Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
70 results about "Descendent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Someone deriving or descending from an ancestor.
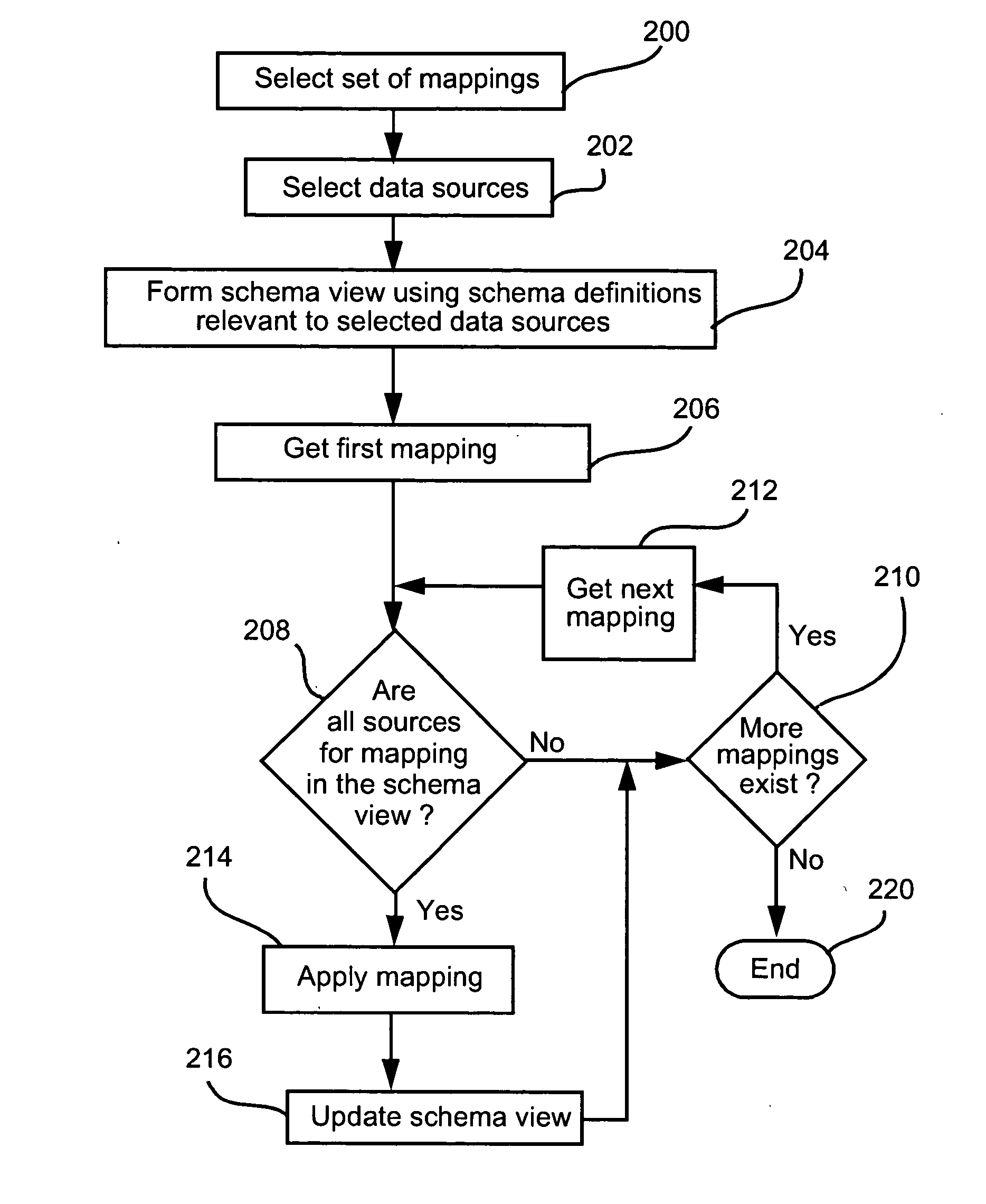
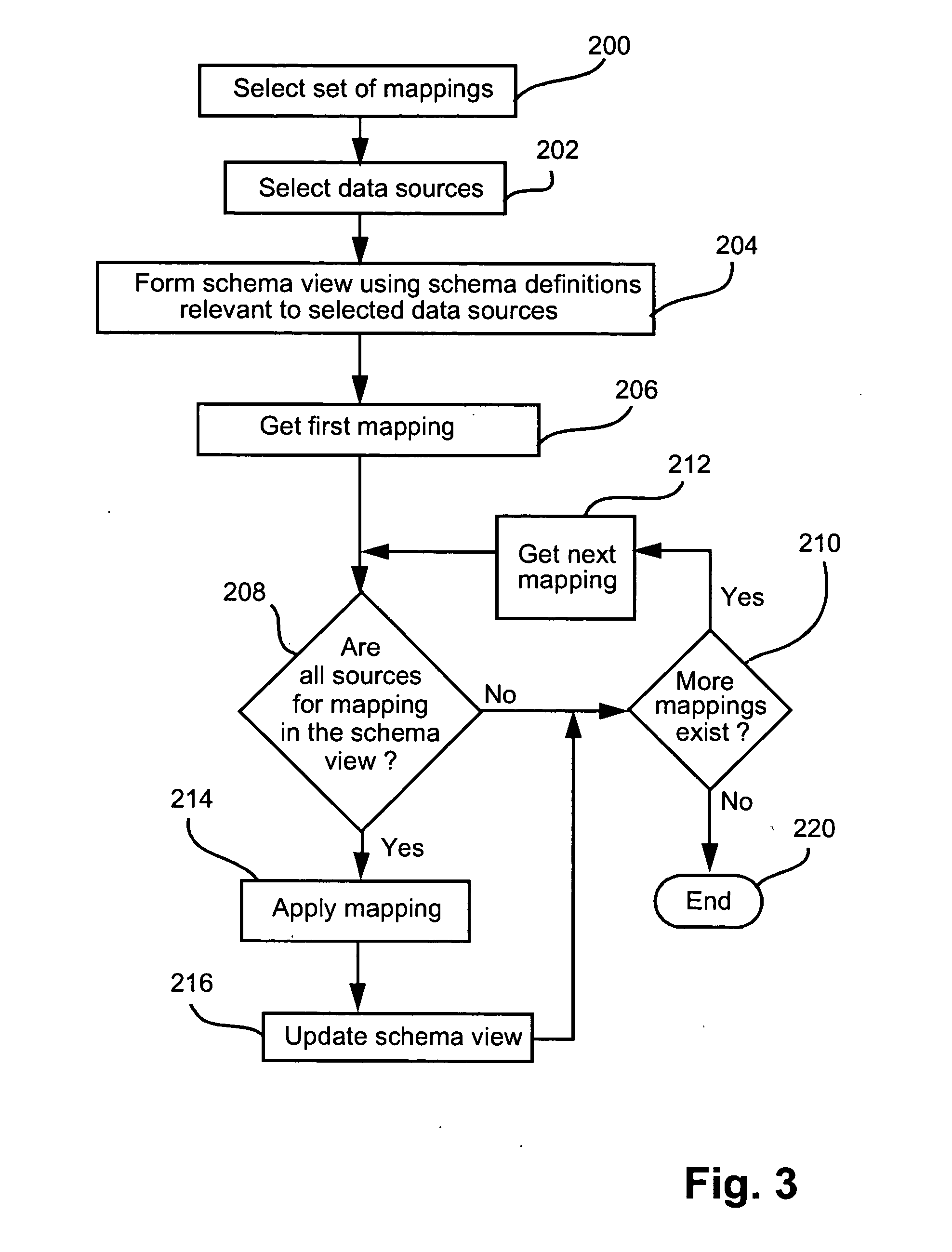
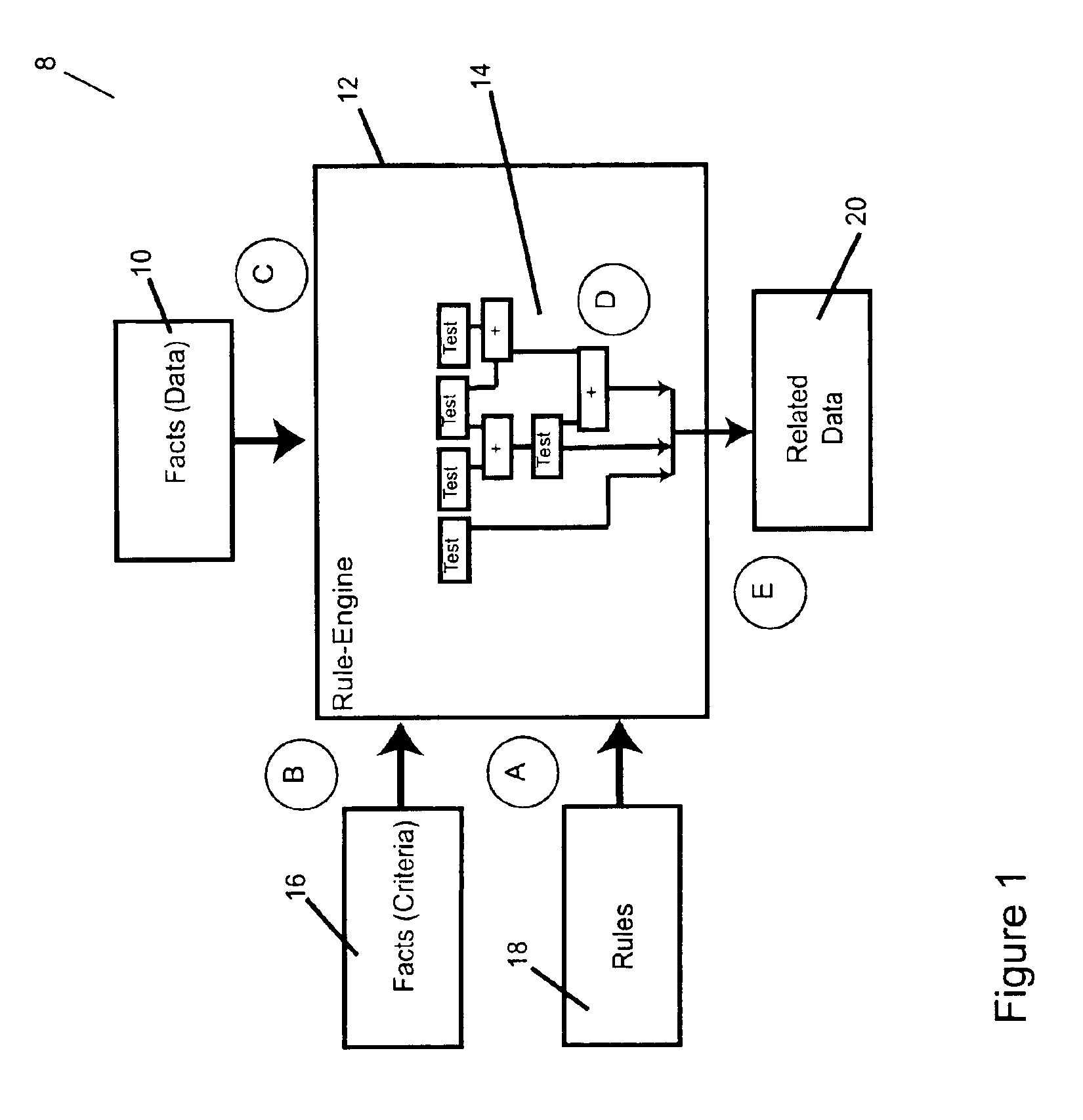
Method for presenting hierarchical data
InactiveUS20050060647A1Easy to operateDatabase management systemsDigital computer detailsHyperlinkDisplay device
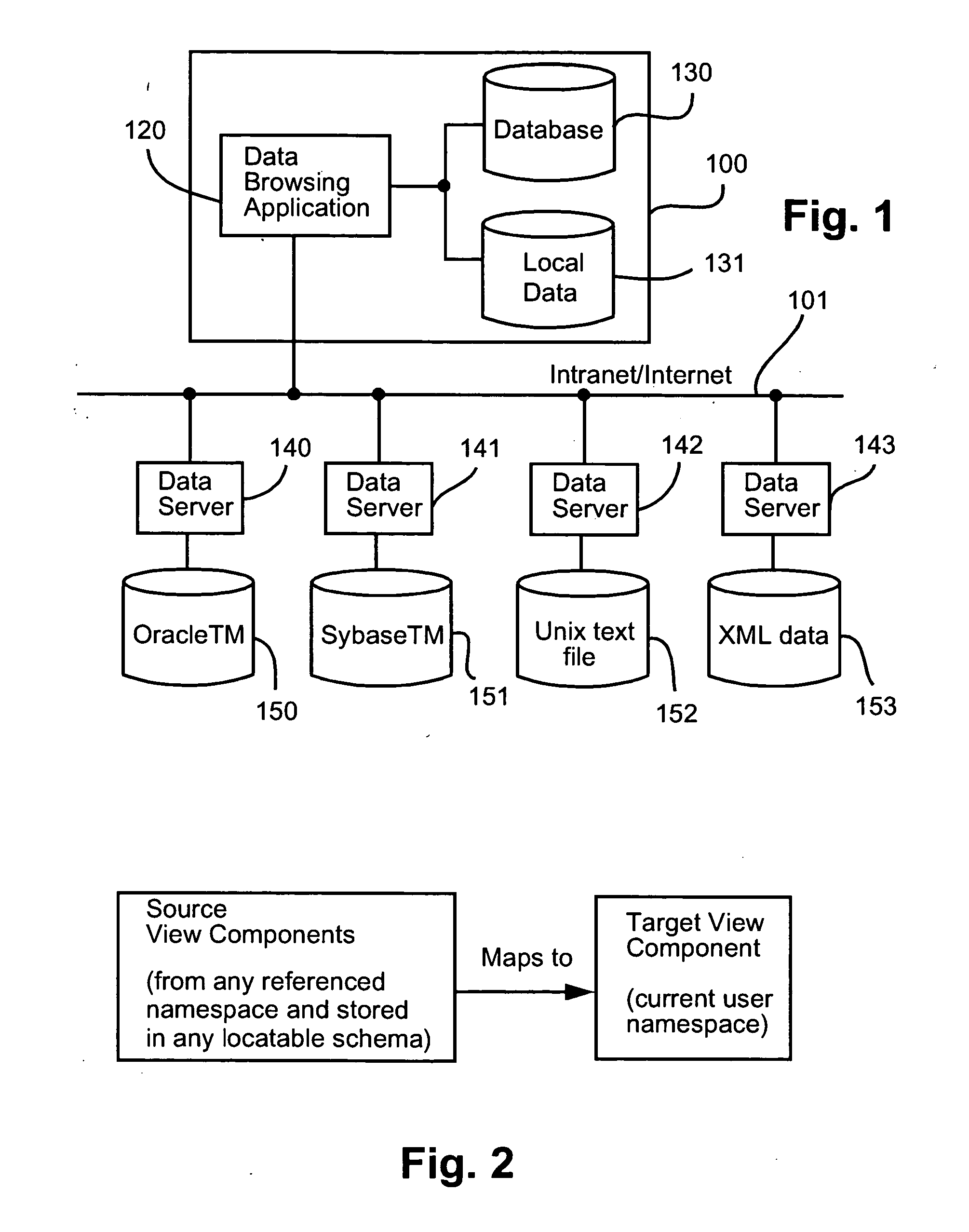
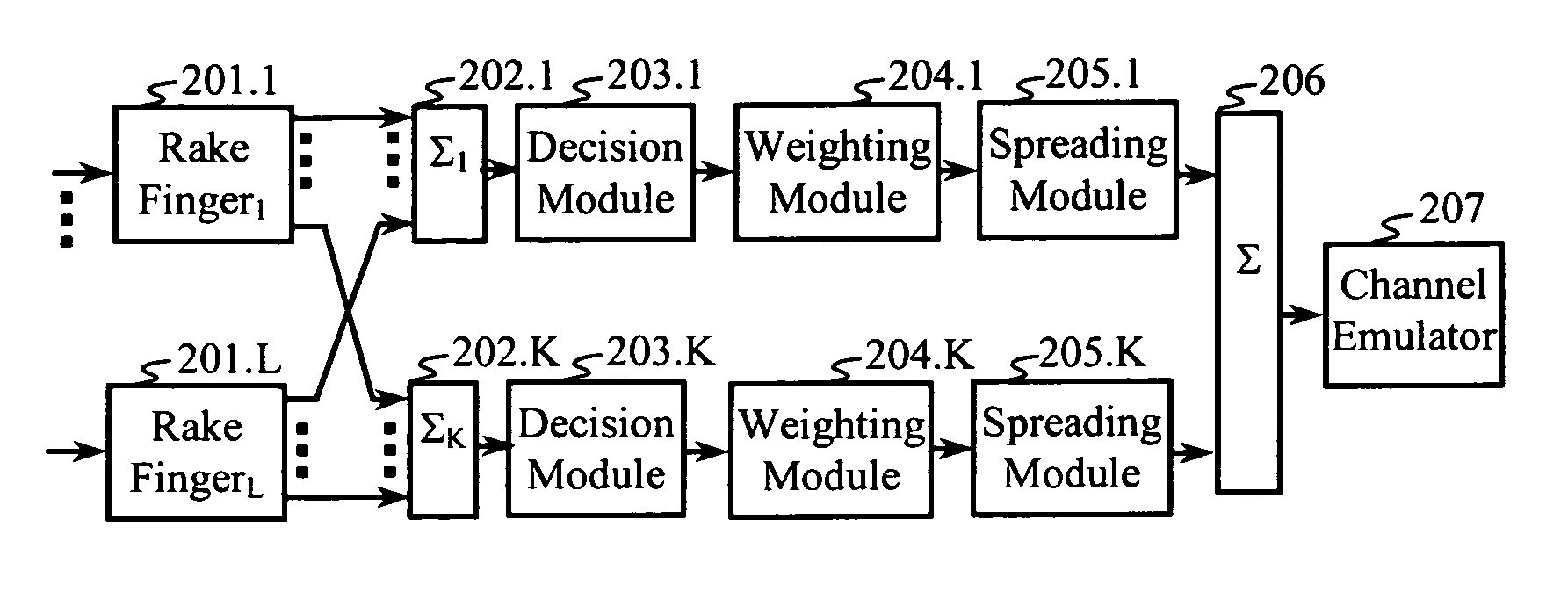
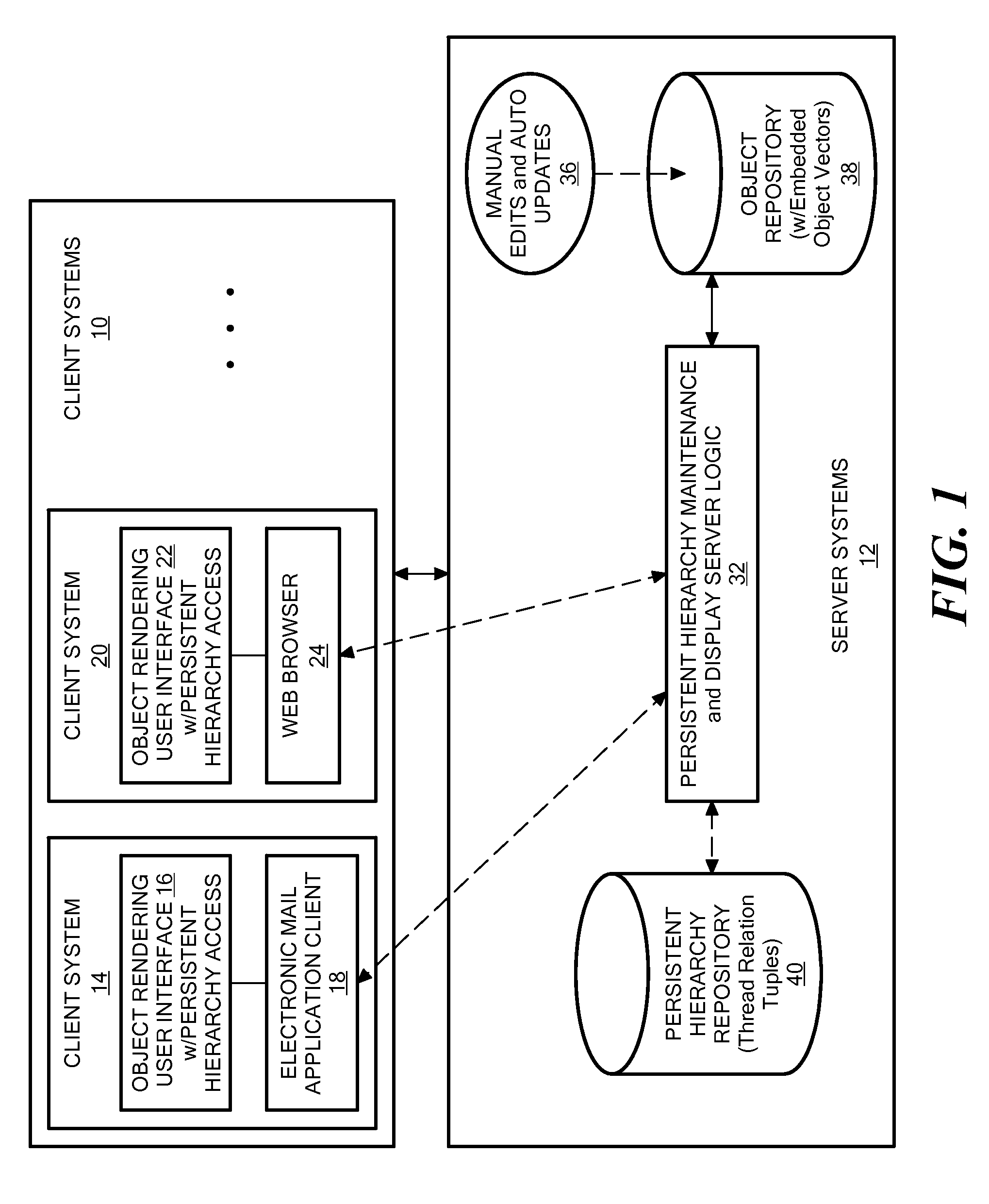
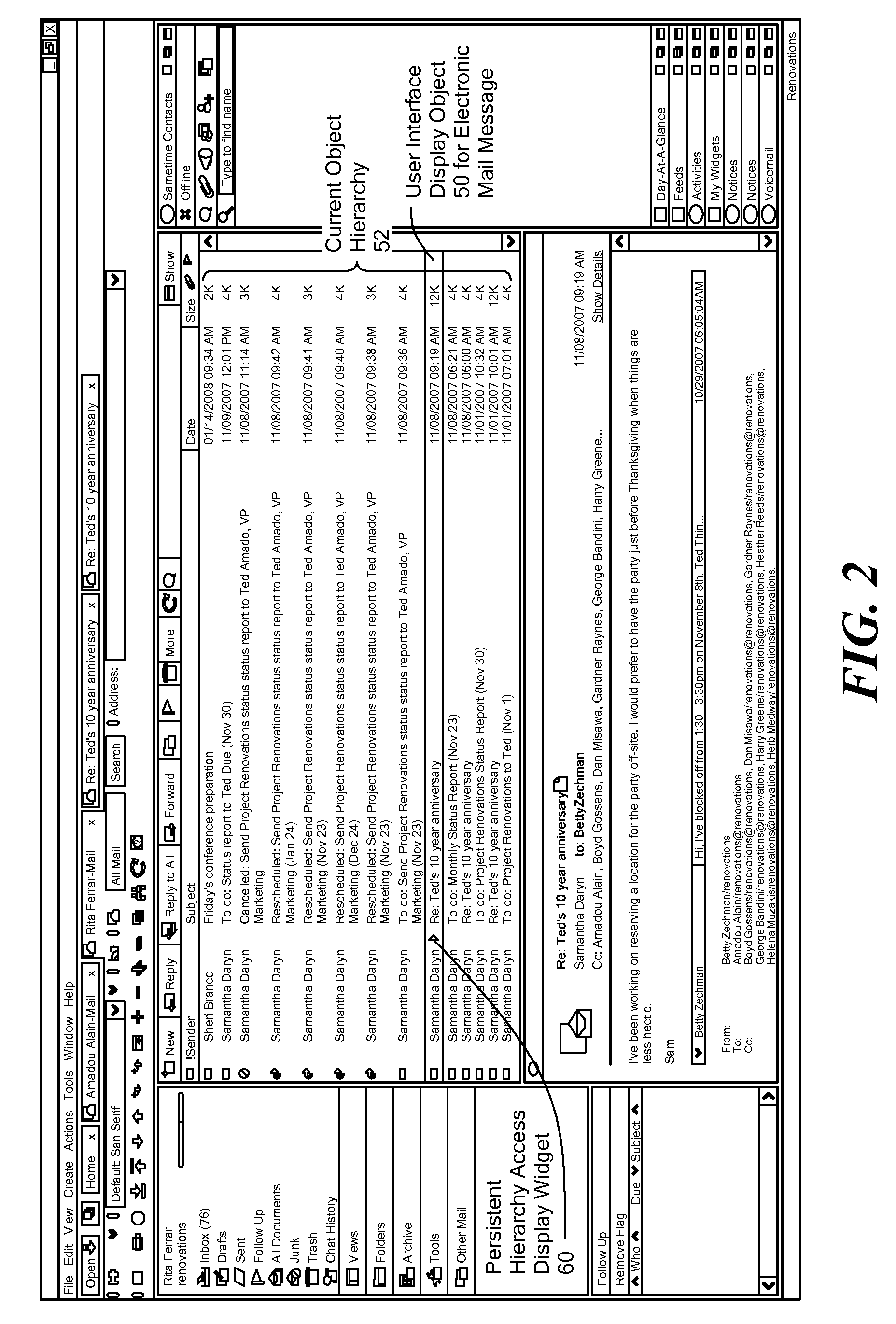
Methods, programs (120) and apparatus (100) are disclosed for accessing and heterogenous data sources (150-153) and presenting information obtained therefrom. Specifically, the data sources may have hierarchical data, which may be presented by identifying a context data node from the data, the context data node having one or more descendent data nodes. At least one data pattern is determined in the descendent data nodes. At least one display type is assigned to the current context data node on the basis of the at least one data pattern. Thereafter, the method presents at least a subset of the descendent data nodes according to one of the assigned display types. Also disclosed is a method of browsing an hierarchically-represented data source. A user operation is interpreted to identify a context data node from the data source, the context data node having one or more descendent data nodes. At least one data pattern in the descendent data nodes is then determined and at least one display type is assigned to the current context data node on the basis of the at least one data pattern. A subset of the descendent data nodes is then presented according to one of the assigned display types, the subset including at least one hyperlink (3401,3402) having as its target a descendant data node of the current context data node. A further user operation is then interpreted to select the at least one hyperlink, the selection resulting in the current context data node being replaced with the data node corresponding to the target of the selected hyperlink. These steps may be repeated until no further hyperlinks to descendent data nodes are included in the subset. Other methods associated with access and presentation are also disclosed.
Owner:CANON KK
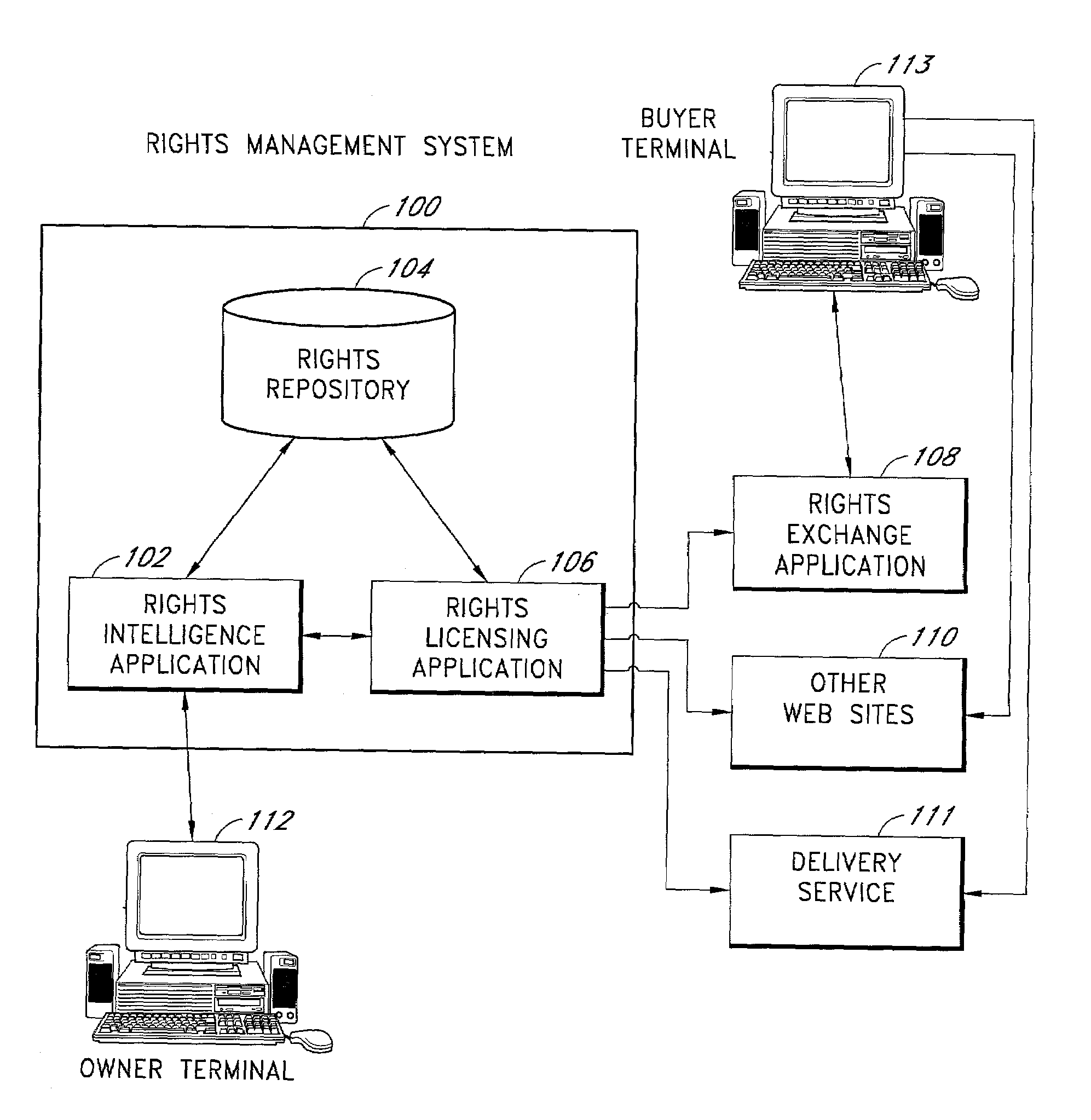
Apparatus and methods for intellectual property database navigation
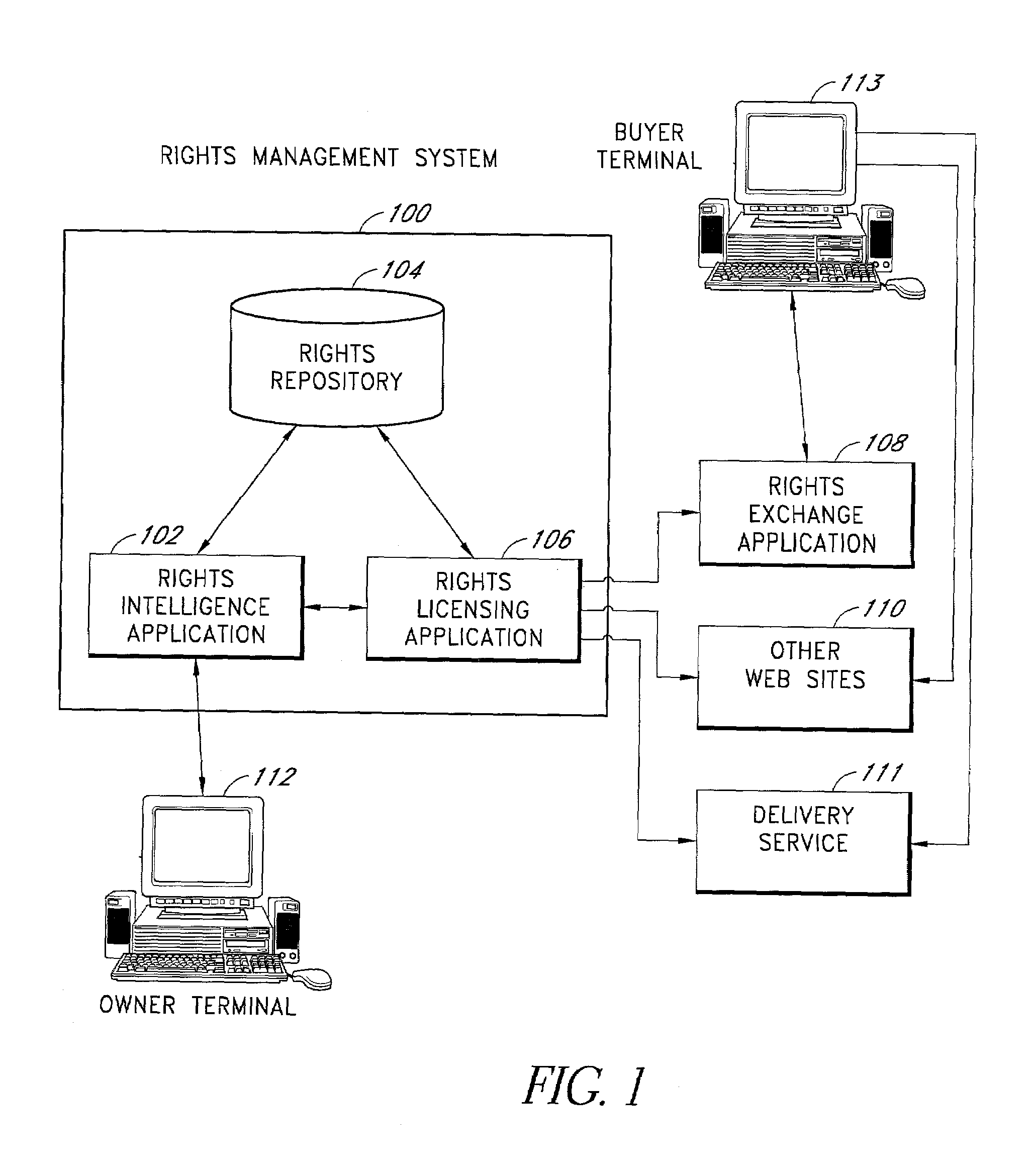
InactiveUS7092953B1Fast and efficient techniqueData processing applicationsProgram/content distribution protectionIntellectual propertyRights management
The present invention advantageously provides a rights management system. In one embodiment, a specification of a general level of rights owned by a first intellectual property rights owner is received. A query is received for a lower level right that is a descendent of at least one of the general level of rights. The system determines if the lower level rights is available for licensing by forming at least a first implicit relationship between the general level of rights owned, and a general level of rights licensed out.
Owner:RIGHTSLINE +1
Techniques for retaining hierarchical information in mapping between XML documents and relational data
ActiveUS7103611B2Data processing applicationsDigital data information retrievalXML treeRelational database
Techniques for managing XML data in an SQL compliant DBMS include receiving an SQL statement. The SQL statement includes a particular operator that operates on a first instance of XML type that represents a first set of XML elements. During execution of the SQL statement, the particular operator is evaluated by generating an ordered collection of instances of XML type. Each different instance in the ordered collection is based on a different XML element from the first set; and there is an instance in the ordered collection for every XML element from either the first set or from the first set and its descendents. When descendents are included, each entry in the ordered collection indicates a level in the XML tree. In another aspect, an aggregate operator in the SQL statement operates on a collection of instances, with associated levels, to generate a single instance of XML type.
Owner:ORACLE INT CORP
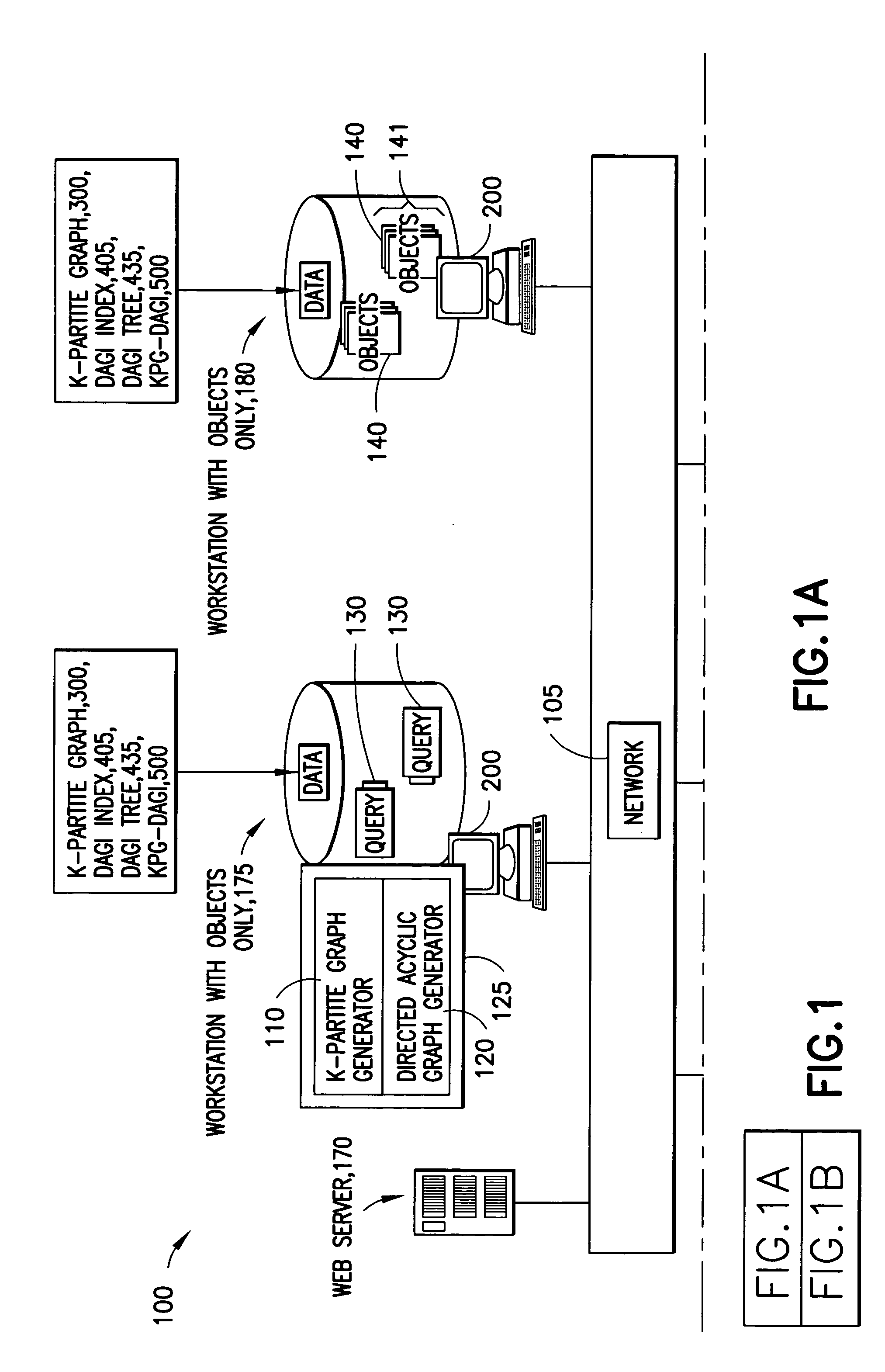
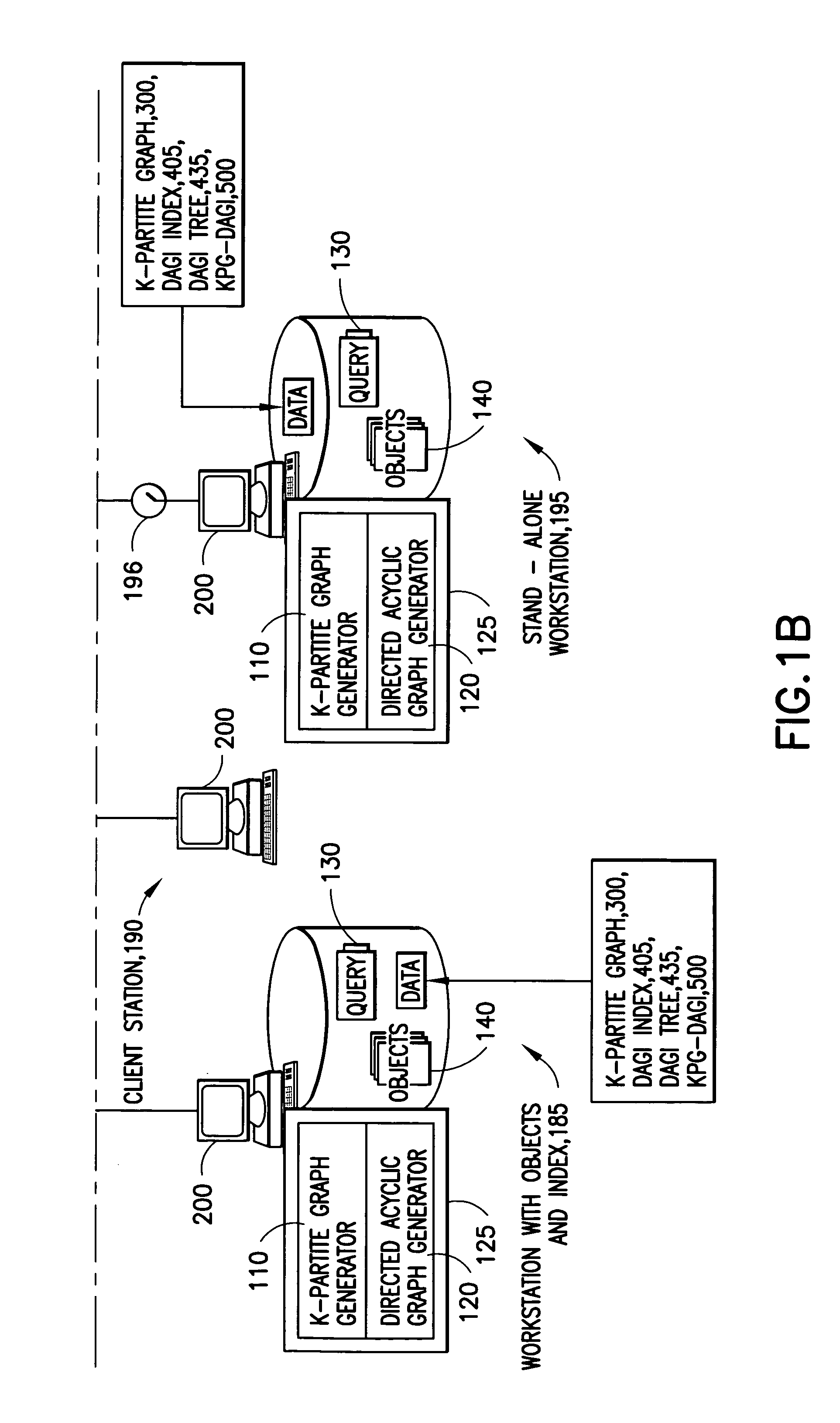
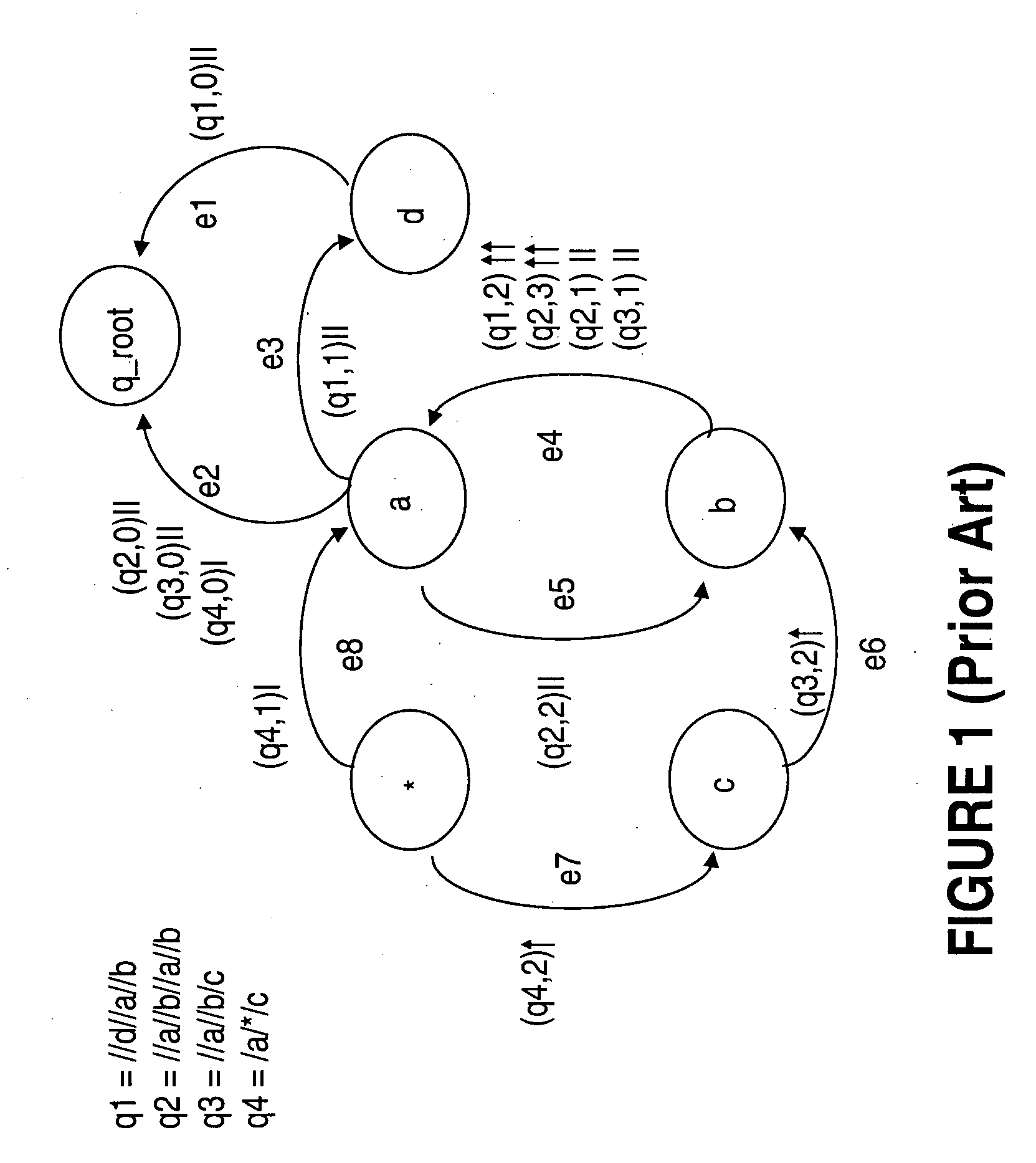
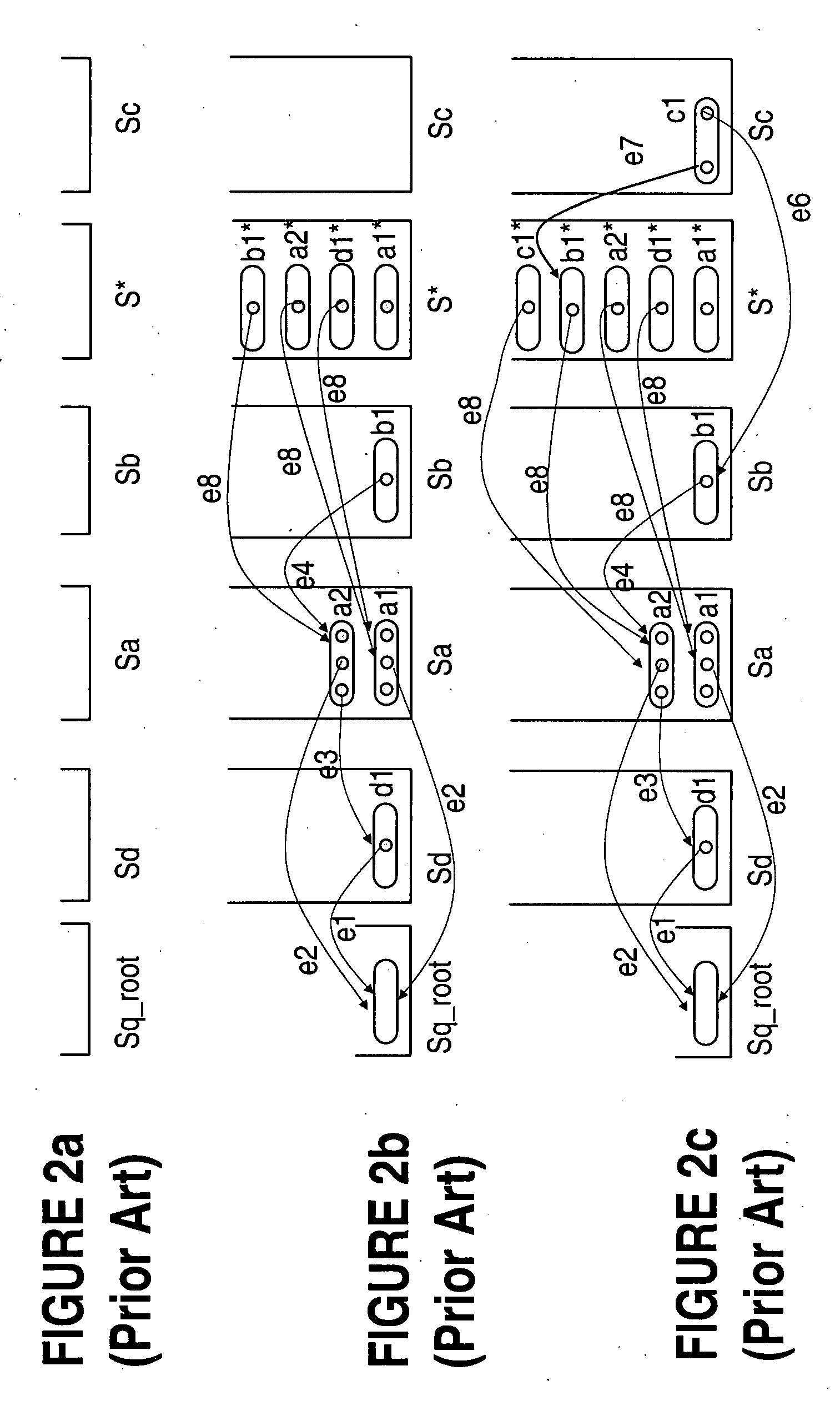
System and method for simplifying and manipulating k-partite graphs
InactiveUS20050038533A1High frequencySampled-variable control systemsData processing applicationsTheoretical computer scienceMultiple category
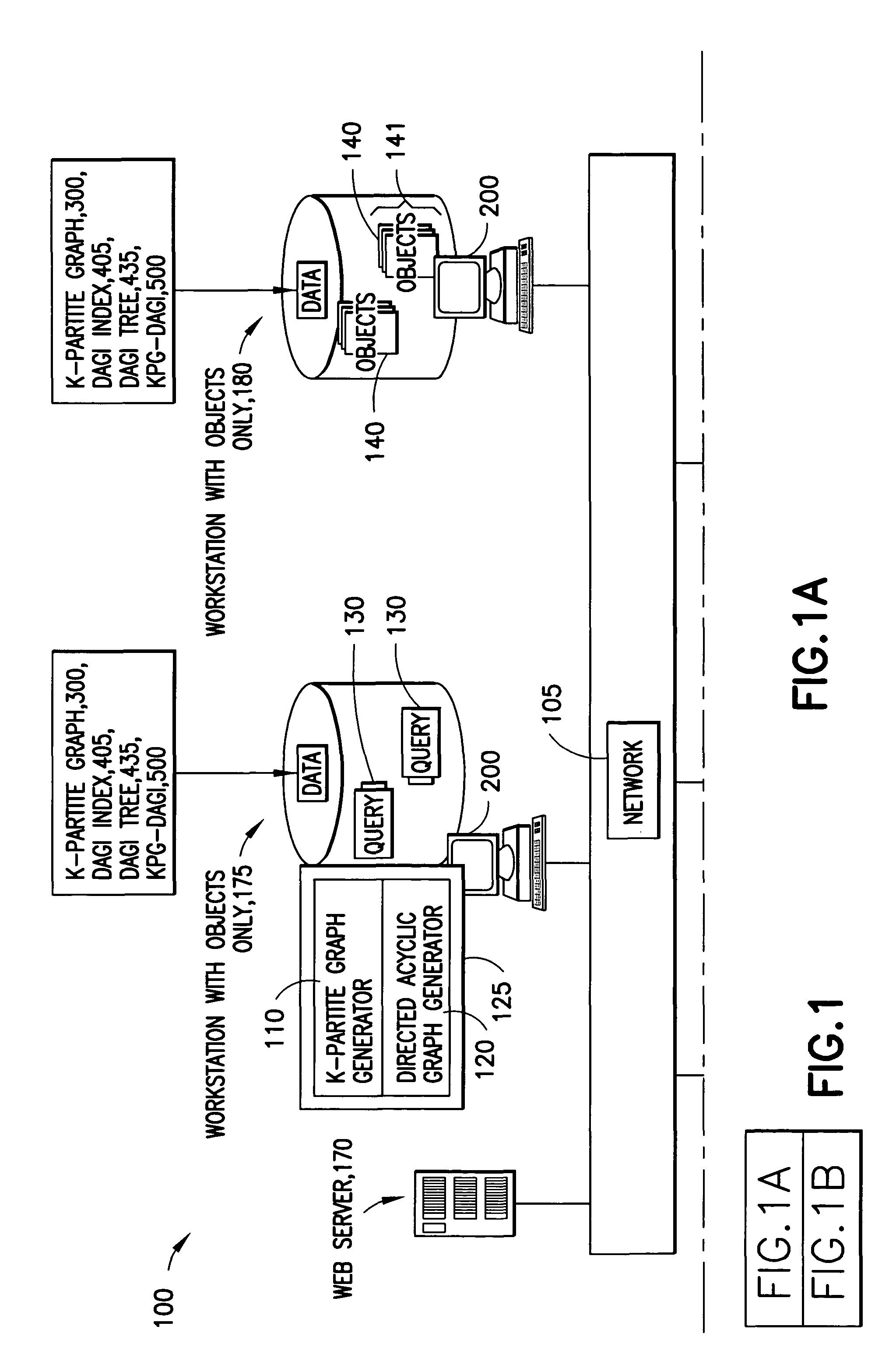
The system has a collection of a plurality of objects. Each object defines a node in a k-partite graph, such that, the nodes can e divided into a number of mutually exclusive sets such that all of the nodes are in exactly one of the sets; further edges occur only between nodes in different sets; The system also has a simplification process that aggregates one or more of the nodes into one or more categories and identifies a category node corresponding to each category. The category node inherits the mode and the edges of all the nodes in the respective category. Further, the system contains Directed Acyclic Graphs Indices (DAGIs) whose nodes may have a 1-1 mapping with the nodes in the k-partite graph. These indices can be used to aggregate and hide nodes in the k-partite graph. Aggregation occurs by selecting one or more non-leaf nodes in the DAGI and aggregating all descendent nodes. Hiding occurs by selecting some set of DAGI nodes, thus selecting some corresponding set of nodes in the k-partite graph, and requesting this set of nodes be hidden which effectively removes them from further consideration until they are restored by explicit request.
Owner:IBM CORP
System and method for implementing dynamic set operations on data stored in a sorted array
ActiveUS7069272B2Easy to implementData processing applicationsRelational databasesArray data structureSorted array
A system and method are disclosed for implementing dynamic set operations on data stored in a sorted array using a hybrid red-black binary search tree as a data structure. More particularly, the subject invention facilitates the implementation of a binary search to access data items stored in a sorted array by position, rather than by key value. This is accomplished by generating a balanced red-black binary search tree for a sorted array of data items wherein the information stored at each node of the tree includes: a key value; a color; a left pointer to indicate the presence of a child to the left of the node; a right pointer to indicate the presence of a child to the right of the node; a count of descendents along a branch to the left of the node; and a count of descendants along a branch to the right of the node.
Owner:BLACKROCK FINANCIAL MANAGEMENT
System And Method For Analyzing Social Media Trends
ActiveUS20140143405A1Digital computer detailsData switching networksGeneral Population CohortSocial media
Disclosed are methods for identifying topical experts from a seed set of experts by identifying “second tier” influencers for the topic. New concepts detected among a pool of experts and second tier influencers are monitored among the general population and their significance evaluated. Reports may be generated for these detected trends. Trends in social media for a concept represented in a taxonomy may be detected by monitoring content for descendent nodes for the concept. Correlations between social media activity with respect to the concept and sales of products corresponding to the concept may be made and sales predicted for the same or different products that correspond to descendants of the concept in the taxonomy.
Owner:WALMART APOLLO LLC
Method and appliance for XML policy matching
ActiveUS20090037379A1Digital data information retrievalSpecial data processing applicationsStreaming XMLTheoretical computer science
An XML matching engine and method are provided, where policy rules expressed using XPath / XQuery policies are matched to streaming XML documents. Two distinct data structures are used: a combined modified DFA data structure for storing simple XPath queries (no wildcards or descendents) and a modified AFilter structure for storing complex queries (with wildcards or / and descendents). As the matching engine receives XML tags from XML parser, matching is performed in both structures in parallel.
Owner:RPX CORP
Complex path-based query execution
InactiveUS20110131200A1Digital data information retrievalDigital data processing detailsXPathPaper document
Systems, methods, computer program product embodiments are provided for executing a function in a path-based query when extracting data from a markup language document for return as a relational table, the markup language document organized hierarchically into nodes. An embodiment includes receiving a path-based query including a complex row pattern and column definition, forming multiple sets of nodes based on a simplified row pattern and column definition, determining ancestor-descendent pairings for the nodes in the column definition set, and utilizing the ancestor-descendent pairings with the simplified row pattern to return a relational table satisfying the complex path-based query. An embodiment further includes extensible markup language (XML) as the markup language, and an XPath query expression as the complex path-based query.
Owner:SYBASE INC
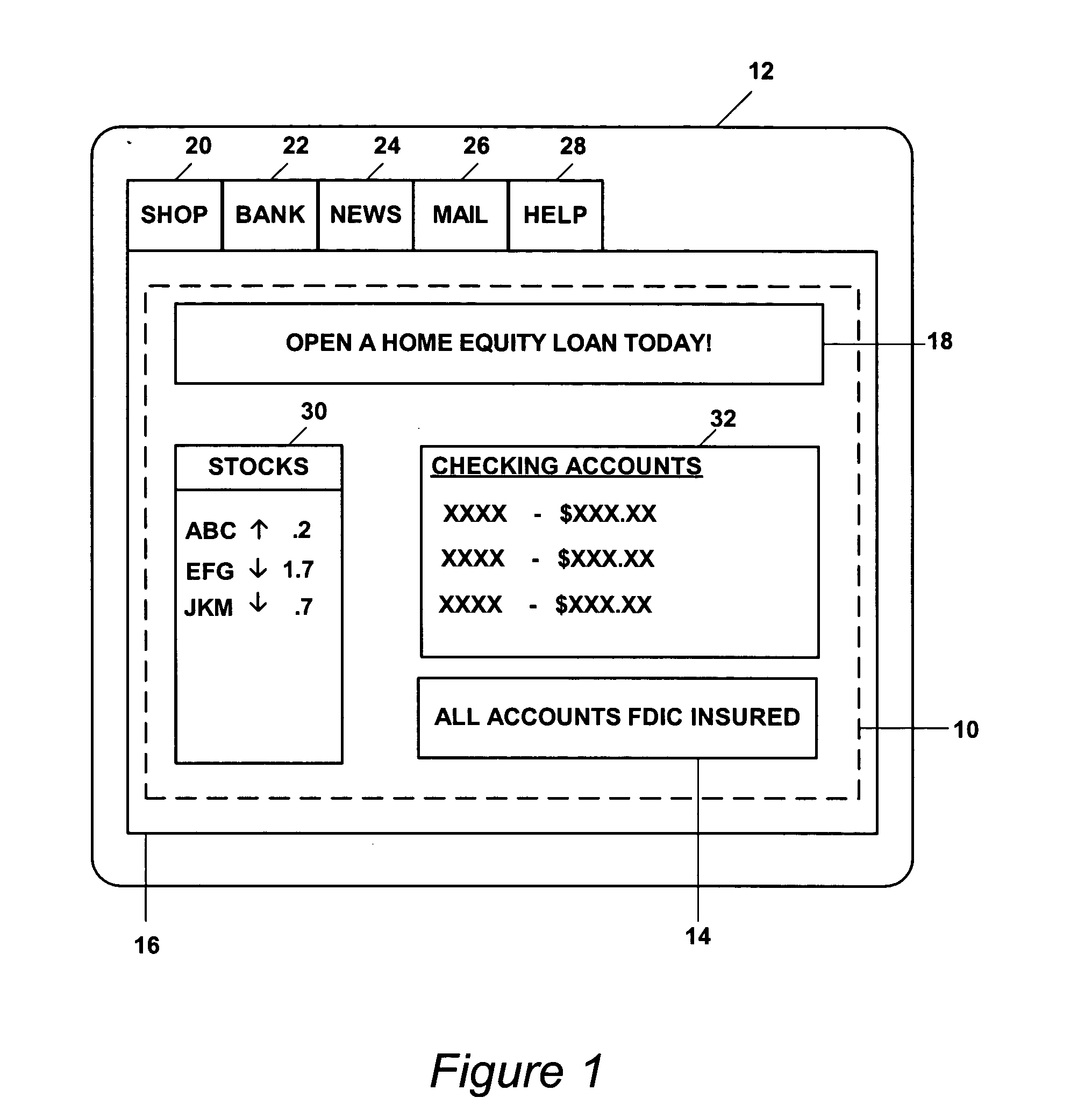
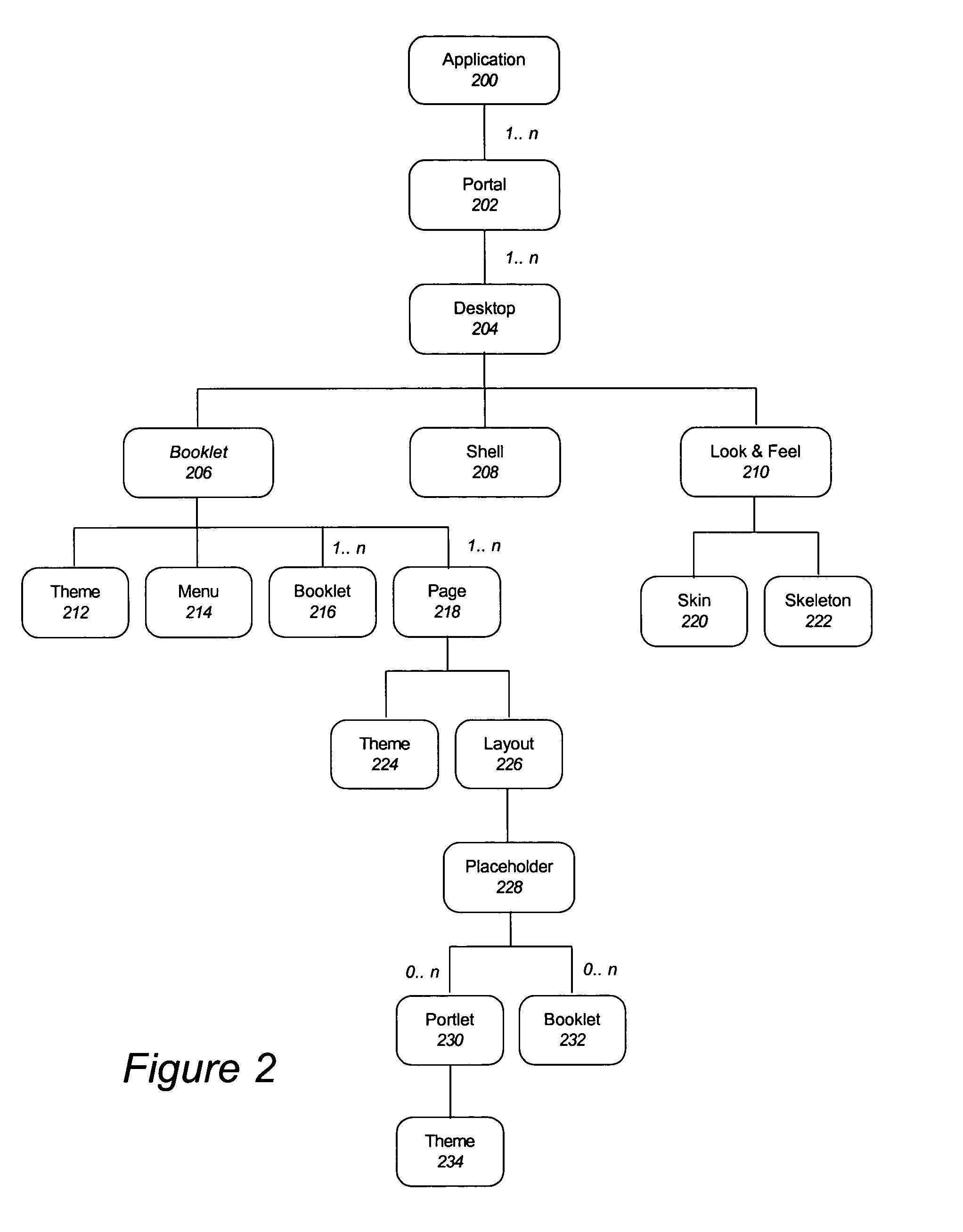
Method for utilizing look and feel in a graphical user interface
ActiveUS20050005243A1Software engineeringCathode-ray tube indicatorsGraphicsGraphical user interface
A method for rendering a graphical user interface (GUI), comprising providing for the representation of the GUI as a set of objects wherein the objects are organized in a logical hierarchy, associating a theme with a first object in the set of objects, rendering the first object according to the theme, rendering any descendents of the first object according to the theme, wherein any descendents of the first object can override the theme, and wherein one of the set of objects can communicate with another of the set of objects.
Owner:ORACLE INT CORP
Method for electrochemical depositing solar cell metallic electrode
ActiveCN101257059AAvoid unevennessAvoid damagePhotovoltaic energy generationSemiconductor devicesElectrochemical responseMetallic electrode
Owner:WUXI SUNTECH POWER CO LTD
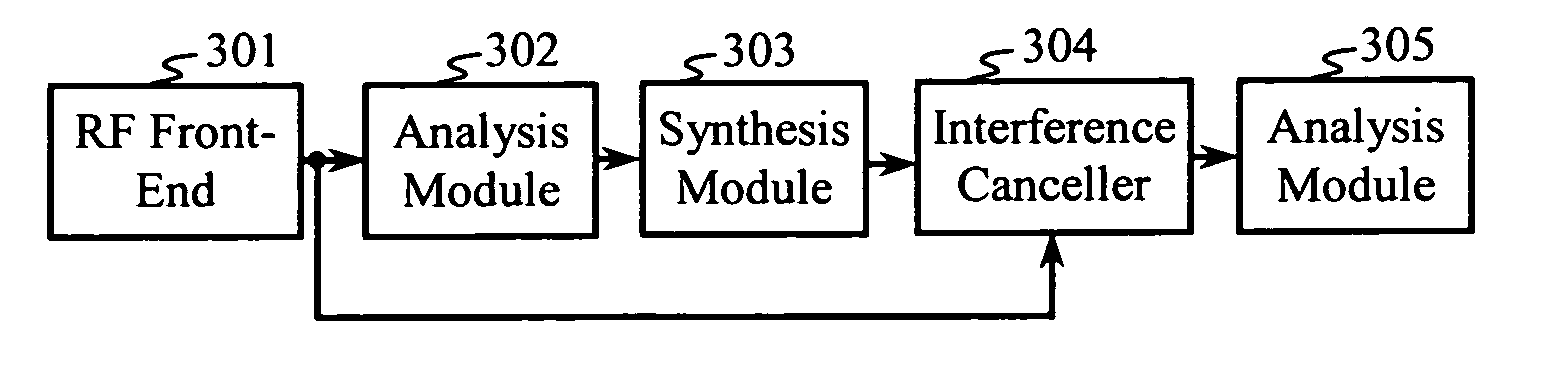
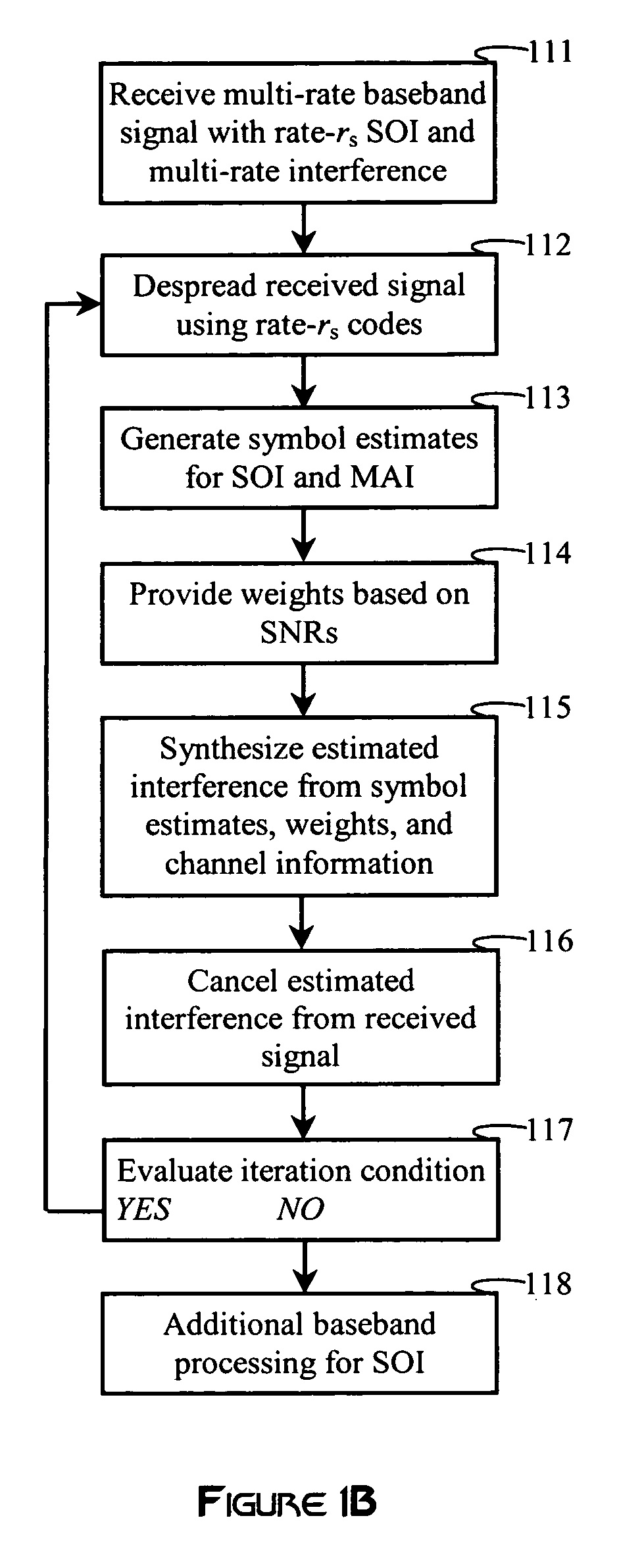
Interference cancellation in variable codelength systems for multi-access communication
A receiver employs low-rate processing to synthesize the effect of high-rate interference in a received multi-rate signal. Each high-rate subchannel is analyzed on its low-rate descendents to produce symbol estimates for each low-rate symbol interval. The symbol estimates are applied to low-rate descendent subchannels, which are then combined to synthesize the effects of the high-rate interference. An interference canceller processes the synthesized interference with the received signal for producing an interference-cancelled signal. Alternatively, analogous steps may be applied at high-rate to analyze, synthesize, and cancel the effects of low-rate interference in a multi-rate signal.
Owner:III HLDG 1
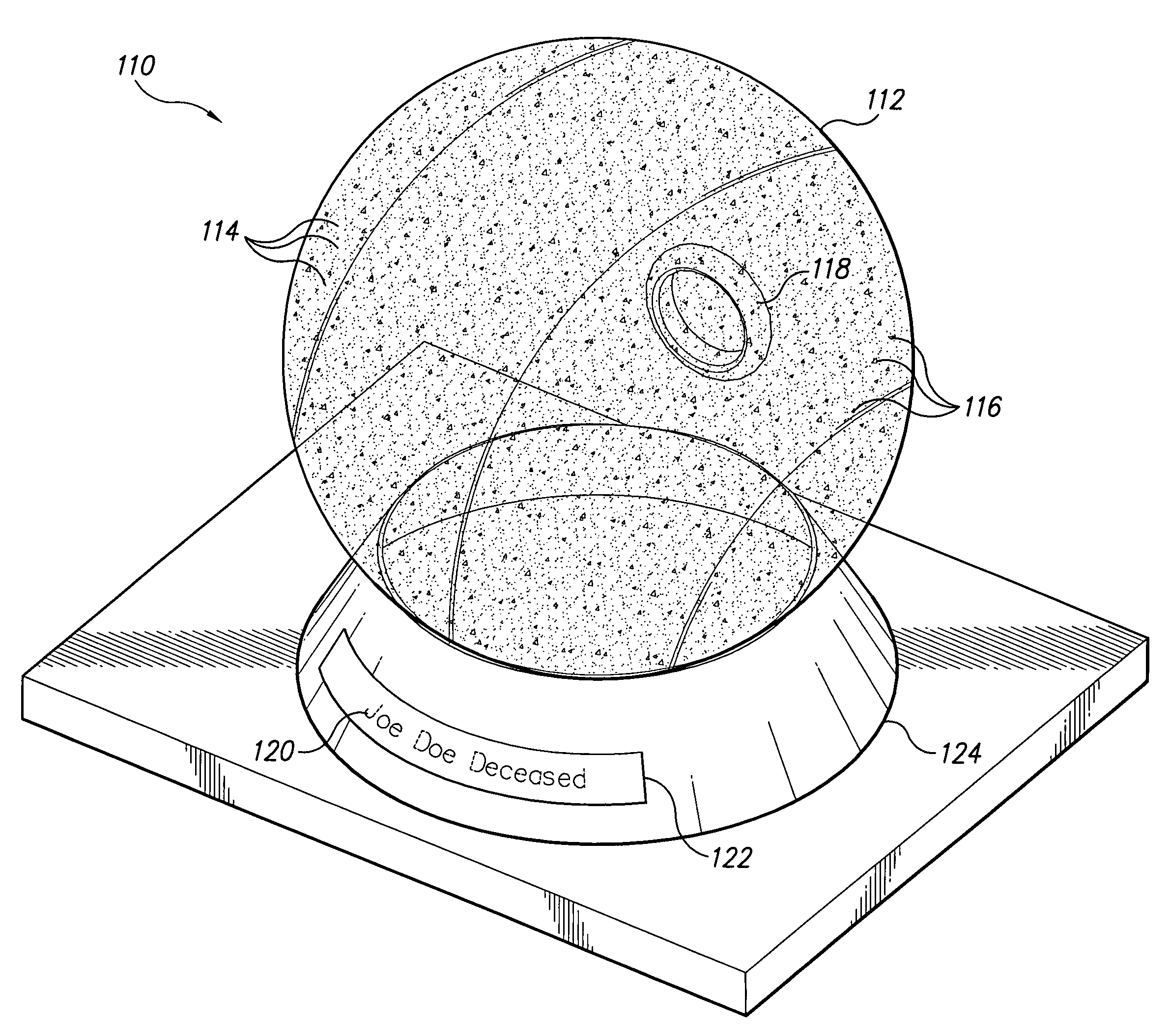
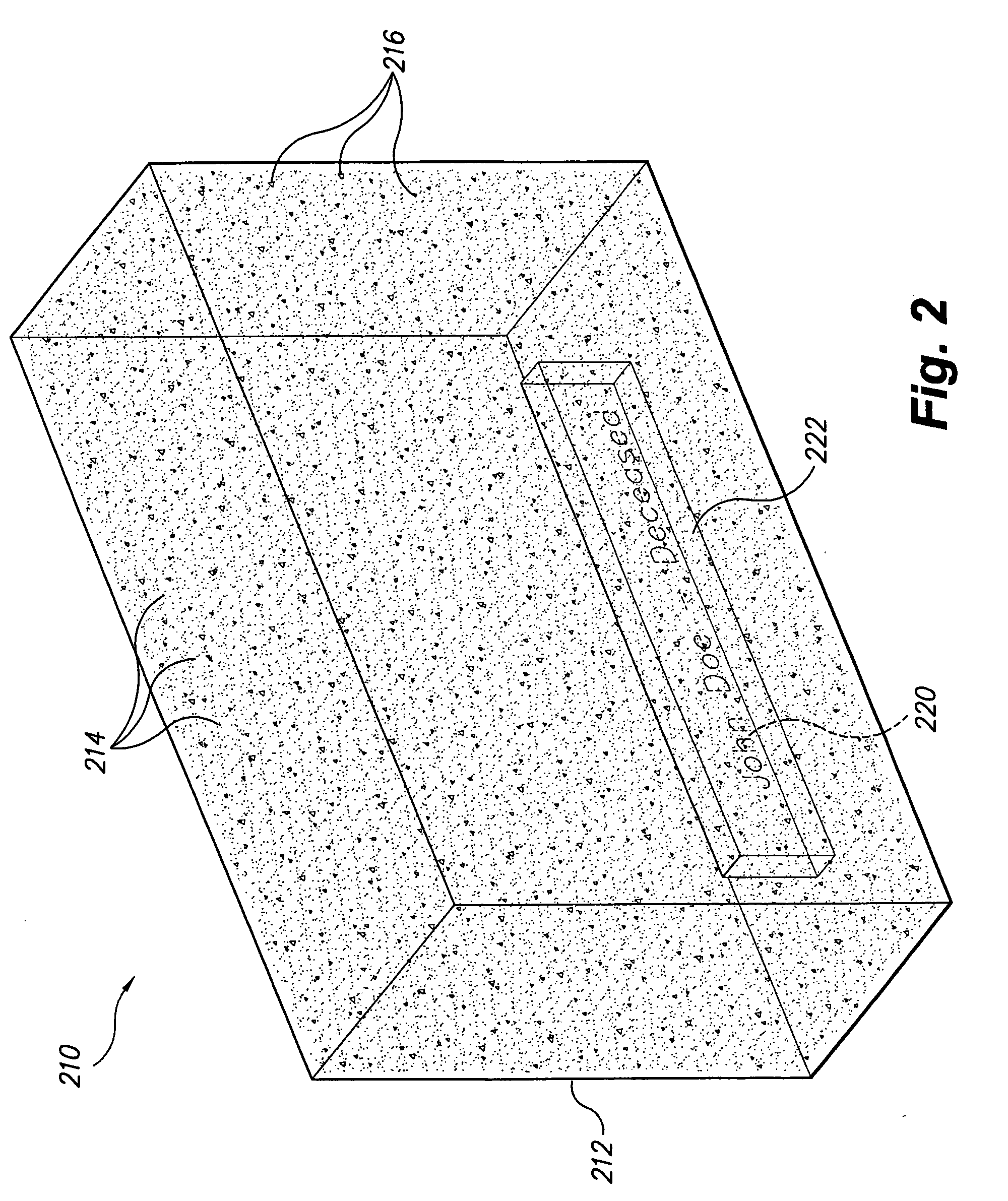
Memorial with cremains
InactiveUS20100199476A1Readily apparentGlass drawing apparatusGlass forming apparatusBottleGlass fusing
The memorial with cremains provides a transparent or translucent glass memorial containing the cremains of the deceased with an article(s) of significance to the deceased and / or family and descendents. A method of forming the memorial comprises melting the glass to at least a plastic consistency, mixing the cremains therein, adding the article(s) of significance either in its entirety or disintegrated, optionally adding an inscribed placard within the molten glass, forming the glass to the desired shape, cooling the glass, and adding an inscription directly to the glass or separate placard if not included within the glass earlier. The glass may comprise or contain glass from another article favored by the deceased, e.g., a wine glass or bottle from a favorite beverage, etc. The article included therein may survive in its solid state or may be melted and fused with the glass, depending upon its melting point relative to the glass.
Owner:CUMMINGS ROBERT S +1
Method and mechanism for managing hierarchical data for implementing region query
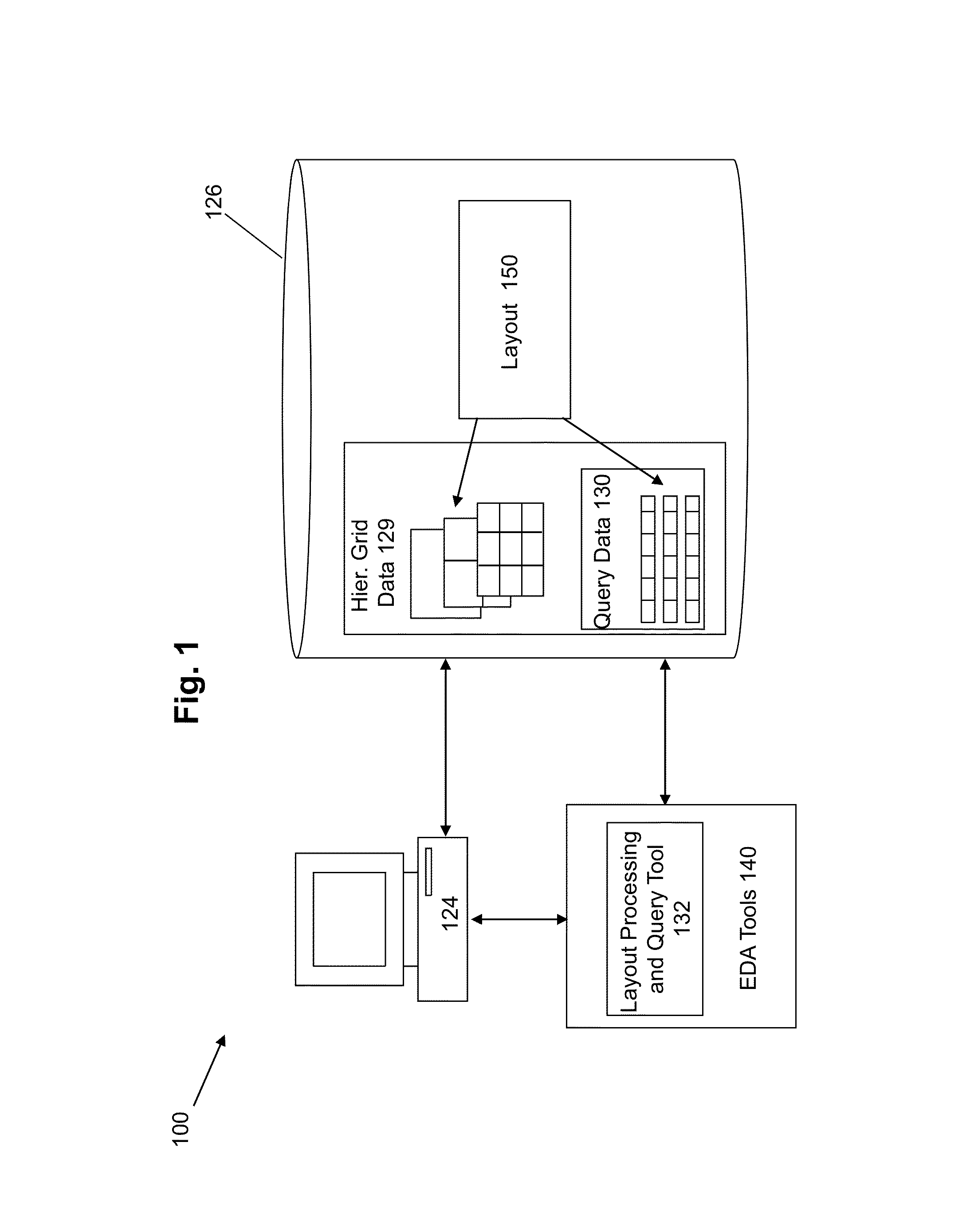
ActiveUS8453091B1Enhancing desirable characteristicFast query timeComputer aided designSpecial data processing applicationsMemory footprintTerm memory
Disclosed is an improved approach for managing, tracking, and querying hierarchical data in layouts. According to some aspects, hierarchical grids are employed utilizing a scheme that organizes physical objects into a set of gradually refined grids that avoids the need to maintain duplicates while enhancing the desirable characteristics of existing schemes, including fast query times, fast data structure initialization and reduced memory footprint. Each grid-cell may be further partitioned into sub-containers to more efficiently provide space pruning during query operations. According to one approach, structures maintained to track existence of objects in a descendent hierarchy.
Owner:CADENCE DESIGN SYST INC
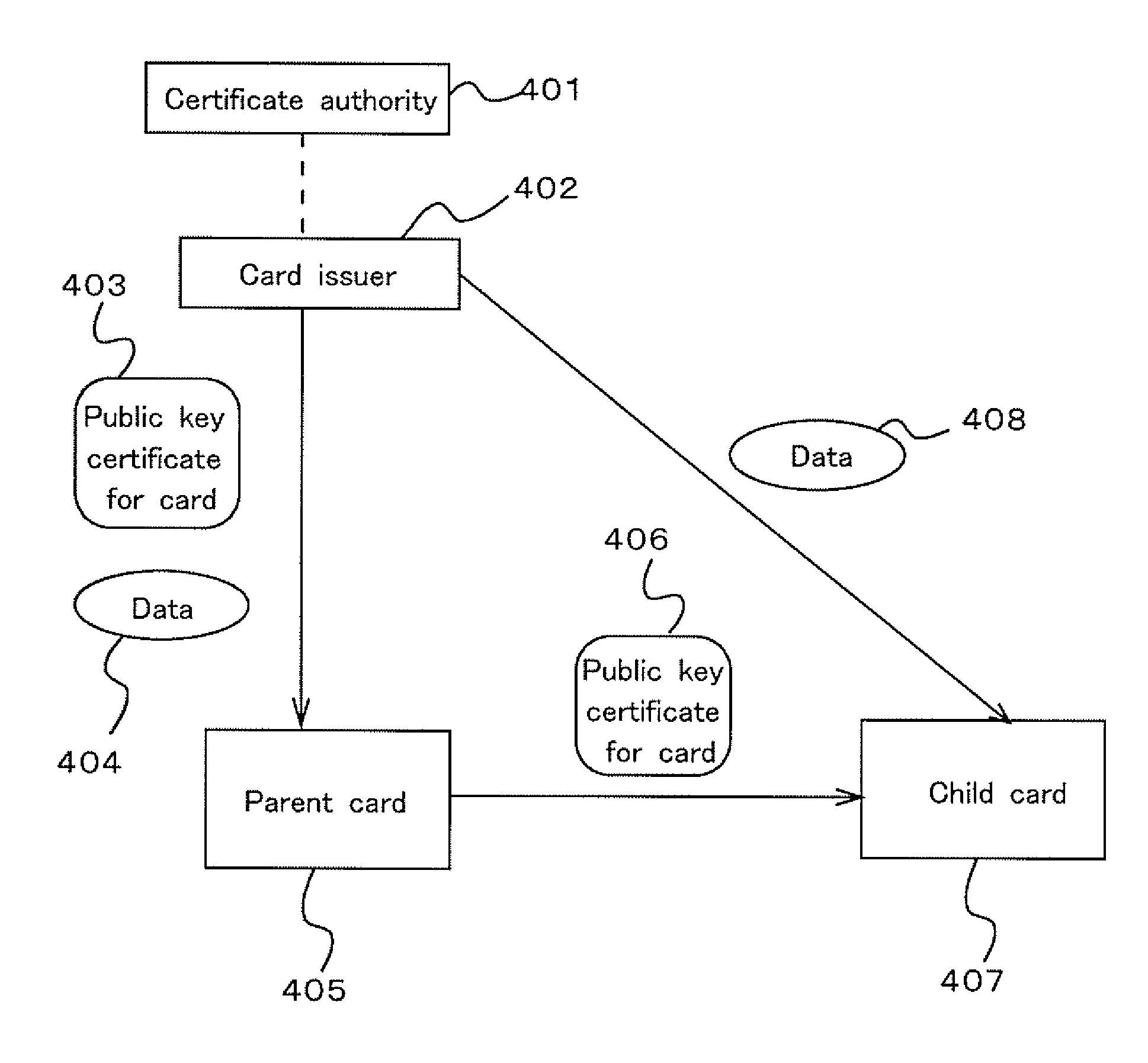
Parent-Child Card Authentication System
InactiveUS20070226793A1Easily grant authorityEasy to useKey distribution for secure communicationDigital data processing detailsComputer hardwarePublic key authentication
When a special relationship is present between IC card owners, authority of one of the IC card owners cannot be easily given to the other owner of the IC card. However, an IC card of a second owner can issue a public key certificate of the IC card of a first owner so that the IC card of the first owner can be recognized as a child card of the IC card of the second owner. Thus, the first generation card authenticated by a route authentication station is set as an ancestor which can generate a descendent card which receives the authentication. By checking which parent card has issued the public key authentication owned by the child card, it is possible to given the authority of the parent card to the child card.
Owner:PANASONIC CORP
Method for entitling a user interface
InactiveUS20050028105A1Software engineeringCathode-ray tube indicatorsGraphicsGraphical user interface
A method for rendering a graphical user interface (GUI), comprising providing for the representation of the GUI as a set of controls wherein the controls are organized in a logical hierarchy and wherein each one of the controls has an entitlement that can be used to determine whether or not the control is visible when rendered, traversing the representation, wherein the traversing comprises associating a theme with a first control in the set of controls, rendering the first control according to the theme, rendering any descendents of the first control according to the theme, wherein any descendents of the first control can override the theme, and wherein one of the set of controls can communicate with another of the set of controls.
Owner:BEA SYST INC
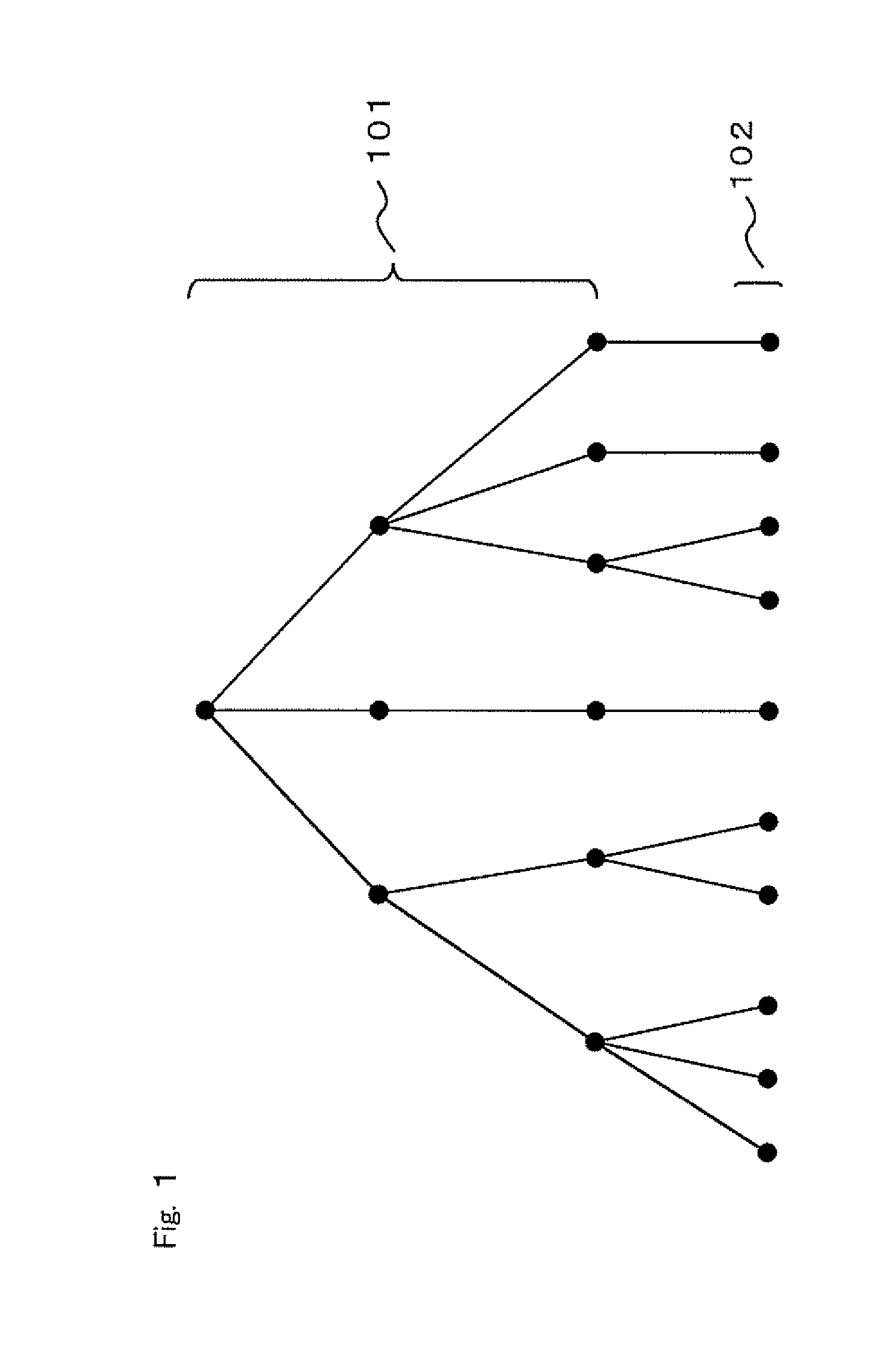
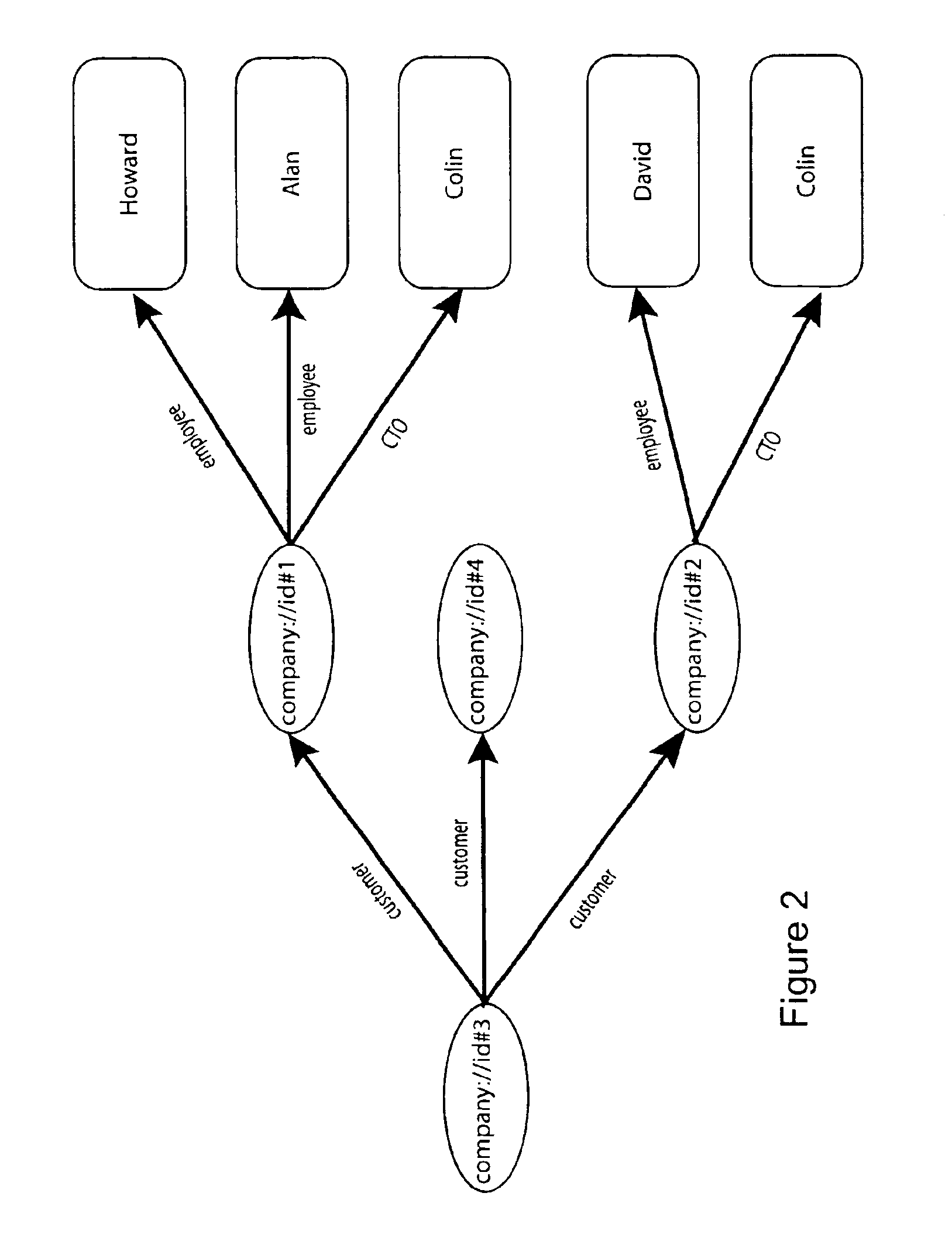
Methods and apparatus for identifying related nodes in a directed graph having named arcs
ActiveUS6954749B2Criterion of becomes complexData processing applicationsDigital data information retrievalNODALData set
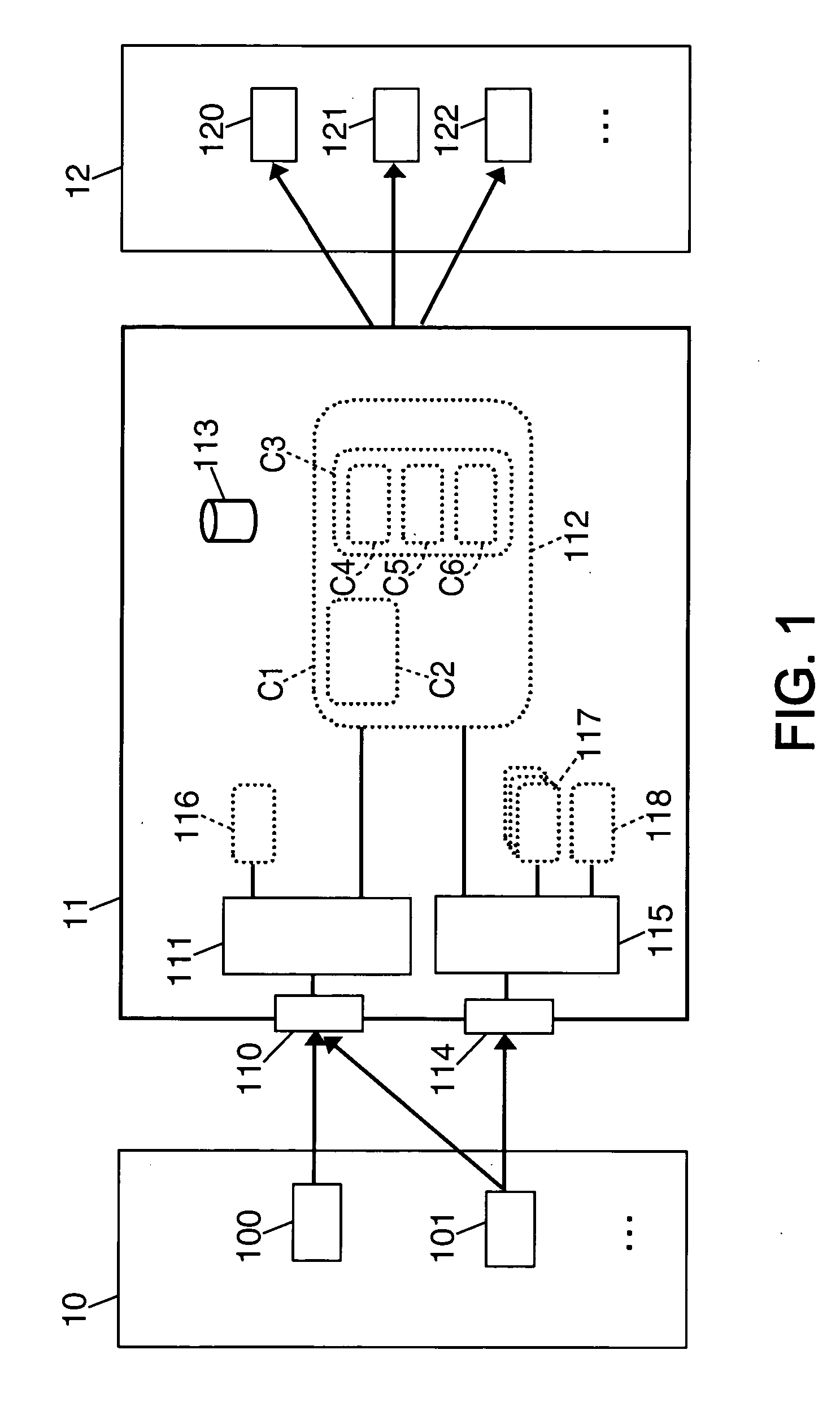
The invention provides methods for identifying related data in a directed graph (e.g., an RDF data set). A “first” step—though the steps are not necessarily executed in sequential order—includes identifying (or marking) as related data expressly satisfying the criteria. A “second” step includes identifying as related ancestors of any data identified as related, e.g., in the first step, unless that ancestor conflicts with the criteria. A “third” step of the method is identifying descendents of any data identified, e.g., in the prior steps, unless that descendent conflicts with the criteria or has a certain relationship with the ancestor from which it descends. The methods generates, e.g., as output, an indication of each of the nodes identified as related in the three steps.
Owner:OBJECT STORE INC
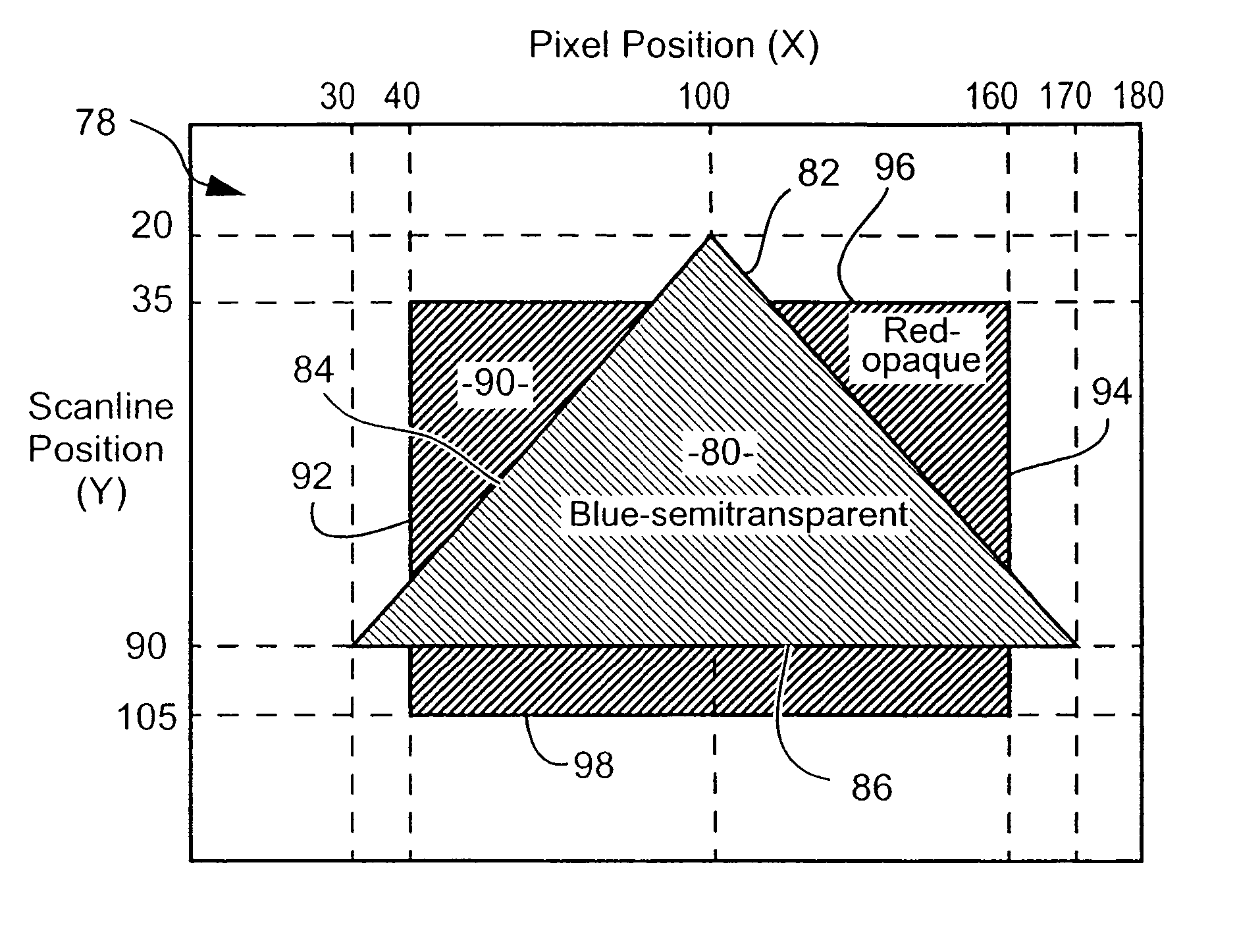
Tree-based compositing system
InactiveUS20050122337A1Reduce complexityDrawing from basic elementsCharacter and pattern recognitionGraphicsOperand
A method of rendering a graphical image described by an expression tree is disclosed. The expression tree has one or more parent nodes and one or more leaf nodes, each parent node representing a graphical operator and having branches to respective descendent nodes. Each of the leaf node represents a graphic object. The method determines regions of one or more pixel locations in an output space of the image, with each region corresponding to a combination in the image of one or more the graphical objects. Next, for each said region, an activity state of corresponding parent nodes is determined using a predefined function for each corresponding operator. The method then generates, in parallel (1098), for each active one of the operators, compositing instructions and pixel generation instructions. The compositing instructions are stored in an operator queue and pixel colors are generated using the pixel generation instructions, the pixel colors being buffered in an operand queue (1300). Lastly, the generated pixel colors are composited (1400), for each pixel in the region, using the operators defined in the operator queue, to output (800) a composited pixel value for each pixel in the region. Other processing operations including operator reduction, flat color bypass, and operand comparison are also discussed.
Owner:CANON KK
Mechanism for dynamically resolving polymorphic type dependencies between parallel heterogenous run-time environments
InactiveUS20120185824A1Specific program execution arrangementsMemory systemsRunning timeDependency relation
Owner:BRITISH BROADCASTING CORP
Adaptive topology discovery in communication networks
InactiveUS7911978B1Reduce spendingEfficient networkingTime-division multiplexData switching by path configurationRouting tableTopology information
A topology discovery process is used to discover all of the links in an ad hoc network and thereby ascertain the topology of the entire network. One of the nodes of the network, referred to as the coordinator, receives the topology information which can then be used to, for example, distribute a routing table to each other node of the network. The process has a Diffusion phase in which a k-resilient mesh, k>1, is created by propagating a topology request message through the network. Through this process, the nodes obtain information from which they are able to discern their local neighbor information. In a subsequent, Gathering phase, the local neighbor information is reported upstream from a node to its parents in the mesh and thence to the parents' parents and so forth back to the coordinator. The robustness of the Diffusion phase is enhanced by allowing a node to have more than one parent as well as by a number of techniques, including use of a so-called diffusion acknowledgement message. The robustness of the Gathering phase is enhanced by a number of techniques including the use of timeouts that ensure that a node will report its neighbor information upstream even if it never receives neighbor information from one or more downstream neighbors and the use of a panic mode that enhances the probability that a node will get its neighbor information, and its descendents' neighbor information, reported upstream even if that node has lost connectivity with all of its parents.
Owner:AT&T INTPROP II L P
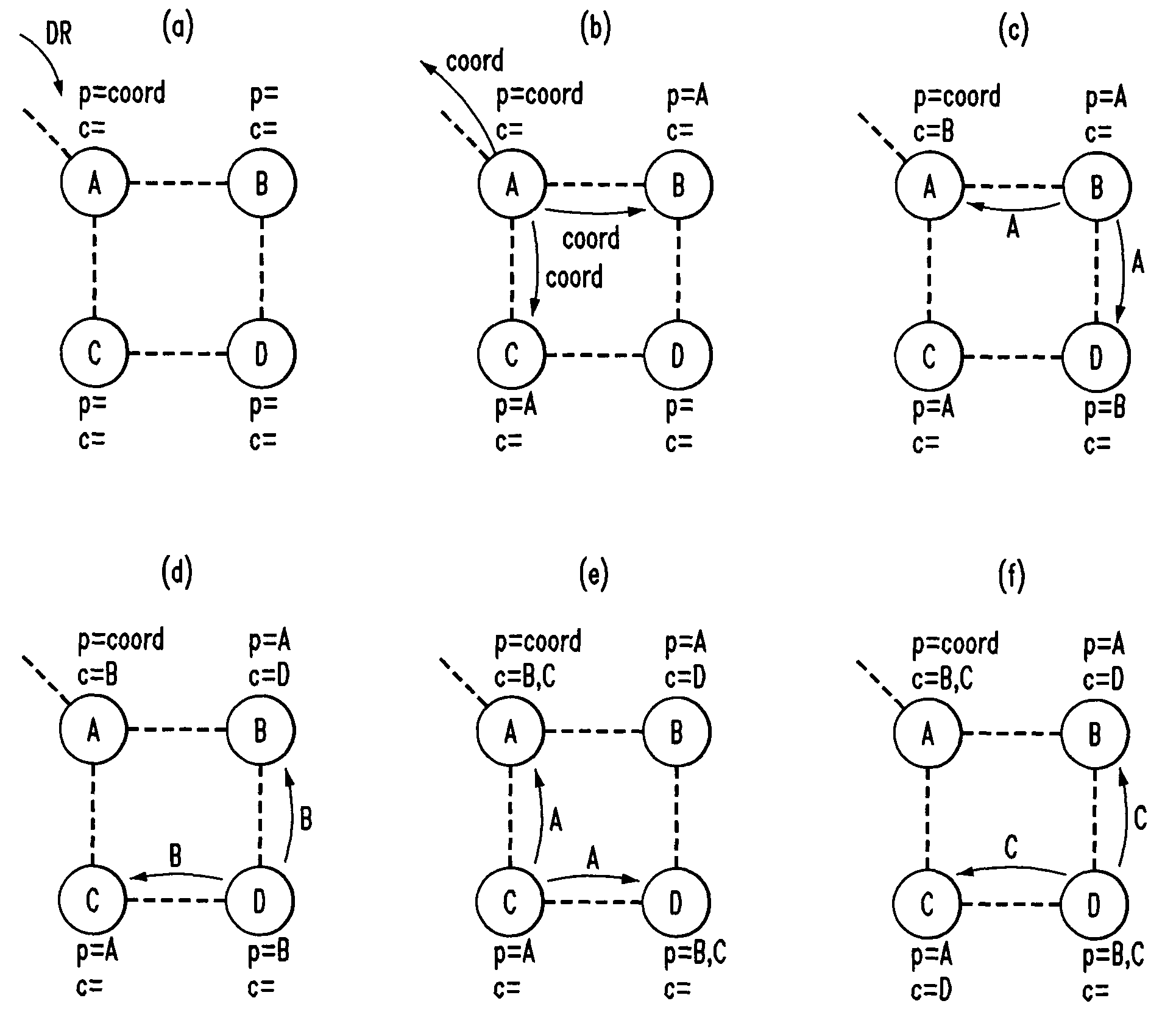
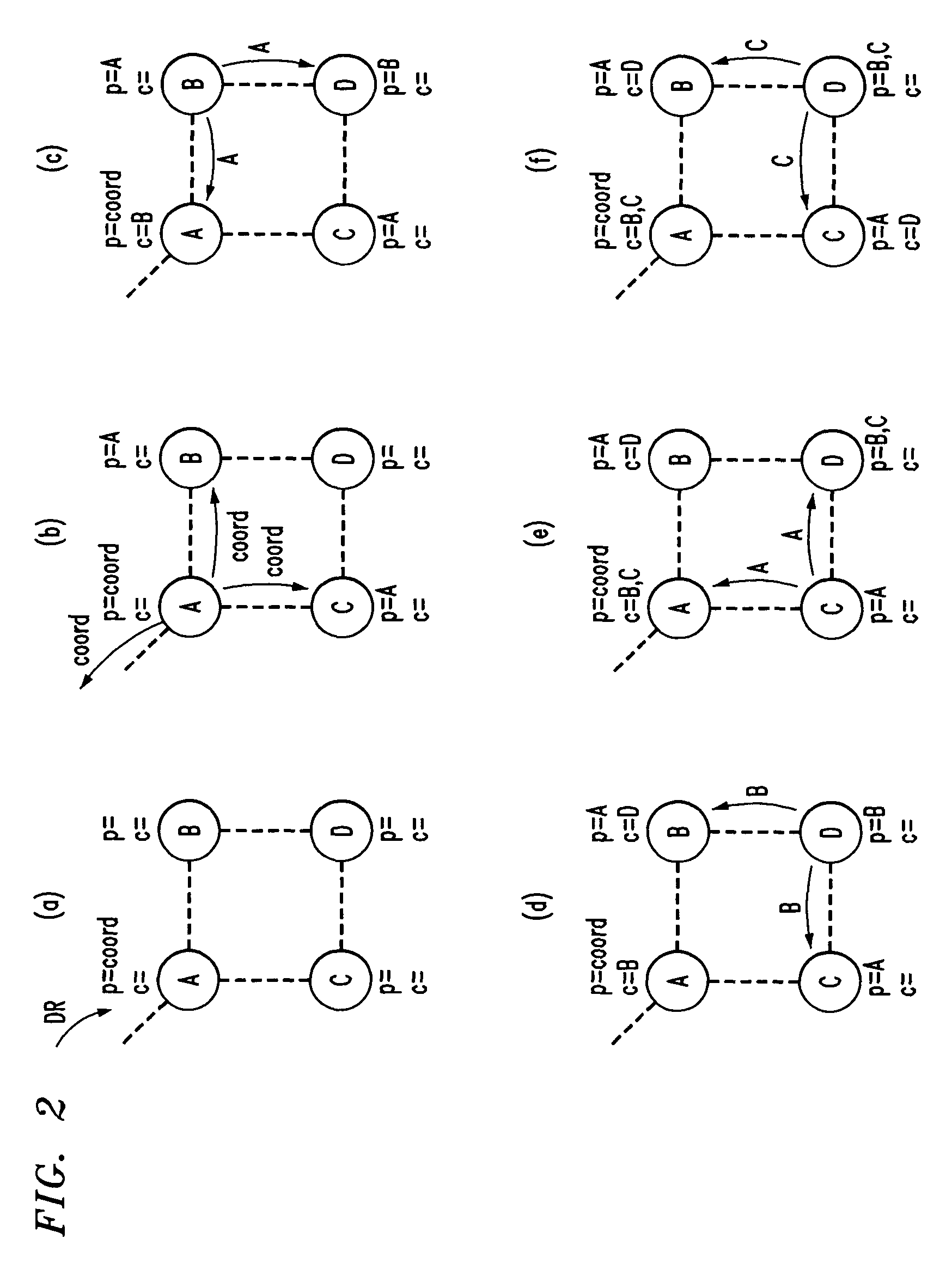
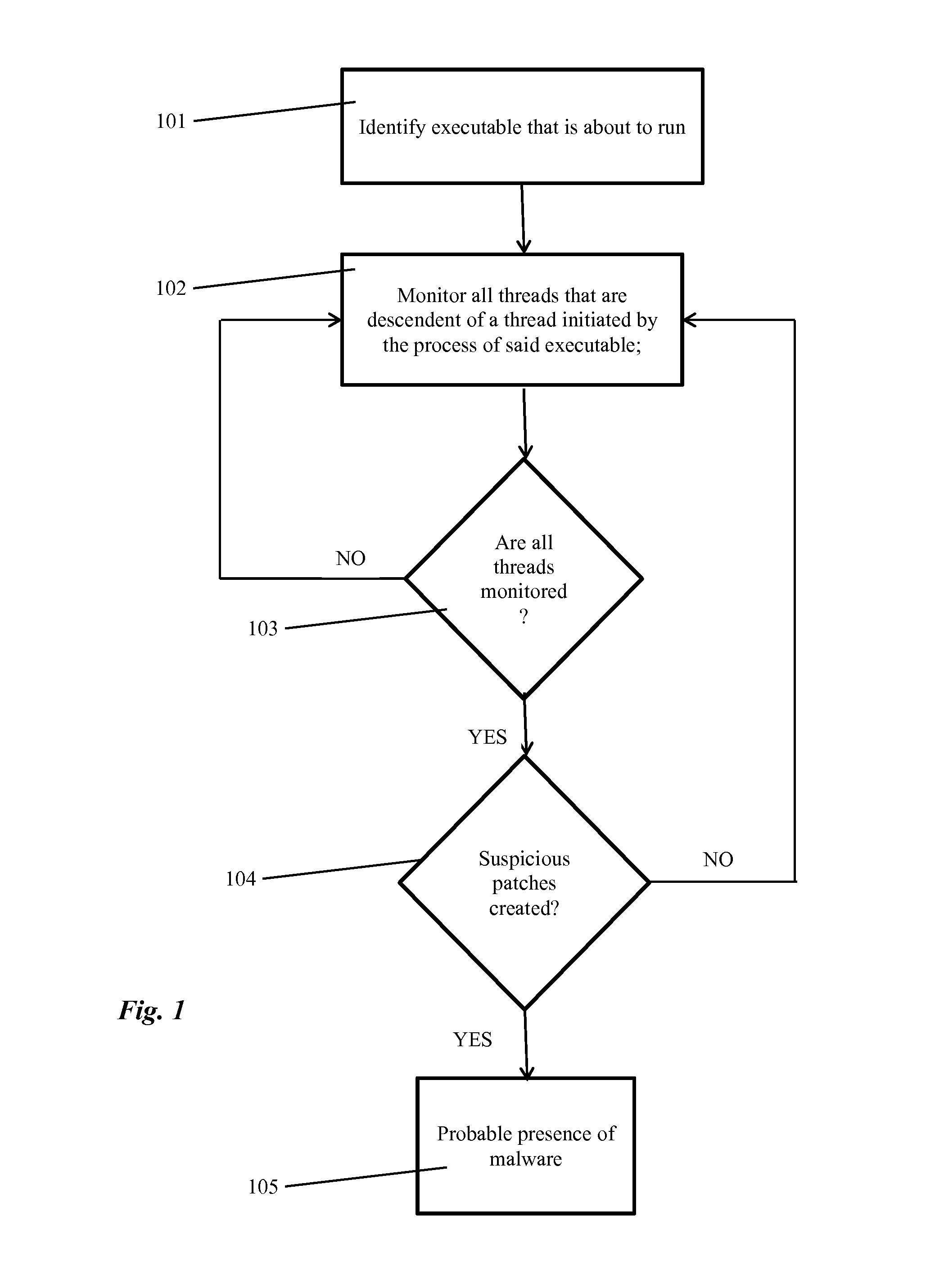
Malware Discovery Method and System
ActiveUS20140289851A1Easy to operateStreamlined operationMemory loss protectionError detection/correctionHigh probabilityMalware
A process for identifying potentially harmful malware, comprises the steps of: a) identifying an executable that is about to run; b) providing a monitoring agent that monitors all threads that are descendent of a thread initiated by the process of said executable; and c) configuring said monitoring agent to conclude that a high probability of malware presence exists, if one of said descendent threads reaches a target process in which suspicious patches are created.
Owner:CROWDSTRIKE
Interference cancellation in variable codelength systems for multi-access communication
A receiver employs low-rate processing to synthesize the effect of high-rate interference in a received multi-rate signal. Each high-rate subchannel is analyzed on its low-rate descendents to produce symbol estimates for each low-rate symbol interval. The symbol estimates are applied to low-rate descendent subchannels, which are then combined to synthesize the effects of the high-rate interference. An interference canceller processes the synthesized interference with the received signal for producing an interference-cancelled signal. Alternatively, analogous steps may be applied at high-rate to analyze, synthesize, and cancel the effects of low-rate interference in a multi-rate signal.
Owner:III HLDG 1
System of bath, shower, drying, massage and sauna for people
A system for bathing, showering, drying, massaging and sauna, which includes a container having a vertical arrangement, a main body, a bottom surface, a water-drainage orifice and a door for allowing entrance of a user in a wheelchair. The bottom surface is at the same level as the door in an open position. The bottom surface has a small descendent inclination towards the water-drainage orifice. The door has an edge acting as slight connecting ramp with a floor of a room in which the system is placed. The door has pawls or iron straps, which lodge and are retained in recesses formed the main body for fastening the door, and the door has magnets for maintaining the door in a closed position.
Owner:SAIZ MANUEL +1
Malware discovery method and system
A process for identifying potentially harmful malware, comprises the steps of: a) identifying an executable that is about to run; b) providing a monitoring agent that monitors all threads that are descendent of a thread initiated by the process of said executable; and c) configuring said monitoring agent to conclude that a high probability of malware presence exists, if one of said descendent threads reaches a target process in which suspicious patches are created.
Owner:CROWDSTRIKE
System and method for analyzing social media trends
Disclosed are methods for identifying topical experts from a seed set of experts by identifying “second tier” influencers for the topic. New concepts detected among a pool of experts and second tier influencers are monitored among the general population and their significance evaluated. Reports may be generated for these detected trends. Trends in social media for a concept represented in a taxonomy may be detected by monitoring content for descendent nodes for the concept. Correlations between social media activity with respect to the concept and sales of products corresponding to the concept may be made and sales predicted for the same or different products that correspond to descendants of the concept in the taxonomy.
Owner:WALMART APOLLO LLC
Persistent Object Linkage Using Ghosting
InactiveUS20090240725A1Effective presentationVersion controlSpecial data processing applicationsHierarchical positionPersistent object
A system that persistently maintains and exposes one or more previous object hierarchies to which an object belonged across one or more hierarchy destroying operations, such as operations that delete parent objects, add parent objects subsequent to addition of their descendent objects, forward objects to or from the hierarchy, and / or modify hierarchy determining rules. A user interface object allows user access to one or more persistent hierarchies for the corresponding object. A hierarchy list or the like allows a user to select a desired one of the persistent hierarchies. A persistent hierarchy can be accessed in the disclosed system through a display object associated with any object within the hierarchy, including the root, leaves, and any intervening objects. When objects are deleted, “ghost” objects are maintained and displayed to the user in the hierarchical positions of the deleted objects when a persistent hierarchy is displayed.
Owner:IBM CORP
System and method for simplifying and manipulating k-partite graphs
InactiveUS7805440B2Sampled-variable control systemsData processing applicationsTheoretical computer scienceMultiple category
The system has a collection of a plurality of objects. Each object defines a node in a k-partite graph, such that, the nodes can be divided into a number of mutually exclusive sets such that all of the nodes are in exactly one of the sets; further edges occur only between nodes in different sets; The system also has a simplification process that aggregates one or more of the nodes into one or more categories and identifies a category node corresponding to each category. The category node inherits the mode and the edges of all the nodes in the respective category. Further, the system contains Directed Acyclic Graphs Indices (DAGIs) whose nodes may have a 1-1 mapping with the nodes in the k-partite graph. These indices can be used to aggregate and hide nodes in the k-partite graph. Aggregation occurs by selecting one or more non-leaf nodes in the DAGI and aggregating all descendent nodes. Hiding occurs by selecting some set of DAGI nodes, thus selecting some corresponding set of nodes in the k-partite graph, and requesting this set of nodes be hidden which effectively removes them from further consideration until they are restored by explicit request.
Owner:INT BUSINESS MASCH CORP
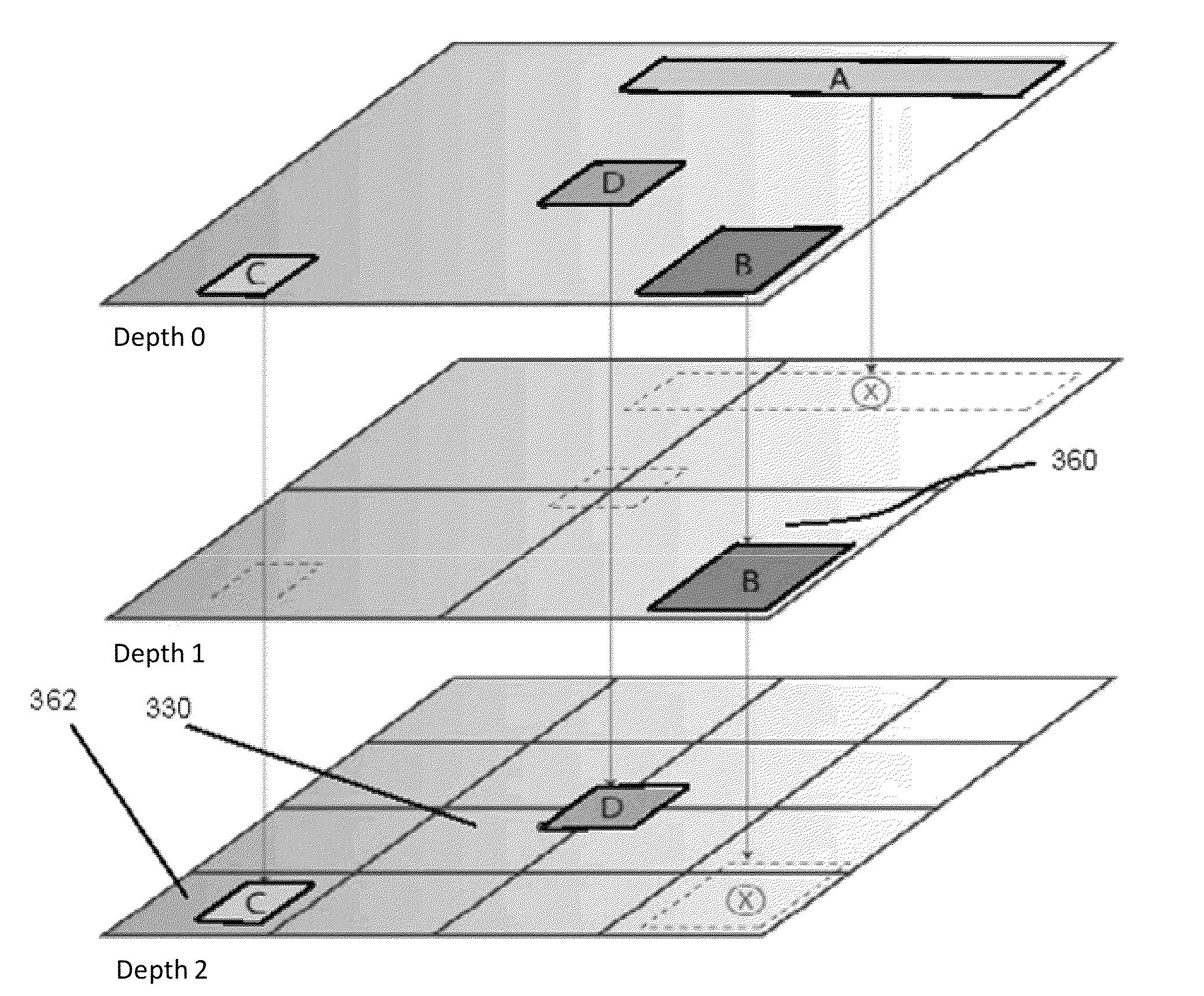
Visualization of value resolution for multidimensional parameterized data
Owner:PIXAR ANIMATION
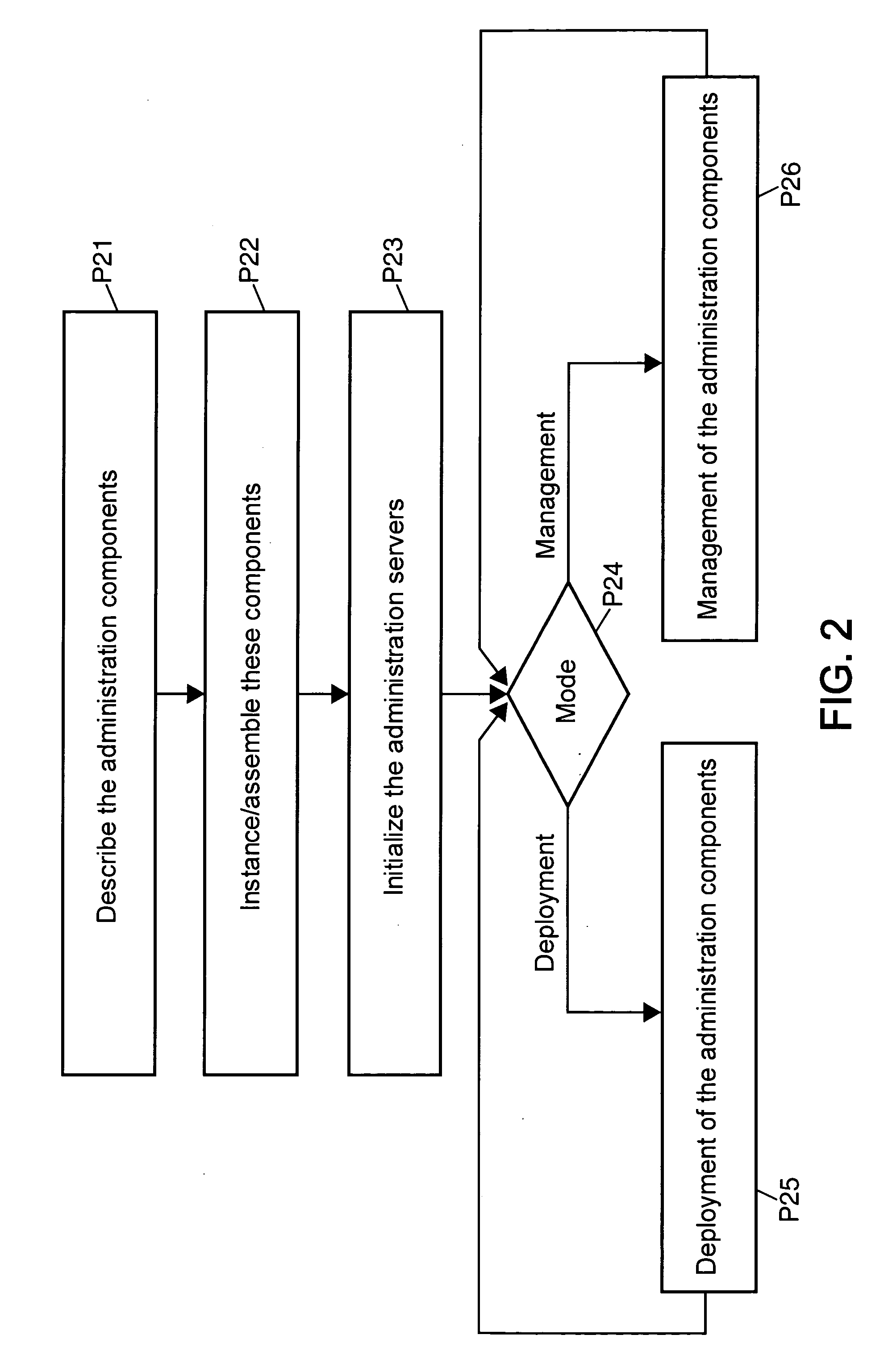
Method and system of administration in a JMX environment comprising an administration application and software systems to be administered
A method of administration in a JMX environment of software systems to be administered, represented by first respective MBeans, and at least one administration application, in which the administration acts produce the exposure of MBeans in at least one MBeanServer server, characterized in that it is implemented by means of a mediation device and that it comprises the following steps: a tree structure of administration components representing first MBeans, in which each component is identified by a unique name, is constructed following the receipt of the name of an administration component, the mediation device dispatches a determined command to the administration component thus identified which, if it represents an MBean, exposes in the MBeanServer this Mbean; when the administration component possesses descendent administration components in the hierarchical structure, the mediation device propagates the command to the descendents.
Owner:FRANCE TELECOM SA
Querying markup language data sources using a relational query processor
InactiveUS20070250503A1Data processing applicationsDigital computer detailsPaper documentSchema for Object-Oriented XML
An XML wrapper queries an XML document in an on-the-fly manner so that only parent nodes in the document that satisfy the query are extracted and then unnested. The parent nodes and associated descendent nodes are located using XPath expressions contained as options in data definition language (DDL) statements. The parent nodes satisfying the query and associated descendent nodes are extracted and stored outside of a database according to a relational schema. The wrapper facilitates applications that use convention SQL queries and views to operate on that information stored according to the relational schema. The wrapper also responds to query optimizer requests for costs associated with queries against external data sources associated with the wrapper.
Owner:IBM CORP
System and method for optical bypass routing and switching
InactiveUS20110129222A1Error preventionFrequency-division multiplex detailsTraffic capacityIp router
Optical bypass circuits are selected and created with a desired amount of traffic on each circuit to offload from the IP routers, the maximum possible amount of traffic. In a first phase, each node in a network independently determines the maximum number of optical bypass circuits, configured to their maximum capacity, to as many destinations, that could possibly originate at that node. The determination is made by aggregating traffic from a given traffic matrix. The optical bypass circuit transports traffic that originates at the node plus transient traffic that the node receives from other nodes. In the second phase, the node will eliminate an optical bypass circuit found in the first phase if any of its parent nodes created a necessarily longer optical bypass circuit to the same destination. In addition, if a descendent node has more aggregate traffic to fill more bypass circuits than the parent node, then the extra optical bypass circuits from the descendent node are also created.
Owner:TELCORDIA TECHNOLOGIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com