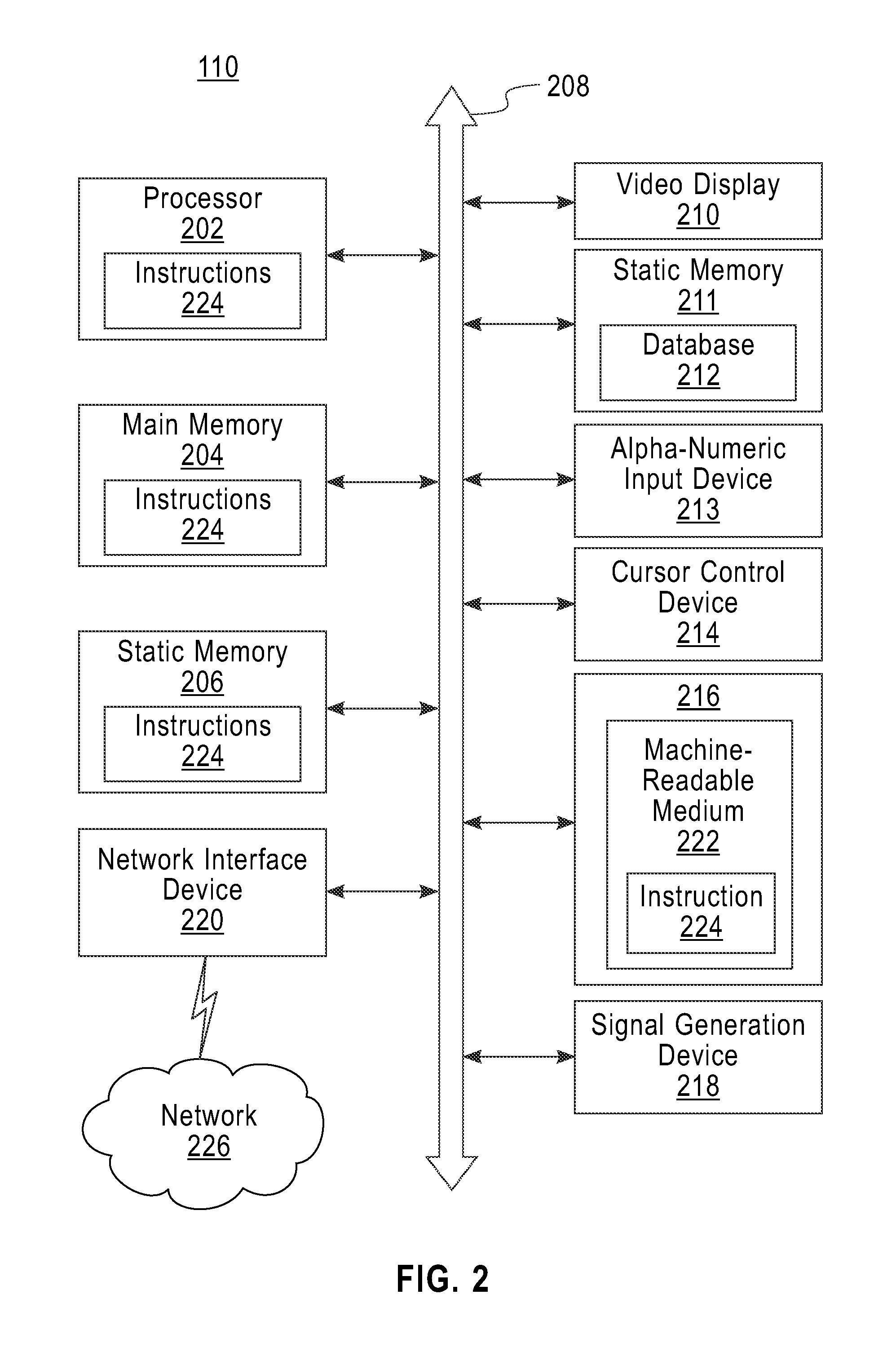
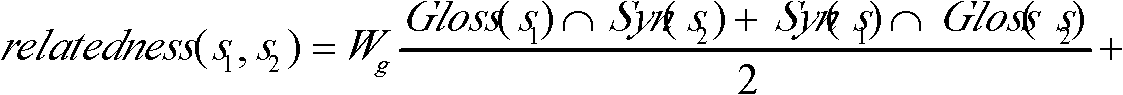Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
438 results about "Backtracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Backtracking is a general algorithm for finding all (or some) solutions to some computational problems, notably constraint satisfaction problems, that incrementally builds candidates to the solutions, and abandons a candidate ("backtracks") as soon as it determines that the candidate cannot possibly be completed to a valid solution.
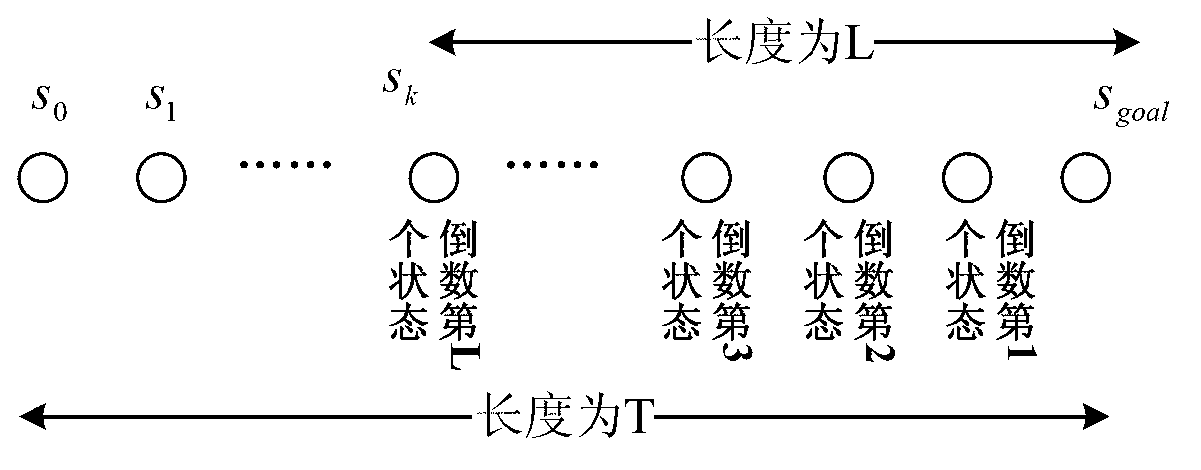
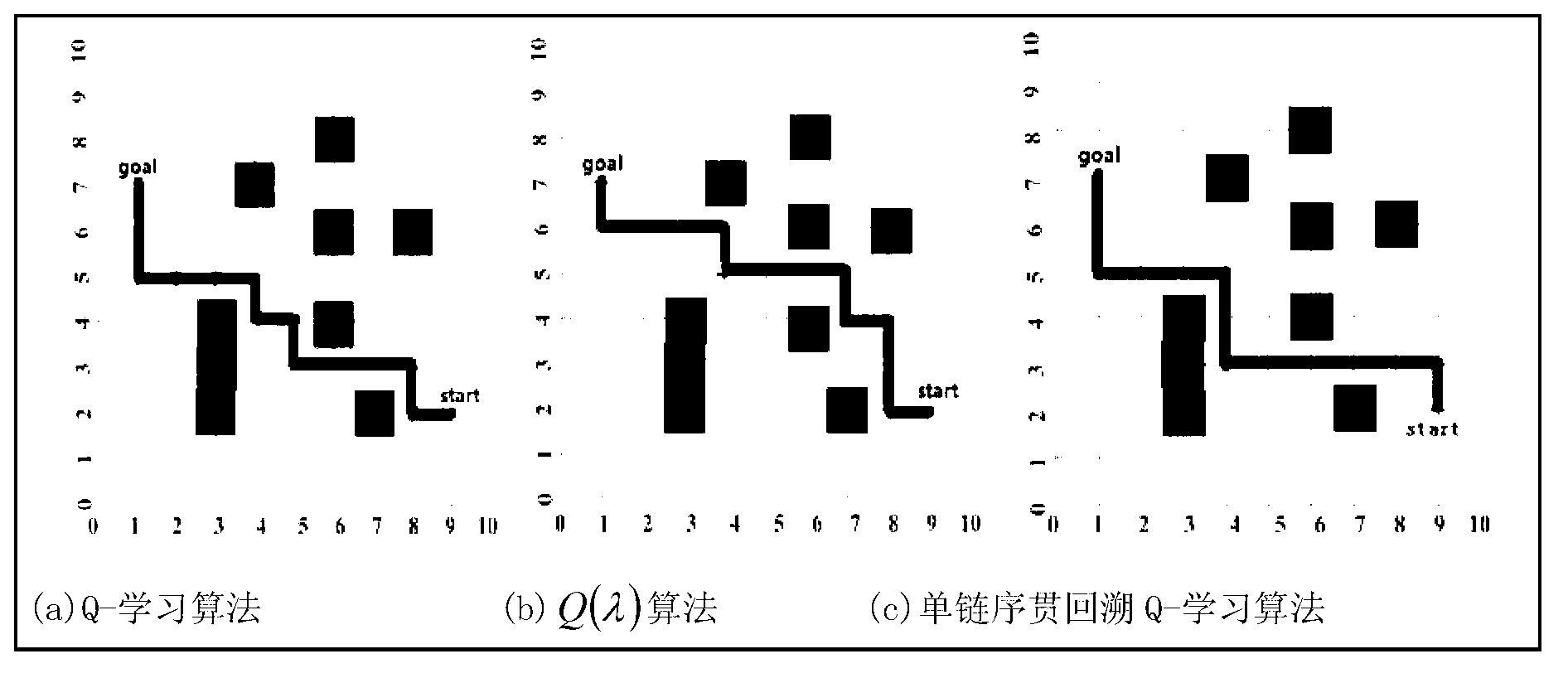
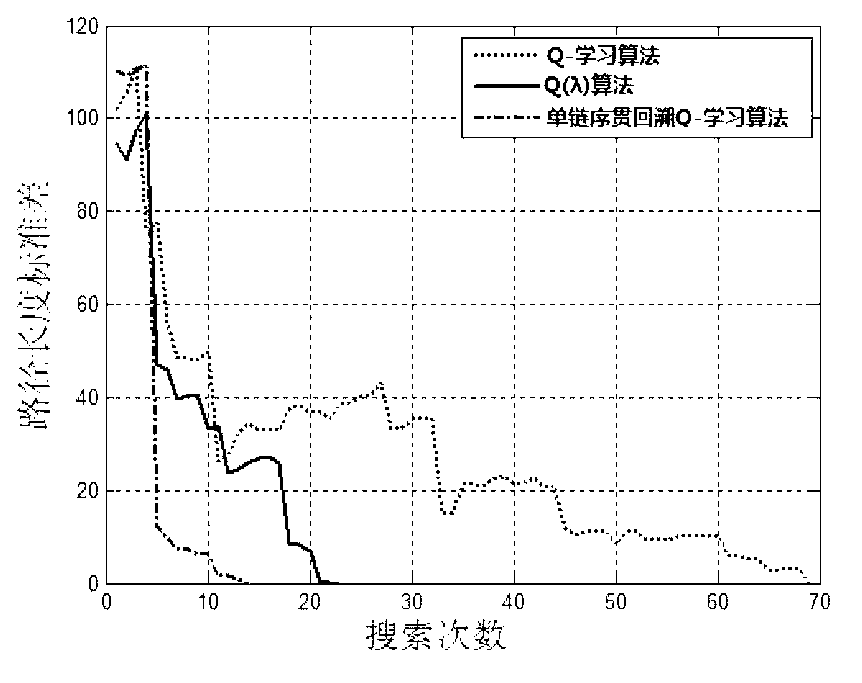
Mobile robot path planning algorithm based on single-chain sequential backtracking Q-learning
InactiveCN102799179AImprove learning efficiencyShort learning timePosition/course control in two dimensionsMobile robots path planningPath plan
The invention provides a mobile robot path planning algorithm based on single-chain sequential backtracking Q-learning. According to the mobile robot path planning algorithm based on the single-chain sequential backtracking Q-learning, a two-dimensional environment is expressed by using a grid method, each environment area block corresponds to a discrete location, the state of a mobile robot at some moment is expressed by an environment location where the robot is located, the search of each step of the mobile robot is based on a Q-learning iterative formula of a non-deterministic Markov decision process, progressively sequential backtracking is carried out from the Q value of the tail end of a single chain, namely the current state, to the Q value of the head end of the single chain until a target state is reached, the mobile robot cyclically and repeatedly finds out paths to the target state from an original state, the search of each step is carried out according to the steps, and Q values of states are continuously iterated and optimized until the Q values are converged. The mobile robot path planning algorithm based on the single-chain sequential backtracking Q-learning has the advantages that the number of steps required for optimal path searching is far less than that of a classic Q-learning algorithm and a Q(lambda) algorithm, the learning time is shorter, and the learning efficiency is higher; and particularly for large environments, the mobile robot path planning algorithm based on the single-chain sequential backtracking Q-learning has more obvious advantages.
Owner:SHANDONG UNIV
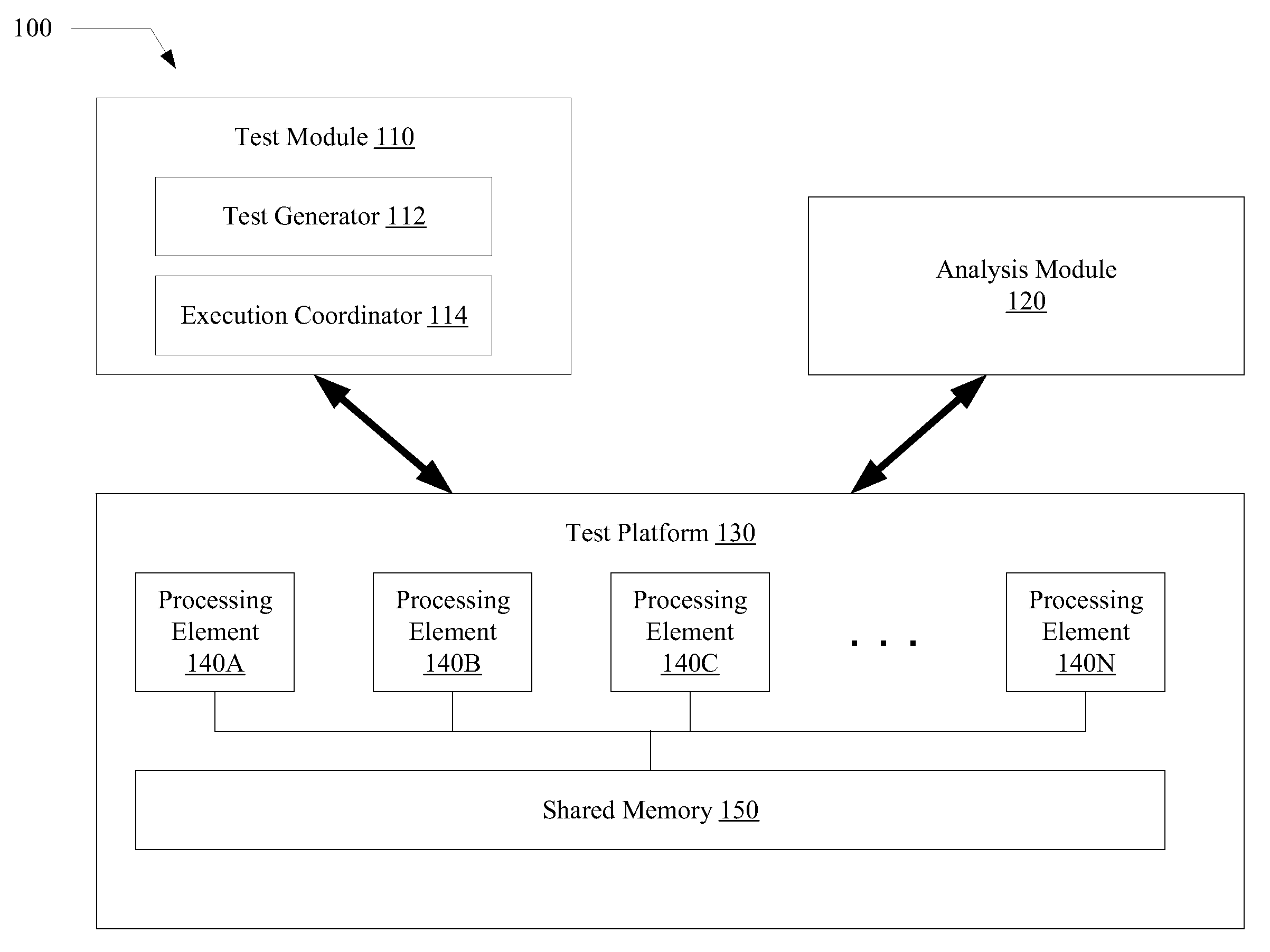
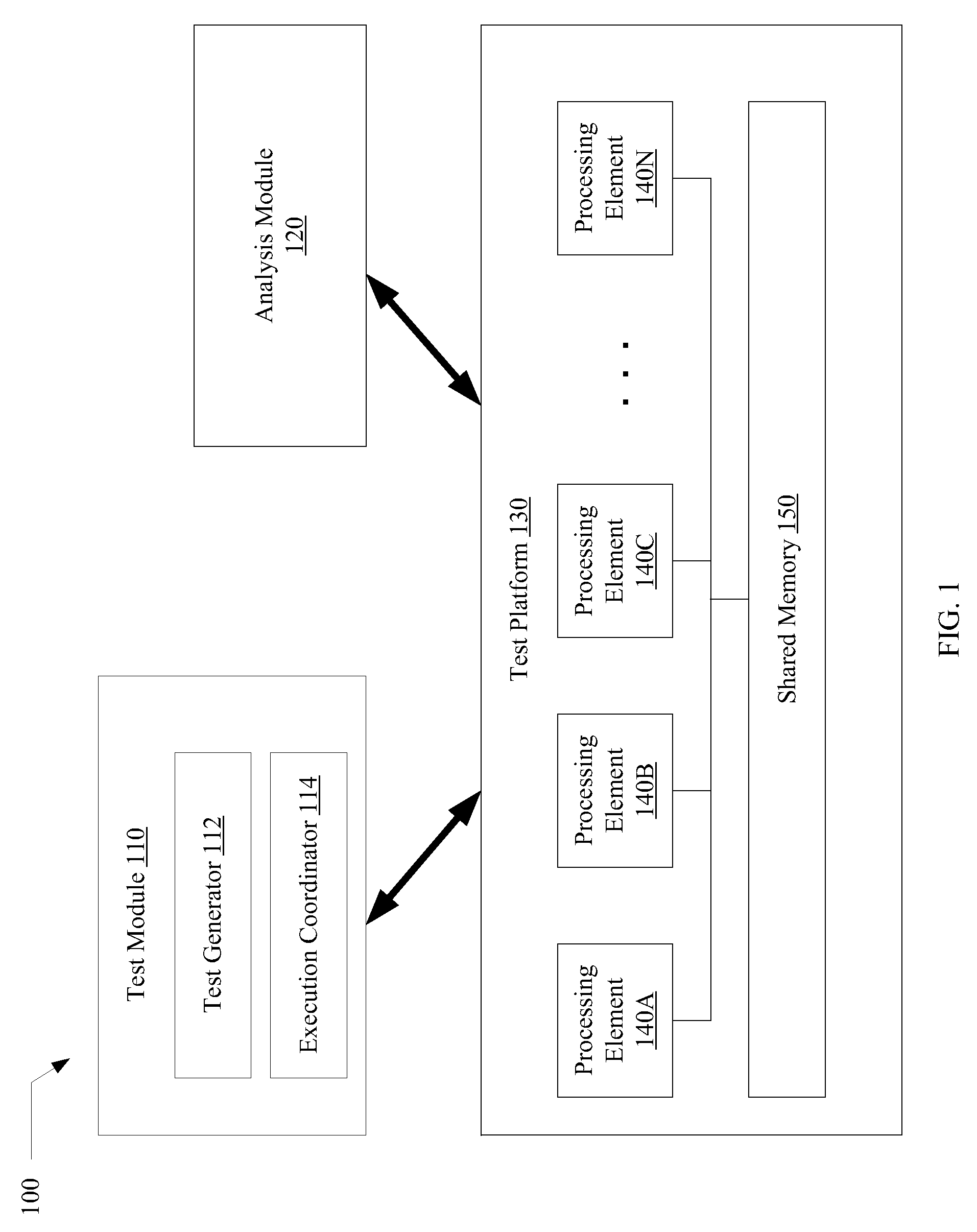
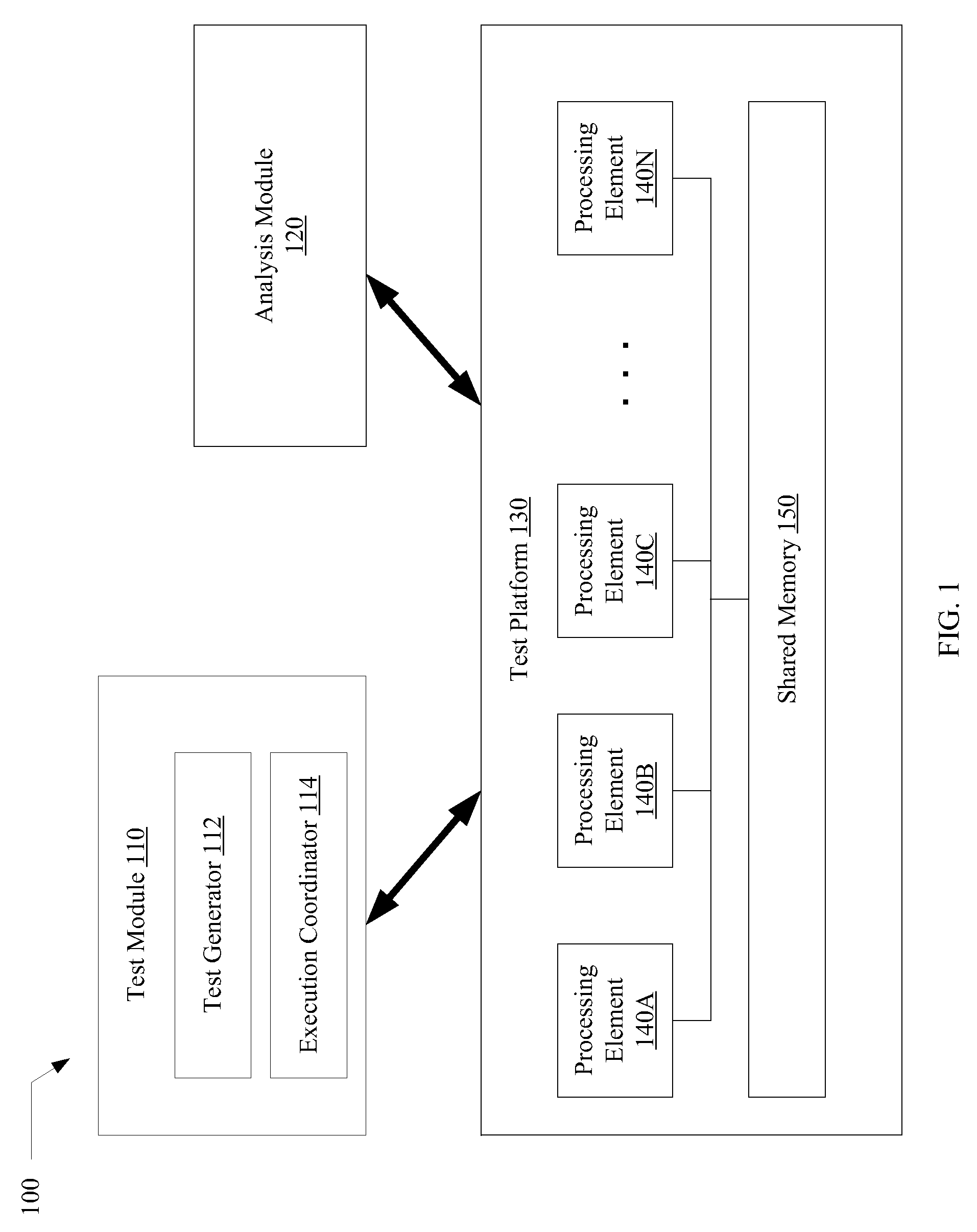
Verification of memory consistency and transactional memory
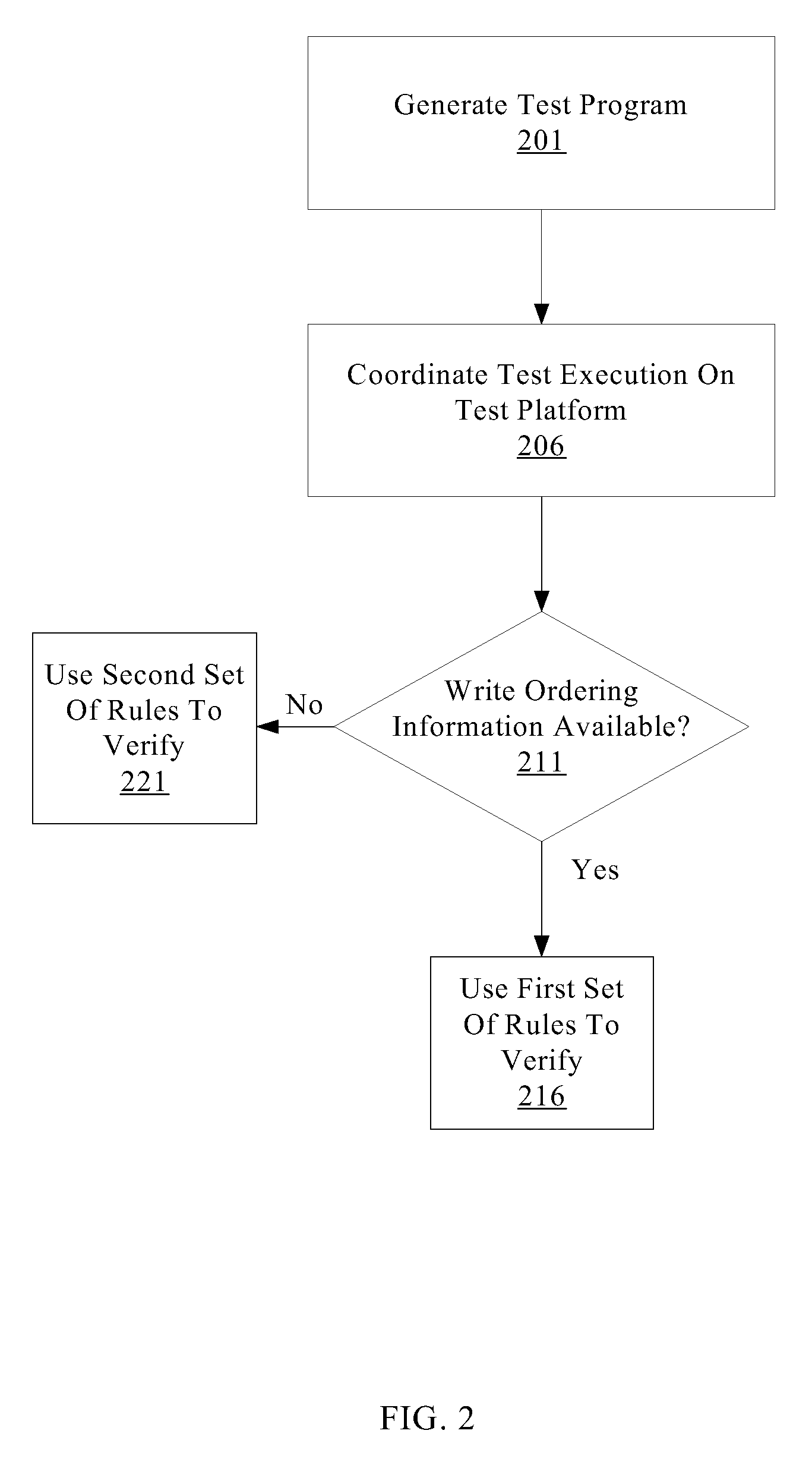
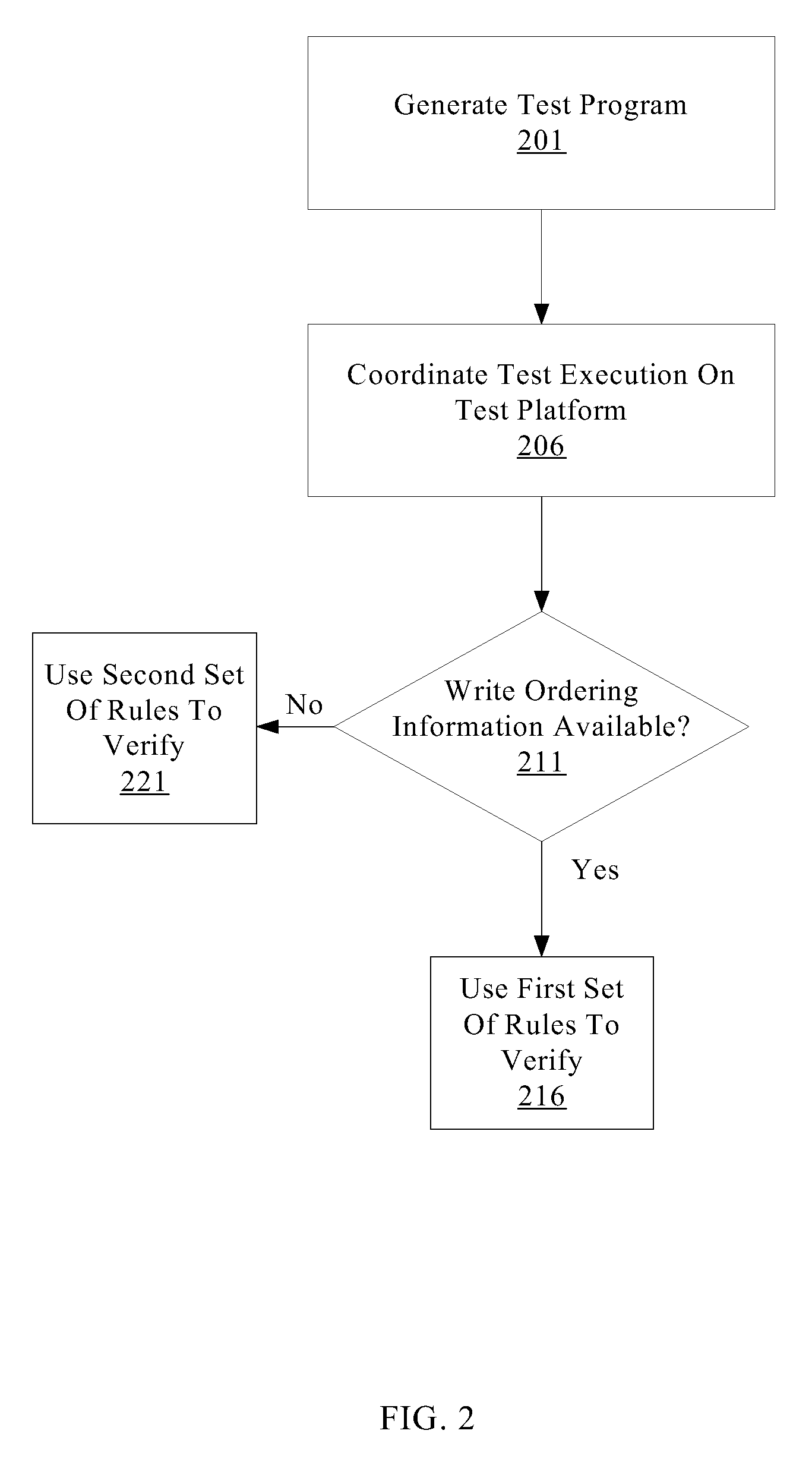
A system for efficiently verifying compliance with a memory consistency model includes a test module and an analysis module. The test module may coordinate an execution of a multithreaded test program on a test platform. If the test platform provides an indication of the order in which writes from multiple processing elements are performed at shared memory locations, the analysis module may use a first set of rules to verify that the results of the execution correspond to a valid ordering of events according to a memory consistency model. If the test platform does not provide an indication of write ordering, the analysis module may use a second set of rules to verify compliance with the memory consistency model. Further, a backtracking search may be performed to find a valid ordering if such ordering exists or show that none exists and, hence, confirm whether or not the results comply with the given memory consistency model.
Owner:ORACLE INT CORP
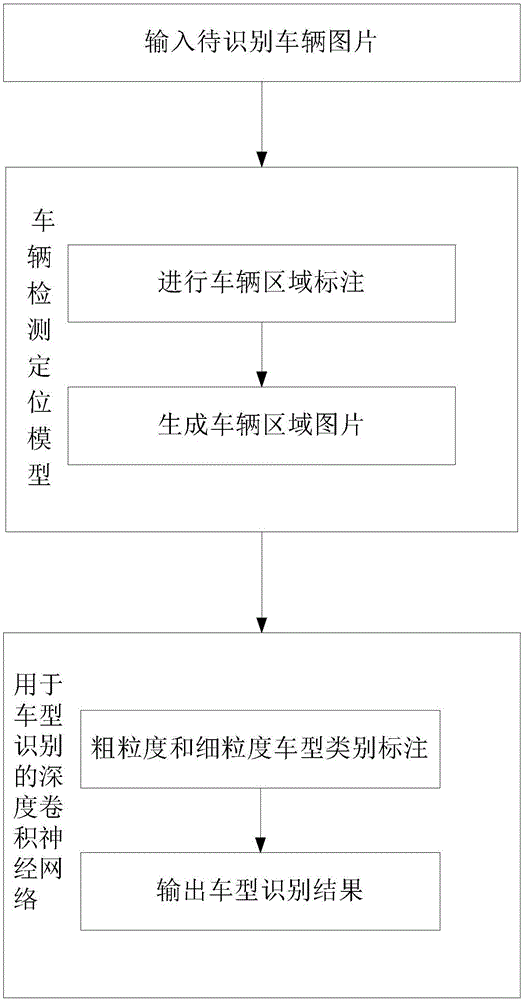
Vehicle model recognition model construction method based on depth learning and vehicle model recognition method based on depth learning
ActiveCN106570477AFast convergenceImprove classification accuracyCharacter and pattern recognitionNeural learning methodsNetwork ConvergenceNetwork structure
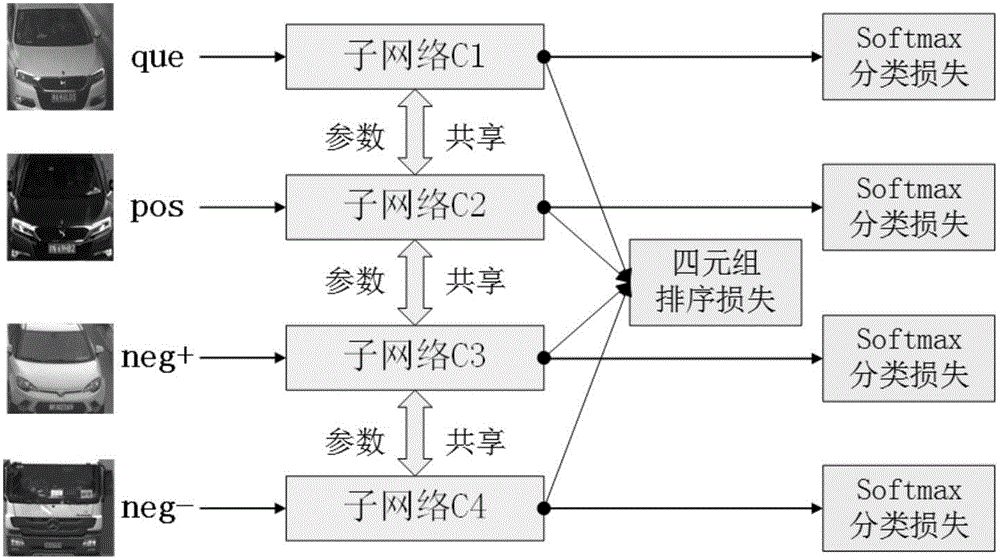
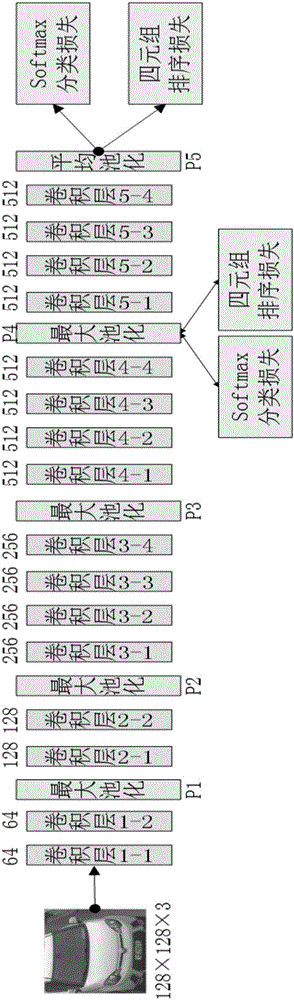
The invention provides a vehicle model recognition model construction method based on depth learning. According to the method, a deep convolution neural network structure is designed for vehicle model recognition; softmax classification loss and sorting loss which is built through a vehicle model type hierarchical structure and is based on tetrad are used together to supervise the deep convolution neural network training; and intra-class differences and inter-class differences of vehicle models are constrained at the same time to learn character representation with rich semantic information and a discriminating classifier. In order to speed up network convergence, an online difficult sample mining policy and an improved gradient backtracking optimization algorithm are used, which greatly reduces the network training time. The invention further provides a vehicle model recognition method based on depth learning. The vehicle model recognition method uses the model constructed by the model construction method to recognize the vehicle type in a vehicle picture, which effectively improves the vehicle model classification accuracy.
Owner:OBJECTEYE (BEIJING) TECH CO LTD
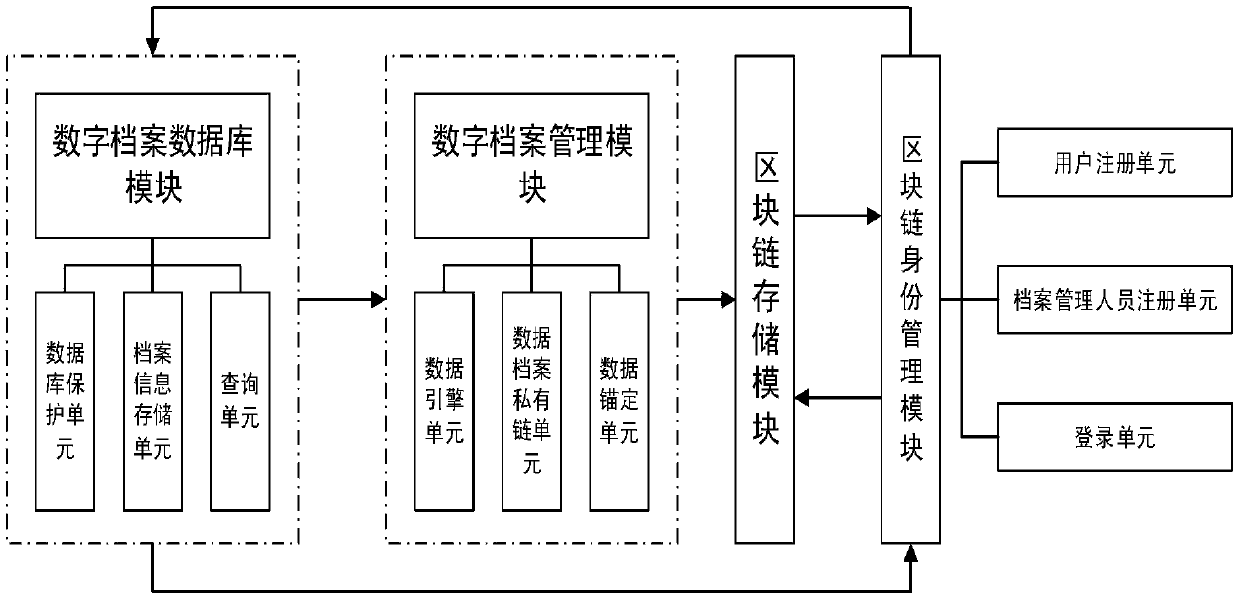
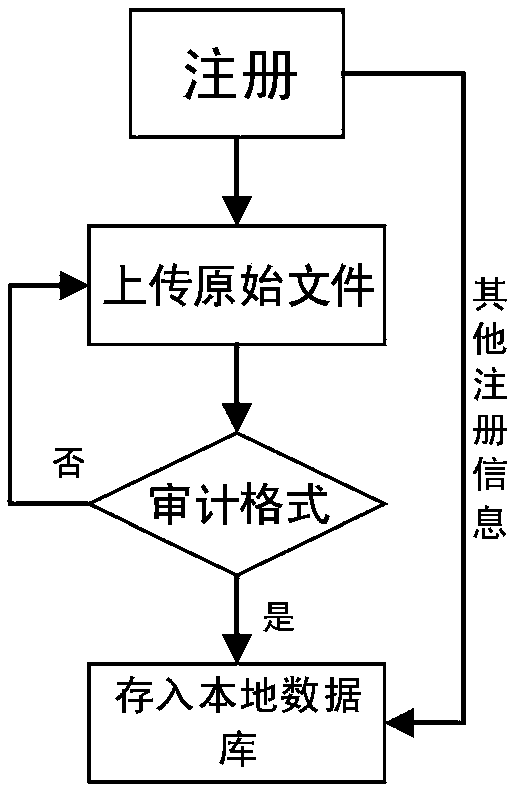
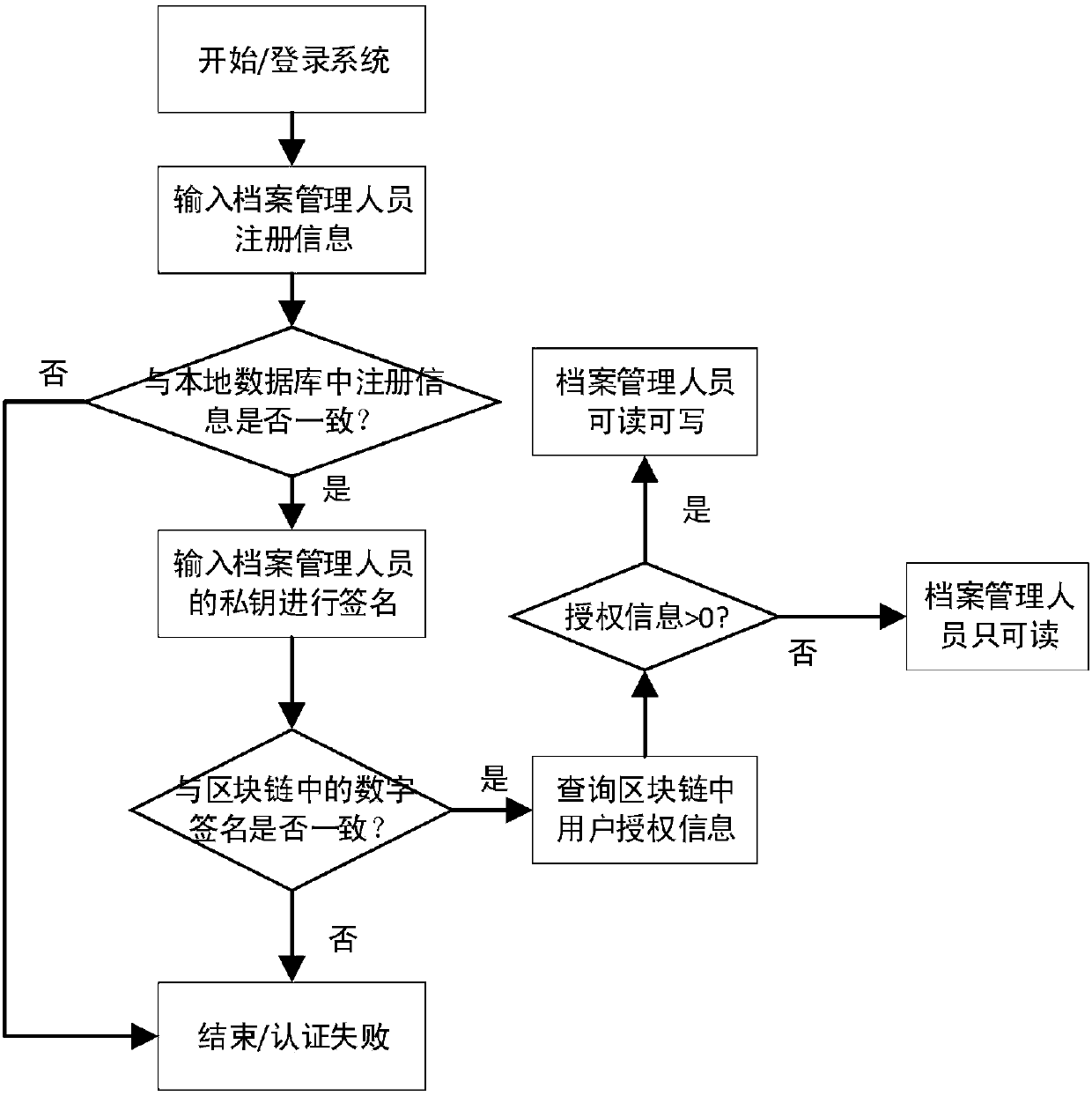
Digital archives management method and system based on blockchain technology
ActiveCN107947922AOvercome the complexity of the management processReduce the consumption of manpower and material resourcesKey distribution for secure communicationSpecial data processing applicationsPrivacy protectionDigital rights management
The invention discloses a digital archives management system based on a blockchain technology and a method thereof. The system comprises a database protection unit, an archives information storage unit, a query unit, a data engine unit, a digital archives private chain unit, a data anchoring unit, a user registration unit, an archivist registration unit, a login unit and a blockchain storage module. The scheme of the invention aims to digitize the existing archives management, realize blockchain storage of archives information, and realize authority management and operation backtracking of archivists, and thus the current archives information management process can be simplified, non-tampered archives information can be realized, and the privacy protection of the archives information can be enhanced.
Owner:安徽中科晶格技术有限公司
Verification of memory consistency and transactional memory
ActiveUS20080288834A1Efficiently verifying complianceError detection/correctionStatic storageProcessing elementTest platform
A system for efficiently verifying compliance with a memory consistency model includes a test module and an analysis module. The test module may coordinate an execution of a multithreaded test program on a test platform. If the test platform provides an indication of the order in which writes from multiple processing elements are performed at shared memory locations, the analysis module may use a first set of rules to verify that the results of the execution correspond to a valid ordering of events according to a memory consistency model. If the test platform does not provide an indication of write ordering, the analysis module may use a second set of rules to verify compliance with the memory consistency model. Further, a backtracking search may be performed to find a valid ordering if such ordering exists or show that none exists and, hence, confirm whether or not the results comply with the given memory consistency model.
Owner:ORACLE INT CORP
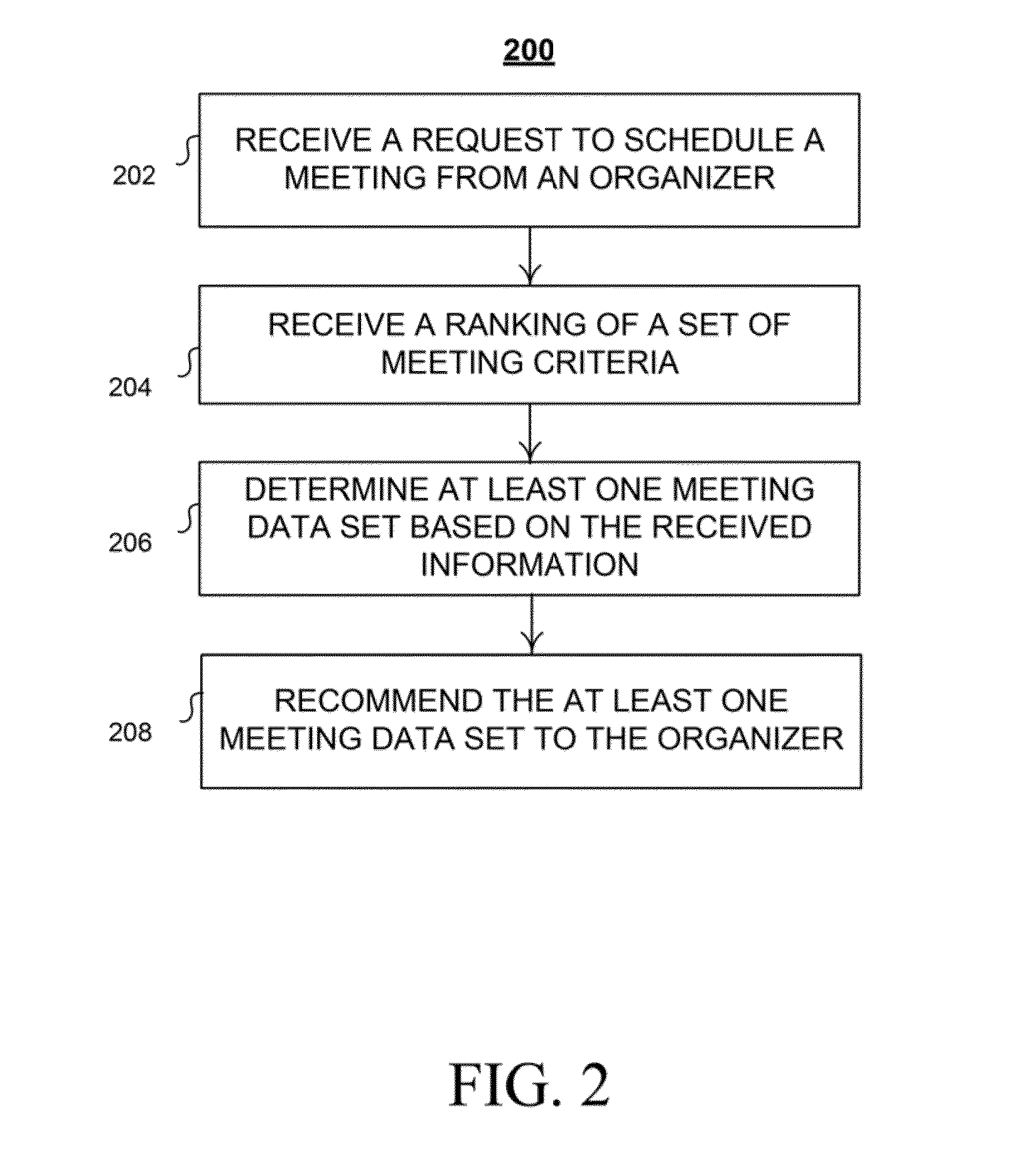
Method and system for scheduling a meeting
A method is provided for scheduling a meeting. The method includes receiving a request from an organizer to schedule a meeting, executing a constraint satisfaction algorithm to determine at least one meeting data set comprising a value for at least one variable in a set of variables. The meeting data set defines at least one of a proposed time, room or participants for the meeting. Executing the constraint satisfaction algorithm involves performing a backtracking search within a solution domain to determine the meeting data set for the set of variables that satisfies a set of meeting constraints. If no meeting data set is determined, the set of variables and the solution domain can be revised. A next backtracking search can be performed to determine the meeting data set for the revised set of variables in the revised solution domain that satisfies one or more of the meeting constraints.
Owner:FMR CORP
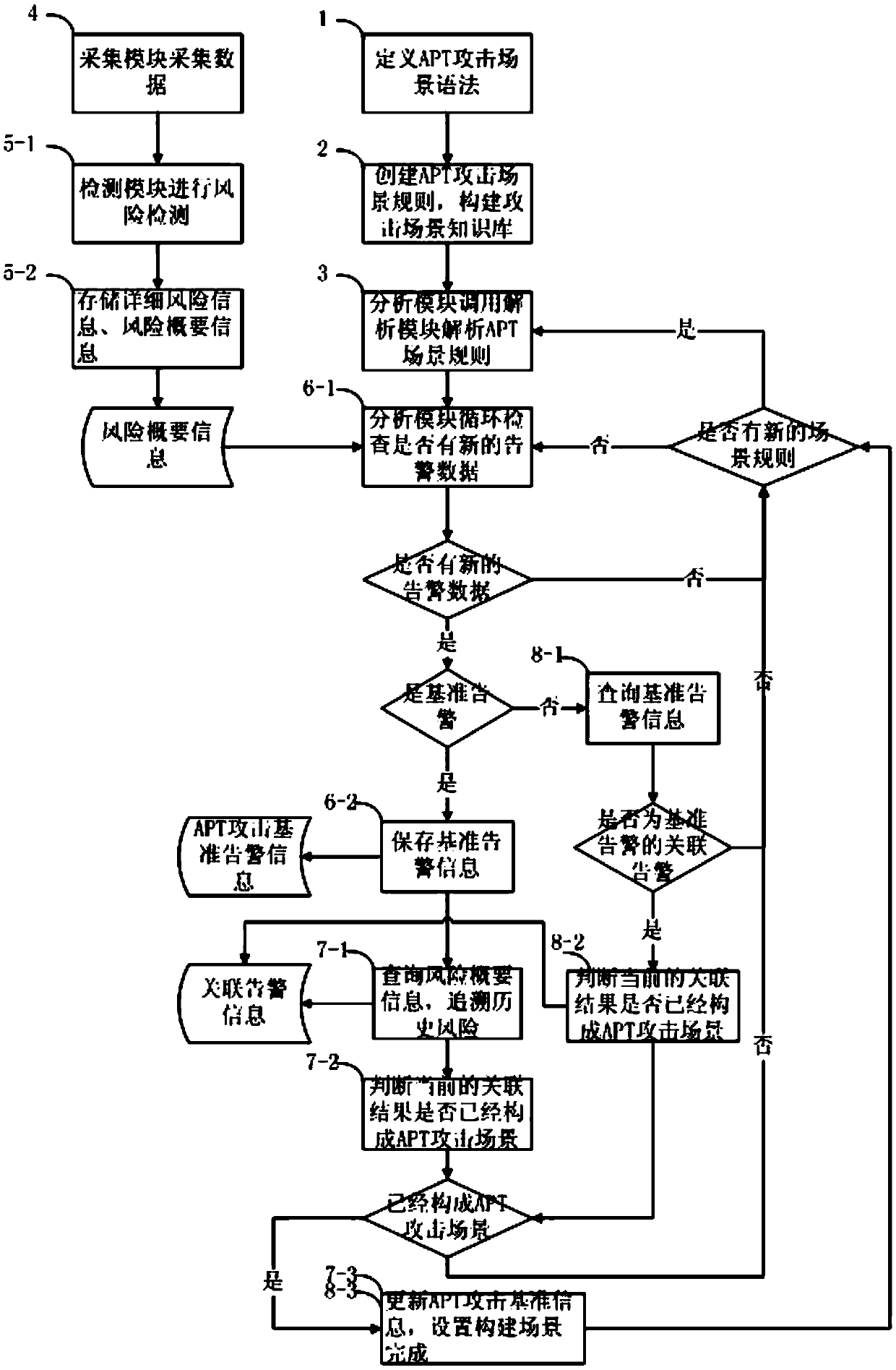
Rule-based detection method of ATP attack behavior
The invention relates to the field of APT detection, and aims at providing a rule-based detection method of an ATP attack behavior. The rule-based detection method of the ATP attack behavior comprises the following steps: defining grammar used for creating an APT attack scene rule; creating the APT attack scene rule, and constituting an APT attack scene knowledge base; dispatching a rule analysis module to analyze and load the APT attack scene rule by an analysis module; collecting full flow of an application layer protocol by a collection module to obtain flow data; screening data; analyzing important alarm; identifying a behavior; and constituting processing of ATP attack behavior failure. With regard to the ATP attack behavior, multiple attach exposure points always exist in the entire attach process, backtracking association is carried out on related flow by the rule-based detection method provided by the invention on this basis, the traditional situation of matching features based on a single time point is changed, and association analysis is carried out on the data of a long time window to identify the complete attack intention of an attacker.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
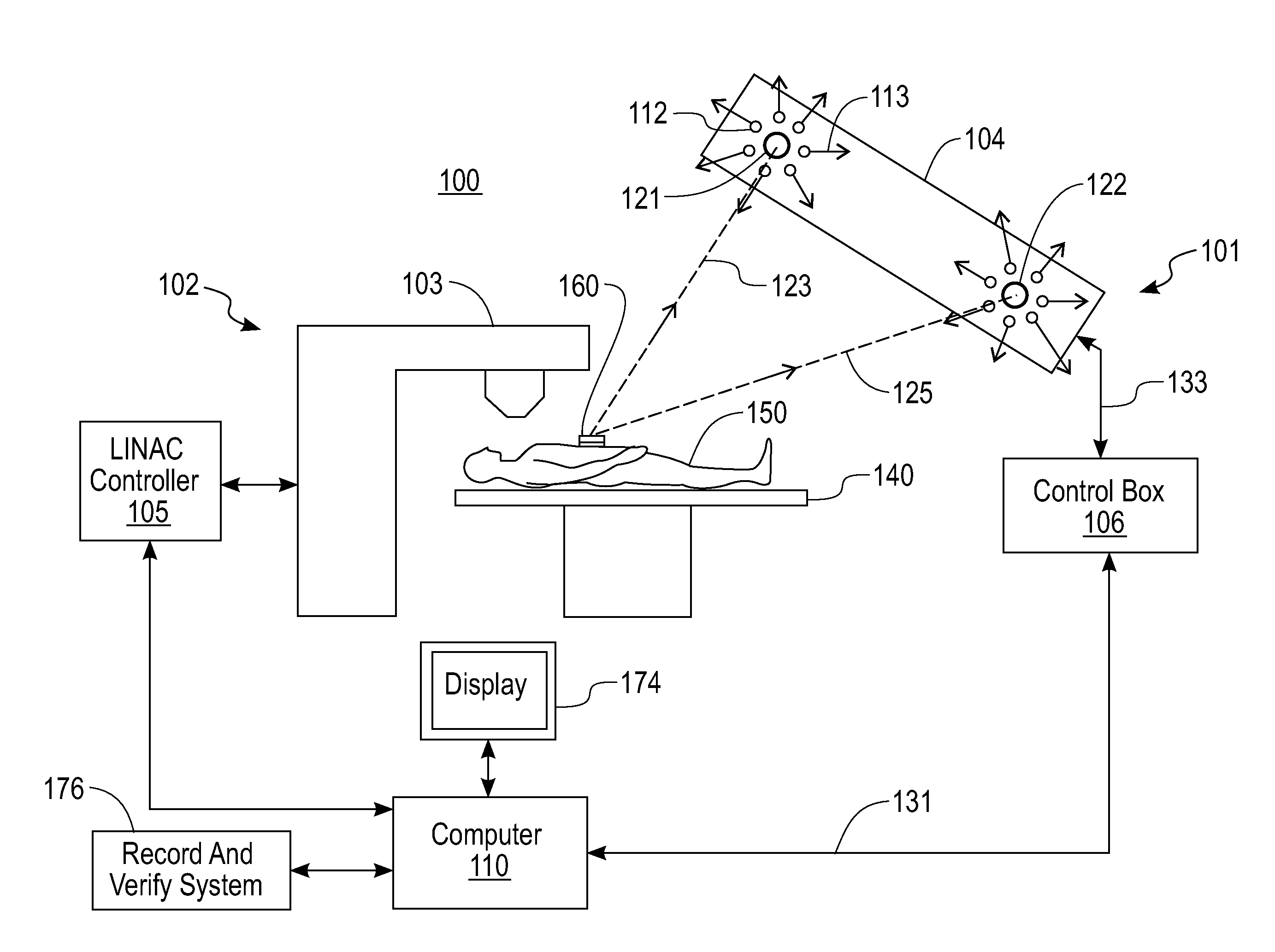
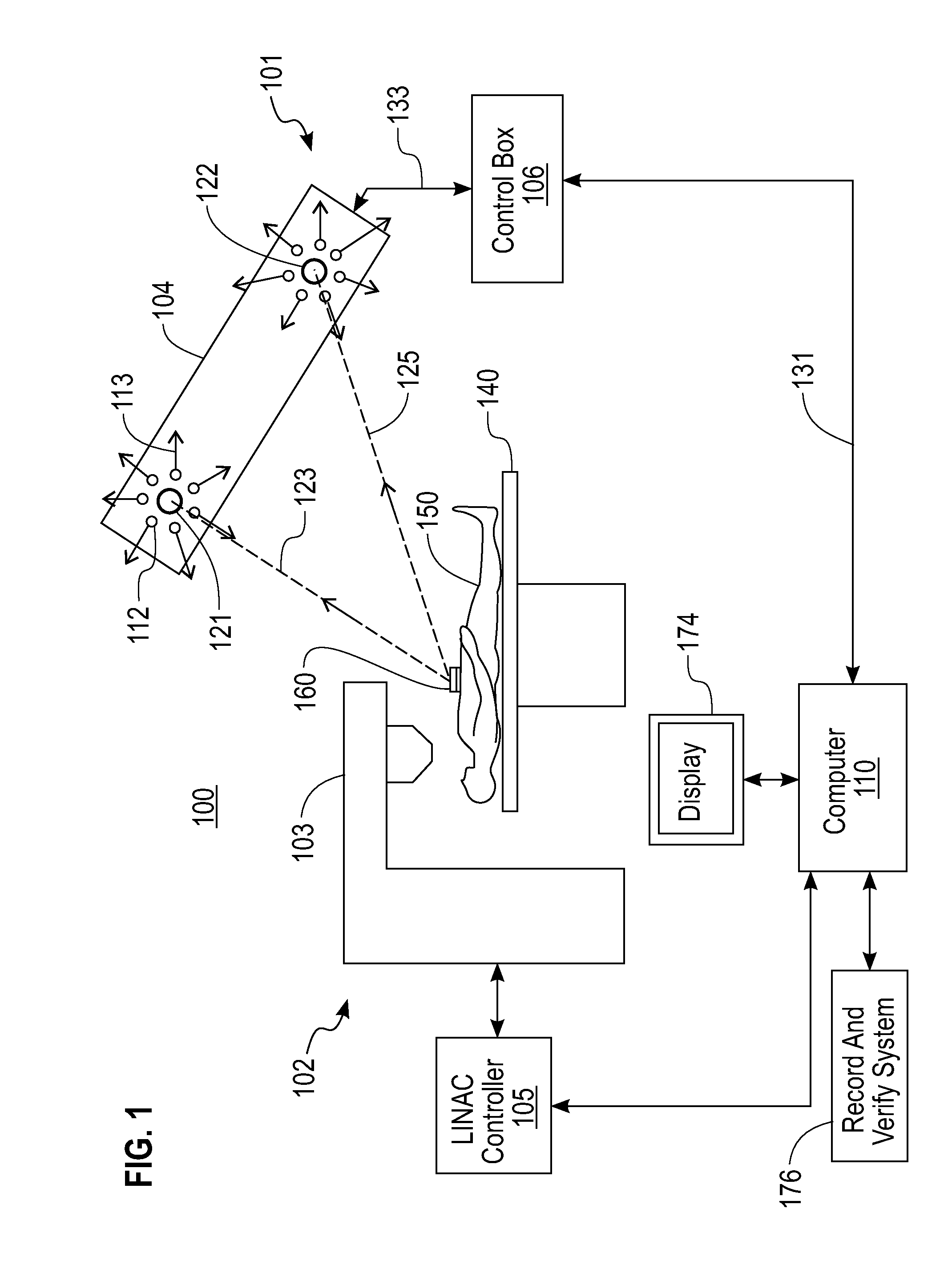
Ambiguity-free optical tracking system
An ambiguity-free optical tracking system (100) includes a position sensor unit (104), a control box (106), a computer (110) and software. The position sensor unit includes two cameras (121 and 122) that track a plurality of individual infra-red reflecting markers (160) affixed on a patient's skin. Coordinates of the cameras in a coordinate system of the cameras are determined as part of a system calibration process by intentionally creating ambiguous markers with two true markers. Using this information, an ambiguity elimination algorithm automatically identifies and eliminates ambiguous markers. A recursive backtracking algorithm builds a one-to-one correspondence between reference markers and markers optically observed during treatment. By utilizing a concept of null markers, the backtracking algorithm deals with missing, misplaced and occluded markers.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Test program control stream path set creation method based on base path
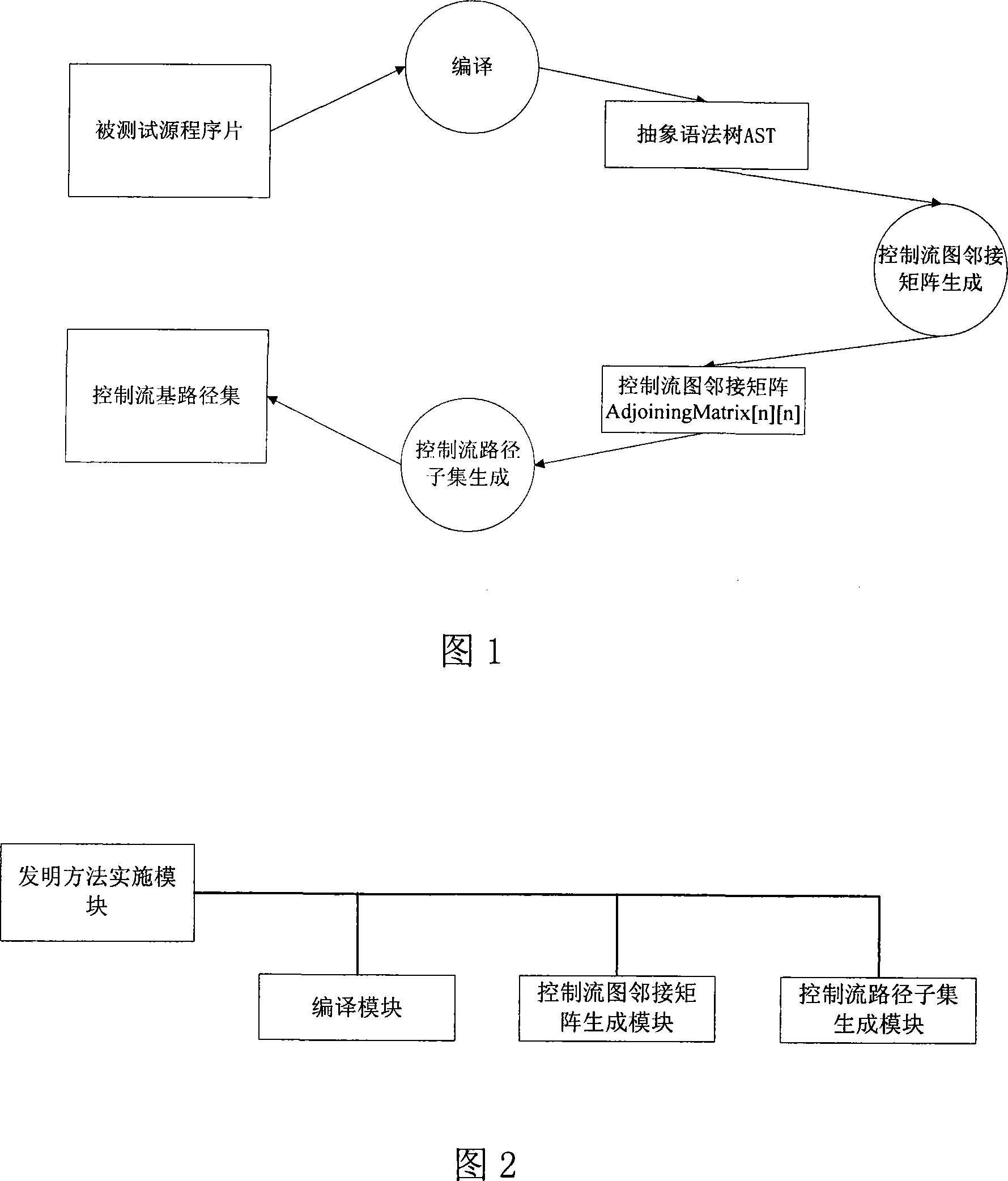
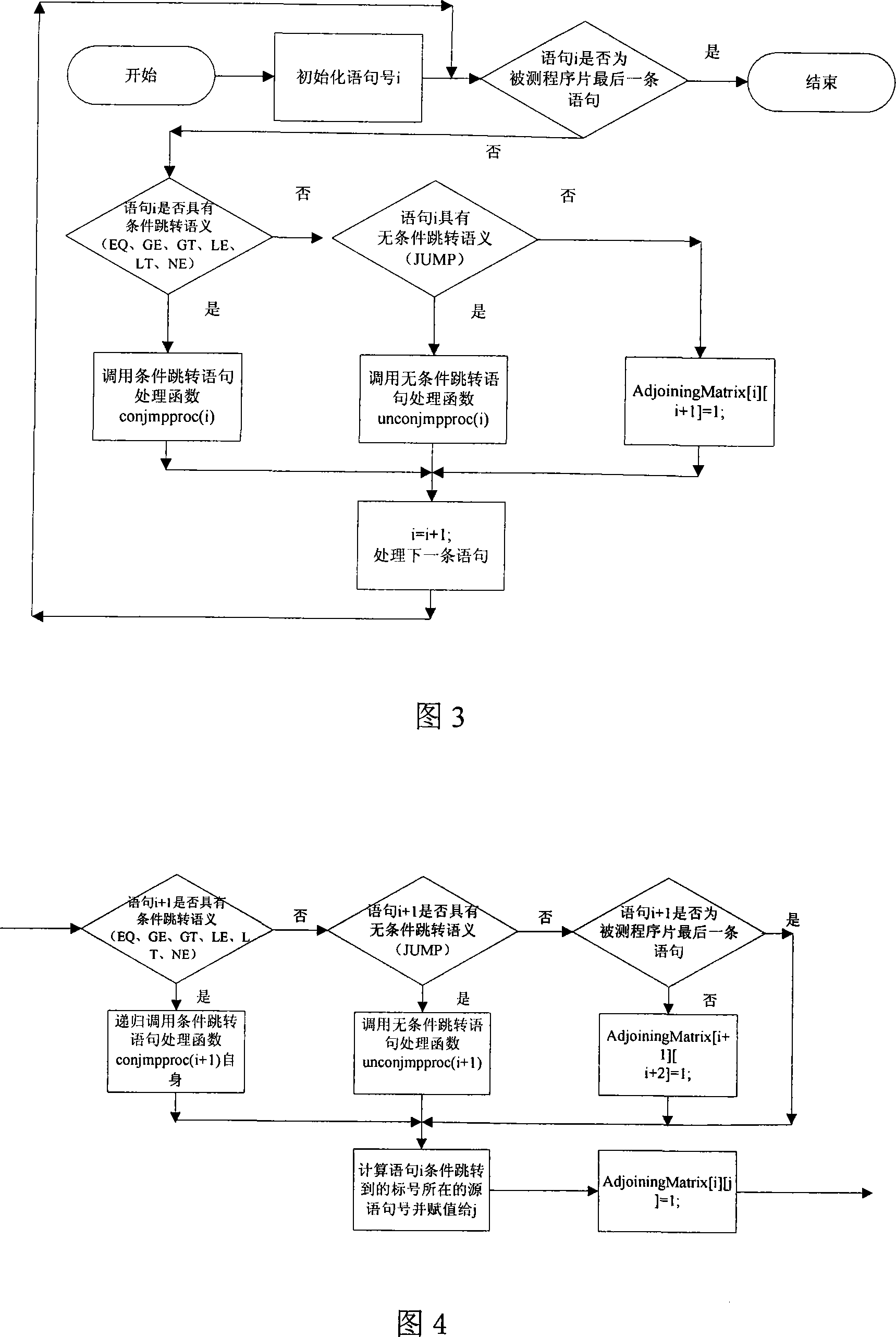
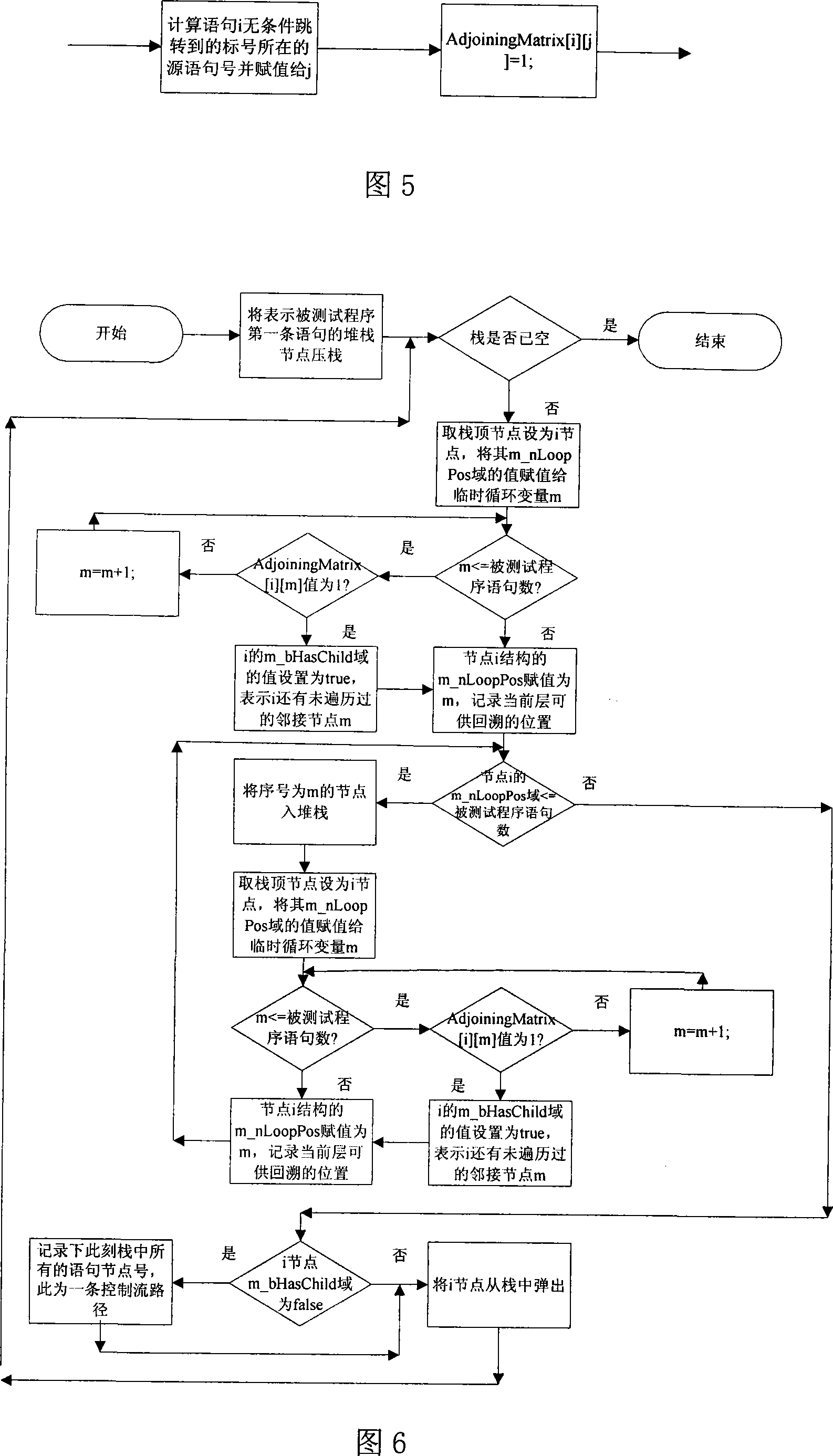
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
Solar tracker drive
ActiveUS20150377518A1Increase productionReduce power outputSolar heating energySolar heat collector controllersAngular deviationEngineering
A sun-tracking solar drive can include hardware and / or be operated in accordance with a method in which angular deviations are compensated for operation including during forward tracking and backtracking. For example, the effects of thermal expansion and mechanical slop associated with certain components can be calculated and used for calculation of target angles that can provide for increased power output and improved shading avoidance.
Owner:SUNPOWER CORPORATION
Video abstract generation and video backtracking method and system
ActiveCN104581437ACompactBacktracking quicklyImage analysisMultimedia data retrievalComputer graphics (images)Backtracking
The invention provides a video abstract generation and video backtracking method and system. According to the method, moving objects in an original video are separated, the separated moving objects are identified and classified, and a highly concentrated video abstract file with compact content is generated with a scalable image fusion technology and a multi-mode information fusion method. During video backtracking, firstly, the number and types of the objects appearing in a video image are elastically controlled according to the number of the objects appearing in the image selected by a user as well as an object which the user is interested in. When the user clicks one object in the image, the system can quickly backtrack the original video on a server and present the whole appearing process of the object to the user.
Owner:CHINACCS INFORMATION IND
Method and device for detecting security flaws of source files
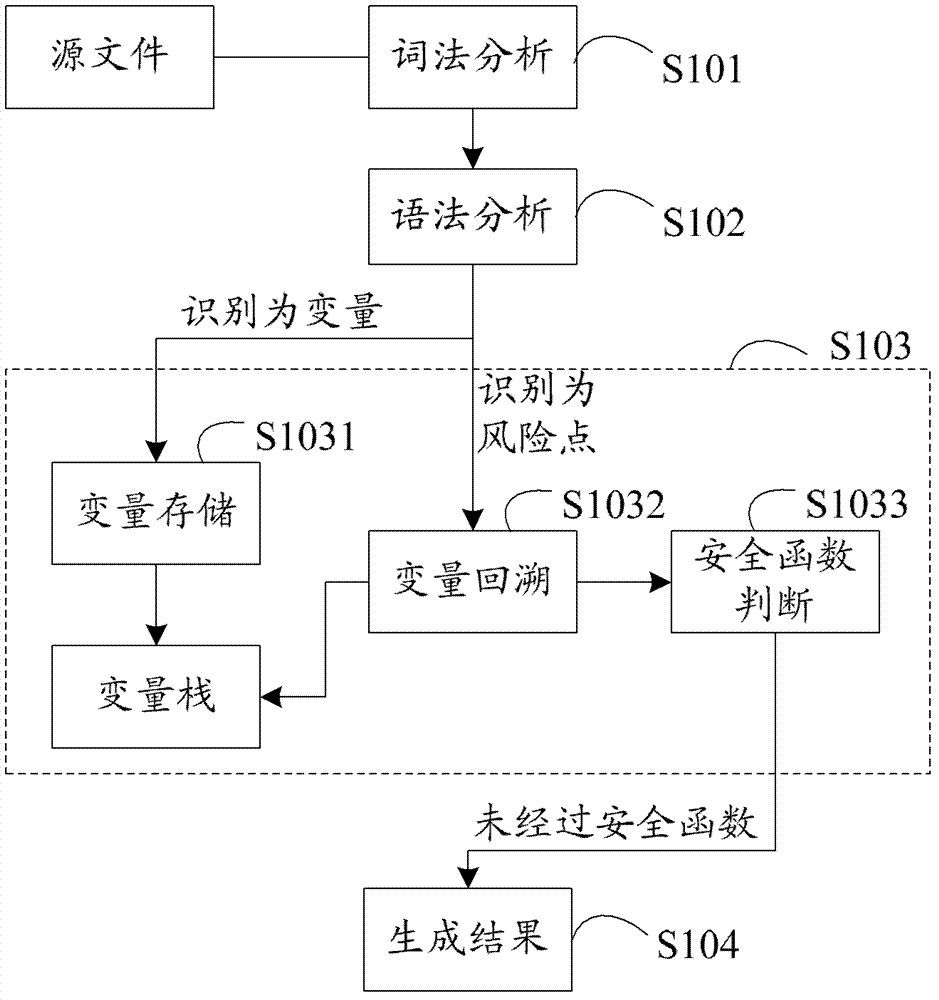
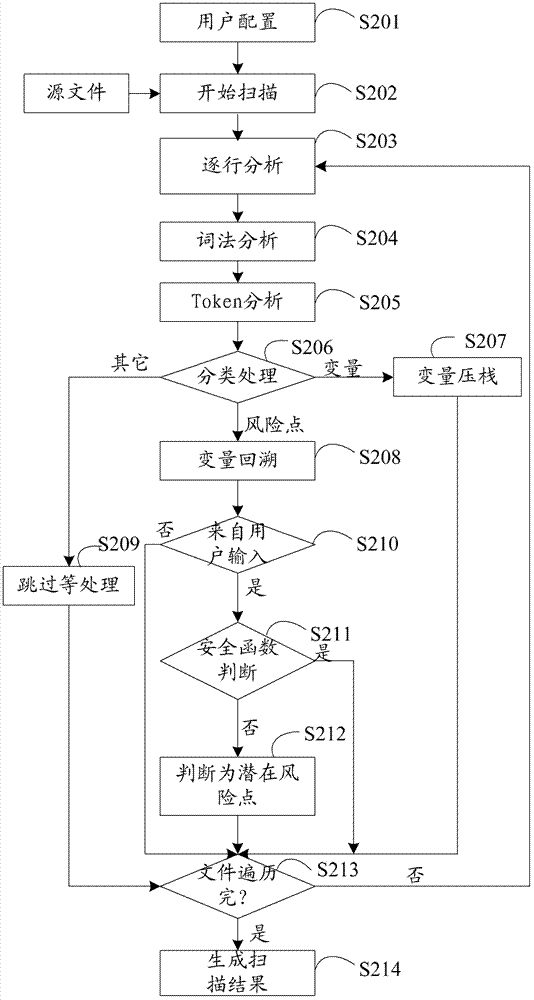
ActiveCN102955914ASave resourcesImprove scanning efficiencyPlatform integrity maintainanceIdentifying VariableLexical analysis
The invention provides a method and a device for detecting security flaws of source files. The method includes scanning the source files one by one and executing steps on the scanned source files including subjecting the source files to lexical analysis and grammatical analysis, performing variable identification operation and risk point identification operation in the process of the lexical analysis, wherein the variable identification operation includes identifying variables and storing identified variables; the risk point identification operation includes identifying risk points, backtracking the stored variables by means of parameters of the risk points which are identified, and if the parameters of the risk points can be backtracked to an importable point, considering the risk point is potential risk points to cause security flaws when without security function processing in the process of backtracking. Compared with the prior art, the method for detecting security flaws of the source files has no need to build up an abstract syntax tree, processing procedures are simplified, resources of a testing system are saved, and code scanning efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Mobile-robot route planning method based on improved genetic algorithm
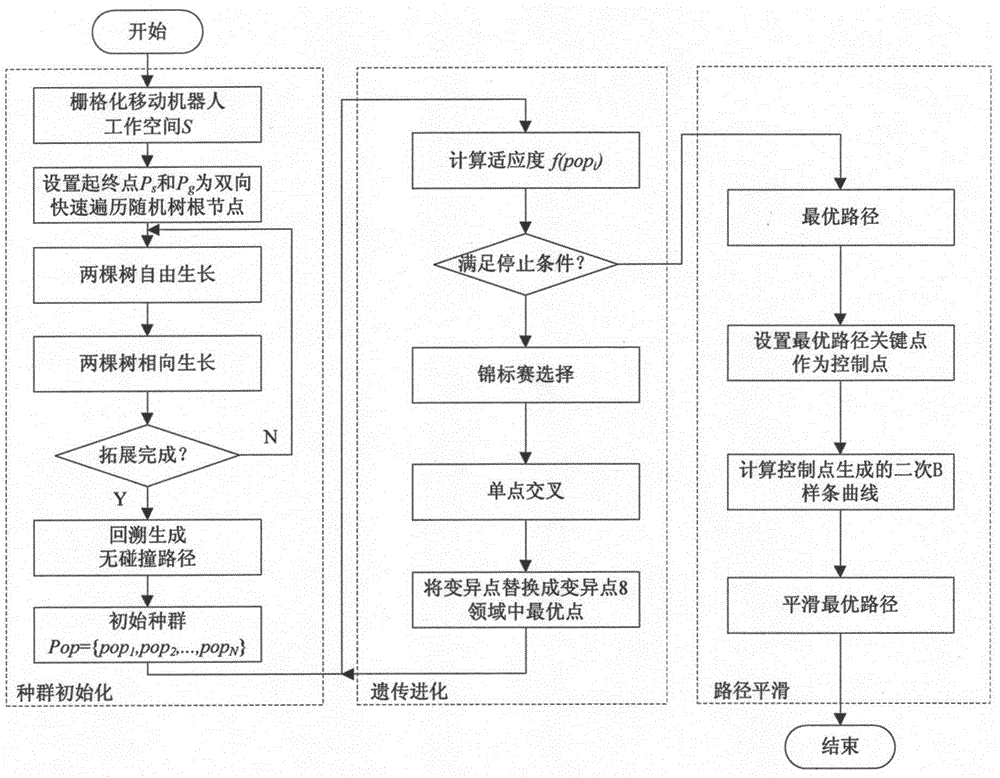
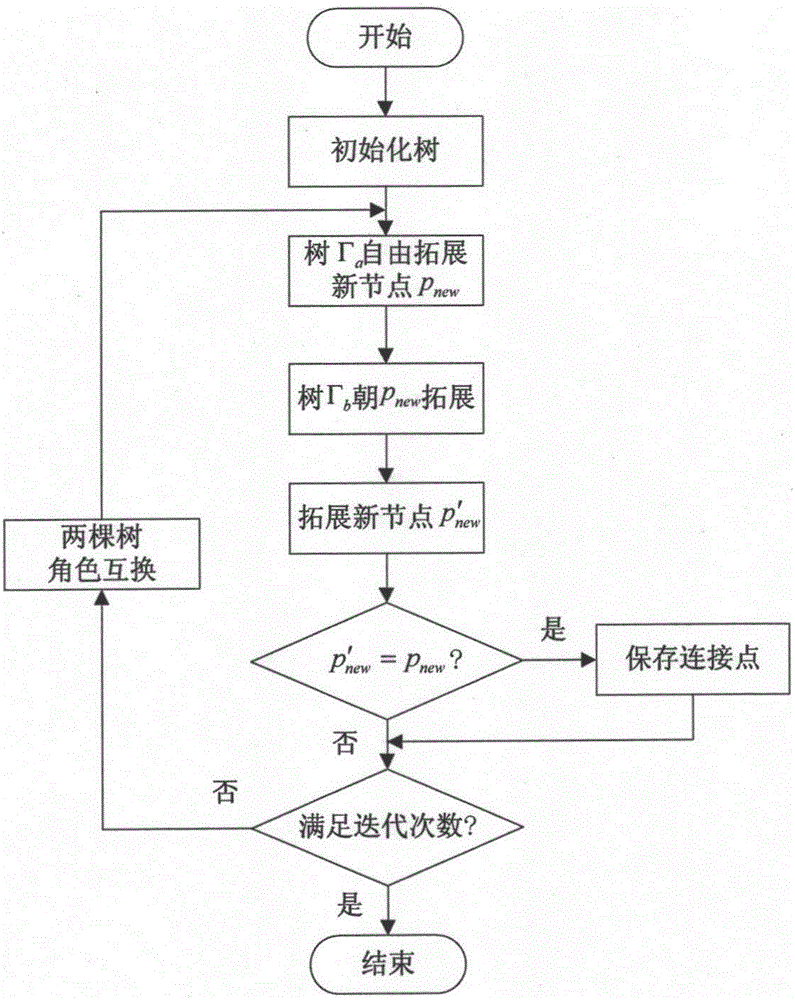
InactiveCN106843211AImprove environmental adaptabilityStrong optimal path search abilityPosition/course control in two dimensionsGenetic algorithmsProximal pointTournament selection
The invention relates to a mobile-robot route planning method based on an improved genetic algorithm. A raster model is adopted to preprocess a working space of a mobile robot, in a rasterized map, an improved rapid traversing random tree is adopted to generate connections of several clusters between a start point and a target point, portions for the mobile robot to freely walk on in the working space are converted into directed acyclic graphs, and a backtracking method is adopted to generate an initial population which is abundant in diversity and has no infeasible path on the basis of the directed acyclic graphs. Three genetic operators, namely a selection operator, a crossover operator and a mutation operator, are adopted to evolve the population, wherein the selection operator uses a tournament selection strategy, the crossover operator adopts a single-point crossover strategy, and the mutation operator adopts a mutation strategy which displaces an aberrance point with an optimal point in eight-neighbor points of the aberrance point. A quadratic b-spline curve is adopted to smooth an optimal route, and finally, a smooth optimal route is generated. According to the method, the route planning capability of the mobile robot under a complex dynamic environment is effectively improved.
Owner:DONGHUA UNIV
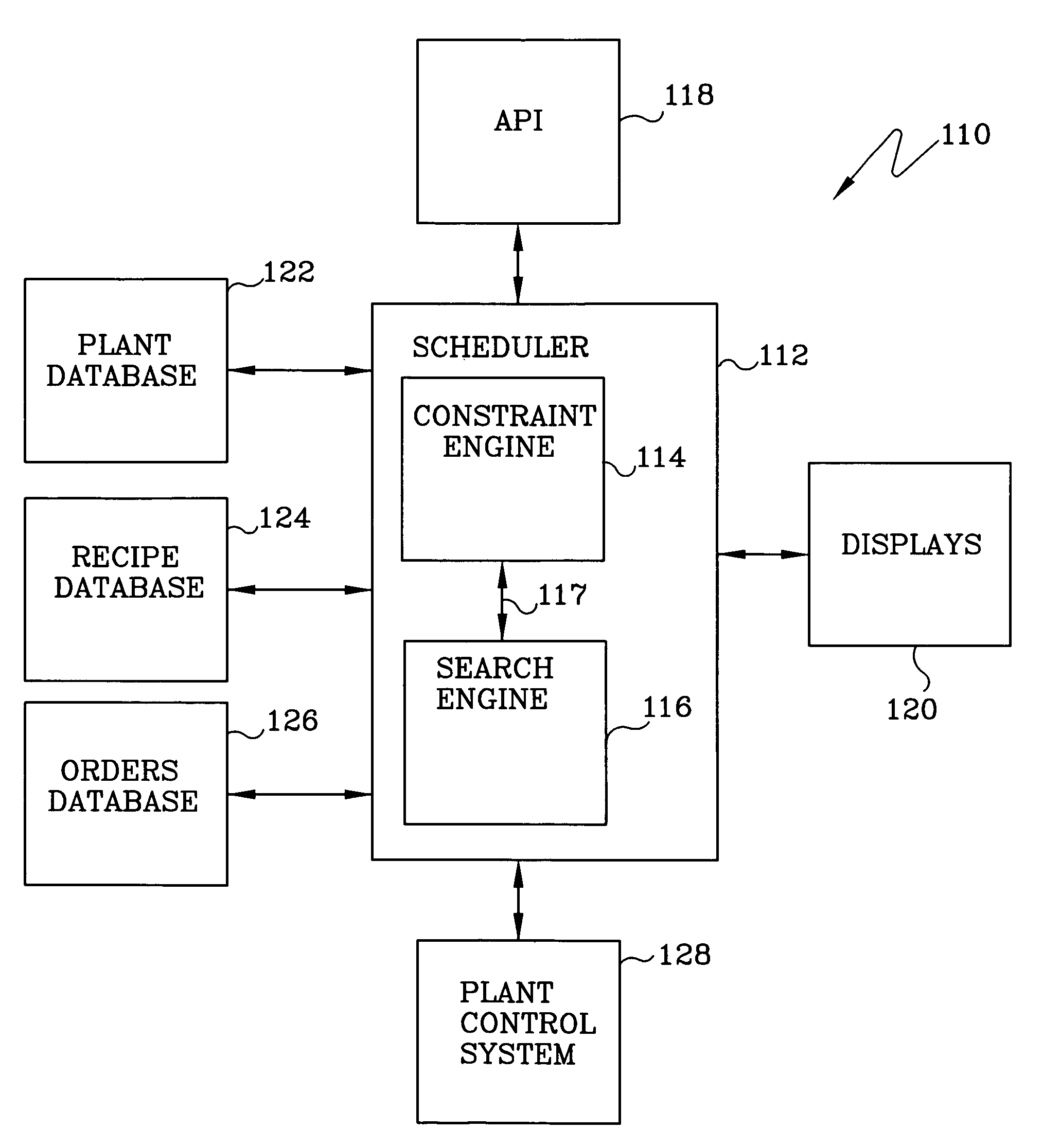
Automated finite capacity scheduler
InactiveUS7505827B1Optimize plant resource utilizationFlexible and efficientResourcesLogisticsTime scheduleResource utilization
A scheduler for a finite capacity process provides a schedule based on an integrated assessment of both discrete and continuous constraints. Given a list of products to be provided, the scheduler generates a set of activities required to produce the products and identifies resources required and the discrete and continuous constraints related to such resources. Activities are resized, and timelines are established for the activities as a function of deadlines for the product delivery for which the activities are related. Resource balancing heuristics are used to redistribute resource utilization to prevent bottlenecks. Data structures are used to keep track of constraints. Both discrete and continuous constraints are defined. Separate solver engines for the discrete and continuous constraint problems modify the constraints. The data structures are used to share and propagate constraints between the two engines. Infeasibilities of meeting product delivery times are detected during the scheduling and backtracking and rescheduling of resources based on under and over utilization and availability of equivalent resources is performed.
Owner:HONEYWELL INC
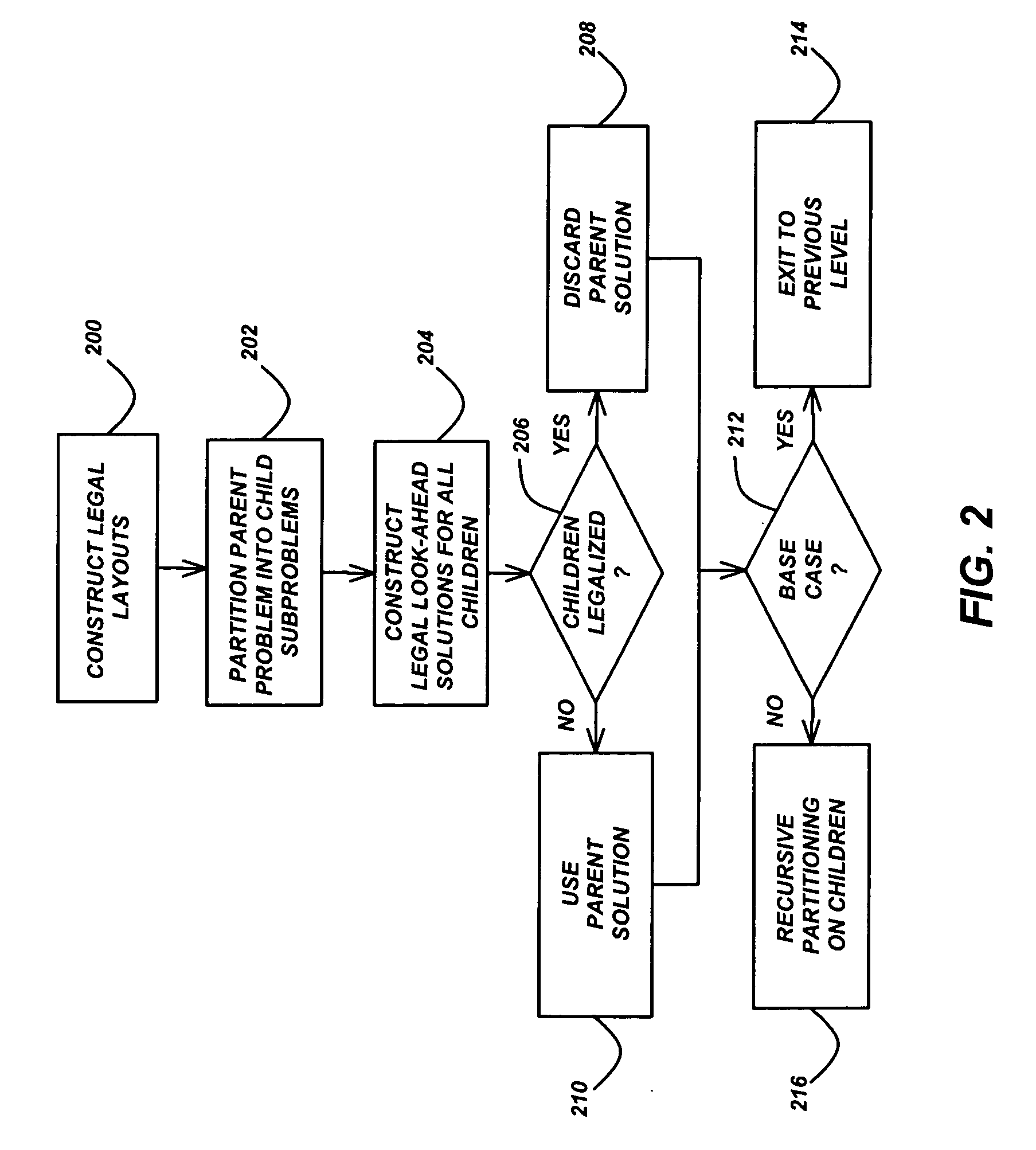
Circuit floorplanning and placement by look-ahead enabled recursive partitioning
InactiveUS20060190889A1Less run timeWirelength resultComputer aided designSoftware simulation/interpretation/emulationBacktrackingSatisfiability
Placement or floorplanning of an integrated circuit is performed by constructing legal layouts at every level of a hierarchy of subsets of modules representing the integrated circuit, by scalably incorporating legalization into each level of the hierarchy, so that satisfiability of constraints is explicitly enforced at every level, in order to eliminate backtracking and post-hoc legalization.
Owner:RGT UNIV OF CALIFORNIA
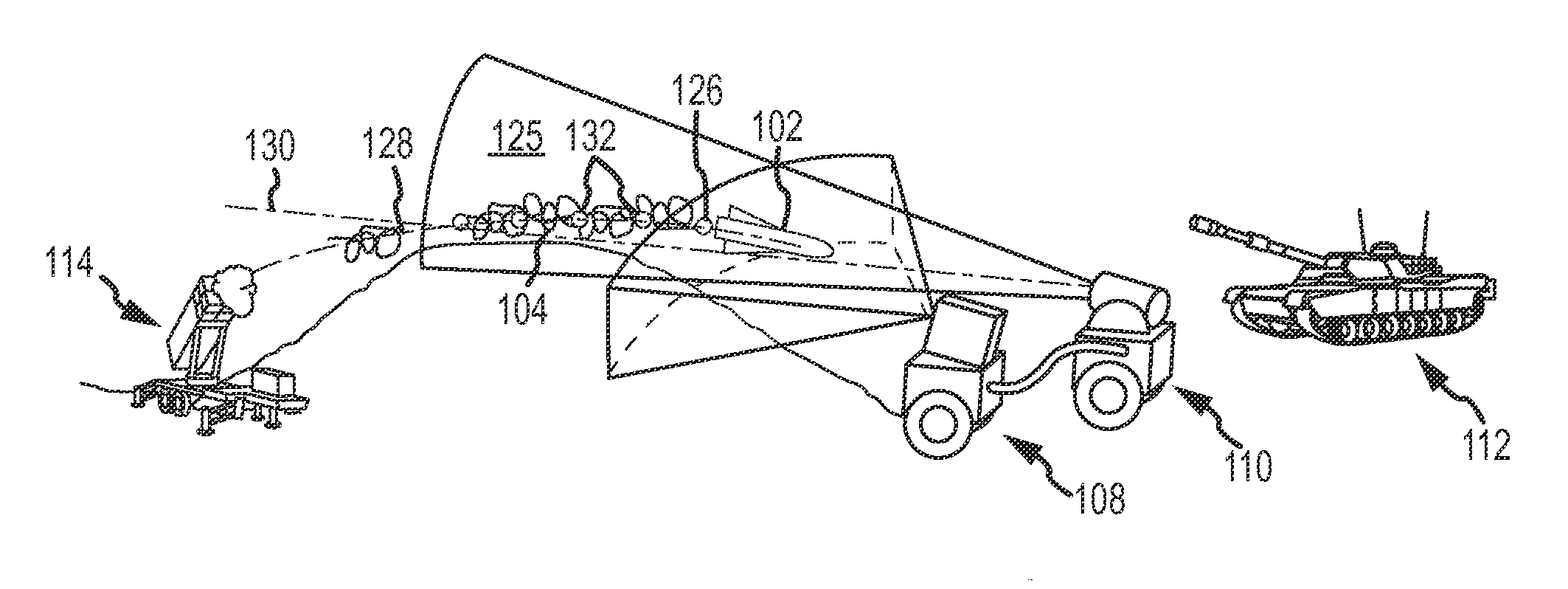
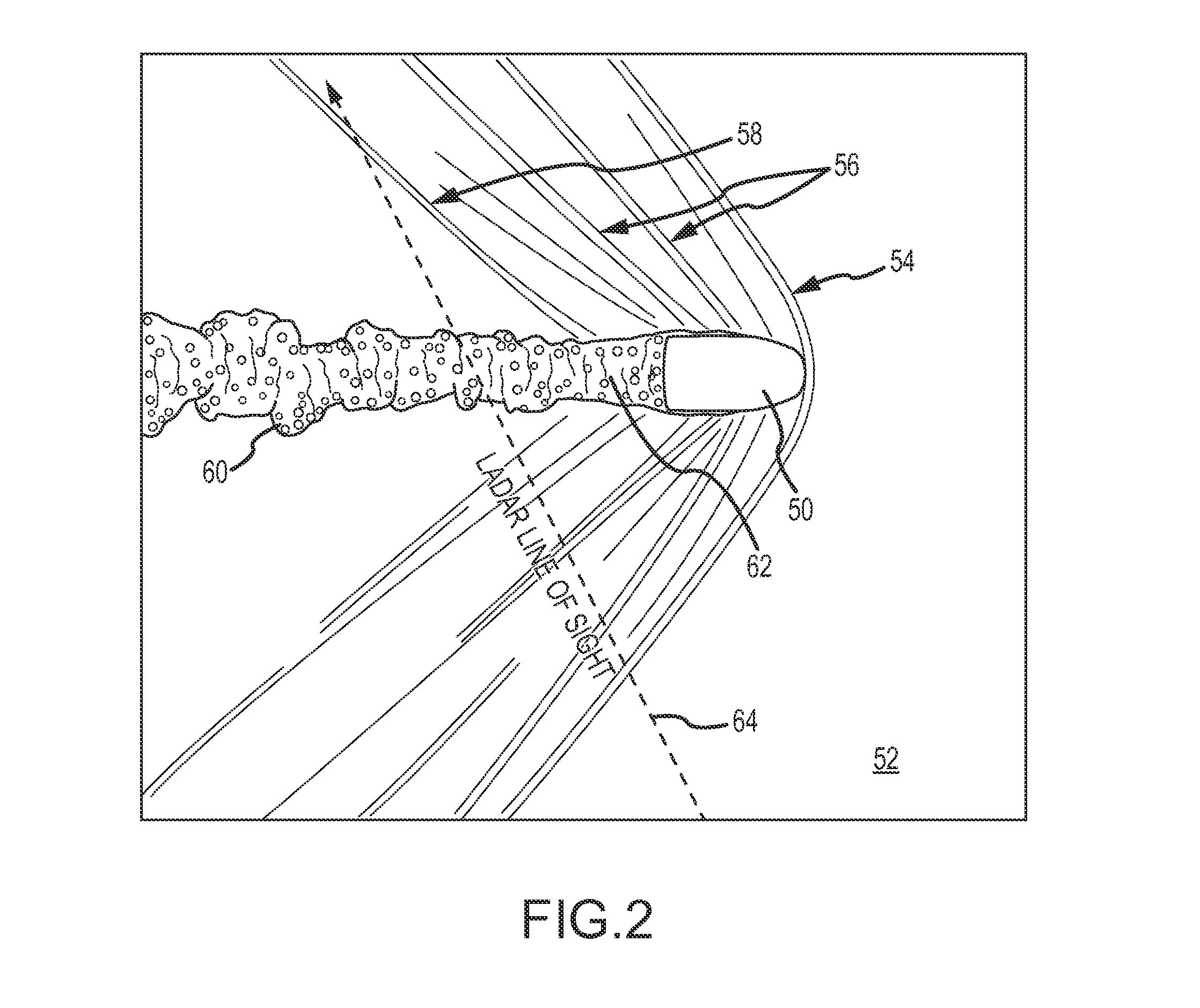
Ladar backtracking of wake turbulence trailing an airborne target for point-of-origin estimation and target classification
ActiveUS20150015869A1Well formedDevices using optical meansWeapons typesLocation trackingEngineering
A weapon-locating ladar system estimates a backward trajectory of an airborne target by using flow field measurements to follow the wake turbulence trailing the airborne target from a position at which the target is detected backwards until the wake is no longer observable. The system may use the backward trajectory to estimate the point-of-origin of the target. The system may also use the flow field measurements along the backward trajectory to classify the target. Target classification may be used to refine the point-of-origin estimate, to influence counter-fire or to adapt the flow field measurements.
Owner:RAYTHEON CO
Complete coverage path planning method for multi-robot system
ActiveCN106979785AImprove coverage efficiencyAchieve synergyNavigational calculation instrumentsPath lengthMultirobot systems
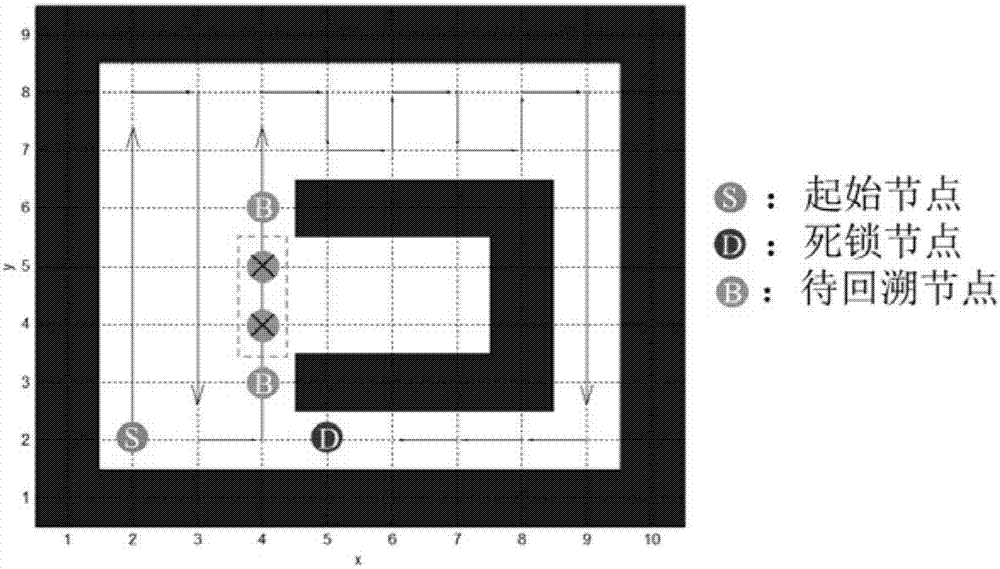
The present invention discloses a complete coverage path planning method for a multi-robot system. This method combines a biologically inspired neural network model with a backtracking mechanism to reduce the repeated coverage path and shorten the time needed by complete coverage. The method concretely comprises the following steps: every robot uses the biologically inspired neural network model to cover surrounding environment until the robot enters a deadlock state, robots use the backtracking mechanism to select an optimum backtracking node without waiting for the attenuation of a neuron activity value, and a dynamic A star algorithm is used to plan out a path to the backtracking node; and the robots continue to enter a coverage mode after moving to the backtracking node. When one of the robots is deadlocked, the backtracking mechanism of the invention chooses the most suitable backtracking node according to a market mechanism, and the bidding process in the market mechanism considers the path length of the robot during backtracking and the conflict relationship with other robots, so the total time needed by the complete coverage is greatly shortened.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
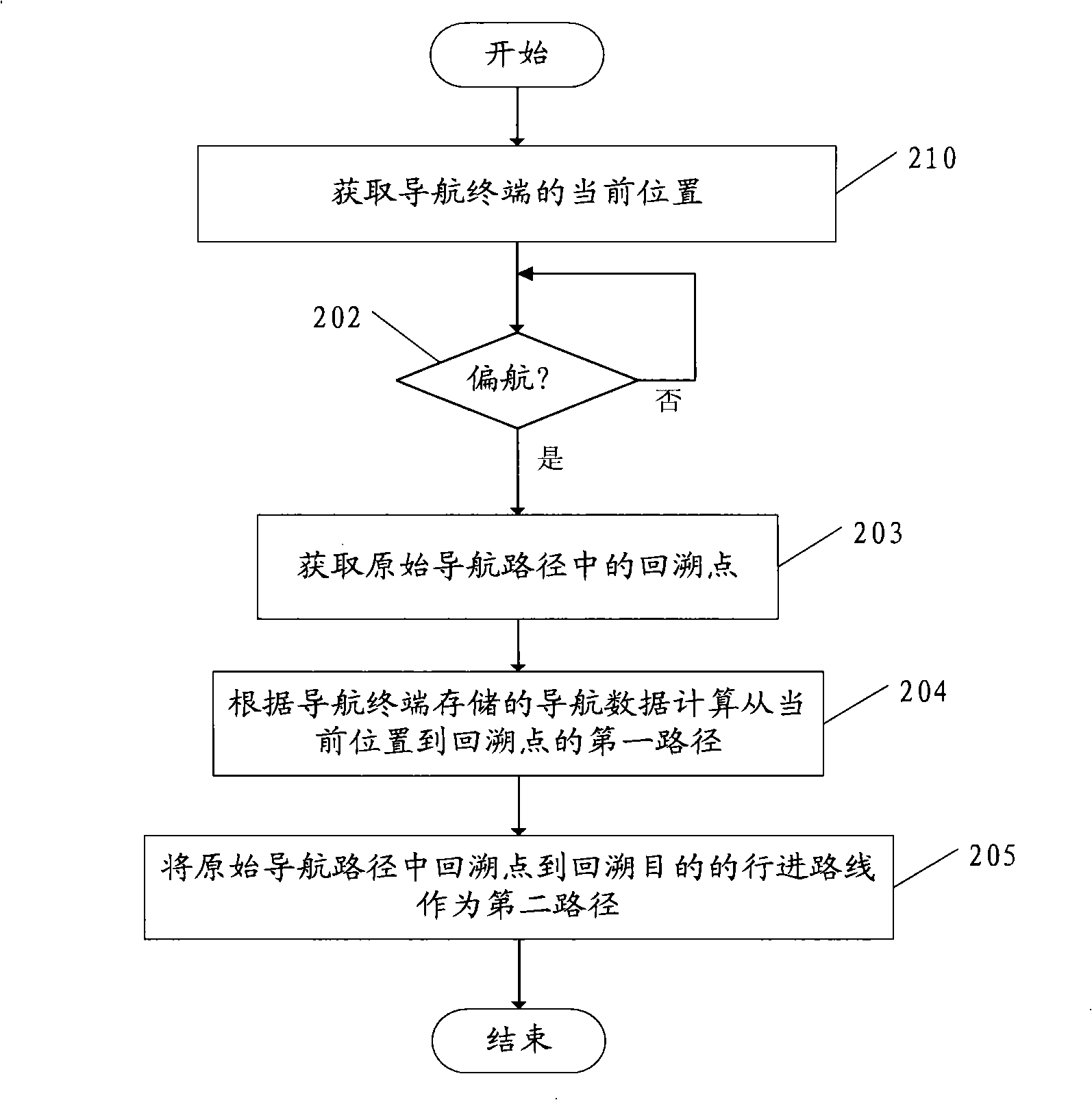
Method for calculating optimum navigation path and communication navigation apparatus
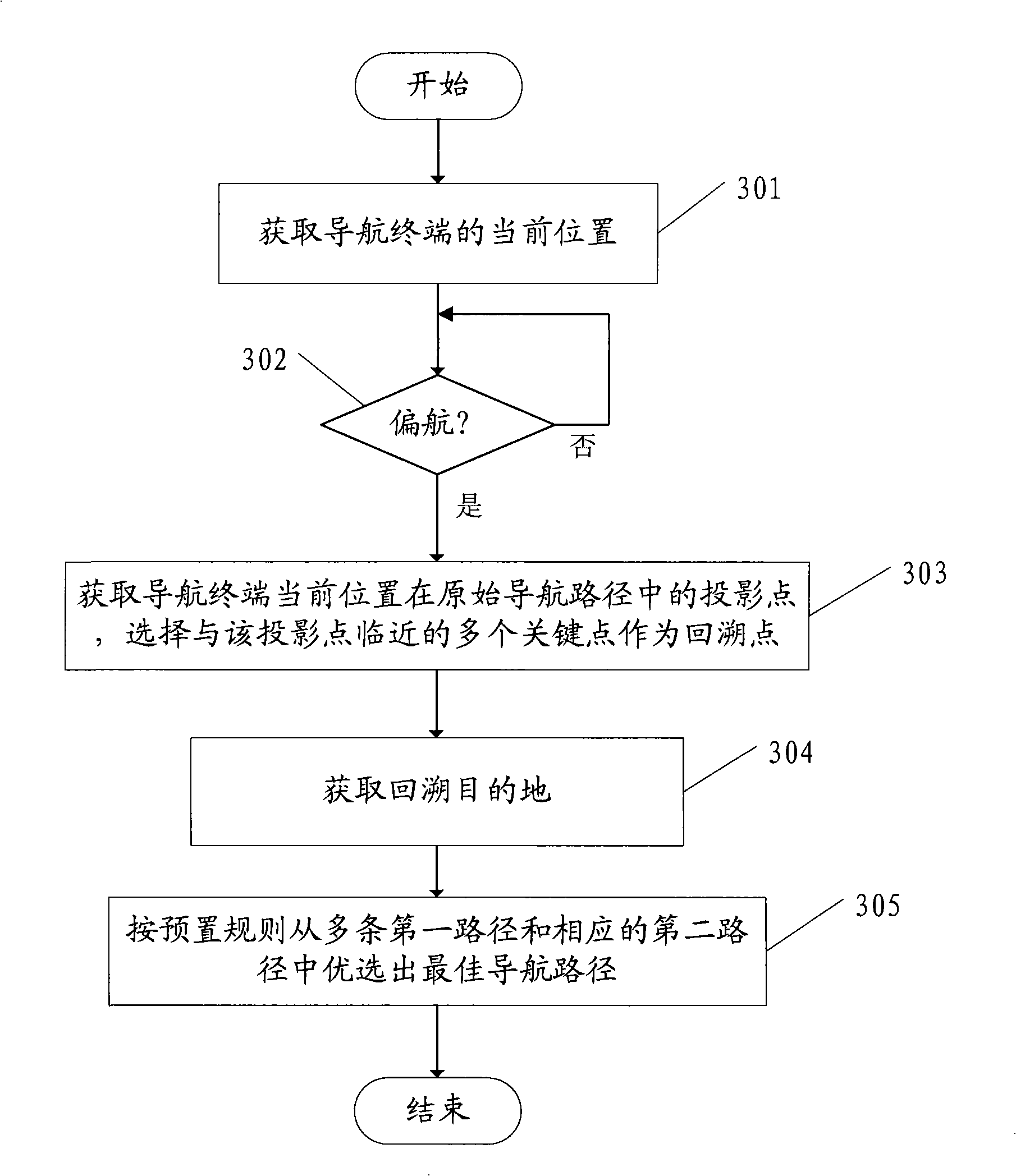
InactiveCN101408428ASave computing resourcesLow costInstruments for road network navigationNetwork communicationData storing
The invention discloses a method for calculating optimal navigation route and a communicating navigation device thereof. The method comprises: obtaining the current position of a navigation terminal and judging whether yawing exists, if yes, calculating the optimal navigation route from the current position of the navigation terminal to an original destination according to navigation data stored in the navigation terminal; the navigation data comprises an original navigation route and the optimal navigation route includes a first route from the current position of the navigation terminal to a backtracking point and a second route from the backtracking point to the backtracking destination; the backtracking point and the backtracking destination are both arranged in the original navigation route. The invention solves the problem that the navigation terminal needs to request a new navigation route from a sever again when in yawing, thus leading the cost of network communication to be increased in the existing communicating navigation technology, and the problems of the time delay and the optimal correction yawing time delay caused by recalculating and transmitting navigation data.
Owner:BEIJING LINGTU SOFTWARE TECH CO LTD
Customized path recommending method in Internet of Vehicles environment
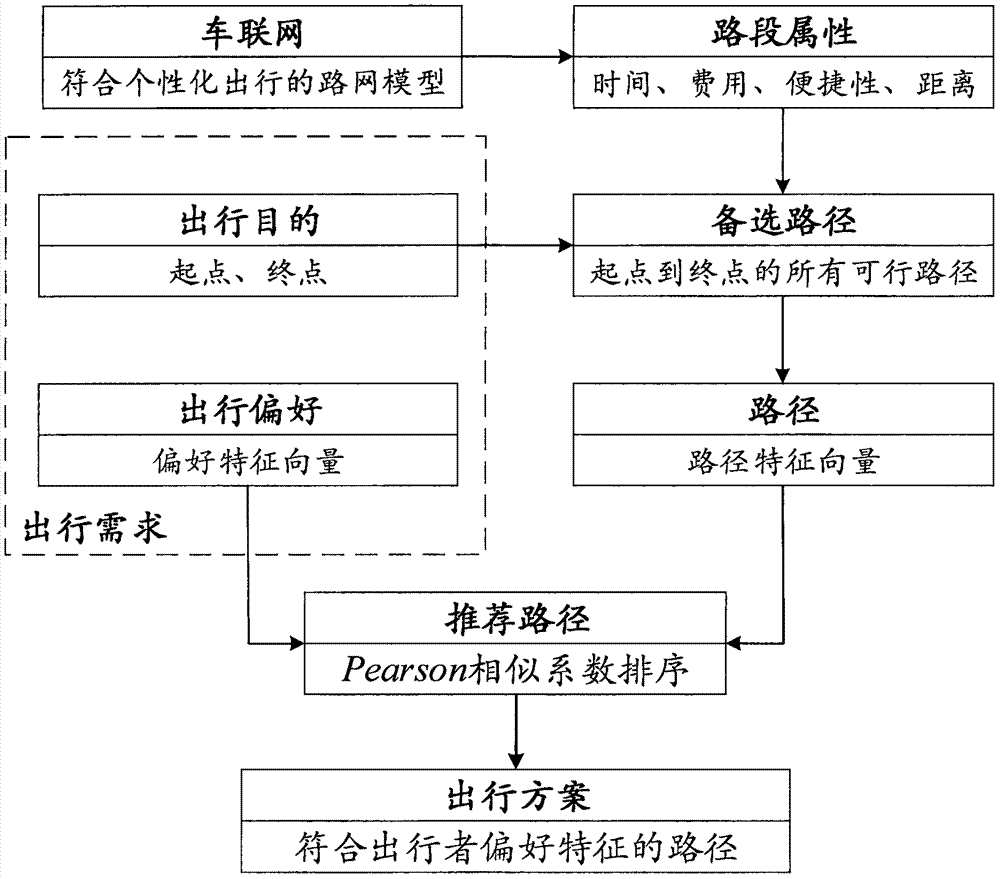
InactiveCN106940829ARealize private customizationReal-time response to unexpected traffic conditionsRoad vehicles traffic controlForecastingCorrelation coefficientFeature vector
The invention discloses a customized path recommending method in an Internet of Vehicles environment. According to the method, in customized path recommending processes, a set of four trip factors including time factors, fee factors, convenience factors and distance factors are taken into account; in a traffic network, a stack idea-based backtracking algorithm for solving a set of all feasible paths from a starting point to an end point is adopted, and a Pearson correlation coefficient-based path recommending algorithm which is implemented according to traveler personality preference characteristic vectors and feasible path characteristic vectors is adopted. According to the method, a plurality kinds of accurate real-time traffic information provided by the Internet of Vehicles is fully used, customized trip demand of a traveler is taken into account, path recommending service in line with individual preference demand can be provided for the traveler, an individual trip path can be customized, accident traffic conditions can be responded to in real time, and customized path recommending service can be provided when traffic accidents occur.
Owner:LANZHOU JIAOTONG UNIV
Intelligent streaming framework
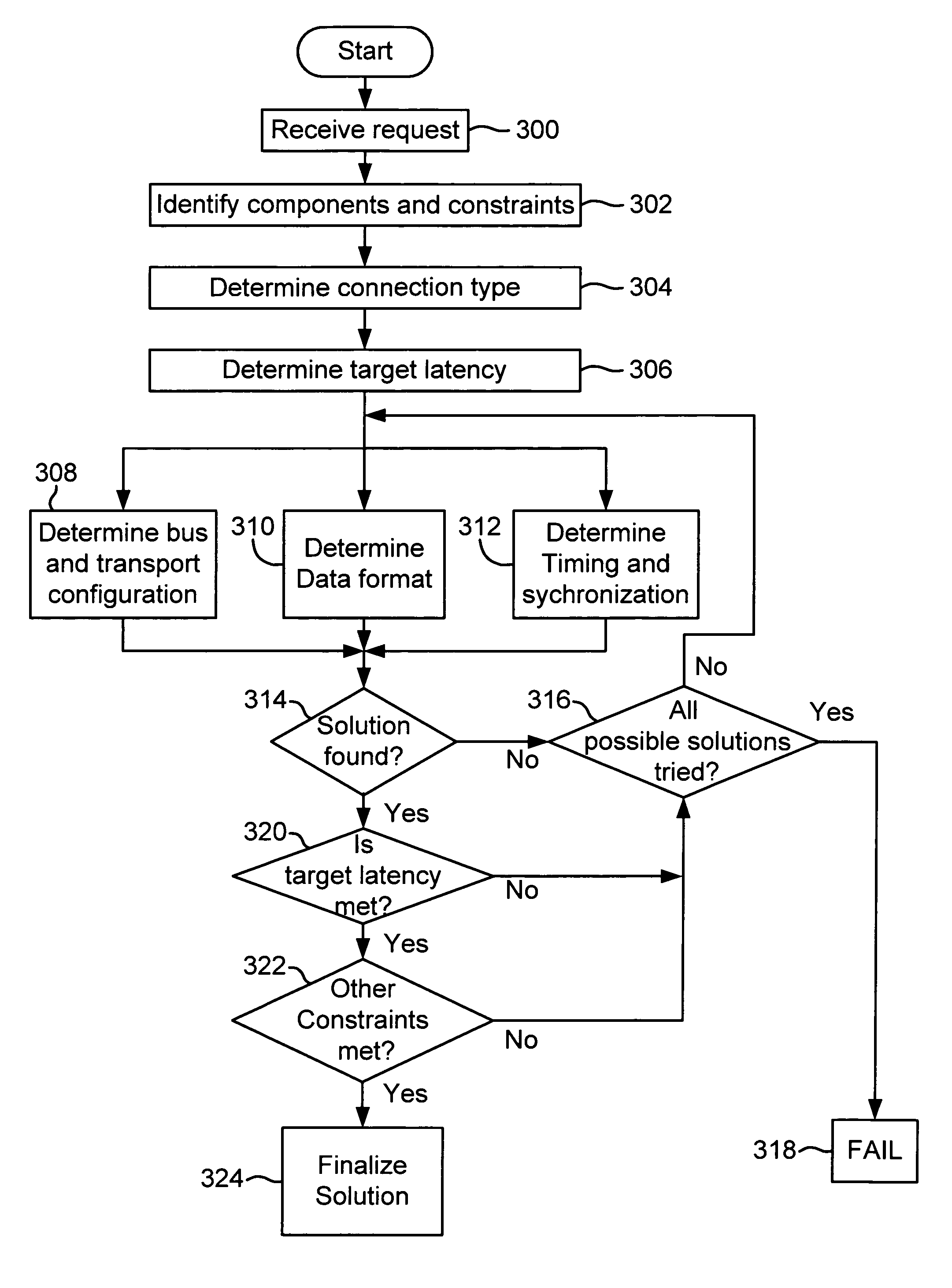
The present invention analyzes a user's or client application's requirements and searches for a solution based on the end-to-end latency requirements (requested or derived), data formats, control protocols, timing and synchronization, local streaming, and resource availability. The search for a solution is tracked to allow backtracking from the point of no solution. Once a solution is determined, the system translates the solution into requirements for the individual components of the graph.
Owner:MICROSOFT TECH LICENSING LLC
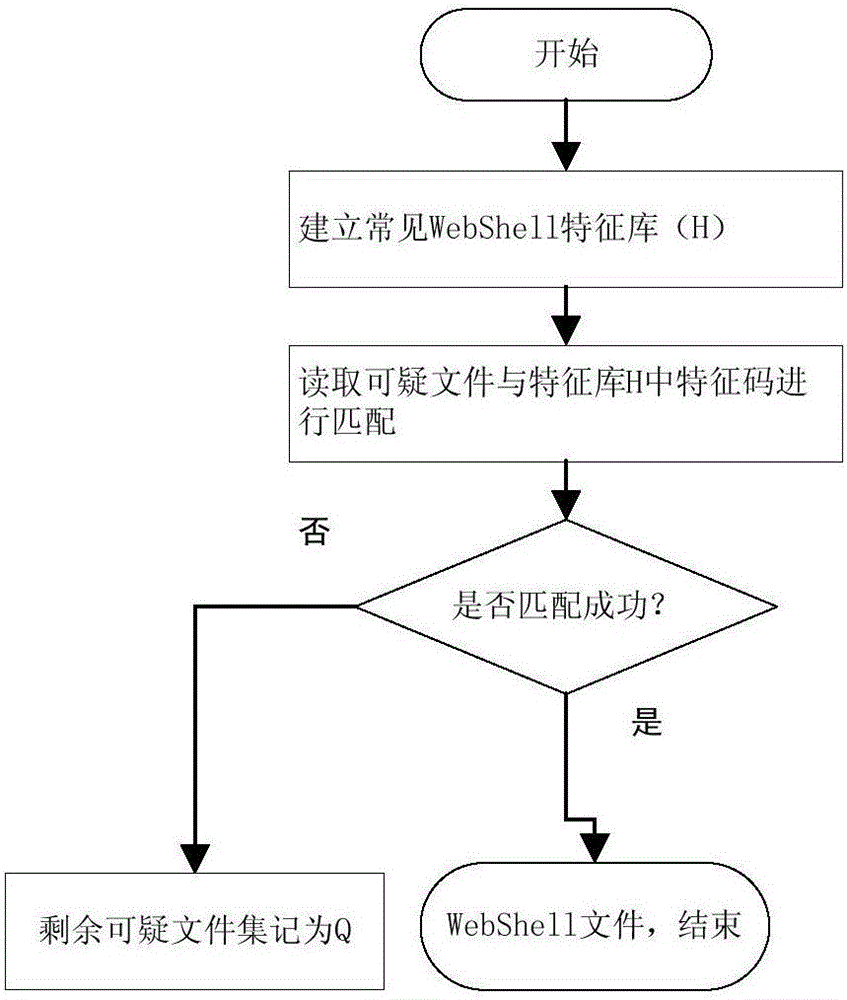
Method and apparatus for detecting WebShell file
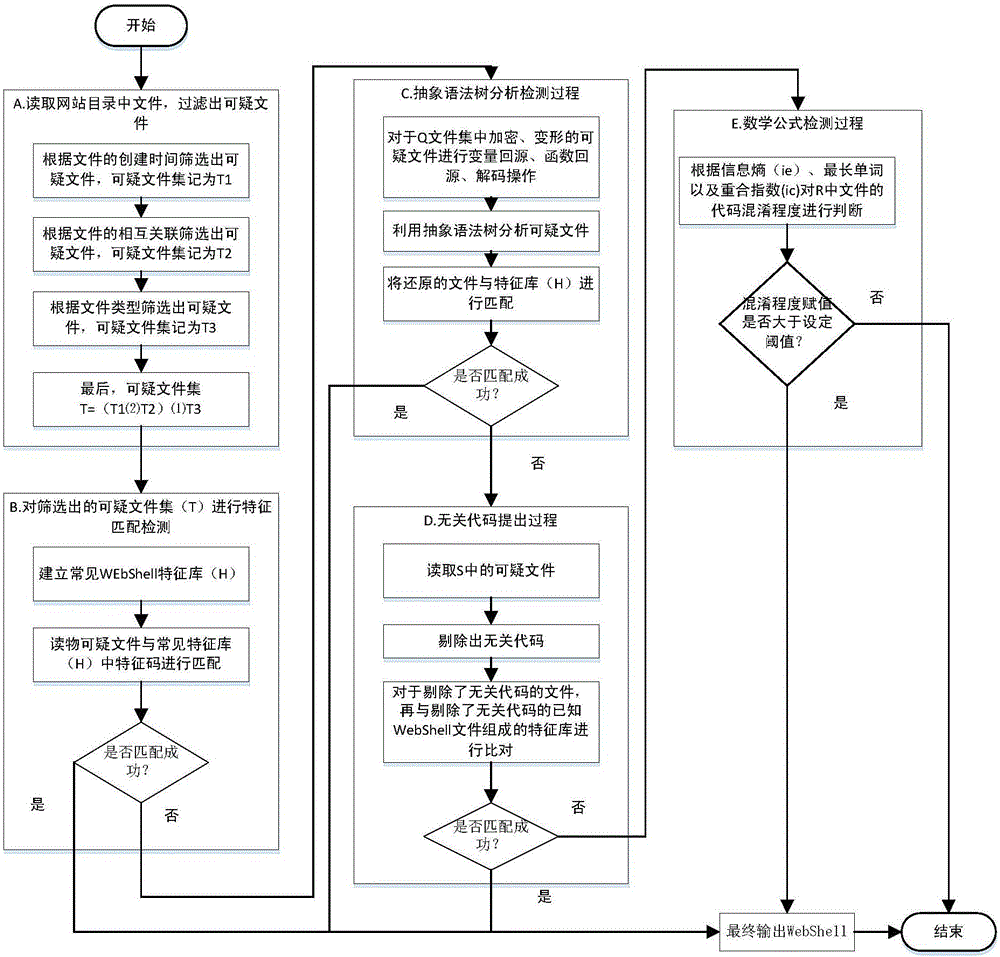
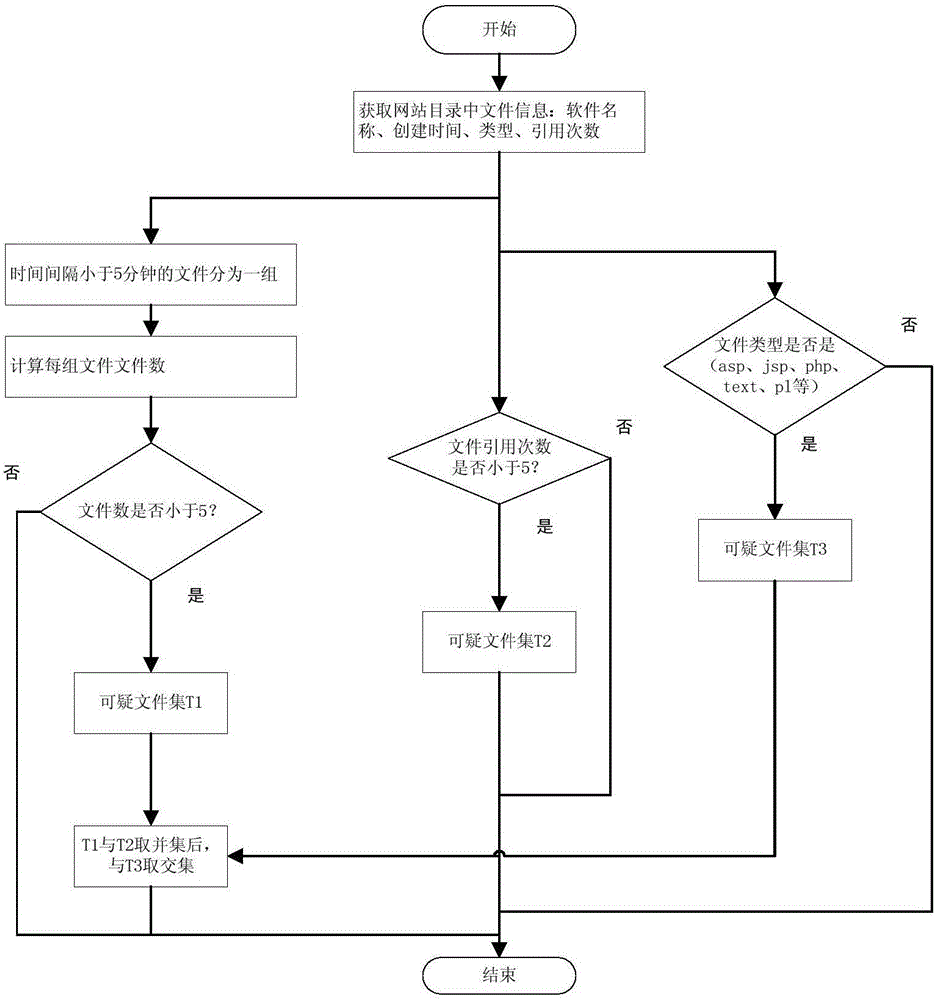
ActiveCN106572117AEnsure safetyImprove detection efficiencyTransmissionWeb serviceAbstract syntax tree
The invention discloses a method and apparatus for detecting a WebShell file. According to the method, on the basis of variable backtracking and an abstract syntax tree, webshell detection is carried out on a plurality of files in a catalogue; a suspicious file screening process, a feature matching detection process, an abstract syntax tree analysis and detection process, an irrelevant code removing process and a mathematical formula detection process are executed successively and then a determined webshell file is outputted. In addition, the detection apparatus comprises a suspicious file screening unit, a feature matching unit, an abstract syntax tree detection analysis unit, an irrelevant code removing unit, and a mathematical formula detection unit; and the units are used for realizing webshell file detection. According to the technical scheme disclosed by the invention, webshell detection can be realized comprehensively, systematically, rapid, and accurately; the detection efficiency is high; and the false alarm rate is low; and thus web service security can be guaranteed.
Owner:BEIJING ANPRO INFORMATION TECH
System and method for packet delivery backtracking
ActiveUS20130128726A1Maximize chanceTransmission systemsFrequency-division multiplex detailsCentralized managementDependability
Owner:RAJANT CORP
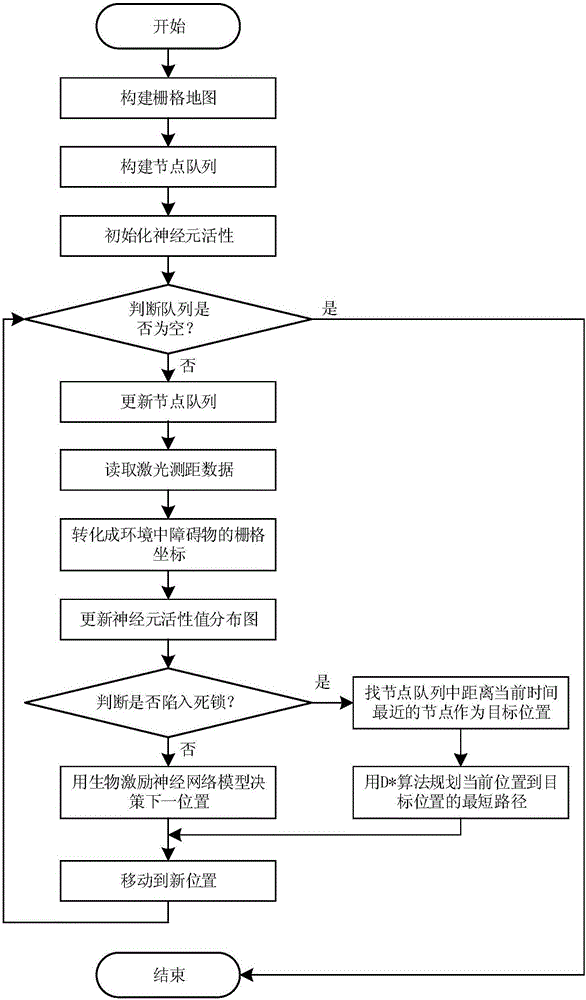
Biological excitation robot complete traverse path planning method based on backtracking search
ActiveCN106843216AThere is no local minimum problemSmall amount of calculationNeural architecturesPosition/course control in two dimensionsReciprocating motionSimulation
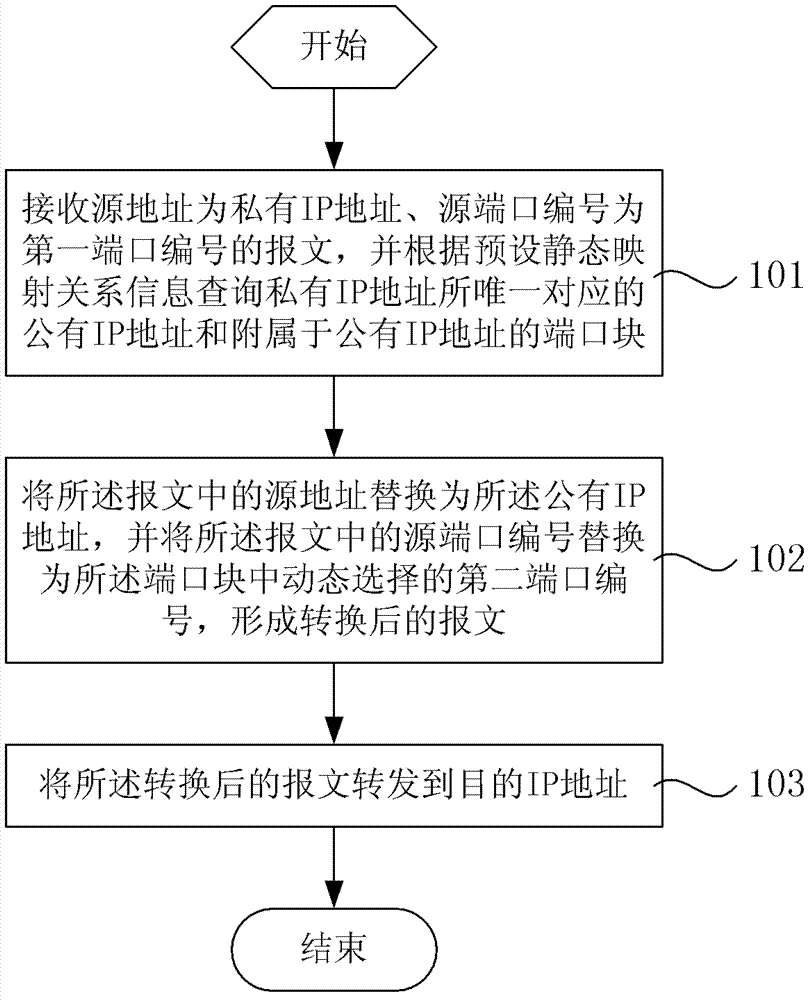
The invention discloses a biological excitation robot complete traverse path planning method based on backtracking search. The method is combined with the advantages of a biological excitation neural network algorithm, a backtracking algorithm and a D * (D star) algorithm to enable a robot to achieve complete transverse path planning in a complicated environment. The method specifically comprises the steps that 1, the biological excitation neural network model is used for simulating a dynamic environment to guide the reciprocating motion of the robot; 2, when the robot deadlocks, firstly, the backtracking algorithm is used for rapidly finding a target position for escaping from deadlocking, and then, and the D* algorithm is used for planning a shortest path from a current position to the target position. According to the biological excitation robot complete traverse path planning method based on the backtracking search, not only are the advantages kept that a path generated by the biological excitation algorithm is smooth and corner turning is less, but also the speed for the robot to escape from the deadlocking is increased, and therefore the robot is capable of covering a whole work space rapidly. According to the biological excitation robot complete traverse path planning method based on the backtracking search, a local minimum problem does not exist, the calculated amount is small, the implementation is simple, and a good adaptability exists in a dynamic unknown environment.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
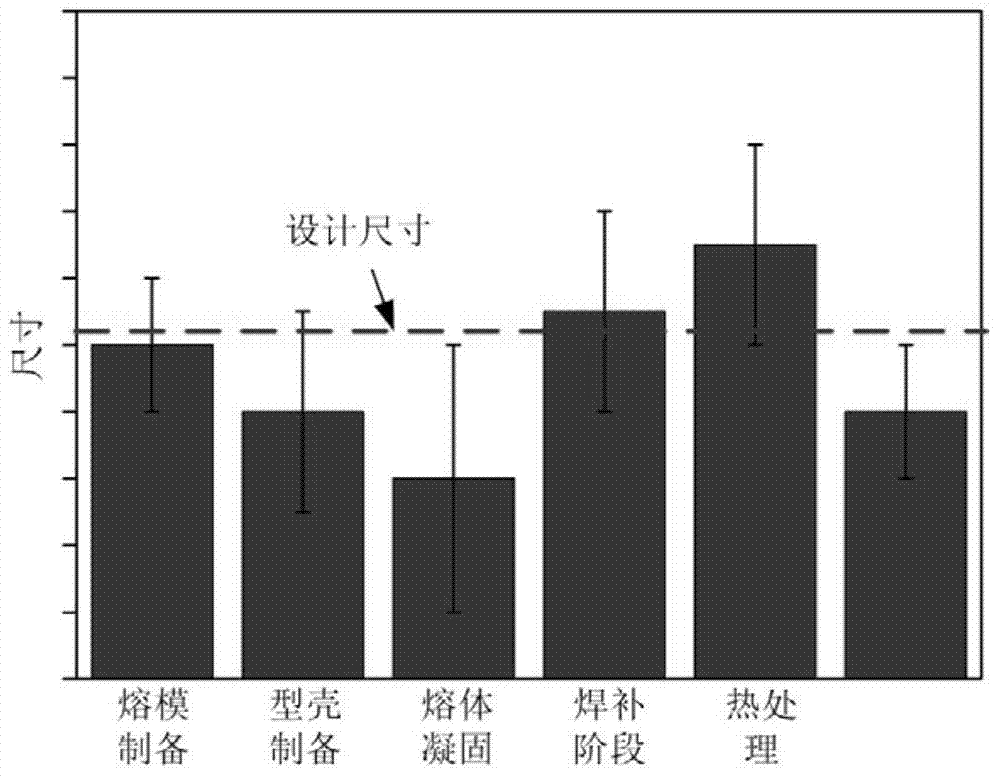
Method for determining shrinking percentages of investment pattern precision casting mold
InactiveCN104504195ALess Corrective WorkHigh precisionFoundry mouldsFoundry coresPre deformationInvestment casting
The invention relates to a method for determining the shrinking percentages of an investment pattern precision casting mold. The method comprises the steps of (1) establishing numerical analysis models for various operation stages of investment casting, (2) taking the analog output of a previous numerical analysis model as the analog input of a next numerical analysis model, establishing an error flow of the whole process and obtaining the final casting simulation deformation result, (3) performing reversible deformation to a mold design stage from the final casting simulation deformation result and determining the profile shrinking percentage of each key dimension. Compared with the prior art, the method has the advantages that the error flow is established or the error evolution of the key dimensions, more accurate and detailed shrinking percentages can be obtained based on the backtracking of the error flow, and the design detail accuracy of the mold design can be enriched; besides, pre-deformation is performed on the error evolution of the whole process of the castings at the source of the mold design, and therefore, the correction work on the castings in the subsequent steps can be saved, the workload is saved and the precision of the castings is improved.
Owner:SHANGHAI JIAO TONG UNIV
Operating-level network address conversion method, operating-level network address conversion equipment and network system
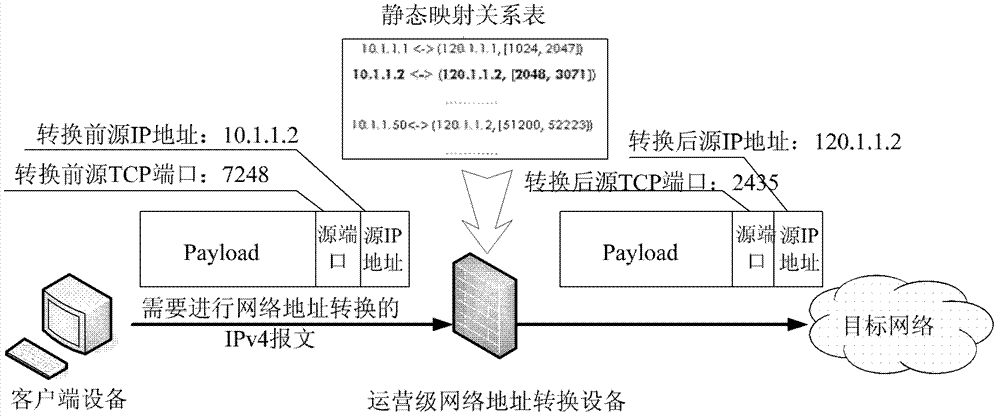
InactiveCN102957754ARealize address traceabilityImplement single point of authenticationTransmissionIp addressStatic mapping
The invention relates to an operating-level network address conversion method which includes steps of receiving a source address as a private IP (internet protocol) address, a source port serial number as a message of the first port serial number; inquiring a public IP address uniquely corresponding to the private IP address and a port block affiliated to the public IP address according to preset static mapping relation information; substituting the source address in the message by the public IP address, substituting the source port serial number in the message by a dynamically selected second port serial number in the port block; and transferring the message after conversion to a target IP address. The invention further relates to operating-level network address conversion equipment a network system. The message is converted by the static mapping relation information, the source address and the source port serial number are substituted by corresponding IP addresses and port serial number selected from the port block, and accordingly, massive log data of the IP address conversion relation are not required to be stored and processed in real time, and address backtracking and single-point authentication can be realized by the static mapping relation information.
Owner:CHINA TELECOM CORP LTD
Terms disambiguation method based on semantic dictionary
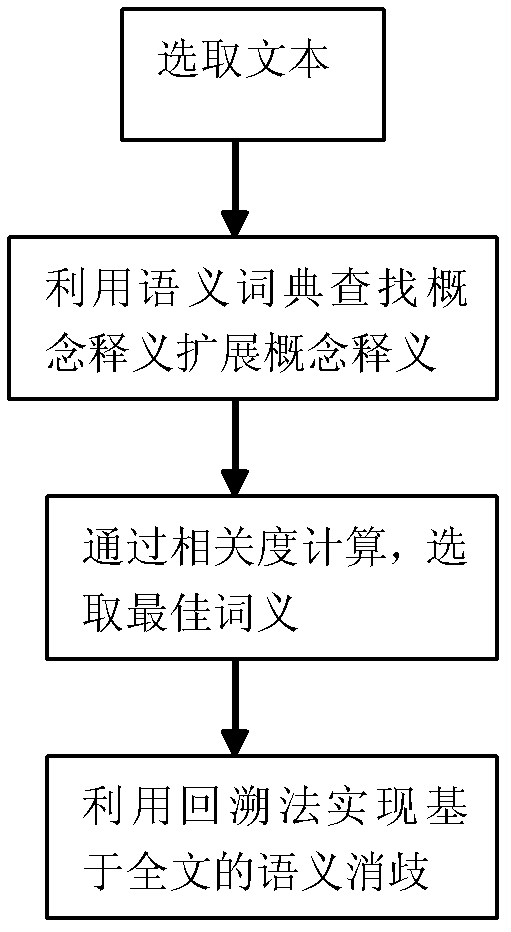
InactiveCN102306144AAchieve disambiguationImprove Disambiguation EfficiencySpecial data processing applicationsParaphraseSynonym
The invention provides a terms disambiguation method based on a semantic dictionary. In the method, term concept relevance is calculated to realize pretreatment on automatic text summarization, namely term disambiguation; the correlativity of concepts is used for realizing the term disambiguation method; requirements of the concept, concept paraphrase, synonym of the concept, expanded paraphrase of the concept, synset of expanded concept and other factors as well as sentence coherence are comprehensively considered; and a correlation degree calculation formula of the concept and a backtracking method are used for selecting the optimum meaning of a word, thus realizing the semantic disambiguation based on the context. An experiment proves that recall and accuracy of the semantic disambiguation can be improved and the method can be better used in acquisition of text summarization.
Owner:NANJING UNIV OF POSTS & TELECOMM
Syntactic analysis method based on sliding semantic string matching
InactiveCN103500160ASolve backtracking difficultiesSolve the problem of insufficient jurisdictionSpecial data processing applicationsContext-sensitive grammarSyntax
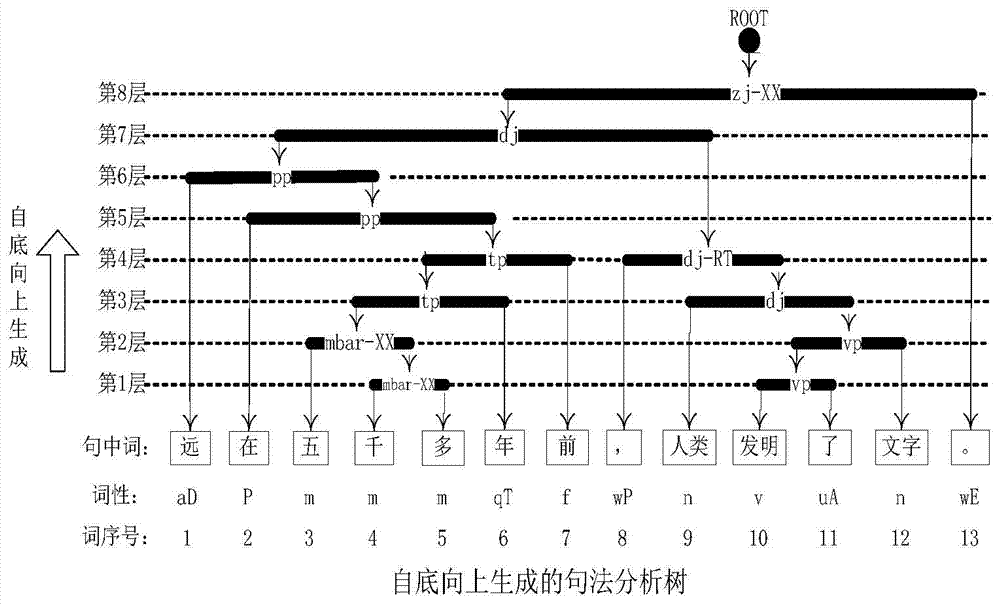
The invention belongs to the field of computer natural language processing, and relates to a method for carrying out high-quality syntactic analysis on human natural language sentences, in particular to a syntactic analysis method based on sliding semantic string matching. The method is characterized in that when a rule base is built, hierarchic flattening transformation is firstly carried out on a usual phrase syntax tree, then semantic code labeling is carried out on the chunking information of each layer, and therefore the chunking rules of context-sensitive grammar of N elements are extracted; in the syntactic analysis process, the optimal chunking rules are matched to carry out stacking chunking type analysis through a sliding semantic string matching model; errors in the lower layer are found and corrected in the higher layer through an error correction template, and heuristic backtracking in the stacking chunking type syntactic analysis is achieved; template information is directly added to a semantic template index, and a machine can learn new syntactic rules immediately. The method solves the problems that a PCFG type syntactic analysis level can hardly be further improved and the correct chucking rules are hard to choose in the stacking chunking type syntactic analysis, and improves the existing syntactic analysis level.
Owner:DALIAN UNIV OF TECH
Method and system for acquiring real-time traffic status information
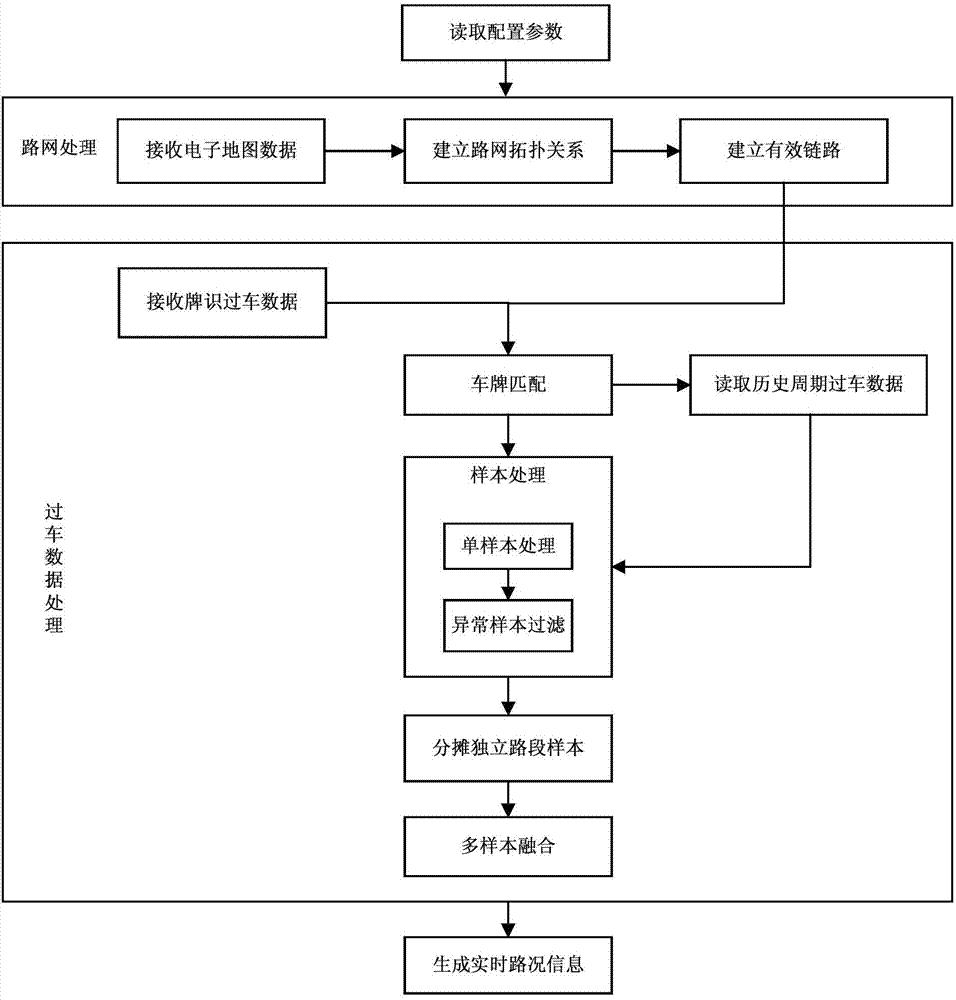
ActiveCN104715604AImprove accuracySolve the problem of real-time traffic information coverageDetection of traffic movementSingle sampleRoad networks
The invention relates to the field of intelligent transportation, and discloses a method and system for acquiring real-time traffic status information. The method includes the following steps that all road sections in a road network are traversed, so that effective links with the starting nodes and the terminal nodes being each provided with a checkpoint device are generated; the vehicle passing data of all the checkpoint devices in the current road condition period or the previous historical period within the license plate backtracking period are read in; the effective links are read one by one, and vehicle passing records corresponding to the starting nodes and the terminal nodes of the links are screened out in the vehicle passing data; the vehicle passing data matched with license plates are searched for, accordingly, the section vehicle speed and the reliability of single samples are calculated, and abnormal samples are filtered; the samples of all the effective links are distributed to all the road sections to generate the real-time traffic status information. According to the method and system, foundation road network data are processed to generate the effective links, the license recognition vehicle passing data are analyzed on this basis, the concept of the sample reliability is introduced, and the accuracy rate of the real-time traffic status information and the information coverage of the complex road network can be improved.
Owner:SHANGHAI GOLDWAY INTELLIGENT TRANSPORTATION SYST CO LTD
Mechanism for facilitating backtracking
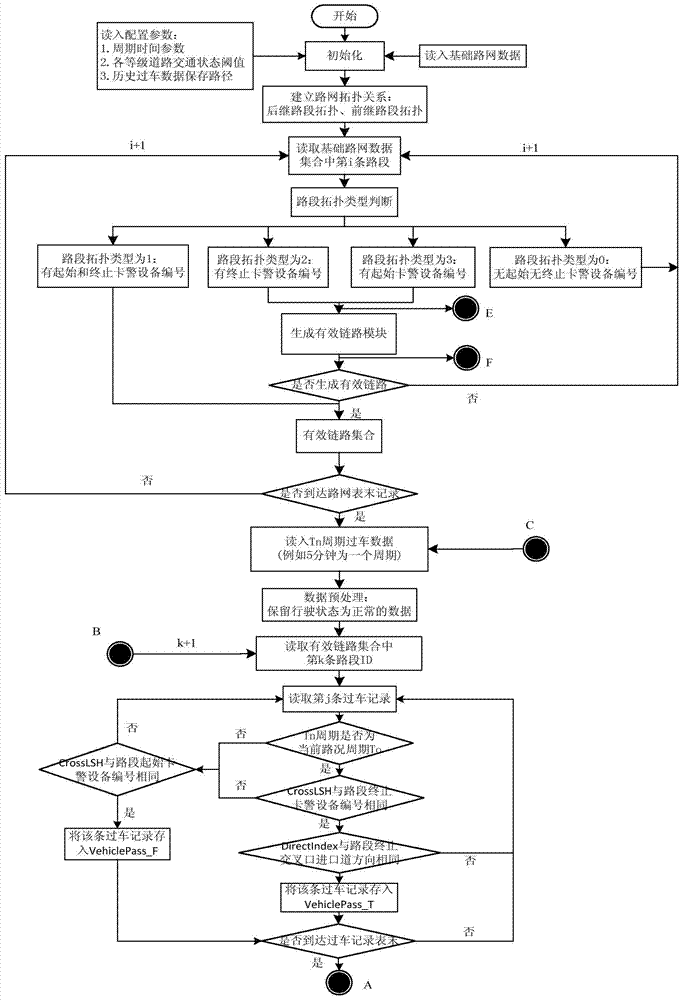
InactiveUS6928449B2Facilitating backtrackingSure easyData processing applicationsSoftware testing/debuggingSubject matterBacktracking
In processing a source entity with a transformation entity, an action set forth in a portion of the transformation entity is executed. A portion of the source entity is the subject of this action. This action causes a particular portion of a result entity to be generated. After this portion of the result entity is generated, a set of history information is associated therewith, which comprises a reference to the portion of the transformation entity that gave rise to the action, and a reference to the portion of the source entity that was the subject of the action. Given this information, it is possible to perform backtracking at a later time, so that when this particular portion of the result entity is selected, those portions of the transformation and source entities that gave rise to the particular portion of the result entity can be indicated to a user.
Owner:ORACLE INT CORP
Unmanned aerial vehicle obstacle avoidance method
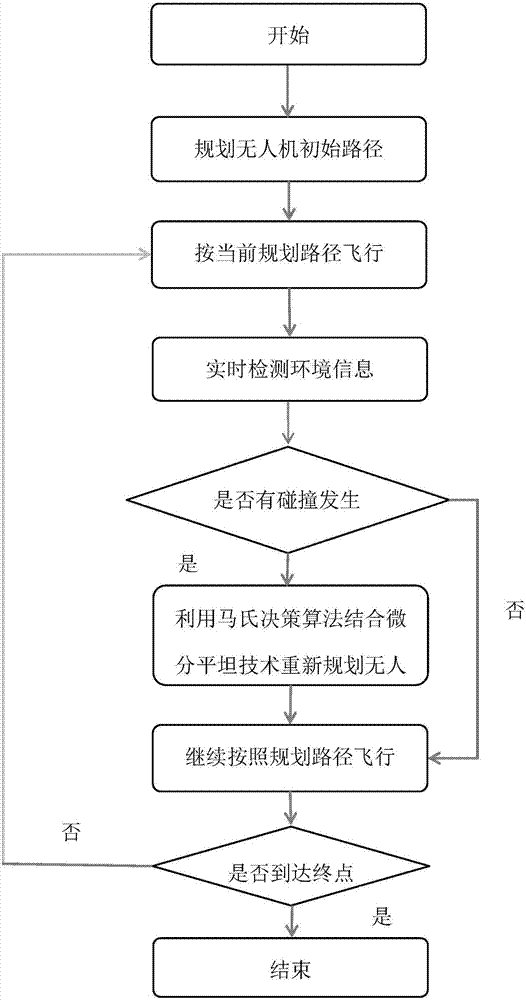
InactiveCN106919181AAvoid local pitfallsMeet flight envelope restrictionsPosition/course control in three dimensionsCollision detectionUncrewed vehicle
The invention discloses an unmanned aerial vehicle obstacle avoidance method, which comprises the steps of planning an initial flight path for an unmanned aerial vehicle; detecting position and speed information of an obstacle within a certain distance of the unmanned aerial vehicle by using a sensor in the flying process of the unmanned aerial vehicle; calculating whether collision occurs or not in flight according to the initial path by adopting a collision detection algorithm; working out a collision avoidance path by using a policy iteration algorithm according to a collision region information predicted by the collision detection algorithm and a destination of the unmanned aerial vehicle; correcting the collision avoidance path by using a backtracking method, and preventing the unmanned aerial vehicle from being caught in a local obstacle trap; and performing differential flattening processing on the corrected collision avoidance path according to dynamic performance characteristics of the unmanned aerial vehicle. According to the method provided by the invention, flight envelope restriction requirements of the unmanned aerial vehicle in reality are met, a common problem of local obstacle traps in the path planning algorithm is effectively avoided, and multiple obstacles can be avoided in real time under the premise of meeting the dynamic performance.
Owner:HUNAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com