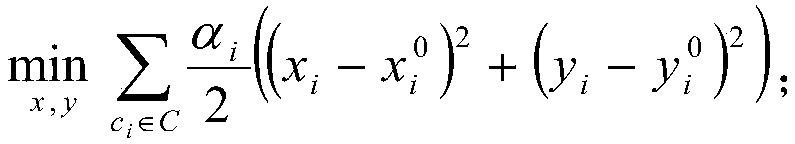Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
67 results about "Legalization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Legalization (also spelled legalisation) is the process of removing a legal prohibition against something which is currently not legal. Legalization is a process often applied to what are regarded, by those working towards legalization, as victimless crimes, of which one example is the consumption of illegal drugs (see drug legalization).
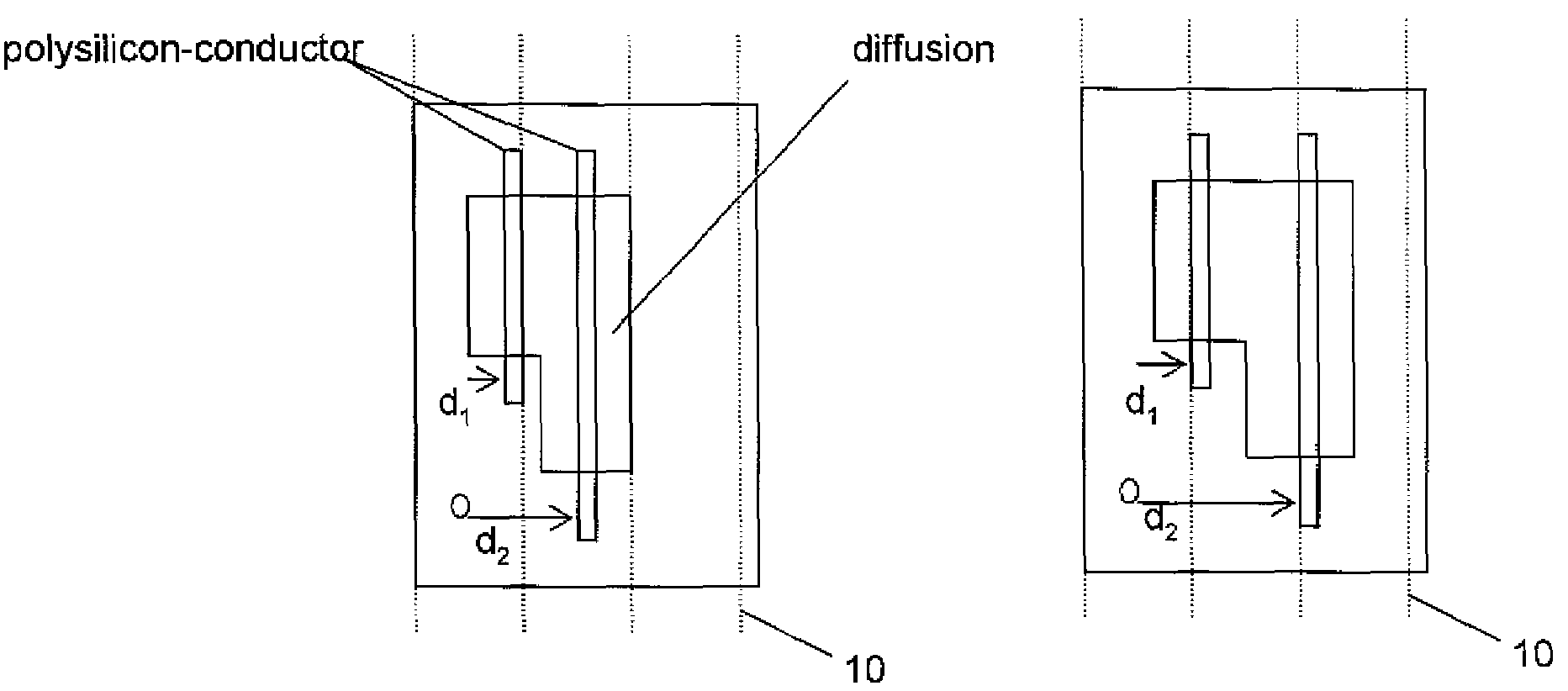
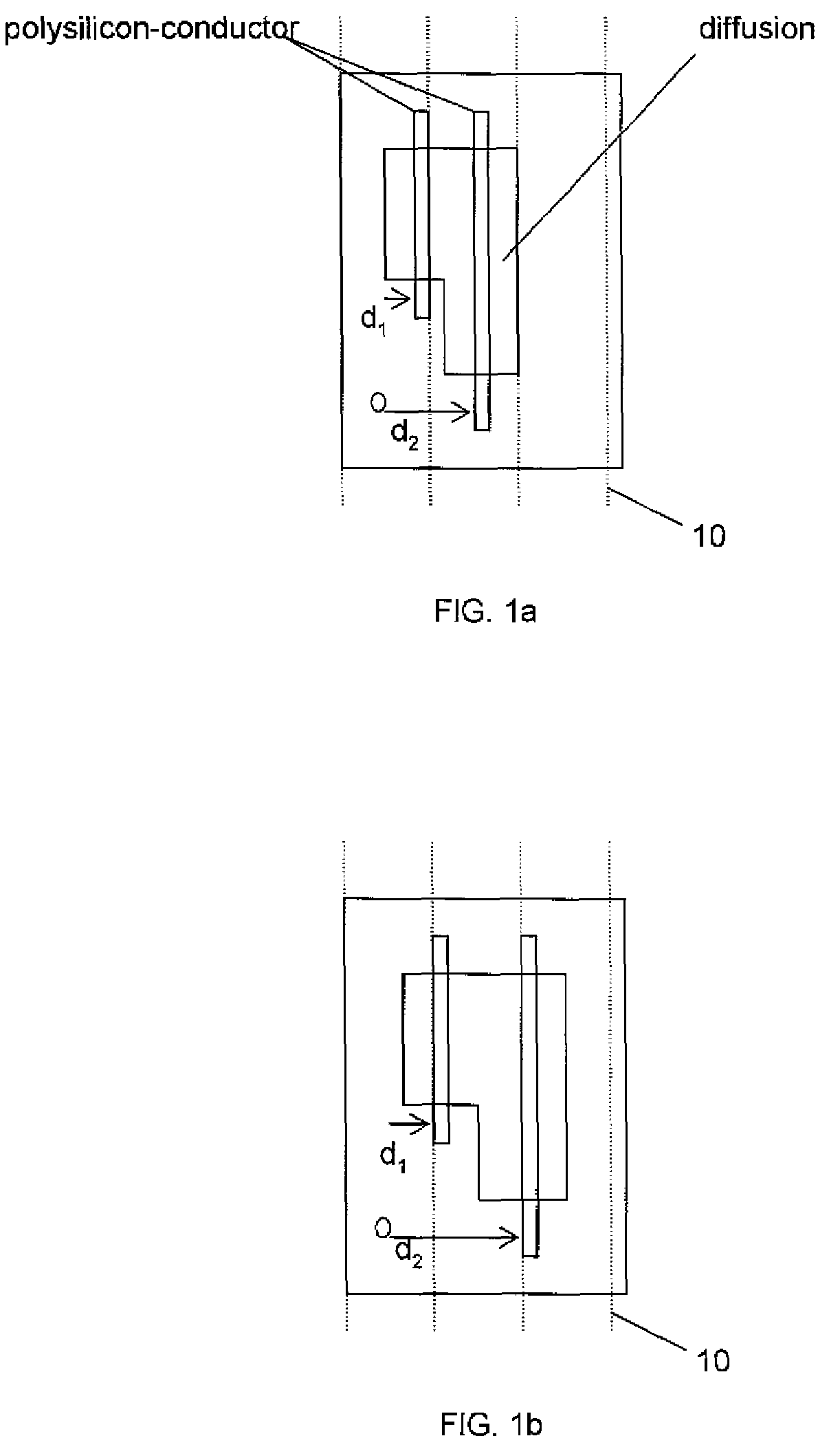
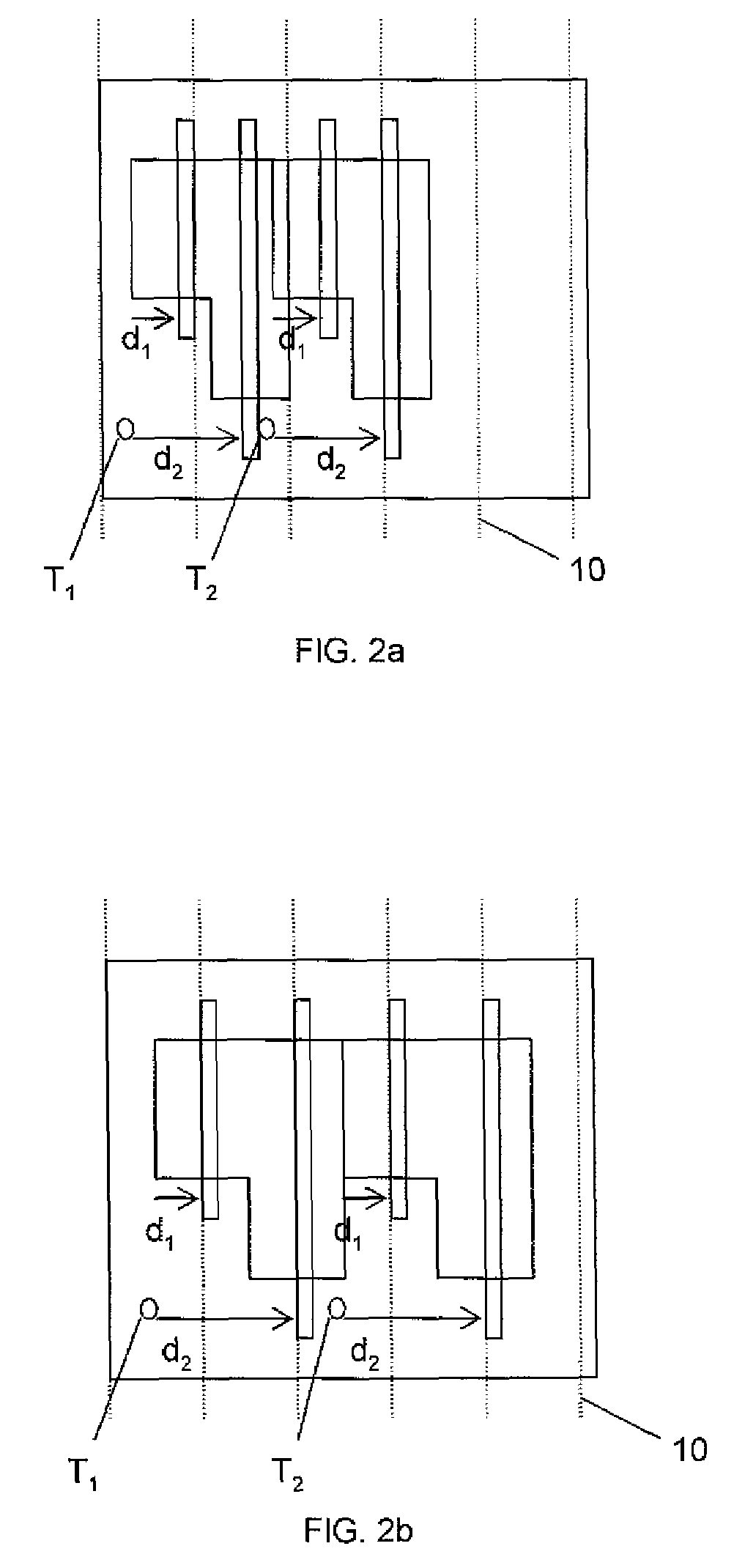
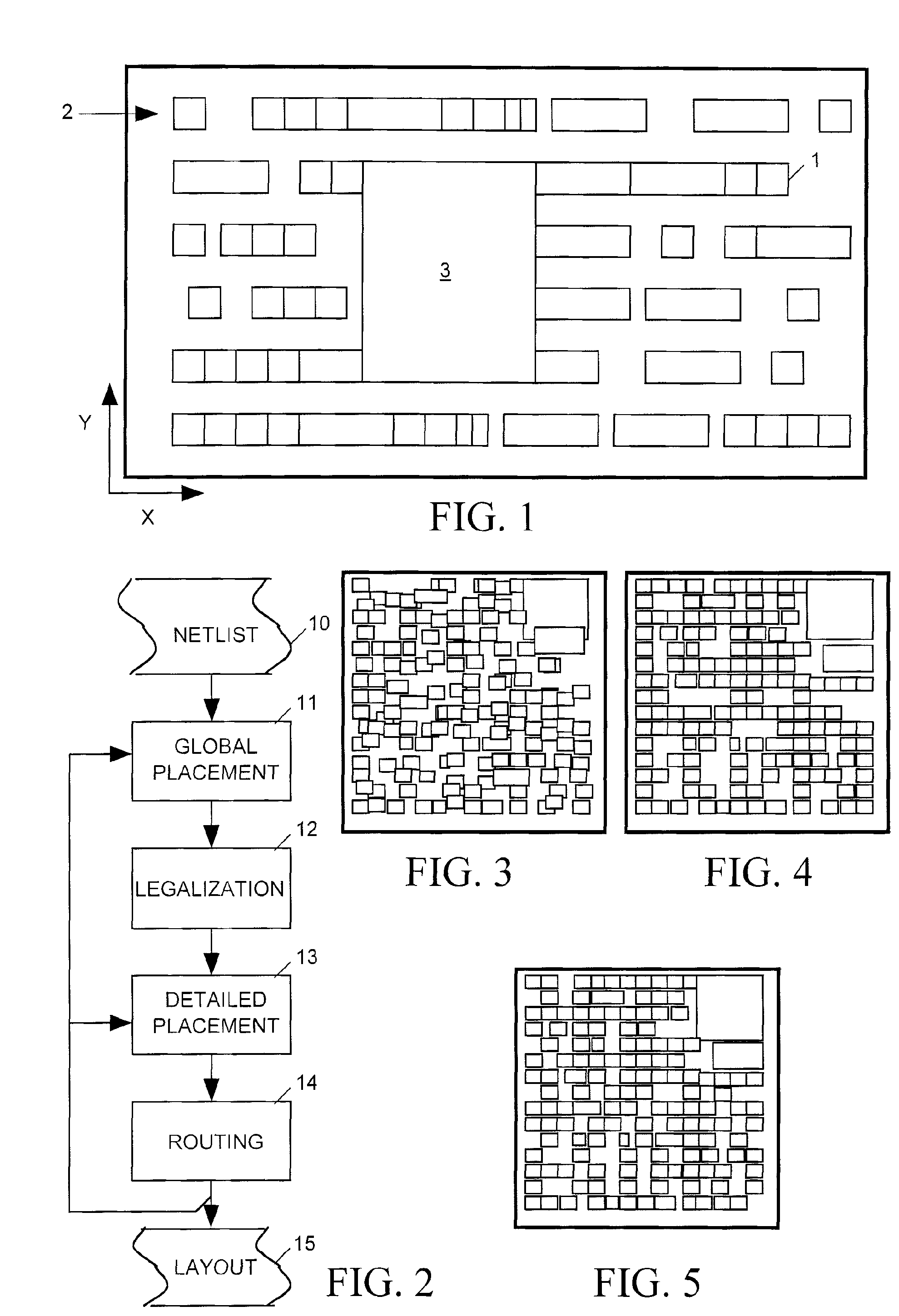
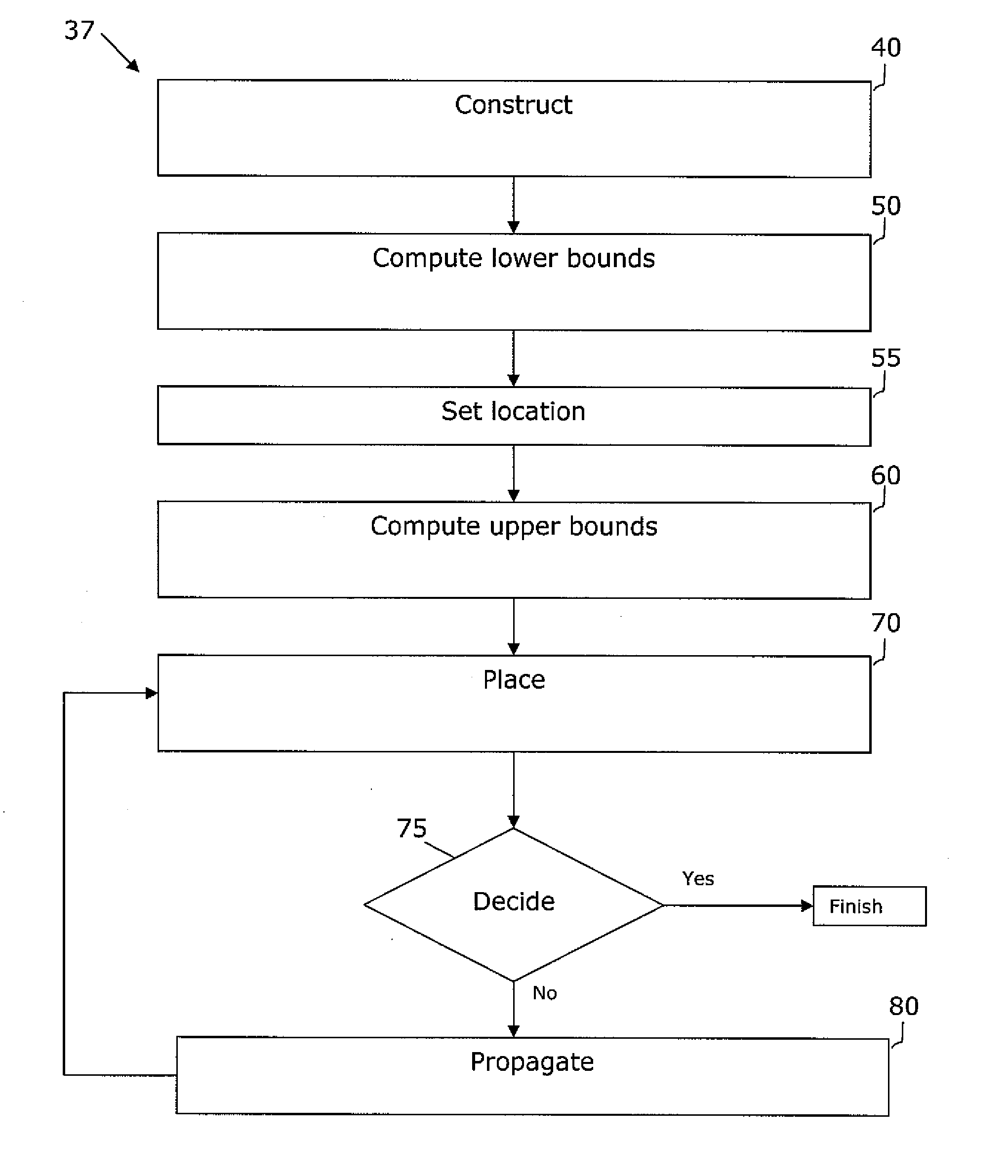
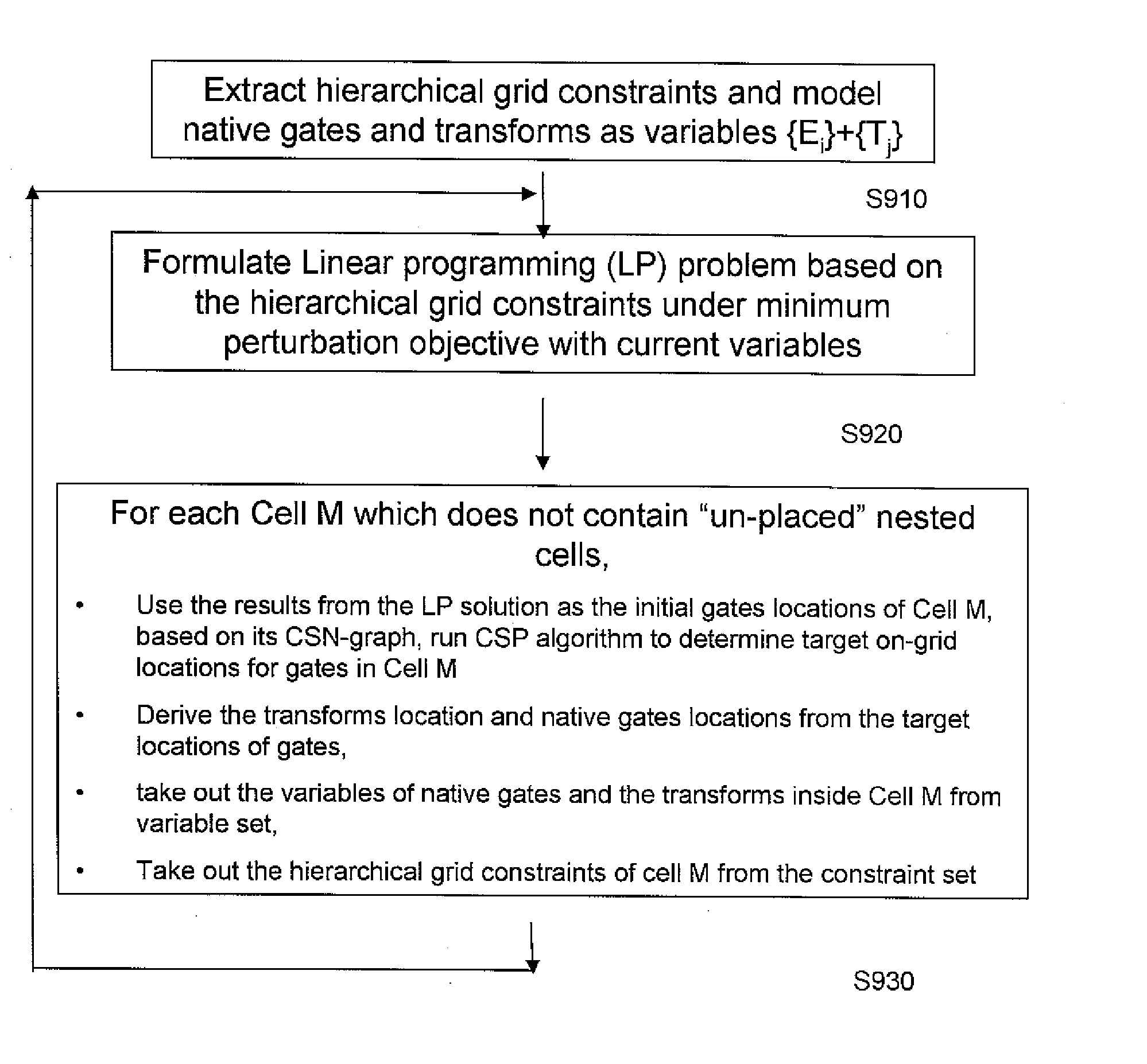
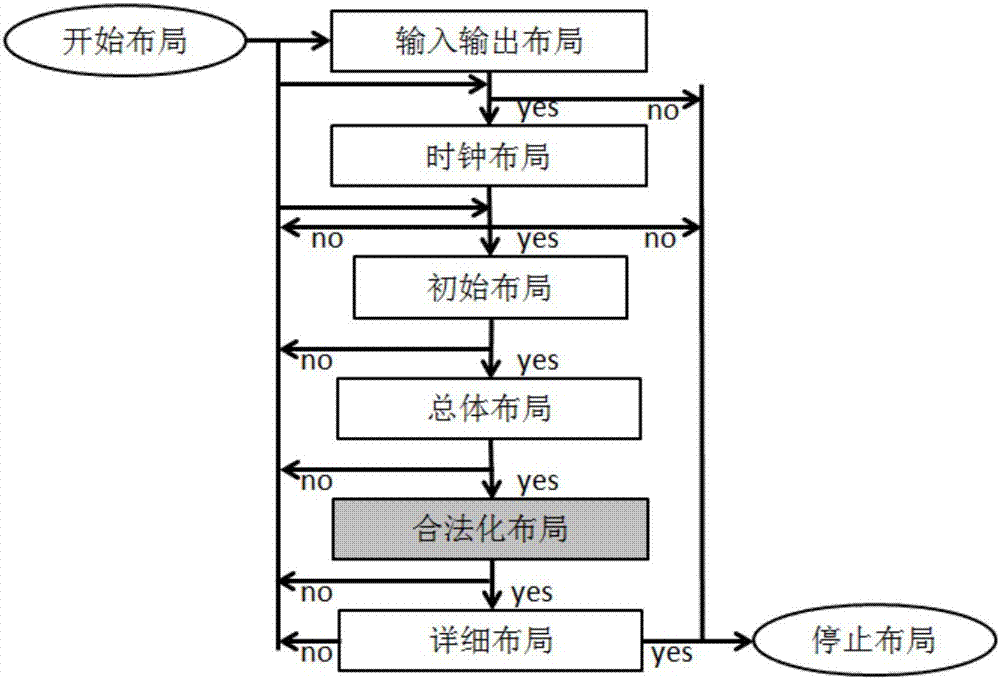
Minimum layout perturbation-based artwork legalization with grid constraints for hierarchical designs
InactiveUS7484197B2Computer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceHierarchical design
A method comprises extracting a hierarchical grid constraint set and modeling one or more critical objects of at least one cell as a variable set. The method further comprises solving a linear programming problem based on the hierarchical grid constraint set with the variable set to provide initial locations of the critical objects of the at least one cell and determining target on-grid locations of the one or more critical objects in the at least one cell using the results of the linear programming solution.
Owner:GLOBALFOUNDRIES INC
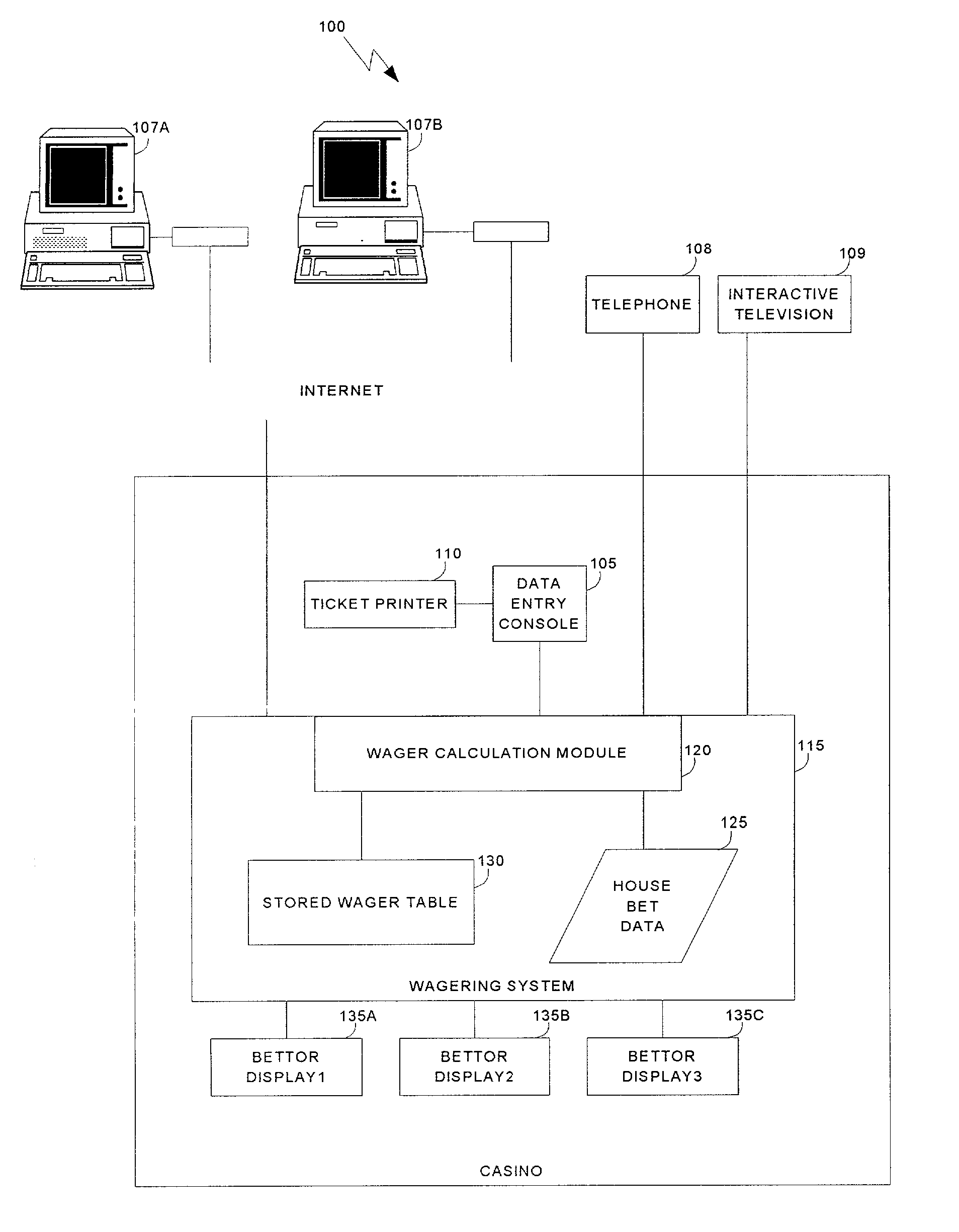
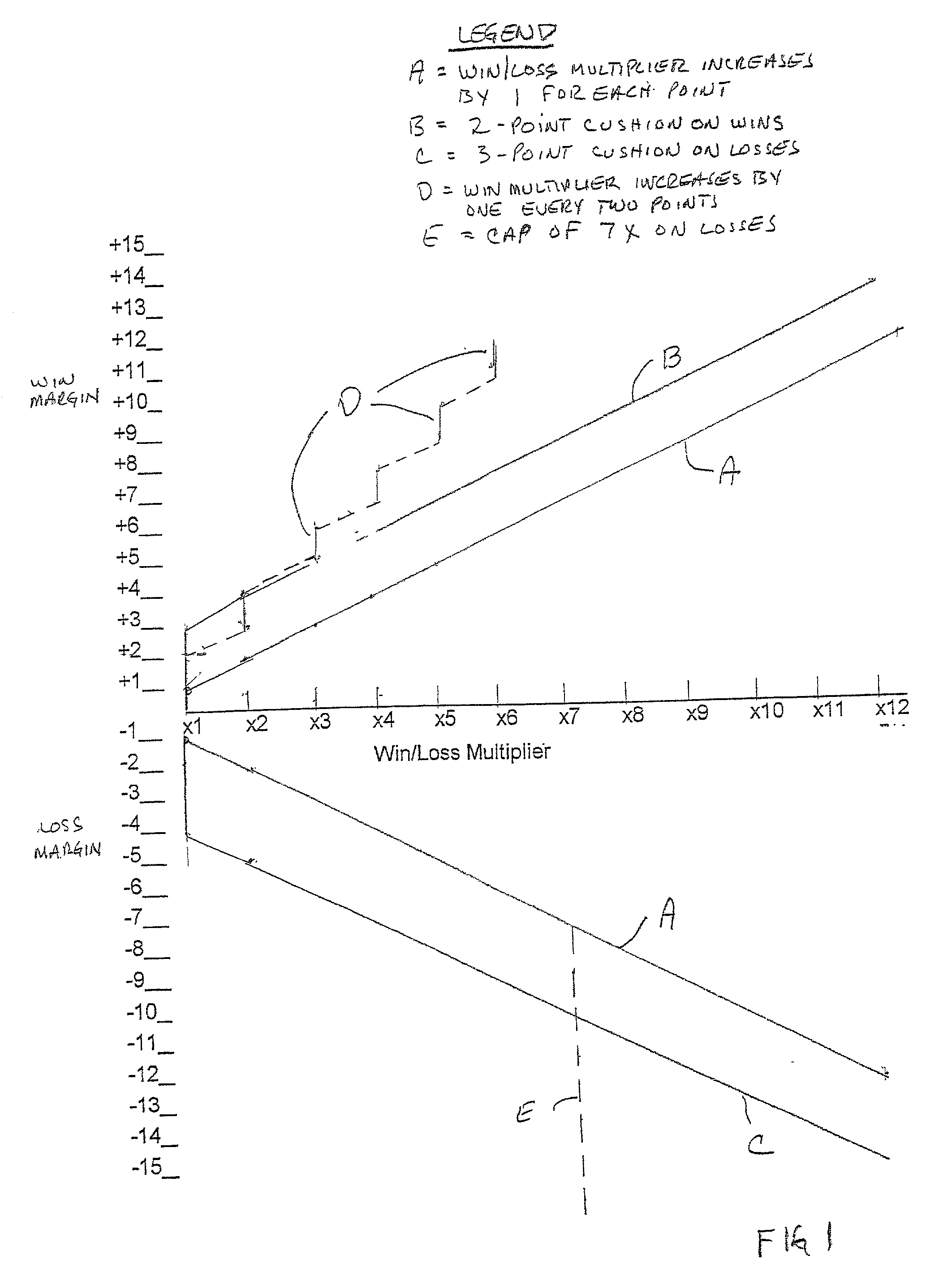
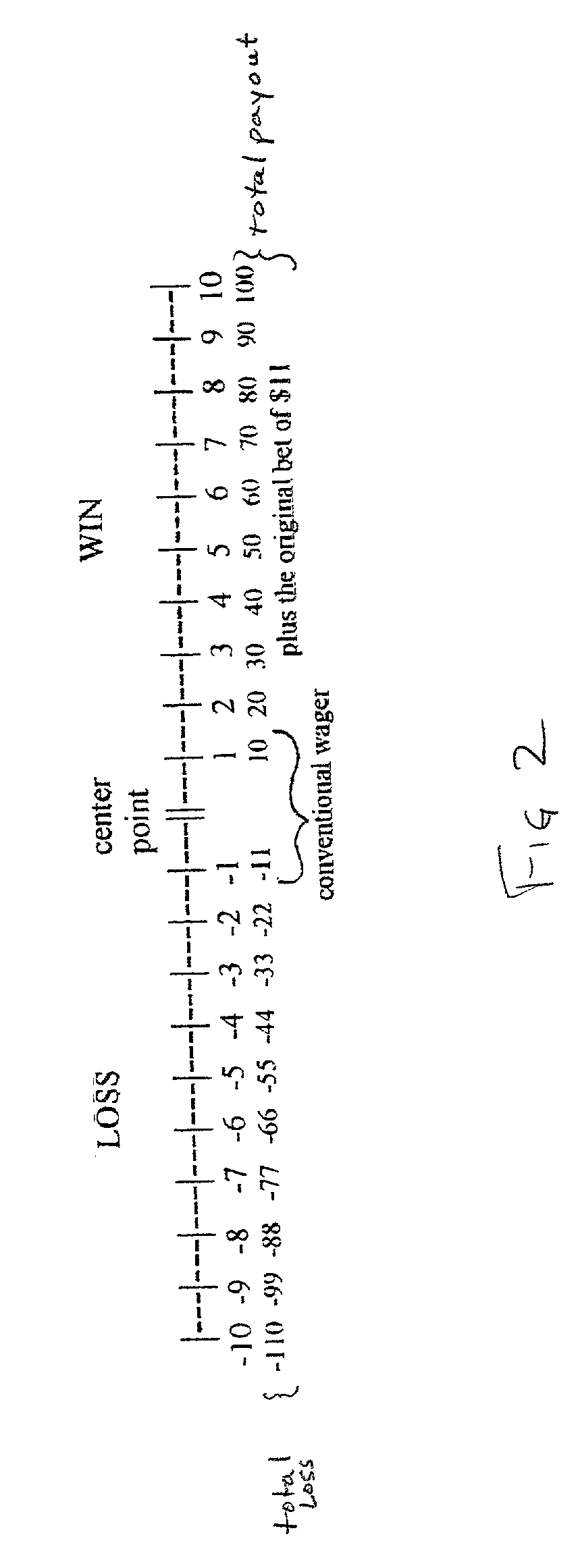
Method of effecting multiple wagers on a sports or other event
InactiveUS20020153656A1Overall betting pool becomes much largerDeposition can be largeData processing applicationsBoard gamesPaymentEngineering
A wagering system is provided in which the payment on either side of a "neutral" bet, or center point, increases as the amount of win or loss diverges from the center point. The system is particularly applicable to bets placed in legalized bookmaking establishments, which set a line for sports betting and permit bettors to wager on either side of the line. In a preferred embodiment, the amount of win or loss increases arithmetically with the departure of the final result from the center point. The system also includes the potential for placing caps (maximums) on the win / loss multiples, and providing cushions (i.e., deviations proximate to the center point) before which the increased wins and / or losses commence.
Owner:CASINO ADVISORY SERVICES
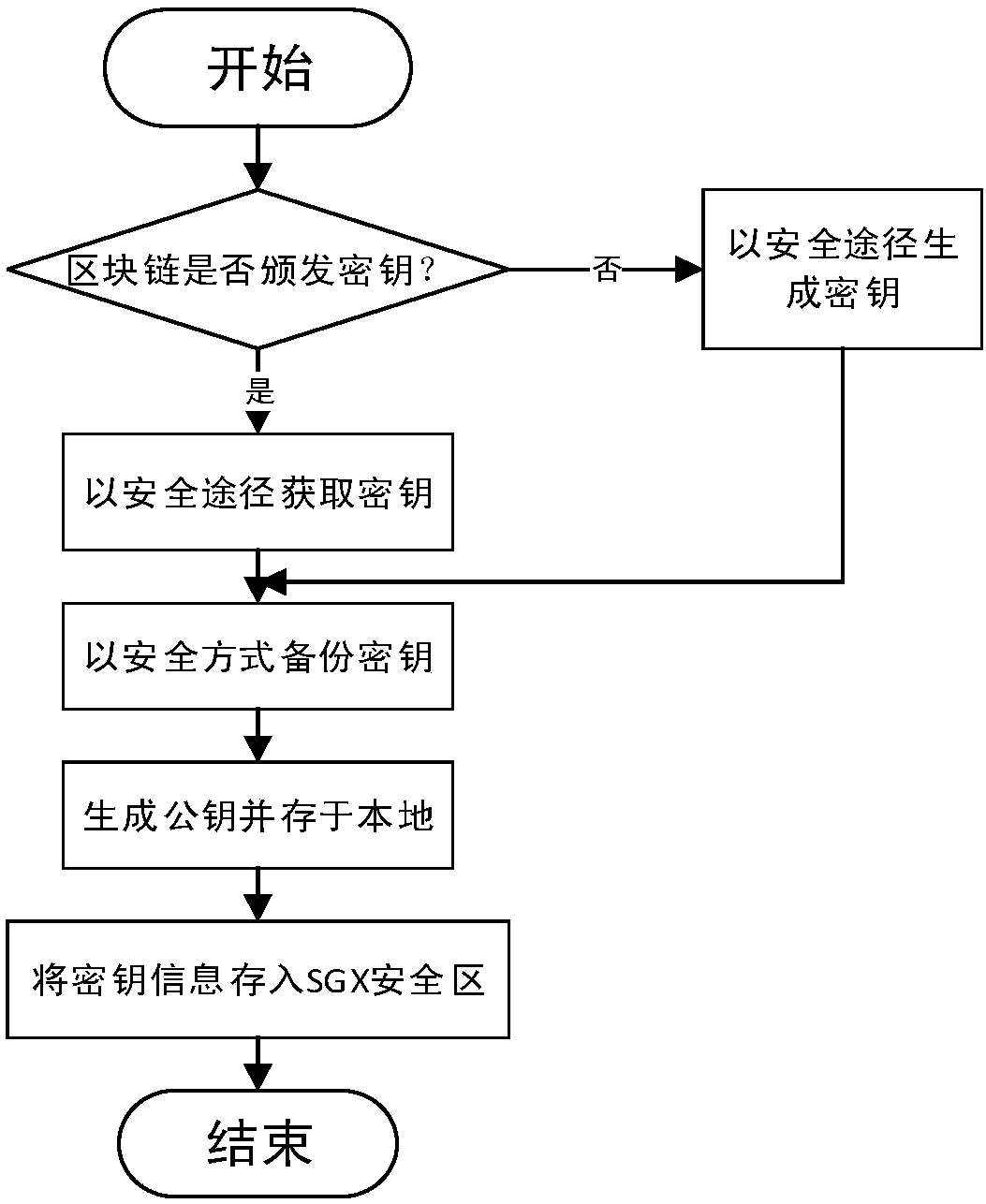
SGX-based secret key protection method and device for blockchain user
ActiveCN107919954AInviolableSafety and securityKey distribution for secure communicationPayment protocolsMalwareSoftware protection
The invention discloses an SGX-based secret key protection device for a blockchain user. The device comprises an SGX encryption module, a transaction common recognition module and a transaction construction module; the SGX encryption module generates a trustable space on the basis of a software protection expanded instruction, and generates an access secret key for verifying the access authority of the trustable space; the trustable space is used to store a user secret key and a secret key operation function of a blockchain network; the transaction common recognition module receives a transaction from the blockchain network, accesses the SGX encryption module via the access secret key, calls the secret key operation function, and realizes verification common-recognition of the transaction;and the transaction construction module initiates the transaction according to intention of the user, accesses the SGX encryption module via the access secret key, calls the secret key operation function, realizes filling and legalization of transaction information, and broadcasts the transaction to the blockchain network. The invention also discloses an SGX-based secret key protection method fora blockchain user. The method can be used to prevent malicious software from sniffing and cracking the local secret key of the user, and blockchain assets of the user are protected against intrusion.
Owner:ZHEJIANG UNIV
Hostile attack preventing method and network system
InactiveCN105208026AReduce load pressurePrevent malicious attacksTransmissionNetworked systemFiltering rules
The invention discloses a hostile attack preventing method and a network system. The method comprises the steps that a second server receives first data sent by client sides, wherein the first data are connection request data from all the client sides; the second server obtains a filter rule, wherein the filter rule comprises a request address list and a parameter rule; the second server filters the first data through the filter rule, and the first data meeting the filter rule are sent to a first server. The network system comprises at least one client side, the first server and the second server. For illegal requests with request parameter filtering not meeting the rule, error information is directly returned at the second server, the information does not directly enter the first server for parameter legalization verification, the load pressure of the first server can be reduced, and some hostile attacks are prevented.
Owner:NUBIA TECHNOLOGY CO LTD
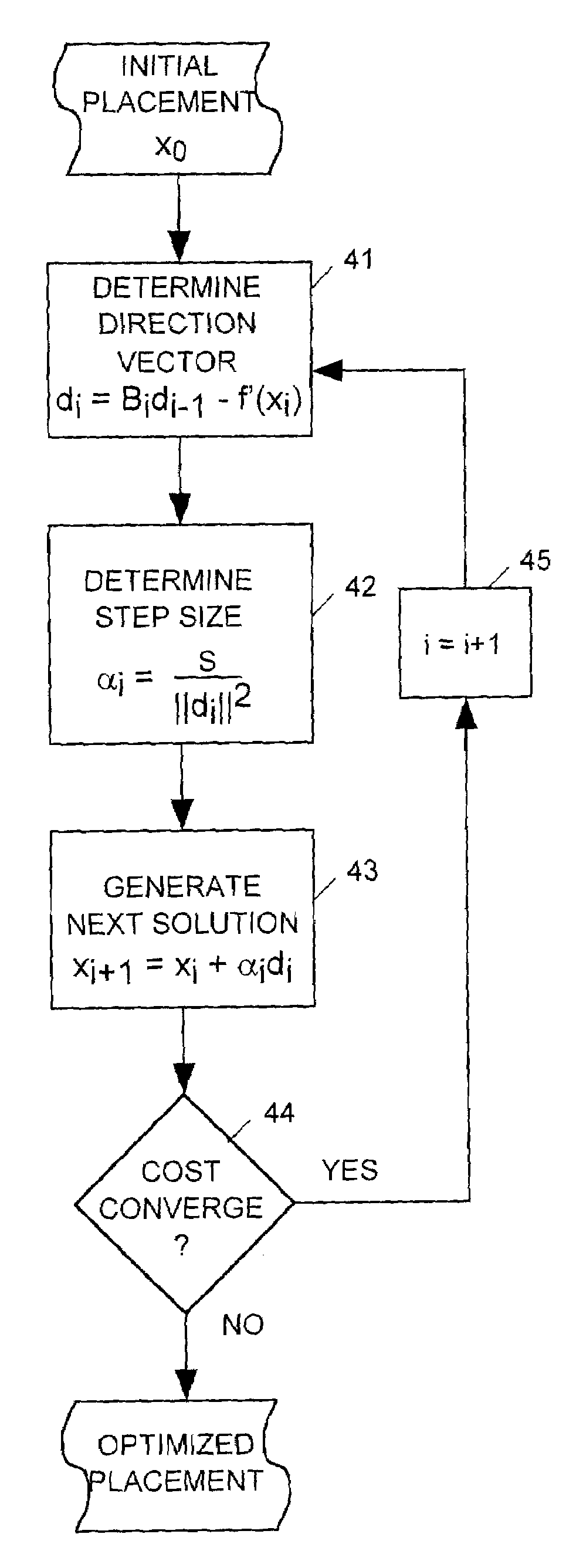
Analytical global placement for an integrated circuit
ActiveUS20090031269A1Improve routabilityMaximizes routabilityComputer aided designSoftware simulation/interpretation/emulationTheoretical computer sciencePyramid
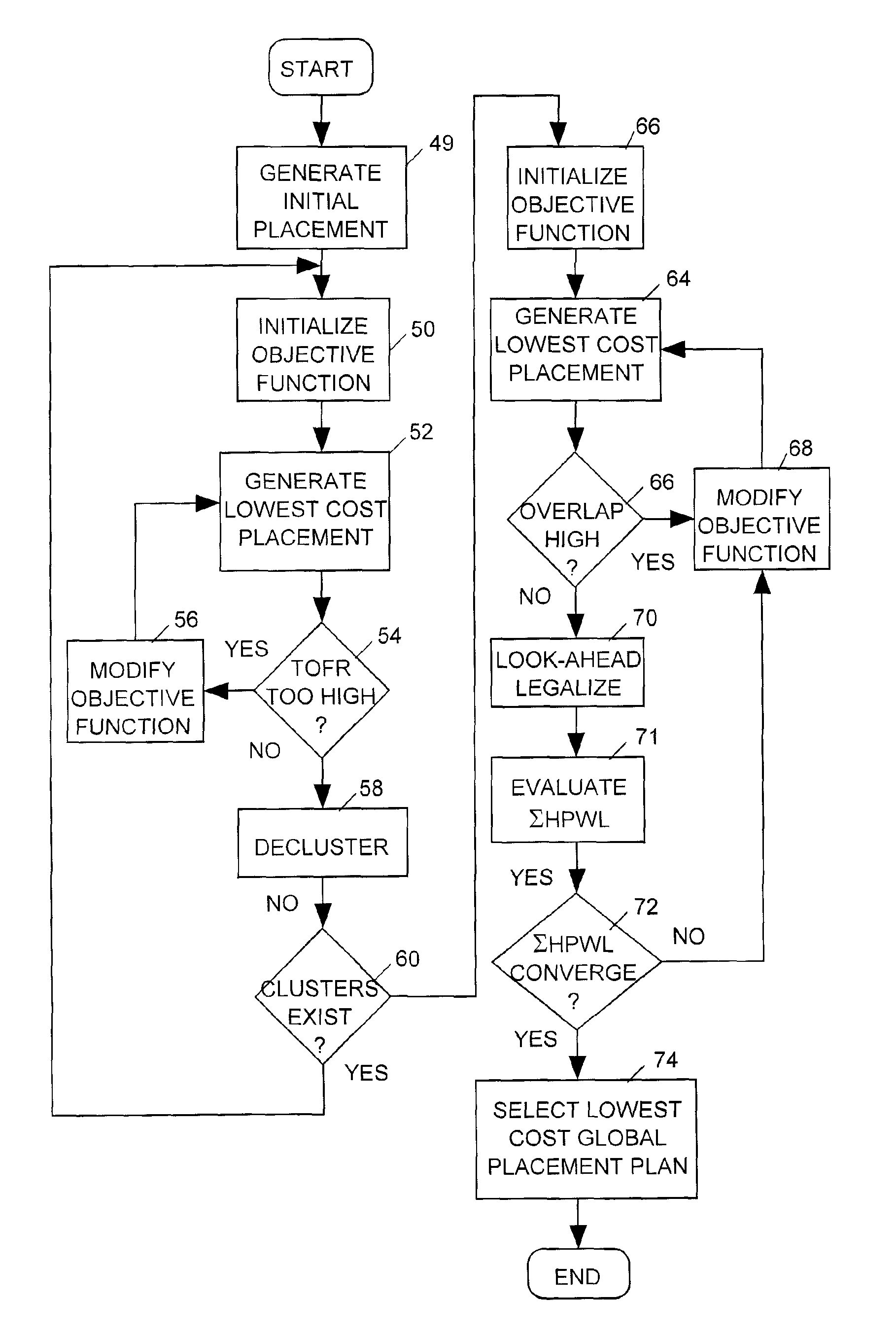
A placer produces a global placement plan specifying positions of cell instances to be interconnected by nets within an integrated circuit (IC) by initially clusterizing cell instances to form a pyramidal hierarchy of blocks and generating an initial global placement plan specifying a position of each block at a highest level of the hierarchy. The placer then declusterizes the global placement plan by replacing the highest level blocks with their component blocks and then improves the routability of the global placement plan by iteratively moving specified block positions in directions and by distances dynamically determined by analyzing the global placement plan and an objective function having a total wirelength term and having a bin density term reflecting density of blocks in specified areas (bins) of the IC. The placer iteratively repeats the declusterization and routability improvement process until the global placement plan specifies positions of all blocks residing at the lowest level of the hierarchy, with weighting of the bin density term adjusted when necessary during each iteration of the routability improvement process to provide sufficient white space in each bin. The placer employs a look-ahead legalization technique to move low level blocks to legal positions during later iterations of the plan improvement process.
Owner:SYNOPSYS INC
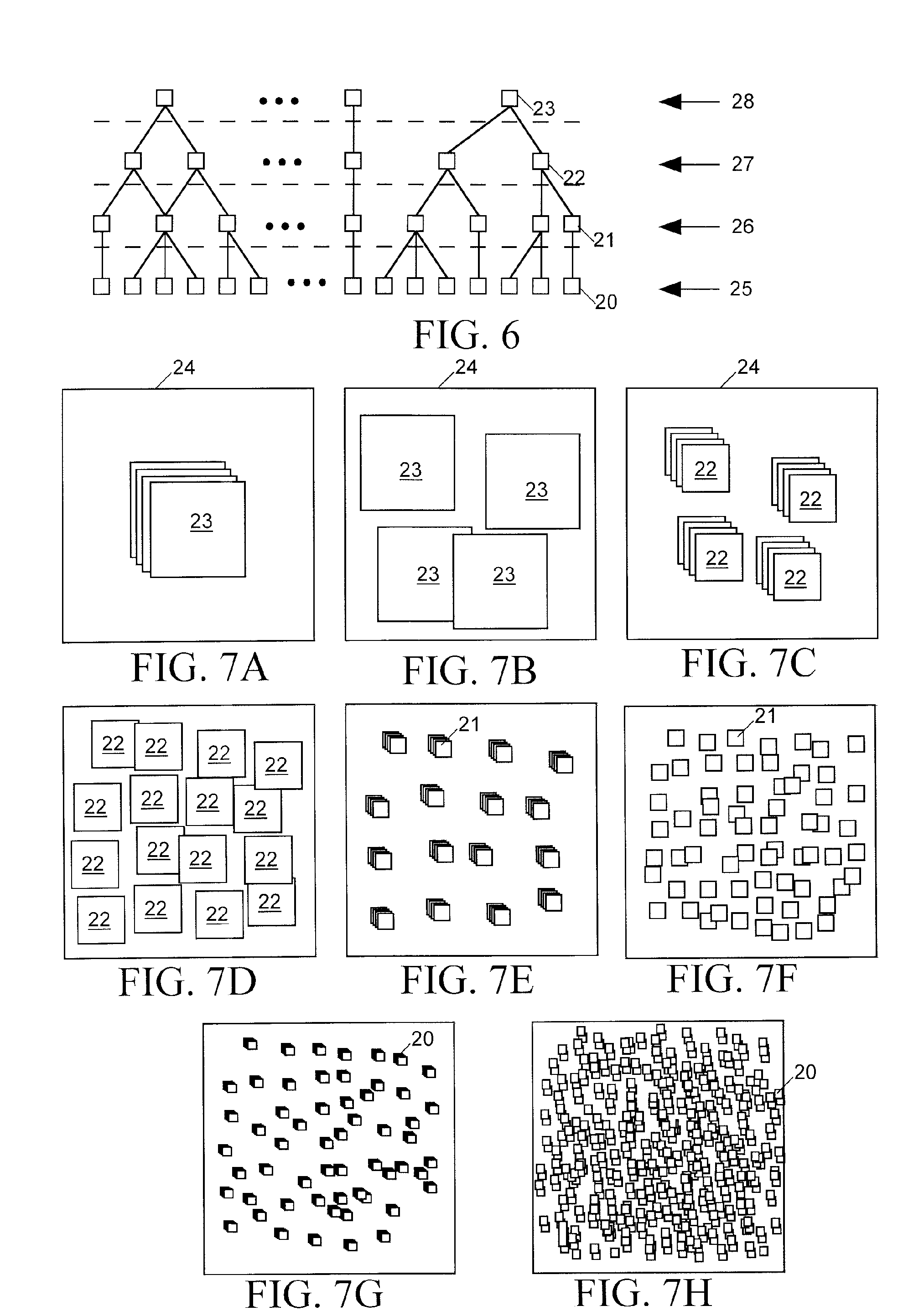
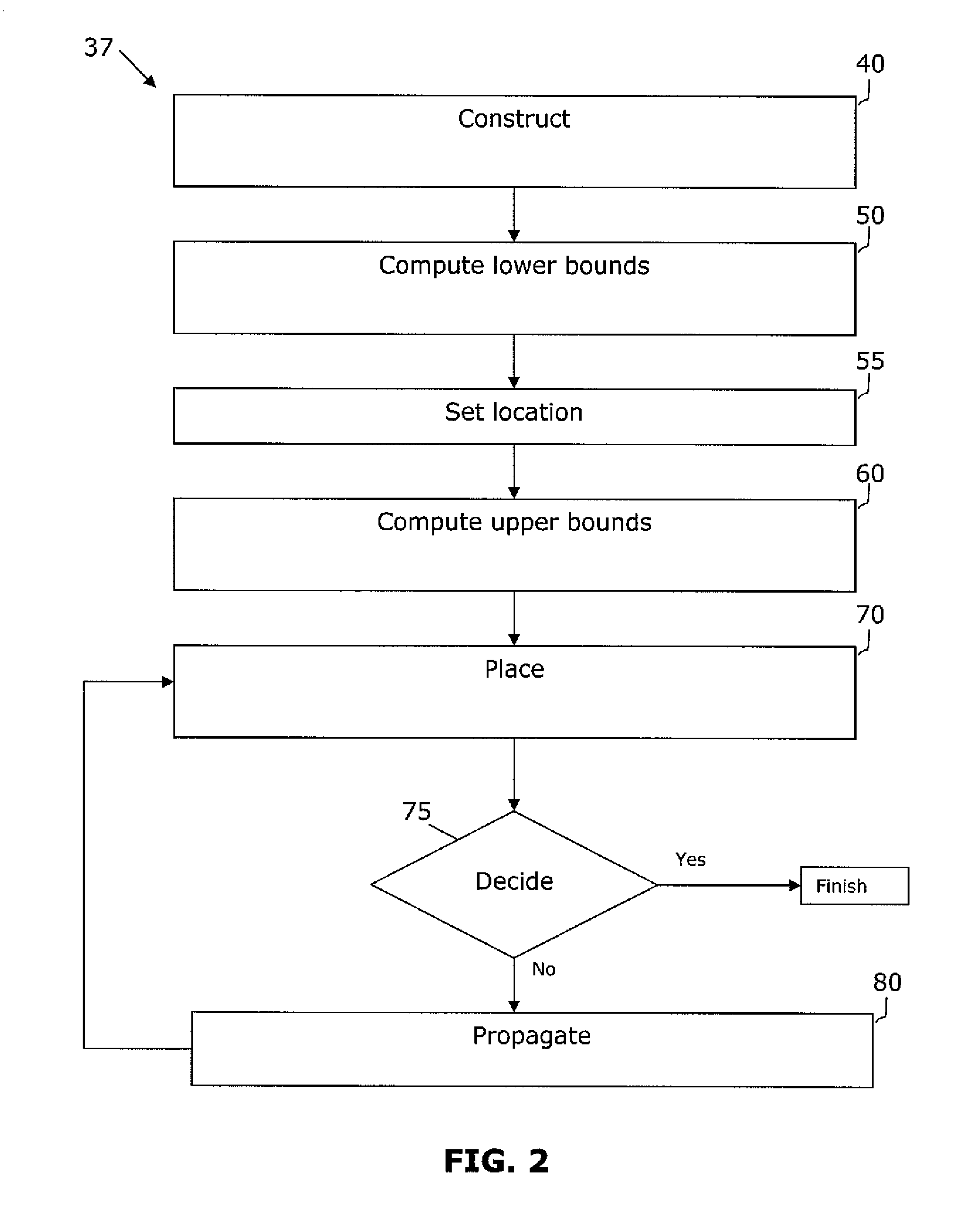
Circuit floorplanning and placement by look-ahead enabled recursive partitioning
InactiveUS20060190889A1Less run timeWirelength resultComputer aided designSoftware simulation/interpretation/emulationBacktrackingSatisfiability
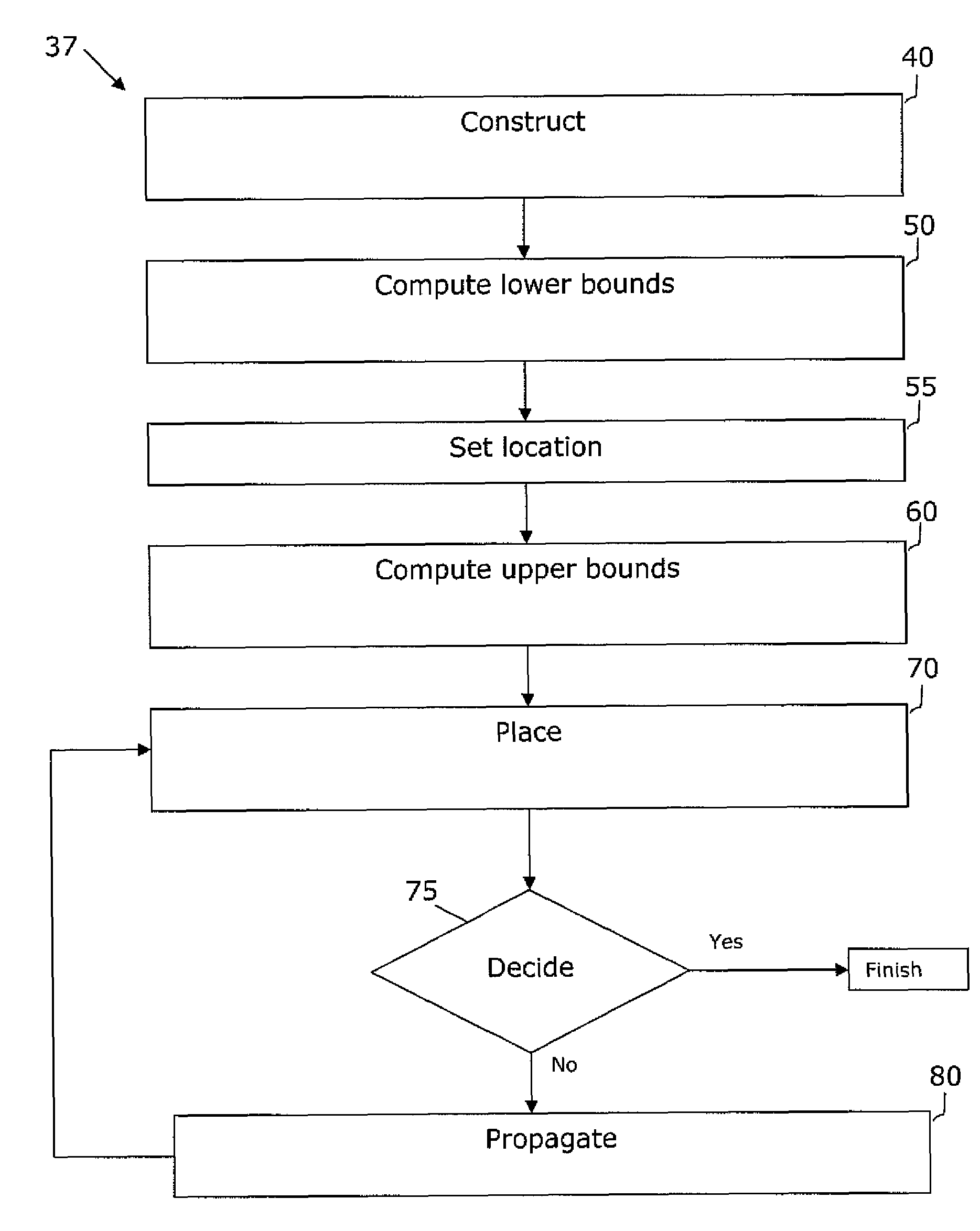
Placement or floorplanning of an integrated circuit is performed by constructing legal layouts at every level of a hierarchy of subsets of modules representing the integrated circuit, by scalably incorporating legalization into each level of the hierarchy, so that satisfiability of constraints is explicitly enforced at every level, in order to eliminate backtracking and post-hoc legalization.
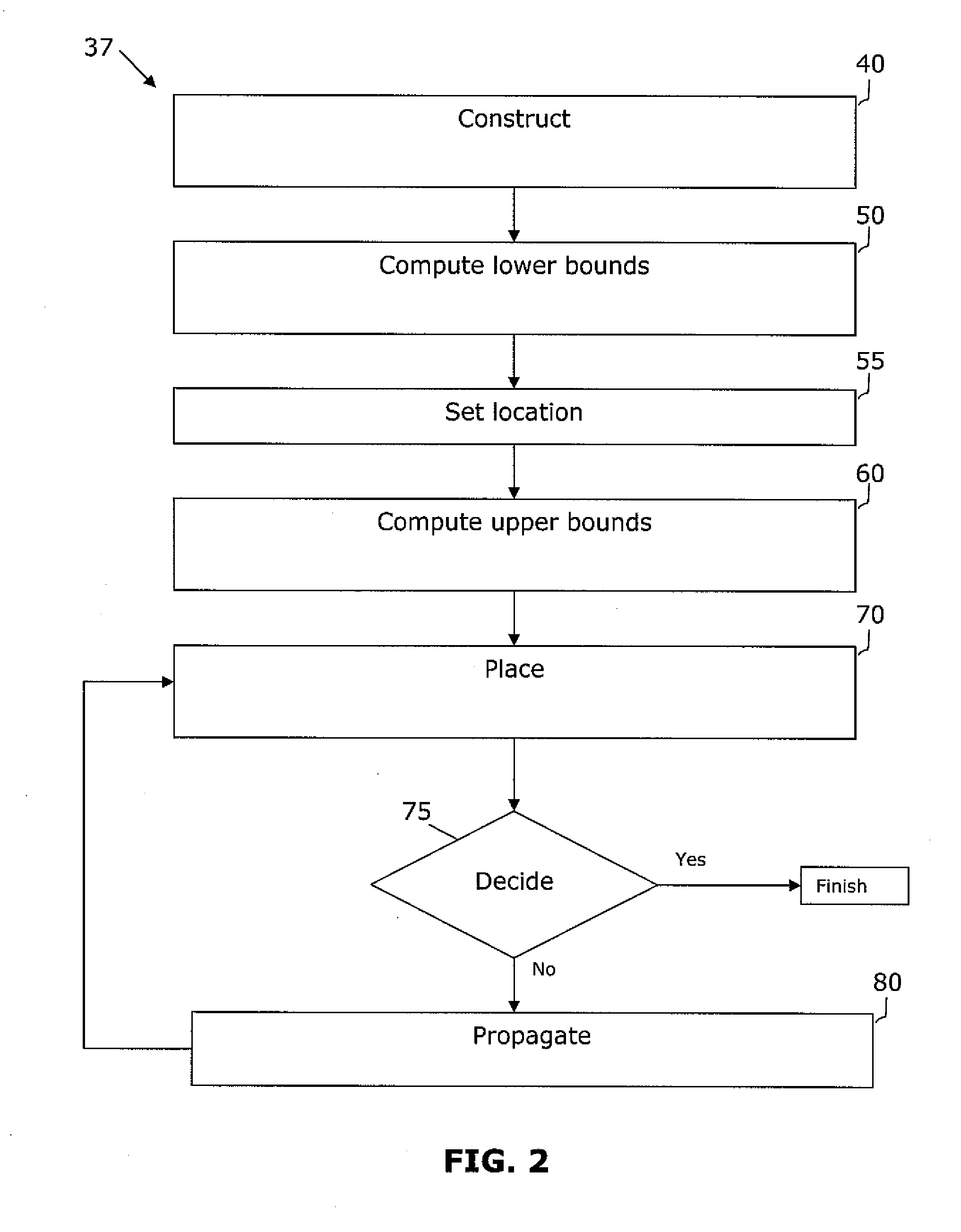
Owner:RGT UNIV OF CALIFORNIA
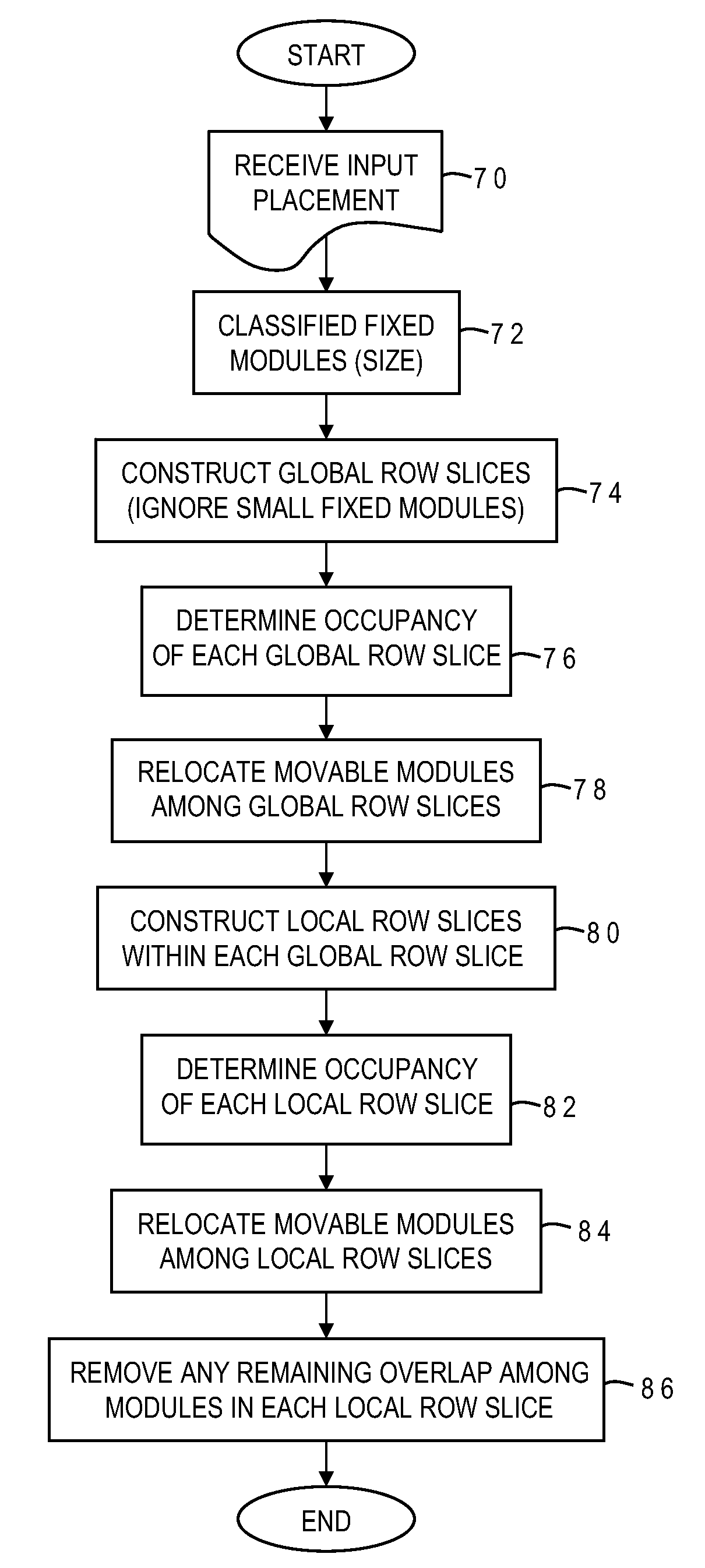
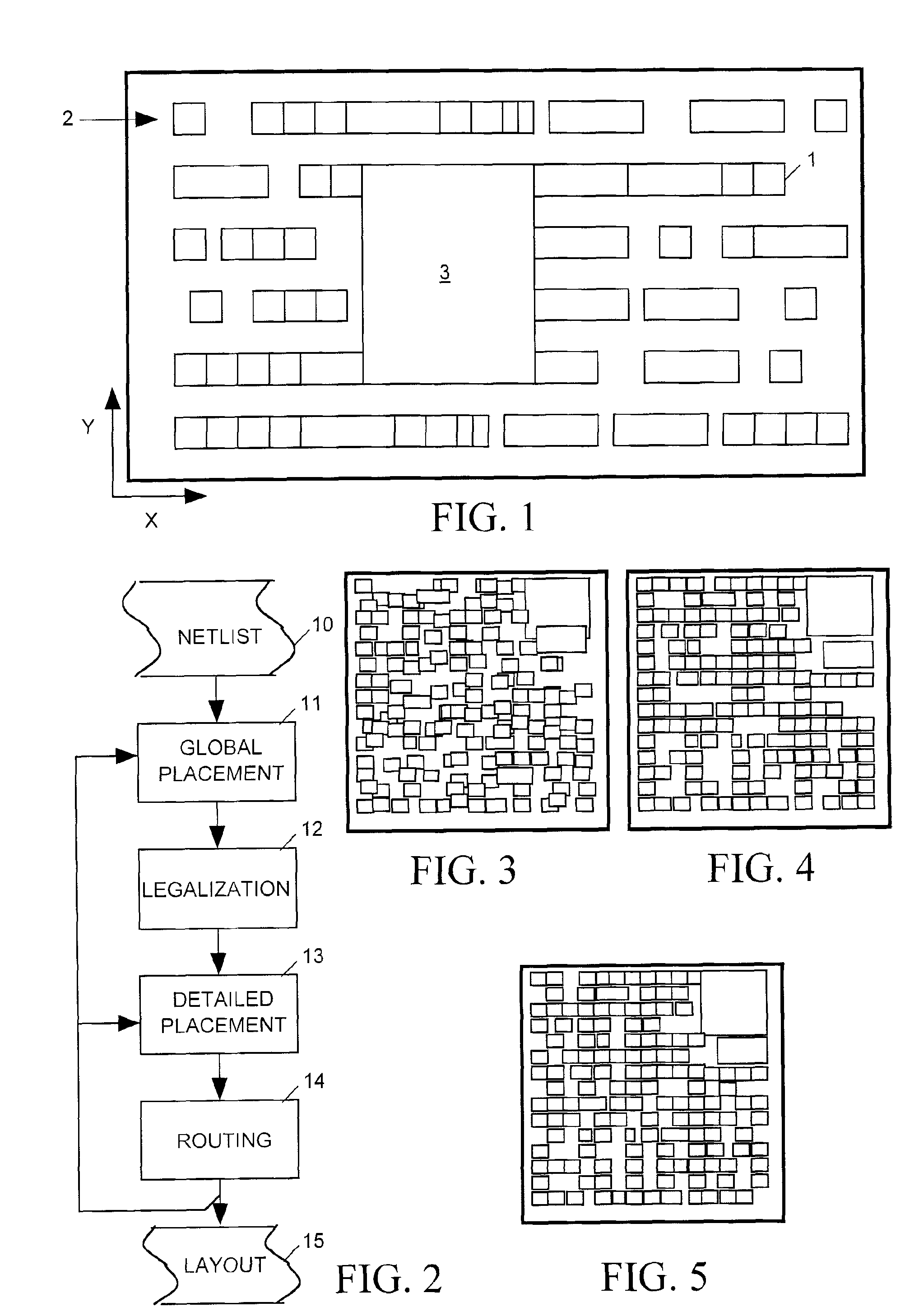
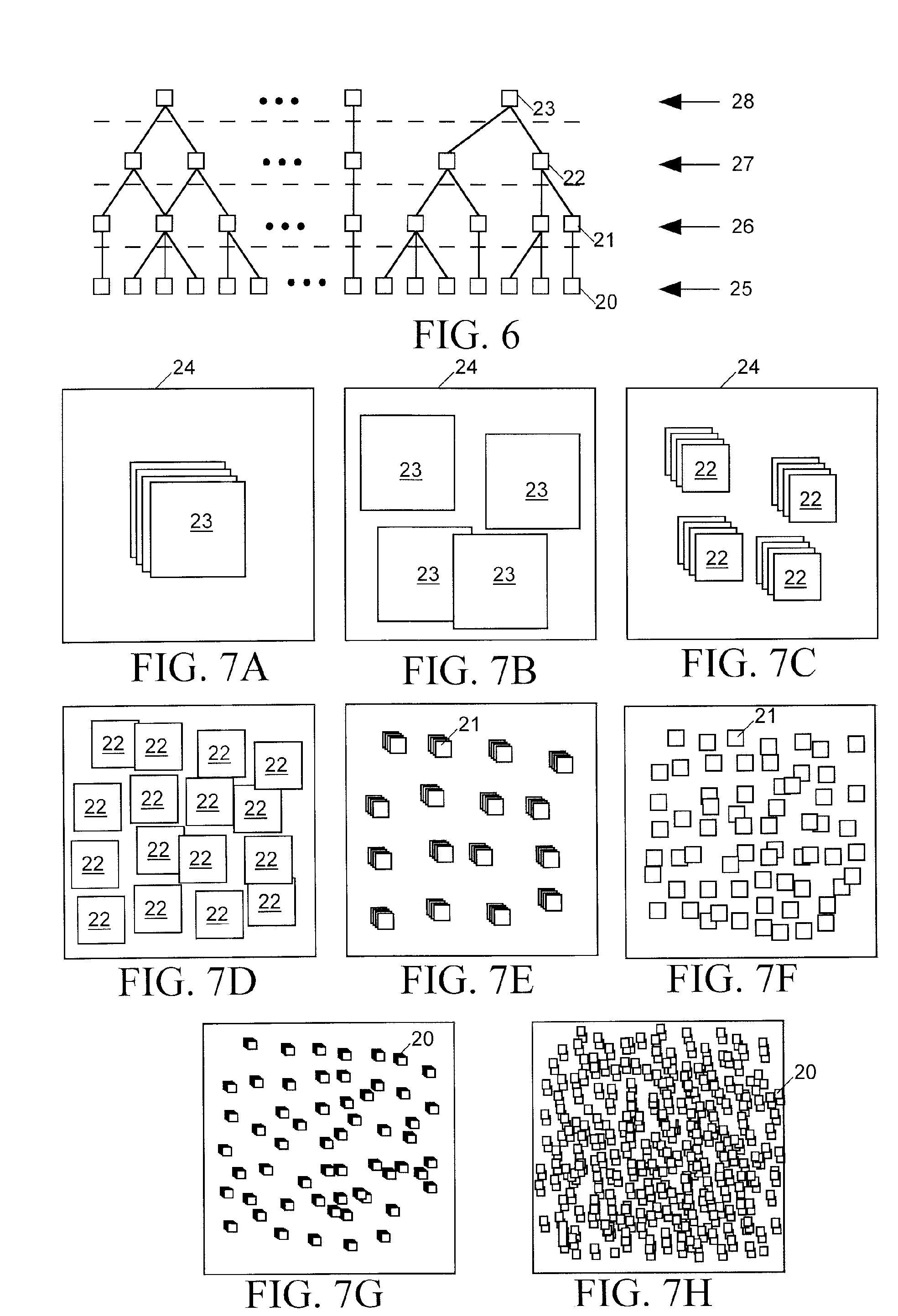
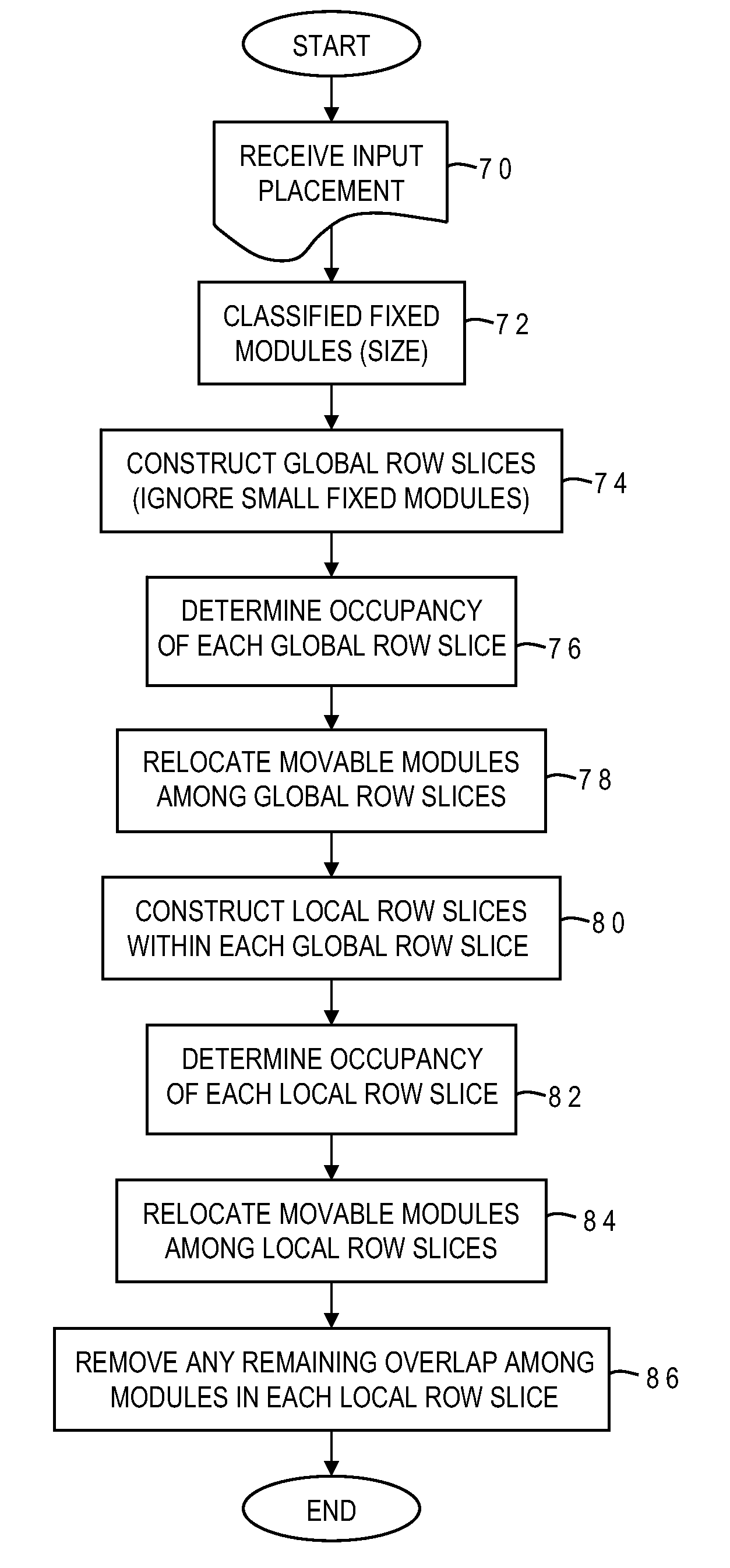
Legalization of VLSI circuit placement with blockages using hierarchical row slicing
ActiveUS20090271752A1Easy to handleReduced and minimal perturbationComputer aided designSpecial data processing applicationsComputer architectureLogic cell
A hierarchical method of legalizing the placement of logic cells in the presence of blockages selectively classifies the blockages into at least two different sets based on size (large and small). Movable logic cells are relocated first among coarse regions between large blockages to remove overlaps among the cells and the large blockages without regard to small blockages (while satisfying capacity constraints of the coarse regions), and thereafter the movable logic cells are relocated among fine regions between small blockages to remove all cell overlaps (while satisfying capacity constraints of the fine regions). The coarse and fine regions may be horizontal slices of the placement region having a height corresponding to a single circuit row height of the design. Cells are relocated with minimal perturbation from the previous placement, preserving wirelength and timing optimizations. The legalization technique may utilize more than two levels of granularity with multiple relocation stages.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
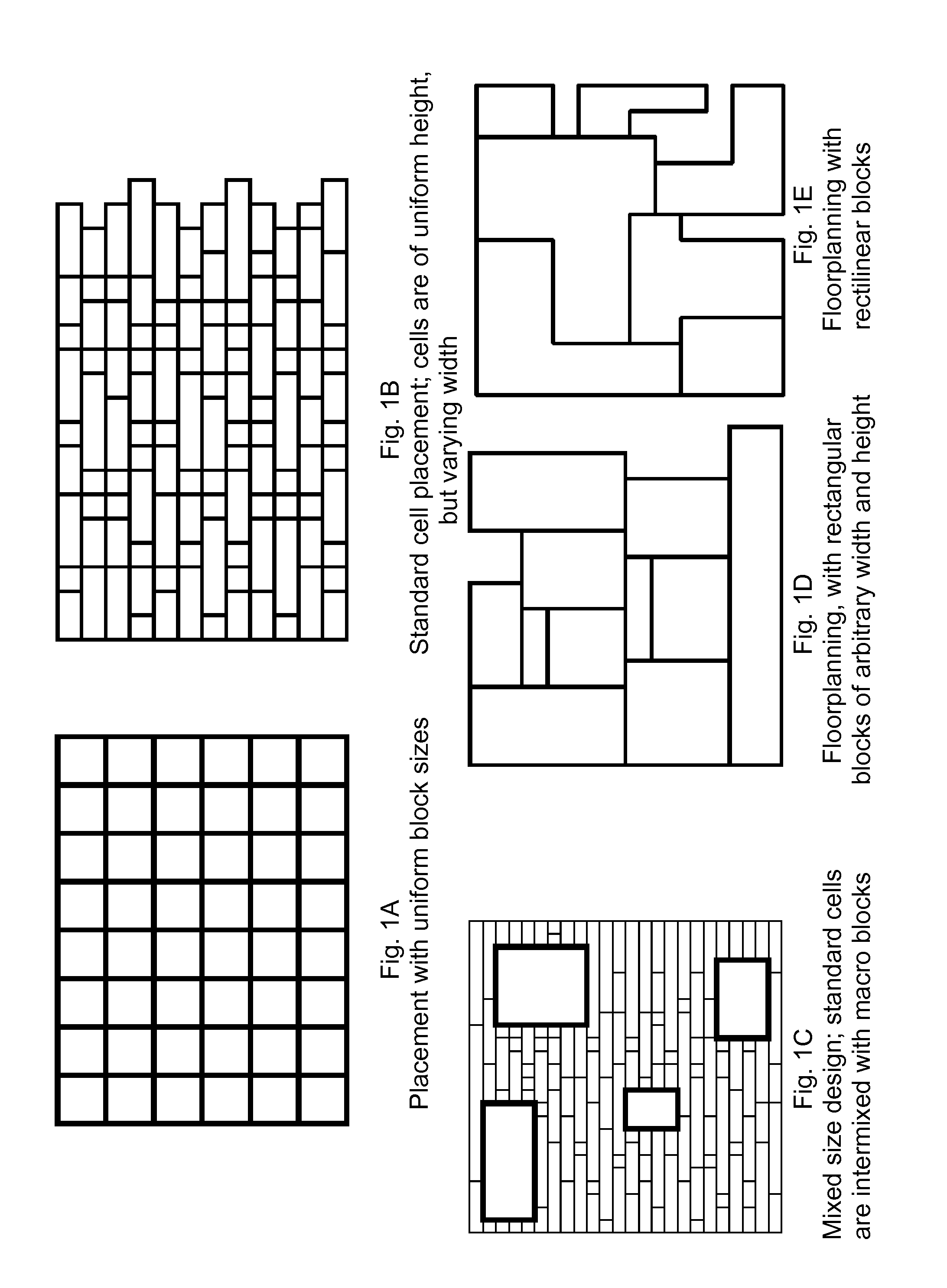
Standard block design: an effective approach for large scale floorplanning
InactiveUS7685540B1Easy to implementPromote resultsComputer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceAlternative methods
As circuit sizes have increased, designs have become increasingly hierarchical. It is common for designs to have large numbers of macro blocks; many of these blocks are “soft,” and may have variable width and height. The present invention provides an alternate method to handle designs with large numbers of blocks. Rather than approaching them as expanded floorplanning, the problems are re-cast as traditional mixed size placement, and many macro blocks are treated as standard cells. Using existing mixed size placement tools, the superior reported are obtained. First, an effective “standard block design” methodology is provided. Second, new mixed size placement legalization algorithms that are more robust than the widely-used mixed-size Tetris algorithm is presented.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
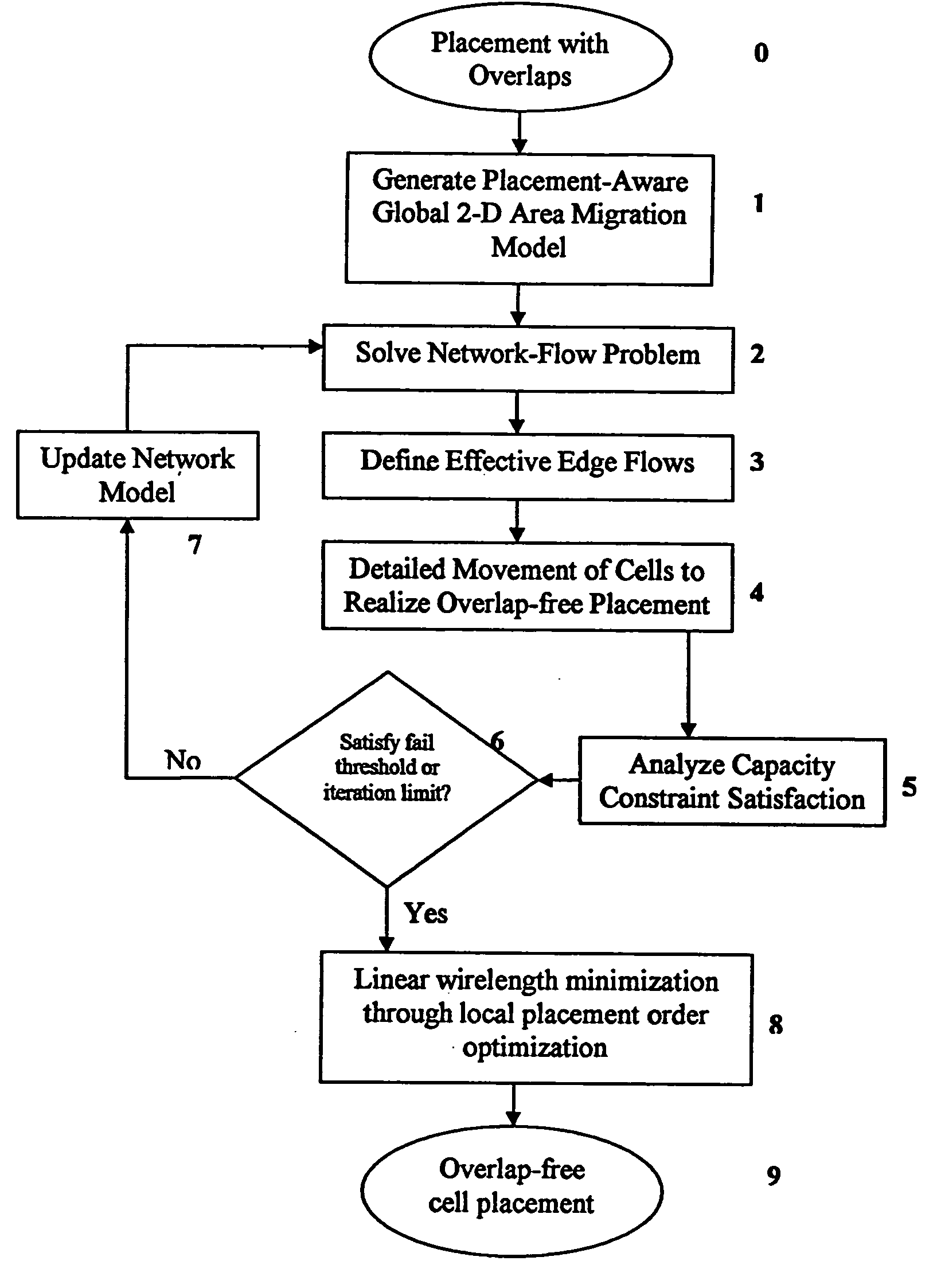
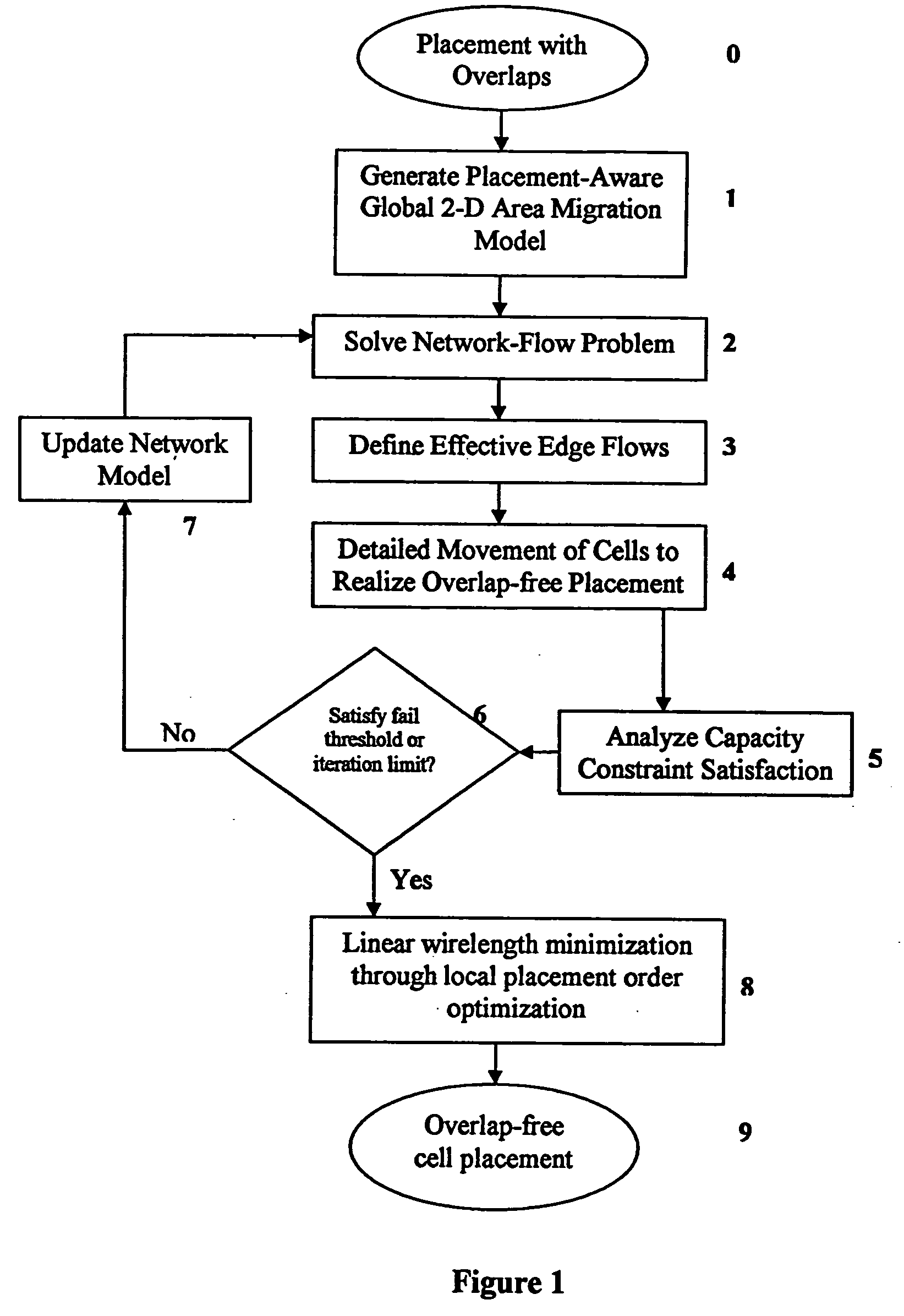
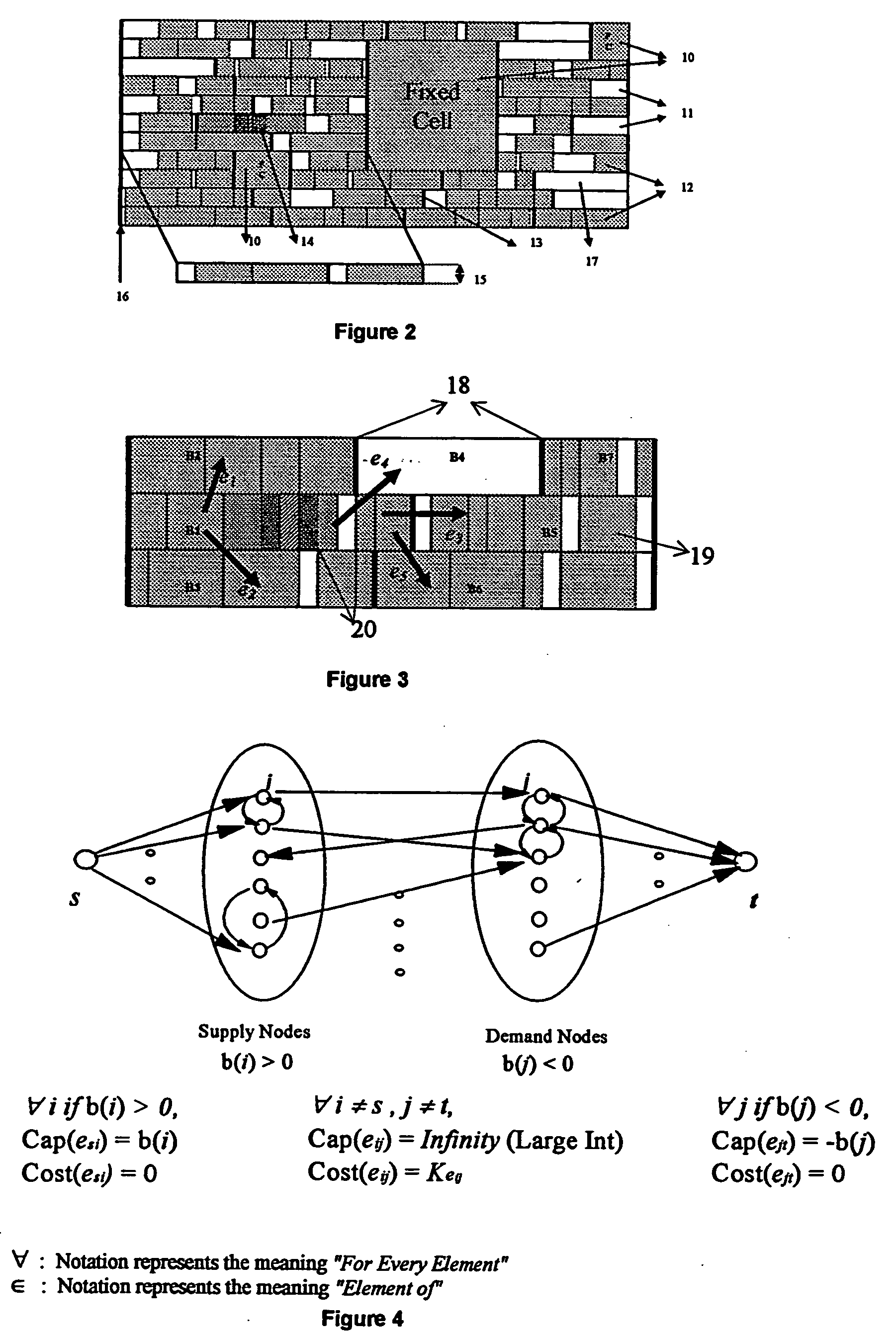
Method for legalizing the placement of cells in an integrated circuit layout
InactiveUS20050166169A1Maintain qualityAutomatically resolve cell overlapsComputer aided designSoftware simulation/interpretation/emulationHigh cellIntegrated circuit layout
A method for resolving overlaps in the cell placement (placement legalization) during the physical design phase of an integrated chip design is described. This problem arises in several contexts within the physical design automation area including global and detailed placement, physical synthesis, and ECO (Engineering Change Order) mode for timing / design closure The method involves capturing a view of a given placement, solving a global two-dimensional area migration model and locally perturbing the cells to resolve the overlaps with minimal changes to the given placement. The method first captures a two-dimensional view of the placement including blockage-space, free-space and the given location of cells by defining physical regions. The desired global area migration across the physical regions of the placement image is determined such that it satisfies area capacity-demand constraints. The method also provides moving the cells between physical regions along previously computed directions of migration to minimize the movement cost. Also provided is an approximate method to model the movement of multi-row high cells.
Owner:IBM CORP
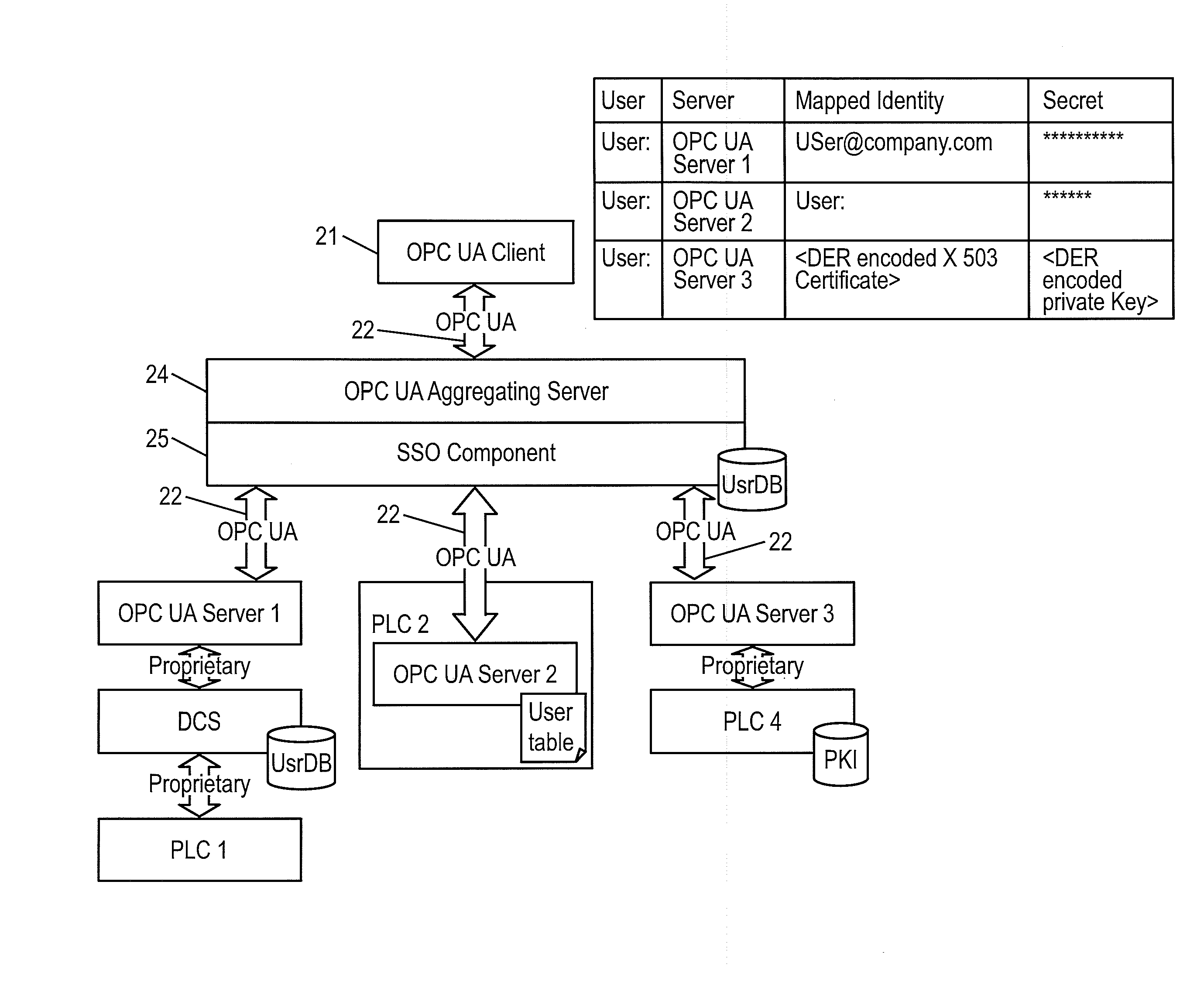
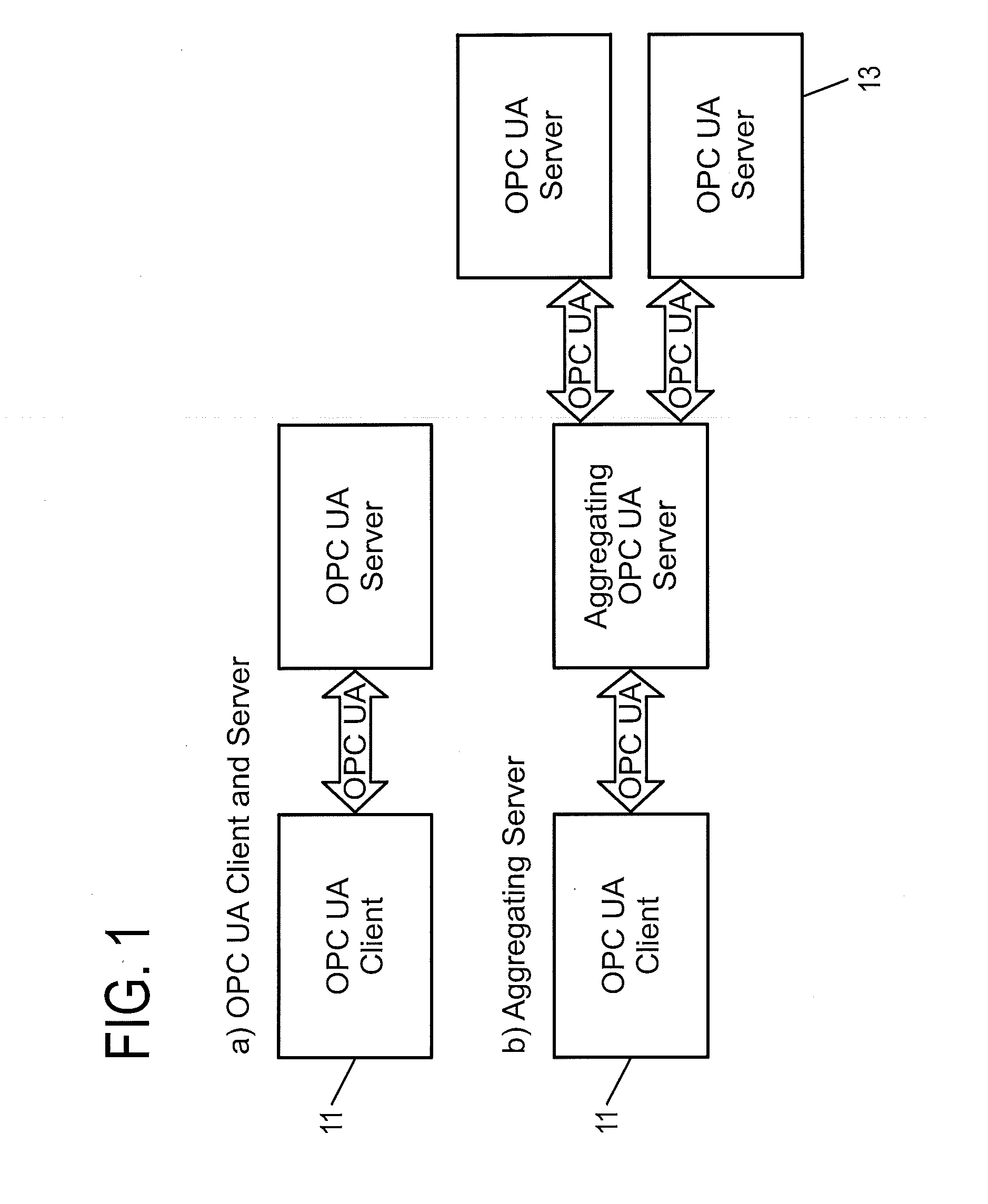
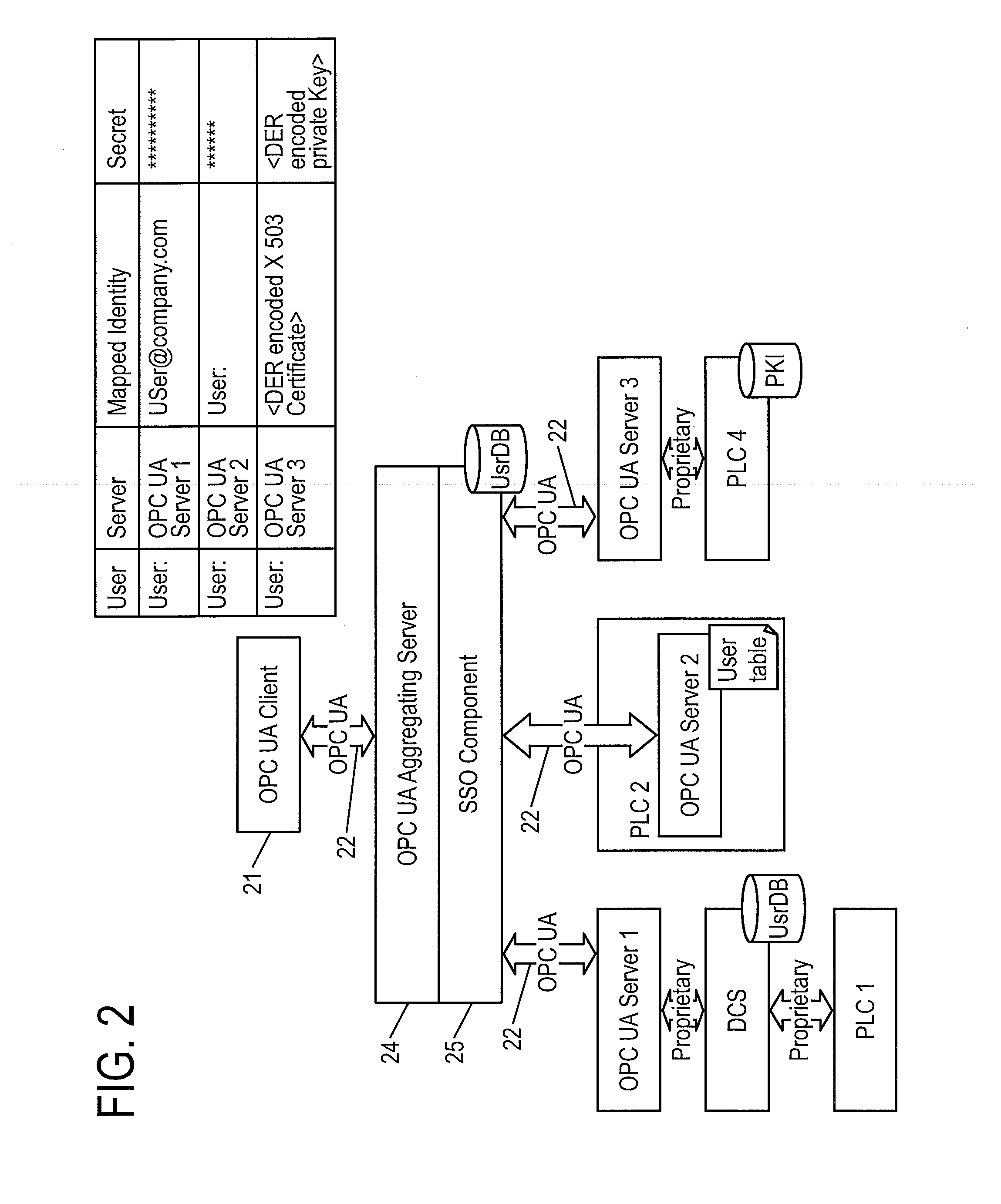
Client/server system for communicating according to the standard protocol opc ua and having single sign-on mechanisms for authenticating, and method for performing single sign-on in such a system
ActiveUS20110035792A1Digital data processing detailsMultiple digital computer combinationsUser authenticationClient-side
A method and device are provided for integrating single sign-on (SOS) mechanisms in a client / server system using communication according to the standard protocol OPC UA, and for performing SOS for user authentication and authorization in the system. A client is connected to an aggregating server, and the aggregating server is connected to subordinated servers via a communication network. To integrate SOS mechanisms, the aggregating server is provided with an SSO component for mapping user legitimation data used in a service call to identities in the form in which the identities are stored in the subordinate servers. To perform SOS using the SSO component, user legitimation data associated with a service call are used to automatically search for corresponding mapped identities and affected servers, and to call up an active session service for each match in each server via the mapped identity, to establish the desired access to data from the user's service invocation.
Owner:ABB (SCHWEIZ) AG
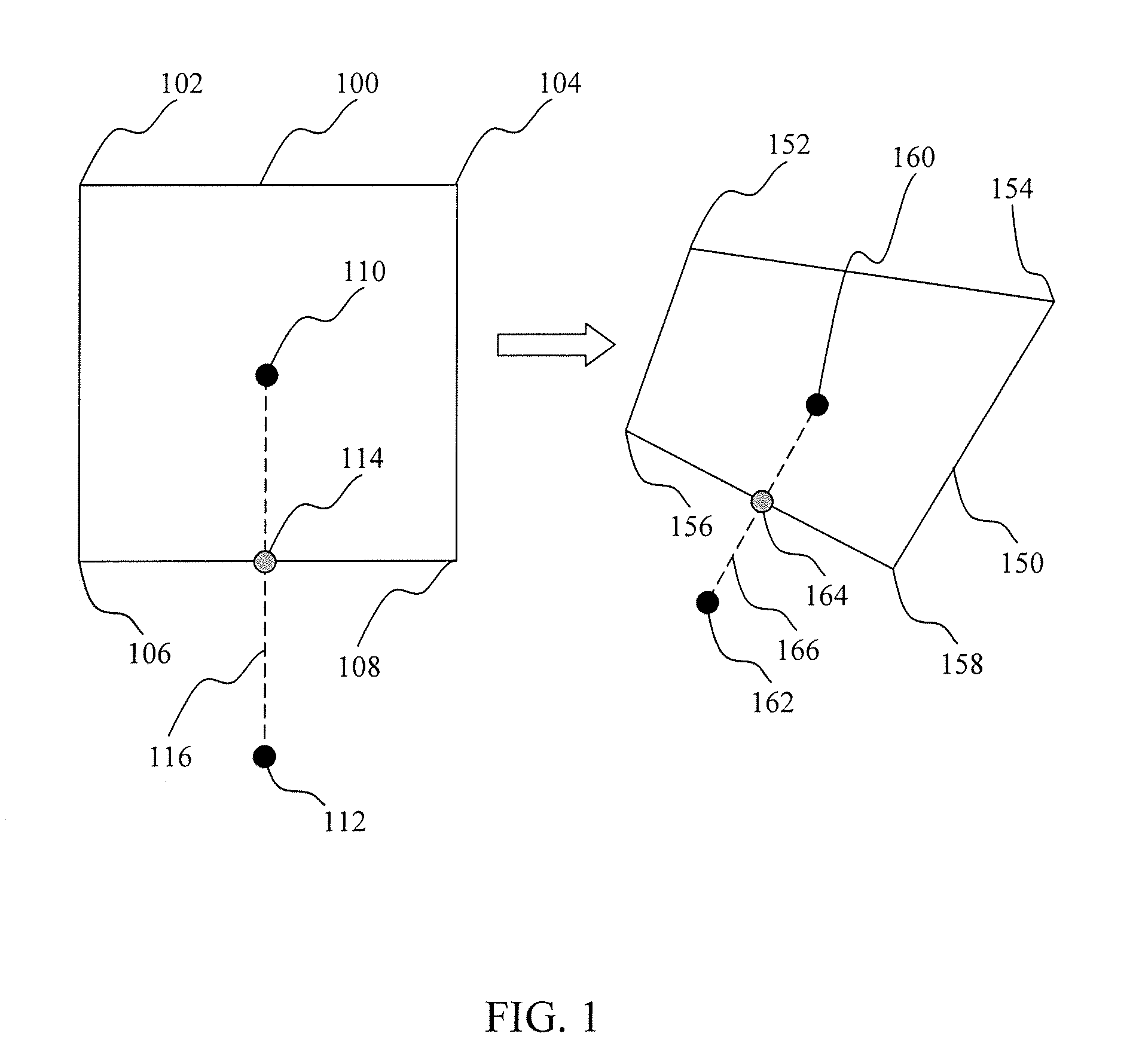
VLSI artwork legalization for hierarchical designs with multiple grid constraints
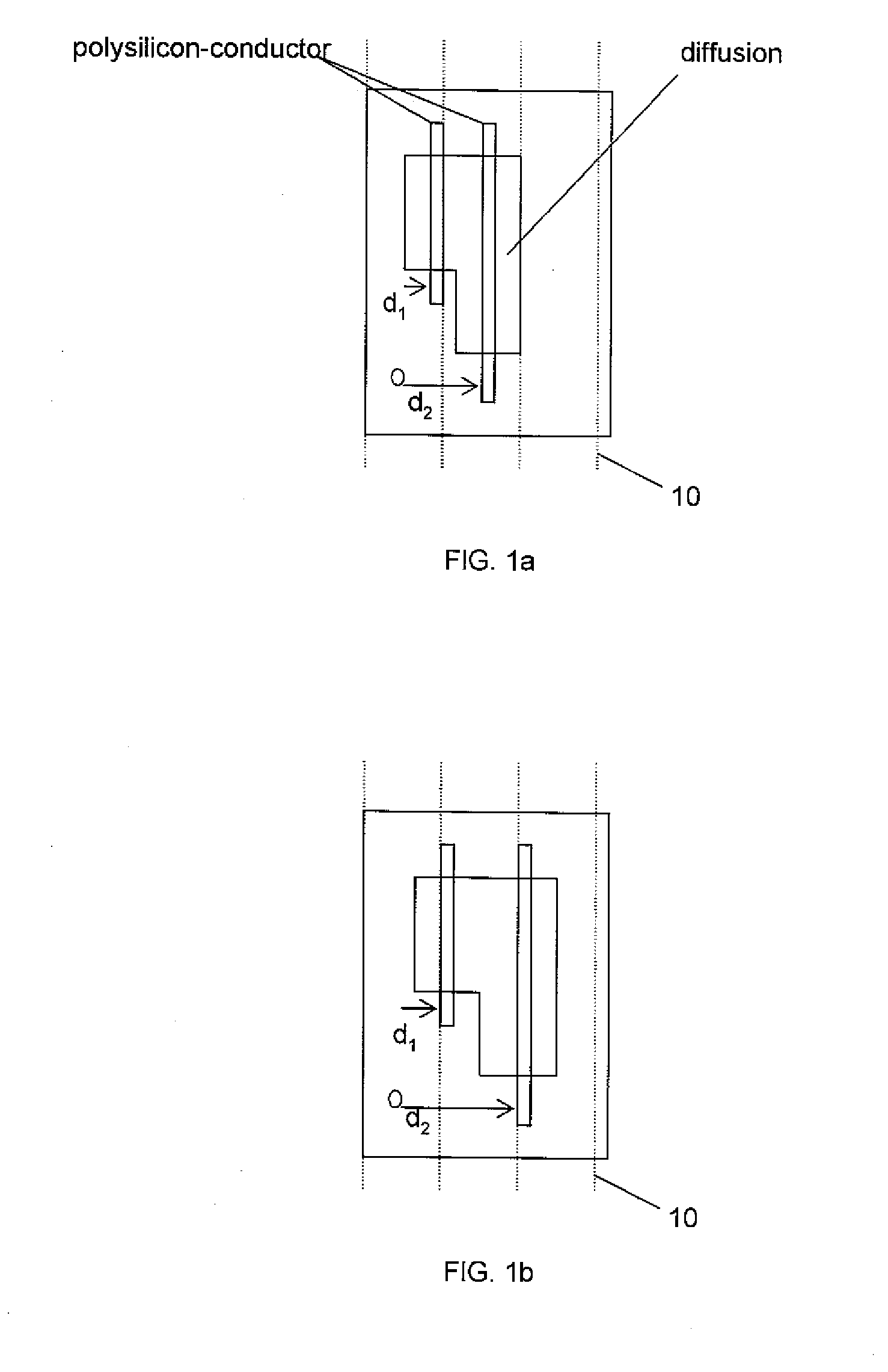
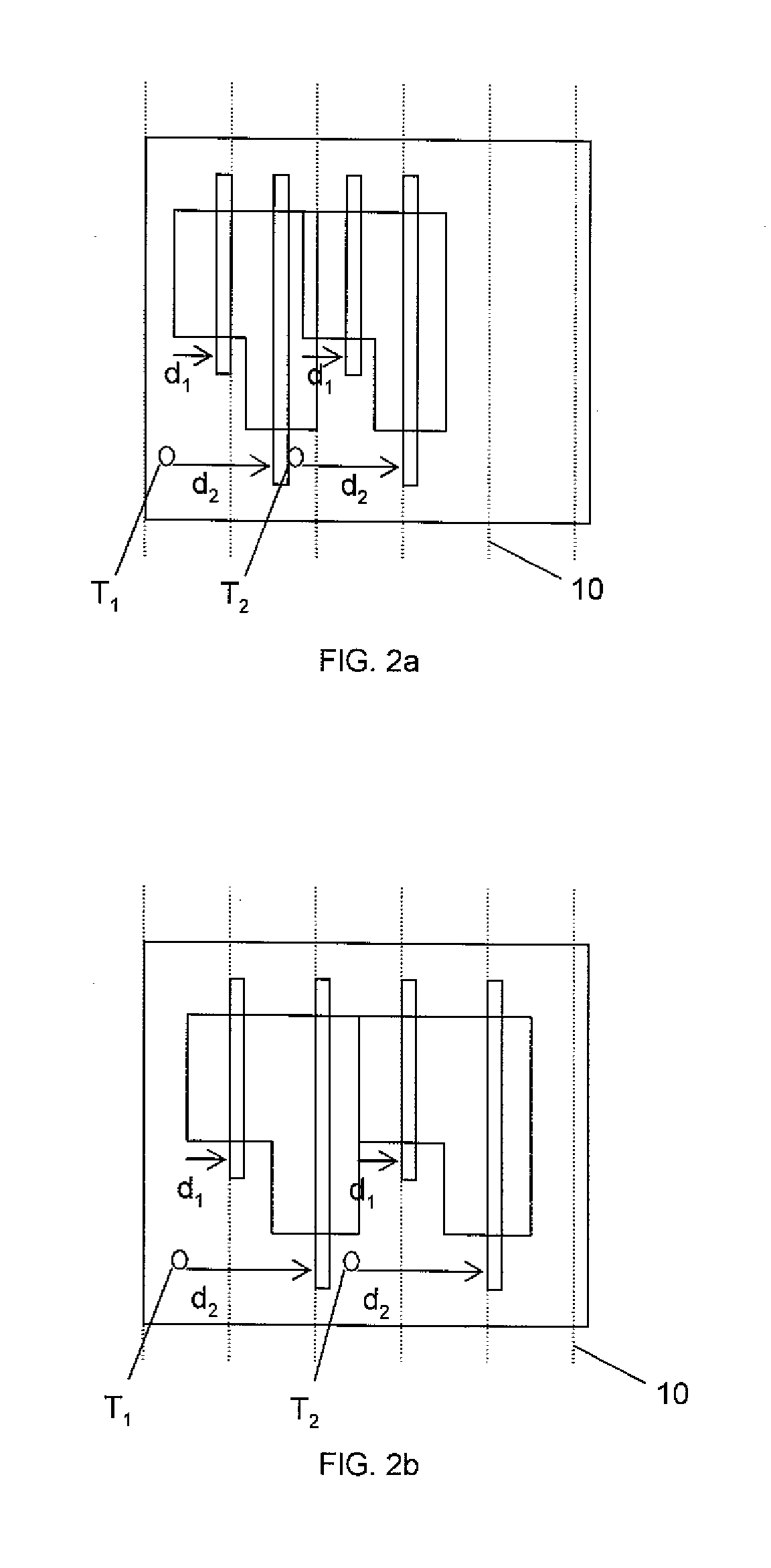
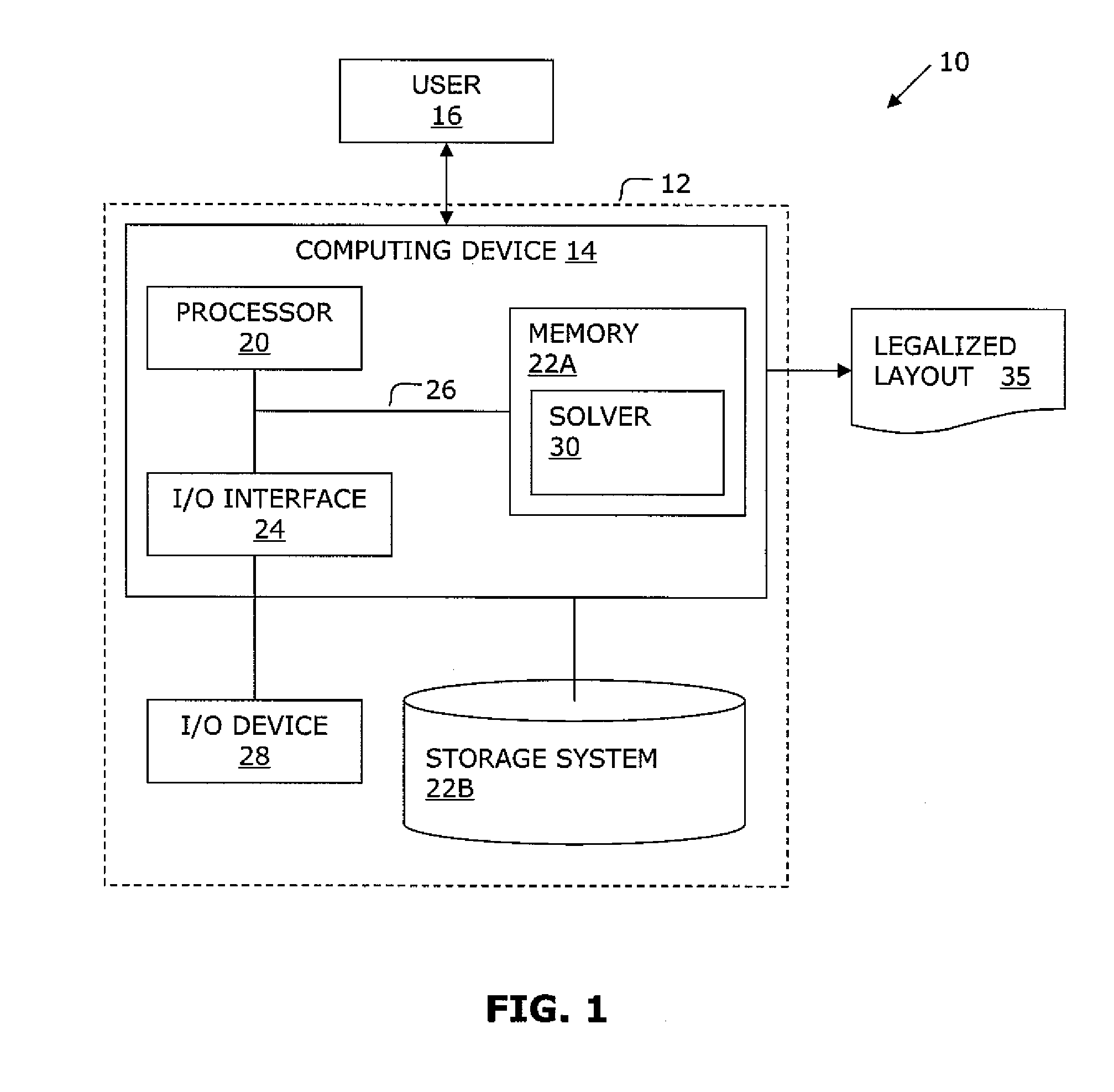
A system and method are disclosed for legalizing a flat or hierarchical VLSI layout to meet multiple grid constraints and conventional ground rules. Given a set of ground rules with multiple grid constraints and a VLSI layout (either hierarchical or flat) which is layout-versus-schematic (LVS) correct but may not be ground rule correct, the system and method provide a legalized layout which meets the multiple grid constraints while maintaining LVS correctness and fixing the ground rule errors as much as possible with minimum layout perturbation from the input design. The system and method support multiple grid pitch constraints for hierarchical design, and provide for LVS correctness to be maintained while an on-grid solution possibly with some spacing violations.
Owner:GLOBALFOUNDRIES US INC
Case generation method for semi-legalized fuzz test of network protocol based on finite-state machine
ActiveCN105095075AQuality improvementReduce sizeSoftware testing/debuggingGranularityFinite-state machine
The invention discloses a case generation method for a semi-legalized fuzz test of a network protocol based on a finite-state machine. The case generation method comprises following steps: analyzing a protocol interaction process based on the network protocol of the finite-state machine and according to a network protocol specification and constructing a network protocol model based on the finite-state machine; establishing the complete test sequence aimed at the finite-state machine, wherein the test sequence is a set composed of all state transition paths of the finite-state machine; constructing a message set of deformity agreements after variation in protocol messages md; sequentially selecting one of the message set of deformity agreements from md as a md used for substituting the complete test sequence in order to obtain one fuzz test sequence related to md so that p fuzz test sequences related to md can be obtained; and finally obtaining all fuzz test sequences from m0 to m(n-1) as cases for the fuzz test. The case generation method is utilized such that cases, with finer granularity, for the fuzzy test of the network protocol can be obtained.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Minimum layout perturbation-based artwork legalization with grid constraints for hierarchical designs
InactiveUS20070245283A1Solve problemsComputer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceHierarchical design
A method comprises extracting a hierarchical grid constraint set and modeling one or more critical objects of at least one cell as a variable set. The method further comprises solving a linear programming problem based on the hierarchical grid constraint set with the variable set to provide initial locations of the critical objects of the at least one cell and determining target on-grid locations of the one or more critical objects in the at least one cell using the results of the linear programming solution.
Owner:GLOBALFOUNDRIES INC
Hierarchy-based analytical placement method for an integrated circuit
ActiveUS7984410B2Improve routabilityMaximizes routabilityComputer aided designSoftware simulation/interpretation/emulationProgram planningTheoretical computer science
A placer produces a global placement plan specifying positions of cell instances to be interconnected by nets within an integrated circuit (IC) by initially clusterizing cell instances to form a pyramidal hierarchy of blocks and generating an initial global placement plan specifying a position of each block at a highest level of the hierarchy. The placer then declusterizes the global placement plan by replacing the highest level blocks with their component blocks and then improves the routability of the global placement plan by iteratively moving specified block positions in directions and by distances dynamically determined by analyzing the global placement plan and an objective function having a total wirelength term and having a bin density term reflecting density of blocks in specified areas (bins) of the IC. The placer iteratively repeats the declusterization and routability improvement process until the global placement plan specifies positions of all blocks residing at the lowest level of the hierarchy, with weighting of the bin density term adjusted when necessary during each iteration of the routability improvement process to provide sufficient white space in each bin. The placer employs a look-ahead legalization technique to move low level blocks to legal positions during later iterations of the plan improvement process.
Owner:SYNOPSYS INC
Legalization of VLSI circuit placement with blockages using hierarchical row slicing
ActiveUS7934188B2Easy to handleReduced and minimal perturbationComputer aided designSpecial data processing applicationsComputer architectureGranularity
A hierarchical method of legalizing the placement of logic cells in the presence of blockages selectively classifies the blockages into at least two different sets based on size (large and small). Movable logic cells are relocated first among coarse regions between large blockages to remove overlaps among the cells and the large blockages without regard to small blockages (while satisfying capacity constraints of the coarse regions), and thereafter the movable logic cells are relocated among fine regions between small blockages to remove all cell overlaps (while satisfying capacity constraints of the fine regions). The coarse and fine regions may be horizontal slices of the placement region having a height corresponding to a single circuit row height of the design. Cells are relocated with minimal perturbation from the previous placement, preserving wirelength and timing optimizations. The legalization technique may utilize more than two levels of granularity with multiple relocation stages.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Placement driven routing
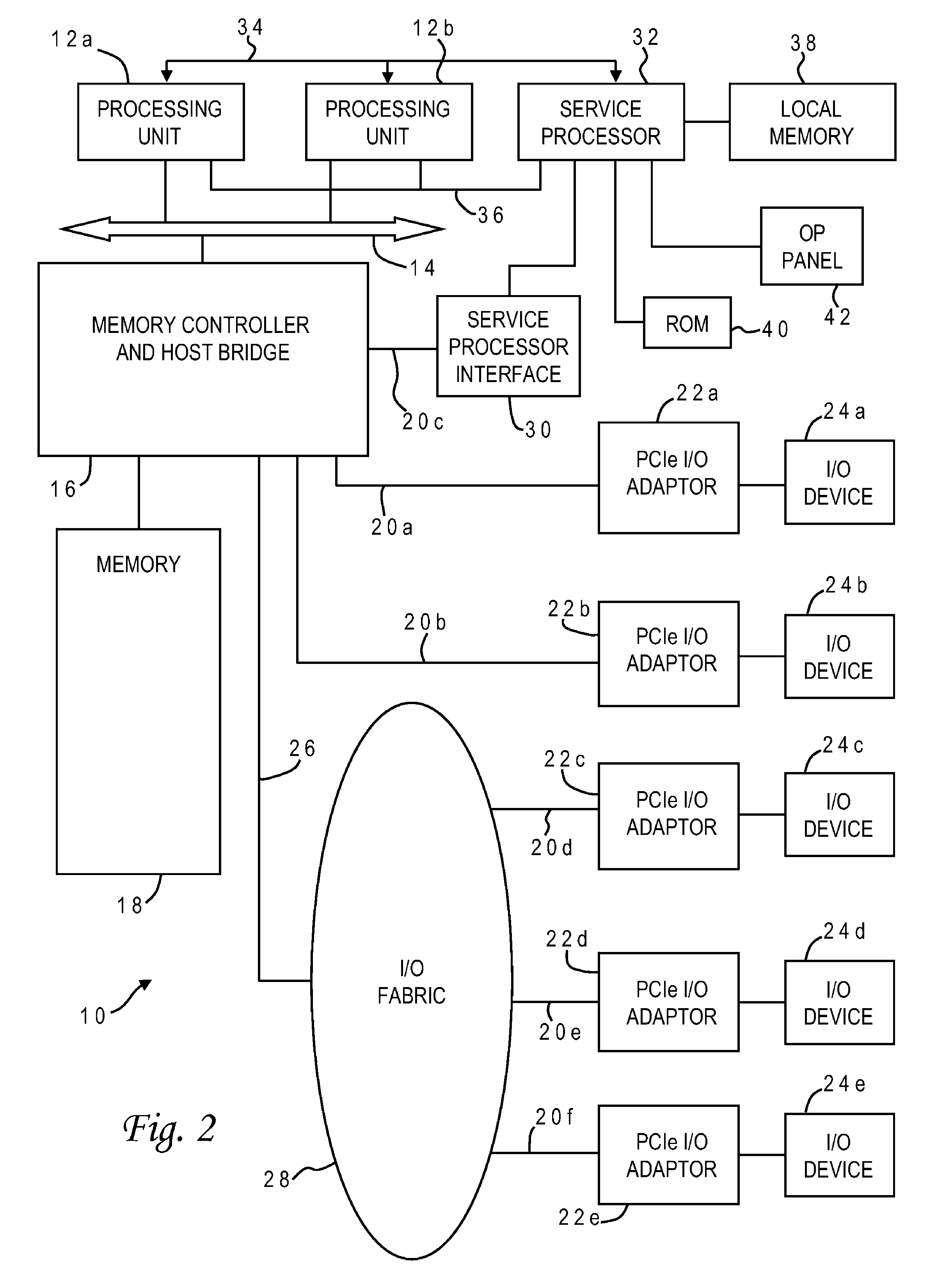
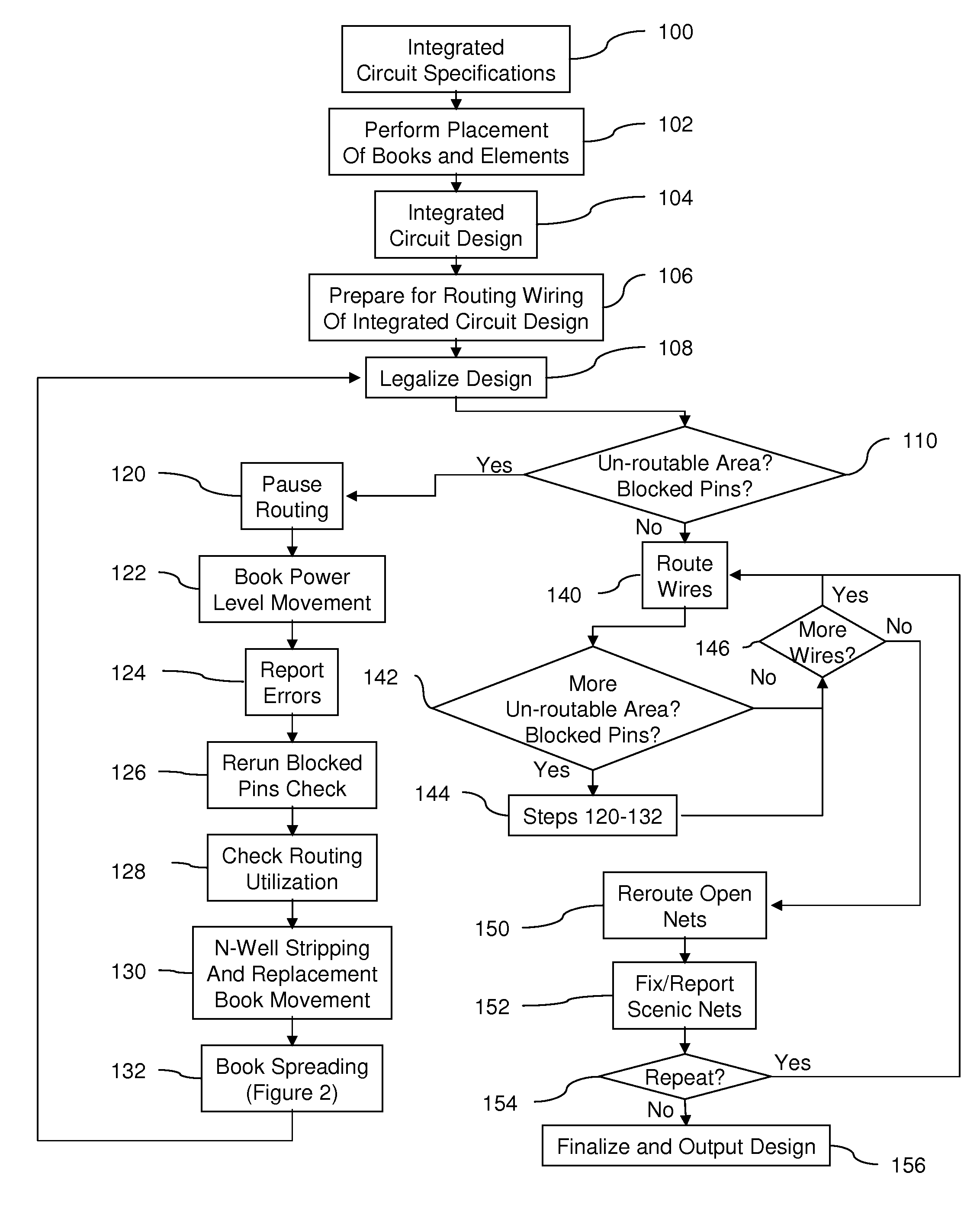
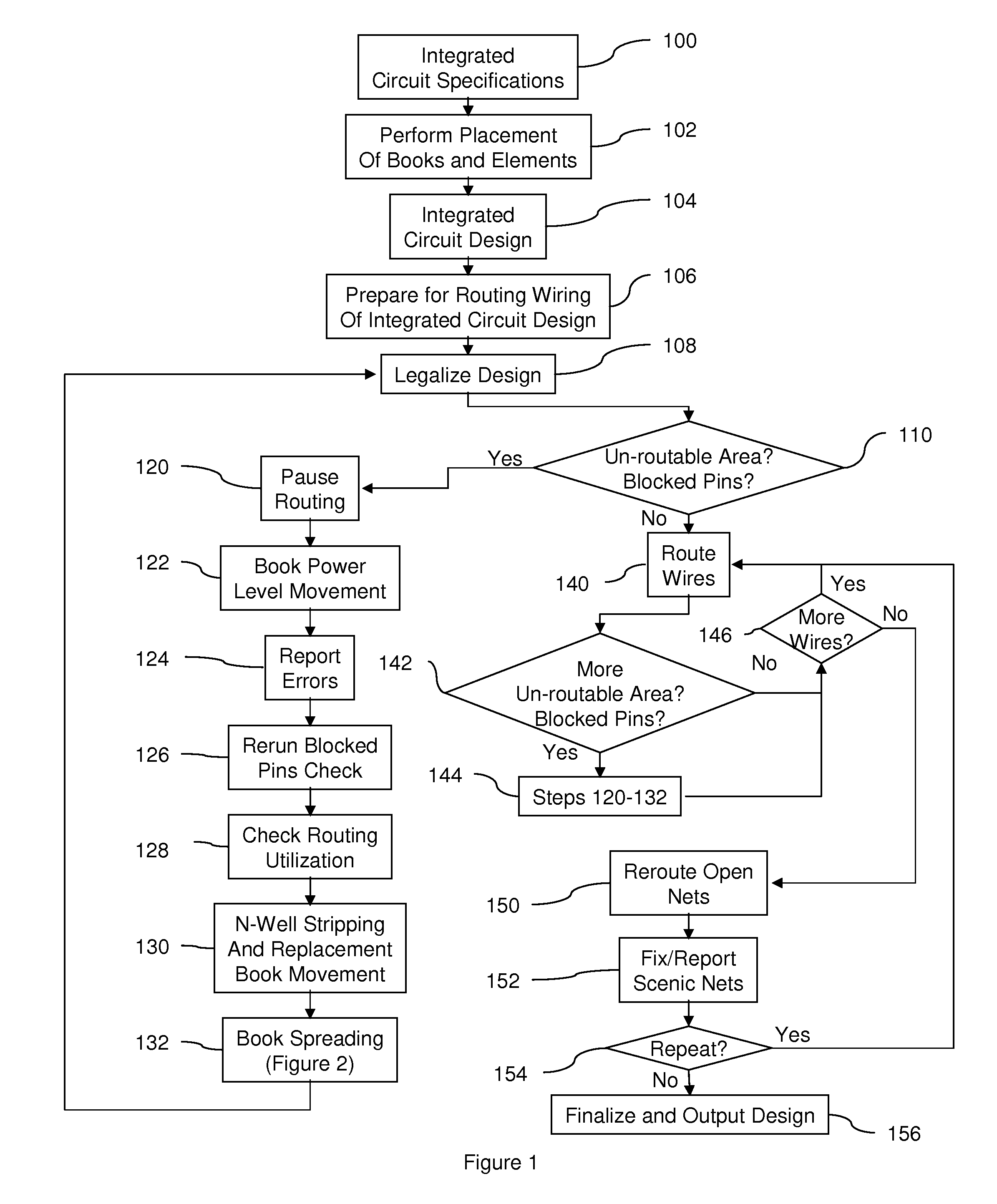
ActiveUS20090187870A1Minimal impactQuantity minimizationComputer aided designSpecial data processing applicationsEngineeringCircuit design
A method placing items routing wiring pursuant to integrated circuit specifications to create an integrated circuit design. Once the initially placed design is legalized, rather that just starting wiring routing, the method identifies books in the integrated circuit design which contain blocked items. The method allows the routing process to be paused temporarily, and for the items to be moved to a certain extent. This movement process is controlled (limited according to signal power output by the associated books) so that the timing of the integrated circuit design is not affected by any such “mid-routing” movement. If the books do not have any blocked items, the process continues to route wires between the items and the books. If at any point before or during the routing of the wires it is found that the books do have blocked items, the process pauses the routing of the wires and performs any number of different processes to solve the blocked item situation (unblock the blocked items).
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
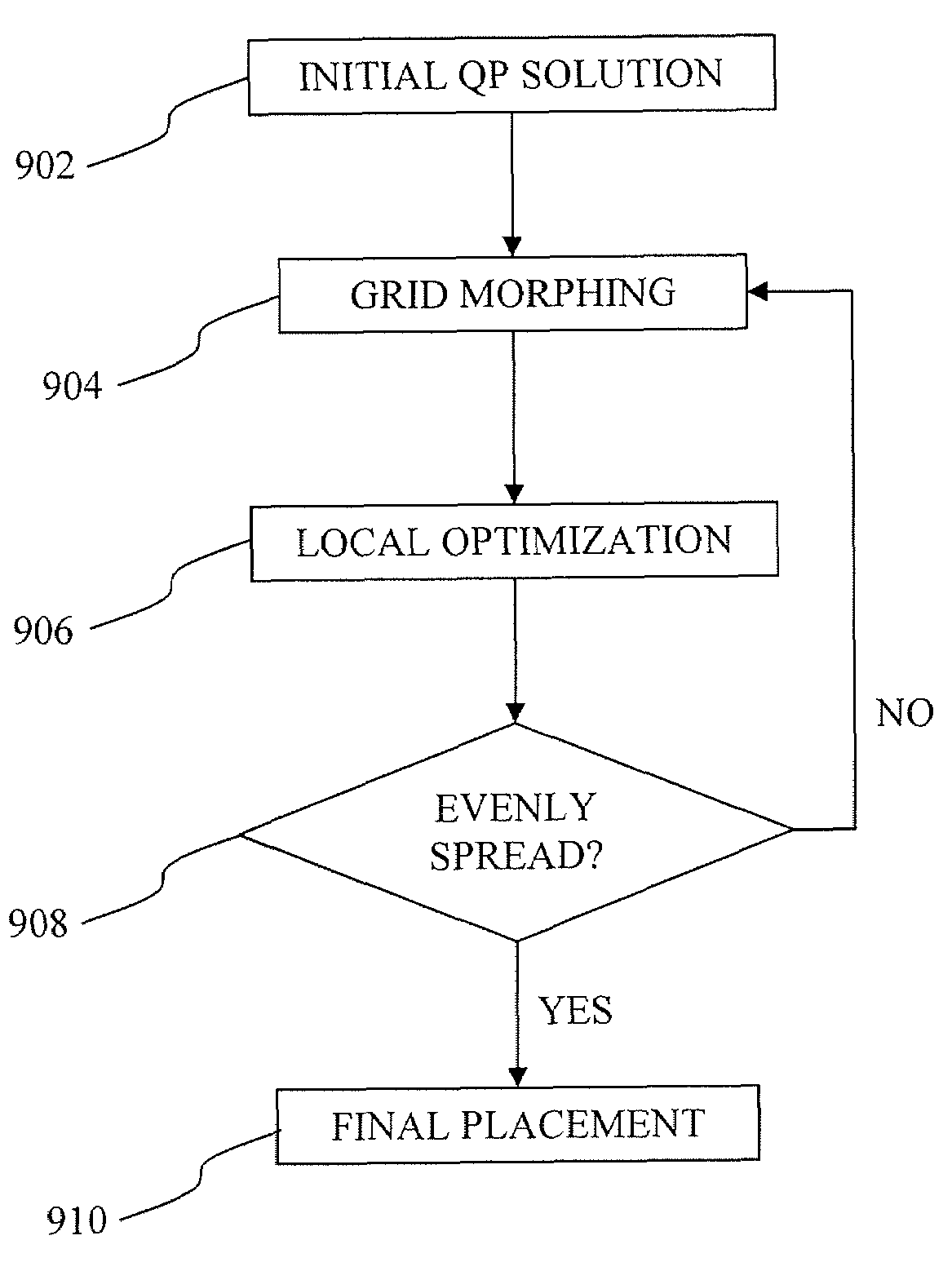
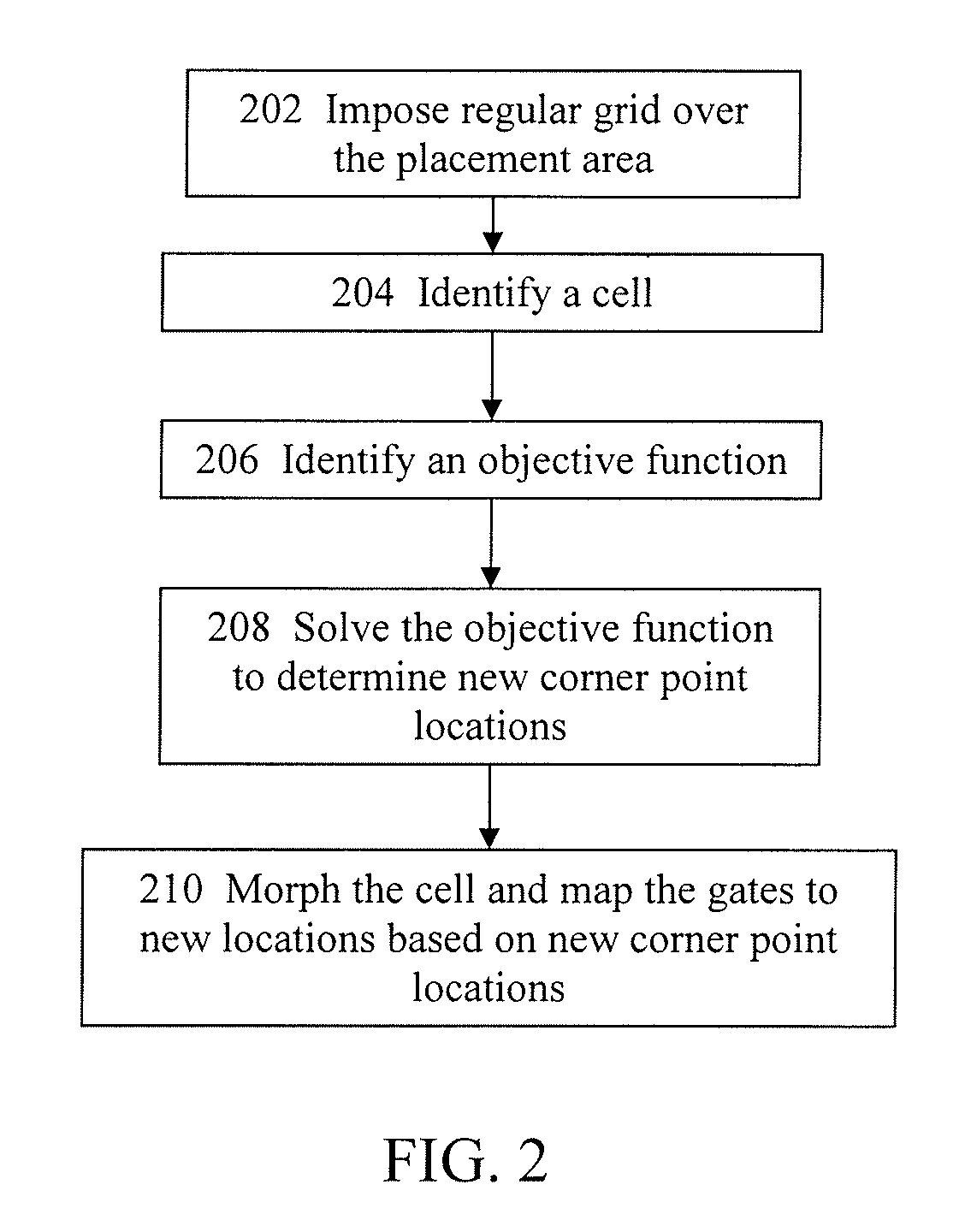
Methods, systems, and computer program products for grid-morphing techniques in placement, floorplanning, and legalization
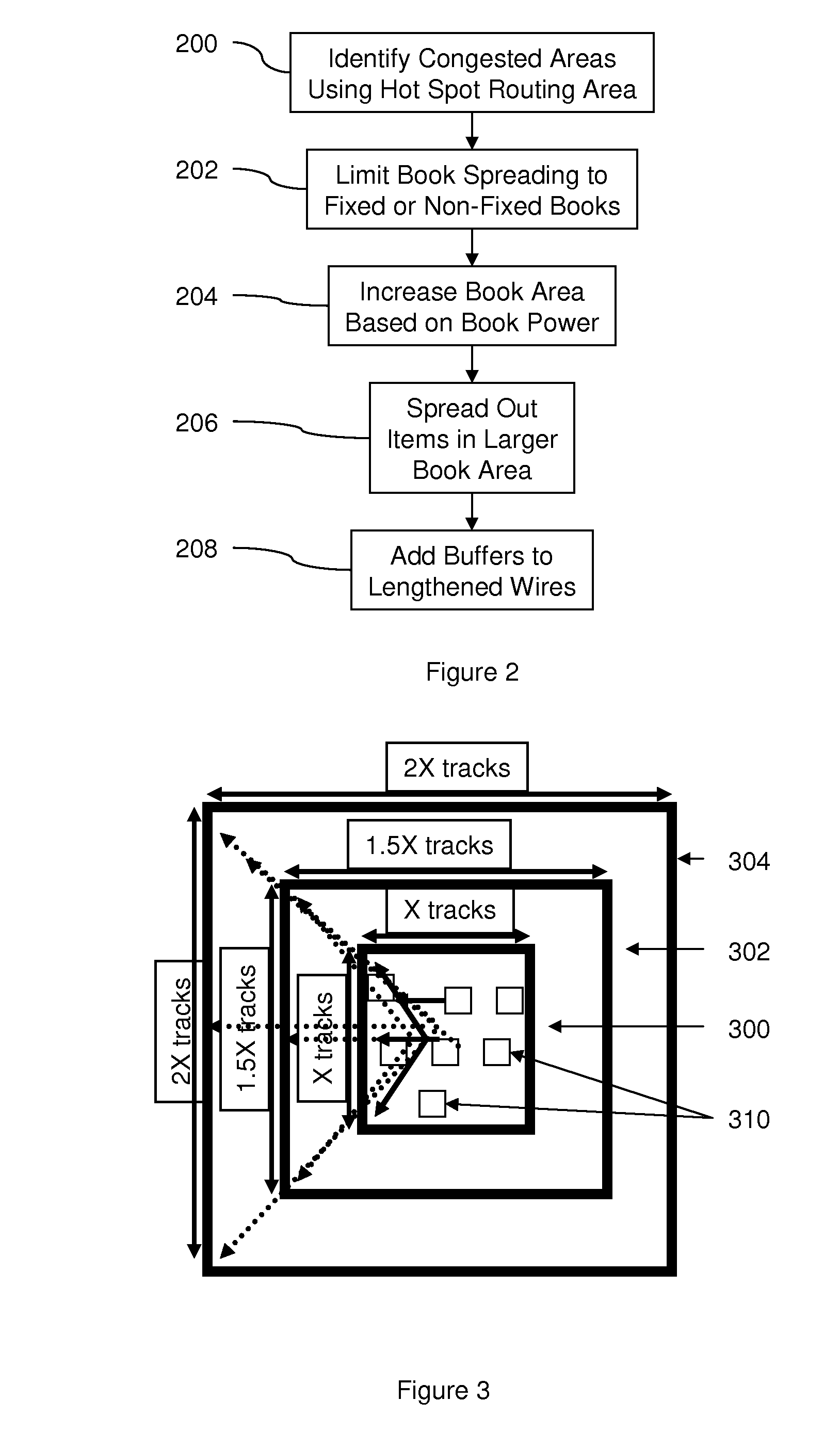
InactiveUS7739644B1Increase demandEasy to placeComputer aided designSpecial data processing applicationsMorphingTheoretical computer science
Disclosed are methods, systems, and computer program products for performing grid morphing technique for computing a spreading of objects over an area such that the final locations of the objects are distributed over the area and such that the final locations of the objects are minimally perturbed from their initial starting locations and the density of objects meets certain constraints. The minimization of perturbation, or stability, of the approaches disclosed, is the key feature which is the principal benefit of the techniques disclosed. The methods described herein may be used as part of a tool for placement or floorplanning of logic gates or larger macroblocks for the design of an integrated circuit.
Owner:CADENCE DESIGN SYST INC +1
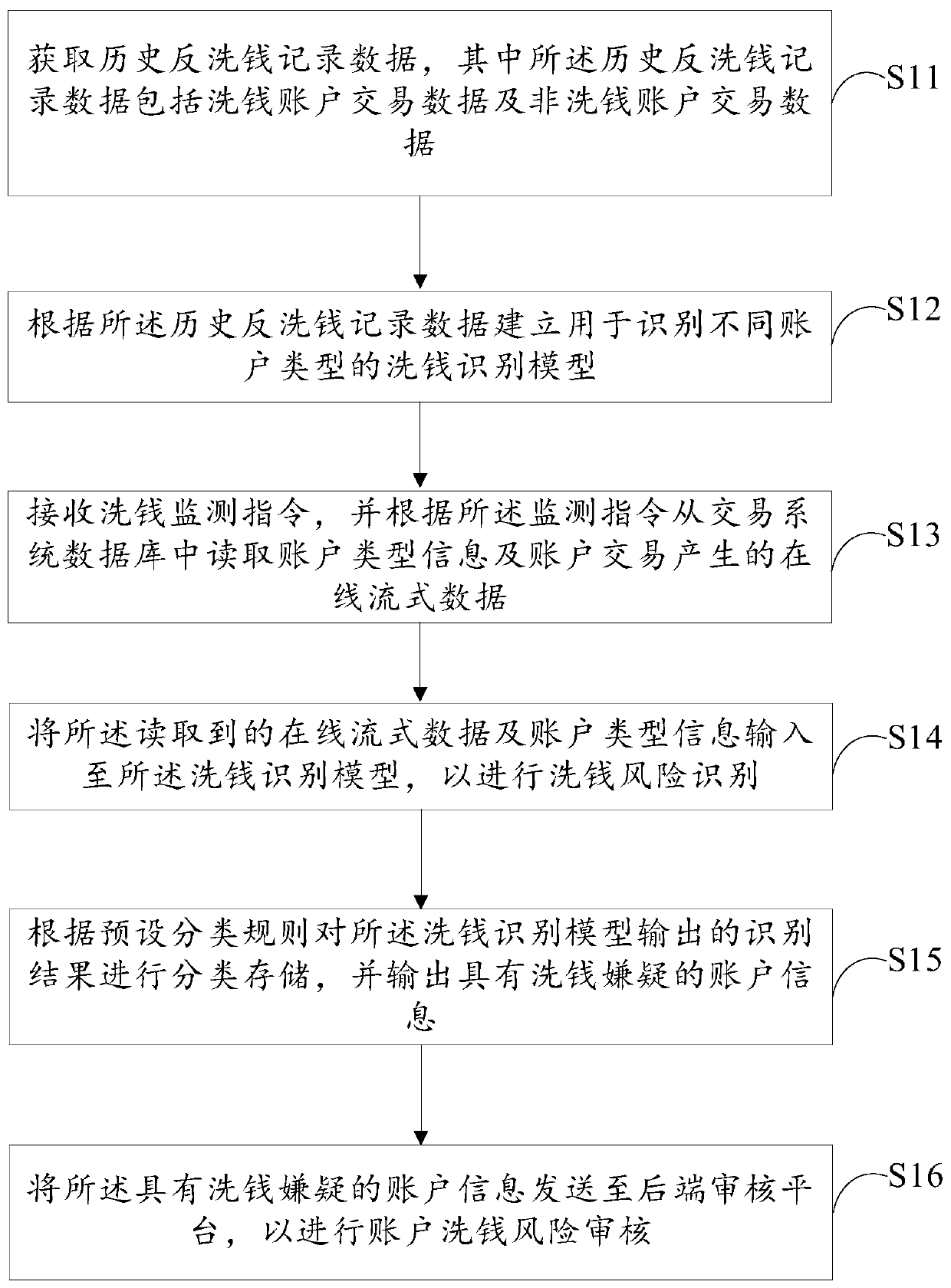
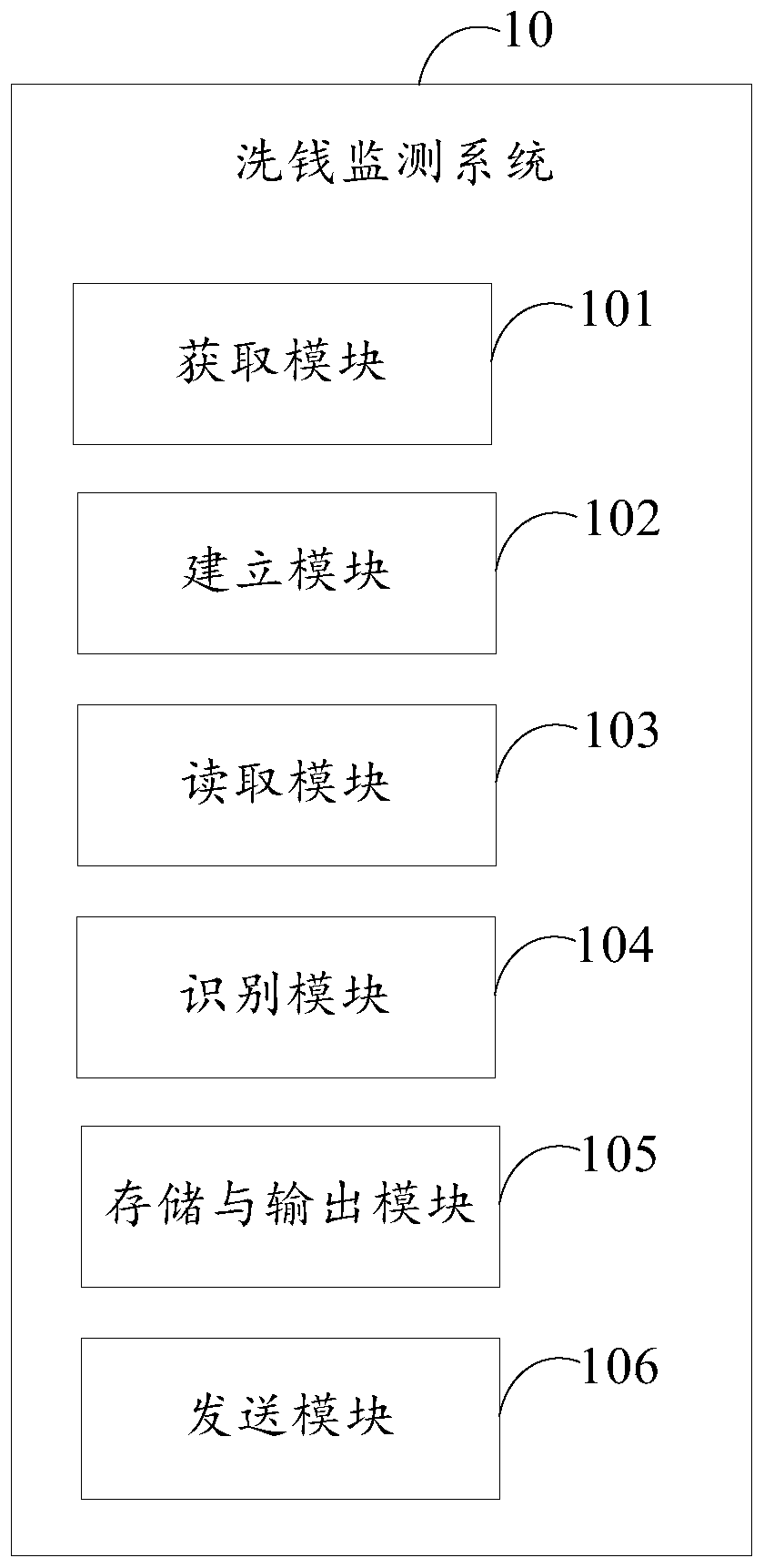
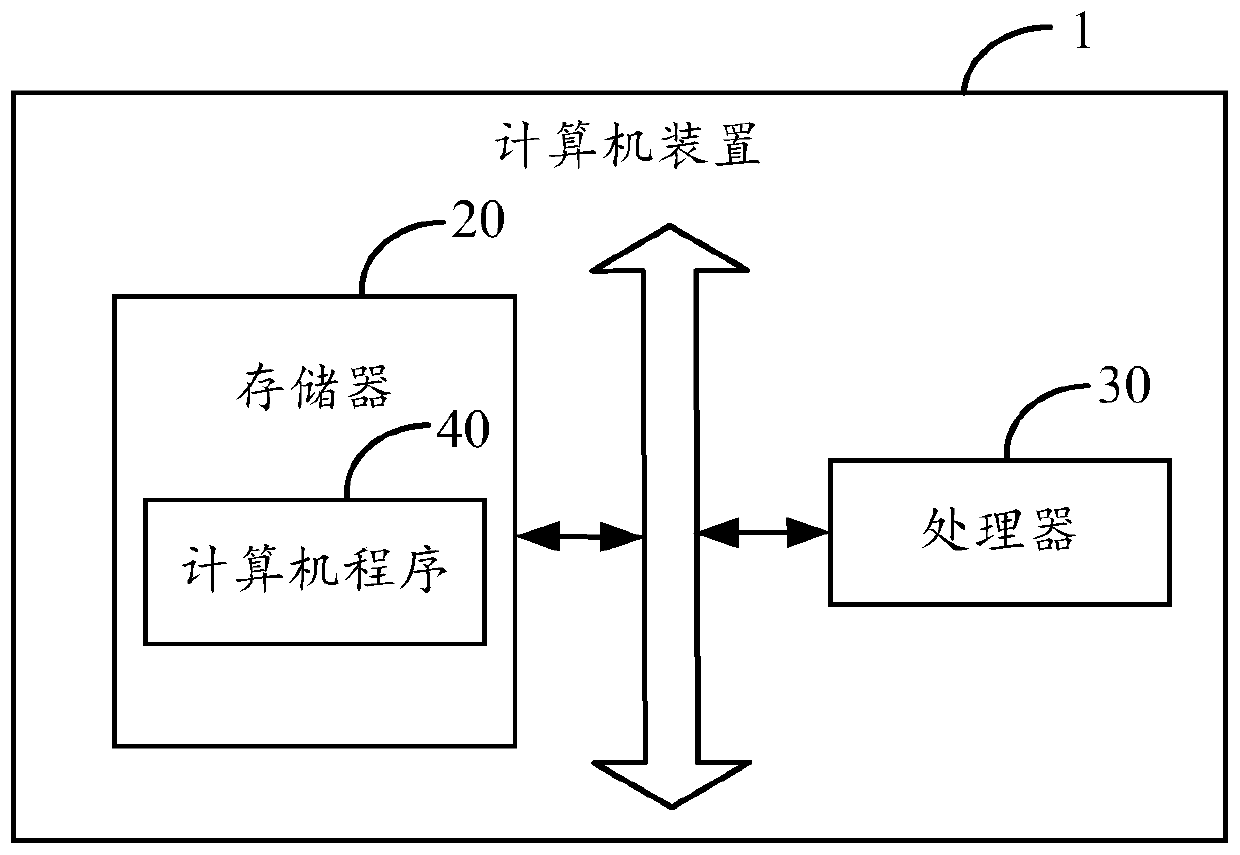
Illegal income legalization behavior monitoring method and system, computer device and medium
The invention provides an illegal income legalization behavior monitoring method and system, a computer device and a computer readable storage medium. The illegal income legalization behavior monitoring method comprises the following steps: obtaining historical anti-money laundering record data; establishing money laundering recognition models for recognizing different account types according to the historical anti-money laundering record data; receiving a money laundering monitoring instruction, and reading account type information and online streaming data generated by an account transactionfrom a transaction system database according to the monitoring instruction; inputting the read online streaming data and account type information into the money laundering recognition model to carryout money laundering risk recognition; classifying and storing the recognition result output by the money laundering recognition model according to a preset classification rule, and outputting accountinformation with money laundering suspicion. According to the invention, the money laundering recognition model is established based on the neural network, money laundering recognition can be carriedout on the online transaction streaming data, and the anti-money laundering behavior monitoring timeliness is high.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
VLSI artwork legalization for hierarchical designs with multiple grid constraints
ActiveUS7437691B2Geometric CADComputation using non-denominational number representationGraphicsLayout Versus Schematic
A system and method are disclosed for legalizing a flat or hierarchical VLSI layout to meet multiple grid constraints and conventional ground rules. Given a set of ground rules with multiple grid constraints and a VLSI layout (either hierarchical or flat) which is layout-versus-schematic (LVS) correct but may not be ground rule correct, the system and method provide a legalized layout which meets the multiple grid constraints while maintaining LVS correctness and fixing the ground rule errors as much as possible with minimum layout perturbation from the input design. The system and method support multiple grid pitch constraints for hierarchical design, and provide for LVS correctness to be maintained while an on-grid solution possibly with some spacing violations.
Owner:GLOBALFOUNDRIES U S INC
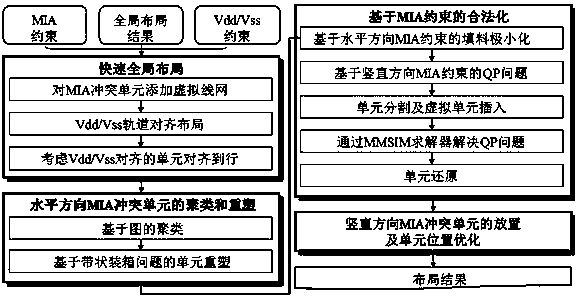
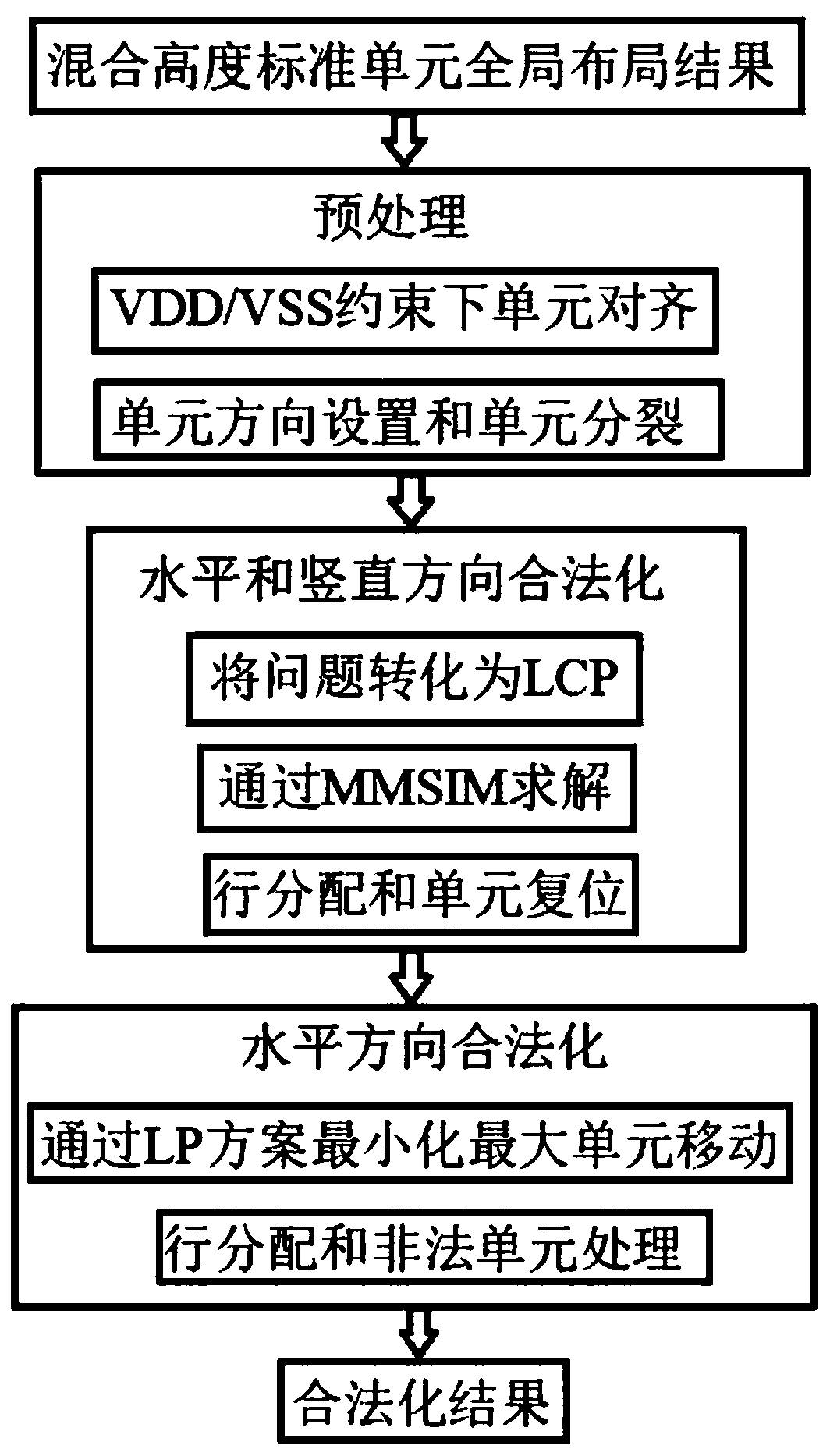
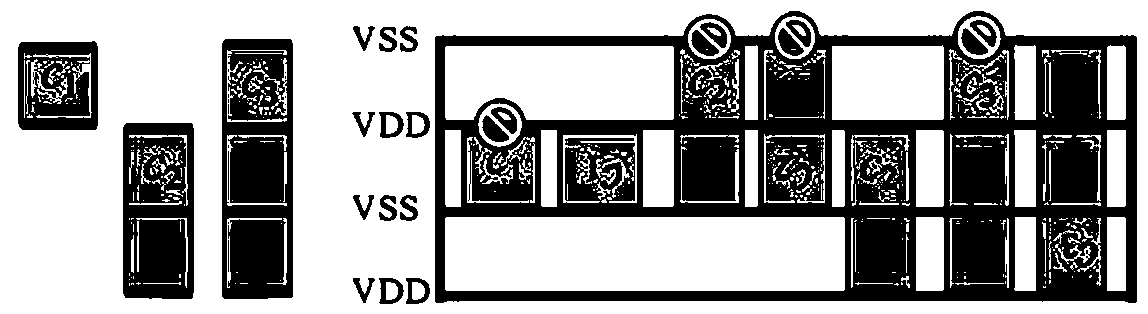
Mixed height unit layout design method based on minimum implantation region constraint
ActiveCN108846169AReduce filler usageReduce line length incrementsSpecial data processing applicationsAlgorithmDesign methods
The invention provides a mixed height unit layout design method based on a minimum implantation region constraint. The method comprises the following steps: step S1, fast global layout; step S2, applying graph-based clustering and reshaping to the horizontal MIA conflict units; step S3, legalization of the constraint based on the MIA; and step S4: allocation and optimization of the unit position.The HVT / LVT units with the same voltage are placed closer together by adding a weighted virtual wire network. The variation of the line length can be globally minimized by depicting the Vdd / Vss constraint through the cost function and conjugate gradient solution. The regional area can be compressed and the use of packing can be reduced by using graph-based clustering method and matching-based method. The constraint based on the vertical MIA is transformed into QP problem and solved by the MMSIM solver. In order to further optimize the layout result, unit allocation and unit position optimization are also carried out finally.
Owner:FUZHOU UNIV
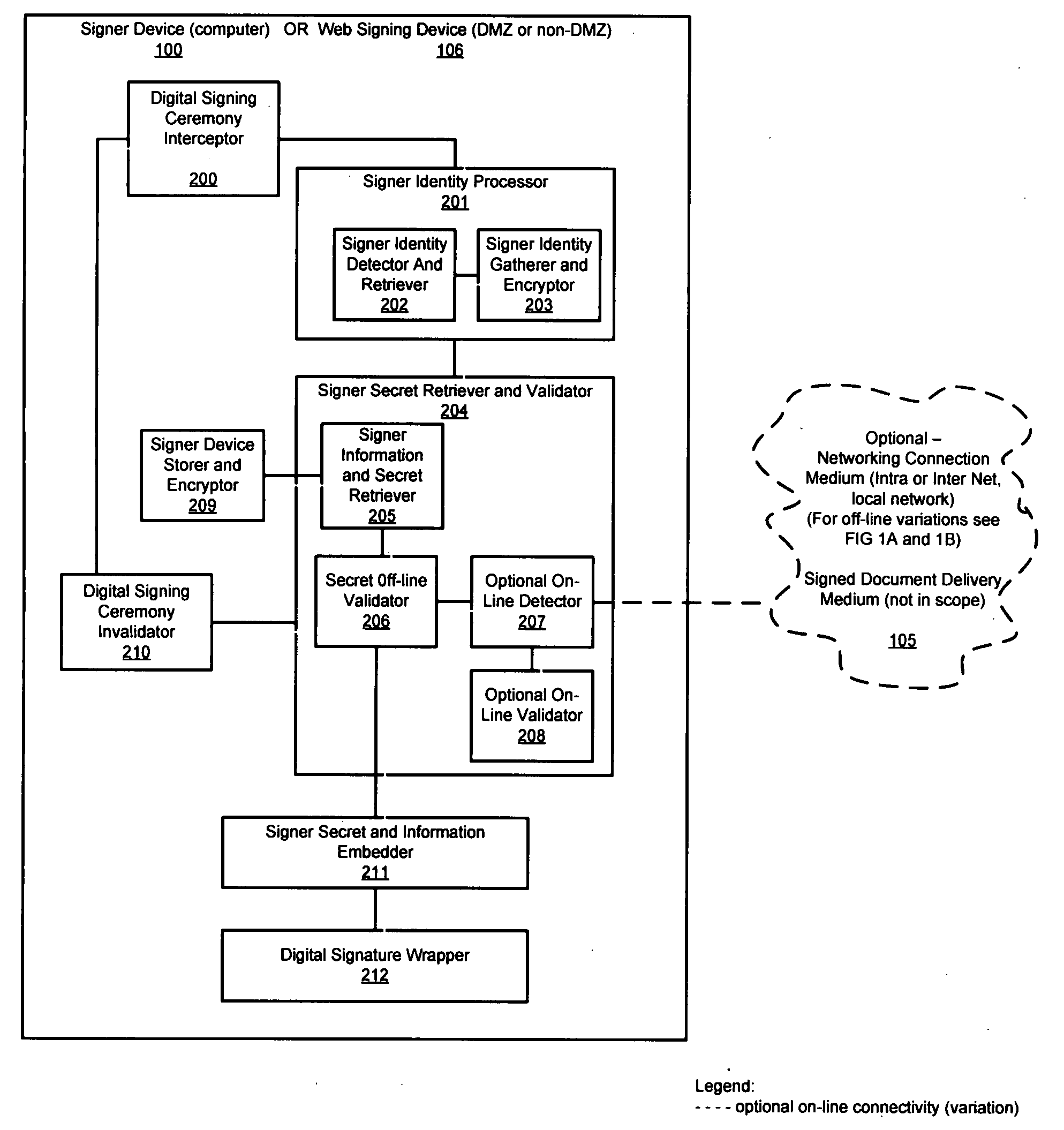
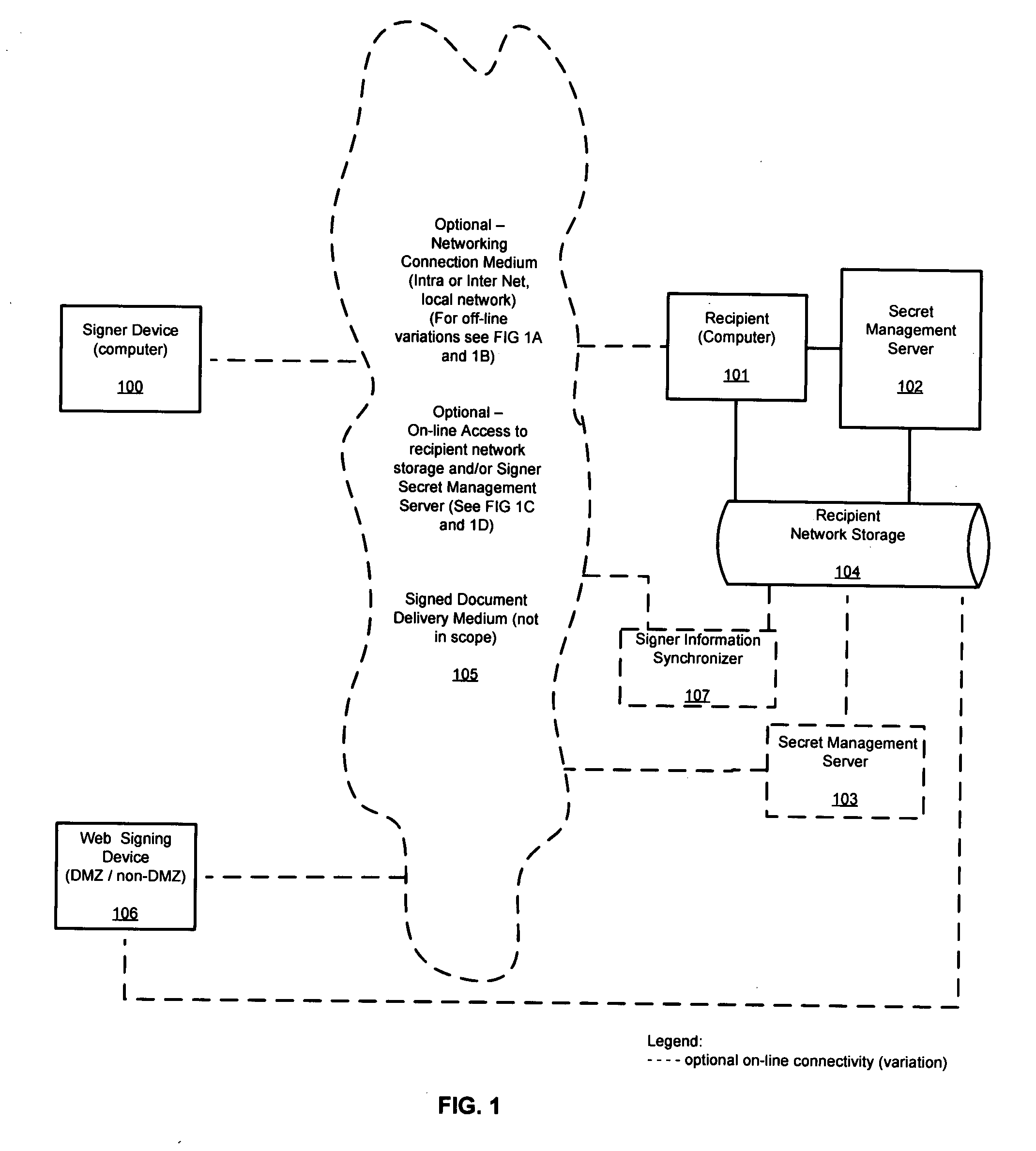
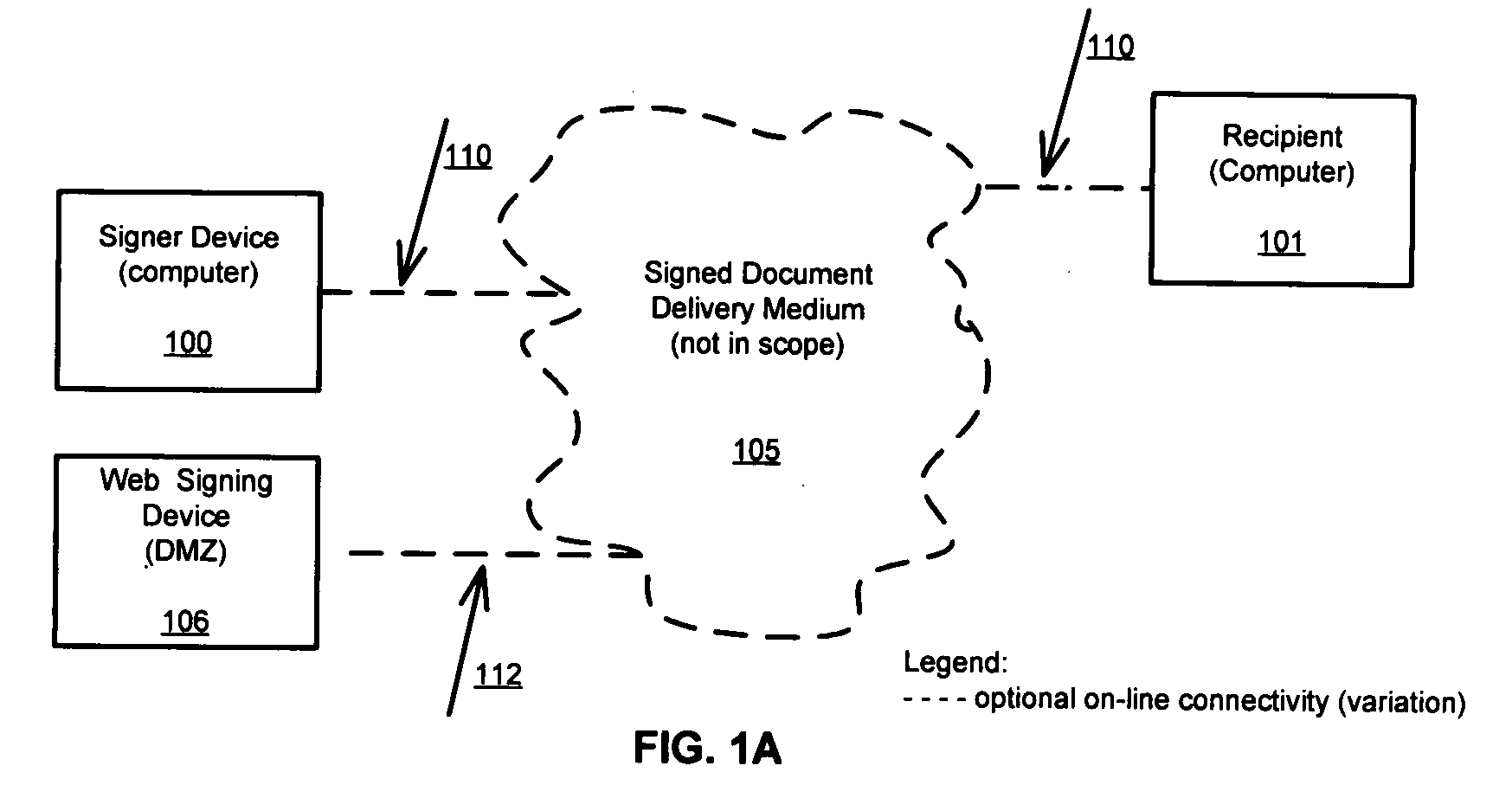
Method and system for signer self-managed, encryption-based identification and signature secret management to verify signer and to legitimize basic digital signature without the use of certificates, tokens or PKI (private key infrastructure)
InactiveUS20090094460A1Easy maintenanceEasy to manageUser identity/authority verificationElectronic documentDigital signature
Method and system for signer self-managed, encryption-based identification and signature secret management to verify the signer and to legitimize basic electronic signature without the use of certificates, tokens or PKI while signing electronic document off-line, on-line (corporate network) or on-line using a web based document. When form is completed, the signing procedure is intercepted by the software to check if signer secret and signer information is present on signer device, else the signer can enter required information and additional system information is gathered. The signature information is validated against the stored encrypted signer information. Both the signature ceremony and the encrypted signer secrets and identification information are embedded in the document for delivery to document recipient. The signer's secret is never compromised, as it is at all times created or updated by signer via self-management software and never revealed to an administrator.
Owner:DEDEK RADIM
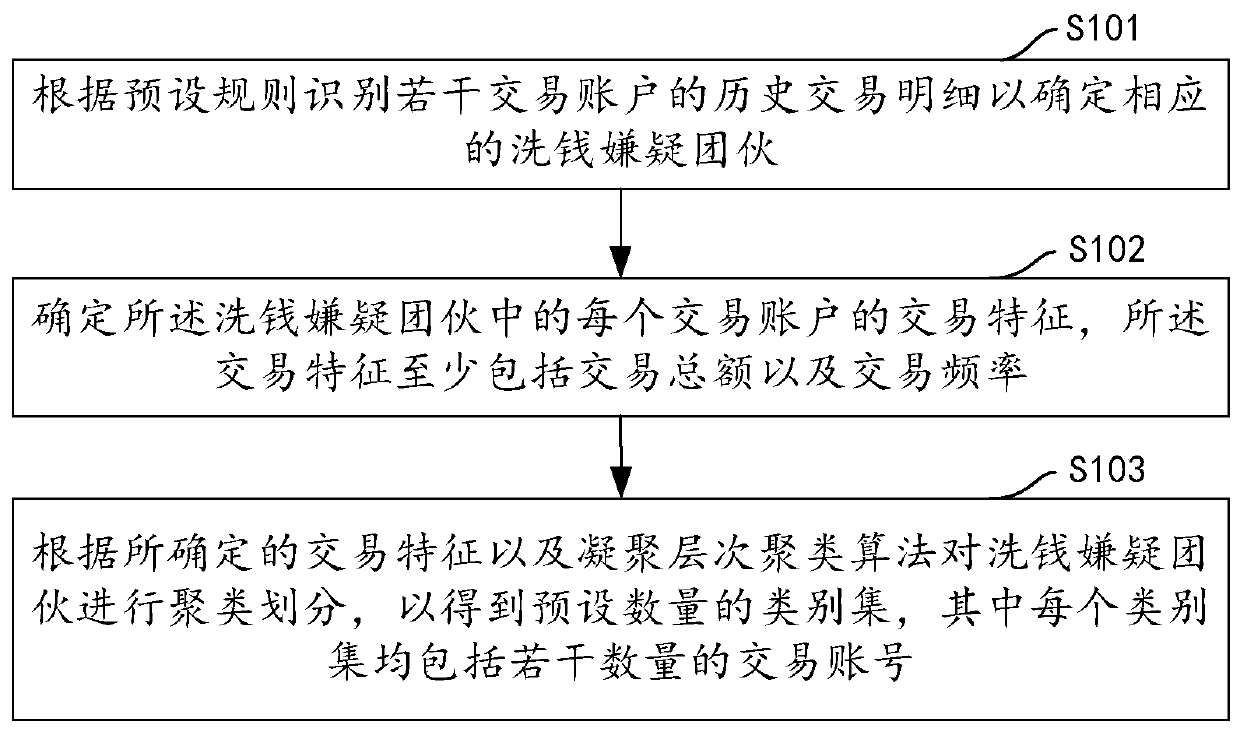
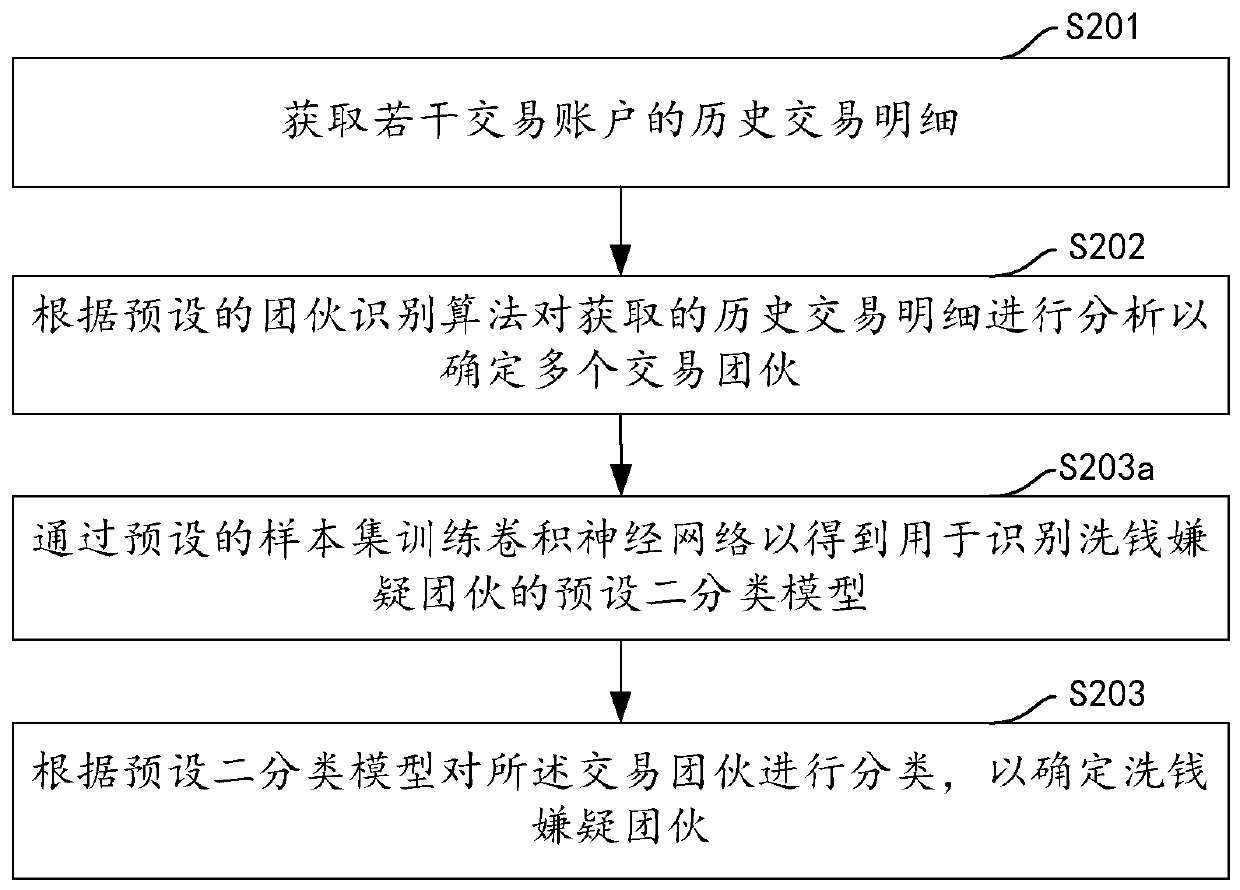
Account classification method and device involving non-legal legalization behavior, computer equipment and storage medium
PendingCN109872232AImprove work efficiencyAccurate automatic classificationFinanceCharacter and pattern recognitionHierarchical cluster algorithmClassification methods
The embodiment of the invention discloses an account classification method and device related to non-legal legalization behaviors, computer equipment and a storage medium. The method comprises the steps of identifying historical transaction details of a plurality of transaction accounts according to a preset rule to determine corresponding money laundering suspicion gangs; determining transactioncharacteristics of each transaction account in the money laundering suspicion gangs, wherein the transaction characteristics at least comprise a transaction total amount and a transaction frequency; and performing clustering division on the money laundering suspicion gangs according to the determined transaction characteristics and a condensation hierarchical clustering algorithm to obtain a preset number of category sets, each category set comprising a plurality of transaction accounts. The money laundering accounts can be accurately and automatically classified through data analysis, the working efficiency of account classification is improved, and repeated work is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
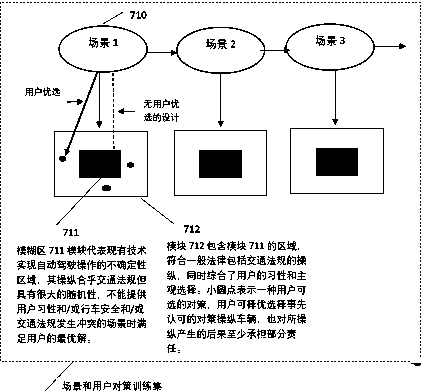
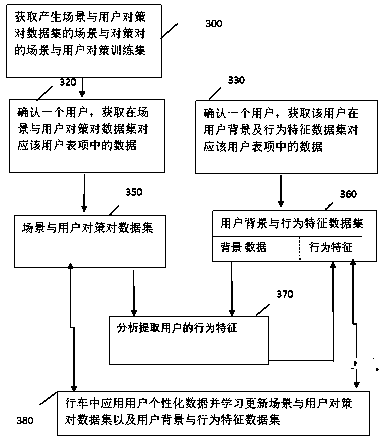
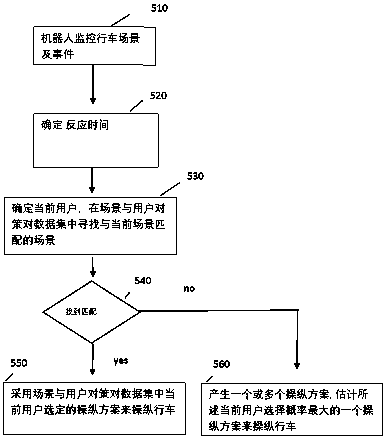
Customized driving method and driving legalization system of autonomous vehicles
The invention relates to a customized driving method and a driving legalization system of autonomous vehicles. The method comprises the following steps that 1) a customized driving database is obtained; 2) before passenger carrying driving of an autonomous vehicle, it is confirmed that one passenger of the vehicle is a present user; 3) customized driving data of the present user in the database isused to aid control driving of the autonomous vehicle. Thus, customized driving habits and / or moral or civil traits of users of the autonomous vehicle are obtained, the habits and / or traits of the users are combined with driving control of the vehicle during design, production and driving of the vehicle, the technical bottlenecks and disputes in production and use of the autonomous vehicle are overcome, and the autonomous vehicle can be marketed more rapidly.
Owner:深圳瑞尔图像技术有限公司
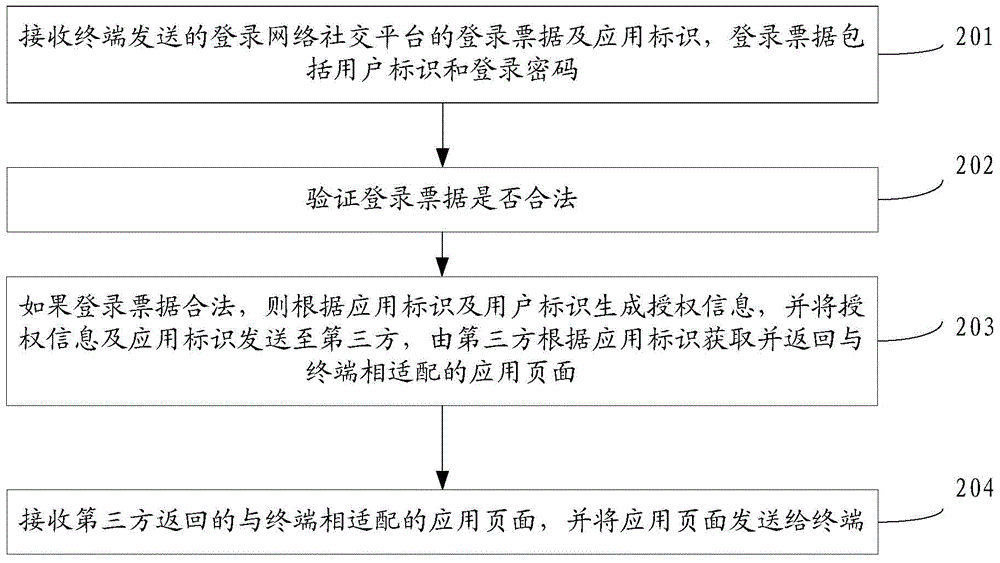
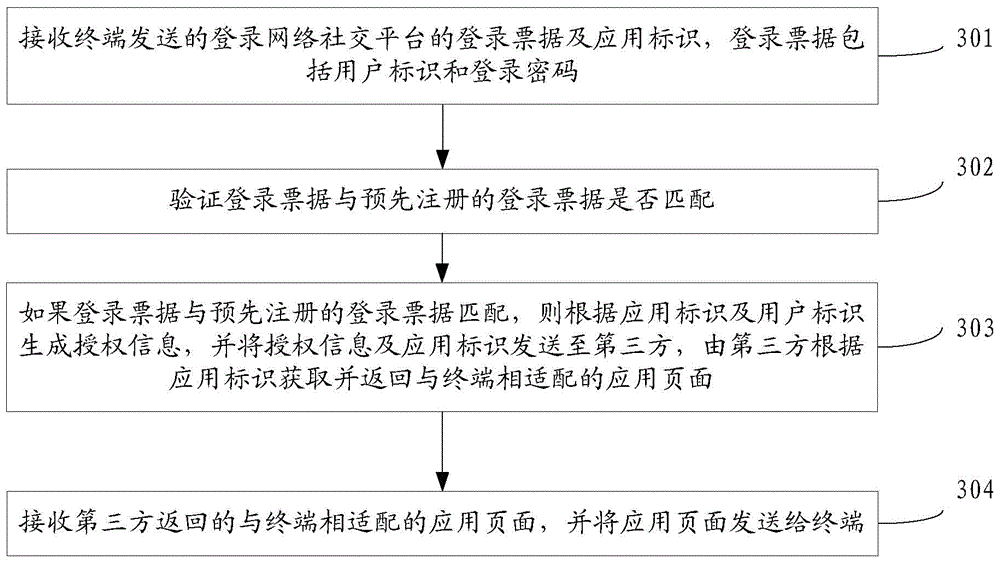
Method and device for acquiring application pages
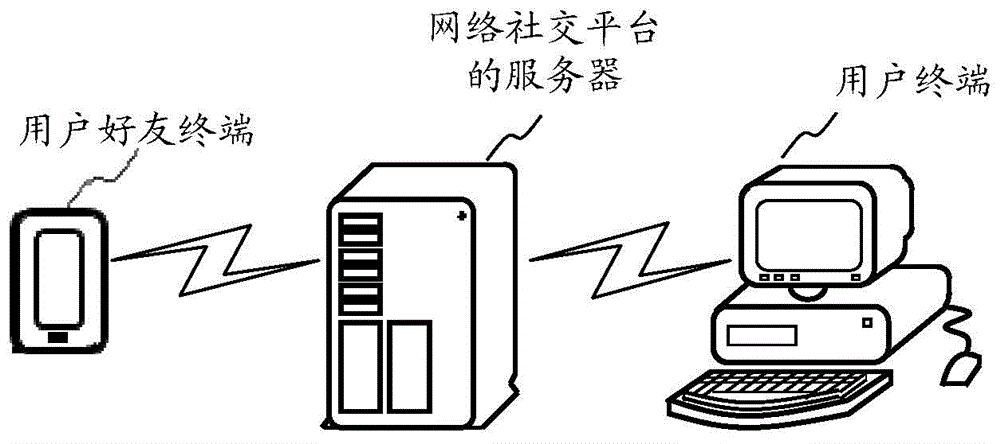
ActiveCN104702650AImprove experienceSimple processUser identity/authority verificationSpecial data processing applicationsThird partyPassword
The invention discloses a method and a device for acquiring application pages, and belongs to the technical field of network application. The method includes receiving network social platform login tickets and application identification; verifying the login tickets to determine whether the login tickets are legal or not; generating authorization information according to the application identification and user identification if the login tickets are legal, transmitting the authorization information and the application identification to a third party, and acquiring and feeding the application pages by the aid of the third party according to the application identification; receiving the application pages matched with a terminal and fed by the third party, and transmitting the application pages to the terminal. The login tickets and the application identification are transmitted by the terminal, and the login tickets comprise the user identification and login passwords. The application pages acquired and fed by the third party are matched with the terminal. The method and the device have the advantages that the authorization information is generated according to the application identification and the user identification after the legalization of the login tickets transmitted by the terminal is verified, the authorization information and the application identification are transmitted to the third party, the application pages are acquired and fed by the third party and are transmitted to the terminal, accordingly, user participation can be omitted in application page acquisition procedures, and the user experience can be improved.
Owner:TENCENT TECH (BEIJING) CO LTD
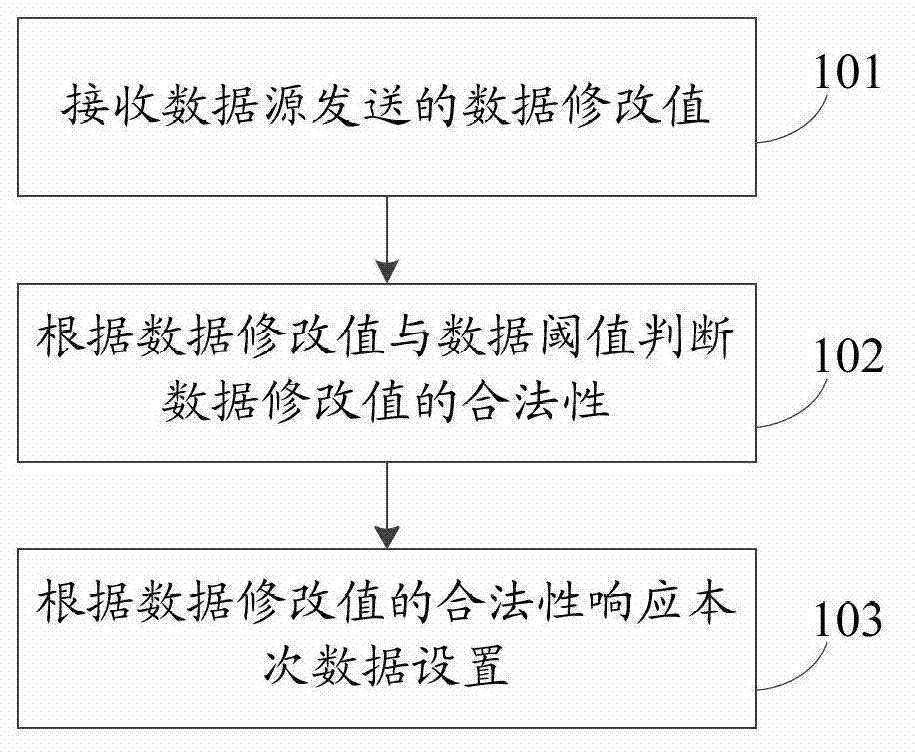
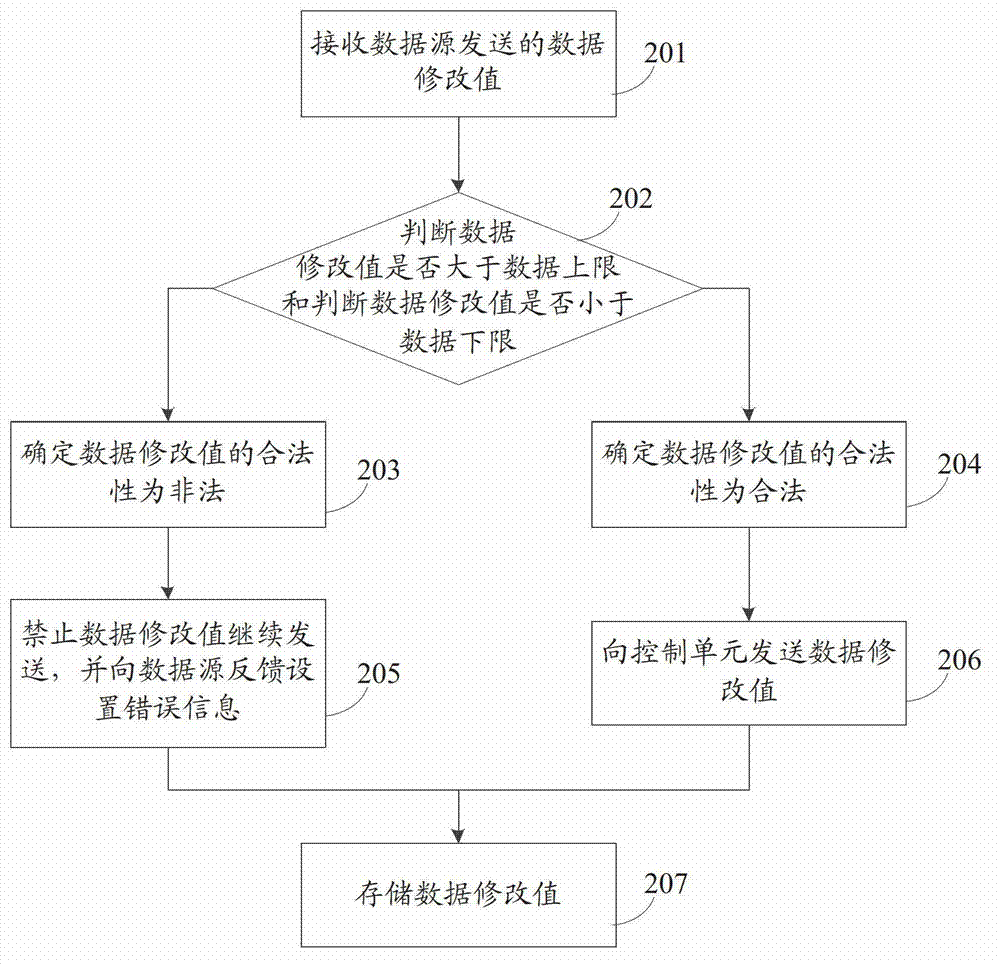
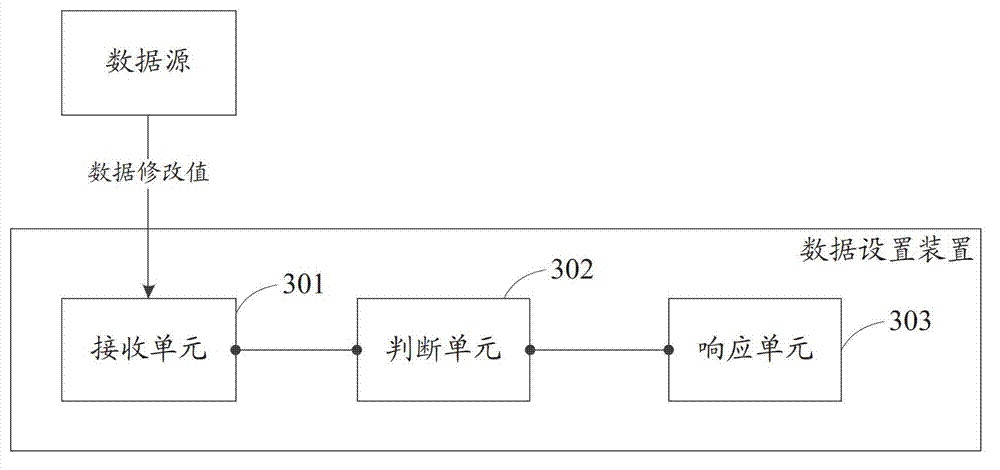
Processing method and device for data setting
InactiveCN102930219ARestriction settings control the behavior of dataEliminate the problem of controlling dataDigital data protectionData setData source
An embodiment of the invention discloses a processing method and device for data setting, and the processing method and device is used for limiting setting of control data. The method includes receiving a data modified value sent by a data source; determining legalization of the data modified value according to the data modified value and a data threshold value which is an extreme value of control data when equipment is in normal operation and can not be modified; and responding the data setting according to legalization of the data modified value. According to the technical scheme, the action that a user sets control data can be limited, so that the problem that the user sets control data of equipment secretly can be solved, and potential safety hazards to the public can be eliminated.
Owner:龚莉雅
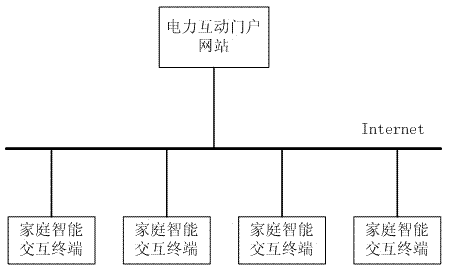
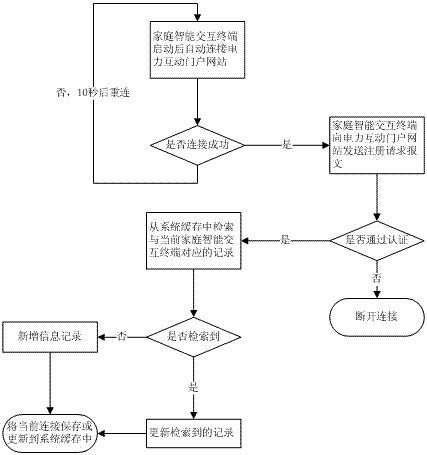
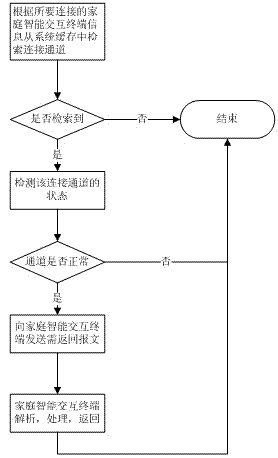
Information interaction method for family intelligent interaction terminal
InactiveCN102821152ARealize online interactionRelieve pressureData switching by path configurationPower utilityWeb site
The invention relates to an information interaction method for a family intelligent interaction terminal. After the family intelligent interaction terminal is started, an electric power interaction portal web site is automatically connected, and in addition, an information approving message is sent for requesting the registration; the electric power interaction portal wet site carries out message analysis and legalization checking, and after the message analysis and the legalization checking are successful, a connecting passage is stored or updated into the system; and when the data on the family intelligent interaction terminal needs to be obtained, the connecting passage is firstly retrieved, then, the data request message is sent, the family intelligent interaction terminal carries out analysis processing on the message, the data message required by the electric power interaction portal web site is returned, and the information interaction is completed. The method provided by the invention has the advantages that the access mode is not limited by the IP (Internet protocol) address length of the IPV4 (Internet protocol version 4); the pressure of the electric power interaction portal web site is greatly reduced through the connecting state maintenance by the family intelligent interaction terminal; and all connections are long connections, and the system resource expenditure for frequency connection building is omitted. The method really realizes the Internet operation of the intelligent family, and great convenience is provided for electric power users and electric power companies.
Owner:XJ ELECTRIC +2
Illegal wireless AP (Access Point) detection method and device
ActiveCN106792715AImprove detection rateReduce security risksSecurity arrangementDetection rateWireless
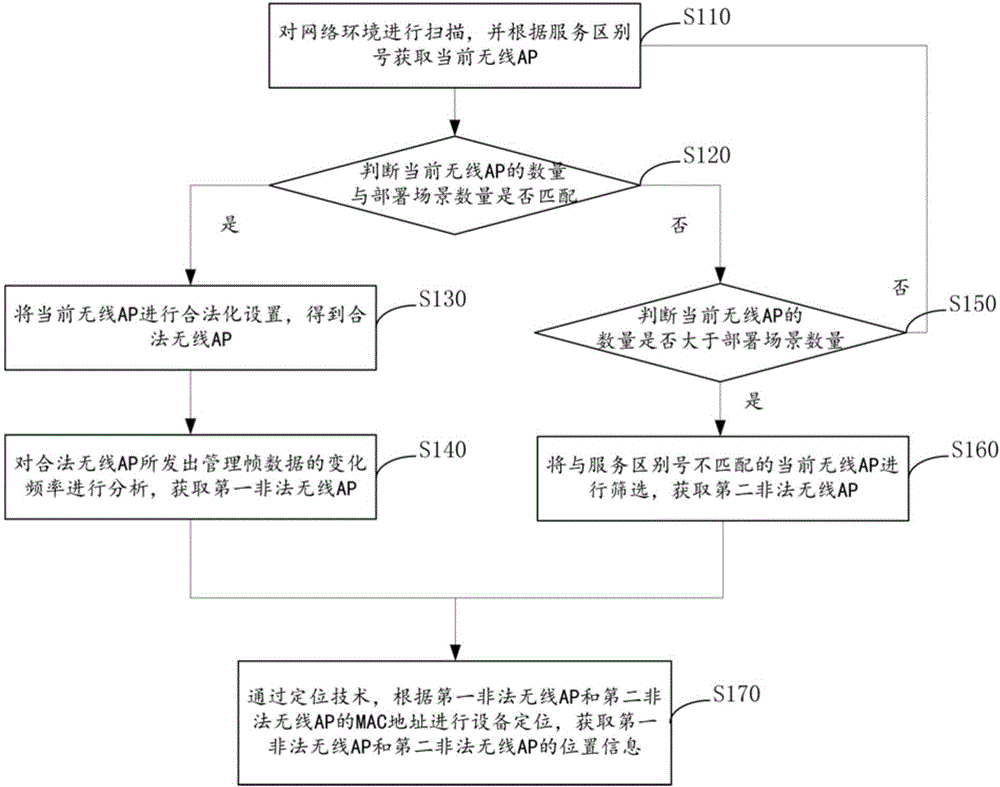
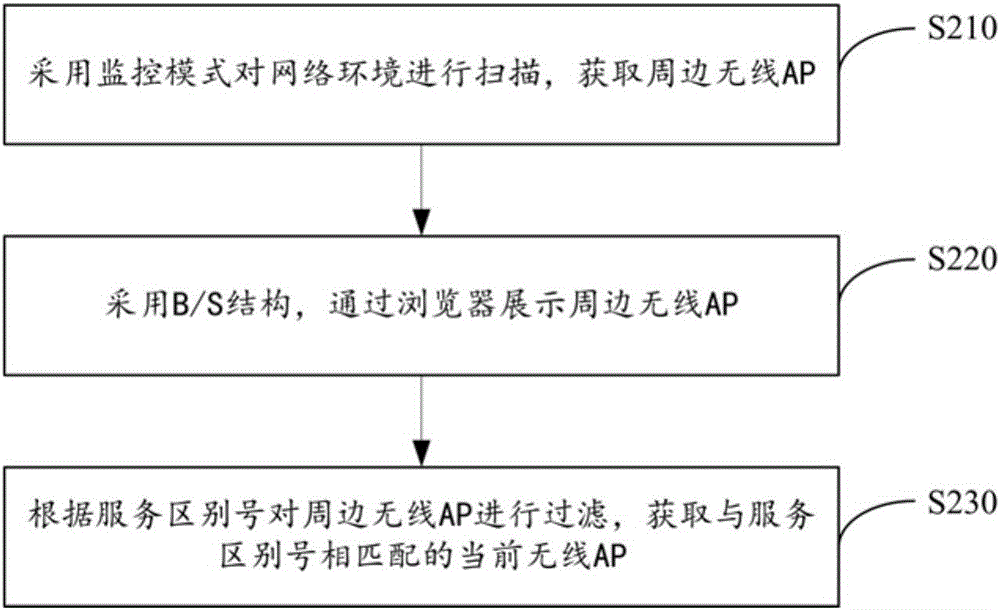
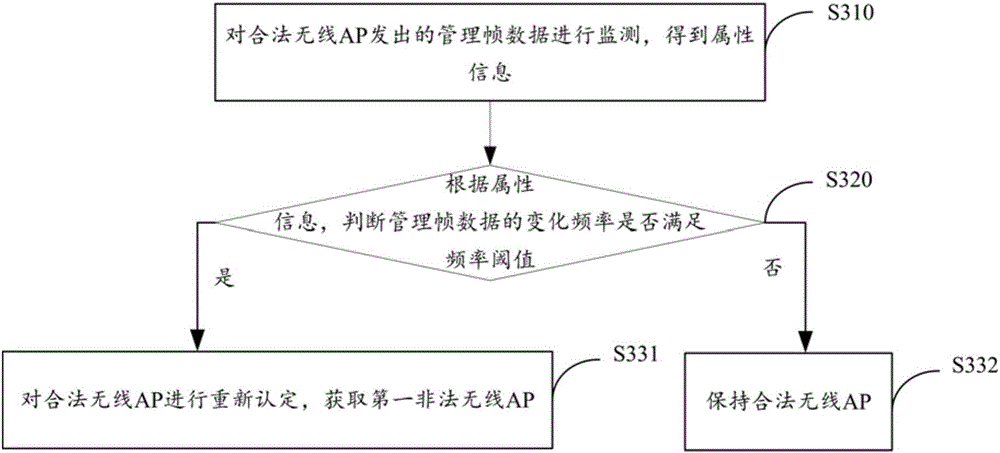
The invention provides an illegal wireless AP (Access Point) detection method and device and relates to the technical field of network safety. The method comprises the following steps: scanning a network environment, acquiring current wireless APs according to service dot marks, judging whether the quantity of the current wireless APs is matched with the quantity of deployment scenarios or not, performing legalized setting on the current wireless APs if the two are matched, thereby obtaining legal wireless APs; analyzing change frequency of management frame data transmitted by the legal wireless APs, acquiring the first illegal wireless AP, and judging whether the quantity of the current wireless APs is more than the quantity of the deployment scenarios if the two are not matched; and screening the current wireless APs which are mismatched with the service dot marks under the condition that the quantity of the current wireless APs is more than the quantity of the deployment scenarios, thereby obtaining the second illegal wireless AP. According to the method and device provided by the invention, the detection rate of the illegal AP can be improved, and the network security risk is reduced.
Owner:杭州亚古科技有限公司
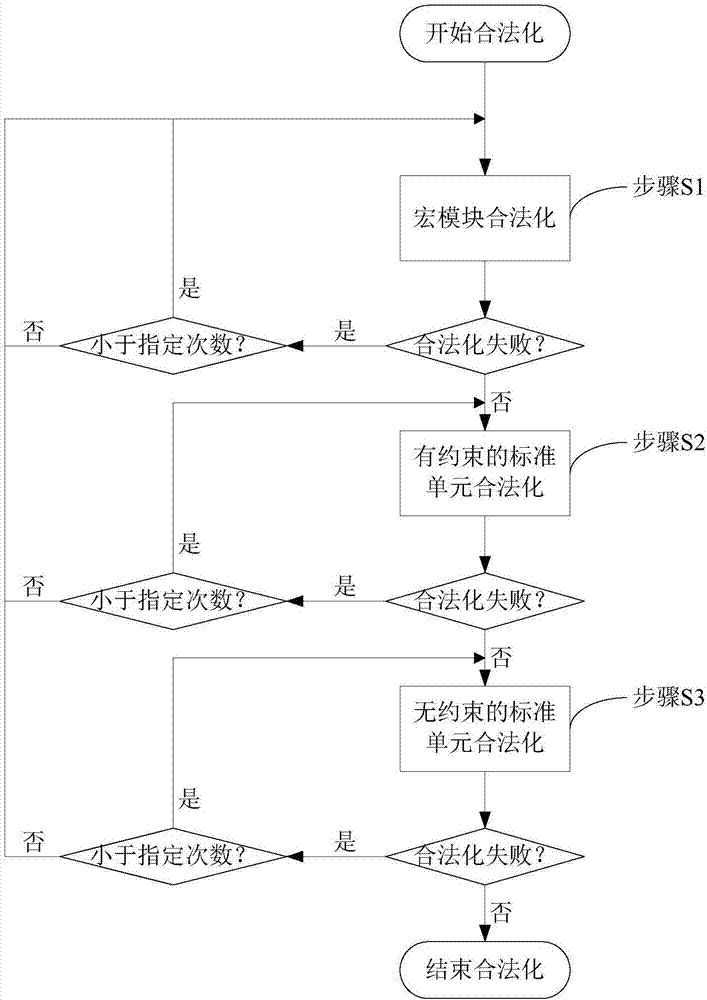
Method for legalizing overall layout of FPGA
ActiveCN107967372AAvoid damageReduce local congestionSpecial data processing applicationsLocal congestionComputer science
A method for legalizing the overall layout of an FPGA comprises the steps that firstly, an integer programming mode and a network flow mode are used for legalization of a macroblock; secondly, a constrained standard unit is legalized in a graded integer programming mode; finally, an unconstrained standard unit is legalized in a graded network flow mode. According to the method, by processing legalization of different types of unit modules with different constraints, legalization operation is conducted through small-range unit moving under the condition that an overall layout result is damagedas little as possible, and the effectiveness of the overall layout is guaranteed; the local congestion degree is reduced, so that damage of legalization to the overall layout is reduced; a legalized frame is very easy to expand through a graded mode, and the layout legalization efficiency is obviously improved.
Owner:SHANGHAI FUDAN MICROELECTRONICS GROUP
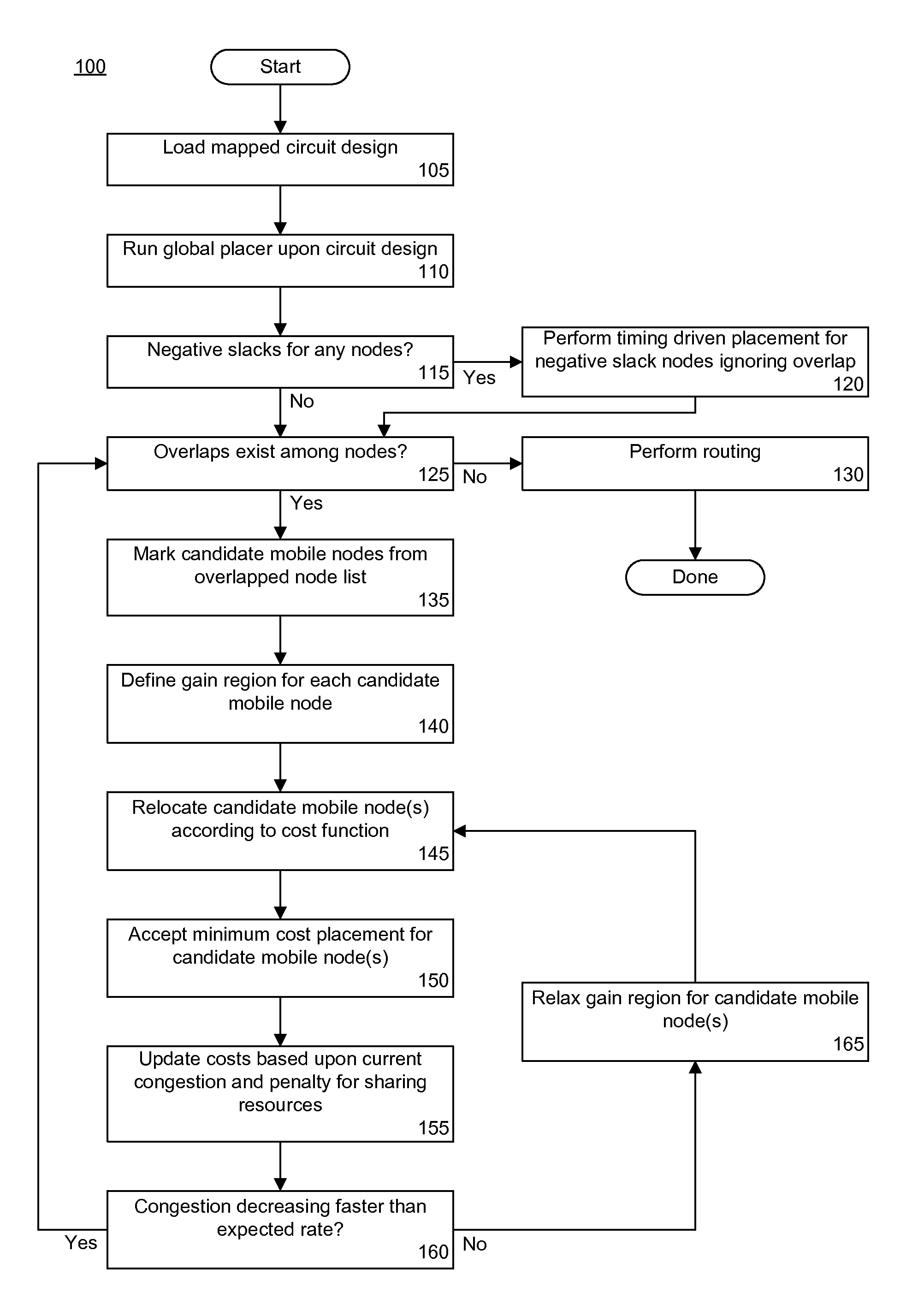
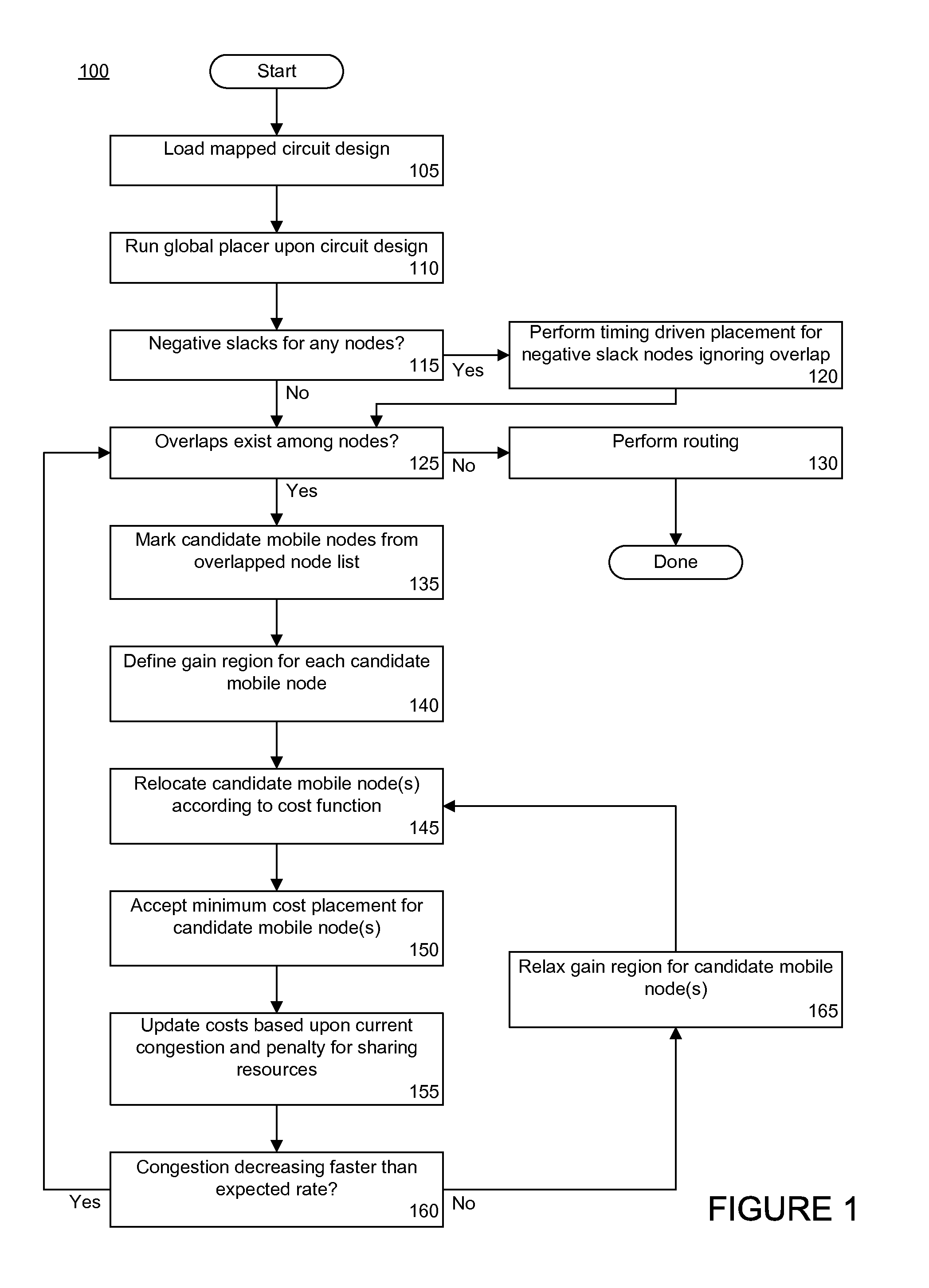
Cost-based performance driven legalization technique for placement in logic designs
A method of placing a circuit design can include selecting one or more candidate mobile nodes from a plurality of overlapped nodes of the circuit design and determining a gain region for each candidate mobile node. The method also can include assigning the candidate mobile node to a site within a gain region according to a cost function. The gain region is associated with the candidate mobile node. The method further can include iteratively selecting and assigning candidate mobile nodes according to a measure of overlap for the circuit design.
Owner:XILINX INC
Mixed height unit legalization method for minimizing average and maximum movements
InactiveCN108804793AQuality assuranceMeet the requirements of convergenceSpecial data processing applicationsMixed integer quadratic programmingMatrix splitting
The invention relates to a mixed height unit legalization method for minimizing average and maximum movements. The method comprises the steps of representing a circuit as a hypergraph model; after directions are set for units, aligning the units to a power supply rail line which is adjacent and correctly matched; preprocessing the multi-line high-standard unit, and by analyzing and reconstructingan objective function and a constraint, planning a mixed height standard unit legalization model as a mixed integer quadratic programming model; converting the mixed integer quadratic programming model into a quadratic programming model; converting the quadratic programming model into a corresponding linear complementary model; solving the linear complementary model by using a matrix splitting iteration method based on modulus; carrying out line redistribution and restoring the multi-line high-standard unit; and legalizing the minimum movement unit by adopting a linear programming-based methodand a Kuhn-Munkres algorithm. According to the method provided by the invention, all the units are optimized at the same time, so that the requirements of a mixed height standard unit legalization stage of current VLSI can be met.
Owner:FUZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com