Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
104 results about "General level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
"On a more general level" means "basically," so use "on" when speaking to an audience less educated on your specific topic because the audience's knowledge is less specialized. "At a more general level" means "generally," so use "at" to explain that the concept can be generalized.
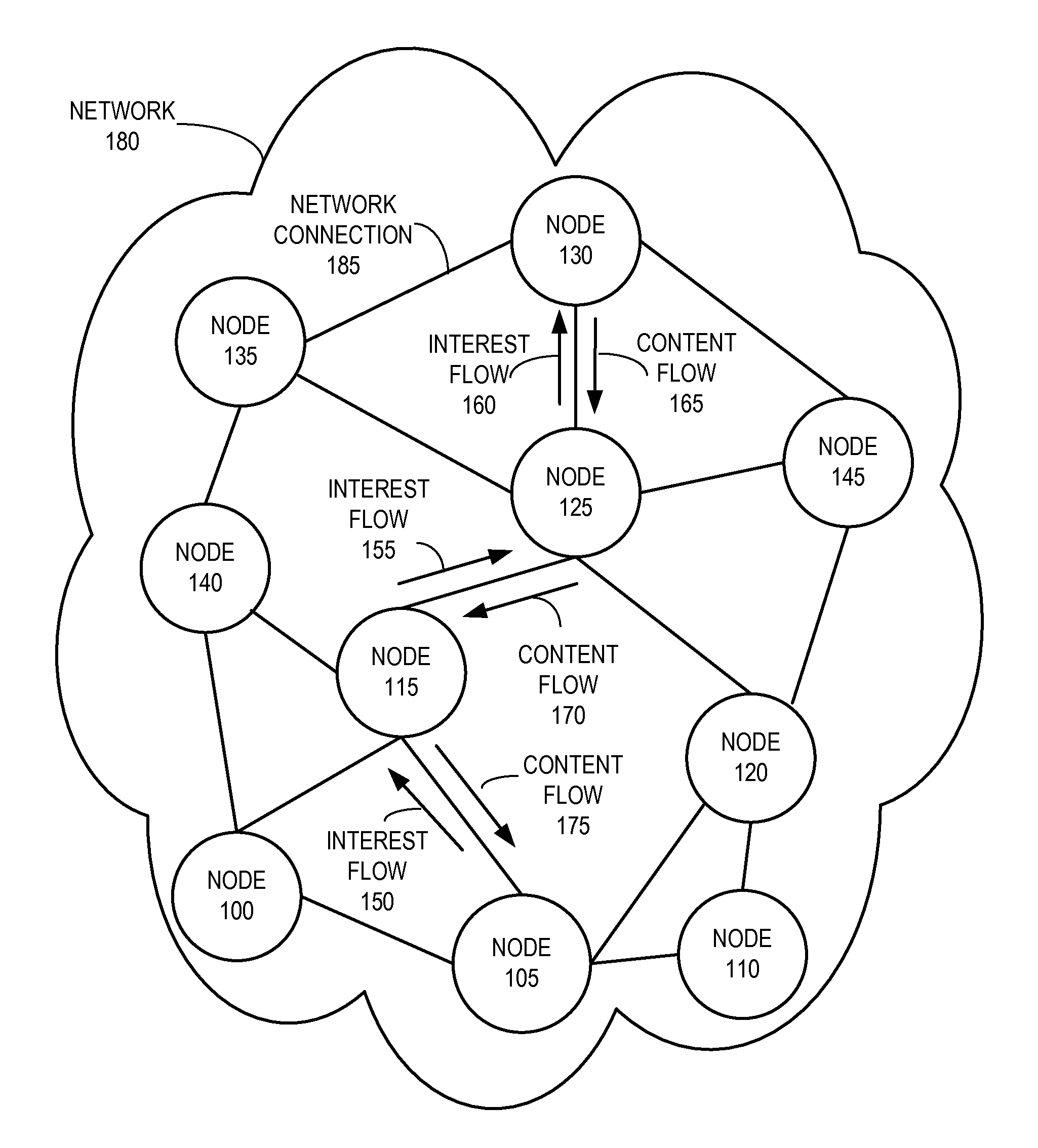
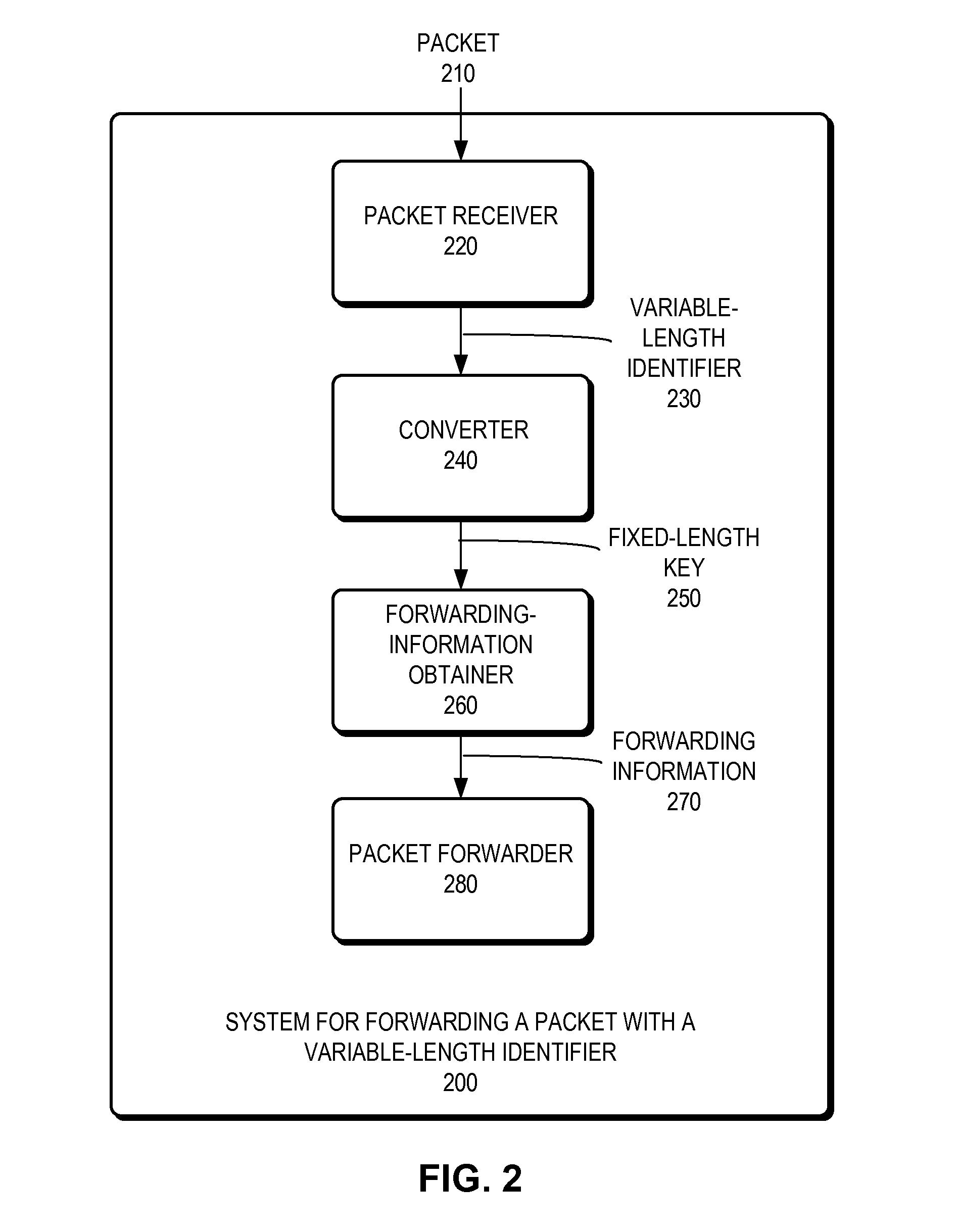
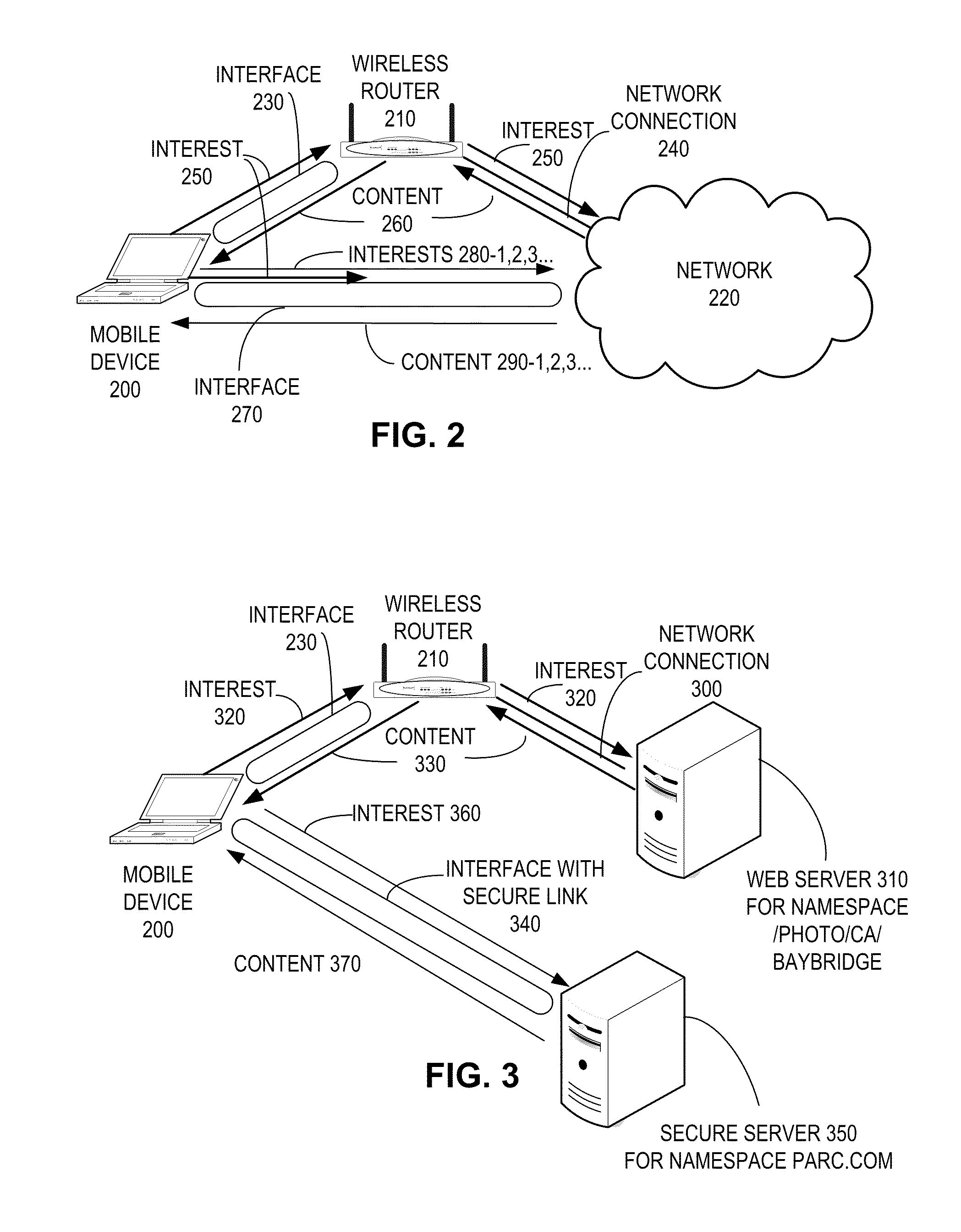
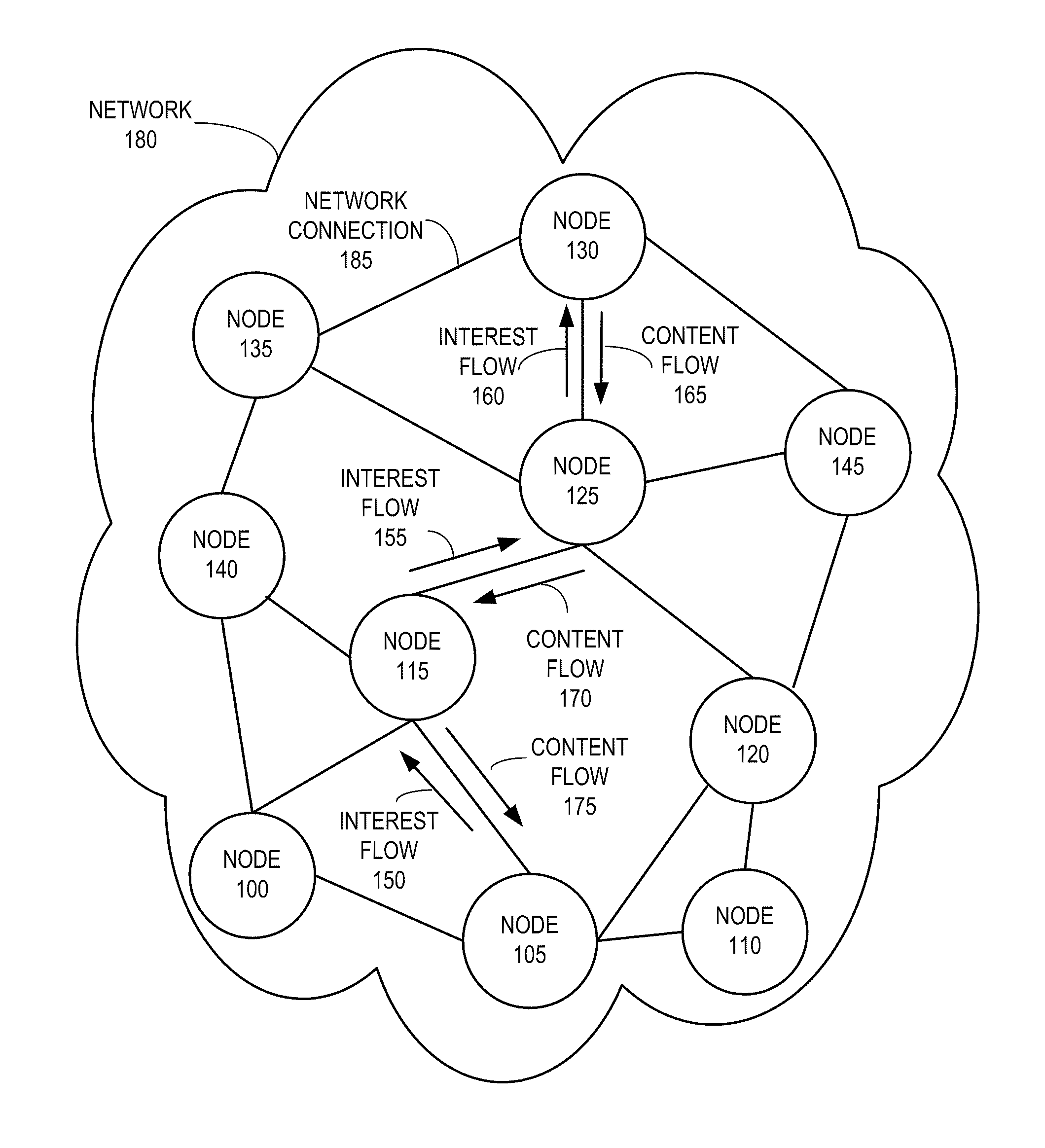
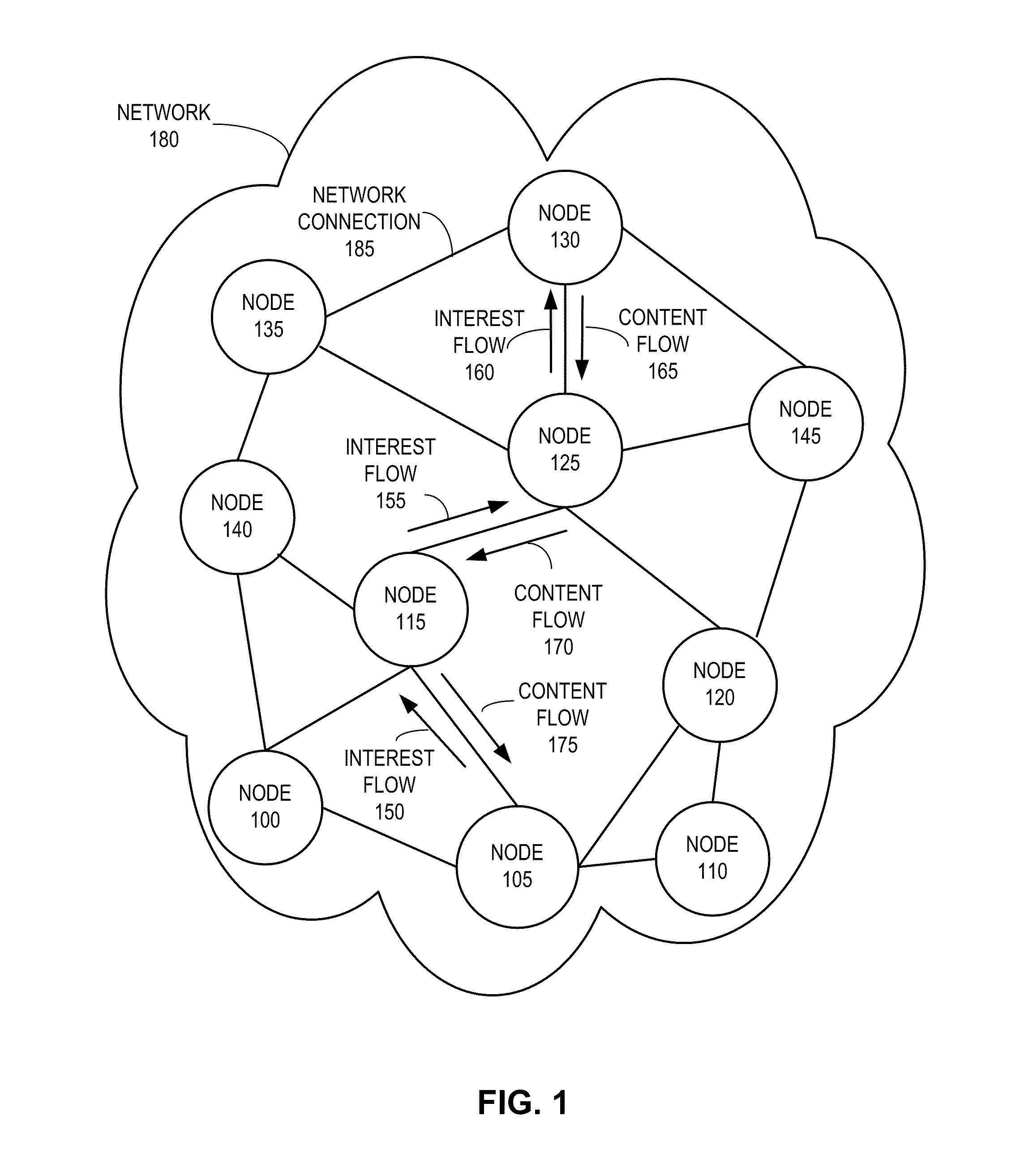
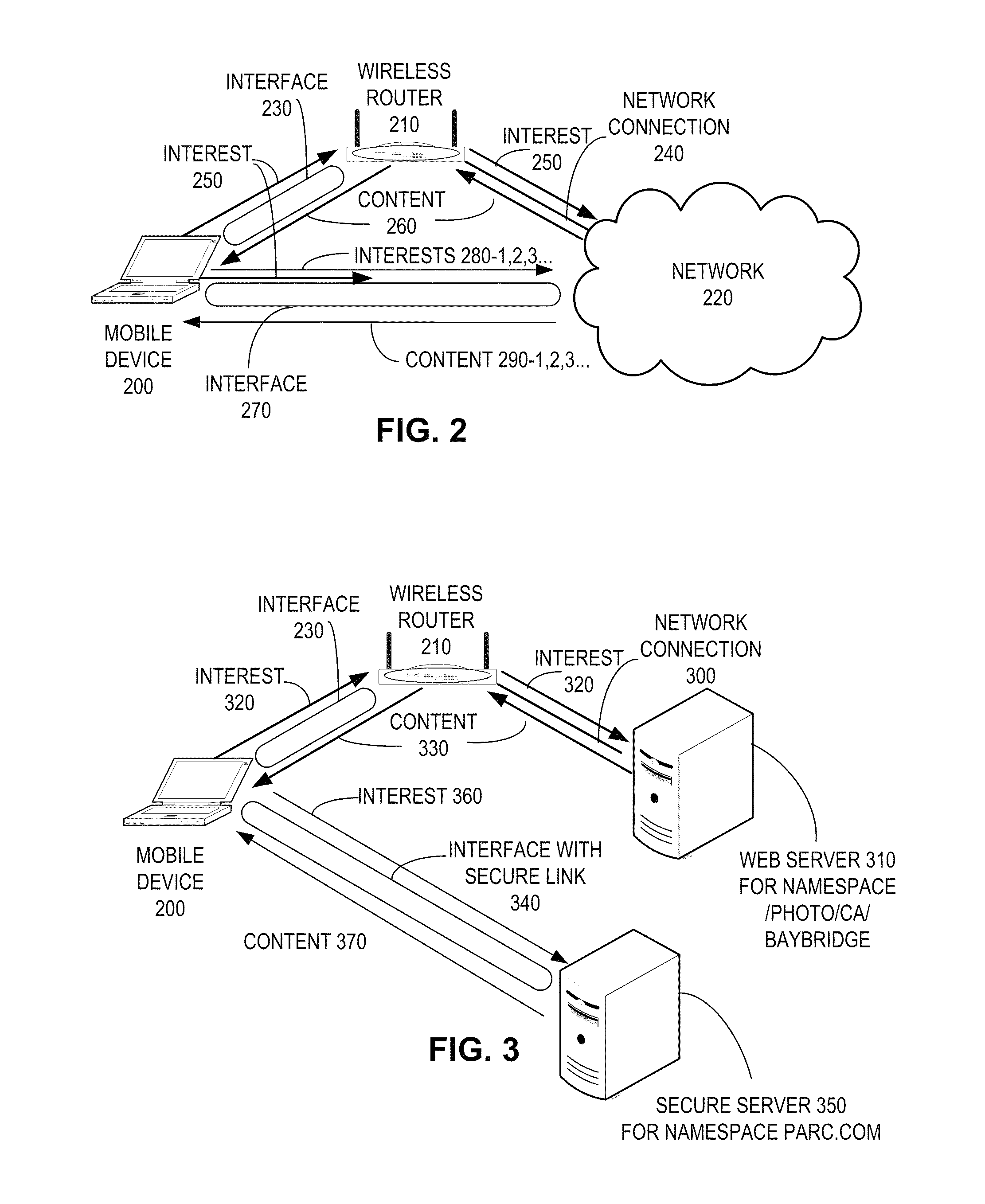
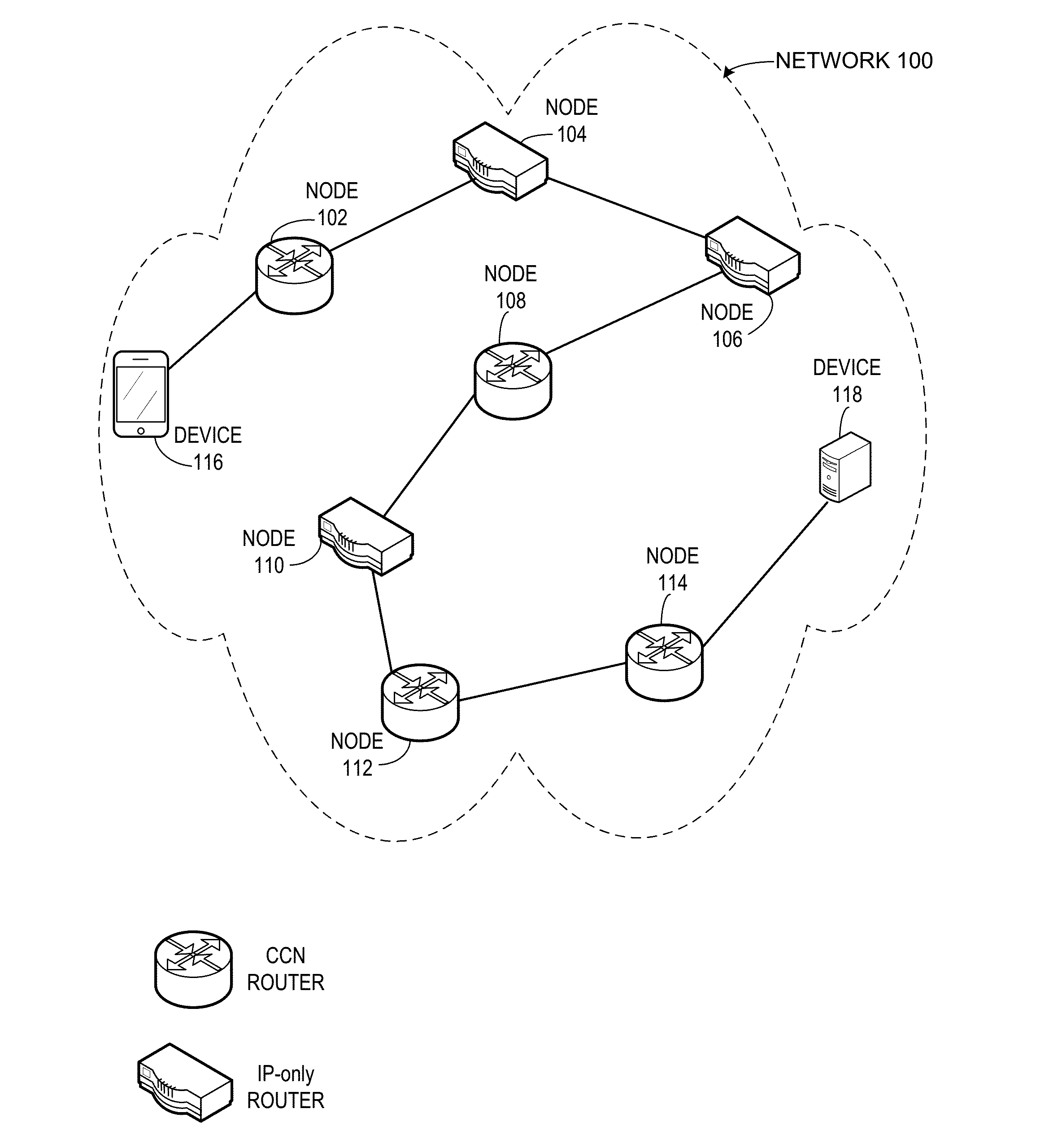
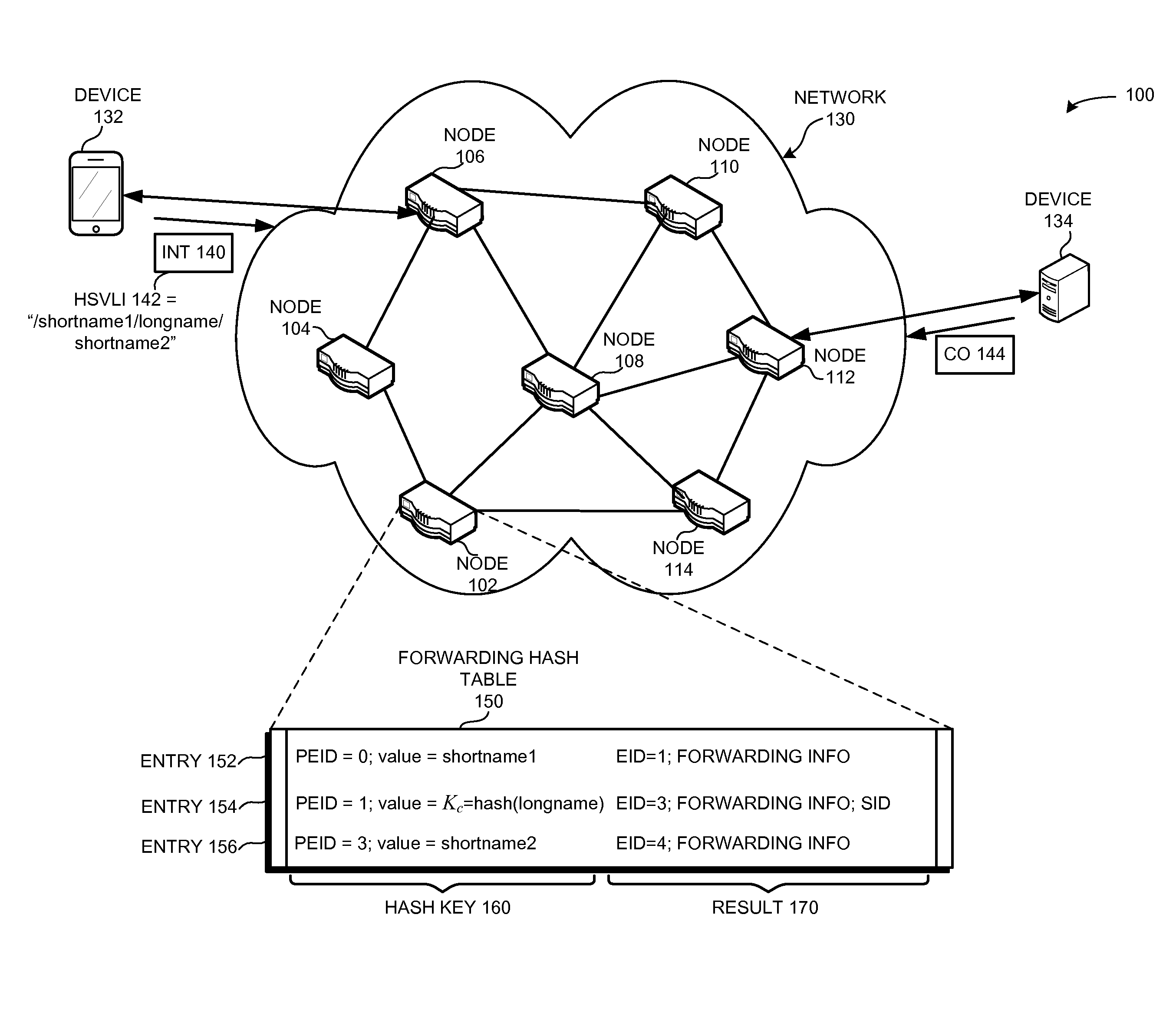
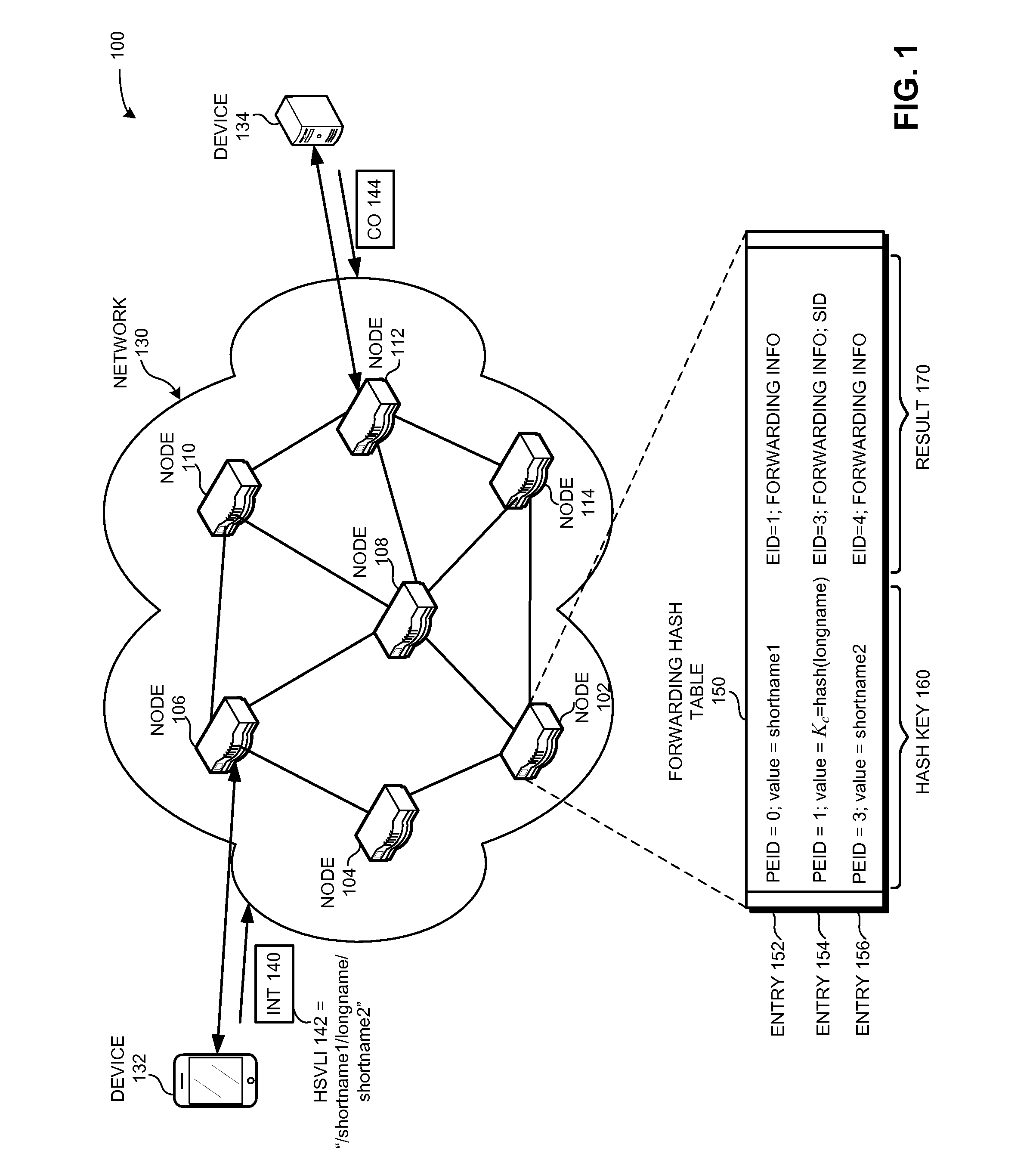
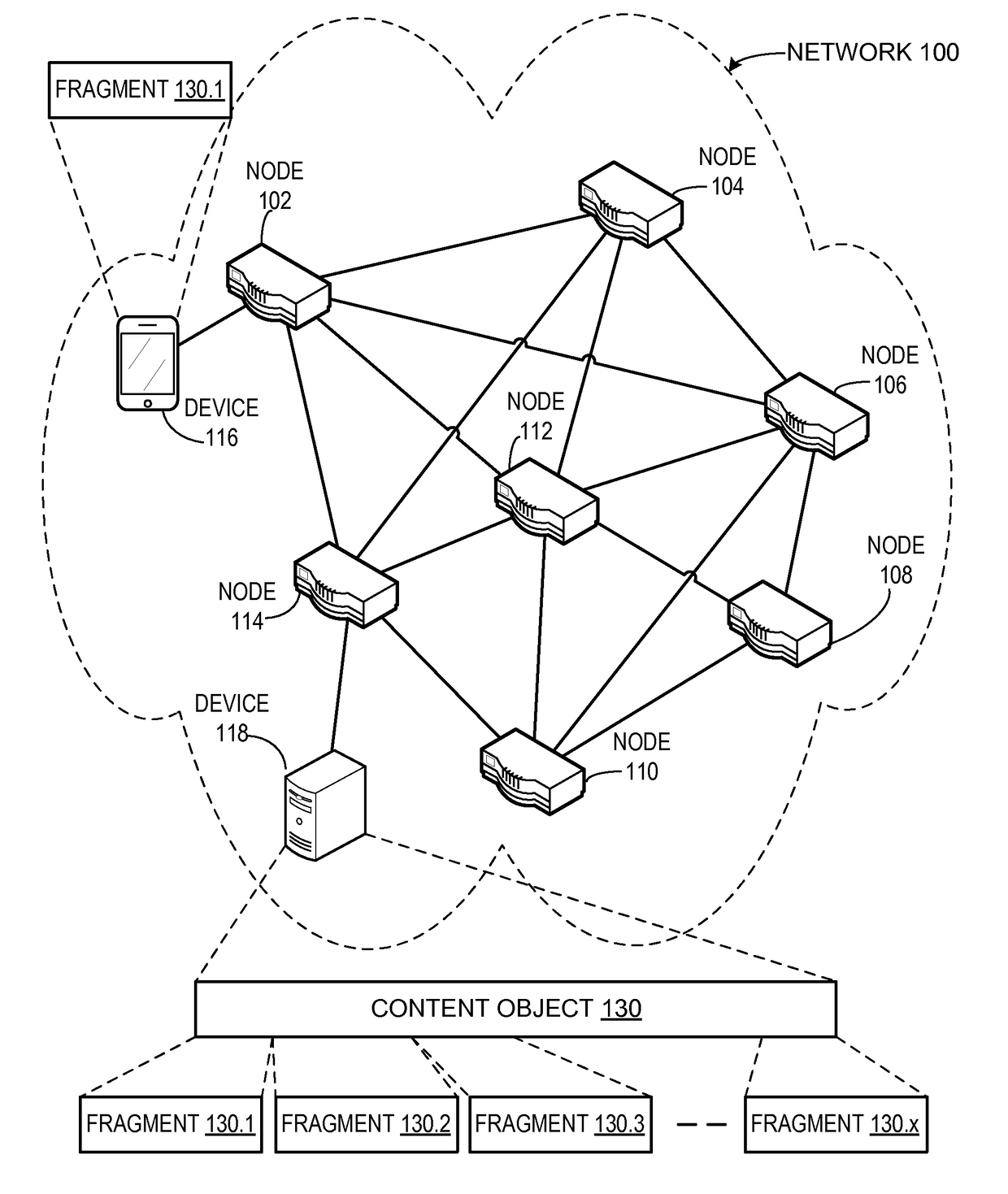
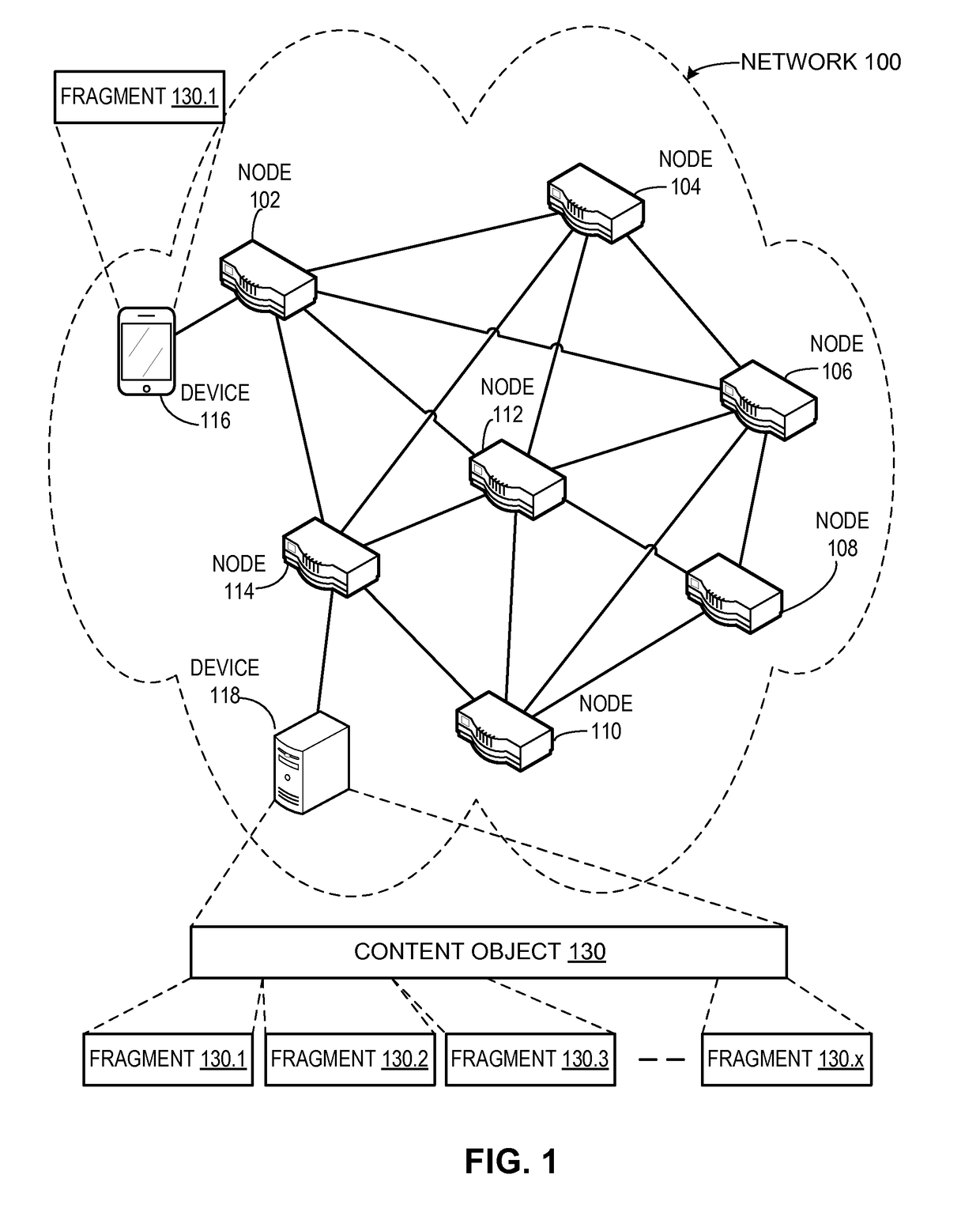
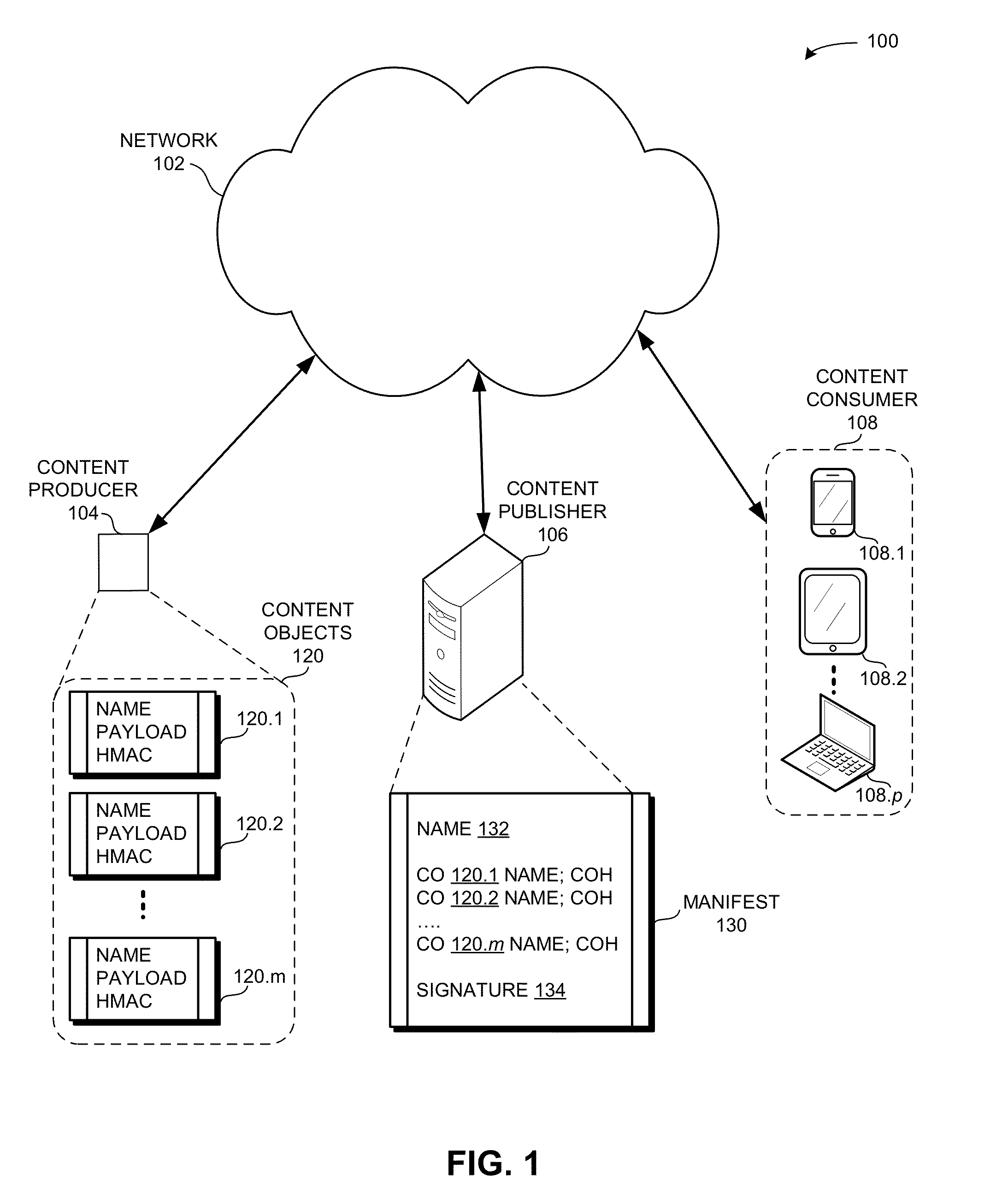
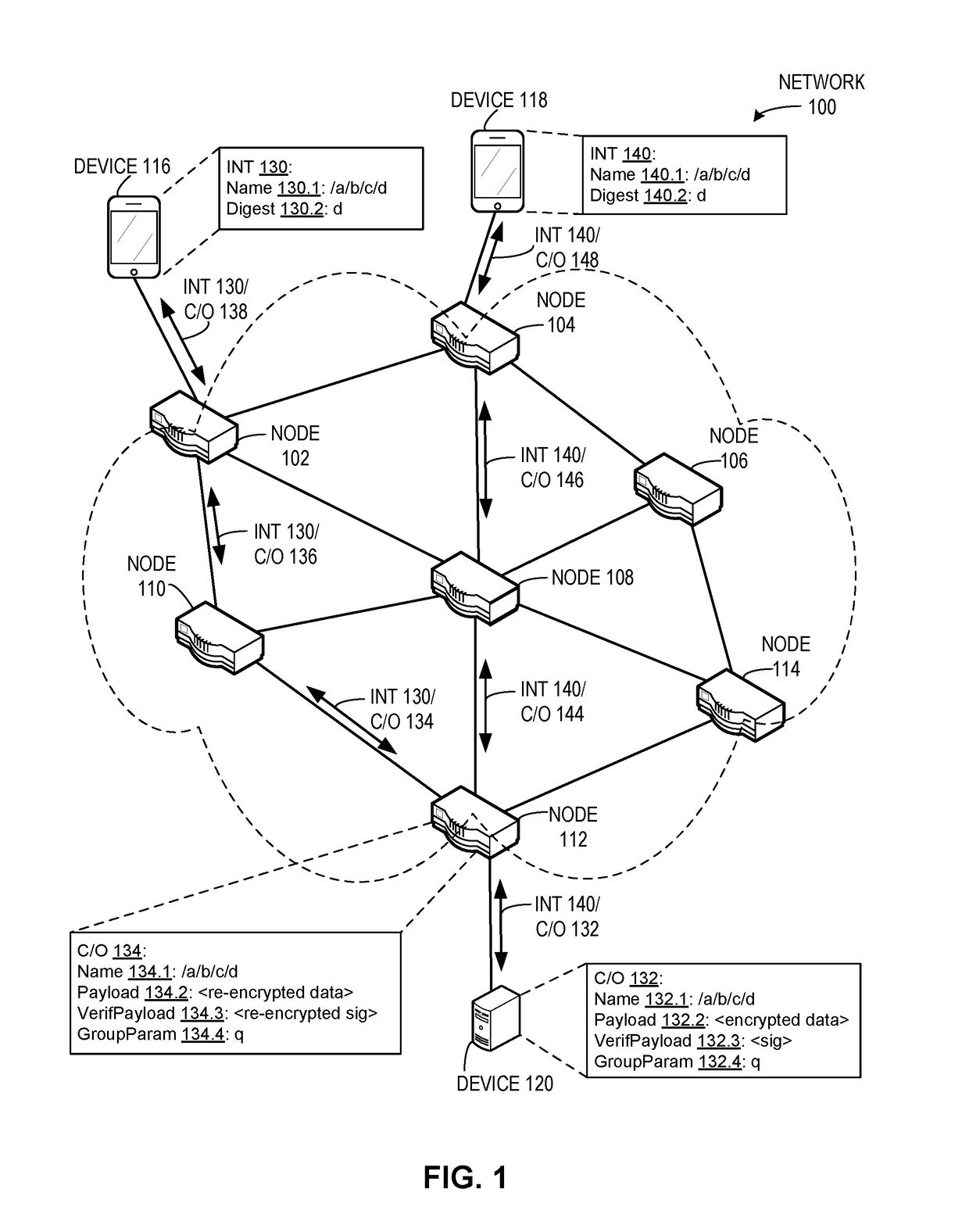
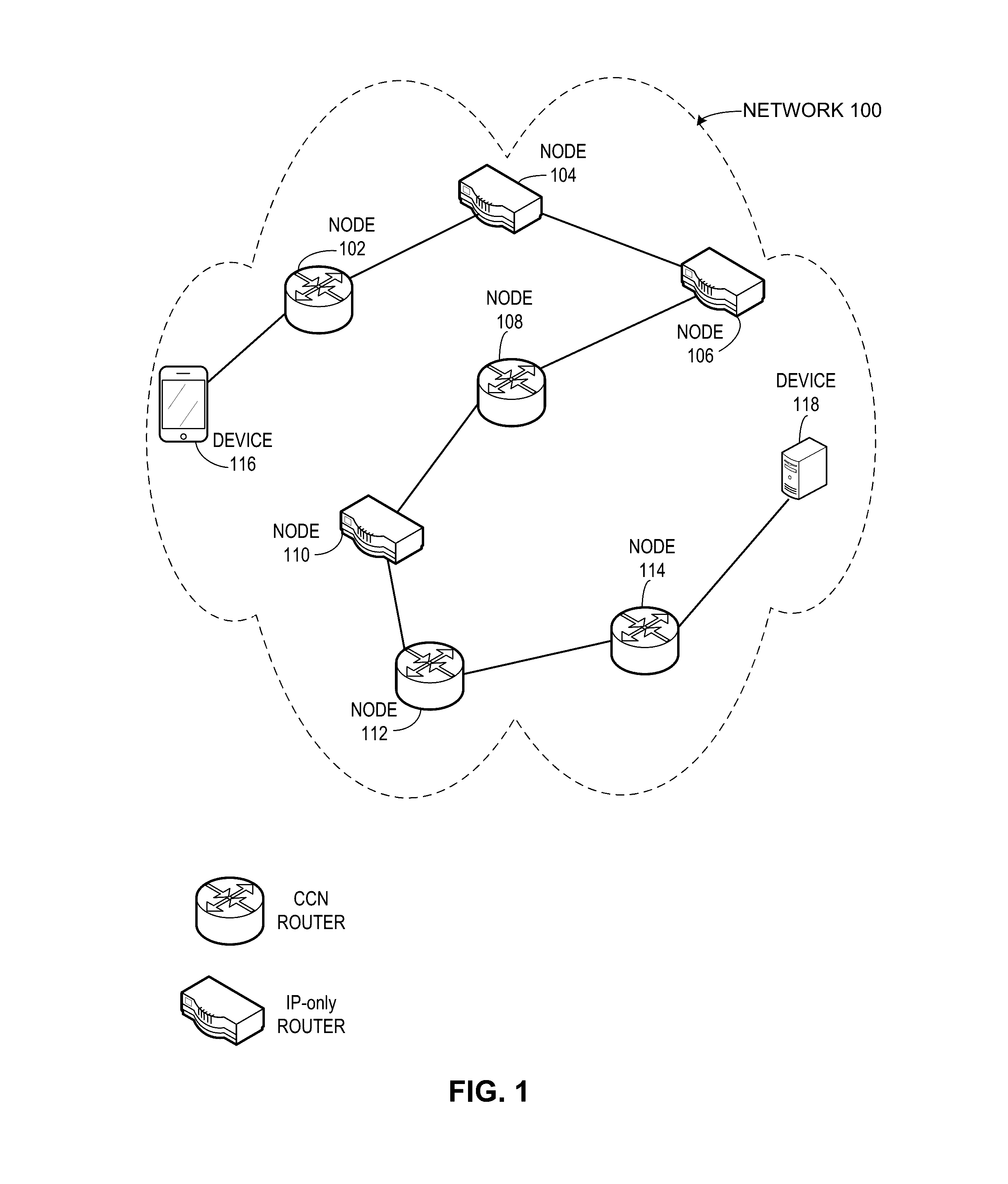
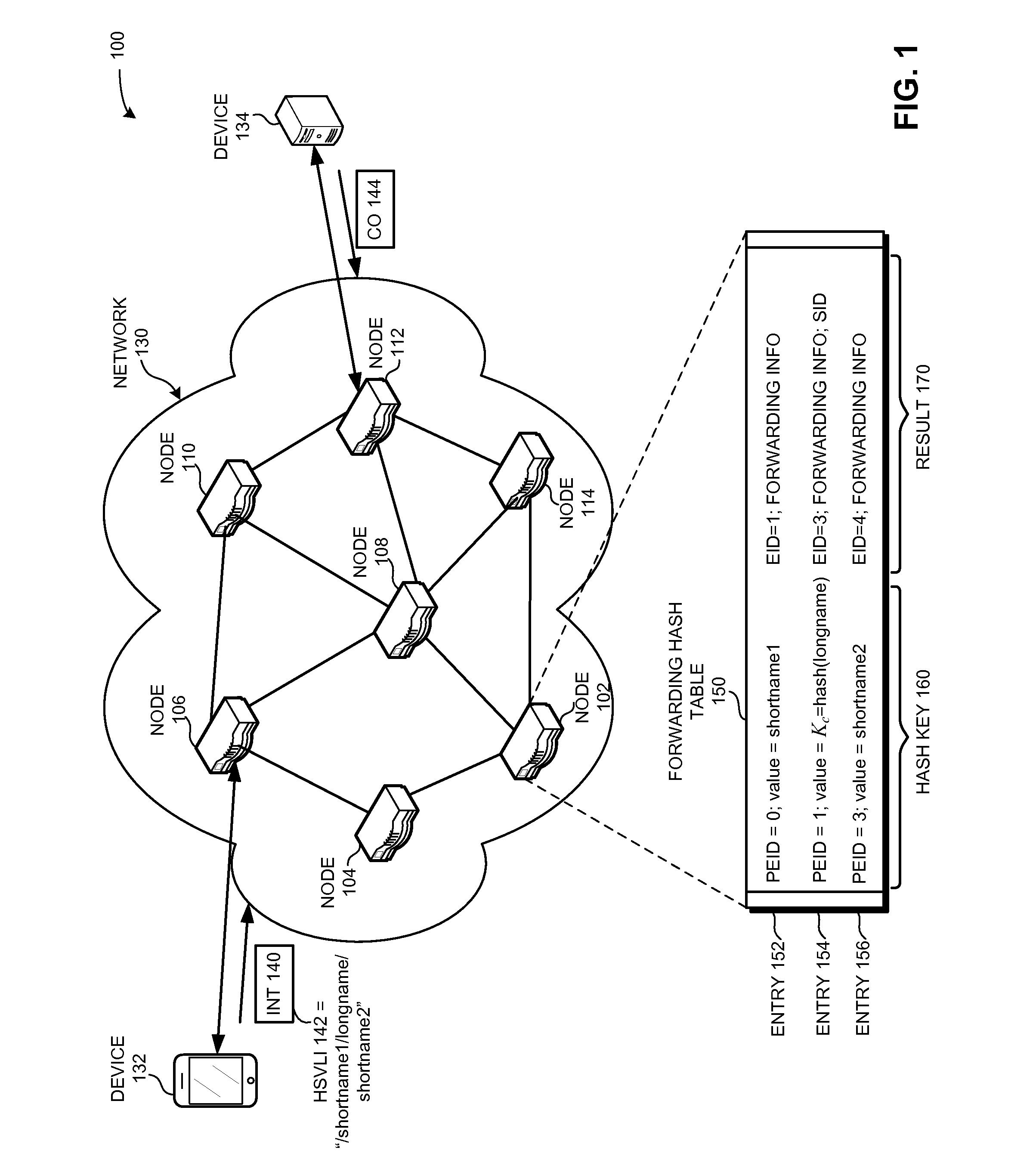
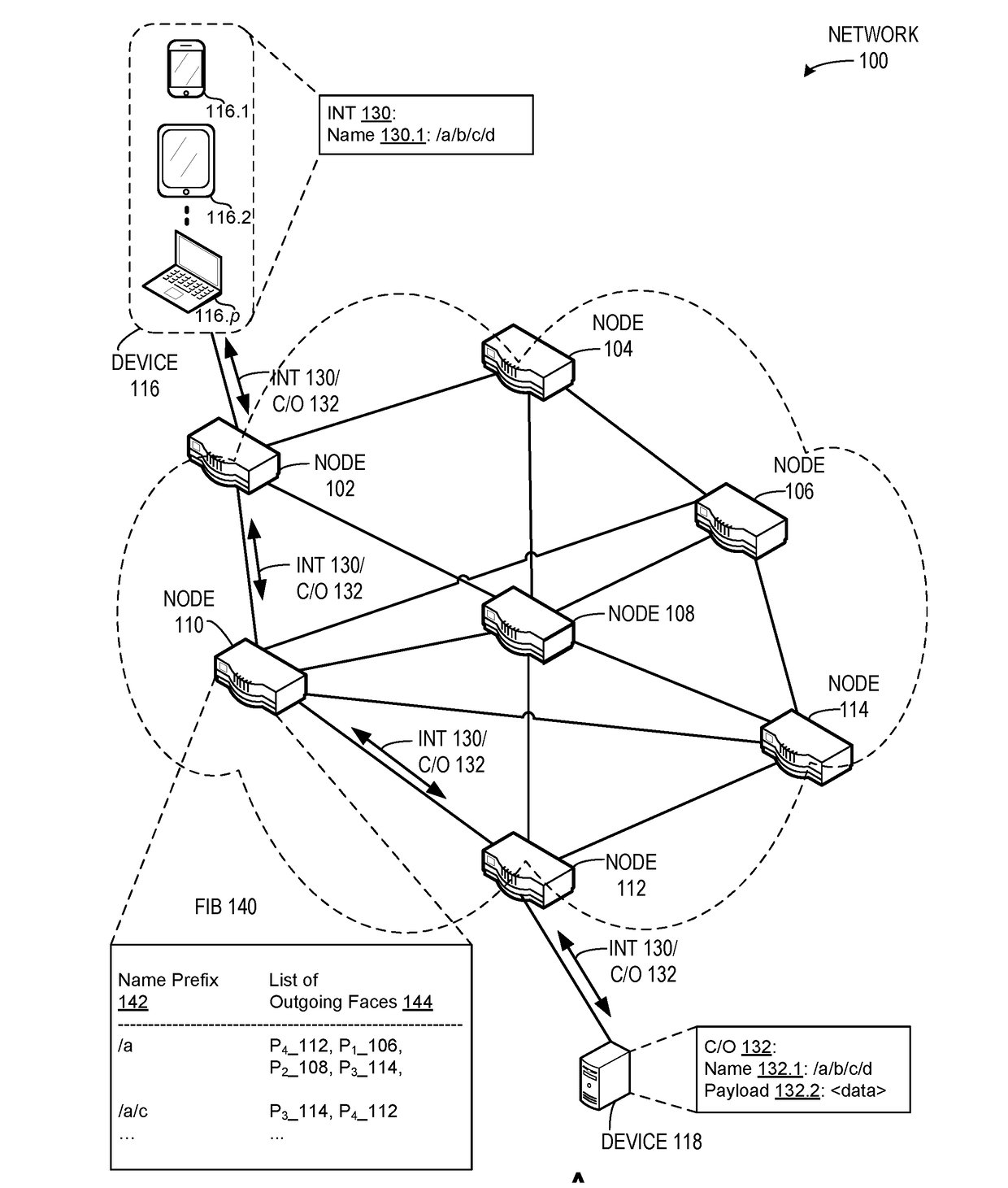
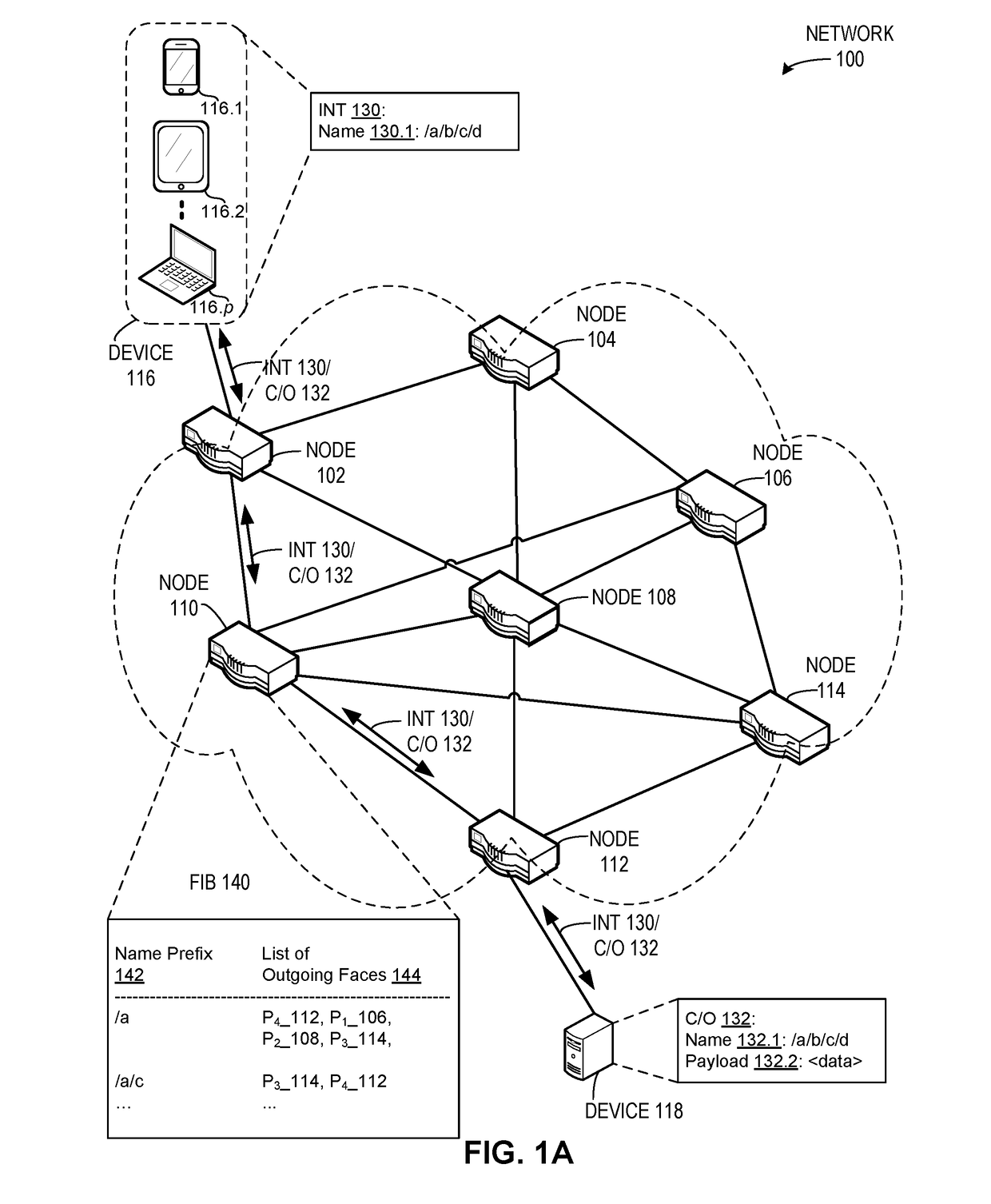
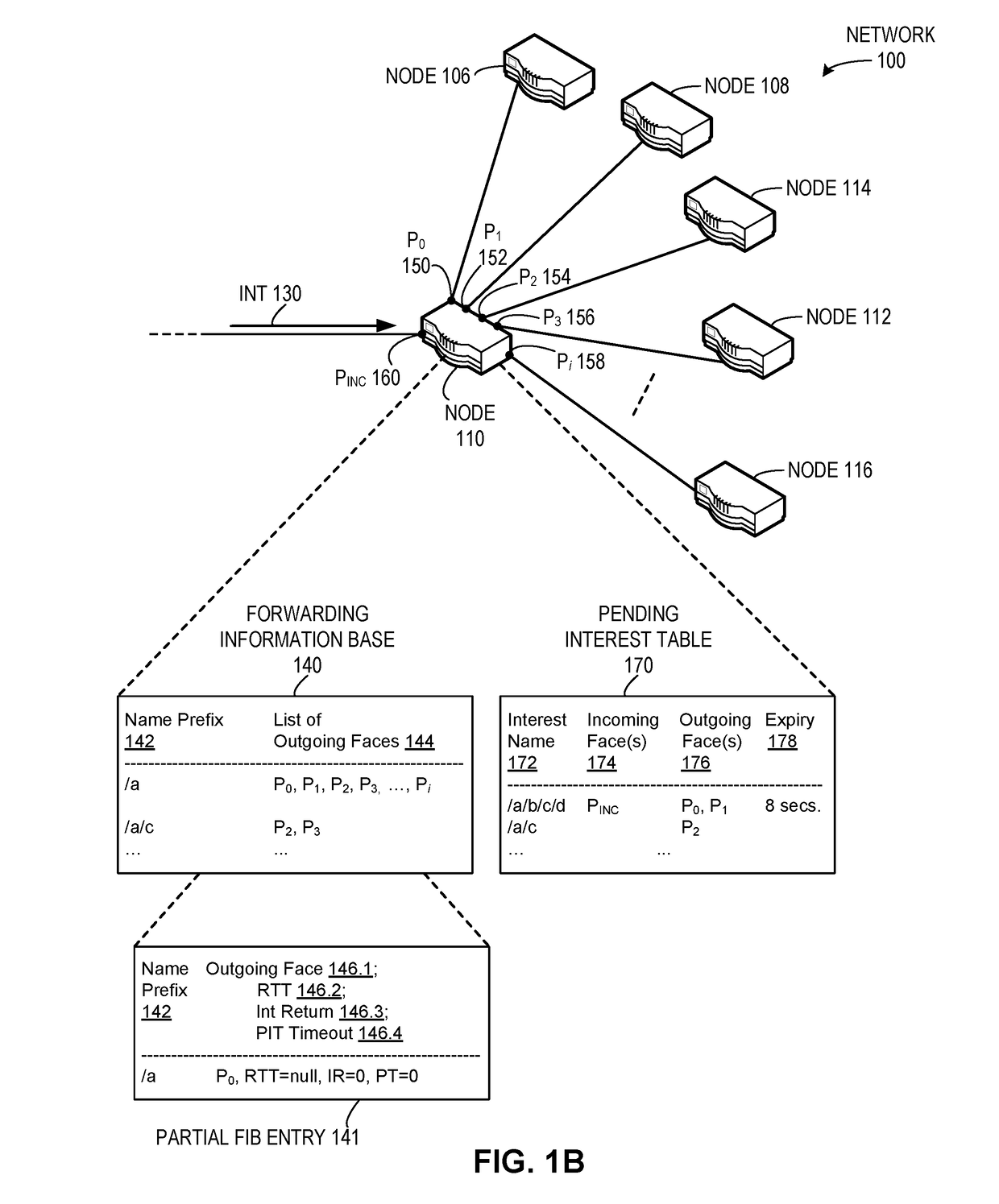
System for forwarding a packet with a hierarchically structured variable-length identifier
ActiveUS8160069B2Data switching by path configurationStructure of Management InformationLongest prefix match
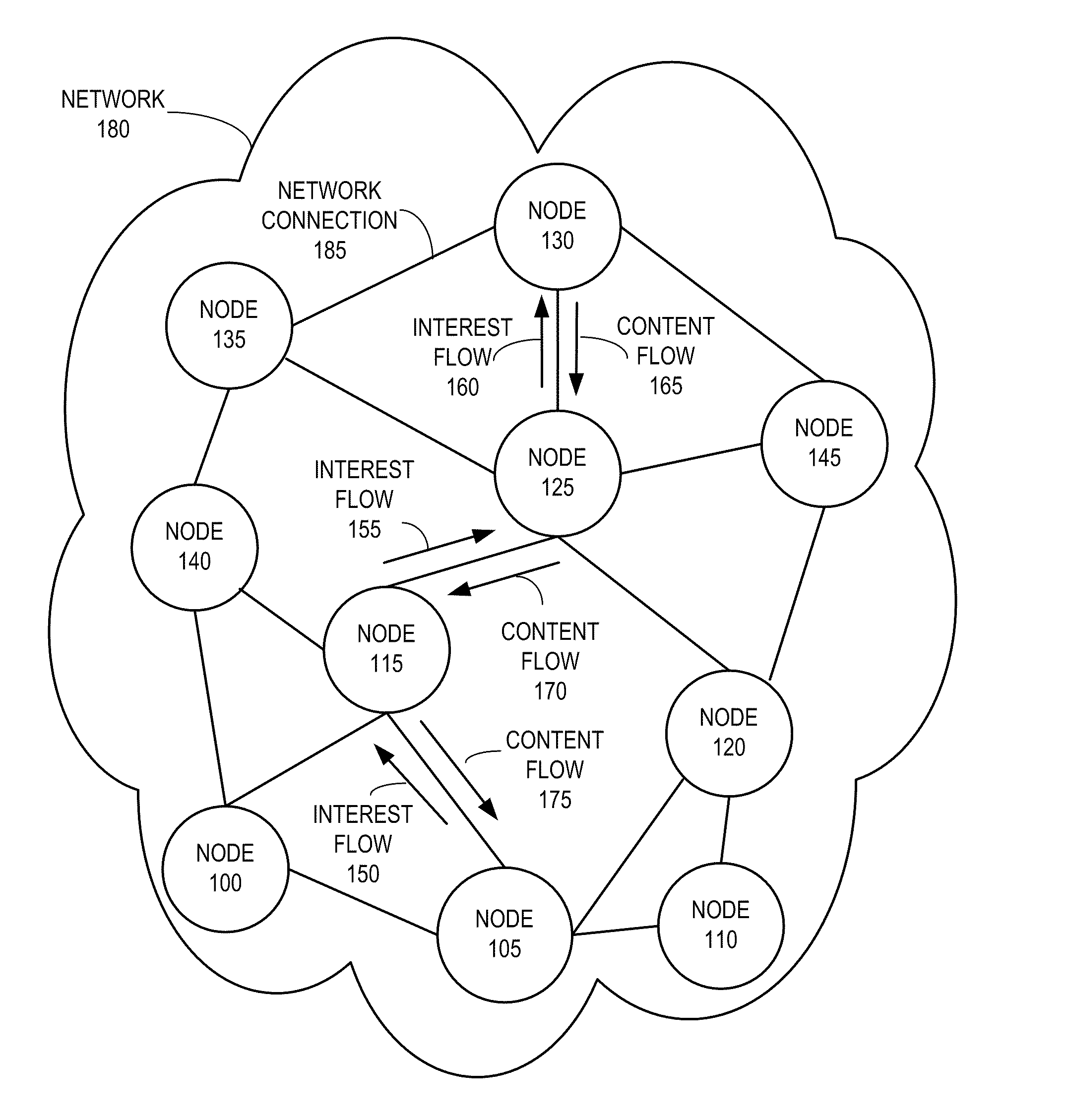
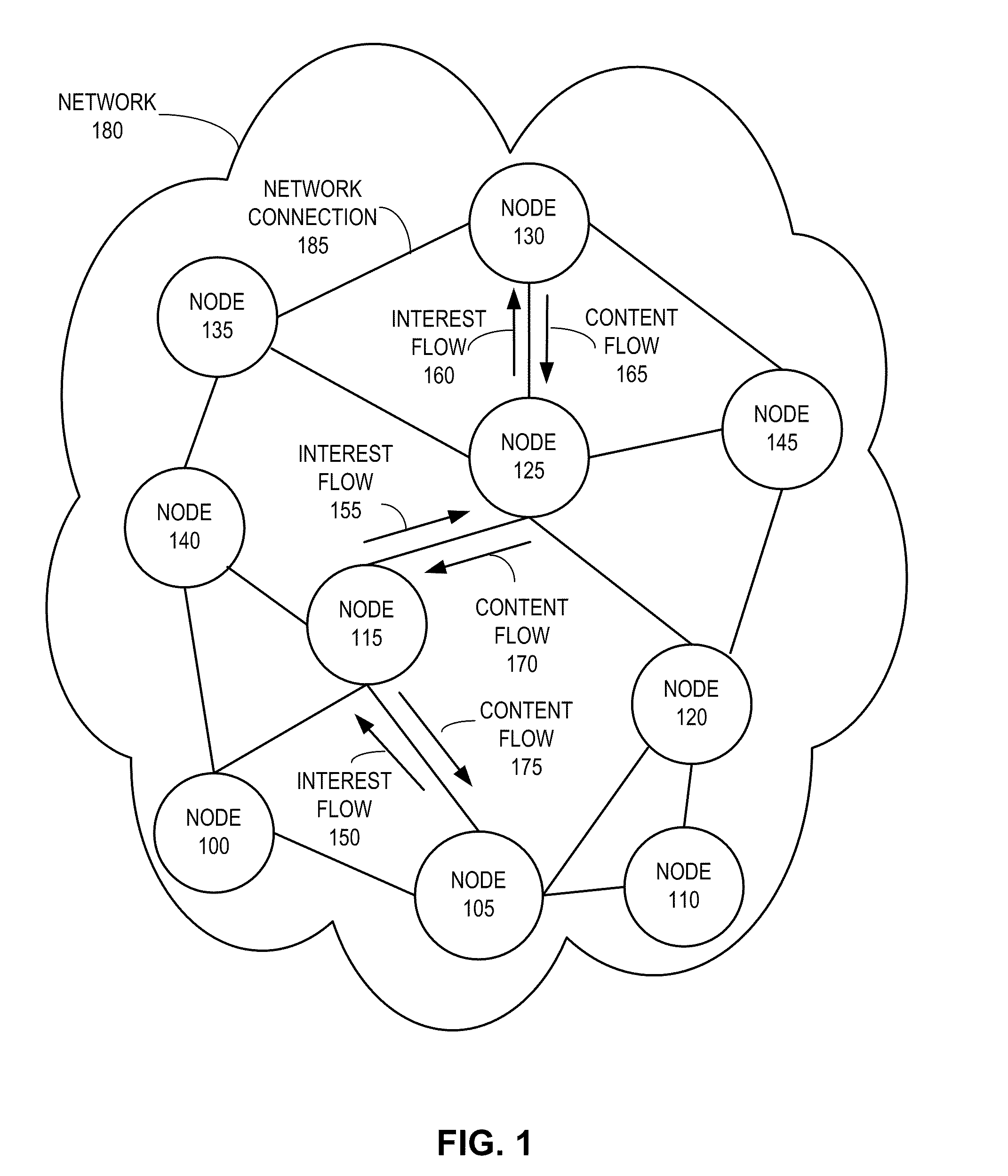
One embodiment provides a system that receives a packet with a hierarchically structured variable-length identifier (HSVLI). An HSVLI indicates a piece or collection of content and may be hierarchically structured, comprising contiguous components ordered from a most general level to a most specific level. The length of a respective identifier is not fixed. During operation, the system converts the HSVLI into a fixed-length key. Subsequently, the system obtains forwarding information based on one or more longest-prefix matches with a longest-prefix-match lookup engine using the fixed-length key. Next, the system forwards the packet to an output port based on the forwarding information.
Owner:CISCO TECH INC
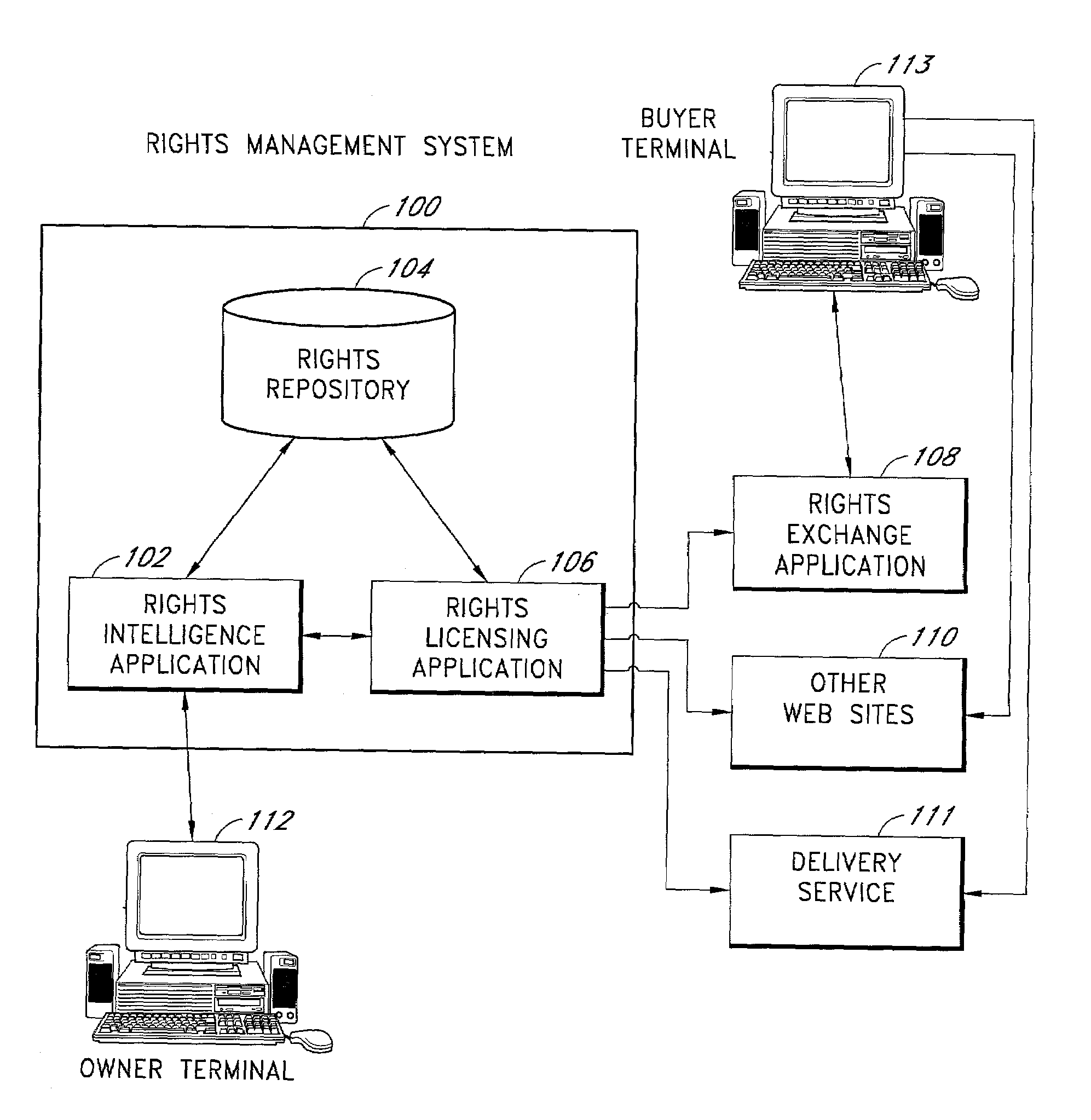
Apparatus and methods for intellectual property database navigation
InactiveUS7092953B1Fast and efficient techniqueData processing applicationsProgram/content distribution protectionIntellectual propertyRights management
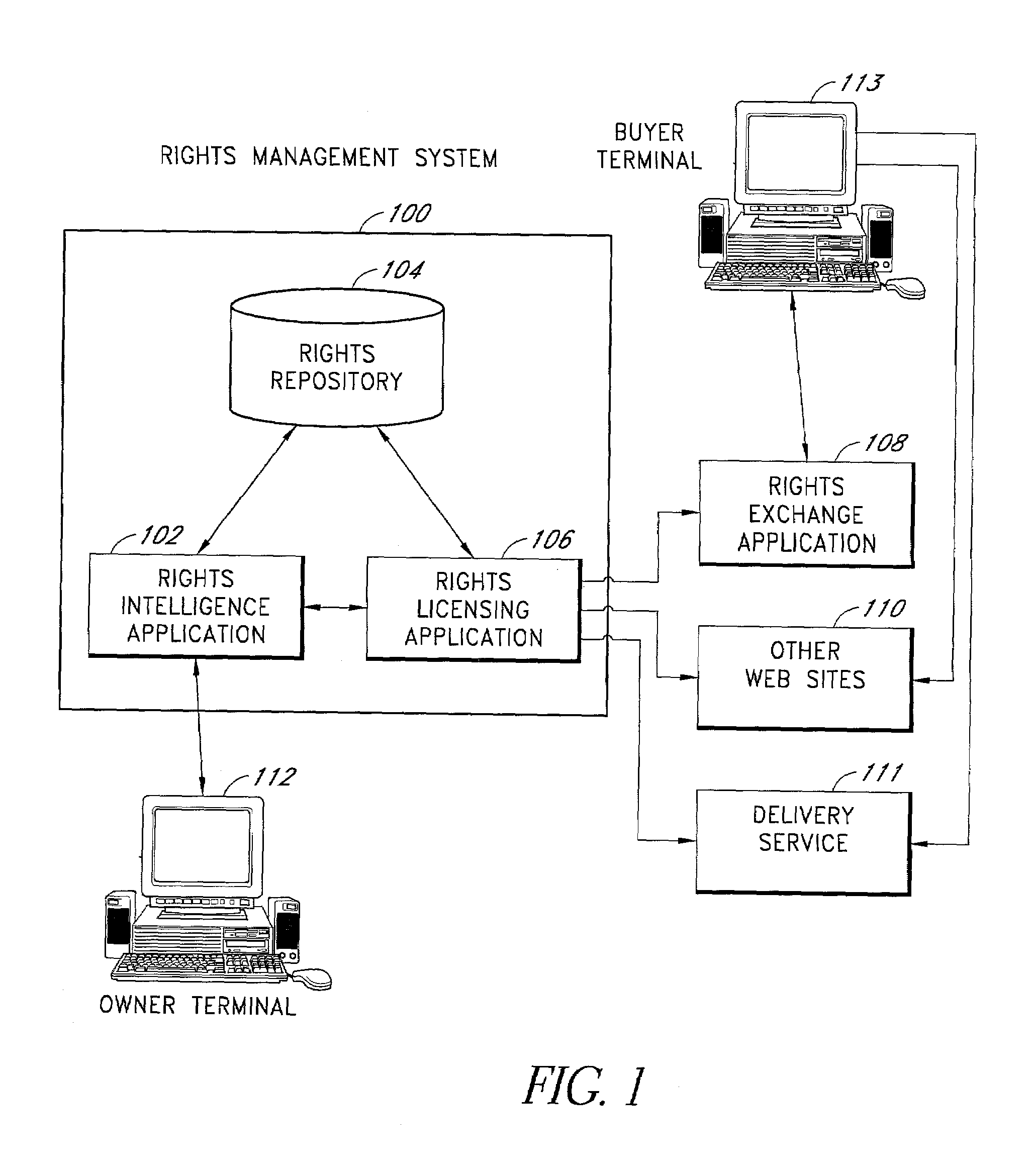
The present invention advantageously provides a rights management system. In one embodiment, a specification of a general level of rights owned by a first intellectual property rights owner is received. A query is received for a lower level right that is a descendent of at least one of the general level of rights. The system determines if the lower level rights is available for licensing by forming at least a first implicit relationship between the general level of rights owned, and a general level of rights licensed out.
Owner:RIGHTSLINE +1
Adaptive multi-interface use for content networking
InactiveUS20110090908A1Web data retrievalData switching by path configurationVariable lengthDistributed computing
One embodiment provides a system that forwards a packet with a hierarchically structured variable-length identifier (HSVLI) in a network. An HSVLI indicates a piece of content and indicates a hierarchical structure of contiguous components ordered from a most general level to a most specific level. The length of the HSVLI is not fixed. During operation, the system receives a packet which contains an interest for a piece of content with an HSVLI. Subsequently, the system determines forwarding information for the HSVLI based on one or more of: knowledge of content which matches the HSVLI, a forwarding policy, and contextual information about the network. Next, the system configures a forwarding engine with the forwarding information. The system then forwards the packet based on the forwarding information.
Owner:CISCO TECH INC
Adaptive multi-interface use for content networking
One embodiment provides a system that forwards a packet with a hierarchically structured variable-length identifier (HSVLI) in a network. An HSVLI indicates a piece of content and indicates a hierarchical structure of contiguous components ordered from a most general level to a most specific level. The length of the HSVLI is not fixed. During operation, the system receives a packet which contains an interest for a piece of content with an HSVLI. Subsequently, the system determines forwarding information for the HSVLI based on one or more of: knowledge of content which matches the HSVLI, a forwarding policy, and contextual information about the network. Next, the system configures a forwarding engine with the forwarding information. The system then forwards the packet based on the forwarding information.
Owner:CISCO TECH INC
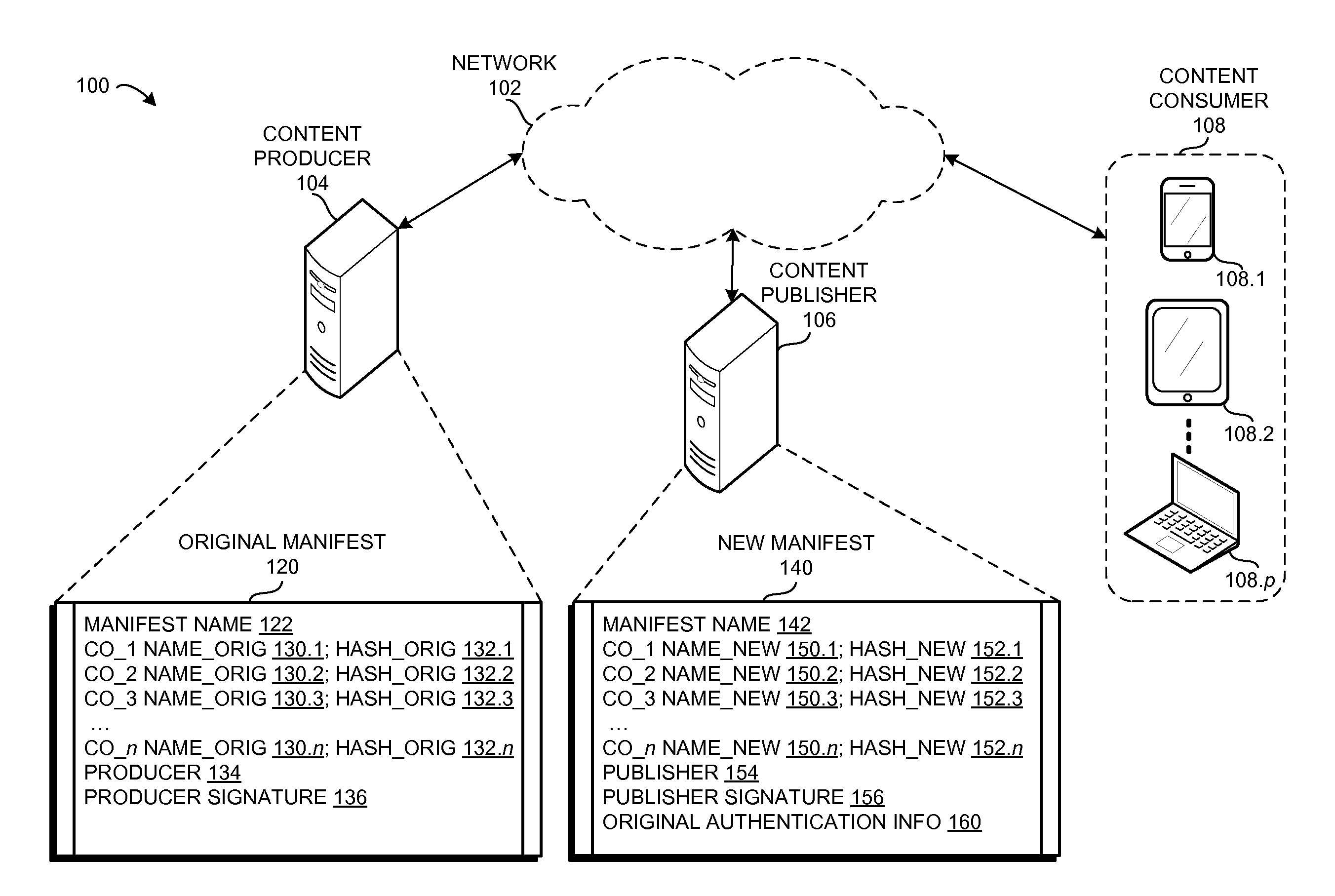
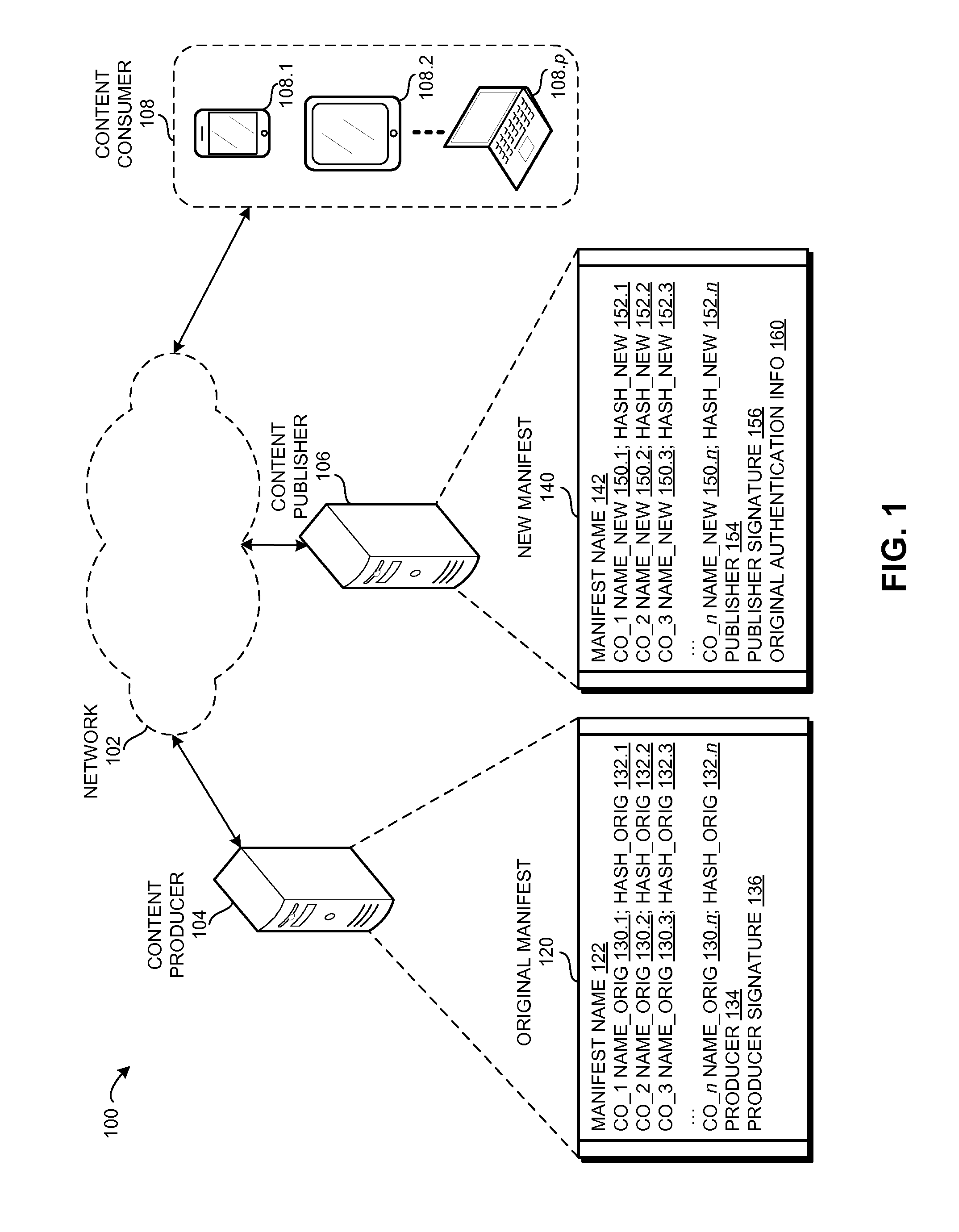
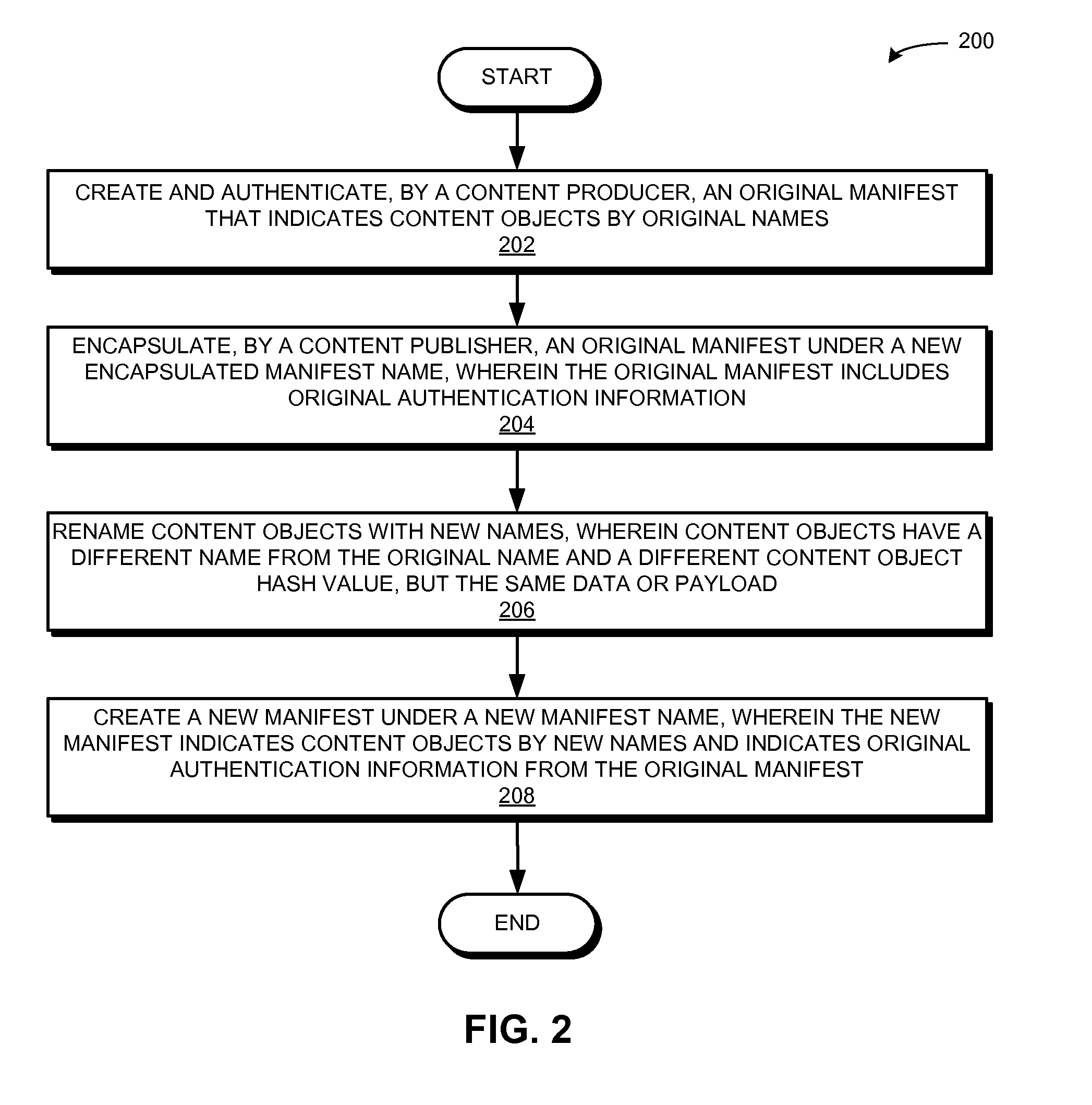
Method and system for verifying renamed content using manifests in a content centric network
ActiveUS20160171184A1Promote redistributionDigital data processing detailsUnauthorized memory use protectionInternet privacyContent centric
One embodiment provides a system that facilitates redistribution of content objects with a different name without requiring re-computation of the original authentication information. During operation, the system determines, by a content producing device, an original manifest which indicates at least an original name associated with a content object, wherein the name is a hierarchically structured variable length identifier (HSVLI) which comprises contiguous name components ordered from a most general level to a most specific level. The system renames the content object with a new name. The system also creates a new manifest which indicates the new name, wherein the new manifest includes original authentication information associated with the original manifest.
Owner:CISCO TECH INC
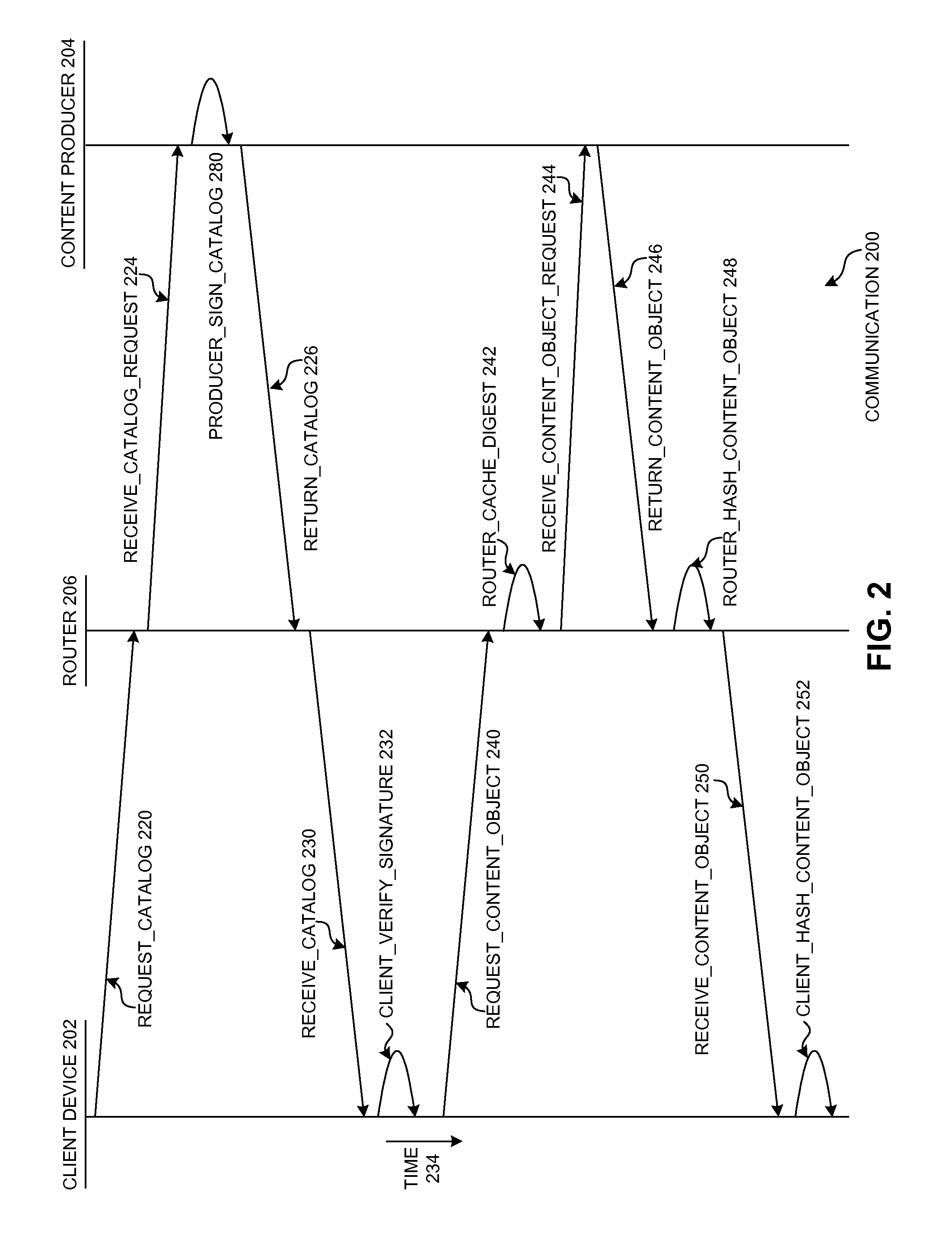
Aggregate signing of data in content centric networking
ActiveUS20150280918A1Facilitates routers in verifying content objectsData processing applicationsPublic key for secure communicationIndication of interestDigital signature
One embodiment provides a system that facilitates routers in verifying content objects in a cost-effective manner by aggregating content objects into a secure content catalog. During operation, a client computing device receives a secure content catalog, which indicates a set of content objects and their corresponding digests. The catalog is digitally signed with the private key of a producer of the catalog. The client computing device constructs an interest for a content object, where the interest indicates a name for the content object and the corresponding digest for the content object, which is based on the secure content catalog. The name for the request content object is a hierarchically structured variable length identifier (HSVLI) which comprises name components ordered from a most general level to a most specific level.
Owner:CISCO TECH INC
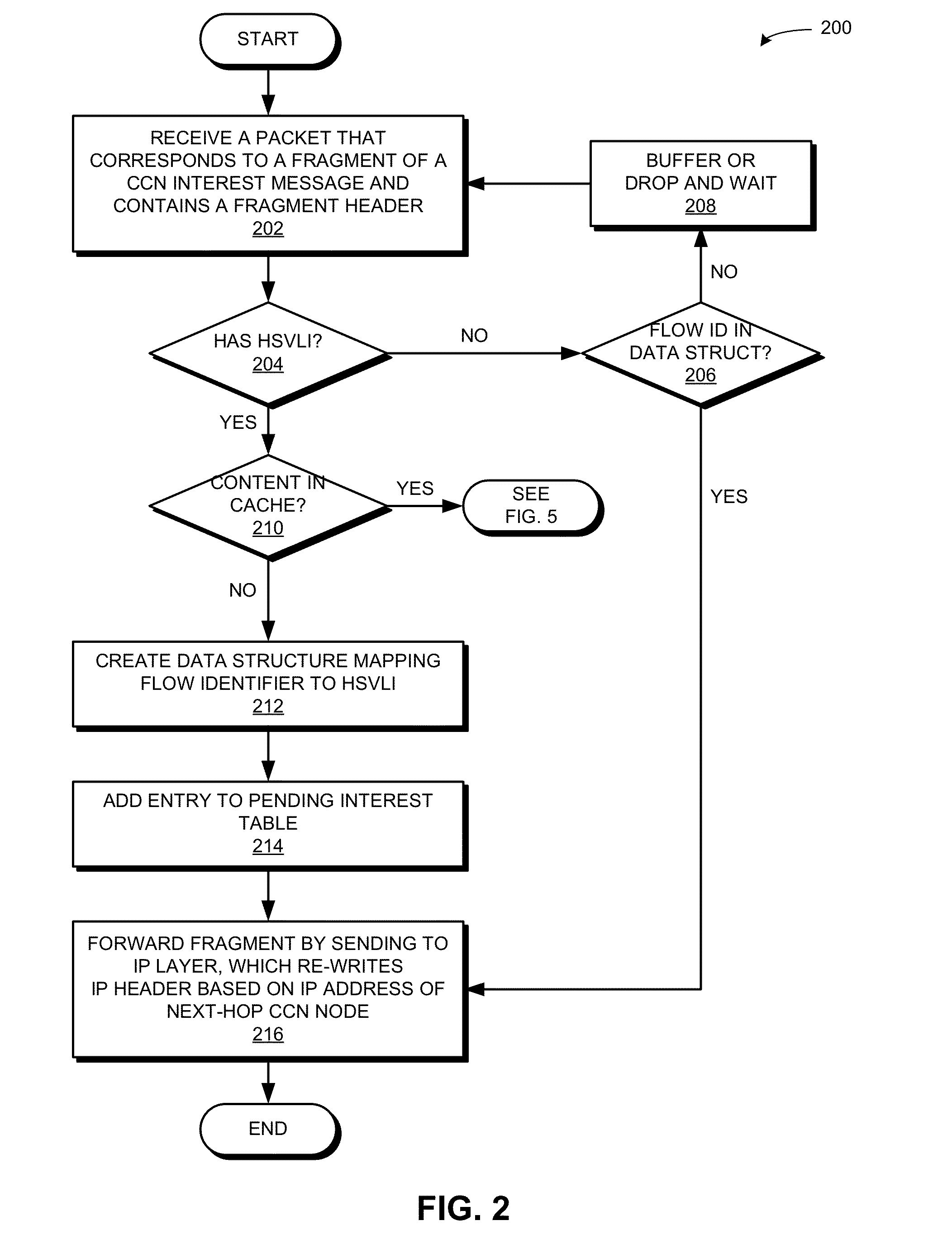
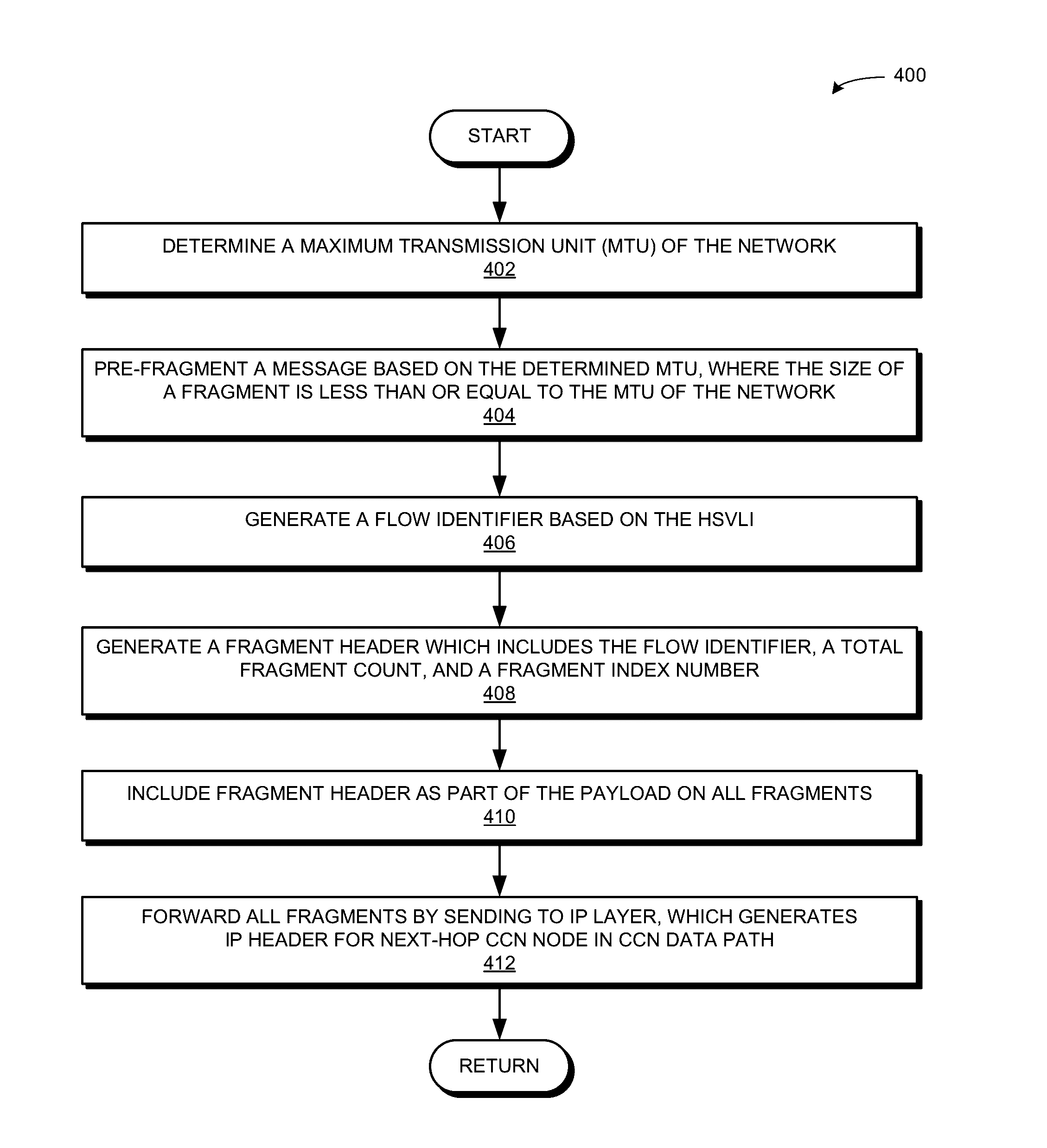
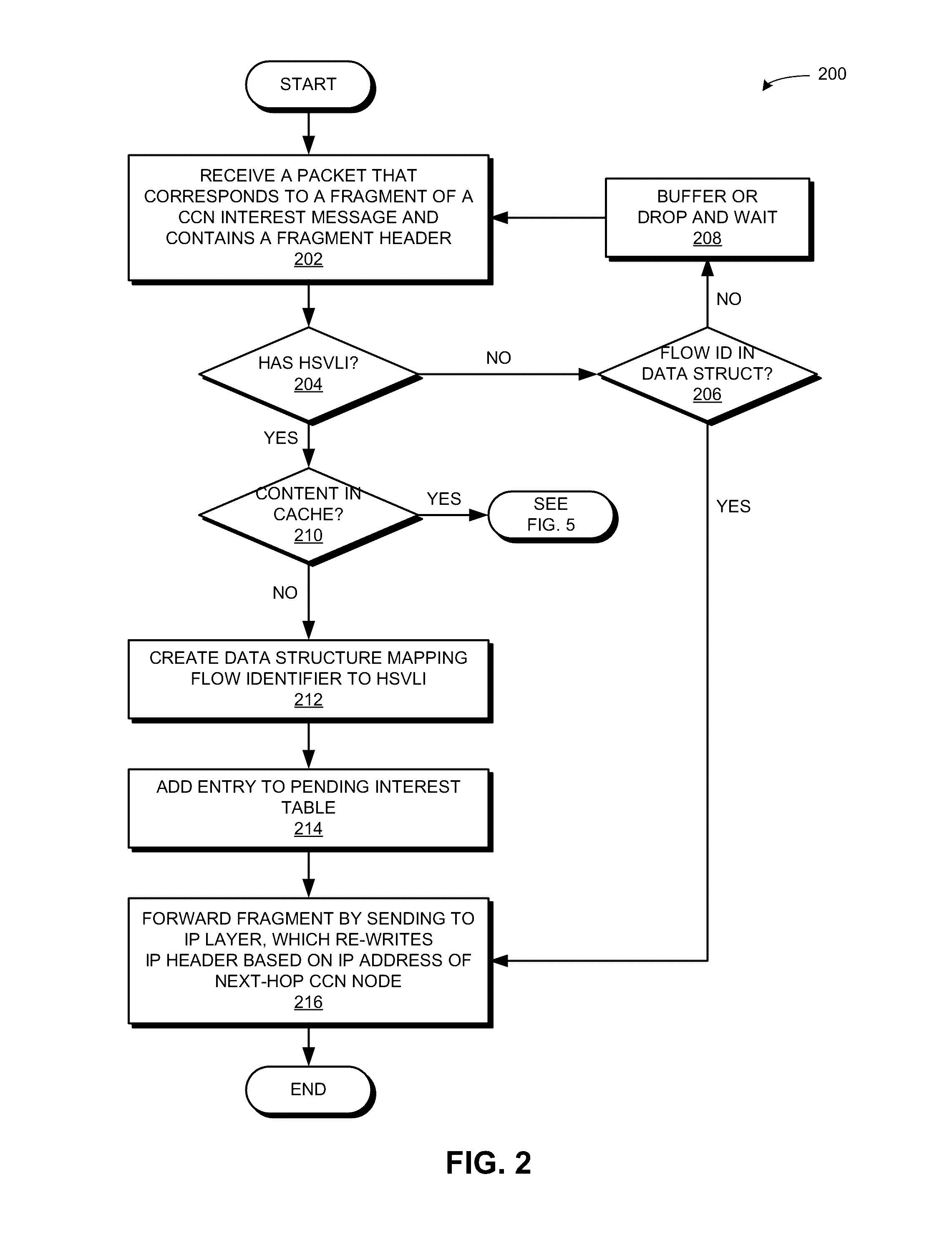
CUT-THROUGH FORWARDING OF CCNx MESSAGE FRAGMENTS WITH IP ENCAPSULATION
ActiveUS20150373162A1Facilitates cut-through forwardingFacilitating cut-through forwardingData switching by path configurationVariable lengthDistributed computing
One embodiment provides a system that facilitates cut-through forwarding of message fragments over a network. During operation, the system receives a packet that corresponds to a fragment of a message and contains a fragment header. The system stores in a data structure a mapping relationship between the fragment header and a hierarchically structured variable-length identifier (HSVLI), wherein the HSVLI comprises contiguous name components ordered from a most general level to a most specific level. The system makes a forwarding decision for the packet based on the fragment header prior to receiving all fragment packets associated with the message, thereby facilitating cut-through forwarding of the message fragments over a network.
Owner:CISCO TECH INC
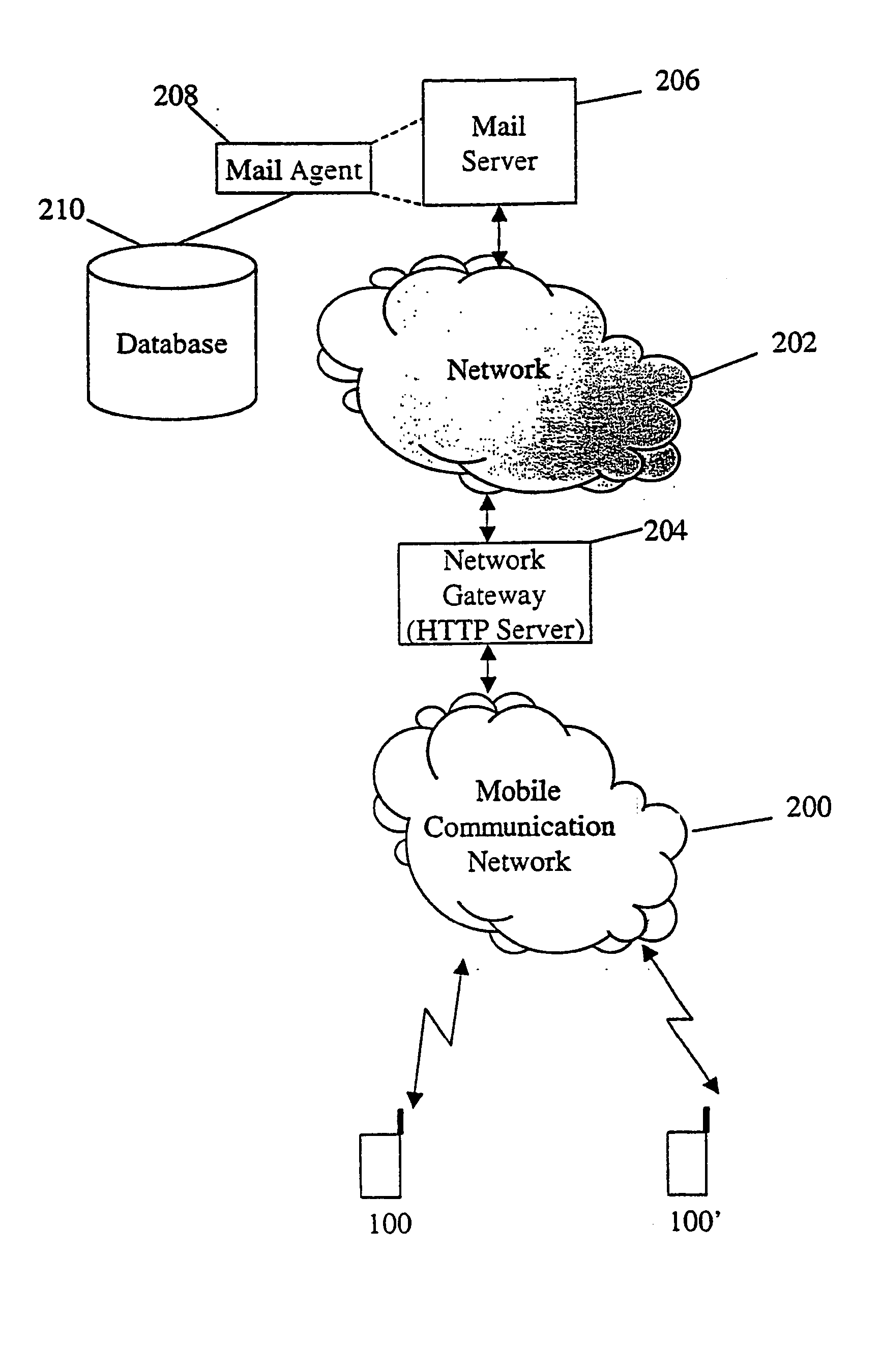
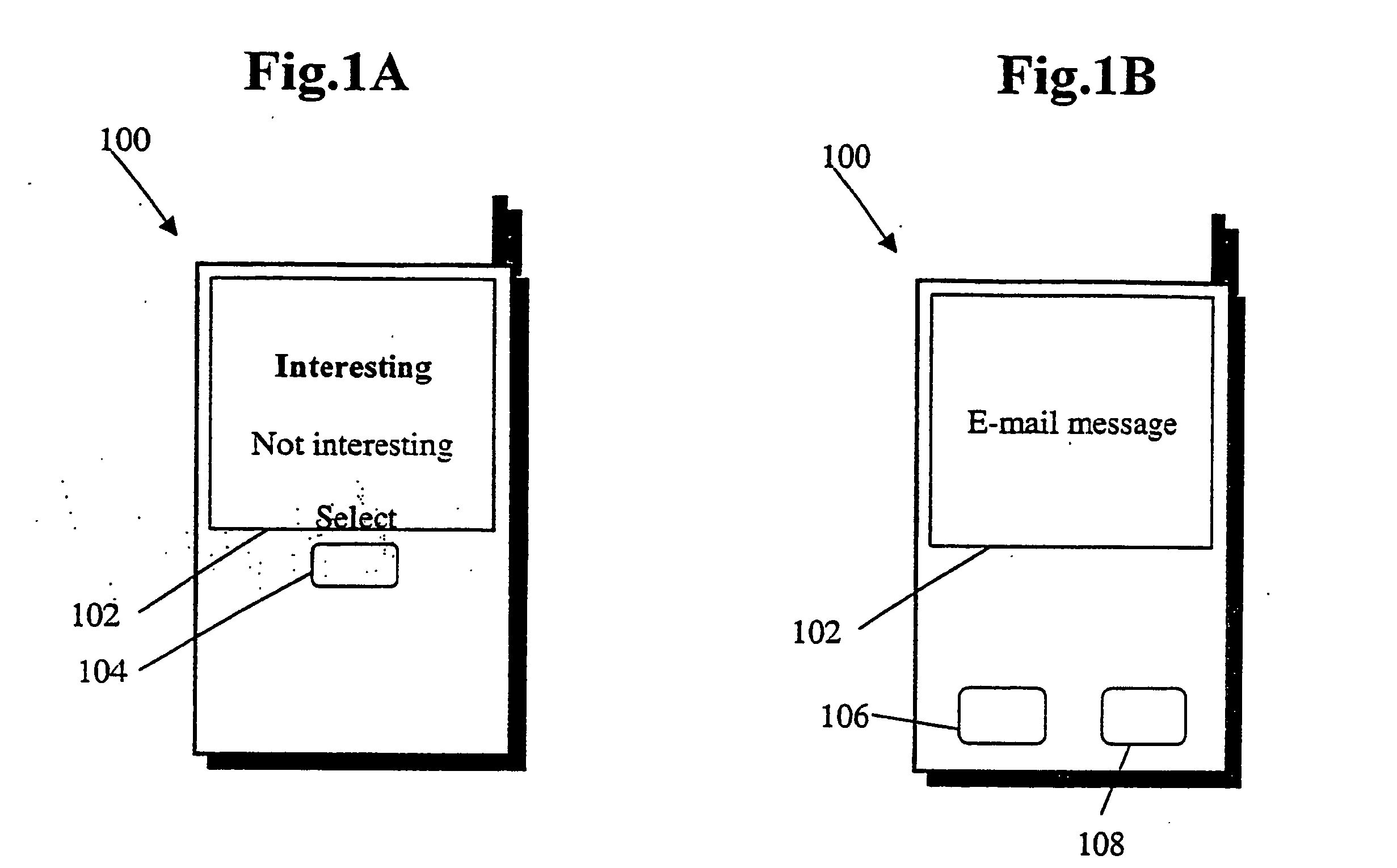
Method and arrangement for obtaining an electronic mail service
ActiveUS20060017983A1Reduce the burden onImprove fitNatural language data processingMessaging/mailboxes/announcementsStatistical analysisMobile context
The a user interface (UI) residing in a mobile environment, which has a possibility of indicating after reading each message whether or not the message is divergent from the normal / general level as to the importance of the message. Advantageously, the user does not need to do the indication every time when reading the mail. In the interface, after a given mail has been read (or a part of the given mail has been read), there occurs a possibility to choose between two alternatives: interesting or non-interesting. Advantageously, there is not required other extra work from the user. Gradually, a mail agent collects information about what kind of mail the user prefers and does not prefer. The result will be a prearranged list by preference in the incoming mail. Any mail similar to the ones previously indicated as important will appear first to the user. The applied algorithm in the methods and systems is based on statistical analysis of the linguistic contents of the mail.
Owner:NOKIA TECHNOLOGLES OY
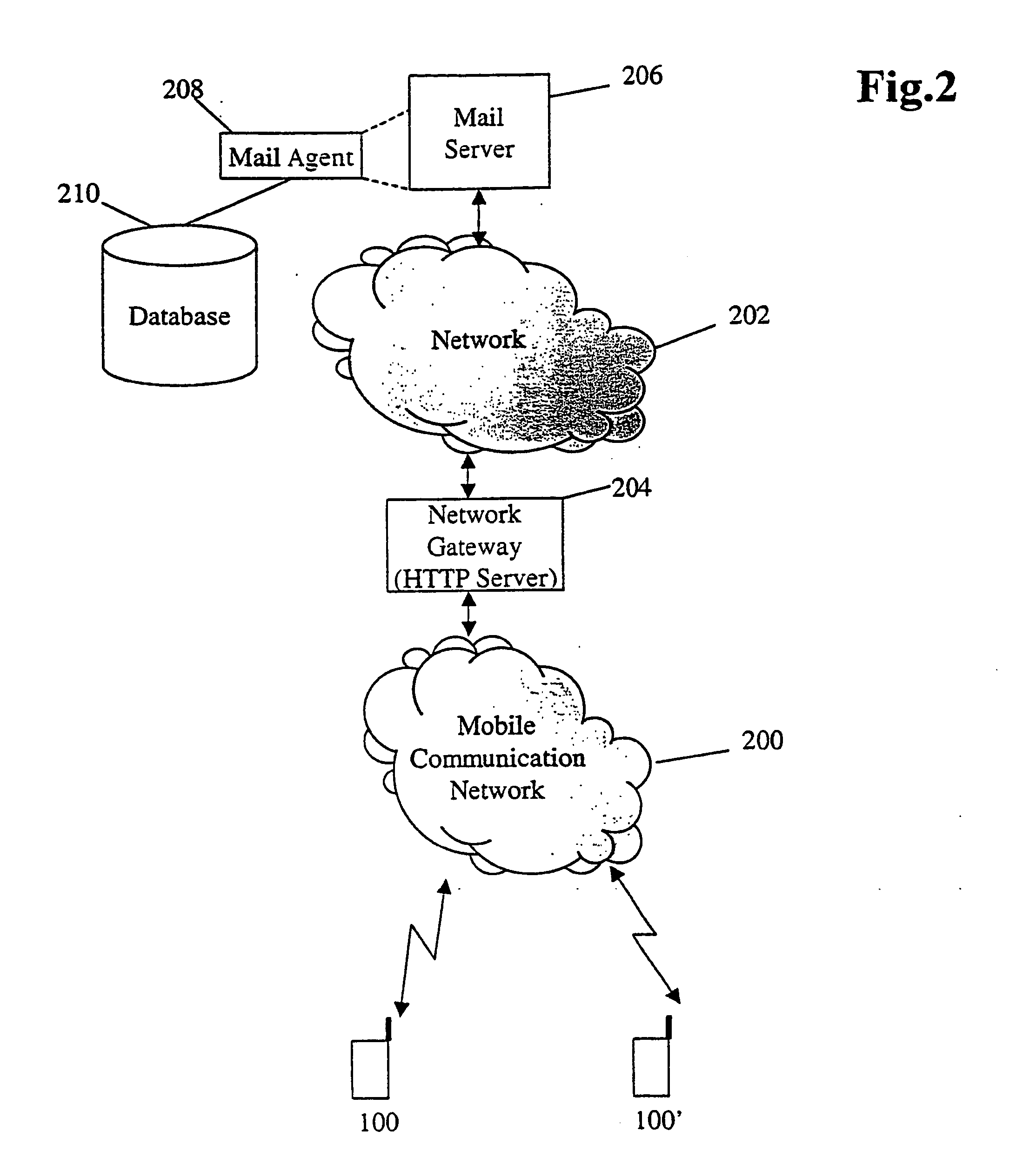
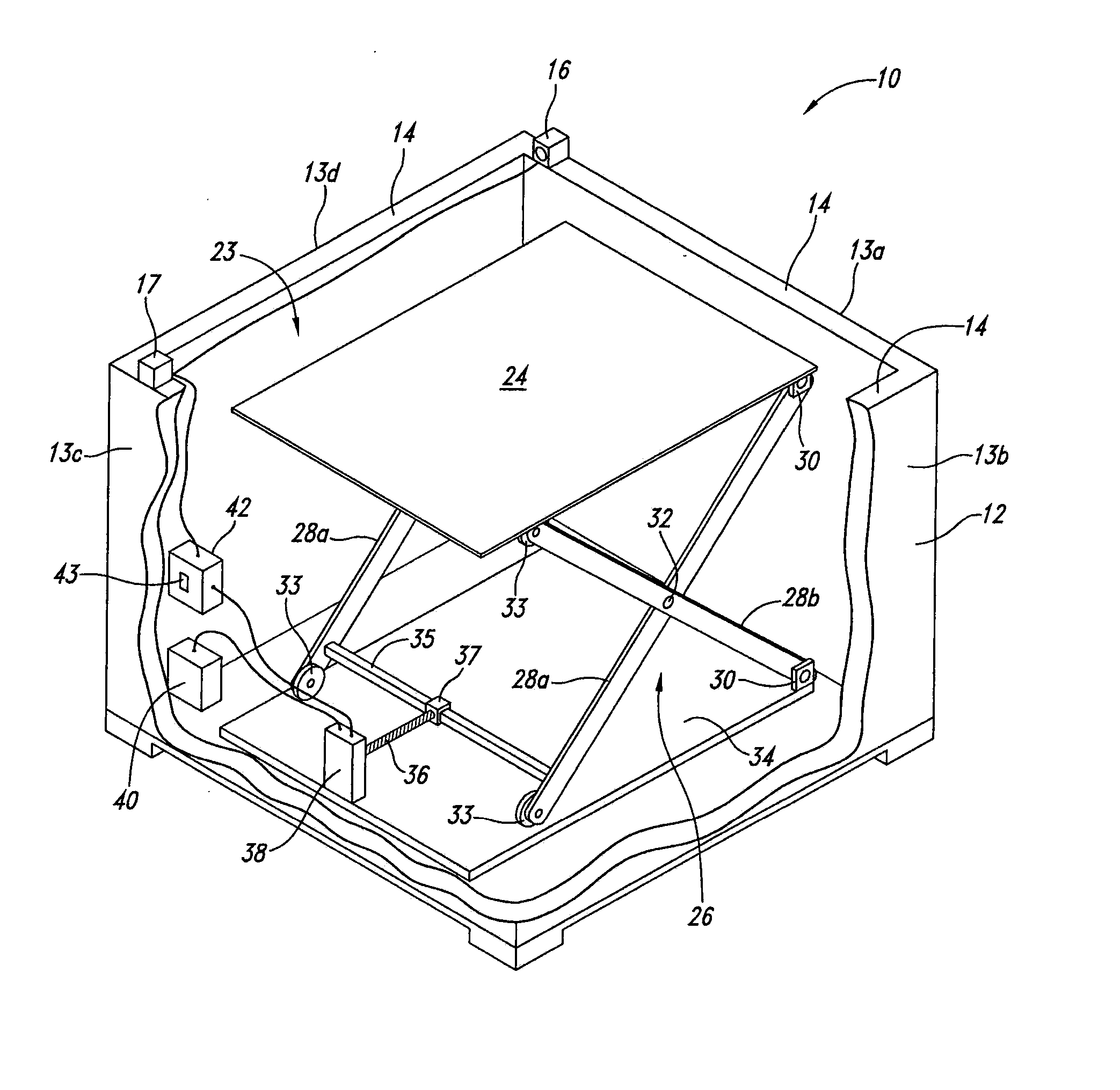
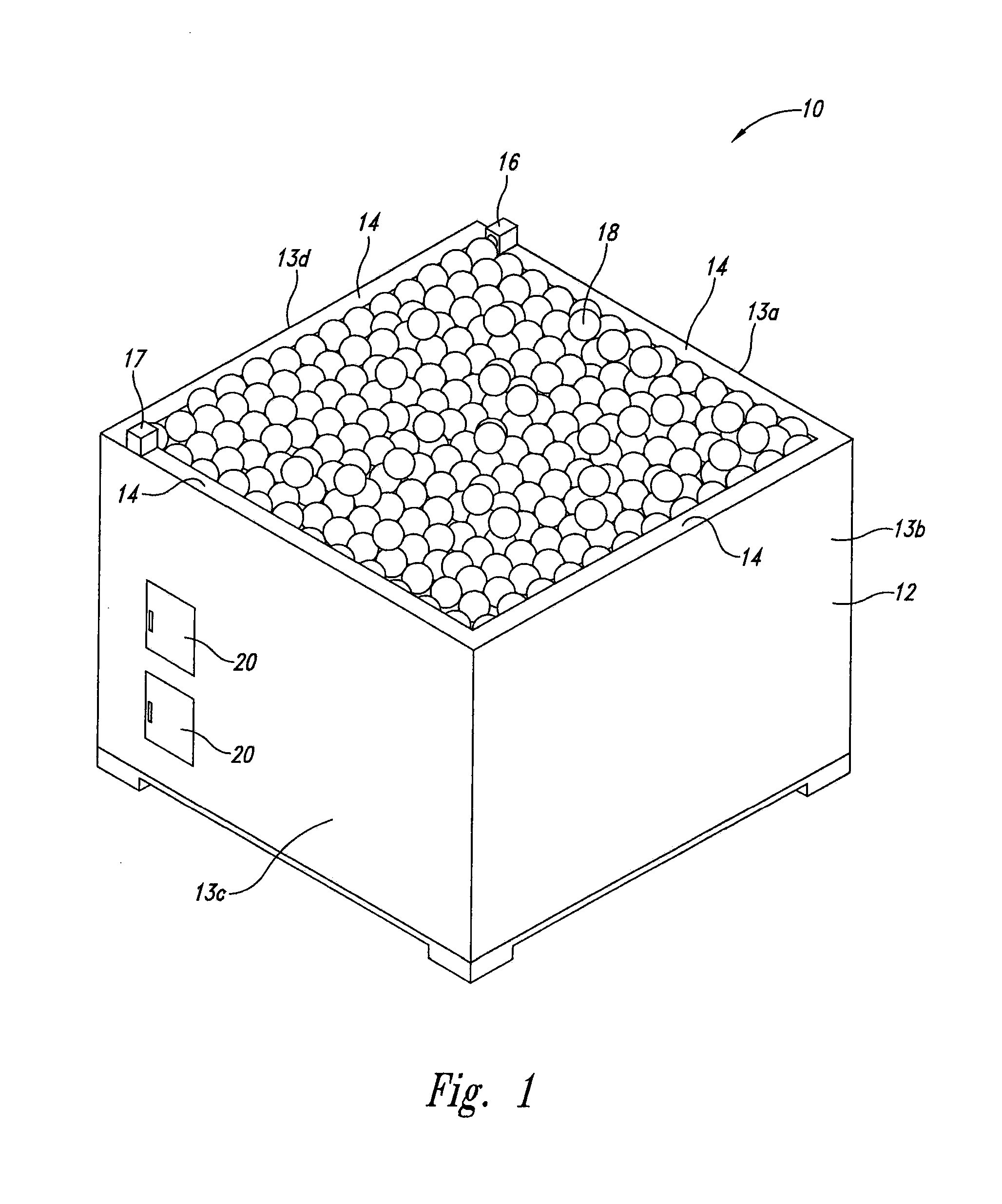
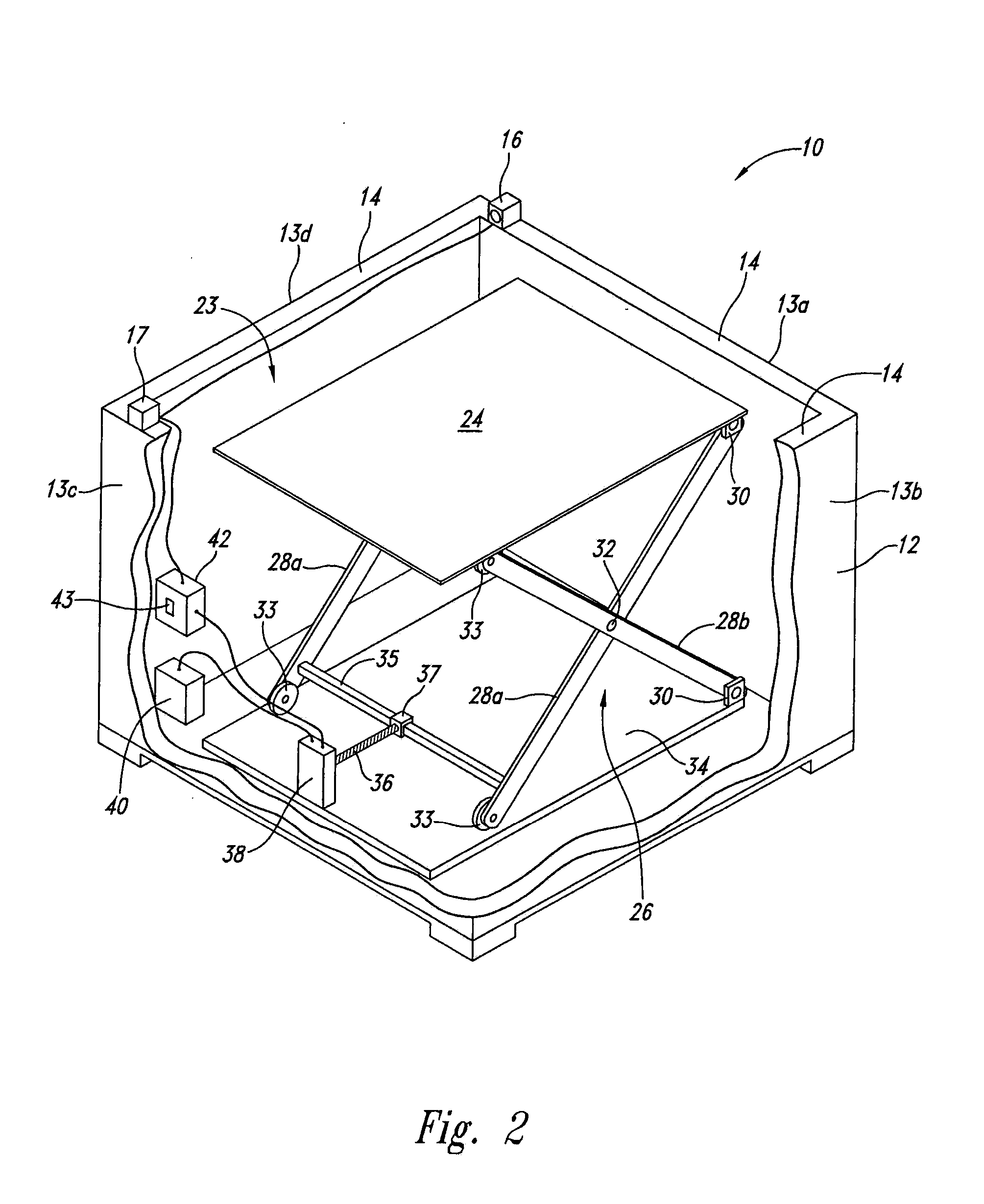
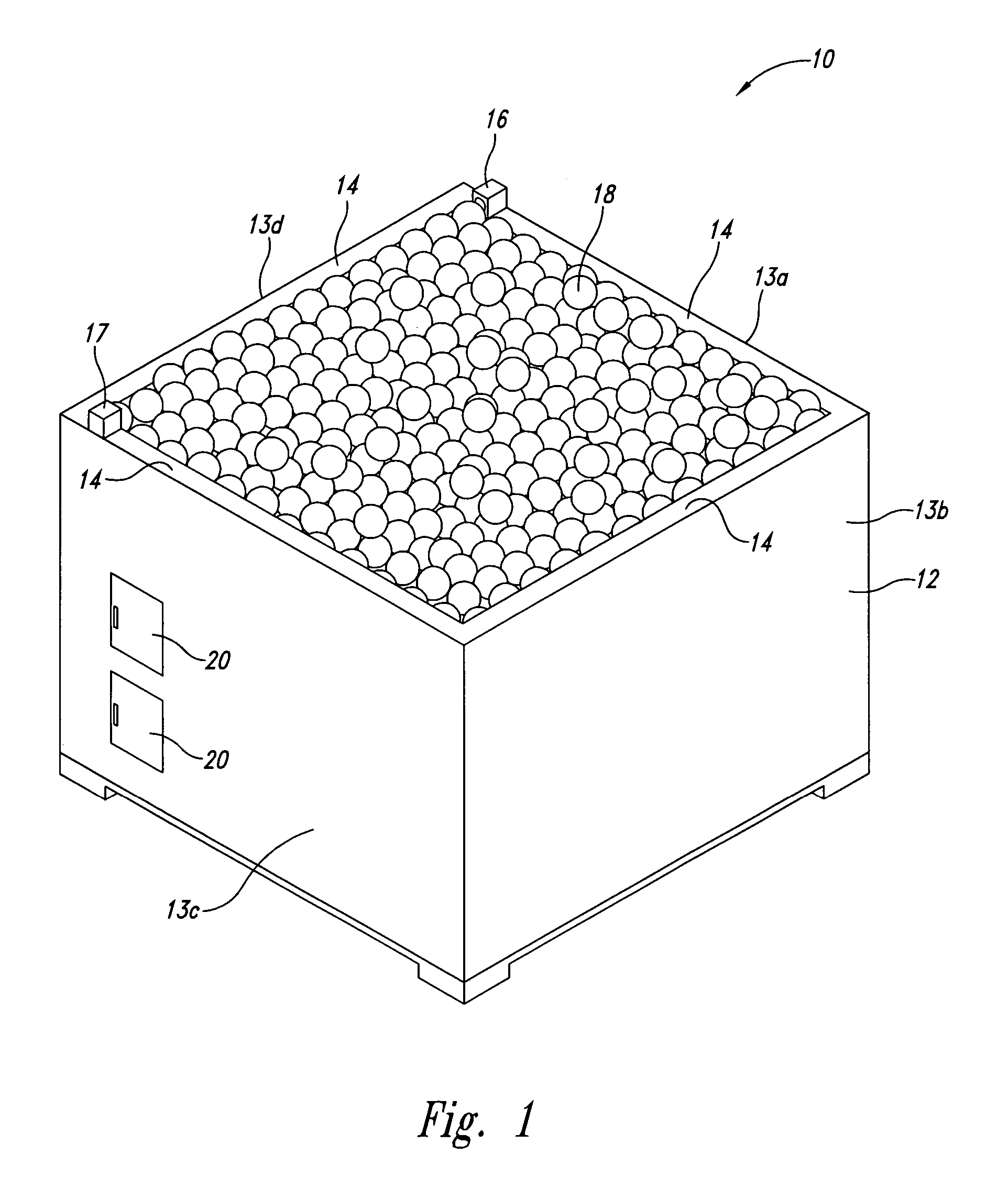
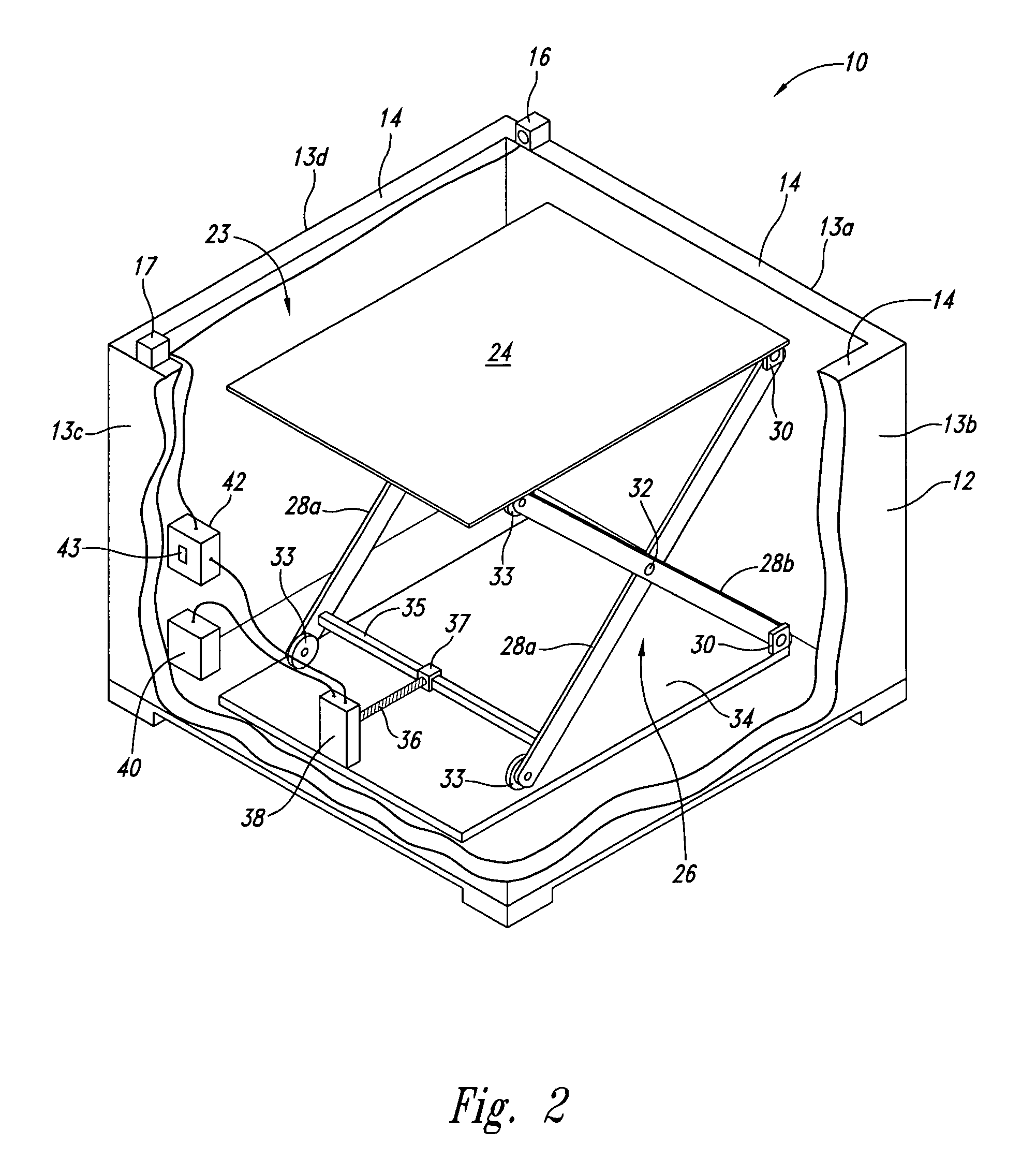
Self-adjusting goods display system and method
A self-adjusting goods display system maintains a proper shelf level for a display bin containing goods. An implementation has an open bin with side walls having top edges and a moveable shelf to receive a pile of goods. A light source and a light receiver are positioned on the top edges of opposing walls of the bin, and the light source generates light to be received by the light receiver. When the pile of goods is reduced so that the pile no longer obstructs the light from being received by the light receiver a signal indicates a need to raise the general level of the remaining pile contained in the bin. A controller receives the signal and controls operation of a motor to raise the height of the shelf until the remaining pile of the shelf again blocks the light, or the shelf is at a position of maximum height.
Owner:PACIFIC BIN CORP
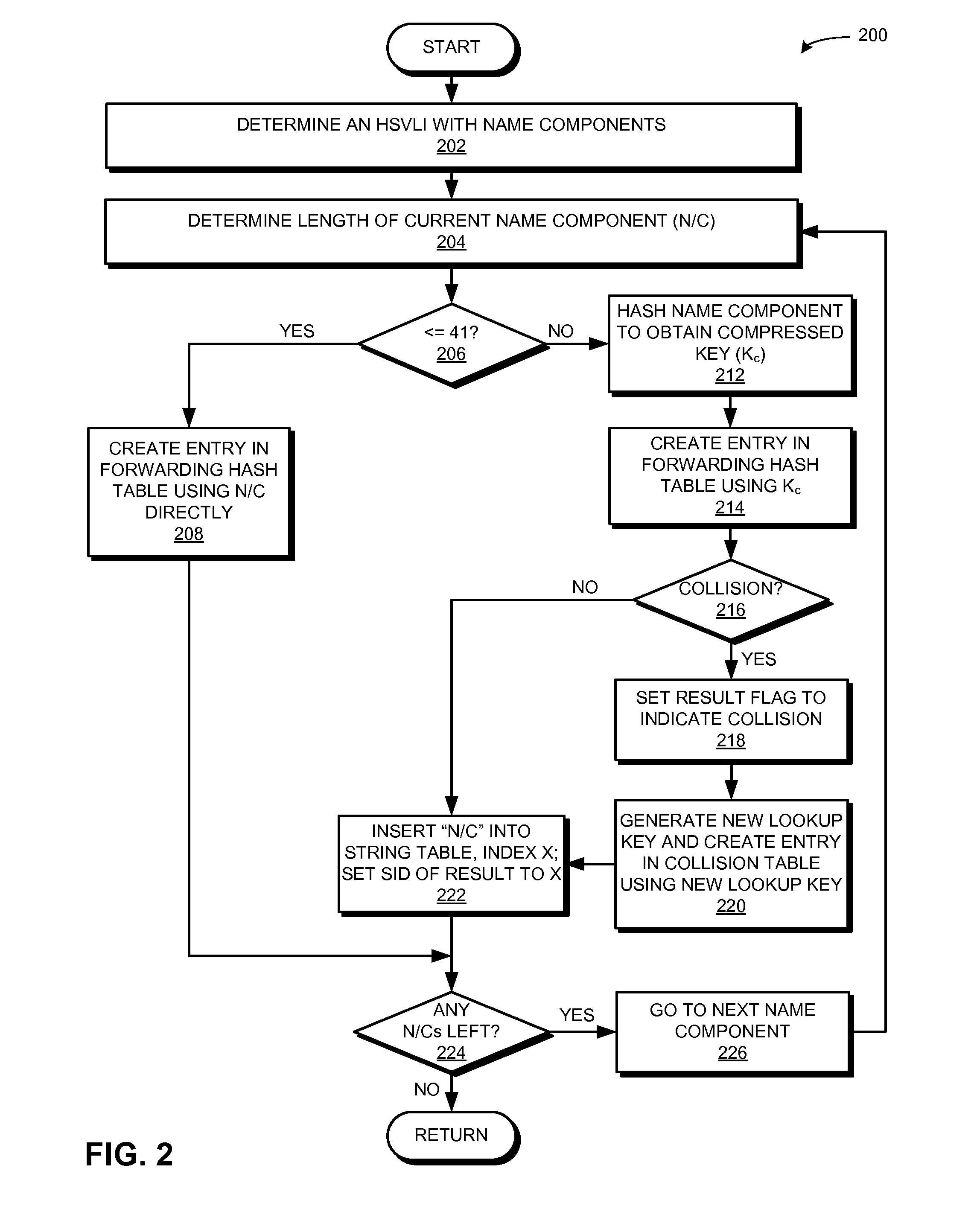
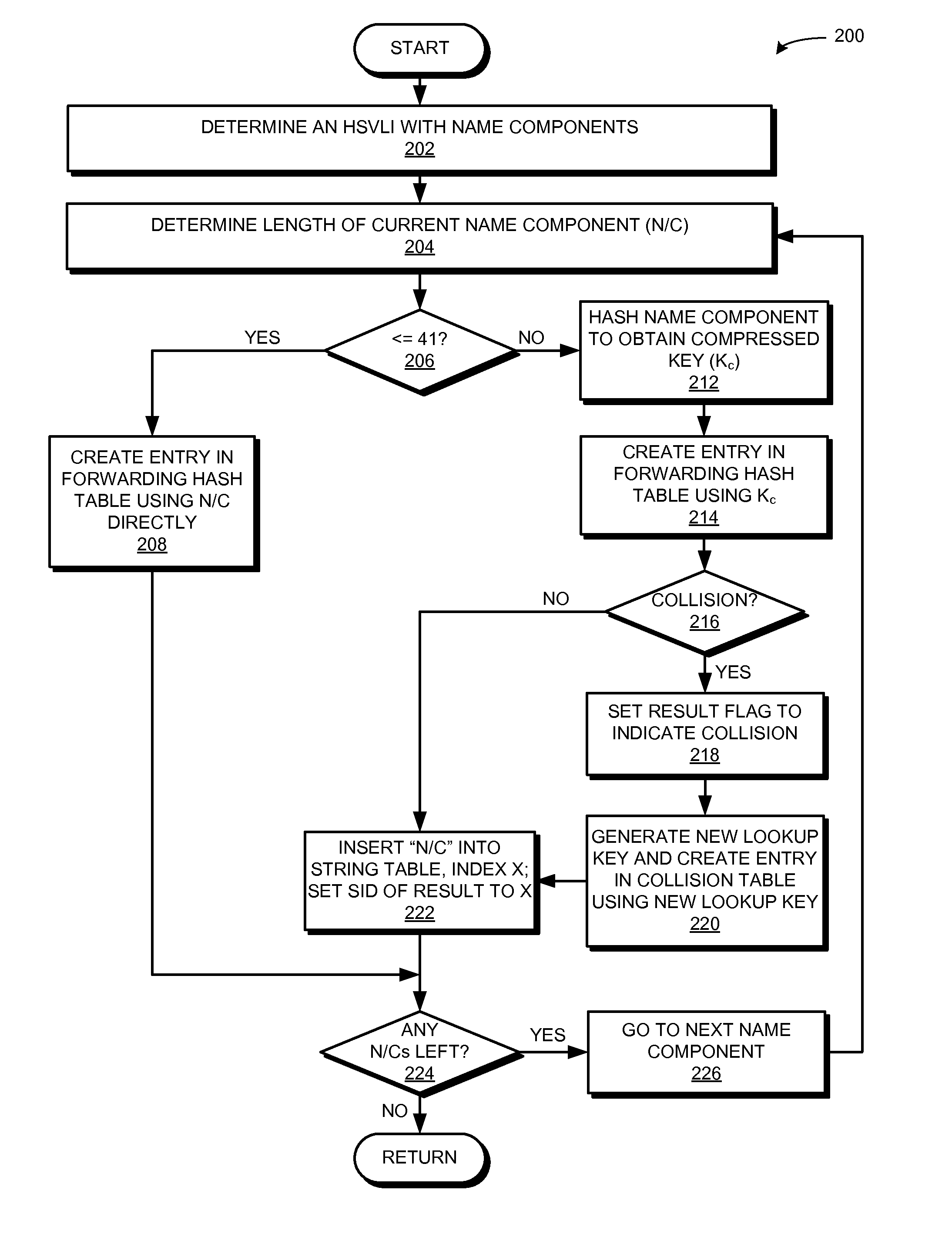
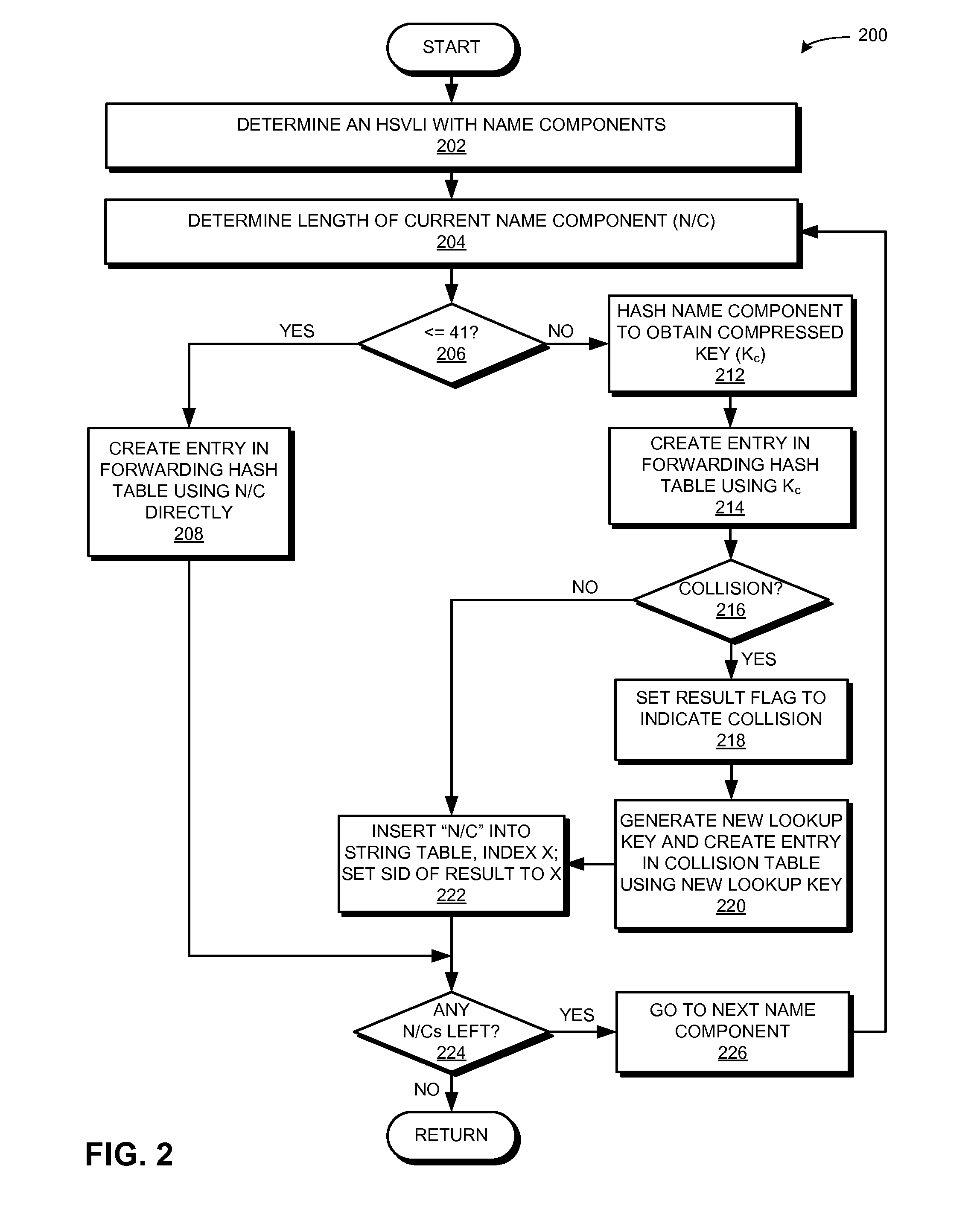
Ccn routing using hardware-assisted hash tables
ActiveUS20160173445A1Good for forwardingData switching by path configurationLongest prefix matchVariable length
One embodiment provides a system that facilitates forwarding of packets with variable length names. During operation, the system receives a packet with a hierarchically structured variable length identifier (HSVLI) which comprises contiguous name components ordered from a most general level to a most specific level. The system performs a longest prefix match lookup by selecting an entry from a first data structure of entries. The entries indicate a name component, forwarding information for the name component, and a plurality of entry identifiers that chain an entry to another entry. If a size of the name component is less than or equal to a predetermined threshold, the system selects an entry based on the name component. If the size is greater, the system selects an entry based on a compressed key which can be a hash of the name component. The system also resolves collisions associated with the selected entry.
Owner:CISCO TECH INC
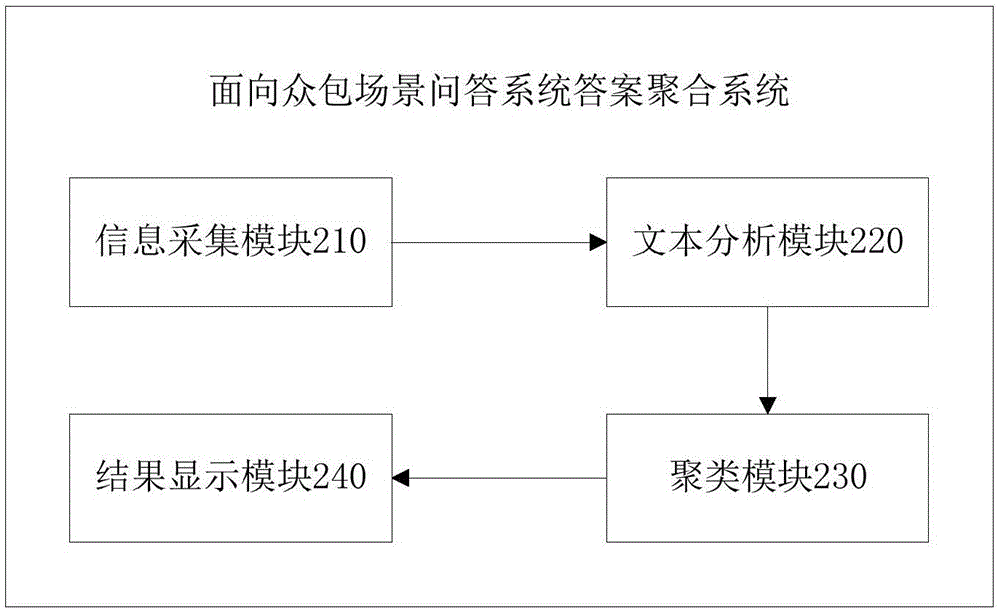
Answer aggregation method and system facing crowdsourcing scene question-answering system
InactiveCN106446287AReduce redundant timeEffective judgmentSpecial data processing applicationsText database clustering/classificationData scienceGeneral level
The invention discloses an answer aggregation method and system facing crowdsourcing scene question-answering system. The method comprises the steps of obtaining multiple reply texts with respect to a specified question, wherein each reply text comprises a pro vote and a con vote of other users; conducting text analysis of a theme and key words on each reply text, and further creating a vector set; clustering all vector sets, combining all similar replies into a sort, and calculating the pro votes and the con votes of each sort of similar replies; supplying a questioner with the replies with a preset number of replies in the each sort of similar replies and a calculation result corresponding to the pro votes and the con votes. The answer aggregation method and system facing crowdsourcing scene question-answering system has the advantages that by supplying the questioner with sorts of the answers and the calculation result of the pro votes and the con votes corresponding to the sorts of the answers, redundant time for the questioner to read a lot of answers with similar meanings is saved, a more general level of support of public opinion is presented for the questioner, and the users can be helped to make own judgment and determination more efficiently.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Coating on a Medical Substrate and a Coated Medical Product
InactiveUS20090012523A1Increase chanceGood coating performanceImpression capsVacuum evaporation coatingProduction rateOptical scanners
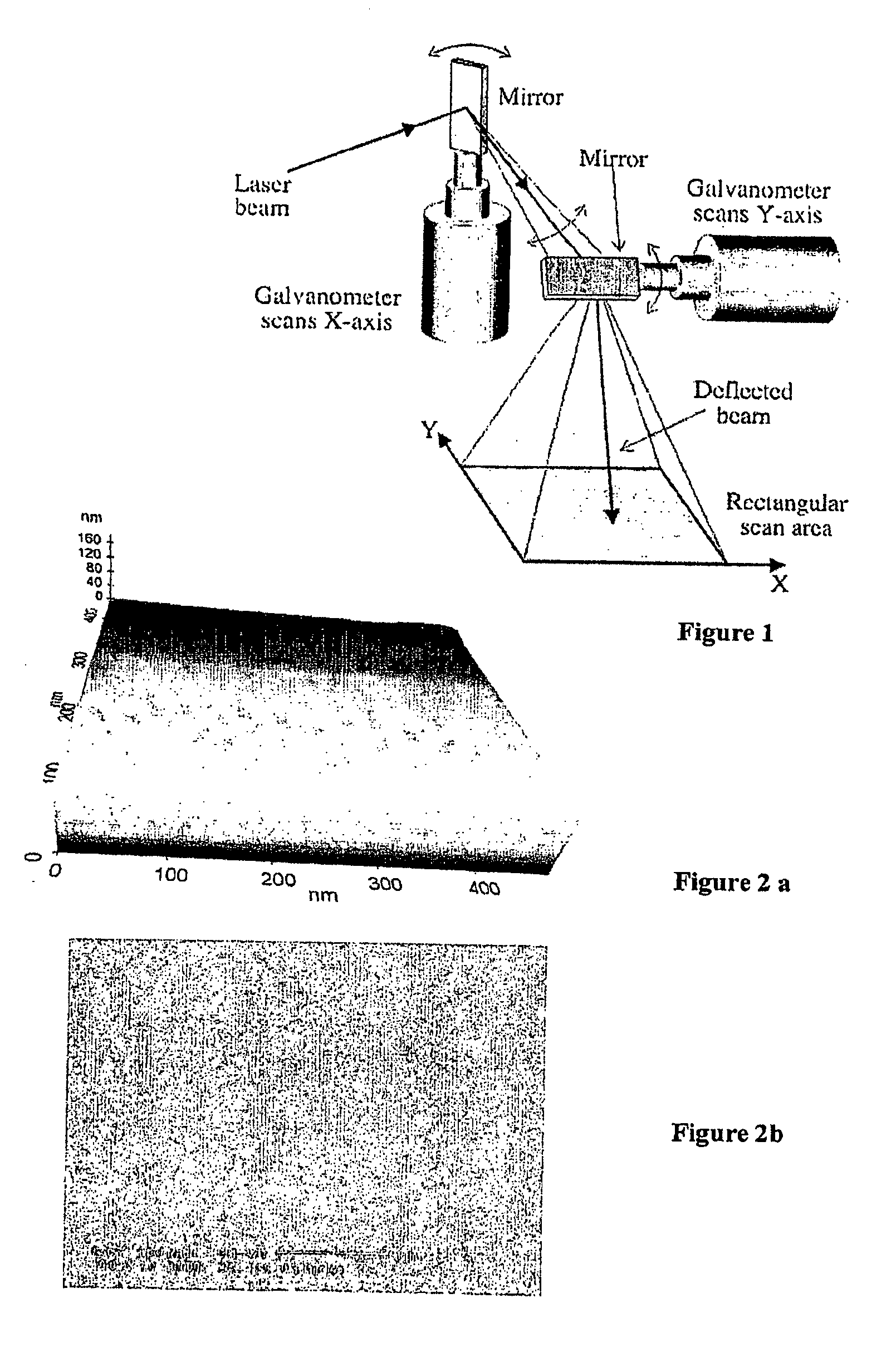
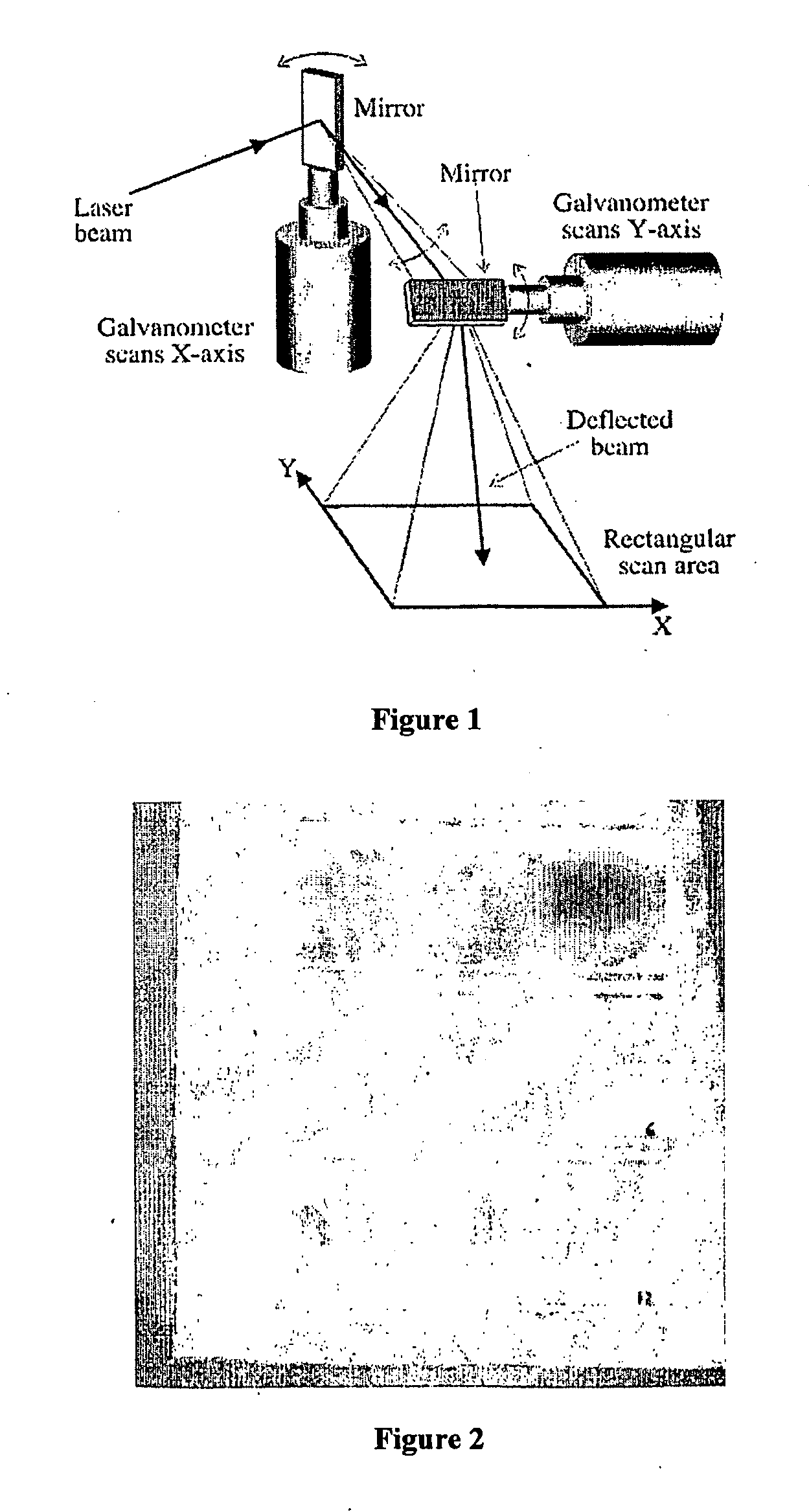
The invention relates in general level to a method for coating articulating surfaces of medical products. The invention also relates to coated medical products manufactured by the method. The coating is carried out by employing ultra short pulsed laser deposition wherein pulsed laser beam is preferably scanned with a rotating optical scanner including at least one mirror for reflecting the laser beam. The invention has several both industrially and qualitatively advantageous effects such as high coating production rate, excellent coating properties and overall low manufacturing costs.
Owner:PICODEON OY
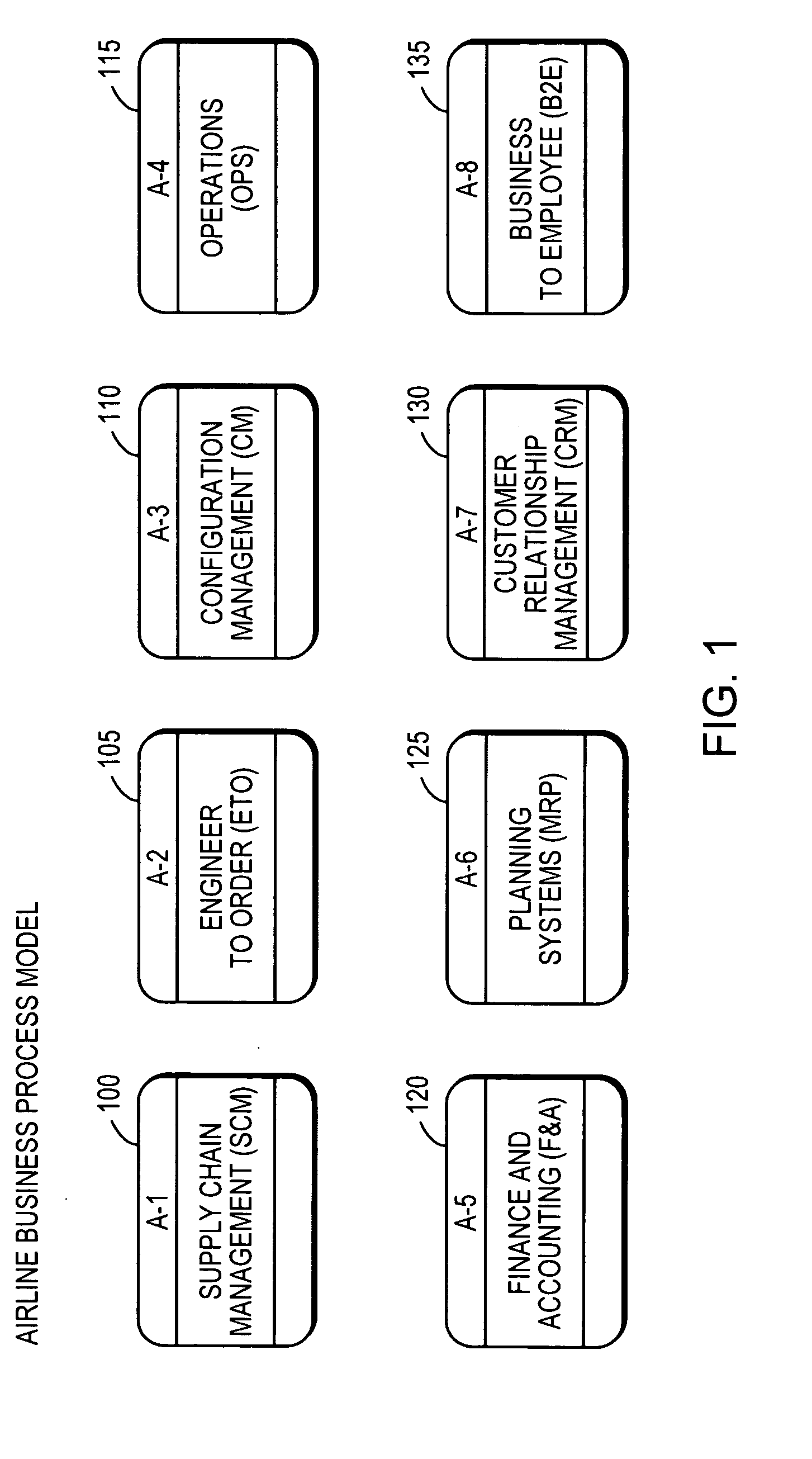
Linked hierarchical airline maintenance process modeling
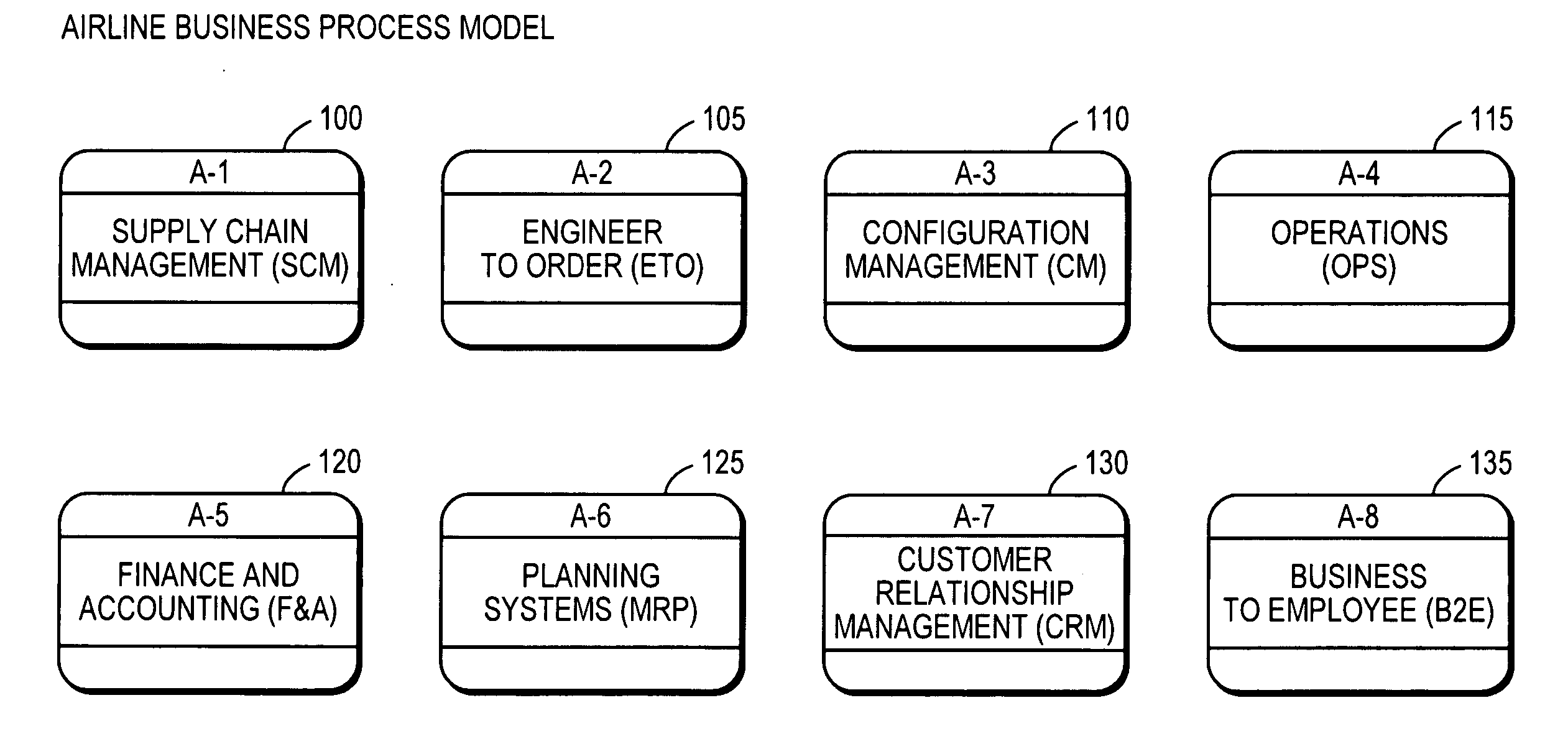
A plurality of display files representing aircraft maintenance processes are generated and linked in a hierarchy. A general level display file defines a number of divisions of aircraft maintenance processes that can include managerial as well as labor related divisions. Linked display files appearing below the general level file in the hierarchy refine the general level divisions until a basic level diagram is reached where the tasks required to perform the aircraft maintenance processes are defined and the input elements for the respective tasks are shown along with output elements. The display files are linked so that selecting items on a diagram causes corresponding lower level diagrams to be displayed. The linked display files representing the aircraft maintenance processes provide graphical information regarding dependencies and relationships between processes that can be used in selectively implementing aircraft maintenance applications across segments of an aircraft maintenance operation.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Power grid fault tracking method based on data mining technology
InactiveCN107016507AAvoid bulk accumulationTightly boundCharacter and pattern recognitionResourcesSelf-healingData set
The invention discloses a power grid fault tracking method based on data mining technology. The method includes taking various types of data acquisition systems of an intelligent substation as an original data source; selecting a decision tree to classify the information in the station, and providing decision support for the fault tracking program on a dispatching side; classifying the data filtered by the decision tree according to the supervision model into three classes: protection rejection signals, signal channel fault signals, and breaker rejection signals; and after the classification algorithm of the decision tree on the training samples is completed, predicting the data set in the unknown class, and corresponding to the power grid fault tracking process, namely, analyzing the various kinds of data of the transformer station layer to give the protection or breaker rejection reasons. The power grid fault tracking method can monitor the other data of the lower transformer station layer at the dispatching center, for example, the general level and forecasting level alarm data, can determine the condition of protection and breaker rejection according to the data, timely know the condition of the power system, and saves time for the power grid fault self-healing.
Owner:STATE GRID OF CHINA TECH COLLEGE +1
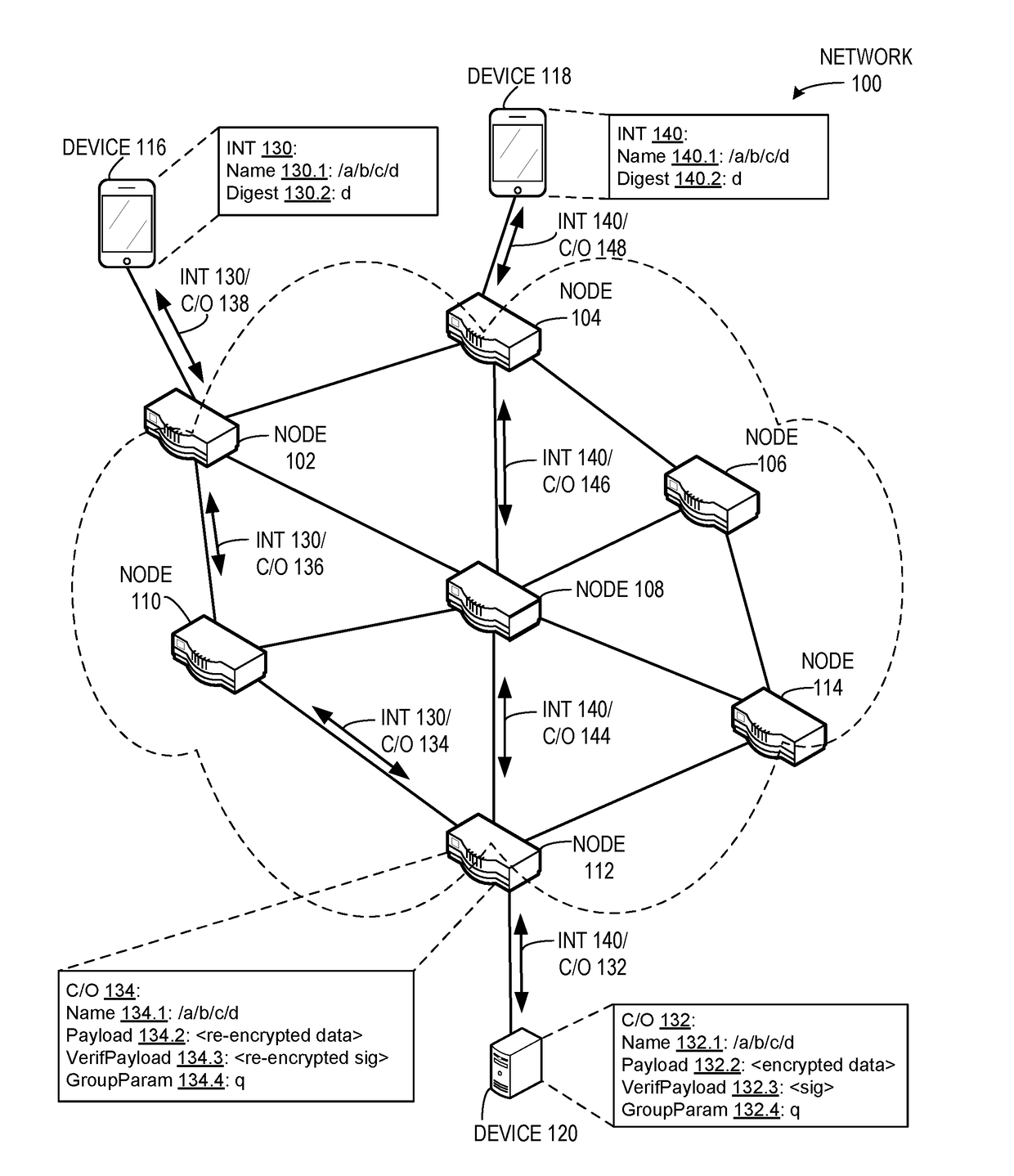
Interest return control message
ActiveUS20160019110A1Easy to processNon-redundant fault processingData switching networksContent centricStructure of Management Information
One embodiment provides a system that facilitates processing of error-condition information associated with a content-centric network (CCN) message transmitted over a network. During operation, the system receives, by a first node, a packet that corresponds to a CCN message, where a name for the CCN message is a hierarchically structured variable length identifier (HSVLI) which comprises contiguous name components ordered from a most general level to a most specific level. Responsive to determining that the CCN message triggers an error condition, the system generates an interest return message by pre-pending a data structure to the CCN message, where the data structure indicates the error condition. The system transmits the interest return message to a second node.
Owner:CISCO TECH INC
Radiation Arrangement
InactiveUS20100181706A1Increased Radiation PowerMirrorsVacuum evaporation coatingVaporizationTurbine
The invention relates in general level to radiation transference techniques as applied for utilisation of material handling. The invention relates to a radiation source arrangement comprising a path of radiation transference, or an improved path of radiation transference, which path comprises a turbine scanner or an improved turbine scanner. The invention also concerns a target material suitable for vaporization and / or ablation. The invention concerns an improved turbine scanner. The invention concerns also to a vacuum vaporization / ablation arrangement that has a radiation source arrangement according to invention. The invention concerns also a target material unit, to be used in coating and / or manufacturing target material.
Owner:PICODEON OY
Coating on a fiber substrate and a coated fiber product
InactiveUS20090061210A1Increase chanceGood coating performanceElectric discharge heatingLayered productsProduction rateFiber
The invention relates in general level to a method for coating fiber products including large surface areas. The invention also relates to coated fiber products manufactured by the method. The coating is carried out by employing ultra short pulsed laser deposition wherein pulsed laser beam is scanned with a rotating optical scanner including at least one mirror for reflecting the laser beam. The invention has several both industrially and qualitatively advantageous effects such as high coating production rate, low-temperature coating conditions accomplishing coating of fiber-products excellent coating properties and overall low manufacturing costs.
Owner:PICODEON OY
Coating on a metal substrate and a coated metal product
InactiveUS20090017318A1Easy to wearExcellent chemicalRadiation applicationsVacuum evaporation coatingProduction rateOptical scanners
The invention relates in general level to a method for coating metal products including large surface areas. The invention also relates to coated metal products manufactured by the method. The coating is carried out by employing ultra short pulsed laser deposition wherein pulsed laser beam is scanned with a rotating optical scanner including at least one mirror for reflecting the laser beam. The invention has several both industrially and qualitatively advantageous effects such as high coating production rate, excellent coating properties and overall low manufacturing costs.
Owner:PICODEON OY
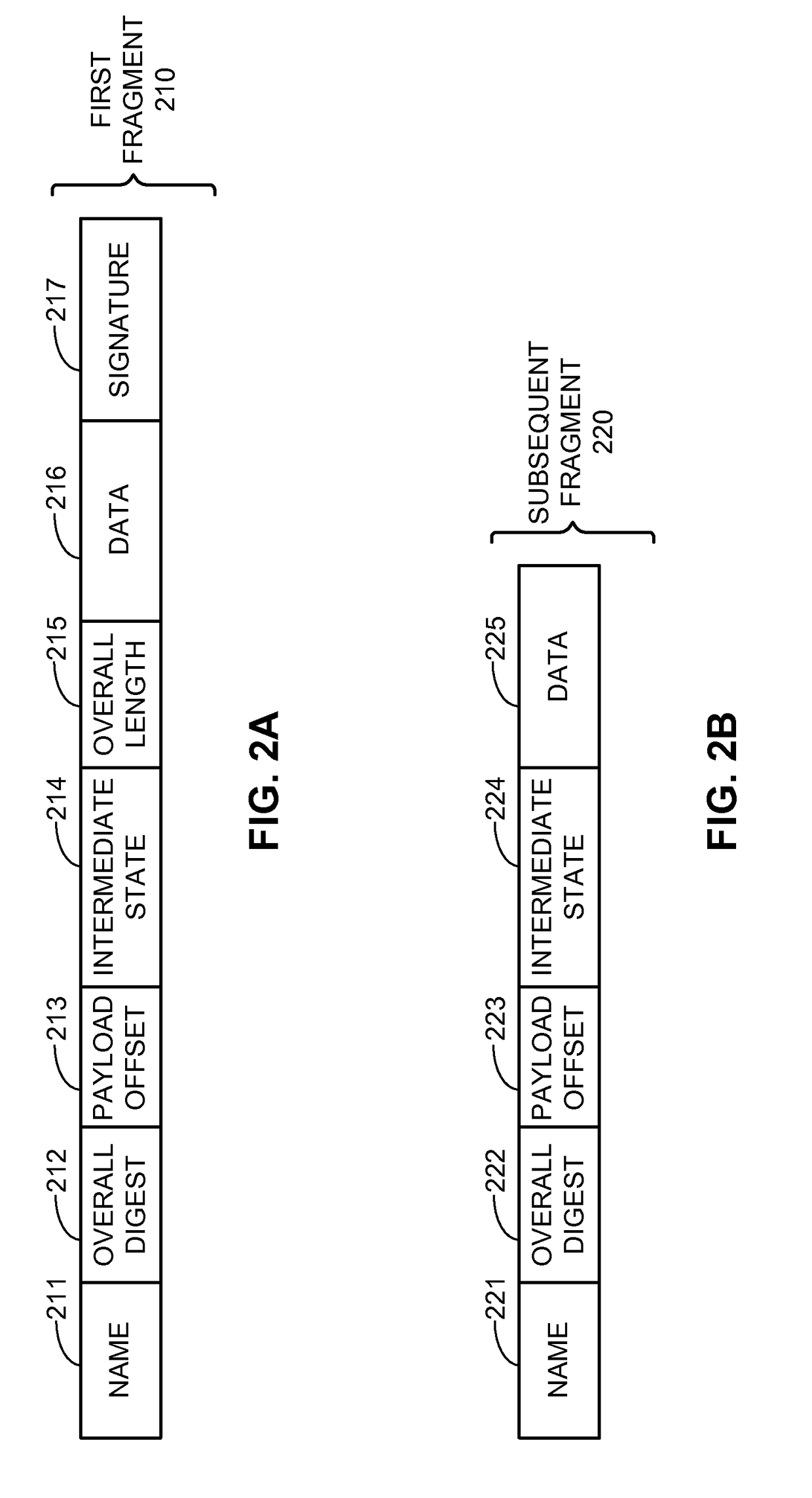
Network named fragments in a content centric network
ActiveUS20170078199A1Facilitates efficient and secure transportationData switching networksSecuring communicationHash functionContent centric
One embodiment provides a system that facilitates efficient and secure transportation of content. An intermediate node receives a packet that corresponds to a fragment of a content object message that is fragmented into a plurality of fragments. One or more fragments of the plurality of fragments indicate a unique name that is a hierarchically structured variable-length identifier that comprises contiguous name components ordered from a most general level to a most specific level. The received fragment indicates an intermediate state which is based on a hash function performed on an intermediate state from a previous fragment and data included in the received fragment. In response to determining that the received fragment is a first fragment, the system identifies a first entry in a pending interest table for an interest with a name that is based on a hash of a content object and that corresponds to the first fragment.
Owner:CISCO TECH INC
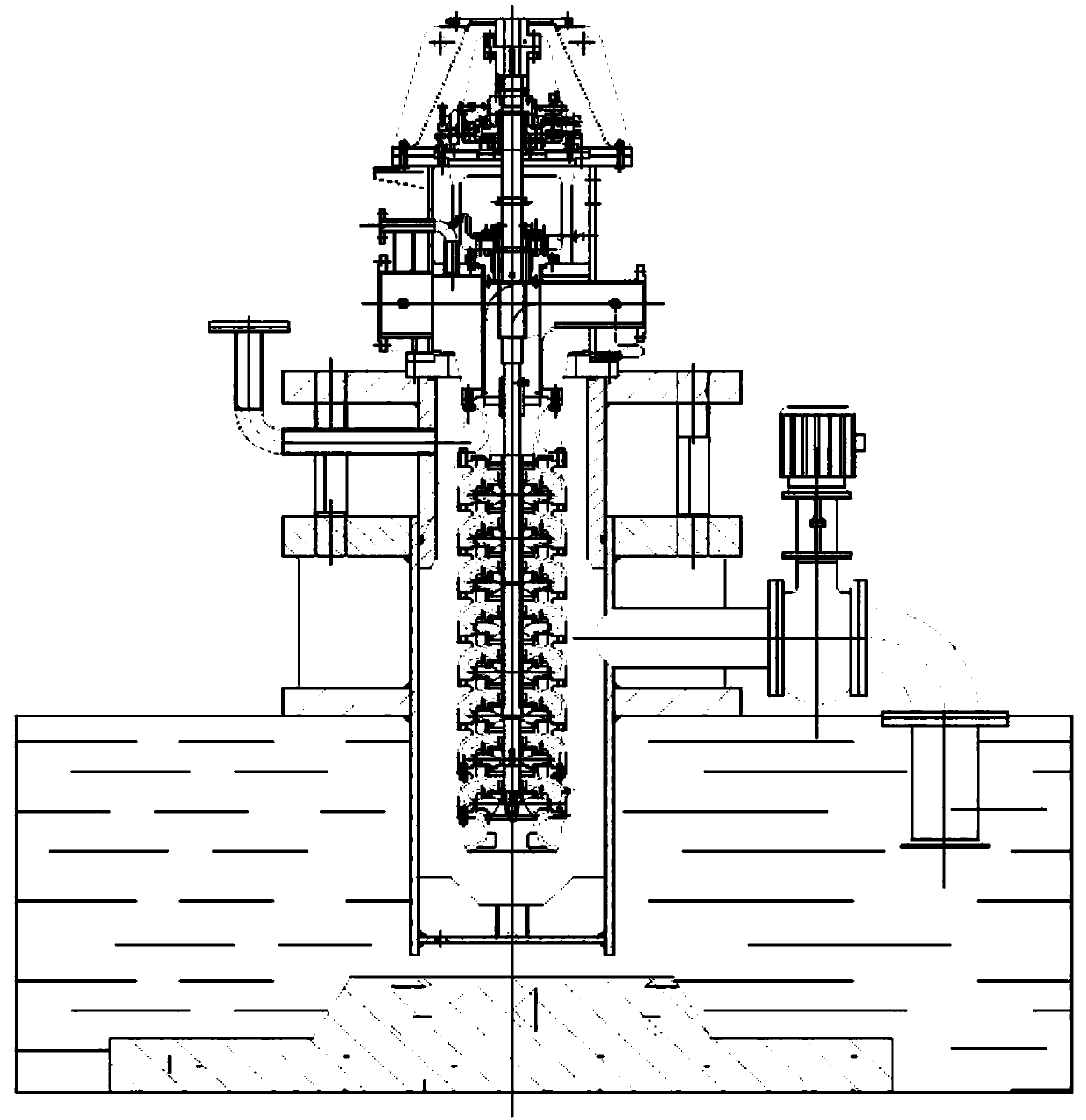
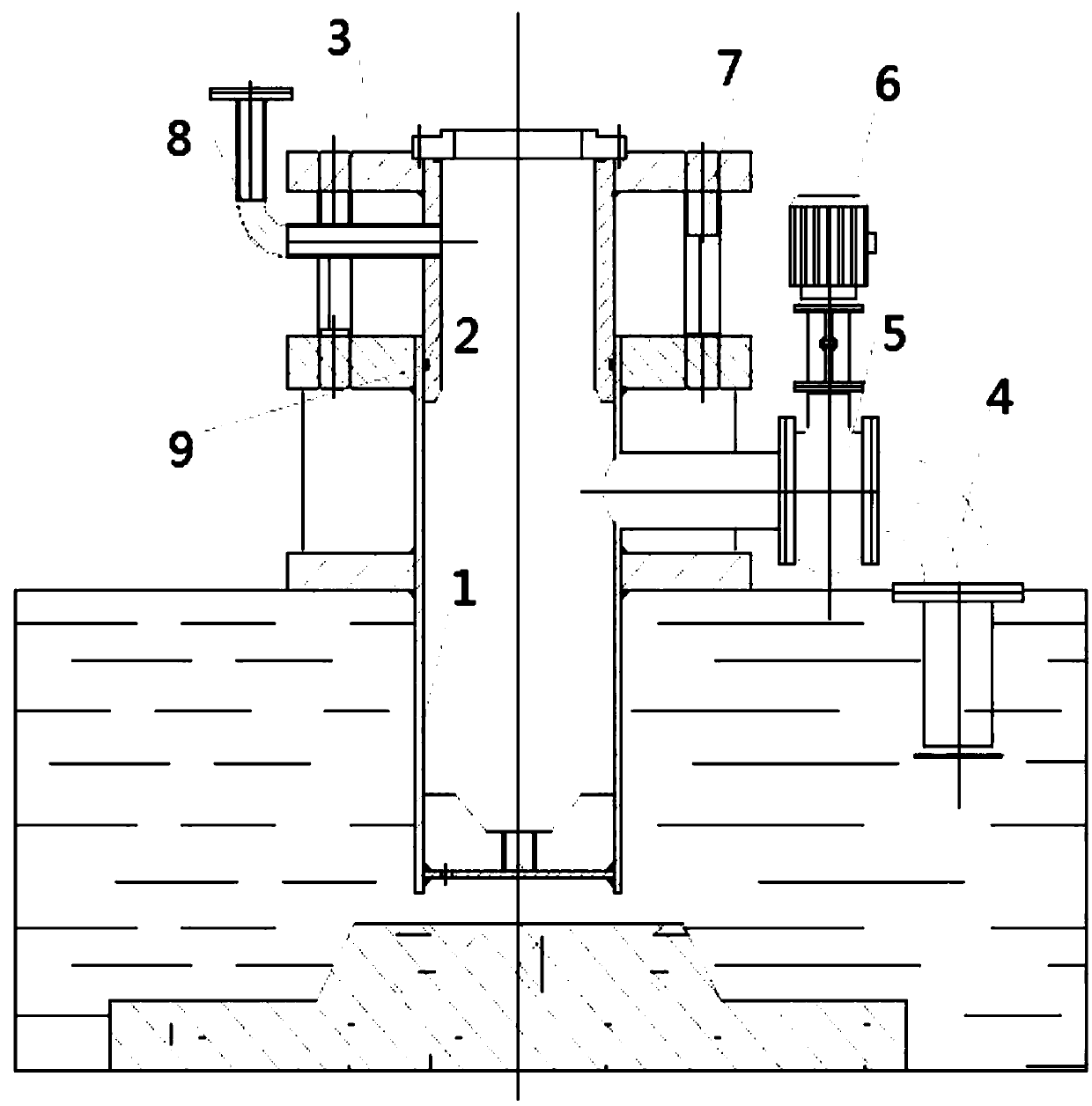
Semi-submersible type hydraulic testing device for vertical and axial suction centrifugal pump
PendingCN107747548AHigh degree of versatilityGood application effectPump controlNon-positive displacement fluid enginesPulp and paper industryProficiency testing
The invention relates to the technical field of machines, in particular to a semi-submersible type hydraulic testing device for a vertical and axial suction centrifugal pump. The semi-submersible typehydraulic testing device comprises a testing cylinder, a lifting platform, a water sucking pipeline, an execution motor, adjusting lead screws and a degassing pipe. The water sucking pipeline is arranged on one side of the testing cylinder and connected with the testing cylinder. The water sucking pipeline is further provided with a regulating valve. The lifting platform is provided with adaptorplates, and therefore a pump body to be tested can be conveniently installed on the lifting platform through the adaptor plates. The adjusting lead screws are arranged between the lifting platform andthe adaptor plates, and the position adjustment of the lifting platform in the vertical direction is achieved through the adjusting lead screws. The execution motor is arranged on the water sucking pipeline and connected with the regulating valve. The other side of the testing cylinder is further provided with the degassing pipe. The semi-submersible type hydraulic testing device can adapt to andbe matched with various types of vertical pumps, the universal degree and the application ability of the testing device are improved, and convenience is brought to installation and adjustment of thevertical centrifugal pump in the testing process.
Owner:SHANGHAI PUMP MFR
Low-cost authenticated signing delegation in content centric networking
One embodiment provides a system that delegates signature production in a CCN. During operation, a first content producing device monitors content objects created by a second content producing device. A content object can be identified by a name that is a hierarchically structured variable length identifier (HSVLI) which comprises contiguous name components ordered from a most general level to a most specific level. The first device retrieves the content objects and authenticates a message authentication code for each content object based on a key shared by the first and second device. The first device creates a manifest with a name and a content object hash value for each content object, produces a digital signature for the manifest based on a private key of the first device, and includes the digital signature in the manifest, thereby delegating signature production to the first device for content objects created by the second device.
Owner:CISCO TECH INC
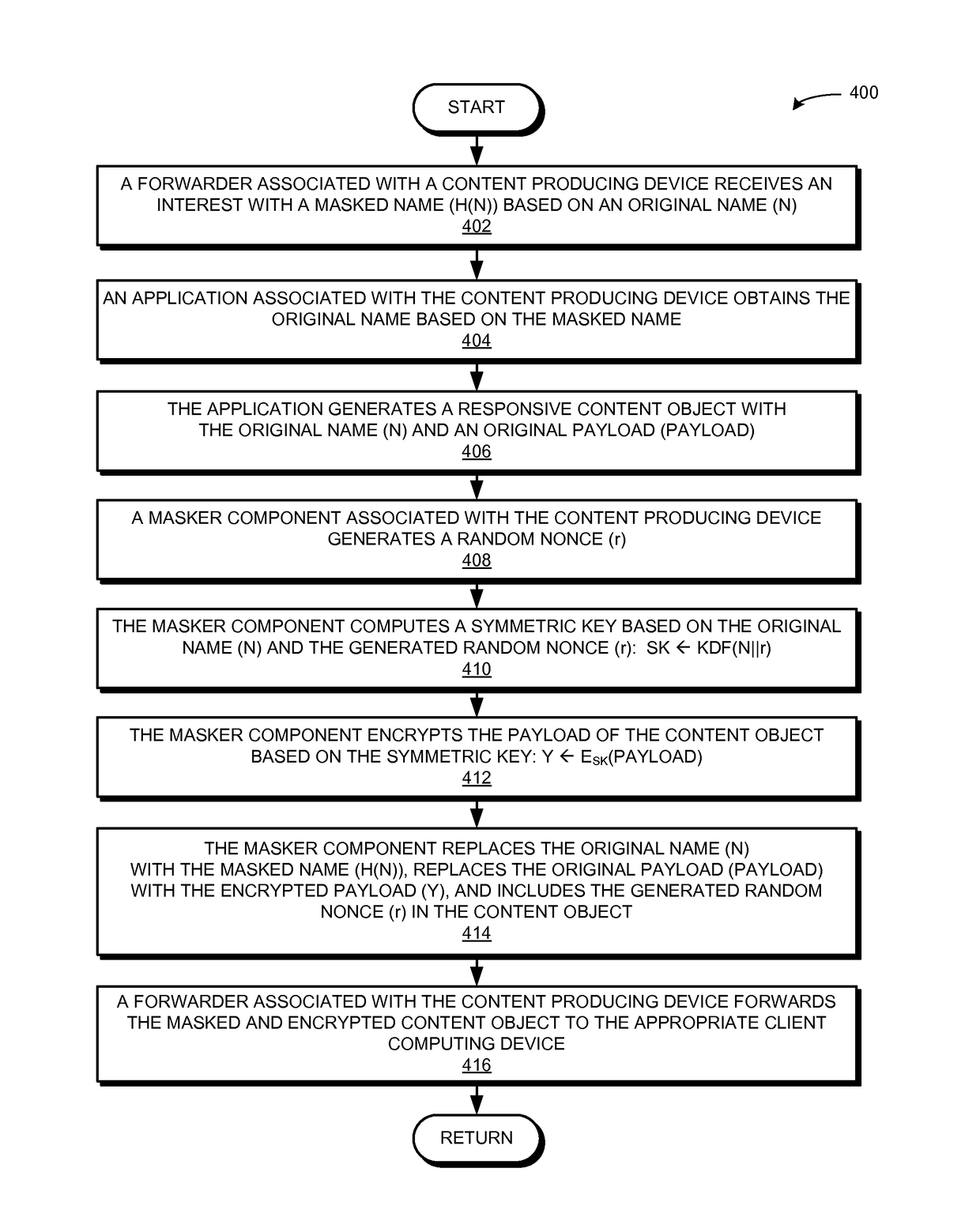
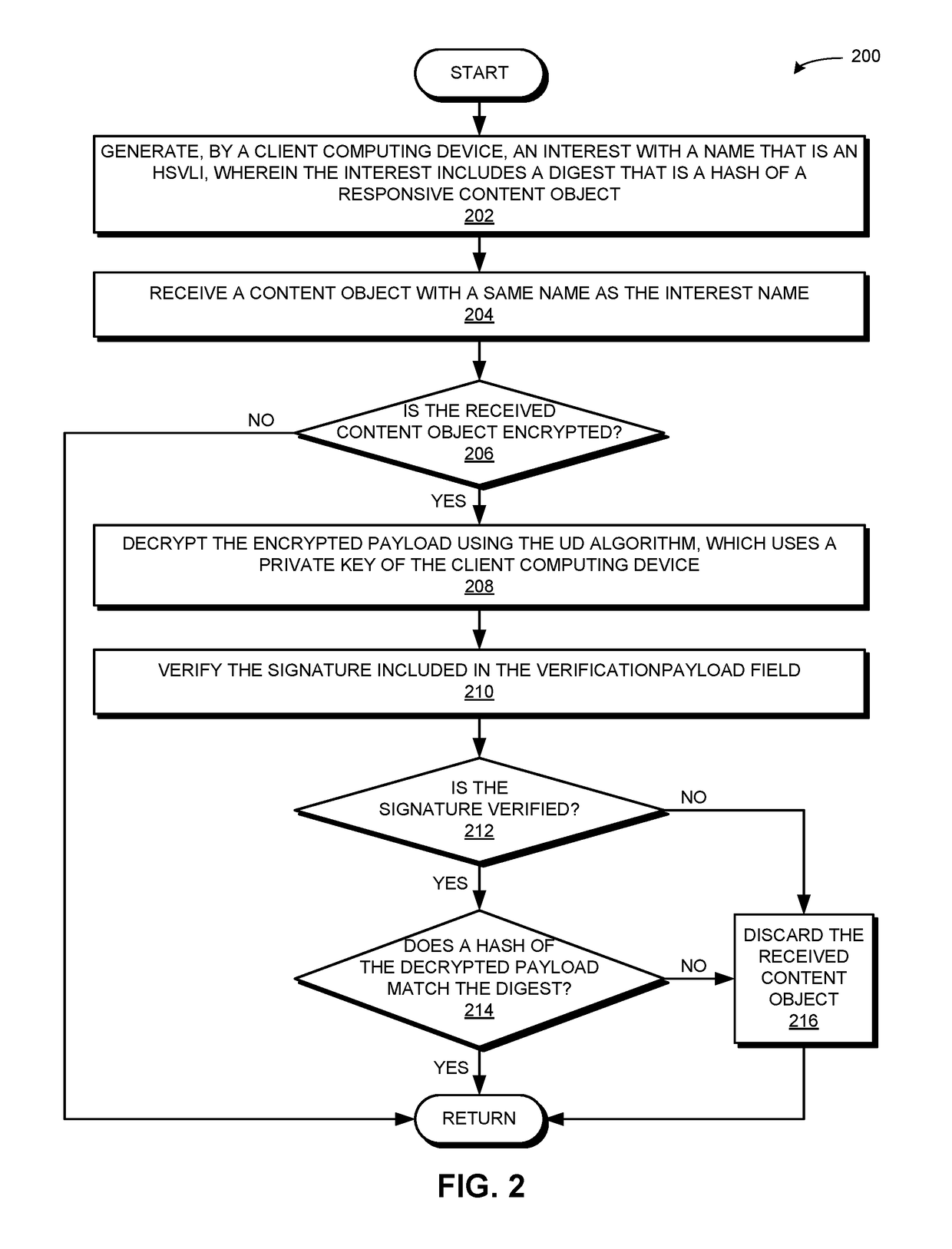
Transparent encryption in a content centric network
InactiveUS20170149747A1Improve efficiencyFacilitates transparent encryptionKey distribution for secure communicationPublic key for secure communicationContent centricVariable length
One embodiment provides a system that facilitates efficient and transparent encryption of packets between a client computing device and a content producing device. During operation, the system receives, by a content producing device, an interest packet that includes a masked name which corresponds to an original name, wherein the original name is a hierarchically structured variable length identifier that includes contiguous name components ordered from a most general level to a most specific level. The system obtains the original name based on the masked name. The system computes a symmetric key based on the original name and a generated nonce. The system generates a content object packet that corresponds to the original name and includes the masked name, the nonce, and a payload encrypted based on the symmetric key, wherein the content object packet is received by a client computing device.
Owner:CISCO TECH INC
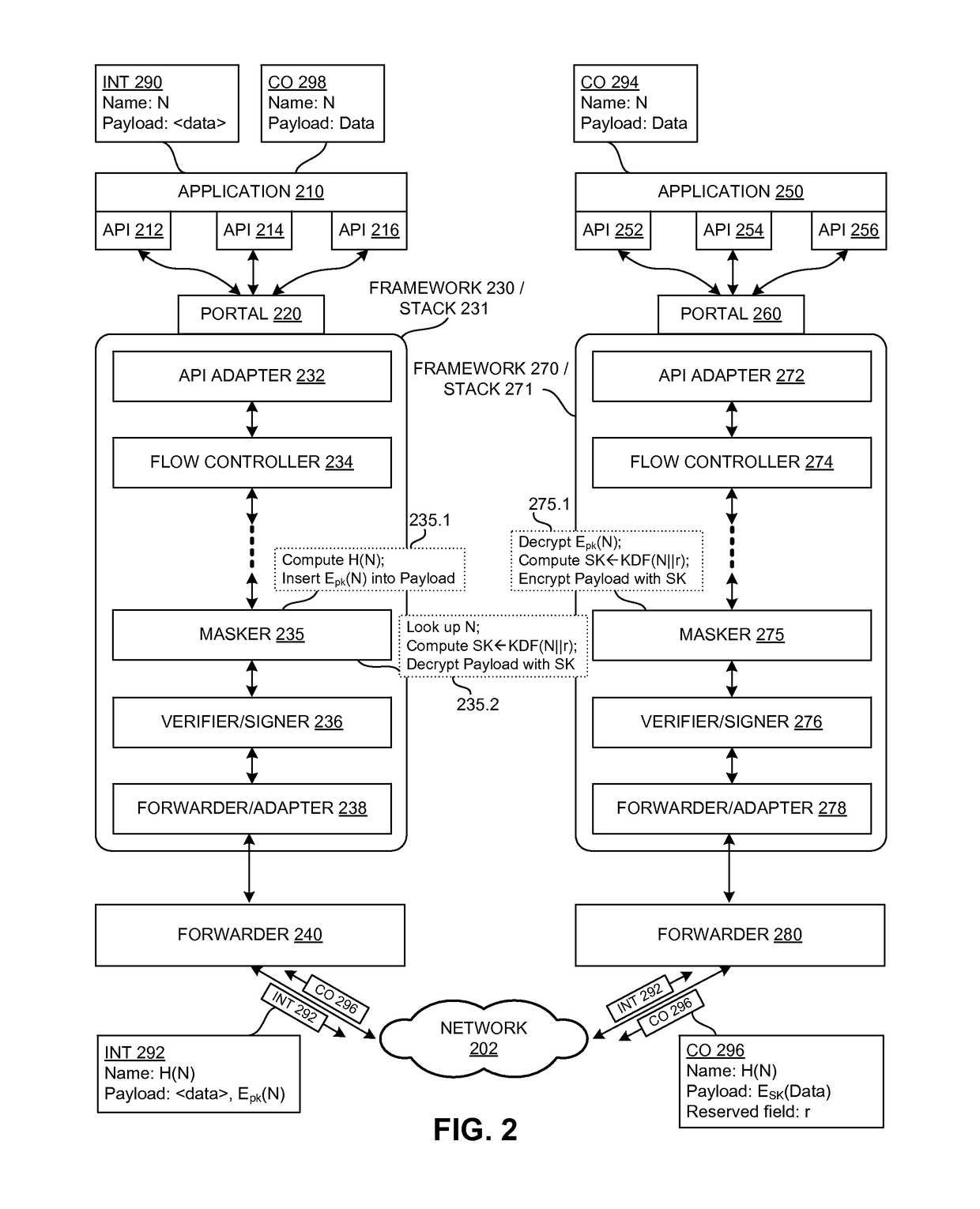
Method and system for mutating and caching content in a content centric network
ActiveUS20170289114A1Multiple keys/algorithms usageUser identity/authority verificationContent centricVariable length
One embodiment provides a system that facilitates mutating and caching content in a CCN. During operation, the system receives, by an intermediate node, a content object that indicates an encrypted payload, a signature, and a parameter for a group to which the content object belongs, wherein the content object includes a name that is a hierarchically structured variable length identifier which comprises contiguous name components ordered from a most general level to a most specific level. The system re-encrypts the content object based on the encrypted payload and the parameter to obtain a new encrypted payload and a new signature, wherein re-encrypting is not based on a private key or a public key associated with the encrypted payload. The system transmits the re-encrypted content object to a client computing device, thereby allowing the client computing device to decrypt the re-encrypted content object and verify the new signature.
Owner:CISCO TECH INC
Cut-through forwarding of CCNx message fragments with IP encapsulation
ActiveUS9516144B2Facilitates cut-through forwardingFacilitating cut-through forwardingData switching networksVariable lengthDistributed computing
Owner:CISCO TECH INC
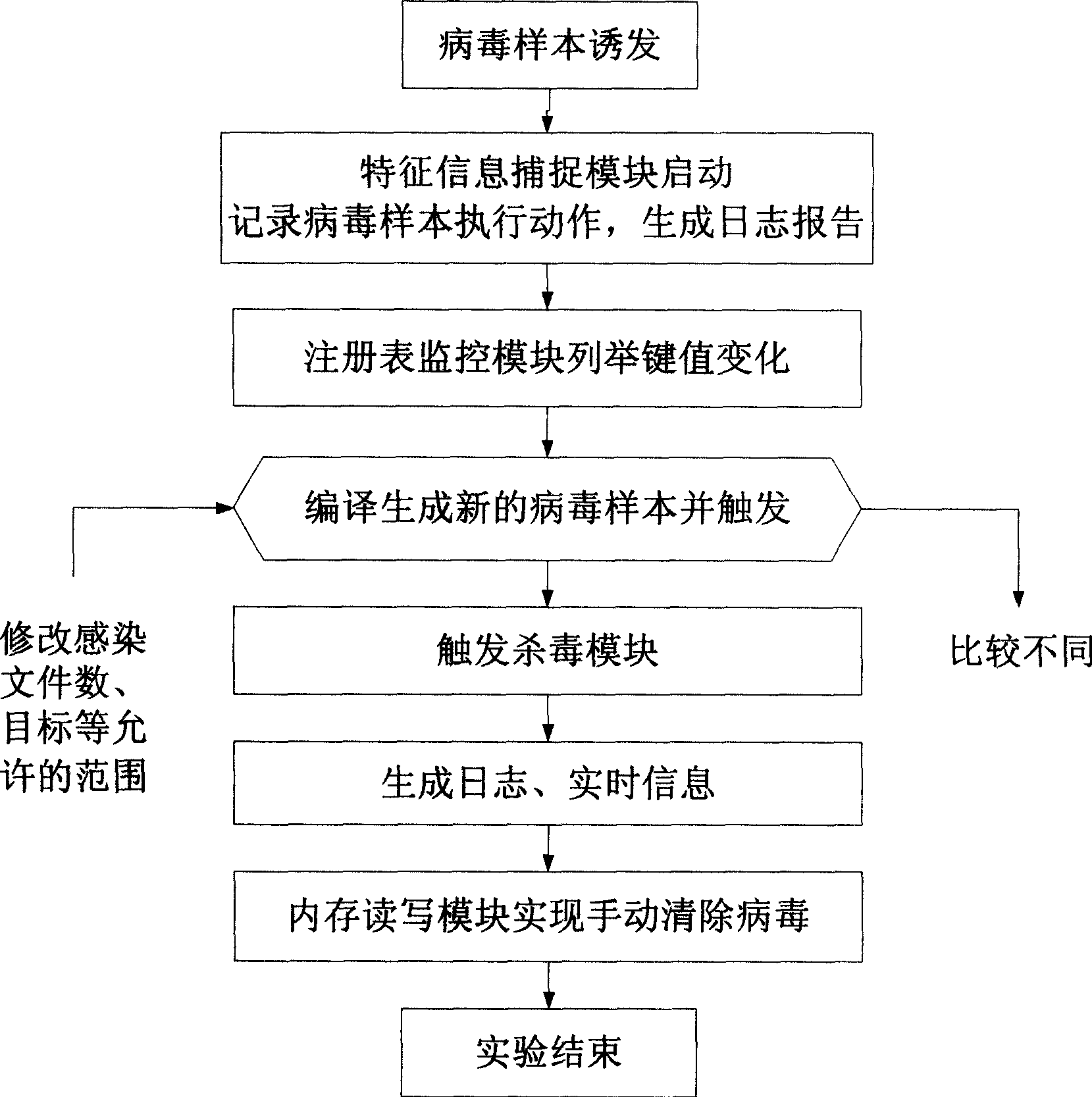
Computer virus experimental method of supporting multiuser concurrency conrol in large scale
InactiveCN1760883ARealize visualizationEasy to operatePlatform integrity maintainanceTransmissionThe InternetOperability
The method includes following three aspects: (1) user management: when user is in logging in, checking userí»s ID and cipher identifies userí»s ID; restricting total number of logging in user in one time; assigning authorities in different levels for users divided into administrator level and general level; building induced environment for meeting to virus trigger mechanism; (2) visualization and operability for virus infection and clearing away virus; dynamic procedure for capturing infection of virus and clearing away virus by combination of capturing attributive information, memory format map of file, and registration table monitoring; (3) controllable propagation of virus: in range of LAN, simulating Internet environment of propagating virus, planning propagation path as well as safeguarding and controlling range of virus propagation. Features are: large scale, concentrative management, visual, operability and controllability.
Owner:SHANGHAI JIAO TONG UNIV
CCN routing using hardware-assisted hash tables
One embodiment provides a system that facilitates forwarding of packets with variable length names. During operation, the system receives a packet with a hierarchically structured variable length identifier (HSVLI) which comprises contiguous name components ordered from a most general level to a most specific level. The system performs a longest prefix match lookup by selecting an entry from a first data structure of entries. The entries indicate a name component, forwarding information for the name component, and a plurality of entry identifiers that chain an entry to another entry. If a size of the name component is less than or equal to a predetermined threshold, the system selects an entry based on the name component. If the size is greater, the system selects an entry based on a compressed key which can be a hash of the name component. The system also resolves collisions associated with the selected entry.
Owner:CISCO TECH INC
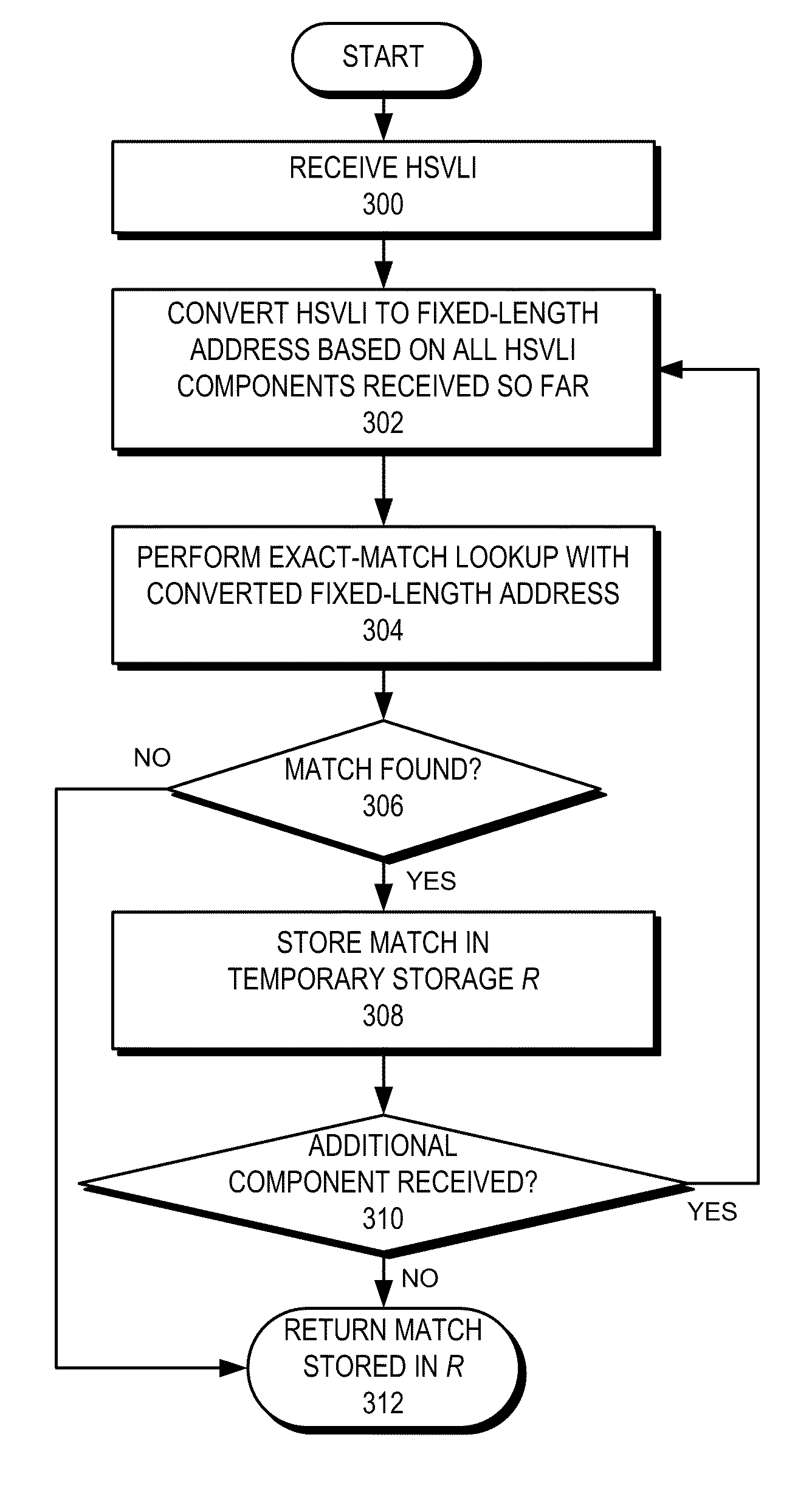
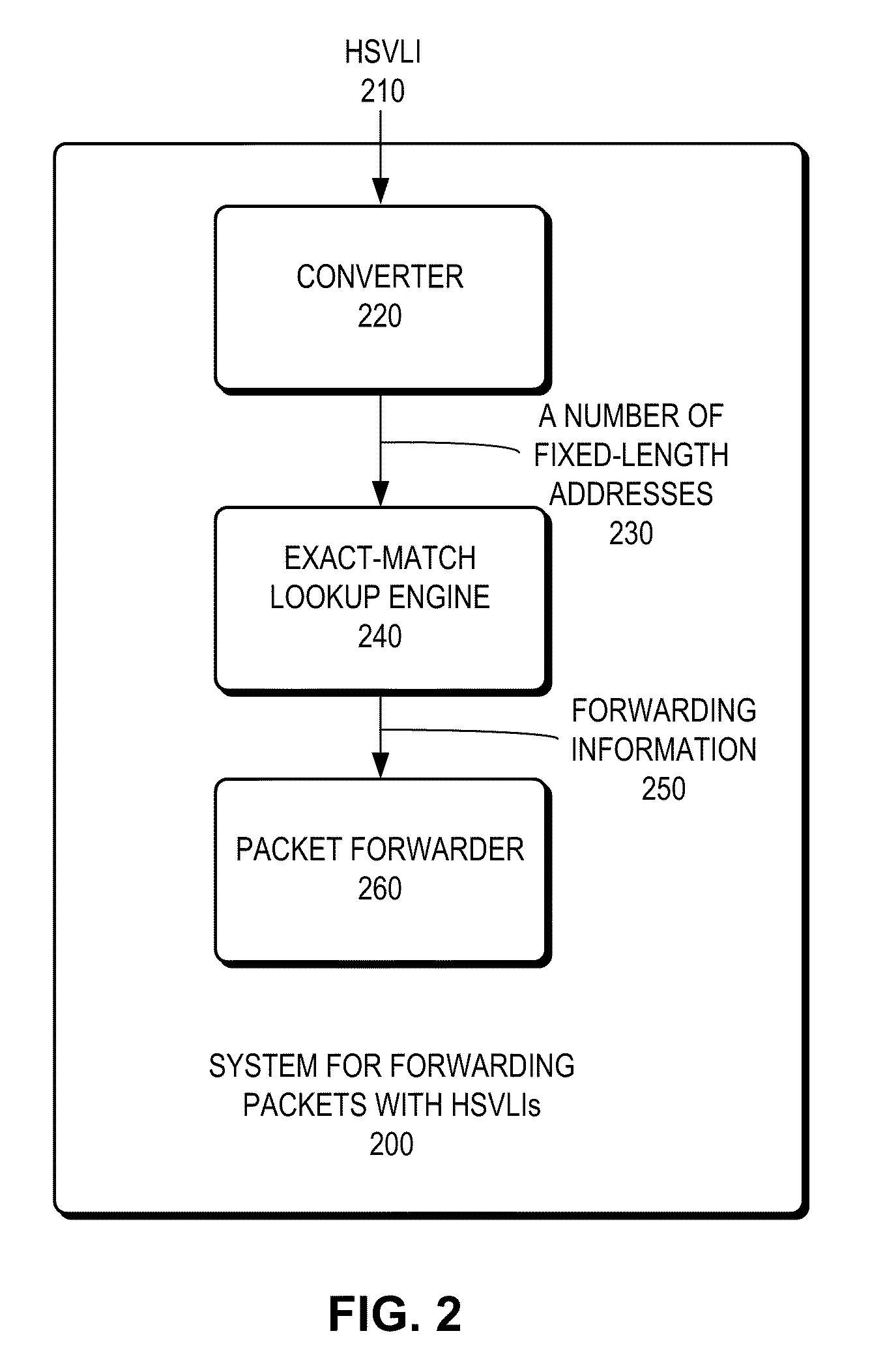
System for forwarding packets with hierarchically structured variable-length identifiers using an exact-match lookup engine
ActiveUS8243735B2Reduce chanceEasy to find laterCoin-freed apparatus detailsData switching by path configurationExact matchNetwork packet
One embodiment provides a system for forwarding packets with hierarchically structured variable-length identifiers (HSVLIs), wherein the computer includes a processor. During operation, the system converts an HSVLI into a number of fixed-length addresses, wherein the HSVLI indicates a piece of content and is hierarchically structured, and comprises contiguous components ordered from a most general level to a most specific level. In addition, the length of a respective HSVLI is not fixed. The system further performs an effective longest-prefix-match lookup by performing multiple exact-match lookups based at least on the fixed-length addresses.
Owner:CISCO TECH INC
Transport session state protocol
ActiveUS20170257284A1Efficient transportImprove network efficiencyMetering/charging/biilling arrangementsTransmission protocolVariable length
One embodiment provides a system that facilitates an efficient transport protocol. During operation, the system receives a first interest which indicates a query for optimal transport parameters, wherein a name for an interest is a hierarchically structured variable length identifier that includes contiguous name components ordered from a most general level to a most specific level, wherein the query is based on a name prefix that includes one or more contiguous name components. The system computes the optimal parameters based on historical information associated with the name prefix. The system transmits a first response which includes the computed optimal parameters to a requesting entity, thereby facilitating a transport protocol which increases network efficiency.
Owner:CISCO TECH INC
Self-adjusting goods display system and method
A self-adjusting goods display system maintains a proper shelf level for a display bin containing goods. An implementation has an open bin with side walls having top edges and a moveable shelf to receive a pile of goods. A light source and a light receiver are positioned on the top edges of opposing walls of the bin, and the light source generates light to be received by the light receiver. When the pile of goods is reduced so that the pile no longer obstructs the light from being received by the light receiver a signal indicates a need to raise the general level of the remaining pile contained in the bin. A controller receives the signal and controls operation of a motor to raise the height of the shelf until the remaining pile of the shelf again blocks the light, or the shelf is at a position of maximum height.
Owner:PACIFIC BIN CORP
Adjusting entries in a forwarding information base in a content centric network
ActiveUS20170264536A1Convenient for dynamic adjustmentDigital computer detailsResourcesInformation repositoryContent centric
One embodiment provides a system that facilitates dynamic adjustment of forwarding information in a CCN. During operation, the system receives, by forwarding circuitry, an interest with a name that is a hierarchically structured variable length identifier which comprises contiguous name components ordered from a most general level to a most specific level. The system identifies in a first data structure an entry for one or more name components of the name, wherein the entry includes a list of outgoing interfaces associated with the one or more name components. The system determines network properties in response to forwarding the interest to a first interface of the list. The system reorders the list in order of priority based on the network properties, thereby facilitating the forwarding circuitry to dynamically adjust a likelihood of using a respective interface for forwarding interests associated with the one or more name components.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com