Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1025 results about "Computational environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
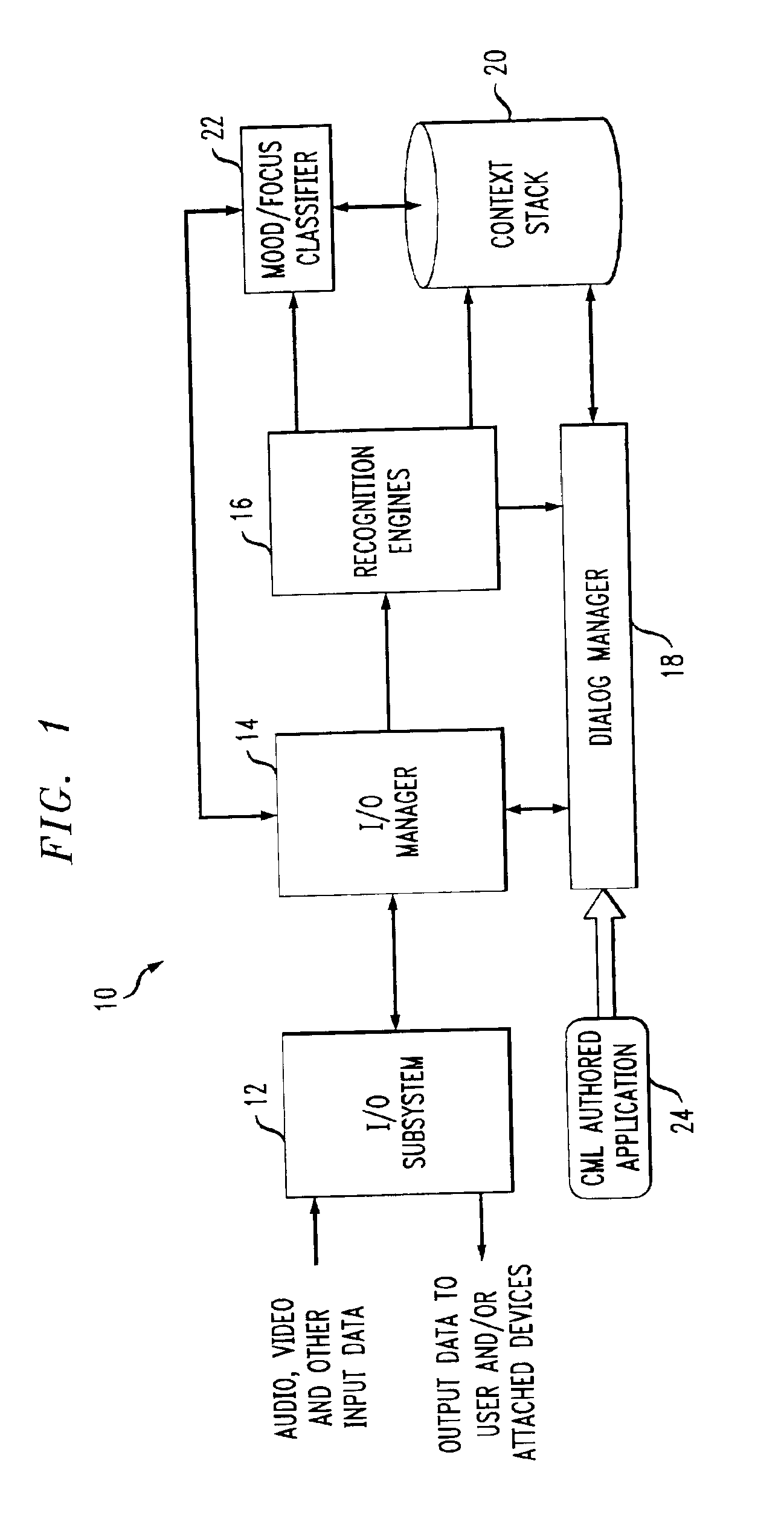
System and method for multi-modal focus detection, referential ambiguity resolution and mood classification using multi-modal input
InactiveUS6964023B2Effective conversational computing environmentInput/output for user-computer interactionData processing applicationsOperant conditioningComputer science
Owner:IBM CORP
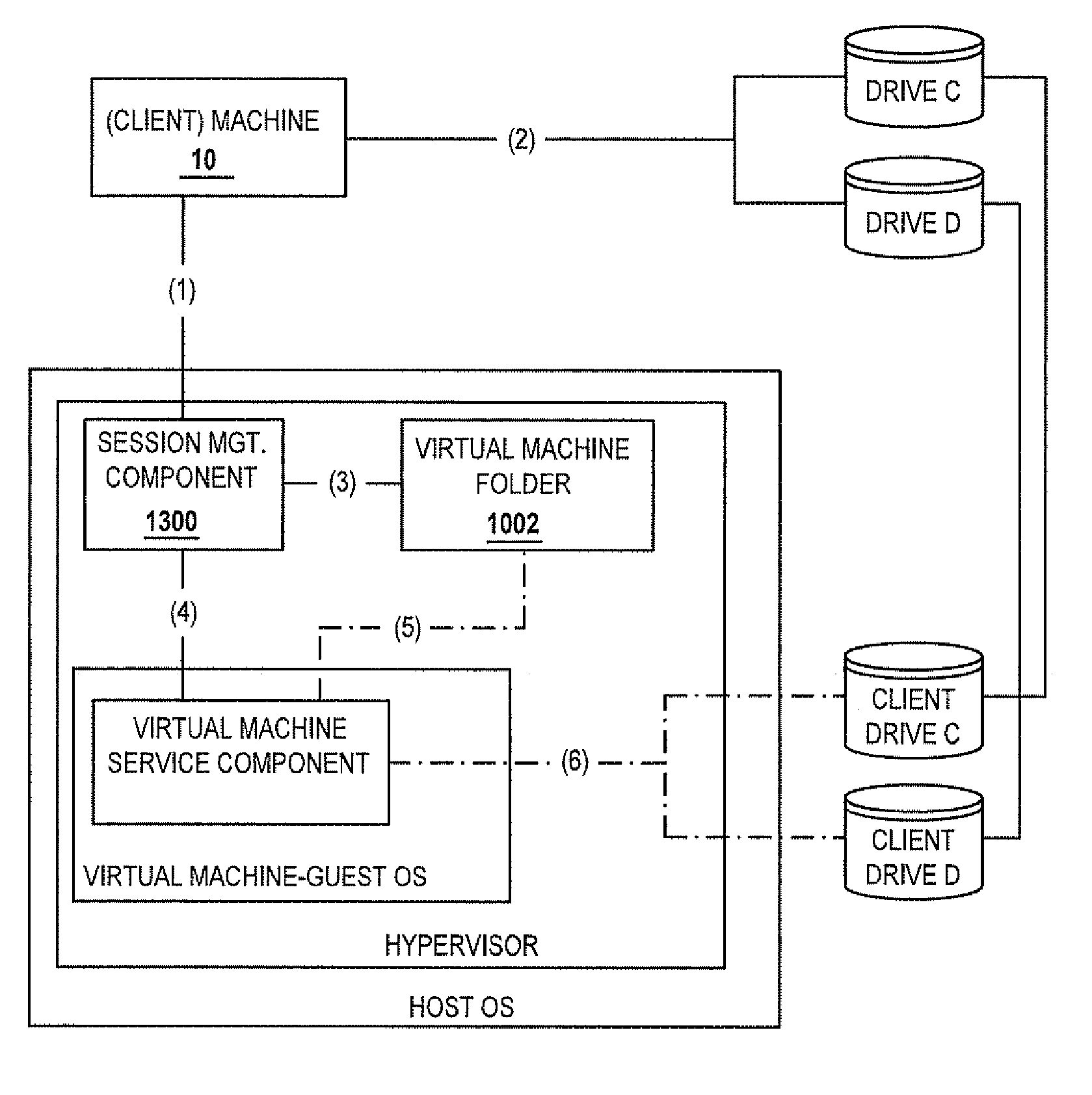
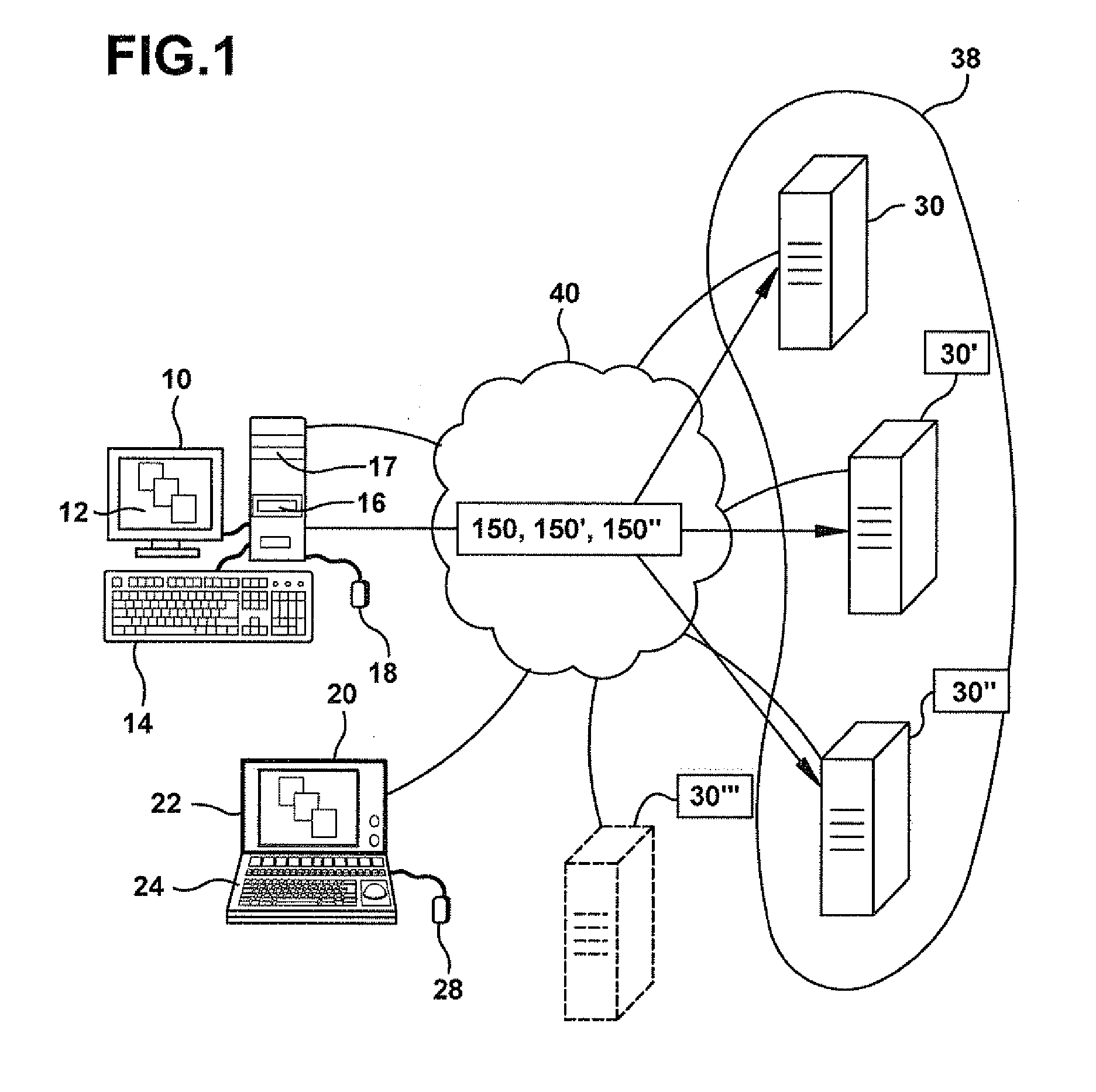
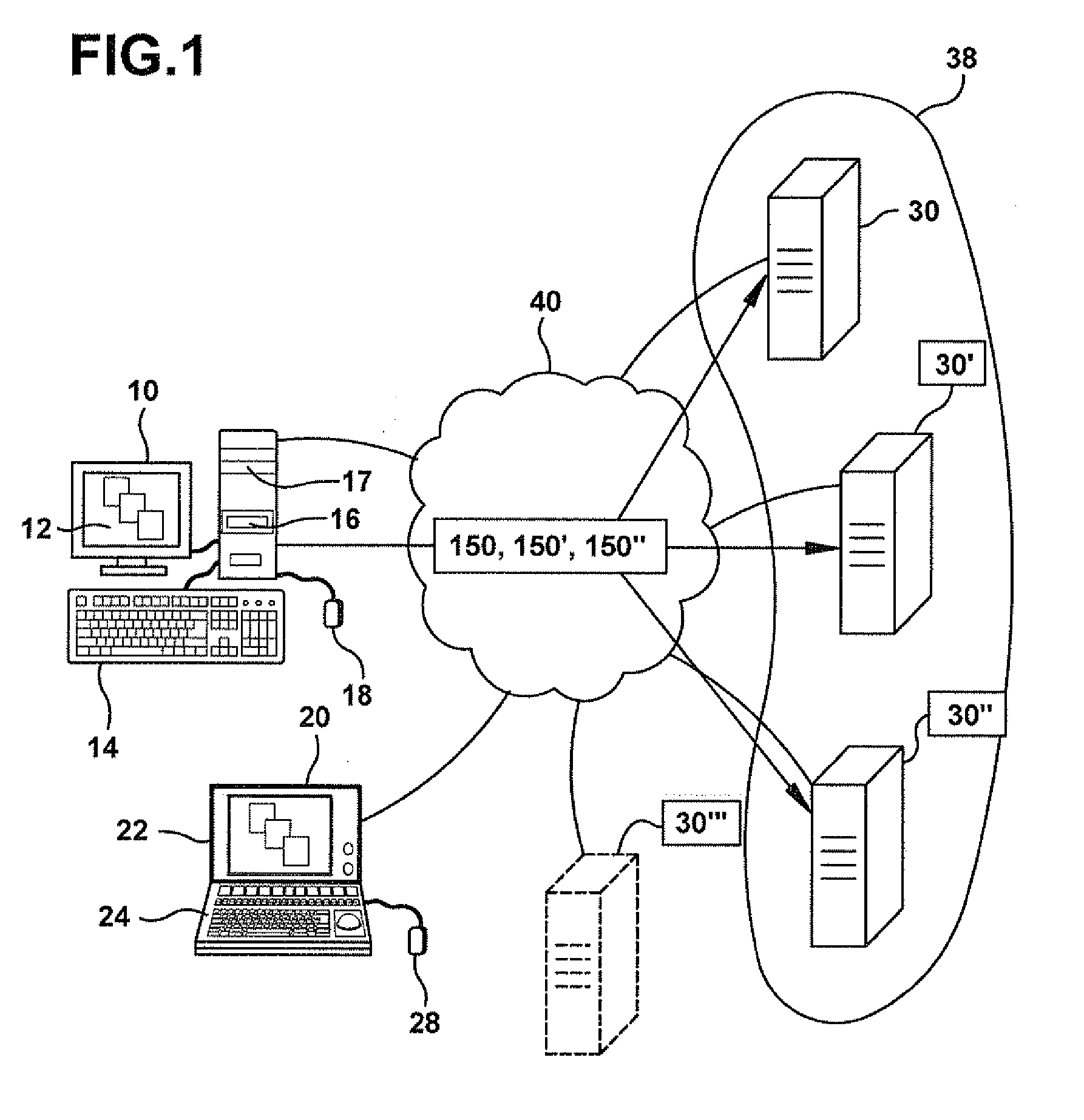
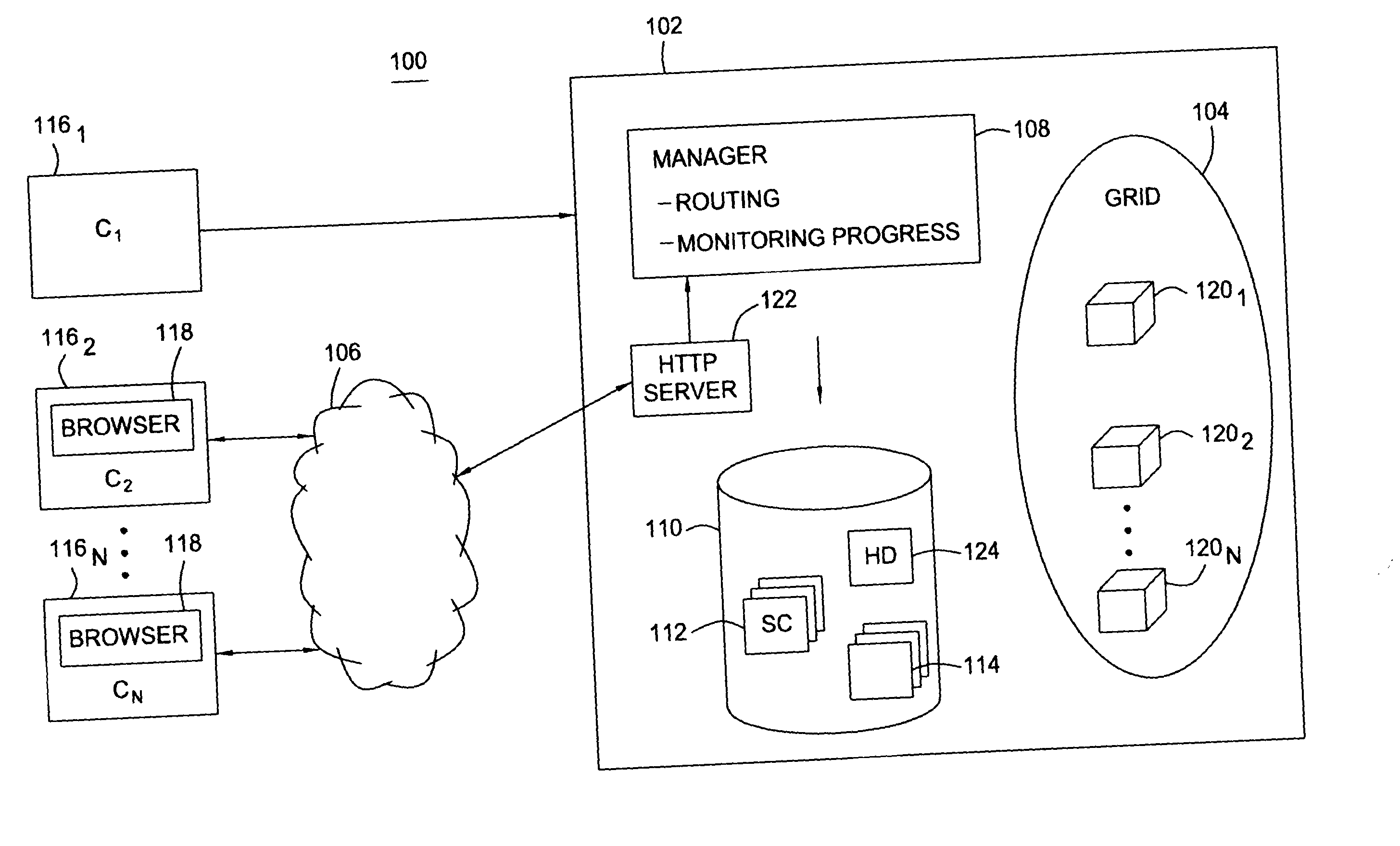
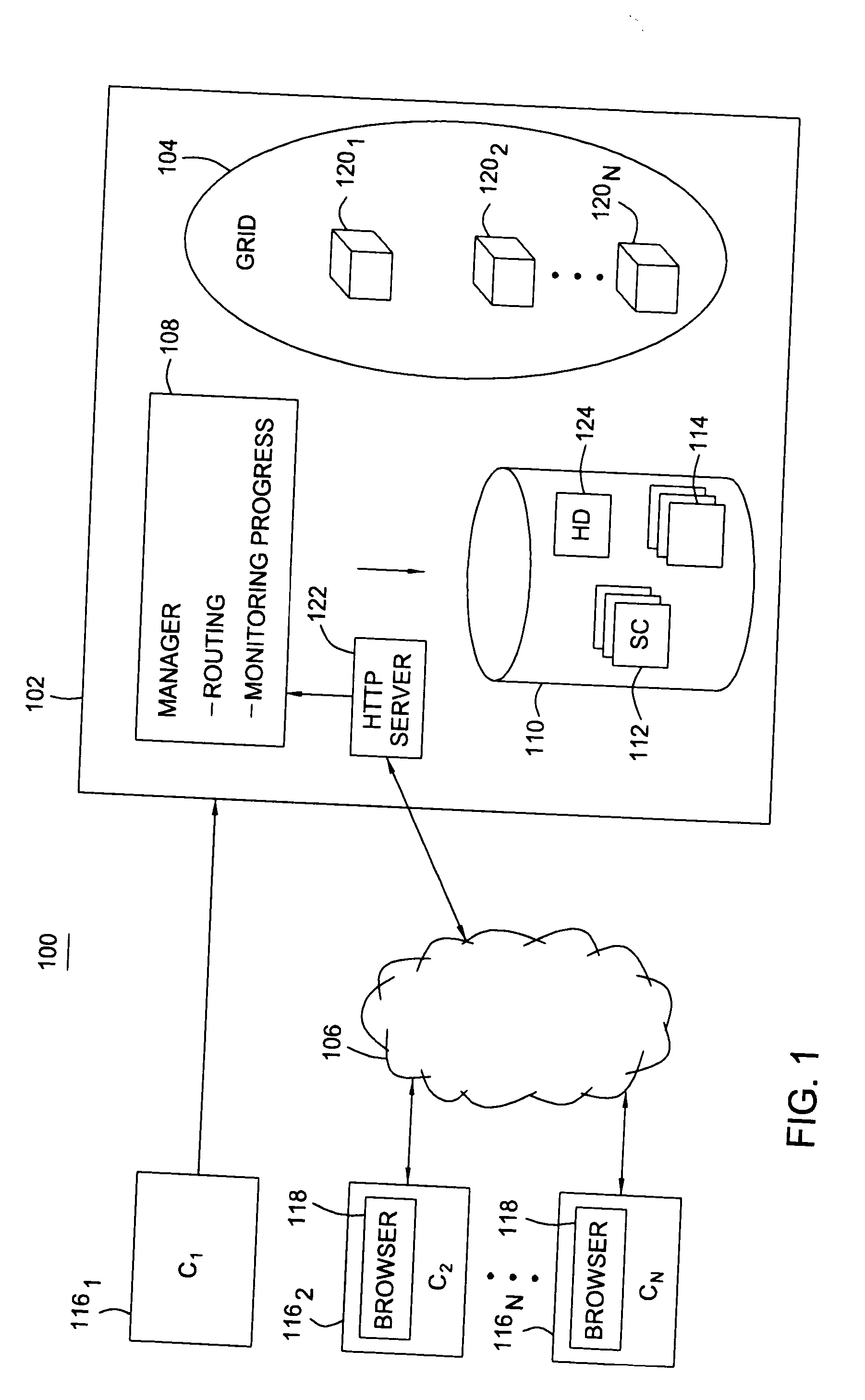
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
Methods and systems for assigning access control levels in providing access to resources via virtual machines
ActiveUS20070180493A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
Owner:CITRIX SYST INC
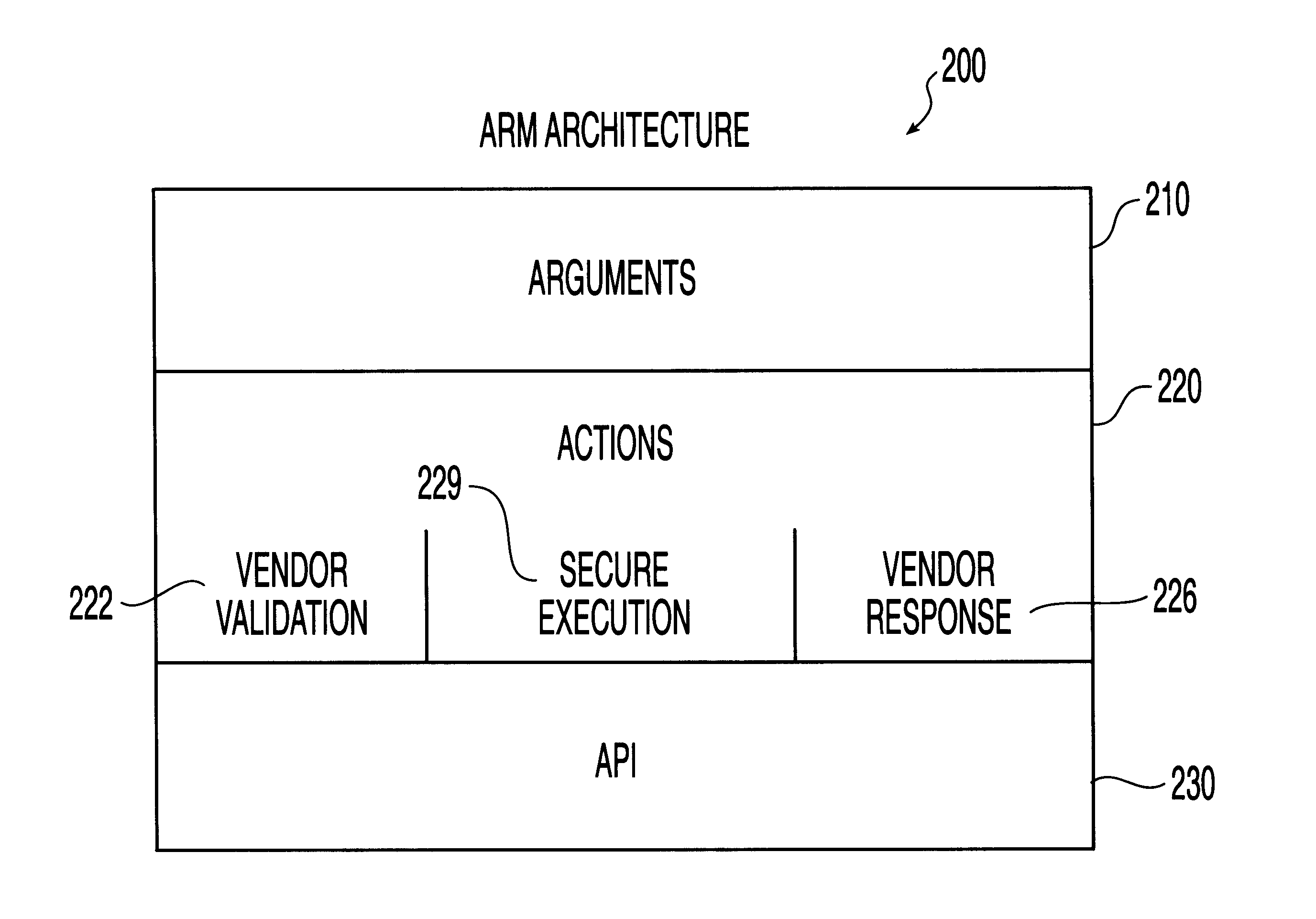
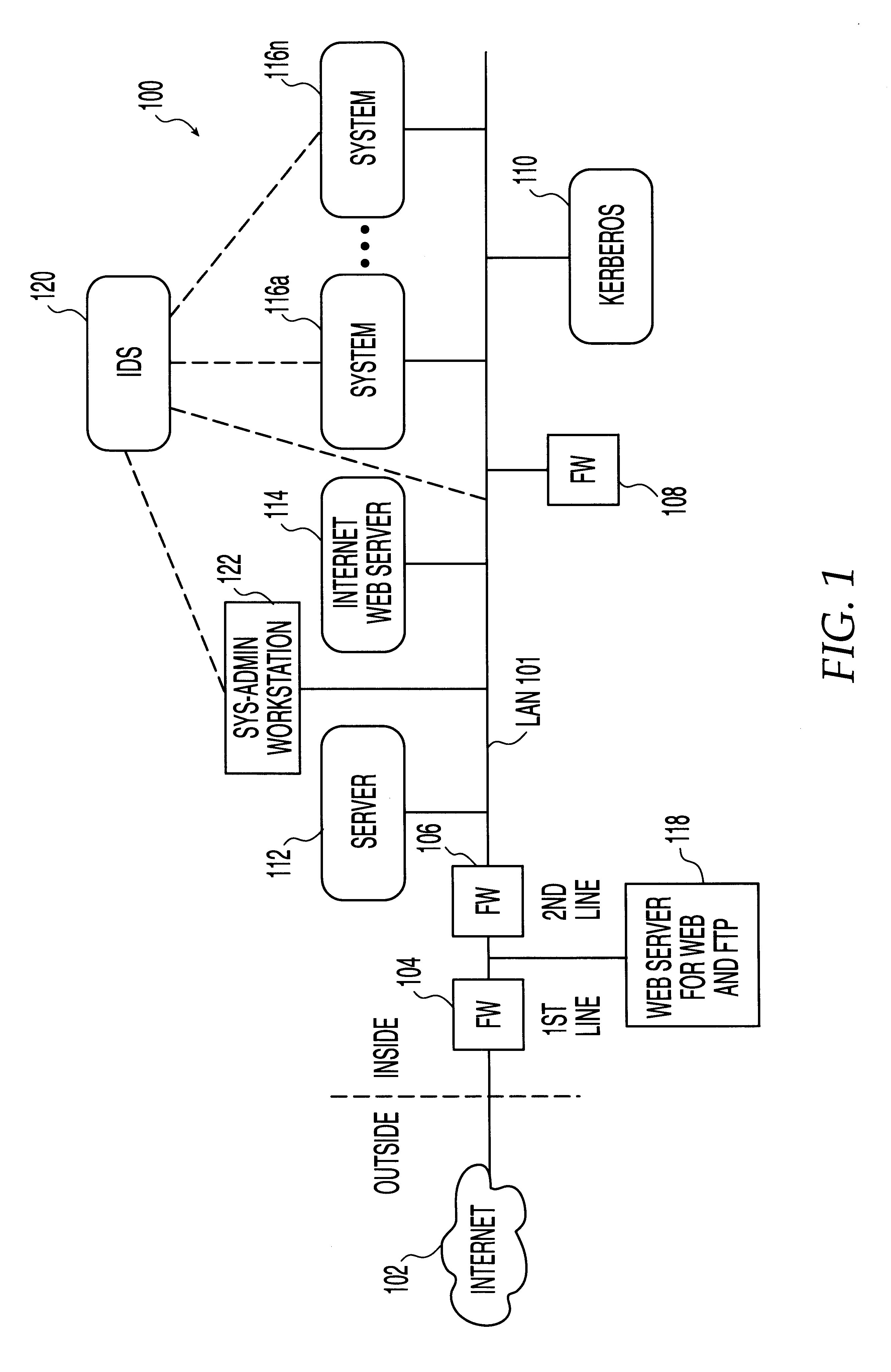
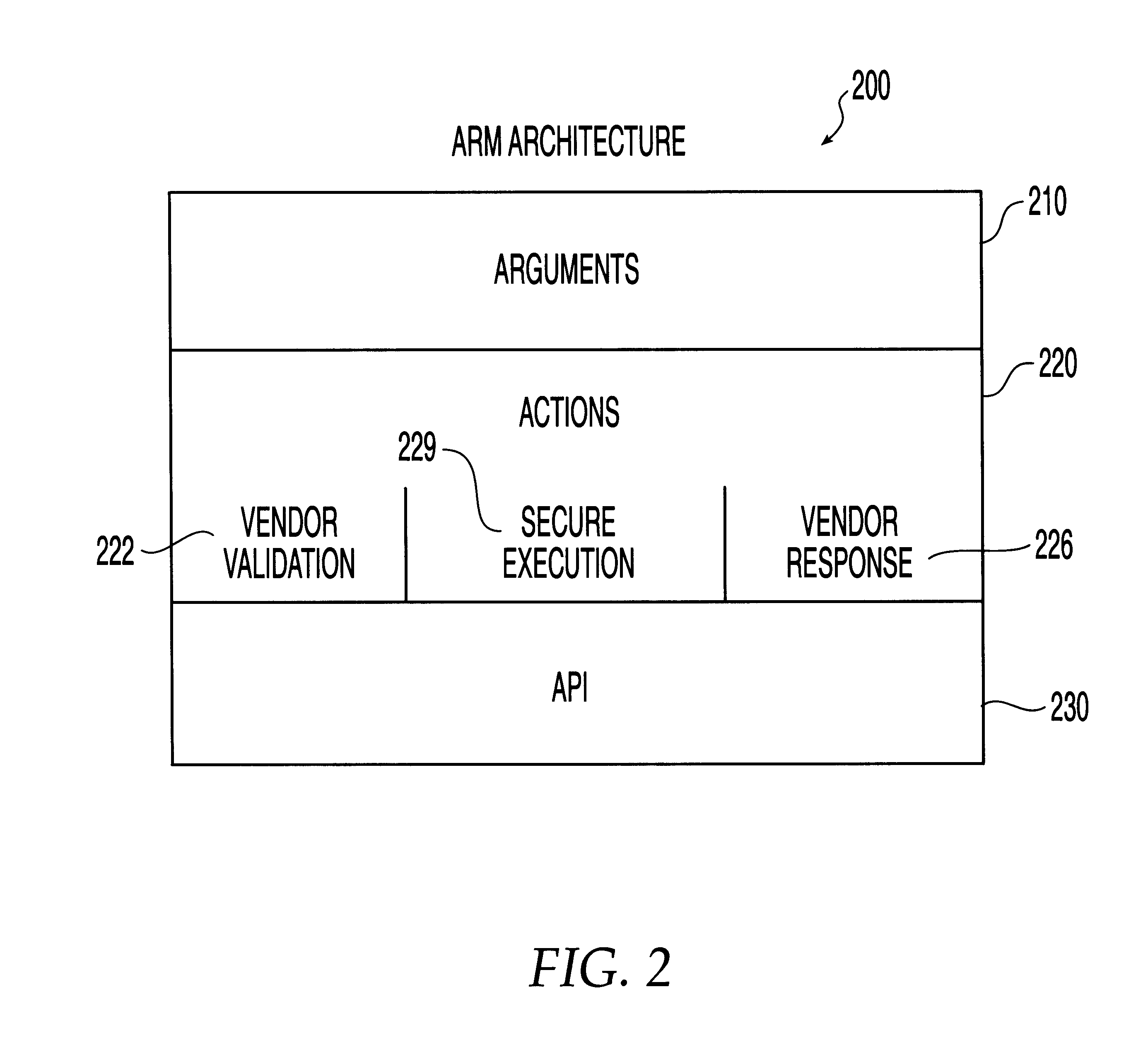
System, method and computer program product for automatic response to computer system misuse using active response modules
InactiveUS6275942B1Rapid responseMemory loss protectionDigital data processing detailsSoftware engineeringSecurity level
A system, method and computer program product for automatic response to computer system misuse using active response modules (ARMs). ARMs are tools that allow static intrusion detection system applications the ability to dynamically increase security levels by allowing real-time responses to detected instances of computer misuse. Several classes of ARMs exist which allow them to interface with several types of network elements found within a computing environment (e.g., firewalls, web servers, Kerberos severs, certificate authorities, etc.). The ARMs, once defined, are deployed in a "plug and play" manner into an existing intrusion detection system within a computing environment. A user (e.g., system administrator) may then configure the ARMs by linking them to specific computer misuses. Upon receipt of an instance of the computer misuse from the intrusion detection system, each ARM linked to the misuse collects pertinent data from the intrusion detection system and invokes a response specified by the ARM class and the collected pertinent data.
Owner:MCAFEE LLC +1
Methods and systems for selecting a method for execution, by a virtual machine, of an application program
ActiveUS20070180450A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideClient machine
A method for selecting a method of execution for an application includes the step of receiving credentials. A plurality of applications available to a client machine is enumerated responsive to the received credentials. A request to execute an enumerated application is received. One of a predetermined number of methods for executing the requested application is selected responsive to a policy, the predetermined number of methods including a method for executing the requested application in a computing environment provided by a virtual machine.
Owner:CITRIX SYST INC
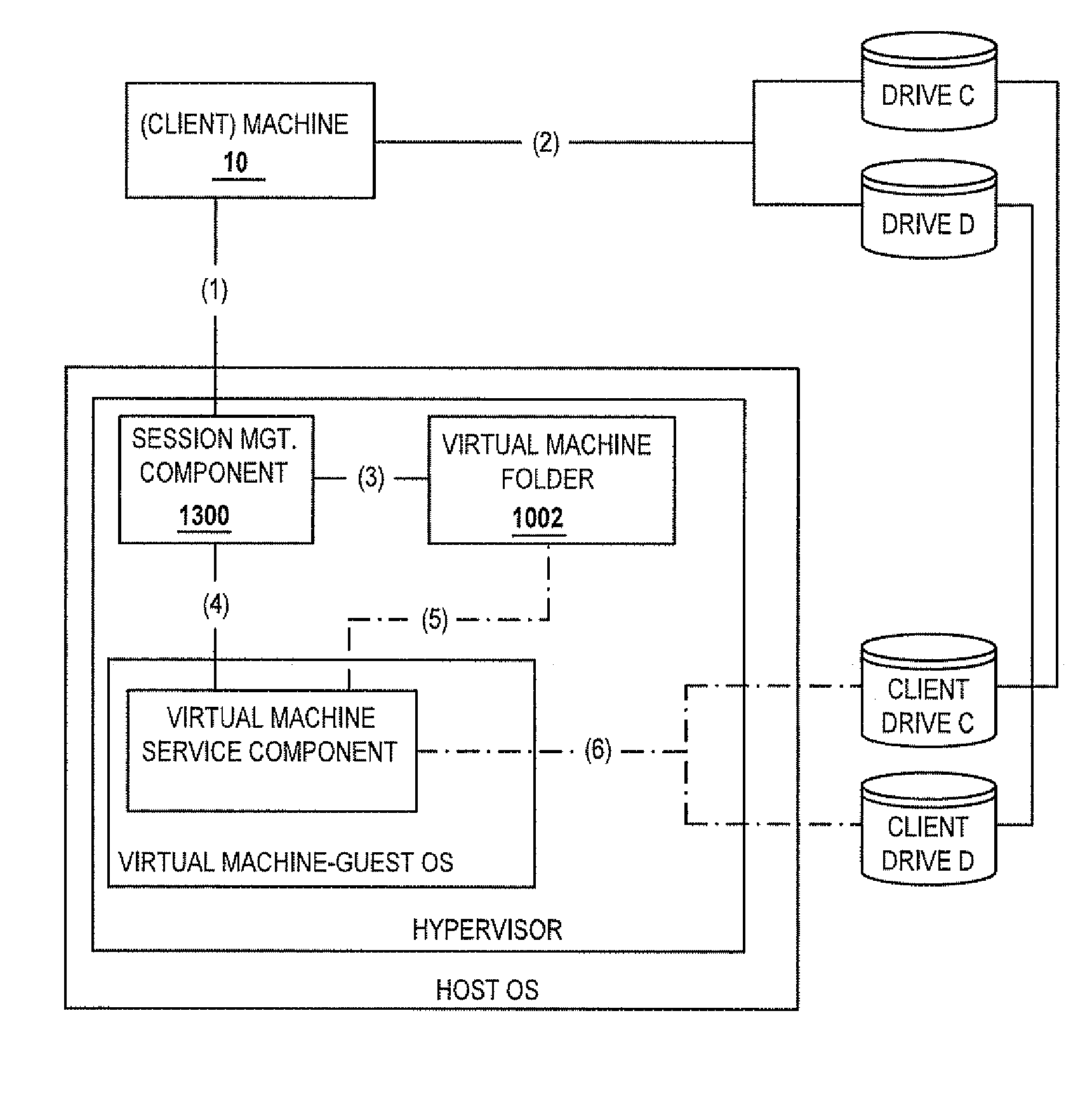
Methods and systems for providing access to a computing environment provided by a virtual machine executing in a hypervisor executing in a terminal services session
ActiveUS20070180448A1Low costReduce difficultyDigital data information retrievalInterprogram communicationSession managementClient-side
A method for providing access to a computing environment includes the step of receiving, by a broker machine, a request from a client machine for access to a computing environment, the request including an identification of a user of the client machine. One of a plurality of virtual machines is identified by a session management component, the identified virtual machine providing the requested computing environment. One of a plurality of execution machines is identified, the identified execution machine providing a terminal services session in which a hypervisor executes to provide access to hardware resources required by the identified virtual machine. The hypervisor launches the identified virtual machine. A connection is established between the client machine and the identified virtual machine, via the terminal services session.
Owner:CITRIX SYST INC
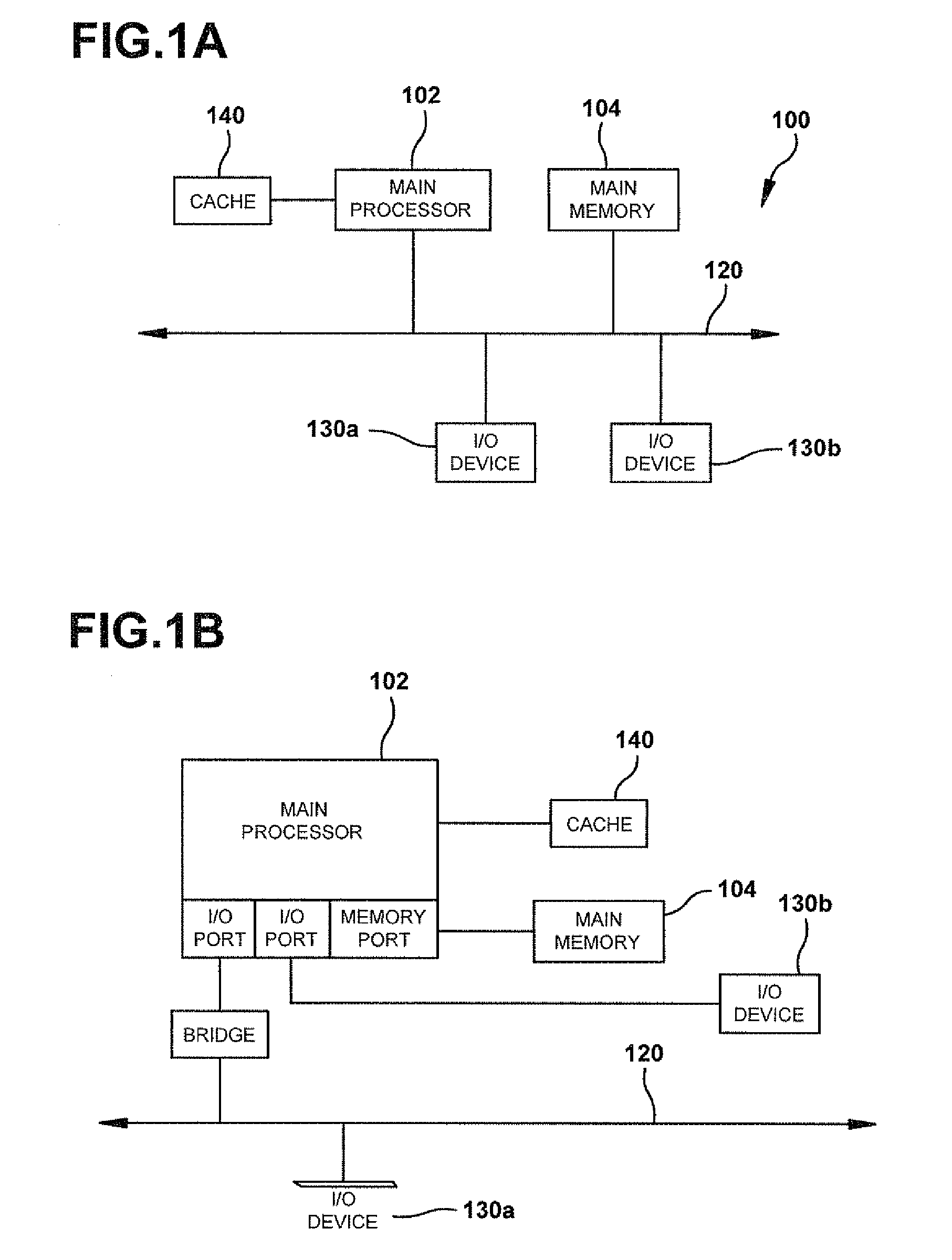
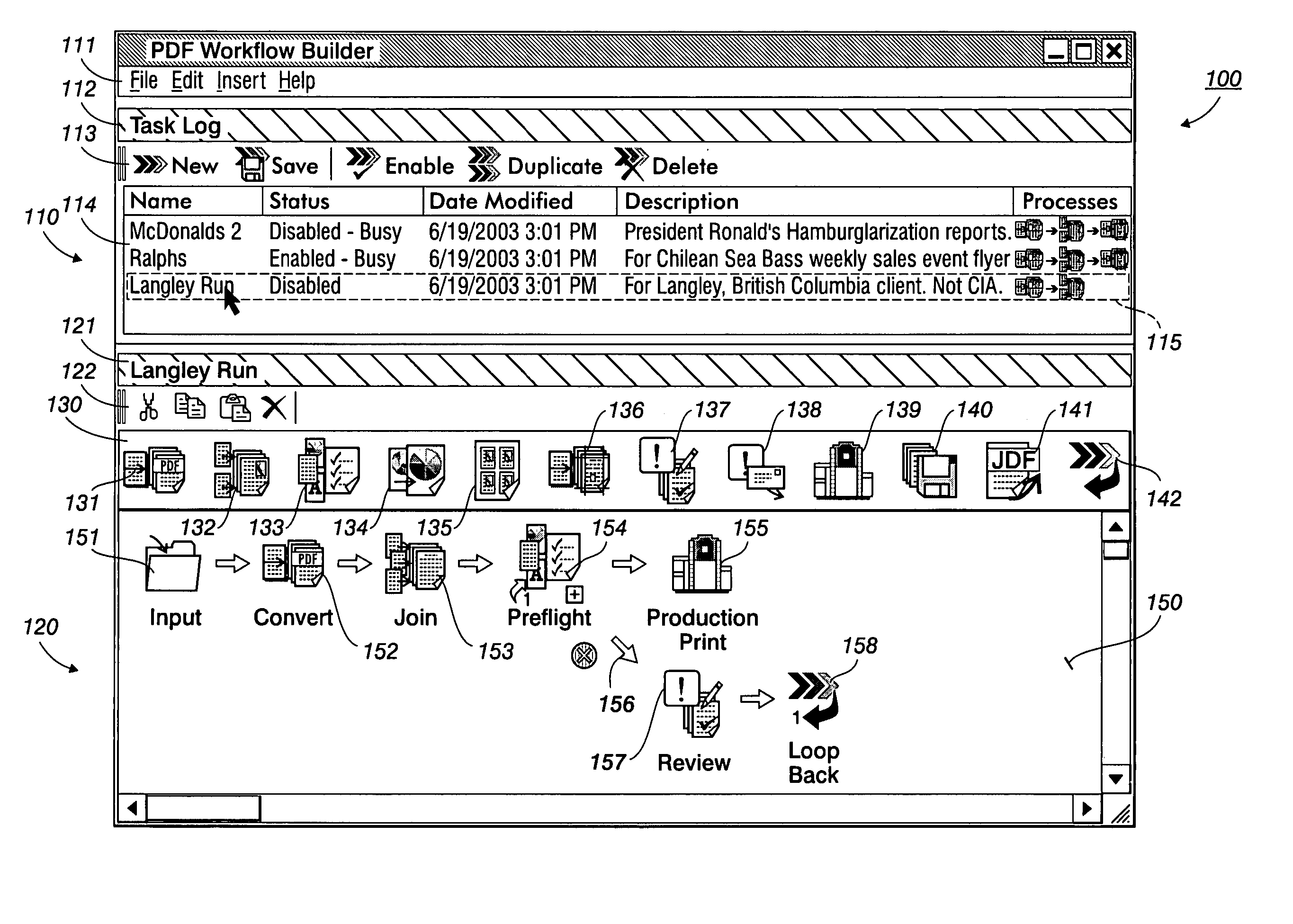
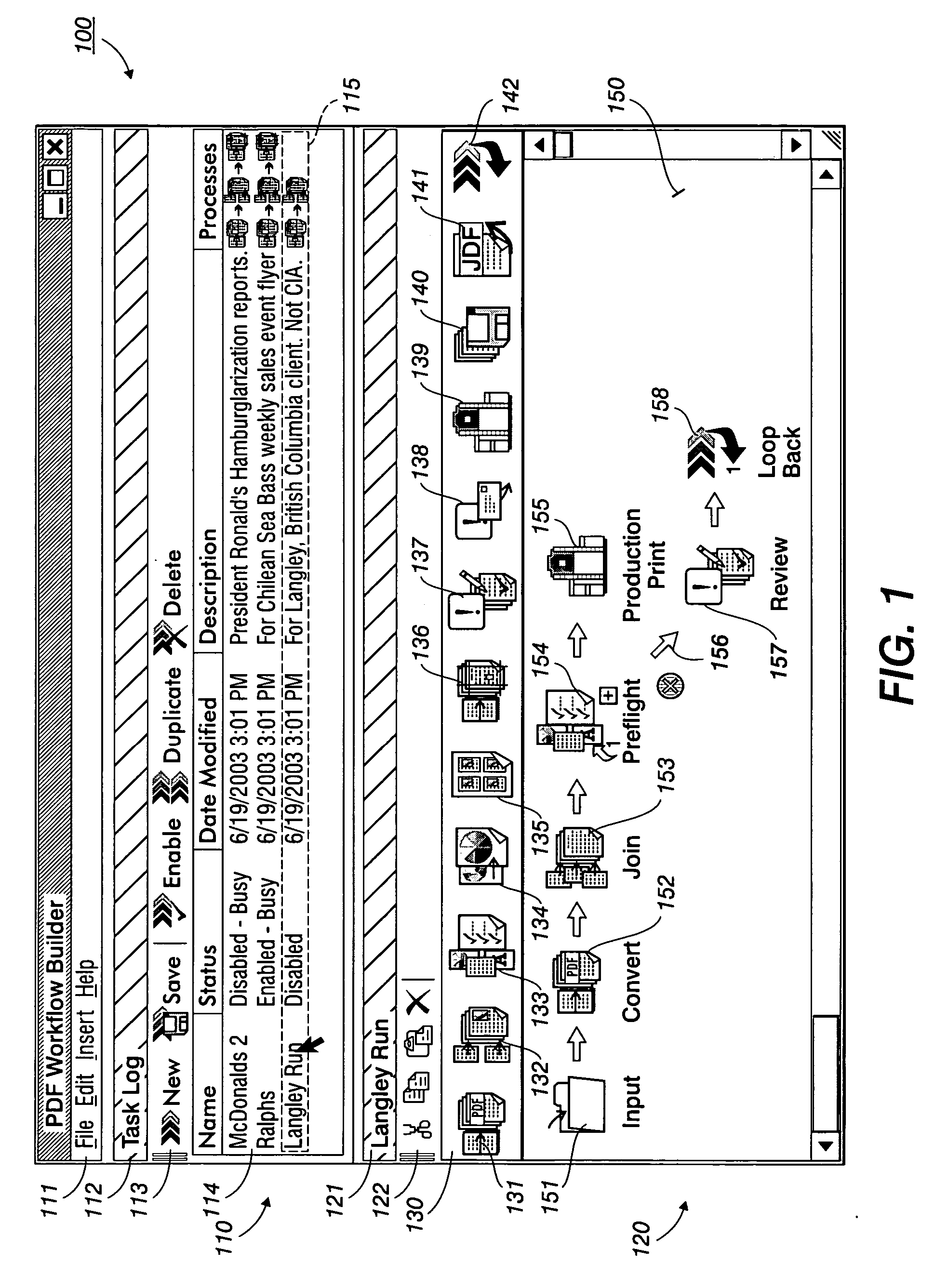
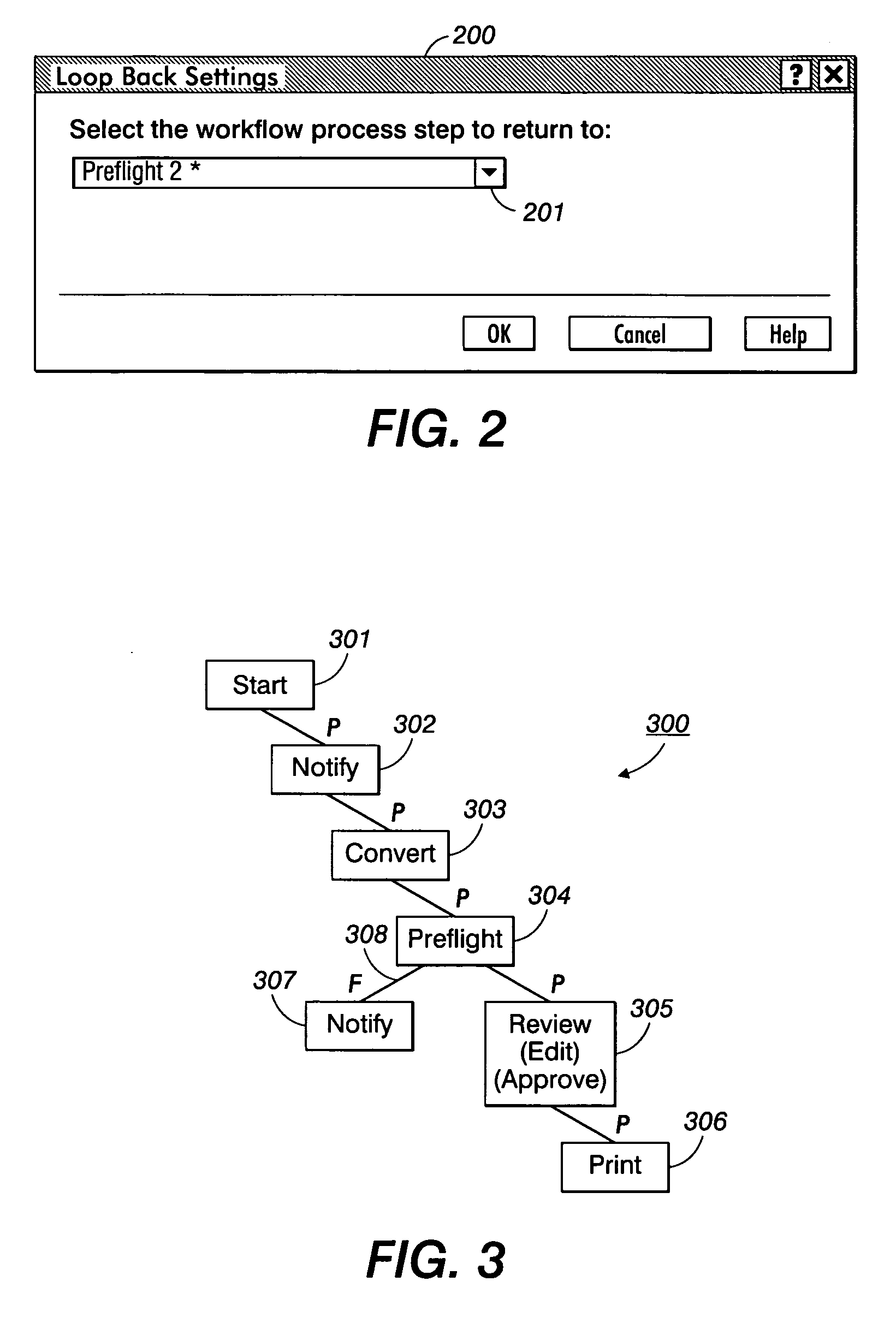
Systems, methods and user interfaces for document workflow construction
InactiveUS20060080616A1Efficient constructionExecution for user interfacesInput/output processes for data processingDrag and dropMain branch
Context sensitive drag-and-drop systems, methods and user interfaces are provided in a Graphical User Interface (GUI) computing environment. Icons representing various tasks may be interactively drag-and-dropped to an adjoining graphically-based workspace in a context-based task-drop location to simply and intuitively construct a graphically-based workflow solution. A collapsible error handling failure branch may be constructed concurrently with the main branch of the workflow process. A loopback path to a higher branch may optionally be constructed for the failure branch. The workflow solution may be applied in a document printing environment for document production, a document copying environment, or an accounting environment, for example, for clear and efficient generation of workflows.
Owner:XEROX CORP
Replication systems and methods for a virtual computing environment
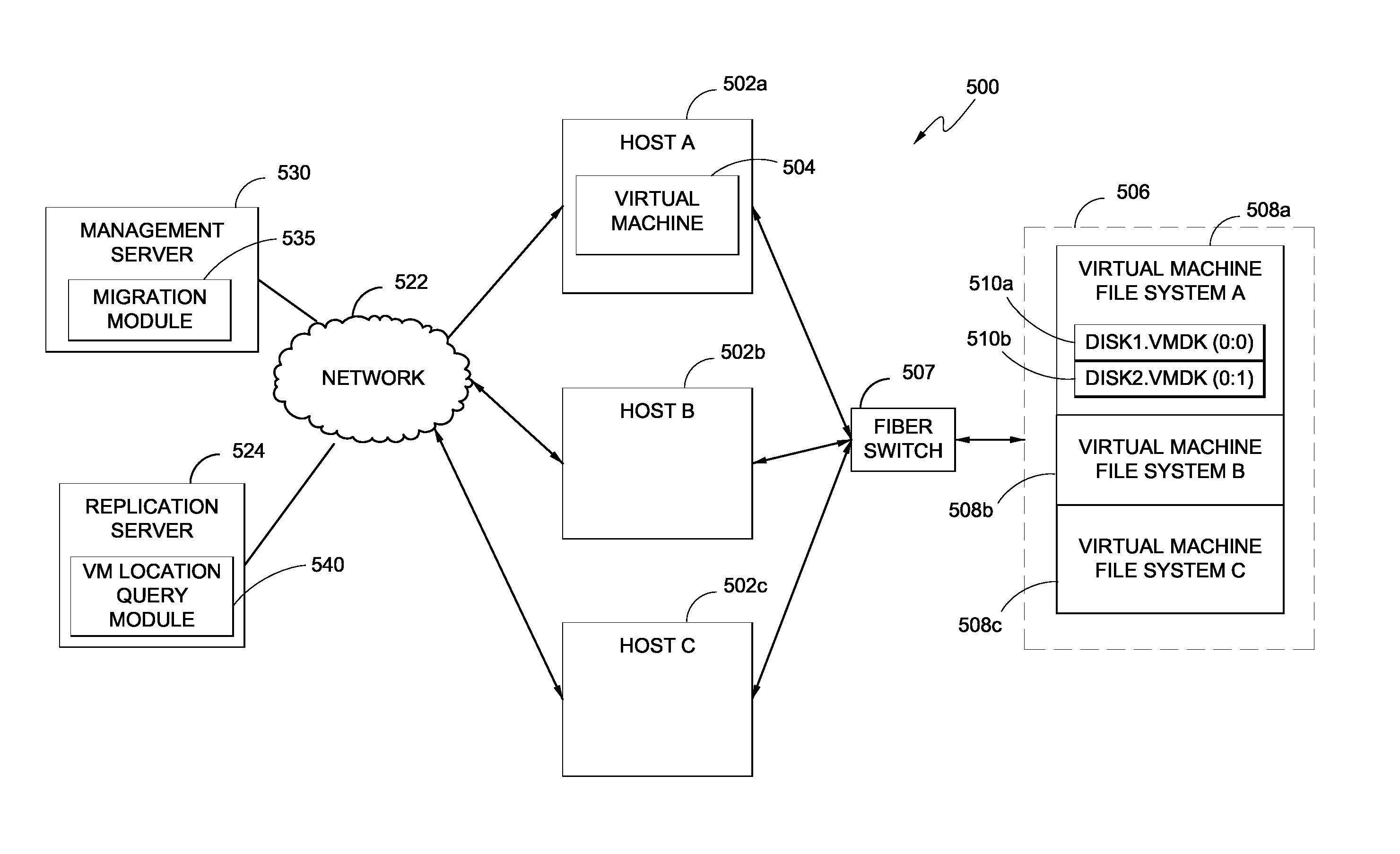
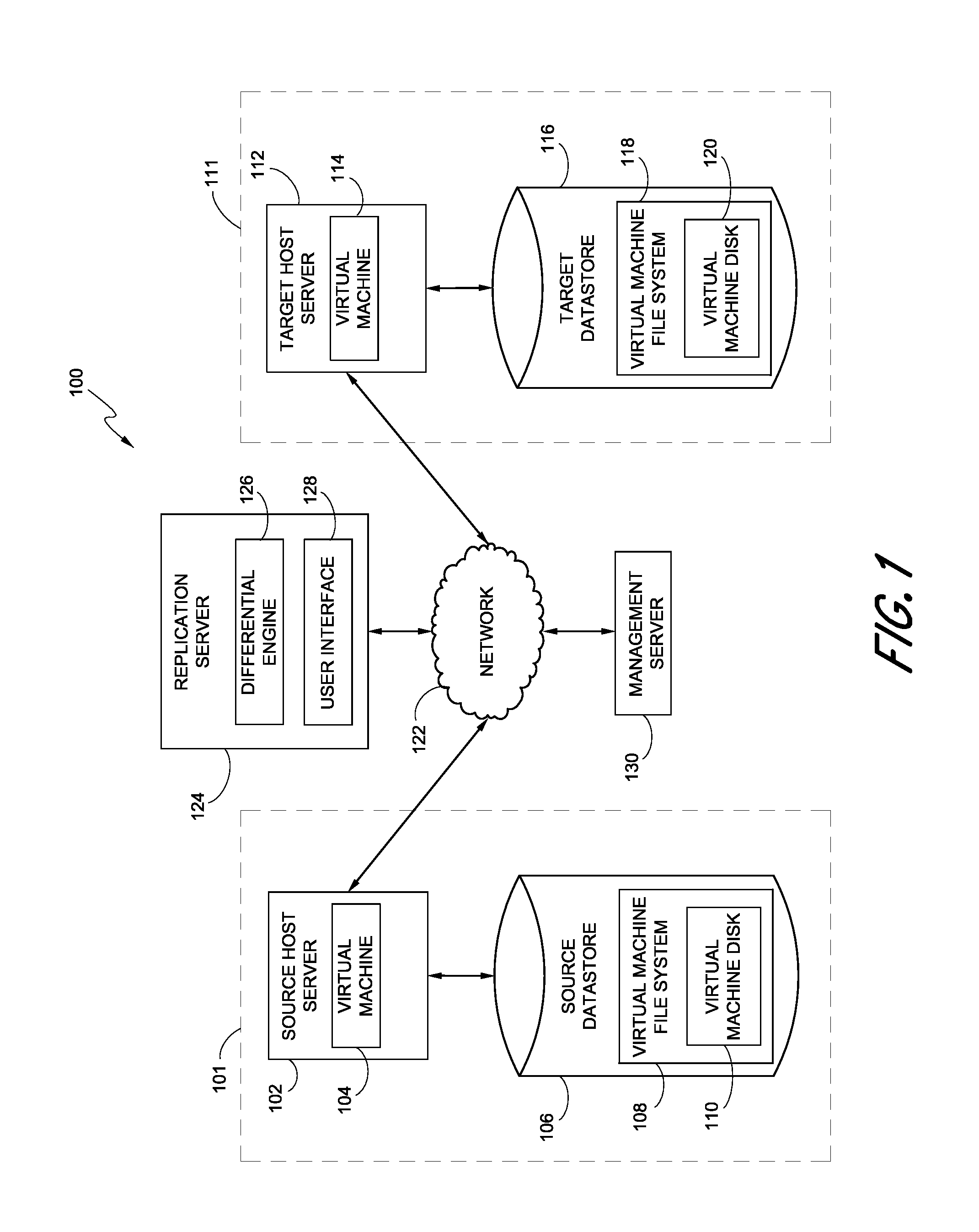
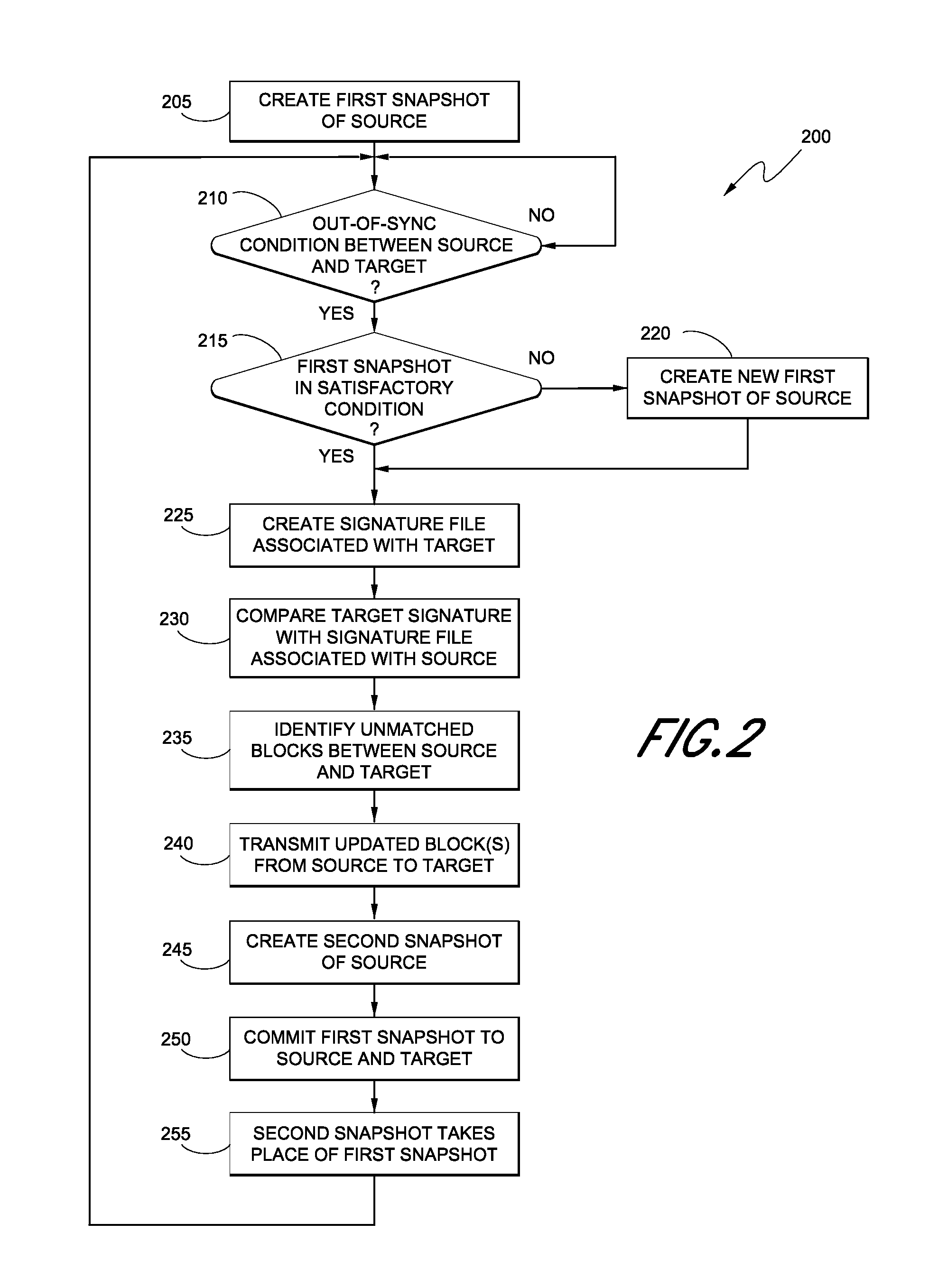
Hybrid replication systems and methods for a virtual computing environment utilize snapshot rotation and differential replication. During snapshot rotation, data modifications intended for a source virtual machine disk (VMDK) are captured by a primary snapshot. Once a particular criterion is satisfied, the data modifications are redirected to a secondary snapshot while the primary snapshot is committed to both source and target VMDKs. The secondary snapshot is then promoted to primary, and a new secondary snapshot is created with writes redirected thereto. If the VMDKs become out-of-sync, disclosed systems can automatically perform a differential scan of the source data and send only the required changes to the target server. Once the two data sets are synchronized, snapshot replication can begin at the previously configured intervals. Certain systems further provide for planned failover copy operations and / or account for migration of a virtual machine during the copying of multiple VMDKs.
Owner:QUEST SOFTWARE INC
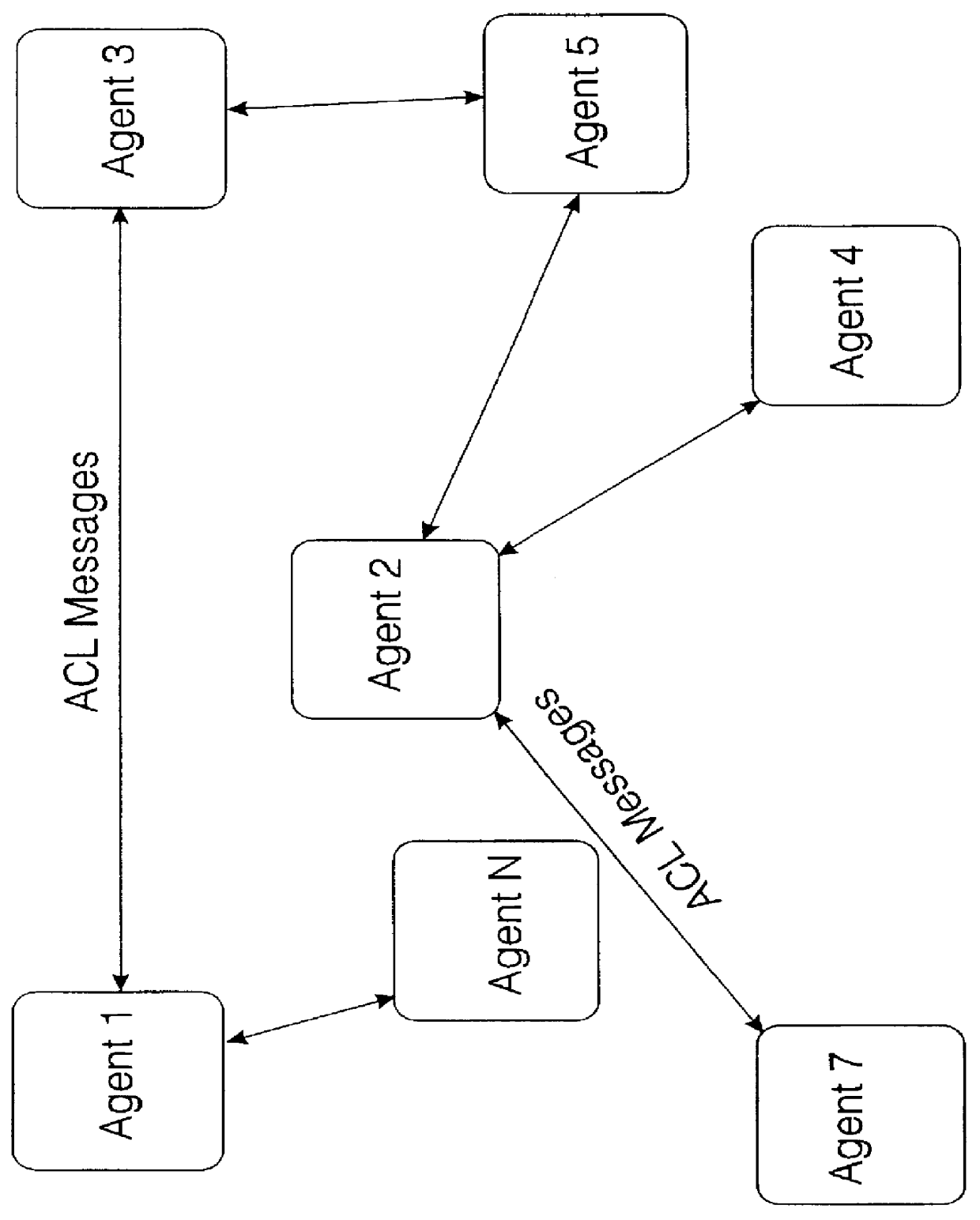
Communications network incorporating agent oriented computing environment
InactiveUS6049819AEfficiently identify each otherQuick functionResource allocationMultiple digital computer combinationsProxy serviceCommunication language
An agent oriented computing environment is disclosed comprising an "agent shell" means which can be used by developers for constructing agent computing entities according to their own functionality requirements; an agent enabling layer, providing basic communication, brokering, and negotiation facilities between agent computing entities; and an underlying transport mechanism based on a prior art CORBA platform. Agents communicate with each other using an agent communication language enabling them to interact to domain specific problems. Agents can pass information to each other in ACL messages describing their own vocabularies concerning logic (ontologies). Various services for locating and connecting agents are provided in the agent oriented environment, such as a broker service for locating and finding agents. A collection of agents may communicate with each other where the agents remain static, maintaining their physical locations on their corresponding host physical resource devices, or alternatively agents may be transported across a plurality of physical resources, through the CORBA platform. The environment supports encapsulation of legacy objects, databases, standard and proprietary protocols and interfaces.
Owner:RPX CLEARINGHOUSE
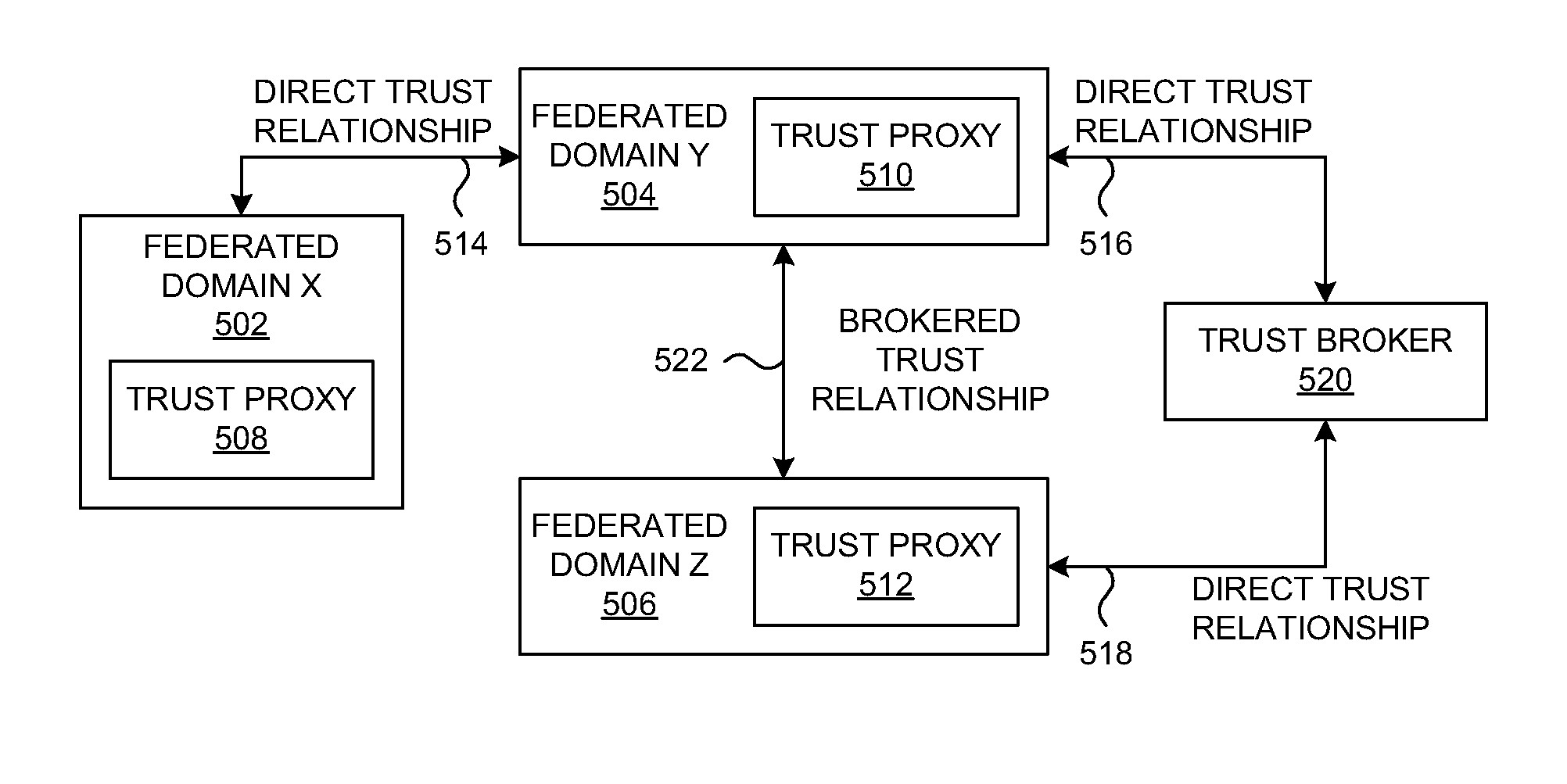
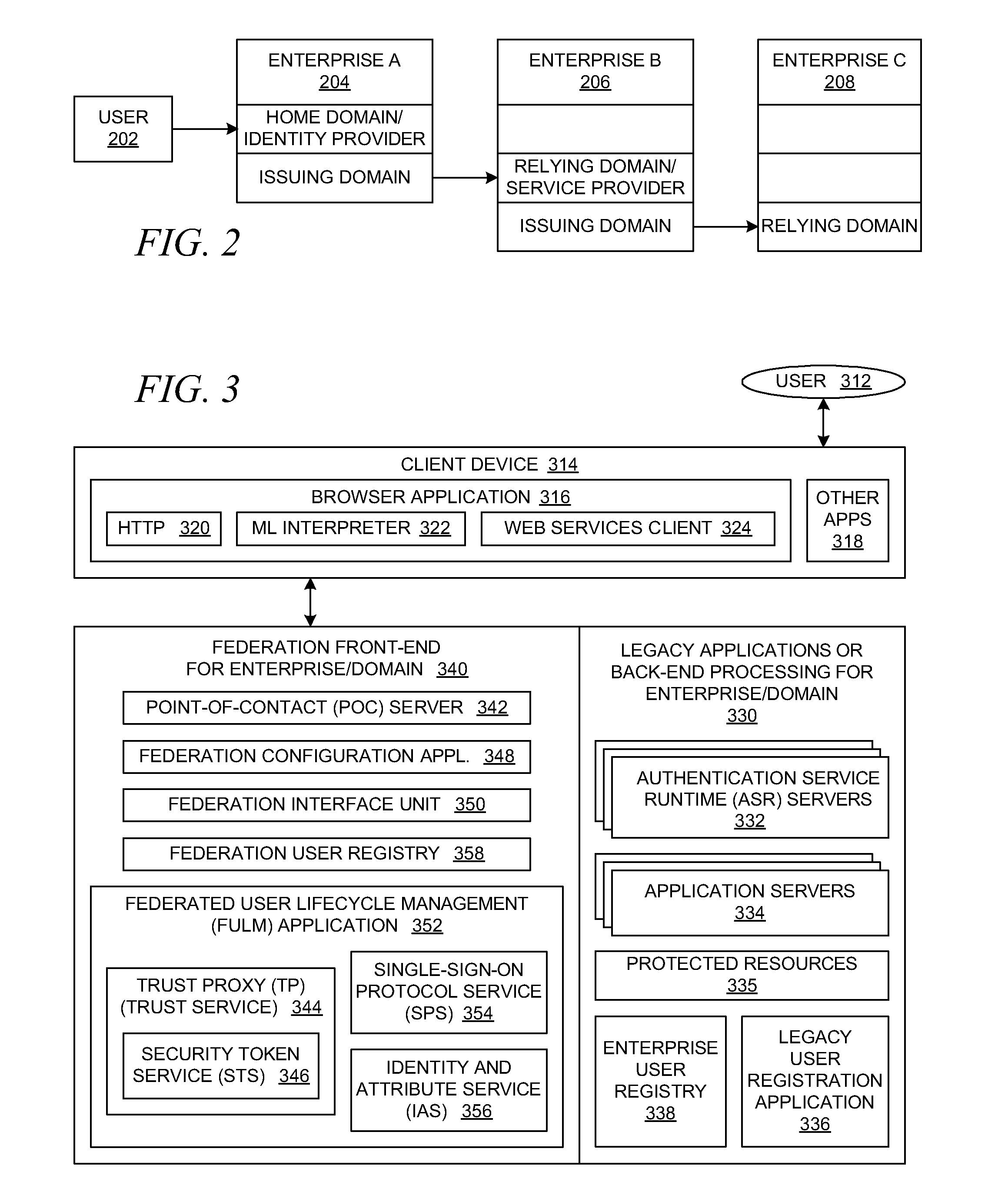
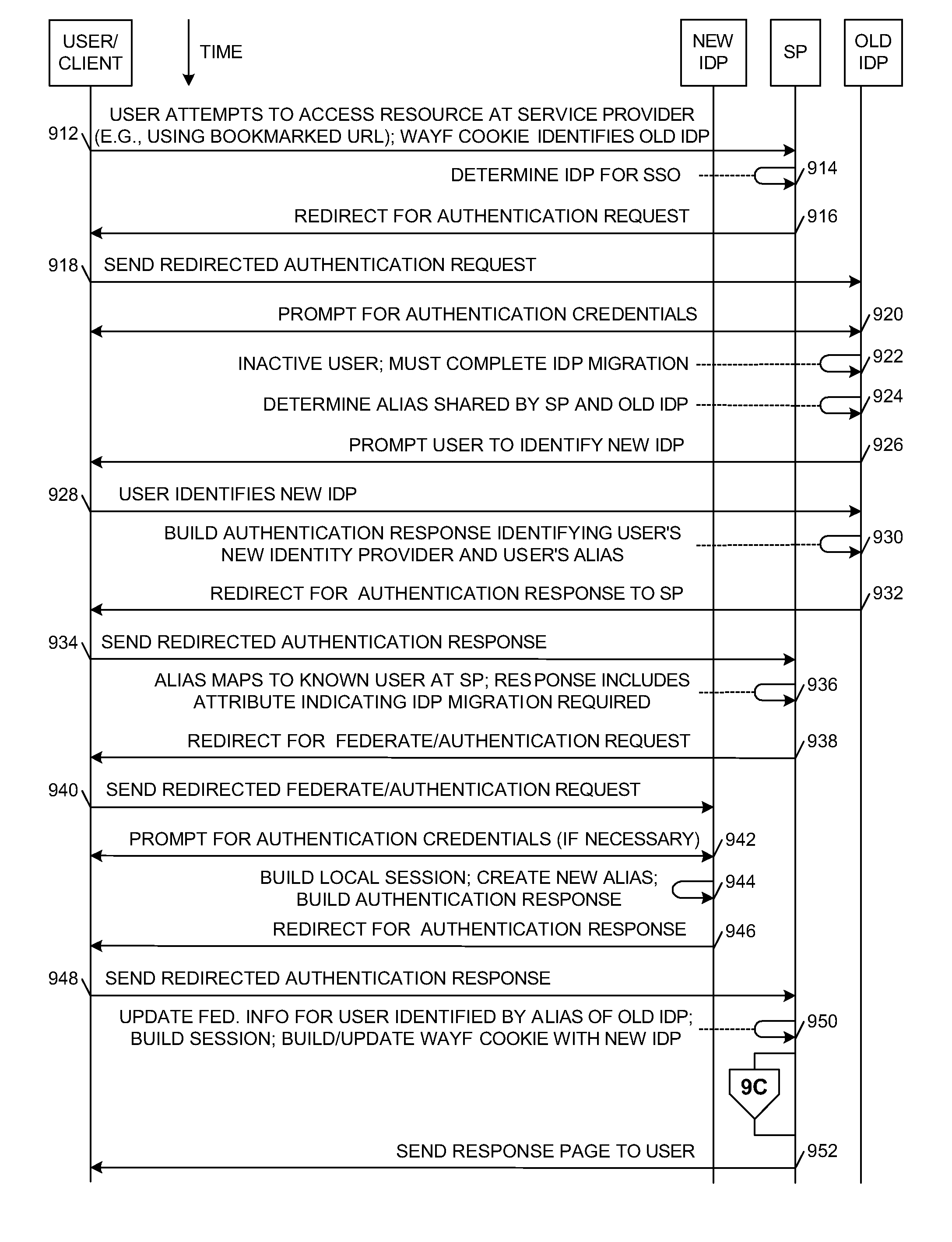
Method and system for identity provider migration using federated single-sign-on operation
ActiveUS20080021997A1Digital data processing detailsMultiple digital computer combinationsInternet privacyIdentity provider
A method is presented for performing an identity provider migration operation with respect to a user within a federated computational environment, wherein the user has a first user account at a first identity provider, a second user account at a second identity provider, and a third user account at a service provider. A request to access a resource is received by the service provider, after which a federated single-sign-on operation for the user is performed between the service provider and the first identity provider. Prior to sending a response to the request to access the protected resource, information in the third user account is modified to indicate that the service provider relies upon the second identity provider to authenticate the user on behalf of the service provider rather than the first identity provider. A response for the request to access the resource is then returned by the service provider.
Owner:SERVICENOW INC
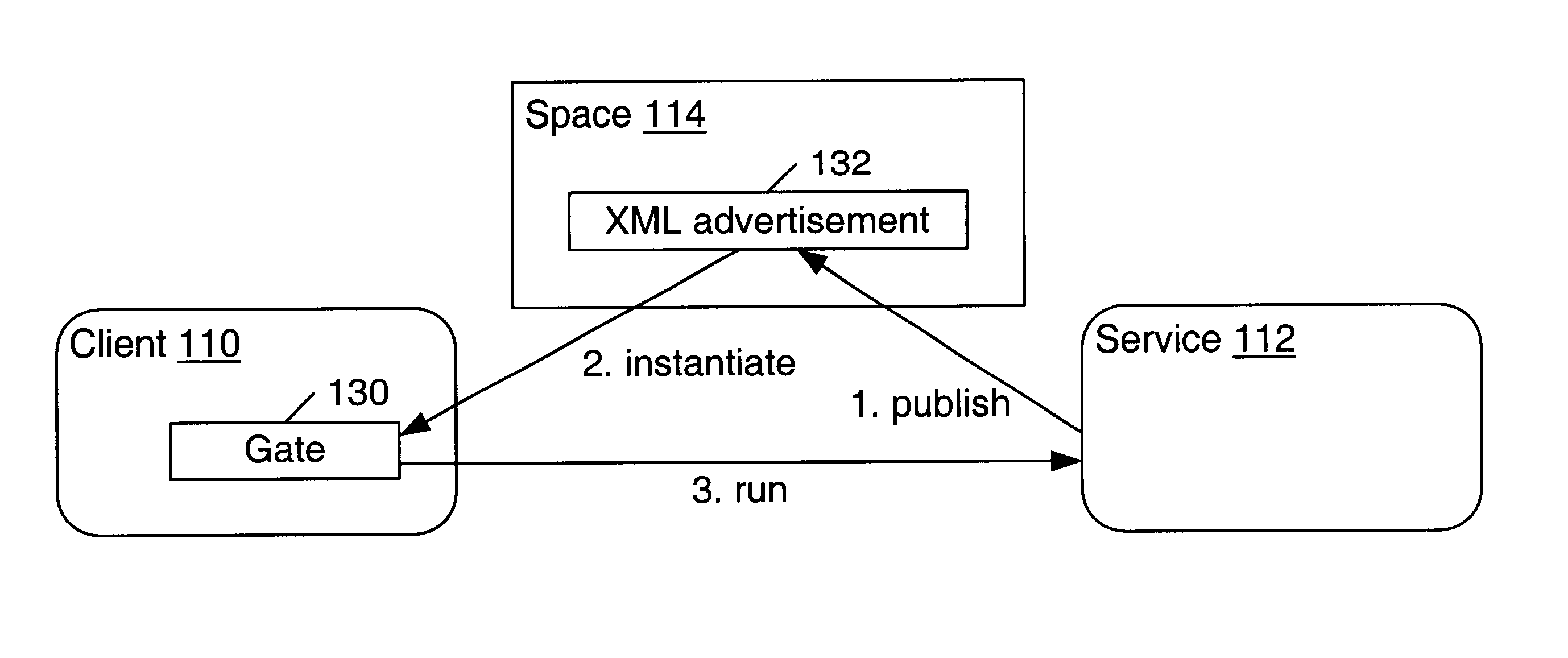
Trusted construction of message endpoints in a distributed computing environment
InactiveUS6792466B1Multiple digital computer combinationsTransmissionXML schemaDistributed Computing Environment
In a distributed computing environment, a message gate may be the message endpoint for a client or service to communicate with another client or service. Devices may have a gate factory (e.g. message endpoint constructor) that is trusted code on the device for generating gates based on XML message descriptions. The use of the gate factory may ensure that the gate it generates is also trusted code, and that the code is correct with respect to a service advertisement. A service advertisement may indicate, for a particular service, a message schema, service URI and authentication service URI. In one embodiment, the pieces the gate factory needs to construct a gate are the XML schema of the service and the URI of the service. In another embodiment, an authentication credential may also be obtained and used in gate construction by running an authentication service specified in the service advertisement. A gate factory for a device may generate gate code that may incorporate the language, security, type safety, and / or execution environment characteristics of the local device platform. By constructing gates itself, a device has the ability to ensure that the generated gate code is relatively bug-free, produces only valid data, and provides type-safety.
Owner:ORACLE INT CORP
Power on demand tiered response time pricing
Methods, articles of manufacture, and systems for determining a fee to be charged for requests processed in a grid computing environment based. In one embodiment the fee may be determined based on the time it takes to process a request and / or pricing schedules that may vary depending on a variety of pricing criteria. In another embodiment, a completion time criterion that defines a maximum acceptable time to complete a request may be specified. If the amount of time needed to perform the request is less than the maximum acceptable time specified, returning the results may be delayed to avoid providing services valued in excess of what the customer has paid for.
Owner:EBAY INC
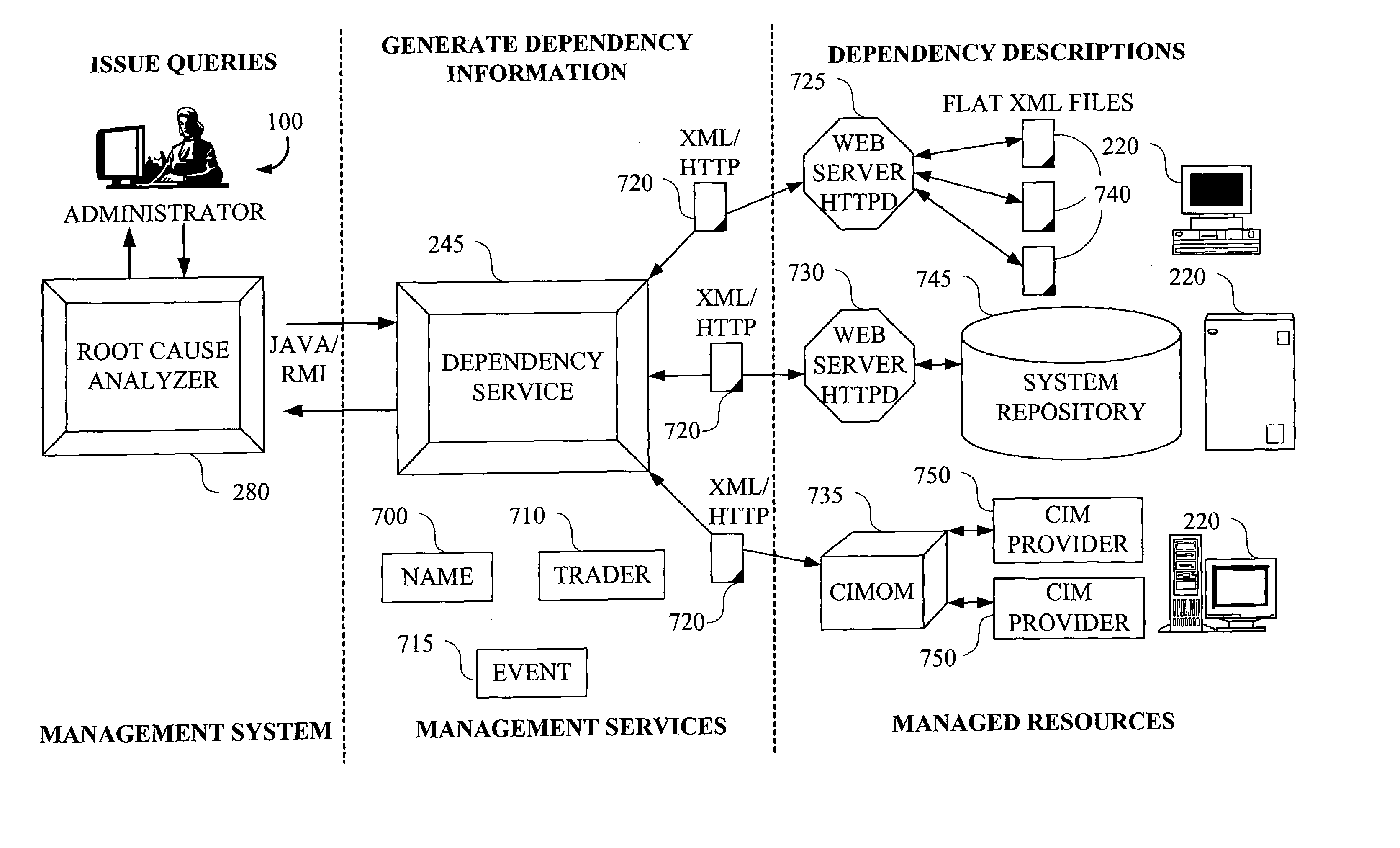
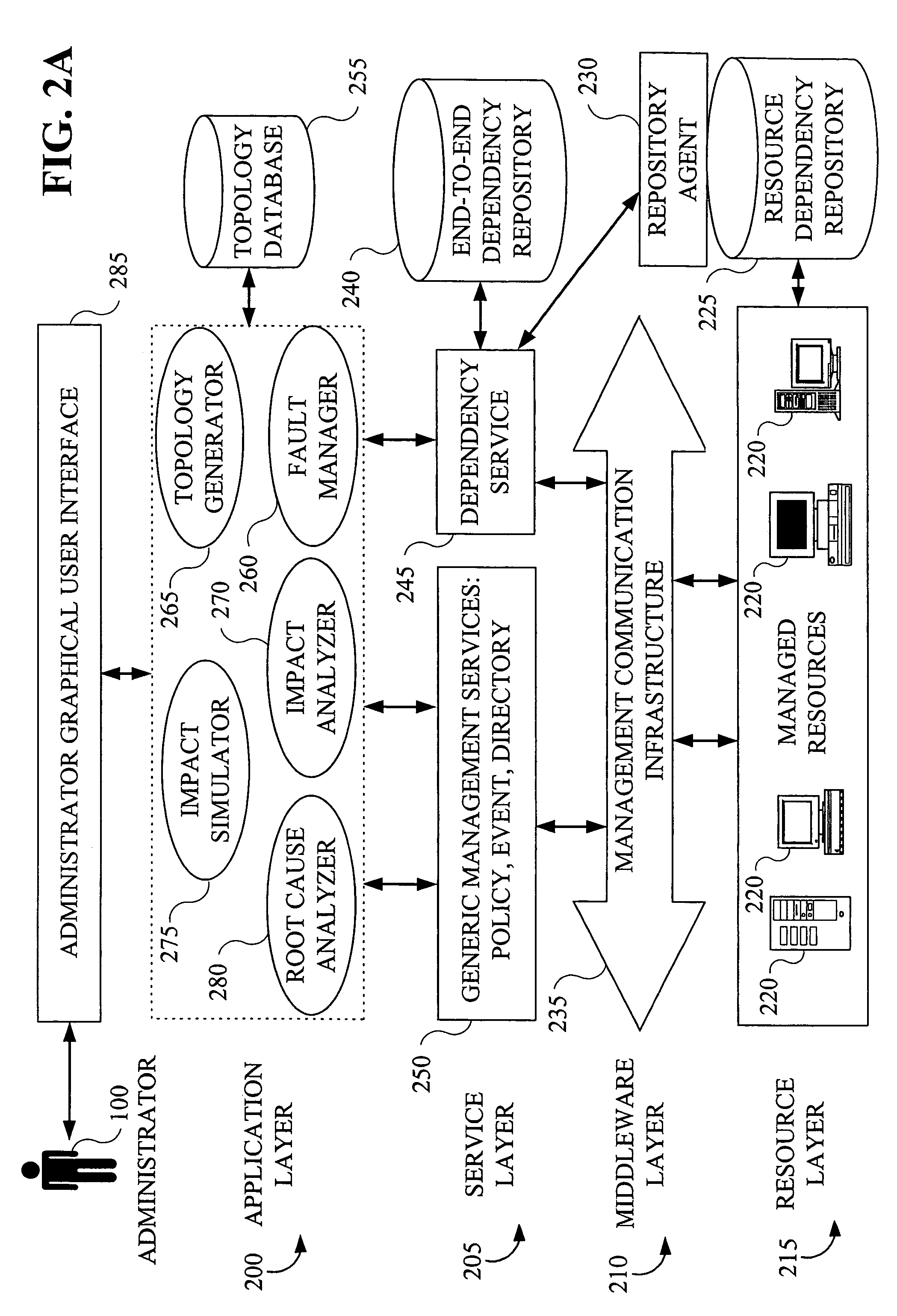
Methods and apparatus for root cause identification and problem determination in distributed systems
InactiveUS7096459B2Logical operation testingHardware monitoringDistributed Computing EnvironmentCondition status
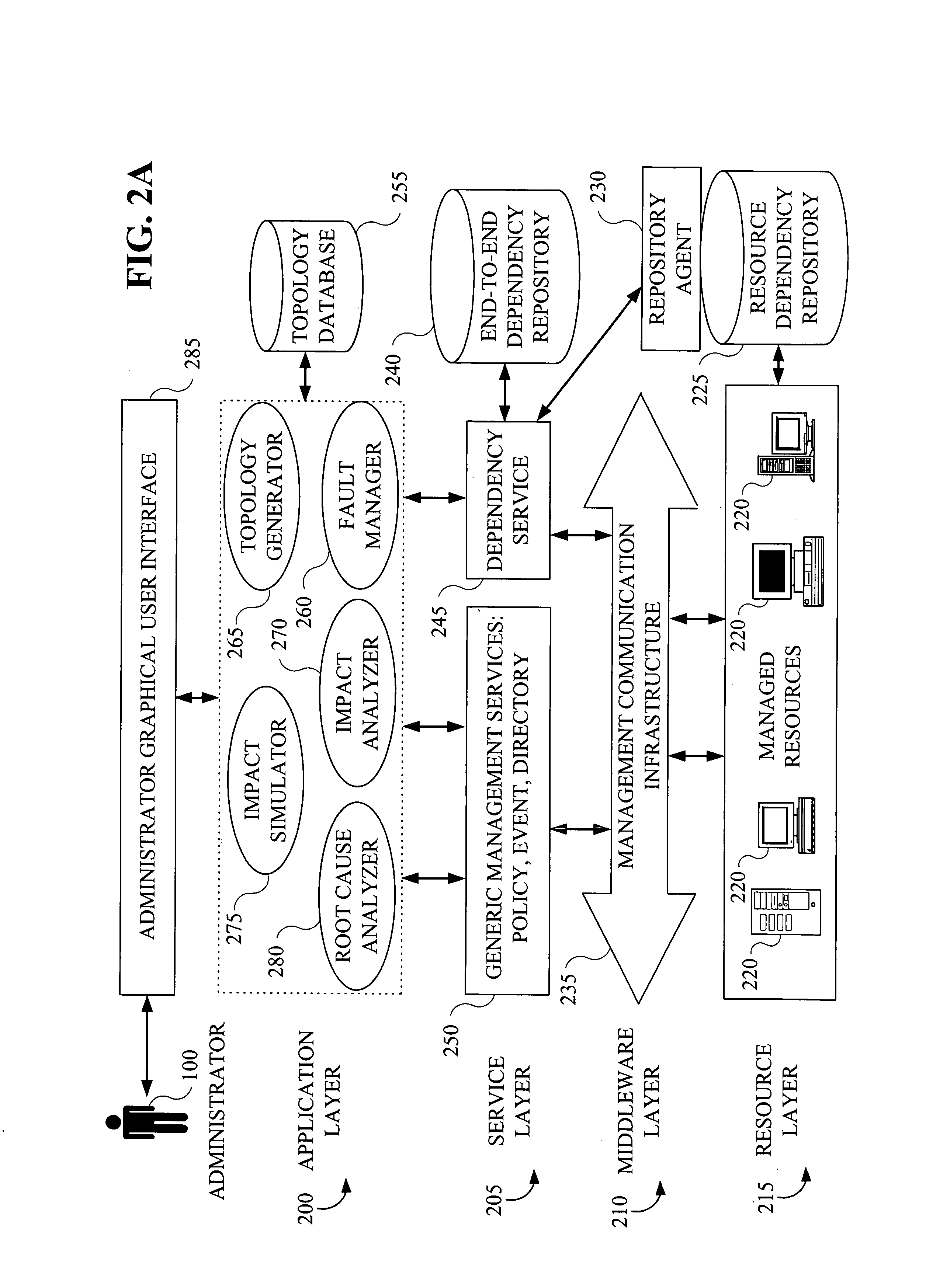
A technique for determining a root cause of a condition (e.g., service outage) of at least one subject component in a computing environment comprises the following steps / operations. First, one or more components in the computing environment upon which the at least one subject component depends (e.g., antecedents) are identified. Identification comprises traversing at least a portion of a model representative of an existence of one or more relationships associated with at least a portion of components of the computing environment and which is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Then, one or more procedures are performed in accordance with the one or more identified components to determine a condition status associated with each of the one or more identified components. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:IBM CORP
System and method for continuous optimization of computing systems with automated assignment of virtual machines and physical machines to hosts
ActiveUS20140019966A1Software simulation/interpretation/emulationMemory systemsEvent triggerComputing systems
A system and method for automatically reconfiguring a computing environment comprises a consumption analysis server, a placement server, a deployment server in communication with a set of virtual machine monitors and a data warehouse in communication with a set of data collection agents, and a database. The consumption analysis server operates on measured resource utilization data in the data warehouse to yield a set of resource consumptions, available capacities and host and virtual machine configurations from the computing environment. The deployment server continuously monitors an event triggering condition and when the triggering condition is met, the placement server assigns a set of target virtual machines to a target set of hosts in a new placement and the deployment server implements the new placement through communication with the set of virtual machine monitors. The placement server right-sizes the virtual machines and the target set of hosts.
Owner:CA TECH INC
Integrated intelligent server based system and method/systems adapted to facilitate fail-safe integration and/or optimized utilization of various sensory inputs
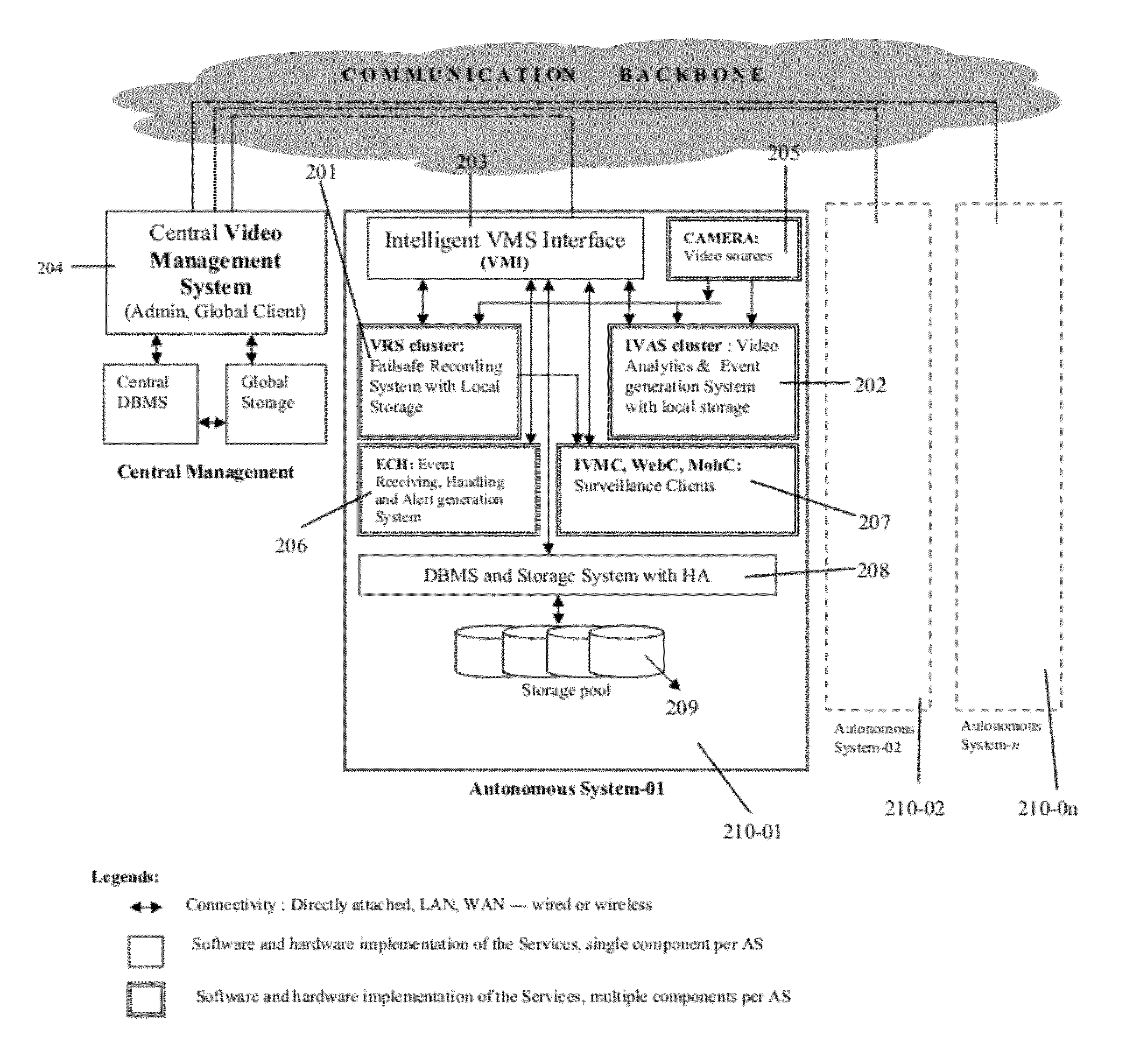
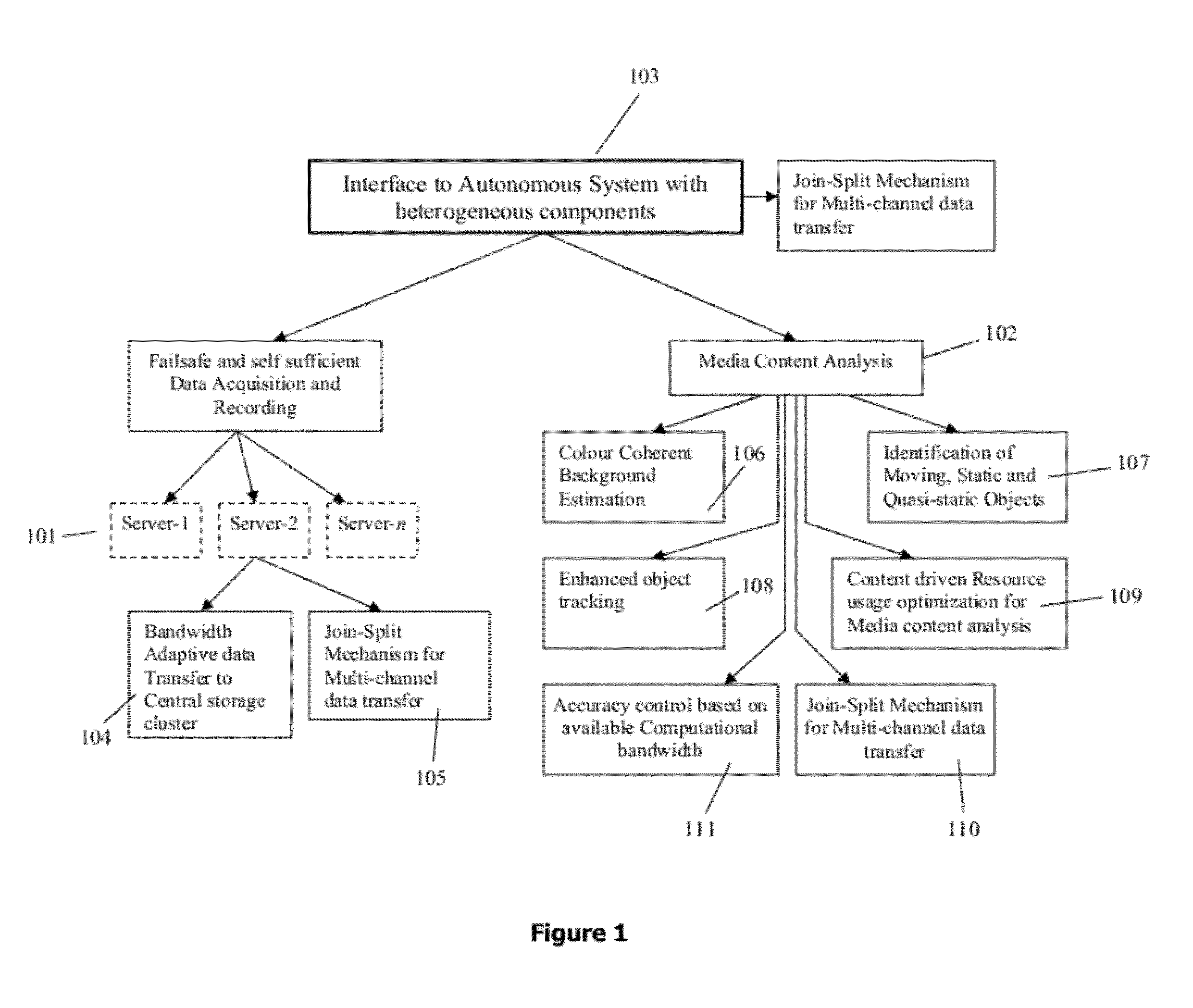
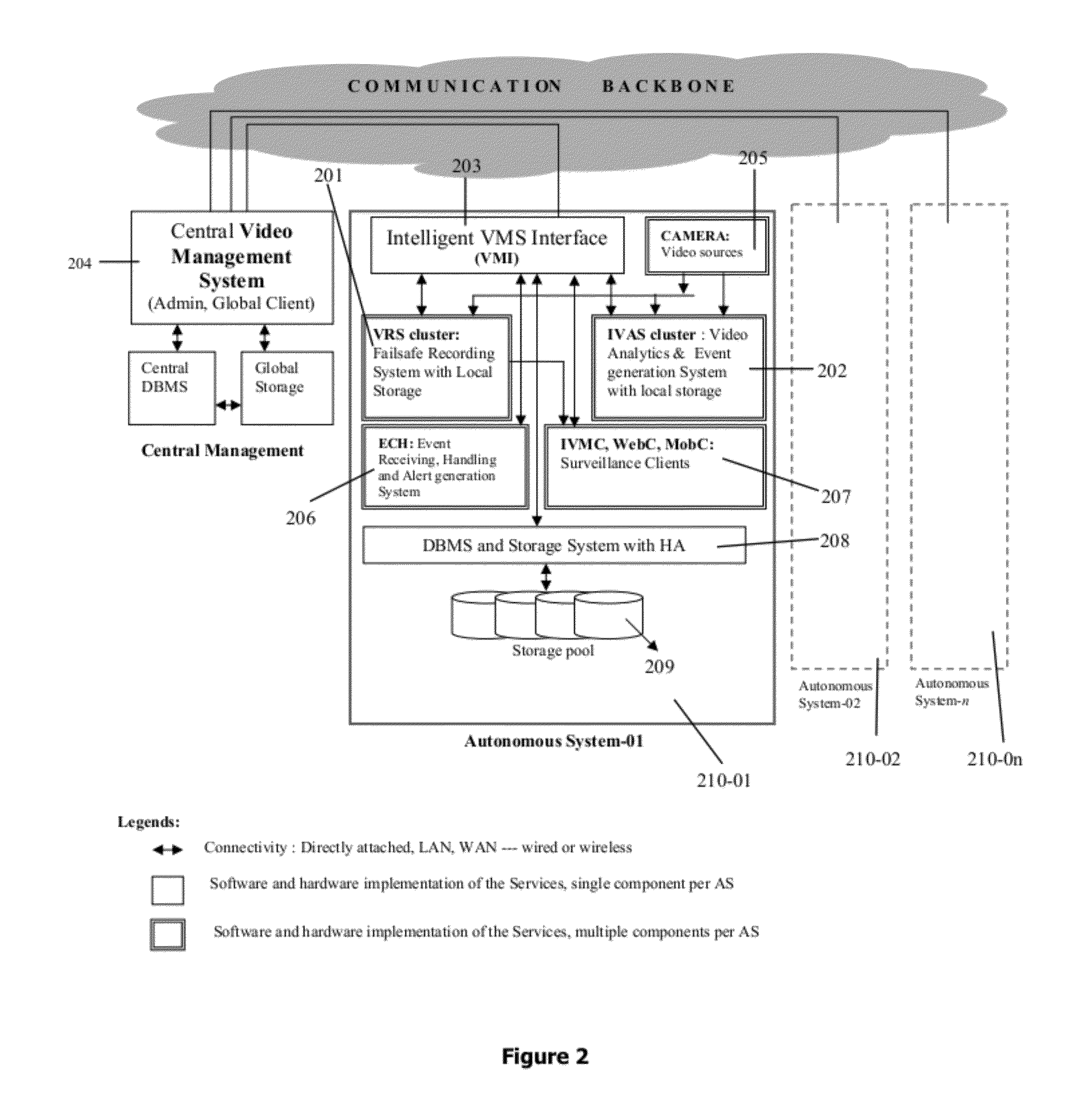
ActiveUS20120179742A1Accurate predictive colour background estimationPrecise positioningTelevision system detailsRoad vehicles traffic controlFace detectionOperational system
Integrated intelligent system adapted for any operating system and / or multi-OS computing environment seamlessly having sensory input / data acquisition cum recording server group and / or analytics server group enabling fail-safe integration and / or optimized utilization of various sensory inputs for various utility applications. Also disclosed as added advancements include intelligent method / system for cost-effective and efficient band adaptive transferring / recording sensory data from single or multiple data sources to network accessible storage devices, fail safe and self sufficient server group based method for sensory input recording and live streaming in a multi-server environment, intelligent and unified method of colour coherent object analysis, face detection in video images and the like, resource allocation for analytical processing involving multi channel environment, multi channel join-split mechanism adapted for low and / or variable bandwidth network link, enhanced multi-colour and / or mono-colour object tracking and also an intelligent automated traffic enforcement system.
Owner:VIDEONETICS TECH PRIVATE
System and method for distributed computation based upon the movement, execution, and interaction of processes in a network
InactiveUS6016393AResource allocationInterprogram communicationDistributed Computing EnvironmentEngineering
A distributed computing environment in which agent processes direct their own movement through a computer network. Place processes provide a computing context within which agent processes are interpreted. An agent process controls its movement from one place process to another within the network by using a ticket. An agent process which moves from one place process to another transports definitions of classes of which objects included in the agent process are members. An agent process which moves from one place process to a second place process avoids unnecessary transportation of objects included in the agent process by substituting equivalent objects which are found in the second place process. An agent process sends clones of the agent process to several place processes simultaneously. If two clones travel along paths which are coextensive for an initial portion thereof, a single clone is transported along the initial portion of the paths and other clones are formed from the single clone, thereby avoiding transferring redundant information along communications media. Two agent processes, which occupy a single place process, interact by exchanging references to one another. The single place process ensures that neither agent process receives a reference to the other agent process without simultaneously giving to the other agent process a reference to the former agent process. Unauthorized or inadvertent excessive use of network resources by an agent process, or a place process, is prevented by associating with each process a permit which defines various capabilities and resource allowances of the process.
Owner:INTELLECTUAL VENTURES I LLC
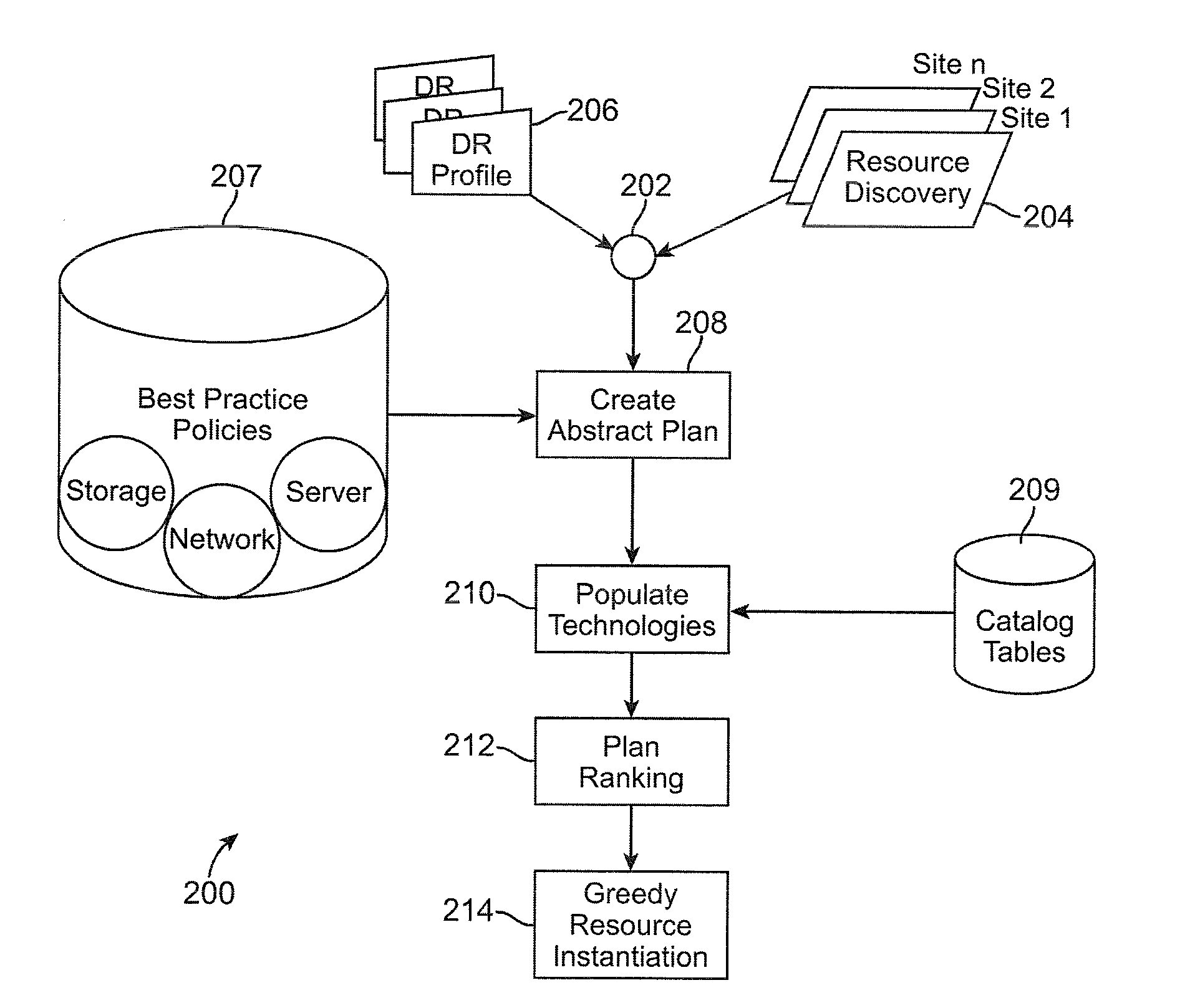
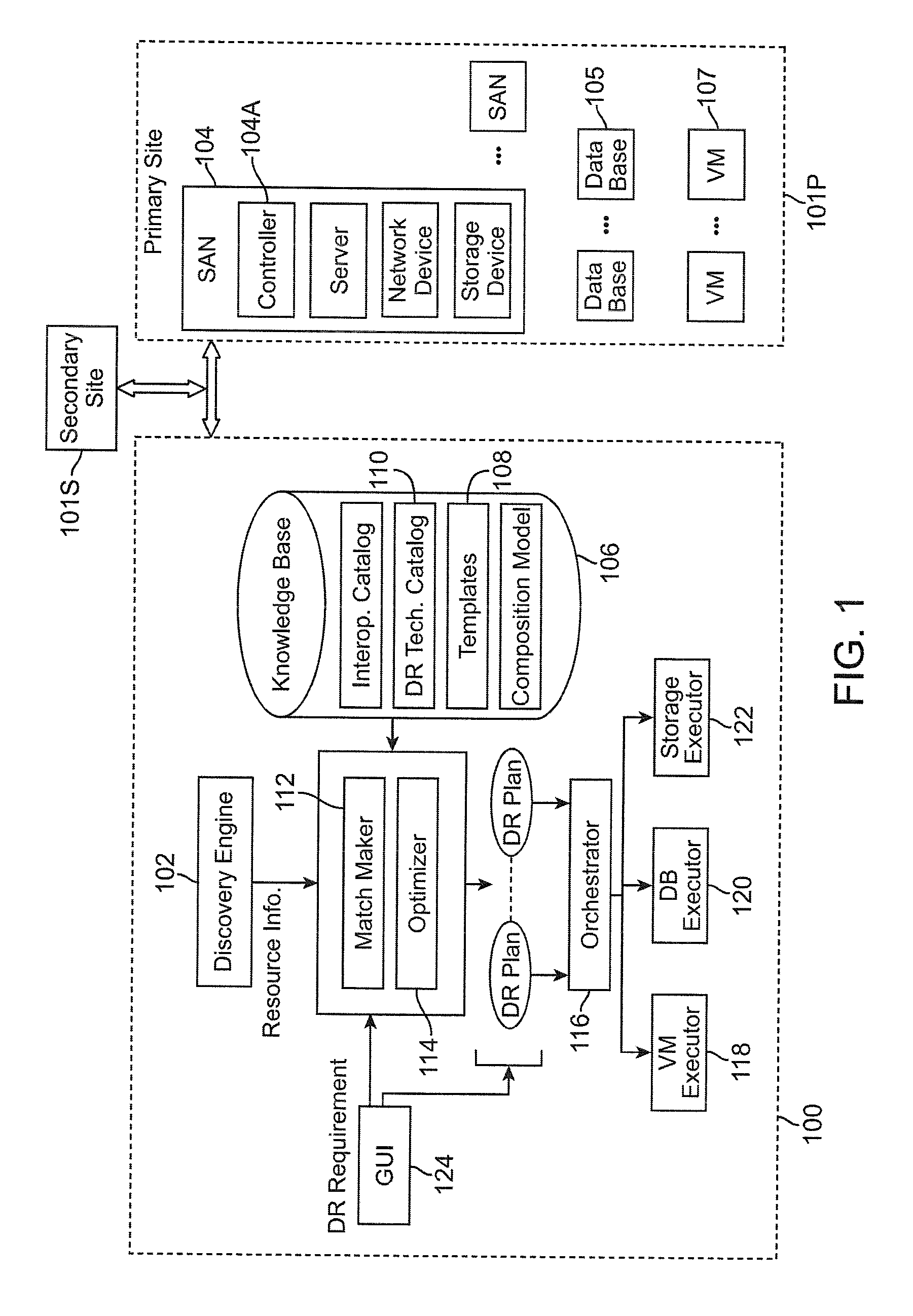
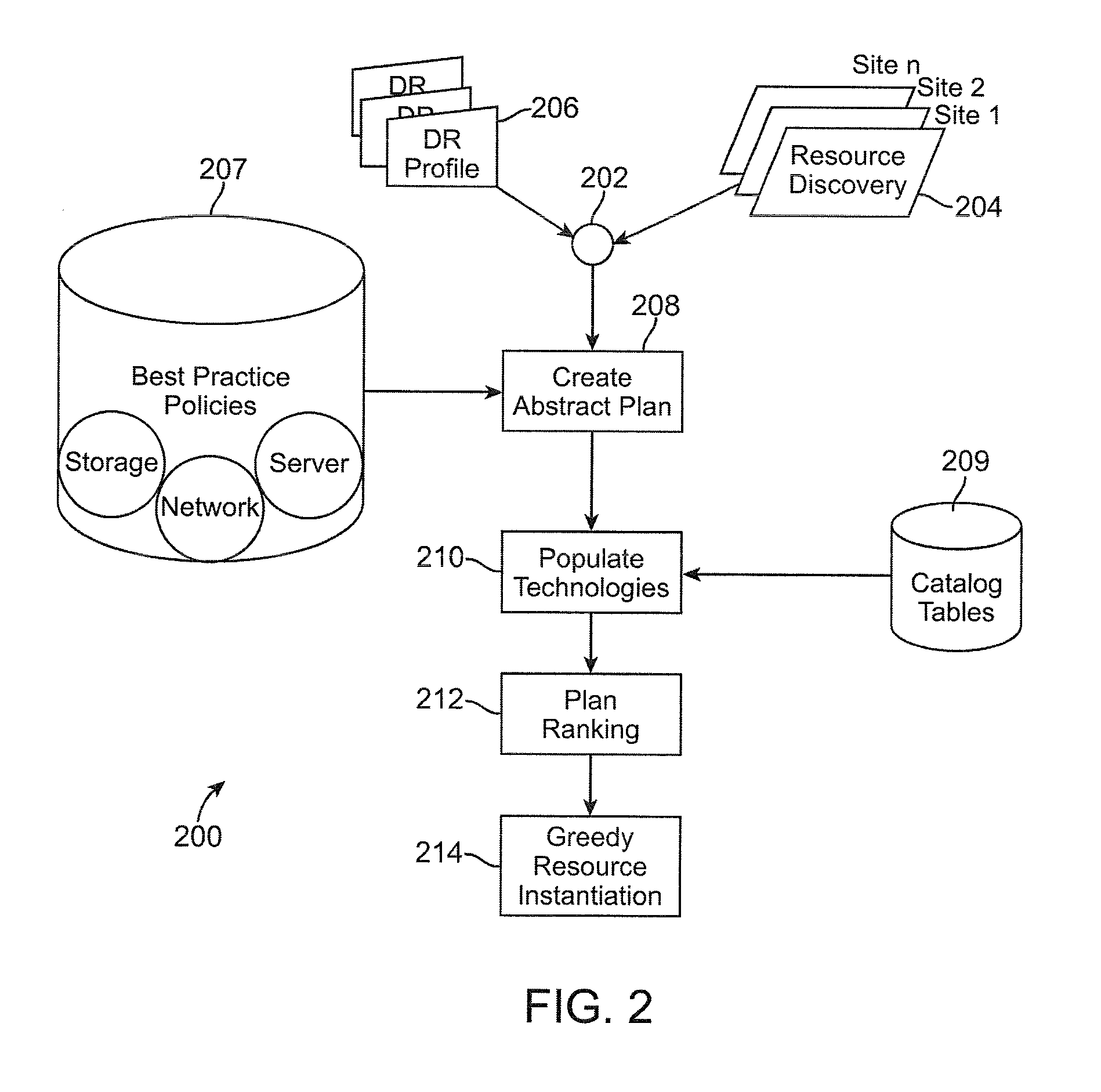
Method and system for automated integrated server-network-storage disaster recovery planning
ActiveUS20090307166A1Knowledge representationInference methodsReplication (computing)Disaster recovery plan
An automated disaster recovery (DR) planning system for a computing environment is provided. A discovery module discovers servers, networks, and storage devices in a computing environment. An expert knowledge base module captures best practices in planning, and capabilities, interoperability, limitation and boundary values for different DR technologies. A match-making module determines multiple DR plans as combinations of one or more replication technologies that can be used to satisfy DR requirements. And, an optimizer configured for assessing a feasible DR plan from said multiple DR plans, to deploy for DR planning of a primary computing environment.
Owner:DAEDALUS BLUE LLC
Managing a workload of a plurality of virtual servers of a computing environment
ActiveUS20120110164A1Overcomes shortcomingEnhanced advantageResource allocationDigital computer detailsHybrid systemEngineering
An integrated hybrid system is provided. The hybrid system includes compute components of different types and architectures that are integrated and managed by a single point of control to provide federation and the presentation of the compute components as a single logical computing platform.
Owner:IBM CORP
Methods and Systems for Evaluating Historical Metrics in Selecting a Physical Host for Execution of a Virtual Machine
ActiveUS20130042123A1Maximize power efficiencyMaximum efficiency of power useVolume/mass flow measurementPower supply for data processingResource consumptionCloud computing
Methods and systems for improved management of power utilization and resource consumption among physical hosts in a cloud computing environment. The management server may provide functionality facilitating the identification and optimized placement of a virtual machine within a cloud computing environment by evaluating historical and heuristic metrics data associated with both the physical hosts and the virtual machines. The management server utilizes the metrics data to generate scores for a plurality of physical host based on physical resources available in a cloud of computing resources. The management server identifies a physical host on which to place a virtual machine using the metrics data, generated scores, and numerous, configurable criteria. The management server responds to the identification of the physical host on which to place a virtual machine by adjusting processor performance and / or operating states for one or more of the physical hosts in the cloud computing environment.
Owner:CITRIX SYST INC
Methods and apparatus for managing computing deployment in presence of variable workload
ActiveUS7350186B2Efficient and effectiveAccommodating unanticipated workloadResource allocationReliability/availability analysisWorkloadDistributed computing
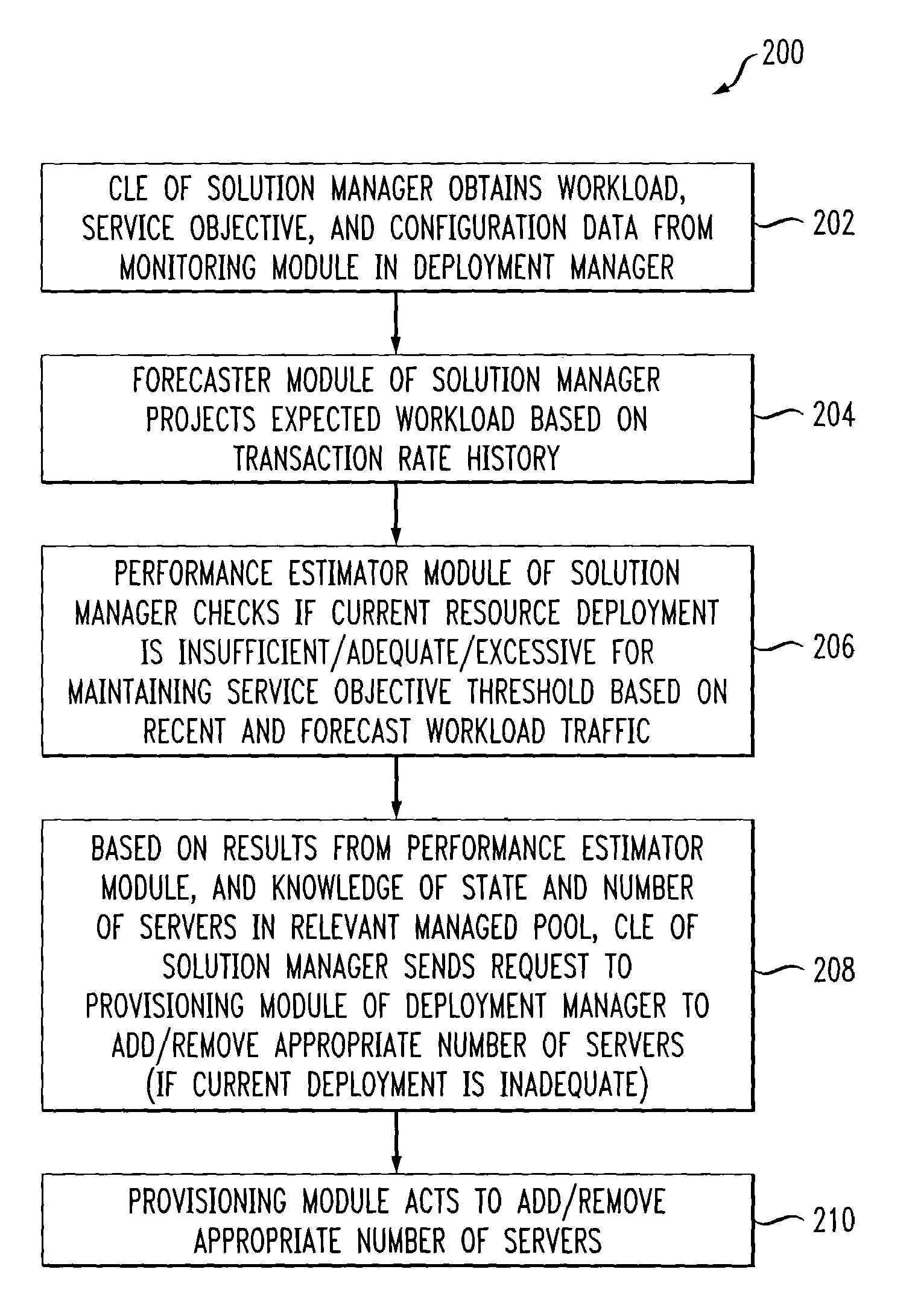
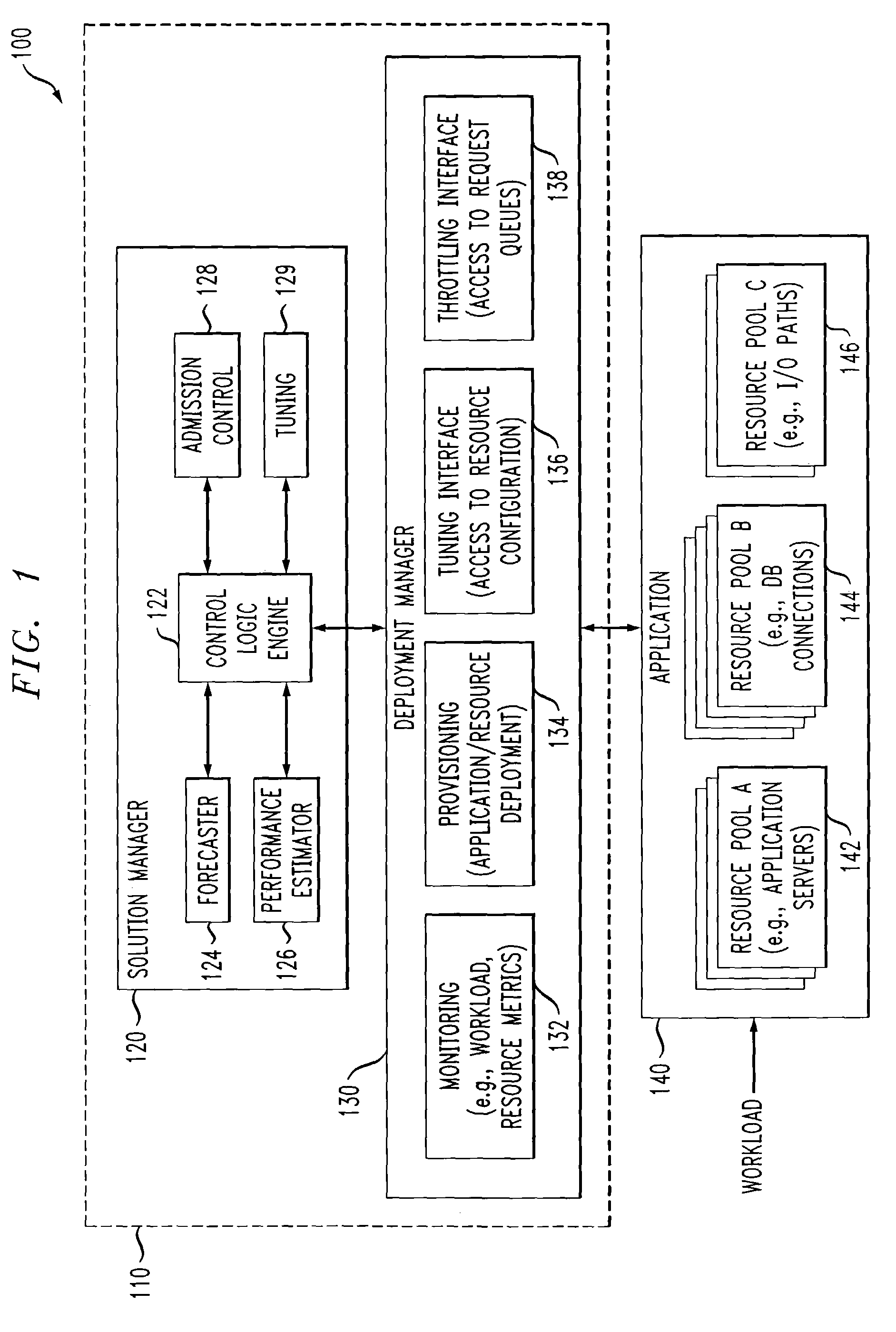
Automated or autonomic techniques for managing deployment of one or more resources in a computing environment based on varying workload levels. The automated techniques may comprise predicting a future workload level based on data associated with the computing environment. Then, an estimation is performed to determine whether a current resource deployment is insufficient, sufficient, or overly sufficient to satisfy the future workload level. Then, one or more actions are caused to be taken when the current resource deployment is estimated to be insufficient or overly sufficient to satisfy the future workload level. Actions may comprise resource provisioning, resource tuning and / or admission control.
Owner:GOOGLE LLC
Neural network learning and collaboration apparatus and methods
ActiveUS20140089232A1Reinforce similar learning experienceIncrease macroNeural architecturesSpecial data processing applicationsNeural network learningArtificial intelligence
Apparatus and methods for learning and training in neural network-based devices. In one implementation, the devices each comprise multiple spiking neurons, configured to process sensory input. In one approach, alternate heterosynaptic plasticity mechanisms are used to enhance learning and field diversity within the devices. The selection of alternate plasticity rules is based on recent post-synaptic activity of neighboring neurons. Apparatus and methods for simplifying training of the devices are also disclosed, including a computer-based application. A data representation of the neural network may be imaged and transferred to another computational environment, effectively copying the brain. Techniques and architectures for achieve this training, storing, and distributing these data representations are also disclosed.
Owner:BRAIN CORP
Method and apparatus for correlation of events in a distributed multi-system computing environment
InactiveUS7003781B1Overcome problemsHardware monitoringProgram controlData processing systemApplication software
A method and system is disclosed for monitoring an operation of a distributed data processing system. The system can include a plurality of applications running on a plurality of host processors and communicating with one another, such as through a message passing technique. The method includes steps executed in individual ones of the plurality of applications, of (a) examining individual ones of generated API calls to determine if a particular API call meets predetermined API call criteria; (b) if a particular API call meets the predetermined API call criteria, storing all or a portion of the content of the API call as a stored event; (c) processing a plurality of the stored events to identify logically correlated events, such as those associated with a business transaction; and (d) displaying all or a portion of the stored API call content data for the logically correlated events.
Owner:MICRO FOCUS LLC
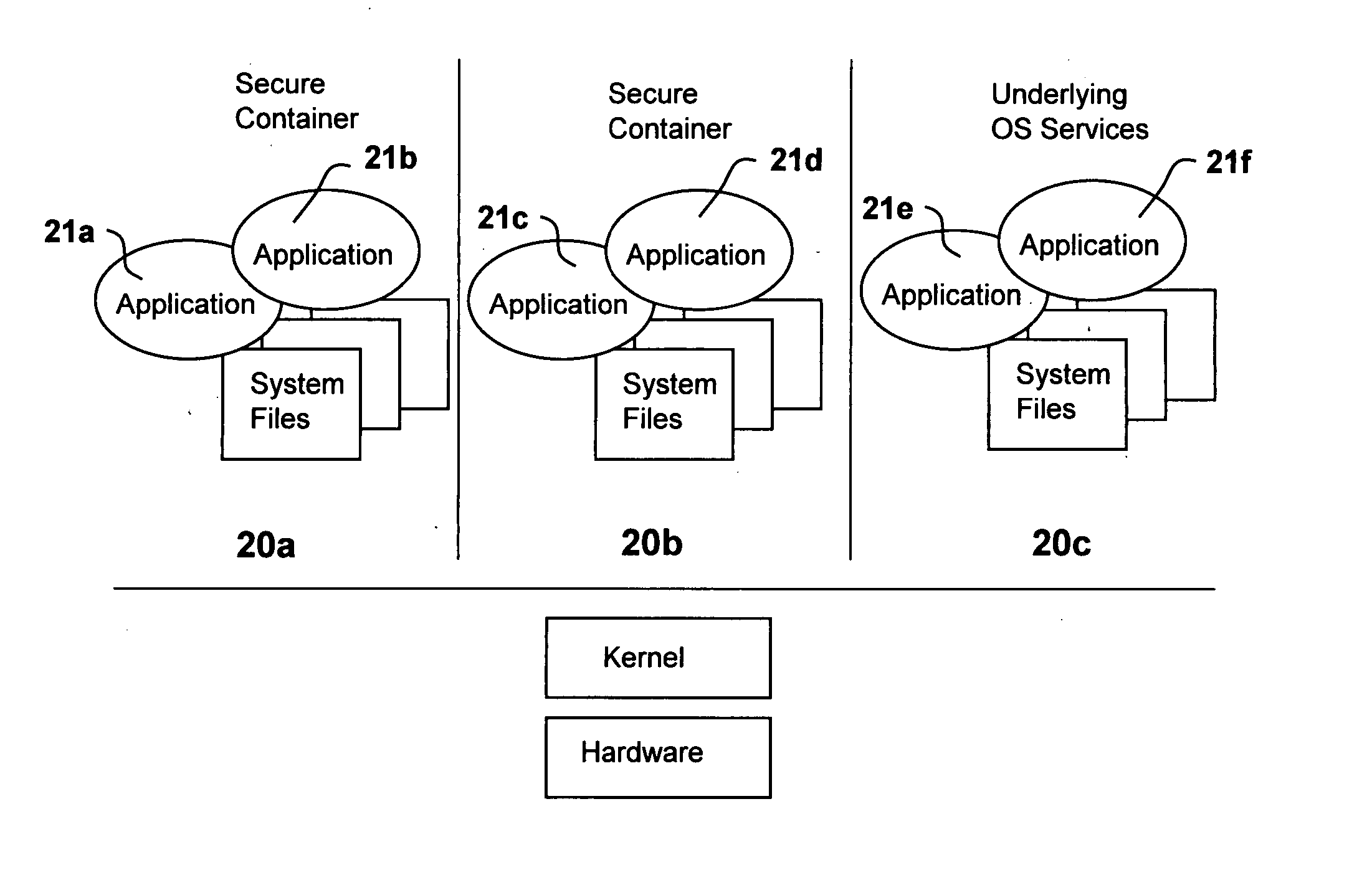
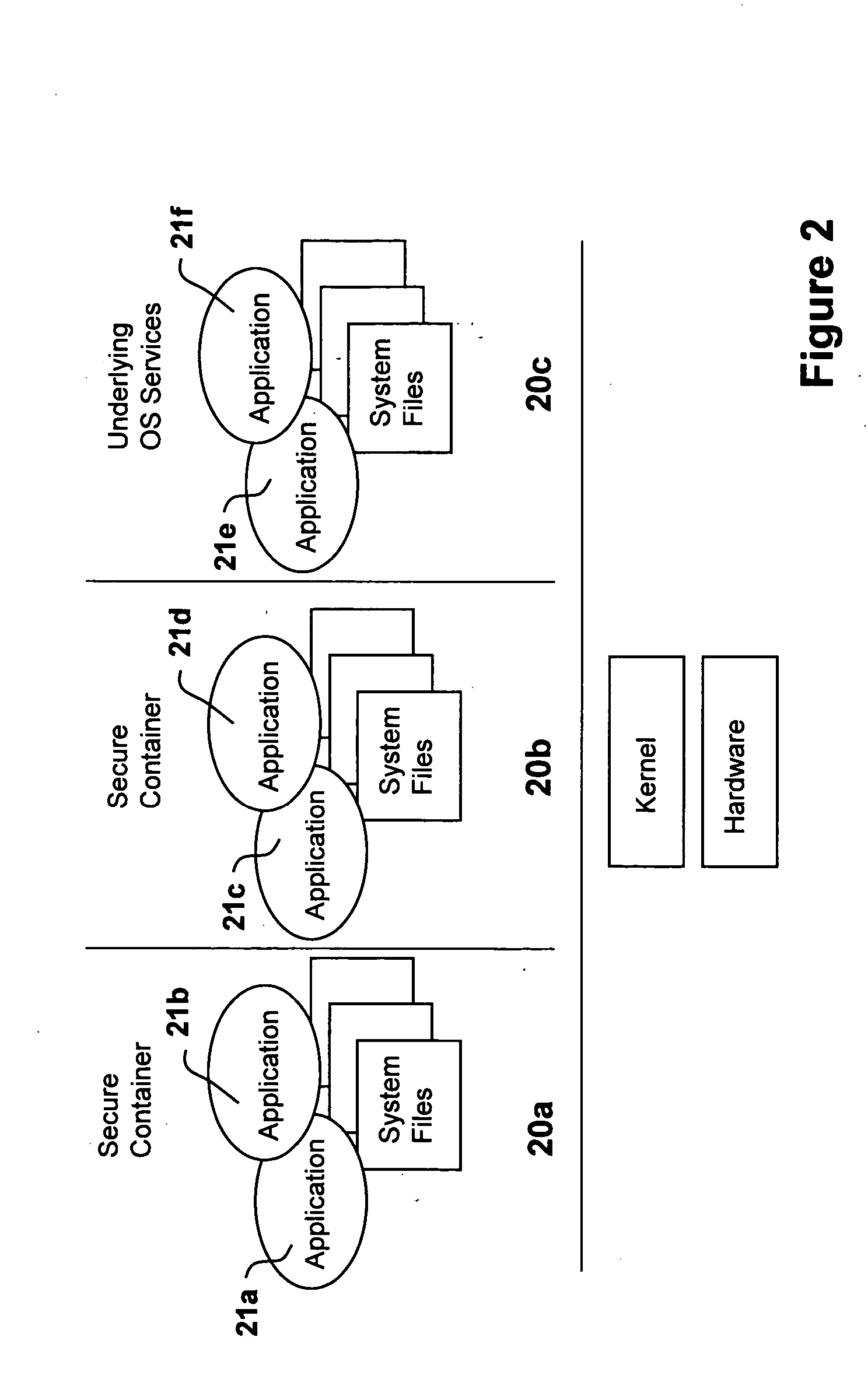
System for containerization of application sets
ActiveUS20050060722A1Specific access rightsMultiple digital computer combinationsMultiple applicationsApplication software
A system is disclosed having servers with operating systems that may differ, operating in disparate computing environments, wherein each server includes a processor and an operating system including a kernel a set of associated local system files compatible with the processor. This invention discloses a method of providing at least some of the servers in the system with secure, executable, applications related to a service, wherein the applications may be executed in a secure environment, wherein the applications each include an object executable by at least some of the different operating systems for performing a task related to the service. The method of this invention requires storing in memory accessible to at least some of the servers a plurality of secure containers of application software. Each container includes one or more of the executable applications and a set of associated system files required to execute the one or more applications, for use with a local kernel residing permanently on one of the servers. The set of associated system files are compatible with a local kernel of at least some of the plurality of different operating systems. The containers of application software exclude a kernel; and some or all of the associated system files within a container stored in memory are utilized in place of the associated local system files resident on the server.
Owner:TRIGENCE CORP
Method and system for identity provider migration using federated single-sign-on operation
ActiveUS7657639B2Digital data processing detailsMultiple digital computer combinationsInternet privacyIdentity provider
A method is presented for performing an identity provider migration operation with respect to a user within a federated computational environment, wherein the user has a first user account at a first identity provider, a second user account at a second identity provider, and a third user account at a service provider. A request to access a resource is received by the service provider, after which a federated single-sign-on operation for the user is performed between the service provider and the first identity provider. Prior to sending a response to the request to access the protected resource, information in the third user account is modified to indicate that the service provider relies upon the second identity provider to authenticate the user on behalf of the service provider rather than the first identity provider. A response for the request to access the resource is then returned by the service provider.
Owner:SERVICENOW INC
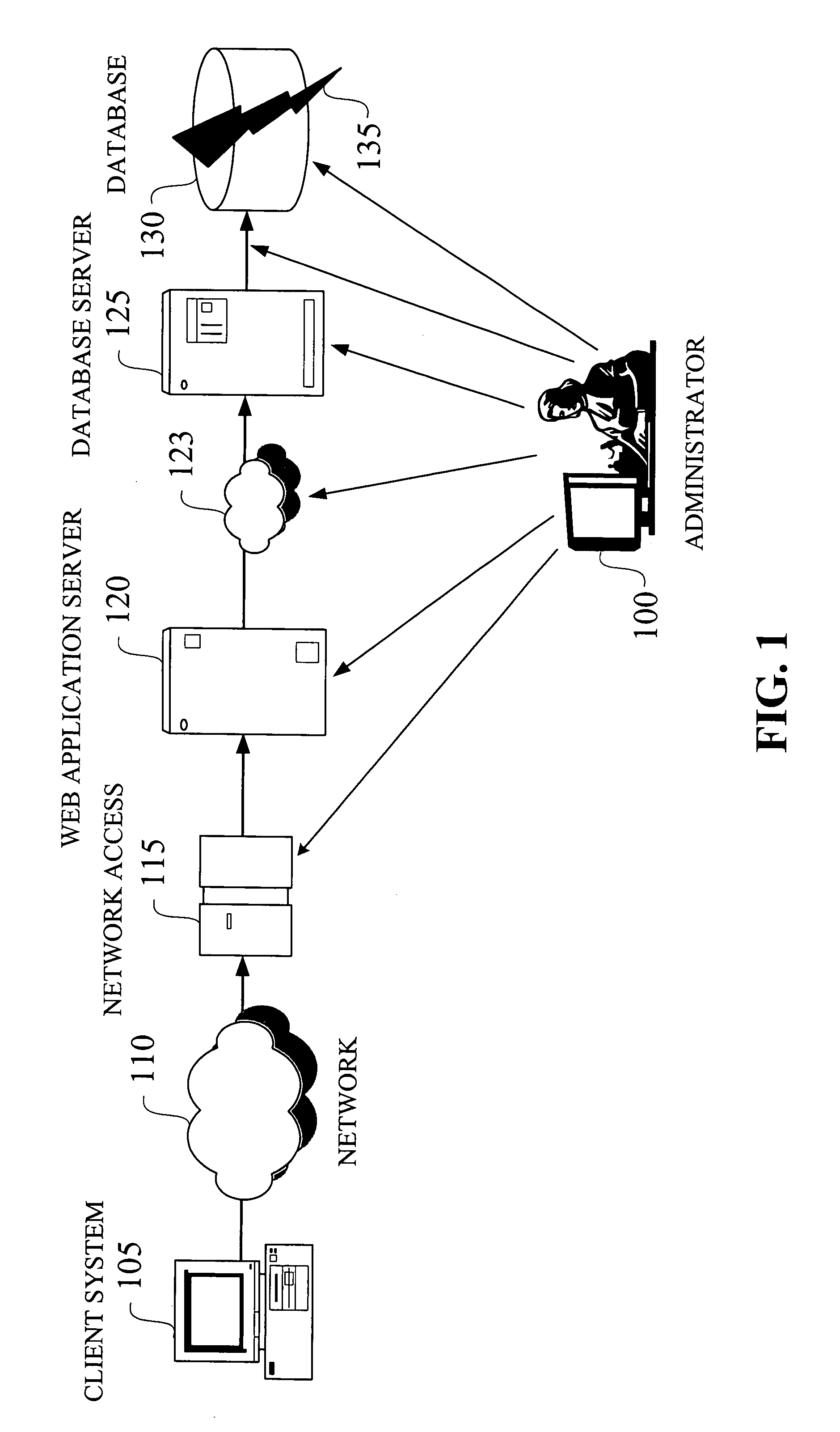
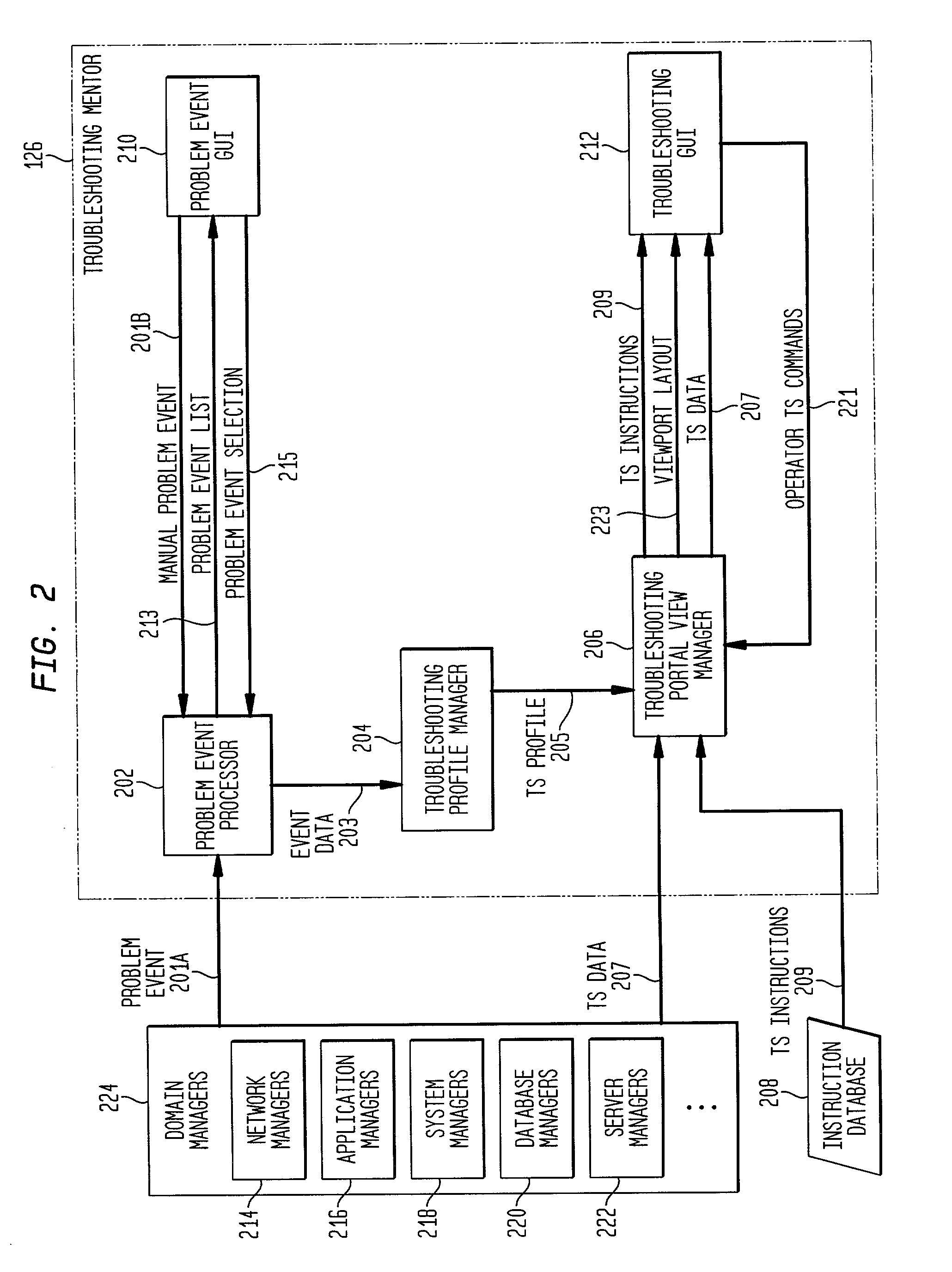
Dynamic generation of context-sensitive data and instructions for troubleshooting problem events in information network systems
InactiveUS20020161875A1Easy diagnosisEliminate needError detection/correctionDigital computer detailsDiagnostic dataRelevant information
A system and method for dynamically providing information to an administrator of a computing environment such as an administrator of a network system that is relevant to a particular problem event. This information includes contextual instructions and diagnostic data that will assist the network administrator in the analysis of the problem event. Generally, the invention automatically obtains from relevant computing environment entities pertinent information likely to be necessary to troubleshoot the particular problem event. The context-sensitive information is presented dynamically on a display for consideration and interaction by the network administrator. Specifically, the invention includes a database of executable troubleshooting (TS) profiles each specifically designed for a particular type of problem event. Each such TS profile references one or more troubleshooting data miner modules included in a library of such modules that accesses particular hardware or software entities in the network system for particular information. When a TS profile is invoked to assist a network administrator troubleshoot a particular type of problem event, the referenced data miner modules are executed and generate or cause the generator of troubleshooting instructions and diagnostic data which is then displayed to the network administrator.
Owner:VALTRUS INNOVATIONS LTD
Methods and apparatus for impact analysis and problem determination
ActiveUS7505872B2Digital computer detailsNuclear monitoringDistributed Computing EnvironmentCondition status
A technique for determining an impact of a condition (e.g., service outage) of at least one subject component in a computing environment comprises the following steps / operations. First, one or more components in the computing environment which depend on the at least one subject component (e.g., dependents) are identified. Identification comprises traversing at least a portion of a model representative of an existence of one or more relationships associated with at least a portion of components of the computing environment and which is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Then, one or more procedures are performed in accordance with the one or more identified components to determine a condition status associated with each of the one or more identified components. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:HUAWEI TECH CO LTD
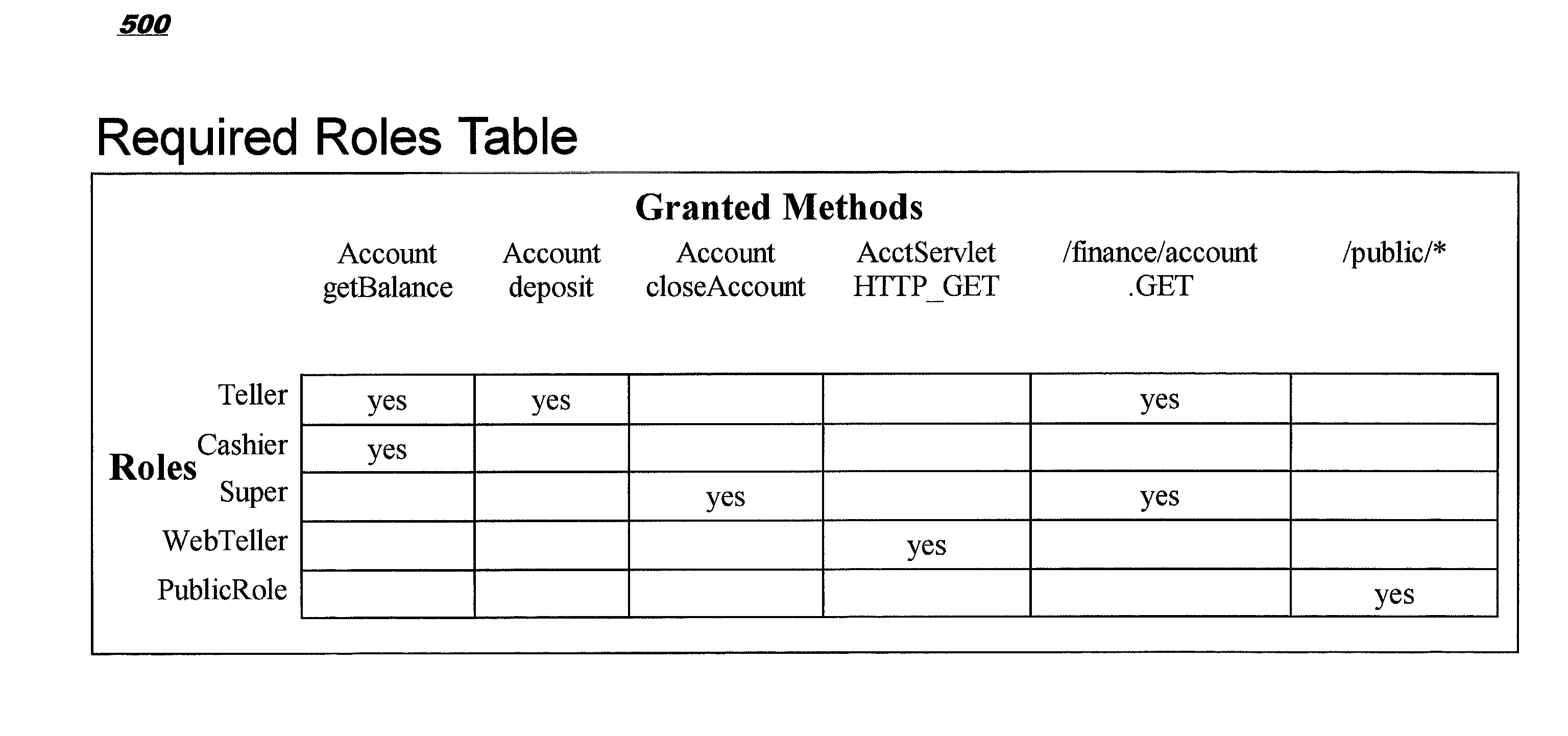
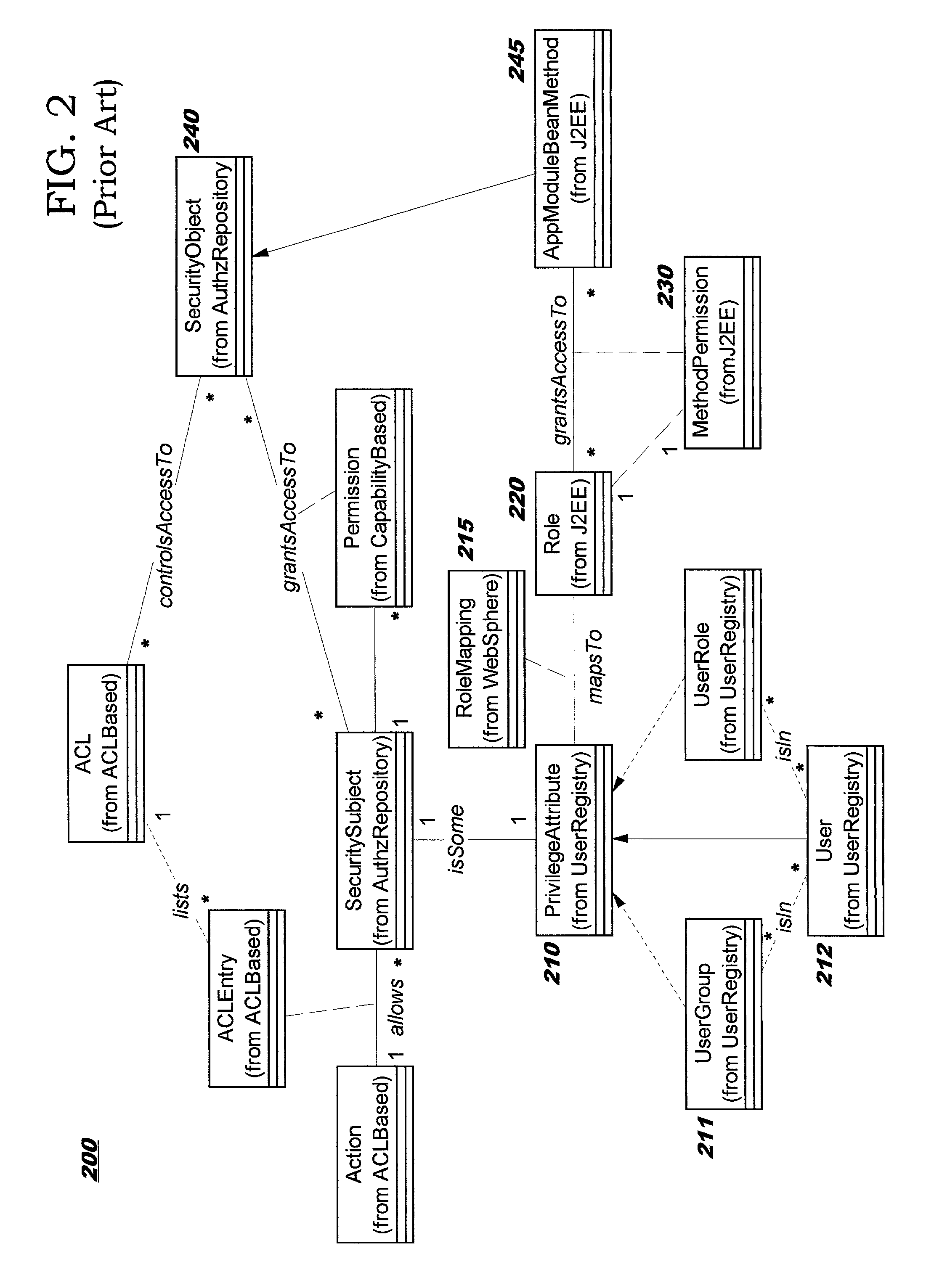
Role-permission model for security policy administration and enforcement
InactiveUS7124192B2Efficient and more manageableData processing applicationsDigital data processing detailsDistributed Computing EnvironmentSecurity policy management
Methods, systems, and computer program products are disclosed for protecting the security of resources in distributed computing environments. The disclosed techniques improve administration and enforcement of security policies. Allowed actions on resources, also called permissions, (such as invocations of particular methods, read or write access of a particular row or perhaps a particular column in a database table, and so forth) are grouped, and each group of permissions is associated with a role name. A particular action on a particular resource may be specified in more than one group, and therefore may be associated with more than one role. Each role is administered as a security object. Users and / or user groups may be associated with one or more roles. At run-time, access to a resource is protected by determining whether the invoking user has been associated with (granted) at least one of the roles required for this type of access on this resource.
Owner:INT BUSINESS MASCH CORP
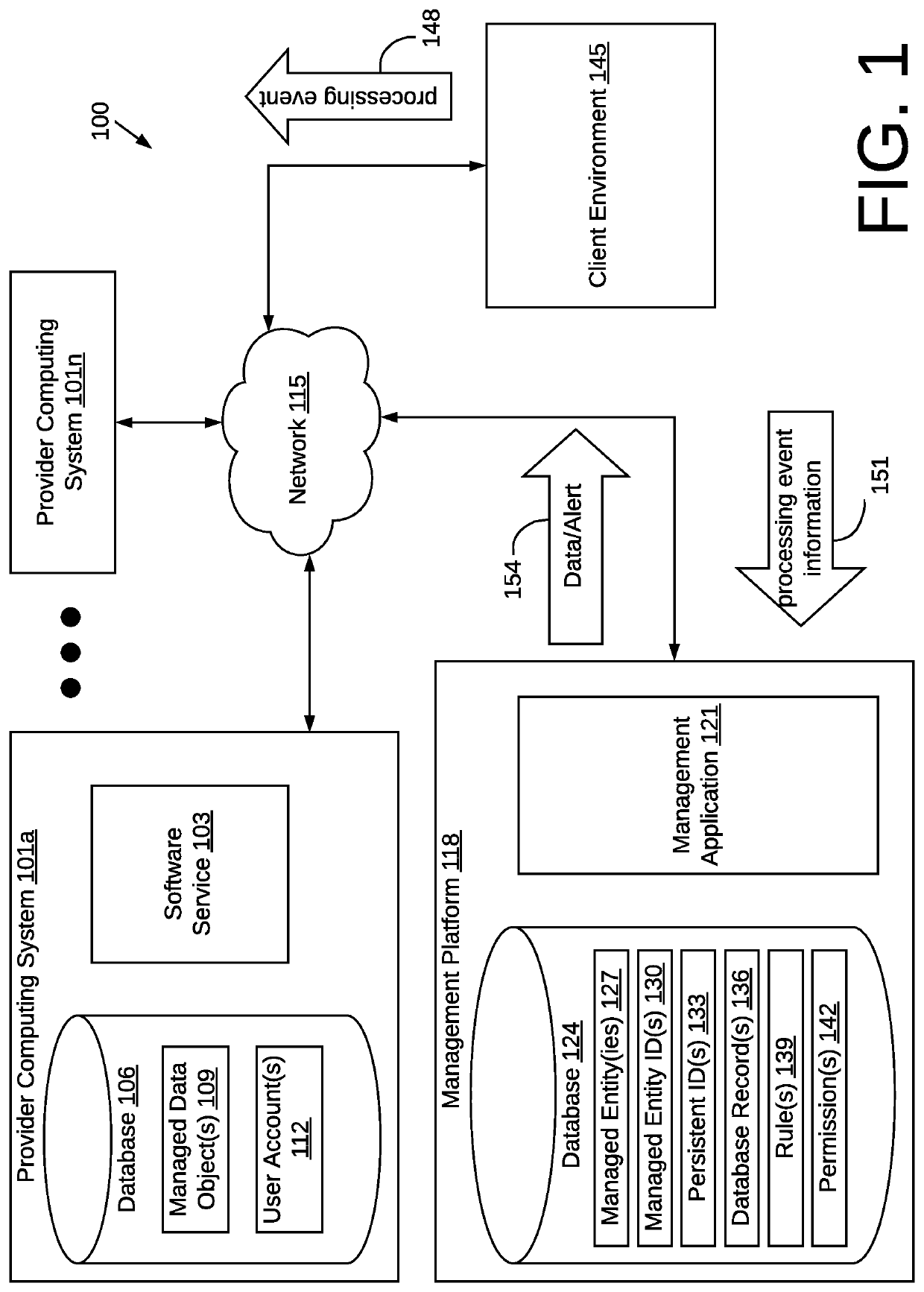
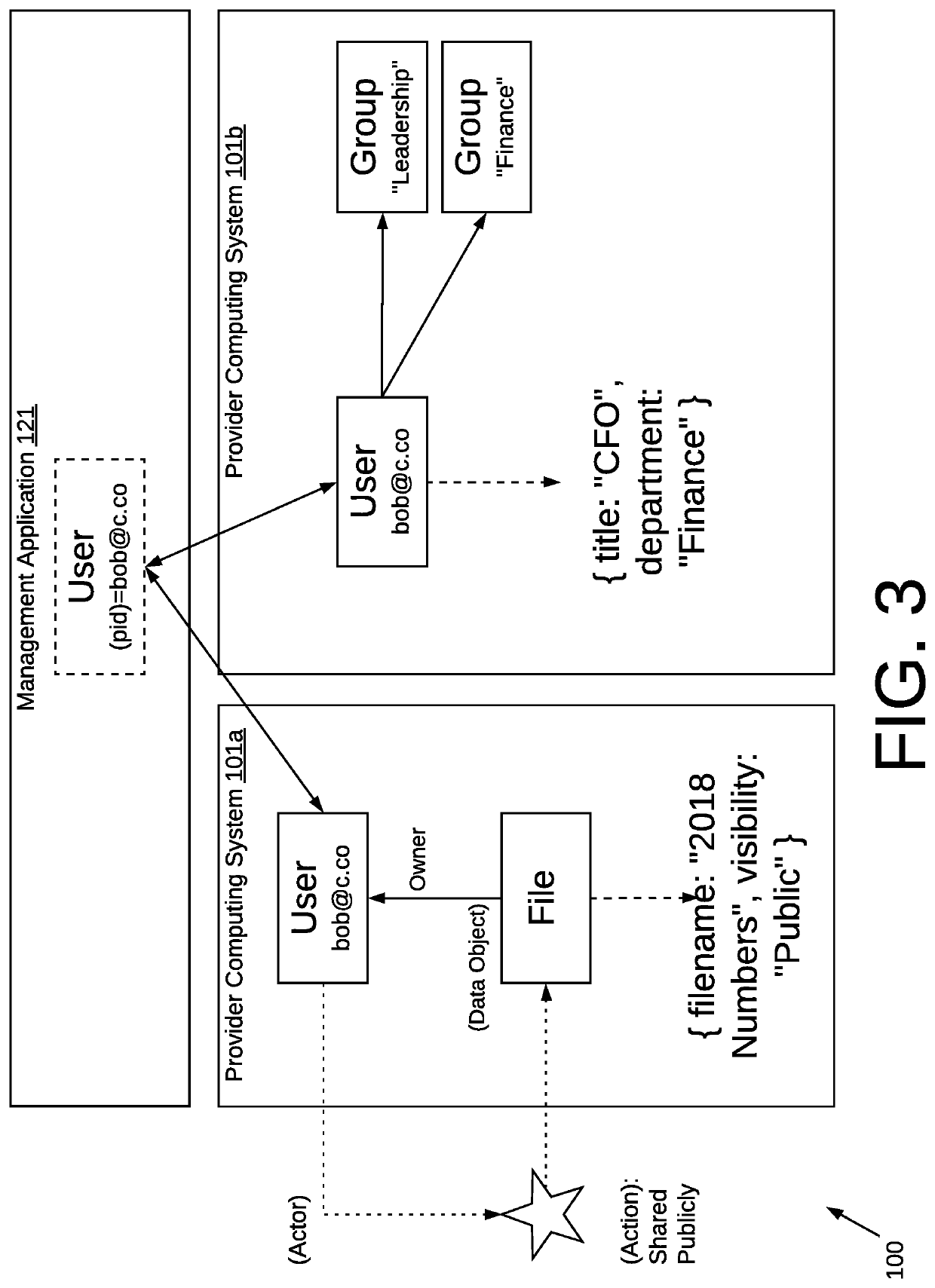
Methods and systems to manage data objects in a cloud computing environment
ActiveUS10965547B1Computer security arrangementsData switching networksData graphPersistent identifier
The present disclosure relates to managing activity taken with respect to cloud-based software services. A platform manages data objects processed by software services and / or those entities that initiate processing events. The platform uses identifiers such as, for example, a persistent identifier (PID) to track processing events. The platform implements rules and / or permissions related to the managed data objects and / or managed entities to determine whether processing events are in compliance. The platform may update database records, send alerts, send data graphs, or provide a real-time stream related to the managed data objects and / or managed entities. In addition, embodiments involve determining whether a PID-associated managed data object has been modified during processing to generate an additional version of the PID-associated managed data object and, if an object version is present, processing the additional version of the PID-associated managed data object to generate an integrated first PID-associated managed data object.
Owner:BETTERCLOUD INC
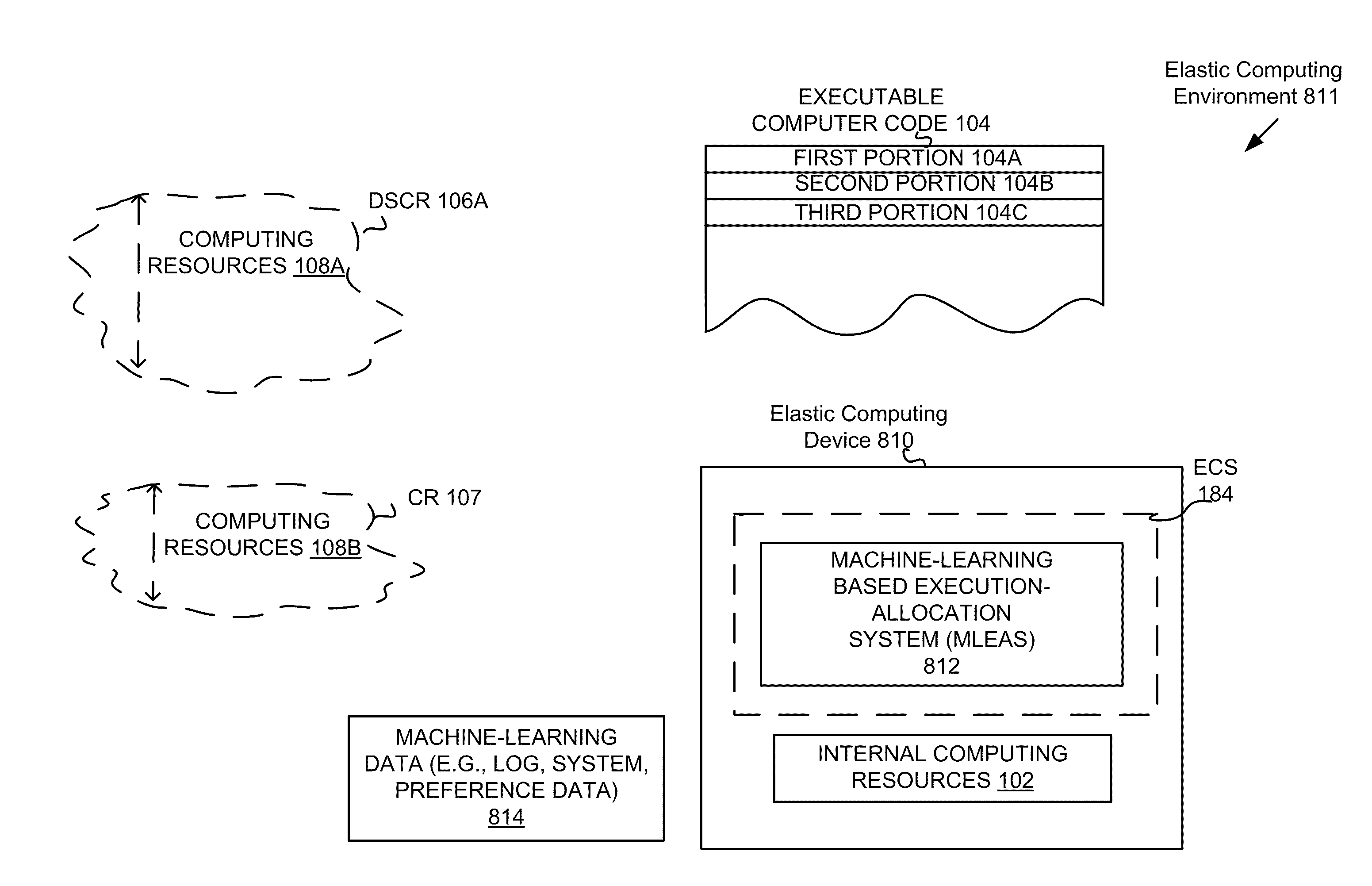
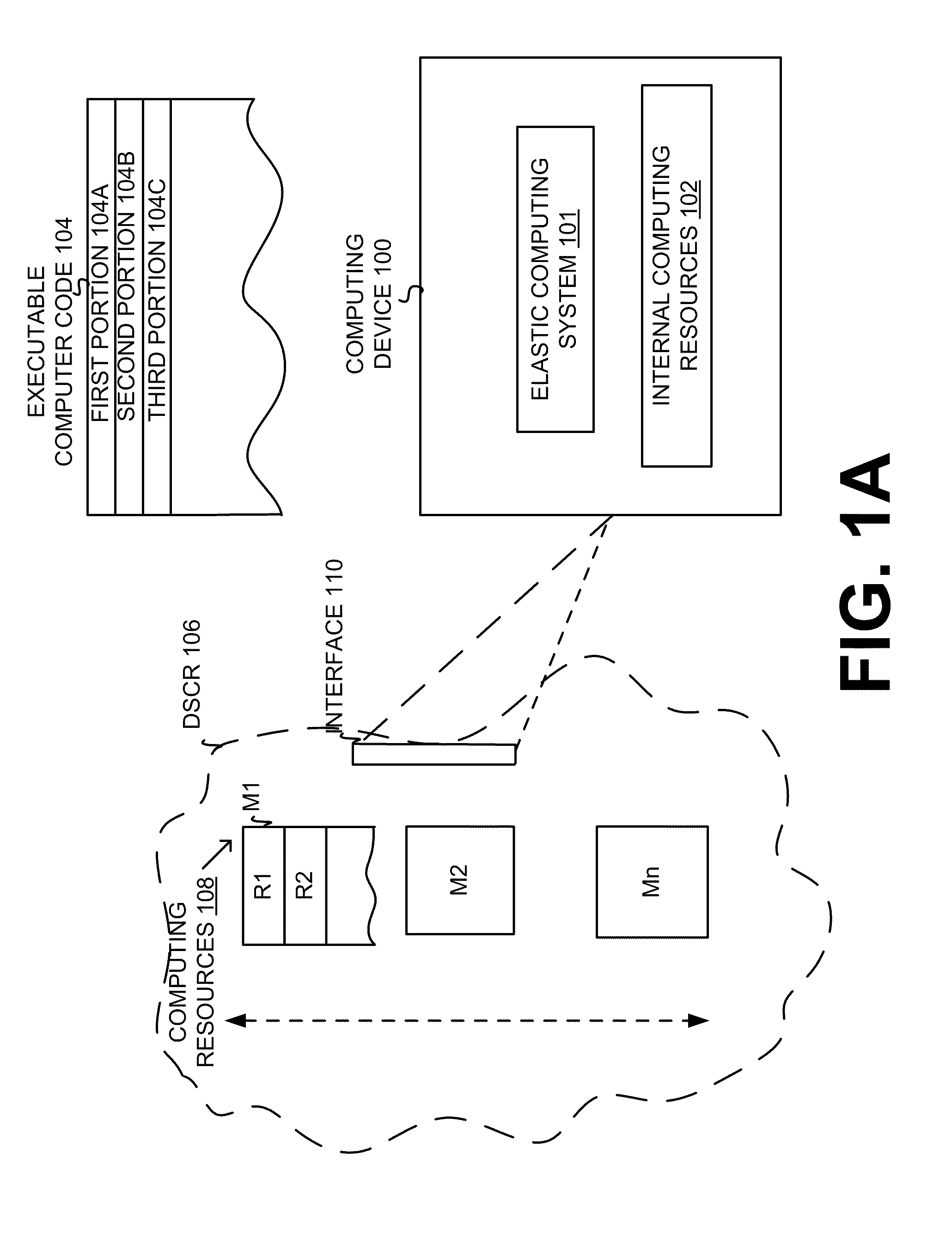
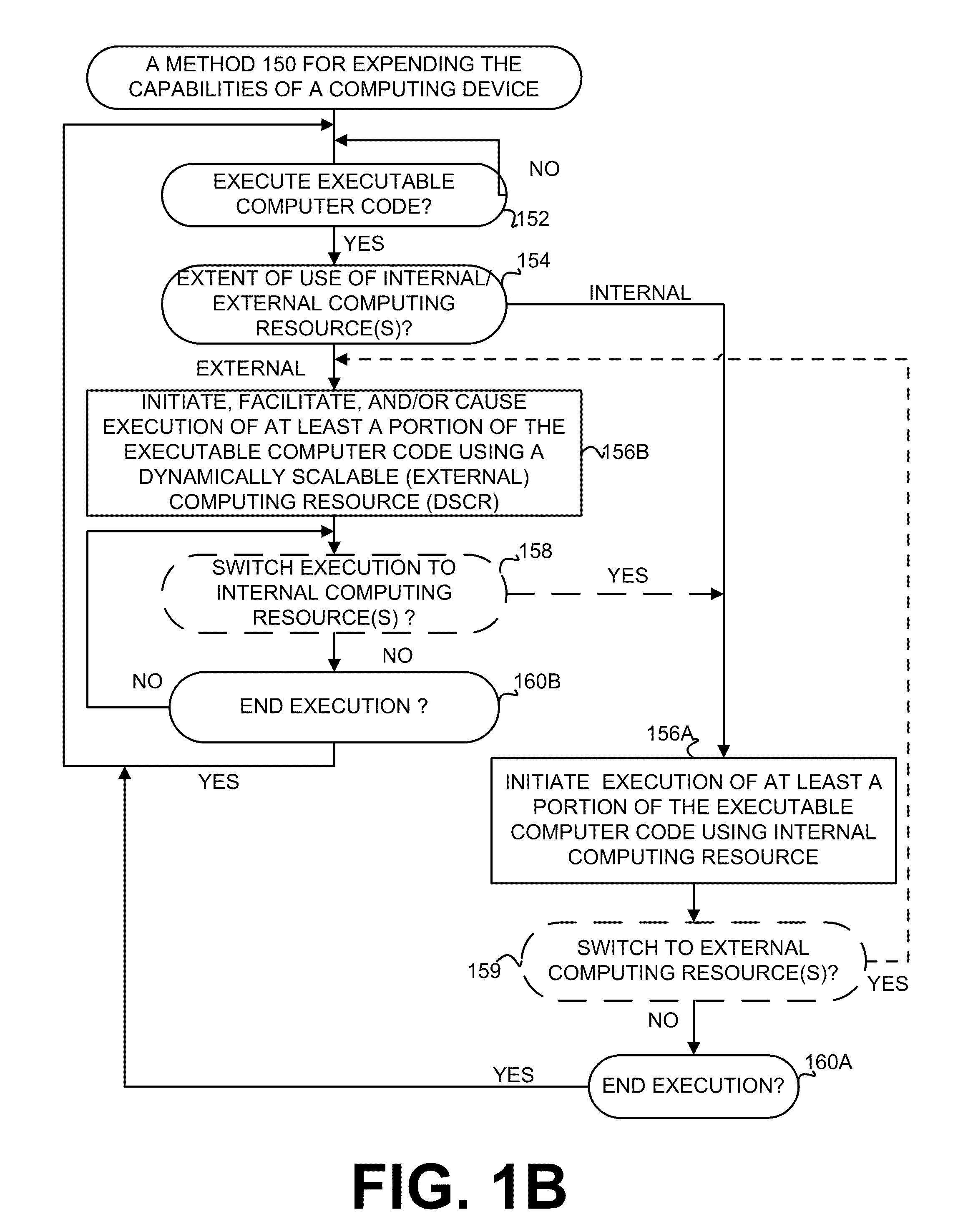
Execution allocation cost assessment for computing systems and environments including elastic computing systems and environments
InactiveUS20110004574A1Computing capabilities of a computing systemEffective resourcesResource allocationDigital computer detailsScalable computingParallel computing
Techniques for allocating individually executable portions of executable code for execution in an Elastic computing environment are disclosed. In an Elastic computing environment, scalable and dynamic external computing resources can be used in order to effectively extend the computing capabilities beyond that which can be provided by internal computing resources of a computing system or environment. Machine learning can be used to automatically determine whether to allocate each individual portion of executable code (e.g., a Weblet) for execution to either internal computing resources of a computing system (e.g., a computing device) or external resources of an dynamically scalable computing resource (e.g., a Cloud). By way of example, status and preference data can be used to train a supervised learning mechanism to allow a computing device to automatically allocate executable code to internal and external computing resources of an Elastic computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com