Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
893 results about "Microservices" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
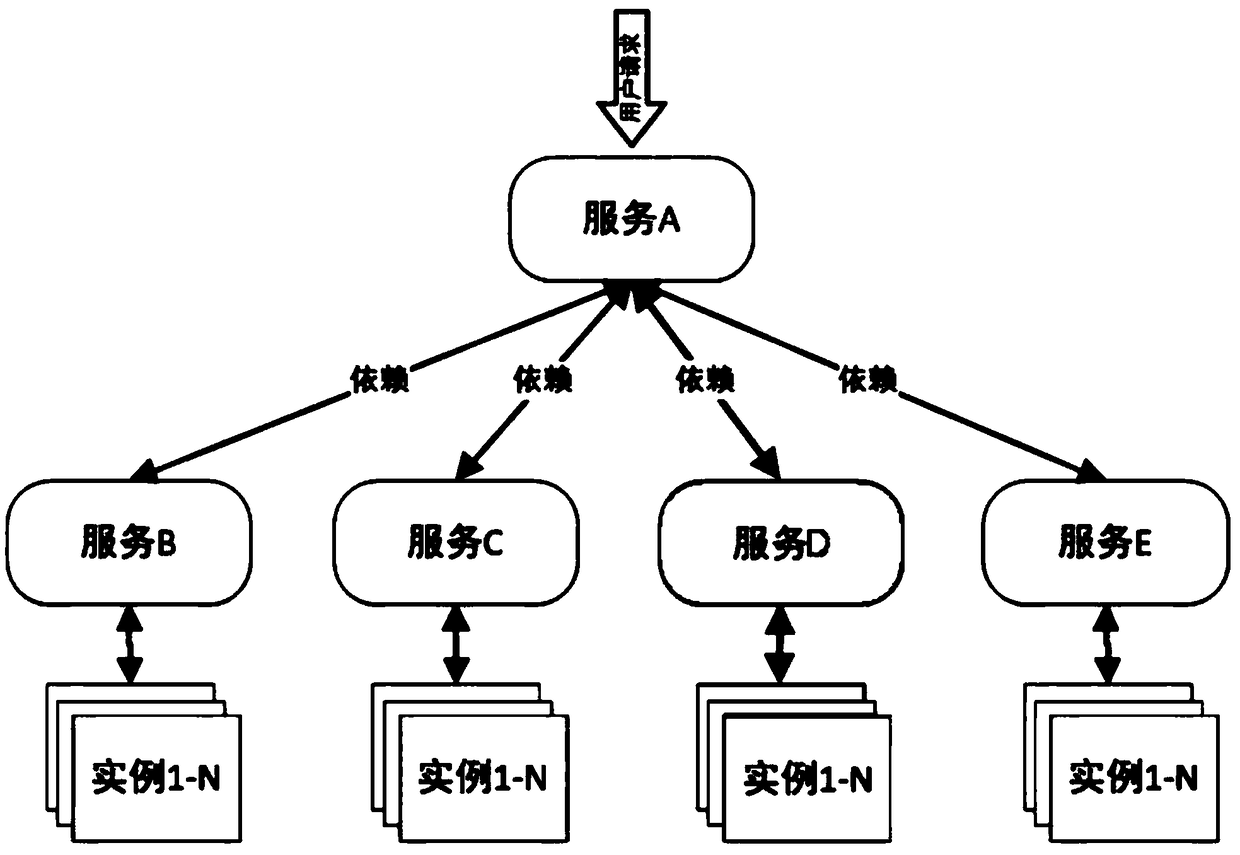
Microservices are a software development technique—a variant of the service-oriented architecture (SOA) architectural style that structures an application as a collection of loosely coupled services. In a microservices architecture, services are fine-grained and the protocols are lightweight. The benefit of decomposing an application into different smaller services is that it improves modularity. This makes the application easier to understand, develop, test, and become more resilient to architecture erosion. It parallelizes development by enabling small autonomous teams to develop, deploy and scale their respective services independently. It also allows the architecture of an individual service to emerge through continuous refactoring. Microservice-based architectures facilitate continuous delivery and deployment.
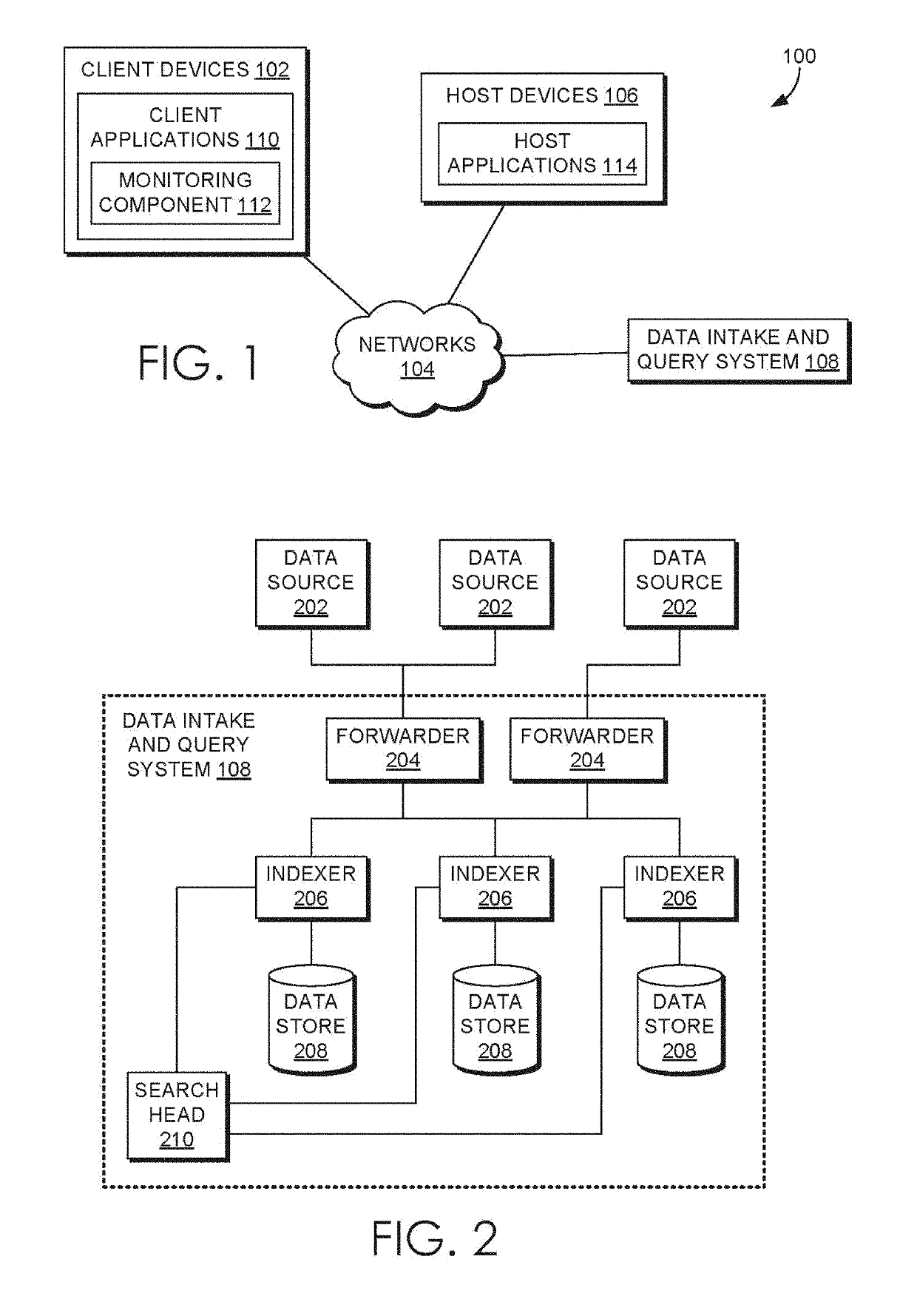
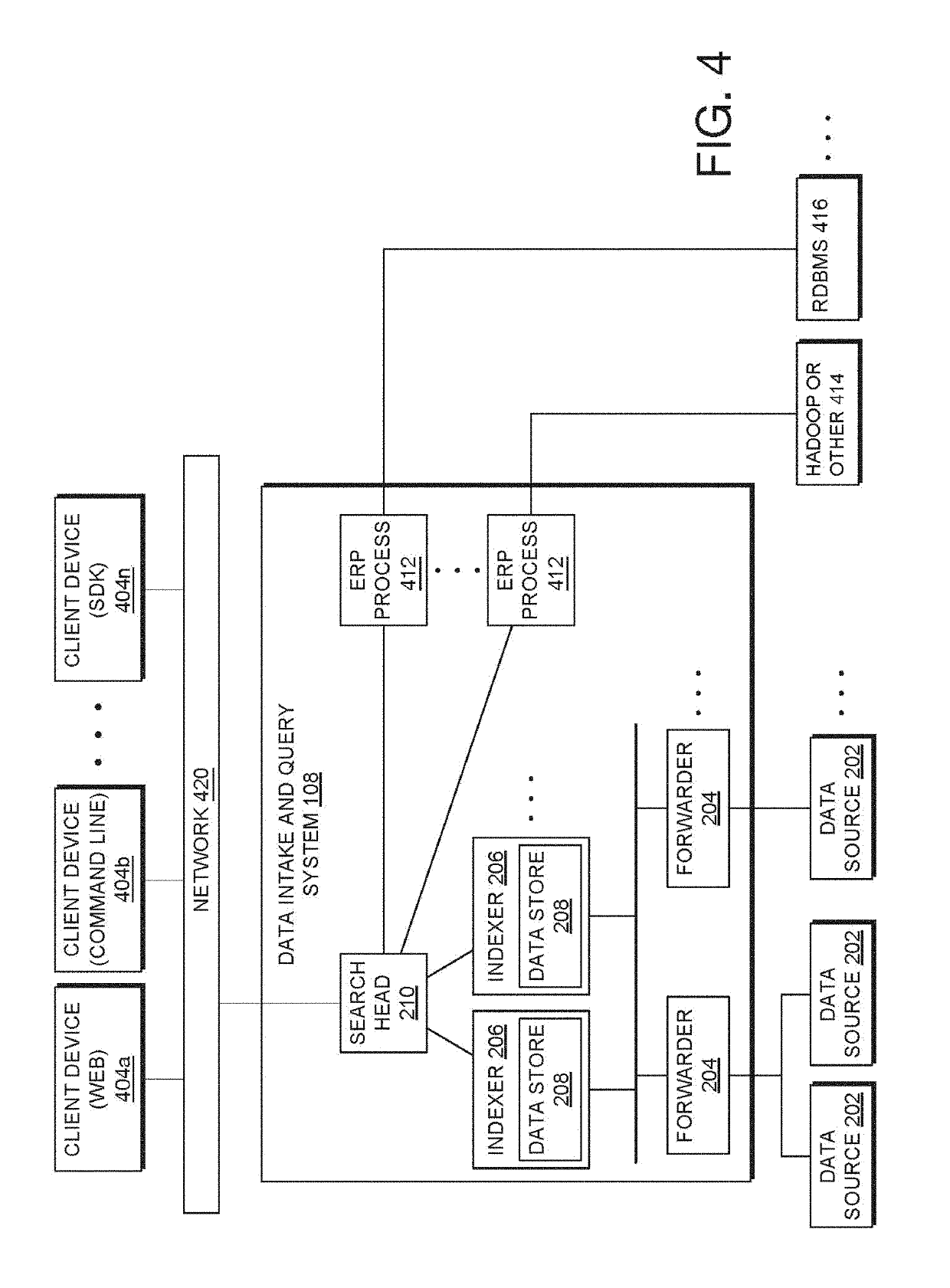
Proxying hypertext transfer protocol (HTTP) requests for microservices
In various embodiments, a gateway application generates an outgoing Hypertext Transmission Protocol (HTTP) request based on an incoming HTTP request. In operation, the gateway application receives the incoming HTTP request and identifies an upstream service based on at least one of an HTTP method and a header included in the incoming HTTP request. Subsequently, the gateway application generates an outgoing HTTP request based on the upstream service and the incoming HTTP request. Finally, the gateway application issues the outgoing HTTP request. The outgoing HTTP request causes the upstream service to perform an action requested in the incoming HTTP request. Advantageously, the gateway application enables underlying upstream services to perform actions specified via incoming HTTP requests without directly exposing the upstream services to users.
Owner:SPLUNK INC
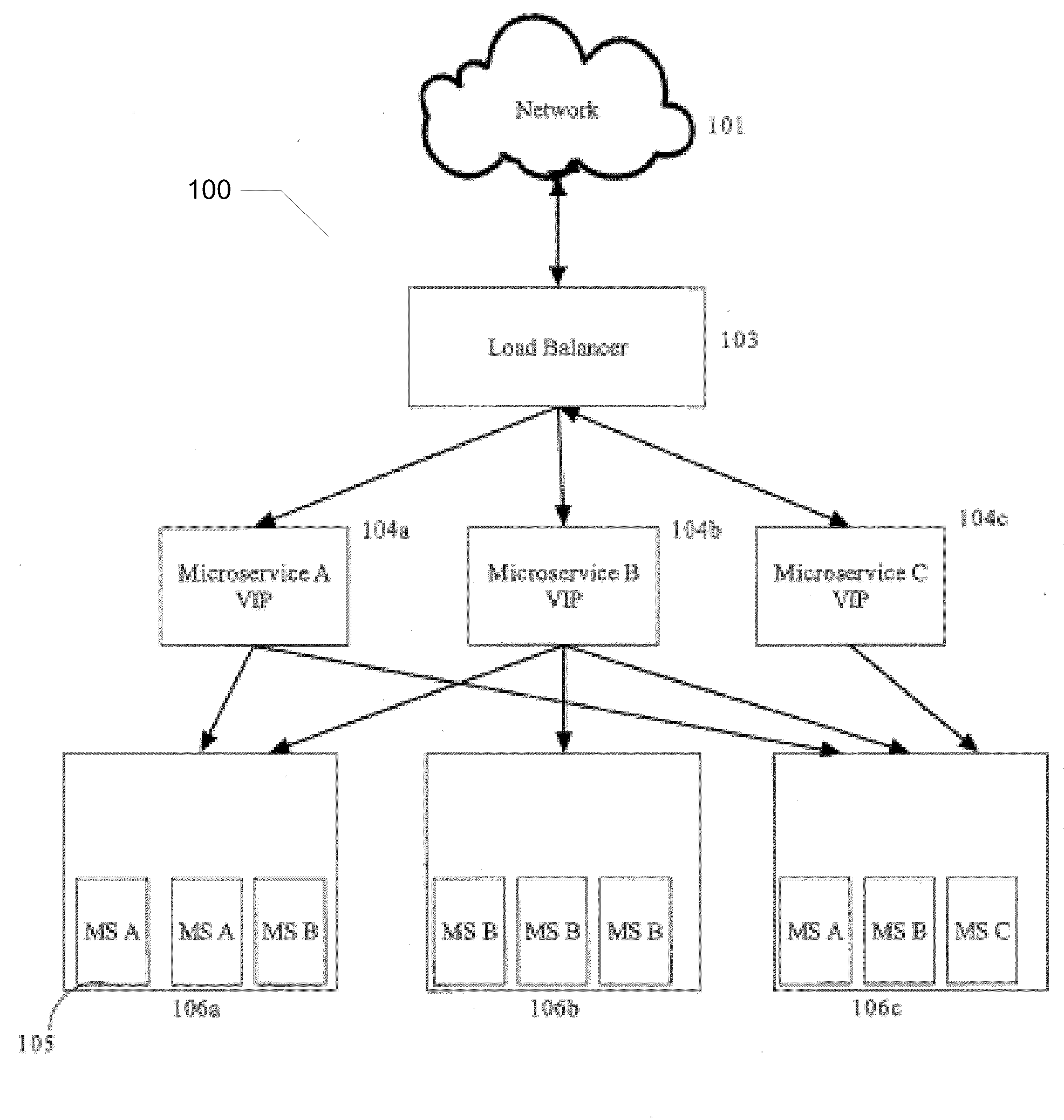
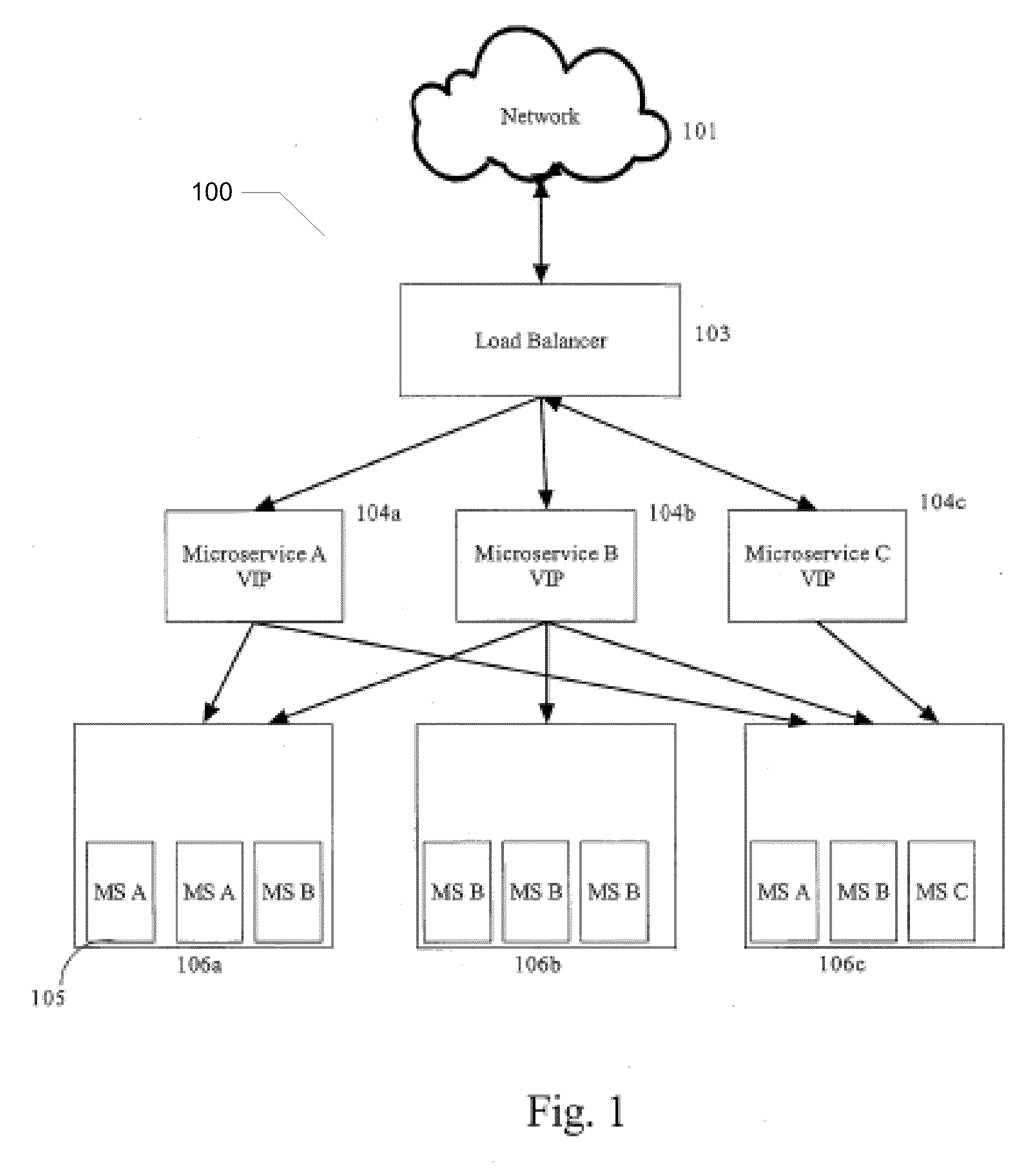
Web Service System and Method
ActiveUS20100299437A1Quick identificationEasy to implementDigital computer detailsTransmissionWeb serviceMicroservices
A system for providing a web service on a network of addressable nodes, said web service comprising a plurality of discrete, individually-addressable microservices, said system comprising: (a) at least one load balancer configured for routing a request from a node for a microservice to one of a plurality of virtual addresses, each virtual address corresponding to a unique microservice, and (b) one or more physical nodes associated with each virtual address, each physical node comprising one or more microservices, each microservice comprising a microservice-specific module for executing a particular function, said microservice-specific module linked to an interface for communicating over said network, each microservice being one of a plurality of individually-addressable microservices constituting a web service.
Owner:COMCAST INTERACTIVE MEDIA
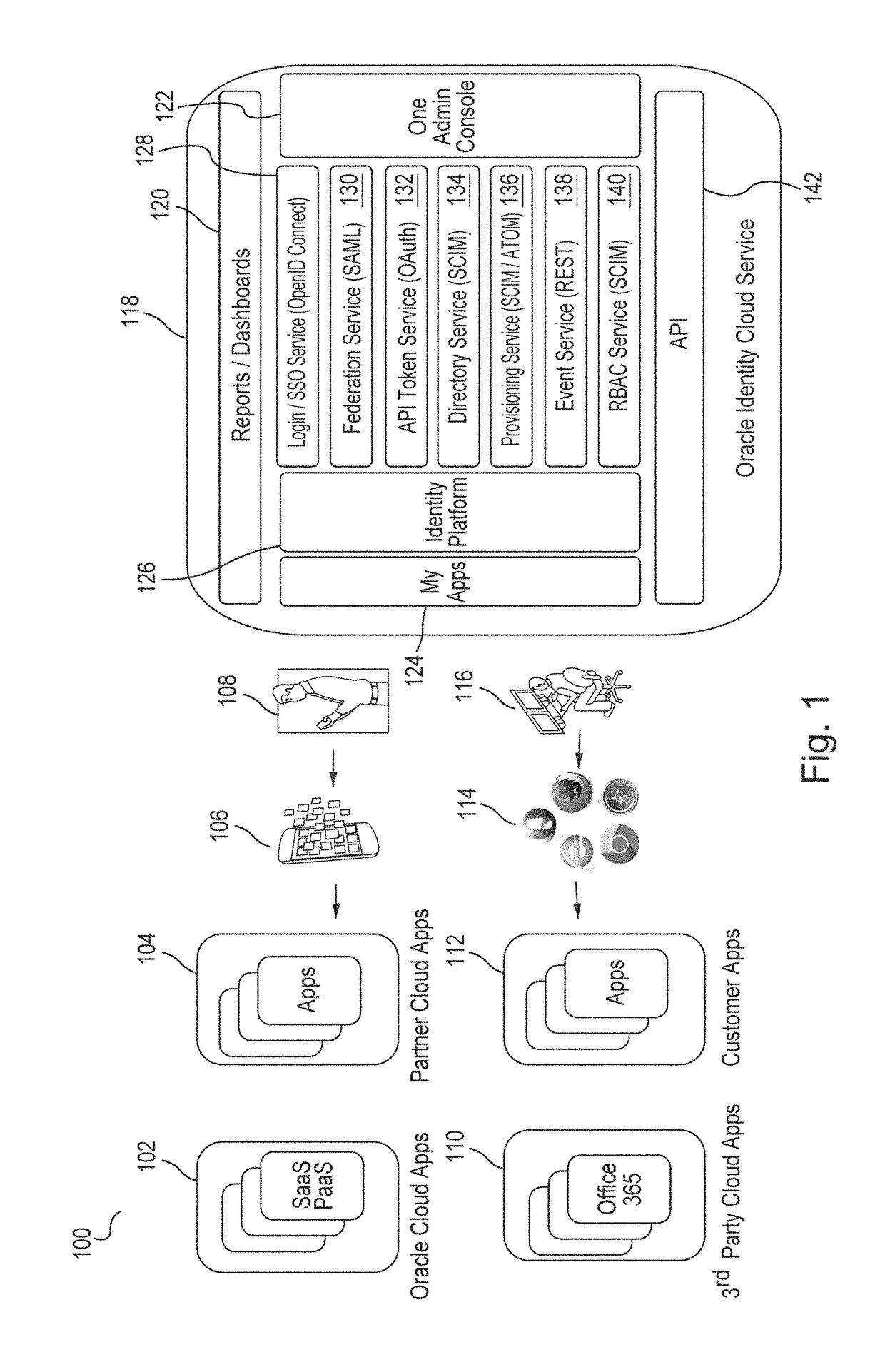
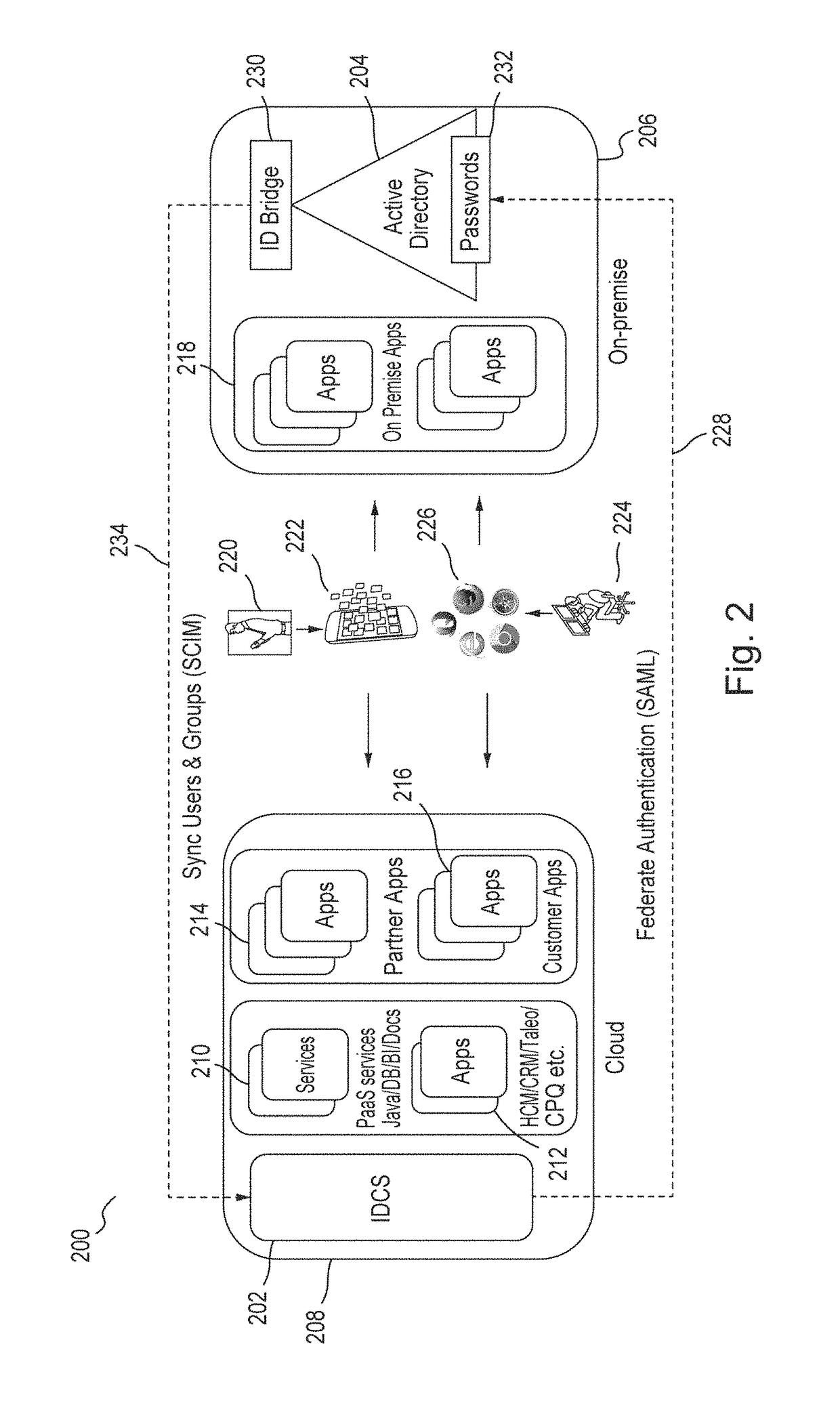
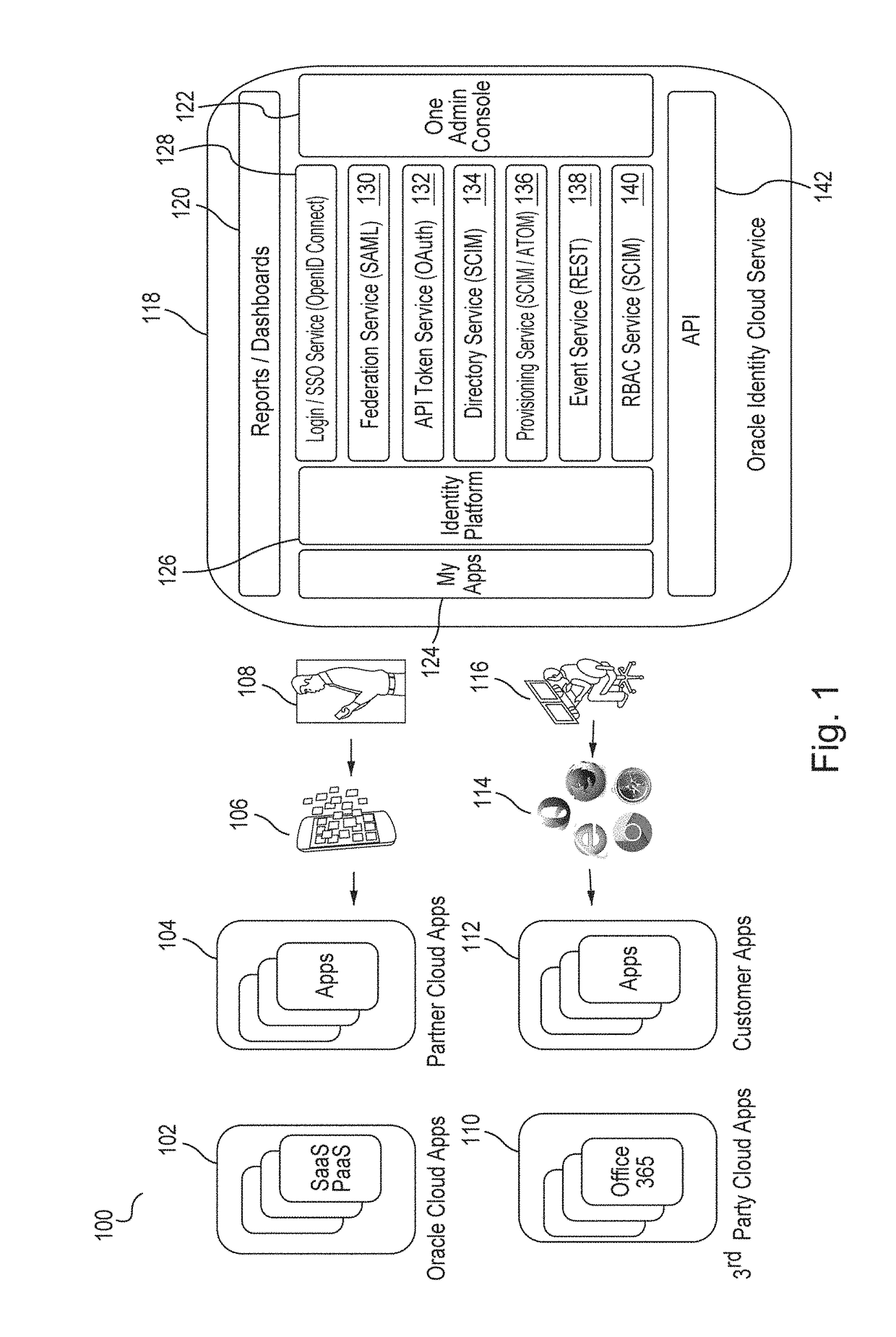
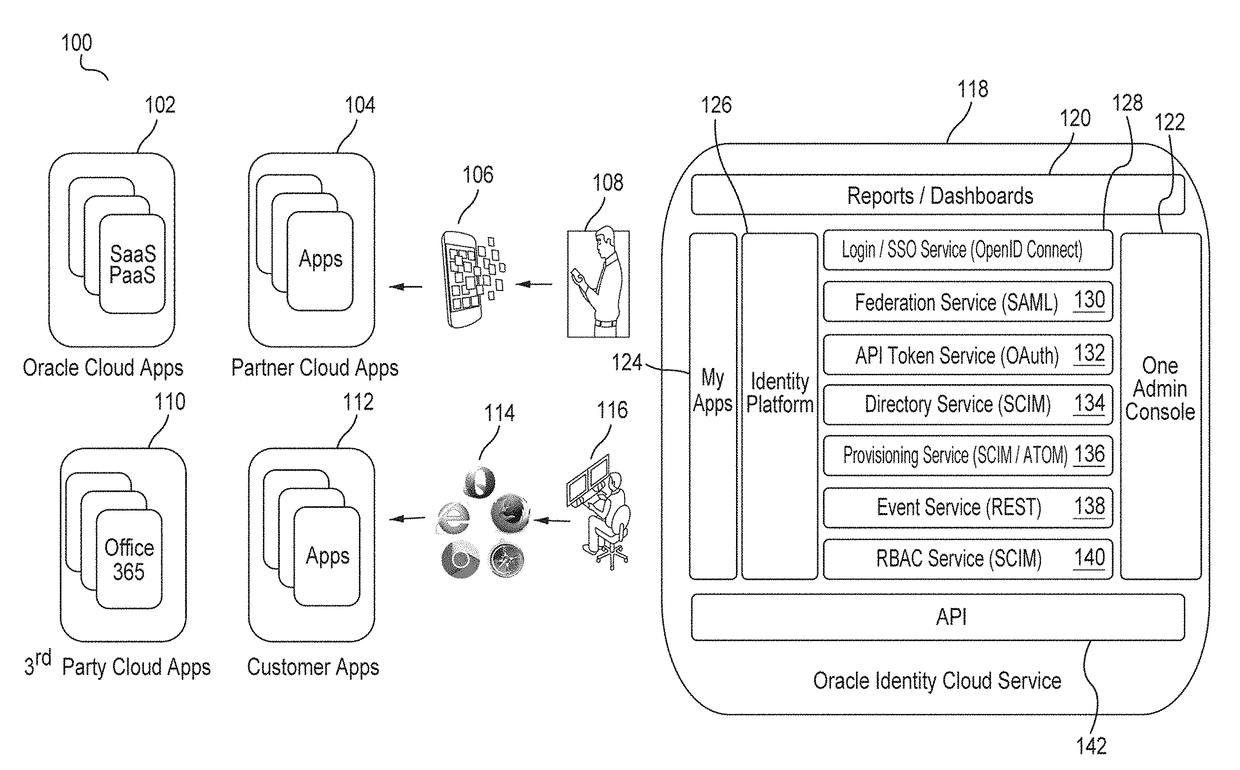
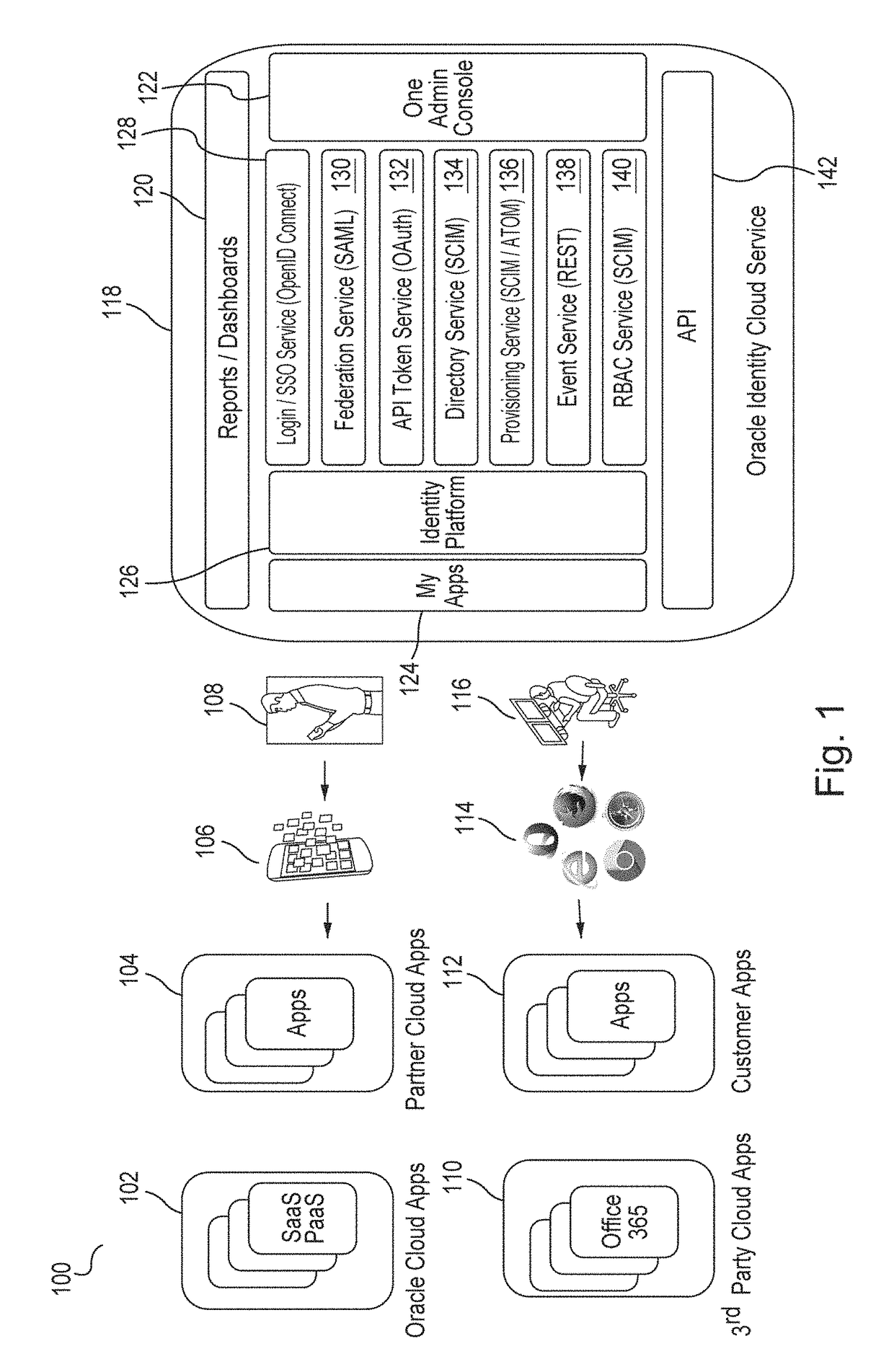
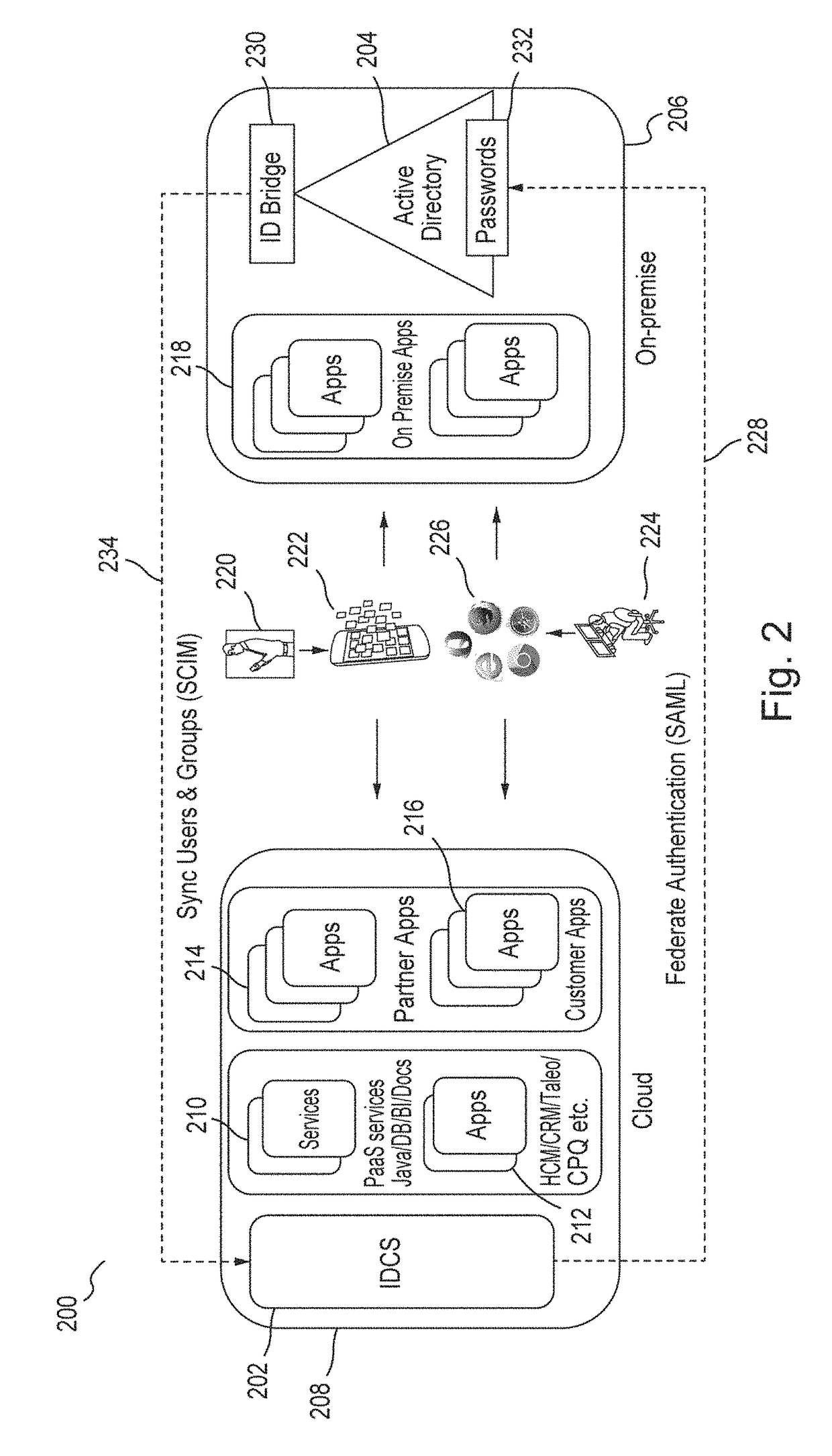
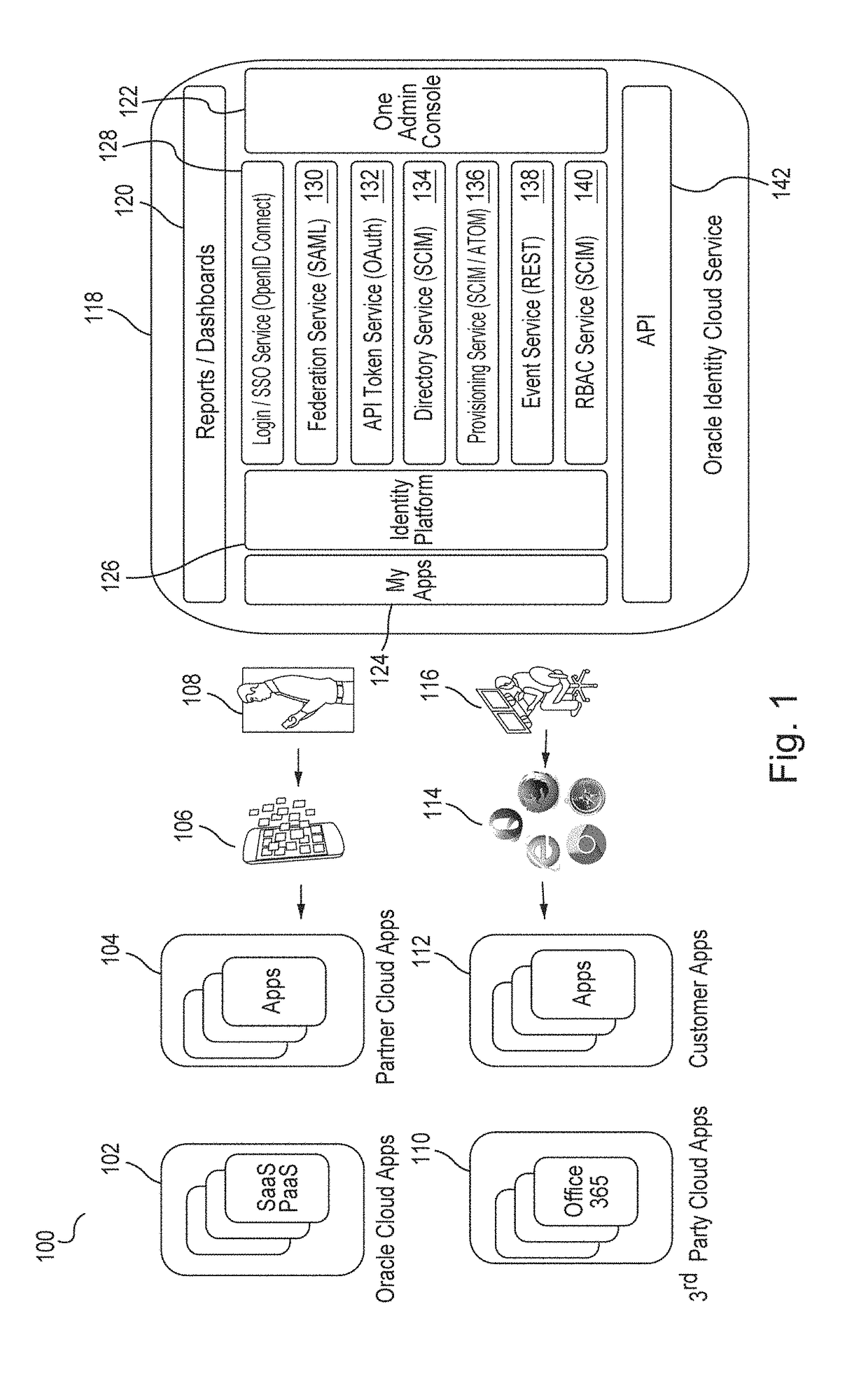
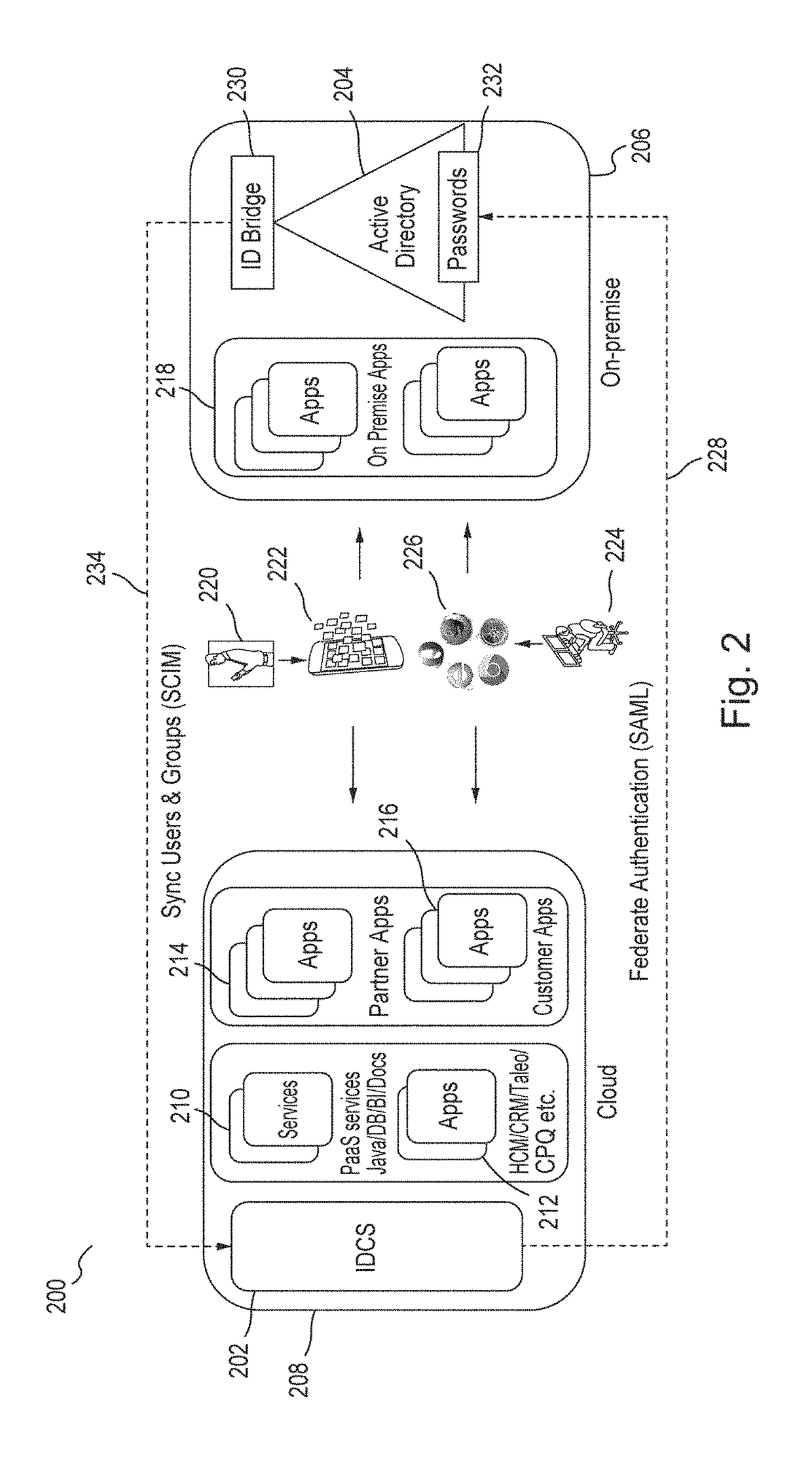
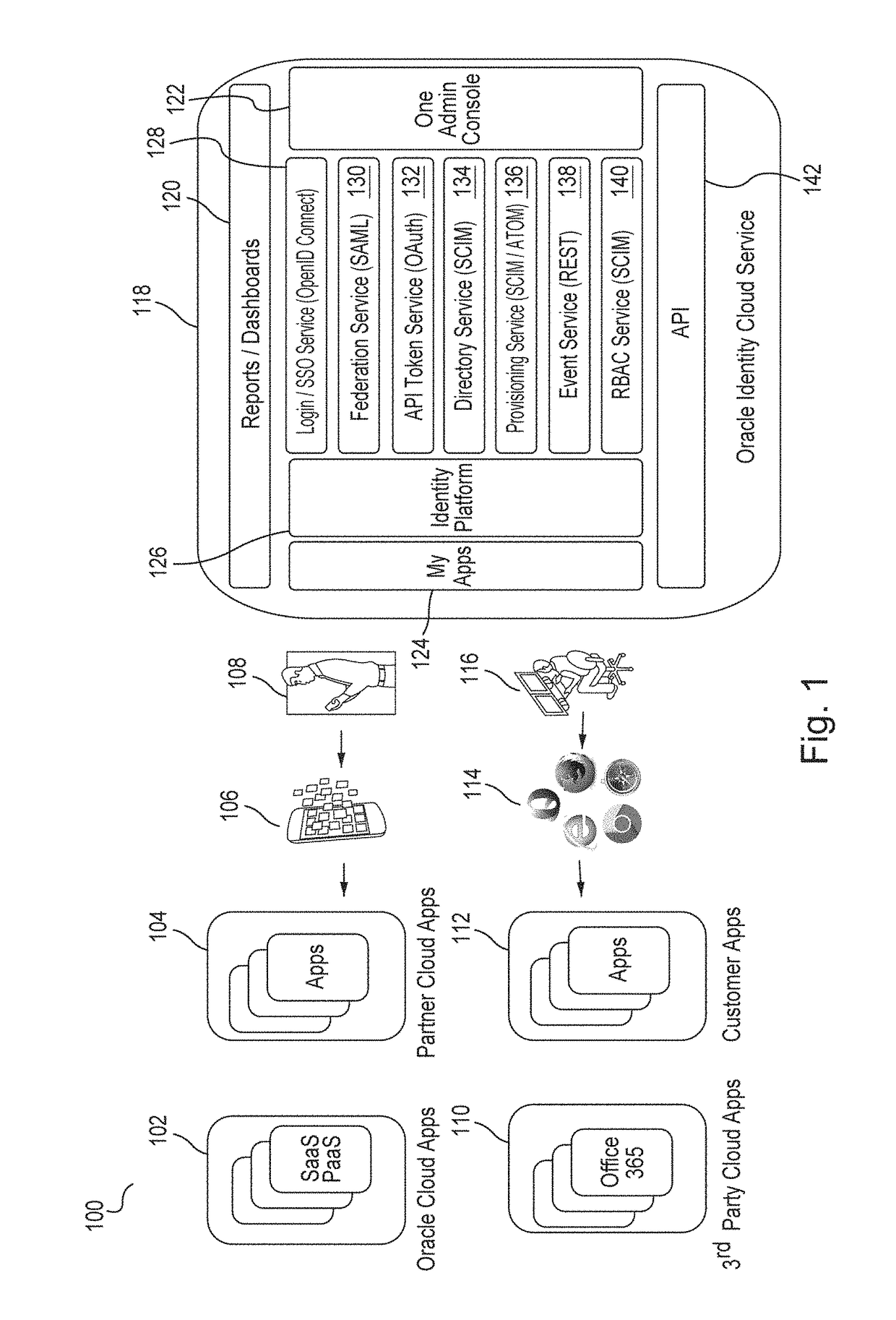
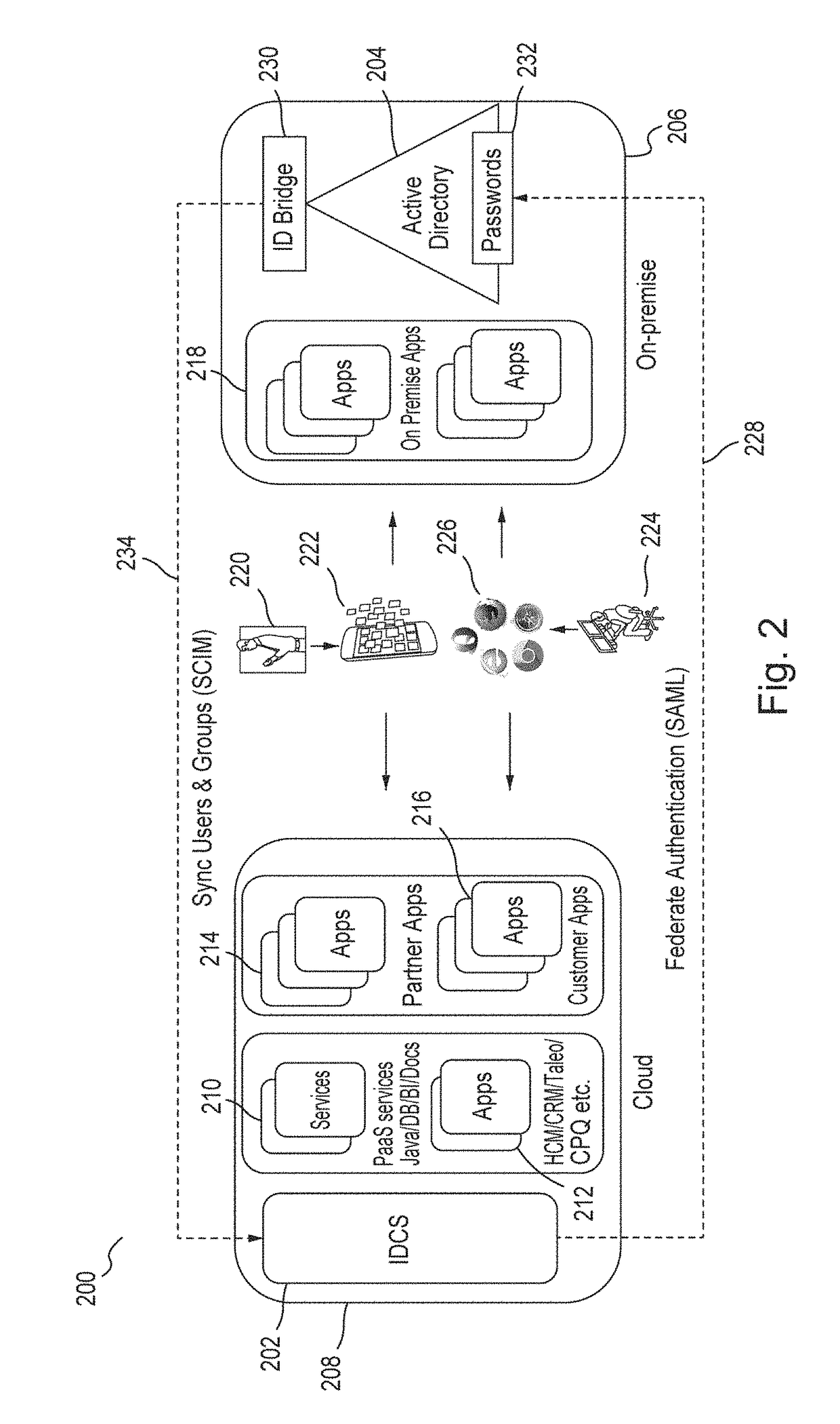
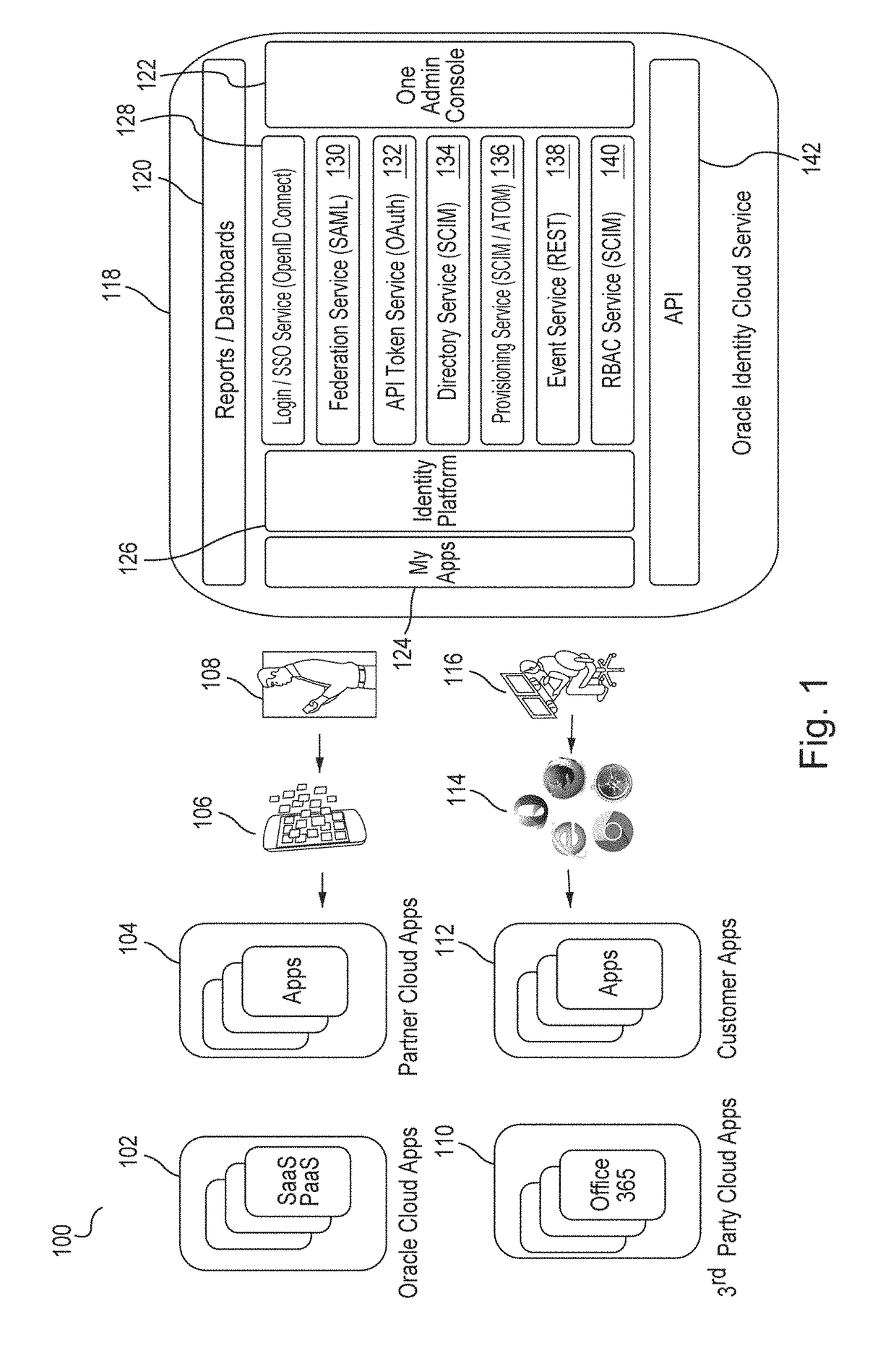
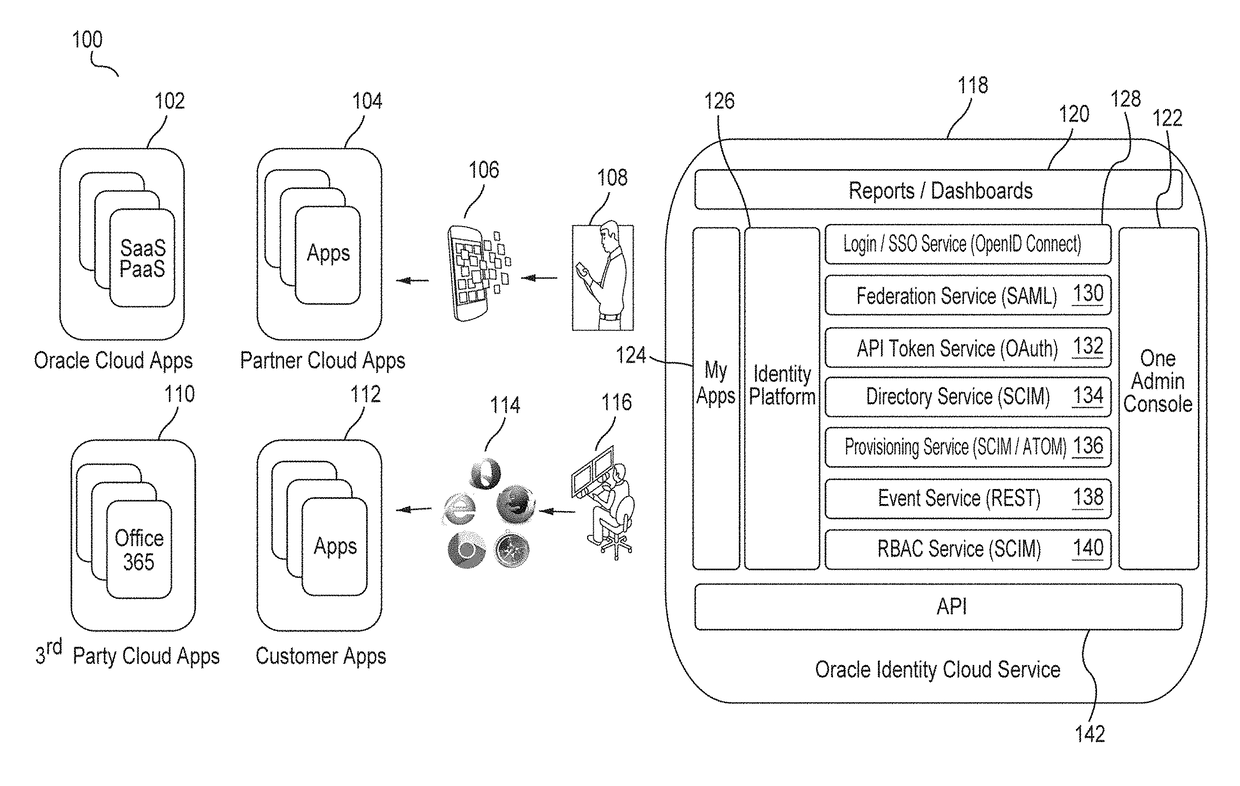
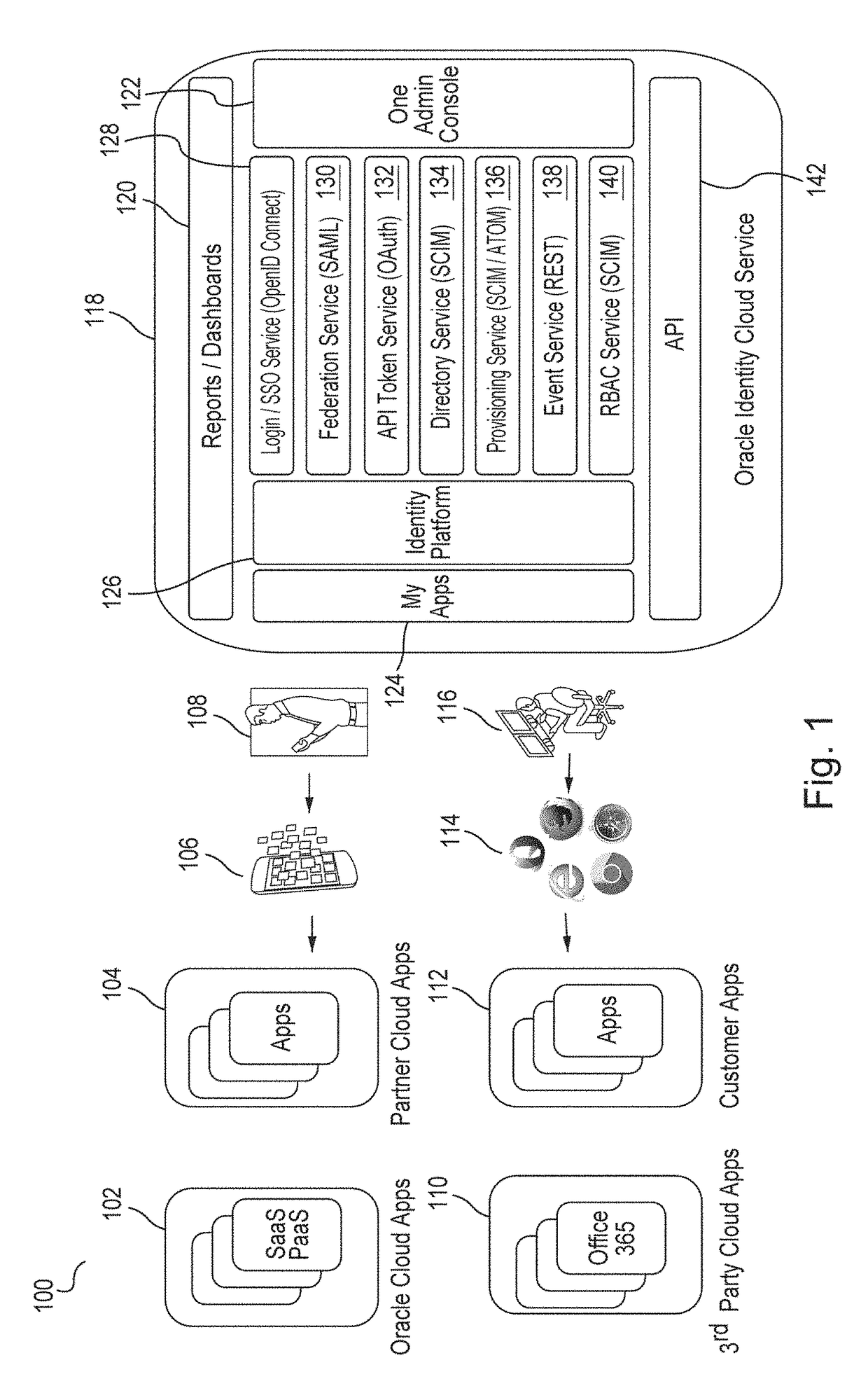
Single sign-on functionality for a multi-tenant identity and data security management cloud service
ActiveUS20180075231A1Digital data information retrievalDigital data authenticationInternet privacyCloud base
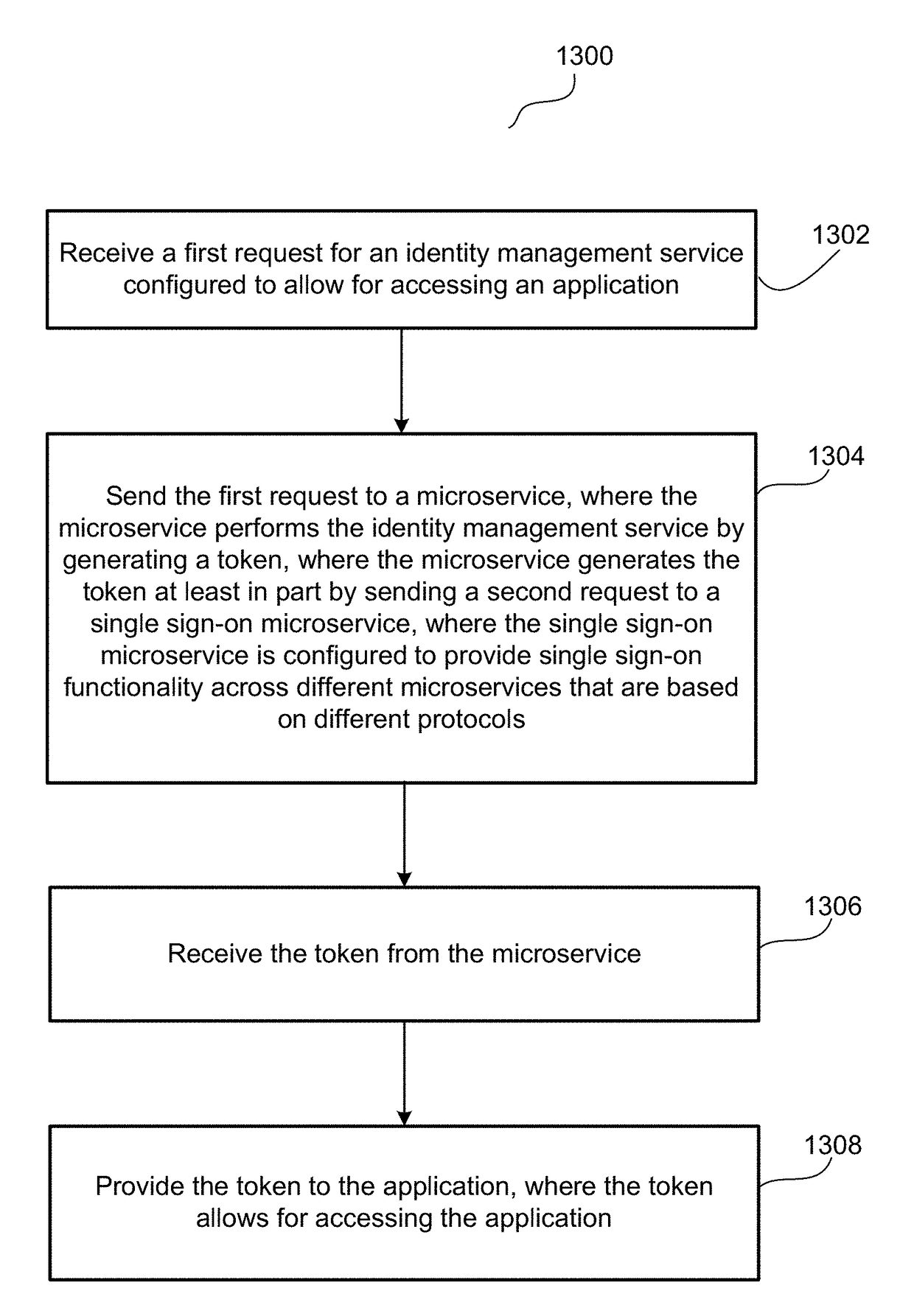
A cloud-based identity and access management system that implements single sign-on (“SSO”) receives a first request for an identity management service configured to allow for accessing an application. Embodiments send the first request to a first microservice which performs the identity management service by generating a token. The first microservice generates the token at least in part by sending a second request to a SSO microservice that is configured to provide SSO functionality across different microservices that are based on different protocols. Embodiments then receive the token from the first microservice and provide the token to the application, where the token allows for accessing the application.
Owner:ORACLE INT CORP
Autonomously healing microservice-based applications
ActiveUS20170046146A1Improve technical effectPerformance issueVersion controlSoftware testing/debuggingProcess engineeringMicroservices
An embodiment includes a method for autonomous healing of an application comprising a plurality of microservices. The method comprises the steps of detecting a performance degradation of at least a portion of the application; and responsive to detecting the performance degradation, downgrading at least one of the plurality of microservices within the application. The downgrading comprises deploying a prior version of the at least one of the plurality of microservices; and routing at least a portion of traffic to the prior version instead of a current version of the at least one of the plurality of microservices.
Owner:IBM CORP
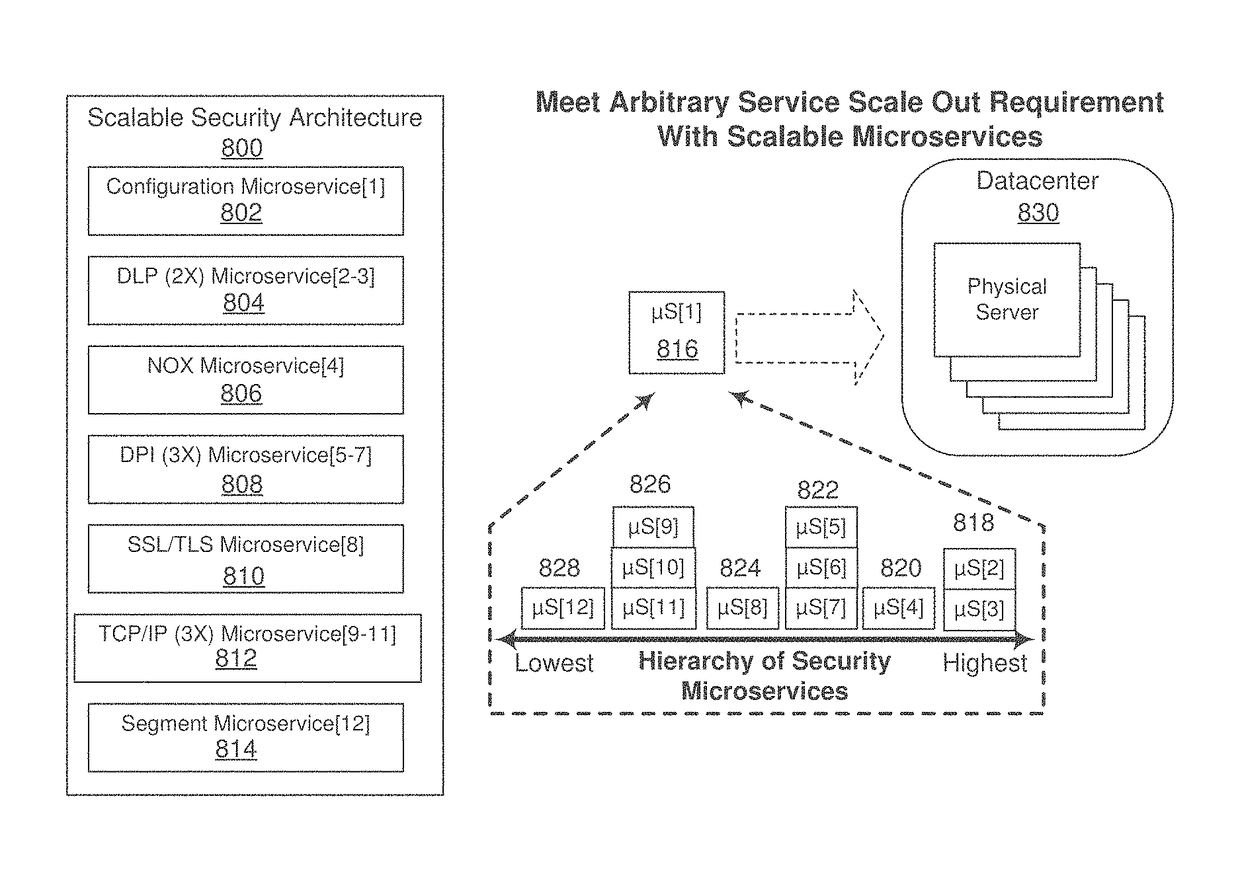
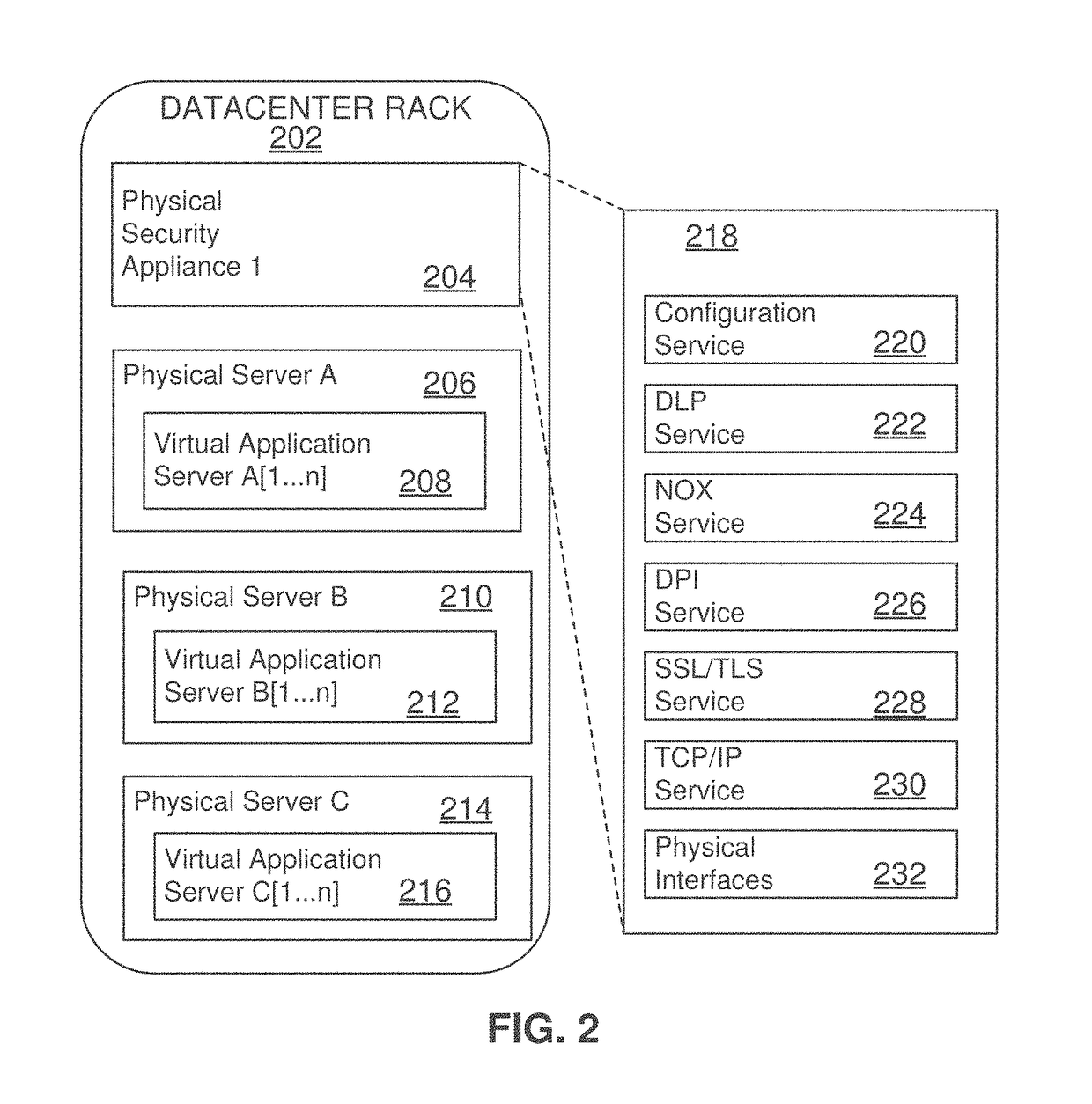
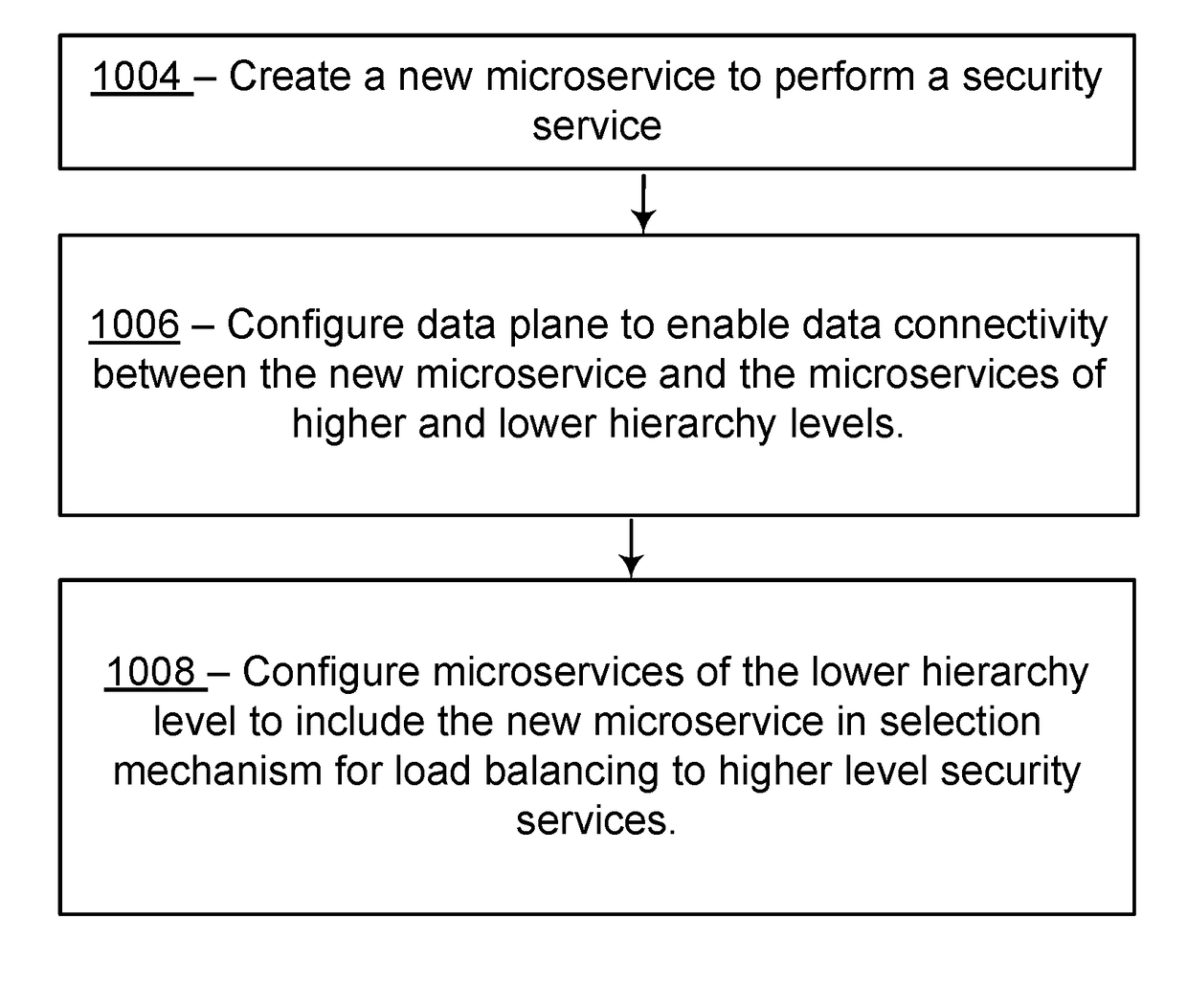
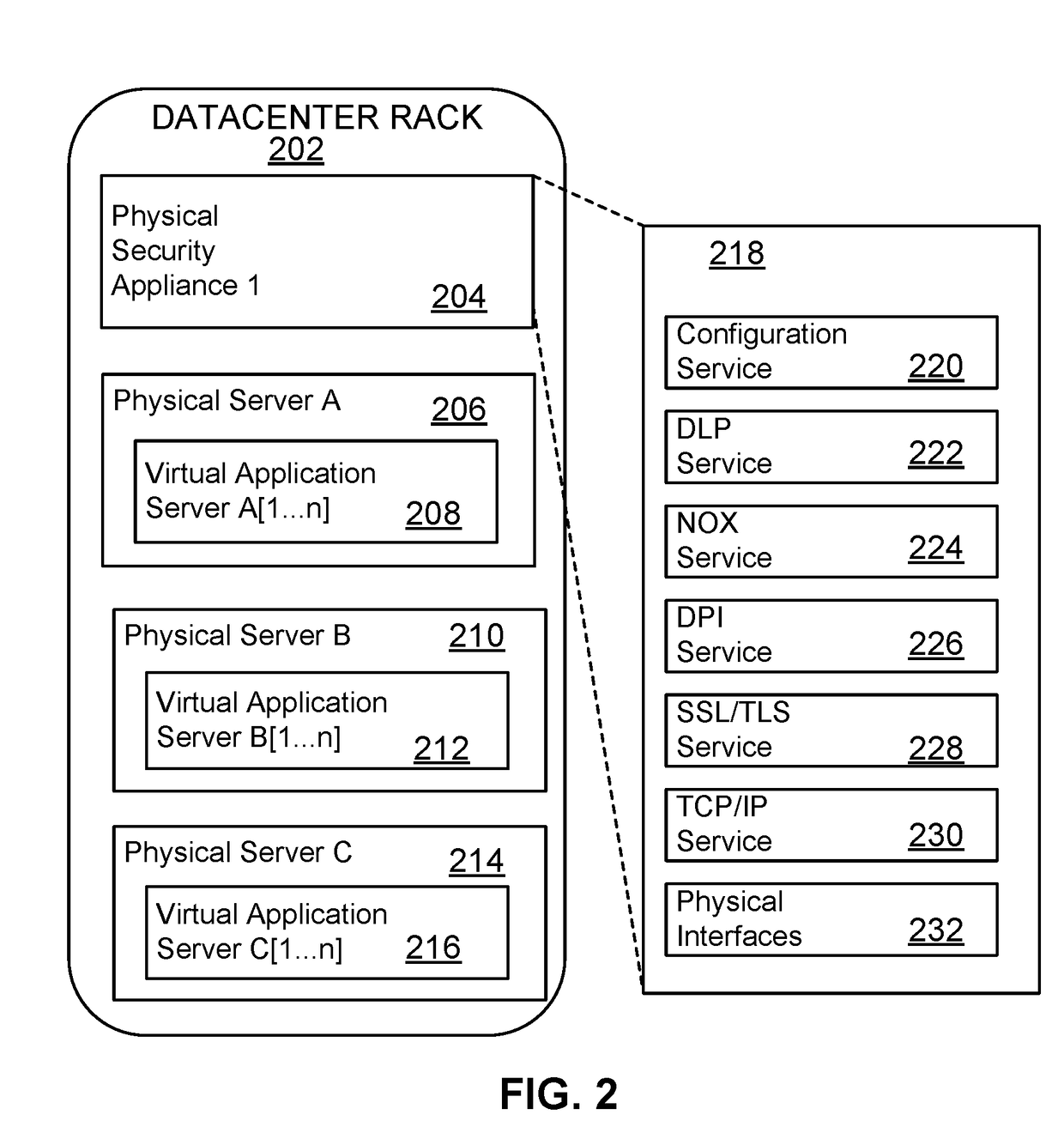
Dynamic, load-based, auto-scaling network security microservices architecture
System, methods, and apparatuses used to monitor network traffic of a datacenter and report security threats are described. For example, one embodiment scales out a hierarchy of microservices in a security system. In particular, the embodiment calls for scaling out a hierarchy of microservices in such a security system, creating a new microservice of a first hierarchy, configuring data plane connectivity between the new microservice and a microservice of a second, higher-level hierarchy; configuring data plane connectivity between the new microservice and a microservice of a third, lower-level hierarchy; and configuring the microservices of the third level of hierarchy to include the new microservice in load balancing decisions to the first hierarchy.
Owner:FORTINET
Affinity of microservice containers
A particular software container hosting a particular microservice is identified that is to implement at least a portion of a software program. A set of other containers hosting other microservices are determined to be interoperable with the particular microservice and an affinity value corresponding to the particular container is determined for each other container in the set, each of the affinity values representing a respective degree of correspondence between the particular container and the corresponding other container. A listing of at least a subset of the set of other containers are presented together with an indication of the corresponding affinity value of each of the subset of other containers.
Owner:CA TECH INC
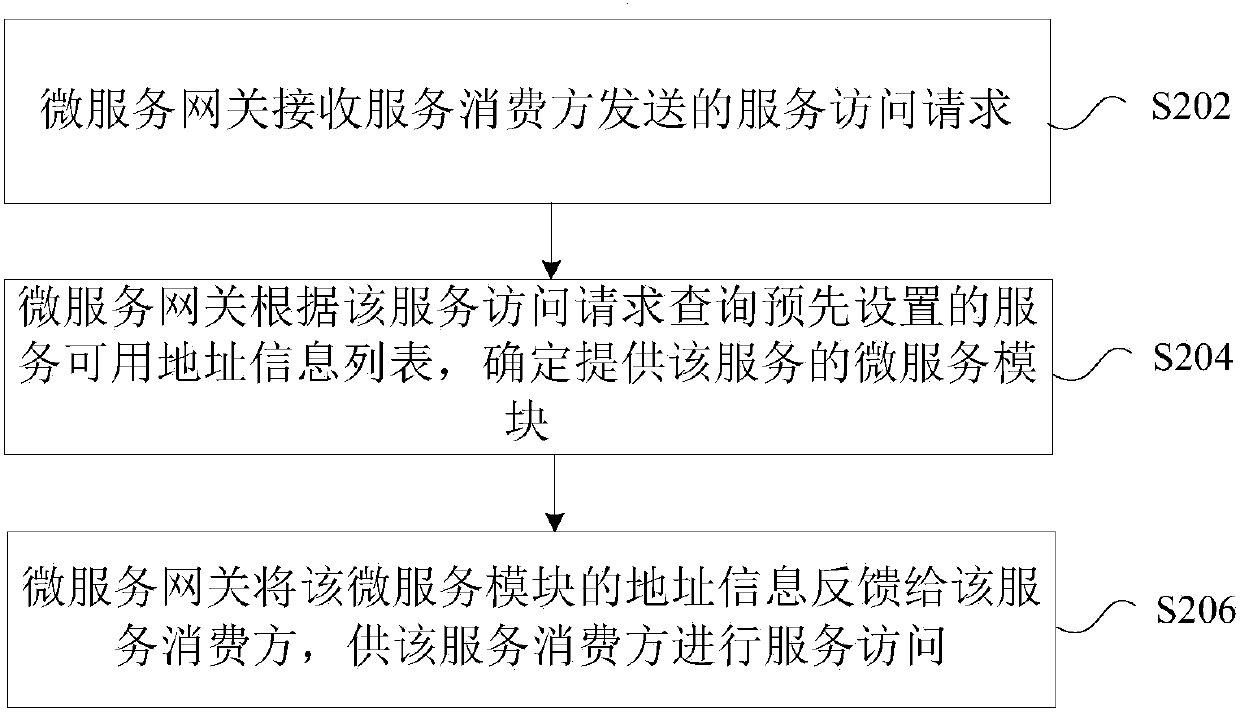
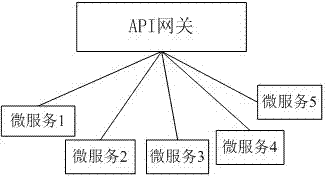
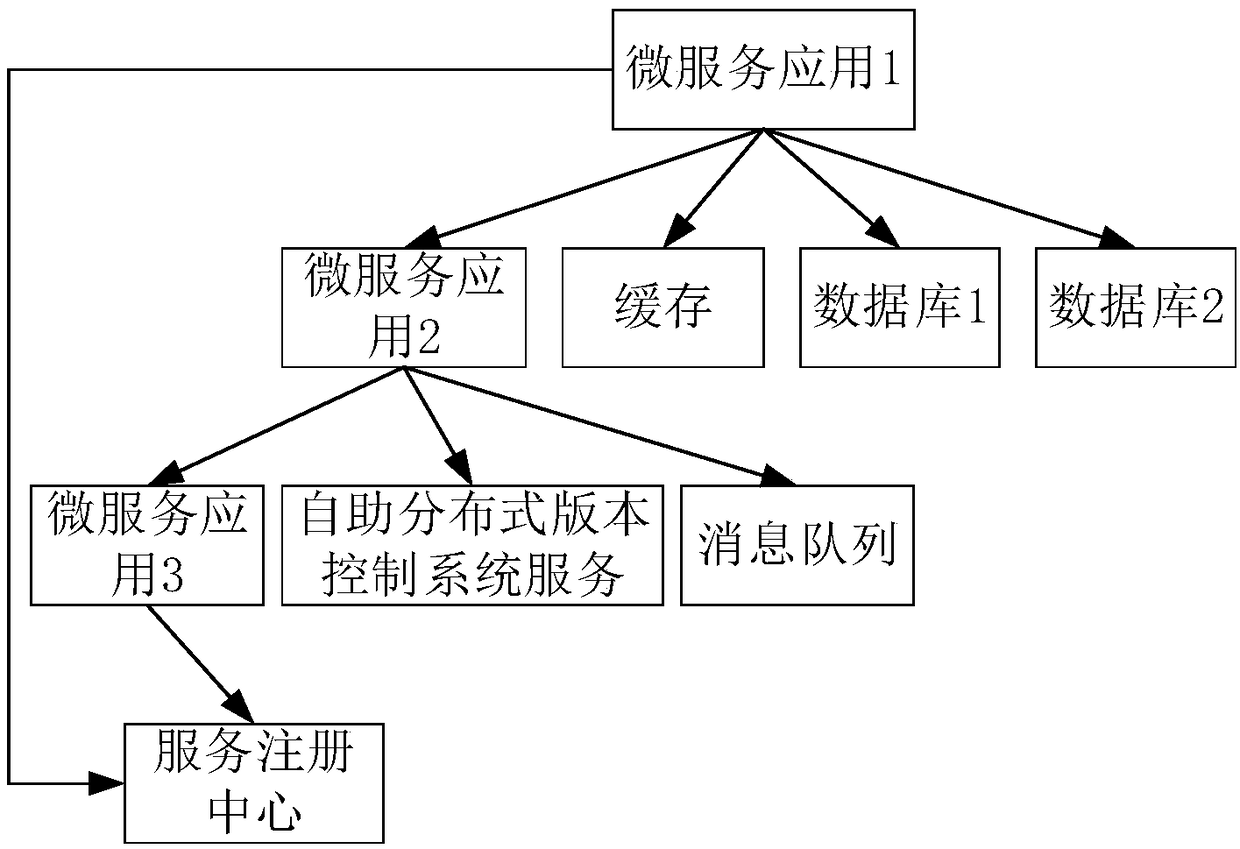
Microservice providing method, device and system
The invention discloses a microservice providing method, device and system. The method includes the steps of receiving, by a microservice gateway, a service access request sent by a service consumer;querying a preset service available address information list according to the service access request, and determining a microservice module that provides the service; and feeding back address information of the microservice module to the service consumer for service access by the service consumer. The problem in the related art that during the dynamic expansion and deployment of the microservice module through a container, the release of the microservice requires manual configuration and management is solved, the service self-registration is achieved, and the control flow and data flow separation is supported.
Owner:深圳市远行科技股份有限公司
Zero down time upgrade for a multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request for performing an identity management service. The request identifies the service and a current version of a microservice. The current version of the microservice is in a first stateless middle tier in a first topology that includes a first web tier. The system performs the identity management service by the current version of the microservice using tenant data stored in a database. The system then determines an upgrade to be applied to the microservice, and deploys a second topology that implements the upgrade. The second topology includes a second web tier and a second stateless middle tier including a new version of the microservice. The system tests the new version of the microservice in the second topology using test data stored in the database, promotes the second topology, and drains and shuts down the first topology.
Owner:ORACLE INT CORP
SaaS application construction method based on microservice architecture
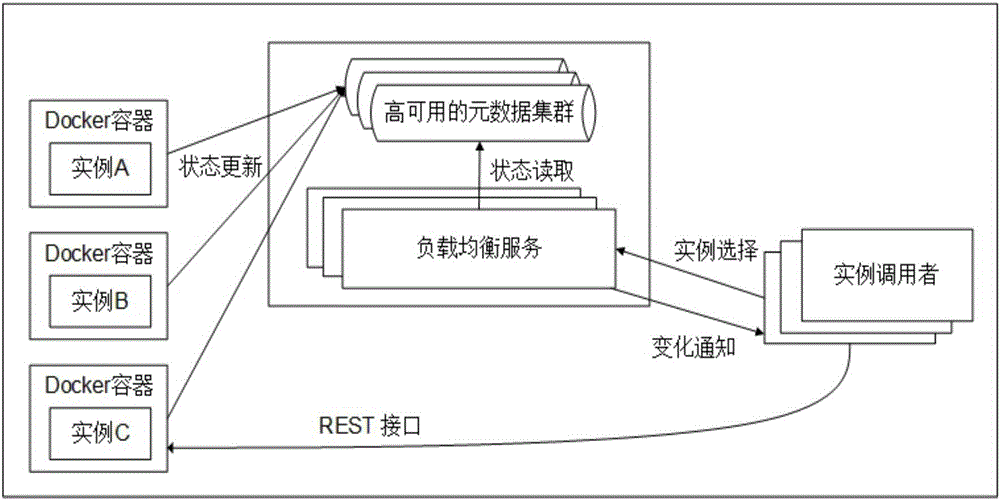
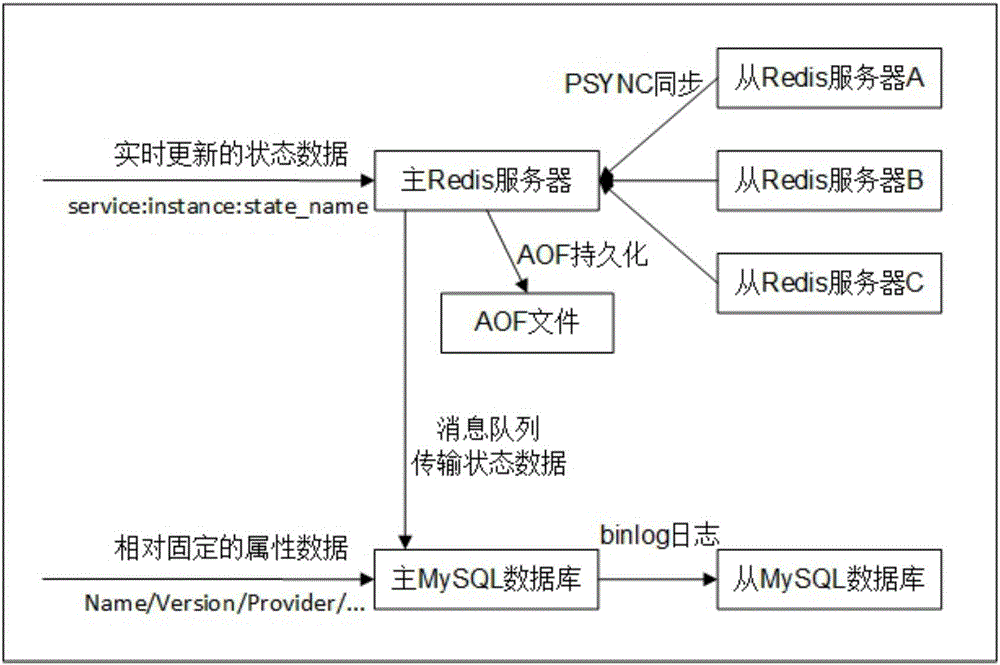
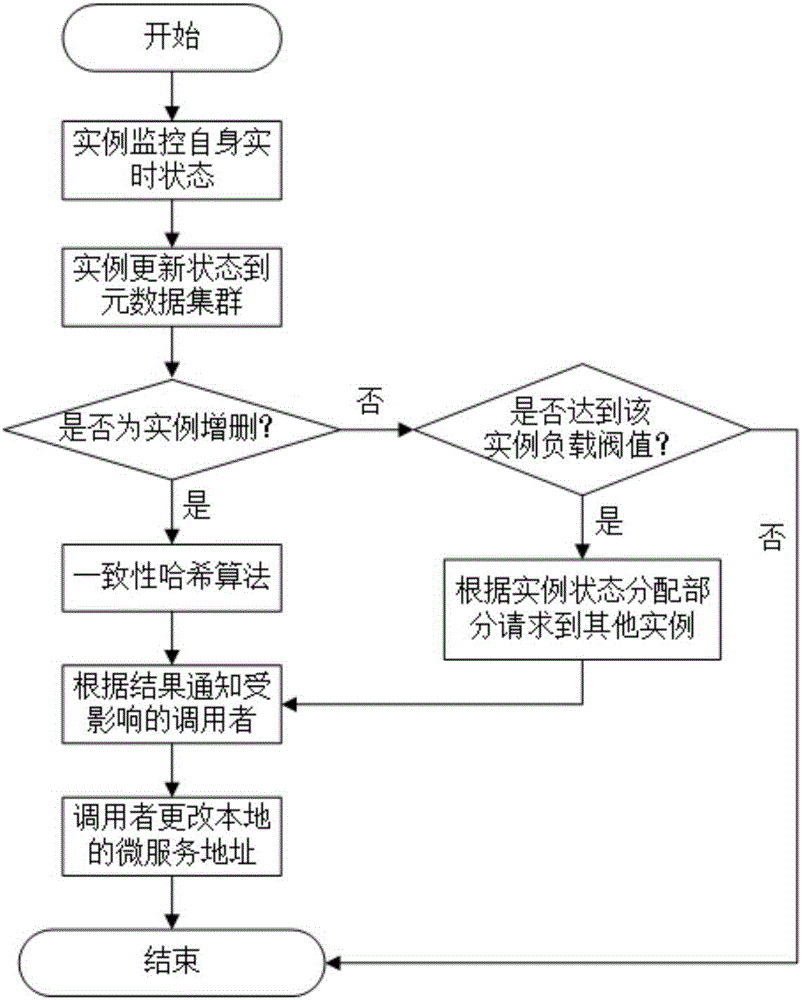
The present invention provides an SaaS application construction method based on a microservice architecture. Aiming at the defects in the construction method based on the traditional SOA architecture in the prior art, the method provided by the invention comprises: formulating the design rule and the attribute model for developing the microservice, and realizing the deployment of the microservice example through a Docker container; building a distributed microservice metadata cluster, and performing unified management of the metadata of the microservice, the microservice providers and the microservice users; aiming at the real-time updating state data and the relatively fixed attribute data, designing a highly available storage scheme; aiming at the real-time highly concurrent reading-write requirement of the metadata, designing a scheme through combination of Redis main and slave server models and a reading-writing separation architecture; and aiming at the microservice example dynamic addition and deletion condition, designing a load balance strategy based on the consistency hash algorithm. The SaaS application construction method based on the microservice architecture solves the microservice development, deployment and management schemes so as to improve the development efficiency of the SaaS application.
Owner:SOUTH CHINA UNIV OF TECH
Generating derived credentials for a multi-tenant identity cloud service
A multi-tenant system that provides cloud-based identity management receives a request to execute a job, where the job has a scheduled start time, or a timeframe to complete, that exceeds the validity time of a request access token. The system generates the request access token corresponding to the job, where the request access token has access privileges. The system schedules the job and persists the request access token. The system triggers the job at the scheduled start time and generates a derived access token based on the request access token, where the derived access token includes the access privileges. The system then injects the derived access token during runtime of the job and calls a microservice using the derived access token to execute the job.
Owner:ORACLE INT CORP
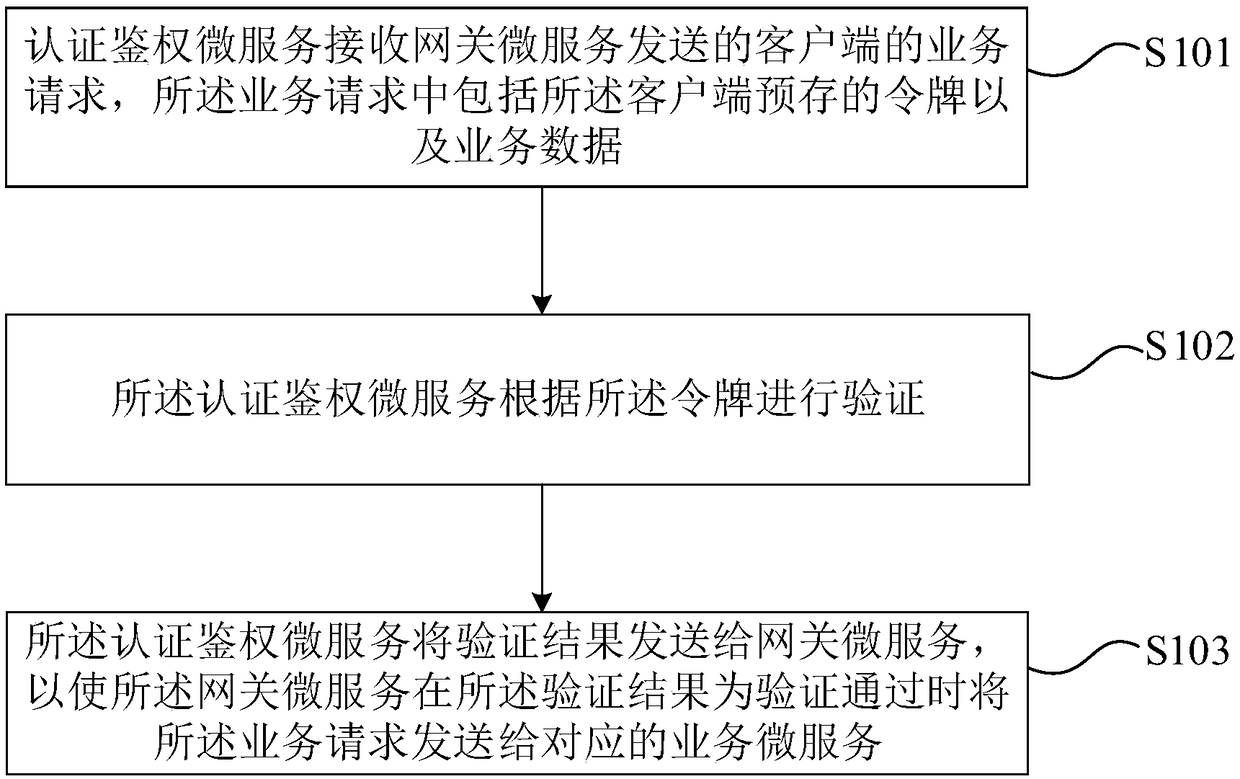
Authentication method and device as well as storage medium
InactiveCN109327477AAvoid the risk of cross-site request forgery)Easy to decoupleTransmissionExtensibilityMicroservices
The invention provides an authentication method and device as well as a storage medium. The method comprises the following steps: sending a service request to a gateway microservice by virtue of a client, wherein the service request comprises a token prestored by the client as well as service data; sending the service request to an authentication microservice by the gateway microservice, verifyingthe authentication microservice according to the token, sending a verification result to the gateway microservice, and sending the service request to a corresponding service microservice to perform aservice flow when the gateway microservice passes verification. The method provided by the invention takes authentication as an independent basic microservice, and other microservices under a microservice architecture respectively can call the authentication microservice to perform authentication, so that decoupling performance is good, and the authentication management problem under the microservice architecture is solved; only a client needs to prestore the token, and each microservice side does not need to store Session information, so that statelessness and extensibility are realized; anduser identity information is transmitted independent of Cookie, and a CSRF risk is avoided.
Owner:TAIKANG LIFE INSURANCE CO LTD
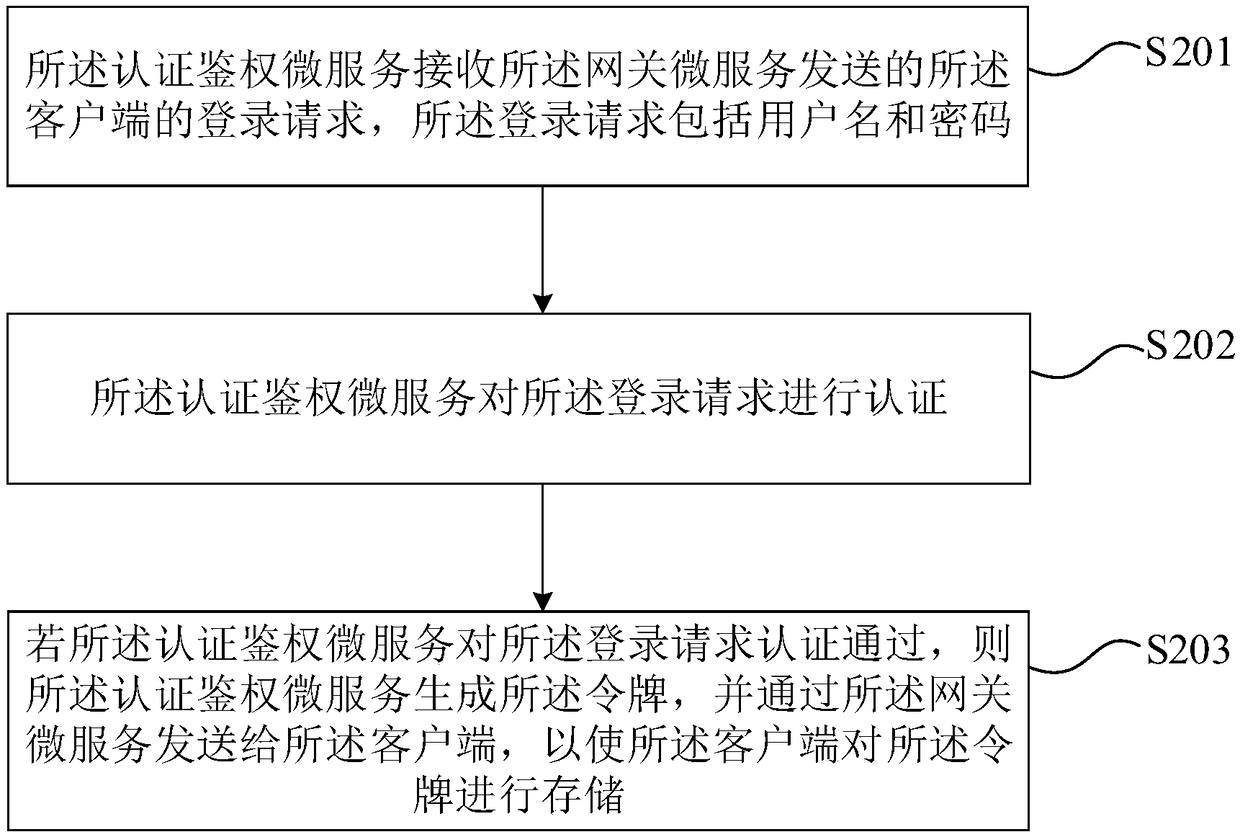
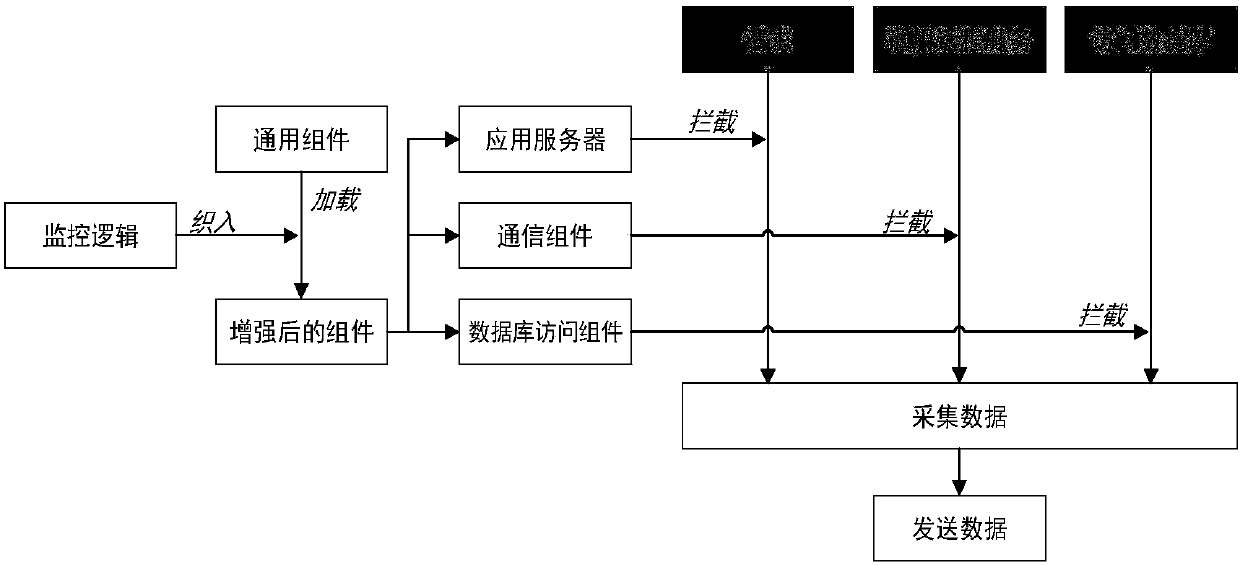
Microservice architecture span process tracking-oriented monitoring system and method
InactiveCN107766205AEffective positioningInterprogram communicationDatabase distribution/replicationMessage queueData acquisition
The invention discloses a microservice architecture span process tracking-oriented monitoring system and method. The system mainly includes a data collection module, a data transmission module and a data storage module. The data collection module adopts dynamic AOP technology to embed monitoring logic code into a common component without the need for modifying service code, and ensures transparency of a monitoring function to an application system. The data transmission module adopts an asynchronous manner based on a message queue, uses message middleware to realize accessing and transmissionof monitoring data, mitigates the problem that speeds of both data transmission and data processing are not synchronized, and also reduces coupling between the data collection module and the data storage module at the same time. For data storage, a user transaction request is used as a unit to record situations, which contain multiple service spans, for the one transaction request. The monitoringsystem uses a column-type model database for data storage.
Owner:WUHAN UNIV
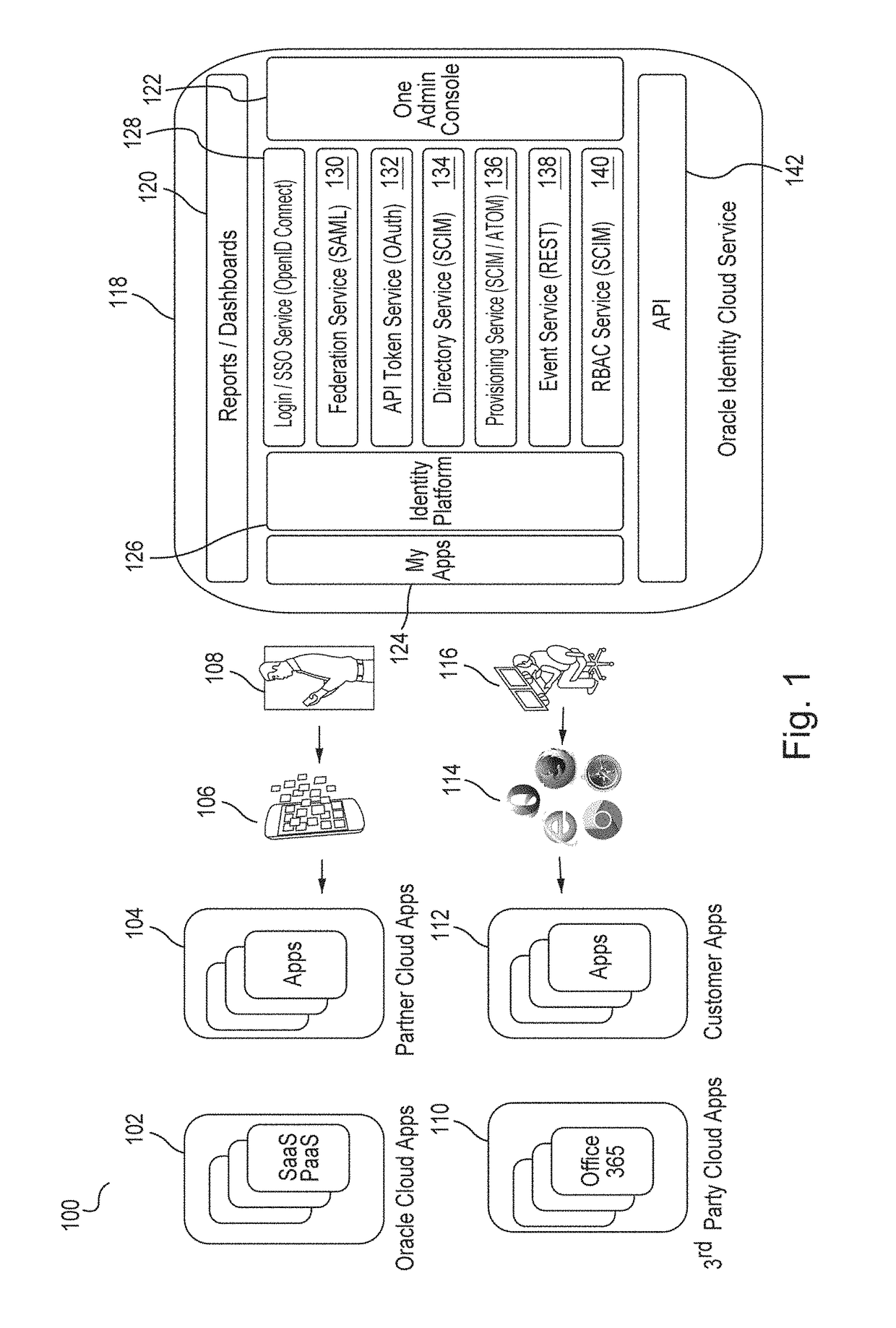
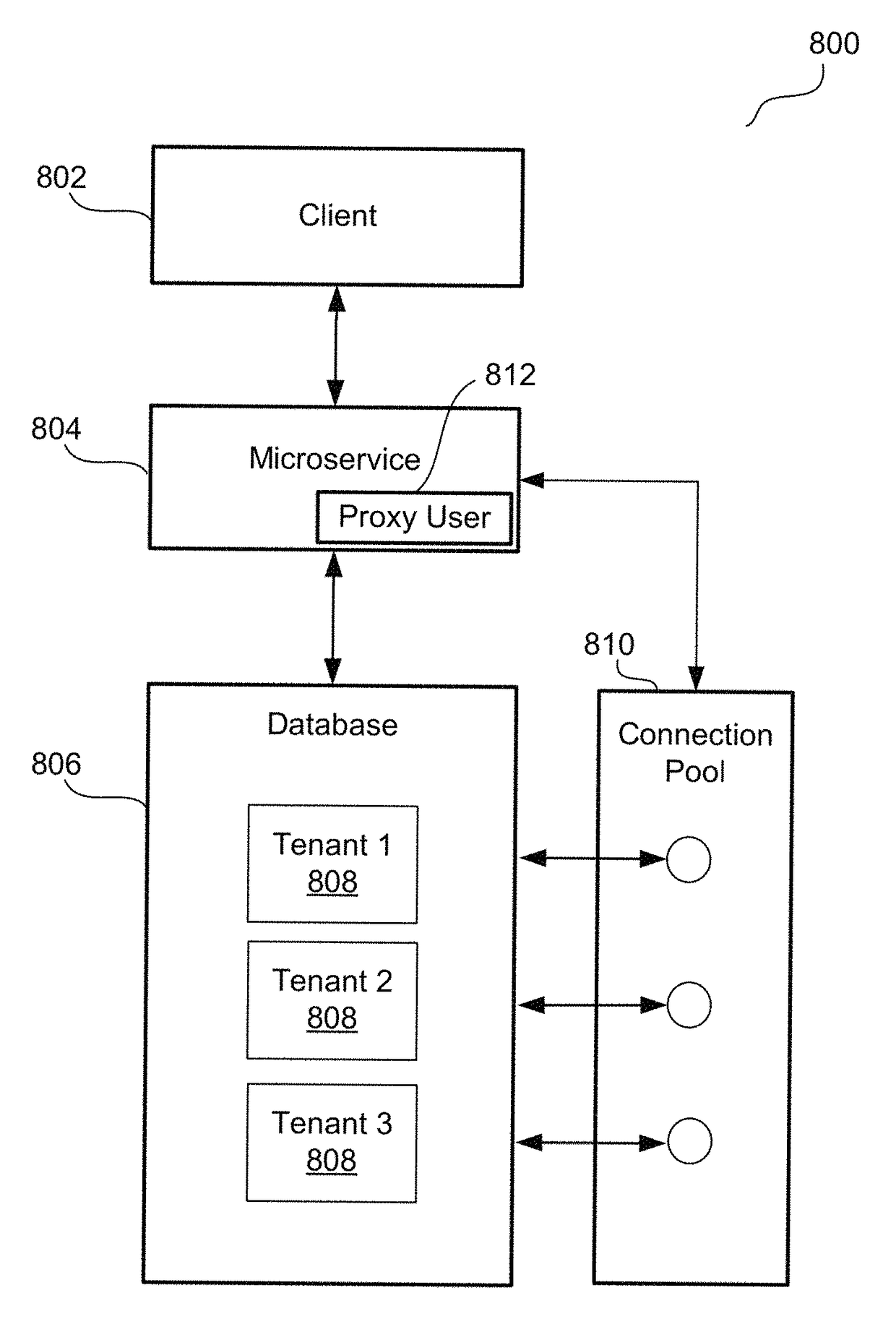
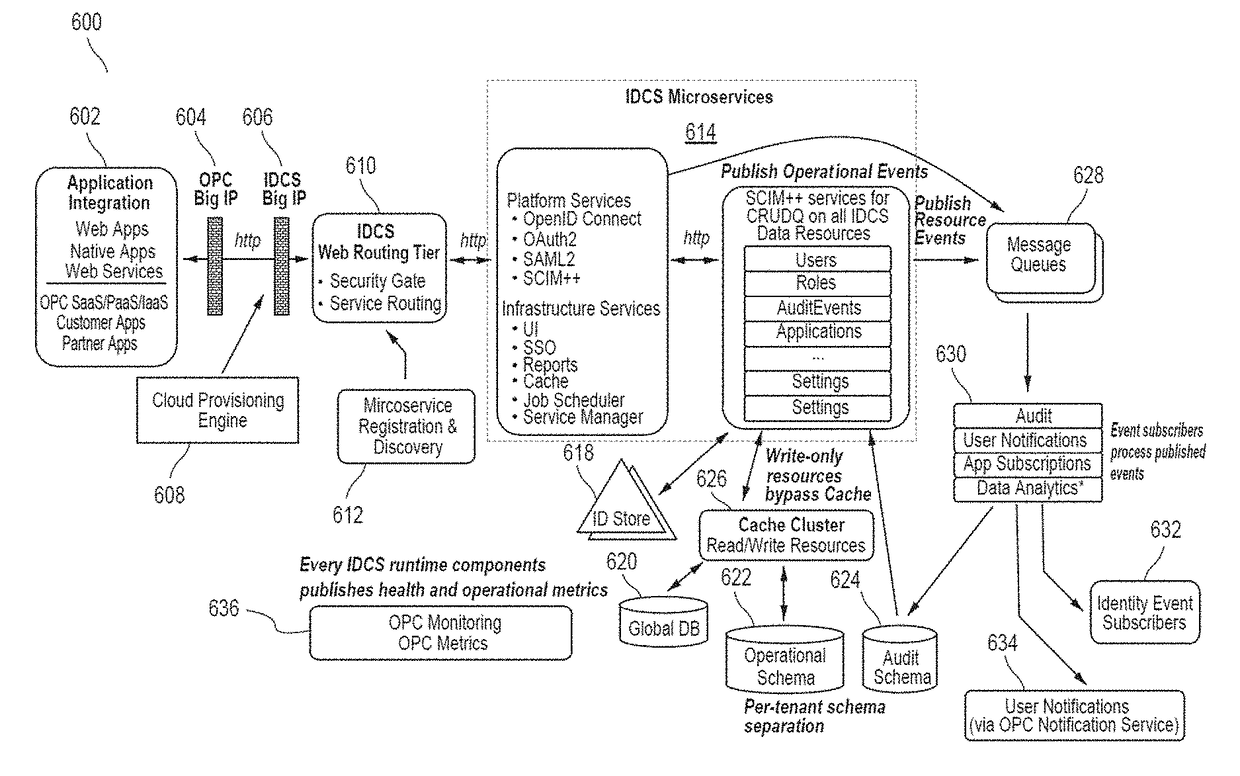
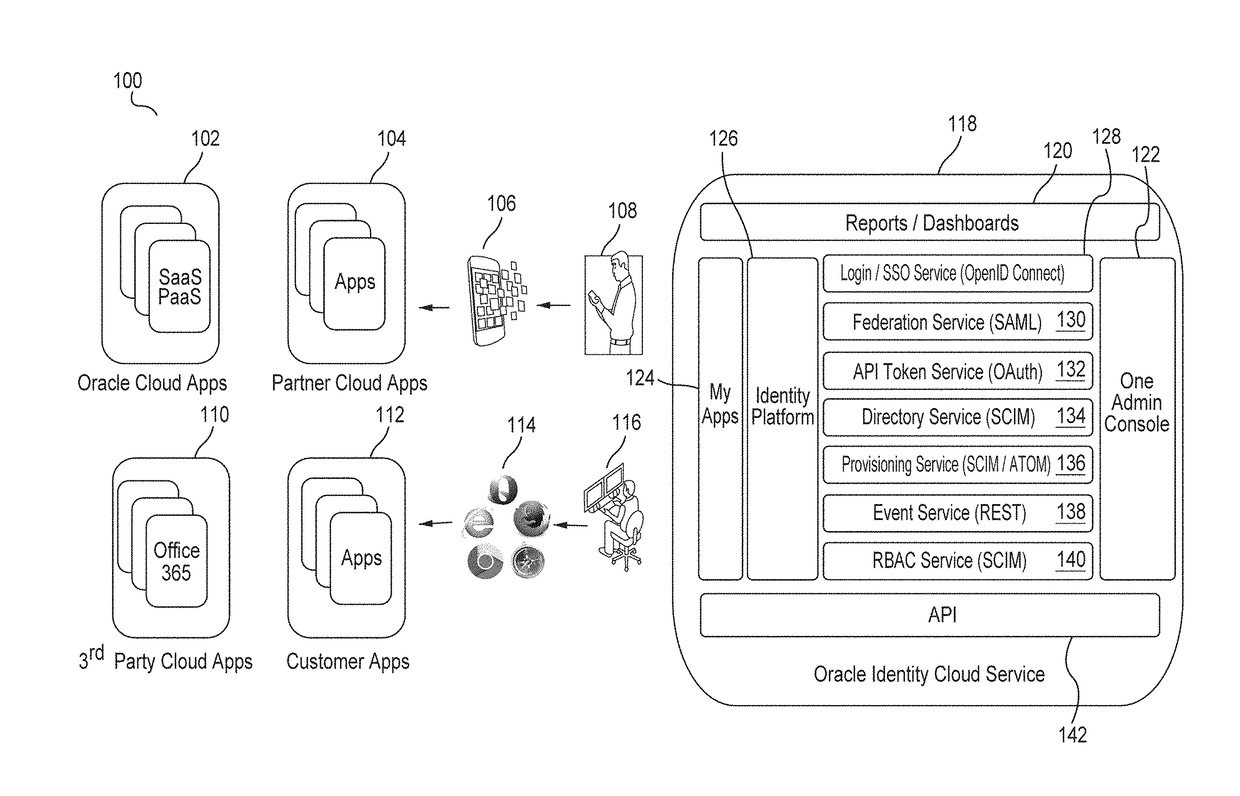
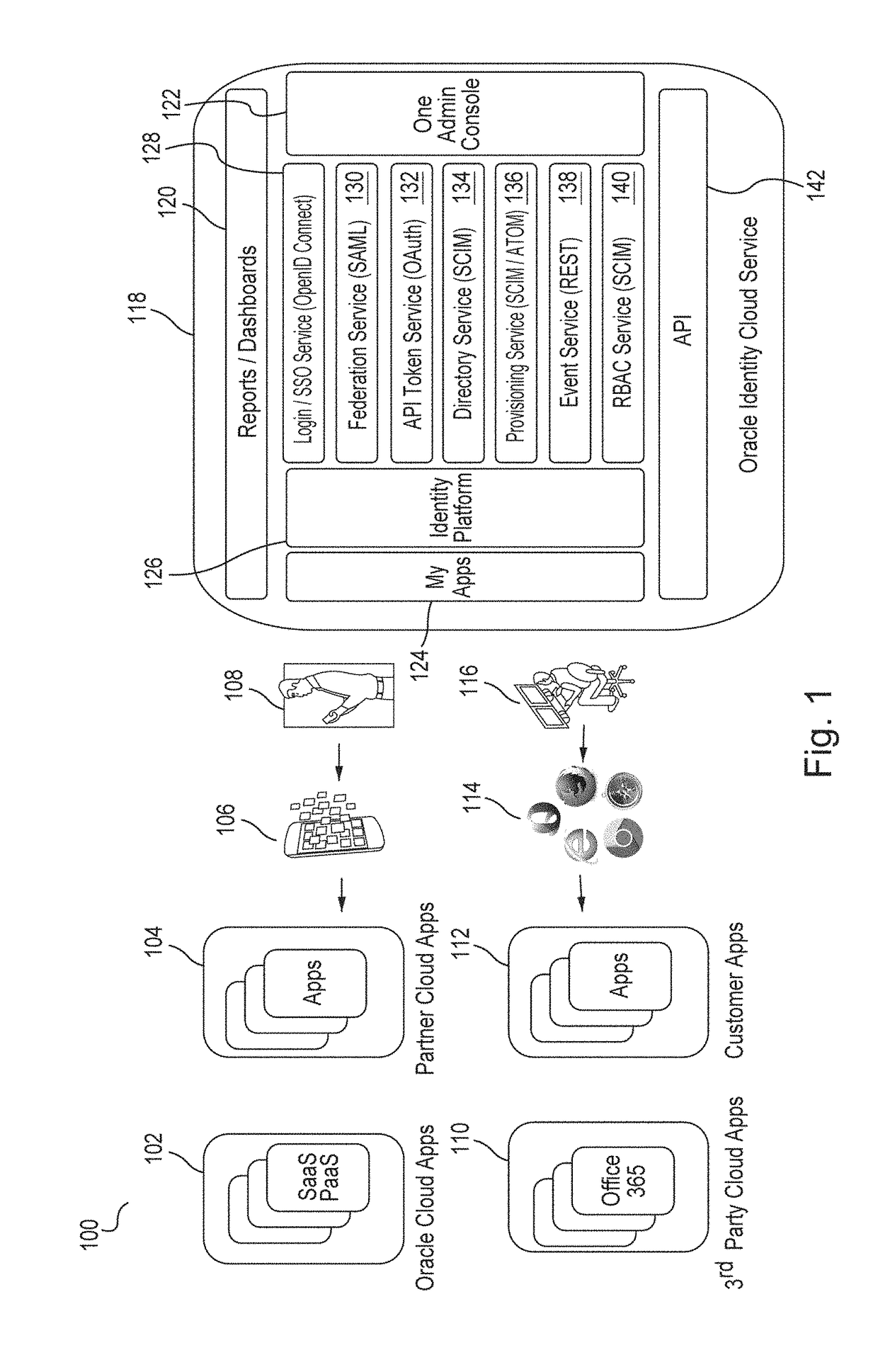
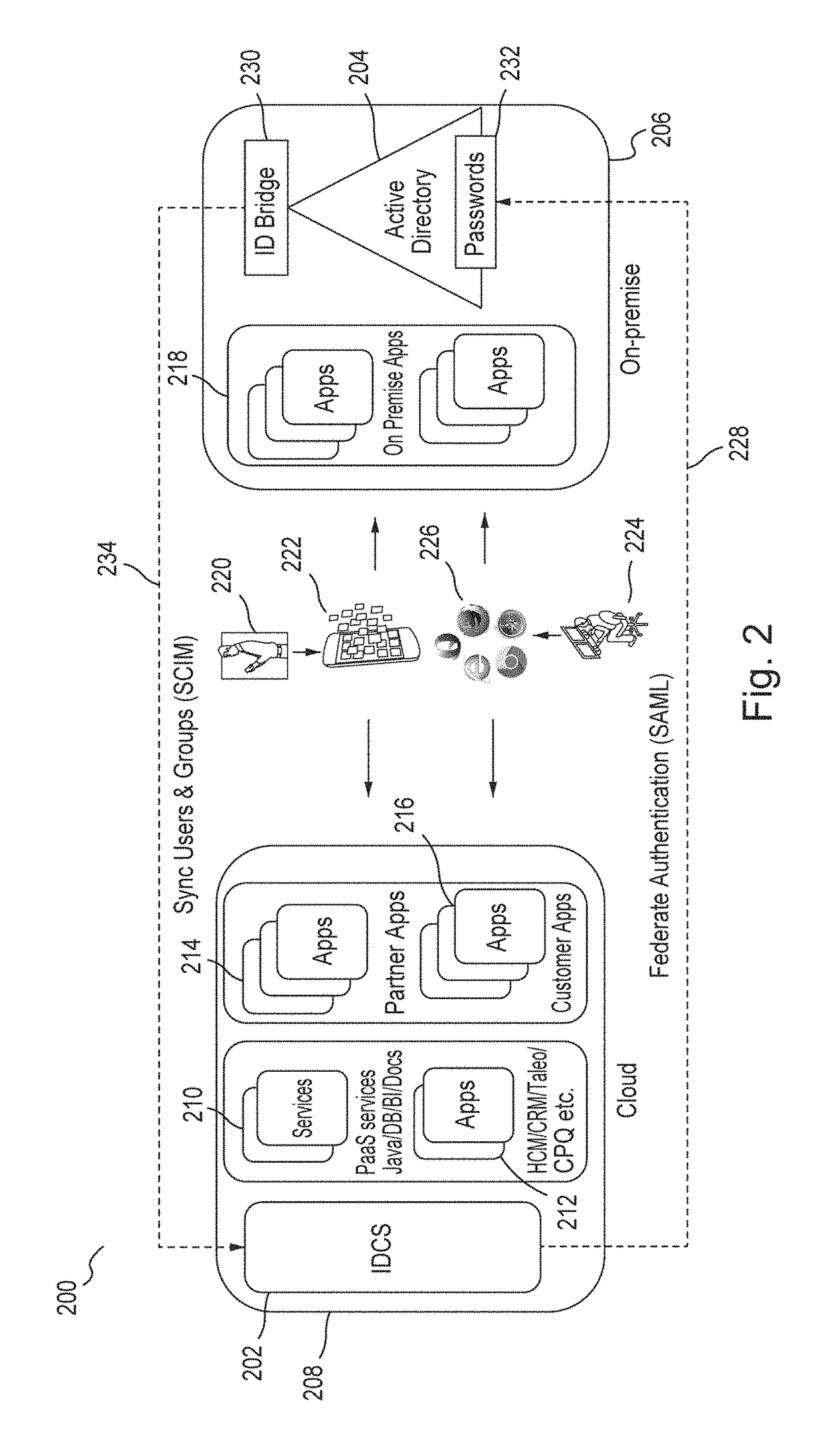
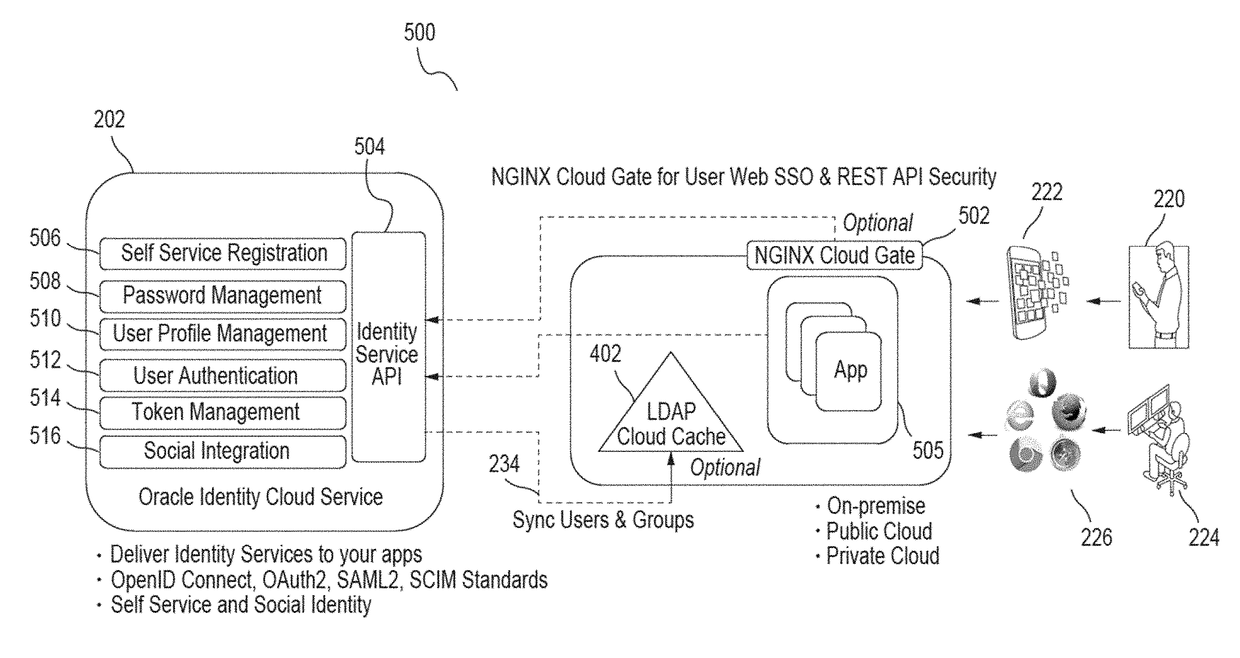
Multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request from a client for an identity management service, authenticates the request, and accesses a microservice based on the request. The system determines, based on the request, a tenancy of the client, a tenancy of a user, and a tenancy of a resource. The system retrieves data from the determined tenancies as required to process the request, where the data is retrieved by the microservice using a connection pool that provides connections to the database. The system then performs the identity management service by the appropriate microservice responsible for processing the received request.
Owner:ORACLE INT CORP
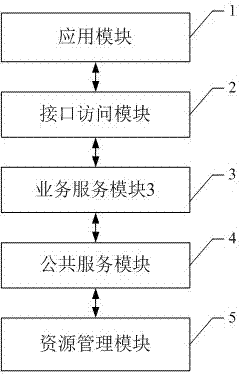
System based on integrated microservice configuration
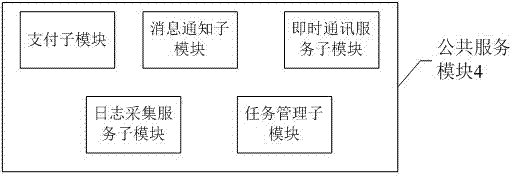
InactiveCN106878393AImprove schedulabilityFast and accurate developmentTransmissionResource managementMicroservices
The invention discloses a system based on integrated microservice configuration, and the system comprises an application module, an interface access module, a business service module, a public service module, and a resource management module. The application module transmits a data request. The interface access module is used for receiving and processing the data request transmitted by the application module, and determines a microservice unit, executing the data request, according to the data request. The business service module is used for receiving the microservice unit information transmitted by the interface access module, and carrying out the call of the microservice according to the microservice unit information. The public service module is used for searching a corresponding service according to the corresponding relation between a preset microservice and a service, wherein the searched service is used for receiving a microservice instruction. The resource management module is used for storing the data of the service in the public service module, and is used for transmitting the corresponding data to the public service module according to a service request. The business service module enables the data to be transmitted to the application module through the interface access module. According to the invention, the system provides the reliable guarantee for the improvement of the schedulability and the quick and accurate development of new demands.
Owner:深圳市商沃科技发展有限公司
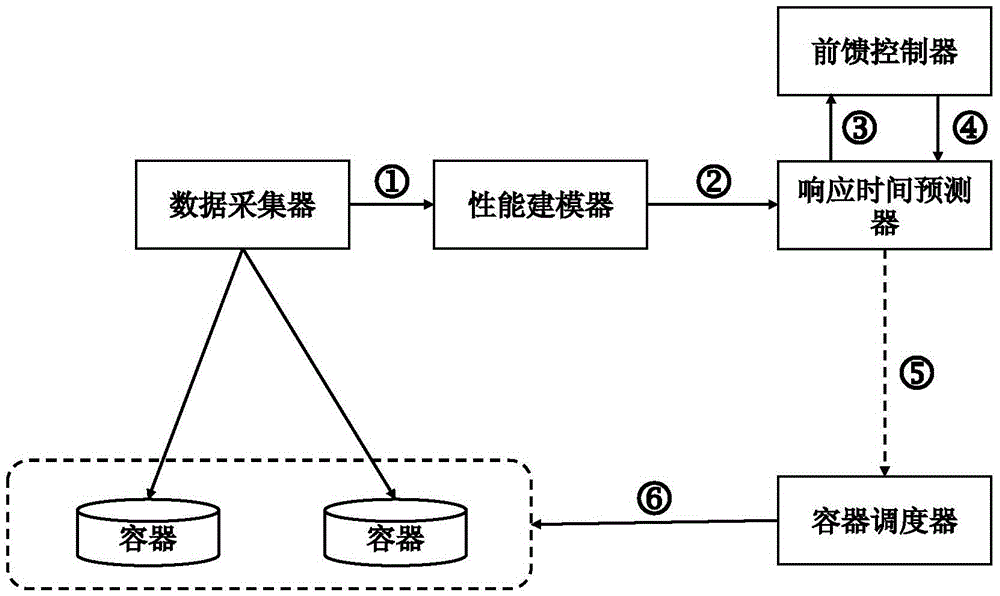
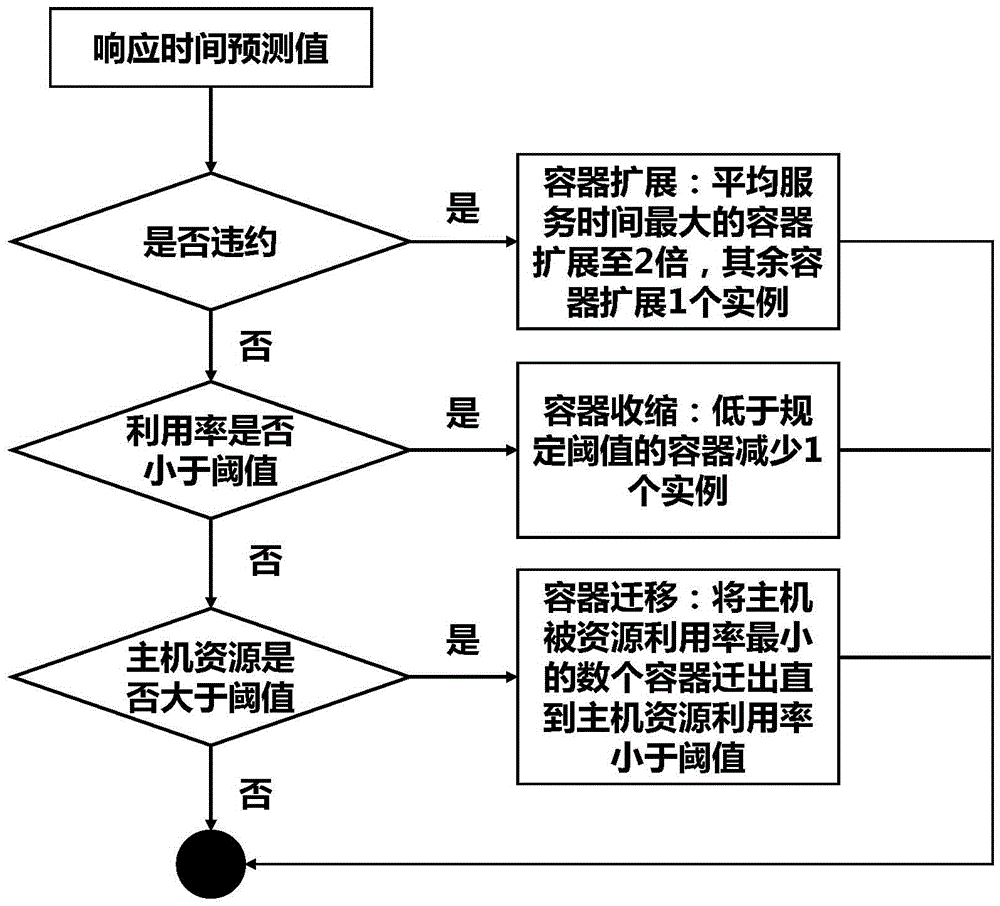
Microservice-oriented container level flexible resource supply system and method
ActiveCN105631196AGuaranteed accuracyImprove effectivenessSpecial data processing applicationsInformaticsData acquisitionMicroservices
The invention relates to a microservice-oriented container level flexible resource supply system and method. The system comprises a data acquisition device, a performance modeling device, a feedforward controller, a response time predictor and a container scheduler. According to the system and method, the deficiencies of difficulty in suitability for a sudden load mode and difficulty in user service quality guarantee in an existing method are made up for.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
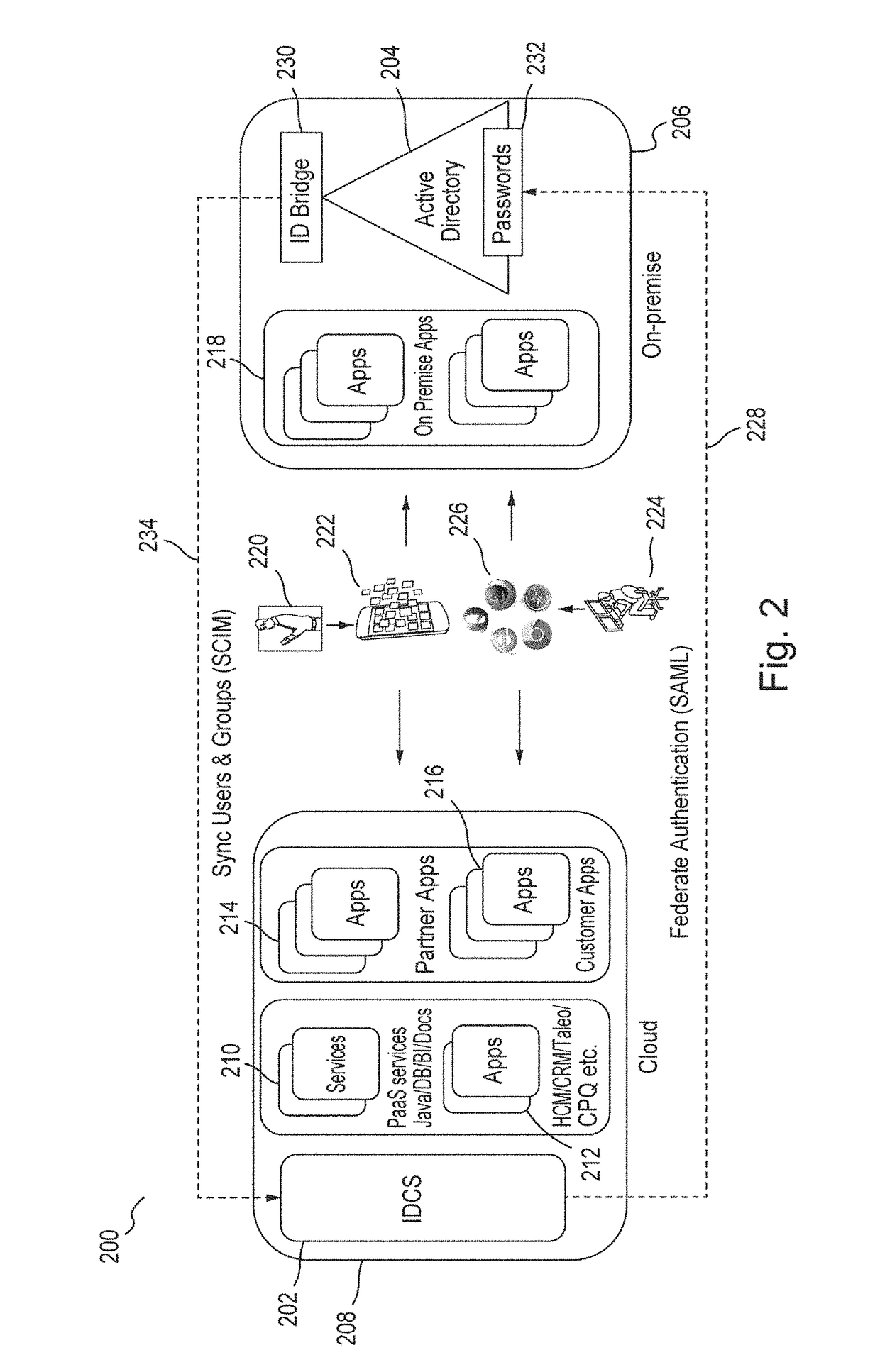
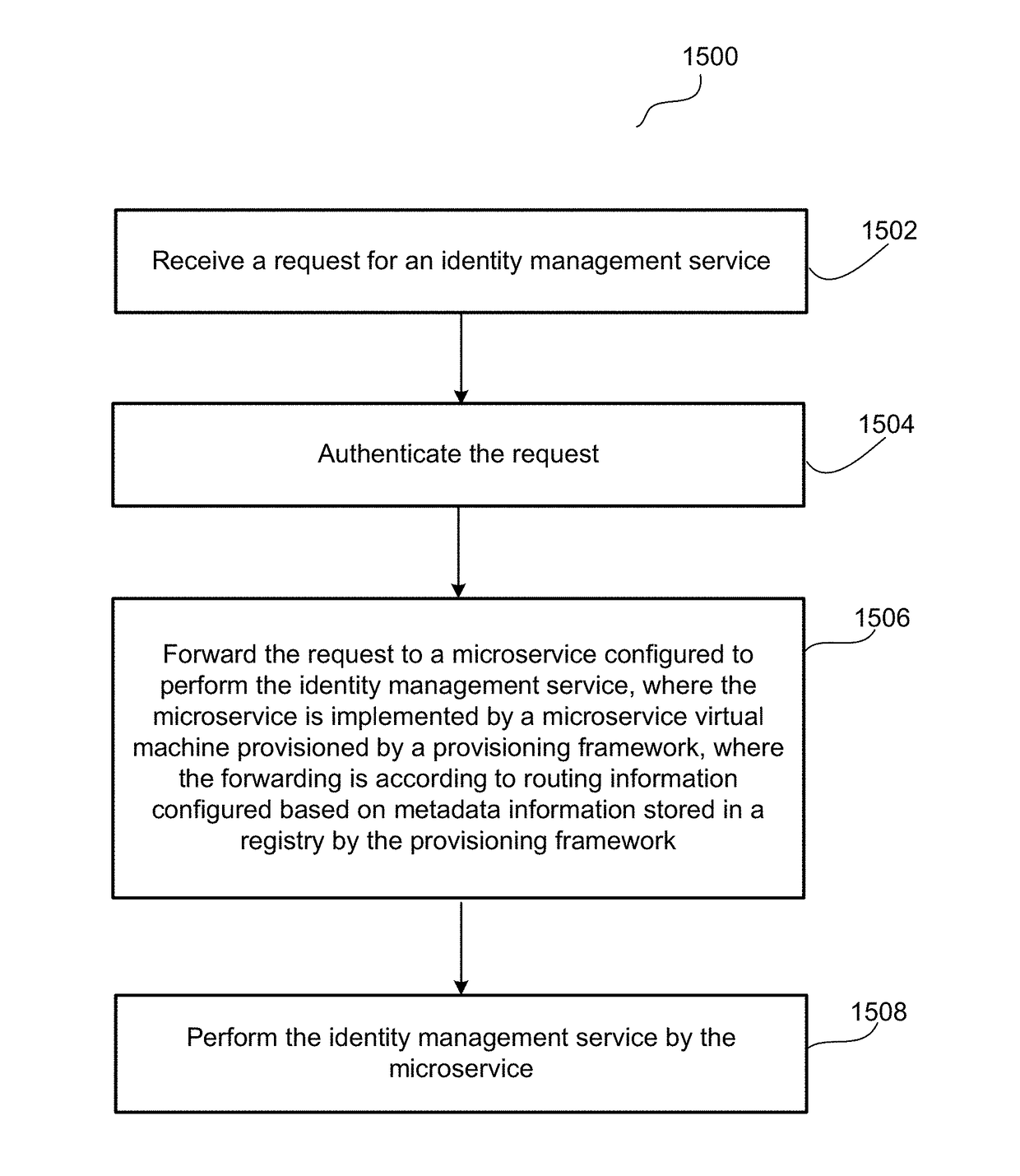
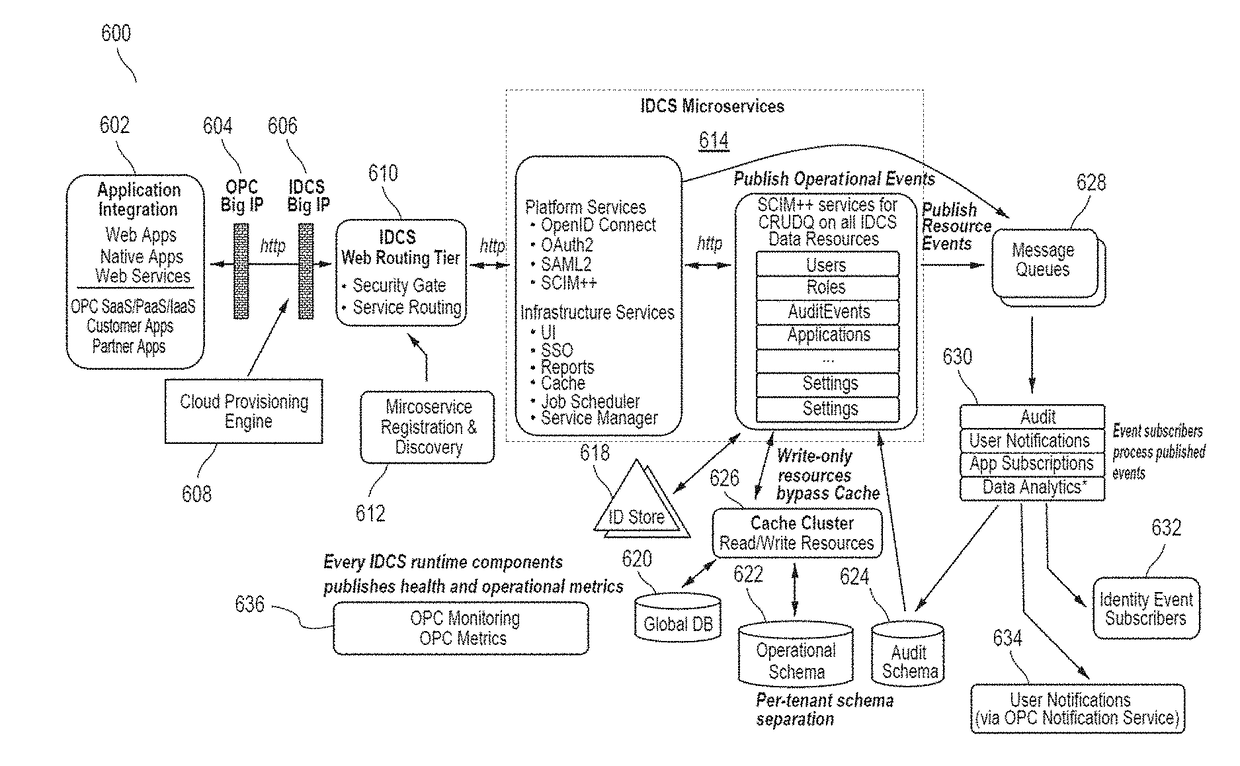
Service discovery for a multi-tenant identity and data security management cloud service
ActiveUS20180041515A1Digital data authenticationPlatform integrity maintainanceCloud baseMicroservices
A system provides cloud-based identity and access management. The system receives a request for an identity management service, authenticates the request, and forwards the request to a microservice configured to perform the identity management service, where the microservice is implemented by a microservice virtual machine provisioned by a provisioning framework, and the forwarding is according to routing information configured based on metadata information stored in a registry by the provisioning framework. The system then performs the identity management service by the microservice.
Owner:ORACLE INT CORP
Microservices based multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request for performing an identity management service, where the request includes a call to an application programming interface (“API”) that identifies the identity management service and a microservice configured to perform the identity management service. The system authenticates the request, accesses the microservice, and performs the identity management service by the microservice.
Owner:ORACLE INT CORP
Dynamic, Load-Based, Auto-Scaling Network Security Microservices Architecture
System, methods, and apparatuses used to monitor network traffic of a datacenter and report security threats are described. For example, one embodiment selects a first microservice of a first hierarchy, configures the microservices of a second lower-level hierarchy to remove the first microservice from load balancing decisions to the first hierarchy, moves the first microservice to another server, configures data plane connectivity to the first microservice to reflect a change in server, and configures the microservices of the second hierarchy to include the first microservice in load balancing decisions to the first hierarchy.
Owner:FORTINET
Microservice application arrangement and deployment method and device and computer terminal
ActiveCN108762769AImprove devops (software engineeringImprove technical operationsSoftware simulation/interpretation/emulationSoftware deploymentContinuous integrationComputer terminal
The invention provides a microservice application arrangement and deployment method and device and a computer terminal. The method comprises the steps of reading a dependency tree of a pre-stored microservice application, wherein the microservice application is a root node of the dependency tree; traversing all nodes in the dependency tree according to a preset rule and determining a starting sequence of all nodes; and deploying applications corresponding to all nodes to an operation environment according to the starting sequence, thereby finishing deploying the microservice application. According to the method, the device and the computer terminal, the condition that a user directly writes a complex program to realize the arrangement and deployment of the applications is avoided, a plurality of sets of environments for operating microservice are set up rapidly, the continuous integration, continuous delivery and continuous deployment are facilitated, all applications are deployed through a key, and a technical level of an enterprise is improved.
Owner:万惠投资管理有限公司
Caching framework for a multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request from a client for a resource, authenticates the request, and accesses a microservice based on the request. The system determines, by the microservice, whether the resource is cached in a near cache or in a remote cache, retrieves the resource from the near cache or from the remote cache when the resource is cached, and calls an administration microservice to obtain the resource when the resource is not cached. The system then provides the resource to the client.
Owner:ORACLE INT CORP
Cookie based state propagation for a multi-tenant identity cloud service
A system that provides cloud based identity management, at a first microservice, saves a current state on a cookie that is stored on a browser, where the current state is saved in a format specific to the first microservice. The system performs an operation on the first microservice that generates a first portion of information and a second portion of information. The system stores the first portion of information related to the operation on the cookie, the first portion including the current state. The system provides a second portion of information related to the operation to a second microservice as a query parameter on a redirect Uniform Resource Locator (“URL”), where the second portion is removed from the cookie.
Owner:ORACLE INT CORP
Data management for a multi-tenant identity cloud service
Cloud based identity management is provided by receiving a request from an application by a web gate for a resource, where the request includes an operation on a resource type out of a plurality of resource types and the request specifies a tenant out of a plurality of tenants. Embodiments access a microservice based on the request, resolve the resource type, and validate that the operation is supported by the resource type based on metadata. Embodiments get a data provider associated with the tenant, call the data provider to perform the operation, and then return the resource.
Owner:ORACLE INT CORP
Policy enforcement point for a multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request by a web gate for an identity management service for reaching an application, and determines a tenancy from a header value of the request. The system looks up a policy configured to be applied for the tenancy, and applies the policy to the request. The system then sends the request to a microservice based on a result of the applying of the policy to the request, where the microservice performs the identity management service for reaching the application.
Owner:ORACLE INT CORP
Microservices based multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request for performing an identity management service, where the request includes a call to an application programming interface (“API”) that identifies the identity management service and a microservice configured to perform the identity management service. The system authenticates the request, accesses the microservice, and performs the identity management service by the microservice.
Owner:ORACLE INT CORP
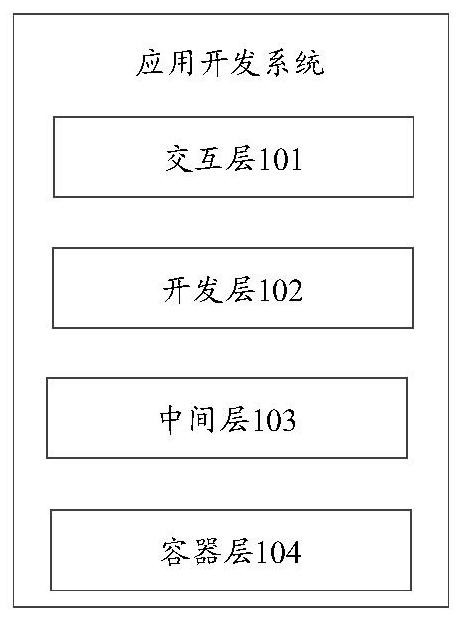
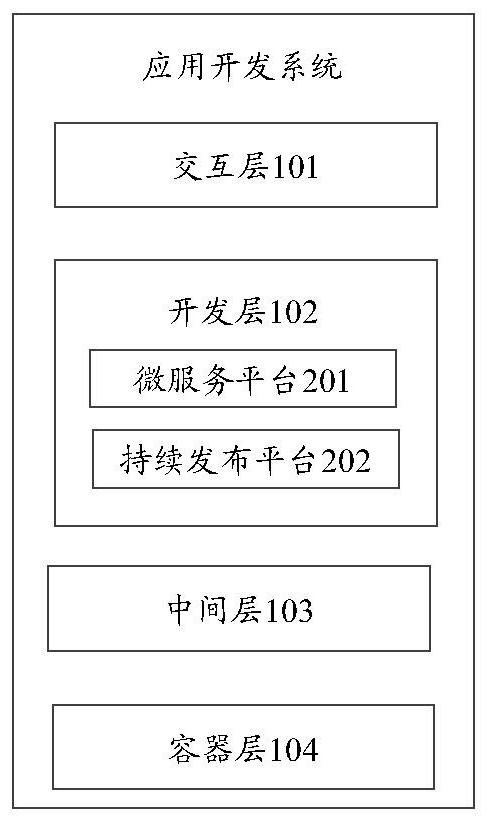
Application development system, operation method, equipment and storage medium
PendingCN111831269AShorten the timeImprove R&D efficiencyData switching networksSoftware simulation/interpretation/emulationInteraction layerEngineering
The embodiment of the invention provides an application development system, an operation method, equipment and a storage medium, and the system comprises: an interaction layer which is used for providing an operation interface, transmitting a creation request triggered on the operation interface to a development layer, and receiving and displaying a completed micro-service, wherein the creation request is used for requesting to create a micro-service of a to-be-developed business item; the development layer that is used for generating a calling request according to the microservice and sendingthe calling request to the intermediate layer so as to call the target intermediate component, and further, in the micro-service framework, a completed micro-service of the business item is created by utilizing the target intermediate component; the middle layer that is used for sending a calling request to the container layer to call the target container and creating a target middle component byutilizing the target container; the container layer that is used for providing at least two containers for setting up different intermediate components and feeding back a target container to the intermediate layer in response to the calling request; in this way, developers can focus on business development, and therefore the research and development efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
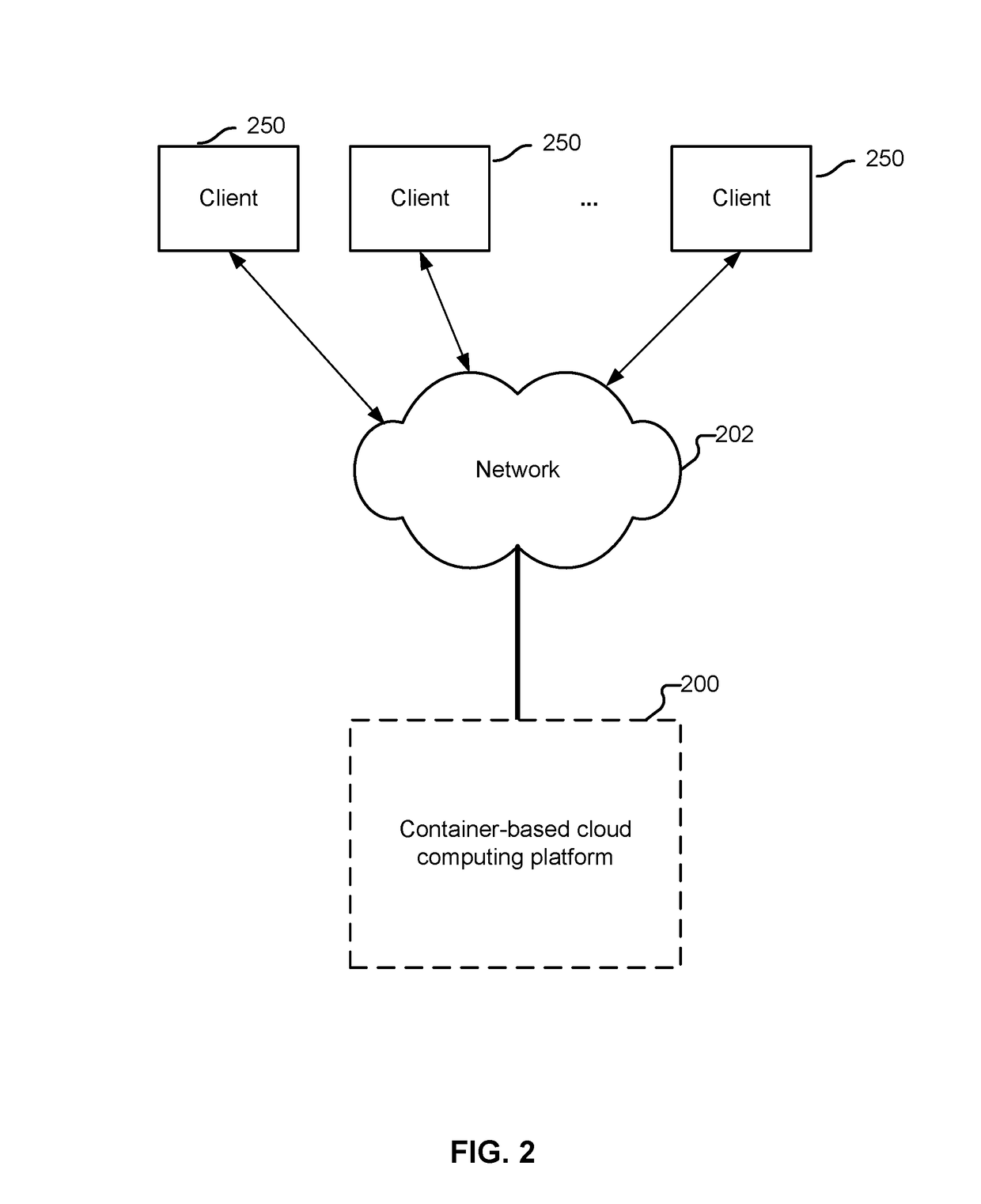
Traffic pattern detection and presentation in container-based cloud computing architecture
Determining and presenting traffic patterns includes: obtaining a first set of traffic metrics pertaining to network traffic associated with a plurality of containers of a container-based cloud computing platform, wherein: the plurality of containers supports a plurality of microservices; and a microservice has one or more corresponding microservice instances that execute on one or more of the plurality of containers; transforming the first set of traffic metrics into a second set of traffic metrics, the second set of traffic metrics comprising network traffic information pertaining to at least some of the plurality of microservices, the transformation being based at least in part on information pertaining to the plurality of containers and the plurality of microservices supported by the plurality of containers; constructing a microservice map based on the second set of traffic metrics; and outputting the microservice map.
Owner:VMWARE INC
Systems and methods for adaptive and intelligent network functions virtualization workload placement
A method for adaptive and intelligent Network Functions Virtualization (NFV) workload placement includes monitoring operation of a network with resources including one or more Virtual Network Functions (VNFs) and microservices; responsive to a request for a service in the network, decomposing the service into interconnected functional atoms, with the functional atoms located in one or more network domains including one or more of different data centers in the network and a user device associated with the service, wherein the functional atoms are decompositions of the VNFs and the microservices into a smaller level of functionality than the VNFs and microservices, wherein the functional atoms are based on isolability, observability, and measurability; and instantiating the service in the network based on the determined placement of the functional atoms.
Owner:CIENA
Implementation method for high availability of cluster microservices
InactiveCN108712464AImprove usabilityImprove discovery efficiencyTransmissionHigh availabilityMicroservices
The invention provides an implementation method for high availability of cluster microservices, comprising the following steps: deploying a service architecture to synchronously sense the newly-published microservices by all the nodes in the cluster; performing load balancing adjustment on the microservices by establishing an IPTABLES forwarding rule by the service agents of each node in the cluster; running the service load monitoring program on each node in the cluster, periodically collecting and integrating the load status of all microservices of each node, and accordingly performing the operation for dynamically increasing or deleting the backend instances of the microservices. So that, after the new service is released, all the nodes in the cluster may be perceived, and an adaptive load balancing policy is implemented on this basis, so as to dynamically adjust the local IPTABLES forwarding rule according to the adaptive load balancing policy when performing capacity expansion andshrinkage, thereby ensuring load balancing after the capacity expansion and shrinkage, that is, playing a role to realize the high availability of cluster microservices from different stages and perspectives.
Owner:INST OF INFORMATION ENG CAS
Local Microservice Development for Remote Deployment
Managing microservice function requests is provided. A request originating from a browser of the computer to execute a function corresponding to a microservice locally deployed on the computer is received using a software development kit operating in the computer. The request to execute the function is routed to the microservice using a local reverse proxy running in the software development kit. Other requests originating from the browser of the computer to execute one or more other functions corresponding to one or more microservices in a remotely deployed microservice architecture that interact with the function corresponding to the microservice are received using the software development kit. The other requests to execute the one or more other functions corresponding to the one or more microservices in the remotely deployed microservice architecture are routed, via a single uniform resource locator corresponding to a remote reverse proxy, using the local reverse proxy.
Owner:IBM CORP
Microservices based multi-tenant identity and data security management cloud service
A system provides cloud-based identity and access management. The system receives a request for performing an identity management service, where the request includes a call to an application programming interface (“API”) that identifies the identity management service and a microservice configured to perform the identity management service. The system authenticates the request, accesses the microservice, and performs the identity management service by the microservice.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com