Computer virus experimental method of supporting multiuser concurrency conrol in large scale
A computer virus and experimental method technology, applied in the field of information security, can solve the problems that have not yet been discovered and cannot support large-scale multiple users to concurrently access teaching experiments, etc., and achieve the effect of good promotion prospects, good scalability and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
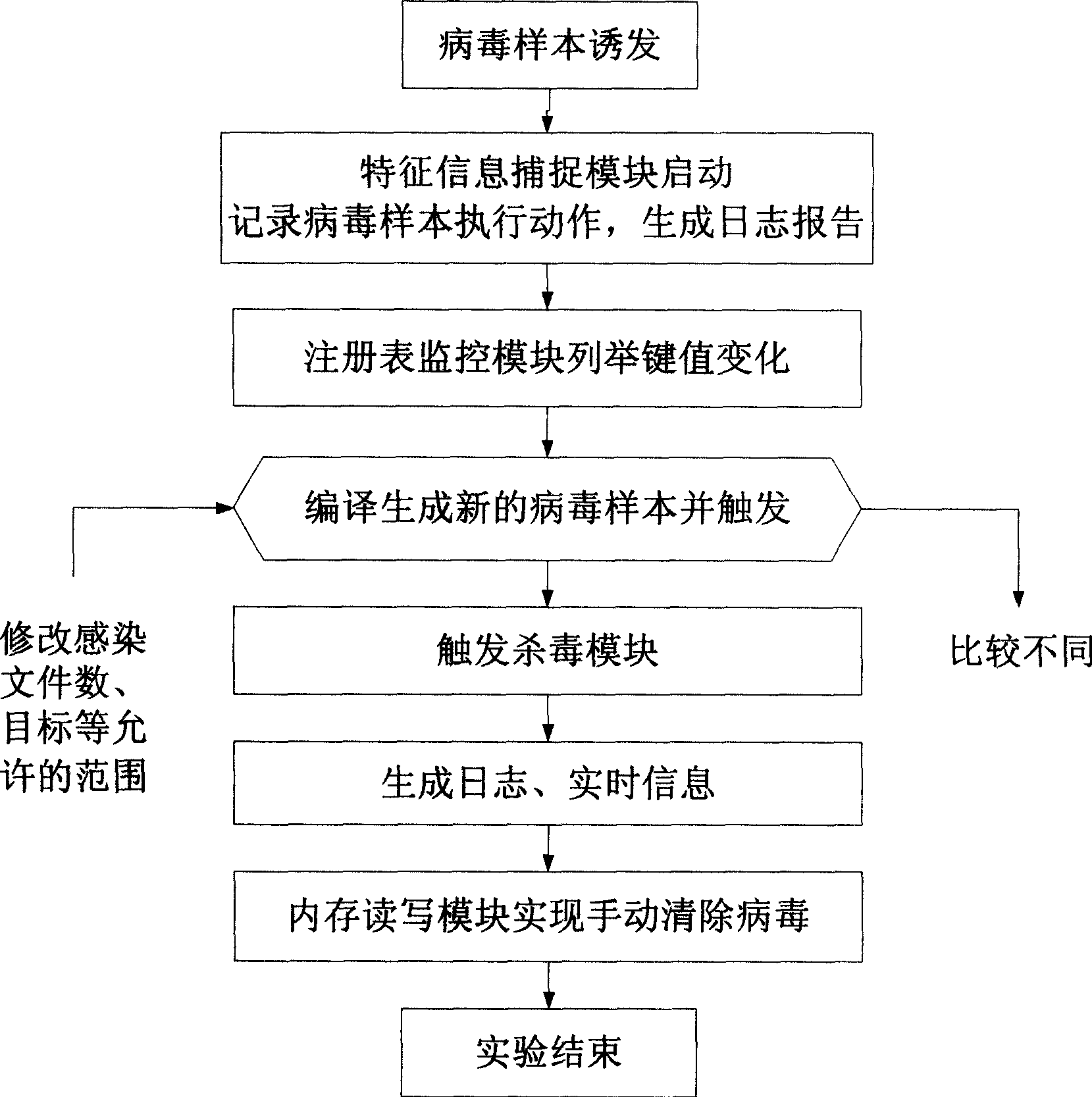
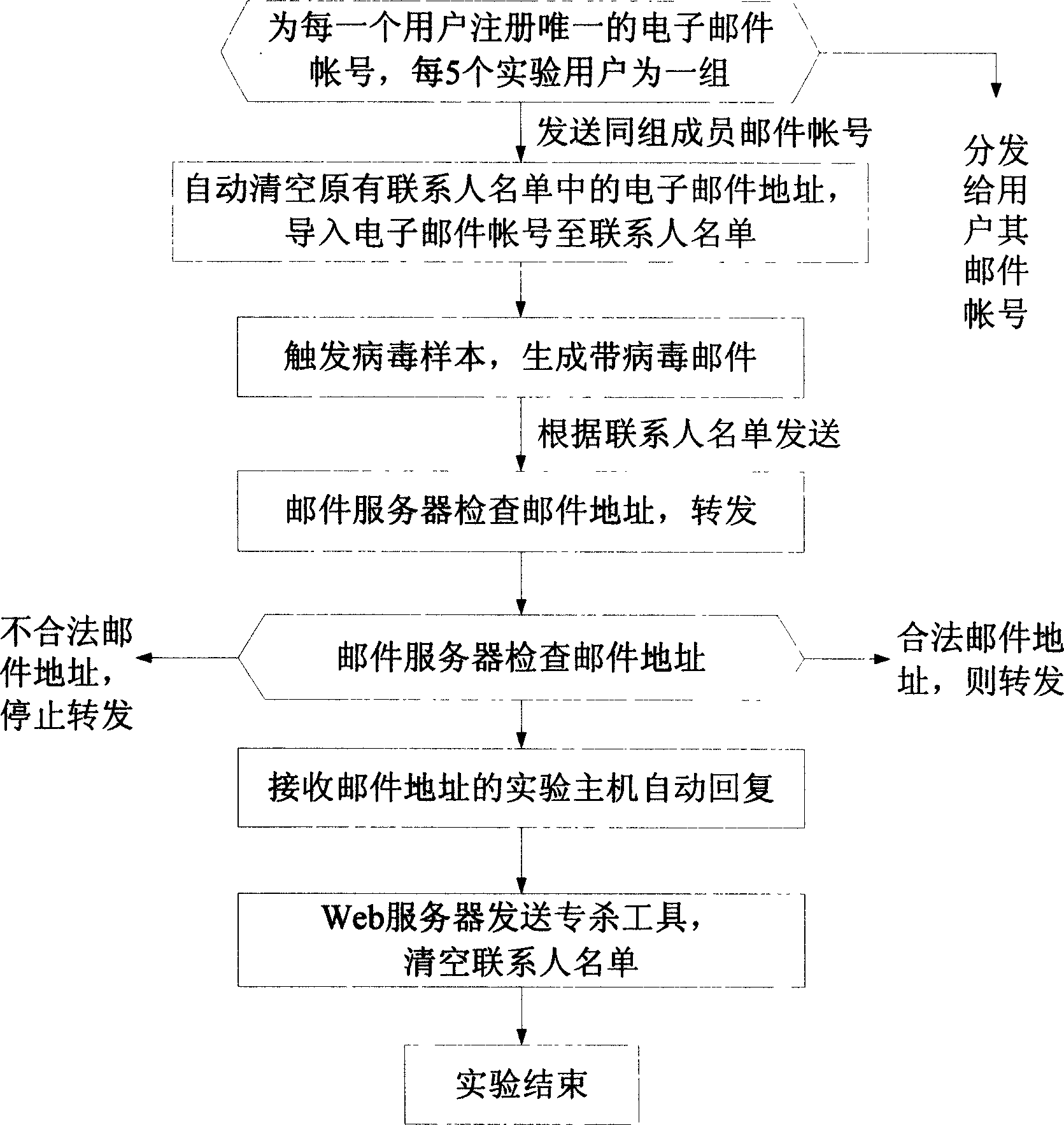
[0021] The system based on this method is divided into four parts, the client running on the user's computer, the Web server, the mail server and the database server. The web server side provides unified identity authentication services for users, determines the types of services available to users and ensures that the number of users served by the experimental system does not exceed the limit value. Users query typical virus sample information through the Web server, download virus samples and special virus removal tools, run the virus locally and spread it within a limited range by the mail server in the system, and the database server stores user information and experimental results. The realization of the technical solution of the present invention is described in detail below in conjunction with accompanying drawing:
[0022] 1. User Management
[0023] Because it is necessary to support hundreds of people to participate in the experiment at the same time, the user manag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com