Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1755 results about "Extensible markup" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Extensible Markup Language (XML) is a markup language that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable.
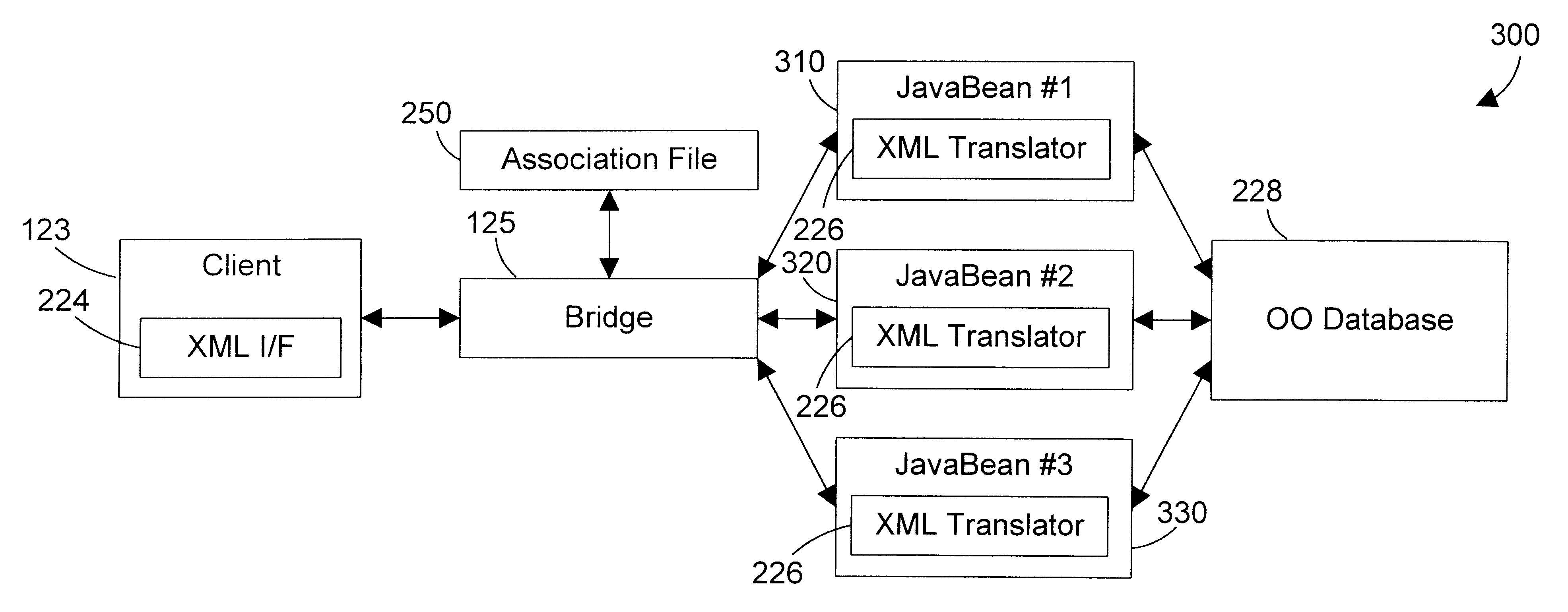
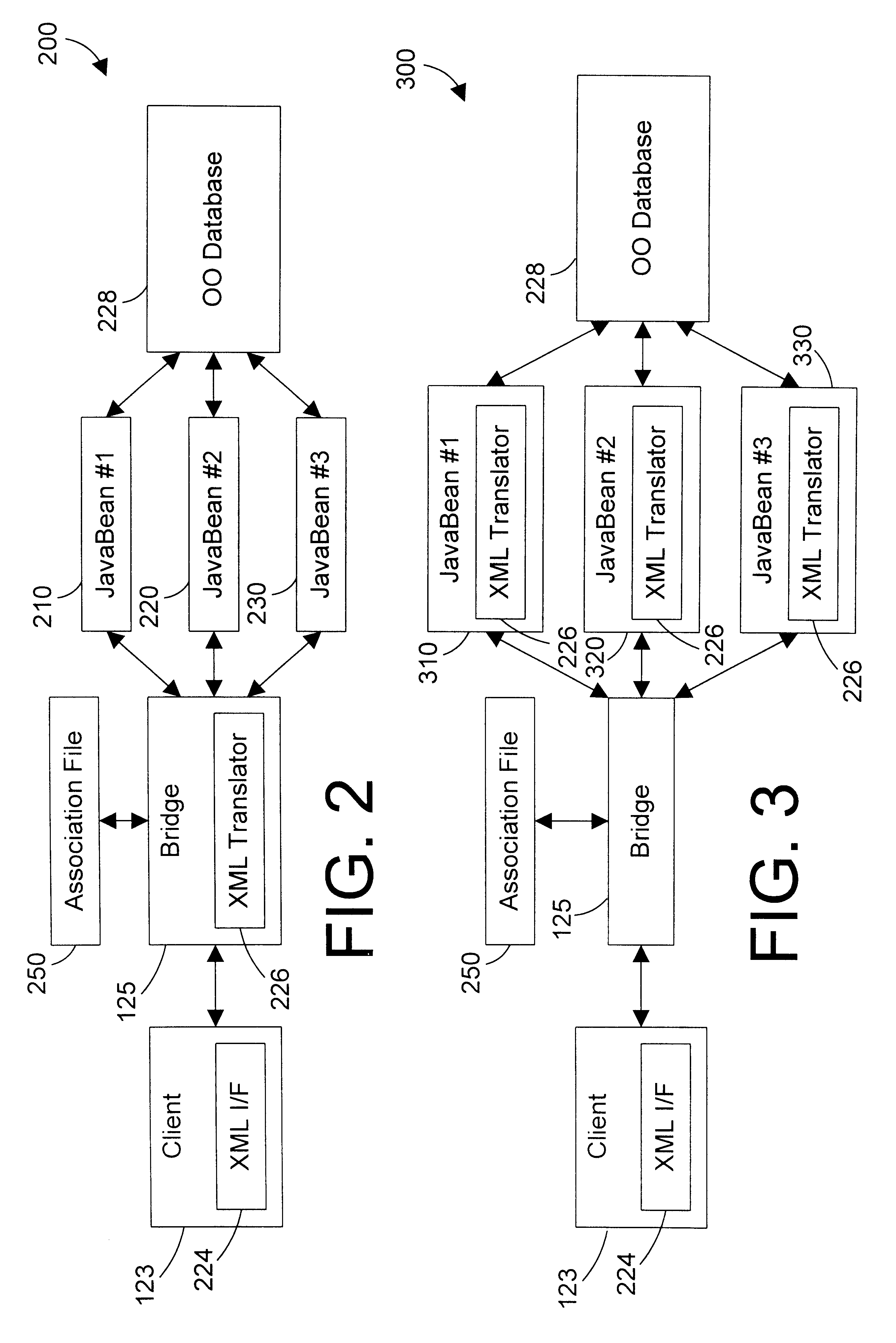
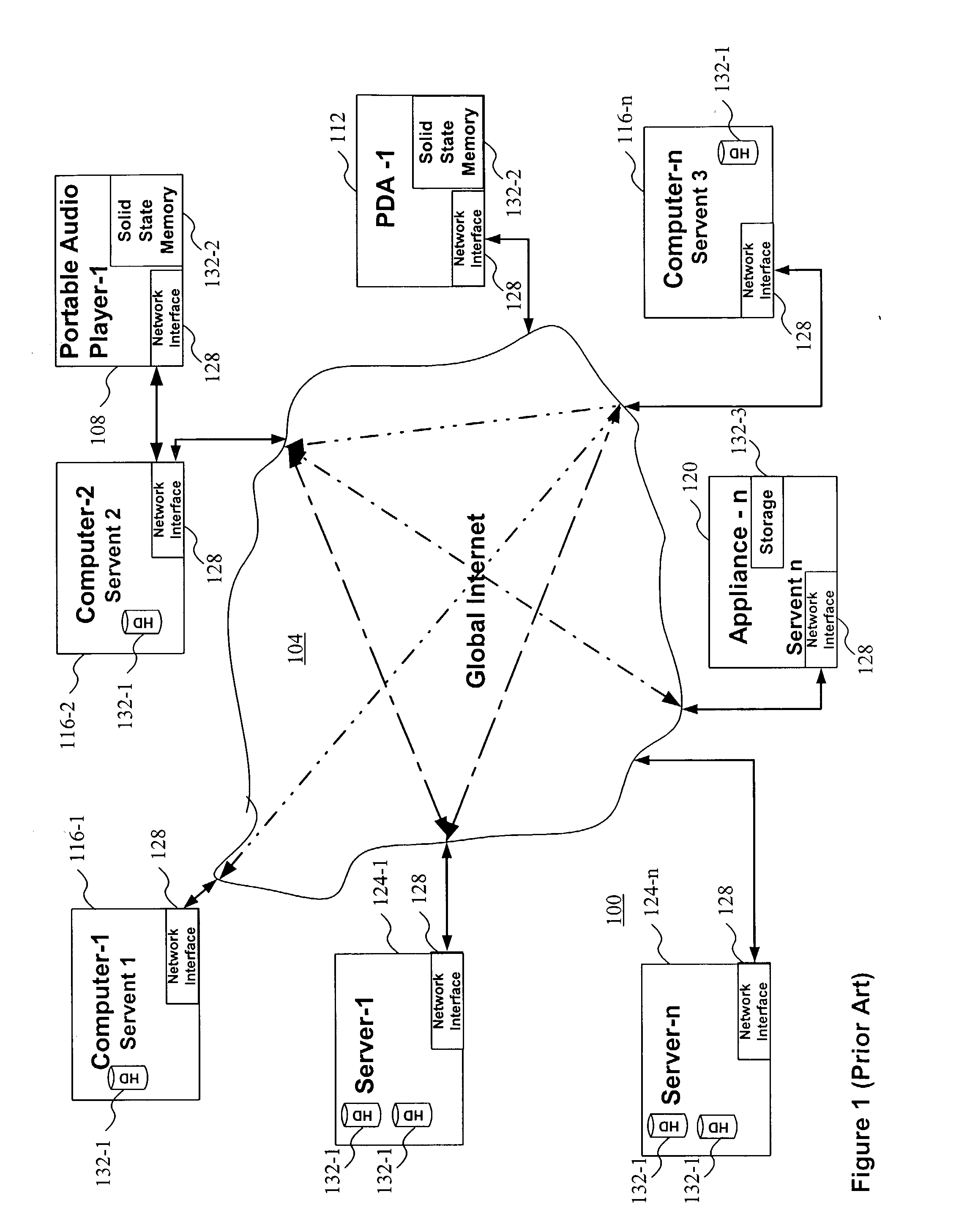
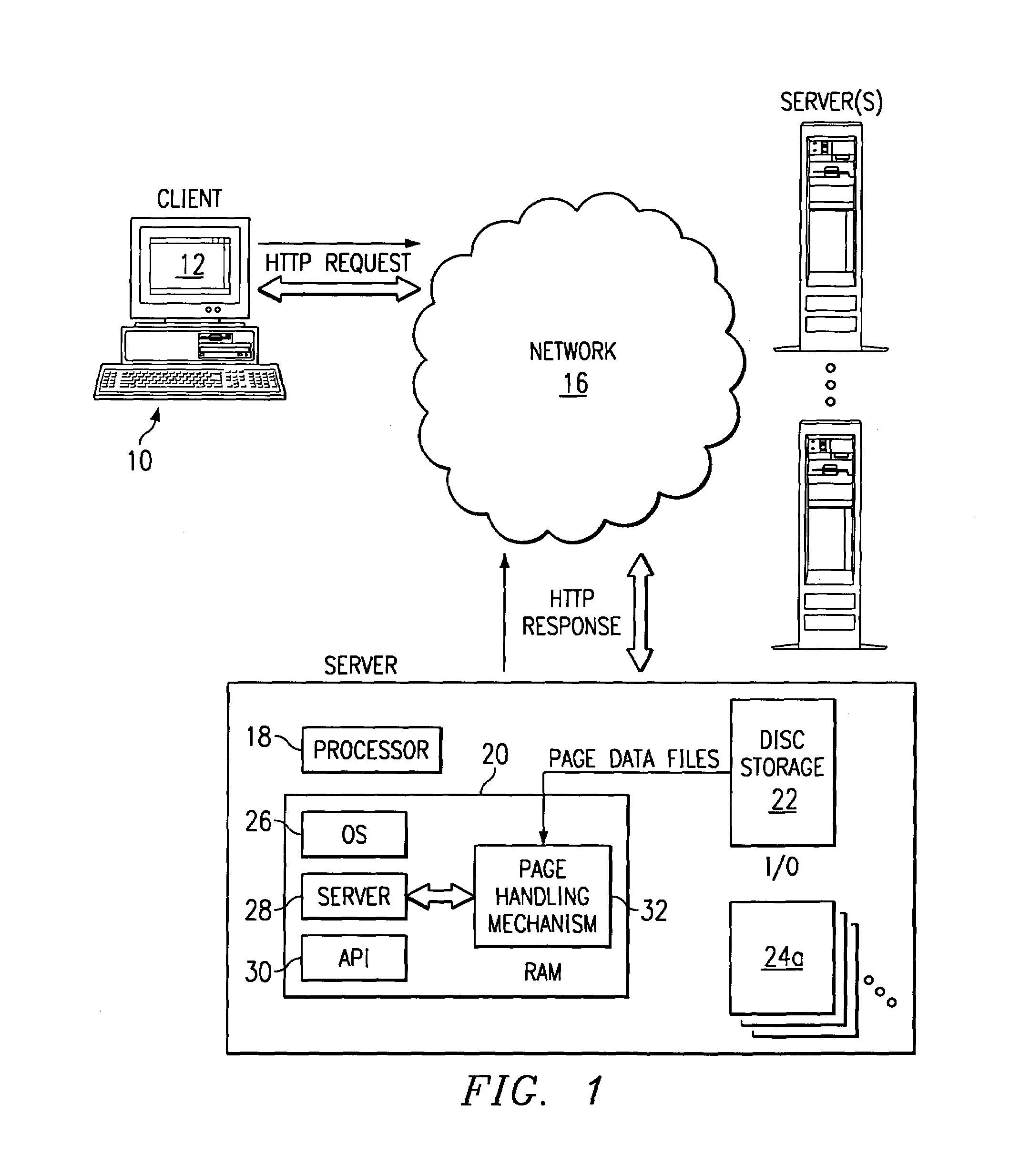
Tagged markup language interface with document type definition to access data in object oriented database
InactiveUS6480860B1Data processing applicationsWebsite content managementExtensible markupDocument preparation
An apparatus and method defines a markup language for accessing data in a database. The markup language is preferably defined in extensible markup language (XML) by creating suitable document type definitions (DTDs), which define the grammar for accessing data in the database using the markup language. A bridge interprets the data request from the client in markup language format, a suitable database query for the database is formulated, and the data is then placed within a document for delivery in markup language format to the user. As new data types are added to the database, corresponding document type definitions (DTDs) may be dynamically generated, allowing a user to access new kinds of data in a database with a software tool that has a user-friendly graphical user interface without having to manually update the software tool for each new data type that is added to the database.
Owner:IBM CORP
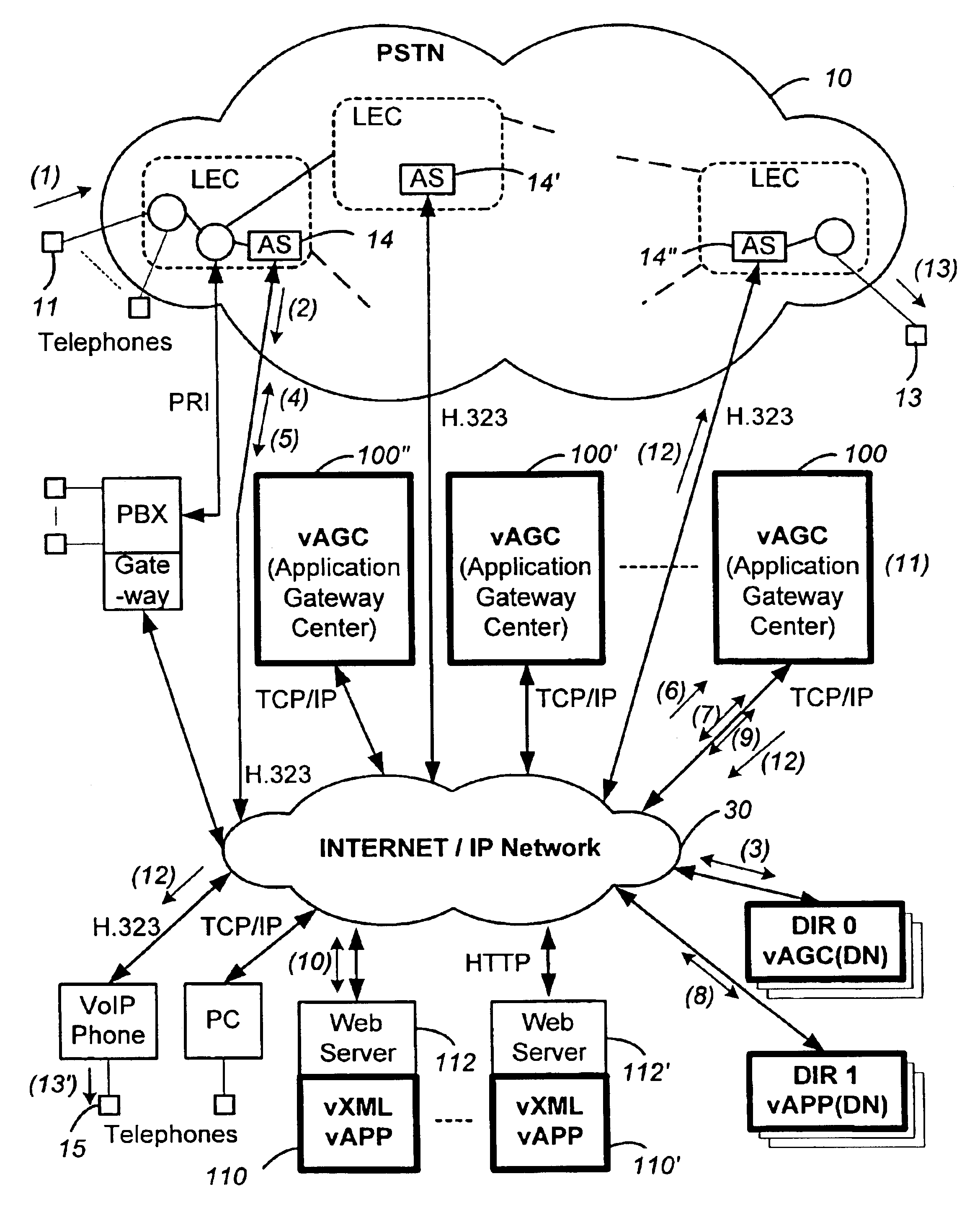
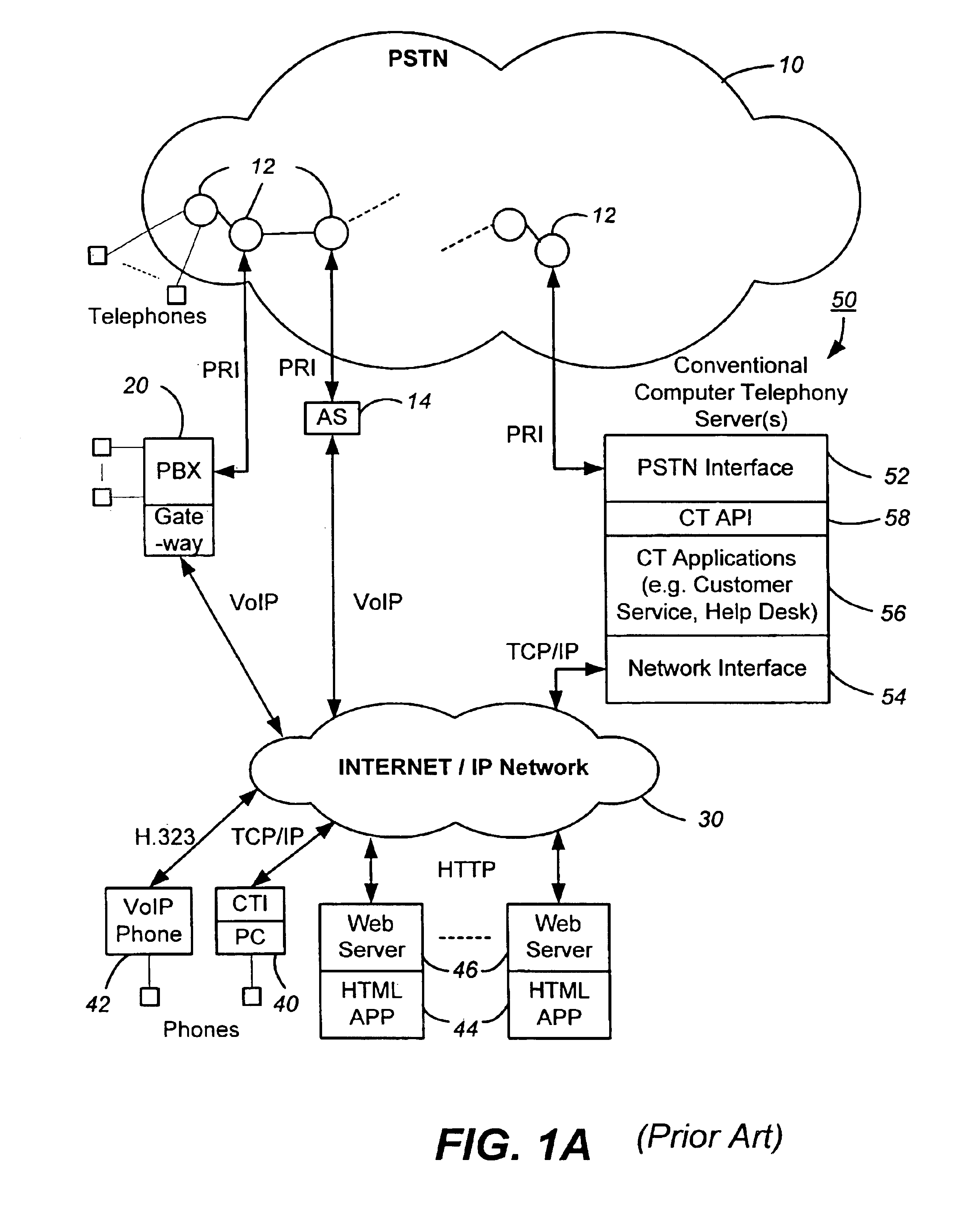
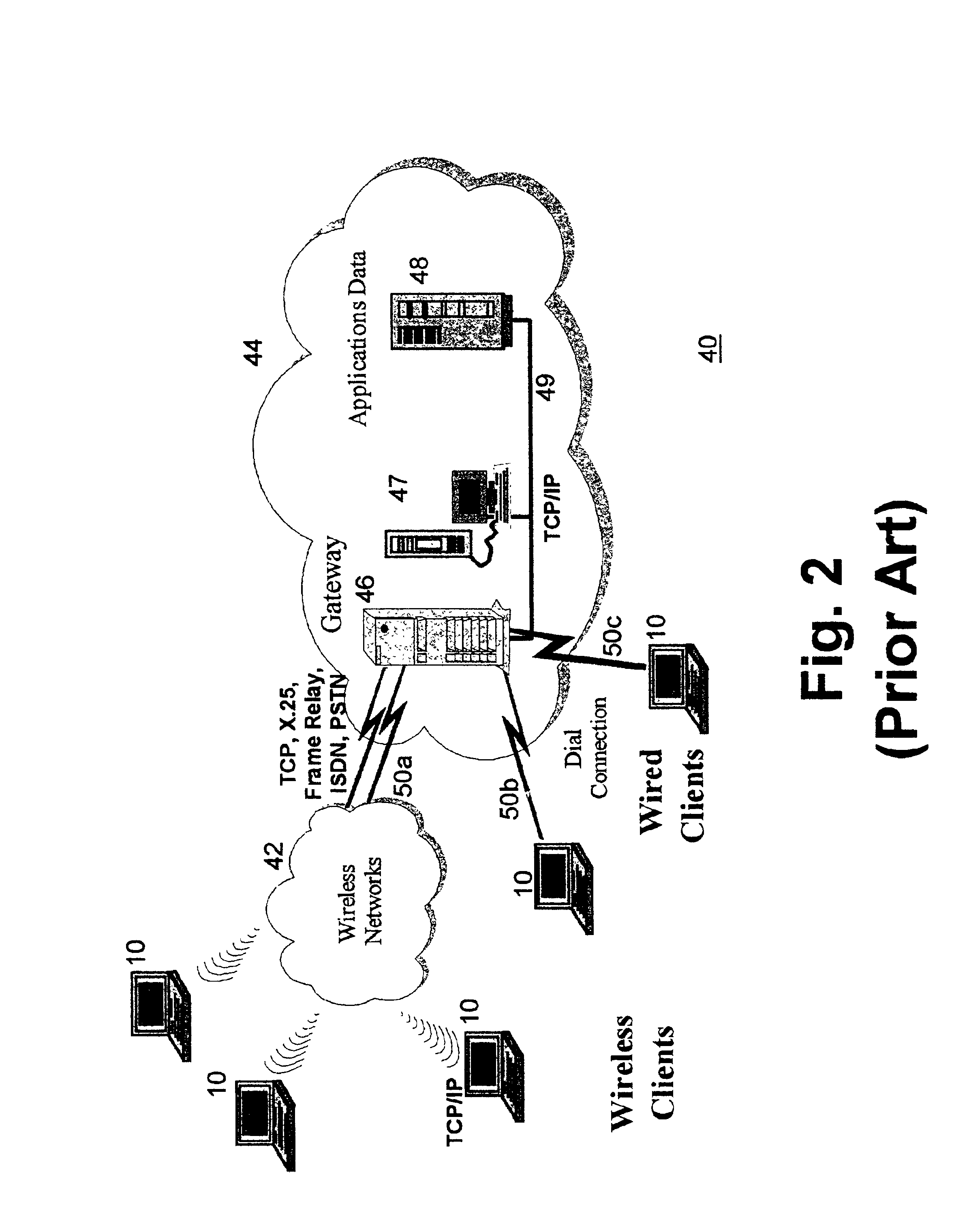
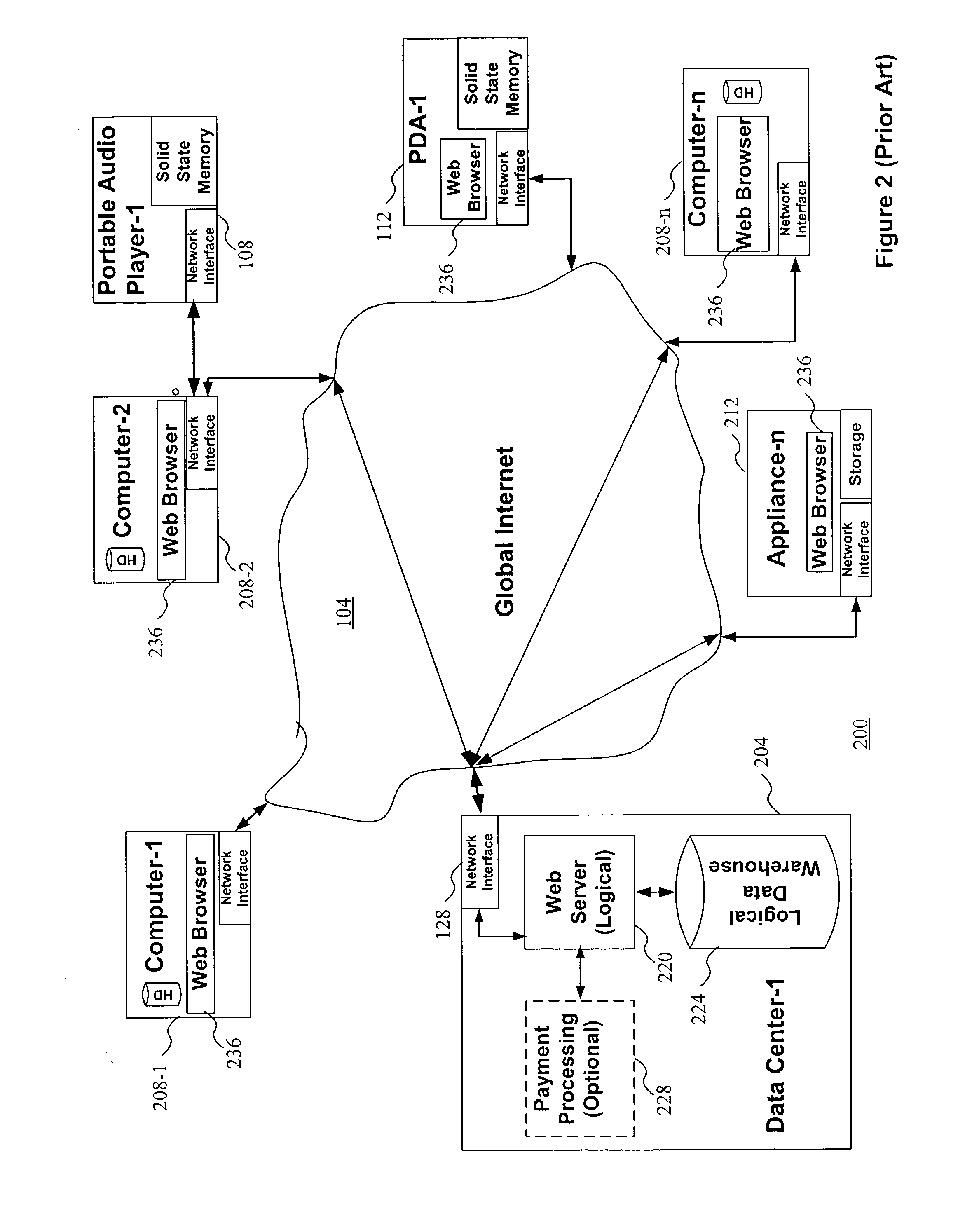
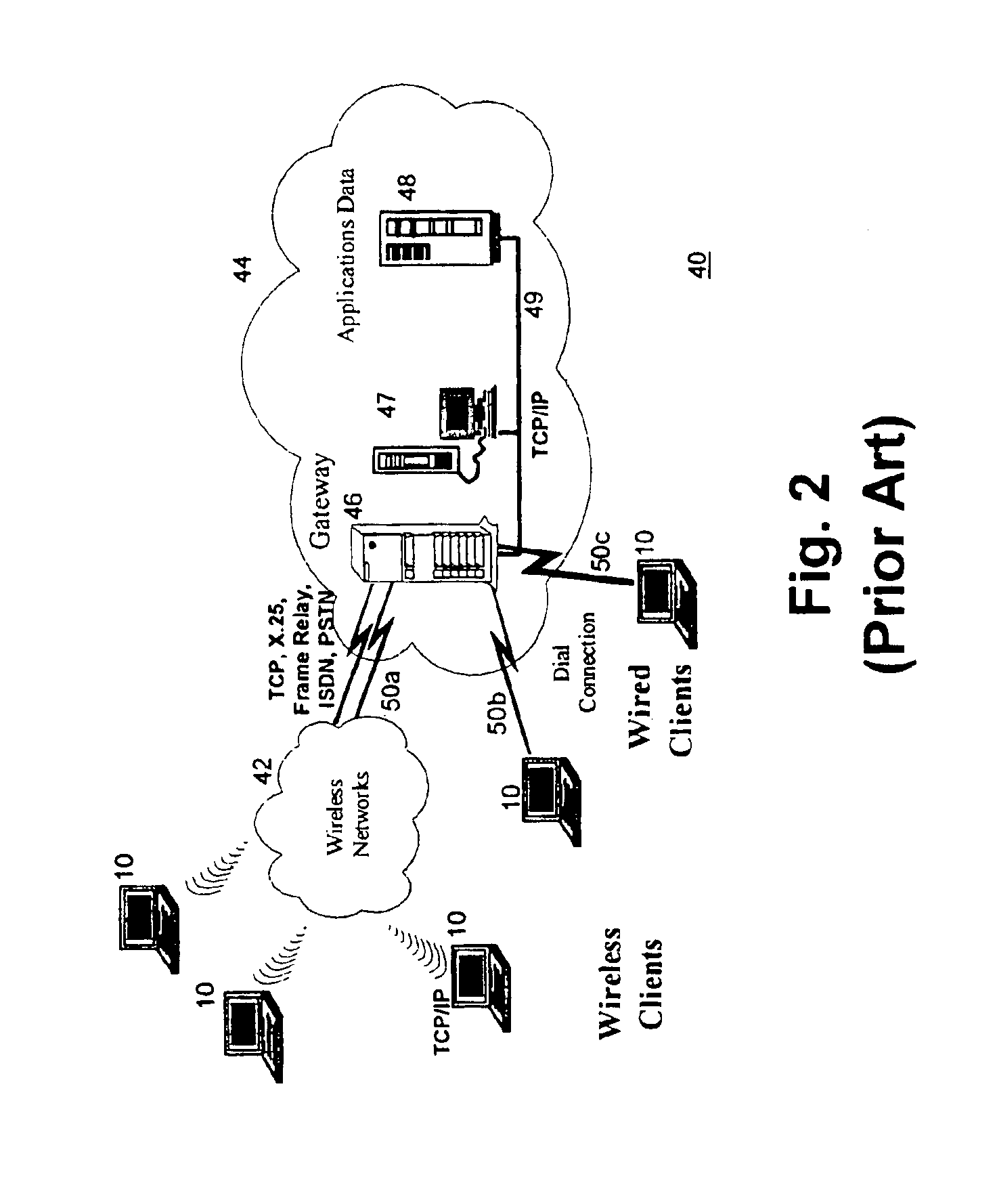
Networked computer telephony system driven by web-based applications
InactiveUS6922411B1Improve developmentEasy to deploySpecial service for subscribersData switching by path configurationQuality of serviceThe Internet
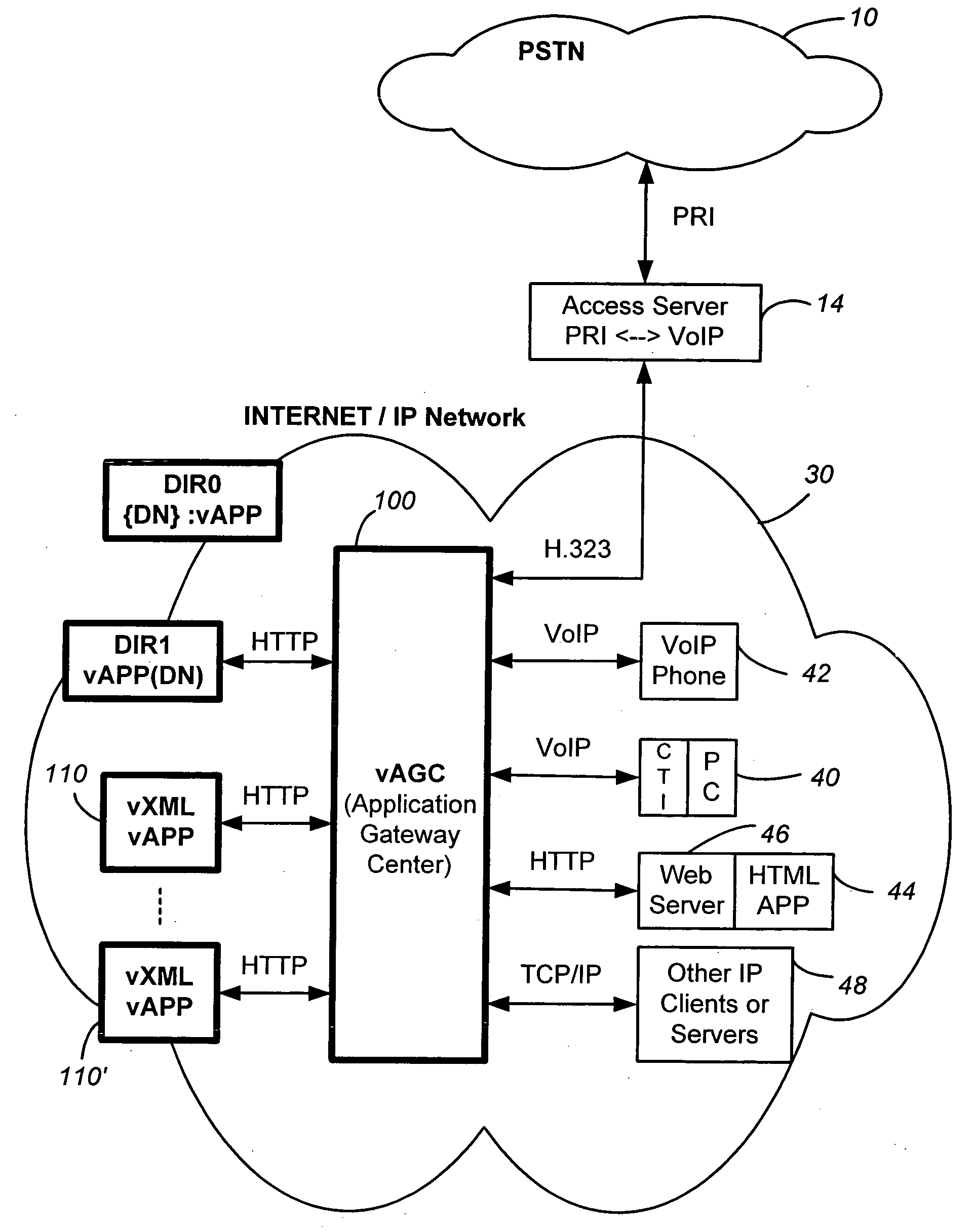
A networked telephony system and method allow users to deploy on the Internet computer telephony applications associated with designated telephone numbers. The telephony application is easily created by a user in XML (Extensible Markup Language) with predefined telephony XML tags and easily deployed on a website. The telephony XML tags include those for call control and media manipulation. A call to anyone of these designated telephone numbers may originate from anyone of the networked telephone system such as the PSTN (Public Switched Telephone System), a wireless network, or the Internet. The call is received by an application gateway center (AGC) installed on the Internet. Analogous to a web browser, the AGC provides facility for retrieving the associated XML application from its website and processing the call accordingly. The architecture and design of the system allow for reliability, high quality-of-service, easy scalability and the ability to incorporate additional telephony hardware and software and protocols.
Owner:ALVARIA INC
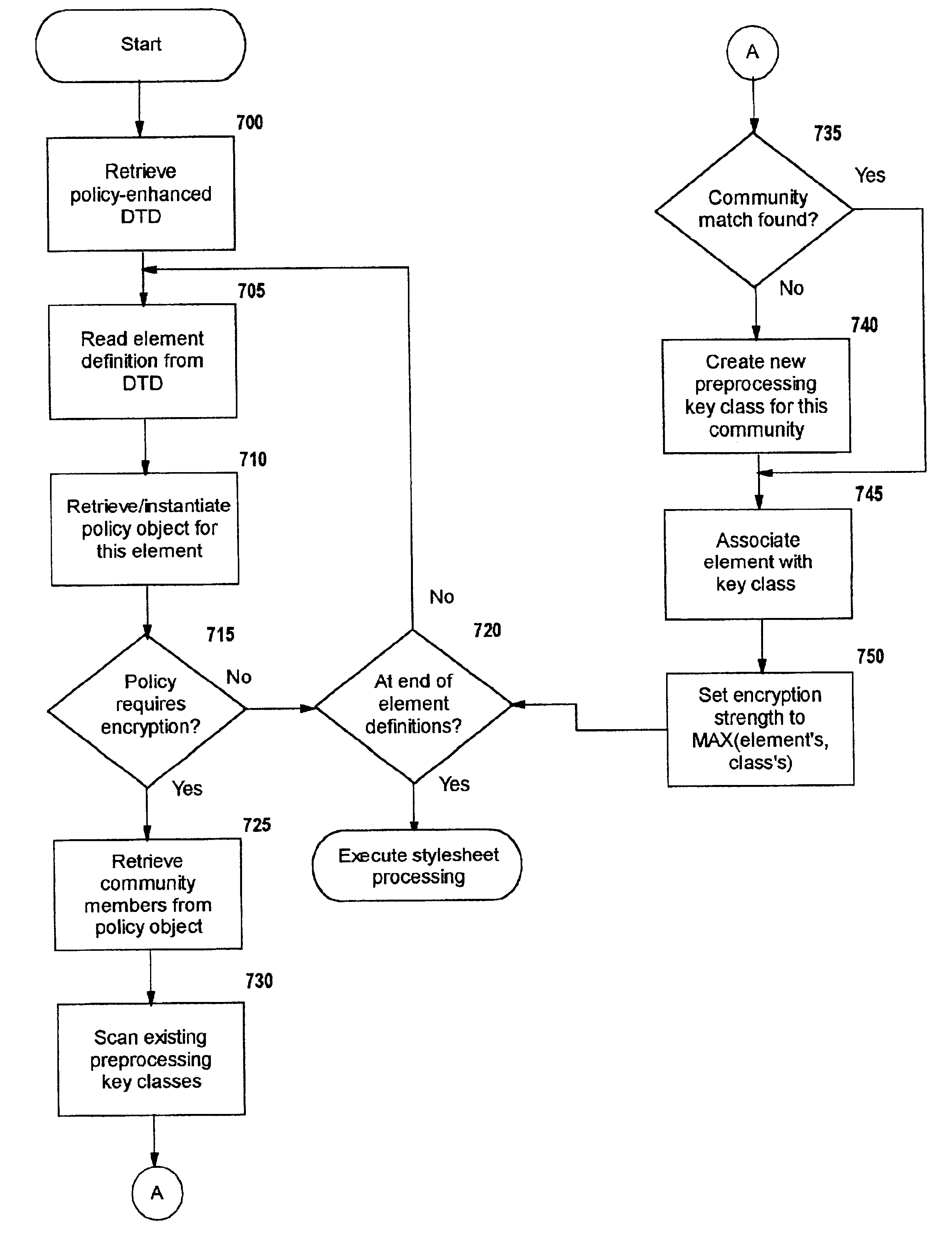
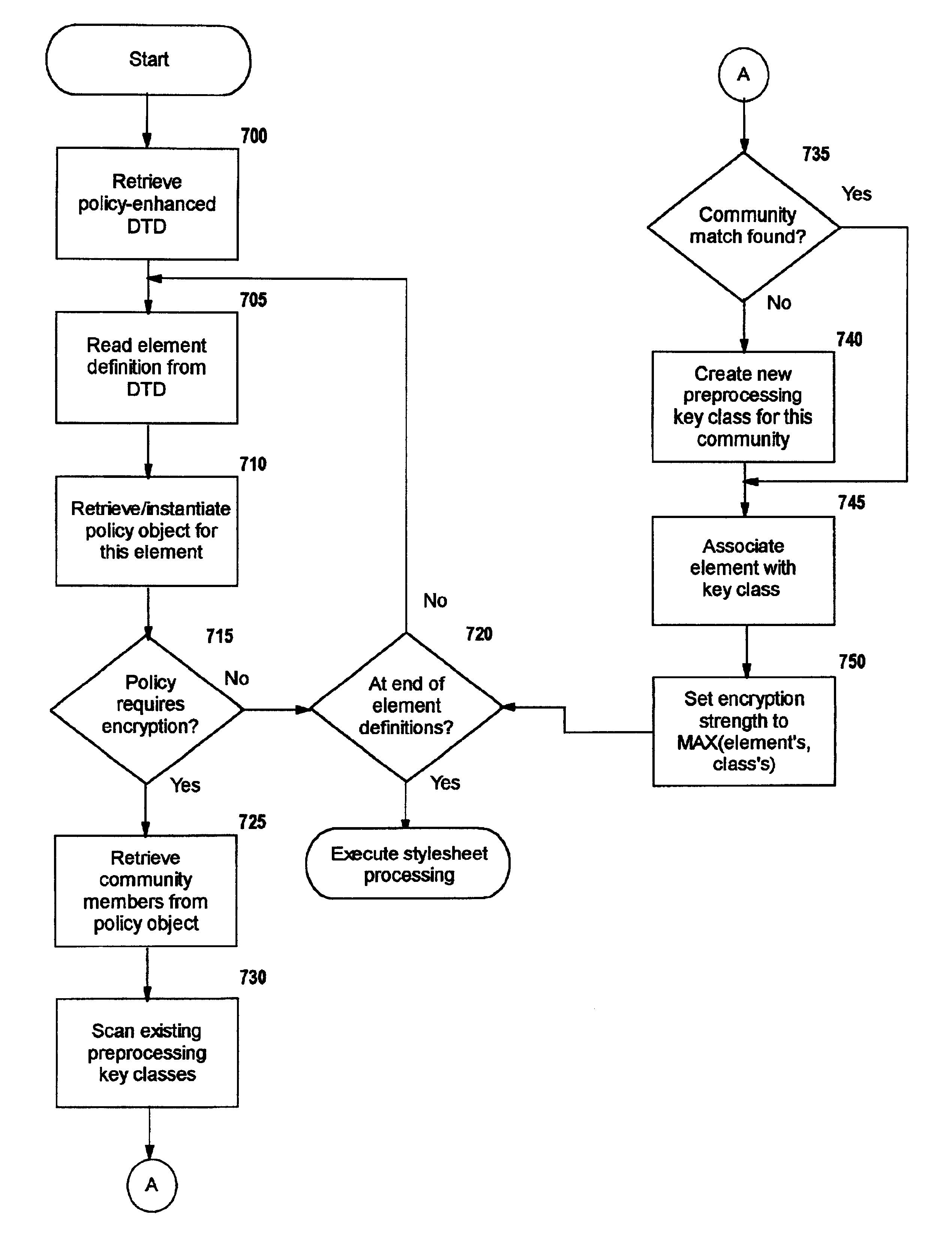
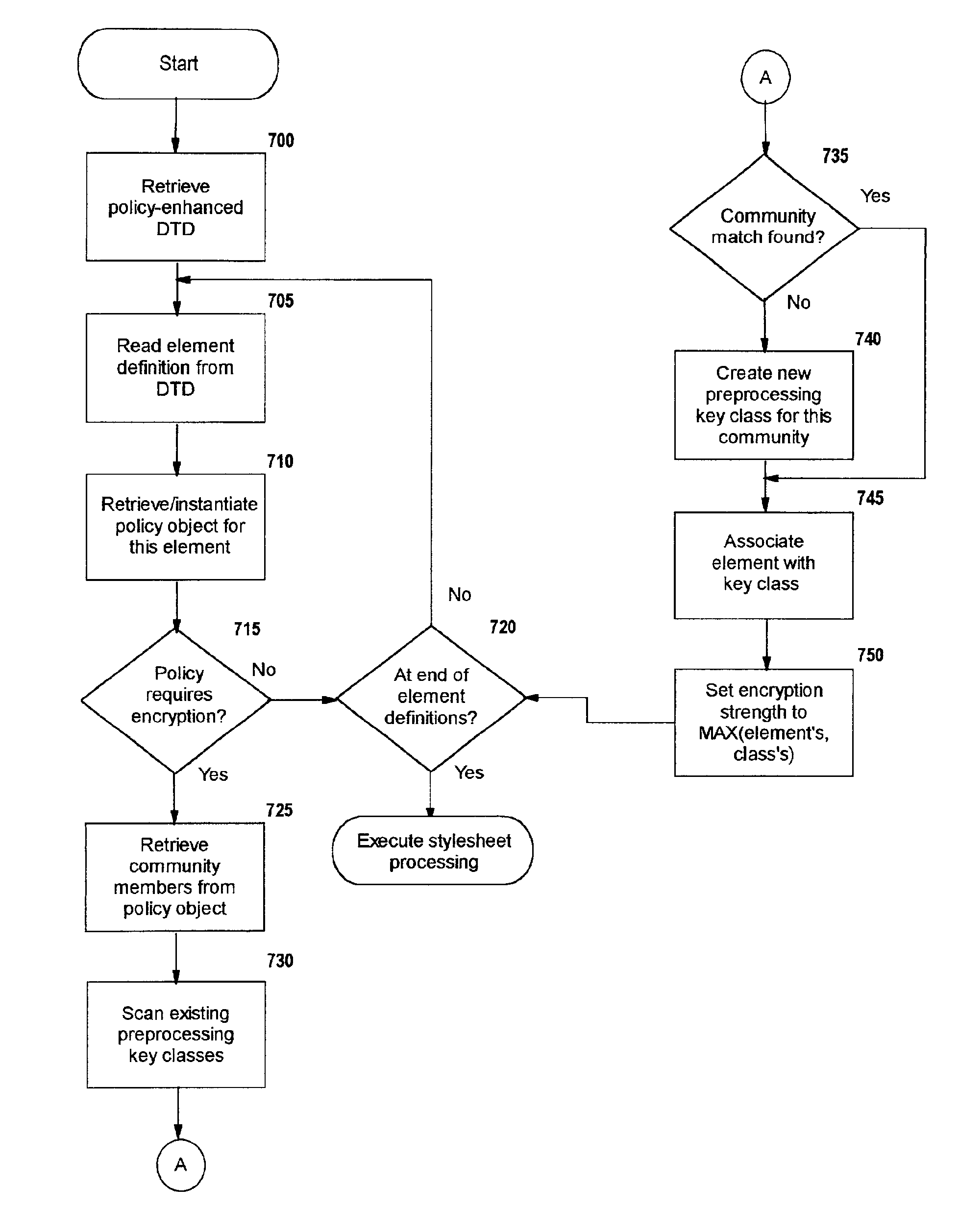
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
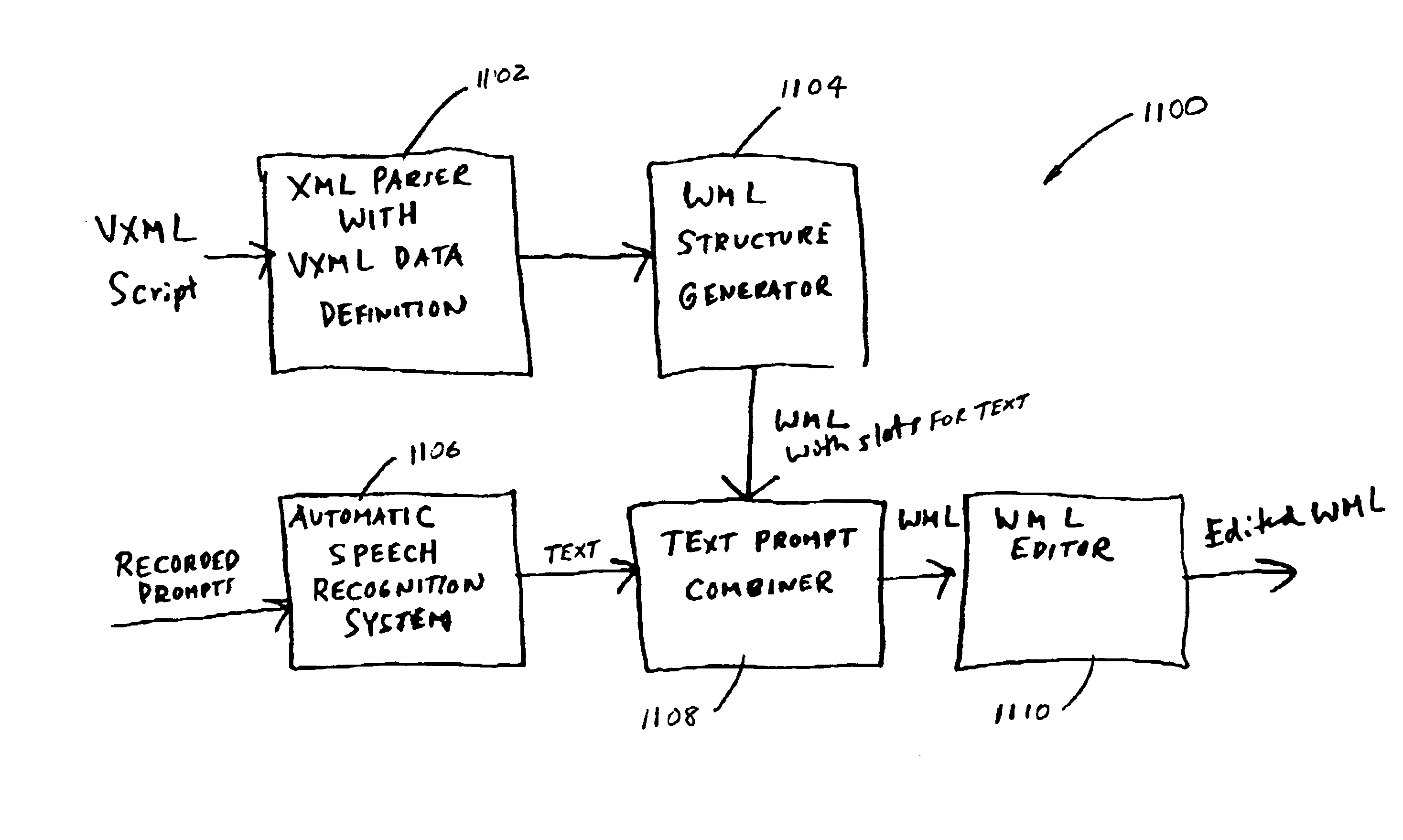
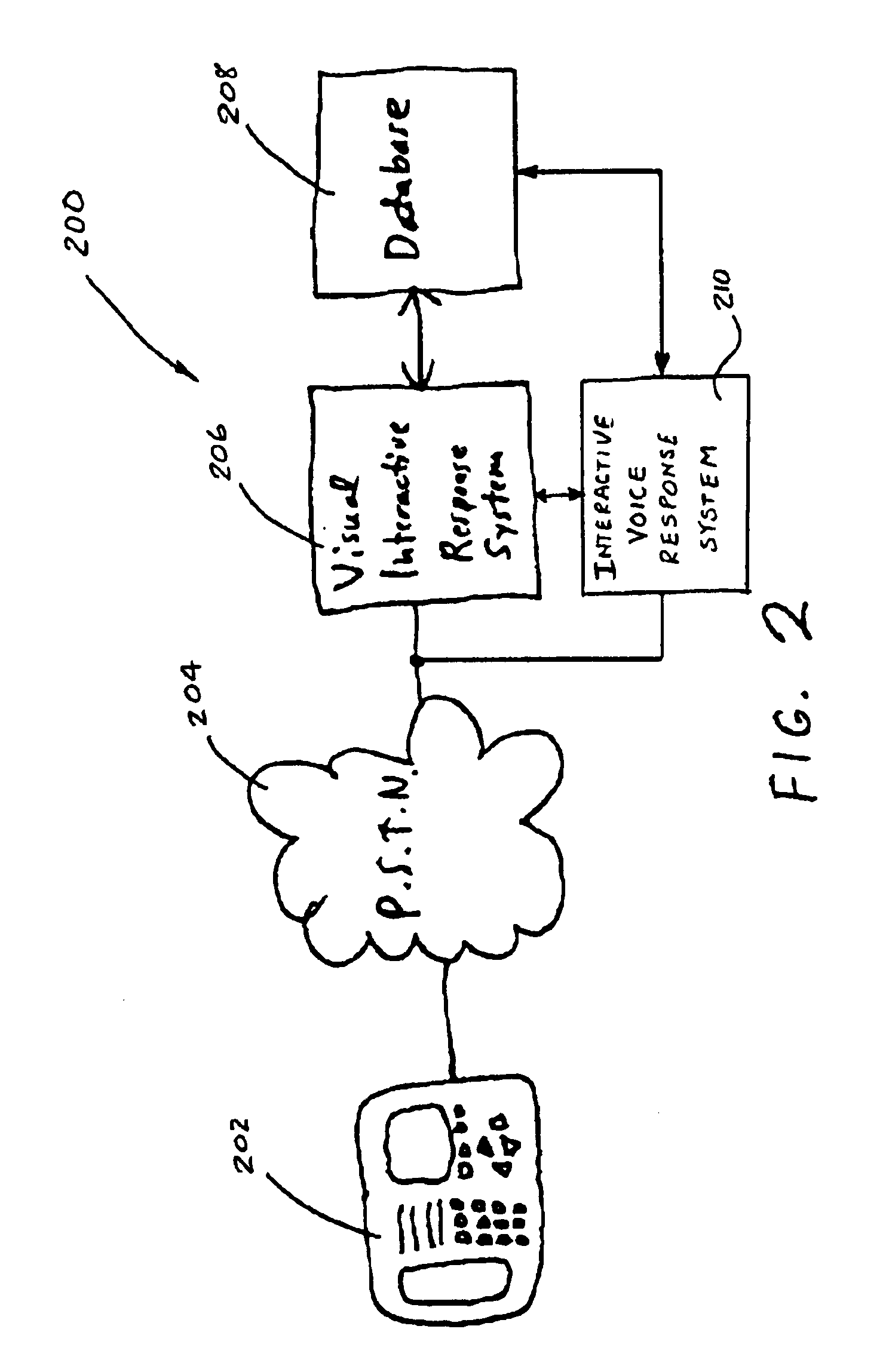
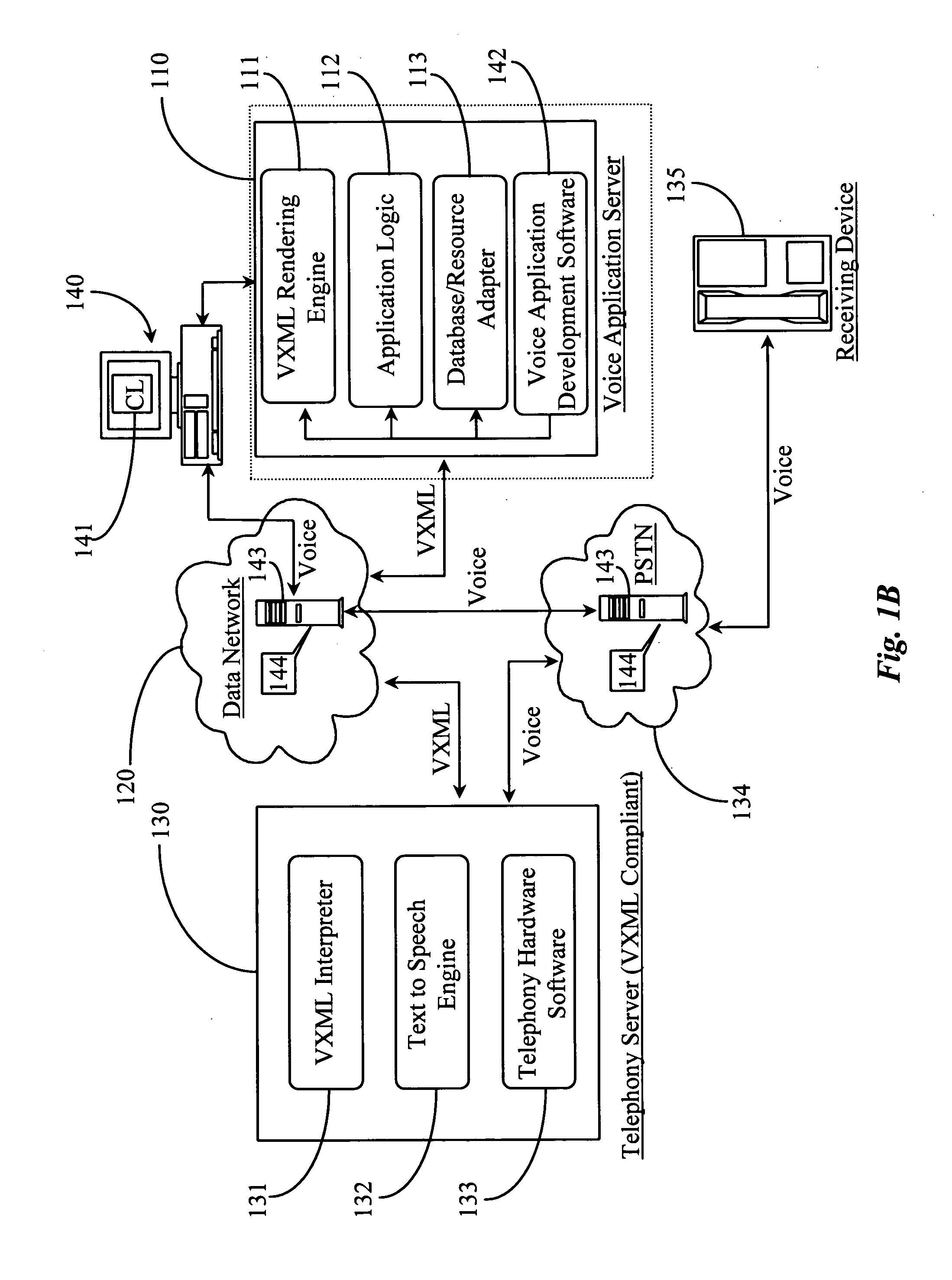
Visual interactive response system and method translated from interactive voice response for telephone utility
InactiveUS6920425B1Interconnection arrangementsAutomatic exchangesInteractive voice response systemWireless Markup Language
A system, method, and computer readable medium storing a software program for translating a script for an interactive voice response system to a script for a visual interactive response system. The visual interactive response system executes the translated visual-based script when a user using a display telephone calls the visual interactive response system. The visual interactive response system then transmits a visual menu to the display telephone to allow the user to select a desired response, which is subsequently sent back to the visual interactive response system for processing. The voice-based script may be defined in voice extensible markup language and the visual-based script may be defined in wireless markup language, hypertext markup language, or handheld device markup language. The translation system and program includes a parser for extracting command structures from the voice-based script, a visual-based structure generator for generating corresponding command structure for the visual-based script, a text prompt combiner for incorporating text translated from voice prompts into command structure generated by the structure generator, an automatic speech recognition routine for automatically converting voice prompts into translated text, and an editor for editing said visual-based script.
Owner:RPX CLEARINGHOUSE
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Message gates in a distributed computing environment
InactiveUS6850979B1Multiple digital computer combinationsBuying/selling/leasing transactionsDistributed Computing EnvironmentExtensible markup
Embodiments of message gates are described. A message gate is the message endpoint for a client or service in a distributed computing environment. A message gate may provide a secure endpoint that sends and receives type-safe messages. Gates may perform the sending and receiving of messages between clients and services using a protocol specified in a service advertisement. In one embodiment, the messages are eXtensible Markup Language (XML) messages. For a client, a message gate represents the authority to use some or all of a service's capabilities. Each capability may be expressed in terms of a message that may be sent to the service. Creation of a message gate may involve an authentication service that generates an authentication credential, and that may negotiate the desired level of security and the set of messages that may be passed between client and service. A message gate may perform verification of messages against a message schema to ensure that the messages are allowed. Message gates may embed the authentication credential in outgoing messages so that the receiving message gate may authenticate the message. Messages may also include information to allow the receiving gate to verify that the message has not been compromised prior to receipt.
Owner:ORACLE INT CORP
Relational database system providing XML query support
InactiveUS6799184B2Efficient accessImprove efficiencyData processing applicationsDigital data information retrievalRelational databaseFile system
A system providing methods enabling data in Extensible Markup Language ("XML") format to be extracted, transformed and stored in a database, file system or main memory is described. The extraction and transformation process is generalized and can be used on various types of XML data, enabling XML data to be stored and queried using standard database query methodologies. The system includes parse-time functionality to transform XML documents into a structure having an interface that enables efficient access to the underlying data. The system also includes query execution-time functionality providing greater efficiency by bringing only the relevant portions of transformed XML data into memory in response to a query. The system parses and translates queries into a structure that can be executed without the need to write custom application-specific navigation code to search XML data. The system also enables original XML documents (or portions thereof) to be recomposed when required.
Owner:SYBASE INC
Method and system for modelling a communications network
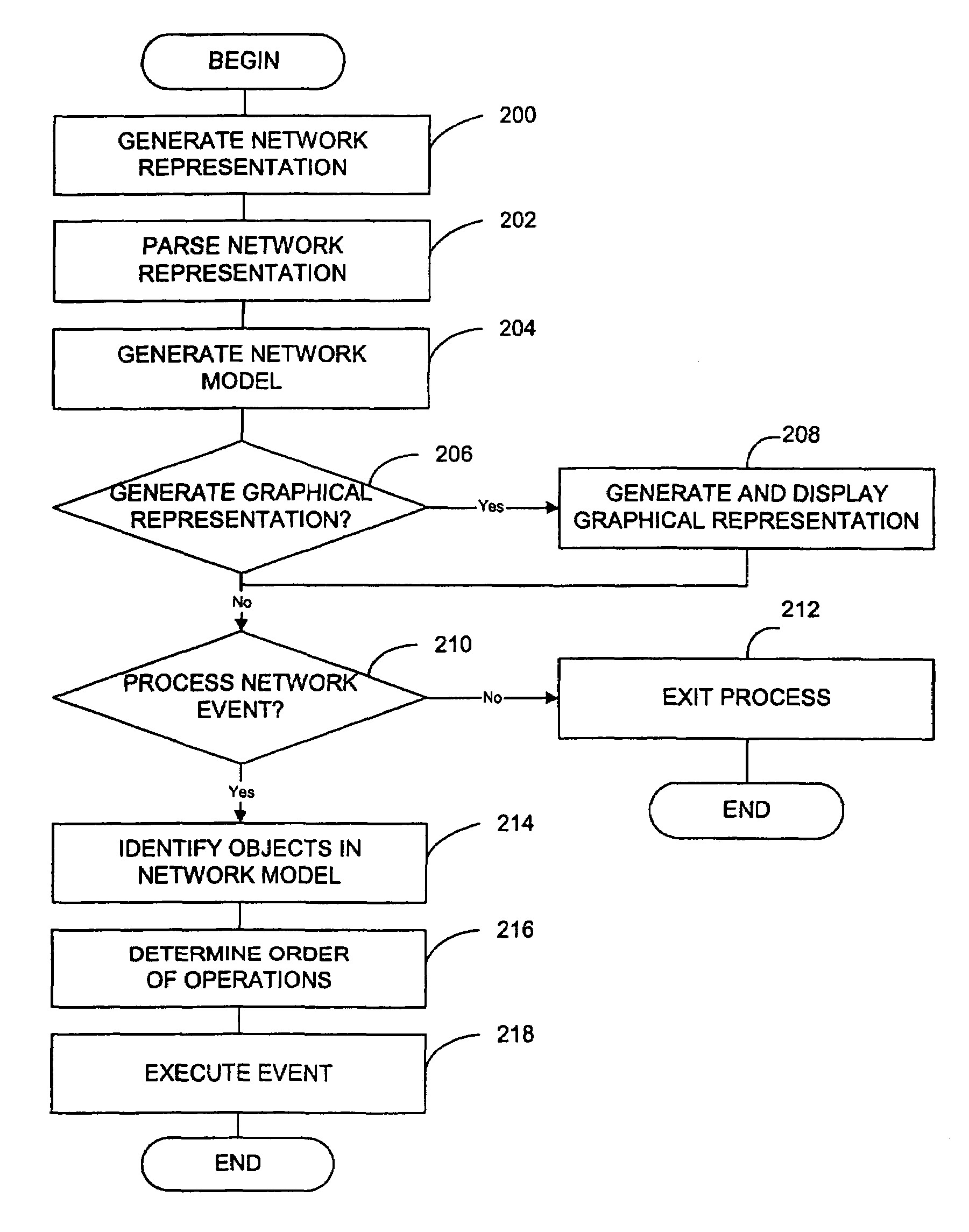
ActiveUS7392300B2Analogue computers for electric apparatusDigital computer detailsOrder of operationsNetwork model
A system and method of modelling a communications network using a computer system is disclosed, the method including generating a network representation using computer-readable code that represents structured information; parsing the network representation; generating a network model using the parsed network representation, the network model including a plurality of network objects and relationships between the plurality of network objects; and storing the network model in memory. Any type of network may be modeled. The computer-readable code may be any suitable language or instructions for representing structured information such as, for example, extensible mark-up language (XML). A network inventory adapter receives the network representation from the network. The network inventory adapter is a software component that may be used to connect applications to the network. The network inventory adapter receives the network representation from the network and reads and parses the network representation to determine which network objects are to be operated on and the order of operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods for rights enabled peer-to-peer networking
InactiveUS20030120928A1User identity/authority verificationUnauthorized memory use protectionDigital rights managementRights management
The present invention relates to digital rights management. In one embodiment, persons, processes, and / or computers and appliances locate, share, publish, retrieve, and use all kinds of digital information that has been protected using digital rights management technologies. Rights management includes securely associating rules for authorized use with the digital information. Rules and / or digital information may be encapsulated in a cryptographically secure data structure or "container" ("CSC") to protect against unauthorized use, to ensure secrecy, to maintain integrity, and to force the use of a rights management system to access the protected information. Attributes or metadata information describing at least some of the rules ("rules-metadata information") and optionally any associated rule parameter data with respect to the protected information are created. This rules-metadata information may be organized, structure, encoded, and / or presented using a self-defining data structure such as those created using Extensible Markup Language (XML). In one embodiment, the XML-encoded rules-metadata information is also made available unencrypted, in plain text, to facilitate P2P search and file transfer. Having at least some of the rules-metadata information outside or external to a CSC allows greater flexibility in searching based at least in part upon the rules-metadata information. Some embodiments may hold the rules-metadata information in a separate CSC. Putting the rules-metadata information in a separate CSC more easily allows authentication and maintains the integrity of the rules-metadata information. In another embodiment, the rules metadata may be in an unencrypted portion of a CSC itself or concatenated with a CSC in a single file.
Owner:CATO MILES +2
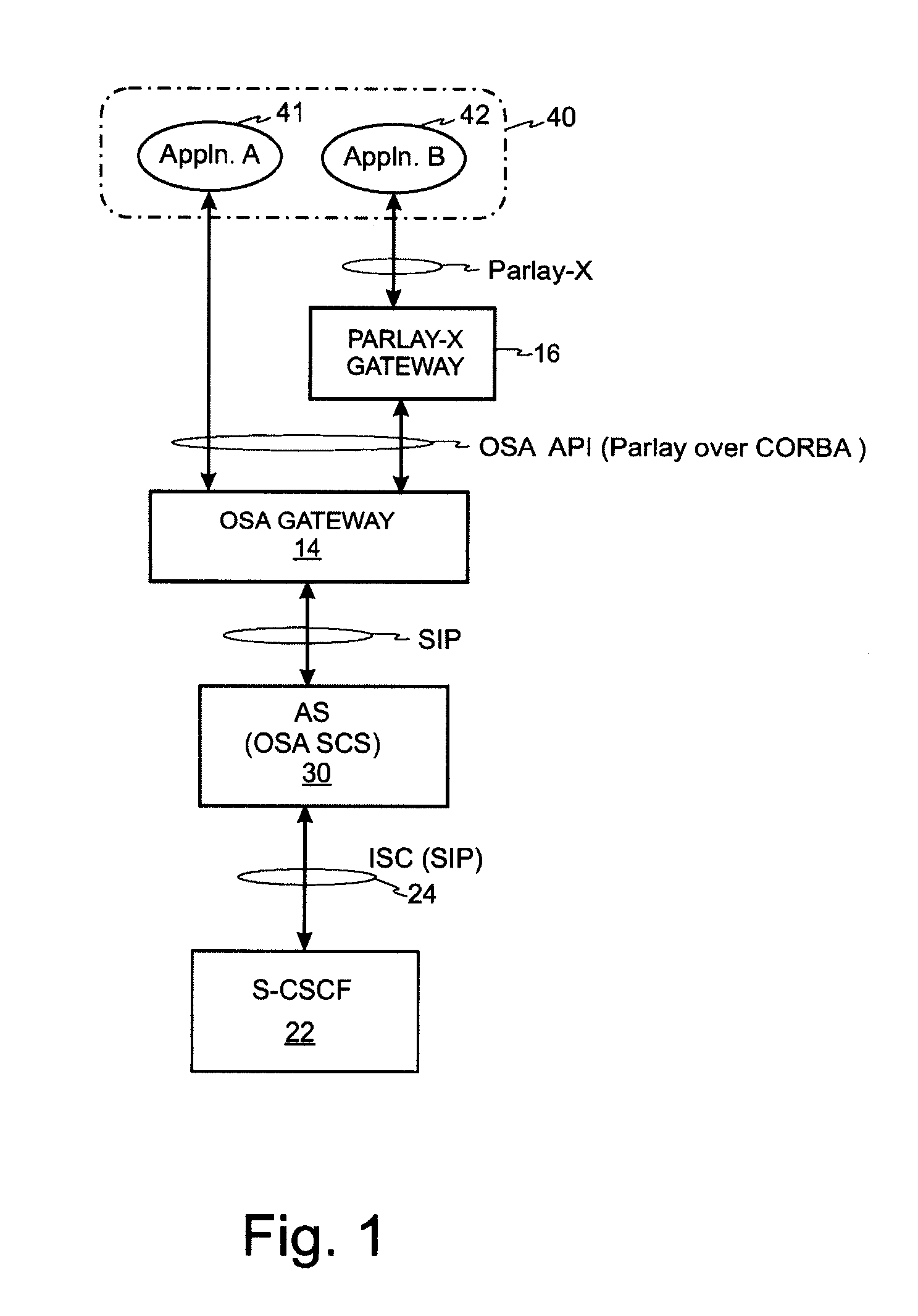
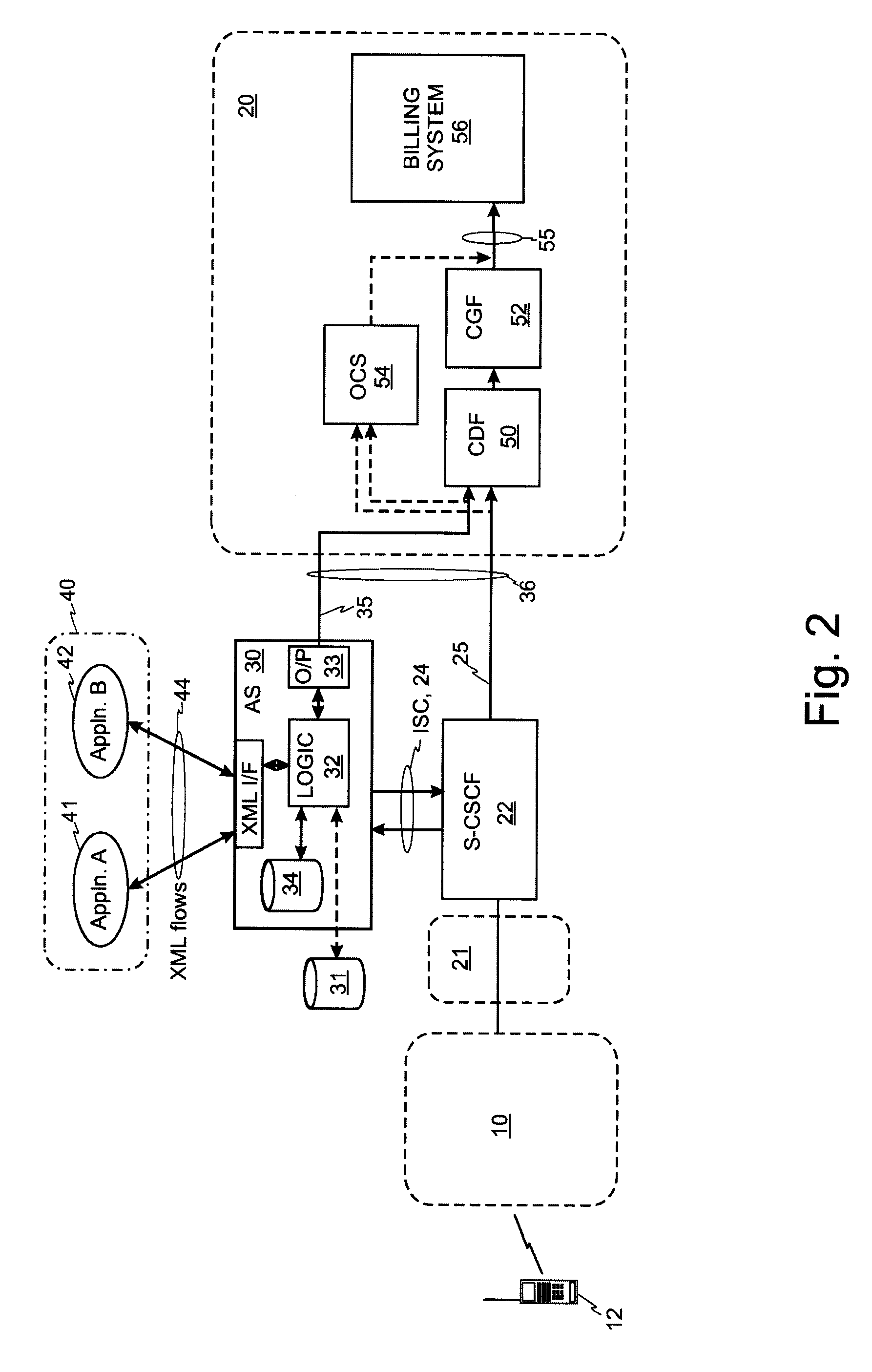
Application Server Billing
InactiveUS20080082643A1Accurate monitoringAvoid the needCredit schemesMultiple digital computer combinationsApplication serverParlay X
An Application Server entity in an IP Multimedia Subsystem (IMS) network comprises an interface for interfacing with an application and control logic which is arranged to inspect signalling information received from the application via the interface in the form of Extensible Markup Language (XML). The received signalling information is compared with stored rule data which specifies a relationship between an element in the signalling information and an action that should be taken and output data is generated based on the comparison. The Application Server can output operational measurements and / or charging information which more accurately reflect usage made of the Application Server resources. The need for a separate OSA / Parlay-X gateway can be avoided.
Owner:RPX CLEARINGHOUSE
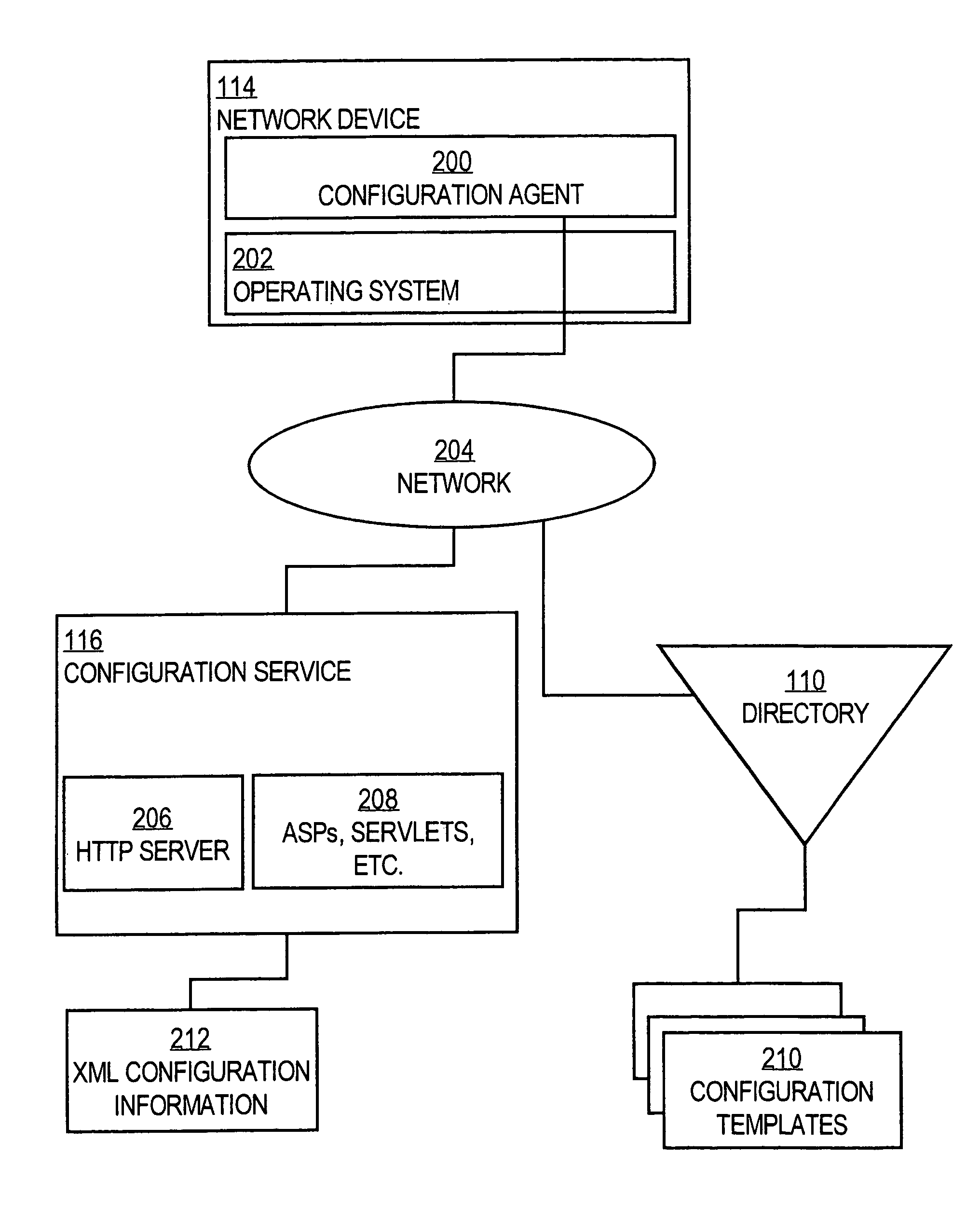
Method and apparatus for provisioning network devices using instructions in extensible markup language
InactiveUS7054924B1Reliable transportationMultiple digital computer combinationsTransmissionReliable transmissionExtensible markup
A method is disclosed for carrying out network device provisioning and configuration, and communication of other information to a network device, automatically and in an assured manner. A configuration service receives a request from a network device to provide configuration information. The configuration service retrieves a template representing the configuration from a storage location, e.g., a directory service. The configuration service also retrieves one or more parameter values specific to the device. Device-specific values are instantiated for the generic parameters in the template, based on the retrieved values. The resulting configuration is stored in XML format using XML tags to delimit configuration commands, tested for well-formed-ness, and syntax checked. A reliable transport protocol carries the configuration information to the device. At the device, a configuration agent syntax checks the embedded configuration information, and then applies the configuration information to the device. As a result, automatic network provisioning may be accomplished remotely, without requiring a skilled technician to visit customer premises to carry out configuration. The process may be integrated with an event service to enable multiple devices to concurrently receive re-configuration without special synchronization logic.
Owner:CISCO TECH INC
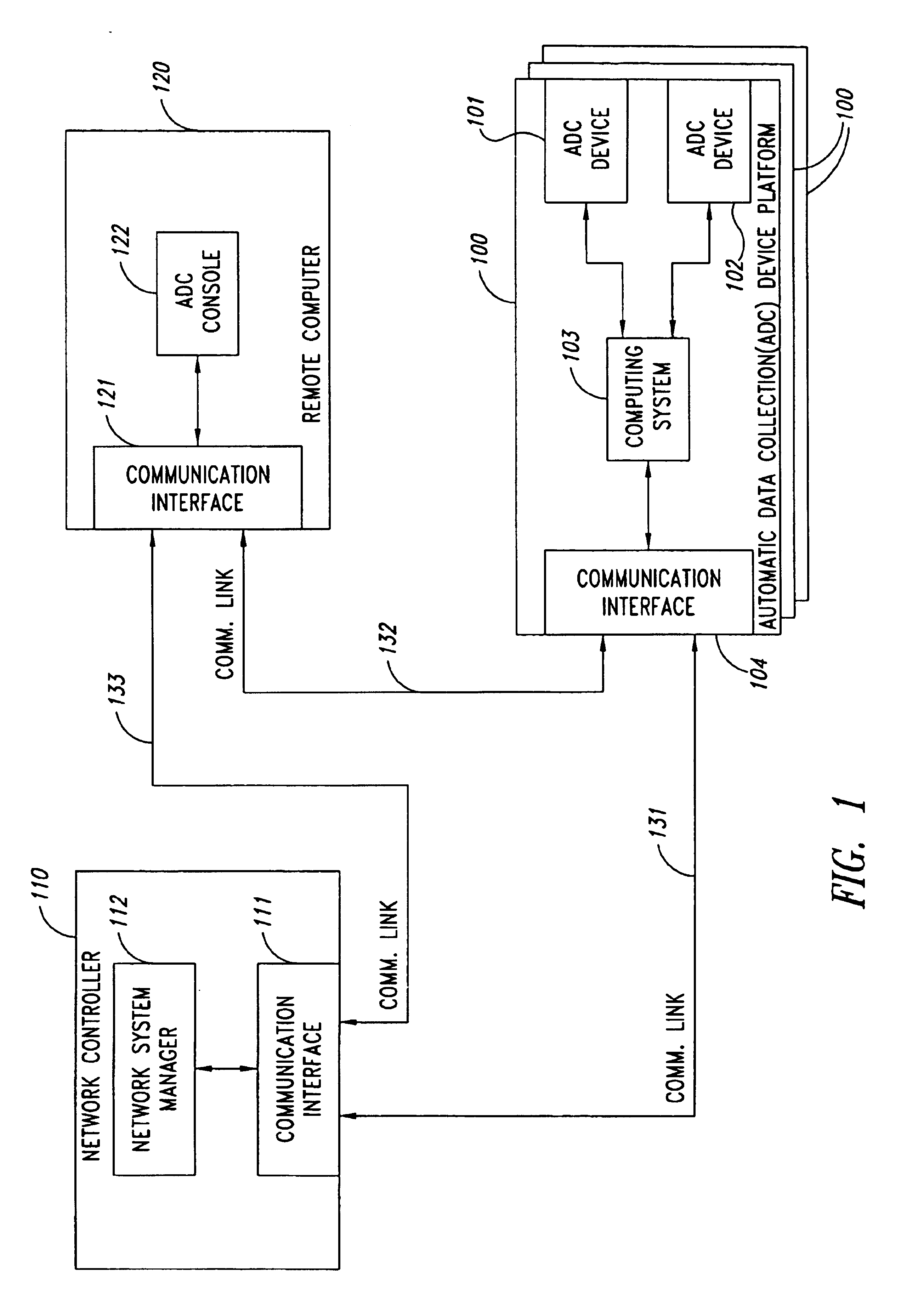
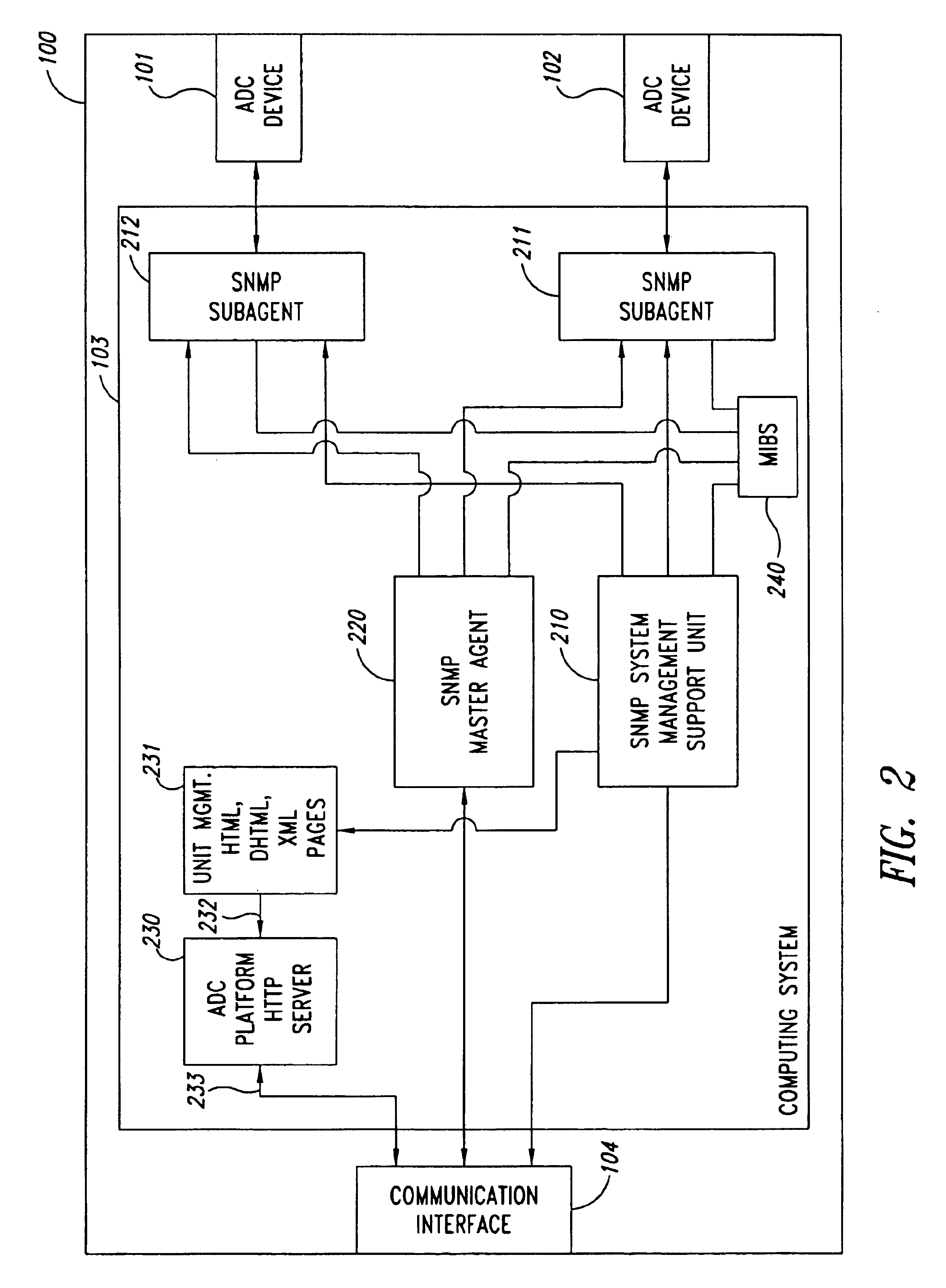
Remote anomaly diagnosis and reconfiguration of an automatic data collection device platform over a telecommunications network
InactiveUS6857013B2Detecting faulty hardware by remote testDigital computer detailsTelecommunications linkExtensible markup
Owner:INTERMEC IP CORP
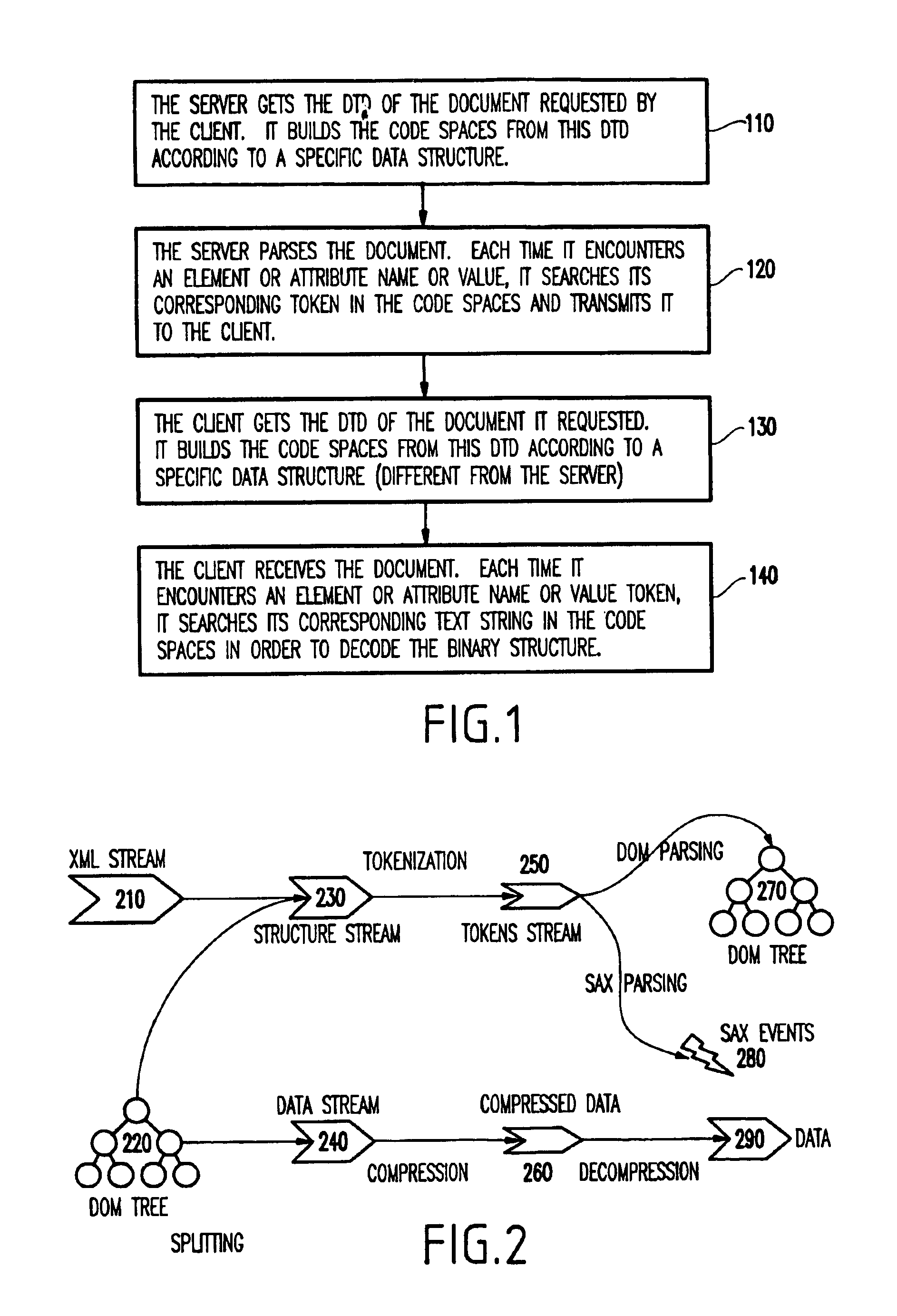
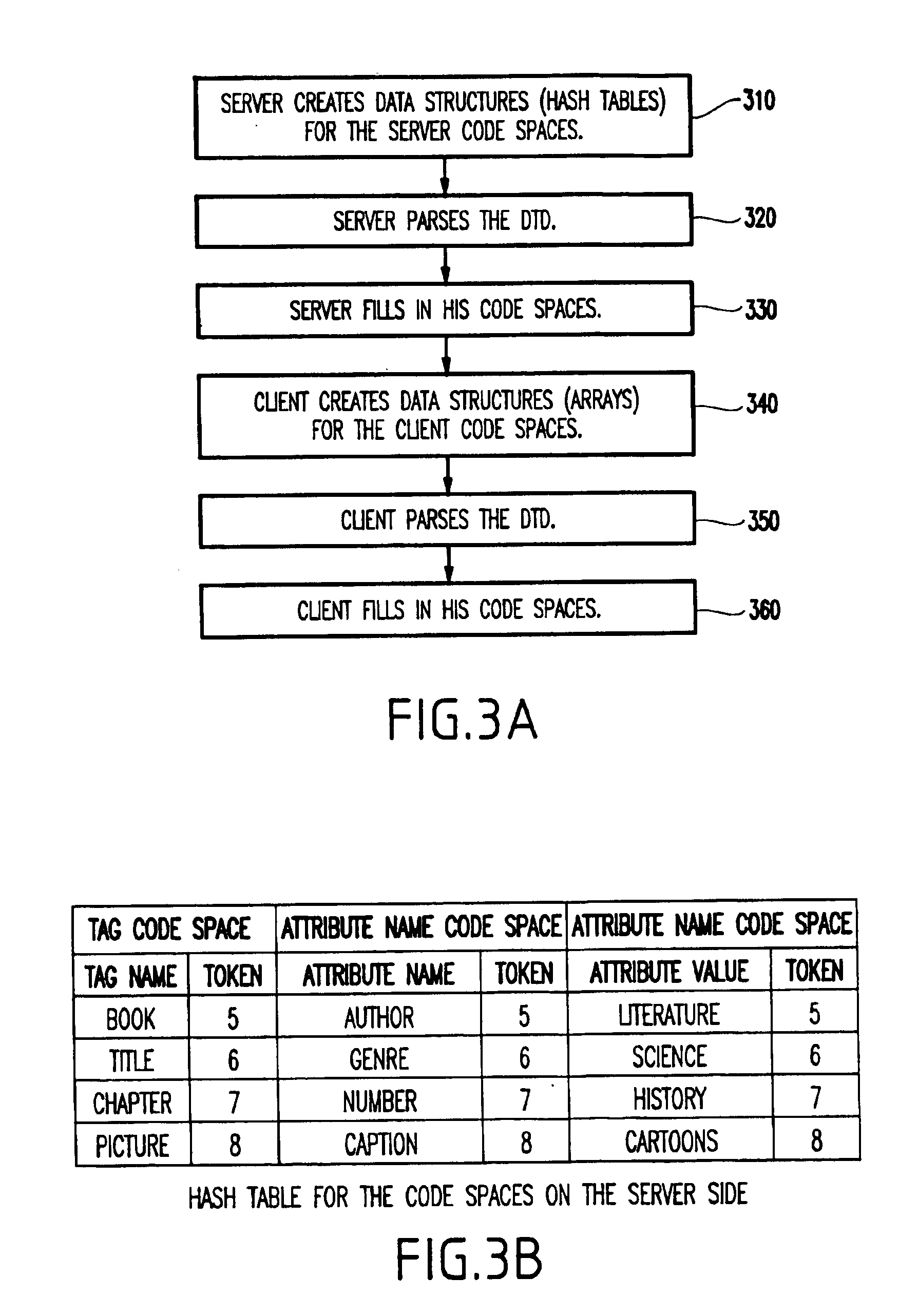
System and method for schema-driven compression of extensible mark-up language (XML) documents
InactiveUS6883137B1Easy to rebuildEfficient compressionDigital computer detailsCode conversionExtensible markupDocumentation
A method (and system) for compressing an extensible markup language (XML) document, includes compressing an XML document such that information in a markup portion therein is maintained in a compressed form to allow the document to be reconstructed. During the compressing, the markup portion and a non-markup portion of the document are separated, and the non-markup component is compressed using a first compression method and the markup component is compressed using a second compression method.
Owner:PENDRAGON NETWORKS
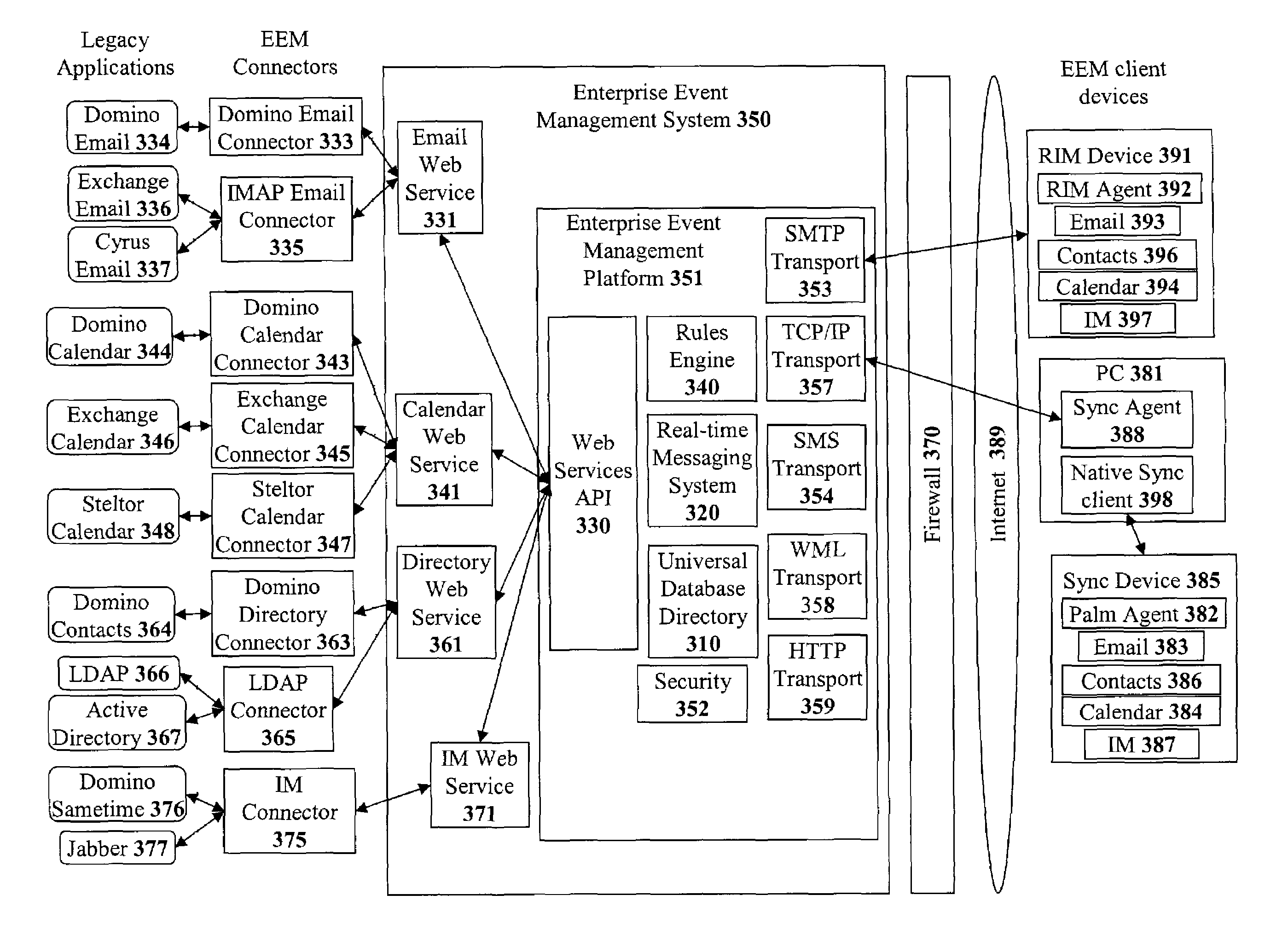
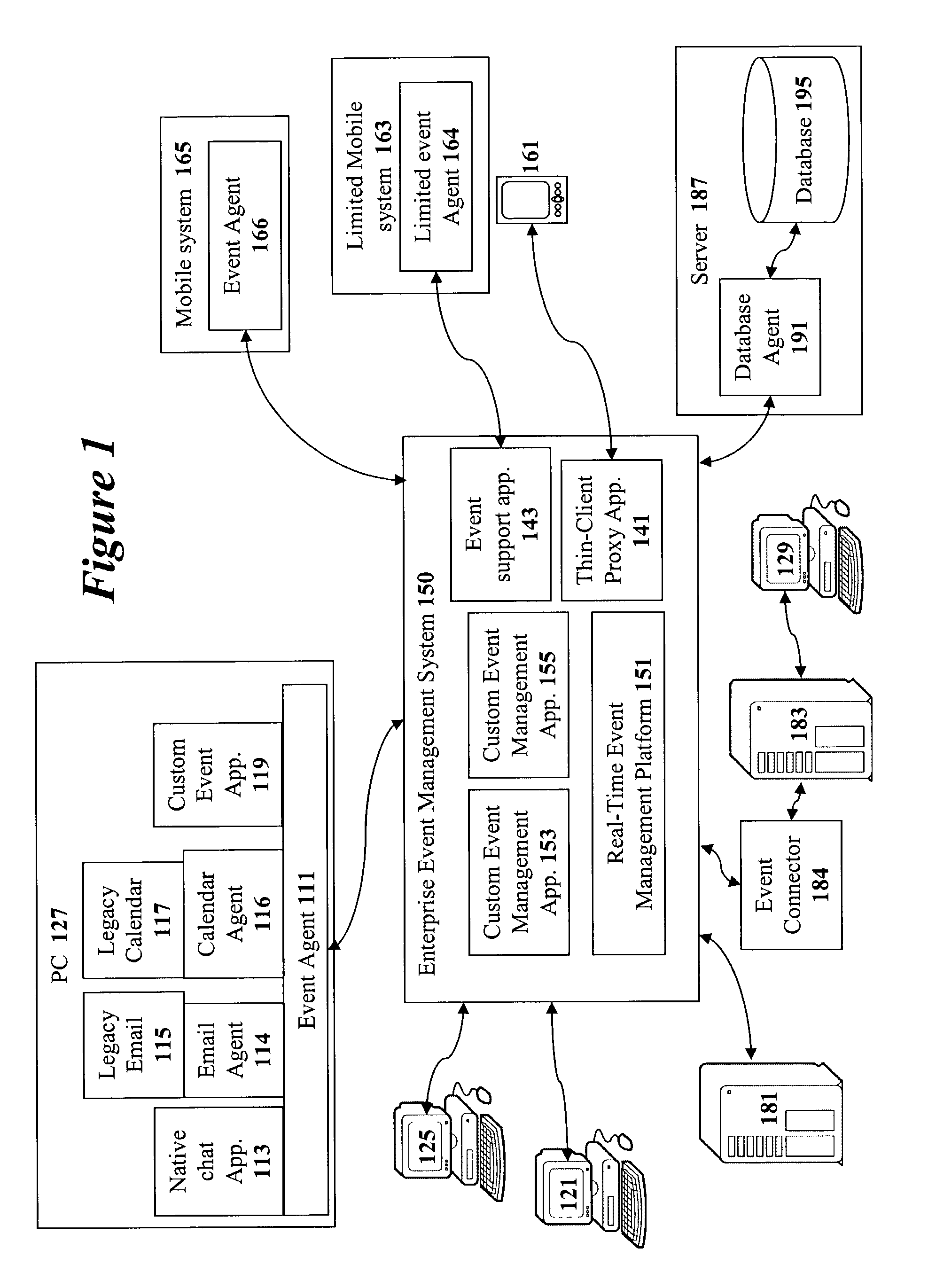
Method and apparatus for implementing a real-time event management platform
ActiveUS7454459B1Multiple digital computer combinationsOffice automationExtensible markupDocumentation
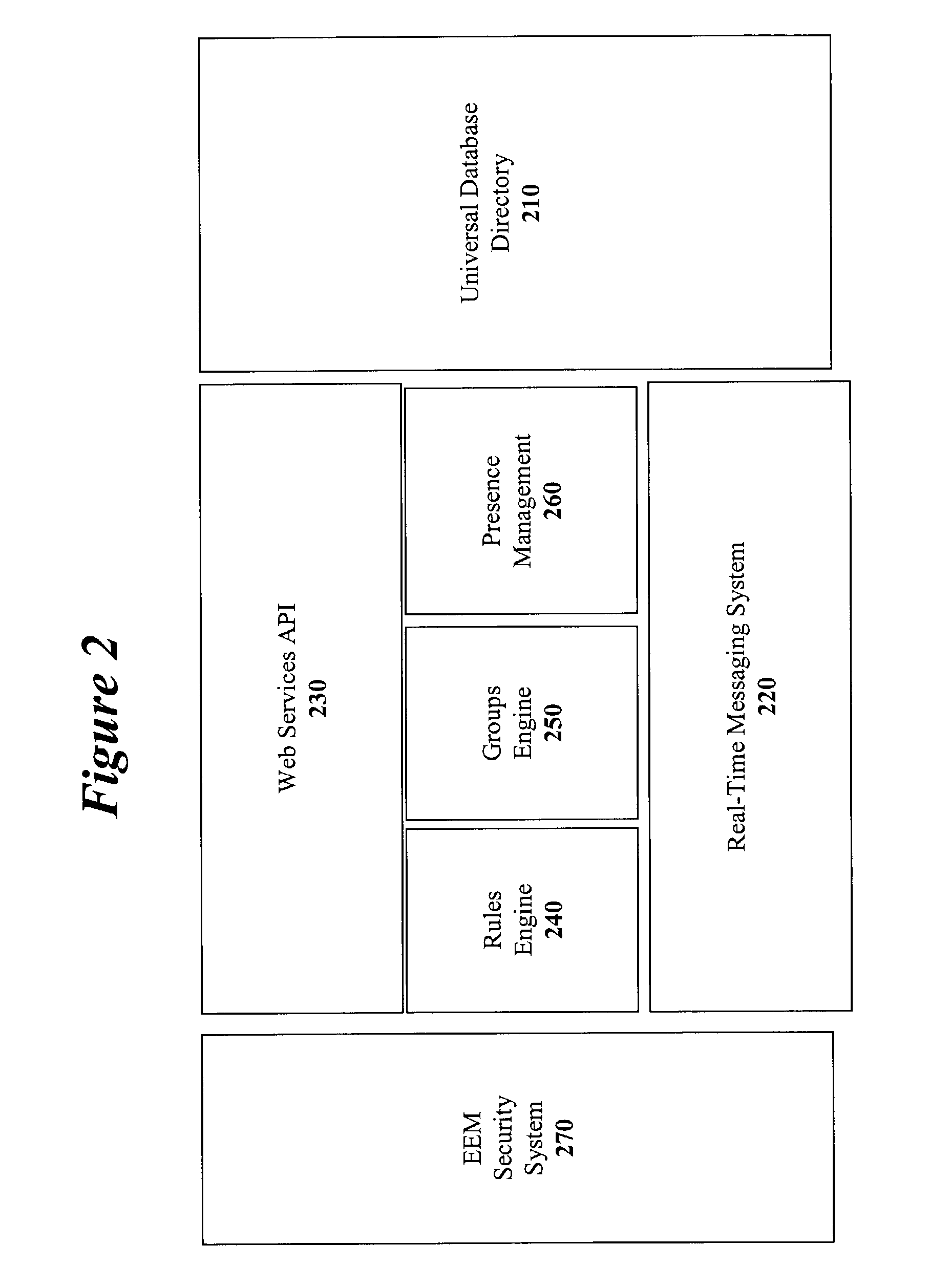
A method and apparatus for implementing a real-time enterprise event management system is disclosed. The enterprise event management (EEM) system couples together various “event aware” computing resources that publish and subscribe to “events” that provide information about the state computing resources. All of the events are represented as eXtensible Mark-up Language (XML) documents. Chains of related events are known as “event streams”. In the real-time event management platform, the event streams are available to all other event-aware computing resources operating in the shared event driven environment. The three main components are a real-time messaging system or handing event messages, a rules engine for allowing specific event message handing rules to be created, and a enterprise directory schema for providing a comprehensive directory of all the available resources and the means in which the resources may be accessed.
Owner:MALIKIE INNOVATIONS LTD
Networked computer telephony system driven by web-based applications
InactiveUS20050240659A1Easy development and deploymentLow costSpecial service for subscribersData switching by path configurationQuality of serviceWeb browser
A networked telephony system and method allow users to deploy on the Internet computer telephony applications associated with designated telephone numbers. The telephony application is easily created by a user in XML (Extensible Markup Language) with predefined telephony XML tags and easily deployed on a website. The telephony XML tags include those for call control and media manipulation. A call to anyone of these designated telephone numbers may originate from anyone of the networked telephone system such as the PSTN (Public Switched Telephone System), a wireless network, or the Internet. The call is received by an application gateway center (AGC) installed on the Internet. Analogous to a web browser, the AGC provides facility for retrieving the associated XML application from its website and processing the call accordingly. The architecture and design of the system allow for reliability, high quality-of-service, easy scalability and the ability to incorporate additional telephony hardware and software and protocols.
Owner:ALVARIA INC
System and method for construction, storage, and transport of presentation-independent multi-media content
InactiveUS7028252B1Increase contentEnsure consistencyData processing applicationsAutomatic exchangesCompositional dataExtensible markup
Owner:ORACLE INT CORP
Chart view for reusable data markup language
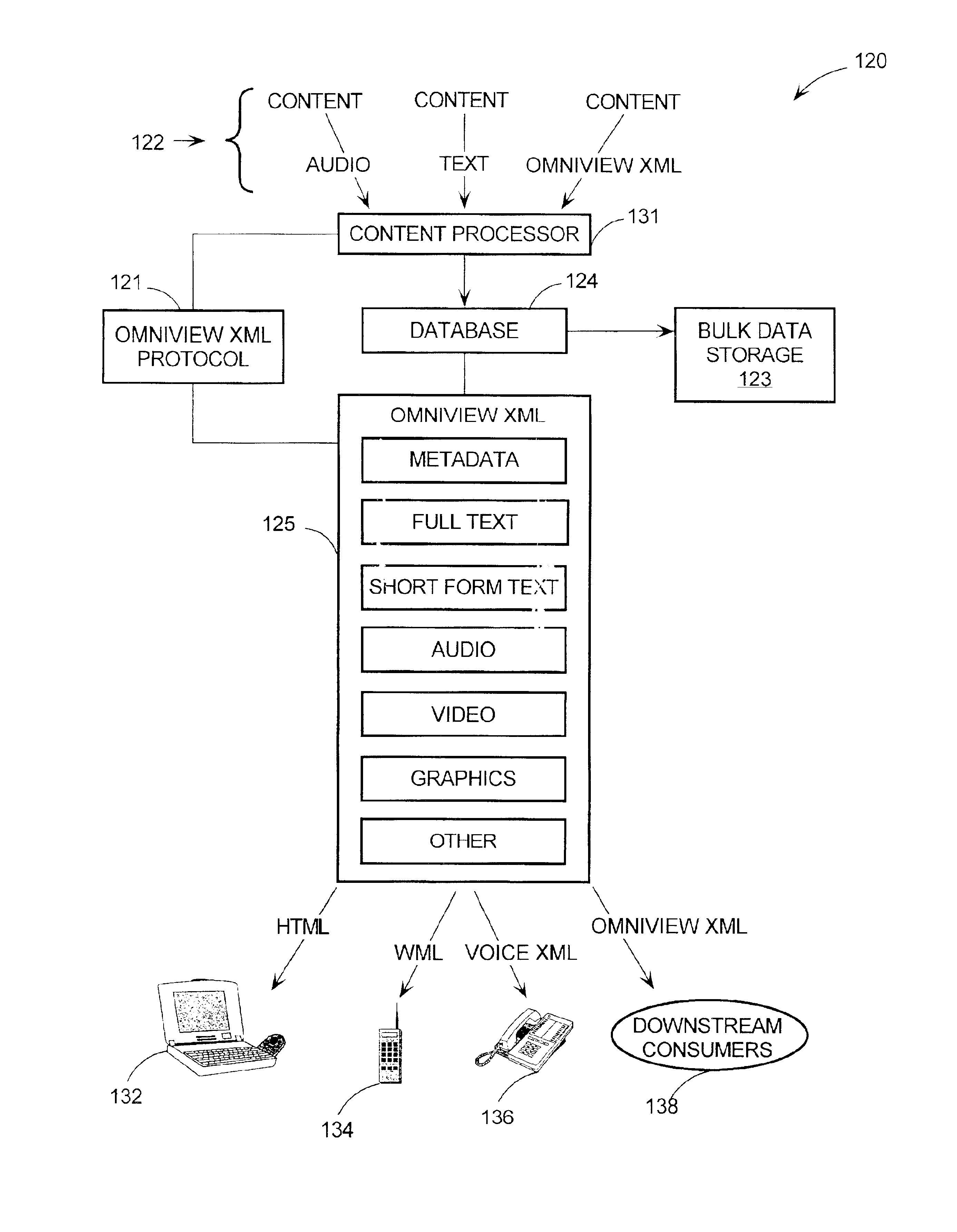
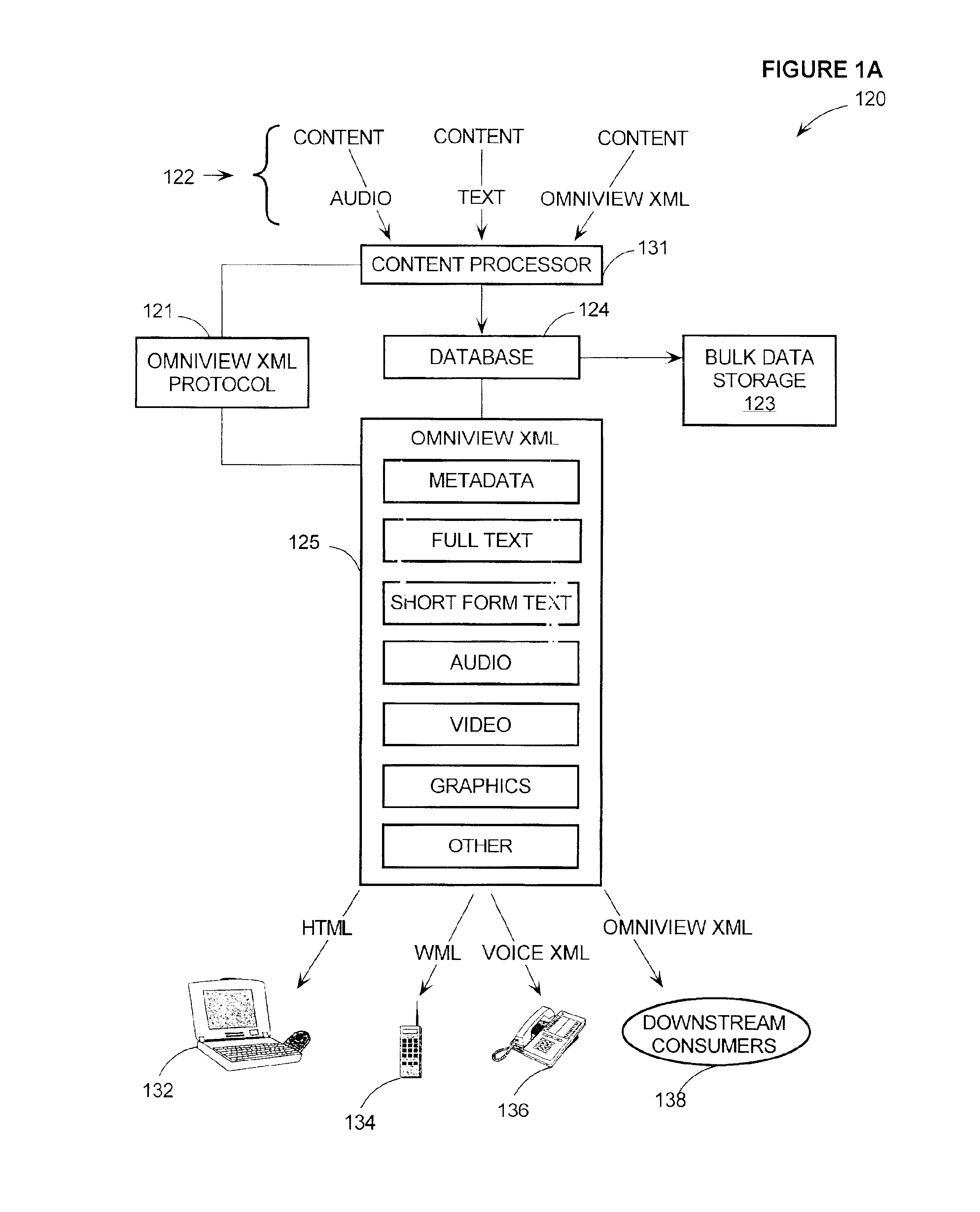
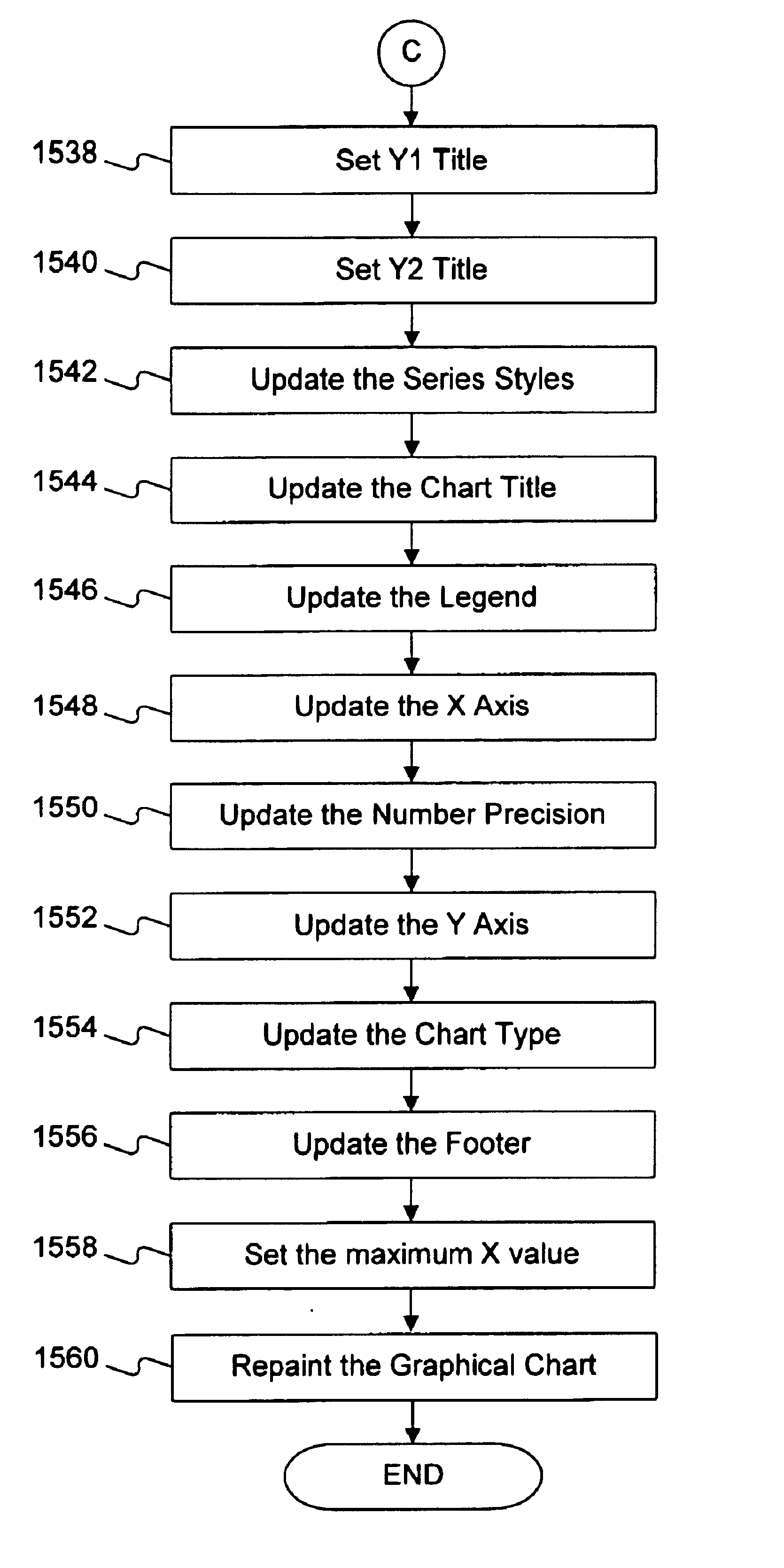
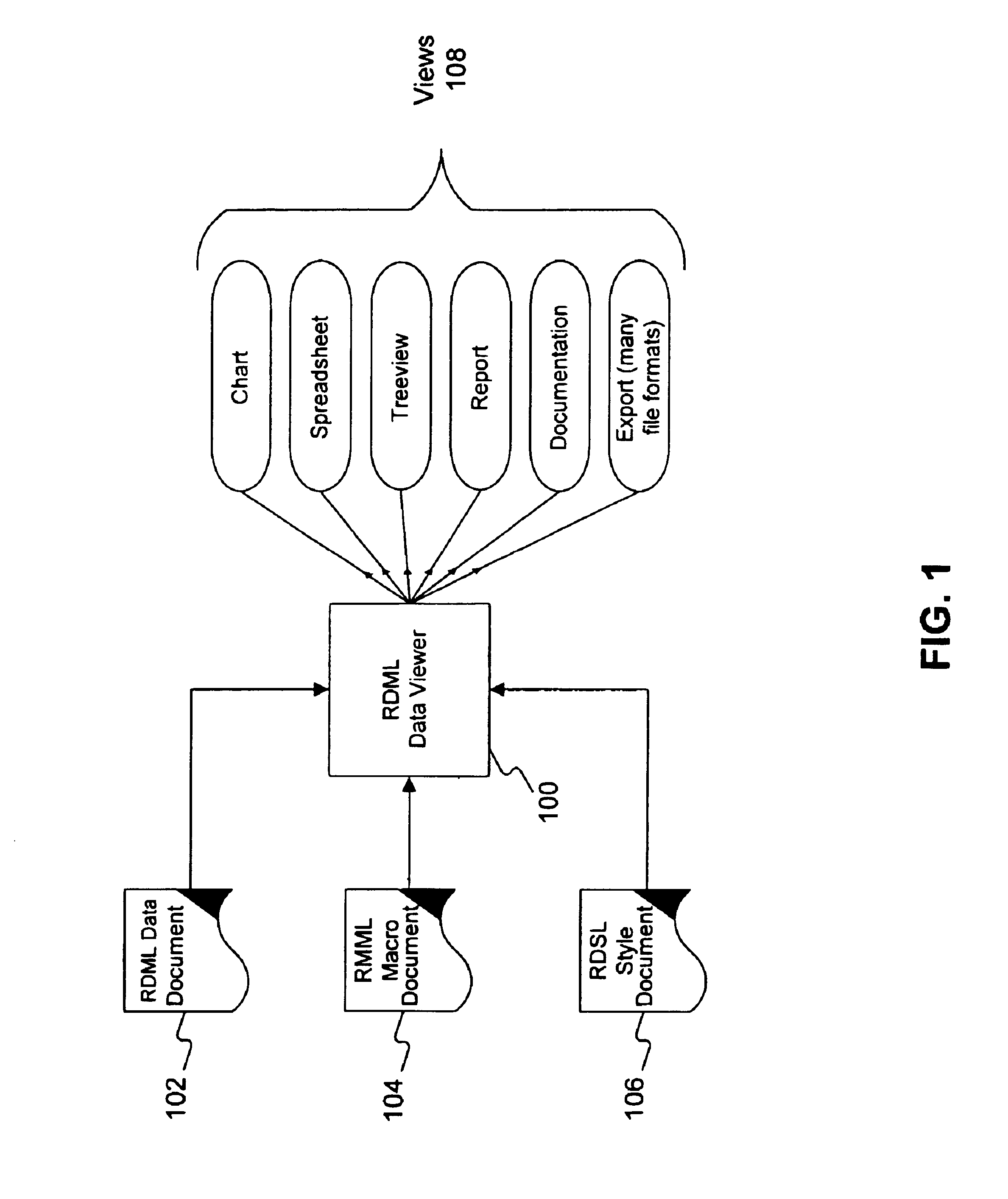
InactiveUS6920608B1Widespread accessibilityWritten quickly and cheaplyDigital data processing detailsNatural language data processingGraphicsDocumentation procedure
Methods and systems provide a “chart view” for a markup language referred to as Reusable Data Markup Language (“RDML”). Generally, a chart view comprises the components necessary for automatically manipulating and displaying a graphical display of numerical data contained in RDML markup documents. RDML is a markup language, such as the Hypertext Markup Language (“HTML”) or the Extensible Markup Language (“XML”). Generally, RDML facilitates the browsing and manipulation of numbers, as opposed to text as in HTML, and does so by requiring attributes describing the meaning of the numbers to be attached to the numbers. Upon receiving RDML markup documents, the chart view transforms, formats, manipulates and displays data stored in the markup documents using the attributes describing the meaning of the data. The chart view uses the attributes of the numbers to, for example, facilitate the simultaneous display of different series of numbers of different types on a single chart and automatically display appropriate axis labels, axis titles, chart titles, number precision, etc. A chart view may be a component of a data viewer used to retrieve, manipulate, and view documents in the RDML format.
Owner:E NUMERATE SOLUTIONS INC
Method and system for the generation of a voice extensible markup language application for a voice interface process
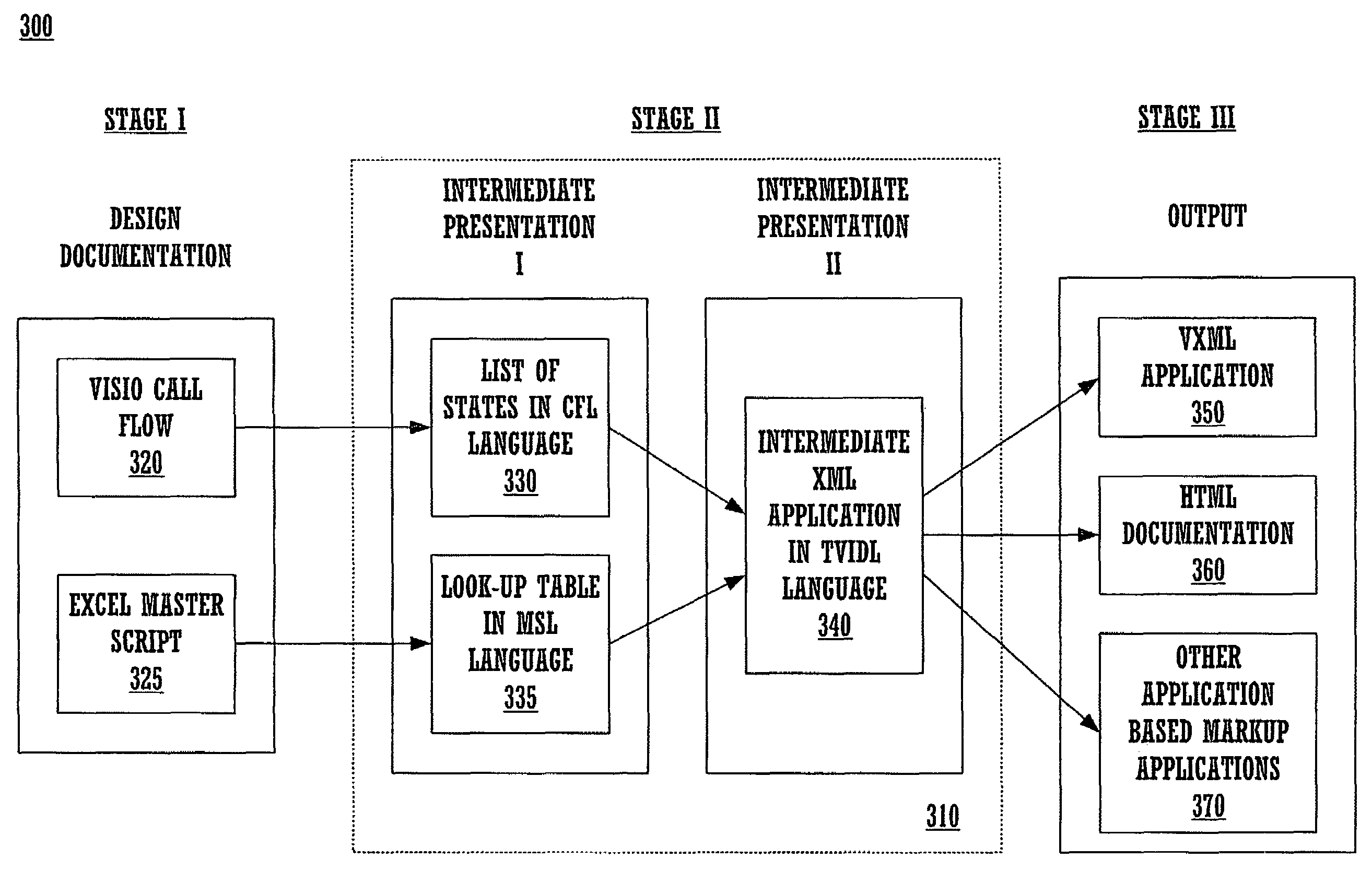
InactiveUS7287248B1Reduce chanceEfficient use ofDigital data information retrievalSpeech recognitionSoftware engineeringLookup table
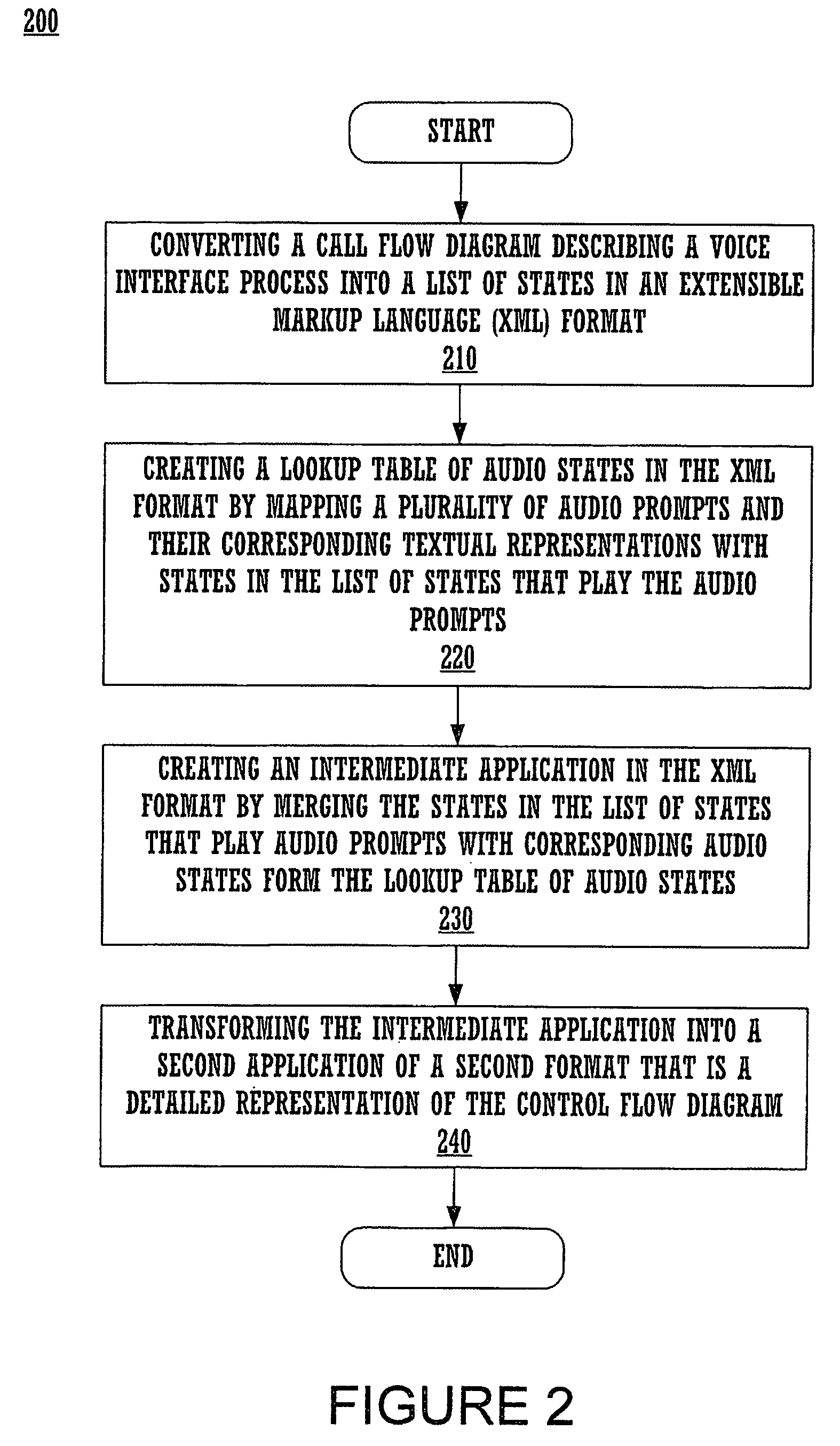
A method and system for Extensible Markup Language (XML) application transformation may include converting a call flow diagram describing a voice interface process into a list of states in a XML format, and creating a lookup table of audio states in the XML format by mapping a plurality of audio prompts and their corresponding textual representations with states of a list of states that play audio files associated with the plurality of audio prompts. The method and system may include creating an intermediate application in the XML format and from the list of states by merging audio prompts in the lookup table with states of the list of states that play audio files, and transforming the intermediate application into a second application of a second format that is a representation of the call flow diagram.
Owner:MICROSOFT TECH LICENSING LLC
Method, computer system and computer program product for processing extensible markup language streams
InactiveUS6925631B2Digital computer detailsNatural language data processingSoftware engineComputerized system
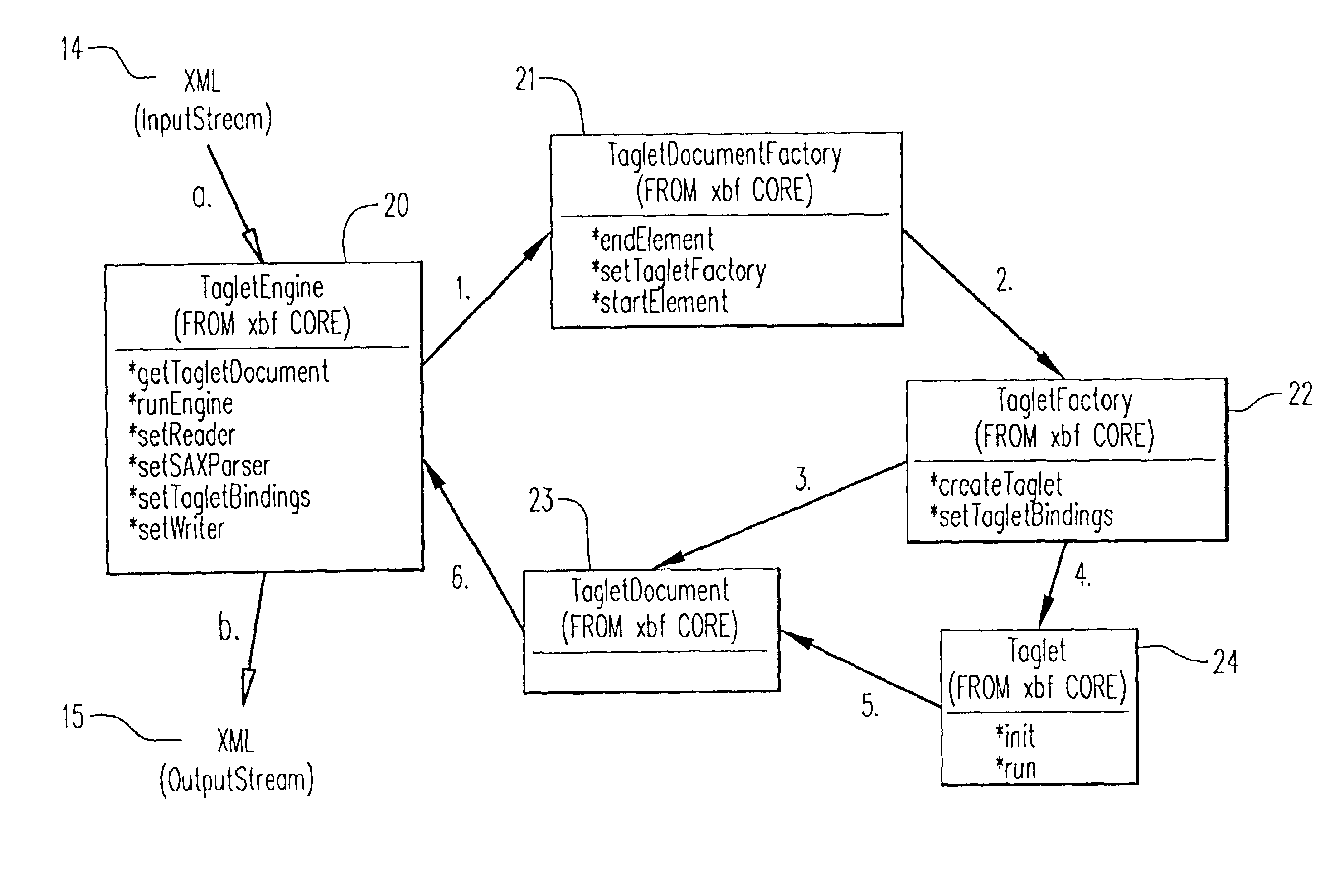
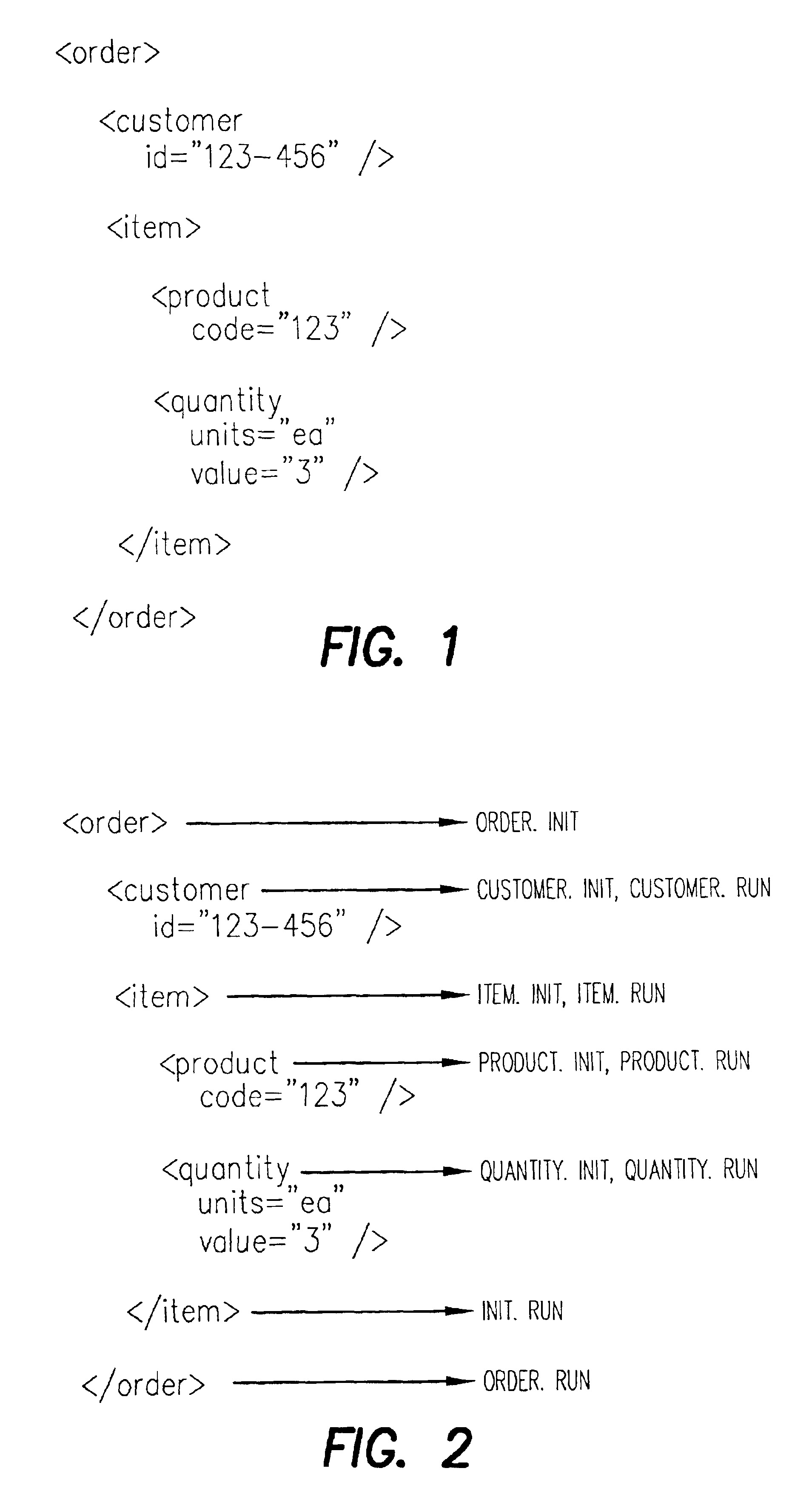
The invention is directed to a method performed by a computer system to process an extensible markup language input stream using discrete software components mapped to tags contained in the input stream, comprising: parsing the input stream; as a tag is parsed, invoking the software component mapped to it. The invention is also directed to a computer system, comprising: a processing unit and storage for processing programs; bindings representing a mapping between tags and discrete software components; a software engine comprising: a reader component that reads an extensible markup language input stream containing at least one tag; a parser component that parses the input stream; an execution component that, as a tag is parsed, invokes the software component mapped to the tag. The invention is also directed to a corresponding computer program product.
Owner:MOSAID TECH
High-performance extensible document transformation
InactiveUS6941511B1Reduce processing timeImproved performance characteristicsDigital data information retrievalDigital computer detailsBusiness-to-businessDocument transformation
The present invention provides a method, system, and computer program product for applying transformations to extensible documents, enabling reductions in the processing time required to transform arbitrarily-structured documents having particular well-defined elements. Signatures for structured document types are defined, along with one or more transformations to be performed upon documents of that type. The transformations are specified using syntax elements referred to as maps. A map specifies an operation code for the transformation to be performed, and describes the input and output of the associated transformation. A special map processing engine locates an appropriate transformation object to a particular input document at run-time, and applies the transformation operation according to the map definition. This technique is preferably used for a set of predetermined core transformations, with other transformations being processed using stylesheet engines of the prior art. The input documents may be encoded in the Extensible Markup Language (XML), or in other structured notations. The techniques of the present invention are particularly well suited to use in high-volume and throughput-sensitive environments such as that encountered by business-to-business transaction servers.
Owner:IBM CORP
Data collection system having reconfigurable data collection terminal
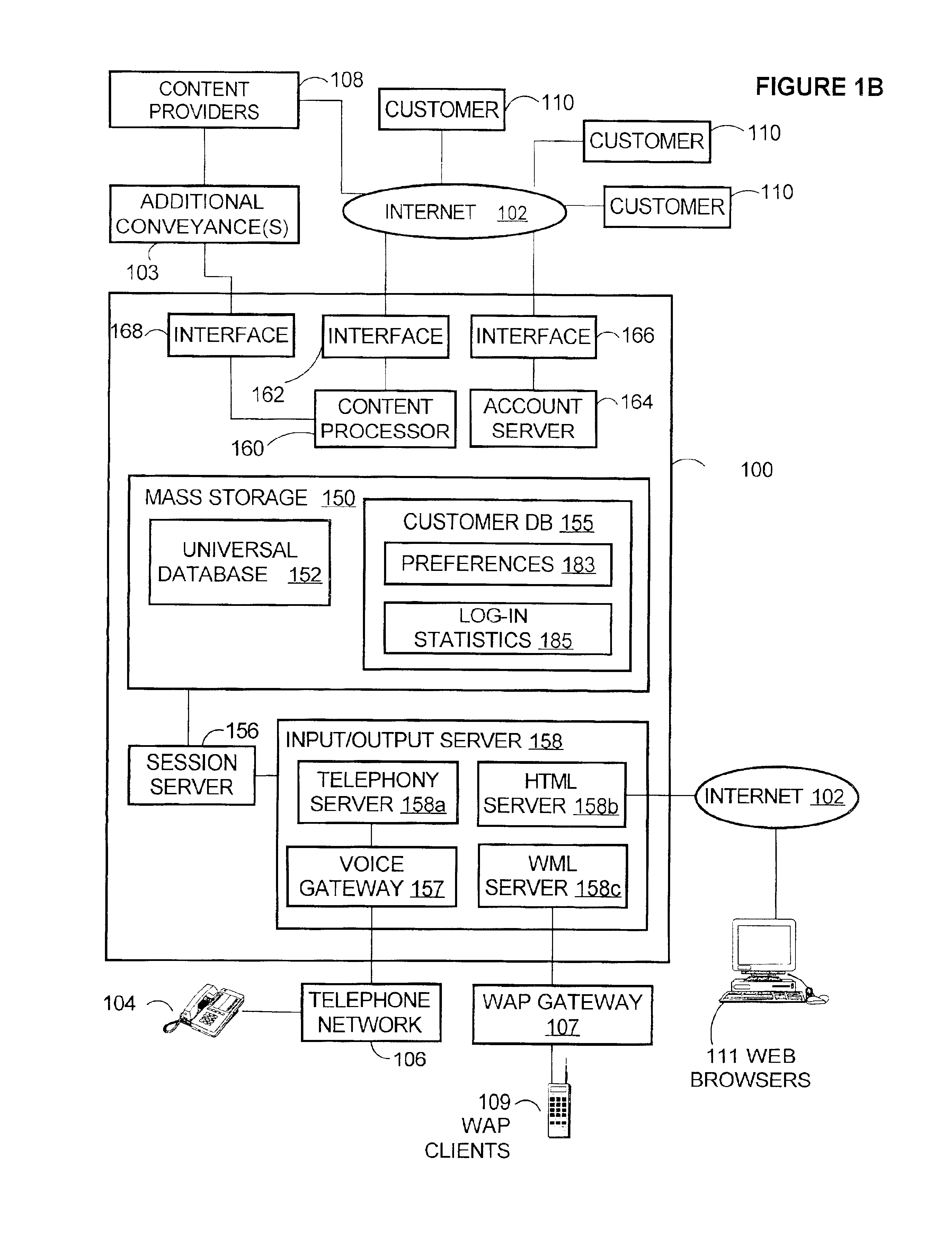
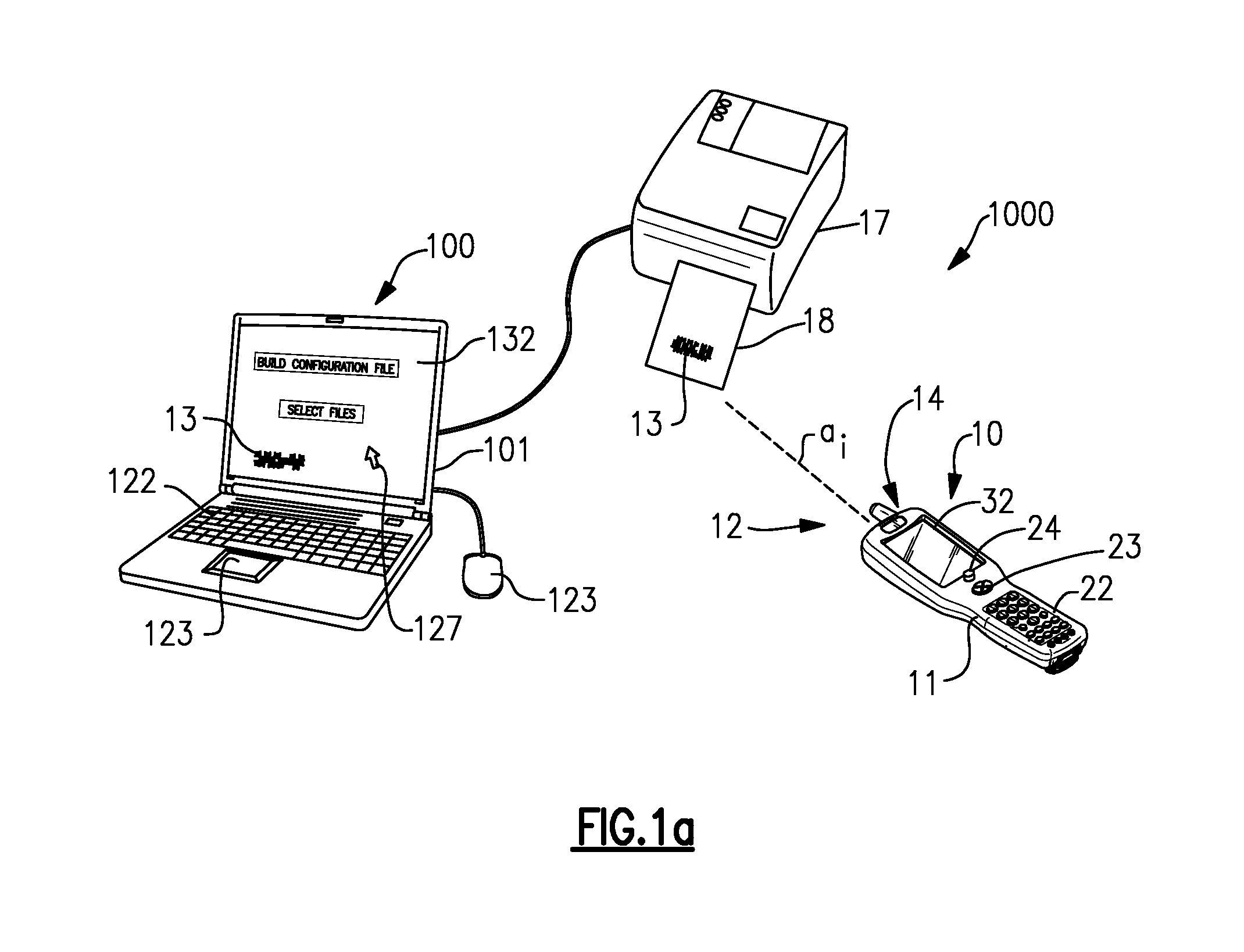
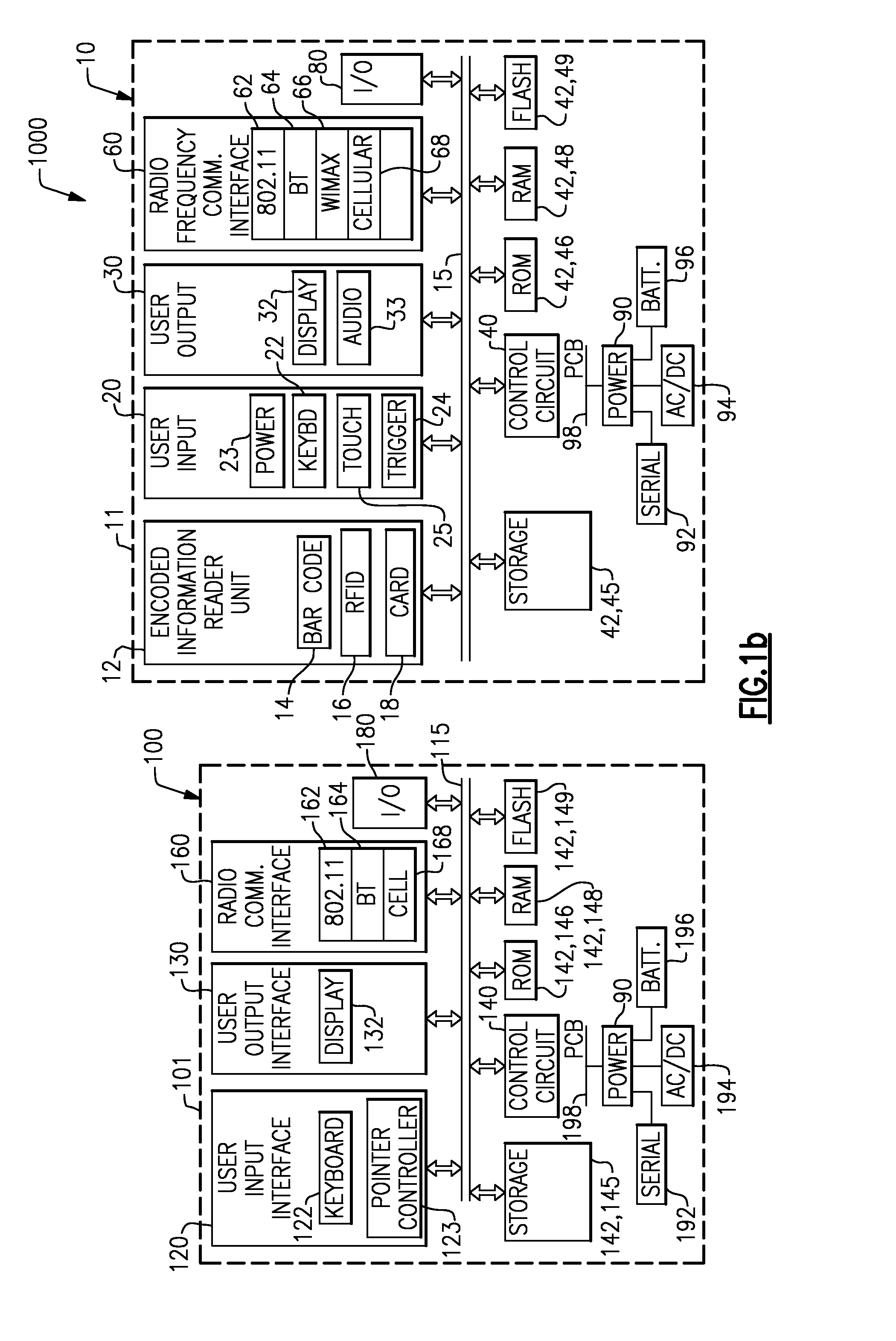
ActiveUS20070152058A1Semi-structured data indexingNatural language data processingNetwork packetExtensible markup
There is provided in one embodiment a data collection system including a data collection terminal having an encoded information reader device and a computer spaced apart from the data collection terminal. The data collection terminal in one embodiment can be configured to be responsive to configuration data expressed in an extensible markup language. The computer in one embodiment can use an existing extensible markup language document to create a data entry screen to received desired parameter settings for the data collection terminal within data entry fields of the data entry screen. The computer can further combine the extensible markup language document with the desired parameter settings to create configuration data and can initiate a transfer of the configuration data to the data collection terminal. The computer in one embodiment can be used to create for transfer to the data collection terminal a data package including file data corresponding to one or more selected files, together with additional data. The system provided can be used to transfer data, including but not limited to configuration data, between computers that are not data collection terminals and which are devoid of encoded information reader devices.
Owner:HAND HELD PRODS
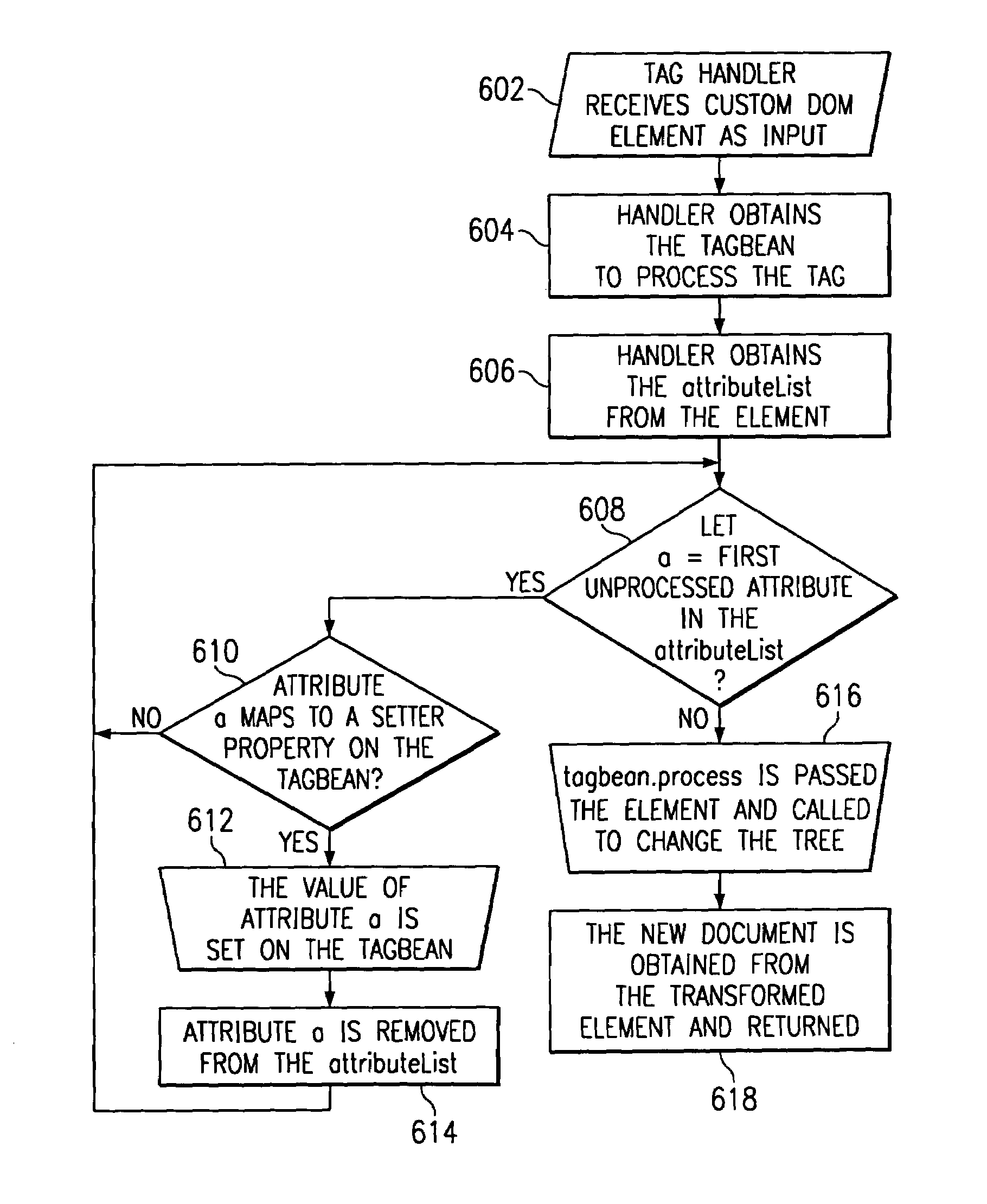
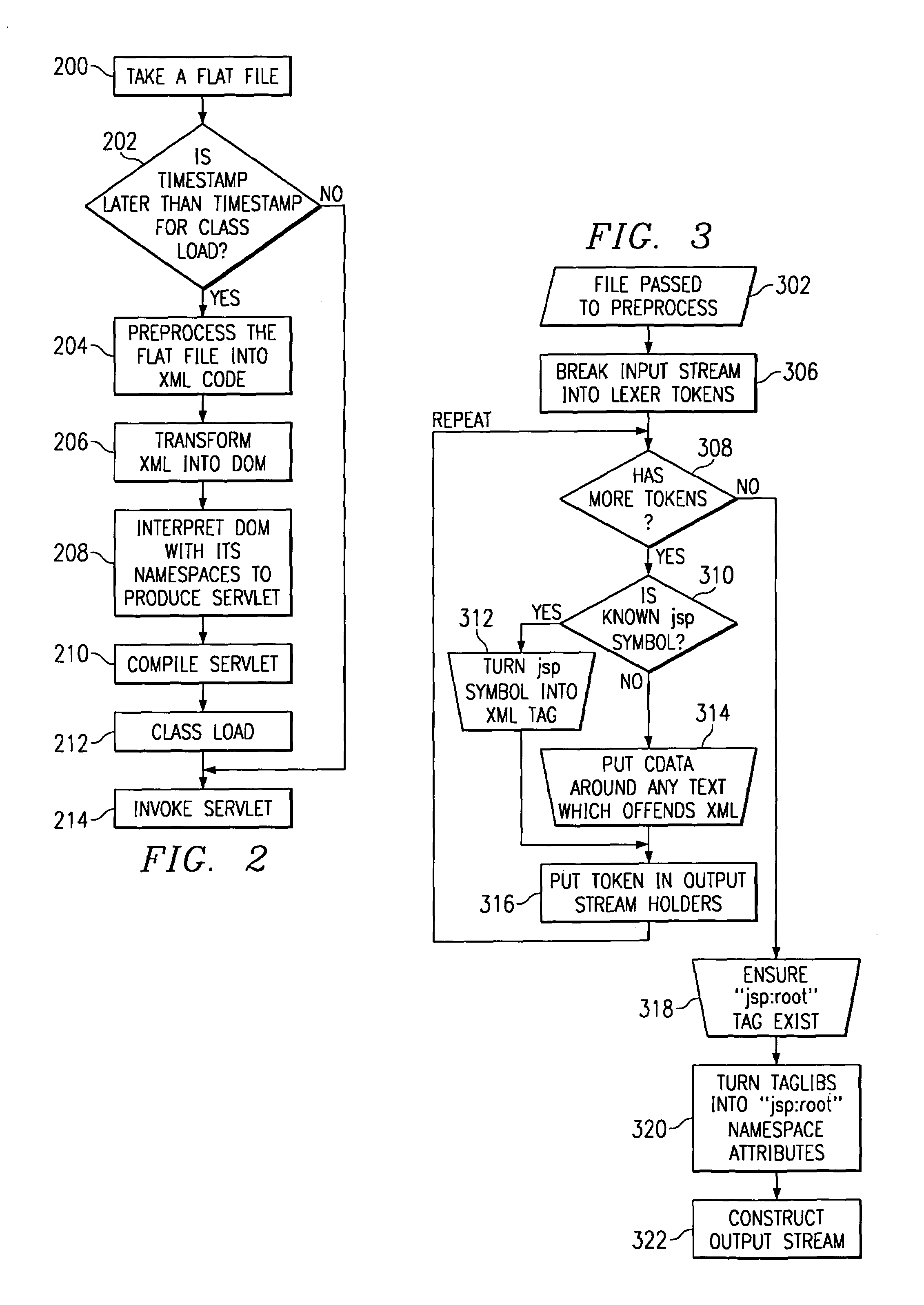
Extensible markup language (XML) server pages having custom document object model (DOM) tags
InactiveUS6981212B1Improve performanceMultiple digital computer combinationsWebsite content managementComponent Object ModelExtensible markup
A method for serving a web page uses eXtensible Markup Language (XML) server pages. The first time a page is accessed, a given flat file is parsed into an XML Document Object Model (DOM), and required tag libraries are loaded. The DOM tree is then traversed, preferably in a depth-first, inside-out manner to locate custom tags. Upon locating a custom tag, if the tag is registered as a Java object, the object is loaded. A process method is then called on the object, passing the custom tag's tree node. The Java object then examines the custom tag and replaces it with an object, e.g., script code. Alternatively, if the tag is registered as an XSL stylesheet, the stylesheet is loaded and passed, together with the DOM, to an XSL processor. The processor applies the template to the custom tag and replaces it with given script code. Once all custom tags are reduced to HTML and script code, the DOM is compiled into a Java servlet to service the client request.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
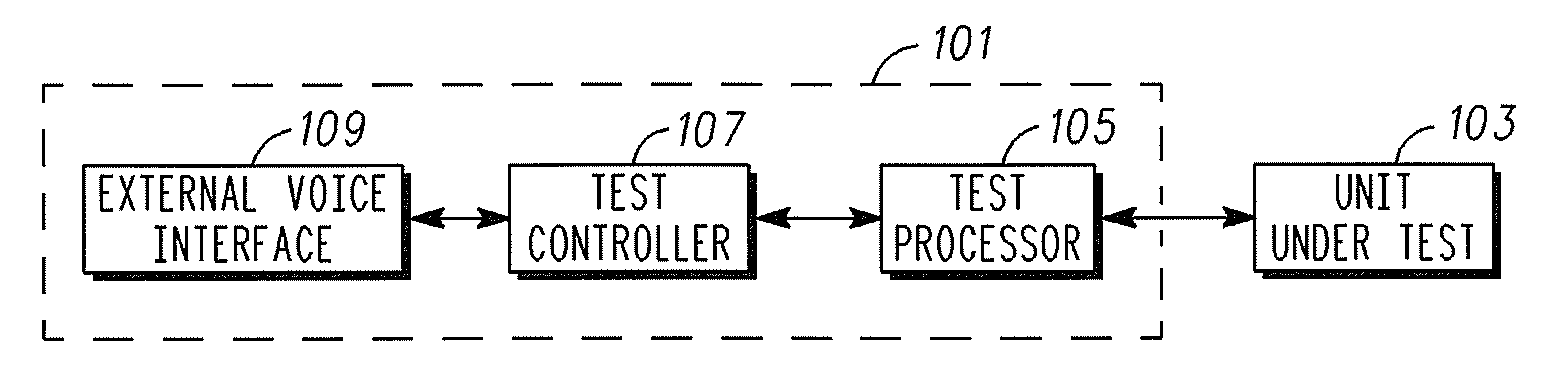
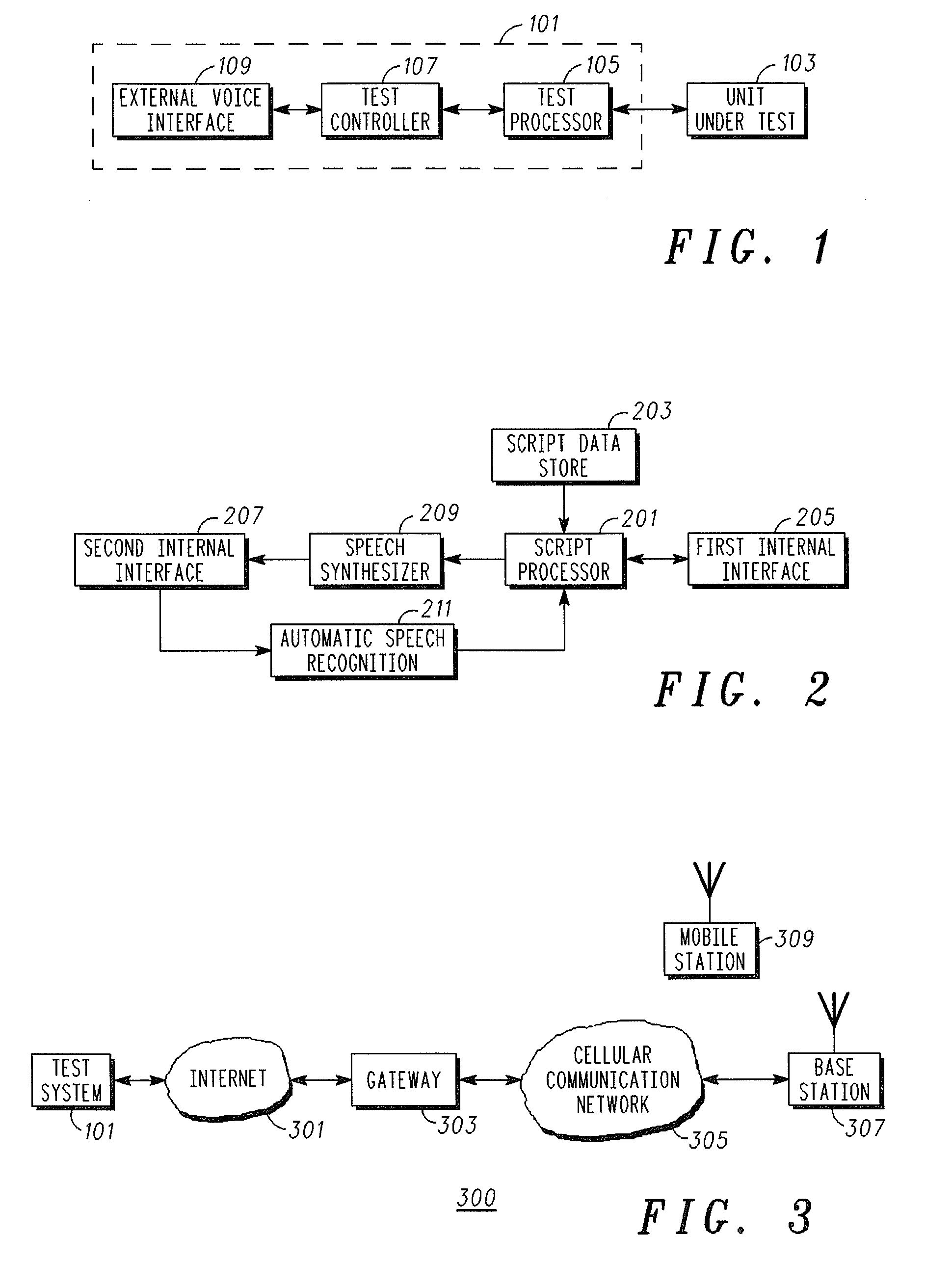
A Test System and method of Operation
InactiveUS20070291905A1Remote control is implementedGood user interfaceDevices with voice recognitionSupervisory/monitoring/testing arrangementsScripting languageComputer hardware
A test system comprises a test processor which is arranged to perform hardware level tests on a unit under test. A voice interface interfaces to an external voice communication link coupled to a remote voice communication unit. A test controller is coupled to the test processor and the voice interface and comprises a script processor for executing a test control script. The test control script is in accordance with a voice scripting language standard, such as the Voice extensible Markup Language, VXML, standard. The script processor comprises a first interface for interfacing with the test processor in response to the test control script and a second interface for interfacing with the voice interface in response to the test control script. The invention may allow a user friendly speech interface to a hardware level test system.
Owner:EMERSON NETWORK POWER EMBEDDED COMPUTING
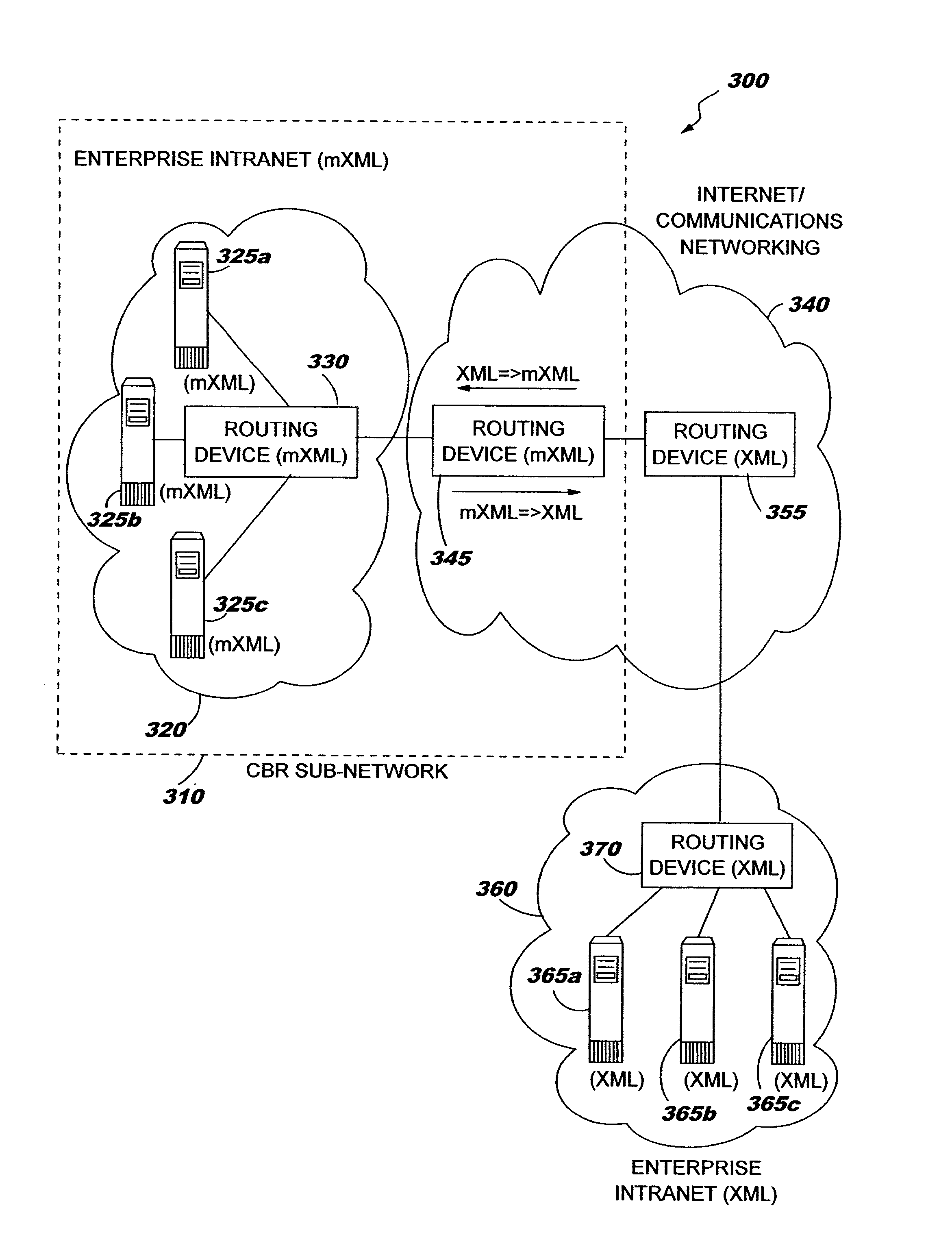
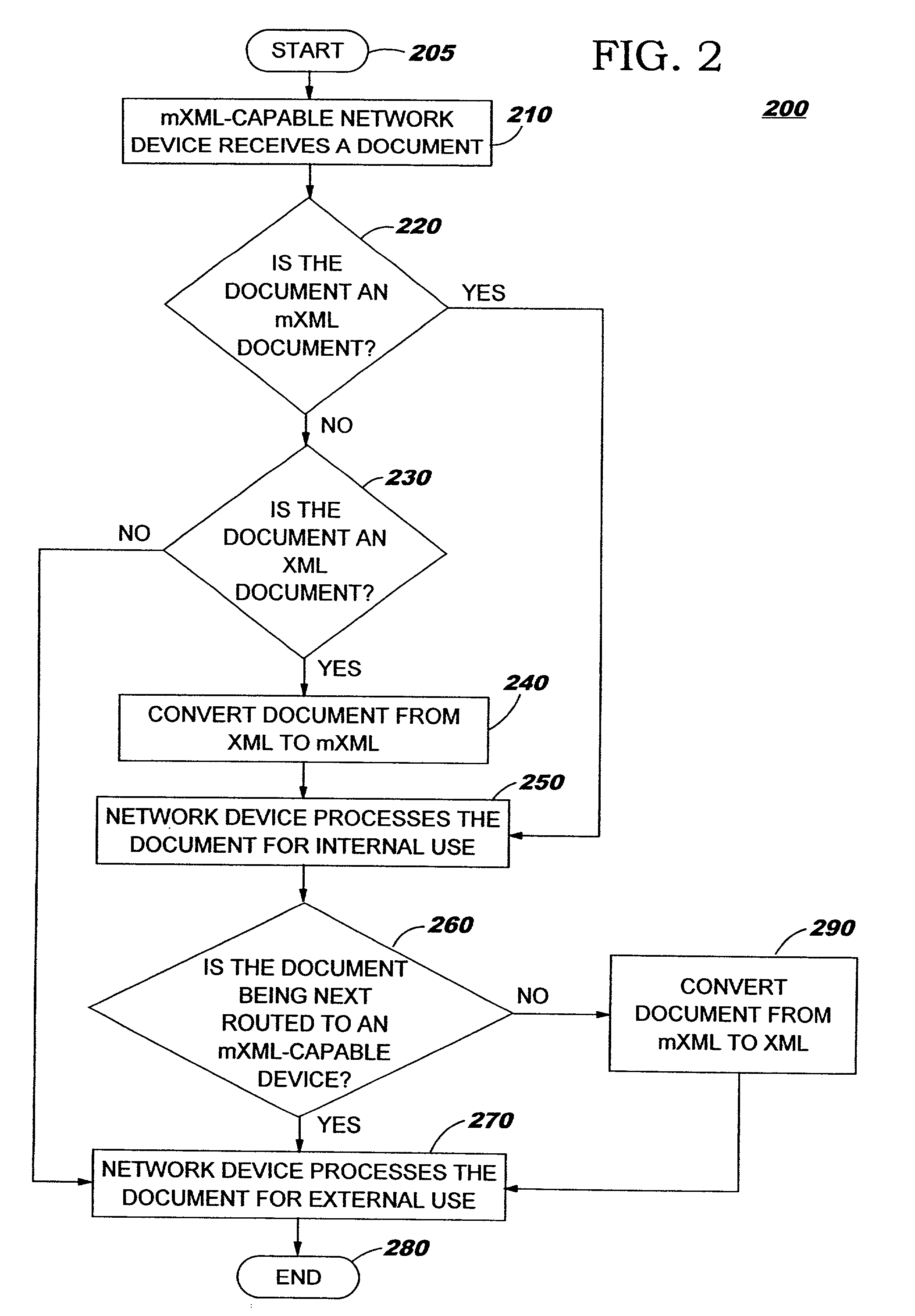
Conversion of documents between XML and processor efficient MXML in content based routing networks
InactiveUS7134075B2Efficient processingImprove performanceNatural language data processingSpecial data processing applicationsSemanticsExtensible markup
A method, system, and computer program product for efficient processing of Extensible Markup Language (XML) documents in Content Based Routing (“CBR”) networks. Specifically, the method involves converting existing XML documents to a machine-oriented notation (“mXML”) which is significantly more compact than XML, while still conveying the content and semantics of the data and the structure of the document. Documents are converted from XML to mXML upon entering a CBR subnetwork and / or upon receipt by an mXML-capable device. The documents are then processed in mXML format. Devices within the inventive system are provided with an awareness of whether target devices or processes are mXML-capable. Documents being routed to a target which is mXML-capable are passed in mXML format while documents being routed to a target which is not mXML-capable are converted to XML before they are passed.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Method and system for presenting dynamic commercial content to clients interacting with a voice extensible markup language system
InactiveUS20050246174A1Speech analysisSpecial service for subscribersInteraction interfaceSpoken dialog
A system for selecting a voice dialog, which may be an advertisement or information message, from a pool of voice dialogs and for causing the selected voice dialog to be utilized by a voice application for presentation to a caller during an automated voice interactive session includes a voice-enabled interaction interface hosting the voice application; and, a sever monitoring the voice-enabled interaction interface for selecting the voice dialog and for serving at least identification and location of the dialog to be presented to the caller via the voice application.
Owner:APPTERA
Method and apparatus for adapting a voice extensible markup language-enabled voice system for natural speech recognition and system response
A system for analyzing natural language spoken through a voice recognition system comprising: a language separator for separating a natural language expression into multiple word segments; and a grammar module for creating XML-based description sets or binary sets using word segments as input. In a preferred embodiment, the word segments are further processed as class objects and then organized according to original spoken order and wherein content fields are created to contain the class objects for comparison during voice interaction using the voice recognition system.
Owner:APPTERA
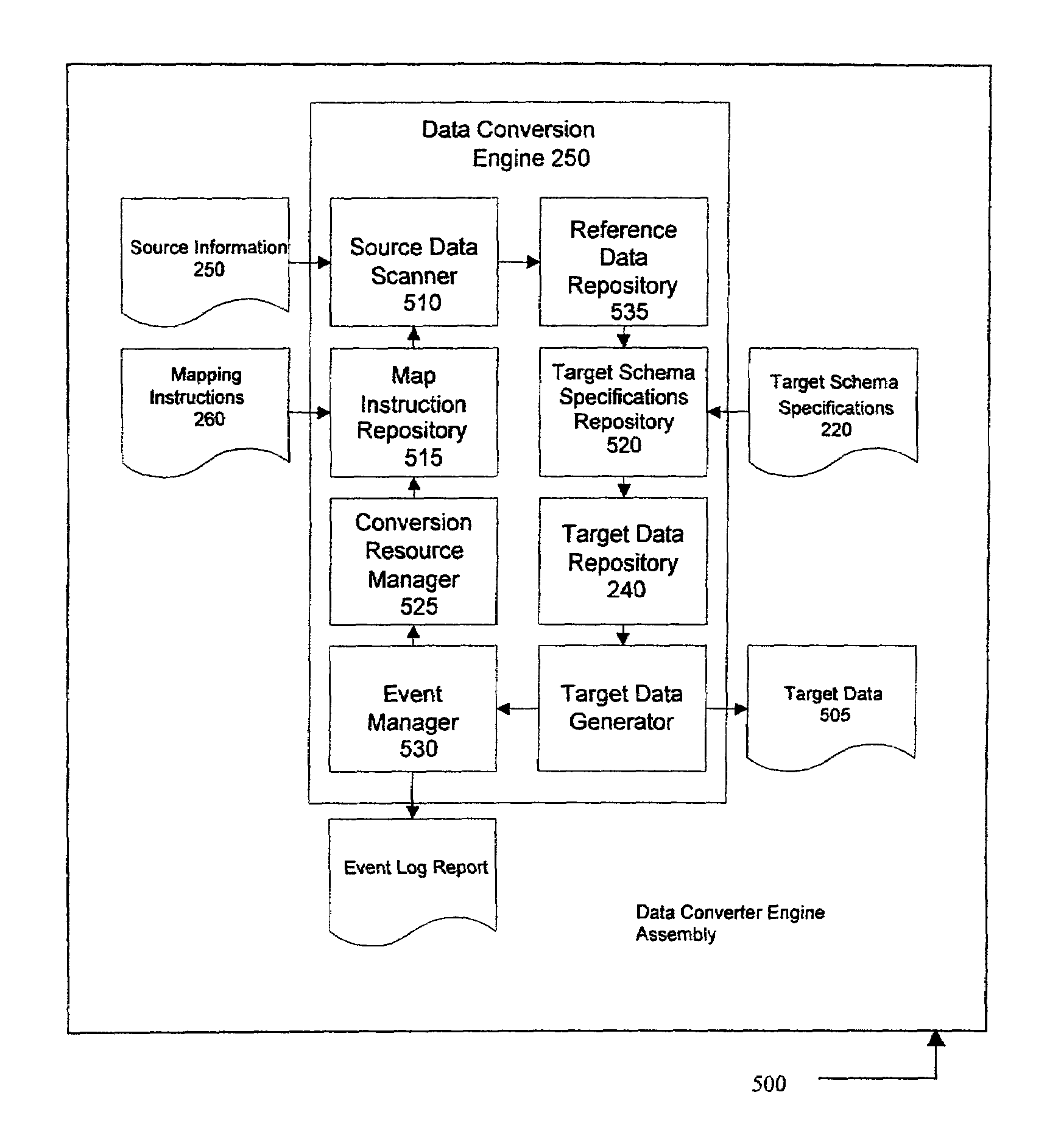
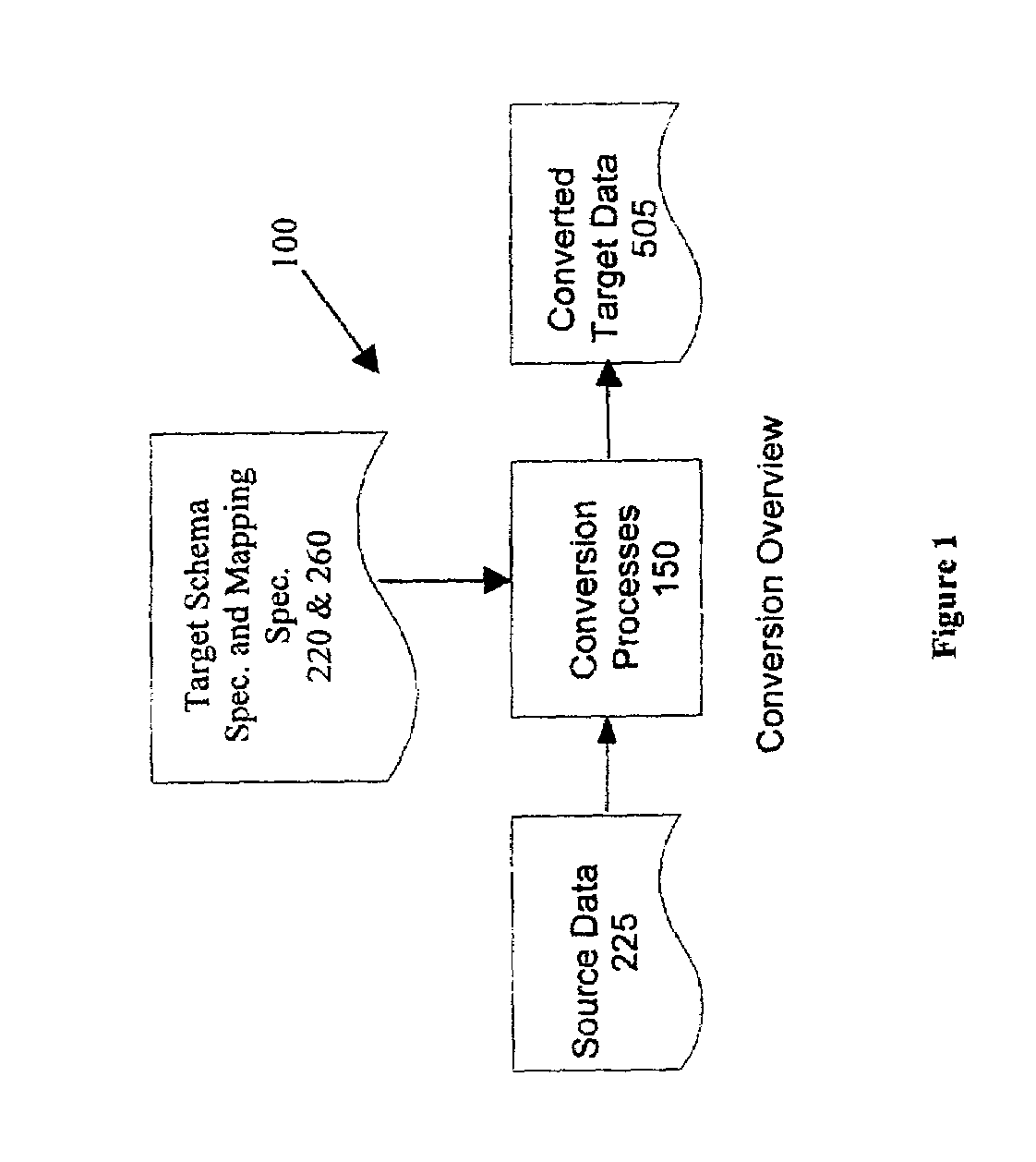
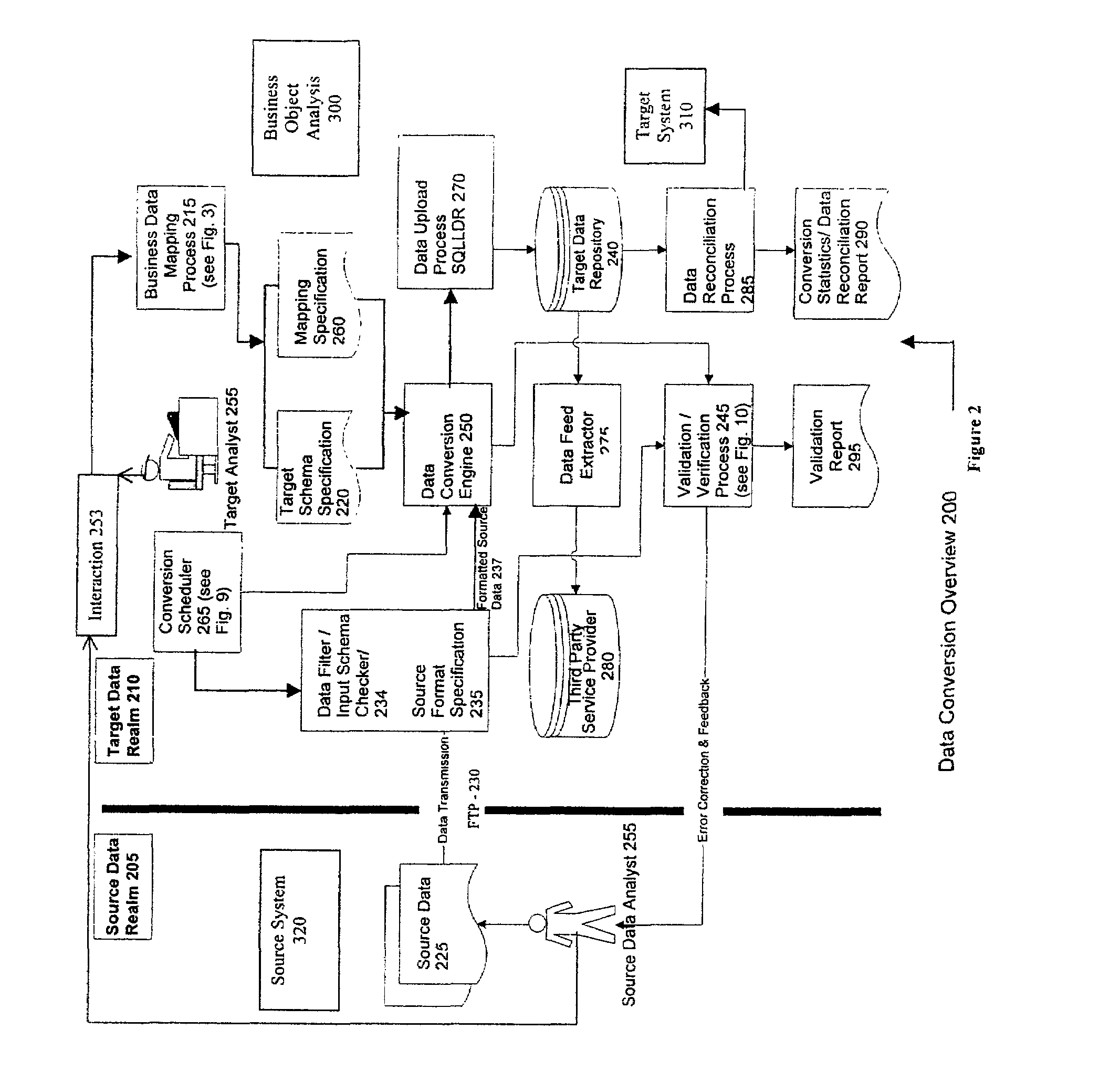
System and method for database conversion
InactiveUS6996589B1Improve performanceFlexiblyData processing applicationsDigital data information retrievalData feedExtensible markup
A database conversion engine comprising a method and system to convert business information residing on one system to another system. A generic, extensible, scalable conversion engine may perform conversion of source data to target data as per mapping instructions / specifications, target schema specifications, and a source extract format specification without the need for code changes to the engine itself for subsequent conversions. A scheduler component may implement a scalable architecture capable of voluminous data crunching operations. Multi-level validation of the incoming source, data may also be provided by the system. A mechanism may provide data feeds to third-party systems as a part of business data conversion. An English-like, XML-based (extensible markup language), user-friendly, extensible data markup language may be further provided to specify the mapping instructions directly or via a GUI (graphical user interface). The system and method employs a business-centric approach to data conversion that determines the basic business object that is the building block of a given conversion. This approach facilitates identification of basic minimum required data for conversion leading to efficiencies in volume of data, performance, validations, reusability, and conversion turnover time.
Owner:NETCRACKER TECH SOLUTIONS
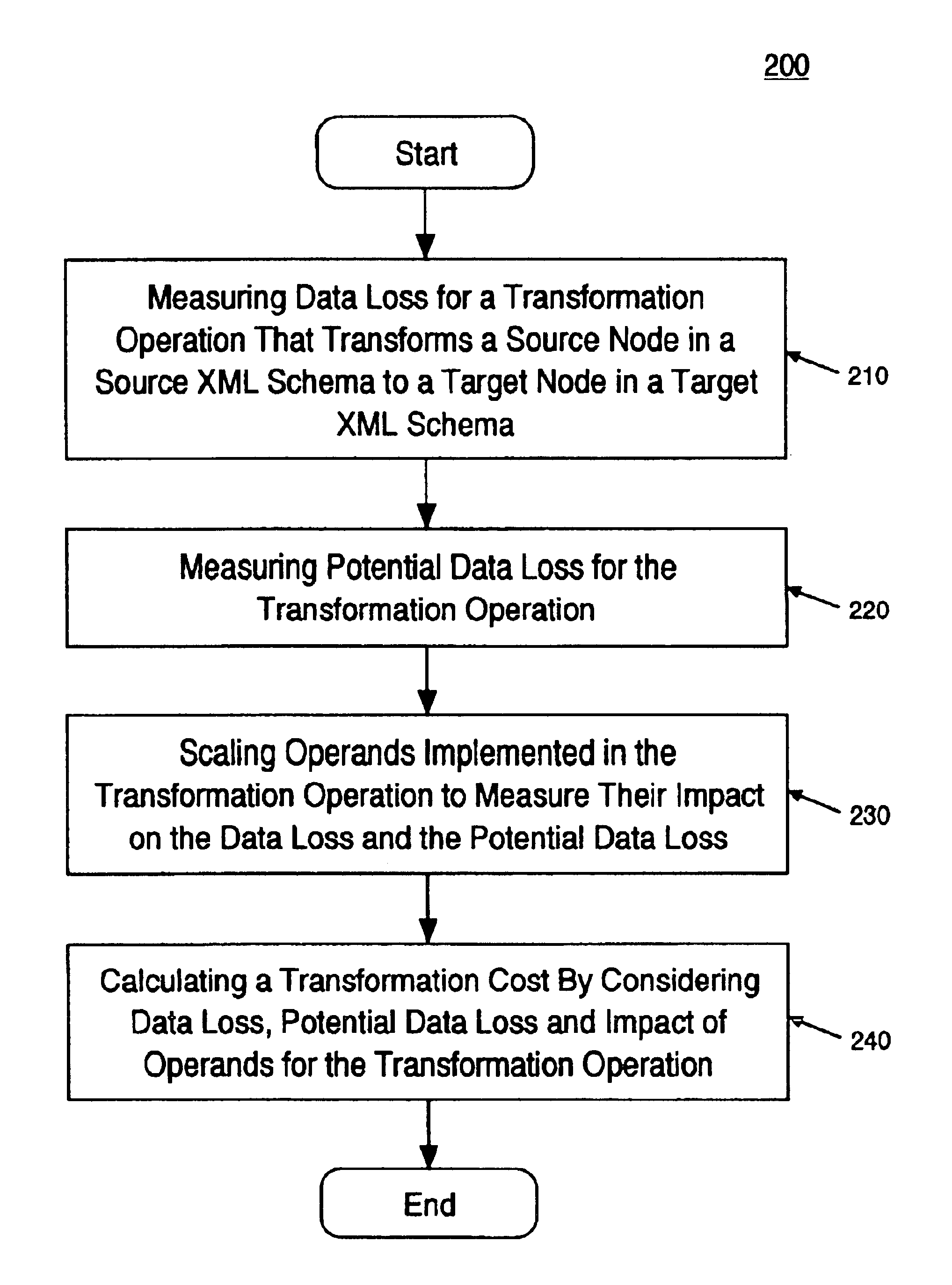
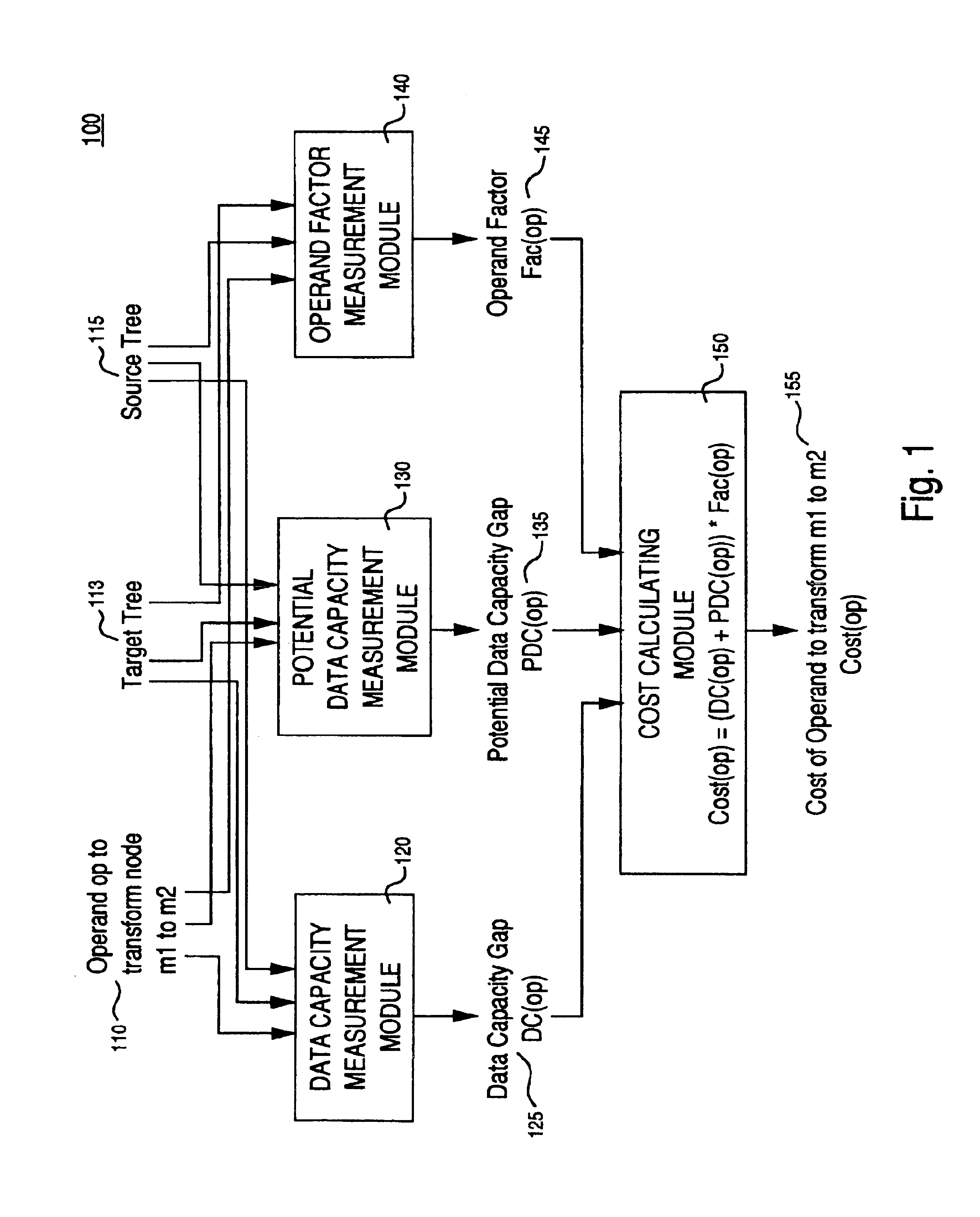
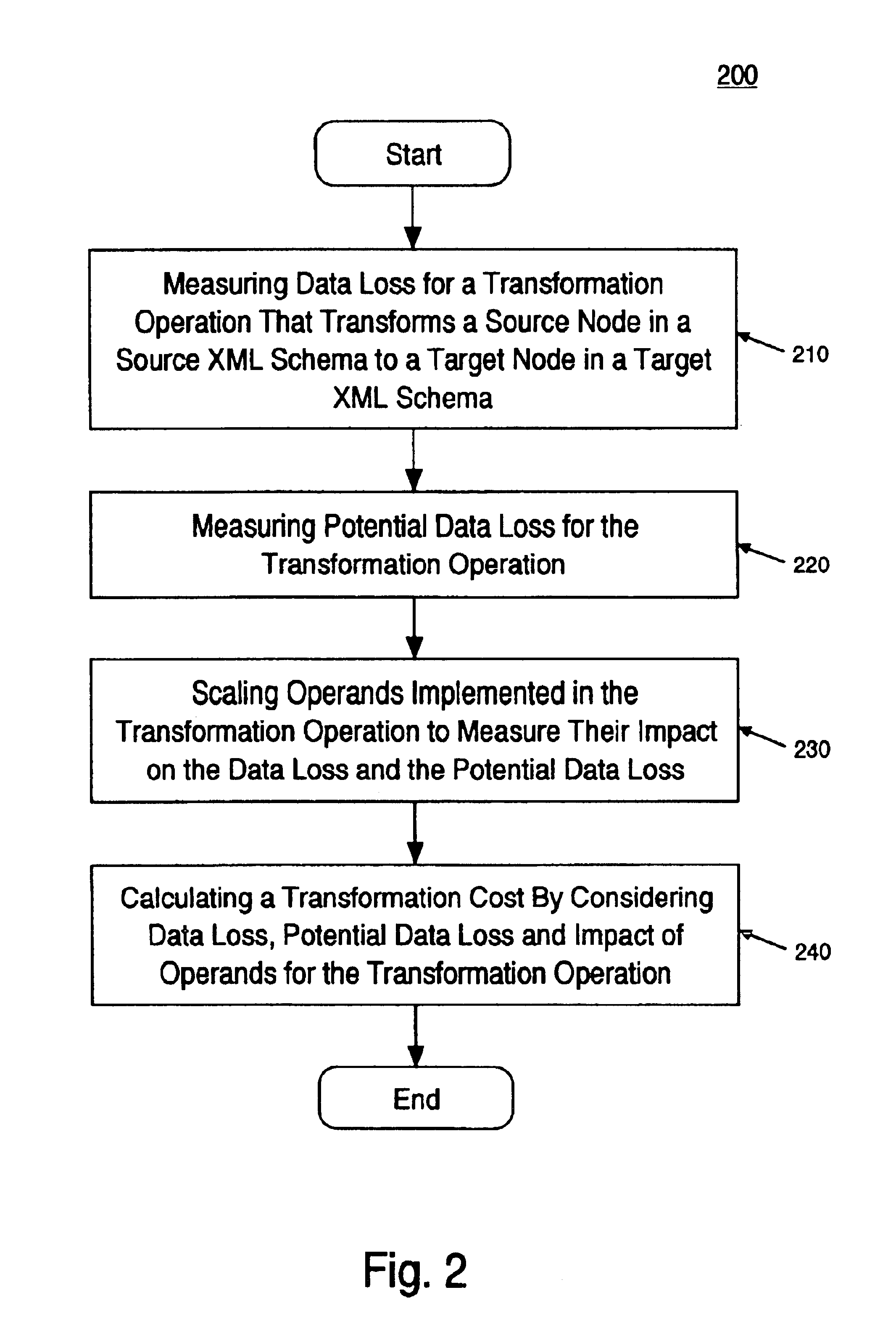
Method and system of valuing transformation between extensible markup language (XML) documents
InactiveUS6845380B2Data processing applicationsDigital data processing detailsOperandExtensible markup
A method and system of valuing transformation between XML documents. Specifically, one embodiment of the present invention discloses a method for calculating a transformation cost for a transformation operation that transforms a source node in a source XML document to a target node in a target XML document. A data loss and potential data loss is measured for the transformation operation. Also, the operands in the transformation operation are scaled to measure their impact on the data loss and potential data loss. A transformation cost is calculated by considering the data loss, potential data loss, and scaling.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com