Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
504 results about "Software protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System for securing protected software from unauthorized use in computer networks
InactiveUS6101606ADigital data processing detailsAnalogue secracy/subscription systemsSoftware protectionAuthorization
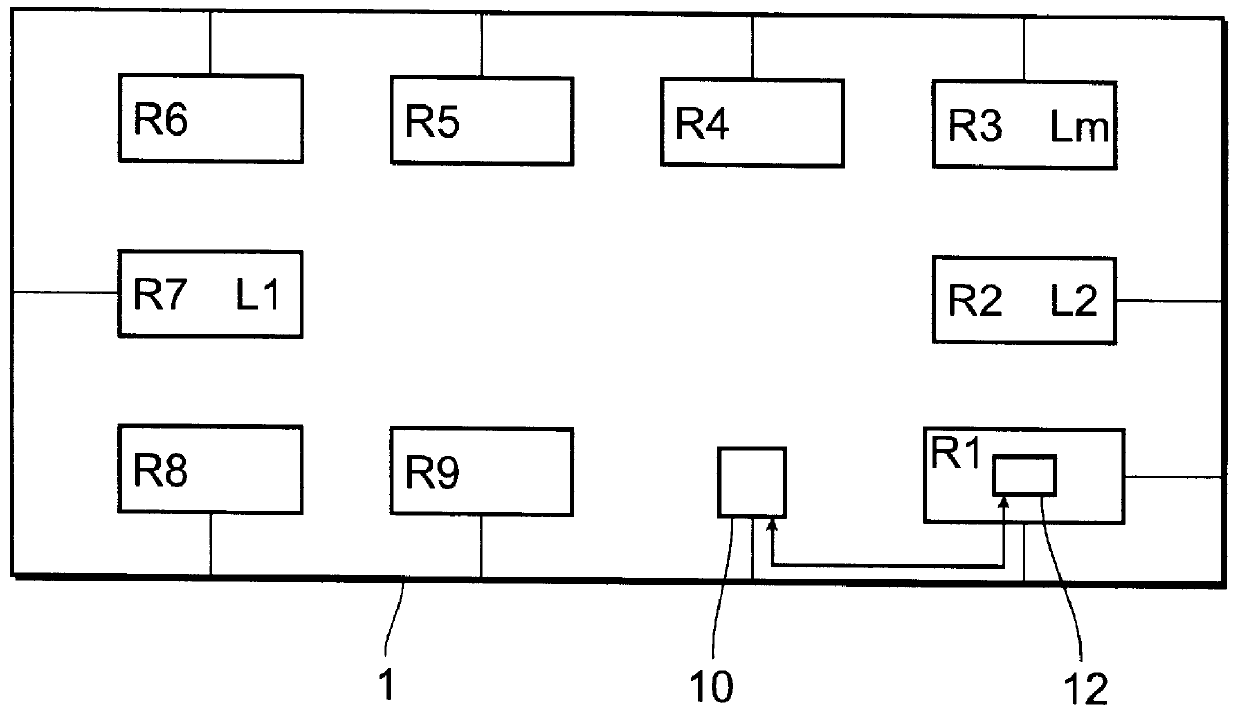
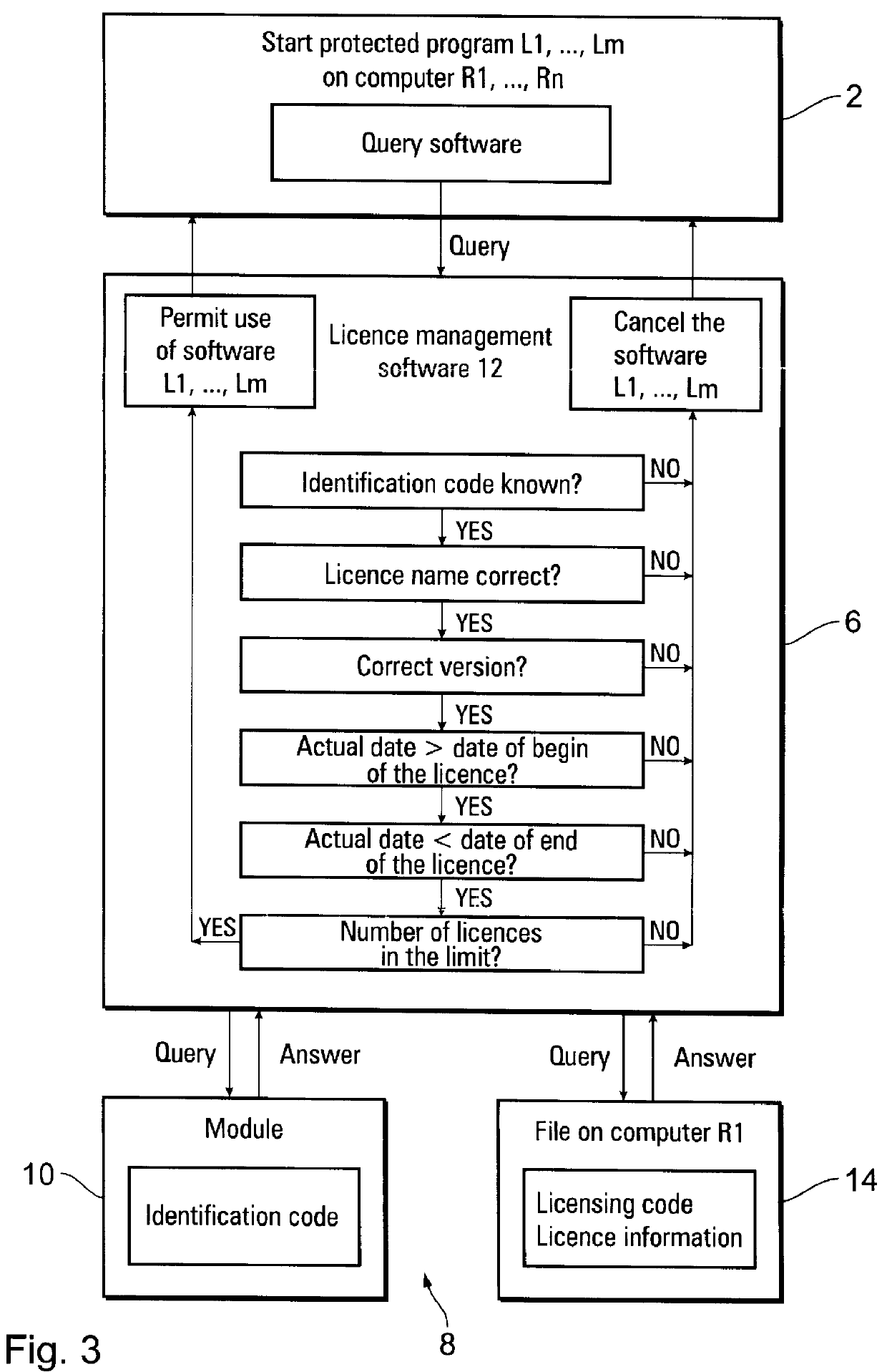
The invention relates to a system for securing protected software against unauthorized, i.e. non-licensed, use in computer networks. The difficulty in licensing of software in a network is that simultaneous and multi-use of the licensed software on several or all computers integrated in the network have to be realized. Without software protection the software producer will lose potential customers. This concerns local networks as well as so-called wide area networks which can be operated across national or continental boundaries. In accordance with the invention the object is accomplished by a system for securing protected software against unauthorized use in computer networks consisting of a query component, a management component and an authorization component whereby the query component communicates with the management component in a bidirectional exchange of information and the management component communicates with the authorization component in a bidirectional exchange of information, wherein the authorization component is a module or licence box having a unique identification code and is separate, independent of any computer in the network and integrable into the computer network in any way.
Owner:WASY GES FUER WASSERWIRTSCHAFT DE
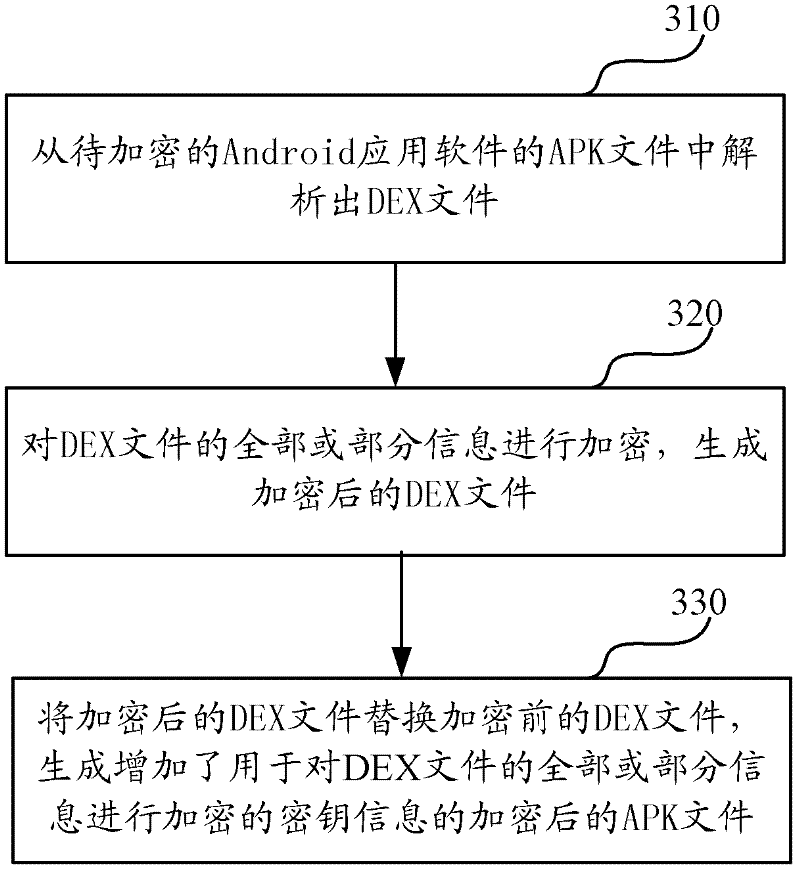
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
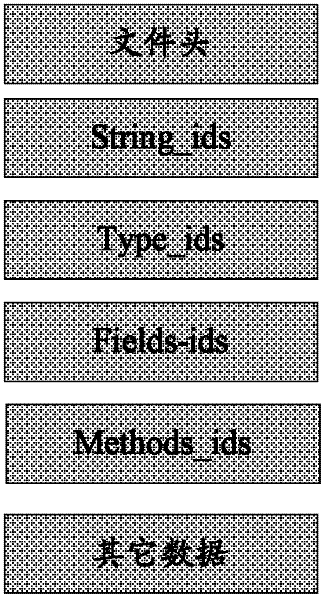
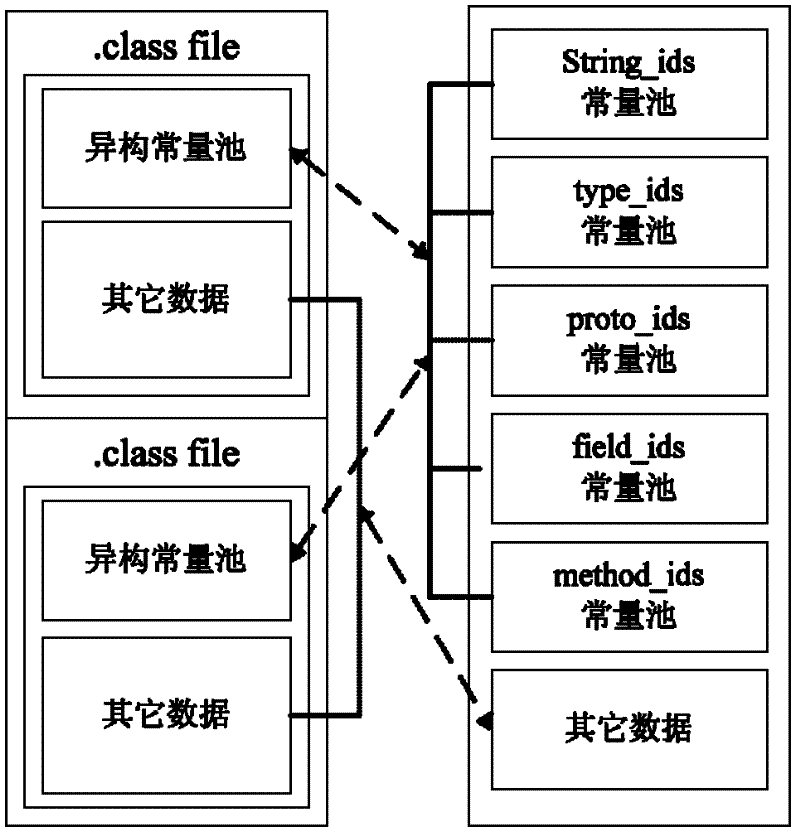
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
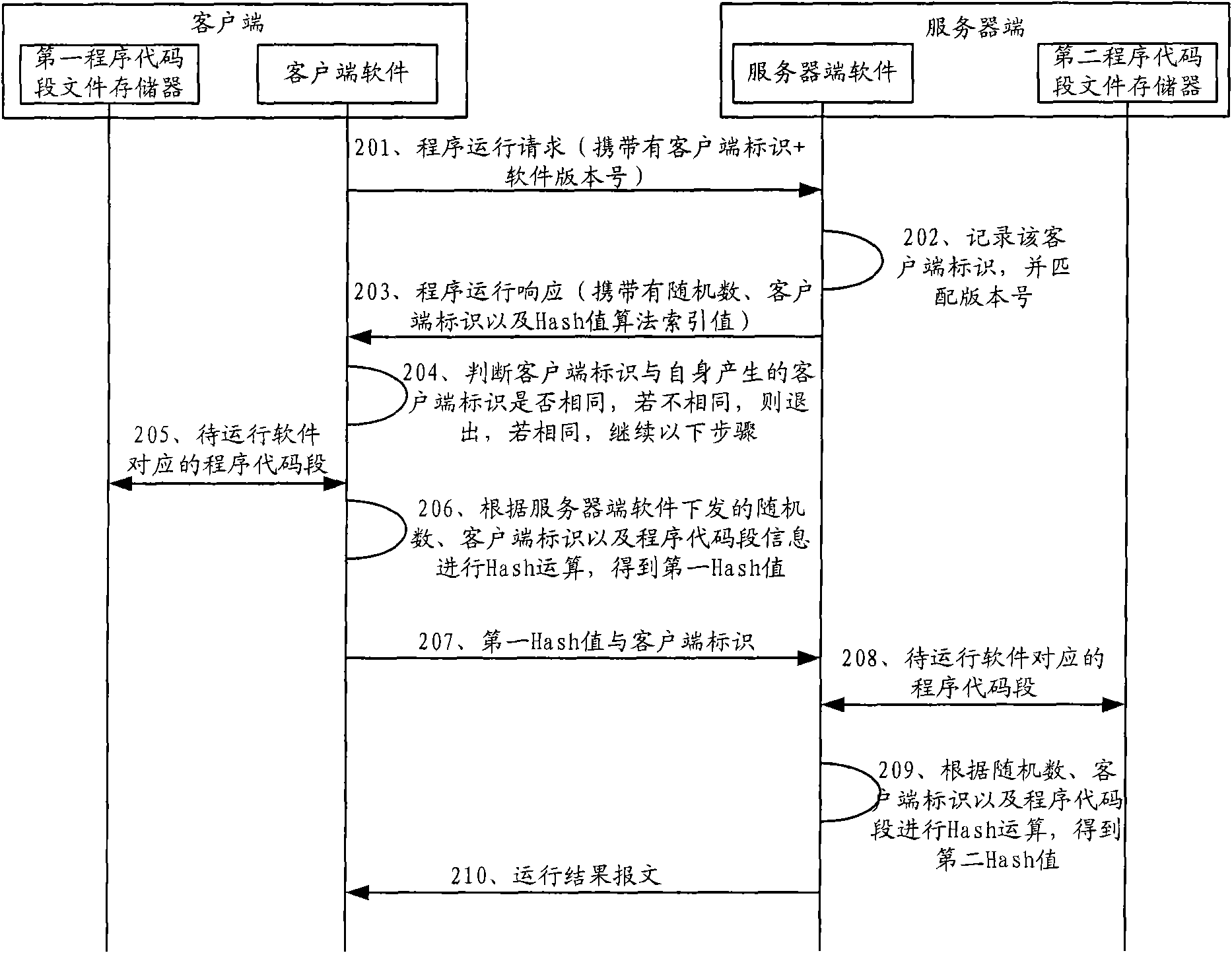
Software protection method based on network, client side and server
ActiveCN101783801AImprove detection effectivenessNot easy to tamper withTransmissionProgram/content distribution protectionClient-sideSoftware protection
The invention discloses a software protection method based on network, a client side and a server, which is used for improving the accuracy and the effectiveness for detecting whether client side software is distorted. The method comprises: a server side receives a program operation request sent by the client side and sends random data to the client side according to the program operation request; the client side adopts a set Hash algorithm to determine a first Hash value according to client side identification, random data and a program code segment which is stored in the client side and corresponds to the edition information of software to be operated; the server side adopts the set Hash algorithm to determine a second Hash value according to client side identification, random data and a program code segment which is stored in the client side and corresponds to the edition information of software to be operated; the first Hash value and the second Hash value are compared to determine whether the client side is permitted to execute the program according to the comparison result. The technical scheme of the invention improves the accuracy and the effectiveness for detecting whether client side software is distorted.
Owner:RUIJIE NETWORKS CO LTD
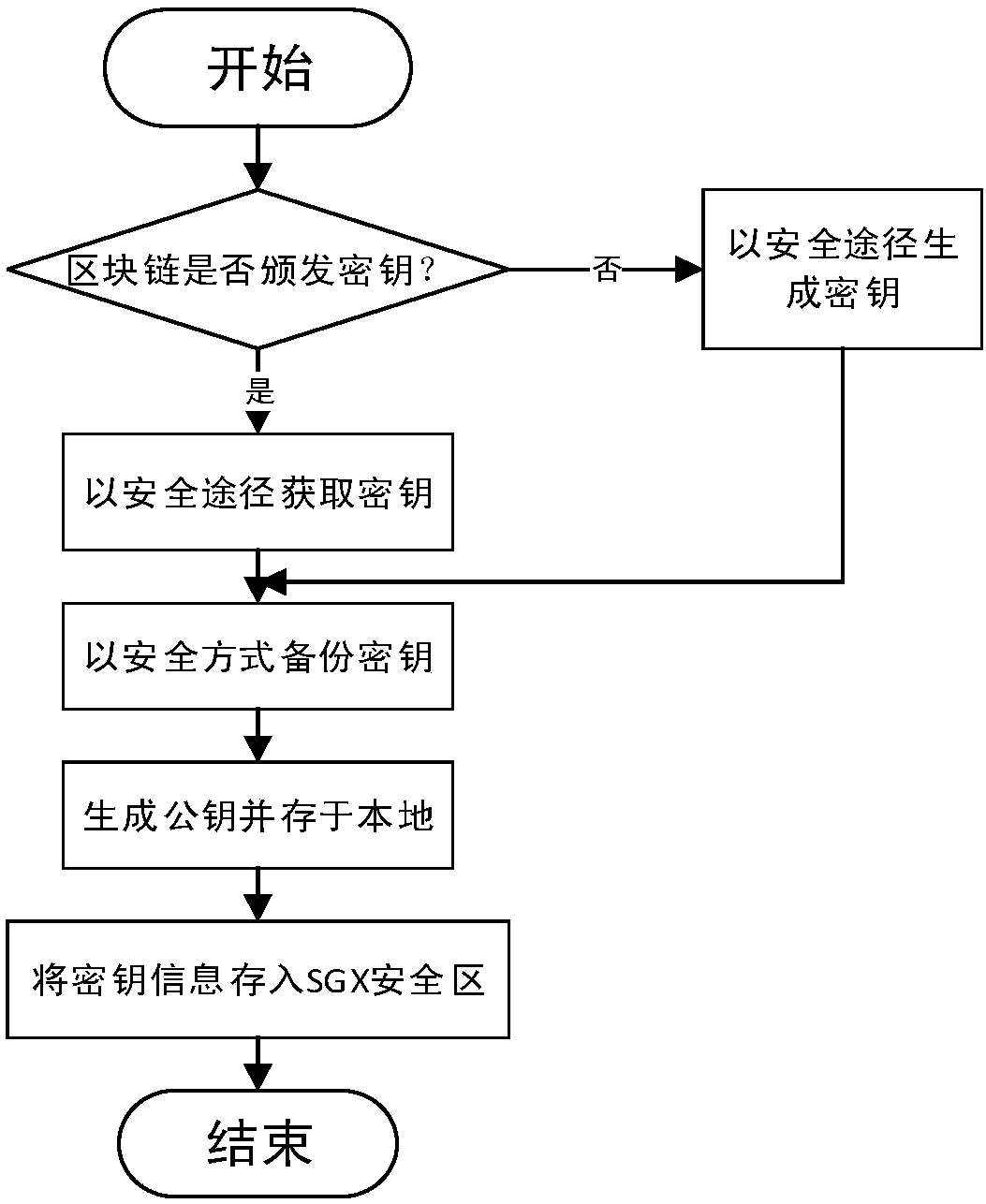
SGX-based secret key protection method and device for blockchain user
ActiveCN107919954AInviolableSafety and securityKey distribution for secure communicationPayment protocolsMalwareSoftware protection
The invention discloses an SGX-based secret key protection device for a blockchain user. The device comprises an SGX encryption module, a transaction common recognition module and a transaction construction module; the SGX encryption module generates a trustable space on the basis of a software protection expanded instruction, and generates an access secret key for verifying the access authority of the trustable space; the trustable space is used to store a user secret key and a secret key operation function of a blockchain network; the transaction common recognition module receives a transaction from the blockchain network, accesses the SGX encryption module via the access secret key, calls the secret key operation function, and realizes verification common-recognition of the transaction;and the transaction construction module initiates the transaction according to intention of the user, accesses the SGX encryption module via the access secret key, calls the secret key operation function, realizes filling and legalization of transaction information, and broadcasts the transaction to the blockchain network. The invention also discloses an SGX-based secret key protection method fora blockchain user. The method can be used to prevent malicious software from sniffing and cracking the local secret key of the user, and blockchain assets of the user are protected against intrusion.
Owner:ZHEJIANG UNIV
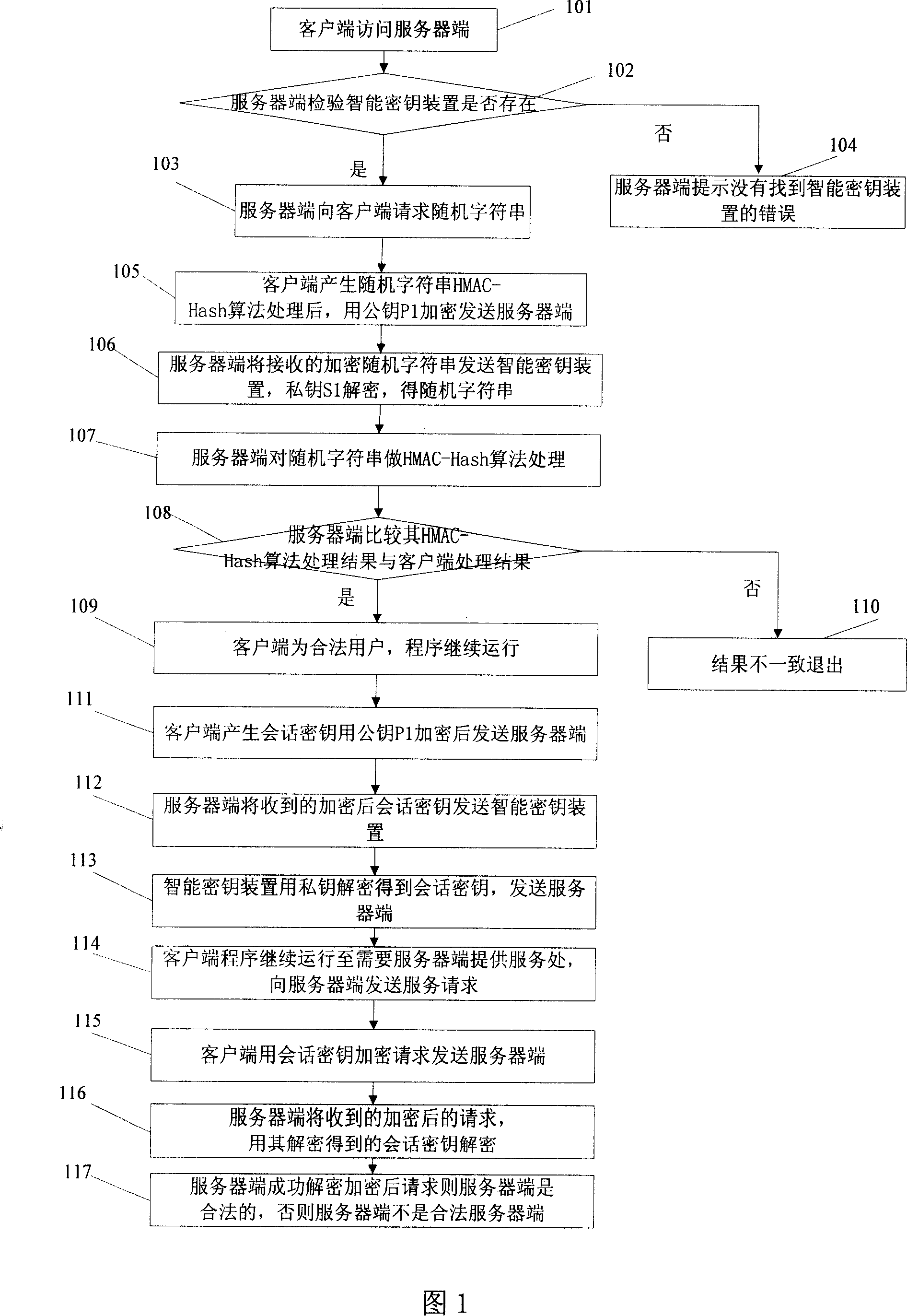
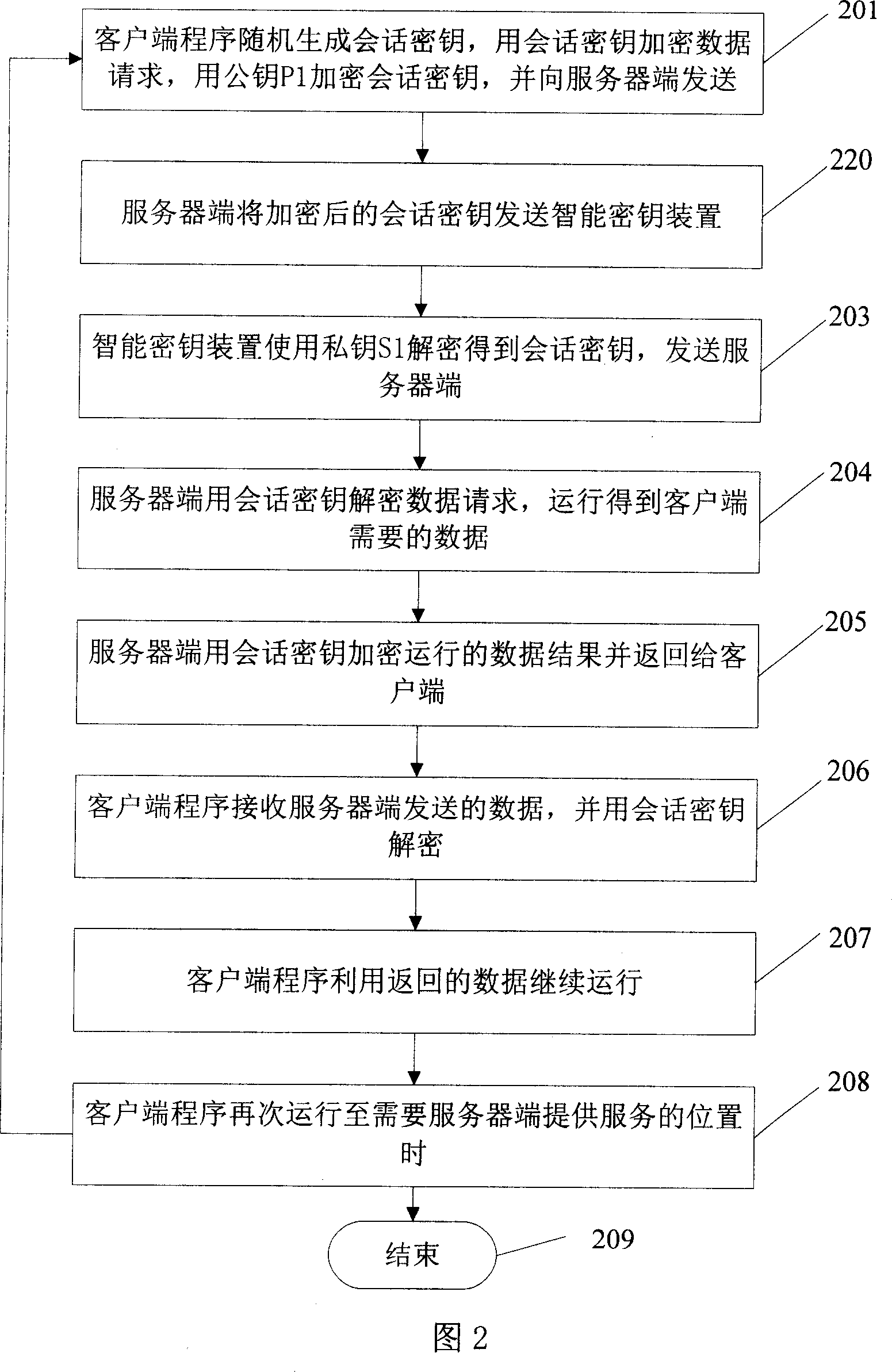
Server and software protection method and system
ActiveCN101005361AImprove securityEnsure safetyUser identity/authority verificationProgram/content distribution protectionNetwork communicationClient-side
The method combines server end with intelligent cipher key device. Network communication is carried out between server end and client end under C / S or B / S structure. ID of client end is authenticated by server end. Program at client end runs and generates session key. Client end sends service request encrypted by session key to server end, and sends session key encrypted by public key. After receiving encrypted service request, server end runs service corresponding to client end, and returns session key encrypted run result to the client end. The server end is bound to the intelligent cipher key device, which is safety carrier capable of preventing interpolating and embezzling internal information. Intelligent cipher key device allows private key used inside equipment. The private key cannot be reproduced and attacked to enhance security of software at server end.
Owner:FEITIAN TECHNOLOGIES
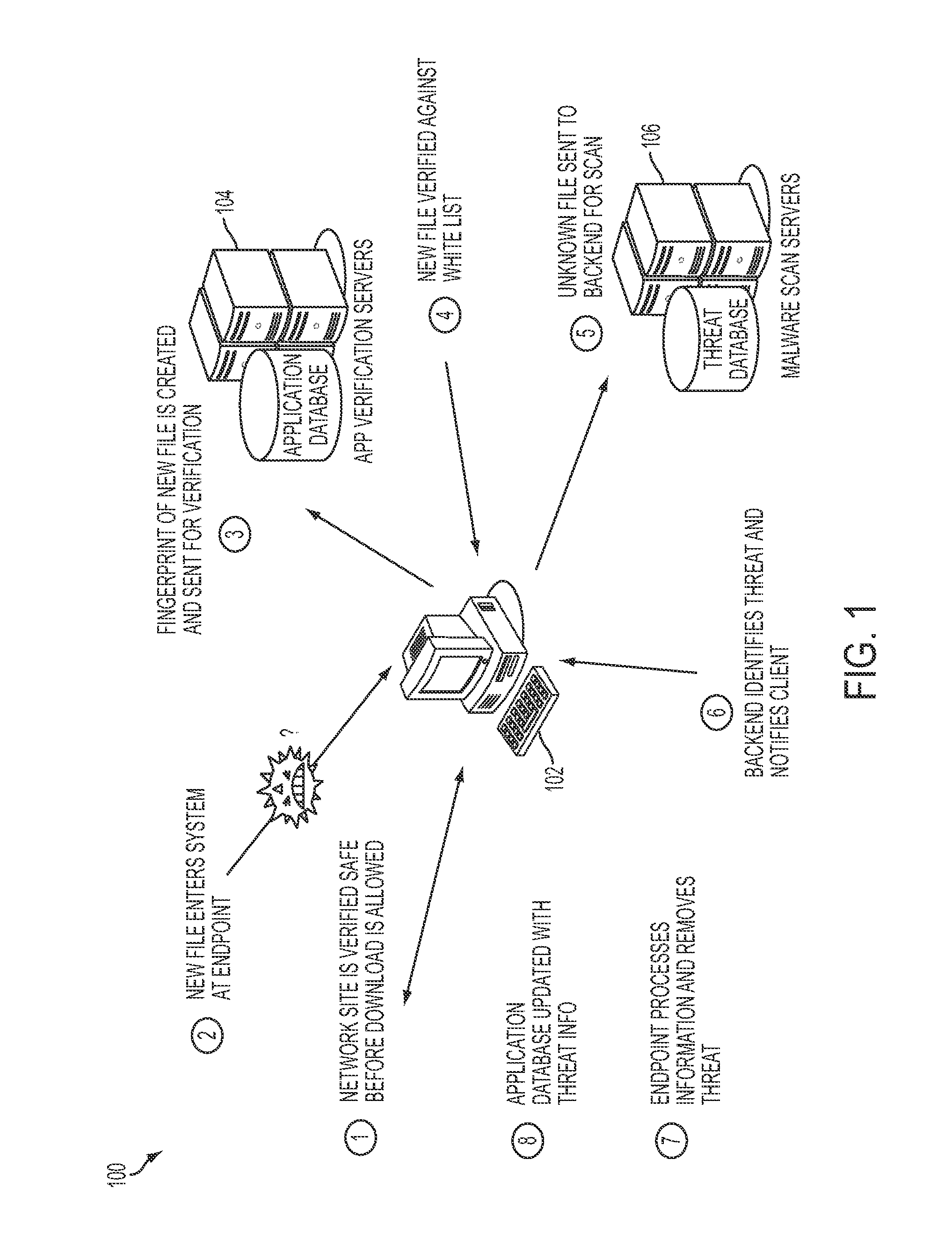
Method and system for protecting endpoints
A malware-protection method and a malware-protection system for protecting a computer from malware infection by preventing infected files from executing on the computer before they can do harm. The malware-protection method employs a number of techniques and relies on multiple layers of protection to identify trusted files, prevent execution of untrustworthy files, accurately detect corrupted files, analyze questionable files, and quarantine files. The malware-protection system includes a client-based verification, detection, blocking, and quarantine application that interacts and coordinates protection methods with application-verification servers, scan servers, definition-update servers, and policy servers to deliver intelligent malware protection as a Software-as-a-Service (SaaS) service. All users of the malware-protection system benefit from the detection of malicious files by any other user. The first time a malicious file is detected by any part of the malware-protection system, all the components of the malware-protection system are immediately protected against the malicious file.
Owner:AVAST SOFTWARE
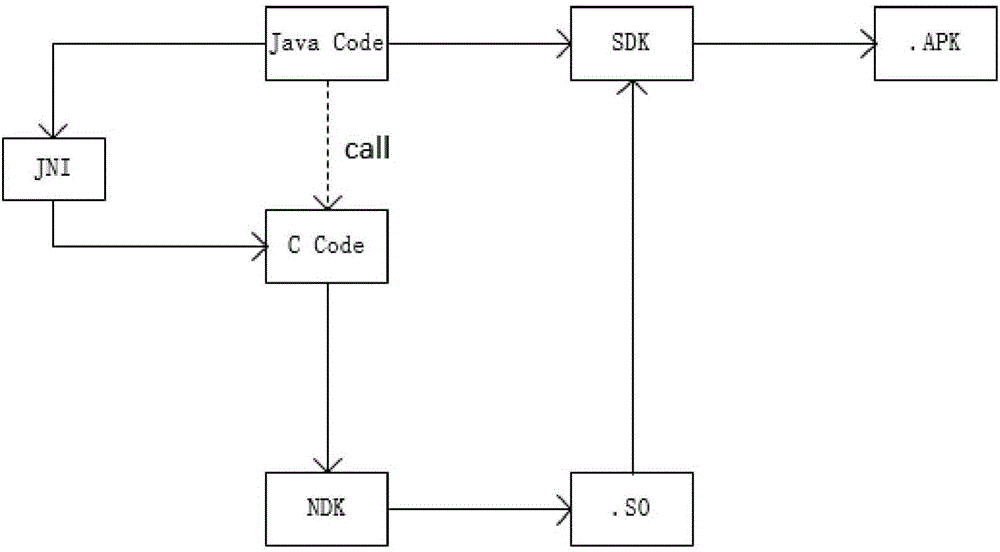
Android application reinforcing method baed on C source code mixing
InactiveCN106326694AImprove reusabilityImprove protectionProgram/content distribution protectionReusabilityC programming language
The invention discloses an Android application reinforcing method based on C source code mixing. The method comprises writing program key codes by using C programming languages and mixing C source codes. The reinforcement of Android application is achieved by mixing the C source codes in the Android application program, and the Android application program codes are protected. The Android application reinforcing method based on C source code mixing specifically includes the steps of writing the key part of the program by using C programming languages, writing programs into .so dynamic-link library file, invoking the dynamic-link library by using JNI technology in Java language, and then mixing the C source codes, so as to achieve the reinforcement of Android application. According to the Android application reinforcing method based on C source code mixing, important codes are saved in the C dynamic-link library by adopting NDK programming, and then the C source codes are mixed, the software protection is improved. At the same time, the important codes are written in a so library, the reusability of the codes are increased, ready-made so library can be directly introduced into other applications, so as to eliminate the troubles of secondary development.
Owner:北京鼎源科技有限公司
Protecting method and protecting system for authentication server software copyright
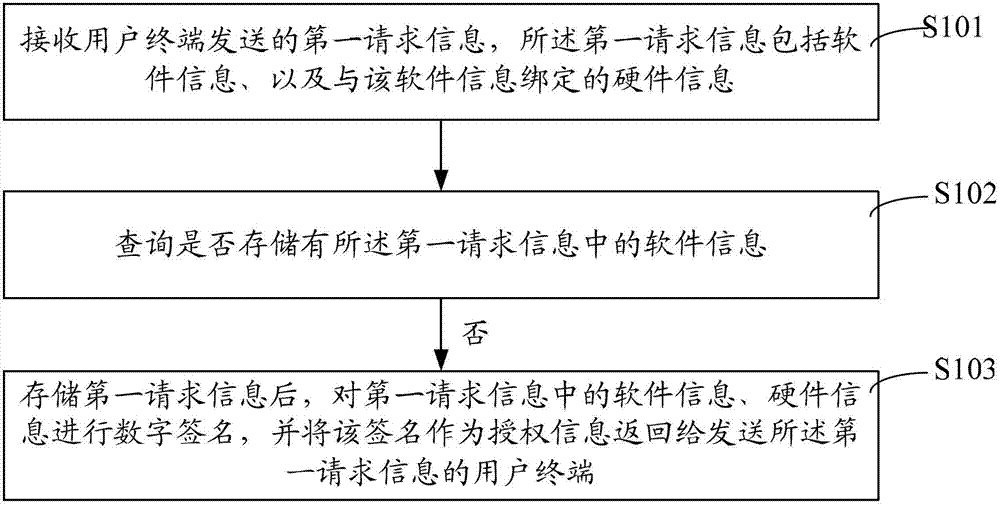
ActiveCN102780699AProtect intellectual propertyEasy to installUser identity/authority verificationComputer security arrangementsIntellectual propertyDigital signature
The invention discloses a protecting method and a protecting system for authentication server software copyright. The protecting method includes authorization request. The authorization request includes the steps that first request information sent by a user terminal is received, and the first request information comprises software information and hardware information bound with the software information; whether the software information in the first request information is stored is queried; and if the software information in the first request information is not stored, after the first request information is stored, a digital signature is conducted on the software information and the hardware information in the first request information, and the signature is used as authorization information and sent to the user terminal of the first request information. By combining the software information and the hardware information, authentication server software can only be installed and operated on legal hardware and can not be operated on other hardware, and therefore intellectual property of vast authorization server software developers is completely protected. Numerous modules are not required to be installed on a client terminal due to an online software protecting method, and therefore installing, deployment and maintaining are easy.
Owner:GCI SCI & TECH
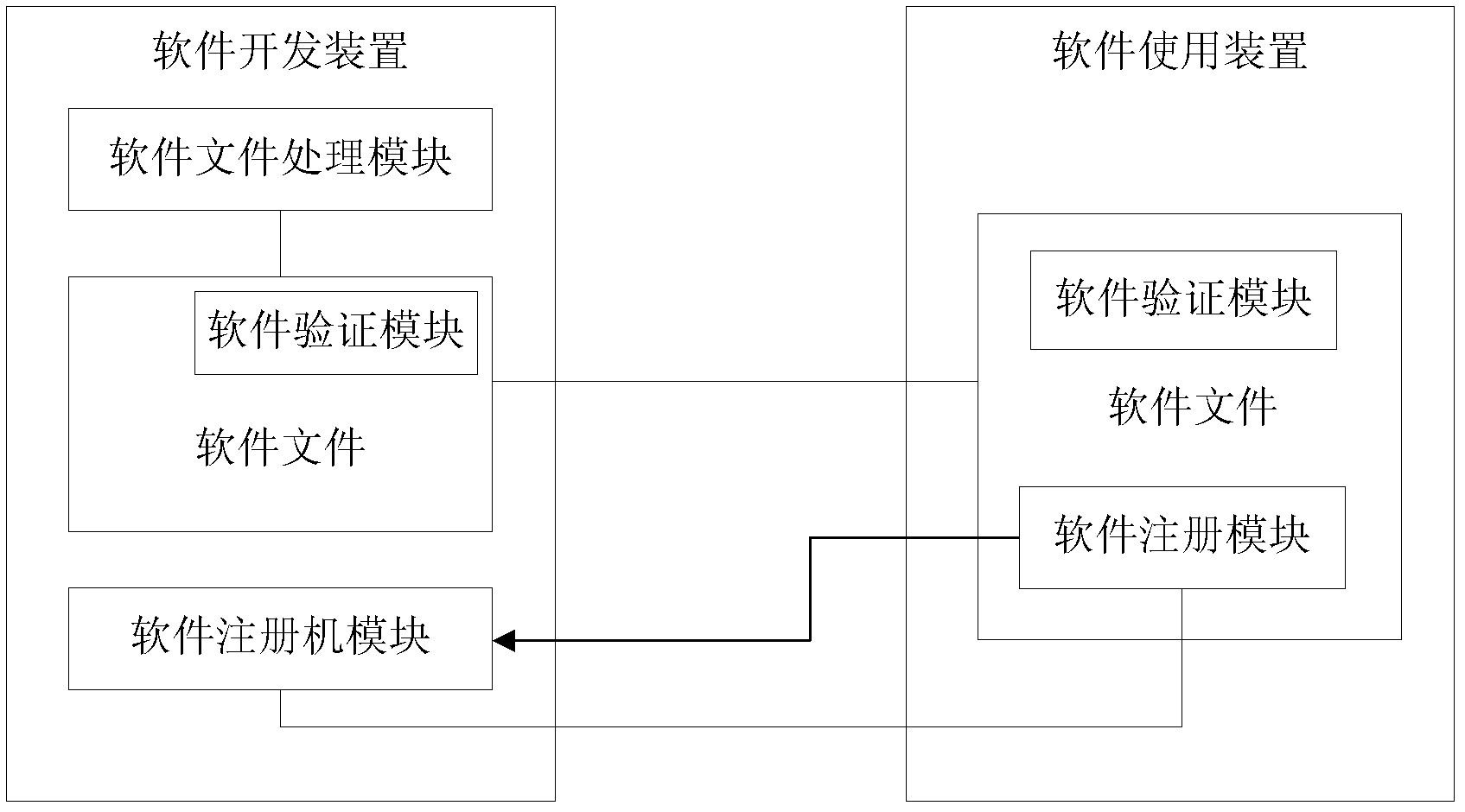
System and method for realizing software protection
ActiveCN102314578AProtect interestsAvoid using effectsProgram/content distribution protectionDigital signatureComputer module
The invention provides a system and a method for realizing software protection, wherein the system comprises a software development device and a software application device; the software development device is used for implanting a software verification module into developed software and for writing a digital signature which is generated aiming at the content of a program file in the developed program file; and the software application device is used for carrying out authorization verification on the software through the implanted software verification module when the software is started to run by a user. With the adoption of the system and the method for realizing the software protection provided by the invention, the software can be greatly protected so as to prevent unauthorized users from using and unlocking the software, so that the benefit of software developers is greatly protected, and the software industry of China develops towards the healthy direction.
Owner:广西浪潮云计算服务有限公司
Security control methods for date transmission process of software protection device and device thereof
ActiveCN101008972AProtection securityIncrease the difficulty of decipheringComputer security arrangementsSecuring communicationInterference (communication)Software engineering
This invention relates to one software protection device data transmission process safety control method, which comprises the following steps: sending the data between computer and software protection device by code form to make the whole process data without clear data in the communication circuit; due to random interference type and coding process of data, it makes each same order sent from protection software into software protection device and the feedback order from software protection device is variable.
Owner:FEITIAN TECHNOLOGIES
System and Method for Software Protection and Secure Software Distribution
ActiveUS20100262824A1Improve securityDigital data processing detailsUser identity/authority verificationComputer hardwareSoftware distribution
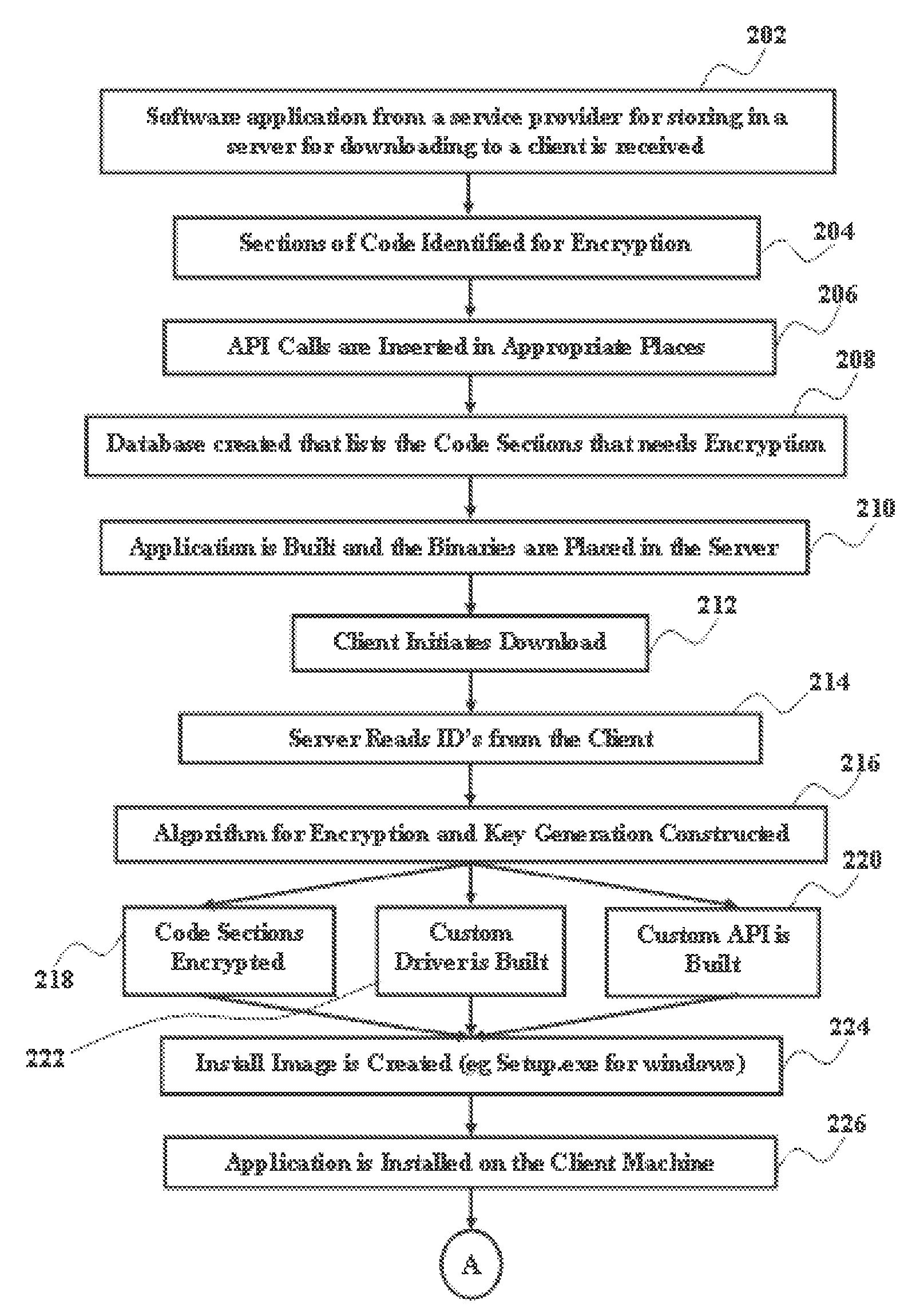
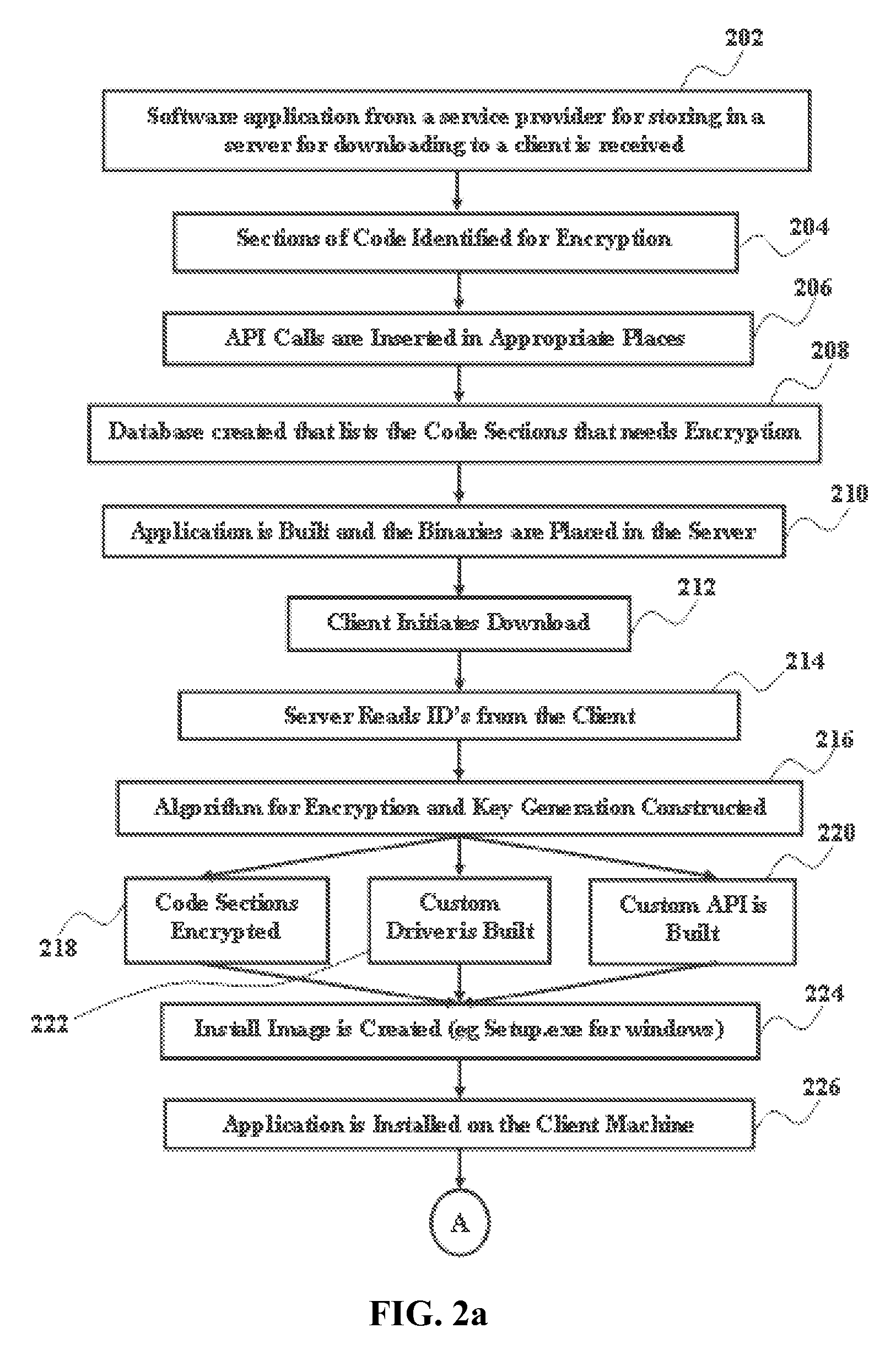
The various embodiments of the present invention provide a secure software distribution and execution method. According to the method, a server receives software from service provider for downloading to a client and identifies the sections for encoding. APIs are inserted in the identified sections. A unique ID is created based on the identity of the each client to generate an encryption algorithm, decryption key and decryption algorithm. The identified sections are encrypted with the generated encryption algorithm. The encrypted application along with encryption algorithm, decryption key and decryption algorithm are downloaded to the driver of the client machine. The API makes call to the driver by sending the encrypted segment when the encrypted portion is reached during the execution of software in the client machine so that the driver decrypts the encoded portion using the received key and the decryption algorithm to enable the continuous execution of the downloaded software.
Owner:AVENTYN
Software protection method based on intermediate result compiling
ActiveCN104091100APrevent illegal crackingAvoid analysisProgram/content distribution protectionSoftware engineeringConfusion
The invention discloses a software protection method based on intermediate result compiling. The software protection method includes the following steps (1), software source codes are compiled to obtain an original object file (OBJ); (2), the original OBJ is analyzed to obtain partitioned data aiming at the original OBJ; (3), the analysis result of the step (2) is preprocessed; (4), system function call is concealed, redundant functions are inserted, and global character strings used for a system are encrypted; (5), deformation is performed for a common instruction; (6), the scattered data obtained through processing in the processes are recombined to form the OBJ, and then an executable file is generated through link of a linker. Confusion and protection at the instruction level for the OBJ are achieved, errors can be avoided, the confusion effect and the confusion quality are improved, and software is prevented from being illegally cracked or analyzed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
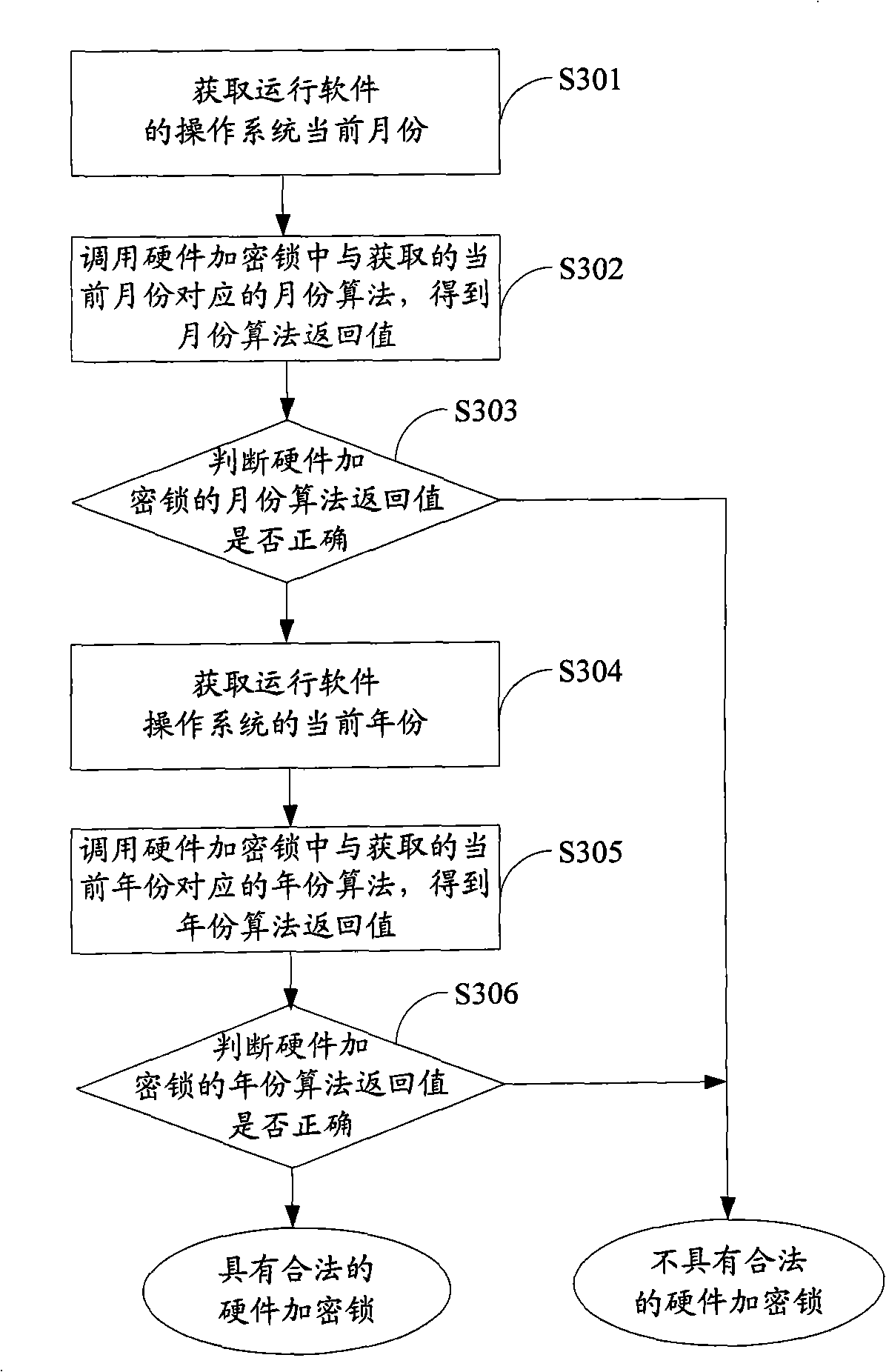
Software protection method, apparatus and equipment
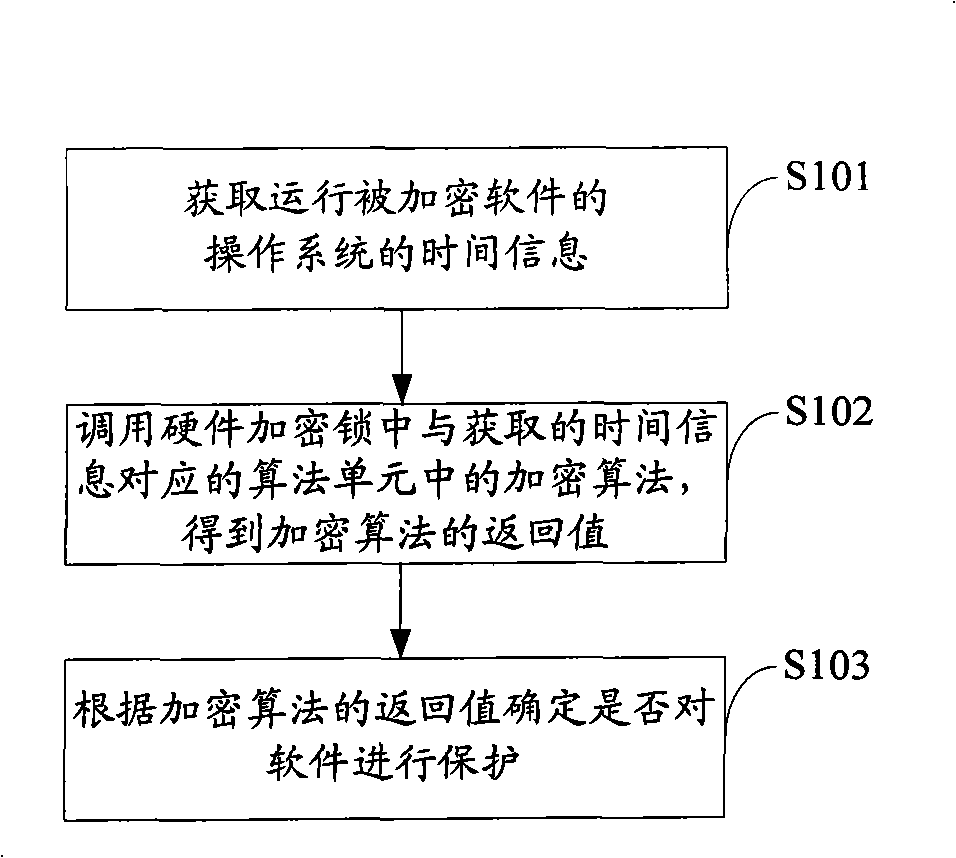
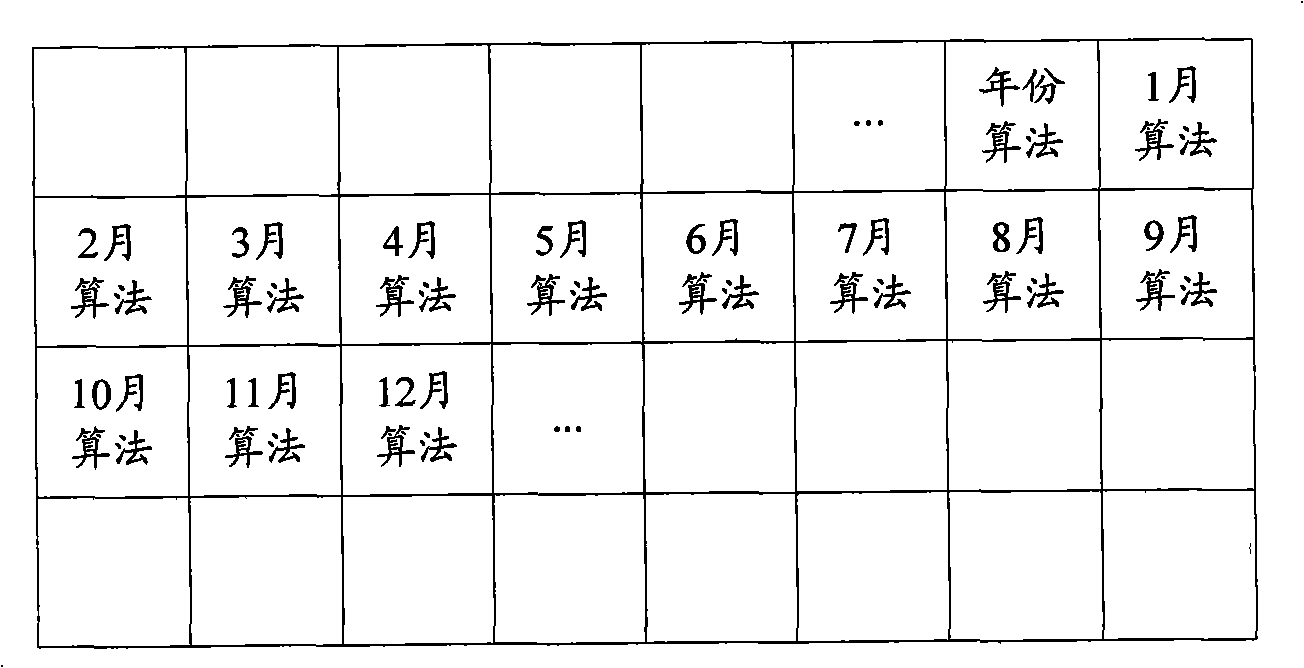
ActiveCN101404056AAchieve protectionReduce the risk of eavesdroppingPlatform integrity maintainanceProgram/content distribution protectionTemporal informationComputer hardware
The invention is applicable to the communication safety field and provides a software protection method, a device and equipment. The method comprises the following steps: current time information of an operation system which operates an encrypted software is obtained; an encryption algorithm in an algorithm unit which is corresponding to the obtained current time information is called from a hardware encryption lock, thereby obtaining a return value of the encryption algorithm; whether a software is protected or not is judged according to the return value of the encryption algorithm. The embodiment of the invention realizes the protection of the software and reduces the risk that communication information between the encrypted software and the hardware encryption lock is eavesdropped effectively by obtaining the time information of the operation system and calling the encryption algorithm which is corresponding to the time information from the hardware encryption lock.
Owner:KINGDEE SOFTWARE(CHINA) CO LTD
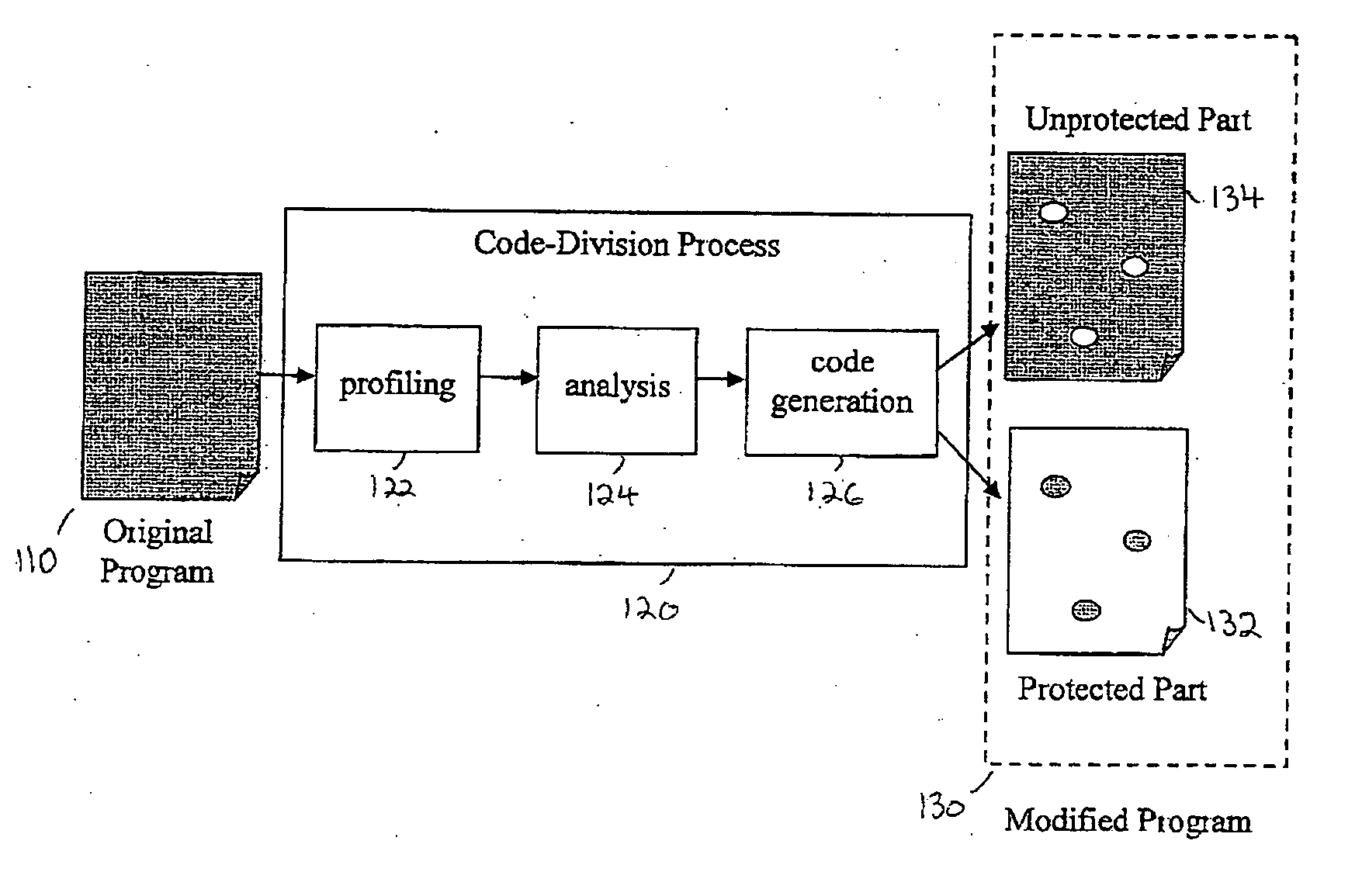
System and method of controlling and monitoring computer program usage
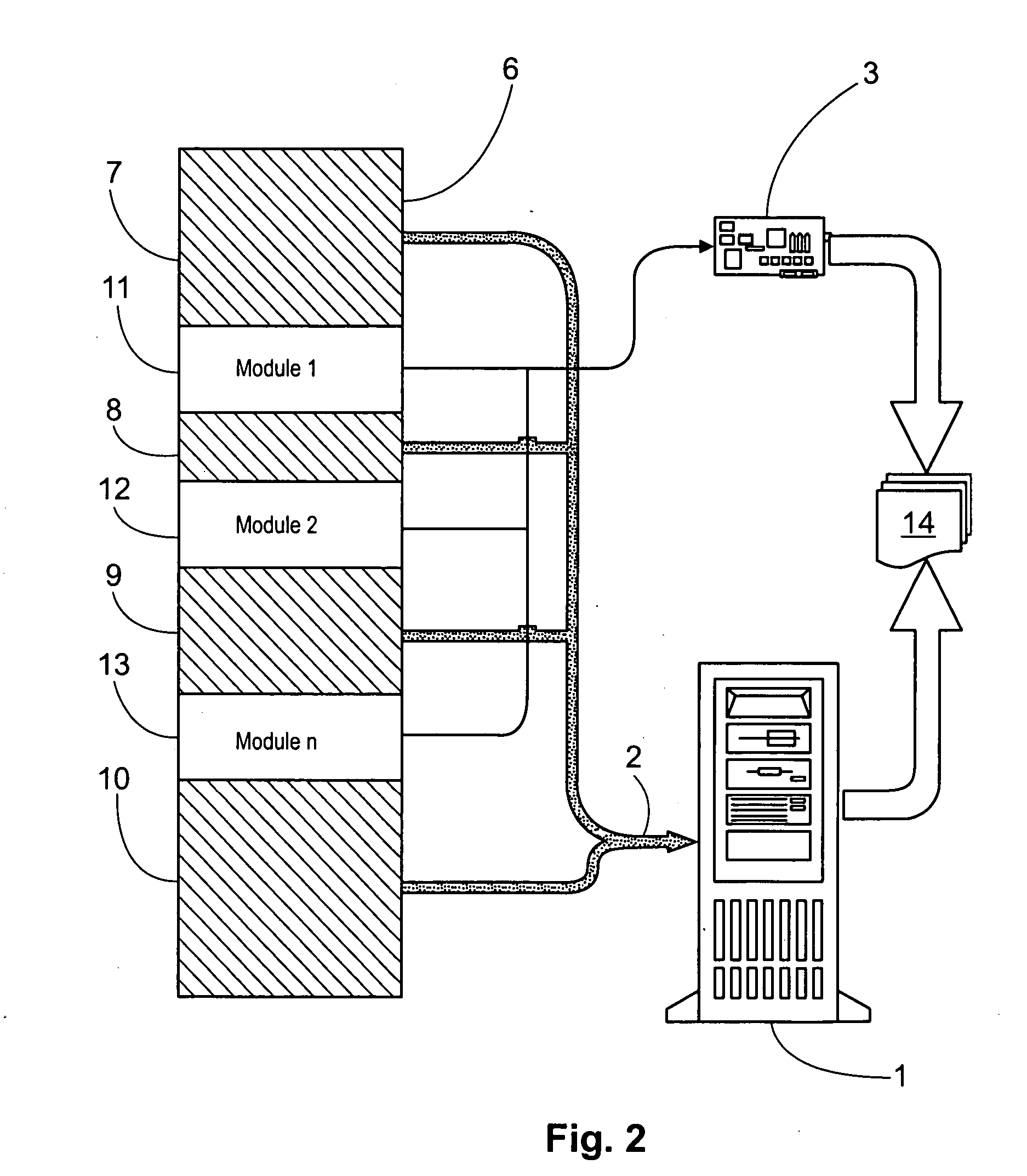
InactiveUS20060259981A1Complicate reverse engineering taskEffort is complicatedDigital data processing detailsUser identity/authority verificationResource consumptionParallel computing
Embodiments of the present invention include a method of modifying a computer program to control and monitor usage, e.g., for software protection, by dividing the computer program code into protected and unprotected parts. According to some demonstrative embodiments of the invention, the protected part of the divided program may include logical operations and computations that influence resource-releasing instructions relating to resources used by the unprotected part of the program. The divided program may be indistinguishable to a user from the original version in terms of execution performance. Embodiments of the present invention include a method of profiling a computer program to collect statistics regarding resource consumption and related operations; analyzing the statistics to identify suitable operations; and generating code for a divided version of the computer program. Other features are described and claimed.
Owner:APPROTECT
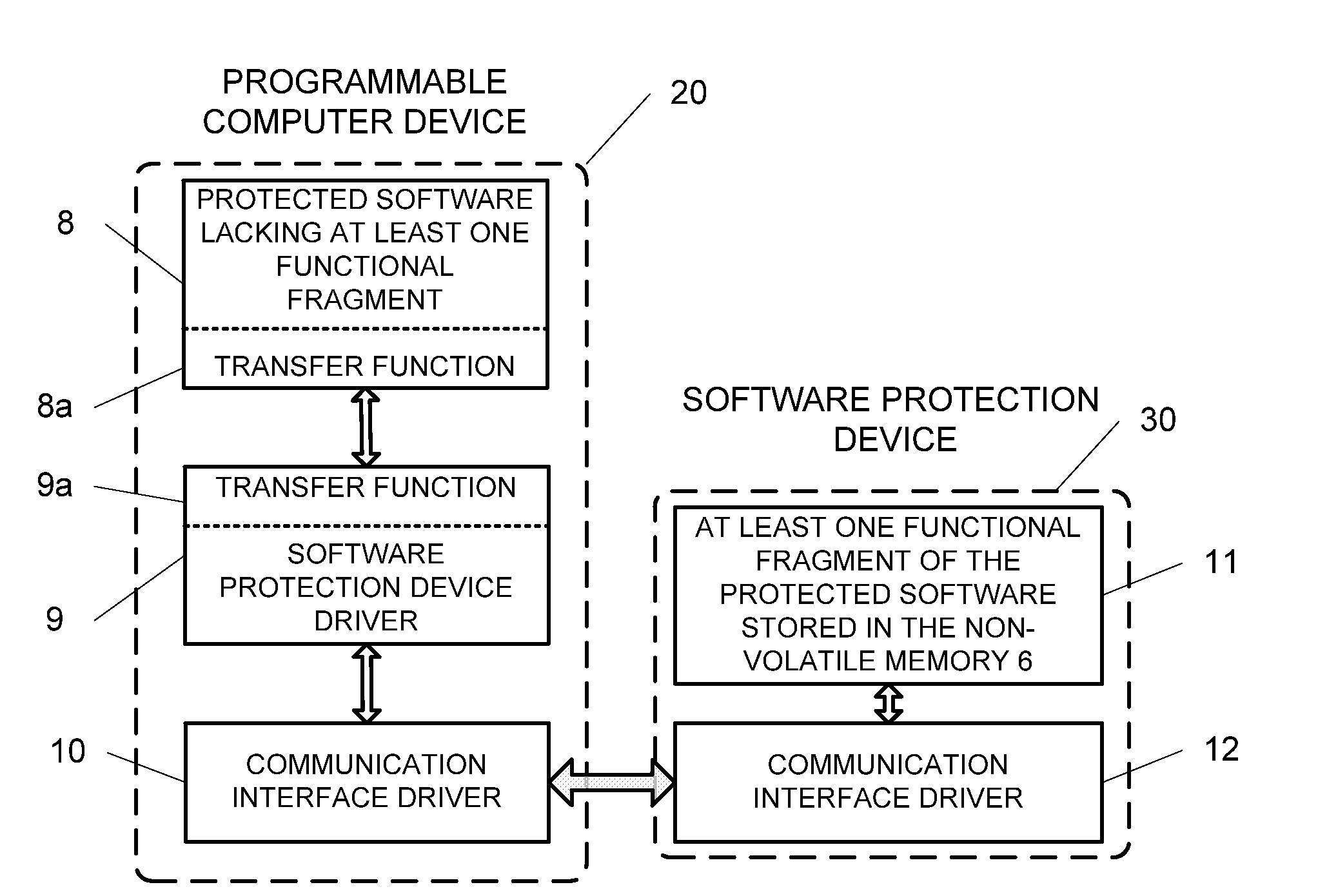
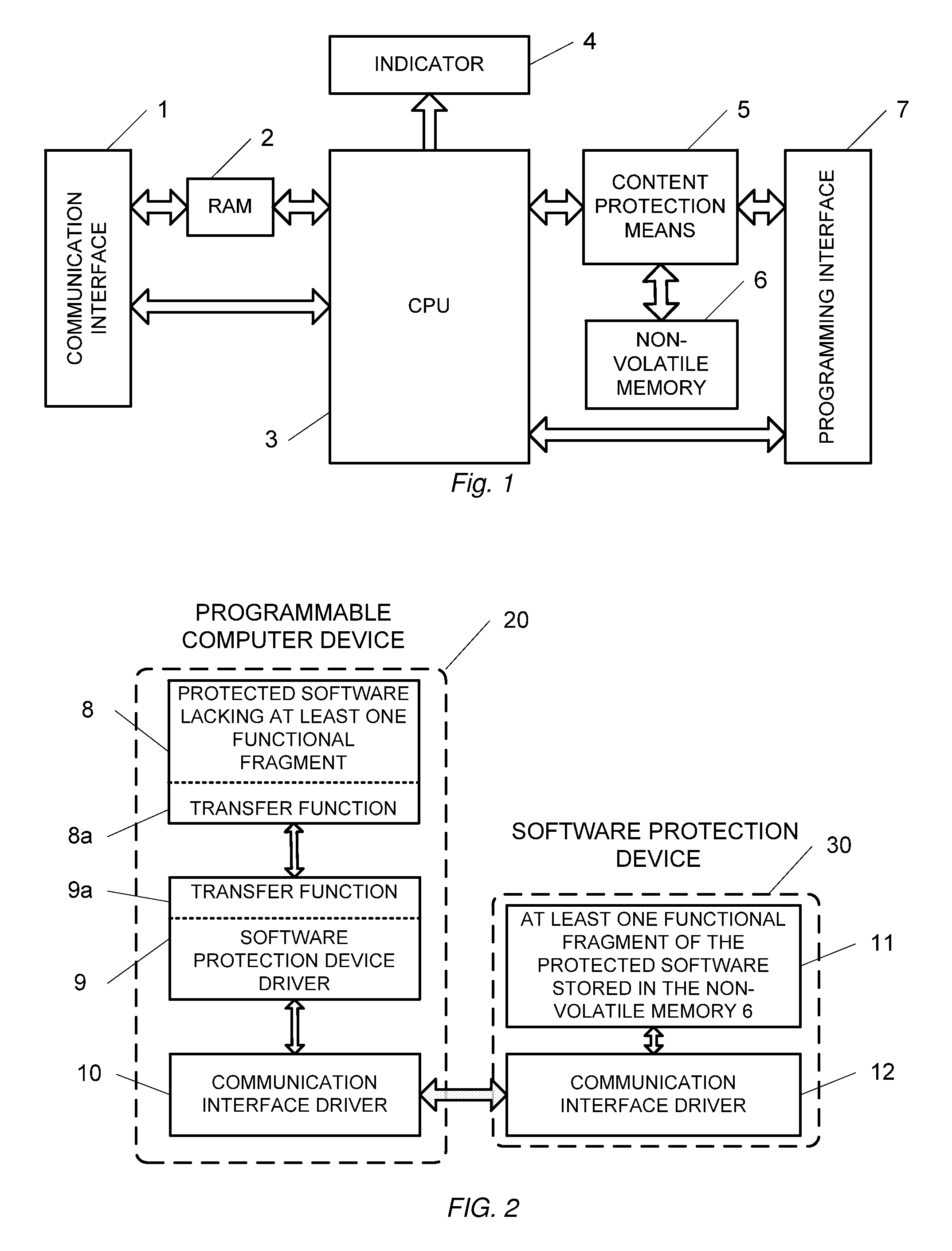
Method and device for protecting software from unauthorized use
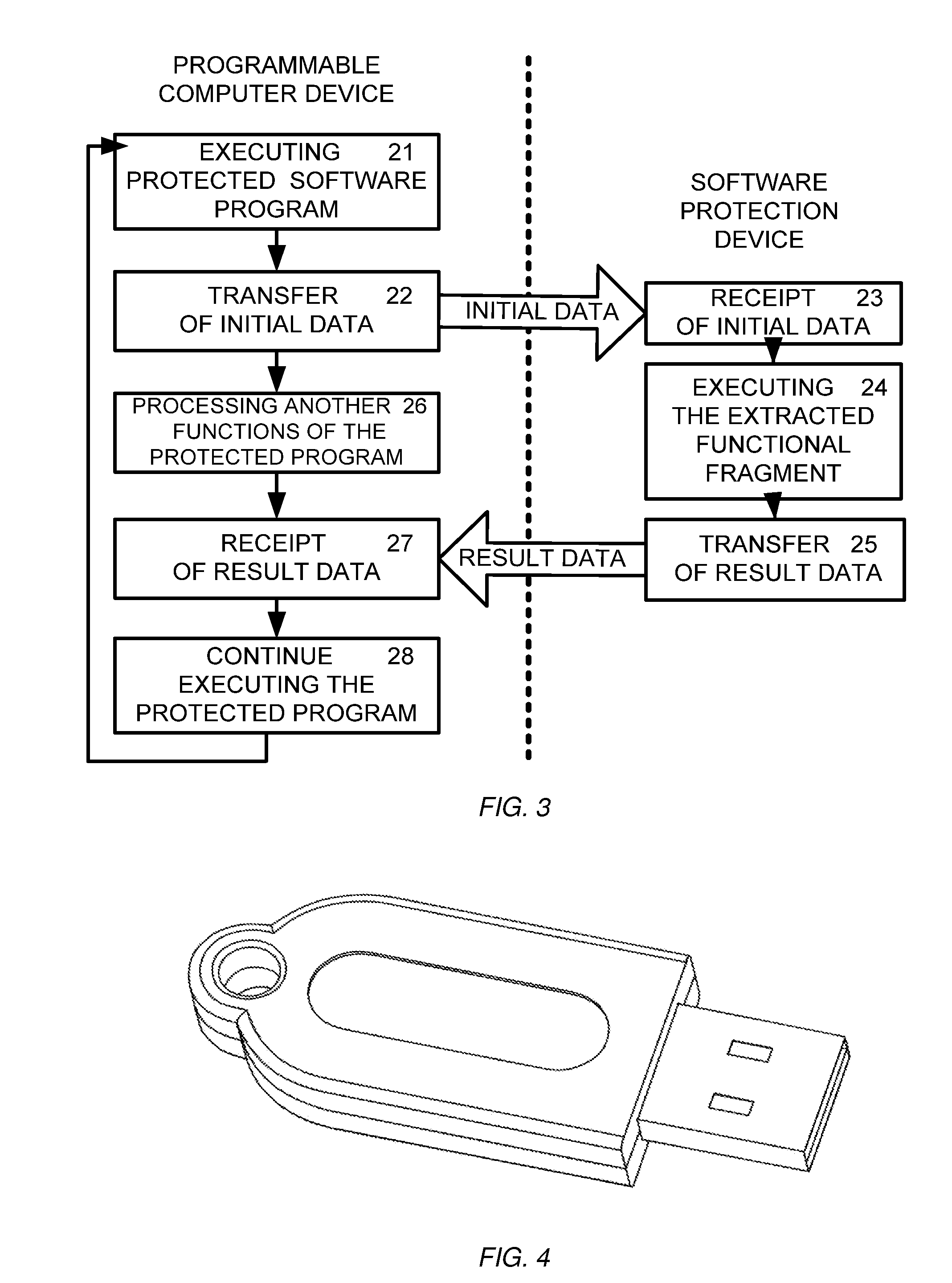
InactiveUS20090094601A1Improve protectionPreclude obtainingMemory adressing/allocation/relocationProgram loading/initiatingCommunication interfaceComputer module
The present invention relation to a method and device for protecting a software program from unauthorized use, comprising a processor, a non-volatile memory, a content protection means, and a communication interface, wherein the non-volatile memory records and stores at least one functional fragment extracted from the said software program, wherein at least one transfer function is embedded into the remaining part of the software program for sending to the software protection device initial data and / or commands initiating execution of the extracted fragment to produce result data, and sending the result data to the programmable computer device, thus preventing hacking of the said software program. The software protection device can be implemented as an external or internal computer module.
Owner:VSTOVSKIY VLADIMIR NIKITICH +2
Software protection
ActiveUS20110307961A1Improved software protectionLow costDigital data processing detailsInstruction analysisParallel computingProgrammable circuits
Owner:NXP BV
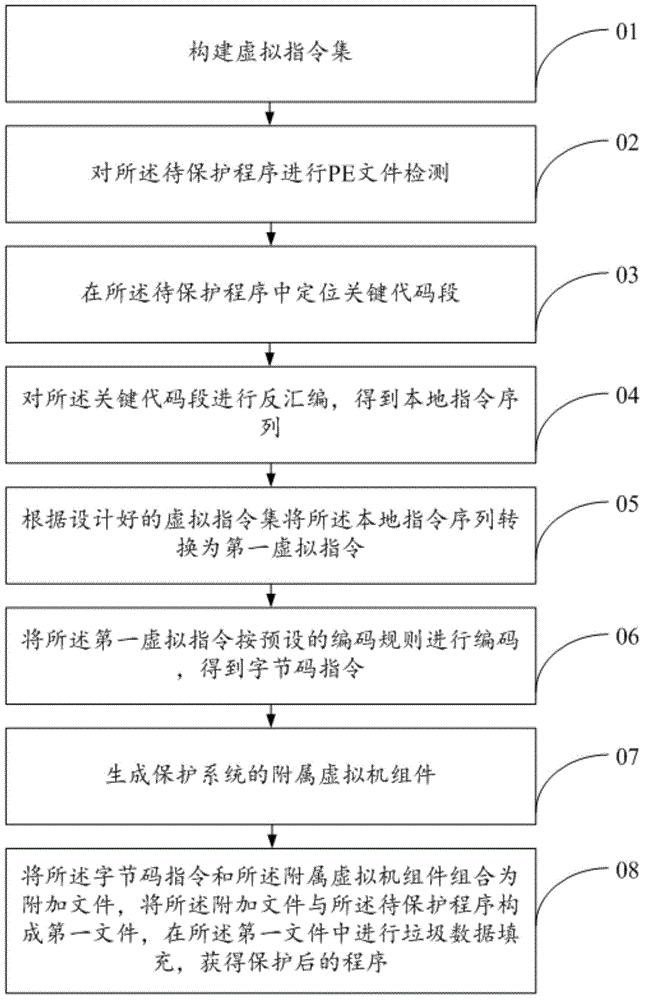
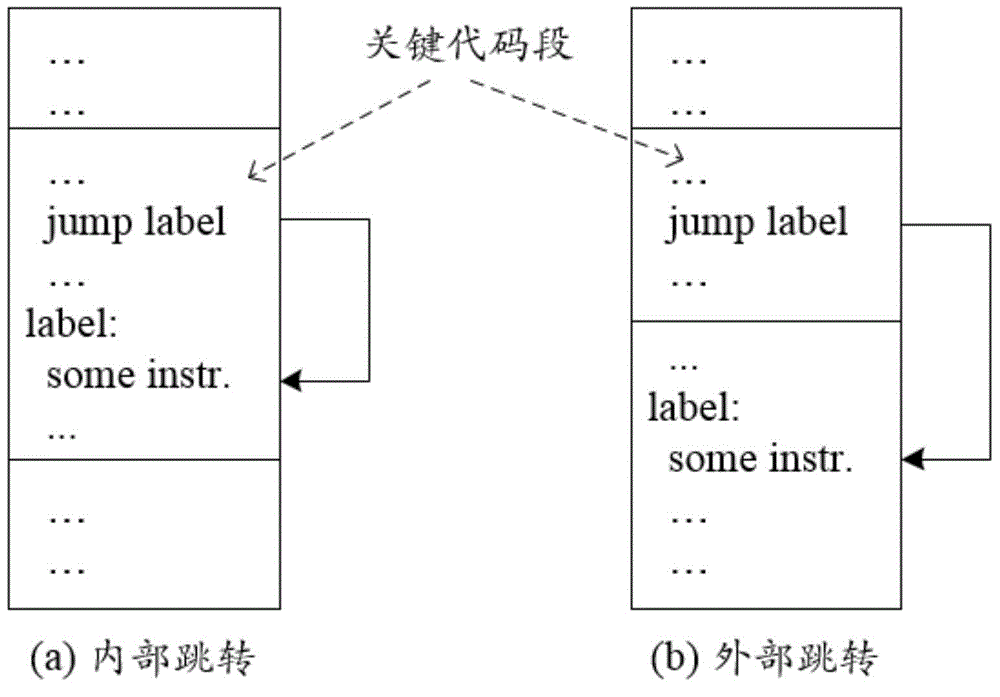
Code virtualization software protection system realizing instruction set randomization
InactiveCN105046117AIncreased complexityLong analysis timePlatform integrity maintainanceProgram/content distribution protectionVirtualizationRandomization
The invention discloses a code virtualization software protection system realizing instruction set randomization, and belongs to the field of computer software security. According to the code virtualization software protection system, a virtual instruction set is built in the system; key code in a program to be protected is disassembled to obtain a local instruction sequence; then, the local instruction sequence is converted into a first virtual instruction according to the virtual instruction set of architecture; the first virtual instruction is coded to obtain a byte code instruction; the byte code instruction is combined with a generated attached virtual machine assembly to obtain an attached file; the attached file is combined with the program to be protected to obtain a first file; and junk data filling is performed on the first file to obtain the final protected program. The code virtualization software protection system has the advantages that the complexity of the program to be protected can be improved; and the analysis time of an analyzer on the program to be protected is prolonged, so that the protection capability of the program to be protected is enhanced.
Owner:NORTHWEST UNIV(CN)
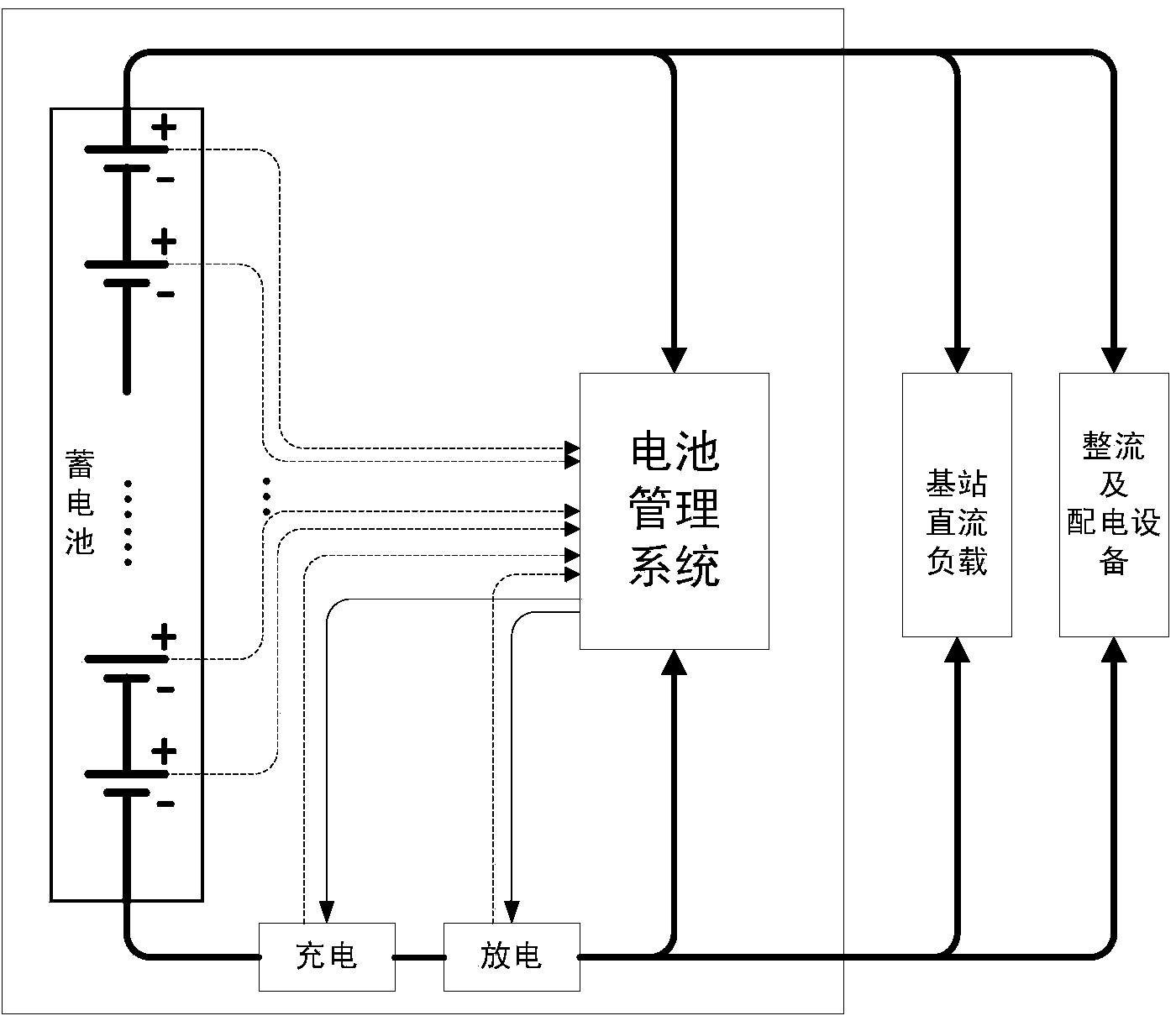
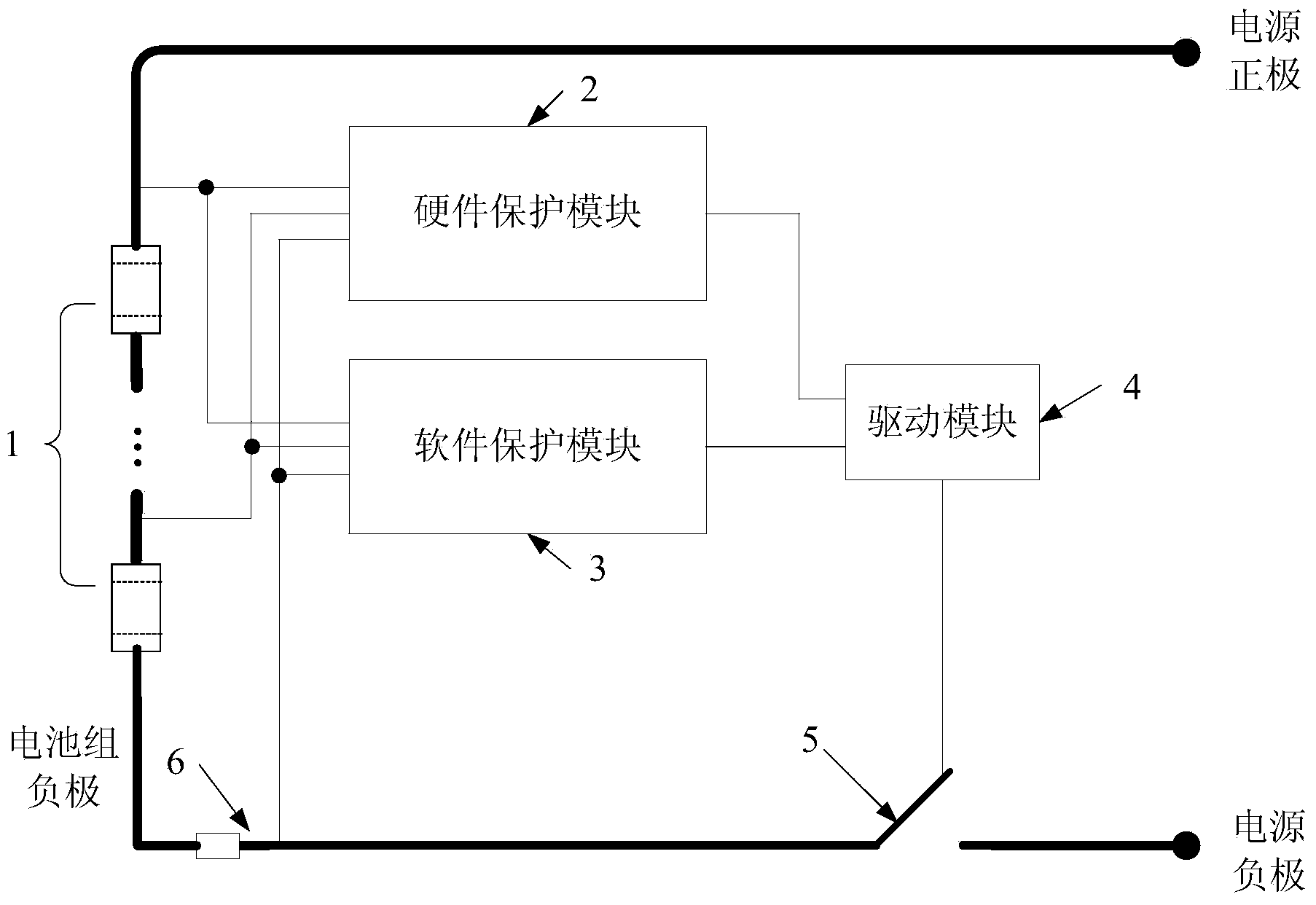
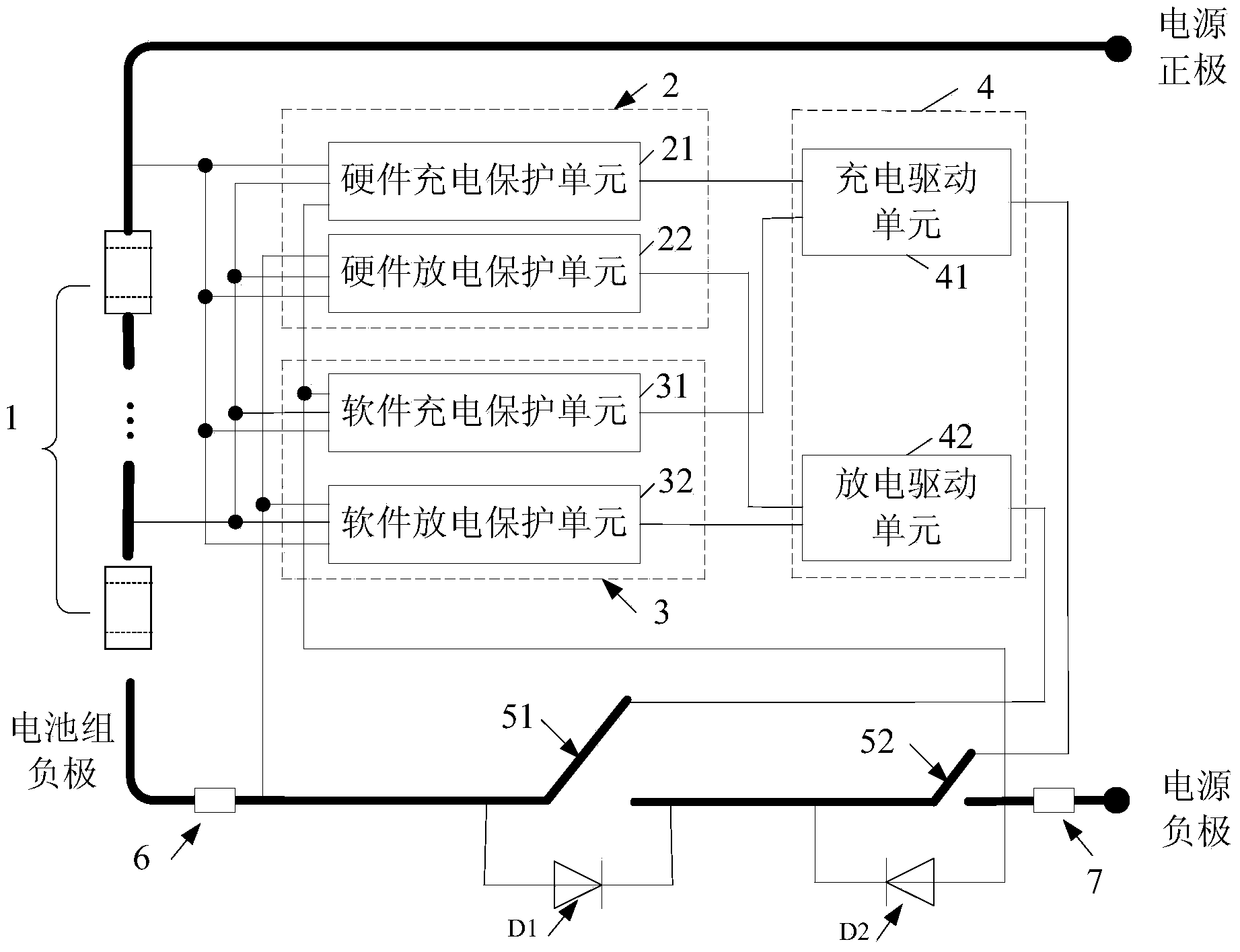
Dual-protection system and method for batteries
InactiveCN103972869AReduce the chance of accidentsExtended service lifeEmergency protective circuit arrangementsElectricityEngineering
The invention discloses a dual-protection system and method for batteries. The dual-protection system comprises a hardware protection module, a software protection module, a drive module, a current sensing resistor and a protection switch, wherein the current sensing resistor is electrically connected with the negative electrode of a battery pack and then connected with the protection switch in series; the input end of the hardware protection module and the input end of the software protection module are electrically connected among the positive electrodes of all the batteries in the battery pack, the protection switch and the current sensing resistor, the output end of the hardware protection module and the output end of the software protection module are electrically connected with the input end of the drive module, and the output end of the drive module is electrically connected to the control end of the protection switch to control the protection switch to be turned off. The dual-protection system and method can improve the reliability of the battery pack and reduce the accident probability of the battery pack.
Owner:深圳市诺比邻科技有限公司
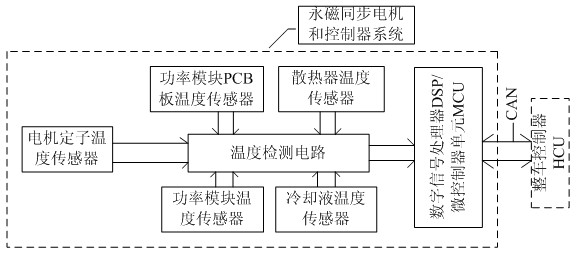
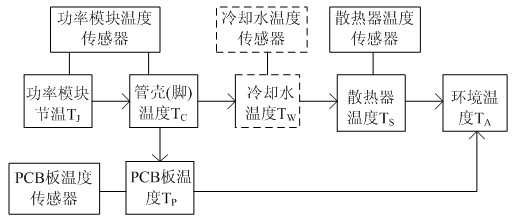
Temperature control method for permanent magnet synchronous motor and intelligent power unit system of pure electric vehicle
ActiveCN102255282ARealize temperature protection functionEnsure safetySpeed controllerElectric machinesPermanent magnet synchronous motorElectric cars
The invention discloses a temperature control method for a permanent magnet synchronous motor and intelligent power unit (IPU) system of a pure electric vehicle. A control chip of an intelligent power unit adopts a digital signal processor (DSP) or a micro control unit (MCU). Each path of input signals acquired by temperature sensors are transmitted to the DSP / MCU after passing through a temperature detection circuit, and the temperature signals are computed and processed to realize functions of performing temperature detection, processing and protection on the motor and IPU system. The method comprises hardware temperature detection and conversion and software protection processing, wherein a hardware method comprises the detection, processing, A / D conversion and the like of the stator temperature of a motor, the power module temperature of the IPU, power module radiator temperature, cooling fluid inlet and outlet temperature and power module printed circuit board (PCB) temperature signals; and a software method comprises software flow processing performed on the temperature signals according to a protocol policy by the DSP / MCU and a hybrid control unit (HCU).
Owner:深蓝汽车科技有限公司
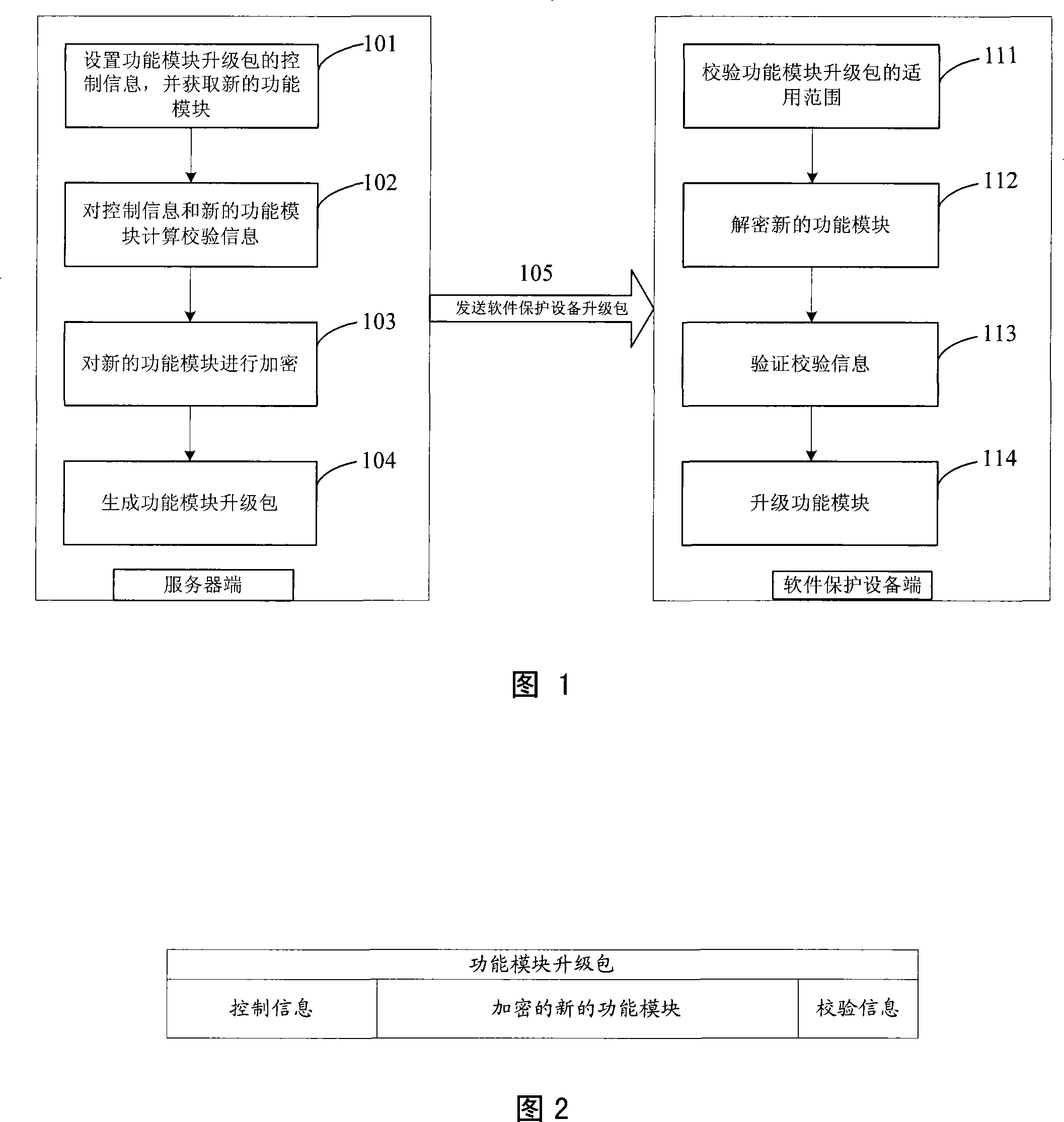
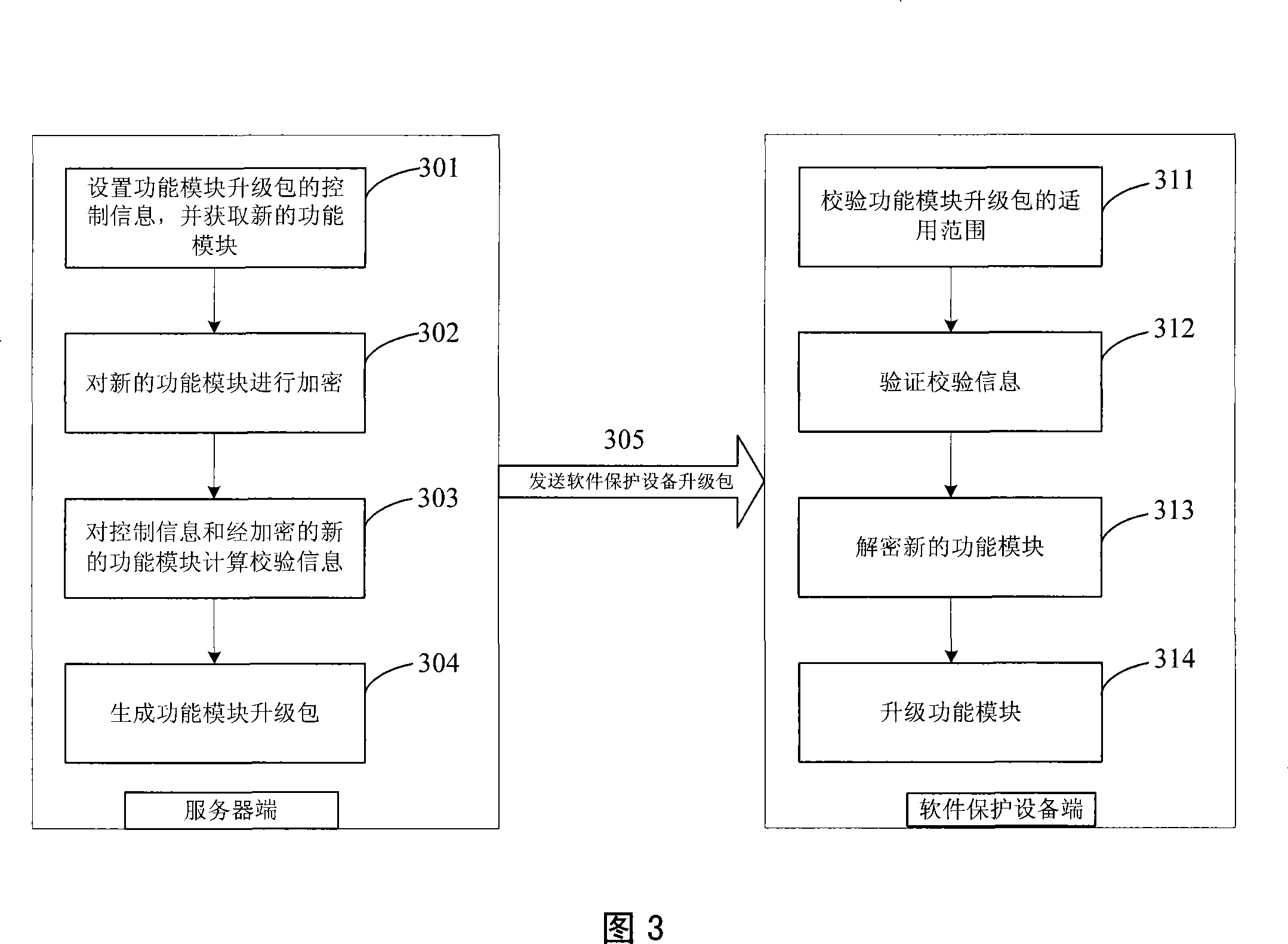
Method for performing safety controllable remote upgrade for software protecting device
InactiveCN101251883AReduce the risk of impactReduce stepsComputer security arrangementsProgram loading/initiatingSoftware protectionServer-side
The invention provides a safe and controlled remote update method for a software protection device, the method is as follows: control information of a function module update pack is arranged at the terminal of a server and a new function module is obtained; the new function module is encrypted after the control information and the new function module are calculated to obtain calibration information, or after the new function module is encrypted, the control information and the encrypted new function module are calculated to obtain the calibration information; and then the control information, the encrypted new function module and the calibration information are combined to form the function module update pack which is sent to the software protection device; the software protection device check the control information in the received function module update pack, the new function module is obtained after decrypting, the calibration information in the update pack is validated according to the control information and the new function module, and the own update can be performed through using the new function module if the validation is passed. The function module in the function module update pack of the safe and controlled remote update method for a software protection device is all cryptograph in the transmission process, thus the safe and controlled remote update for the software protection device is effectively realized.
Owner:BEIJING SENSESHIELD TECH
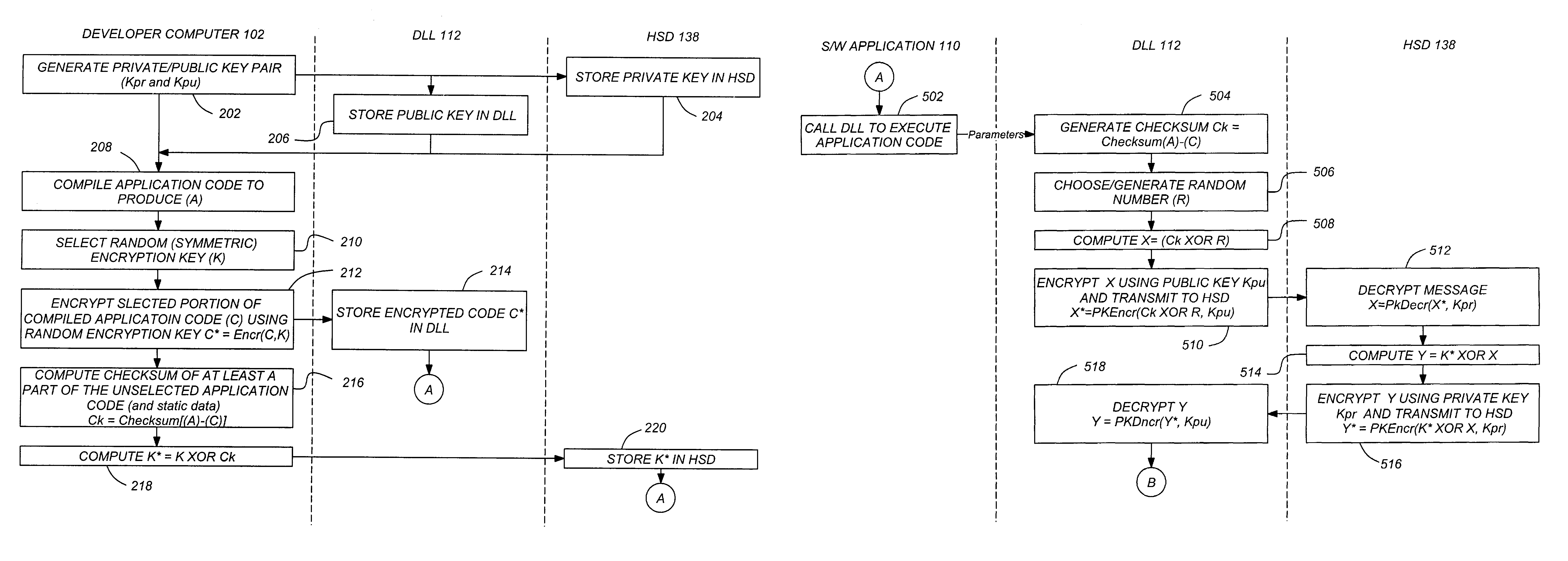
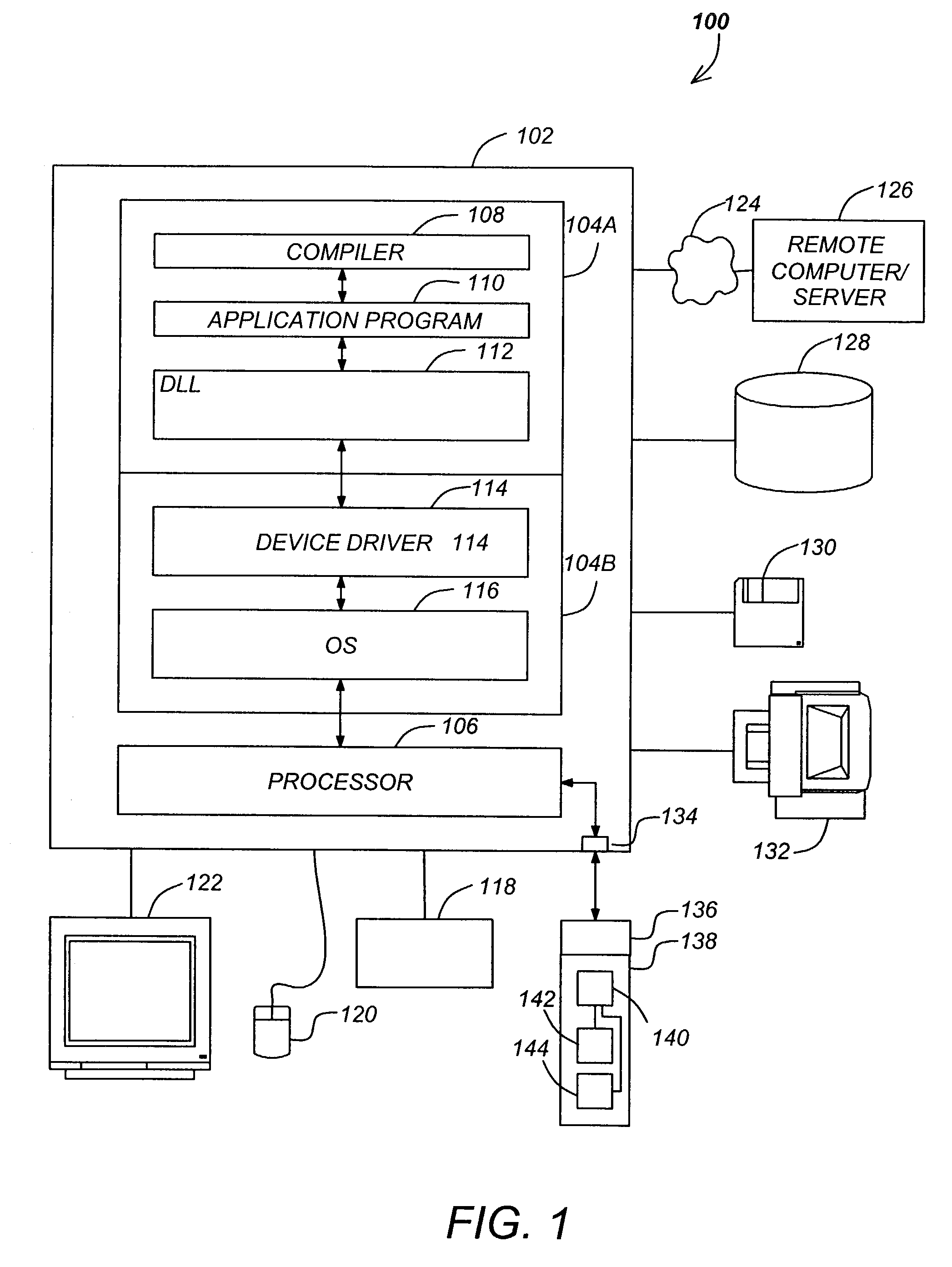
Software protection method utilizing hidden application code in a protection dynamic link library object
ActiveUS7320075B2User identity/authority verificationUnauthorized memory use protectionOperational systemApplication software
A system and method in which the operating system of the user computer loads the software application and a DLL having a portion of the application execution code stored therein into memory is disclosed. At selected points during its execution, the software application calls the DLL to execute a portion of the application code that was saved into the DLL before delivery to the end user. Since this code is encrypted and the encryption key is stored in a hardware security device and not in the DLL or the software application, the application code portion cannot be executed without recovering the key.
Owner:THALES DIS CPL USA INC
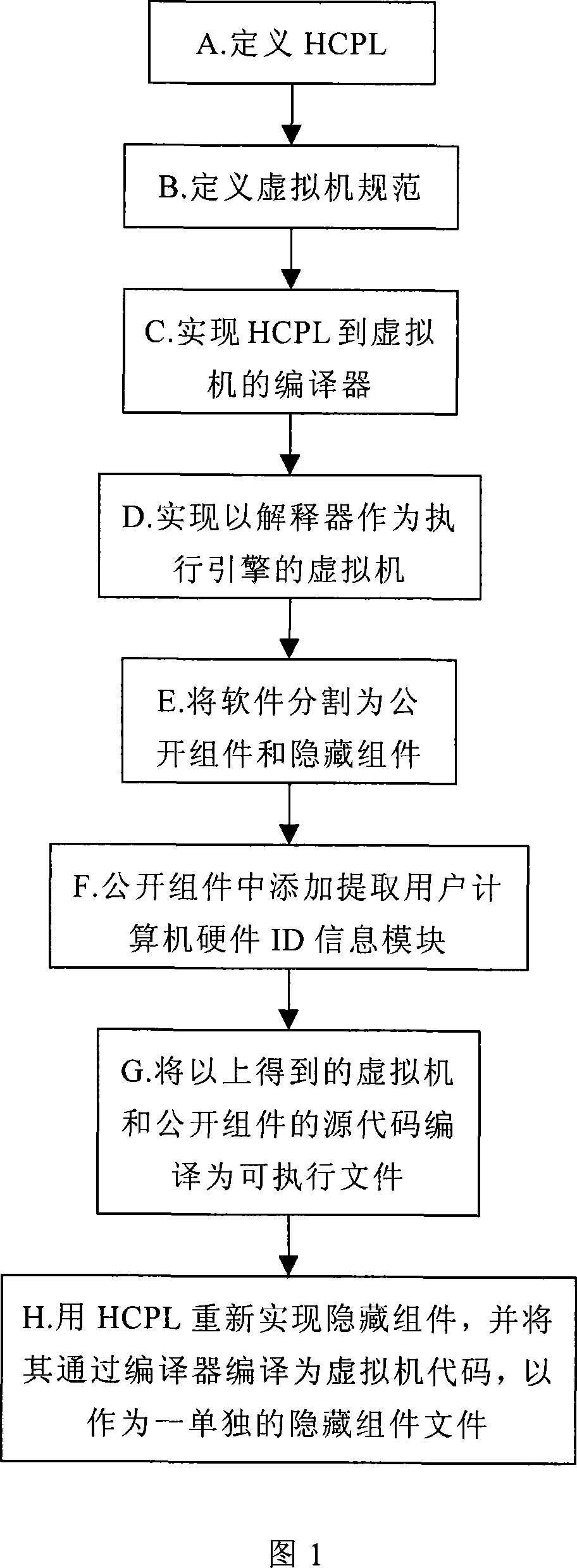
Software protection method based on virtual machine
InactiveCN101201883APrevent piracyStrong anti-illegal tampering functionPlatform integrity maintainanceProgram controlSoftware engineeringResponse delay
The invention discloses a method for protecting software based on a virtual computer, which comprises the steps that: a high level programming language applied to compiling hidden components is defined; virtual computer specification is defined; a compiler of exclusive instruction set from the high level programming language to the virtual computer is realized; the virtual computer taking an interpreter as an execution engine is realized; the software is divided into open components and hidden components; the open components are added with a module to get the hardware ID information of the computer of users; source code of the virtual computer and the open components obtained in the steps are compiled into executable files; the hidden components are again realized through the high level programming language and complied into the code of the virtual computer as independent hidden component files. The invention has high performance of safe operation environment and little response delay between open and hidden components and greatly improves the experience of users. The invention provides a method for preventing software piracy effectively for software developers, which realizes on-line software issuing and decreases the cost of software greatly.
Owner:北京赛柏科技有限责任公司
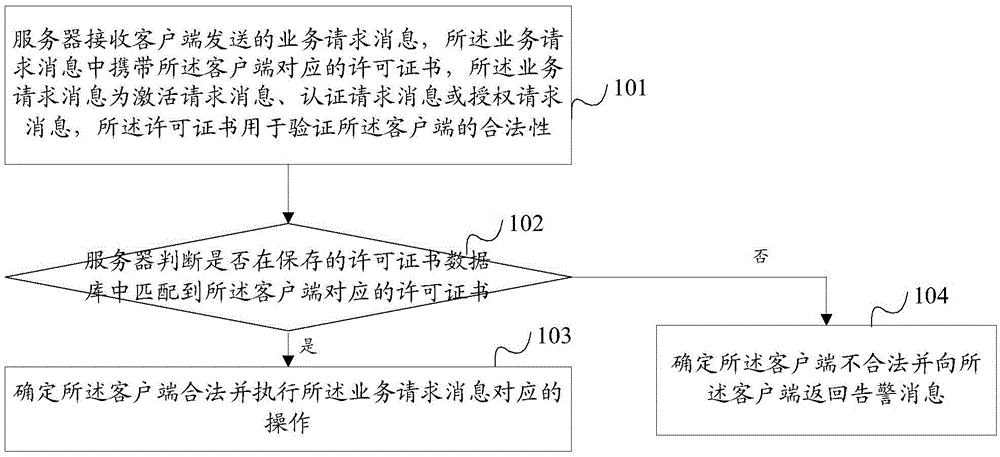
Client software protection method and device, and client
The invention provides a client software protection method and device, and a client. The method comprises that: a server receives a piece of business request message that is sent by a client, wherein the business request message carries a certificate corresponding to the client, the business request message is activation request message, authentication request message or authorization request message, and the certificate is used to verify the validity of the client; the server judges whether the certificate corresponding to the client is matched with the stored certificate database; if so, the client is judged as valid and operations corresponding to the business request message are executed; otherwise, the client is judged as invalid and a piece of warning message is sent to the client. By means of the invention, client software is protected at the server side, thereby improving the security of the client software and strengthening the protection of the client software.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +2
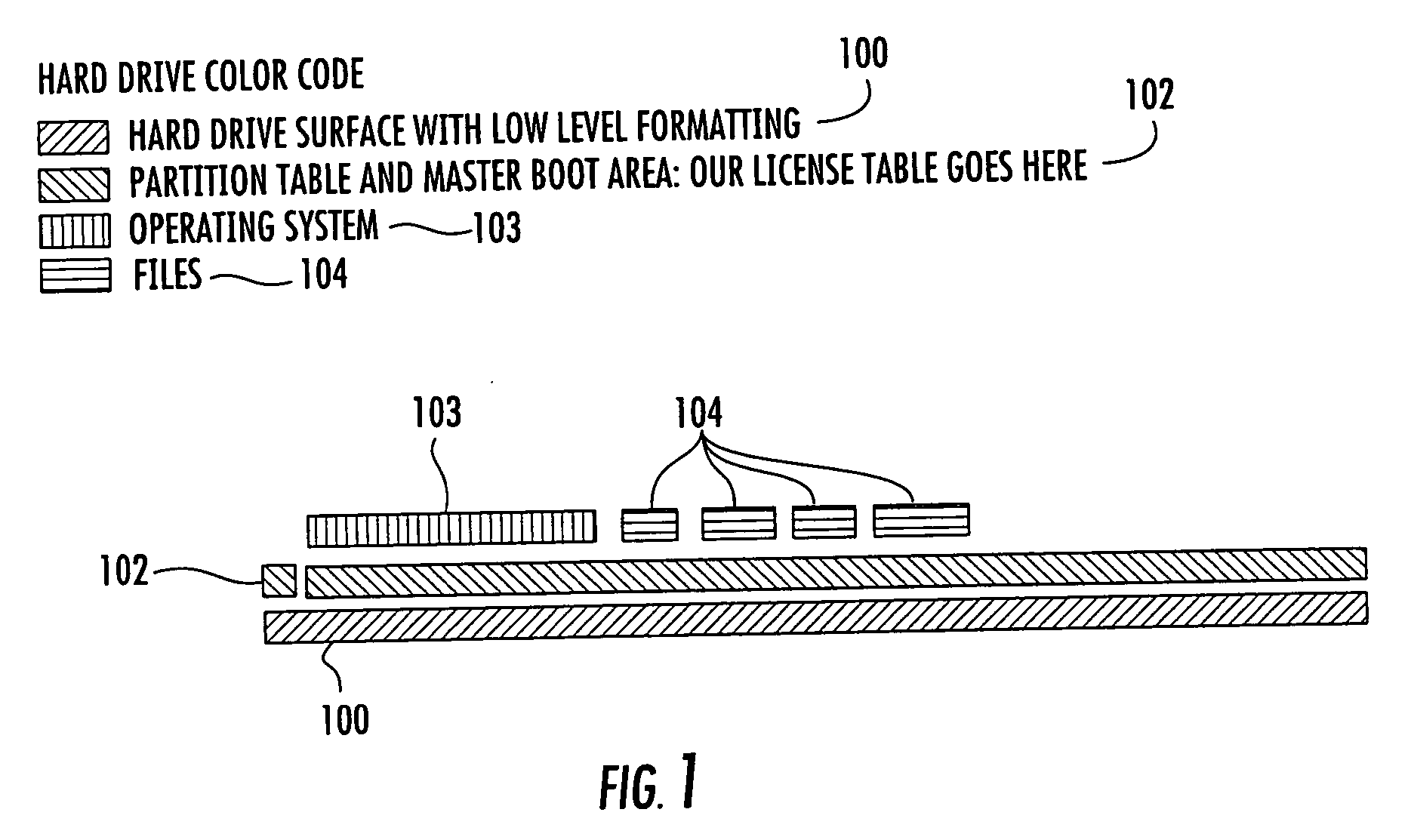
License table for software protection
InactiveUS20060212649A1Improve protectionEasy to storeDigital computer detailsProgram controlSoftware engineeringSoftware protection
A method and apparatus for creating a table of information stored on a disk is disclosed. A first track is located on a hard disk which is unaffected and immune to changes in an operating system or any programs using the operating system. The table of information contains a unique marker signifying the beginning of the table. A series of table entries follow the table marker expanding through the sectors of the hard disk. The sectors are analyzed to determine whether the operating system, boot record or partition table make use of them. The table is written to the usable sectors of the track and may be in non-contiguous sectors.
Owner:NALPEIRON
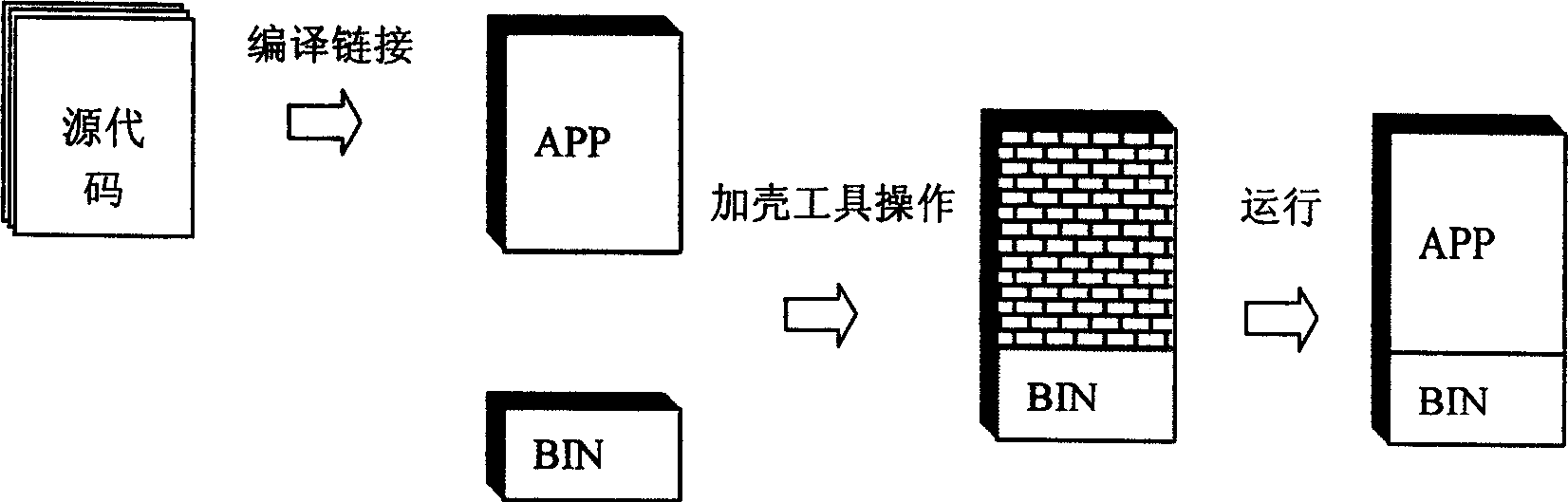
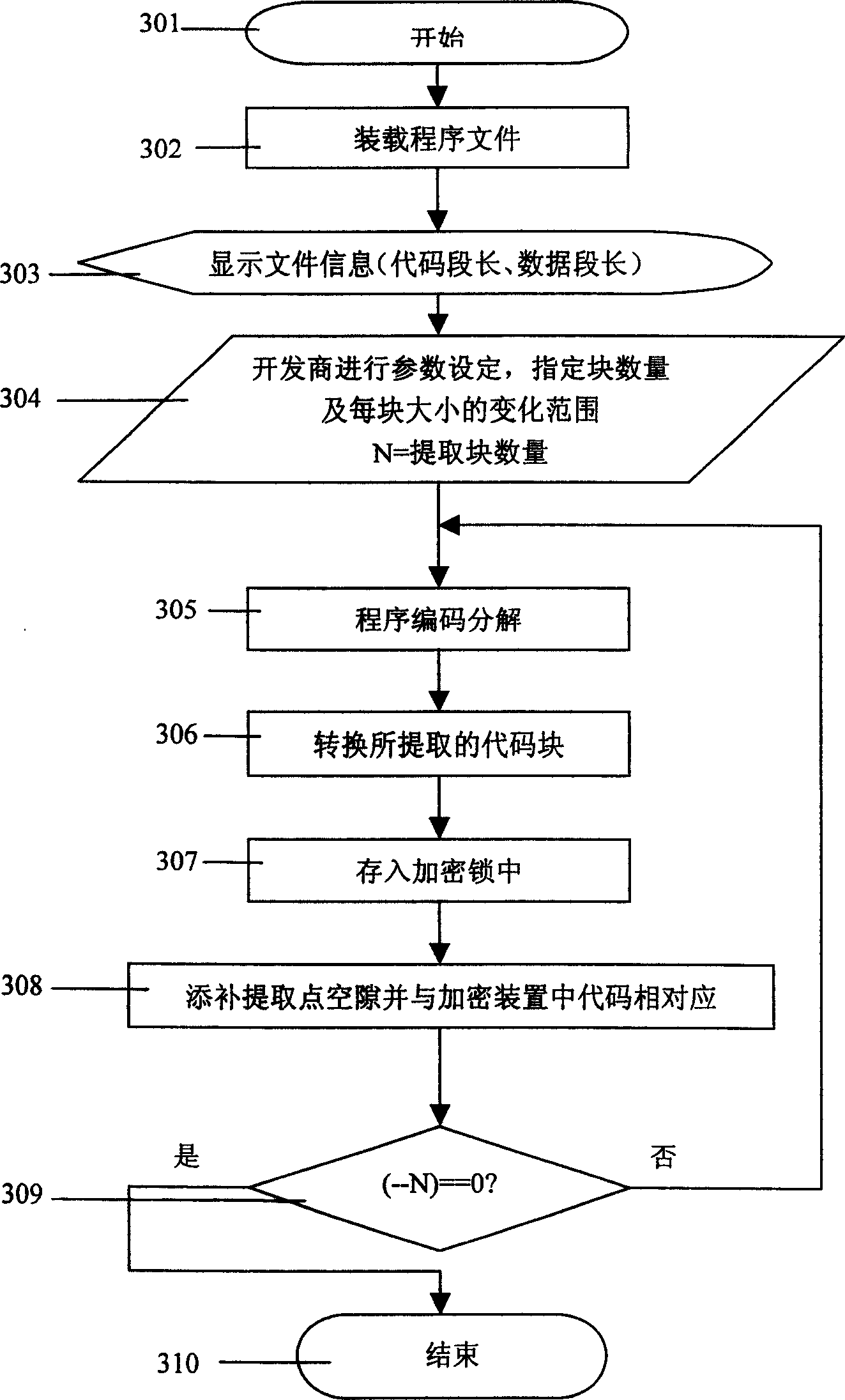
Software copy right protecting method for extracting partial code to enciphed device from software
ActiveCN1749915AIncrease the difficulty of crackingNo burdenDigital data processing detailsSoftware engineeringSoftware development
The present invention relates to software copyright protecting method, and is especially software copyright protecting method by extracting partial codes from program file to the enciphering device. The compiled program file has its codes decomposed into partial codes running in the enciphering device and the other in the computer, and this makes it possible for the software developer to raise the enciphering safety degree without increasing load in developing software protecting functional module. The software copyright protecting method is superior to traditional shell enciphering method.
Owner:北京坚石诚信科技有限公司
IGBT overcurrent protection apparatus and method of PFC circuit
ActiveCN108923377AAvoid damageImprove reliabilityTransistorEfficient power electronics conversionOvercurrentEngineering
The invention discloses an IGBT overcurrent protection apparatus and method of a PFC circuit. The IGBT overcurrent protection apparatus comprises: a PWM control module; an input voltage detection module detecting an input voltage, setting a hardware protection voltage, comparing the input voltage with the hardware protection voltage, generating a hardware voltage protection signal and outputting the hardware voltage protection signal to the PWM control module; an output voltage detection module detecting an output voltage; a current detection module detecting an input current; a current overcurrent protection module setting a hardware protection current, comparing the input current with the hardware protection current, generating a first hardware current protection signal and a second hardware current protection signal and transmitting the second hardware current protection signal to the PWM control module, wherein the PWM control module outputs a PWMout signal according to the hardware voltage protection signal and the second hardware current protection signal; and a PFC control module separately connected with the above modules, receiving the input voltage, the input current, thefirst hardware current protection signal and the output voltage, setting a software protection current, outputting a PWM signal to the PWM control module according to various values, and controllingthe PWM control module to output the PWMout signal.
Owner:HISENSE (SHANDONG) AIR CONDITIONING CO LTD
Software protection system and method
InactiveUS20040098613A1Fast processingMemory loss protectionError detection/correctionSoftware protectionAuthorization
A system and method for preventing a computer program from being used, cracked, copied and duplicated without authorization, wherein the system comprises an outer protection device that is connectable to a port of a computer and contains, stored therein, at least a portion of the program while a remaining portion of the program is for storing into the computer, and the program is executed by executing the two portions of the program by the computer and the protection device by sharing the memory and resources of the computer.
Owner:SCHIAVONI JUAN JOSE +3
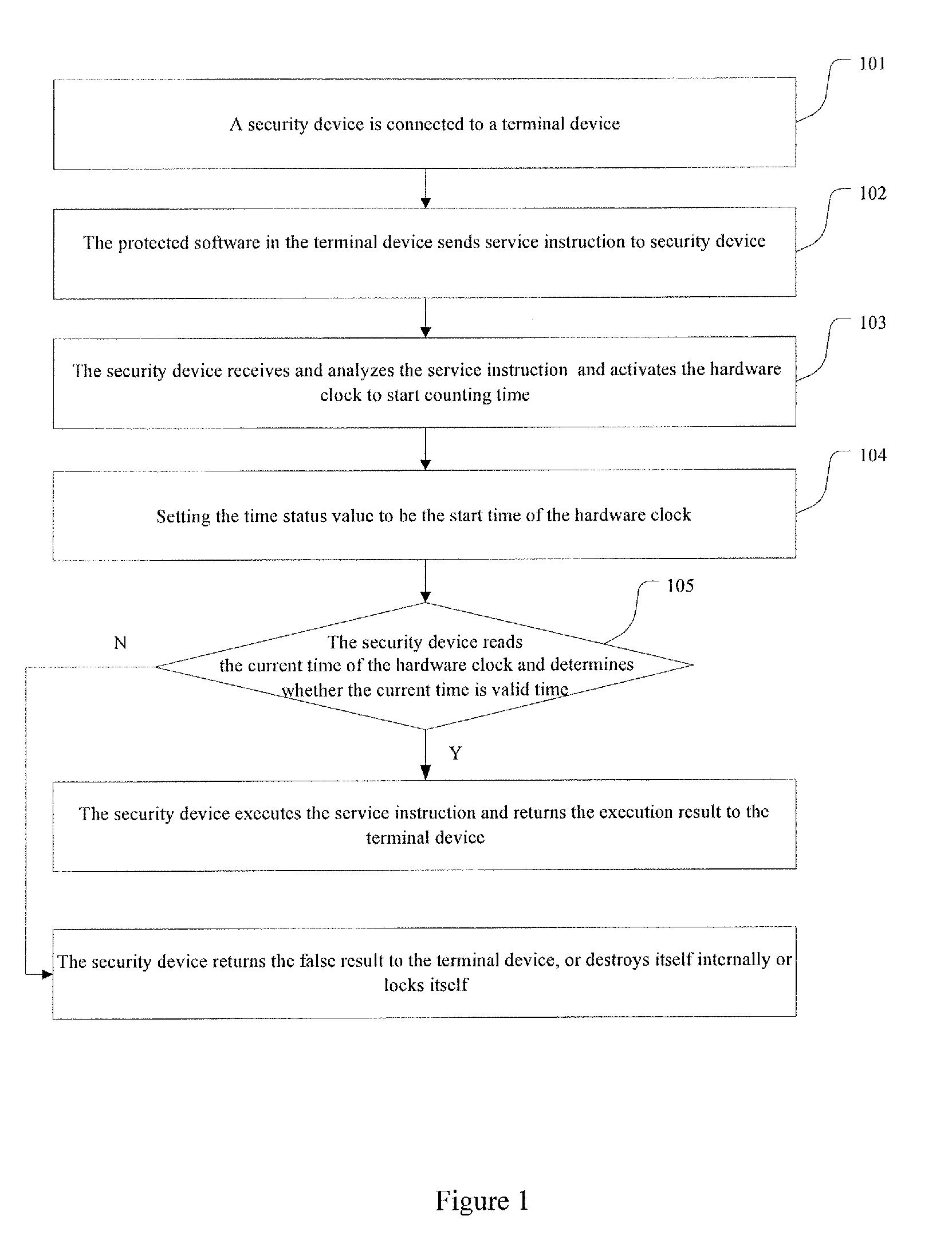
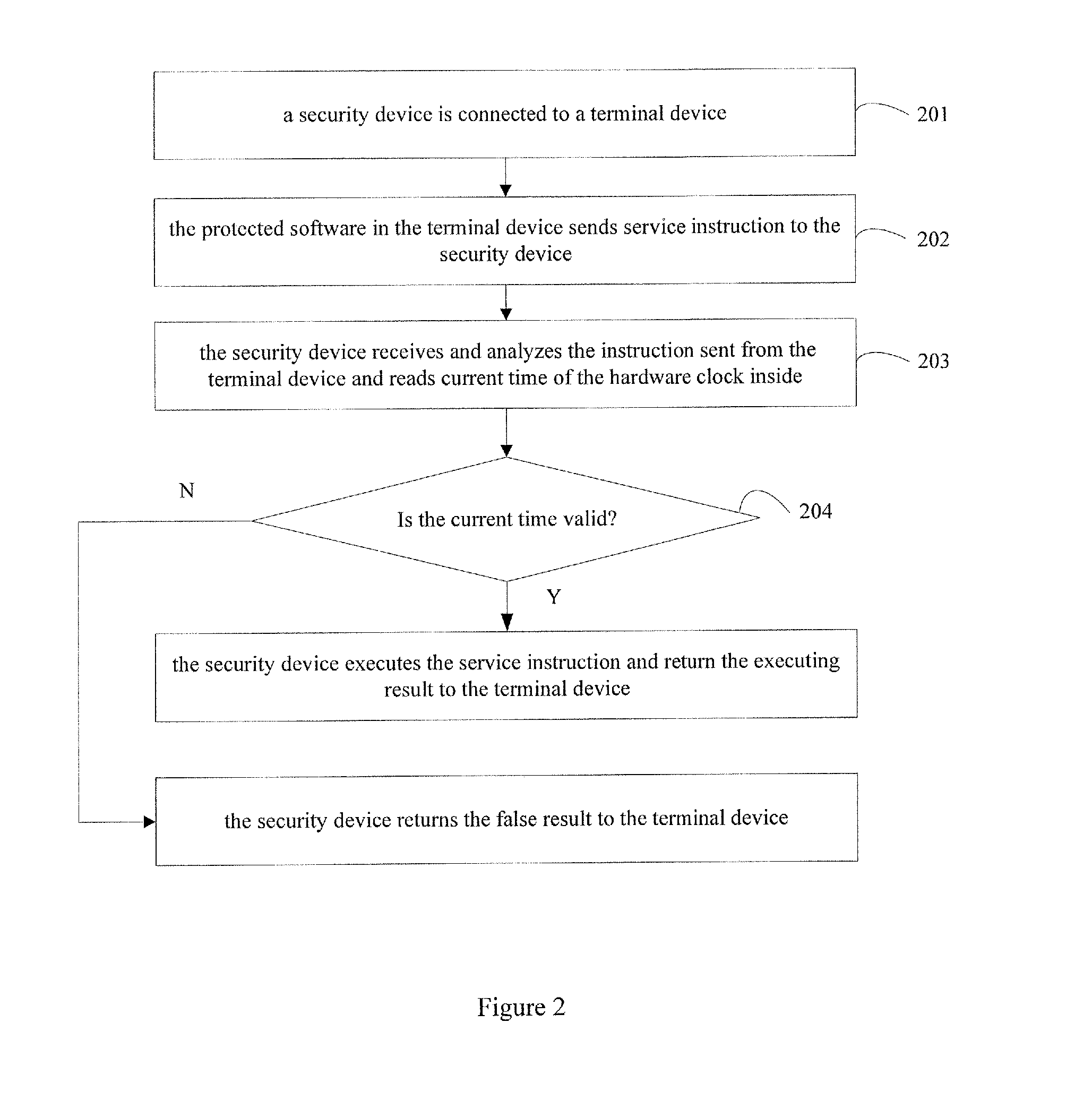
Method for protecting software based on clock of security device and security device thereof
InactiveUS20120131679A1Convenient bindingImprove securityDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareStart time
The invention discloses a software protecting method based on clock of a security device and a security device thereof. The method includes connecting to a terminal device to the security device, receiving the service instruction sent from protected software of the terminal device, protecting the protected software of the terminal device by the security device via the preset time protecting function. The security device includes an interface module and a control module. Thereby, the control module includes a communicating unit and a software protecting unit. The security device of the invention binds with functions such as time and date easily according to the time limit information which limits the time of using the security device and controls the start time and expiring time of using the security device accurately which provides safer service for protecting the software.
Owner:FEITIAN TECHNOLOGIES
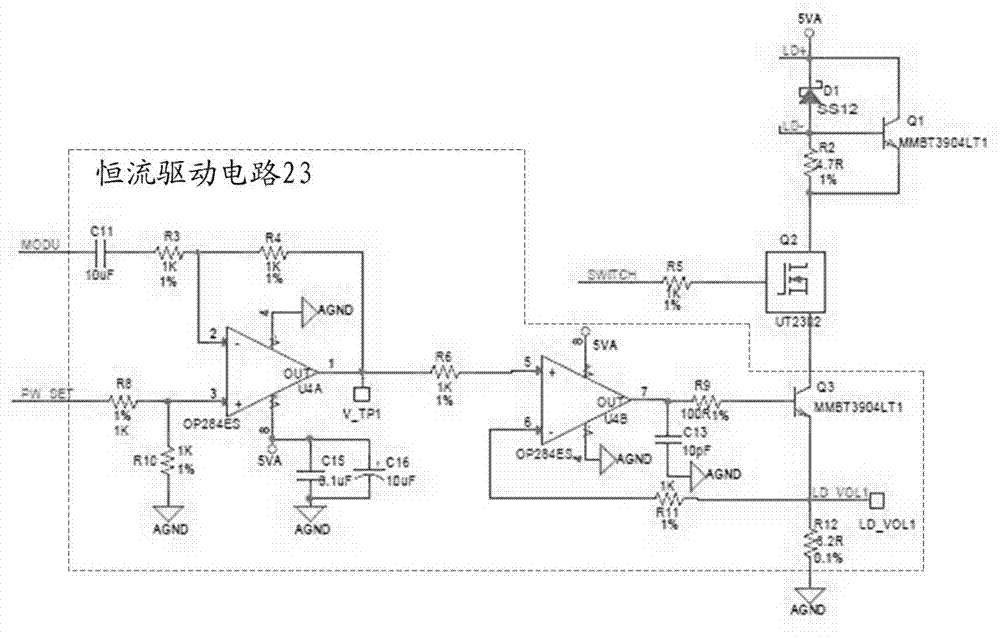
Work protection system for DFB (distributed feed back) laser
InactiveCN103701033AFast protection responseStable jobLaser detailsSemiconductor lasersDriver circuitProtection system
The invention discloses a work protection system for a DFB (distributed feed back) laser. A laser diode and a semiconductor refrigerator are arranged in the DFB laser; the work protection system comprises a constant-current protection system and a temperature-constant protection system, wherein the constant-current protection system comprises a constant-current voltage comparison circuit, a switching circuit and a constant-current drive circuit; the constant-temperature protection system comprises a temperature-constant voltage comparison circuit and a temperature-constant drive circuit. The work protection system for the DFB laser has the following benefits: the on / off of the constant-current drive circuit is controlled by arranging the constant-current voltage comparison circuit and the switching circuit, and the on / off of the constant-temperature drive circuit is controlled by arranging the temperature-constant voltage comparison circuit, so that hardware protection is provided for the DFB laser, and the hardware protection responses quickly and works stably; three types of sampling circuits are arranged for monitoring the work of the laser in real time, and the constant-current drive circuit and the constant-temperature drive circuit can be controlled remotely, so that software protection is provided for the DFB laser, and the software protection is convenient to operate.
Owner:SHANGHAI BOOM FIBER SENSING TECH +1
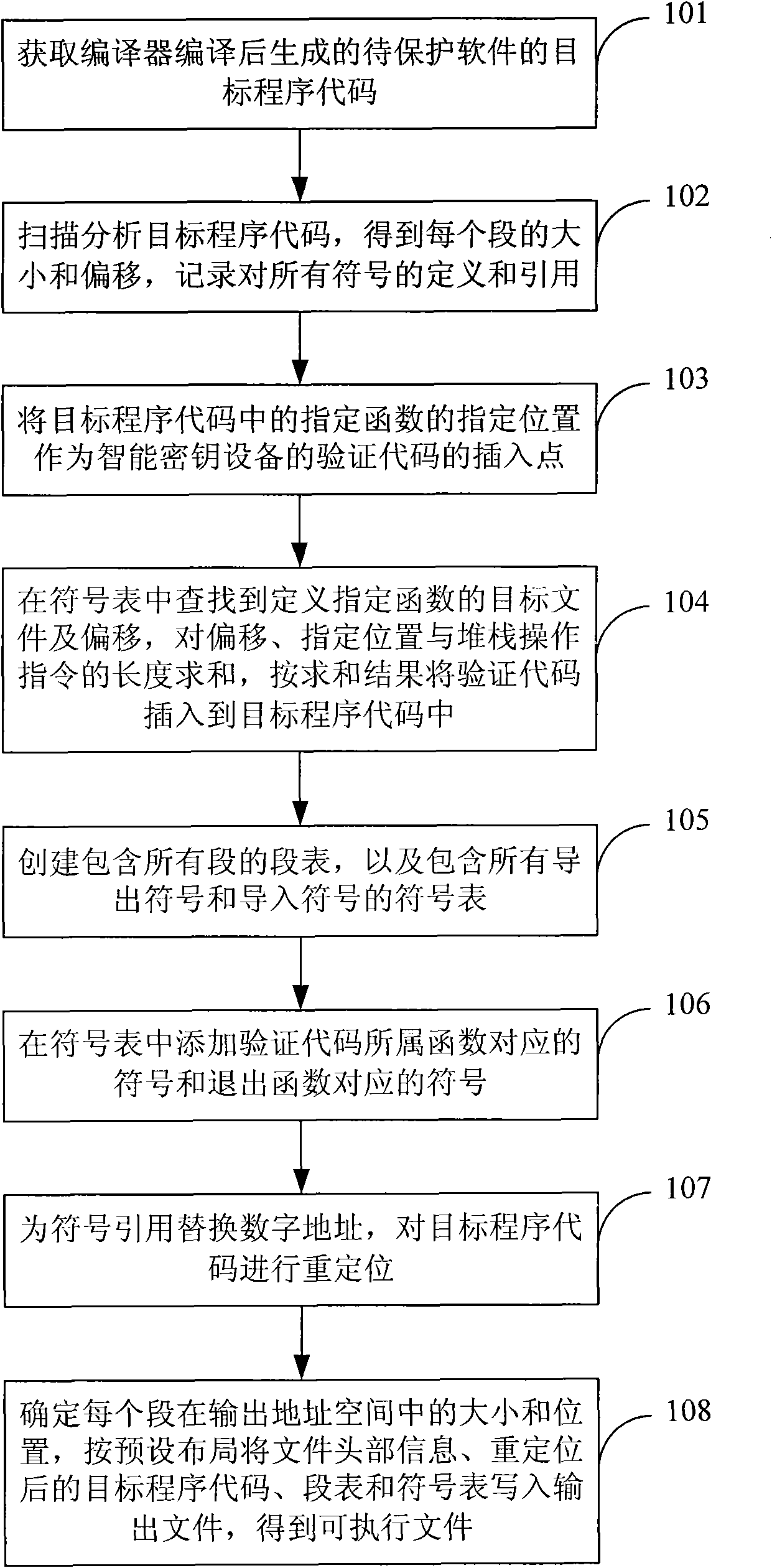
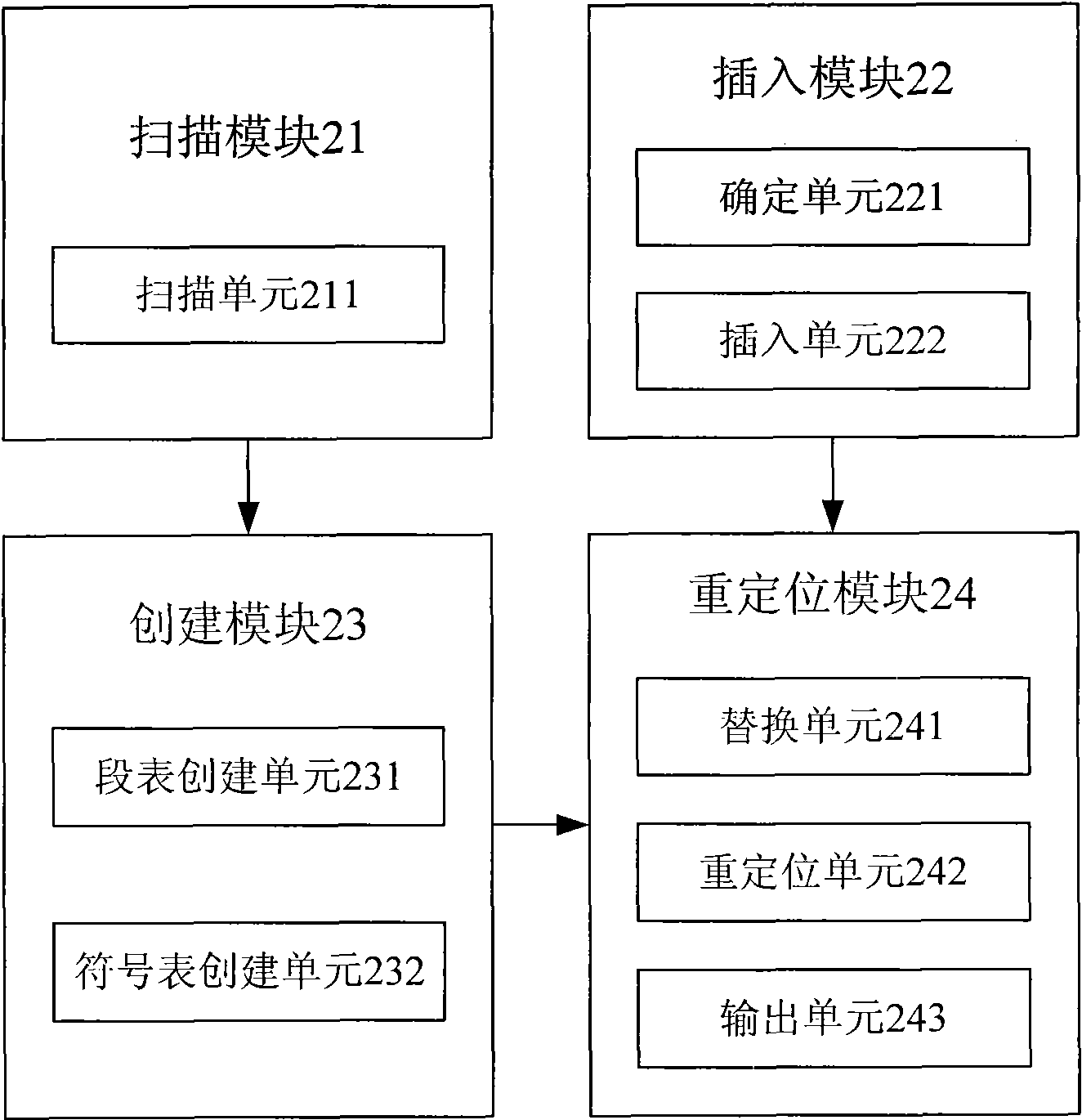
Link method and linker
ActiveCN101650664ATo achieve the purpose of copyright protectionReduce complexityProgram controlProgram/content distribution protectionSoftware protectionProgram code
The invention discloses a link method and a linker, which belong to the field of software security. The method comprises the following steps: scanning the objective program codes of software to be protected, wherein the codes are generated after the compiling of a compiler; determining the inserting point of the identification codes of an intelligent key facility, and inserting the identificationcodes in the objective program codes; creating a segment table and a symbol table according to scanning information, adding symbols respectively corresponding to identification code functions and exitfunctions in the symbol table, and using the functions to which the identification codes belong to identify the intelligent key facility; if successful, allowing the software to operate, and if fail,calling the exit functions and completing the operation; repositioning the objective program codes, writing the head information of a file, the repositioned objective program codes, the segment tableand the symbol table in an output file to obtain an executable file. The linker comprises a scanning module, an insertion module, a creation module and a repositioning module. The invention realizessoftware protection, simplifies and reduces the complexity and the difficulty of software protection.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com