Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
311 results about "Transactional memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
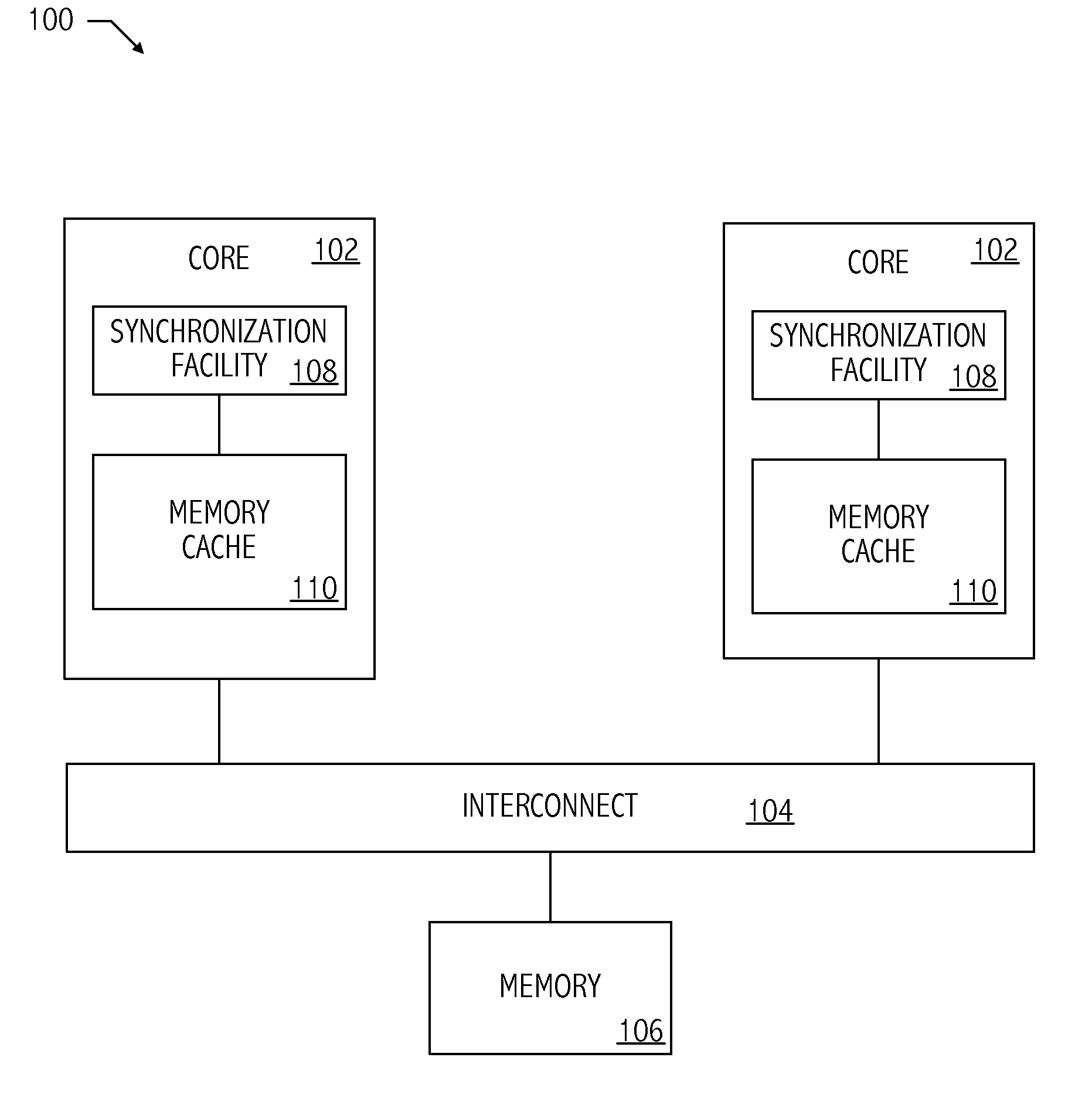
In computer science and engineering, transactional memory attempts to simplify concurrent programming by allowing a group of load and store instructions to execute in an atomic way. It is a concurrency control mechanism analogous to database transactions for controlling access to shared memory in concurrent computing. Transactional memory systems provide high-level abstraction as an alternative to low-level thread synchronization. This abstraction allows for coordination between concurrent reads and writes of shared data in parallel systems.
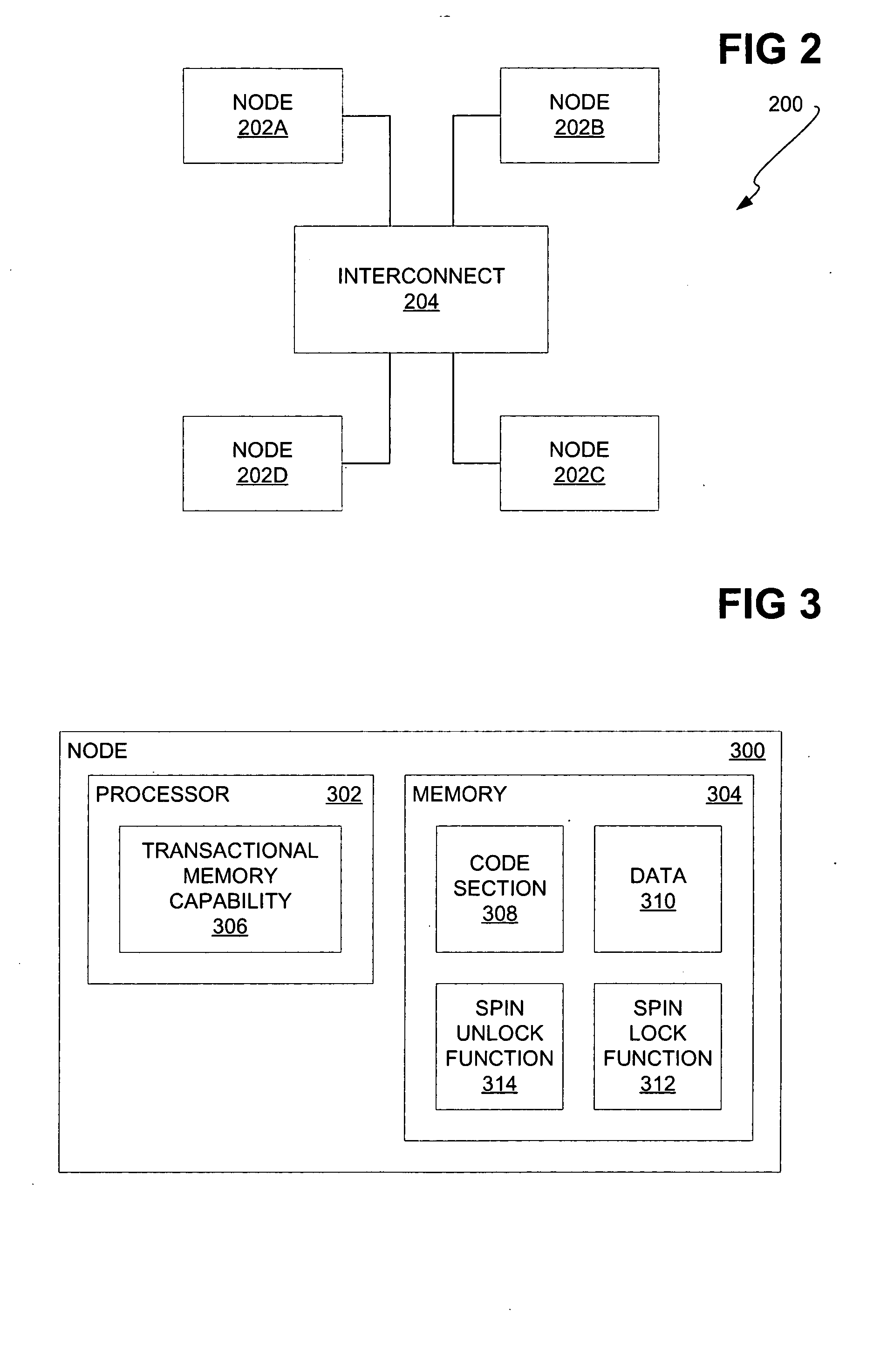
Transactional memory execution utilizing virtual memory
ActiveUS7685365B2Memory adressing/allocation/relocationTransaction processingVirtual memoryTransactional memory
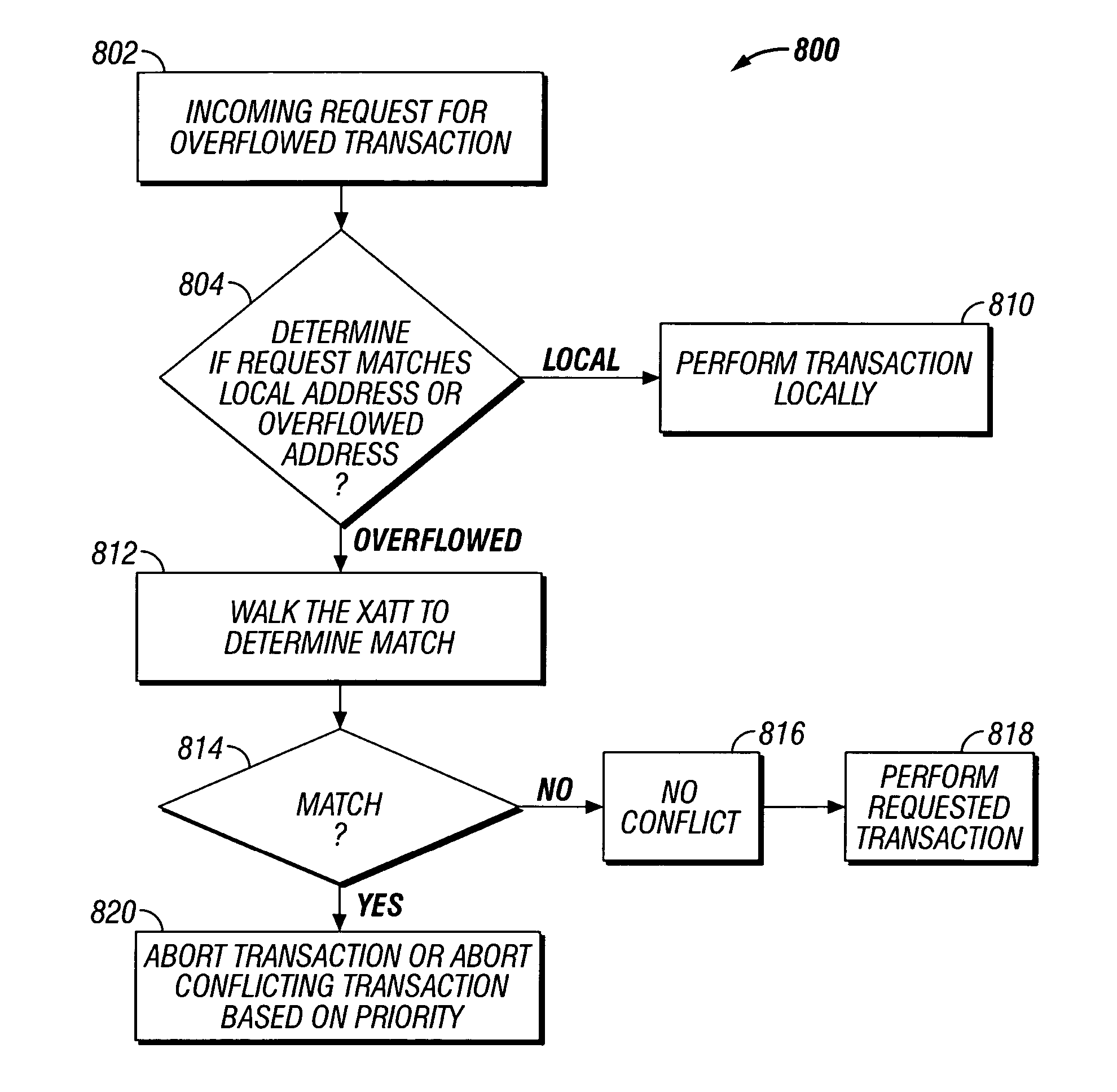
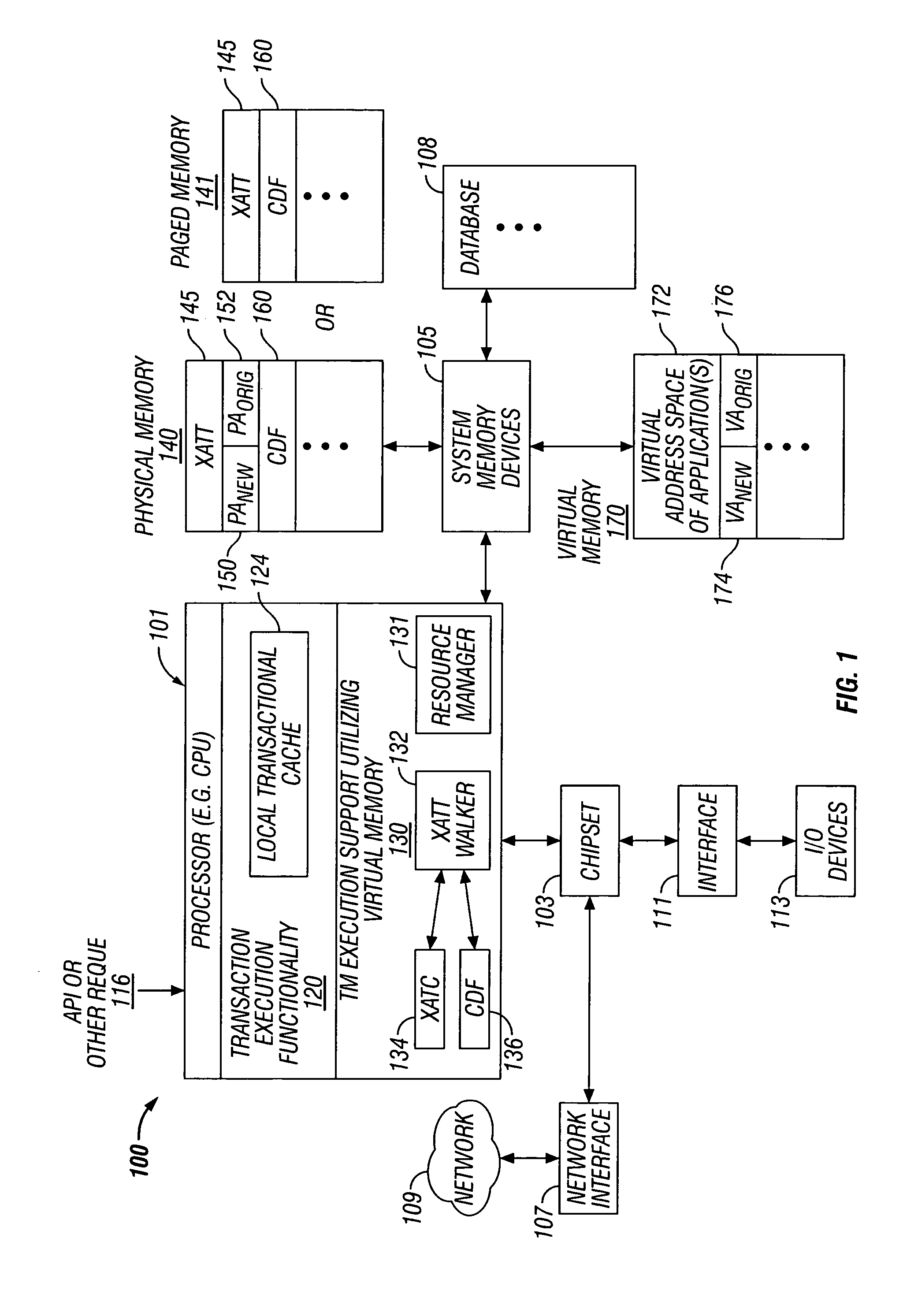
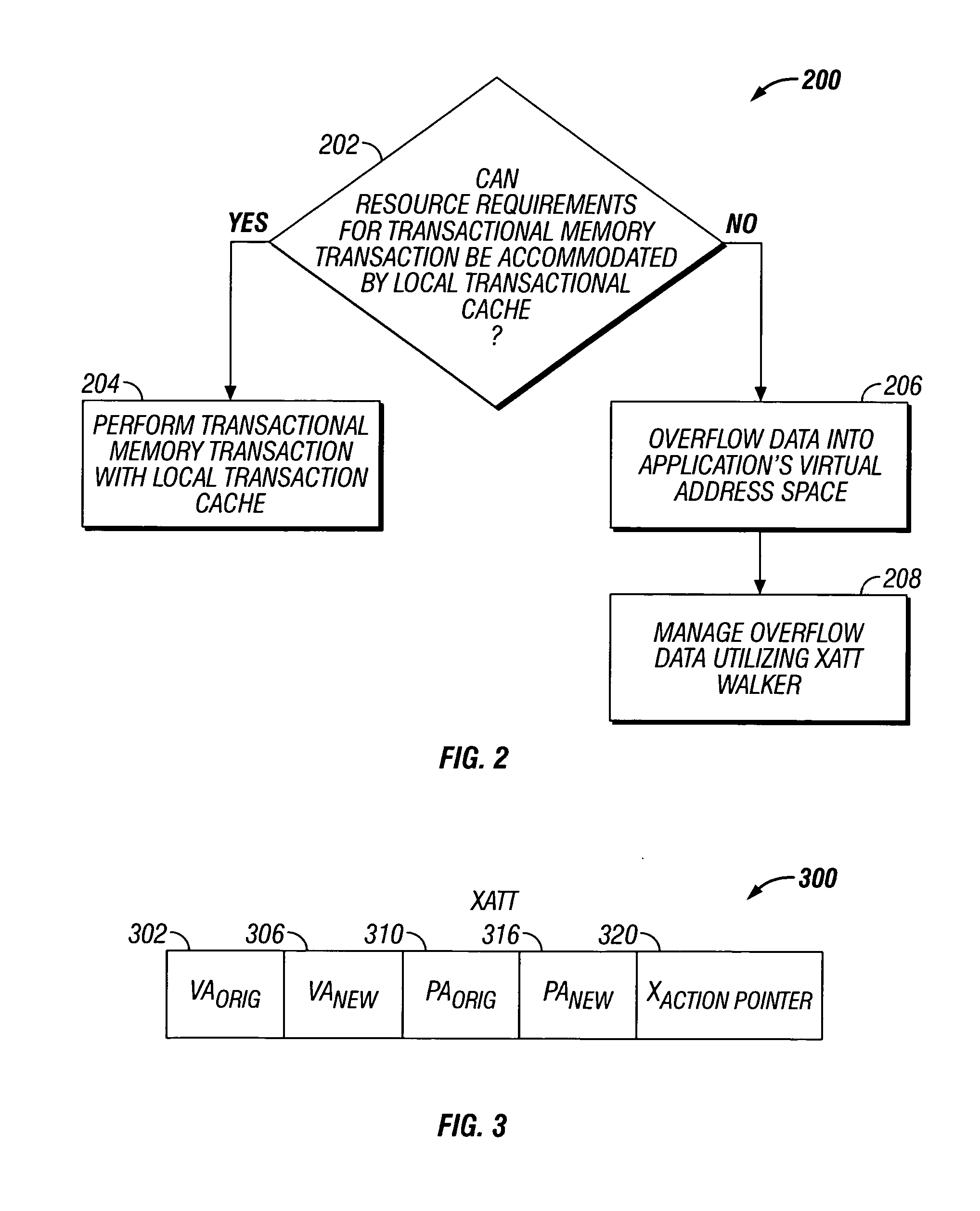
Embodiments of the invention relate to transactional memory execution utilizing virtual memory. A processor includes a local transactional cache and a resource manager. The resource manager responsive to a transactional memory transaction request from a requesting thread determines whether the local transactional cache is capable of accommodating the transactional memory transaction request and, if so, the local transactional caches performs the transactional memory transaction. However, if the local transactional cache is not capable of accommodating the transactional memory transaction request, data for the transactional memory transaction request is overflowed into an application's virtual address space associated with the requesting thread.
Owner:INTEL CORP
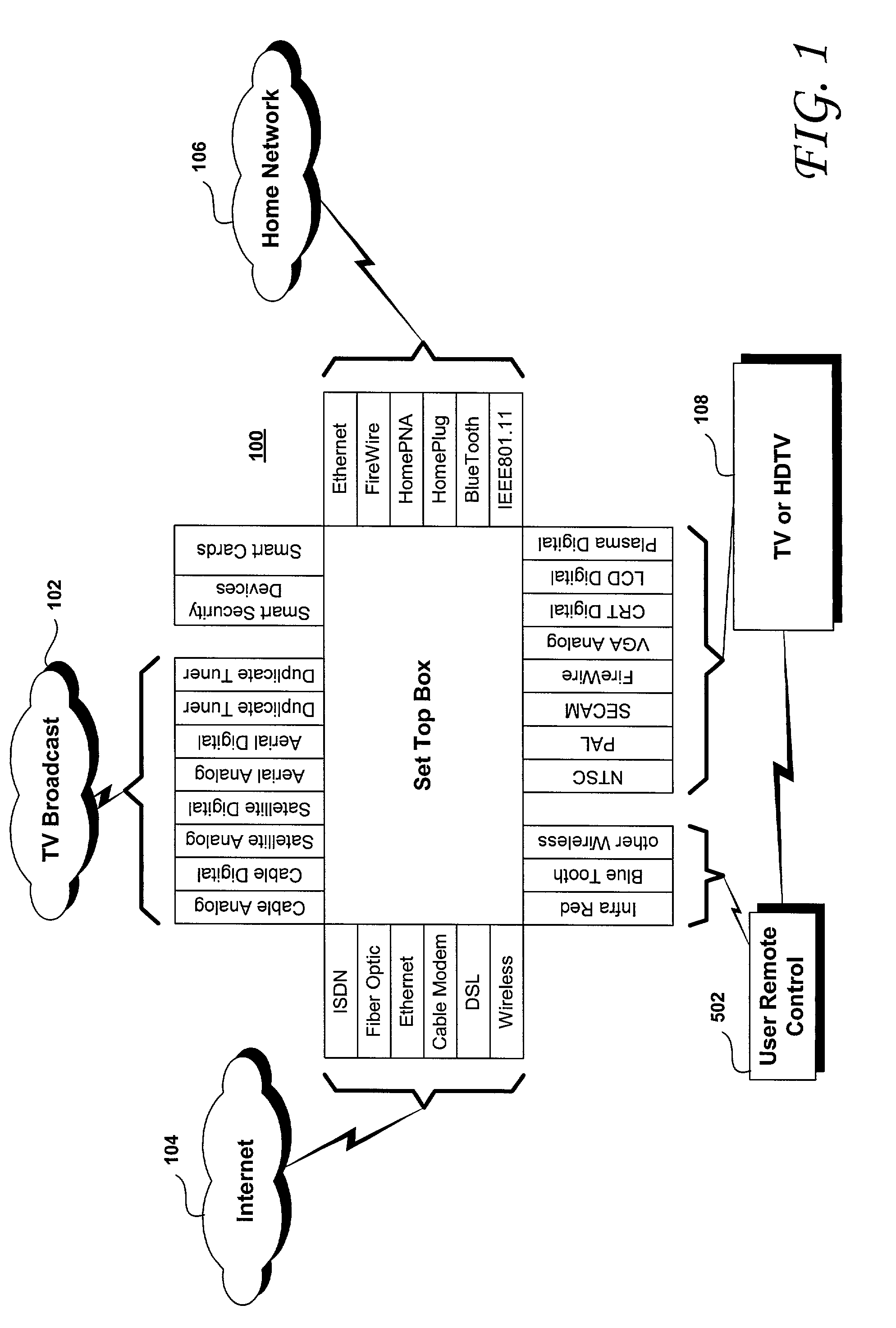
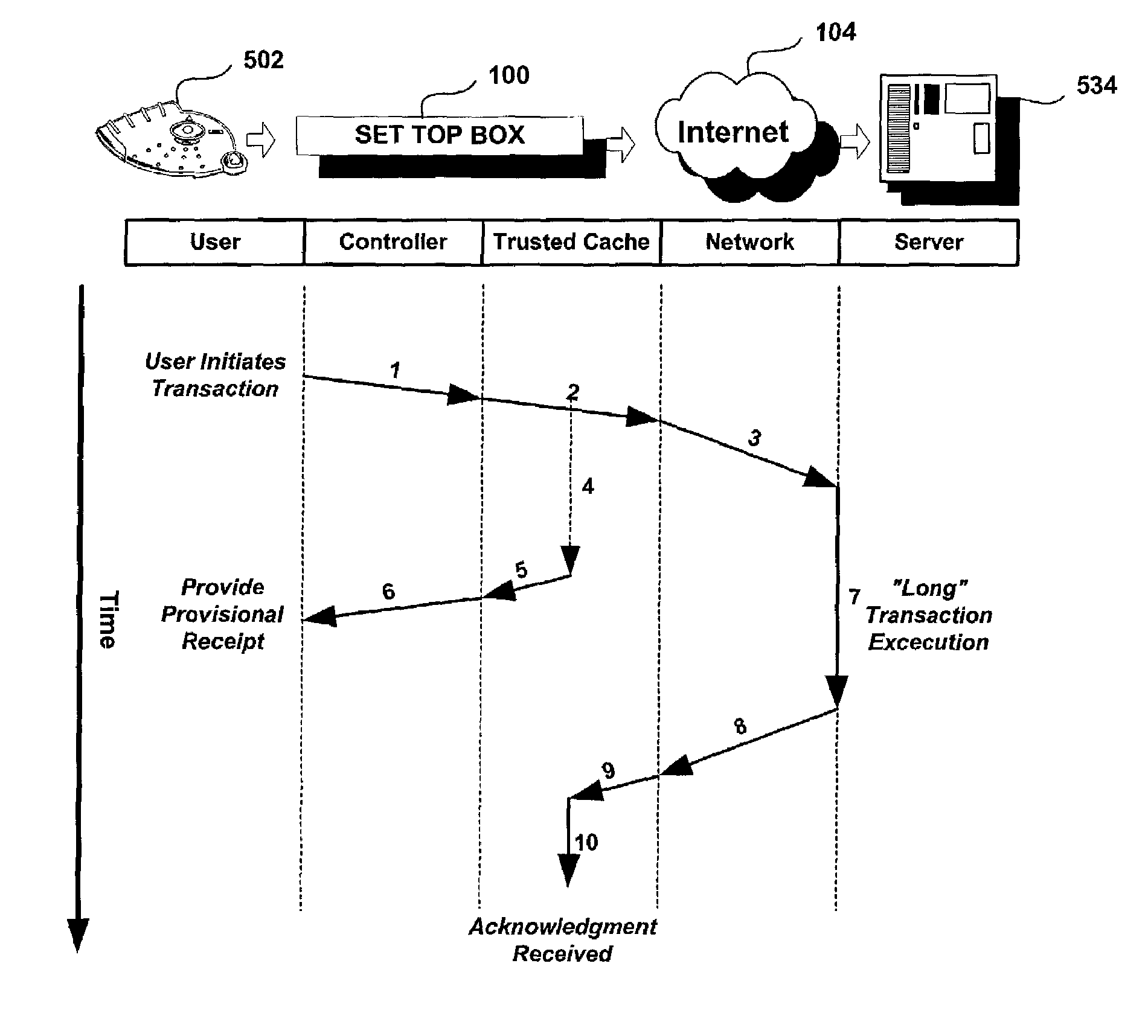
Trusted transactional set-top box
InactiveUS20020174444A1Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsTransactional memorySet top box
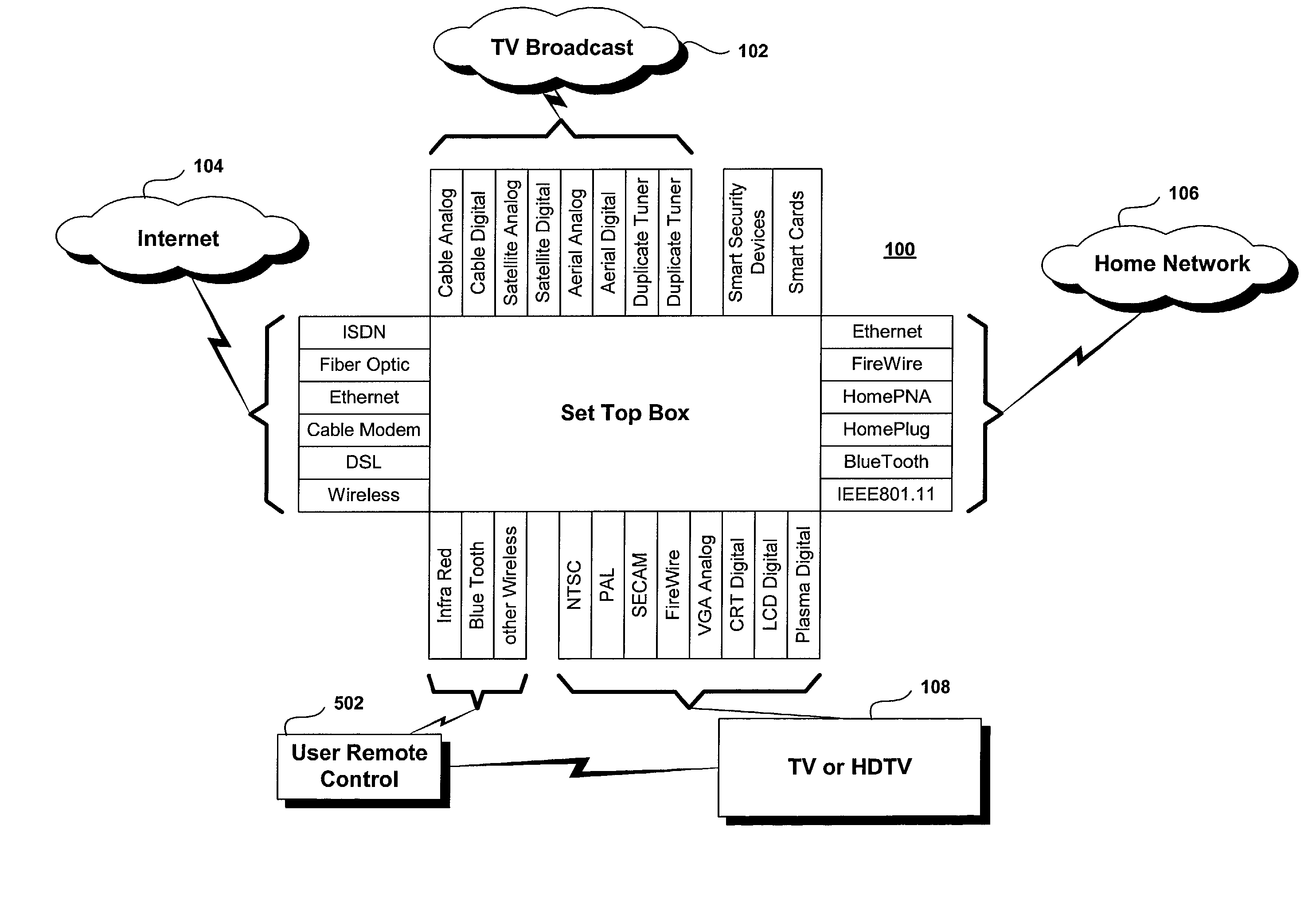
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
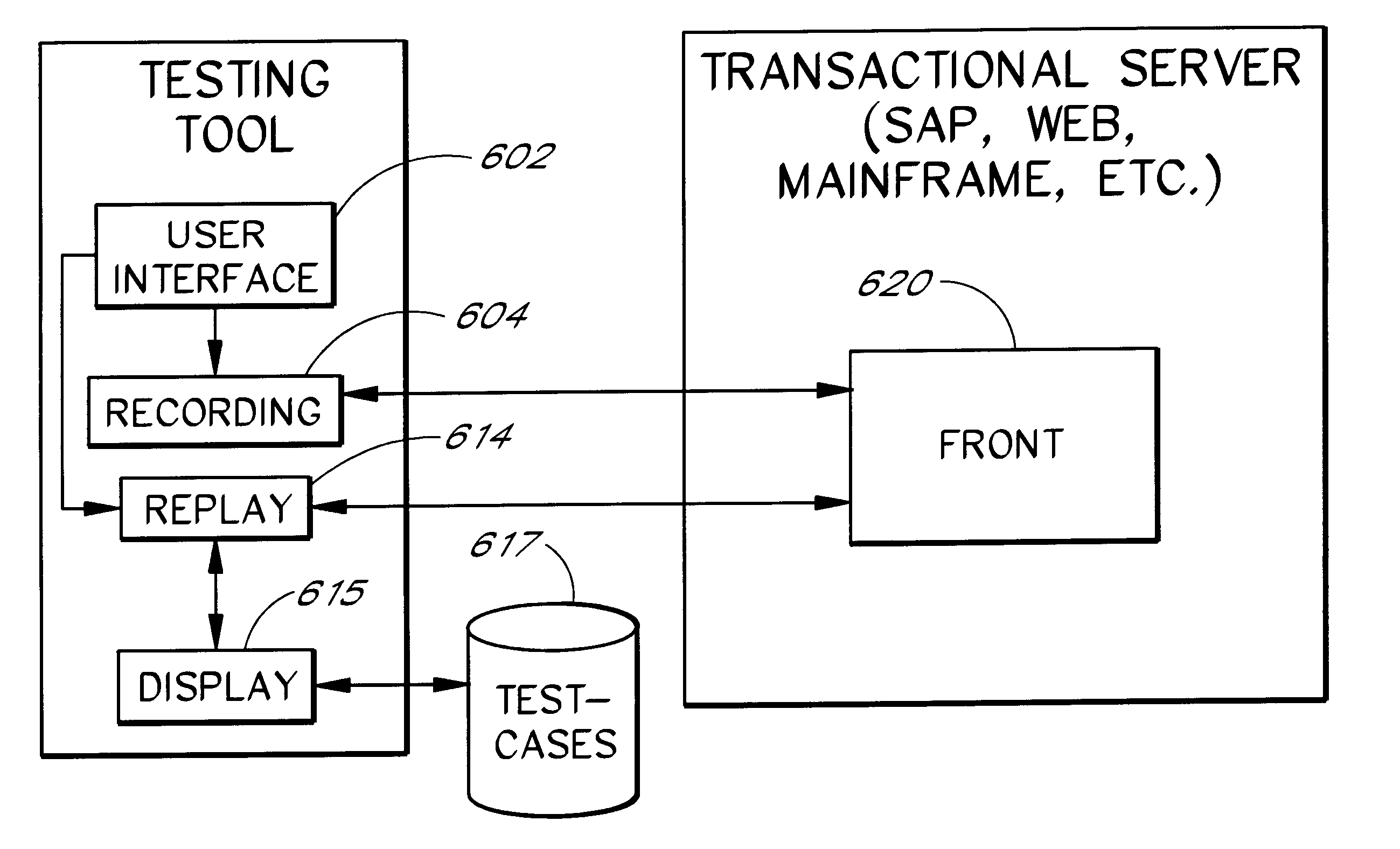
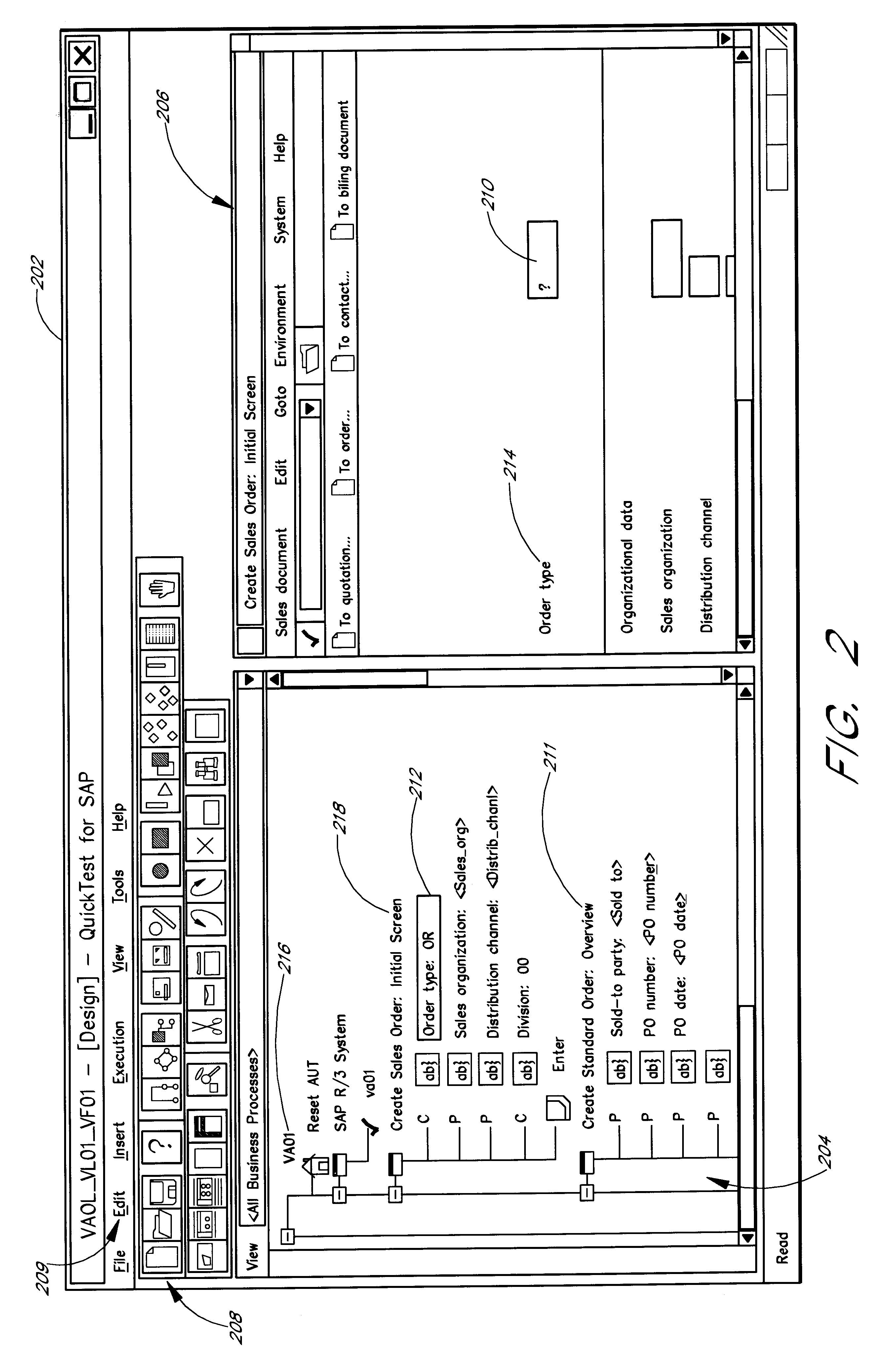
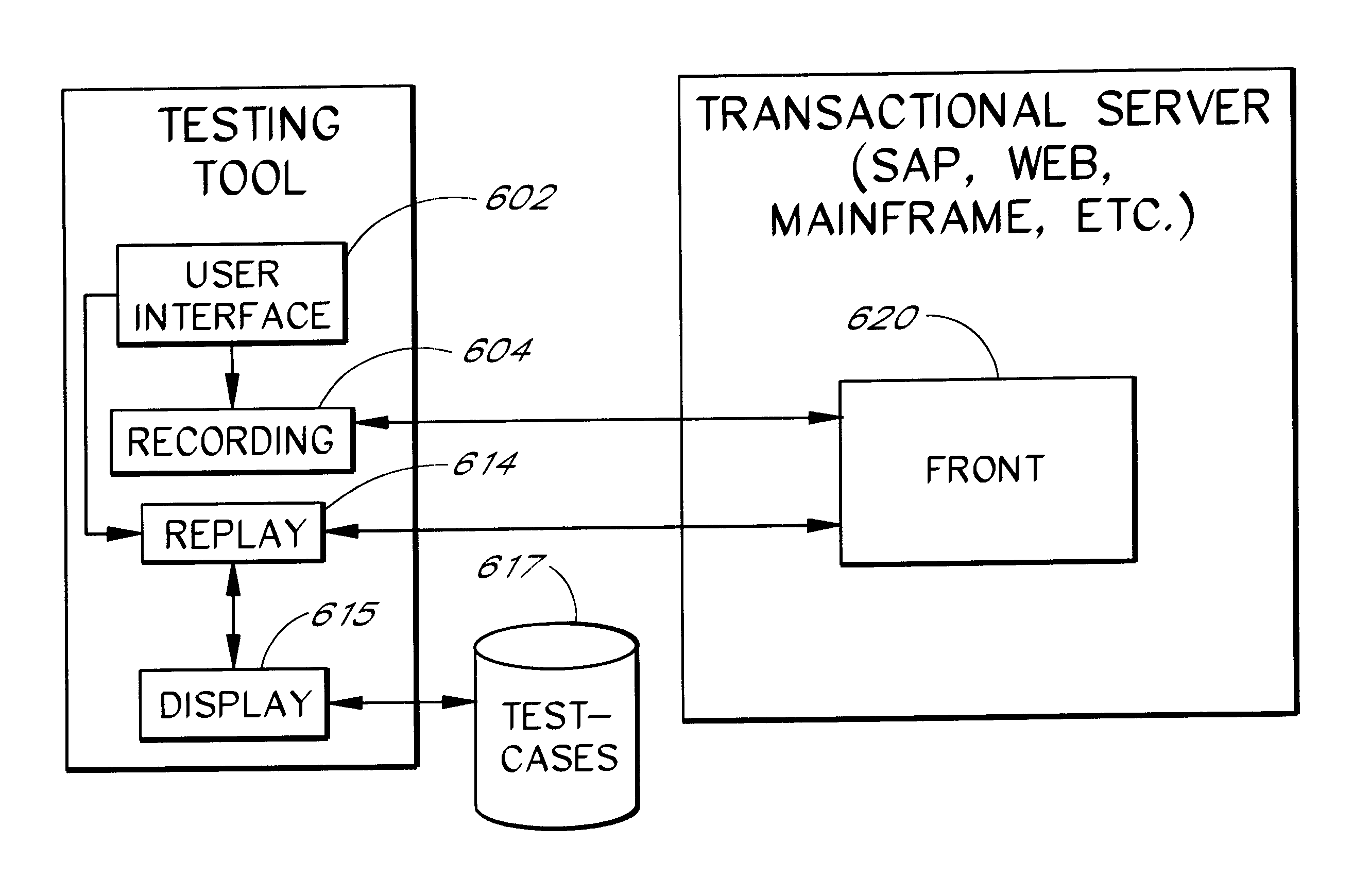
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:MICRO FOCUS LLC
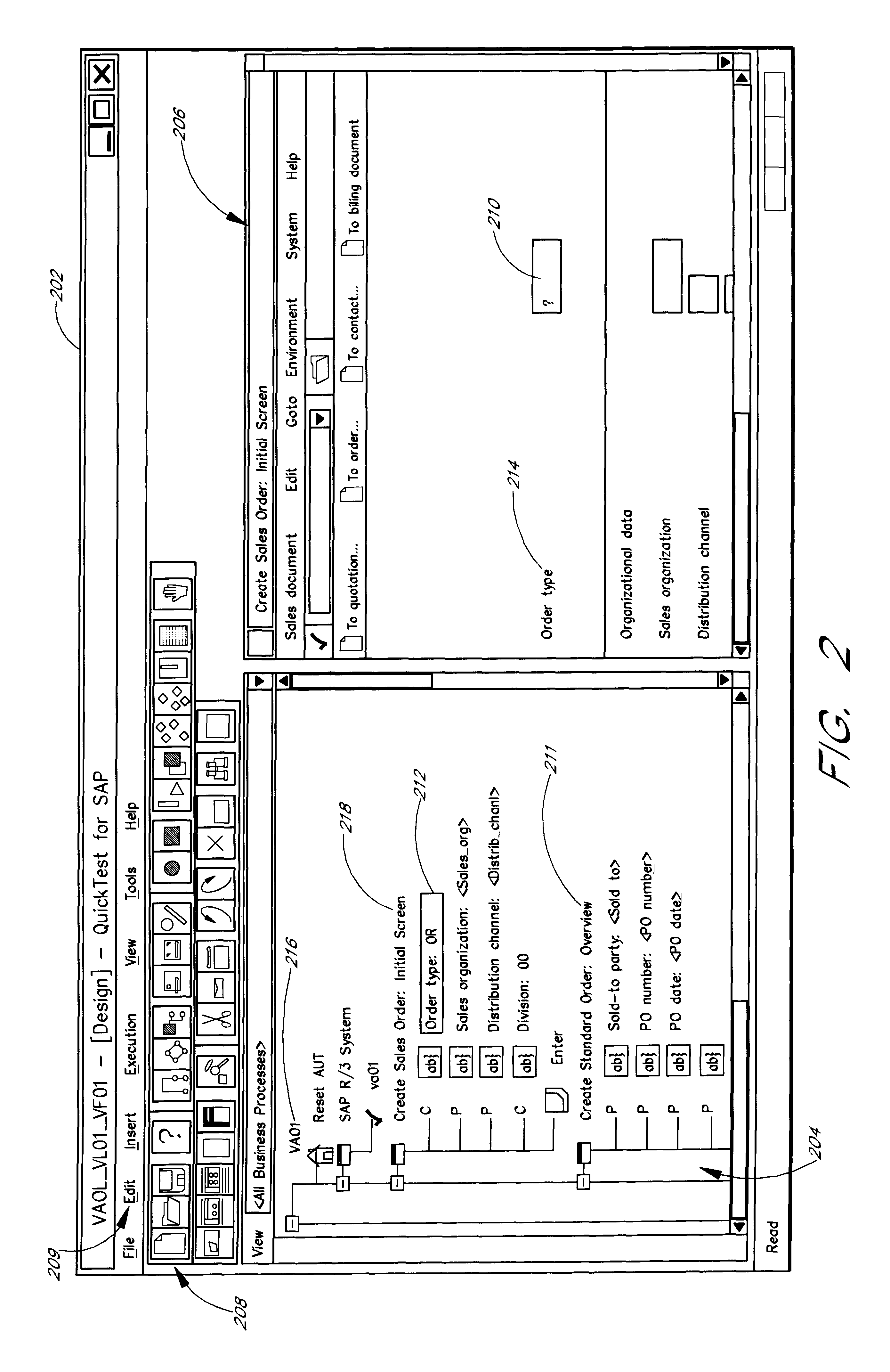
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:AMAZON COM +1
Inverted default semantics for in-speculative-region memory accesses
InactiveUS20110208921A1Unauthorized memory use protectionTransaction processingDirect memory accessMulti processor
A method for accessing memory by a first processor of a plurality of processors in a multi-processor system includes, responsive to a memory access instruction within a speculative region of a program, accessing contents of a memory location using a transactional memory access to the memory access instruction unless the memory access instruction indicates a non-transactional memory access. The method may include accessing contents of the memory location using a non-transactional memory access by the first processor according to the memory access instruction responsive to the instruction not being in the speculative region of the program. The method may include updating contents of the memory location responsive to the speculative region of the program executing successfully and the memory access instruction not being annotated to be a non-transactional memory access.
Owner:ADVANCED MICRO DEVICES INC
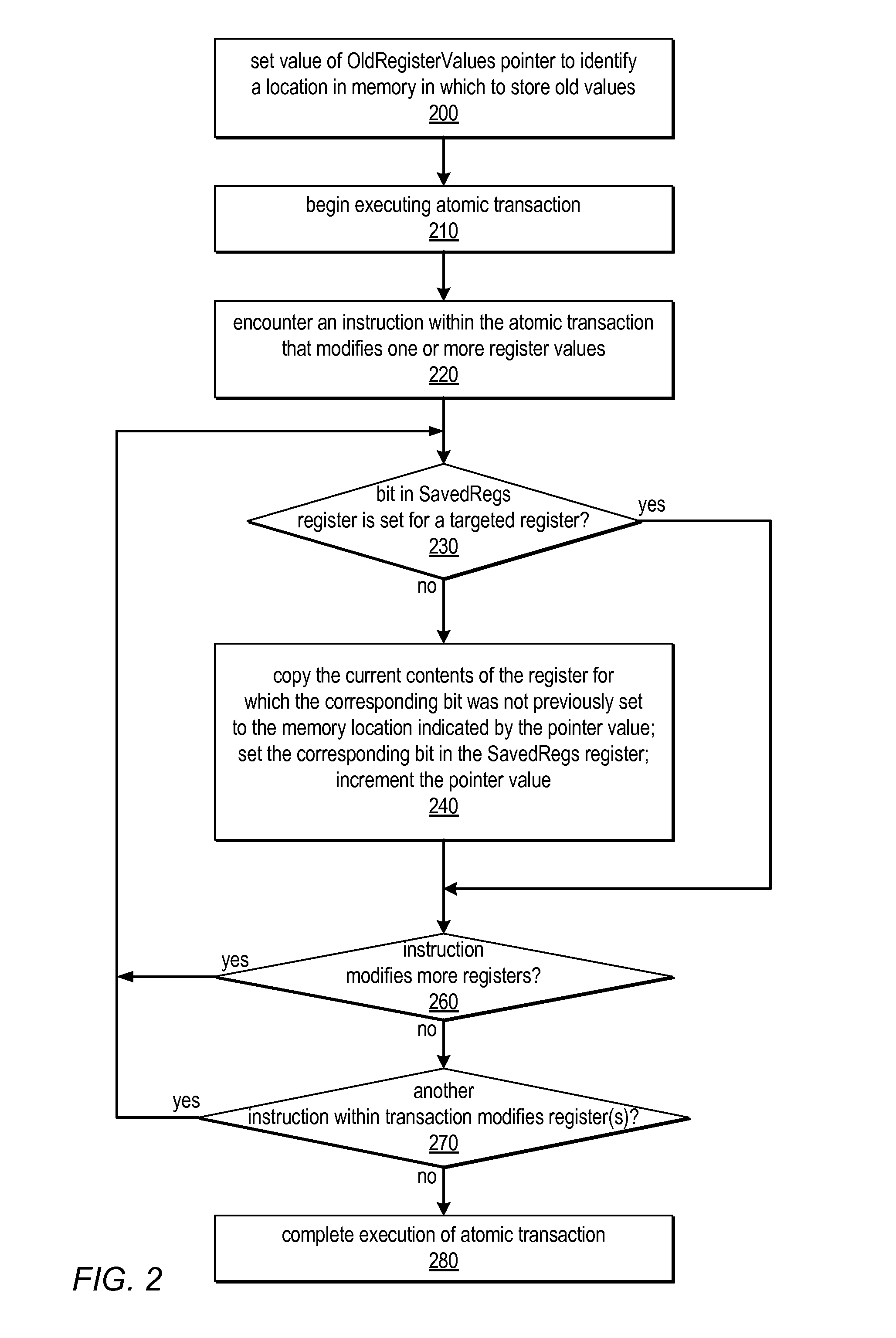
System and Method for Performing Incremental Register Checkpointing in Transactional Memory
ActiveUS20120005461A1Reduce overheadSimpler and flexibleDigital computer detailsSpecific program execution arrangementsSpeculative executionProcessor register
Systems and methods described herein for performing incremental register checkpointing may employ a special register to indicate which registers have already been checkpointed. This register may include one bit per register. These systems may also include a special pointer register whose value identifies a location in user memory or in dedicated on-chip storage at which a copy of a register's value should be saved by a checkpointing operation. Only registers modified during speculative execution or execution of a transaction may be checkpointed (e.g., when register modifying instructions are encountered) and subsequently restored (e.g., due to misspeculation or transaction abort), rather than all of the registers of the processor. Each register may be checkpointed at most once for a given speculative episode or atomic transaction. Setting a bit in the special register may prevent checkpointing of the corresponding register. Setting all of the bits in the special register may disable checkpointing.
Owner:ORACLE INT CORP
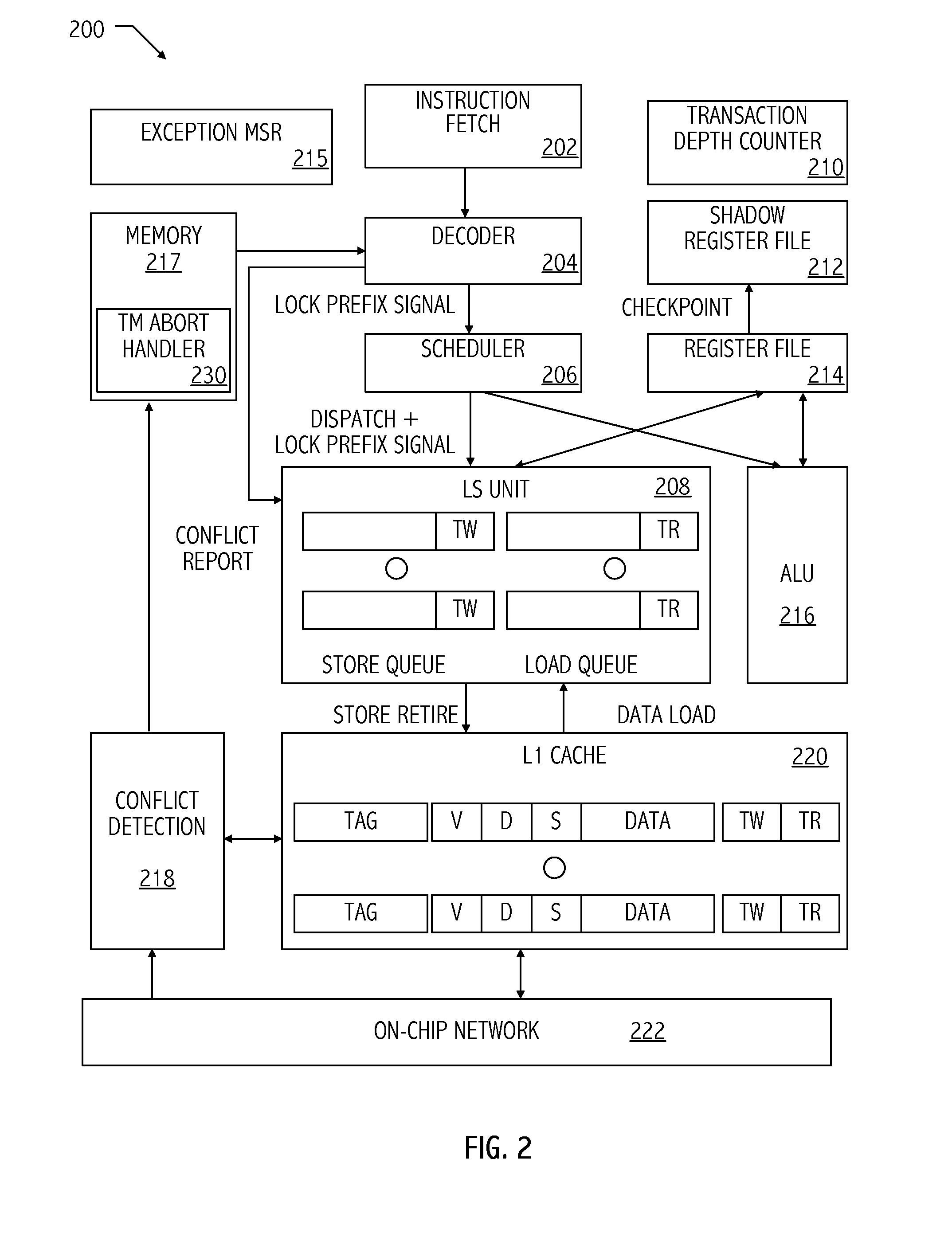
Instrumentation of hardware assisted transactional memory system
ActiveUS20110145498A1Error detection/correctionMemory adressing/allocation/relocationParallel computingTransactional memory
Monitoring performance of one or more architecturally significant processor caches coupled to a processor. The methods include executing an application on one or more processors coupled to one or more architecturally significant processor caches, where the application utilizes the architecturally significant portions of the architecturally significant processor caches. The methods further include at least one of generating metrics related to performance of the architecturally significant processor caches; implementing one or more debug exceptions related to performance of the architecturally significant processor caches; or implementing one or more transactional breakpoints related to performance of the architecturally significant processor caches as a result of utilizing the architecturally significant portions of the architecturally significant processor caches.
Owner:MICROSOFT TECH LICENSING LLC
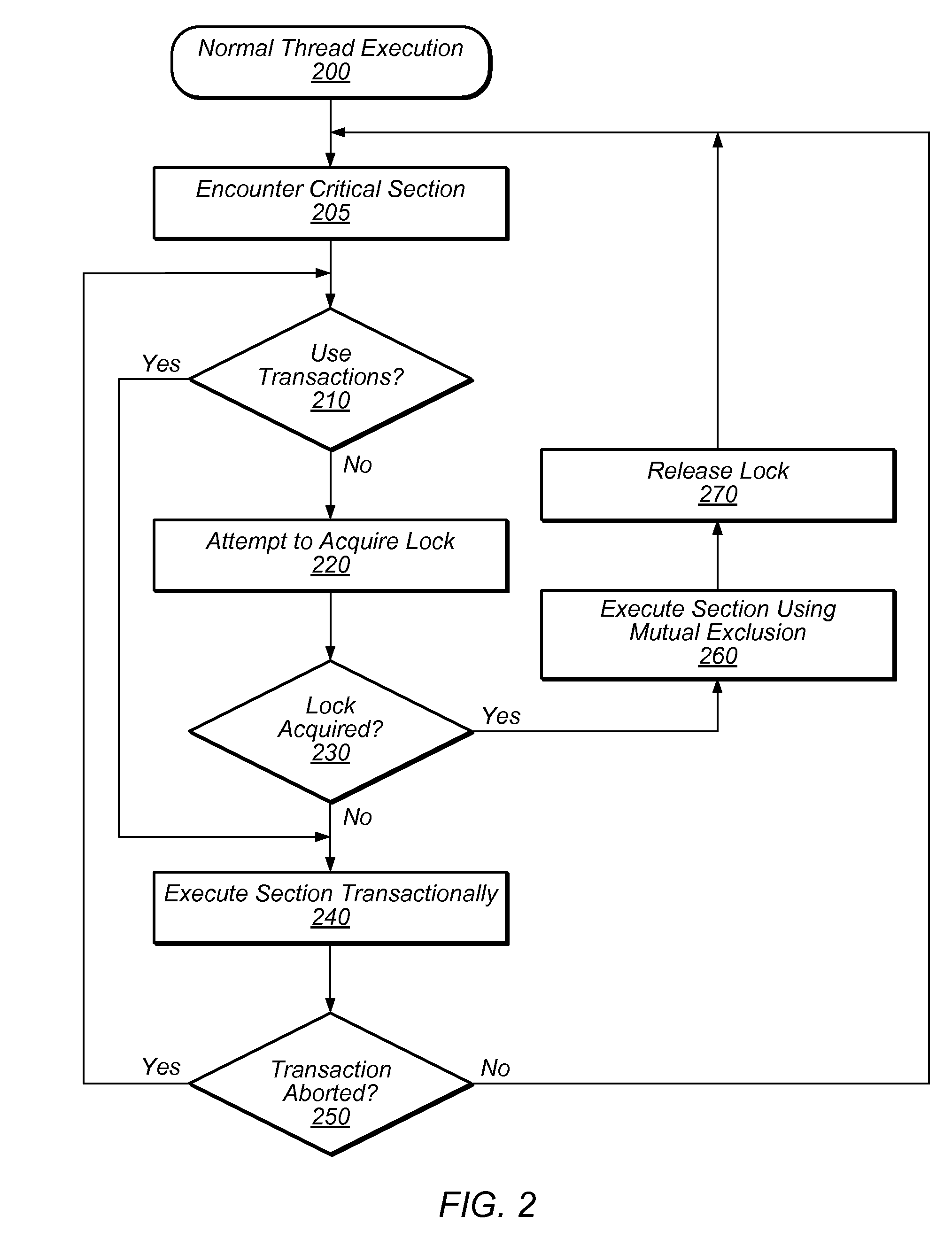
Method and System for Reducing Abort Rates in Speculative Lock Elision using Contention Management Mechanisms
ActiveUS20100169623A1Reduce transactional abort rateWaste system resourceDigital computer detailsSpecific program execution arrangementsSpeculative executionCritical section
Hardware-based transactional memory mechanisms, such as Speculative Lock Elision (SLE), may allow multiple threads to concurrently execute critical sections protected by the same lock as speculative transactions. Such transactions may abort due to contention or due to misidentification of code as a critical section. In various embodiments, speculative execution mechanisms may be augmented with software and / or hardware contention management mechanisms to reduce abort rates. Speculative execution hardware may send a hardware interrupt signal to notify software components of a speculative execution event (e.g., abort). Software components may respond by implementing concurrency-throttling mechanisms and / or by determining a mode of execution (e.g., speculative, non-speculative) for a given section and communicating that determination to the hardware speculative execution mechanisms, e.g., by writing it into a lock predictor cache. Subsequently, hardware speculative execution mechanisms may determine a preferred mode of execution for the section by reading the corresponding entry from the lock predictor cache.
Owner:SUN MICROSYSTEMS INC
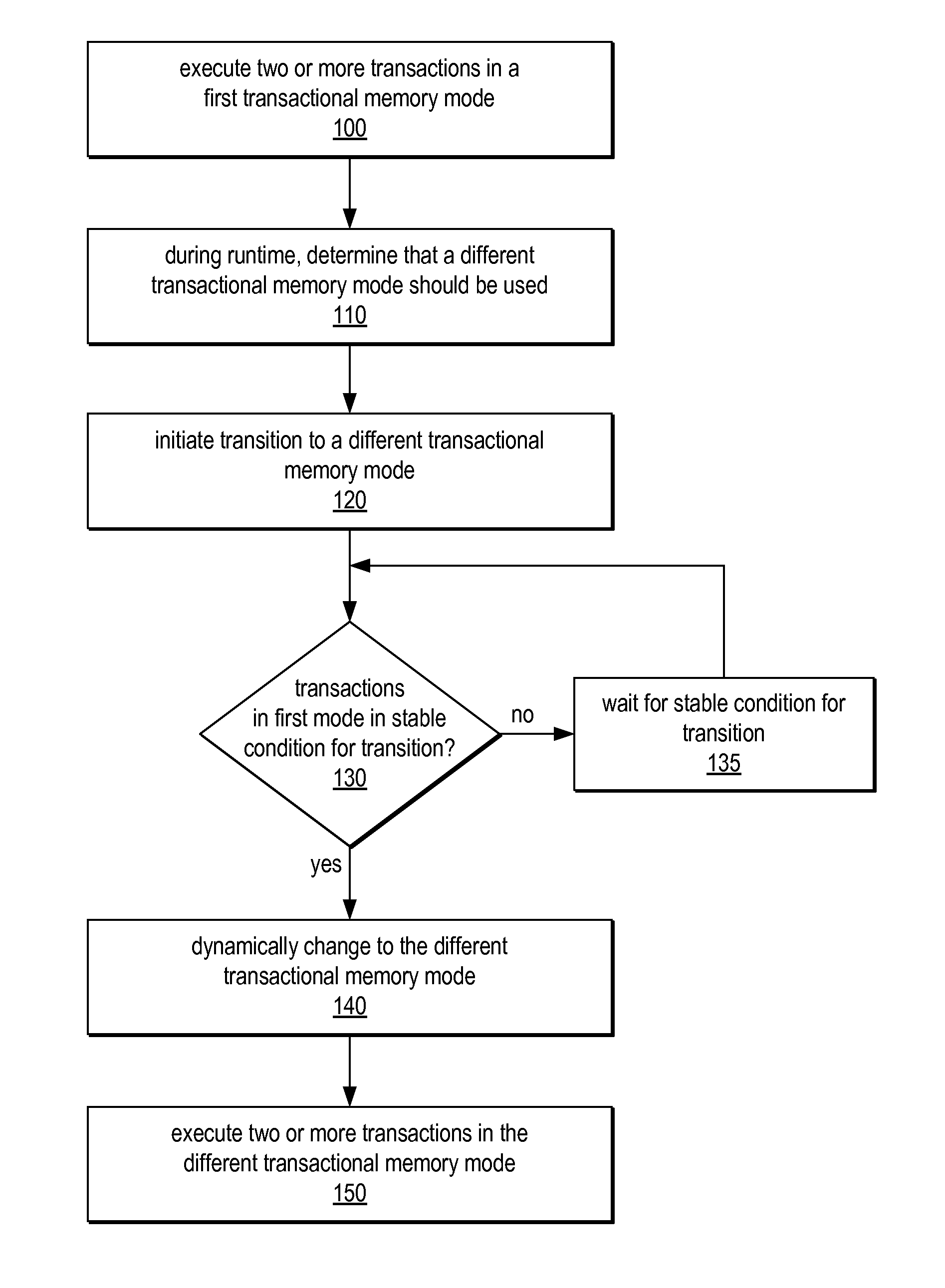
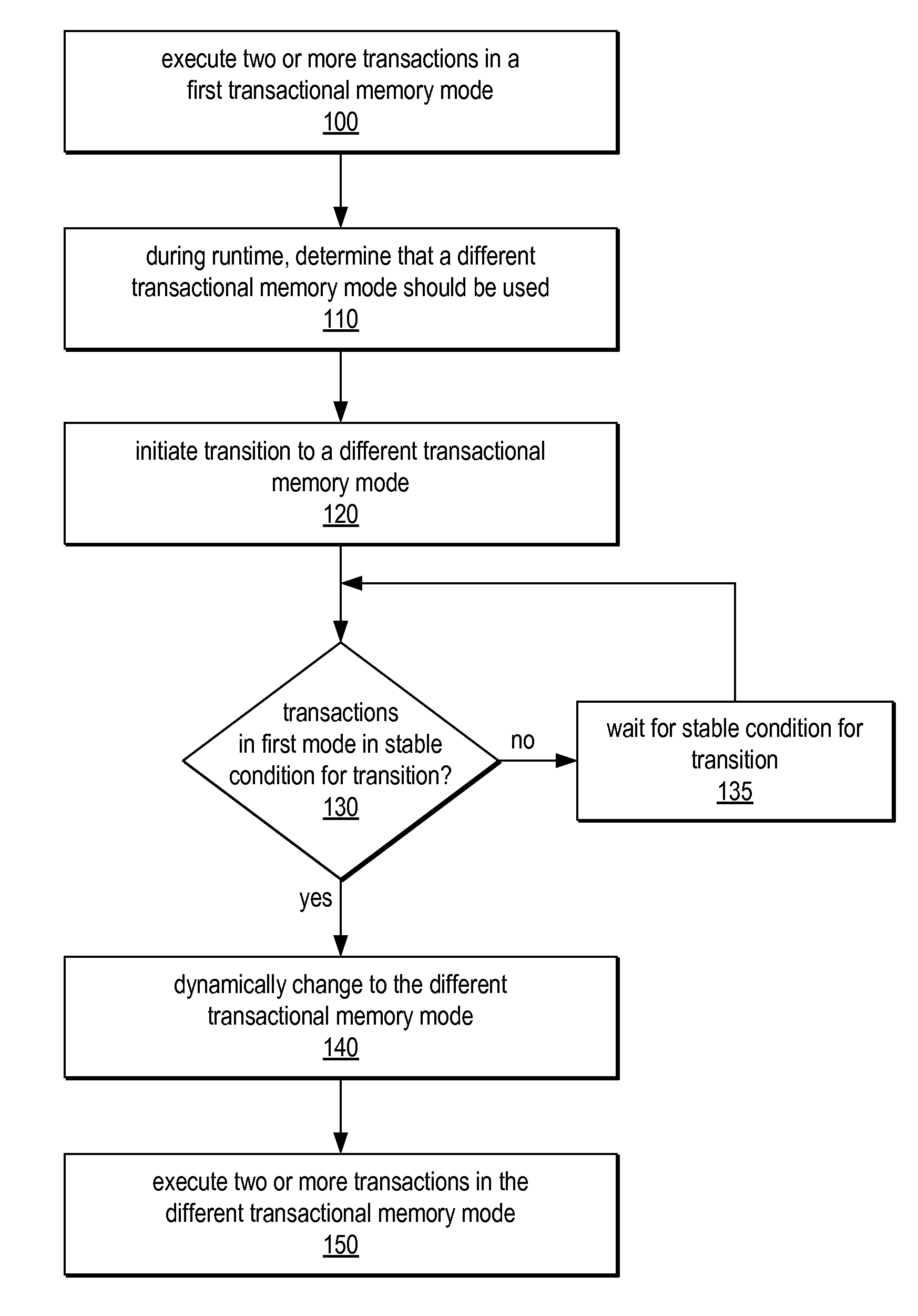
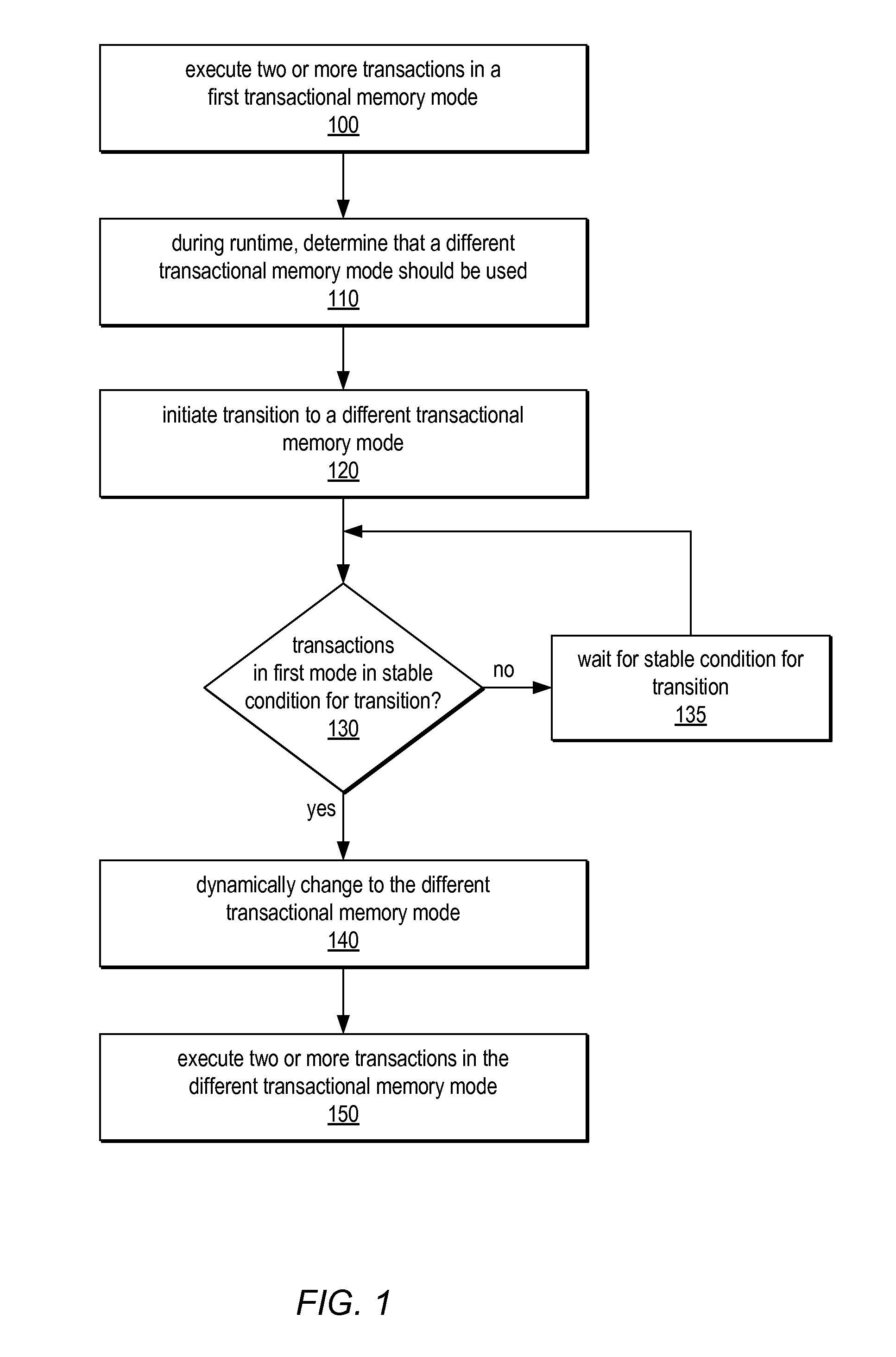
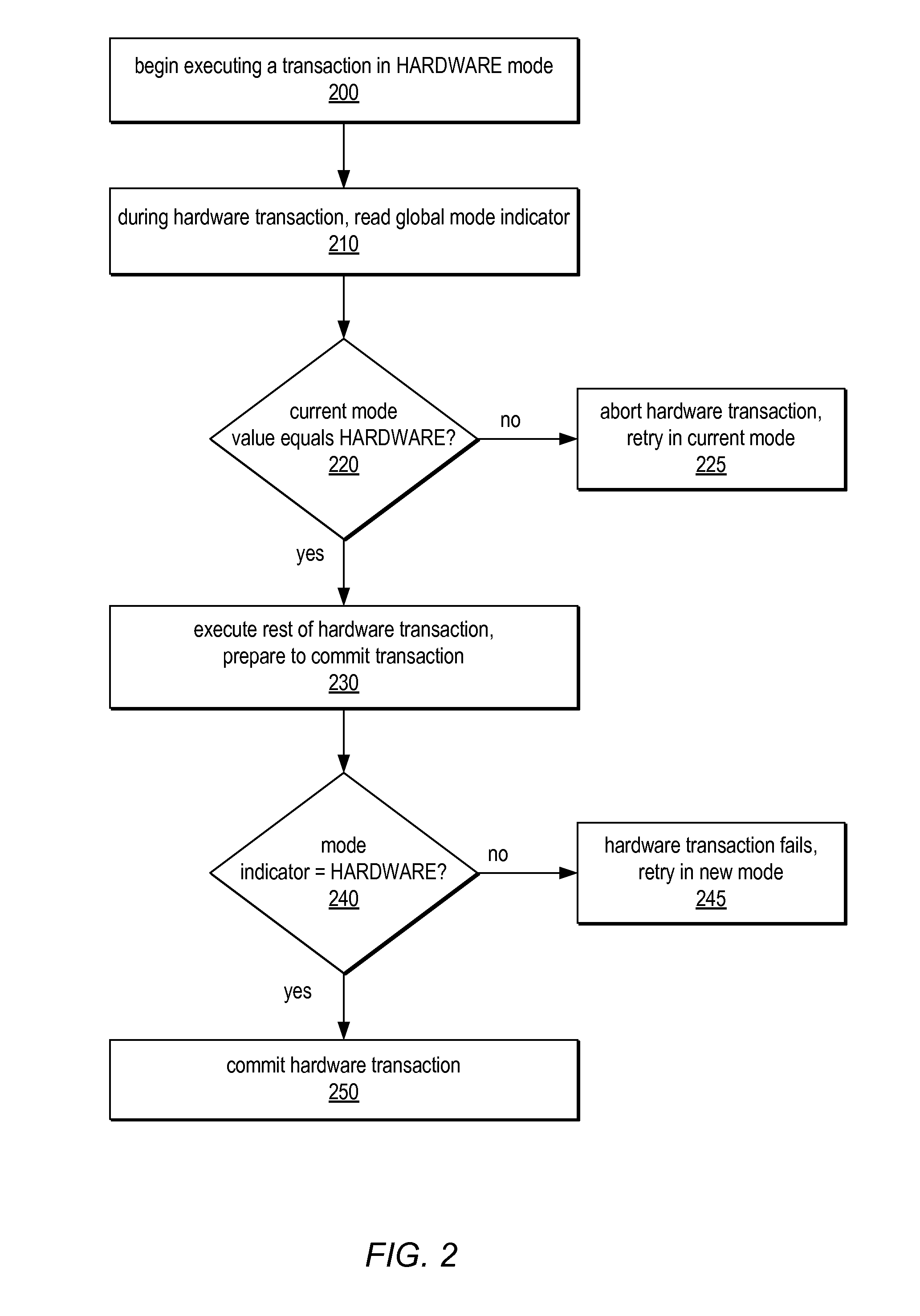
System and Method for Supporting Phased Transactional Memory Modes
ActiveUS20090172306A1Reduce difficultyMaximum flexibilityProgram control using stored programsDigital computer detailsParallel computingTransactional memory
A phased transactional memory (PhTM) may support a plurality of transactional memory implementations, including software, hardware, and hybrid implementations, and may provide mechanisms for dynamically transitioning between transactional memory modes in response to changing workload characteristics; upon discovering that the current mode does not perform well, is not suitable, or does not support functionality required for particular transactions; or according to scheduled phases. A system providing PhTM may be configured to transition from a first transactional memory mode to a second transactional memory mode while ensuring that transactions executing in the first transactional memory mode do not interfere with correct execution of transactions in the second transactional memory mode. The system may be configured to abort transactions in progress or to wait for transactions to complete, be aborted, or reach a safe transition point before transitioning to a new mode, and may use a global mode indicator in coordinating transitions.
Owner:ORACLE INT CORP
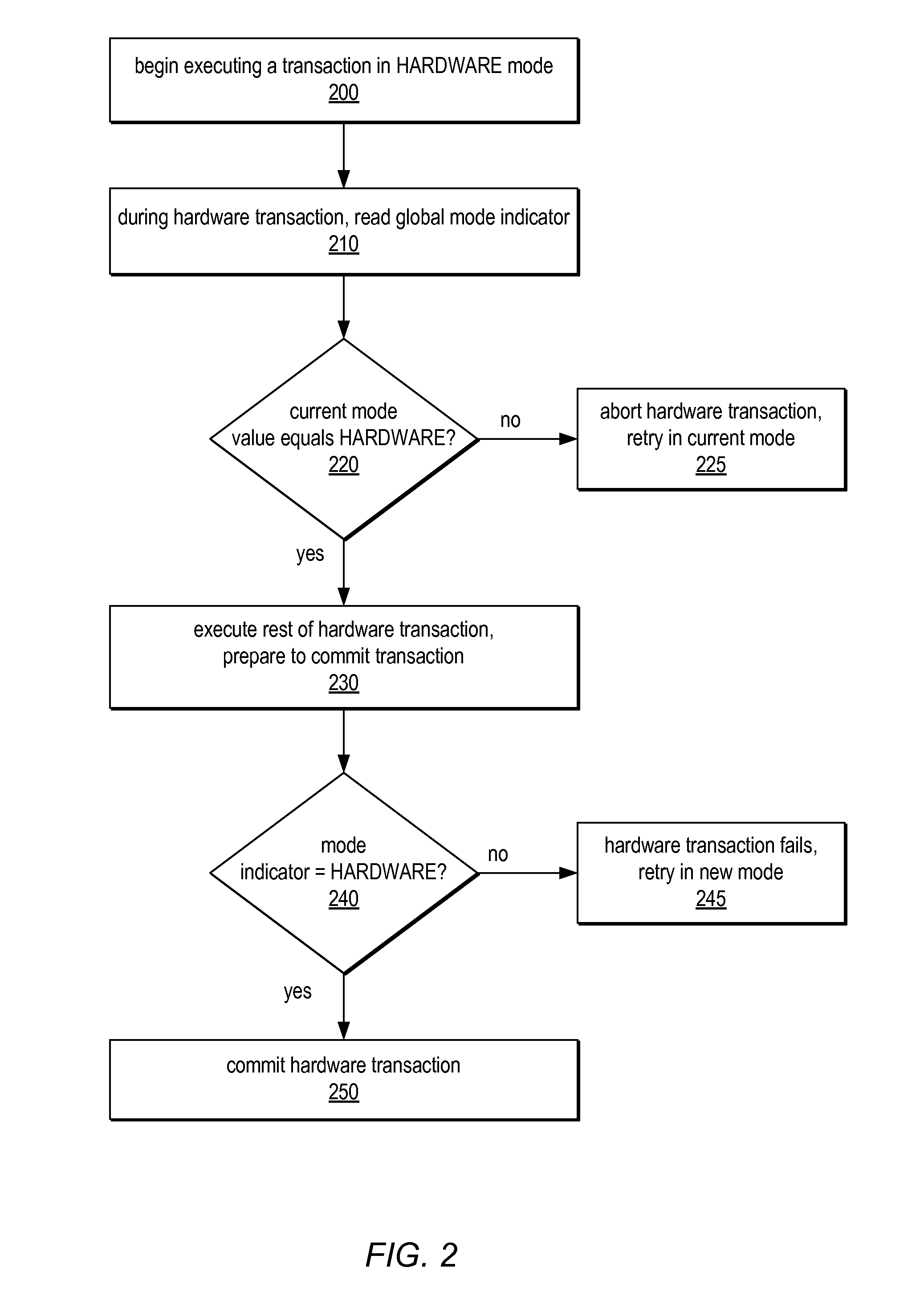
Advice-based feedback for transactional execution
ActiveUS20100332901A1Easy to implementImprove responseDigital data processing detailsNon-redundant fault processingState dependentTransactional memory
One embodiment provides a system that facilitates the execution of a transaction for a program in a hardware-supported transactional memory system. During operation, the system records a failure state of the transaction during execution of the transaction using hardware transactional memory mechanisms. Next, the system detects a transaction failure associated with the transaction. Finally, the system provides an advice state associated with the recorded failure state to the program to facilitate a response to the transaction failure by the program.
Owner:ORACLE INT CORP
Hybrid Transactional Memory System (HybridTM) and Method
InactiveUS20110119452A1Simple/cost-effective hardware designAdd supportNon-redundant fault processingMemory systemsOperational systemHandling system
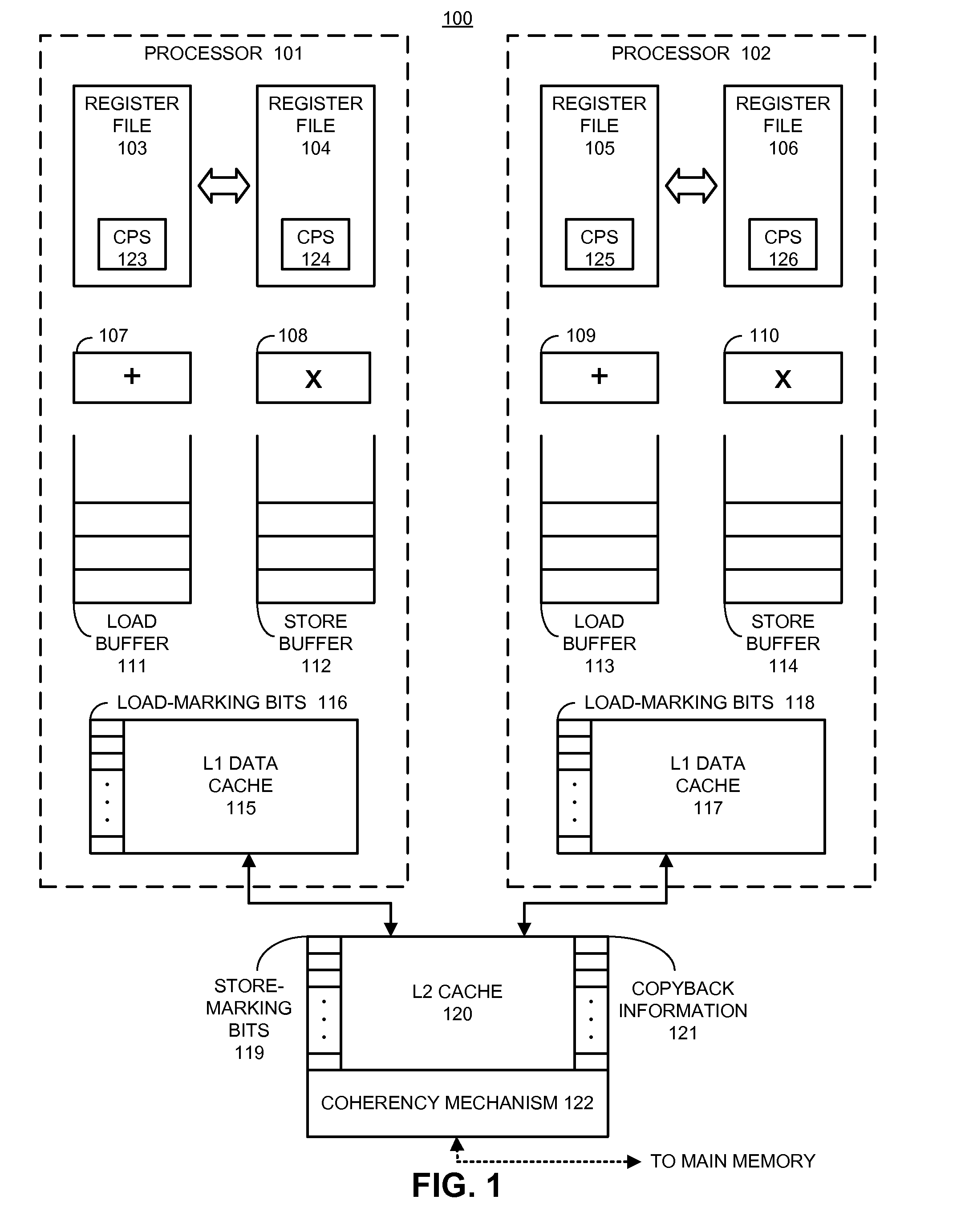
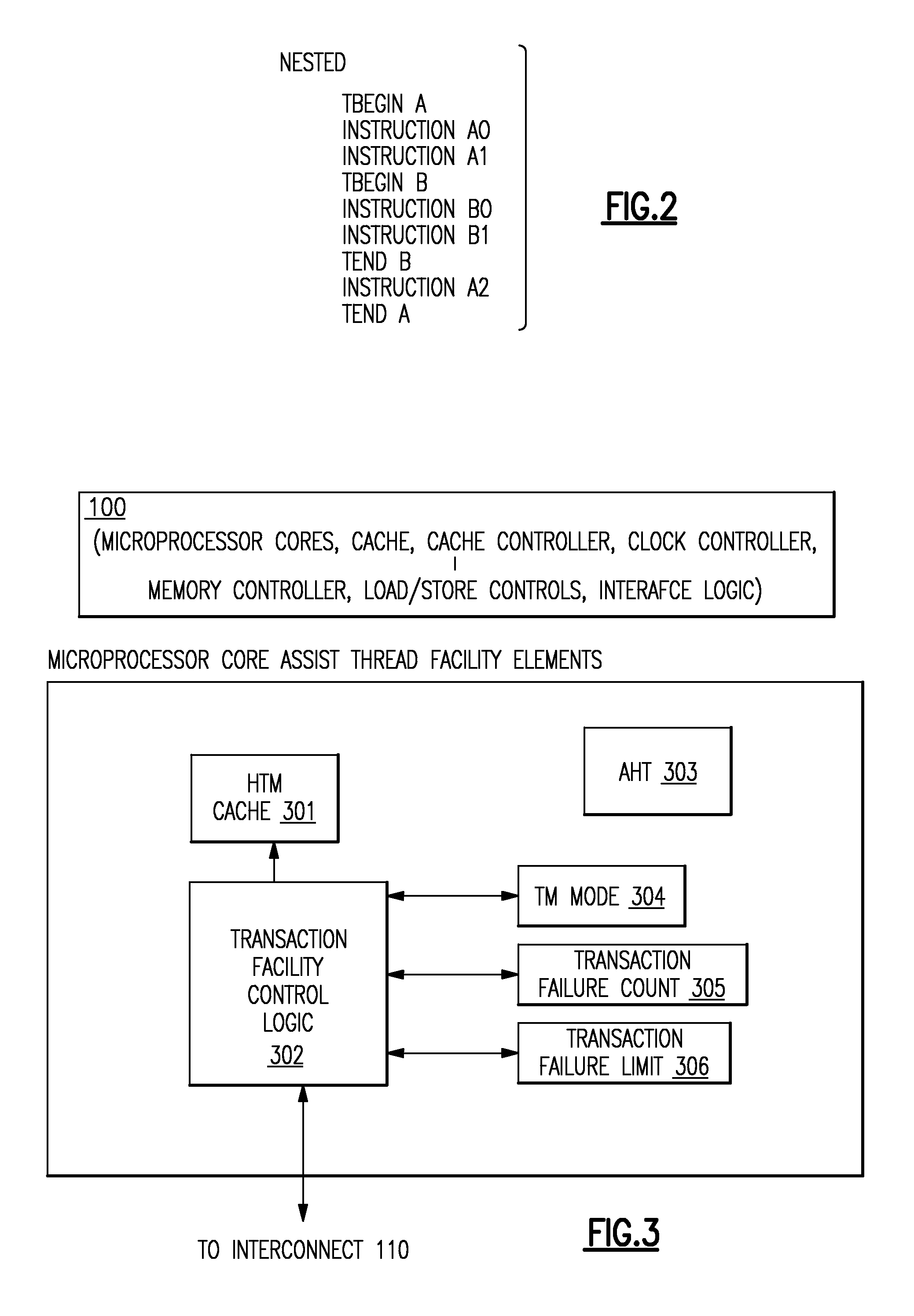
A computer processing system having memory and processing facilities for processing data with a computer program is a Hybrid Transactional Memory multiprocessor system with modules 1 . . . n coupled to a system physical memory array, I / O devices via a high speed interconnection element. A CPU is integrated as in a multi-chip module with microprocessors which contain or are coupled in the CPU module to an assist thread facility, as well as a memory controller, cache controllers, cache memory, and other components which form part of the CPU which connects to the high speed interconnect which functions under the architecture and operating system to interconnect elements of the computer system with physical memory, various 1 / 0, devices and the other CPUs of the system. The current hybrid transactional memory elements support for a transactional memory system that has a simple / cost effective hardware design that can deal with limited hardware resources, yet one which has a transactional facility control logic providing for a back up assist thread that can still allow transactions to reference existing libraries and allows programmers to include calls to existing software libraries inside of their transactions, and which will not make a user code use a second lock based solution.
Owner:IBM CORP
Utilizing software locking approach to execute code upon failure of hardware transactional approach
Utilizing a software locking approach to execute a code section, upon failure of a hardware transactional approach, is disclosed. A method is disclosed that includes utilizing a hardware approach to transactional memory to execute a code section relating to memory. Where utilizing the hardware approach fails a threshold in executing the code section, the software approach is instead utilized to execute the code section relating to the memory. The threshold may include the hardware approach aborting execution of the code section a predetermined one or more times. The hardware approach includes starting a transaction inclusive of the code section, conditionally executing the transaction, and upon successfully completing the transaction, committing execution to memory. The software locking approach includes placing a lock on memory, executing the code section, committing execution of the code section to the memory as the code section is executed, and then removing the lock from the memory.
Owner:IBM CORP
Hardware accelerated transactional memory system with open nested transactions
ActiveUS20100332538A1Well formedDigital data information retrievalDigital data processing detailsComputer hardwareSoftware lockout
Hardware assisted transactional memory system with open nested transactions. Some embodiments described herein implement a system whereby hardware acceleration of transactions can be accomplished by implementing open nested transaction in hardware which respect software locks such that a top level transaction can be implemented in software, and thus not be limited by hardware constraints typical when using hardware transactional memory systems.
Owner:MICROSOFT TECH LICENSING LLC
Hardware transactional memory acceleration through multiple failure recovery
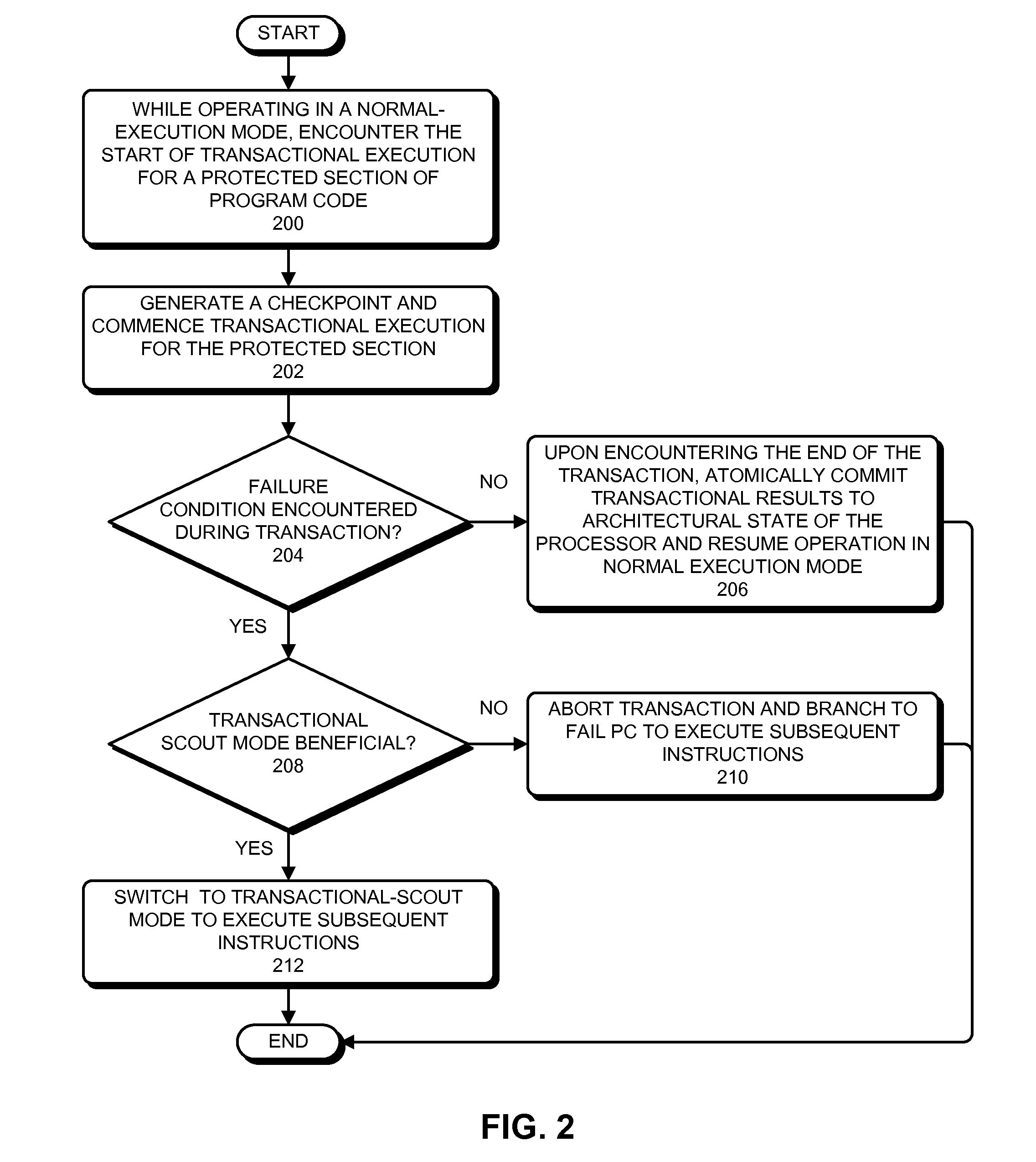
ActiveUS20110119528A1Error detection/correctionDigital computer detailsParallel computingTransactional memory
The described embodiments provide a processor (e.g., processor 102) for executing instructions. During execution, the processor starts by transactionally executing instructions from a protected section of program code. The processor then encounters a transactional failure condition while transactionally executing the instructions from the protected section of program code. In response to encountering the transactional failure condition, the processor enters a transactional-scout mode and speculatively executes subsequent instructions in the transactional-scout mode.
Owner:ORACLE INT CORP
System and method for supporting phased transactional memory modes
ActiveUS7966459B2Reduce difficultyMaximum flexibilityDigital computer detailsSpecific program execution arrangementsParallel computingTransactional memory
A phased transactional memory (PhTM) may support a plurality of transactional memory implementations, including software, hardware, and hybrid implementations, and may provide mechanisms for dynamically transitioning between transactional memory modes in response to changing workload characteristics; upon discovering that the current mode does not perform well, is not suitable, or does not support functionality required for particular transactions; or according to scheduled phases. A system providing PhTM may be configured to transition from a first transactional memory mode to a second transactional memory mode while ensuring that transactions executing in the first transactional memory mode do not interfere with correct execution of transactions in the second transactional memory mode. The system may be configured to abort transactions in progress or to wait for transactions to complete, be aborted, or reach a safe transition point before transitioning to a new mode, and may use a global mode indicator in coordinating transitions.
Owner:ORACLE INT CORP
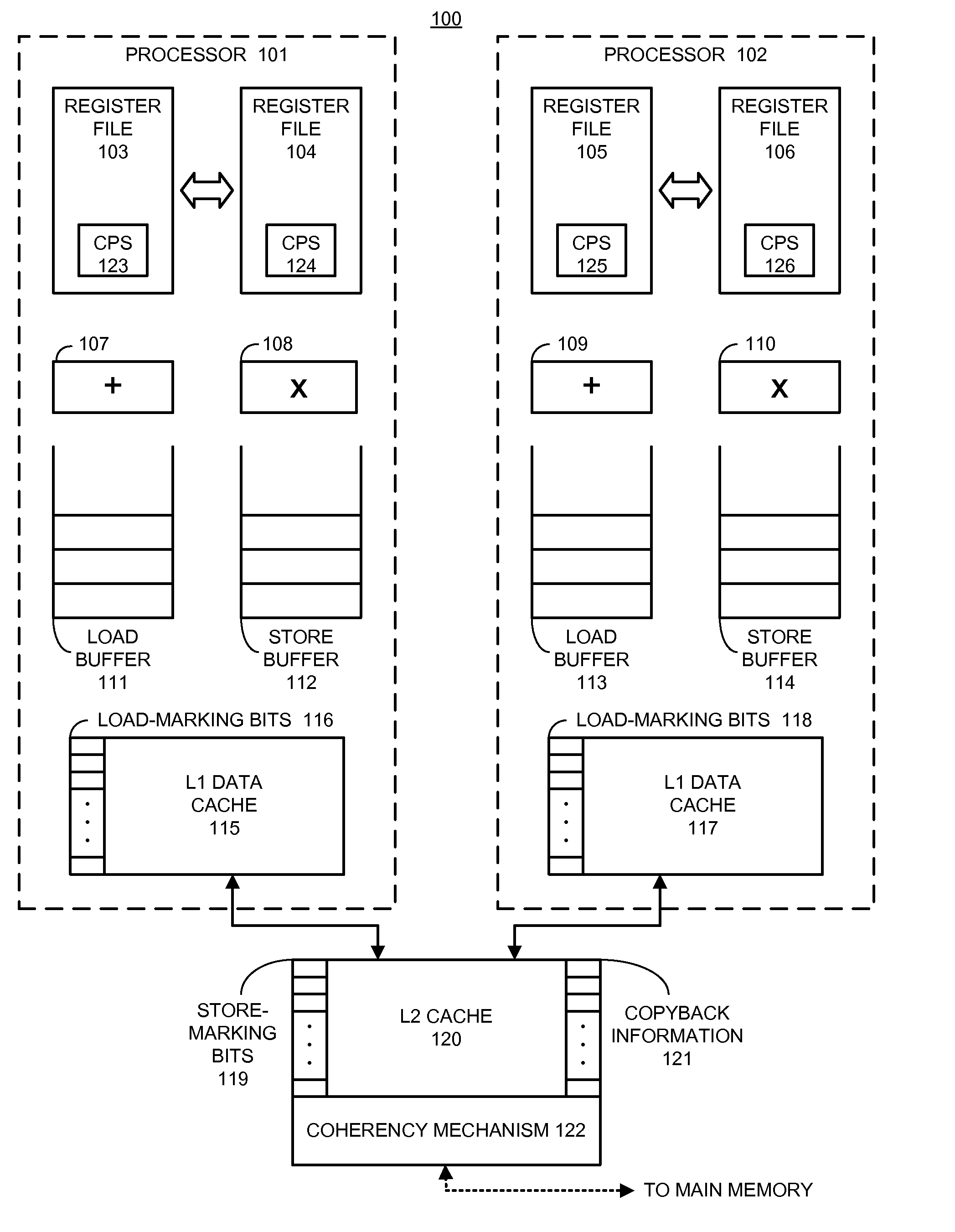
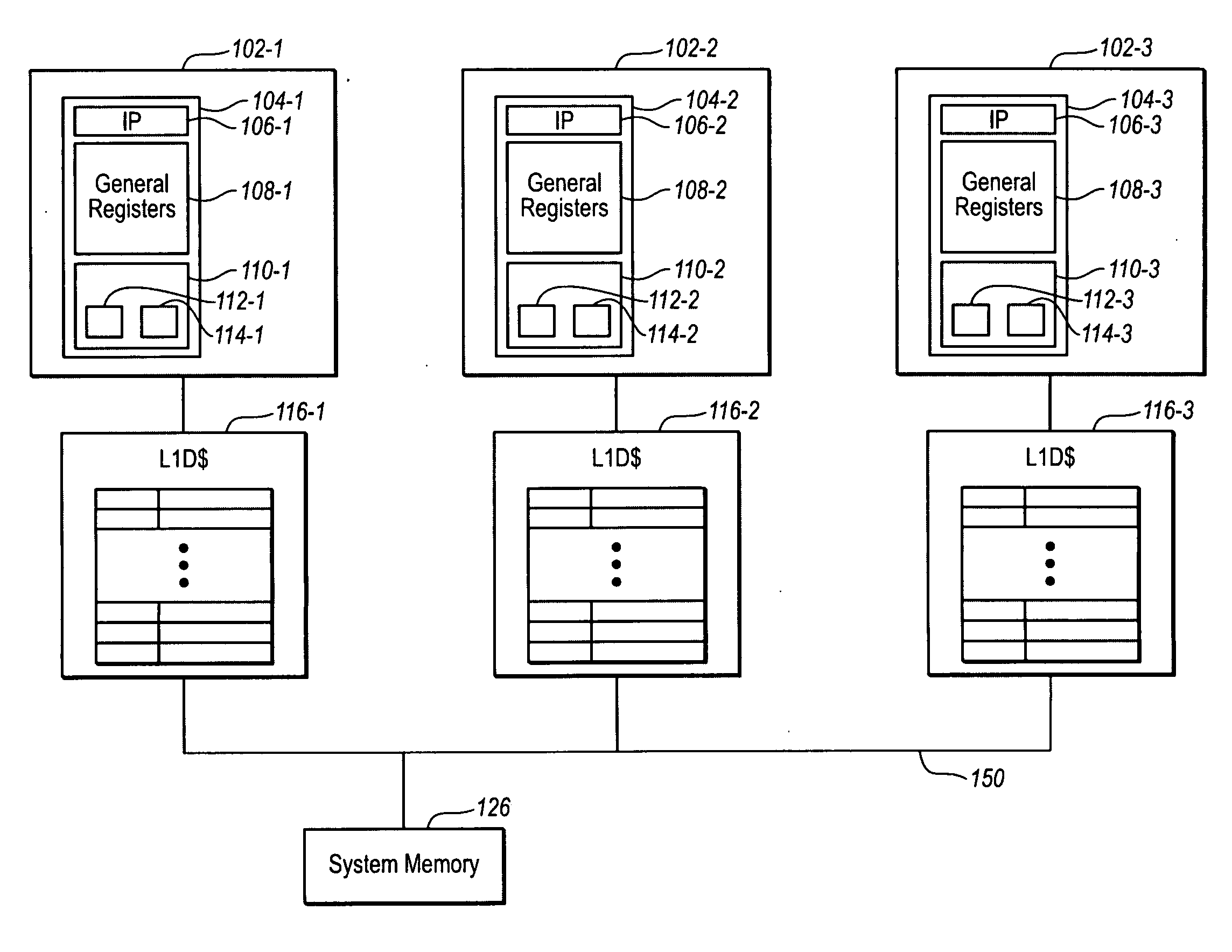
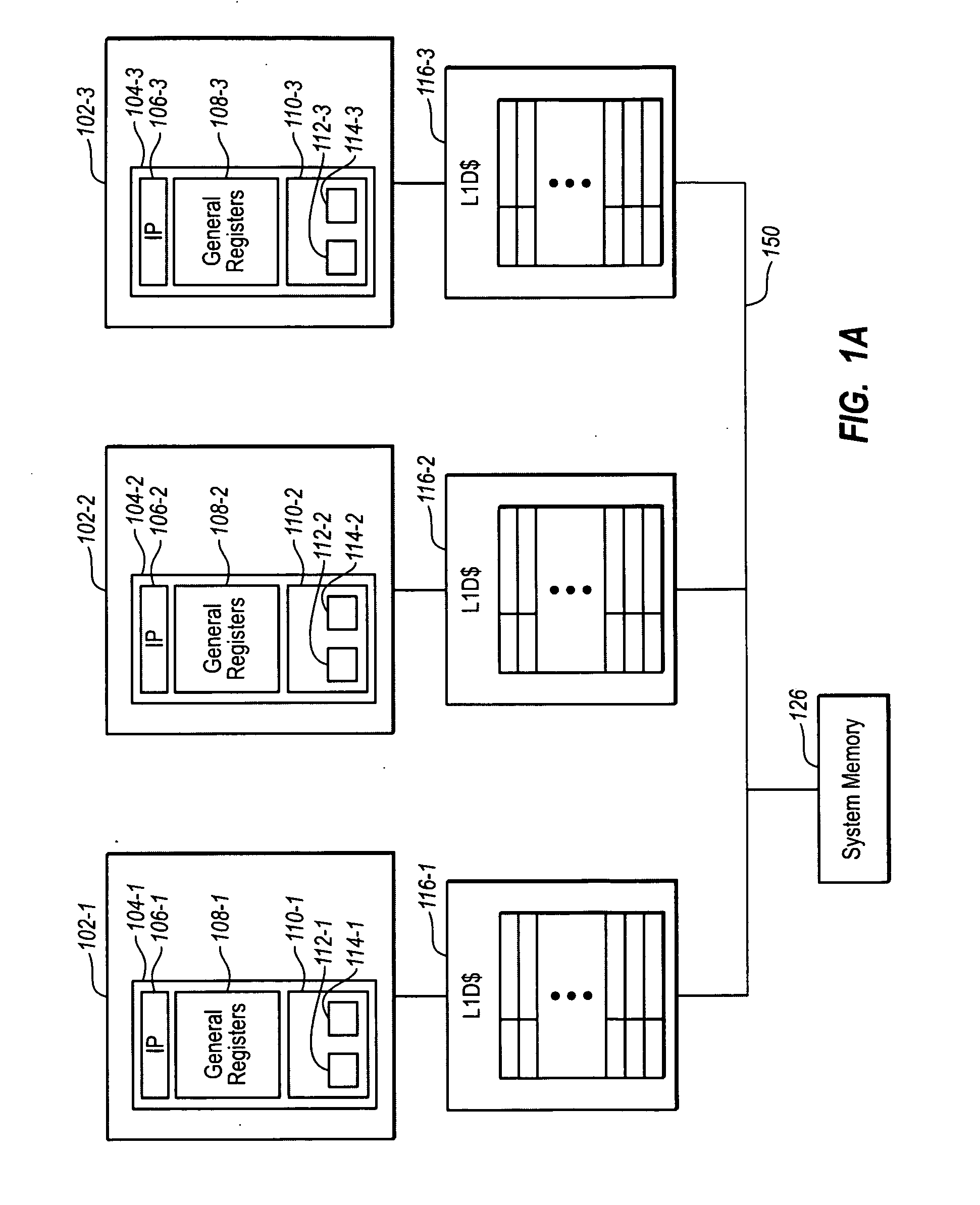
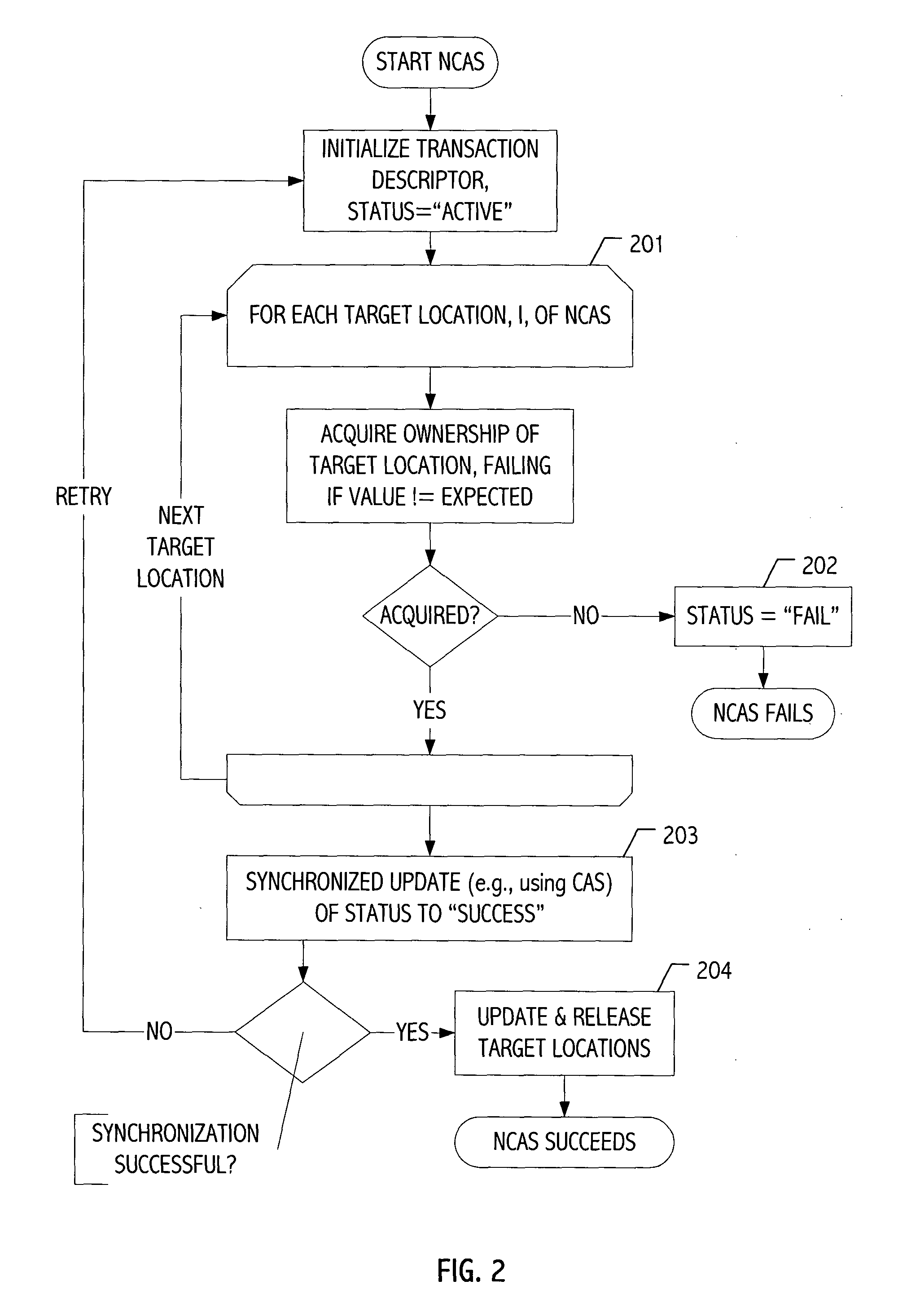
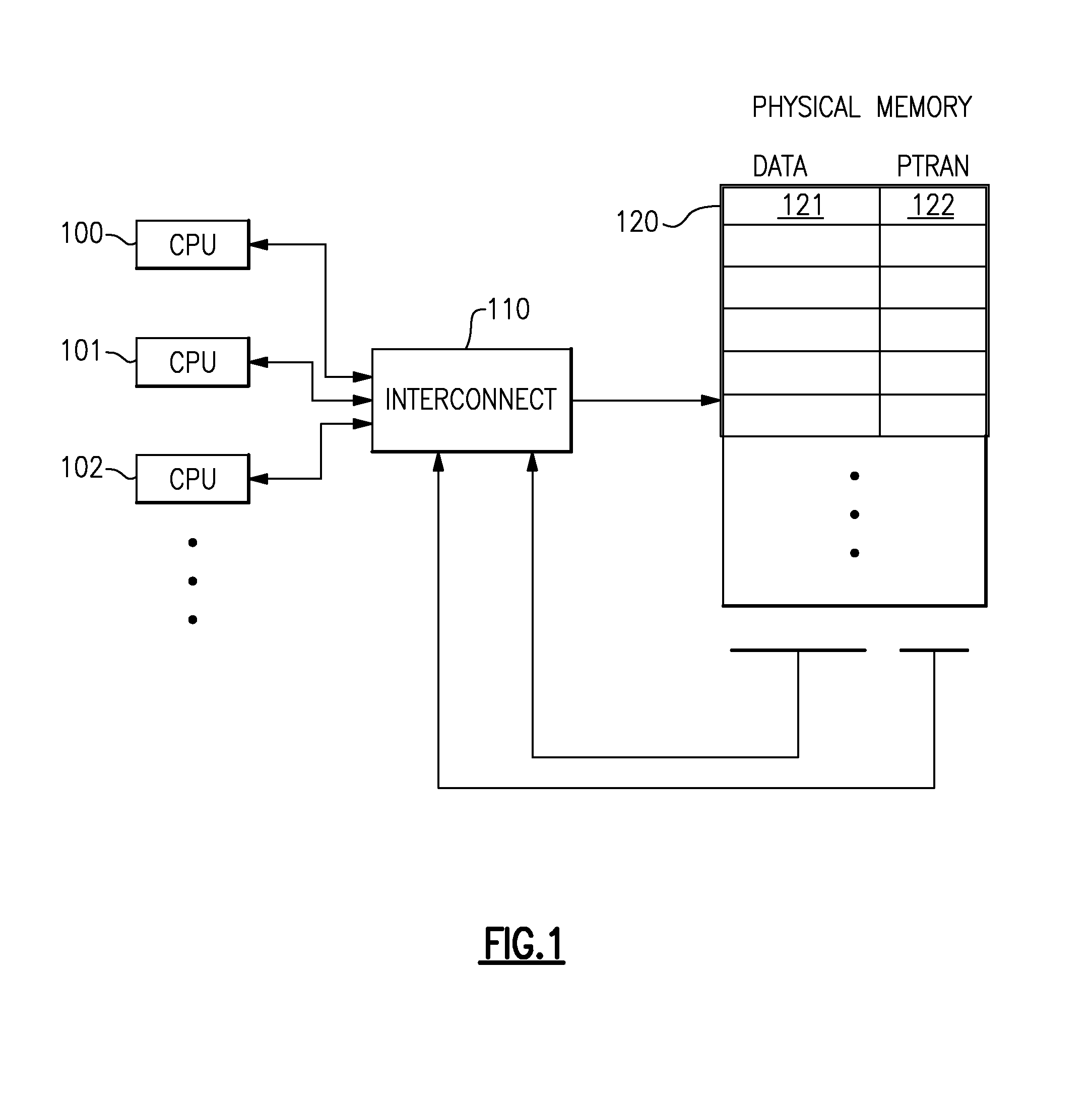
Computing System with Transactional Memory Using Millicode Assists
InactiveUS20080288819A1FasterSolve excessive overheadRuntime instruction translationDigital computer detailsProcess memoryTransactional memory
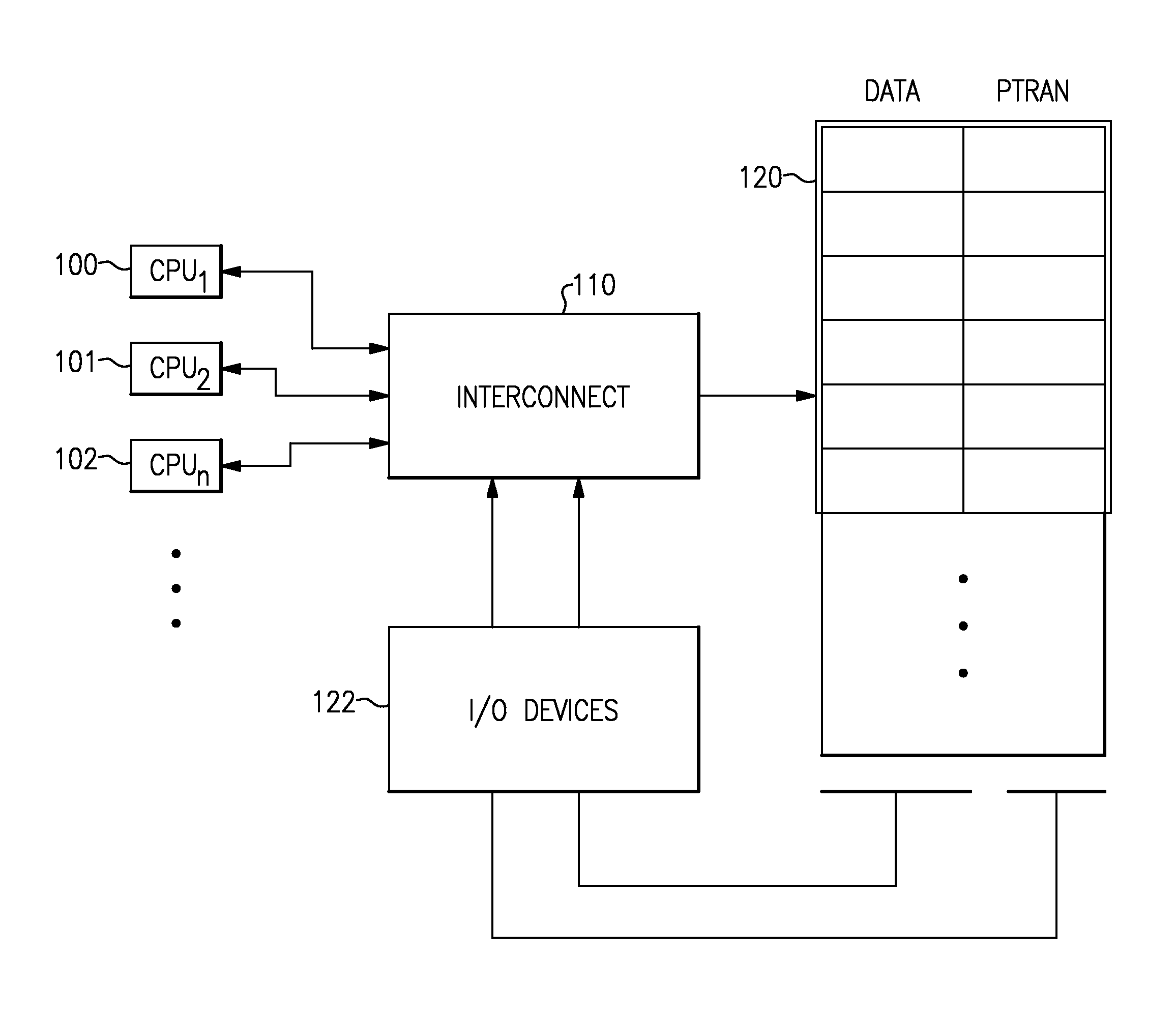
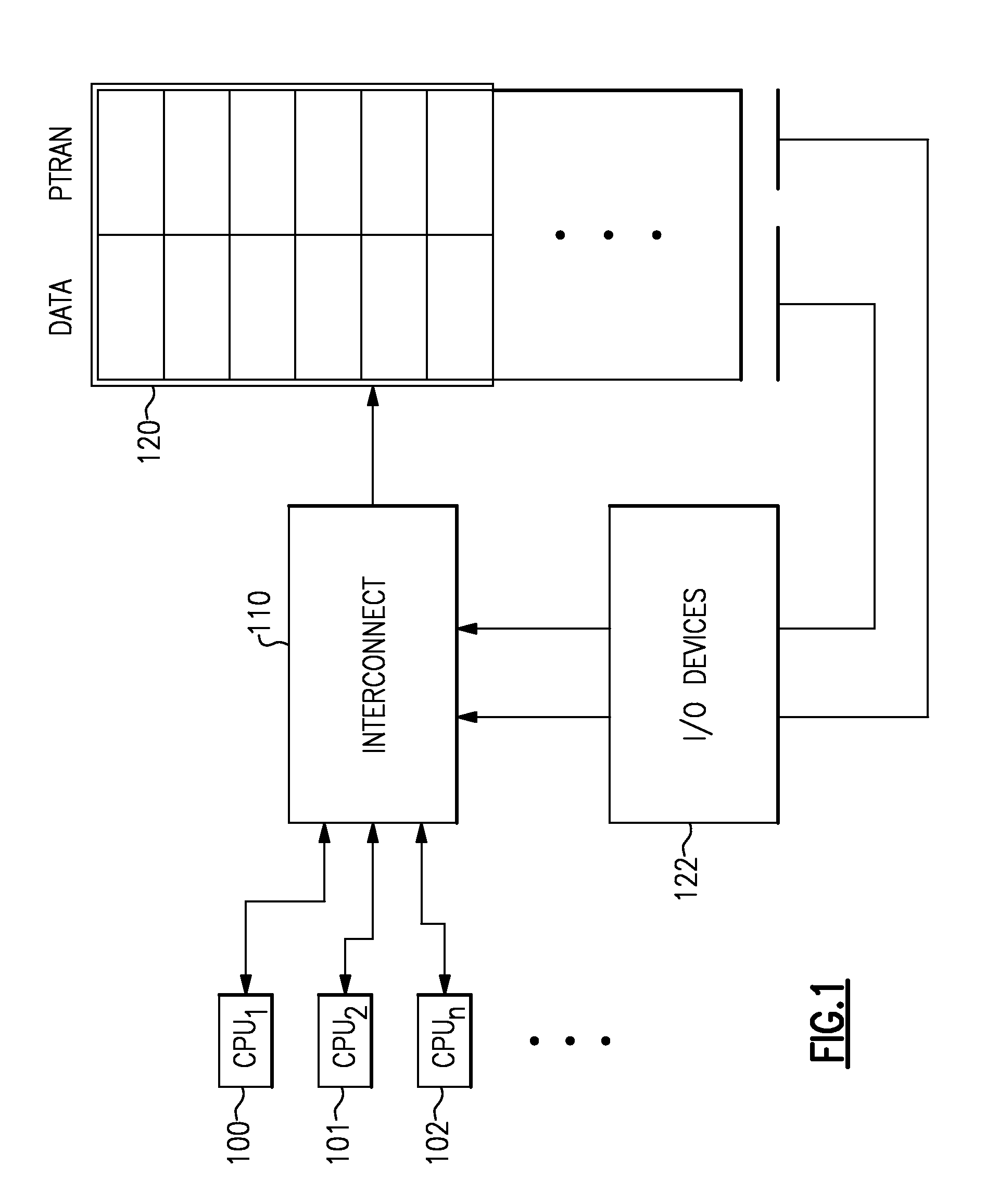
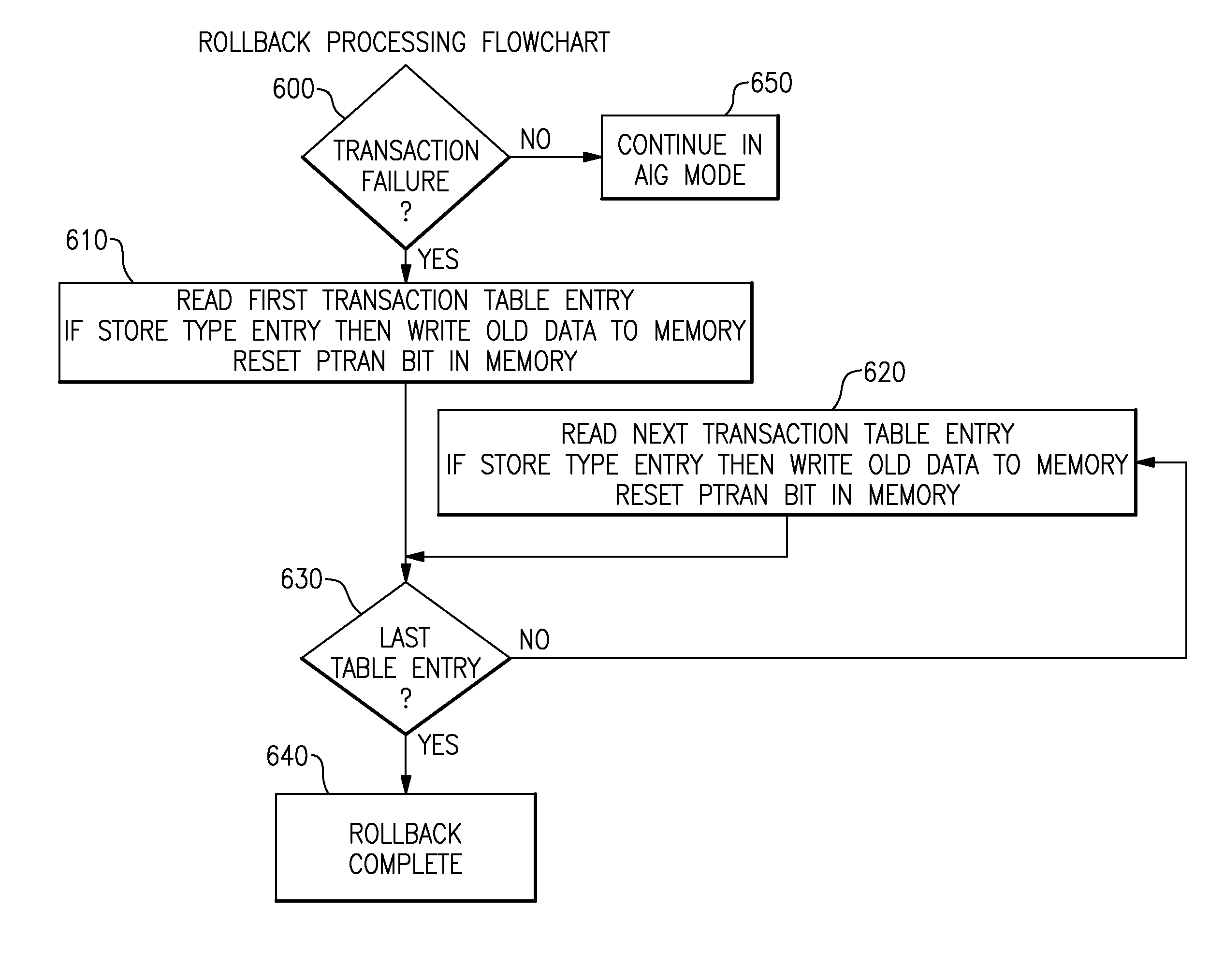
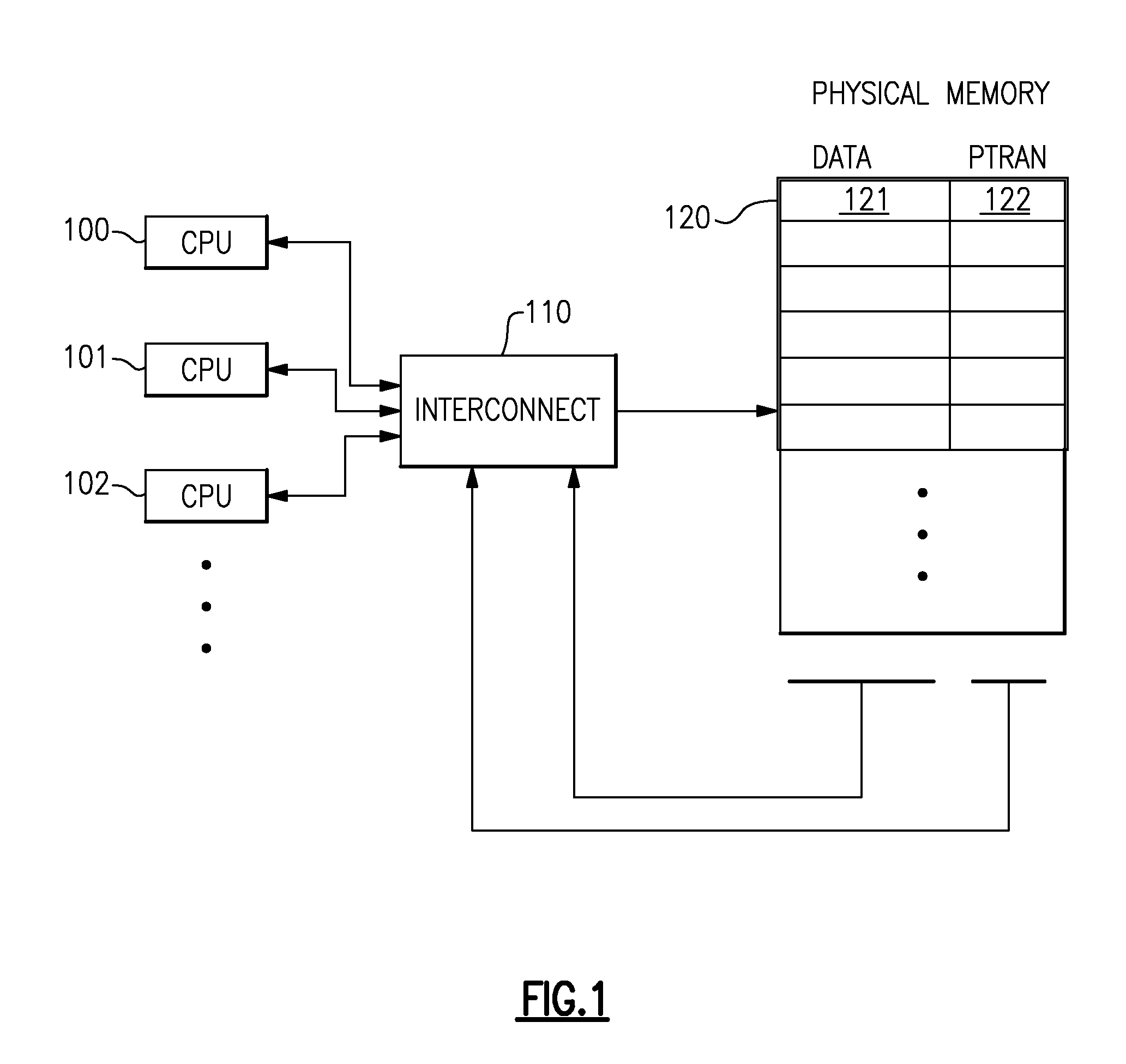
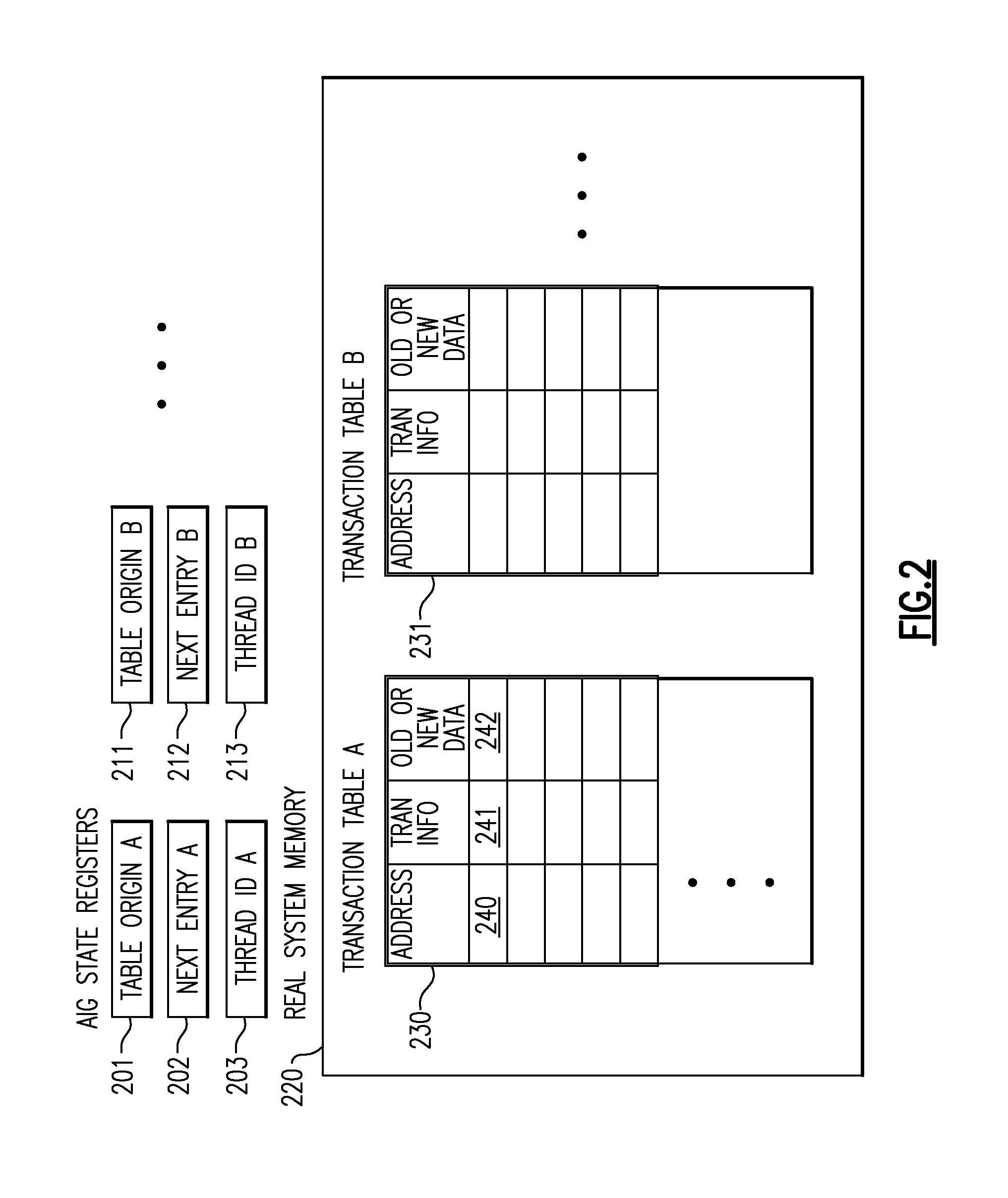
A computing system processes memory transactions for parallel processing of multiple threads of execution with millicode assists. The computing system transactional memory support provides a Transaction Table in memory and a method of fast detection of potential conflicts between multiple transactions. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system. Program millicode provides transactional memory functions including creating and updating transaction tables, committing transactions and controlling the rollback of transactions which fail.
Owner:IBM CORP
System and Method for Executing a Transaction Using Parallel Co-Transactions
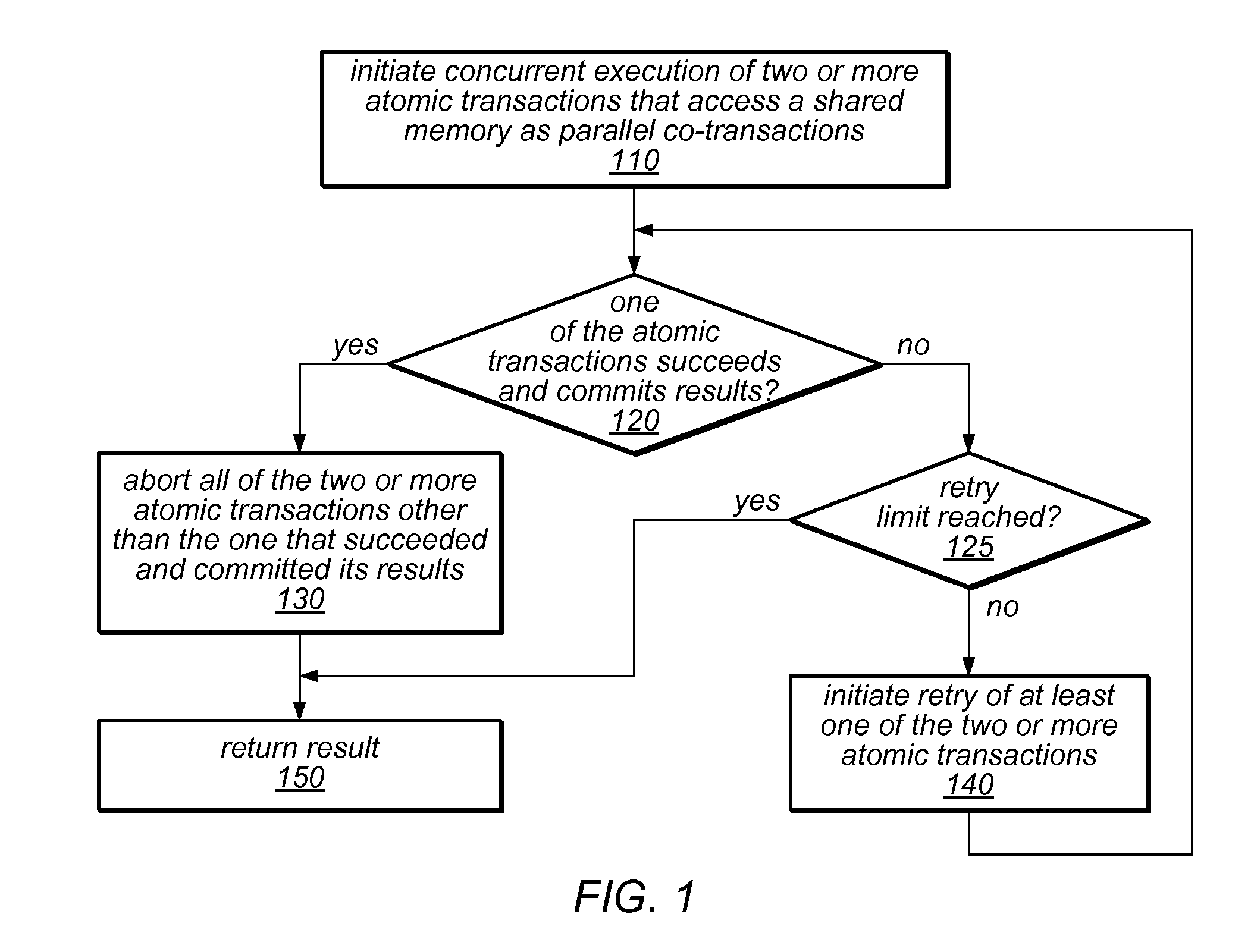
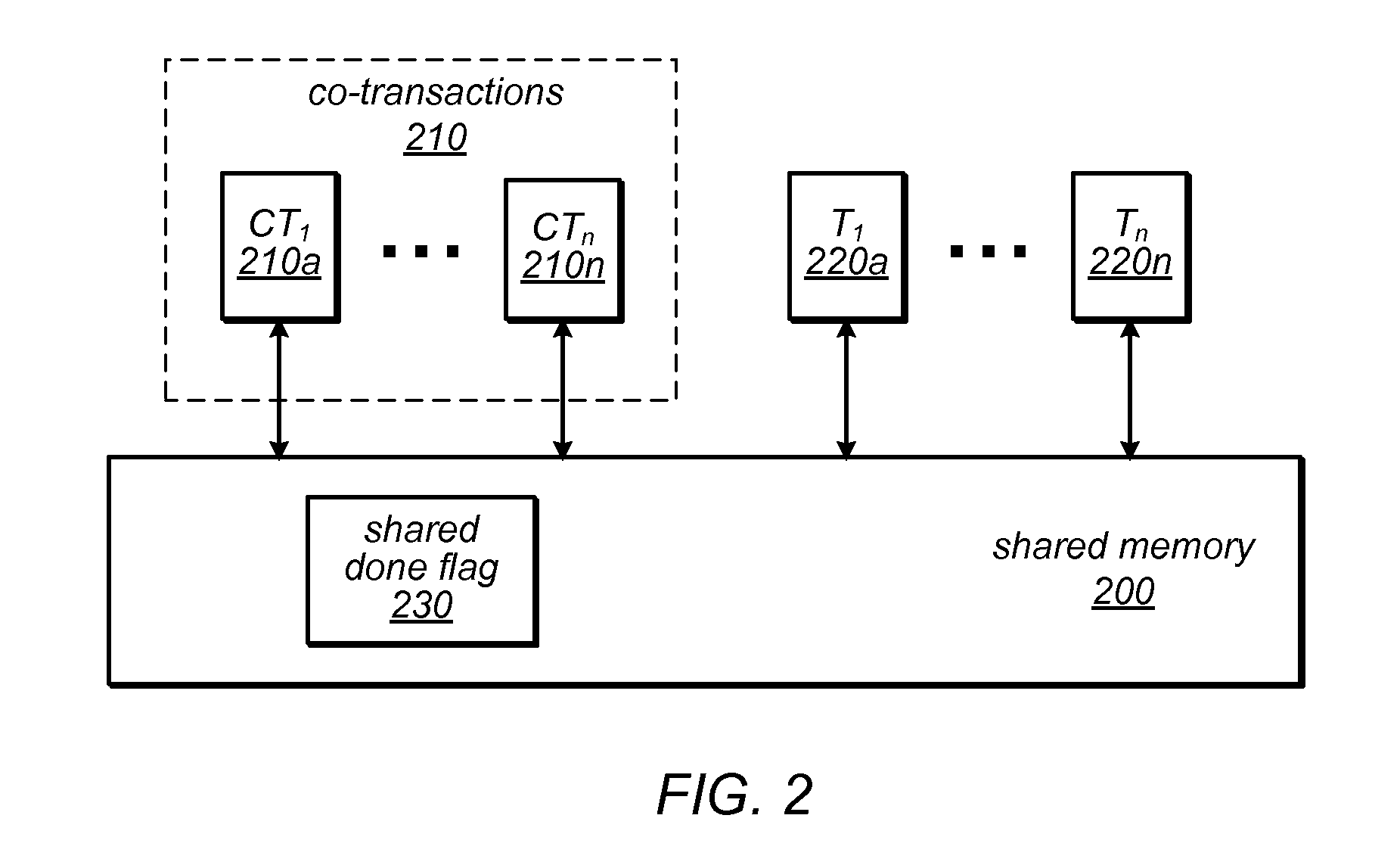
ActiveUS20110246993A1Improve programming performanceSimple and efficient implementationMemory systemsTransaction processingTransactional memoryShared memory
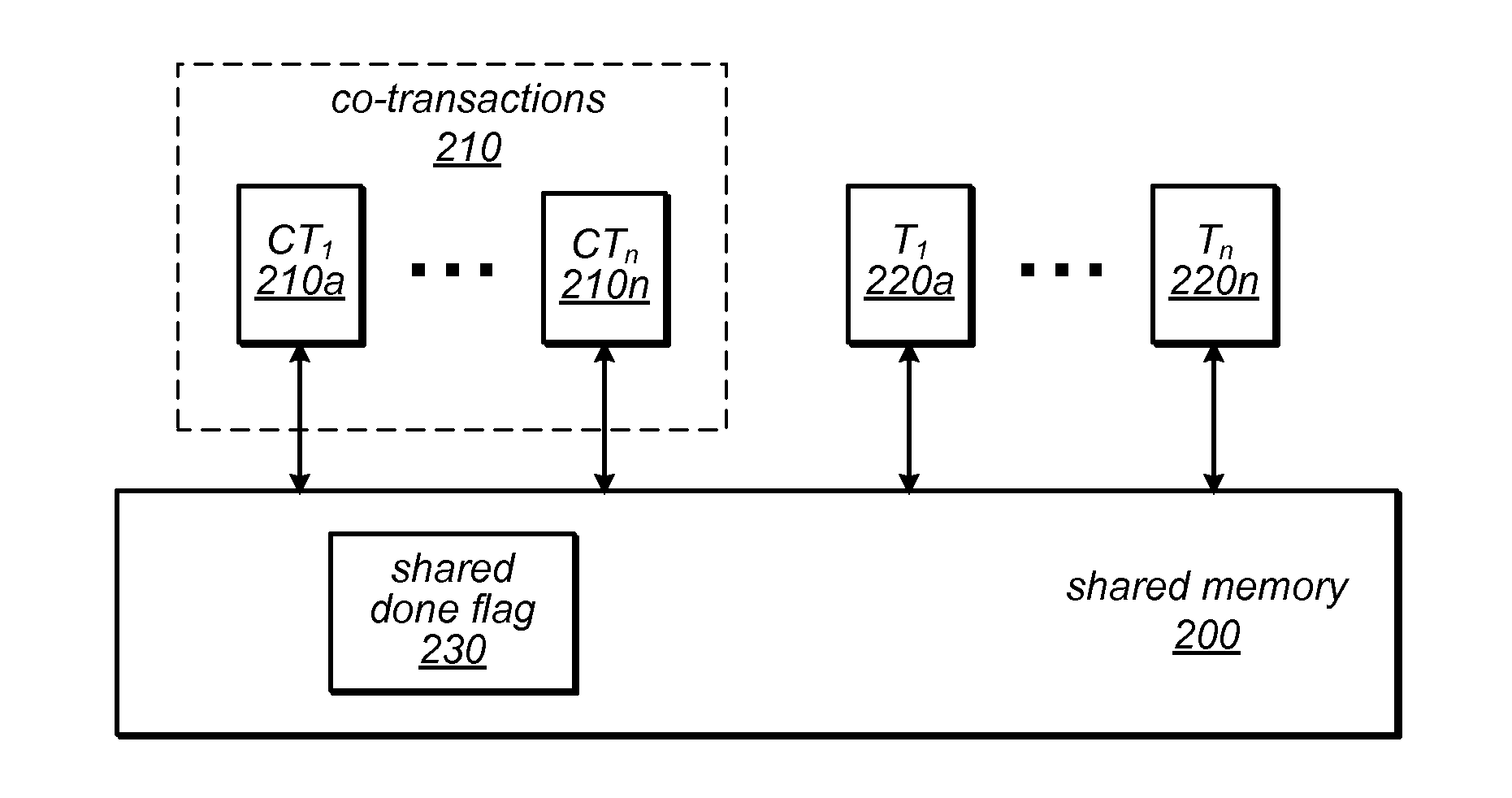
The transactional memory system described herein may implement parallel co-transactions that access a shared memory such that at most one of the co-transactions in a set will succeed and all others will fail (e.g., be aborted). Co-transactions may improve the performance of programs that use transactional memory by attempting to perform the same high-level operation using multiple algorithmic approaches, transactional memory implementations and / or speculation options in parallel, and allowing only the first to complete to commit its results. If none of the co-transactions succeeds, one or more may be retried, possibly using a different approach and / or transactional memory implementation. The at-most-one property may be managed through the use of a shared “done” flag. Conflicts between co-transactions in a set and accesses made by transactions or activities outside the set may be managed using lazy write ownership acquisition and / or a priority-based approach. Each co-transaction may execute on a different processor resource.
Owner:ORACLE INT CORP
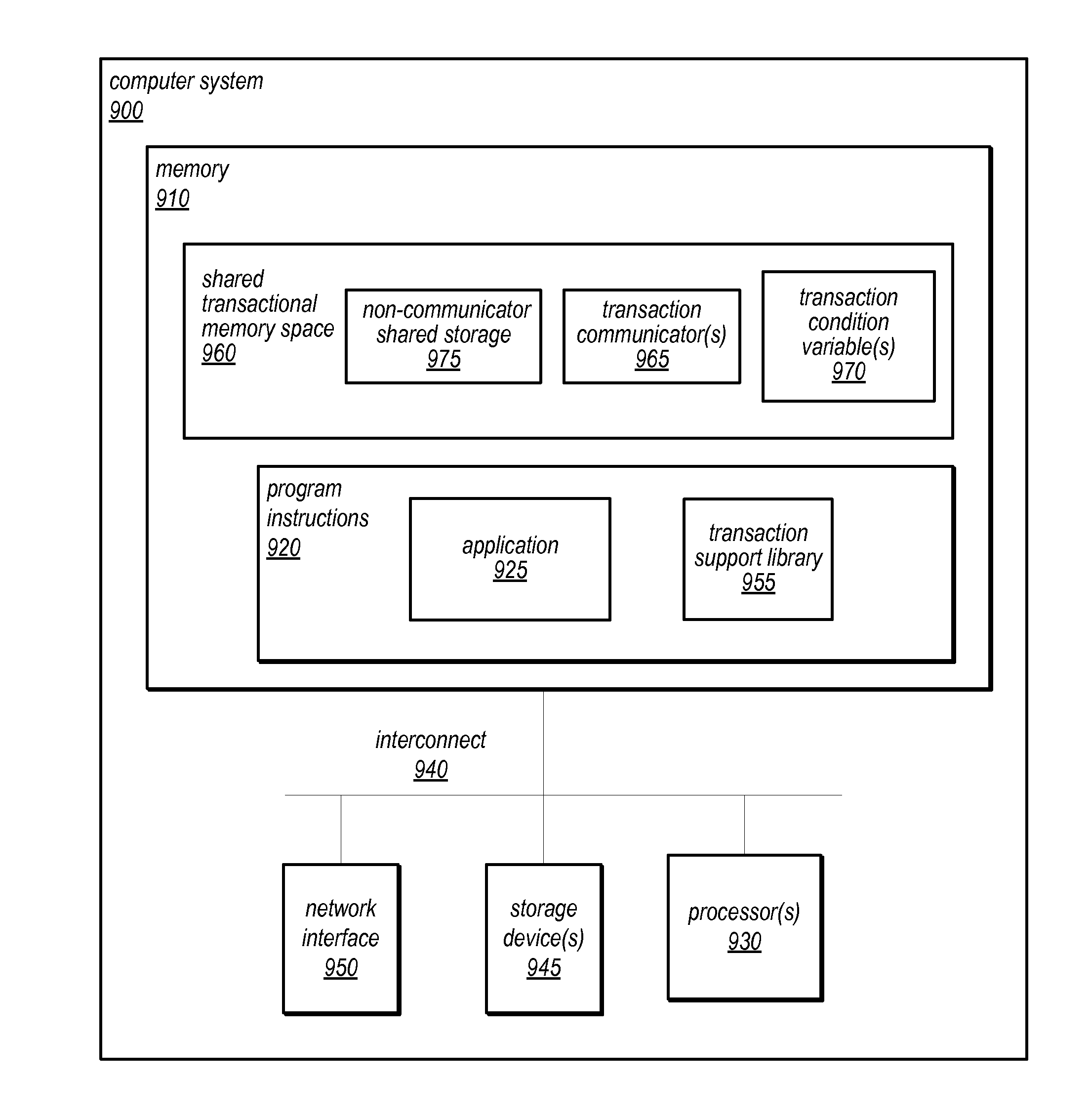
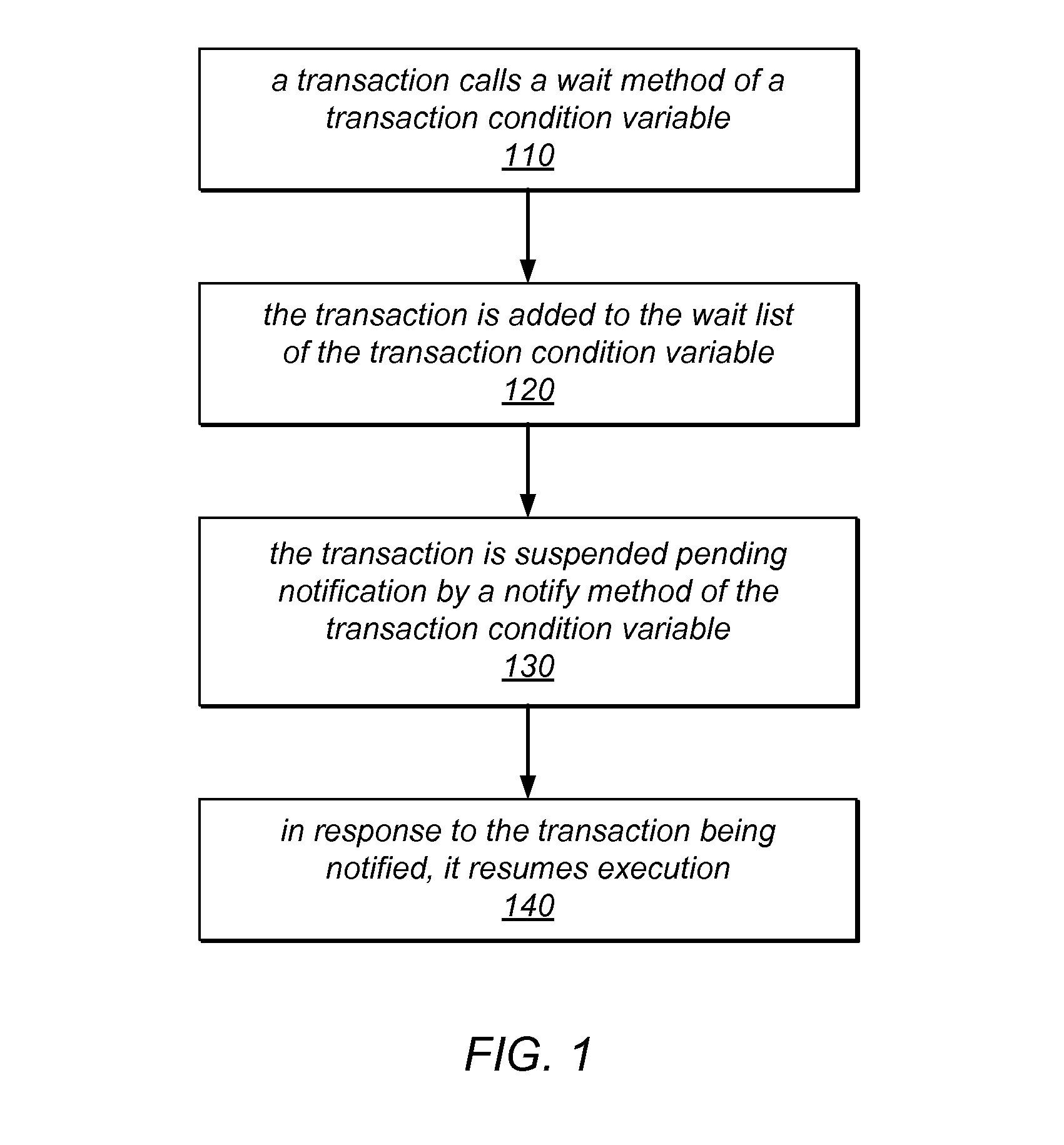
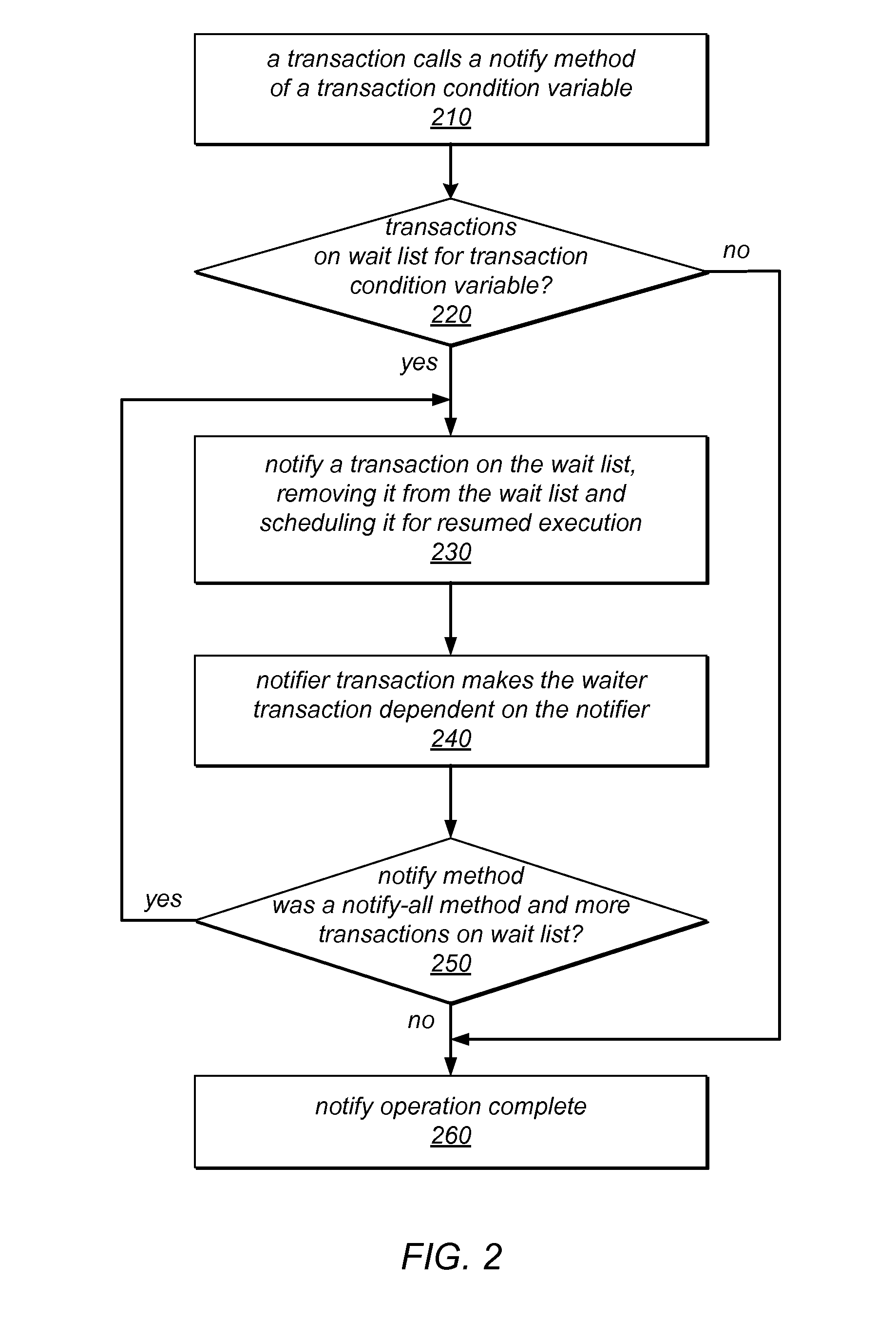
System and Method for Synchronization Between Concurrent Transactions Using Transaction Condition Variables
ActiveUS20120311273A1Ensure isolationGuaranteed isolationMemory systemsTransaction processingWaiters/waitressesTransactional memory
The systems and methods described herein may extend transactional memory implementations to support transaction communicators and / or transaction condition variables for which transaction isolation is relaxed, and through which concurrent transactions can communicate and be synchronized with each other. Transactional accesses to these objects may not be isolated unless called within communicator-isolating transactions. A waiter transaction may invoke a wait method of a transaction condition variable, be added to a wait list for the variable, and be suspended pending notification of a notification event from a notify method of the variable. A notifier transaction may invoke a notify method of the variable, which may remove the waiter from the wait list, schedule the waiter transaction for resumed execution, and notify the waiter of the notification event. A waiter transaction may commit only if the corresponding notifier transaction commits. If the waiter transaction aborts, the notification may be forwarded to another waiter.
Owner:ORACLE INT CORP
System and Method for Providing Locale-Based Optimizations In a Transactional Memory
ActiveUS20110246724A1Reduce cache pressureImprove localityMemory systemsTransaction processingTransactional memoryMetadata
The system and methods described herein may reduce read / write fence latencies and cache pressure related to STM metadata accesses. These techniques may leverage locality information (as reflected by the value of a respective locale guard) associated with each of a plurality of data partitions (locales) in a shared memory to elide various operations in transactional read / write fences when transactions access data in locales owned by their threads. The locale state may be disabled, free, exclusive, or shared. For a given memory access operation of an atomic transaction targeting an object in the shared memory, the system may implement the memory access operation using a contention mediation mechanism selected based on the value of the locale guard associated with the locale in which the target object resides. For example, a traditional read / write fence may be employed in some memory access operations, while other access operations may employ an optimized read / write fence.
Owner:ORACLE INT CORP
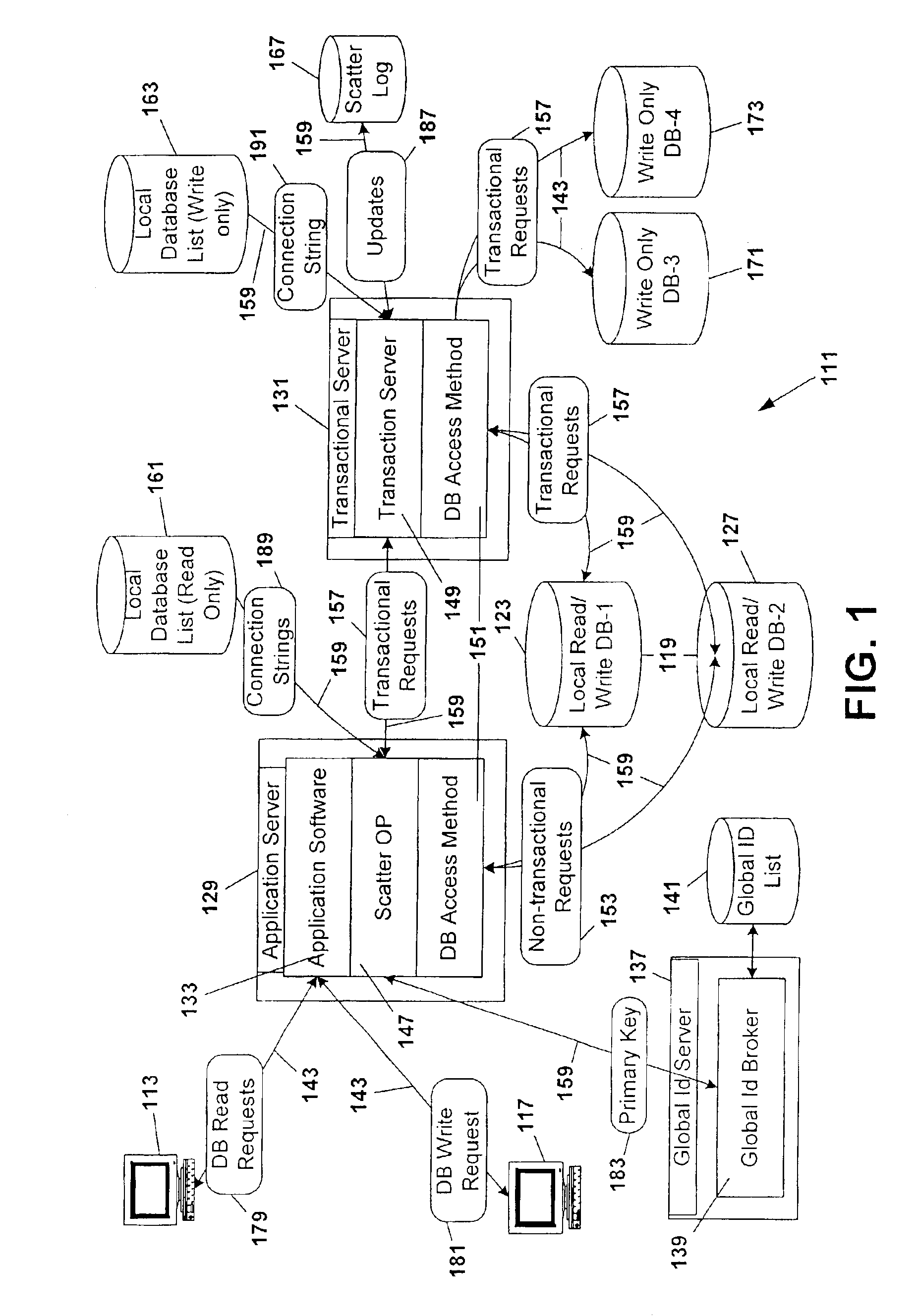
Database scattering system
InactiveUS6898609B2Reduce needPermit scalabilityDigital data information retrievalData processing applicationsComputerized systemData content
A computer system for providing load balancing and scalable access to a network database system by providing multiple database instances with each instance being substantially identical in data content, database structure, and primary key system. Requests from users are received by the system, examined to determine their nature as transactional or non-transactional and, in the case of non-transactional queries, scattered among the multiple database instances. Such scattering of queries permits multiple instances of the database to be serving responses to multiple users at substantially the same time. In the case of transactional queries, the system automatically propagates the transactional query to all instances of the database to maintain homogeneity.
Owner:ENTERPRISEDB
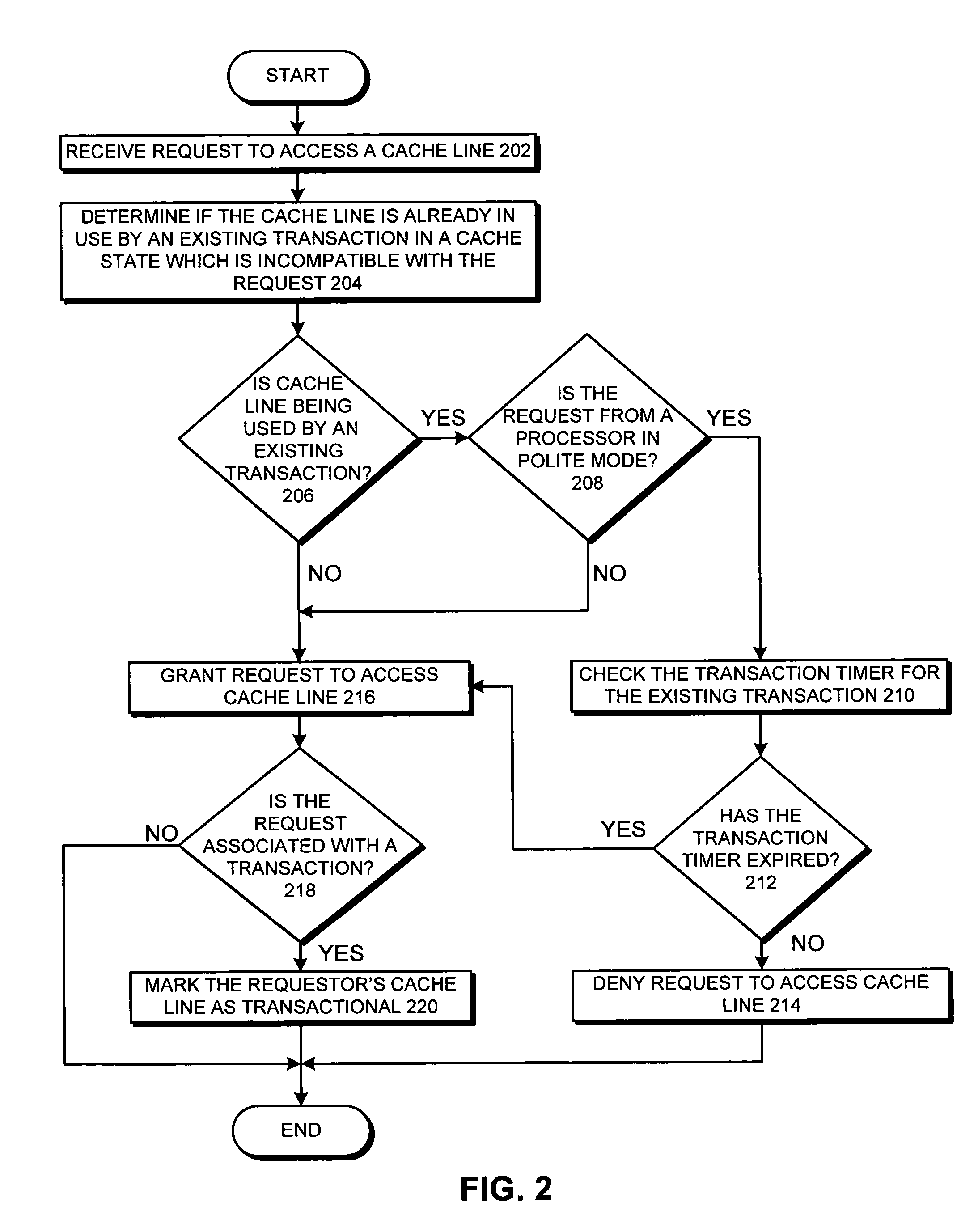
Controlling contention via transactional timers among conflicting transactions issued by processors operating in insistent or polite mode
A system for controlling contention between conflicting transactions in a transactional memory system. During operation, the system receives a request to access a cache line and then determines if the cache line is already in use by an existing transaction in a cache state that is incompatible with the request. If so, the system determines if the request is from a processor which is in a polite mode. If this is true, the system denies the request to access the cache line and continues executing the existing transaction.
Owner:ORACLE INT CORP
Performing escape actions in transactions
ActiveUS20100332807A1Memory adressing/allocation/relocationDigital computer detailsHardware threadFinancial transaction
Performing non-transactional escape actions within a hardware based transactional memory system. A method includes at a hardware thread on a processor beginning a hardware based transaction for the thread. Without committing or aborting the transaction, the method further includes suspending the hardware based transaction and performing one or more operations for the thread, non-transactionally and not affected by: transaction monitoring and buffering for the transaction, an abort for the transaction, or a commit for the transaction. After performing one or more operations for the thread, non-transactionally, the method further includes resuming the transaction and performing additional operations transactionally. After performing the additional operations, the method further includes either committing or aborting the transaction.
Owner:MICROSOFT TECH LICENSING LLC
Trusted transactional set-top box
InactiveUS7346917B2Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsPrivate networkThe Internet
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
Method and apparatus for improving transactional memory interactions by tracking object visibility
ActiveUS20070150509A1Avoid overheadAvoid accessSpecific program execution arrangementsSpecial data processing applicationsProgramming languageVisibility
In a multi-threaded computer system that uses transactional memory, object fields accessed by only one thread are accessed by regular non-transactional read and write operations. When an object may be visible to more than one thread, access by non-transactional code is prevented and all accesses to the fields of that object are performed using transactional code. In one embodiment, the current visibility of an object is stored in the object itself. This stored visibility can be checked at runtime by code that accesses the object fields or code can be generated to check the visibility prior to access during compilation.
Owner:ORACLE INT CORP
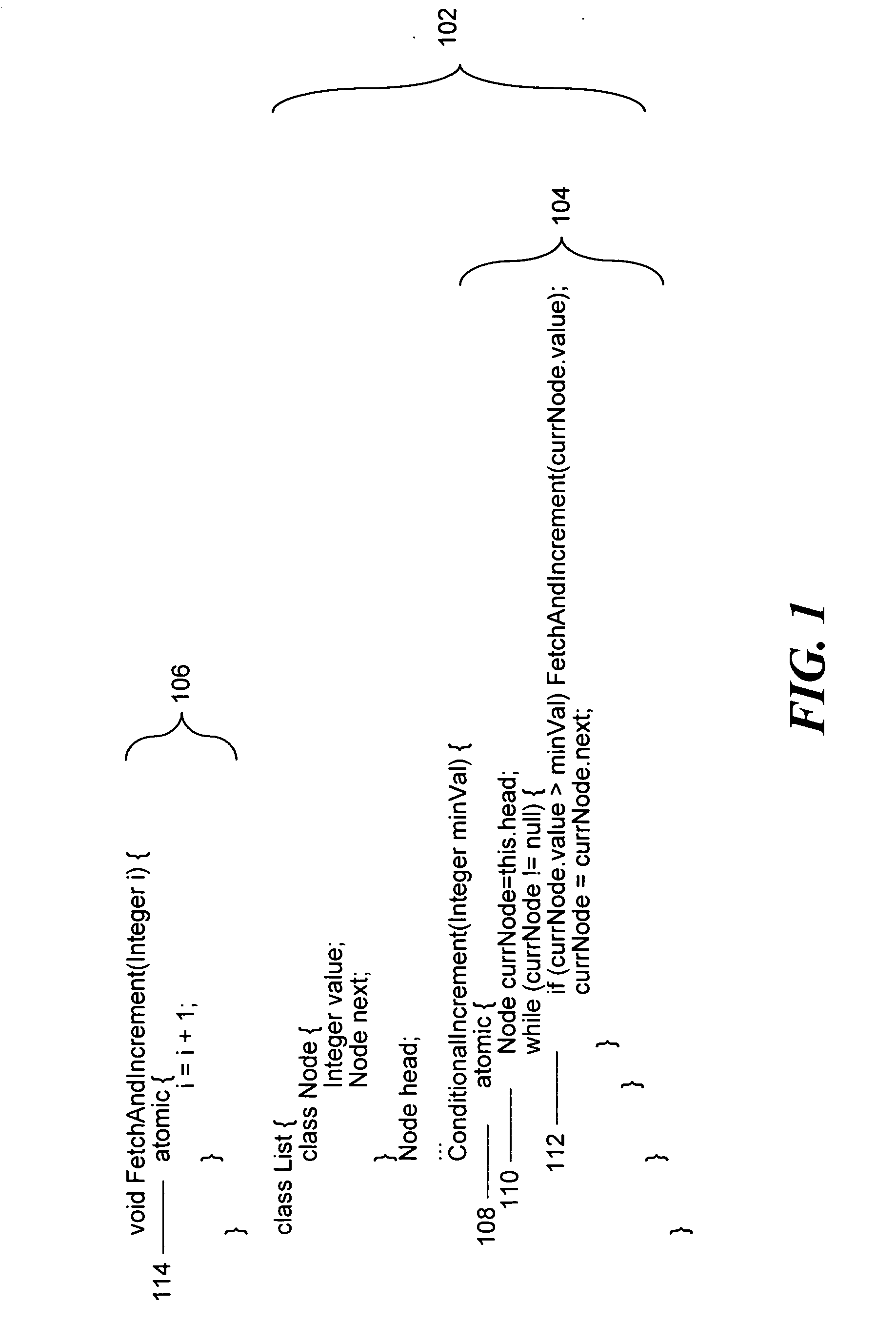
Obstruction-free mechanism for atomic update of multiple non-contiguous locations in shared memory
ActiveUS20040034673A1Data processing applicationsError preventionTransactional memoryMulti targeting
We present a technique for implementing obstruction-free atomic multi-target transactions that target special "transactionable" locations in shared memory. A programming interface for using operations based on these transactions can be structured in several ways, including as n-word compare-and-swap (NCAS) operations or as atomic sequences of single-word loads and stores (e.g., as transactional memory).
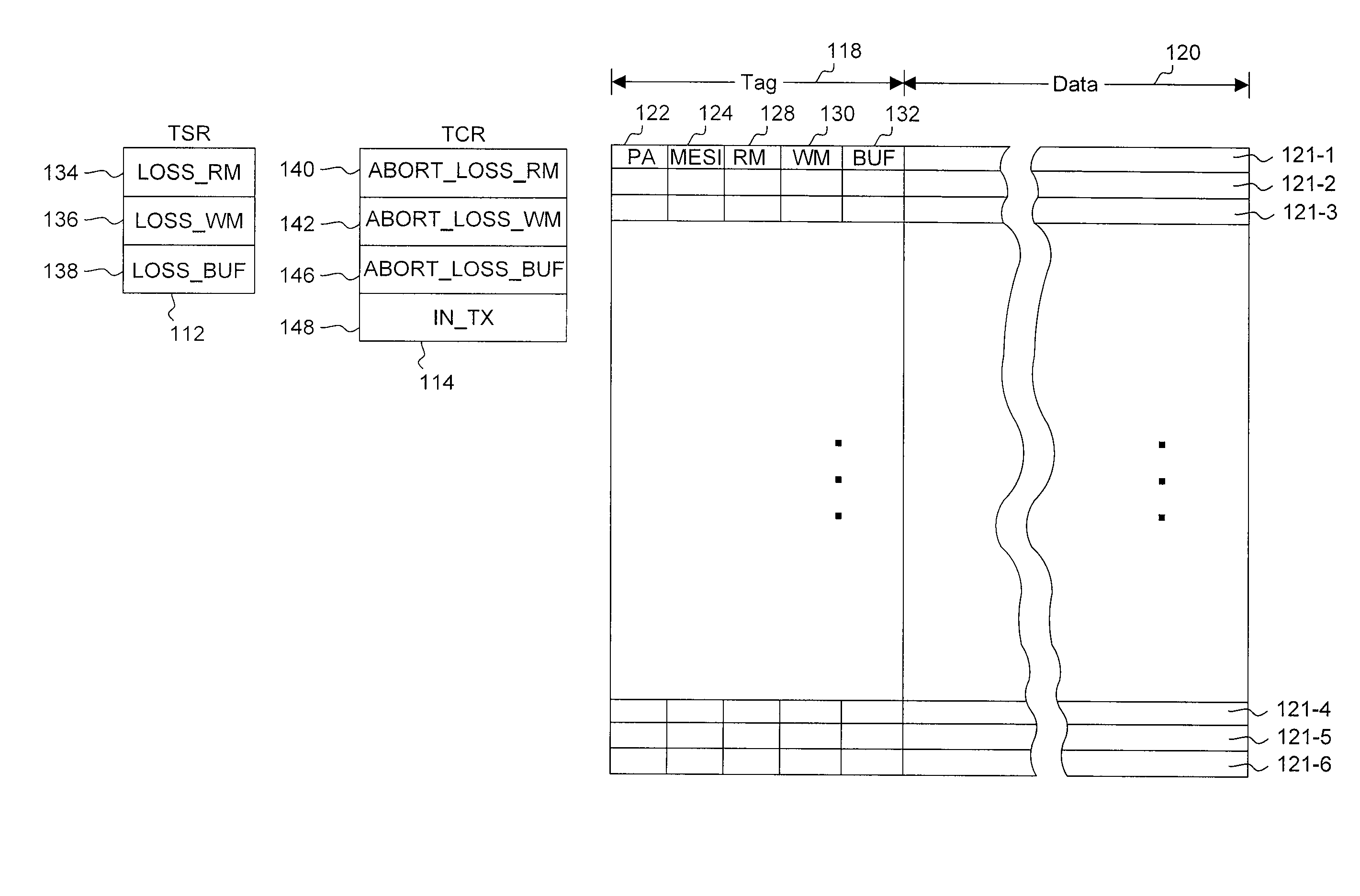
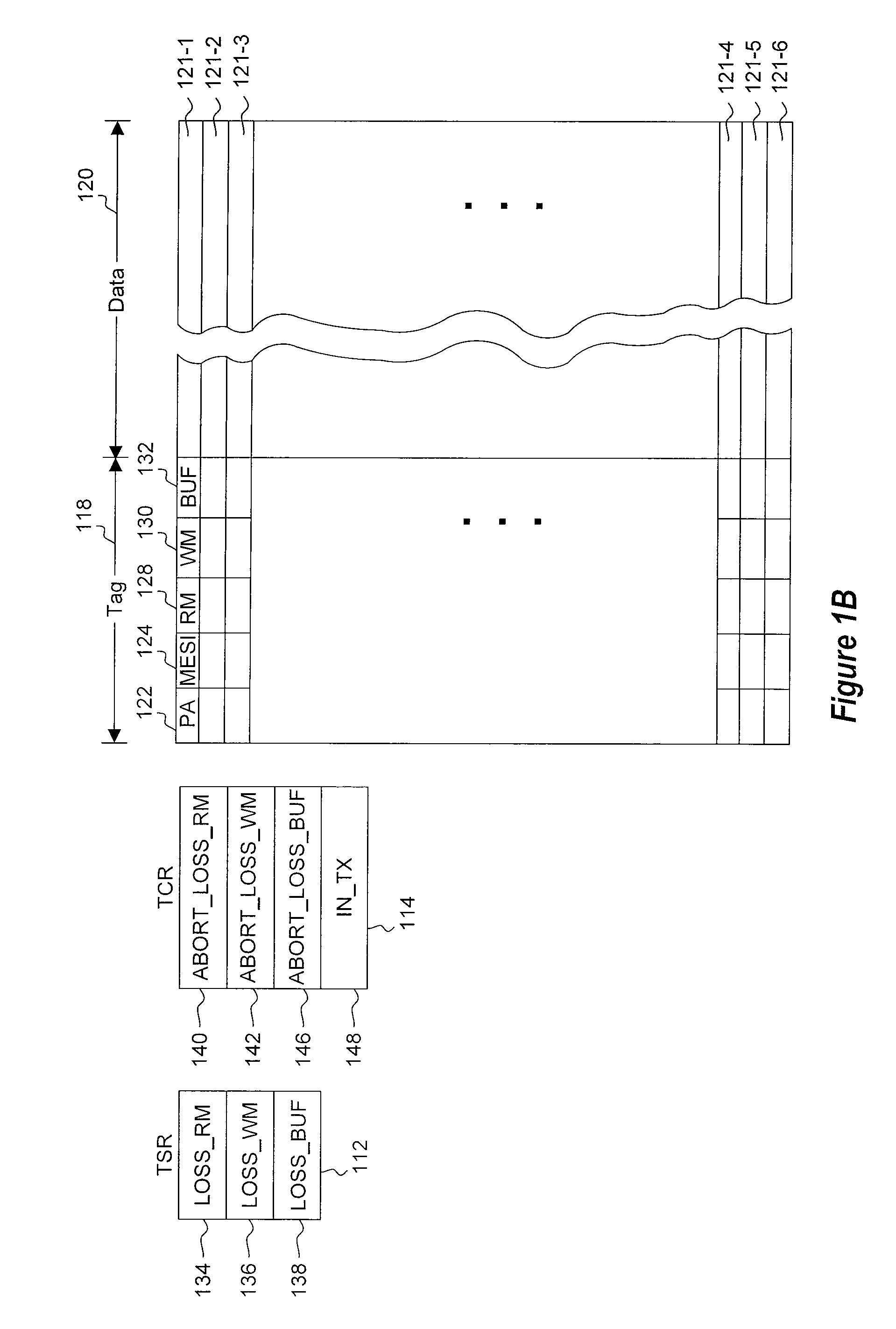
Owner:ORACLE INT CORP
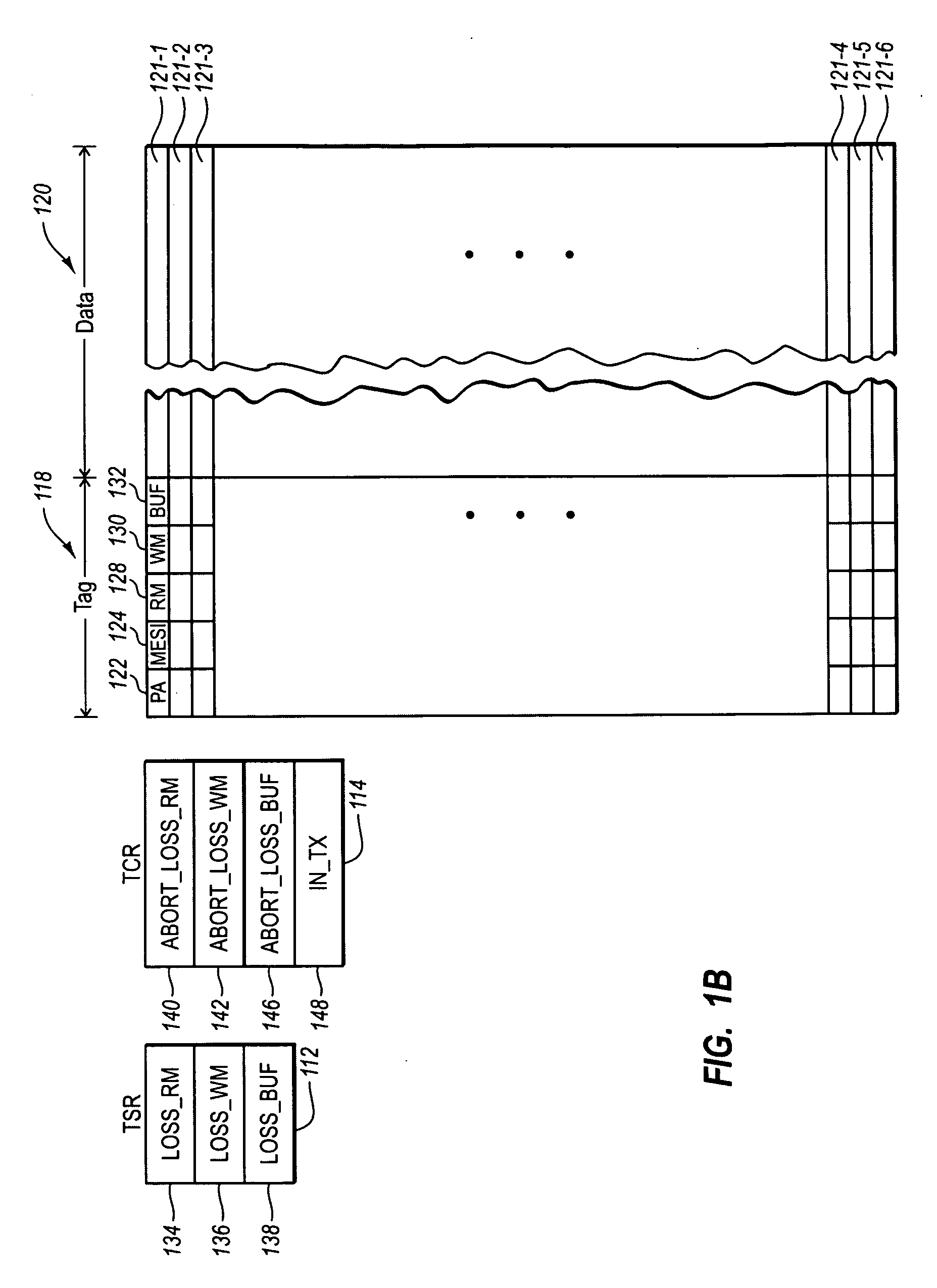
Transactional Memory System Which Employs Thread Assists Using Address History Tables
A computing system uses specialized “Set Associative Transaction Tables” and additional “Summary Transaction Tables” to speed the processing of common transactional memory conflict cases and those which employ assist threads using an Address History Table and processes memory transactions with a Transaction Table in memory for parallel processing of multiple threads of execution by support of which an application need not be aware. Special instructions may mark the boundaries of a transaction and identify memory locations applicable to a transaction. A ‘private to transaction’ (PTRAN) tag, directly addressable as part of the main data storage memory location, enables a quick detection of potential conflicts with other transactions that are concurrently executing on another thread of said computing system. The tag indicates whether (or not) a data entry in memory is part of a speculative memory state of an uncommitted transaction that is currently active in the system.
Owner:IBM CORP
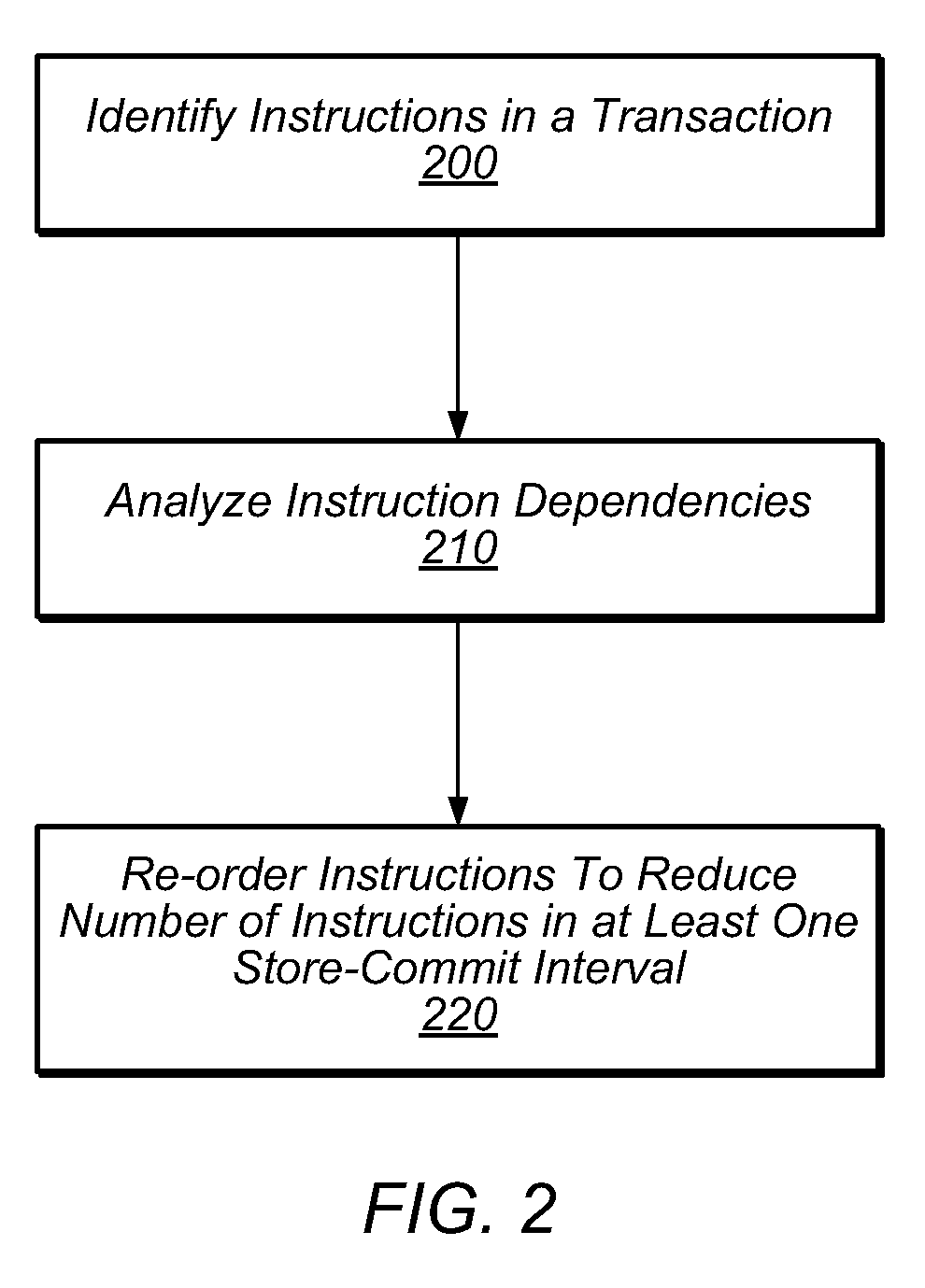
System and Method for Reducing Transactional Abort Rates Using Compiler Optimization Techniques
ActiveUS20100169870A1Reduce probabilityReduce transactional abortsSoftware engineeringSpecific program execution arrangementsLong latencyTransactional memory
In transactional memory systems, transactional aborts due to conflicts between concurrent threads may cause system performance degradation. A compiler may attempt to minimize runtime abort rates by performing one or more code transformations and / or other optimizations on a transactional memory program in an attempt to minimize one or more store-commit intervals. The compiler may employ store deferral, hoisting of long-latency operations from within a transaction body and / or store-commit interval, speculative hoisting of long-latency operations, and / or redundant store squashing optimizations. The compiler may perform optimizing transformations on source code and / or on any intermediate representation of the source code (e.g., parse trees, un-optimized assembly code, etc.). In some embodiments, the compiler may preemptively avoid naïve target code constructions. The compiler may perform static and / or dynamic analysis of a program in order to determine which, if any, transformations should be applied and / or may dynamically recompile code sections at runtime, based on execution analysis.
Owner:SUN MICROSYSTEMS INC
System and Method for Reducing Serialization in Transactional Memory Using Gang Release of Blocked Threads
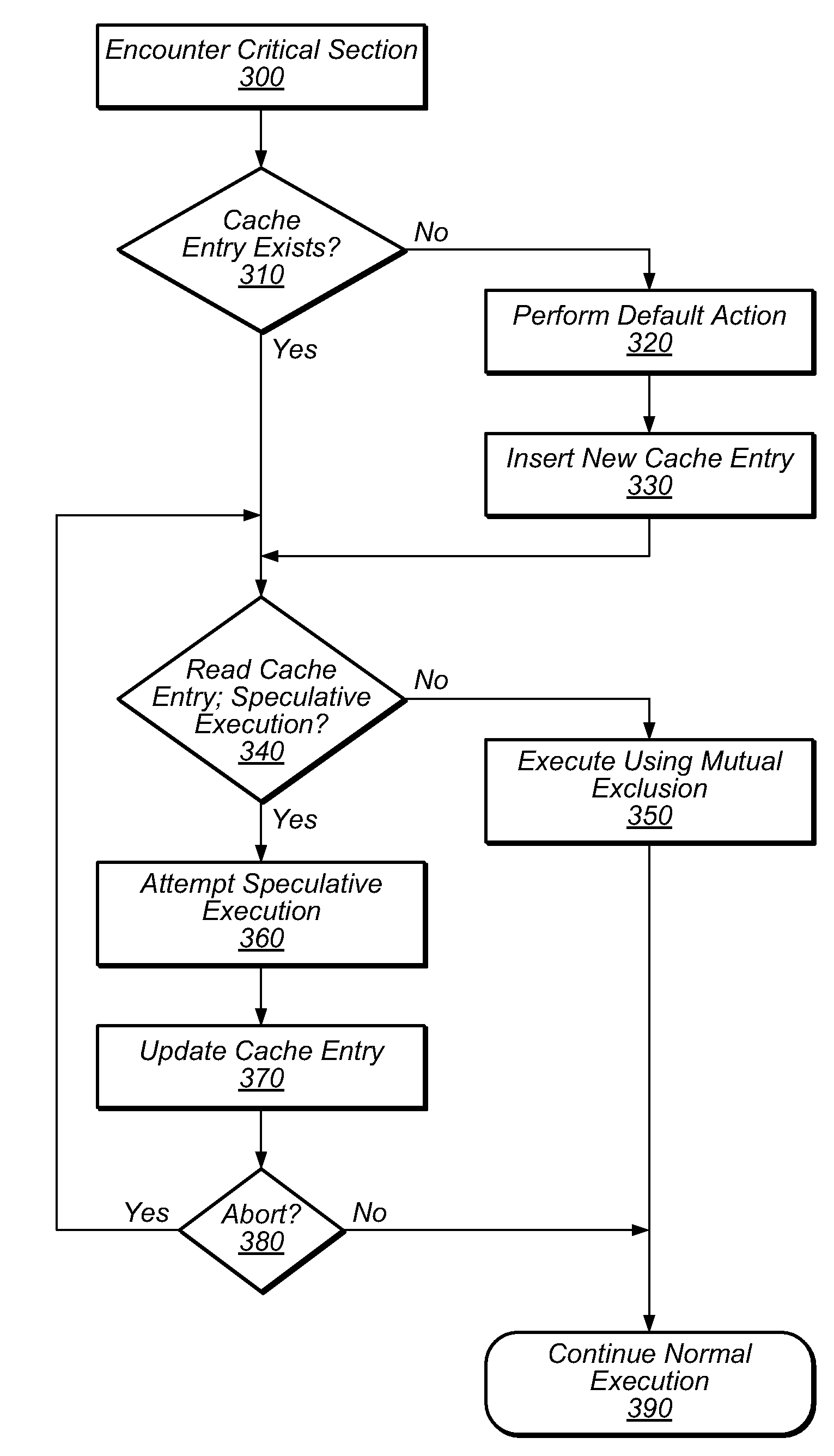
ActiveUS20100138836A1Reduce the impactProgram synchronisationMemory systemsCritical sectionParallel computing
Transactional Lock Elision (TLE) may allow multiple threads to concurrently execute critical sections as speculative transactions. Transactions may abort due to various reasons. To avoid starvation, transactions may revert to execution using mutual exclusion when transactional execution fails. Because threads may revert to mutual exclusion in response to the mutual exclusion of other threads, a positive feedback loop may form in times of high congestion, causing a “lemming effect”. To regain the benefits of concurrent transactional execution, the system may allow one or more threads awaiting a given lock to be released from the wait queue and instead attempt transactional execution. A gang release may allow a subset of waiting threads to be released simultaneously. The subset may be chosen dependent on the number of waiting threads, historical abort relationships between threads, analysis of transactions of each thread, sensitivity of each thread to abort, and / or other thread-local or global criteria.
Owner:SUN MICROSYSTEMS INC
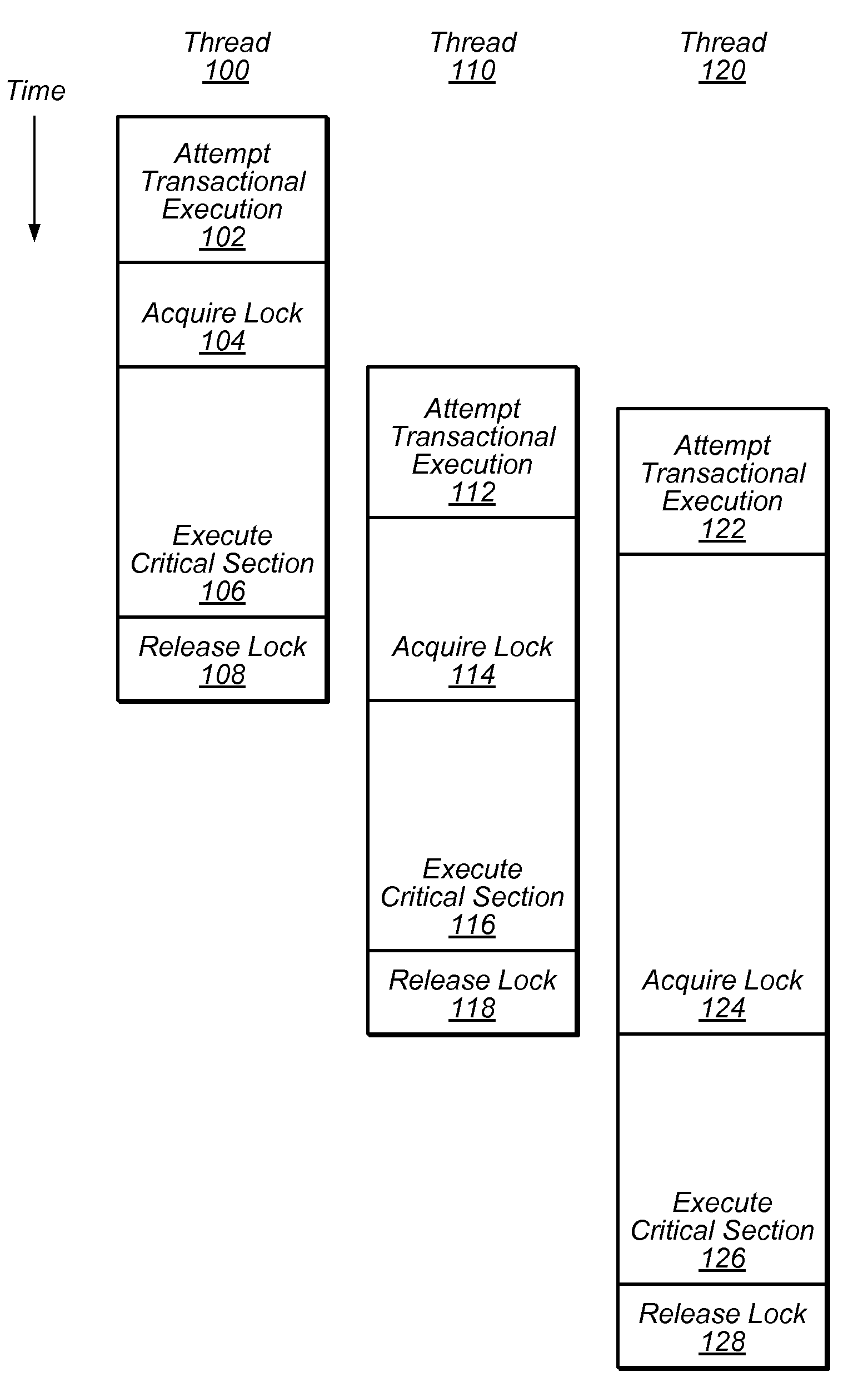
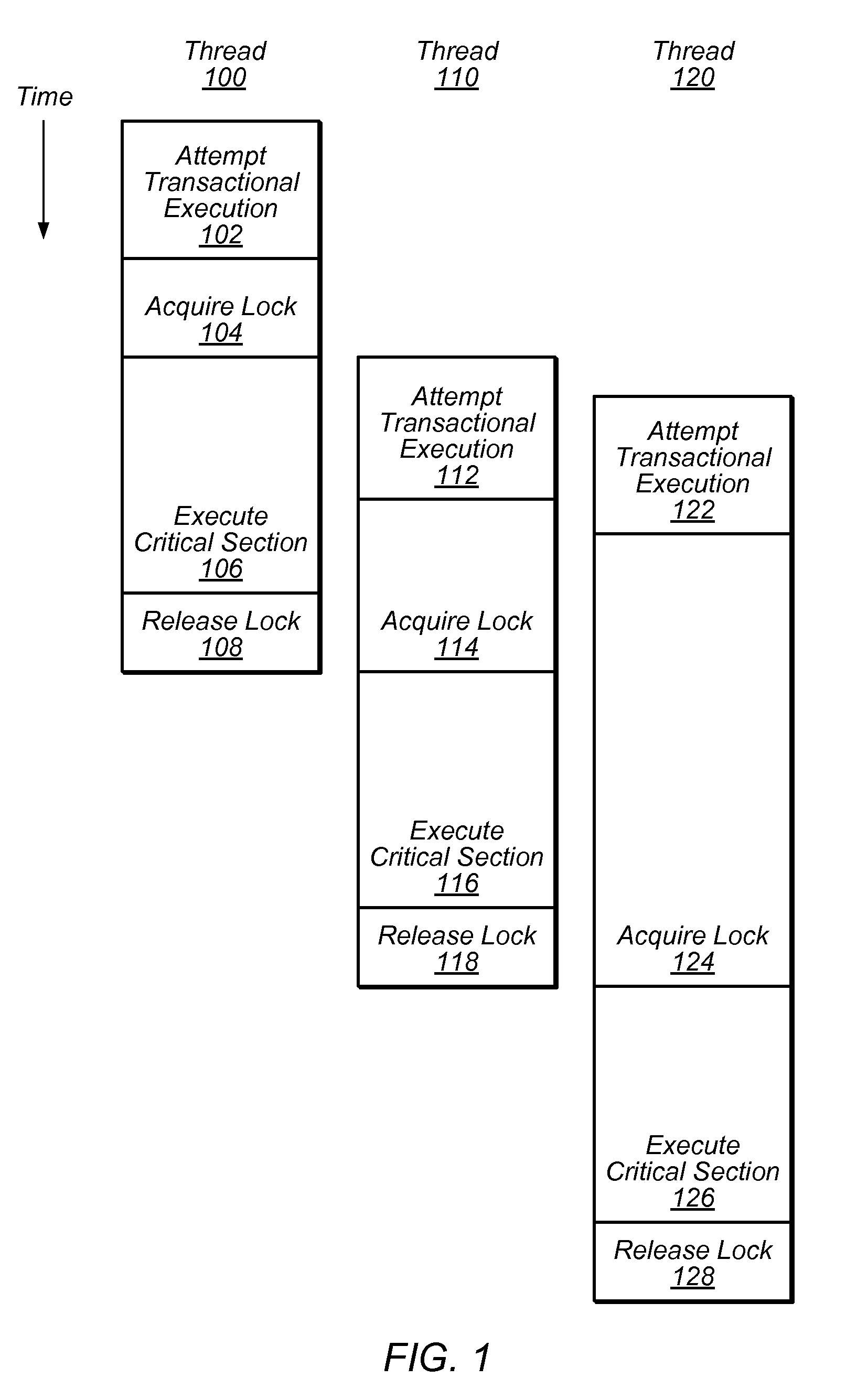
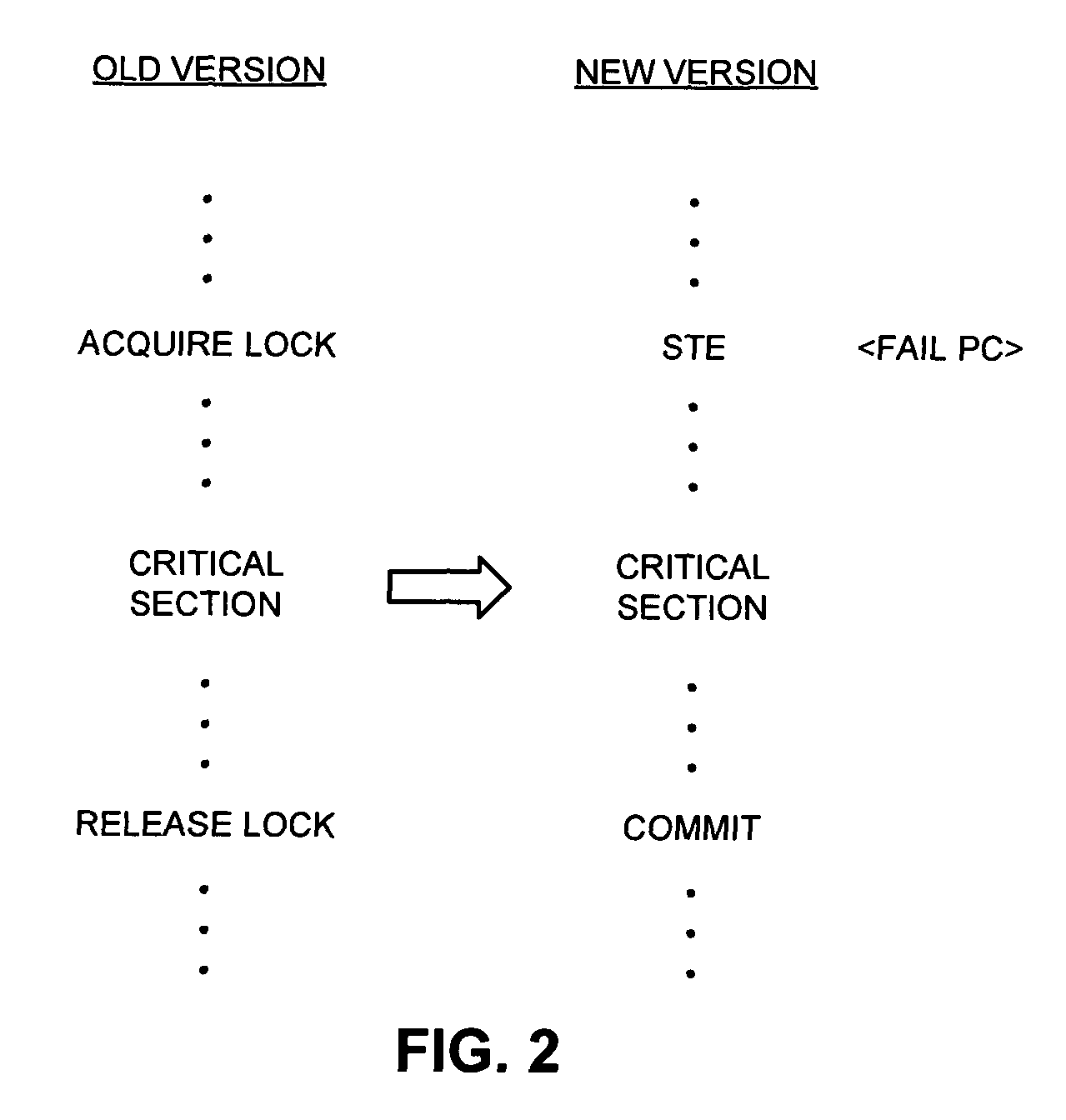
Method and apparatus for synchronizing threads on a processor that supports transactional memory
One embodiment of the present invention provides a system that synchronizes threads on a multi-threaded processor. The system starts by executing instructions from a multi-threaded program using a first thread and a second thread. When the first thread reaches a predetermined location in the multi-threaded program, the first thread executes a Start-Transactional-Execution (STE) instruction to commence transactional execution, wherein the STE instruction specifies a location to branch to if transactional execution fails. During the subsequent transactional execution, the first thread accesses a mailbox location in memory (which is also accessible by the second thread) and then executes instructions that cause the first thread to wait. When the second thread reaches a second predetermined location in the multi-threaded program, the second thread signals the first thread by accessing the mailbox location, which causes the transactional execution of the first thread to fail, thereby causing the first thread to resume non-transactional execution from the location specified in the STE instruction. In this way, the second thread can signal to the first thread without the first thread having to poll a shared variable.
Owner:ORACLE INT CORP
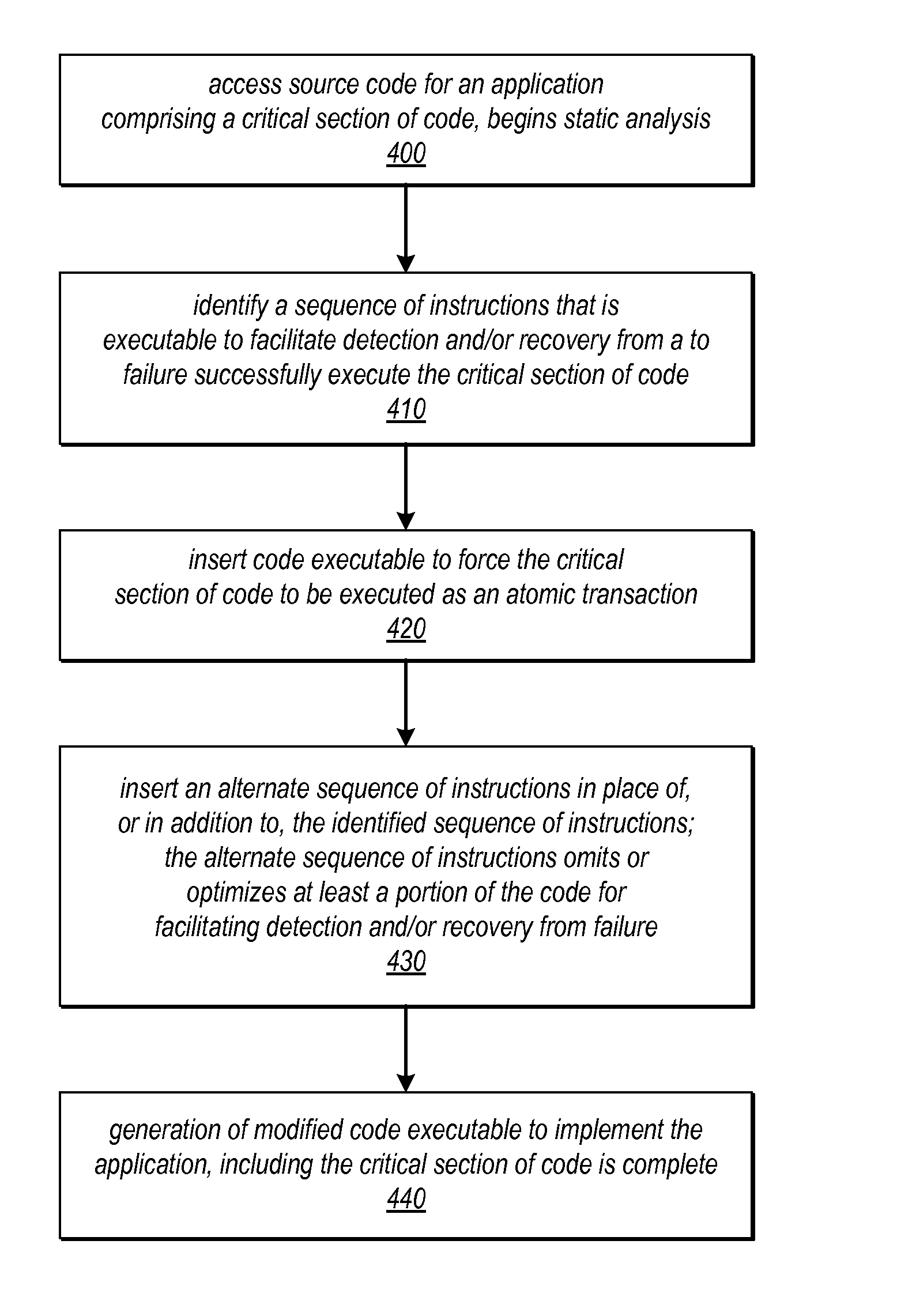
System and Method for Optimizing a Code Section by Forcing a Code Section to be Executed Atomically
ActiveUS20120254846A1Easy to detectOptimizationSoftware engineeringMemory systemsParallel computingCritical section
Systems and methods for optimizing code may use transactional memory to optimize one code section by forcing another code section to execute atomically. Application source code may be analyzed to identify instructions in one code section that only need to be executed if there exists the possibility that another code section (e.g., a critical section) could be partially executed or that its results could be affected by interference. In response to identifying such instructions, alternate code may be generated that forces the critical section to be executed as an atomic transaction, e.g., using best-effort hardware transactional memory. This alternate code may replace the original code or may be included in an alternate execution path that can be conditionally selected for execution at runtime. The alternate code may elide the identified instructions (which are rendered unnecessary by the transaction) by removing them, or by including them in the alternate execution path.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com