Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6416 results about "Data request" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
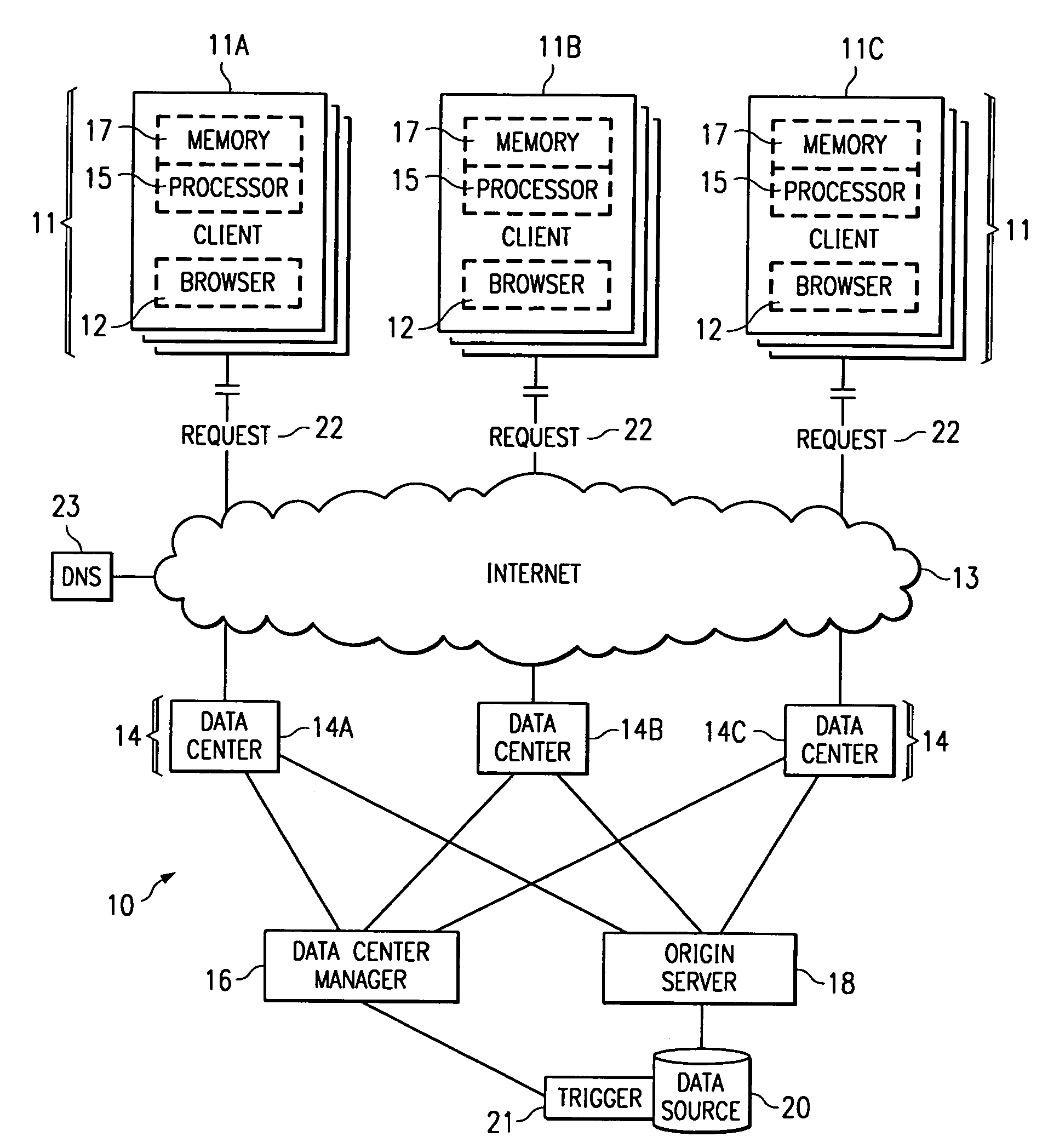
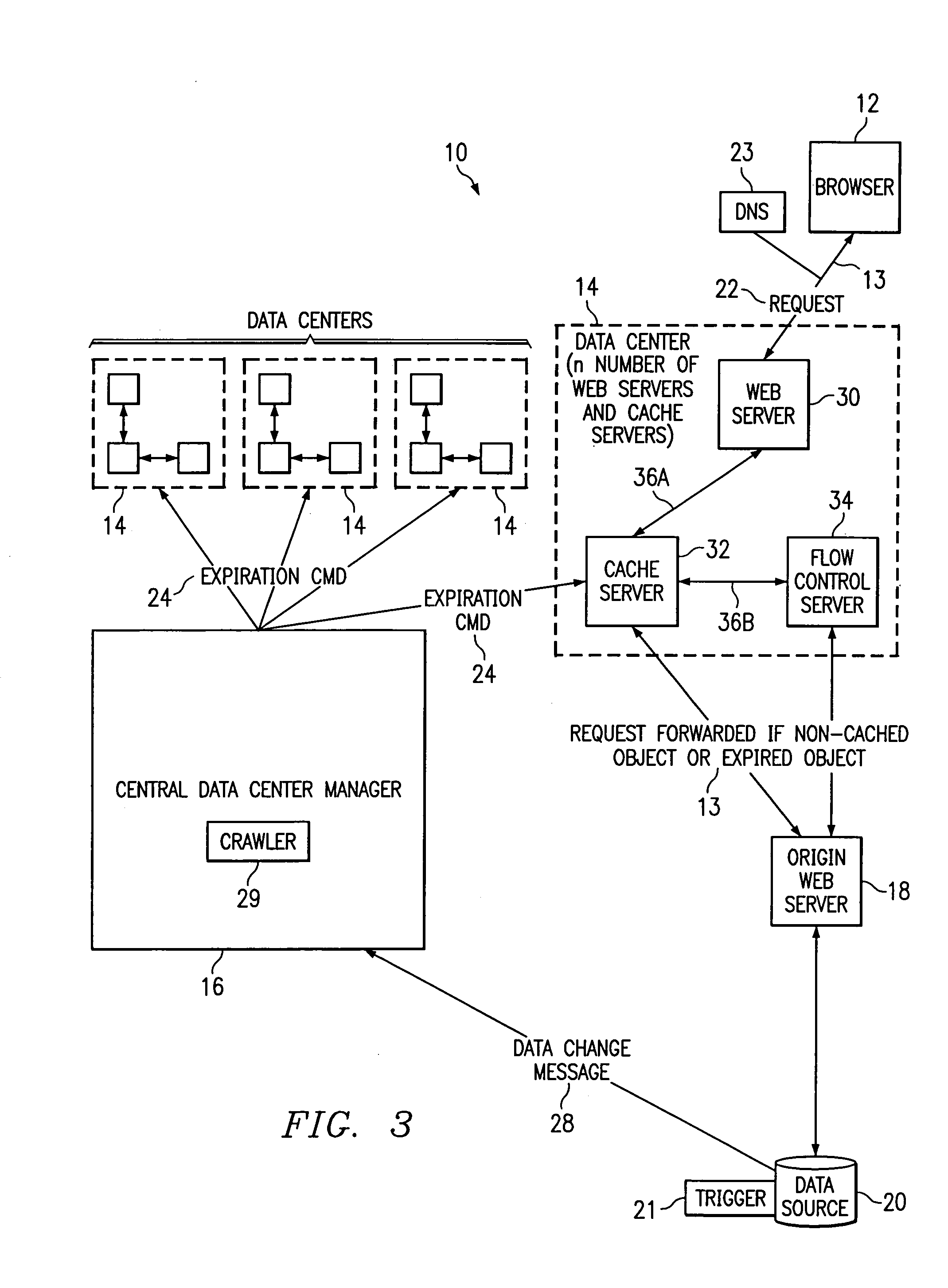
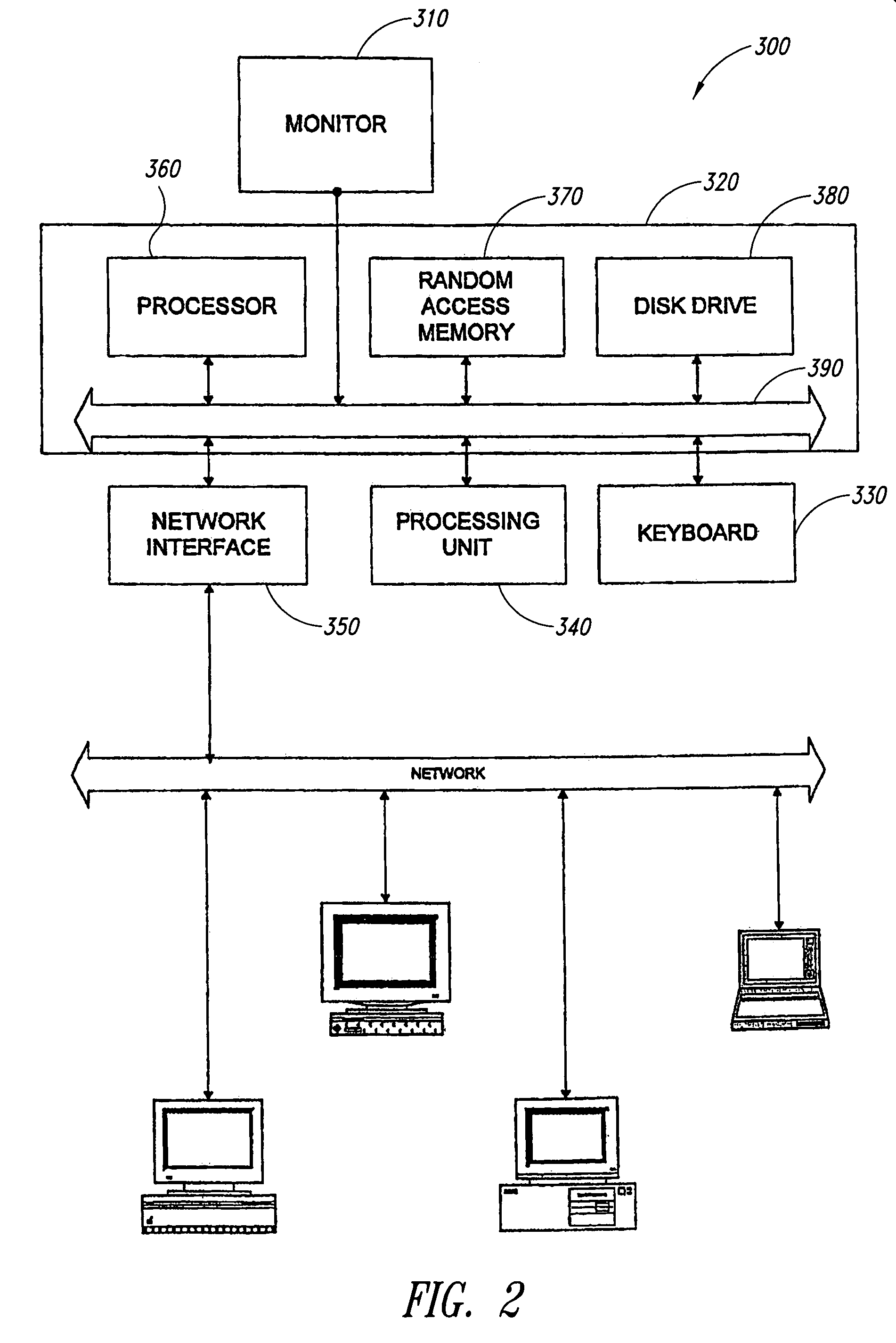
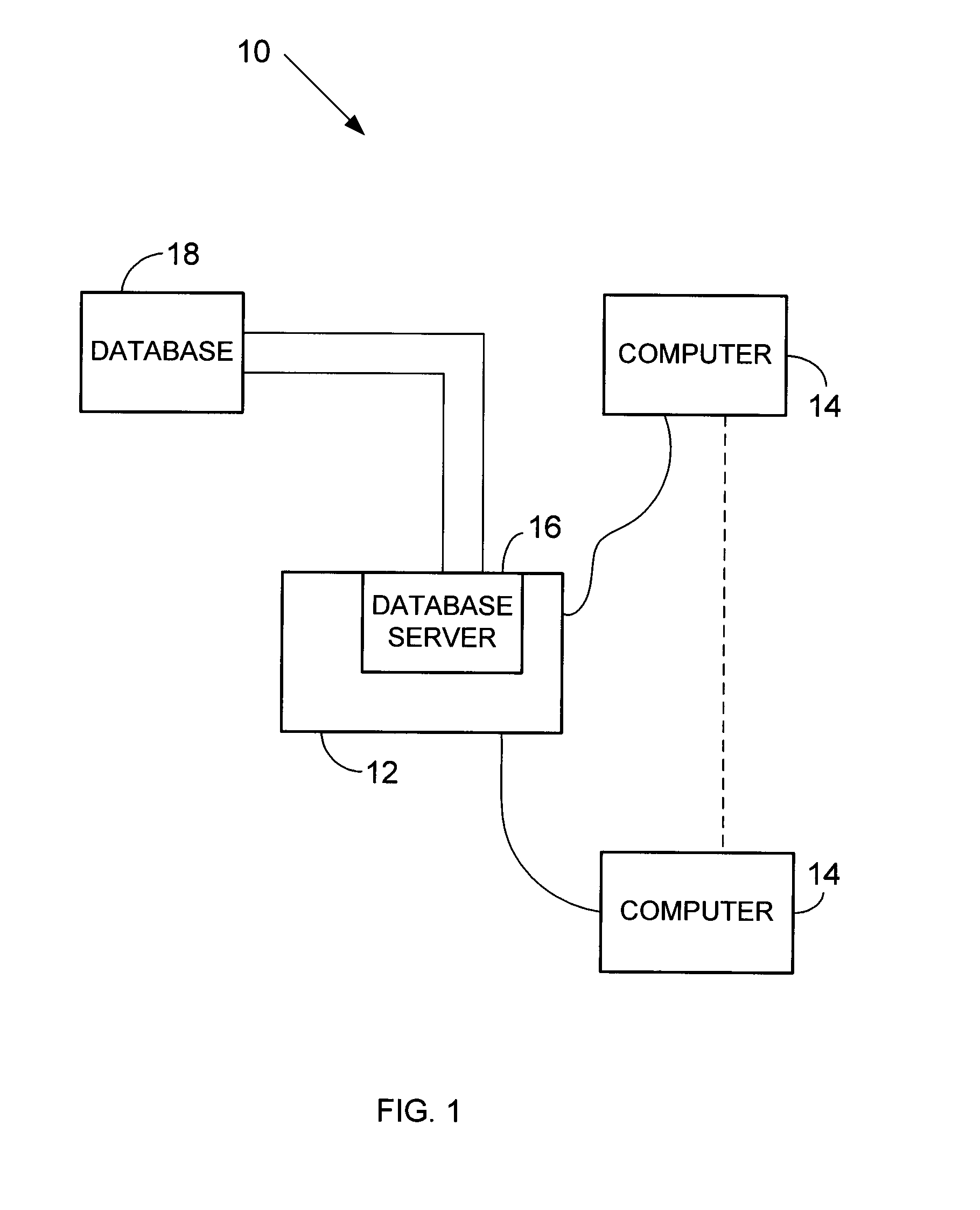
Method and apparatus for dynamic data flow control using prioritization of data requests
InactiveUS7454457B1Independent controlImprove efficiencyMultiple digital computer combinationsTransmissionData centerDynamic data
A data center (14) receives a request (22) for content from a browser (12) on a client (11). The data center determines whether the requested content is available at the data center. The content is available when the content is both present at the data center and current. The content may be expired and marked as non-available in response to an expiration command (24). When the requested content is available at the data center, the data center returns the requested content to the data center. When the requested content is locally unavailable at the data center, the requested content is retrieved from an origin server (18). The retrieval of the content from the origin server may be delayed based on the processing load at the origin server. When retrieval of the content is delayed, the request is prioritized and placed in a queue for handling by the origin server based on the priority of the request. Also, when retrieval of the content is delayed, a status page may be communicated to the browser to inform a user of the delay and provide alternate content (139) and status information related to the request determined as a function of the request or the current state of the origin server.
Owner:PARALLEL NETWORKS
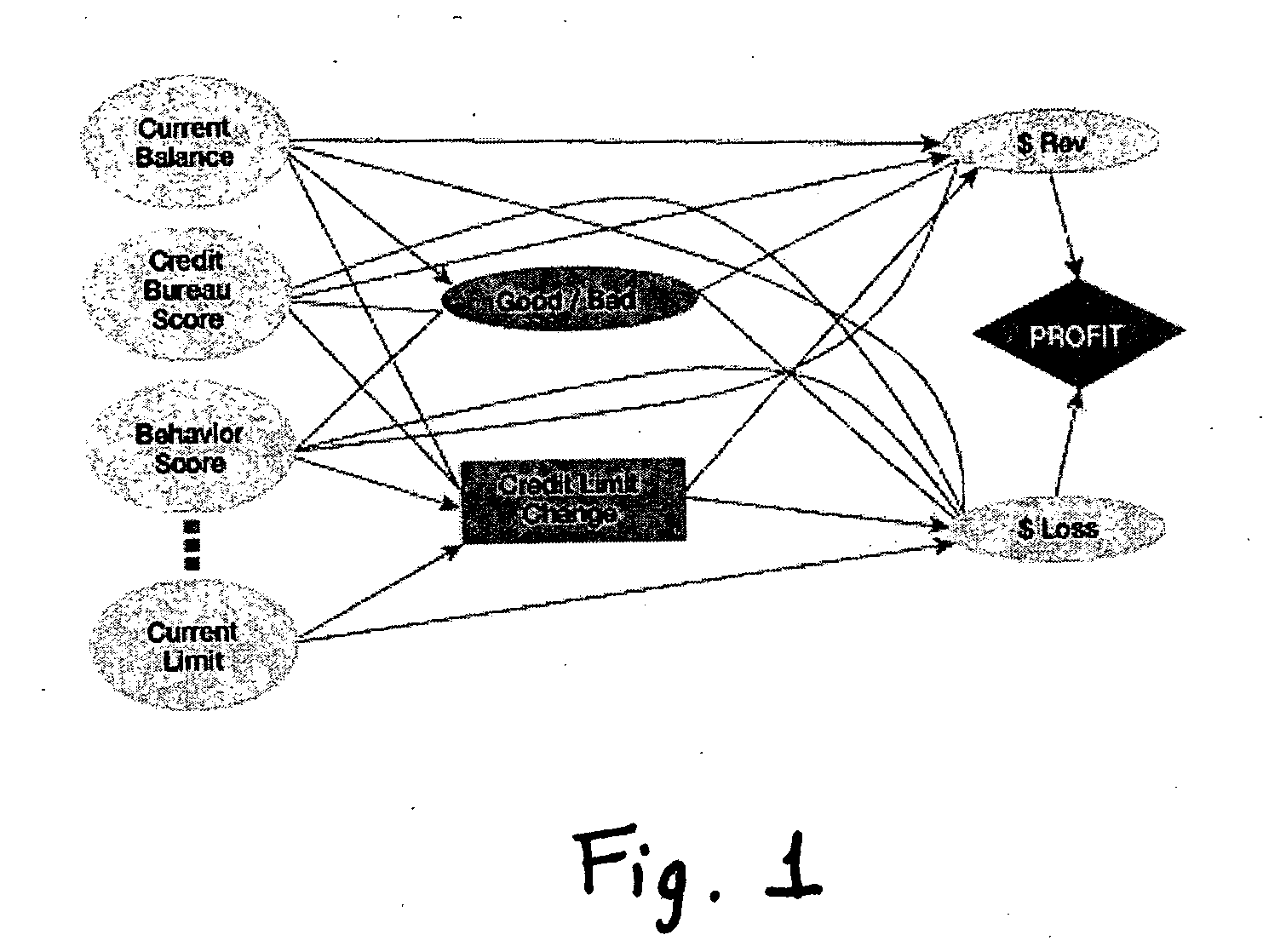
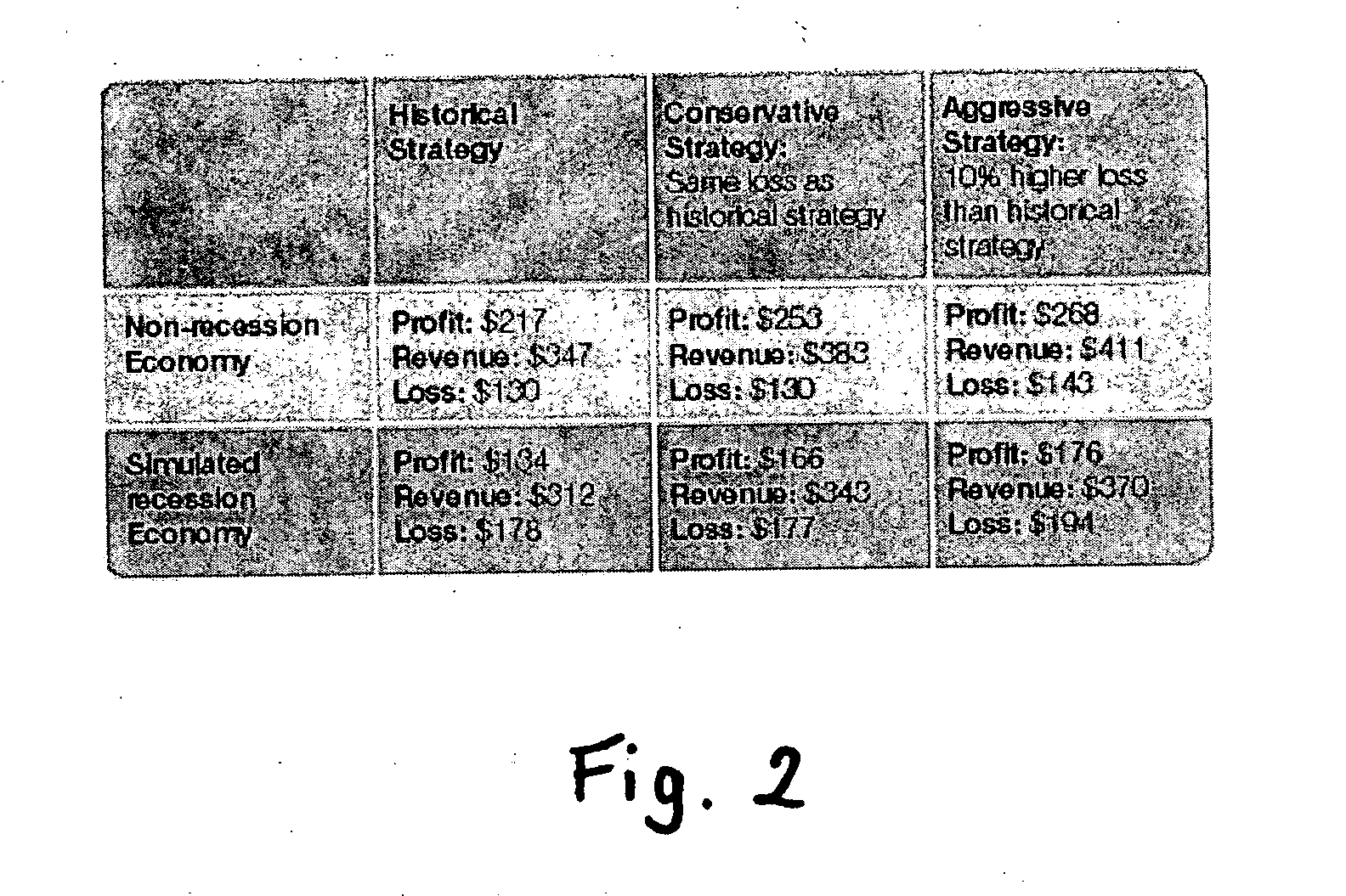
Method and apparatus for creating and evaluating strategies
A method and apparatus for strategy science methodology involving computer implementation is provided. The invention includes a well-defined set of procedures for carrying out a full range of projects to develop strategies for clients. One embodiment of the invention produces custom consulting projects that are found at one end of the full range of projects. At the other end of the range are, for example, projects developing strategies from syndicated models. The strategies developed are for single decisions or for sequences of multiple decisions. Some parts of the preferred embodiment of the invention are categorized into the following areas: Team Development, Strategy Situation Analysis, Quantifying the Objective Function, Data Request and Reception, Data Transformation and Cleansing, Decision Key and Intermediate Variable Creation, Data Exploration, Decision Model Structuring, Decision Model Quantification, An Exemplary Score Tuner, Strategy Creation, An Exemplary Strategy Optimizer, An Exemplary Uncertainty Estimator, and Strategy Testing. Each of the sub-categories are described and discussed in detail under sections of the same headings. The invention uses judgment in addition to data for developing strategies for clients.
Owner:FAIR ISAAC & CO INC
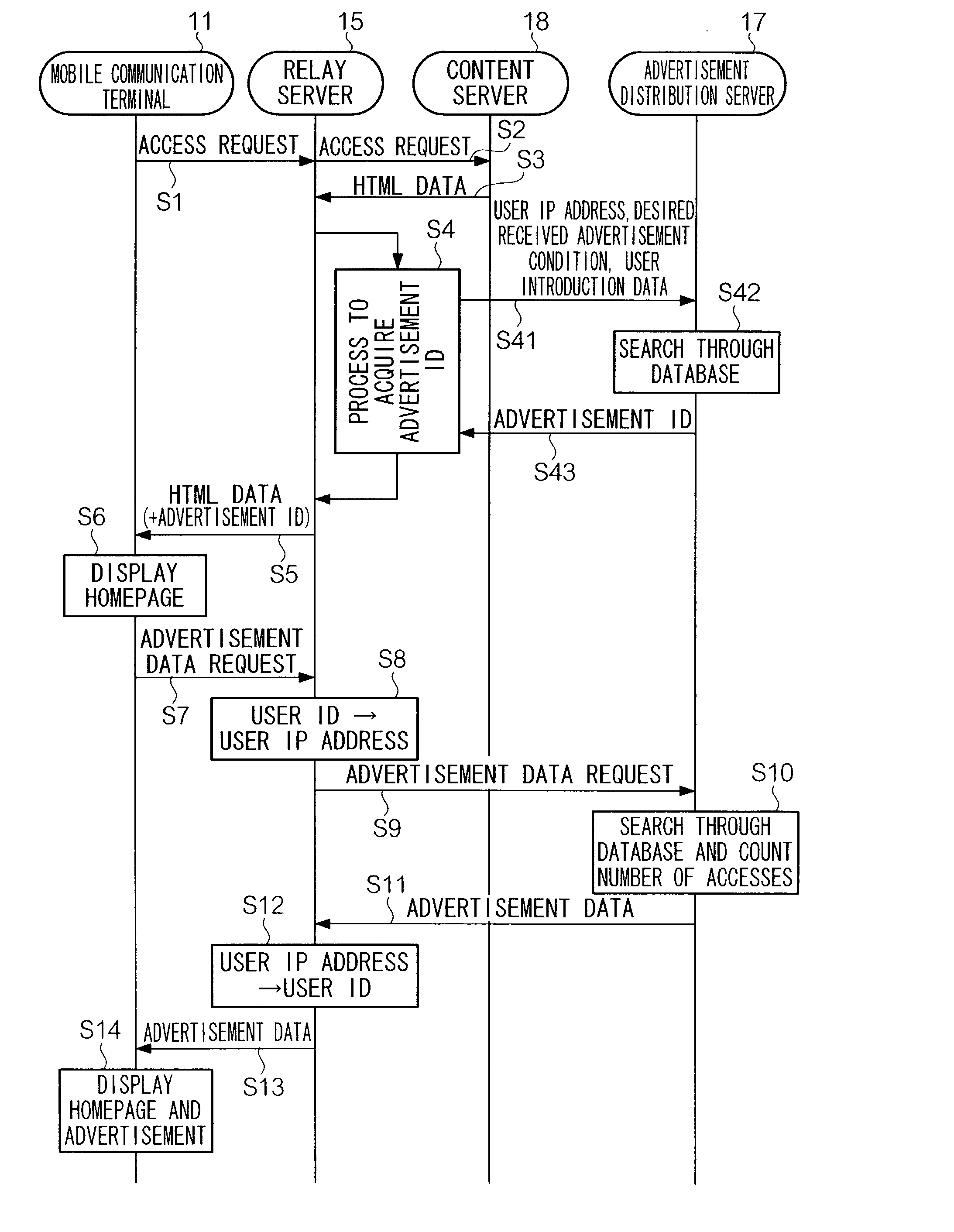
Method and system for distributing advertisements over network
A communication terminal sends an access request to a WWW server connected to a network to a relay server in the network. The relay server sends this access request to the WWW server and receives display data from the WWW server and sends an advertisement ID specifying an advertisement satisfying a predefined condition to the communication terminal together with the display data. The communication terminal displays a screen by this display data and sends an advertisement data request including an advertisement ID received from the relay server through the relay server to an advertisement distribution server. When receiving an advertisement data request, the advertisement distribution server sends the advertisement ID contained in the advertisement data request to the communication terminal through the relay server. When receiving the advertisement data, the communication terminal displays an advertisement corresponding to the advertisement data along with the screen corresponding to the display data.
Owner:NTT DOCOMO INC
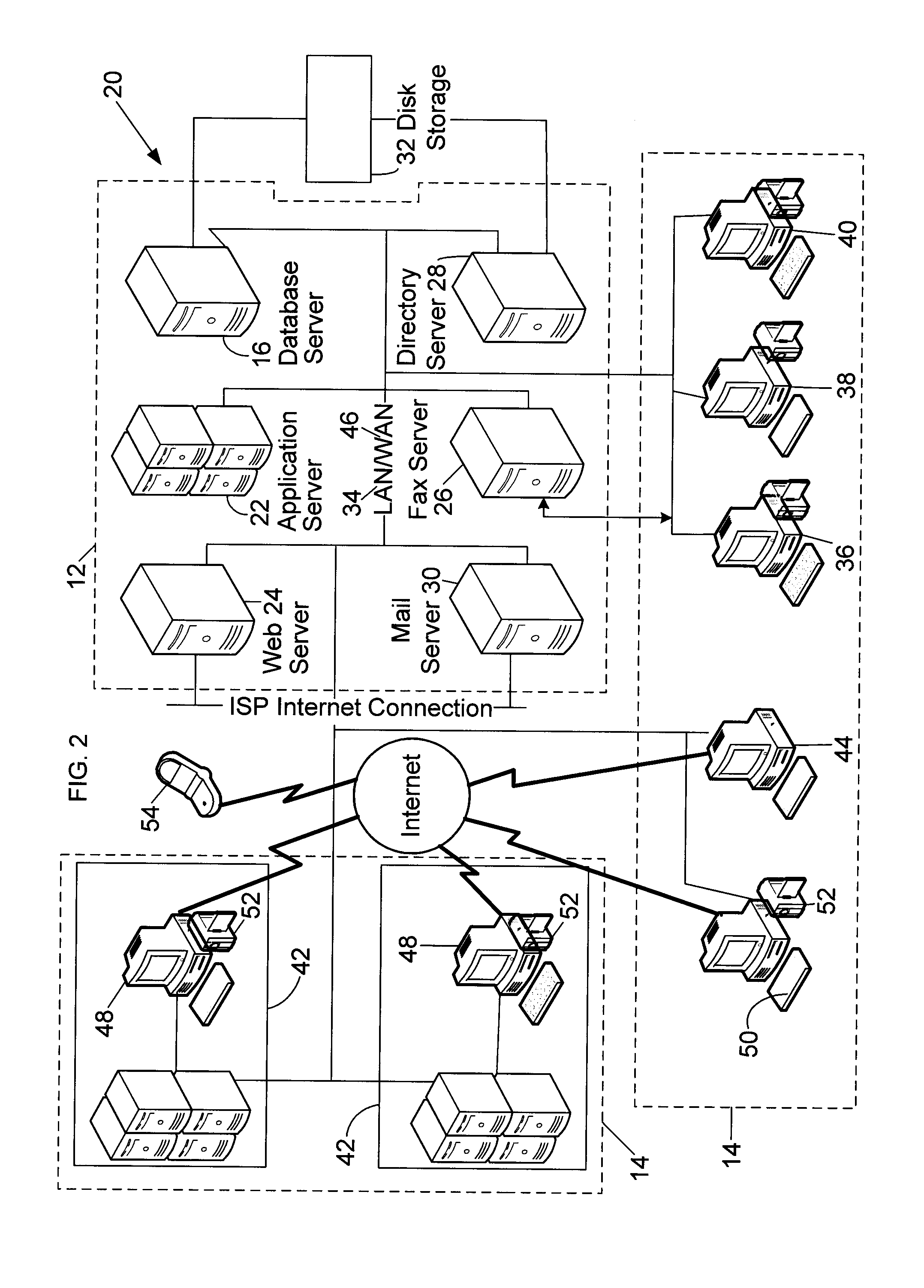
Systems and methods for user identification, user demographic reporting and collecting usage data usage biometrics
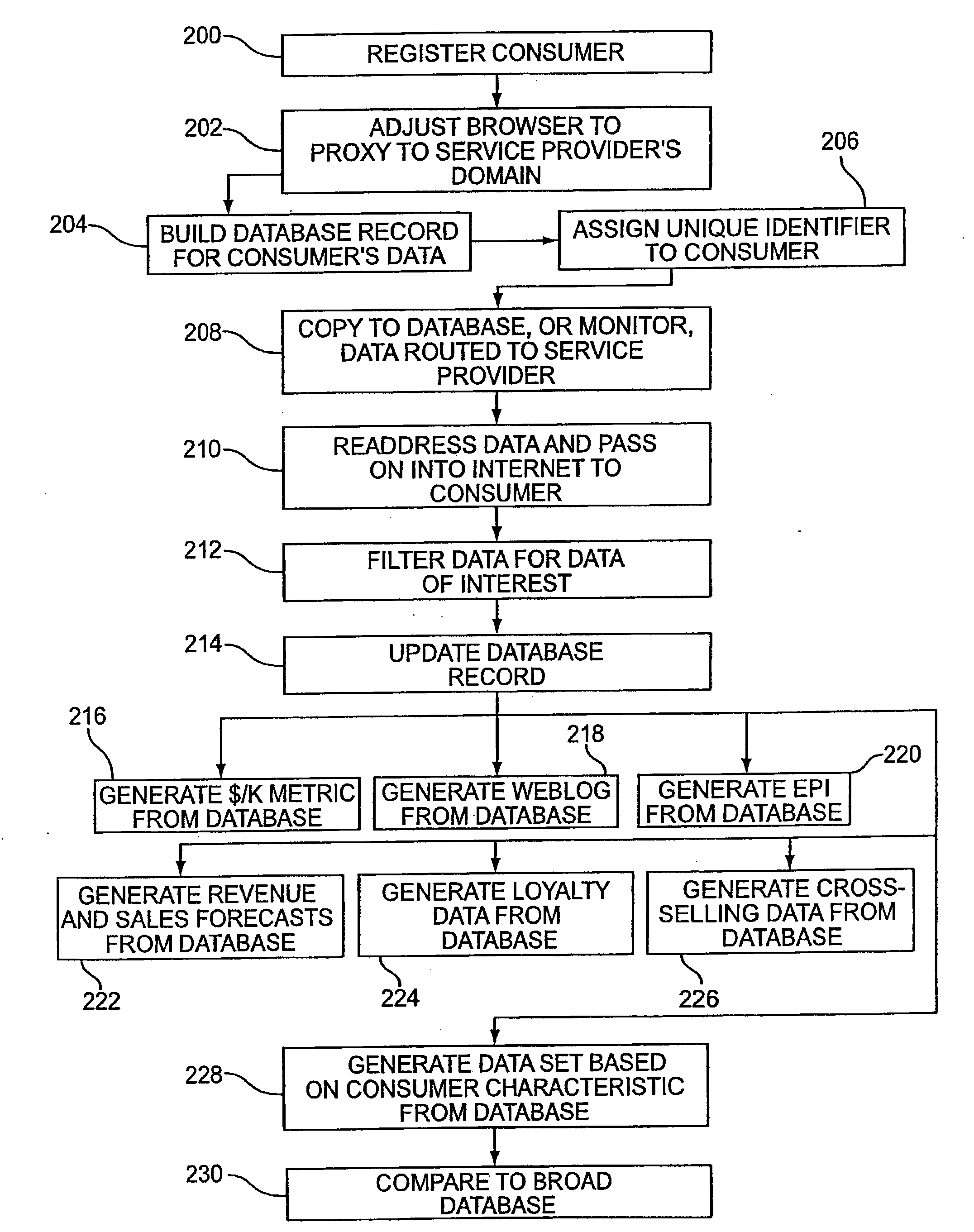
InactiveUS7260837B2Digital data information retrievalDigital data processing detailsData setDatabase server
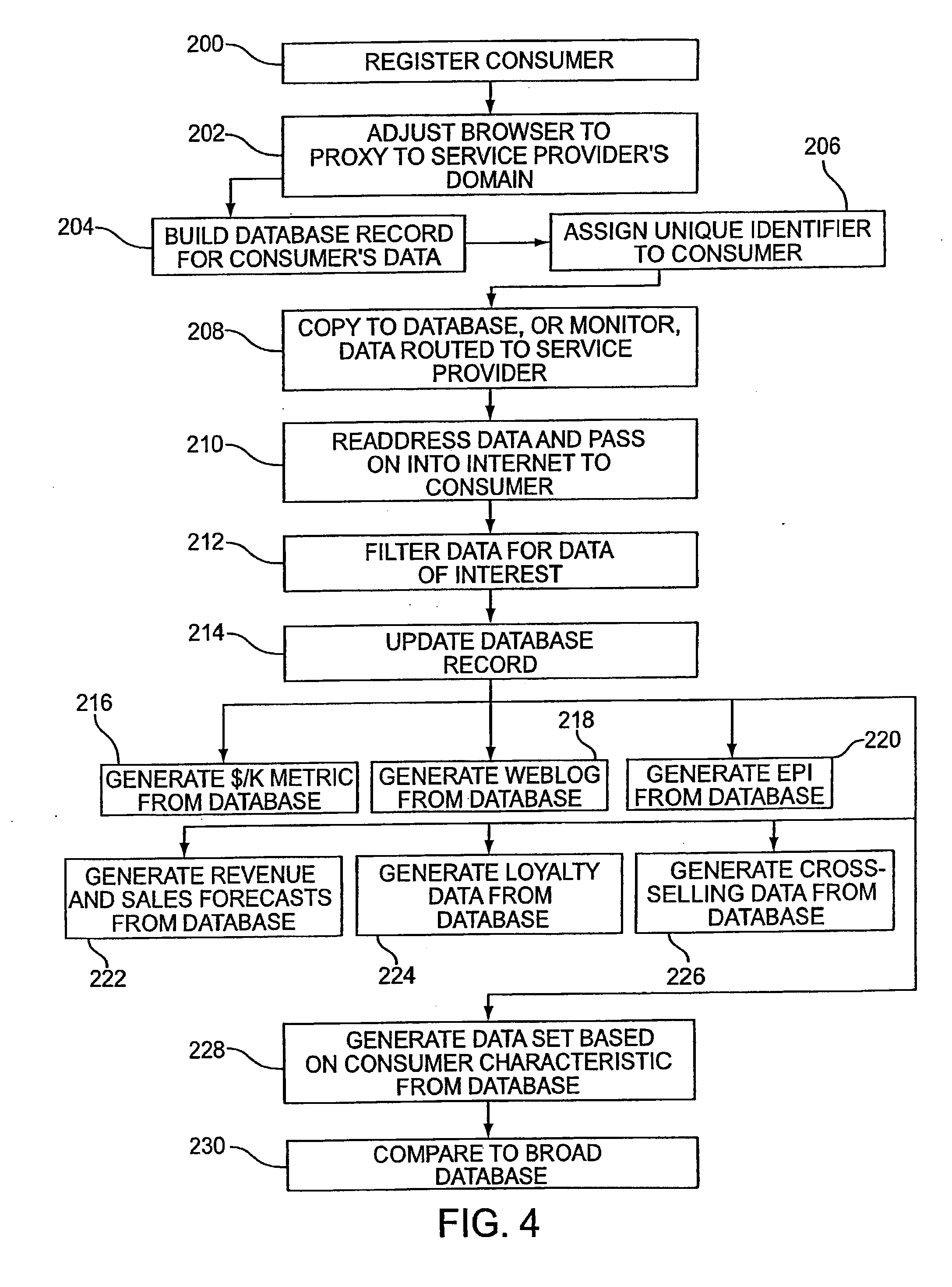
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
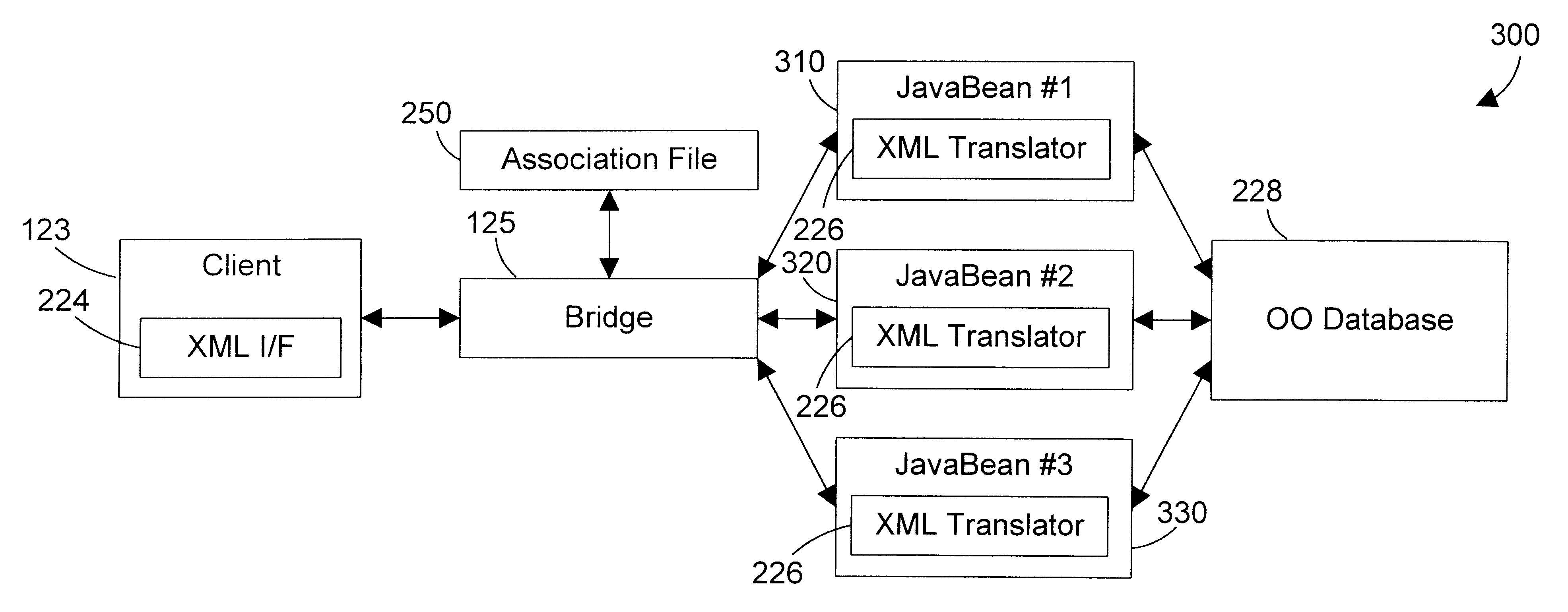
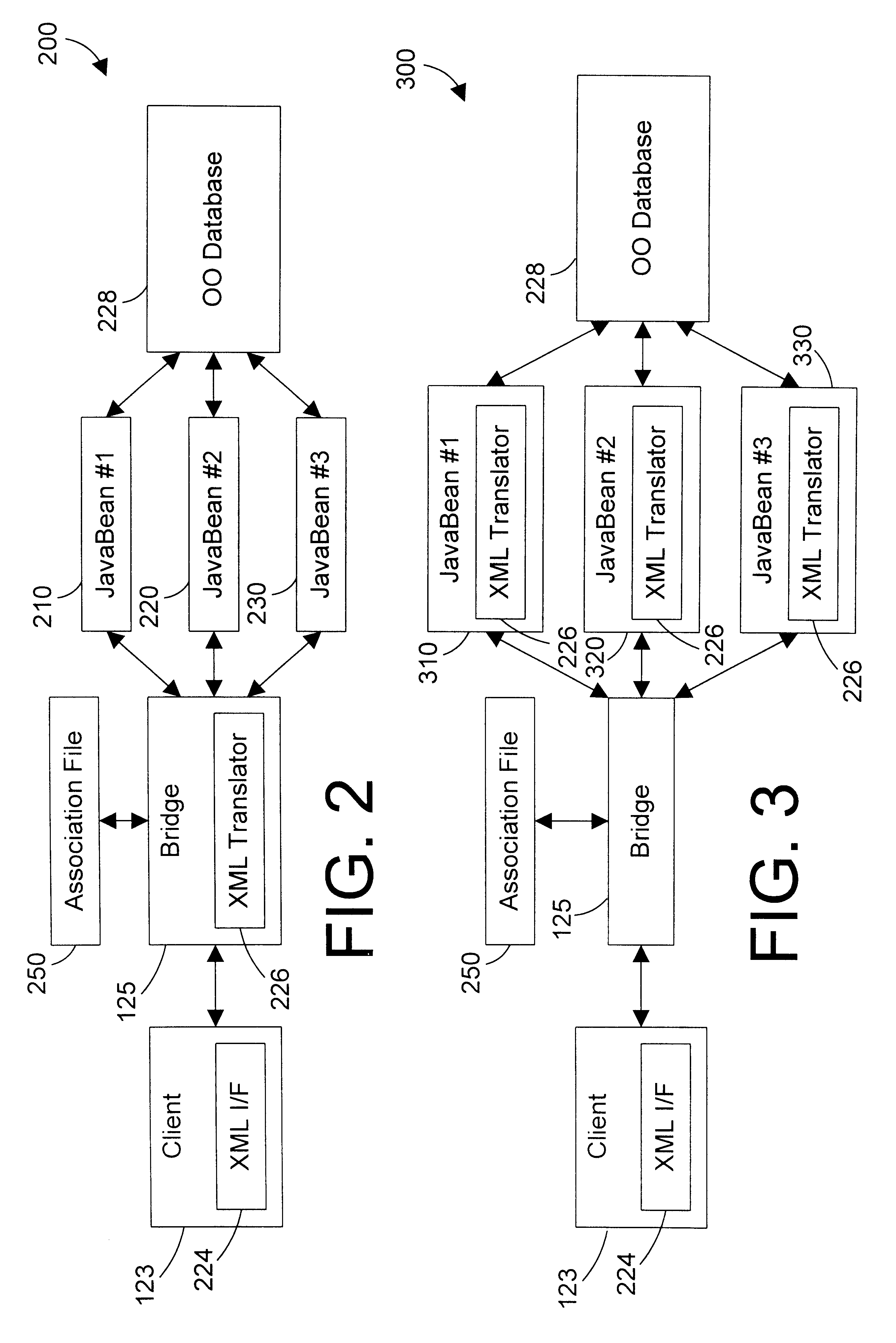
Tagged markup language interface with document type definition to access data in object oriented database
InactiveUS6480860B1Data processing applicationsWebsite content managementExtensible markupDocument preparation
An apparatus and method defines a markup language for accessing data in a database. The markup language is preferably defined in extensible markup language (XML) by creating suitable document type definitions (DTDs), which define the grammar for accessing data in the database using the markup language. A bridge interprets the data request from the client in markup language format, a suitable database query for the database is formulated, and the data is then placed within a document for delivery in markup language format to the user. As new data types are added to the database, corresponding document type definitions (DTDs) may be dynamically generated, allowing a user to access new kinds of data in a database with a software tool that has a user-friendly graphical user interface without having to manually update the software tool for each new data type that is added to the database.
Owner:IBM CORP
Client-side performance optimization system for streamed applications
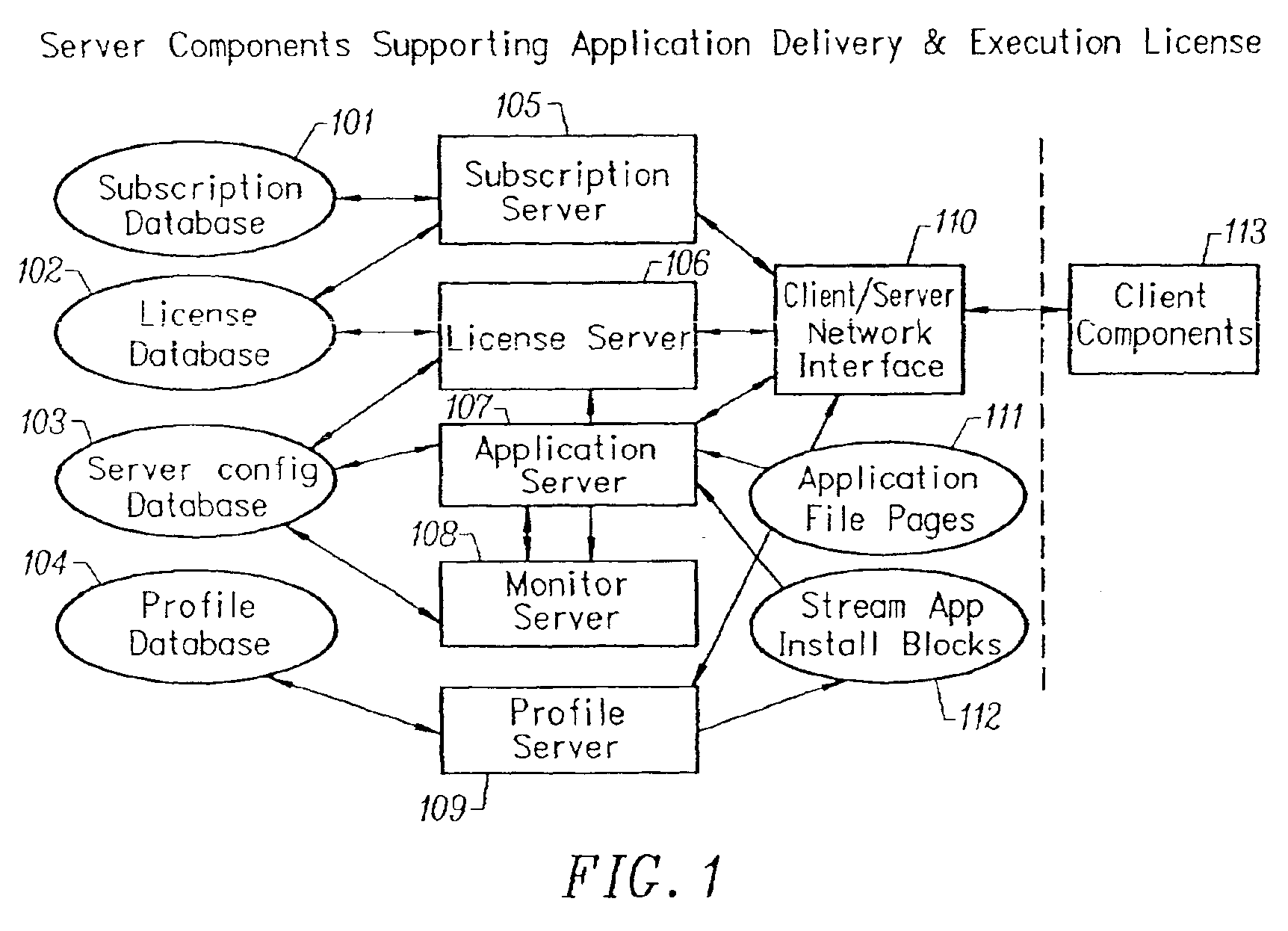
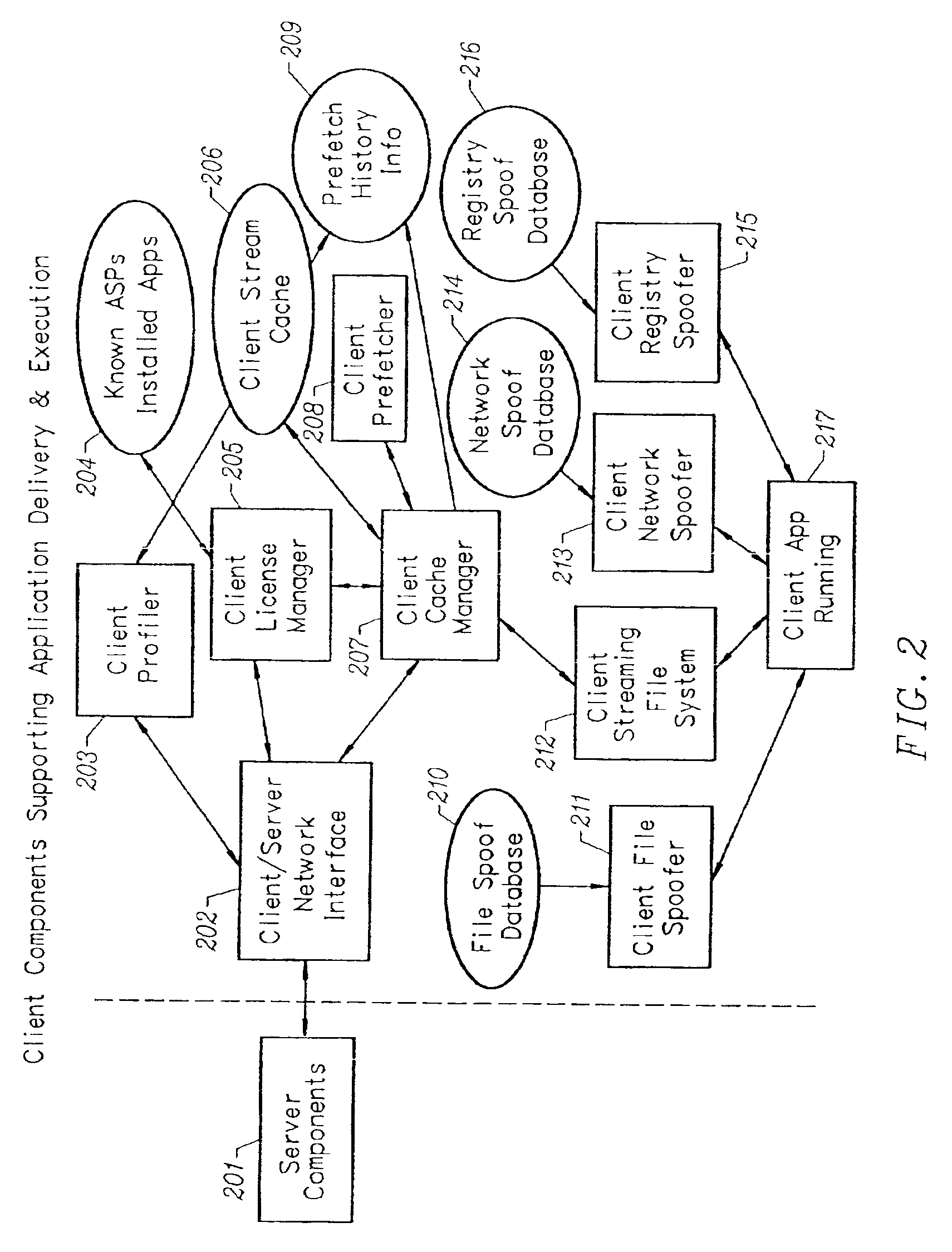
InactiveUS6959320B2Efficiently stream and executeEasily integrates into client system 's operating systemMultiple digital computer combinationsProgram loading/initiatingApplication serverData file
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
User identification in the header of data packets
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE NETWORKS
Method and system for selecting grammars based on geographic information associated with a caller
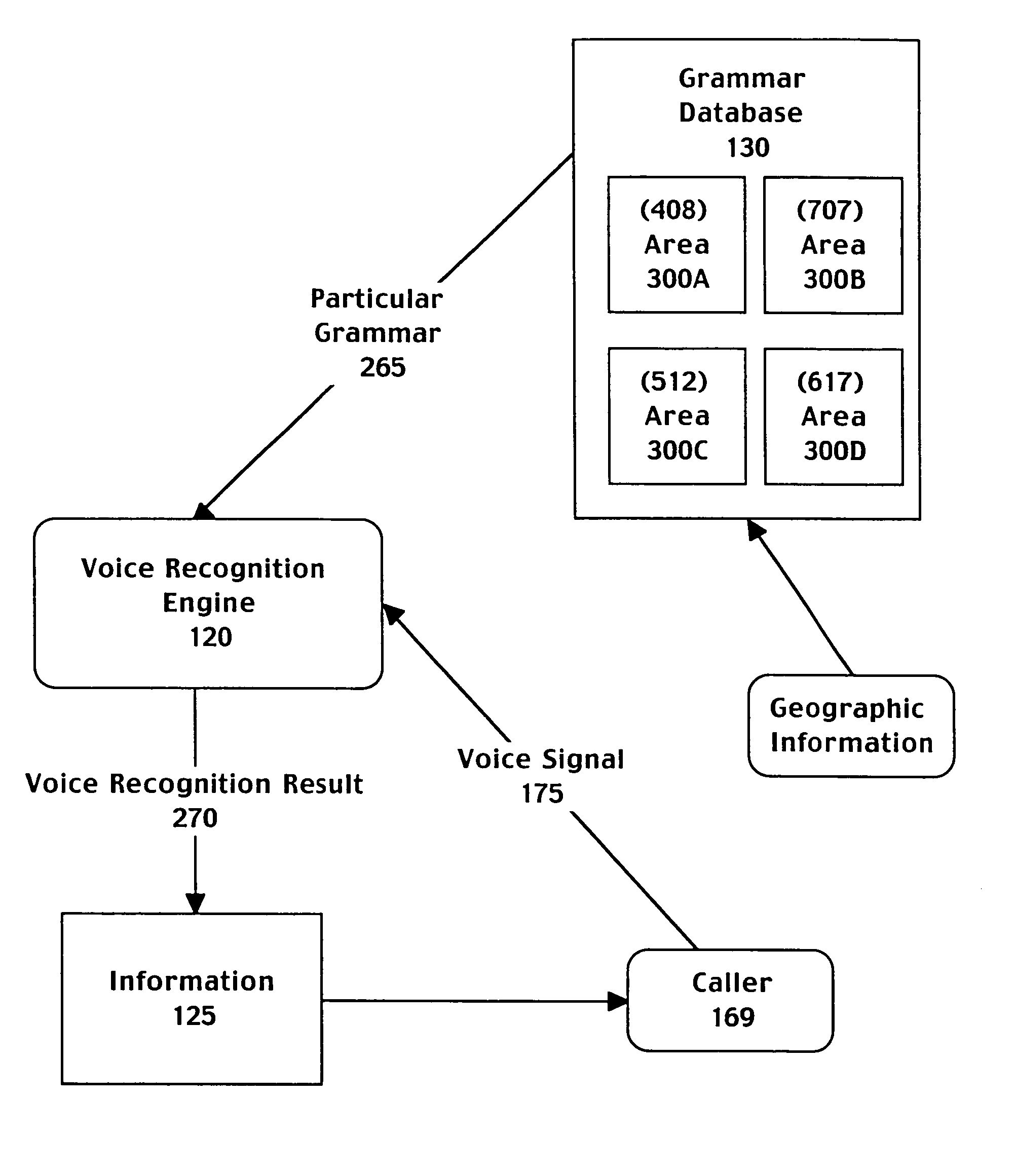
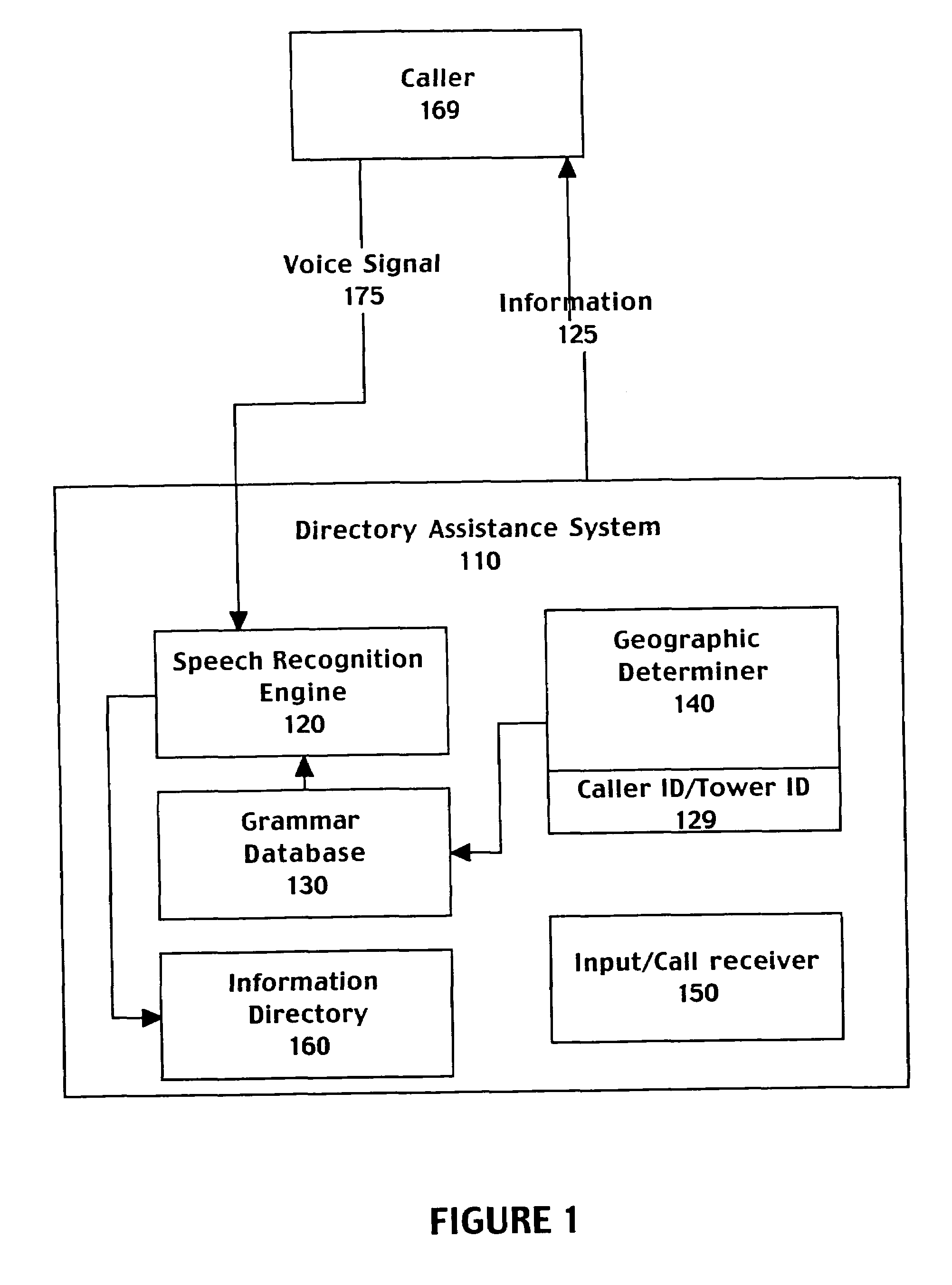
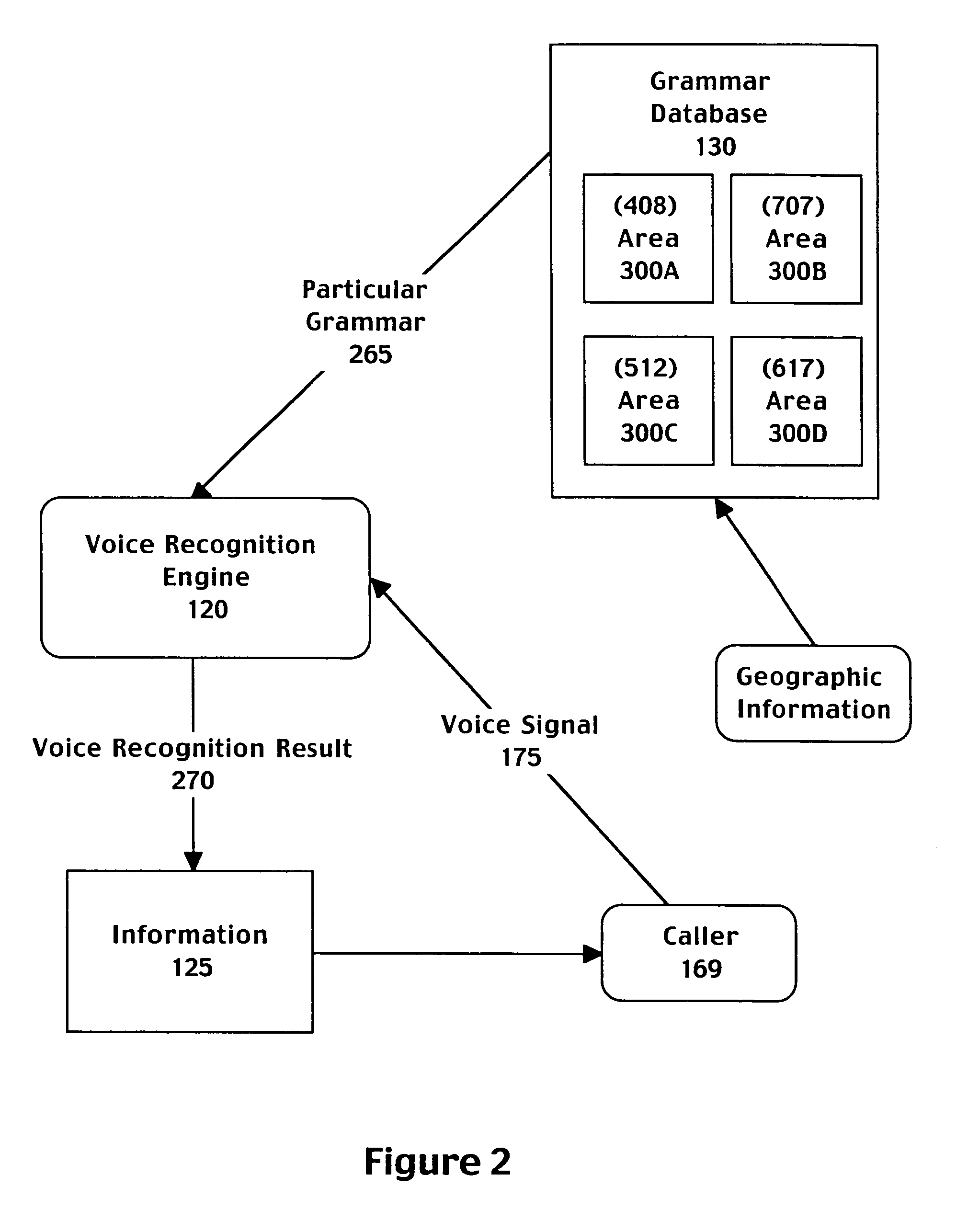
A computer implemented method for automatically processing a data request comprising accessing a voice signal from a caller, determining geographic information associated with the caller from telephone network information associated with a call made by the caller, and retrieving a speech recognition grammar customized to the geographic information associated with the caller. The method further includes recognizing the voice signal by matching the voice signal to an entry of the speech recognition grammar and providing a directory listing to the caller based on the entry of the speech recognition grammar. The selected grammar may be customized to bias speech recognition to more frequently recognize cities local to the geographic information.
Owner:MICROSOFT TECH LICENSING LLC
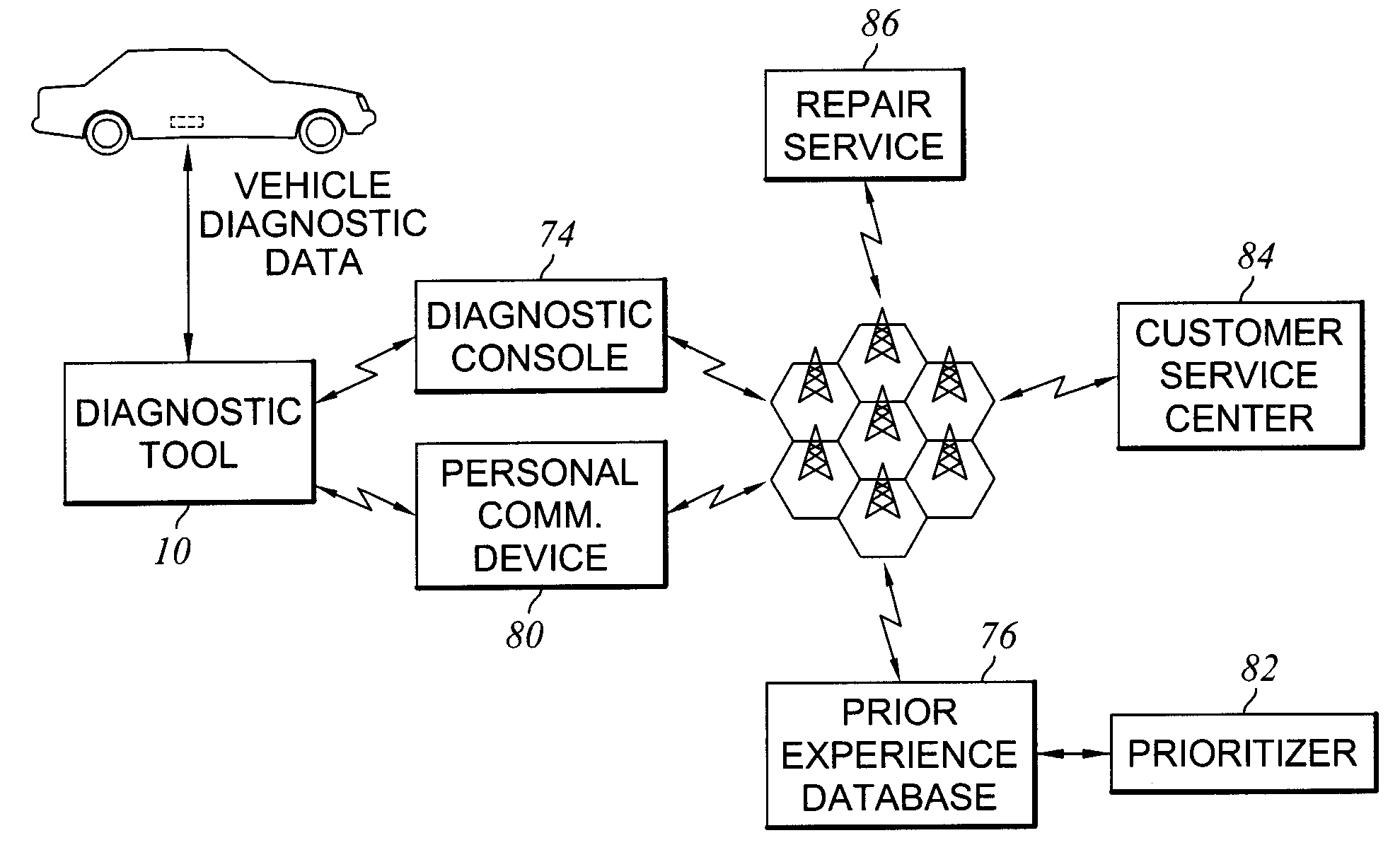
Handheld Automotive Diagnostic Tool with VIN Decoder and Communication System
ActiveUS20090276115A1Quickly and easily determiningVehicle testingRegistering/indicating working of vehiclesCommunications systemHand held
Provided is a method of receiving data from a vehicle onboard computer. The onboard computer is configured to transmit vehicle identification data in response to receipt of an identification request, which is transmitted in a basic communication protocol. The onboard computer is further configured to transmit private operational data in response to receipt of a private data request. The private data request is transmitted in a diagnostic protocol. The method includes connecting a scan tool to the onboard computer, and polling the onboard computer to identify the basic communication protocol. The identification request is then transmitted to the onboard computer. Vehicle identification data is subsequently received from the onboard computer. A protocol database having a plurality of diagnostic protocols is then accessed. Each diagnostic protocol is associated with respective vehicle identification data. The diagnostic protocol is then determined based on the received vehicle identification data.
Owner:INNOVA ELECTRONICS
System for redirecting requests for data to servers having sufficient processing power to transcast streams of data in a desired format
InactiveUS6981045B1Attenuation bandwidthReduce deliveryMultiple digital computer combinationsTwo-way working systemsBandwidth requirementDistributed computing
A method includes polling a first plurality of one-hop gateway serves for available bandwidth and available number of CPU cycles for each respective one-hop gateway server, receiving a request to provide data to a media sink in a desired format, determining a bandwidth requirement and an estimated number of CPU cycles required for servicing the media sink, determining a second plurality of one-hop gateway servers having an available bandwidth greater or equal to the bandwidth requirement and an available number of CPU cycles greater or equal to the estimated number of CPU cycles, determining a one-hop gateway server from the second plurality of one-hop gateway servers appropriate for providing the data to the media sink and configured to receive data in a second format, and transcoding the data from a first format to the second format. An example gateway server and a computer program product usable therewith are also provided.
Owner:ADAPTIVE STREAMING INC
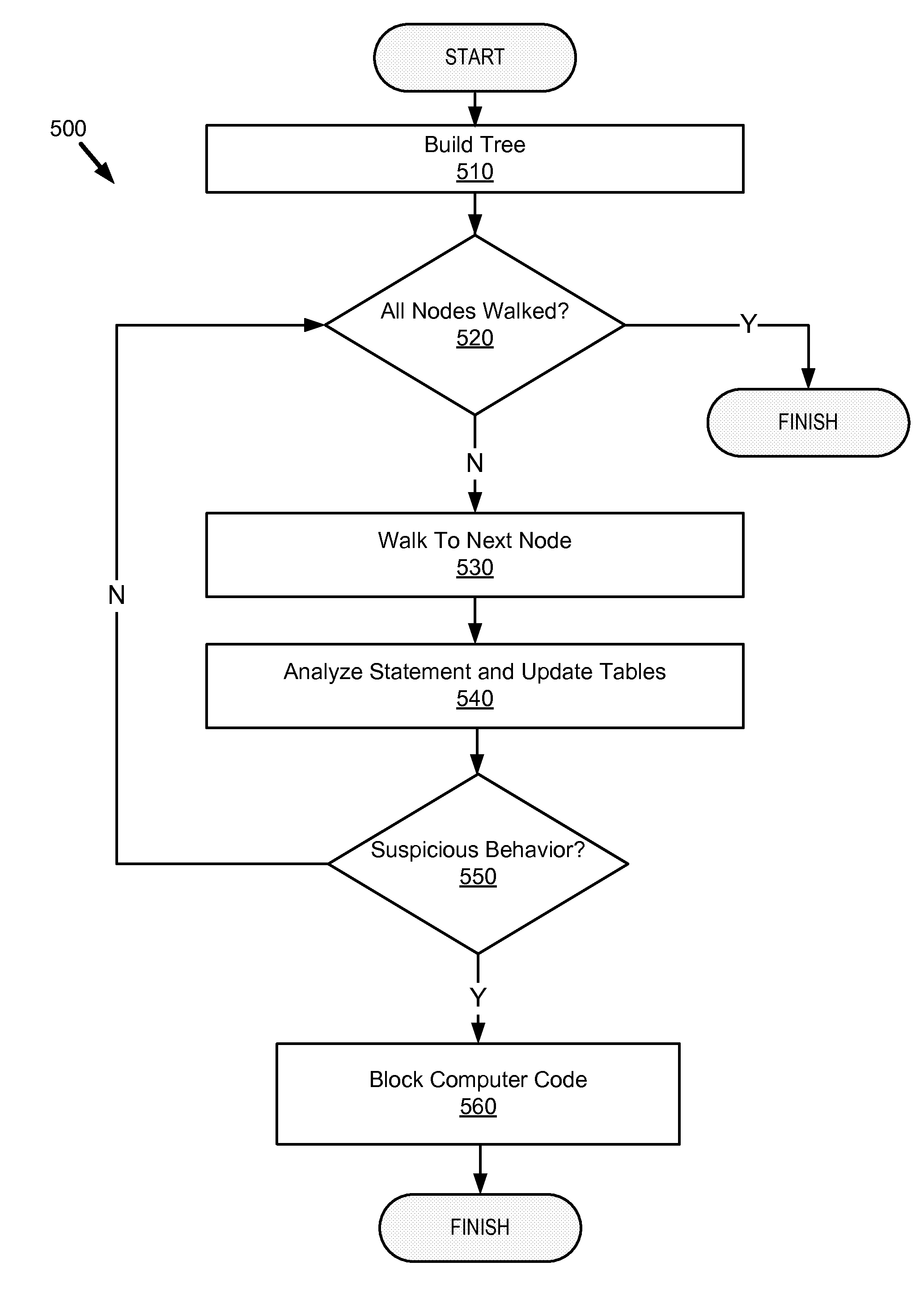
System and method for analyzing malicious code using a static analyzer
Owner:TRUSTWAVE HOLDINGS
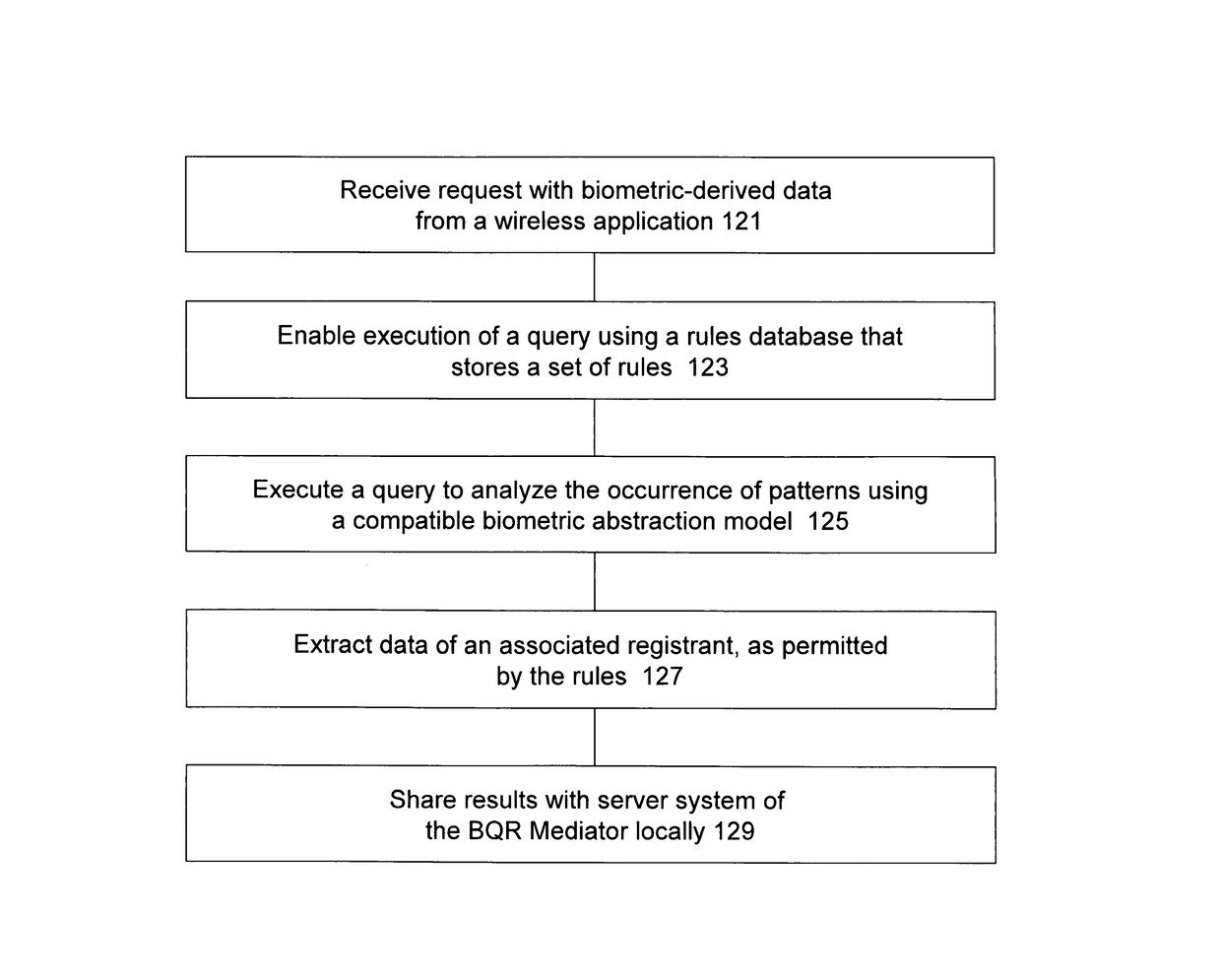
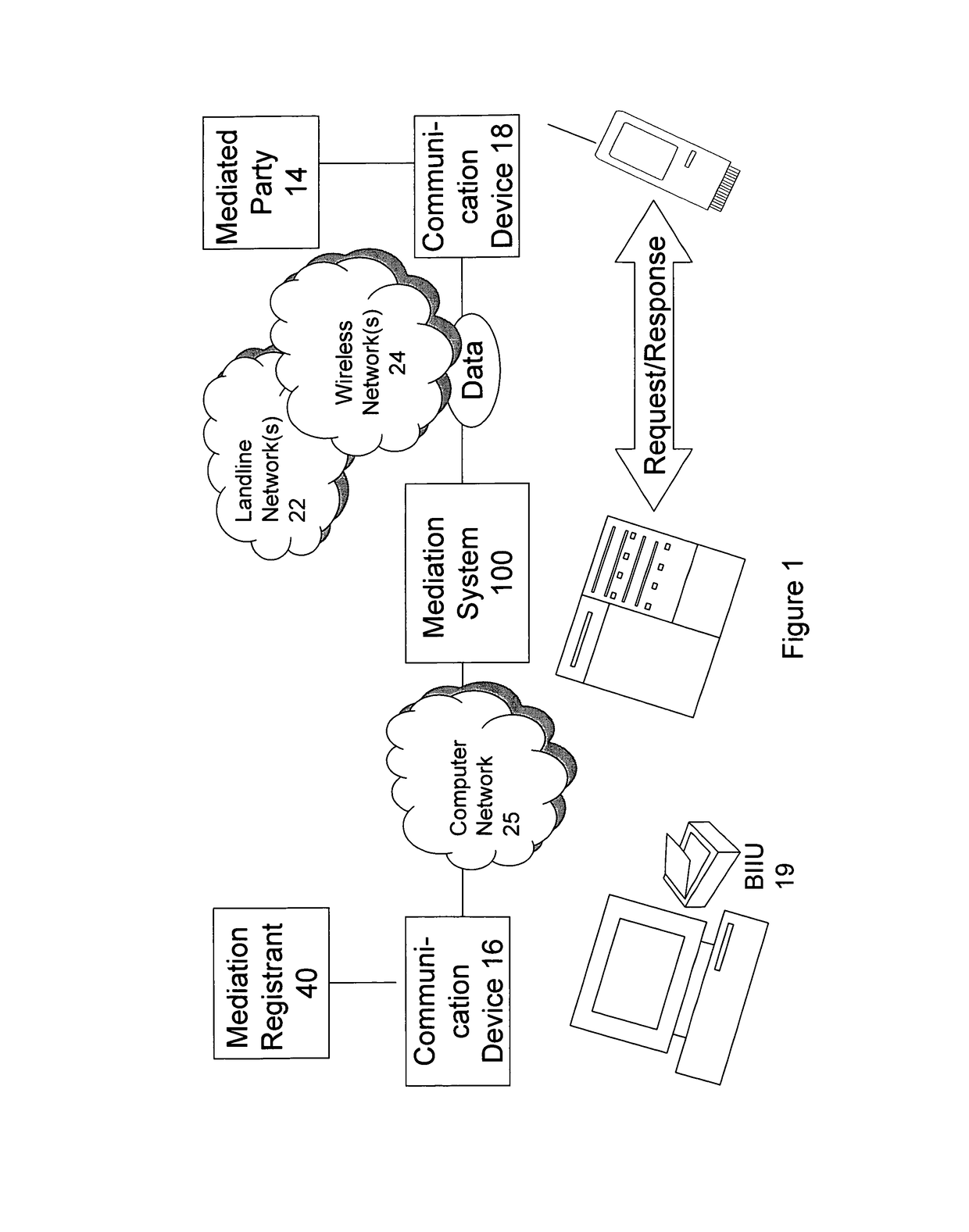
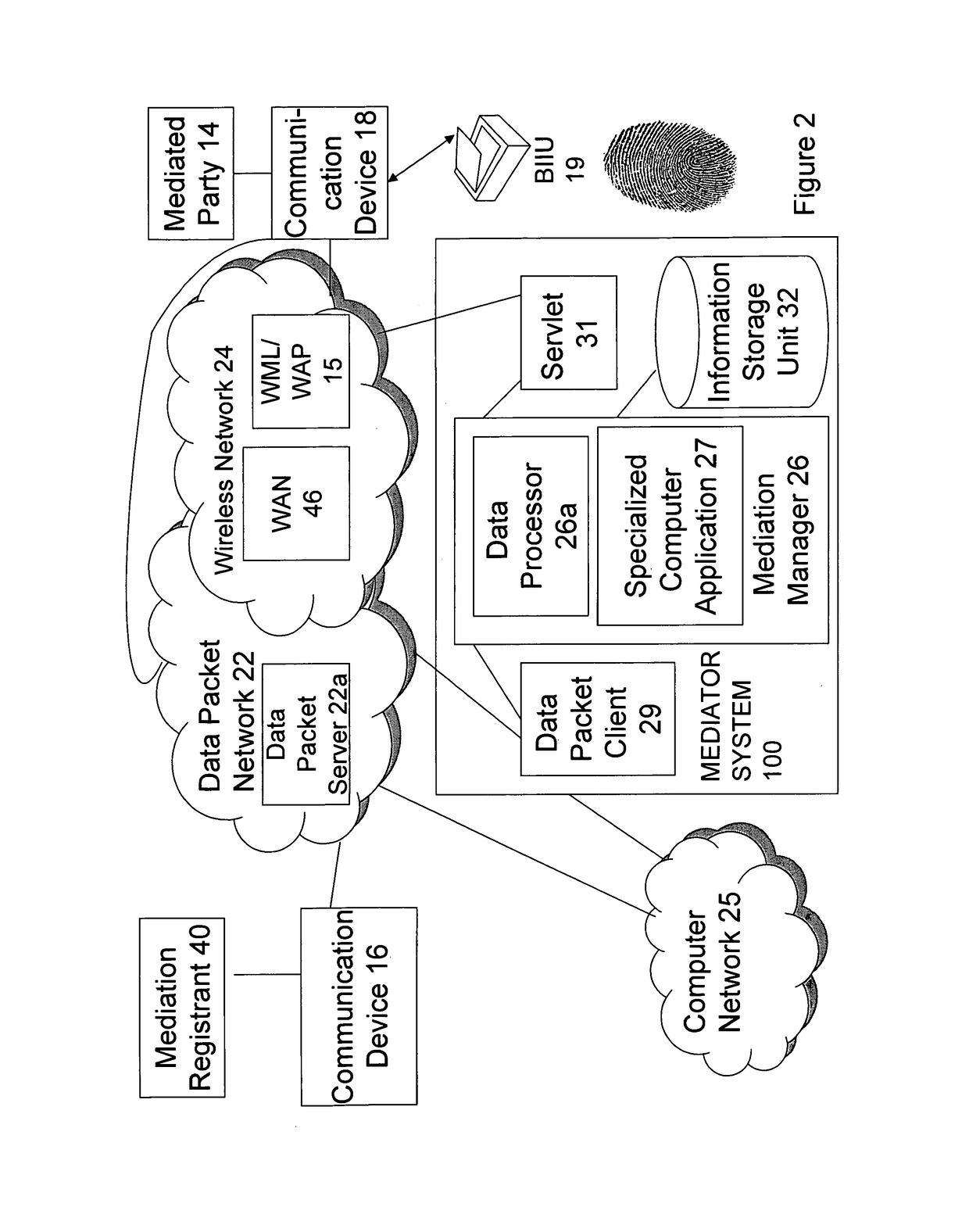
Methods using mediation software for rapid health care support over a secured wireless network; methods of composition; and computer program products therefor
ActiveUS9928379B1Increased riskImprove privacyMedical data miningWeb data indexingBiometric dataPrivacy rule
Some of these new methods harness distributed computing capabilities to integrate biometric abstraction processes, wireless network connectivity, and specialized software for mediation, to produce a unified result set. A mediator that enables rapid health care support is used in a computer system having a database of information to be shared with authorized requesters, under privacy rules or other pre-defined constraints. The methods, using specialized software for mediation, are preferably enabled to process a securely transmitted remote data request as a query to verify or identify an individual, whether it is sent via a network that is wireless in any part, or not. Upon receiving a remote request, typically sent by a requesting application other than one operated by the individual who is the subject of the request, the mediator uses the individual's transformed biometric data of the request to rapidly advance query resolution, under all query preprocessing rules, and query results post-processing rules, that apply.
Owner:HOFFER STEVEN M
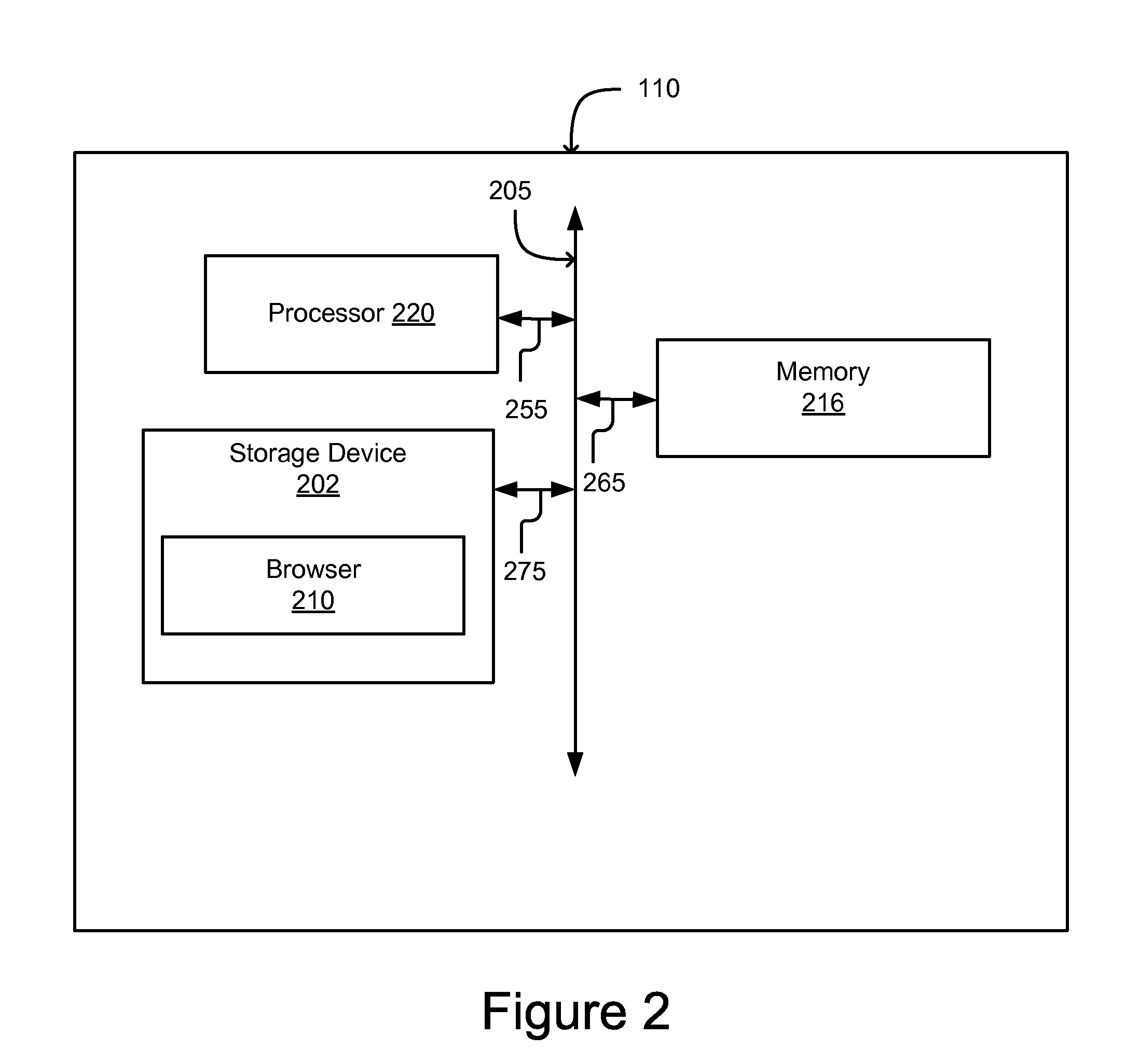
Method and system for confirming the identity of a user
InactiveUS7690032B1Digital data processing detailsUser identity/authority verificationBiometric dataInternet privacy
A method of confirming the identity of a user includes processing biometric credentials, generating a user configurable policy including identities of a plurality of authenticating entities, storing the user configurable policy in a device, presenting the device to an authenticating entity at an authentication station, and requesting biometric and personal data of the user from the device data. The biometric data corresponds to at least one biometric feature desired for authenticating the user and the requesting operation is performed by a workstation of the authenticating entity. Moreover, the method includes consulting the user configurable policy in response to the requesting operation to determine whether the requested biometric data is permitted to be released from the device data, and releasing the requested biometric and personal data from the device data to the authenticating entity when the default rule associated with the one authenticating entity permits releasing the requested biometric and personal data.
Owner:DAON HLDG
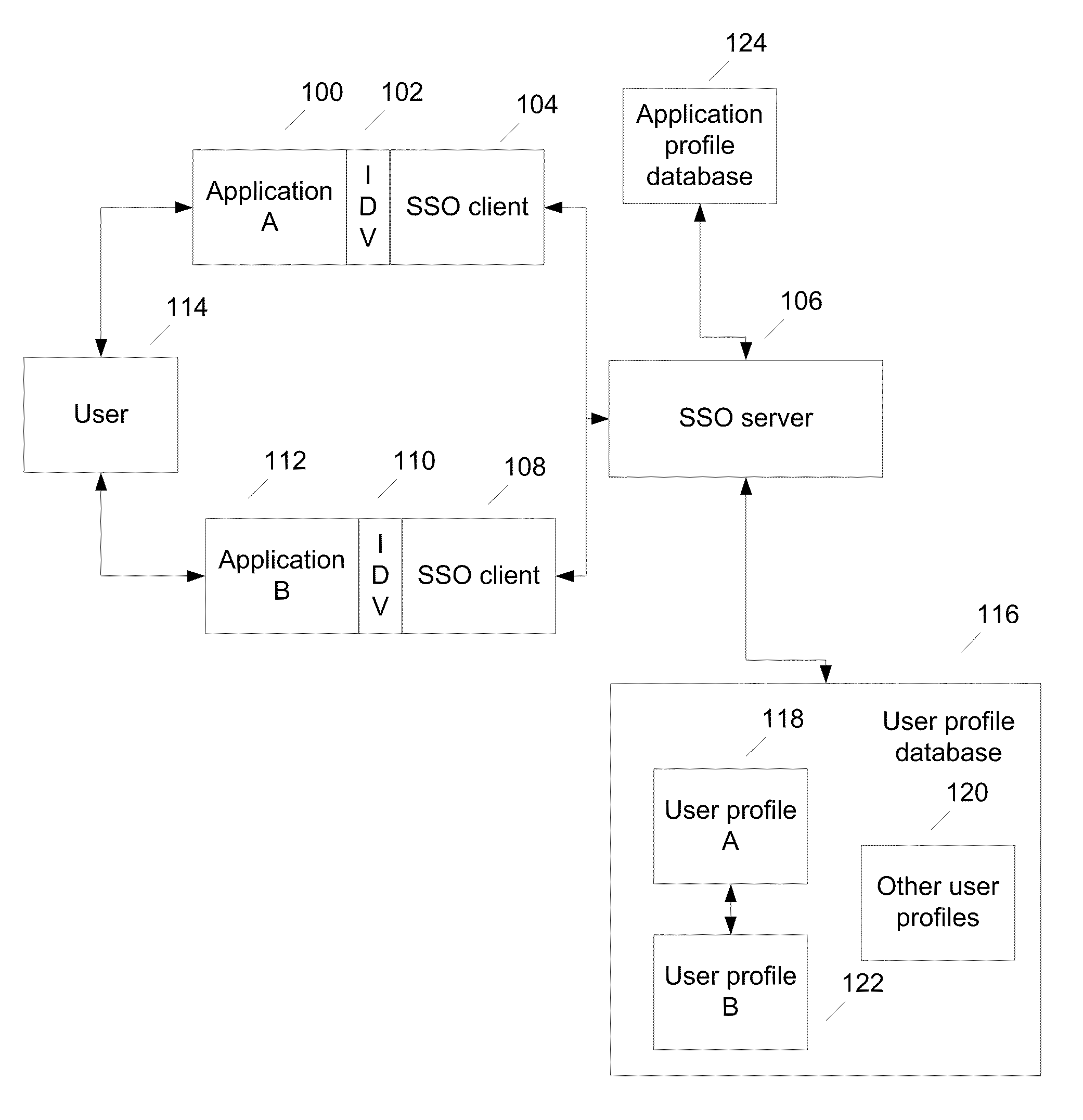
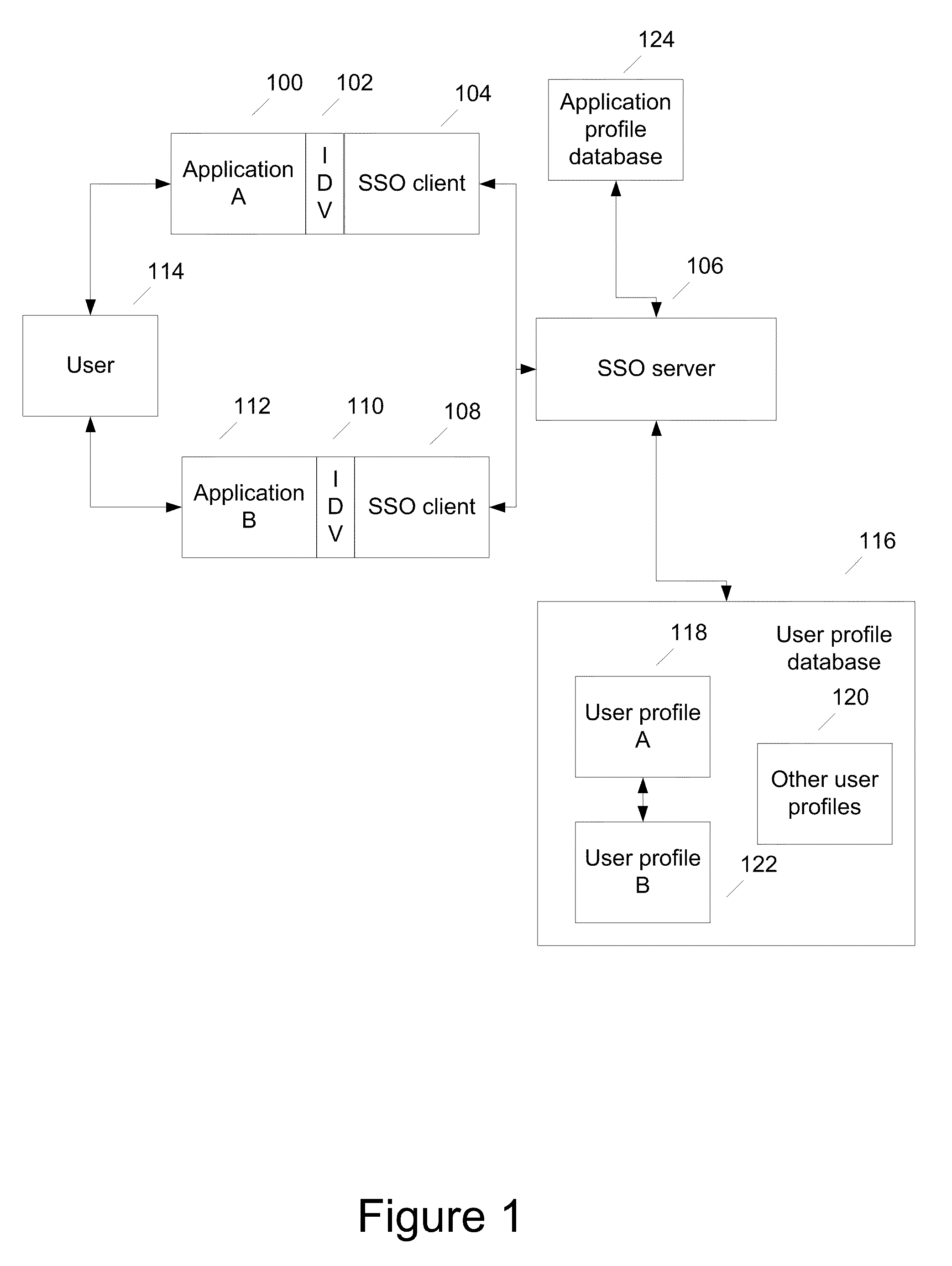
Methods and systems for single sign on with dynamic authentication levels
ActiveUS20090292927A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyApplication software
Method and systems for single sign on with dynamic authentication levels is described. The method include receiving a data request for access to a second application, where the user is already authenticated to the first application at a first authentication level. Application information about the authentication level necessary to access the second application is retrieved. In response to a request, the user provides the further authentication data for accessing the second application. The type of the further authentication data required is based on the first authentication level and the minimum authentication level necessary to access the second application. The user is then authenticated to the second application at the minimum authentication level necessary to access the second application.
Owner:HSBC TECH & SERVICES (USA) INC
Methods and apparatus providing automatic client authentication
ActiveUS7194761B1Avoid disruptionDigital data processing detailsUser identity/authority verificationClient-sideServer appliance
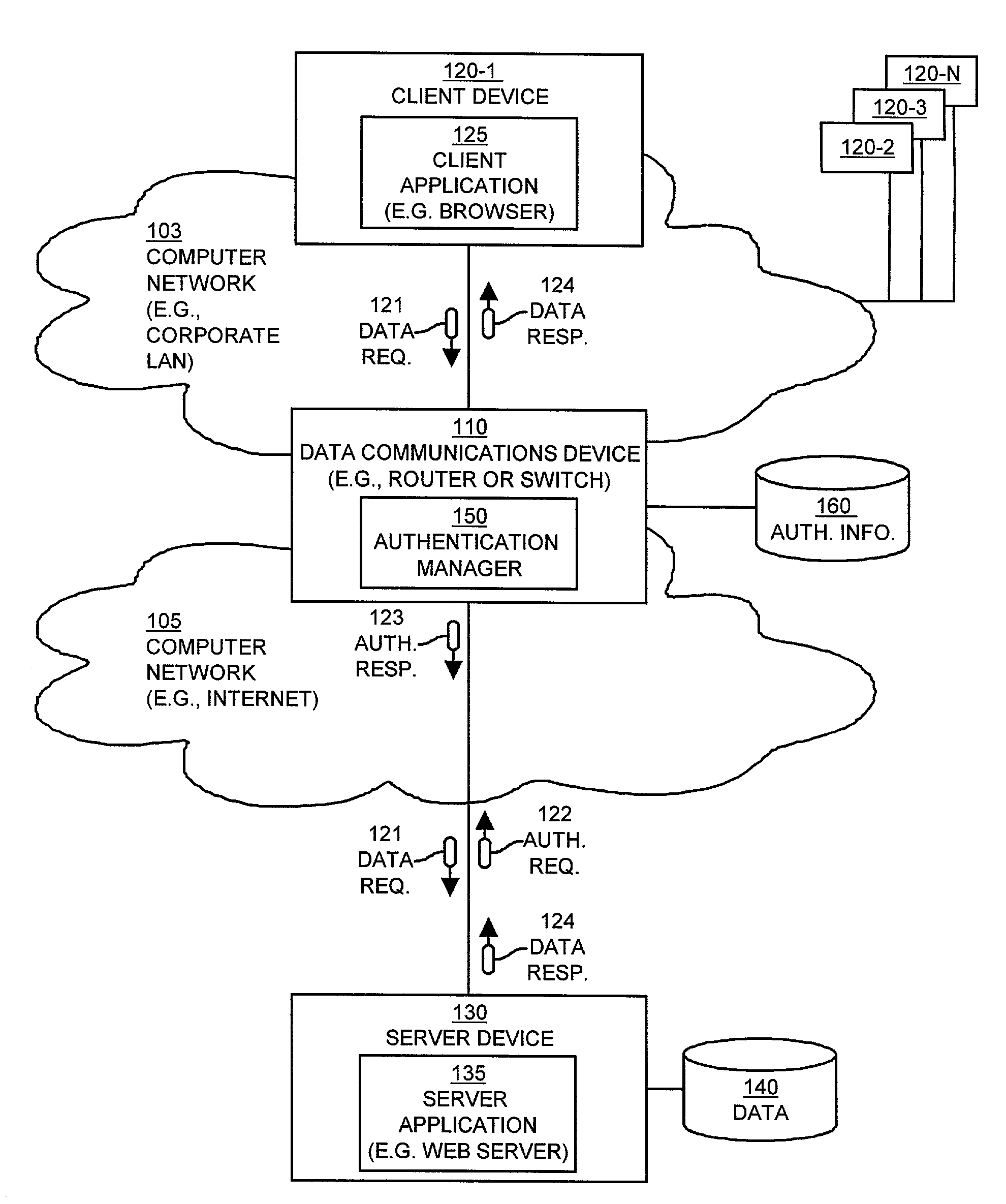
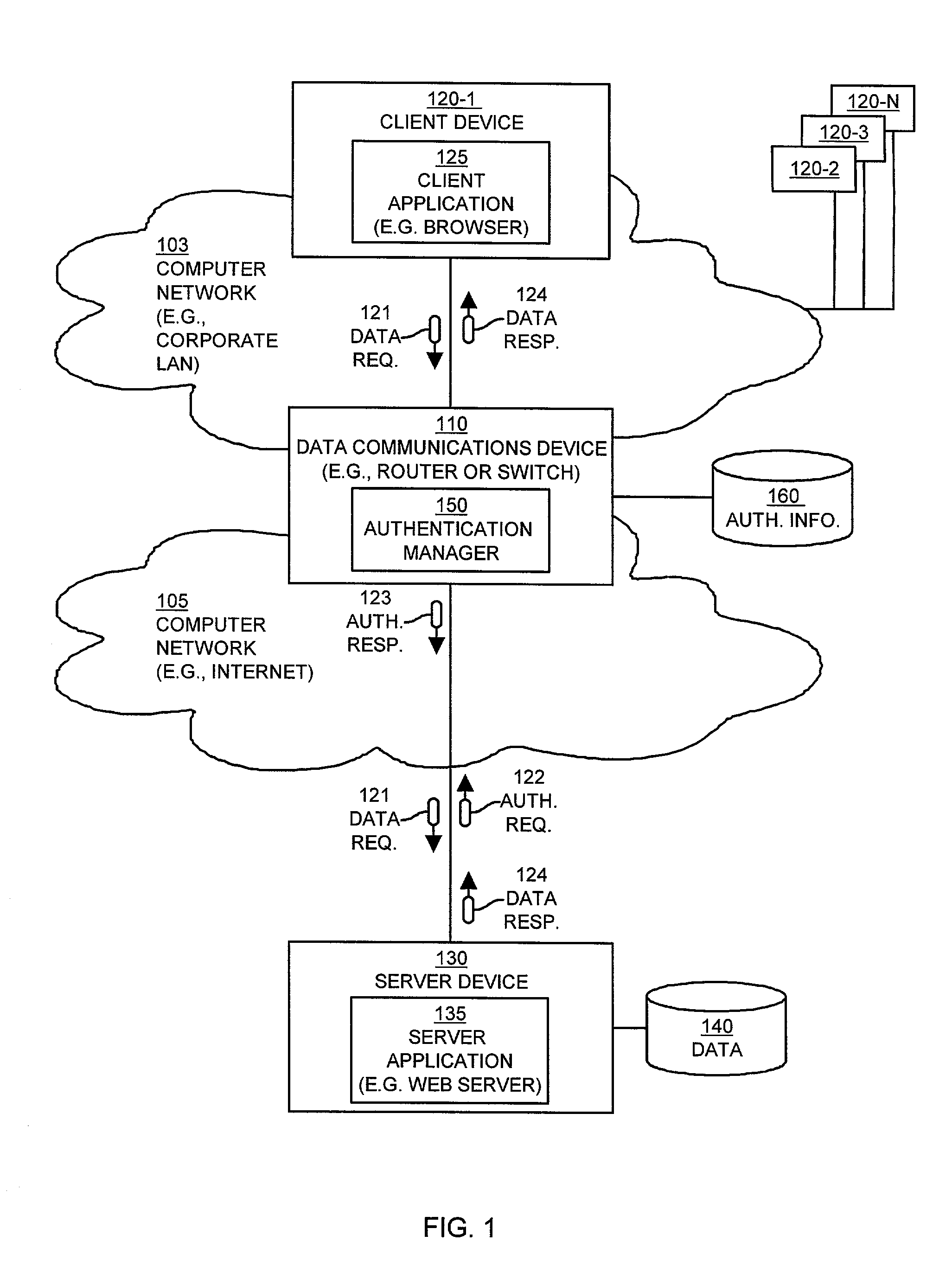
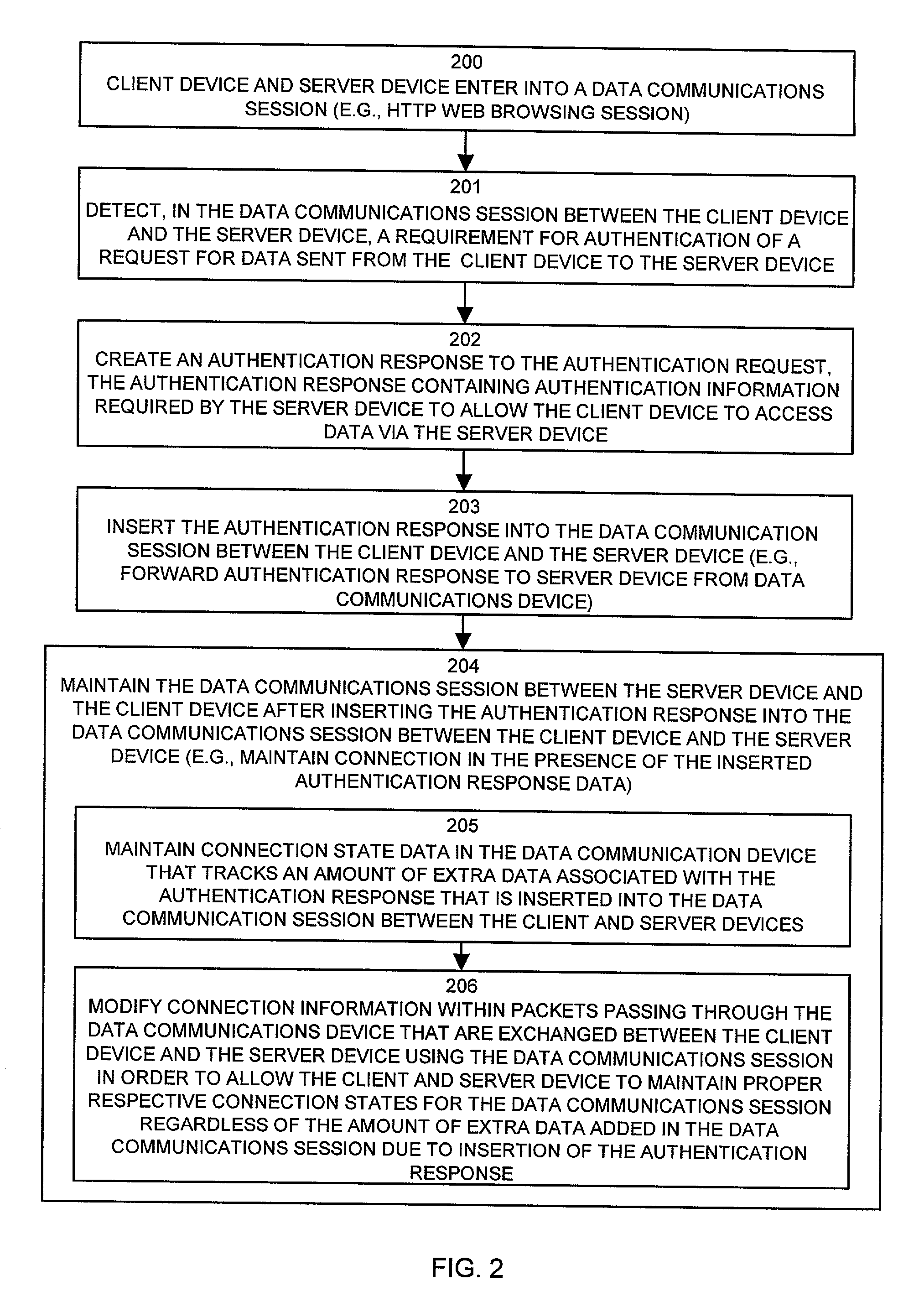
Mechanisms and techniques provide a system that operates in a data communications device to provide automatic authentication of a client device to a server device. The mechanisms and techniques (i.e., the system) operate to detect a requirement for authentication of a request for data sent from a client device to a server device. In response, the system creates an authentication response in response to detecting the requirement for authentication. The authentication response contains authentication information required by the server device to allow the client device to access data via the server device. The system then automatically inserts the authentication response into the data communications session between the client device and the server device. The authentication response authenticates, to the server device, access to the data by the client device. The system also maintains the data communications session between the server device and the client device in the presence of authentication response information inserted into the data communications session between the client device and the server device.
Owner:CISCO TECH INC
Network-distributed data routing
InactiveUS20060167985A1Facilitate delivery of contentEasy transferMultiple digital computer combinationsTransmissionTelecommunications linkData source
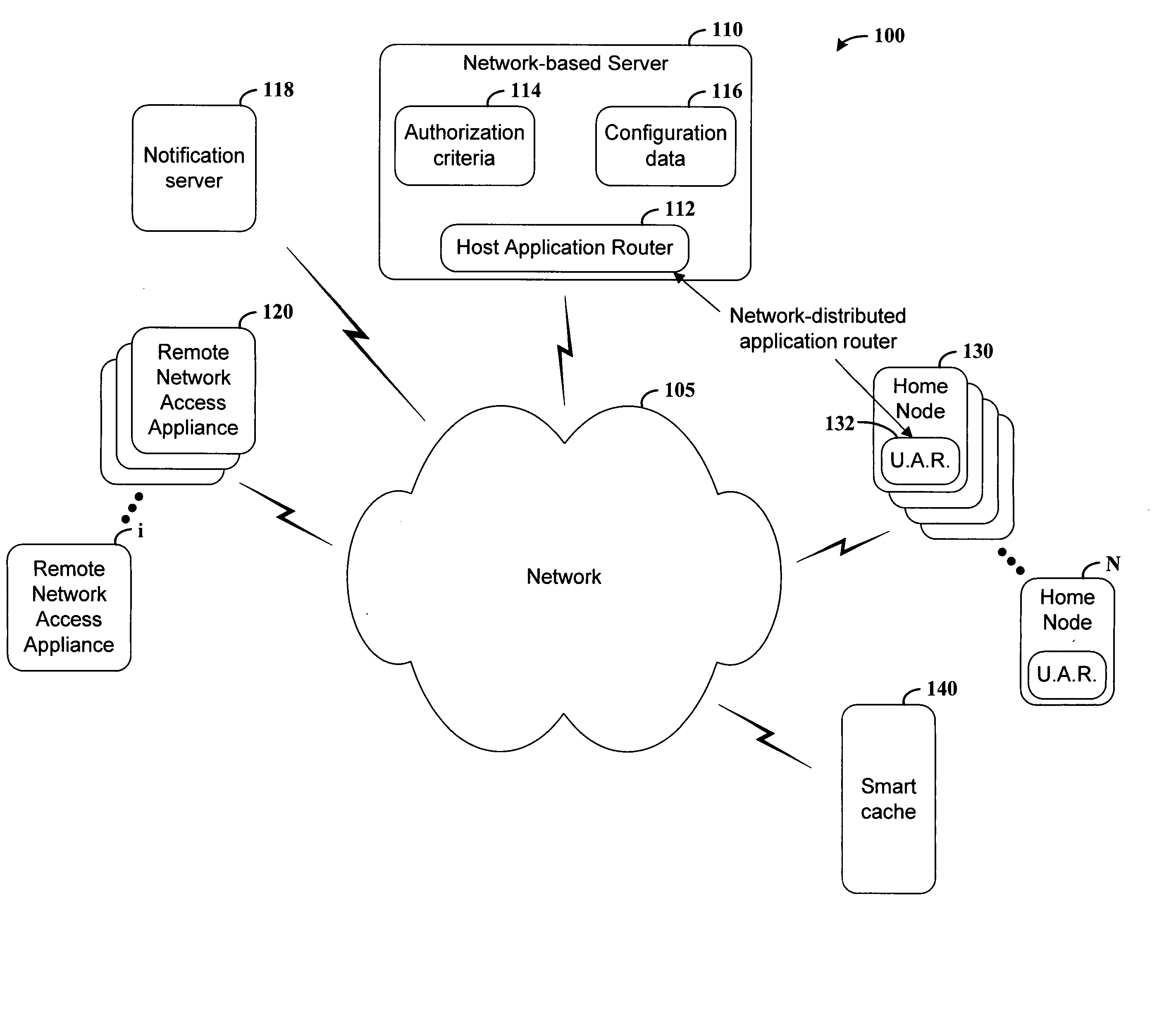
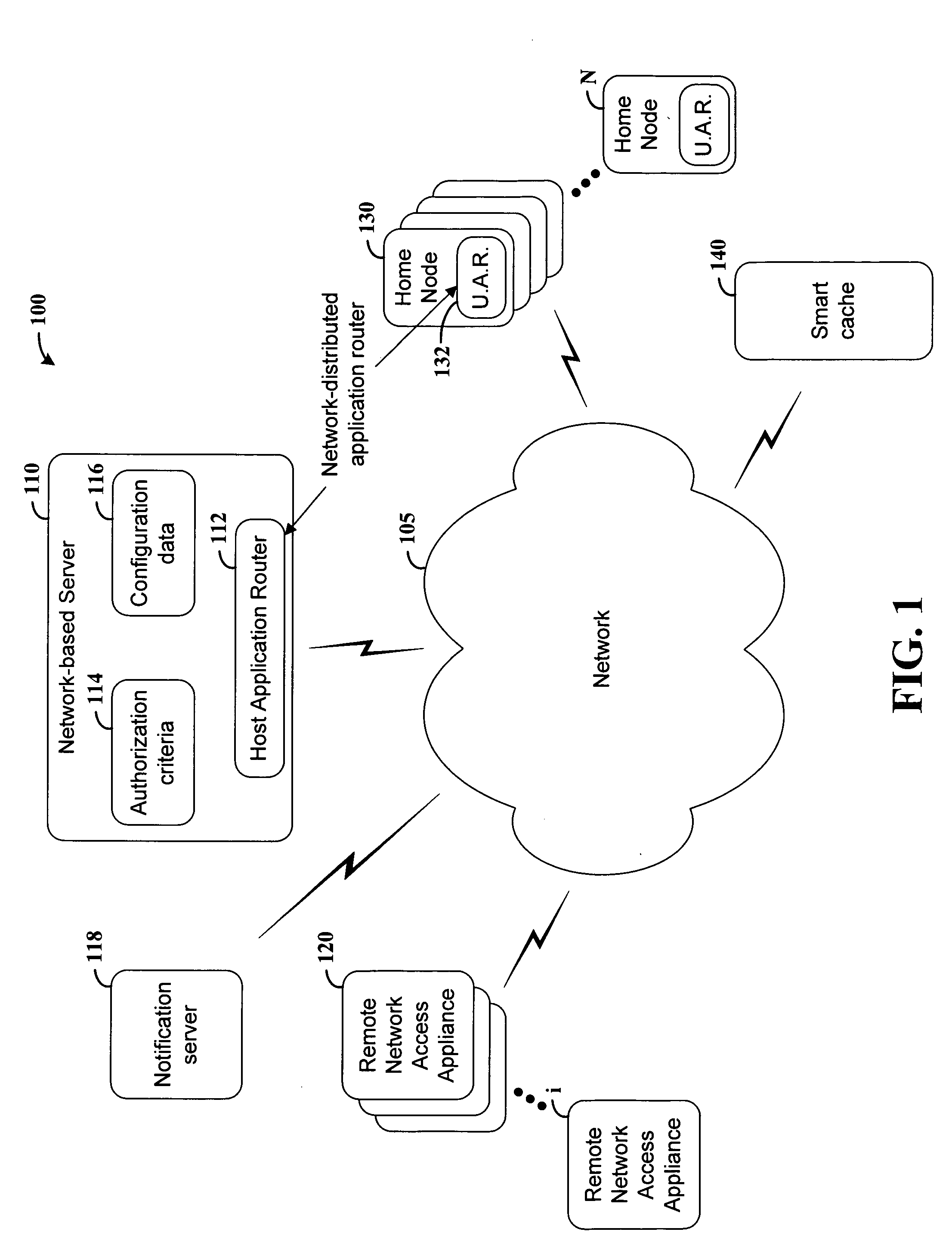
Data transfer over an network is effected in a manner that facilitates the use of available communications channels and makes possible enhanced data routing control and monitoring. According to an example embodiment of the present invention, data is transferred over a network having a plurality of communication links. A home (e.g., data source) node coupled to the network supplies data for transfer on the network. A network-distributed application routing controller is implemented at a host server and at the home node, and is configured for controlling the home node for passing data on the network. A data request from a remote network access appliance, such as a laptop or mobile telephone, is received at the host server. In response to the request, the host server implements the network-distributed application routing controller to transfer data from a home node to the remote network access appliance.
Owner:NOKIA CORP
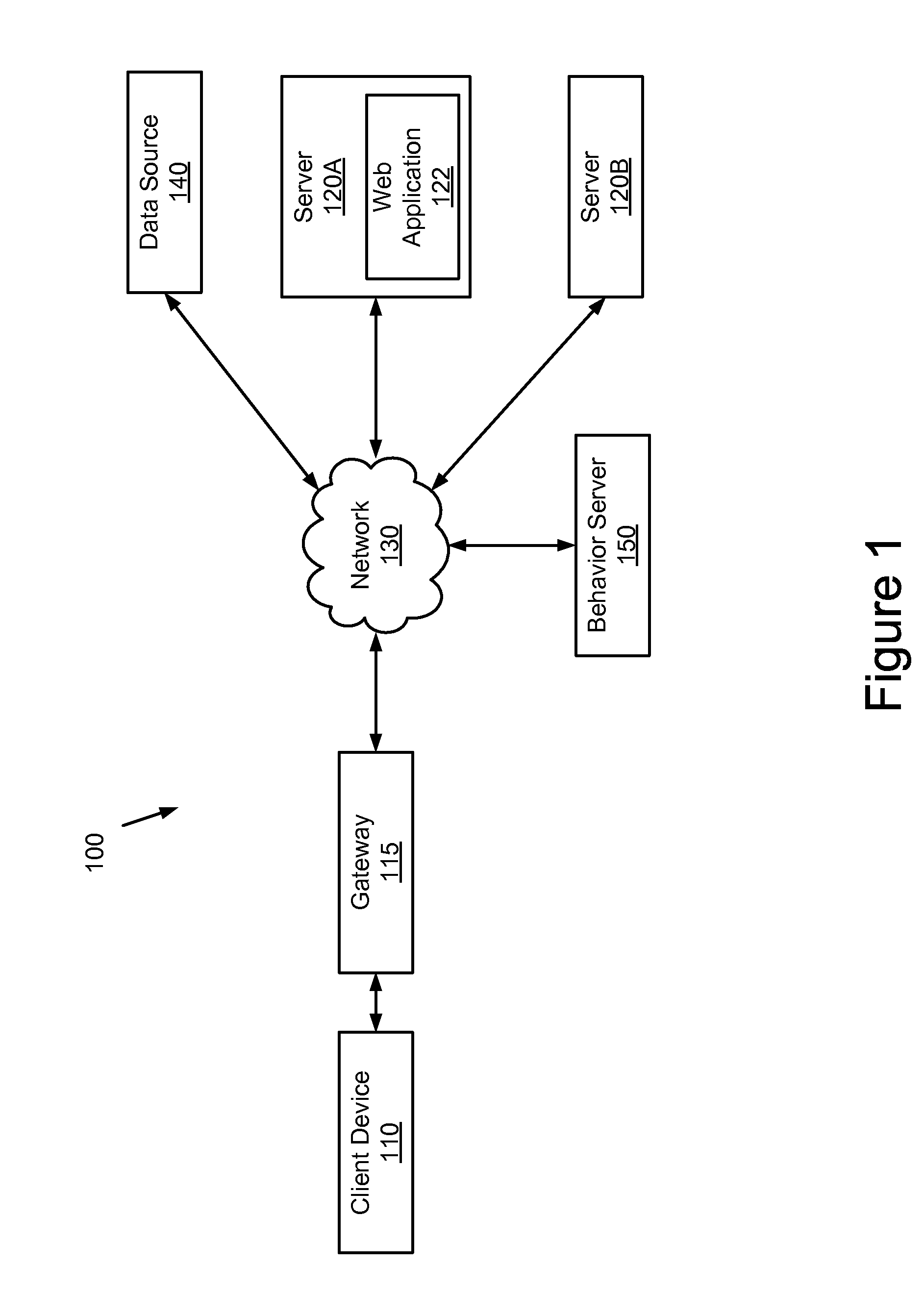
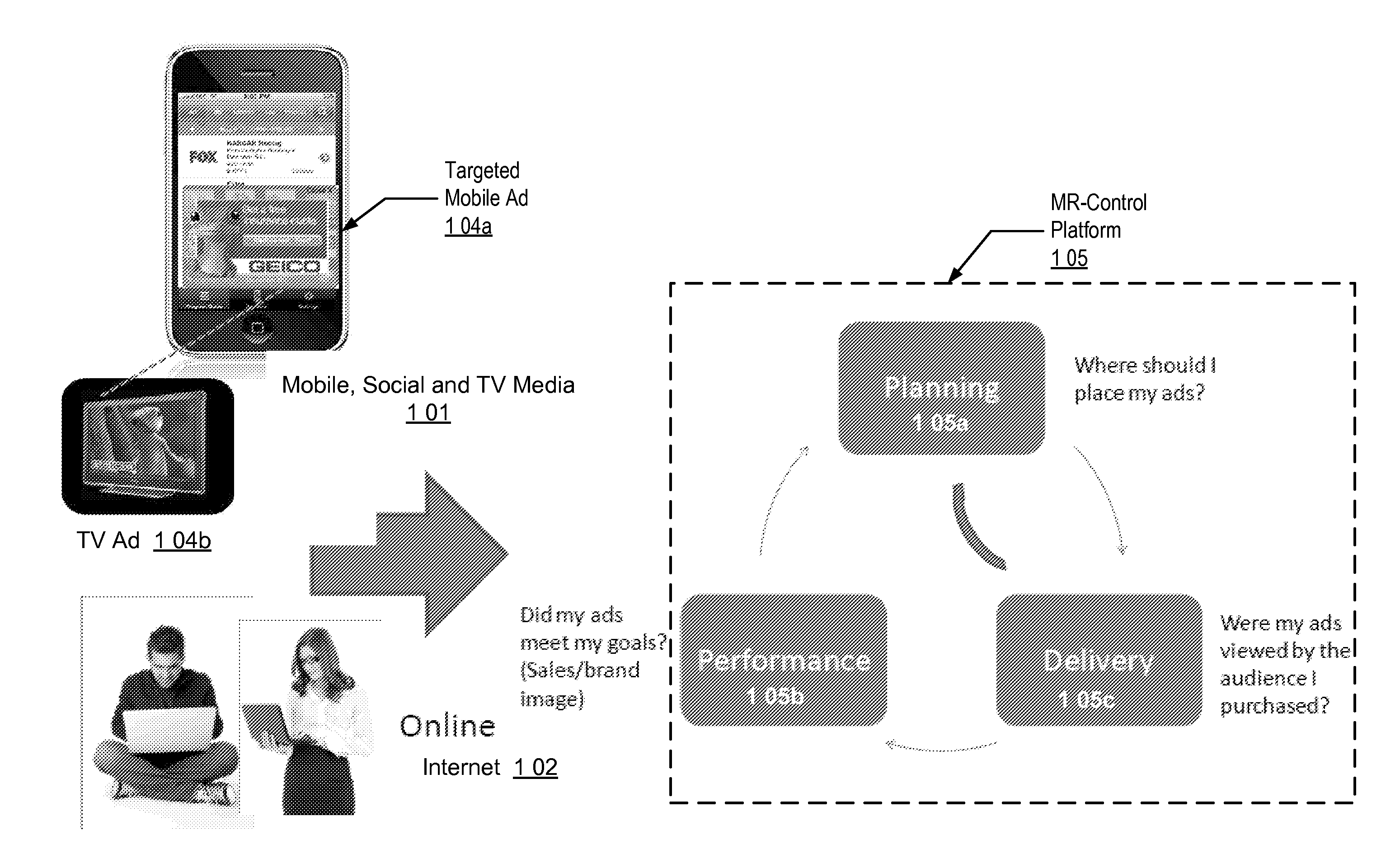
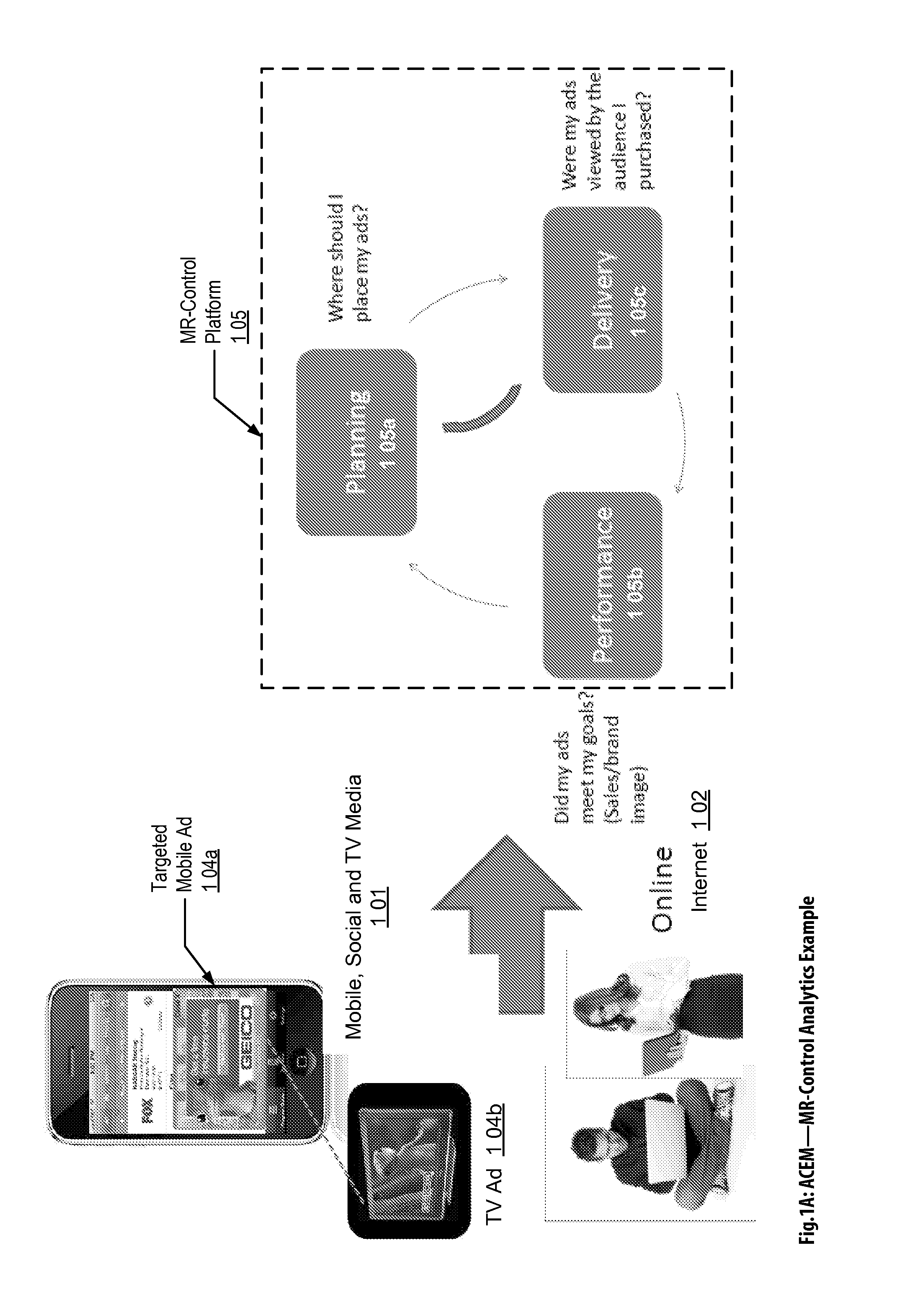
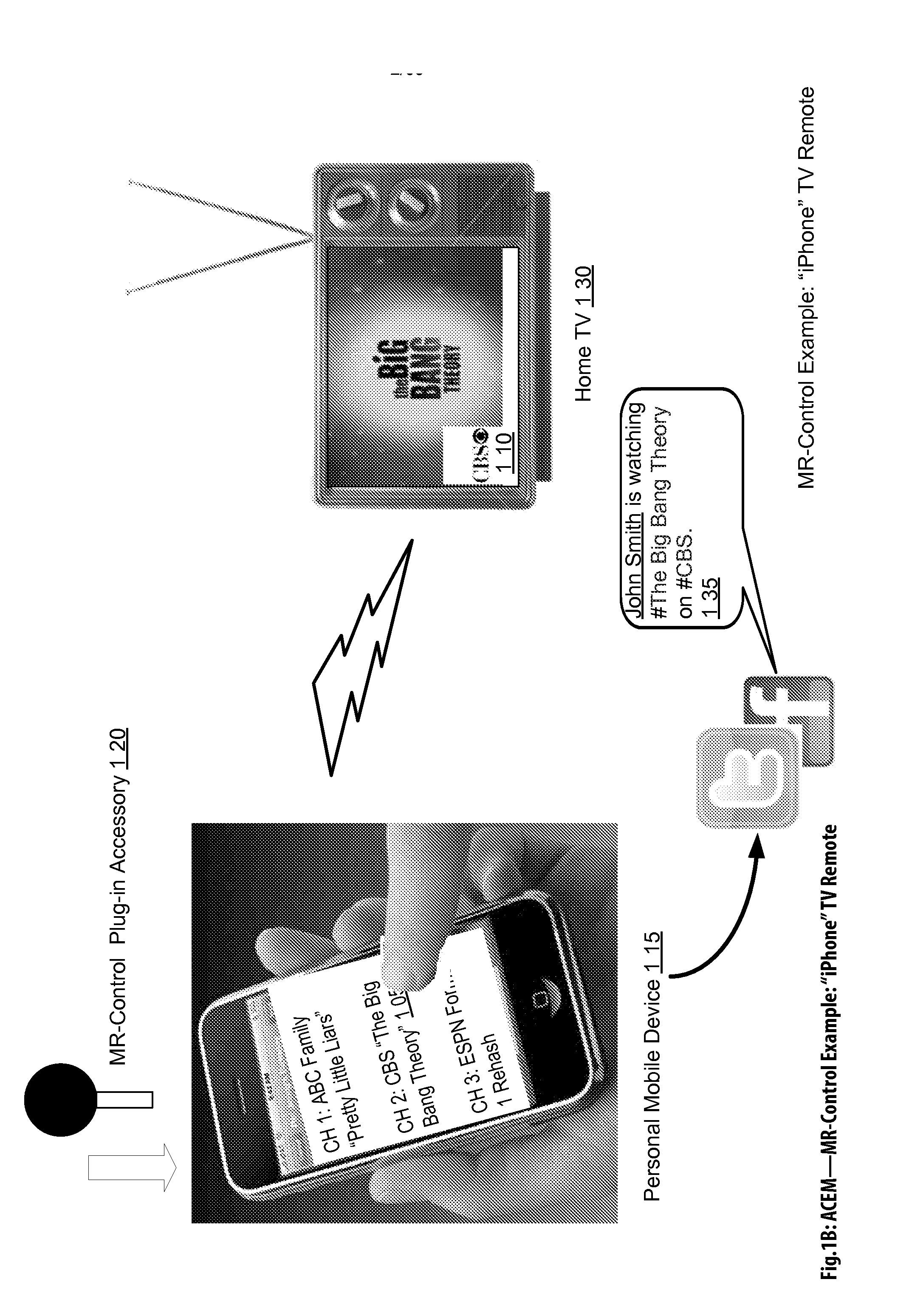
Audience Content Exposure Monitoring Apparatuses, Methods and Systems
ActiveUS20160007083A1Analogue secracy/subscription systemsBroadcast information monitoringSocial mediaMobile device
The Audience Content Exposure Monitoring Apparatuses, Methods and Systems (“ACEM”) transforms pulsing request (e.g., 1107), viewing status, purchase request, channel selection, survey request, sentiment request, atmospherics, social media posts, response events, data request and access token, app / device input monitoring, check-in, URL access, etc. inputs via ACEM components into atmospherics sampling record (e.g., 1106), ad contents (e.g., 1115), RT data / records, ad tags, media program, full page content outputs. In some embodiments, the ACEM provides a mobile metering system that configures the data collection of audience environment atmospherics to evaluate audience media exposure. In one implementation, the ACEM may employ media data collection technology using a combination of mobile device metering app and cloud hosted server side technology to determine when and how often a user mobile device should record and / or generate monitoring atmospherics of audience environment; and to determine what content the audience has been exposed to based on the collected monitoring data.
Owner:SYMPHONY ADVANCED MEDIA
Method and apparatus for efficient SQL processing in an n-tier architecture
ActiveUS7580971B1Efficient processingFree of ChargeDigital data information retrievalMultiple digital computer combinationsData setCache server
A method and apparatus for efficiently processing data requests in a network oriented n-tier database environment is presented. According to one embodiment of the invention, certain or all data from the tables of a database server device can be maintained in tables on the client device in a client side database cache server system. This local cache allows the network oriented n-tier database system to eliminate the expense of repetitive network transmissions to respond to duplicate queries for the same information. Additionally, the local client device may also keep track of what data is cached on peer network nodes. This allows the client to request that data from a peer database cache server and off load that burden from the database server device. Moreover, the local client may also keep statistics regarding the frequency of requested data in order to optimize the data set maintained in the local database cache server.
Owner:ORACLE INT CORP
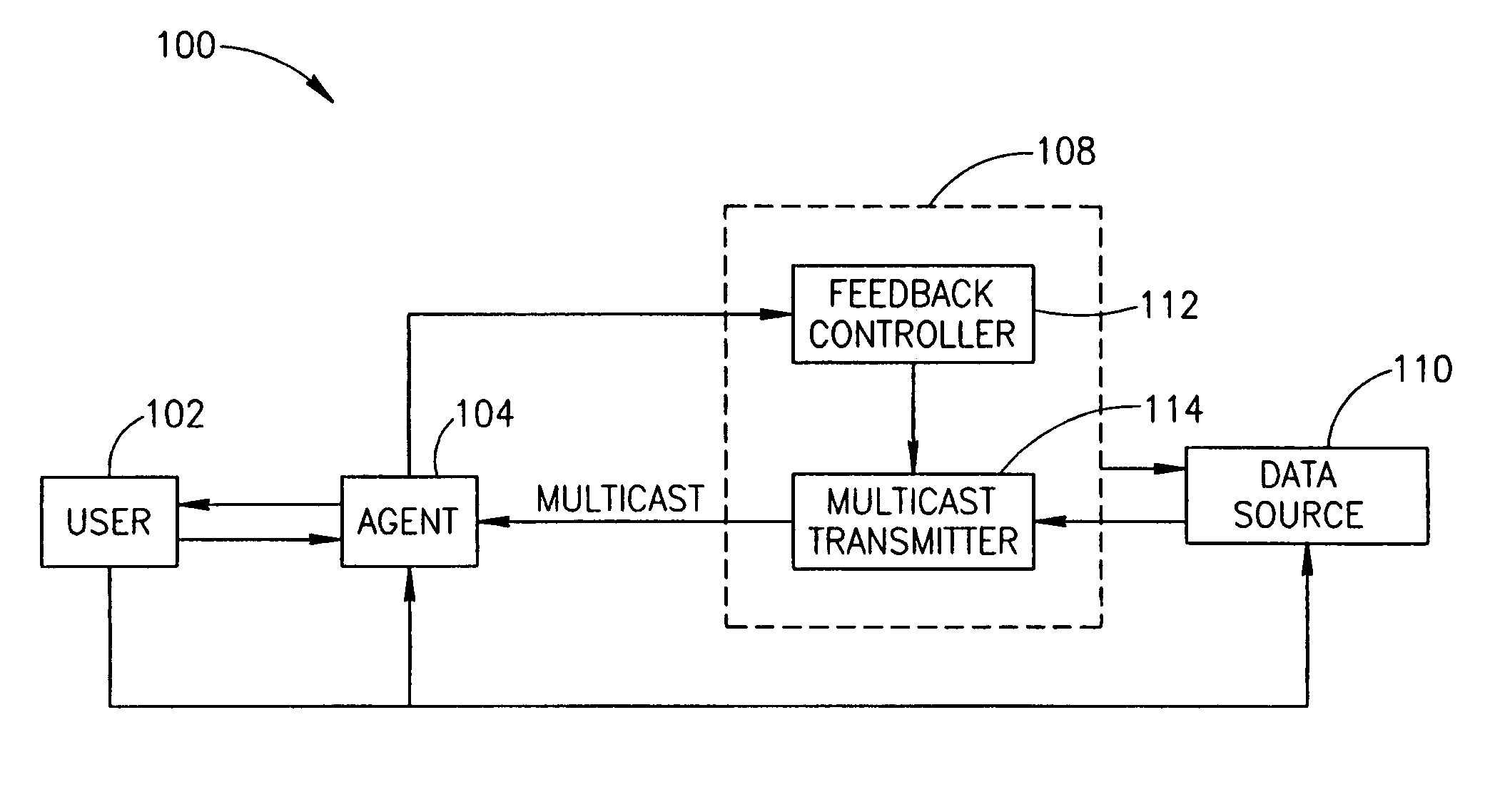
Broadcast system
InactiveUS20050259682A1Quick searchEasy retrievalSpecial service provision for substationTime-division multiplexClient-sideData request
A method of emulating an interactive connection, comprising: generating a request for interactive data from an interactive server, at a client; intercepting said request by an agent; responsive to said request, retrieving at least some of said data from a continuous retransmission of said data, by said agent; and displaying said data including said retrieved data at said client.
Owner:BANDWIZ
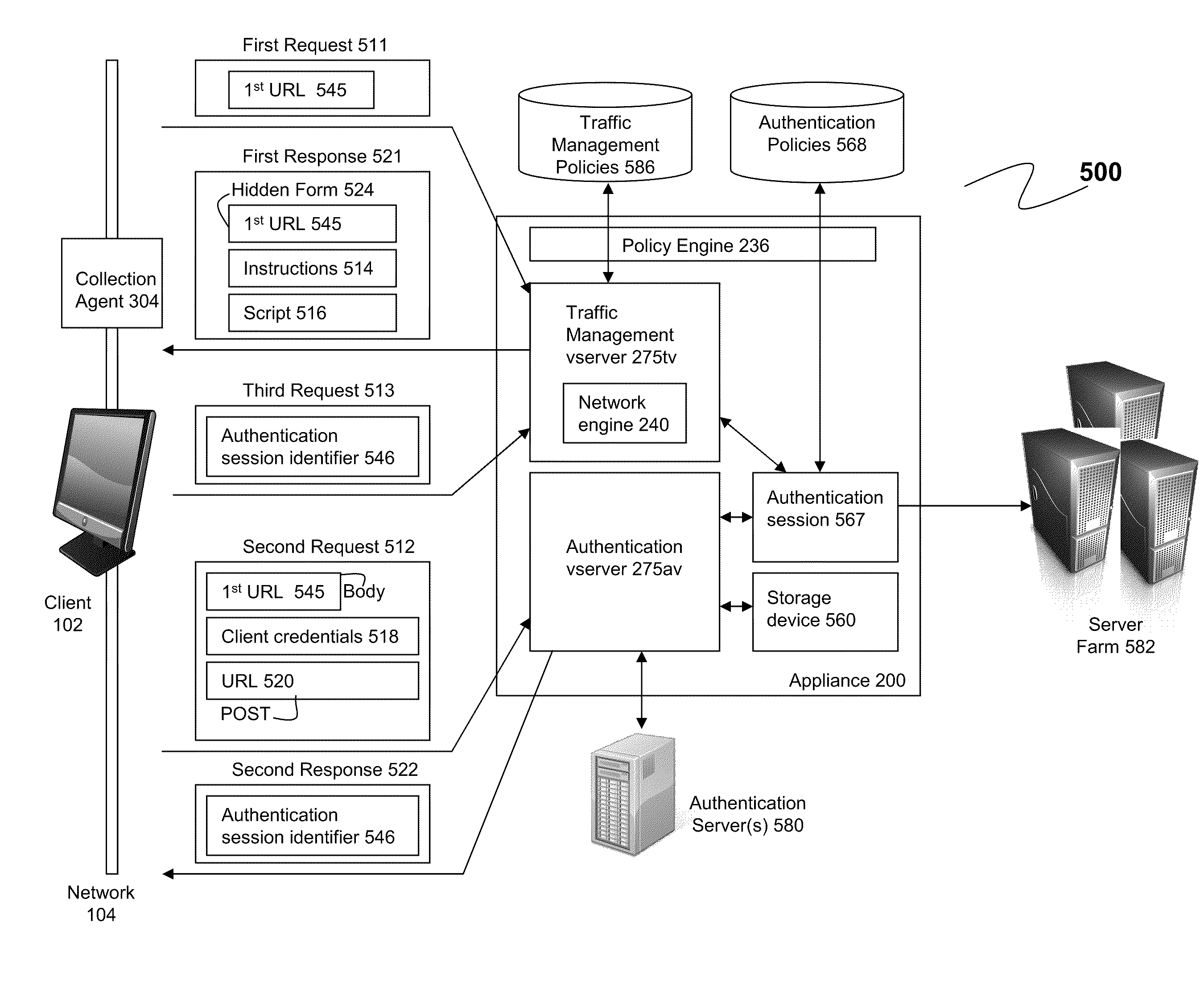
Systems and methods for aaa-traffic management information sharing across cores in a multi-core system
ActiveUS20110154443A1Digital data processing detailsMultiple digital computer combinationsClient-sideTraffic volume
A method for propagating authentication session information to a plurality of cores of a multi-core device includes establishing, by an authentication virtual server executing on a first core of a device intermediary to at least one client and server, a session for a user, the authentication virtual server authenticating the session. A traffic management virtual server executes on a second core of device, and receives a request to access a server via the session. The traffic management virtual server may identify, responsive to a determination that the session is not stored by the second core, from an identifier of the session that the first core established the session. The second core may send to the first core a request for data for the session identified by the identifier. The second core may receive from the first core a response to the second request identifying whether the session is valid.
Owner:CITRIX SYST INC
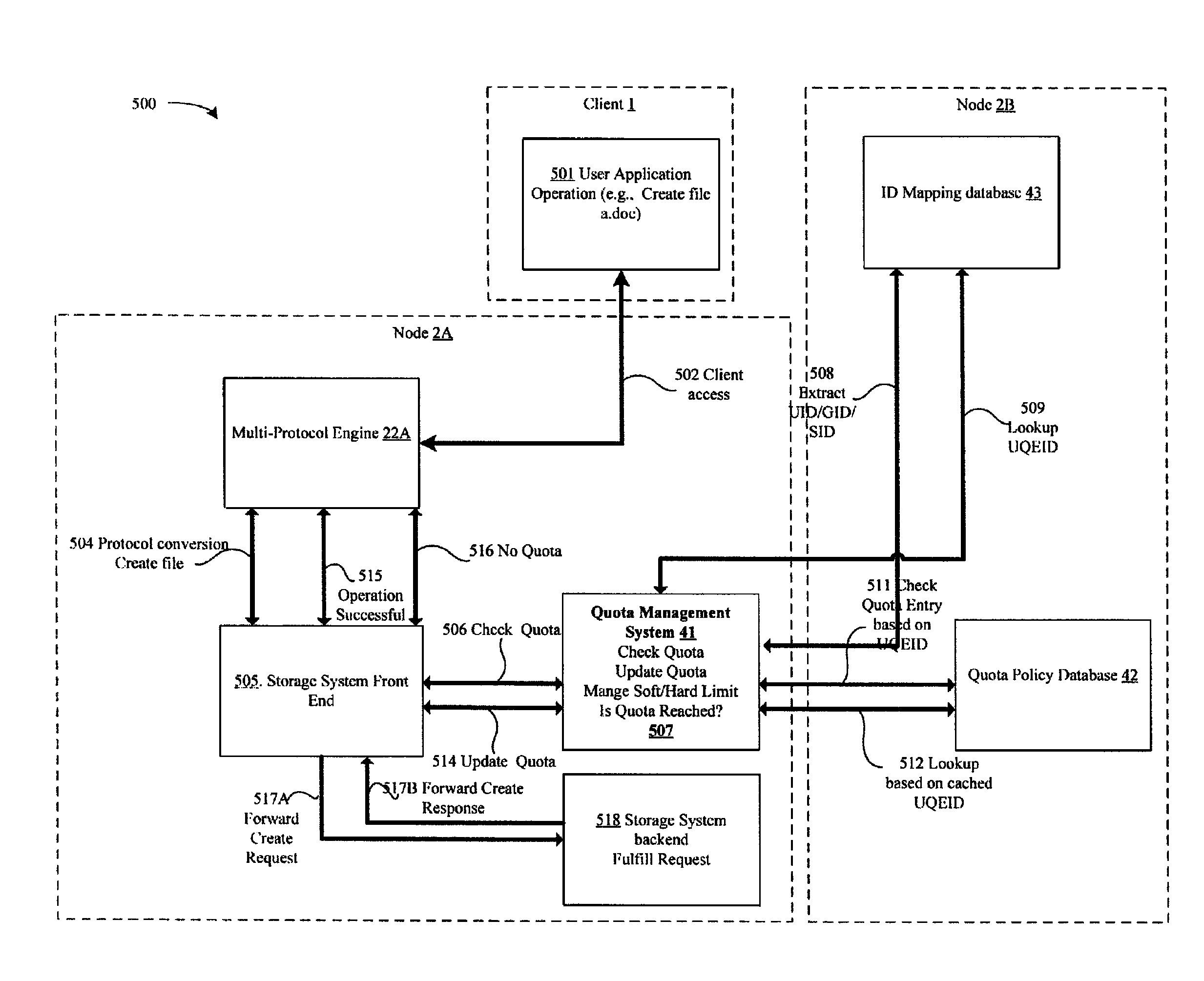
Universal quota entry identification
ActiveUS8046378B1Data processing applicationsDigital data information retrievalMultiple platformData store
An apparatus and a method for determining whether a quota has been violated by using a platform-identification value, instead of the platform-specific identification value. The method may include receiving a quota-sensitive data request from a user at a data storage system, which includes a platform-specific identification value. The method further includes performing a lookup operation on a first data store using the platform-specific identification value to determine a platform-independent identification value that corresponds to the user, and translating the platform-specific identification value into a platform-independent identification value. The first data store includes multiple entries that map multiple platform-specific identification values that correspond to the same user on different platforms to the same platform-independent identification value. Once the platform-specific identification value is translated, the quota-sensitive data request is determined whether a quota is violated using the platform-independent identification value.
Owner:NETWORK APPLIANCE INC
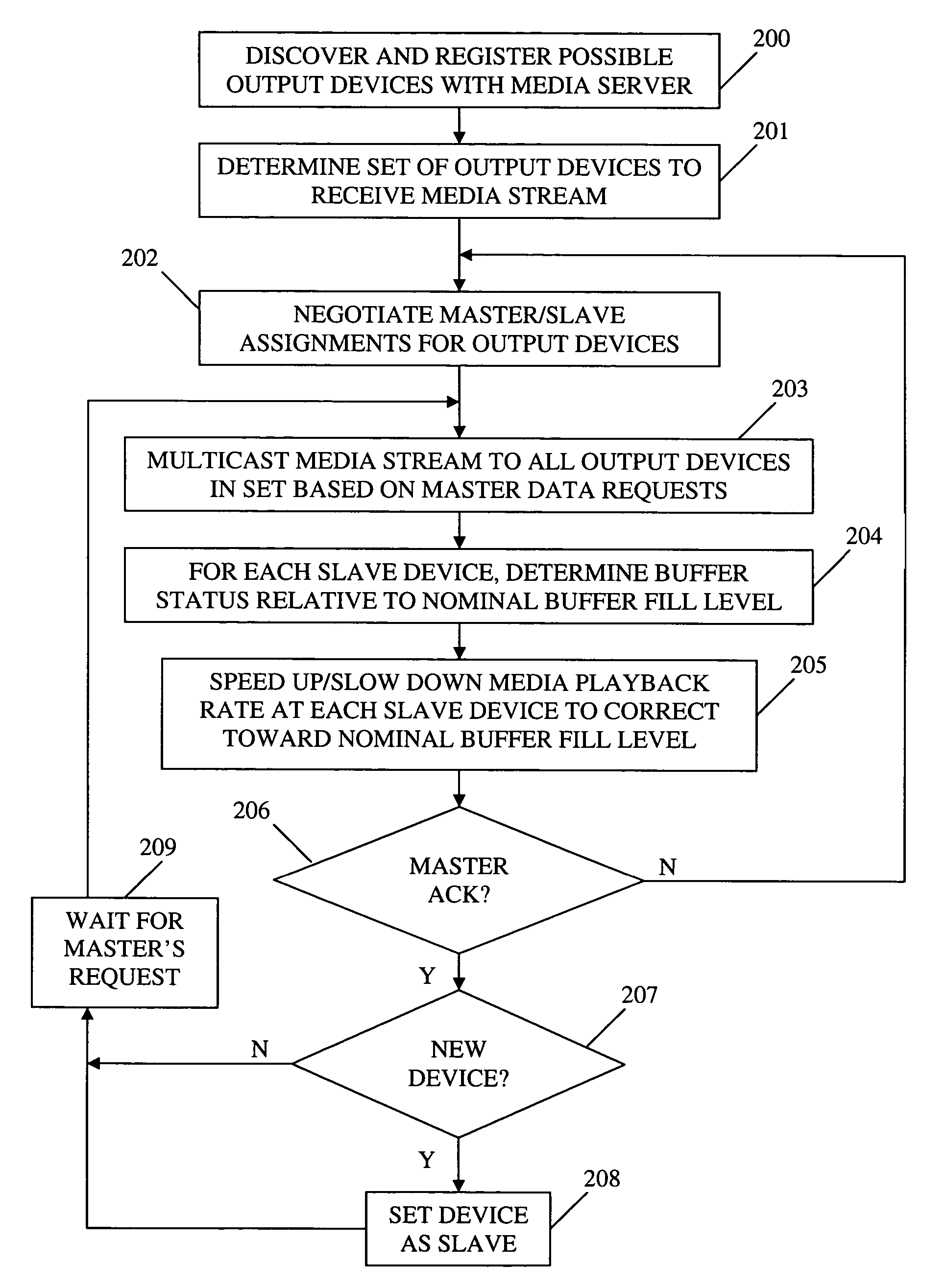
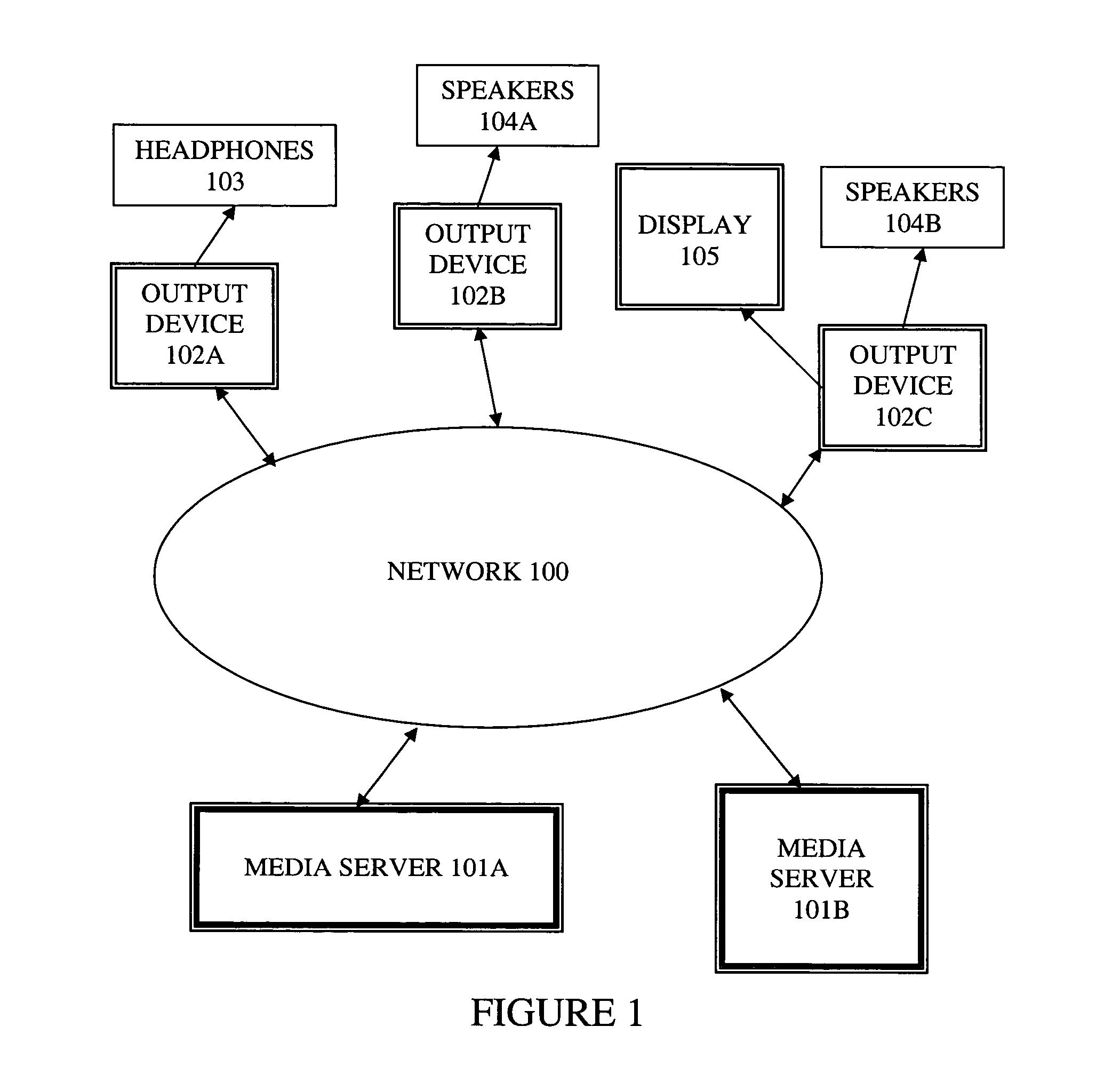
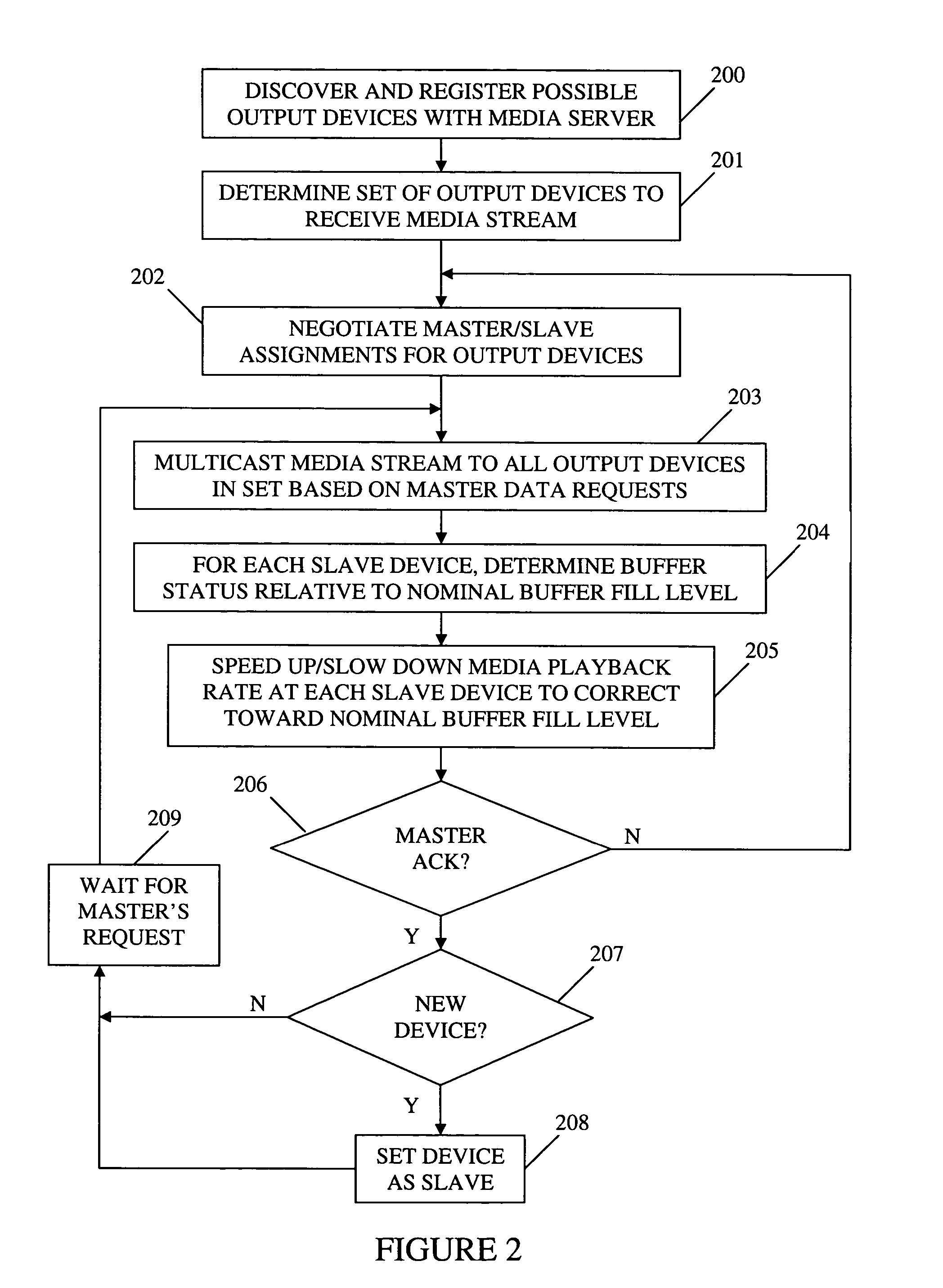
Method and apparatus for synchronizing playback of streaming media in multiple output devices
ActiveUS8015306B2Maintaining average timing synchronizationError preventionTransmission systemsTimestampNetwork packet
A method and apparatus for synchronizing streaming media with multiple output devices. One or more media servers serve media streams to one or more output devices (i.e., players). For playback synchronization, one output device is the “master”, whereas the remaining output devices are “slaves”. More data is requested from the media server by the “master” device to maintain a nominal buffer fill level over time. The “slave” devices receive streamed data from the media server at the rate determined by the master device's data requests, and the average rate of data flow over the streaming network is thus controlled by the frequency of the single “master” device's crystal. “Slave” devices make playback rate corrections to maintain respective buffer fill levels within upper and lower threshold levels. For slow networks, each media data packet timestamp is calculated from the time the master's buffer reaches nominal level.
Owner:SNAP ONE LLC
Systems and methods for promotion of calculations to cloud-based computation resources
ActiveUS20100057831A1Digital data processing detailsMultiple digital computer combinationsHigh bandwidthElectronic form
Embodiments relate to systems and methods for the promotion of calculations to cloud-based computation resources. One or more applications, such as spreadsheet applications, can prepare the calculation of a relatively large-scale computation, such as running statistical reports on large (e.g., greater than 1000 by 1000 cell) spreadsheets or other data objects. If the pending calculation is determined to be greater than a computation threshold for instance in computation intensity or data size, a computation request can be sent to a promotion engine. The promotion engine can identify a set of computation resources located in a cloud or other network and transmit the data request and subject data to the set of computation resources, which afford greater computation speed than the local machine hosting the requesting application. A set of results is returned from the cloud to the requesting application, thereby creating higher bandwidth and faster calculation times for the user.
Owner:RED HAT
Method, product, and apparatus for processing a data request
ActiveUS20080059607A1Saving distribution costMore display spaceDigital data information retrievalMultiple digital computer combinationsWeb resourceData request
When a one or more identifiers and a plurality of data request types is received, a first data request from the one or more identifiers and from a first data request type can be generated and performed. When at least one first result from the first data request can be received, a second data request from the one or more identifiers and from a second data request type can be generated and performed at any time after receiving the one or more identifiers and the plurality of data request types, and then the at least one second result from the second data request can be retrieved either one of a before, during, and after the at least one first result from the first data request is presented. The correspondence between identifiers and request types may be one-to-one, one-to-many, many-to-one, or many-to-many relationship. A response type may employ a plurality of response methods to access multiple network resources corresponding to any generated and / or selected identifiers and / or request types.
Owner:MEC MANAGEMENT LLC
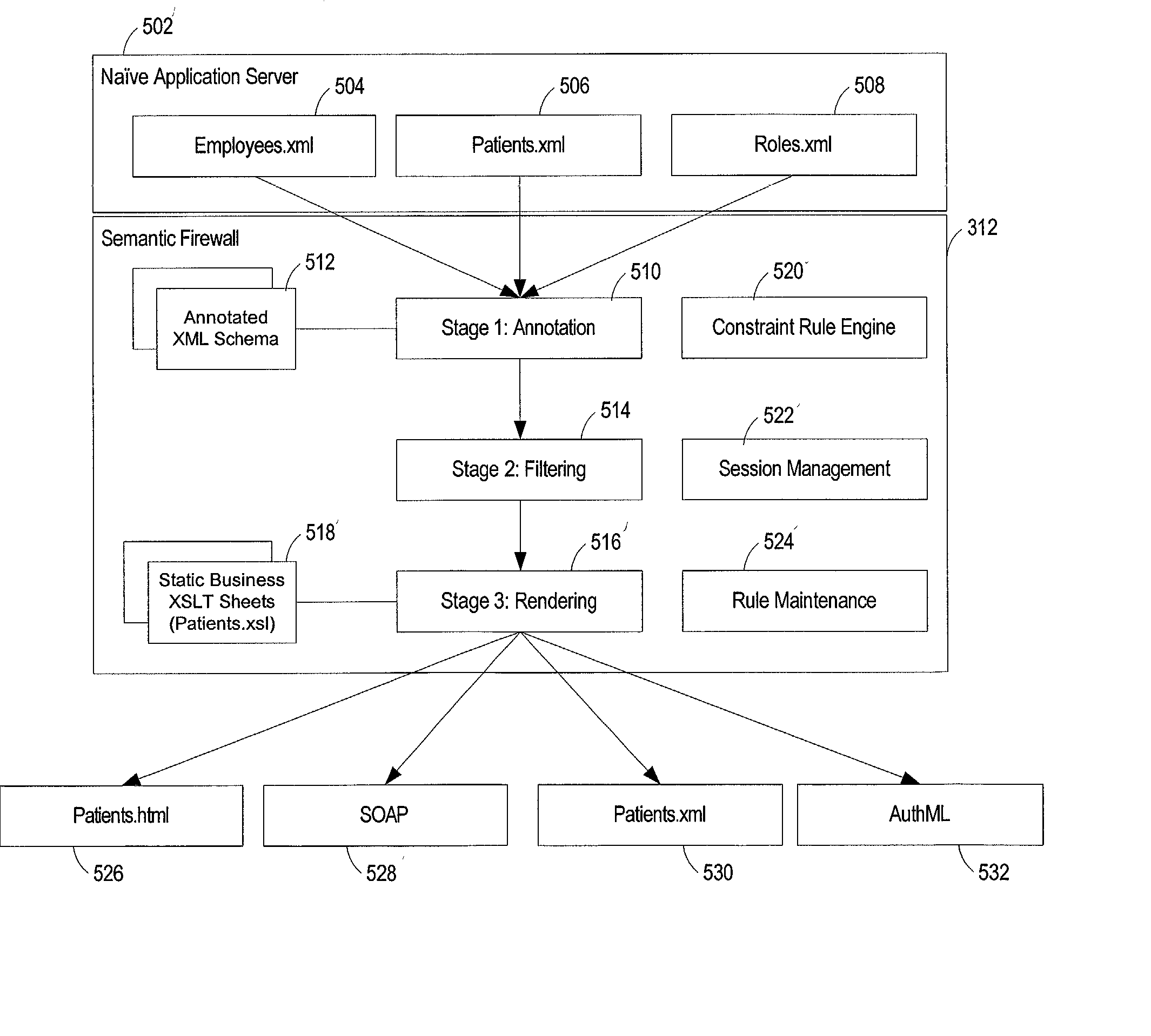
Layering enterprise application services using semantic firewalls
InactiveUS20020157023A1Digital data processing detailsMultiple digital computer combinationsApplication serverApplication software
A system for processing data requests from clients via a network is disclosed. The system has an application server coupled to a network, and a semantic firewall to pass and filter the content between the application server and the clients. The application server provides content from a database to the clients via the network, and the semantic firewall restricts access to a portion of the content for one or more clients.
Owner:SPHERE SOFTWARE CORP
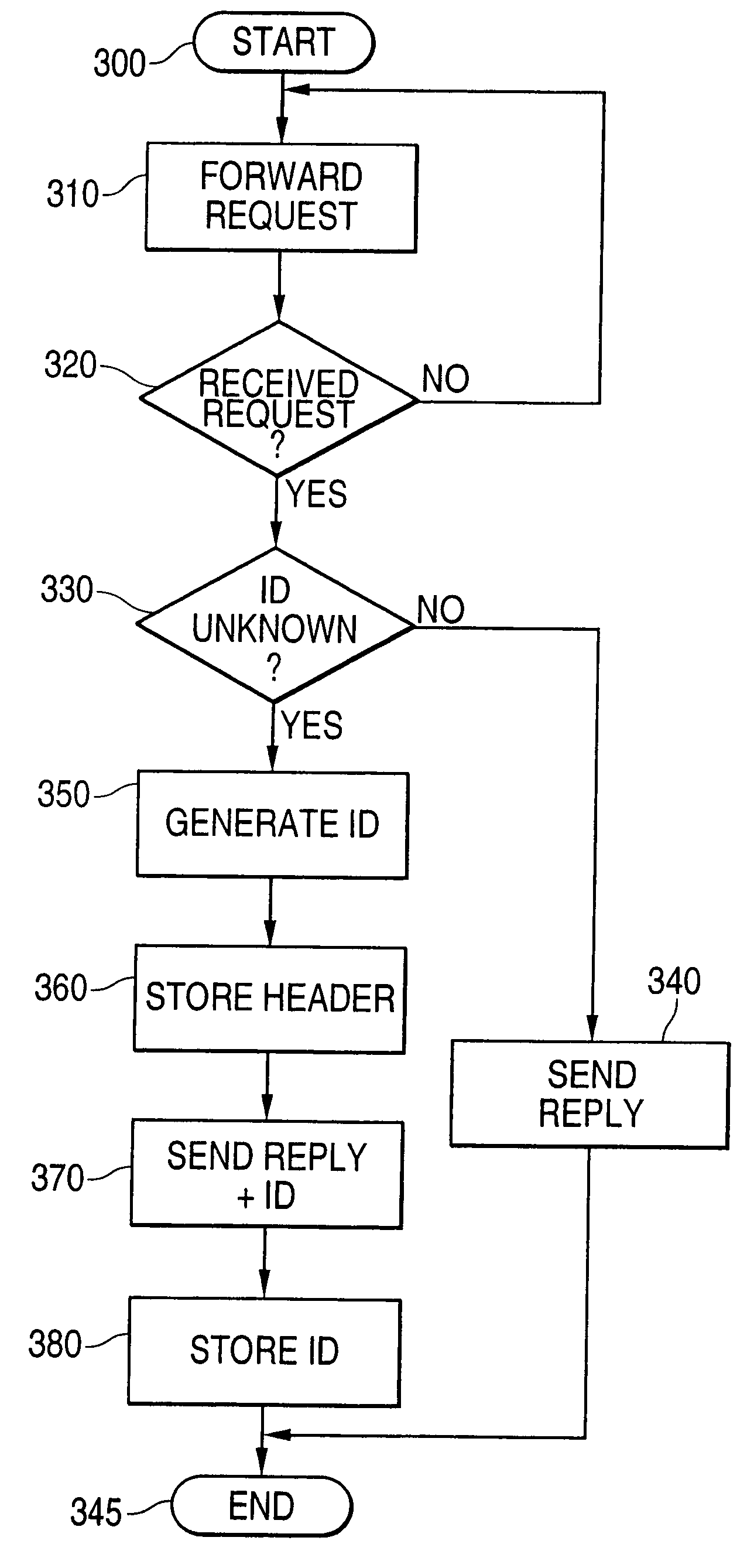
Method of and a network for handling wireless session protocol (WSP) sessions
InactiveUS7103018B1Reduce the amount requiredUnacceptable overheadNetwork traffic/resource managementConnection managementComputer terminalUser profile
A communication terminal initiates a Wireless Session Protocol (WSP) session by forwarding a request of data to a server. The request comprises an identification of the requested data and a communication terminal identification number provided by the server. The server. when receiving a request containing a communication terminal identification number, recalls user profile information from an associated database memory corresponding to said communication terminal identification number. The user profile information indicates a data format which will be handled by the communication terminal. Then the server replies to the request by forwarding the requested data in the format defined by the user profile information.
Owner:NOKIA TECHNOLOGLES OY
System and method for monitoring network traffic
ActiveUS20050063377A1Error preventionFrequency-division multiplex detailsInternet trafficComputer science
A system includes a packet reader configured to scan packets transmitted through a network for pre-specified criteria. The packets include endpoint information and data. A request / response matcher determines whether each packet meets pre-specified criteria, and matches request packets with corresponding response packets when the packets meet the pre-specified criteria. A message analyzer determines the format, or structure, of the data of the matched packets, and analyzes the data of the matched packets to generate at least a portion of a model of the data.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Apparatus and method for profiling system events in a fine grain multi-threaded multi-core processor
A system and method for profiling runtime system events of a computer system may include associating a data source type with detected system events. The system events may be detected dependent on information included in a reply message received by a processor in response to a data request or other transaction request message. The reply message may include information characterizing a source type of a source of data included in the reply message. The source type information may indicate that the source is remote or local; that it is a shared or a private storage location; that the data is supplied via a cache-to-cache transfer; or that the data is sourced from a coherency domain other than that of the requesting process. Instructions, events, messages, and replies may be sampled, and extended address information corresponding to the samples may be stored in an event set database for performance analysis.
Owner:SUN MICROSYSTEMS INC
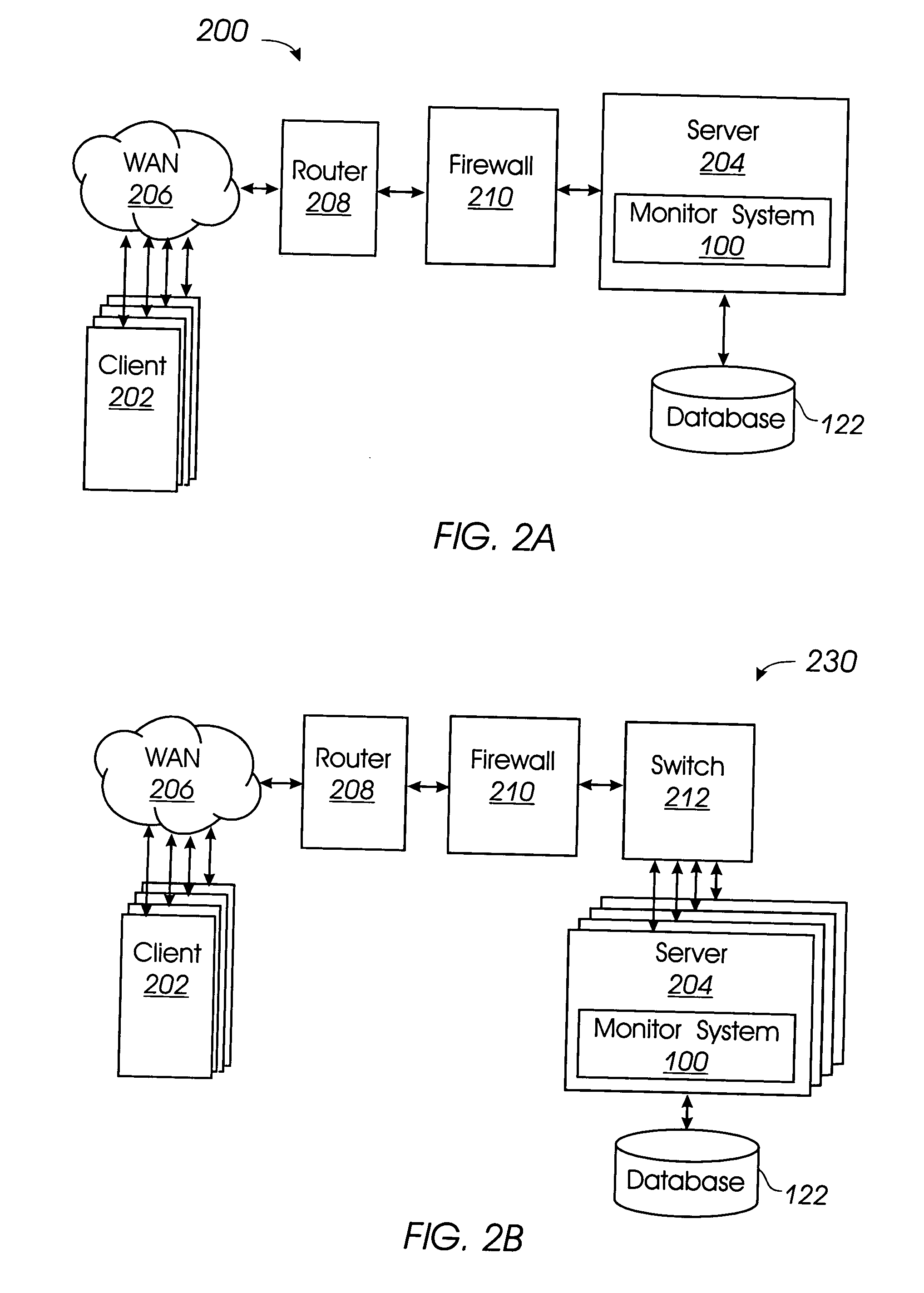
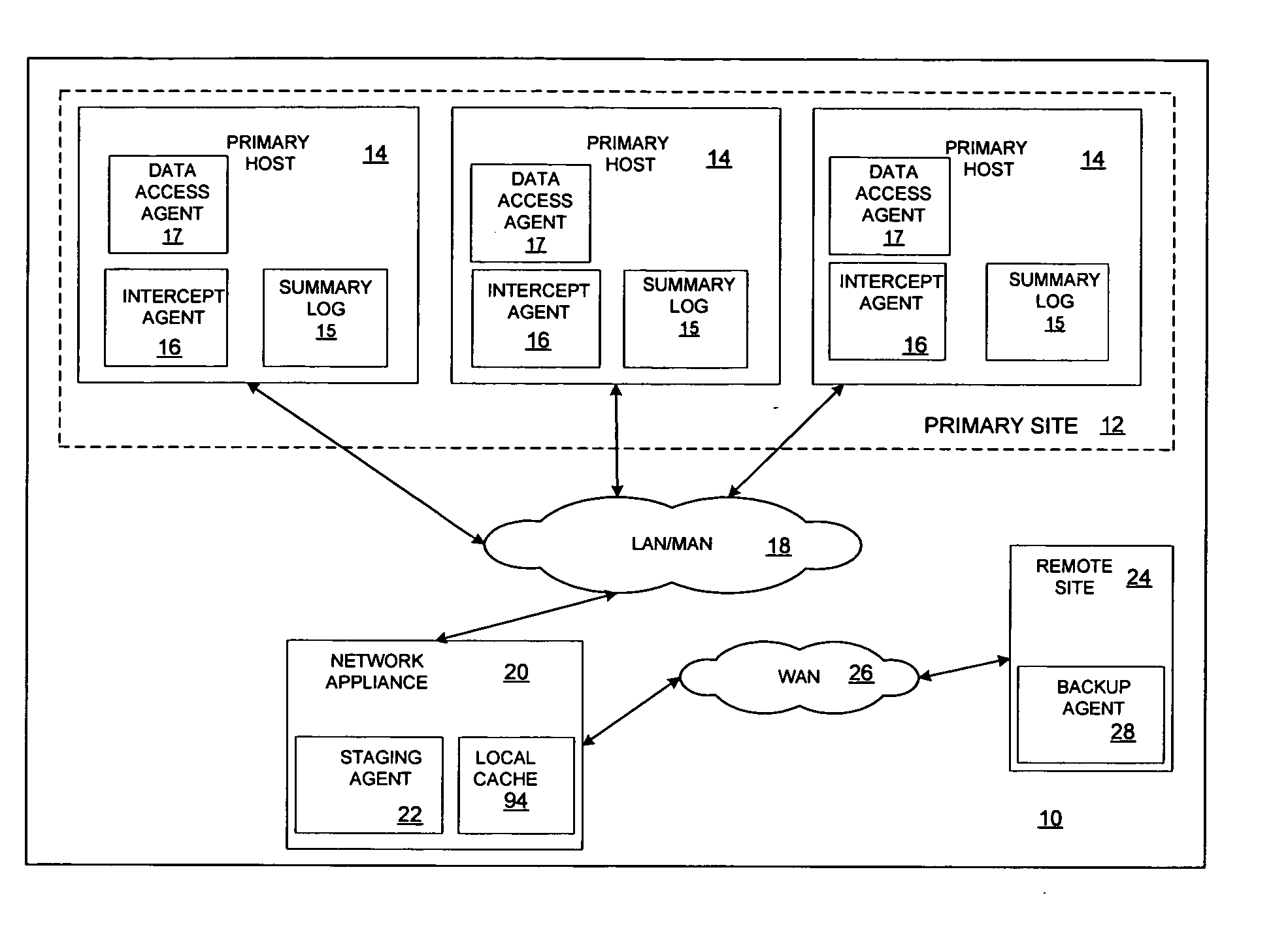
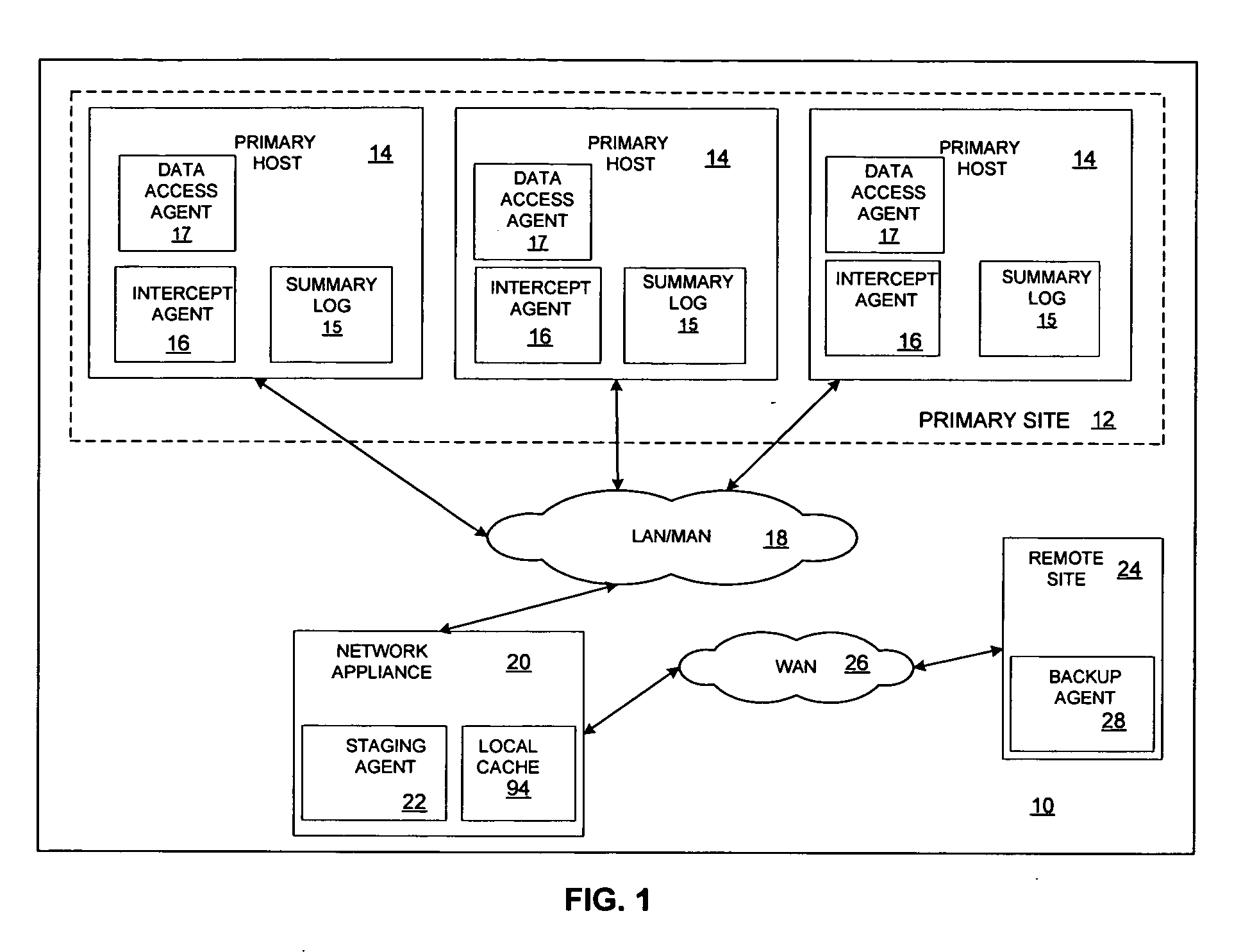
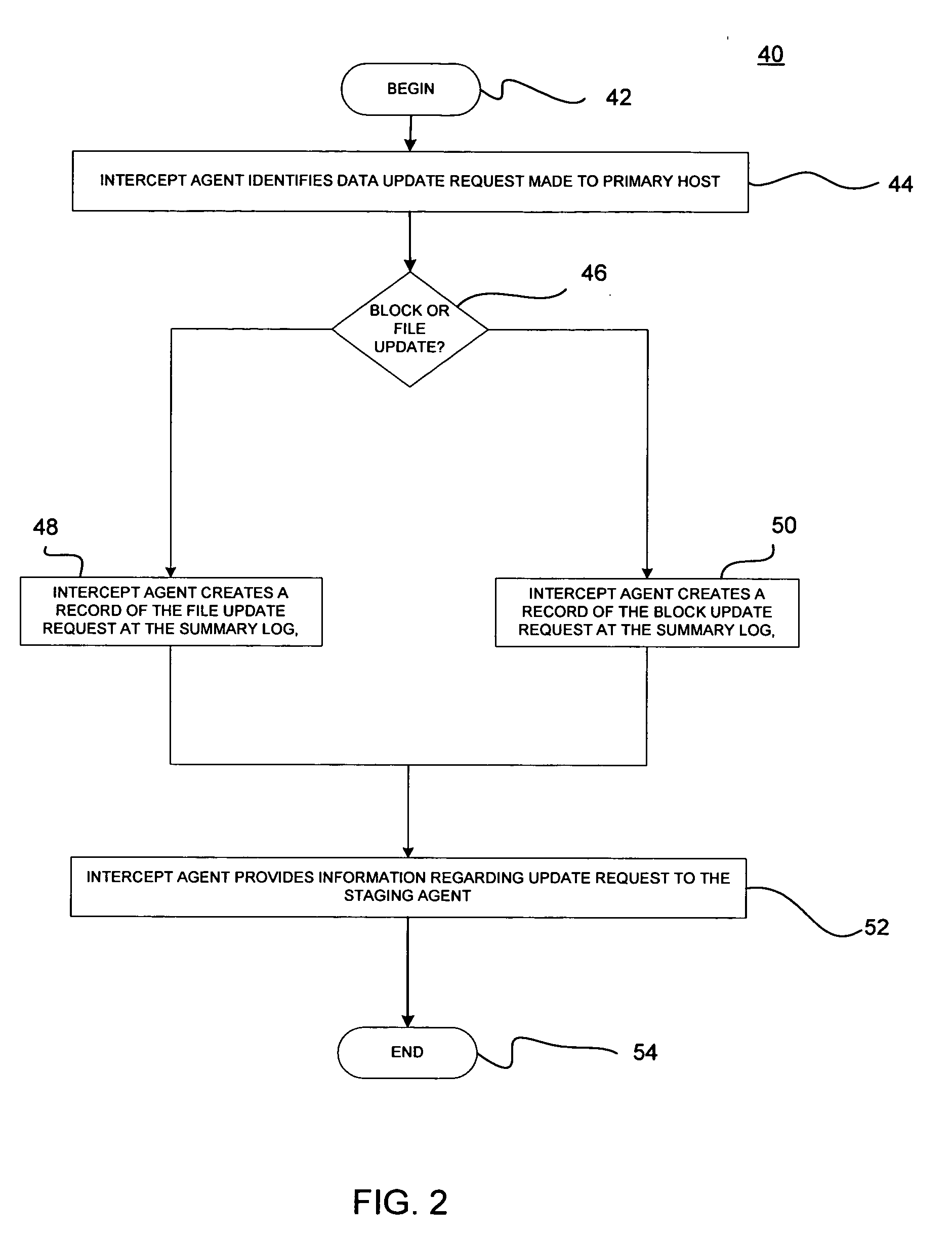
Minimizing resynchronization time after backup system failures in an appliance-based business continuance architecture
ActiveUS20050273654A1Minimize resynchronization timeMinimize timeMemory systemsRedundant hardware error correctionDowntimeSystem failure
A system for minimizing downtime in an appliance-based business continuance architecture is provided. The system includes at least one primary data storage and least one primary host machine. The system includes an intercept agent to intercept primary host machine data requests, and to collect information associated with the intercepted data requests. Moreover, at least one business continuance appliance in communication with the primary host machine and in communication with a remote backup site is provided. The appliance receives information associated with the intercepted data requests from the intercept agent. In addition, a local cache is included within the business continuance appliance. The local cache maintains copies of primary data storage according to the information received. Furthermore, the remote site is provided with the intercepted data requests via the business continuance appliance, wherein the remote site maintains a backup of the primary data storage.
Owner:LENOVO PC INT
Method and network apparatus for requesting data based on content name
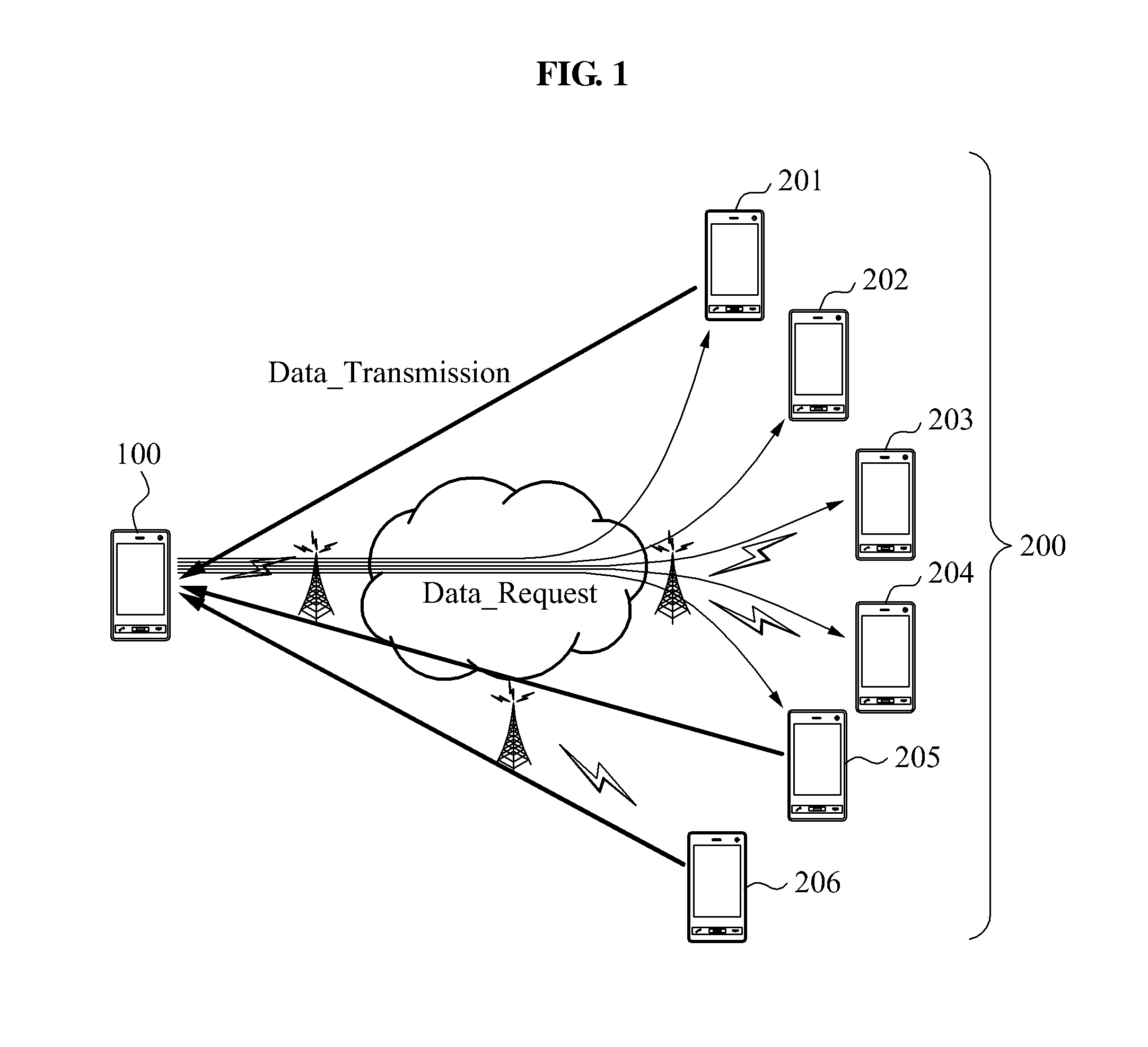
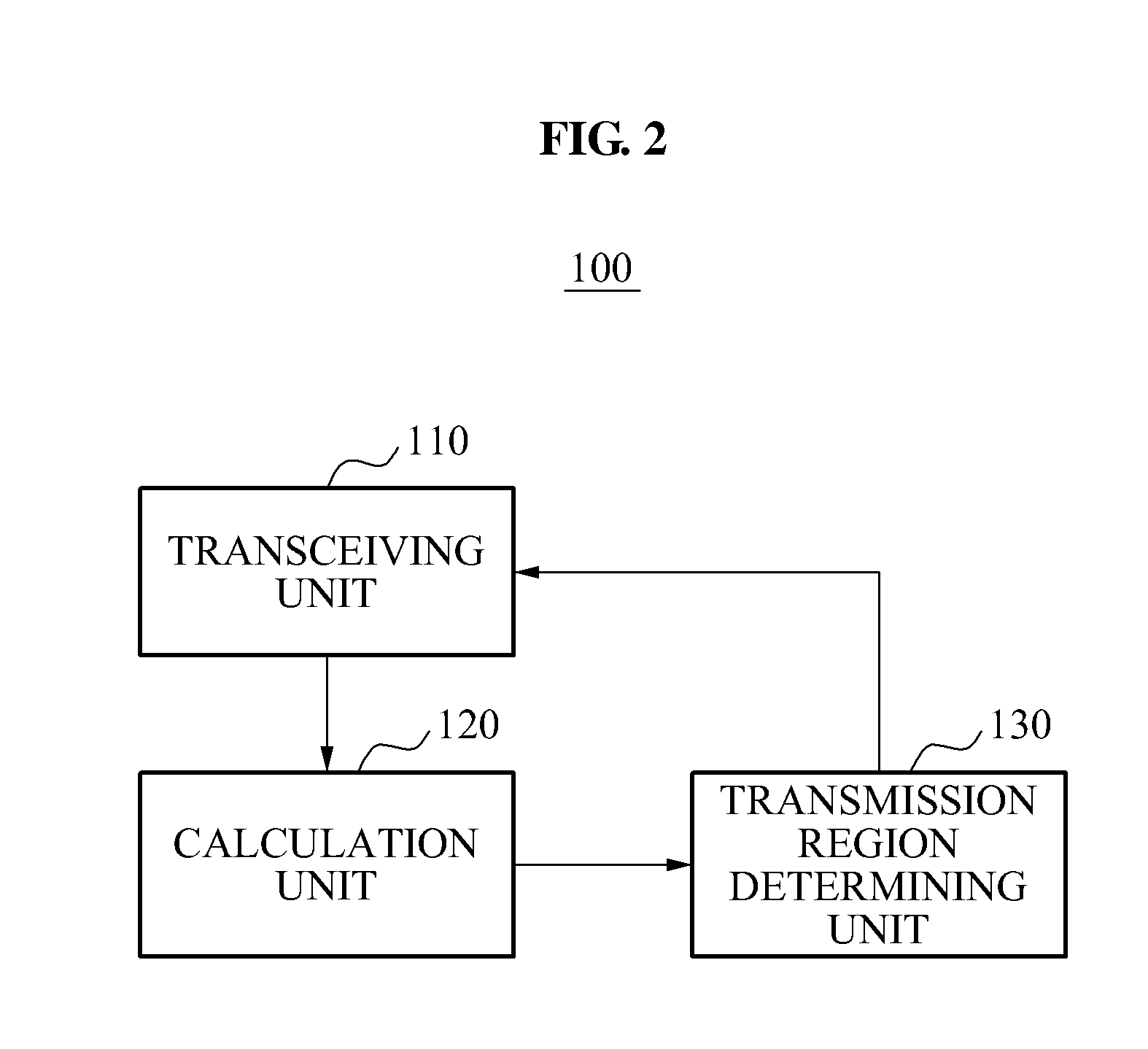
ActiveUS20110161408A1Multiple digital computer combinationsData switching networksDistributed computingData request
Provided are a network apparatus and system that may request or receive the same contents stored in a plurality of network apparatuses. In a network system sharing data, specific segments from a plurality of segments constituting the data may be received from mutually different terminals. For this, a transmission region may be determined by calculating a transmission offset corresponding to the plurality of terminals, and at least one segment included in the determined transmission region may be received from a corresponding terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com