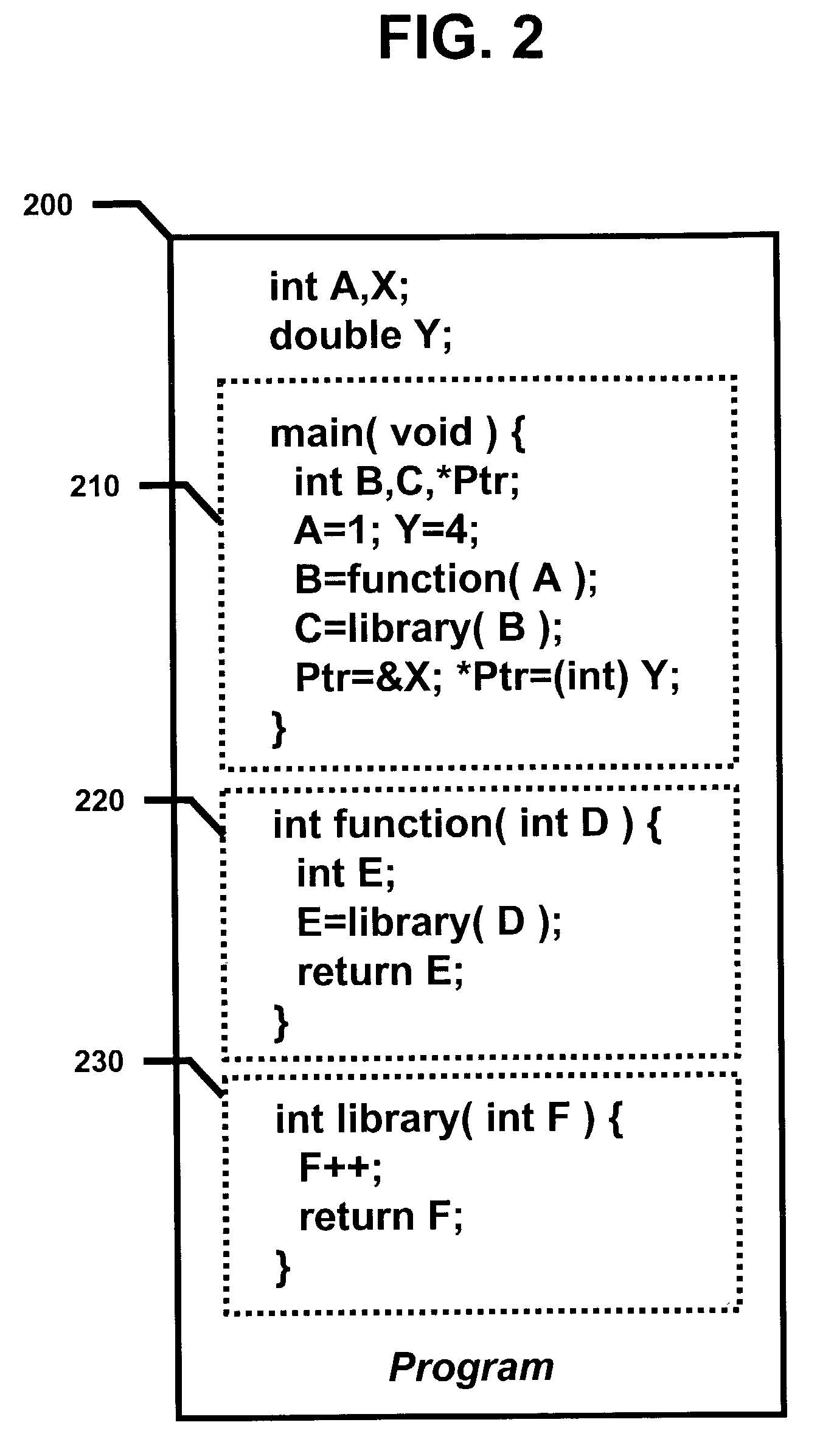
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103 results about "Identifying Variable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The variable that identifies a particular data element.
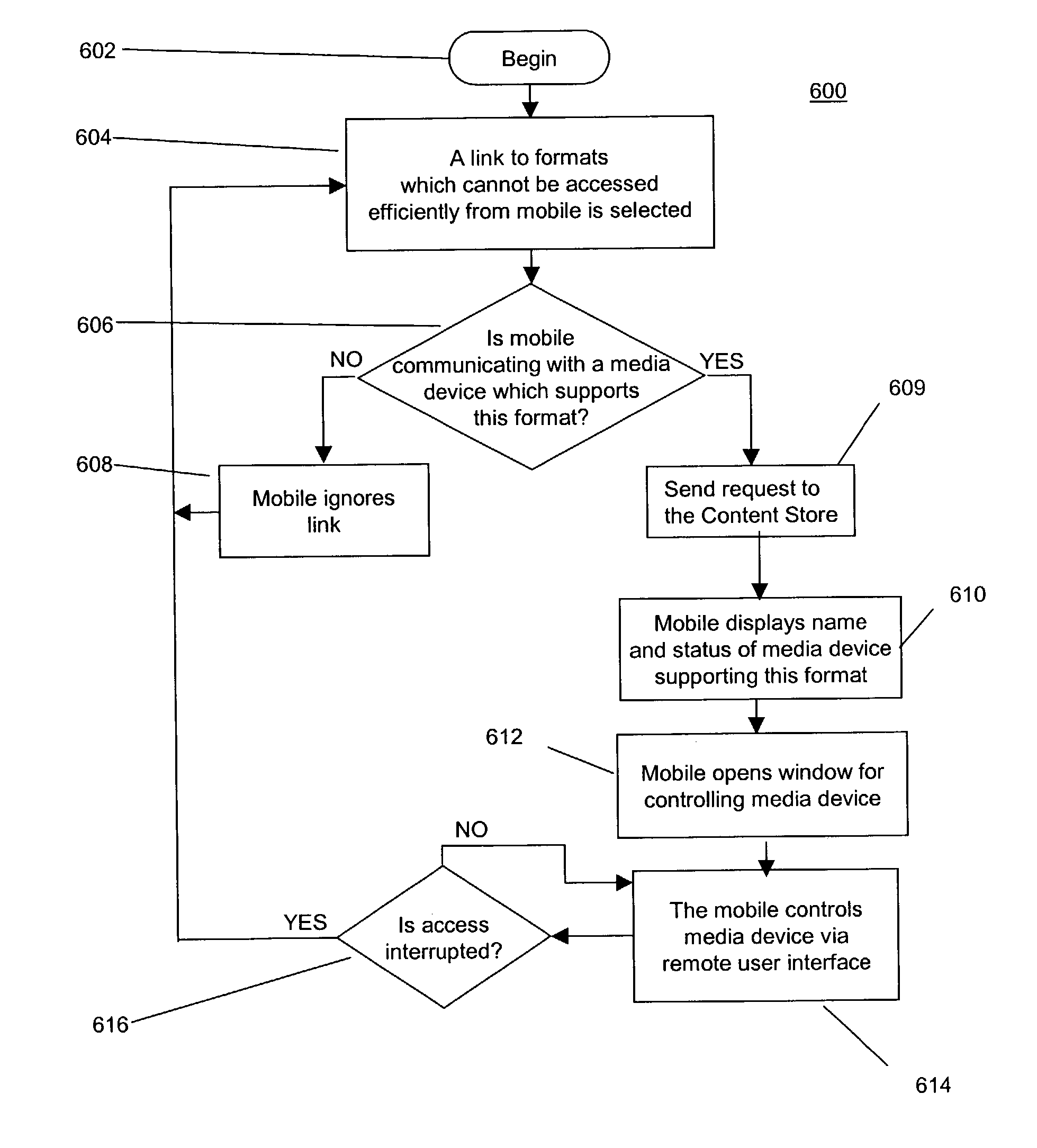
Multimedia control with one-click device selection
ActiveUS7840631B2Digital data processing detailsMultiple digital computer combinationsIdentifying VariableMedia content
Embodiments of a system and method for initiating multimedia control are disclosed. One embodiment comprises a means for discovering a media device including establishing communication with the media device, identifying media formats which the media device supports, and identifying variables to control media device playback; a means for delegating to the media device responsibility for playback of a media content including selecting the media device with a one-click selection and identifying to the media device the media content to be played back; and a means for controlling the media device playback.
Owner:MALIKIE INNOVATIONS LTD
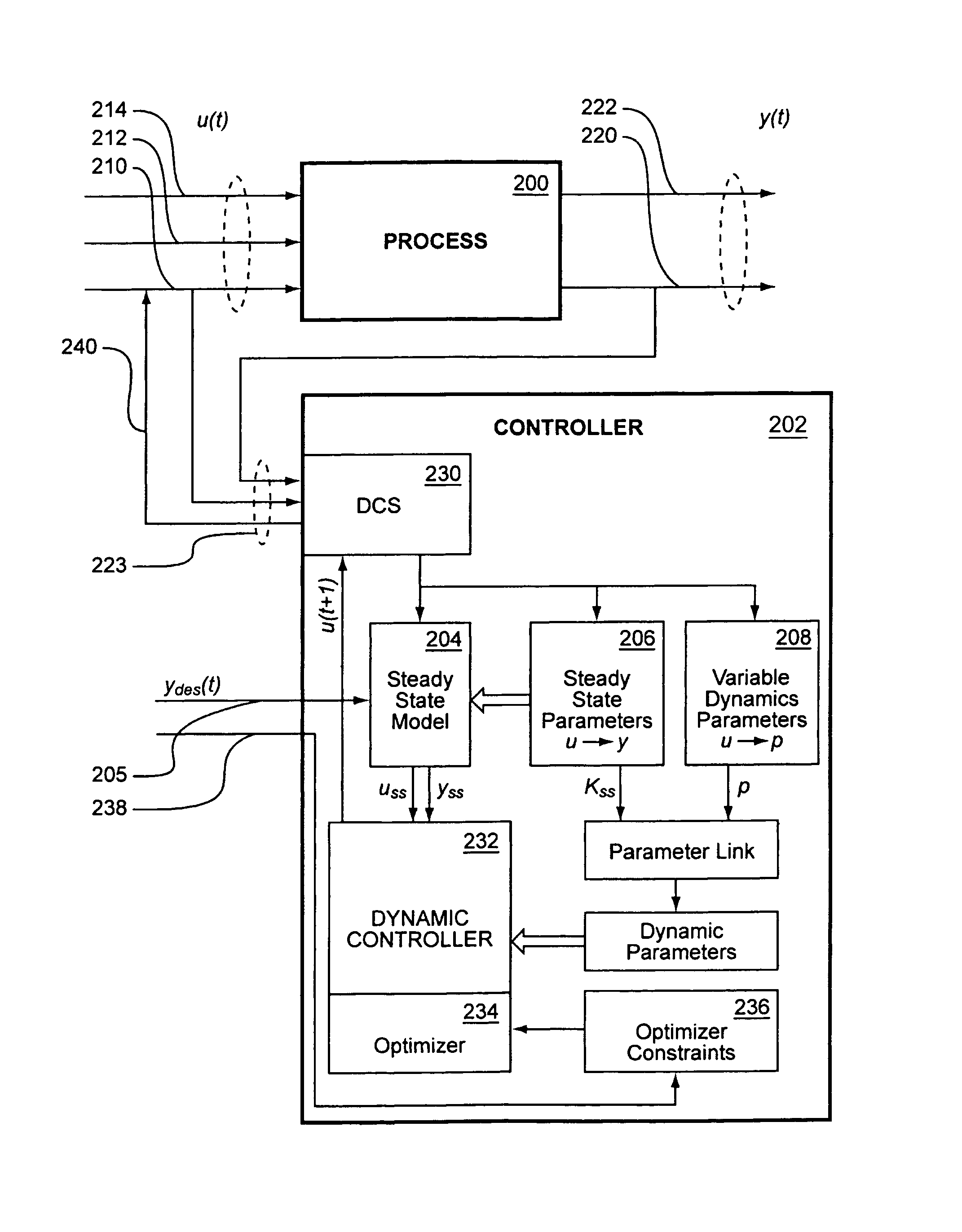
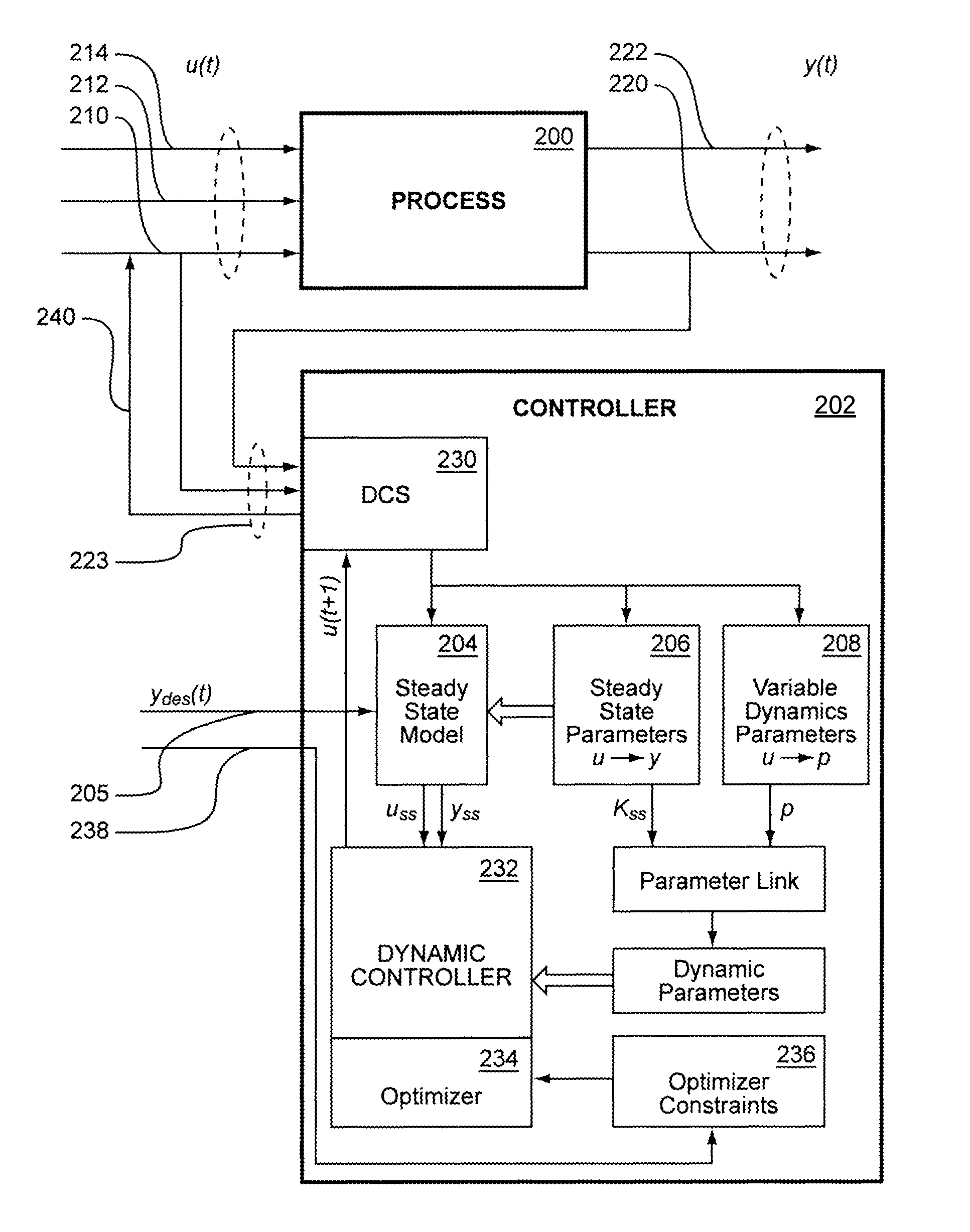
System and method of adaptive control of processes with varying dynamics
InactiveUS7039475B2Efficient collisionMore accurateSimulator controlElectric controllersIdentifying VariableControl system
The present invention provides a method for controlling nonlinear process control problems. This method involves first utilizing modeling tools to identify variable inputs and controlled variables associated with the process, wherein at least one variable input is a manipulated variable. The modeling tools are further operable to determine relationships between the variable inputs and controlled variables. A control system that provides inputs to and acts on inputs from the modeling tools tunes one or more manipulated variable inputs to achieve a desired result like greater efficiency, higher quality, or greater consistency.
Owner:ROCKWELL AUTOMATION TECH
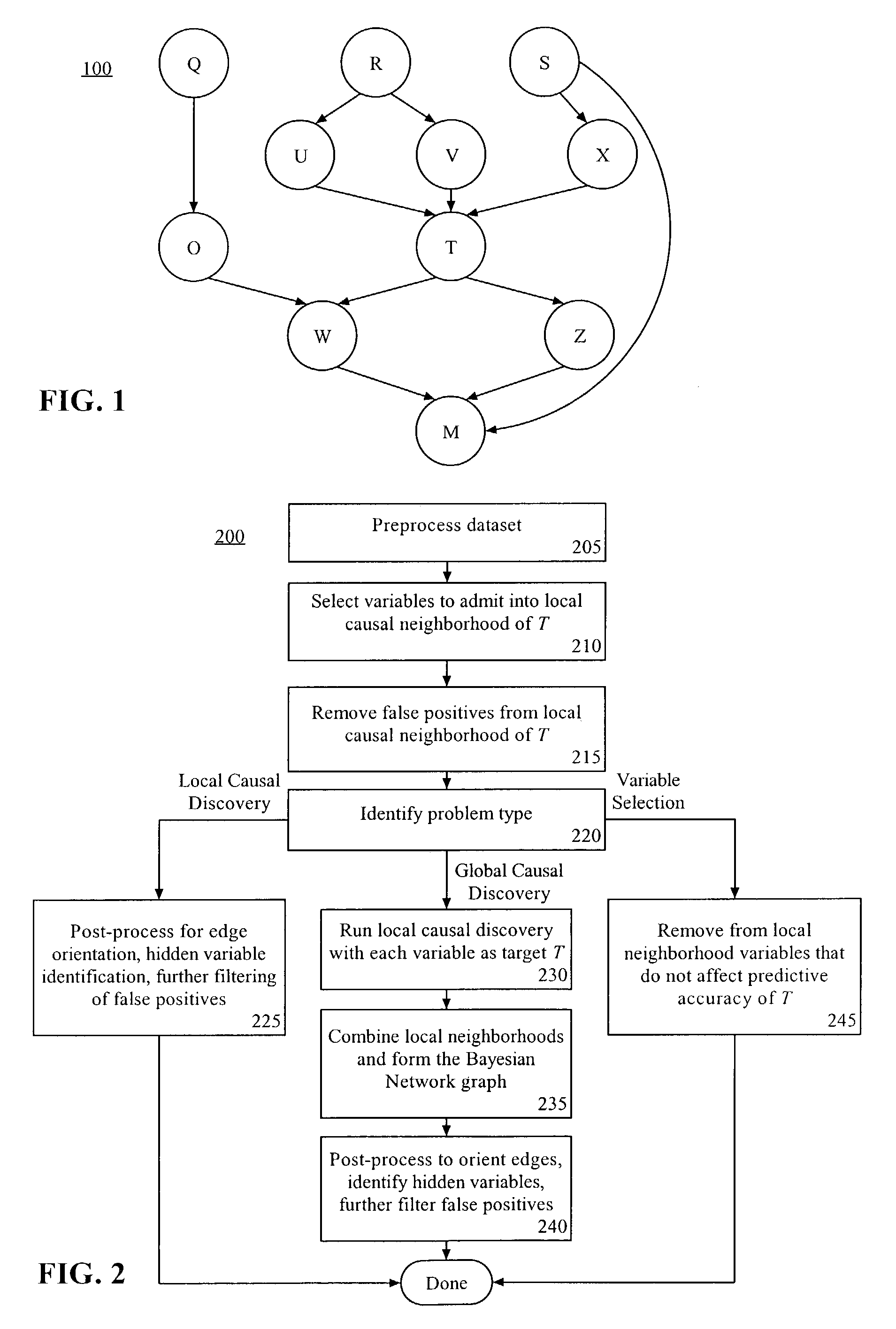
Method, system, and apparatus for casual discovery and variable selection for classification
InactiveUS7117185B1Easy to understandEasy constructionMathematical modelsDigital computer detailsIdentifying VariableData set
A method of determining a local causal neighborhood of a target variable from a data set can include identifying variables of the data set as candidates of the local causal neighborhood using statistical characteristics, and including the identified variables within a candidate set. False positive variables can be removed from the candidate set according to further statistical characteristics applied to each variable of the candidate set. The remaining variables of the candidate set can be identified as the local causal neighborhood of the target variable.
Owner:VANDERBILT UNIV
Electrospun Skin Capable Of Controlling Drug Release Rates And Method
InactiveUS20070087027A1High tensile strengthChange in permeabilityStentsSynthetic resin layered productsFiberDrug release rate
A versatile covering process enabled through the identification and manipulation of a plurality of variables present in the electrospinning method of the present invention. By manipulating and controlling various identified variables, it is possible to use electrospinning to predictably produce thin materials having desirable characteristics. The fibers created by the electrospinning process have diameters averaging less than 100 micrometers. Proper manipulation of the identified variables ensures that these fibers are still wet upon contacting a target surface, thereby adhering with each other to form a cloth-like material and, if desired, adhering to the target surface to form a covering thereon. The extremely small size of these fibers, and the resulting interstices therebetween, provides an effective vehicle for drug and radiation delivery, and forms an effective membrane for use in fuel cells.
Owner:GREENHALGH SKOTT E +1
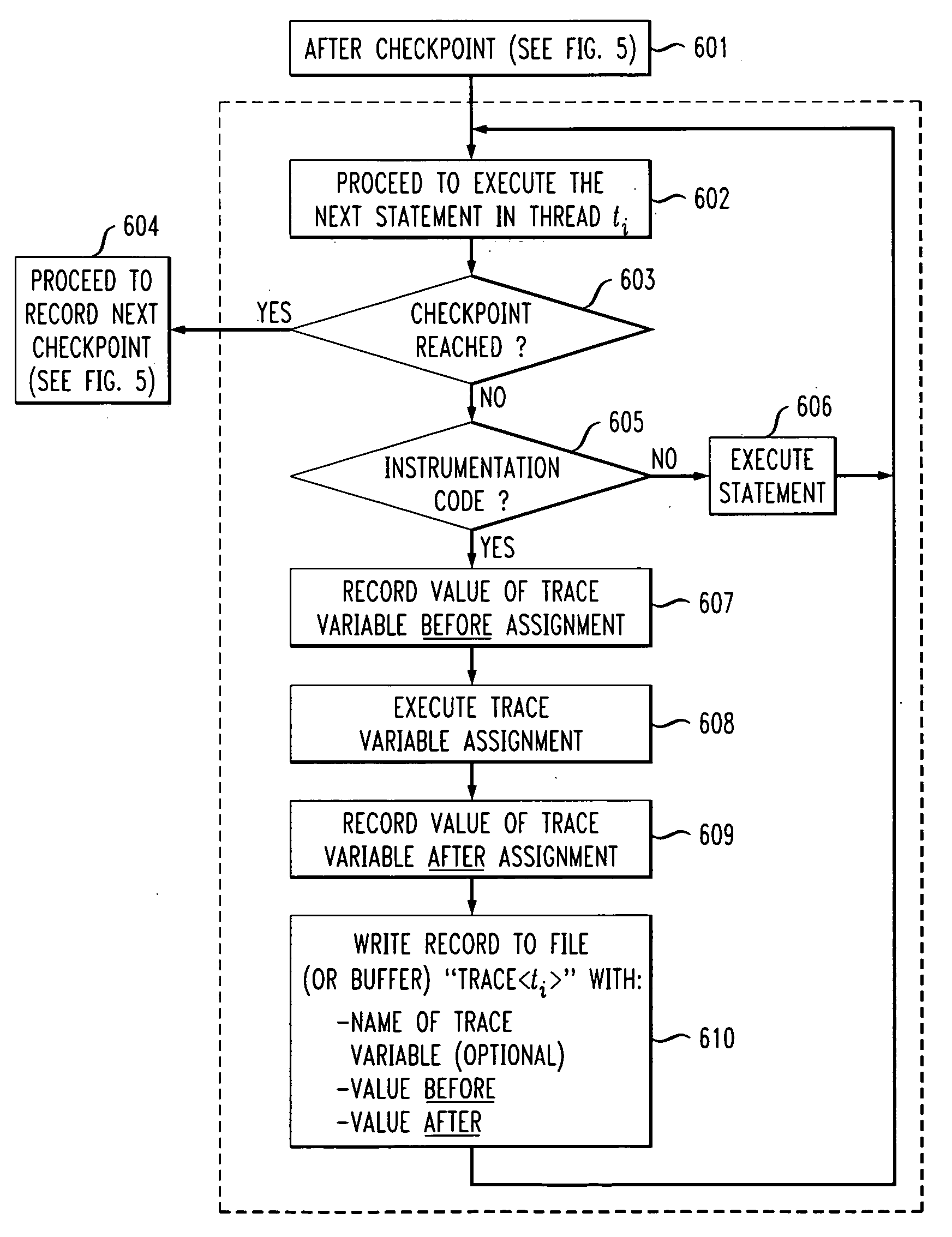
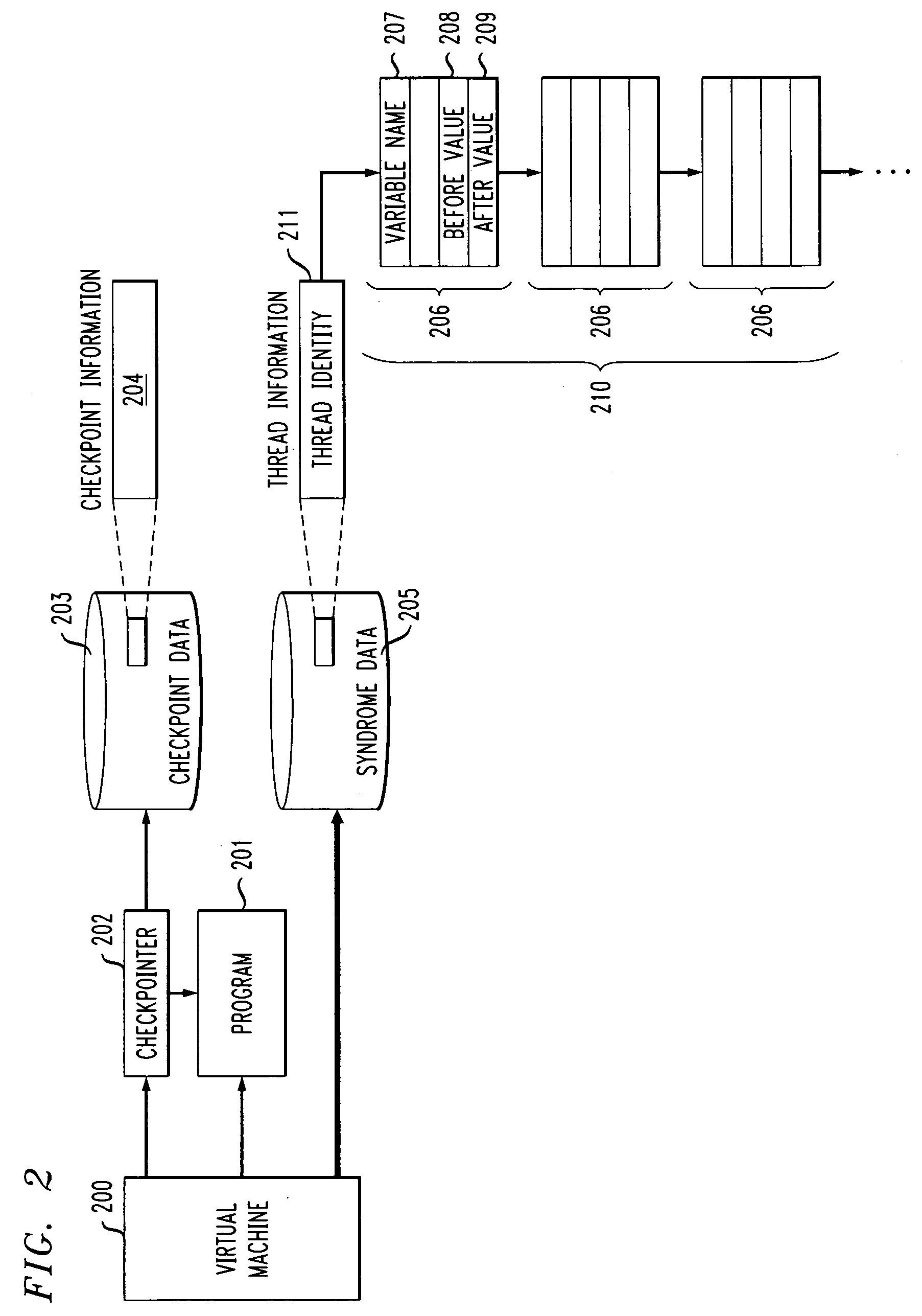
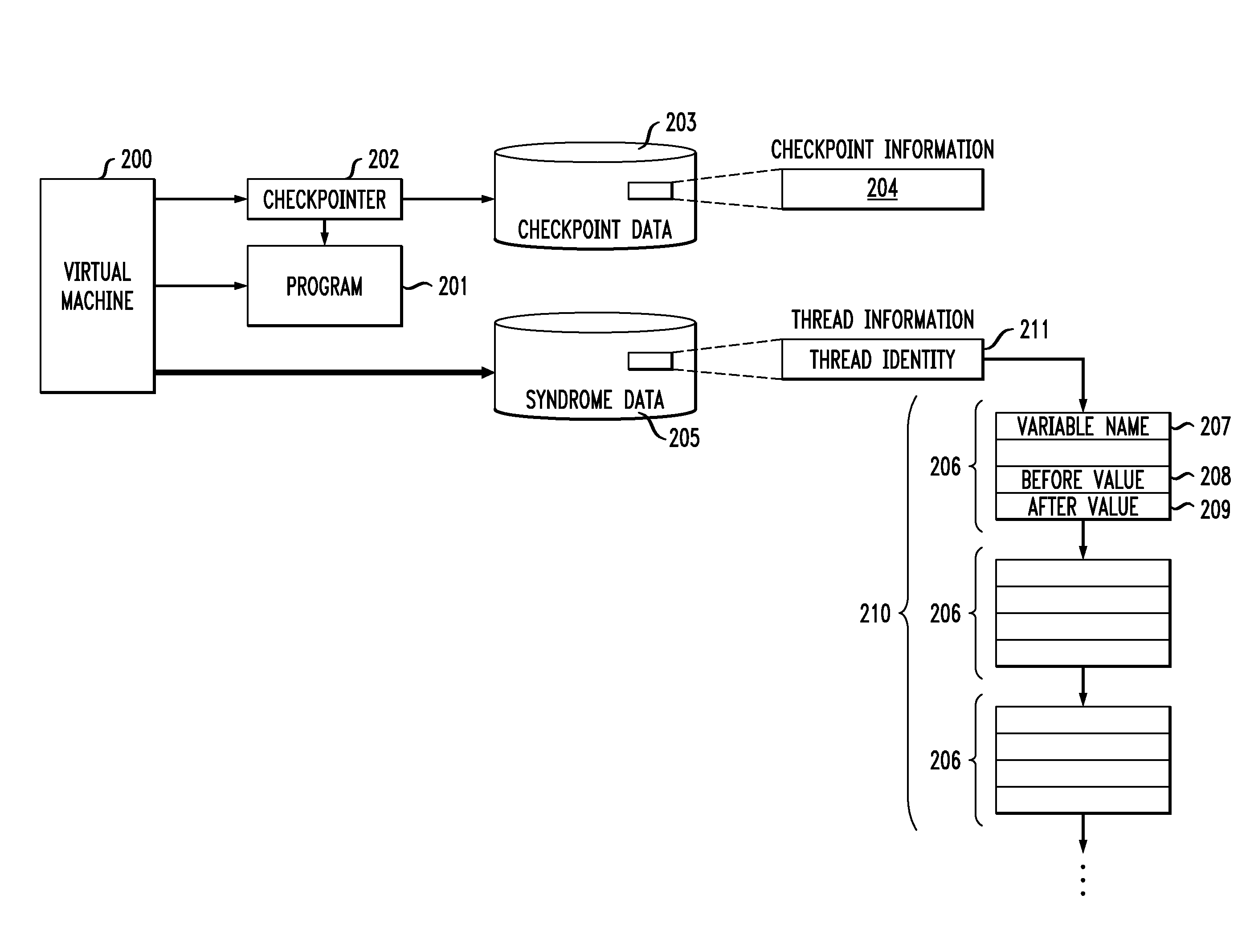
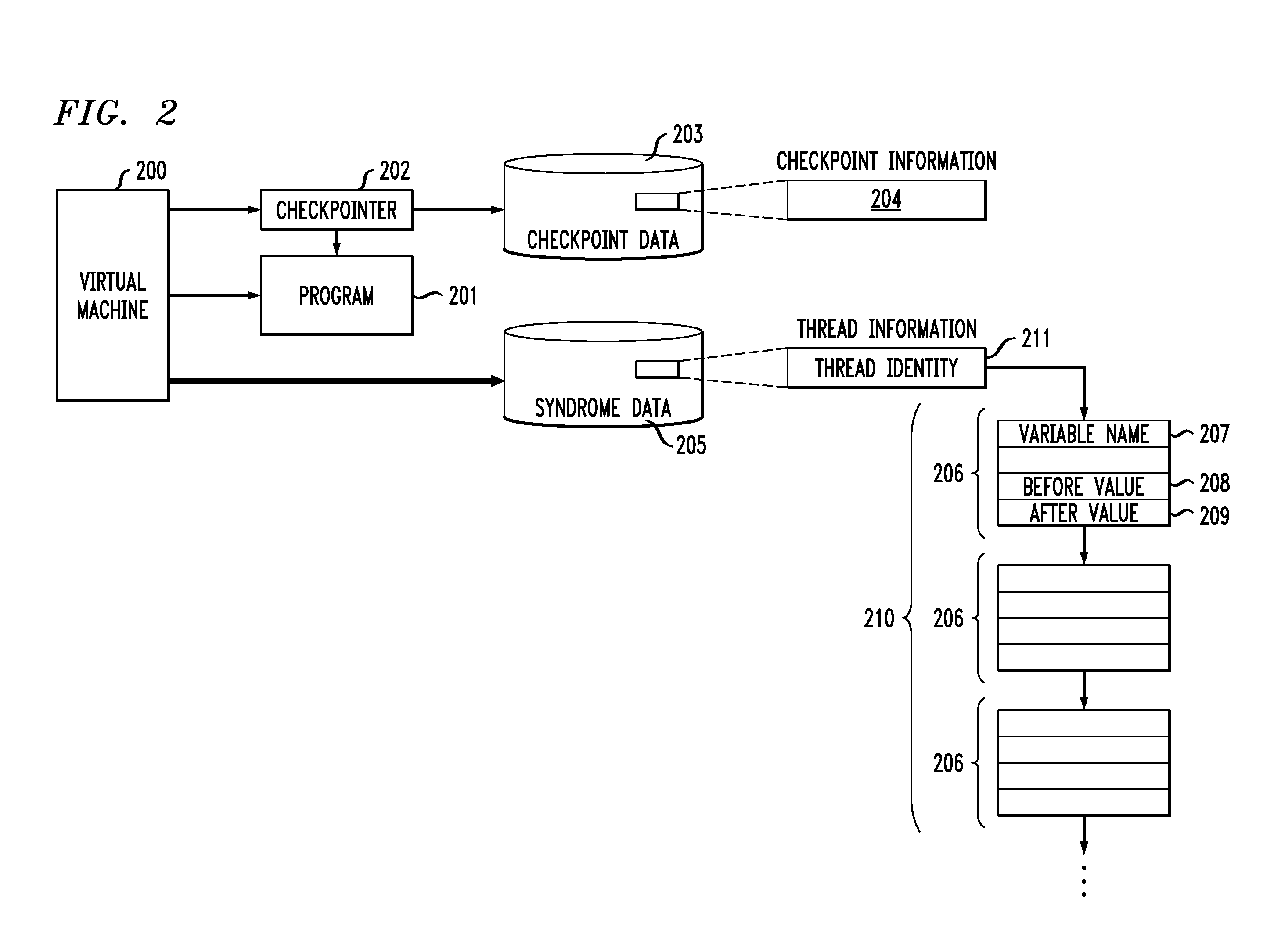
Method and apparatus for non-deterministic incremental program replay using checkpoints and syndrome tracking
InactiveUS20080046699A1Error detection/correctionDigital computer detailsIdentifying VariableTheoretical computer science
Methods and apparatus are provided for non-deterministic incremental program replay using checkpoints and syndrome tracking. Replay of a program proceeds by, for a given execution of the program, recording one or more checkpoints of the program, the one or more checkpoints containing program state information; and a recorded list of values for one or more identified variables executing in one or more threads of the program. Thereafter, during a replay execution of the program, the process continues by commencing execution from a particular one of the recorded checkpoints; restoring the program state information associated with the particular one of the recorded checkpoints; comparing an observed list of values to the recorded list of values for the one or more identified variables executing in each of the one or more threads; and identifying a difference between the observed list of values and the recorded list of values. A perturbation or suspend statement can optionally be introduced into the replay execution of the program.
Owner:IBM CORP
Method and apparatus for identifying access states for variables
A method, apparatus, and computer instructions in a processor for selectively performing operations on data. An operation to be performed on data is identified to form an identified operation. A determination is made as to whether metadata identifying a state of the data is associated with the data. A determination is made as to whether the identified operation can be performed on the data based on the state of the data, in response to the metadata being associated with the data. The operation is performed on the data if the state of the data allows for the operation to be performed. The processor selectively performs the operations based on the state of the data.
Owner:IBM CORP
System and method of applying adaptive control to the control of particle accelerators with varying dynamics behavioral characteristics using a nonlinear model predictive control technology
ActiveUS7184845B2Efficient collisionMore accurateAcceleratorsAdaptive controlParticle acceleratorIdentifying Variable
The present invention provides a method for controlling nonlinear control problems within particle accelerators. This method involves first utilizing software tools to identify variable inputs and controlled variables associated with the particle accelerator, wherein at least one variable input parameter is a controlled variable. This software tool is further operable to determine relationships between the variable inputs and controlled variables. A control system that provides variable inputs to and acts on controller outputs from the software tools tunes one or more manipulated variables to achieve a desired controlled variable, which in the case of a particle accelerator may be realized as a more efficient collision.
Owner:ROCKWELL AUTOMATION TECH
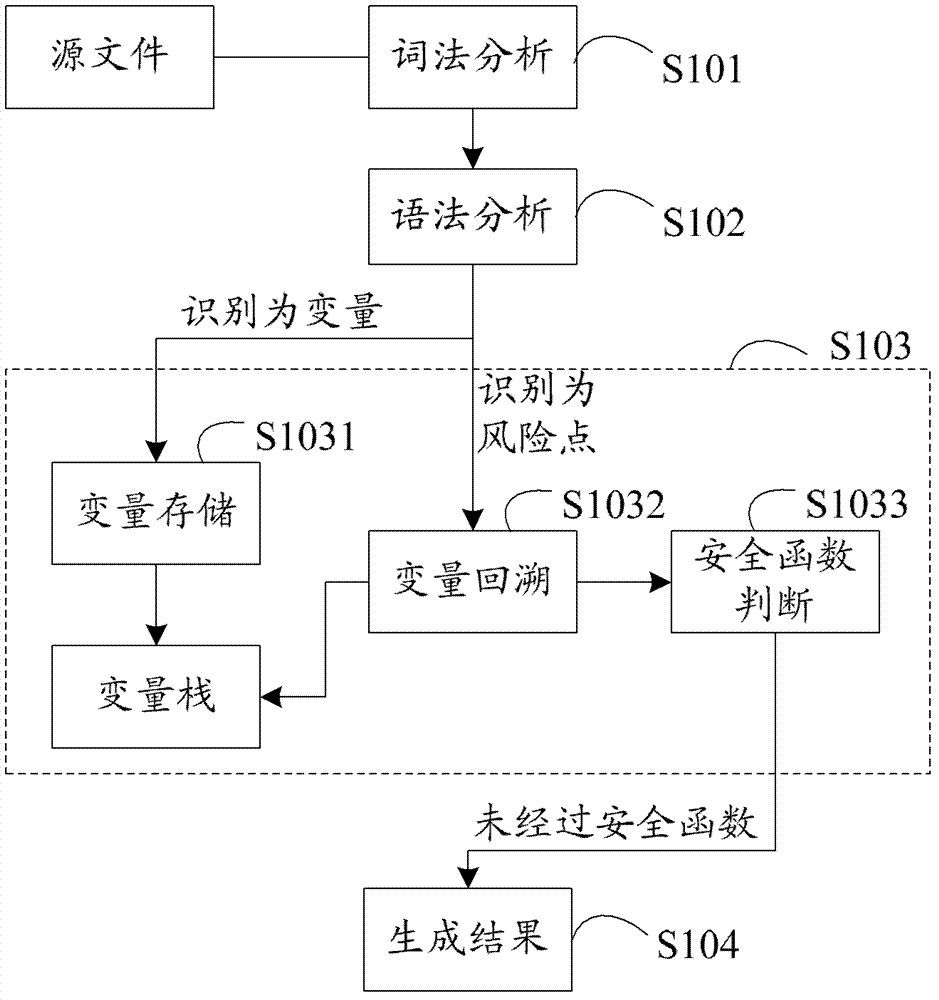
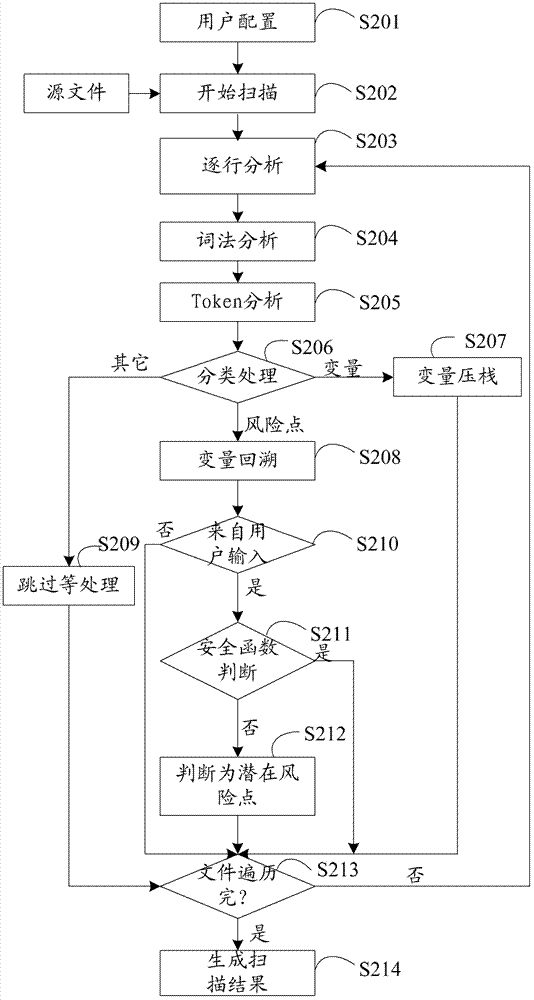
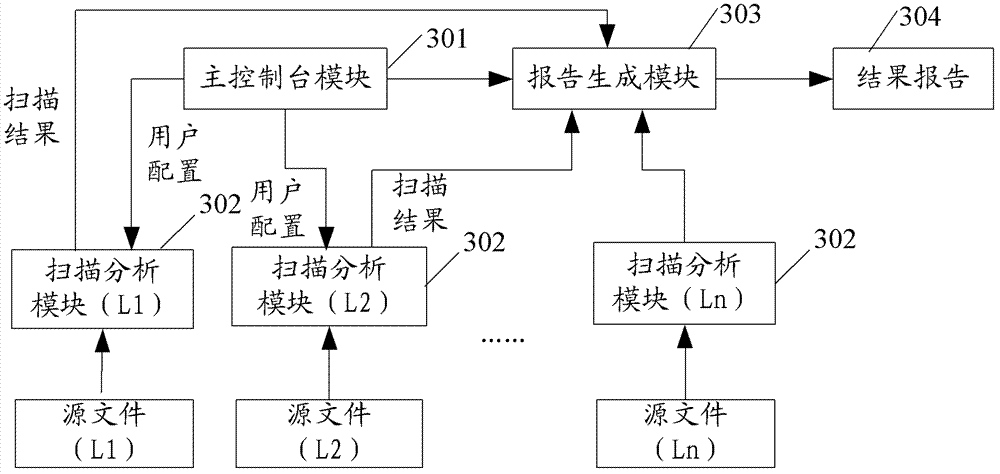
Method and device for detecting security flaws of source files
ActiveCN102955914ASave resourcesImprove scanning efficiencyPlatform integrity maintainanceIdentifying VariableLexical analysis
The invention provides a method and a device for detecting security flaws of source files. The method includes scanning the source files one by one and executing steps on the scanned source files including subjecting the source files to lexical analysis and grammatical analysis, performing variable identification operation and risk point identification operation in the process of the lexical analysis, wherein the variable identification operation includes identifying variables and storing identified variables; the risk point identification operation includes identifying risk points, backtracking the stored variables by means of parameters of the risk points which are identified, and if the parameters of the risk points can be backtracked to an importable point, considering the risk point is potential risk points to cause security flaws when without security function processing in the process of backtracking. Compared with the prior art, the method for detecting security flaws of the source files has no need to build up an abstract syntax tree, processing procedures are simplified, resources of a testing system are saved, and code scanning efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
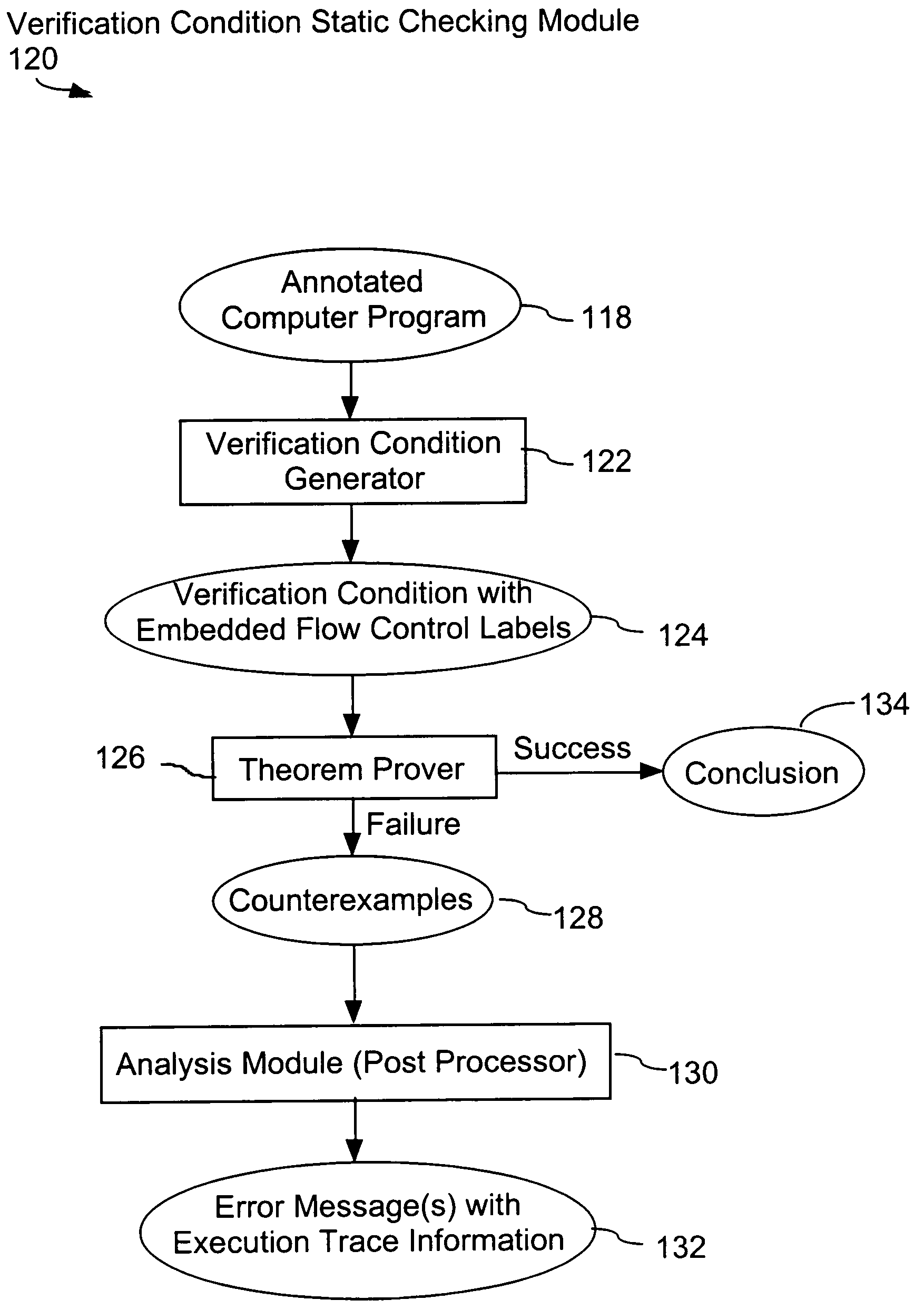
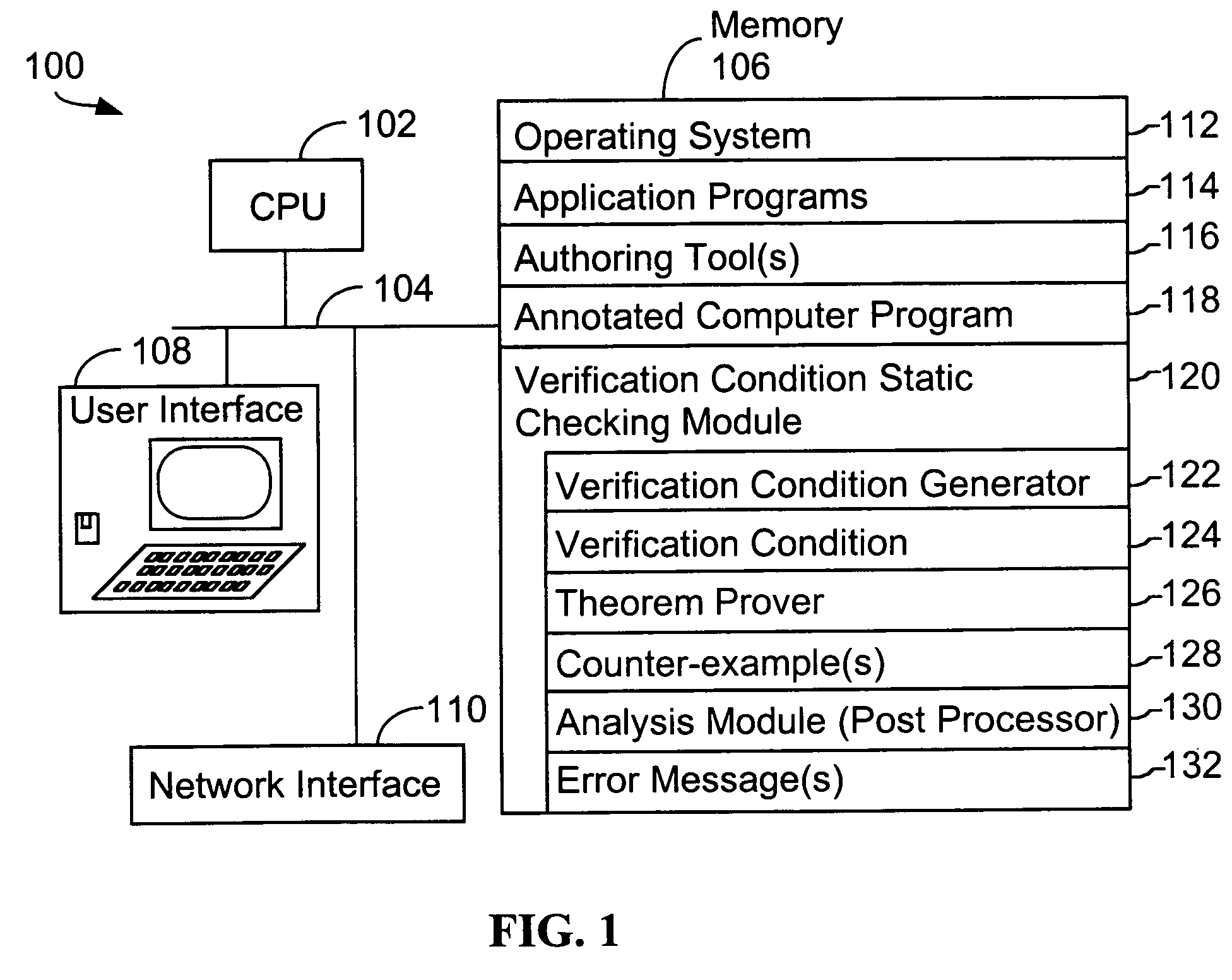
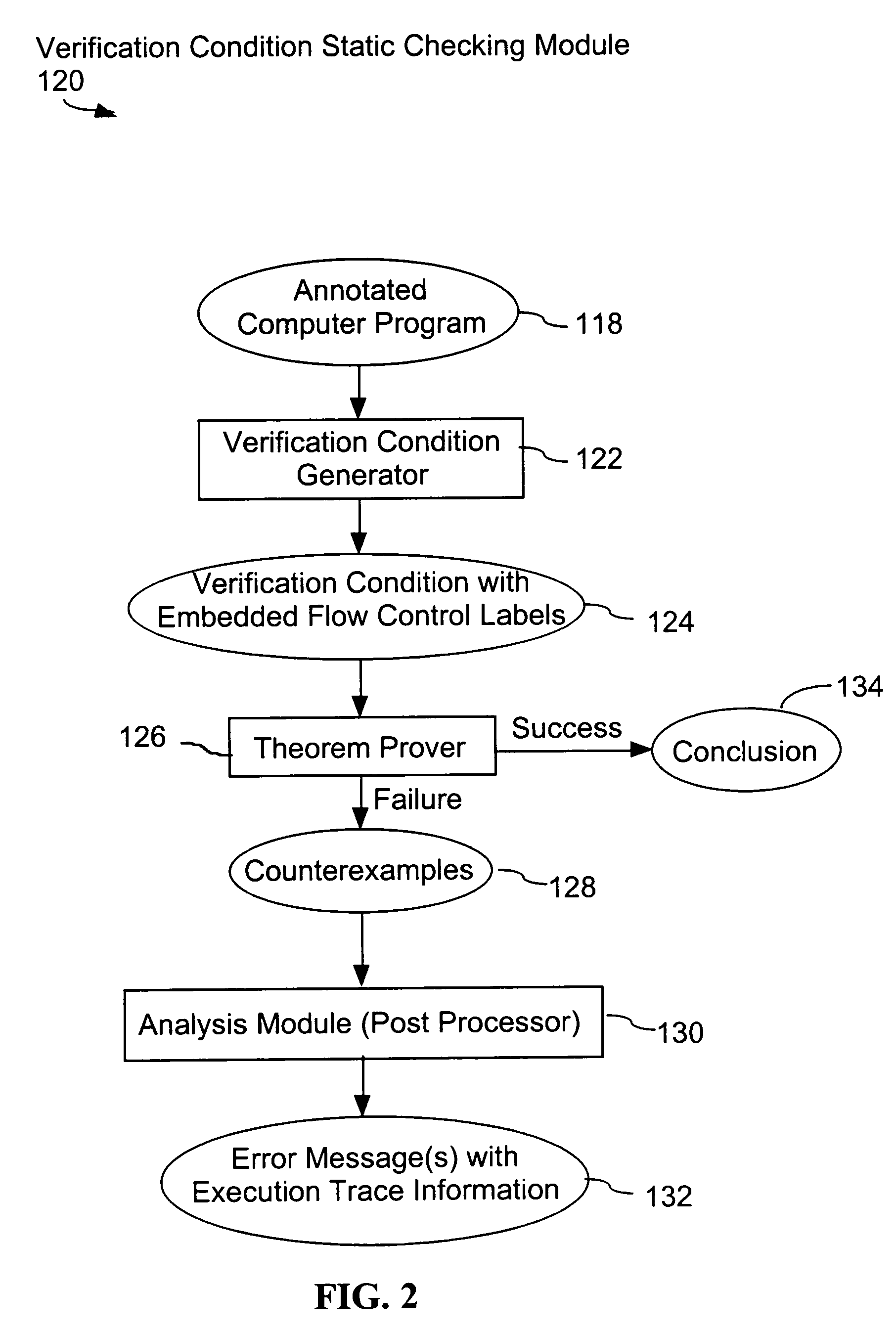
System and method for verifying computer program correctness and providing recoverable execution trace information
In a system for statically analyzing a specified computer, a verification condition generator converts the program into a logical equation, called a verification condition, and inserts program flow control labels into the sub-equations of the verification condition. The flow control labels identify conditional branch points in the specified computer program. A theorem prover is applied to the logical equation to determine truth of the logical equation, and when the truth of the logical equation cannot be proved, the theorem prover generates at least one counter-example identifying one of the conditions, one or more variable values inconsistent with that condition, and any of the flow control labels for conditional branch points of the program associated with the identified variable values. A post processing module converts each counter-example into an error message that includes a program trace when the counter-example identifies one or more of the flow control labels.
Owner:HEWLETT PACKARD DEV CO LP
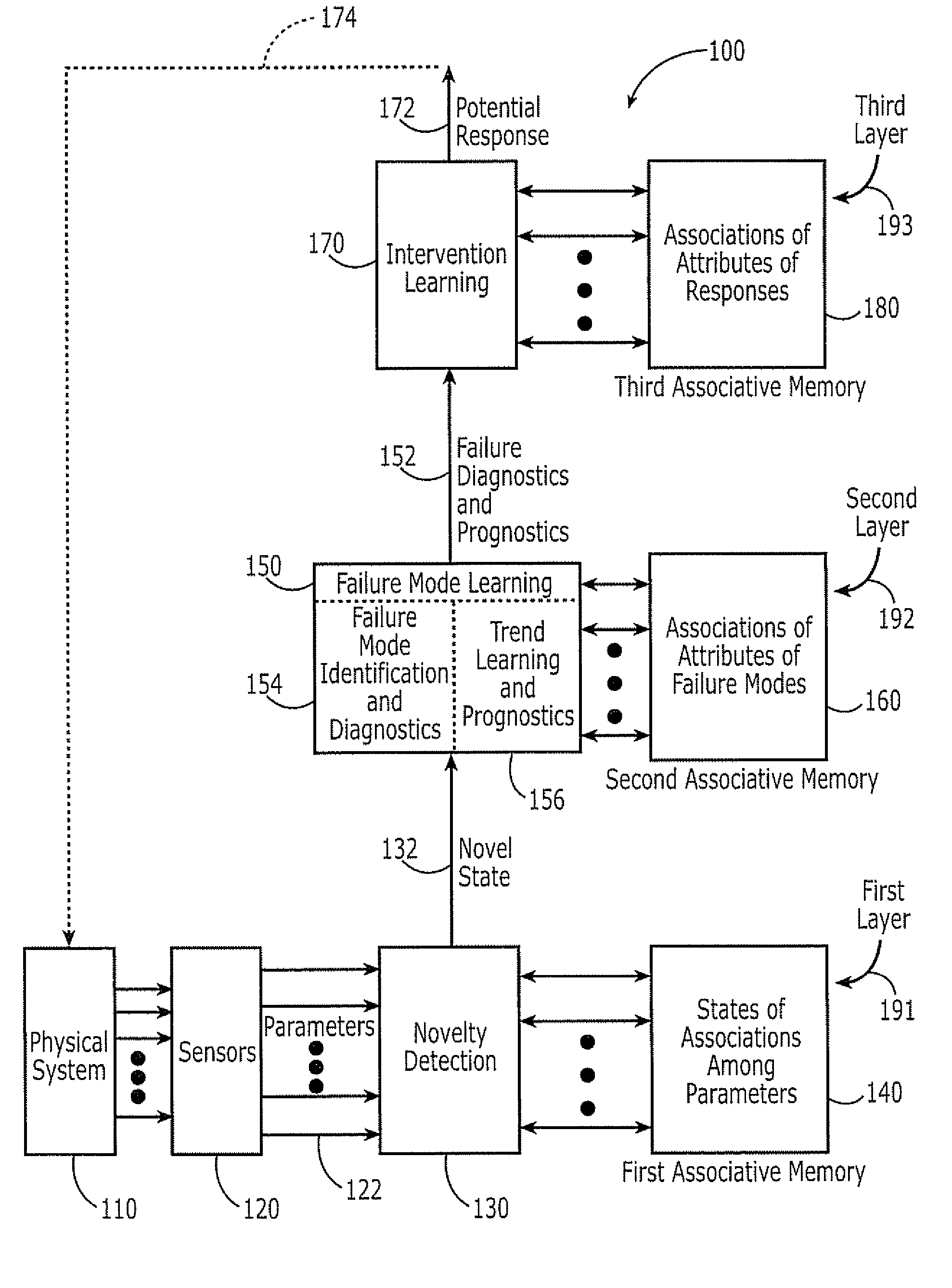
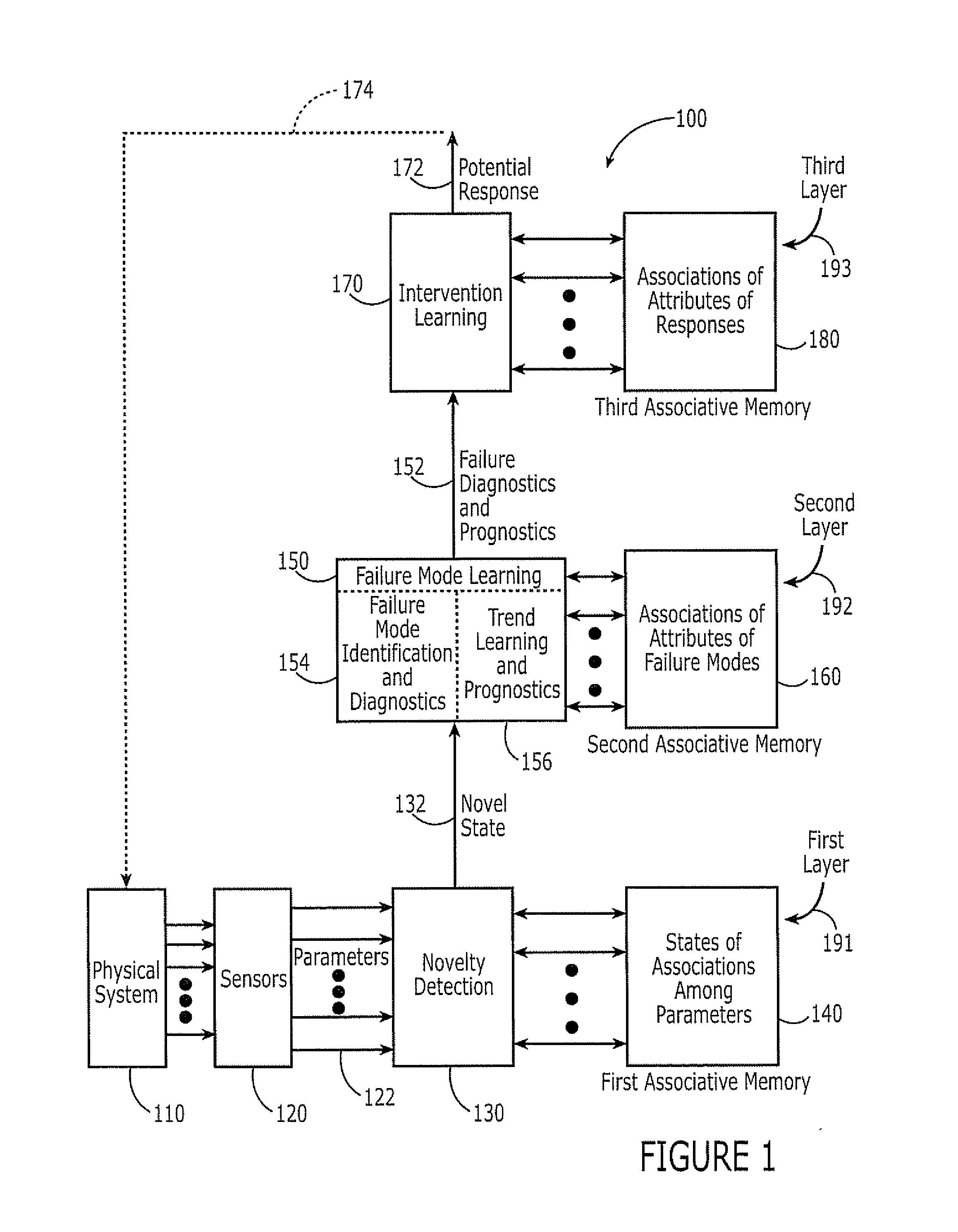
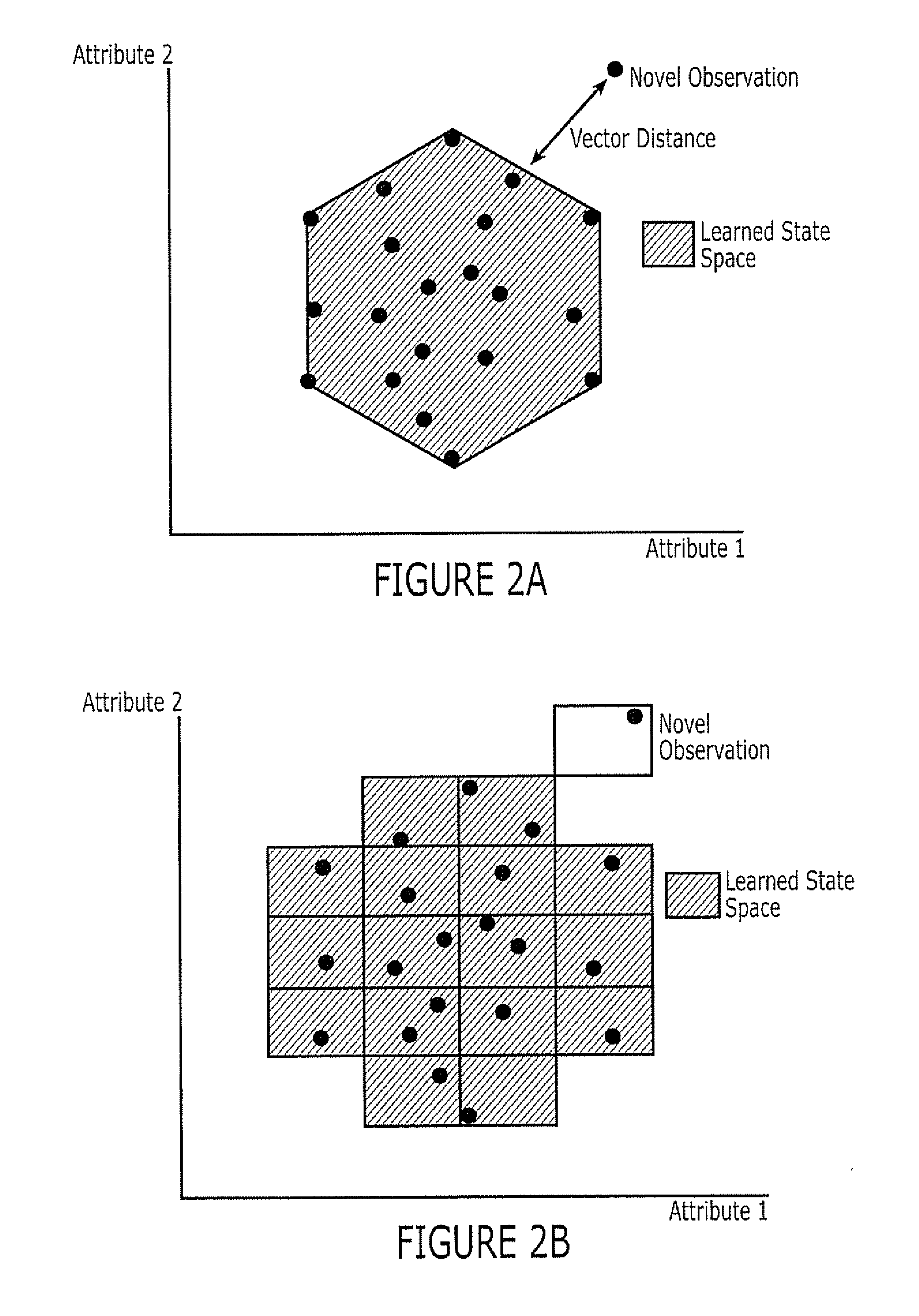
Novelty detection systems, methods and computer program products for real-time diagnostics/prognostics in complex physical systems
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL +1
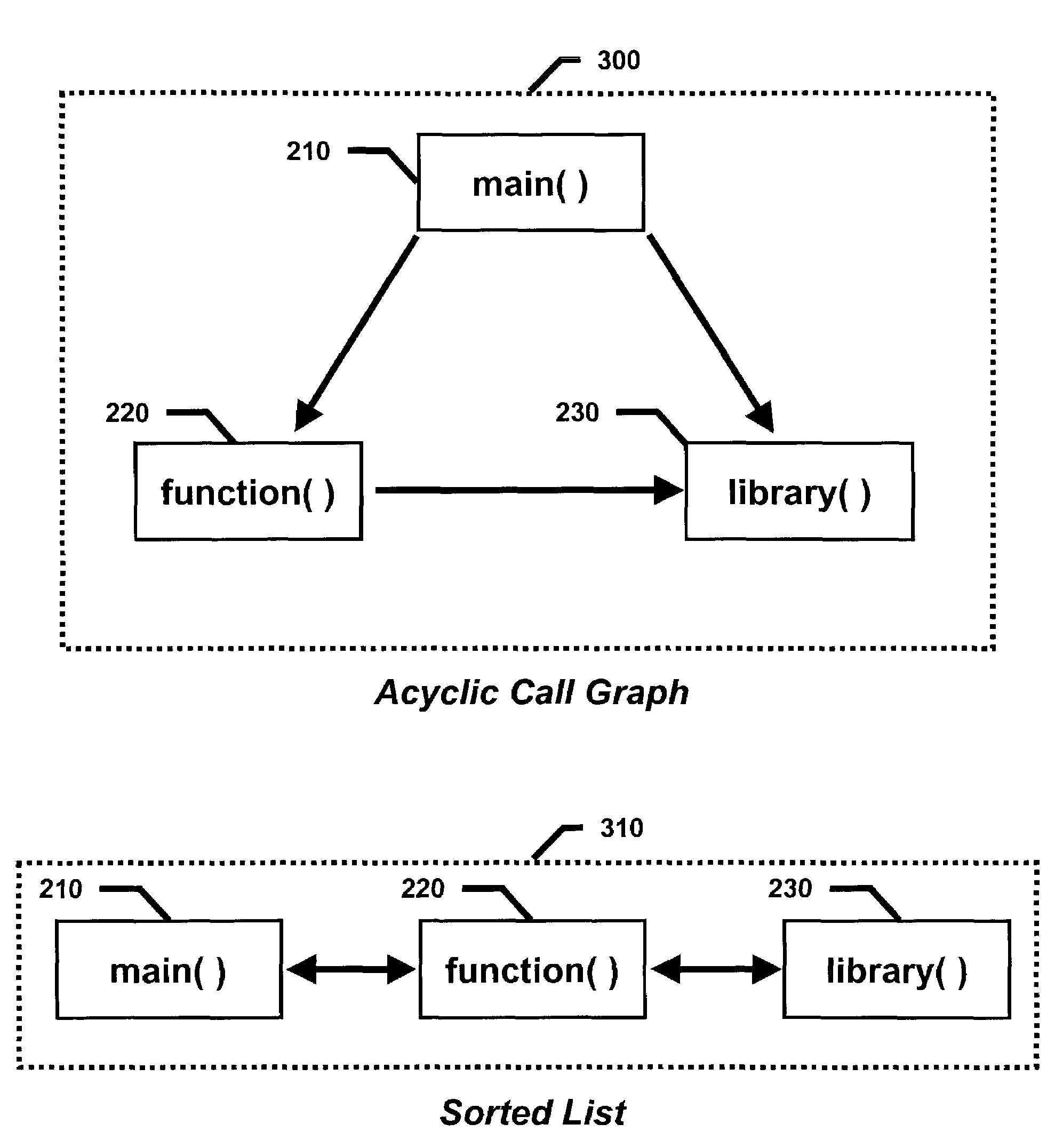
Inter-procedure global register allocation method
Embodiments of the present invention provide a method and system for optimizing processor register allocation. Variables from an acyclic call graph having a plurality of functions may be identified and a plurality of virtual registers may be created by assigning each of the identified variables to at least one virtual register. An interference graph may be constructed based on the plurality of virtual registers and may be colored with a plurality of physical registers. If the interference graph is not colorable, then at least one virtual register may be spilled from the interference graph.
Owner:INTEL CORP
Method and system for determining a least cost path for routing international communications traffic
InactiveUS7352852B1Easily and accurately and efficiently determineFacilitate communicationTelephonic communicationIdentifying VariableTelecommunications network
A method, system, and medium for determining a least-cost, international-routing path to communicate data across a telecommunications network are provided. The path implementation variables can be presented on a user interface or used to automatically generate a switch update transaction that implements the path. The method includes identifying variables that affect the determination of a least-cost path, receiving data values that correspond to the variables, and presenting the data values so that the path can be determined in response to observing the variables. Confidence and route testing can be conducted using the present invention.
Owner:SPRINT CORPORATION
Novelty Detection Systems, Methods and Computer Program Products for Real-Time Diagnostics/Prognostics In Complex Physical Systems
Sensors are configured to repeatedly monitor variables of a physical system during its operation. A novelty detection system is responsive to the sensors and is configured to repeatedly observe into an associative memory, states of associations among the variables that are repeatedly monitored, during a learning phase. The novelty detection system is further configured to thereafter observe at least one state of associations among the variables that are sensed relative to the states of associations that are in the associative memory, to identify a novel state of associations among the variables. The novelty detection system may determine whether the novel state is indicative of normal operation or of a potential abnormal operation. Multiple layers of learning for real-time diagnostics / prognostics also may be provided.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL +1
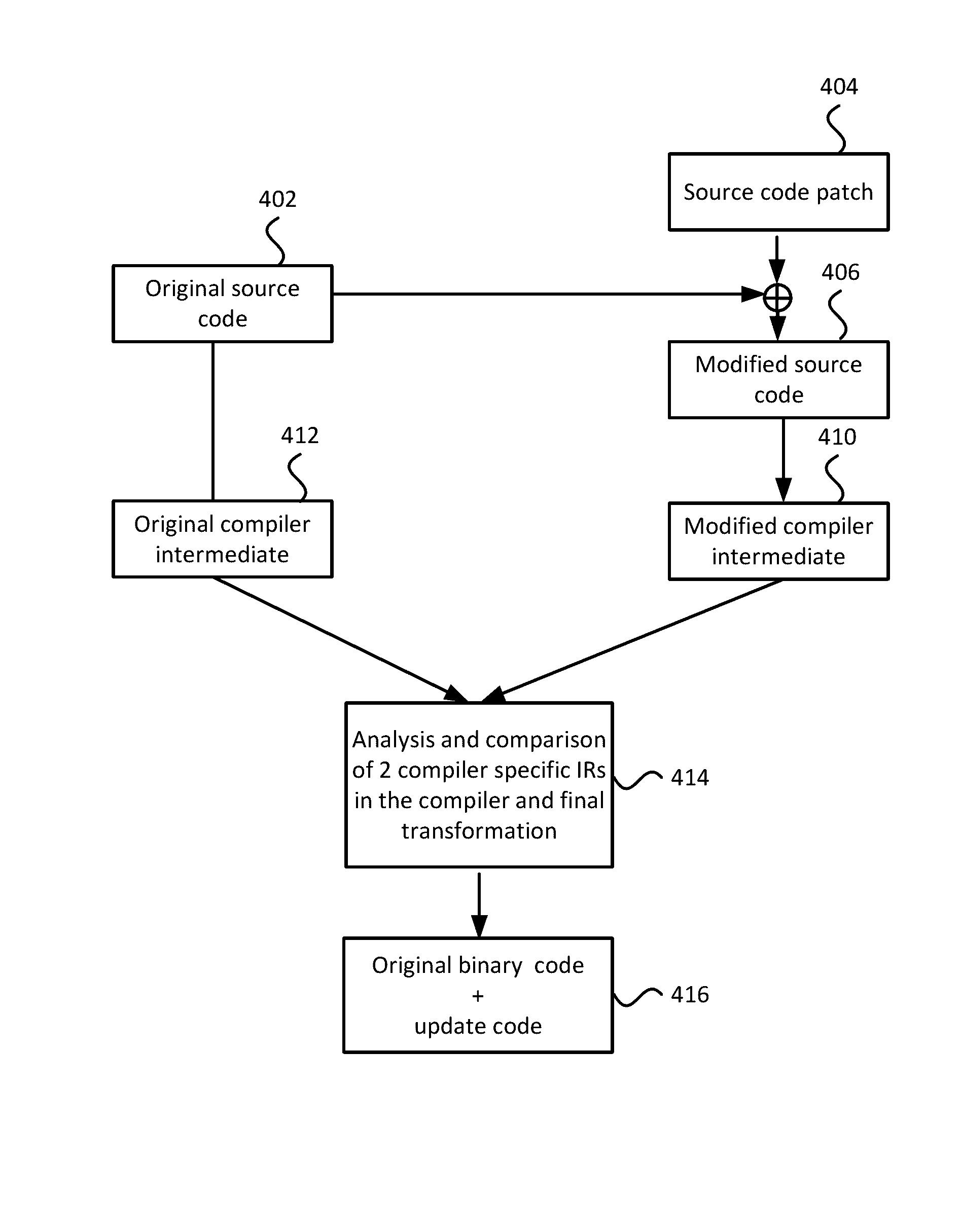
Systems and methods for generating and applying operating system live updates
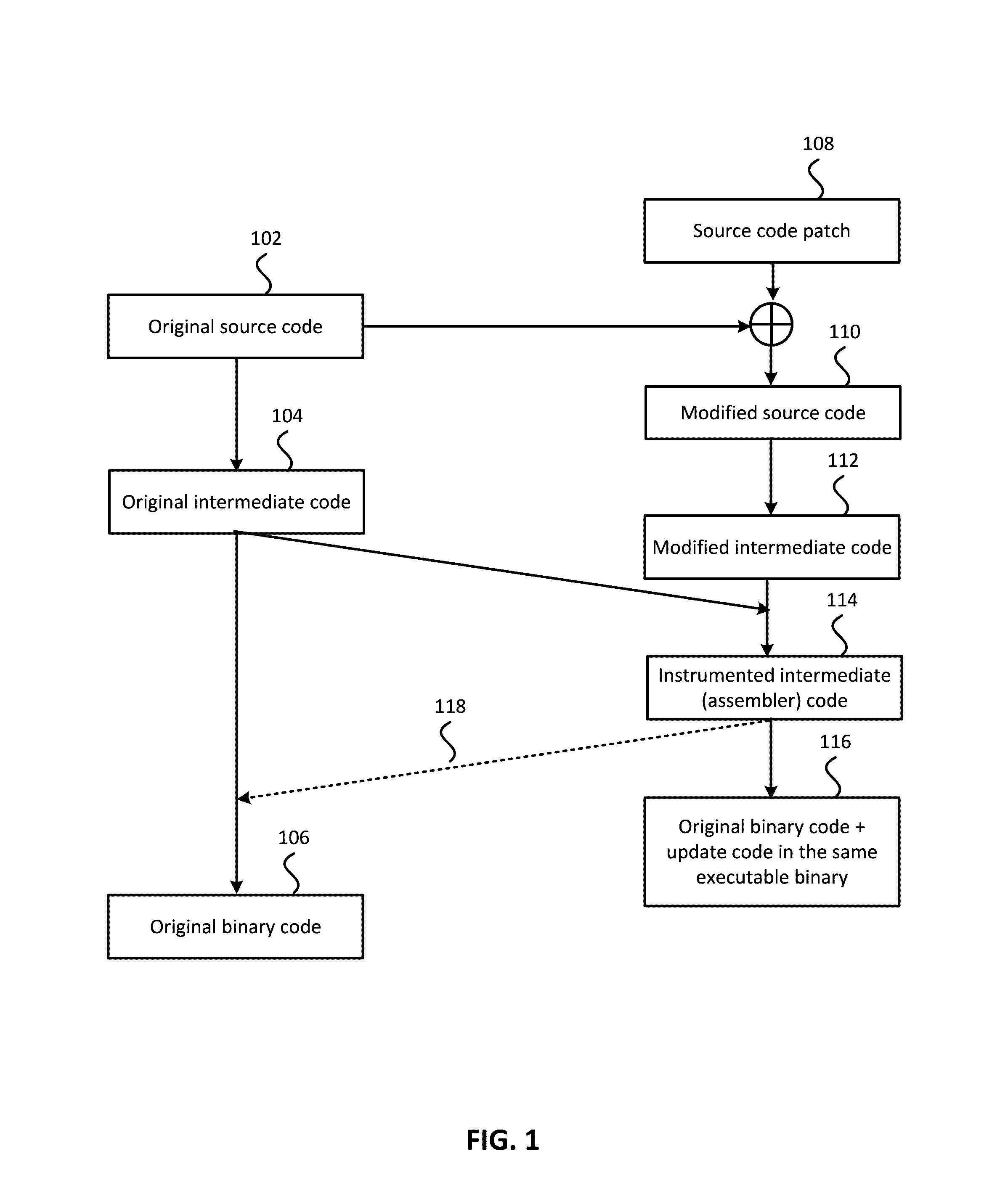
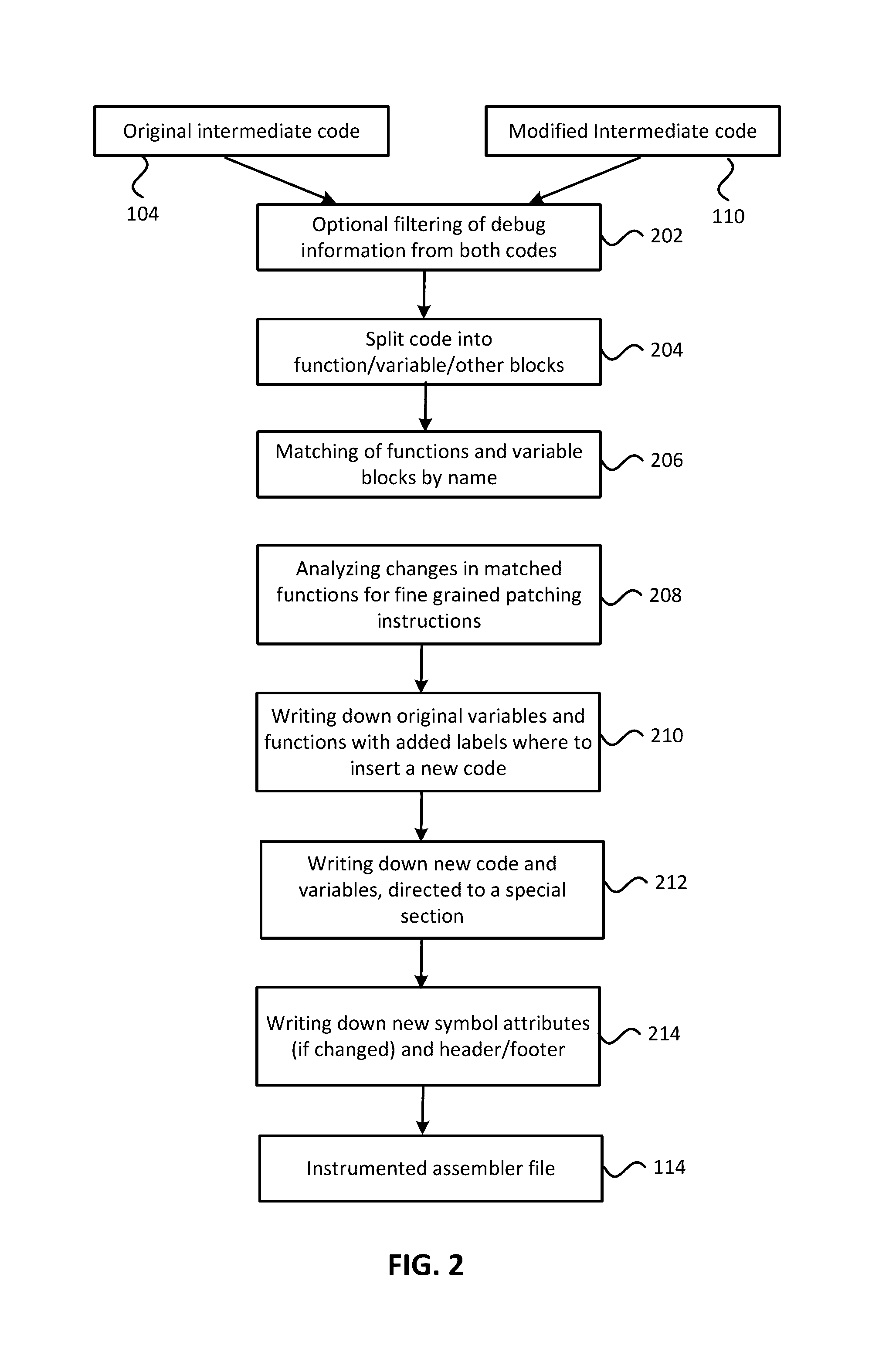
ActiveUS9477461B1Application securityUpdate generationProgram loading/initiatingSpecial data processing applicationsIdentifying VariableData segment
Method for generation of a live update including compiling original source code into a first intermediate representation (IR) code; compiling modified source code into second IR code; analyzing and comparing the first and second IR codes to identify variables and functions that were changed generating a part of final IR code with all the original variables and functions; generating an additional part of final IR code with new code for modified portions of the changed original functions, added functions and variables, and marking it for compilation into special code / data sections; and compiling a new object code and a final executable binary based on the final IR. The final executable object code includes the original code and data from original application binary, and a live update code and data from additional part of final IR generated. The live update code and data refer to original code and data where needed via standard object code relocation information.
Owner:CLOUD LINUX SOFTWARE INC
System and method for computer language migration
ActiveUS20180357055A1Program documentationVisual/graphical programmingIdentifying VariableObject Class
A legacy-to-container (L2C) system converts a computer program in a procedural programming language to an object oriented programming language. The L2C system parses the procedural language to identify program variables and also program sub-elements, such as paragraphs in COBOL for example. The L2C system provides a user interface that allows the user to select which paragraphs should be converted into methods wherein the remaining non-selected paragraphs are to be converted into classes. The L2C system is configured to re-architect the procedural language by (i) creating normal object classes corresponding to the identified variables, (ii) creating methods for the user-selected paragraphs; and (iii) creating classes for the remaining non-selected paragraphs. The L2C further includes various wizards to further facilitate the re-architecting, such as a UI enrichment wizard, a code elimination wizard, and a database optimizer wizard, as well as a code de-duplication wizard, a microservices wizard, and a parallel processing wizard.
Owner:ATOS FRANCE
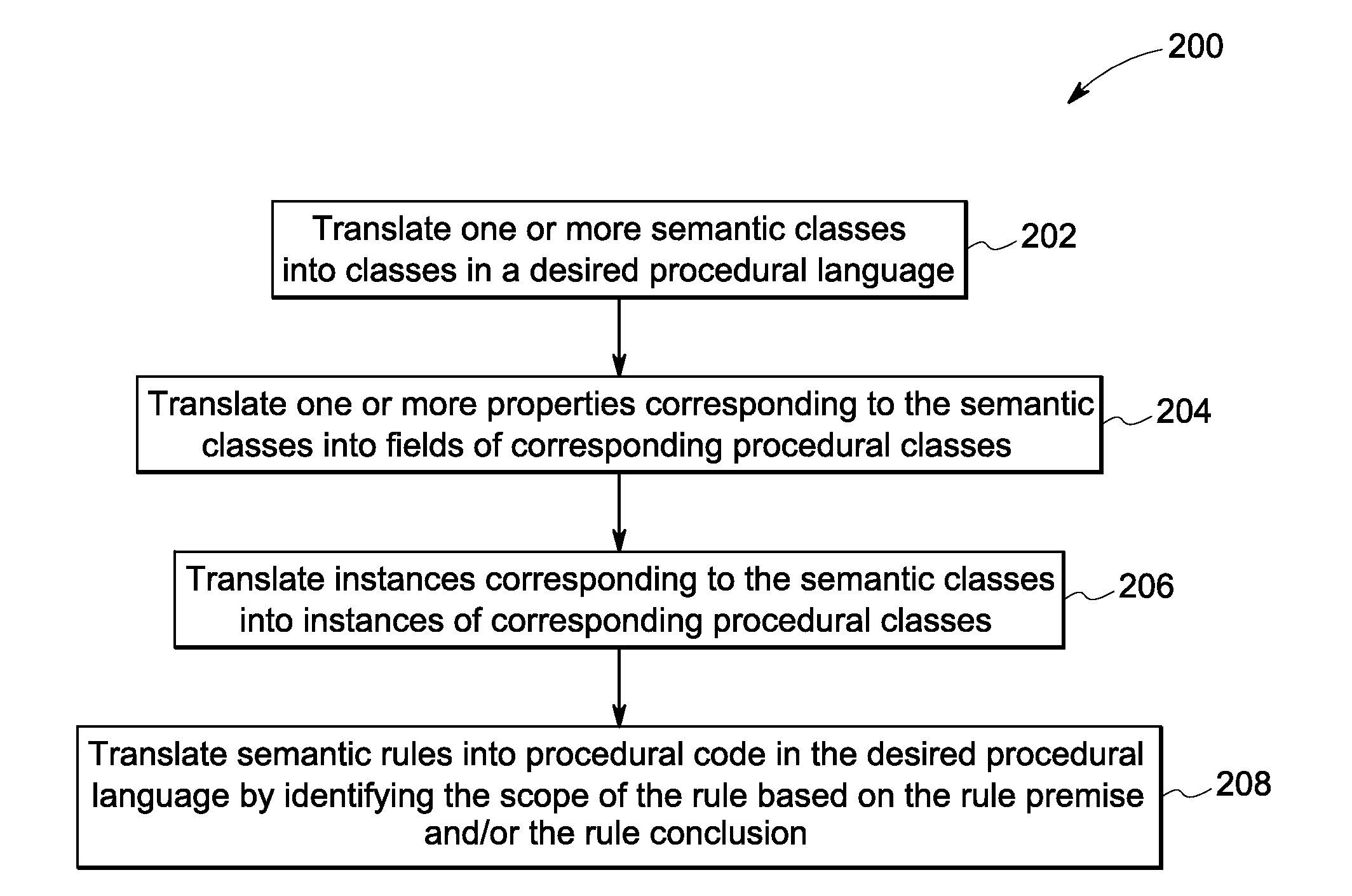
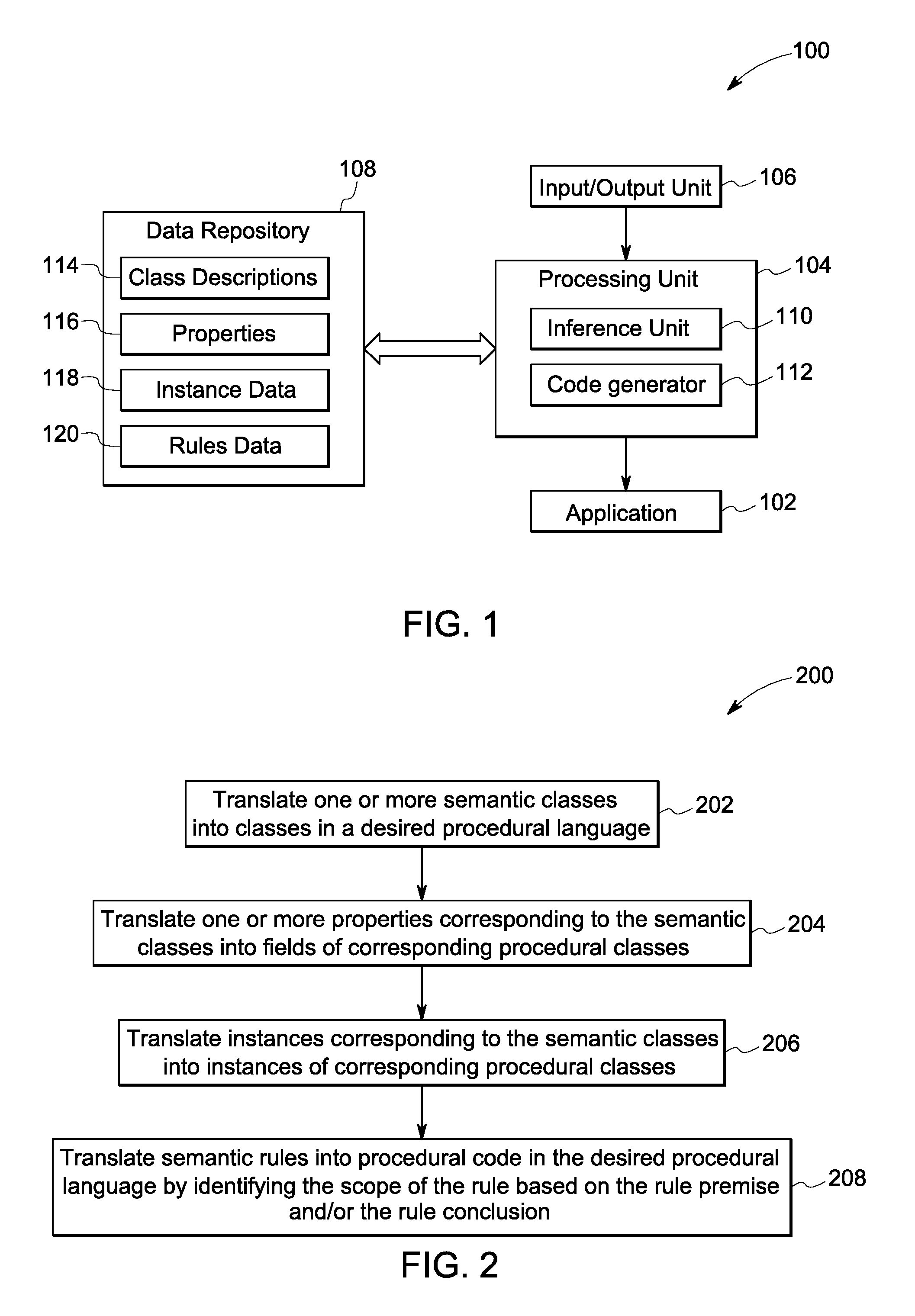
Methods for code generation from semantic models and rules
InactiveUS20120278788A1Specific program execution arrangementsMemory systemsIdentifying VariableSubject matter
Owner:GENERAL ELECTRIC CO
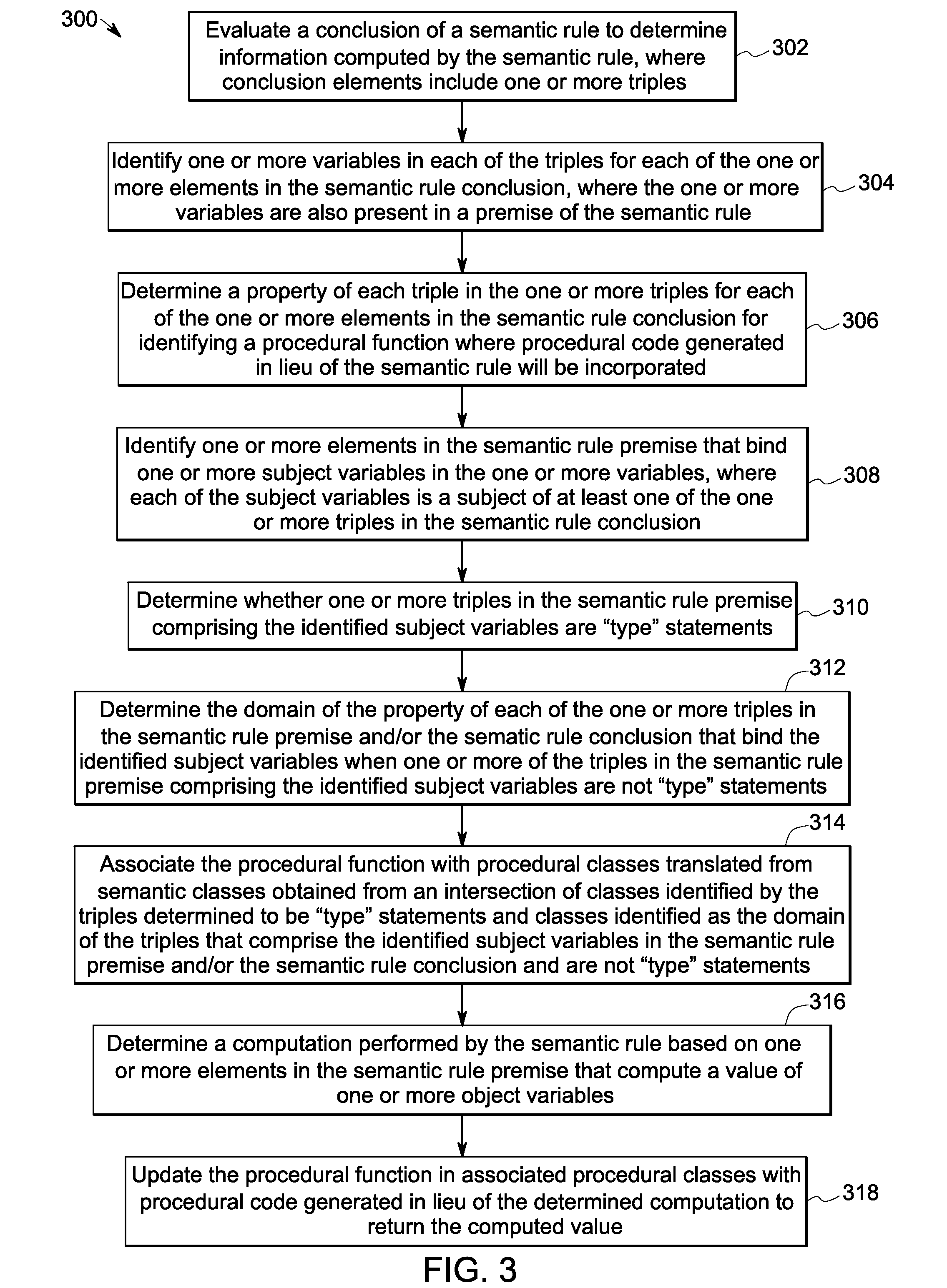
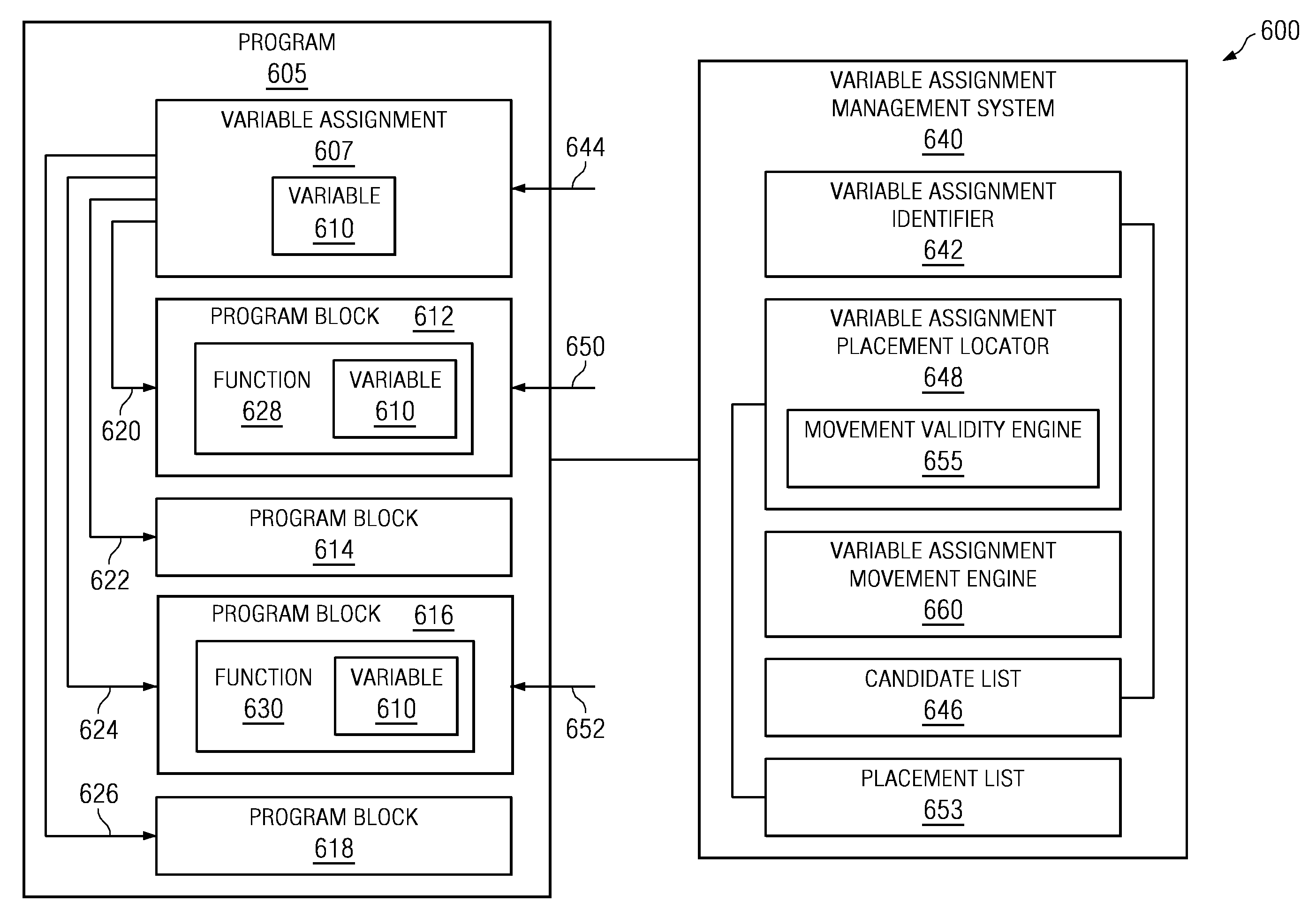
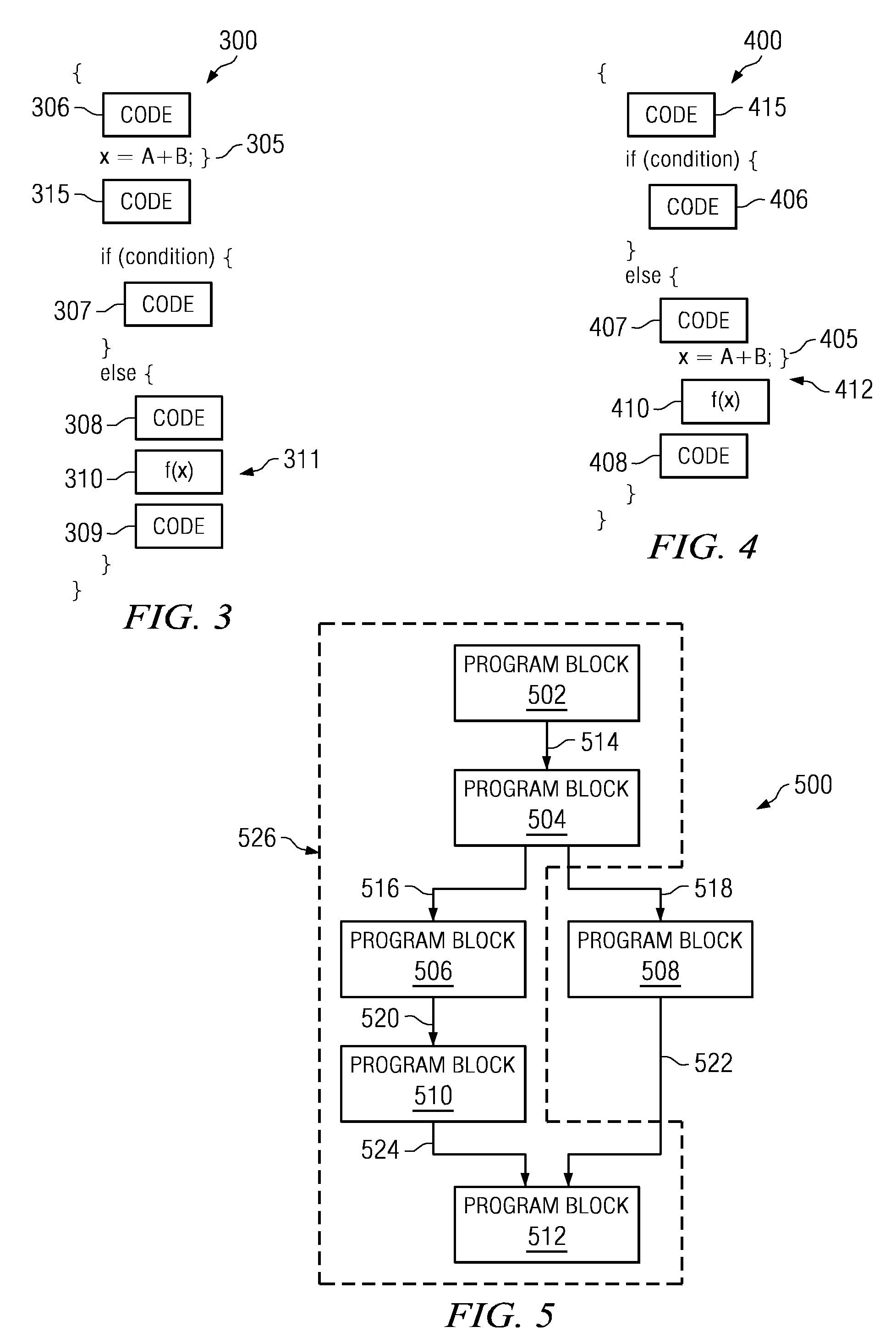
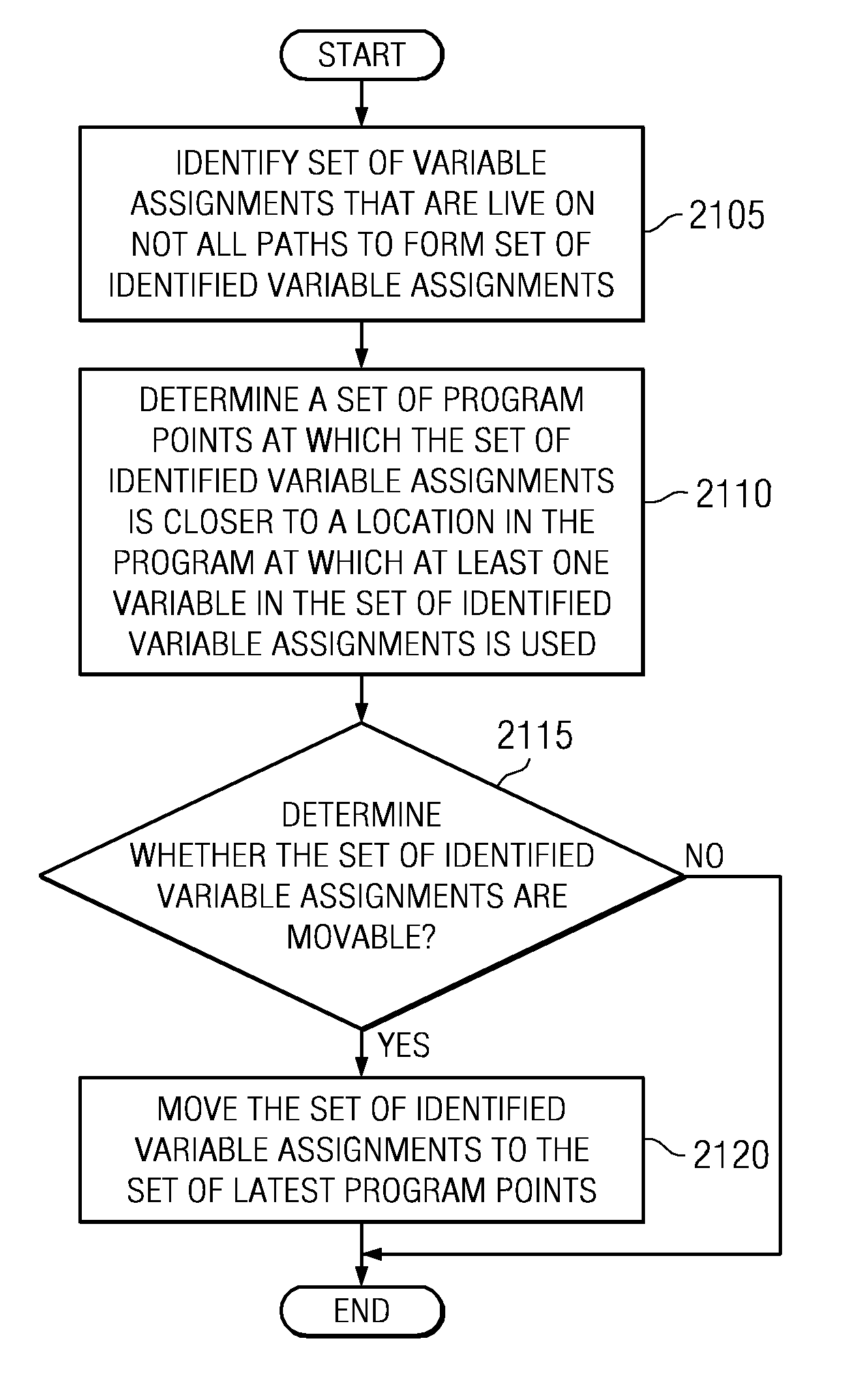
Method and apparatus for managing variable assignments in a program
The illustrative embodiments described herein provide a computer-implemented method, apparatus, and computer program product for managing variable assignments in a program. The process identifies a set of variable assignments that is live on a portion of paths to form a set of identified variable assignments. Each of the set of identified variable assignments assign a value to at least one variable of a set of variables. The process determines a set of program points at which the set of identified variable assignments is live on all paths. The process also moves the set of identified variable assignments to the set of program points in response to determining that the set of identified variable assignments is movable to the set of program points.
Owner:IBM CORP
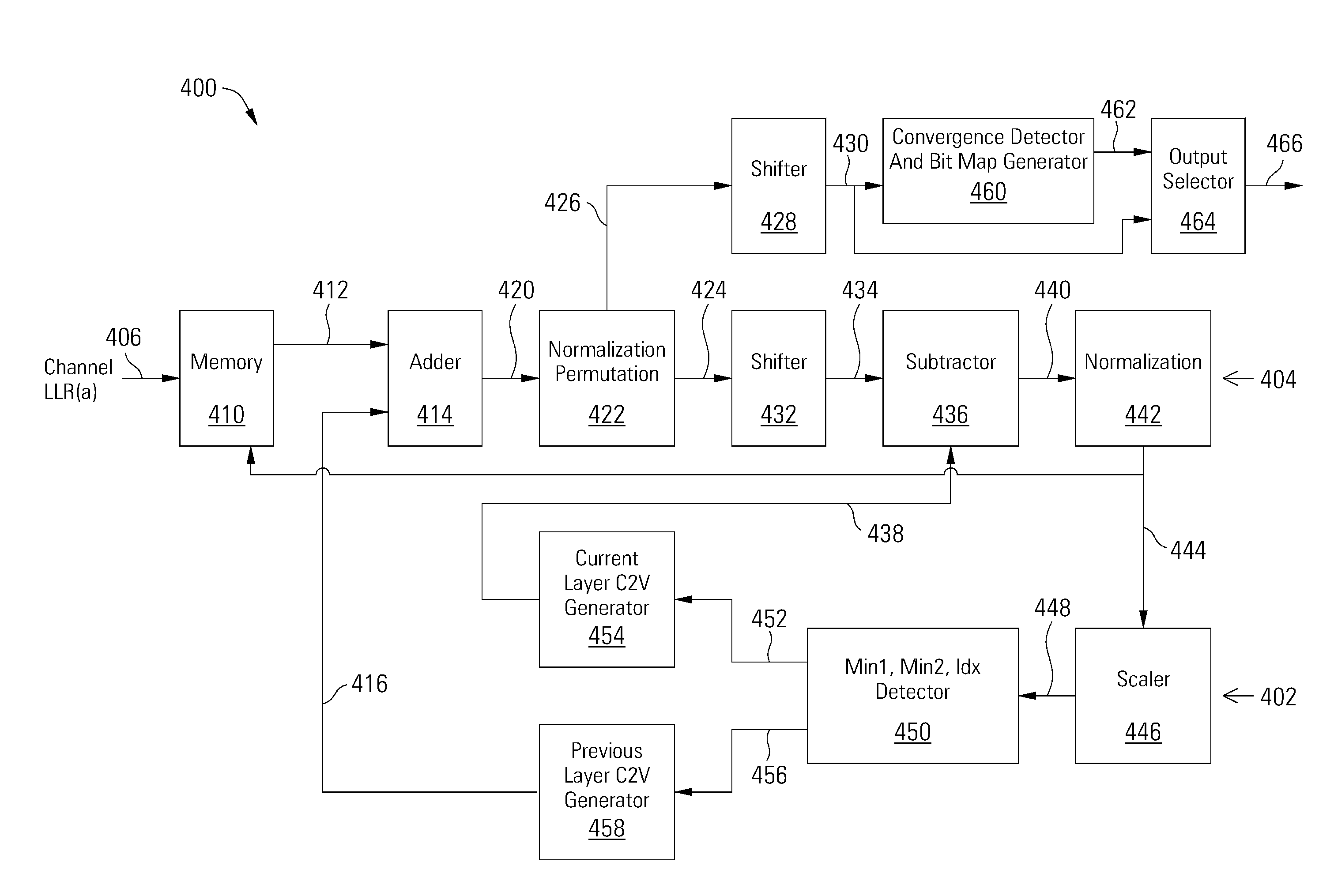
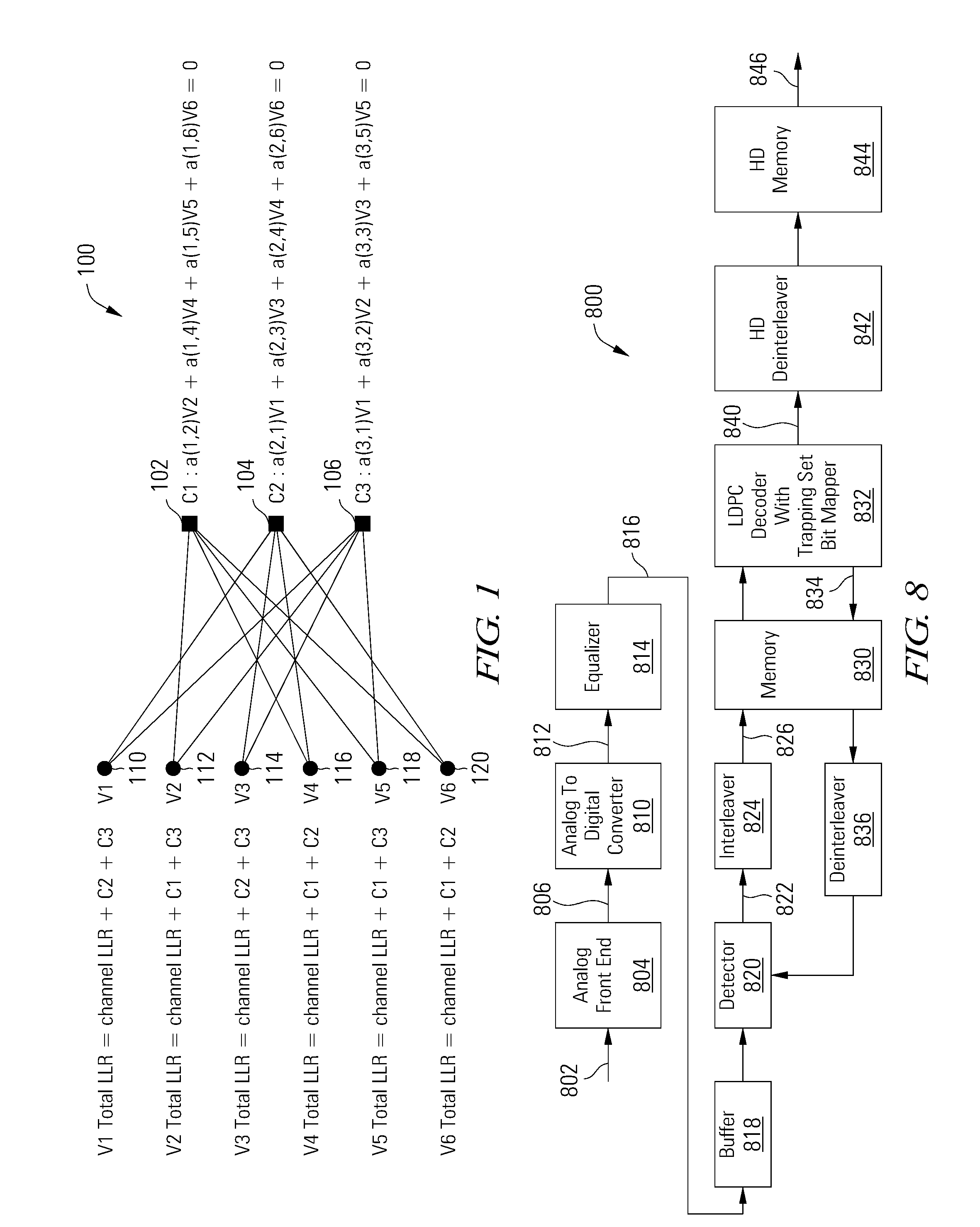
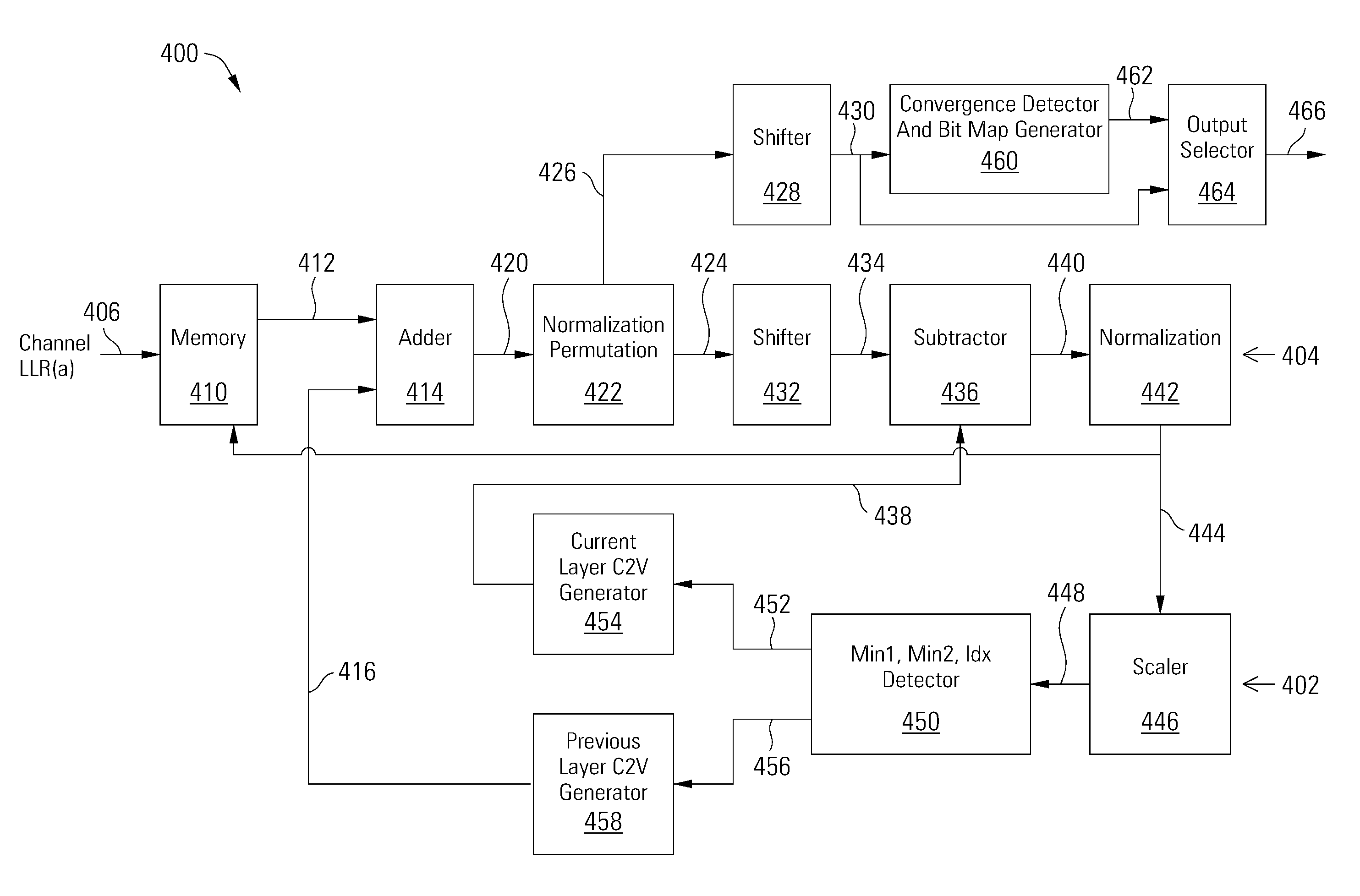
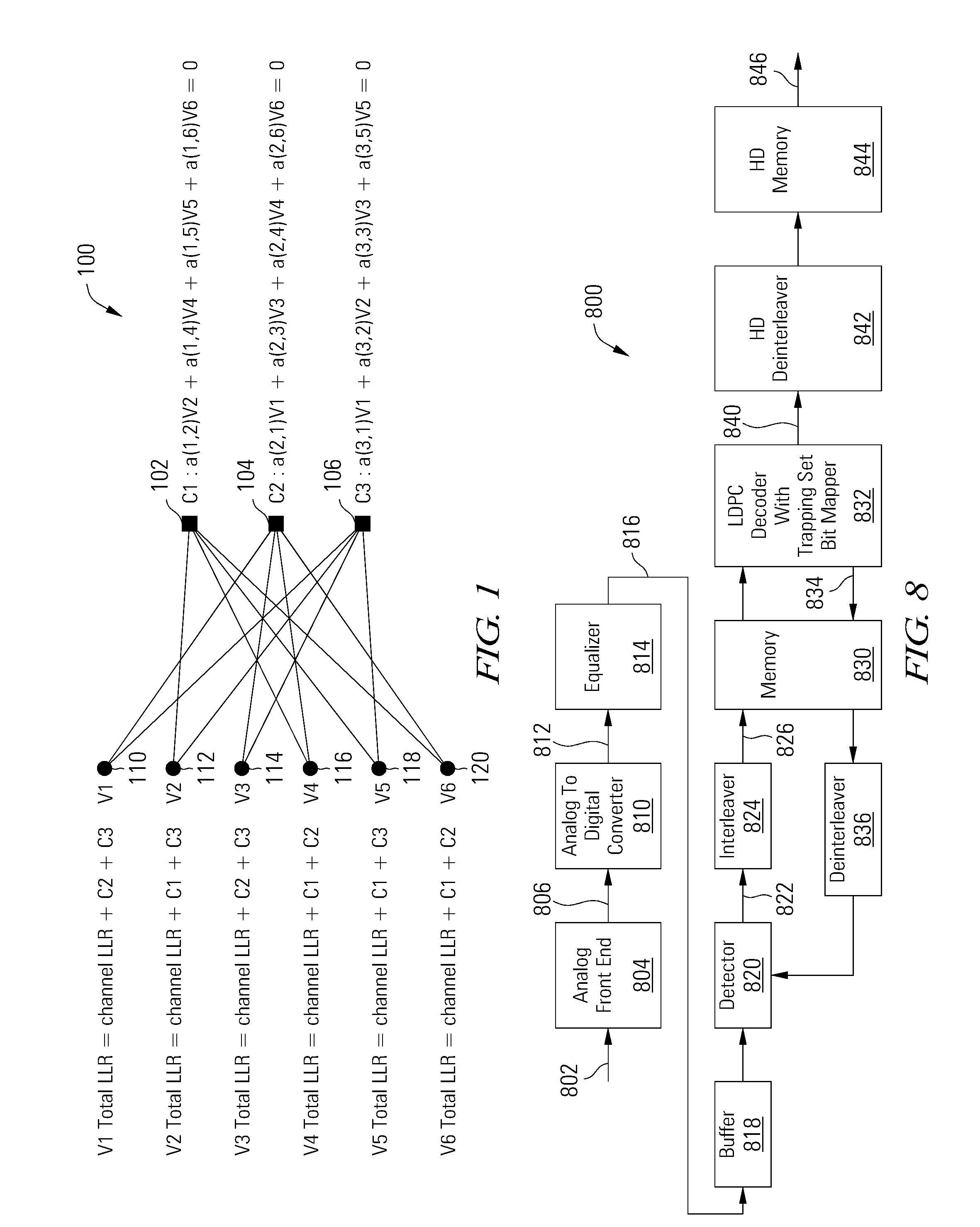
Data Decoder With Trapping Set Flip Bit Mapper
A low density parity check decoder includes a variable node processor operable to generate variable node to check node messages and to calculate perceived values based on check node to variable node messages, a check node processor operable to generate the check node to variable node message vectors and to calculate checksums based on the variable node to check node messages, and a convergence detector and bit map generator operable to convergence of the perceived values and to generate at least one bit map that identifies variable nodes that are connected to check nodes with unsatisfied parity checks.
Owner:SEAGATE TECH LLC
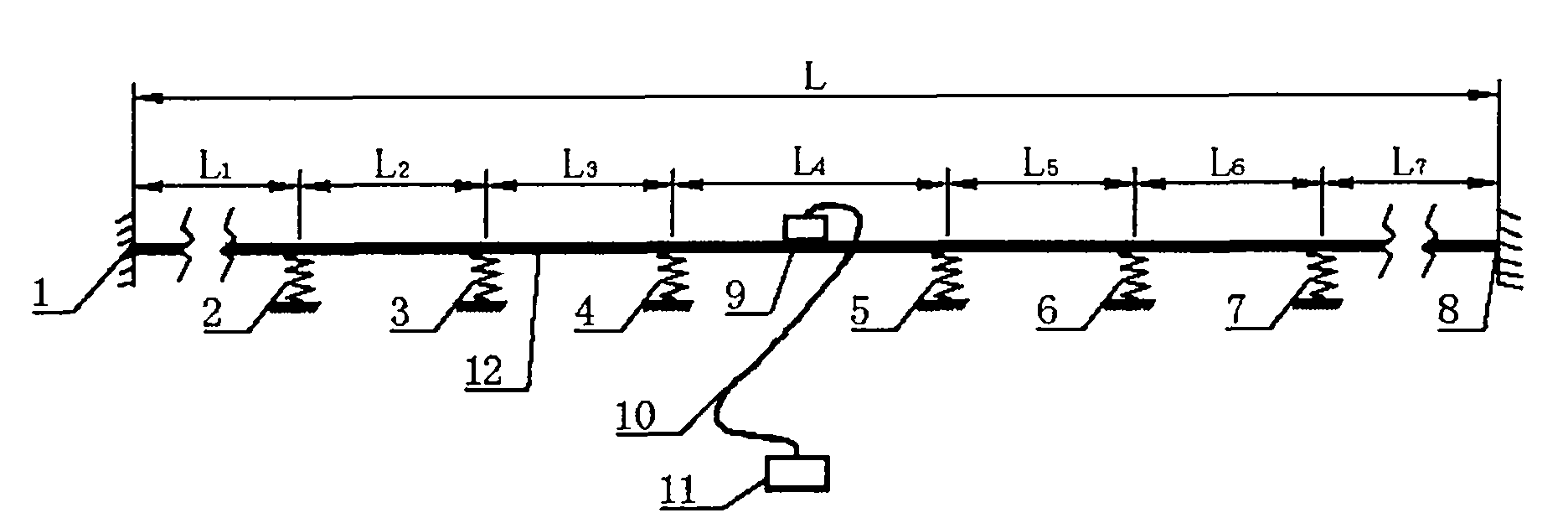
Method for identifying variable boundary cable force of medium or long cable
InactiveCN101900620AImproved frequency methodBreak through the blind zone of frequency testTension measurementSpecial data processing applicationsIdentifying VariableEngineering
The invention discloses a method for identifying a variable boundary cable force of a medium or long cable. The method comprises the following steps of: performing unit discreteness on the cable, dividing the cable into n units (n is in a range of 40 to 400), and calculating a unit rigidity matrix [K]e and a mass matrix [M]e of each unit according to formulas (1) to (2); then arranging rubber cushion blocks on the cable to form external restraint, wherein the number of the rubber cushion blocks is 2 to 6 and the mounting number of the rubber cushion blocks is determined according to the length of the tested cable; and after the total rigidity matrix [K] and the total mass matrix [M] are determined, solving a characteristic value equation l[K]-omega2[M]l=0 of natural vibration frequency of a cable structure by adopting an iteration method to obtain the cable force T. Under the condition that the cable force is not changed, if the boundary condition of the cable is changed, the frequency of the cable is changed, and the equation of the frequency of the cable and the cable force is changed along with the change of the boundary condition of the cable, so the condition that the frequency of the cable cannot be tested under complex environments is solved, and meanwhile the frequency of the cable is in an interval capable of being tested by the conventional instrument by regulating the boundary condition.
Owner:SOUTH CHINA UNIV OF TECH
Method and Apparatus for Non-Deterministic Incremental Program Replay Using Checkpoints and Syndrome Tracking
InactiveUS20080288558A1Error detection/correctionDigital computer detailsIdentifying VariableTheoretical computer science
Methods and apparatus are provided for non-deterministic incremental program replay using checkpoints and syndrome tracking. Replay of a program proceeds by, for a given execution of the program, recording one or more checkpoints of the program, the one or more checkpoints containing program state information; and a recorded list of values for one or more identified variables executing in one or more threads of the program. Thereafter, during a replay execution of the program, the process continues by commencing execution from a particular one of the recorded checkpoints; restoring the program state information associated with the particular one of the recorded checkpoints; comparing an observed list of values to the recorded list of values for the one or more identified variables executing in each of the one or more threads; and identifying a difference between the observed list of values and the recorded list of values A perturbation or suspend statement can optionally be introduced into the replay execution of the program.
Owner:IBM CORP
Adaptive Remediation of Multivariate Risk
ActiveUS20190036971A1Error detection/correctionInternal/peripheral component protectionIdentifying VariableData mining
A method, system and computer-usable medium for adaptively remediating multivariate risk, comprising: detecting a violation of a multivariate security policy, the multivariate security policy comprising a plurality of variables; identifying a variable from the plurality of variables associated with a cause of the violation; associating an entity with the variable associated with the cause of the violation; and, adaptively remediating a risk associated with the entity.
Owner:FORCEPOINT LLC
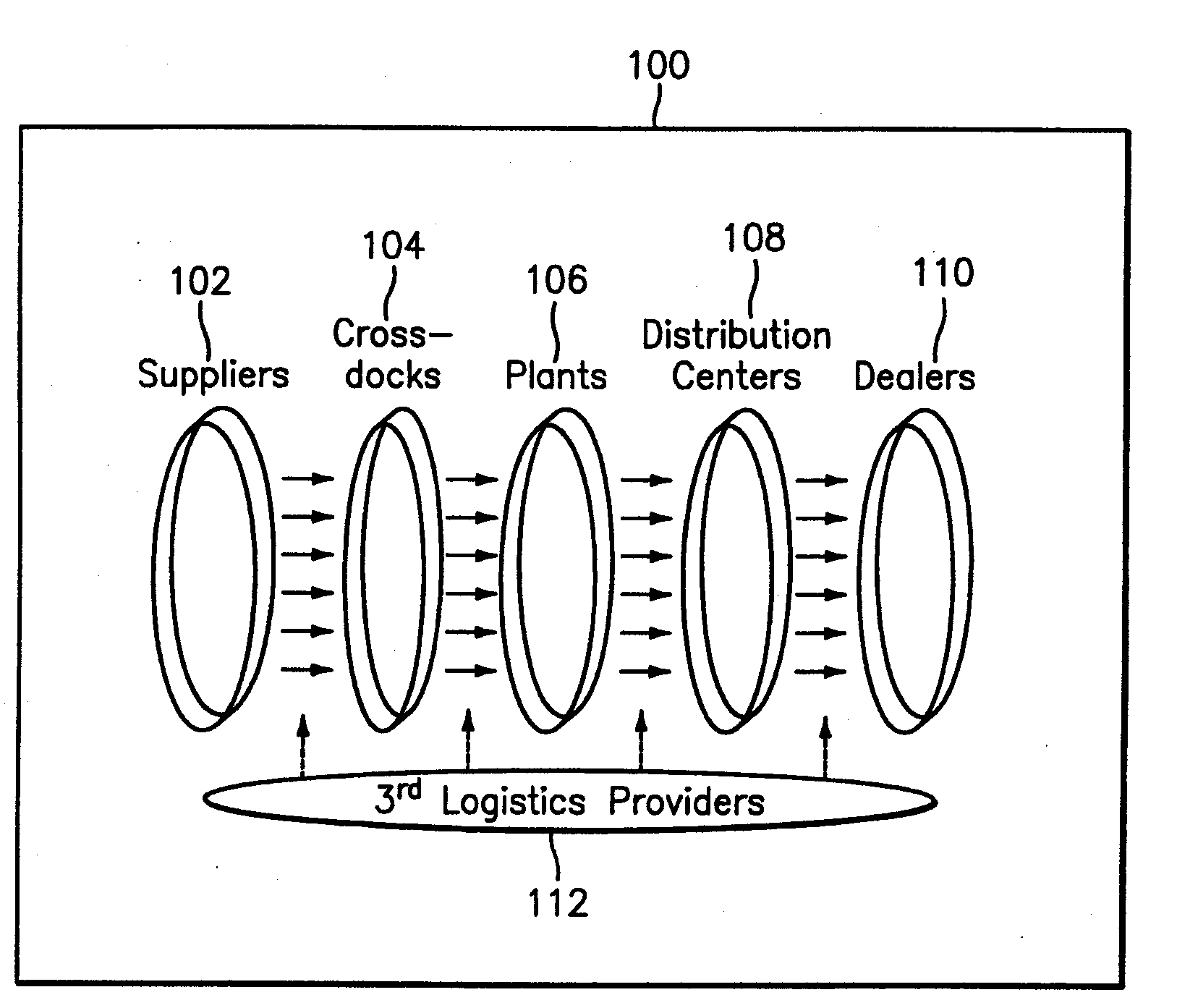
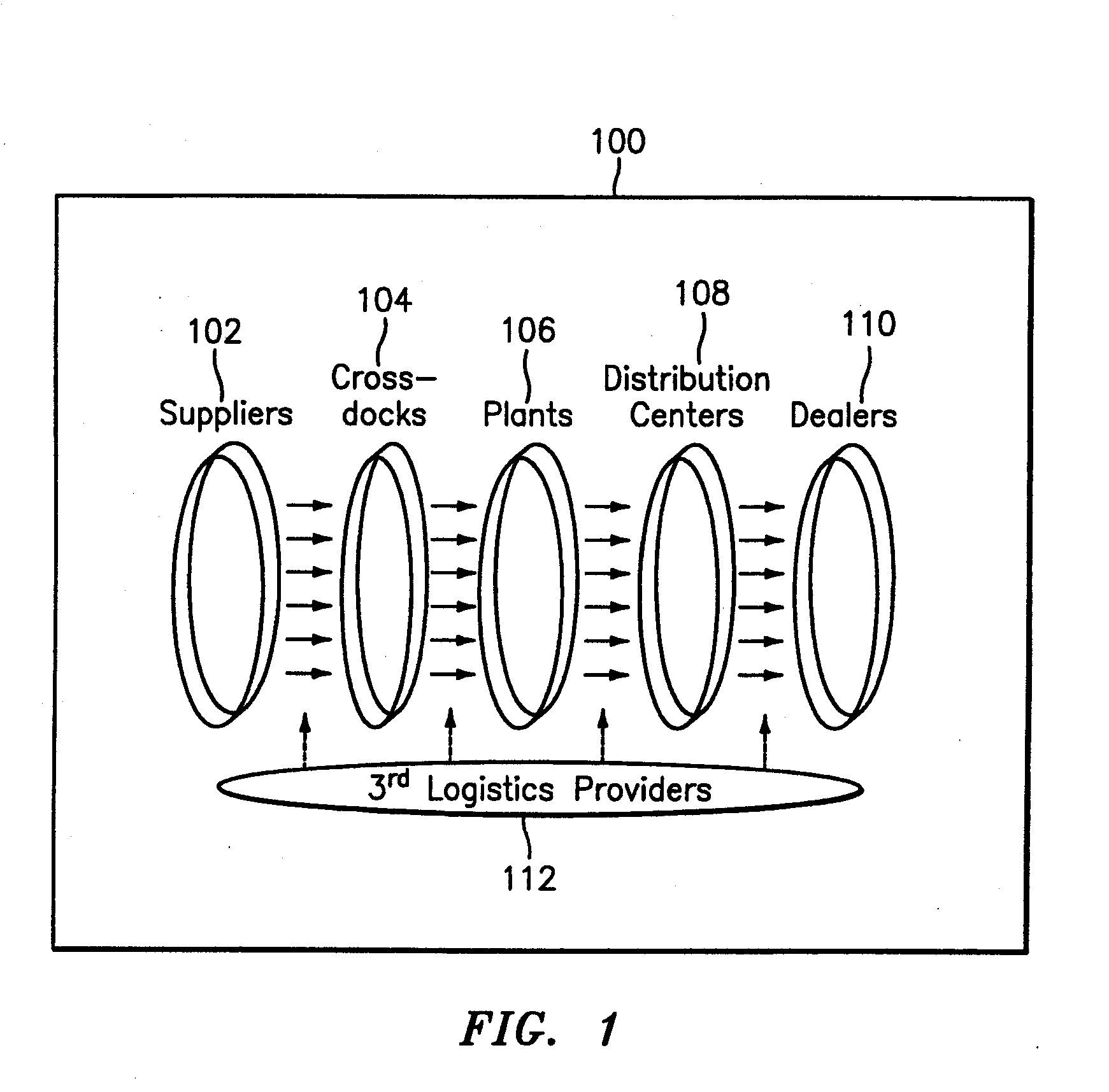
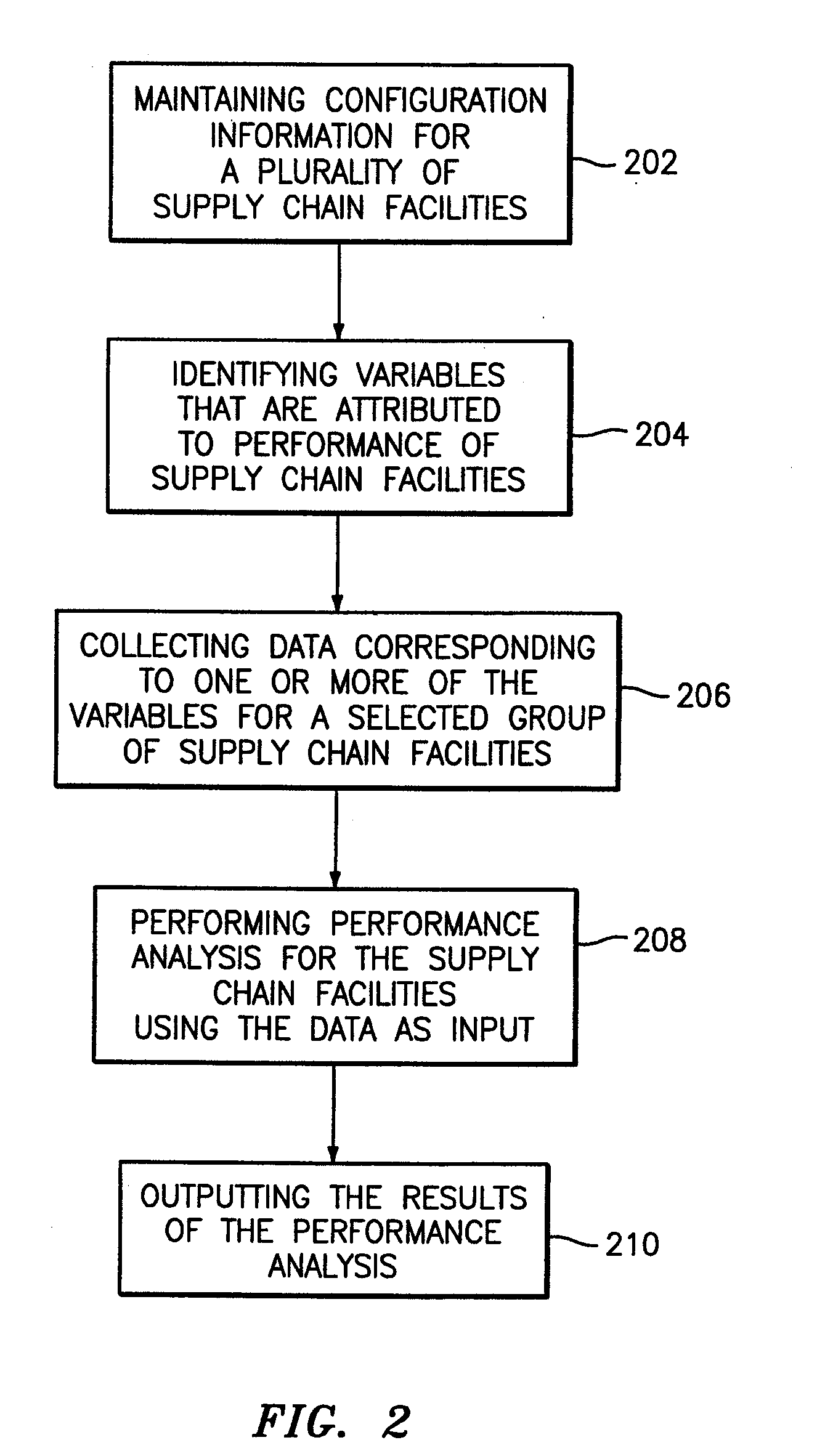
Supply chain facility performance analyzer
InactiveUS20080065436A1Hand manipulated computer devicesCash registersIdentifying VariableStatistical analysis
Methods, systems and computer program products for supporting supply chain facility performance analysis. Methods include maintaining supply chain facility configuration information for a plurality of supply chain facilities. The method also includes identifying variables that are attributed to performance of the supply chain facilities. Data corresponding to one or more of the variables for selected supply chain facilities in the plurality of supply chain facilities is collected. Performance analysis is performed for the selected supply chain facilities using the data as input. The performance analysis includes executing a data envelope analysis (DEA) based three-stage performance analysis model, executing a statistical analysis and executing a sensitivity analysis. The results of the performance analysis are output. The results include a performance ranking of the selected supply chain facilities, a prescription for performance improvement, a correlation analysis, and a sensitivity analysis.
Owner:GM GLOBAL TECH OPERATIONS LLC
Controlling a non-linear process with varying dynamics using non-linear model predictive control
InactiveUS20070198104A1More accuratePromote resultsAdaptive controlIdentifying VariableParticle accelerator
The present invention provides a method for controlling nonlinear control problems within particle accelerators. This method involves first utilizing software tools to identify variable inputs and controlled variables associated with the particle accelerator, wherein at least one variable input parameter is a controlled variable. This software tool is further operable to determine relationships between the variable inputs and controlled variables. A control system that provides variable inputs to and acts on controller outputs from the software tools tunes one or more manipulated variables to achieve a desired controlled variable, which in the case of a particle accelerator may be realized as a more efficient collision.
Owner:ROCKWELL AUTOMATION TECH
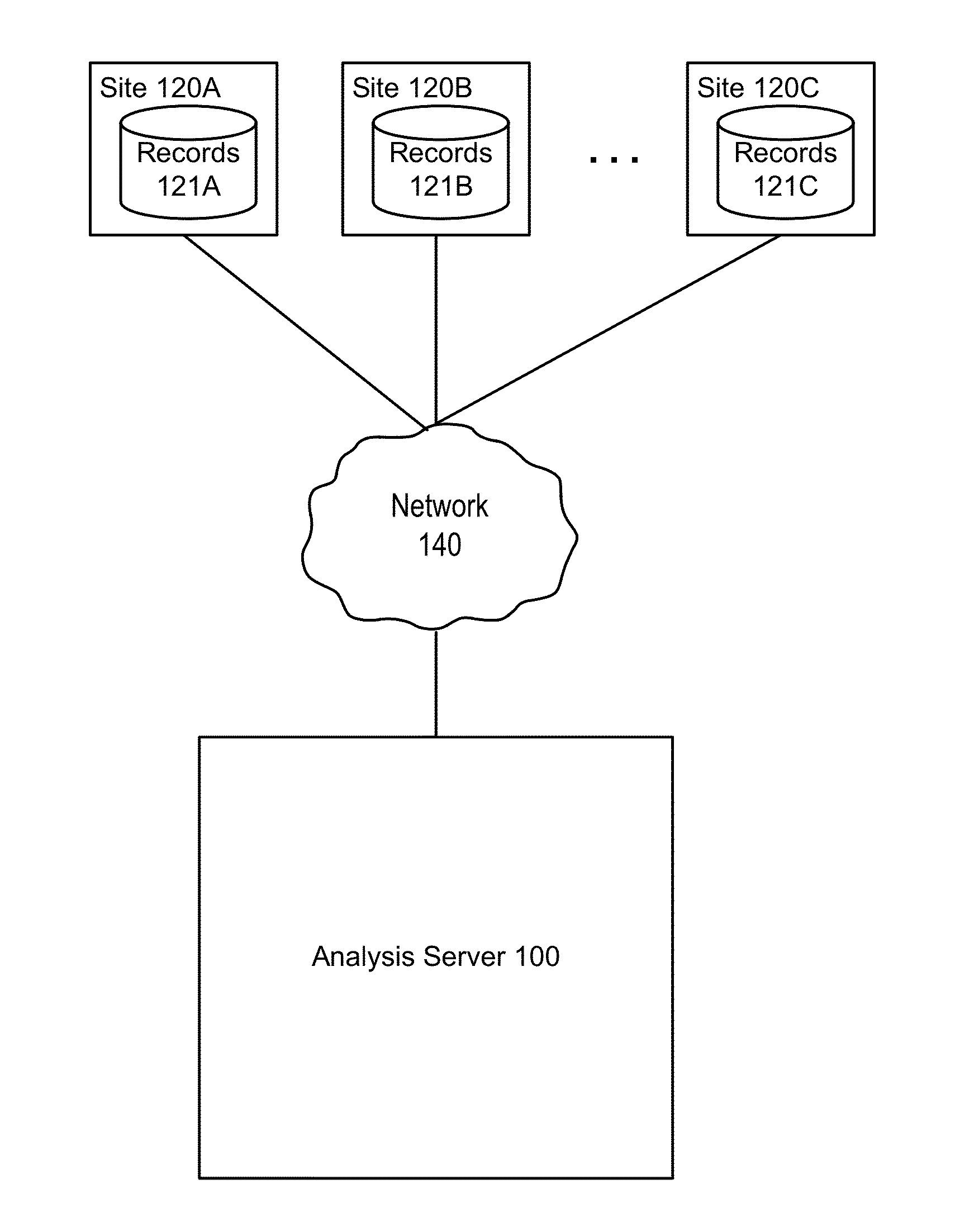
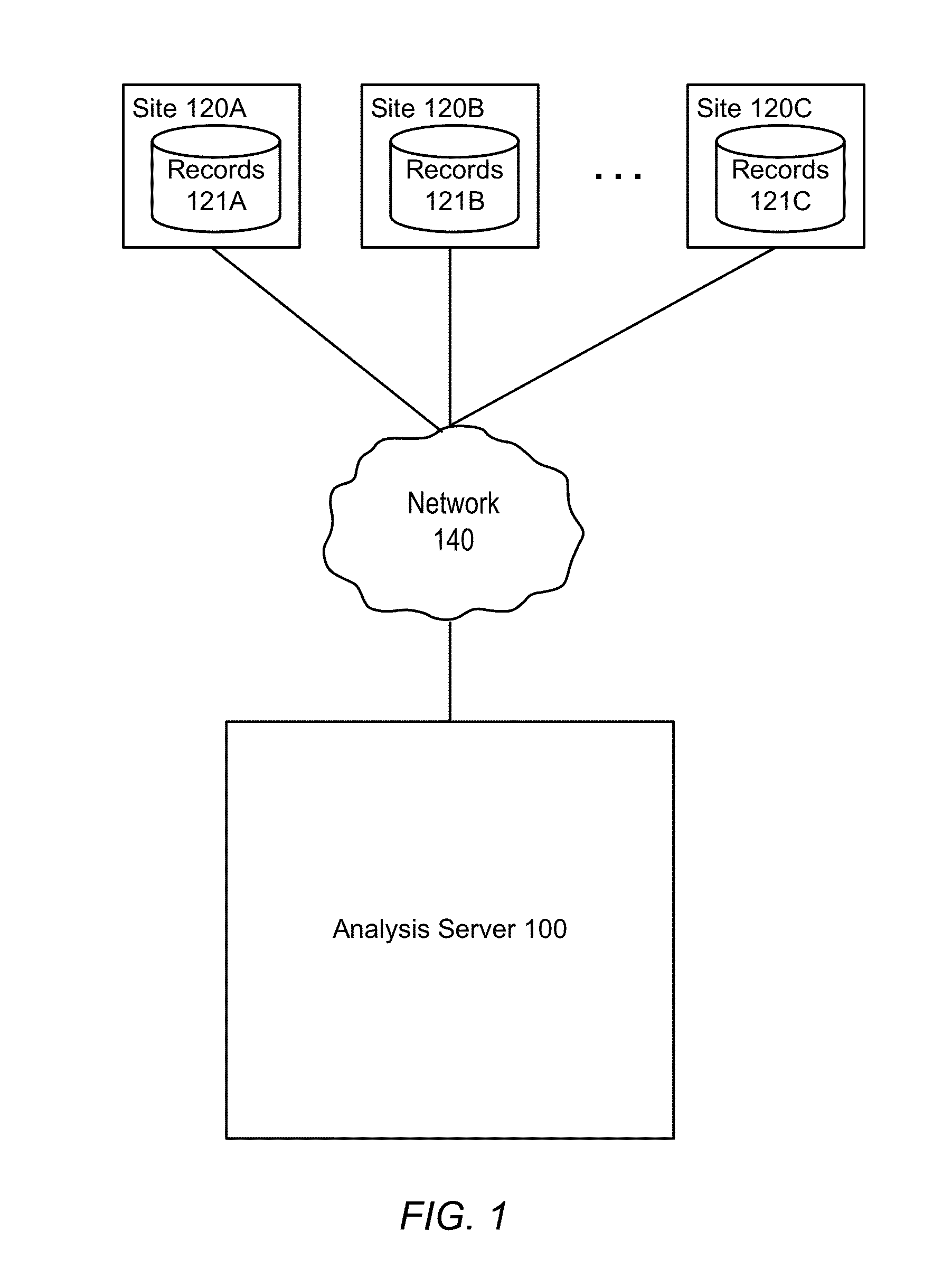
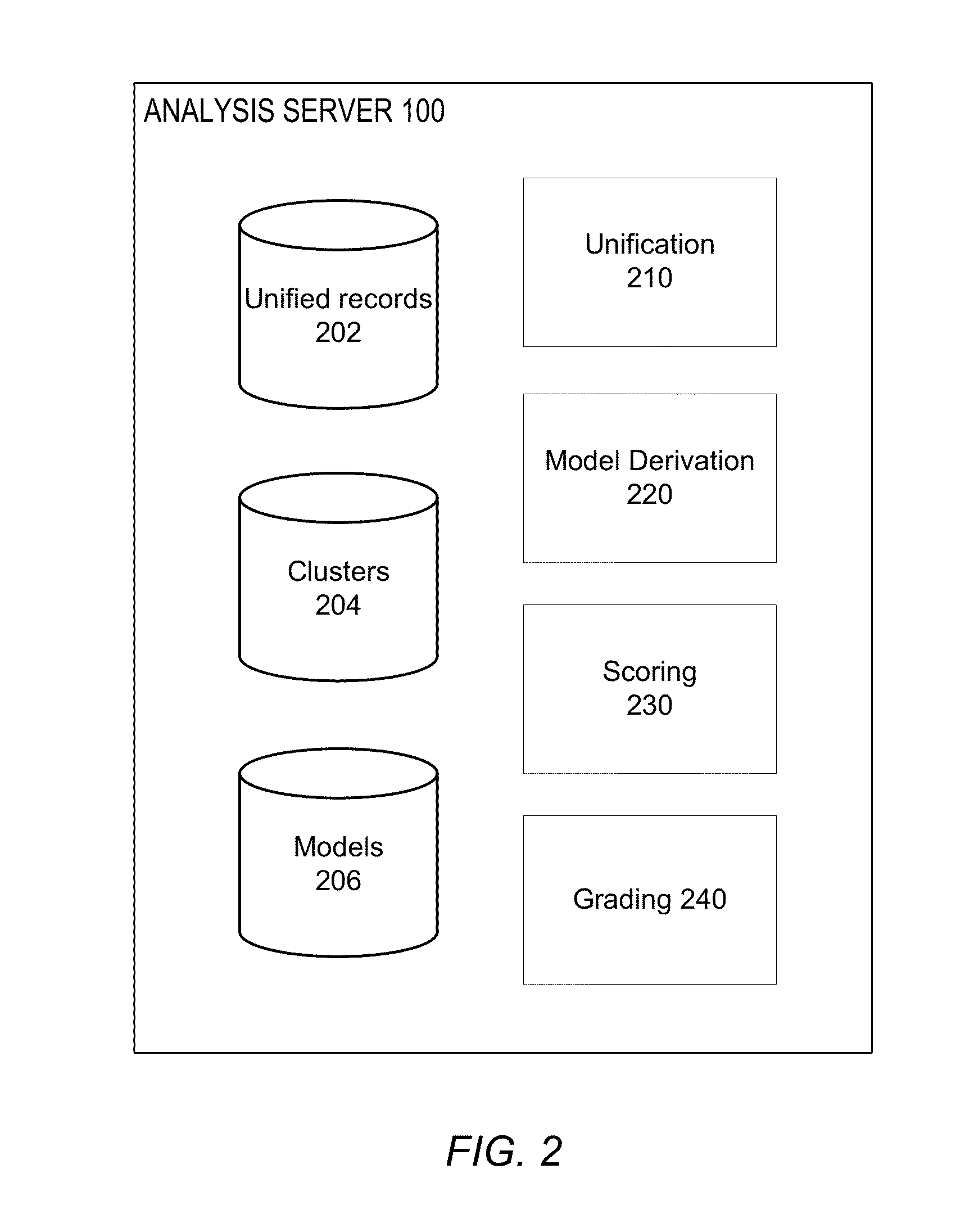
Evaluating Data Quality of Clinical Trials
An analysis server obtains data associated with patients as part of a clinical trial. The analysis server derives models from the patient data, the models specifying how likely it is that a given value of a variable (or values of a pair of variables) are erroneous. The models can be applied to the patient data to identify variable values more likely to be erroneous, and in turn to assess the data quality of patients, sites, and the clinical trial itself.
Owner:PATIENT PROFILES
Data decoder with trapping set flip bit mapper
ActiveUS9459956B2Error correction/detection using multiple parity bitsCode conversionIdentifying VariableChecksum
A low density parity check decoder includes a variable node processor operable to generate variable node to check node messages and to calculate perceived values based on check node to variable node messages, a check node processor operable to generate the check node to variable node message vectors and to calculate checksums based on the variable node to check node messages, and a convergence detector and bit map generator operable to convergence of the perceived values and to generate at least one bit map that identifies variable nodes that are connected to check nodes with unsatisfied parity checks.
Owner:SEAGATE TECH LLC
Process for verifying computer codes and corresponding verification system
ActiveUS20100281466A1Increase independenceError detection/correctionSpecific program execution arrangementsIdentifying VariableTheoretical computer science
A process for detecting errors in computer code in C / C++ language in a computer, which comprises the operations of:—making available in said computer a source computer program (P) containing computer codes in C / C++ language; compiling (Z) said source computer program (P) to obtain an executable program (E); and—executing (240) said executable program (E) to generate (245) an error report (R). According to the invention, said method comprises, prior to the operation of compilation (Z): executing an operation of syntactic analysis (AS) to identify variables (x) having a structure of vector or pointer; modifying said source computer program (P) via the application to said identified variables (x) of a test function (f ( . . . ); io_sper; io_sper2; io_sper3; io_sper4) that is able to veriCy, during the operation of execution, whether an index (y) supplied for said variable x is valid.
Owner:REMOLLINO ANTONIO
Utilizing a dynamic data source to affect business rule management
Dynamic data discovery can identify variables or changes in a business environment which can impact existing business rules and can match identified triggers. A business rule associated with a business rule management system can be identified. The business rule management system can be a component of an enterprise organization. The rule can be an operation, a definition, and a constraint associated with the organization. The organization can be a person, a process, a product, a service, or a computing device. Relevant information can be determined from a dynamic data associated with a data source. The determination can be made through the use of semantic analysis. A business pattern associated with the rule can be semantically matched with a dynamic pattern associated with the information. The pattern can be a semantic pattern of the information. A new business rule can be automatically generated from the dynamic data analysis.
Owner:IBM CORP
Managing variable assignments in a program
ActiveUS8555266B2Software engineeringProgram controlIdentifying VariableTheoretical computer science
Owner:INT BUSINESS MASCH CORP
User configurable language independent code assist engine method, system, article of manufacture, and computer program product
InactiveUS7562343B2Improved code assistIntelligent editorsSpecific program execution arrangementsIdentifying VariableProgram instruction
A code assist function which suggests candidates responsive to a parsing of a partial program instruction statement is provided by parsing a program containing the partial program instruction statement to identify variables contained in the program; parsing the partial program instruction statement to generate proposals; and providing proposals to append to the partial program instruction statement to a user responsive to both the parsing of the program and the parsing of the partial program instruction statement. The code assist function may be performed according to a user-selected programming language dependent file selected from a plurality of programming language dependent files. Candidates may be proposed responsive to a verb of the partial program instruction statement, responsive to a variable type of a variable, or responsive to a portion of the program containing the partial program instruction statement.
Owner:INTELLECTUAL DISCOVERY INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com