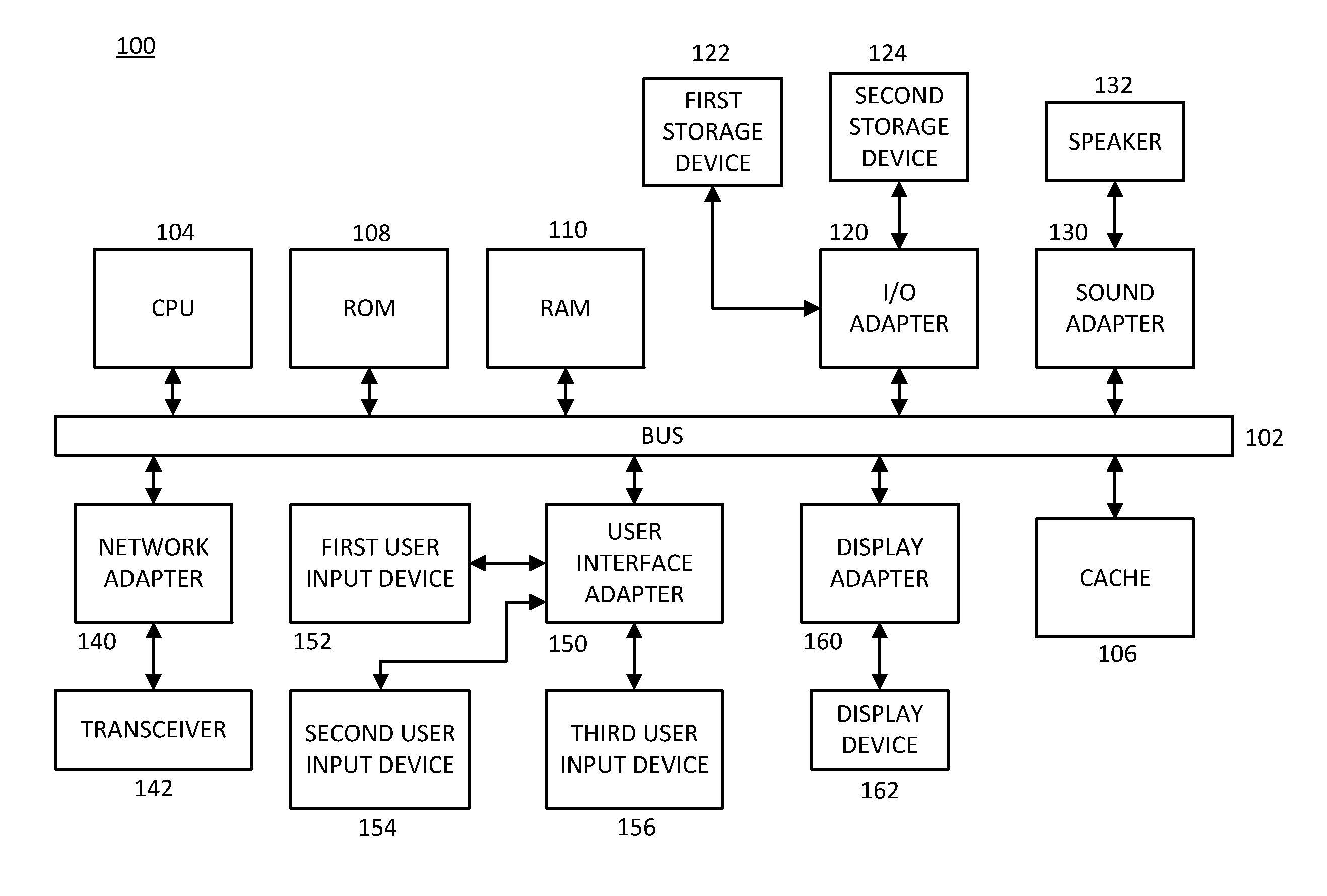
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
354 results about "Dependency graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
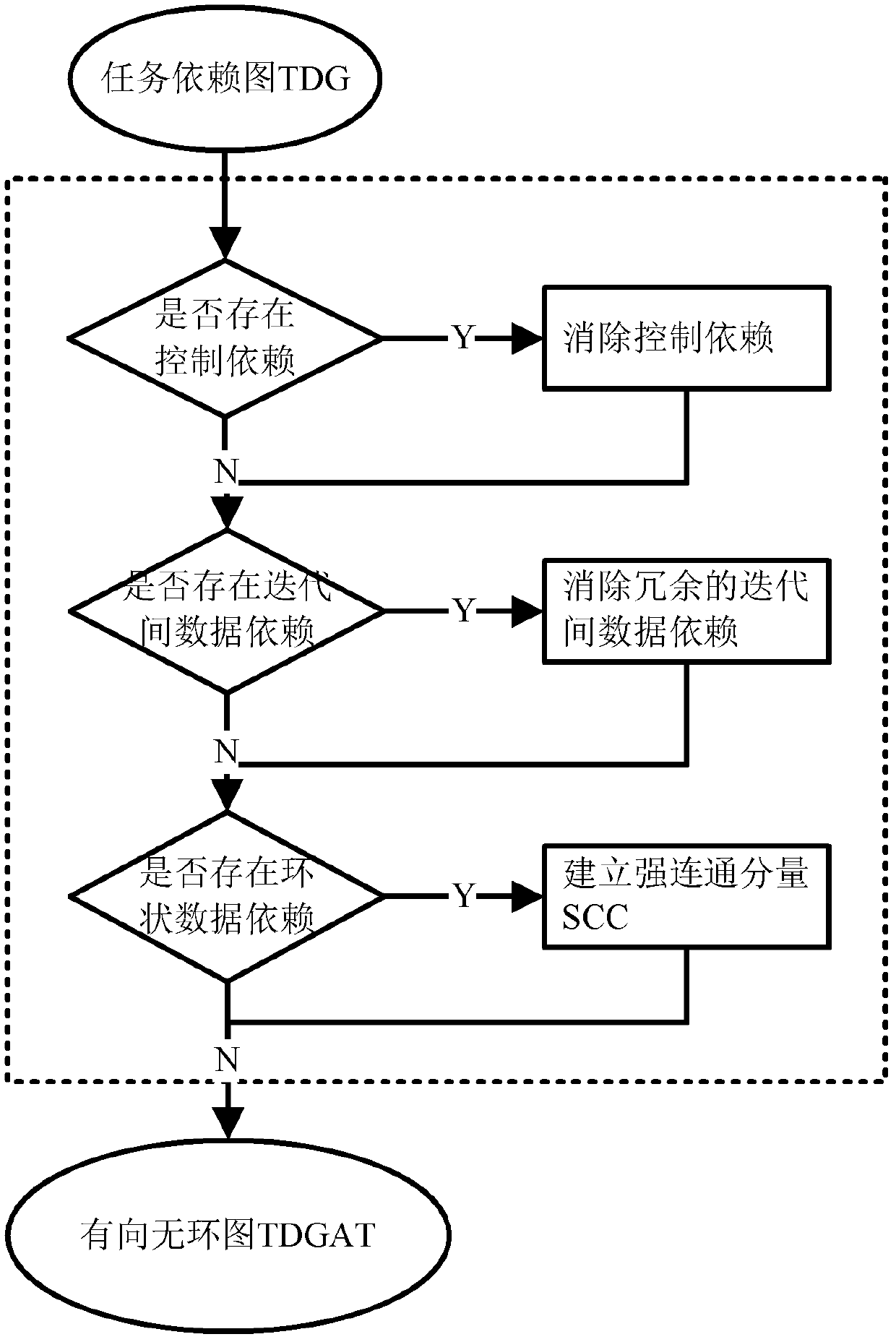
In mathematics, computer science and digital electronics, a dependency graph is a directed graph representing dependencies of several objects towards each other. It is possible to derive an evaluation order or the absence of an evaluation order that respects the given dependencies from the dependency graph.
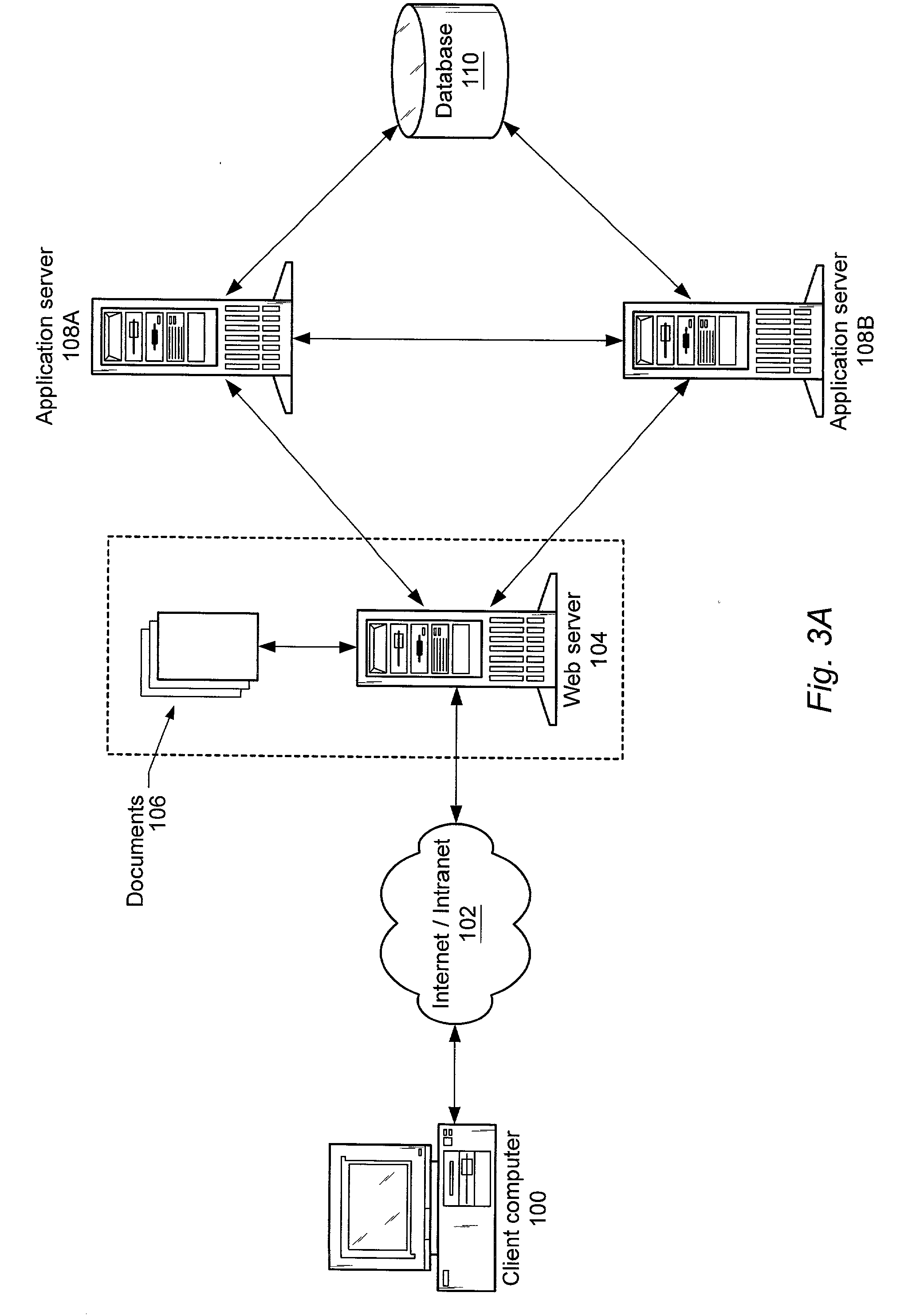
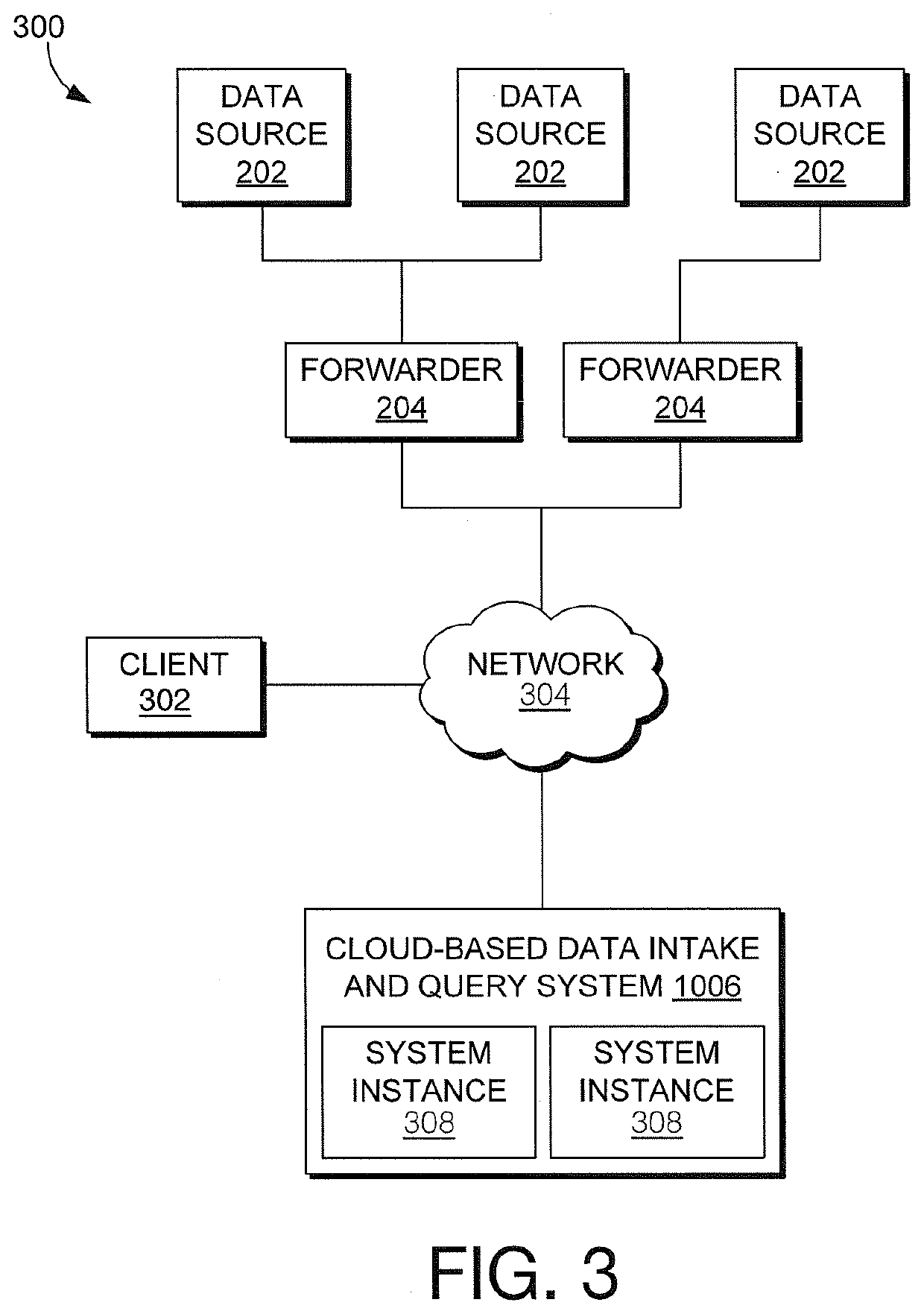
State control of remote hosts for management of distributed applications
Configuring a node. A method includes determining a current state of a target node. The current state of the target node refers to objects currently deployed or running in the remote target node. It includes at least one of an operating system, one or more applications, or configuration setting at the target node. The method further includes determining a desired state for the target node to change the current state. The method further includes accessing a dependency graph based on the version of an agent running on the target node. The dependency graph is supplied to a state machine. The state machine is particular to the target node. The state machine using the current state of the target node, the desired state and the dependency graph, performs operations to drive the target node toward its goal.
Owner:MICROSOFT TECH LICENSING LLC
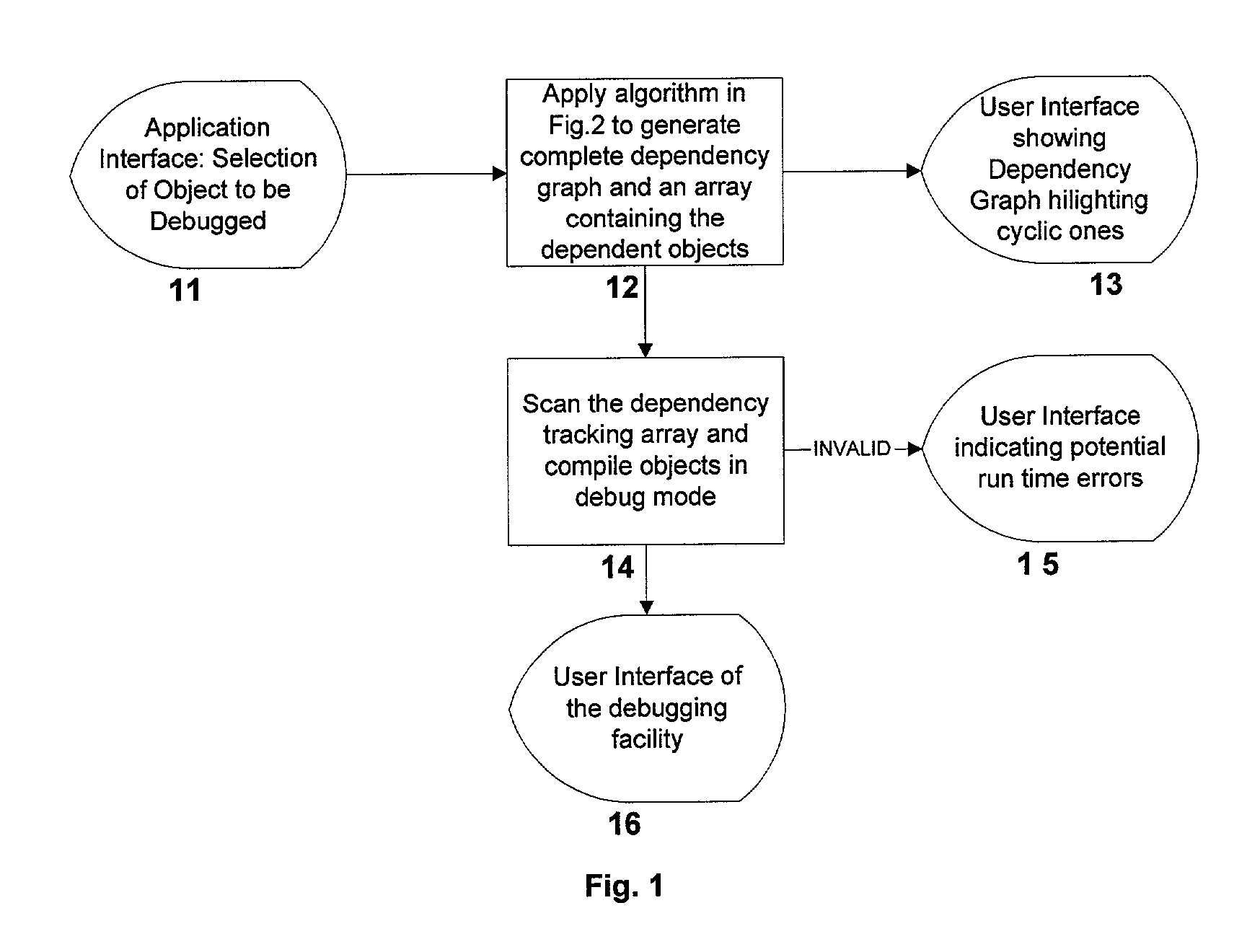
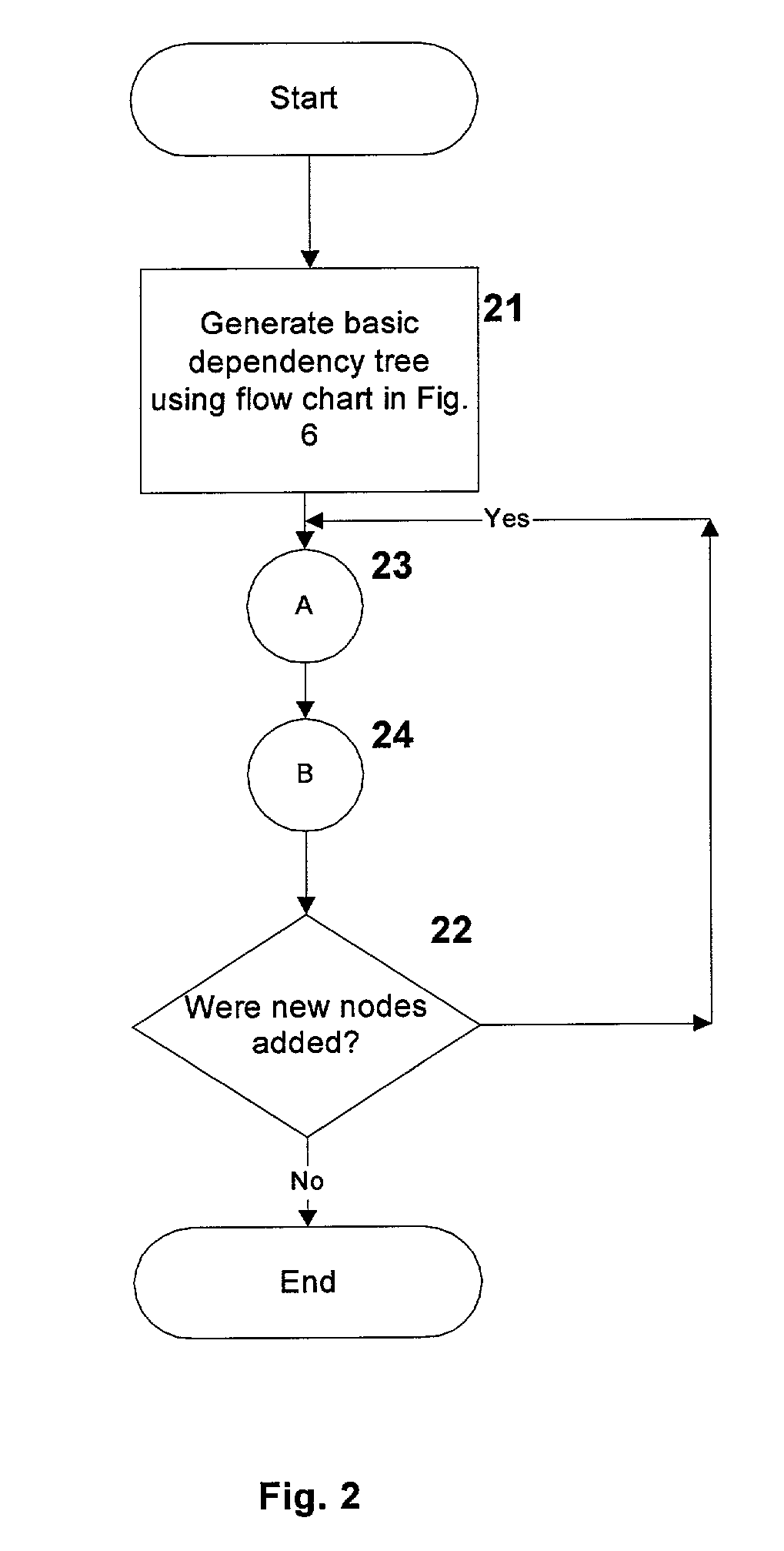
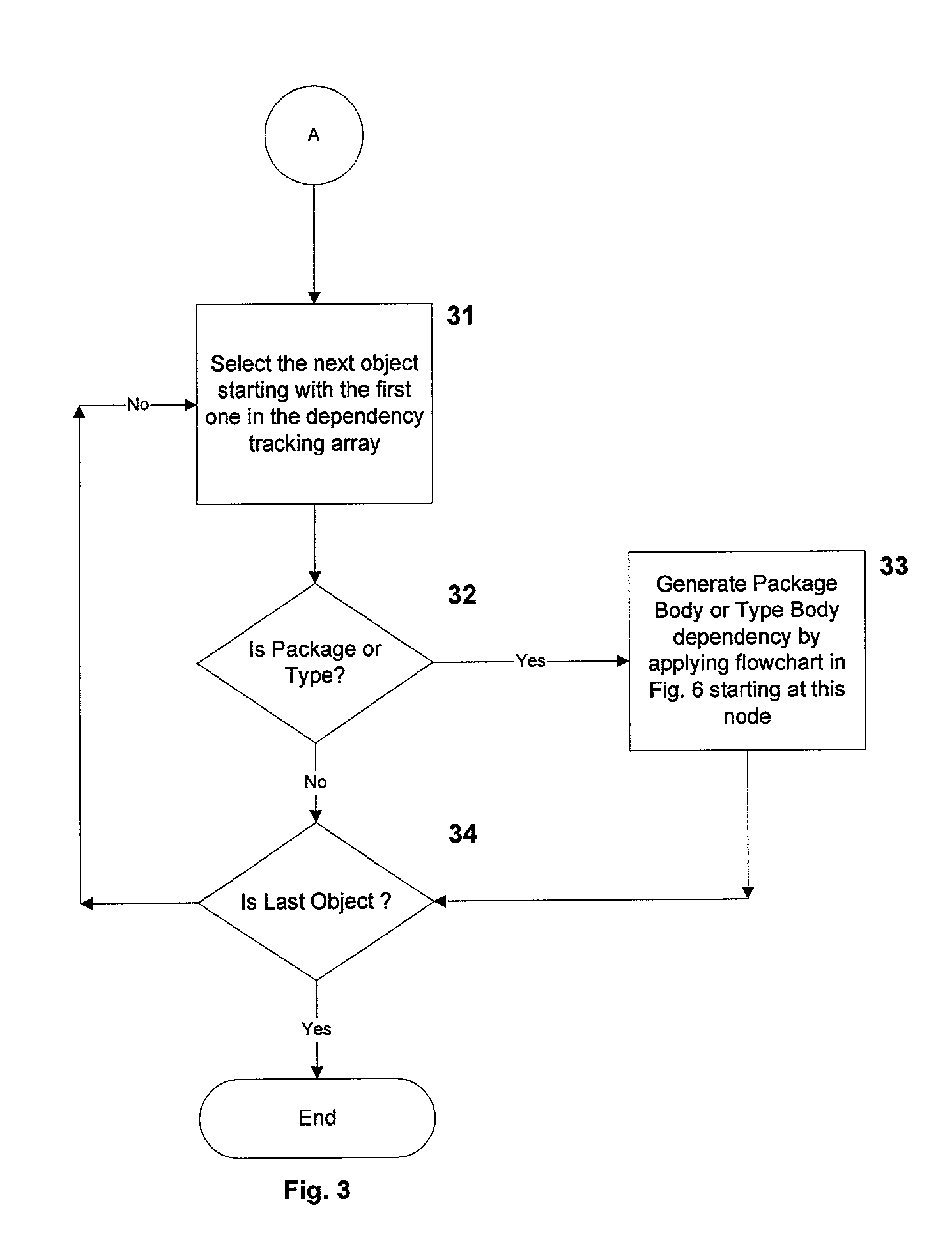
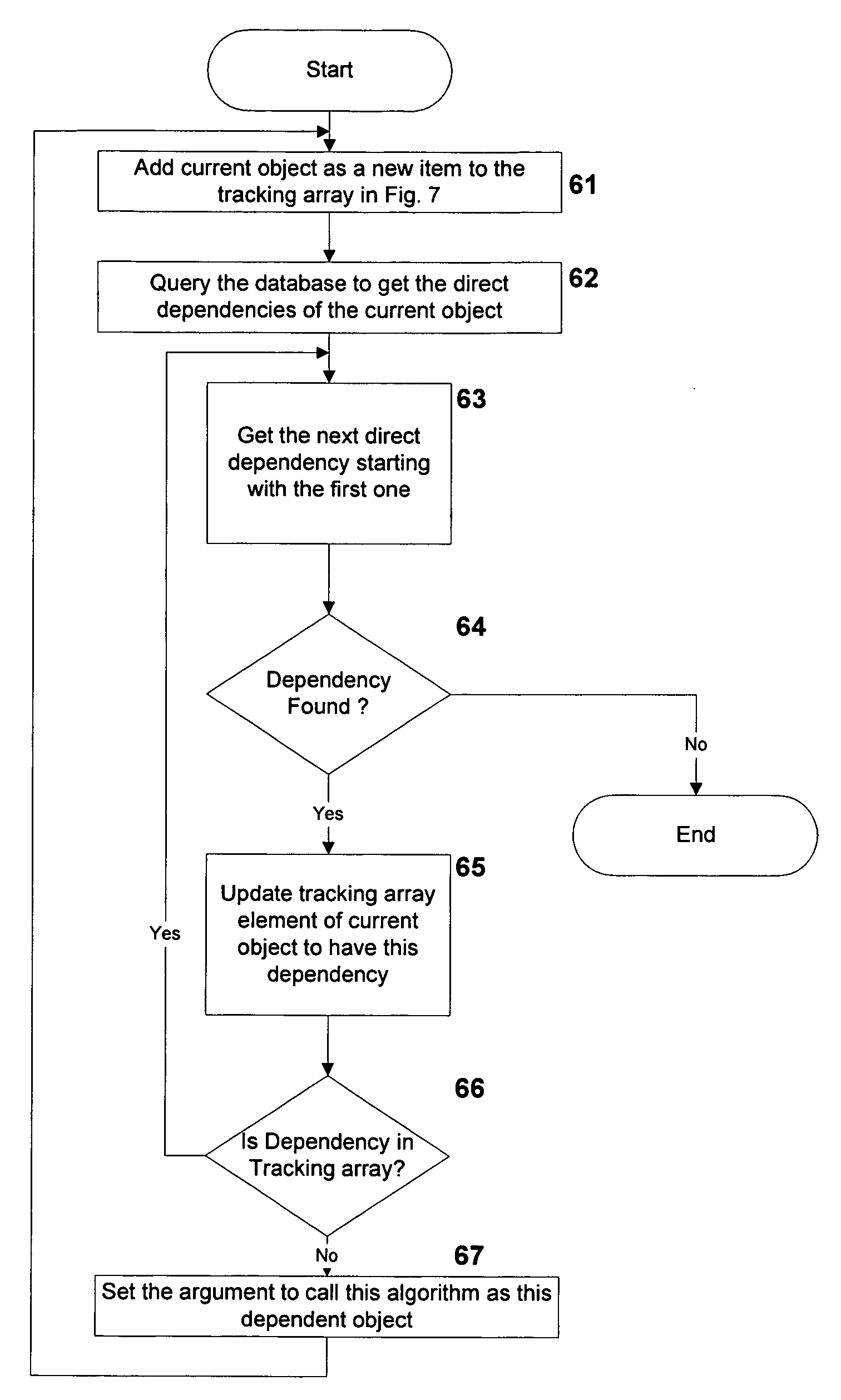
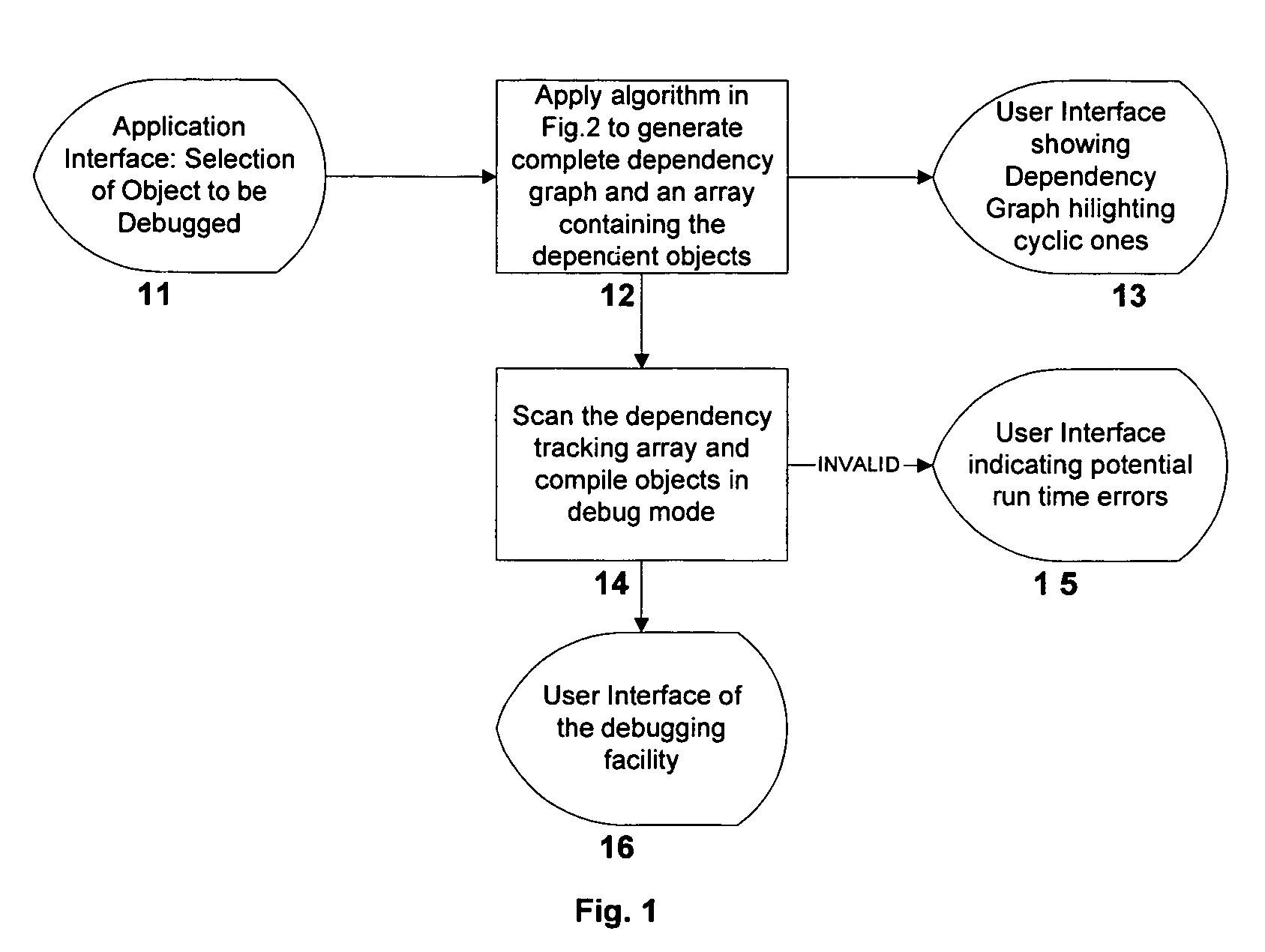
System and method for recursive path analysis of dbms procedures
InactiveUS20010049682A1Data processing applicationsDigital data processing detailsTrack algorithmDependency graph
A system, method and database development tool are disclosed for automatically generating the complete dependency graph for use in debugging stored code objects in a database, by using a recursive dependency tracking algorithm which takes into consideration the indirect dependencies on triggers as well as the dependencies on implementations of object oriented code objects which are represented as separate objects in the database catalog.
Owner:COMP ASSOC THINK INC
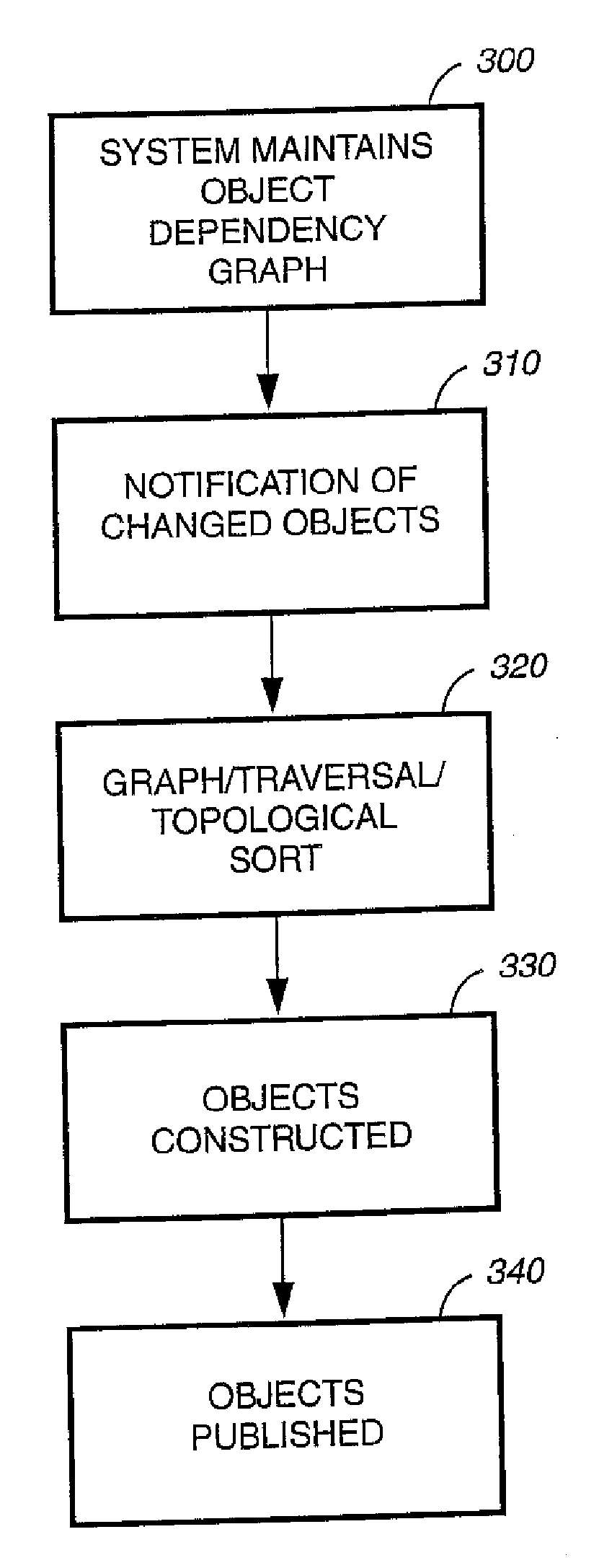
Method and apparatus for end-to-end content publishing system using XML with an object dependency graph
InactiveUS7076728B2Avoid scatterAvoid duplicationDigital computer detailsNatural language data processingData integrityReusability
The system for end-to-end content publishing using XML with an object dependency graph is based on the following two design principles: First, separation of content and style: Information stored in the content management system is independent on how it is going to be presented. The presentation style is encapsulated elsewhere and can be used to customize the look and feel based on the end-user preferences as well as the delivery methods and devices. Second, reusability of information content: By encapsulating common information in fragments and subfragments and making these fragments insertable in other fragments, thereby avoid scattering and duplication of information. This enables a user to restrict the edit operations to a limited number of relevant fragments, to affect global changes. In addition, the present invention provides data consistency and data integrity in the content management.
Owner:IBM CORP
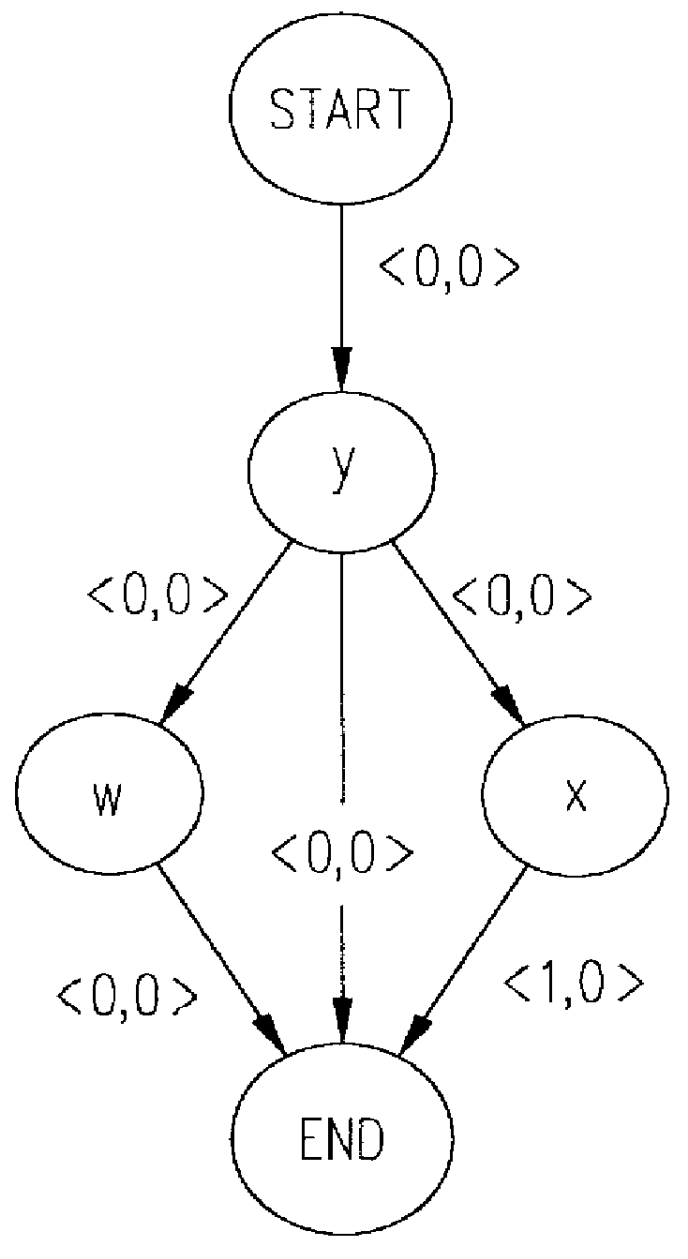
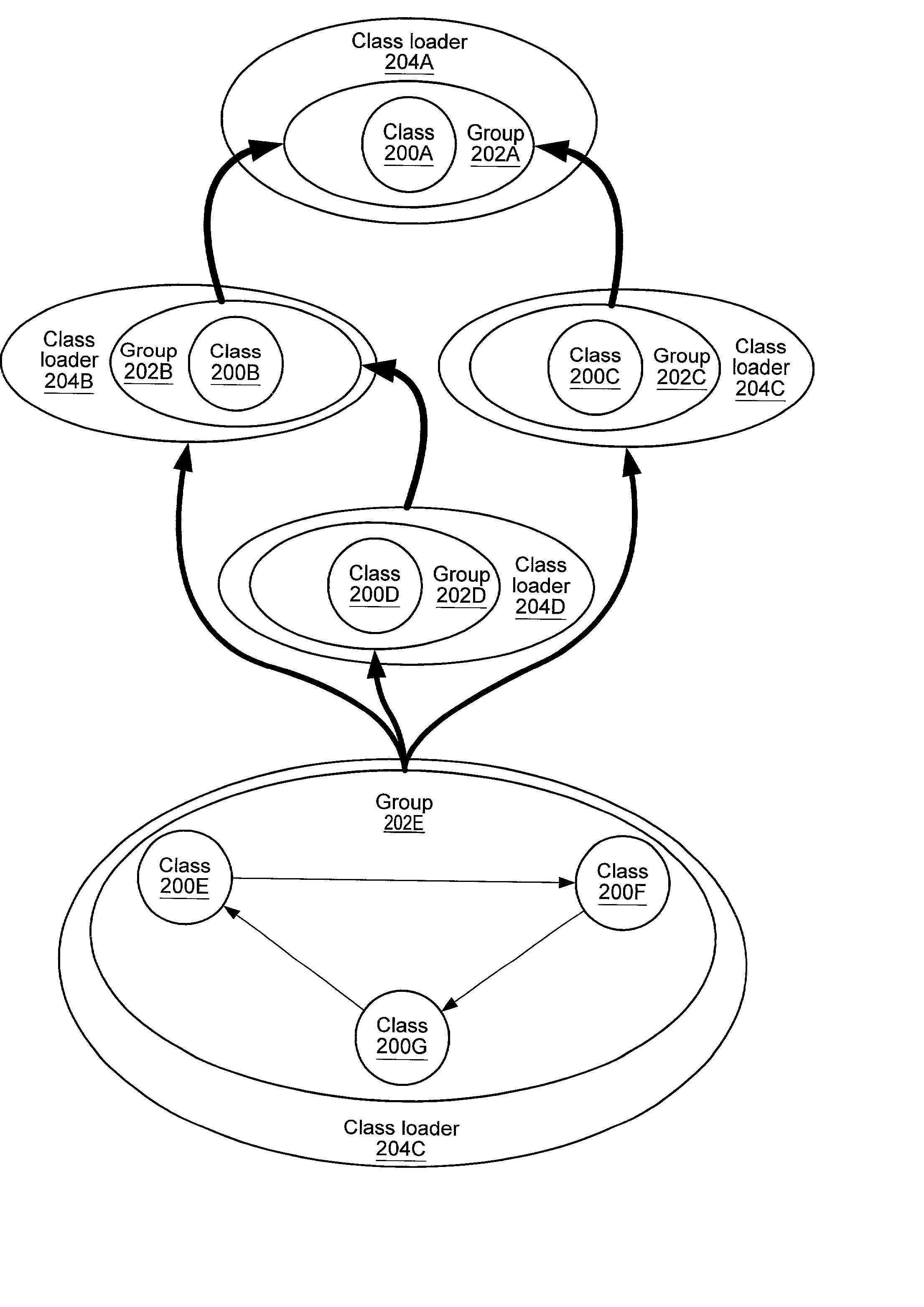
Class dependency graph-based class loading and reloading
Embodiments of a system and method for providing class dependency graph-based class loading and reloading may be used to segregate namespaces in a graph-centric way, and may provide a set of normalized topologies that may be used to efficiently support hot-swapping of programmatic logic such as classes, applets, and beans, among other applications. Embodiments may provide a domain-independent, flexible and robust namespace segregation technique that is based on the dependency between the various classes and not on details like the roles the classes play. The problem of segregating namespaces is formulated as a graph theory problem, and a solution is sought through graph techniques. The graph may be normalized by identifying and grouping interdependent classes and non-interdependent classes in separate groups. A directed dependency relationship of the groups may be determined using the relationships between the member classes of the groups.
Owner:ORACLE INT CORP
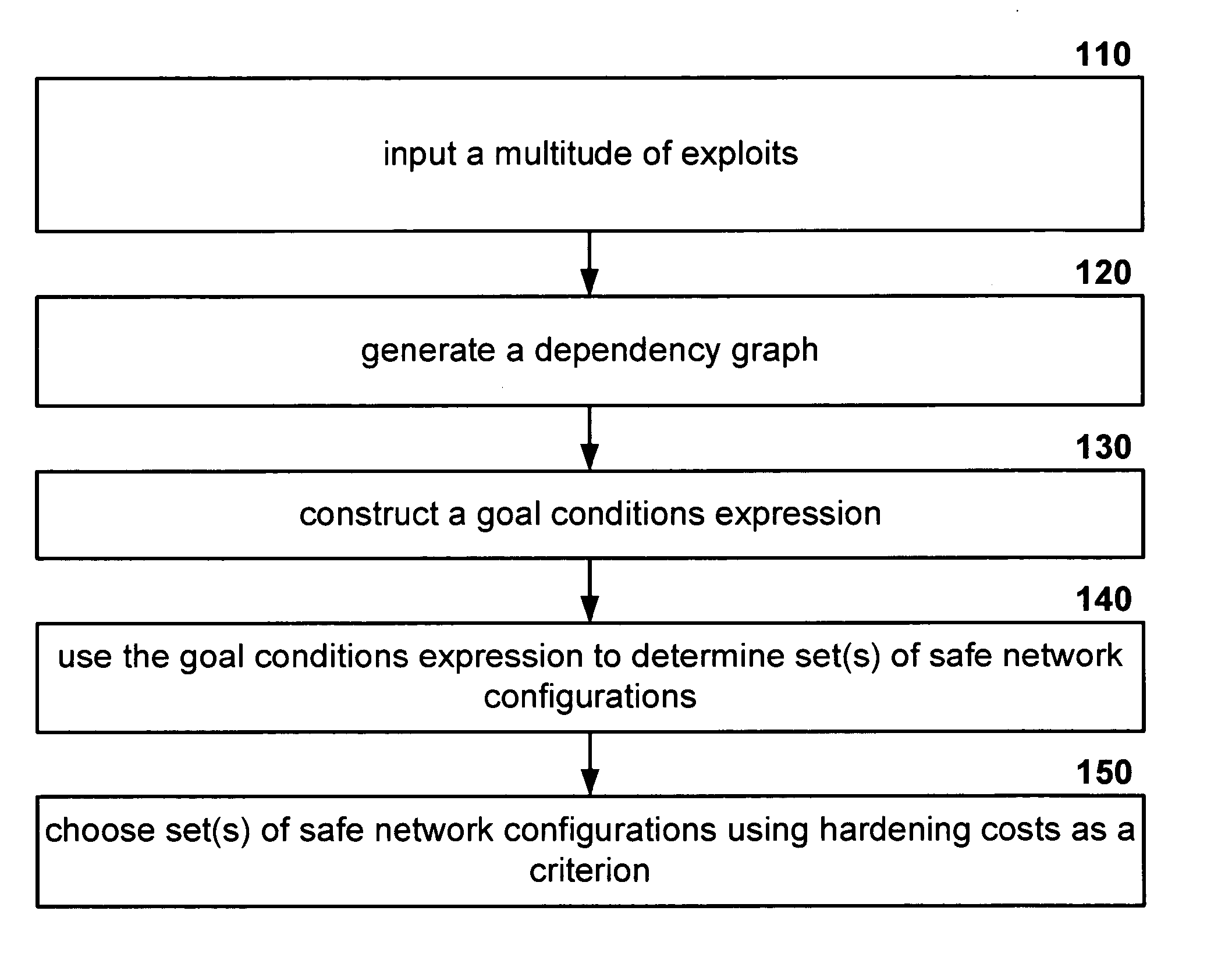
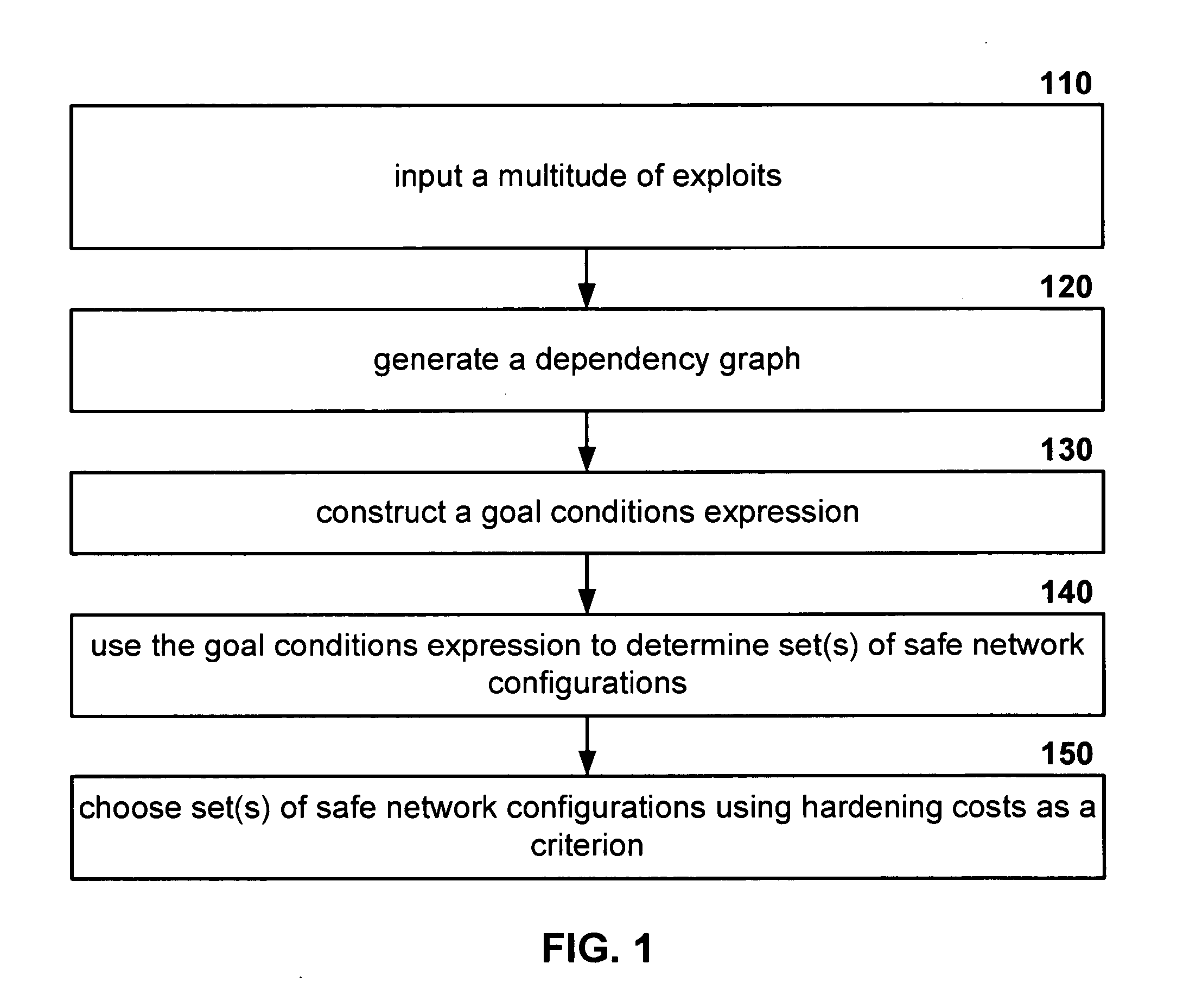
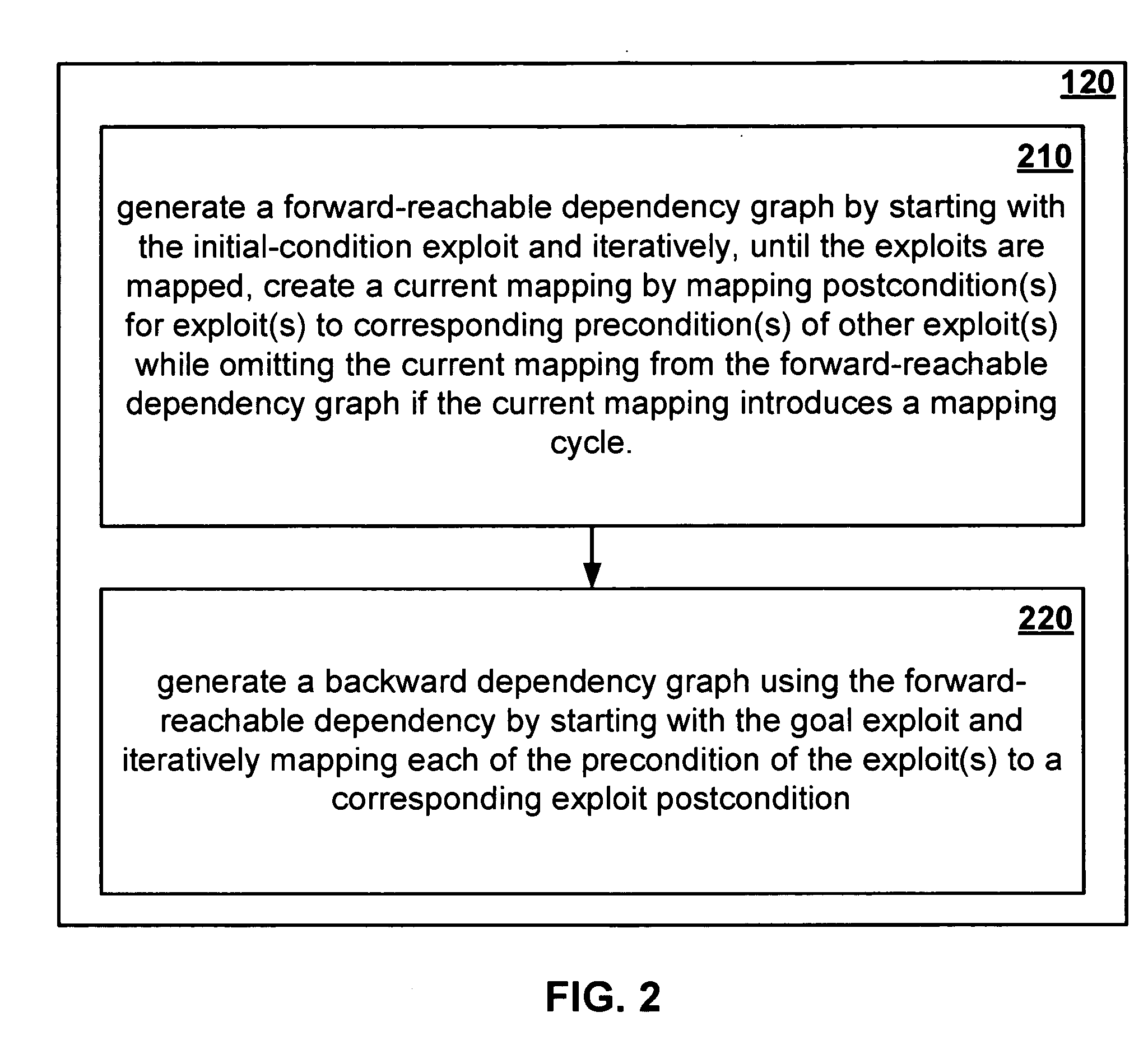
Minimum-cost network hardening
ActiveUS20060085858A1Low costProvide securityMemory loss protectionDigital data processing detailsConditional expressionDependency graph
Disclosed is a network hardening mechanism. The mechanism: generates a dependency graph from a multitude of exploits; constructs a goal conditions expression which may then be used to determine set(s) of safe network configurations. A subset of these safe network configuration sets may then be selected for implementation using hardening costs as a criterion.
Owner:GEORGE MASON UNIVERSITY
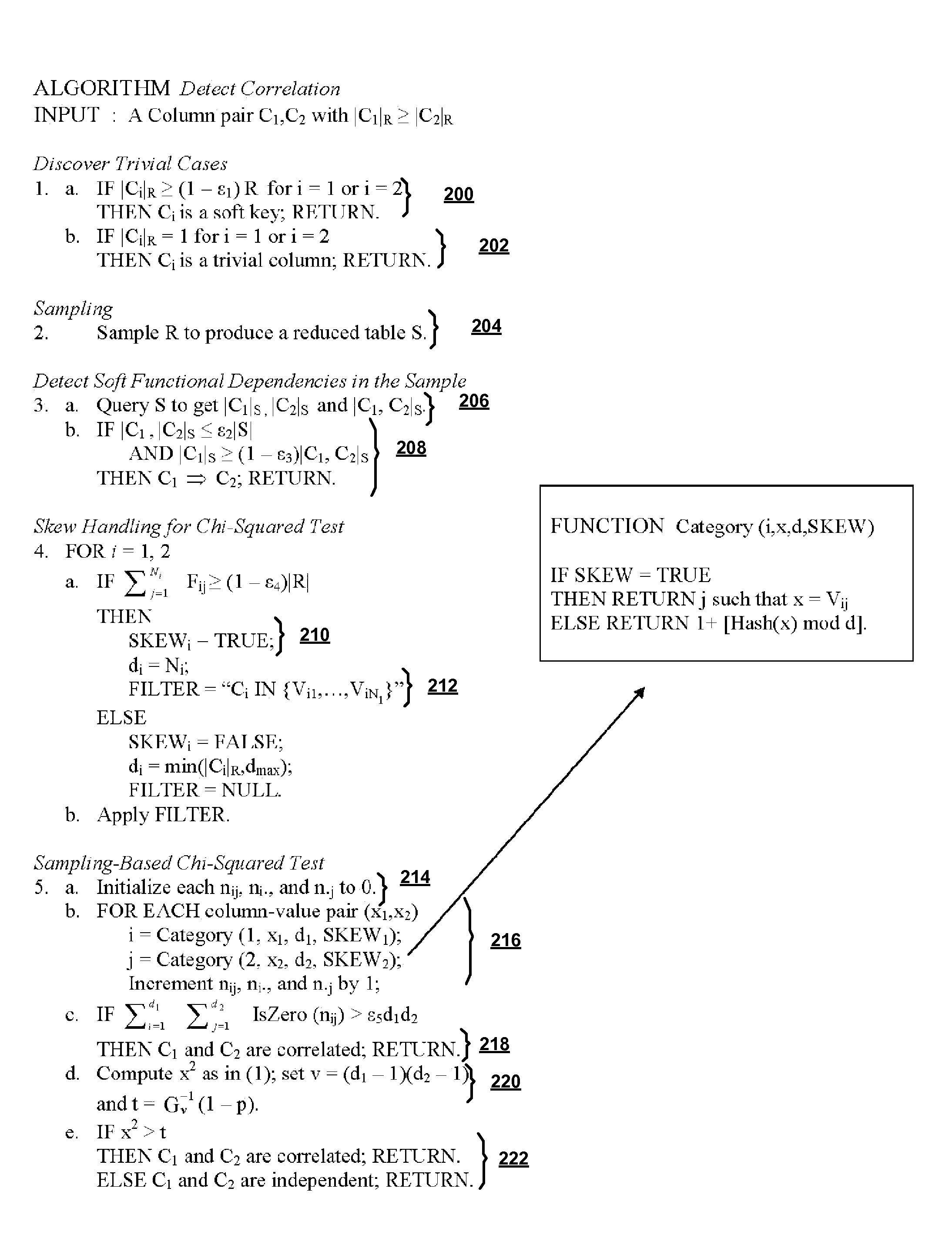
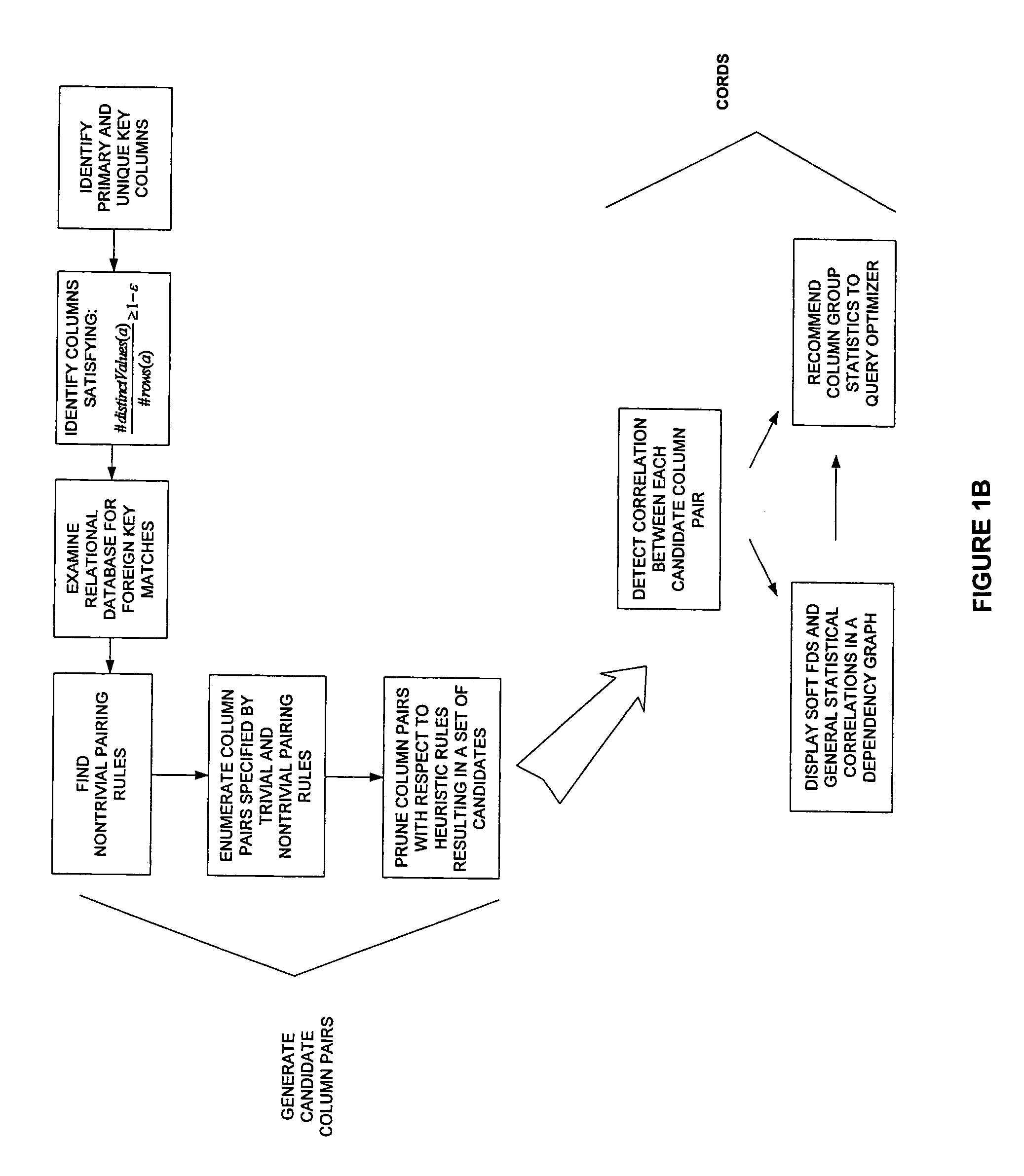
Detecting correlation from data
InactiveUS20050278357A1Improved selectivity estimateImprove impactDigital data information retrievalDigital data processing detailsStatistical correlationQuery optimization
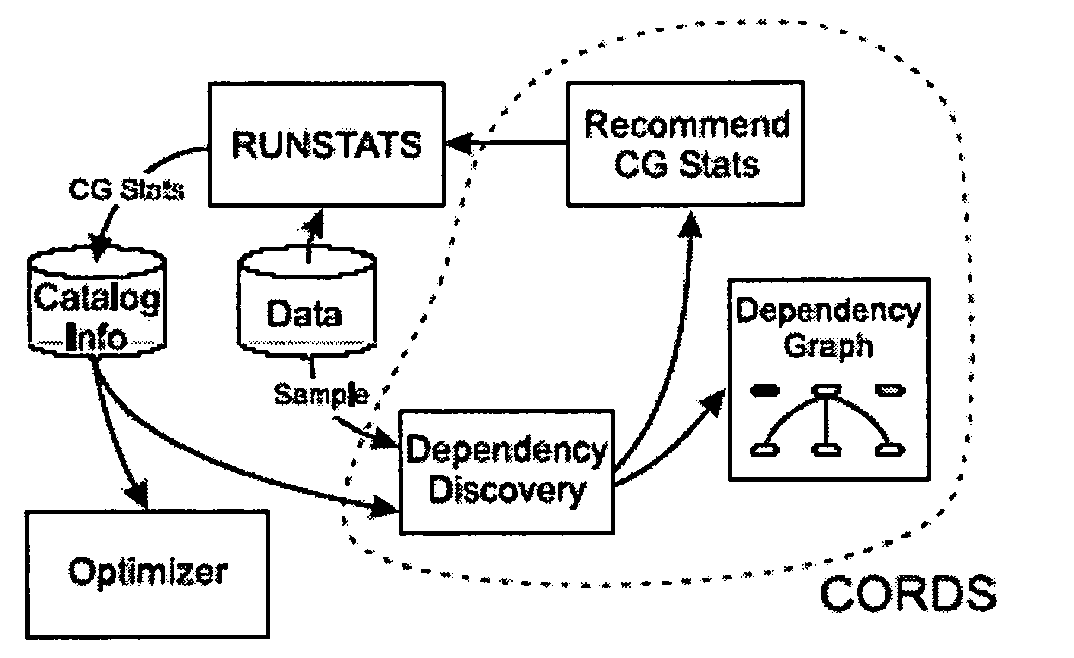
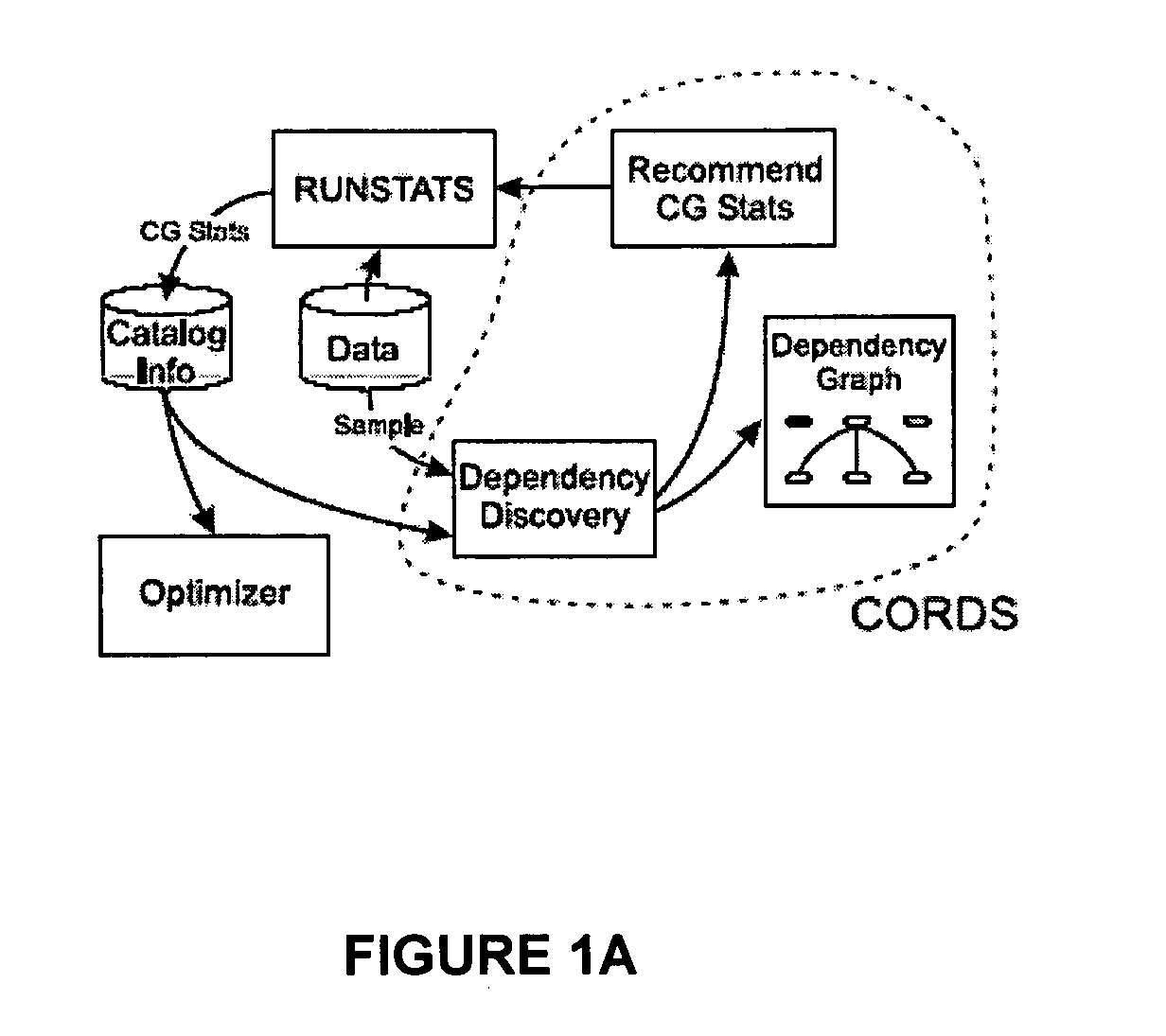
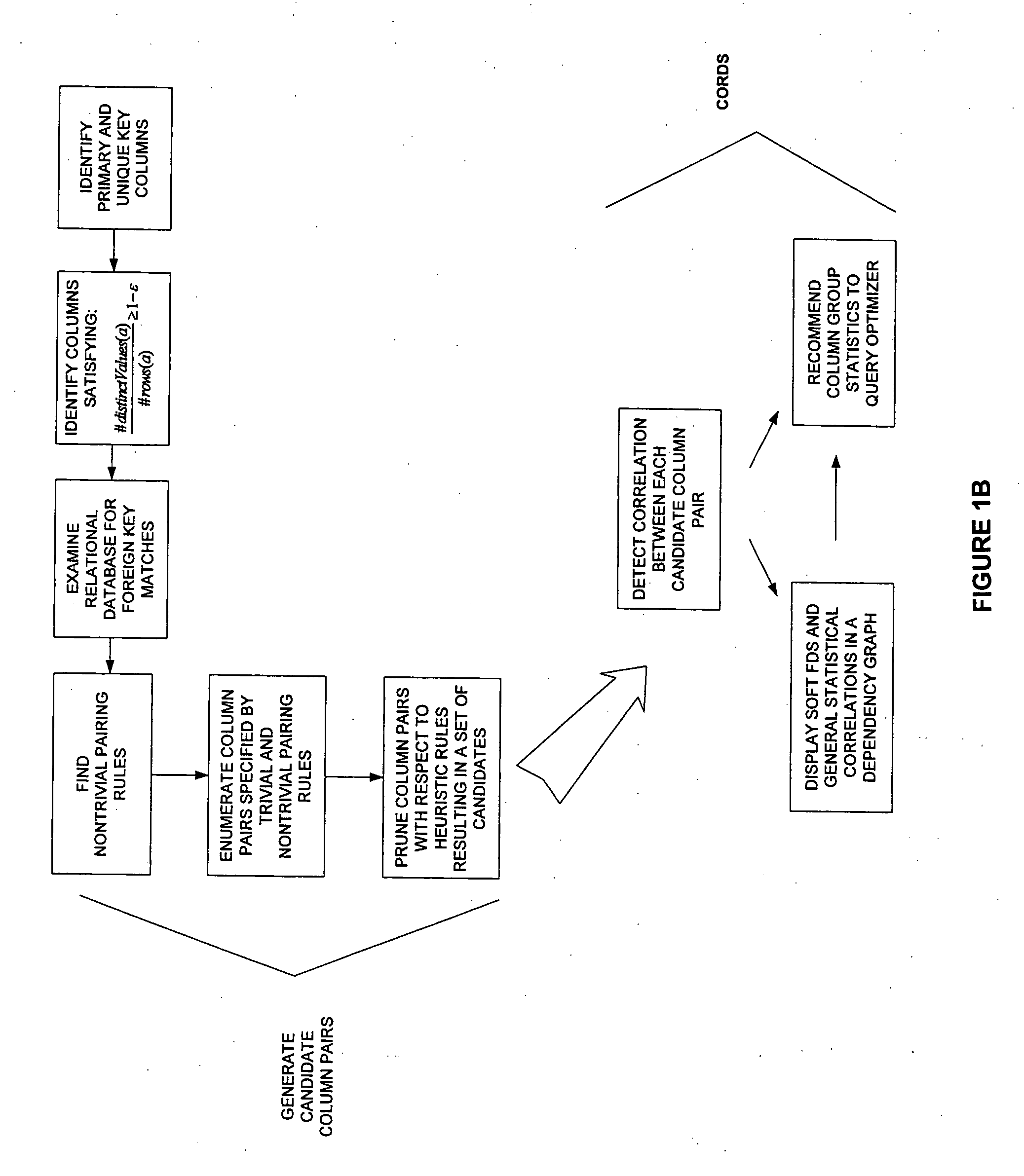
A system and a priori method of discovering dependencies between relational database column pairs and application of discoveries to query optimization is provided. For each candidate column pair remaining after simultaneously generating column pairs, pruning pairs not satisfying specified heuristic constraints, and eliminating pairs with trivial instances of correlation, a random sample of data values is collected. A candidate column pair is tested for the existence of a soft functional dependency (FD), and if a dependency is not found, statistically tested for correlation using a robust chi-squared statistic. Column pairs for which either a soft FD or a statistical correlation exists are prioritized for recommendation to a query optimizer, based on any of: strength of dependency, degree of correlation, or adjustment factor; statistics for recommended columns pairs are tracked to improve selectivity estimates. Additionally, a dependency graph representing correlations and dependencies as edges and column pairs as nodes is provided.
Owner:IBM CORP
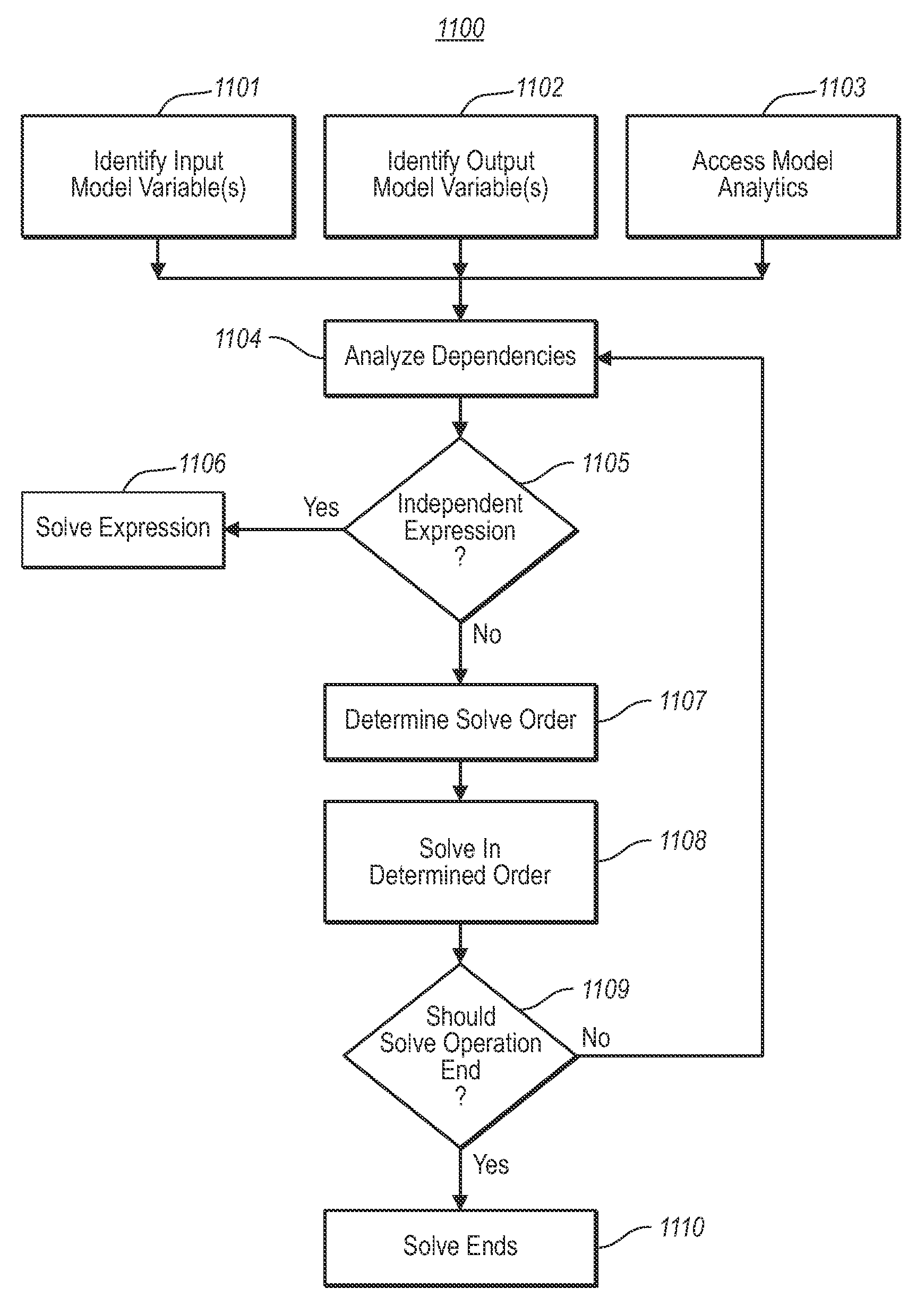
Dependency graph in data-driven model
InactiveUS20110060704A1Digital computer detailsMachine learningTheoretical computer scienceModel parameters
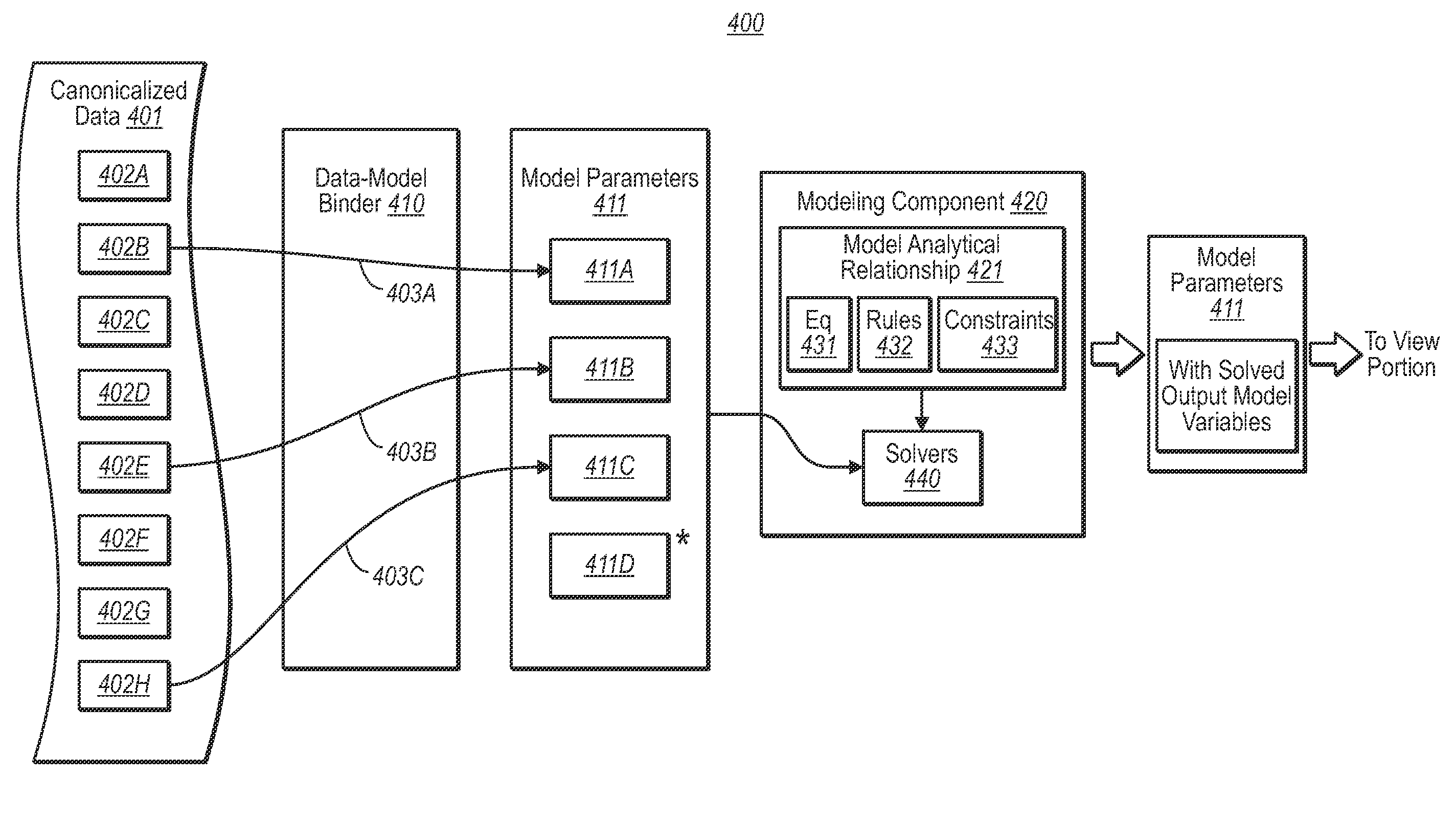
The inference of a dependency graph that represents a graph of solves that leads from input model parameter(s) to output model parameters using analytics. In one embodiment, the dependency graph is part of visually driven analytics in which the output model parameter(s) are used to formulate data-drive scenes. As the identity of the input and / or output model parameter(s) change, or as the analytics themselves change, the dependency graph may also change. This might trigger a resolve of the analytics. In one embodiment, the intermediate parameters involved in the dependency graph may be viewed and evaluated by the user.
Owner:MICROSOFT TECH LICENSING LLC
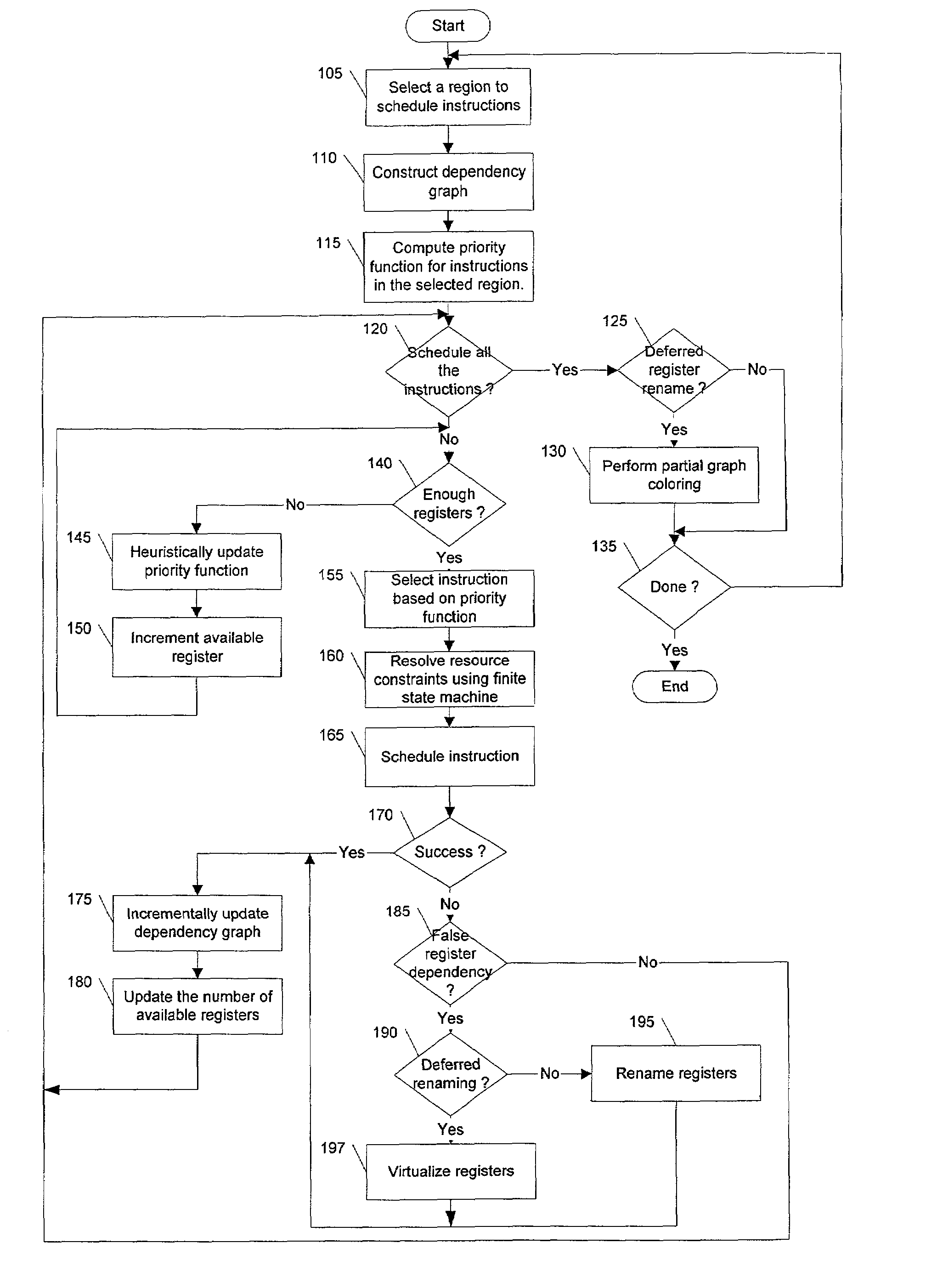
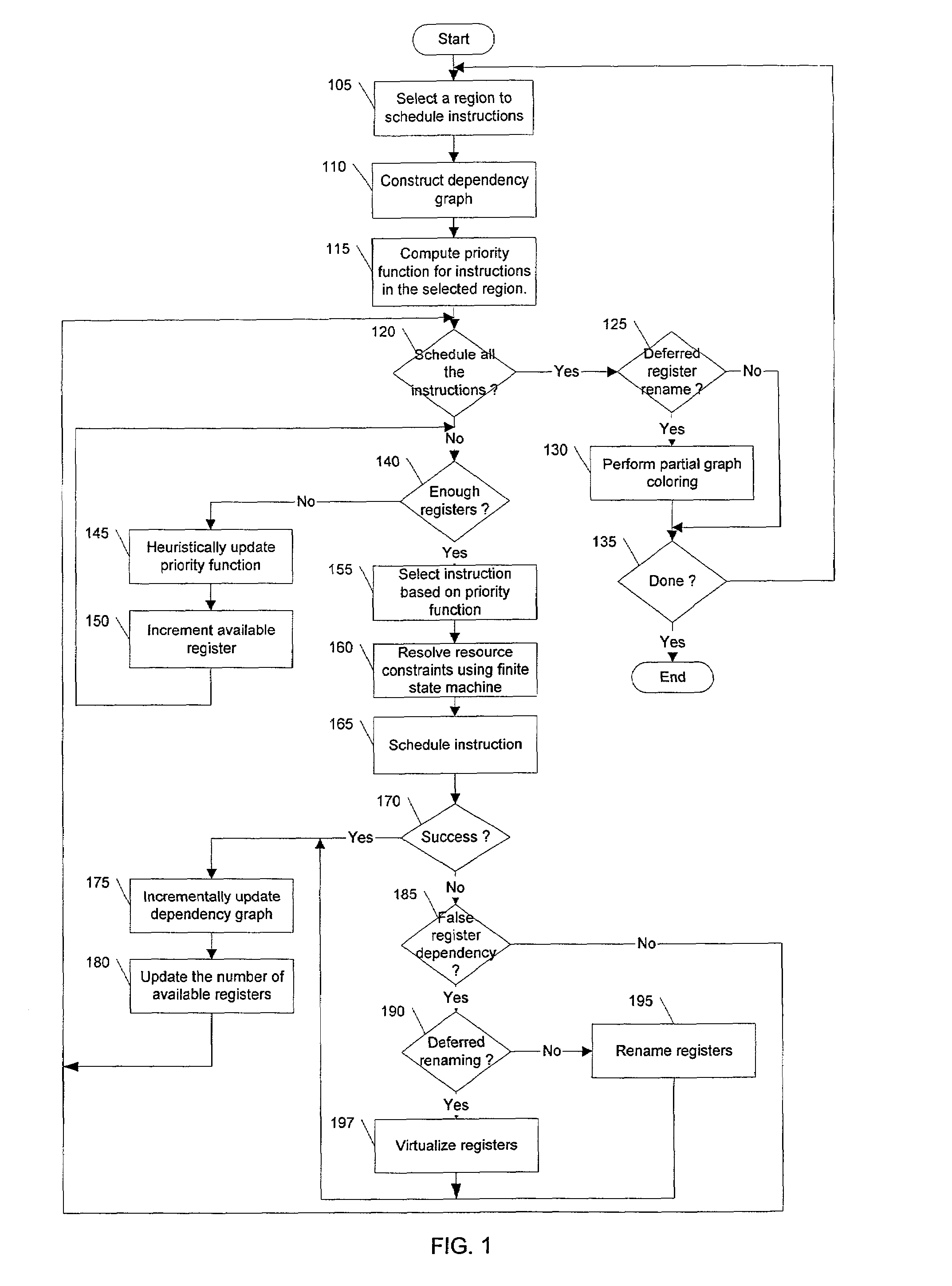
System, method, and program product for loop instruction scheduling hardware lookahead
InactiveUS6044222ASoftware engineeringDigital computer detailsScheduling instructionsComputerized system
Improved scheduling of instructions within a loop for execution by a computer system having hardware lookahead is provided. A dependence graph is constructed which contains all the nodes of a dependence graph corresponding to the loop, but which only contains loop-independent dependence edges. A start node simulating a previous iteration of the loop may be added to the dependence graph, and an end node simulating a next iteration of the loop may also added to the dependence graph. A loop-independent edge between a source node and the start node is added to the dependence graph, and a loop-independent edge between a sink node and the end node is added to the dependence graph. Loop-carried edges which satisfy a computed lower bound on the time required for a single loop iteration are eliminated from a dependence graph, and loop-carried edges which do not satisfy the computed lower bound are replaced by a pair of loop-independent edges. Instructions may be scheduled for execution based on the dependence graph.
Owner:IBM CORP
Class dependency graph-based class loading and reloading
ActiveUS7039923B2Effective supportReduce in quantityVersion controlProgram loading/initiatingGraphicsAlgorithm
Embodiments of a system and method for providing class dependency graph-based class loading and reloading may be used to segregate namespaces in a graph-centric way, and may provide a set of normalized topologies that may be used to efficiently support hot-swapping of programmatic logic such as classes, applets, and beans, among other applications. Embodiments may provide a domain-independent, flexible and robust namespace segregation technique that is based on the dependency between the various classes and not on details like the roles the classes play. The problem of segregating namespaces is formulated as a graph theory problem, and a solution is sought through graph techniques. The graph may be normalized by identifying and grouping interdependent classes and non-interdependent classes in separate groups. A directed dependency relationship of the groups may be determined using the relationships between the member classes of the groups.
Owner:ORACLE INT CORP
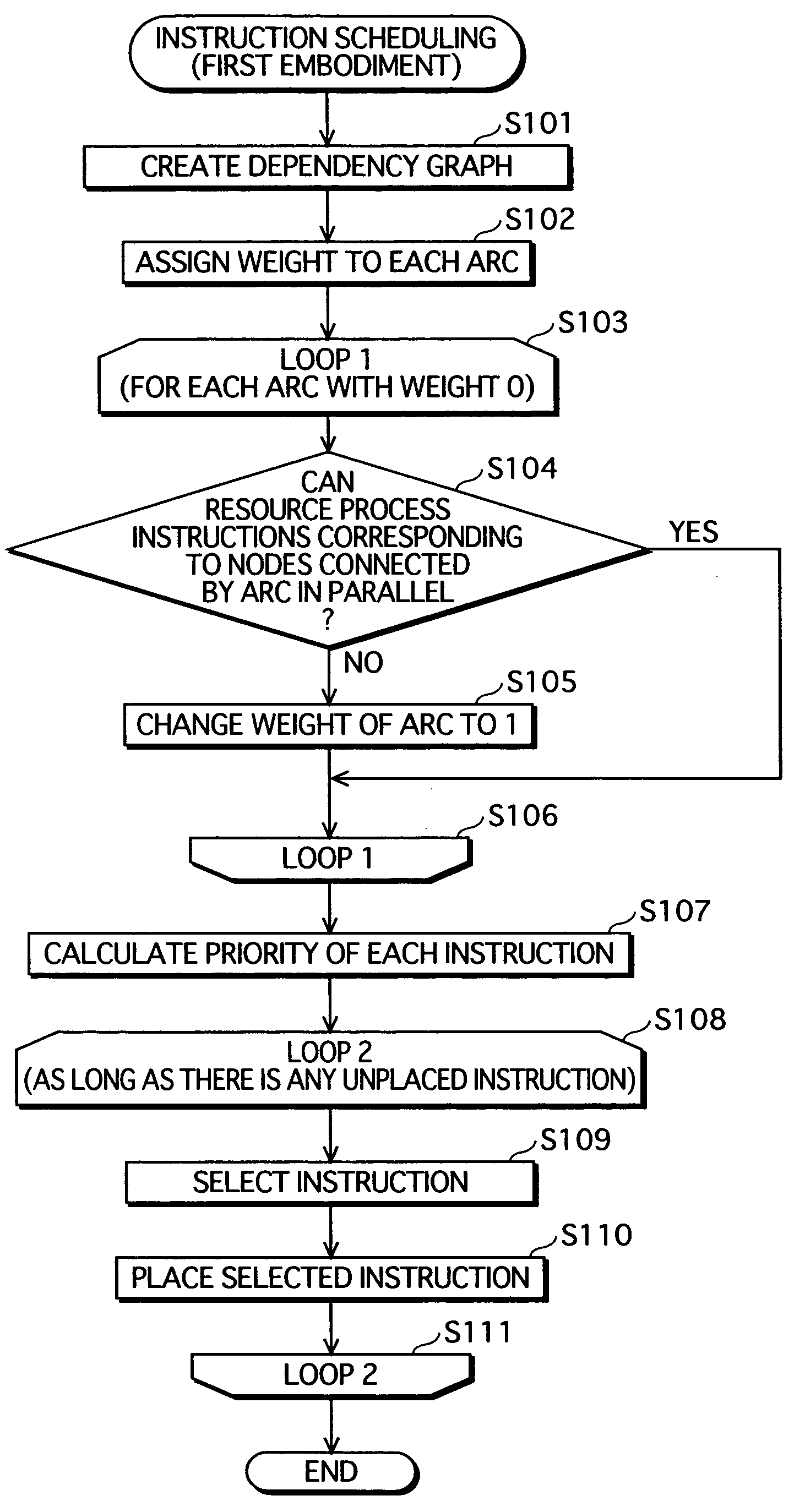
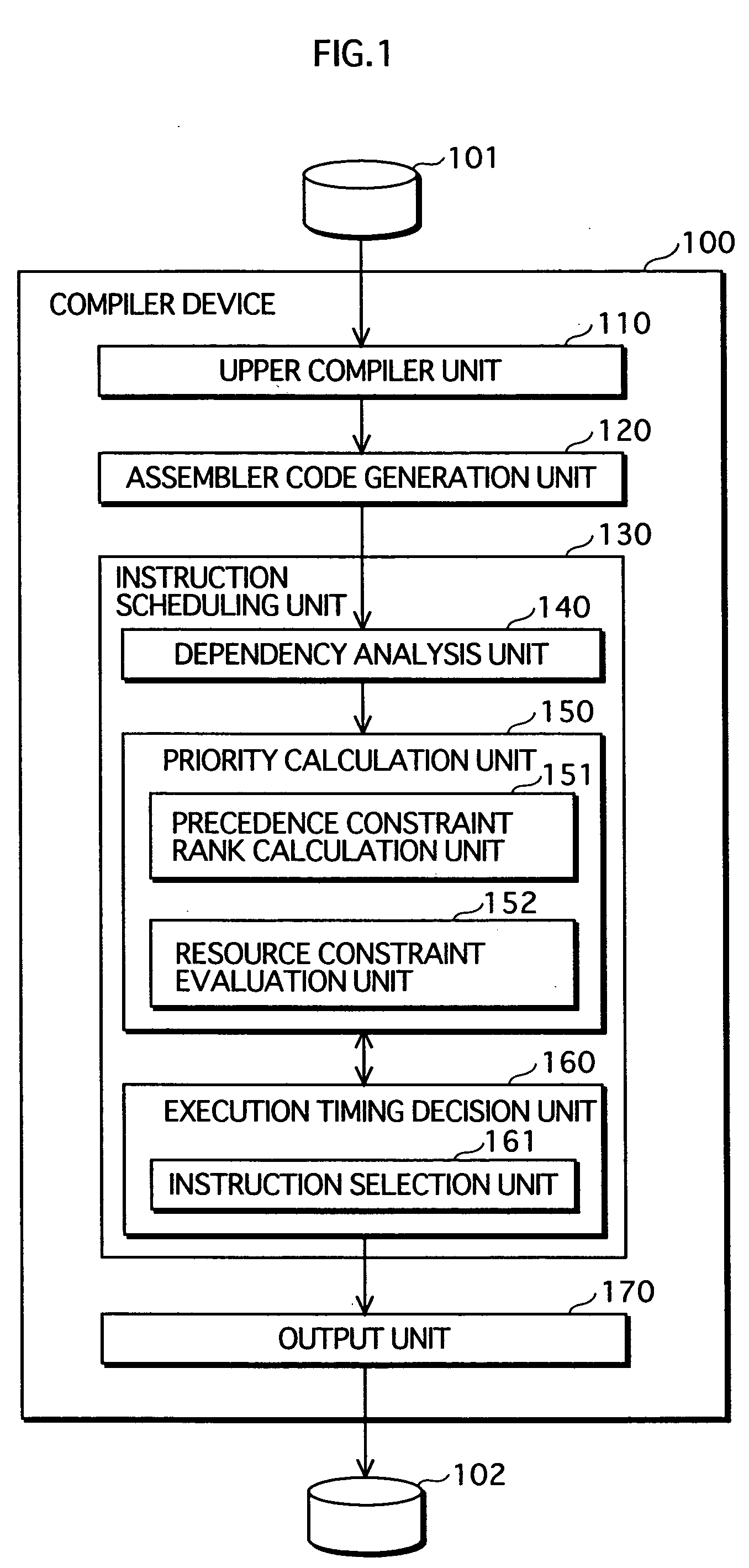
Instruction scheduling method, instruction scheduling device, and instruction scheduling program
InactiveUS20040083468A1Software engineeringProgram controlScheduling instructionsParallel processing
A dependency analysis unit creates a dependency graph showing dependencies between instructions acquired from an assembler code generation unit. A precedence constraint rank calculation unit assigns predetermined weights to arcs in the graph, and adds up weights to calculate a precedence constraint rank of each instruction. When a predecessor and a successor having a dependency and an equal precedence constraint rank cannot be processed in parallel due to a resource constraint, a resource constraint evaluation unit raises the precedence constraint rank of the predecessor. A priority calculation unit sets the raised precedence constraint rank as a priority of the predecessor. An instruction selection unit selects an instruction having a highest priority. An execution timing decision unit places the selected instruction in a clock cycle. The selection by the instruction selection unit and the placement by the execution timing decision unit are repeated until all instructions are placed in clock cycles.
Owner:PANASONIC CORP
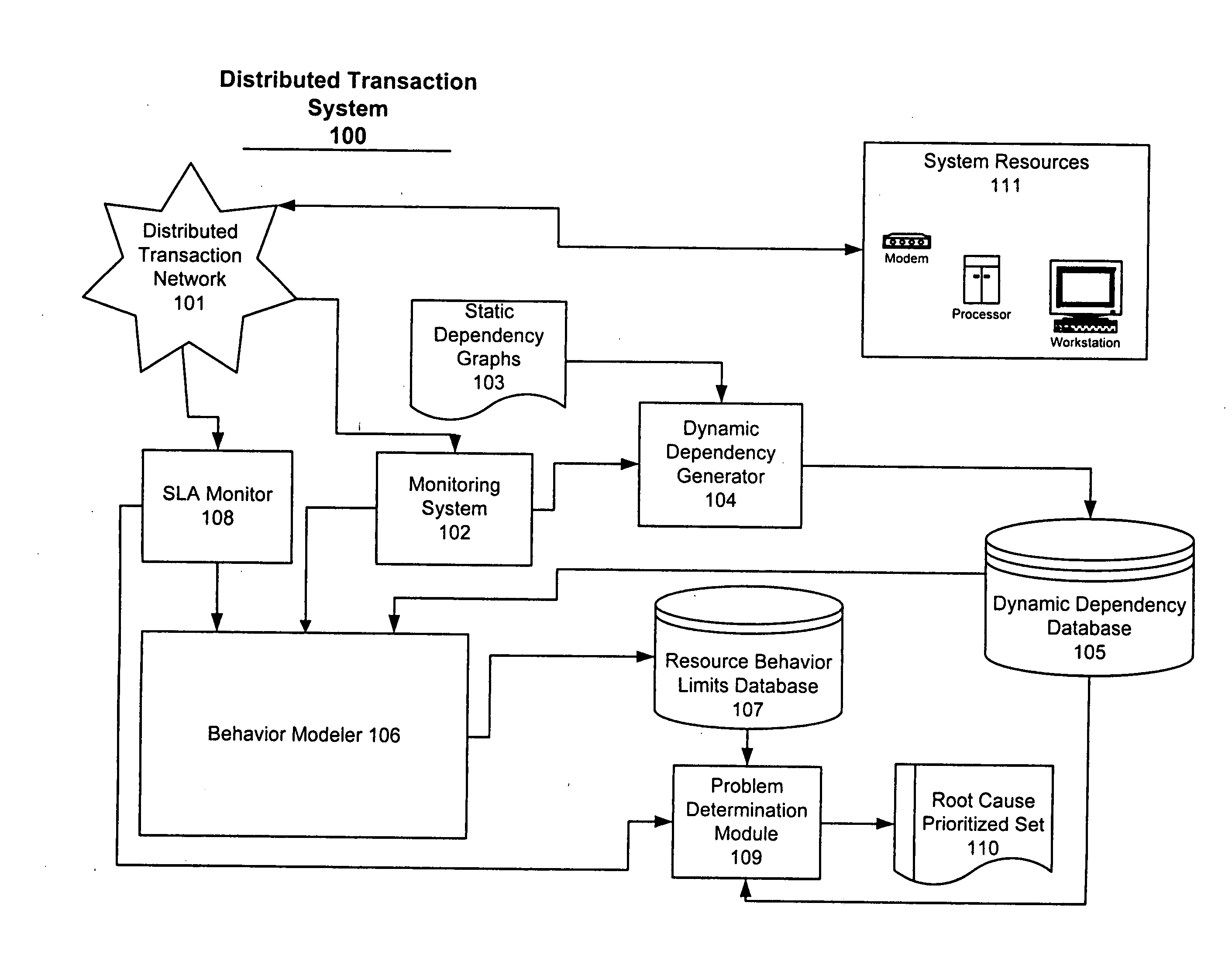
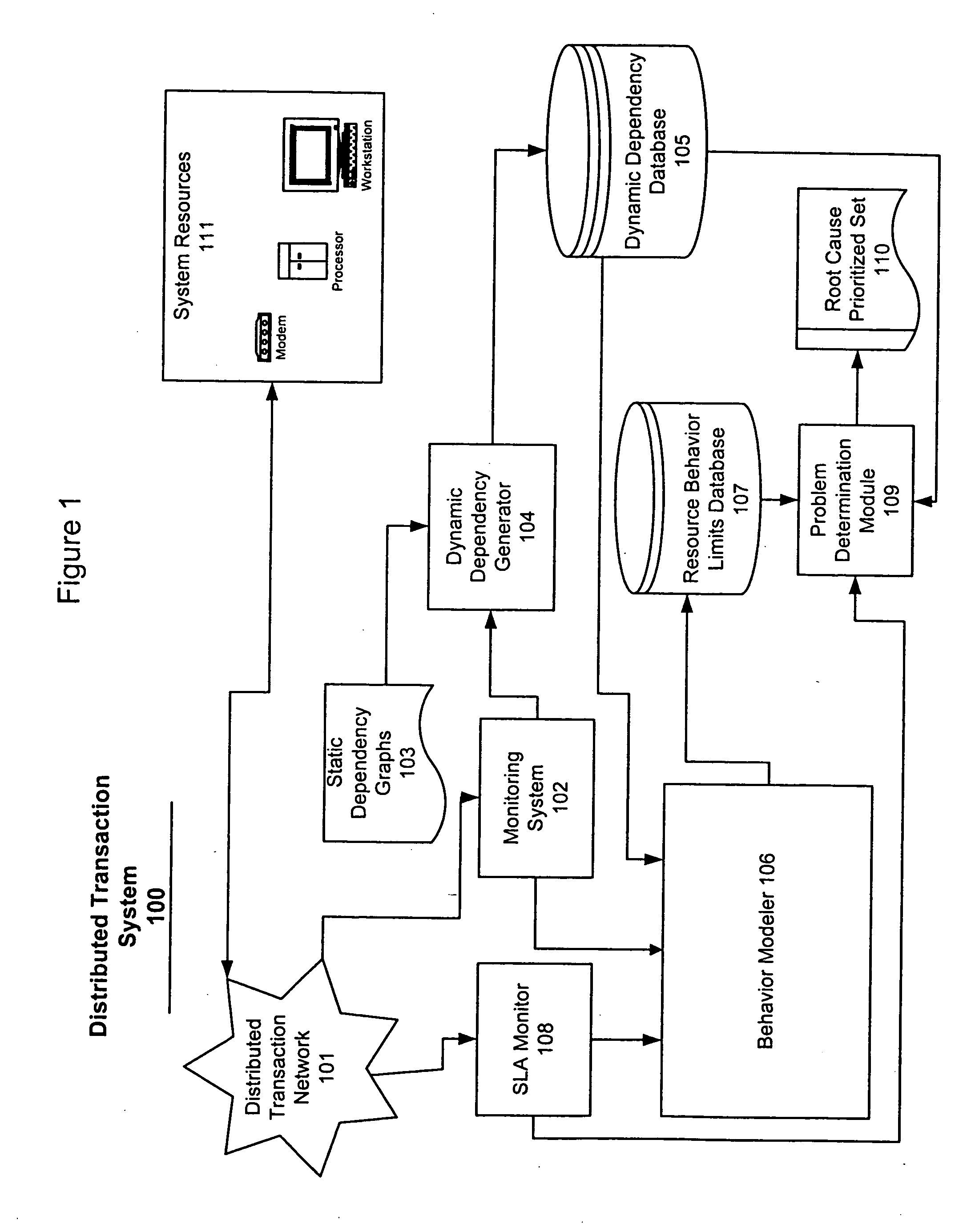
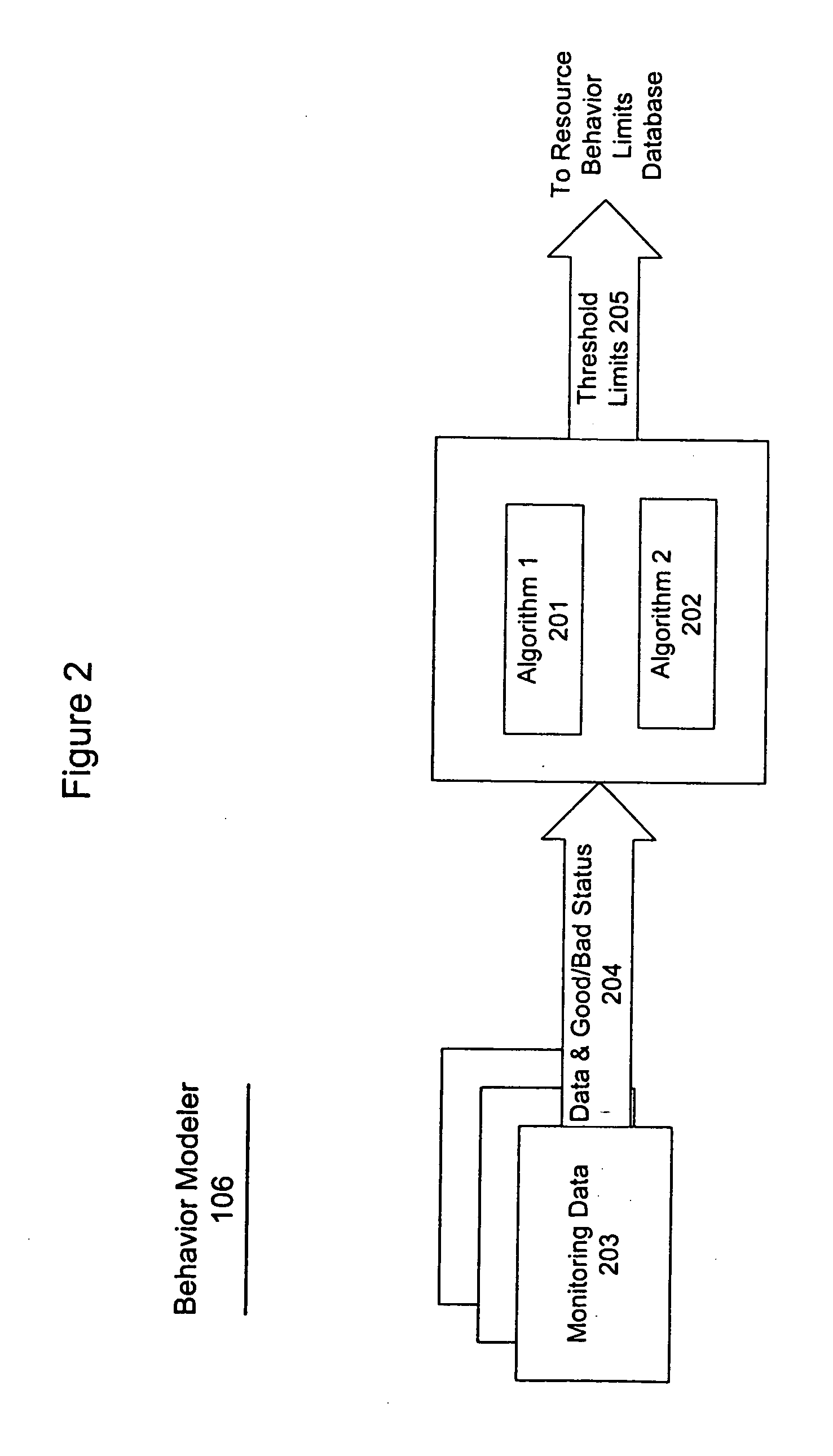
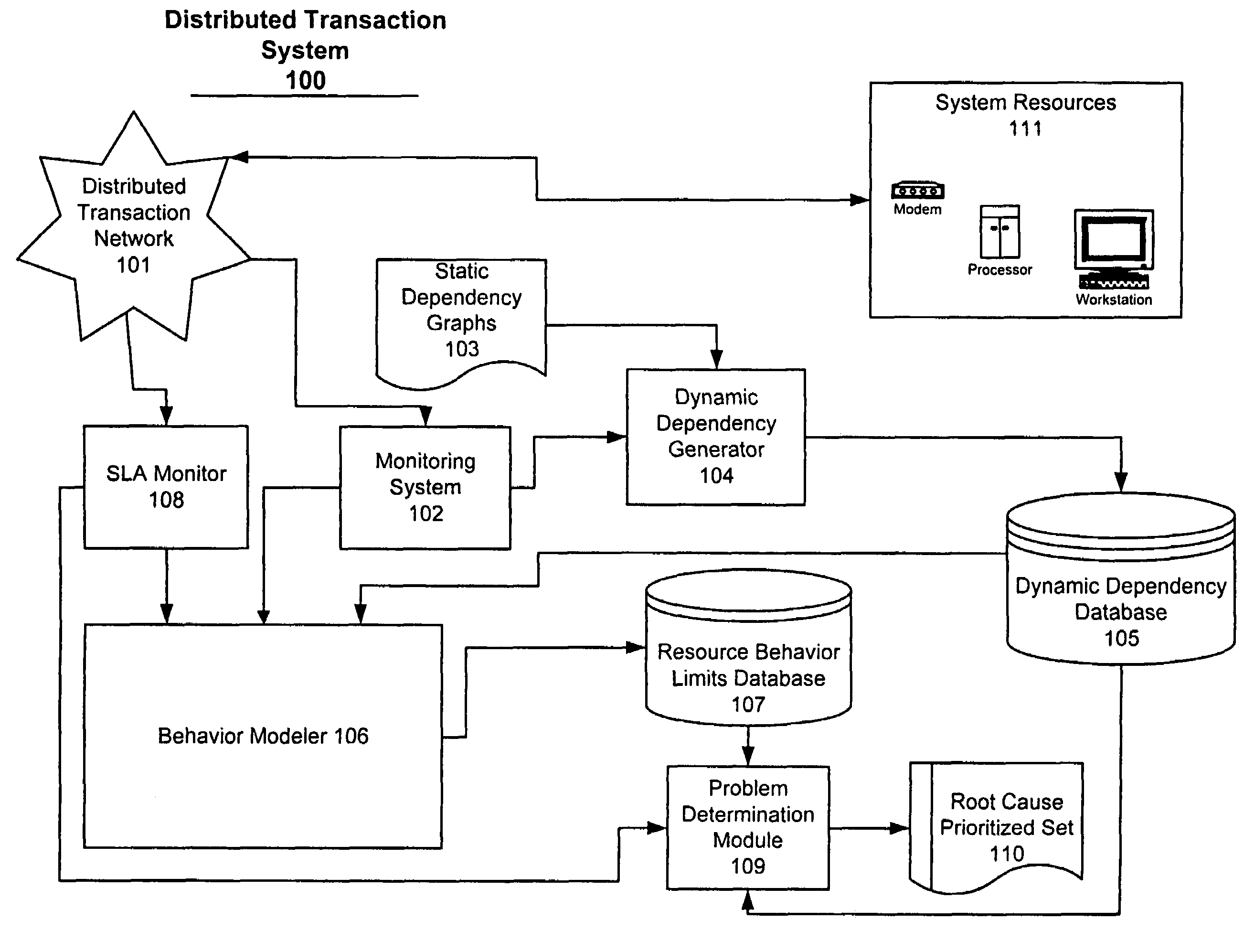
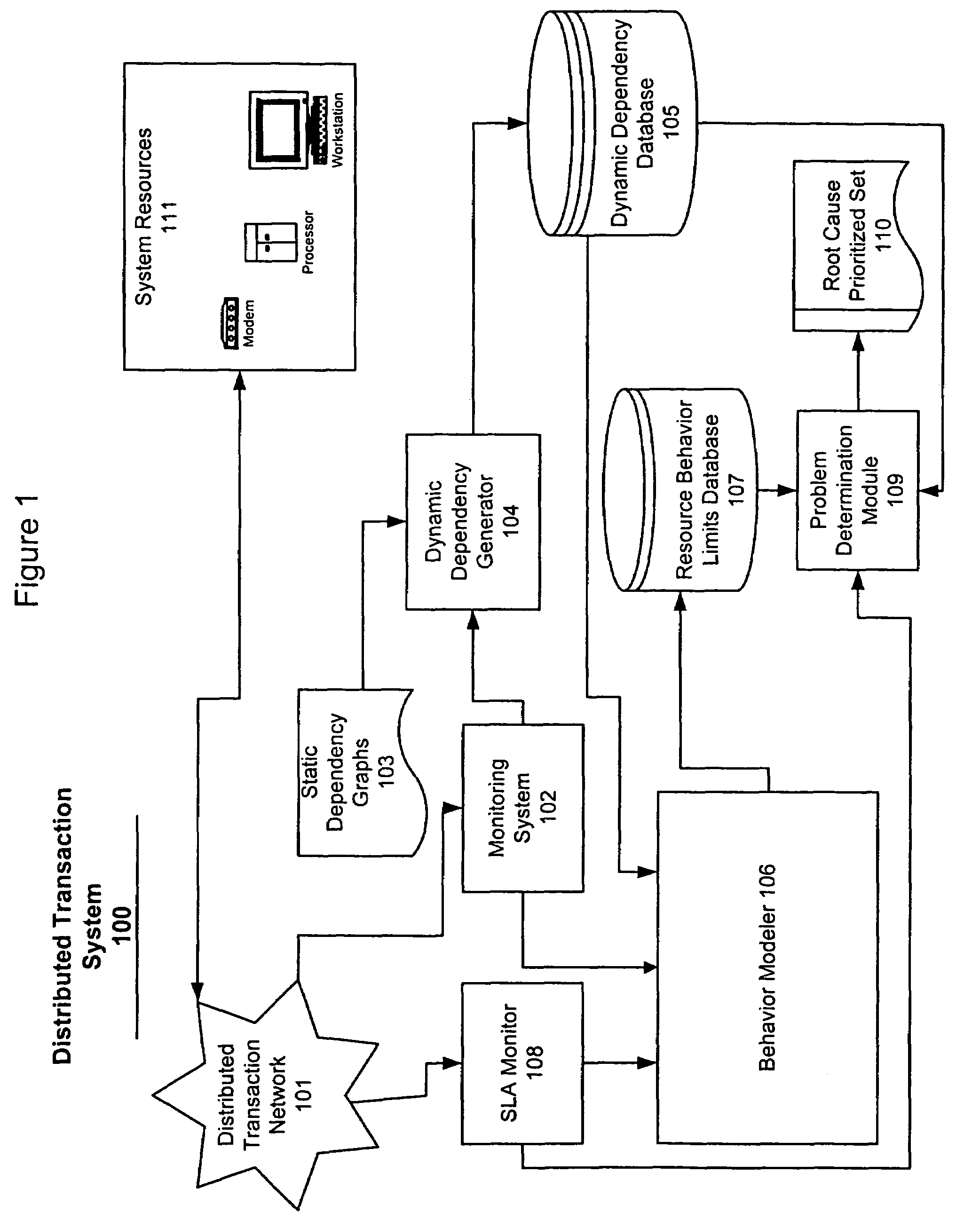
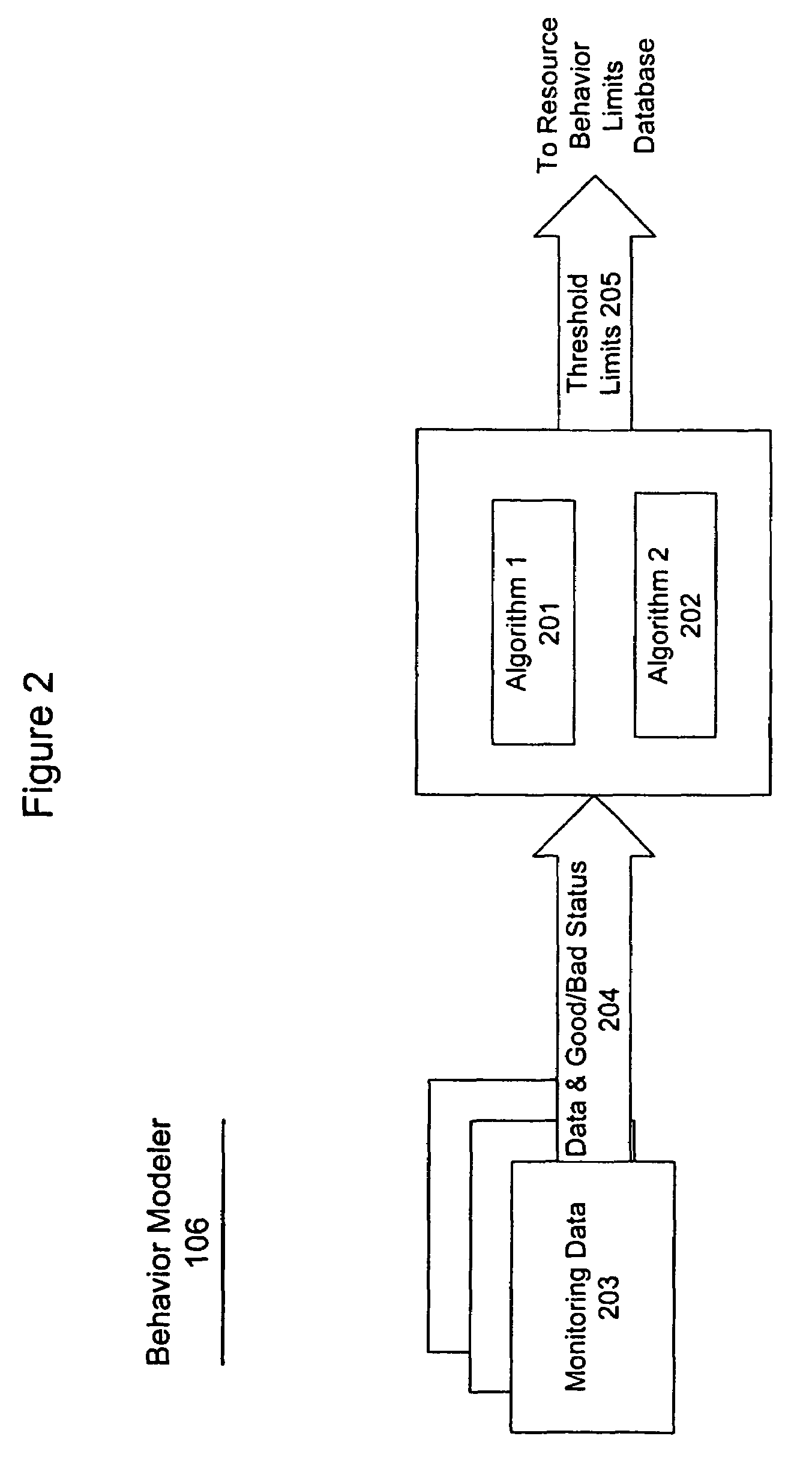
System and method for problem determination using dependency graphs and run-time behavior models
InactiveUS20060101308A1Reduce component countReduce in quantityNon-redundant fault processingMonitoring systemRunning time
A problem determination system and method reduces the time and effort required by system administrators to trouble shot transaction processing difficulties in a large distributed I / T environment by monitoring system component performance and computing operational performance threshold limits based on dependency graphs for the system. Using this data, a prioritized list of suspect components for the I / T system is generated.
Owner:GLOBALFOUNDRIES INC
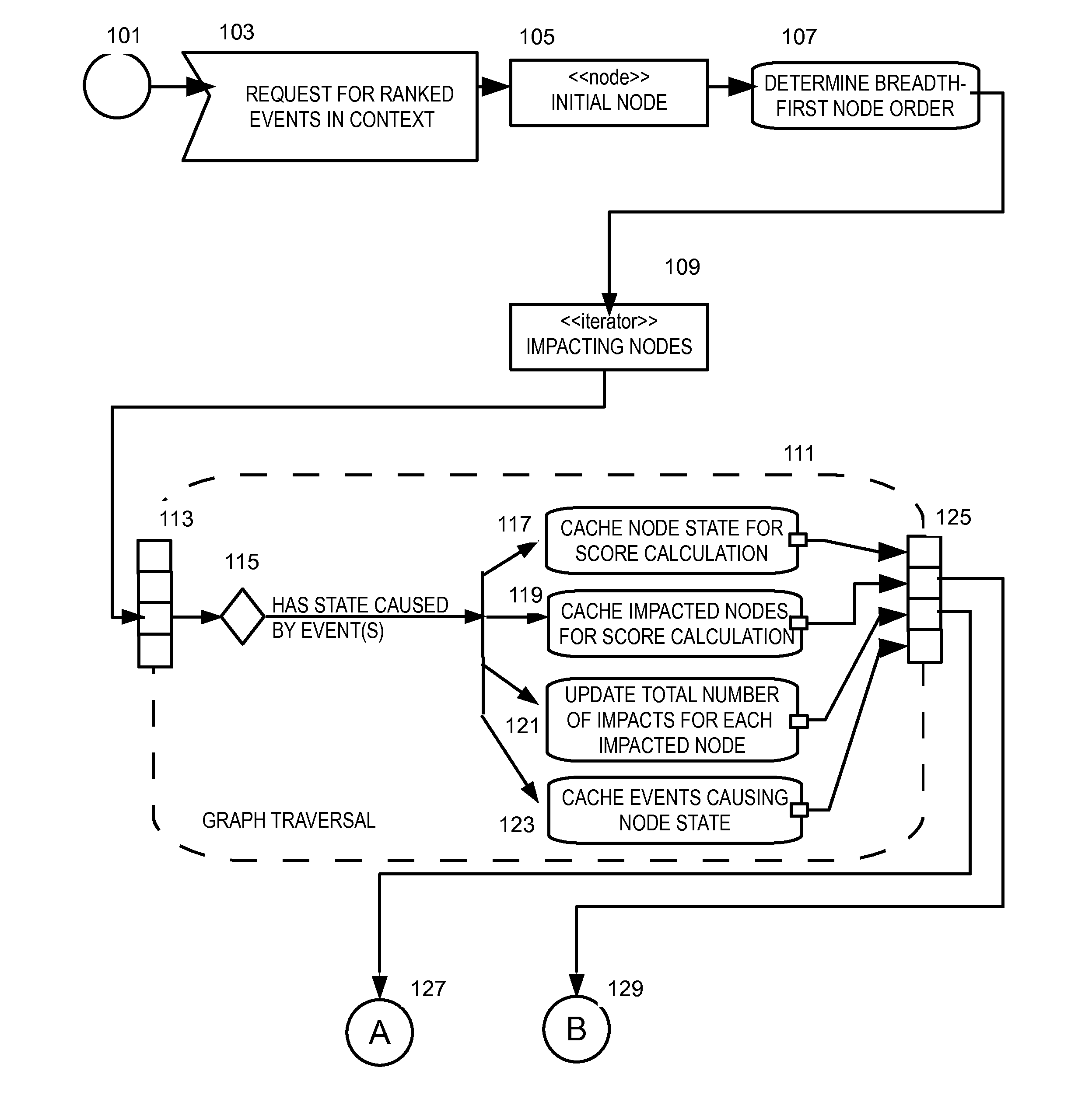
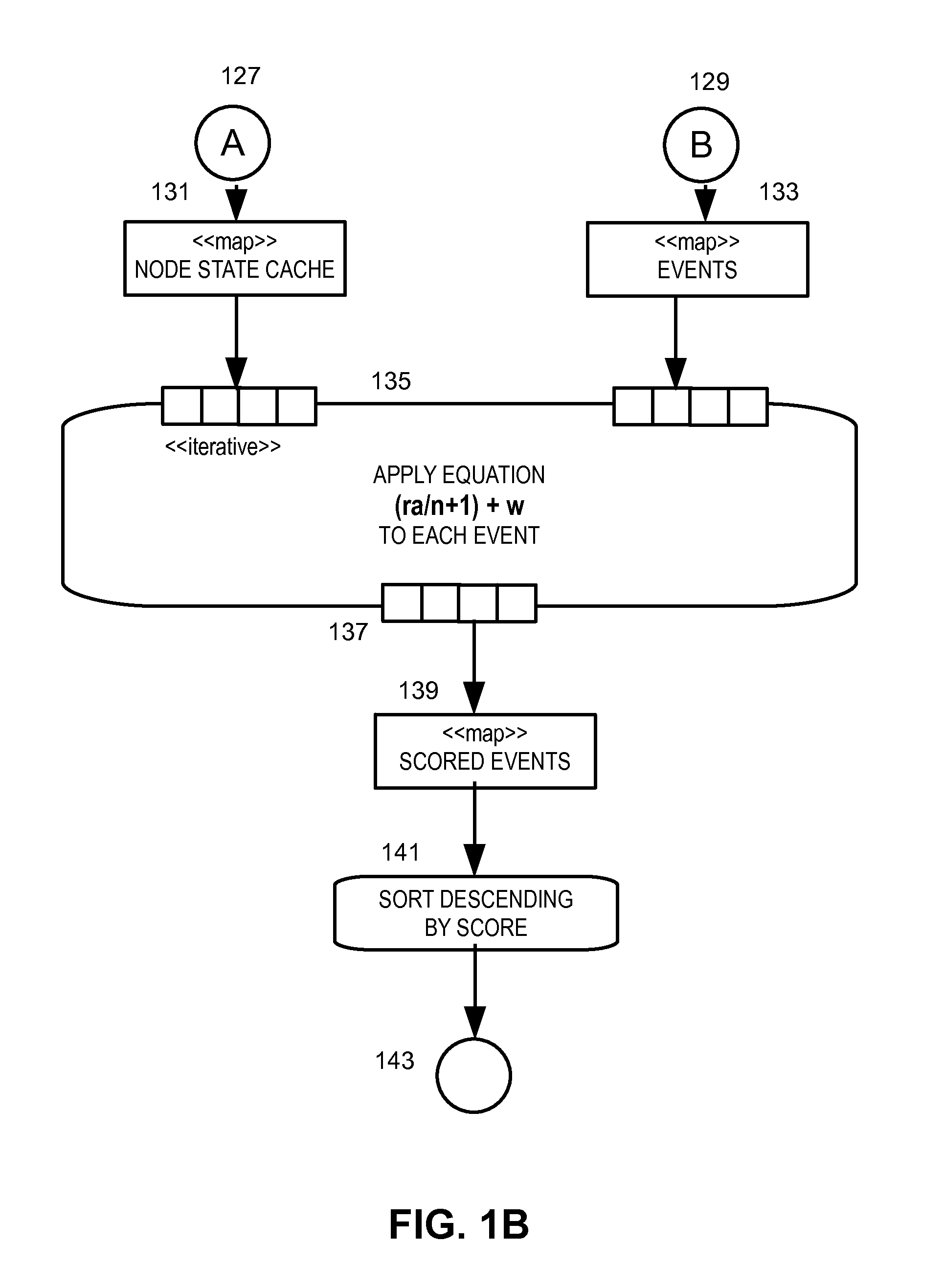
Method and apparatus for analyzing a root cause of a service impact in a virtualized environment
InactiveUS20130097183A1Digital data processing detailsNon-redundant fault processingVirtualizationRoot cause
A dependency graph includes nodes representing states of infrastructure elements in a managed system, and impacts and events among the infrastructure elements in a managed system that are related to delivery of a service by the managed system. Events are received that cause change among the states in the dependency graph. An event occurs in relation to one of the infrastructure elements of the dependency graph. Each individual node that was affected by the event is analyzed and ranked based on (i) states of the nodes which impact the individual node, and (ii) the states of the nodes which are impacted by the individual node, to provide a score for event(s) which is associated with the individual node. Plural events are ranked based on the scores. The root cause of the events with respect to the service is provided based on the events which were ranked.
Owner:ZENOSS
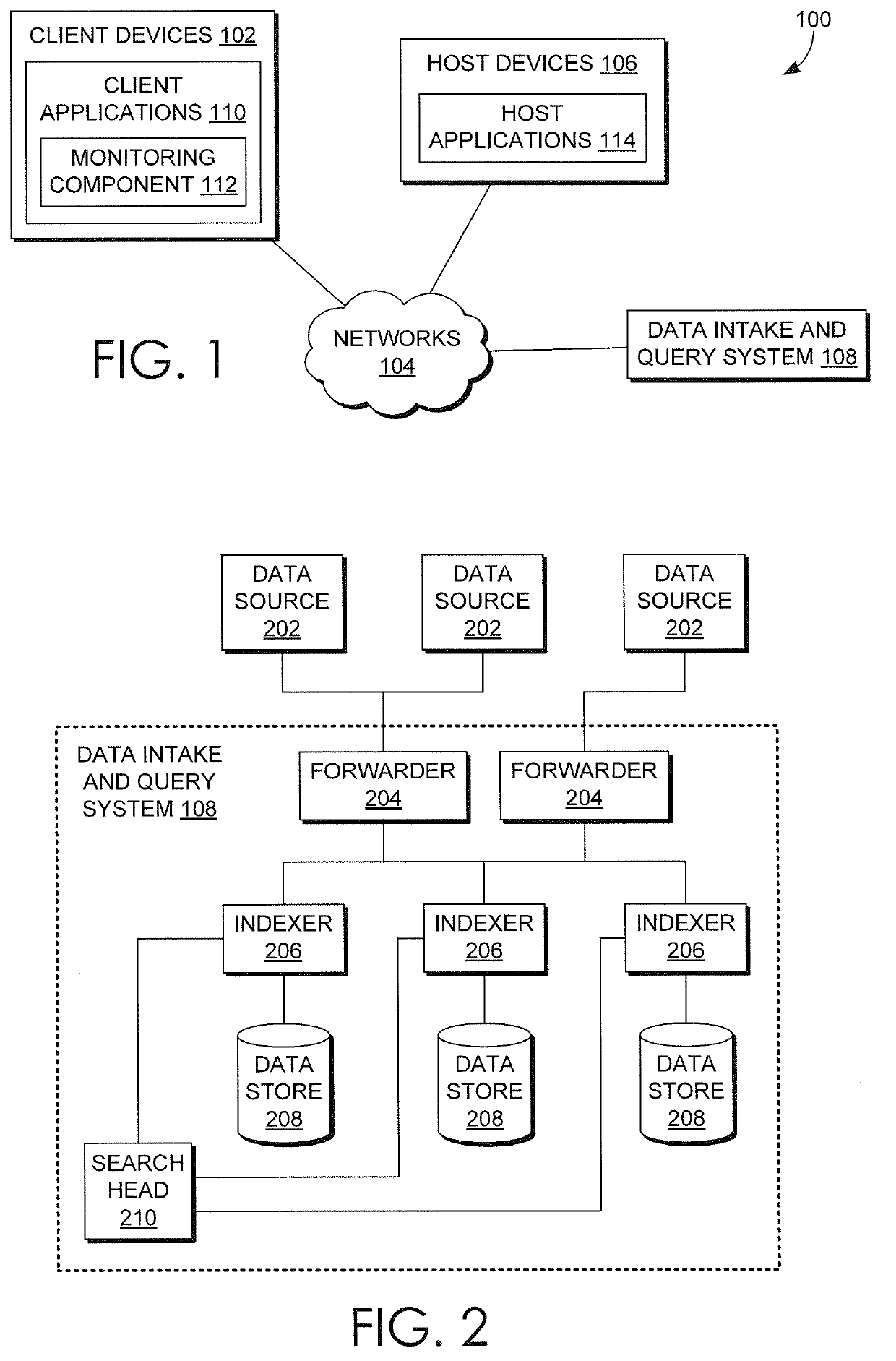
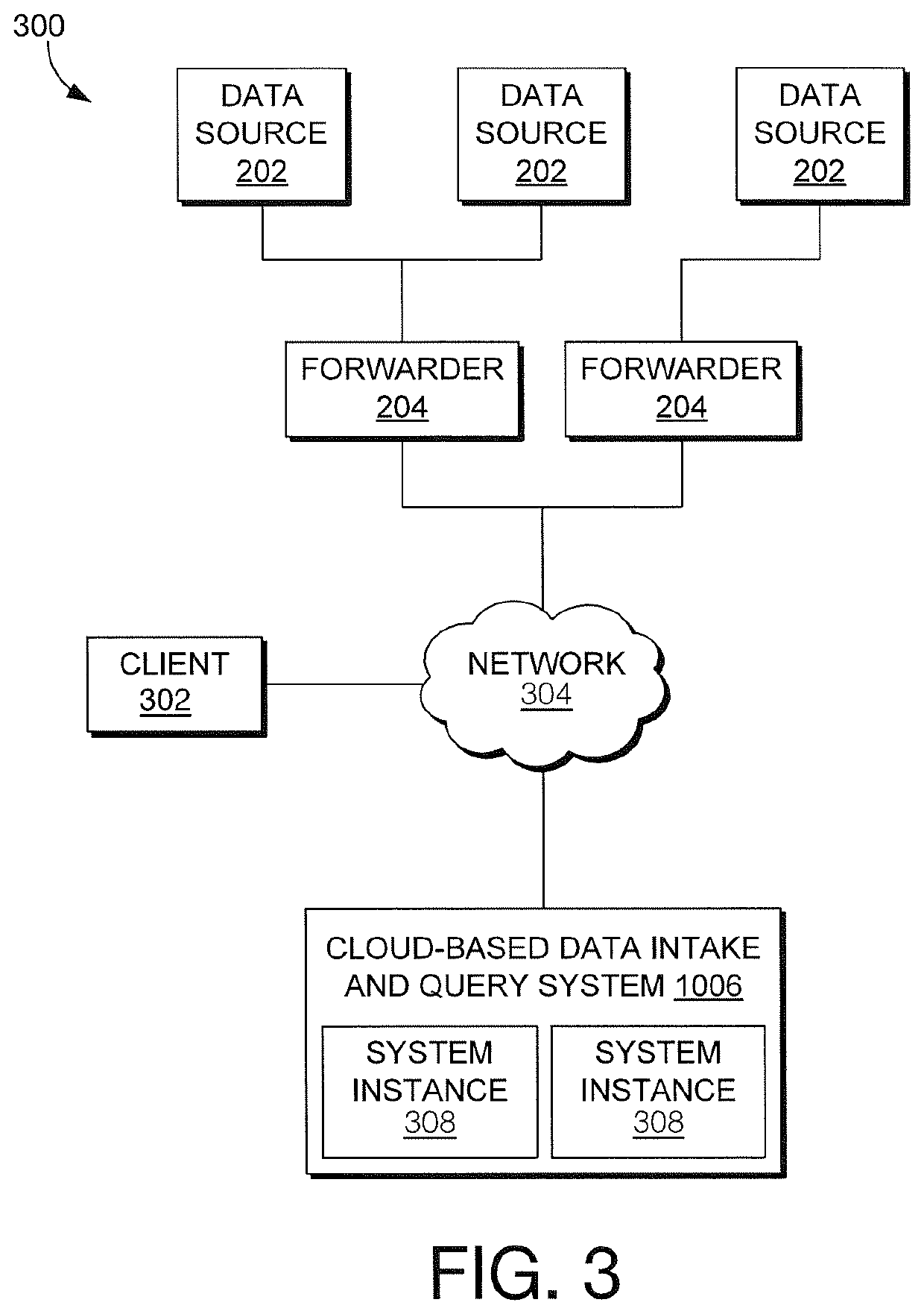
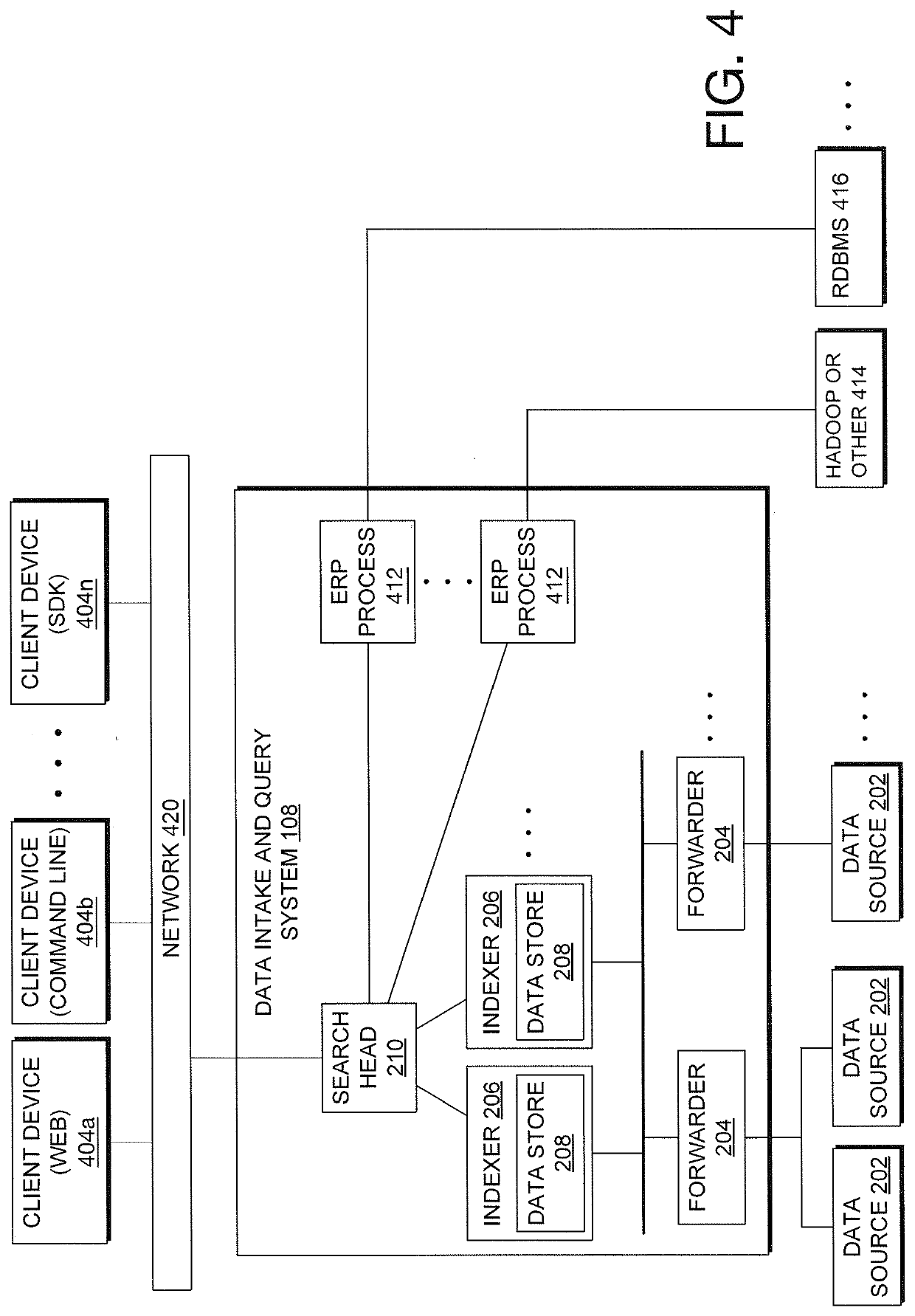
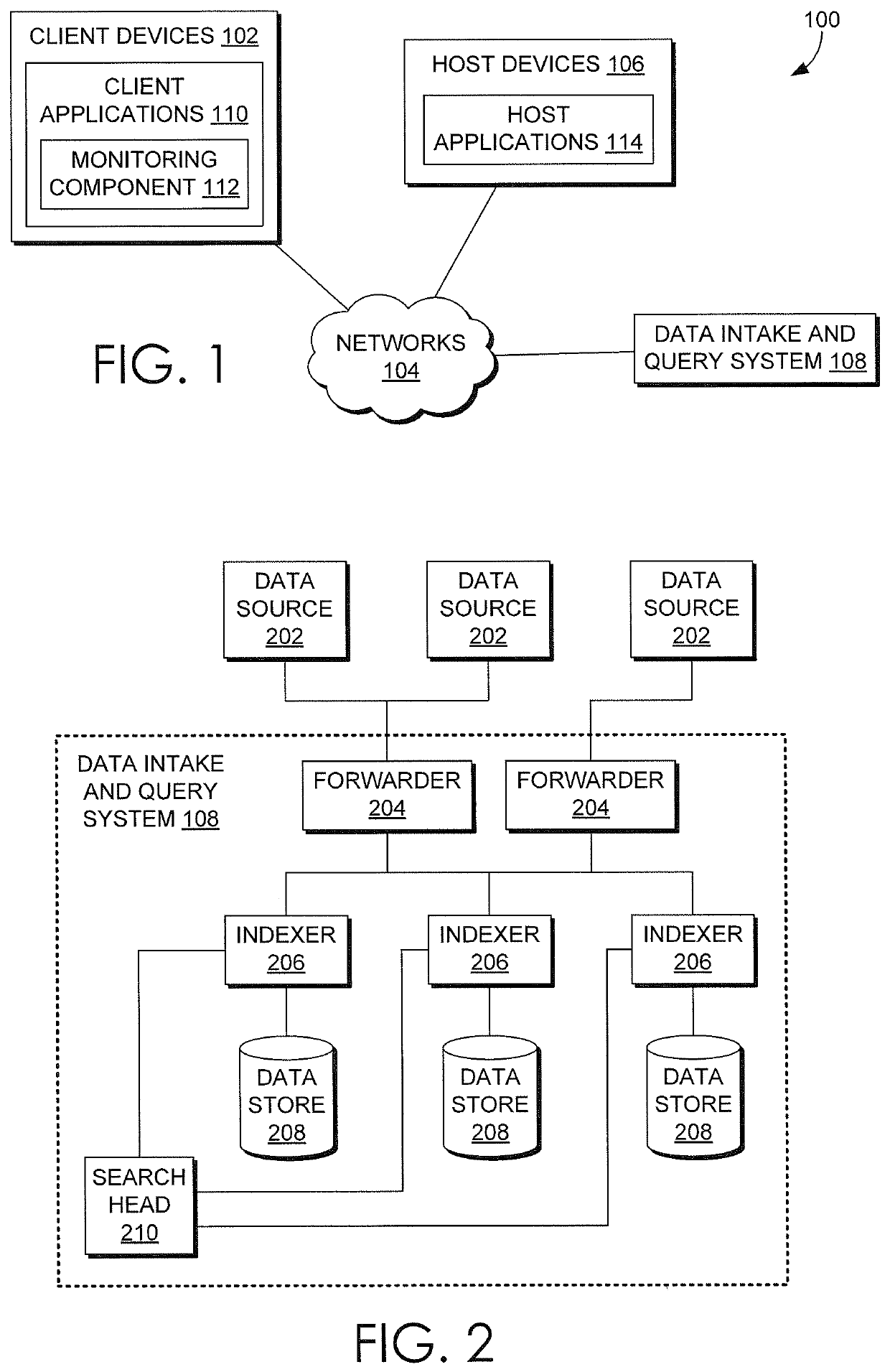
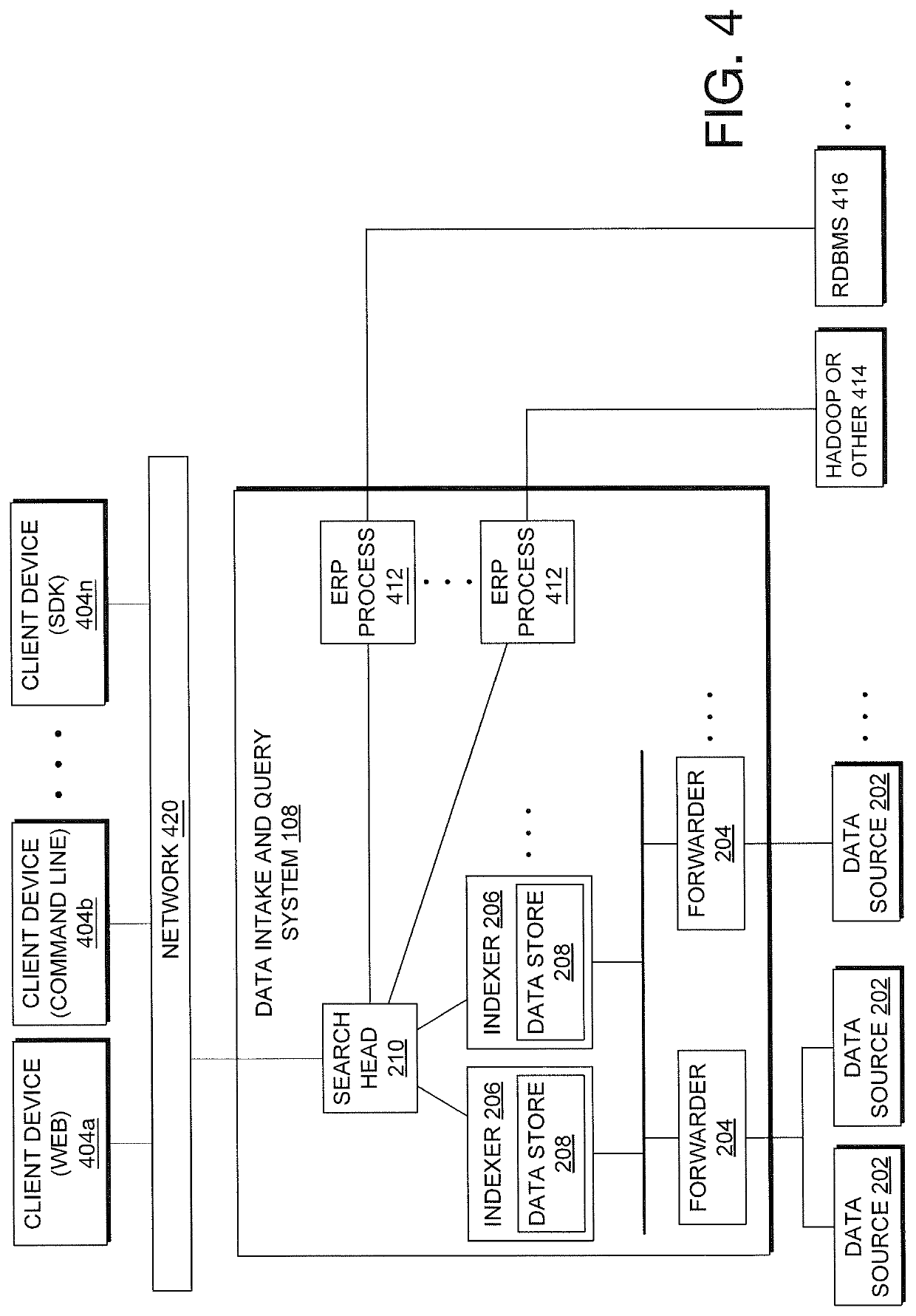
Real-Time Measurement And System Monitoring Based On Generated Dependency Graph Models Of System Components
Machine data is collected from multiple sources of an operating environment such as an information technology system, factory floor, or the like, into a data intake and query system, in one embodiment. Metrics representative of the environment are included in or derived from the data. Users may interact with an interface to depict a representation of various metrics and interdependencies and that depiction is reflected in a computer storage model. Changes to the computer storage model based on the user interaction may also result in training of a machine learning model according to the user interaction, the machine learning model configured to determine a prediction, classification or clustering of a result of a first search query by utilizing a result of at least a second search query as input to the machine learning model.
Owner:SPLUNK INC
System Monitoring Driven By Automatically Determined Operational Parameters Of Dependency Graph Model With User Interface
ActiveUS20200104402A1Relational databasesSpecial data processing applicationsEngineeringStorage model
Machine data is collected from multiple sources of an operating environment such as an information technology system, factory floor, or the like, into a data intake and query system, in one embodiment. Metrics representative of the environment are included in or derived from the data. Users may interact with an interface to depict a representation of various metrics and interdependencies and that depiction is reflected in a computer storage model. Changes to the computer storage model based on the user interaction may also result in automatic changes to control information reflected in the computer storage model that directs the processing of various monitoring functions associated with the metrics.
Owner:SPLUNK INC
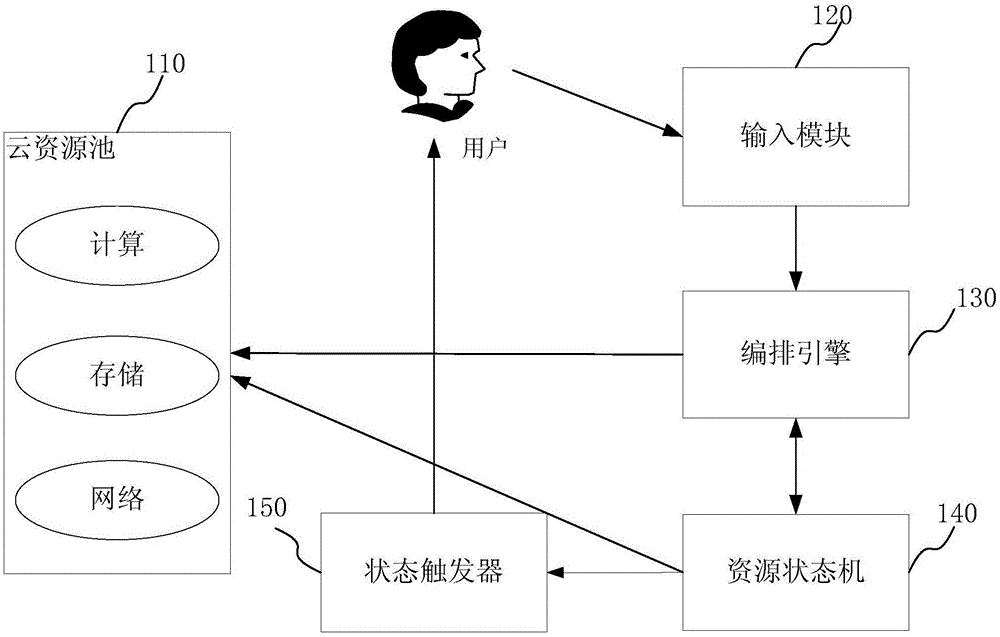
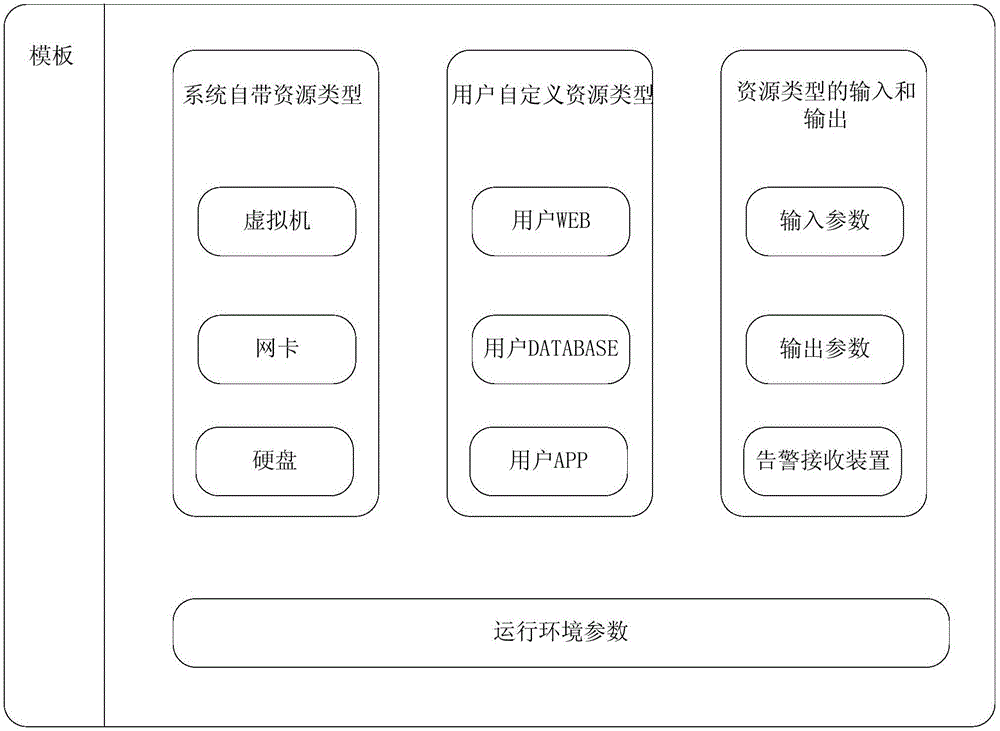
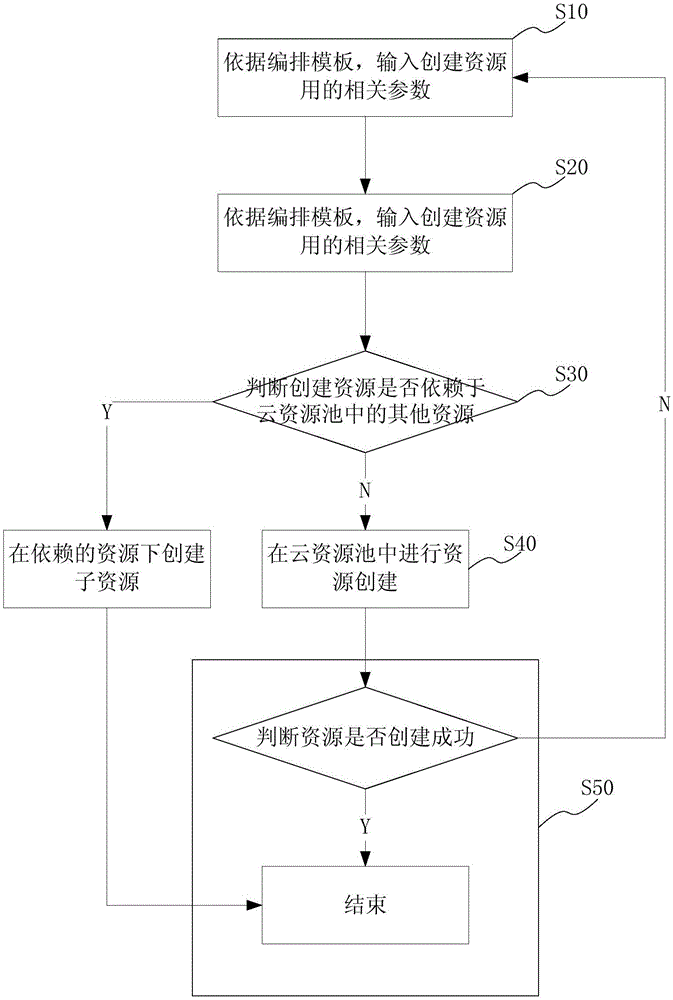
System and method for arranging cloud resources
The invention provides a system and a method for arranging cloud resources. The system comprises a cloud resource pool, an input module, an arranging engine and a resource state machine, wherein the cloud resource pool is used for providing the resources needing to arrange, and the resources are organized as different resource pools by using pooling method and are stored in a classified manner; the input module is used for inputting relative parameters according to an arranging template, wherein the arranging template is established in advance according to different business requirements; the arranging engine is used for analyzing the relative parameters, obtaining a dependency graph of the resources and processing the resources in a multi-path manner according to the dependency graph; the resource state machine is used for maintaining the state of the resources. The system and the method of the invention are used for dynamically deploying the resources according to a requirement type and a degree of an application to the resources to achieve optimal combination of the application and the resources. Simultaneously, the method and the system of the invention improve operation and maintenance efficiency of a data centre and reduce cost and management complexity.
Owner:PHICOMM (SHANGHAI) CO LTD
Method and apparatus for end-to-end content publishing system using XML with an object dependency graph
InactiveUS20060294459A1Avoid scattering and duplicationReusabilityDigital computer detailsNatural language data processingData integrityReusability
The system for end-to-end content publishing using XML with an object dependency graph is based on the following two design principles: First, separation of content and style: Information stored in the content management system is independent on how it is going to be presented. The presentation style is encapsulated elsewhere and can be used to customize the look and feel based on the end-user preferences as well as the delivery methods and devices. Second, reusability of information content: By encapsulating common information in fragments and subfragments and making these fragments insertable in other fragments, thereby avoid scattering and duplication of information. This enables a user to restrict the edit operations to a limited number of relevant fragments, to affect global changes. In addition, the present invention provides data consistency and data integrity in the content management.
Owner:INT BUSINESS MASCH CORP
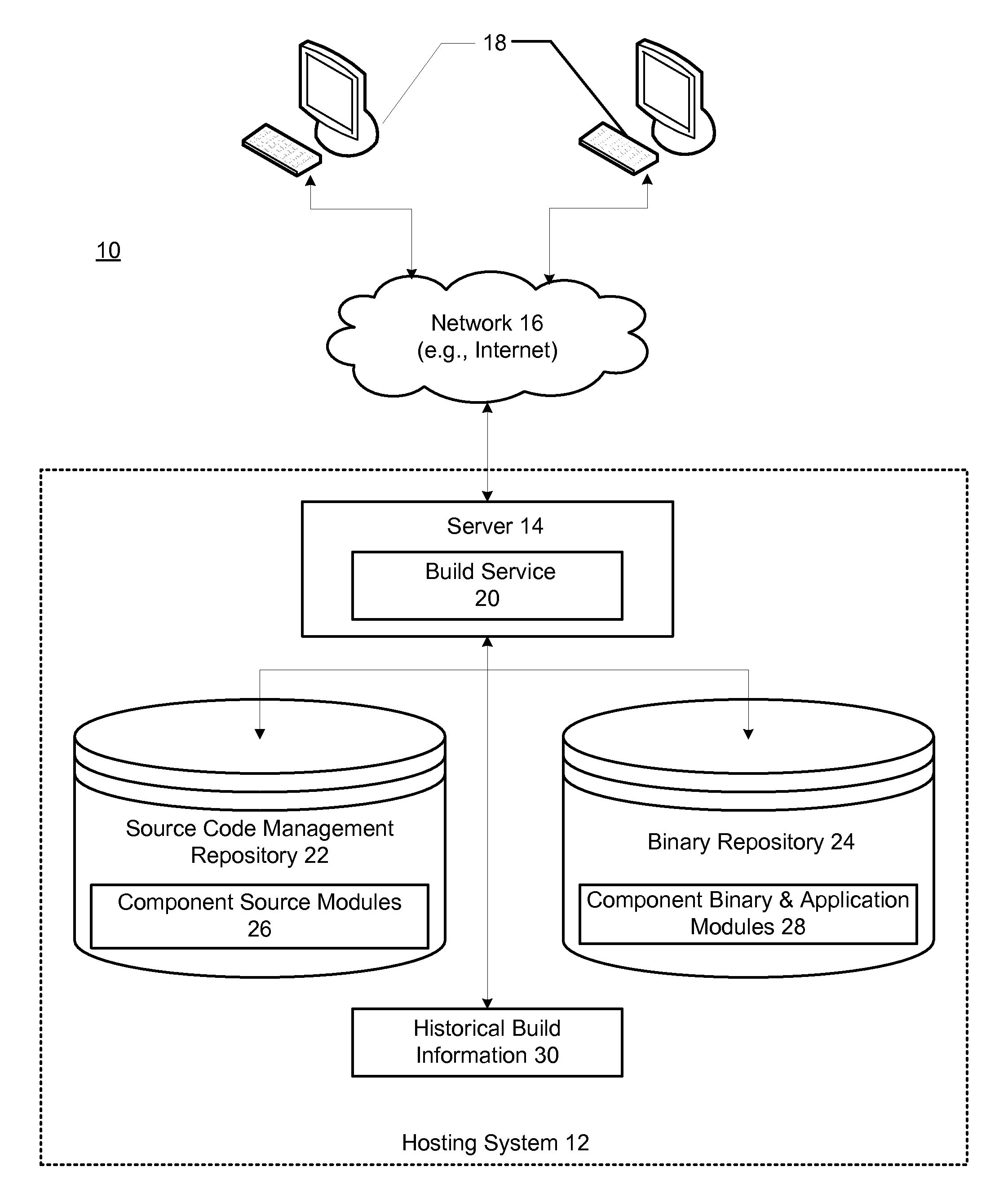
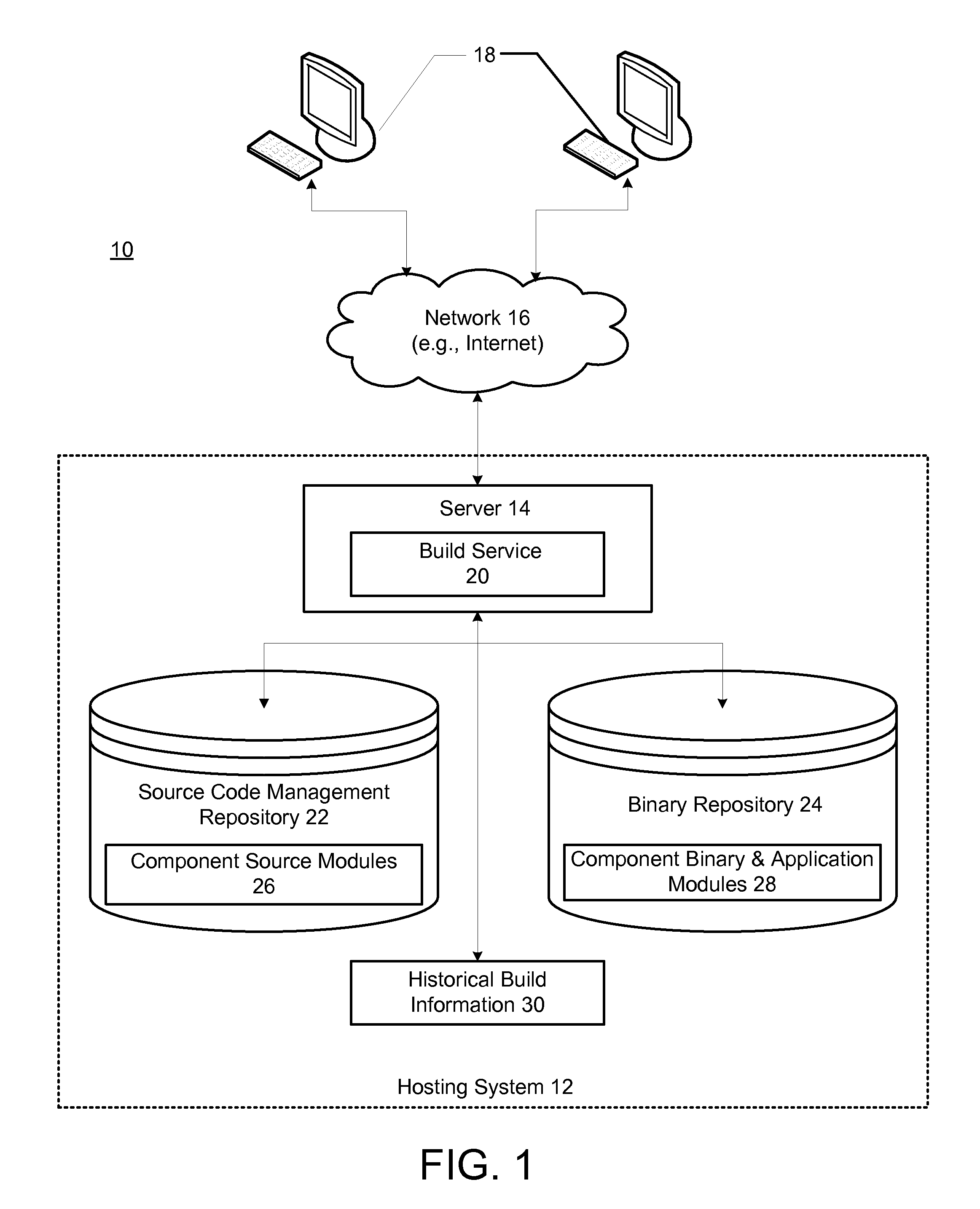
Using build history information to optimize a software build process
InactiveUS20100050156A1Version controlSpecific program execution arrangementsDependency graphComputer science
Methods and systems for optimizing a build order of component source modules comprises creating a dependency graph based on dependency information. Historical build information associated with previous build failures is then used to calculate relative failure factors for paths of the dependency graph; and the relative failure factors are used to determine an order of traversal of the dependency graph during a build process in which component binary modules are built from the component source modules.
Owner:IBM CORP
Detecting correlation from data
InactiveUS7647293B2Improve impactHigh selectivityDigital data information retrievalDigital data processing detailsStatistical correlationQuery optimization
A system and method of discovering dependencies between relational database column pairs and application of discoveries to query optimization is provided. For each candidate column pair remaining after simultaneously generating column pairs, pruning pairs not satisfying specified heuristic constraints, and eliminating pairs with trivial instances of correlation, a random sample of data values is collected. A candidate column pair is tested for the existence of a soft functional dependency (FD), and if a dependency is not found, statistically tested for correlation using a robust chi-squared statistic. Column pairs for which either a soft FD or a statistical correlation exists are prioritized for recommendation to a query optimizer, based on any of: strength of dependency, degree of correlation, or adjustment factor; statistics for recommended columns pairs are tracked to improve selectivity estimates. Additionally, a dependency graph representing correlations and dependencies as edges and column pairs as nodes is provided.
Owner:IBM CORP
Dependency graph in data-driven model
Owner:MICROSOFT TECH LICENSING LLC
Differential dependency tracking for attack forensics
ActiveUS20160105454A1Digital data information retrievalMemory loss protectionDifferential dependenciesDependency graph
Methods and systems for intrusion attack recovery include monitoring two or more hosts in a network to generate audit logs of system events. One or more dependency graphs (DGraphs) is generated based on the audit logs. A relevancy score for each edge of the DGraphs is determined. Irrelevant events from the DGraphs are pruned to generate a condensed backtracking graph. An origin is located by backtracking from an attack detection point in the condensed backtracking graph.
Owner:NEC CORP
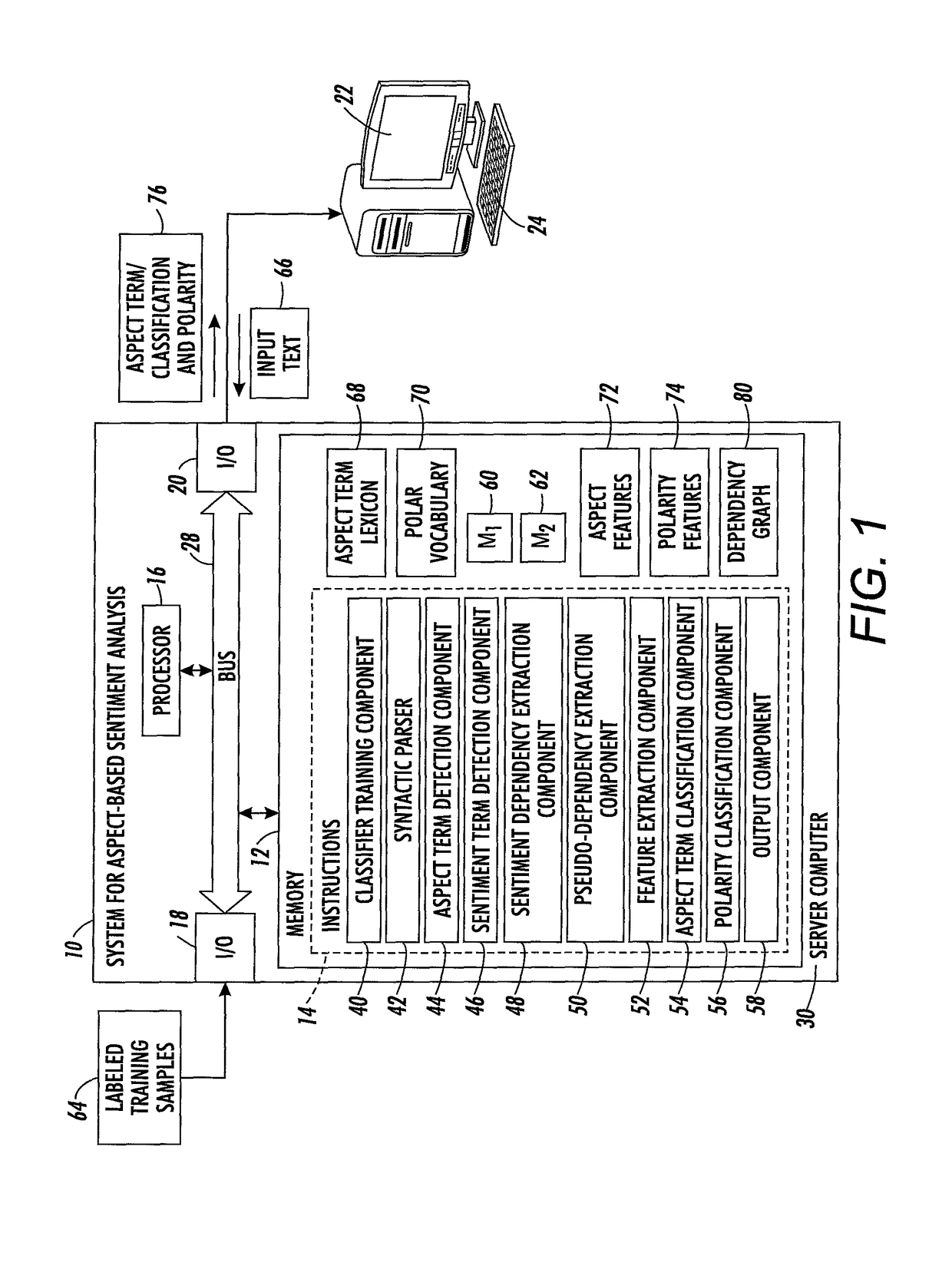
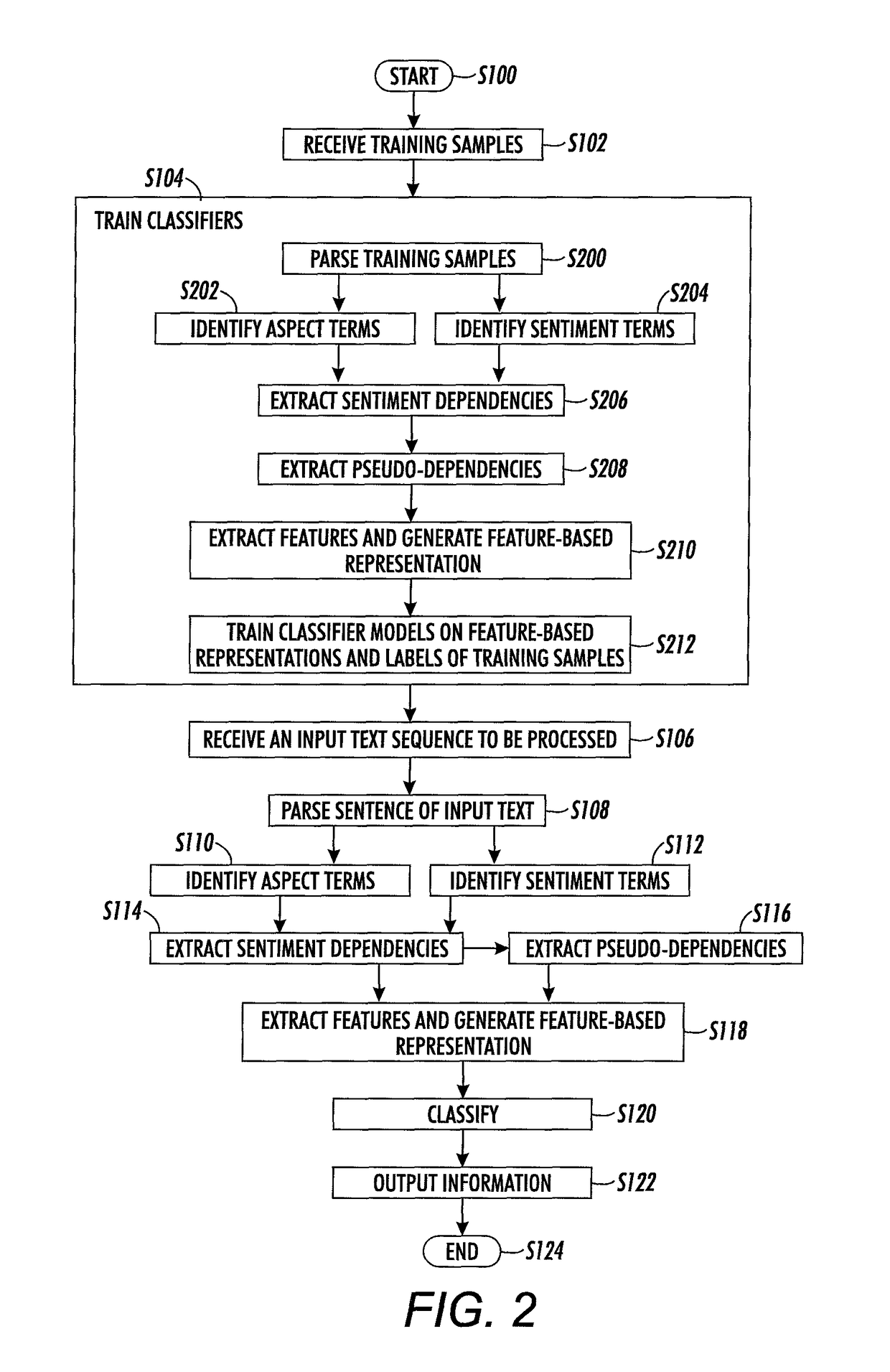
Loose term-centric representation for term classification in aspect-based sentiment analysis
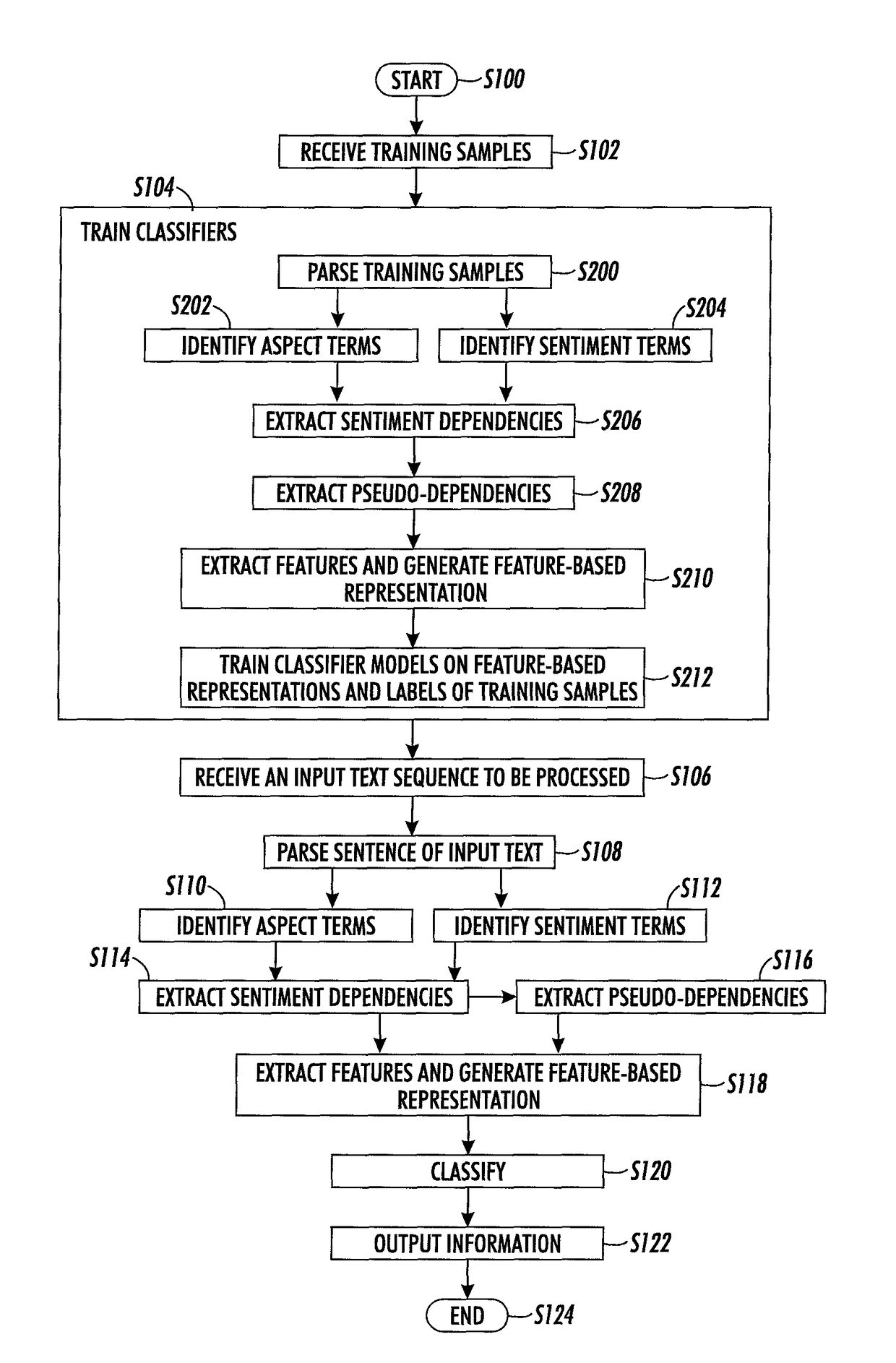
A method for aspect categorization includes receiving an input text sequence and identifying aspect terms and sentiment phrases in the input text sequence, where present. For an identified aspect term, identifying sentiment dependencies in which the aspect term is in a syntactic dependency with one of the identified sentiment phrases, and identifying pseudo-dependencies from a dependency graph of the input text sequence. The dependency graph includes a sequence of nodes. In a pseudo-dependency, a node representing the aspect term precedes or follows a node representing a semantic anchor in the dependency graph without an intervening other aspect term. Features for the aspect term are extracted from at least one of identified sentiment dependencies and identified pseudo-dependencies. With a classifier trained to output at least one of category labels and polarity labels for aspect terms, classifying the identified aspect term based on the extracted features.
Owner:XEROX CORP
System and method for recursive path analysis of DBMS procedures
InactiveUS7526468B2Data processing applicationsDigital data processing detailsTrack algorithmDependency graph
A system, method and database development tool are disclosed for automatically generating the complete dependency graph for use in debugging stored code objects in a database, by using a recursive dependency tracking algorithm which takes into consideration the indirect dependencies on triggers as well as the dependencies on implementations of object oriented code objects which are represented as separate objects in the database catalog.
Owner:COMP ASSOC THINK INC
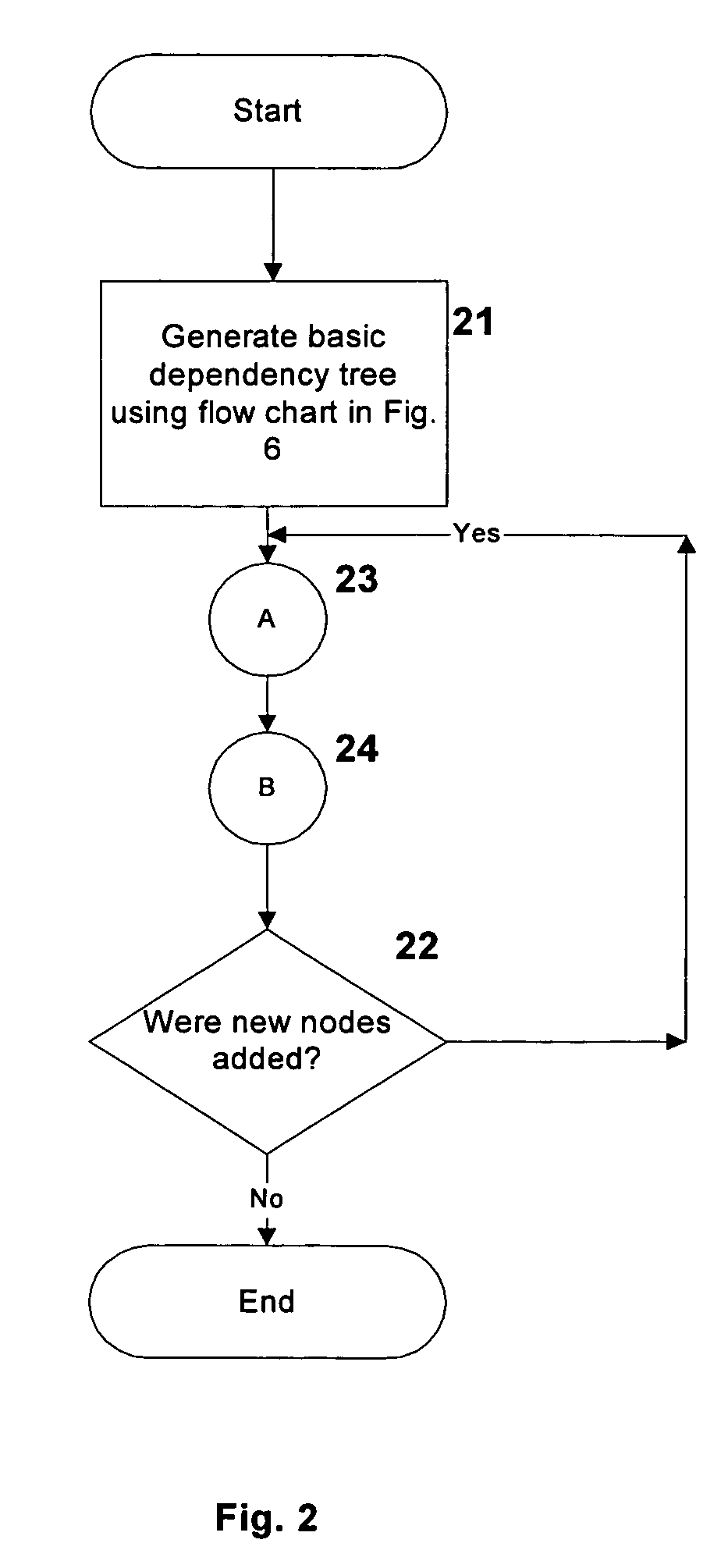
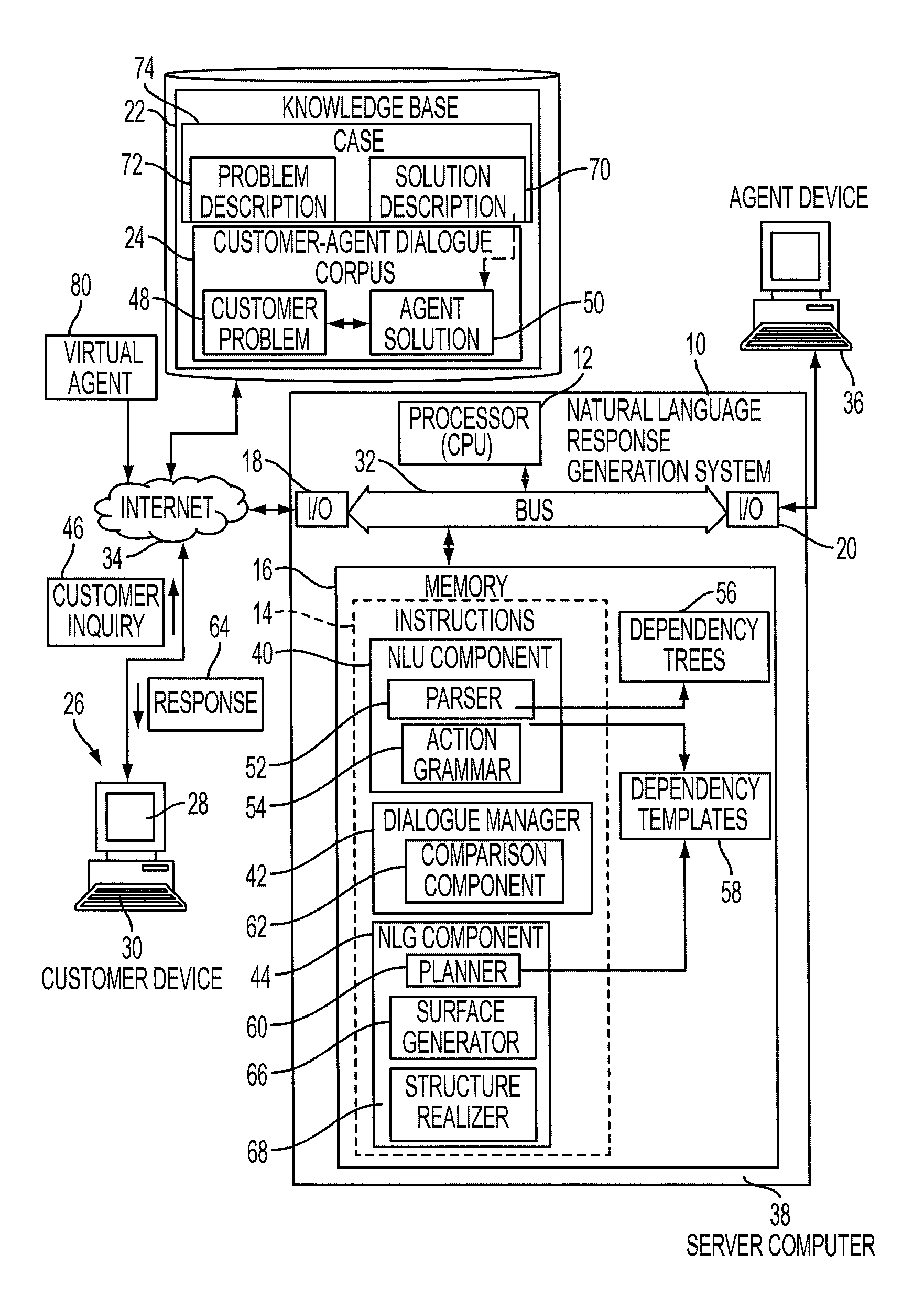
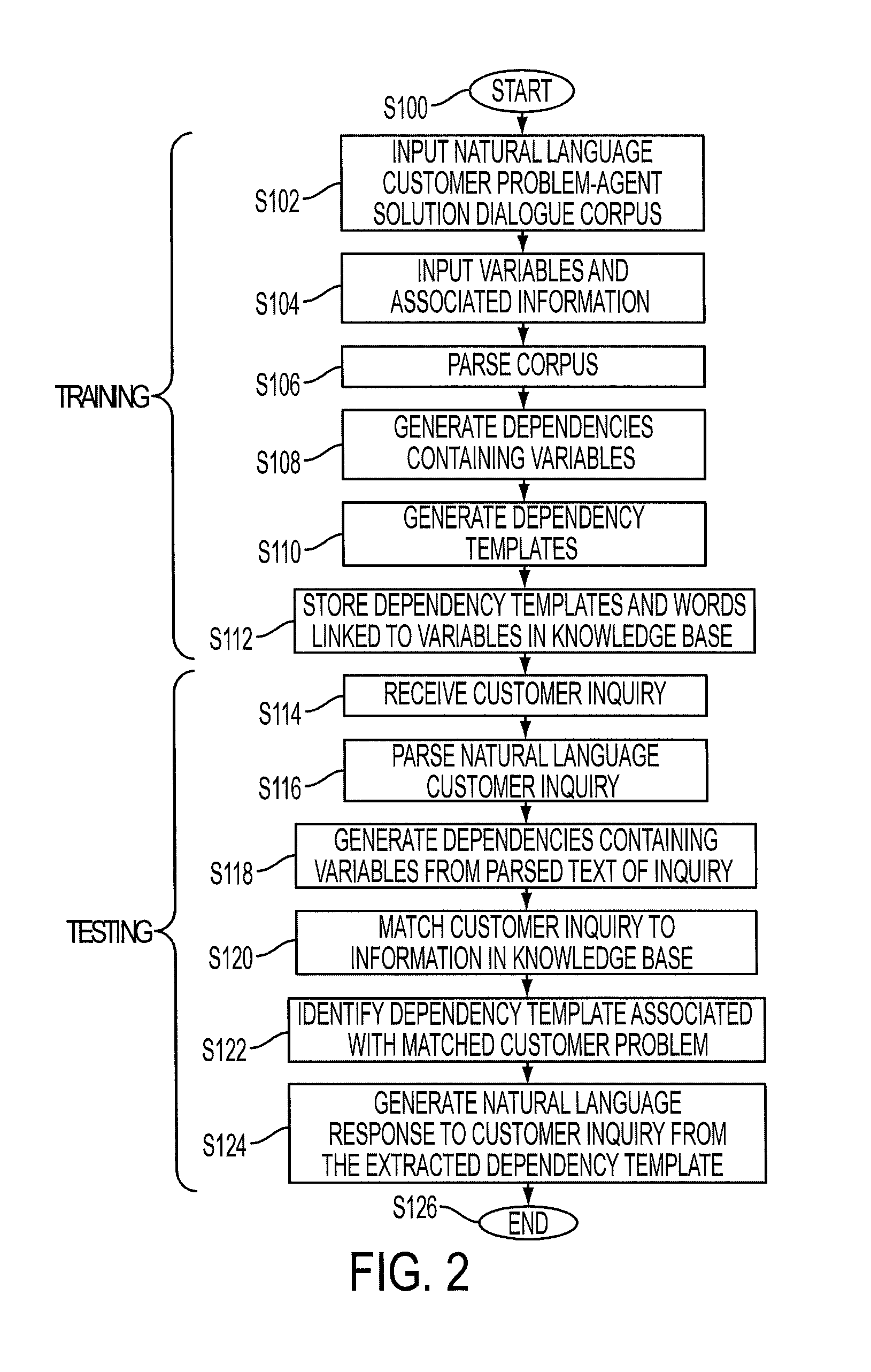
System and method for response generation using linguistic information
A method for generating a natural language response to a customer inquiry includes parsing sentences in a corpus of natural language dialogs between a respective customer and an agent to extract dependencies. Each parsed sentence is represented by a dependency graph, based on the extracted dependencies. Dependency templates are generated, at least some of which are each generated from two or more of the extracted dependency graphs (e.g., using variables which each represent a group of words referring to a same topic) and are stored in a knowledge base. In response to the customer inquiry, one of the stored dependency templates is identified and a natural language response to the inquiry is generated, using the identified dependency template. The natural language response is generated based on words extracted from the natural language dialogs that are linked, in memory, to the identified dependency template.
Owner:CONDUENT BUSINESS SERVICES LLC
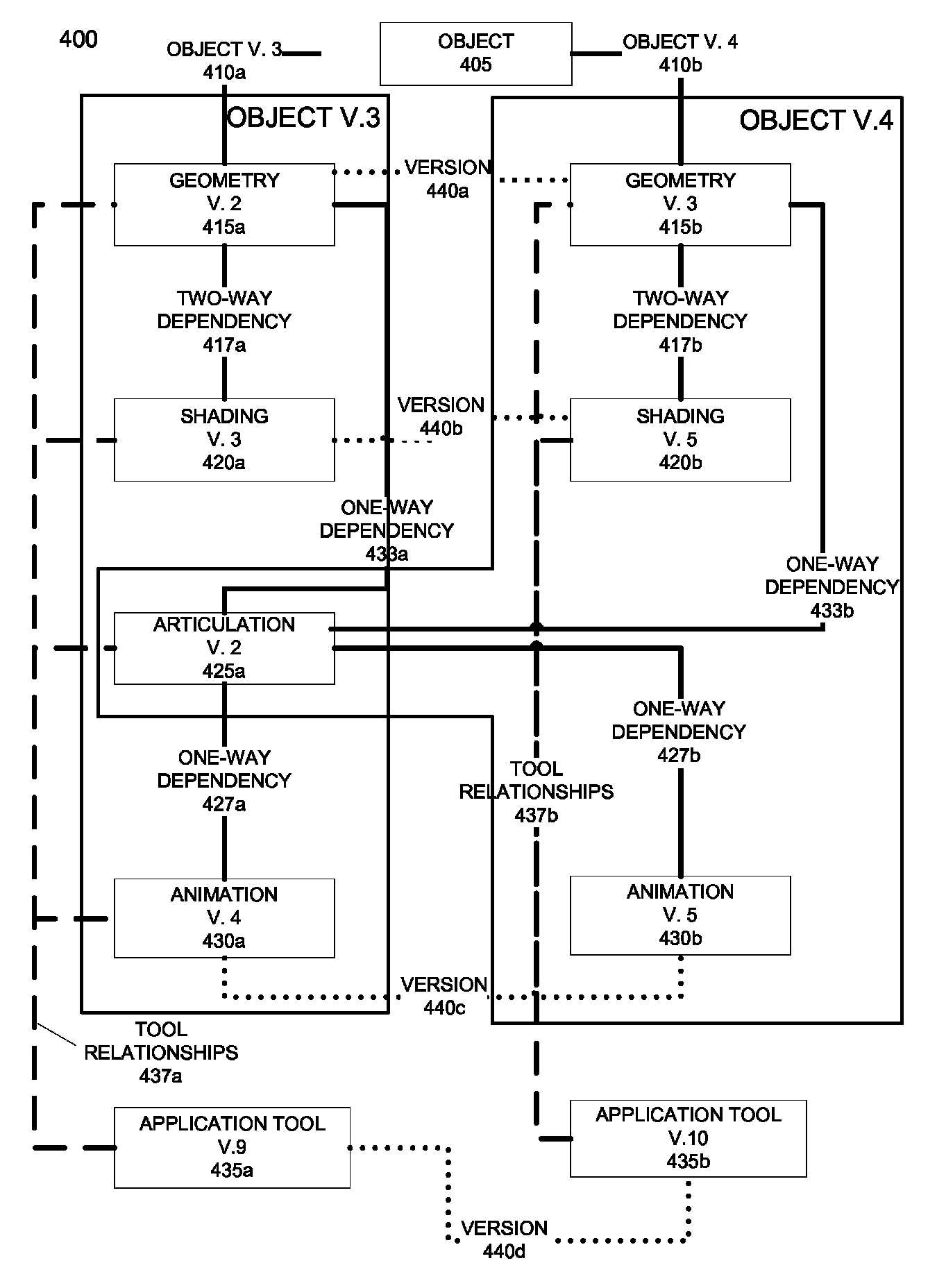
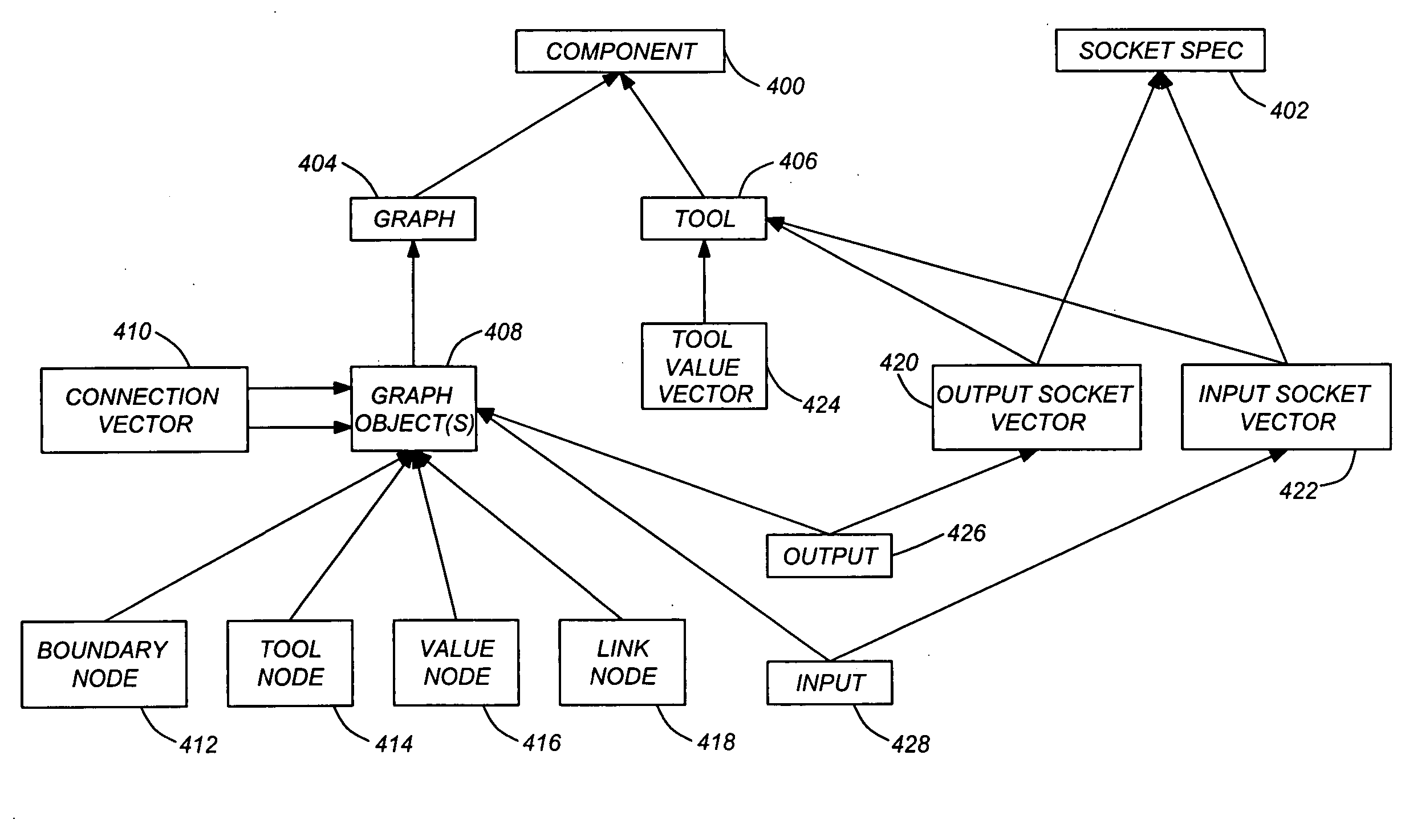
Typed dependency graphs
ActiveUS8624898B1Avoid Compatibility IssuesDrawing from basic elementsDigital data processing detailsData fileDependency graph
Typed dependency graphs represent digital assets as nodes in a graph. The digital assets, data files, and required software applications are represented as connected nodes. Nodes of the graph are connected by typed links, specifying the type of dependency relationship between digital assets, data files, and / or software applications associated with nodes. Type attributes can represent one-way dependencies, two-way dependencies, version relationships, variant relationships, subcomponent relationships, aggregation relationships, and software application / digital asset dependencies. Typed dependency graphs may be automatically created by parsing asset data or data files to determine the characteristics of assets and their relationships with other assets, data files, and software applications. Typed dependency graphs may be traversed based on the type of links, with the result defining a component, subcomponent, version, and / or variant.
Owner:PIXAR ANIMATION
System and method for problem determination using dependency graphs and run-time behavior models
InactiveUS7437611B2Reduce component countReduce in quantityNon-redundant fault processingMonitoring systemRunning time
A problem determination system and method reduces the time and effort required by system administrators to trouble shot transaction processing difficulties in a large distributed I / T environment by monitoring system component performance and computing operational performance threshold limits based on dependency graphs for the system. Using this data, a prioritized list of suspect components for the I / T system is generated.
Owner:GLOBALFOUNDRIES INC
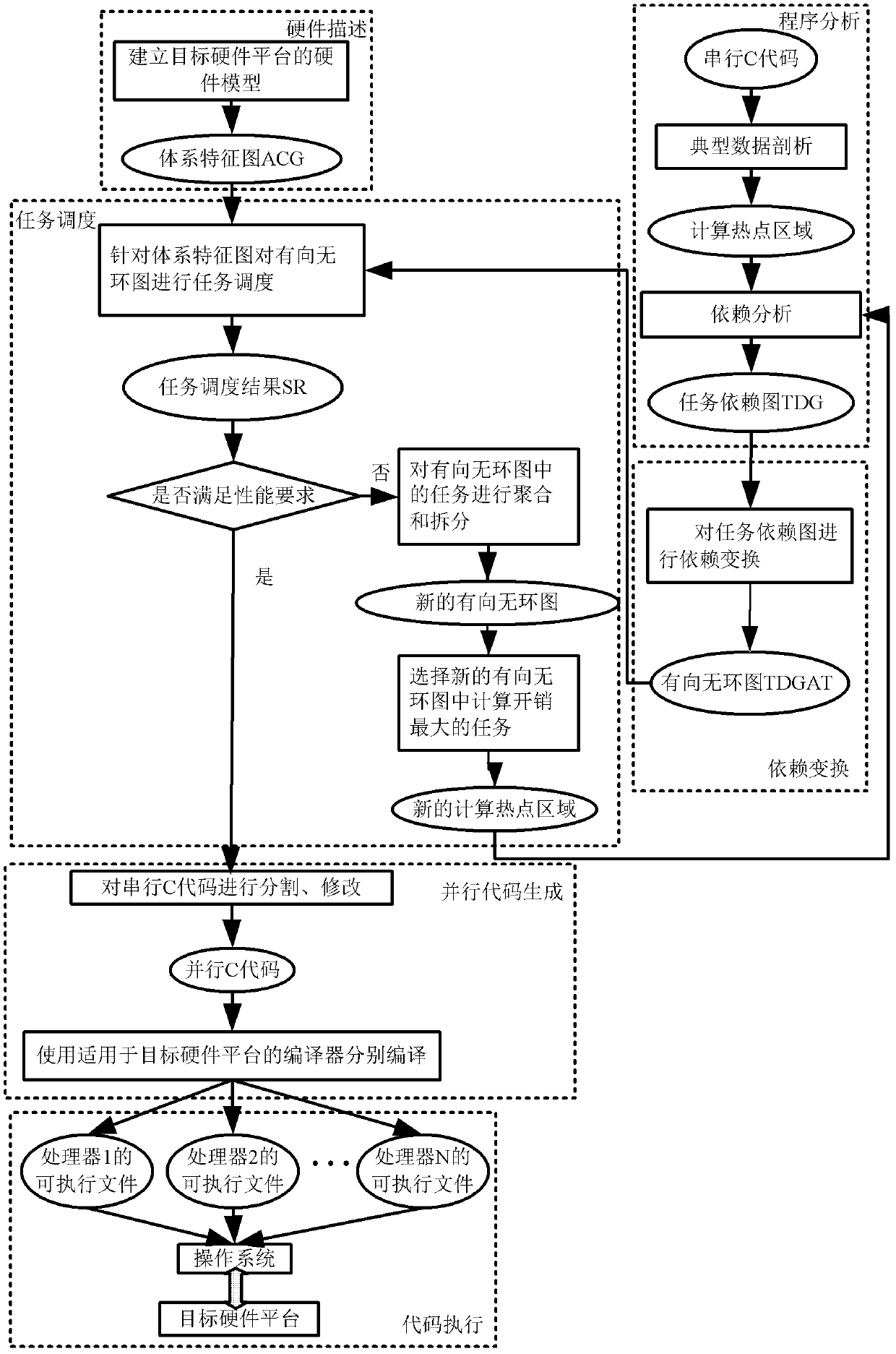
Pipeline parallelization method for coarse-grained streaming application
InactiveCN103377035AEliminate dependenciesEliminate untieProgram initiation/switchingConcurrent instruction executionDependency graphTask dependency
The invention discloses a pipeline parallelization method for coarse-grained streaming applications. The pipeline parallelization method includes performing classic data profiling and dependency analysis on serial C-codes to acquire a task dependence graph, performing dependence transformation on the task dependence graph to acquire a directed acyclic graph, building a system feature graph, performing task scheduling on the directed acyclic graph according to the system feature graph and judging whether a task scheduling result meets performance requirements or not, if not, then aggregating and splitting task of the directed acyclic graph to acquire a new directed acyclic graph, selecting and calculating the highest-cost task of the new directed acyclic graph to acquire a new calculated hot spot region, returning to performing the dependency analysis again, segmenting and modifying the serial C-codes according to the task scheduling result so as to obtain parallelized C-codes, encoding to generate parallel executable files through an encoder, and loading the parallel executable files to a target hardware platform to execute. The pipeline parallelization method is adaptable to multilayer nested loop structures and capable of extracting parallelism of the multilayer loop.
Owner:ZHEJIANG UNIV
Method and apparatus for integrated instruction scheduling and register allocation in a postoptimizer
The present invention describes a method of efficiently optimizing instruction scheduling and register allocation in a post optimizer. The method removes false register dependencies between pipelined instructions by building an incremental (partial) interference graph of register allocation for scheduled instructions. False dependency graph indicates the amount of parallelism in the data flow graph. The incremental interference graph uses a mix of virtual and physical registers. The interference graph is built incrementally as an instruction schedular schedules each instruction. The optimization is done incrementally on localized code. The physical register mapping is maximized and virtual registers are created on demand basis.
Owner:ORACLE INT CORP
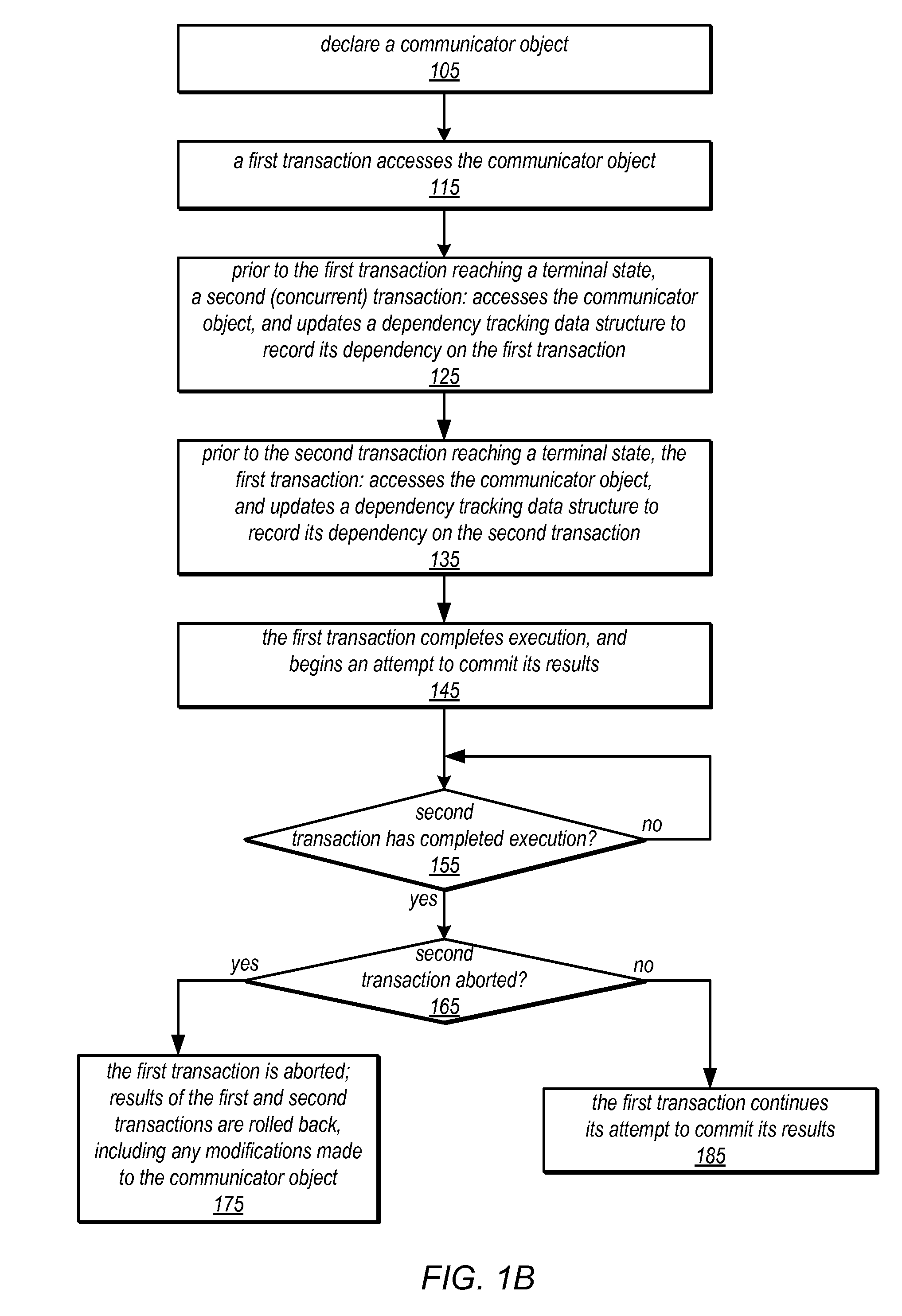
System and Method for Communication Between Concurrent Transactions Using Transaction Communicator Objects
ActiveUS20120005530A1Expand application spaceEnsure isolationDigital computer detailsRedundant operation error correctionTransactional memoryDependency graph
Transactional memory implementations may be extended to include special transaction communicator objects through which concurrent transactions can communicate. Changes by a first transaction to a communicator may be visible to concurrent transactions before the first transaction commits. Although isolation of transactions may be compromised by such communication, the effects of this compromise may be limited by tracking dependencies among transactions, and preventing any transaction from committing unless every transaction whose changes it has observed also commits. For example, mutually dependent or cyclically dependent transactions may commit or abort together. Transactions that do not communicate with each other may remain isolated. The system may provide a communicator-isolating transaction that ensures isolation even for accesses to communicators, which may be implemented using nesting transactions. True (e.g., read-after-write) dependencies, ordering (e.g., write-after-write) dependencies, and / or anti-dependencies (e.g., write-after-read dependencies) may be tracked, and a resulting dependency graph may be perused by the commit protocol.
Owner:ORACLE INT CORP
Database-managed image processing
ActiveUS20070185881A1Quick selectionEasy to collectDigital data information retrievalDigital data processing detailsImaging processingDatabase access
A method, apparatus, system, and article of manufacture provide the ability to track the processing of image data in a collaborative environment. A dependency graph that represents an image composition is obtained. Metadata for each element of the dependency graph are stored in a database that is accessible across a network to multiple users. Access to the database is controlled to allow the multiple users to access the dependency graph via the database simultaneously.
Owner:AUTODESK INC
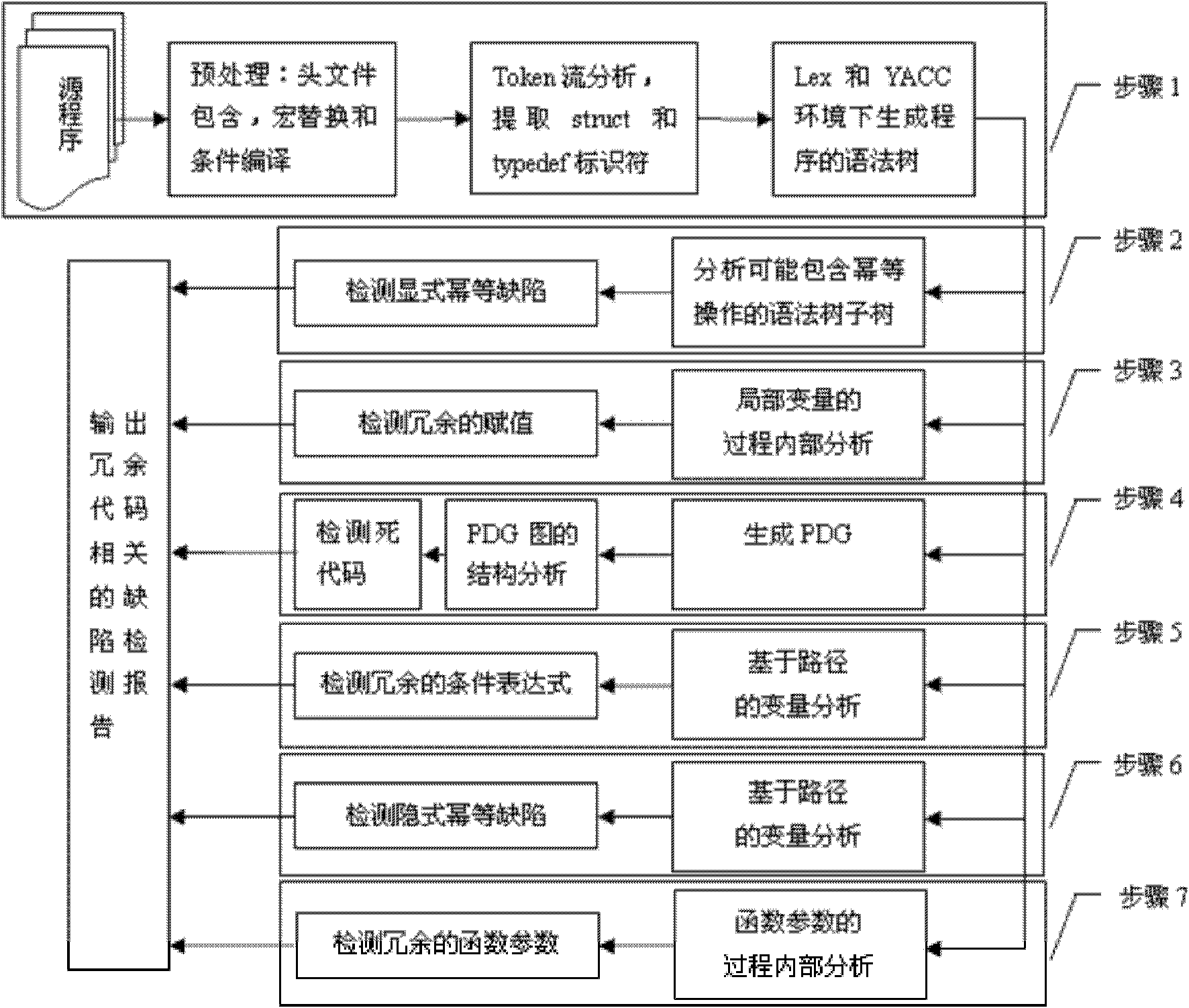
Method for detecting redundant code defects based on static analysis
InactiveCN102231134AReduce false detection rateReduce missed detection rateSoftware testing/debuggingStatic timing analysisAbstract syntax tree
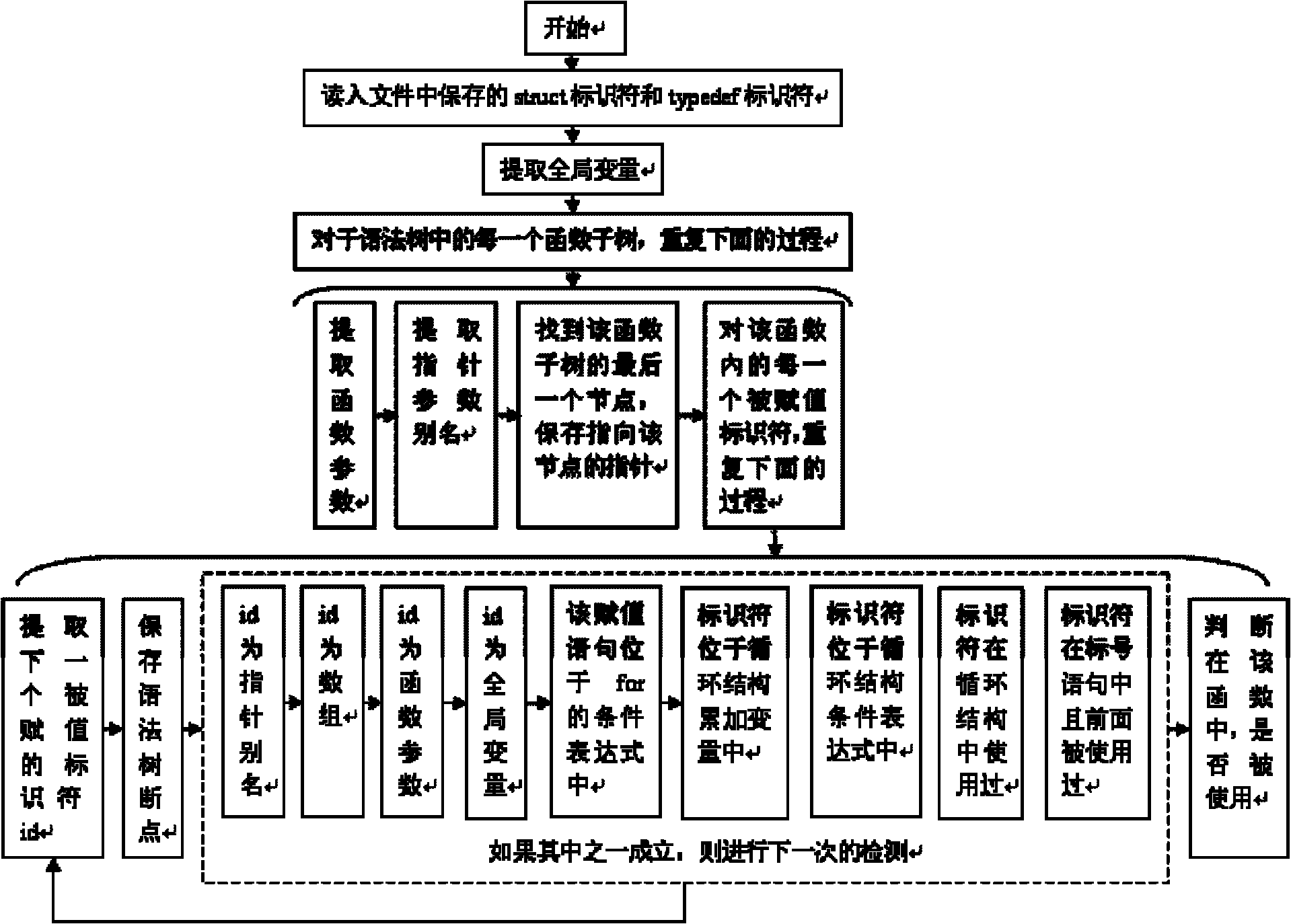
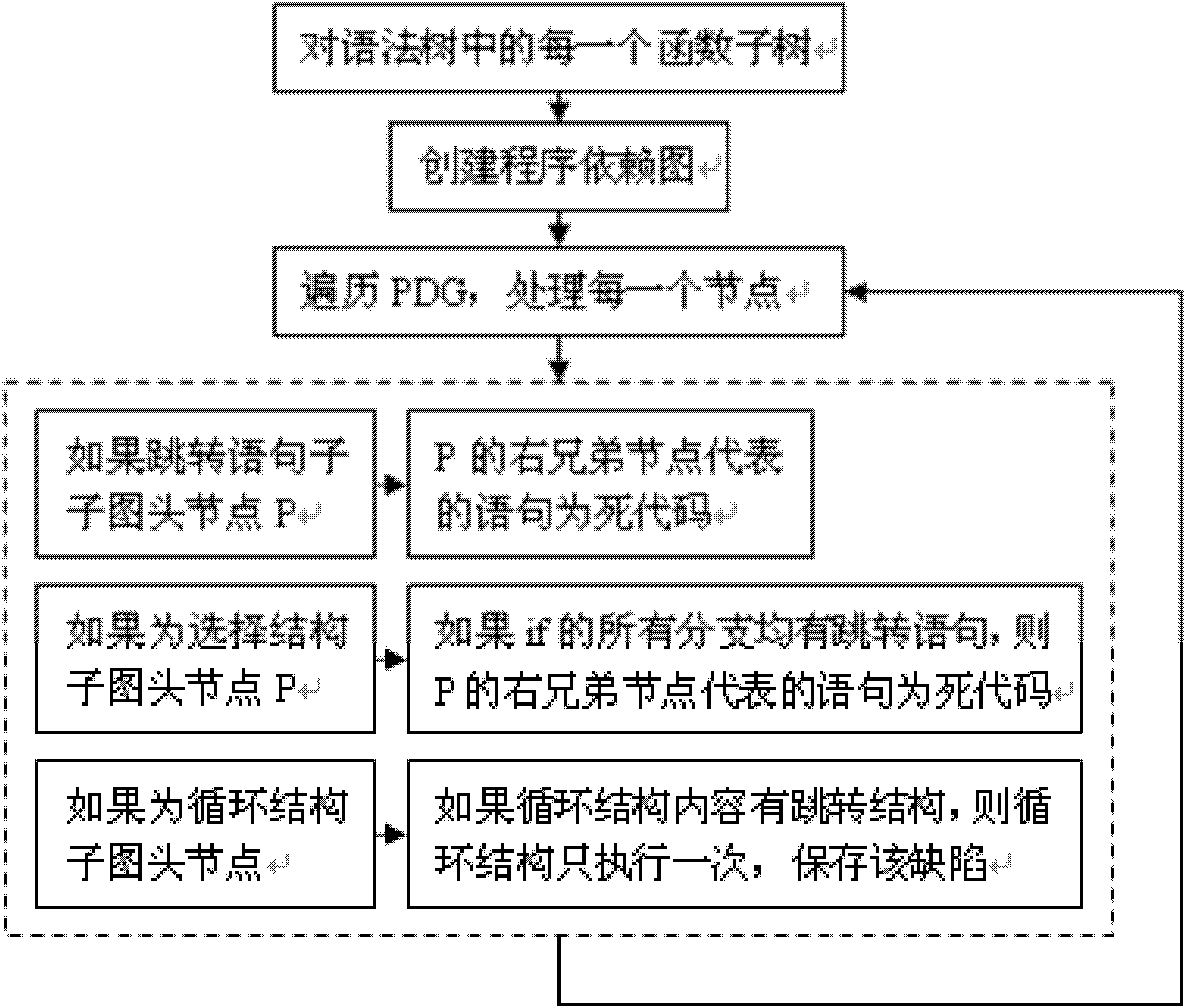
The invention discloses a method for detecting redundant code defects based on static analysis, for solving the problem lacking of a mature method for detecting redundant codes and related defects currently. The method comprises the following steps of: 1, inputting a program to be tested; analyzing the program into an abstract syntax tree; 2, analyzing statements possibly including operations of explicit power and the like; detecting the operations of the explicit power and the like; 3, for locally defined variables, detecting redundant assignment statements by using an internal process analysis method; 4, traversing the abstract syntax tree of the program; searching structures including the defects on the basis of a standardized program dependency graph; detecting dead codes; 5, detecting redundant conditional expressions; 6, detecting operations of implicit power and the like; and 7, detecting redundant function parameters; and giving a defect detection report according to the six defect detection results obtained in the steps 2-7. The method disclosed by the invention is applicable for analyzing large-scale program codes.
Owner:HARBIN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com