Patents
Literature
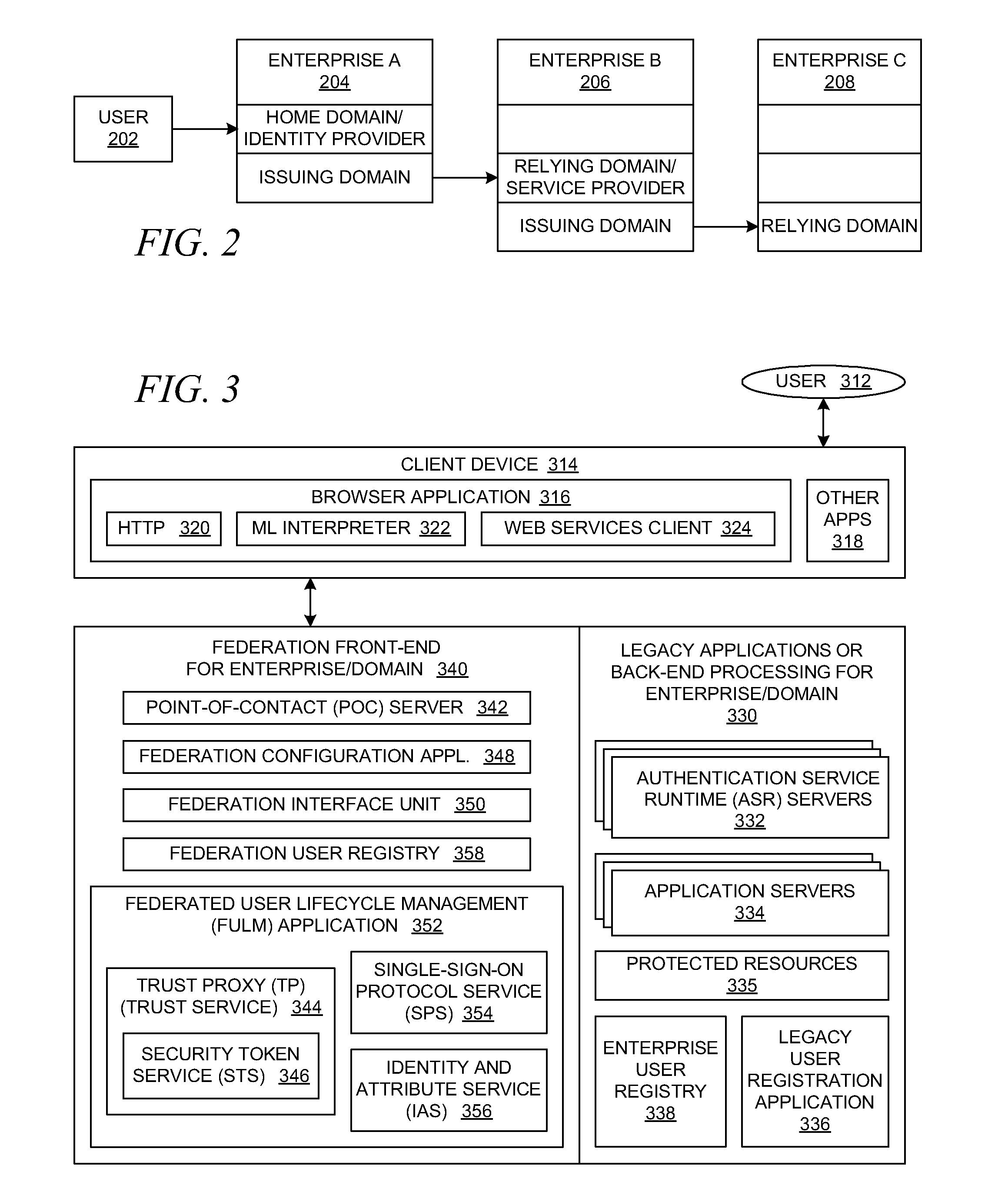
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1269 results about "Single sign-on" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
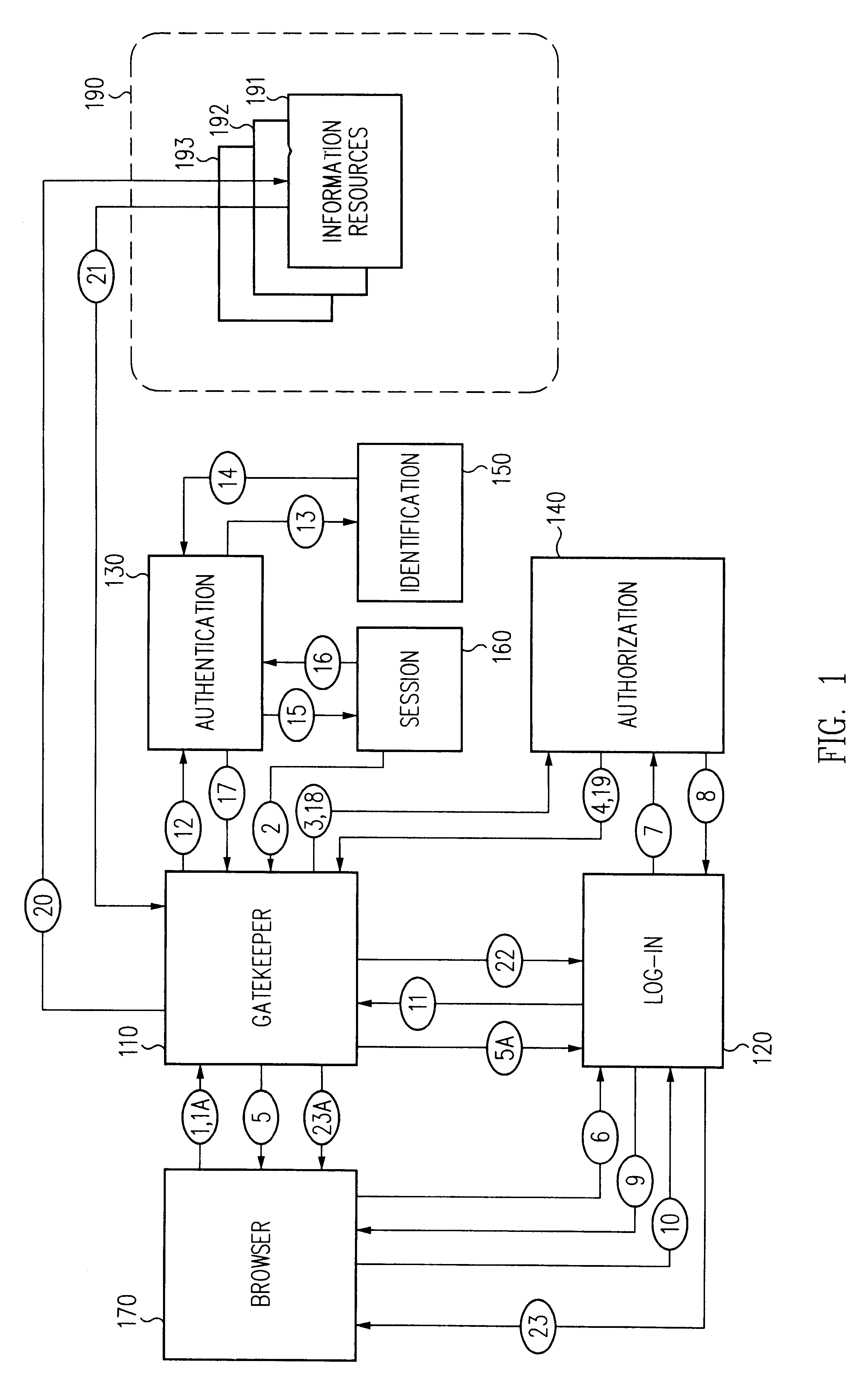
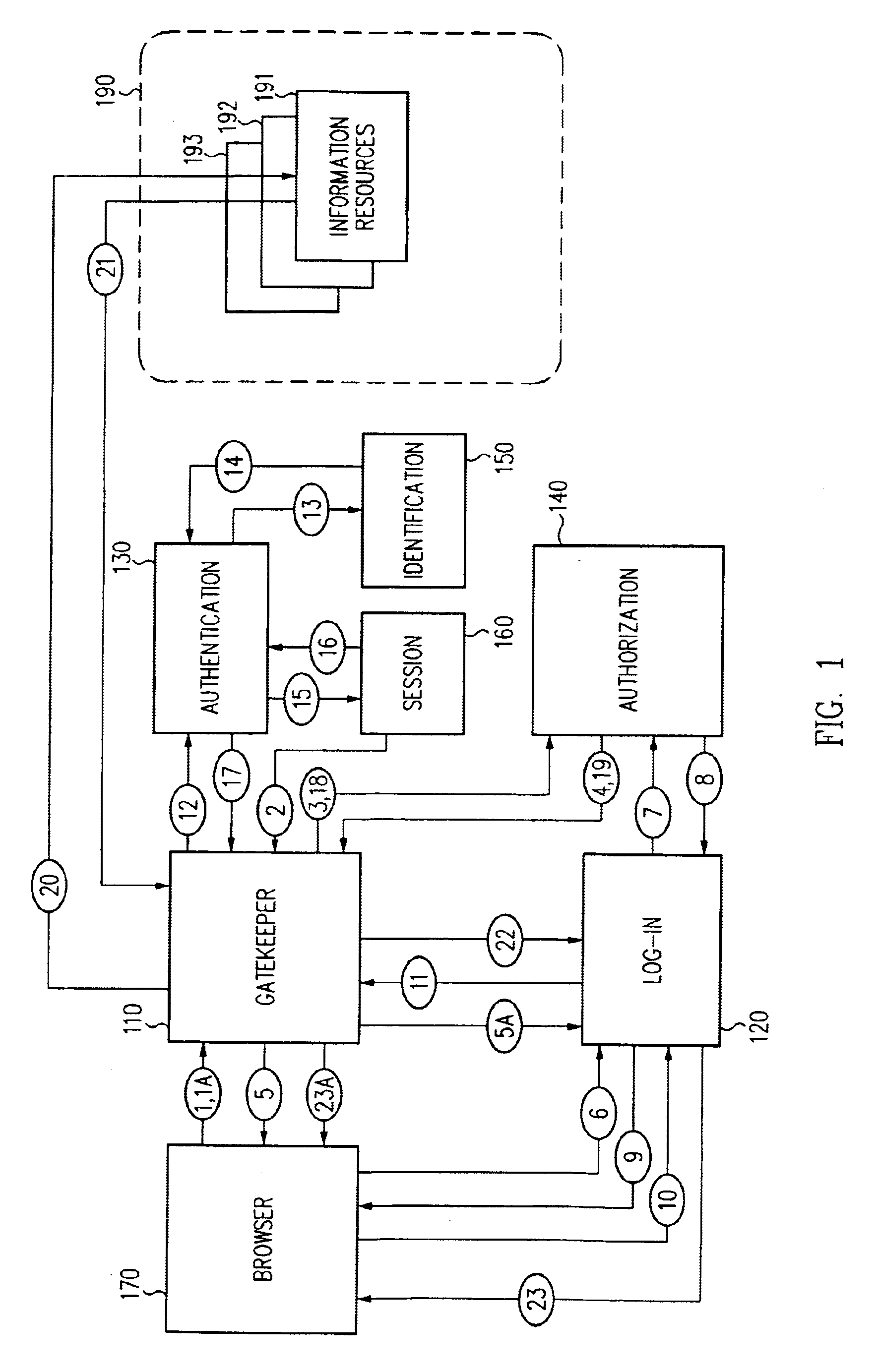
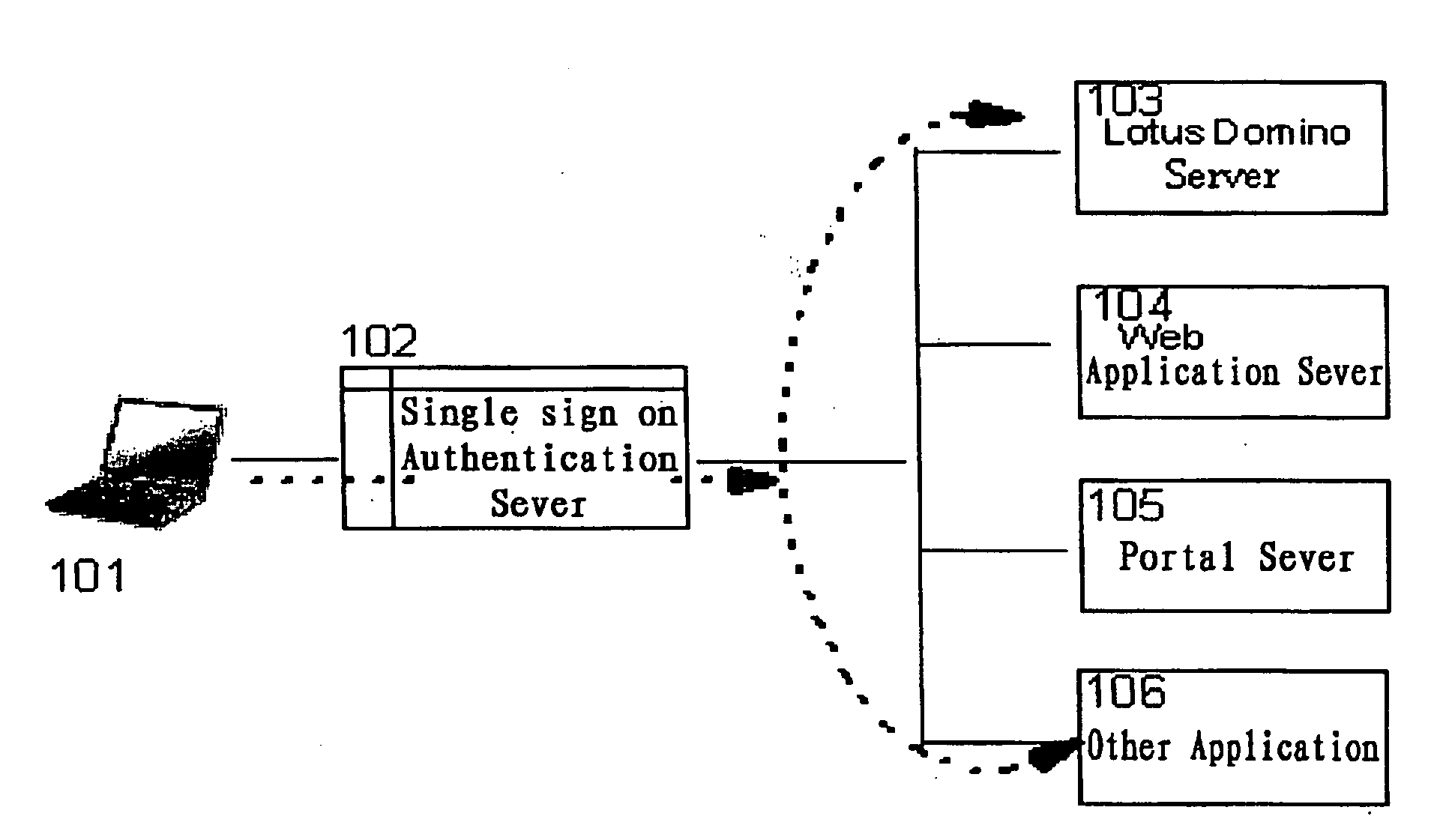
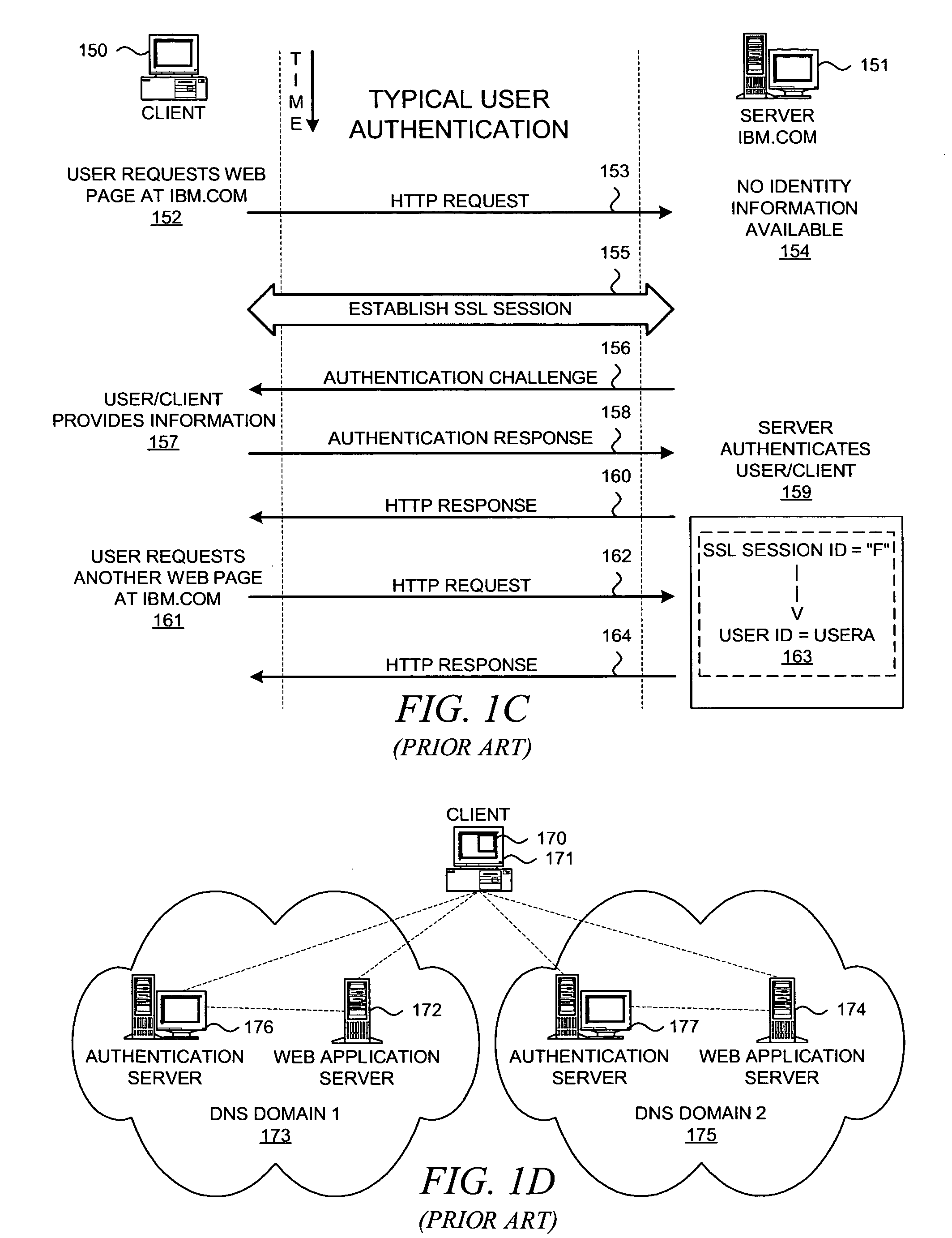
Single sign-on (SSO) is a property of access control of multiple related, yet independent, software systems. With this property, a user logs in with a single ID and password to gain access to any of several related systems. It is often accomplished by using the Lightweight Directory Access Protocol (LDAP) and stored LDAP databases on (directory) servers. A simple version of single sign-on can be achieved over IP networks using cookies but only if the sites share a common DNS parent domain.
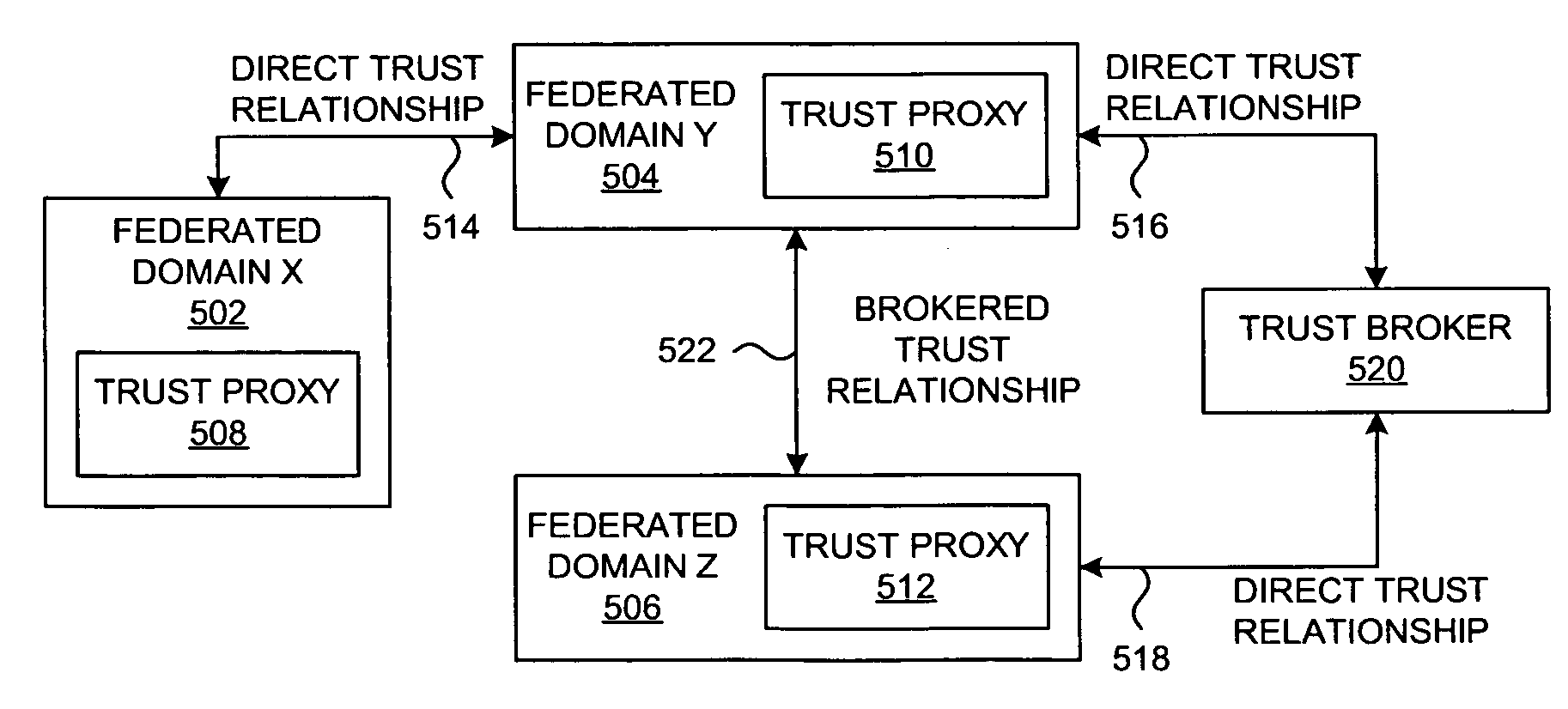
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
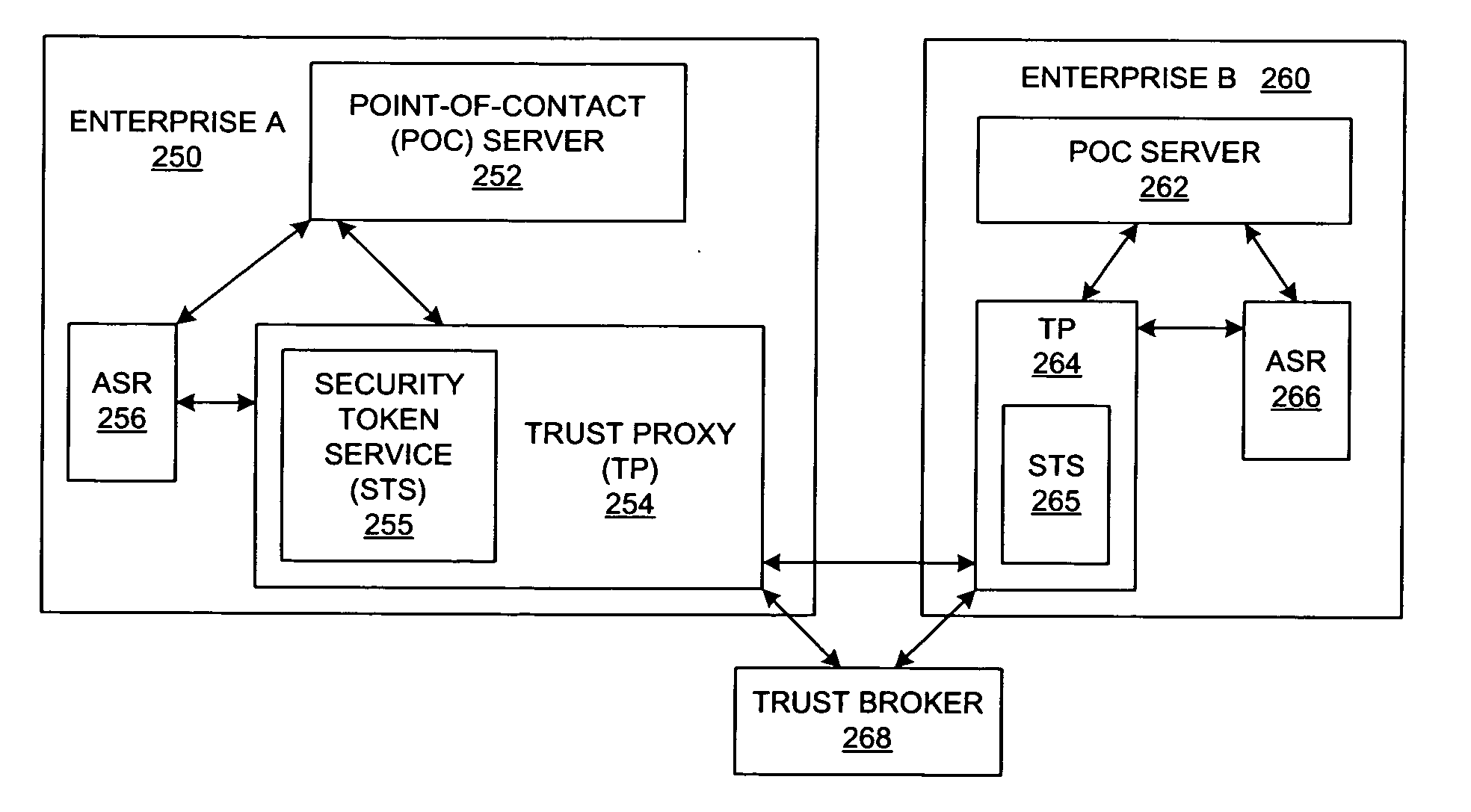
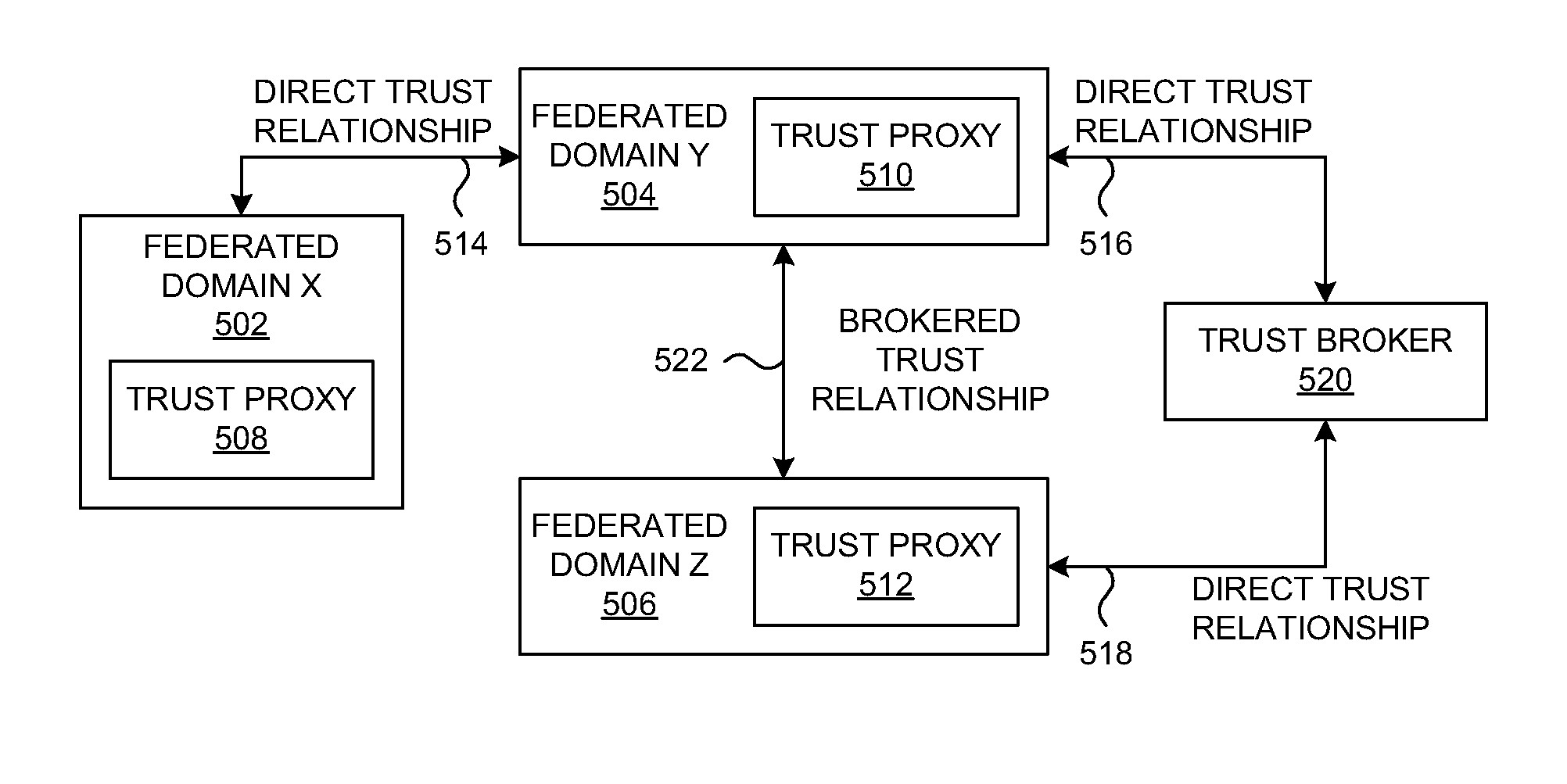
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
Log-on service providing credential level change without loss of session continuity
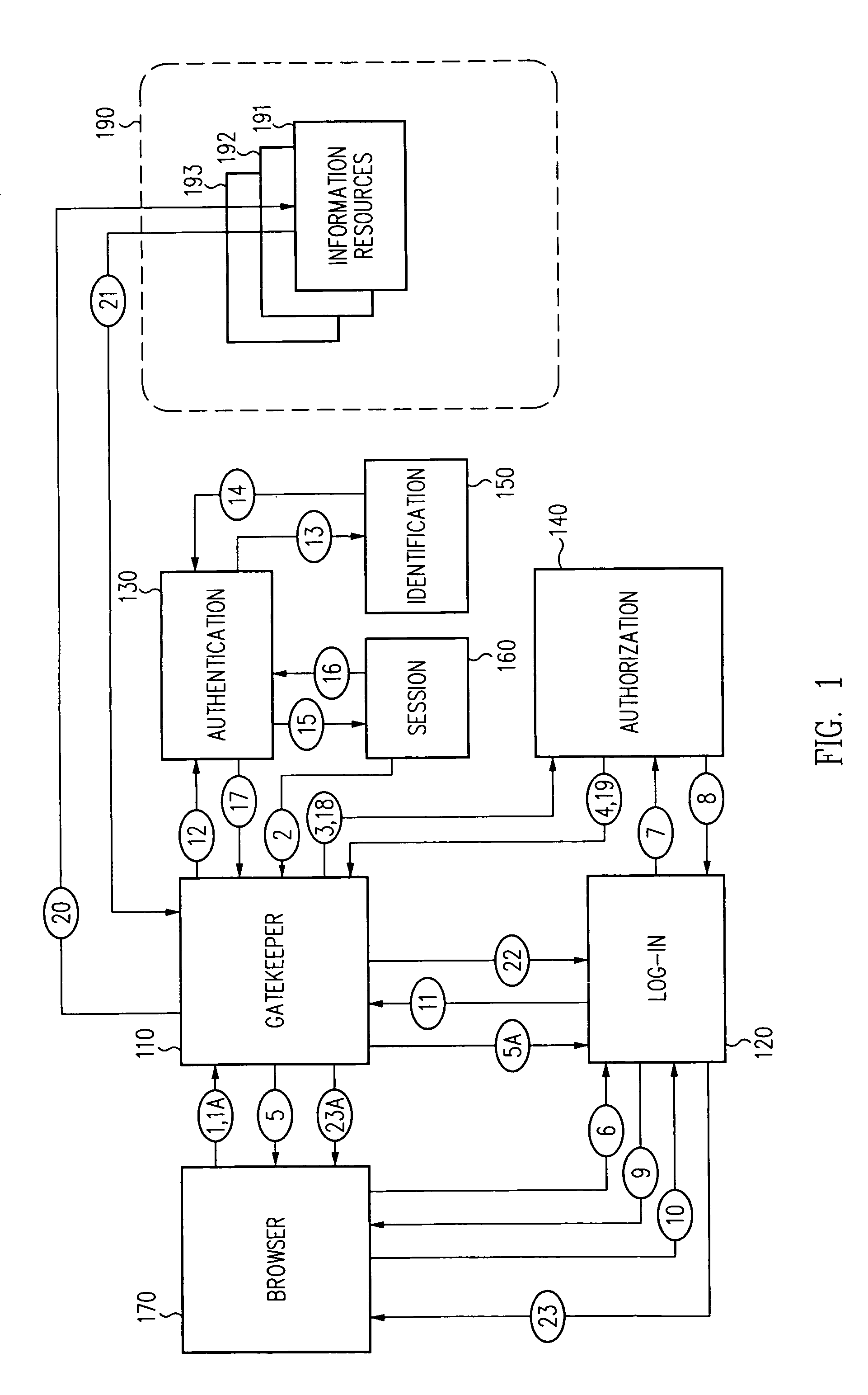
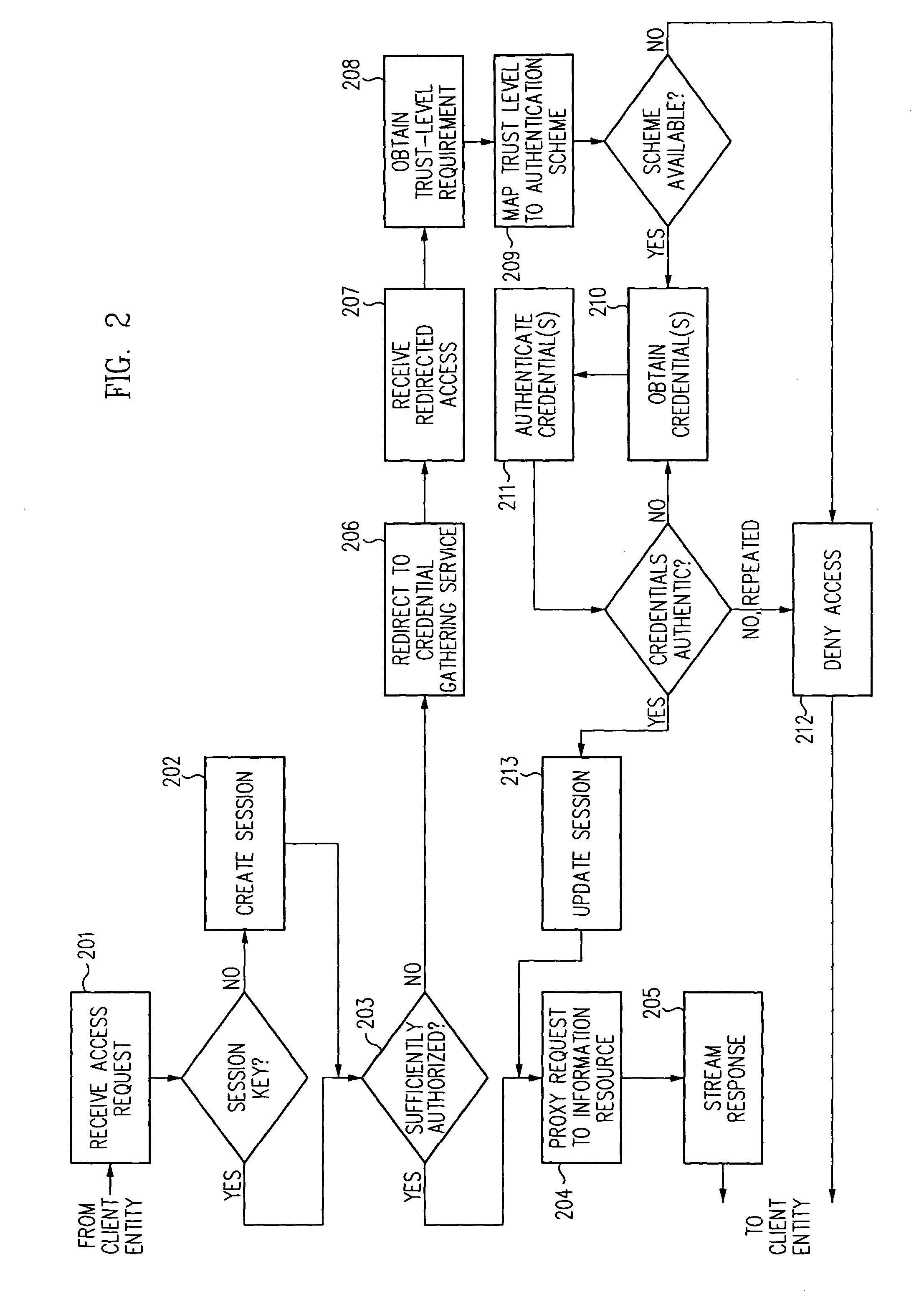
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
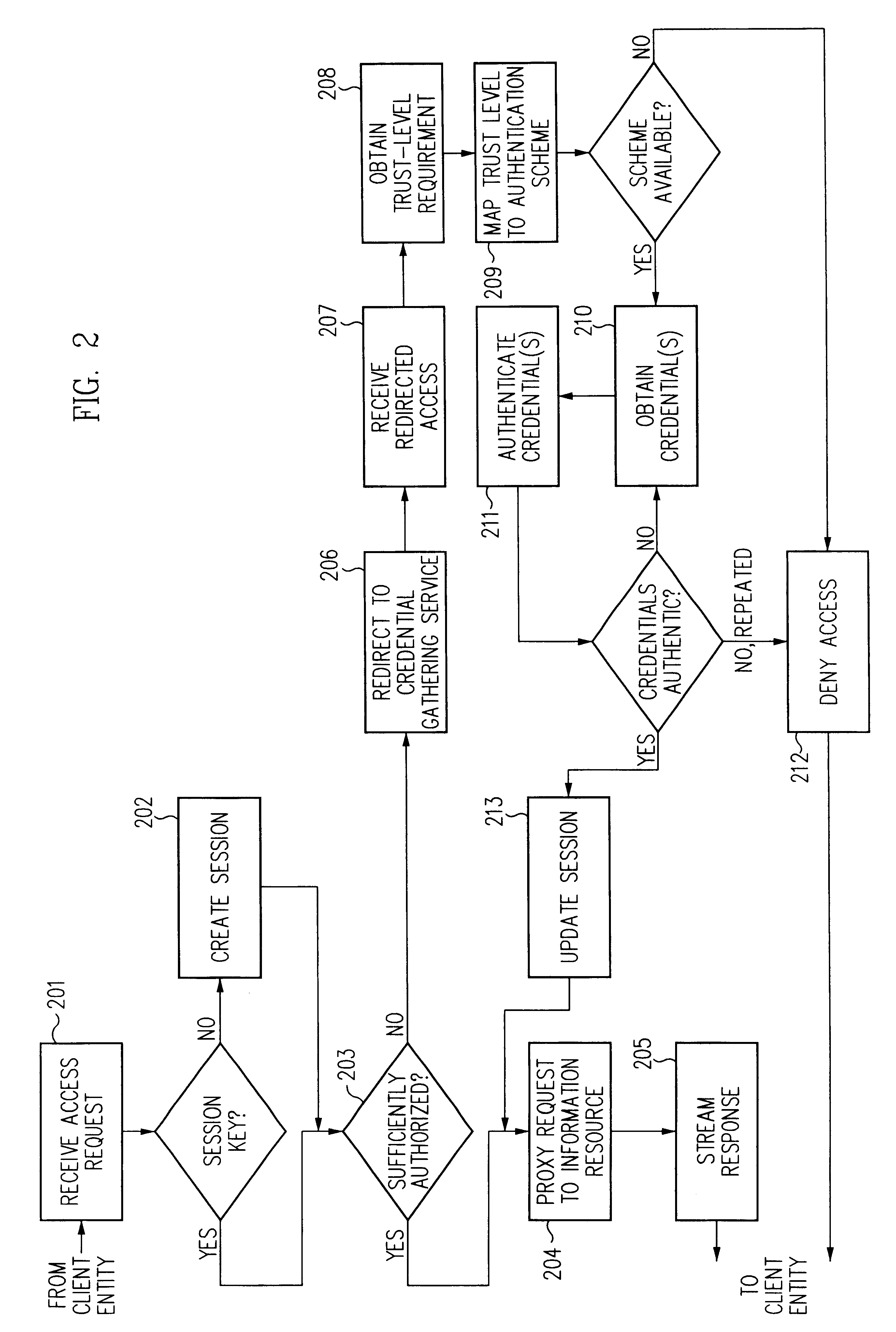
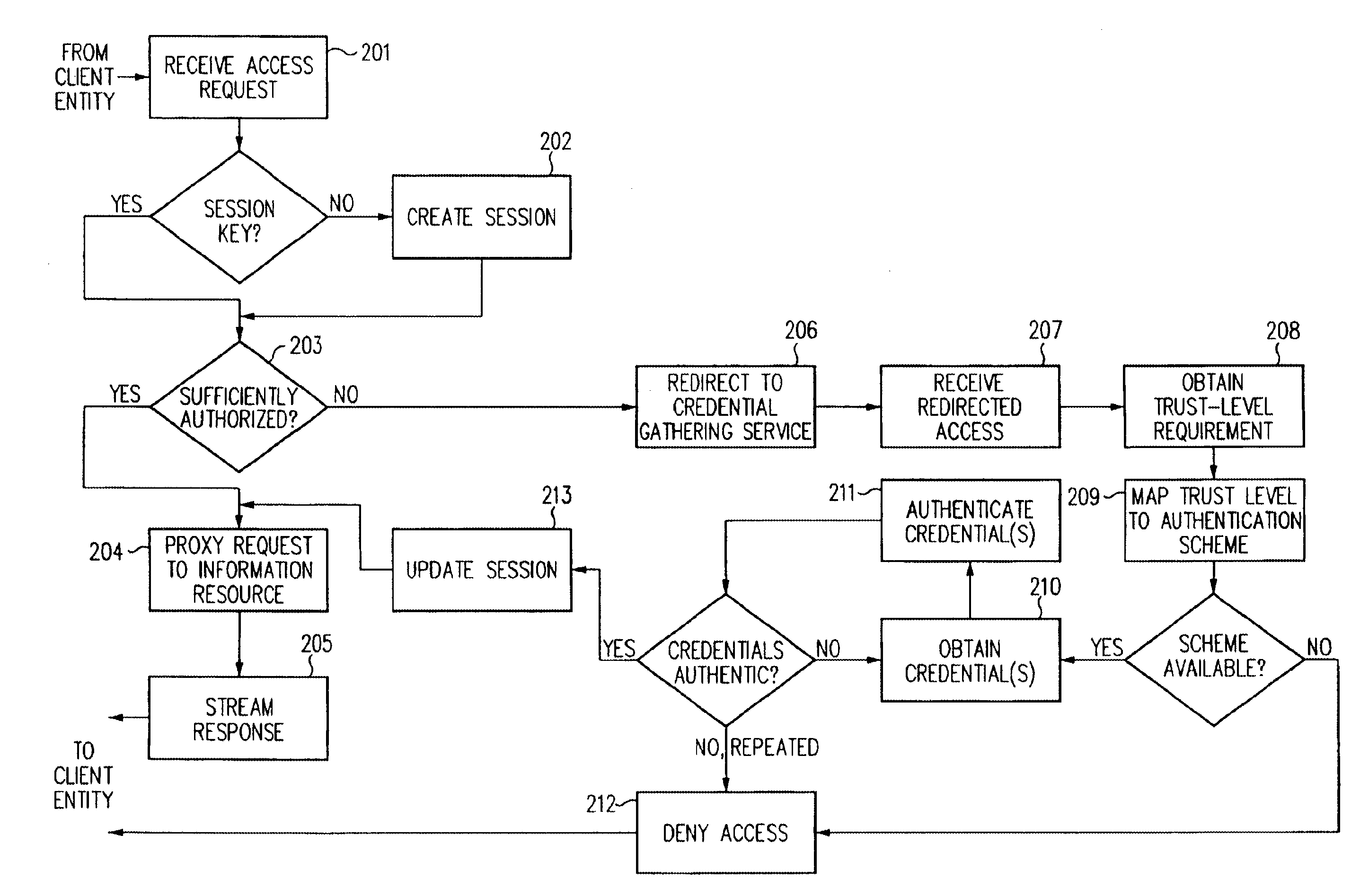
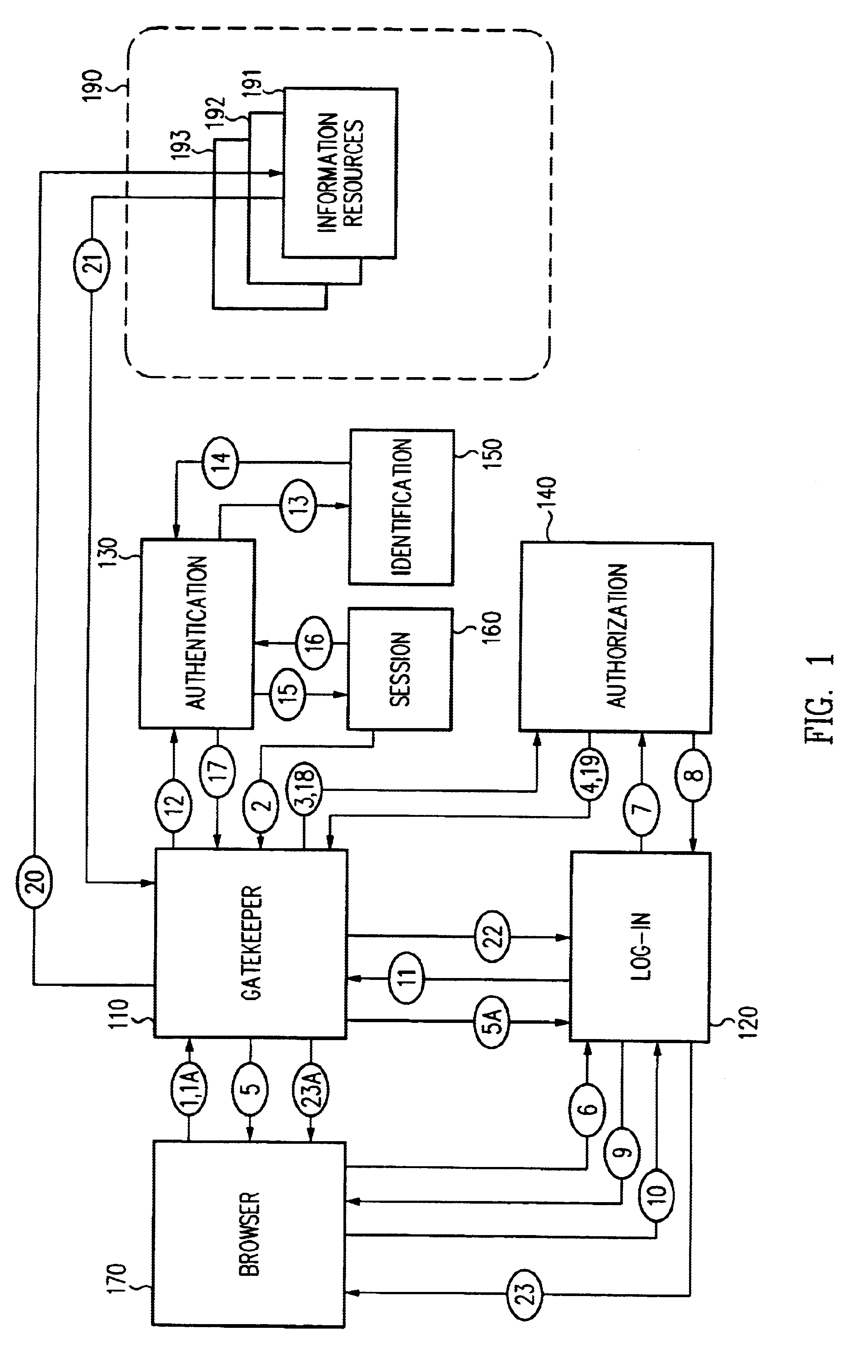
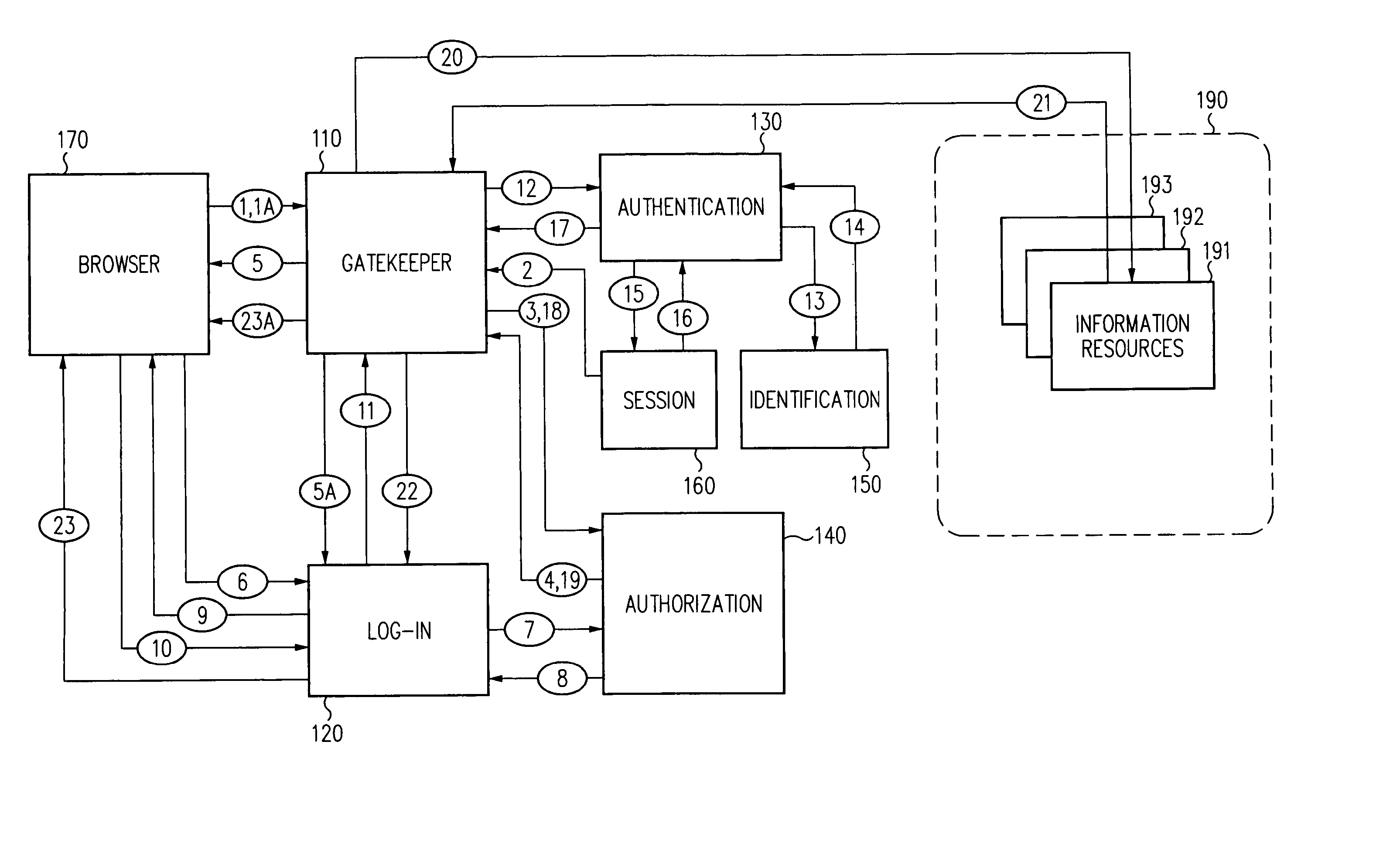
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
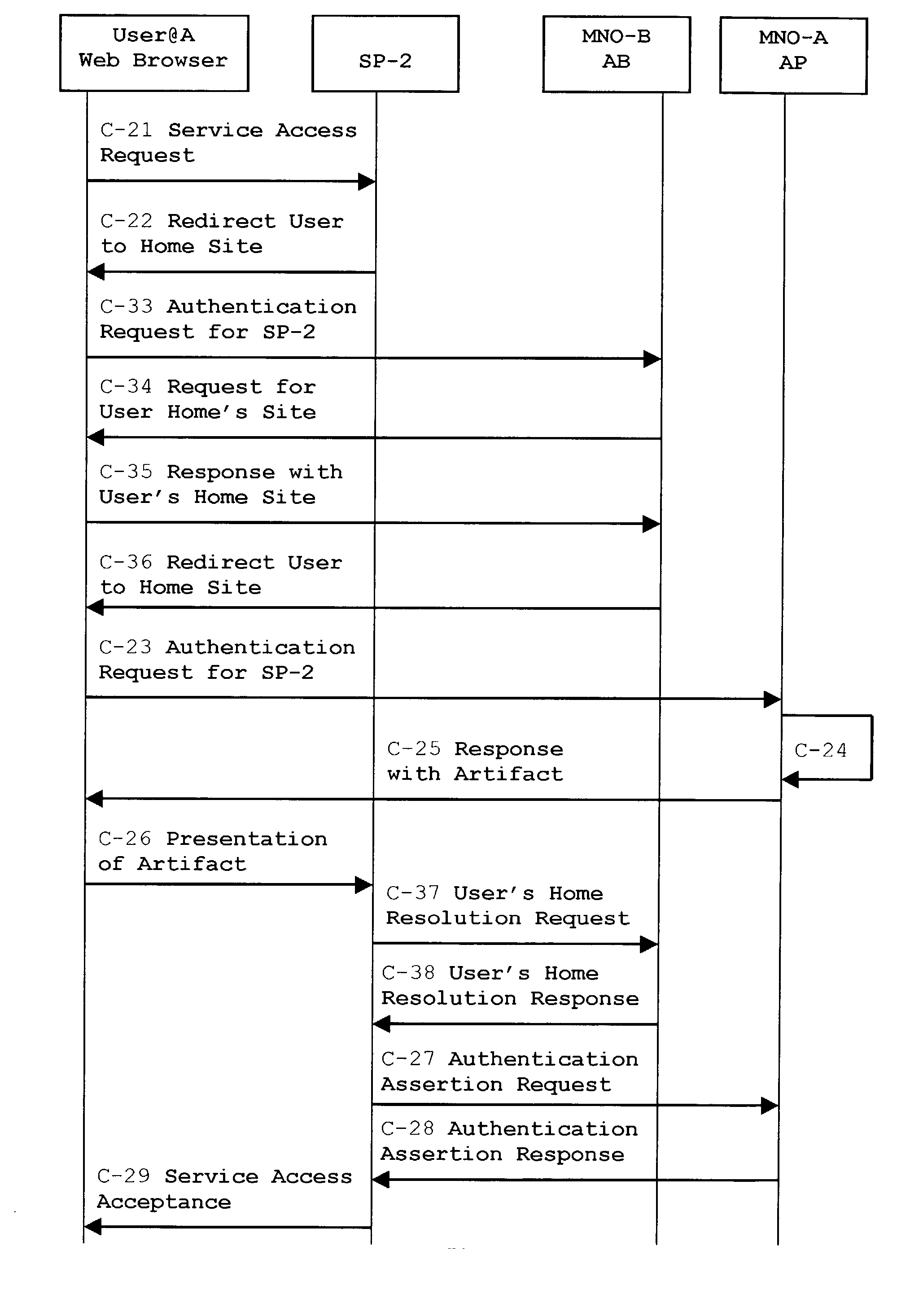
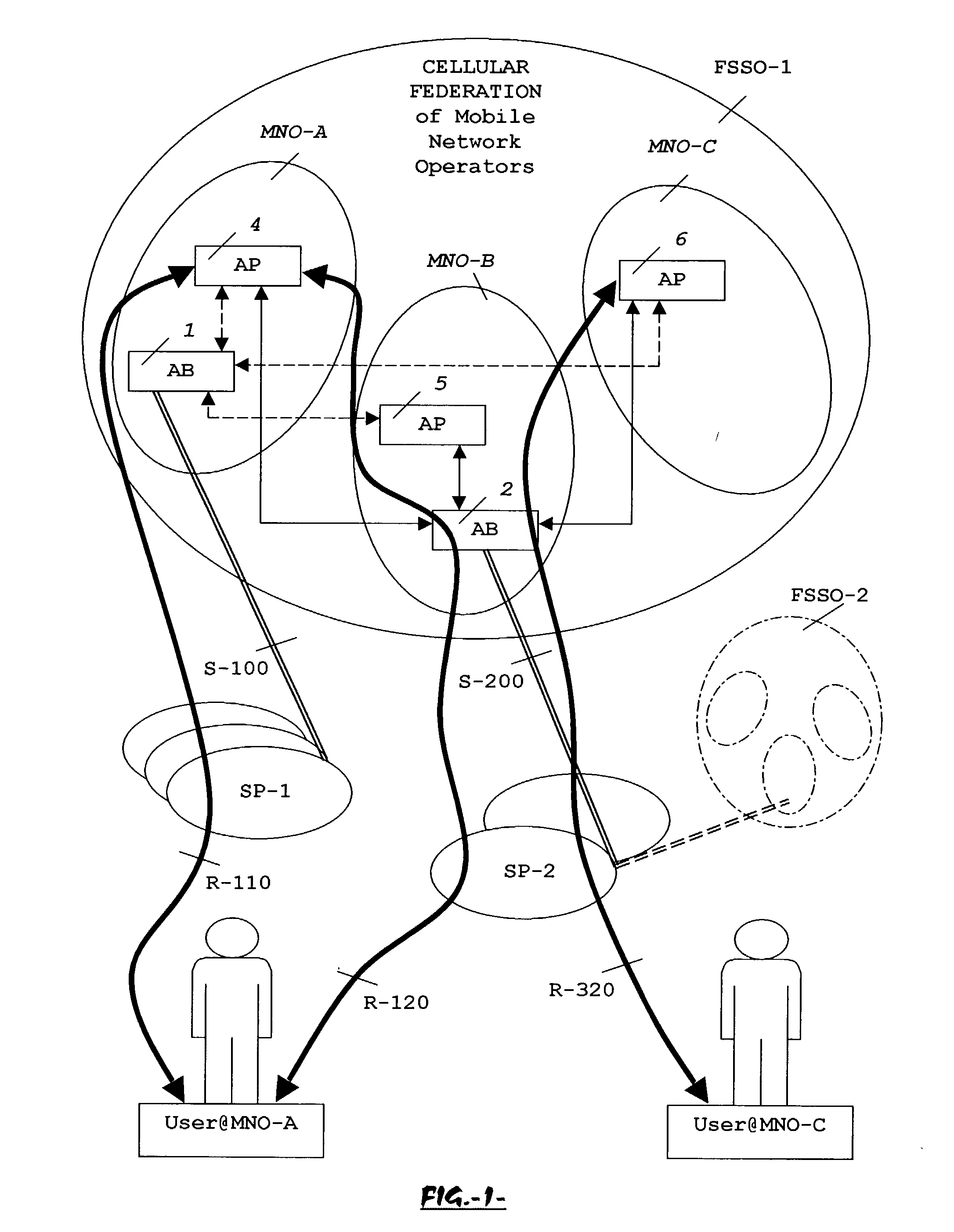
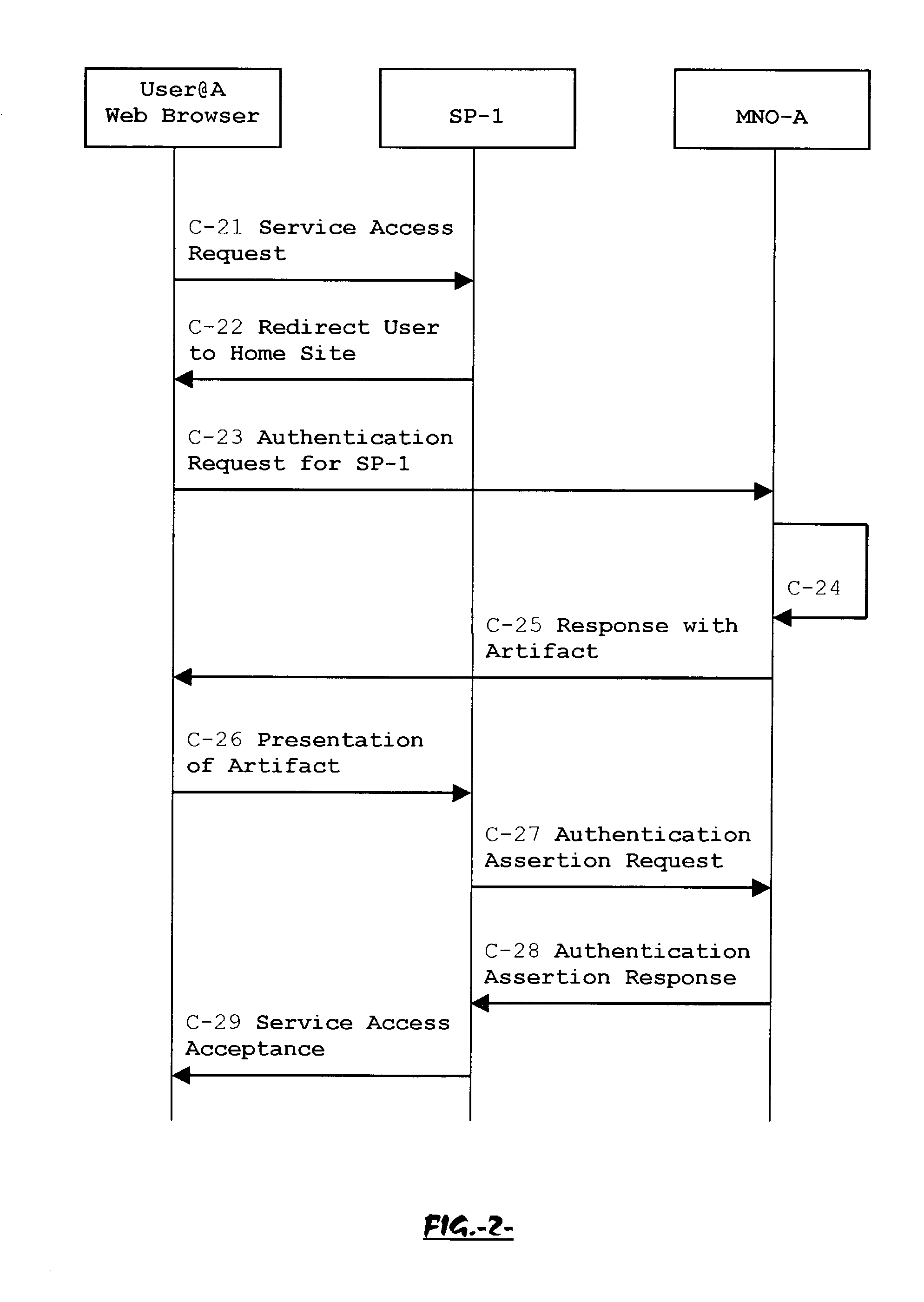
System, method and apparatus for federated single sign-on services
ActiveUS20030163733A1Unauthorised/fraudulent call preventionDigital data processing detailsCyber operationsService domain
The advent of new and sophisticated web services provided by Service Providers to users, services that individually require authentication of user and authorization of access, brings the needs for a new service to facilitate such authentication and access, a service referred to as Single Sign-On (SSO). The basic principle behind SSO is that users are authenticated once at a particular level, and then access all their subscribed services accepting that level of authentication. The present invention provides a system, method and apparatus wherein a cellular Federation of mobile network operators becomes an SSO authentication authority for subscribers of this Federation accessing Service Providers having such agreement with a mobile network operator of the Federation. In accordance with this invention, mobile network operators can leverage their operator-subscriber trust relationship in order to act as SSO authentication authority for those subscribers accessing Service Providers in a service domain other than the mobile network domain.
Owner:TELEFON AB LM ERICSSON (PUBL)
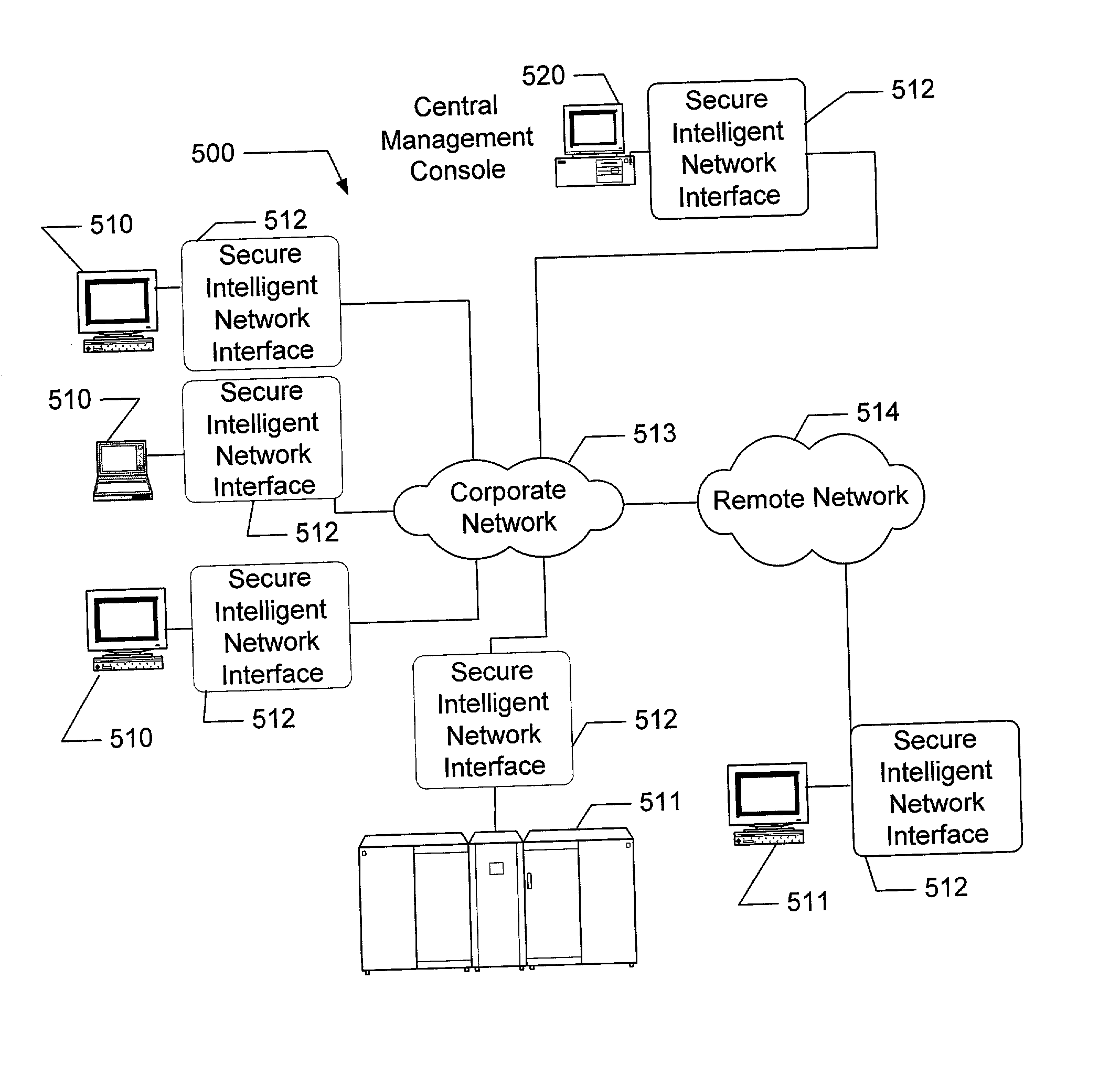
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
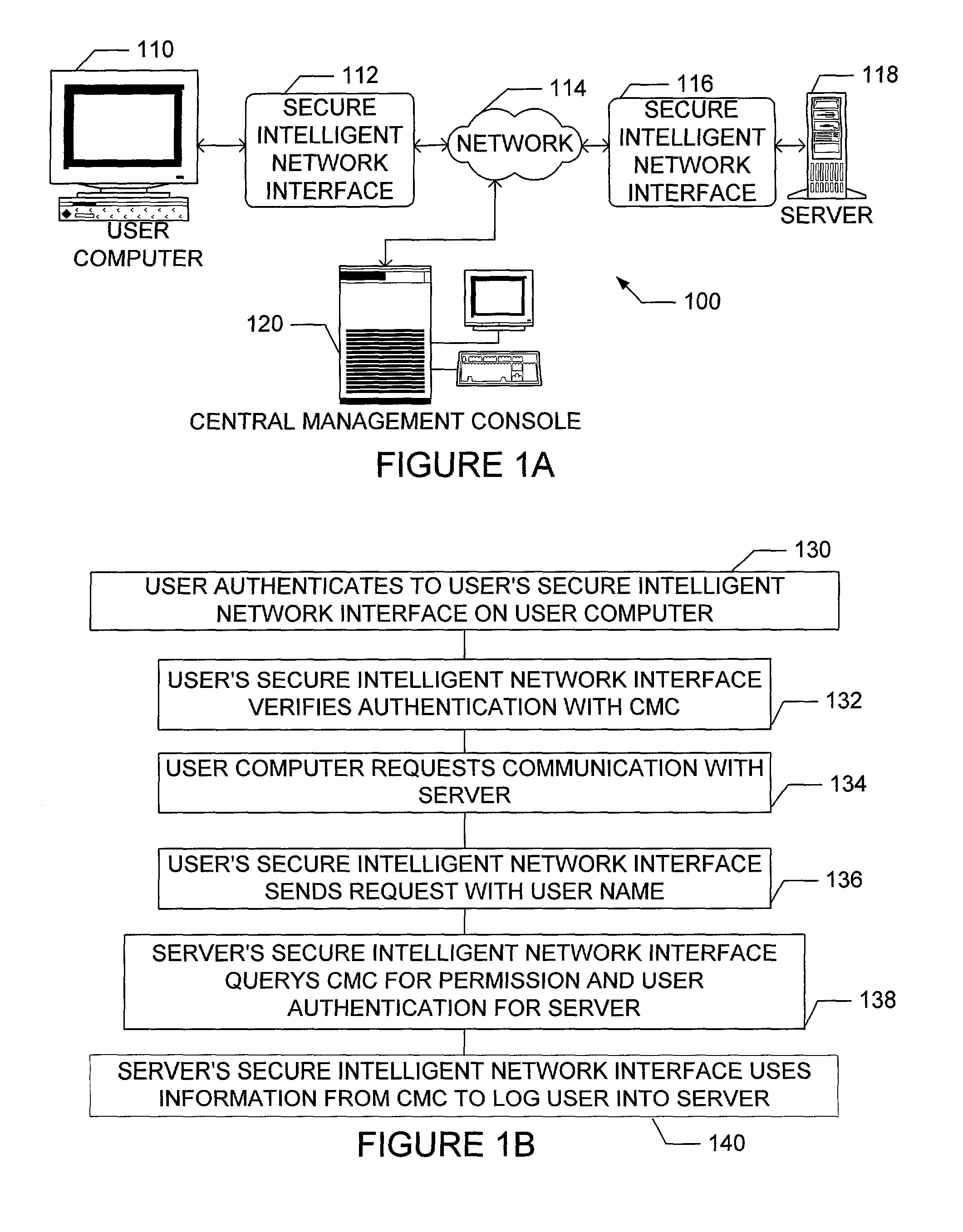
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
Single certificate service system and operational method thereof
ActiveUS20140282983A1Need can be stimulatedEasy to manageDigital data processing detailsMultiple digital computer combinationsTerminal operationMultiple applications
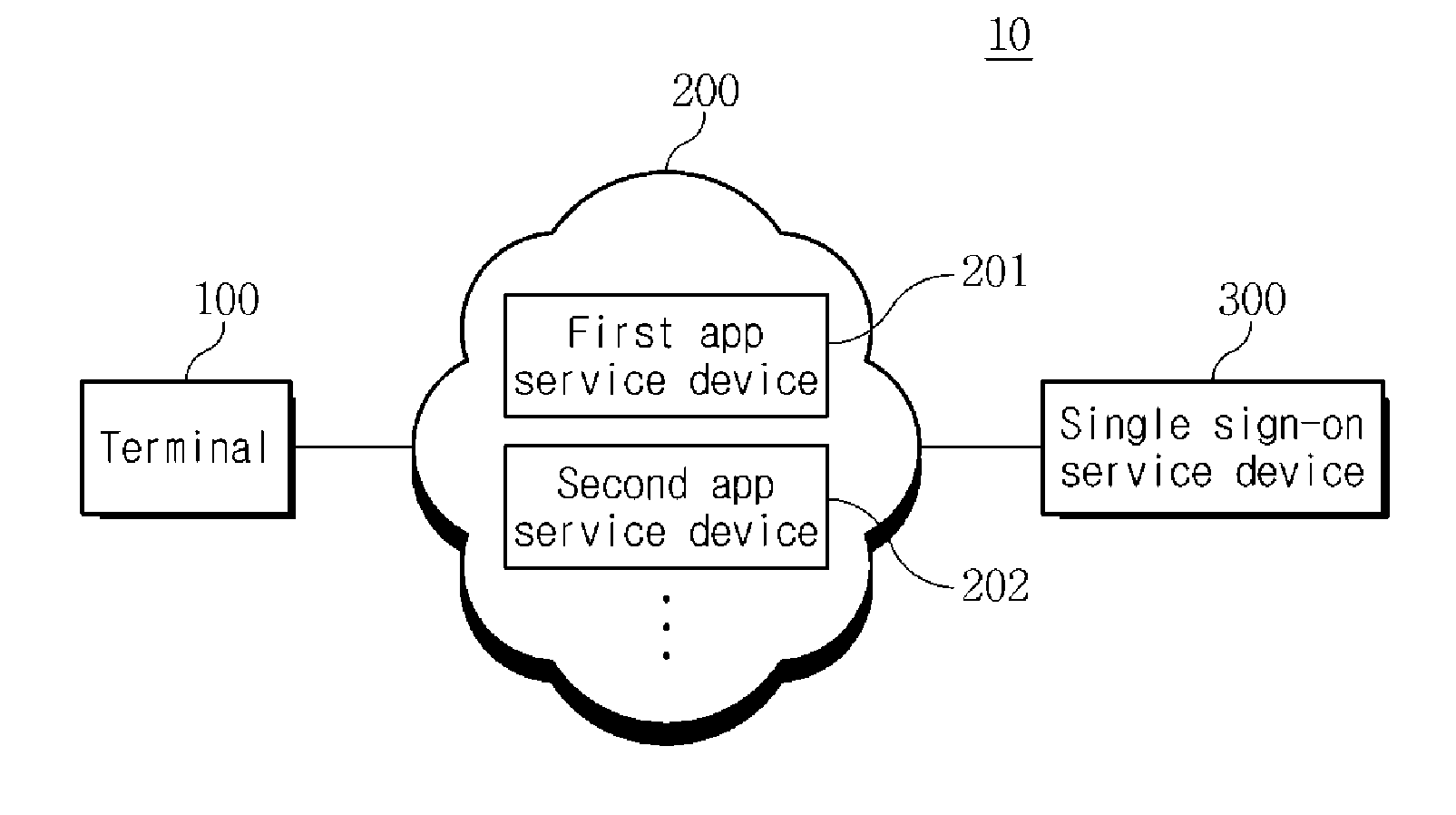
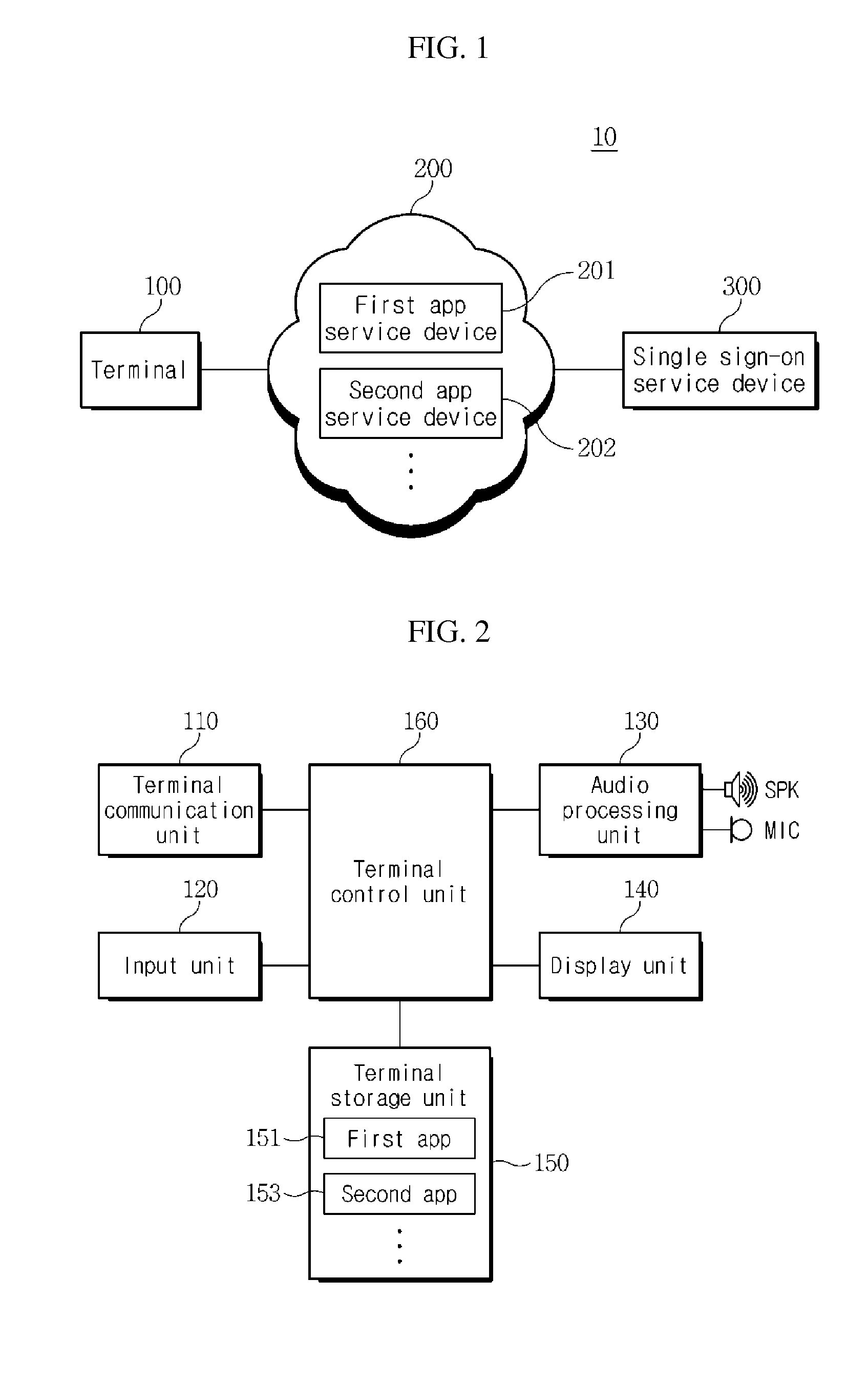
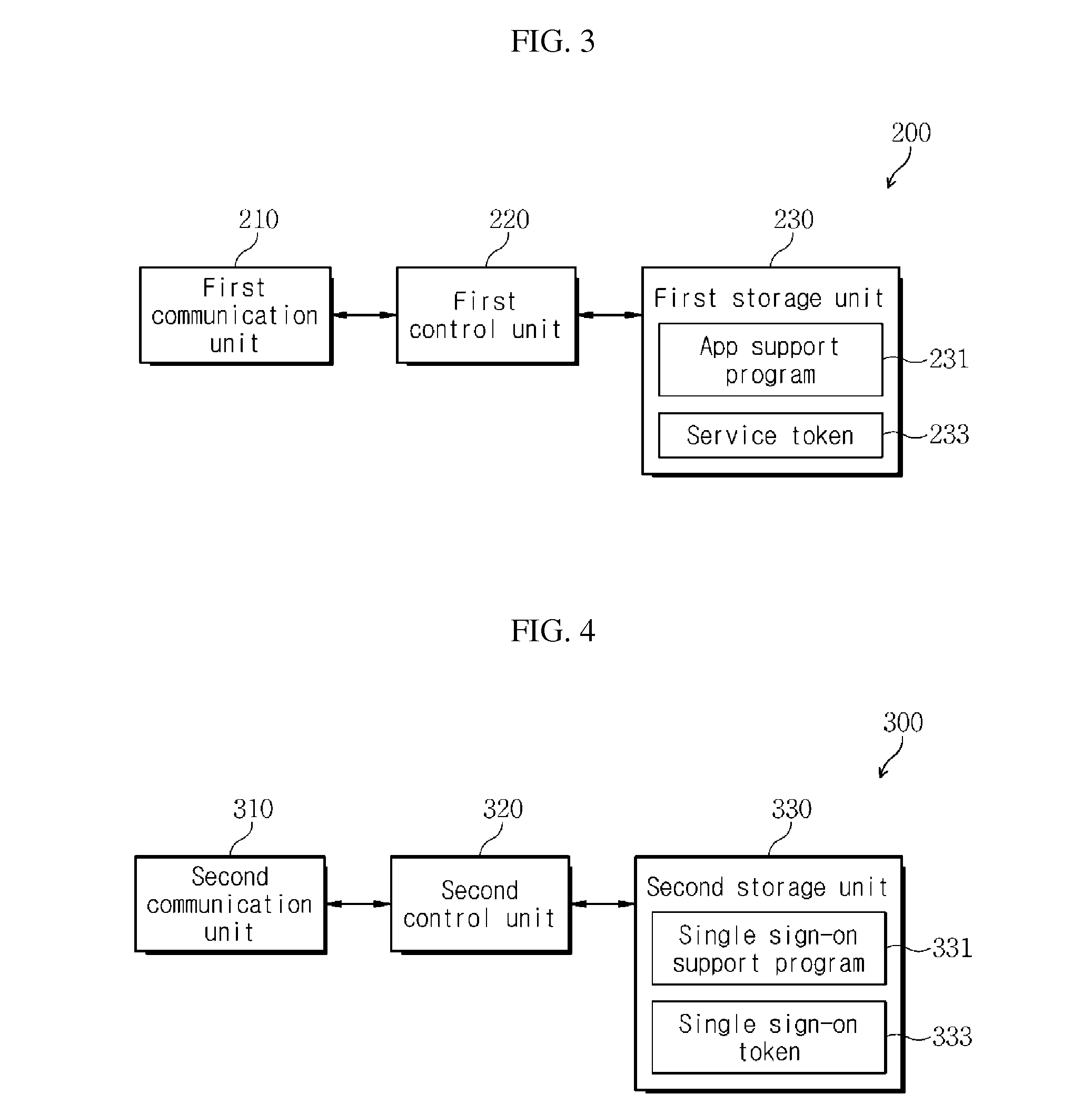
The present invention discloses a single sign-on service system and its respective elements, and an operating method thereof. The single sign-on service system includes a terminal configured to access at least one of a plurality of application service devices according to a request for activating at least one of a plurality of applications, and receive a service token used to operate the application service from each application service device on the basis of a single sign-on token without separately inputting sign-on information, an application service device configured to provide data for operating the application service by the terminal having the service token and when a single sign-on message is received, provide the single sign-on message to a single sign-on service device.
Owner:SK PLANET CO LTD
Authentication and authorization mapping for a computer network
ActiveUS7350229B1User identity/authority verificationComputer security arrangementsApplication softwareAuthorization
A method and apparatus for a network-wide authentication and authorization mapping system for a network is provided. The global authentication and authorization mapping system enables a seamless transition from one web-based application in the network configuration to another web-based application in the network configuration, including a single sign-on capability for users. There are no localized security enforcement processes required to further authenticate a user.
Owner:COMP ASSOC THINK INC
Method and system for single sign-on user access to multiple web servers
InactiveUS7137006B1User identity/authority verificationDigital data authenticationExpiration TimeHyperlink
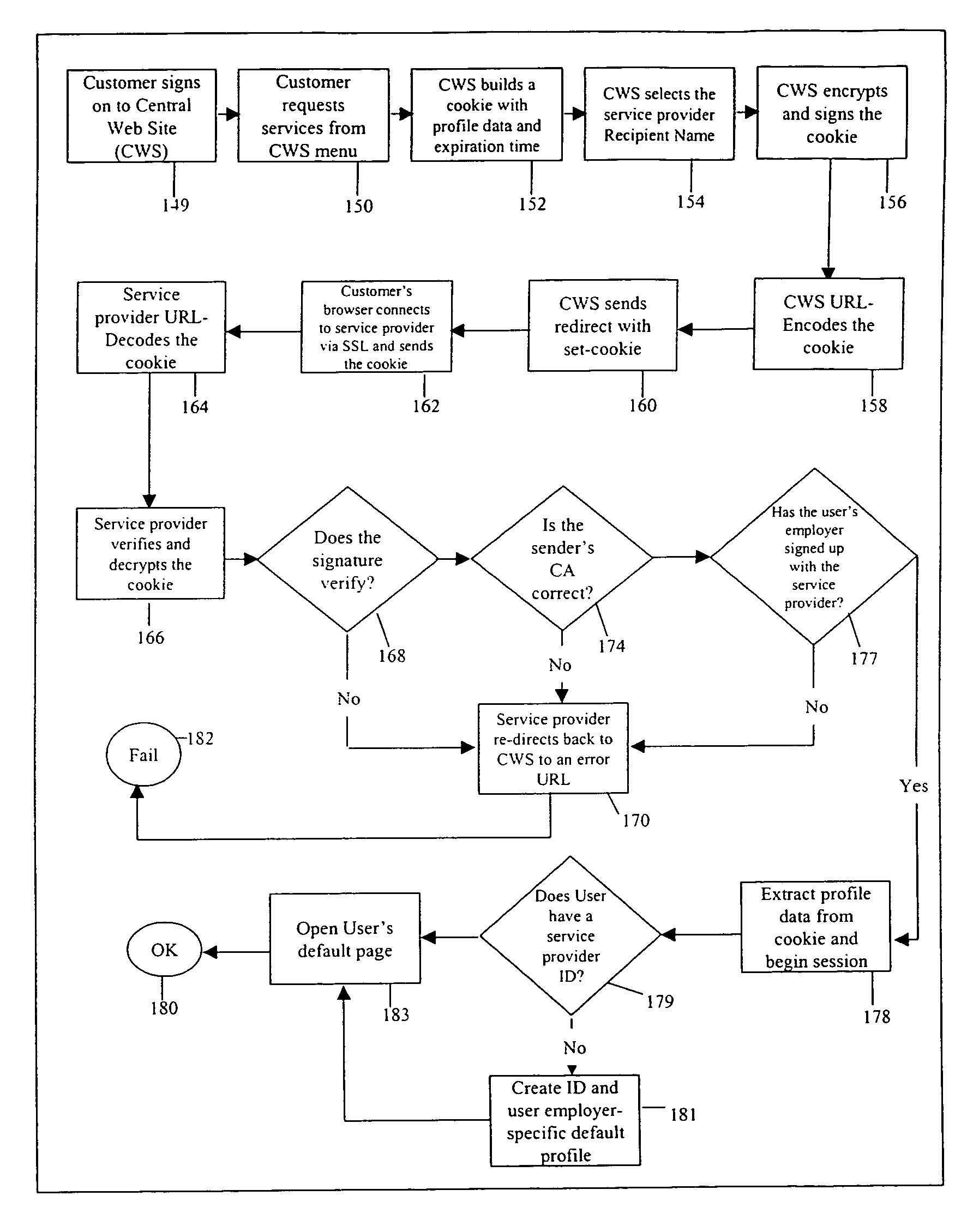
Methods and systems for single sign-on user access to multiple web servers are provided. A user is authenticated at a first web server (e.g., by user name and password). The first web server provides a web page to the user having a service selector (e.g., a hyperlink comprising the URL of a second web server offering the service indicated by the selector). When the user activates the service selector, the first web server constructs and transmits an encrypted authentication token (e.g., a cookie) from the first web server to a second web server via the user client. The first and second web servers share a sub-domain. The authentication token comprises an expiration time and is digitally signed by the first web server and is authenticated at the second web server. Upon authentication, the second web server allows the user to conduct a session at the second web server.
Owner:CITICORP CREDIT SERVICES INC (USA)
Log-on service providing credential level change without loss of session continuity
InactiveUS20040210771A1Digital data processing detailsUser identity/authority verificationInformation resourcePassword
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:SUN MICROSYSTEMS INC
Method And Apparatus For Trusted Federated Identity
InactiveUS20120072979A1Well formedDigital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
System and method for single sign on process for websites with multiple applications and services
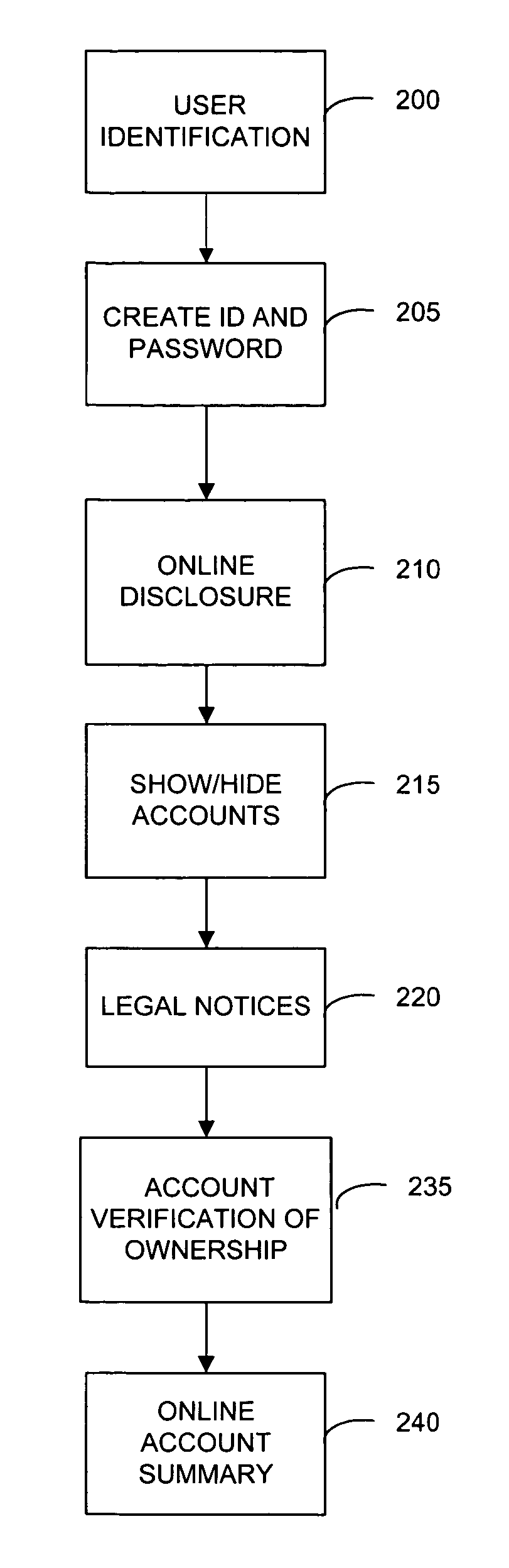
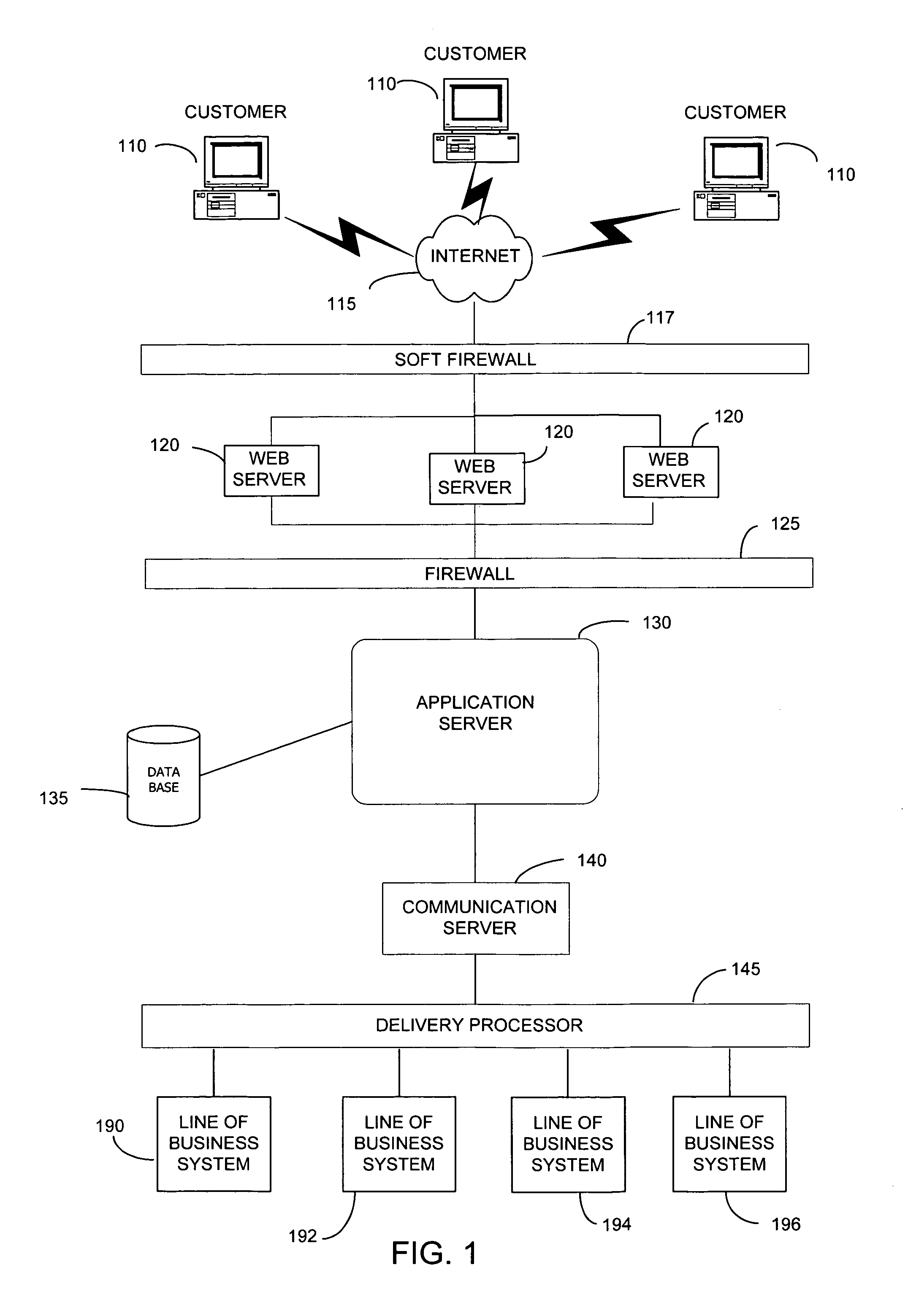
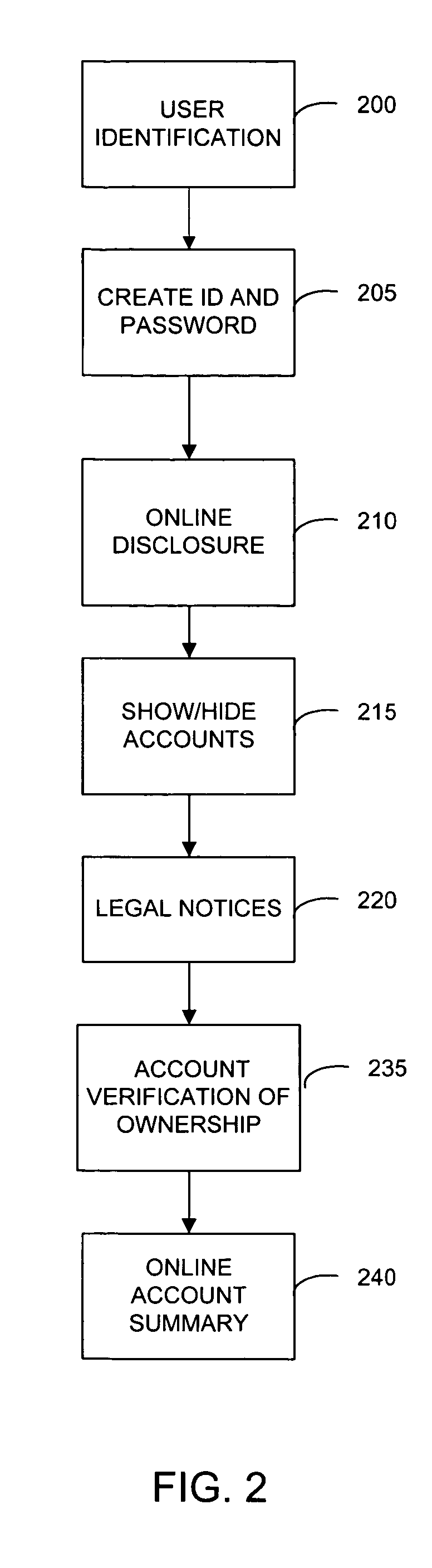
InactiveUS7058817B1Reduce usageReduce supportFinanceUser identity/authority verificationPasswordThe Internet
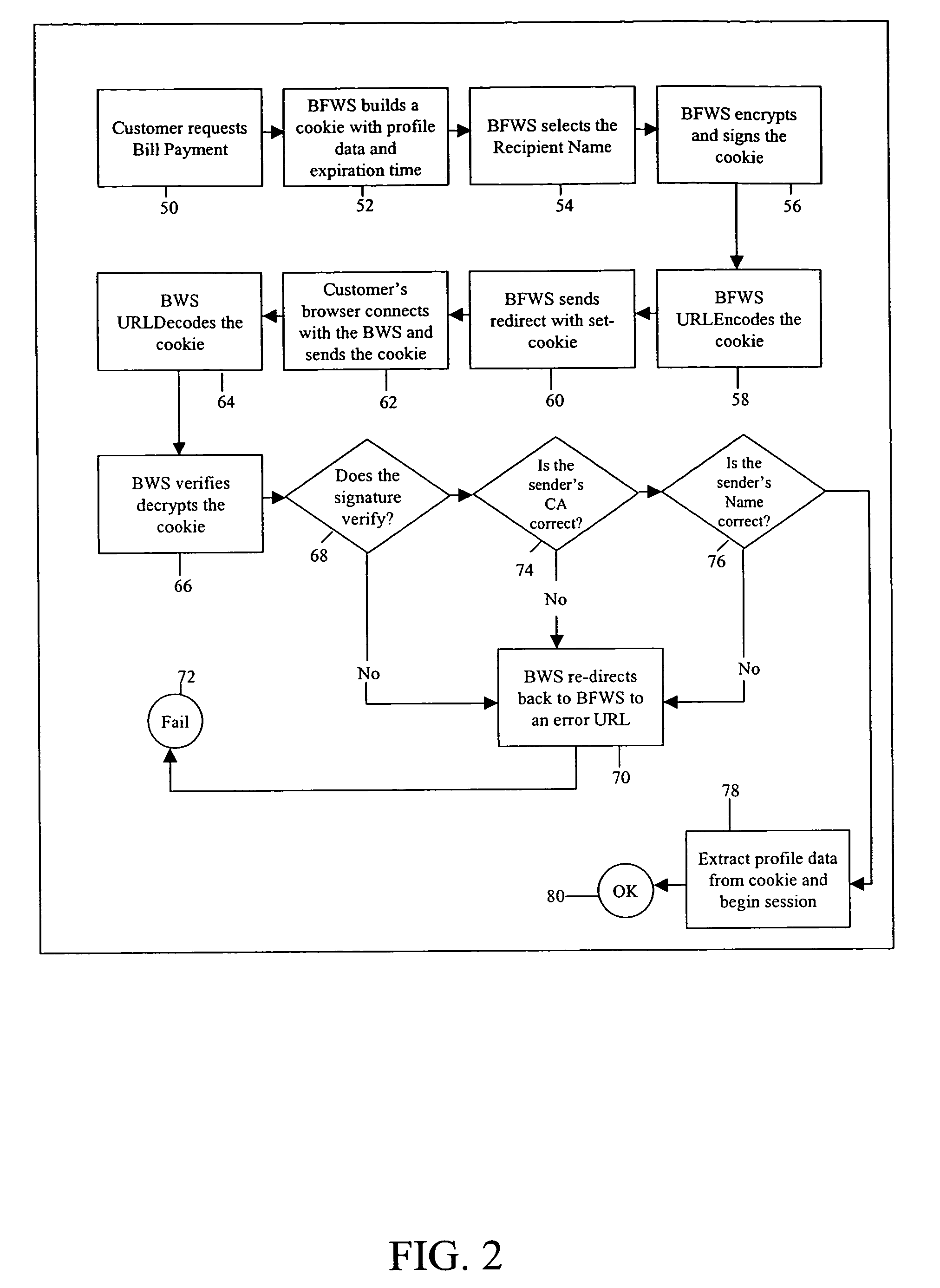
A system and method for integrating the Internet front end sign on processes of the various systems of a financial institution which allows a customer to view and access its various financial accounts with the institution. During the initial sign up for the online access to its accounts, a customer creates it's User ID and password online during the same session. Once the customer has signed on (password) and verified ownership of at least one account, the system displays all of the customer's accounts that are available for access via the Internet website. The online ownership verification uses only a single account of the customer and the ownership verification criteria associated with the account. The account used for verifying a customer is first determined based on the accounts selected by the customer for accessing online. From the selected accounts, the system of the present invention creates a verification hierarchy with respect to the accounts. When determining the verification to use for the single ownership verification, the present invention selects the account from the hierarchy with the most stringent requirements.
Owner:JPMORGAN CHASE BANK NA
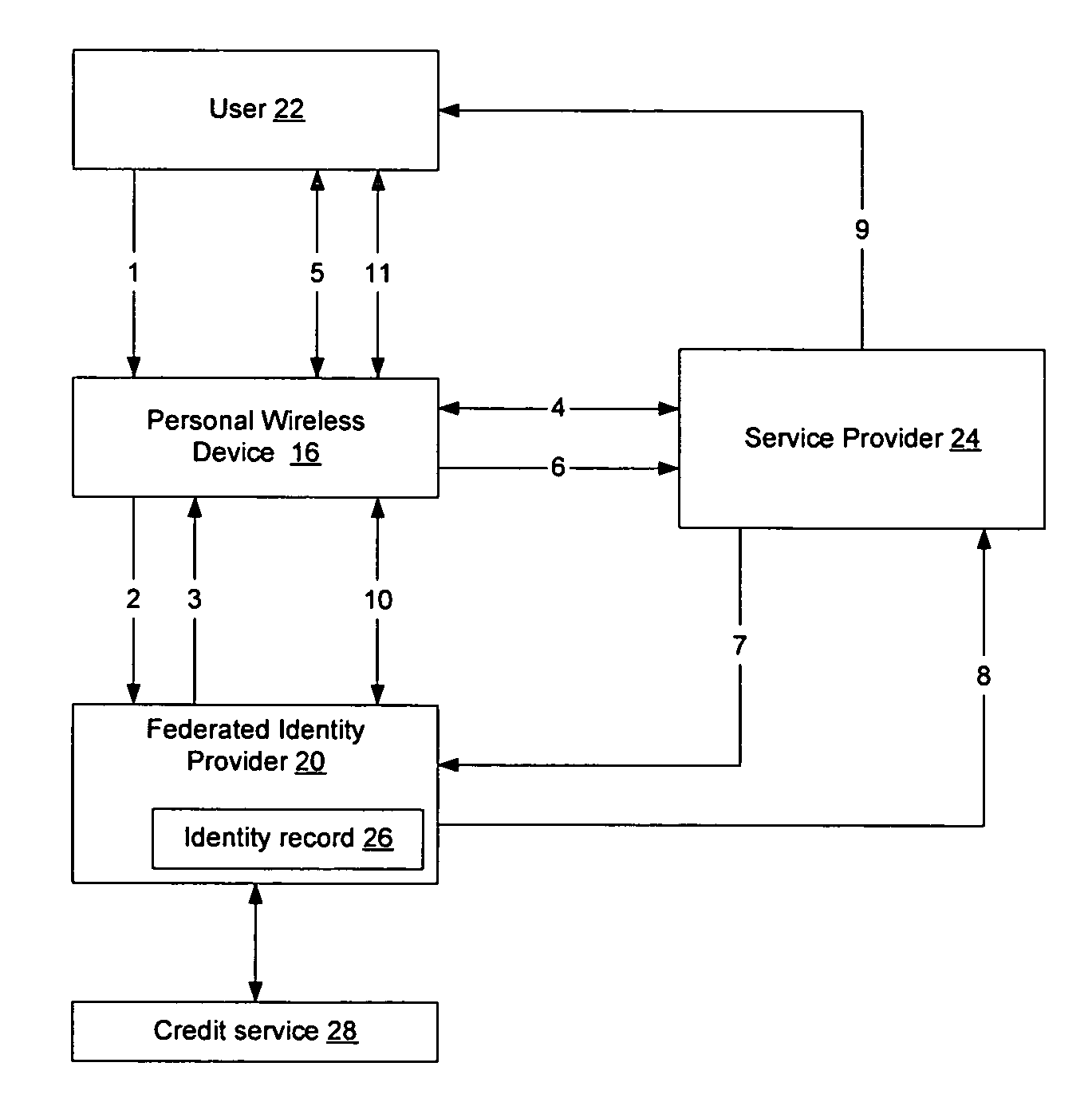
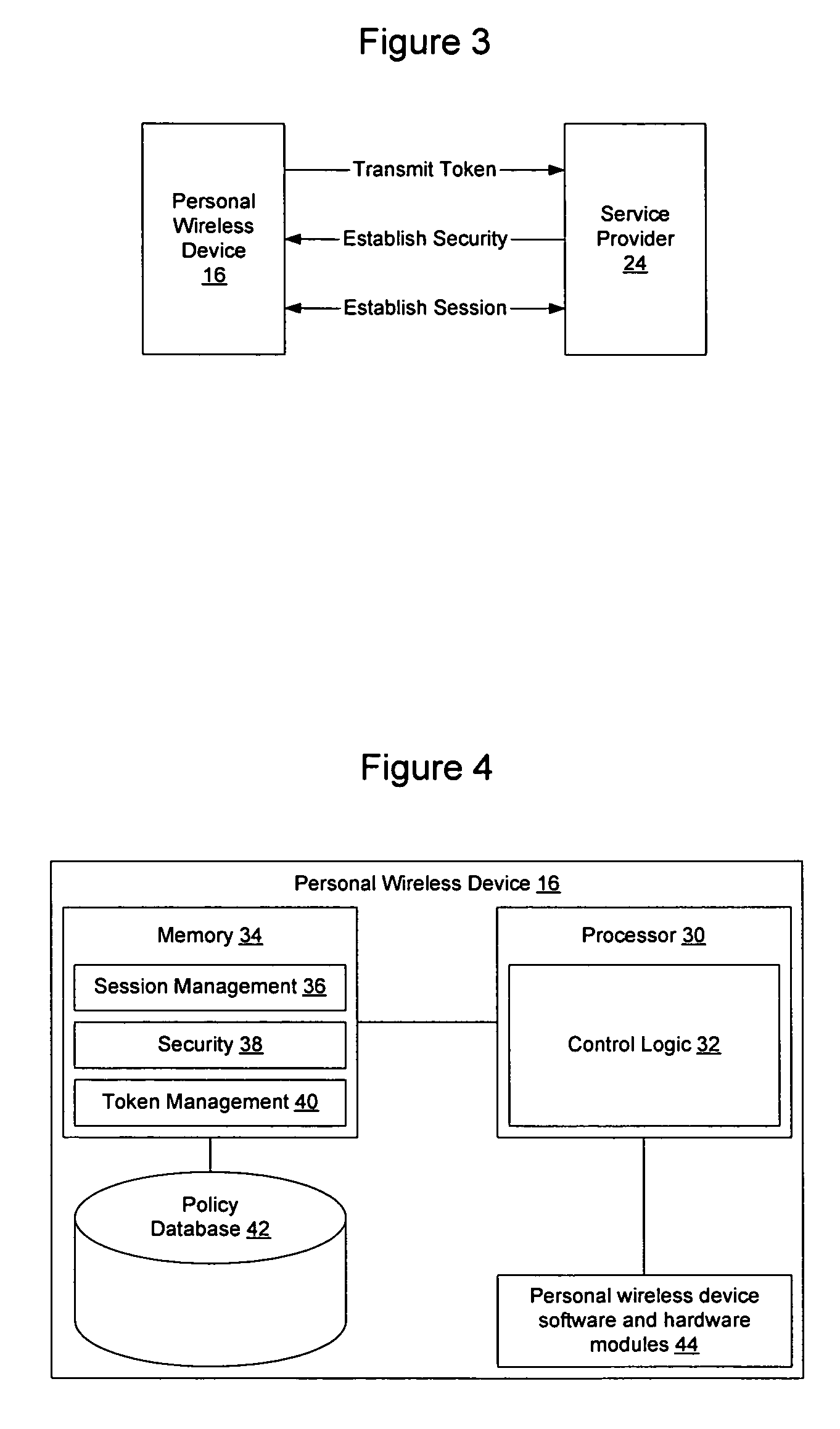
Method and apparatus for establishing a federated identity using a personal wireless device
ActiveUS8522039B2User identity/authority verificationDigital data authenticationCryptographic protocolBluetooth
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
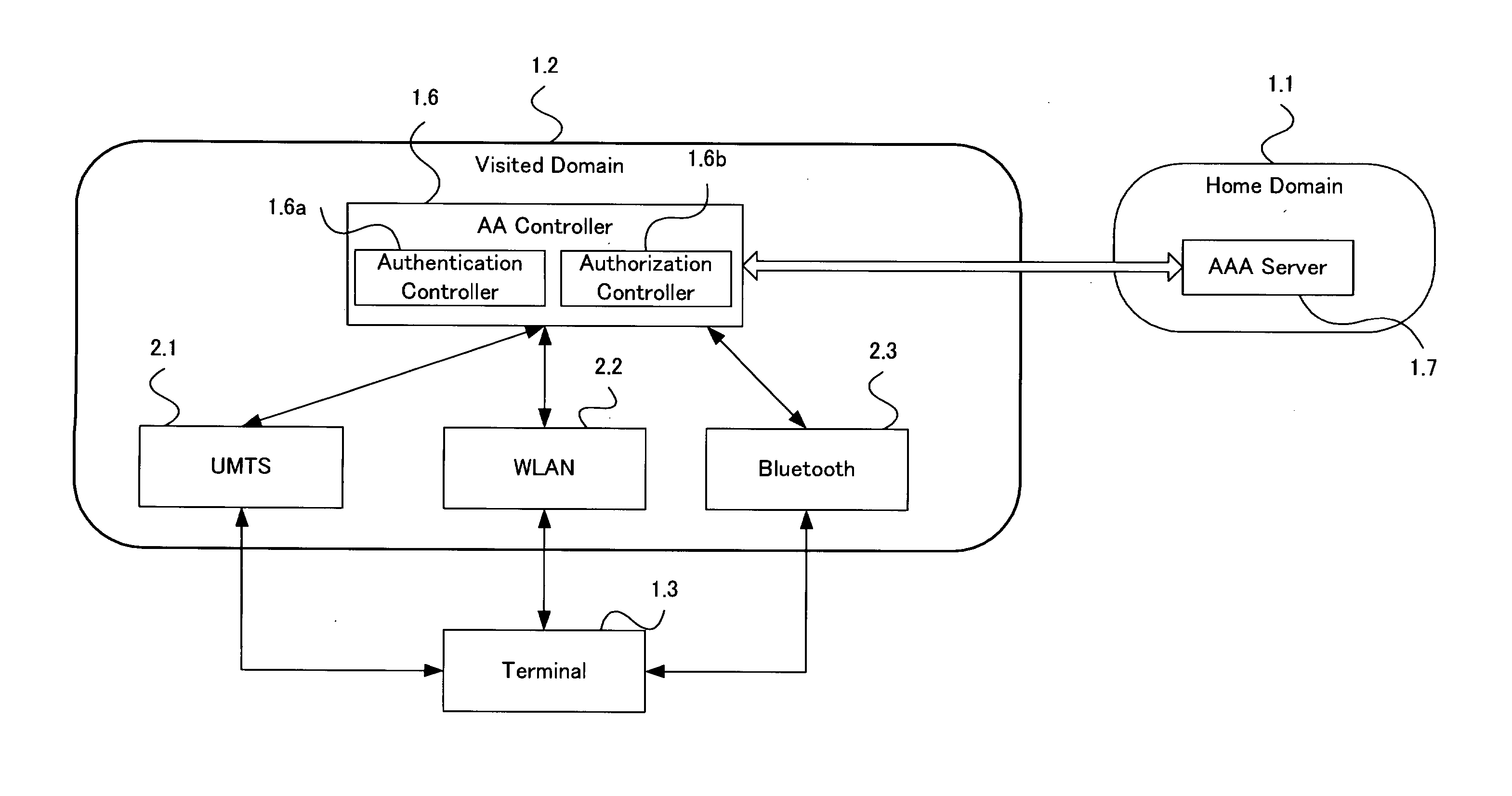
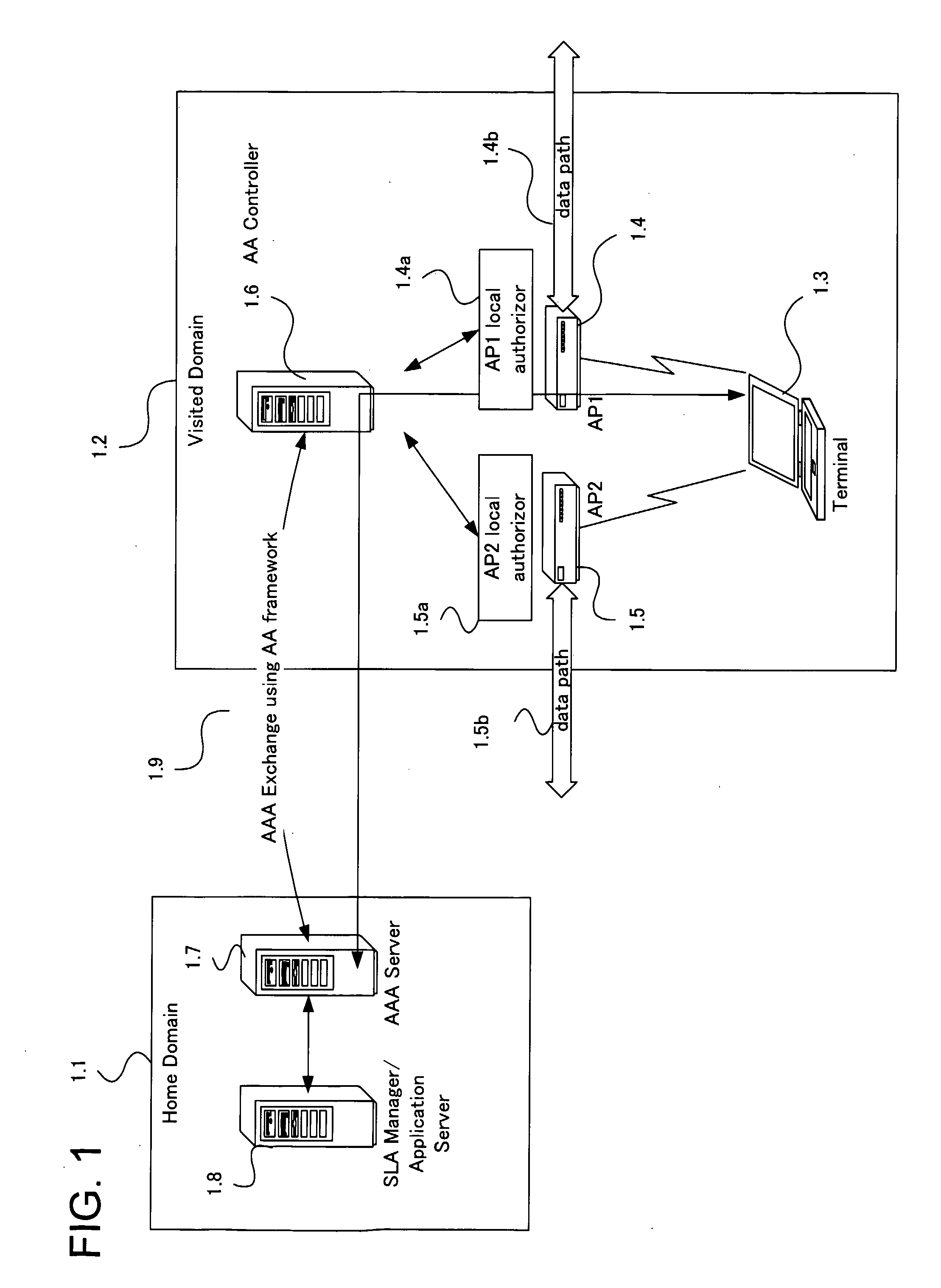
System And Method For Managing User Authentication And Service Authorization To Achieve Single-Sign-On To Access Multiple Network Interfaces
InactiveUS20080072301A1Timely controlShorten the timeDigital data processing detailsUser identity/authority verificationUser authenticationNetwork management
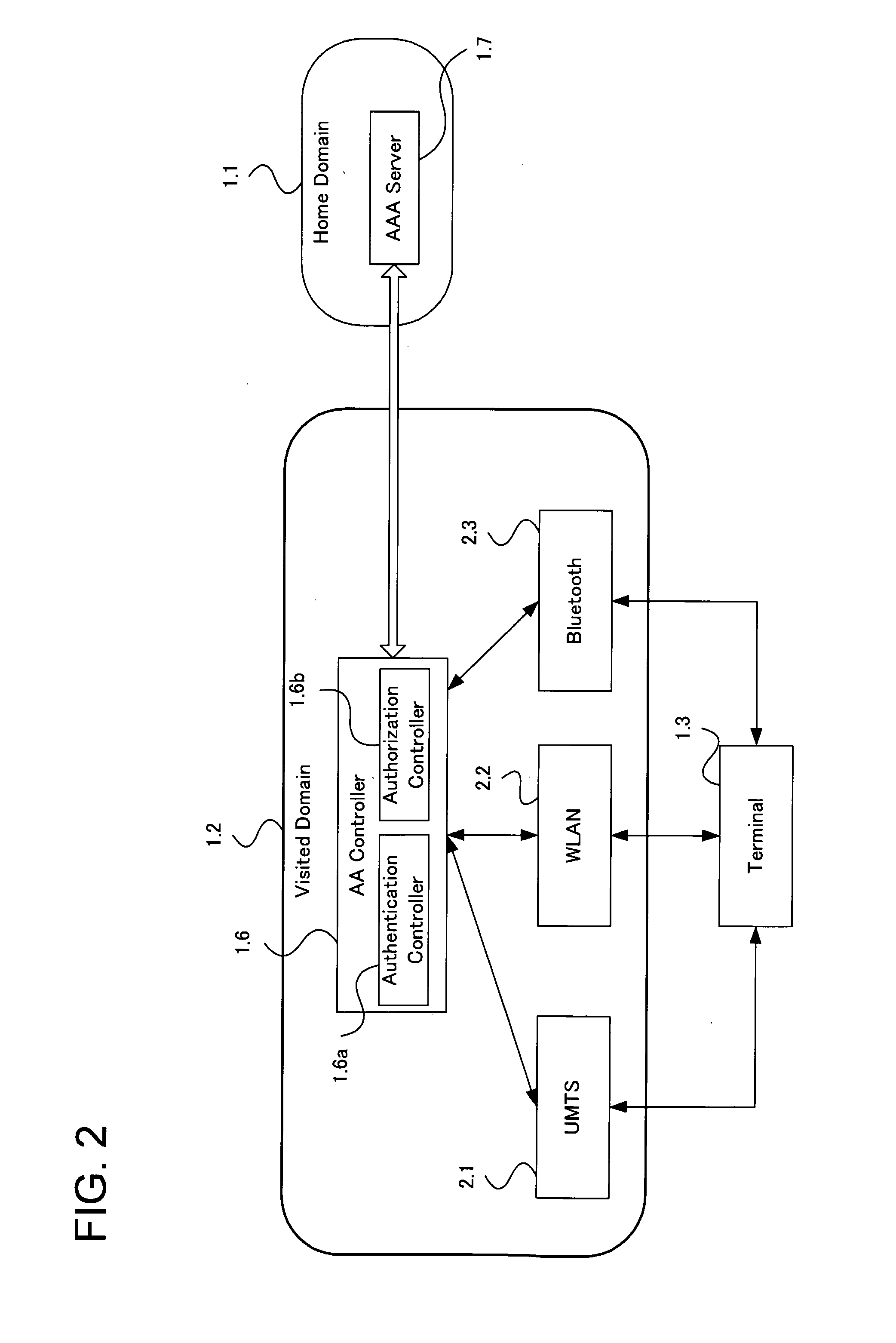
A single-sign-on to access multiple networks residing at multiple domains is disclosed. In particular the single-sign-on features refers to the authentication and the authorization process carried out among the different network administration domains so that the terminal using the end service need not explicitly initiate the authentication process each time it accesses a new service. This invention's single-sign-on feature can be extended for usage in a federated domain environment and non-federated domain environment. The non-federated domains are able to form an indirect federation chain through other domains in order to utilize this invention. Therefore discovery of intermediate domains to form a federation chain is also covered. The management of user credentials to allow a Visited Domain to perform authentication is also covered in this invention.
Owner:PANASONIC CORP
Methods and systems for single sign on with dynamic authentication levels
ActiveUS20090292927A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyApplication software
Method and systems for single sign on with dynamic authentication levels is described. The method include receiving a data request for access to a second application, where the user is already authenticated to the first application at a first authentication level. Application information about the authentication level necessary to access the second application is retrieved. In response to a request, the user provides the further authentication data for accessing the second application. The type of the further authentication data required is based on the first authentication level and the minimum authentication level necessary to access the second application. The user is then authenticated to the second application at the minimum authentication level necessary to access the second application.
Owner:HSBC TECH & SERVICES (USA) INC
Authentication method and apparatus utilizing proof-of-authentication module
ActiveUS7562221B2Unauthorised/fraudulent call preventionDigital data processing detailsComputer hardwareValidation methods
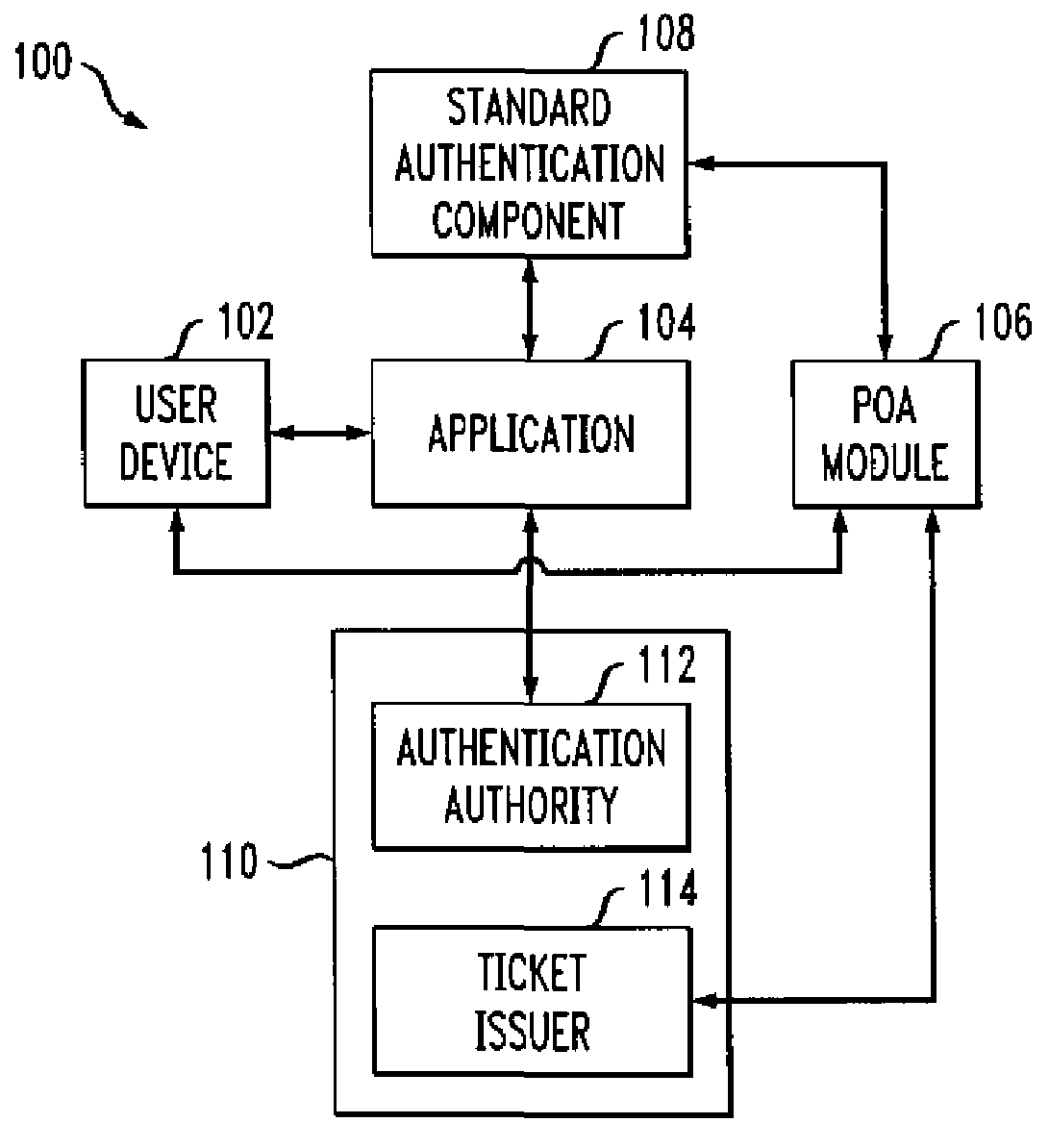
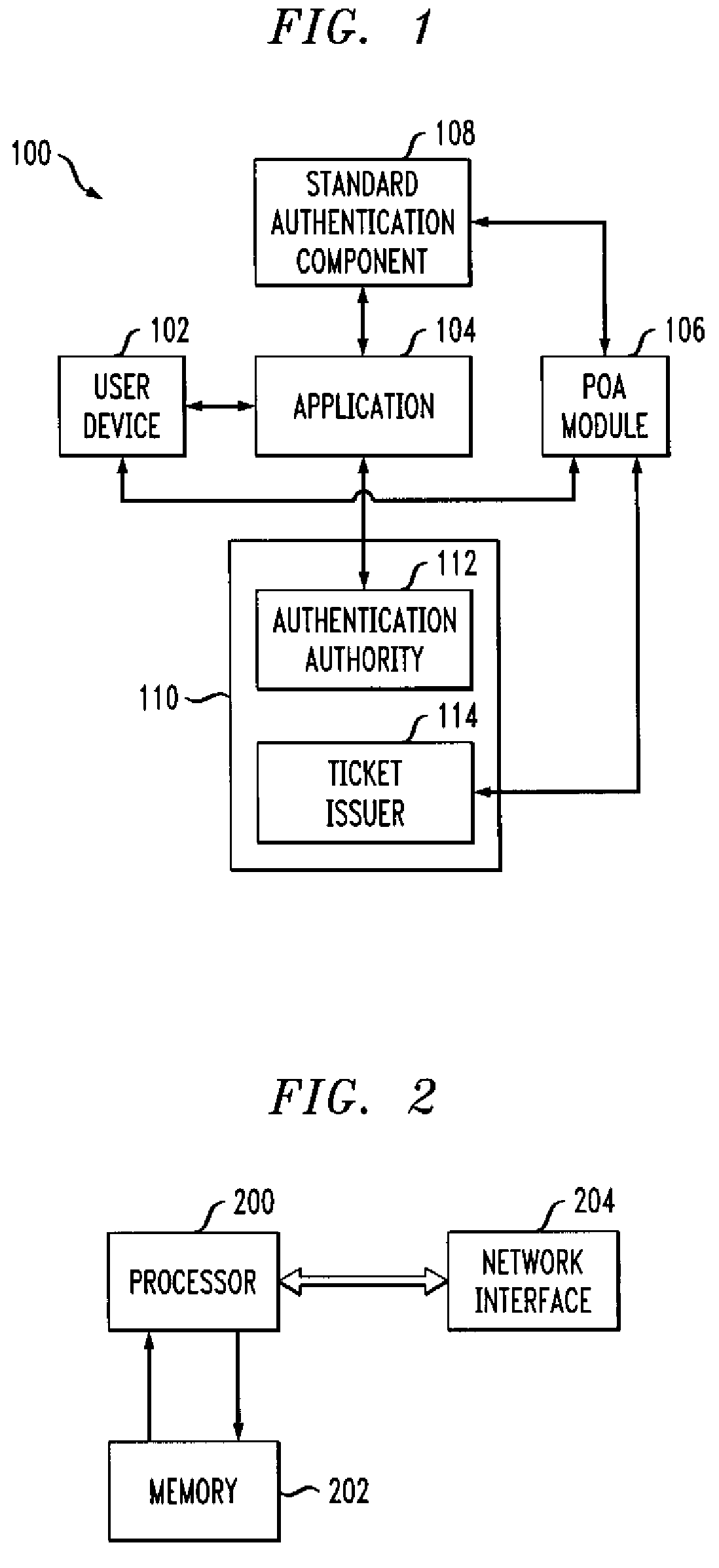
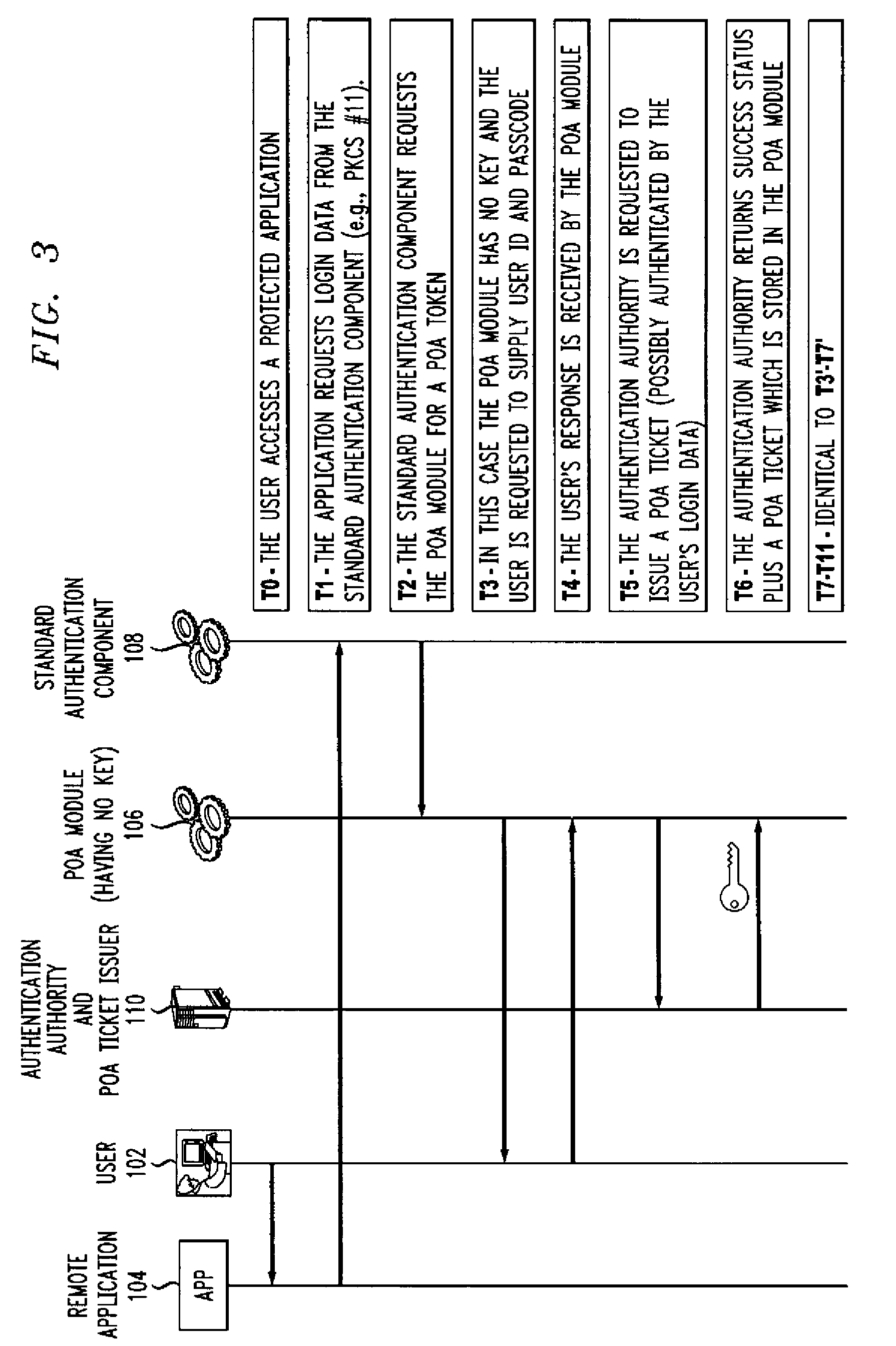
A single sign-on technique allows multiple accesses to one or more applications or other resources using a proof-of-authentication module operating in conjunction with a standard authentication component. The application or other resource issues an authentication information request to the standard authentication component responsive to an access request from the user. The application or other resource receives, responsive to the authentication information request, a proof-of-authentication value from the standard authentication component, and authenticates the user based on the proof-of-authentication value. The standard authentication component interacts with the proof-of-authentication module to obtain the proof-of-authentication value. The proof-of-authentication module is configured to generate multiple proof-of-authentication values for authentication of respective access requests of the user.
Owner:EMC IP HLDG CO LLC
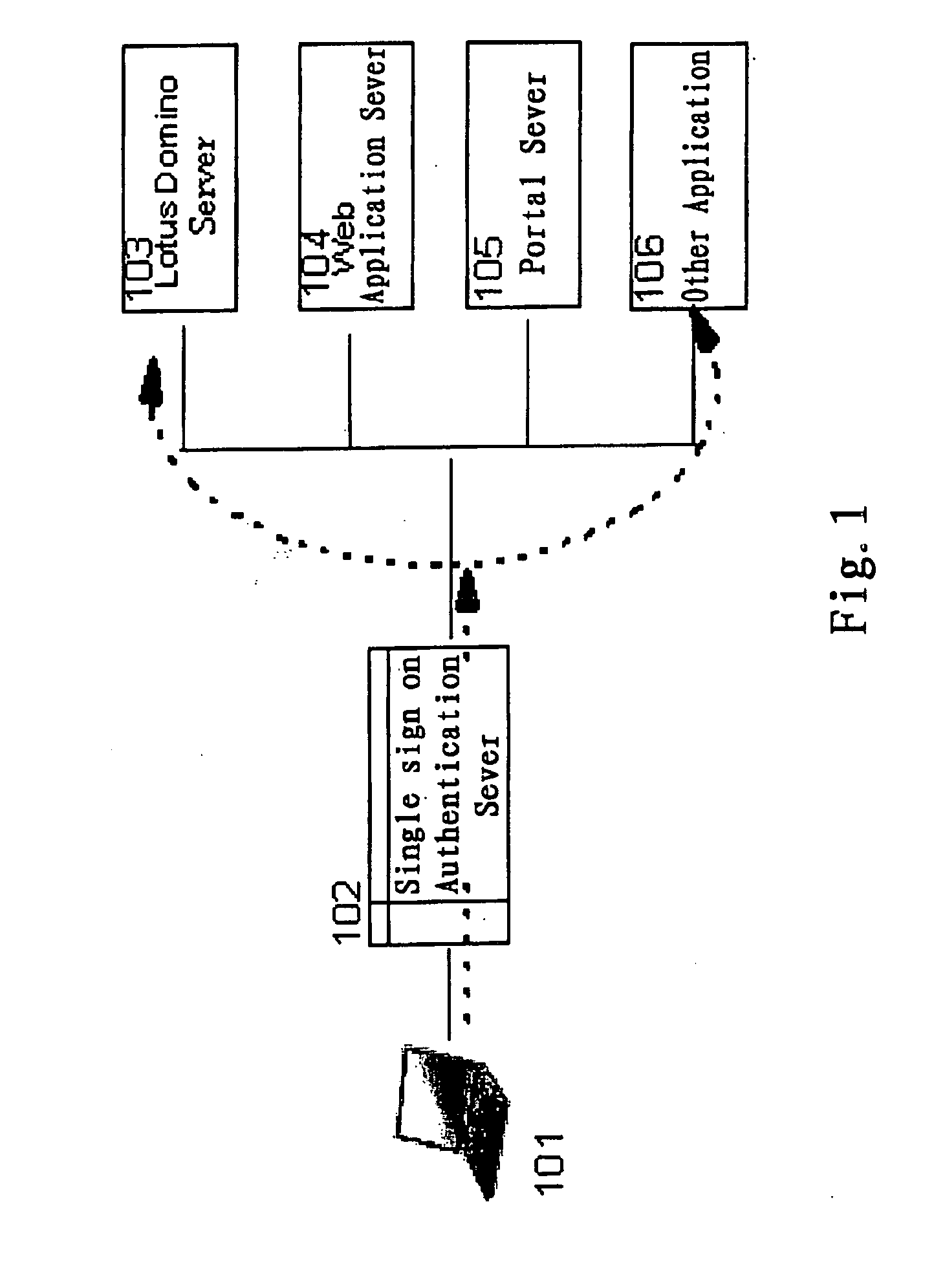
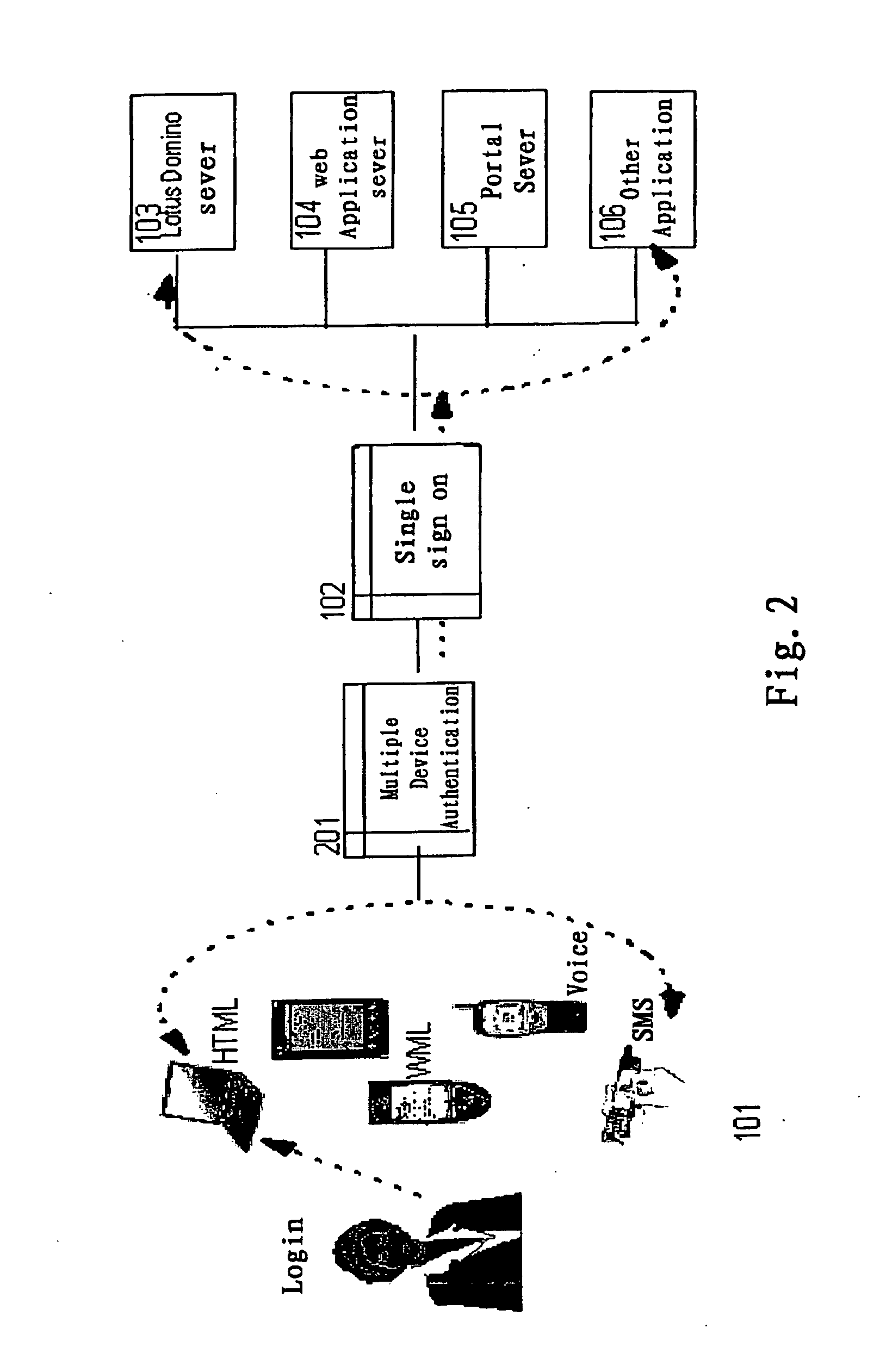
Supporting auto-logon for multiple devices
InactiveUS20050091539A1Save effortSaving user 's effortDigital data processing detailsUser identity/authority verificationUser deviceRegistered user
Enables multiple devices of a same user to logon automatically. An example of a method includes: registering the user and the user's multiple user devices with a Multiple Device Authentication (MDA) apparatus; authenticating at least one of the user's registered devices by the MDA apparatus and selecting the authenticated device as a master device; selecting one or more slave devices from the registered user devices; adding the selected master device and one or more selected slave devices to an active device table; if a user device accessing the MDA apparatus is in the active device table, causing the user device logon directly and automatically without first authenticating the user device. Operation of authentication is needed only once to enable user's multiple devices to logon the server automatically and conveniently. Seamless switch between different devices can be implemented, resulting in improved single-sign-on solution over the prior art.
Owner:LENOVO (SINGAPORE) PTE LTD
Method and system for a runtime user account creation operation within a single-sign-on process in a federated computing environment
ActiveUS20060236382A1Key distribution for secure communicationDigital data processing detailsComputer networkService provision
A method, system, apparatus, and computer program product are presented to support computing systems of different enterprises that interact within a federated computing environment. Federated single-sign-on operations can be initiated at the computing systems of federation partners on behalf of a user even though the user has not established a user account at a federation partner prior to the initiation of the single-sign-on operation. For example, an identity provider can initiate a single-sign-on operation at a service provider while attempting to obtain access to a controlled resource on behalf of a user. When the service provider recognizes that it does not have a linked user account for the user that allows for a single-sign-on operation with the identity provider, the service provider creates a local user account. The service provider can also pull user attributes from the identity provider as necessary to perform the user account creation operation.
Owner:IBM CORP
Method and system for identity provider migration using federated single-sign-on operation
ActiveUS20080021997A1Digital data processing detailsMultiple digital computer combinationsInternet privacyIdentity provider
A method is presented for performing an identity provider migration operation with respect to a user within a federated computational environment, wherein the user has a first user account at a first identity provider, a second user account at a second identity provider, and a third user account at a service provider. A request to access a resource is received by the service provider, after which a federated single-sign-on operation for the user is performed between the service provider and the first identity provider. Prior to sending a response to the request to access the protected resource, information in the third user account is modified to indicate that the service provider relies upon the second identity provider to authenticate the user on behalf of the service provider rather than the first identity provider. A response for the request to access the resource is then returned by the service provider.
Owner:SERVICENOW INC
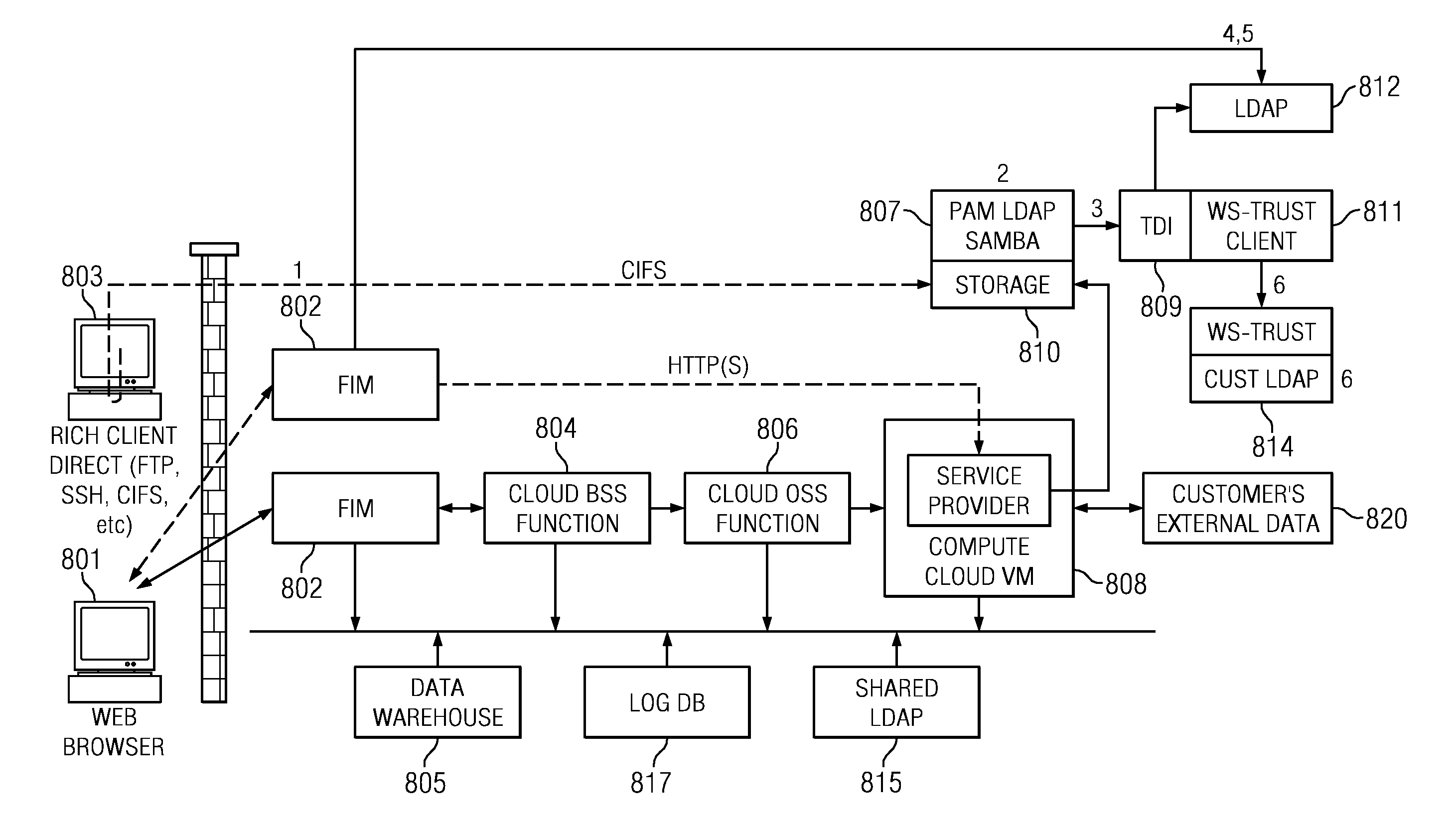
Cross-protocol federated single sign-on (F-SSO) for cloud enablement
ActiveUS20120011578A1Simple on-boarding processRetain controlMultiple keys/algorithms usagePublic key for secure communicationCloud providerCloud resources
A method to enable access to resources hosted in a compute cloud begins upon receiving a registration request to initiate a user's registration to use resources hosted in the compute cloud. During a registration process initiated by receipt of the registration request, a federated single sign-on (F-SSO) request is received. The F-SSO request includes an assertion (e.g., an HTTP-based SAML assertion) having authentication data (e.g., an SSH public key, a CIFS username, etc.) for use to enable direct user access to a resource hosted in the compute cloud. Upon validation of the assertion, the authentication data is deployed within the cloud to enable direct user access to the compute cloud resource using the authentication data. In this manner, the cloud provider provides authentication, single sign-on and lifecycle management for the user, despite the “air gap” between the HTTP protocol used for F-SSO and the non-HTTP protocol used for the user's direct access to the cloud resource.
Owner:SERVICENOW INC
Method and apparatus for handling user identities under single sign-on services
ActiveUS20050154913A1Digital data processing detailsUser identity/authority verificationService provisionWorld Wide Web
Owner:TELEFON AB LM ERICSSON (PUBL)
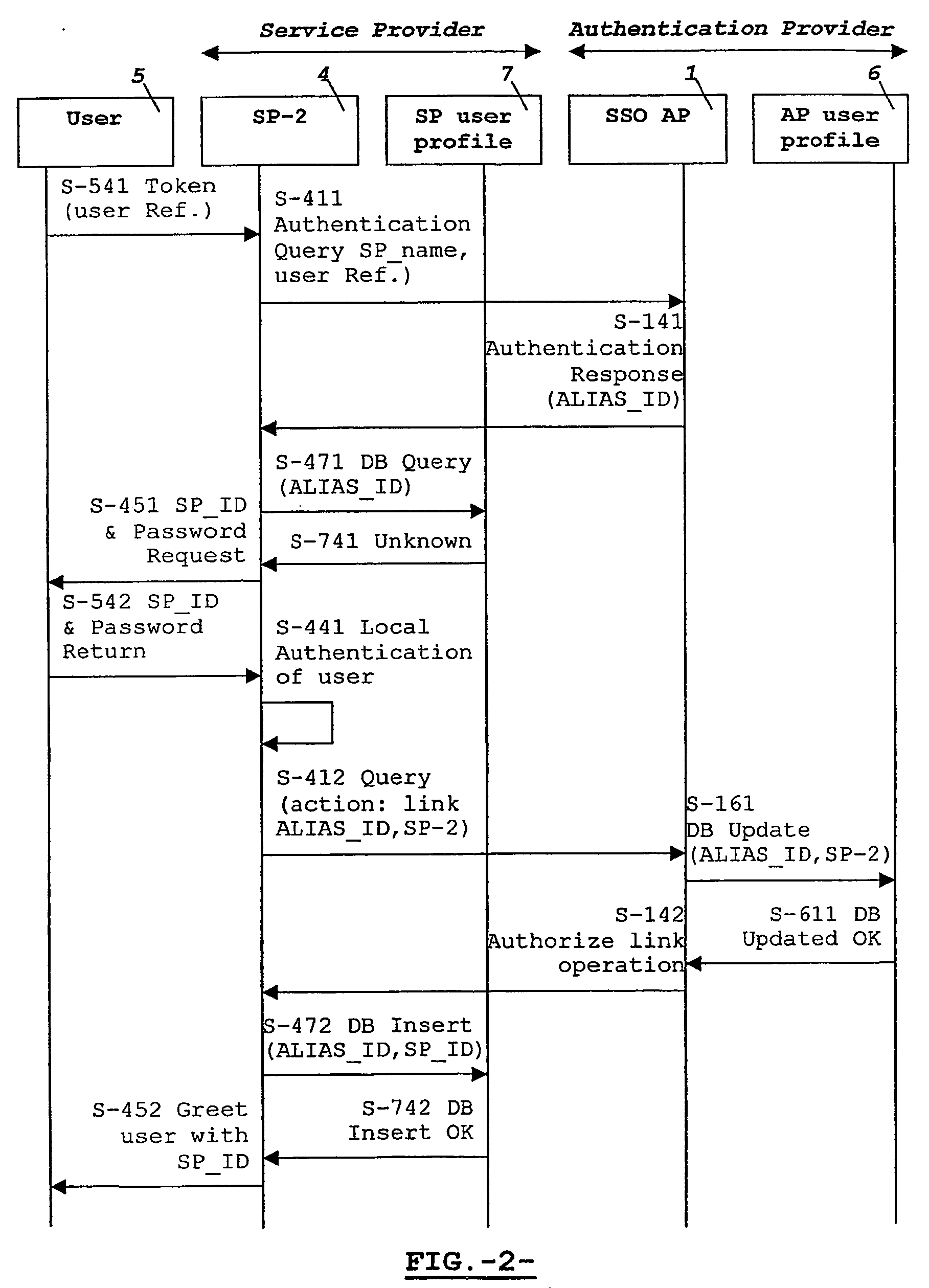
System and method for single-sign-on access to a resource via a portal server
A single-sign-on adapter (SSO Adapter) implementing one or more authentication mechanisms that may be used by Portal middleware on behalf of a portal user. A user seeking access to a resource server through a portal server performs a single sign-on with the portal server at the beginning of a session. When requests a resource from resource server that requires authentication, the authentication is handled by the portal server without requiring an authentication response from the user. The portal server may use stored user credentials, a token-based shared authentication service, or proxy authentication in order to gain access to the resource server on behalf of the portal user.
Owner:SUN MICROSYSTEMS INC
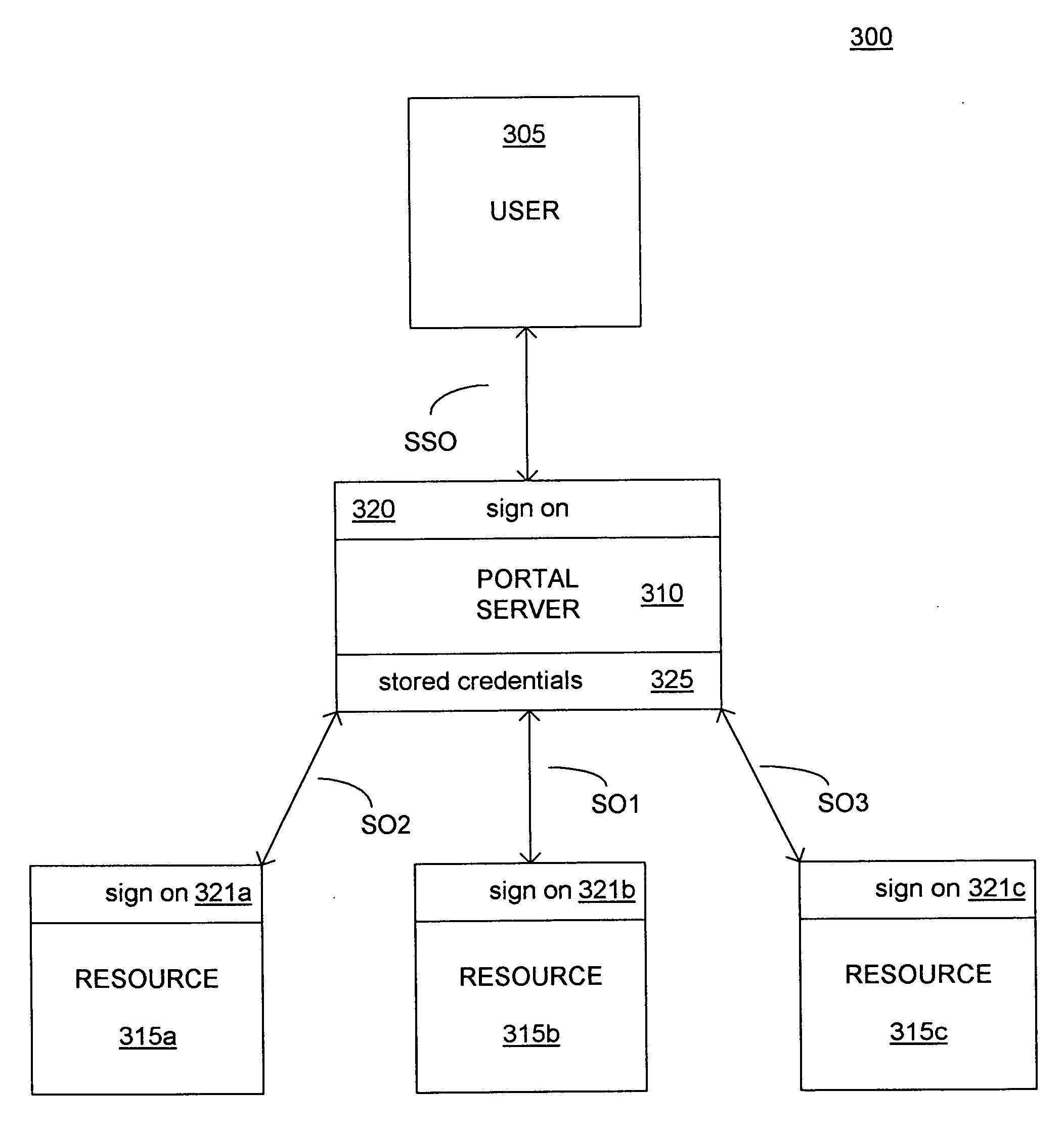
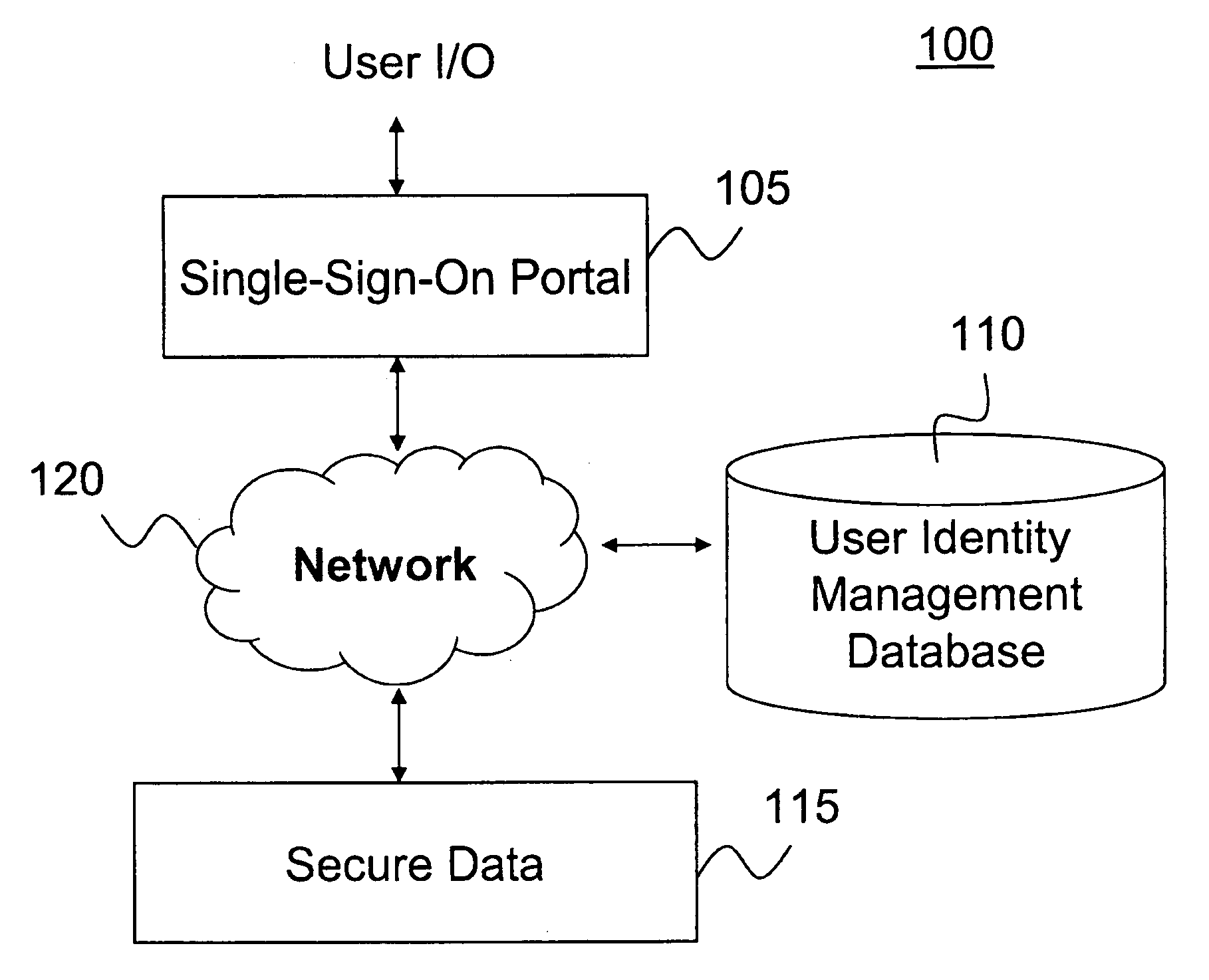
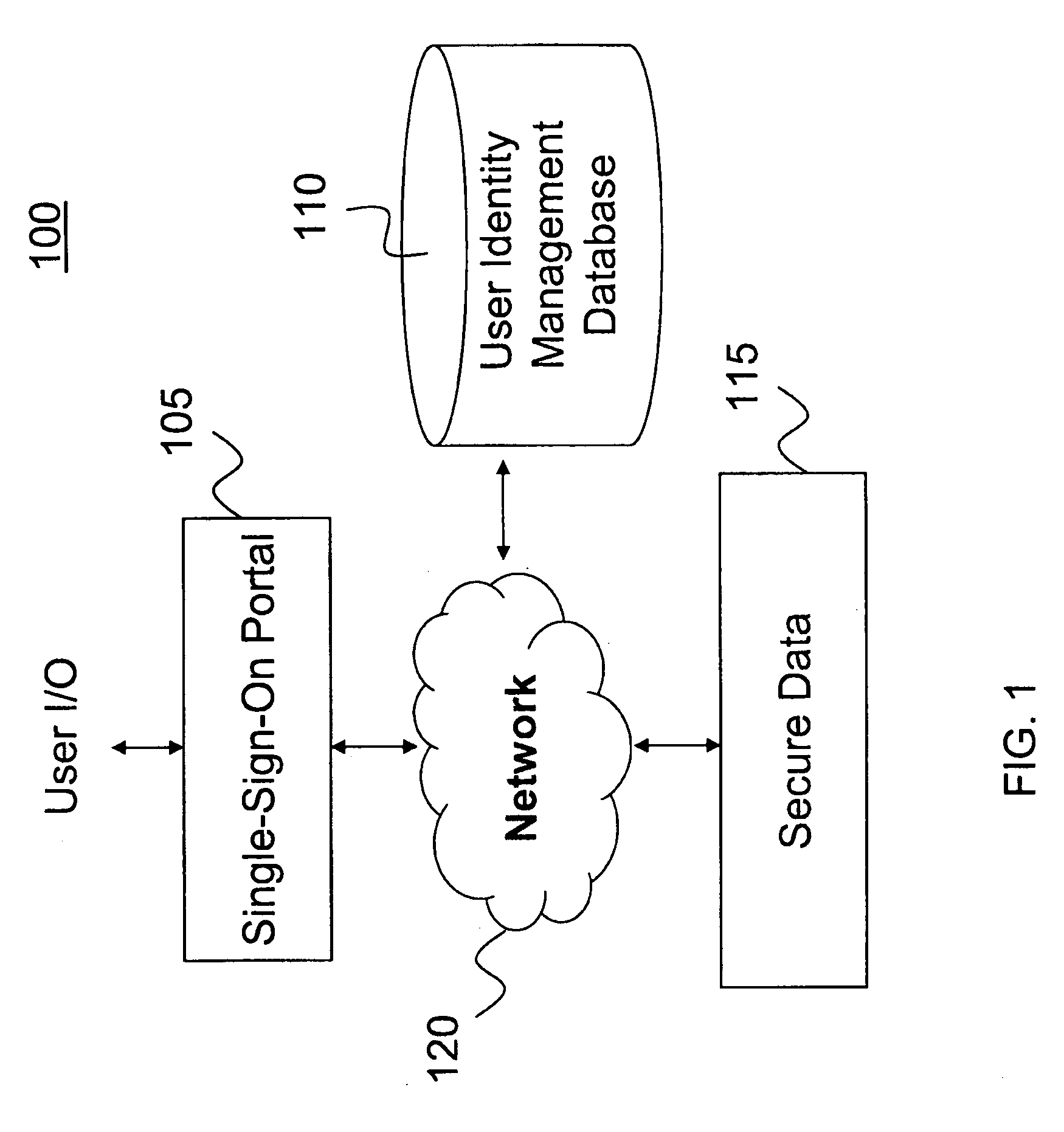
Secure single-sign-on portal system
ActiveUS20090172795A1Reduce decreaseDigital data processing detailsUser identity/authority verificationPasswordThe Internet
A computer-implemented portal system facilitates access to secure data and multiple secure-access internet sites. The system authenticates a user based on a single-sign-on identifier (ID) and password. The system stores user authentication information for the secure-access internet sites so that once the user is authenticated, the system can automatically authenticate the user to the sites, thus allowing the user to access multiple secure sites after a single manual authentication.
Owner:DELUXE CORPORATION
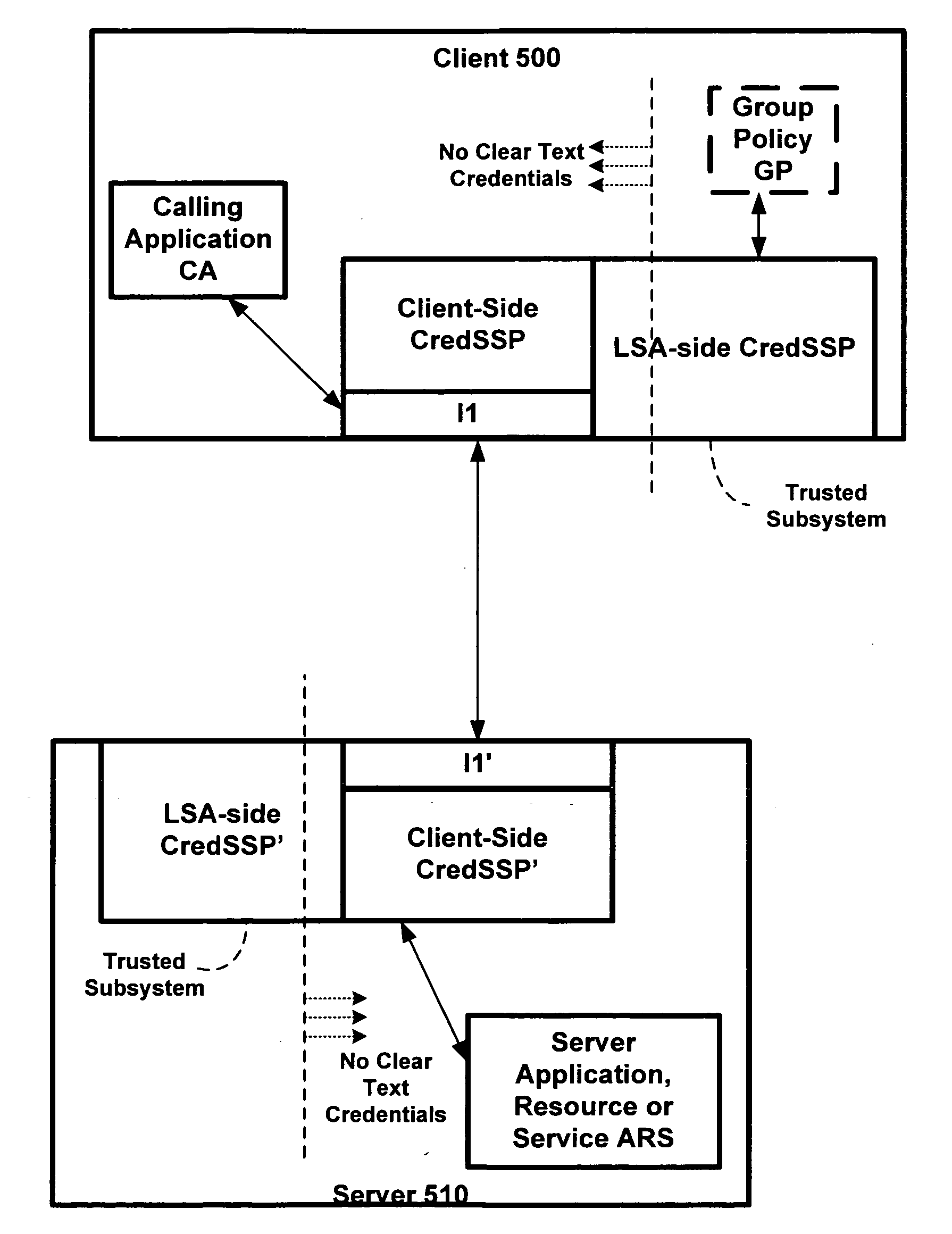
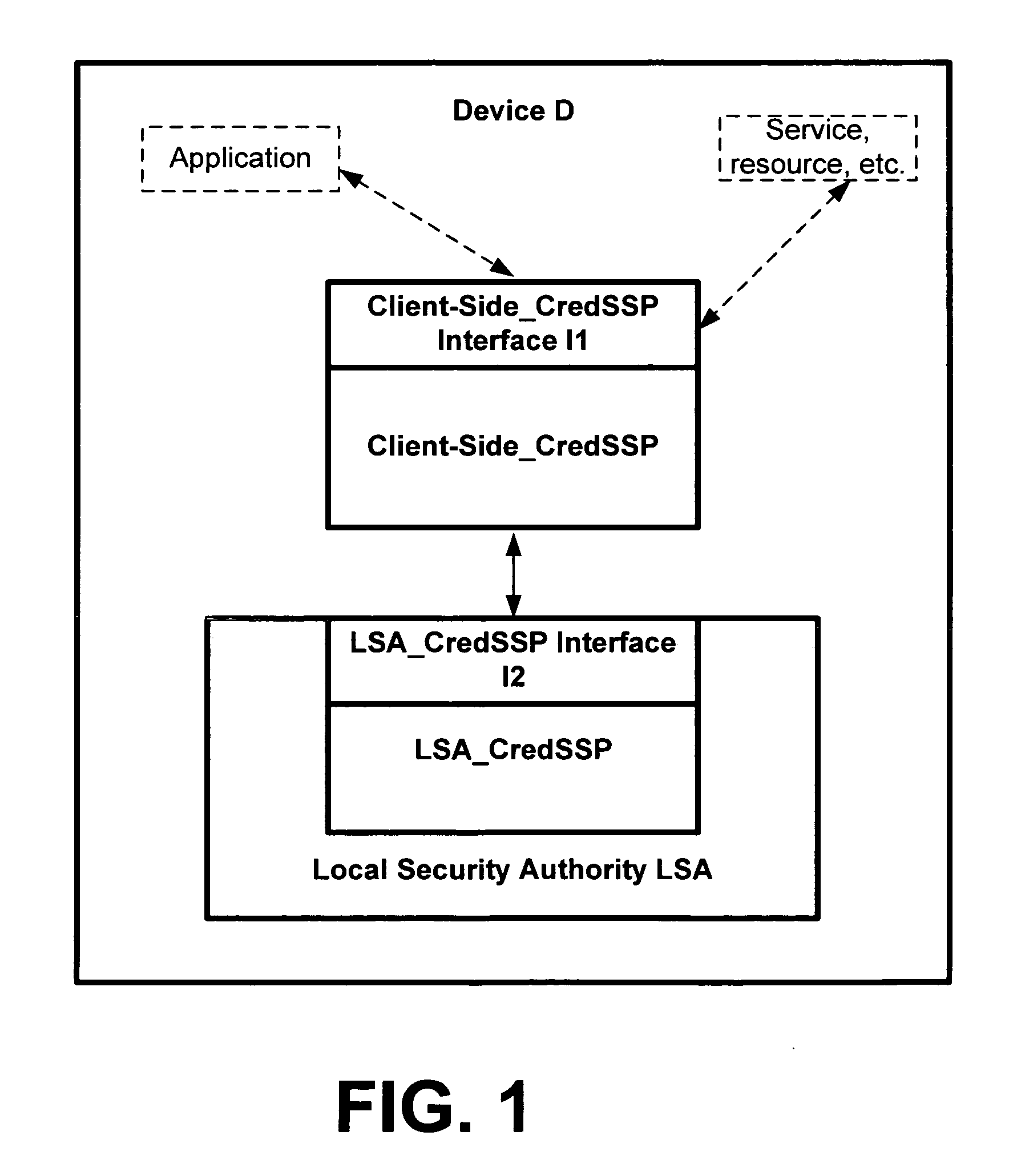
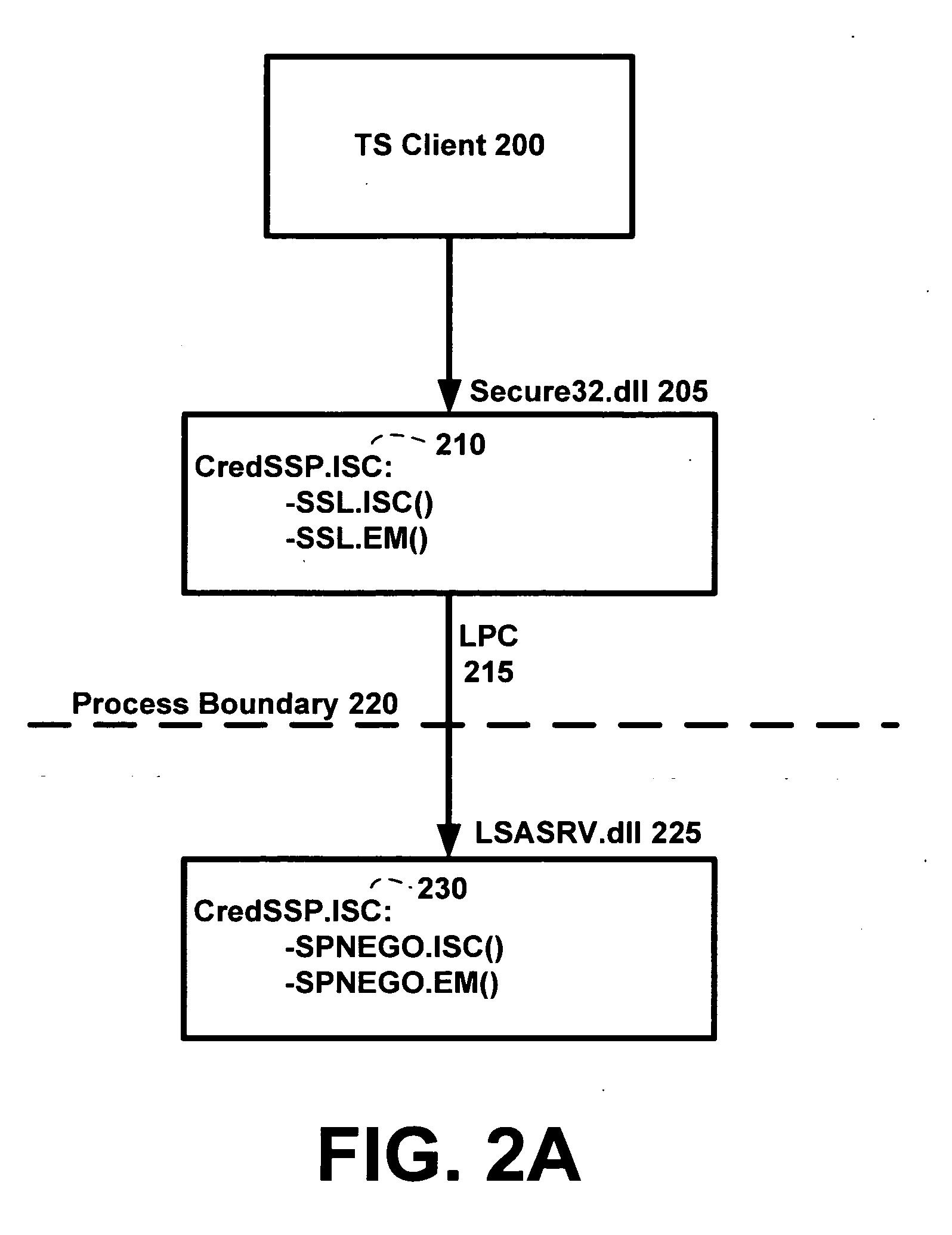
Policy driven, credential delegation for single sign on and secure access to network resources
ActiveUS20070277231A1Wide rangeMemory loss protectionError detection/correctionNetwork conditionsTrust level
A credential security support provider (Cred SSP) is provided that enables any application to securely delegate a user's credentials from the client, via client side Security Support Provider (SSP) software, to a target server, via server side SSP software in a networked computing environment. The Cred SSP of the invention provides a secure solution that is based in part upon a set of policies, including a default policy that is secure against a broad range of attacks, which are used to control and restrict the delegation of user credentials from a client to a server. The policies can be for any type of user credentials and the different policies are designed to mitigate a broad range of attacks so that appropriate delegation can occur for given delegation circumstances, network conditions, trust levels, etc. Additionally, only a trusted subsystem, e.g., a trusted subsystem of the Local Security Authority (LSA), has access to the clear text credentials such that neither the calling application of the Cred SSP APIs on the server side nor the calling application of the Cred SSP APIs on the client side have access to clear text credentials.
Owner:MICROSOFT TECH LICENSING LLC
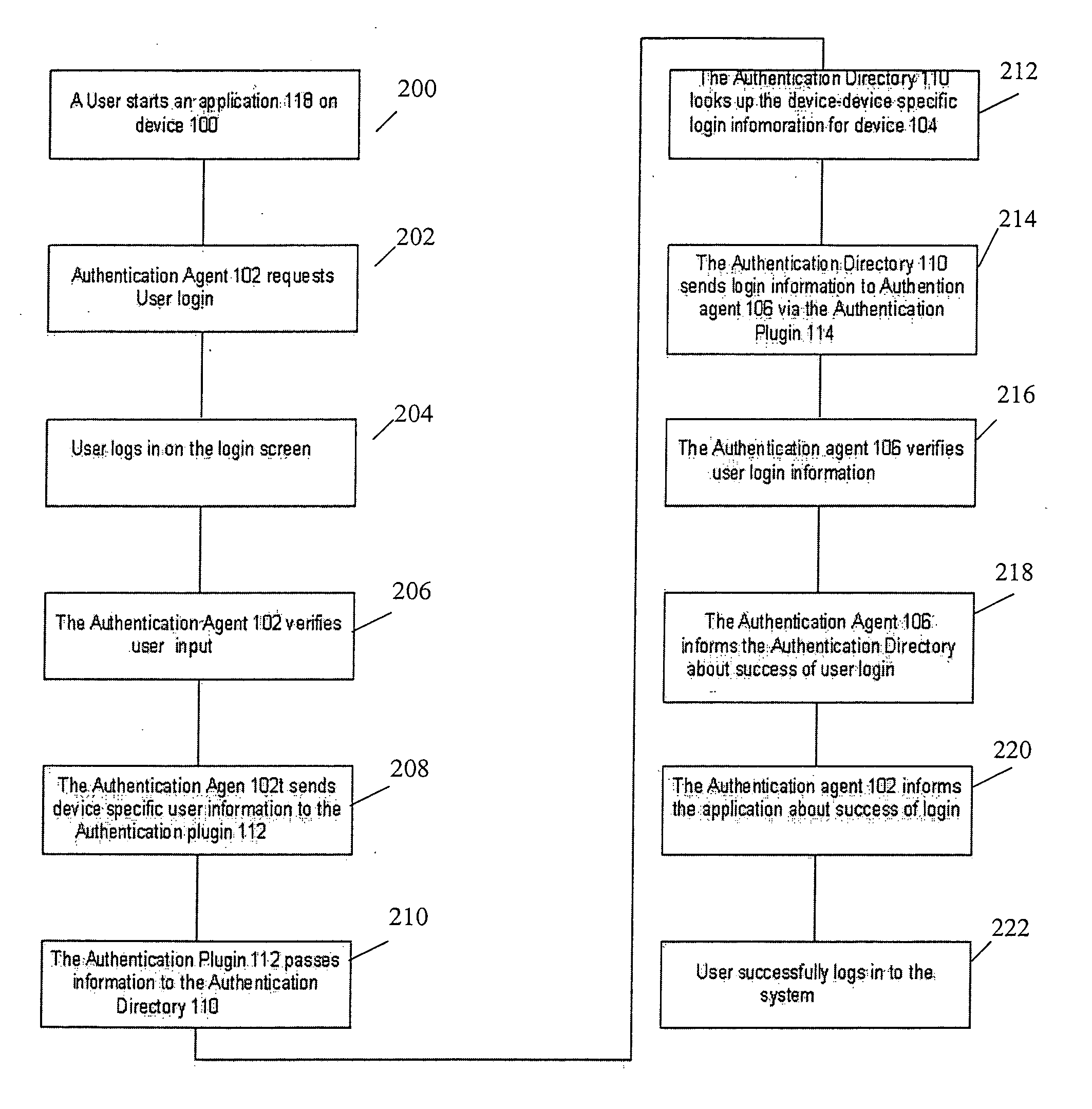
Method and system for single sign-on in a network
InactiveUS20060185004A1Easy to set upDigital data processing detailsMultiple digital computer combinationsInternet privacyAuthentication system
A user identity authentication system in a network is implemented on a device or multiple devices in the network. The authentication system employs a map that translates device-specific user IDs to system-wide user IDs and vice versa. A user is authenticated on a device with a device-specific authentication method. Once a user is authenticated on a specific device, a device-specific user ID is translated into a system-wide user ID. This system-wide user ID is further translated into other device-specific user IDs such that other devices can authenticate the user based on the device-specific user IDs. Further, if a device is not capable of authenticating a user, it can delegate authentication to another device or a proxy.
Owner:SAMSUNG ELECTRONICS CO LTD
Mobile application, single sign-on management
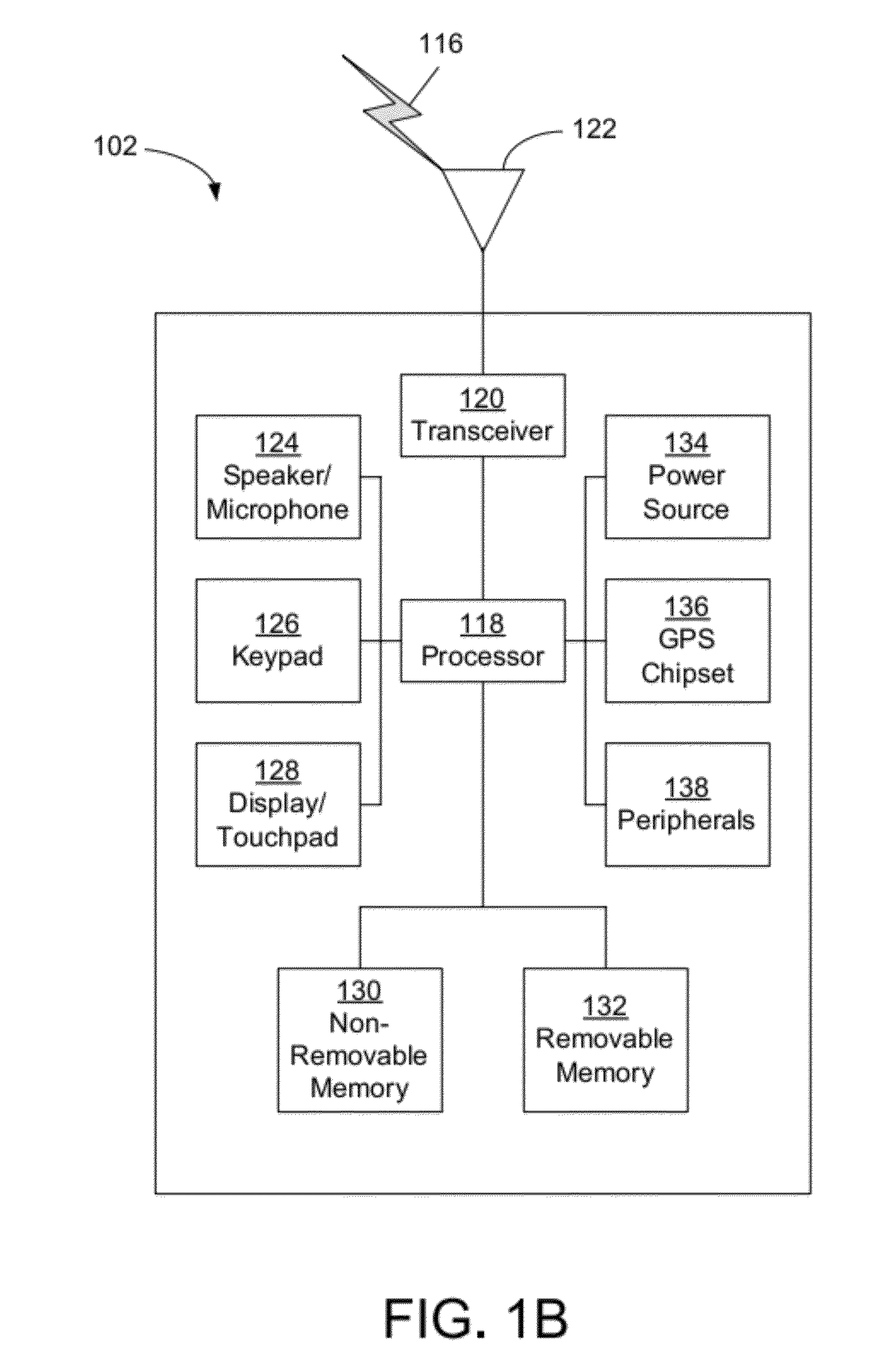
InactiveUS20130086669A1Digital data processing detailsMultiple digital computer combinationsComputer networkApplication software
Techniques for managing single sign-on are provided. in some examples, single sign-on functionality may be provided for use on mobile devices by utilizing mobile applications, cloud applications, and / or other web-based applications. For example, a mobile application or mobile web browser may request to authenticate with or access one or more service providers. Authentication credentials may be requested from a user of the mobile device to facilitate such authentication and / or access. Based at least in part on a successful log-in, access to server resources from other applications on the same mobile device may be provided without successive or repetitive credential requests to the user.
Owner:ORACLE INT CORP
Single sign-on in mixed HTTP and sip environments
InactiveUS20110138453A1Digital data processing detailsUser identity/authority verificationSession Initiation ProtocolWeb service
In a first embodiment of the present invention, a method for providing single sign-on in a network having a HyperText Transfer Protocol (HTTP) portion and a Session Initiation Protocol (SIP) portion is provided, the method performed at a gateway and comprising: receiving an HTTP request for an assertion from a requester over the HTTP portion; generating a SIP request using the request for assertion; sending the SIP request to a SIP registrar over the SIP portion; receiving a SIP response including information regarding an assertion from the SIP registrar; and sending the information regarding the assertion in an HTTP response to the requester, such that the requester can use the information regarding the assertion in authenticating the requester to a web server.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for providing single sign-on service
InactiveUS20090119763A1Possible to useDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
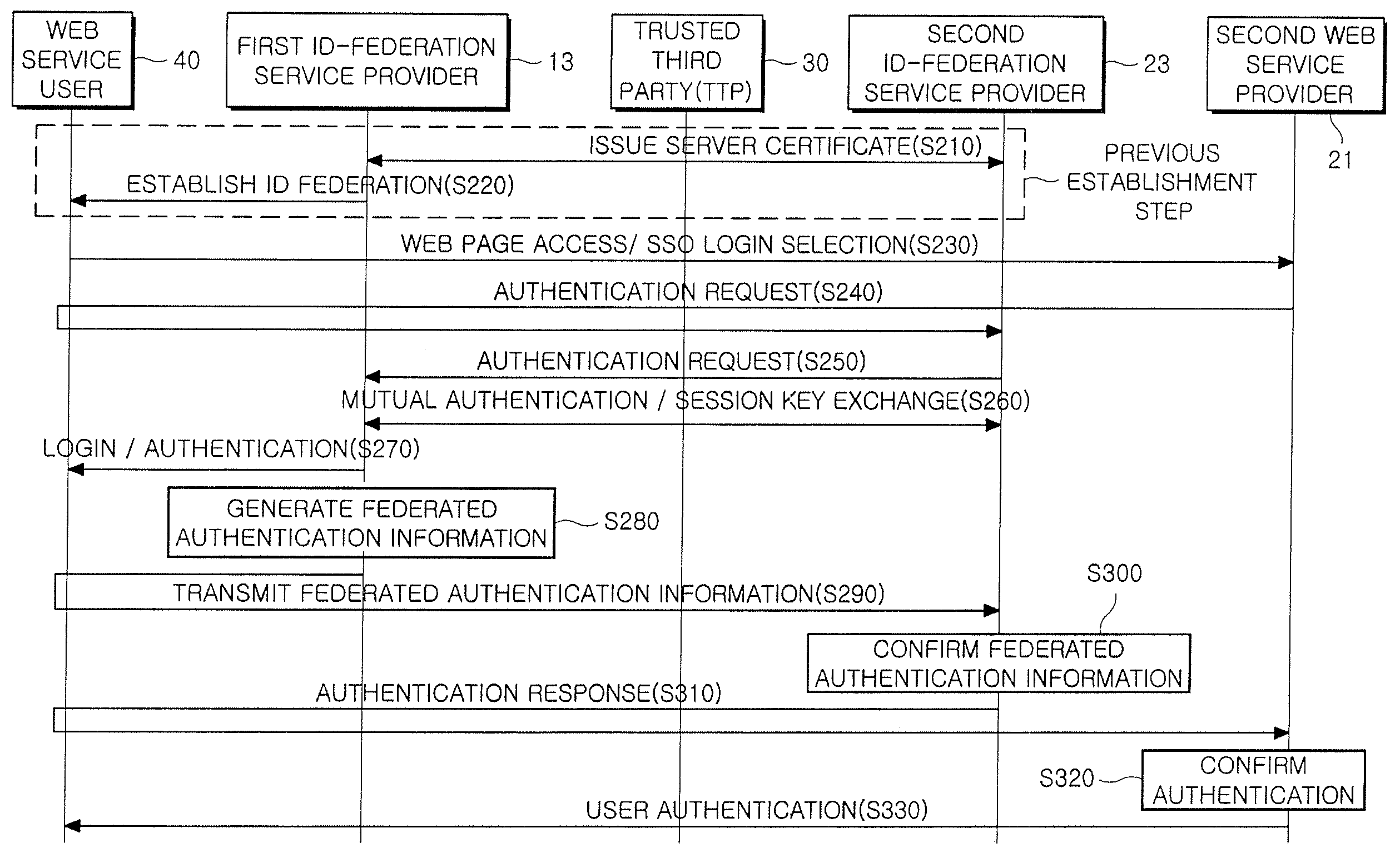
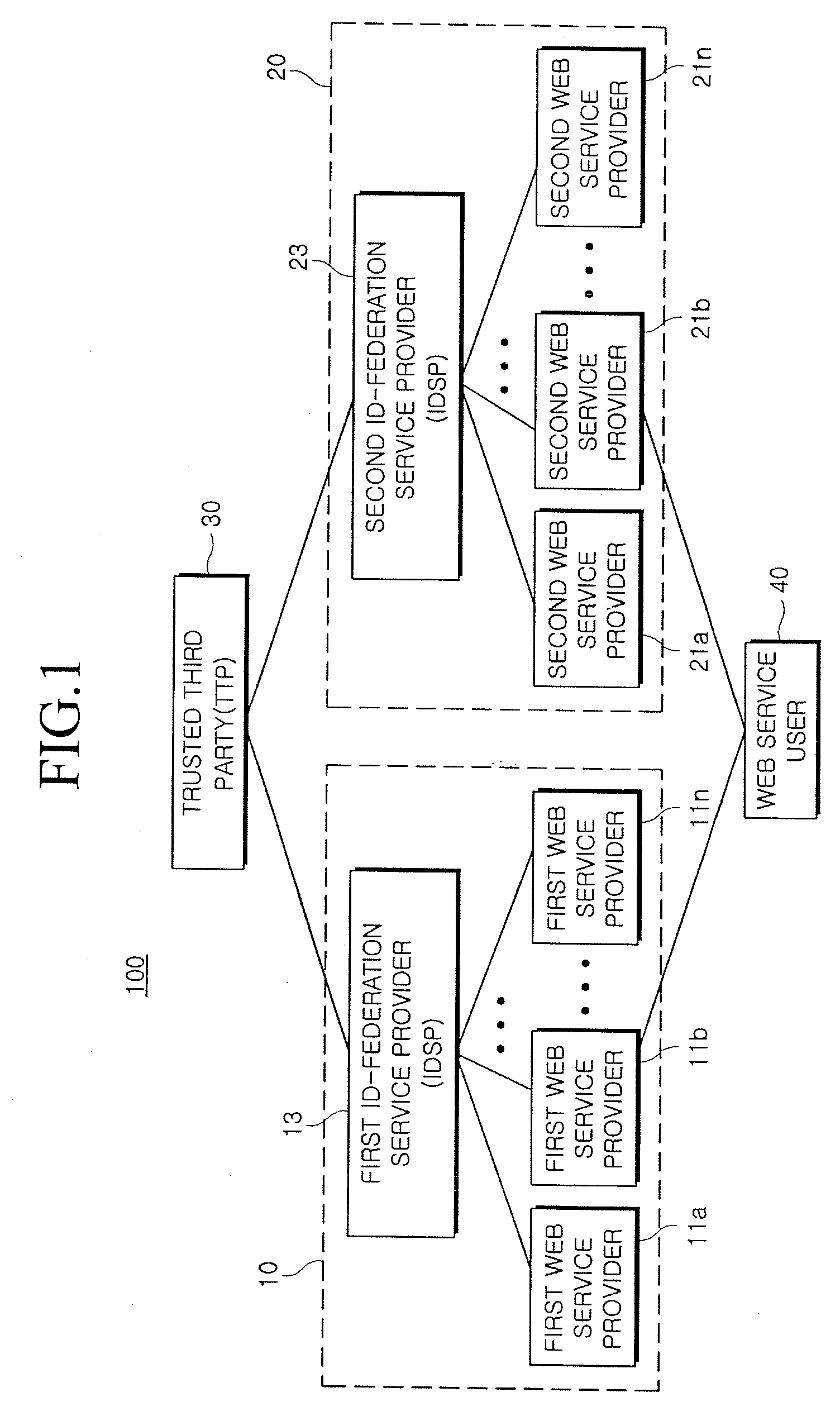
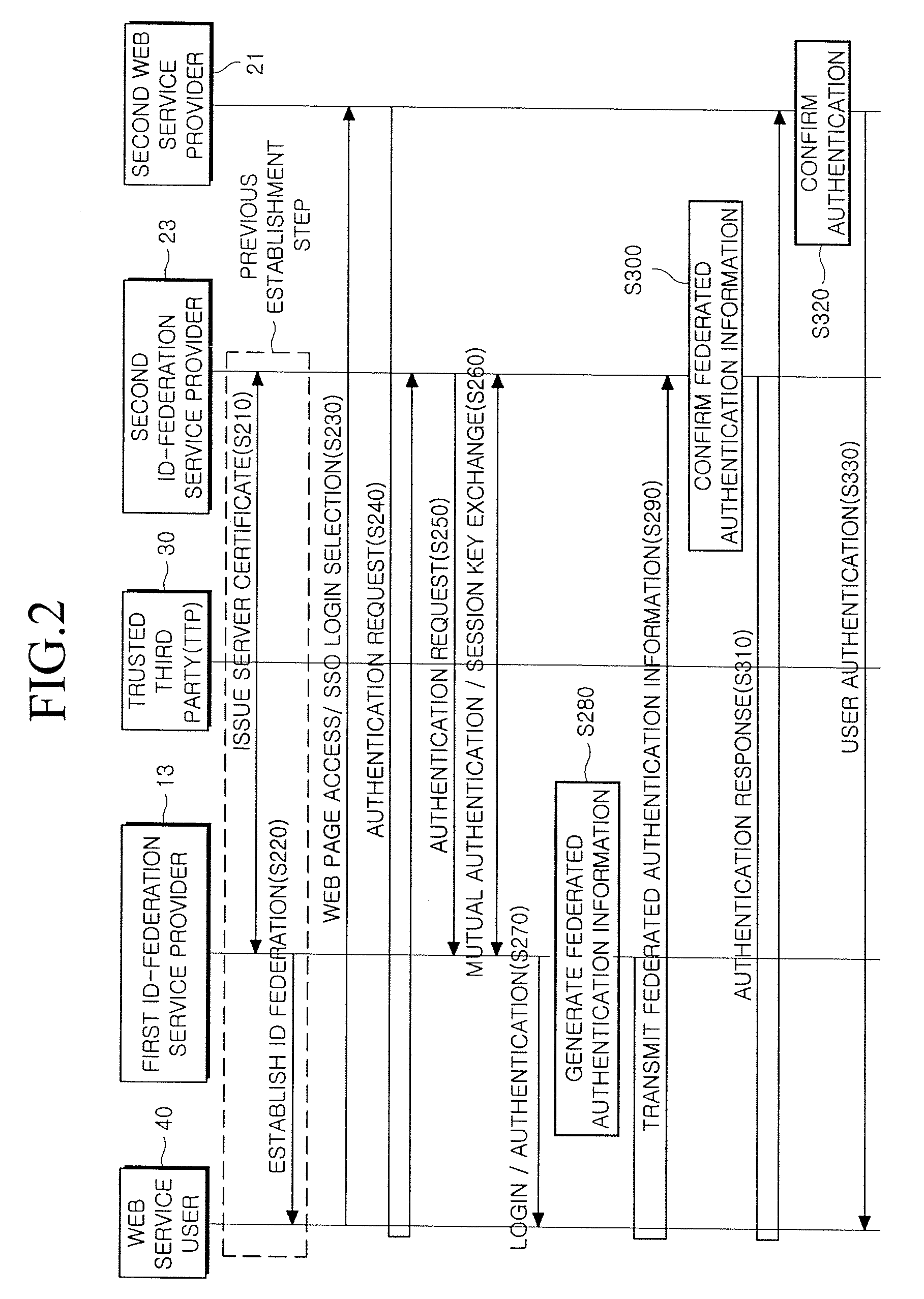
Provided is a method and system for providing an SSO service enabling the use of Web services in different trusted domains through a one-time authentication process. In the method, mutual authentication information is issued from a trusted third party to each of ID-federation service providers managing each of trusted domains, and an ID federation established between the ID-federation service provider and a user in the trusted domain of the ID-federation service provider. The first ID-federation service provider managing the first trusted domain, to which the user belongs to, is confirmed when a Web service provider in the second trusted domain receives a login request from the user in the first trusted domain. User authentication and mutual authentication arc performed between the first ID-federation service provider and a second ID-federation service provider managing the second trusted domain. The Web service provider authenticates the user in the first trusted domain and provides a corresponding Web service.
Owner:ELECTRONICS & TELECOMM RES INST
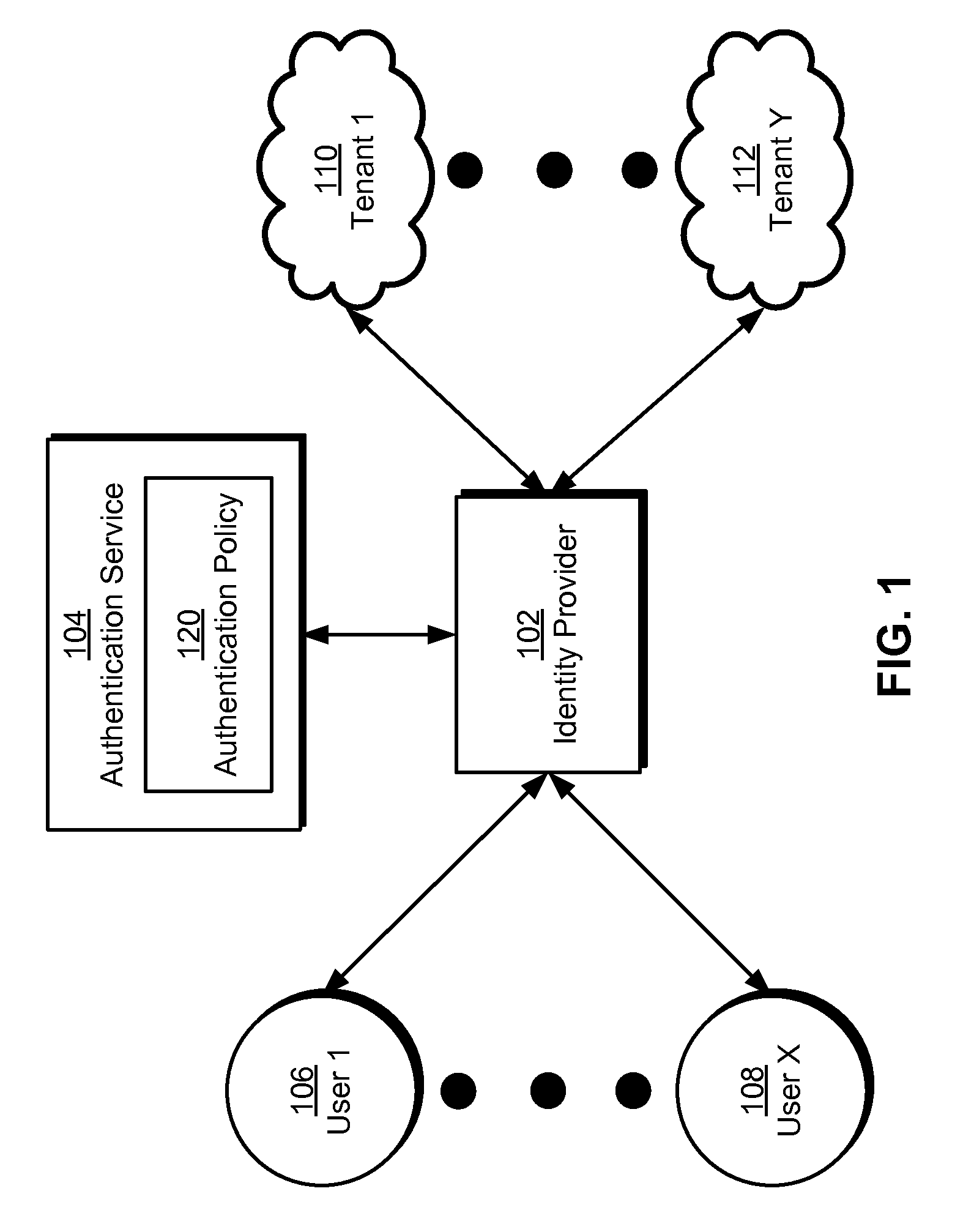
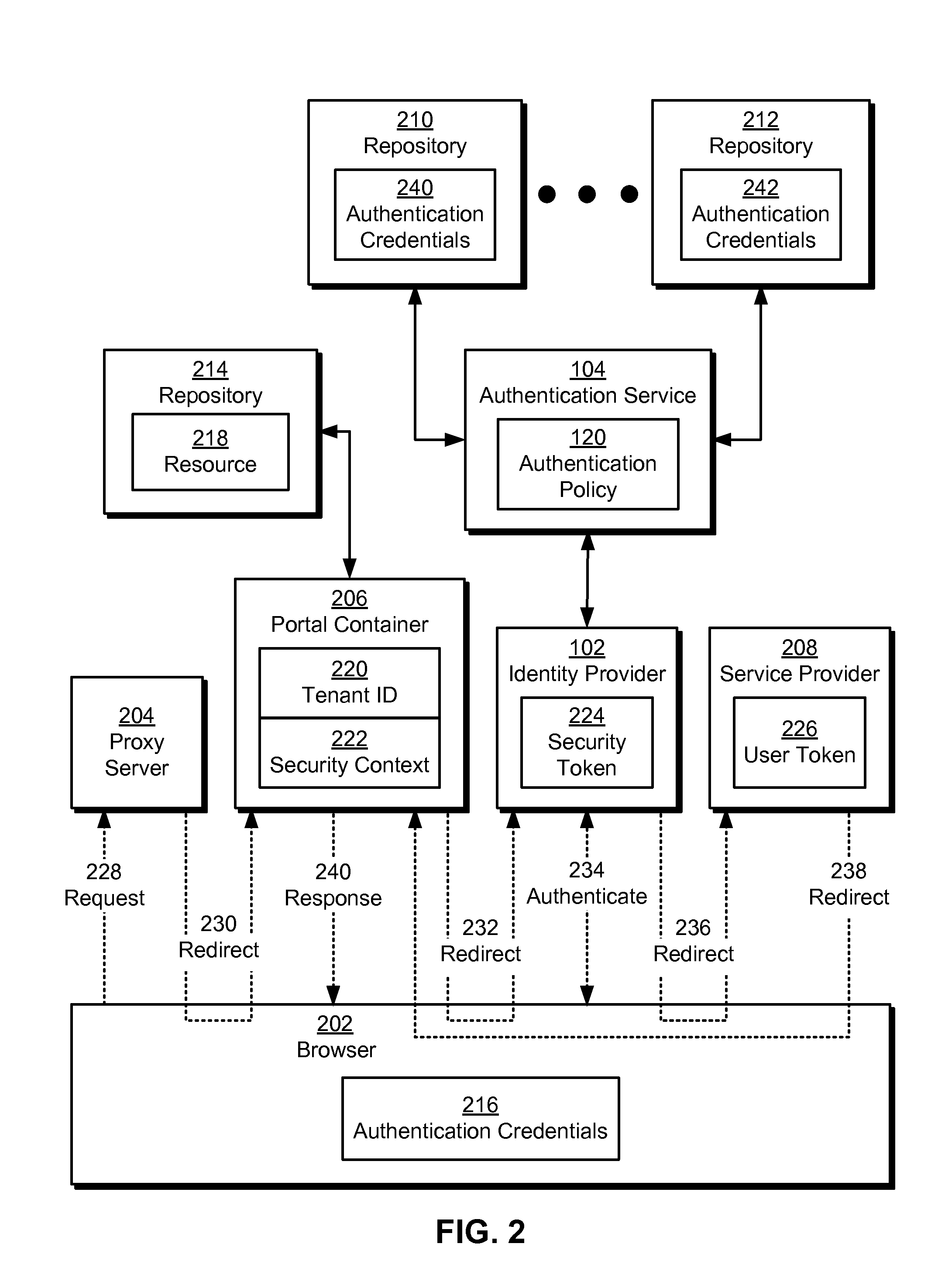
Single sign-on in multi-tenant environments
ActiveUS20140090037A1Digital data processing detailsMultiple digital computer combinationsInternet privacySystem usage
The disclosed embodiments provide a system that authenticates a user. During operation, the system identifies a first tenant associated with a first request for a first resource from the user and obtains an authentication policy for the first tenant. Next, the system uses an authentication mechanism associated with the authentication policy to authenticate the user. Upon authenticating the user, the system provides a first security token for enabling access to the first resource by the user.
Owner:INTUIT INC
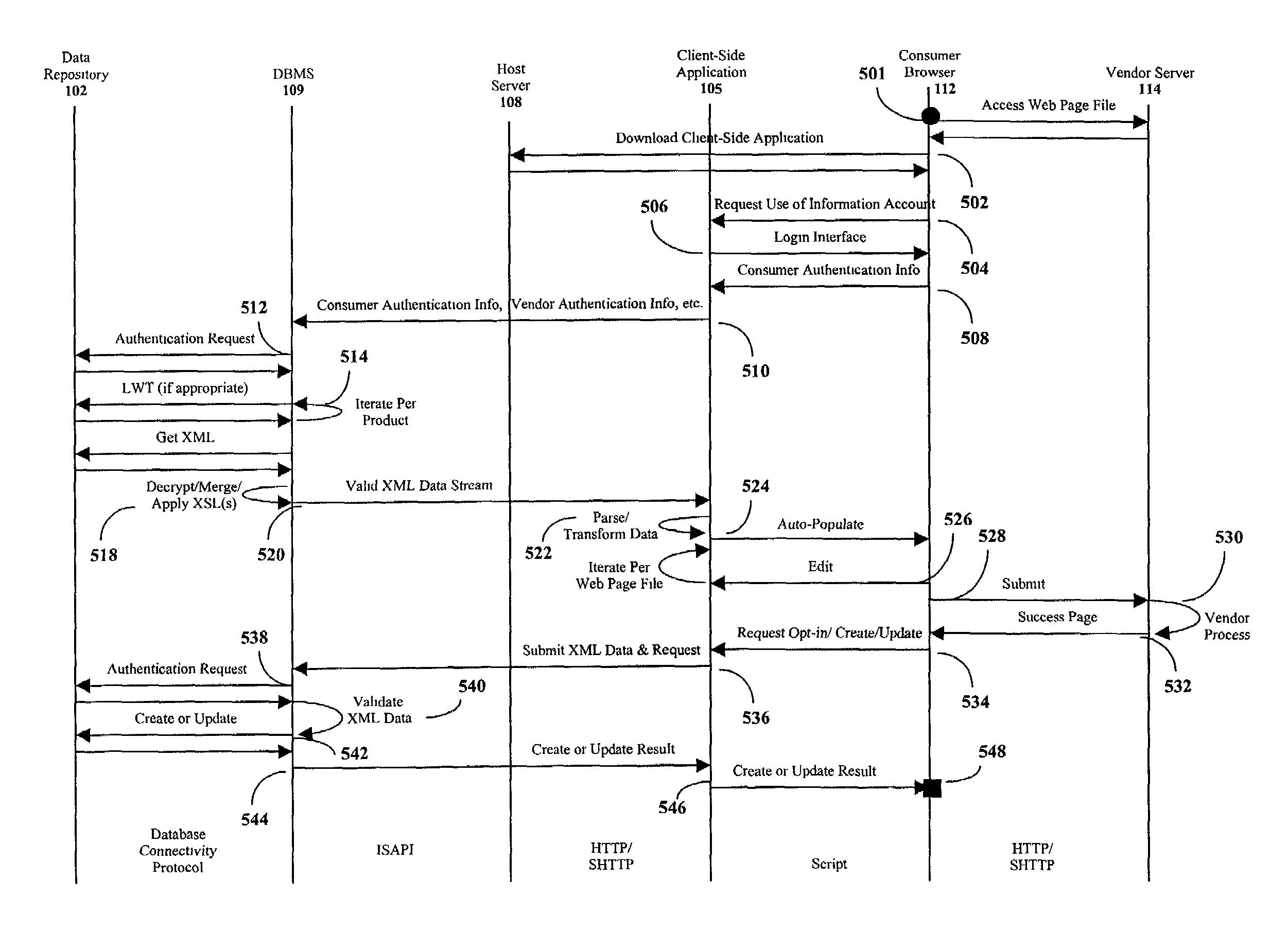
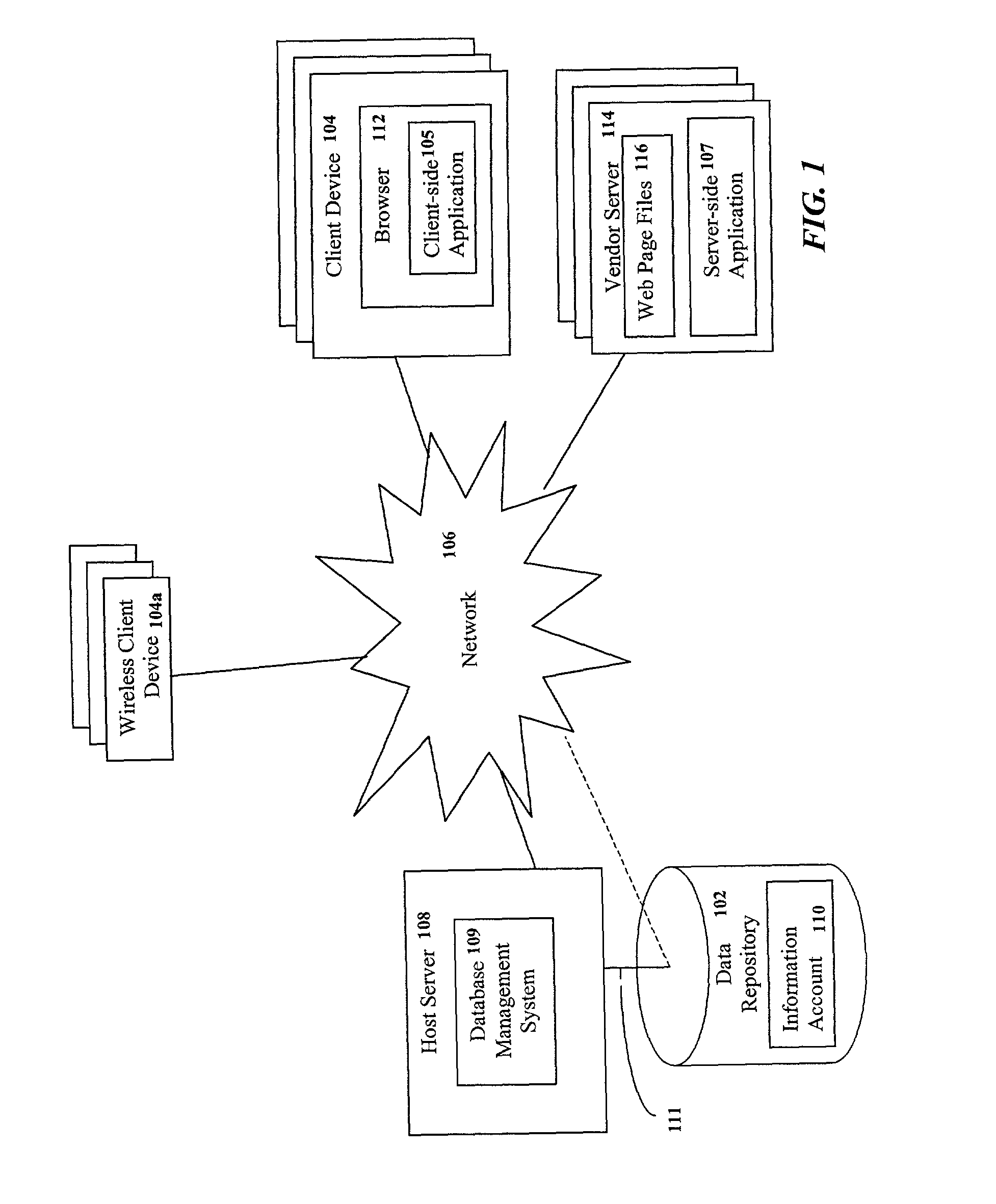
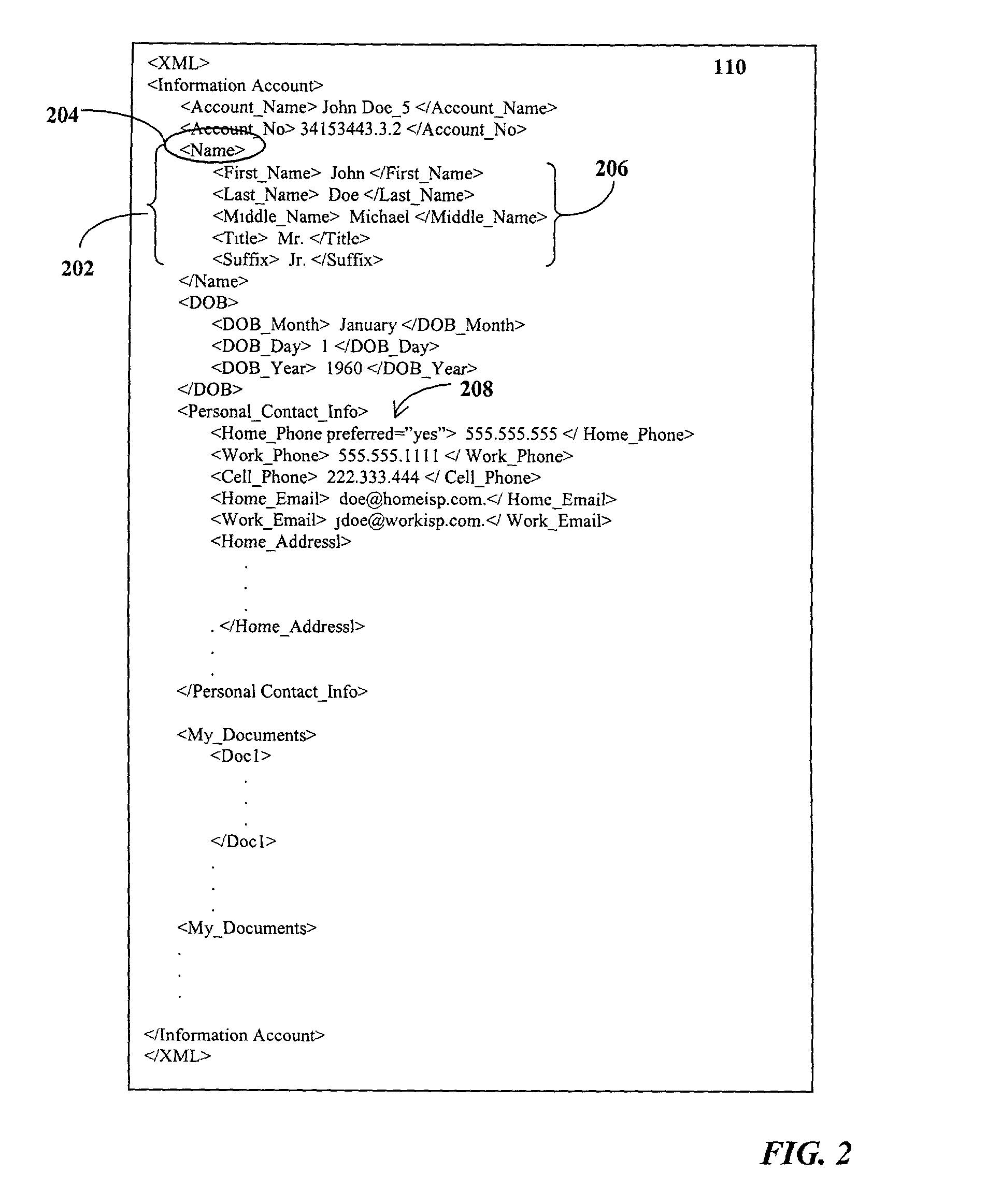
Single sign-on for access to a central data repository
Systems and methods for providing access to an information account stored in a central data repository. The information account is associated with a consumer and is subject to the consumer's control and management. Consumer authentication information is input by the consumer in connection with a first request for access to the information account via a first web-site. Responsive to authentication of the consumer, a single sign-on feature may be activated for automatically managing subsequent authentications of the consumer so that the consumer will not be required to again input the consumer authentication information upon initiating a second request for access to the information account while interacting with a subsequent web-site that is configured to provide access to the information account upon authentication of the consumer. The single sign-on function may be deactivated upon the occurrence of a terminating event, such as the expiration of a time-out interval.
Owner:CXT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com