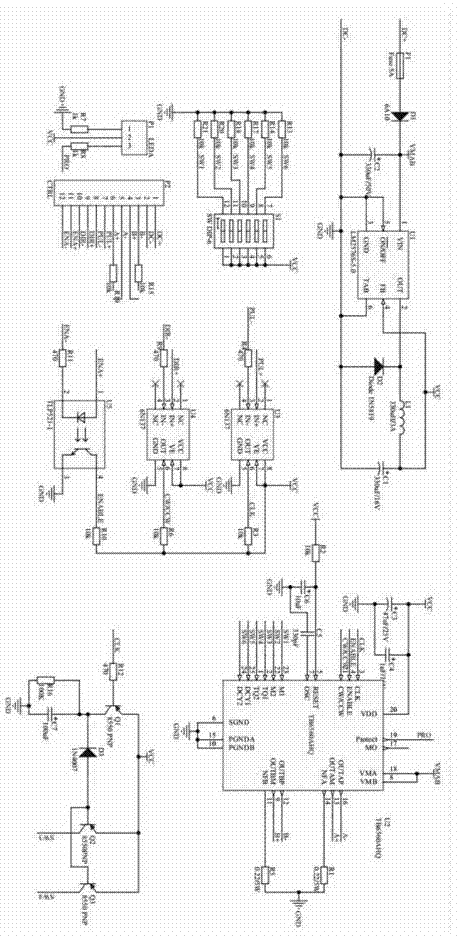
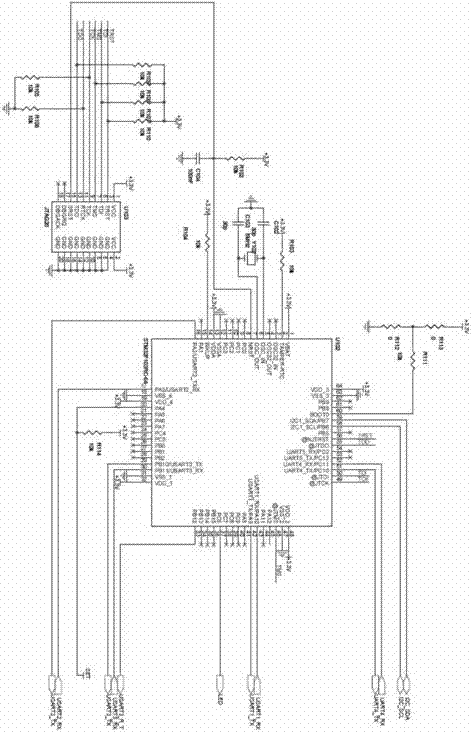
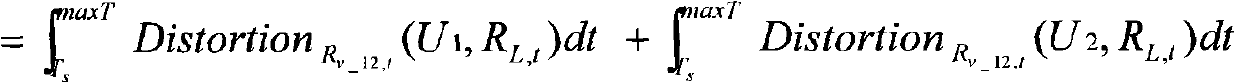Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
552results about How to "Avoid Privacy Leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
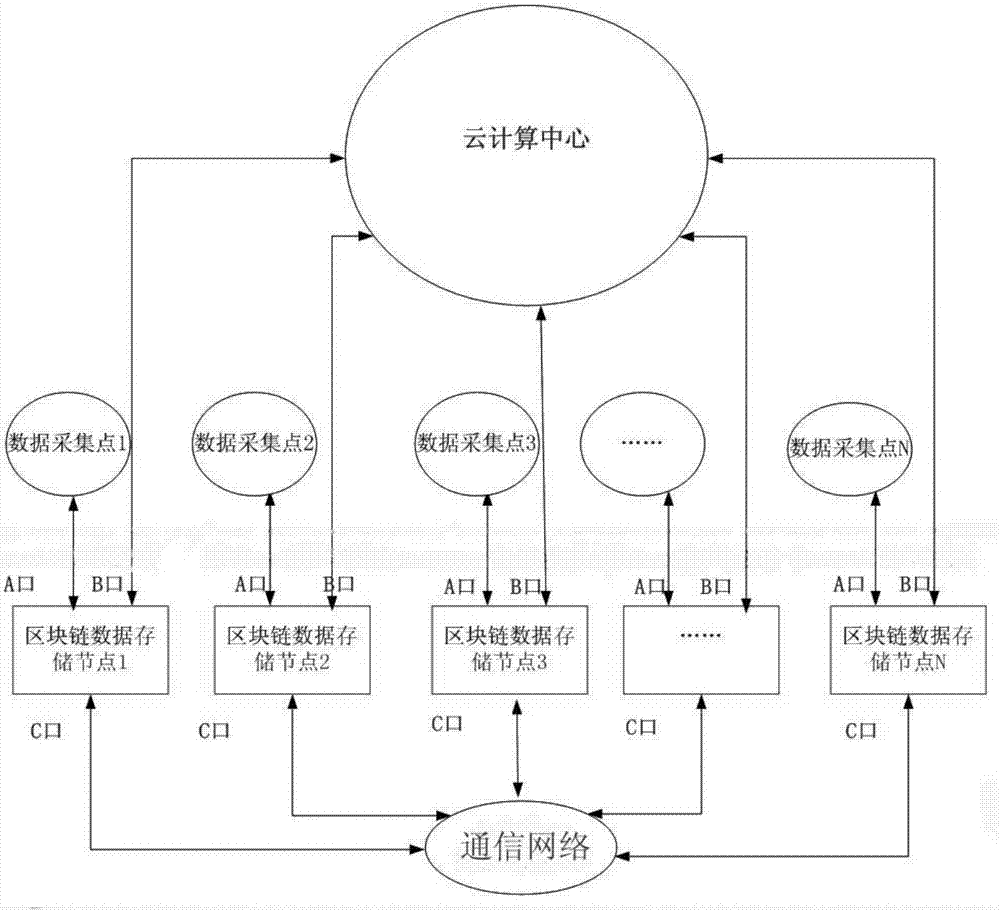
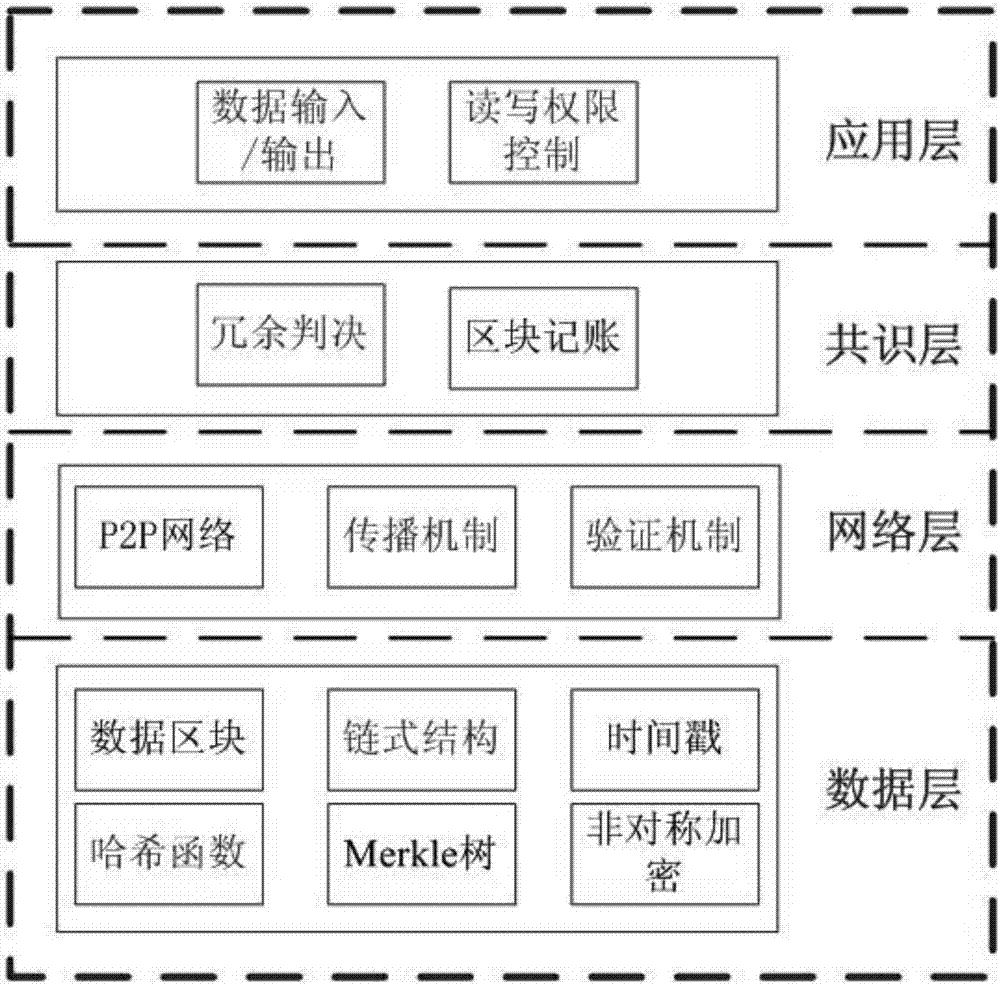
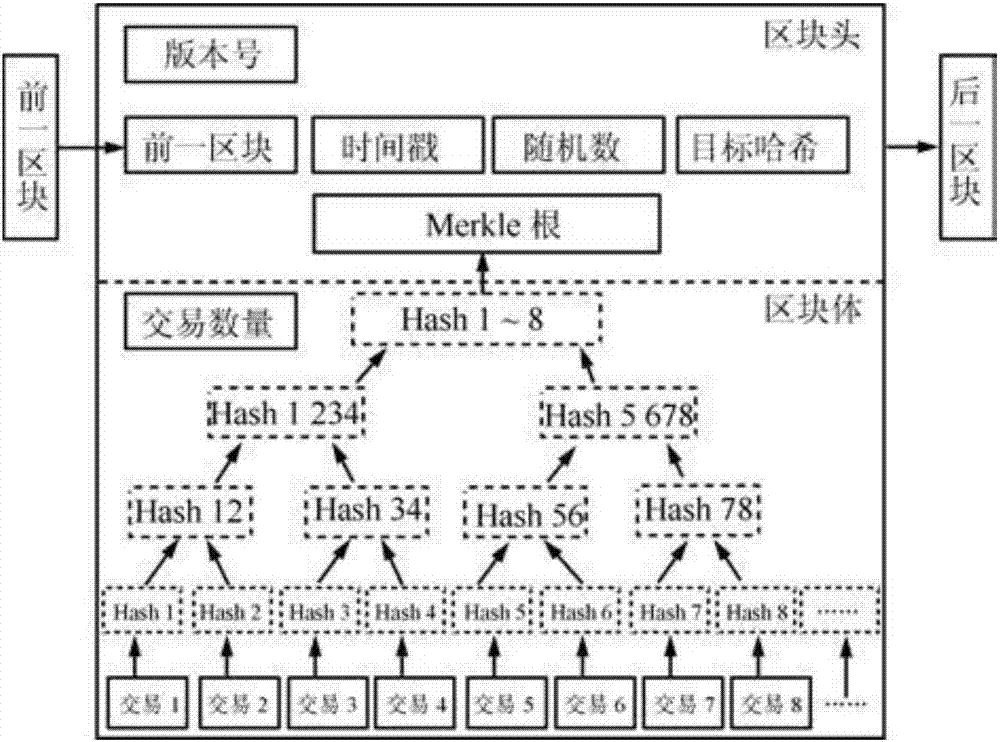
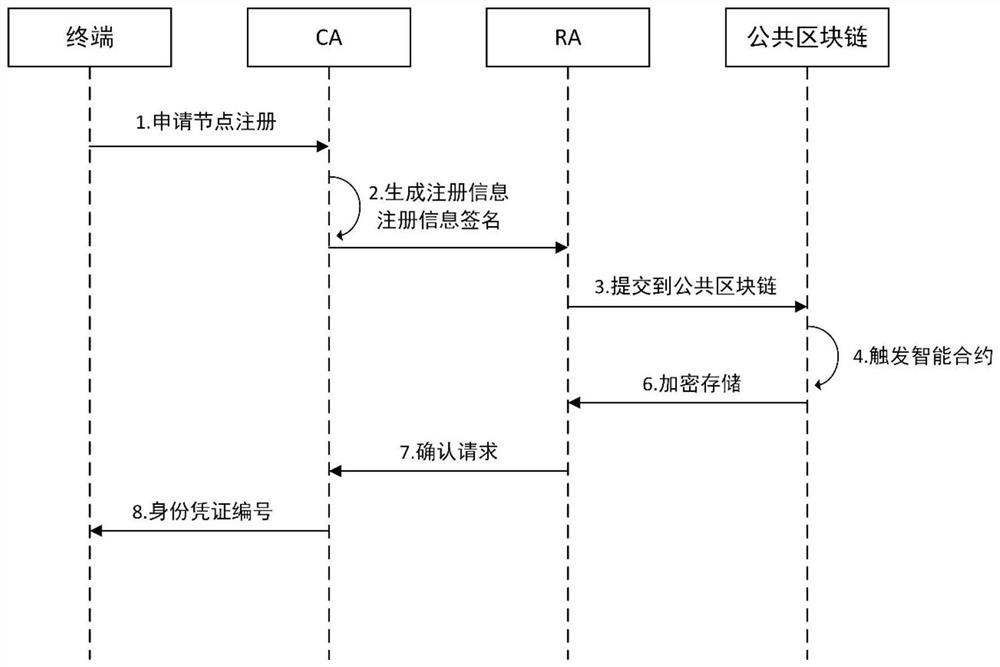
Block chain storage system
InactiveCN107122477APrevent data privacy breachesReach the consensus of the whole networkDigital data protectionTransmissionCloud computingBlockchain
The invention discloses a block chain storage system. The system comprises a plurality of data collection modules and block chain data storage nodes corresponding to the data collection modules, wherein the data collection modules send collected data into the block chain data storage nodes, and all the block chain data storage nodes are connected with a communication network through a wired interface, a wireless interface, an optical interface, a Bluetooth interface or other technical interfaces and can complete synchronization and data communication. The system also comprises a cloud computing center, wherein the cloud computing center can call the data in the block chain data storage nodes, and a user can check the data from the cloud computing center through terminal equipment. The block chain storage system is composed of N block chain data storage nodes, and all the block chain data storage nodes are connected with the communication network through the wired interface, the wireless interface, the optical interface, the Bluetooth interface or other technical interfaces and can complete synchronization and data communication between themselves.
Owner:CHENGDU ZHONGYUANXIN ELECTRONICS TECH
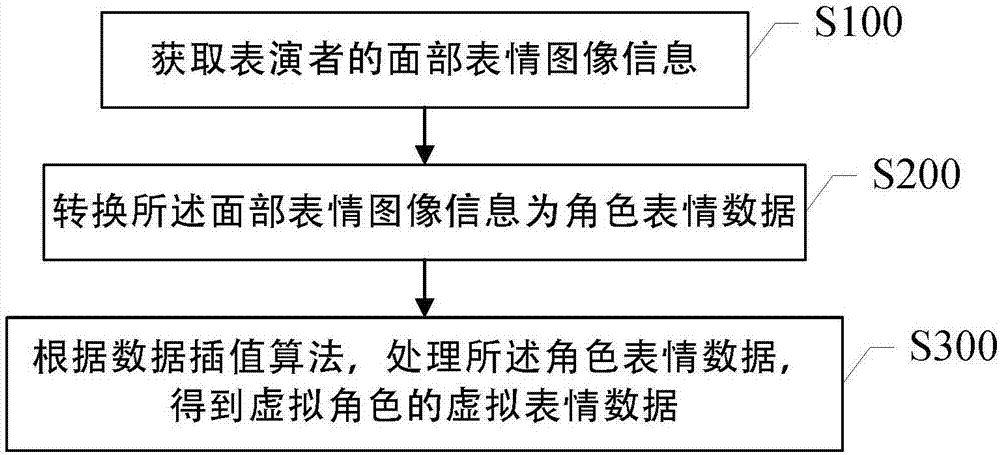
Data processing method and system based on virtual character
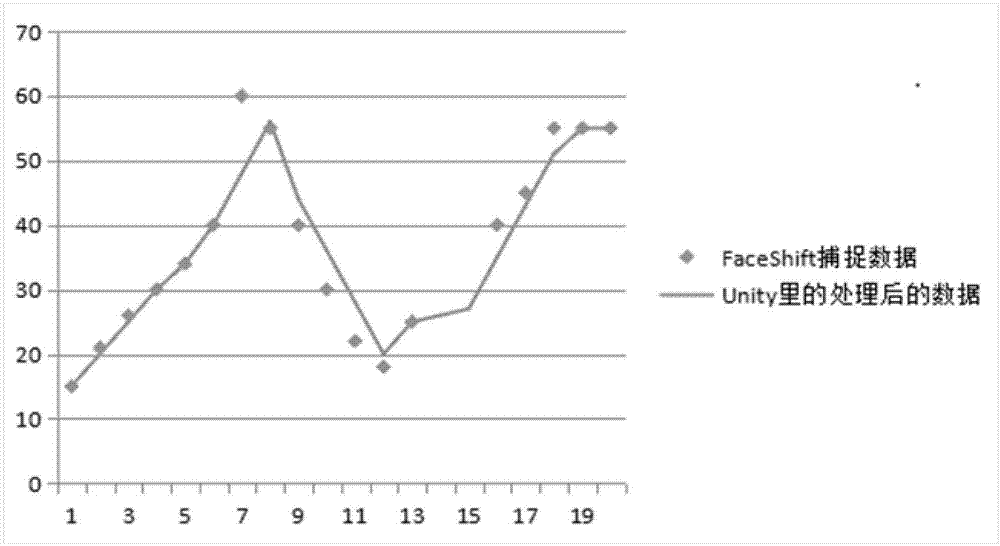
The invention discloses a data processing method and a system based on a virtual character. The invention provides a data processing method based on a virtual character, comprising the following steps: S100, acquiring facial expression image information of a performer; S200, converting the facial expression image information into character expression data; and S300, processing the character expression data according to a data interpolation algorithm to get virtual expression data of a virtual character. The facial movements of a human face can be transferred to any virtual character chosen by users and demonstrated. The current facial expression change of a performer can be reflected in real time through the virtual character. A more vivid virtual character can be created, interest is added, and the user experience is enhanced. Moreover, when there is an identification fault, the action of the character can be stably controlled within an interval to make virtual character demonstration more vivid and natural.
Owner:上海微漫网络科技有限公司
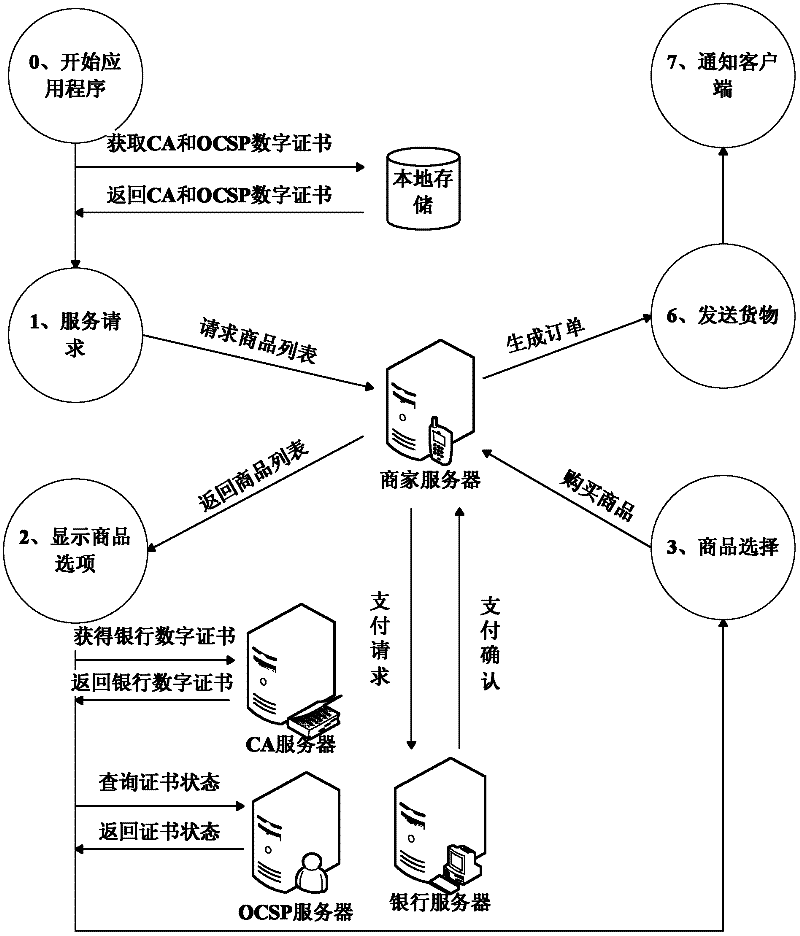
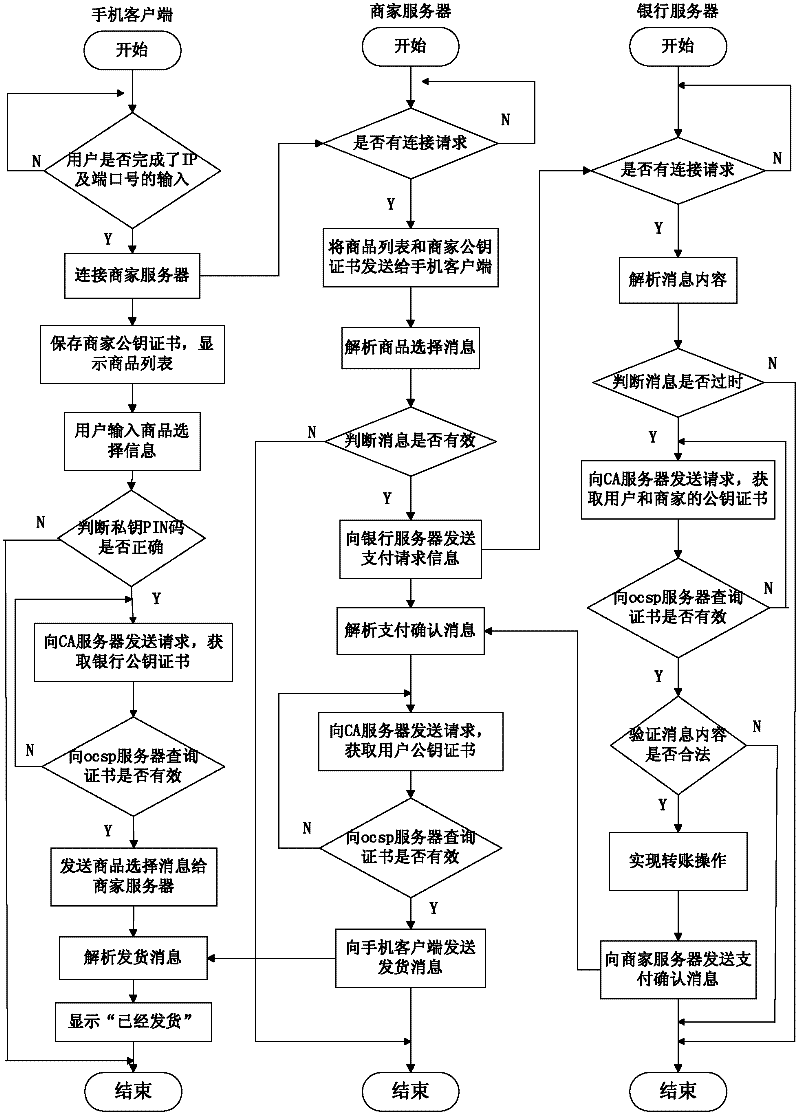
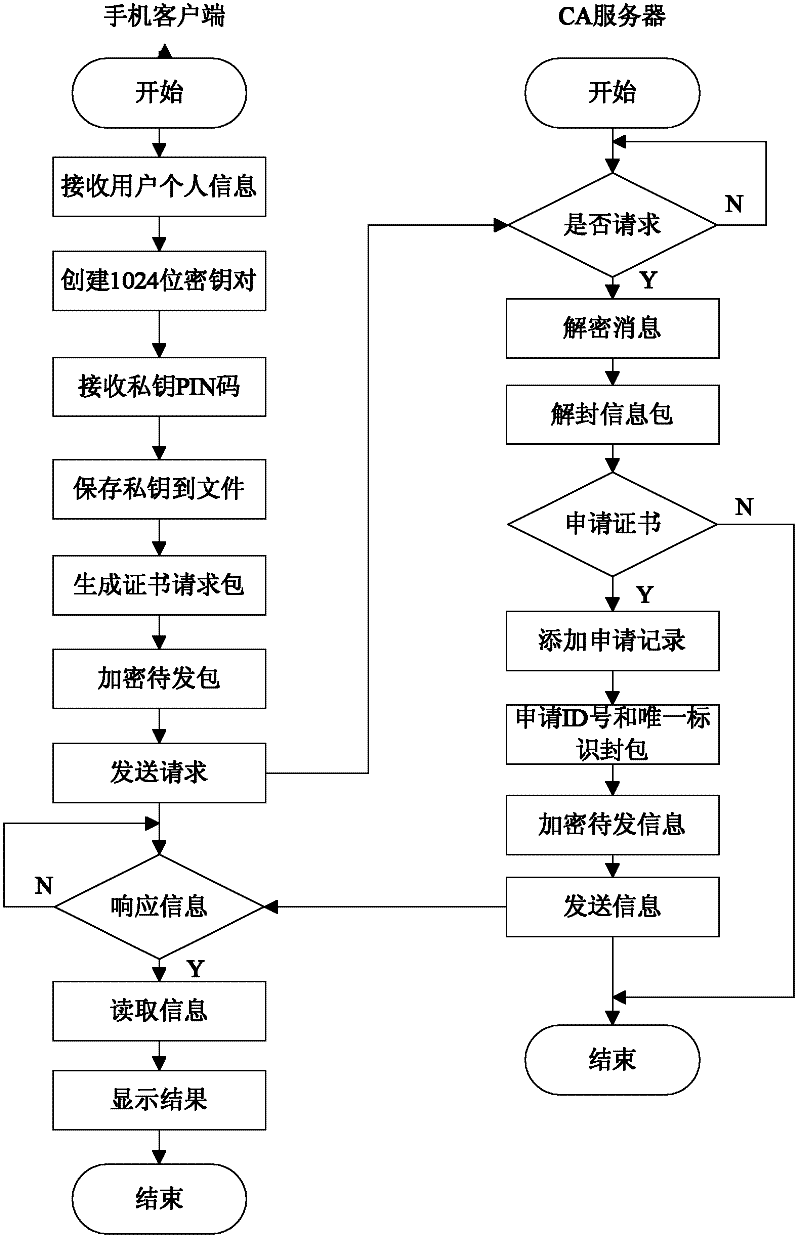
Remote mobile payment system based on digital certificate and payment method
InactiveCN102609841AGuaranteed confidentialityProtect transaction detailsProtocol authorisationConfidentialityDigital signature
The invention relates to a remote mobile payment system based on a digital certificate and a payment method and belongs to the technical field of mobile payment. According to the invention, the digital certificate is used for binding an identity of a user with a public key of the user and the problem of difficulty in managing a secret key during a transaction process is solved. All communication information is encrypted by using the secret key, so that the confidentiality of the transaction information is ensured, the transaction details of the user are protected and the privacy is prevented from being revealed. Meanwhile, each piece of transaction information is digitally signed by using a private key of a sender; as long as a receiver successfully verifies the signature by using the public key of the sender, the sender cannot deny the performed operation of sending the information, so that the undeniable property of information is achieved; an abstract value of the information is calculated for each piece of transaction information; and the receiver firstly compares the abstract value of the information with the received information, so as to judge if the information is distorted and ensure the completeness of the information.
Owner:何文秀
Privacy continuous-query protection method based on location-based service
InactiveCN101866353AAvoid Privacy LeakageQuick serviceSpecial data processing applicationsDatabase serverPrivacy protection
The invention relates to a privacy continuous-query protection method based on a location-based service, which comprises the following steps that: A. a mobile user is used for transmitting a query request to an anonymous server; B. an anonymous engine judges whether the query request Q is a new query or an active query according to a user identification id; C. if the query request is the new query, the anonymous engine can carry out anonymous processing to the query request, and transmits the processed request Q=(id', Rv, t, maxT, con) to a server of a provider; D. the server of the provider carries out the query processing according to the received request Q=(id', Rv, t, maxT, con), and returns a candidate set of a query result to the anonymous server; and E. the anonymous server selects a correct query result from the candidate set returned by the database server and returns the query result to corresponding mobile objects.
Owner:孟小峰
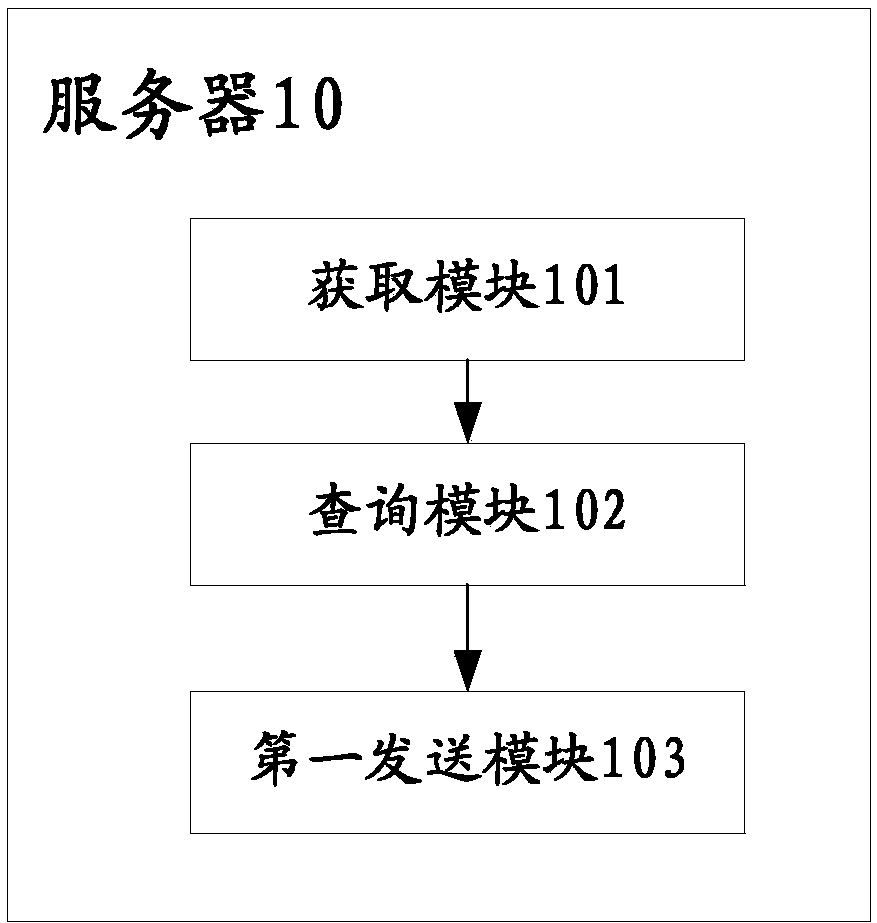
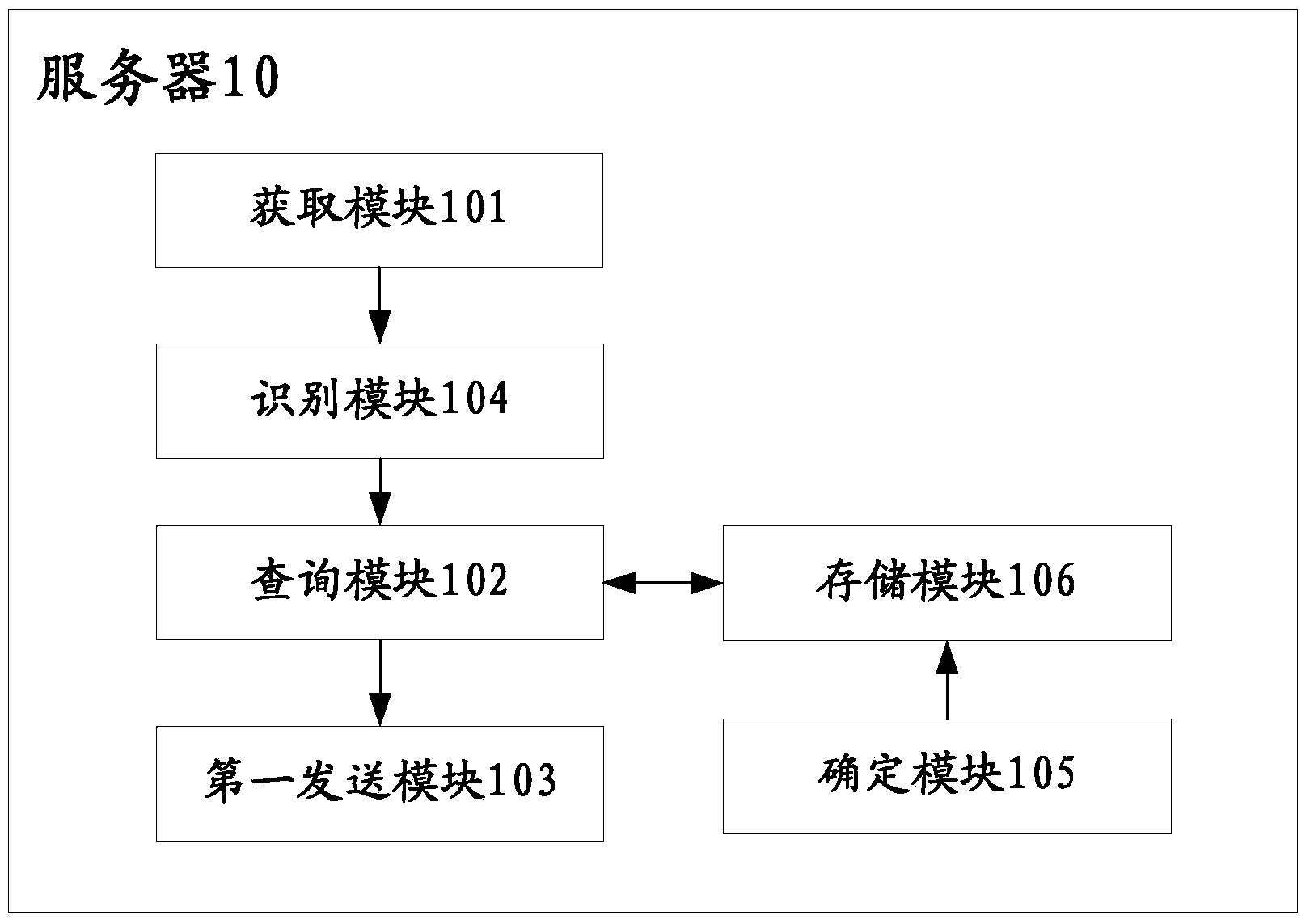
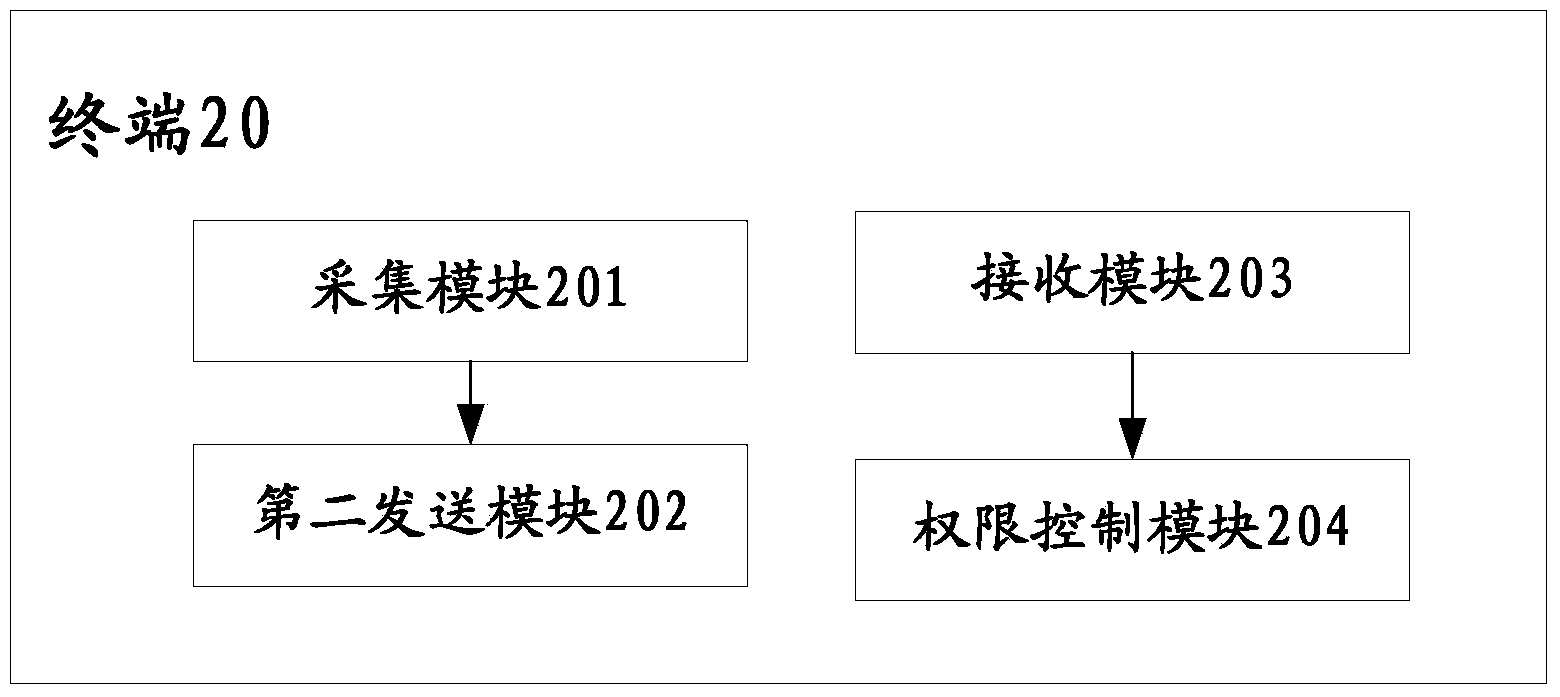
Server, terminal and authority management and permission method
InactiveCN103514397AAvoid cumbersomeImprove experienceDigital data authenticationPlatform integrity maintainanceRights managementApplication software
The invention discloses a server, a terminal and an authority management and permission method. Identification information of an application program to be inquired from the terminal is obtained; an optimal and reasonable permission policy corresponding to the application program to be inquired is inquired and obtained according to the identification information, and the permission policy is sent to the terminal. The tedious process of judging the application software program manually by a user is avoided, and a server sends the optimal permission policy to the terminal directly through inquiring. In addition, the terminal conducts permission limitation on the corresponding application program through the obtained reasonable permission policy, manual permission selection of a user is avoided, the terminal obtains the reasonable permission policy automatically to limit the application program, and user experience is further improved. Meanwhile, the reasonable permission policy is used, inaccurate permission judgment of the user is avoided, and information safety of the user is protected.
Owner:XIAN COOLPAD SOFTWARE TECH CO LTD
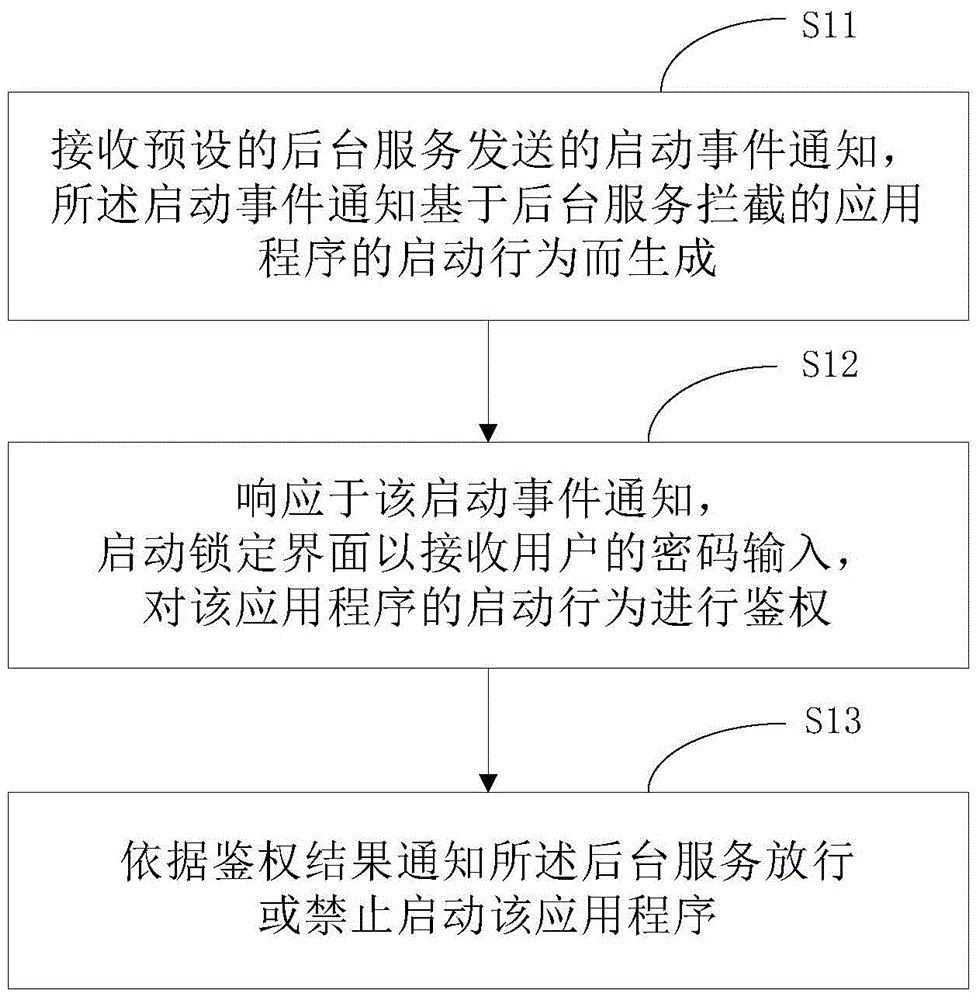
Method and device for application program starting authentication
ActiveCN105095746AImprove experienceAvoid Privacy LeakageDigital data authenticationPasswordApplication software
The invention provides a method for application program starting authentication, which mainly comprises the steps that an event starting notice sent by a preset backstage service is received, wherein the event starting notice is generated based on a starting behavior of an application program intercepted by the backstage service; a response is made to the event starting notice, a locking interface is started to receive password input of a user, and the authentication is carried out to the starting behavior of the application program; and the backstage service is informed by an authentication result to release or prohibit starting of the application program. In addition, the invention also provides a device for the application program starting authentication. The method and the device for the application program starting authentication provided by the invention can realize locking before the self-starting of the application program, and determine whether the starting is realized by the user's authentication, so that the problem about frame blinking during the locking is solved, time wasting caused by timed polling of a CPU is avoided, and a program locking function with better user experience is realized.
Owner:BEIJING QIHOO TECH CO LTD
Rotatable lifting camera and display device
ActiveCN109958870AAvoid leaking privacyThe appearance of the product is simpleStands/trestlesCamera body detailsEngineeringMechanical engineering
The invention provides a rotatable lifting camera and a display device. The rotatable lifting camera comprises a camera module and a drive assembly, wherein the drive assembly comprises a drive piece,a transmission piece, an execution piece, a limiting piece and a locking piece; the camera module is arranged on the execution piece; a non-rotation sliding fit section and a rotatable fit section are formed between the execution piece and the limiting piece; when the execution piece and the limiting piece are located at the non-rotation sliding fit section, the drive piece can drive the execution piece to linearly move in a reciprocating way through the transmission piece; when the execution piece and the limiting piece are located at the rotatable fit section, the locking piece locks the relative rotation between the transmission piece and the execution piece, so that the drive piece drives the camera module to rotate; and the display device comprises the rotatable lifting camera. The invention provides the rotatable lifting camera capable of automatically lifting and rotating segmentally and realizing double actions through a single power source, and the display device with the camera capable of stretching out and drawing back relative to a display screen and rotating after stretching out.
Owner:ONEPLUS TECH SHENZHEN
Screen transfer display method and device
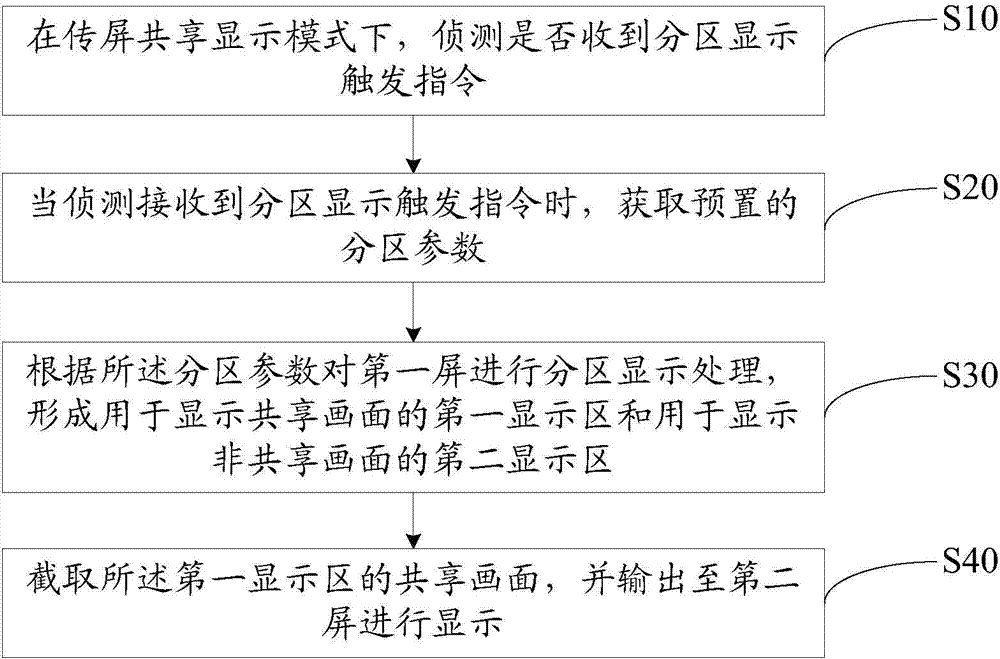
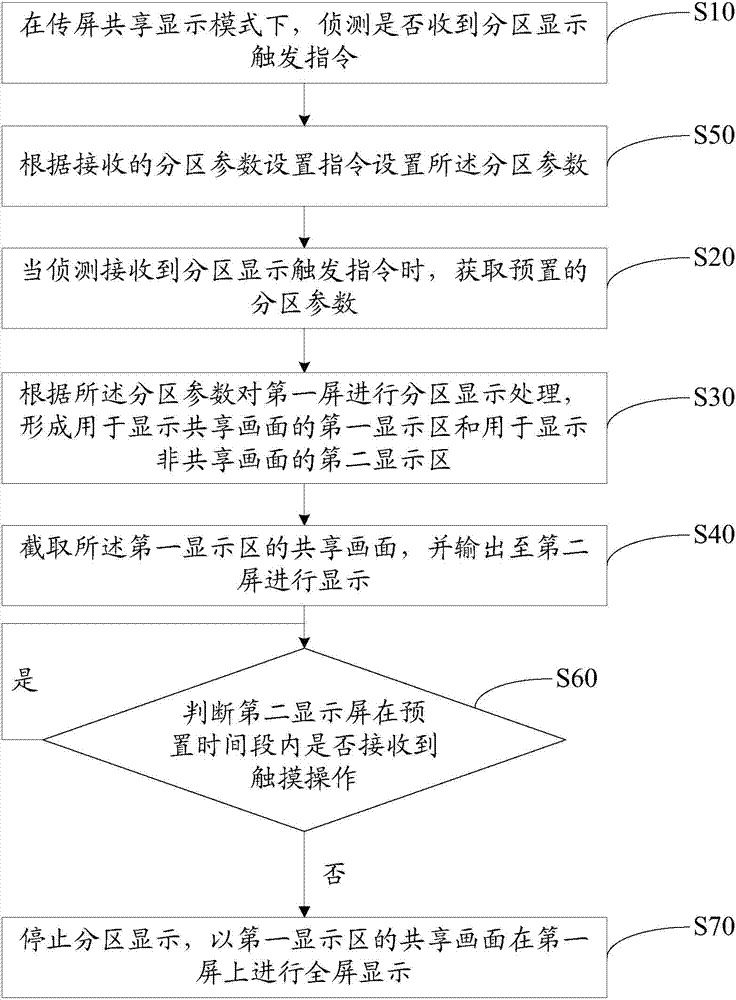
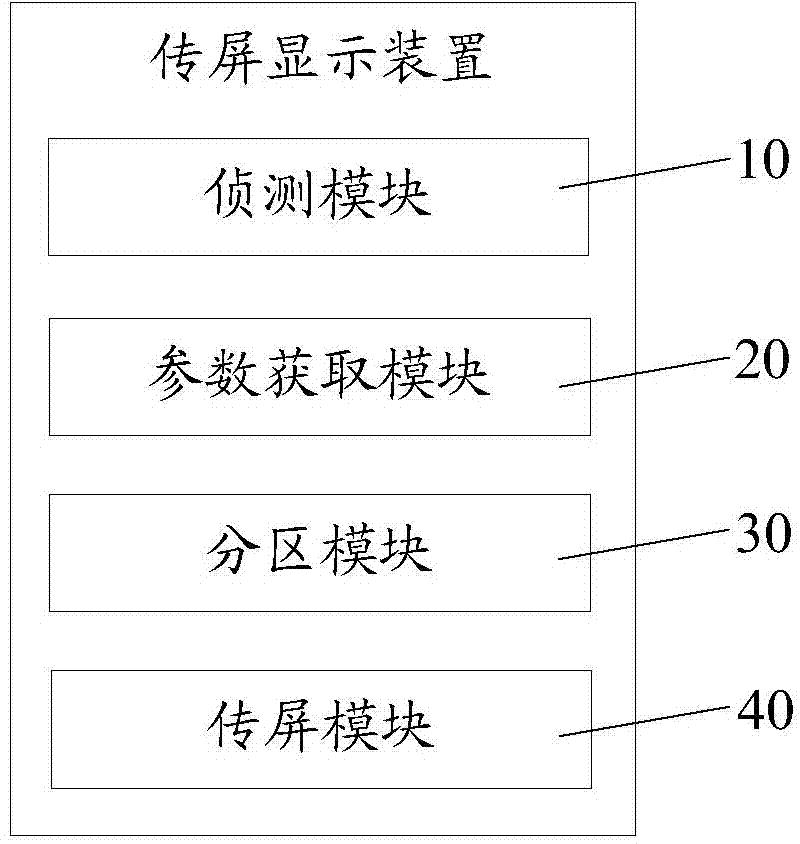
InactiveCN104238986AAvoid Privacy LeakageAvoid interferenceDigital output to display deviceUser privacyDisplay processing
The invention discloses a screen transfer display method. The screen transfer display method comprises the following steps: detecting whether an area display trigger instruction is received or not in a screen transfer sharing display mode; acquiring a preset area parameter when detecting and receiving the area display trigger instruction; performing area display processing on a first screen according to the area parameter to form a first display area for displaying a shared picture and a second display area for displaying a non-shared picture; intercepting the shared picture of the first display area and outputting to the second screen to display. The invention also discloses a screen transfer display device. The screen transfer display method provided by the invention, on one hand, can prevent that viewers are not disturbed by other pictures while watching the picture (such as a film) displayed through the screen transfer sharing to improve the impression of the viewers, and on the other hand, can prevent communication contents, private documents, pictures or the like of a user from being exposed to all the viewers so as to avoid the user privacy leakage.
Owner:NUBIA TECHNOLOGY CO LTD
Intelligent remote social adjuvant therapy robot for autism children
InactiveCN103612252ARealize motion path planning functionReal-time motion joint drive capabilityData processing applicationsDiagnostic recording/measuringHead movementsDrive wheel
The invention belongs to the field of remote control and artificial intelligence and relates to an intelligent adjuvant therapy robot device for performing real-time social capability training for autism children. The device comprises a head movement driver (1), an arm movement driver (2), a device loader (3), a driving-driven wheel type chassis (4) and a casing module (7). A multi-joint combined driving mode is adopted, the collaborated driving capability of the robot for every movement joint is improved, the problem that time delay affects the interaction effect is solved, precise posture control of the robot in the random direction is achieved, a limb movement path planning function for automatically avoiding obstacles is achieved, and intelligent emotion interaction between a human and the robot and a safe and reliable family remote rehabilitation therapy model are achieved in various modes such as voice, images, touch and induction in the man-machine interactive process in response to emotion cognitive disorder which occurs universally in child patients.
Owner:UNIV OF SCI & TECH BEIJING
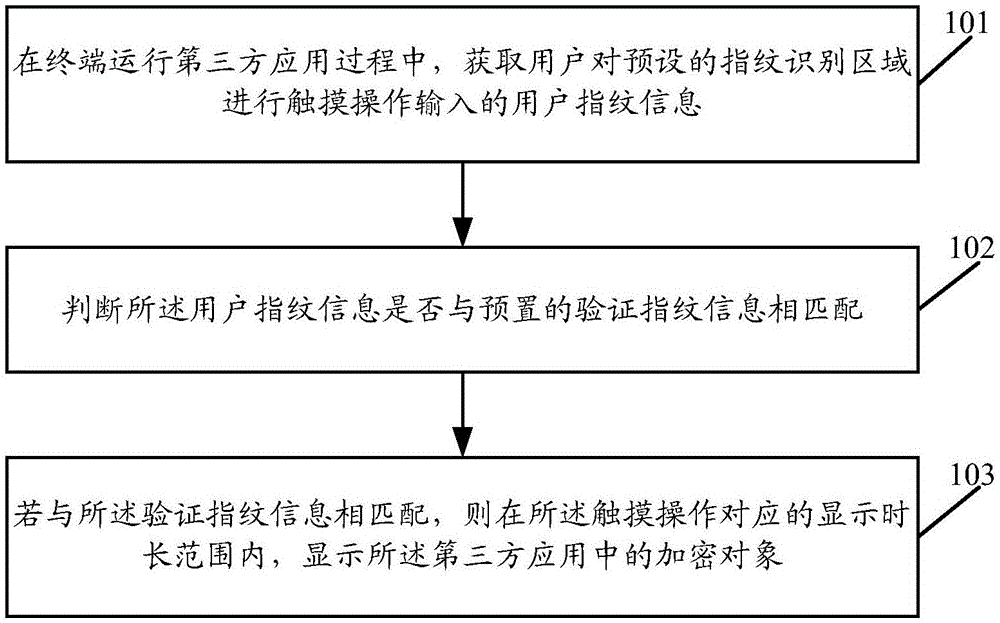
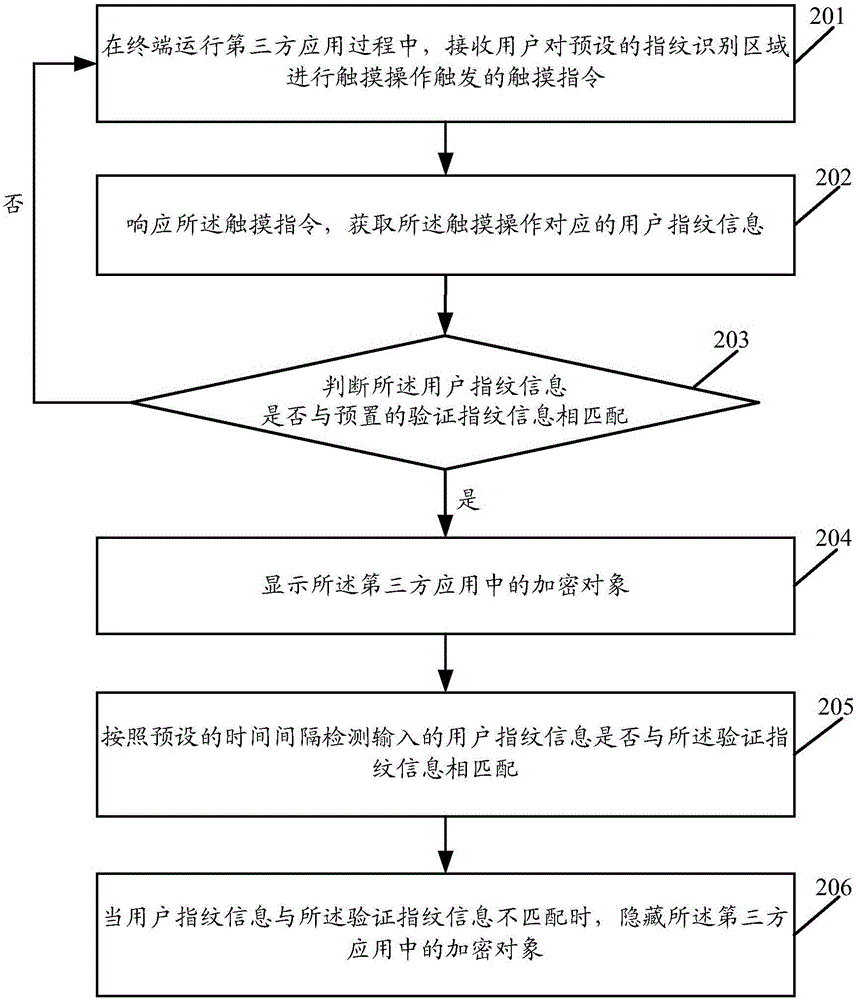
Encrypted object display method and device for application
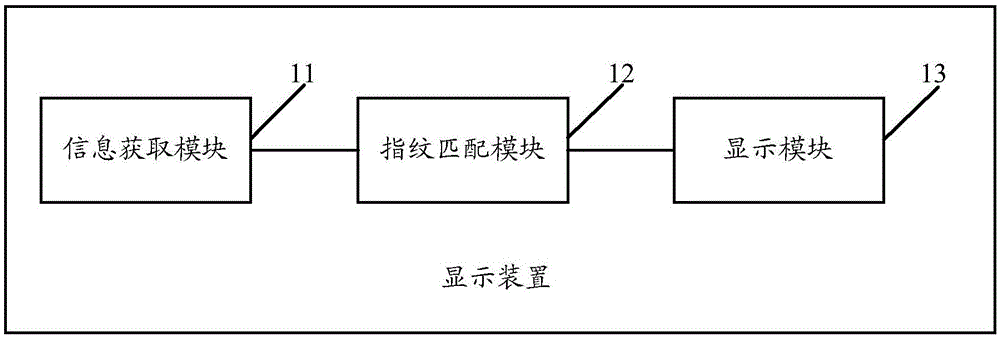
ActiveCN105117663AAvoid Privacy LeakageDigital data protectionDigital data authenticationUser privacyFingerprint
The embodiment of the invention discloses an encrypted object display method and device for an application. The method includes the steps that when a terminal runs the third-party application, user fingerprint information input when a user performs touch operation on a preset fingerprint recognition area is acquired; whether the user fingerprint information is matched with preset verification fingerprint information or not is judged; if yes, an encrypted object of the third-party application is displayed within a display duration range corresponding to the touch operation. By means of the encrypted object display method and device, display of the encrypted object of the application can be controlled according to the user fingerprint information, so that leakage of user privacy is avoided.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Express delivery information privacy protection system based on blockchain, and protection method thereof
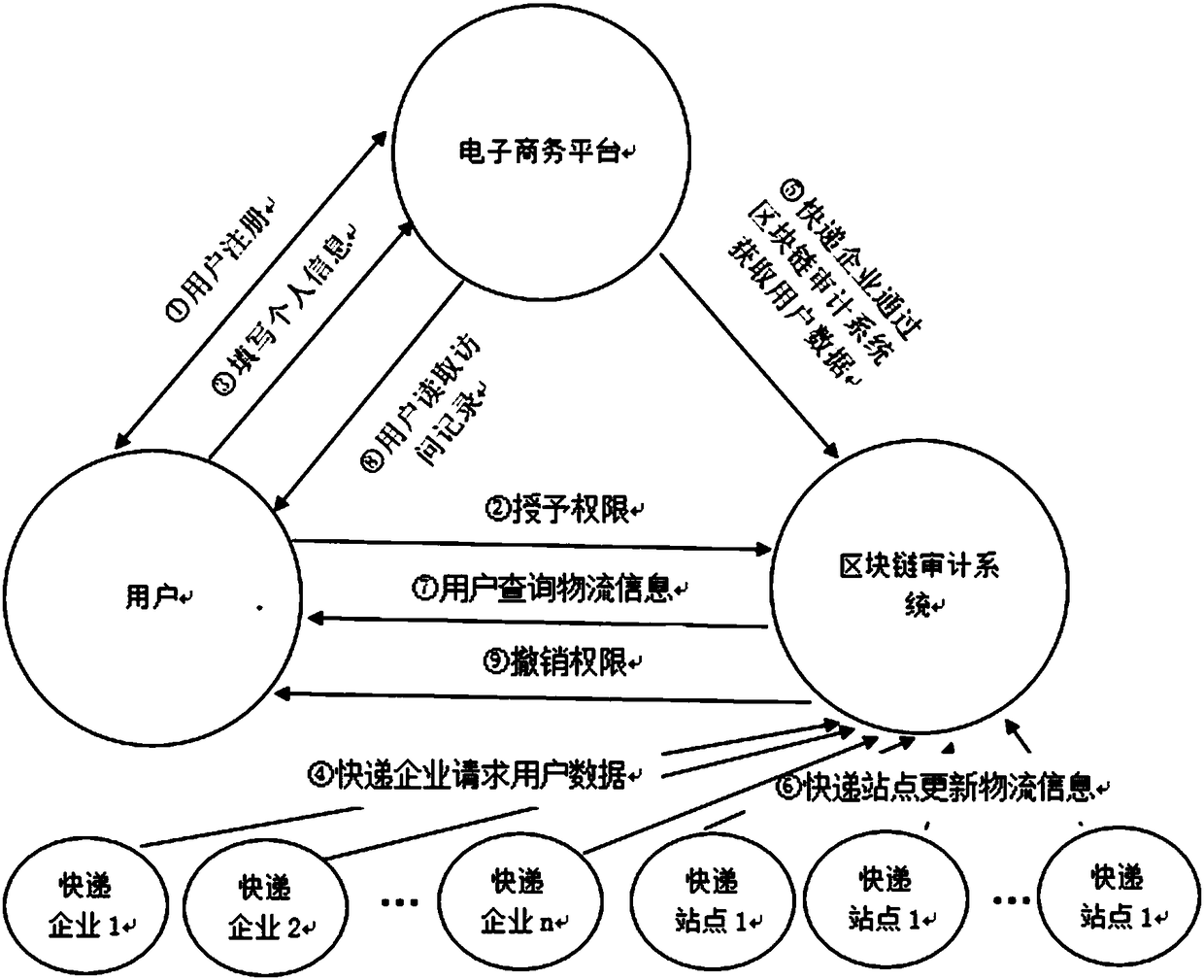
ActiveCN108614974AEnhancing Operational ComplianceAvoid illegal acquisitionDigital data protectionDigital data authenticationPlaintextLogistics management
The invention discloses an express delivery information privacy protection system based on a blockchain, and a protection method thereof. The method records all operational motions of an express delivery enterprise for user data through a blockchain auditing platform, the operation compliance of the express delivery enterprise is enhanced, and the express delivery enterprise can be effectively prevented from illegally obtaining personal information. Meanwhile, a user can read a user data visitor record through an authorization record recorded in the blockchain, the access permission of the express delivery enterprise for the user data is revoked, and the sense of control of the user for personal data is enhanced. In addition, a ciphertext express waybill is used for replacing a plaintext express waybill, so that a possibility that the user data is leaked in each link of an express delivery business process can be lowered. An express delivery package logistics tracking scheme based on the blockchain can assist the user in checking the logistics situation of the express delivery package at any time in a blockchain system, and logistics information which can not be tampered on the blockchain can provide proof-providing information for disputes including delivery losing claims and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
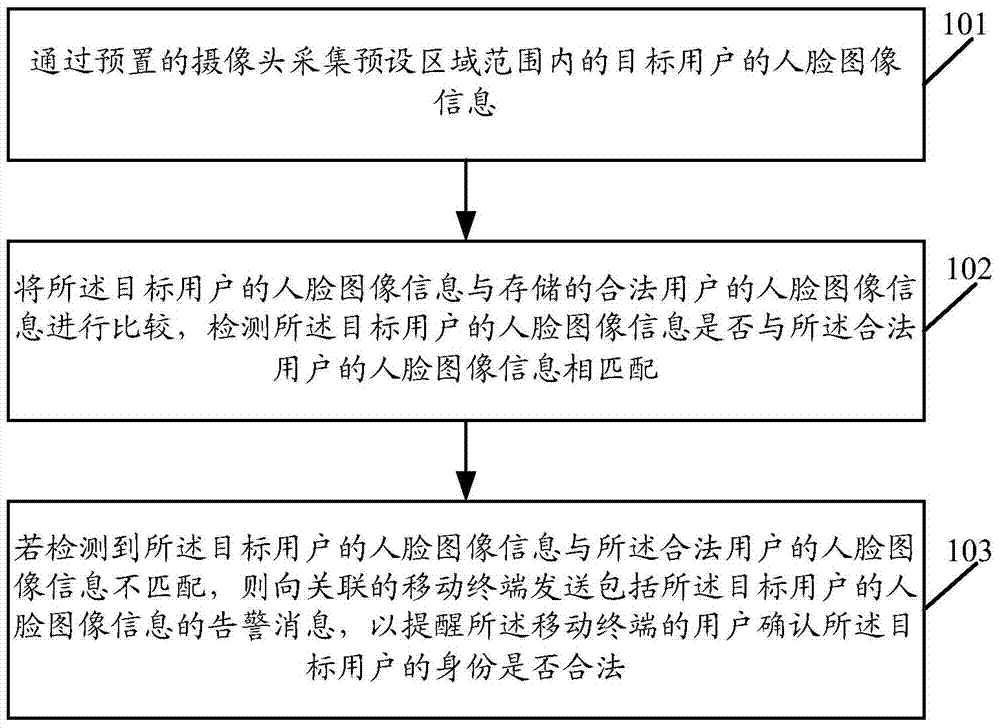
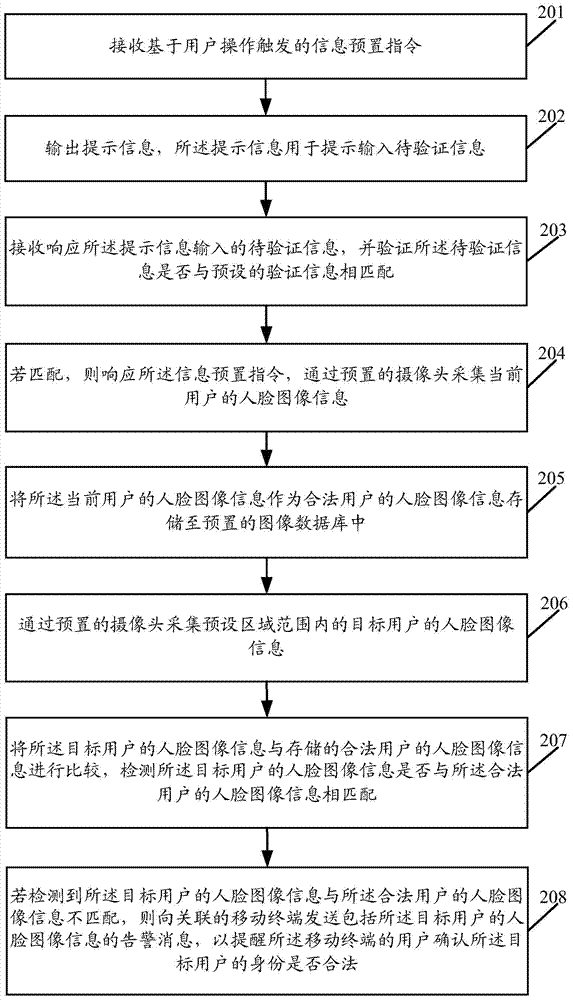
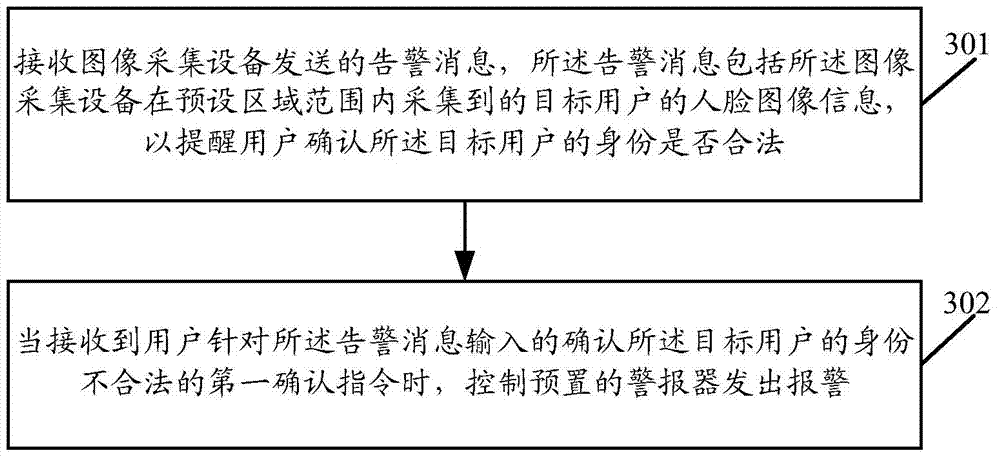
Identity verification method and related equipment
Embodiments of the present invention disclose an identity verification method and related equipment. The method comprises the following steps: collecting facial image information of a target user in a preset area range by a preset camera; comparing the facial image information of the target user with the stored facial image information of legal users and detecting whether the facial image information of the target user is matched with the facial image information of the legal users; and sending a warning message containing the facial image information of the target user to an associated mobile terminal so as to remind a user of the mobile terminal to verify whether the identity of the target user is legal if it is detected that the facial image information of the target user is not matched with the facial image information of the legal users. By virtue of implementation of the embodiments of the present invention, the warning message can be sent to the associated mobile terminal in time to remind the user when the detected facial image information is not matched with the stored facial image information.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
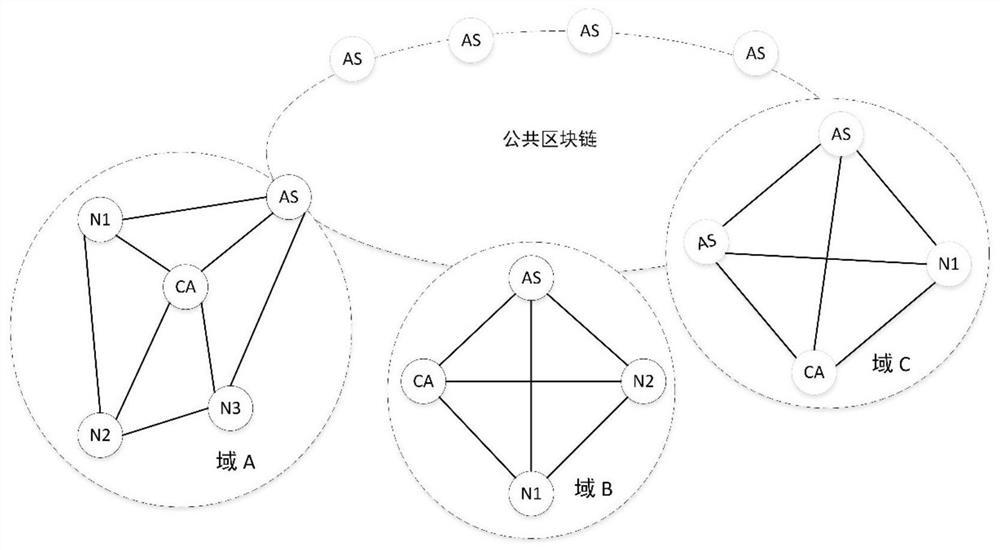
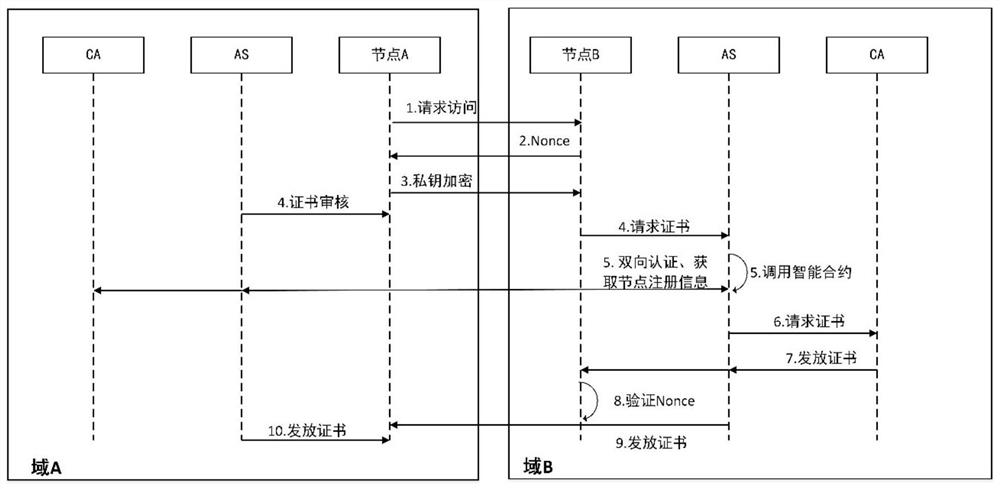
Multi-layer blockchain cross-domain authentication method in Internet of Things application scene
ActiveCN112637189AAvoid Privacy LeakageImprove space utilizationTransmissionInternet privacyThe Internet
The invention relates to a multi-layer blockchain cross-domain authentication method in an Internet of Things application scene, and belongs to the technical field of Internet of Things and blockchains. According to the method, a blockchain identity registration protocol, a cross-domain identity authentication protocol and a node trust degree evaluation method based on delegation proving of rights and interests are used for carrying out distributed node management and security protection on the blockchain in an application scene of the Internet of Things; and when nodes of different blockchains need to carry out cross-chain identity authentication and data exchange, the across-chain trusted identity authentication is carried out by using a public block chain, so that the user privacy and the data security are ensured. The technical scheme includes the contents in the specification. Compared with an original centralized identity authentication mode, the identity authentication efficiency under the distributed application scene of the Internet of Things is improved, the management problem of certificates under a heterogeneous network is solved, and good safety and usability are achieved.
Owner:CHONGQING UNIV +1
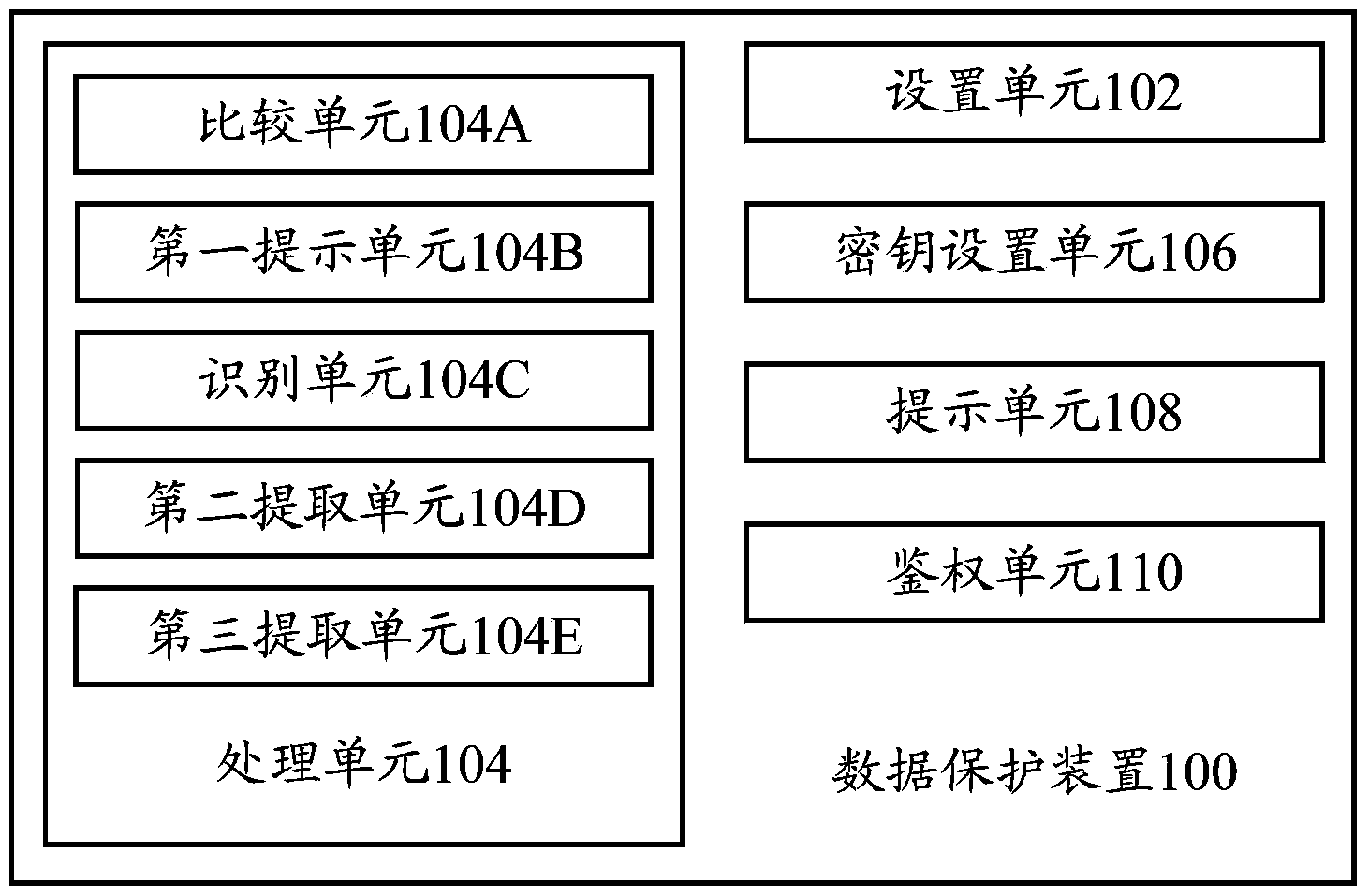
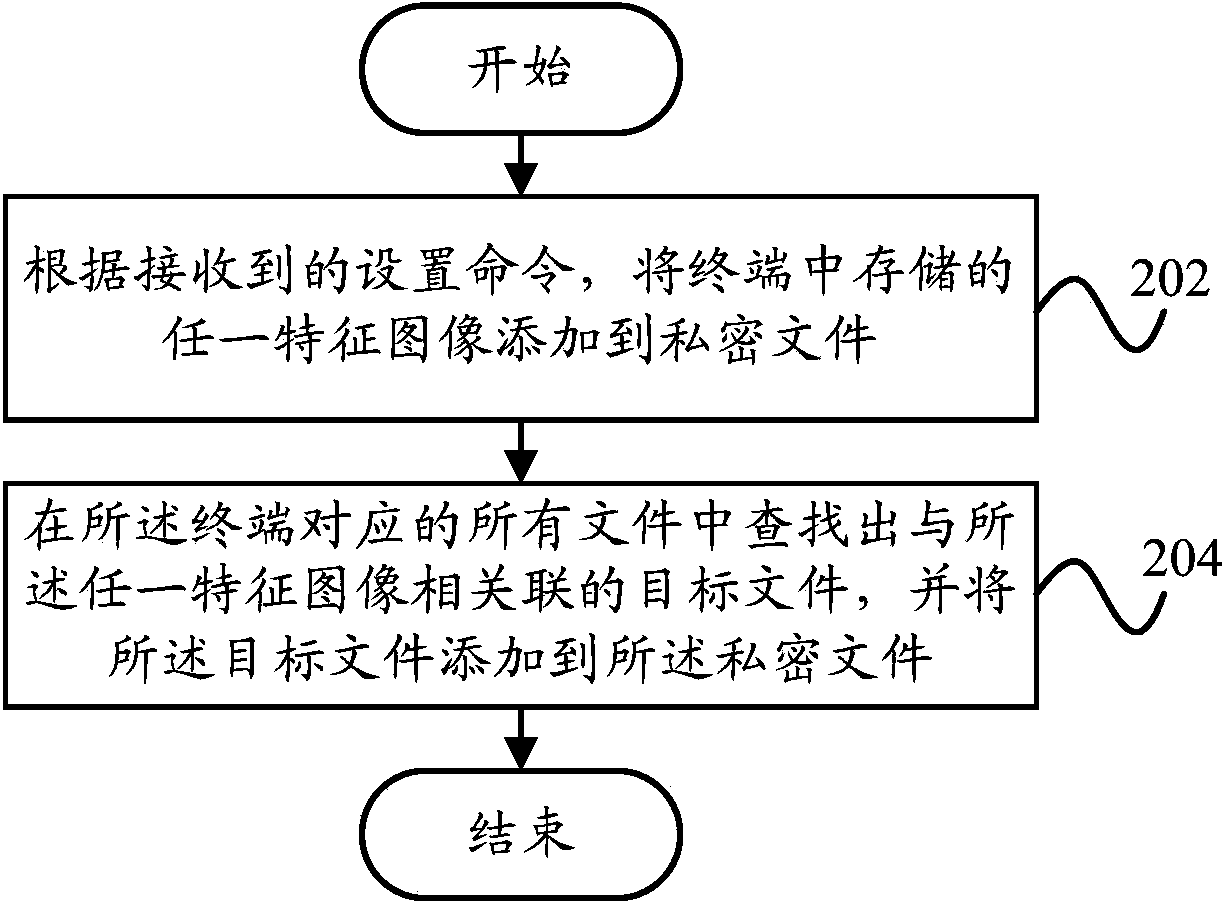
Data protection device and data protection method
InactiveCN103824030AImplement automatic encryptionAvoid privacy leaksDigital data protectionPattern recognitionComputer terminal
The invention provides a data protection device and a data protection method. The data protection device comprises a setting unit and a processing unit. The setting unit adds any feather image in a terminal to a secret file according to a received setting command, wherein the feature images include facial images. The processing unit searches the terminal for a target file related to the feature image and adds the target file to the secret file. The processing unit comprises a comparison unit used for obtaining all the facial images stored in the terminal, and comparing the feather image with each facial image in all the facial images according to the comparison result. The first extraction unit confirms the facial similarity of each facial image and the feature image according to the comparison result, extracts the facial images with the facial similarity larger than preset facial similarity, and adds the facial images to the secret file. By means of the technical scheme, automatic encryption of files can be achieved, and the encryption operation is simplified.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
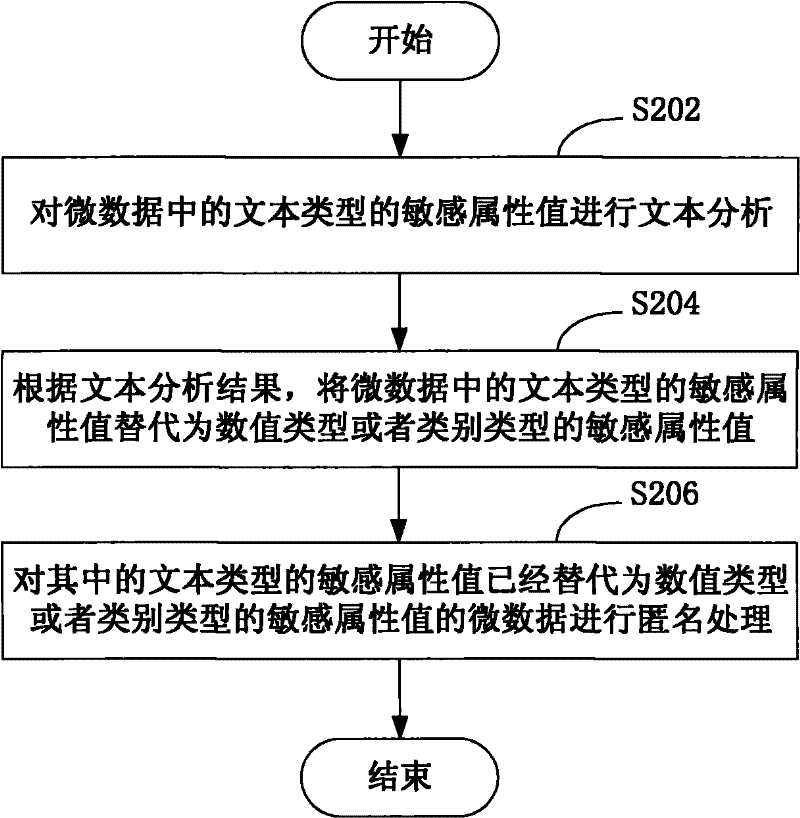
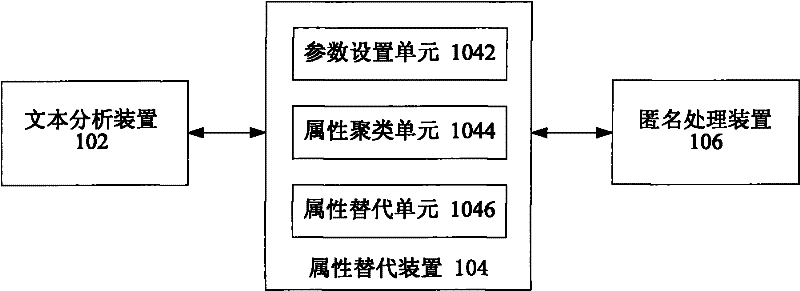
Data anonymization method and system
The invention provides a data anonymization method and system. The data anonymization method comprises the steps of: carrying out text analysis on the attribute value of a text type in data; replacing the attribute value of the text type in the data with the attribute value of a value type or a class type according to text analysis result; and carrying out anonymization processing on the data in which the attribute value of the text type is replaced by the attribute value of the value type or the class type. According to the invention, after anonymization processing, the data comprising the attribute value of the text type not only can prevent the privacy leakage based on the attribute value, but also still has use value.
Owner:NEC (CHINA) CO LTD
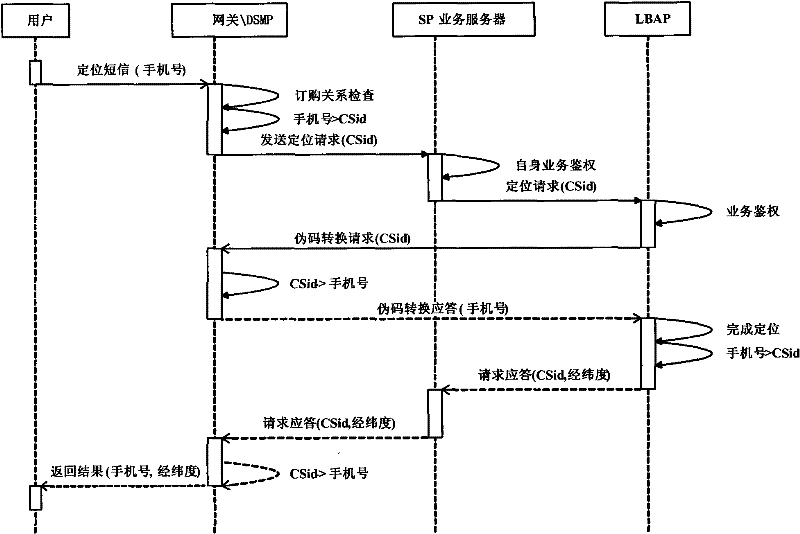
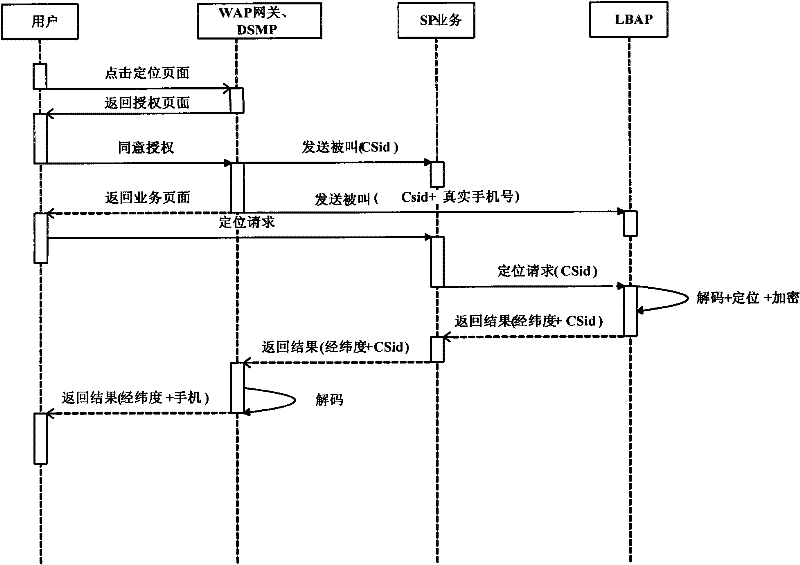
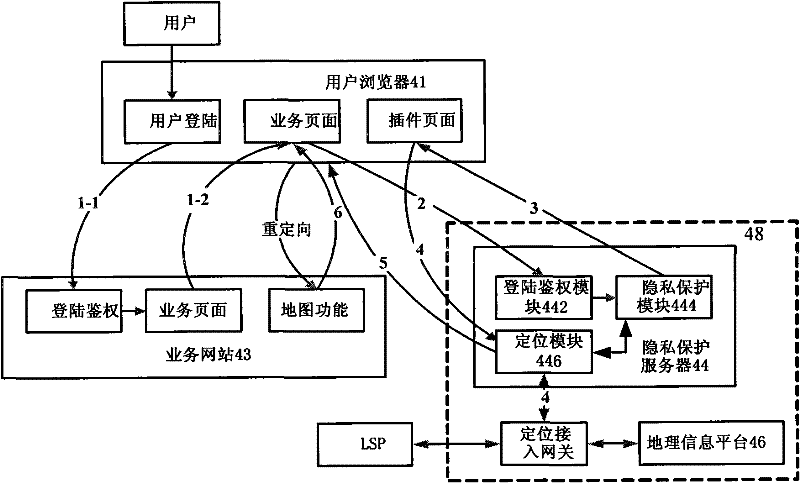
User privacy protection method, equipment and system for location business
InactiveCN102457805AImprove securityAvoid leakage of user privacyLocation information based serviceTransmissionUser privacyPrivacy protection
The invention discloses a user privacy protection method, equipment and a system for a location business, wherein the method comprises the following steps of: receiving a started location positioning request by a user browser end when an internet user visits a business website, and directly sending the location positioning request to privacy protection equipment of a wireless communication network side by the user browser end; verifying the location positioning request by the privacy protection equipment, after the location positioning request is passed, and returning a positioning result corresponding to the location positioning request to the user browser end; and returning positioning result location information requested by the internet user to the business website by the user browser end. In the invention, user privacy protection can be achieved when the internet user uses the location business, safety for user location privacy can be improved, and defects that the user location privacy is leaked and privacy protection for the internet user can not be achieved in the prior art can be solved.
Owner:LIAONING MOBILE COMM
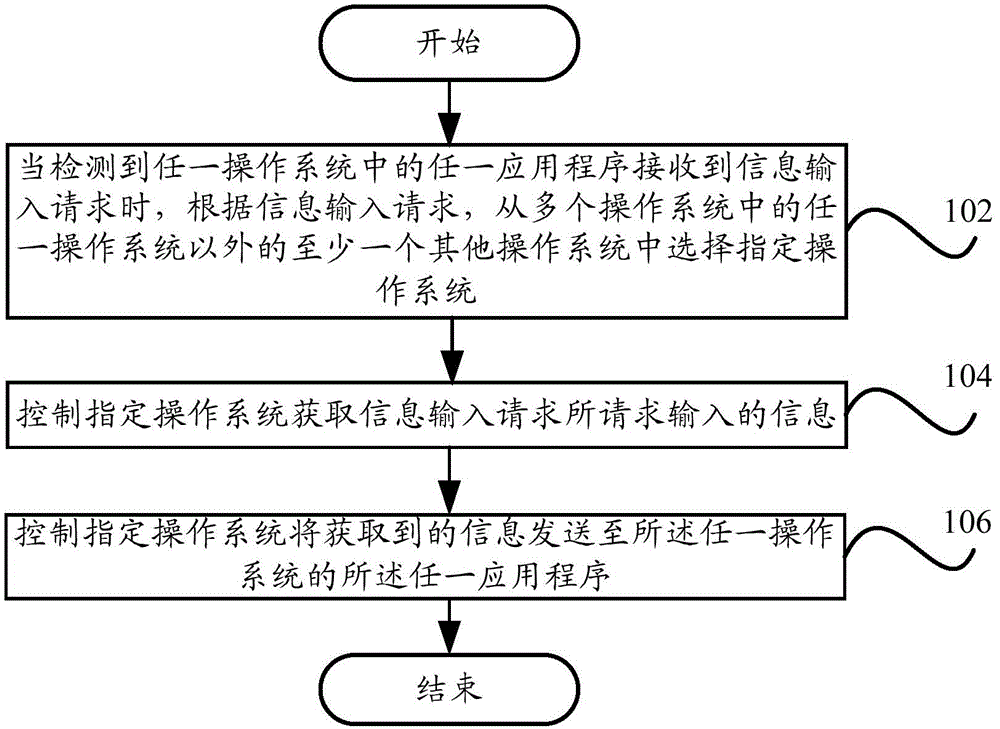
Information input method and information input device of terminal and terminal
ActiveCN104156657AReduce the chance of leaksImprove convenienceInternal/peripheral component protectionDigital data authenticationMalwareApplication software
The invention provides an information input method and information input device of a terminal and the terminal. The terminal comprises a plurality of operating systems, and the information input method comprises the steps that when the fact that any application program in any operating system receives an information input request is detected, a designated operating system is selected from at least one other operating system in the operating systems except for the any operating system; the designated operating system is controlled to acquire information required by the information input request to be input; the designated operating system is controlled to send the acquired information to the any application program of the any operating system. According to the technical scheme, the problem that the information input into the terminal is captured by malicious software, viruses and the like is solved, the information safety of the terminal is effectively protected, the privacy safety of a user is improved, and user experience is enhanced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Screen projection method and system and electronic device
ActiveCN110740363AAvoid Privacy LeakageImprove experienceSelective content distributionData packComputer graphics (images)
The invention discloses a screen projection method and system and an electronic device. The screen projection method is used for displaying multimedia data played on terminal device on playing equipment except the terminal device. The method comprises: acquiring multimedia data, processing the multimedia data into screen projection data, sending the screen projection data to a playing device to bedisplayed, the multimedia data comprising streaming media data, and the screen projection data comprising frame data with a target coding format; in other words, processing the multimedia data into the screen projection data including the frame data in the target coding format during screen projection, sending the screen projection data to the playing device, the playing device can directly achieve screen projection display of the multimedia data according to the screen projection data, and the user experience can be improved.
Owner:HUAWEI DEVICE CO LTD
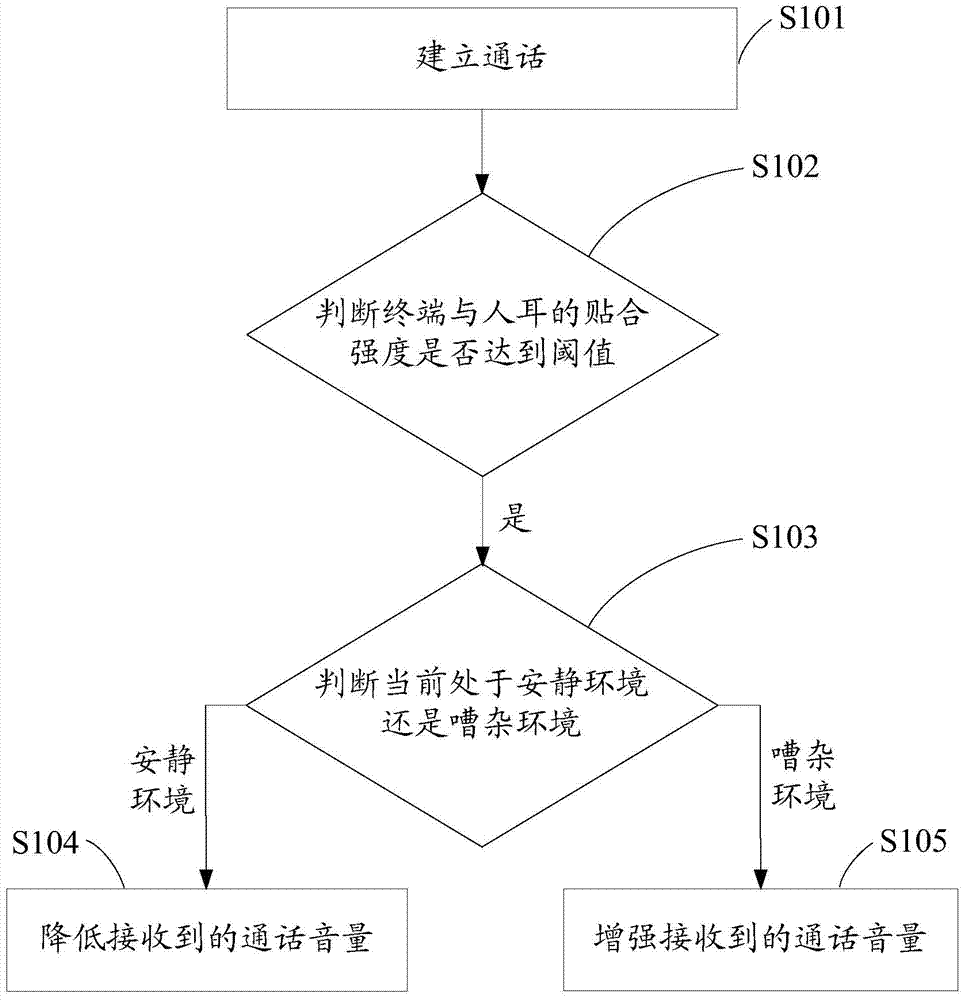
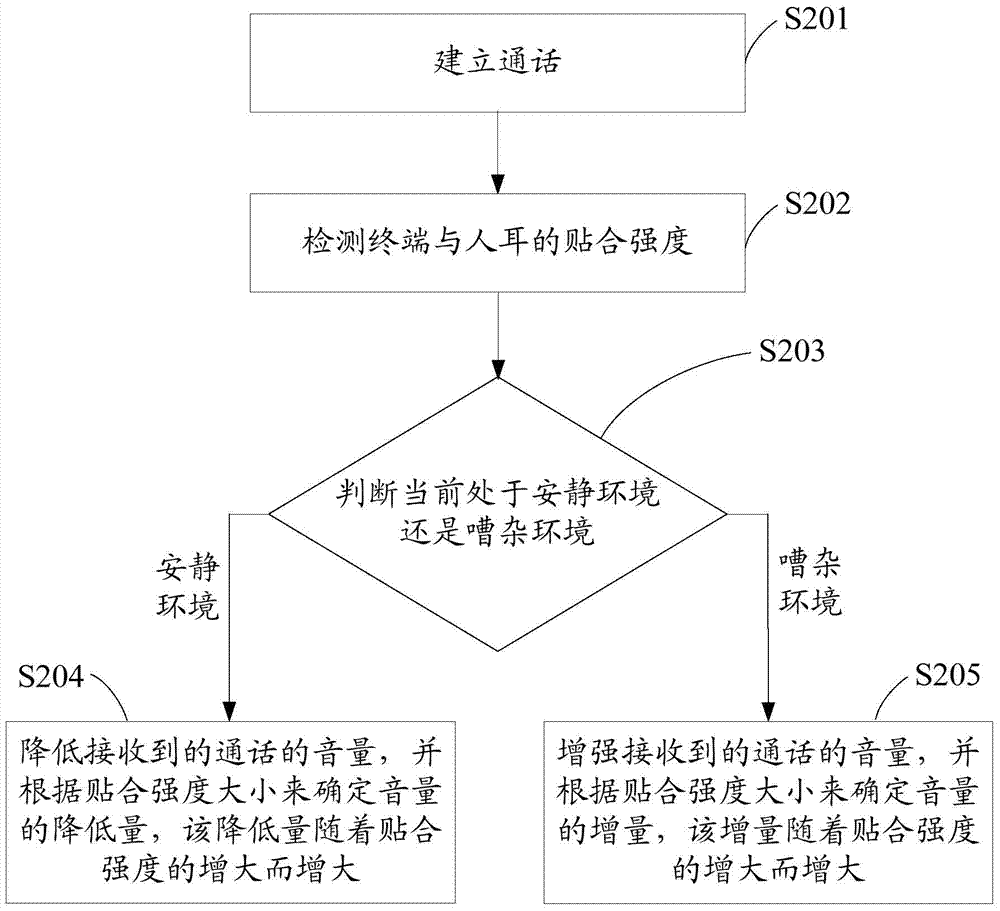
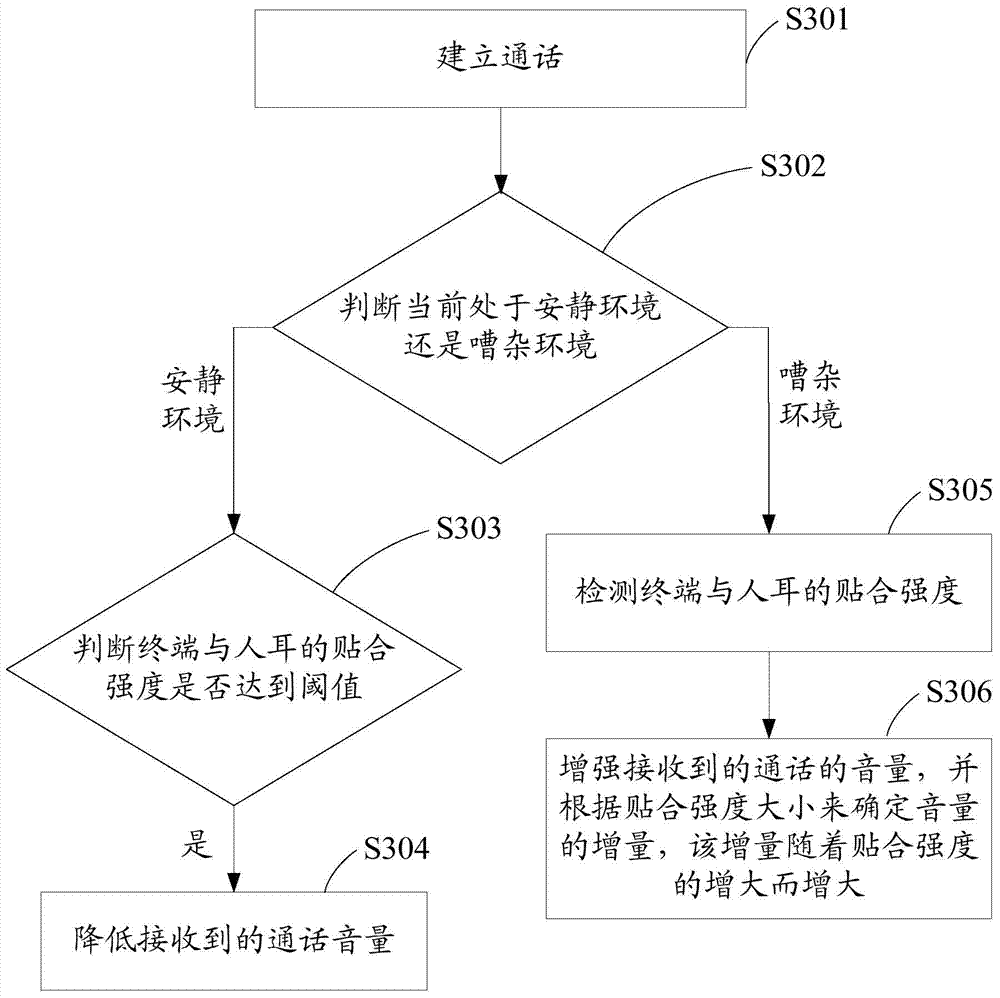
Method for automatically adjusting call volume and communication terminal
ActiveCN103973863AMeet call needsImprove the level of intelligenceSubstation speech amplifiersComputer engineering
The invention discloses a method for automatically adjusting call volume and a communication terminal. The method comprises the following steps: detecting whether the current environment is quiet environment or noisy environment in a calling process, and detecting the call behavior of a user; automatically adjusting the volume of the received call according detection results; automatically lowering the volume of the received call when the user speaks in a lower voice in the quiet environment so as to prevent the leakage of privacy or influence other people due to excessively-great volume; automatically enhancing the volume of the received call according to fitting strength of the terminal with ear in the noisy environment so as to enable the user to listen to the voice of other people clearly, thereby meeting call requirements of the user in different environments, improving the intelligent level of the terminal and improving the user experience.
Owner:NUBIA TECHNOLOGY CO LTD
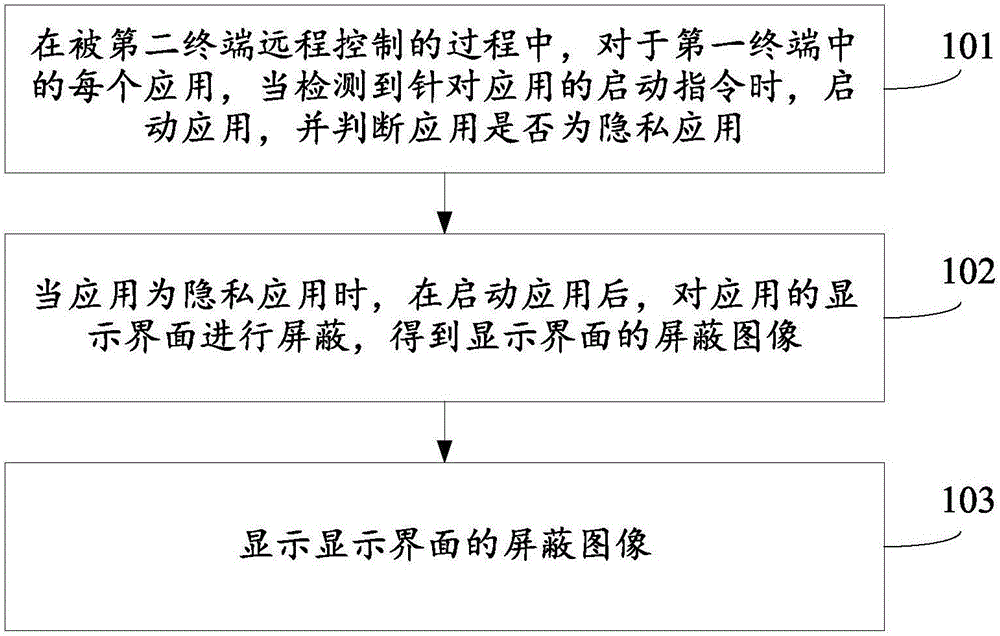
Remote control method and apparatus
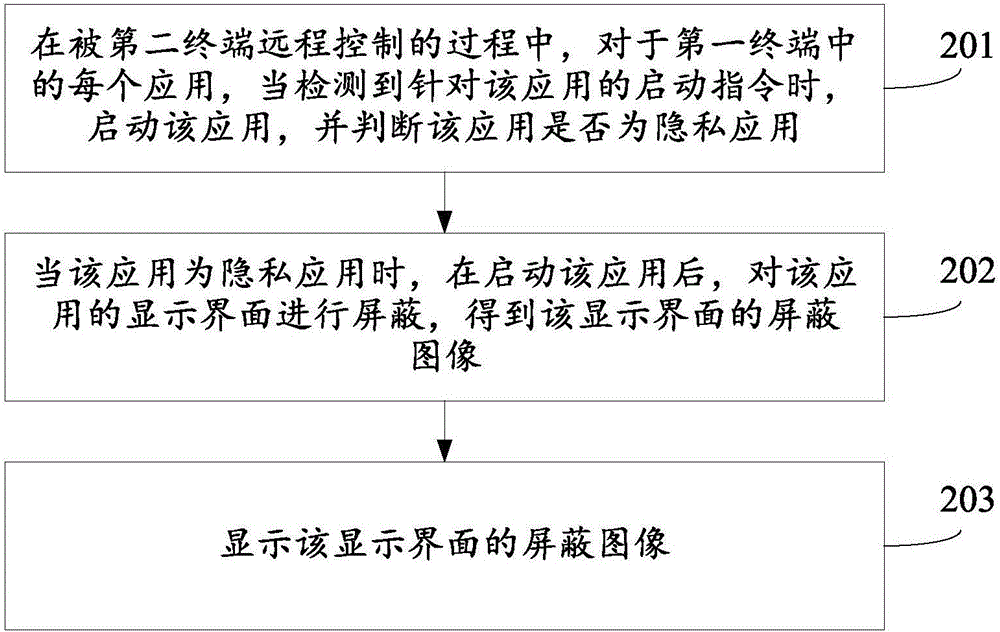
ActiveCN105956486AAvoid Privacy LeakageGuaranteed privacy and securityDigital data protectionRemote controlThe Internet
The invention relates to a remote control method and apparatus, and belongs to the technical field of internet. The method is applied to a first terminal. The method comprises the steps of starting an application when a starting instruction for the application is detected for each application in the first terminal in a process of remote control by a second terminal, and judging whether the application is a private application or not; when the application is the private application, hiding a display interface of the application after starting the application to obtain a hided image of the display interface; and displaying the hided image of the display interface. According to the method and apparatus, the privacy leakage of the first terminal can be effectively prevented to ensure privacy security of the first terminal.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Screen projection method, terminal and computer readable memory medium
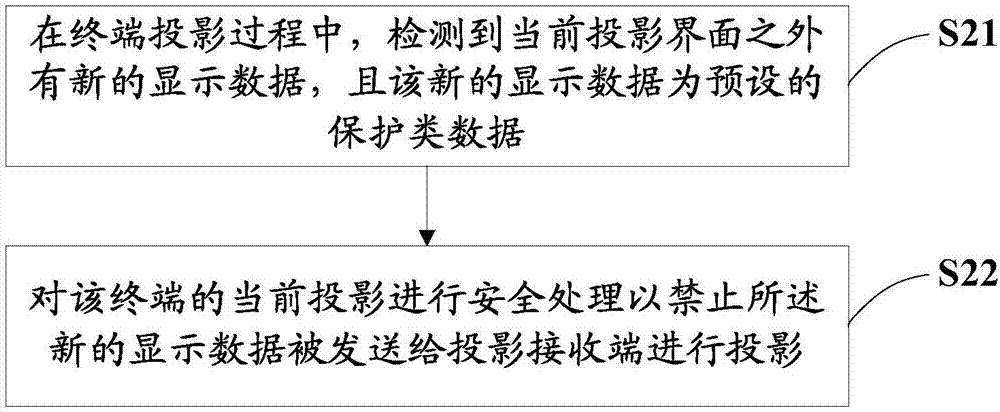
InactiveCN107302624AAvoid Privacy LeakageAvoid lostDigital data protectionSubstation equipmentUser privacyComputer terminal
The invention discloses a screen projection method, a terminal and a computer readable memory medium. In a projection process of a terminal, when it is detected that new display data exists out of a current projection interface, whether the new display data is preset protection type data or not is determined; and if the new display data is the preset protection type data, secure processing is carried out on current projection of the terminal, so the new display data is forbidden to be sent to a projection receiving end for projection. The corresponding protection type data is prevented from being sent to the projection receiving end for projection display. The problem that user privacy is leaked due to the fact that other user can browse and check the protection type data through the projection display of the projection receiving end when the corresponding protection type data is sent to the projection receiving end for projection in the projection process of the screen is effectively avoided; unnecessary losses to the user can be avoided; moreover, the trust of the user for a screen projection function is improved; and the user experience is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Intelligent monitoring method, device and system based on WiFi
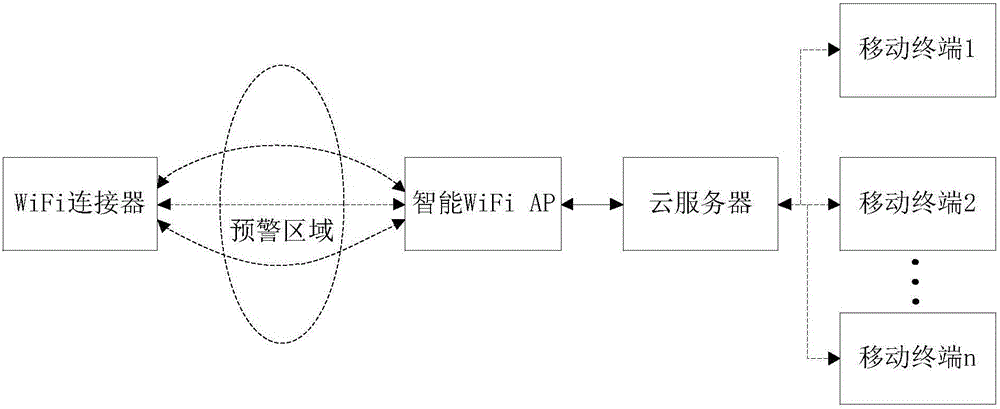
ActiveCN105894703APrevent bandits from invadingAvoid leakage of user privacyBurglar alarm electric actuationUser privacyReal-time computing
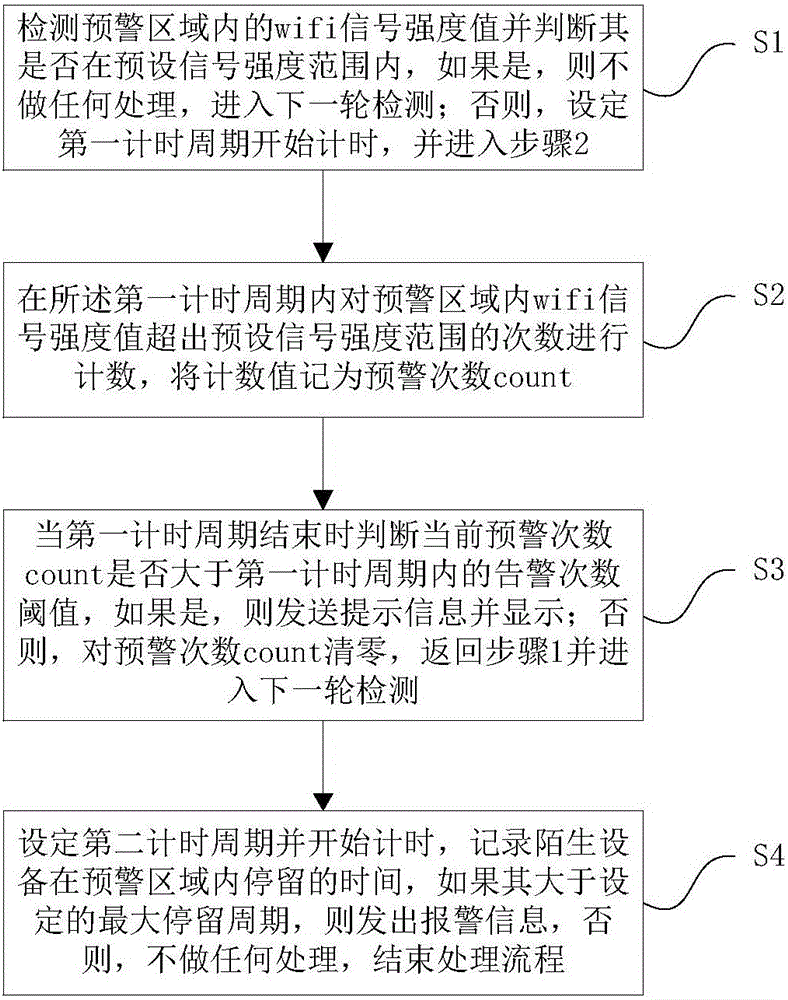
The invention relates to an intelligent monitoring method, device and system based on WiFi. The device comprises an intelligent WiFi AP (Access Point), which is used for detecting a WiFi signal intensity value in an early warning area, judging whether the WiFi signal intensity value is within a preset signal intensity range, judging whether the current early warning count exceeds an early warning count threshold after a set timing cycle, if so, sending and displaying prompt information, otherwise, not carrying out any processing. The method, the device and the system realize intelligent monitoring using the WiFi technology, thereby effectively avoiding user privacy divulgence and missing report defect; and intelligent monitoring can be realized by adding only one WiFi connector and sufficiently utilizing the existing household routing platform, so the method, the device and the system are low in cost, high in security and very suitable for large-area popularization.
Owner:湖南领佰科技有限公司
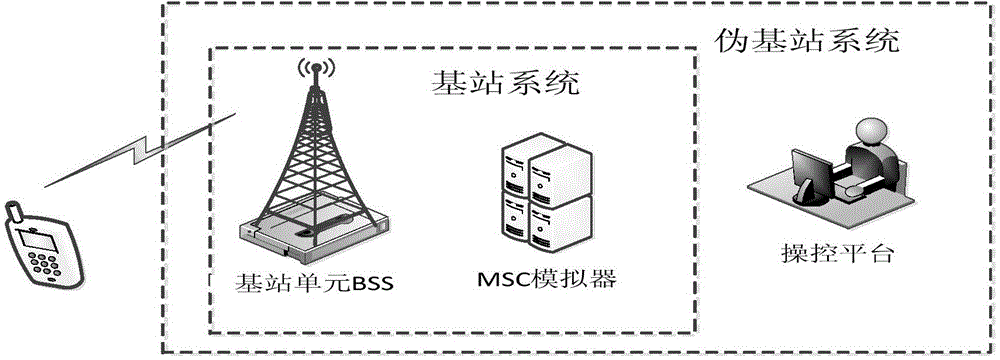
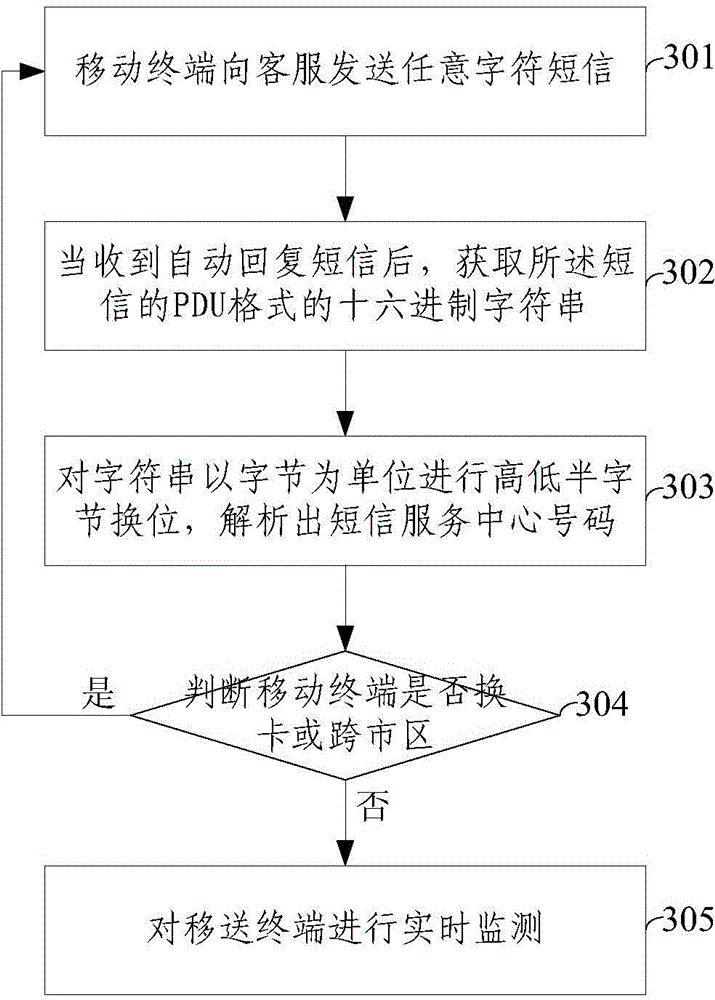
Real-time pseudo base station determining method and system based on short message
The invention provides a real-time pseudo base station determining method based on a short message. The method comprises steps as follows: a mobile terminal analyzes the received short message to acquire a short message service center number; whether the short message service center number is identical with an initialized short message service center number or not is judged, and if the short message service center number is not identical with the initialized short message service center number, the short message is determined to be sent by a pseudo base station; the short message is intercepted, and the short message is displayed as a short message sent by the pseudo base station. The invention further provides a real-time pseudo base station determining system based on the short message. The system comprises an analysis module, a determination module and an interception module. With the adoption of the method and the system, short messages of pseudo base stations can be intercepted in real time, and privacy disclosure can be effectively prevented.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
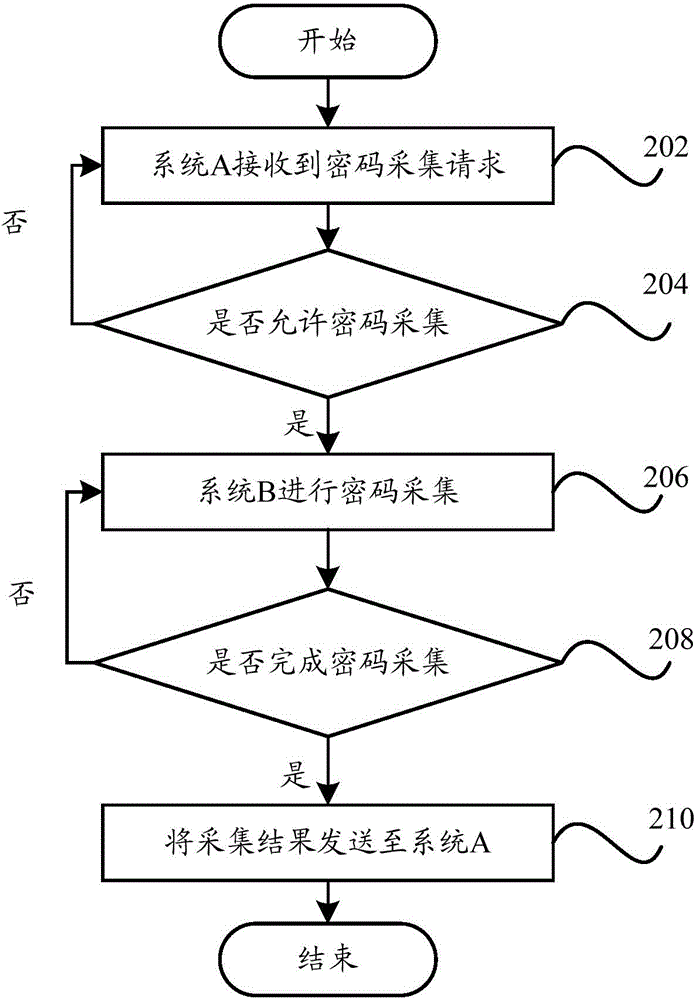
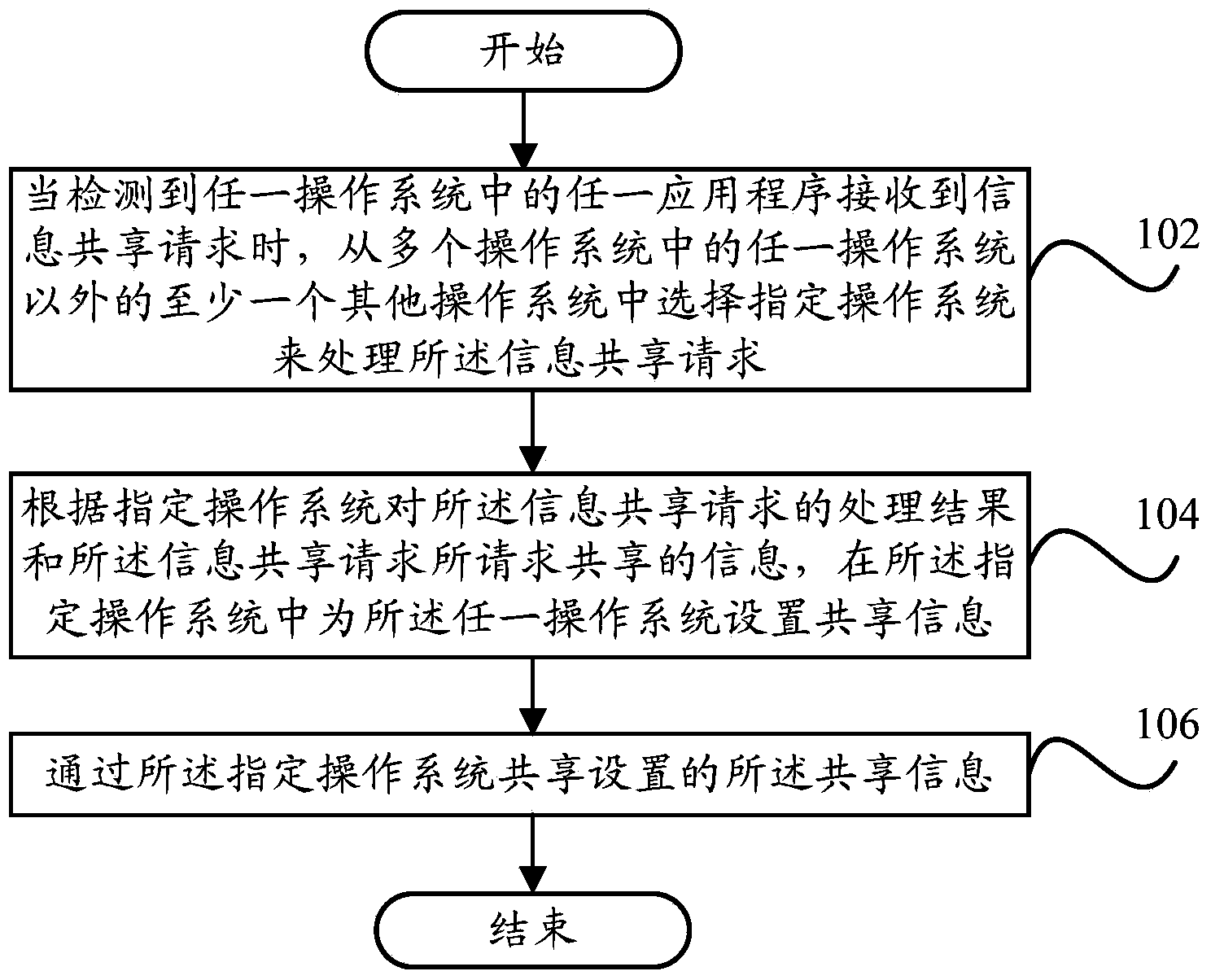
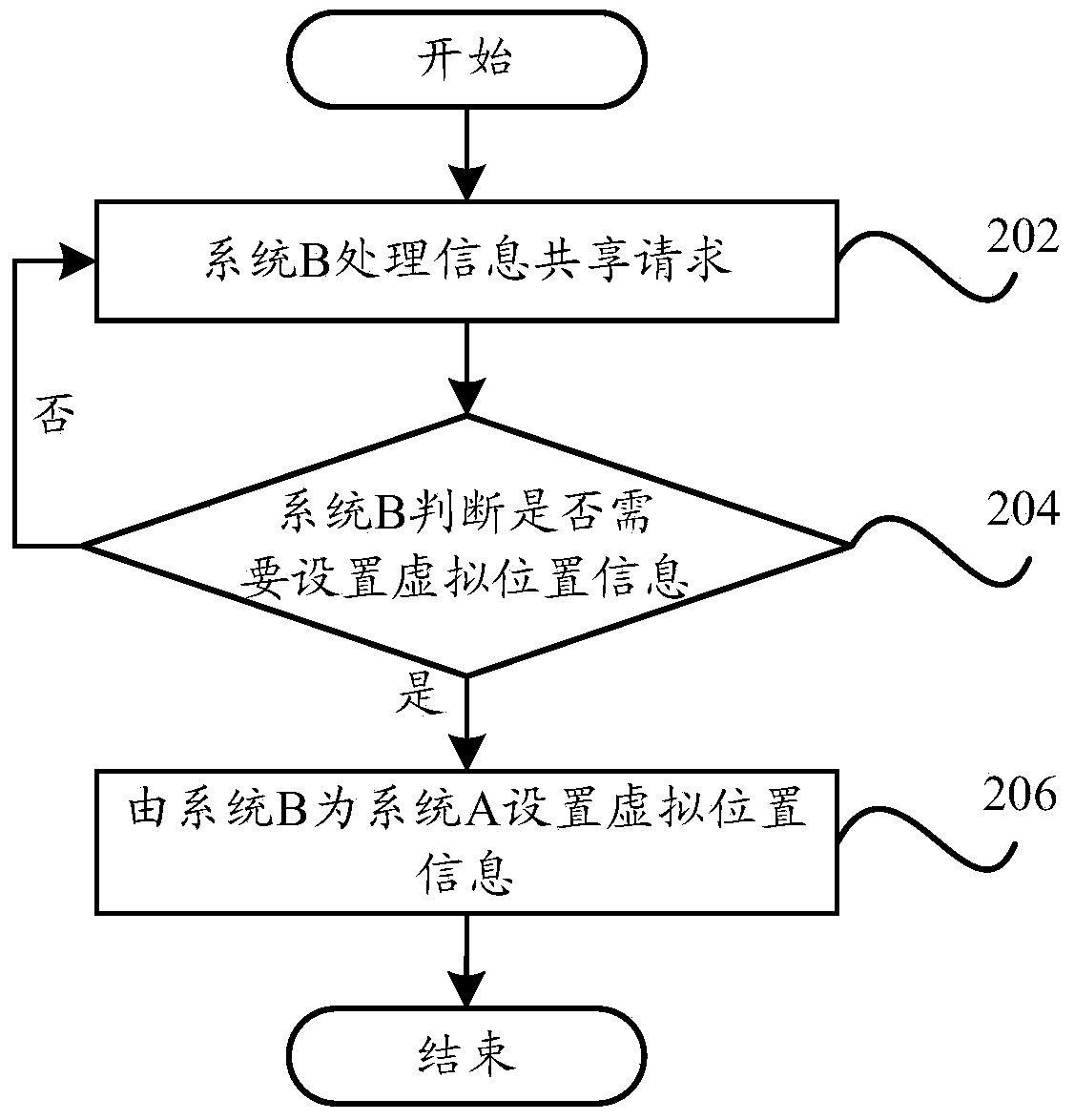
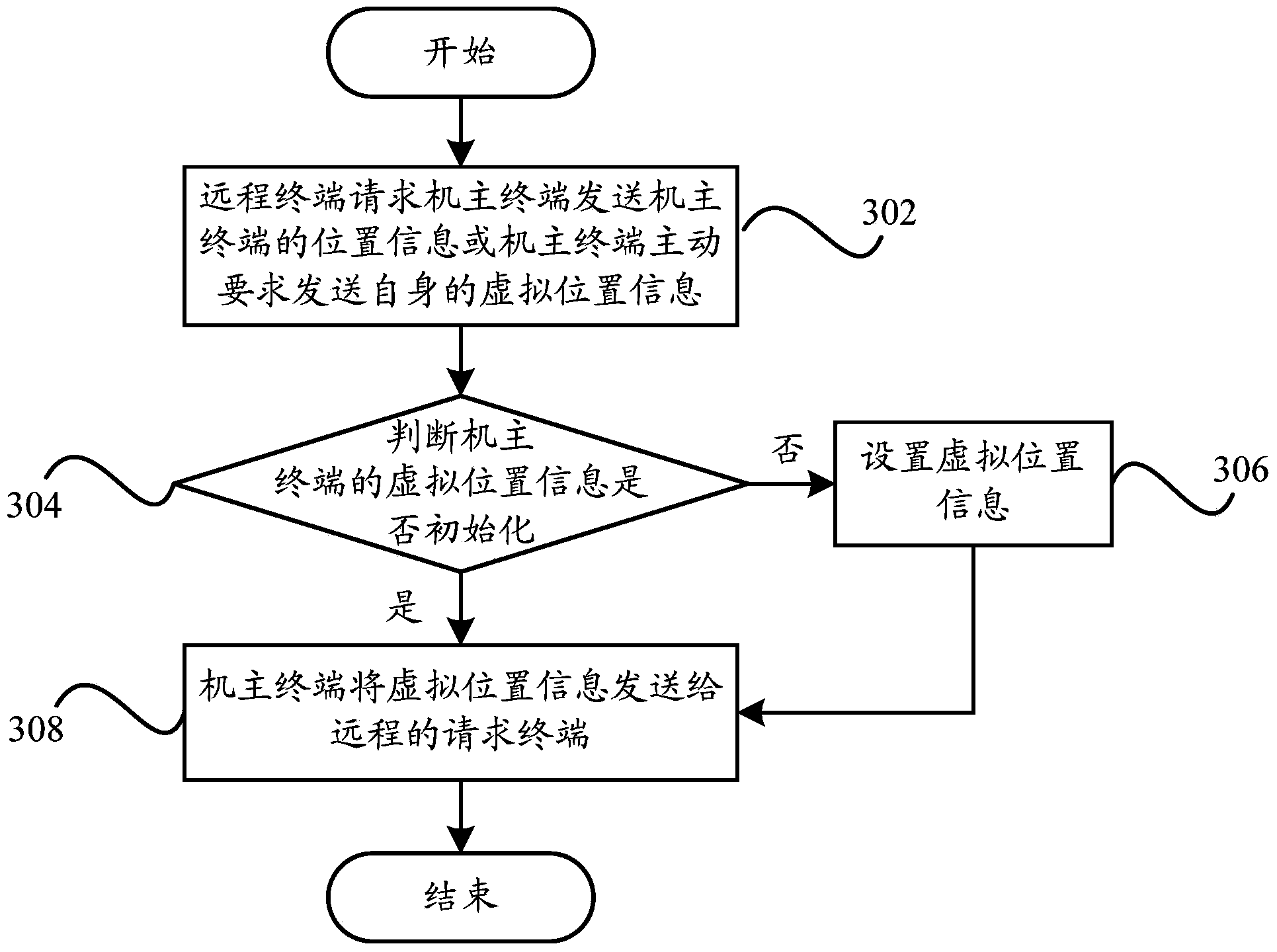
Information sharing method and information sharing device of terminal and terminal
ActiveCN104184738AImprove privacy and securityImprove experienceTransmissionInformation sharingOperational system
The invention provides an information sharing method and an information sharing device of a terminal and the terminal. The information sharing method of the terminal comprises the steps of selecting a designated operating system from at least one of other operating systems of multiple operating systems except any one operating system to handle an information sharing request when detecting any one operating system receives the information sharing request; setting shared information for any one operating system in the designated operating system according to a handling result of the designated operating system handling the information sharing request and information required by the information sharing request to be shared; sharing the set shared information through the designated operating system. By means of the technical scheme, the control ability on personal information of a user is improved, the information security of the terminal is effectively ensured, the privacy security of the user is improved, and the user experience is enhanced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
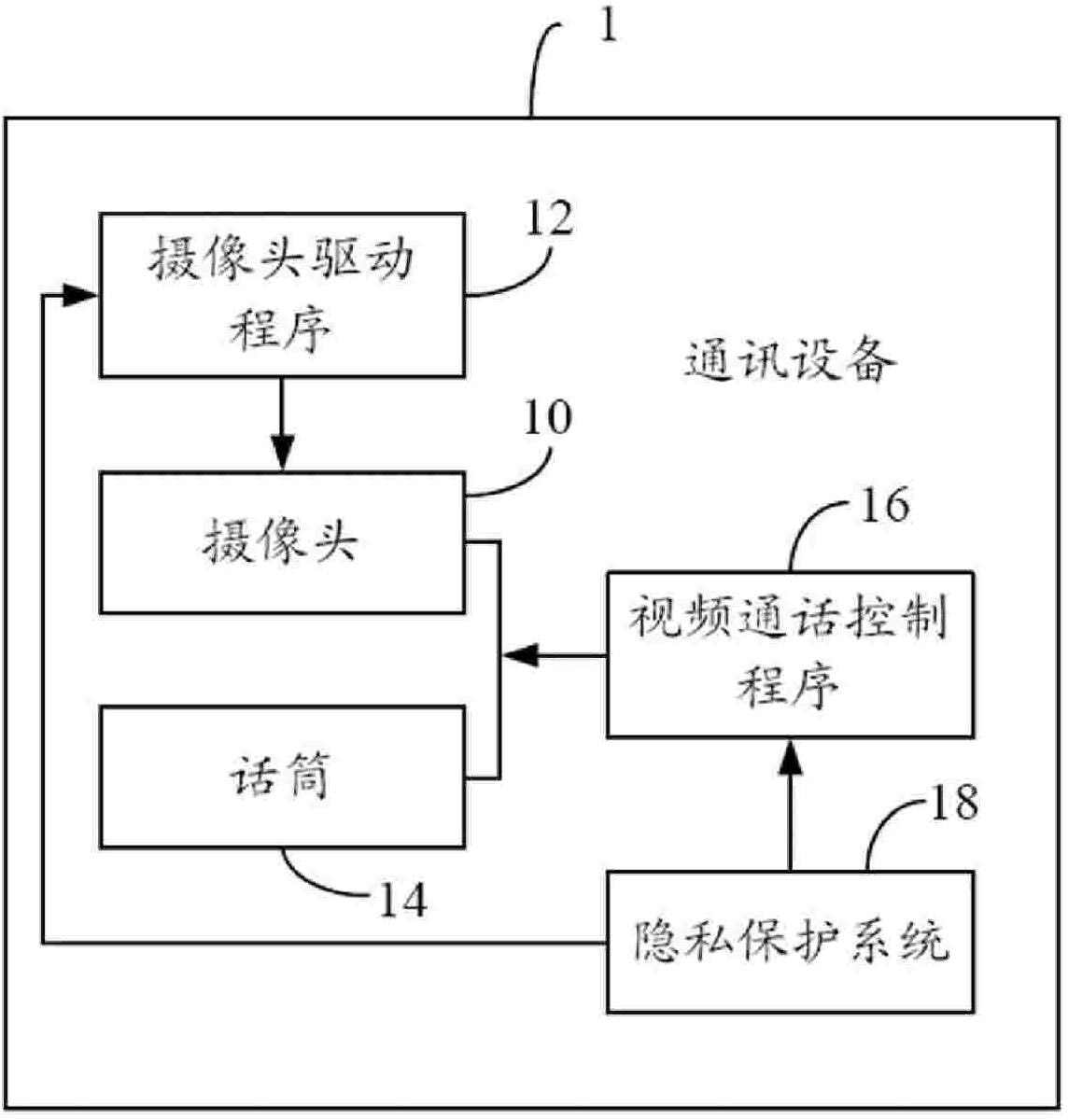
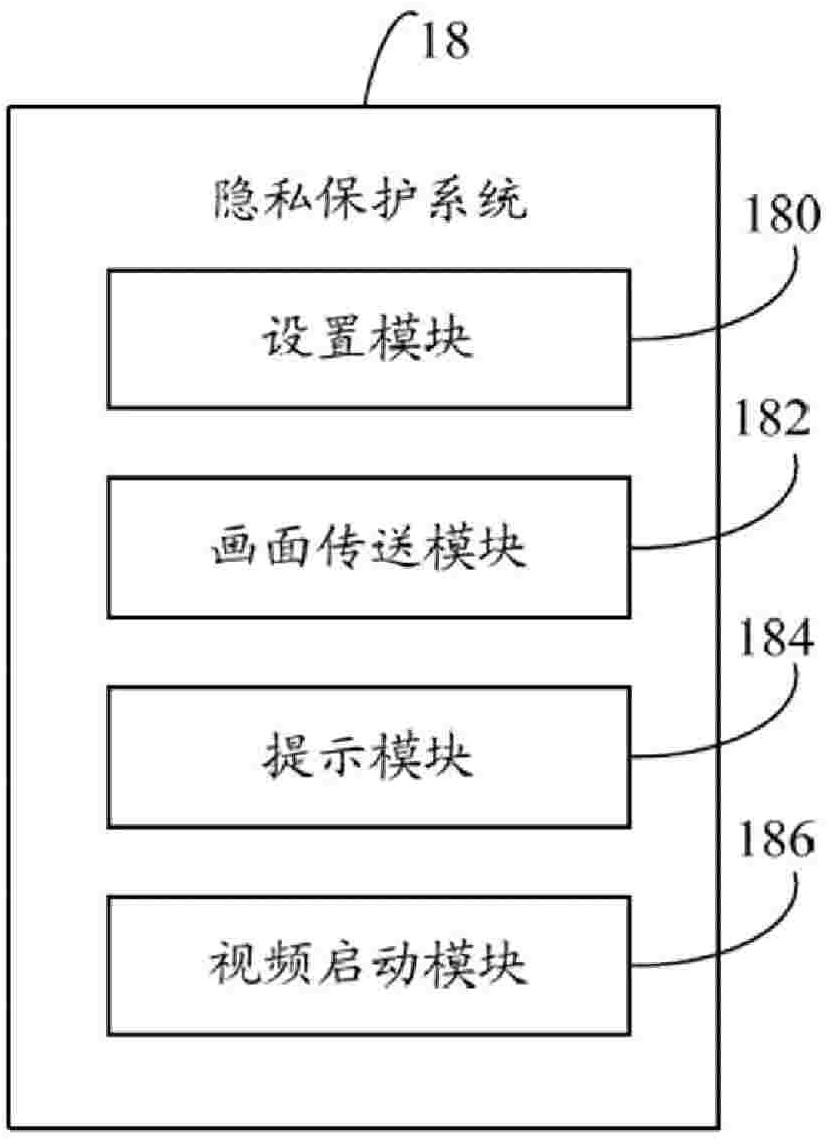
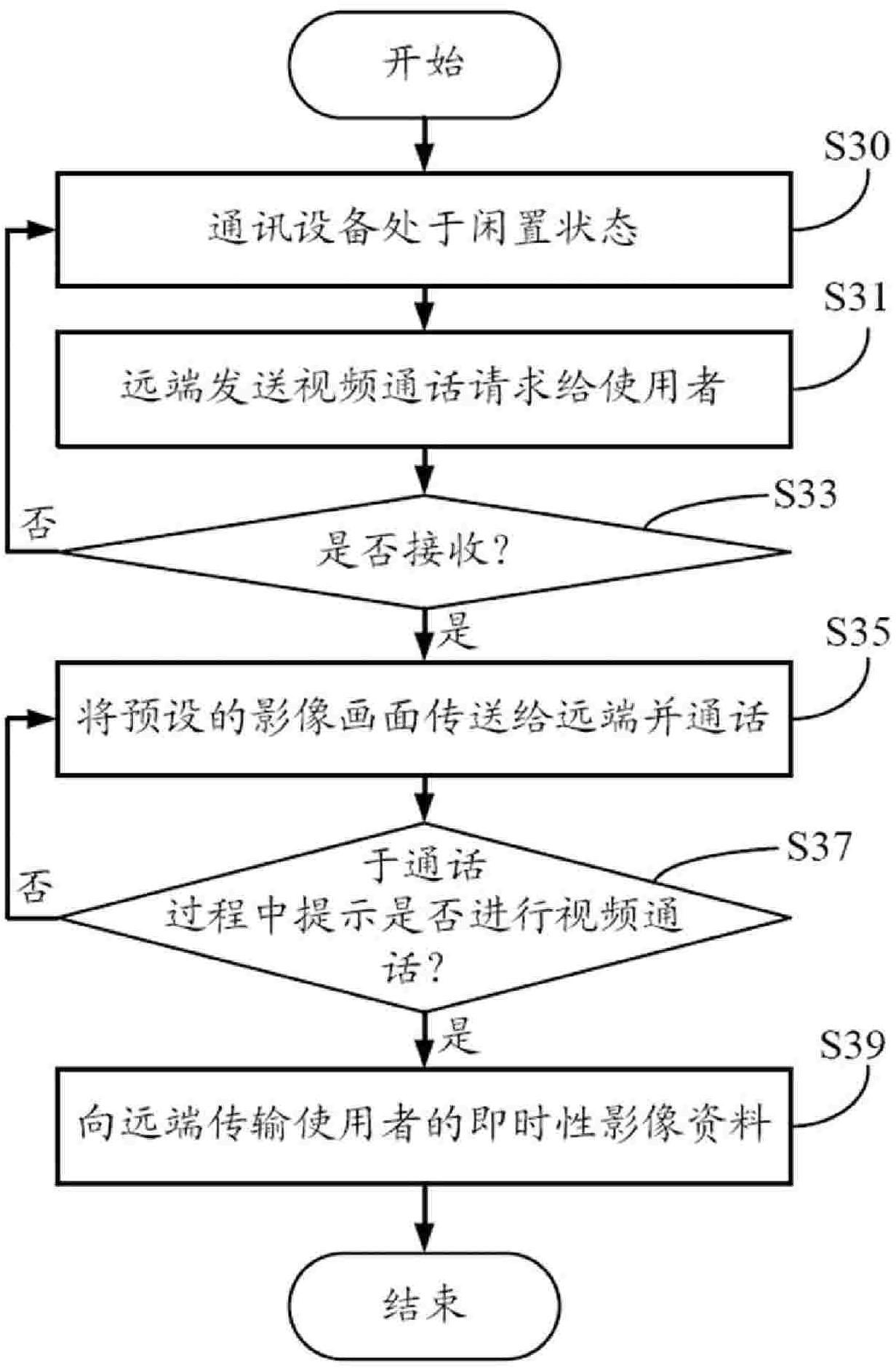
Privacy protecting system and method in video call
InactiveCN102104766AAvoid Privacy LeakageLeak of privacyTwo-way working systemsSelective content distributionVideo transmissionInternet privacy
The invention provides a privacy protecting method in a video call, which comprises the following steps of: sending a video call request by a distal end; if a user is inconvenient to have a video with the distal end, sending a preset image frame to the distal end and talking with the distal end; prompting whether to have the video call during the call; when the user is convenient to have the video call with the distal end, confirming a video call prompt to start the video transmission function; and transmitting real-time image data of the user to the distal end. The invention also provides a privacy protecting system in the video call. Privacy leakage caused by receiving the video call request of the distal end in an emergency by the user can be avoided by using the privacy protecting method.
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD
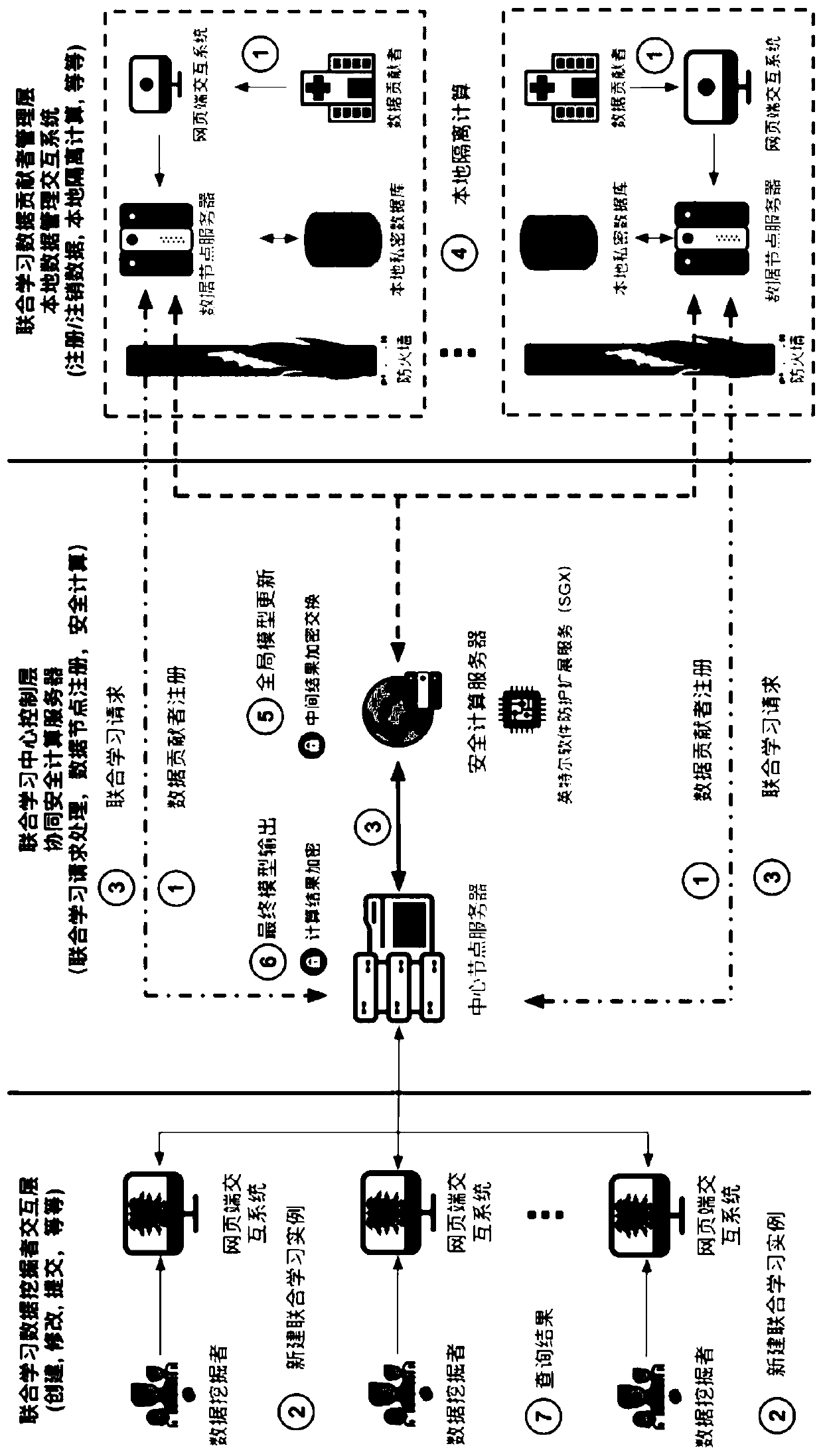
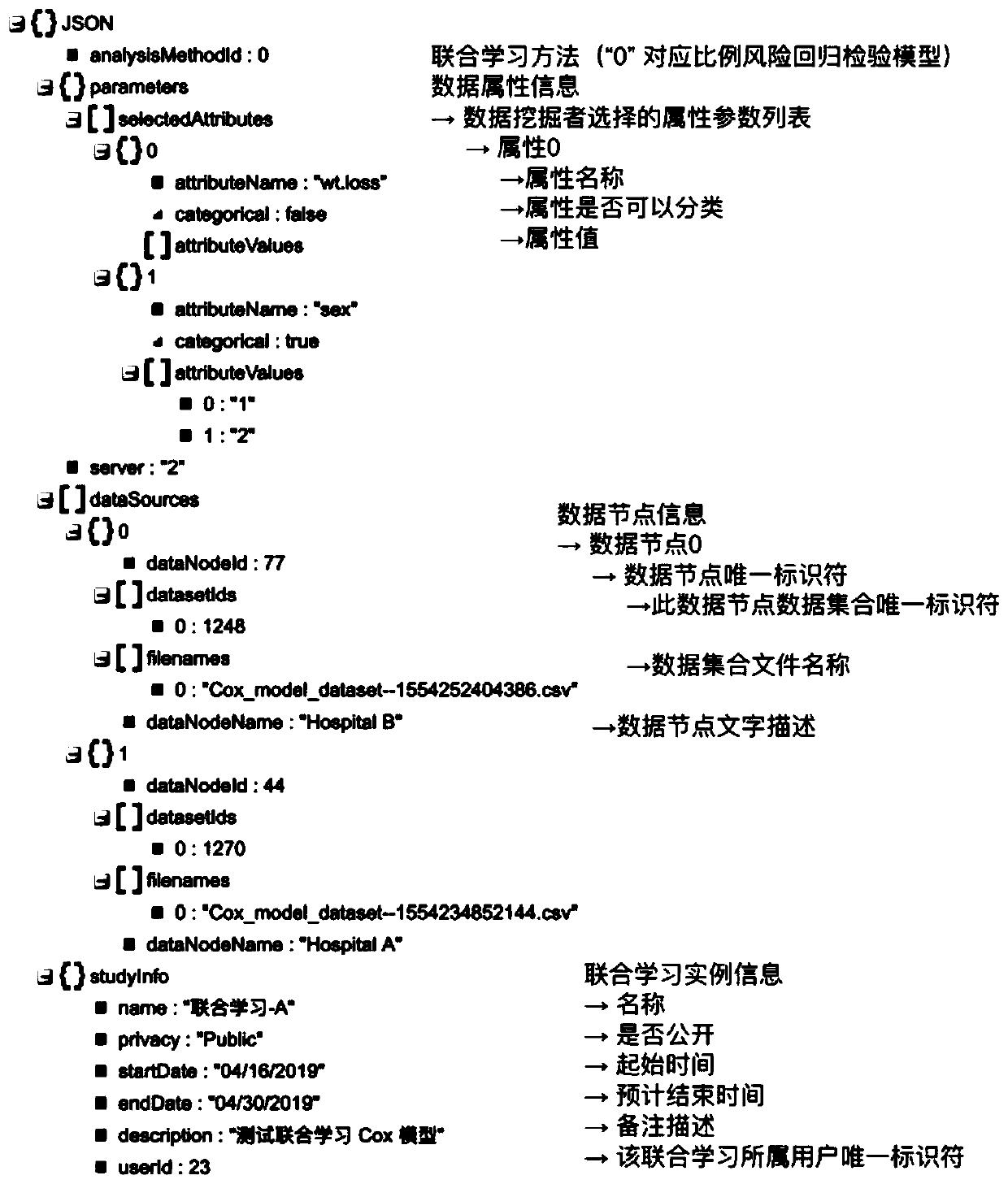
Medical data joint learning system and method based on trusted computing and privacy protection
ActiveCN110197084AStrict and flexible authorization authenticationRealize deep miningMedical data miningDigital data protectionInteraction layerData privacy protection
The invention relates to a medical data joint learning system and method based on trusted computing and privacy protection. A joint learning center control layer receives non-sensitive meta-information uploaded by a data contributor through a data contributor management layer of a data node where the joint learning center control layer is located for filing, and original data is locally registered, stored and subjected to isolation calculation; and the joint learning center control layer processes a joint learning request initiated by the data miner through the data miner interaction layer, summarizes insensitive intermediate results obtained by performing local isolation calculation on the data nodes based on the original data in a safe calculation area, and returns a final joint learningresult to the data miner interaction layer. The invention provides a whole set of service system based on medical big data security sharing, trusted computing, deep mining, authority authentication and multi-platform joint learning, and solves the problems of scattered, single and incomplete medical data privacy protection and data mining at the present stage.
Owner:上海锘崴信息科技有限公司
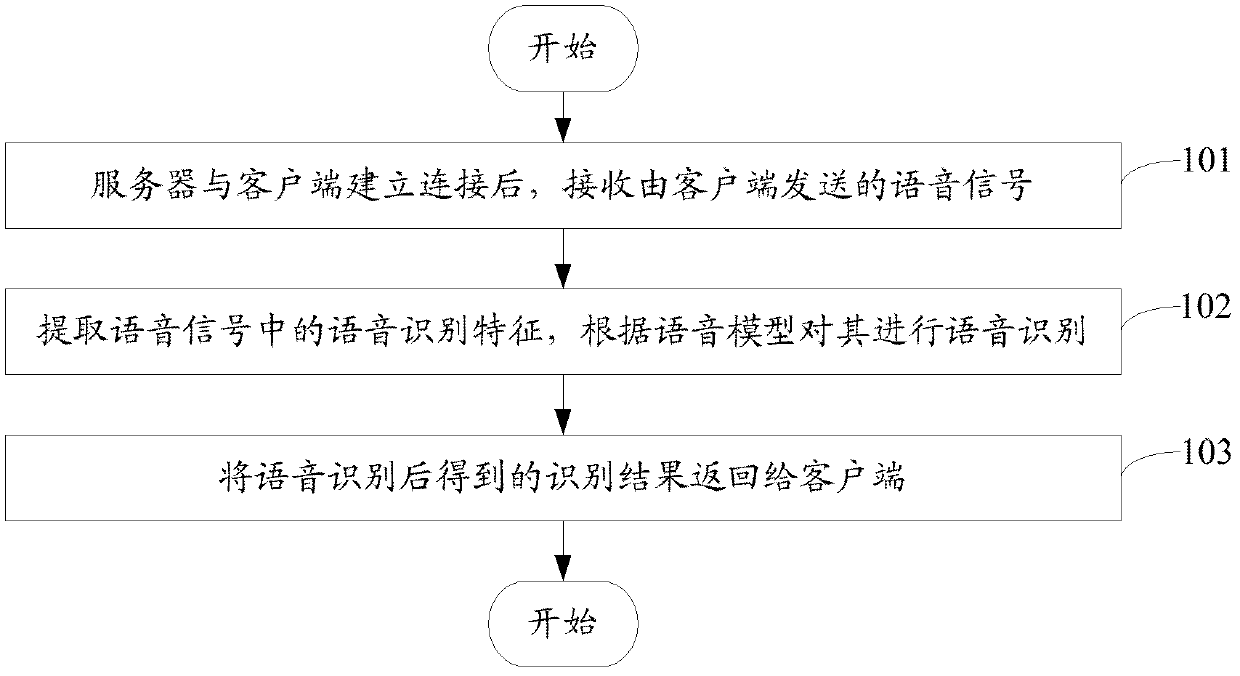
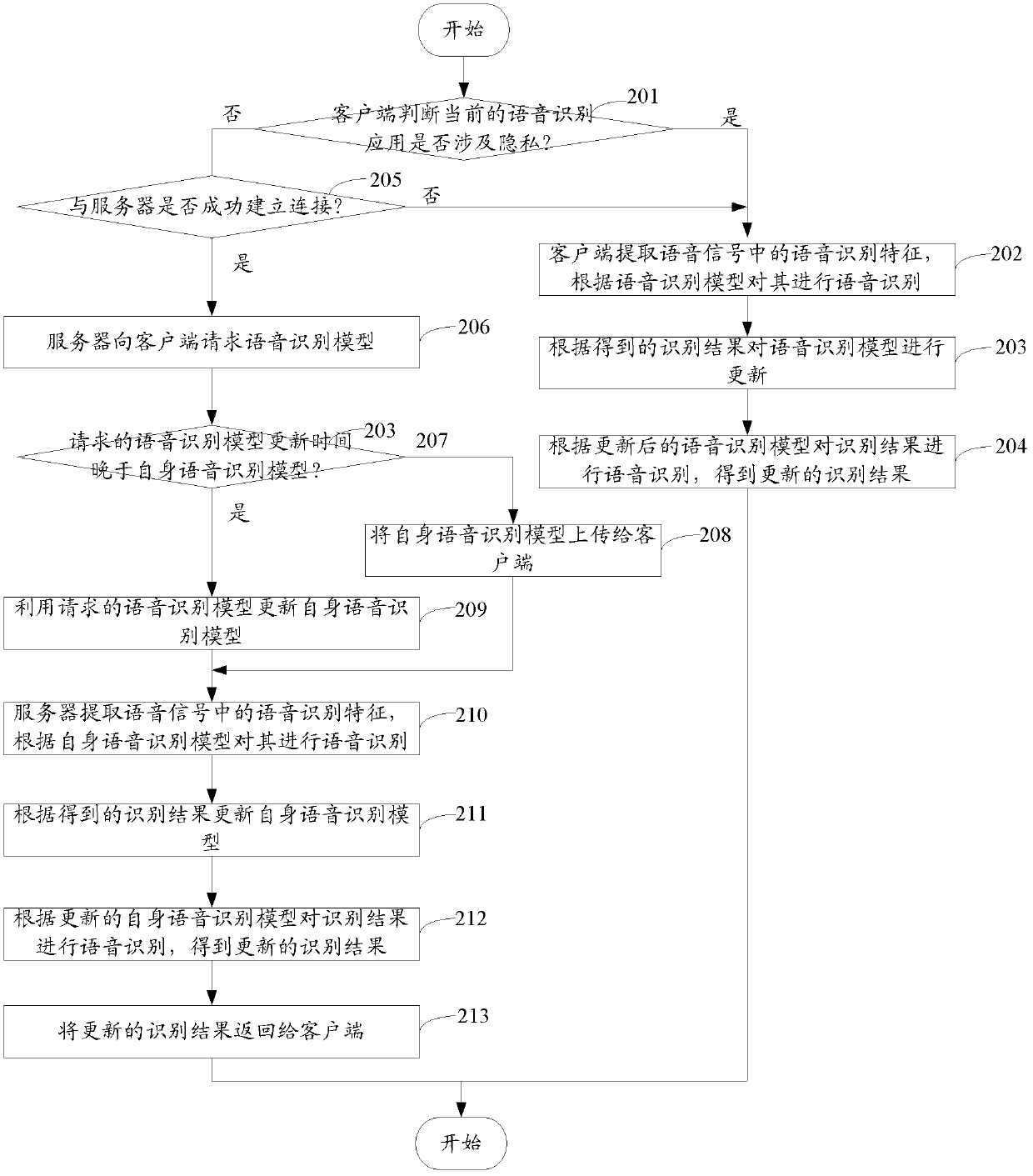
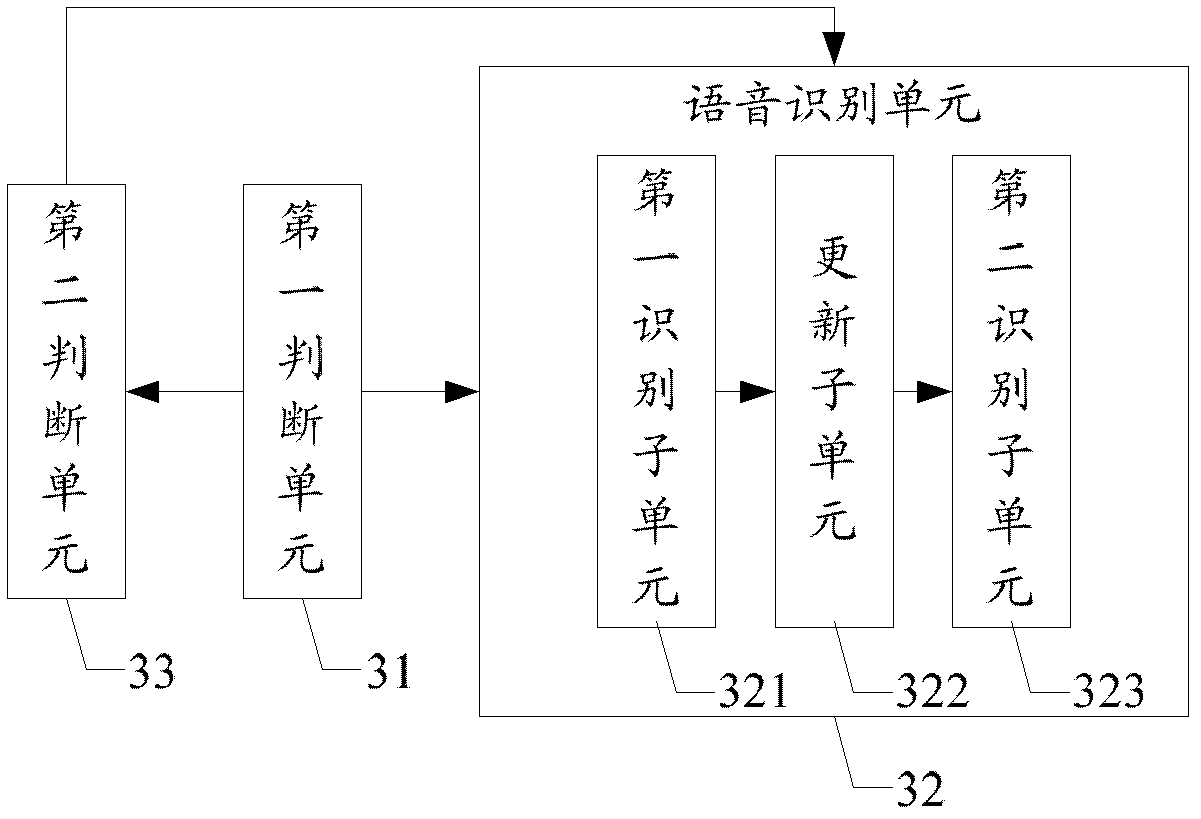
Speech recognition method and client
The invention provides a speech recognition method. The speech recognition method comprises the following steps that a client judges whether current speech recognition application involves privacy, if the current speech recognition application involves privacy, the client conducts speech recognition on collected speed signals; otherwise, the client further judges whether connection between the client and a server is successfully established; if connection between the client and the server is successfully established, the server conducts the speech recognition on the collected speech signals; if the connection between the client and the server is not successfully established, the client conducts the collected speech recognition on the collected speech signals. The invention further discloses the client of the speech recognition. The speech recognition method and the client can achieve the objective that speech recognition is conducted on speech data which contain privacy and is not limited by a network condition.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
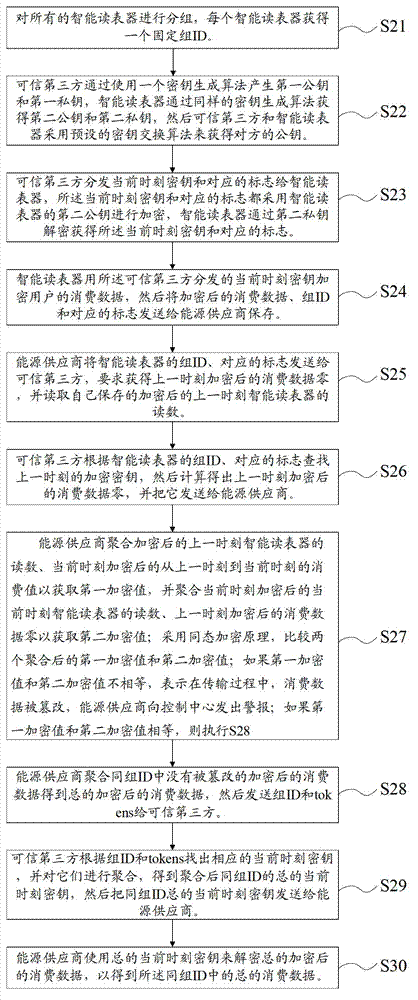
Data protection method and system based on homomorphic encryption
The invention provides a data protection method and a system based on homomorphic encryption. Historical data of users are combined, the data protection method and the system based on the homomorphic encryption utilizes a principle of the homomorphic encryption, methods of calibration for comparing two encrypted values after polymerizations can effectively detect whether the data of the users are intercepted or tampered by opponents or not in the process of transmitting procedure of the data of the users. The data protection method and the system based on the homomorphic encryption can find whether the data of the users are tampered or not, and carry out the deciphering on the whole encrypted consumption data of the same group identification data (ID) so that the whole consumption data of the group are obtained. The data protection method and the system based on the homomorphic encryption don't directly decipher the encrypted consumption data sent by a smart meter reading device so that the privacy disclosure of the users to energy suppliers is avoided.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI +1
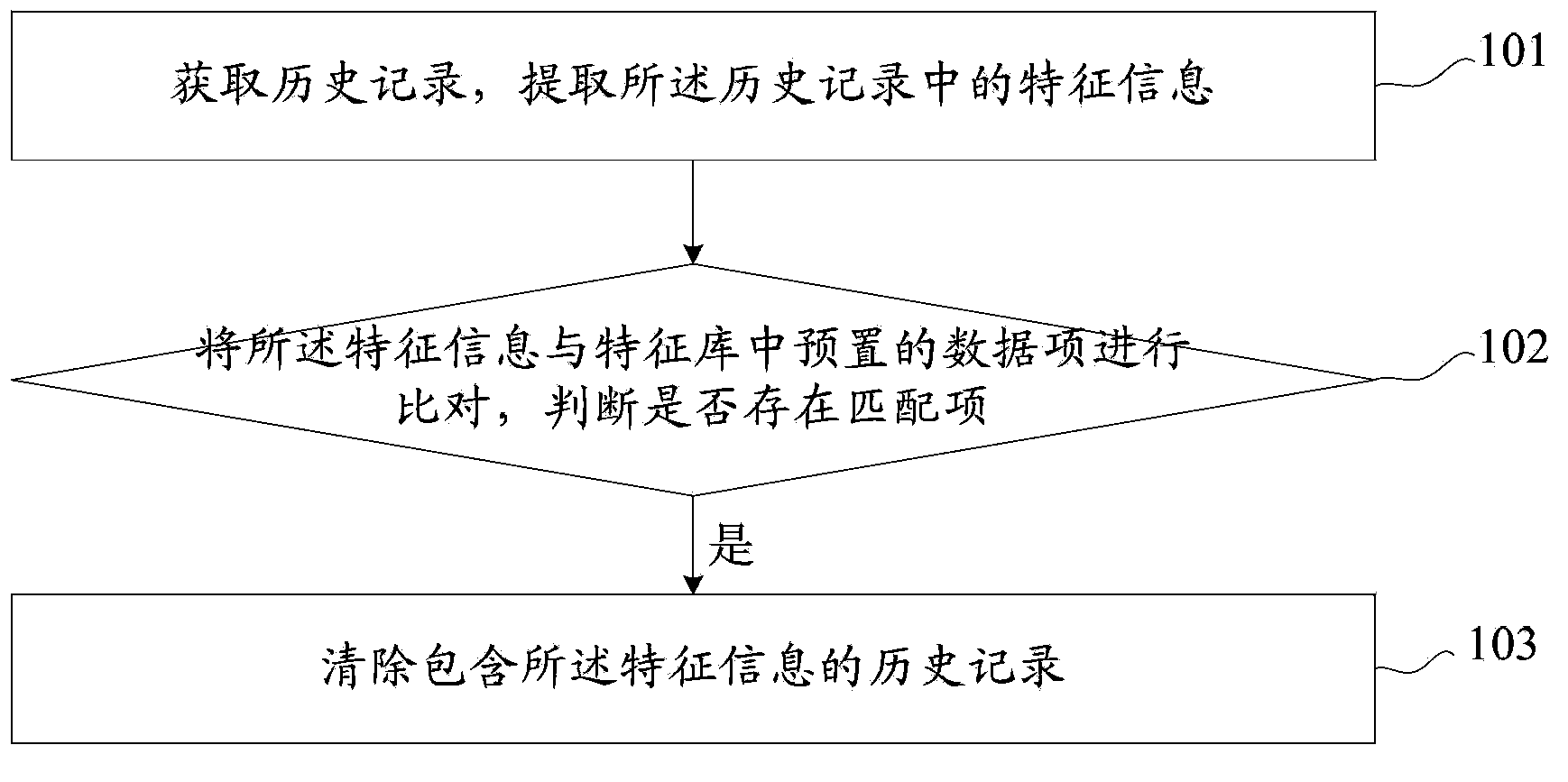
Method and device for clearing historical records
InactiveCN103412901AEasy to operateAvoid Privacy LeakageSpecial data processing applicationsUser deviceInternet privacy
The invention provides a method and a device for clearing historical records. The method comprises the steps as follows: the historical records are acquired, and feature information in the historical records is extracted; the feature information is compared with preset data items in a feature library; and if matched items exist, and the historical records containing the feature information are cleared. According to an embodiment of the method and the device, user operation steps can be simplified, user privacy leak is prevented, and the safety of user equipment is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
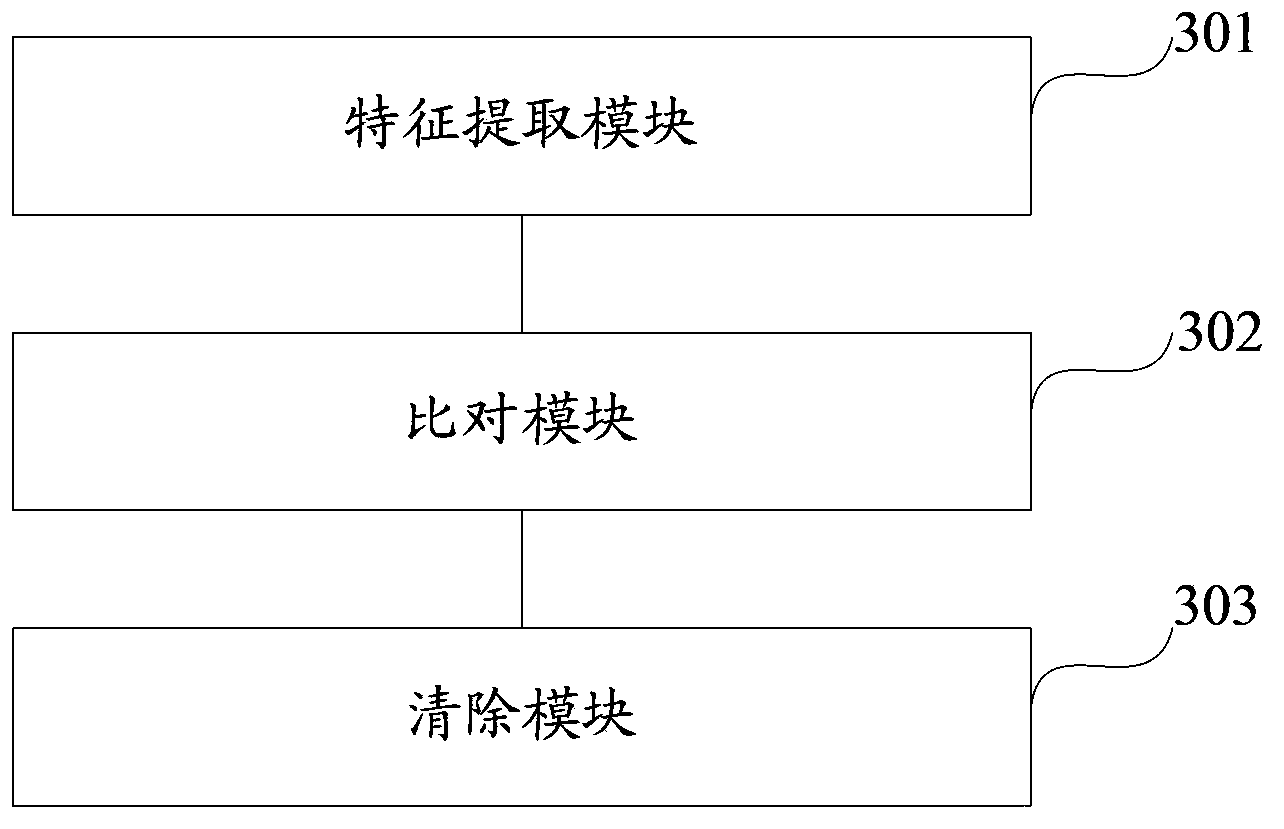
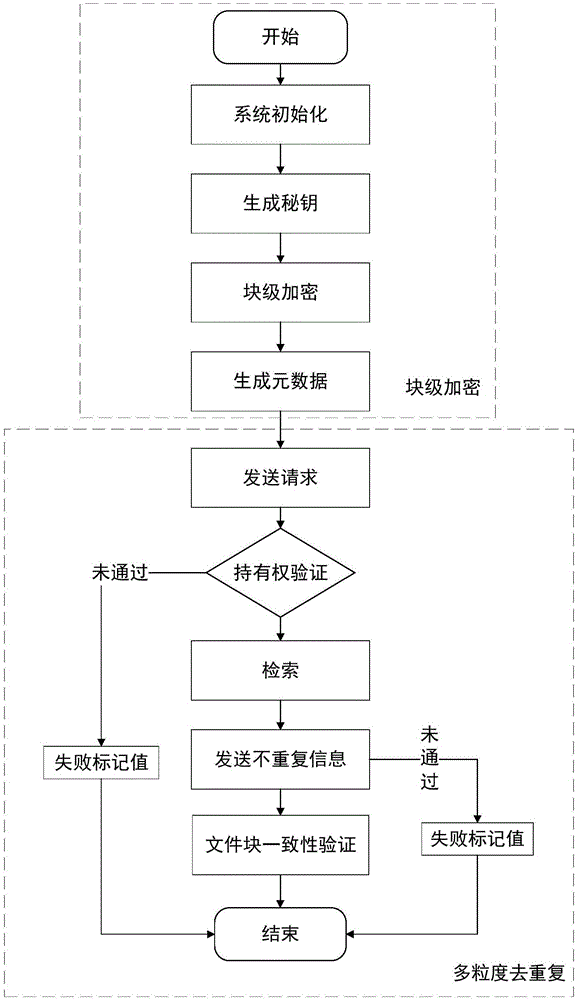
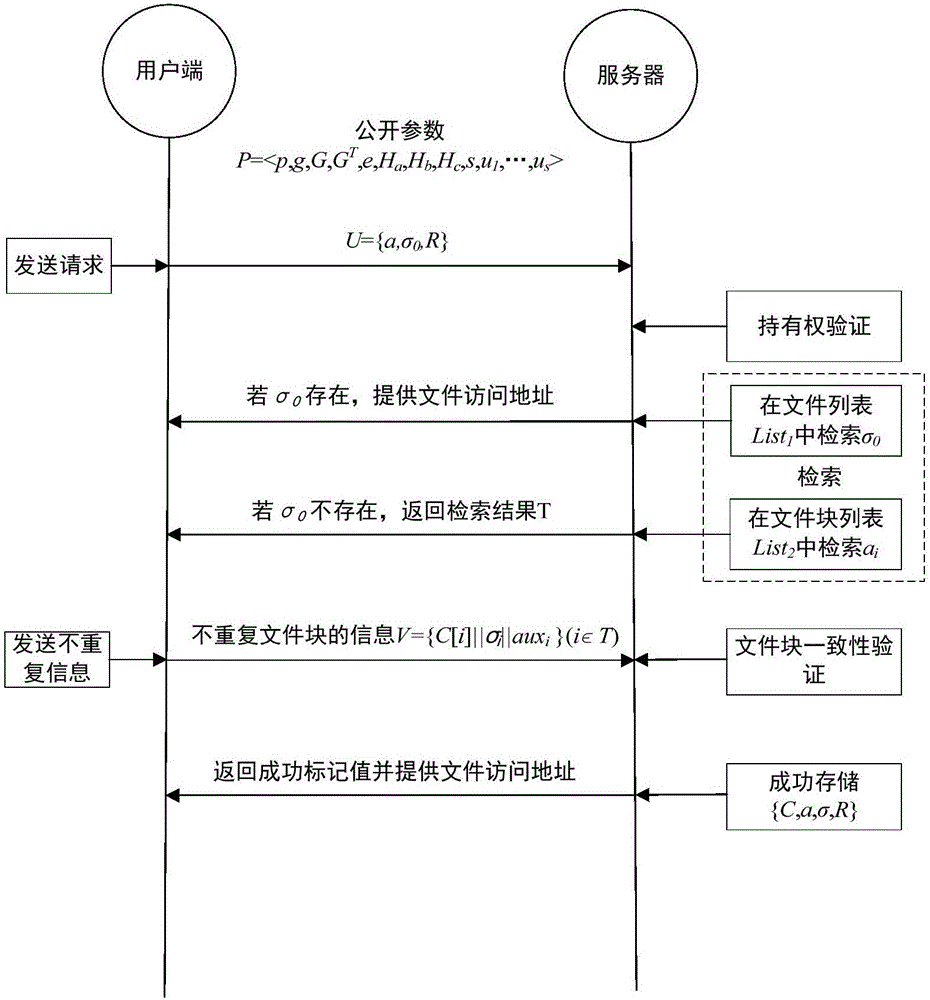
Block level encryption method in cloud storage and multi-granularity deduplication method
ActiveCN106603561ADe-duplicationReduce overheadDigital data protectionTransmissionGranularityCloud storage
The invention discloses a block level encryption method in cloud storage and a multi-granularity deduplication method, belonging to the technical field of network security. The block level encryption method comprises the steps that a system public parameter is set, a user end calculates a key and encryptes a file, and metadata is calculated; and the user end selects a part of metadata as a deduplication request and sends the request to a server, the server verifies the file ownership of a user according to the request and retrieves a file in a storage list, if the file exists, access is provided directly, otherwise the server asks the user end to upload non-repeat information, the server carries out consistency verification on received data, and the server allows the user end to access the file if the verification is passed. The method is suitable for the cloud storage with security and efficiency of data and aims to safely and reliably carry out deduplication on the user data, and the data storage efficiency is high.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com