Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
794 results about "Type safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
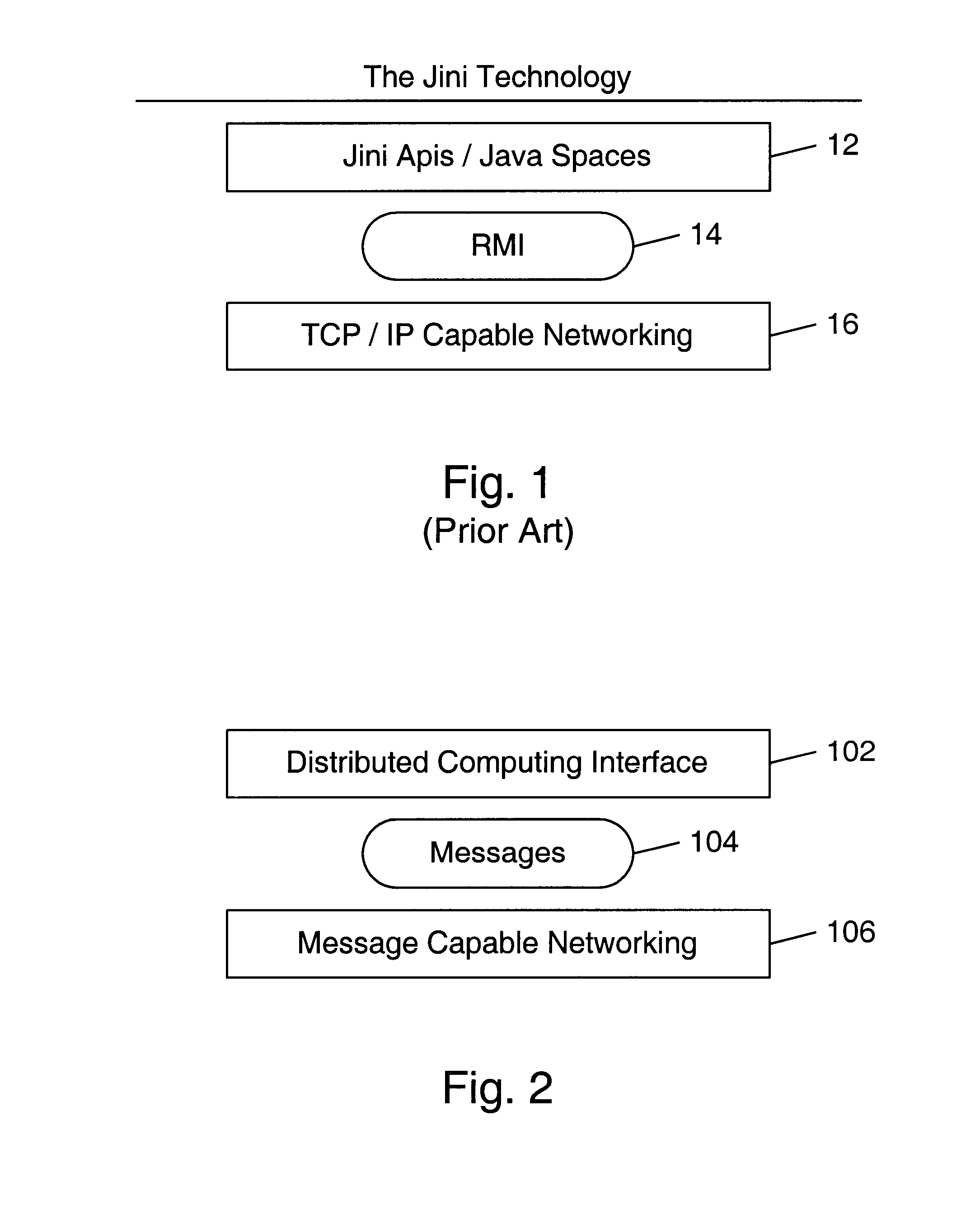
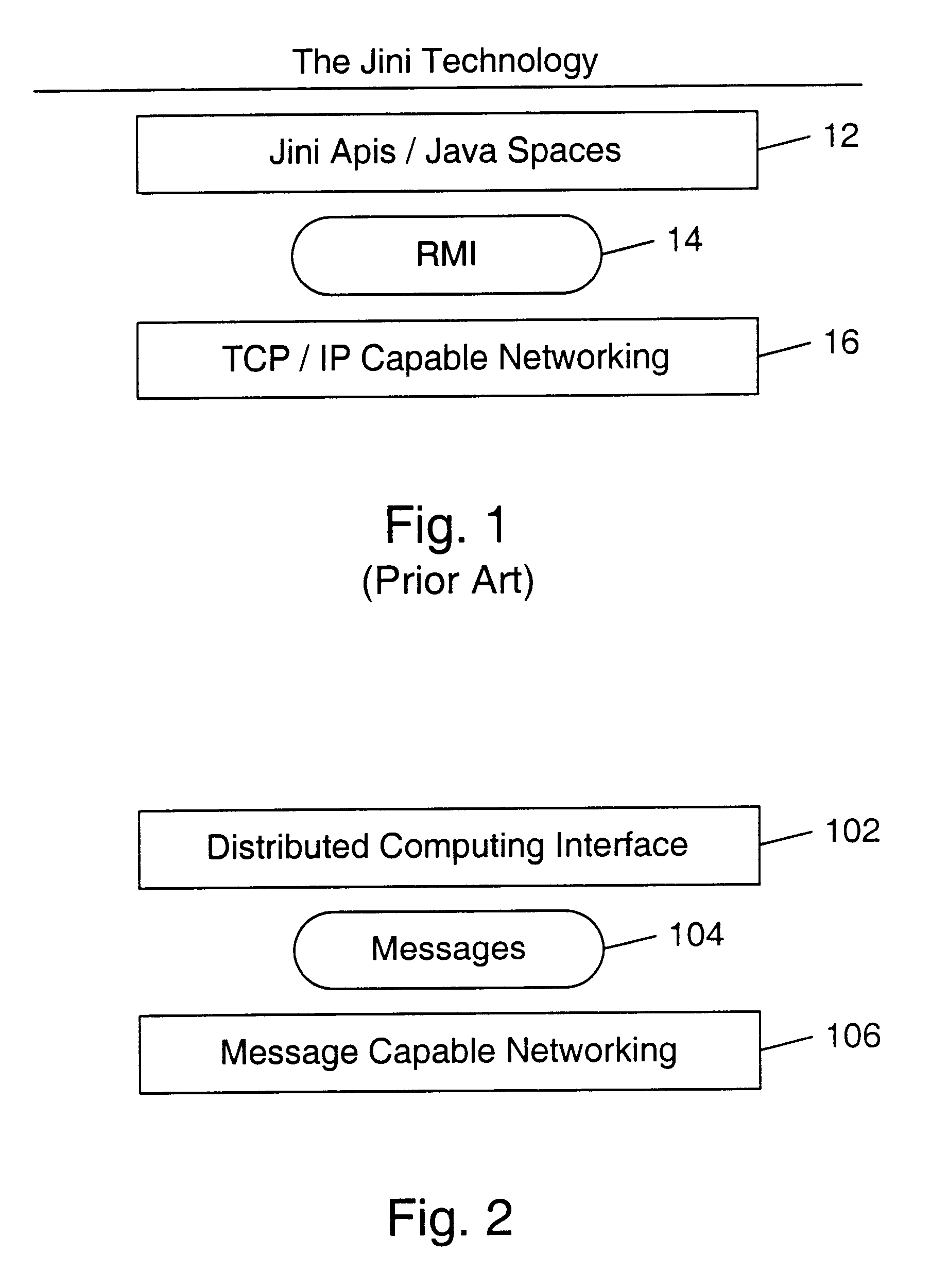
Patent Type
Patent Status
Application Year
Inventor
In computer science, type safety is the extent to which a programming language discourages or prevents type errors. A type error is erroneous or undesirable program behaviour caused by a discrepancy between differing data types for the program's constants, variables, and methods (functions), e.g., treating an integer (int) as a floating-point number (float). Type safety is sometimes alternatively considered to be a property of a computer program rather than the language in which that program is written; that is, some languages have type-safe facilities that can be circumvented by programmers who adopt practices that exhibit poor type safety.
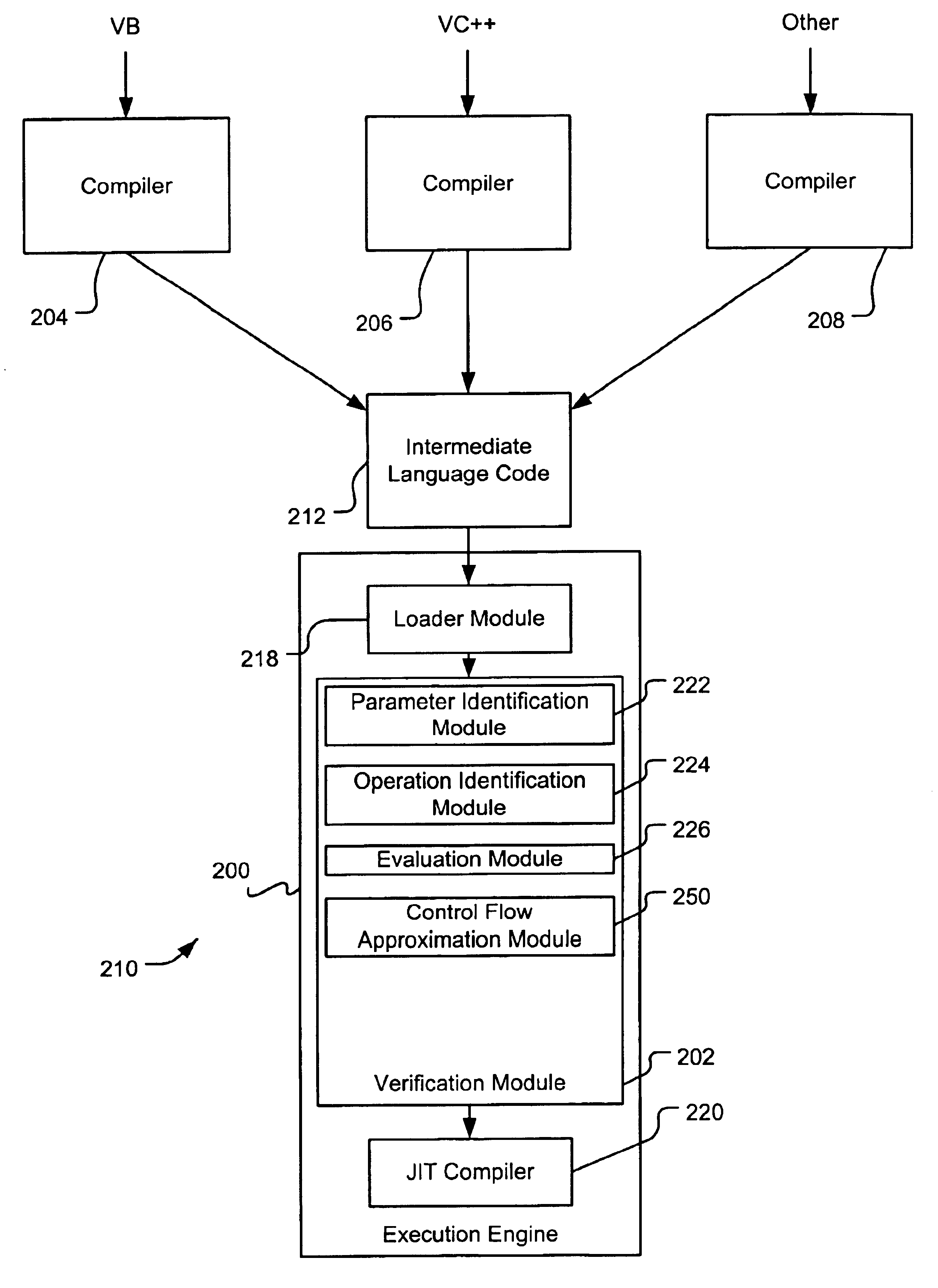
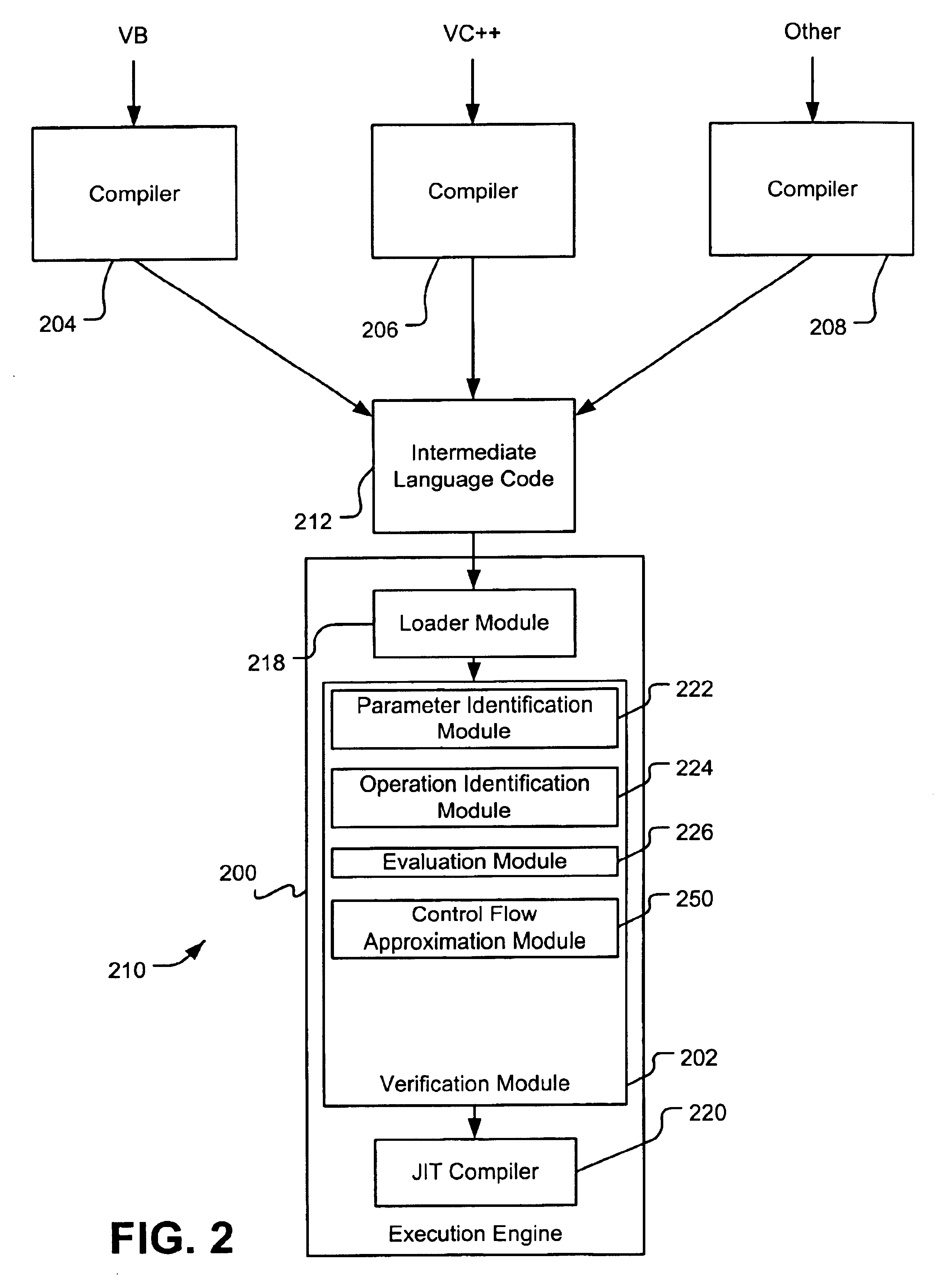
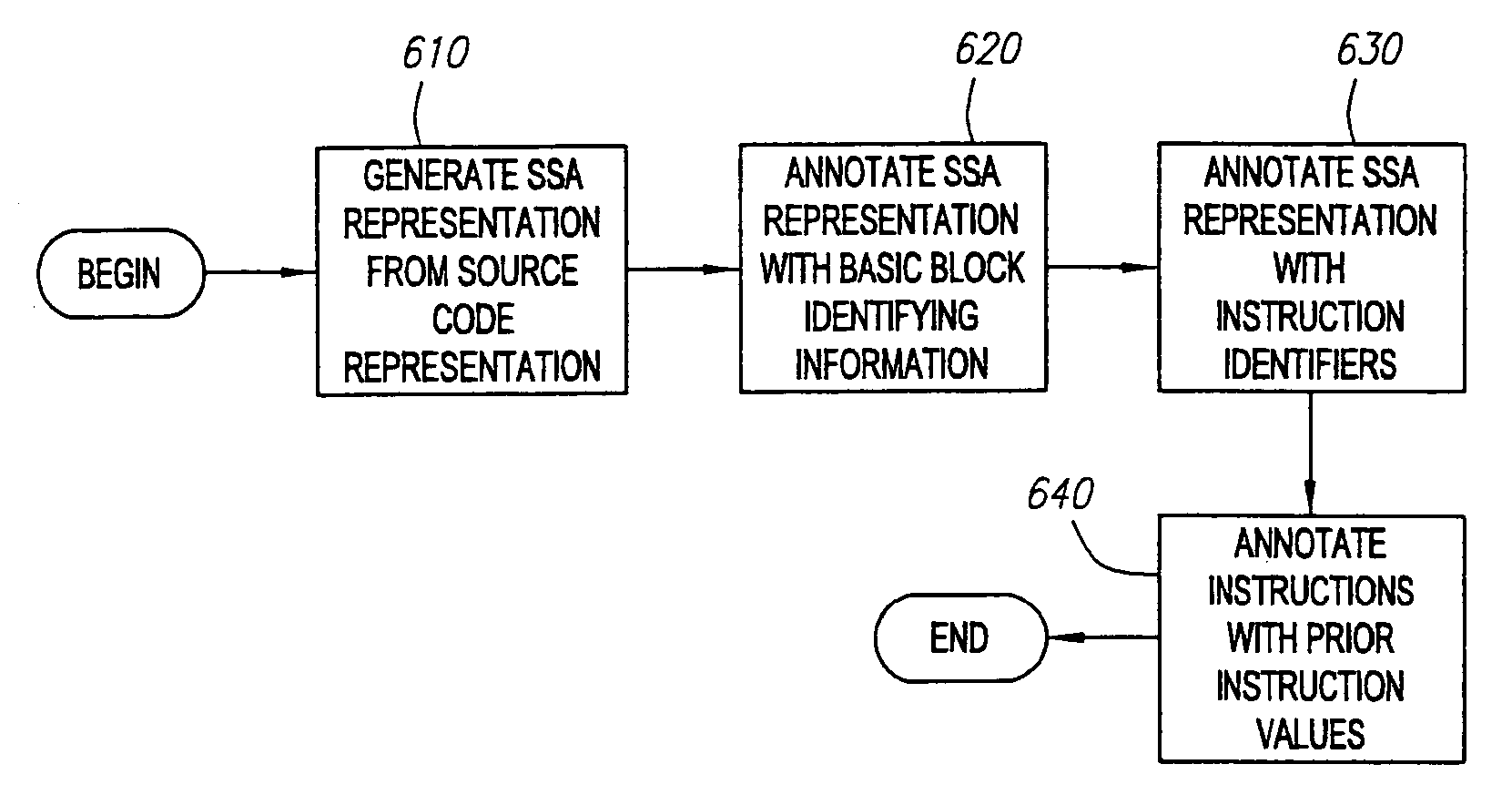
Verifying intermediate language code
InactiveUS6851108B1Existing techniqueRich varietyProgram loading/initiatingMemory systemsLanguage constructComputerized system
A verification module evaluates intermediate language code to verify that the code is type safe before passing the code for execution. Code that is not deemed type safe can cause execution errors, corrupt the runtime environment in which the code is executing, or cause unauthorized access to protected system resources. As such, the verification module protects a computer system from intentional or inadvertent breaches of the computer system's defenses. The verification module verifies the type safety of intermediate language code that supports significant high-level language constructs prohibited by verification modules in the prior art. One exemplary verification module verifies intermediate language code that includes one or more reference-based parameter, such as a pointer (or reference), a value class containing pointers, a RefAny parameter, or a nested pointer.
Owner:MICROSOFT TECH LICENSING LLC
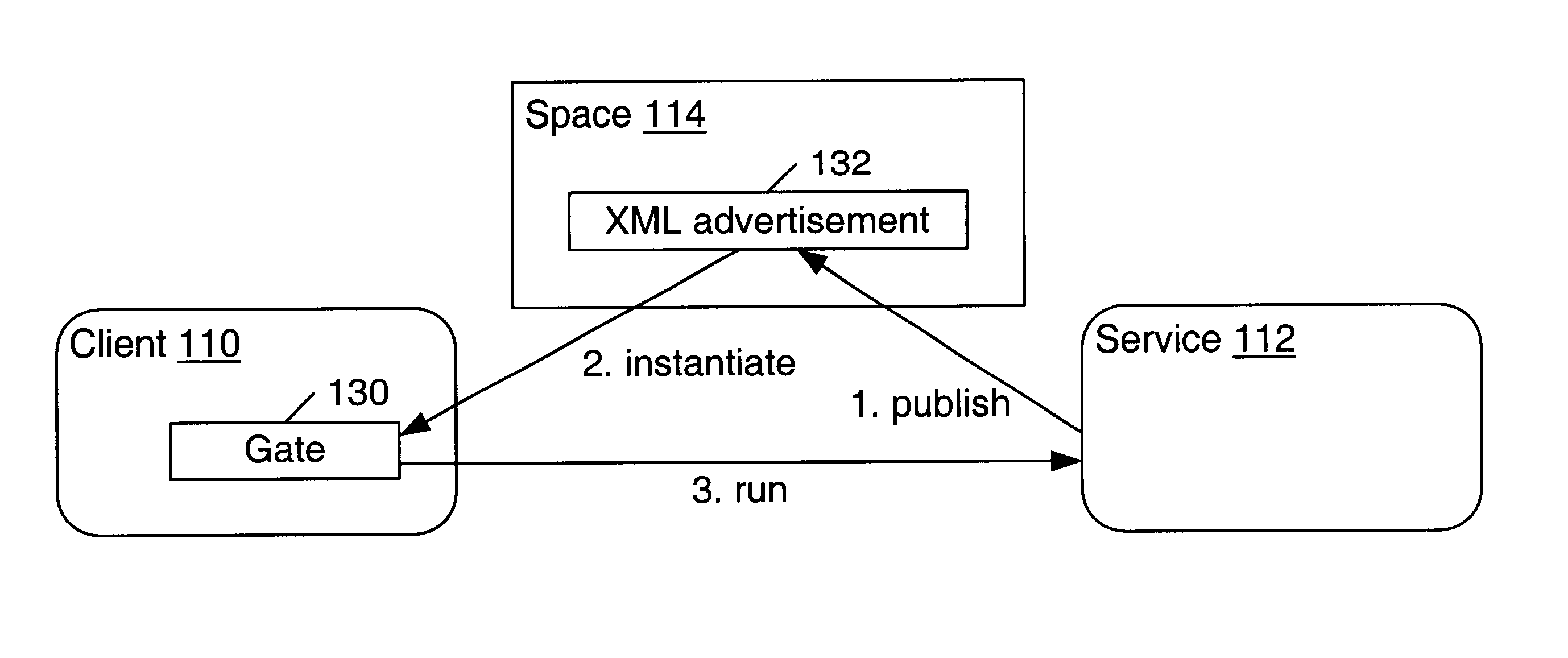
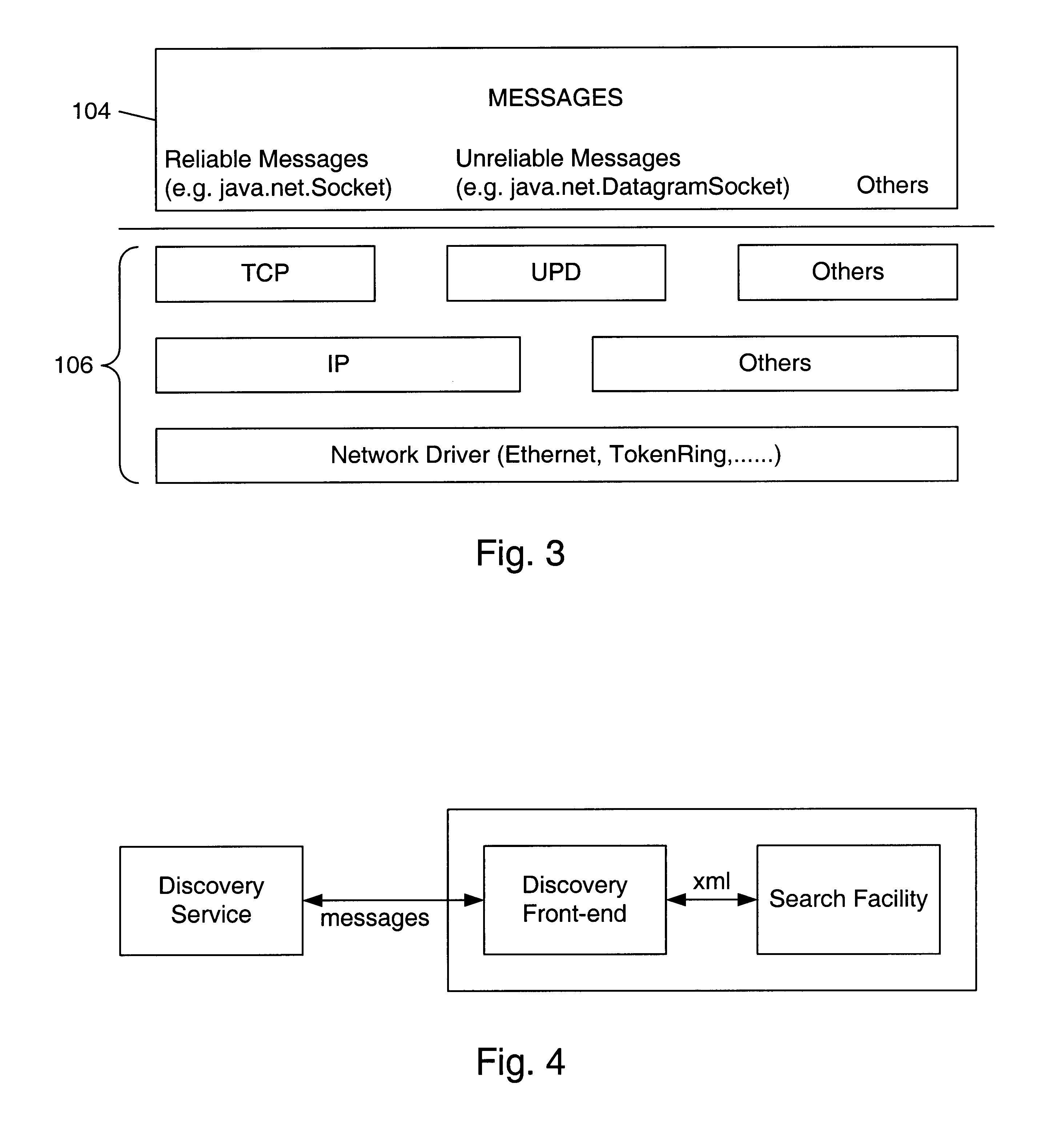
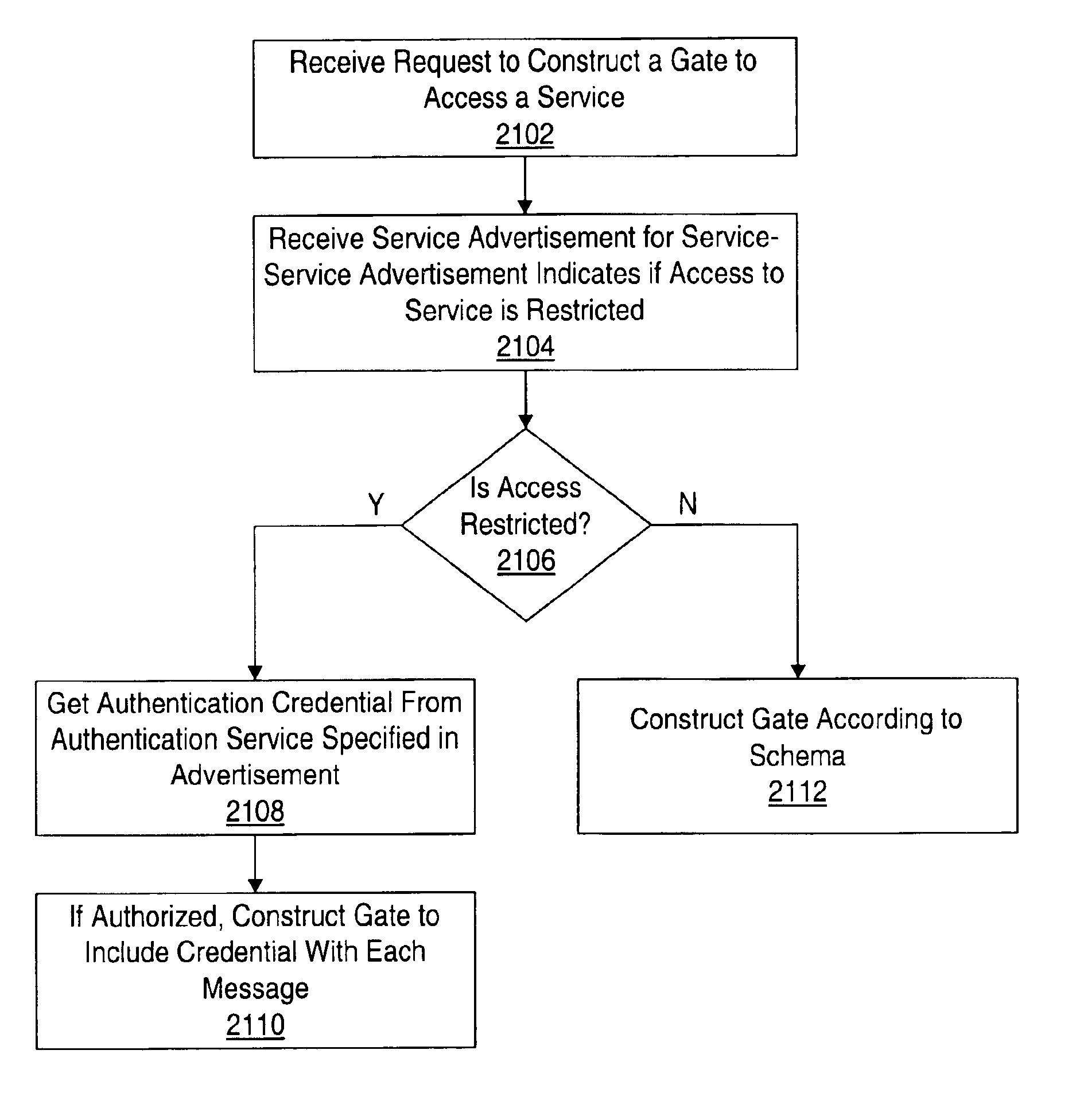
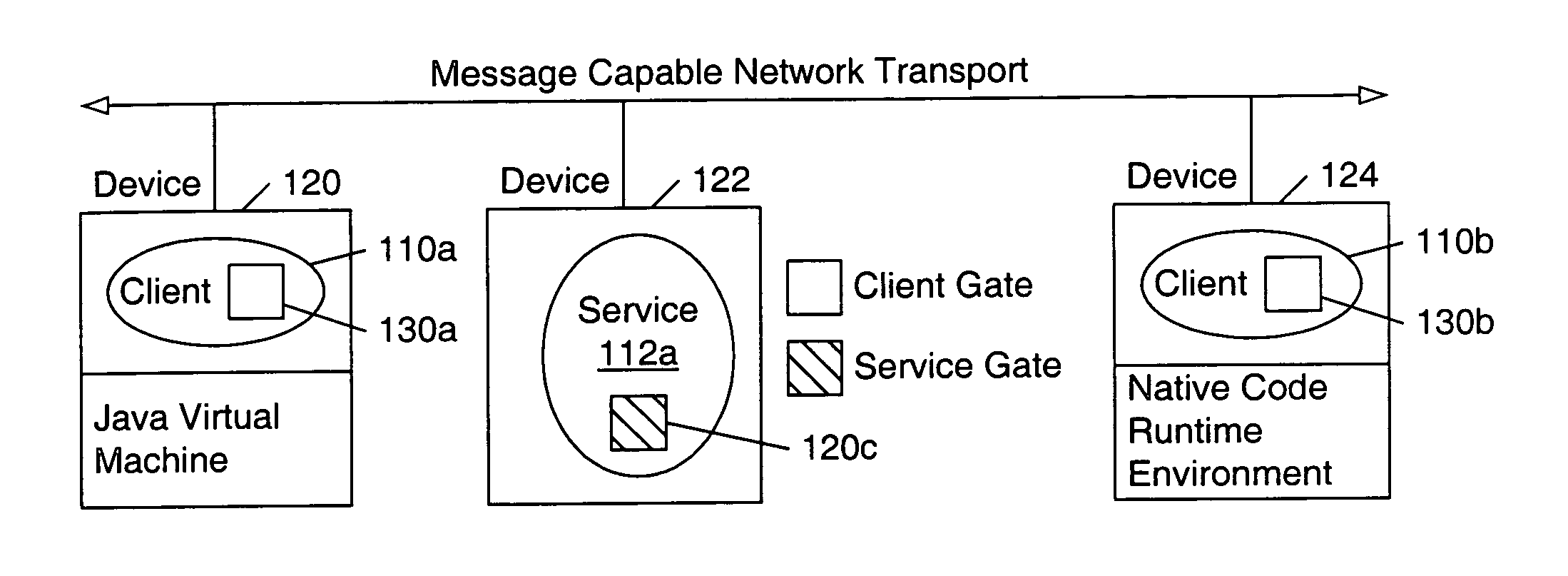
Trusted construction of message endpoints in a distributed computing environment
InactiveUS6792466B1Multiple digital computer combinationsTransmissionXML schemaDistributed Computing Environment
In a distributed computing environment, a message gate may be the message endpoint for a client or service to communicate with another client or service. Devices may have a gate factory (e.g. message endpoint constructor) that is trusted code on the device for generating gates based on XML message descriptions. The use of the gate factory may ensure that the gate it generates is also trusted code, and that the code is correct with respect to a service advertisement. A service advertisement may indicate, for a particular service, a message schema, service URI and authentication service URI. In one embodiment, the pieces the gate factory needs to construct a gate are the XML schema of the service and the URI of the service. In another embodiment, an authentication credential may also be obtained and used in gate construction by running an authentication service specified in the service advertisement. A gate factory for a device may generate gate code that may incorporate the language, security, type safety, and / or execution environment characteristics of the local device platform. By constructing gates itself, a device has the ability to ensure that the generated gate code is relatively bug-free, produces only valid data, and provides type-safety.
Owner:ORACLE INT CORP
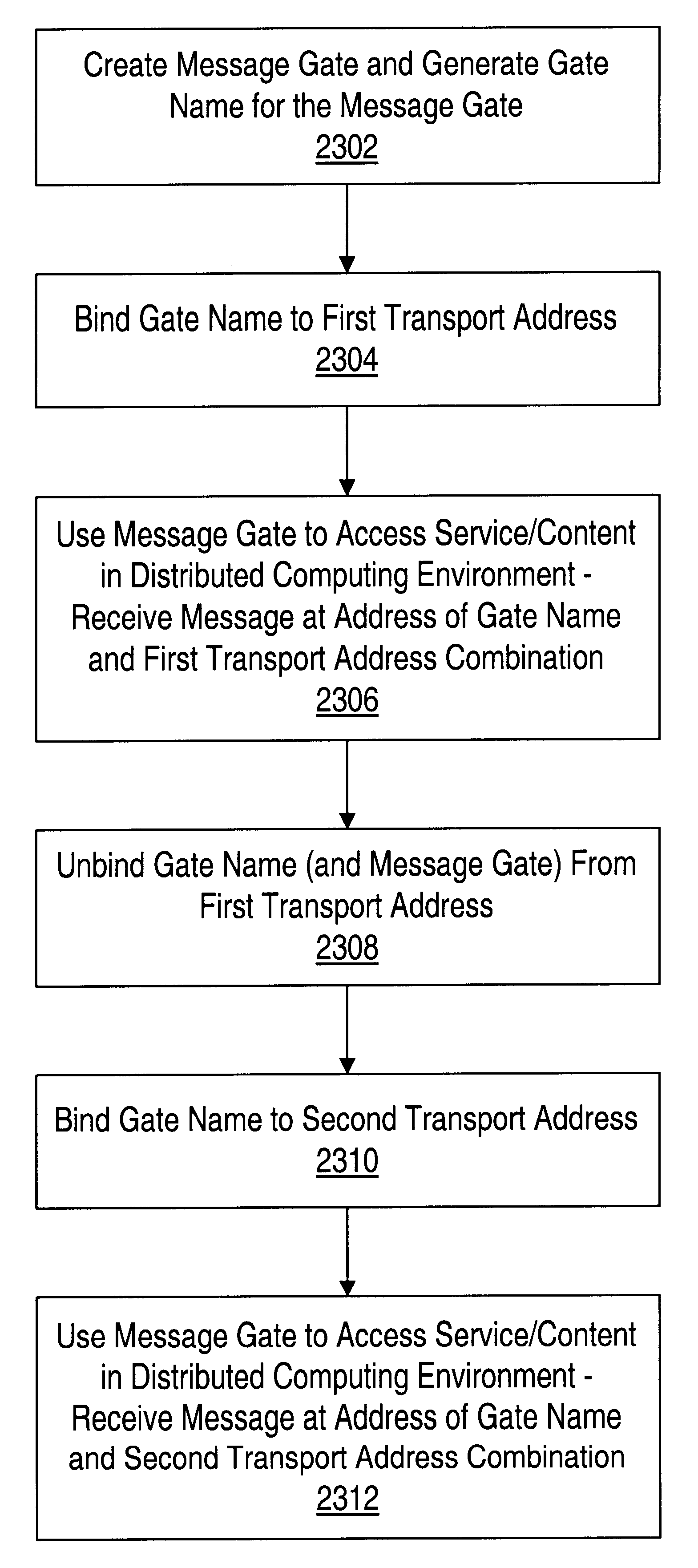
Addressing message gates in a distributed computing environment
InactiveUS6789126B1Multiple digital computer combinationsNetwork connectionsDistributed Computing EnvironmentClient-side
A message gate is the message endpoint for a client or service in a distributed computing environment. A message gate may provide a secure message endpoint that sends and receives type-safe messages. A gate may have a gate name that is a unique ID that refers only to the gate. In one embodiment, a gate is assigned a gate name when the gate is created and the gate name refers to only that gate for the life of the gate. A gate may be addressed using its gate name. The name may allow clients and services to migrate about the network and still work together. In a preferred embodiment, the gate address is independent of the physical message transport address and / or socket layer. Thus, a gate name may provide a virtual message endpoint address that may be bound and un-bound to a message transport address.
Owner:ORACLE INT CORP
Efficient construction of message endpoints
InactiveUS7072967B1Easy constructionAvoid constructionMemory loss protectionError detection/correctionXML schemaDistributed Computing Environment
In a distributed computing environment, a message gate may be the message endpoint for a client or service. A message gate may provide a secure message endpoint that sends and receives type-safe messages. Devices may have a gate factory (e.g. message endpoint constructor) that is trusted code on the device for generating gates based on XML message descriptions. In one embodiment, the gate factory may construct a gate from the XML schema of the service, a URI for the service, and an authentication credential. Access to some services may be unrestricted. For such services, a gate may be constructed without an authentication credential, saving the overhead of running an authentication service and incorporating an authentication credential. Gate construction may also be optimized for certain clients that do not desire to perform checking of messages against a service's XML schema. If verification is not desired, a client may avoid or may chose to avoid building (e.g. by a gate factory) some or all of the gate code that checks the messages against the XML schema. Also, the building of a gate may be made lightweight by appropriate reuse or sharing of pieces used to construct other gates. Devices may maintain a cache of gates to avoid constructing them each time the same service is run.
Owner:ORACLE INT CORP
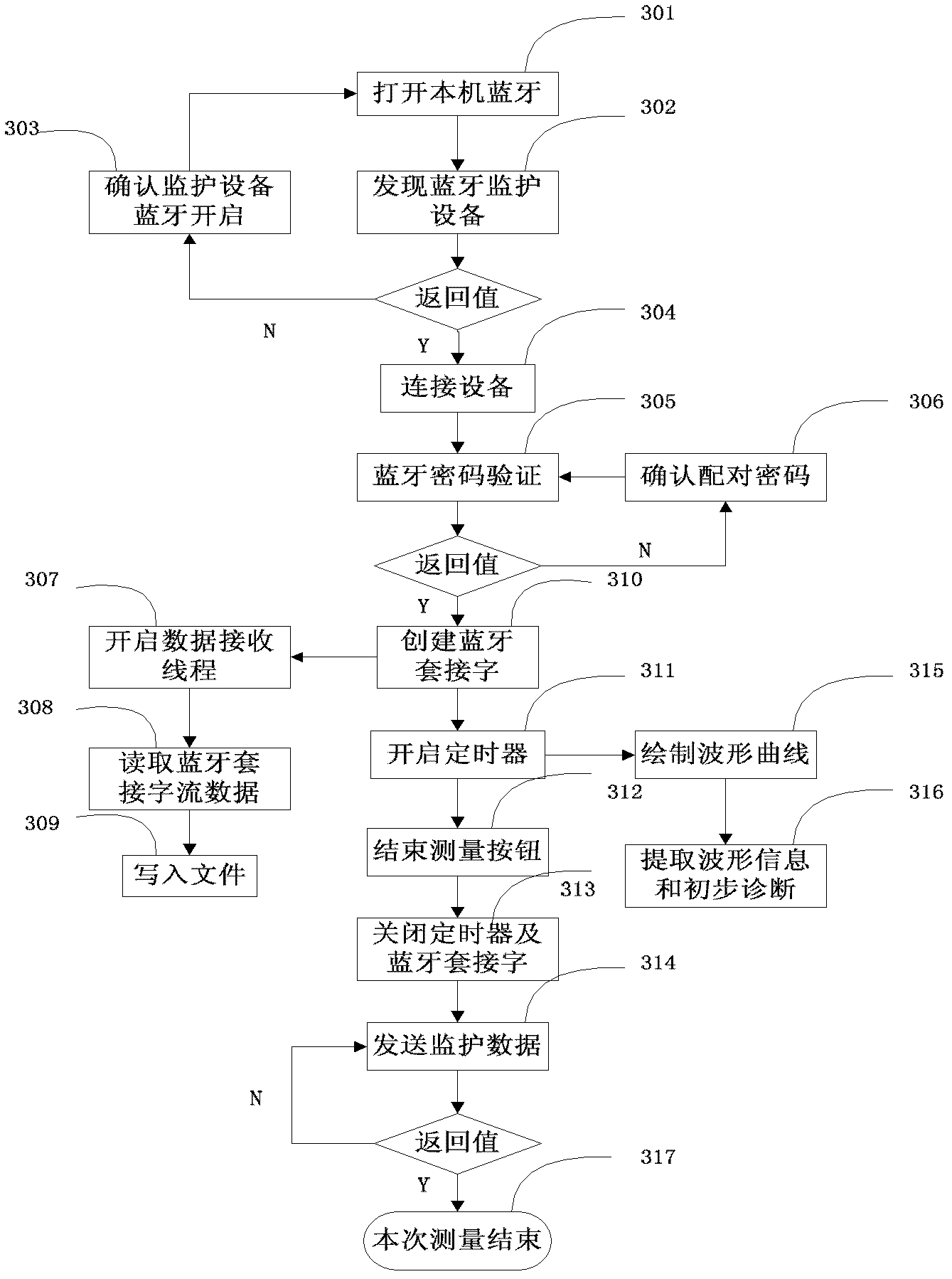
Handheld mobile type safety telemedicine health status monitoring system
InactiveCN102622522AImprove compatibilityImprove scalabilityRespiratory organ evaluationSensorsDiseaseReal time analysis
The invention discloses a handheld mobile type safety telemedicine health status monitoring system, which comprises a biosensor, an intelligent mobile platform, a far-end data center and a doctor workstation. The biosensor transmits acquired patient data to the intelligent mobile platform by means of the Bluetooth, the intelligent mobile platform analyzes and processes the data in real time prior to displaying results and uploading the process results to the far-end data center, and relevant members at the doctor workstation check the uploaded result data and provide diagnosis advices and can contact with patients to request the patients to come to hospitals for examination when necessary. The handheld mobile type safety telemedicine health status monitoring system has the advantages that a client program is realized based on various mobile platform operating systems, and patient health statuses can be monitored anytime and anywhere to prevent diseases while patient identification validity and data transmission safety are guaranteed.
Owner:SHANGHAI INST OF TECHNICAL PHYSICS - CHINESE ACAD OF SCI
Message gates using a shared transport in a distributed computing environment
InactiveUS7010573B1Reduce complexitySmall sizeMultiple digital computer combinationsTransmissionTransport layerNetwork socket
A message gate is the message endpoint for a client or service in a distributed computing environment. A message gate may provide a secure message endpoint that sends and receives type-safe messages. A gate may have a gate name that is a unique ID that refers only to the gate. A gate may be implemented as a layer above a device's transport layer (e.g. networking sockets). The gate name for each gate may be bound to a transport reference. Multiple gates may share the same message transport. The transport reference may be a transport URI or socket reference and may provide a mechanism for naming an underlying transport and sharing the transport with other gates. Multiple local gates may include a reference to the same transport, however, each local gate may behave independently of the other local gates sending and receiving messages to and from its paired remote gate.
Owner:ORACLE INT CORP
Safe computer code formats and methods for generating safe computer code
InactiveUS7117488B1Preventing executionExpending valuable timePlatform integrity maintainanceSpecific program execution arrangementsType safetySource code
An inherently safe code format for representing computer programs is disclosed. The format provides incorruptible referential integrity and uses type separation to achieve intrinsic type safety. The format preserves a safety guarantee found in a source code language representation of the computer program while the computer program proceeds through various stages of the code compilation process.
Owner:RGT UNIV OF CALIFORNIA
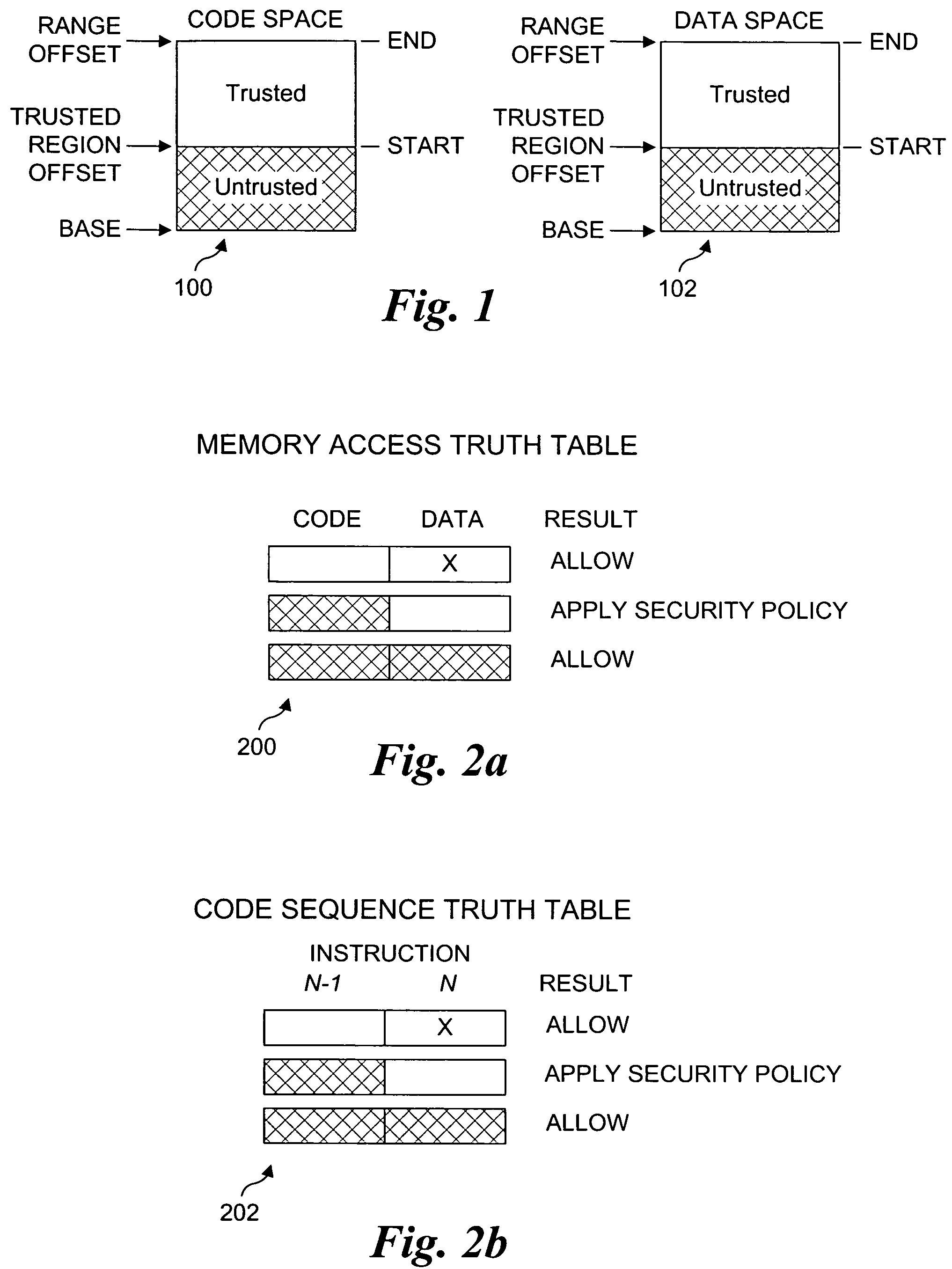
Processor extensions and software verification to support type-safe language environments running with untrusted code
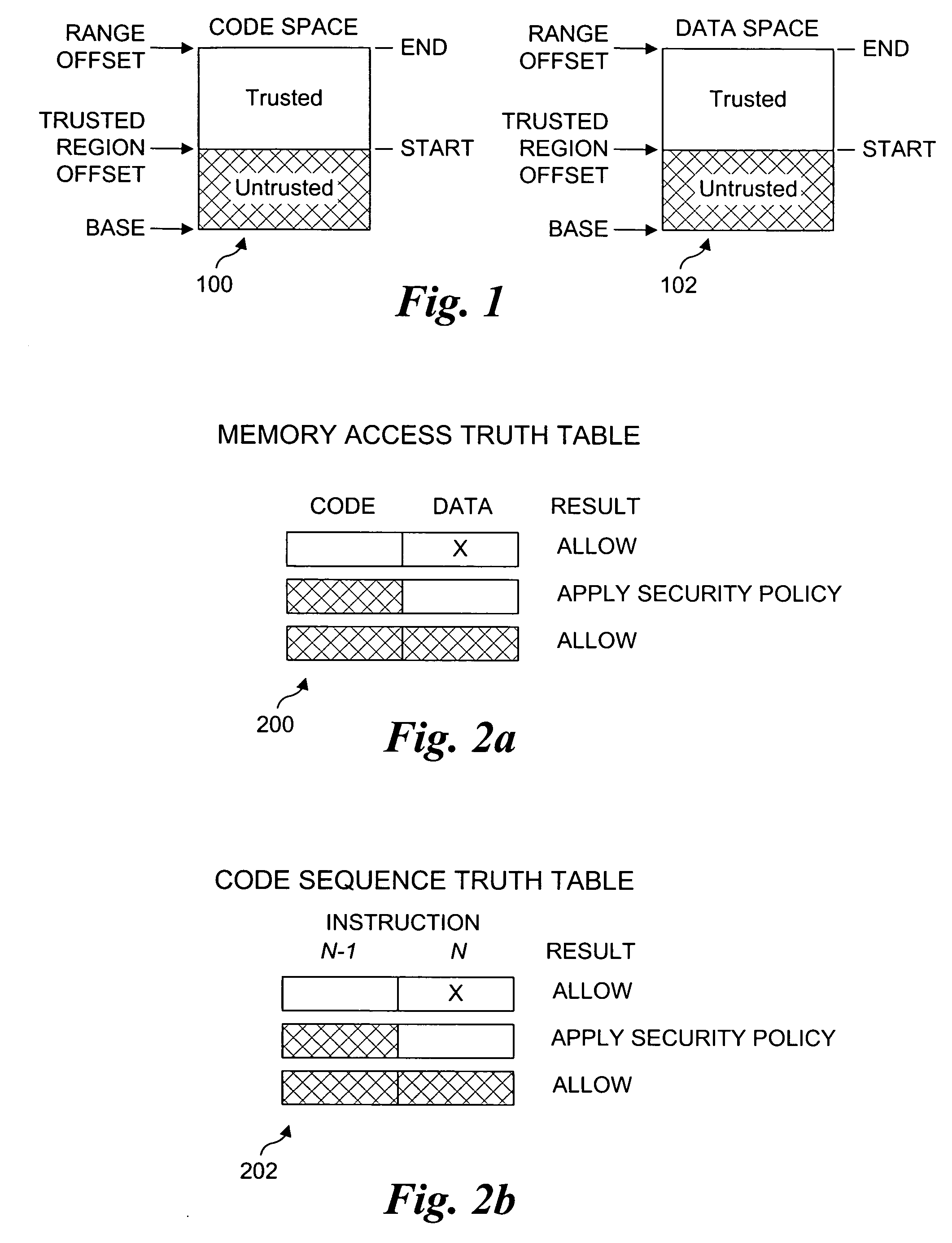
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Core object-oriented type system for semi-structured data
InactiveUS7389498B2Improve abilitiesEnhance layeringError preventionSoftware engineeringSemi-structured dataValidation methods
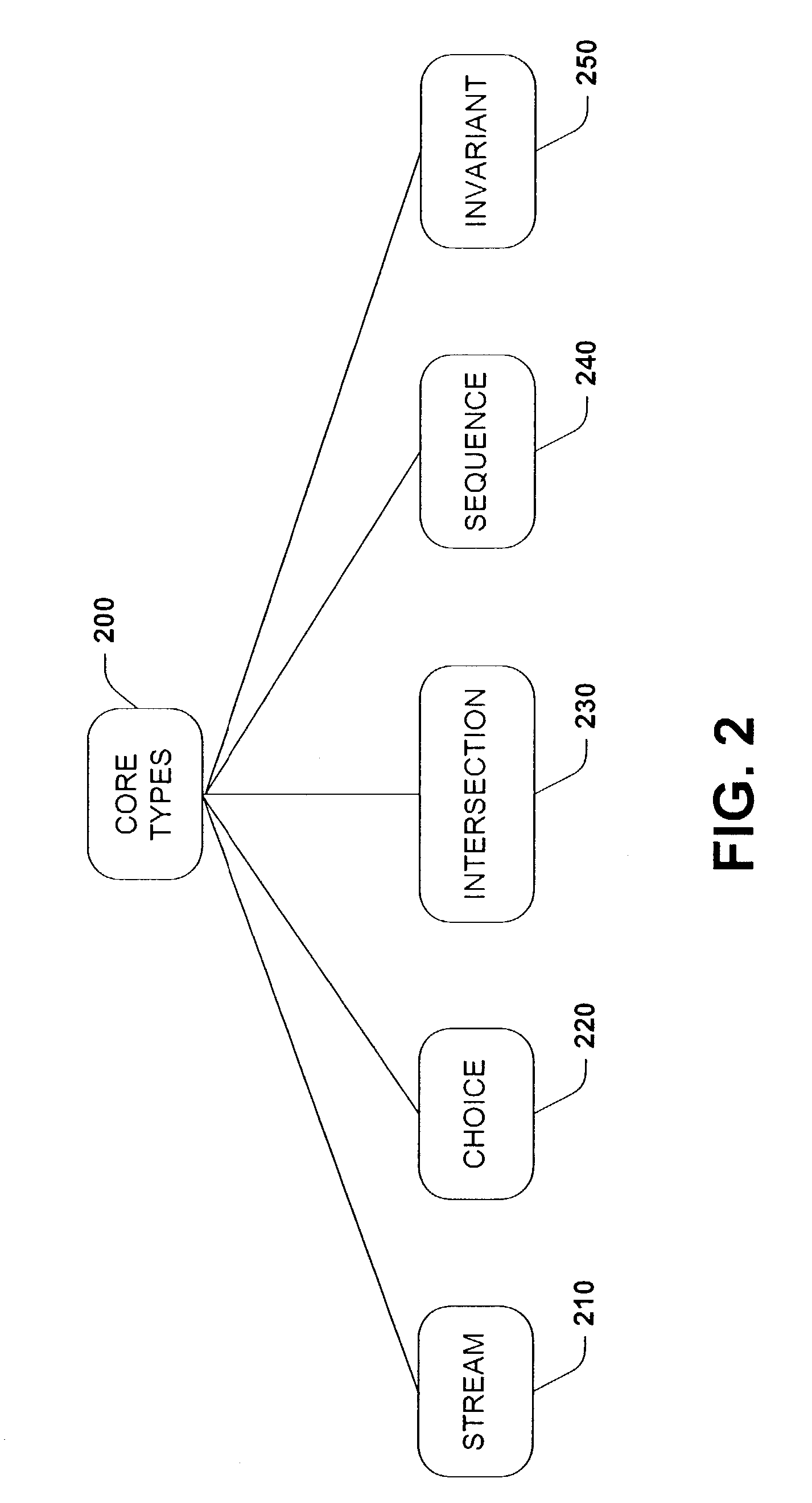
A type system employing structural subtyping is disclosed herein. A core type system supports several structural types, such as stream, choice, intersection and sequence. Also part of the core type system is a new invariant type, which denotes values whose dynamic type is the same as its static type, and type restrictions for limiting a range of a base type. Furthermore, a streamlined structural version of delegates, called structural delegates and a validation method thereof are introduce into the type system. To further facilitate type safety, strict statically checked interface casts are introduced.
Owner:MICROSOFT TECH LICENSING LLC
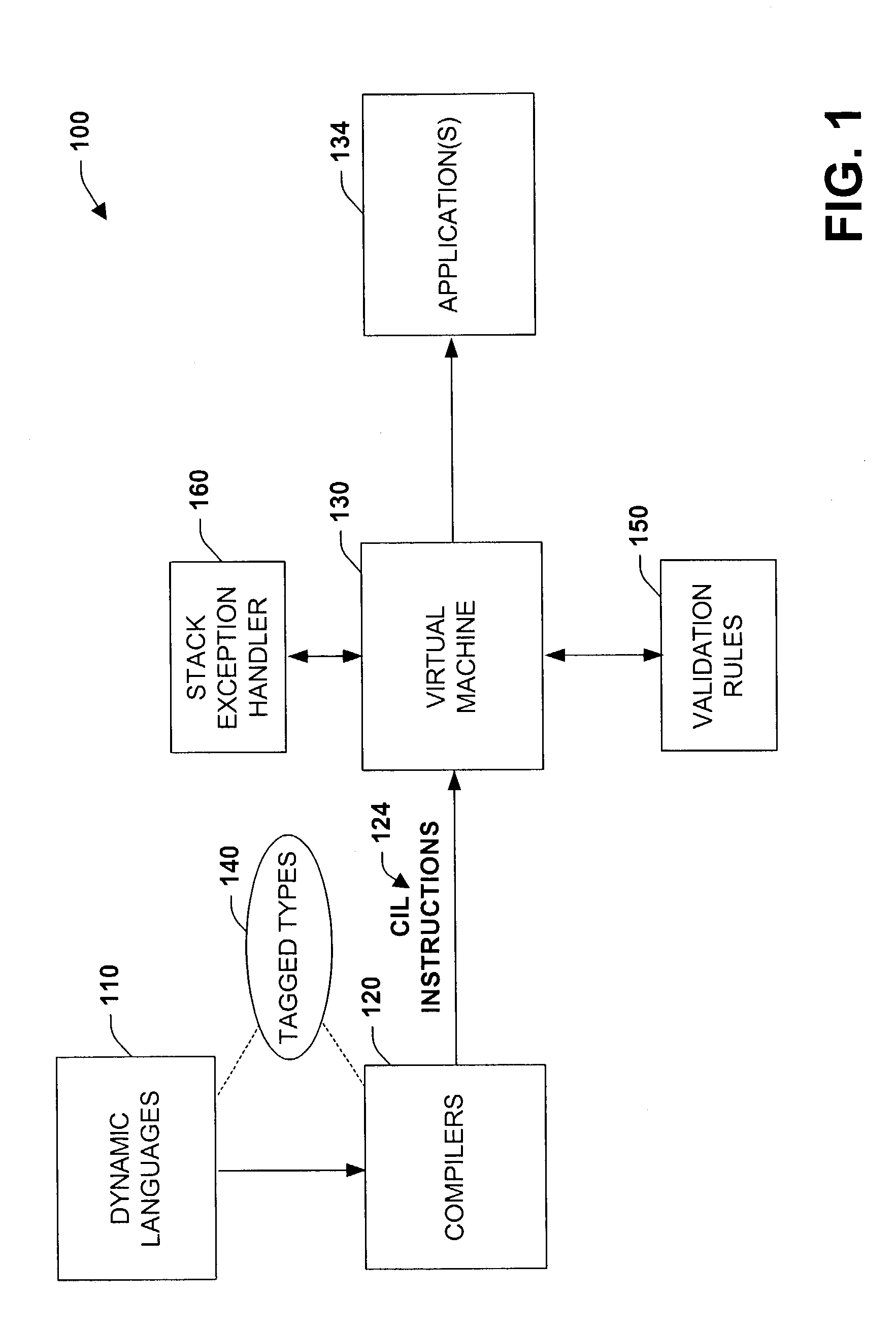
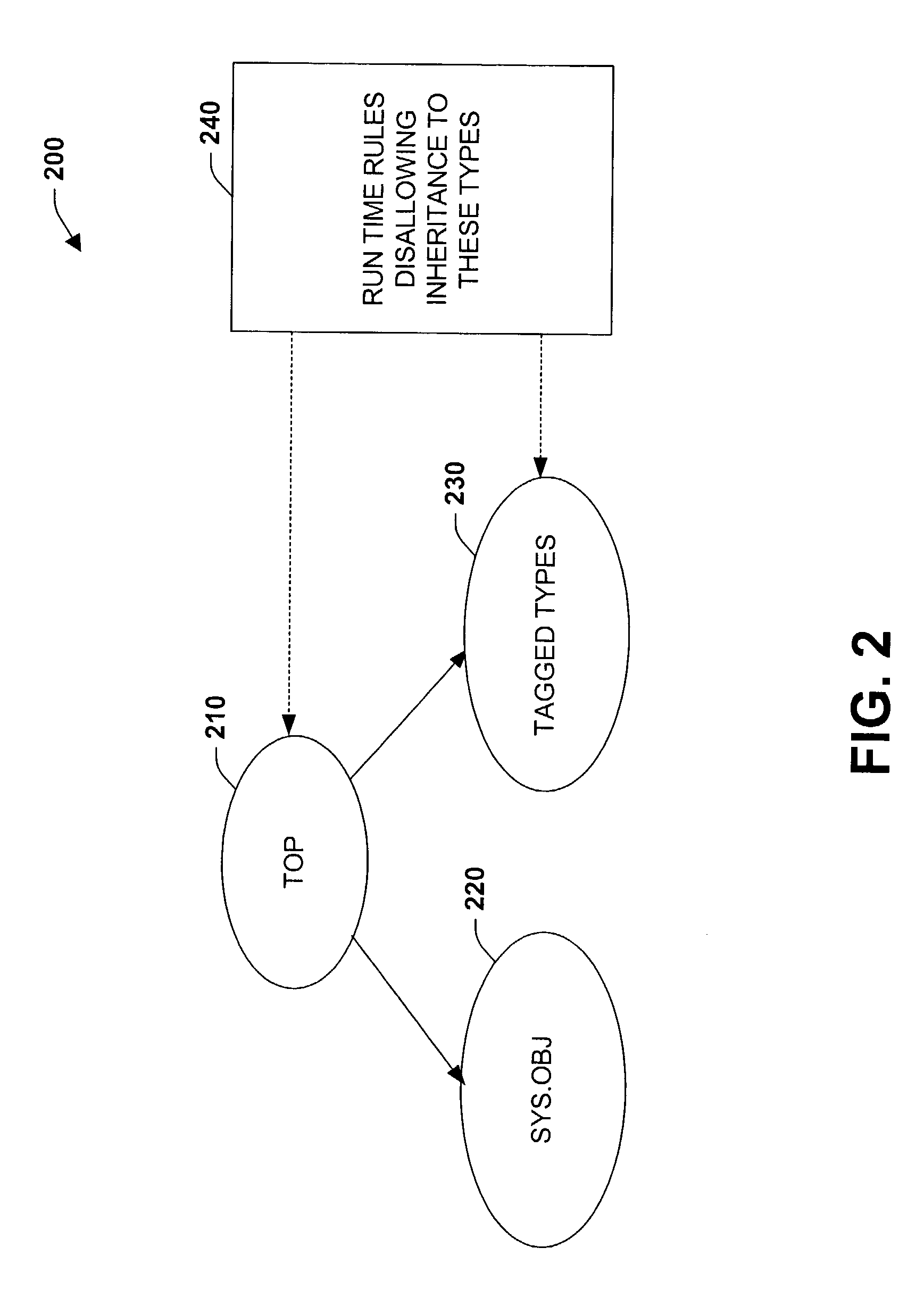
Systems and methods for employing tagged types in a dynamic runtime environment
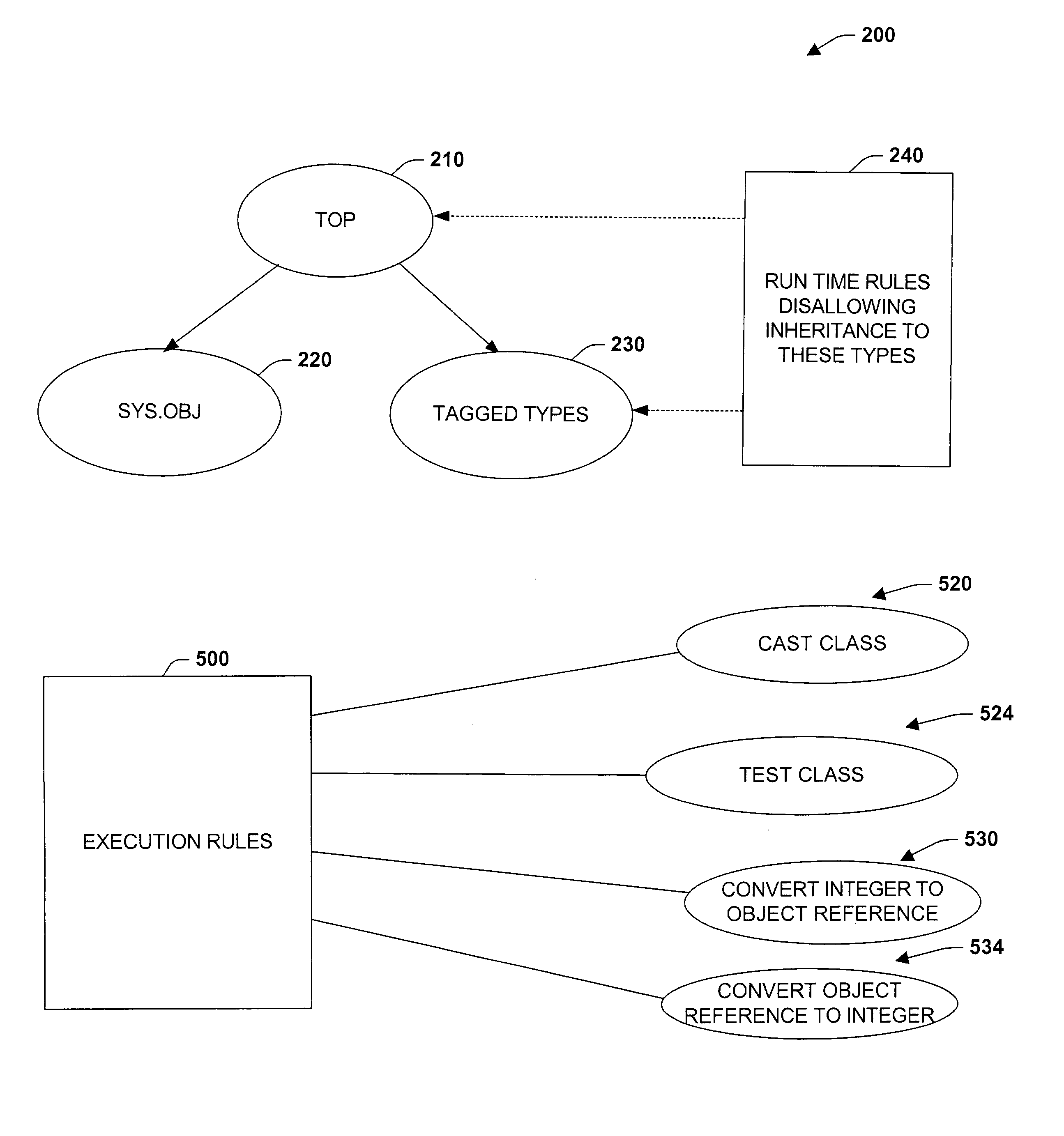
ActiveUS7168063B2Facilitate proper executionReduce dataTransformation of program codeSoftware simulation/interpretation/emulationManaged codeType safety
The present invention relates to systems and methods that facilitate dynamic programming language execution in a managed code environment. A class component is provided that declares an inheritance hierarchy for one or more tagged values associated with a dynamic programming language. During execution of the tagged values, a rules component mitigates user-defined types from inheriting or deriving properties from the tagged values in order to support a type safe runtime environment. A bifurcated class tree is provided that defines non-tagged type elements on one side of the tree and tagged type element values on an alternate branch of the tree. The rules component analyzes runtime extensions that help to prevent data from one component of the tree deriving or inheriting properties from another component of the tree. The runtime extensions include such aspects as cast class extensions, test class extensions, and conversion class extensions for converting data types from one class subtype to another.
Owner:MICROSOFT TECH LICENSING LLC
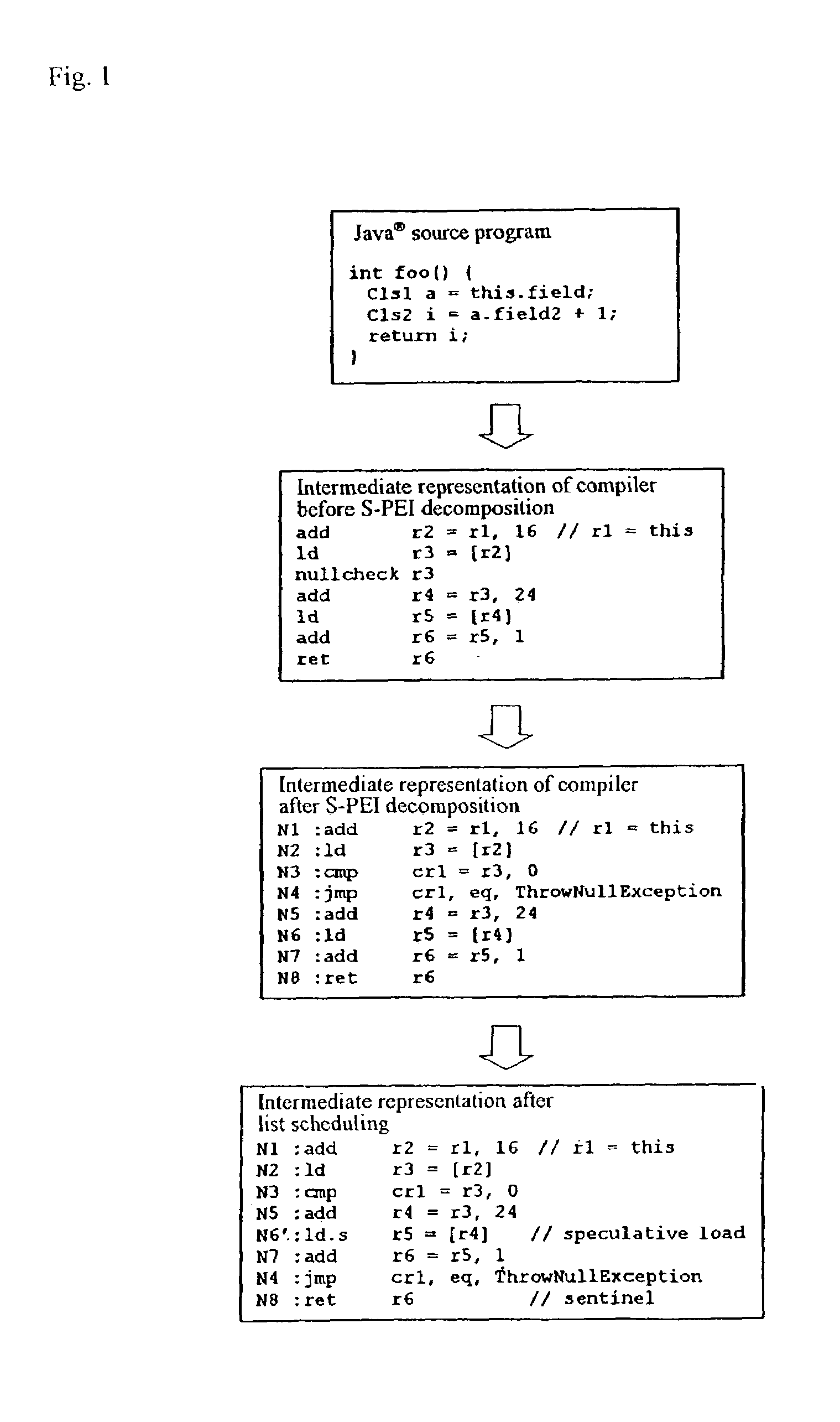
Compiling method, apparatus, and program
InactiveUS7197747B2Overcome problemsImprove executionSoftware engineeringSpecific program execution arrangementsSpeculative executionStart time
A method and system for compiling a program written in a type-safe language. Instructions are reordered for speculative execution while reducing the execution time of the program. A dependency graph is generated wherein exception dependent arcs are discriminated from arcs of other dependency types. Determination is made whether earliest execution start time of the H-PEI will be earlier when executed with or without a constraint by the exception dependent arc. If it is determined that it will be earlier in the latter case, the instruction sequence including the H-PEI is reordered for speculative execution.
Owner:IBM CORP
Processor extensions and software verification to support type-safe language environments running with untrusted code
Processor extensions and software verification to support type-safe language environments running with untrusted code. Code and data spaces are partitioned into trusted and untrusted regions. Type-safe code is loaded into the trusted region of the code space, while non-type-safe code is loaded into the untrusted region of the code space. The trusted region of the data space is allocated to the type-safe code. The untrusted region of the data space is allocated to the non-type-safe code. Hardware-based truth tables are employed for defining allowable and disallowable code sequences and memory access operations. For code sequences, allowable operations are based on the location (i.e., region) of a code sequence including a current instruction and a prior instruction. For memory access, the location of the requesting instruction and data requested are considered. Disallowed code sequence or memory access operations cause the processor to generate a safe access protection trap. In response to the safe access protection trap, a software-based dynamic verifier applies a security policy to determine whether to allow the operation to proceed.
Owner:INTEL CORP
Method and apparatus to guarantee type and initialization safety in multithreaded programs
InactiveUS20050050528A1Initialization safety is also guaranteedImprove performanceMemory loss protectionSpecific program execution arrangementsMultithreadingType safety
A method and apparatus to guarantee type safety in multithreaded programs, and to guarantee initialization safety in well-behaved multithreaded programs. A plurality of bytecodes representing a program are received and examined to identify bytecodes defining object creation operations and object initialization operations. Upon execution of the plurality of bytecodes, memory barrier operations are performed subsequent to the performance of both the object creation operations and the object initialization operations. This guarantees type safety, and further guarantees initialization safety if the program is well-behaved. Optimization algorithms may also be applied in the compilation of bytecodes to improve performance.
Owner:IBM CORP
Compiling executable code into a less-trusted address space
InactiveUS20080127142A1Avoiding security violationWell formedLink editingProgram synchronisationOperational systemManaged code
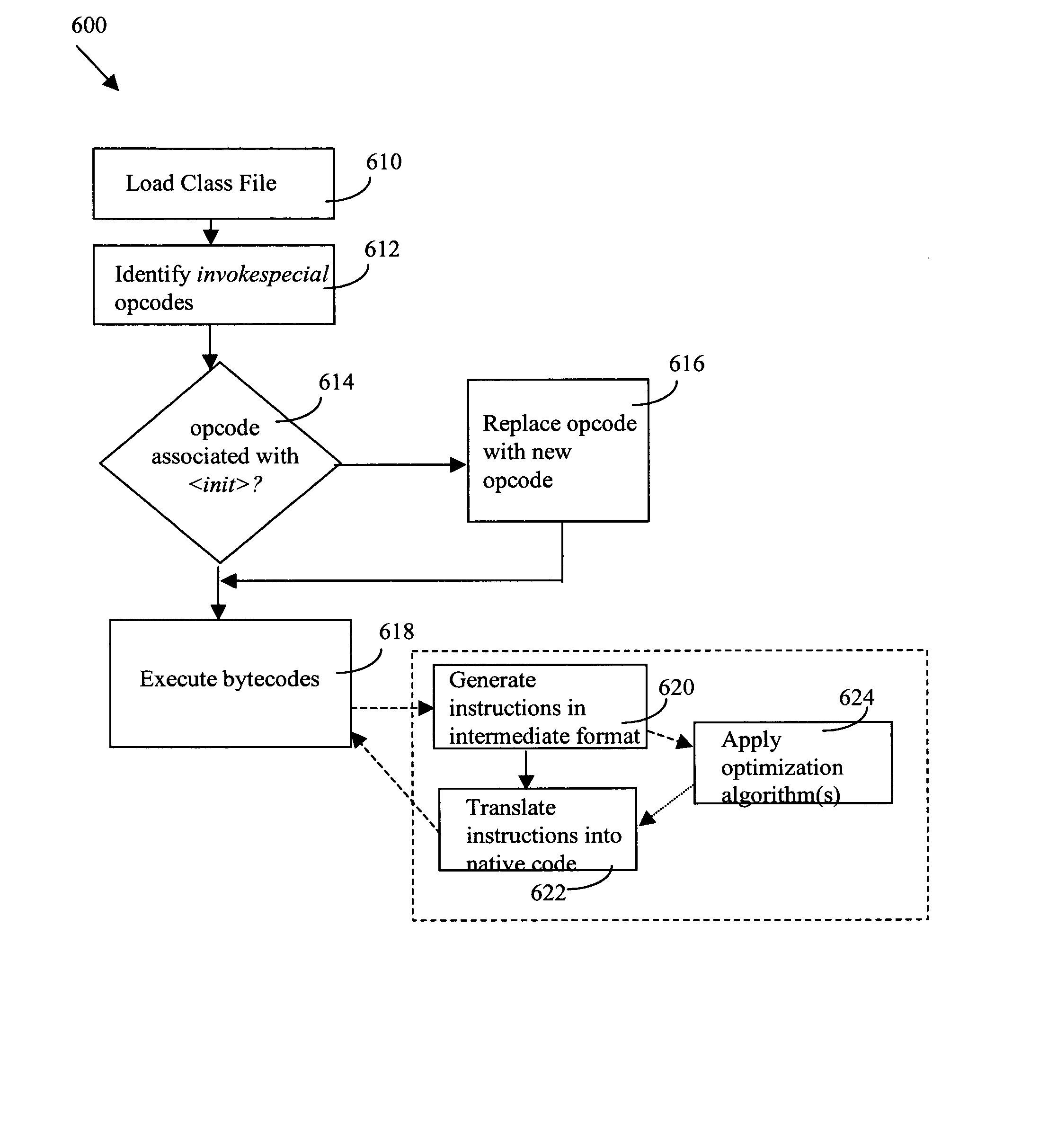
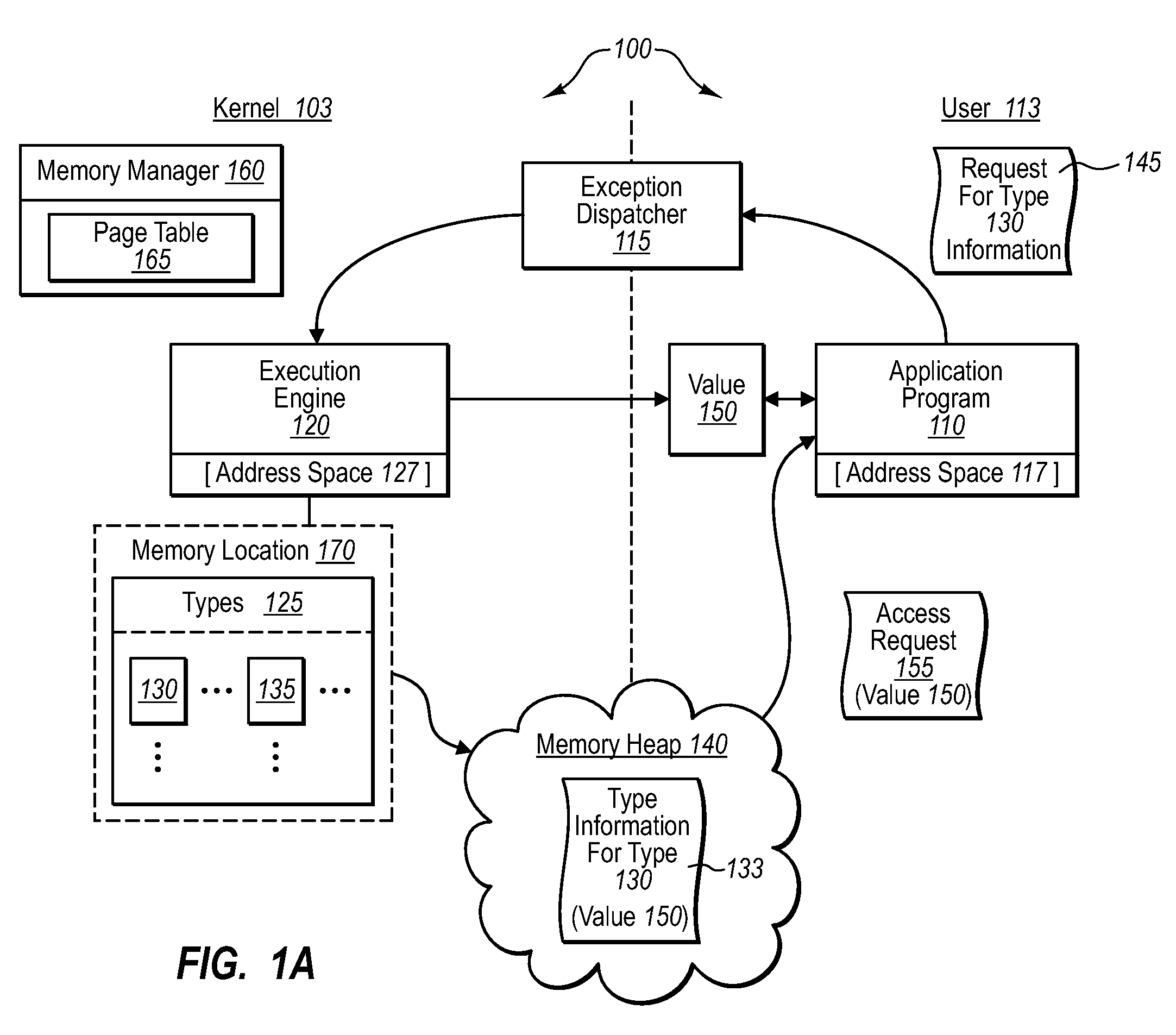
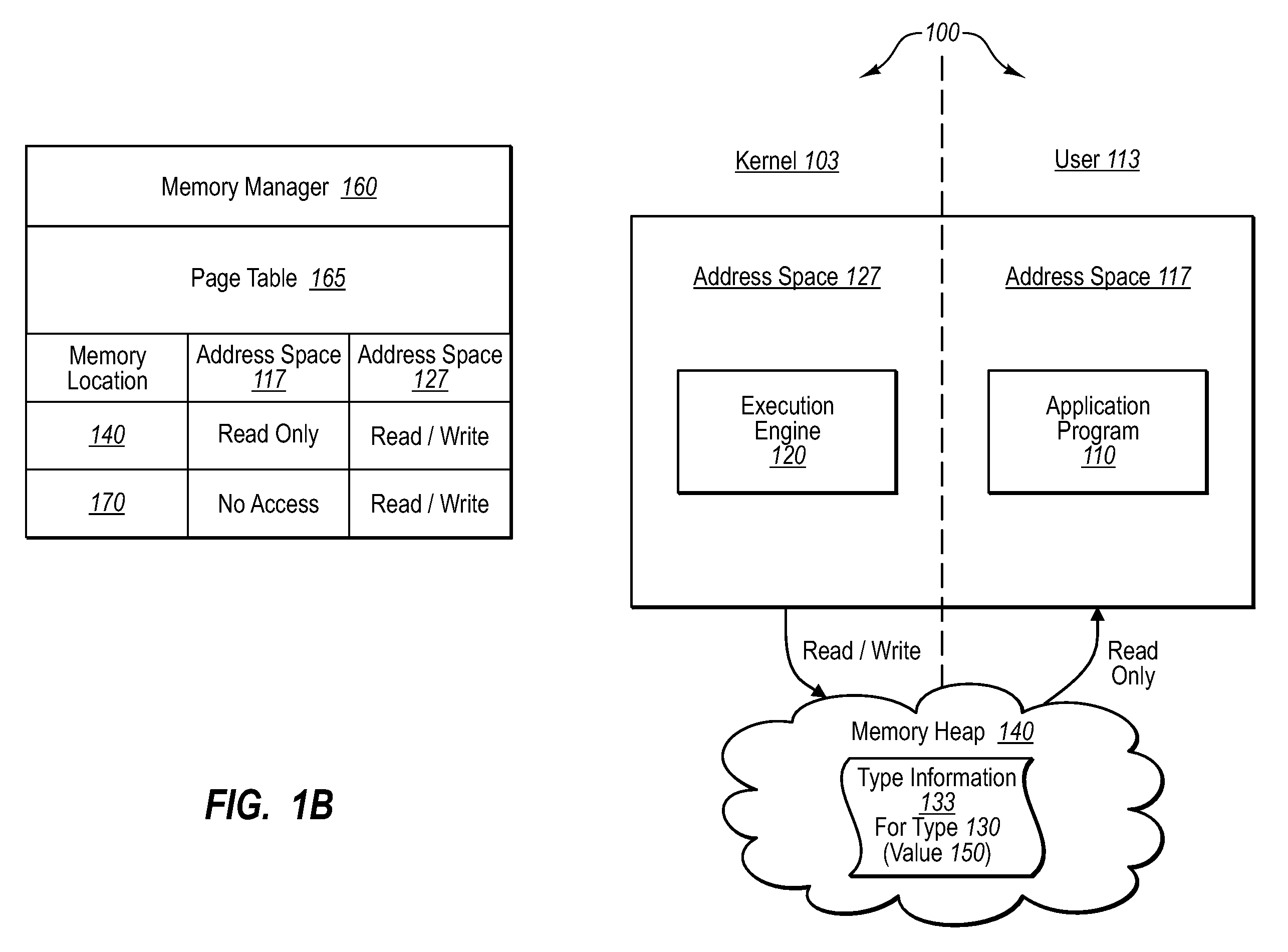
Unsafe application programs that implement managed code can be executed in a secure fashion. In particular, an operating system can be configured to execute an application program in user mode, but handle managed code compilation through a type-safe JIT compiler operating in kernel mode. The operating system can also designate a single memory location to be accessed through multiple address spaces with different permission sets. An application program operating in user mode can be executed in the read / execute address space, while the JIT compiler operates in a read / write address space. When encountering one or more pointers to intermediate language code, the application runtime can send one or more compilation requests to a kernel mode security component, which validates the requests. If validated, the JIT compiler will compile the requested intermediate language code, and the application program can access the compiled code from a shared memory heap.
Owner:MICROSOFT TECH LICENSING LLC
Positioning type safety hand bracelet for children
InactiveCN103906231AExtended use timeKeep abreast of locationEnergy efficient ICTAlarmsMemory chipCommunications system
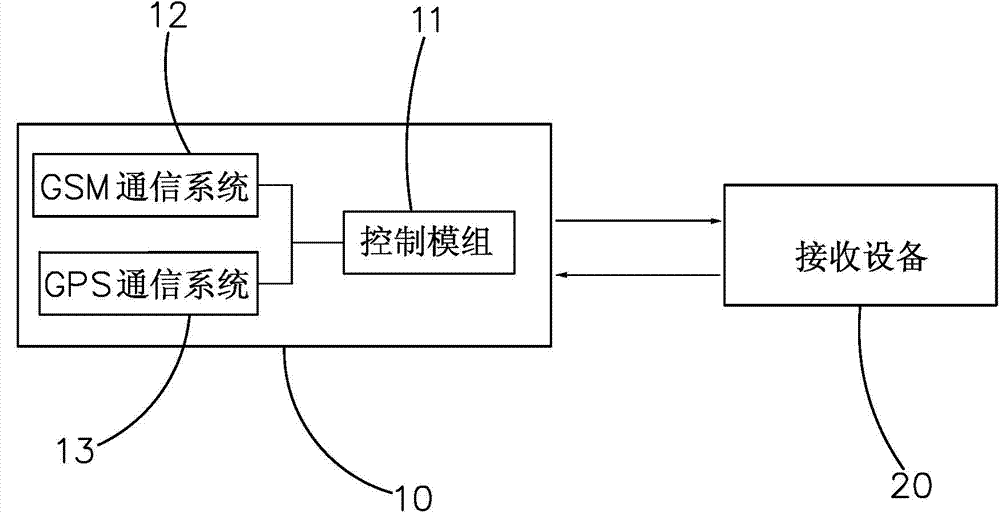
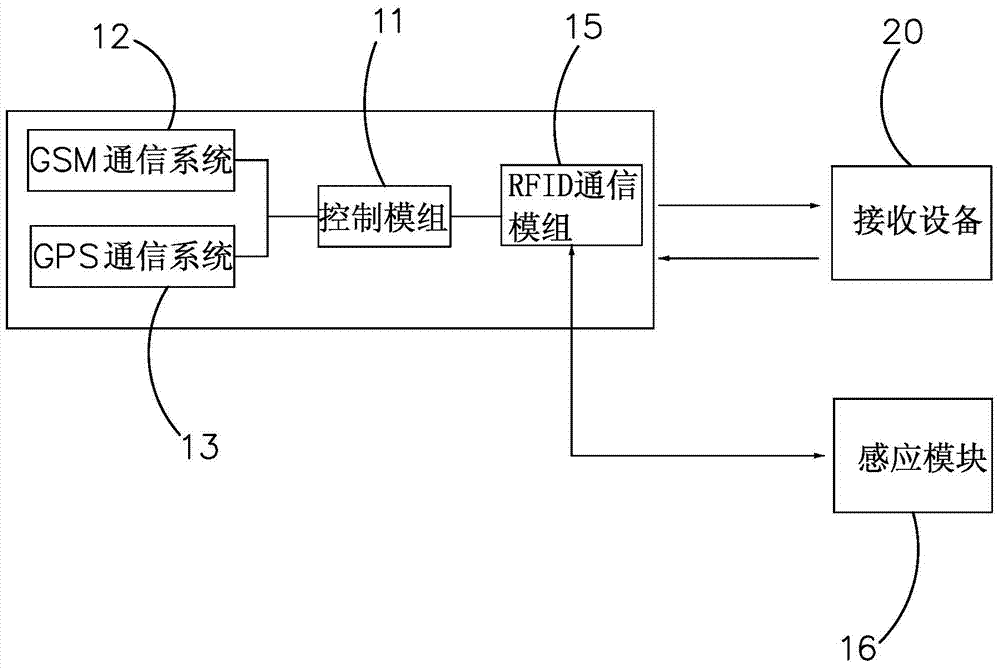
The invention discloses a positioning type safety hand bracelet for children. The positioning type safety hand bracelet for the children comprises a built-in GPS communication system, a built-in GSM communication system and a built-in control module, wherein the GPS communication system and the GSM communication system are respectively connected to the control module. The control module controls the GPS communication system and the GSM communication system inside the positioning type safety hand bracelet for the children to be started at different time periods. The positioning type safety hand bracelet for the children has two working modes, namely the normal working mode and the power saving mode. When the children are in school, the positioning type safety hand bracelet for the children is set to be in the power saving mode; when the children are not in school, the positioning type safety hand bracelet for the children is set to be in the normal working mode. A memory chip is also arranged in the positioning type safety hand bracelet for the children, and records the serial numbers of base stations by which the children pass in the walking path through the GSM communication system. When the positioning type safety hand bracelet for the children is used, by means of the built-in GPS communication system and the built-in GSM communication system, users can know the positions of the children in time, and the children are prevented from being lost.
Owner:福建省道生网络科技有限公司
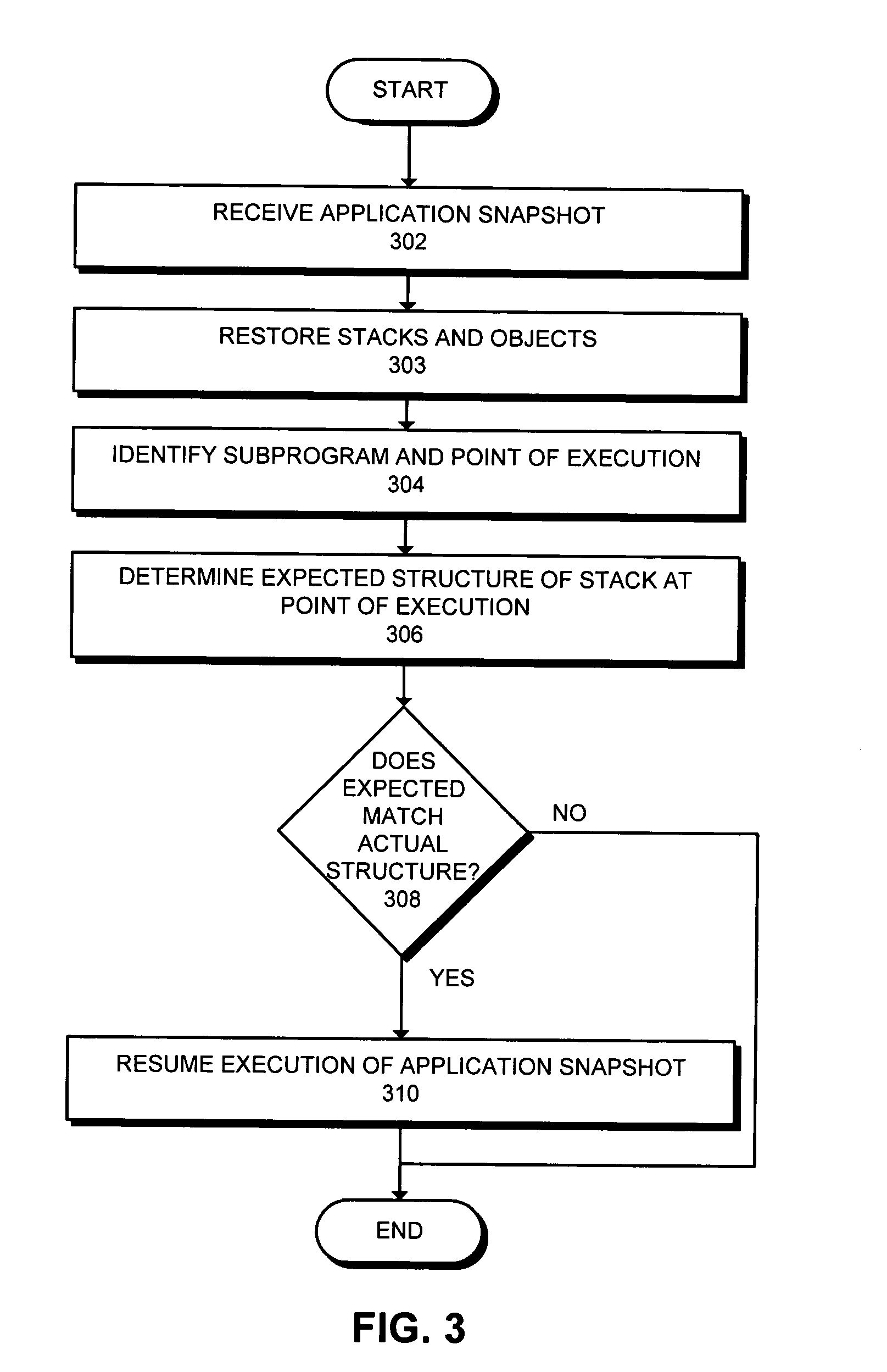
Method and apparatus to verify type safety of an application snapshot
InactiveUS6993761B1Multiprogramming arrangementsMultiple digital computer combinationsOperandType safety
One embodiment of the present invention provides a system for verifying type safety of an application snapshot. This application snapshot includes a state of an executing program that is moved from a first computing device to a second computing device across a network in order to continue execution on the second computing device. The system operates by receiving the application snapshot from the first computing device on the second computing device, wherein the application snapshot includes a subprogram, an operand stack, and a point of execution. The system then examines the application snapshot to identify one or more subprograms and the point of execution within the subprograms. Next, the system examines the subprogram to determine an expected structure of the operand stack at the point of execution. After the expected structure of the operand stack has been determined, the system verifies that the state of the application snapshot on the second computing device does not violate type safety in the sense of a platform-independent programming language. Execution of the application snapshot is resumed on the second computing device if the verification does not fail.
Owner:ORACLE INT CORP
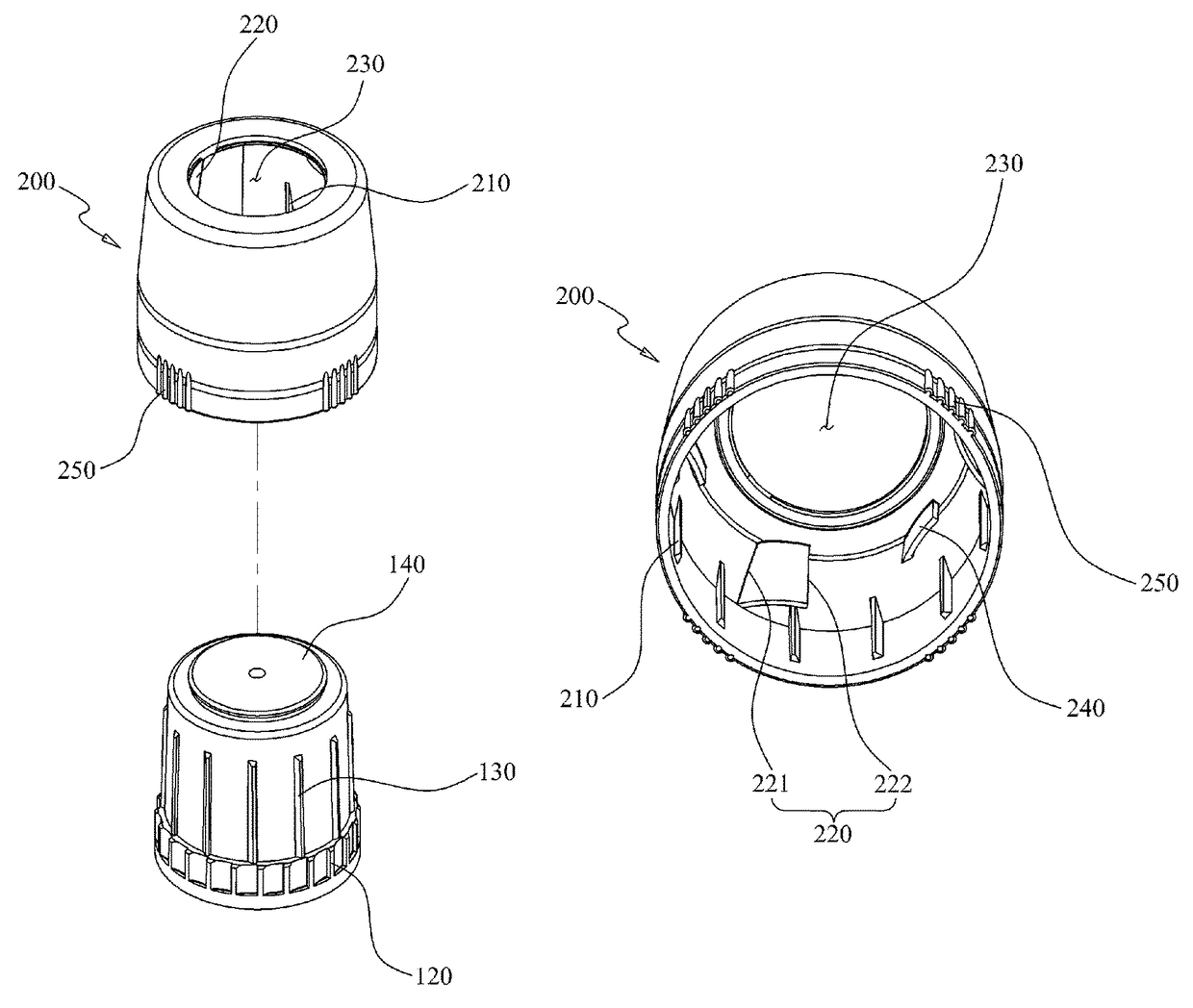
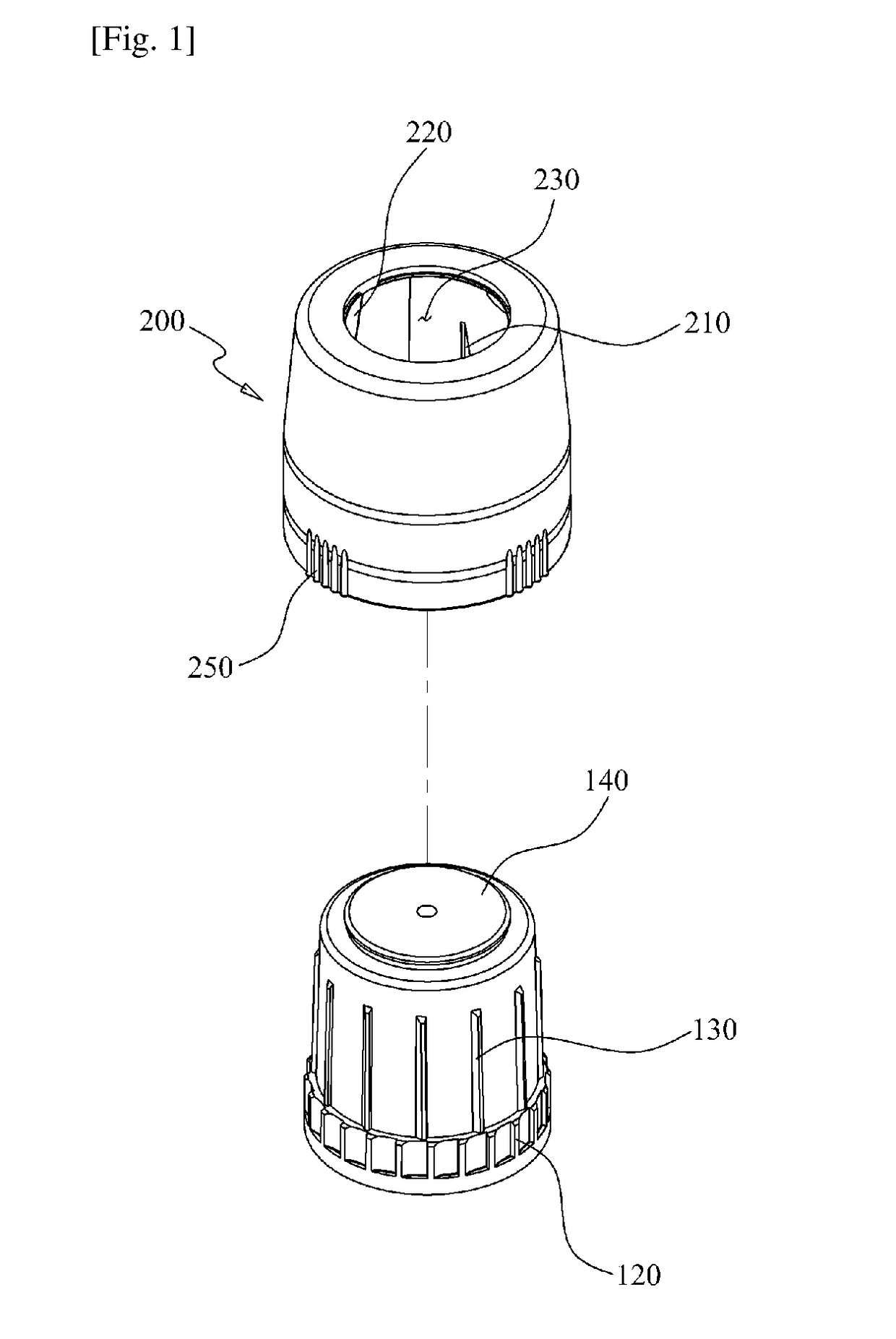
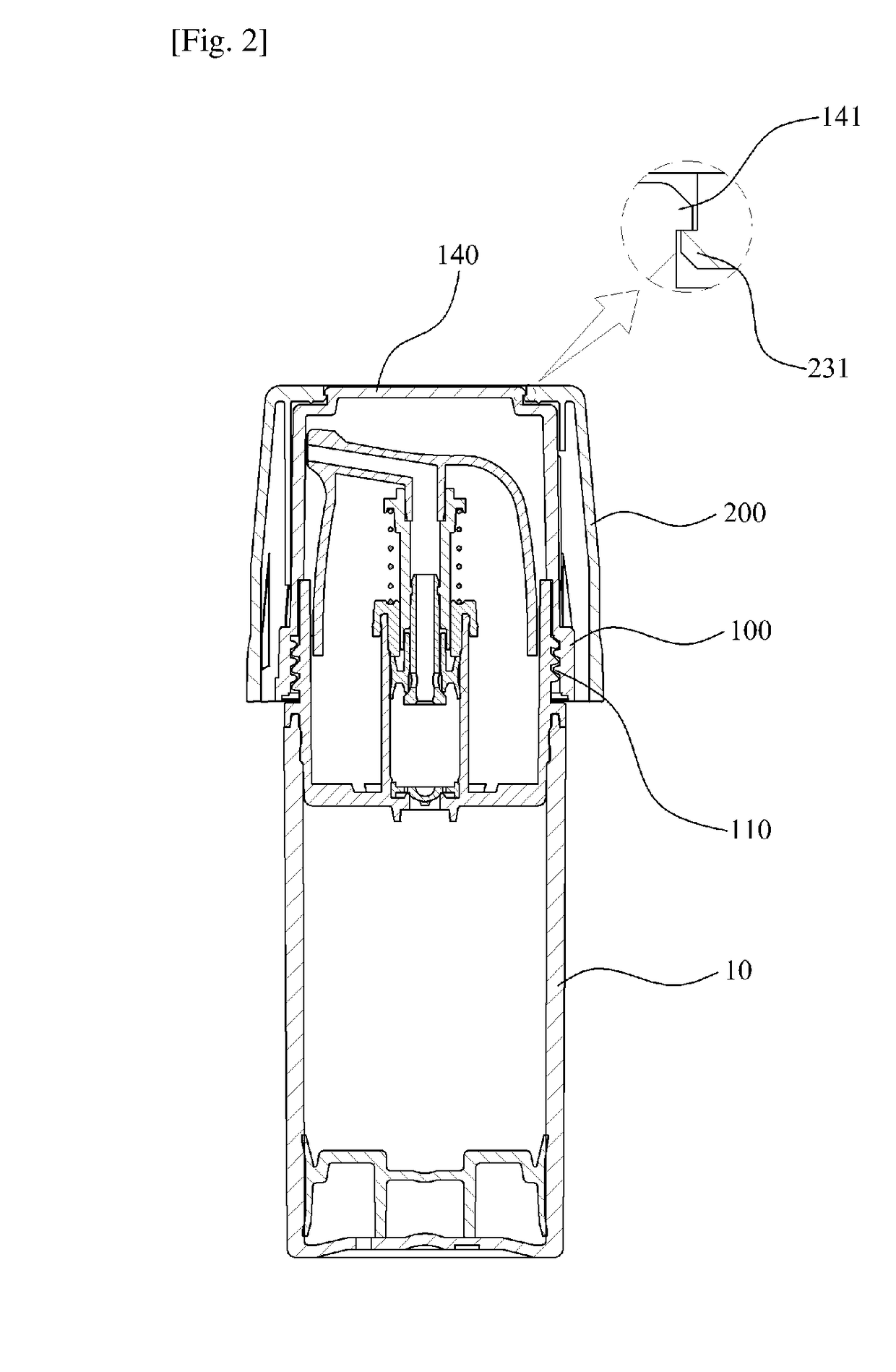
Side press-type safety cap
Owner:YONWOO CO LTD
Safe computer code formats and methods for generating safe computer code
ActiveUS20070006191A1Preventing executionFacilitates prevention from executionPlatform integrity maintainanceSpecific program execution arrangementsType safetySource code
An inherently safe code format for representing computer programs is disclosed. The format provides incorruptible referential integrity and uses type separation to achieve intrinsic type safety. The format preserves a safety guarantee found in a source code language representation of the computer program while the computer program proceeds through various stages of the code compilation process.
Owner:RGT UNIV OF CALIFORNIA
Self-locking reliability performance testing machine for speed differential fall arrester
ActiveCN102297762AReach releaseReach holdMachine part testingBuilding rescueHigh volume manufacturingEngineering
The invention discloses a speed-different type safety catcher self-locking reliability performance test machine which comprises a framework, a base plate 2 and an air pump. The framework is provided with two fixed plates, releasing mechanisms, one or two upper stop blocks, an impact pedestal, a control cabinet, a suspension ring, a weight block set, cylinders, movable plates, a sensor, movable plate gag lever posts, and a weight block gag lever post. Each releasing mechanism 5 comprises an electromagnet, a releasing pawl and a lever mechanism. The releasing pawl extends horizontally and inwardly to form a mobile platform capable of supporting the weight block set. The electromagnet and one end of the lever mechanism form a machinery linkage capable of tripping. The impact pedestal is arranged at a central position of the base plate. Center lines of the impact pedestal, the weight block set and the speed-different type safety catcher are superposed. The impact pedestal is provided witha counting sensor. The speed-different type safety catcher self-locking reliability performance test machine has the advantages of simple structure, low manufacture cost, good processing consistency,suitability of mass production and the like.
Owner:ZHEJIANG HUADIAN EQUIP TESTING INST
Monitoring method in video-type safety-protection system
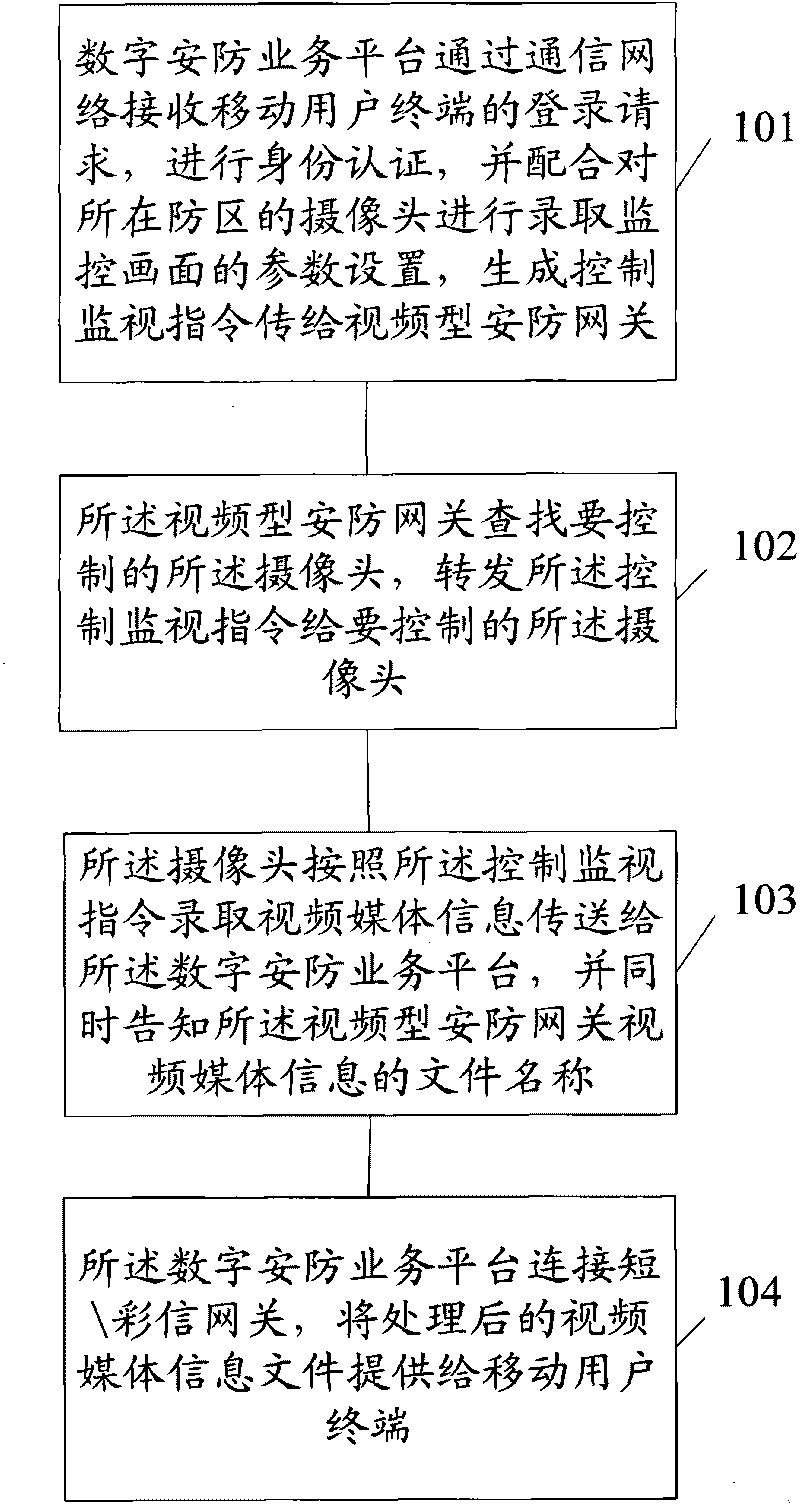
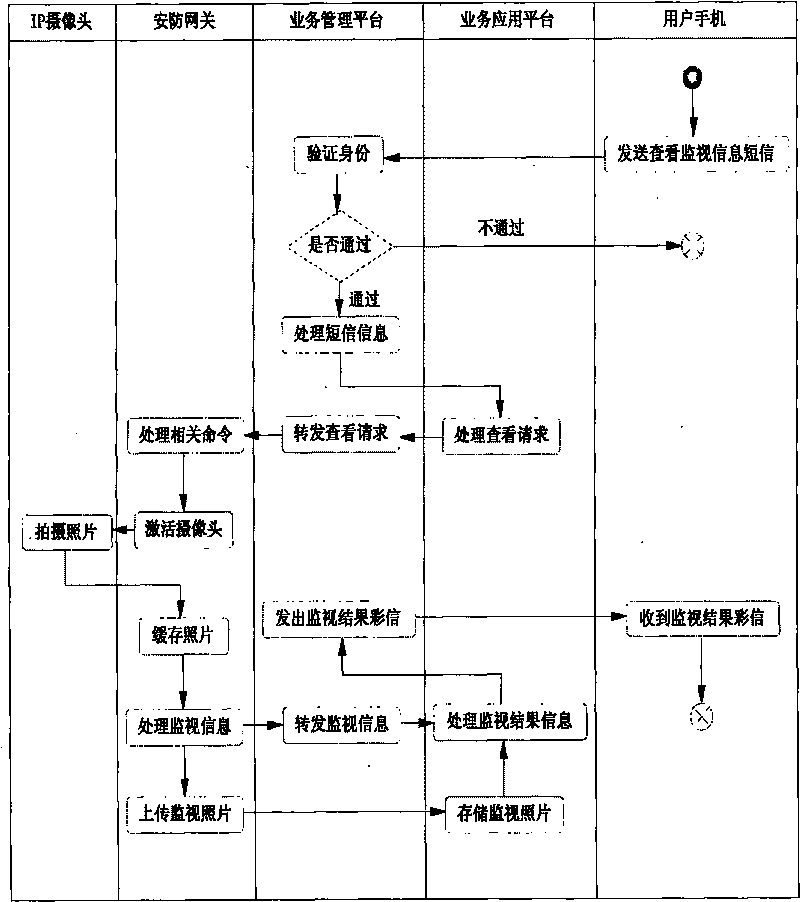
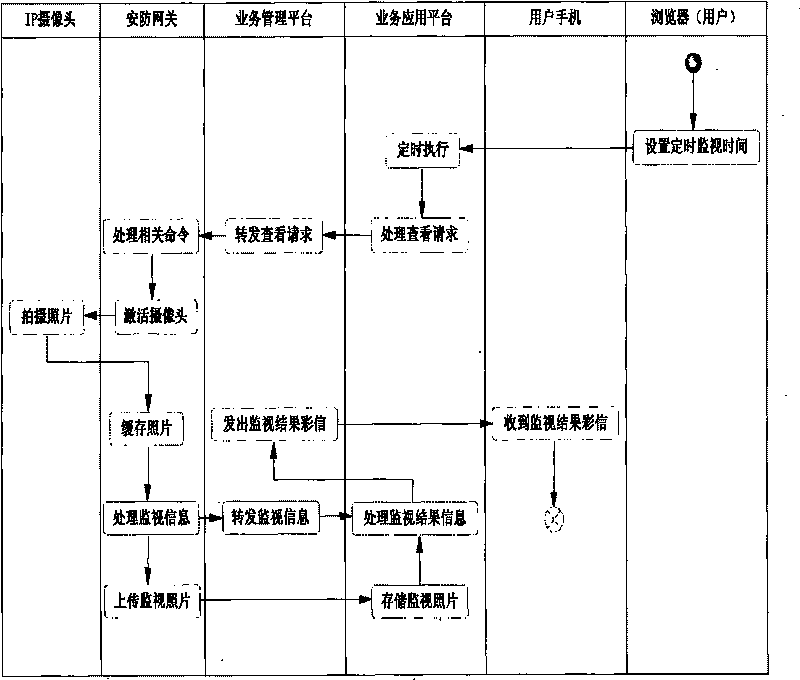
InactiveCN101741898AEase of workReduce riskClosed circuit television systemsTransmissionComputer hardwareUsability
The invention discloses a monitoring method in a video-type safety-protection system, which comprises the following steps: A. a digital safety-protection service platform receives a login request of a mobile user terminal through the communication network, authenticates the identity, sets the parameters for taking the monitoring pictures in cooperation with the camera of the local protection area, generates a control monitoring instruction and transmits the control monitoring instruction to the video-type safety-protection gateway; B. the video-type safety-protection gateway searches the camera to be controlled, and forwards the control monitoring instruction to the camera to be controlled; C. the camera takes the video media information, forwards the video media information to the digital safety-protection service platform and informs of the file name of the video media information; and D. the digital safety-protection service platform is connected to the short / multimedia message gateway, and supplies the processed media information file for the mobile user terminal. The invention greatly enhances the usability of users; and any mobile telephone capable of receiving short messages or multimedia messages can monitor.
Owner:GUANGDONG TRI SUN ELECTRONICS TECH
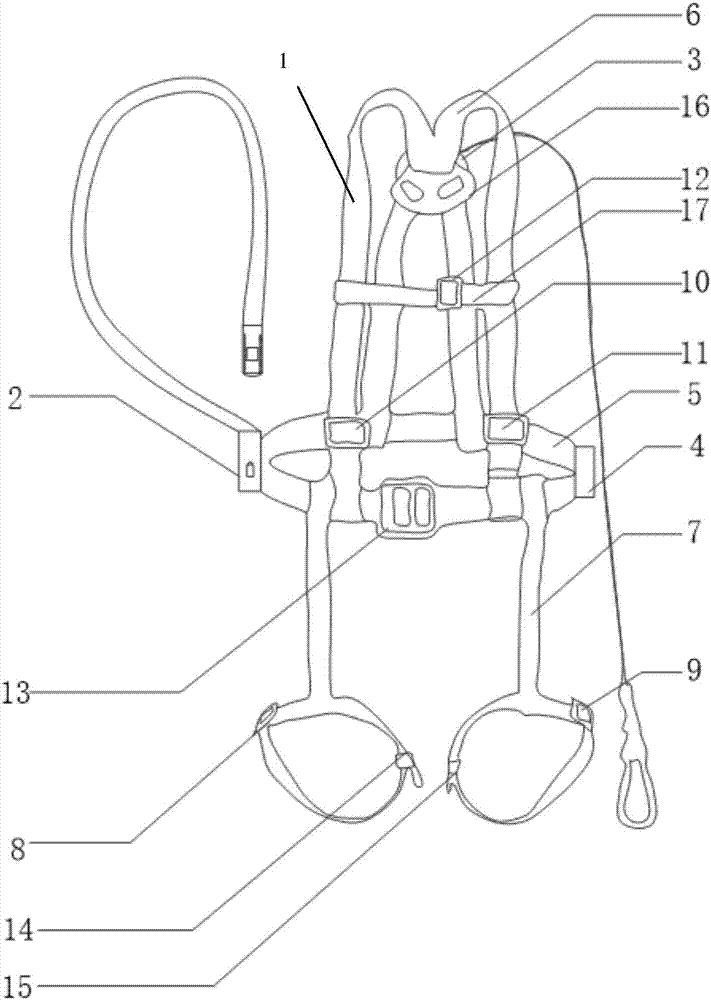
Aerial working safety belt and using method
The invention discloses an aerial working safety belt which comprises a waistcoat type safety belt body, a main hook, an auxiliary hook, braids, braid furling devices, a main hook control device and an auxiliary hook control device. The lower end of a movable hook body of the main hook and the lower end of a movable hook body of the auxiliary hook are both connected with the lower ends of fixed hook bodies through a main hook locking device and an auxiliary hook locking device. A using method of the aerial working safety belt includes the following steps: (1) wearing the aerial working safety belt, (2) starting a main hook electric control device, (3) respectively hooking the main hook and the auxiliary hook, (4) respectively locking the main hook and the auxiliary hook, (5) moving the main hook, (6) moving the auxiliary hook, (7) hooking the main hook or the auxiliary hook again, and (8) taking down the main hook and the auxiliary hook. According to the aerial working safety belt and the using method, a dual-safety mechanism that the main hook and the auxiliary hook are used for hooking at the same time is adopted, the automatic locking function when falling occurs is achieved, and movement space of a worker is enlarged. The self-locking function of the main hook or the auxiliary hook is achieved, the one-way interlocking function between the main hook and the auxiliary hook is achieved, and the aerial working safety is guaranteed.
Owner:镇江天颐装备科技有限公司
Harness type safety belt
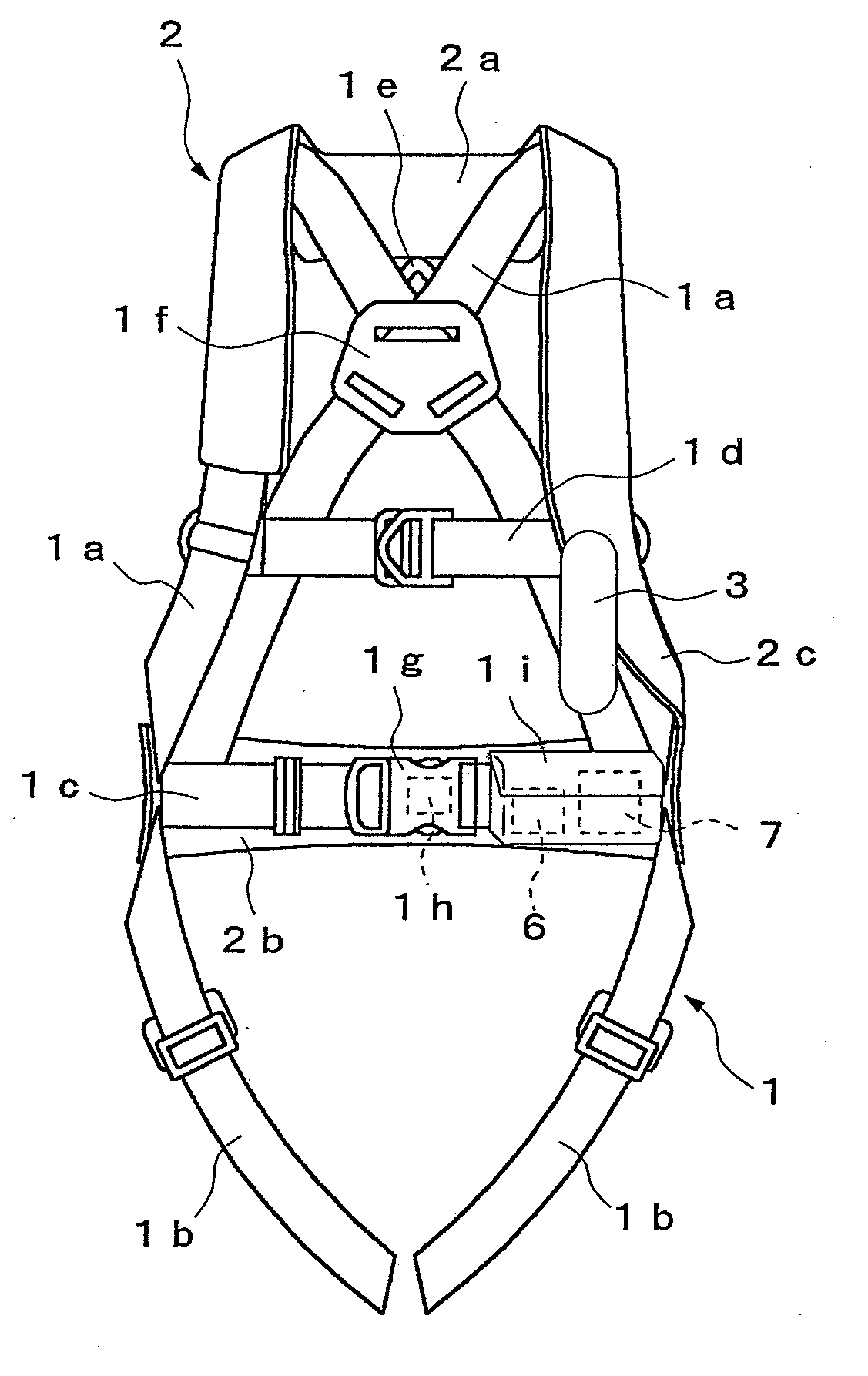
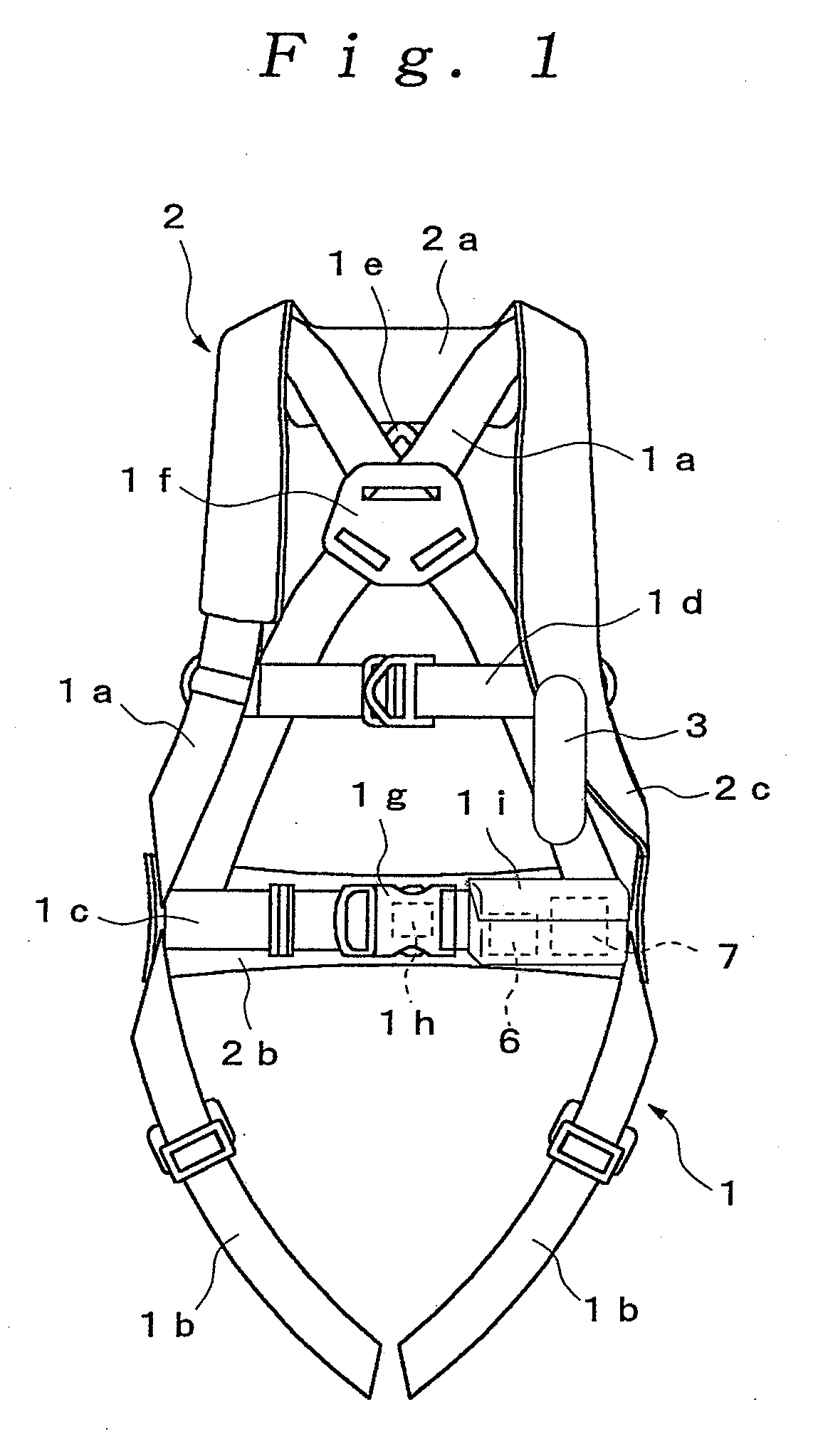
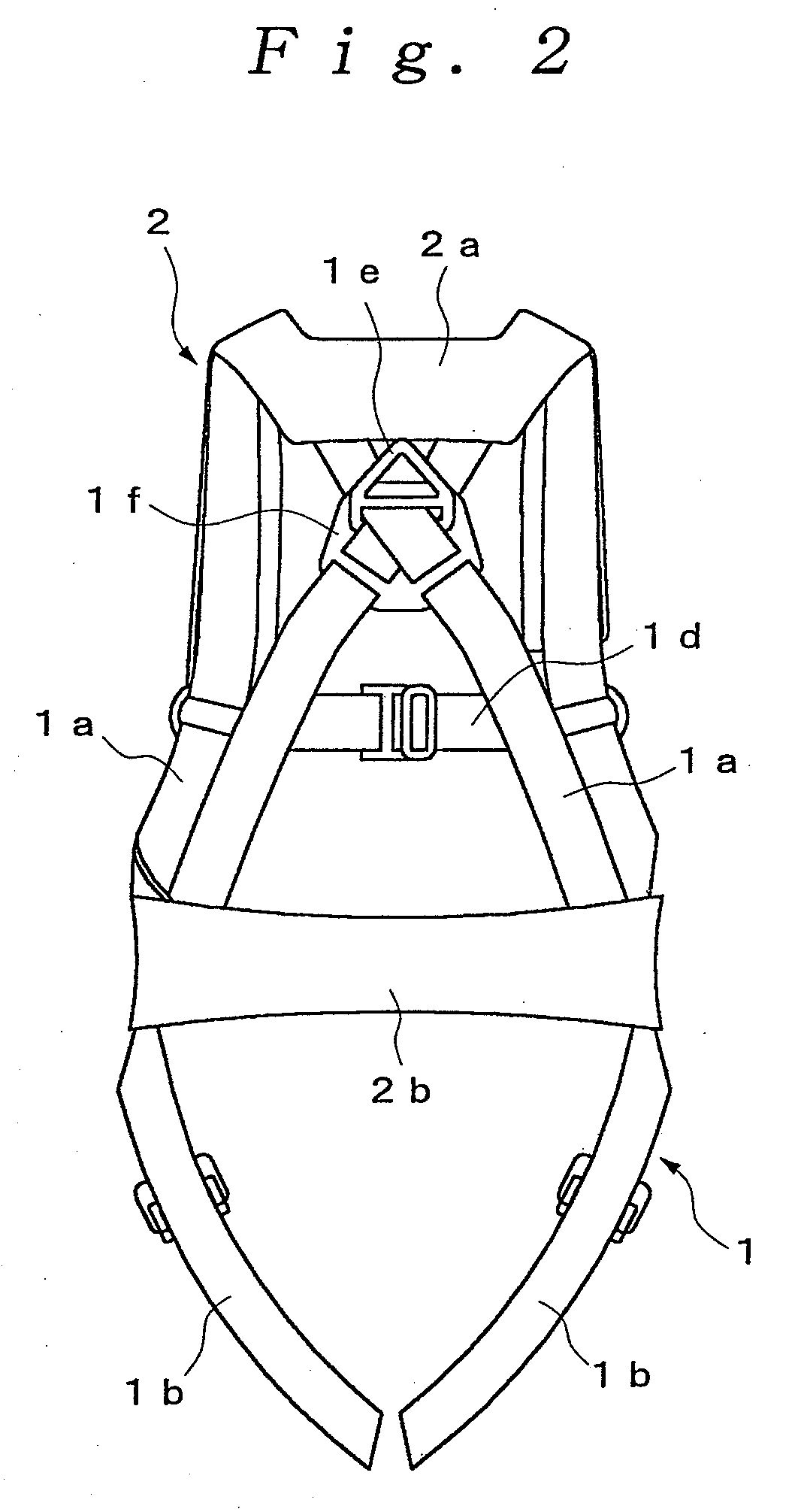
InactiveUS20090019623A1Firm supportReduce the impactChemical protectionHeat protectionDrop impactThigh part
The present invention provides a harness type safety belt capable of absorbing a dropping shock to a user even if the user accidentally falls from an elevated position. According to the present invention, in such a case that a user A fails to apply a hook of a rope to a life line and the user A falls from an elevated position, an air bag 2 provided in a mounting body 1 is inflated. Therefore, the air bag 2 can absorb a dropping shock and the dropping impact applied to the user A can be reduced. In addition, in the case where the user A falls with the hook of the rope being connected to the life line, the user A is suspended by the rope. The body of the user A is supported by not only a waist part belt 1b but also shoulder part belts 1a and thigh part belts 1c. Therefore a tension applied from the rope to the body of the user can be dispersed to each of the belts 1a, 1b and 1c and the body of the user can be stably supported.
Owner:PROP
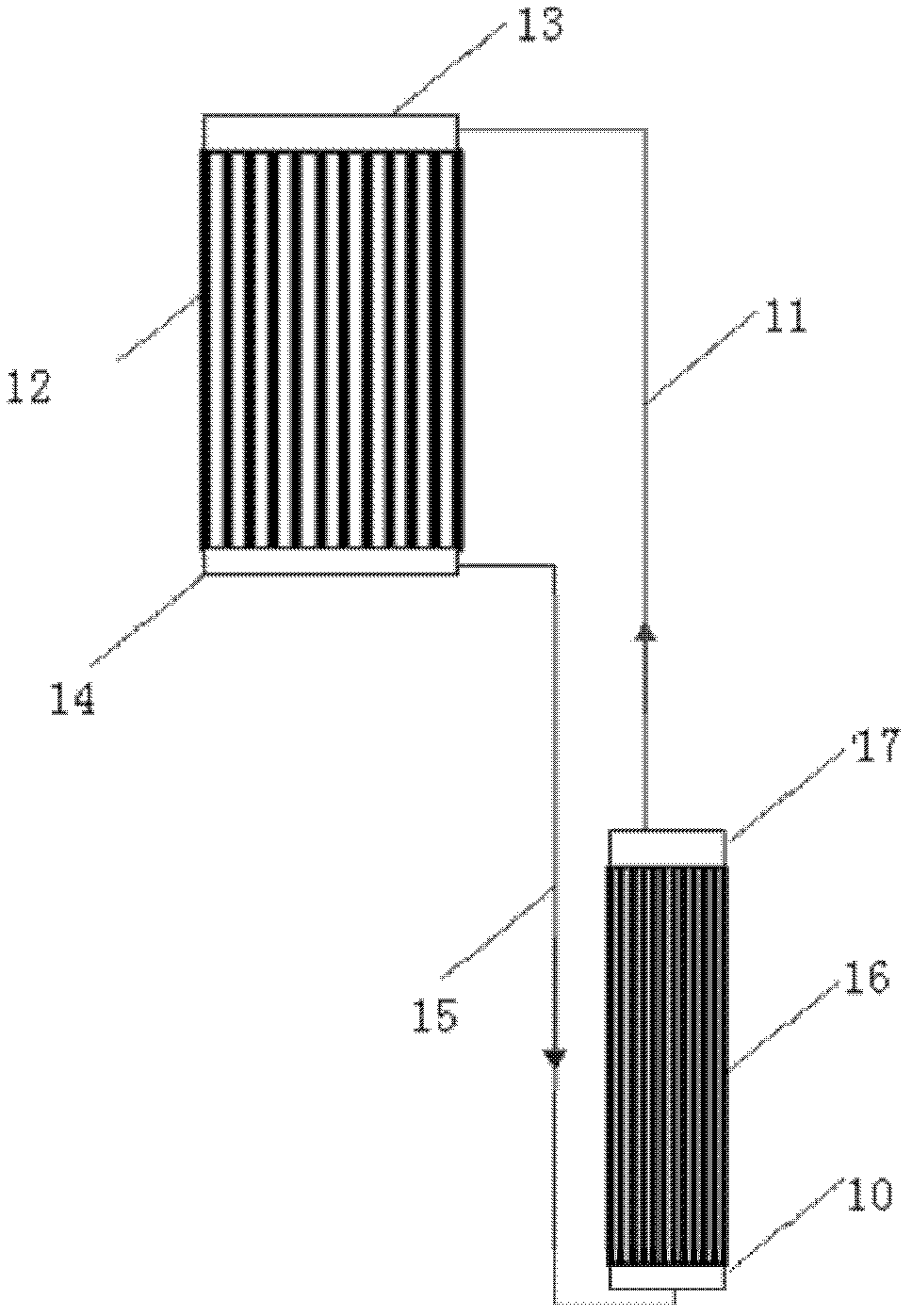
Flooded-type containment complete passive after-heat removal system
ActiveCN103377728APrevent evaporationEliminate dependenciesNuclear energy generationCooling arrangementNuclear engineeringNuclear power
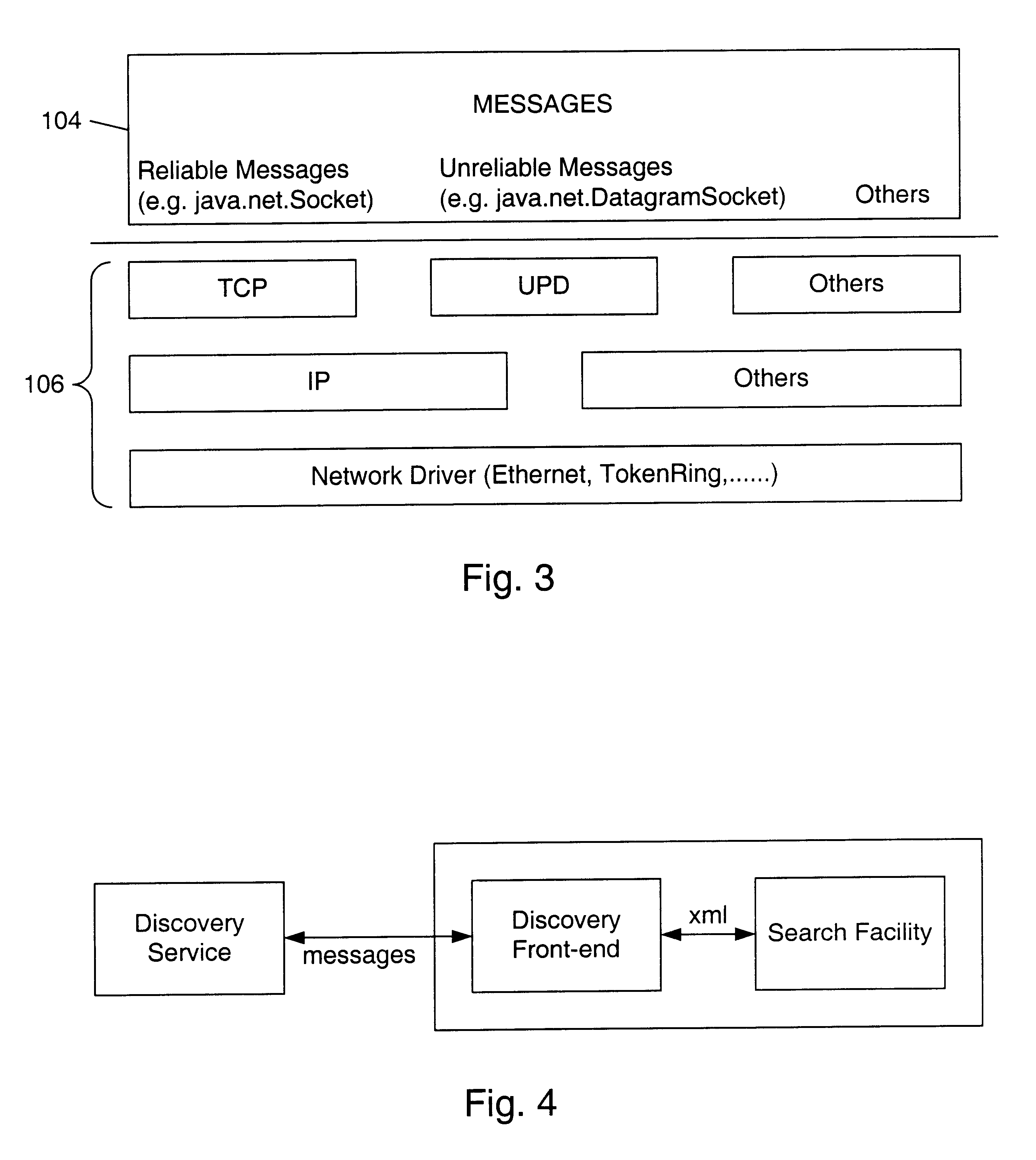
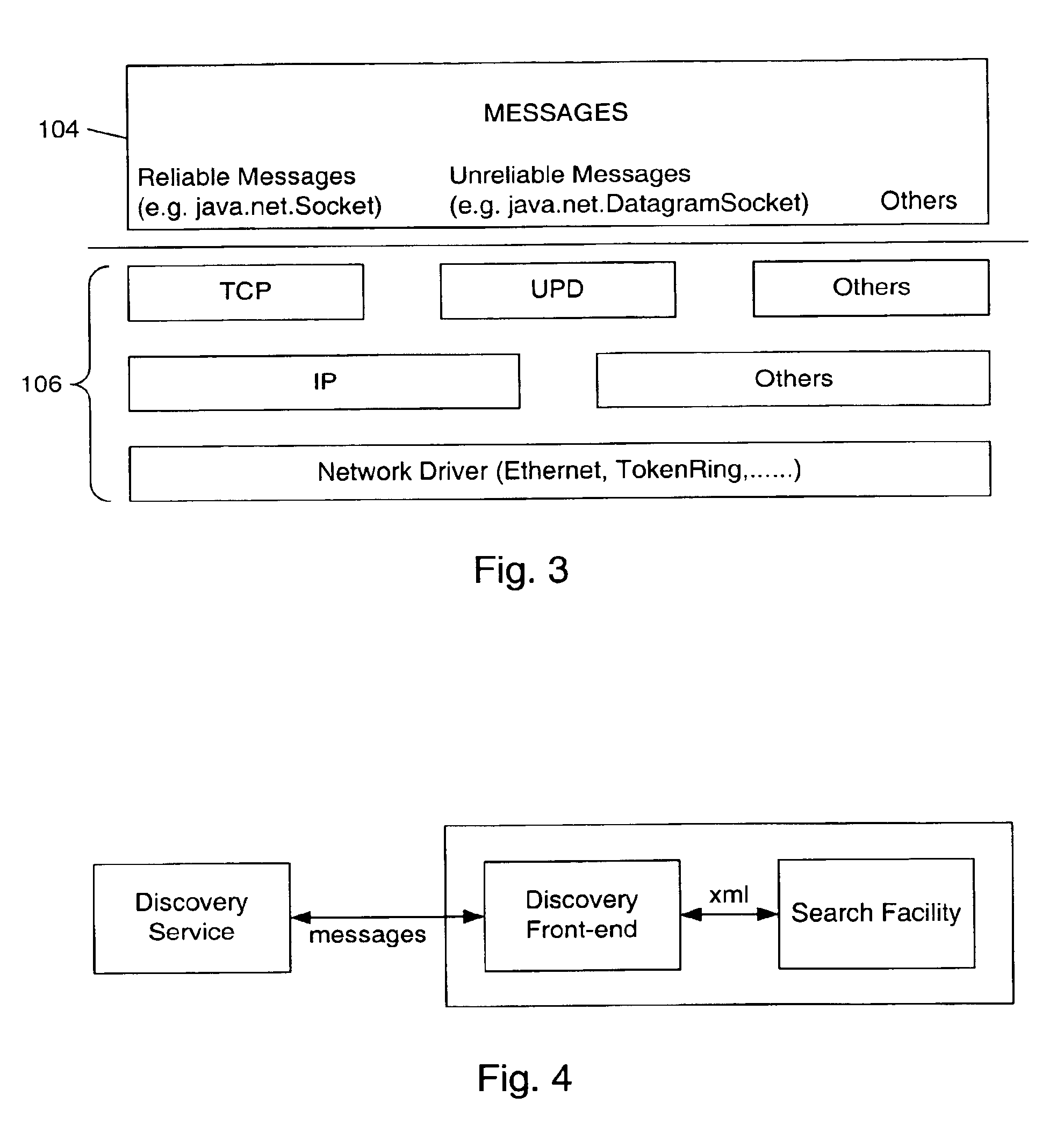
The invention relates to the field of an engineering safety system of a nuclear power station reactor, and in particular relates to a flooded-type containment complete passive after-heat removal system with final hot traps after accidents, in order to solve the problem that after the safety accidents of a nuclear power station, cooling water evaporates completely, and most final hot traps are lost for the flooded-type safety shell. A flow guide plate is in a framework structure with a sealed periphery, and a plurality of limber holes are formed in the lower part of the flow guide plate; the flow guide plate is placed on the bottom of a water tank, surrounds the containment, and is immersed into cooling water; an evaporation end of a separated-type cooling device is placed in cooling water at the outer side area of the flow guide plate; a condensation end of the separated-type cooling device is configured into a chimney. Heat emitted by the containment is transmitted to the separated-type cooling device through the natural circulation of a cooling liquid, and the separated-type cooling device removes heat through the chimney again. The system adopts mature equipment and is driven passively, thus the system running reliability and safety are guaranteed, and further the safety of a nuclear power station is increased obviously.
Owner:SHANGHAI NUCLEAR ENG RES & DESIGN INST CO LTD
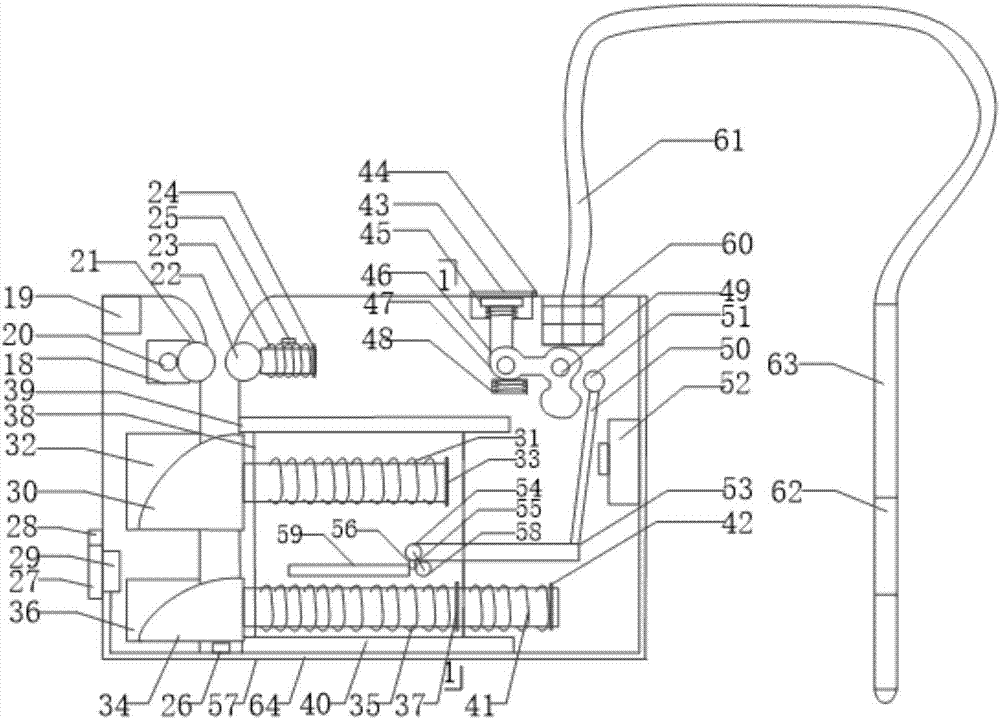
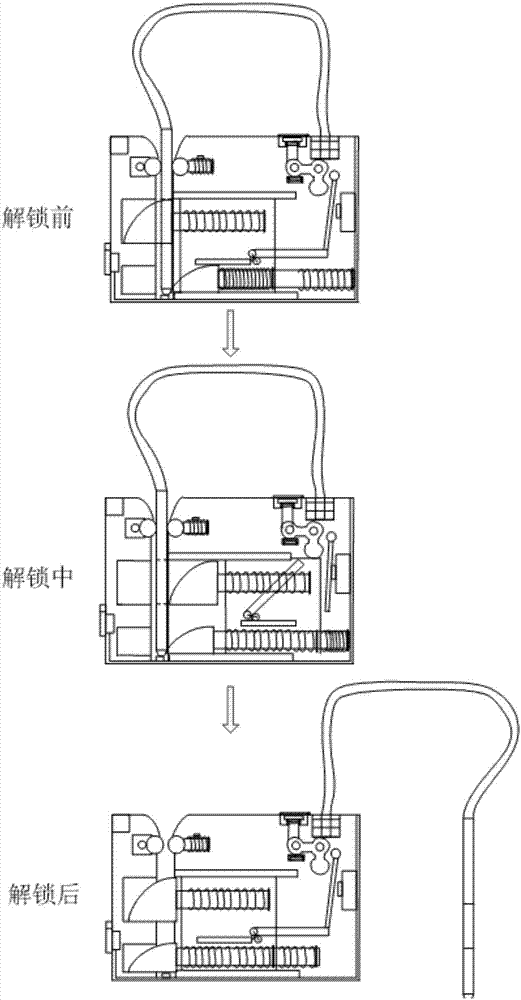
Anti-falling device for steel pipe pole operation of power transmission lines
The invention belongs to the technical field of operating maintenance of power transmission lines, and particularly relates to an anti-falling device for steel pipe pole operation of power transmission lines. The anti-falling device is arranged on a binding type safety belt base body, a steel pipe pole on the safety belt base body is carried by a worker to an operation position, a locked detectiondevice is unlocked and winds across angle iron so as to be tied, and a hanging ring of a falling brake device is hung at a high position. A warning message can be given out if a safety belt is not tied, and an insertion head can be pushed inwards automatically if the insertion head is not fastened. When the worker falls, a central control monitoring unit can provide a brake signal to make the falling brake device to act rapidly, mechanical brake is triggered if an electric fault happens, and thus dual protection is achieved. The work conditions of all components are fed back to ground monitoring personnel in the whole process. The anti-falling device has the advantages that the brake distance is short, noise is avoided in the operation process, reminding and monitoring functions can be achieved, and the anti-falling device is safe and reliable.
Owner:STATE GRID LIAONING ECONOMIC TECHN INST +2
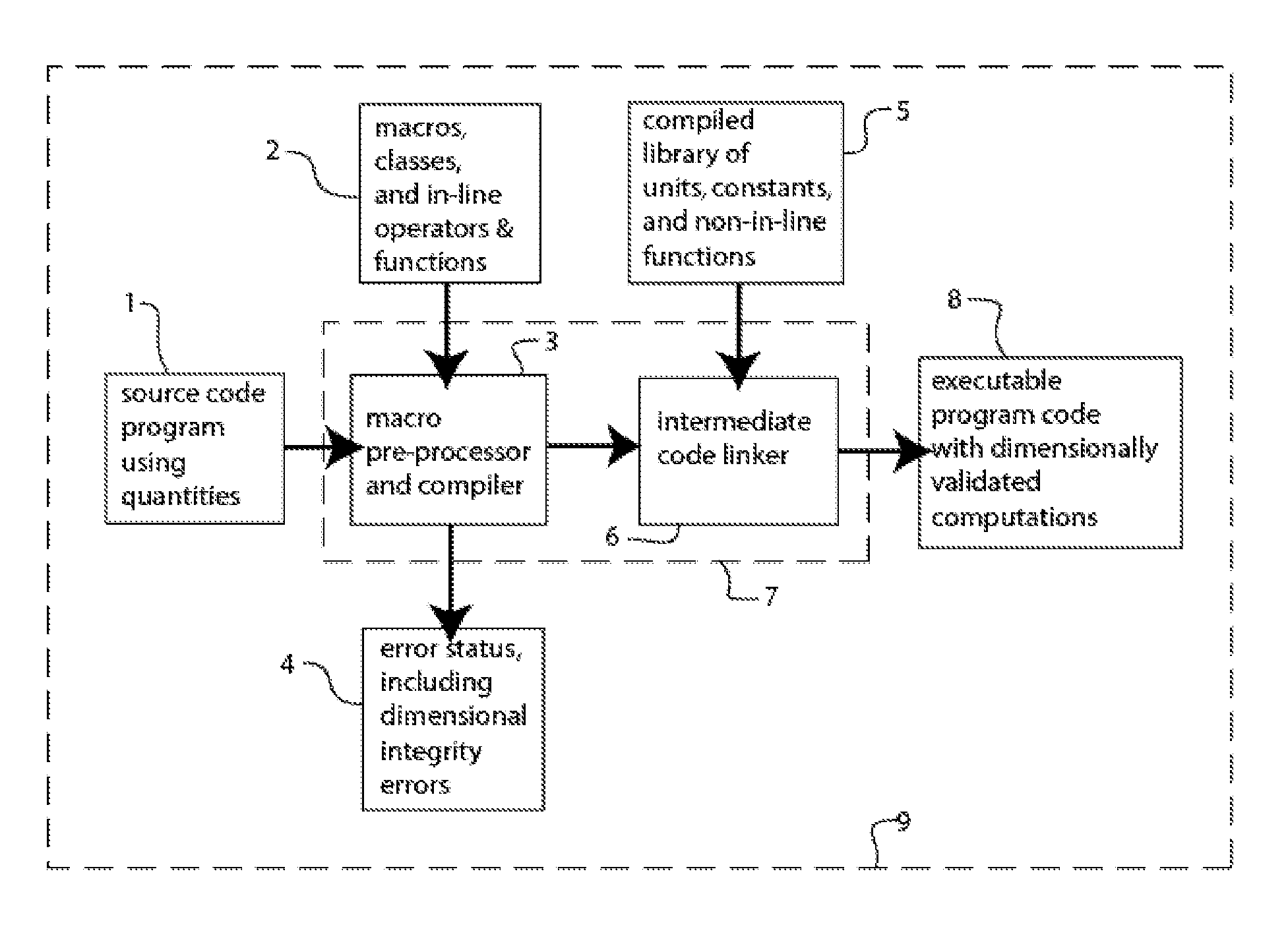
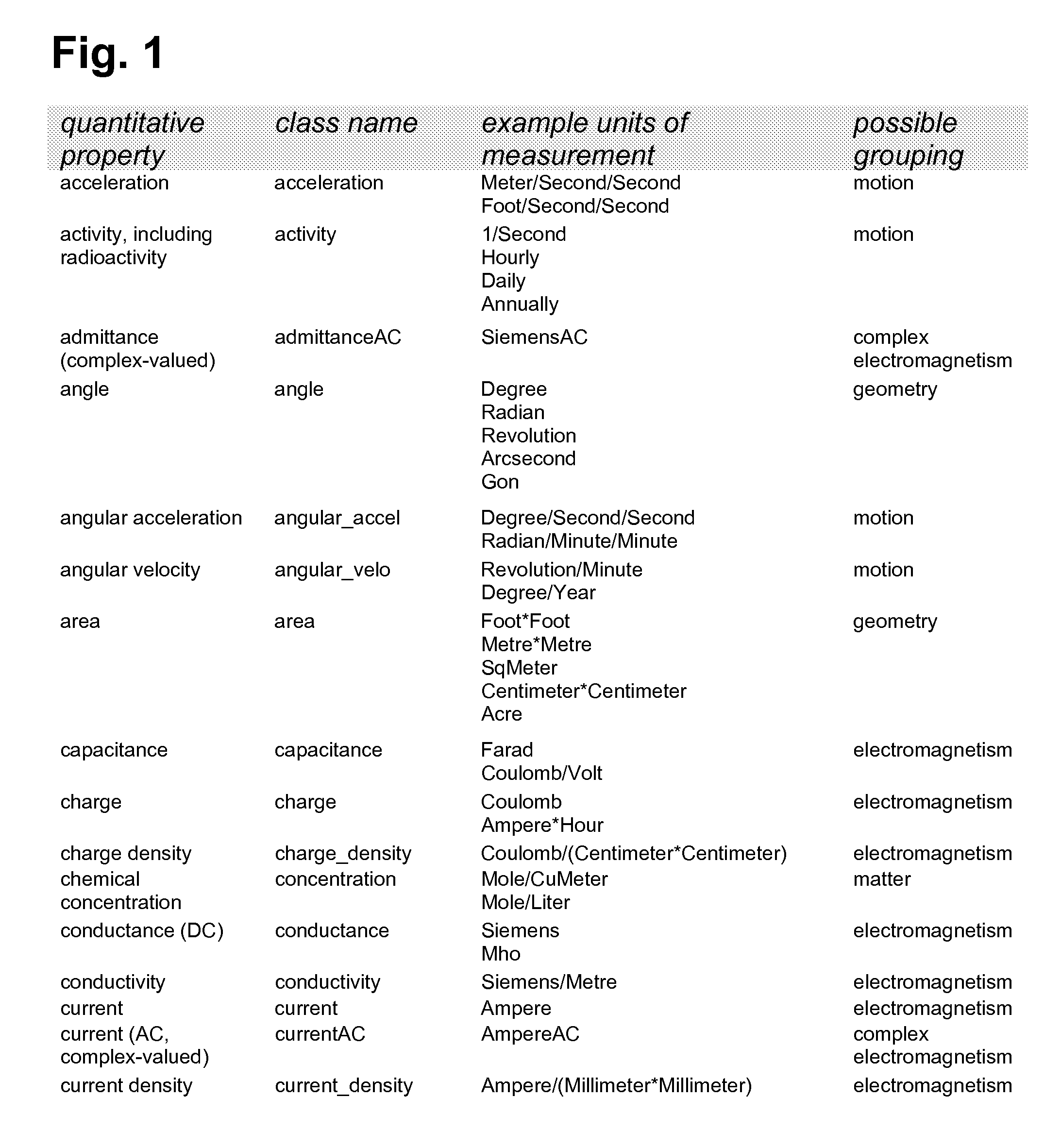
Method and System for Representing Quantitative Properties in a Computer Program and for Validating Dimensional Integrity of Mathematical Expressions
InactiveUS20080247532A1Interconnection arrangementsSoftware engineeringAlgorithmUnits of measurement
A software method and system for efficiently representing values of quantitative properties, or dimensions, such as scientifically measured or computed quantities. Each quantitative dimension may be represented by a class defined in an object-oriented programming language. Each quantity of a dimension is represented by an object of the class representing the dimension objects may be used without knowledge of the internal representation of its objects. The class provides storage and computational efficiency comparable to that of using a computer's native numbers of the same range and precision as the quantities involved. The classes may include object constructors, arithmetic operators, and constants representing conventional units of measurement. Type-safe operators and functions in a mathematical expression accept quantity objects as arguments and compute objects as results. The method and system provide for compile-time validation of the dimensional integrity of the expression.
Owner:SCHULZ WALDEAN ALLEN
Explosion-roof and flameproof ejection type safety surge-absorbing module
ActiveUS20120105191A1Prevent any further accidentSpark gap detailsHeating/cooling contact switchesType safetyHigh heat
An explosion-proof and flameproof ejection type safety surge-absorbing module includes a protective member and a surge-absorbing unit. The protective member comprises a base and an upper lid coupled with the base. The base has two corresponding partitions extending upwards. The surge-absorbing unit includes a body, two connecting leads, and a resilient metallic plate. The body has two sides each defining an electrode surface. The electrode surface is connected with one of the connecting leads. The resilient metallic plate has a first end welded to the electrode surface with a contact member and a second end curved and striding across an outer side of one of the partitions to penetrate through the bottom of the base. In case the body of the surge-absorbing unit is overheated due to high temperature caused by a surge, the contact component will be melted allowing the resilient metallic plate to eject away from the electrode.
Owner:CERAMATE TECH CO LTD
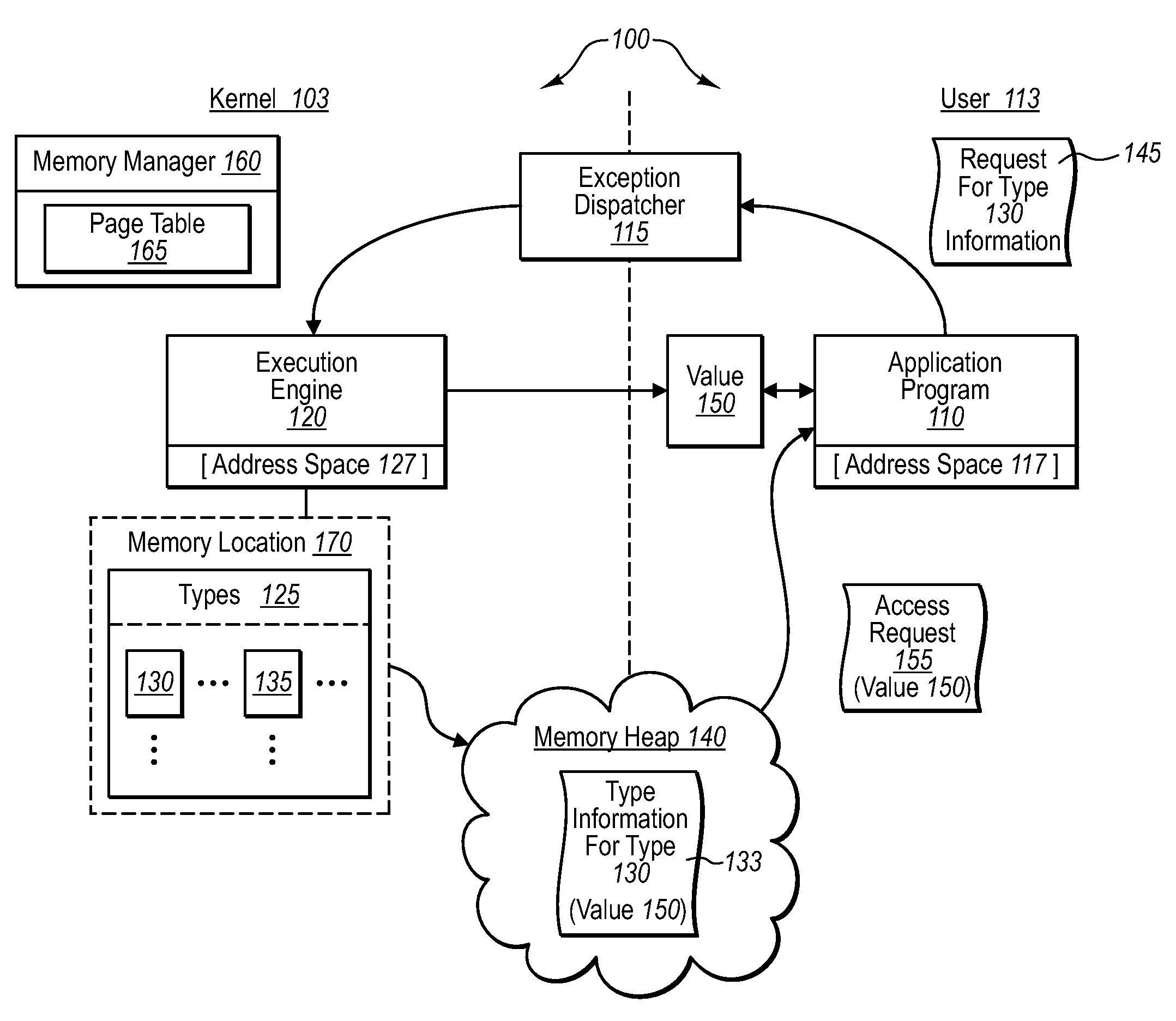
Restricting type access to high-trust components
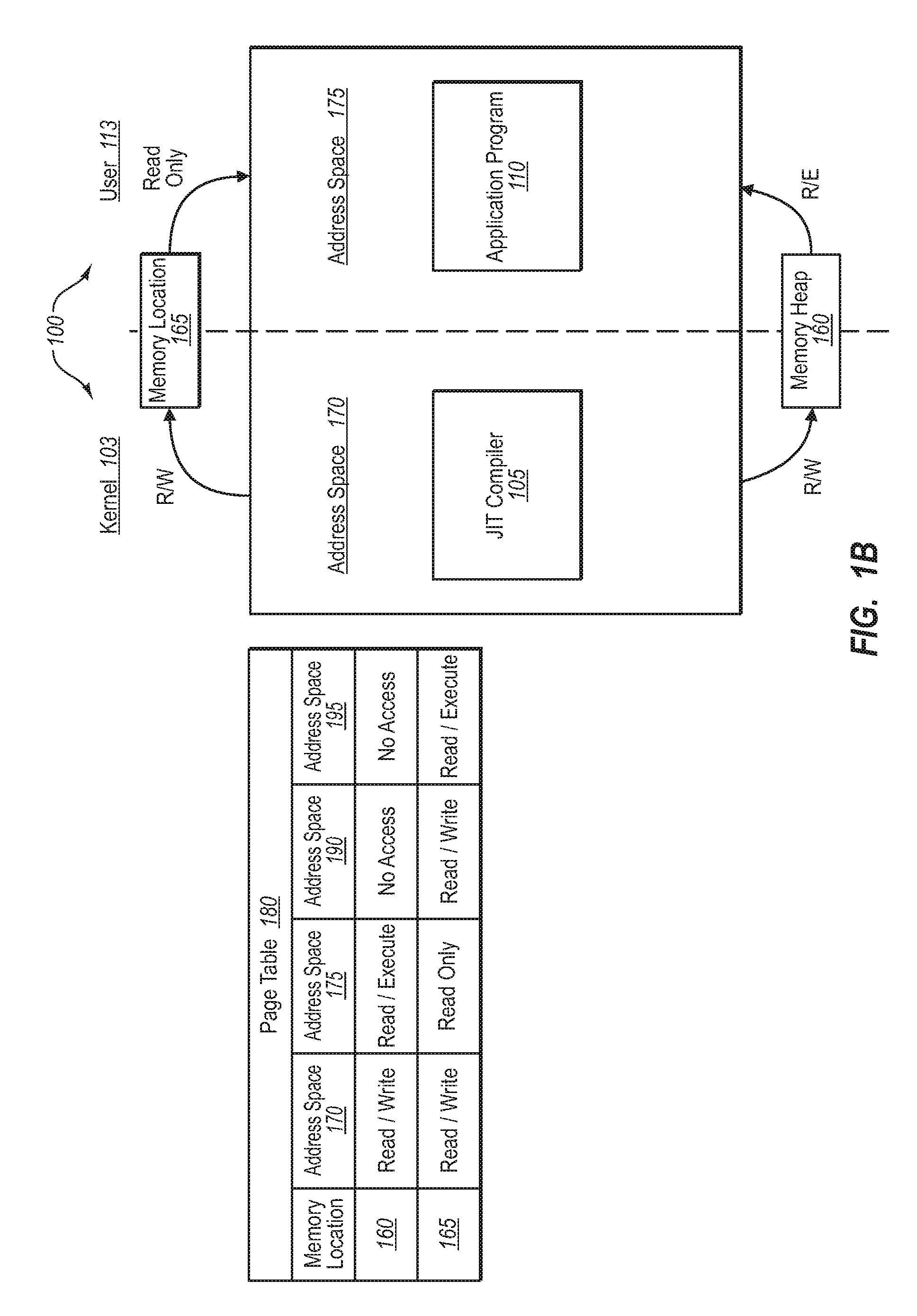
Sensitive data structures, such as type data structures, can be used by untrusted application programs without necessarily exposing the sensitive data structures directly. For example, untrusted components, such as application programs that may or may not be type safe, can be allowed to operate in a lower-privilege mode. In addition, the application programs can be associated with an address space with limited permissions (e.g., read-only) to a shared memory heap. Requests by the untrusted components for sensitive data structures can then be handled by trusted components operating in a higher-privilege mode, which may have broader permissions to the shared memory heap. If the requests by the untrusted components are deemed to be valid, the results of the requests can be shared with the lower-privilege mode components through the shared memory heap.
Owner:MICROSOFT TECH LICENSING LLC
Instantaneous type safety gear for elevator
The invention discloses an instantaneous type safety gear for an elevator, which comprises a gear body which is provided with a channel with a trapezoidal section, wherein the channel is wide at the bottom and narrow at the top; double pin roller groups and a wedge block are mounted on two sides in the gear channel respectively; the double pin roller groups and the wedge block can move up and down along a corresponding gear body inclined surface; one side surface, corresponding to the gear body inclined surface, of the wedge block forms a step, and correspondingly, a step is formed on the inclined surface of the gear body; and when the safety gear is triggered to act until the action is completed, the step of the wedge block is contacted with the step on the gear body inclined surface. According to the instantaneous type safety gear, the matched steps are arranged on the wedge block and the corresponding gear body inclined surface to replace a steel plate in the prior art; and in comparison, the instantaneous type safety gear provided by the utility model has the advantages of larger braking force and simple structure, simplifies the elevator structure, and reduces the elevator load bearing and elevator manufacturing cost.
Owner:HANGZHOU HUNING ELEVATOR PARTS CO LTD
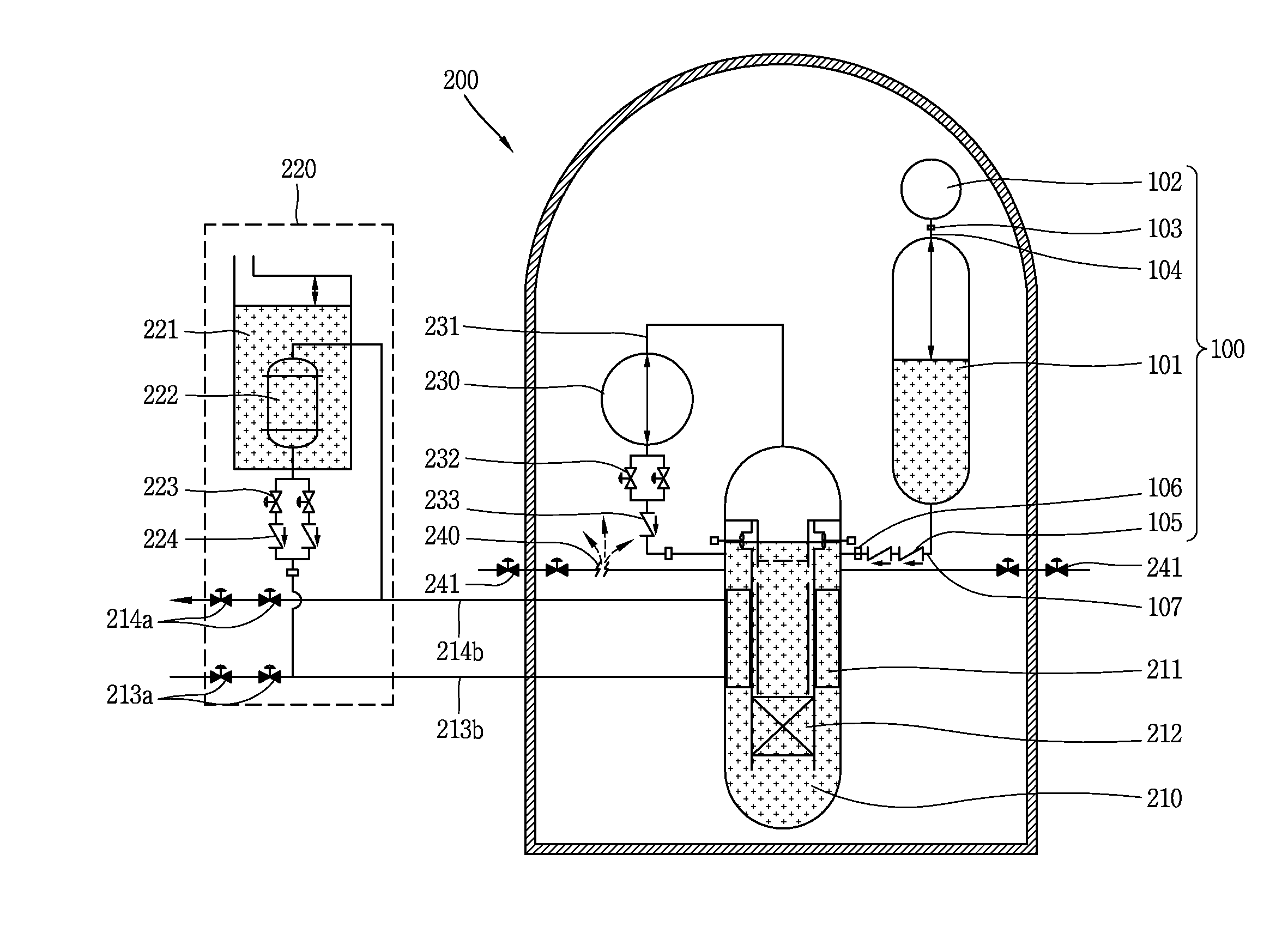
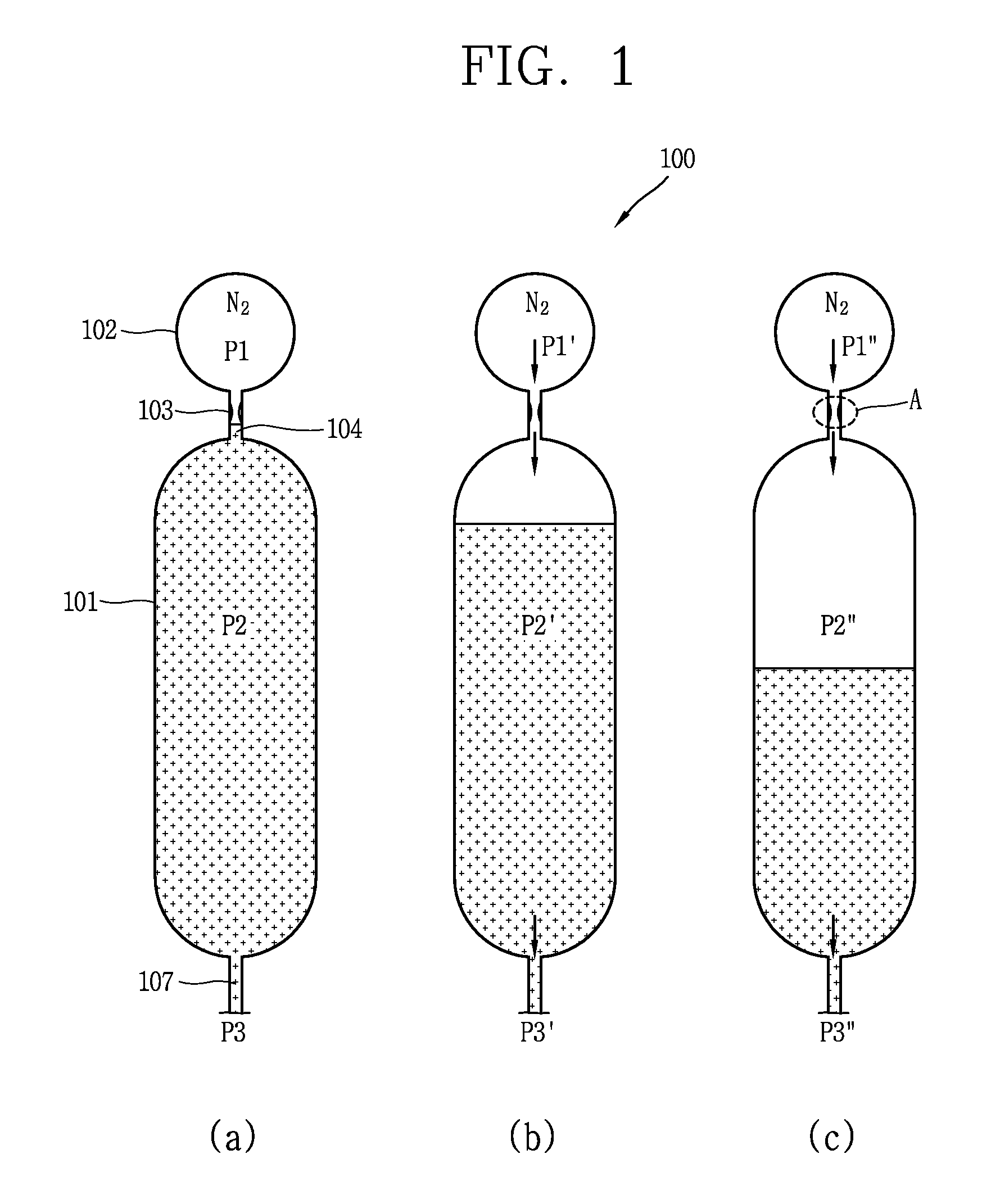
Separate type safety injection tank and integral type reactor having the same
ActiveUS20140050292A1Prevent backflowPower plant safety arrangementIntegral reactorsNuclear engineeringProduct gas
A separate type safety injection tank comprises: a coolant injection unit connected to a reactor coolant system by a safety injection pipe such that coolant stored therein is injected into the reactor coolant system by a pressure difference from the reactor coolant system when a loss-of-coolant-accident (LOCA) occurs; a gas injection unit connected to the coolant injection unit, and configured to pressurize the coolant injected into the reactor coolant system, by introducing gas stored therein to an upper part of the coolant injection unit in the loss-of-coolant-accident; and a choking device disposed between the coolant injection unit and the gas injection unit, and configured to contract a flow cross-sectional area of the gas introduced to the coolant injection unit, and configured to maintain a flow velocity and a flow rate of the gas introduced to the coolant injection unit as a critical flow velocity and a critical flow rate when a pressure difference between the coolant injection unit and the gas injection unit is more than a critical value.
Owner:KOREA ATOMIC ENERGY RES INST
Type safe data proxy
InactiveUS20060242187A1Digital data information retrievalSpecial data processing applicationsTheoretical computer scienceType safety
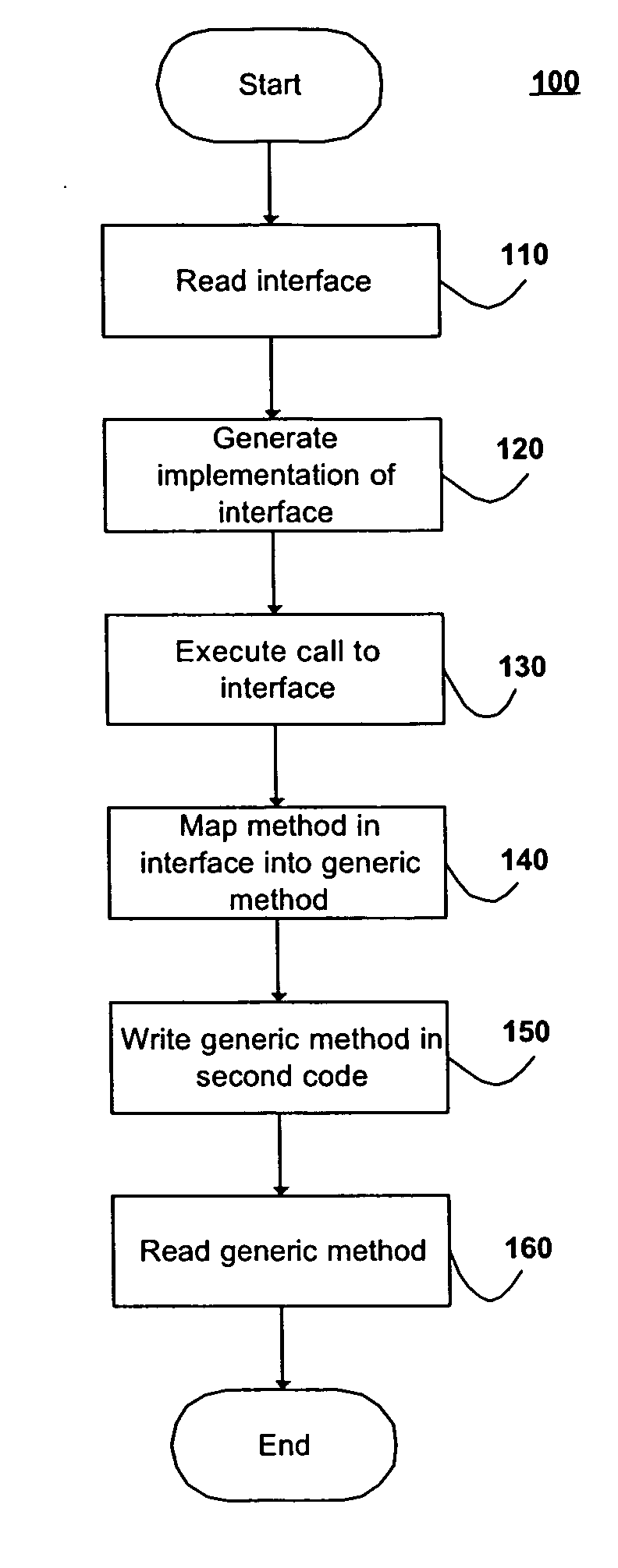
Described is a method for reading a data structure in a first code language, generating an implementation of the data structure and executing a call to the implementation of the data structure to obtain information describing the data structure. The method further includes mapping the data structure to a generic data structure using the information and writing the generic data structure in a second code language, wherein access to the generic data structure is type-safe.
Owner:WIND RIVER SYSTEMS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com