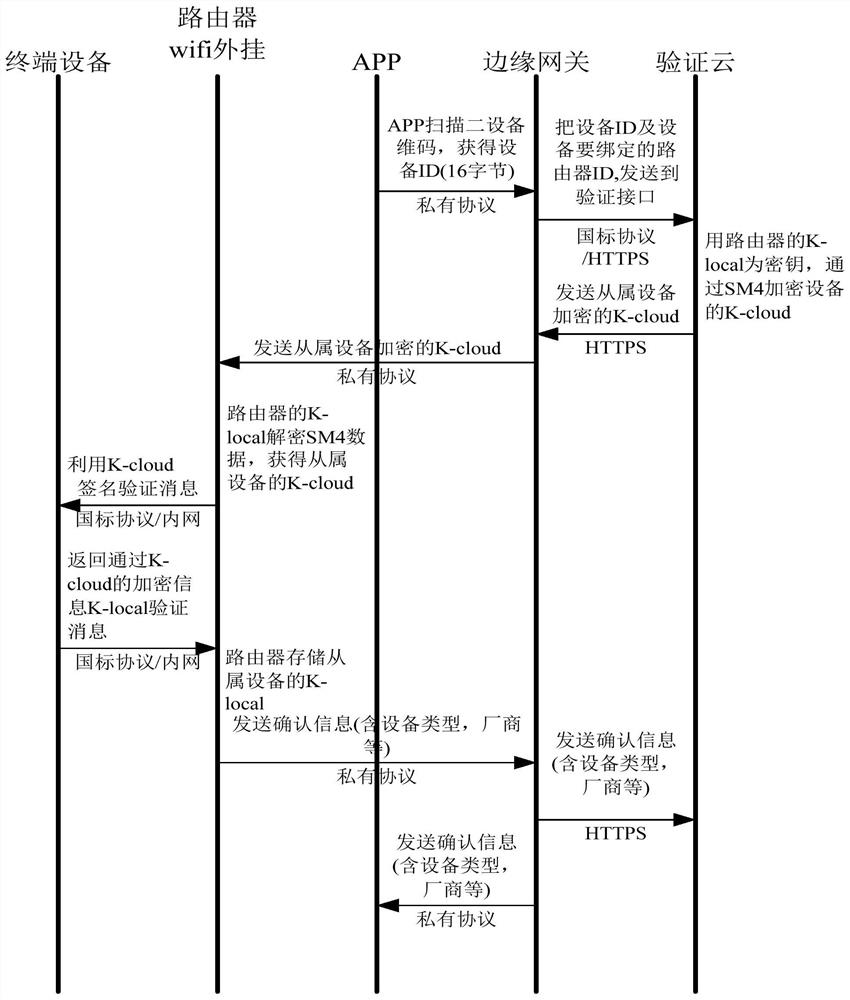
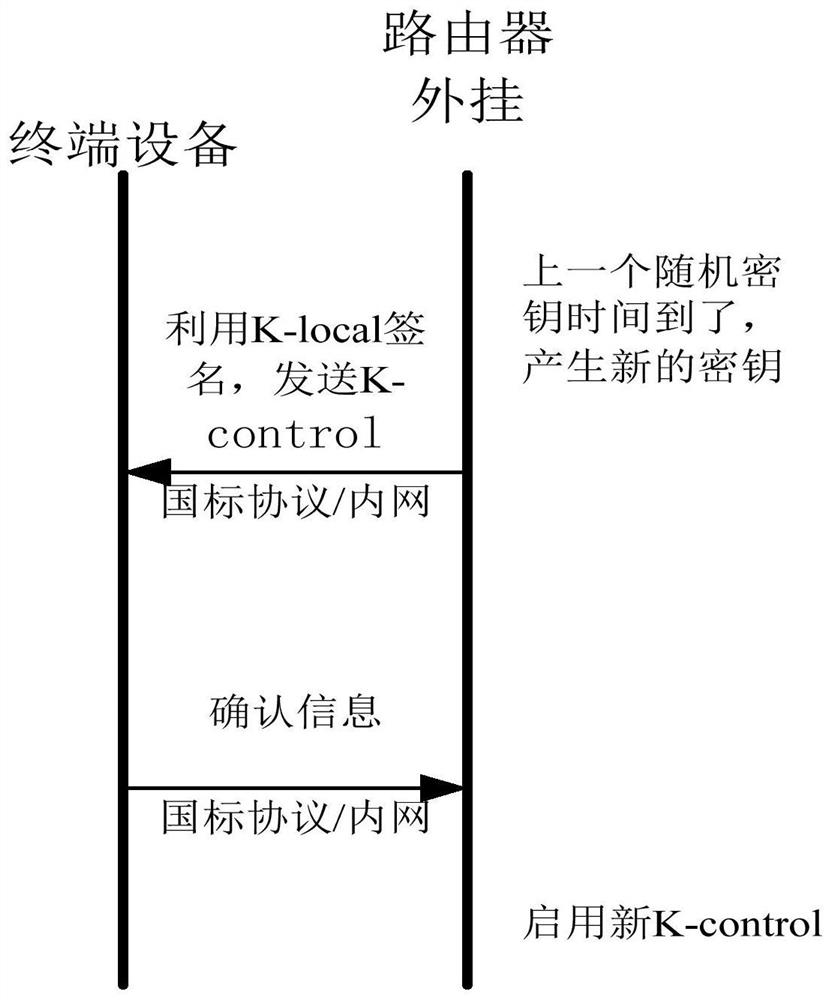
Security verification method and device for household edge computing system
ActiveCN112822274AEnsure safetyReliable data security supportUser identity/authority verificationSignature CodeIdentity recognition
The invention discloses a security verification method for a household edge computing system, and the method comprises the steps: constructing a verification cloud which stores an identity identification code and a cloud verification signature code of a household appliance slave device, and an identity identification code, a cloud verification signature code and a local verification signature code of a communication node device; and when the edge node, the communication node equipment and the household appliance slave equipment are in communication connection, establishing communication connection between the edge node and the communication node equipment as well as between the communication node equipment and the household appliance slave equipment through the cloud verification signature code and the local verification signature code, and controlling and releasing data verification. According to the invention, two-stage security protection can be realized, so that all networked household appliances have self-protection and system-level protection capabilities, and the security of household big data generated by the Internet of Things is improved.
Owner:苏州蓝赫智能科技有限公司
Data transmission method and system
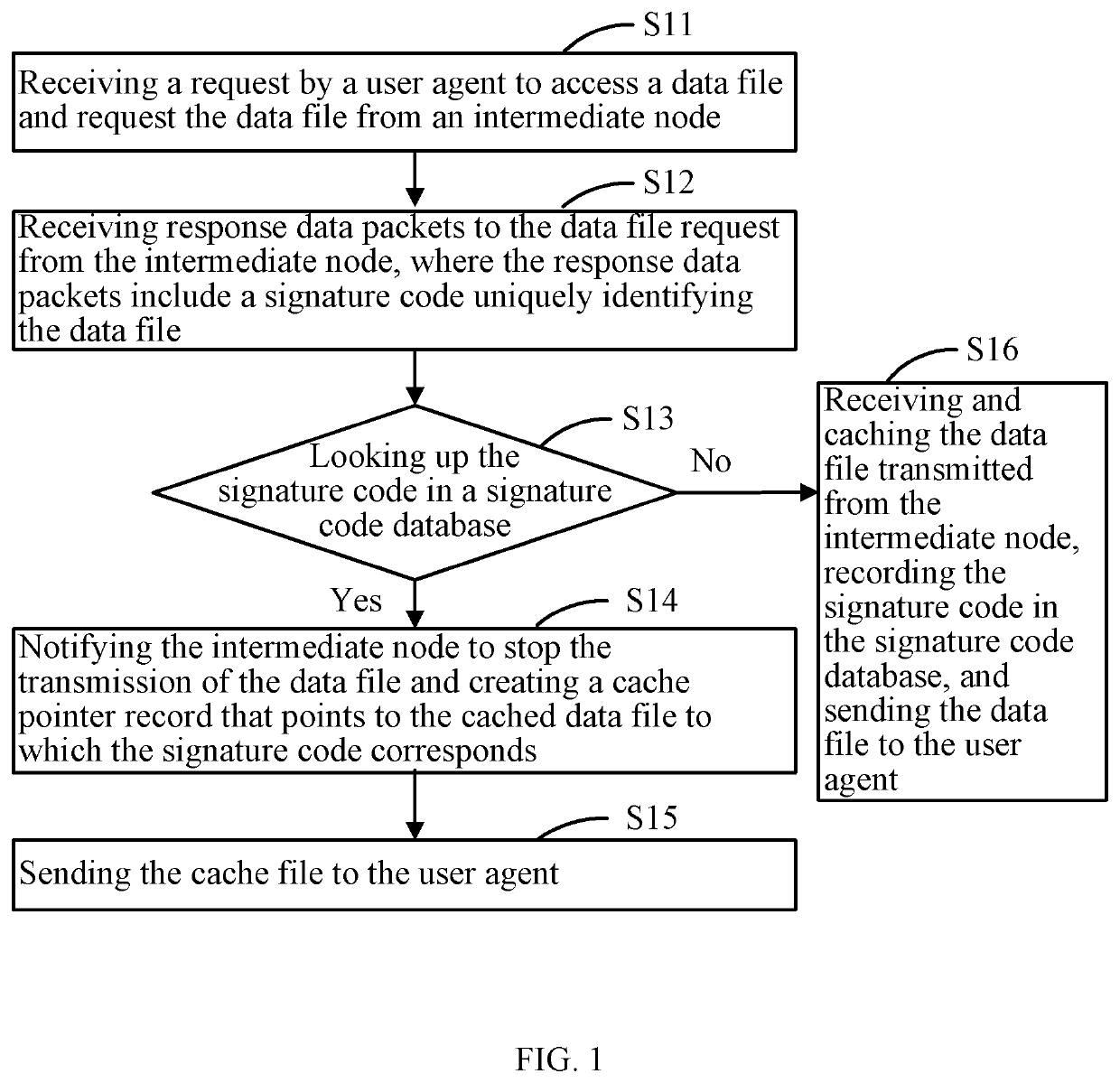
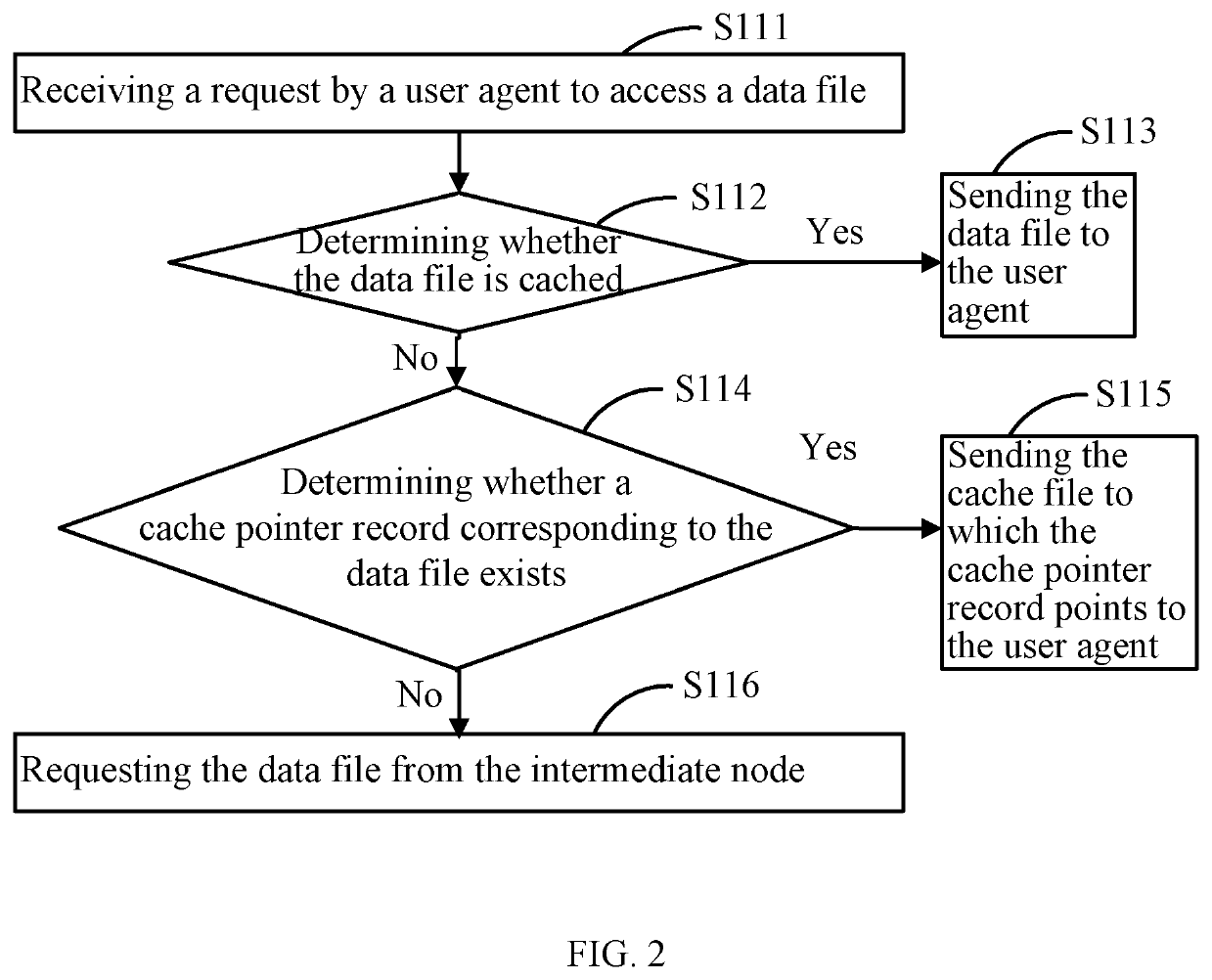
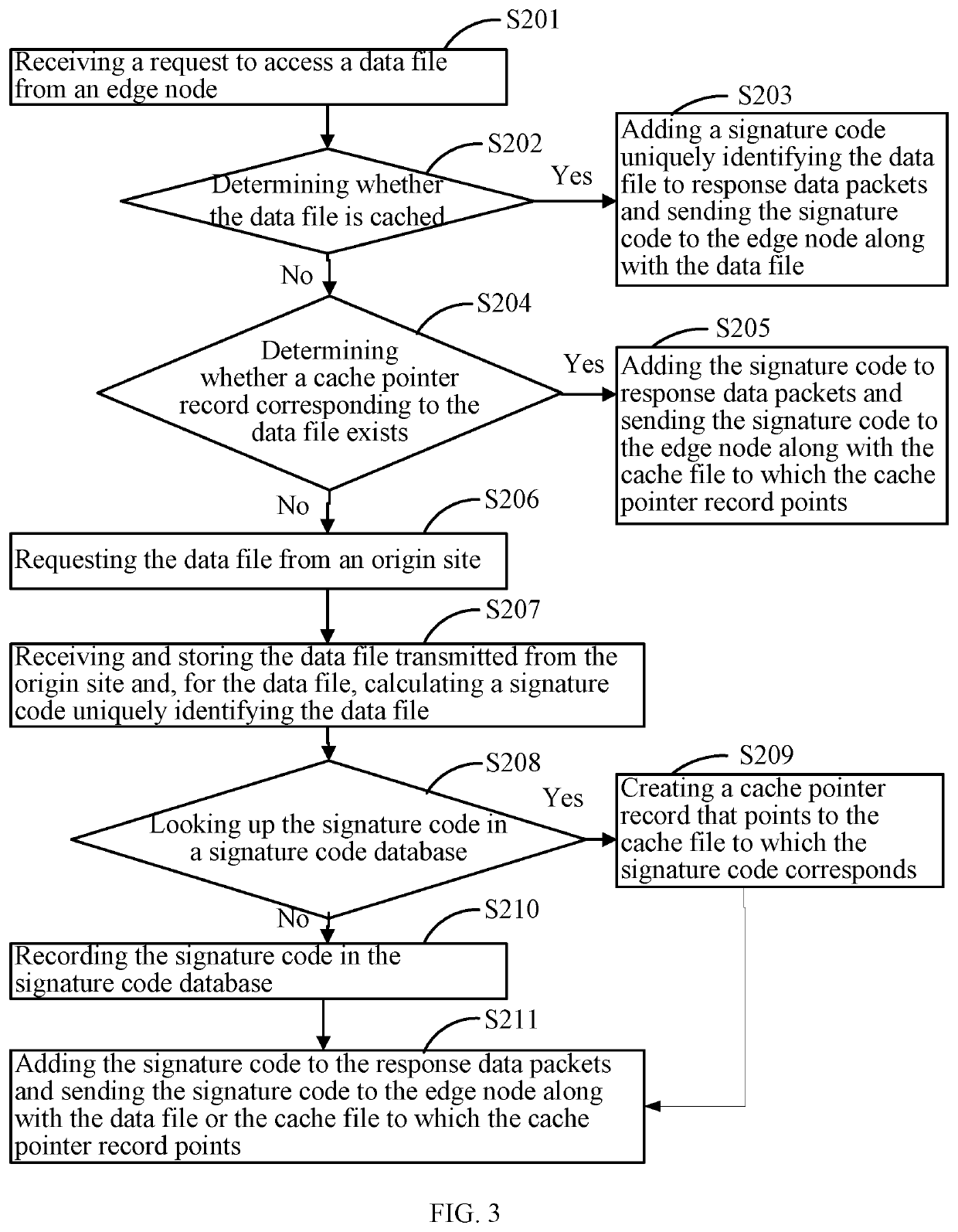
InactiveUS20210203745A1Avoid spreadingTransmissionSpecial data processing applicationsData packSignature Code
The present disclosure provides a data transmission method and system. The method includes: requesting to access a data file from an intermediate node; receiving response data packets of the data file from the intermediate node, where the response data packets include a data file signature code uniquely identifying the data file; looking up the signature code in a signature code database; when the signature code is present in the signature code database, notifying the intermediate node to stop the transmission of the data file, and creating a cache pointer record to point to a cached data file corresponding to the signature code; and sending the cached data file to a user agent.
Owner:CHINANETCENT TECH
Rach receiving apparatus
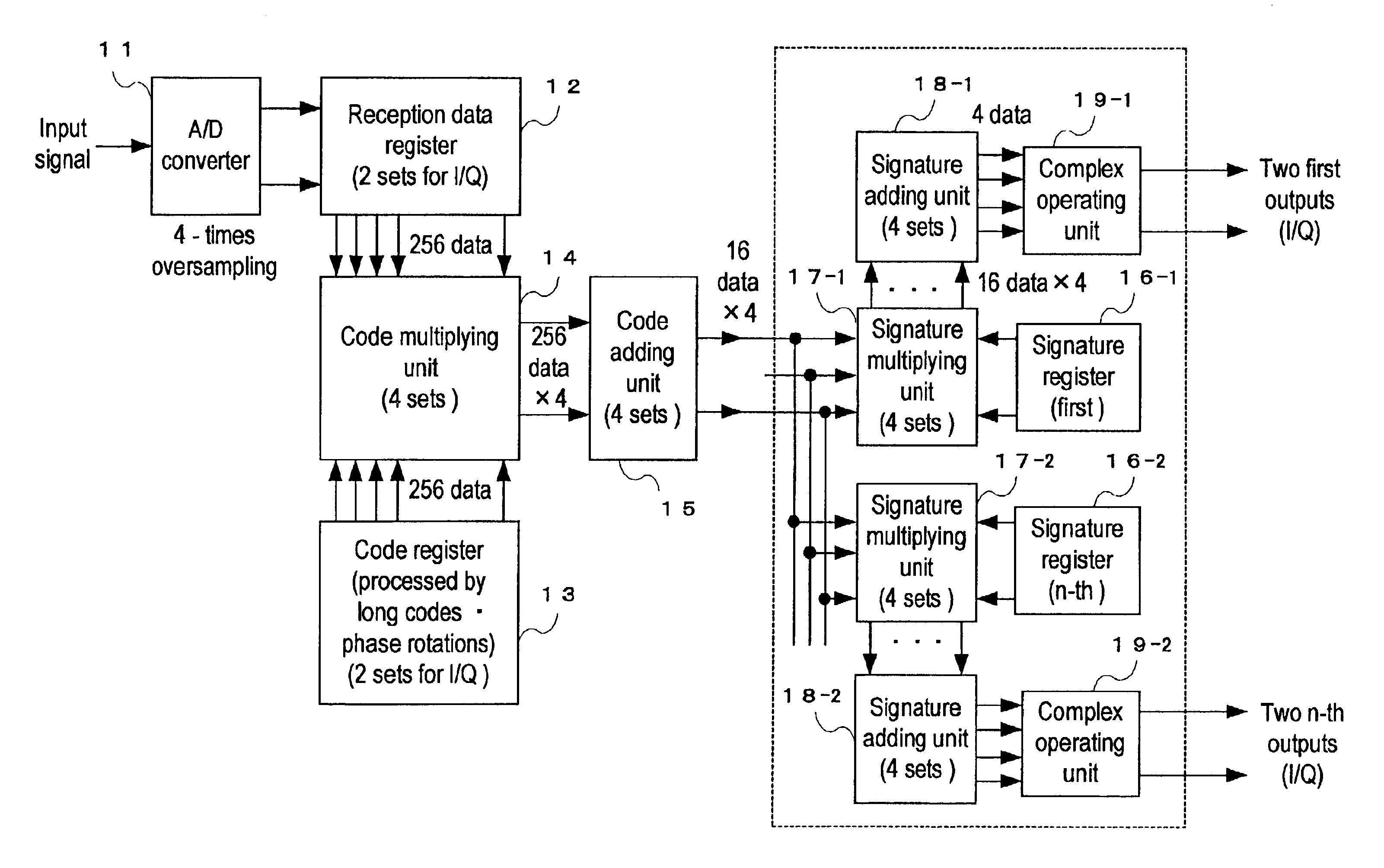
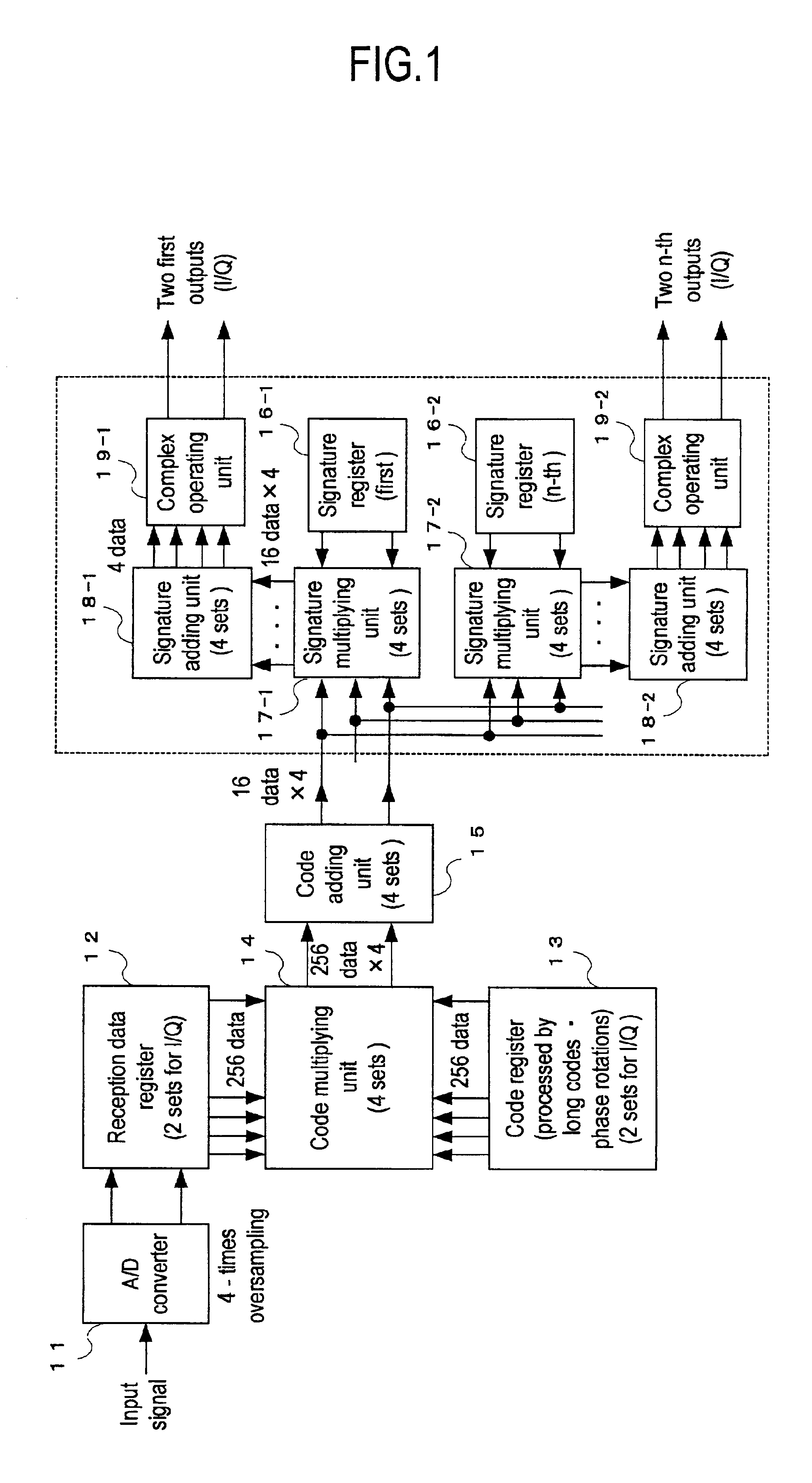
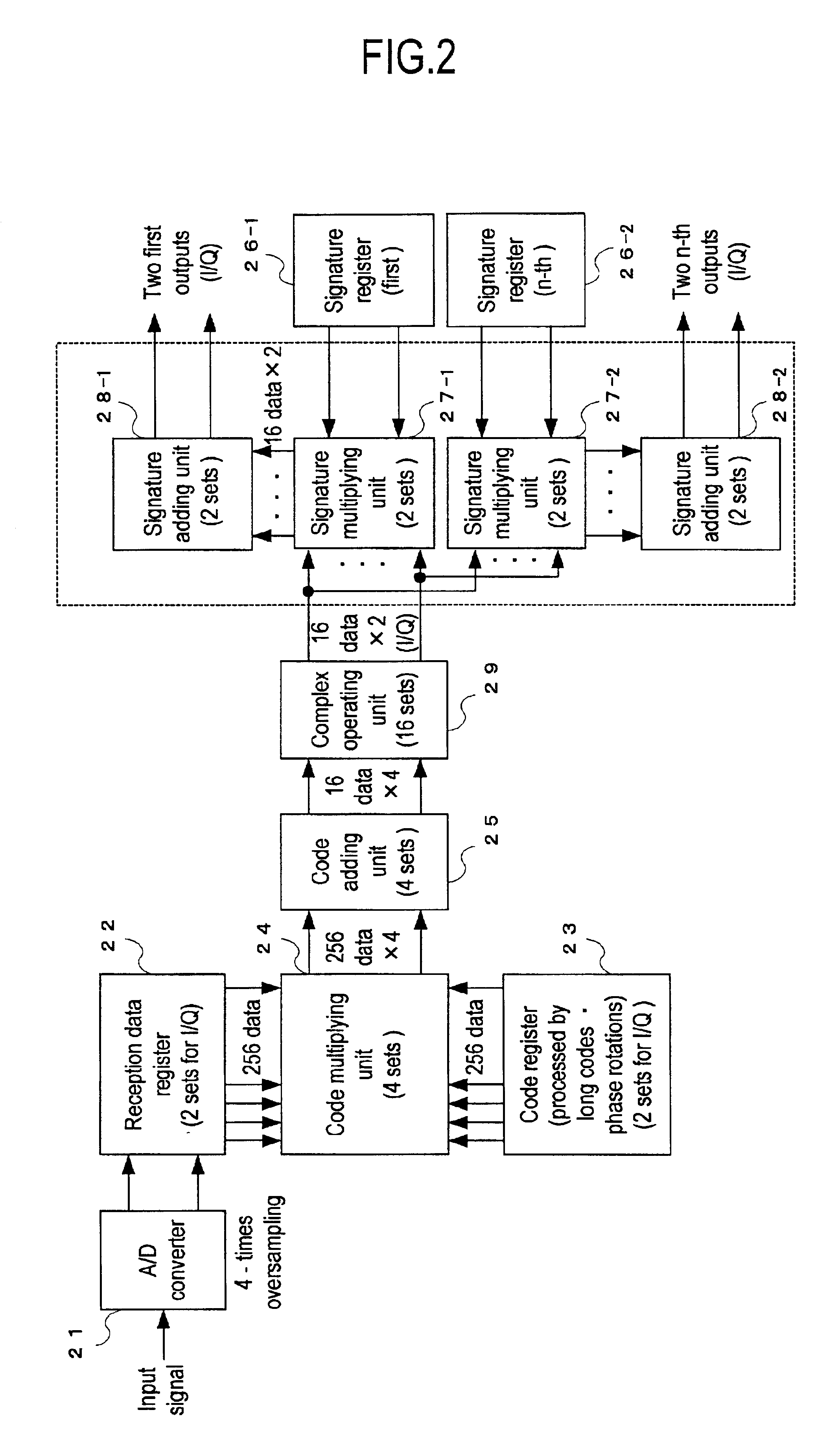
InactiveUS6928103B2Accurate outputReduce circuit sizeSecret communicationMulti-frequency code systemsComputer hardwareSignature Code
The present invention provides an RACH receiving apparatus in which the components can be constructed in a small scale.The RACH receiving apparatus performs a demodulation processing so as to divide it into two stages of a first demodulation processing for multiplying reception data of complex-modulated RACH by sign codes subjected to an arithmetic processing with long codes and phase rotations in a code register multiplying unit, and a second demodulation processing for adding multiplication results every chips and multiplying addition results by signature codes in a signature multiplying unit.
Owner:KOKUSA ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com