Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1638 results about "Rights management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
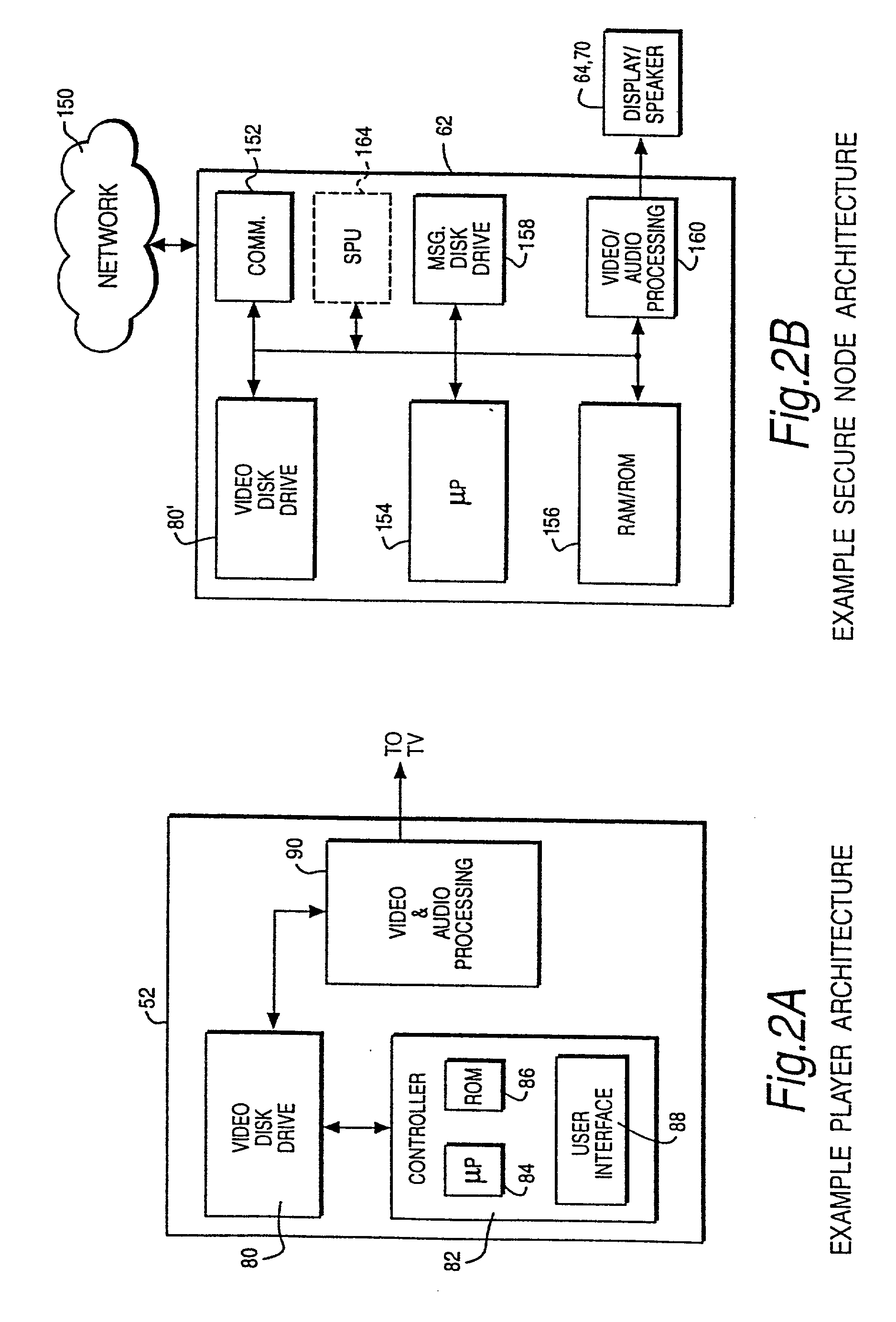
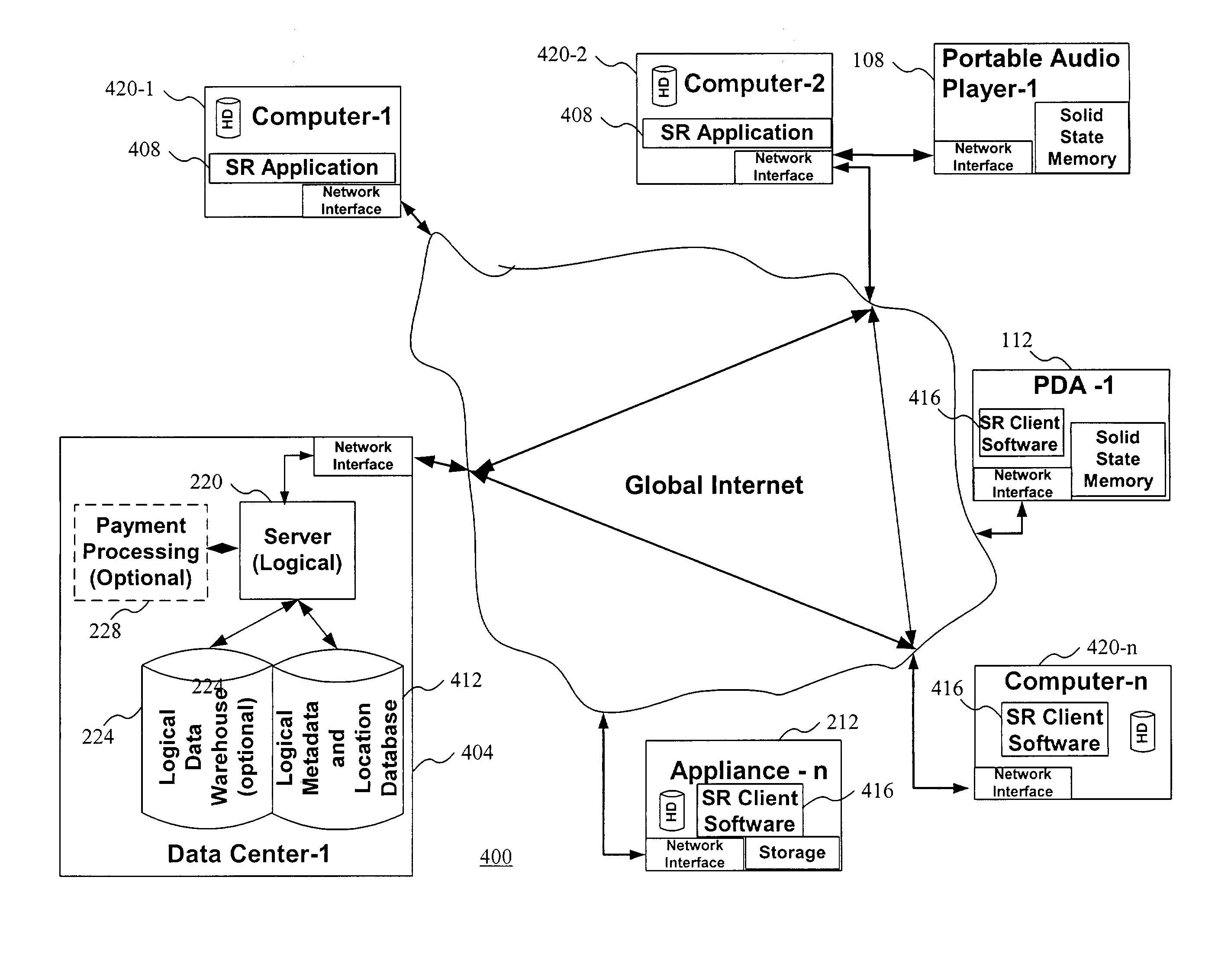
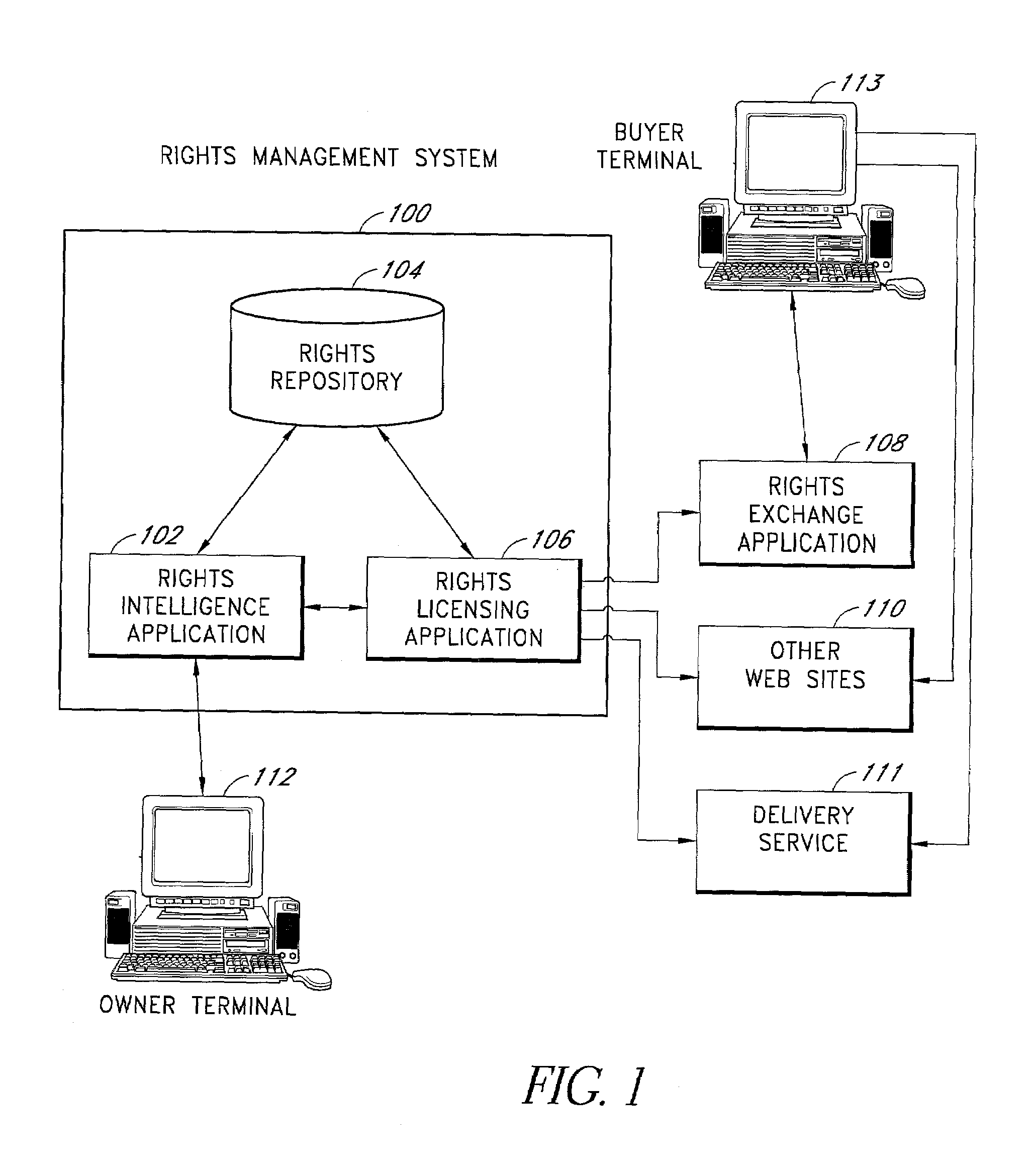
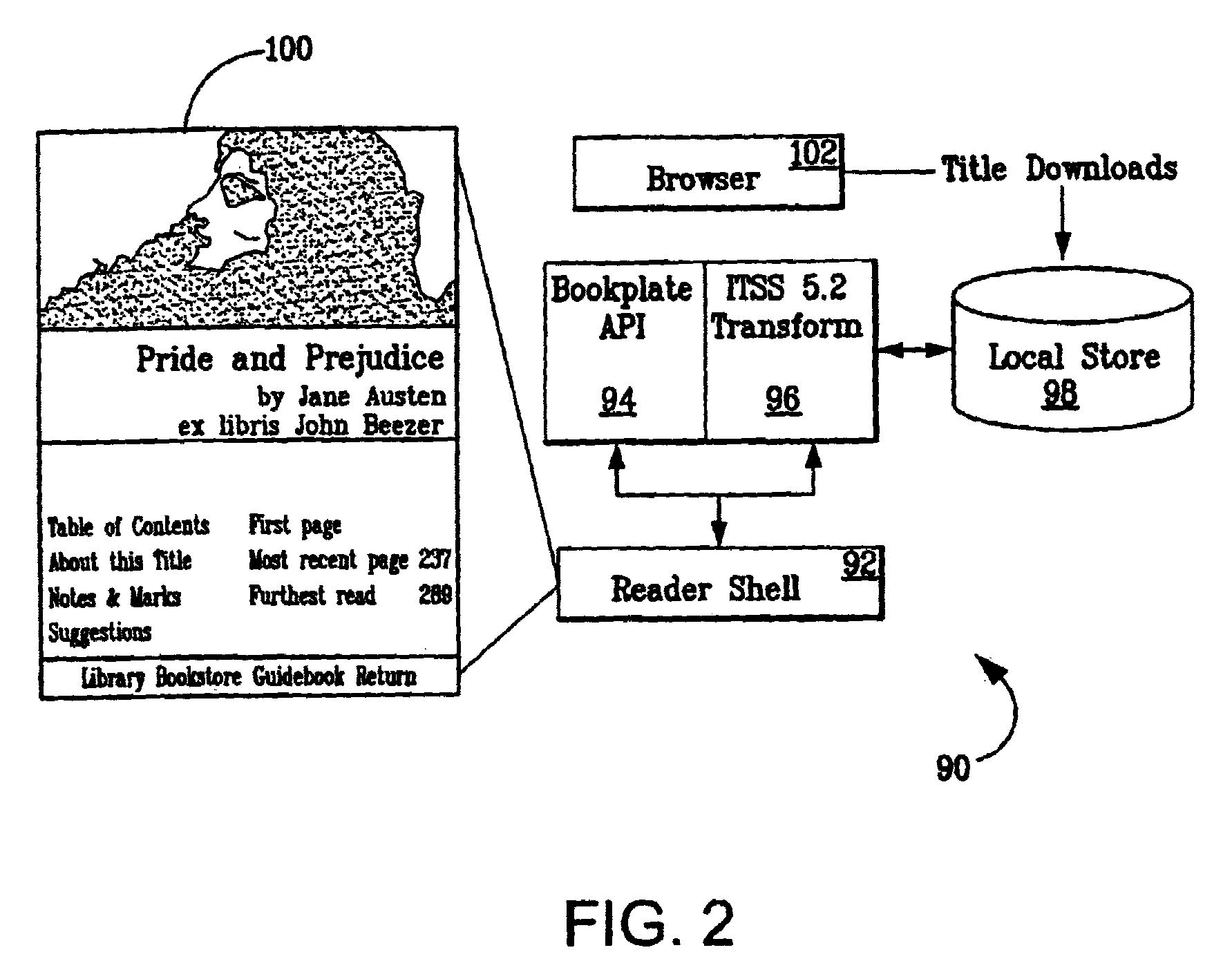
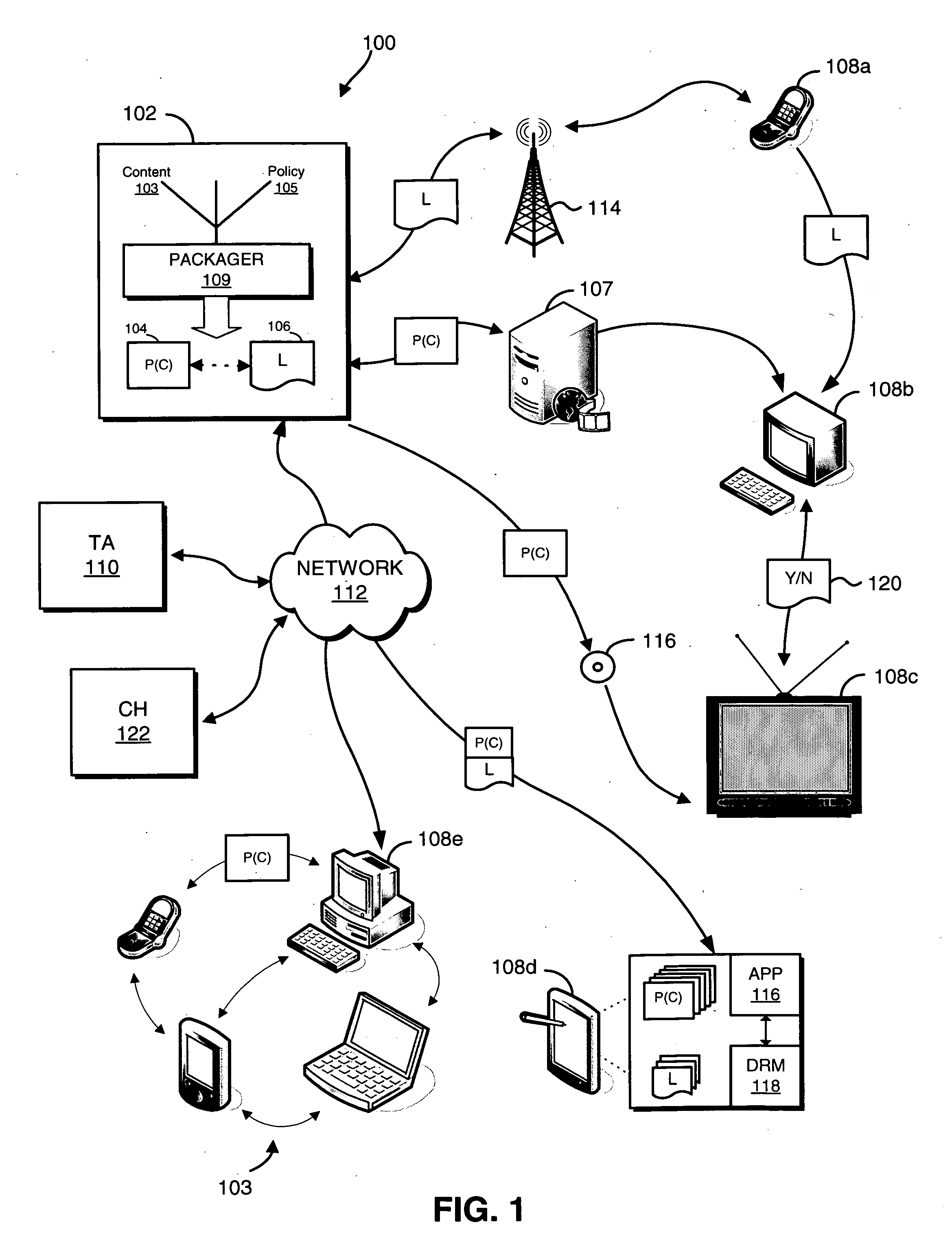
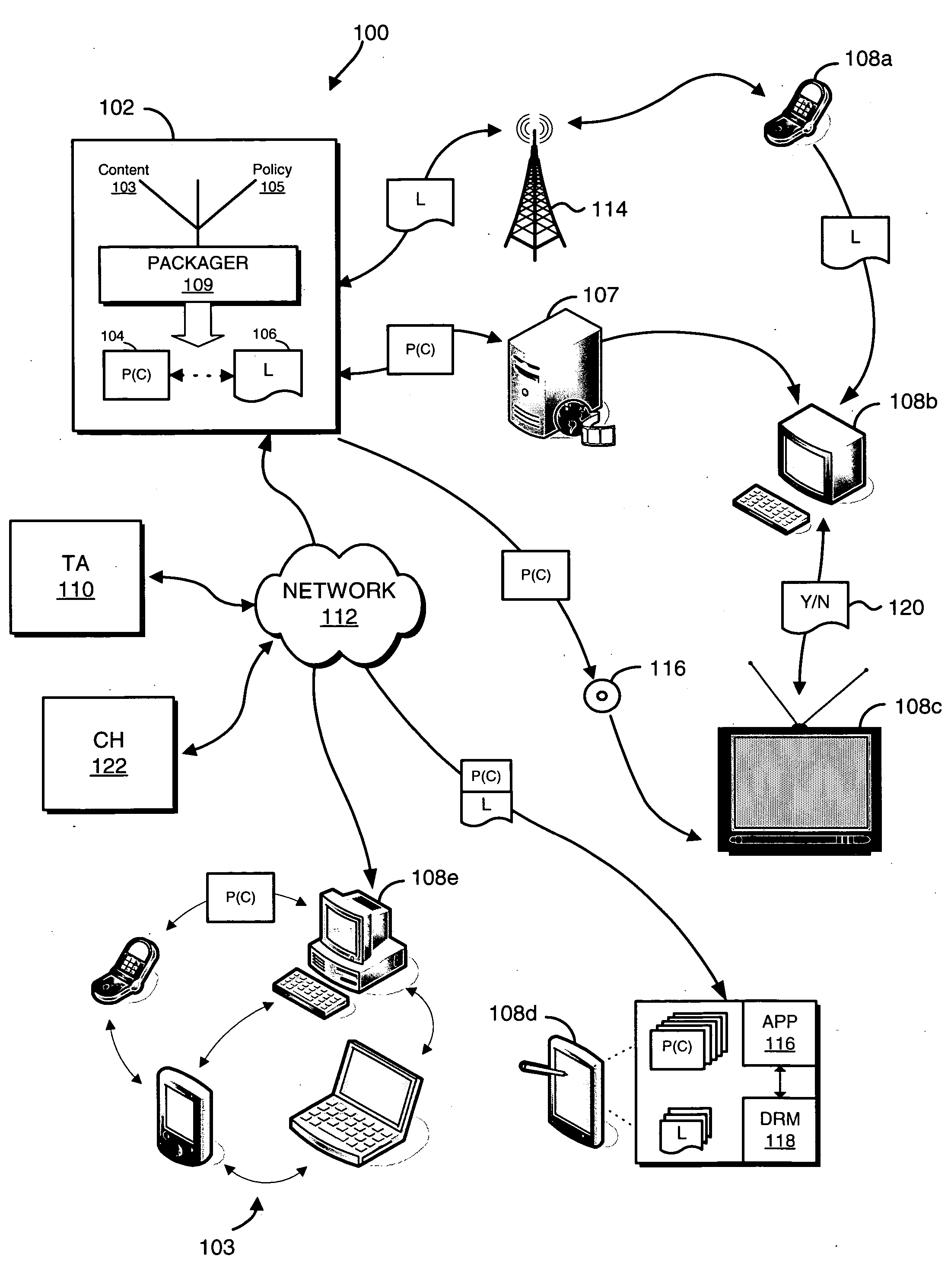
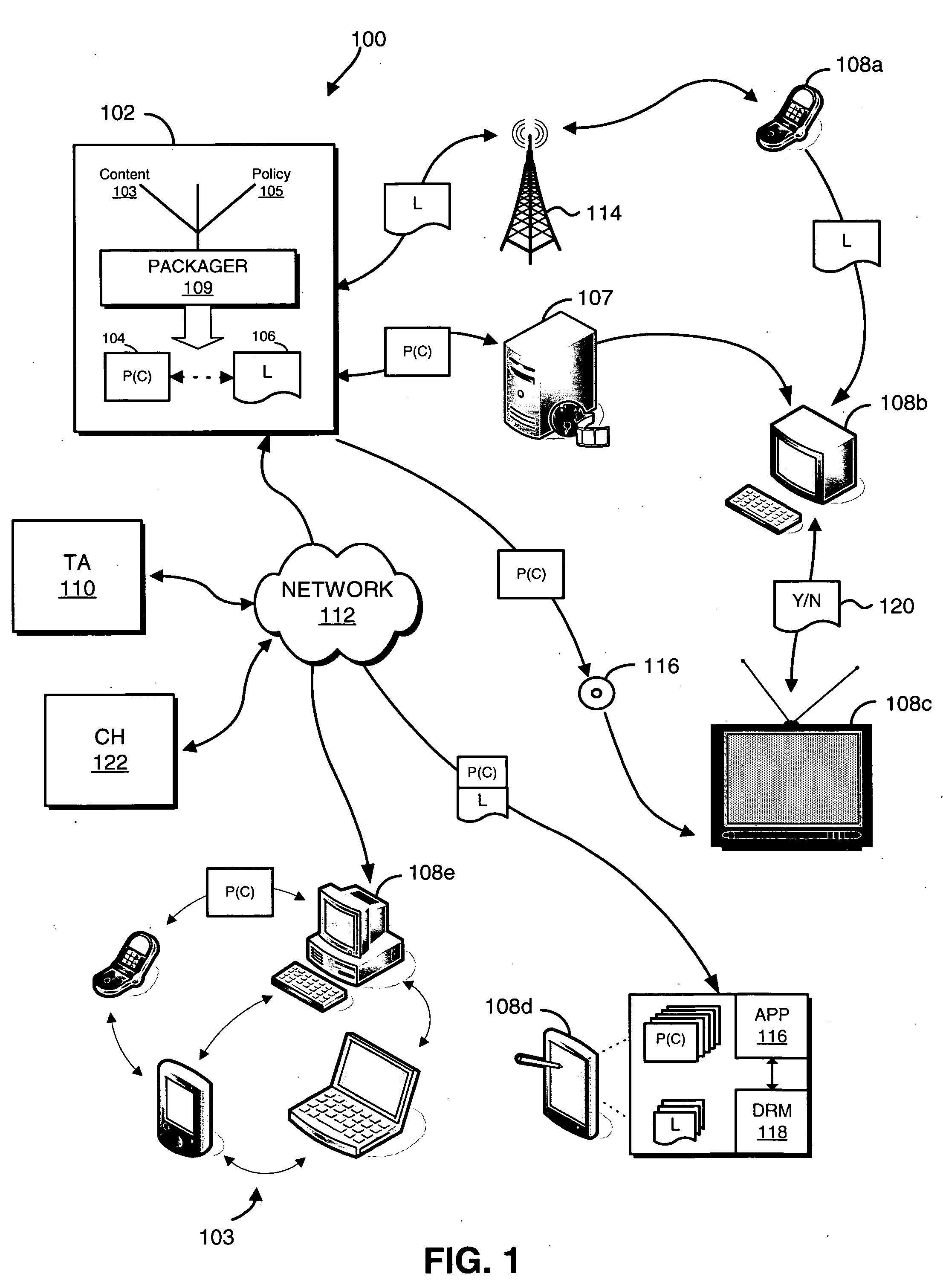
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
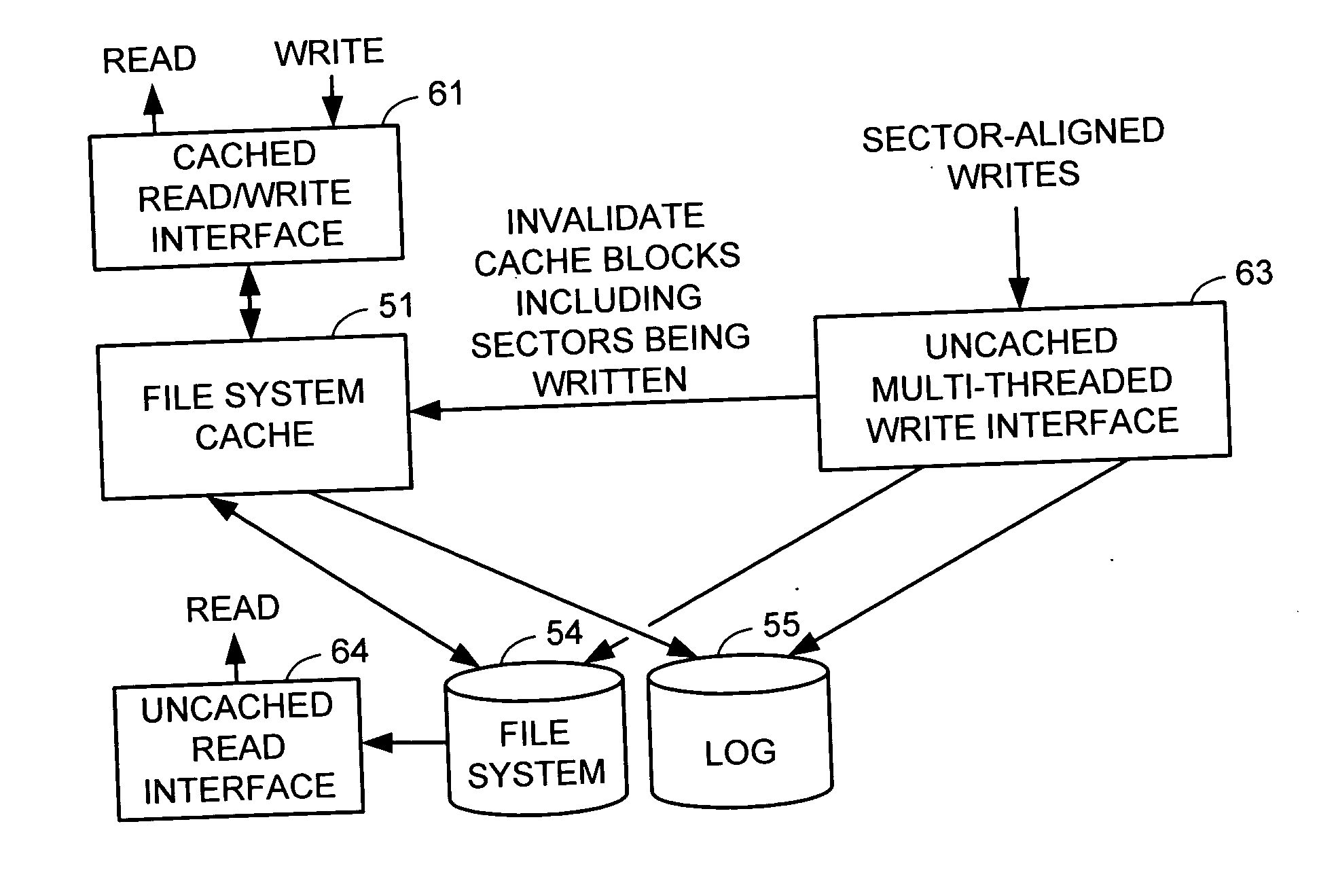
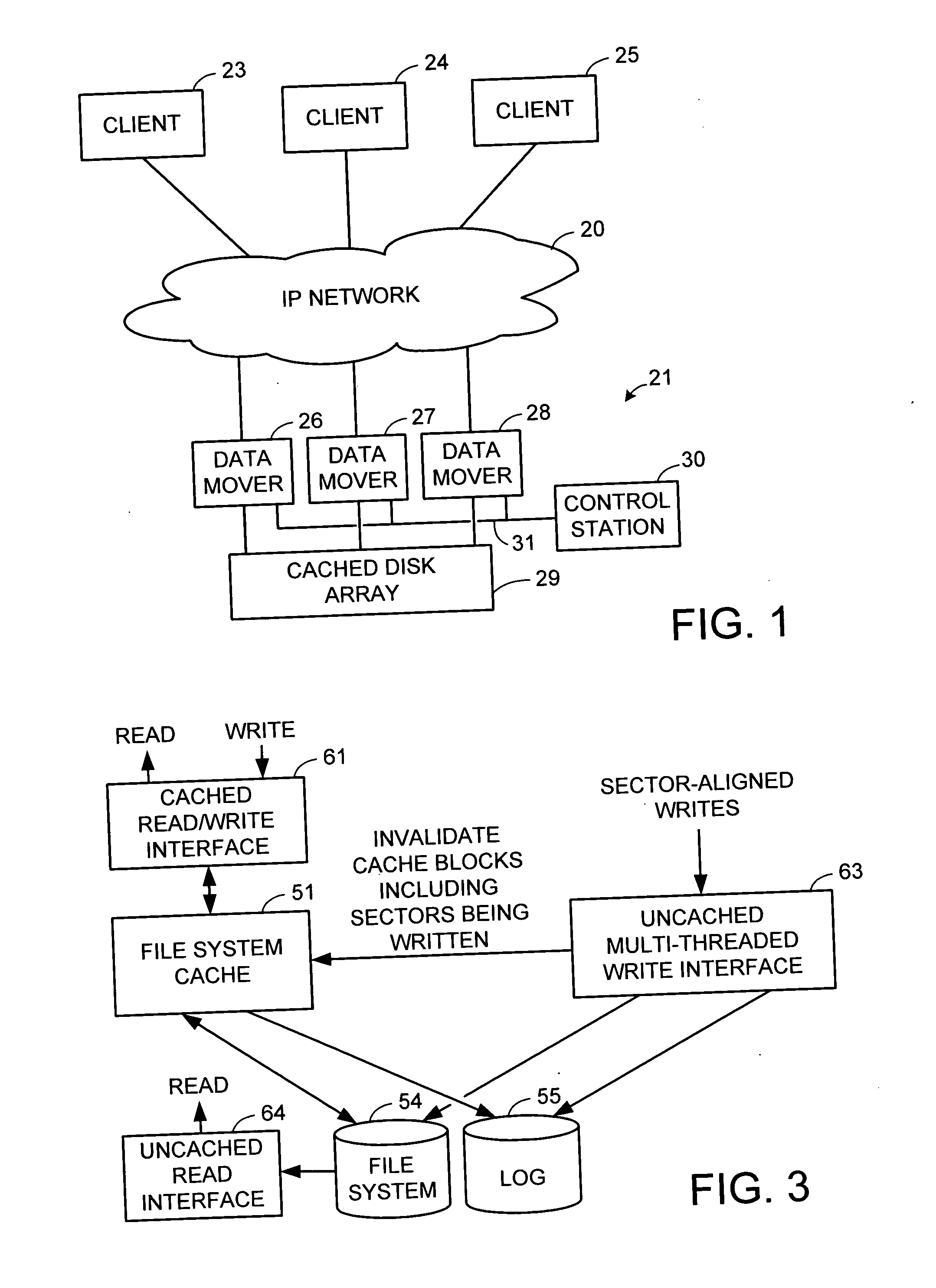
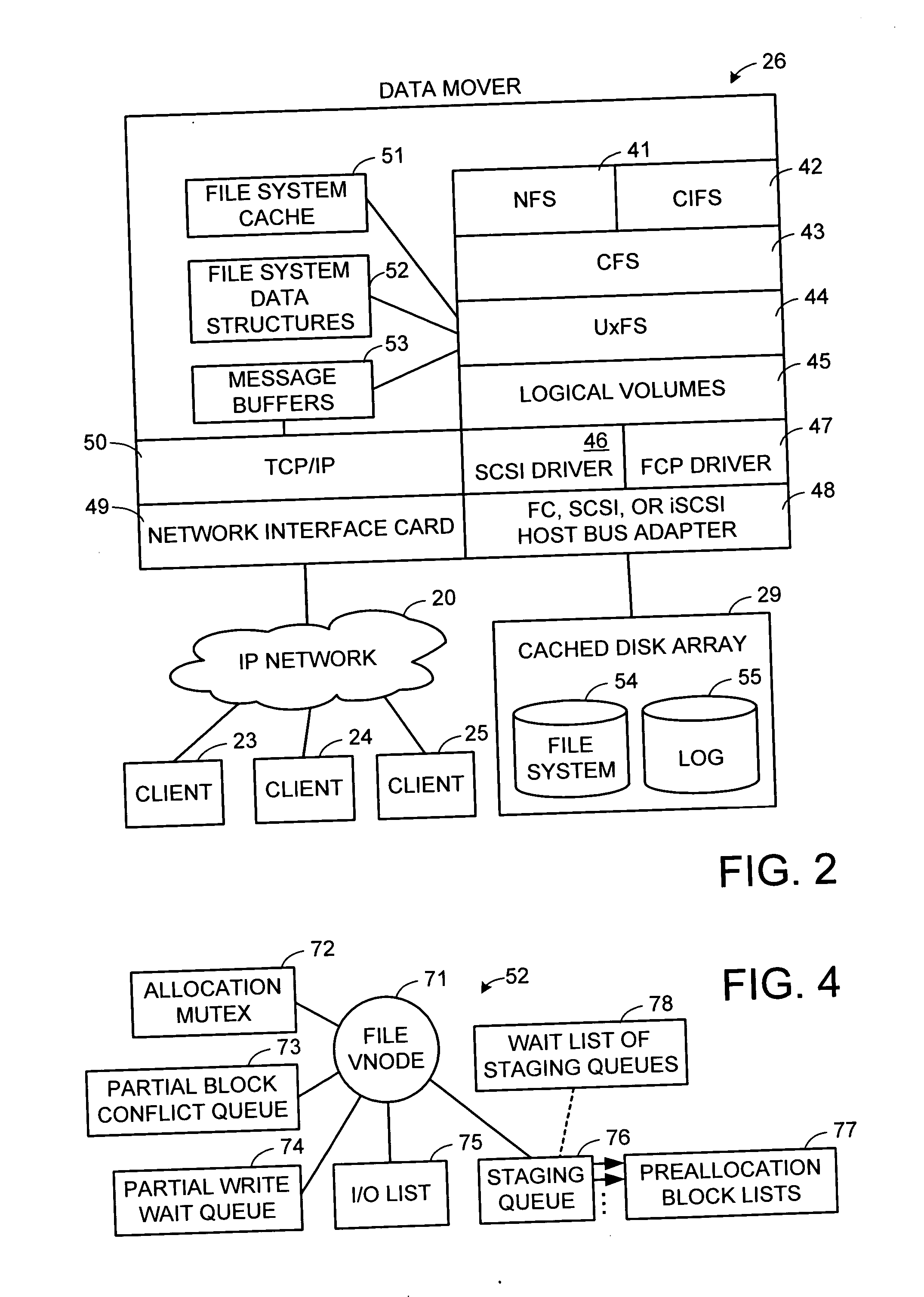
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS20050066095A1Digital data information retrievalDigital data processing detailsData integrityFile allocation
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
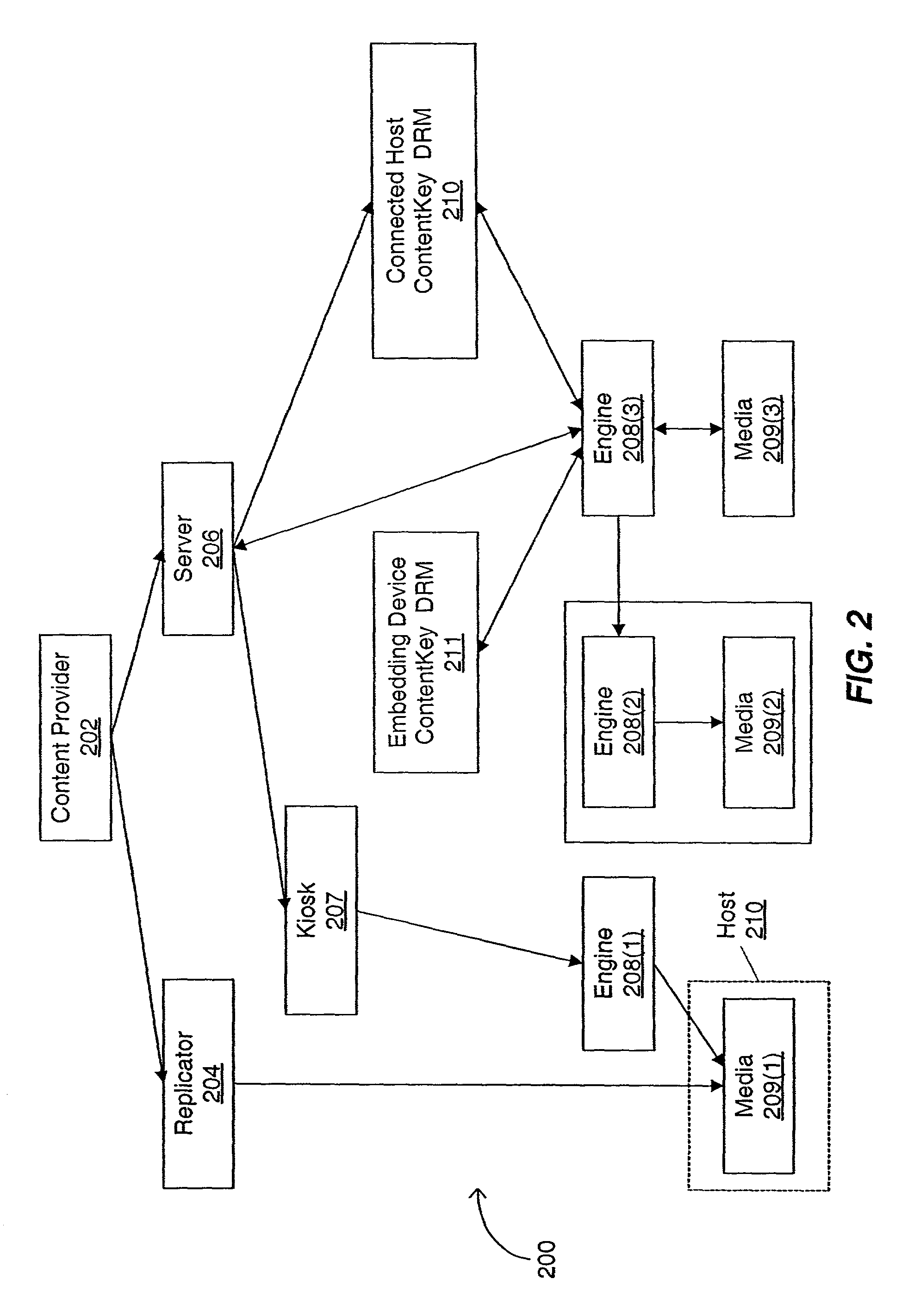
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
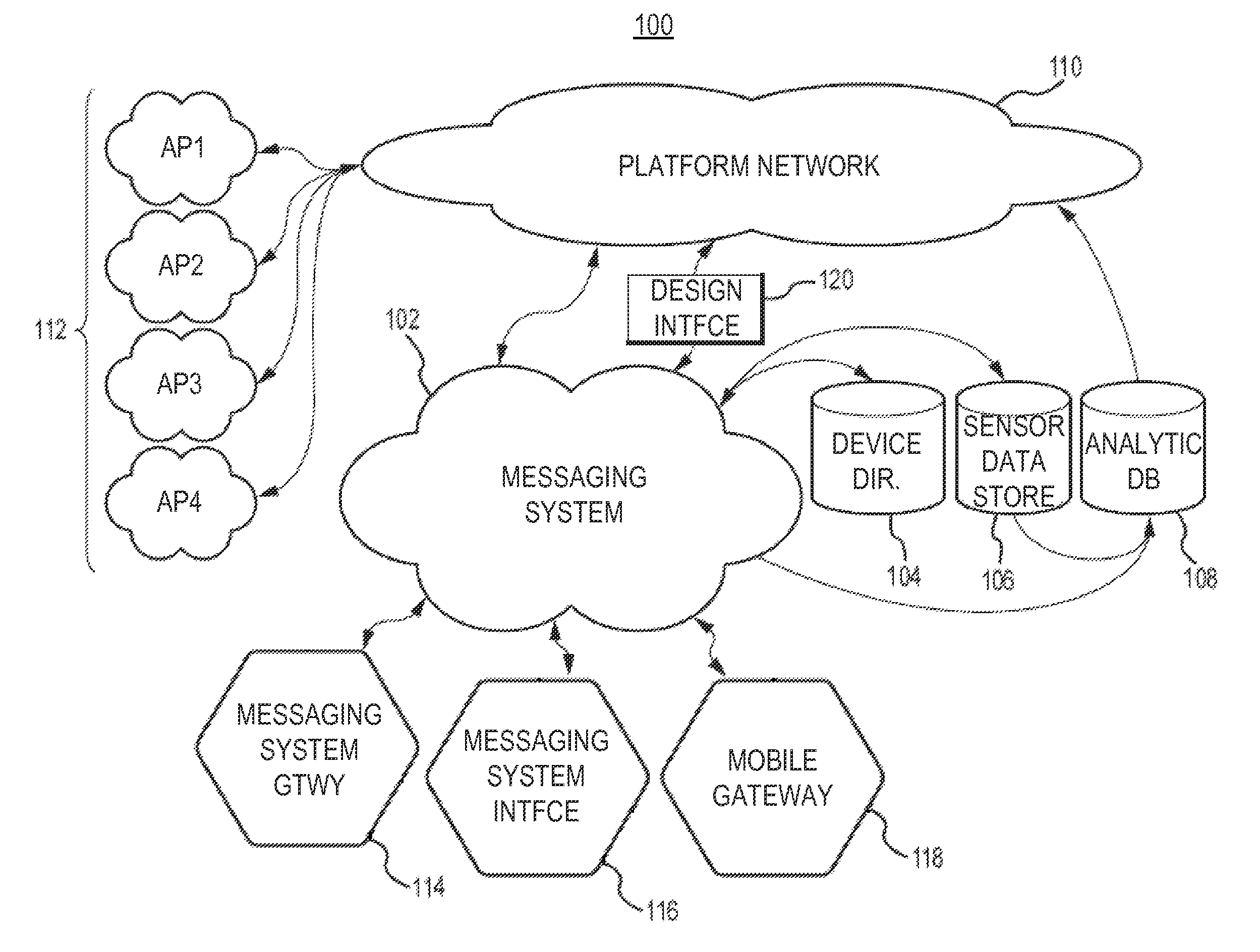
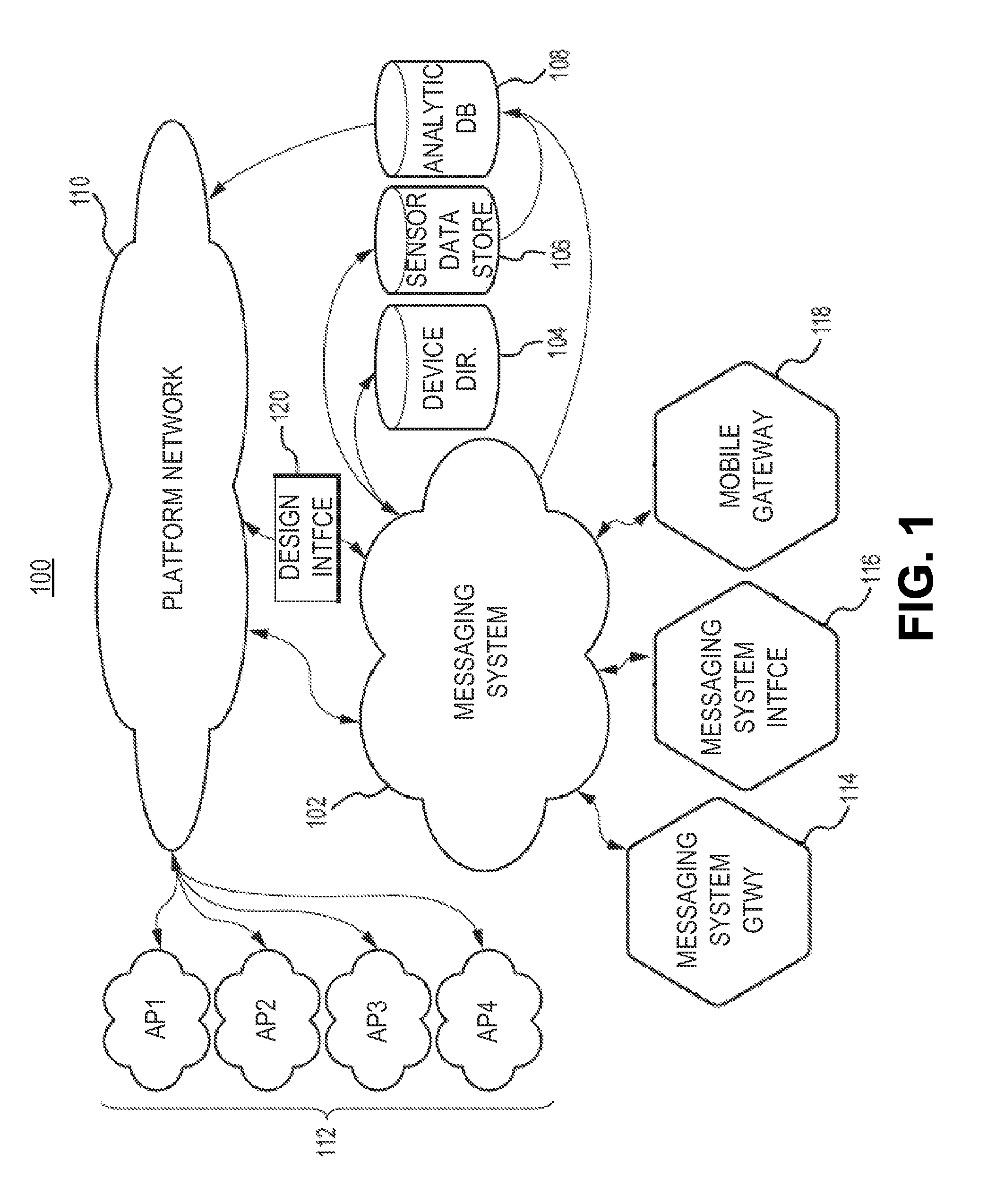
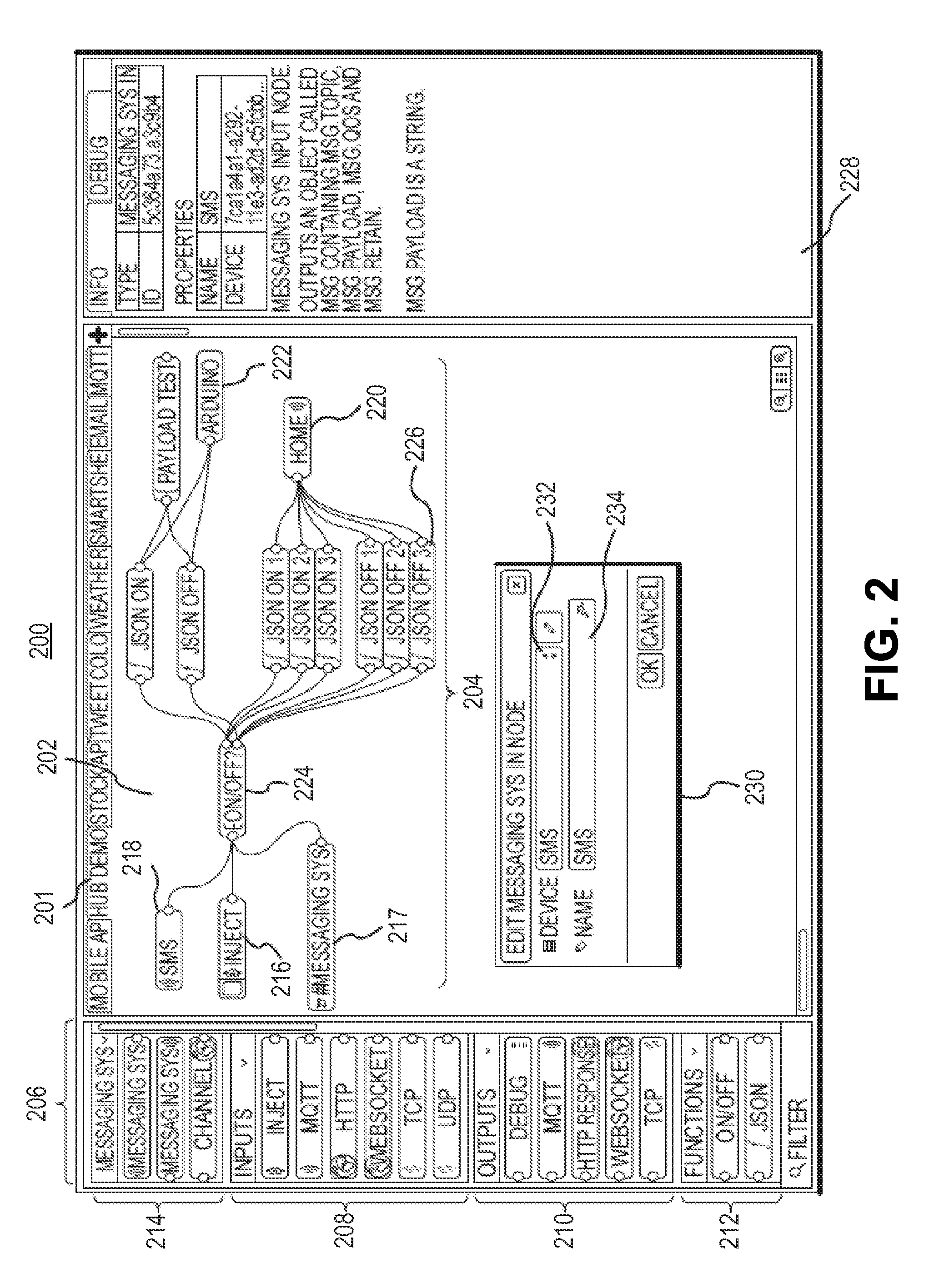
Security and rights management in a machine-to-machine messaging system
Techniques for providing security and rights management in a machine-to-machine messaging system are provided, such as a computing device, a method, and a computer-program product for detecting unauthorized message attempts. For example, the method may receive a communication sent from a first Internet of Things (IoT) device and destined for a second IoT device. The first IoT device is assigned a first universally unique identifier, and the communication includes a second universally unique identifier assigned to the second IoT device. The method may further include obtaining the second universally unique identifier, determining that the second universally unique identifier is assigned to the second IoT device, and determining, using the second universally unique identifier, that the communication received from the first IoT device is an unauthorized message attempt by the first IoT device to exchange a message with the second IoT device.
Owner:CITRIX SYST INC
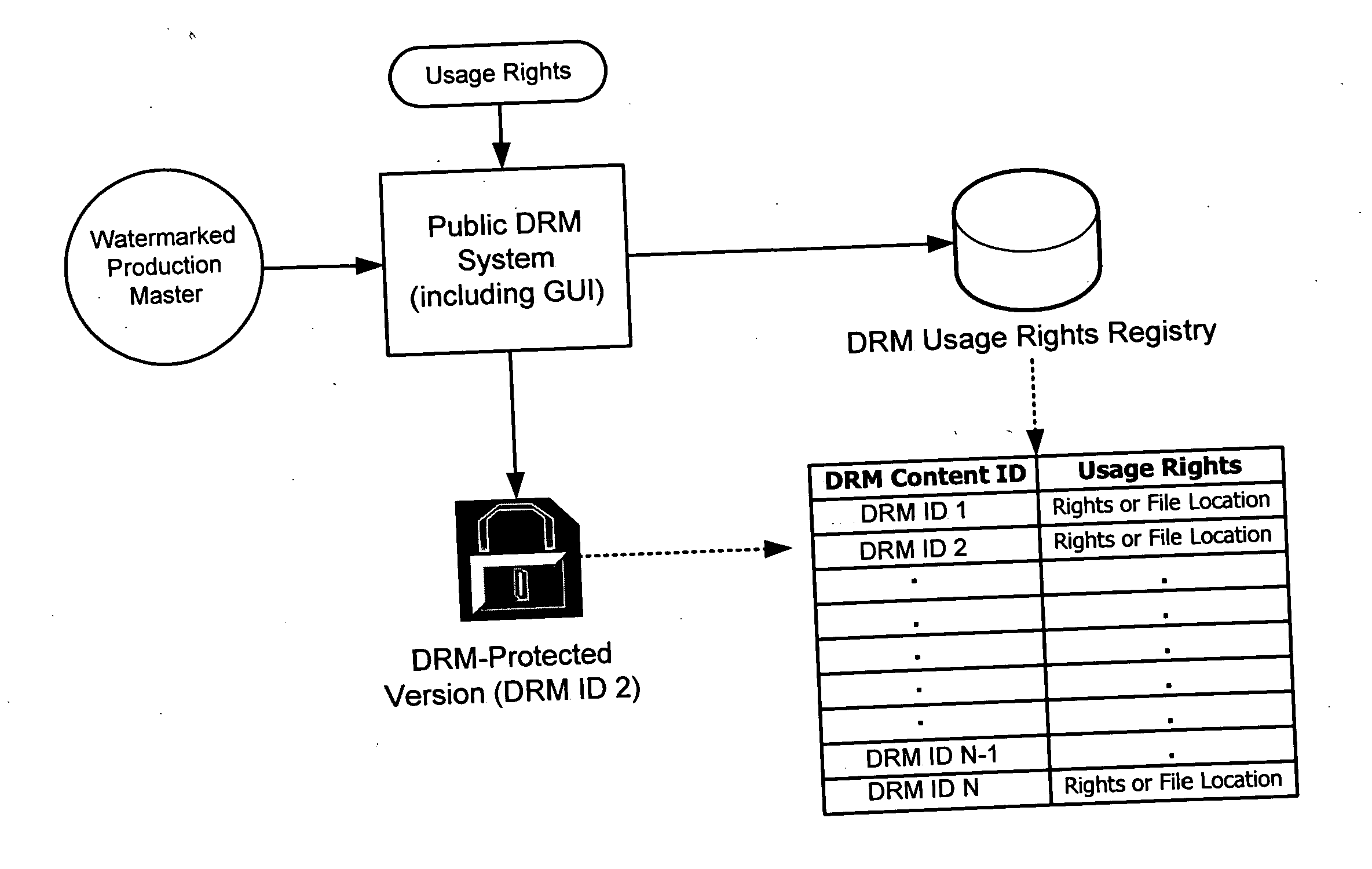
Rights management systems and methods using digital watermarking
ActiveUS20060062426A1Difficult to controlDifficult to trackUser identity/authority verificationAnalogue secracy/subscription systemsContent IdentifierRights management
A digital watermark (DWM) content identifier is steganographically embedded in content. The DWM content identifier provides a link to a rights registry storing usage rights associated with the content. In some implementations the rights registry provides an association between the DWM content identifier and a digital rights management (DRM) content identifier. The DRM content identifier is used to find associated usage rights. The DWM content identifier can also be used to transfer content from a first DRM system to a second DRM system.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
Data rights management of digital information in a portable software permission wrapper
InactiveUS20050114672A1Minimize impactImprove protectionSecret communicationProgram/content distribution protectionEmbedded securityTransaction management
The present invention provides systems and methods for secure transaction management and electronic rights protection. The invention is a software permission control wrapper that is used to encrypt and encapsulate digital information for the purpose of enforcing discretionary access control rights to the data contained in the wrapper. The permission control wrapper enforces rules associated with users, and their rights to access the data. Those rights are based on deterministic security behavior of the permission wrapper based on embedded security policies and rules contained therein and that are based, in part, on the user type, network connectivity state, and the user environment in which the data is accessed.
Owner:ENCRYPTX CORP
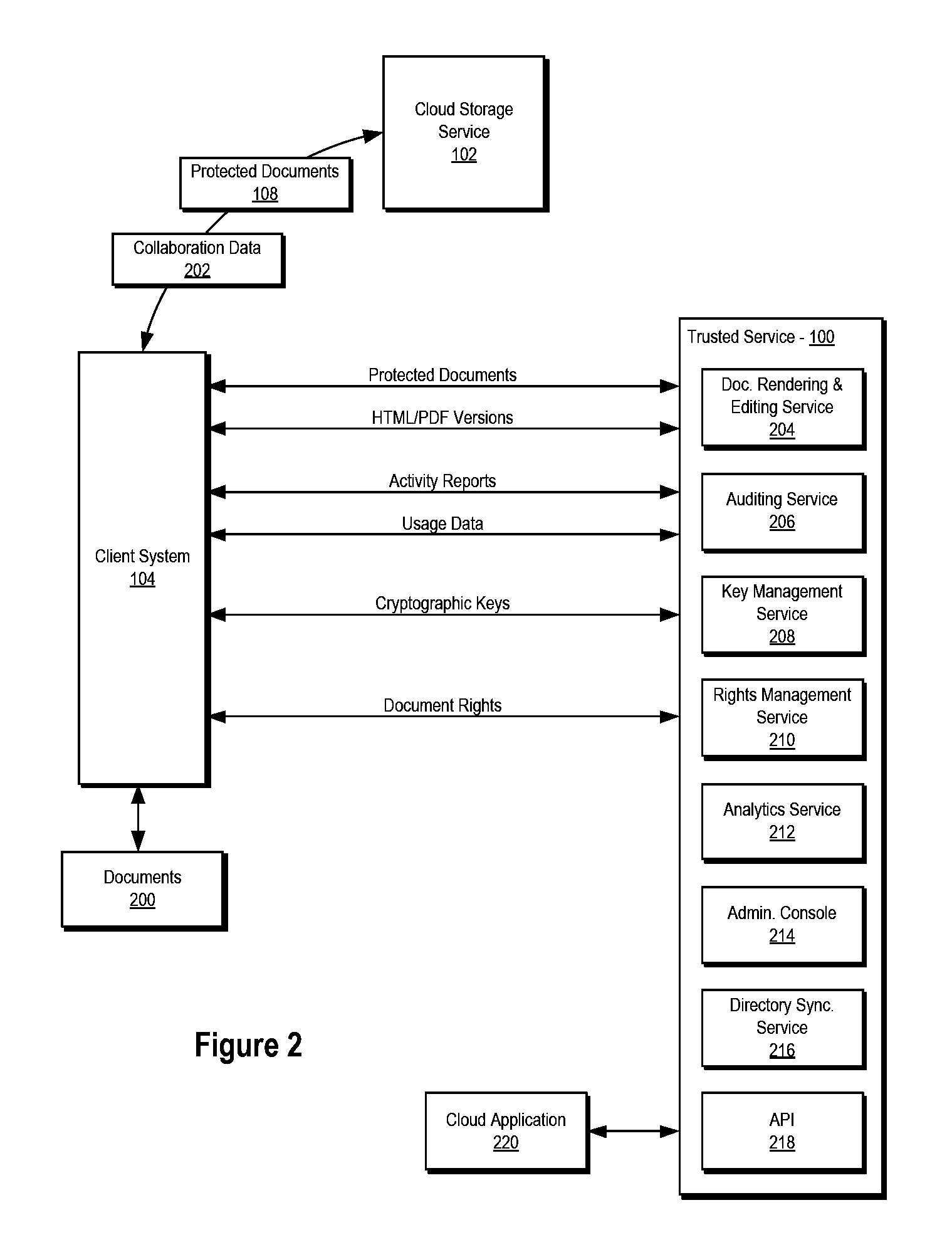
Systems and methods for managing documents and other electronic content
InactiveUS20130254699A1Reduce riskOffice automationSpecial data processing applicationsThird partyInternet privacy
This disclosure relates to systems and methods for managing documents and other electronic works. Certain embodiments relate to enabling secure, governed, and / or audited collaboration and / or document management over cloud storage platforms (e.g., third-party cloud storage platforms). Further embodiments relate to providing key and rights management as well as collaboration services in conjunction with cloud storage services.
Owner:BASHIR TAUSEEF +4
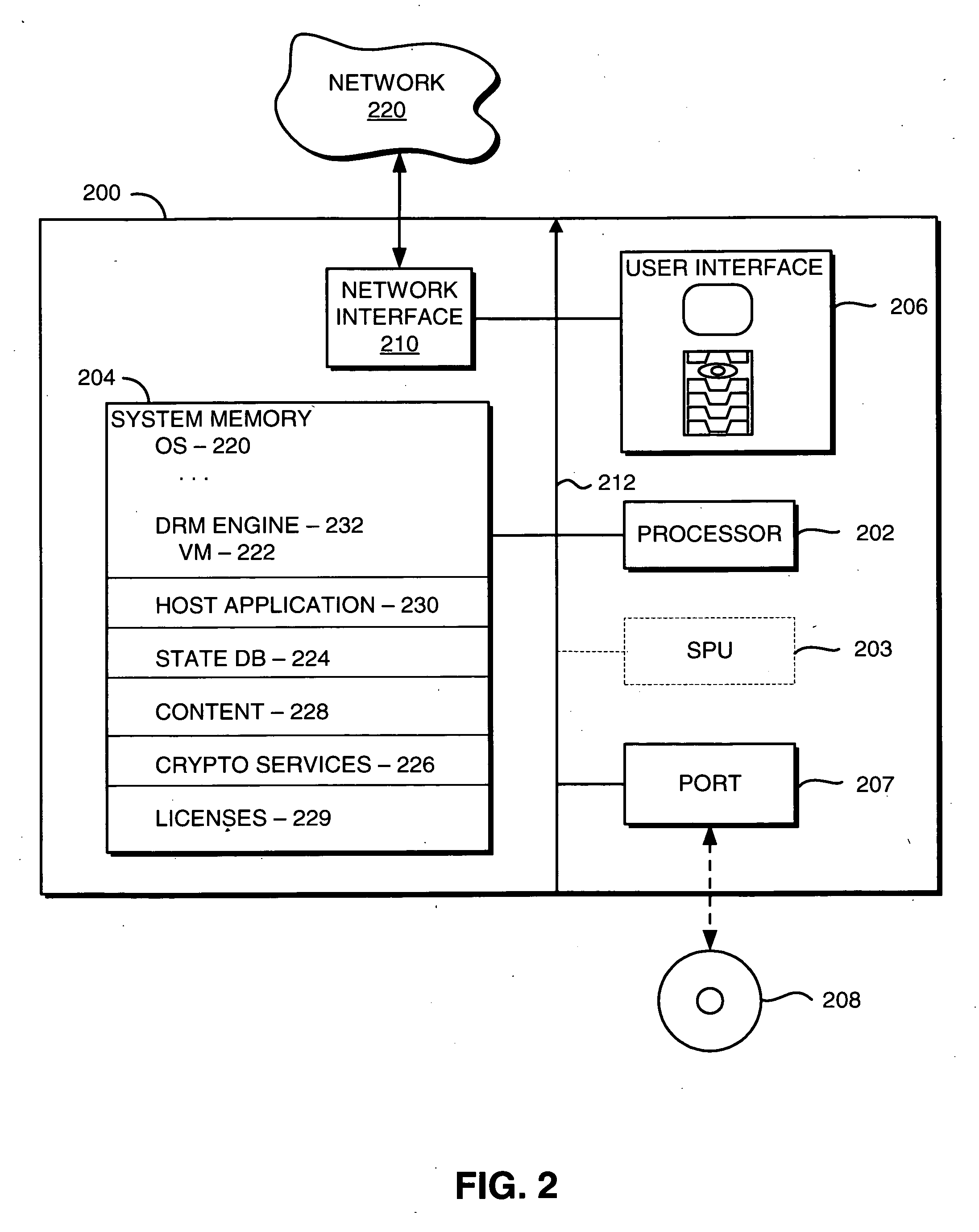
System and method for accessing protected content in a rights-management architecture
InactiveUS6996720B1Digital data processing detailsUnauthorized memory use protectionPersonalizationDigital rights management system
A digital rights management system for the distribution, protection and use of electronic content. The system includes a client architecture which receives content, where the content is preferably protected by encryption and may include a license and individualization features. Content is protected at several levels, including: no protection; source-sealed; individually-sealed (or “inscribed”); source-signed; and fully-individualized (or “owner exclusive”). The client also includes and / or receives components which permit the access and protection of the encrypted content, as well as components that allow content to be provided to the client in a form that is individualized for the client. In some cases, access to the content will be governed by a rights construct defined in the license bound to the content. The client components include an object which accesses encrypted content, an object that parses the license and enforces the rights in the license, an object which obtains protection software and data that is individualized for the client and / or the persona operating the client, and a script of instructions that provides individualization information to a distributor of content so that the content may be individualized for the client and / or its operating persona. Content is generally protected by encrypting it with a key and then sealing the key into the content in a way that binds it to the meta-data associated with the content. In some instances, the key may also be encrypted in such a way as to be accessible only by the use of individualized protection software installed on the client, thereby binding use of the content to a particular client or set of clients.
Owner:MICROSOFT TECH LICENSING LLC
Methods for rights enabled peer-to-peer networking
InactiveUS20030120928A1User identity/authority verificationUnauthorized memory use protectionDigital rights managementRights management
The present invention relates to digital rights management. In one embodiment, persons, processes, and / or computers and appliances locate, share, publish, retrieve, and use all kinds of digital information that has been protected using digital rights management technologies. Rights management includes securely associating rules for authorized use with the digital information. Rules and / or digital information may be encapsulated in a cryptographically secure data structure or "container" ("CSC") to protect against unauthorized use, to ensure secrecy, to maintain integrity, and to force the use of a rights management system to access the protected information. Attributes or metadata information describing at least some of the rules ("rules-metadata information") and optionally any associated rule parameter data with respect to the protected information are created. This rules-metadata information may be organized, structure, encoded, and / or presented using a self-defining data structure such as those created using Extensible Markup Language (XML). In one embodiment, the XML-encoded rules-metadata information is also made available unencrypted, in plain text, to facilitate P2P search and file transfer. Having at least some of the rules-metadata information outside or external to a CSC allows greater flexibility in searching based at least in part upon the rules-metadata information. Some embodiments may hold the rules-metadata information in a separate CSC. Putting the rules-metadata information in a separate CSC more easily allows authentication and maintains the integrity of the rules-metadata information. In another embodiment, the rules metadata may be in an unencrypted portion of a CSC itself or concatenated with a CSC in a single file.
Owner:CATO MILES +2
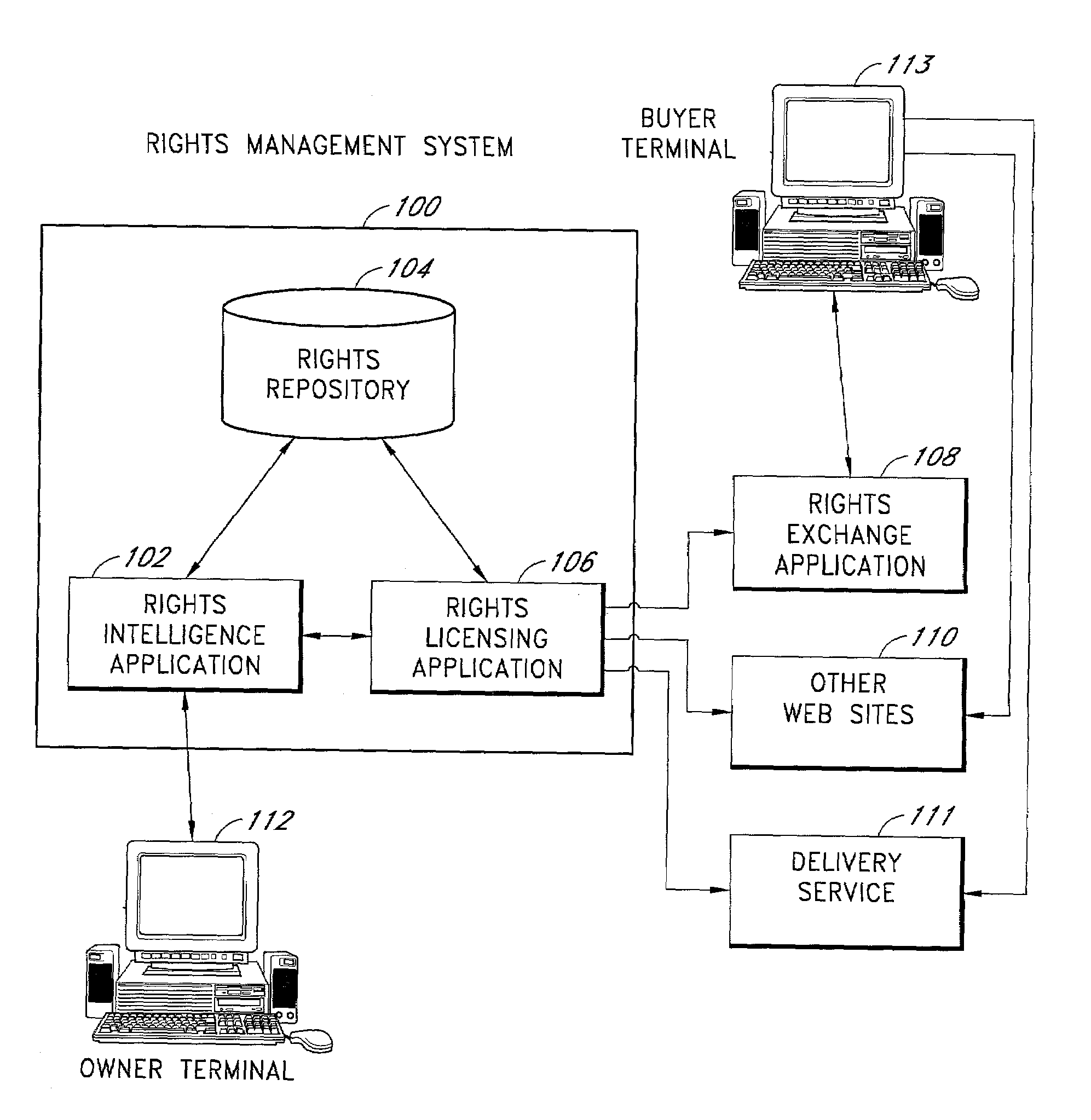
Apparatus and methods for intellectual property database navigation
InactiveUS7092953B1Fast and efficient techniqueData processing applicationsProgram/content distribution protectionIntellectual propertyRights management
The present invention advantageously provides a rights management system. In one embodiment, a specification of a general level of rights owned by a first intellectual property rights owner is received. A query is received for a lower level right that is a descendent of at least one of the general level of rights. The system determines if the lower level rights is available for licensing by forming at least a first implicit relationship between the general level of rights owned, and a general level of rights licensed out.
Owner:RIGHTSLINE +1
System and method for activating a rendering device in a multi-level rights-management architecture
InactiveUS7017189B1Digital data processing detailsUser identity/authority verificationPersonalizationDigital rights management system
Owner:MICROSOFT TECH LICENSING LLC
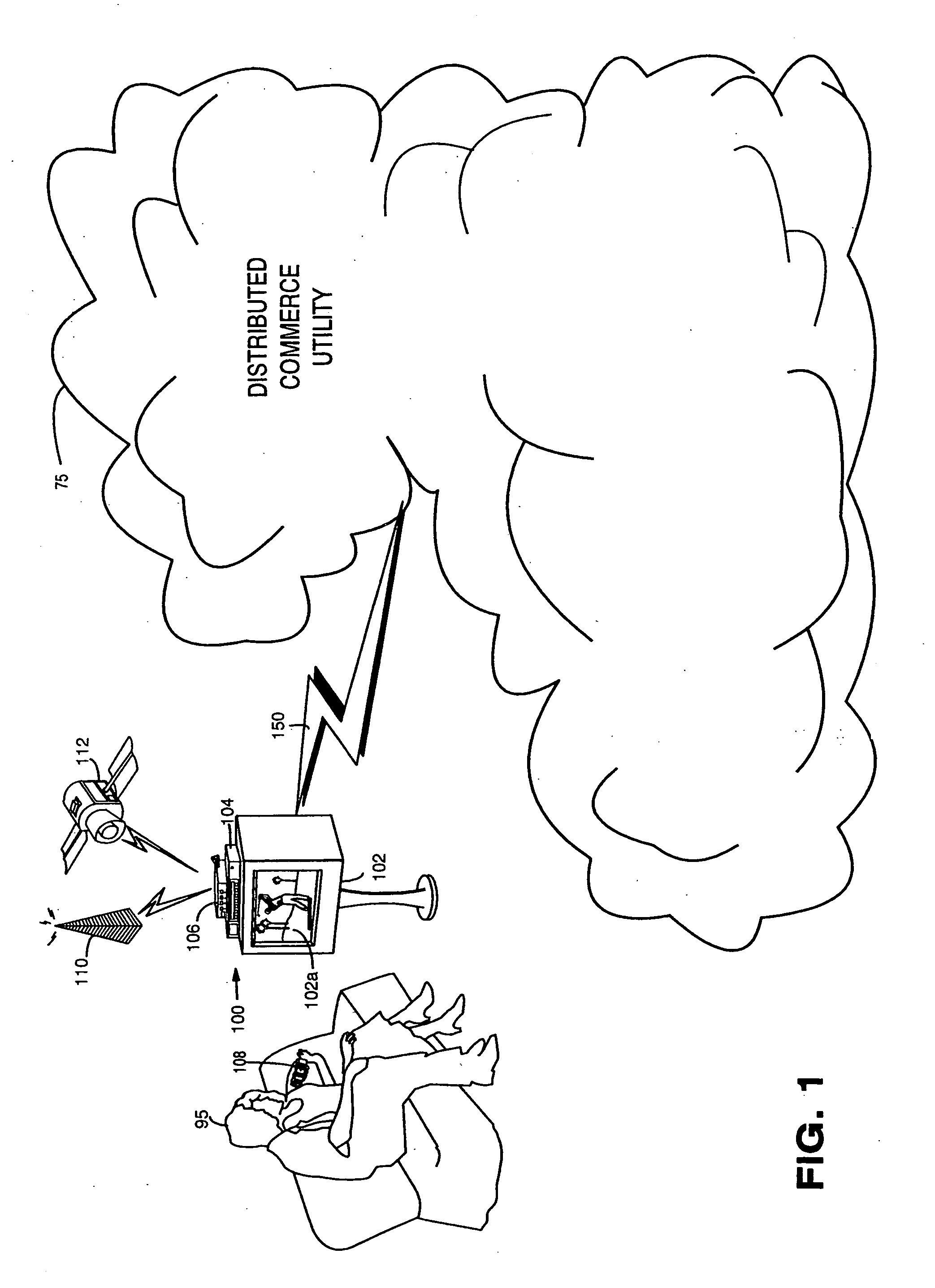
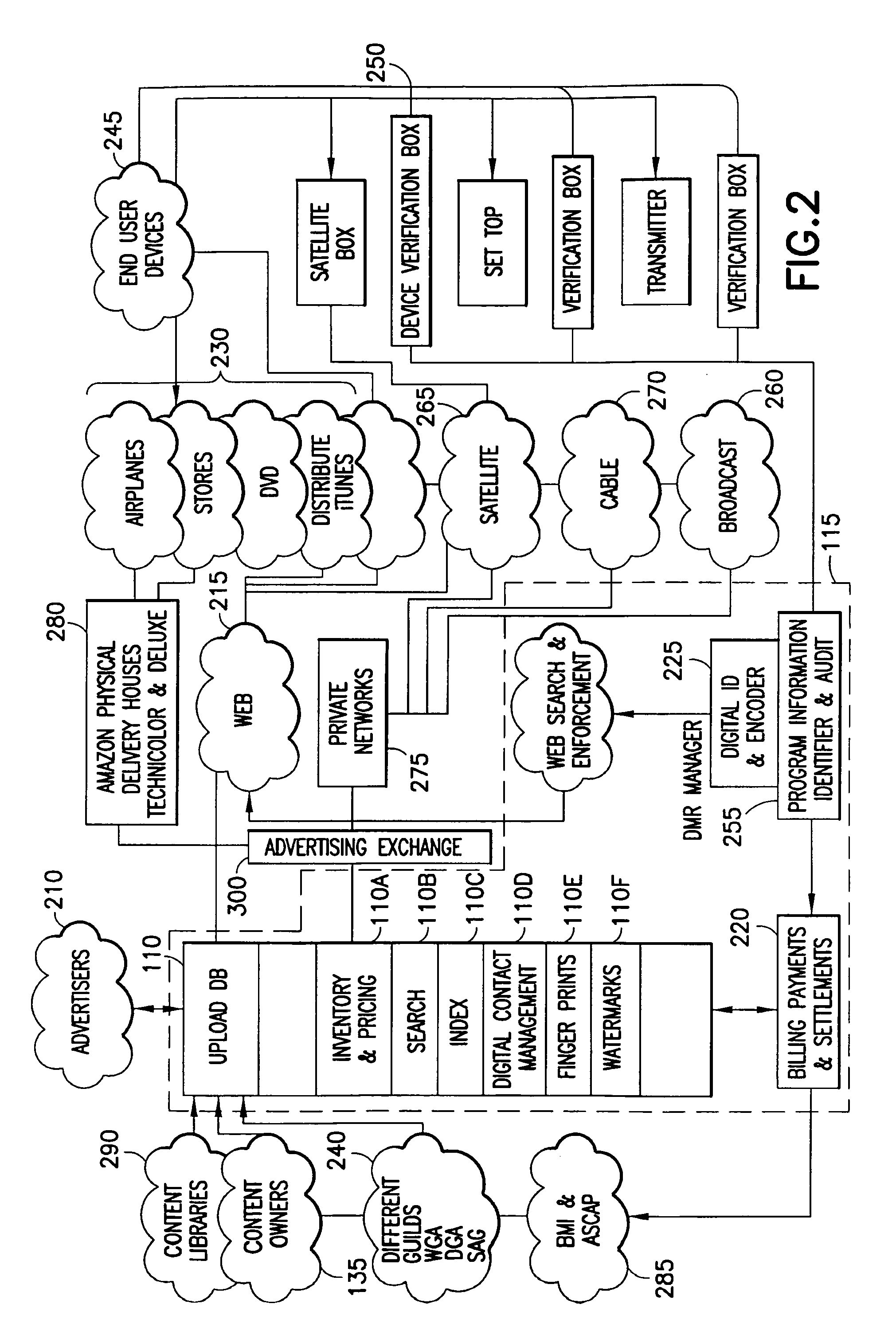
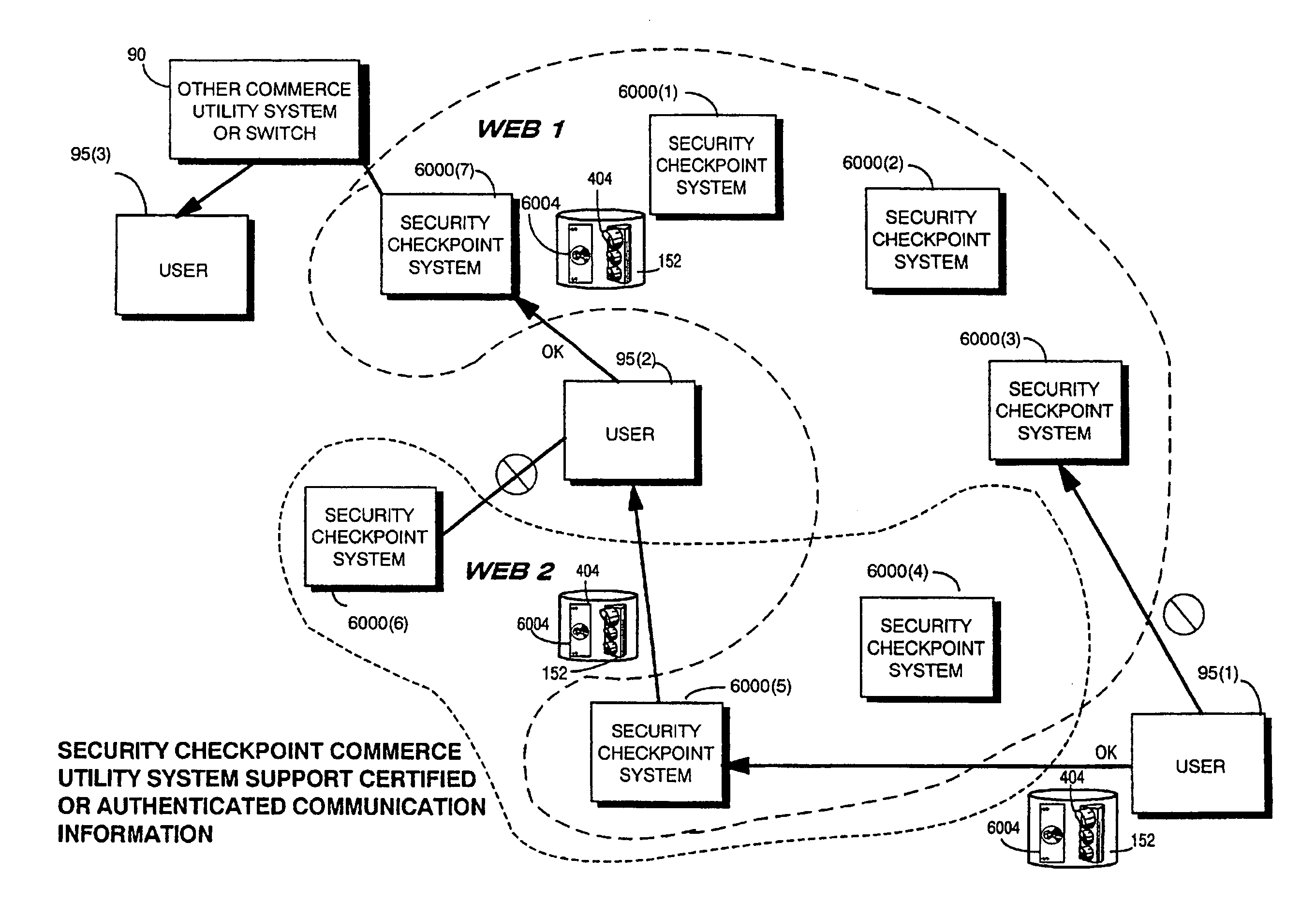
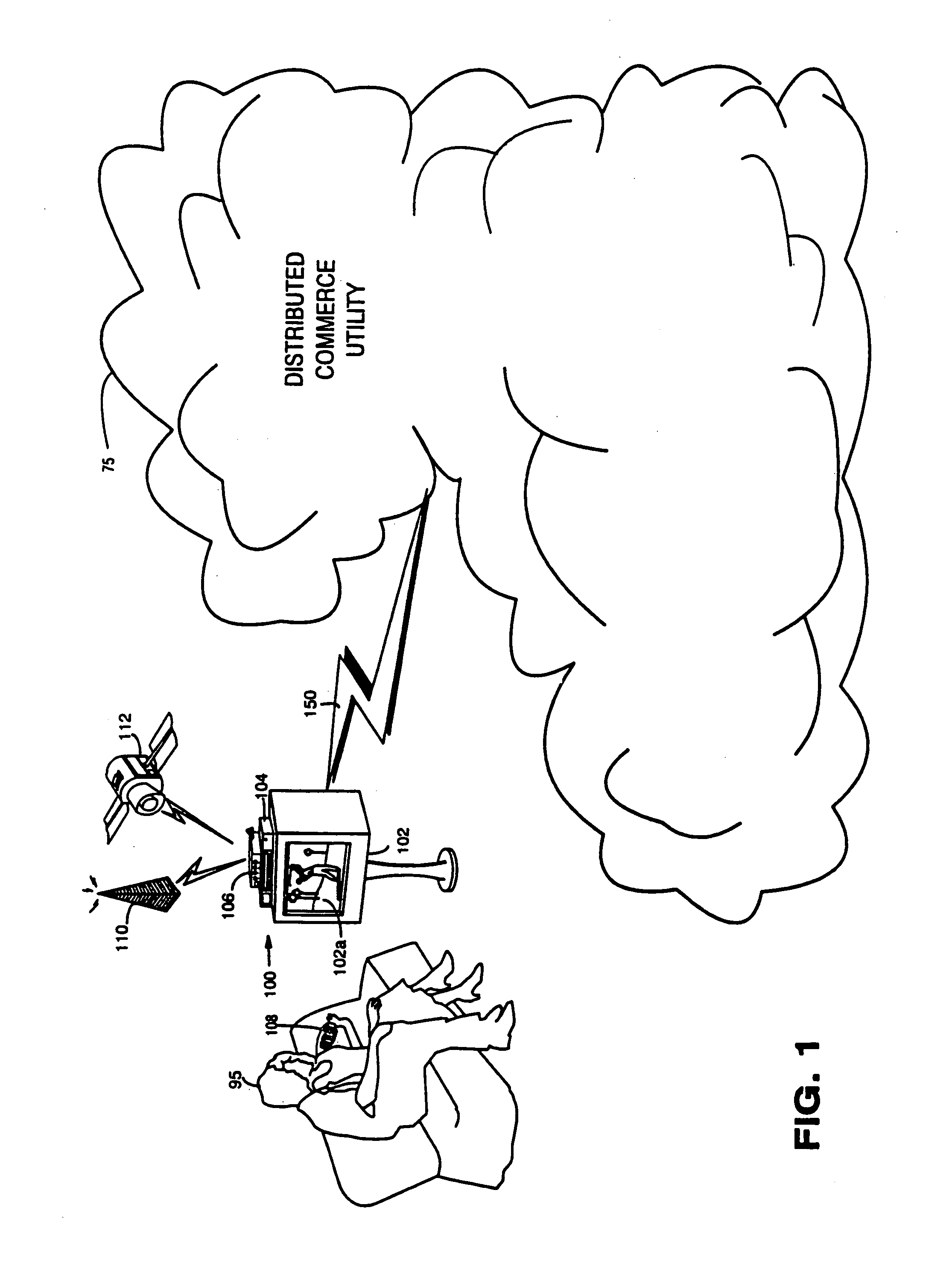
Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management
InactiveUS20050060584A1Flexible and efficient creationSimple designDigital data processing detailsAnalogue secracy/subscription systemsModularityRights management
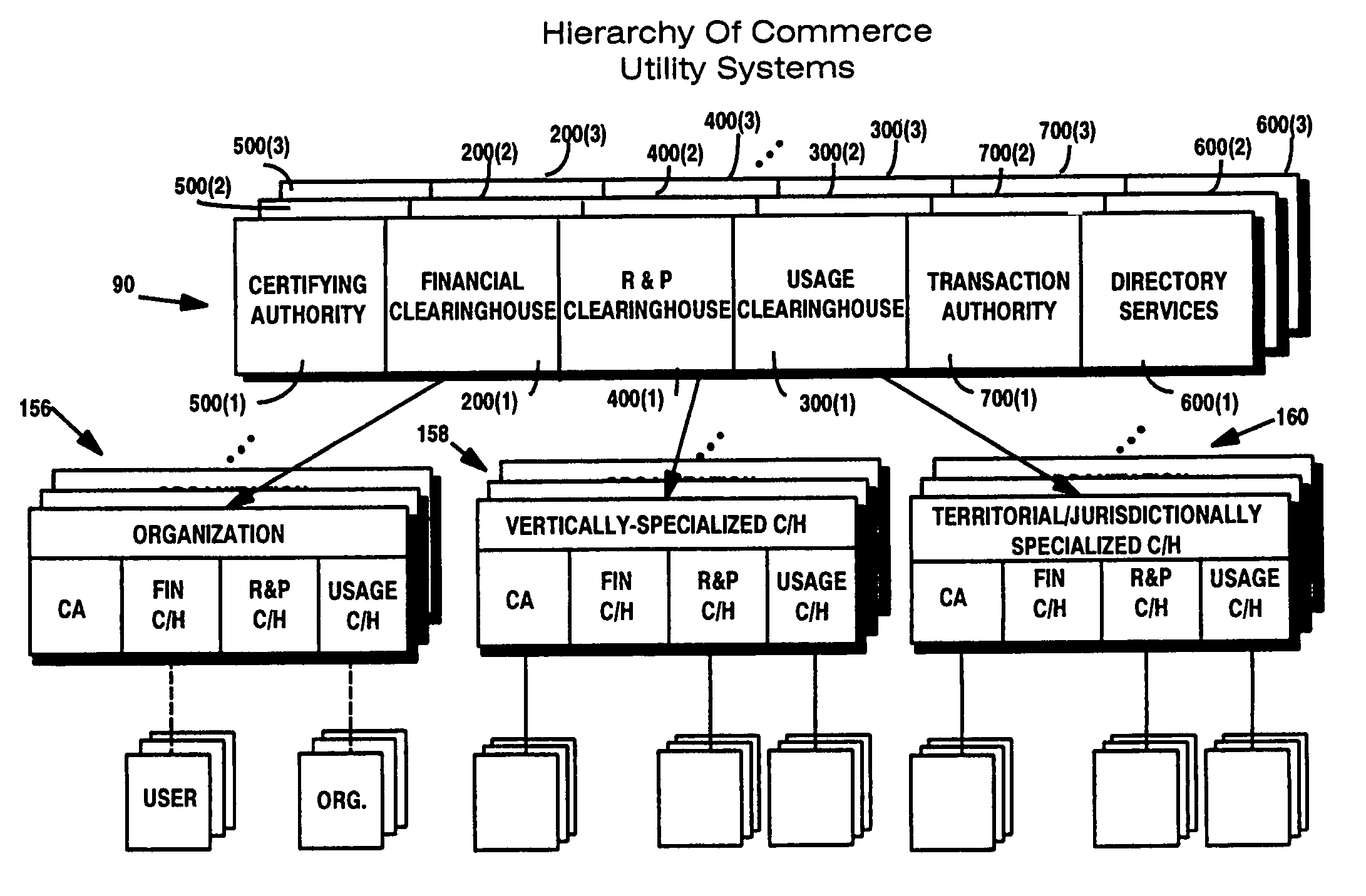
An integrated, modular array of administrative and support services are provided for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting transaction-related capabilities functioning over electronic network-s, and can also be adapted to the specific needs of electronic commerce value chains. In one embodiment, a Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many of its participants. Different support functions can be collected together in hierarchical and / or networked relationships to suit various business models or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes.
Owner:INTERTRUST TECH CORP
Digital rights management engine systems and methods
ActiveUS20070100701A1Limited accessHand manipulated computer devicesDigital data protectionRights managementDigital rights management
Systems and methods are described for performing digital rights management. In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
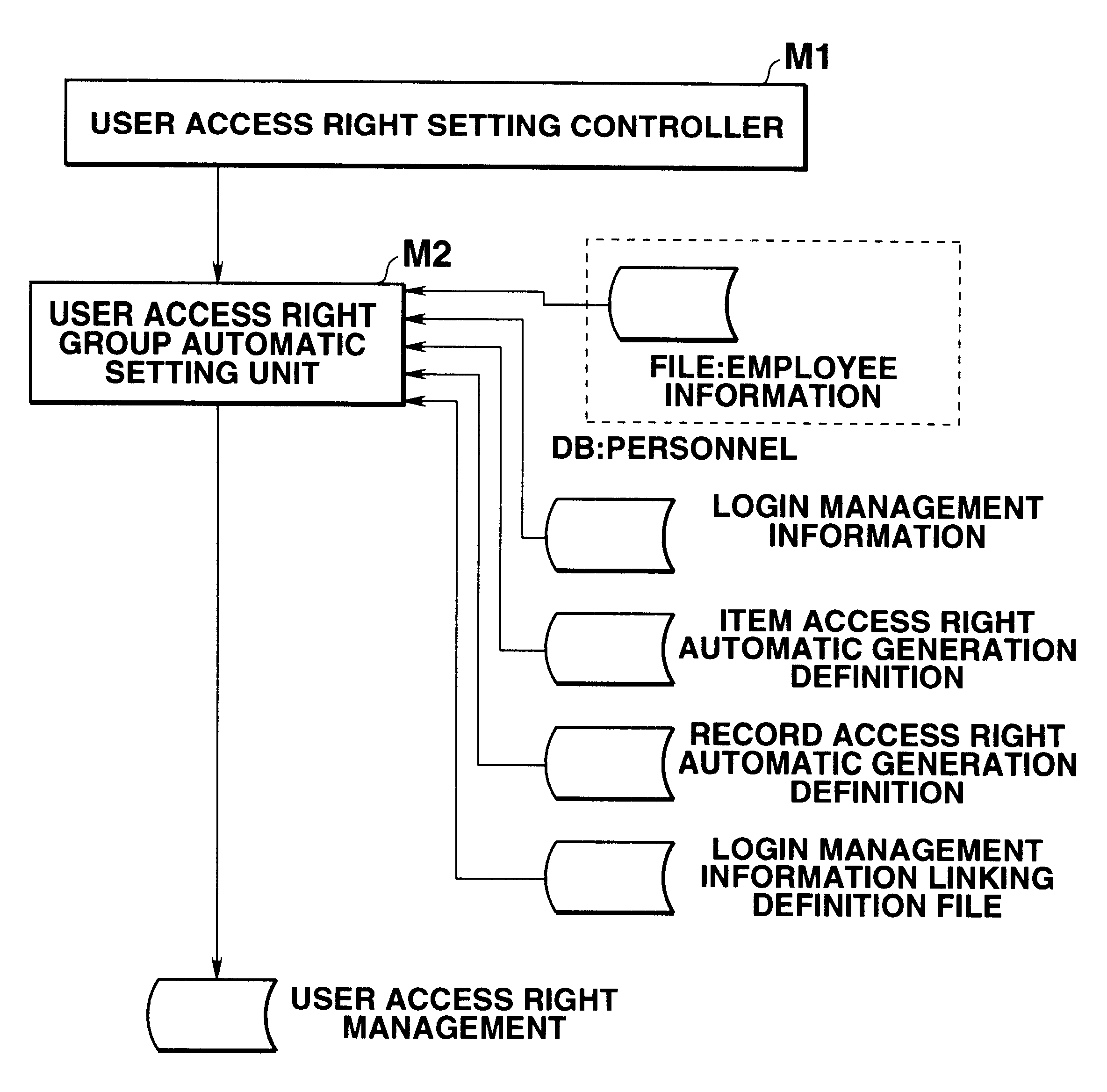
Data access control apparatus for limiting data access in accordance with user attribute
InactiveUS6275825B1Reduce loadPrevent setting errorsData processing applicationsDigital data processing detailsData access controlRights management
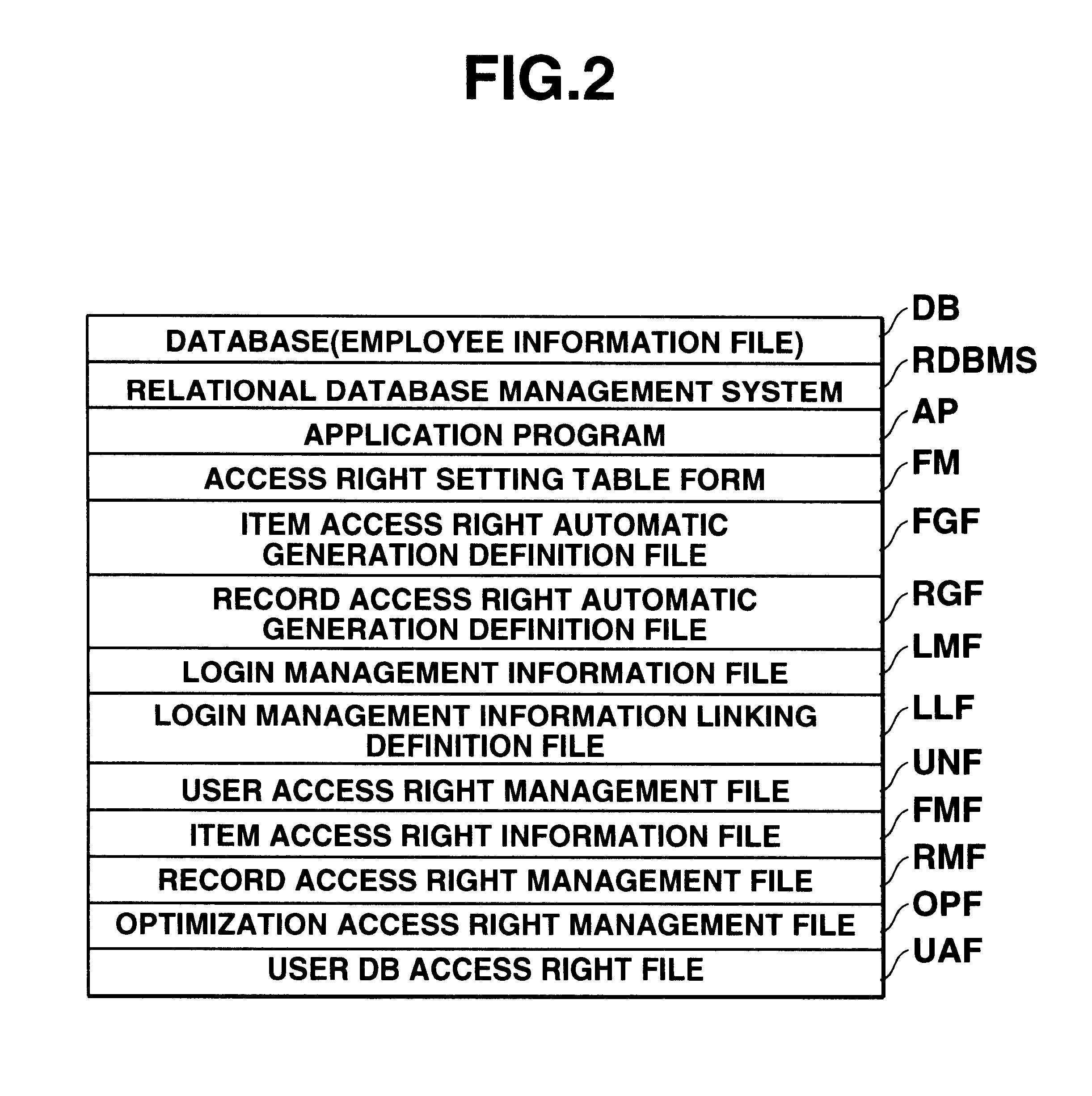
This invention provides a data access control apparatus arranged to automatically set access right information limiting data access, in accordance with a user attribute when a user accesses a database. In setting, for a plurality of users, access right information corresponding to each user, the load on an operator can be reduced, and access right information setting errors can be prevented. An automatic setting unit reads out information from a login management information file and an employee information file on the basis of definition information of a definition files to automatically generate a user access right management file which stores a login ID, an item access right, and a record access right group code for each user. When a login ID is input in accessing the employee information file, a setting controller refers to the management file to determine a user group to which the user belongs and an access enabled / disabled state of the data on the basis of the access right made to correspond to this user group.
Owner:CASIO COMPUTER CO LTD
Method of rights management for streaming media
InactiveUS20030131353A1Low resolution/qualityTelevision system detailsKey distribution for secure communicationComputer networkRights management
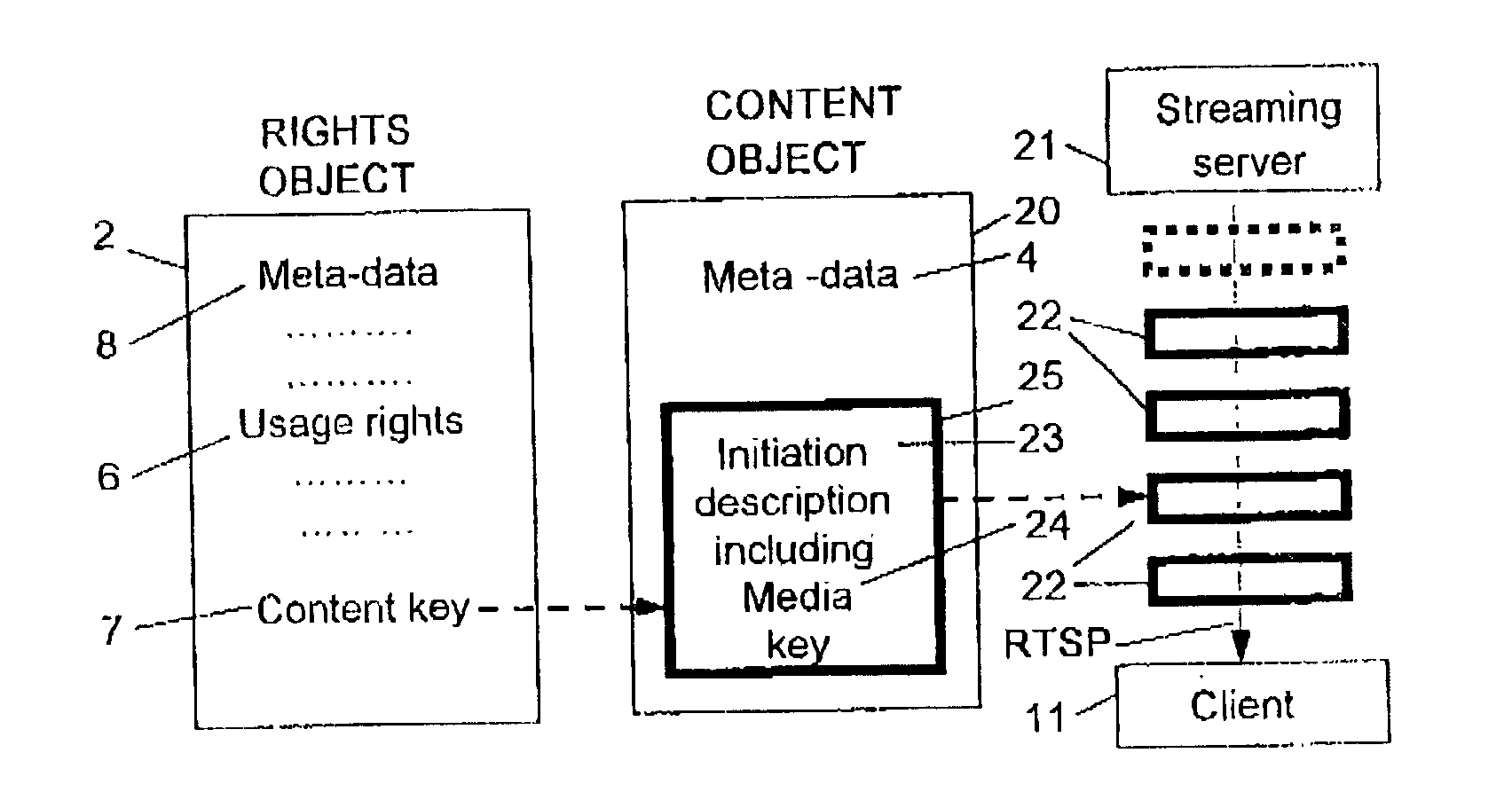
The present invention relates to an arrangement, system and method for managing rights to streaming media using a management mechanism based on a content object and a rights object. In accordance with the invention the content object comprises means for initiation of the streaming media and the rights object comprises usage rules defining the rights to use said streaming media. The invention also relates to a method of delivering and protecting digital streaming media. The initiation may comprise a session description of the streaming media, a SDP description, a URL to said streaming media or a SMIL file. Preview and super-distribution are provided. The content object is delivered like a downloadable object in a rights management system for download, thereby reusing the mechanisms for rights management of said latter system for rights management in a system for transmission of streaming media.
Owner:TELEFON AB LM ERICSSON (PUBL)
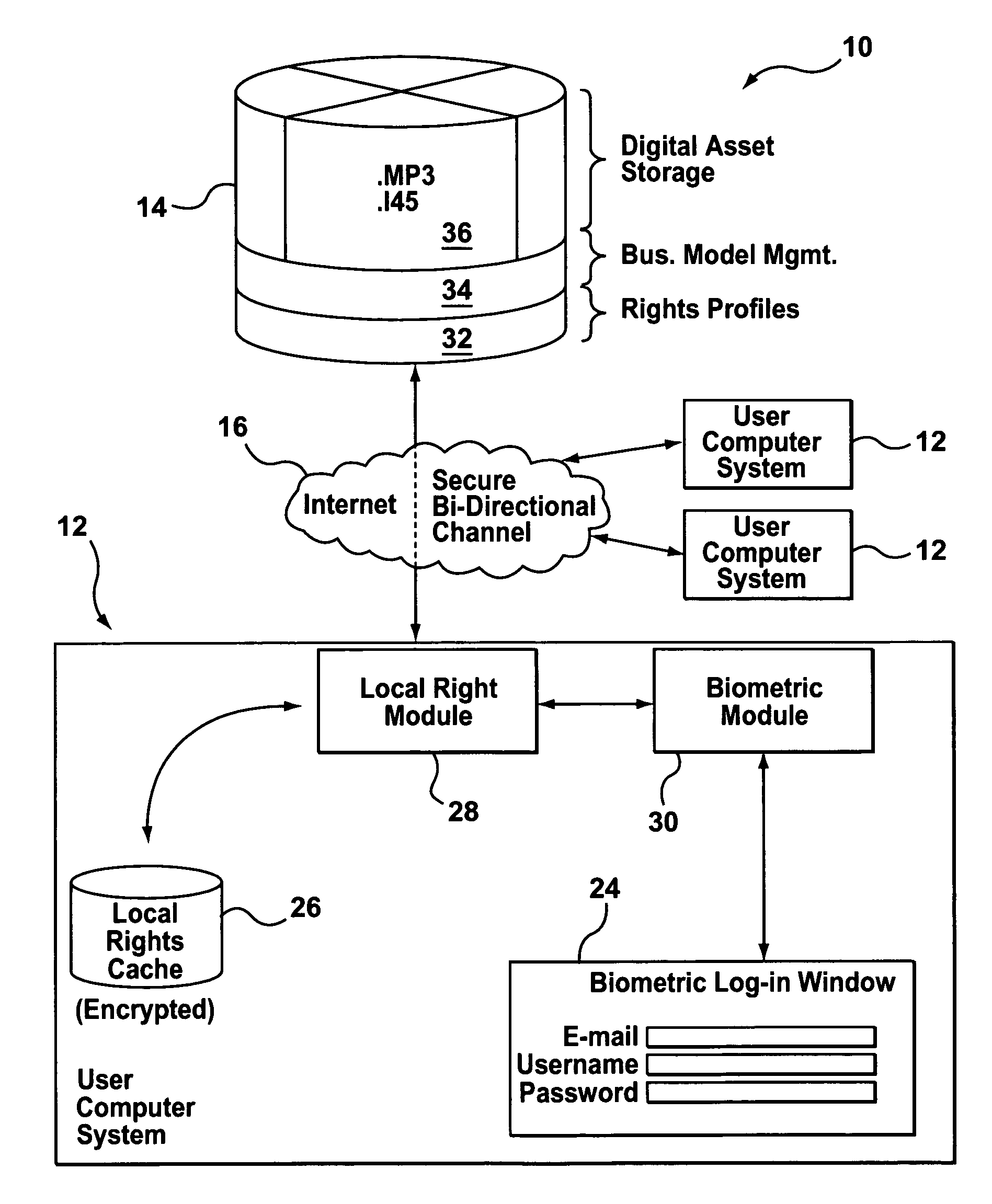
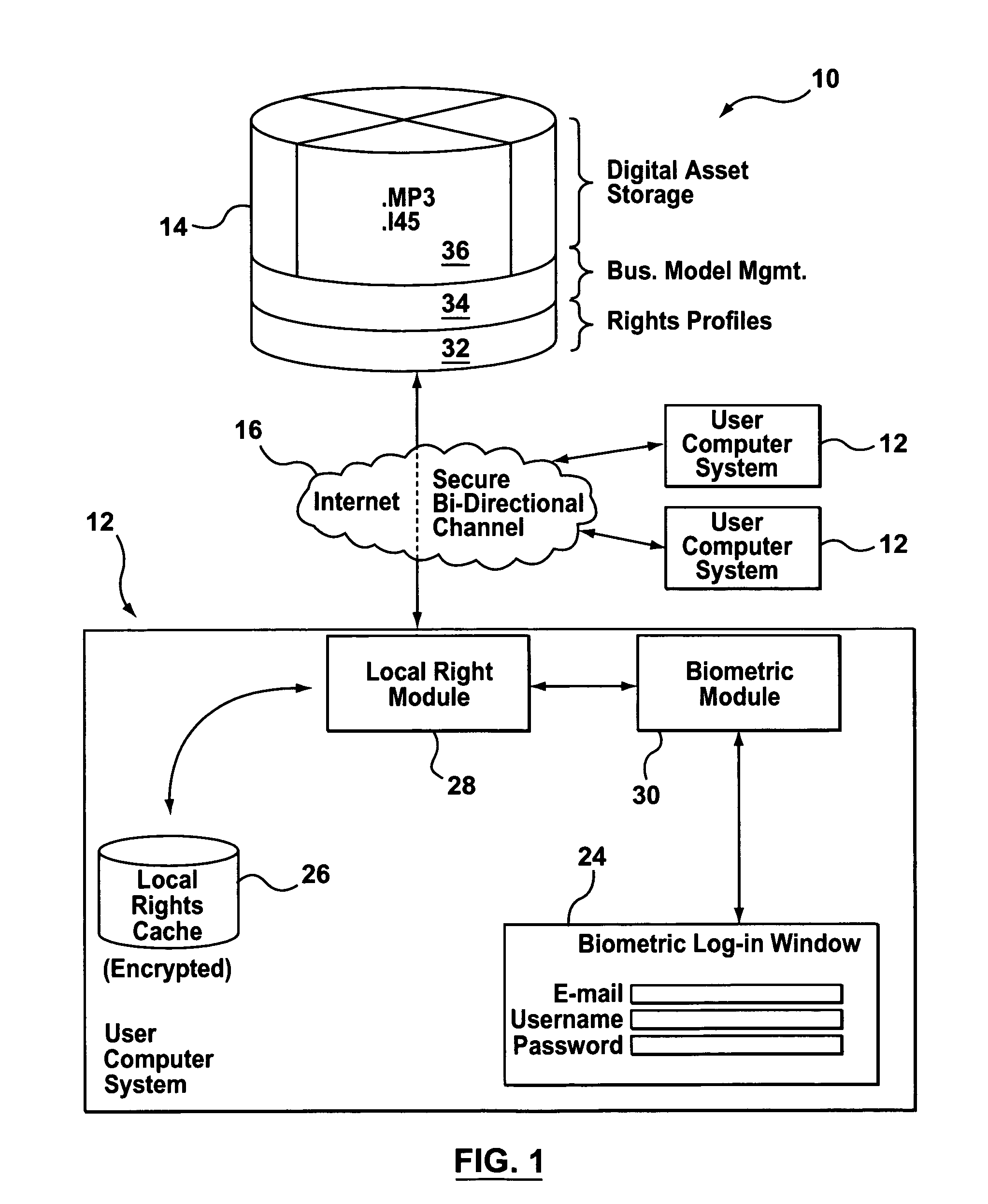
Biometric rights management system
InactiveUS7003670B2User identity/authority verificationSecret communicationThe InternetRights management
An apparatus and method for using biometric information to control access to digital media that is obtained over a network such as the Internet. Encryption, techniques are used in combination with biometric verification technology to control and monitor access to online or locally held media. Biometrics such as keystroke dynamics are measured at a user's computer to confirm the identity of a user for the purpose of allowing the user to audit music files to which the user has authorized access.
Owner:YANGAROO
Digital rights management and data license management
InactiveUS20080228578A1Surpasses efficiencySurpasses convenience factorAdvertisementsDigital computer detailsDigital contentWeb service
A system and method for the exchanging, distributing and managing digital content, along with providing users with the ability to sell and transfer digital rights of products or services purchased from other users, wherein the system and method are used to manage synchronization and the use of applications, web services and media in combination with different digital rights management (DRM) solutions to authenticate and authorize such transactions.
Owner:ALEX MASHINSKY FAMILY TRUST +1
Trusted infrastructure support systems, methods and techniques for secure electronic commerce transaction and rights management
InactiveUS7165174B1Improve efficiencyIncrease flexibilityPublic key for secure communicationDigital data processing detailsTransaction managementBusiness management
The present inventions provide an integrated, modular array of administrative and support services for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting financial management, rights management, certificate authority, rules clearing, usage clearing, secure directory services, and other transaction related capabilities functioning over a vast electronic network such as the Internet and / or over organization internal Intranets.These administrative and support services can be adapted to the specific needs of electronic commerce value chains. Electronic commerce participants can use these administrative and support services to support their interests, and can shape and reuse these services in response to competitive business realities.A Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility makes optimally efficient use of commerce administration resources, and can scale in a practical fashion to accommodate the demands of electronic commerce growth.The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many or all of its participants.Different support functions can be collected together in hierarchical and / or in networked relationships to suit various business models and / or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes. These Commerce Utility Systems can be distributed across a large number of electronic appliances with varying degrees of distribution.
Owner:INTERTRUST TECH CORP
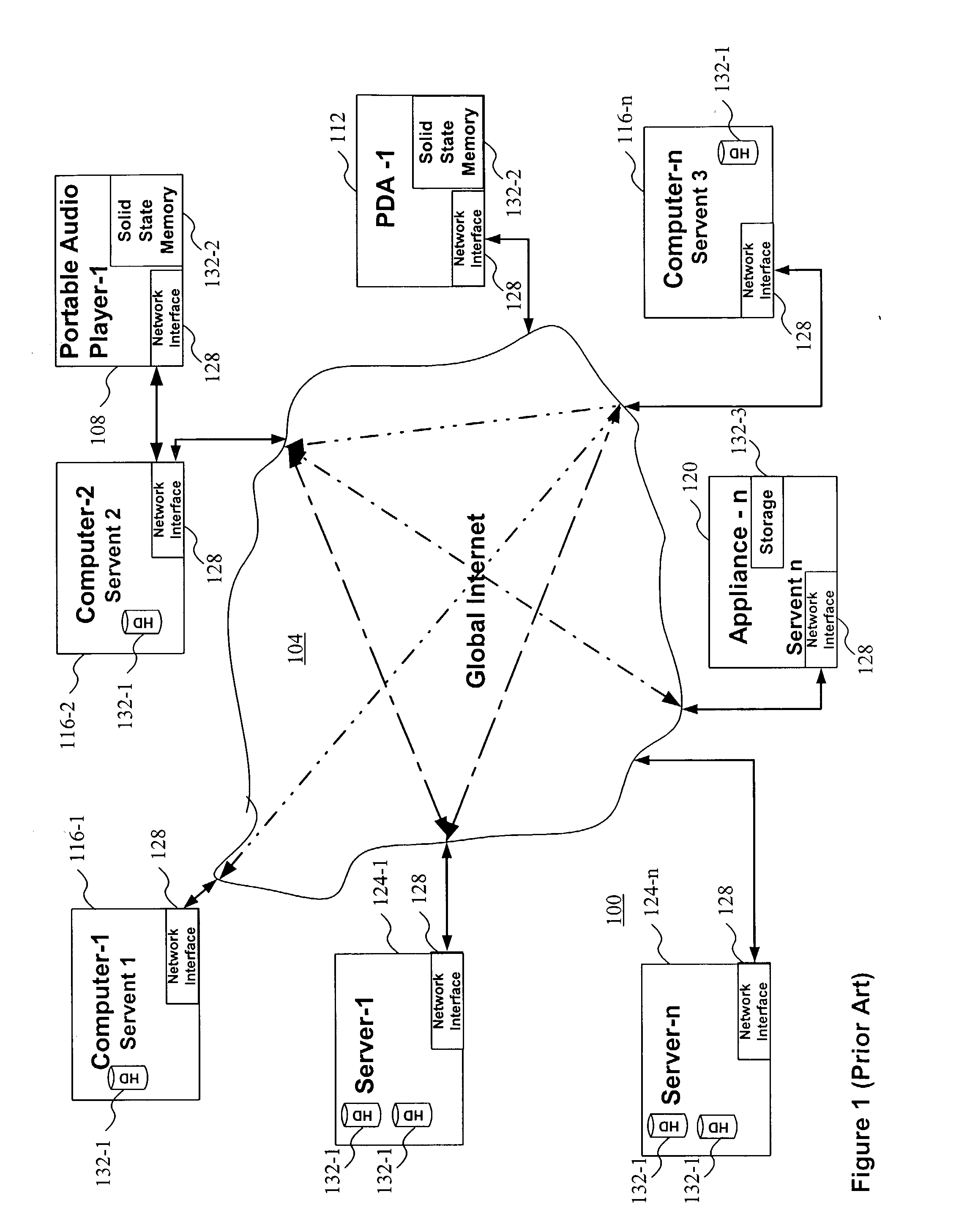
Methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS20030069749A1Increase success rateCostly and inefficientAdvertisementsRelational databasesRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
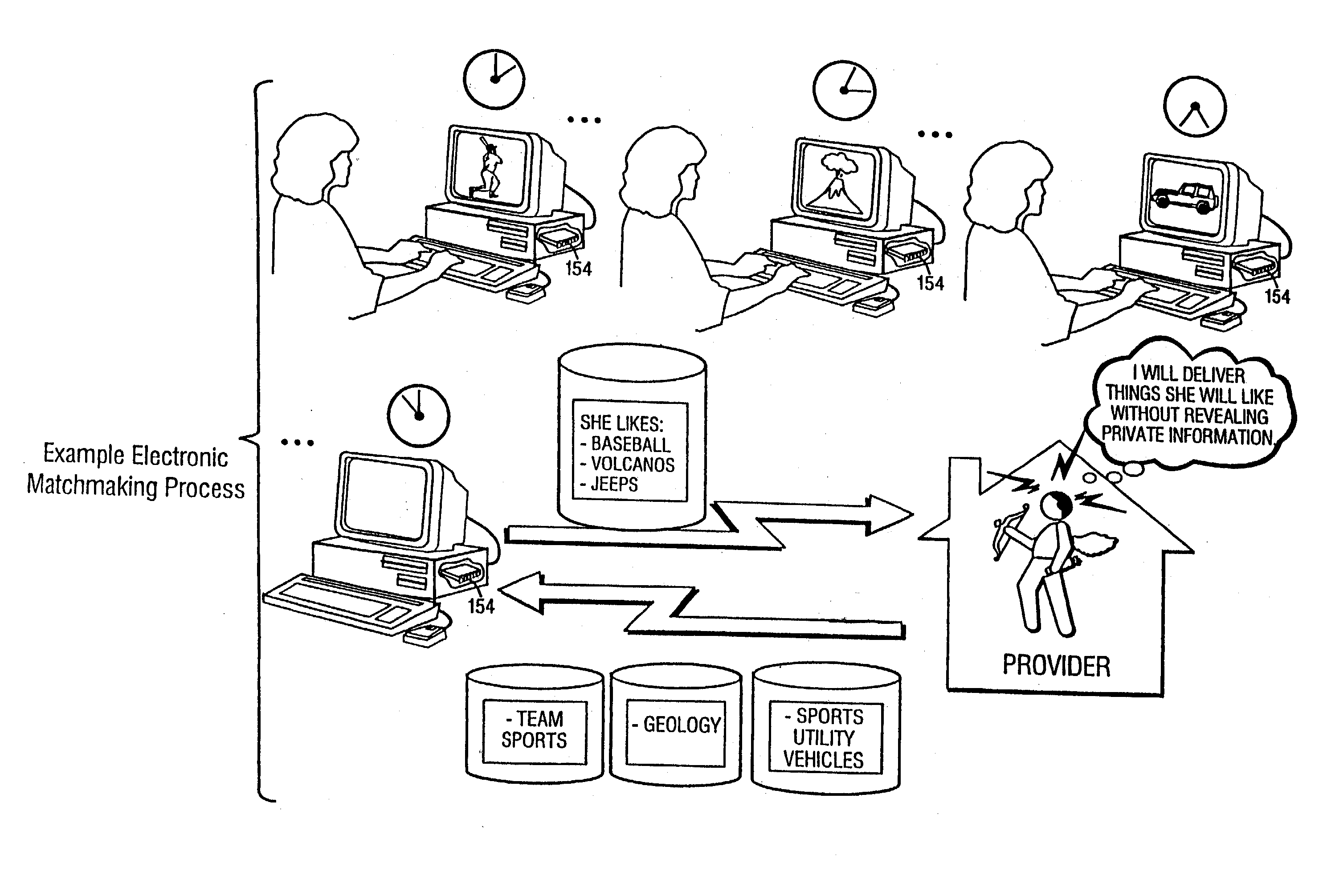
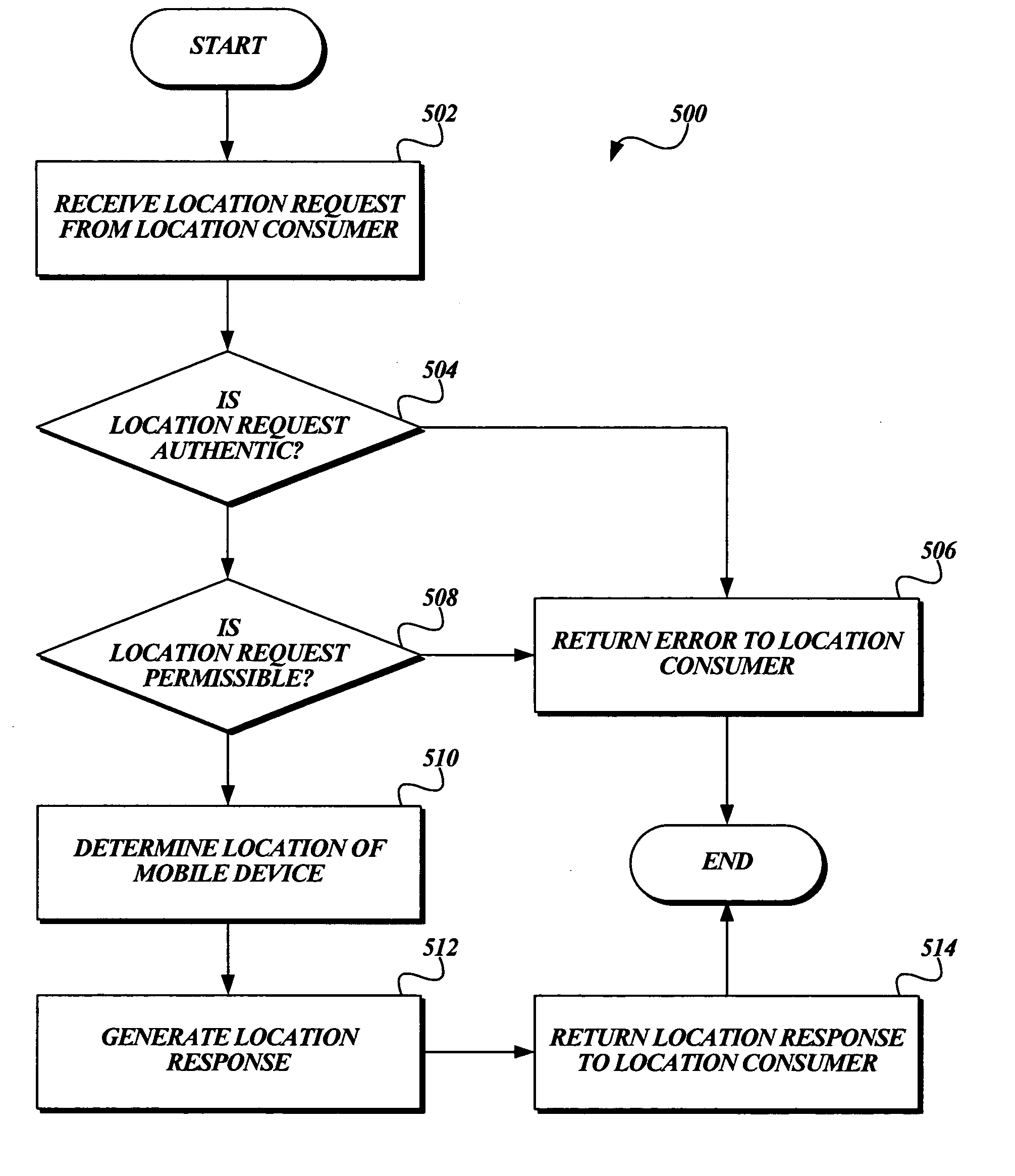
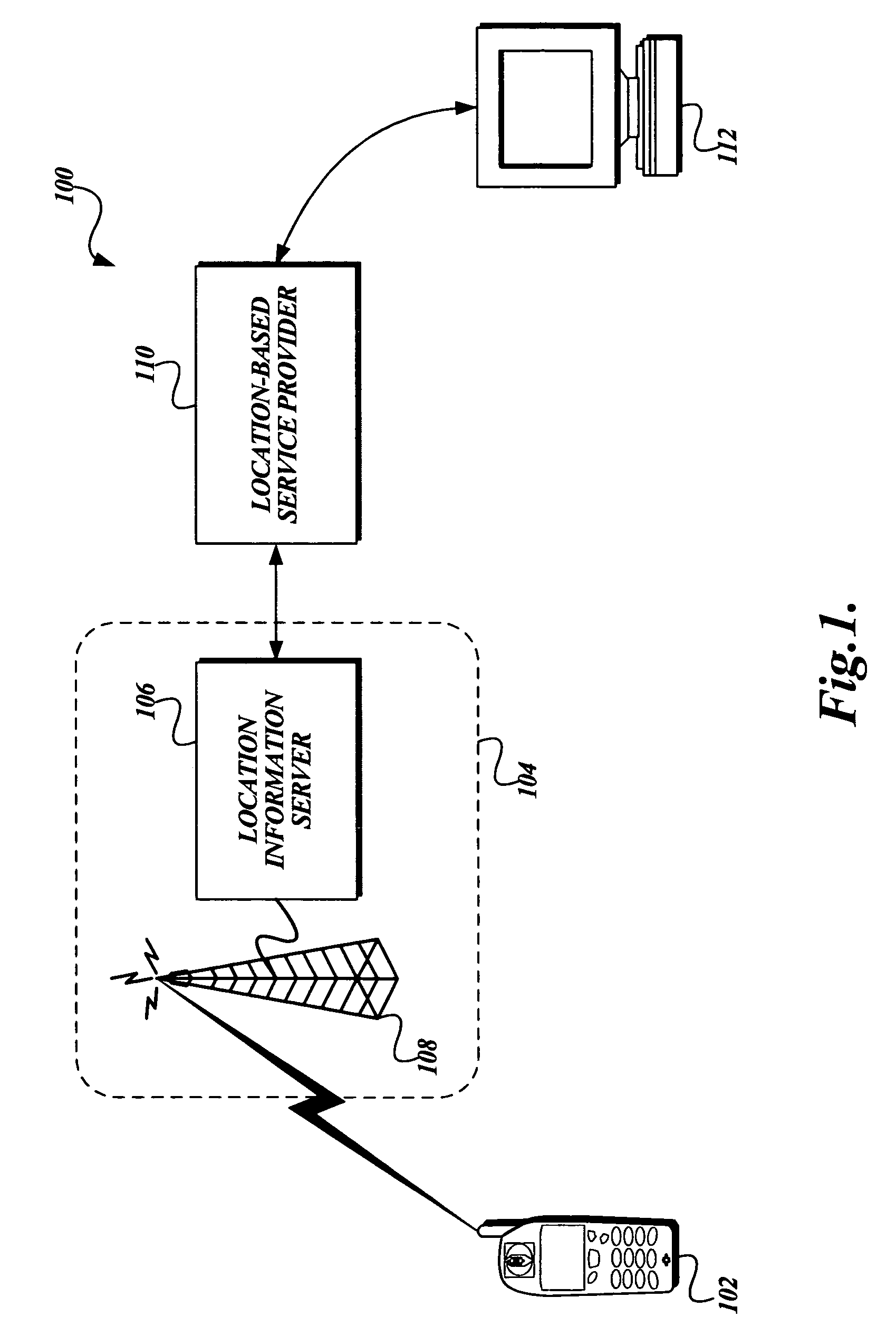
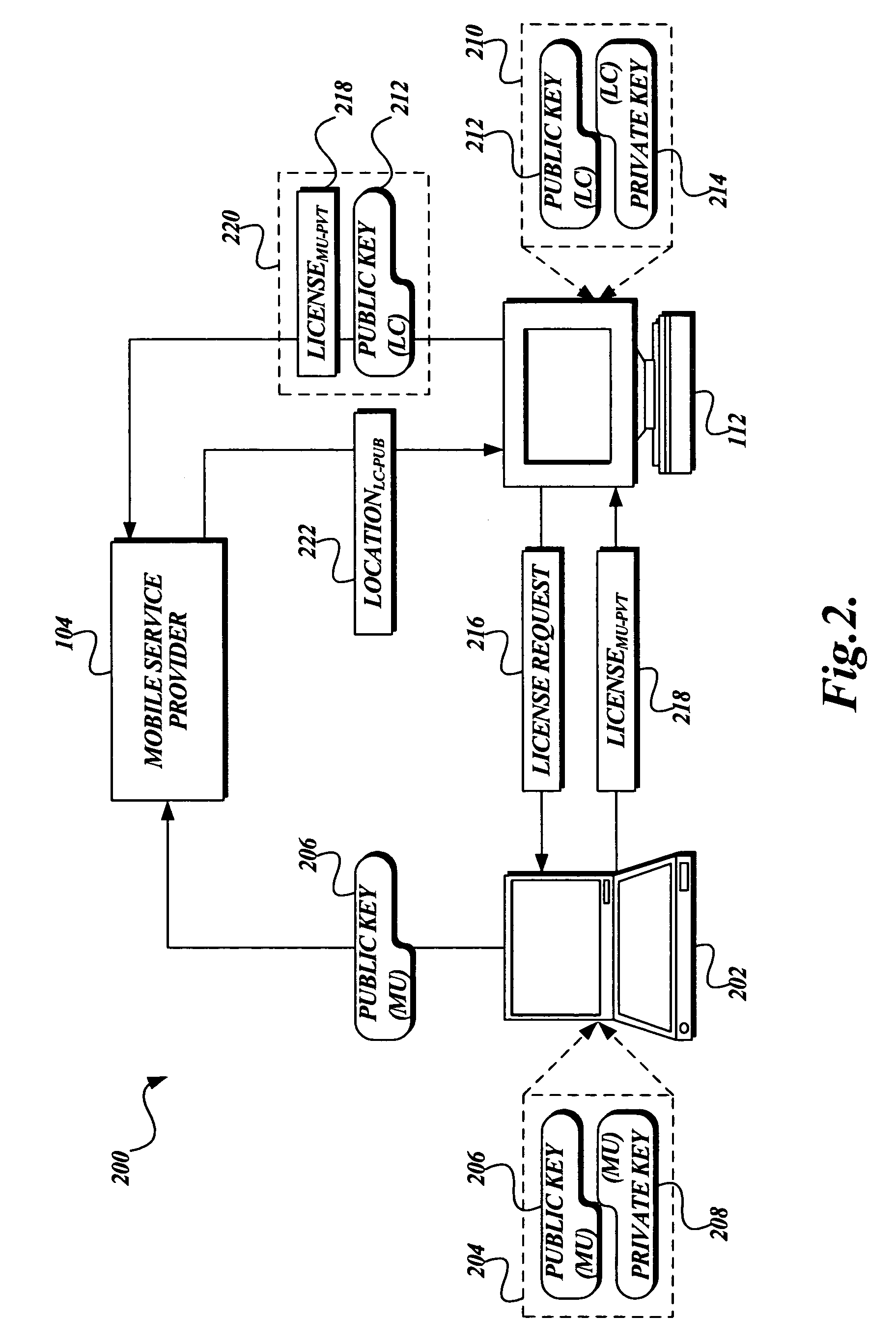
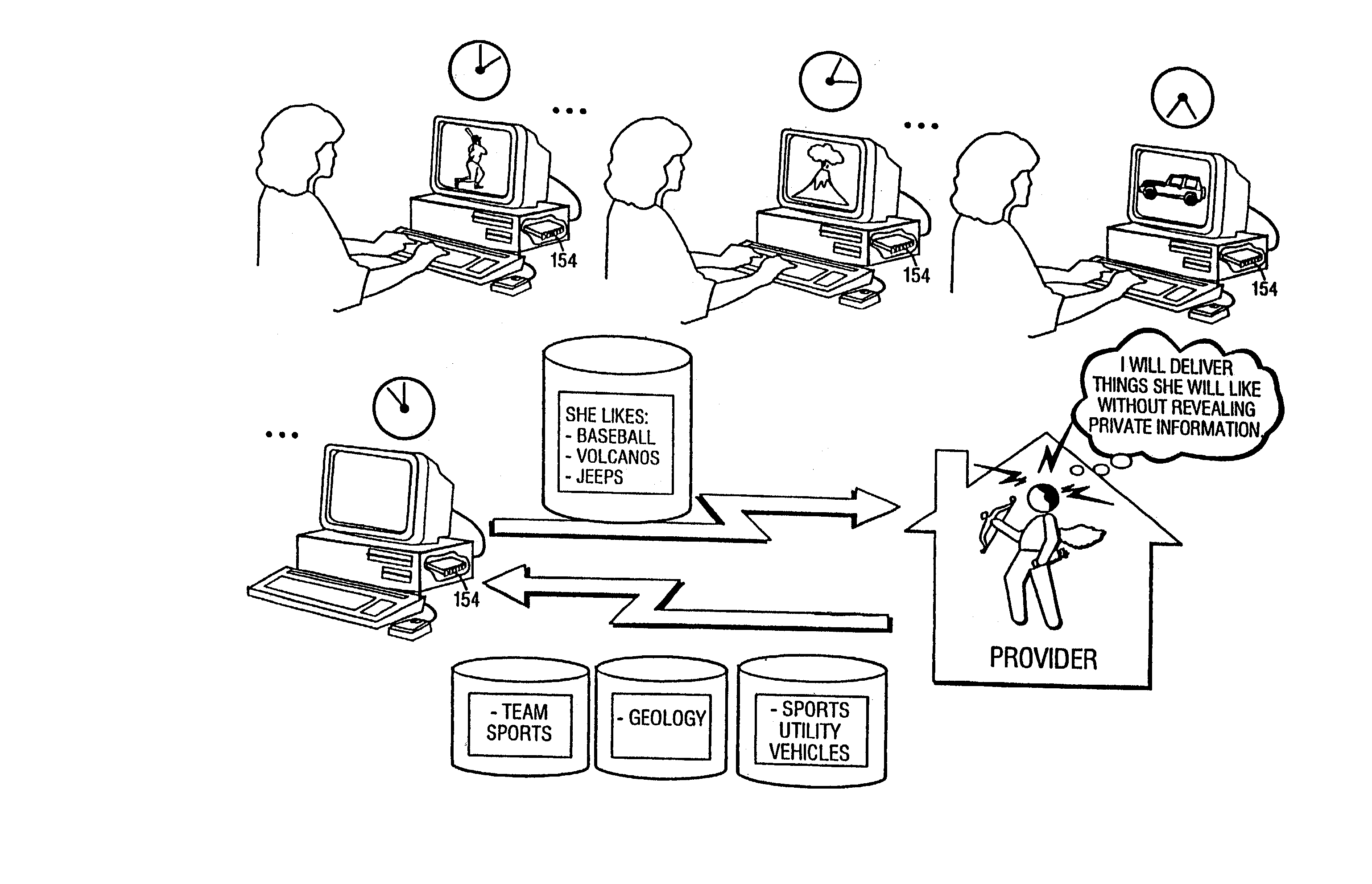
System and method for enforcing location privacy using rights management
InactiveUS20060046744A1Secure deliveryData processing applicationsUser identity/authority verificationRights managementMobile device
A system and method for securely delivering the location information of a mobile device to a location consumer is presented. In operation, the mobile device user issues a license to a location consumer. The license identifies the location consumer and any conditions the mobile device user places on the license. The license is encrypted such that it cannot be modified without invalidating the license. The license is submitted in a location request by the location consumer. A location information server receives the request, validates that the license was issued to the location consumer and that the location request conforms to the conditions of the license. If so, the location information server obtains the mobile device's location information, generates a location response, encrypts some of the location response, and returns the location response to the location consumer.
Owner:MICROSOFT TECH LICENSING LLC
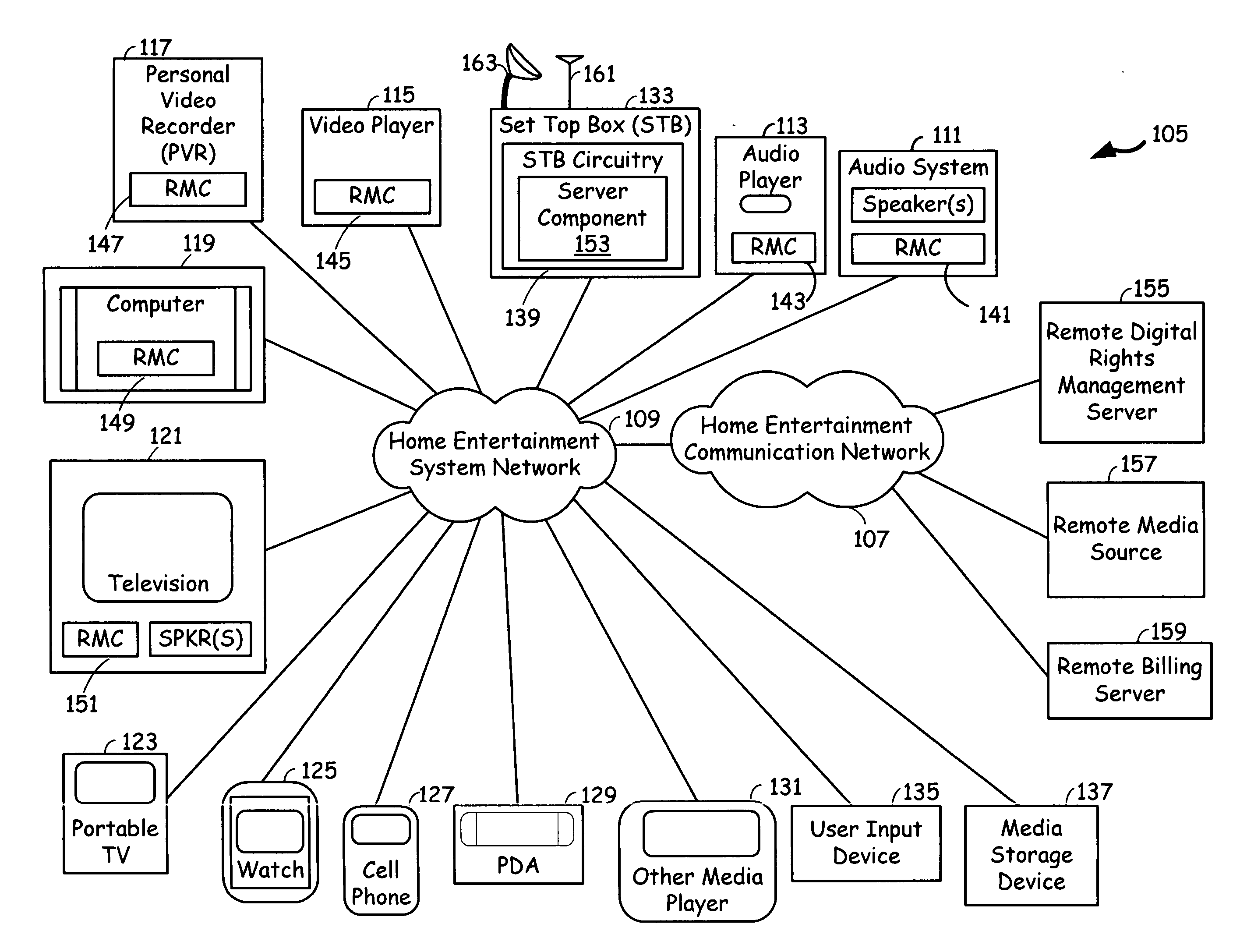
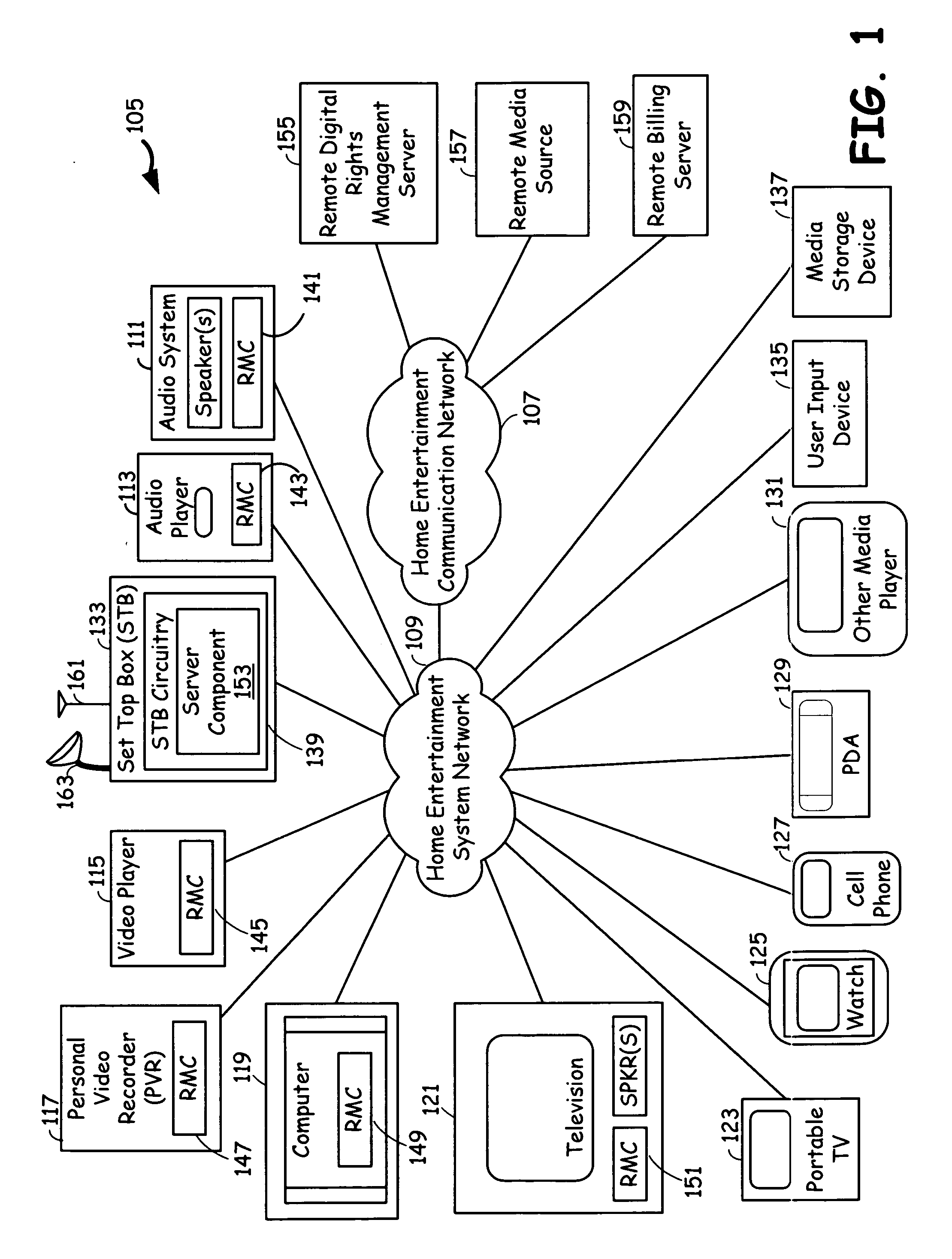
Transcoding and data rights management in a mobile video network with STB as a hub
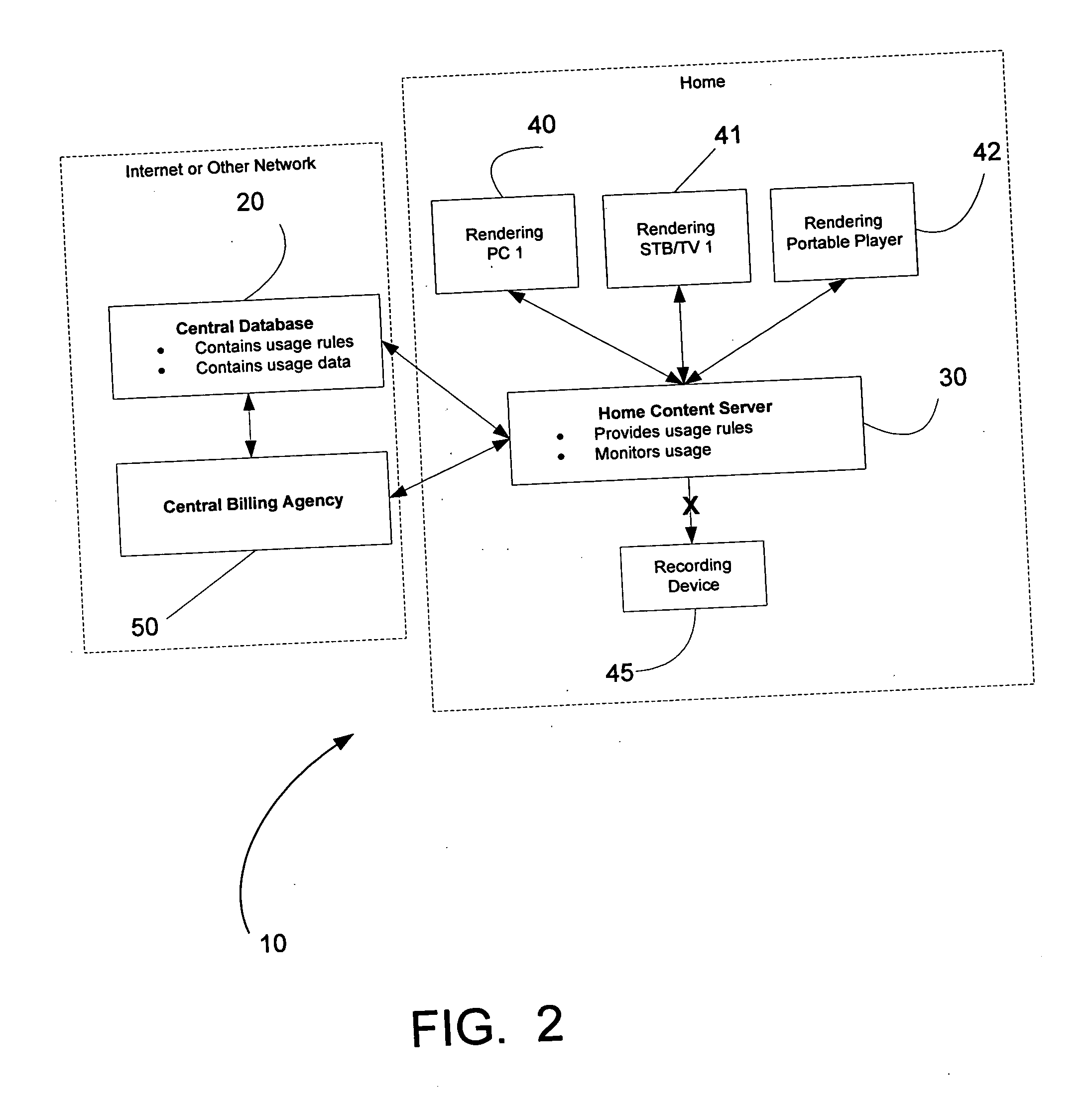
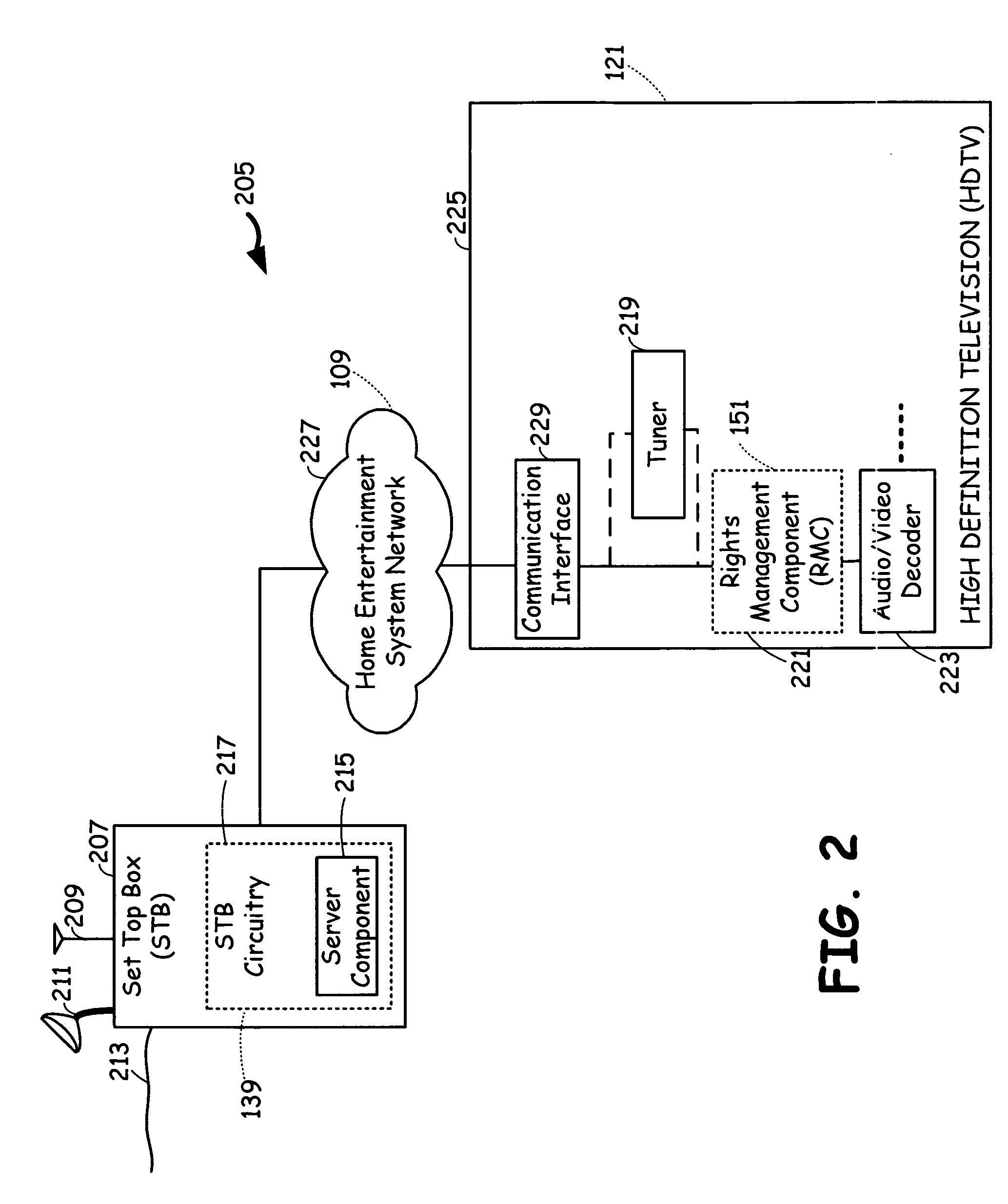
InactiveUS20060117379A1Control consumptionDigital data processing detailsUser identity/authority verificationMediaFLOTranscoding
A home entertainment system that employs DRM (Data Rights Management) data protected multimedia programs and rights management component (RMC), with corresponding hardware and software systems incorporated in to home entertainment systems, to protect rights of the media program providers and the users. The system employs STB (Set Top Box) as a hub. The rights management component is incorporated in to the set top box (STB Circuitry), as well as some of the media devices. Three operational scenarios are envisaged regarding the home entertainment system. The first operational scenario involves a remote media source and the media device interaction via STB Circuitry; where as the STB Circuitry performs the duty of a mediator. The second operational scenario involves remote media source and the media device interaction via STB Circuitry, where as the STB Circuitry having rights to reissue licenses to media players. The third operational scenario involves local media sources incorporating the RMC and interacting with the STB Circuitry to decrypt and transcode the multimedia programs. Further, the STB Circuitry interacts with a remote billing server via the communication network regarding presentation rights, to interact with a user regarding the presentation rights, and to arrange for payment for the presentation rights.
Owner:AVAGO TECH INT SALES PTE LTD
Digital rights management of a digital device
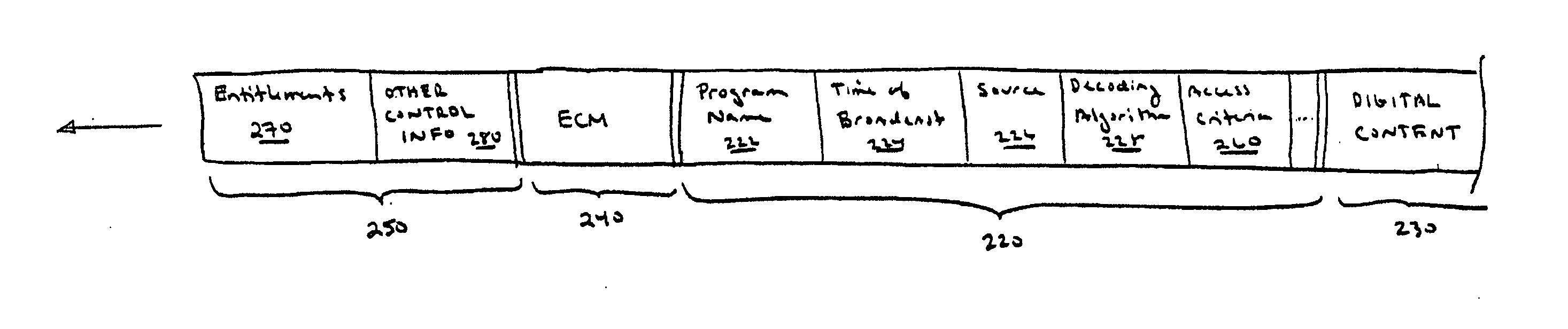
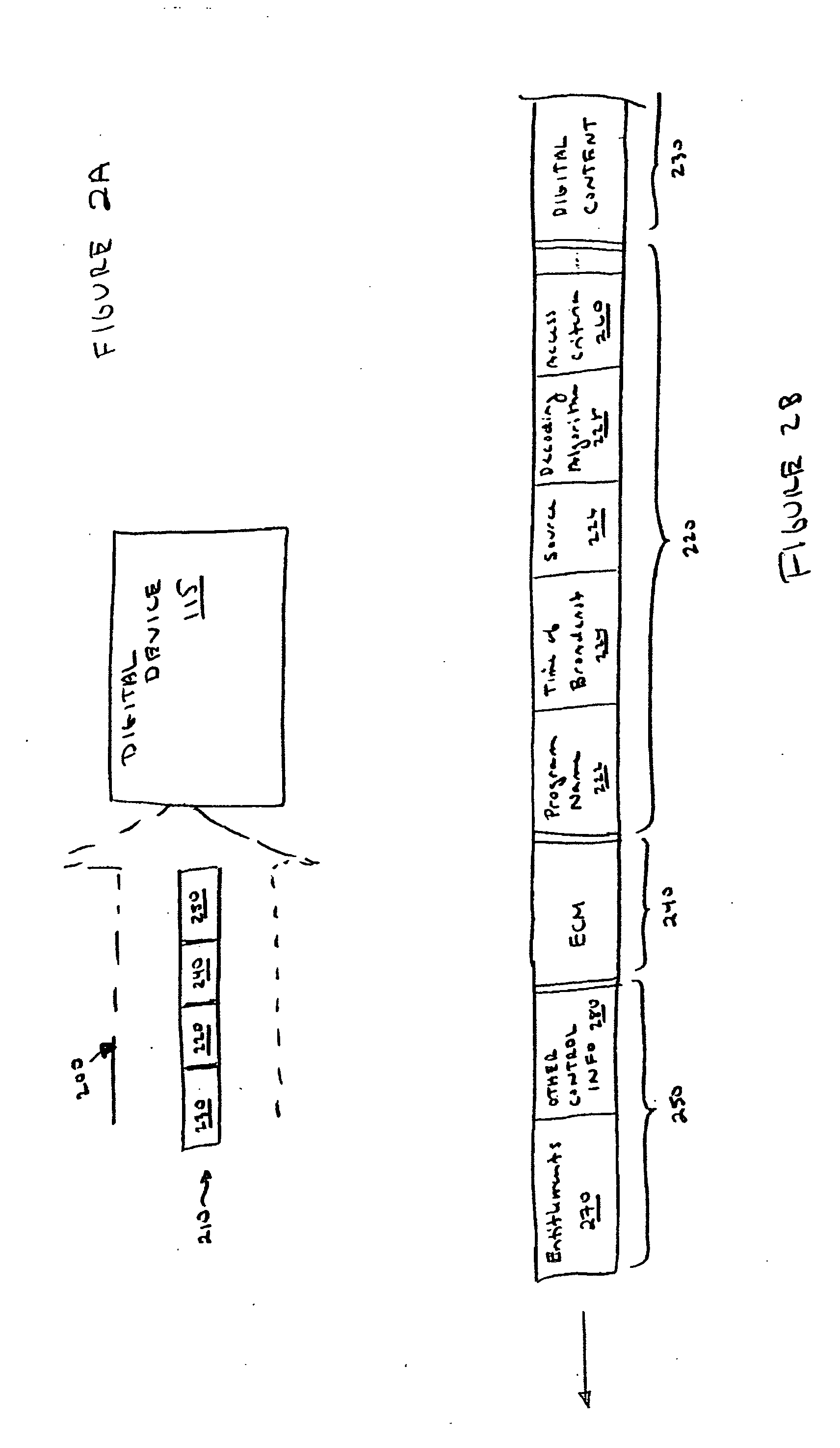
ActiveUS20050063541A1Television system detailsUnauthorized memory use protectionDigital contentRights management
According to one embodiment, an apparatus involves the descrambling of scrambled digital content using a one-time programmable key and digital rights management. The apparatus comprises a processor and a descrambler. The processor is adapted to execute a Digital Rights Management (DRM) function in order to determine whether each entitlement needed to access the digital content is pre-stored. The descrambler is adapted to decrypt encrypted information using a Unique Key stored within the one-time programmable memory. After determining that each entitlement needed to access the digital content is pre-stored, the decrypted information is used to generate a key, which is used to decrypt at least one service key for descrambling the scrambled digital content.
Owner:SONY CORP +1
Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management
InactiveUS7415617B2Efficiently distributedDigital data processing detailsUser identity/authority verificationTransaction managementUtility industry
An integrated, modular array of administrative and support services are provided for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting transaction-related capabilities functioning over electronic network-s, and can also be adapted to the specific needs of electronic commerce value chains. In one embodiment, a Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many of its participants. Different support functions can be collected together in hierarchical and / or networked relationships to suit various business models or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes.
Owner:INTERTRUST TECH CORP
System, method and computer program product for providing digital rights management of protected content
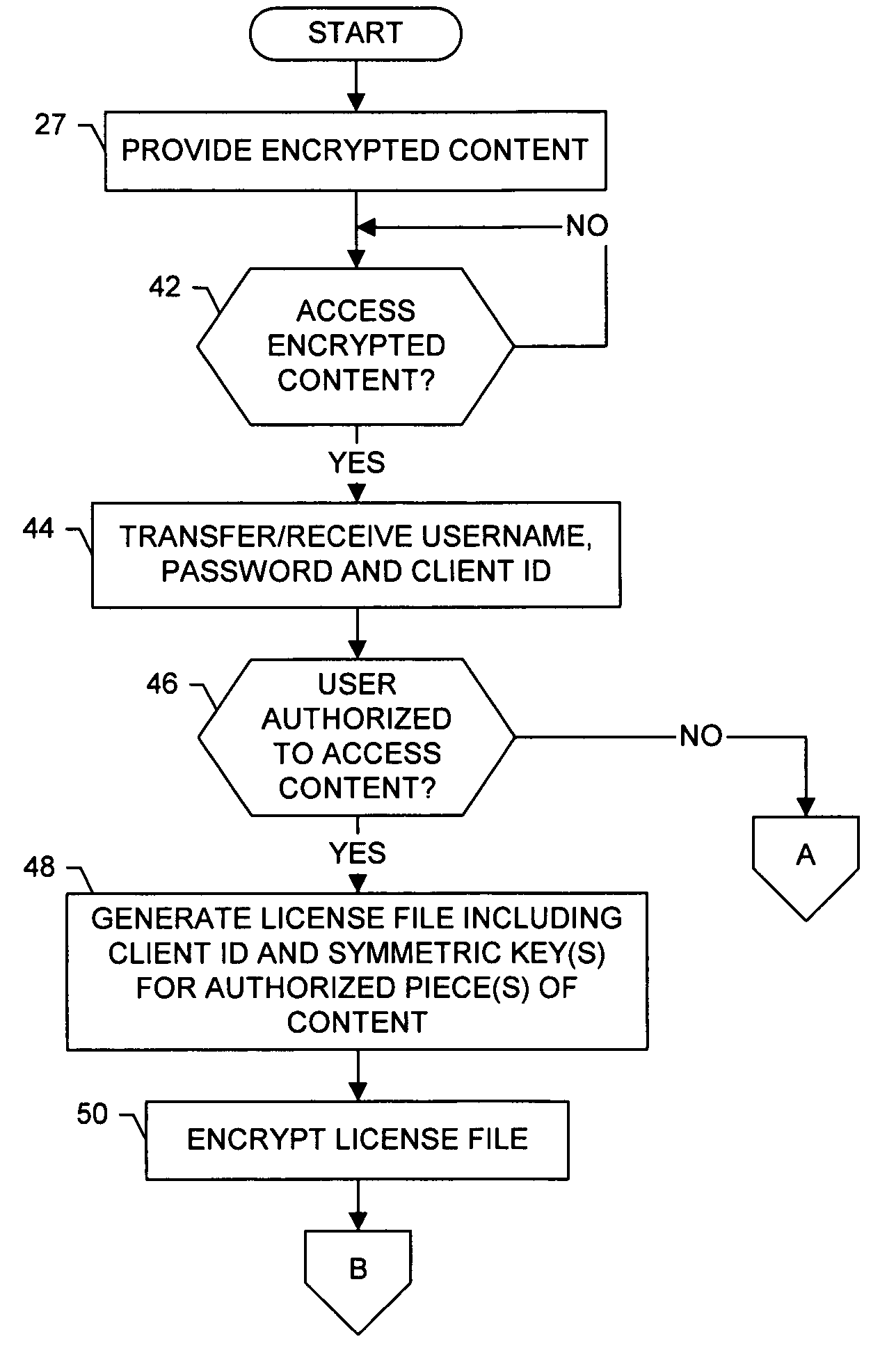
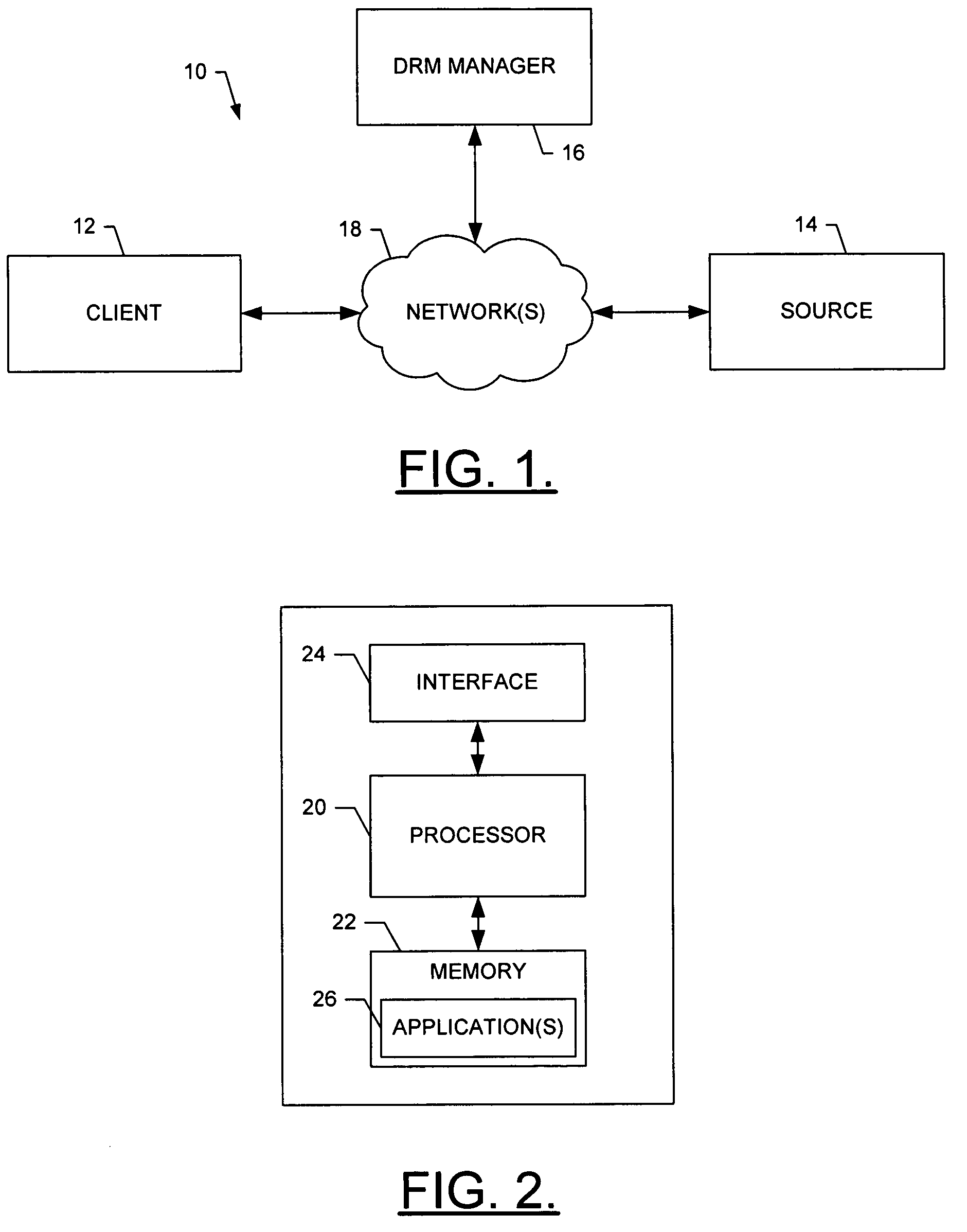
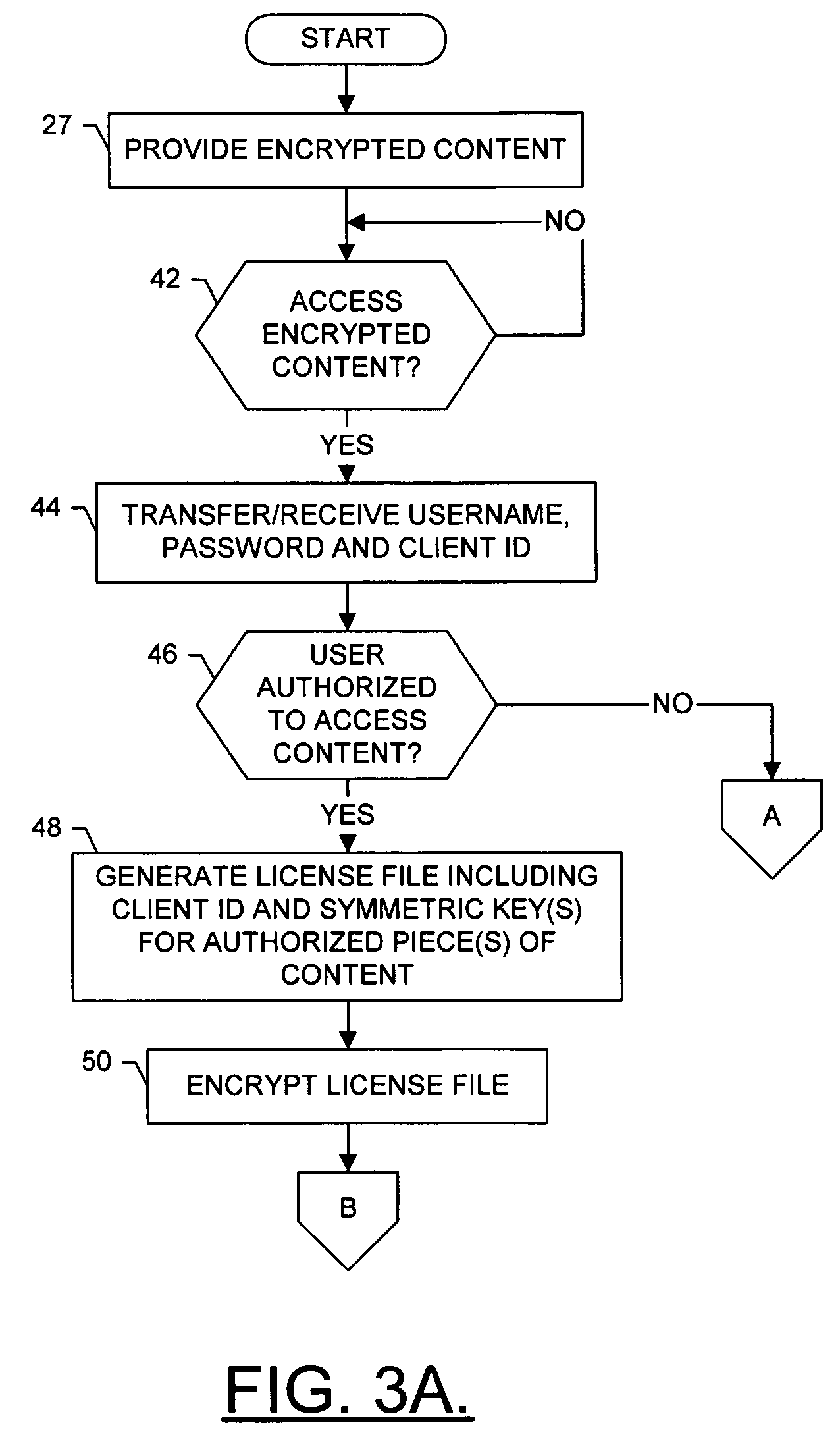
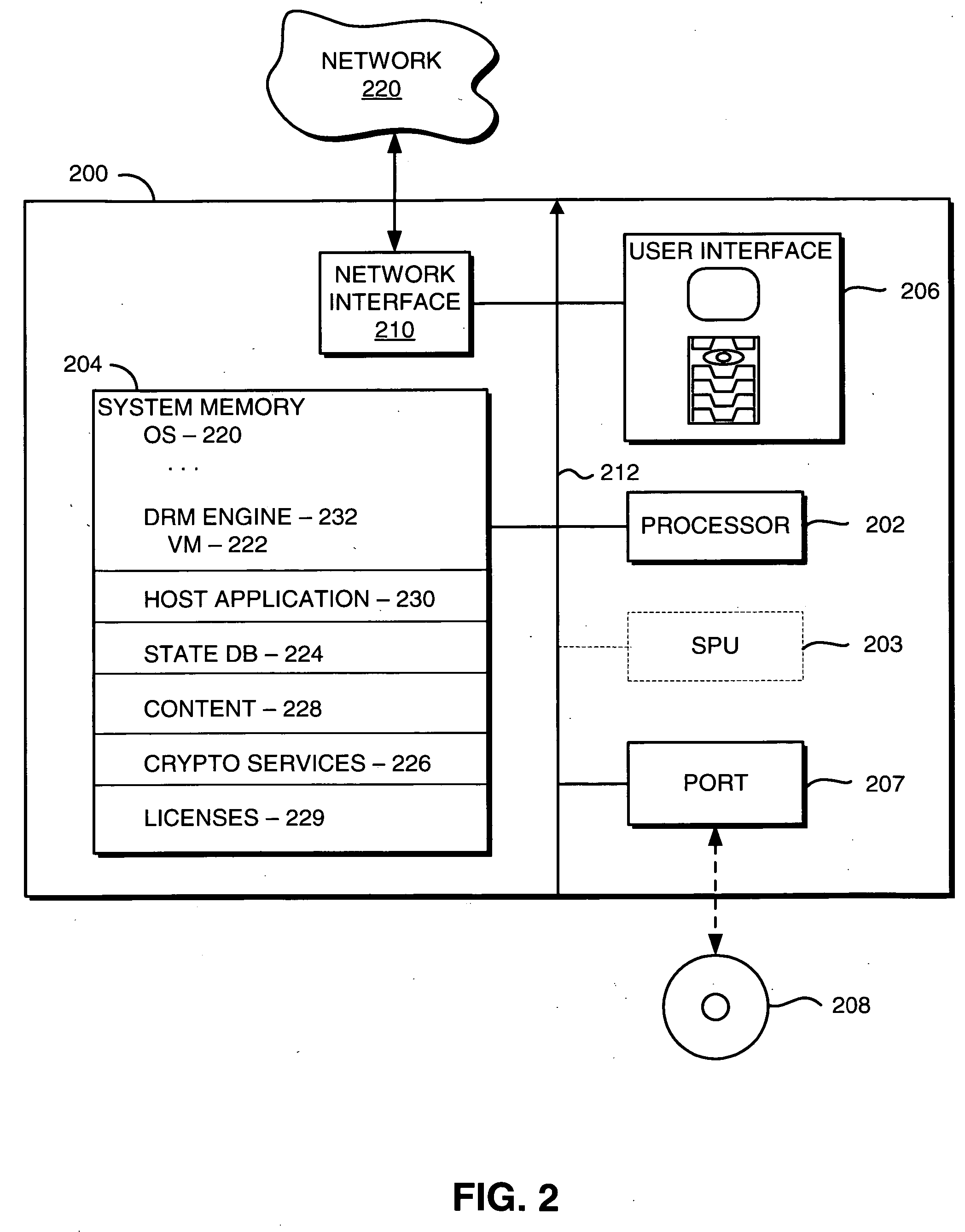
InactiveUS20050273629A1Shorten the timePrecise managementUser identity/authority verificationUnauthorized memory use protectionRights managementDigital rights management
A system for providing digial rights management of protected content includes a client and a DRM manager. The client is capable of receiving at least one piece of content, the piece(s) of content being encrypted with at least one encryption key regardless of client user(s) authorized to access the piece(s) of encrypted content. To facilitate the client accessing one or more of the piece(s) of content, the DRM manager is capable of transferring the encryption key(s) to the client, the encryption key(s) being encrypted with a private key of a public key / private key pair unique to a client user associated with the client. The client can thereafter decrypt the encryption key(s) using the public key of the public key / private key pair unique to the client user. Then, the client can decrypt the piece(s) of content using the decrypted encryption key(s), and access the decrypted piece(s) of content.
Owner:VITALSOURCE TECH INC
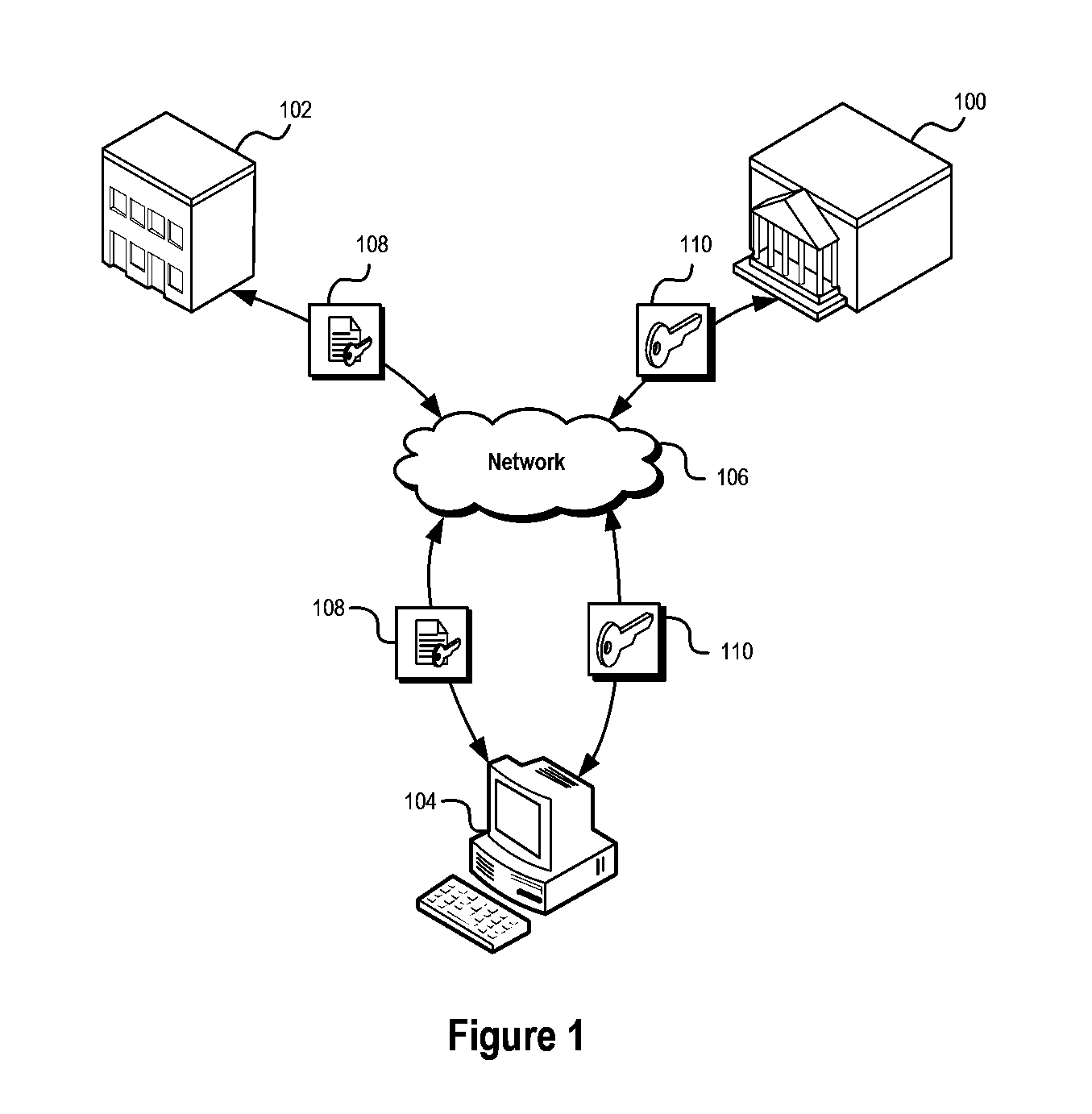
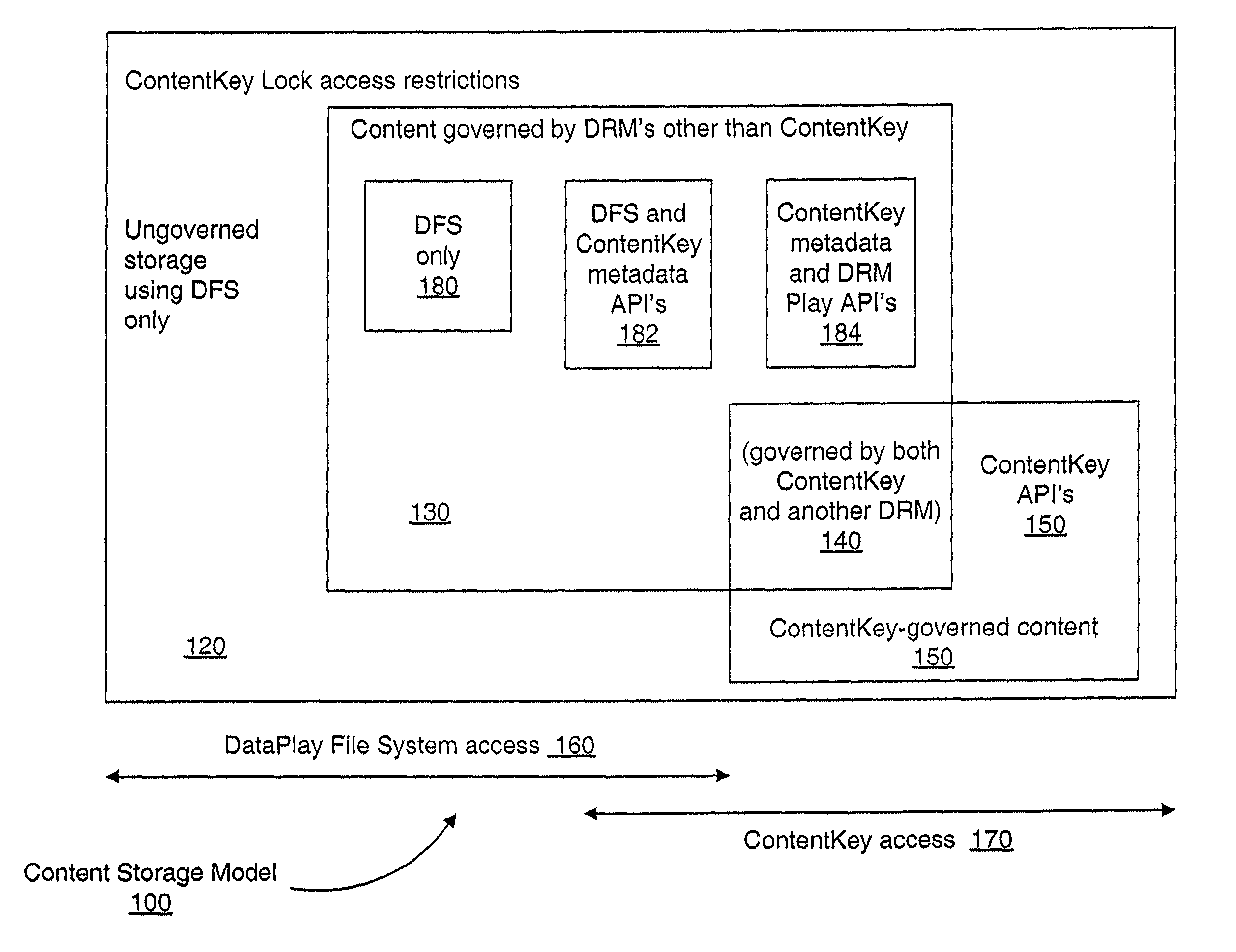
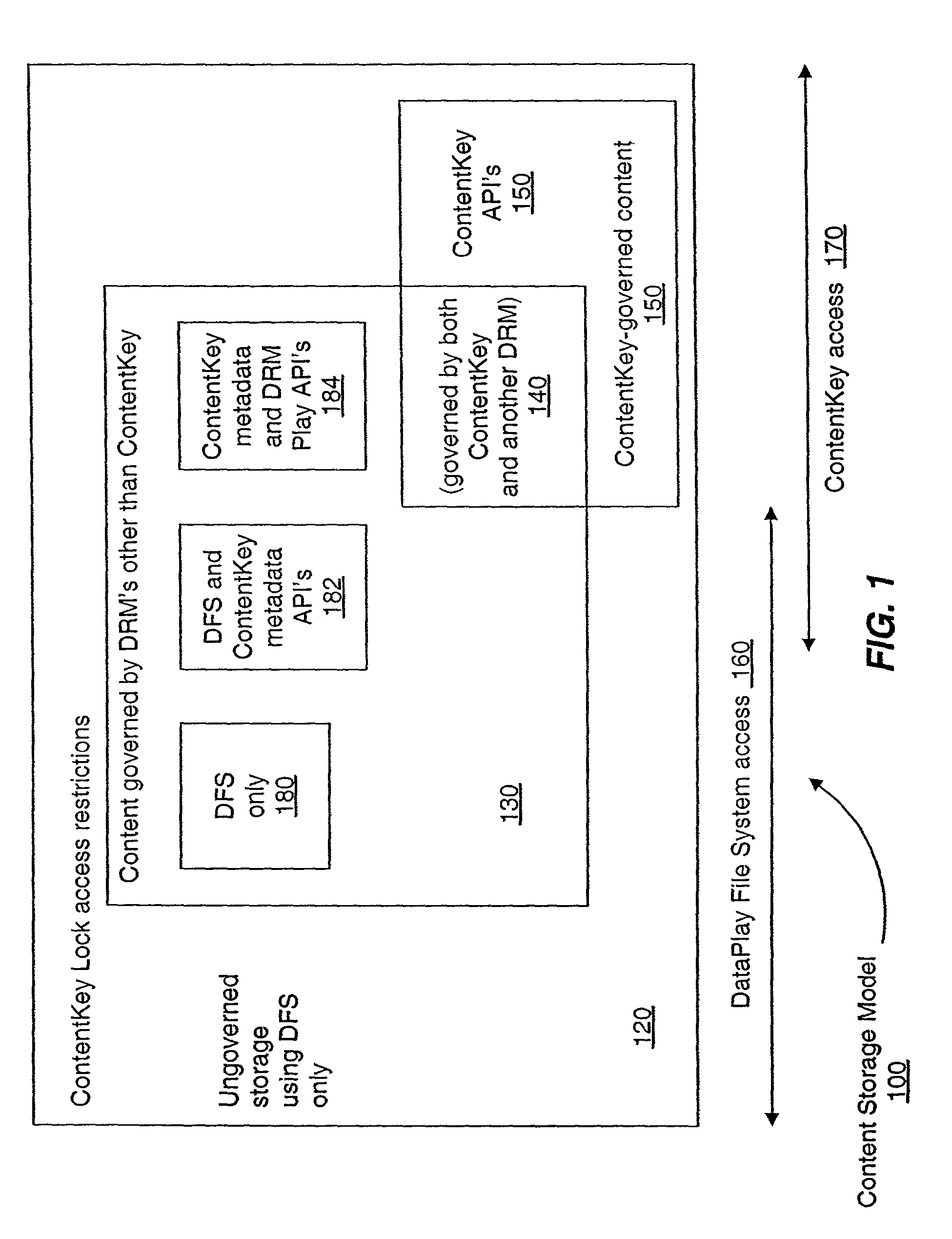
Secure access method and system
A secure electronic content system and method is provided. The system includes a controller including an interface component, a host system coupled to the controller, the host system configured to present content under predetermined conditions, the host system operable with a navigation protocol, the host system further including a system manager operable with an associations component configured to be at least partially run by the host system, a translator configured to provide meanings and generate commands within the host system at least a first digital rights management (DRM) component configured to provide encoding and access rules for the content; and a file system component including a file system application programming interface (API) configured to provide a logical interface between a plurality of components.
Owner:DATAPLAY
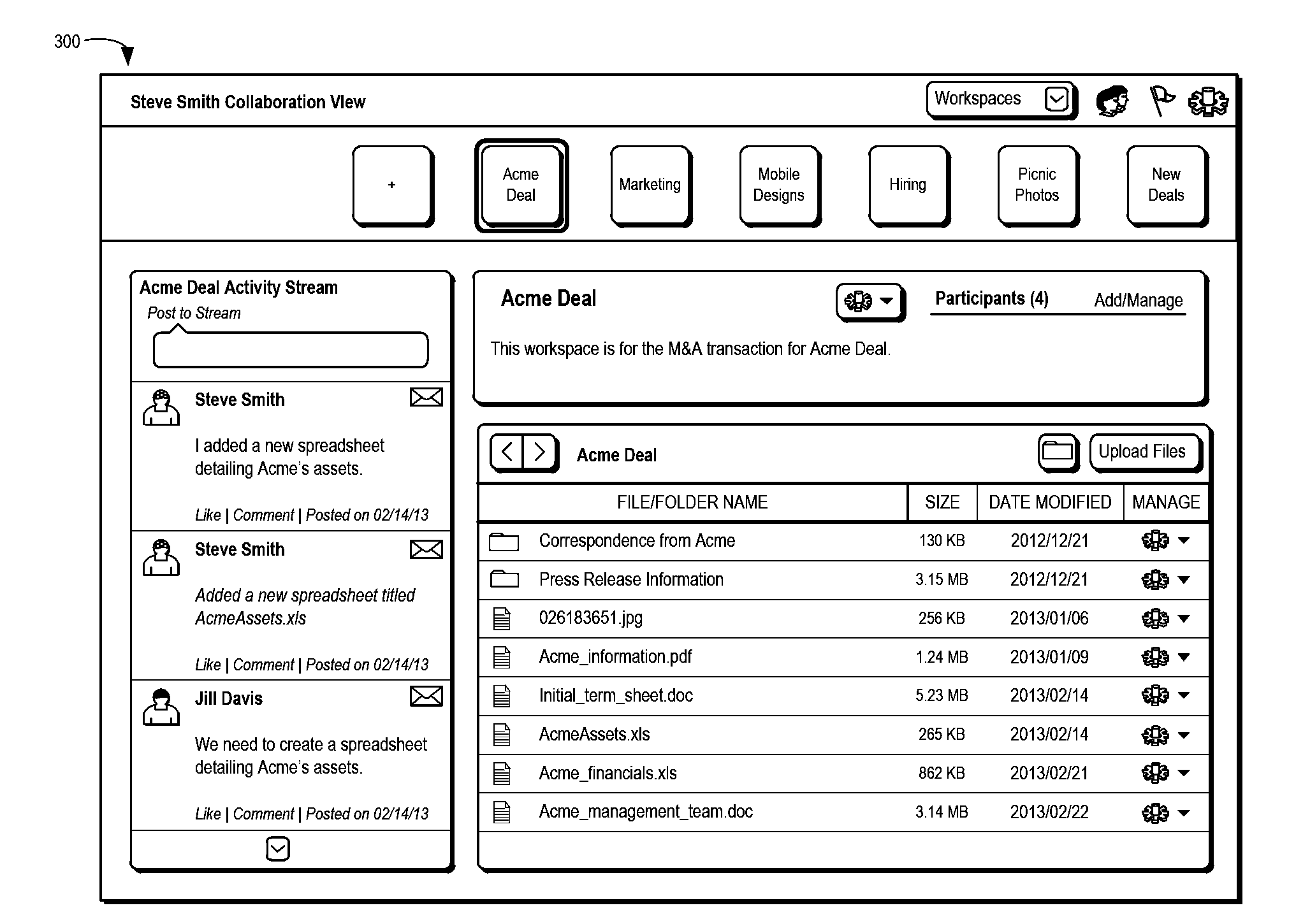
System, method, and computer program product for managing rights of media in collaborative environments
InactiveUS20080133551A1Easy to understandEasily and efficiently share both content and editorial inputProgram/content distribution protectionSpecial data processing applicationsDigital rights managementRights management
A system, method, computer program product, and propagated signal of this collaborative system are adapted to track metadata relating to an online digital asset that captures each user's or group's interest in the asset and thus, in the aggregate, defines a collective interest in the asset and self-selects a relevant market based upon the nature of the asset, the distribution, and the collective group. Further, the system, method, computer program product, and propagated signal implement a rights manager to provide for digital rights management in collaborative systems. The system includes a plurality of communication clients, inter-communicated by a network, each for initiating a collaborative concurrent processing of a resource file; and a rights manager, coupled to each the plurality of communications clients, for authorizing the processing of the resource file responsive to a rights management tag associated with the resource file, the rights manager securing the rights management tag with the resource file to produce a digital resource and the rights manager decrypting the digital resource to produce the resource file and the rights management tag. The method includes initiating a collaborative concurrent processing of a resource file by a particular one communication client of a plurality of communication clients, inter-communicated by a network; and authorizing the processing of the resource file by a rights manager, the authorizing responsive to a rights management tag associated with the resource file, the rights manager securing the rights management tag with the resource file to produce a digital resource and the rights manager decrypting the digital resource to produce the resource file and the rights management tag.
Owner:APEER
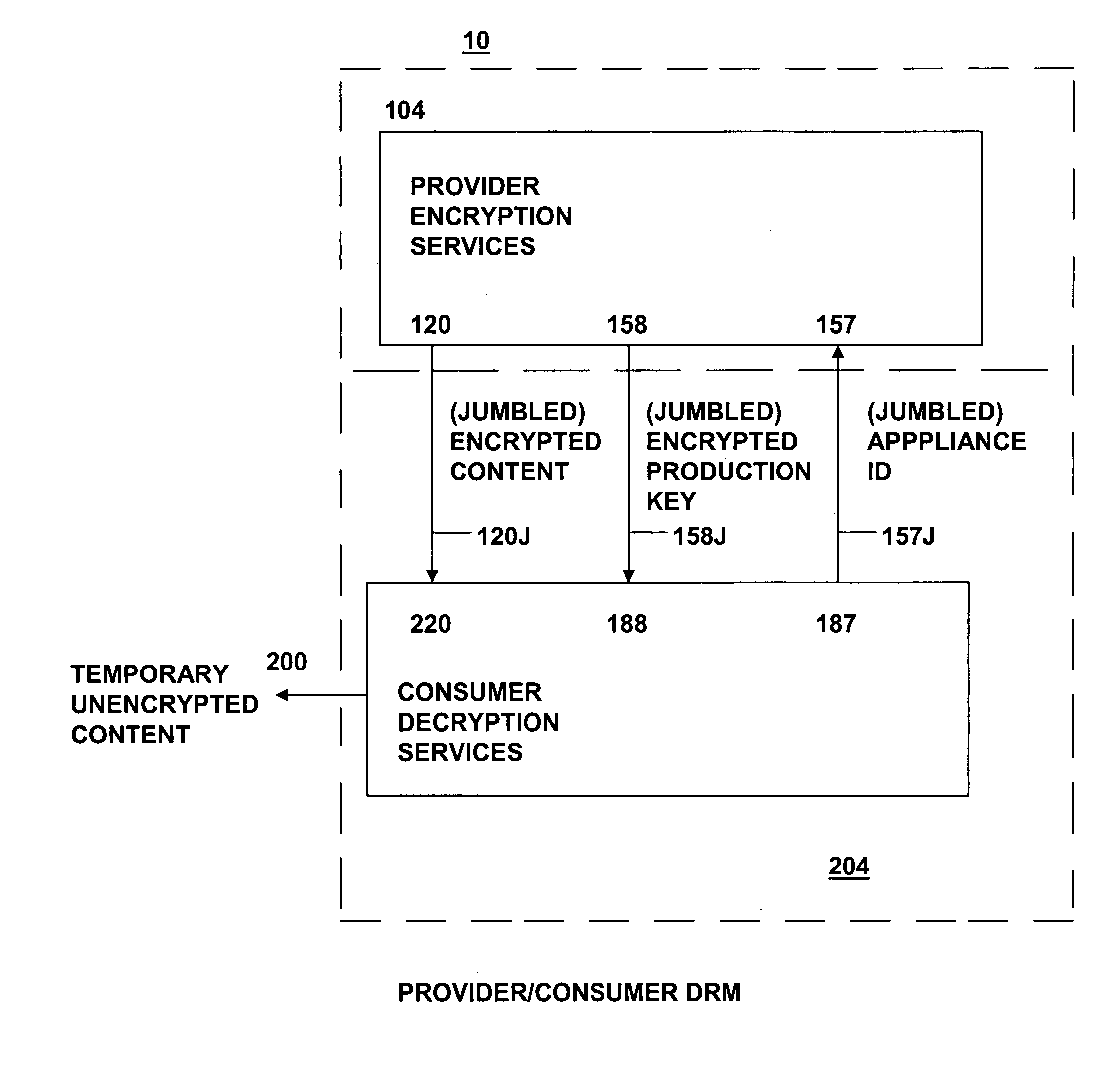
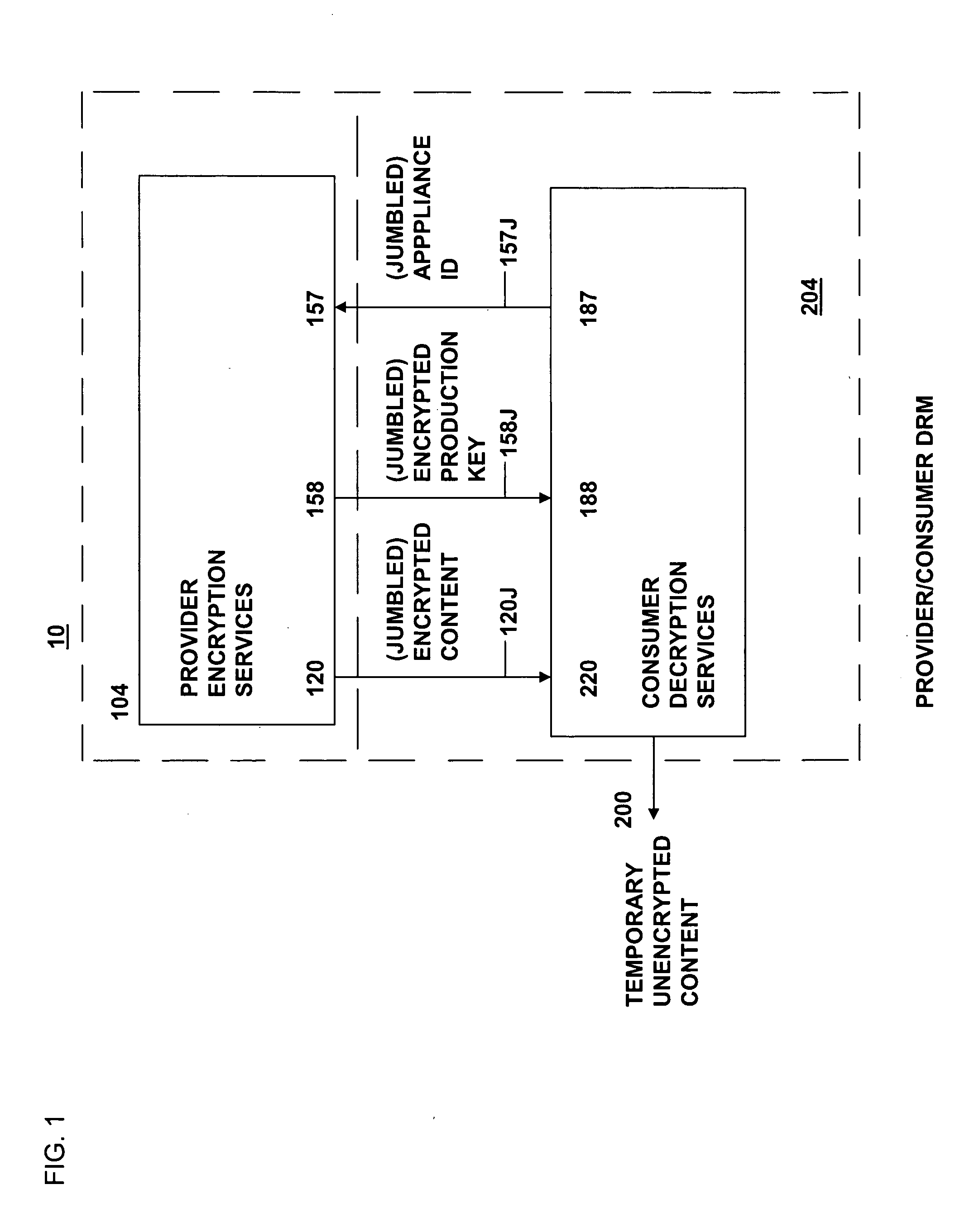
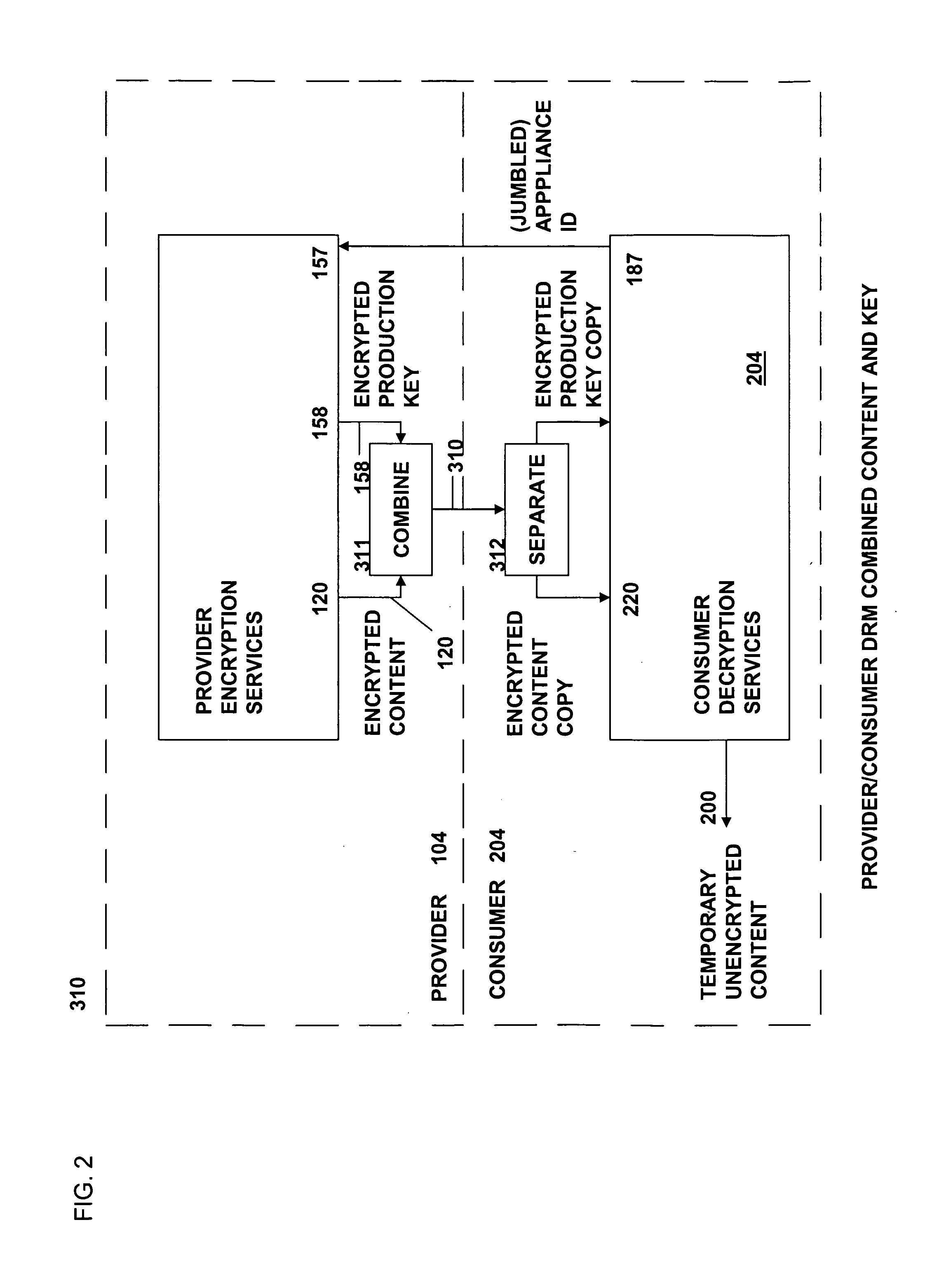
Method and system for secure distribution of selected content to be protected on an appliance-specific basis with definable permitted associated usage rights for the selected content
ActiveUS20080148067A1Unauthorized memory use protectionHardware monitoringApplication program softwareData file
The present invention relates to data rights management and more particularly to a secured system and methodology and production system and methodology related thereto and to apparatus and methodology for production side systems and are consumer side systems for securely utilizing protected electronic data files of content (protected content), and further relates to controlled distribution, and regulating usage of the respective content on a recipient device (computing system) to be limited strictly to defined permitted uses, in accordance with usage rights (associated with the respective content to control usage of that respective content), on specifically restricted to a specific one particular recipient device (for a plurality of specific particular recipient devices), or usage on some or any authorized recipient device without restriction to any one in specific, to control use of the respective content as an application software program, exporting, modifying, executing as an application program, viewing, and / or printing of electronic data files.
Owner:OL SECURITY LIABILITY CO
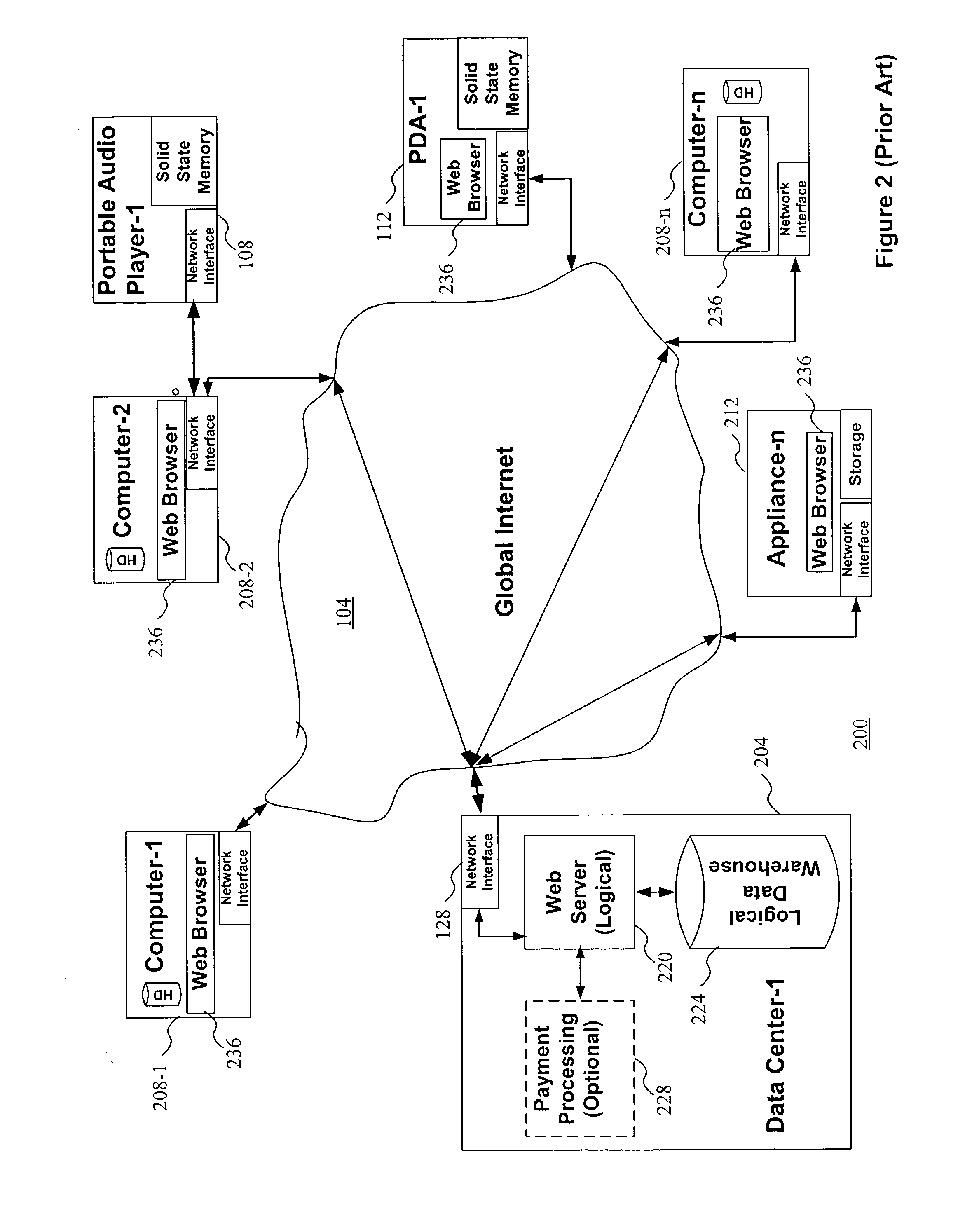
Methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS20030069748A1Difficult to navigateImprove privacyAdvertisementsRelational databasesRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
Data processing system, data processing device, data processing method, and computer program
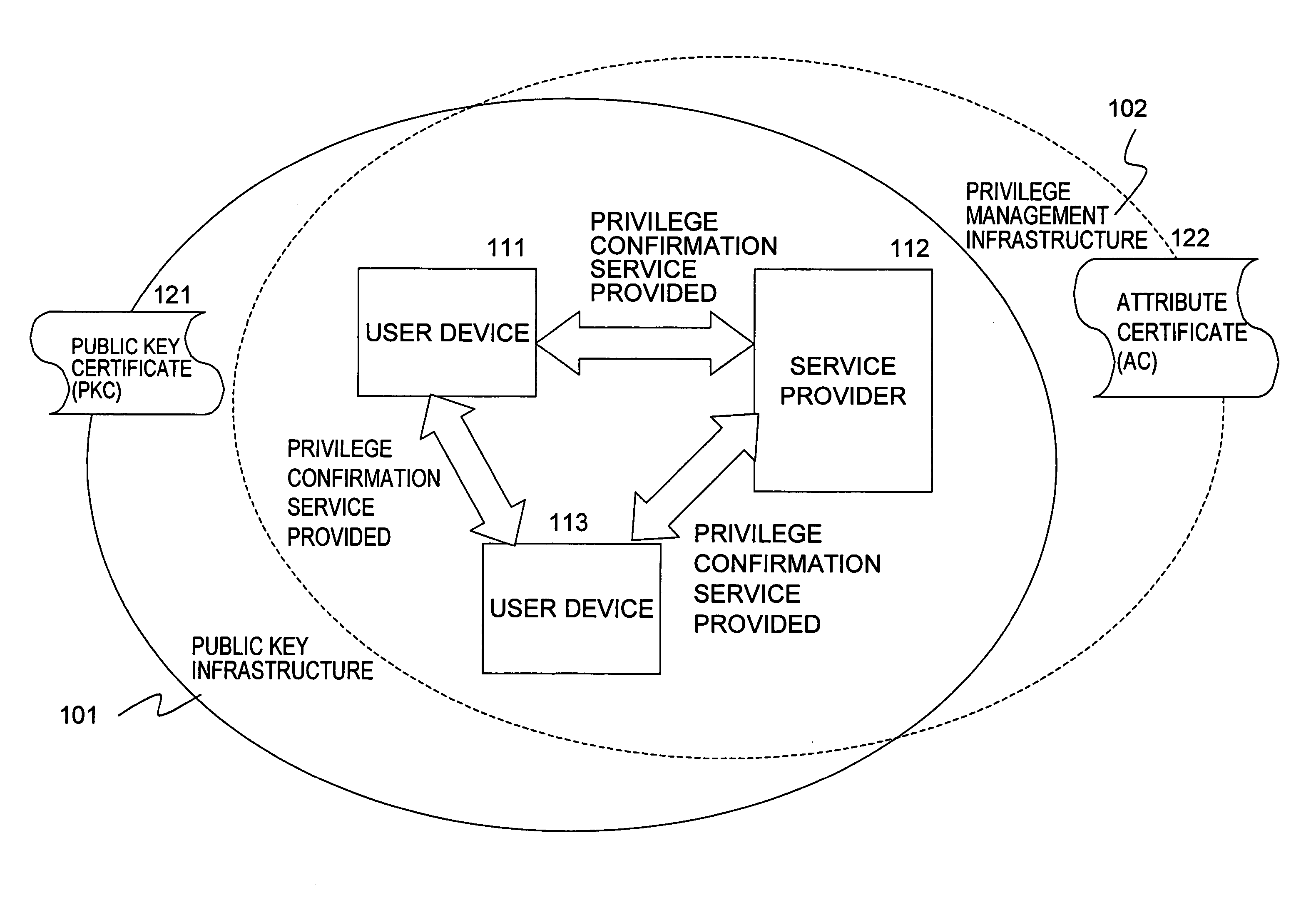
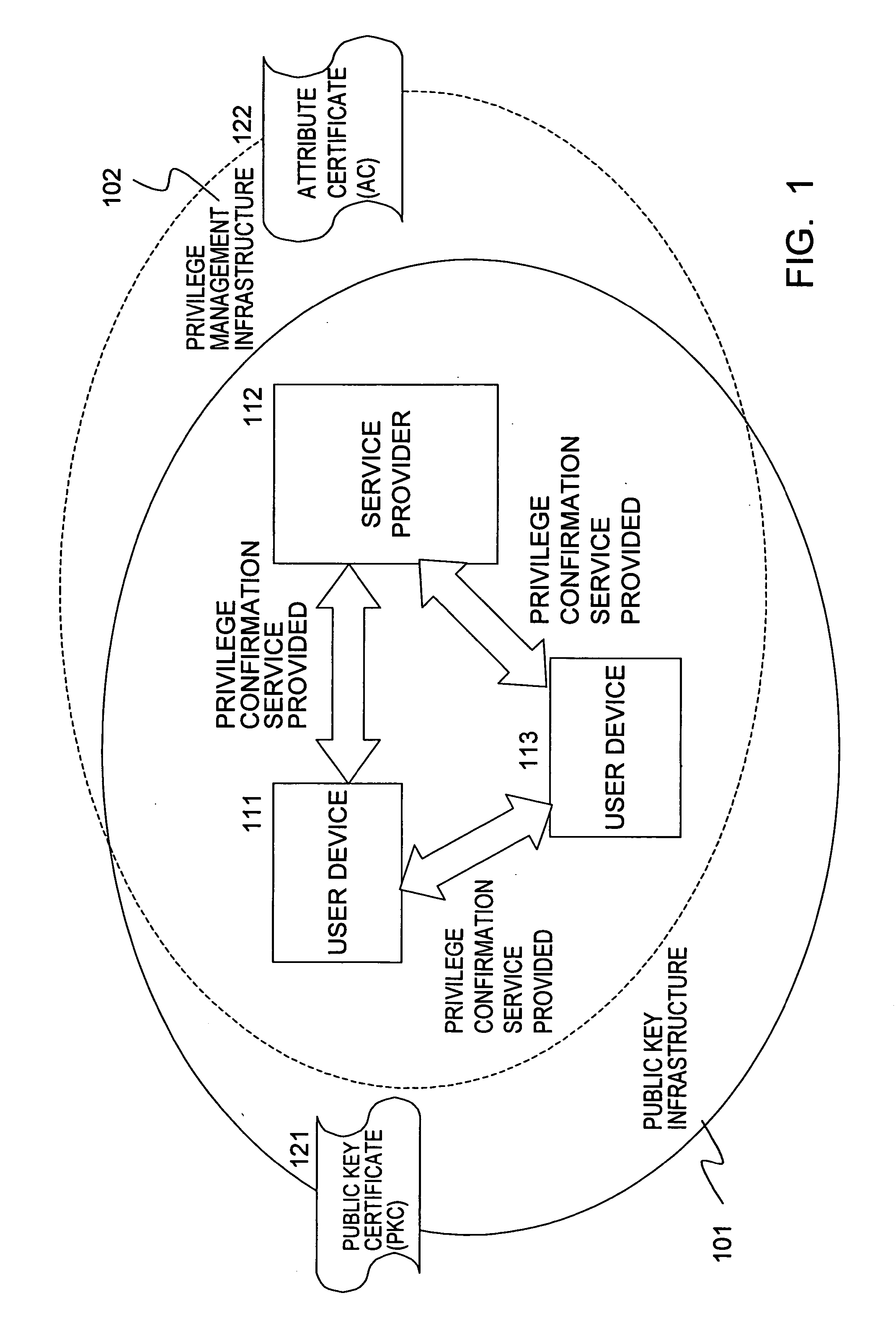
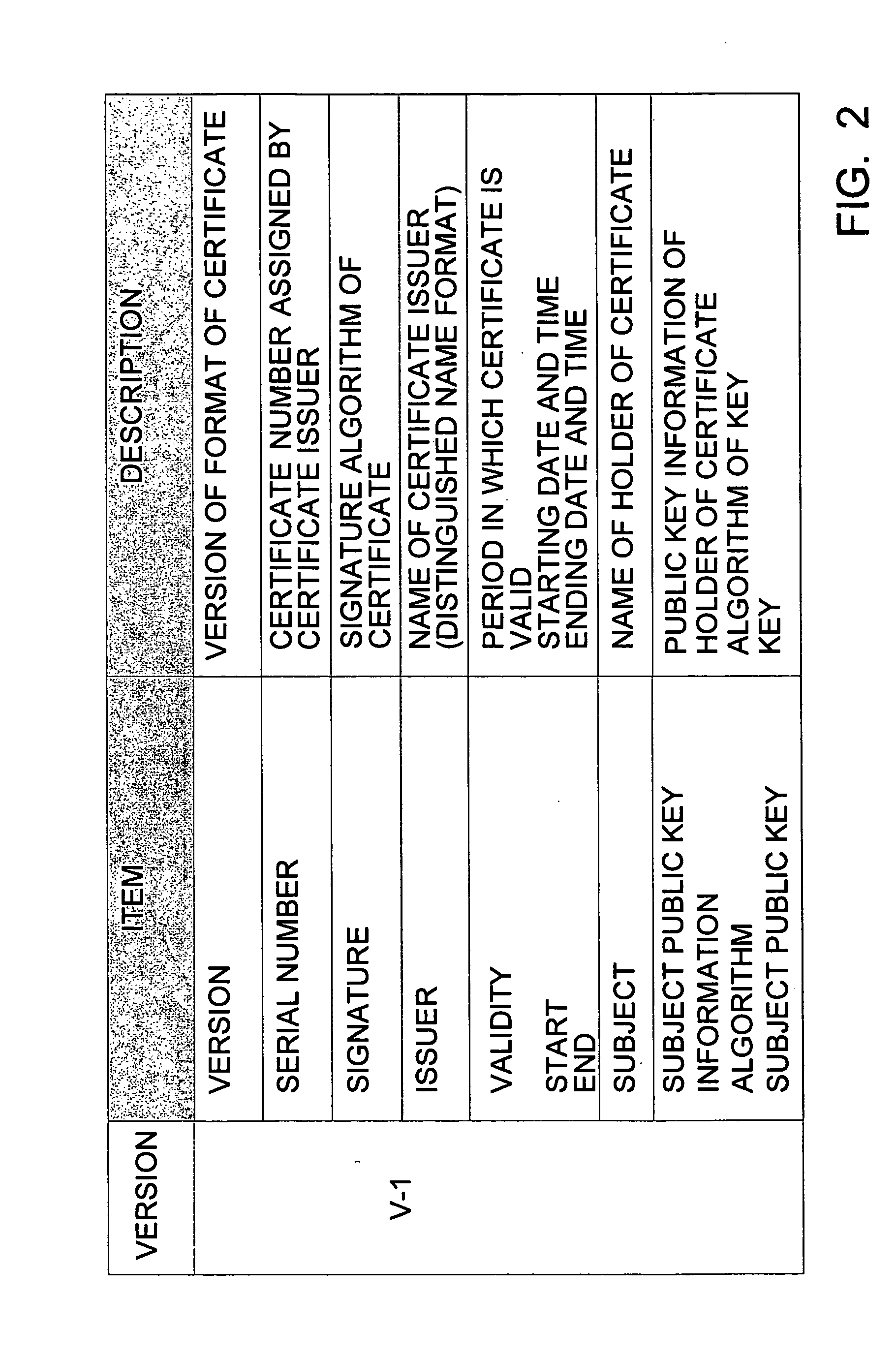
InactiveUS20060106836A1Improve variationEliminating accessDigital data processing detailsUser identity/authority verificationData processing systemUser device
A privilege management system enabling effective privilege management, such as confirmation processing of service receiving privileges and so forth, is realized. A group attribute certificate which has, as stored information, group identification information corresponding to a group which is a set of certain devices or certain users, and also has affixed an electronic signature of an issuer, is issued to a service reception entity, and verification is performed by means of signature verification for of the group attribute certificate presented from the user device regarding whether or not there has been tampering, screening is performed regarding whether or not this is a service-permitted group based on group identification information stored in the group attribute certificate by using a group information database, and determination is made regarding whether or not service can be provided, based on the screening. Centralized privilege confirmation corresponding to various user sets or device sets can be made, so management of individual privilege information can be omitted, thereby enabling effective privilege management.
Owner:SONY CORP
Digital rights management engine systems and methods
InactiveUS20070100768A1Limited accessProvide immunityDigital data protectionSecret communicationRights managementDigital rights management
Systems and methods are described for performing digital rights management. In one embodiment, a digital rights management engine is provided that evaluates license associated with protected content to determine if a requested access or other use of the content is authorized. In some embodiments, the licenses contain control programs that are executable by the digital rights management engine.
Owner:INTERTRUST TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com