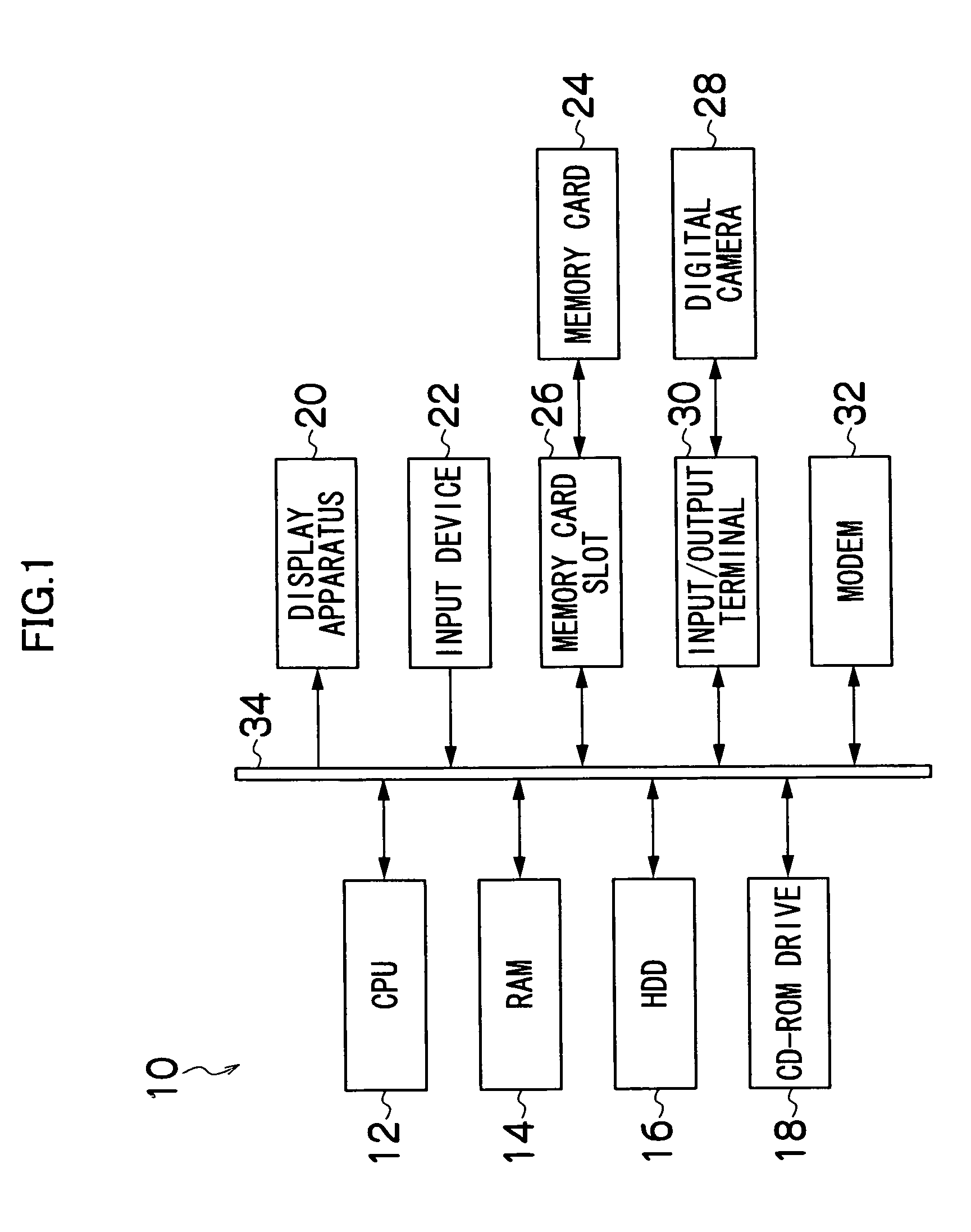
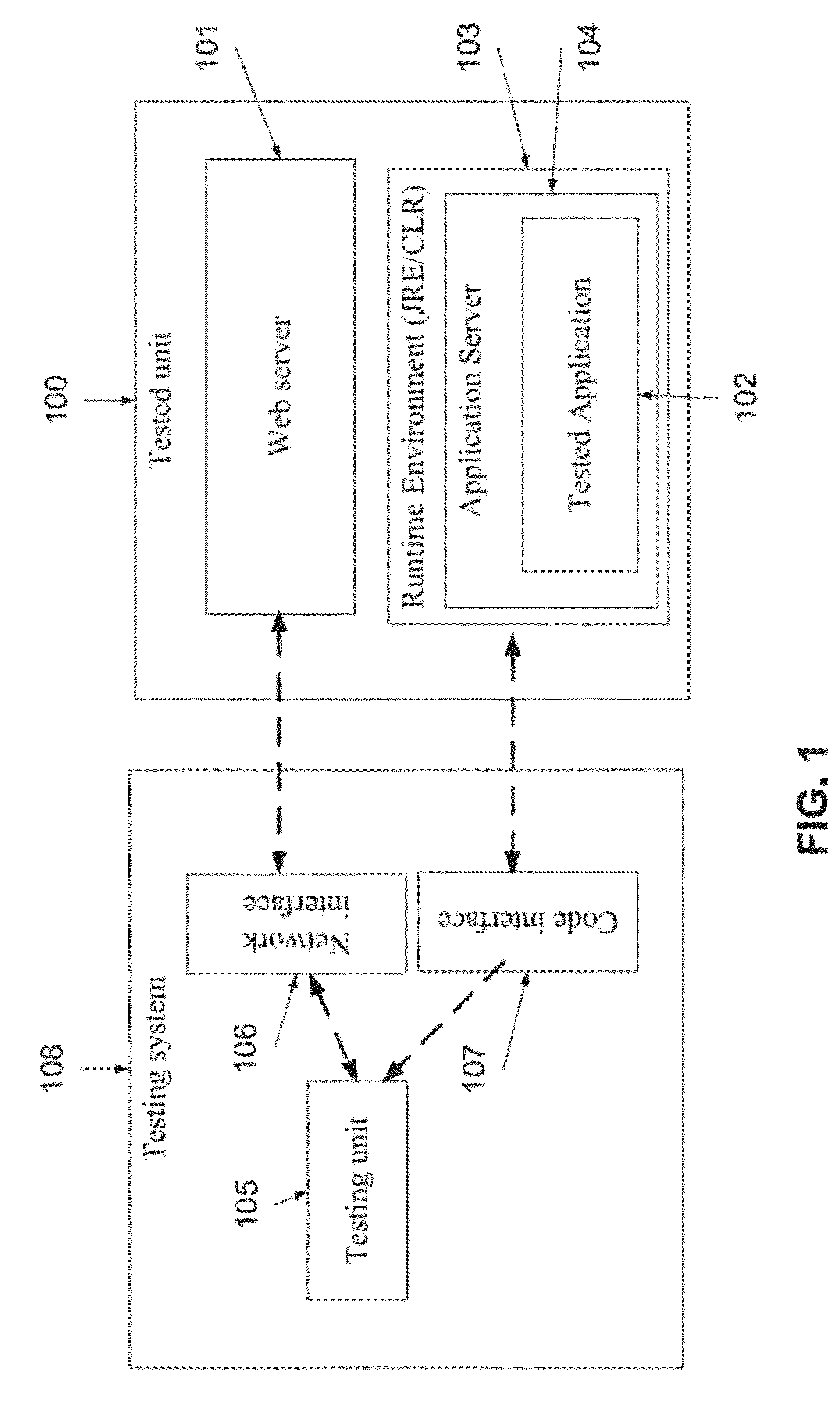
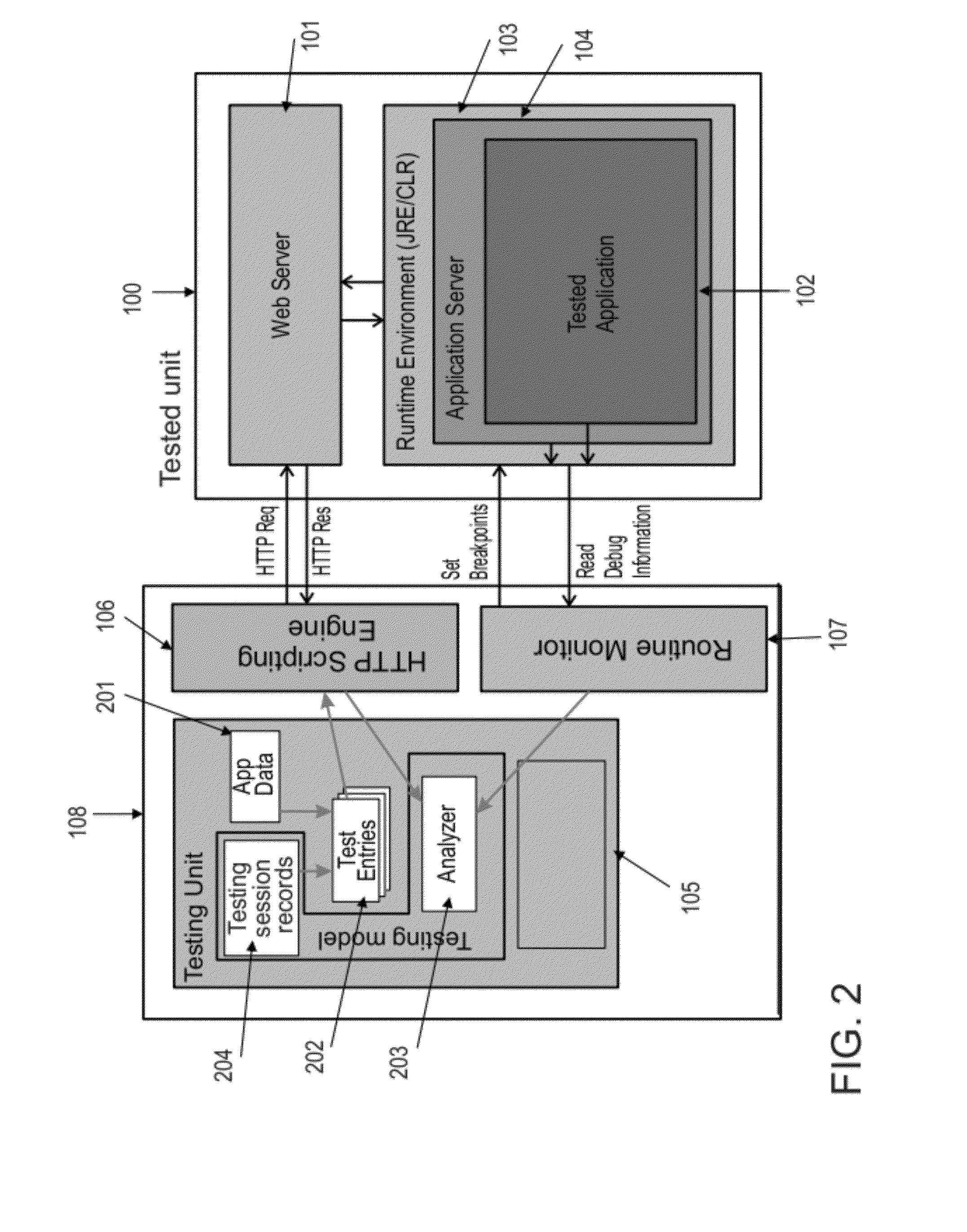
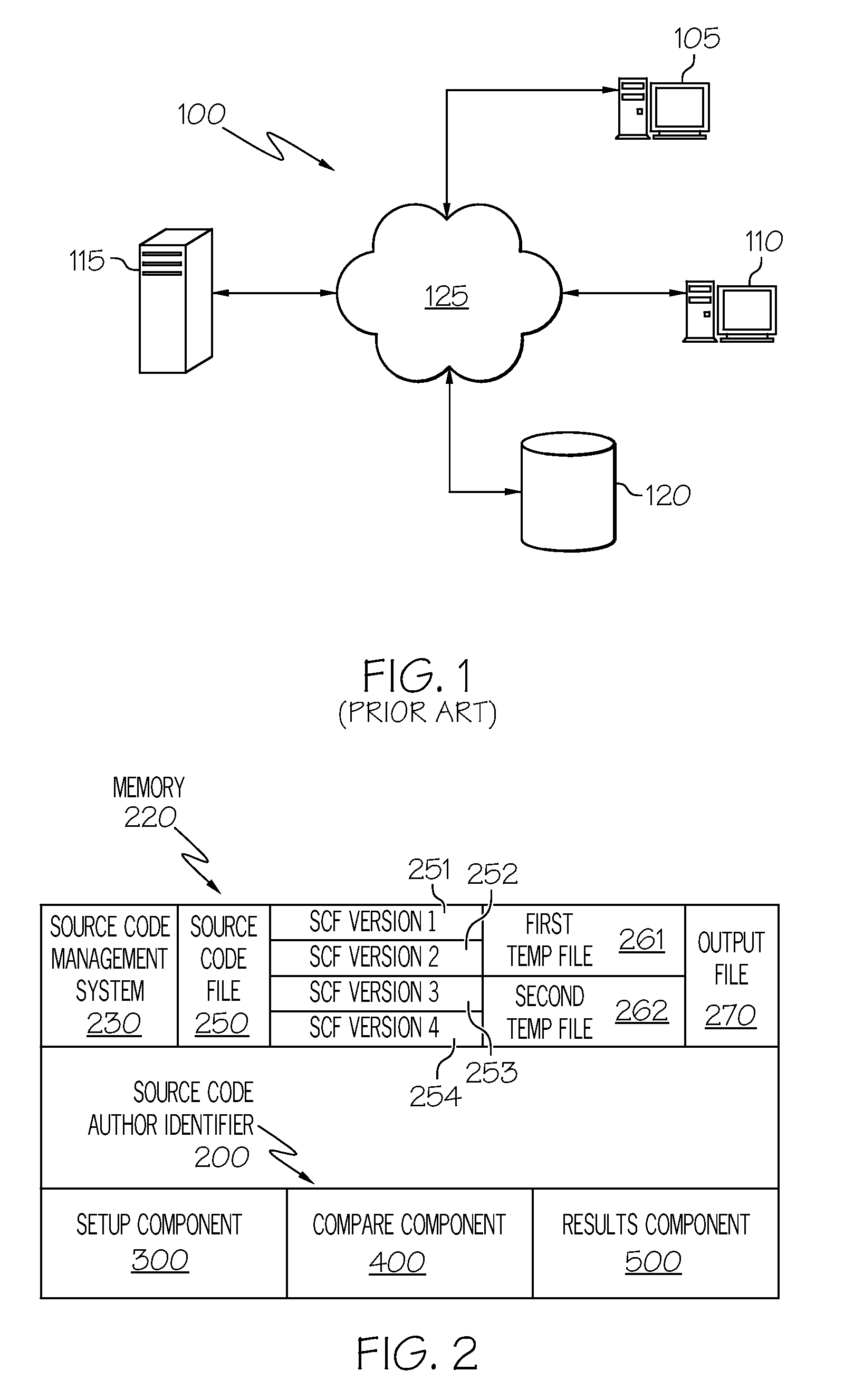
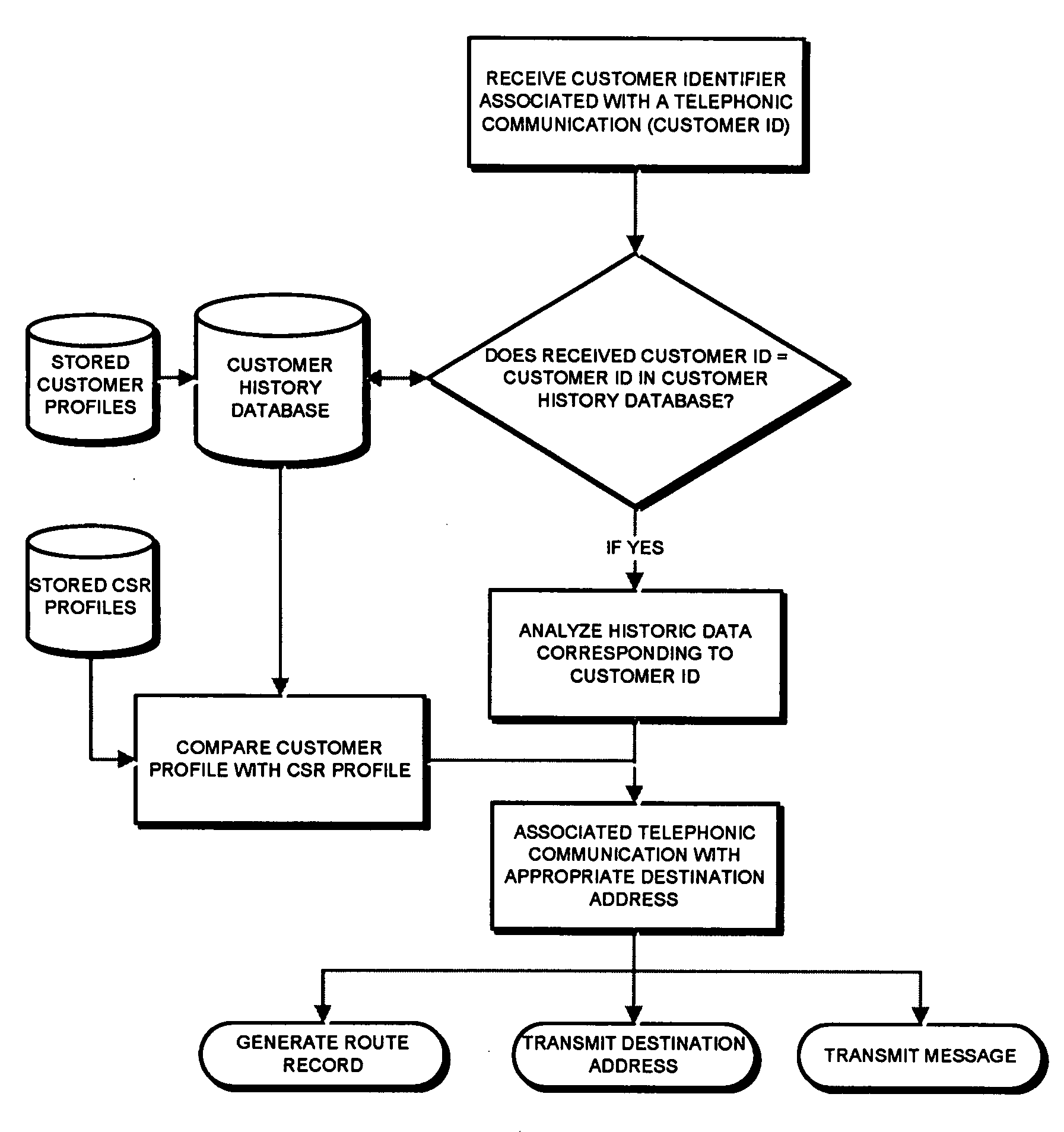
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1569 results about "Code segment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
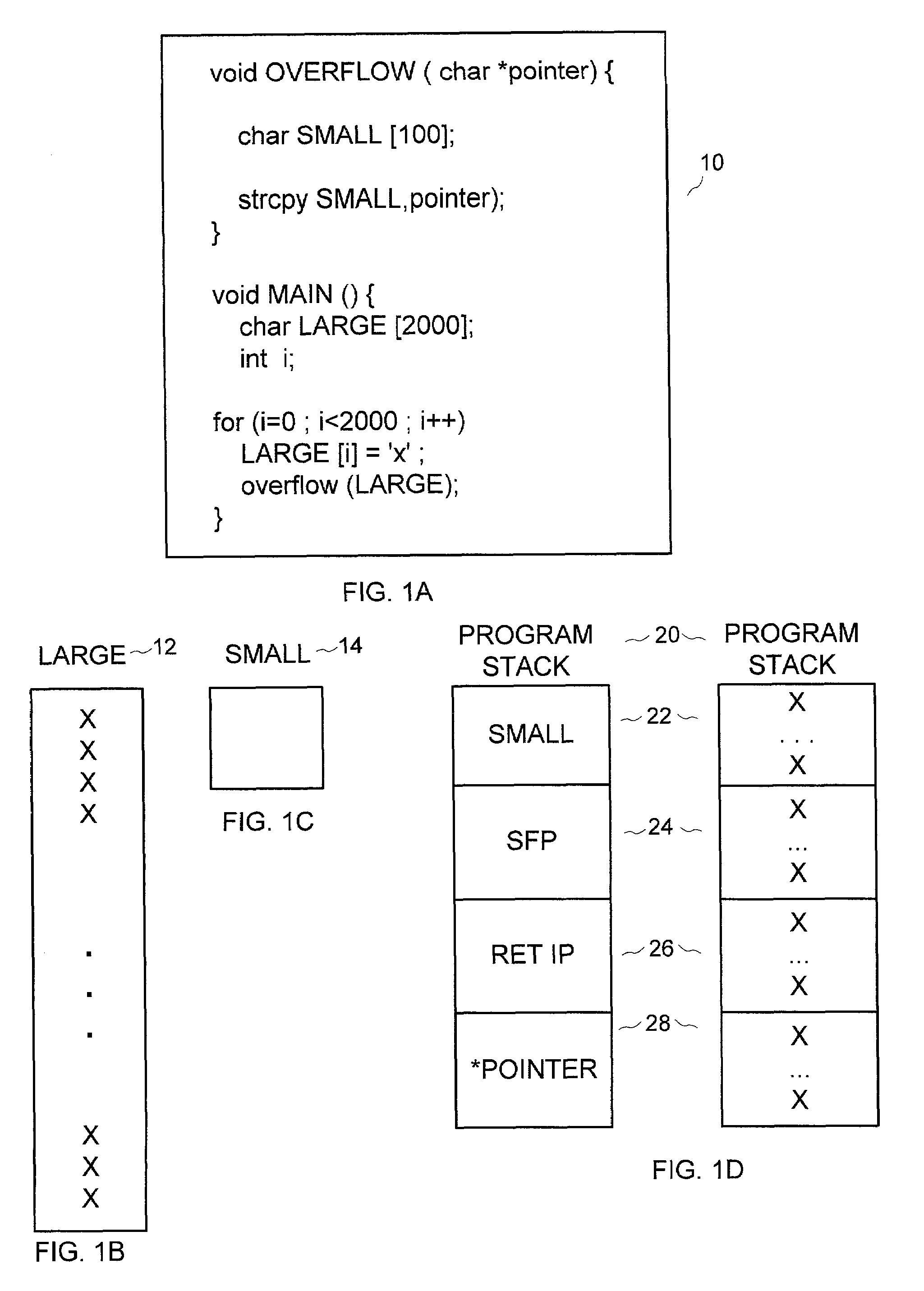
In computing, a code segment, also known as a text segment or simply as text, is a portion of an object file or the corresponding section of the program's virtual address space that contains executable instructions. The term "segment" comes from the memory segment, which is a historical approach to memory management that has been succeeded by paging. When a program is stored in an object file, the code segment is a part of this file; when the loader places a program into memory so that it may be executed, various memory regions are allocated (in particular, as pages), corresponding to both the segments in the object files and to segments only needed at run time. For example, the code segment of an object file is loaded into a corresponding code segment in memory.
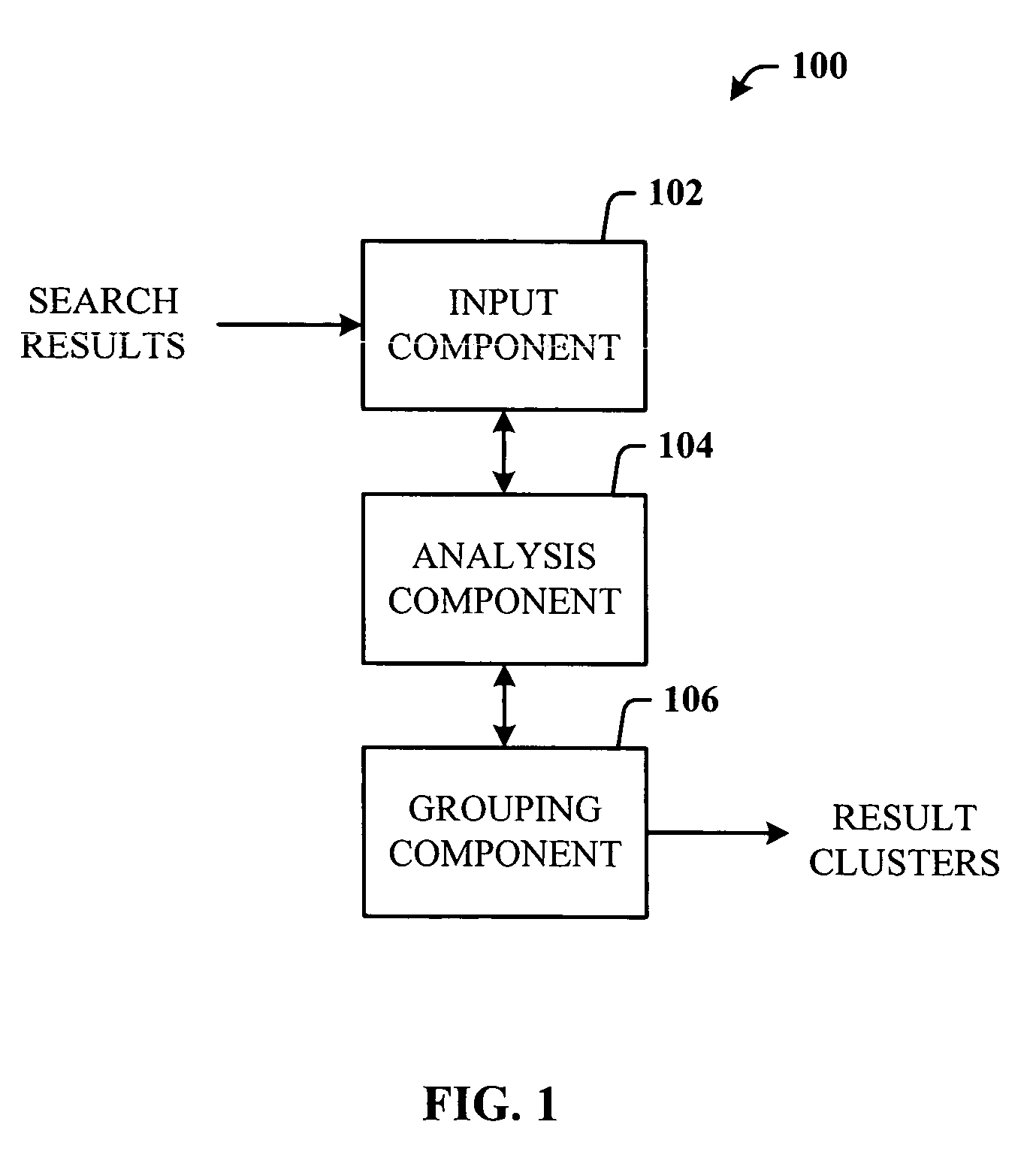
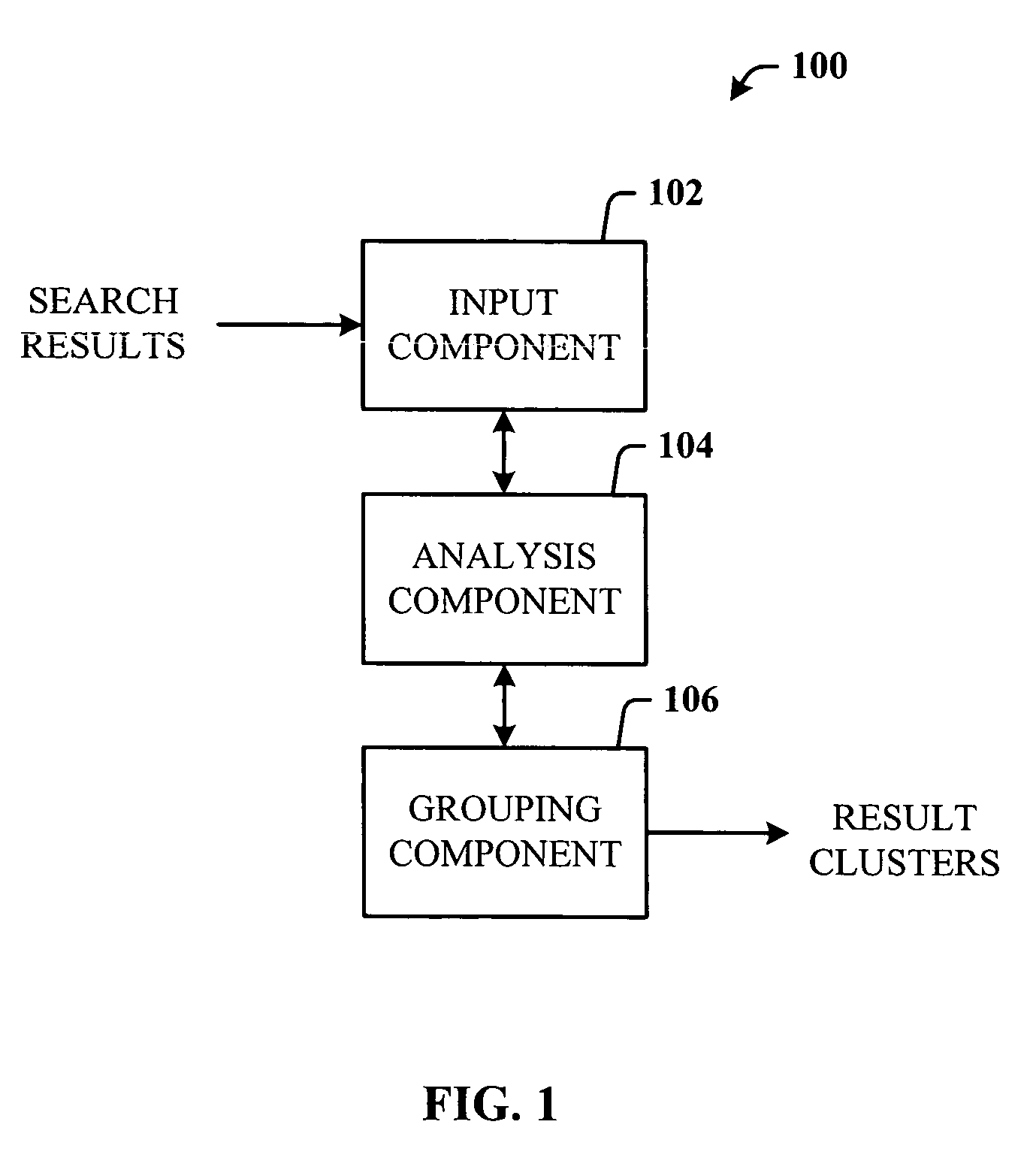
Query-based snippet clustering for search result grouping
InactiveUS20060026152A1Quick identificationEfficient identificationWeb data indexingSpecial data processing applicationsFeature vectorCo-occurrence
Owner:MICROSOFT TECH LICENSING LLC
System and method for identifying and eliminating vulnerabilities in computer software applications
ActiveUS7284274B1Memory loss protectionError detection/correctionParallel computingApplication software
Owner:SYNOPSYS INC
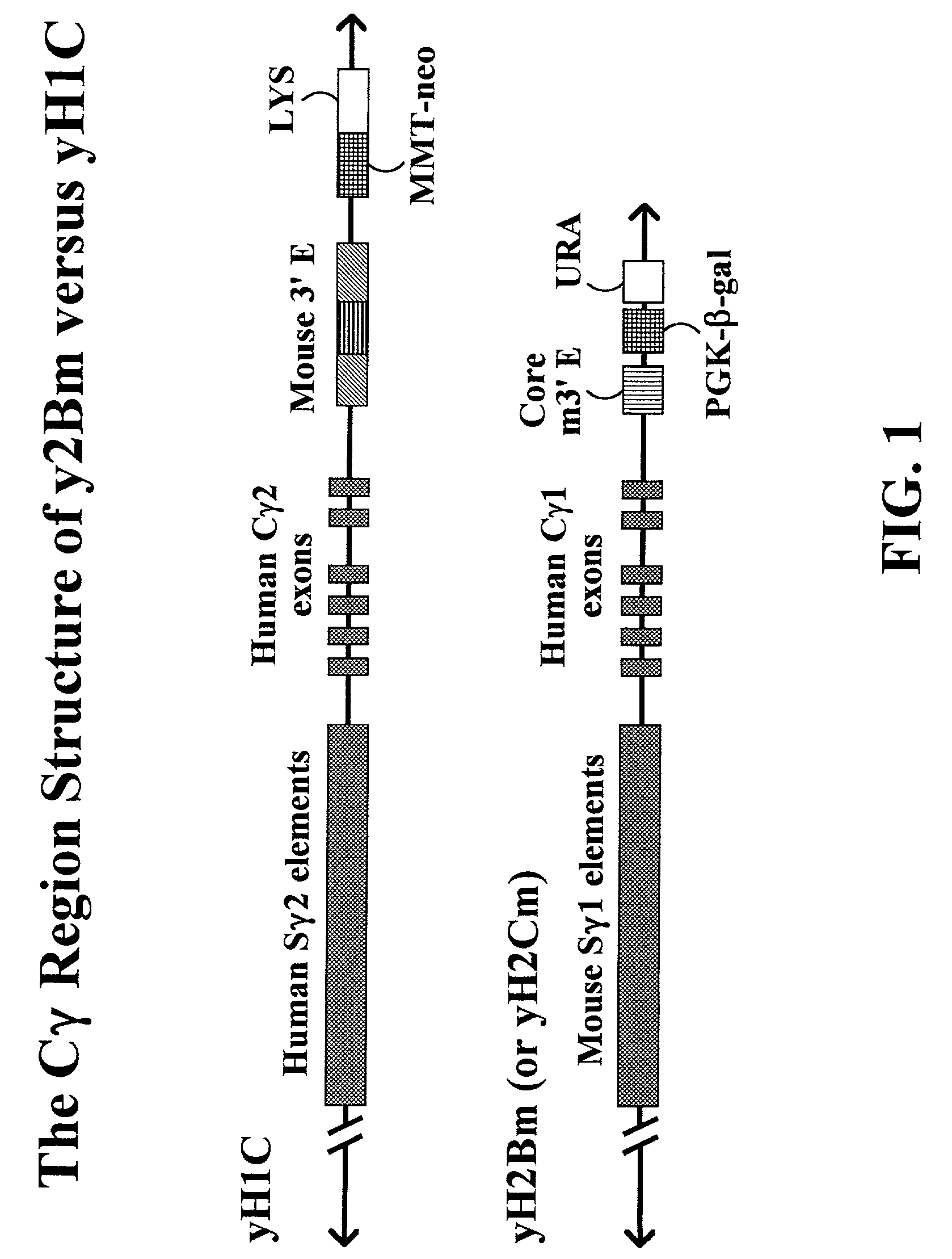
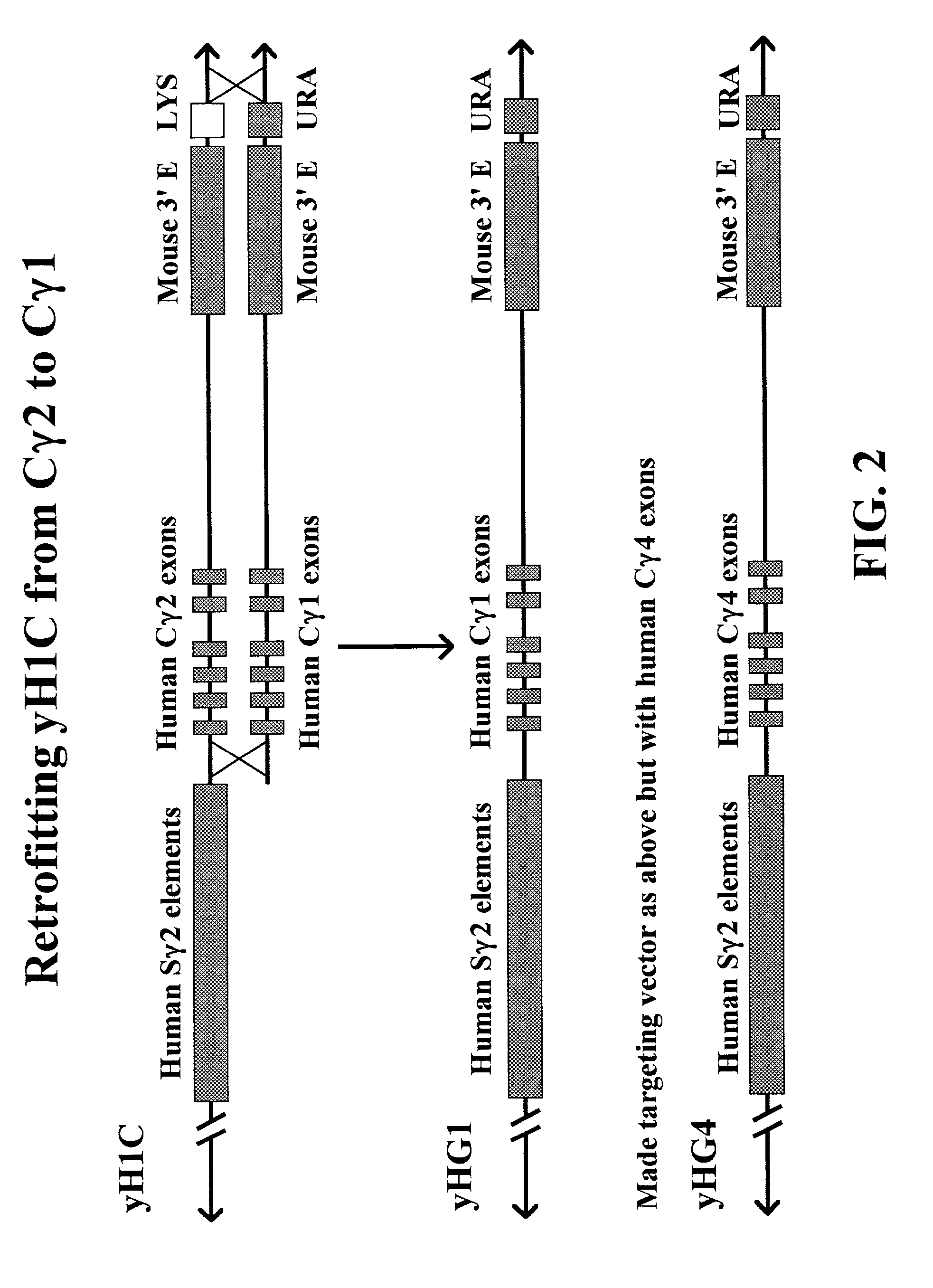
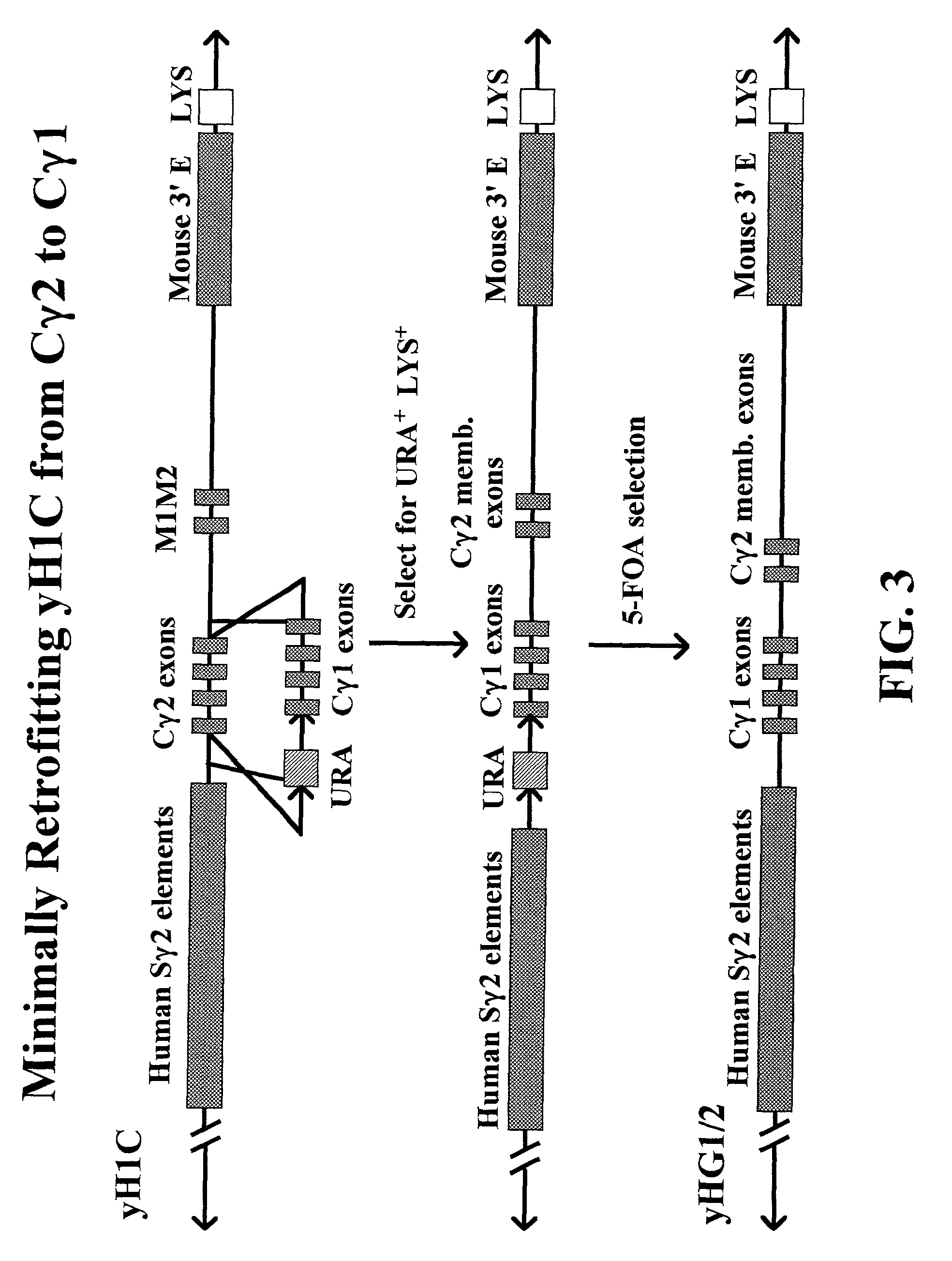
Transgenic animals for producing specific isotypes of human antibodies via non-cognate switch regions
InactiveUS7049426B2Immunoglobulins against cytokines/lymphokines/interferonsImmunoglobulins against cell receptors/antigens/surface-determinantsAntigenExon
The present invention provides fully human antibodies in a transgenic animal of a desired isotype in response to immunization with any virtually any desired antigen. The human immunoglobulin heavy chain transgene in the foregoing animals comprises a human constant region gene segment comprising exons encoding the desired heavy chain isotype, operably linked to switch segments from a constant region of a different heavy chain isotype, i.e., a non-cognate switch region. Said additional constant region segment comprises a switch region and human constant region coding segment, wherein the constant region coding segment is operably linked to a switch region that it is not normally associated with, i.e., a non-cognate switch region. In the transgenes of the invention, the non-cognate switch region may be a switch region from a different species than the constant region coding segment. The switch region and membrane exons of the invention may comprise a human gamma-2 constant region and the secreted constant region exons are from a human gamma-1 or a human gamma-4 constant region.
Owner:ABQENIX INC
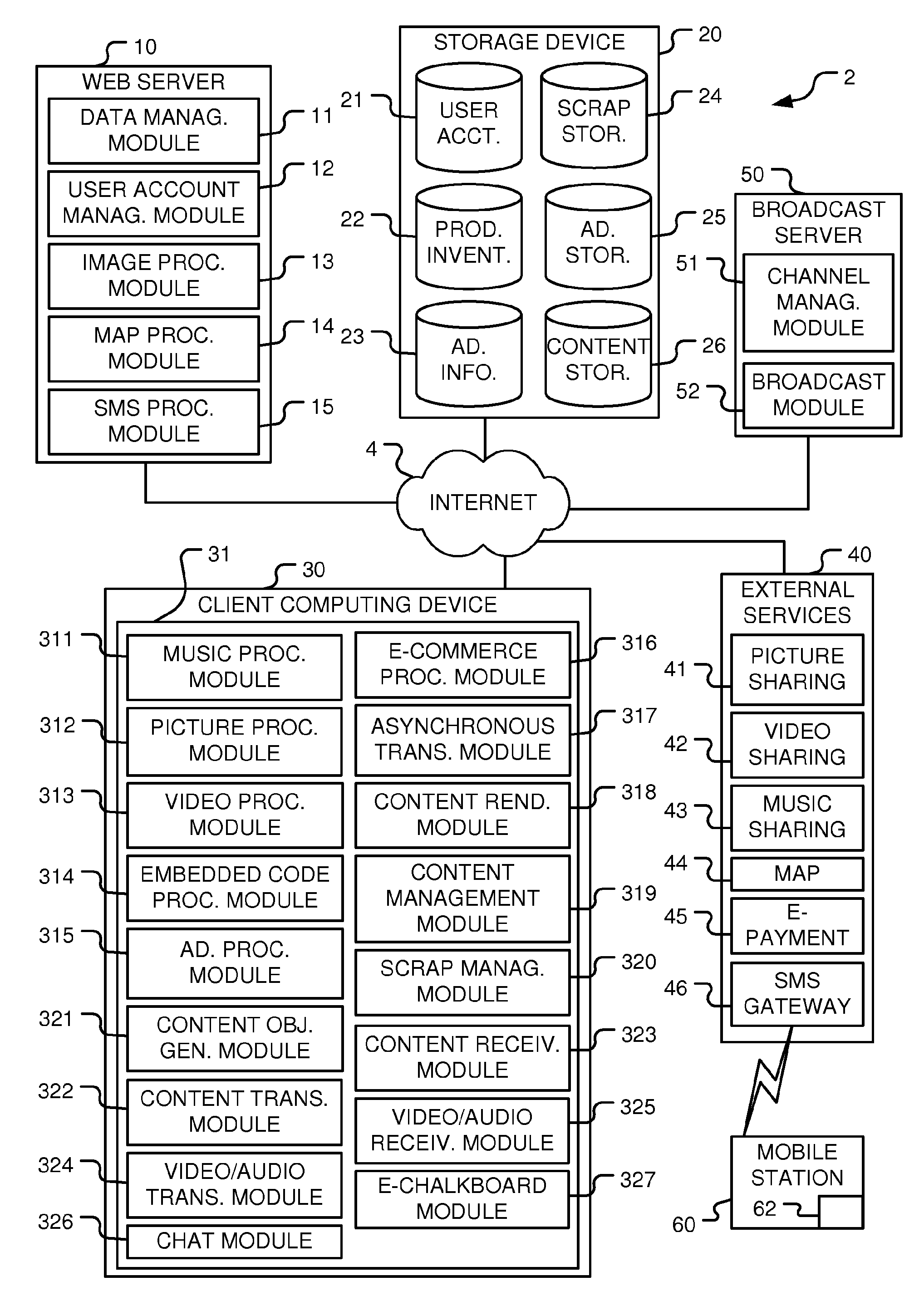
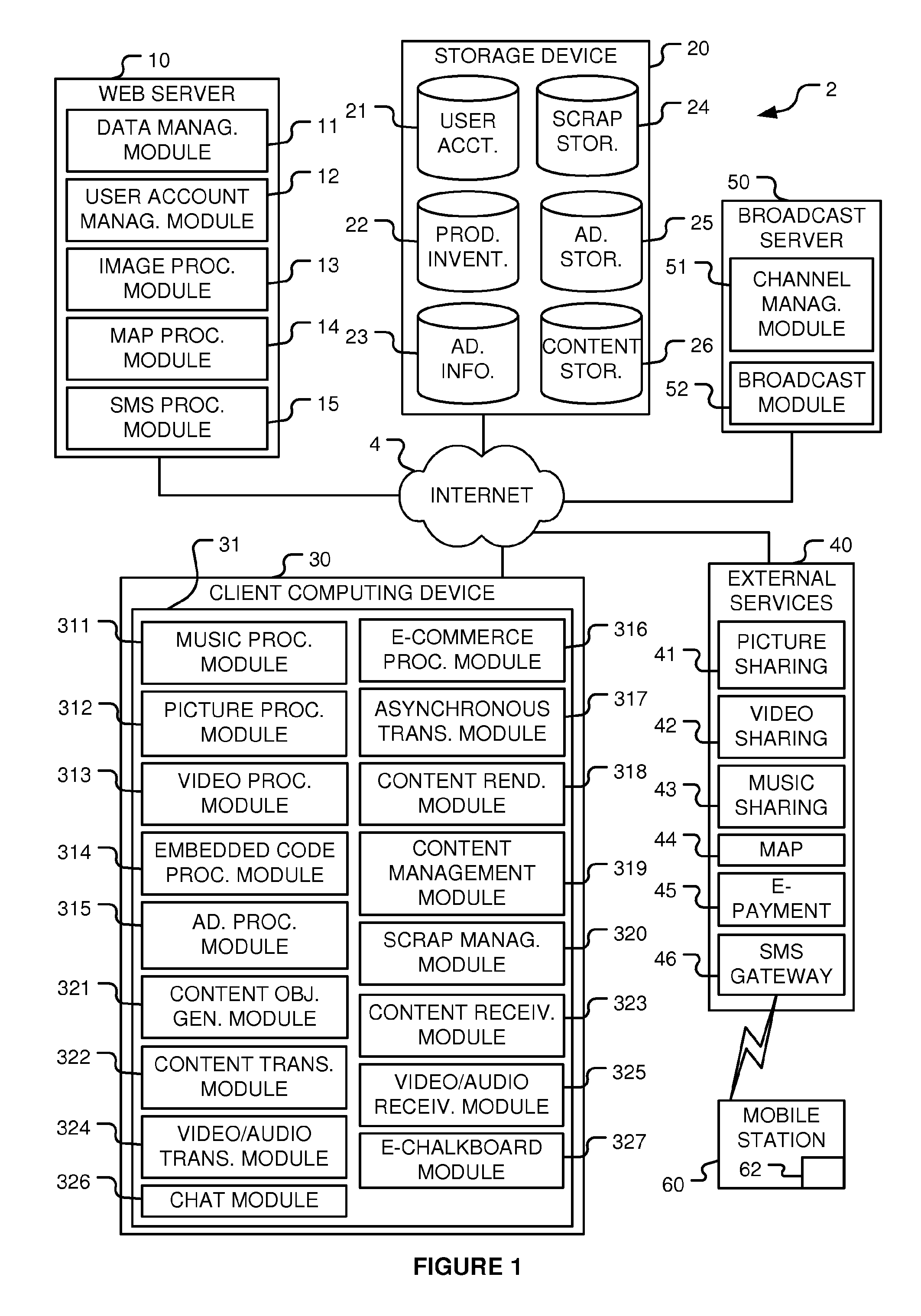
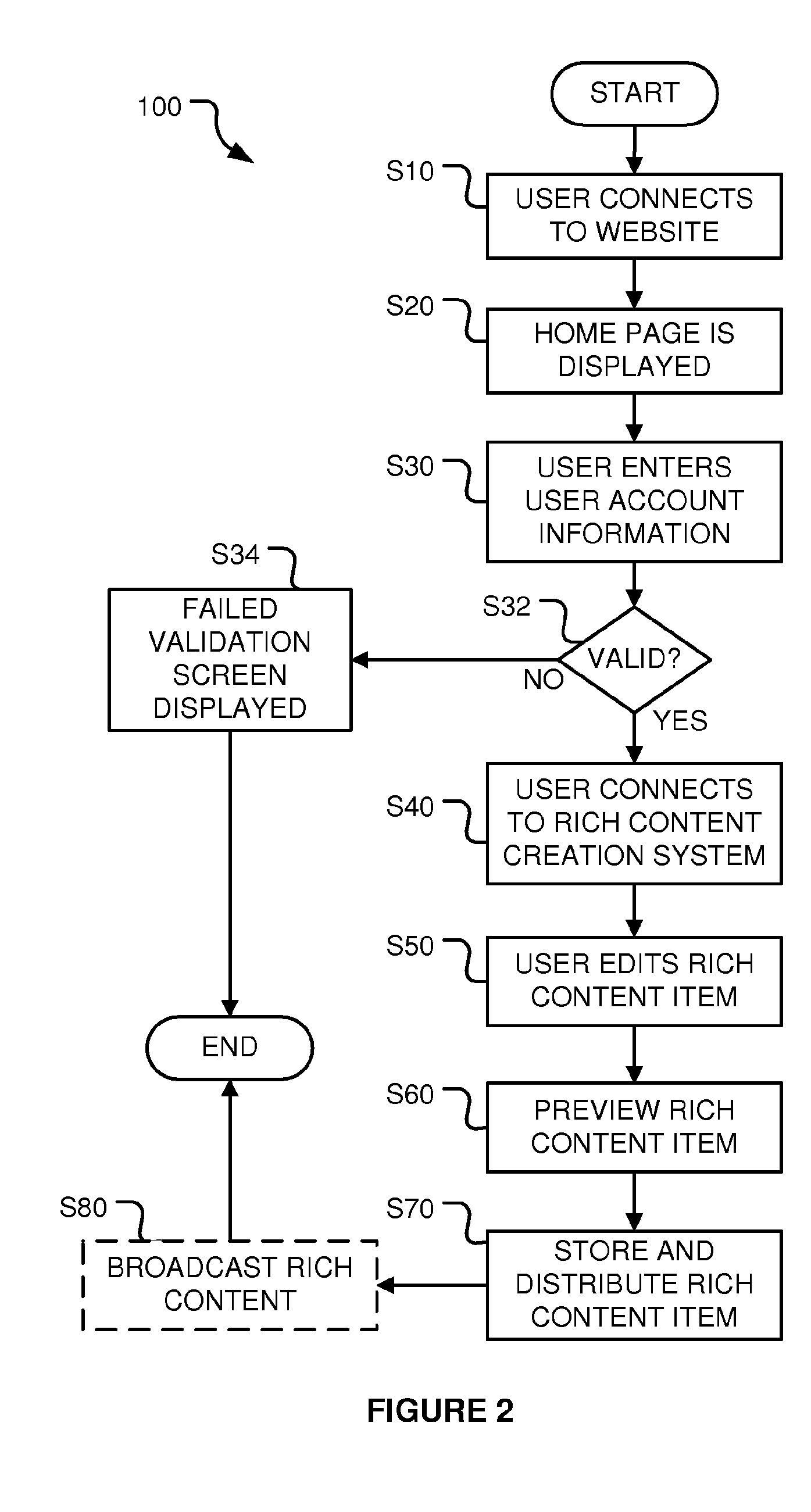
Rich content creation, distribution, and broadcasting system
InactiveUS20110202424A1Multiple digital computer combinationsBuying/selling/leasing transactionsContent creationCode segment
A system for creating rich content displayable on a webpage. The system includes content files stored on a server and an editor displayed by a client in a Rich Internet Application (‘RIA’). The editor has a region into which content objects may be inserted to create a rich content item. At least a portion of the content objects are linked to content files stored on the server. The system generates a code segment operable to generate a display on a webpage based on the rich content item that does not use the RIA. The display is substantially equivalent to the rich content item displayed in the editing region using the RIA. The code segment is configured to be search engine friendly. The system may broadcast a common Rich Content item between a Broadcaster and a viewer both of whom may edit the Rich Content item at the same time.
Owner:MOTIONCLOUD
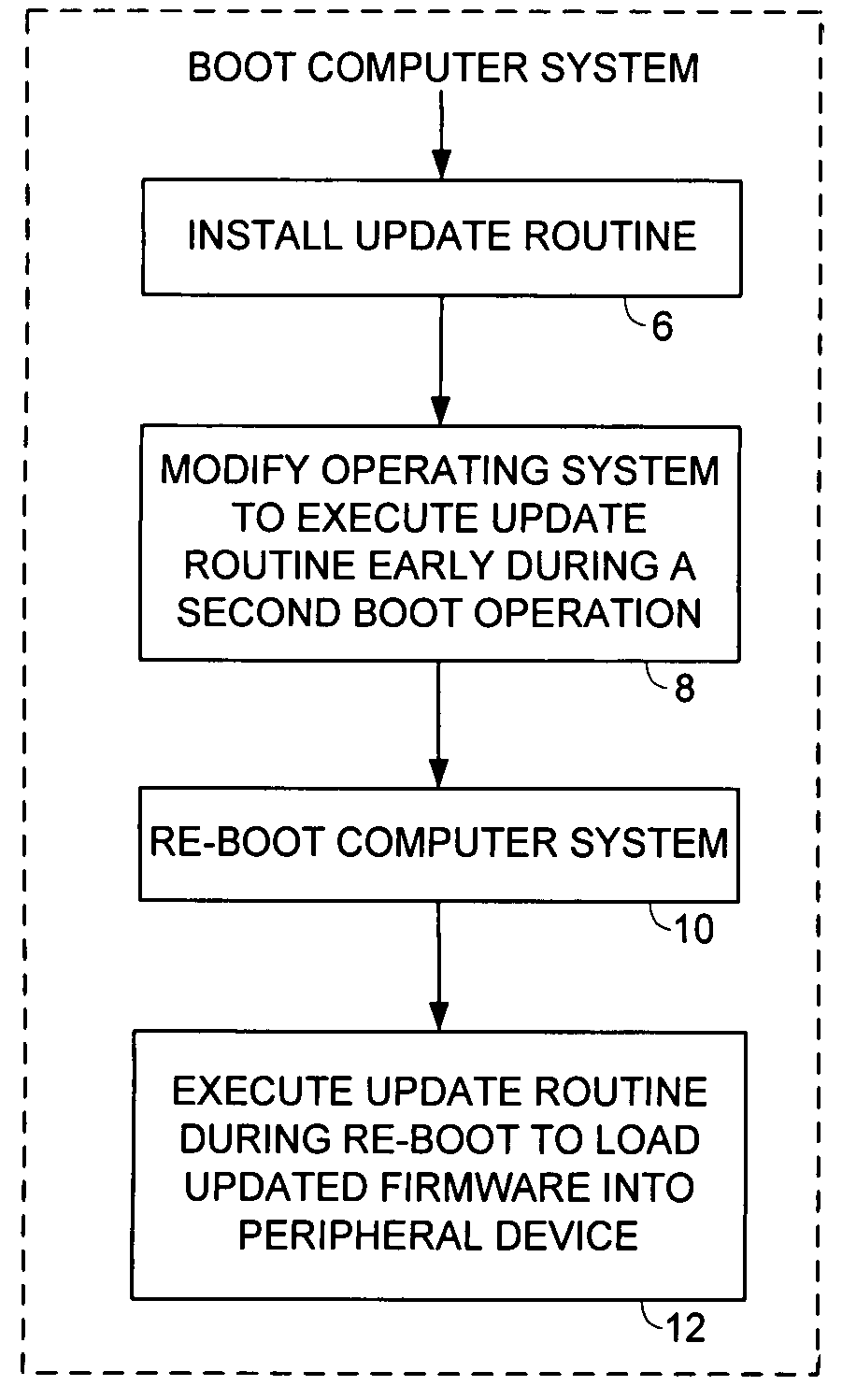
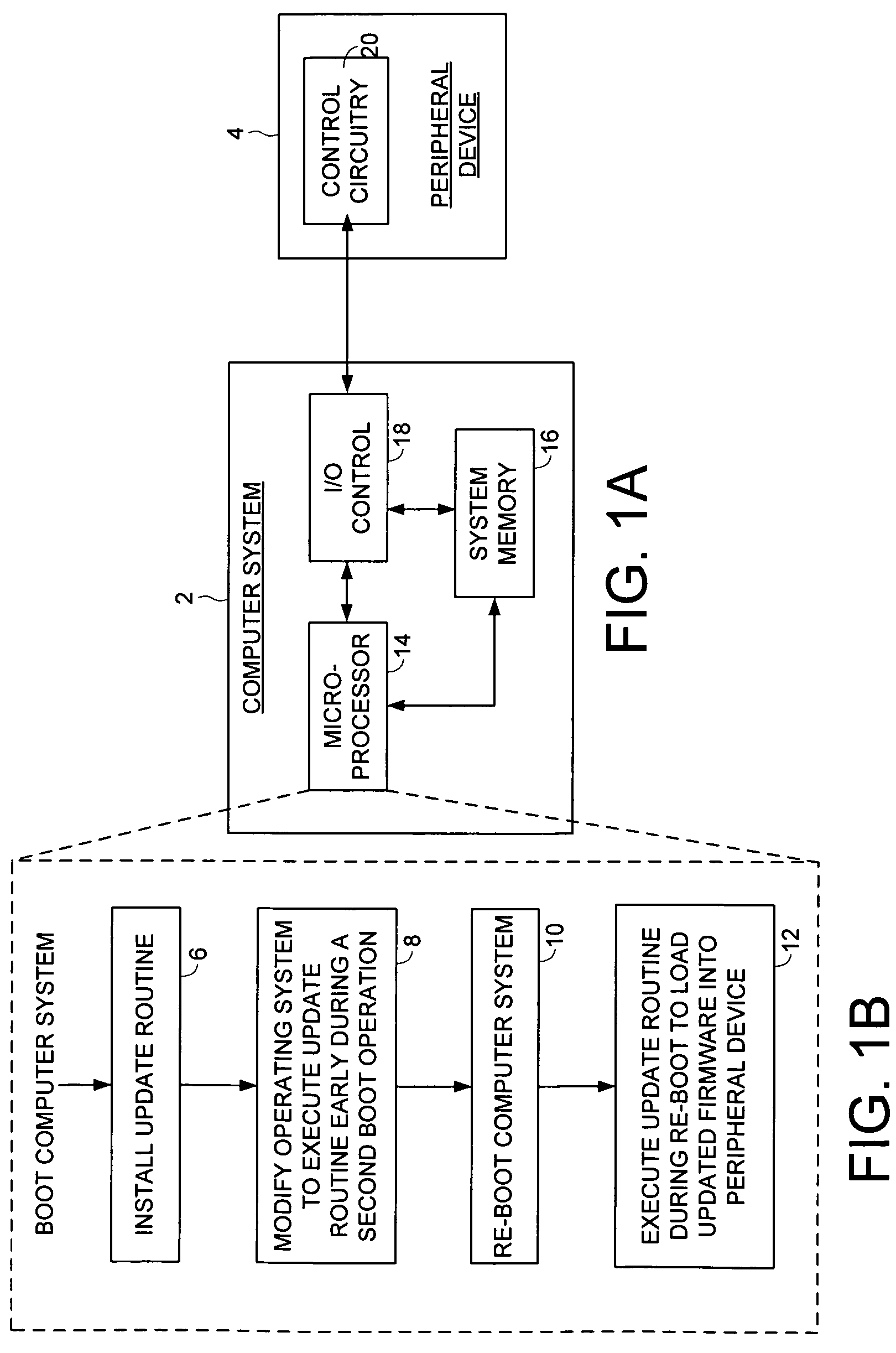
Updating firmware of a peripheral device
An embodiment of the present invention comprises a method of updating firmware of a peripheral device coupled to a computer system. A first boot operation is executed for loading an operating system into the computer system, and an update routine is installed for loading updated firmware into the peripheral device. The operating system is modified so that the update routine is executed early during a second boot operation for loading the operating system into the computer system. The second boot operation is executed, during which the update routine is executed to load the updated firmware into the peripheral device. In one embodiment, the update routine comprises an update driver having a DriverEntry code segment for loading the updated firmware into the peripheral device.
Owner:WESTERN DIGITAL TECH INC
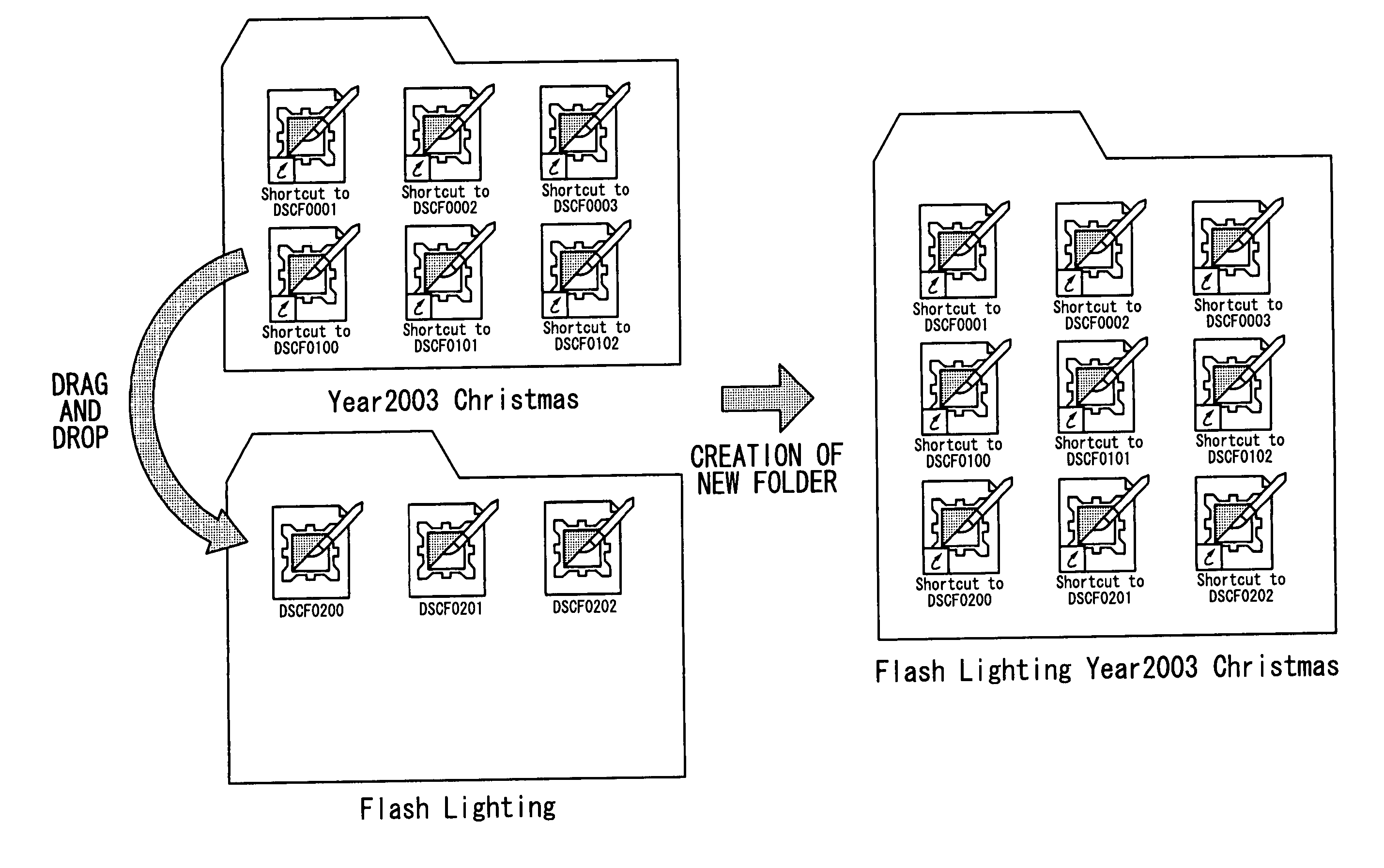
File management program
InactiveUS20050177796A1Simplified managementEasy to manageTelevision system detailsColor television detailsDrag and dropComputer science
The computer readable medium has embodied thereon a file management program for processing by a computer, the file management program comprising: a first code segment for, when an icon of a first folder displayed on a display apparatus is dragged and dropped onto another icon of a second folder displayed on the display apparatus, creating a third folder at the same level as the second folder; and a second code segment for copying a file stored in the first folder and a file stored in the second folder into the third folder.
Owner:FUJIFILM CORP
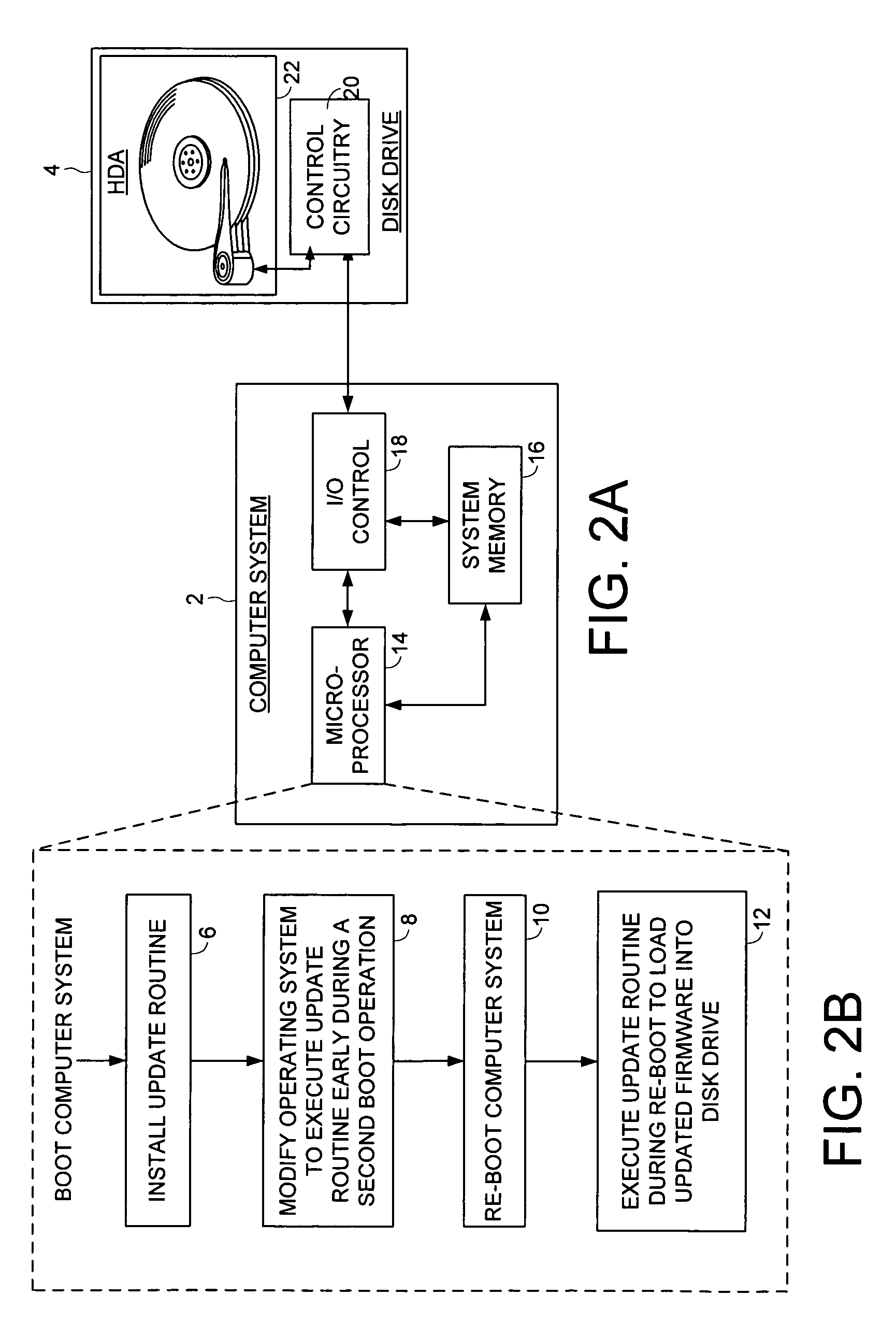
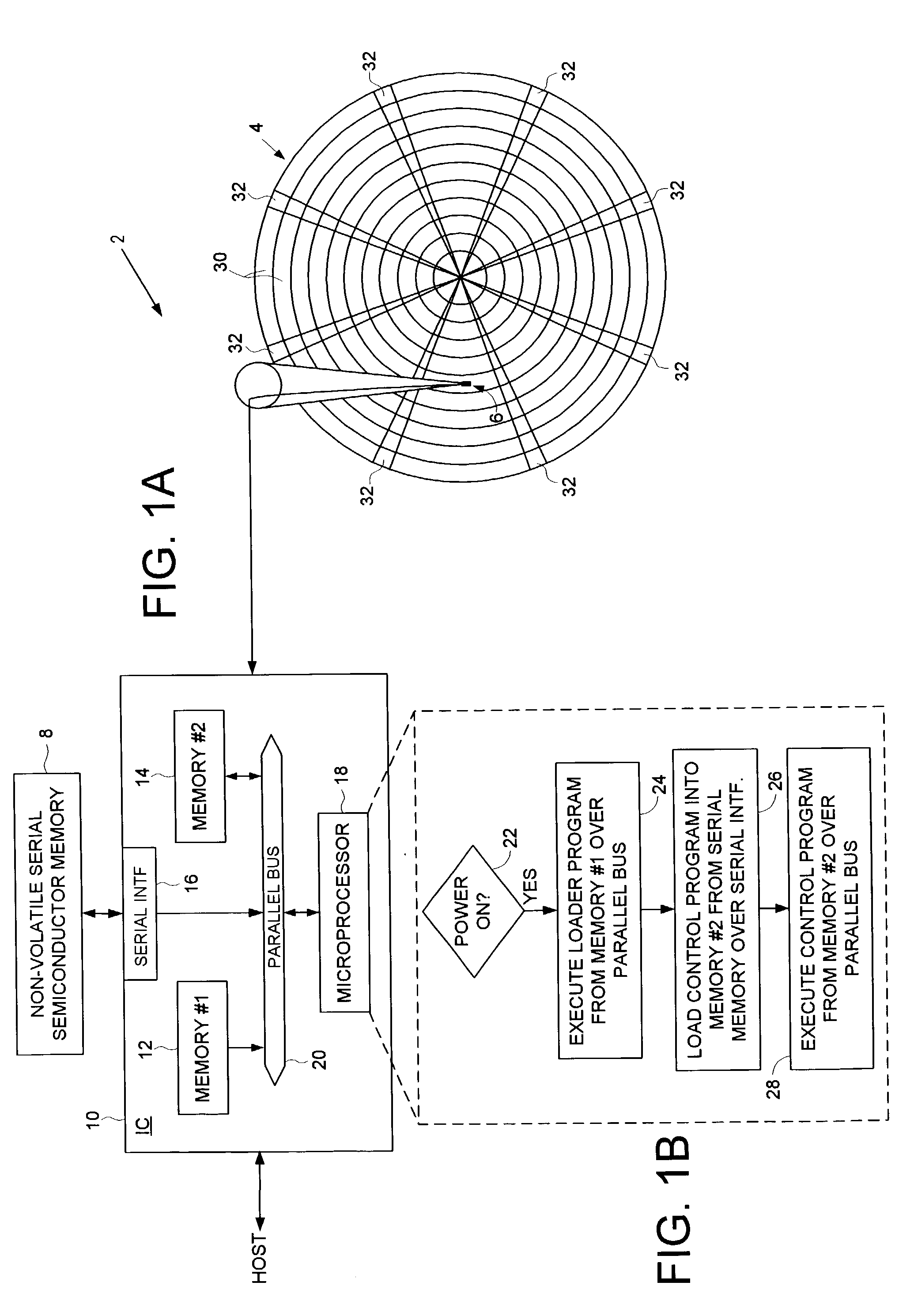
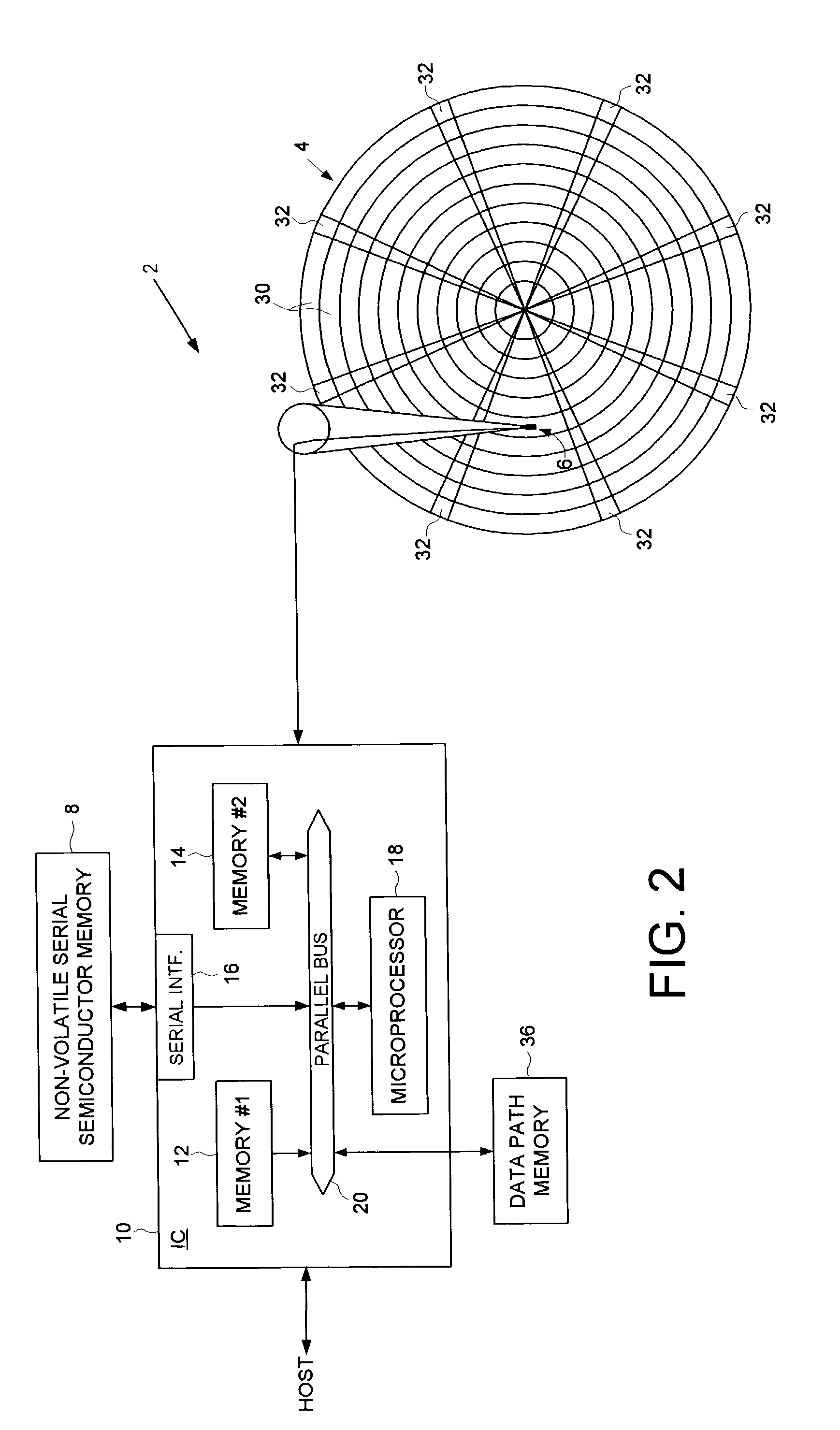
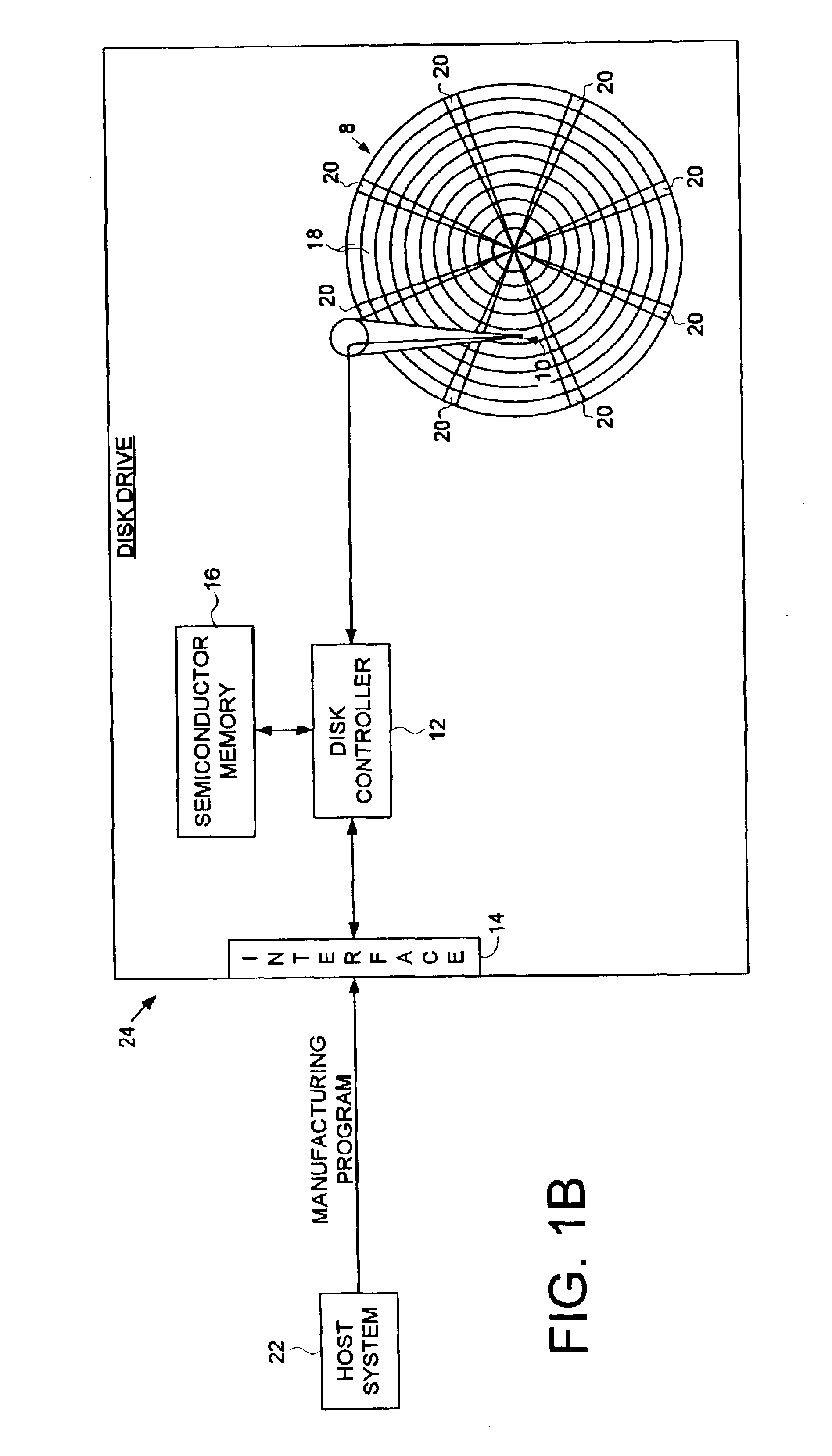
Disk drive employing a non-volatile serial semiconductor memory for storing a control program for a microprocessor
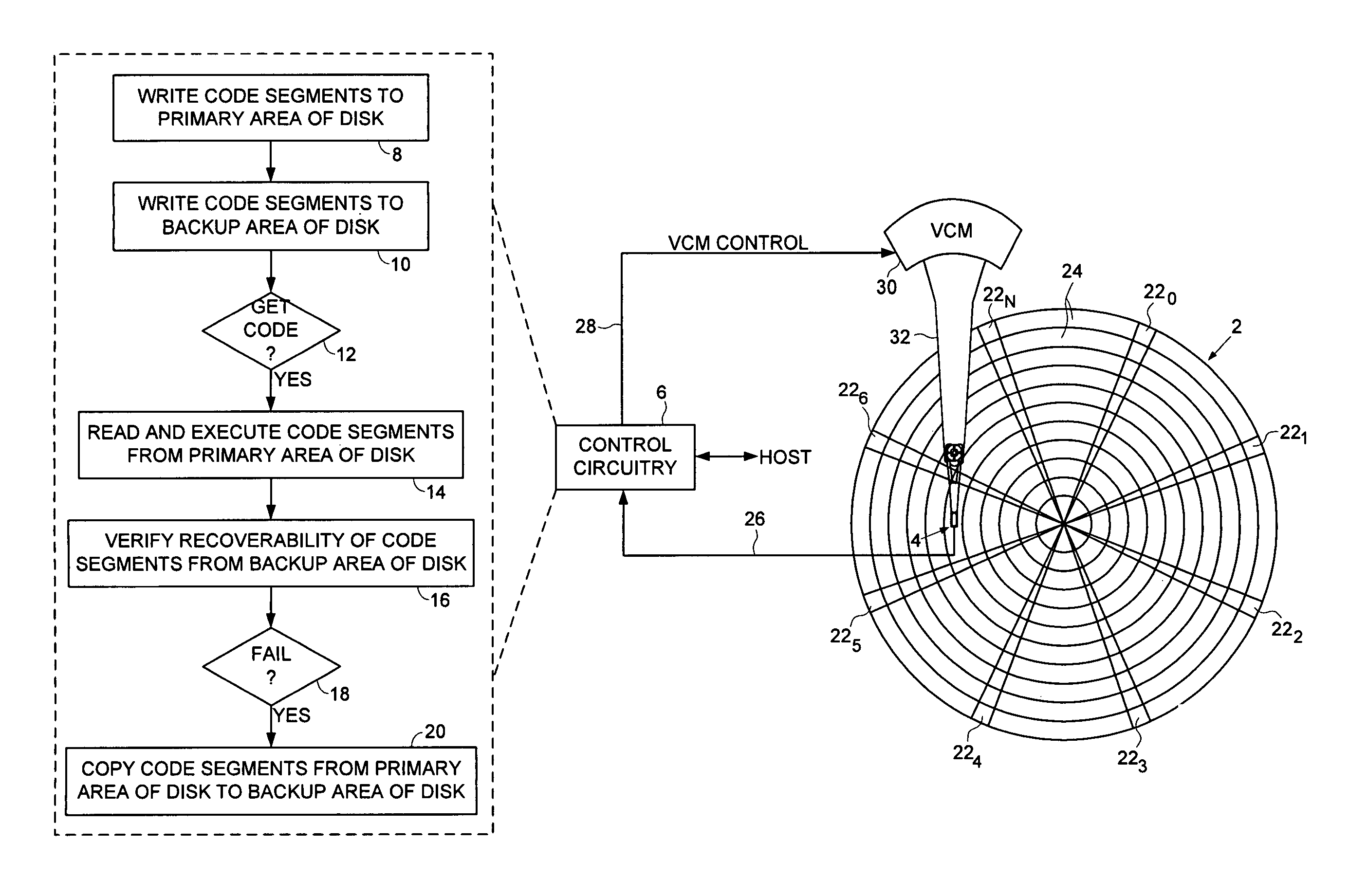
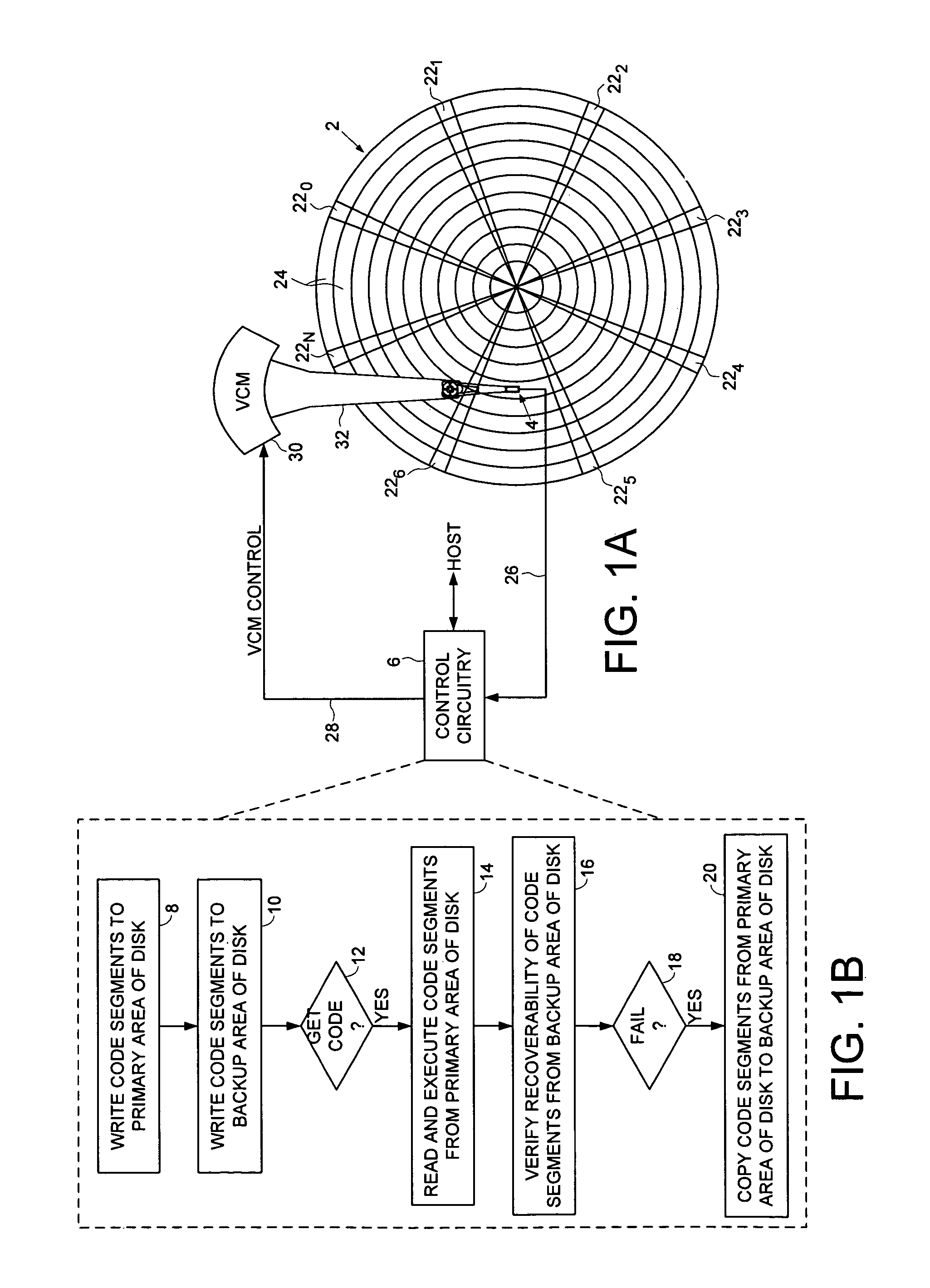
A disk drive is disclosed comprising a microprocessor, a non-volatile serial semiconductor memory for storing code segments of a control program, a first semiconductor memory for storing code segments of a loader program, and a second semiconductor memory for receiving the code segments of the control program. When the disk drive is powered on, the microprocessor executes the loader program from the first semiconductor memory to load the control program from the non-volatile serial semiconductor memory into the second semiconductor memory. The microprocessor then executes the control program from the second semiconductor memory.
Owner:WESTERN DIGITAL TECH INC
Method and mechanism for speculatively executing threads of instructions
InactiveUS6574725B1Program initiation/switchingGeneral purpose stored program computerSpeculative executionOperational system
A processor architecture containing multiple closely coupled processors in a form of symmetric multiprocessing system is provided. The special coupling mechanism allows it to speculatively execute multiple threads in parallel very efficiently. Generally, the operating system is responsible for scheduling various threads of execution among the available processors in a multiprocessor system. One problem with parallel multithreading is that the overhead involved in scheduling the threads for execution by the operating system is such that shorter segments of code cannot efficiently take advantage of parallel multithreading. Consequently, potential performance gains from parallel multithreading are not attainable. Additional circuitry is included in a form of symmetrical multiprocessing system which enables the scheduling and speculative execution of multiple threads on multiple processors without the involvement and inherent overhead of the operating system. Advantageously, parallel multithreaded execution is more efficient and performance may be improved.
Owner:GLOBALFOUNDRIES INC
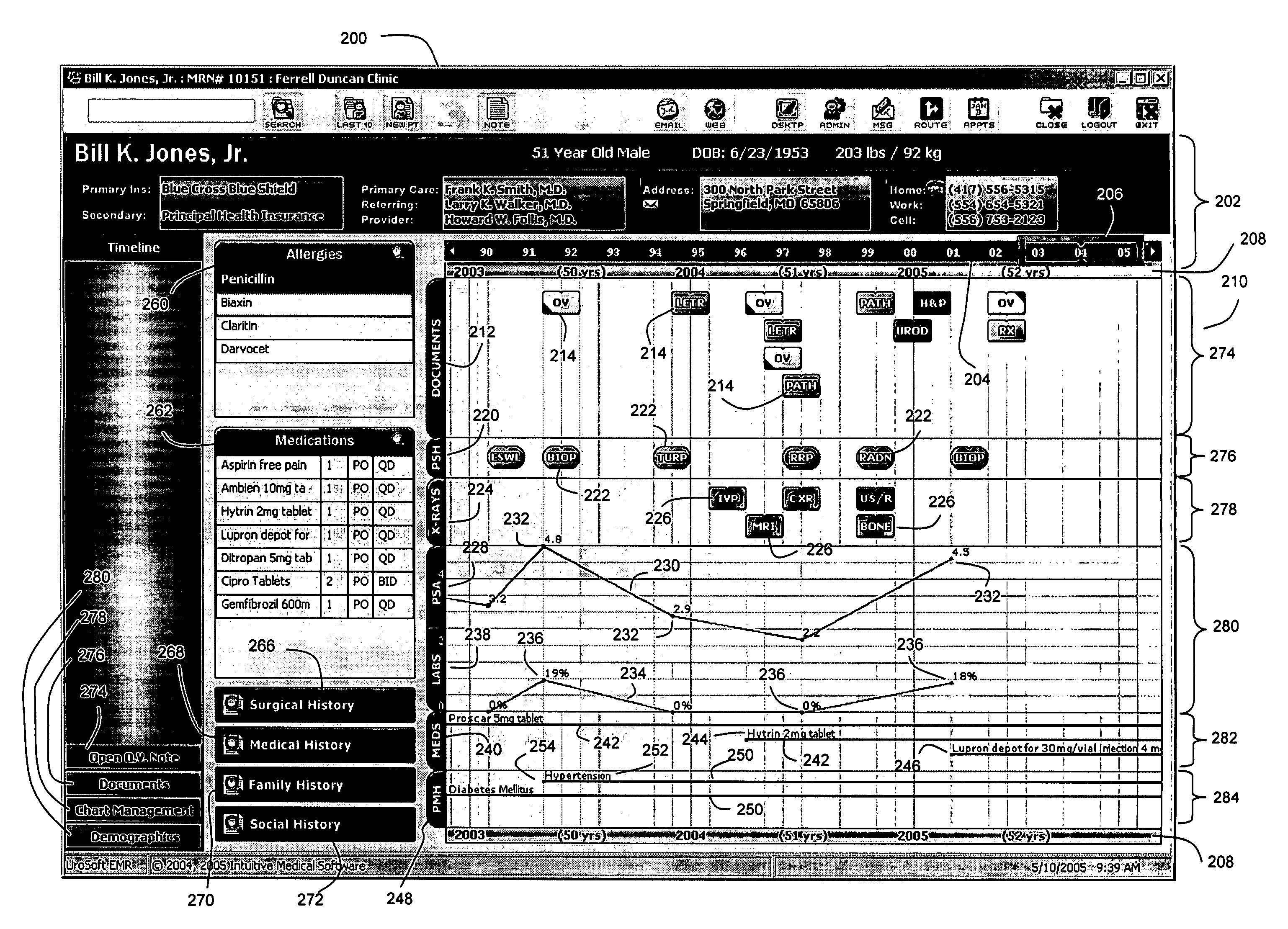
Method, system, and computer-readable medium for providing a patient electronic medical record with an improved timeline
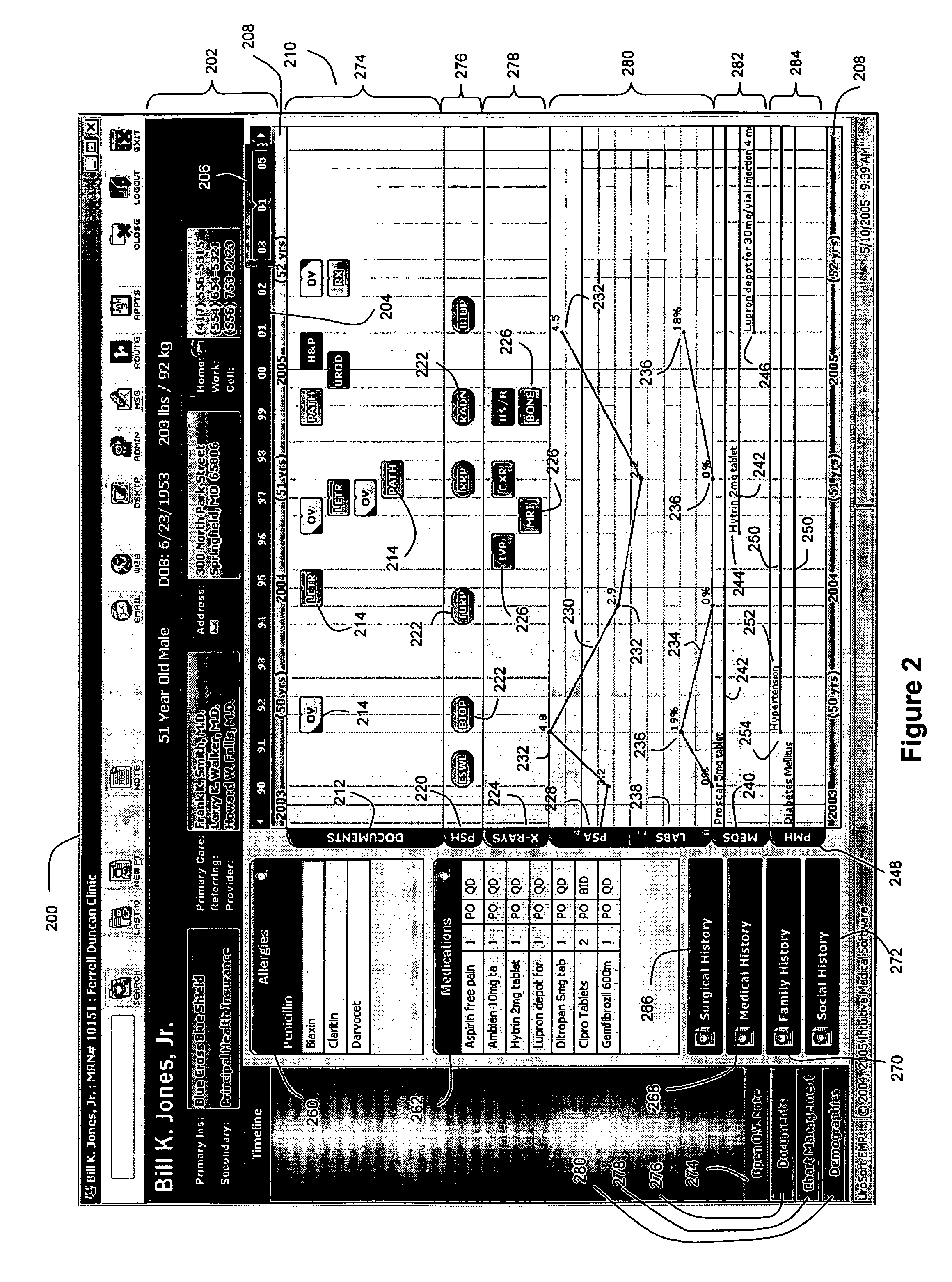
InactiveUS20060265249A1Easy to useEasy accessData processing applicationsMedical report generationMedical recordGraphics
A computer-readable medium for displaying and providing access to a stored patient electronic medical record (EMR), the computer-readable medium comprising a code segment executable by a processor for providing a user interface screen for display to a user, the user interface screen comprising a graphically-displayed timeline, the timeline comprising a first axis for time and a second axis that is substantially perpendicular to the first axis, the second axis being divided into a plurality of sections in parallel with each other, each section corresponding to a different type of patient information, each section comprising a display of patient data corresponding to that section's type of patient information, wherein the displayed patient data in each section is located on the timeline at a position such that the patient data is chronologically-ordered. The displayed timeline can be used as an access point for retrieving a wealth of information about the patient. Also disclosed herein are corresponding methods and systems for displaying and providing access to electronic patient medical records.
Owner:INTUITIVE MEDICAL SOFTWARE
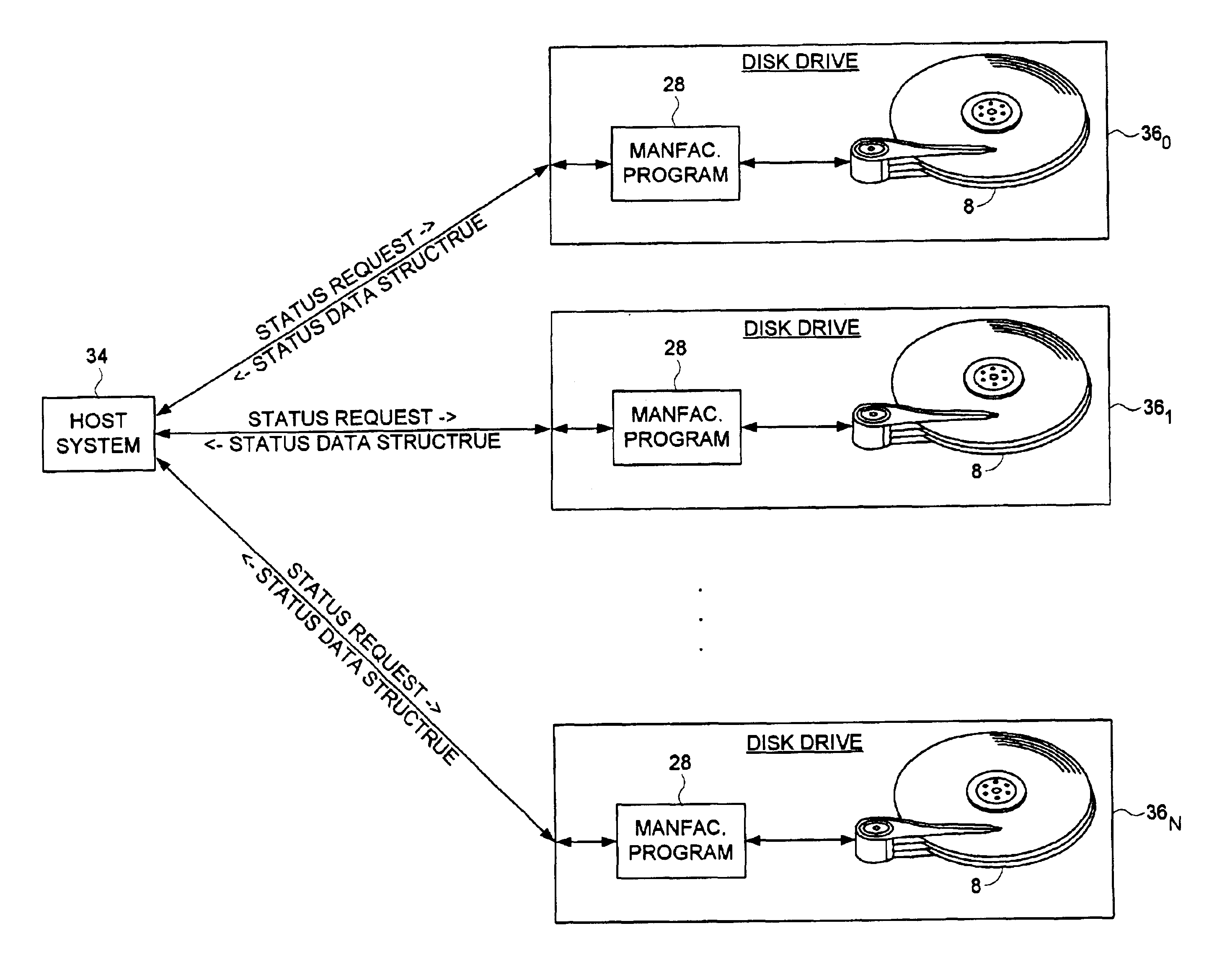
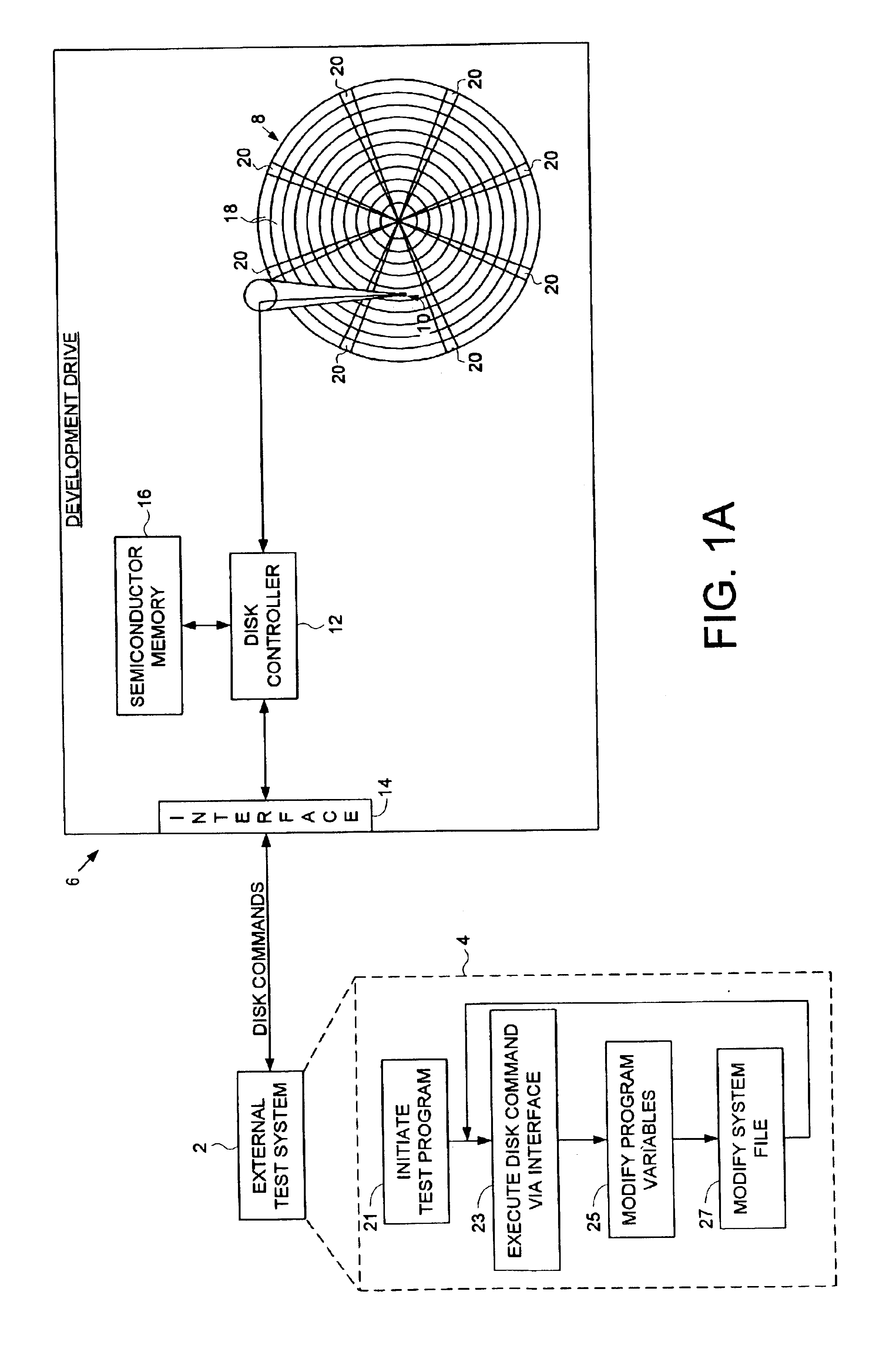
Disk drive executing a manufacturing program internally by executing disk commands through a vector
A disk drive is disclosed for executing a drive operating program and a manufacturing program during a manufacturing process. An external test system executes a test program comprising platform independent executable code segments and host interface executable code segments. The external test system for executing the host interface executable code segments to send disk commands to a development drive. The manufacturing program comprises the platform independent executable code segments of the test program and disk access executable code segments. The drive operating program comprises a disk access procedure for processing disk commands and a disk access vector for calling the disk access procedure. The disk access executable code segments of the manufacturing program execute disk commands by calling the disk access procedure of the drive operating program through the disk access vector.
Owner:WESTERN DIGITAL TECH INC
System and method for automatically filling webpage fields
A computer-implemented method for automatically populating fields of an online webpage. The method includes inserting a code segment into a first webpage that is configured to populate fields included in the first webpage with received data, where the first webpage is displayed on a display device in a web browser application executing on a computer system; receiving data from a second webpage; and executing the code segment to populate the fields based on the received data.
Owner:VERIENT
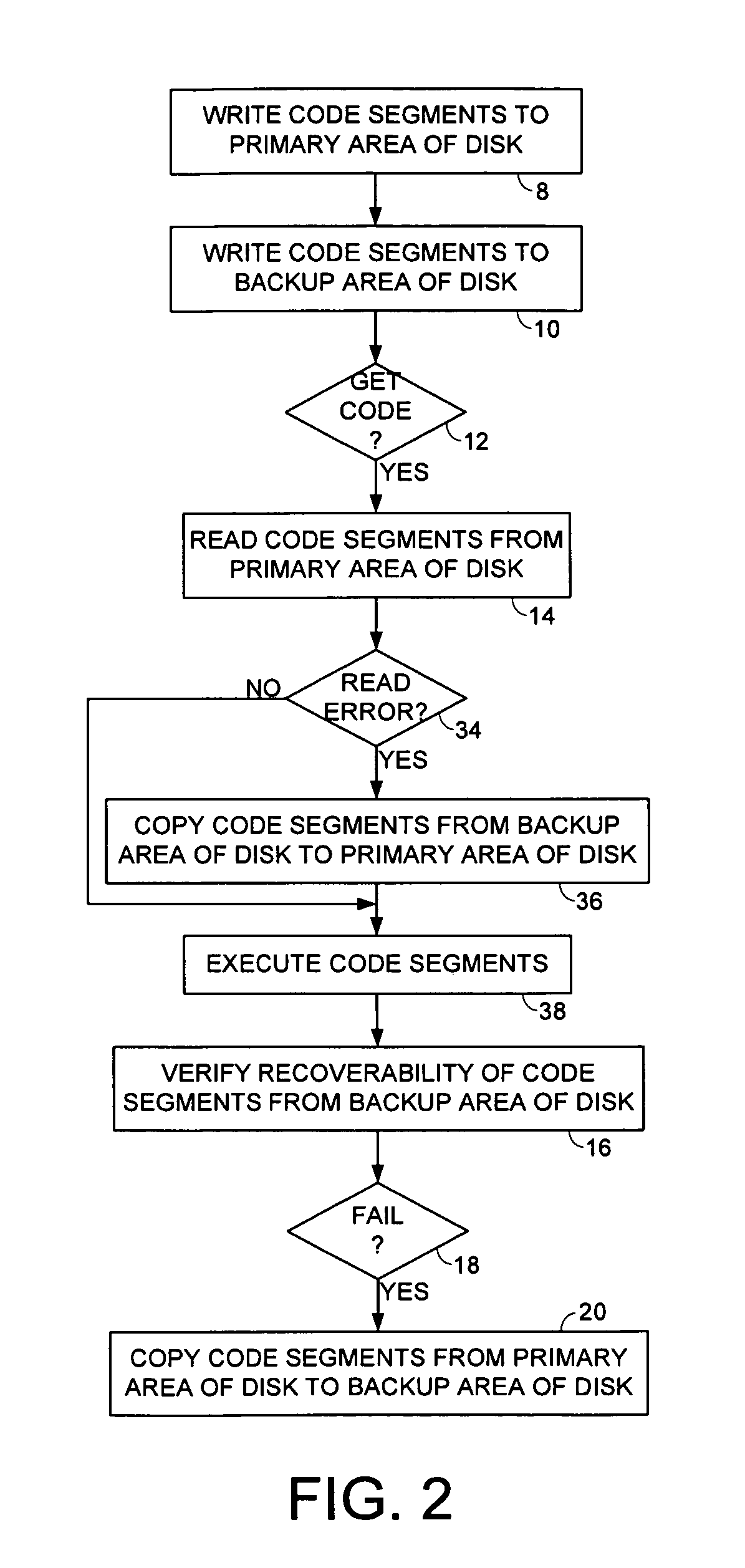
Disk drive maintaining multiple copies of code segments
InactiveUS8190575B1Digital data processing detailsRecord information storageControl circuitCode segment
Owner:WESTERN DIGITAL TECH INC
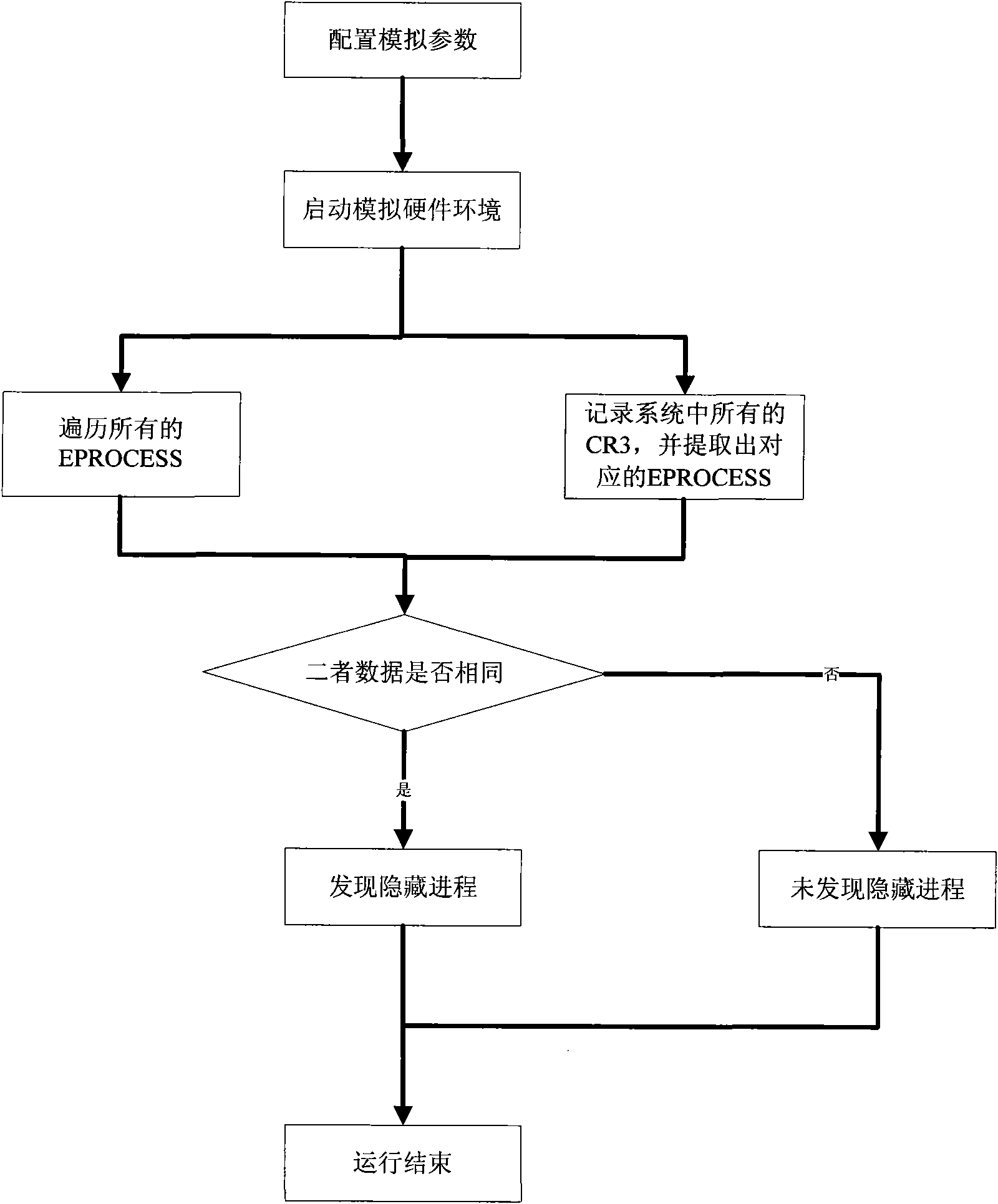
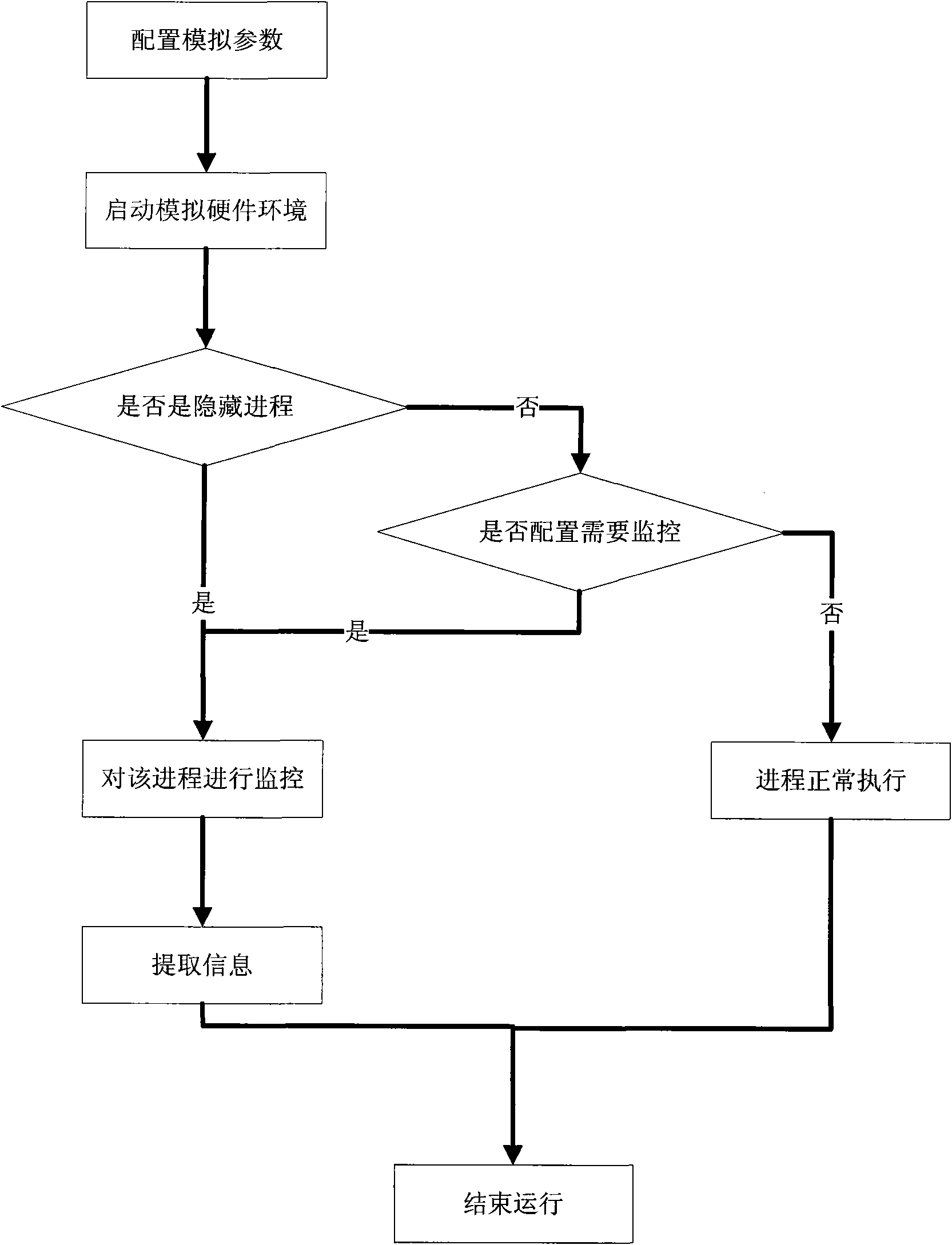
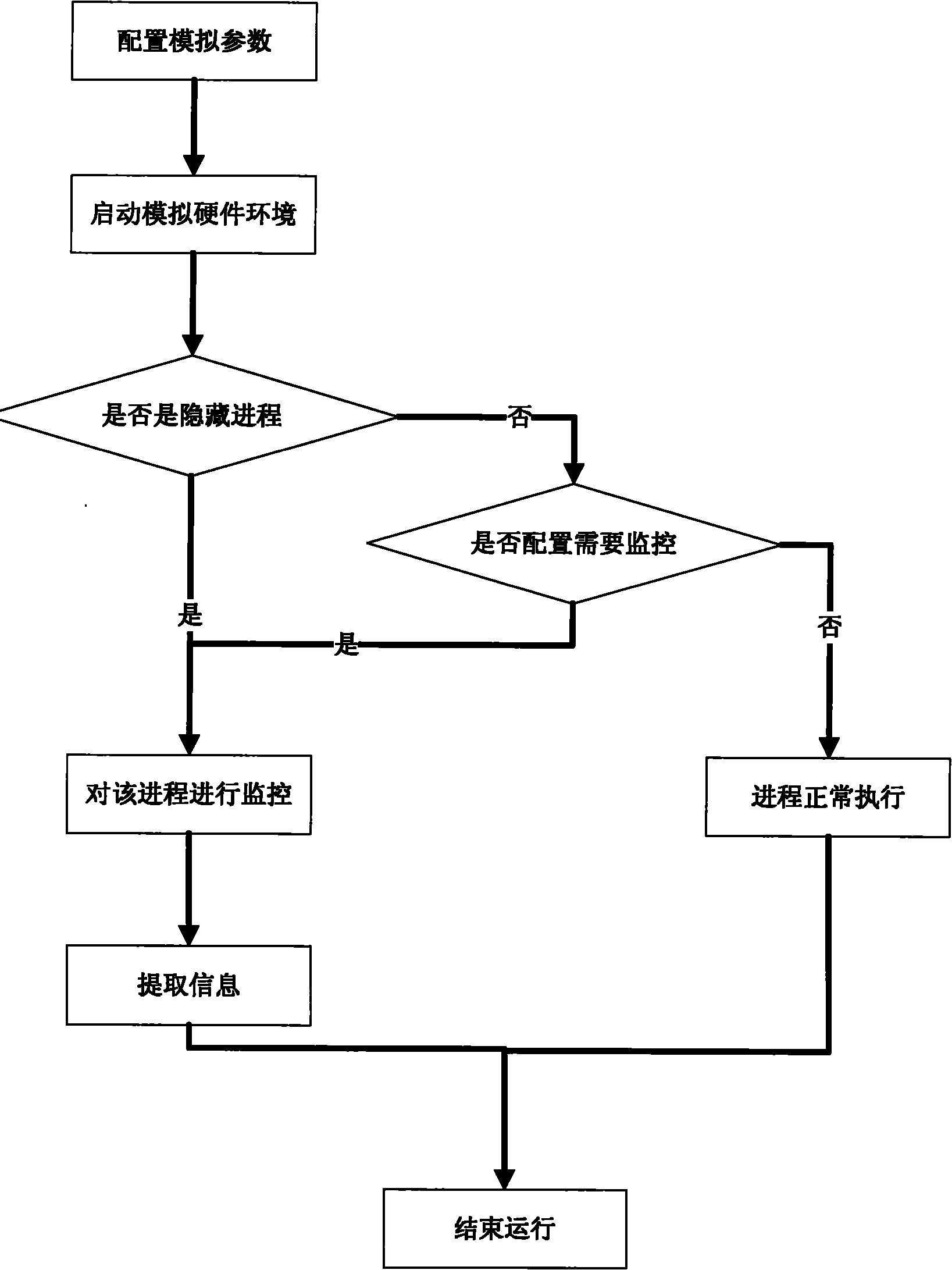
Method for processing hidden process based on hardware simulator
InactiveCN101770551ATransparent analysisEnsure transparencyPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual memoryData acquisition
The invention belongs to the technical field of network security and particularly relates to a method for processing a hidden process based on a hardware simulator. By establishing a running environment of malicious codes in hidden codes in a hardware simulating environment and operating and controlling instructions simulating a CPU and various accessing operations simulating a memory, marked by a CR3 value in a CR3 register, the hidden process is detected, the running process of the hidden process is monitored, and the running information of the malicious codes in the hidden process is recorded by a data acquisition module; and the invention also provides a mirror image which extracts the malicious codes directly from a virtual memory. All instructions of a virtual CPU and various hardware operations of a hardware simulating device are executed in simulation after translation and are not executed in a real machine by using code segments directly, and the running time of the instruction in the instruction running process can be accurately calculated, thus realizing fully transparent analysis of the malicious codes in the hidden process.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
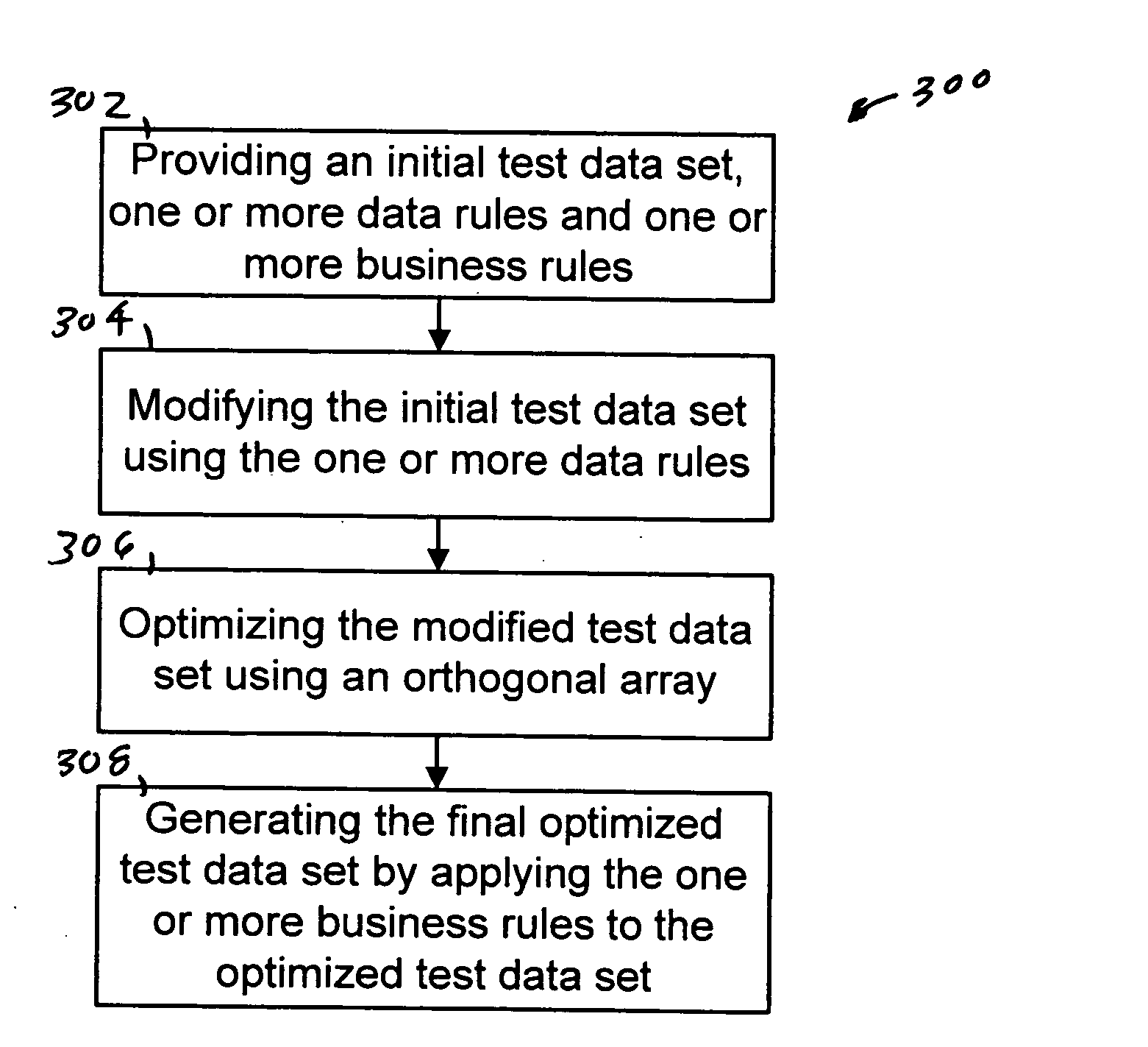
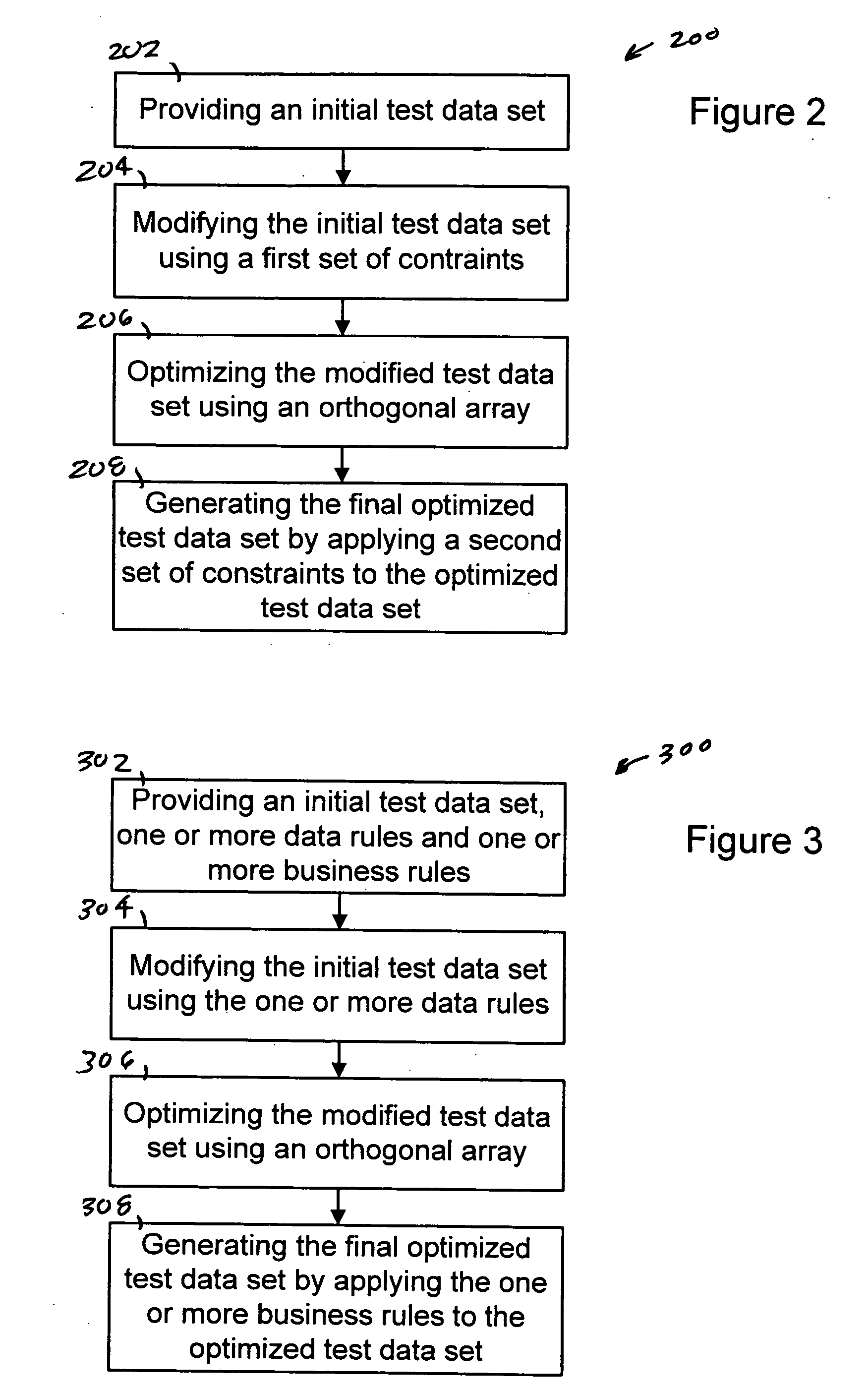
System and method for generating optimized test cases using constraints based upon system requirements
InactiveUS20060010426A1Error detection/correctionSpecific program execution arrangementsData setSystem requirements
The present invention provides a system, method and computer program for generating a final optimized test data set. An initial test data set, one or more data rules and one or more business rules are provided. The initial test data set is then modified using the one or more data rules. The modified test data set is optimized using an orthogonal array. The final optimized test data set is then generated by applying the one or more business rules to the optimized test data. The present invention can be implemented using a computer program embodied on a computer readable medium wherein each step is executed by one or more code segments. The system used to implement the present invention may include a data storage device, a processor and one or more input / output devices.
Owner:SMARTWARE TECH
Utilizing software locking approach to execute code upon failure of hardware transactional approach
Utilizing a software locking approach to execute a code section, upon failure of a hardware transactional approach, is disclosed. A method is disclosed that includes utilizing a hardware approach to transactional memory to execute a code section relating to memory. Where utilizing the hardware approach fails a threshold in executing the code section, the software approach is instead utilized to execute the code section relating to the memory. The threshold may include the hardware approach aborting execution of the code section a predetermined one or more times. The hardware approach includes starting a transaction inclusive of the code section, conditionally executing the transaction, and upon successfully completing the transaction, committing execution to memory. The software locking approach includes placing a lock on memory, executing the code section, committing execution of the code section to the memory as the code section is executed, and then removing the lock from the memory.
Owner:IBM CORP
Query-based snippet clustering for search result grouping
InactiveUS7617176B2Quick resultsEfficient identificationData processing applicationsWeb data indexingFeature vectorCo-occurrence
Owner:MICROSOFT TECH LICENSING LLC
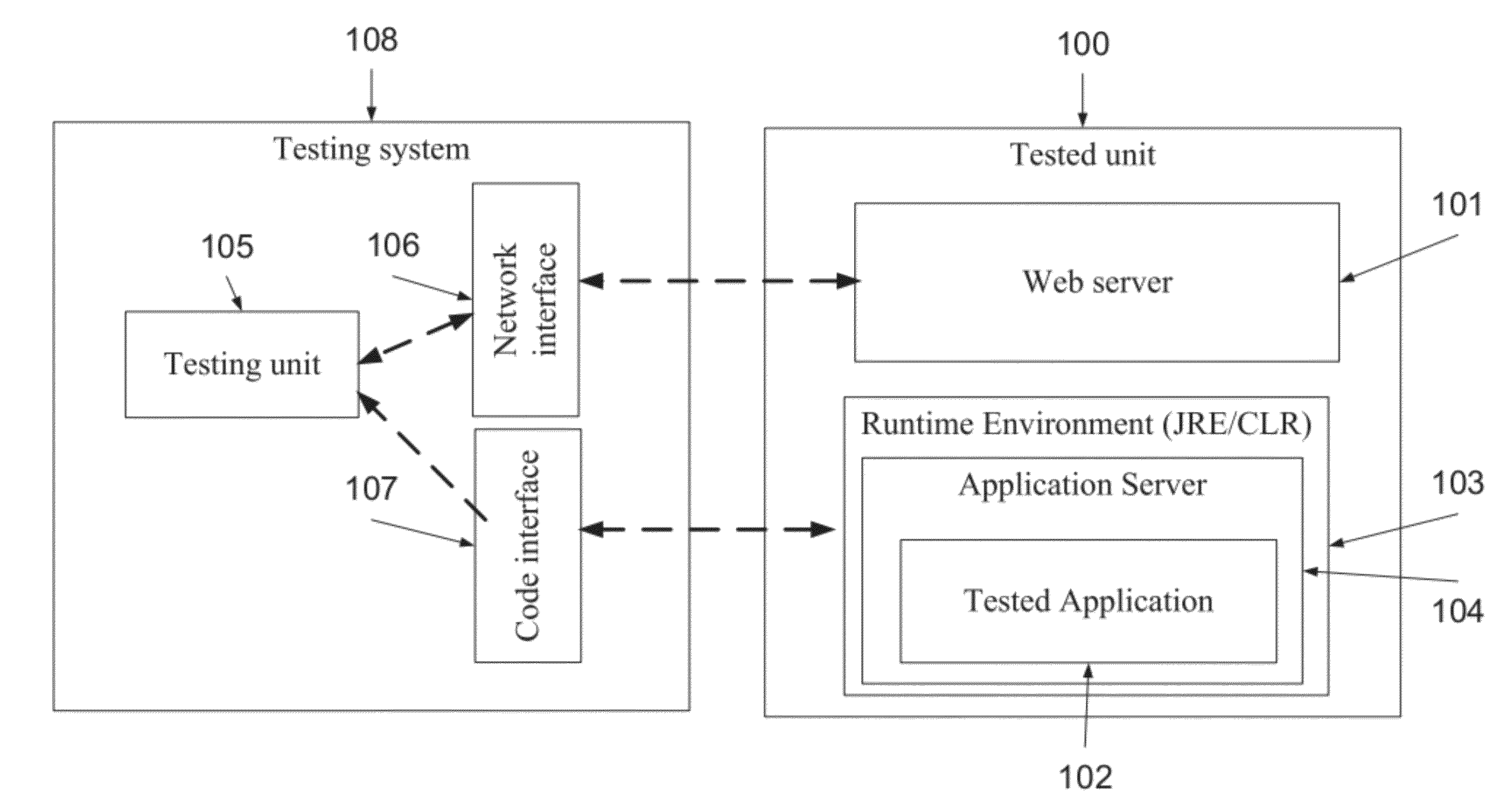
Method and system of runtime analysis
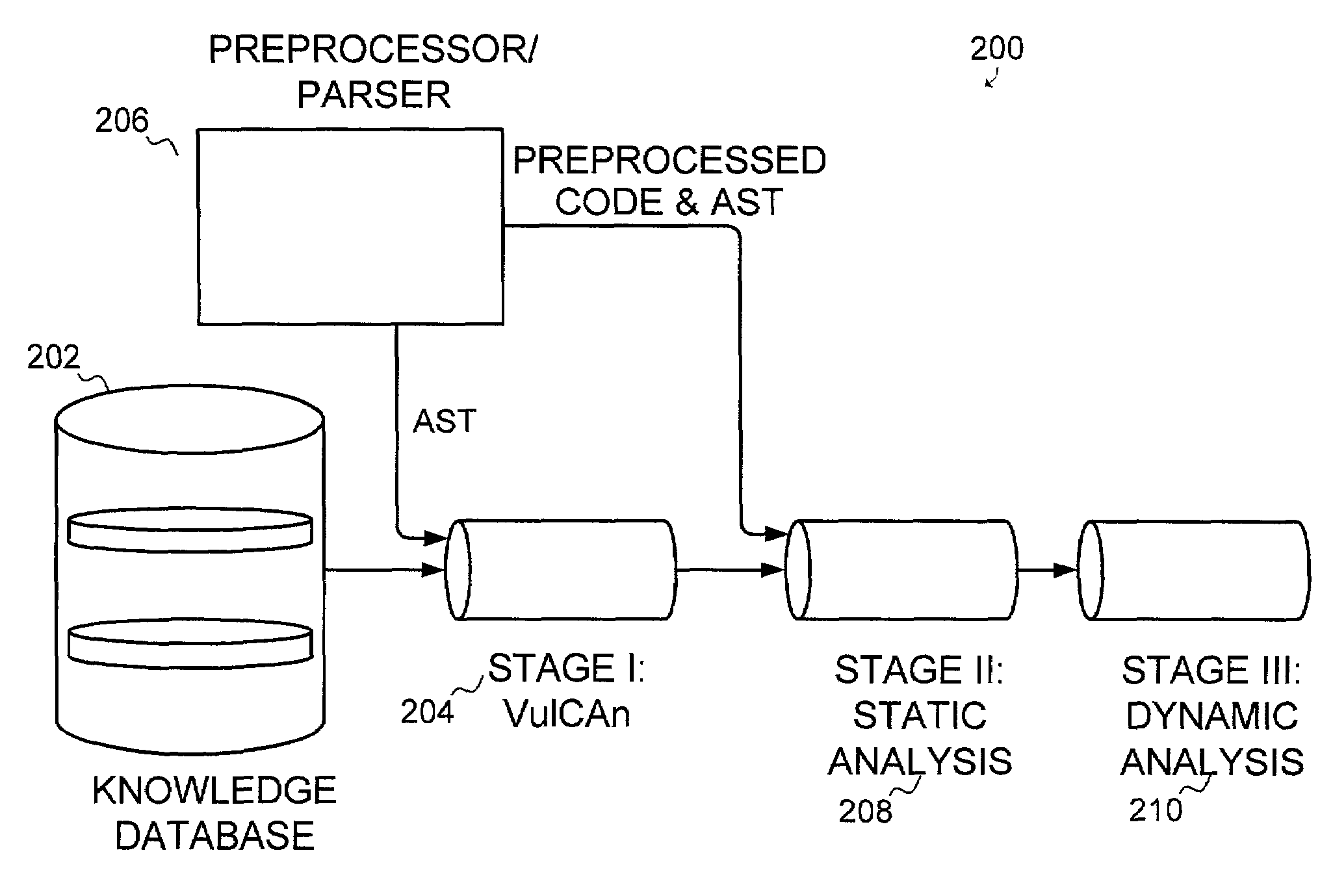
ActiveUS20120260344A1Facilitates code coverageApolipeptidesPeptide/protein ingredientsWeb applicationClient-side
A method and a system for detecting one or more security vulnerabilities. The method comprises providing test instructions for an application, such as a web application or a client server application, adding test code to a code segment of the application according to the test instructions, sending at least one message to the application according to the test instructions at runtime thereof, monitoring test information pertaining to at least one reaction of the application to the at least one message during an execution of the test code, performing an analysis of the at least one reaction, and detecting a presence or an absence of at least one security vulnerability according to the analysis.
Owner:SYNOPSYS INC
Method and Apparatus for Identifying Authors of Changes Between Multiple Versions of a File
InactiveUS20080086718A1Version controlSpecific program execution arrangementsSource code fileCode segment
A Source Code Author Identifier (SCAI) automates the process of manually running a comparison to identify changes between versions of a source code file and associates identified changes with the author who made the change. After a developer identifies a segment of code in a first file, wherein the first file as a newer version of a second file, SCAI compares the segment of code in the first file to a corresponding segment of code in the second file. SCAI identifies the author of the first file whenever a difference is detected between the segment of code in the first file and the corresponding segment of code in the second file. SCAI displays the author of the first file next to the detected difference between the segment of code from the first file and the corresponding segment of code from the second file. SCAI can repeat the comparison across a plurality of versions of the file, comparing each version with the previously created version.
Owner:IBM CORP
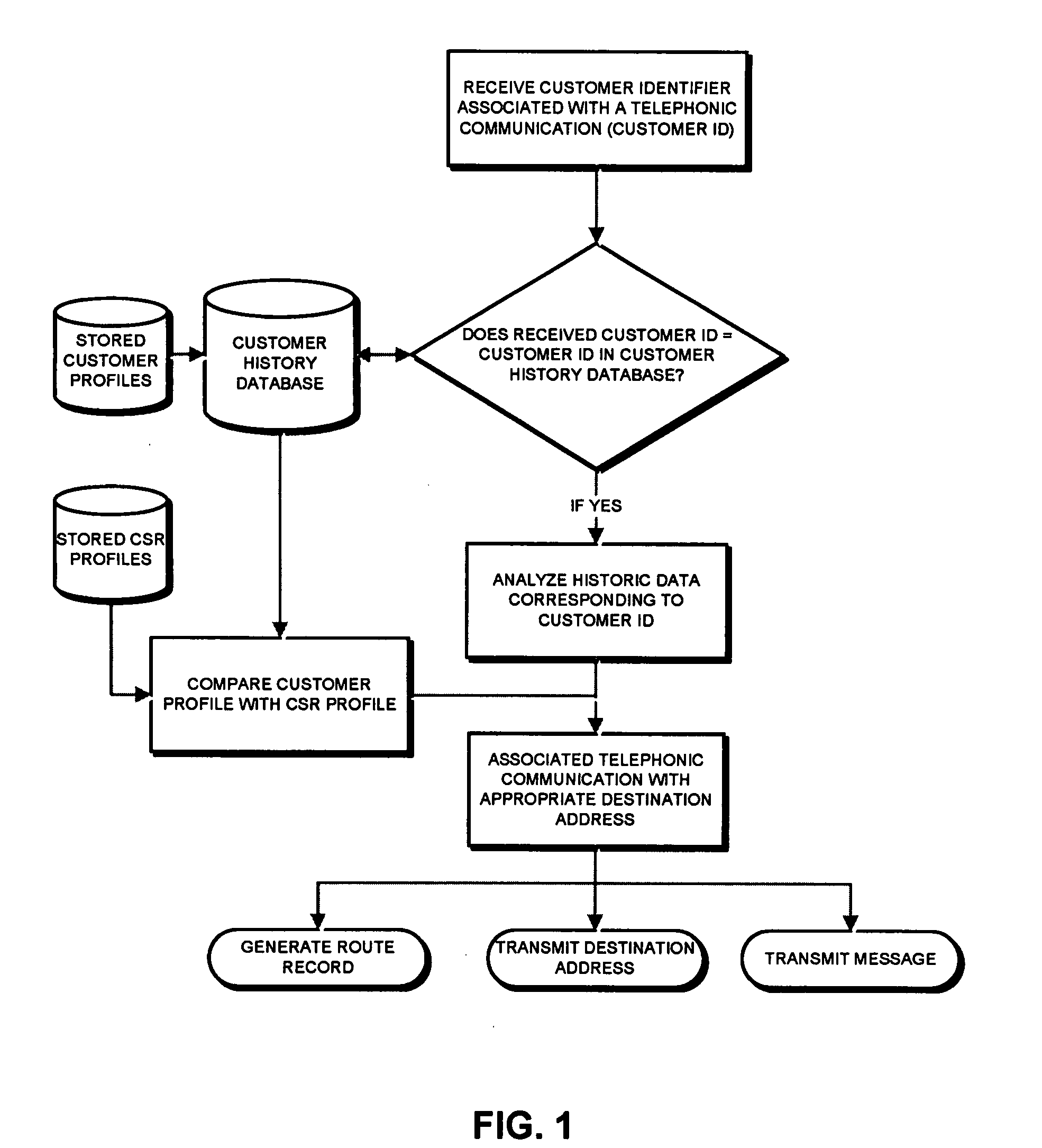
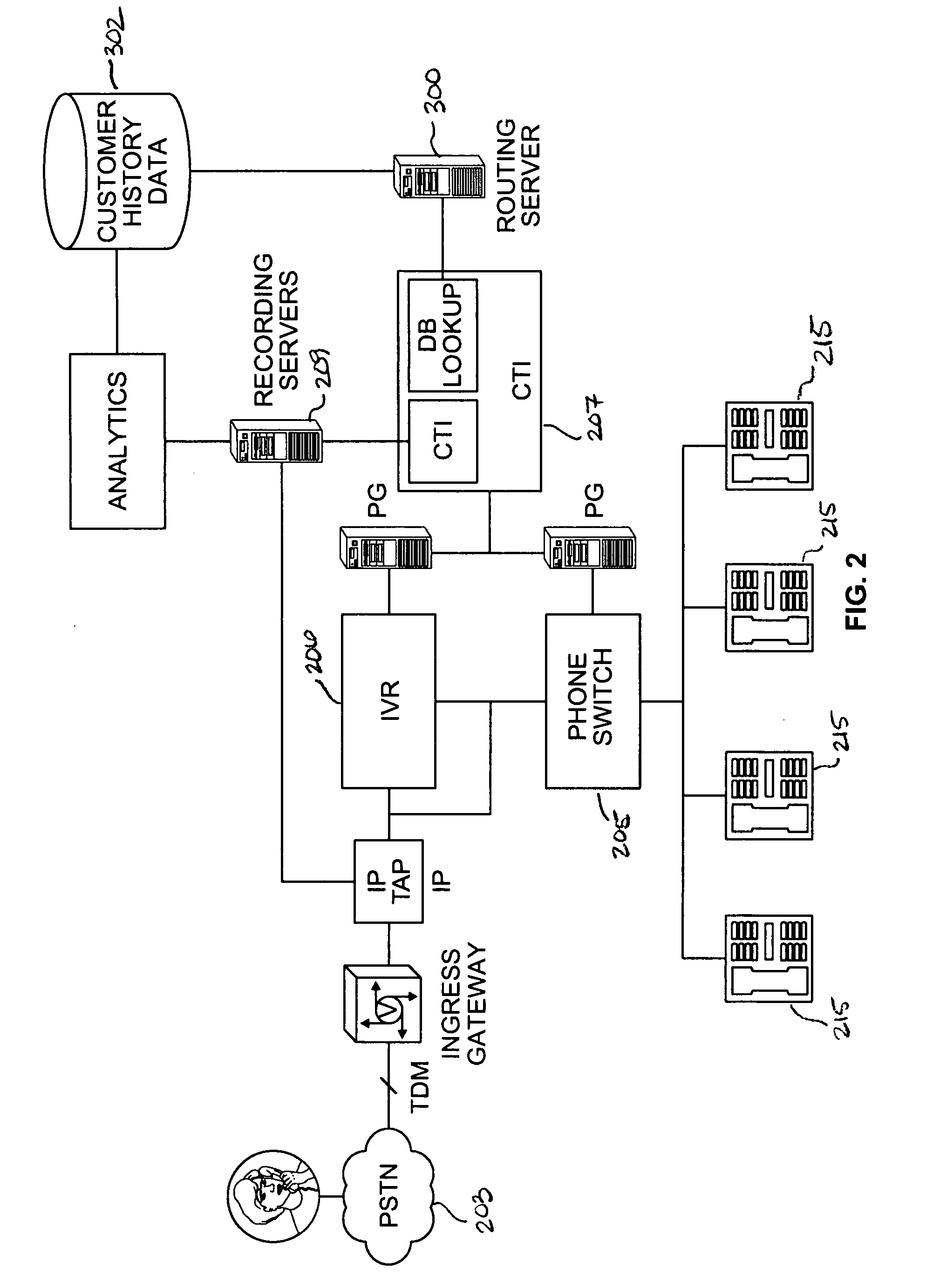
Method and system for automatically routing a telephonic communication base on analytic attributes associated with prior telephonic communication
ActiveUS20080240376A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingSwitching signalAutomatic routing
A method for automatically routing a telephonic communication to at least one of a plurality of communication destination addresses is provided. The method is implemented by a computer readable medium having a plurality of code segments. The method comprises the step of receiving customer identifier and communicating with a customer history database configured to store historic data. The method also includes determining whether the received customer identifier corresponds to a stored customer identifier in the customer history database. Historic data corresponding to the stored customer number is identified based on the comparison of the received customer identifier and the stored customer identifier. The telephonic communication is associated with a predetermined communication destination based on the identified historic data. The associated communication data is transmitted to a switching signal.
Owner:MATTERSIGHT CORP
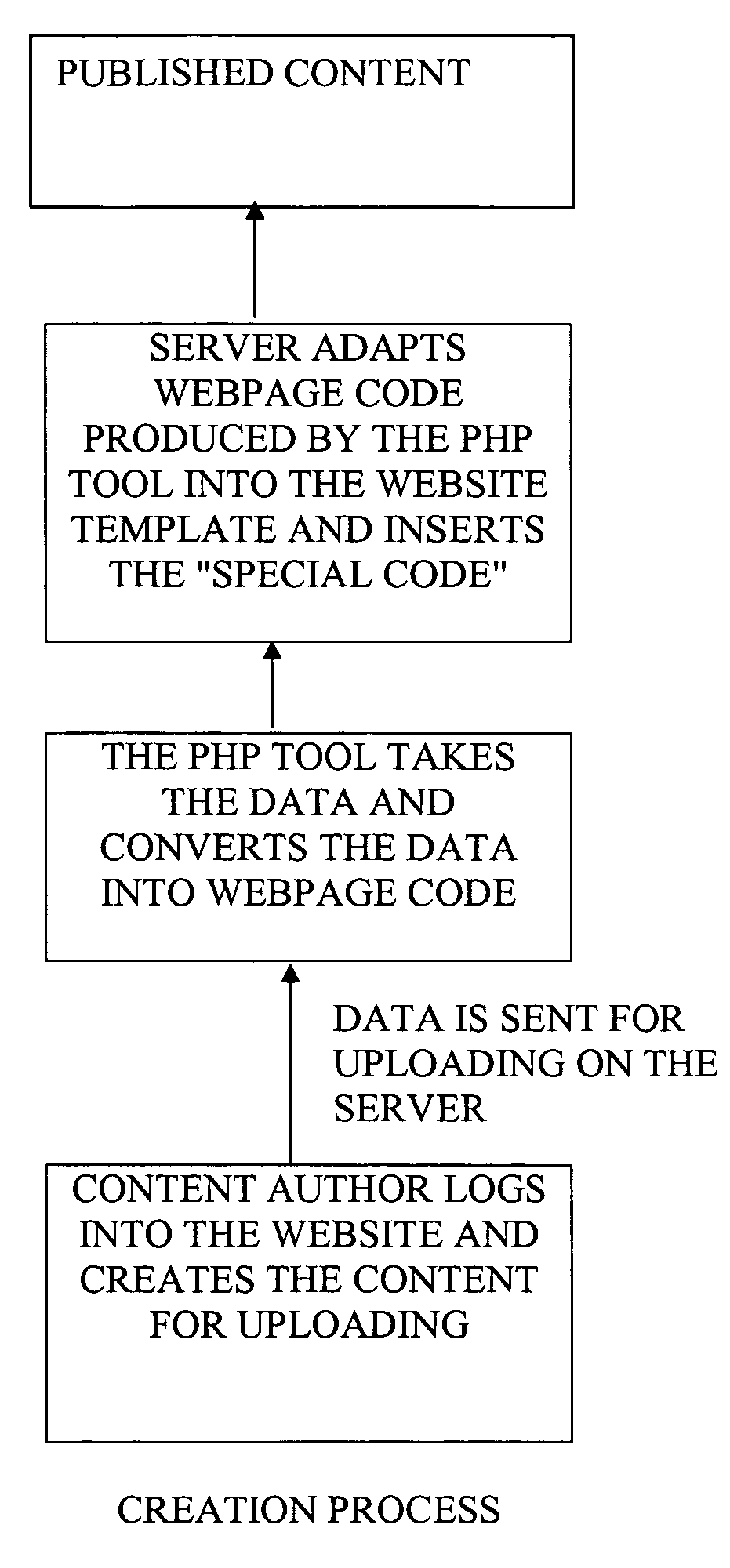
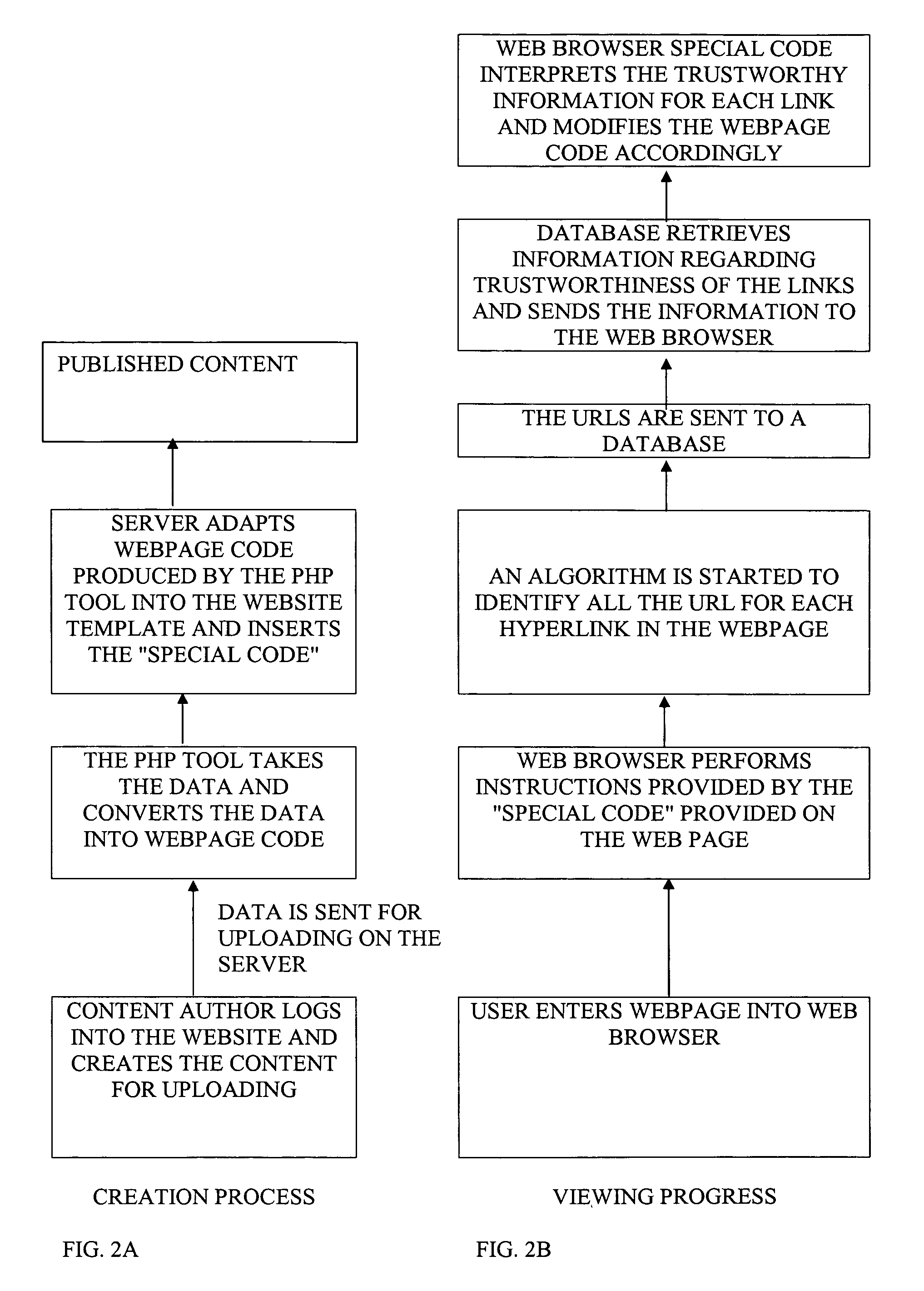
Website content regulation
ActiveUS20100017880A1Simple processReduce loadMemory loss protectionError detection/correctionWeb siteHyperlink
A method of facilitating the scanning of web pages for suspect and / or malicious hyperlinks that includes receiving at a content hosting website, user generated content. A web page or web page containing said content is then generated and, in the web page source code is included a detection code segment or a link from which a detection code segment can be downloaded. The detection code segment is executable by a web browser or web browser plug-in to scan the web page(s), or cause the web page(s) to be scanned, for suspect and / or malicious links.
Owner:FINJAN LLC
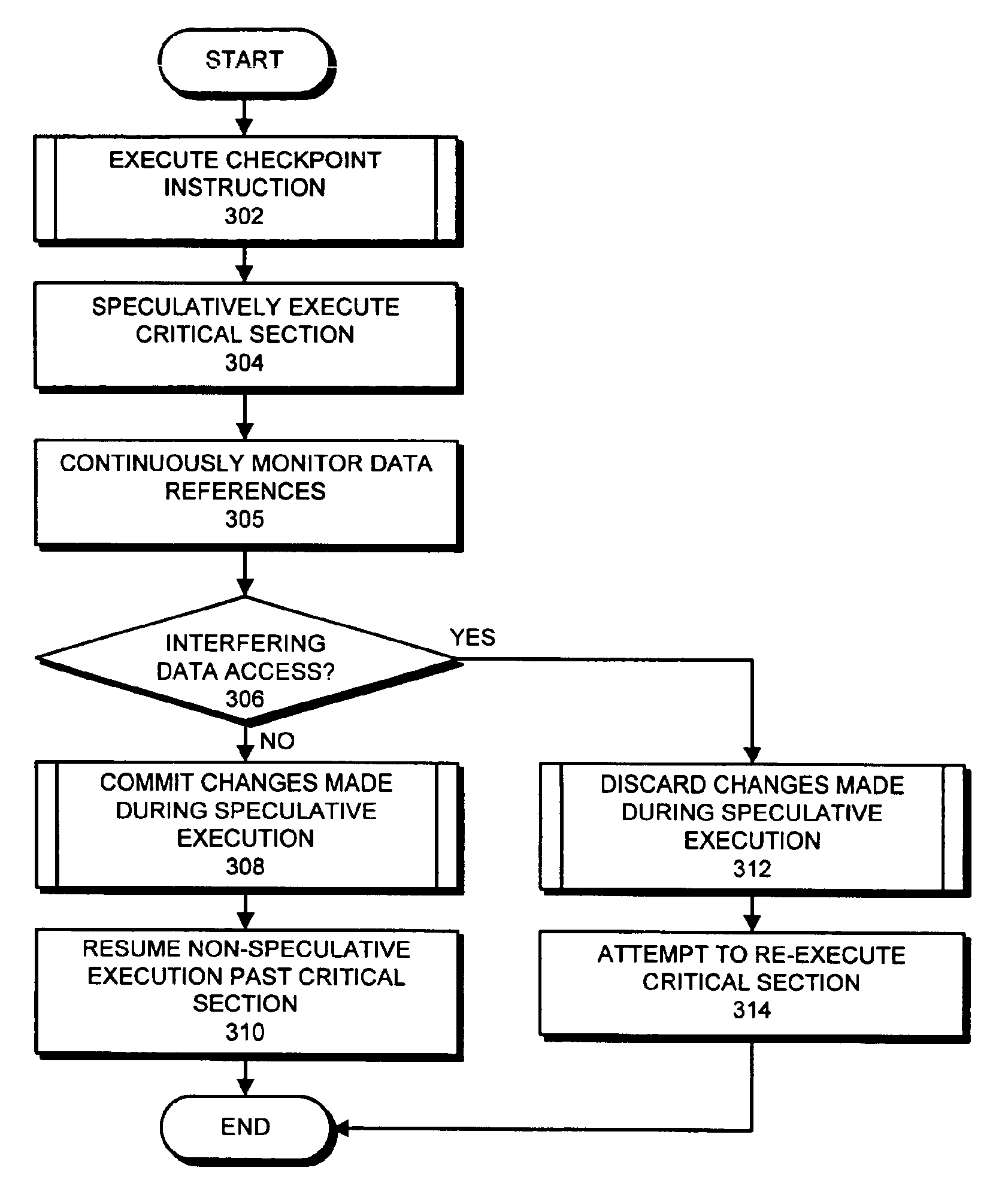
Method and apparatus for avoiding locks by speculatively executing critical sections
InactiveUS6862664B2Easy to solveMemory adressing/allocation/relocationMultiprogramming arrangementsSpeculative executionCritical section
One embodiment of the present invention provides a system that facilitates avoiding locks by speculatively executing critical sections of code. During operation, the system allows a process to speculatively execute a critical section of code within a program without first acquiring a lock associated with the critical section. If the process subsequently completes the critical section without encountering an interfering data access from another process, the system commits changes made during the speculative execution, and resumes normal non-speculative execution of the program past the critical section. Otherwise, if an interfering data access from another process is encountered during execution of the critical section, the system discards changes made during the speculative execution, and attempts to re-execute the critical section.
Owner:ORACLE INT CORP
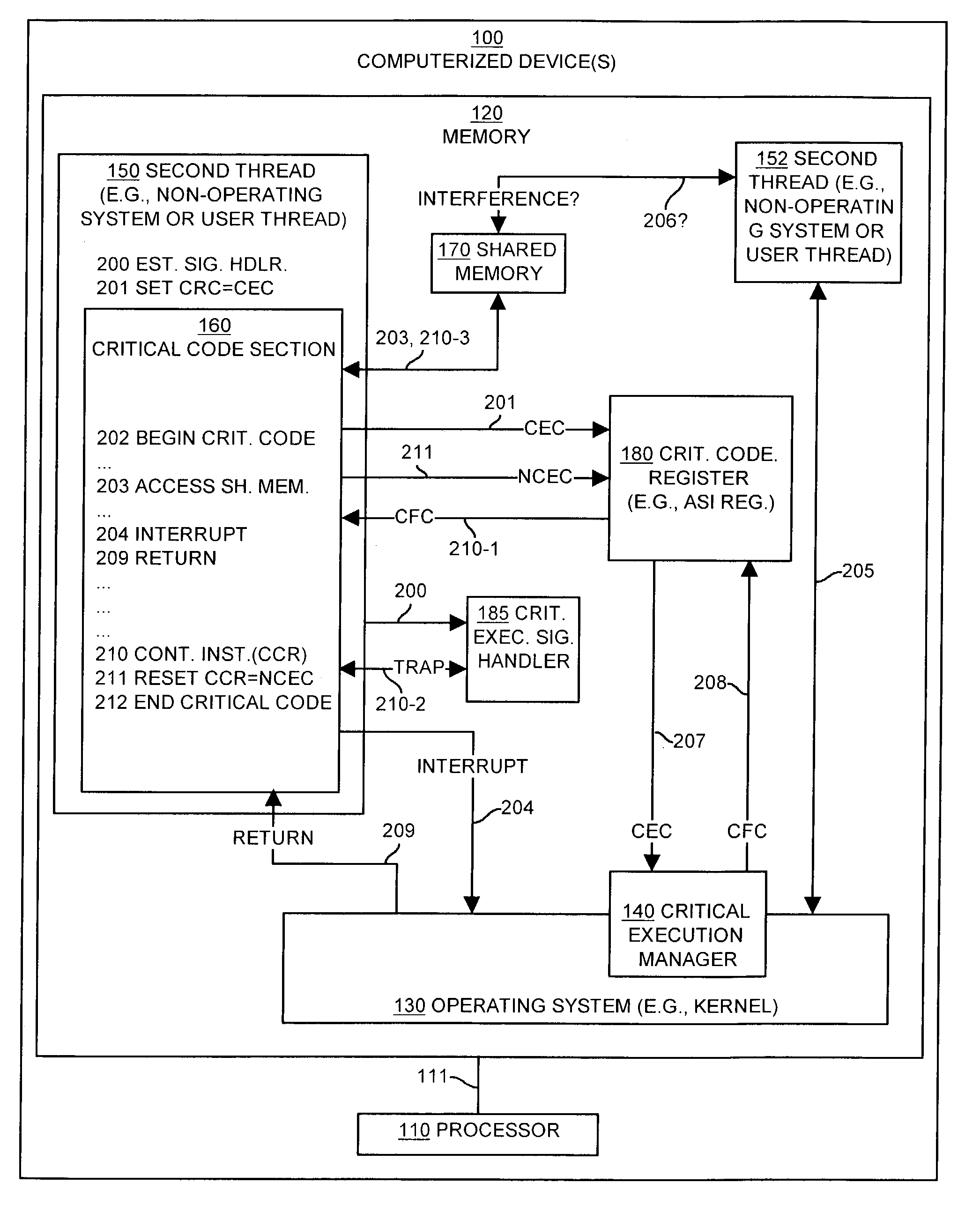
Methods and apparatus for executing code while avoiding interference
ActiveUS7178062B1Inhibition effectAvoid interferenceError detection/correctionDigital computer detailsOperational systemProcessor register
Mechanisms and techniques operate in a scalable or non-scalable processing architecture computerized device to execute critical code while overcoming interference from interruptions. A critical signal handler is registered and a non-operating system thread sets a value of a critical code register to indicate a critical execution condition. The non-operating system thread then executes a critical code section until an interruption occurs. In response to the interruption to the critical code section, an operating system thread detects if the critical code register is equivalent to a critical execution condition and if so, sets the value of the critical code register to indicate a critical execution failure. Upon returning to execution of the critical code section, the critical code section attempts to execute a contingent instruction in the critical code section that is contingent upon the value of the critical code register. The attempted execution of the contingent instruction triggers a critical trap signal when the critical code register is set to a value that indicates the critical execution failure. The critical execution signal handler processes the critical trap signal to avoid any interference that may have been caused by the interruption.
Owner:ORACLE INT CORP
Vehicle diagnostic tool
Owner:INNOVA ELECTRONICS
Polymorphic computational system and method in signals intelligence analysis
ActiveUS7386833B2Multiple digital computer combinationsComputer aided designLogic emulationSignals intelligence
Configuration software is used for generating hardware-level code and data that may be used with reconfigurable / polymorphic computing platforms, such as logic emulators, and which may be used for conducting signals intelligence analysis, such as encryption / decryption processing, image analysis, etc. A user may use development tools to create visual representations of desired process algorithms, data structures, and interconnections, and system may generate intermediate data from this visual representation. The Intermediate data may be used to consult a database of predefined code segments, and segments may be assembled to generate monolithic block of hardware syhthesizable (RTL, VHDL, etc.) code for implementing the user's process in hardware. Efficiencies may be accounted for to minimize circuit components or processing time. Floating point calculations may be supported by a defined data structure that is readily implemented in hardware.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Managing variants of artifacts in a software process
InactiveUS20090083268A1Fine granularityHigh resolutionDigital data information retrievalDigital data processing detailsCode segmentDatabase
In some embodiments the management of revisions to segments of code or artifacts is disclosed. Such management can assist a software developer in the development of software. In some embodiments, a developer can retrieve a versioned file from a repository, modify content of the versioned file to create a variant of the versioned file, compare the variant to the versioned file, and determine a difference between the versioned file and the variant. Then, the one or more attribute can be assigned to the differences and the attributes can be indexed such that the variants can be located in response to a search. In some embodiments variants can be indexed based on a variability point to which they can be matched. Other embodiments are also disclosed.
Owner:IBM CORP
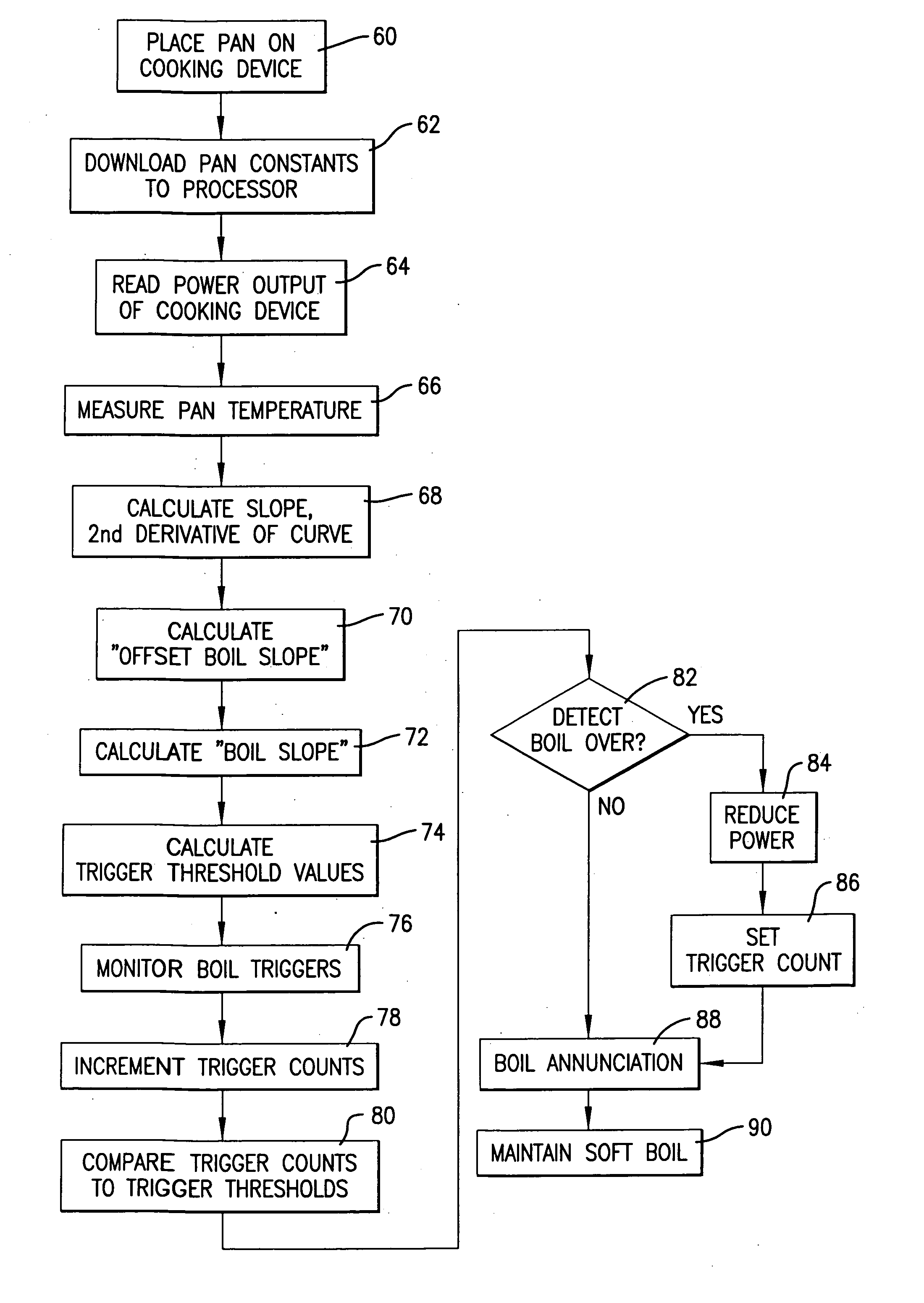
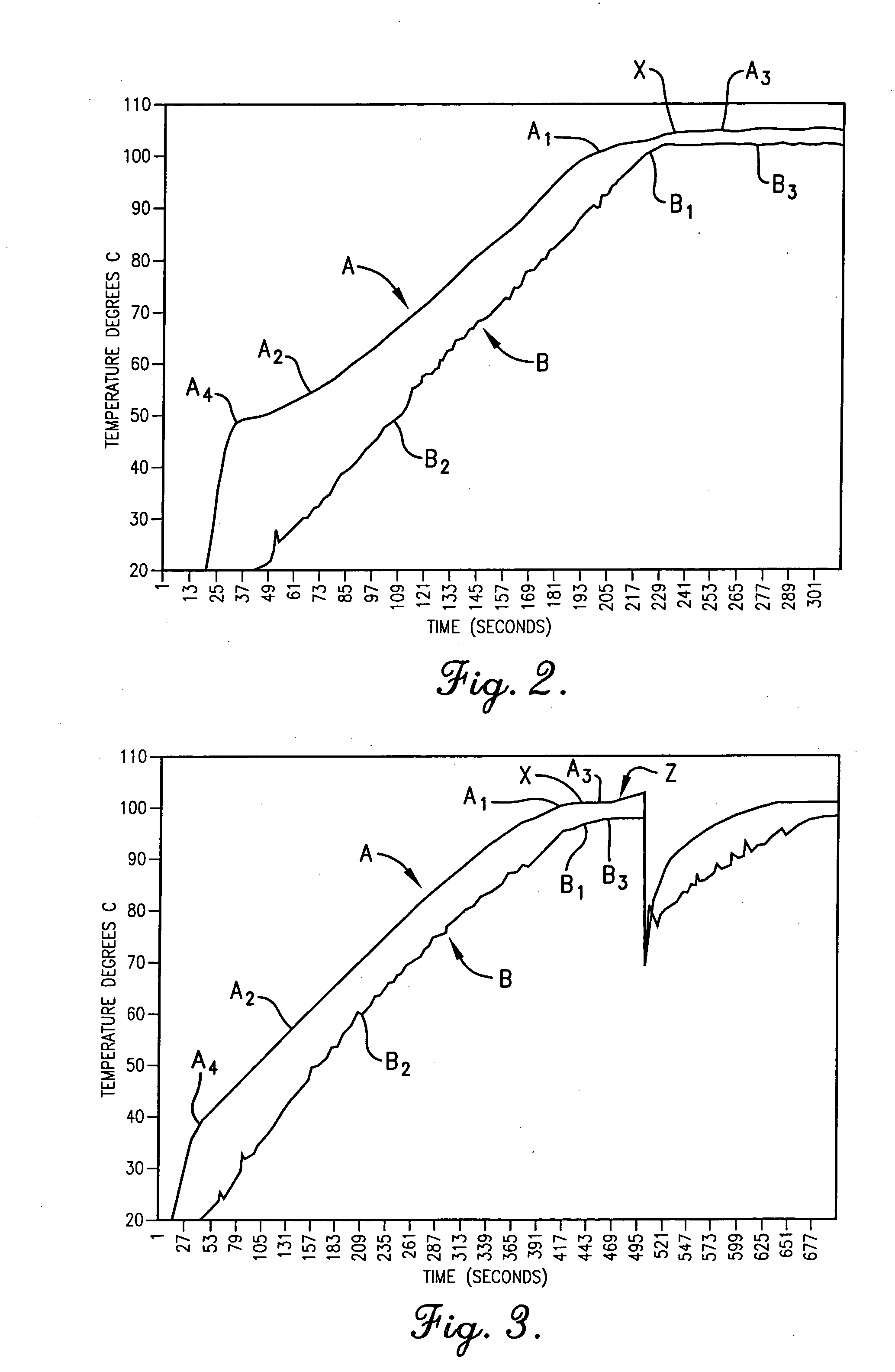
Boil detection method and computer program
A method, computer program, and cooking device for detecting boiling of liquids. The invention is implemented with a computer program executed by a processor or other computing device of a cooking unit such as an induction range. The computer program comprises a code segment for receiving an indication of successive temperatures of the vessel and for calculating a slope of a curve representing the successive temperatures versus time; a code segment for detecting boiling of the liquid based on the slope of the curve; and a code segment for providing an output which may be used to indicate the boiling. The computer program may also include a code segment for receiving variables relating to parameters and / or characteristics of the cooking vessel to refine the boiling detection.
Owner:TSI TECH
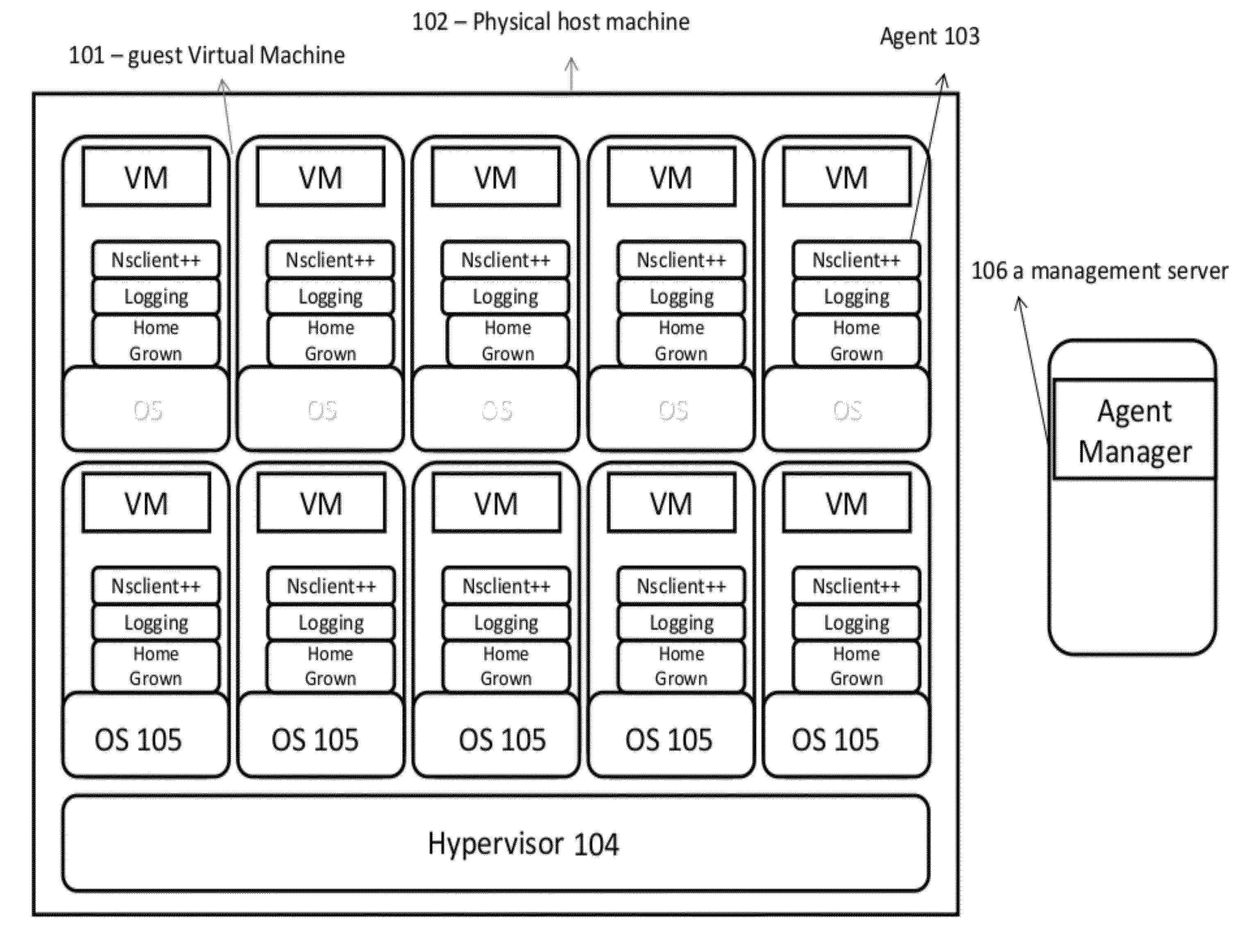
System and method for management of a virtual machine environment
InactiveUS20120066681A1Software simulation/interpretation/emulationMemory systemsHuman–computer interactionCode segment
A system and method for operating an agent. A policy may be generated based on an analysis of a code segment of an agent, analysis of the execution and / or installation of an agent. An interaction with the agent may be intercepted. The interaction may be analyzed according to the policy. A machine for performing an operation related to the interaction may be selected. A proxy on the selected machine may perform the operation and return a result to the agent. In some embodiments, a request to perform a task may be intercepted. A first portion of the task may be performed by an agent and a second portion of the task may be performed by a proxy.
Owner:INTIGUA
Software source asset management
InactiveUS20070006152A1Version controlProgram/content distribution protectionBusiness managementCode segment
Code information is marked by tags and tags are embedded into pieces of code or files called “codetags” that map tags to pieces of code. These tags can then be updated, searched, sorted, recombined, and tracked, among many other feedback mechanisms. These tags and their feedback mechanisms help to illuminate the engineering metadata and business metadata of pieces of code so as to help engineering management and business management of companies to better guide their software resources.
Owner:MICROSOFT TECH LICENSING LLC
Deep learning-based vulnerability detection method and system
ActiveCN107885999AUnlimited Vulnerability TypeImprove accuracyPlatform integrity maintainanceLearning basedTraining program
The invention discloses a deep learning-based vulnerability detection method and system. The method comprises an offline vulnerability classifier training part and an online vulnerability detection part. The offline vulnerability classifier training part comprises the following steps of: calling candidate code sections for a training program extraction library / API function; adding type label for the candidate code sections; converting the candidate code sections into vectors; inputting the vectors into a neural network model to carry out training; and finally outputting a vulnerability classifier. The online vulnerability detection part comprises the following steps of: calling candidate code sections for a target program extraction library / API function; converting the candidate code sections into vectors; classifying the candidate code sections by adoption of the trained vulnerability classifier; and finally outputting the code sections which contain online vulnerabilities in the classification result. According to the method and system, vulnerability features aiming at library / API function calling can be automatically generated, and the operation does not depend on expert knowledges and is not restricted to vulnerability types, so that the false report rate and missing report rate of vulnerability detection in target programs can be remarkably reduced and vulnerability positions can be given.
Owner:HUAZHONG UNIV OF SCI & TECH
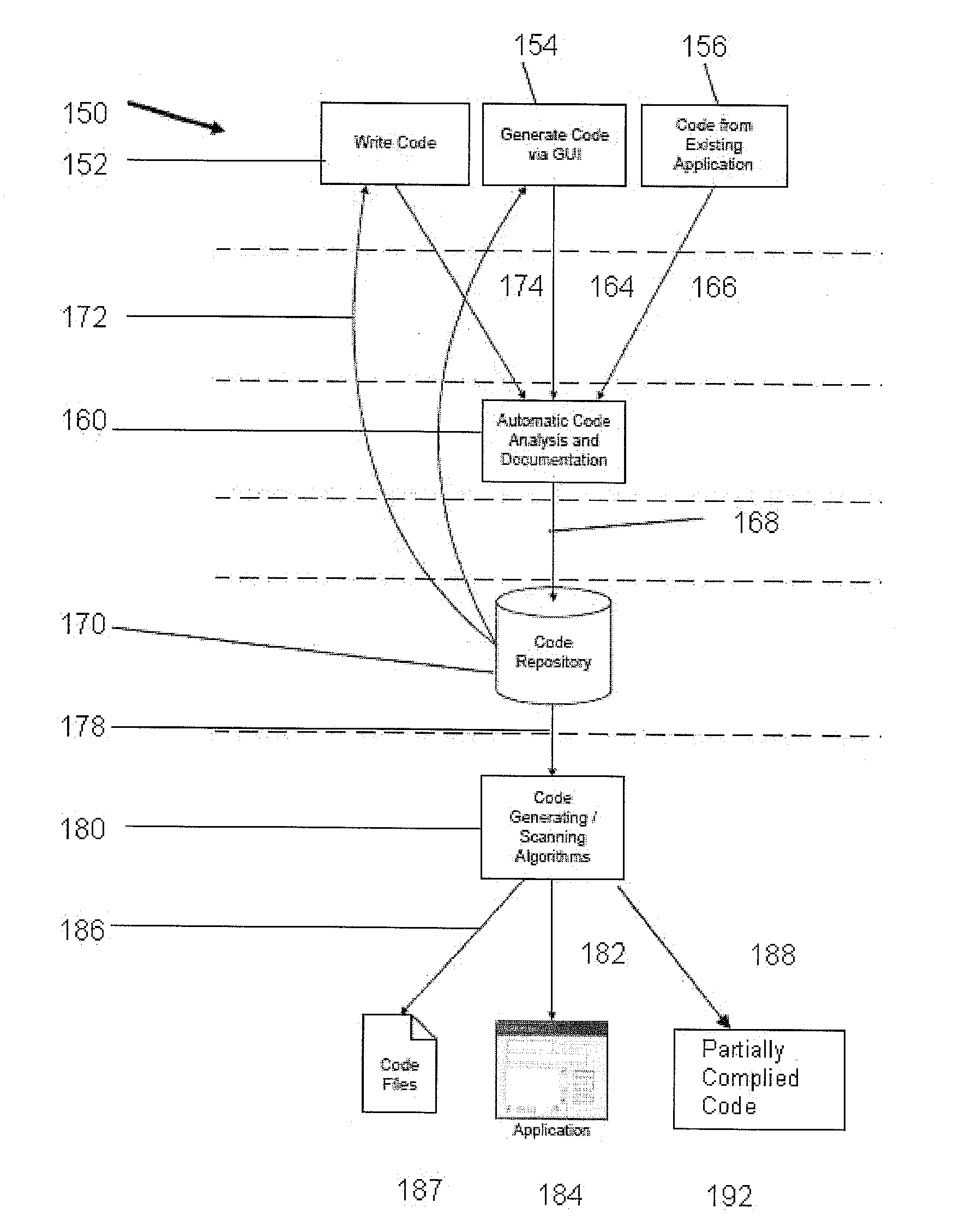
Software database system and process of building and operating the same
InactiveUS20120110030A1Digital data processing detailsCode refactoringDocumentation procedureProgram analysis
A software database system is provided that includes an automatic code analysis and self-documentation program. This program operating on a computer analyzes and fragments input code into constituent code segments and self-documents those segments. A code repository stores the code segments. A code-generating algorithm operating on a microprocessor extracts the code segments from the repository to generate a standard code page that is deployable on a server.
Owner:POMPONIO MARK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com