Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2413 results about "Current mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
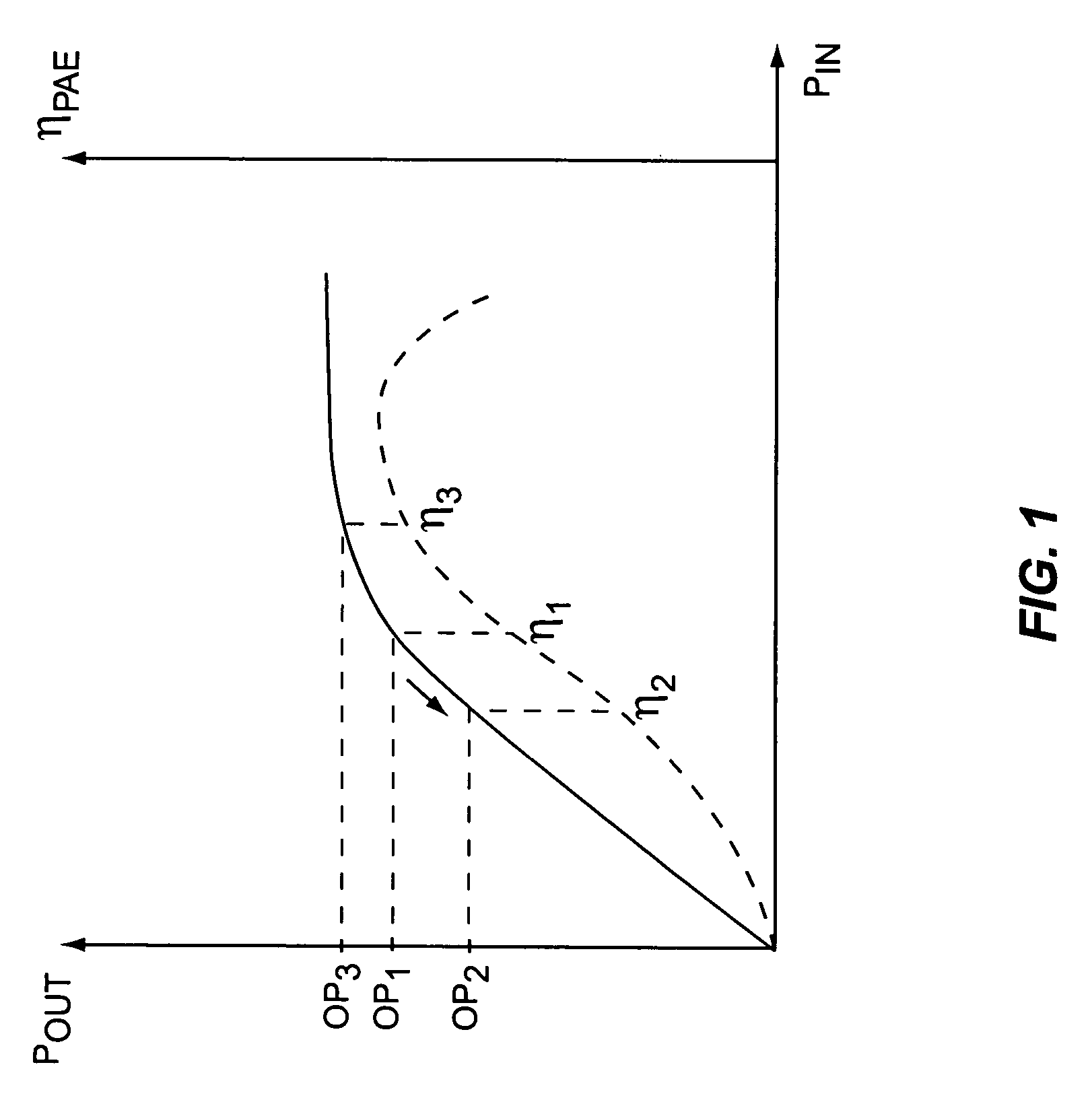
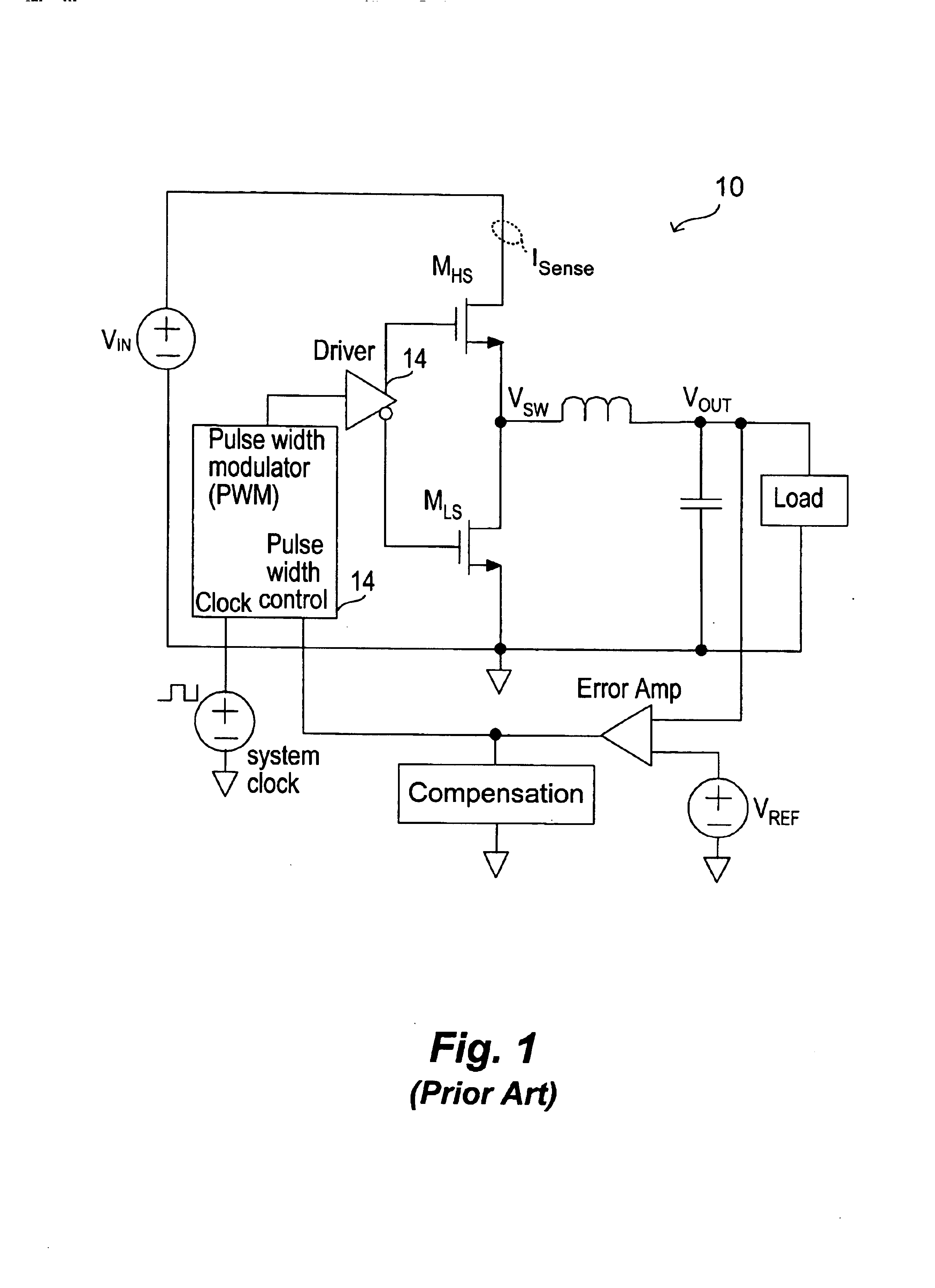
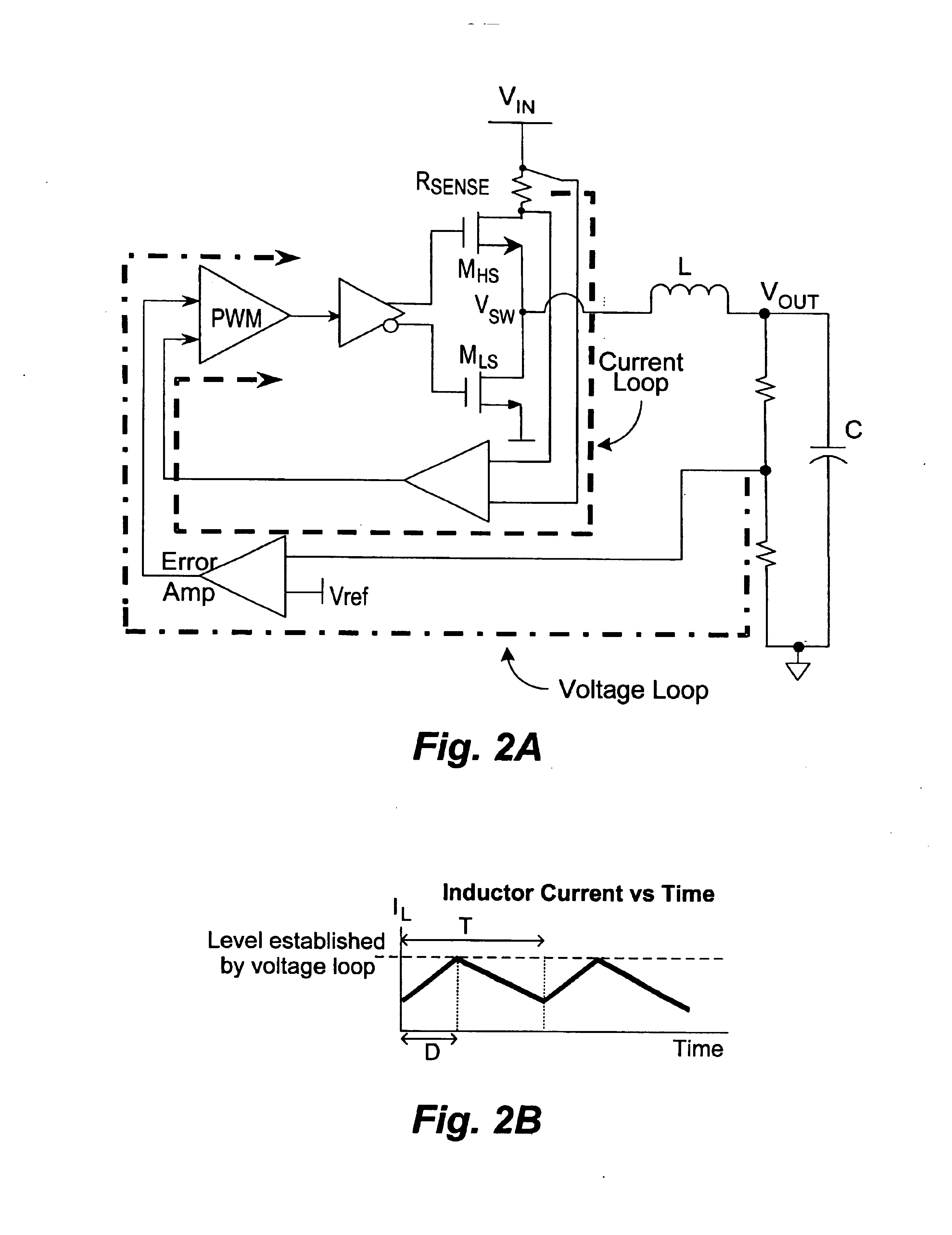
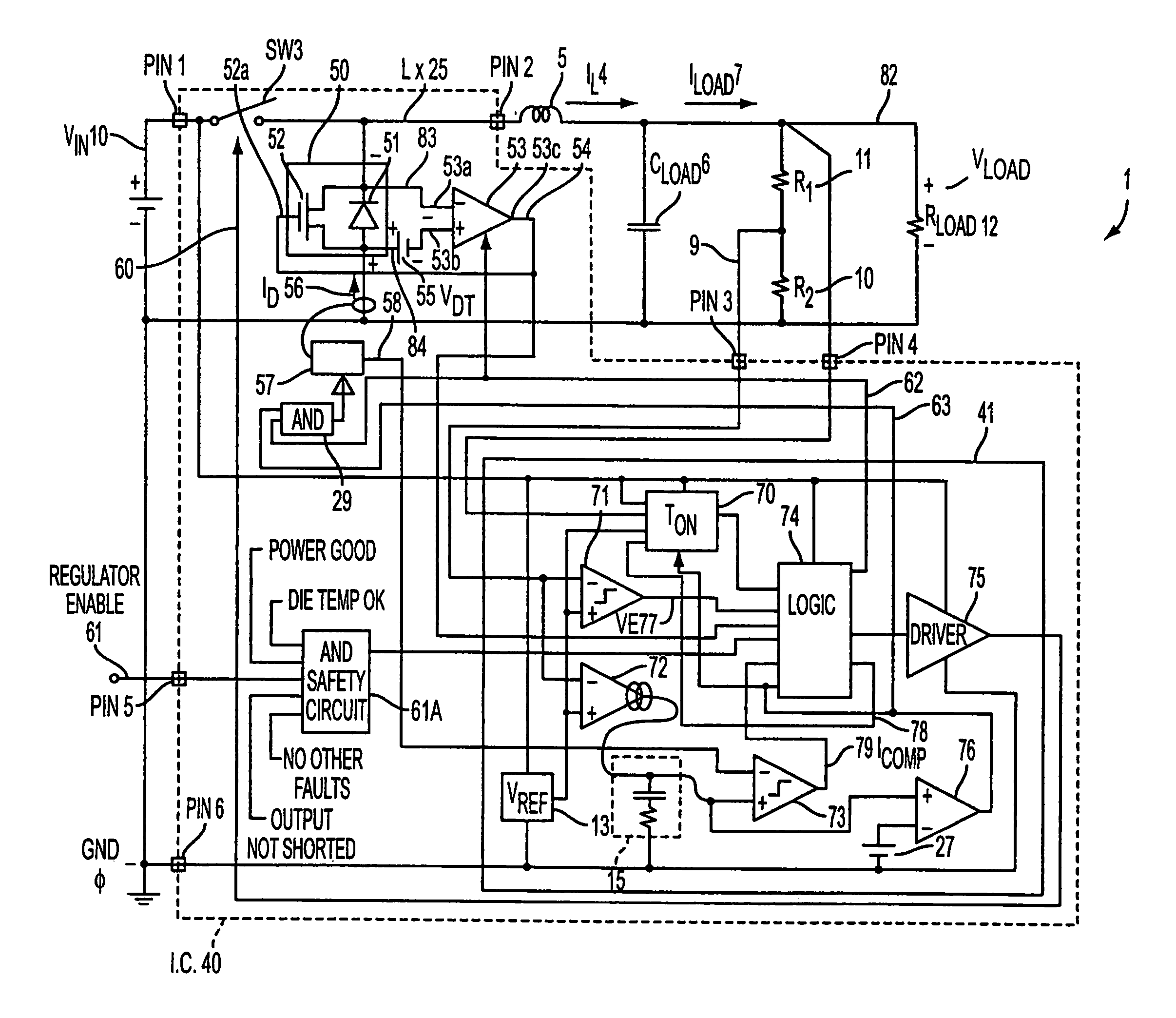
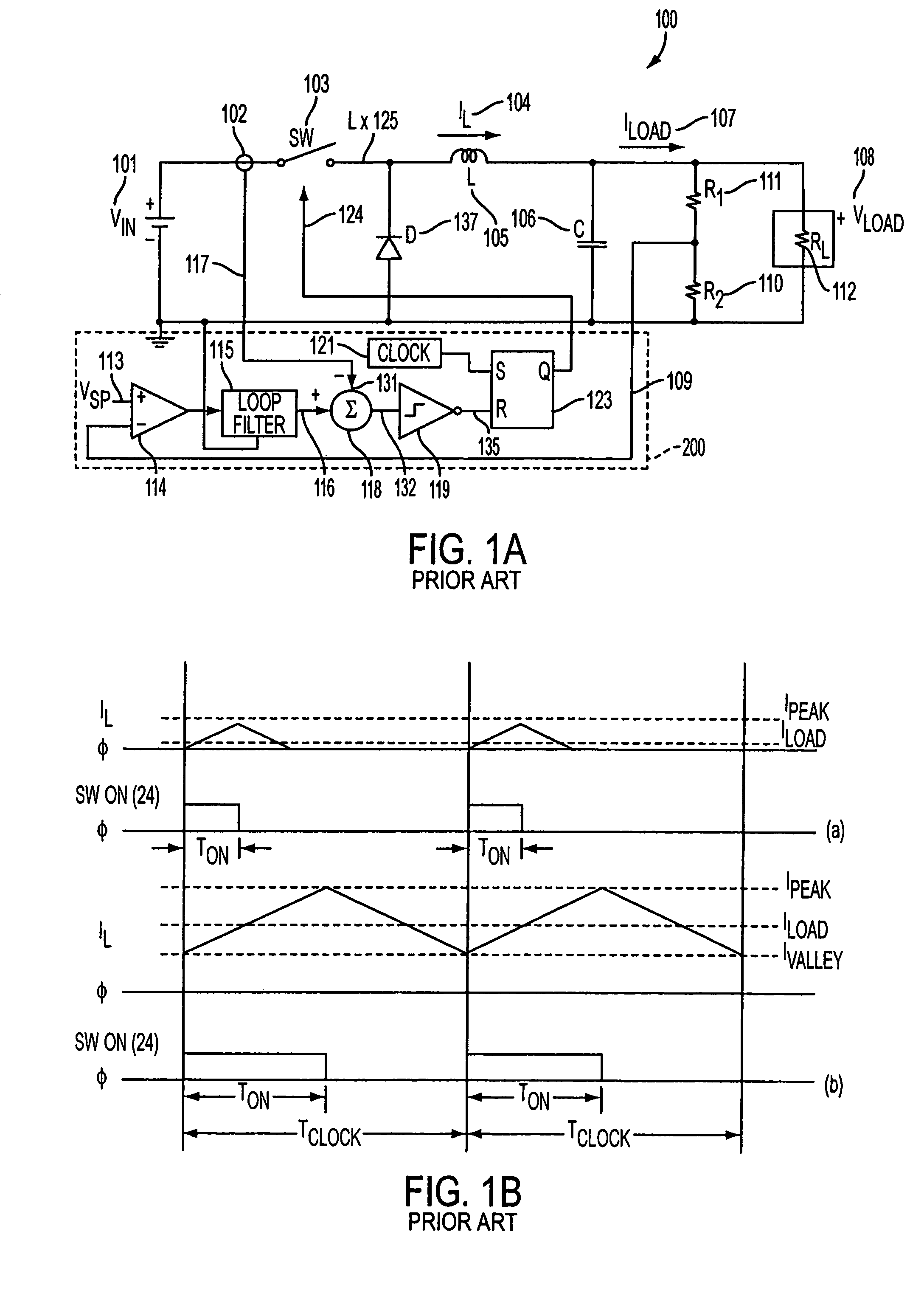
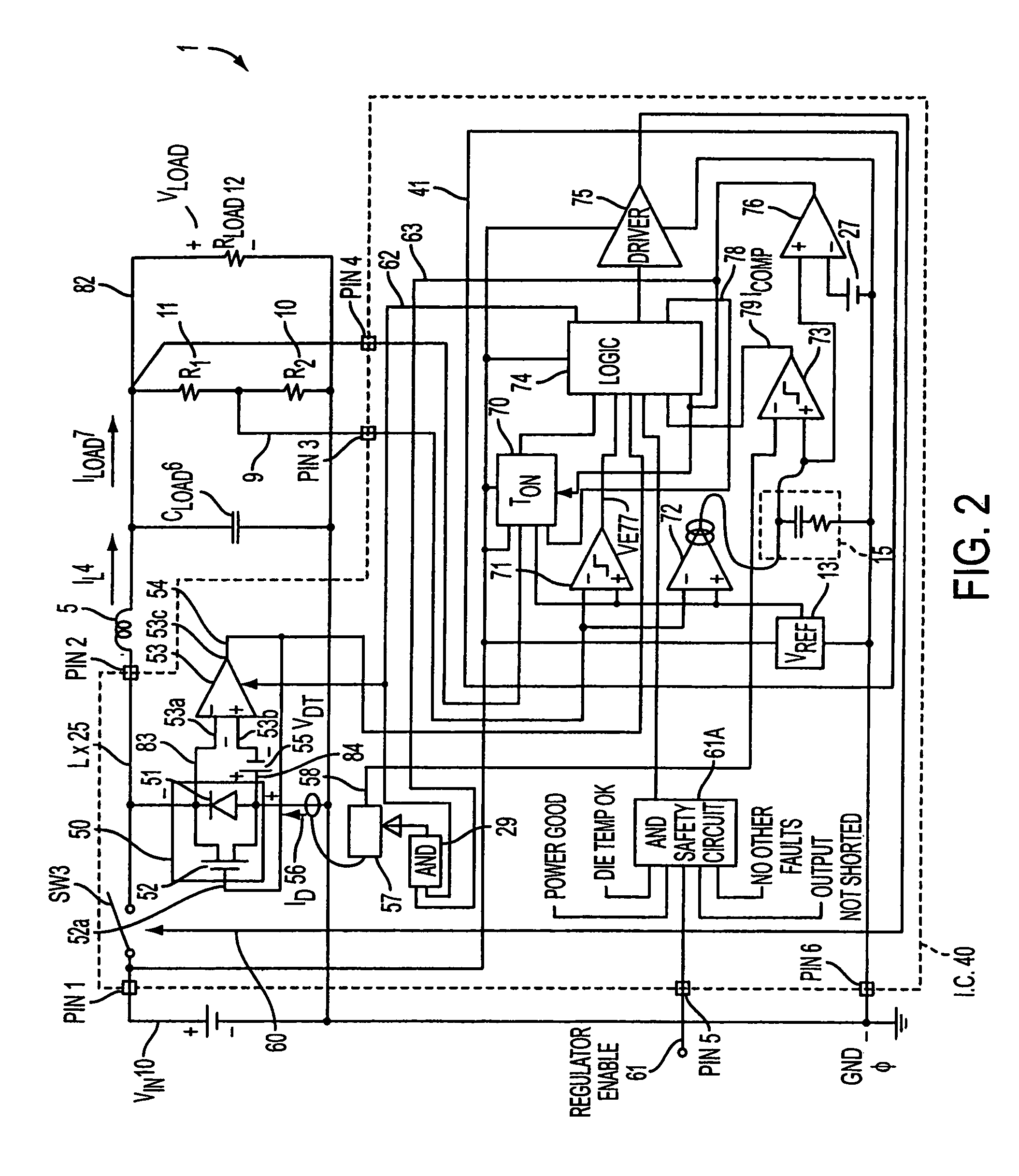
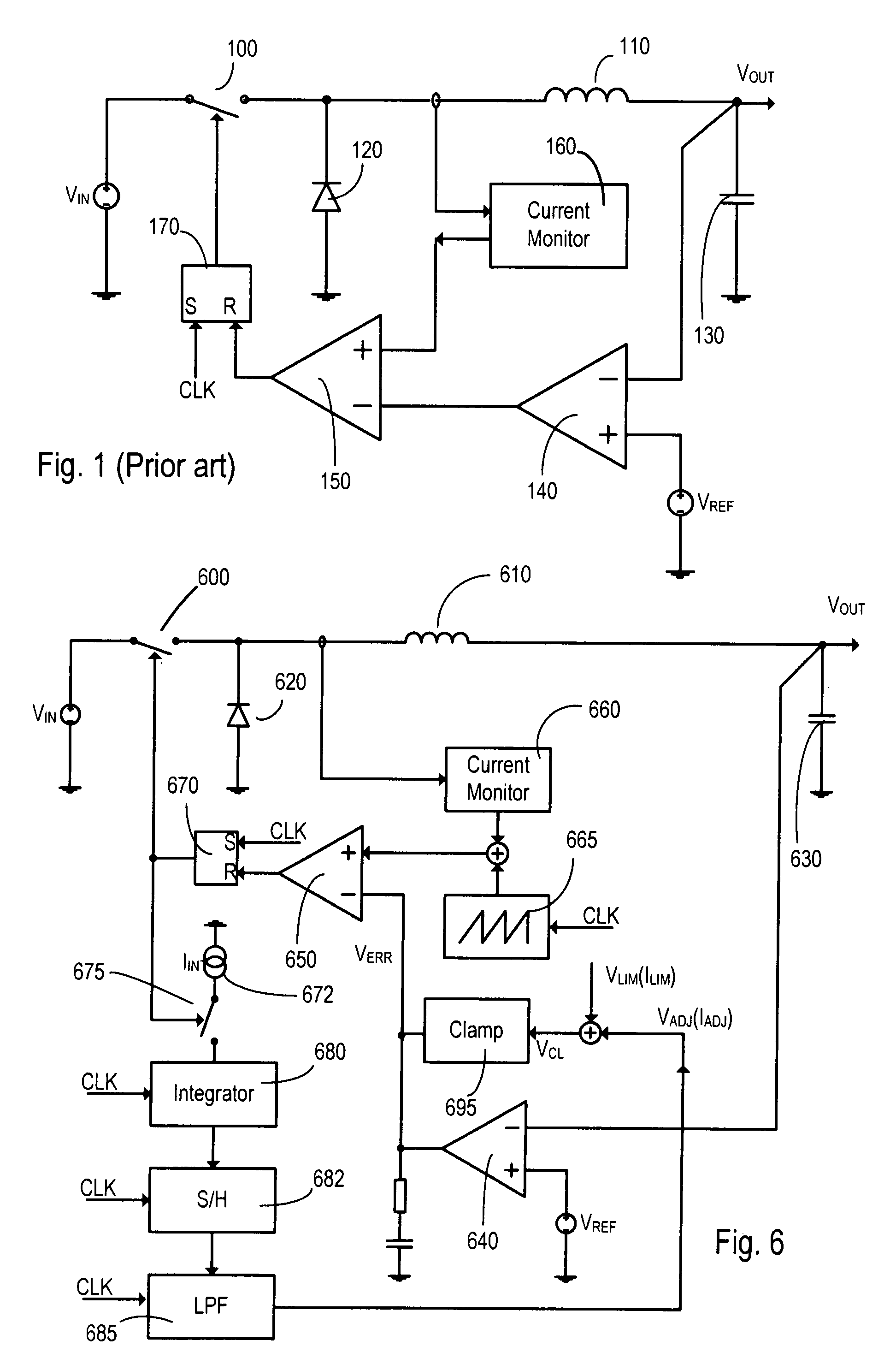
Current mode. The current mode is a modification of voltage mode control, where the inductor current in the circuit is detected and used instead of the triangular waveforms used in the voltage mode control. The current sensing can also be done by using the on-resistance of high side MOSFET or a current sense resistor instead of the inductor current.
Method and system for low power mode management for complex bluetooth devices
Methods and systems for controlling a personal area network access device are disclosed herein. Aspects of the method may comprise receiving an application event associated with a particular application running on a complex Bluetooth® device that is running a plurality of simultaneous applications, and determining whether a low power mode is allowed by the particular application running on the complex Bluetooth® device. If the low power mode is allowed by the particular application running on the complex Bluetooth® device, the complex Bluetooth® device running the particular application may be configured to operate utilizing the allowed low power mode. The allowed low power mode may be switched by the complex Bluetooth® device based on the application event. An active mode may be switched from a current mode prior to switching to the allowed power mode based on the application event.
Owner:AVAGO TECH INT SALES PTE LTD
System for changing modalities
InactiveUS6202212B1Television system detailsPicture reproducers using cathode ray tubesDiagnostic Radiology ModalityRemote control
A method and apparatus allows users to quickly effect a modal change in an appliance having first and second modes. The apparatus captures a user actuation indicative of a modal change. The user actuation may be a mouse button closure, a keyboard button closure, or a remote control button closure. Upon detecting the user actuation indicative of a modal change, the apparatus detects the current mode for the appliance. Based on the current mode of the appliance, the apparatus cycles to the next mode in a round-robin basis and sets the next mode to become the current mode for the appliance. Further, in setting the next mode, the apparatus displays the next mode of the appliance as a mode change item in a menu list. The apparatus also then requests a second user actuation confirming a modal change. Further, in the event that the user confirms the modal change, the apparatus sets the next mode of the appliance to be the current mode for the appliance and maximizes the window associated with the mode of the appliance.
Owner:HEWLETT PACKARD DEV CO LP
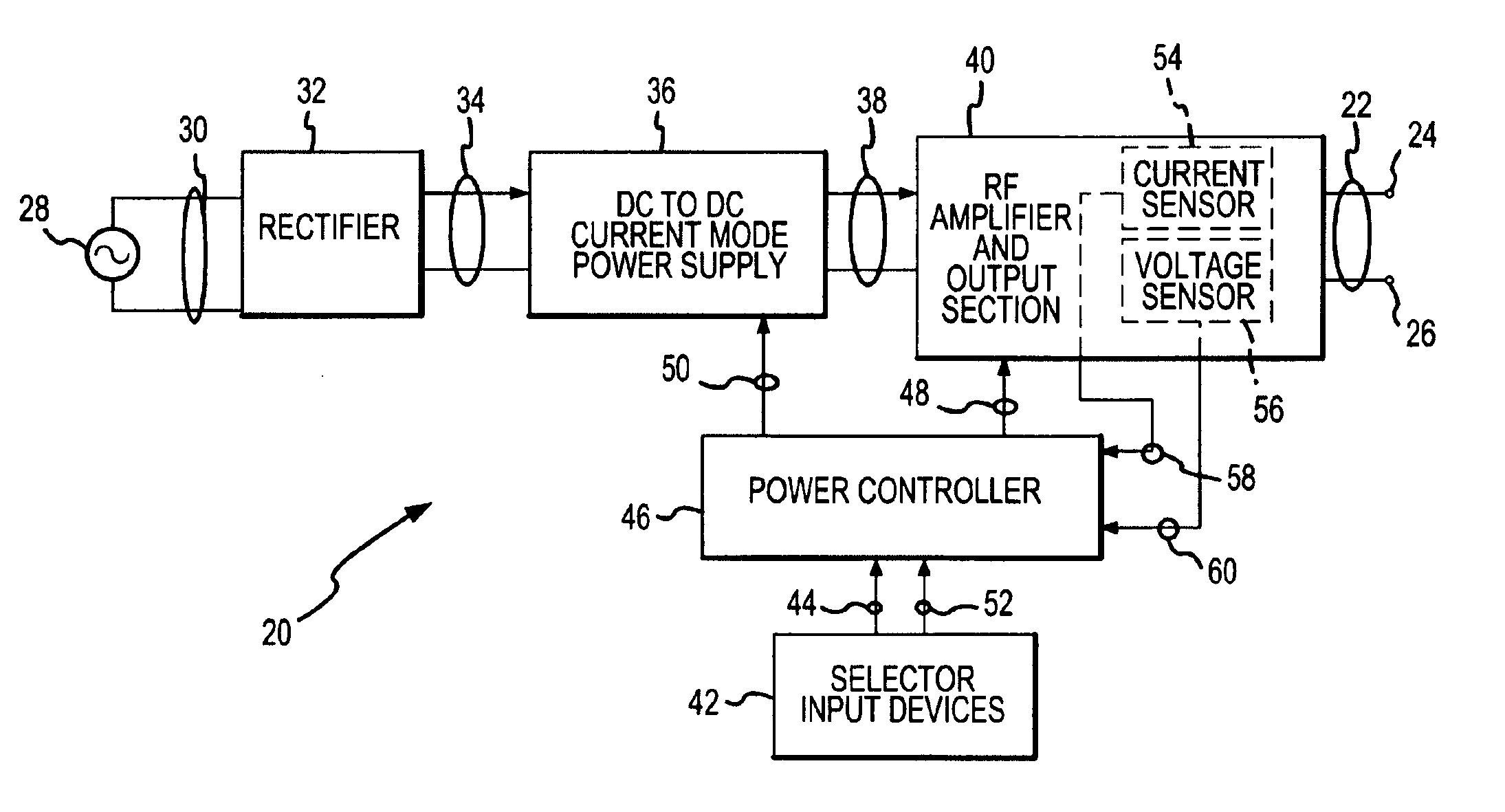
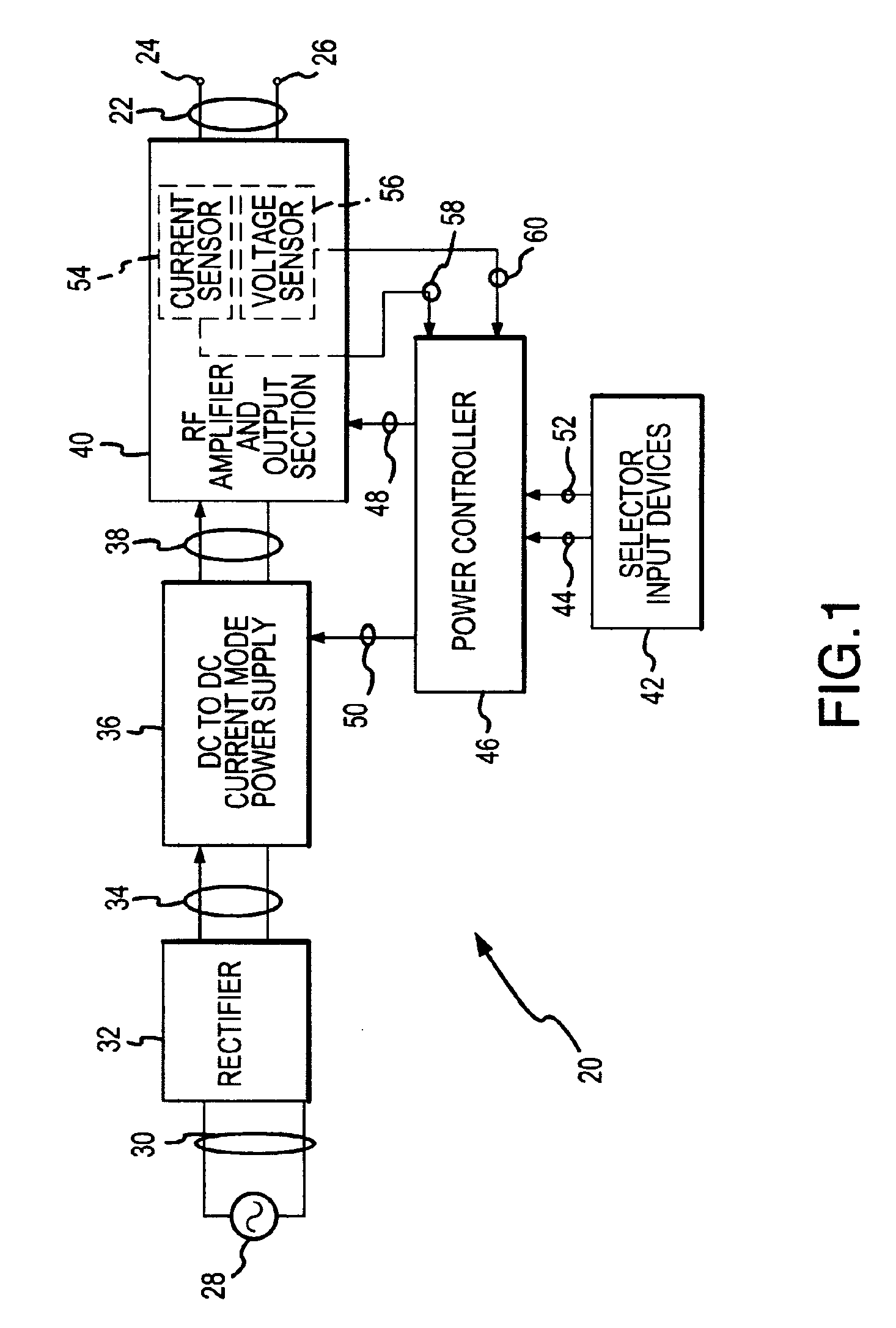
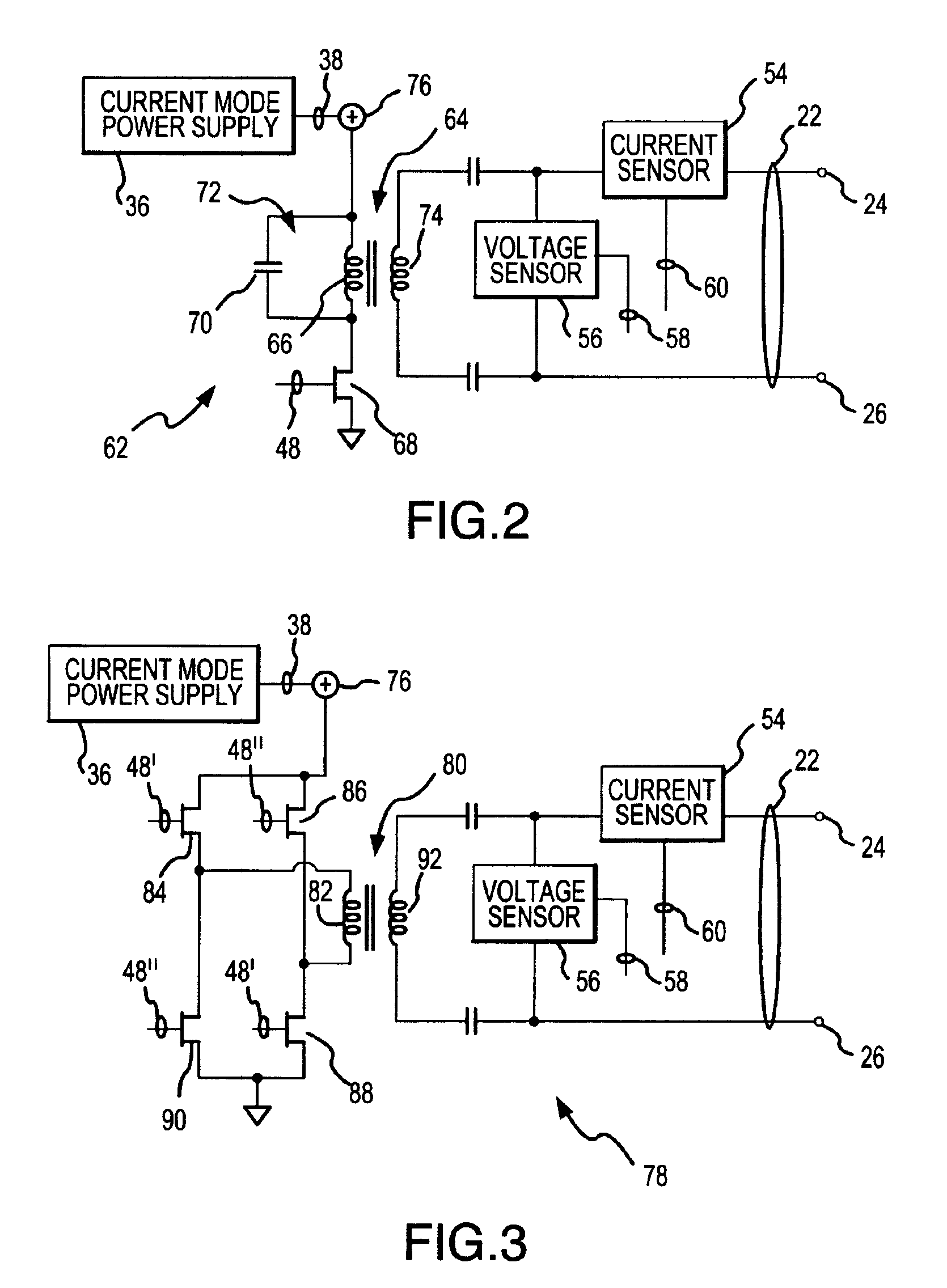
Electrosurgical generator and method with voltage and frequency regulated high-voltage current mode power supply
ActiveUS6939347B2Efficient implementationEfficient and effective power controlDiagnosticsEmergency protective circuit arrangementsSwitched currentTransformer
DC input energy is converted into DC output voltage by the use of a switched current mode high-voltage power supply. Pulses of input current are switched through a conversion transformer and the energy content of each pulse is converted into the DC output voltage. The time widths of the input current pulses are regulated relative to the DC input and output voltages, the magnitude of the current within each input current pulse, and in relation to maintaining a plurality of different selected operational conditions. The rate at which the input current pulses are converted is changed relative to the level of the DC output voltage.
Owner:CONMED CORP
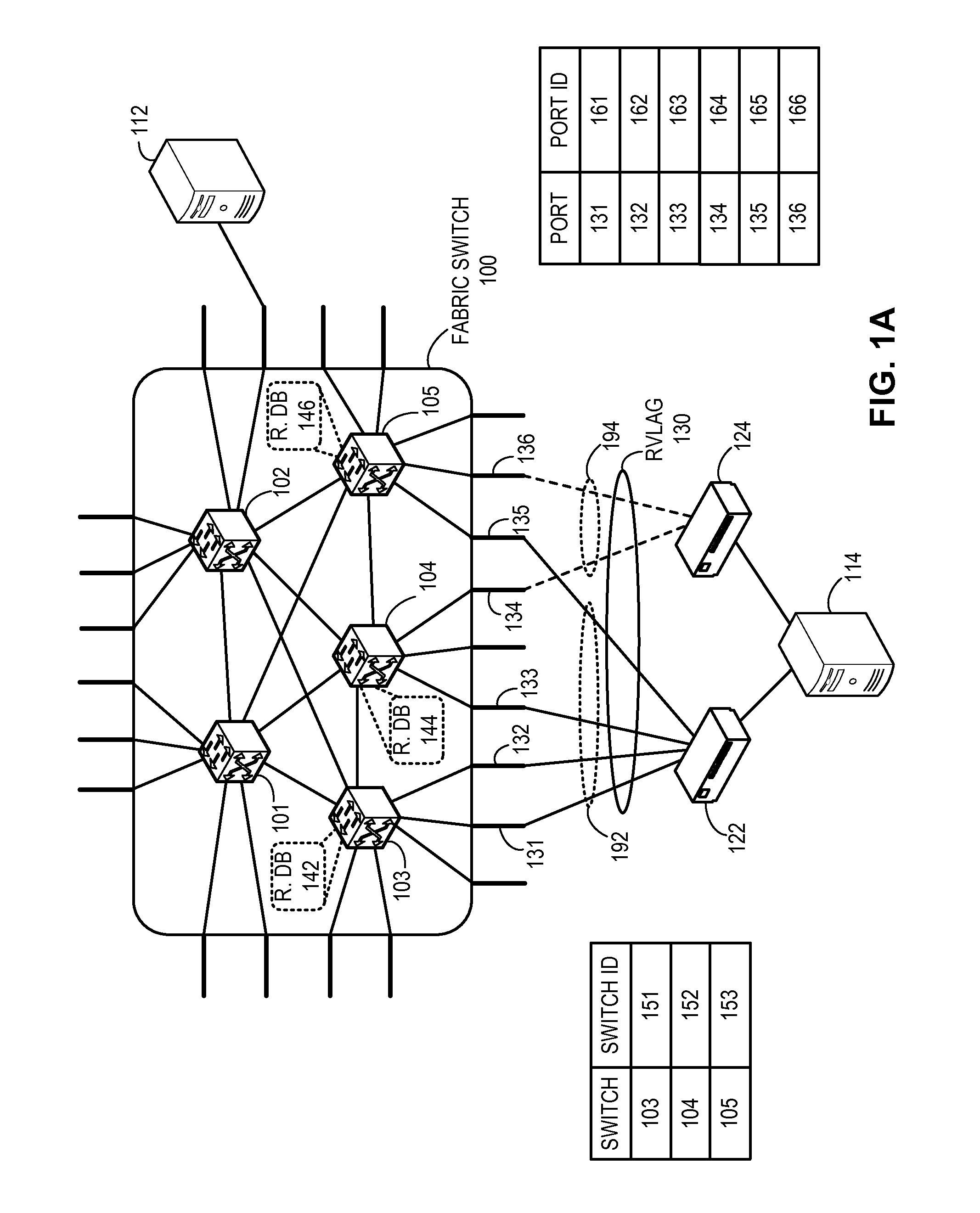
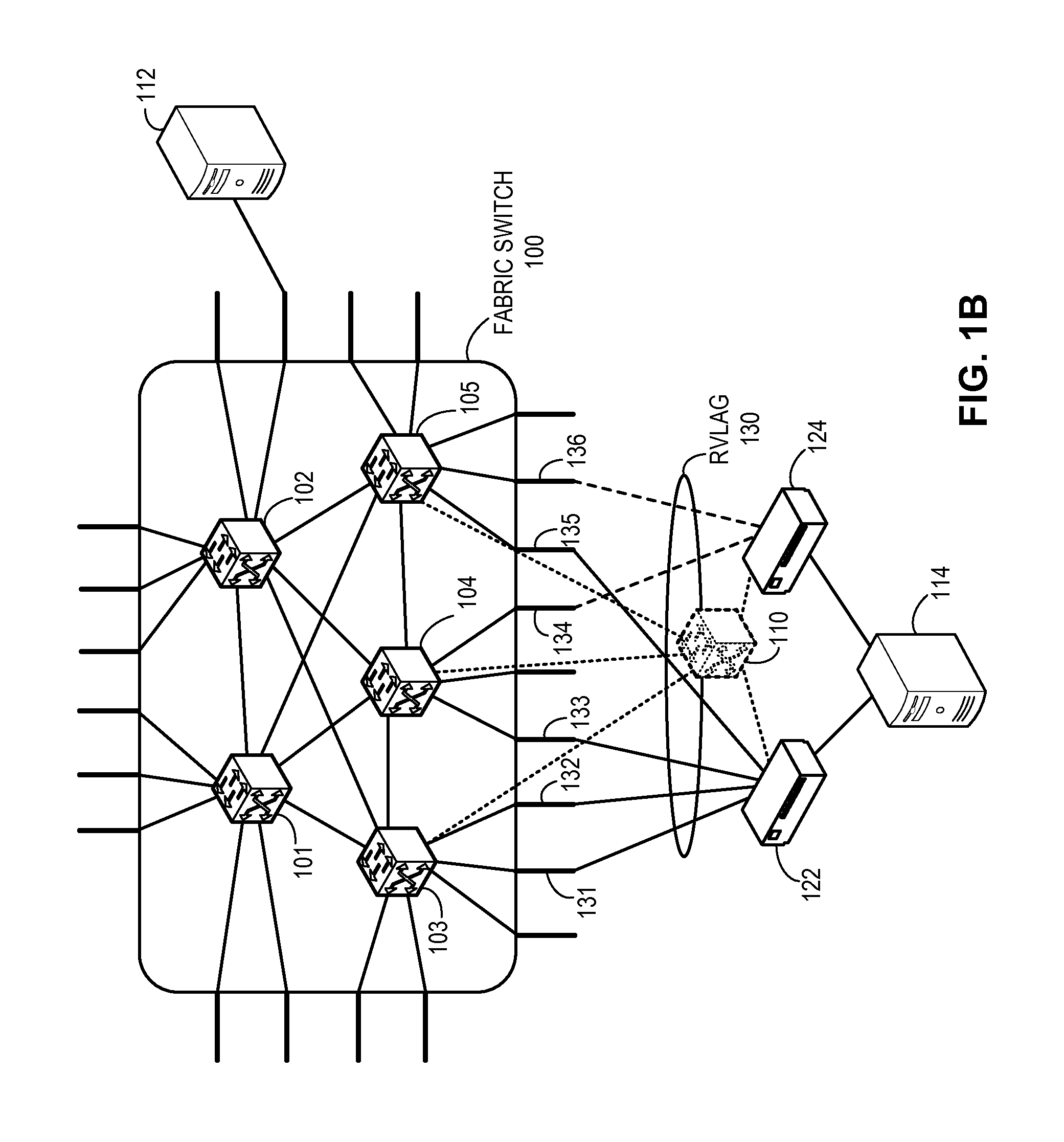
Redundent virtual link aggregation group
One embodiment of the present invention provides a switch. The switch includes a link aggregation module and a link management module. The link aggregation module establishes a virtual link aggregation group comprising a plurality of links coupled to the switch and one or more other switches. The plurality of links includes a first and a second sets of links coupling a first and a second end devices, respectively. The link management module determines a current mode which indicates which of the sets of links is currently active, and operates the first and the second sets of links as active and standby links, respectively, for the virtual link aggregation group based on the current mode and a port role for a port participating in the virtual link aggregation group. The port role indicates whether the port is coupled to an active link or a backup link.
Owner:AVAGO TECH INT SALES PTE LTD
Automatic gain control technique for current monitoring in current-mode switching regulators
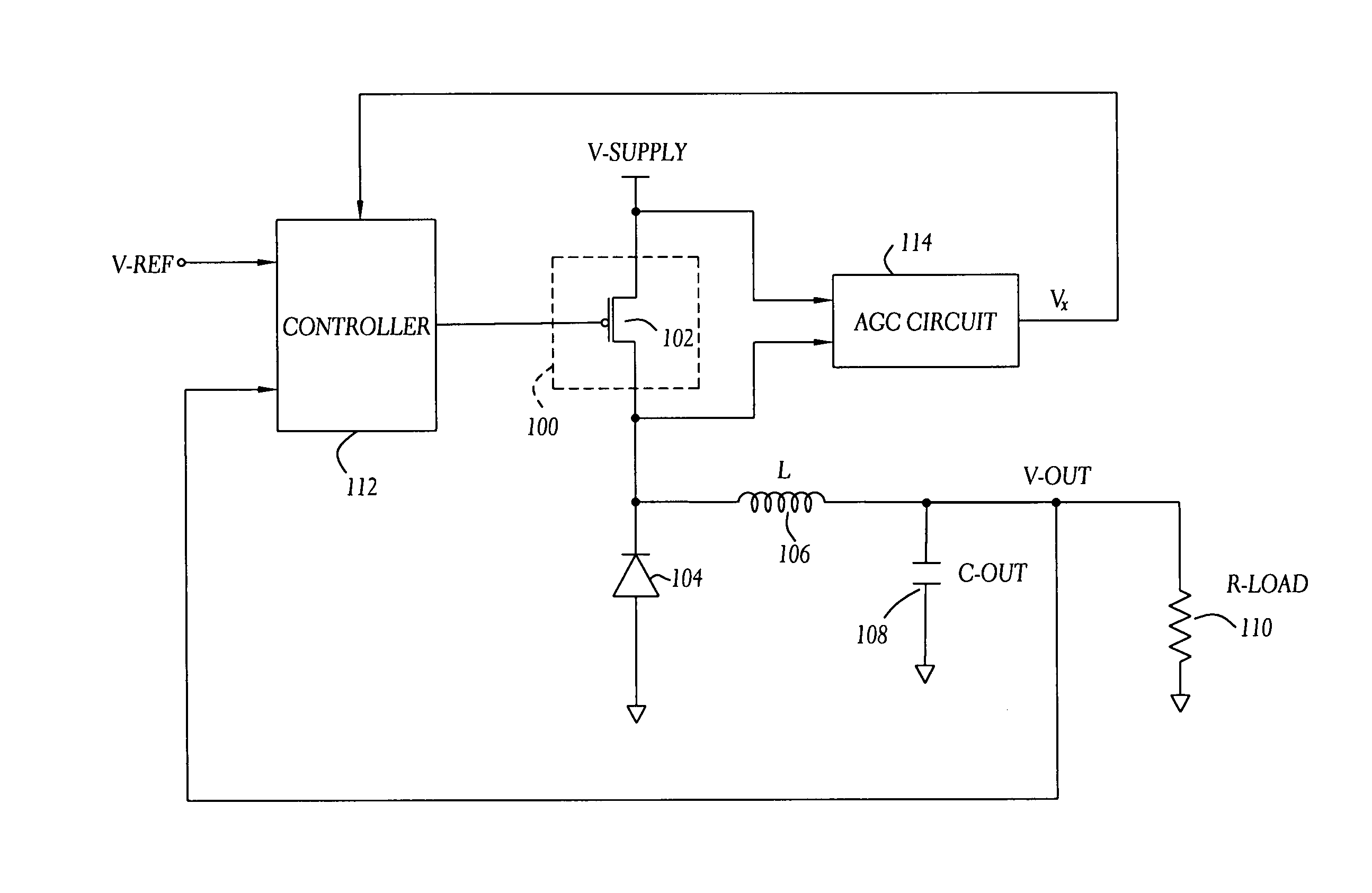
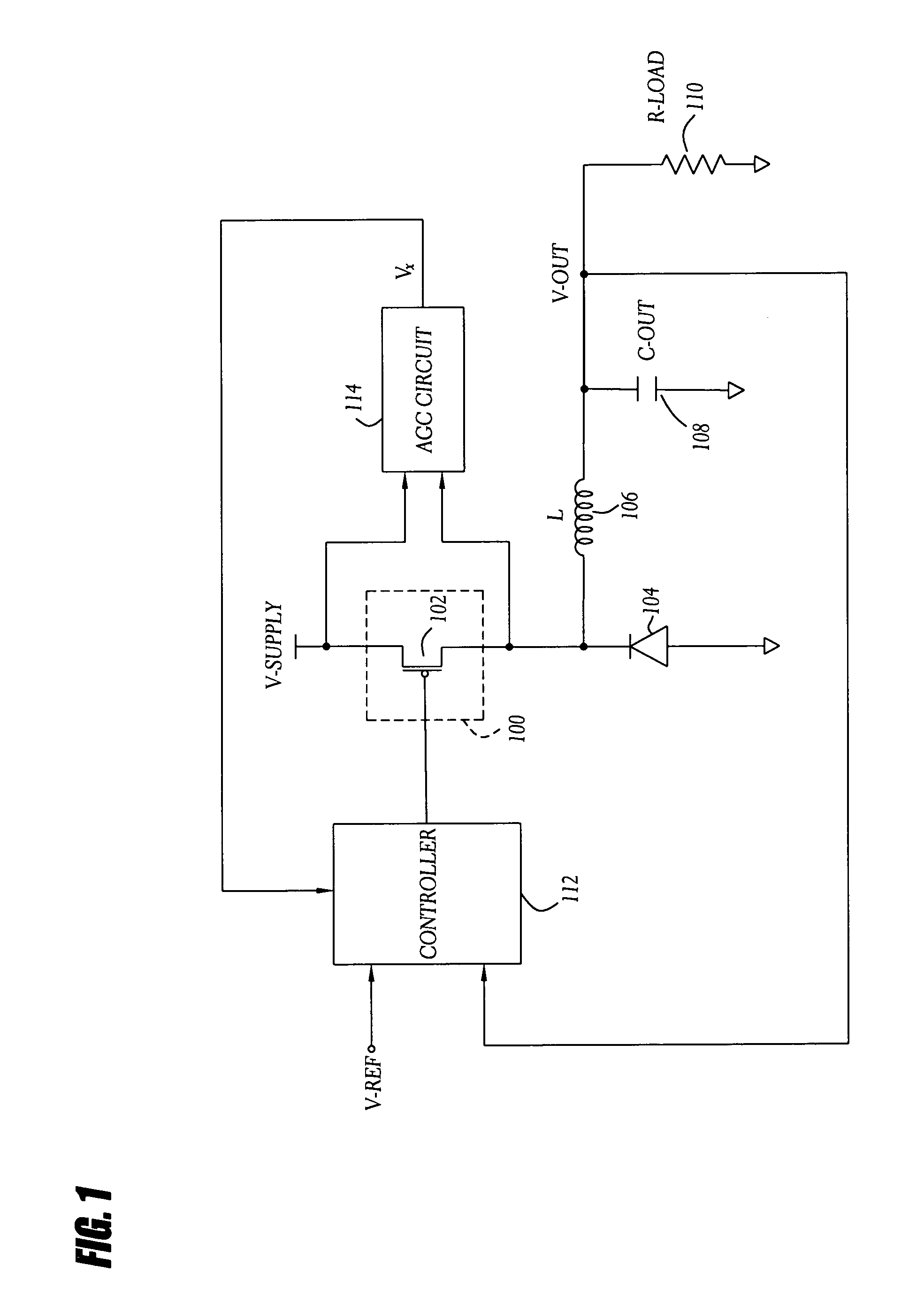
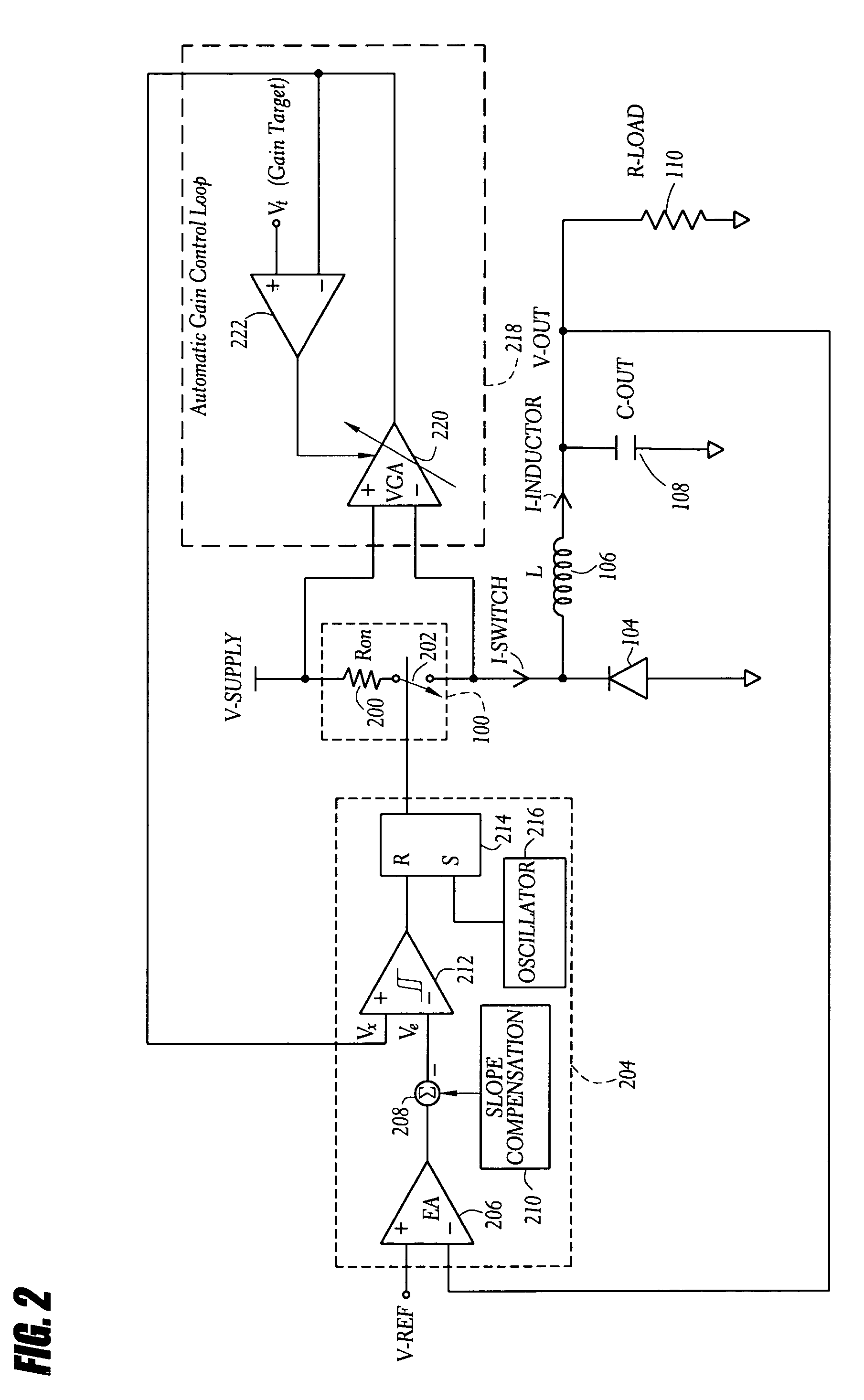
InactiveUS7919952B1Reduce component count and circuit board sizeFacilitates efficient and reliable monitoringDc-dc conversionElectric variable regulationEngineeringCurrent mode
A current-mode switching regulator uses adaptive current sensing to reliably monitor an inductor current in a cost-efficient and power-efficient manner. A semiconductor switch periodically turns on to conduct the inductor current. A voltage drop across the semiconductor switch is monitored when the semiconductor switch is on. A variable gain amplifier with an automatic gain control loop generates a feedback signal from the voltage drop of the semiconductor switch when conducting to provide an indication of the inductor current to a controller. The automatic gain control loop compensates for any variations in the on-resistance of the semiconductor switch.
Owner:MICROSEMI
Contextual menus in an electronic device
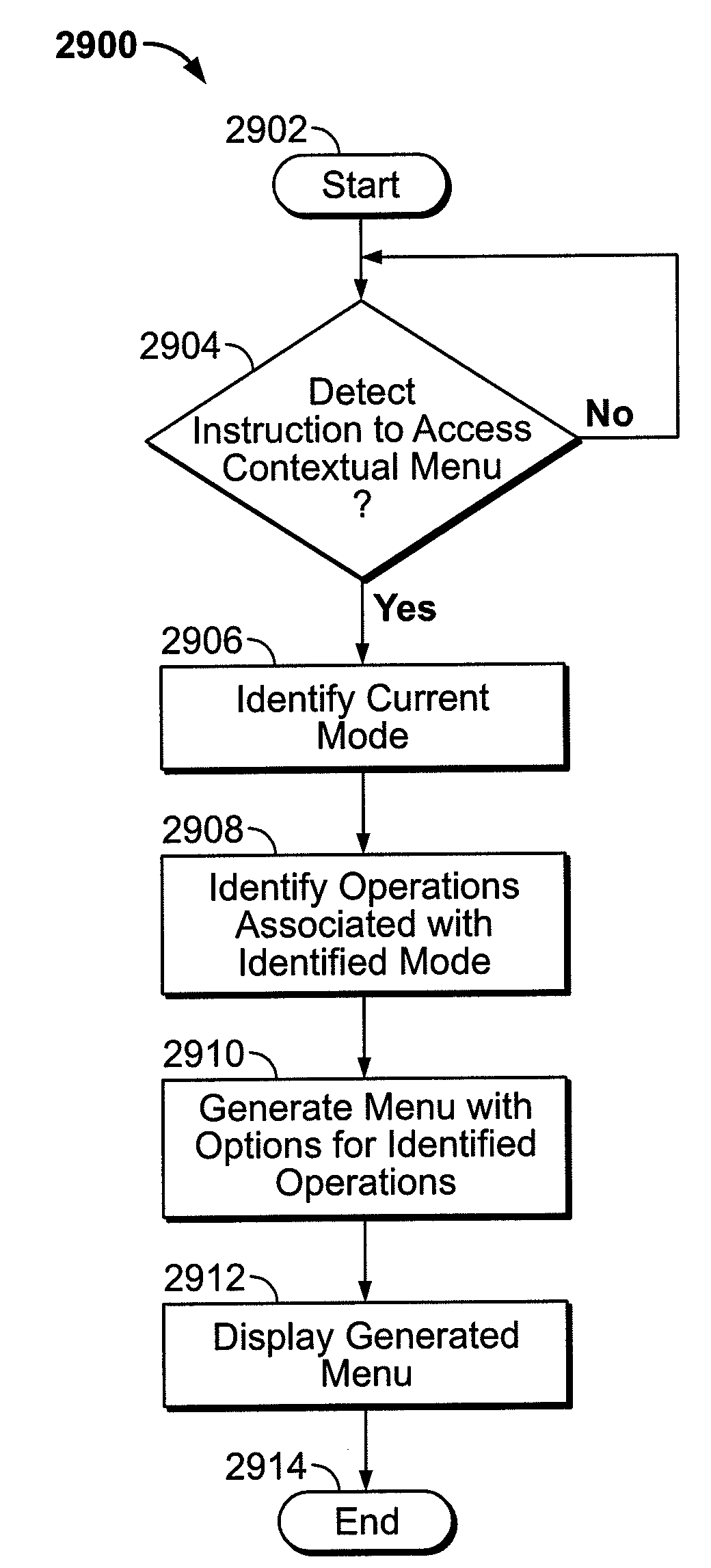
A system and method for displaying menus of selectable options to a user are provided. The menus may include options that are contextually related to a current mode of the device to provide relevant options to a user. The electronic device modes may include, for example, a media mode, a radio mode, a workout mode, a calendar or event mode, a clock mode, a stopwatch mode, or any other suitable mode. To further enhance a user's experience, the displayed menus may not cover the entirety of the screen such that a portion of the content associated with a current mode or application may be visible, thus providing context to the displayed options.
Owner:APPLE INC
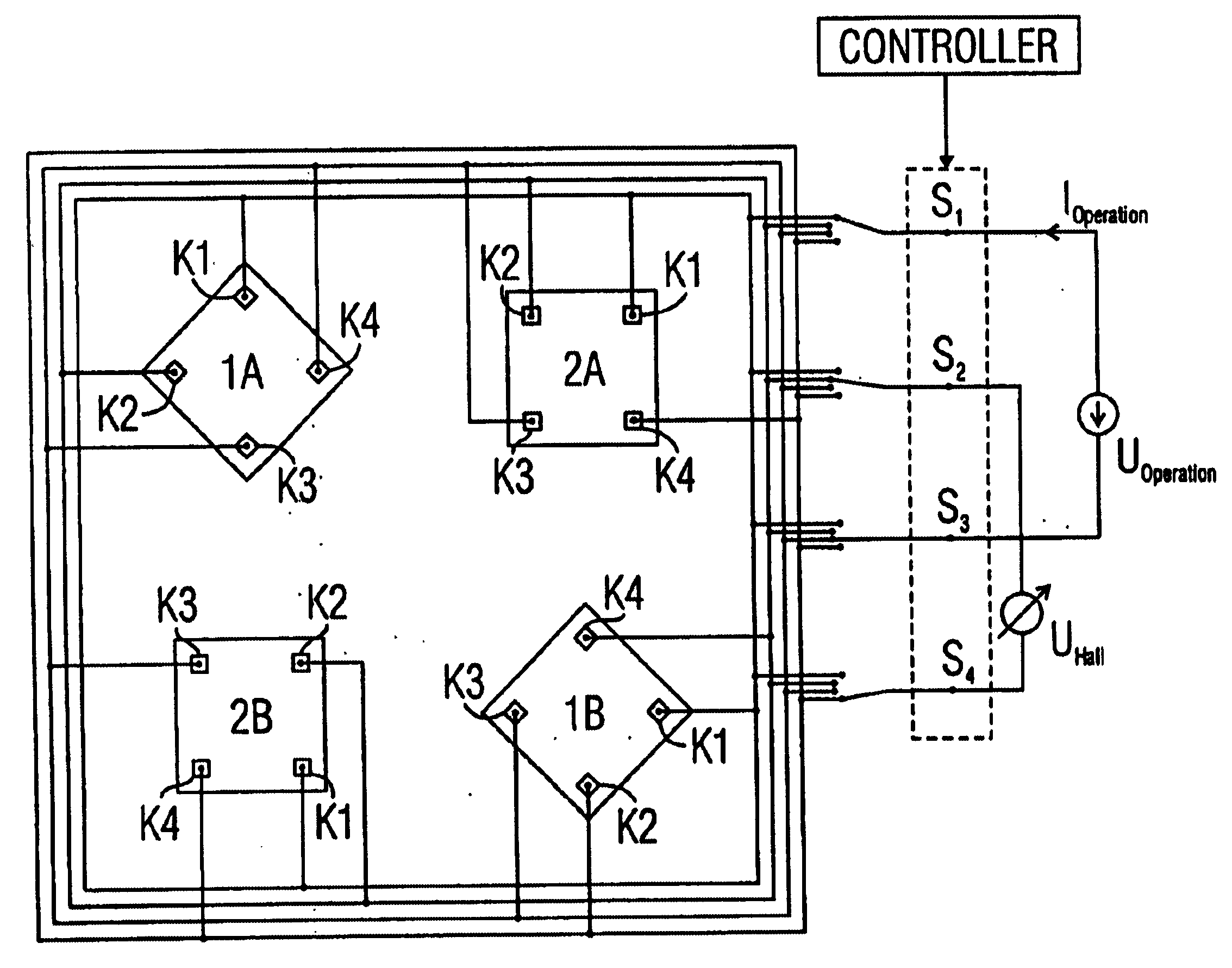
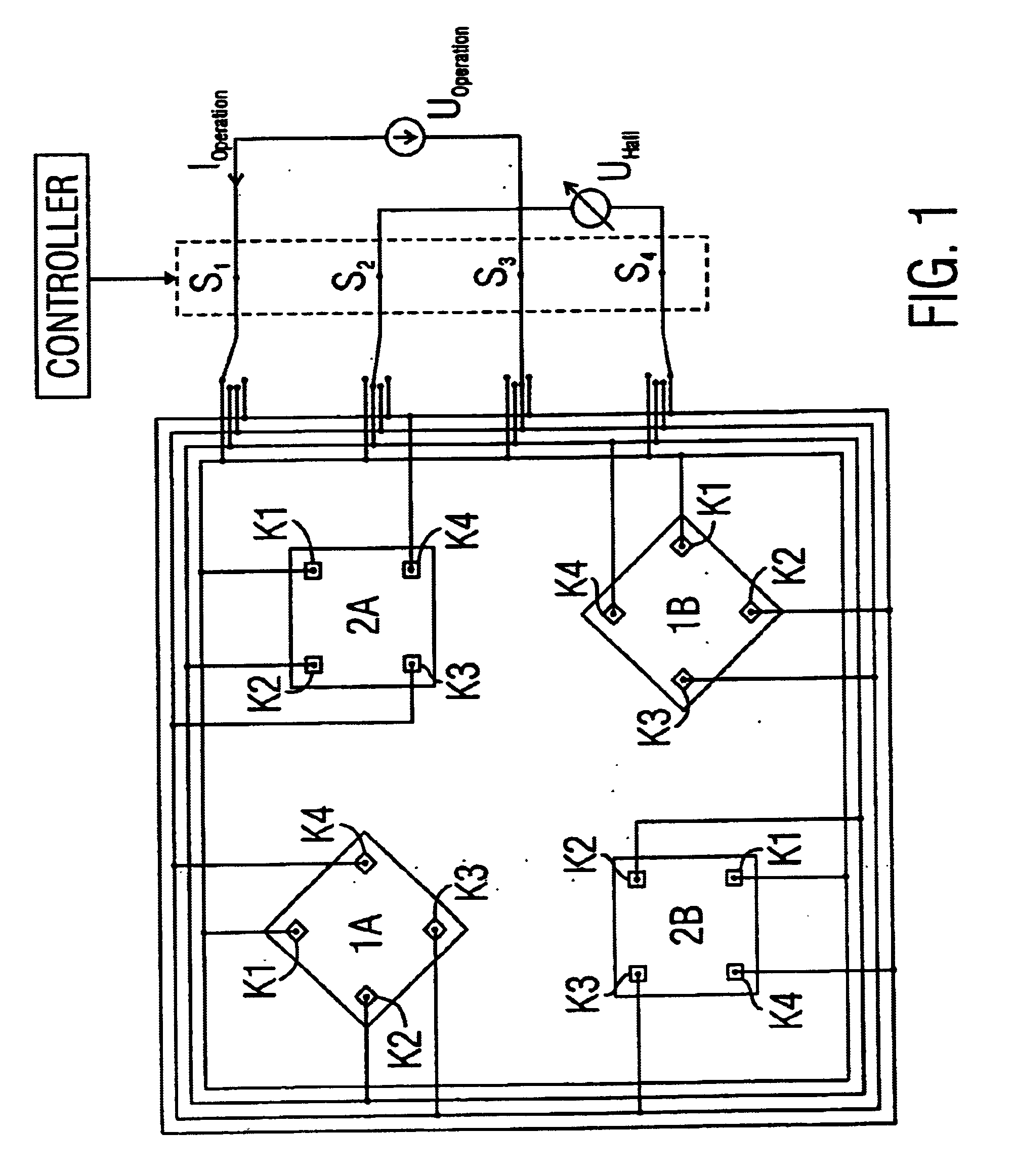
Hall sensor array for measuring a magnetic field with offset compensation
InactiveUS6768301B1Less complicated to manufactureReduce signalingSolid-state devicesMagnetic field measurement using galvano-magnetic devicesSensor arrayVoltage source
A Hall sensor array for offset-compensated magnetic field measurement comprises a first and at least one additional pair of Hall sensor elements. Each Hall sensor element has four terminals, of which two act as power supply terminals for supplying an operating current and two act as measurement terminals for measuring a Hall voltage. Respective first supply terminals of each Hall sensor element are connected together and to a first terminal of a common voltage source and respective second supply terminals of each Hall sensor element are connected together and to a second terminal of the common voltage source so that the common voltage source supplies an operating current for the Hall sensor elements. The Hall sensor elements are operated in the spinning current mode so that the offset voltages of the Hall sensor elements approximately cancel one another out in a revolution so that the Hall signal contributions which actually depend on the magnetic field remain.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Digital multilevel memory system having multistage autozero sensing
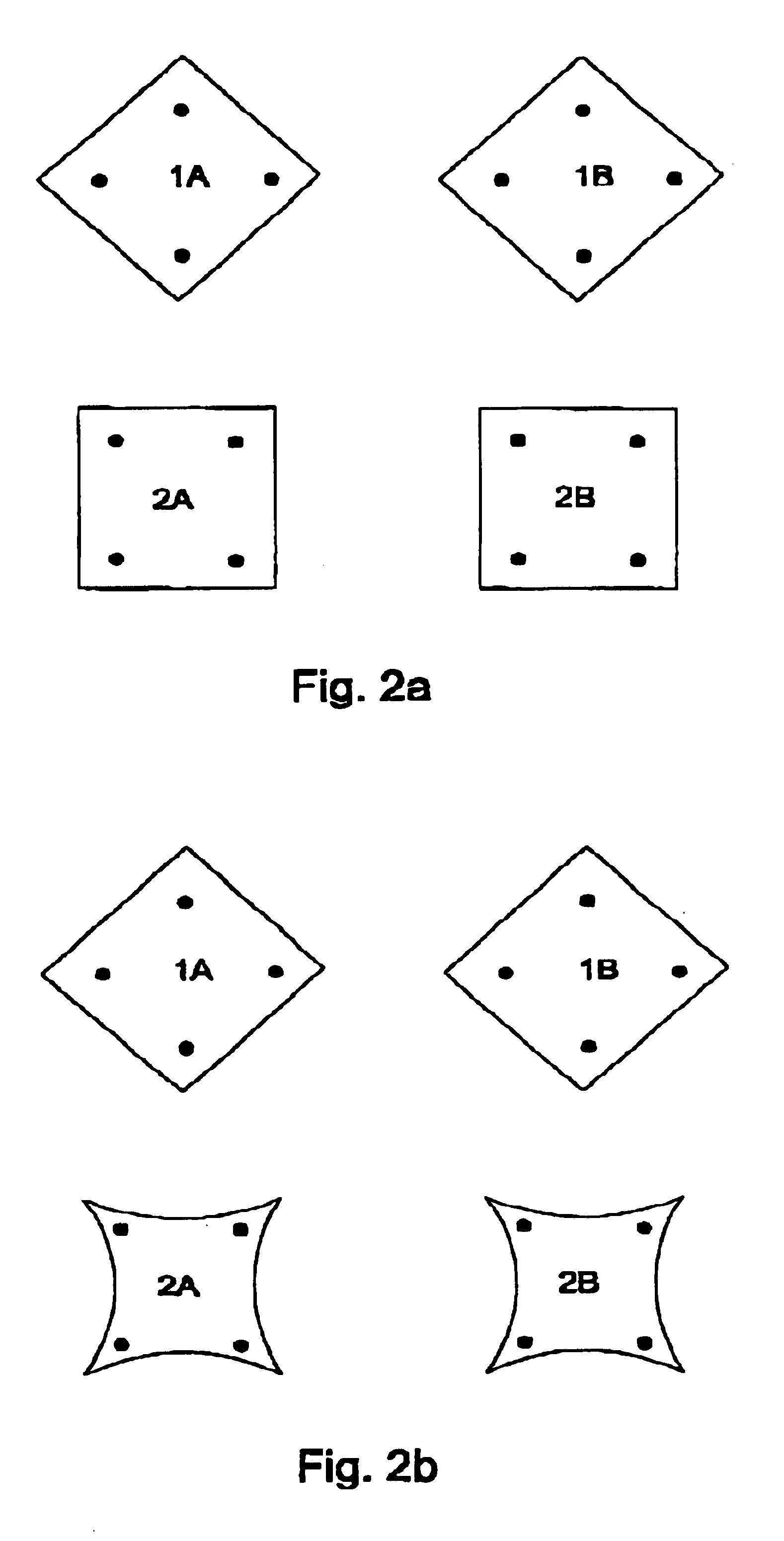
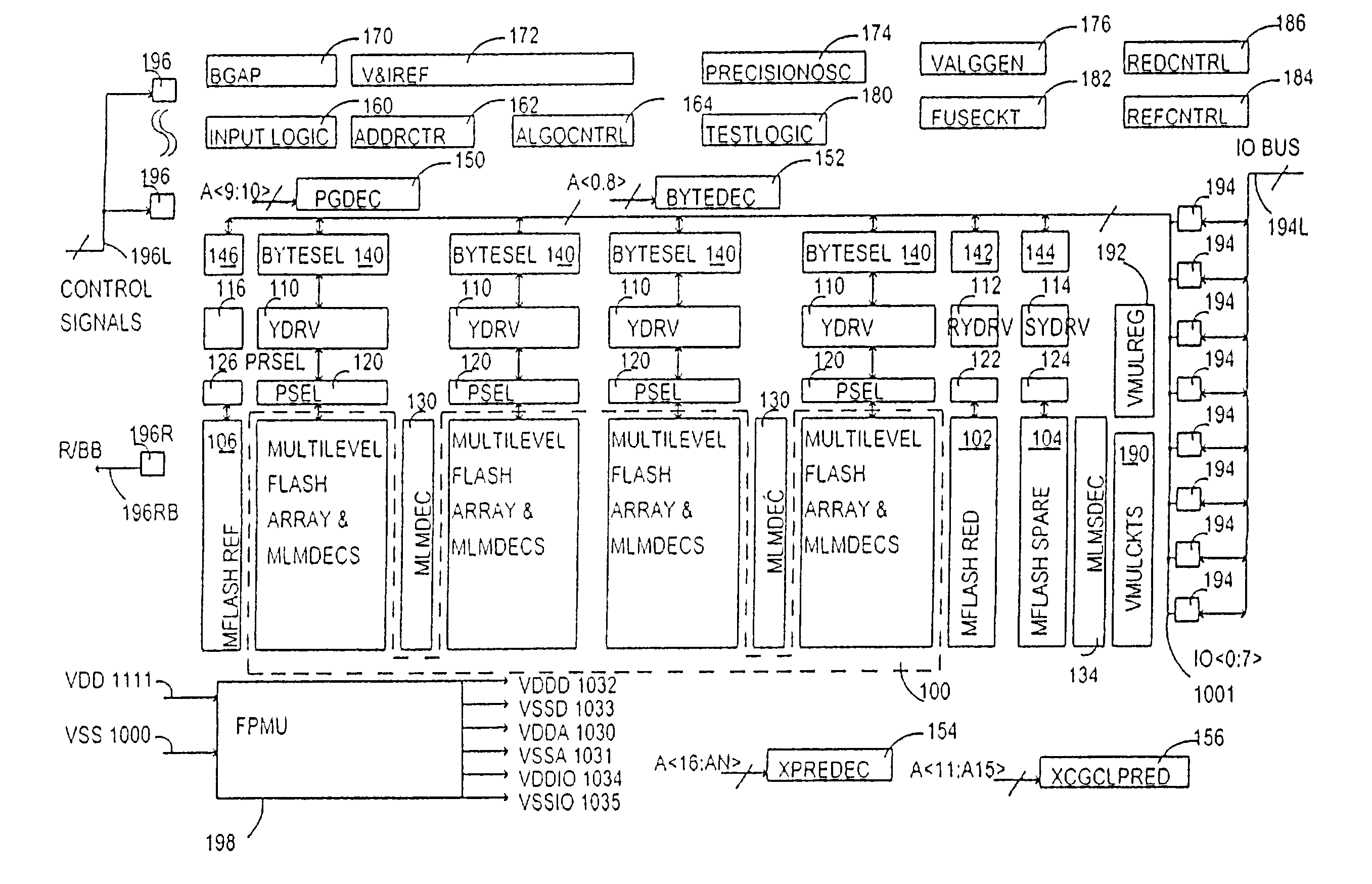
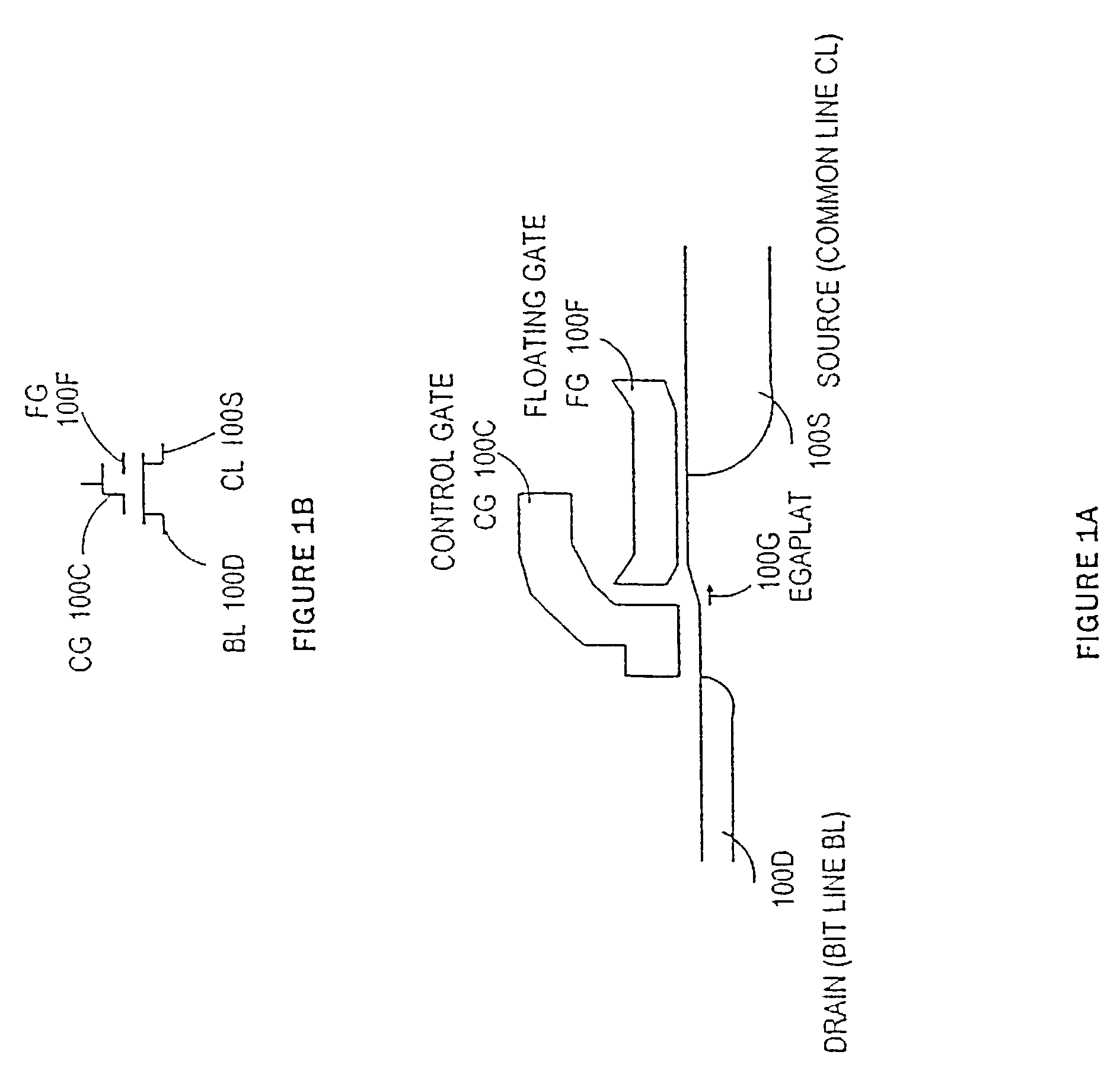
A digital multibit non-volatile memory integrated system includes autozero multistage sensing. One stage may provide local sensing with autozero. Another stage may provide global sensing with autozero. A twisted bitline may be used for array arrangement. Segment reference may be used for each segment. The system may read data cells using a current sensing one or two step binary search. The system may use inverse voltage mode or inverse current mode sensing. The system may use no current multilevel sensing. The system may use memory cell replica sensing. The system may use dynamic sensing. The system may use built-in byte redundancy. Sense amplifiers capable of sub-volt (<<1V) sensing are described.
Owner:SILICON STORAGE TECHNOLOGY
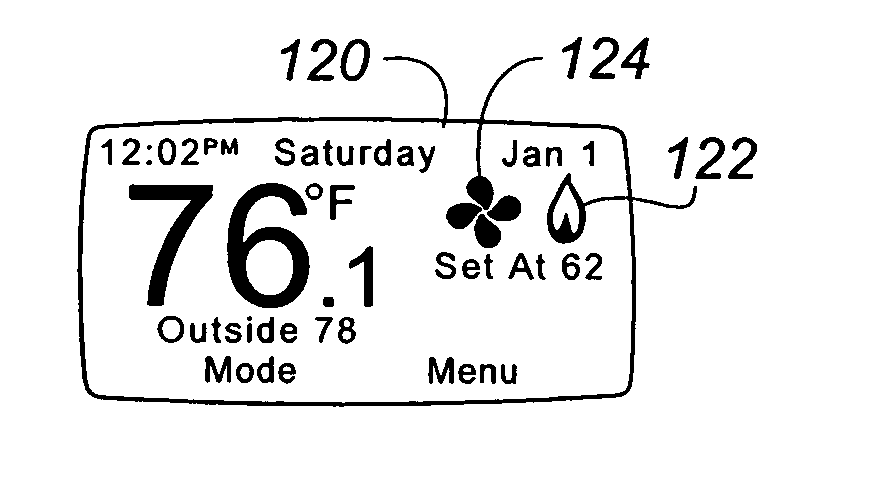
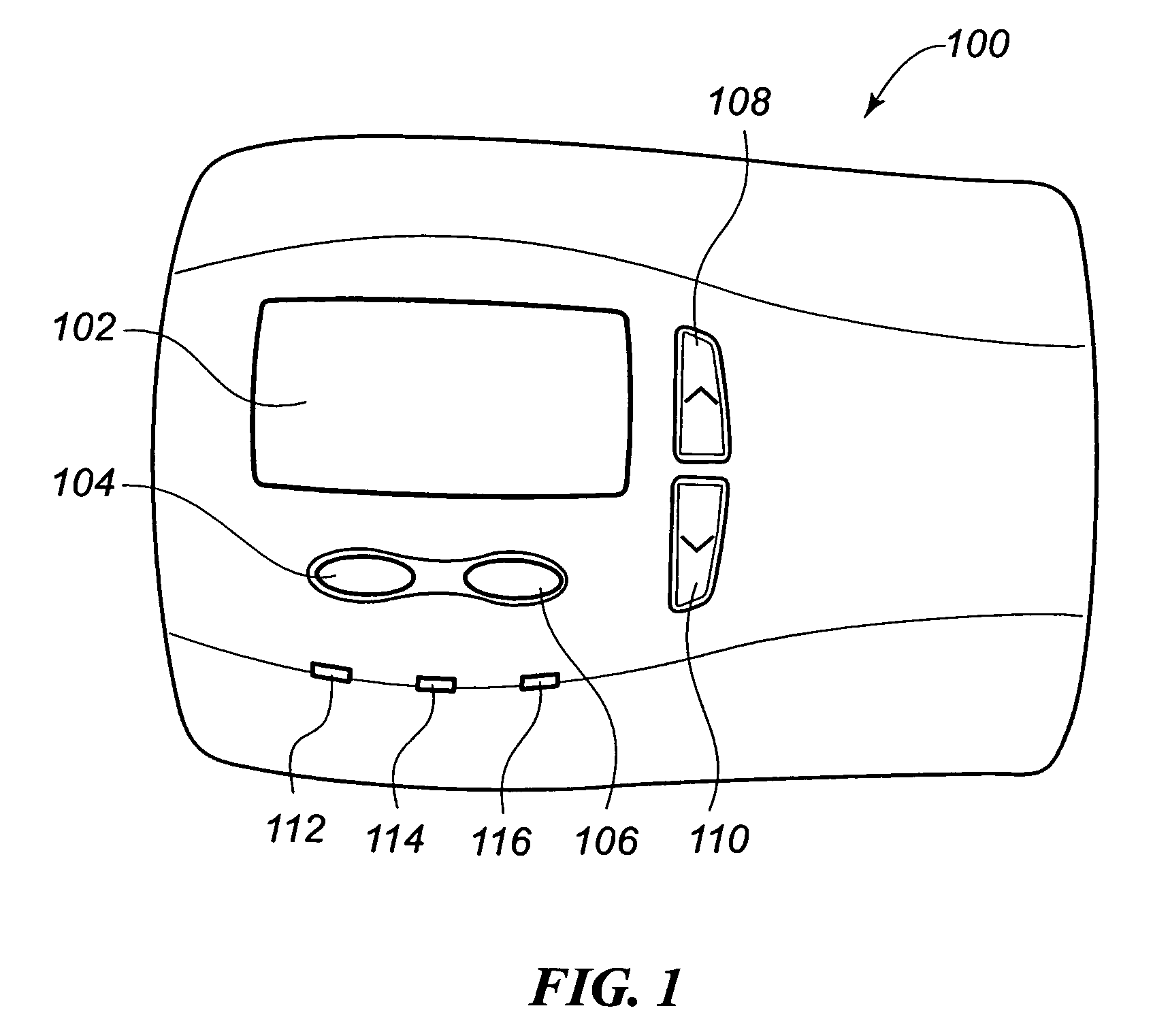
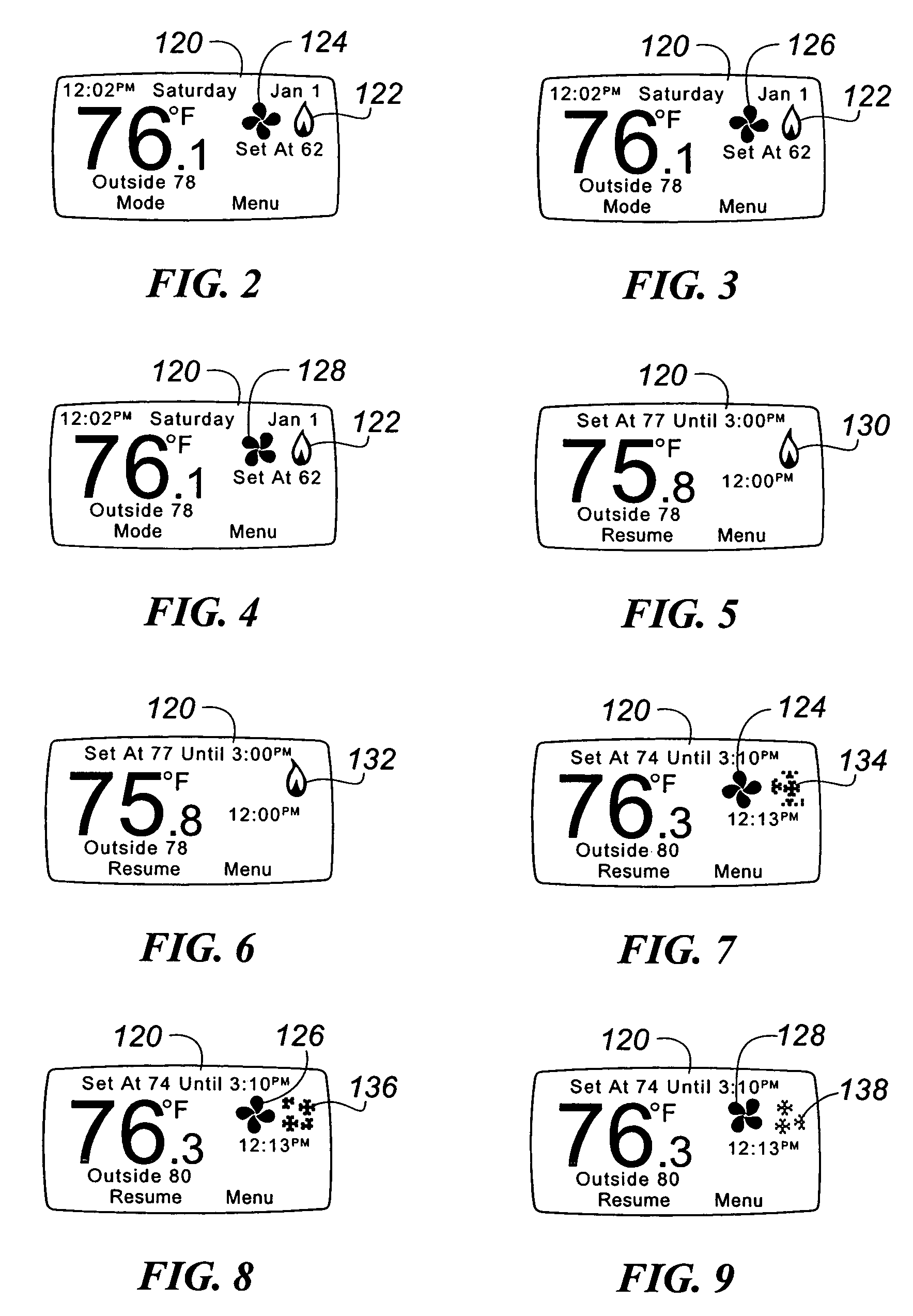
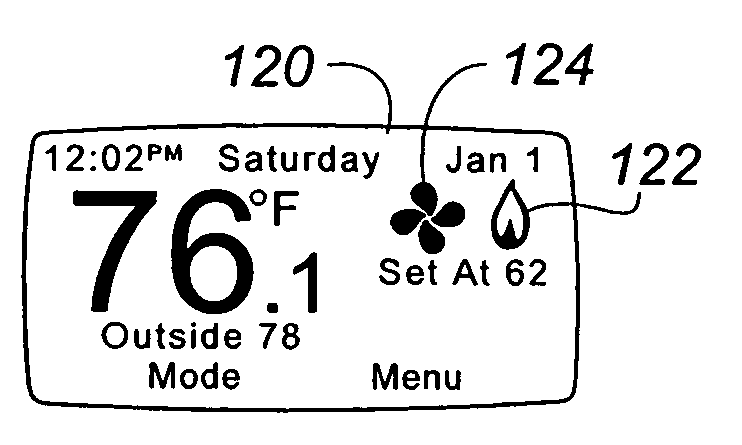
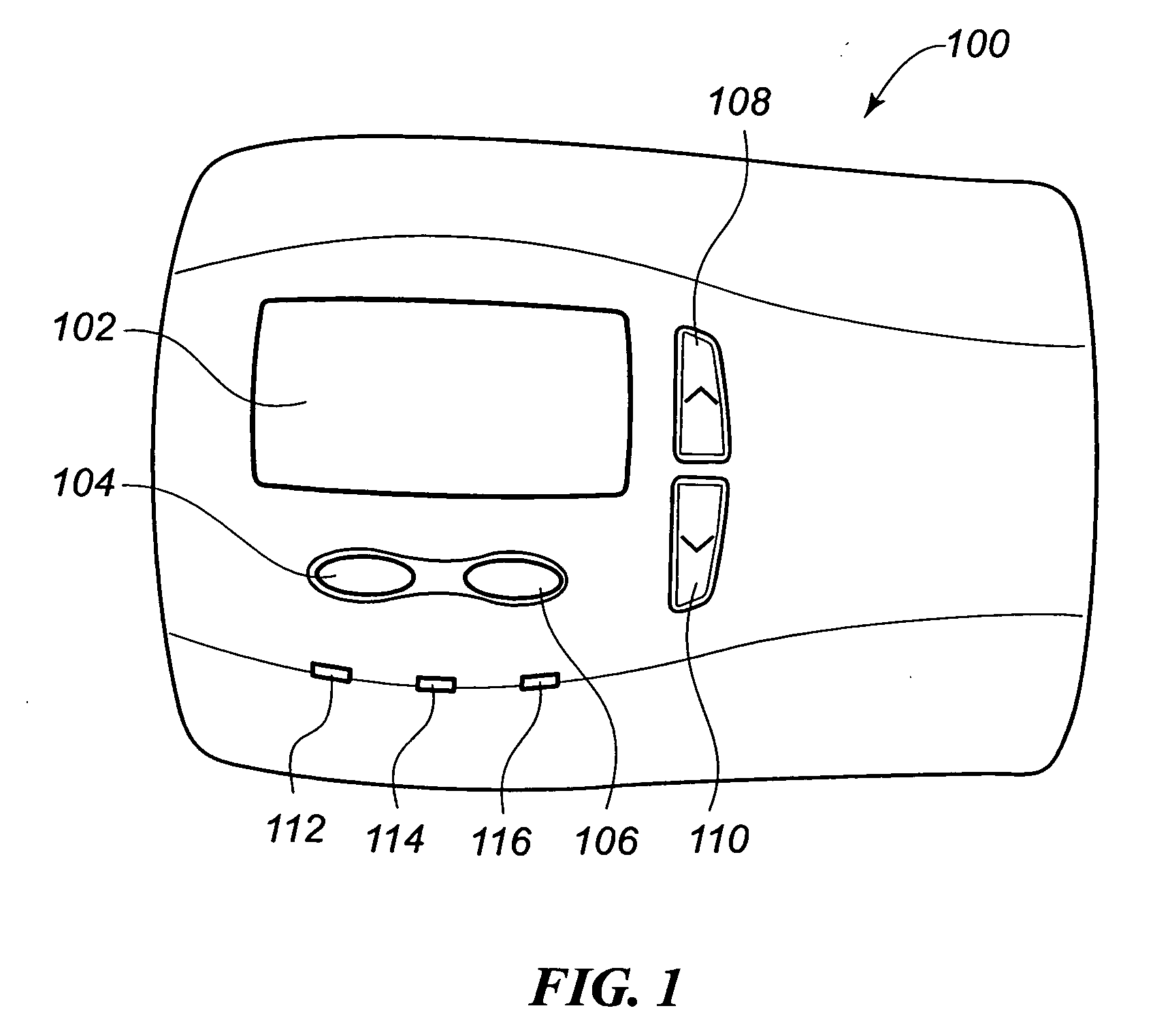
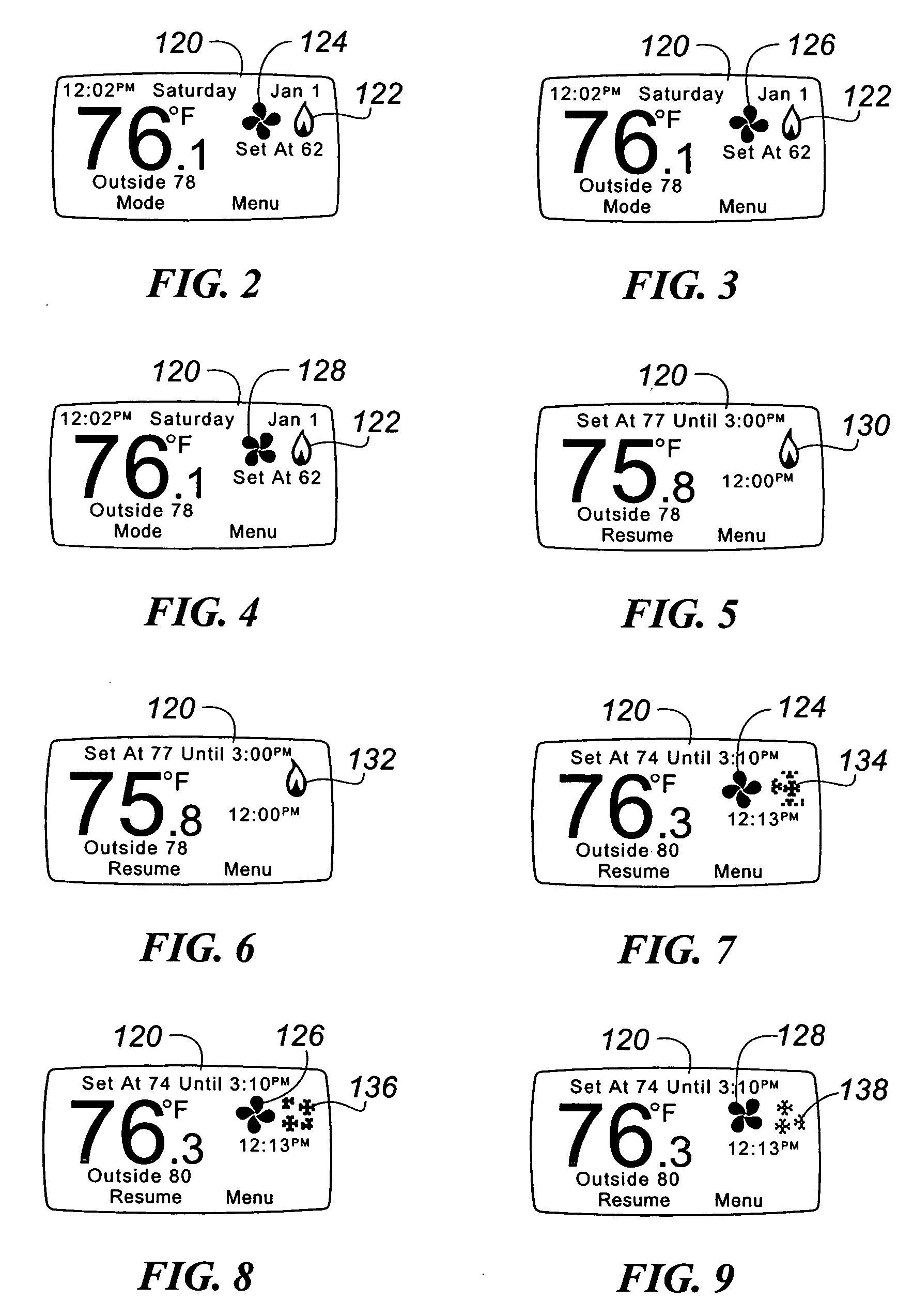
Thermostat display system providing animated icons
InactiveUS7455240B2Energy efficiencyExtend battery lifeMechanical apparatusTemperature control with auxillary non-electric powerAnimationThermostat
A visual display system and method for a digital thermostat having a user display screen to provide operational status information of the heating and / or cooling equipment controlled by the thermostat is provided. This visual display system utilizes animated icons to show operational status of the heating and / or cooling equipment. Static icons may also be used in one embodiment to indicate the current mode of the thermostat. Animated icons for the heating system, the cooling system, and fan operation are provided. The illusion of animation is provided by overwriting or replacing a displayed image with another image at a predetermined frequency. This predetermined frequency may be changed programmatically, and varied to provide different visual effects.
Owner:RANCO OF DELAWARE
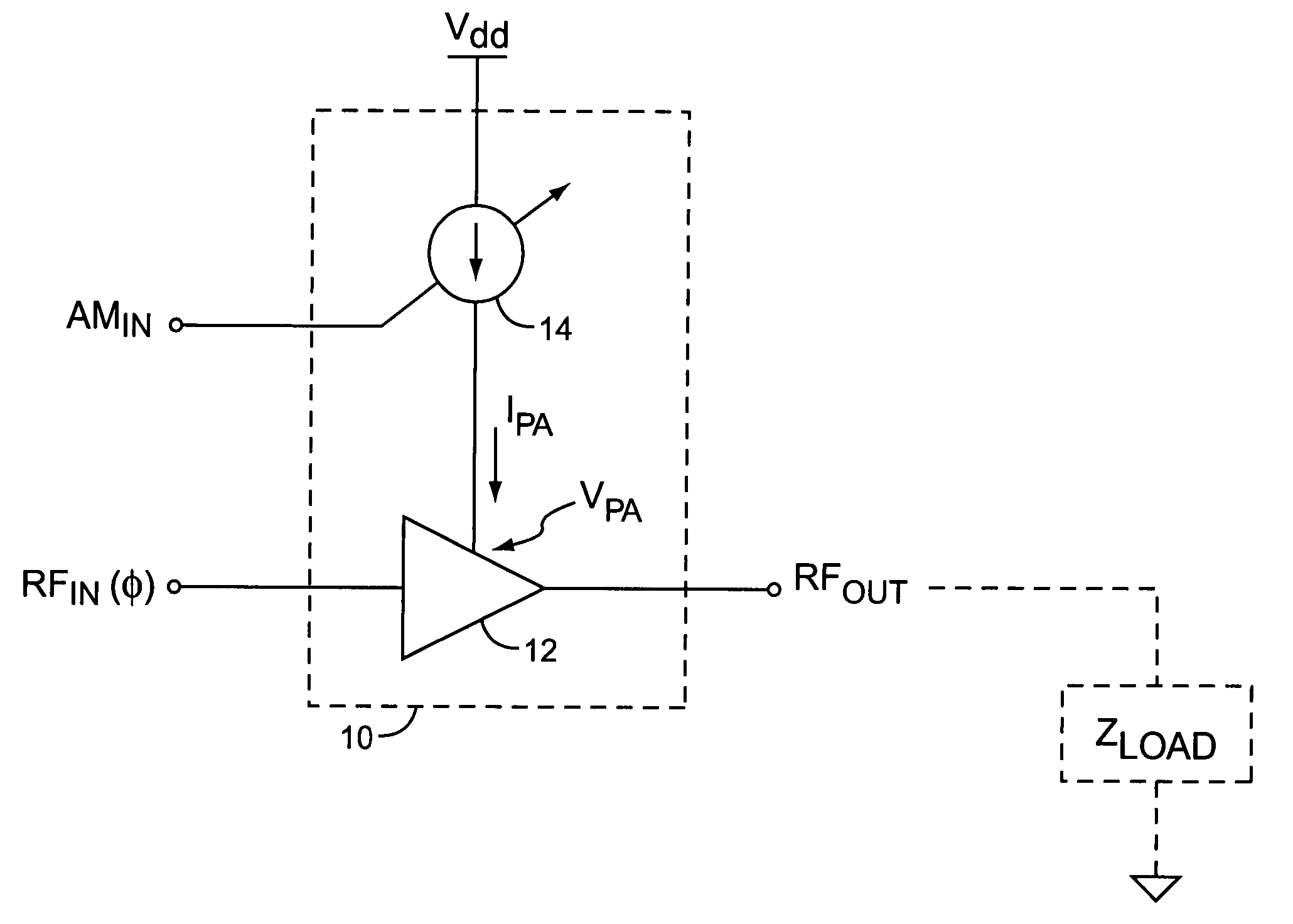
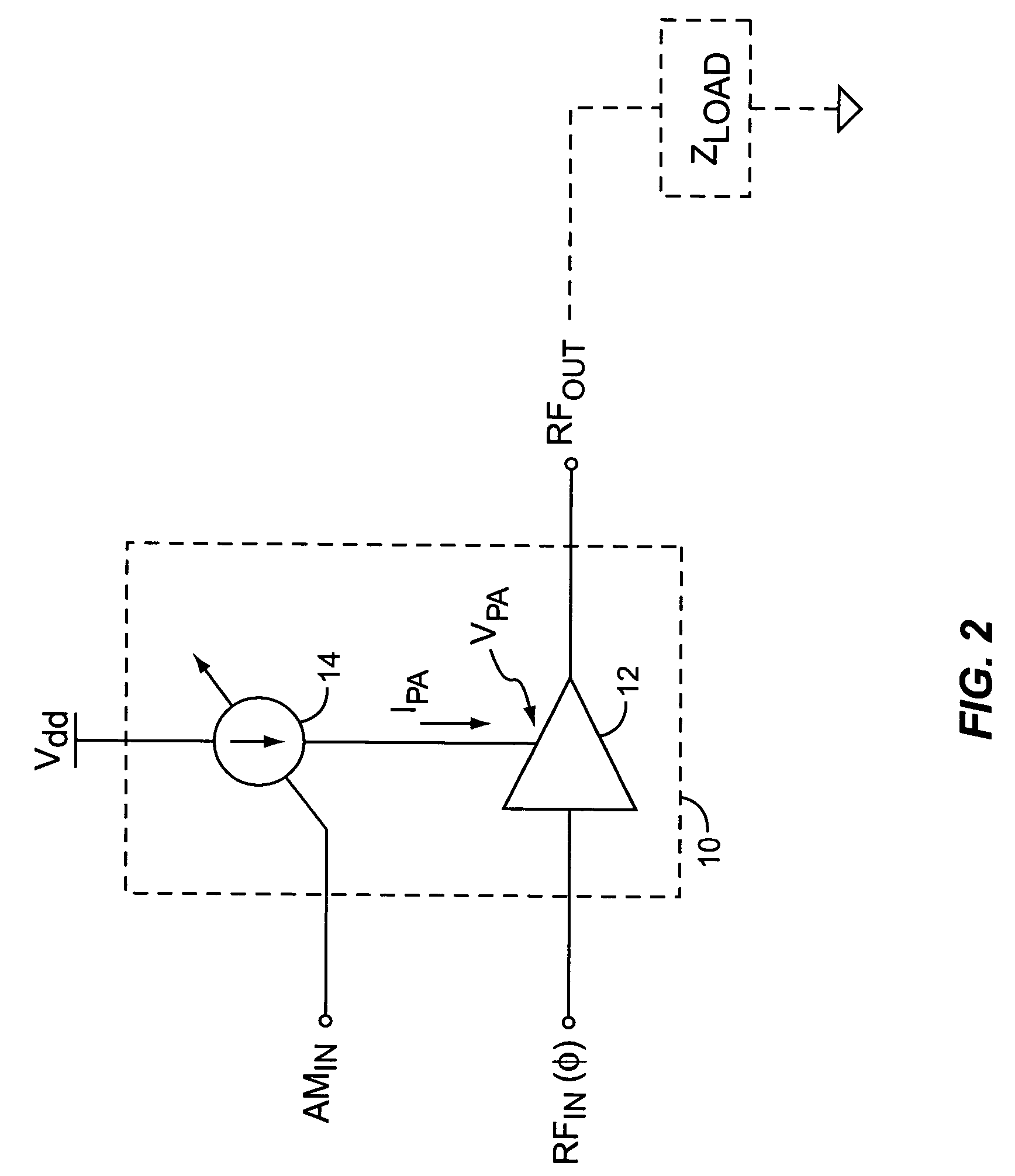
System and method for current-mode amplitude modulation
InactiveUS20050032488A1Efficient and linear amplificationHighly linear envelope modulationSimultaneous amplitude and angle modulationAmplifier modifications to reduce non-linear distortionAntenna impedanceAudio power amplifier
An amplifier circuit includes a power amplifier biased for saturated mode operation, and a controllable current source to provide supply current to the power amplifier. The controllable current source effects desired amplitude modulation of the output signal from the power amplifier by modulating the supply current it provides responsive to an amplitude information signal. In one or more embodiments, the current source includes a circuit that is configured to adjust one or more transmitter operating parameters responsive to detecting changes in the effective DC resistance of the power amplifier. For example, the circuit may generate a compensation signal that reduces the effective DC resistance responsive to detecting that the effective DC resistance has undesirably increased. By way of non-limiting examples, such compensation may be effected by changing a current mirror, an amplifier-to-antenna impedance matching, an amplifier bias or device size, or imposing some form of transmit signal back-off.
Owner:ERICSSON INC
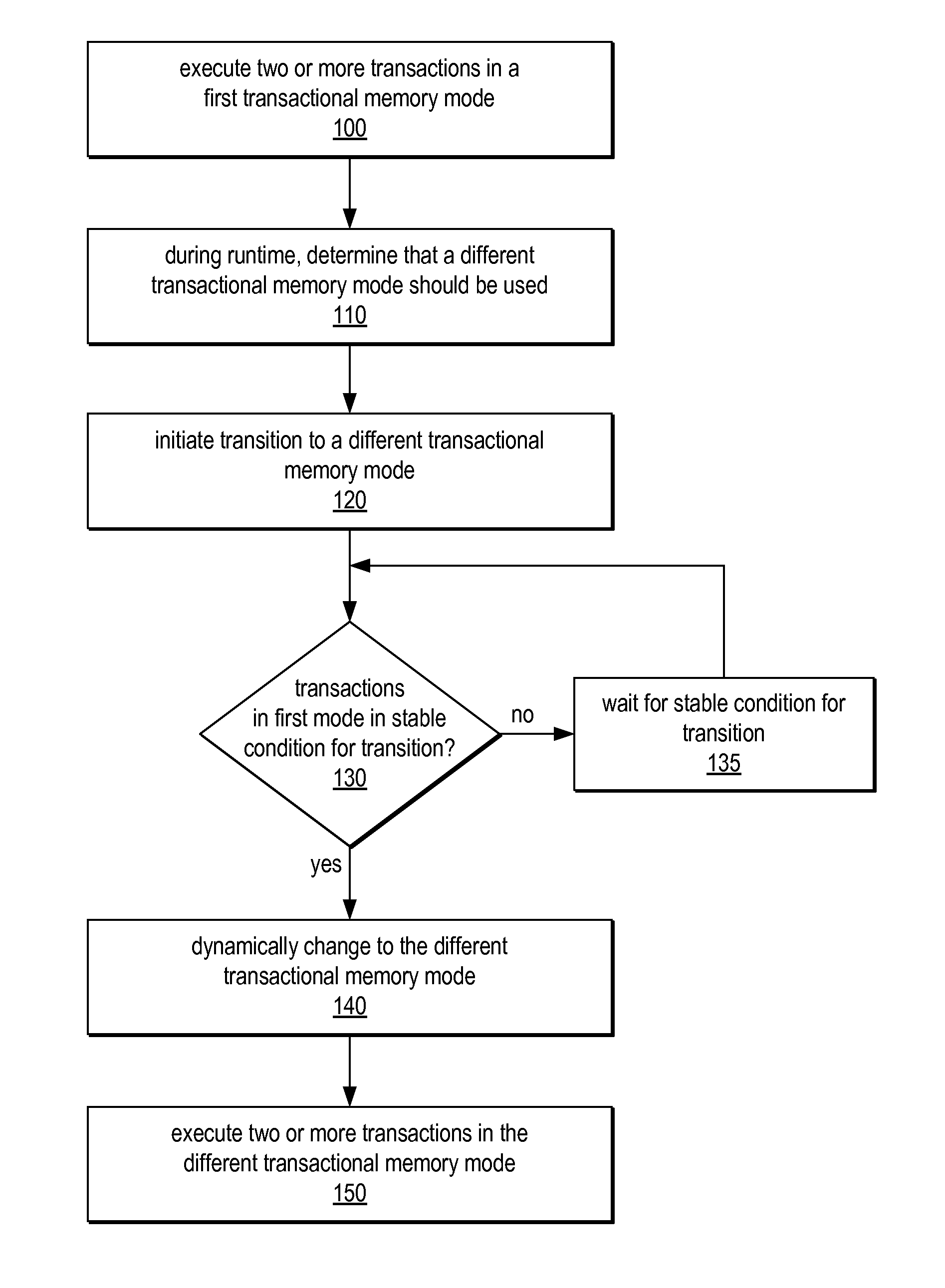
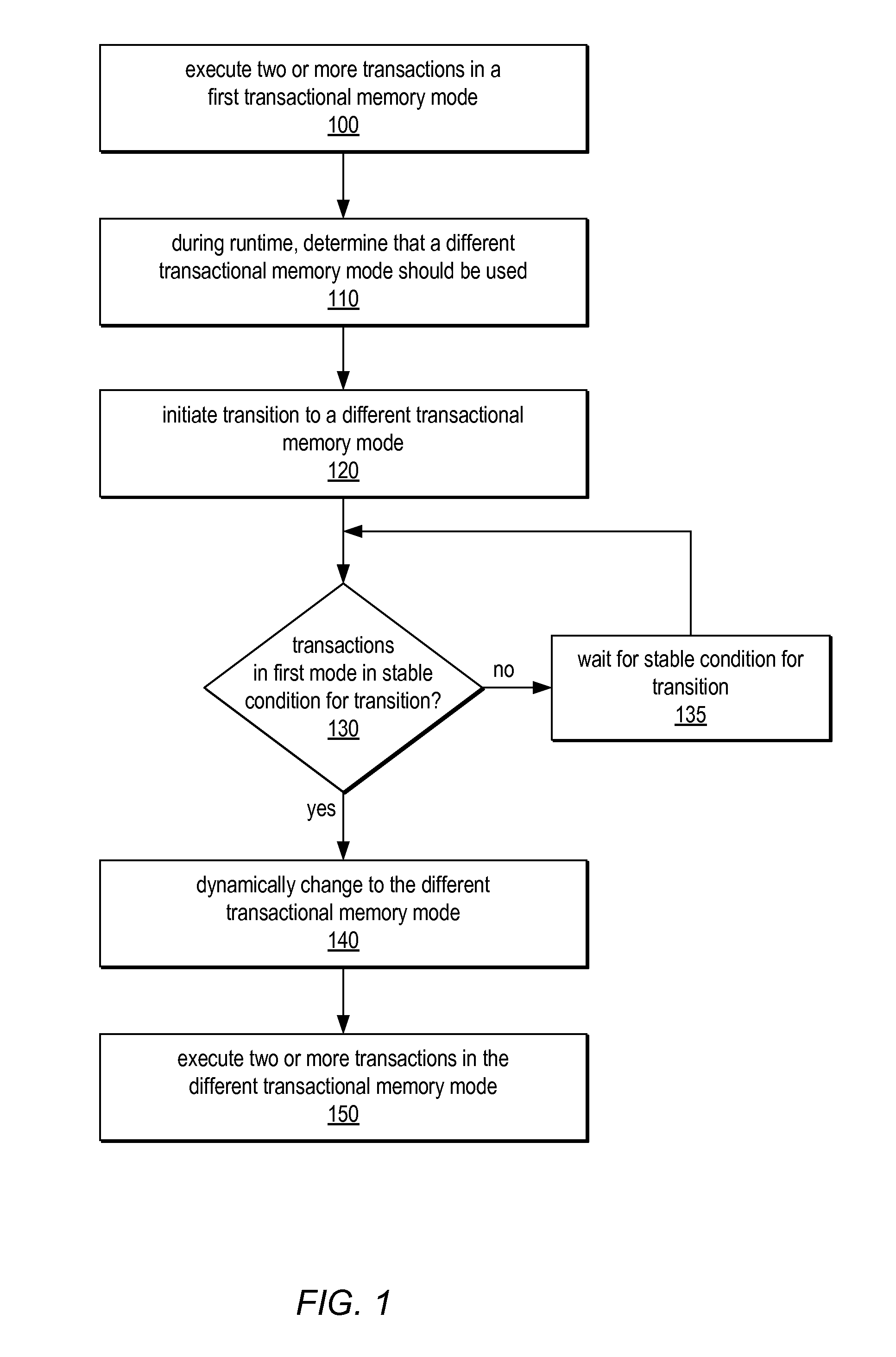
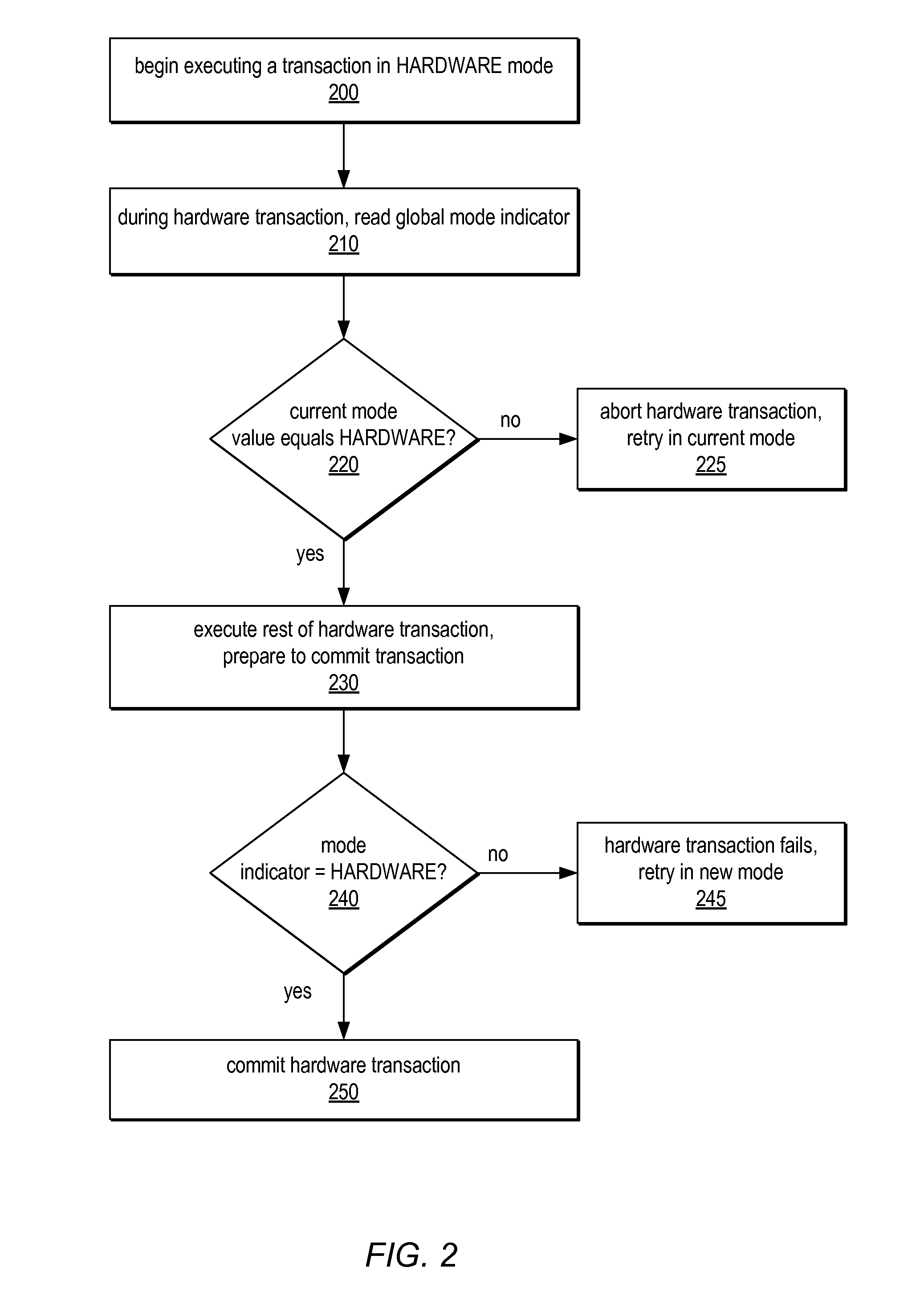
System and Method for Supporting Phased Transactional Memory Modes
ActiveUS20090172306A1Reduce difficultyMaximum flexibilityProgram control using stored programsDigital computer detailsParallel computingTransactional memory
A phased transactional memory (PhTM) may support a plurality of transactional memory implementations, including software, hardware, and hybrid implementations, and may provide mechanisms for dynamically transitioning between transactional memory modes in response to changing workload characteristics; upon discovering that the current mode does not perform well, is not suitable, or does not support functionality required for particular transactions; or according to scheduled phases. A system providing PhTM may be configured to transition from a first transactional memory mode to a second transactional memory mode while ensuring that transactions executing in the first transactional memory mode do not interfere with correct execution of transactions in the second transactional memory mode. The system may be configured to abort transactions in progress or to wait for transactions to complete, be aborted, or reach a safe transition point before transitioning to a new mode, and may use a global mode indicator in coordinating transitions.
Owner:ORACLE INT CORP
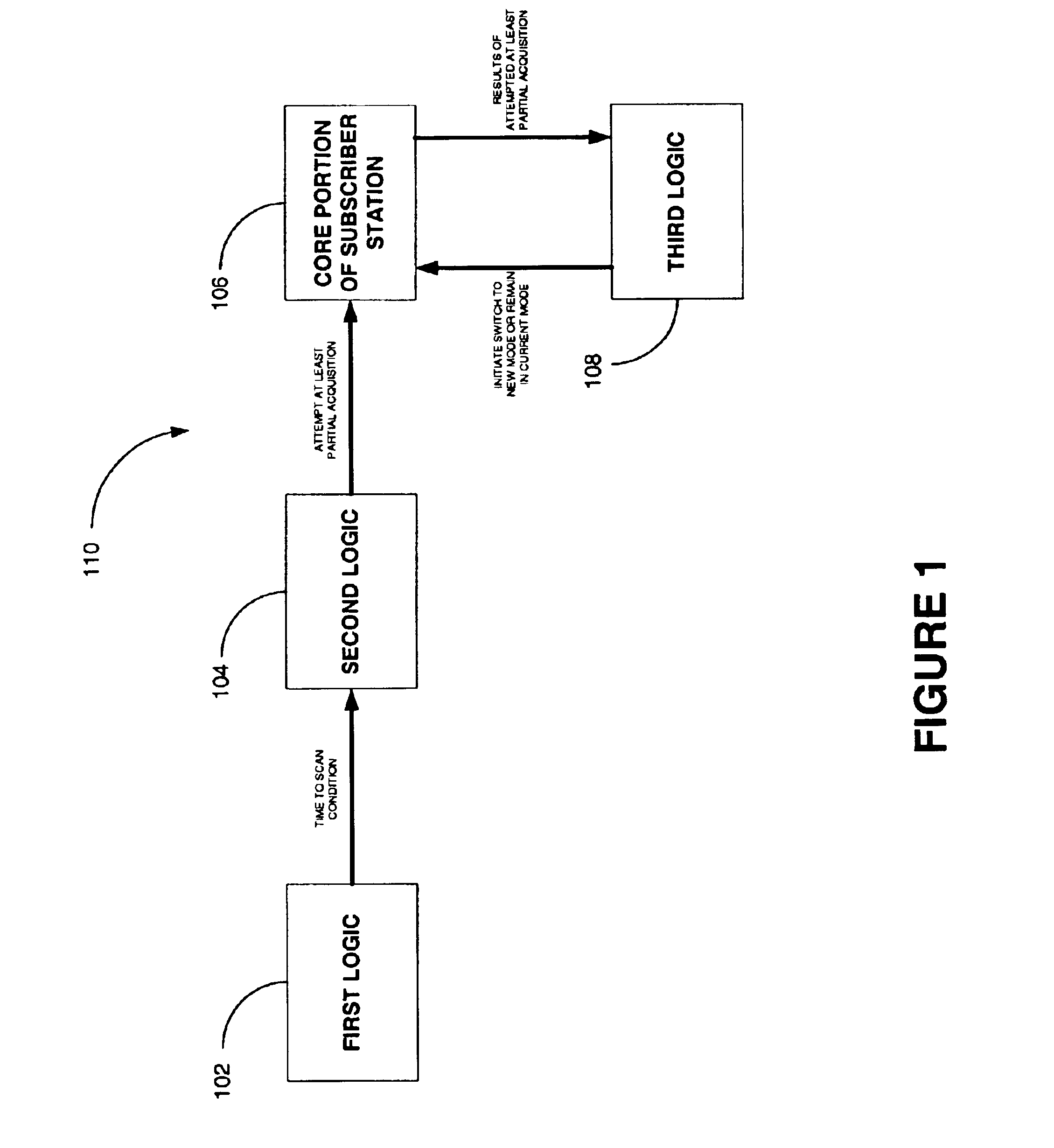
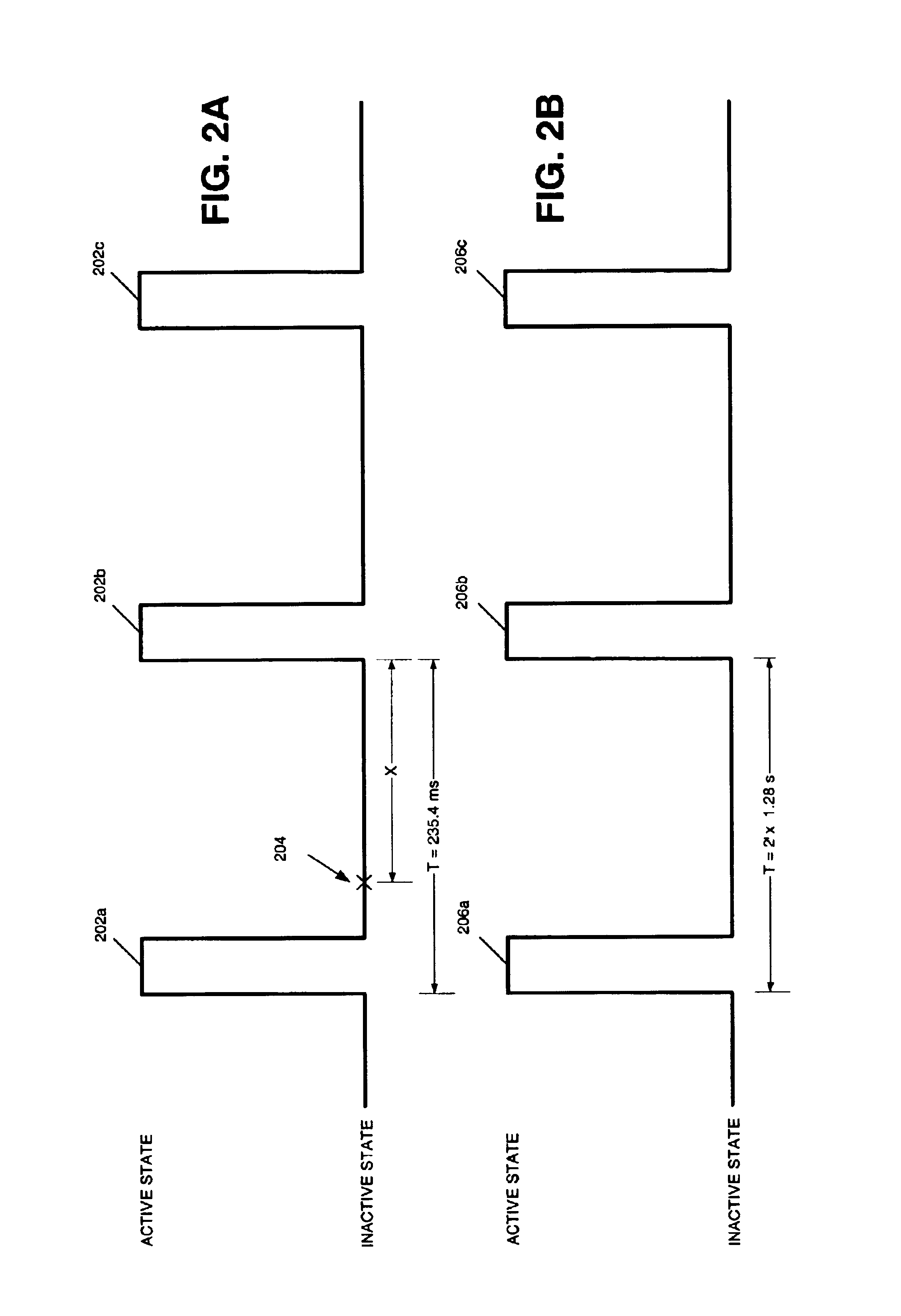
Subscriber station with dynamic multi-mode service acquisition capability
ActiveUS6957068B2Capable of operatingCordless telephonesPower managementTime conditionTelecommunications
A system for providing a dynamic multi-mode service acquisition capability to a subscriber station is provided. The subscriber station is capable of operating in two or more modes of operation. A time to scan condition is indicated while the subscriber station is operating in a current mode of operation having active and inactive states. Responsive thereto, the system stores state information for the current mode of operation, and attempts at least a partial acquisition of communications services in accordance with another mode of operation. The at least partial acquisition attempt is scheduled to be initiated while the subscriber station is operating in the inactive state in the current mode of operation, and completed before the subscriber station transitions back to the active state in the current mode of operation. If the acquisition attempt is successful, the subscriber station transitions to the new mode of operation, maintaining appropriate registration. If unsuccessful, the subscriber station uses the stored state information to resume operating in the current mode of operation.
Owner:QUALCOMM INC
Thermostat display system providing animated icons
InactiveUS20070045433A1Energy efficiencyExtend battery lifeMechanical apparatusComputer controlIllusionAnimation
A visual display system and method for a digital thermostat having a user display screen to provide operational status information of the heating and / or cooling equipment controlled by the thermostat is provided. This visual display system utilizes animated icons to show operational status of the heating and / or cooling equipment. Static icons may also be used in one embodiment to indicate the current mode of the thermostat. Animated icons for the heating system, the cooling system, and fan operation are provided. The illusion of animation is provided by overwriting or replacing a displayed image with another image at a predetermined frequency. This predetermined frequency may be changed programmatically, and varied to provide different visual effects.
Owner:RANCO OF DELAWARE
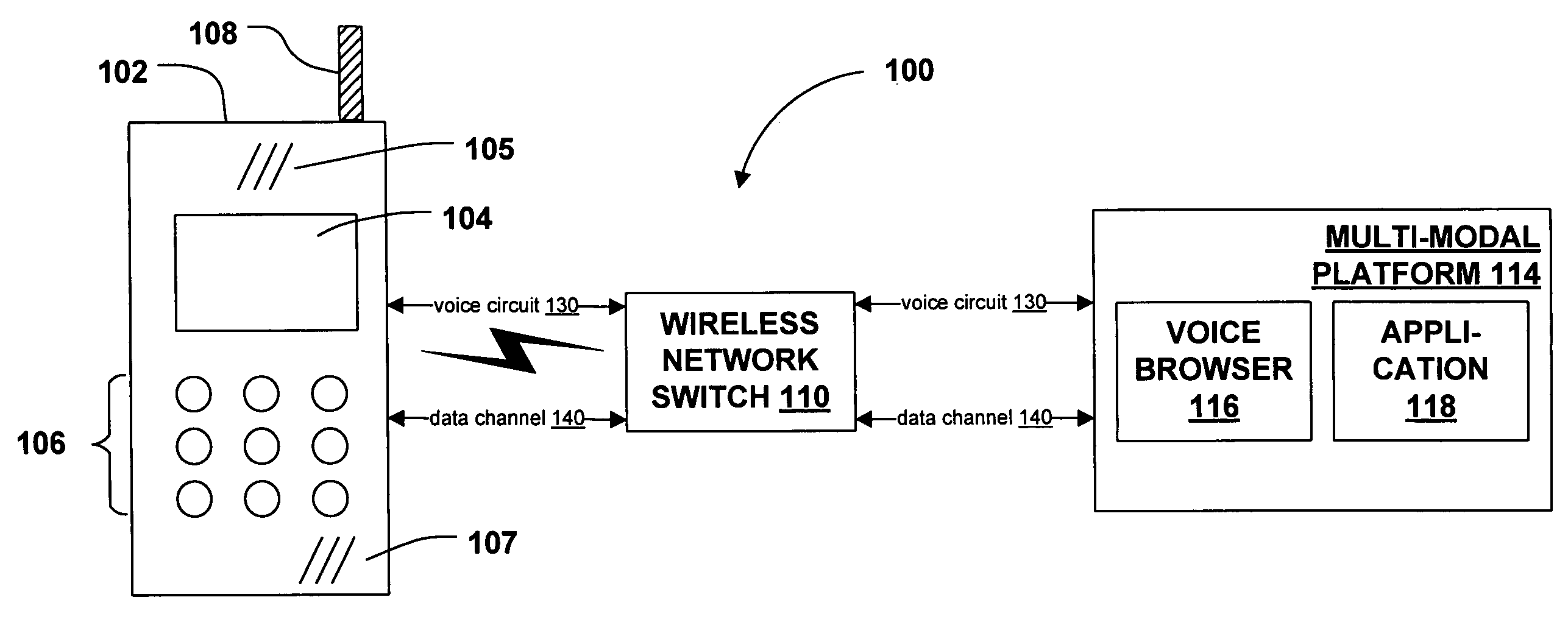
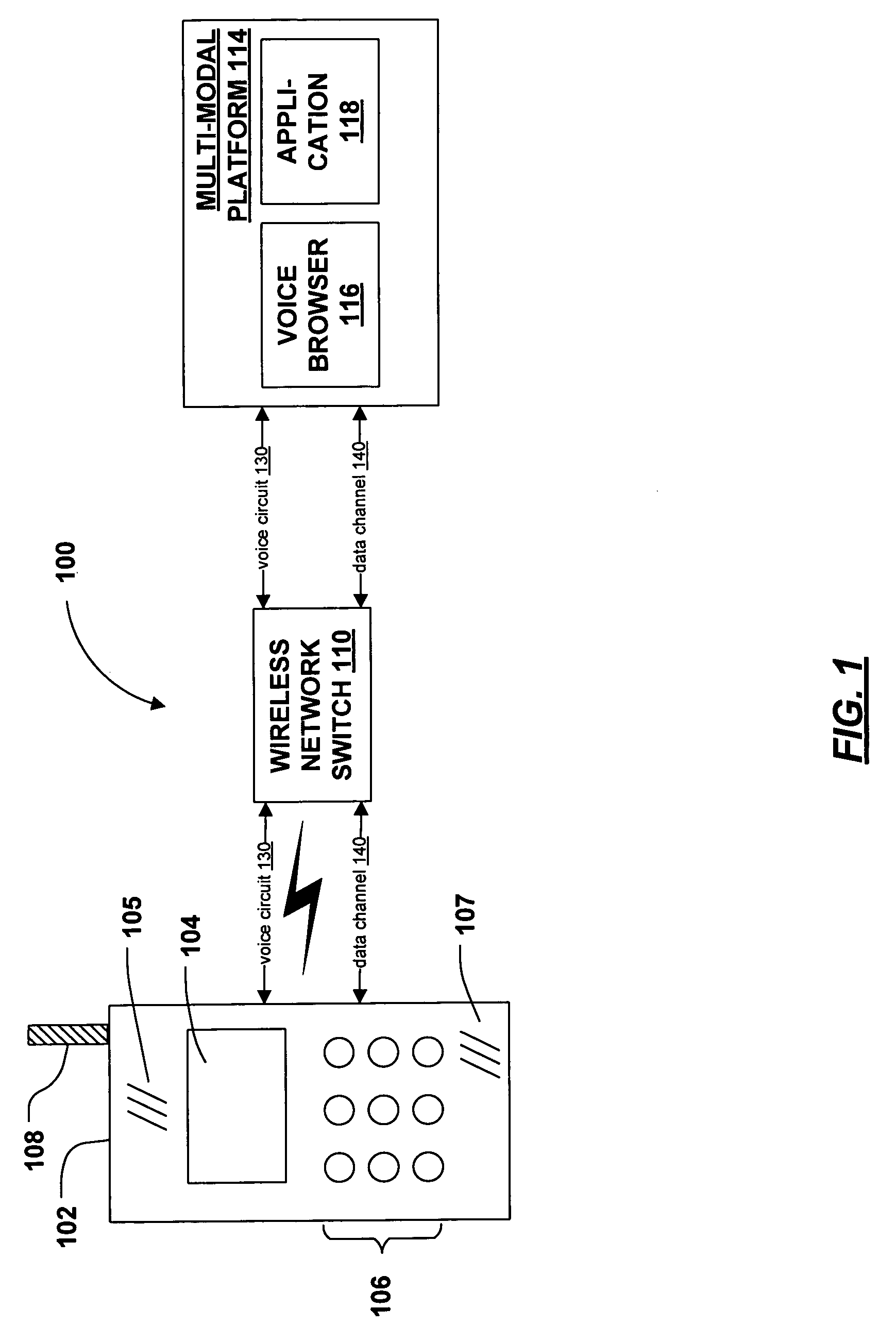
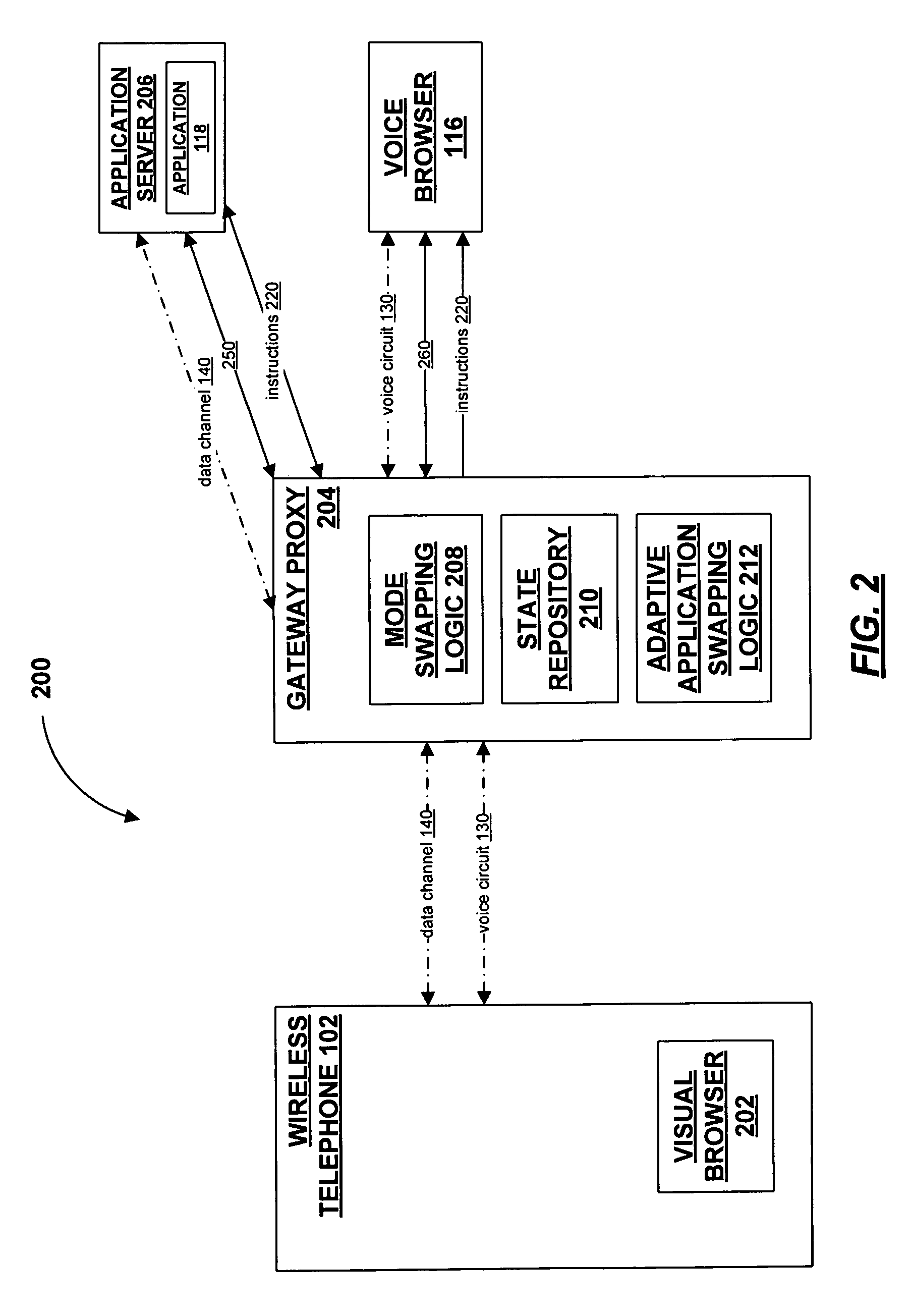
Mode-swapping in multi-modal telephonic applications
Owner:CDN INNOVATIONS LLC
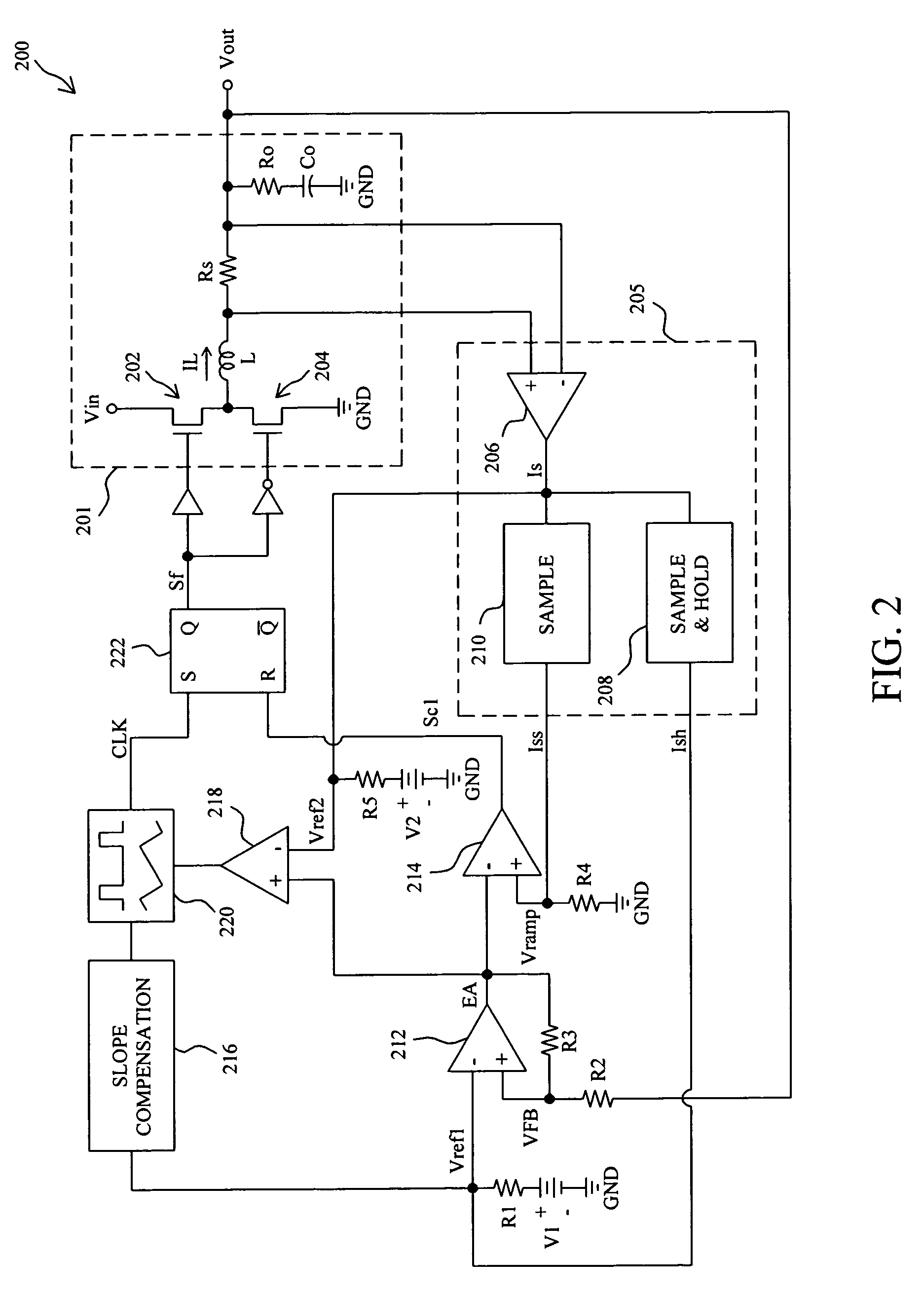
Fixed-frequency current mode converter and control method thereof
InactiveUS20060043943A1Rapid responseDc-dc conversionElectric variable regulationInductorCurrent mode
A fixed-frequency current mode converter comprises a power stage to produce an inductor current and an output voltage, an error amplifier to generate an error signal from the difference between the output voltage and a reference voltage varied with the inductor current, a comparator to compare the error signal with a ramp signal varied with the inductor current to generate a comparison signal, and a PWM generator to generate a PWM signal in response to a fixed-frequency clock and the comparison signal to drive the power stage. A second comparator is further comprised to compare the error signal with a second reference voltage varied with the inductor current, and generates a second comparison signal to reset the clock when the error signal is lower than the second reference voltage.
Owner:RICHTEK TECH
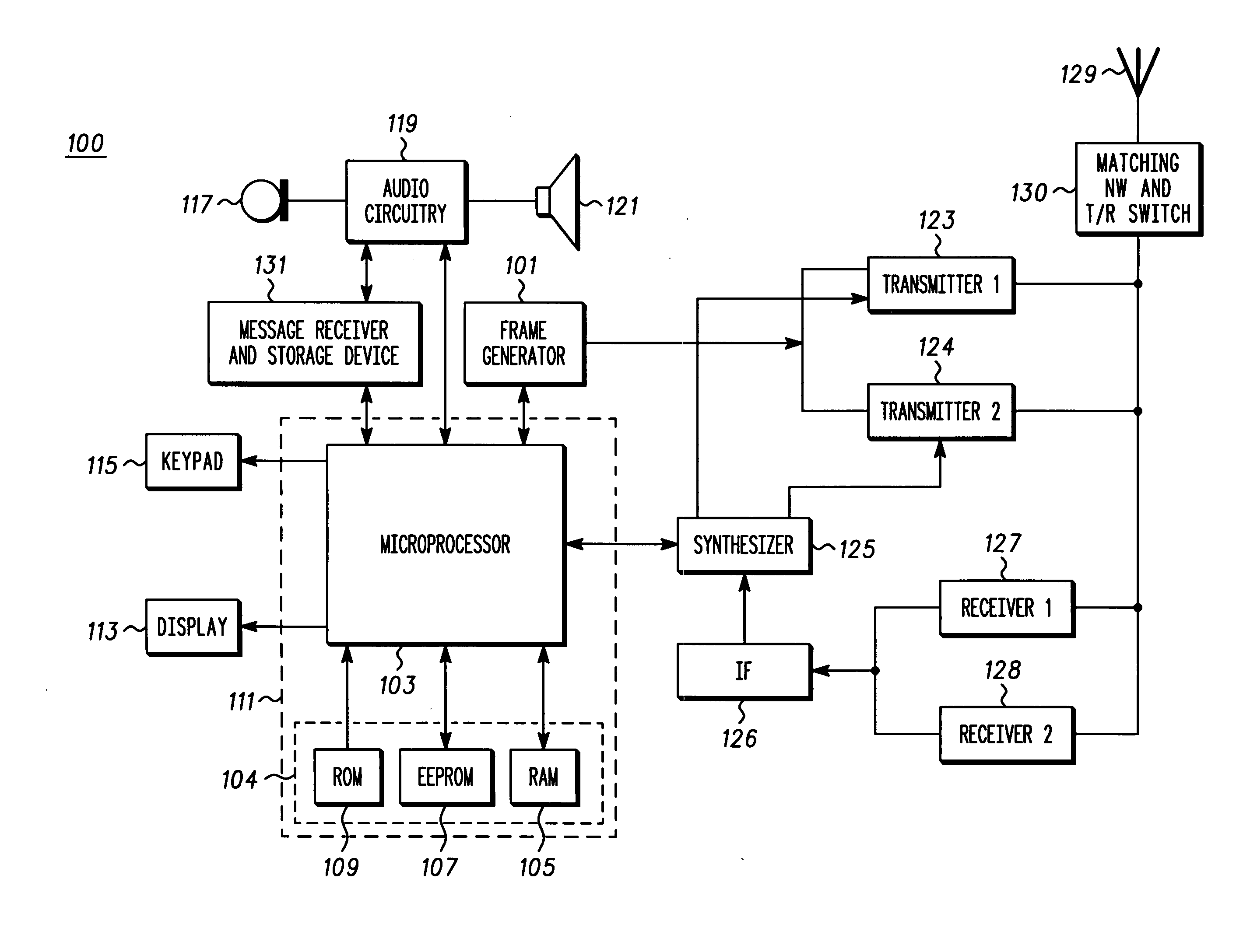
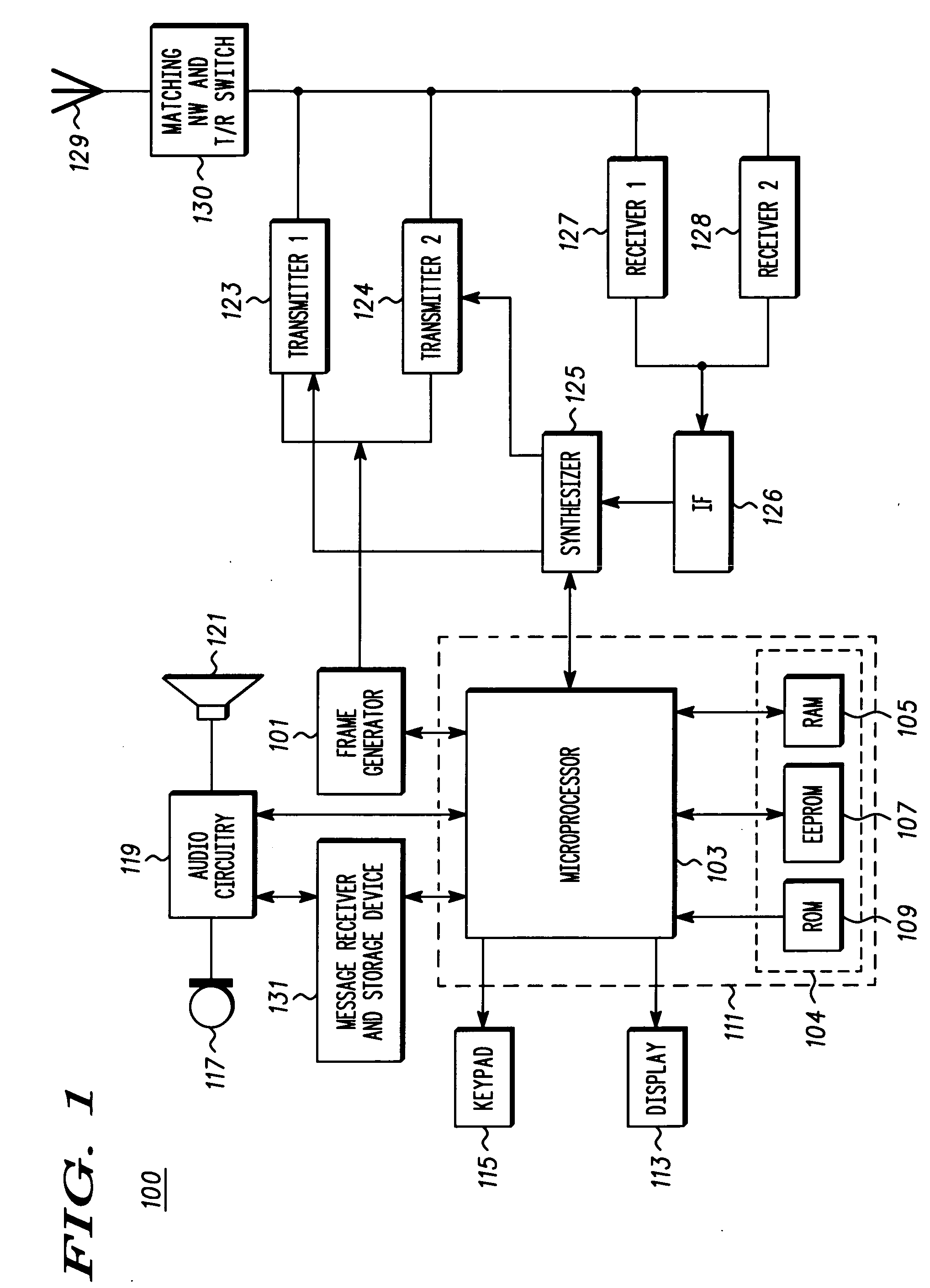
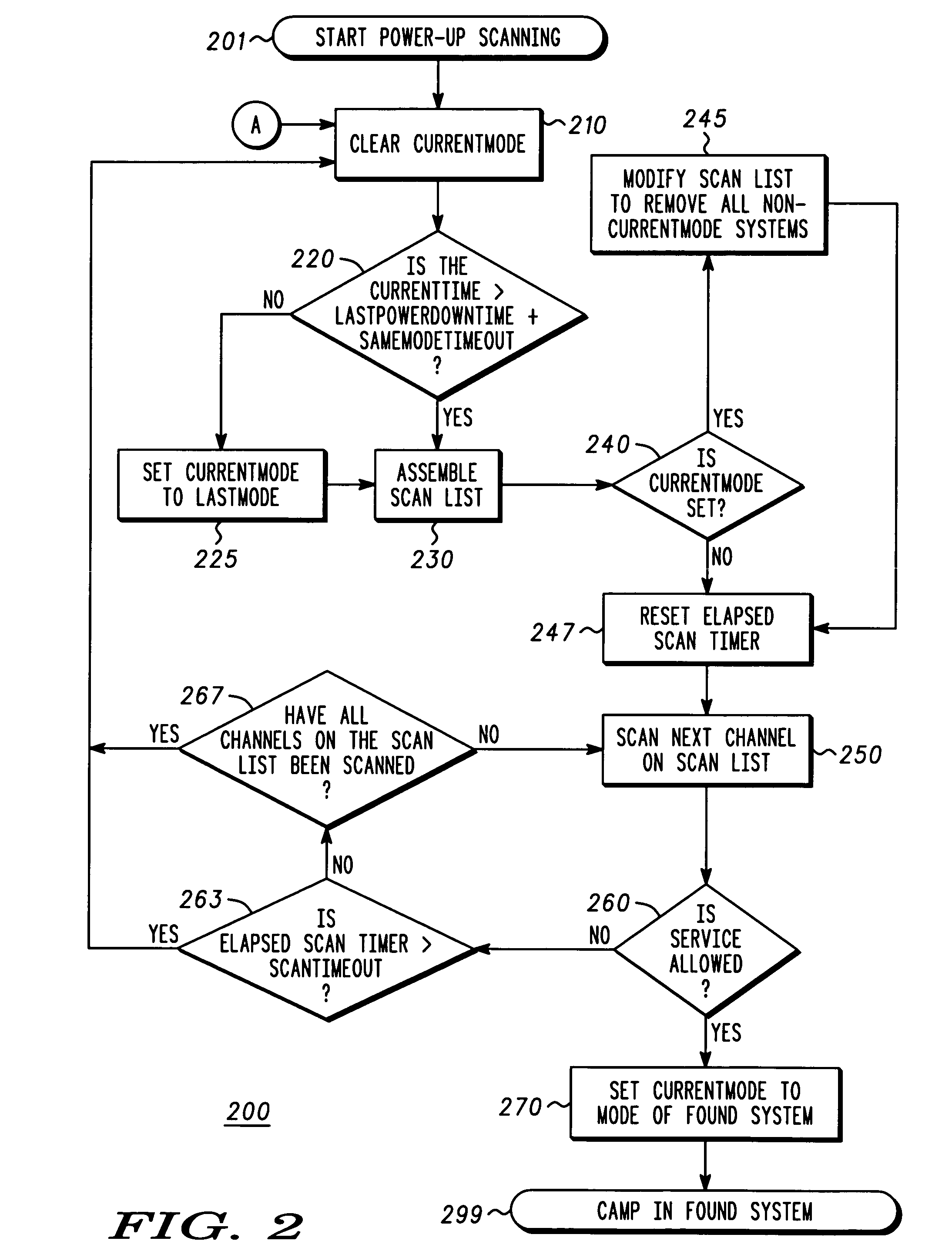
Multiple mode scanning
A method (200) for scanning of channels by a multi-mode communication device includes the steps of making a scan list (230) operative for more than one mode, modifying the scan list (245) to remove all non-current-mode systems, and sequentially scanning (450) a highest priority channel on the modified scan list. If the communication device has recently found service on a particular system in a first mode, the communication device will only search for systems that are associated with that first mode. This use of a modified scan list applies both to power up scanning situations and scanning after power up situations. Modifying a scan list to remove all non-current mode systems allows the multi-mode communication device to avoid scanning for systems that are geographically unavailable and instead acquire a system in less time and with less power consumption.
Owner:MOTOROLA INC
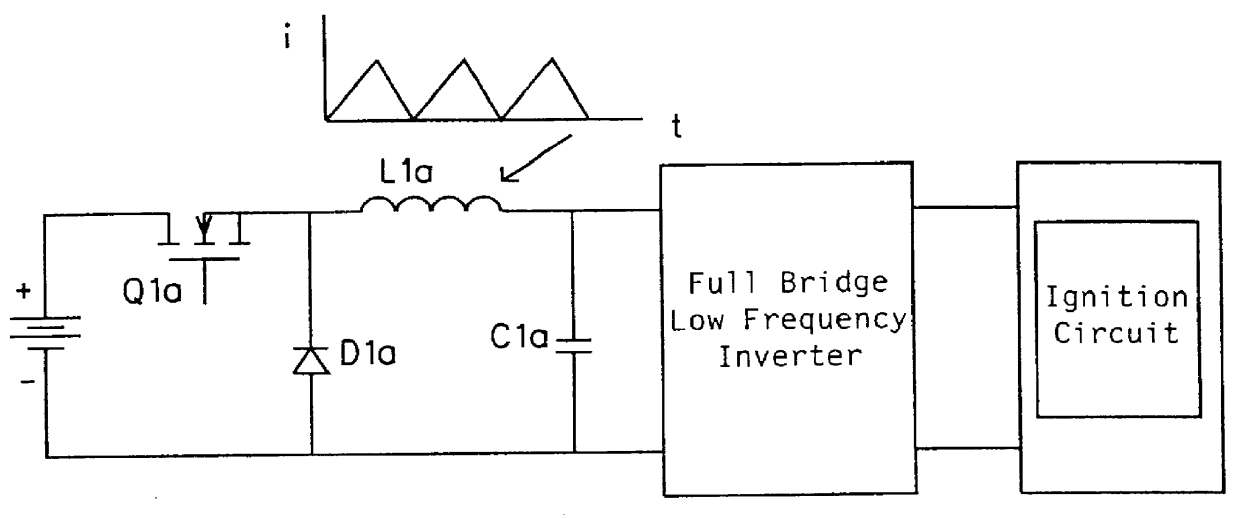
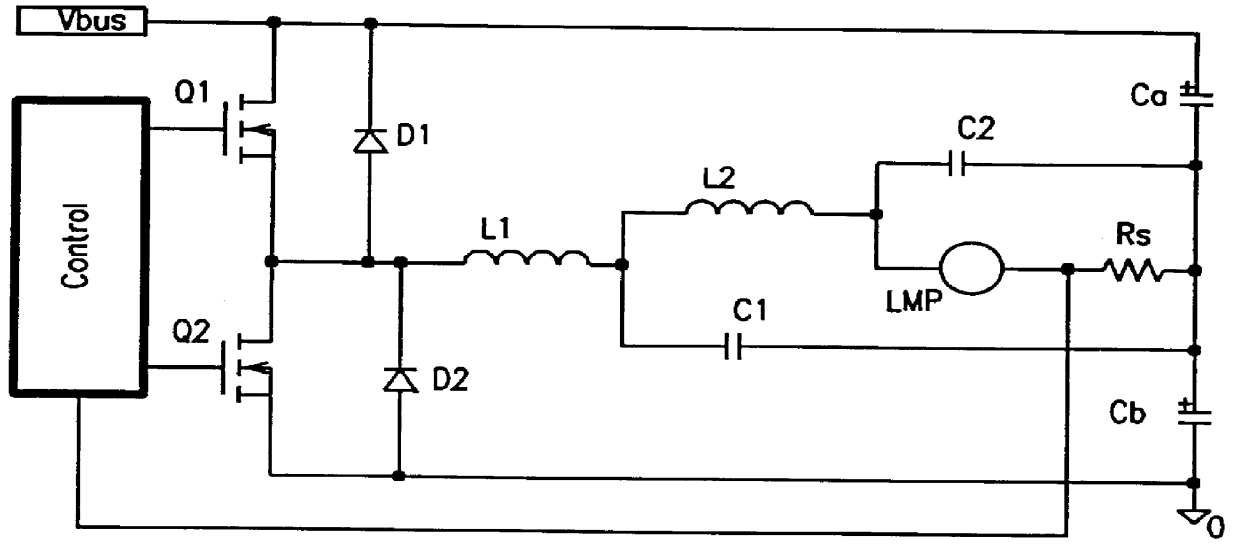
Driving circuit for high intensity discharge lamp electronic ballast
InactiveUS6020691AImprove performanceAvoiding excessive currentElectric light circuit arrangementGas discharge lamp usageLamp currentEngineering
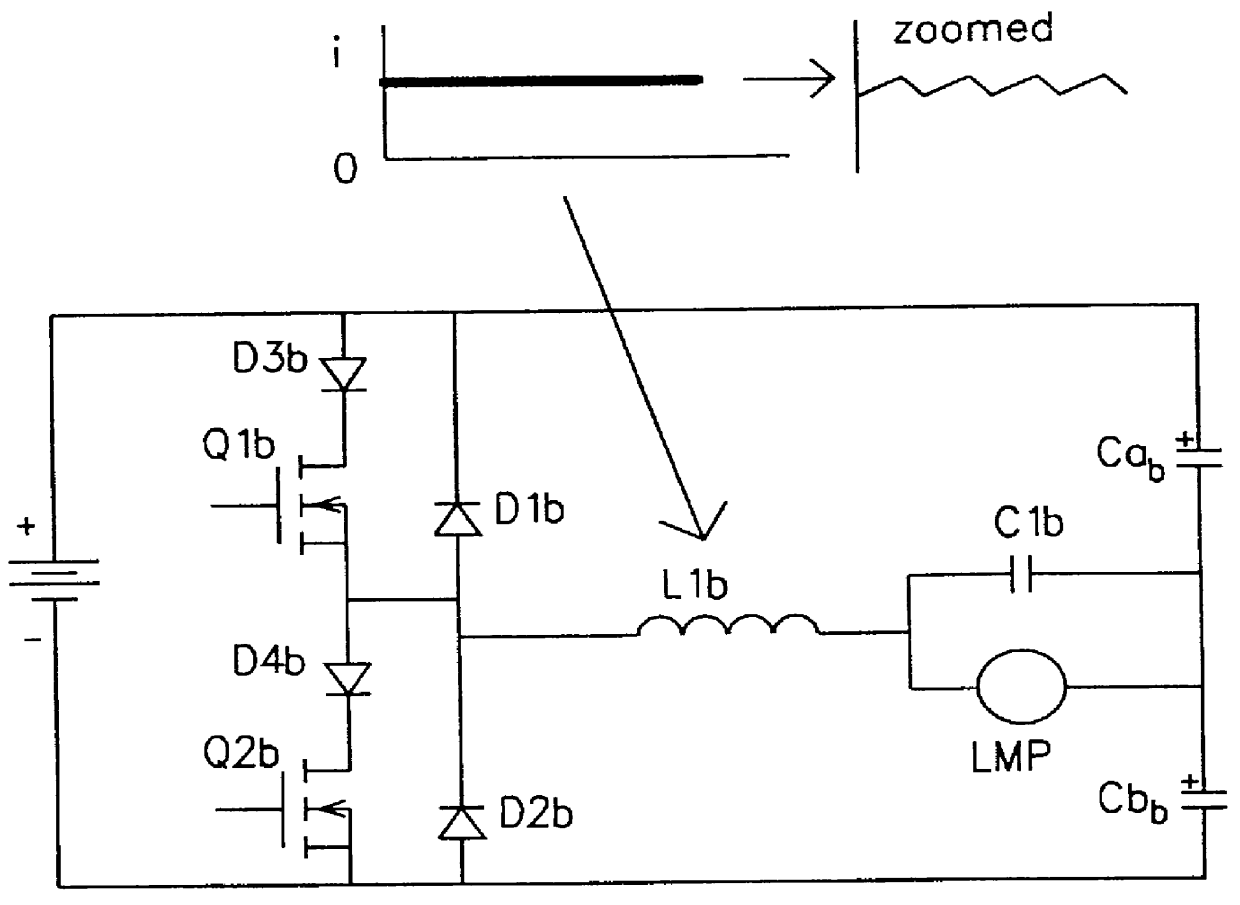
A circuit arrangement and control thereof for igniting a high intensity discharge (HID) lamp, for reducing the high frequency ripple superimposed on the low frequency rectangular waveform lamp current after ignition, and for increased circuit efficiency. The high frequency ignition voltage is only applied to the lamp during ignition phase and is mainly generated by the second stage of the low pass (LP) filter. The first stage of the LP filter whose resonant frequency is below the second stage further attenuates the high frequency ripple current through the lamp in normal operation. The resulting lamp current is a low frequency rectangular wave with less than 10% high frequency ripple. Acoustic resonance is avoided. The inductor in the first stage of LP filter is operated in discontinuous current mode. Doing so, the active switches are in zero current switching (ZCS) to maximize the circuit efficiency.
Owner:MATSUSHITA ELECTRIC WORKS LTD
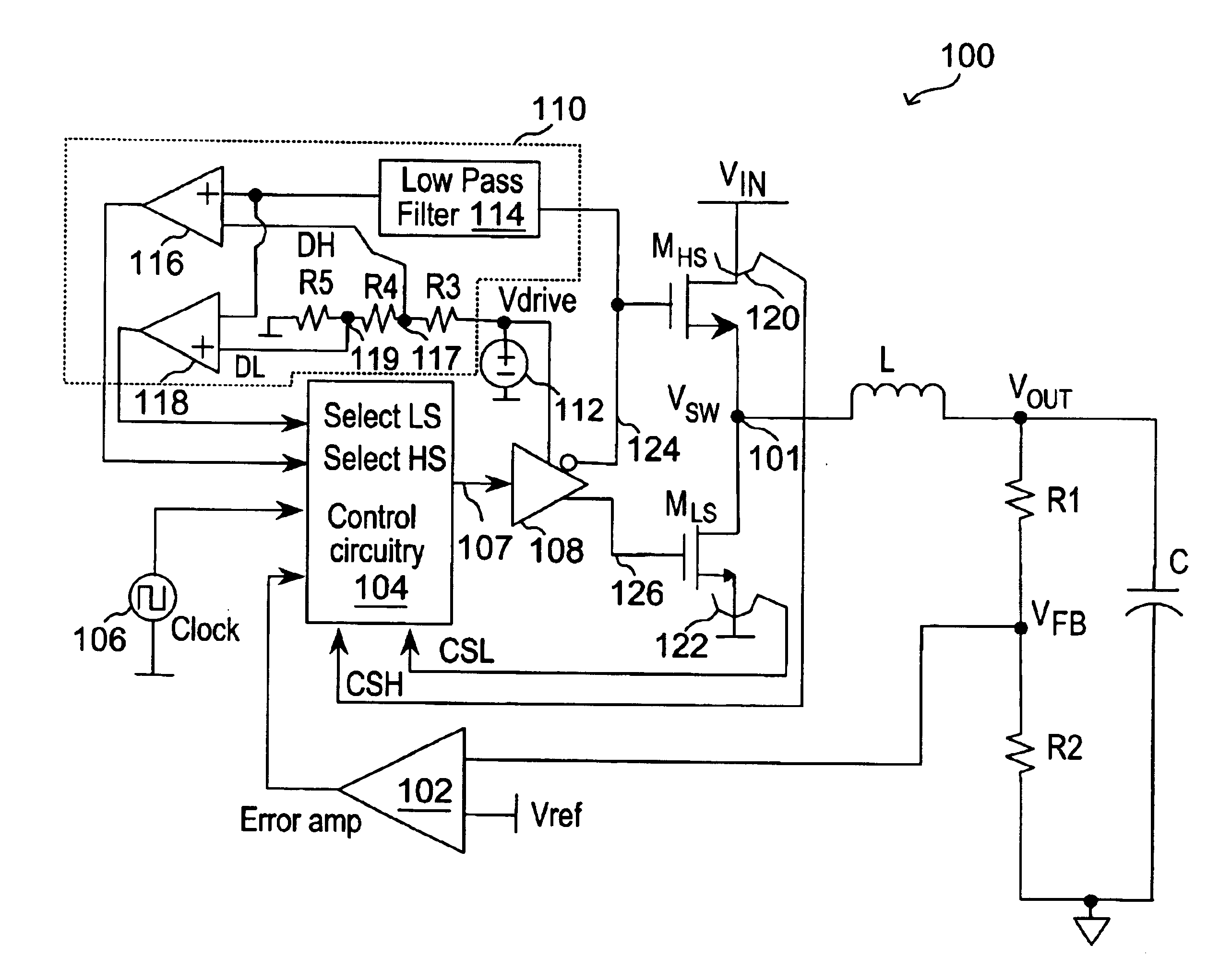
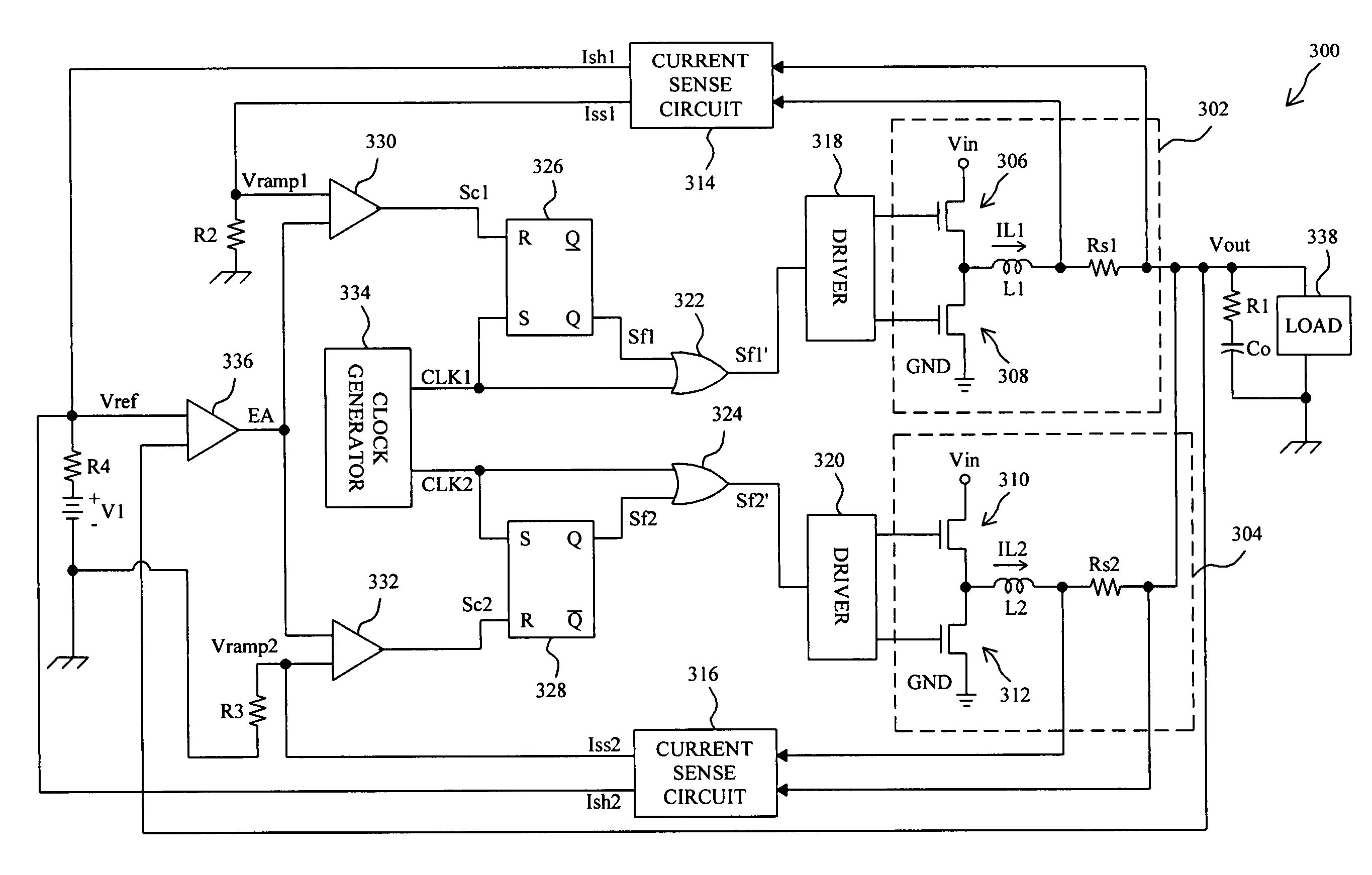
Selective high-side and low-side current sensing in switching power supplies
ActiveUS6853174B1Maintain output voltageIncrease currentEfficient power electronics conversionApparatus without intermediate ac conversionControl signalCurrent mode
A current mode switching regulator implementing a dual sense scheme includes a first current sensing circuit for sensing a current through a first switch and providing a first current sense signal, and a second current sensing circuit for sensing a current through a second switch and providing a second current sense signal. The switching regulator includes a control circuit for generating switch control signals for driving the first and second switches in response to one of the first and second current sense signals. The regulator further includes a duty cycle detection circuit coupled to determine a duty cycle of the switching regulator. The detection circuit asserts a first select signal to select the first current sense signal when the duty cycle exceeds a first threshold level and asserts a second select signal to select the second current sense signal when the duty cycle is less than a second threshold level.
Owner:MICREL
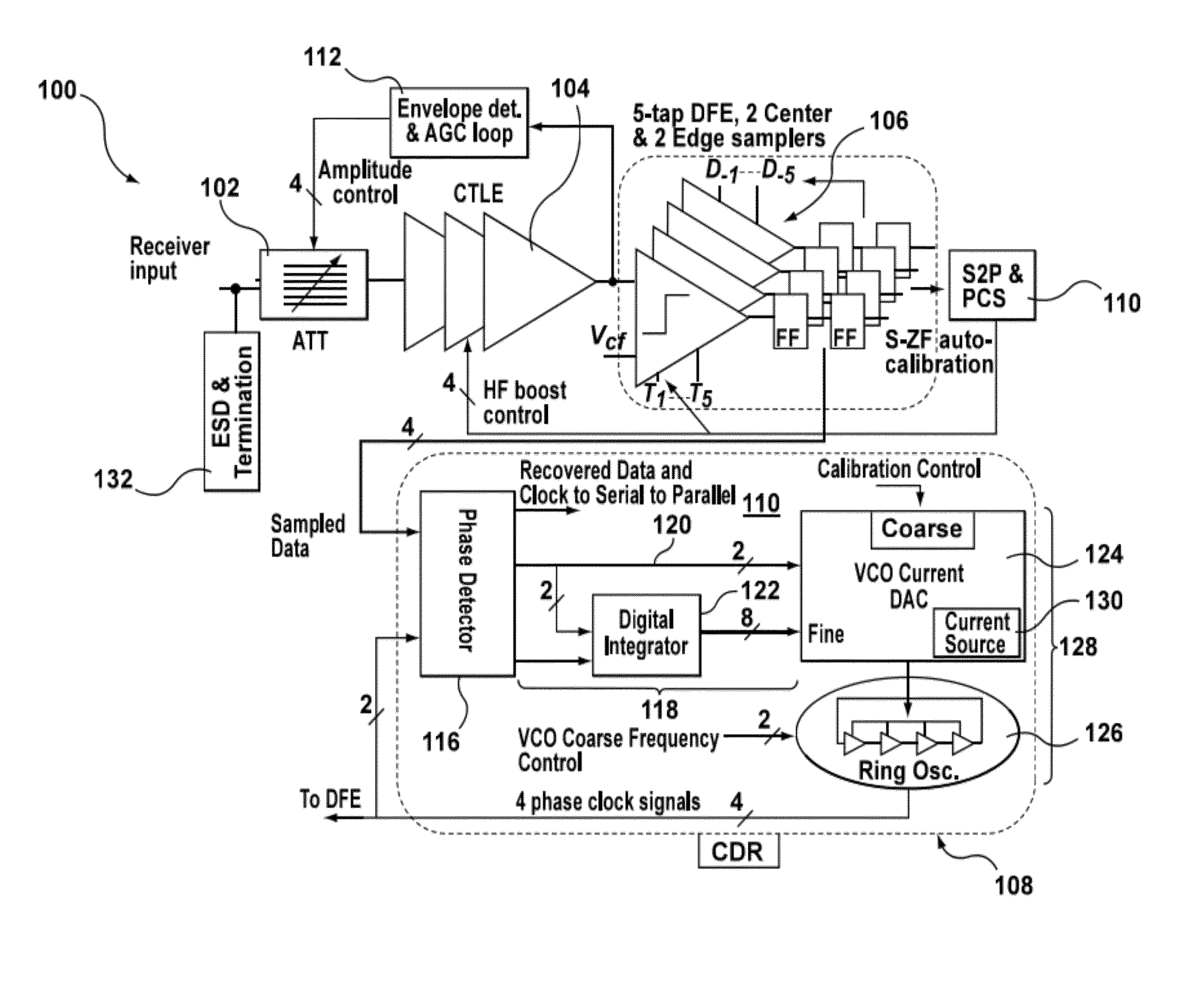
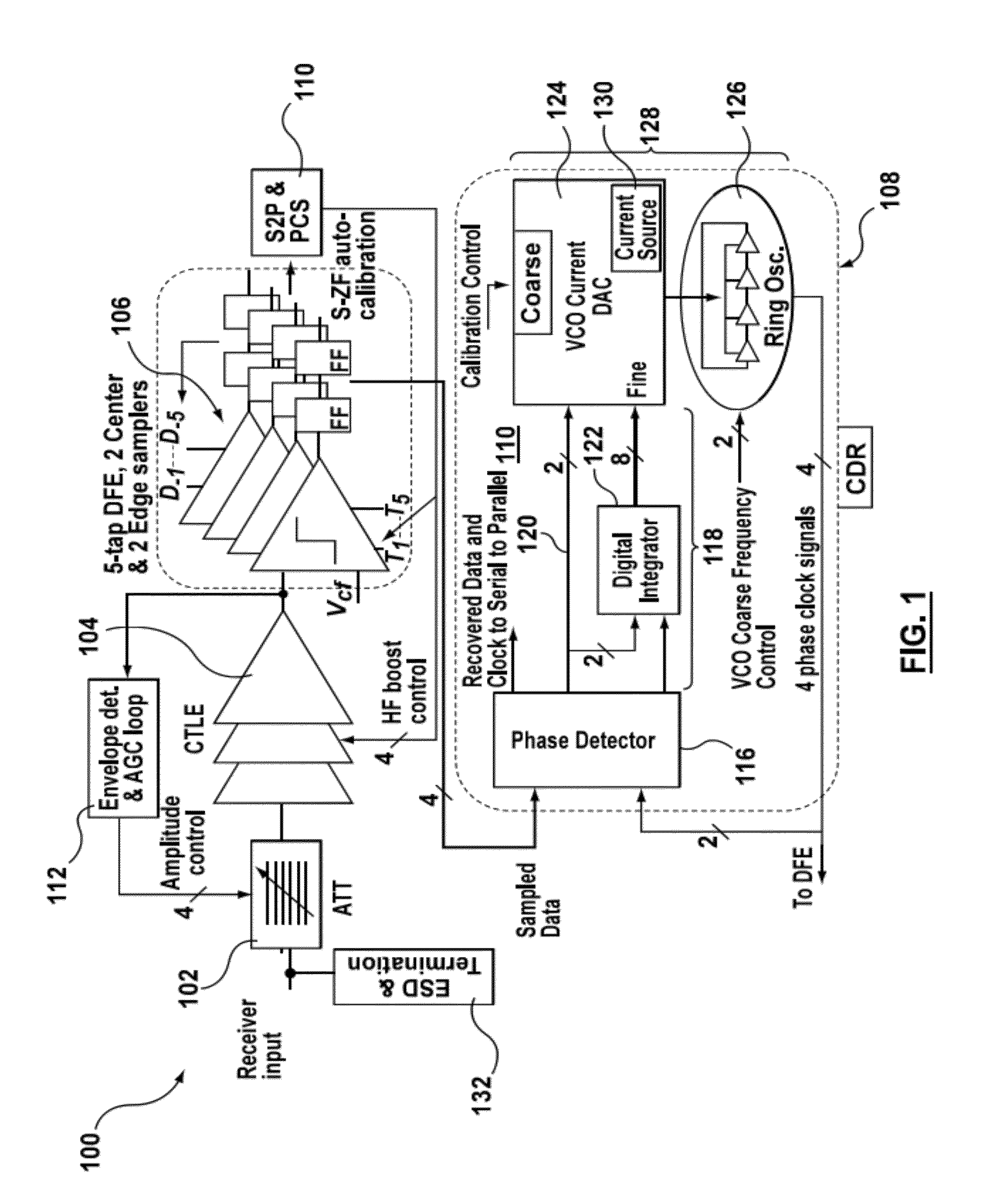
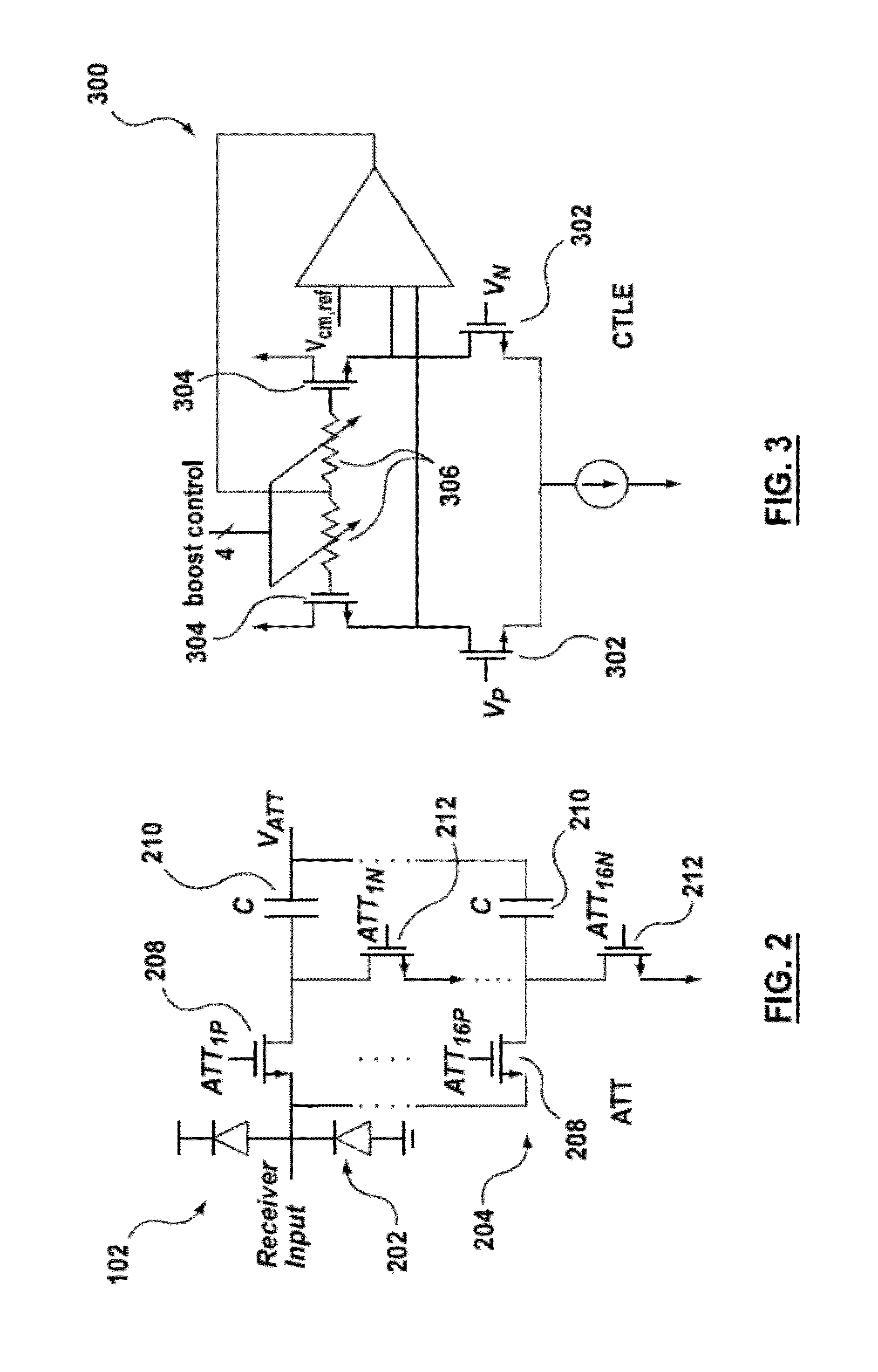
Decision feedback equalizer and transceiver
A decision feedback equalizer, transceiver, and method are provided, the equalizer having at least one comparator, the at least one comparator comprising a first stage, comprising a main branch having two track switches with a resistive load, an offset cancellation branch, a plurality of tap branches with transistor sizes smaller than the main branch, in which previous decisions of the equalizer are mixed with the tap weights using current-mode switching, and a cross coupled latch branch; and a second stage, comprising a comparator module for making decisions based on the outputs of the first stage and a clock input, and a plurality of flip-flops for storing the output of the comparator module.
Owner:RAMBUS INC
Current mode switching regulator with predetermined on time
InactiveUS7250746B2High adjustment accuracyDc-dc conversionElectric variable regulationPower switchingEngineering
Owner:COLLABO INNOVATIONS INC
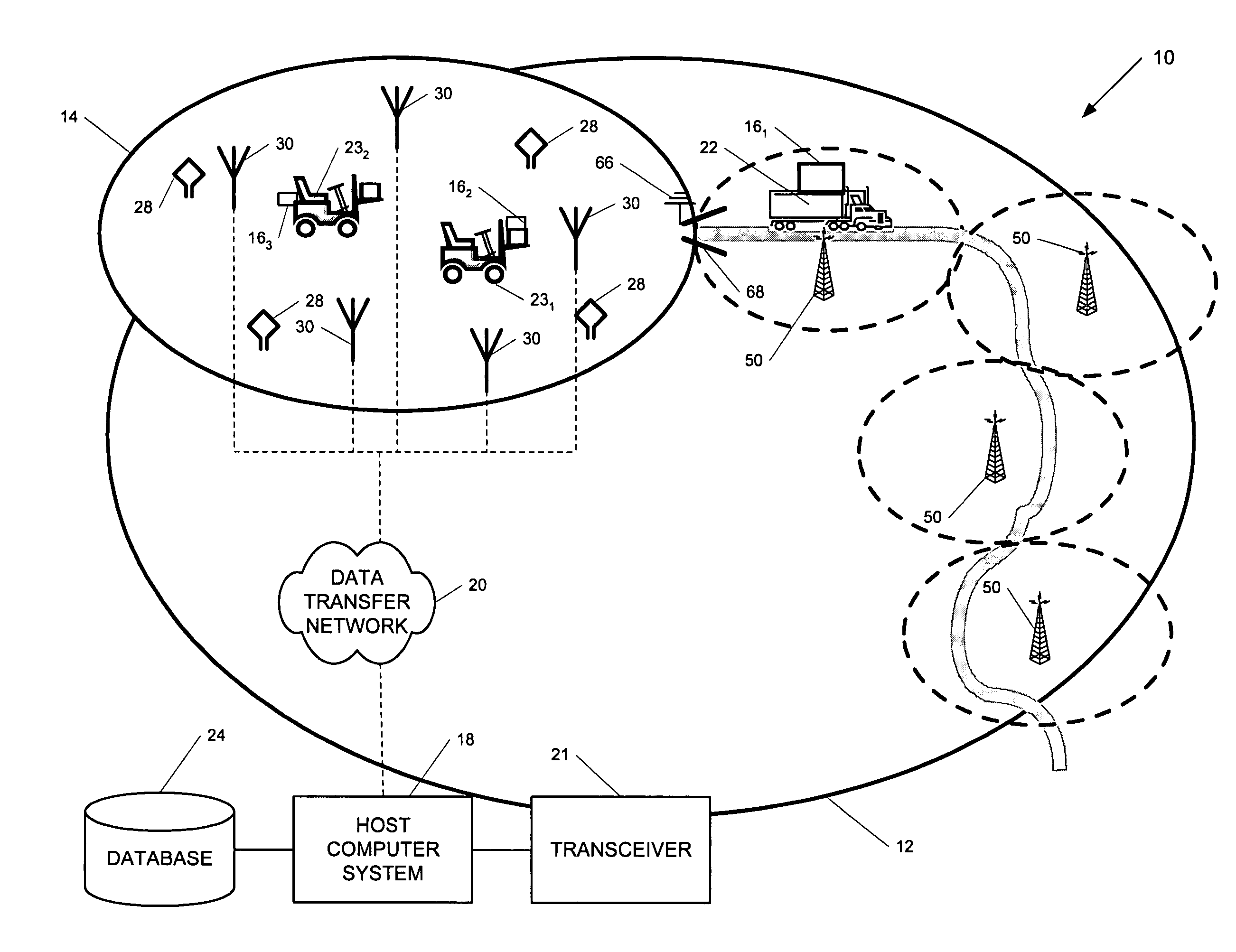
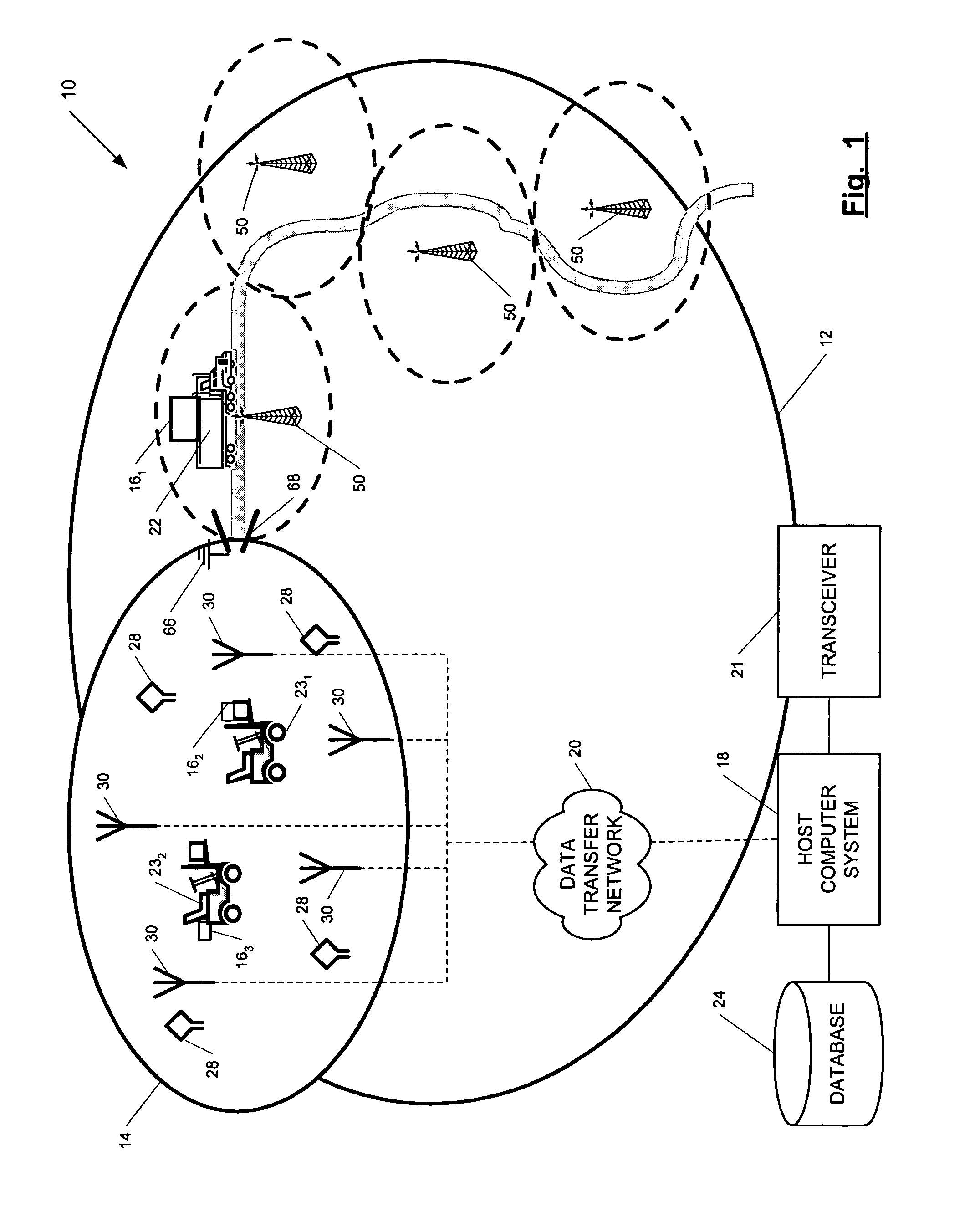
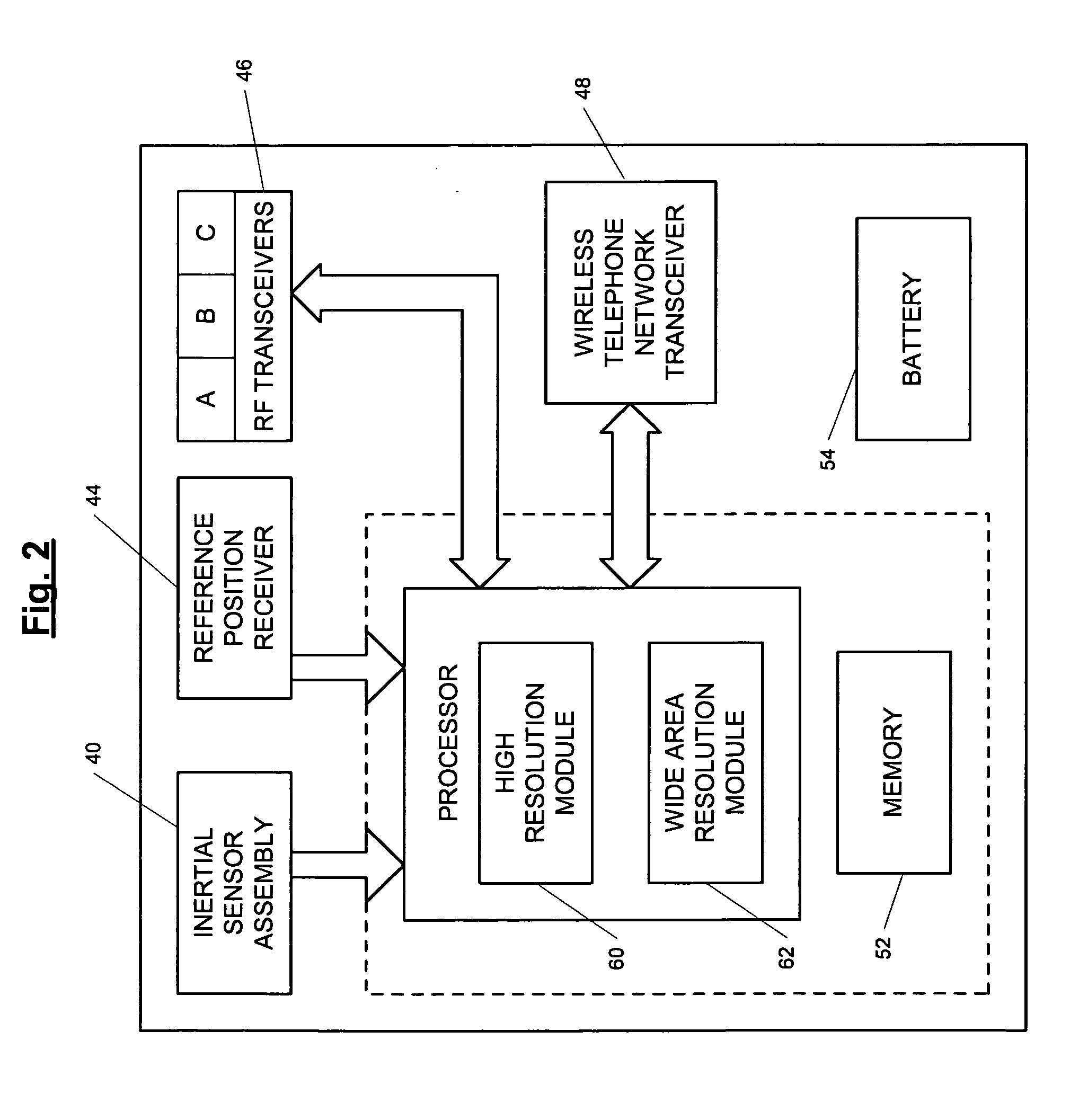
Position-tracking system
ActiveUS7236091B2High position resolutionImprove accuracyRoad vehicles traffic controlElectric/electromagnetic visible signallingObject basedTransceiver
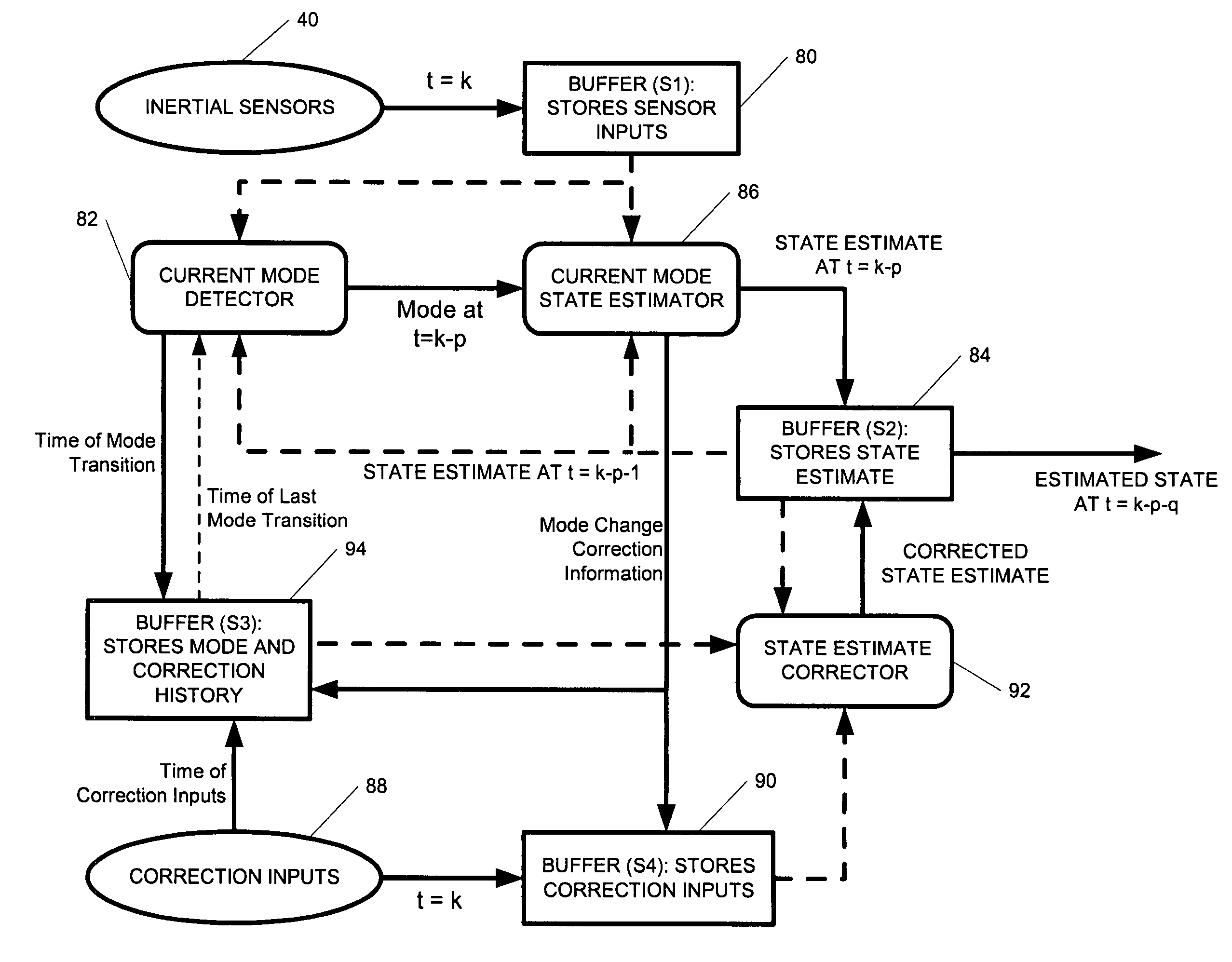
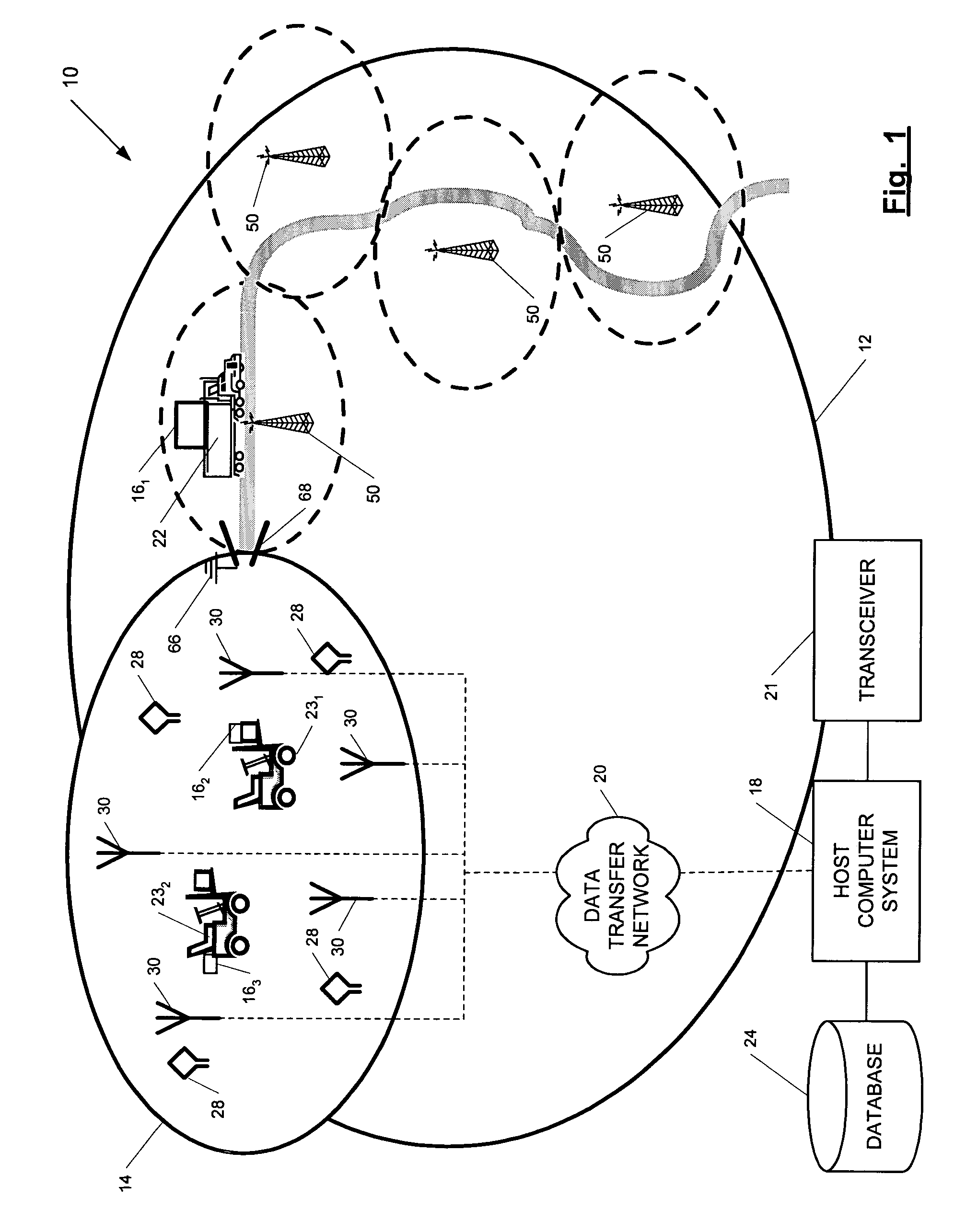
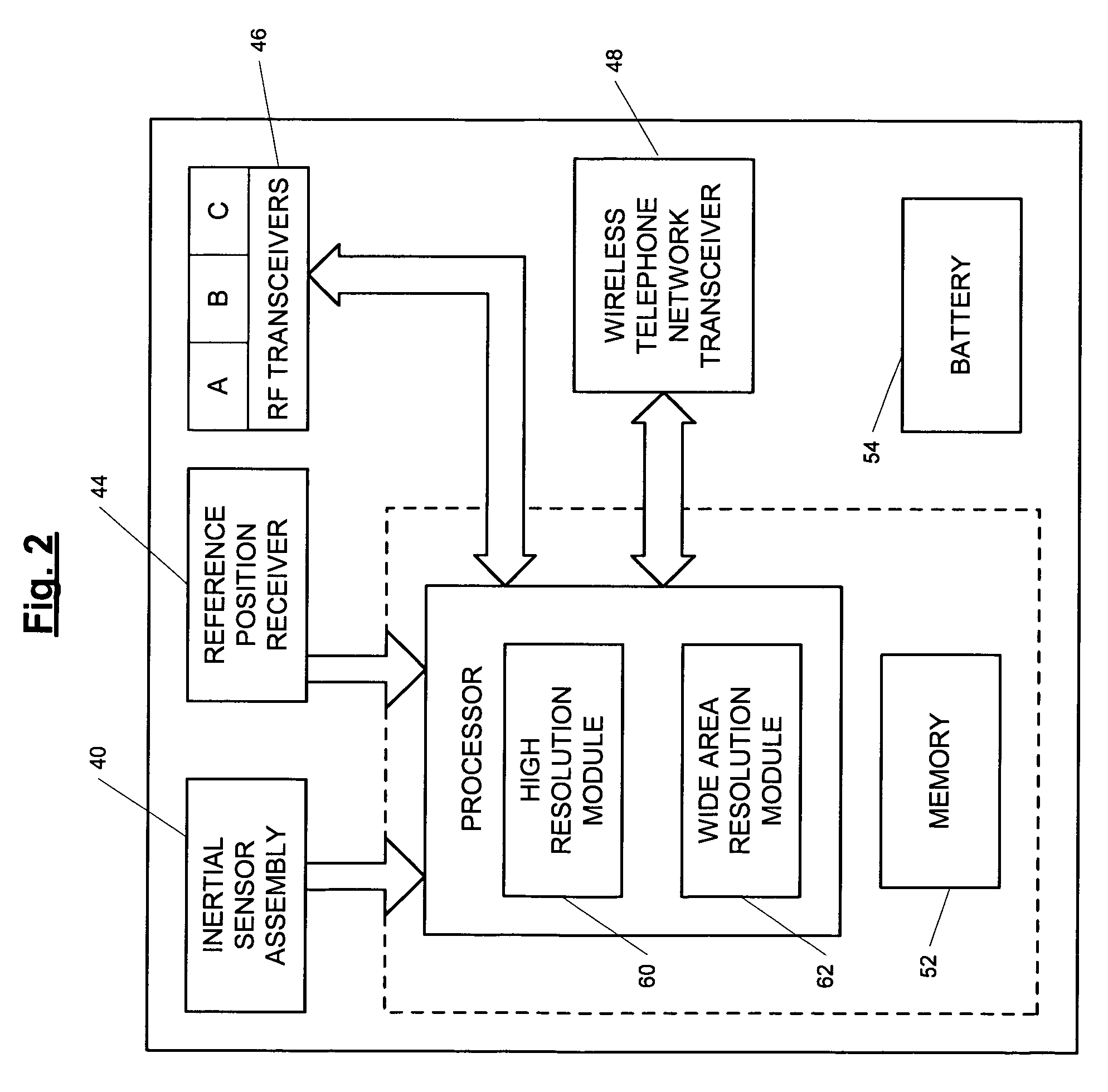
A position-tracking system for tracking the position of an object is disclosed. According to various embodiments, the tracking system includes a tracking device that is connected to or otherwise affixed to the object to be tracked. The tracking device may include, among other things, an inertial sensor assembly, radio transceivers and a processor. The position tracking system may also include a host processing system that is in communication with the tracking device. The position tracking system may provide variable-resolution position information based on the environment in which the object is moving. In a “wide resolution” area, the system may compute a general position for the object based on a wireless telephone network Cell-ID / map correlation architecture. In a high-resolution area, greater position resolution may be realized from the combination of a wireless aiding system and inputs from the inertial sensors. In the high-resolution mode, the system may exploit distinct patterns of motion that can be identified as motion “signatures” that are characteristic of certain types of motion. Kinematic (or object movement) models may be constructed based on these motion signatures and the position tracking system may estimate the state of the object based on the kinematic model for the current mode of the object. Adaptive and cascaded Kalman filtering may be employed in the analysis to more accurately estimate the position and velocity of the object based on the motion pattern identified.
Owner:PINC SOLUTIONS
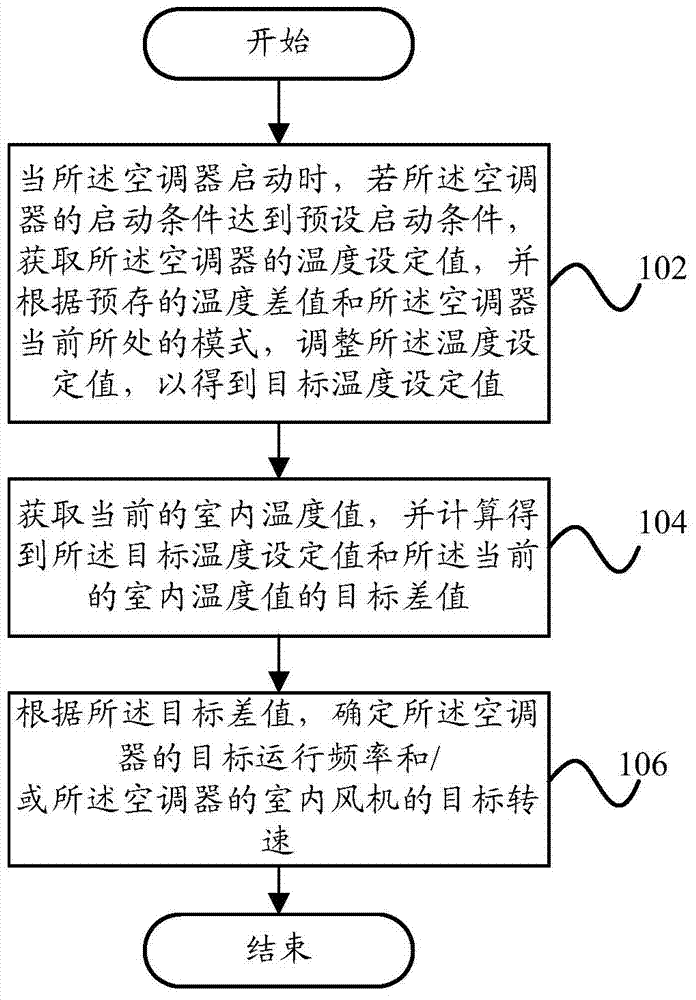
Air conditioner, and control method and device thereof
ActiveCN103940058AMeet the needs of indoor temperature senseImproved cold/hot experienceSpace heating and ventilation safety systemsLighting and heating apparatusEngineeringTemperature difference
The invention provides an air conditioner, and a control method and device of the air conditioner. The control method of the air conditioner includes the steps of obtaining a temperature set value of the air conditioner if the starting condition of the air conditioner reaches the preset starting condition when the air conditioner starts, adjusting the temperature set value according to a pre-stored temperature difference value and the current mode of the air conditioner, thereby obtaining a target temperature set value, obtaining a current indoor temperature value, obtaining a target difference value between the target temperature set value and the current indoor temperature value through calculation, and determining the target operation frequency and / or the target rotation speed of an indoor draught fan of the air conditioner according to the target difference value. By means of the technical scheme, the comfort level of the variable frequency air conditioner is improved, cold / hot experience of users is improved, and the effect of saving electric energy is achieved.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD +1
Low power current input delta-sigma ADC using injection FET reference
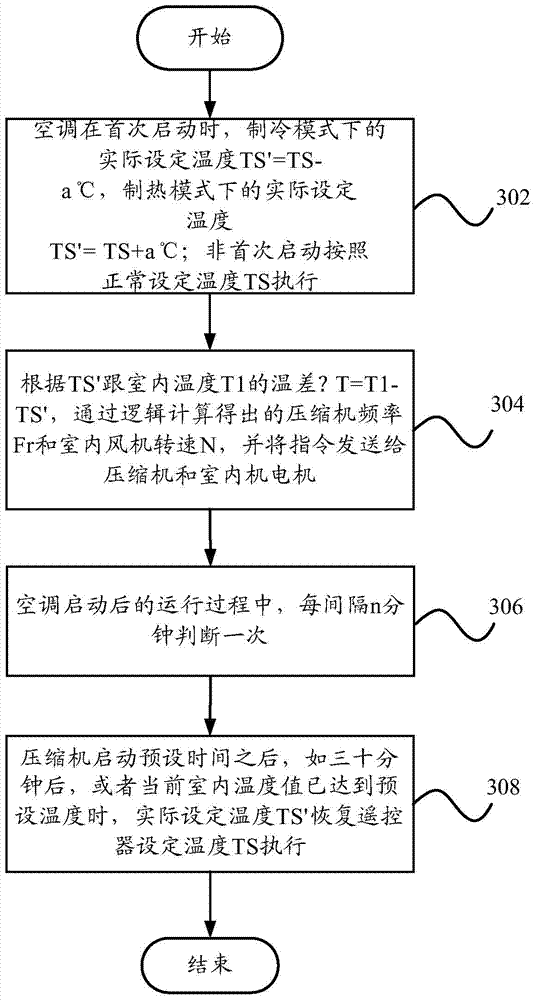
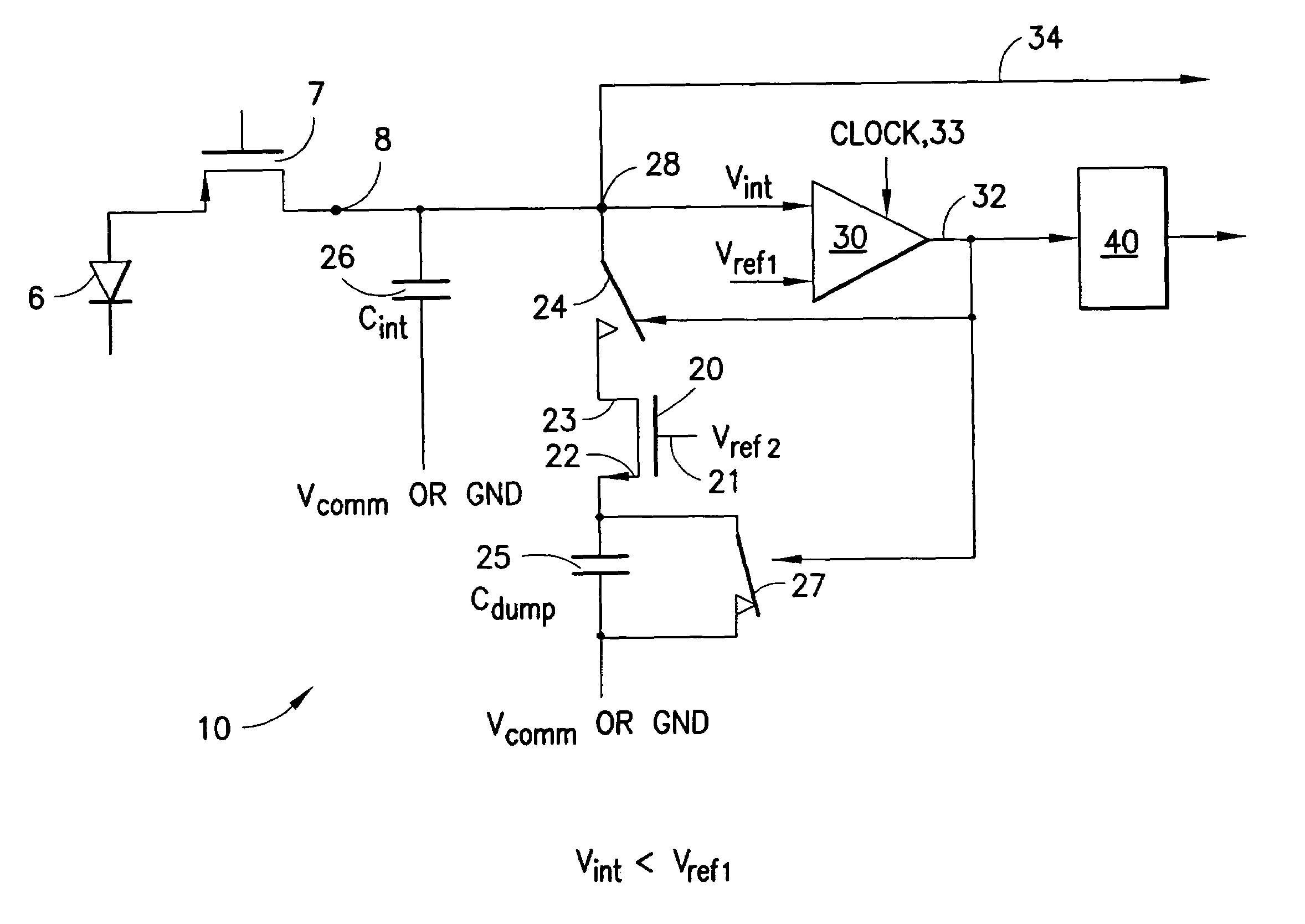
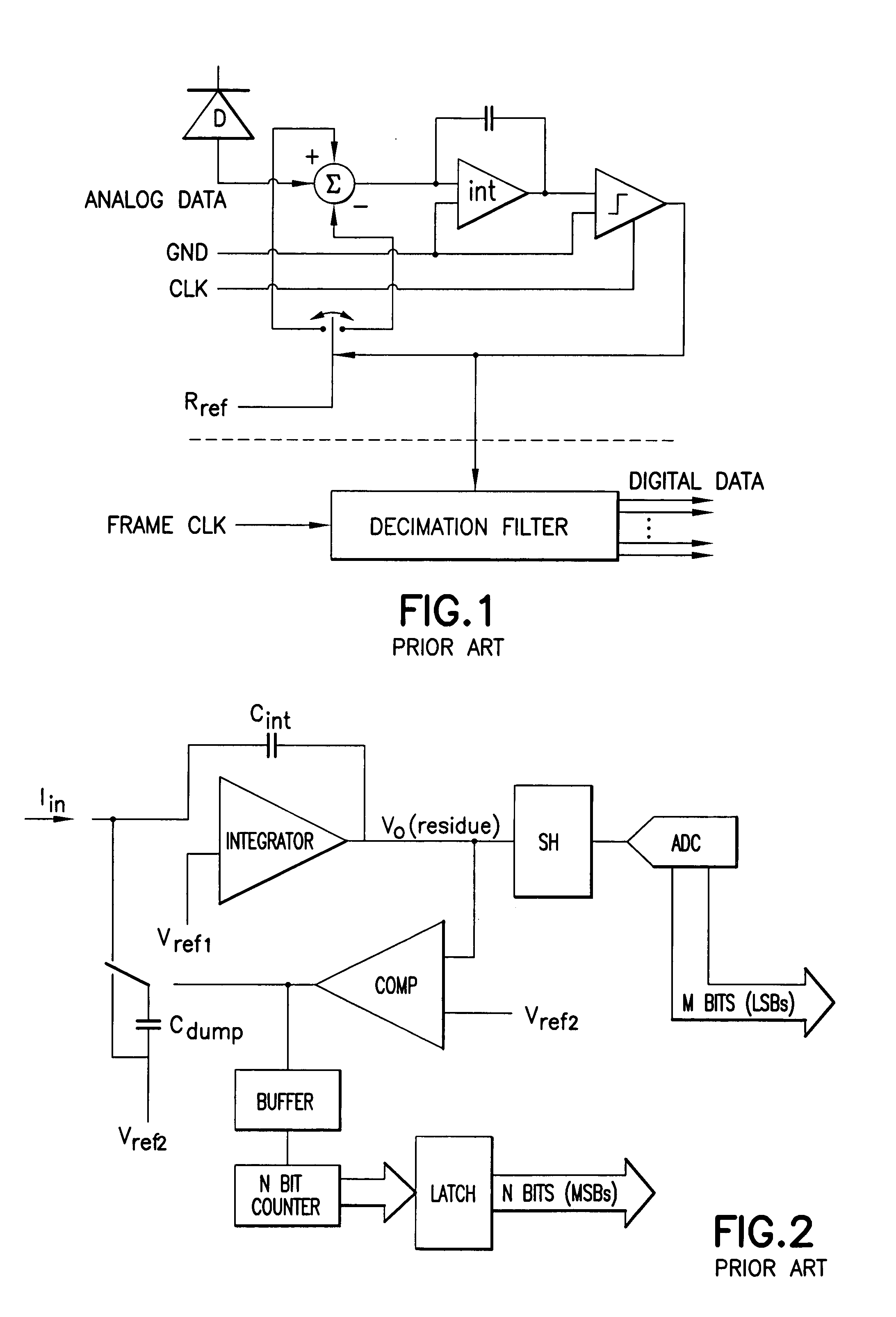
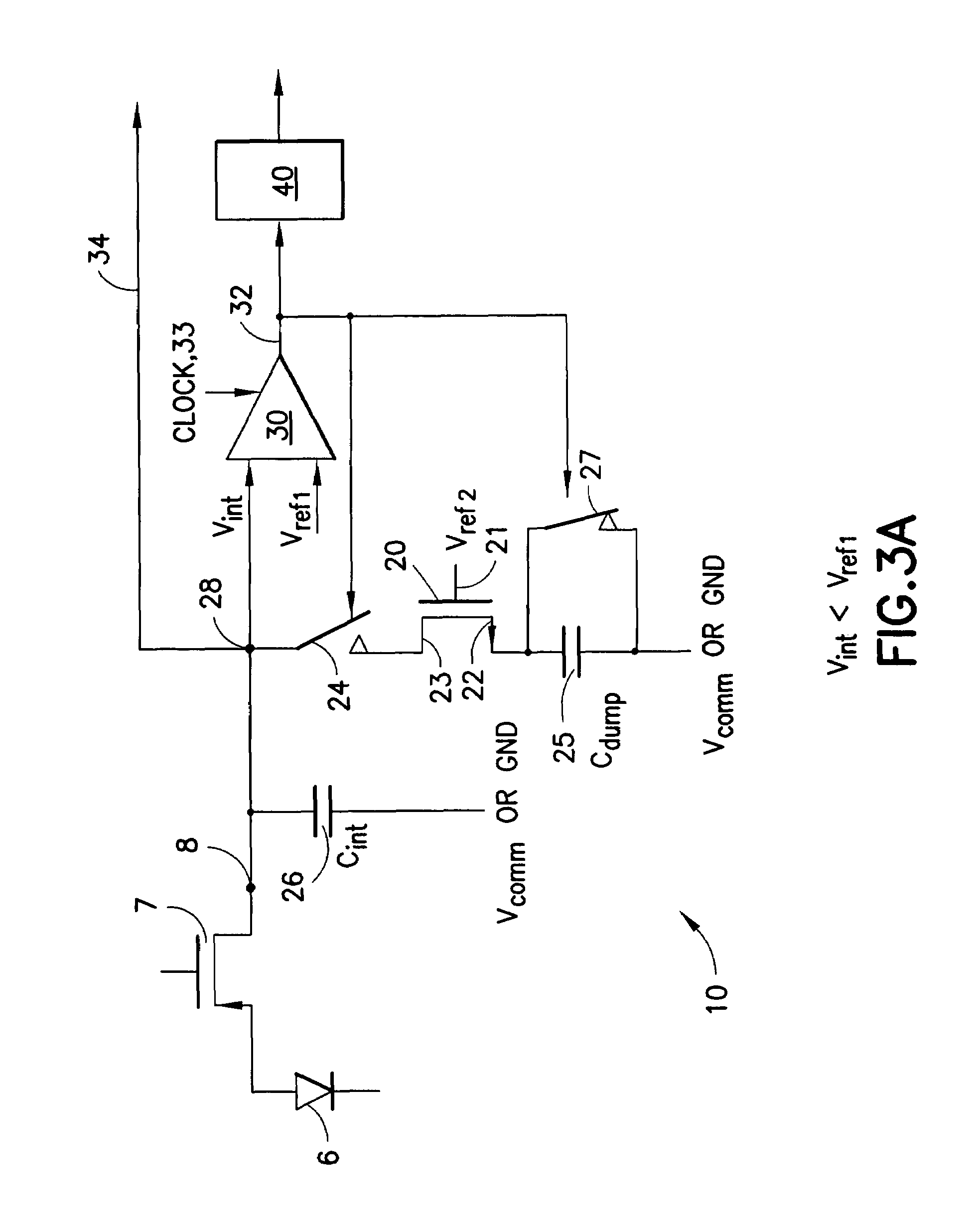
A low power delta-sigma analog to digital converter 10 for converting current mode signals without an amplifier includes an integration capacitor 26, a comparator 30, and a first switch 24 in parallel with one another and coupled to an integration node 28. A FET 20 and the first switch are disposed in series between a dump capacitor 25 and the integration node. A second switch 27 operates to discharge the dump capacitor, and an output of the comparator controls both switches in opposition. Preferably, no op-amps are included in the circuit, and current is supplied by an imaging component 5. In a first comparator state, the first capacitor charges, the first switch is open and the second switch is closed, and the dump capacitor discharges. In a comparator second state, the first switch is closed and the second switch is open, and the integration capacitor transfers a fixed amount of charge into the dump capacitor through an injection FET operating in saturation.
Owner:RAYTHEON CO
Human detection method and apparatus
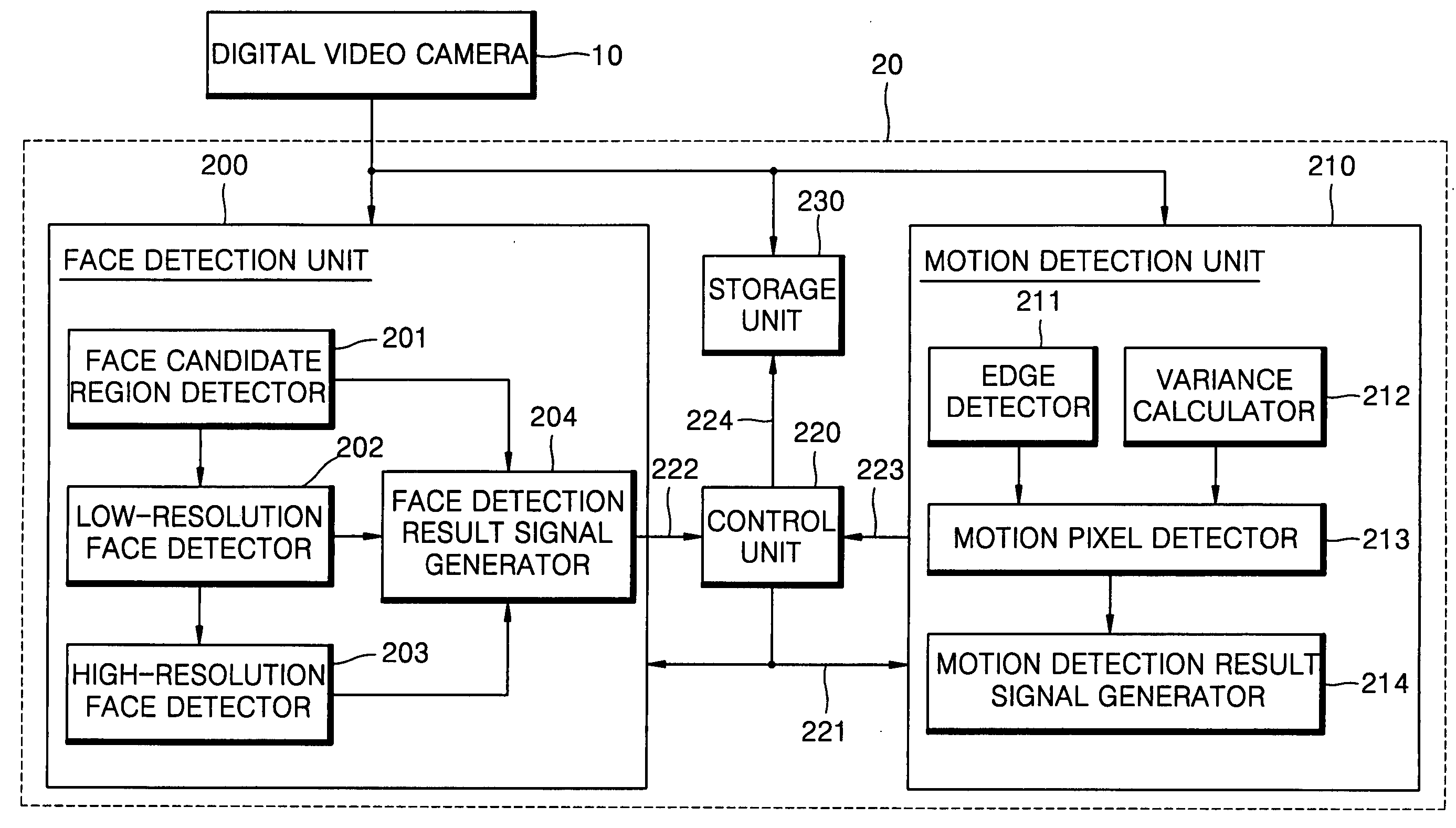
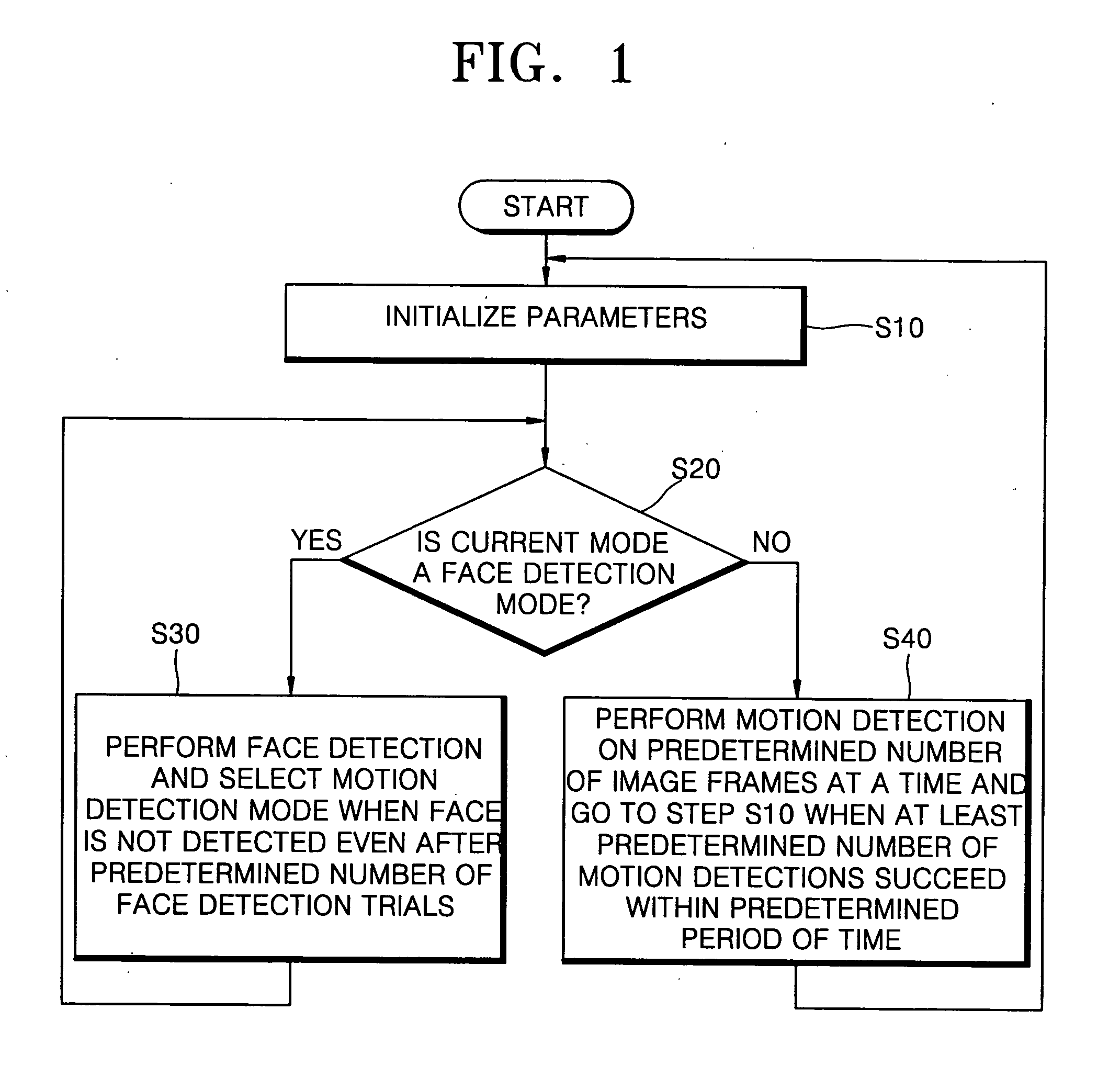
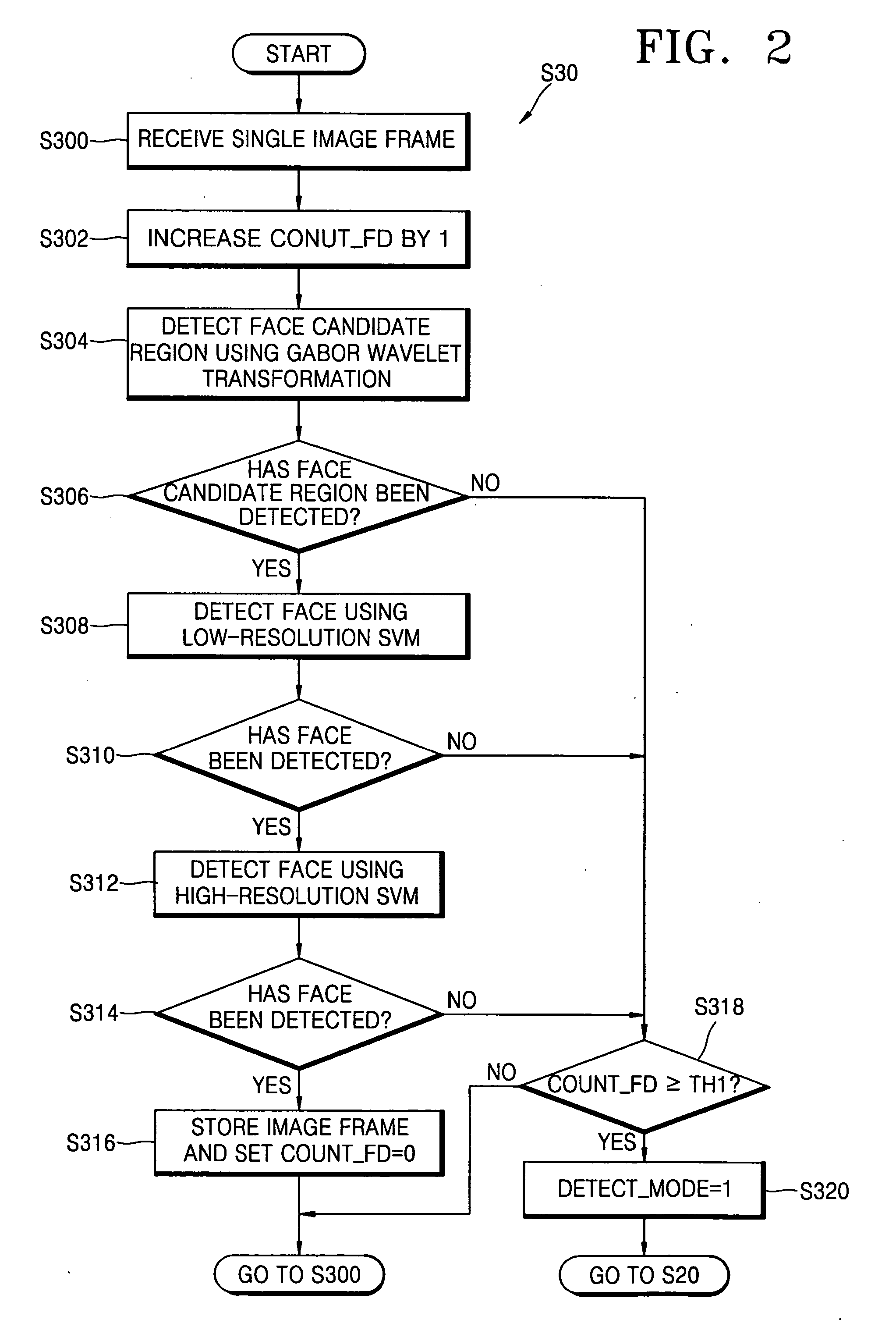
InactiveUS20050094849A1Accurate detectionImprove efficiencyImage enhancementImage analysisFace detectionDigital video
A human detection method and apparatus are provided. In the method, a person is detected from an image provided by a digital video camera. The method includes (a) initializing parameters used for a user detection; (b) determining a current mode; (c) when it is determined that the current mode is the face detection mode, performing a face detection on each of a plurality of image frames, and when a face is not detected even after a predetermined number of face detection trials, selecting a motion detection mode and going back to step (b); and (d) when it is determined that the current mode is the motion detection mode, performing a motion detection on a predetermined number of image frames at a time, and when at least a predetermined number of motion detections are performed successfully within a predetermined period of time, going back to step (a).
Owner:SAMSUNG ELECTRONICS CO LTD
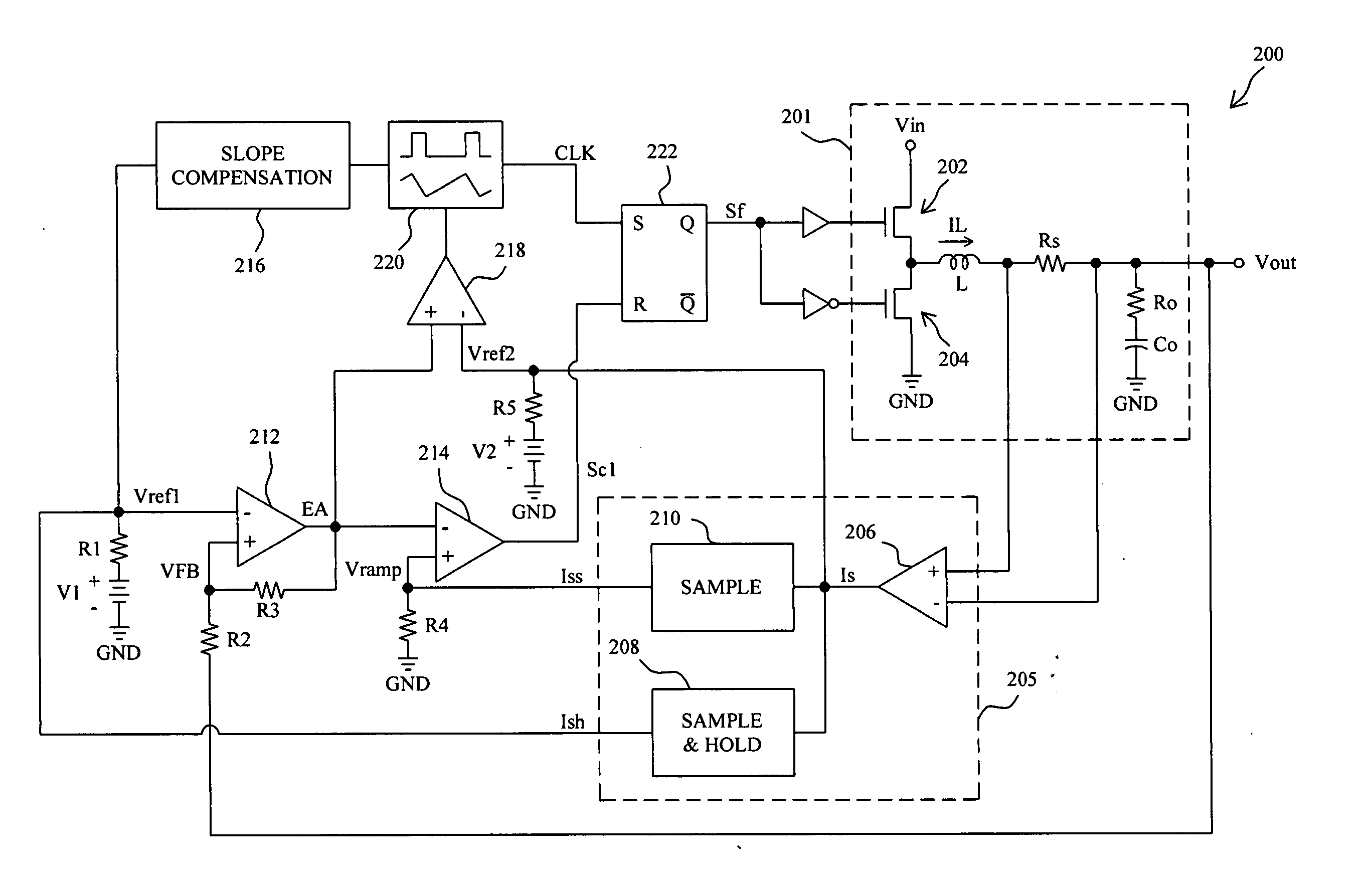
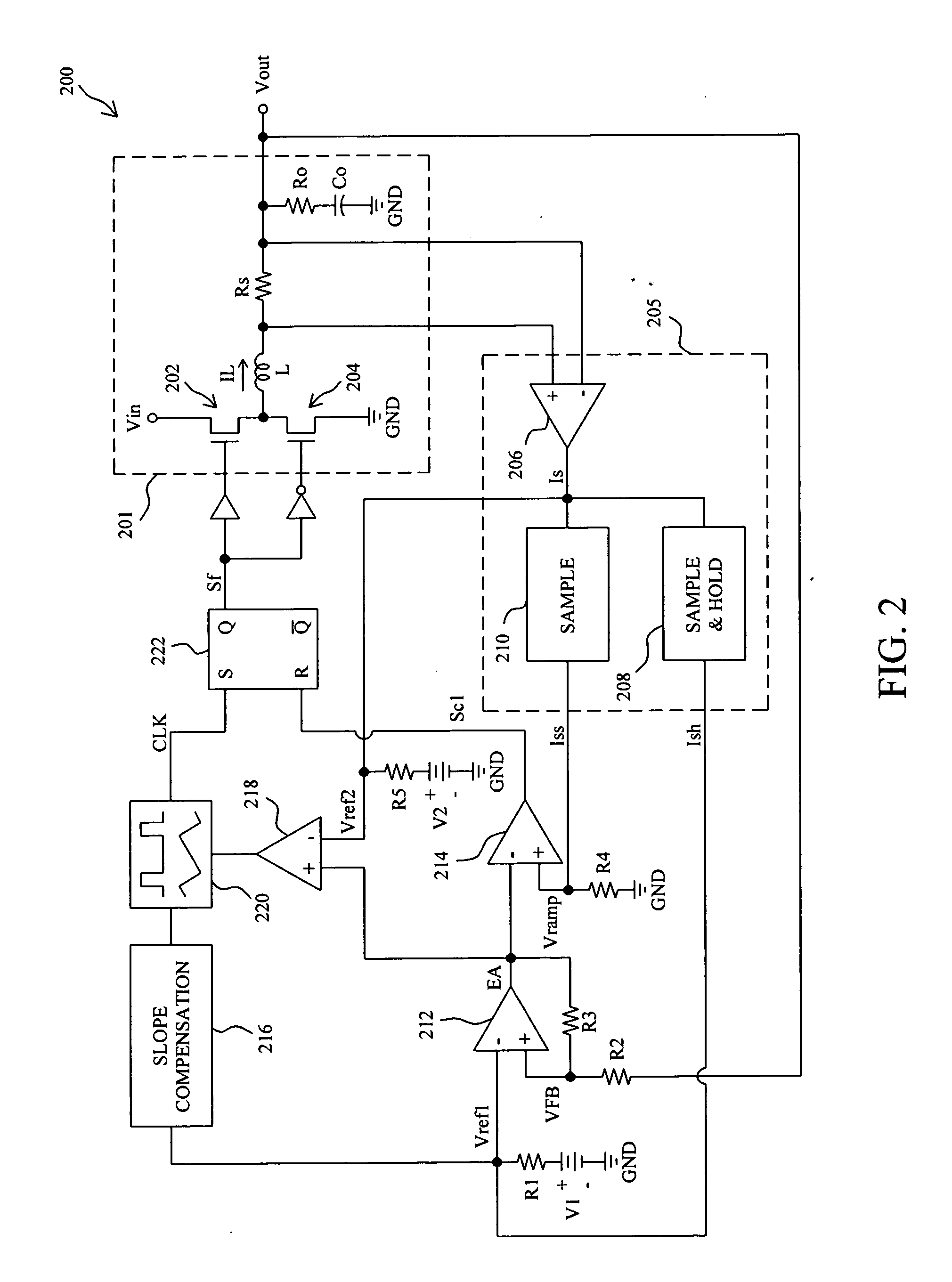
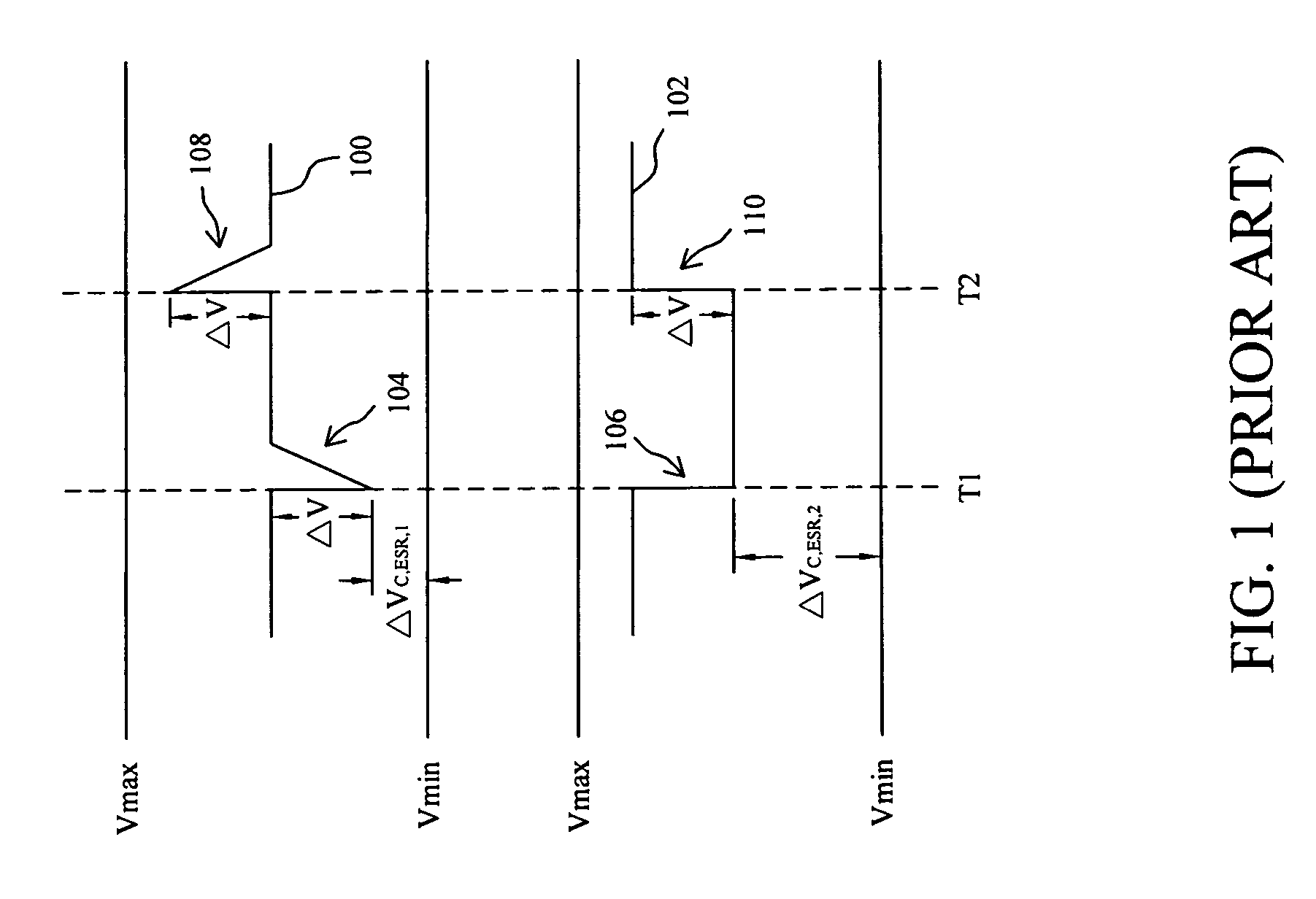
Switching regulator circuits
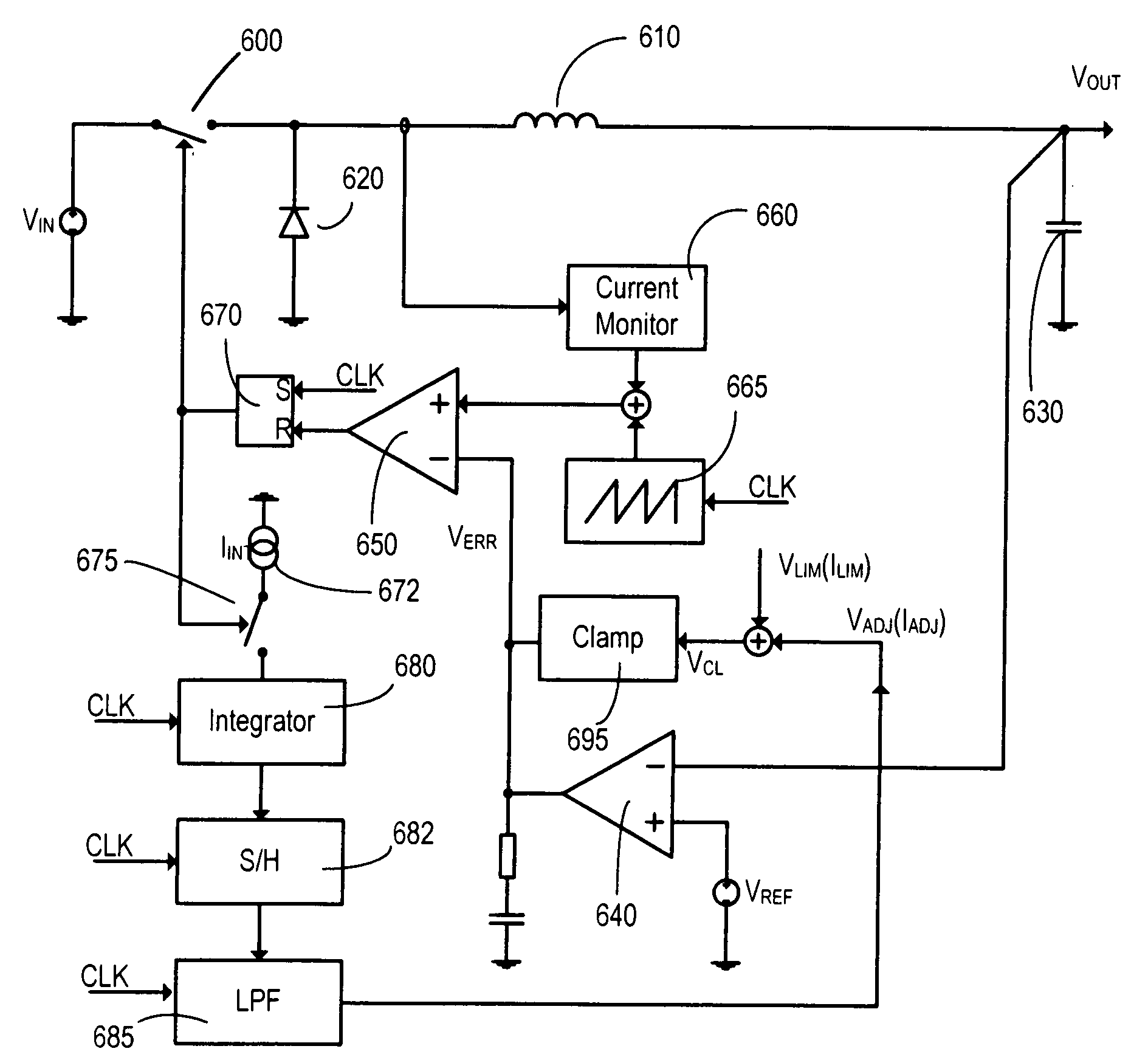
A current-mode switching regulator including at least: an inductor; a main switch for controlling the current flow through the inductor; and a feedback control circuit for operating the main switch cyclically and to vary a duty cycle of the main switch so as to substantially maintain an output voltage of the regulator at a desired level. The feedback control circuit further includes slope compensation circuitry adding slope compensation to a signal representing the inductor current prior to the slope compensated signal being compared to the fed-back output error voltage. The regulator further includes current limiting circuitry for controlling the main switch responsive to a current limit reference signal, the current limit circuitry including adjustment circuitry for adjusting the current limit reference signal in response to the duty cycle of more than one previous cycle so as to limit current in the inductor irrespective of the output voltage and to a value which, in the steady state, is substantially independent of the duty cycle.
Owner:CIRRUS LOGIC INC
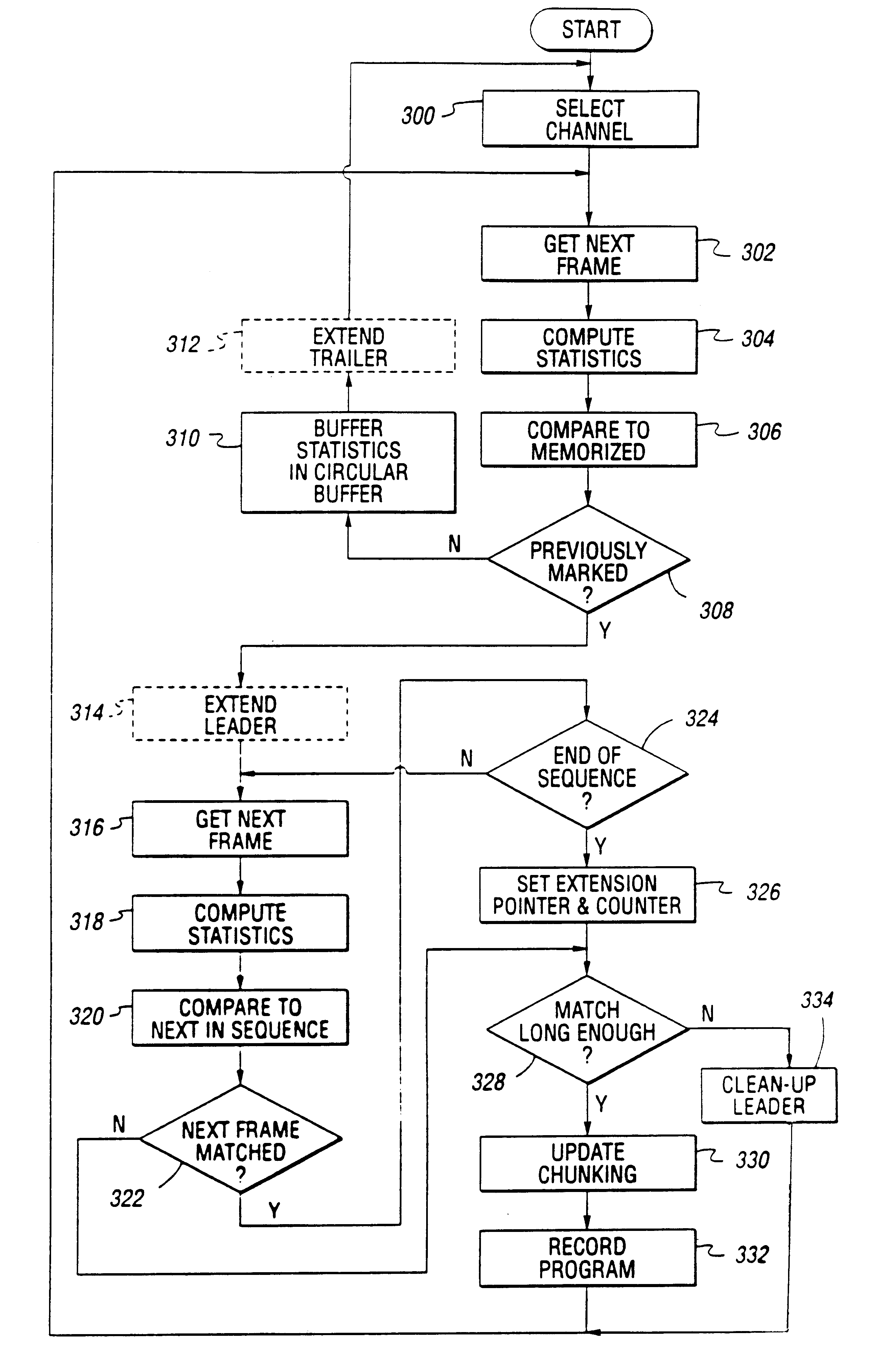
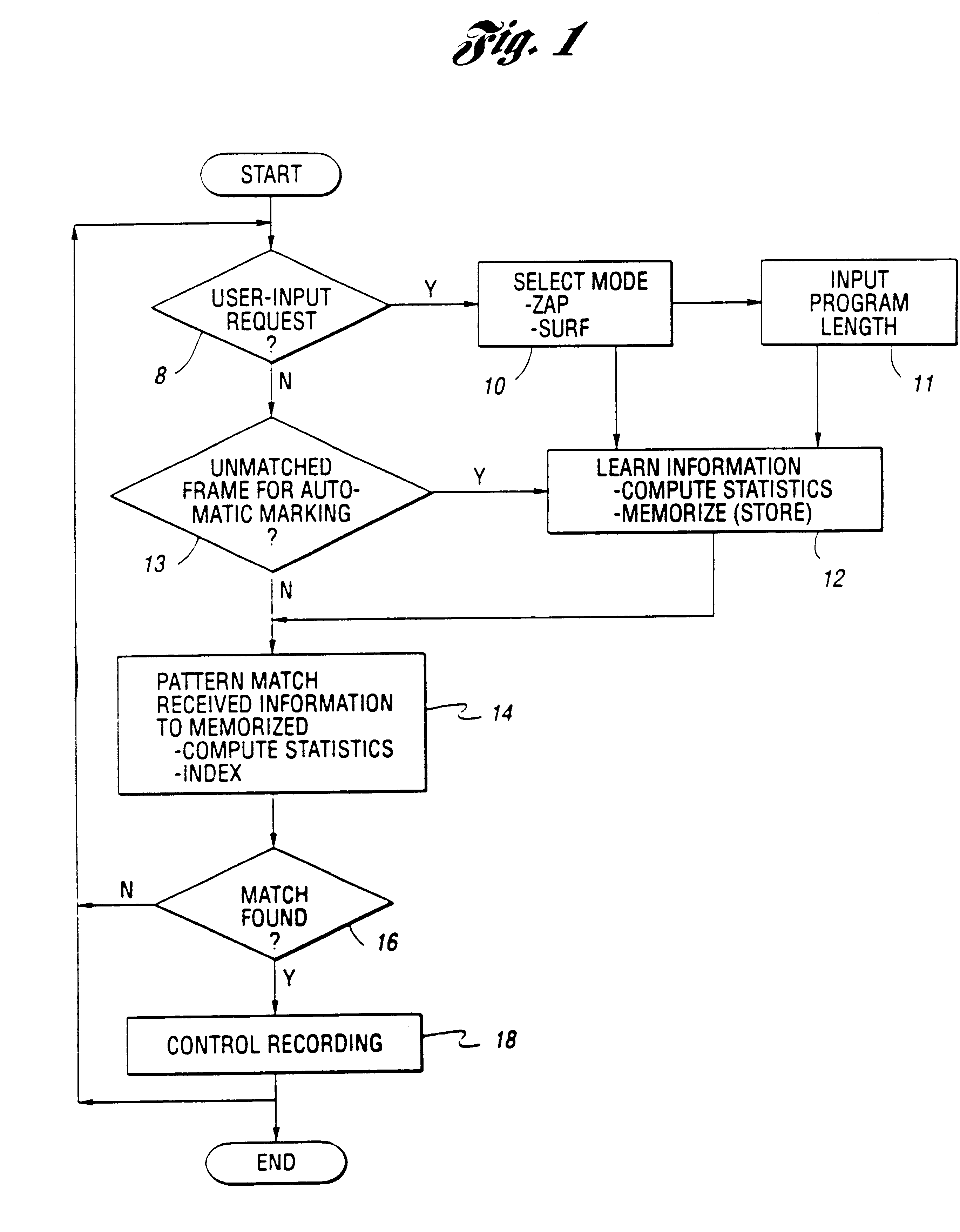
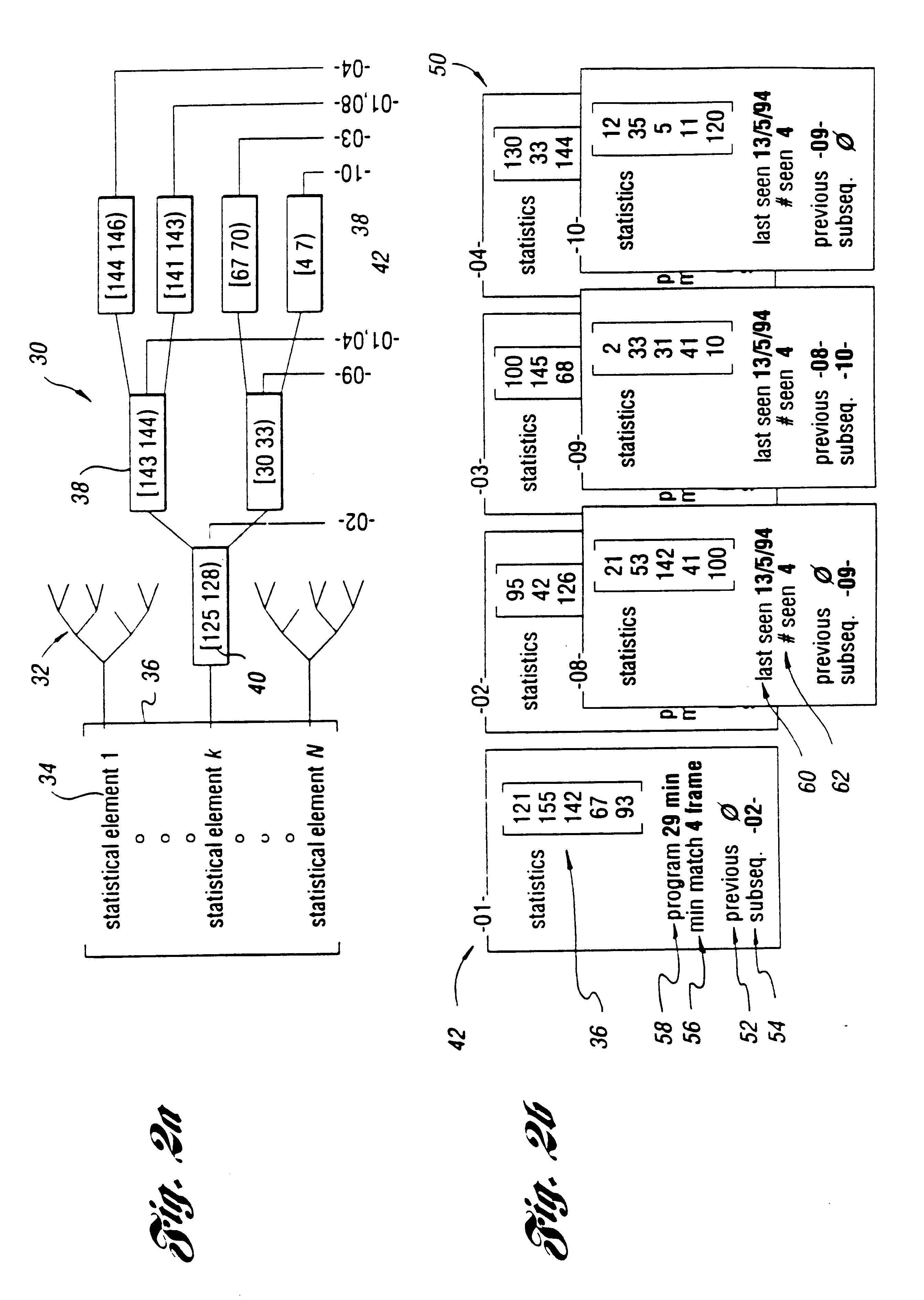
System and method for selective recording of information
InactiveUS6782186B1Reduce and eliminate possibilityEasy to appreciateTelevision system detailsFilamentary/web carriers operation controlPattern matchingOperation mode
A system and method for selective recording of information uses sequential pattern matching of statistical vectors which characterize incoming time-based information to identify previously marked information within an incoming information stream. The system and method generate a signal to control a recording device to either elide the previously marked information from the recording, or to begin recording once the previously marked information is identified, depending upon the current mode of operation. The system and method may be utilized to omit recording of unwanted information, such as commercials in a television broadcast, or to automatically locate desired information on any of a number of available information channels without a priori knowledge of the occurrence time or channel of the information.
Owner:INTERVAL RESEARCH CORPORATION
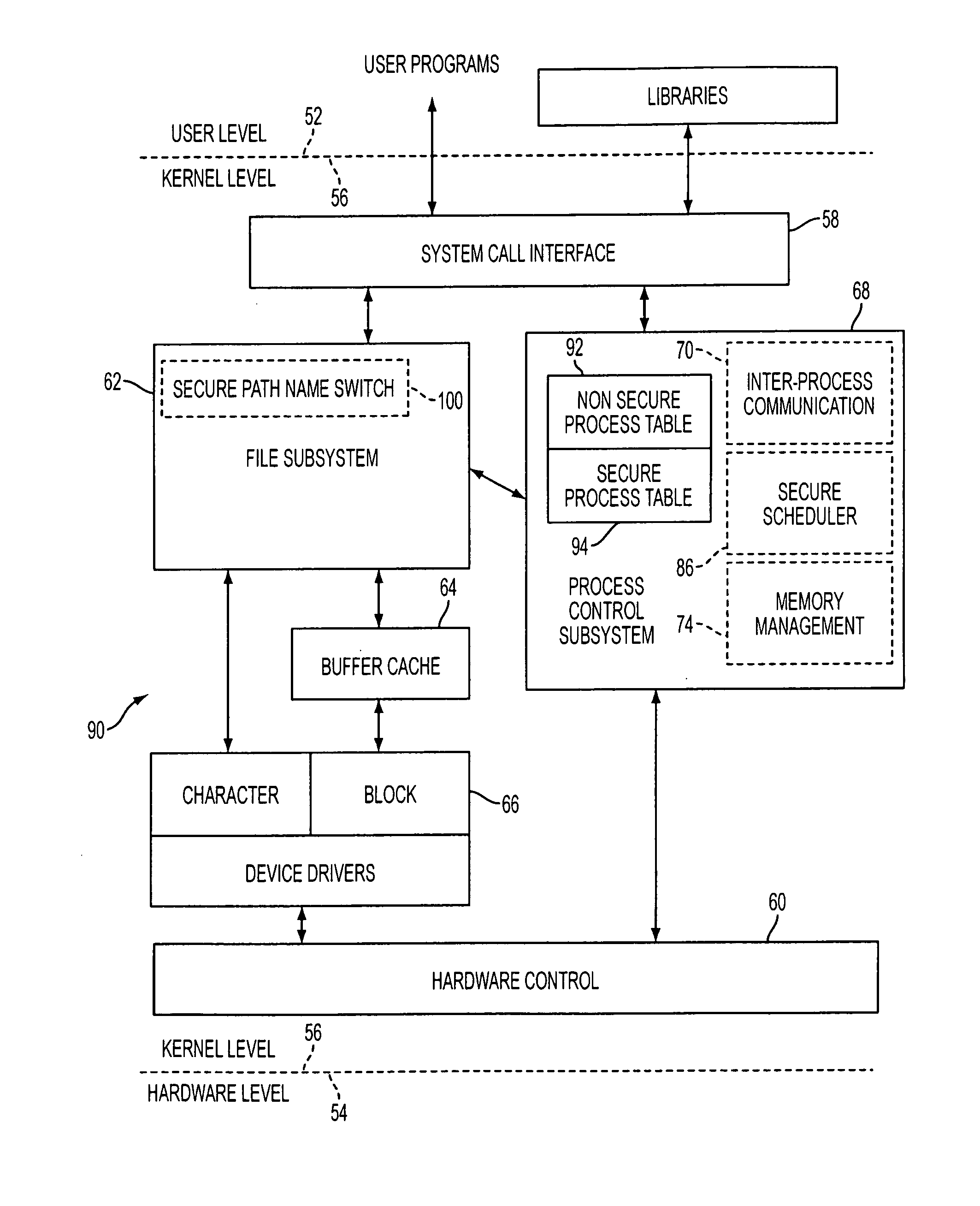
Computer system with dual operating modes
ActiveUS20060212945A1Safely and securely co-existDigital data processing detailsAnalogue secracy/subscription systemsOperation modeCurrent mode
The present invention is a system that switches between non-secure and secure modes by making processes, applications and data for the non-active mode unavailable to the active mode. That is, non-secure processes, applications and data are not accessible when in the secure mode and visa versa. This is accomplished by creating dual hash tables where one table is used for secure processes and one for non-secure processes. A hash table pointer is changed to point to the table corresponding to the mode. The path-name look-up function that traverses the path name tree to obtain a device or file pointer is also restricted to allow traversal to only secure devices and file pointers when in the secure mode and only to non-secure devices and files in the non-secure mode. The process thread run queue is modified to include a state flag for each process that indicates whether the process is a secure or non-secure process. A process scheduler traverses the queue and only allocates time to processes that have a state flag that matches the current mode. Running processes are marked to be idled and are flagged as unrunnable, depending on the security mode, when the process reaches an intercept point. The switch operation validates the switch process and pauses the system for a period of time to allow all running processes to reach an intercept point and be marked as unrunnable. After all the processes are idled, the hash table pointer is changed, the look-up control is changed to allow traversal of the corresponding security mode branch of the file name path tree, and the scheduler is switched to allow only threads that have a flag that corresponds to the security mode to run. The switch process is then put to sleep and a master process, either secure or non-secure, depending on the mode, is then awakened.
Owner:MORGAN STANLEY +1
Position-tracking device for position-tracking system
ActiveUS7245215B2High position resolutionImprove accuracyInstruments for road network navigationRoad vehicles traffic controlTransceiverObject based
A position-tracking system for tracking the position of an object is disclosed. According to various embodiments, the tracking system includes a tracking device that is connected to or otherwise affixed to the object to be tracked. The tracking device may include, among other things, an inertial sensor assembly, radio transceivers and a processor. The position tracking system may also include a host processing system that is in communication with the tracking device. The position tracking system may provide variable-resolution position information based on the environment in which the object is moving. In a “wide resolution” area, the system may compute a general position for the object based on a wireless telephone network Cell-ID / map correlation architecture. In a high-resolution area, greater position resolution may be realized from the combination of a wireless aiding system and inputs from the inertial sensors. In the high-resolution mode, the system may exploit distinct patterns of motion that can be identified as motion “signatures” that are characteristic of certain types of motion. Kinematic (or object movement) models may be constructed based on these motion signatures and the position tracking system may estimate the state of the object based on the kinematic model for the current mode of the object. Adaptive and cascaded Kalman filtering may be employed in the analysis to more accurately estimate the position and velocity of the object based on the motion pattern identified.
Owner:PINC SOLUTIONS
Dual mode flyback converter and method of operating it
ActiveUS20110149614A1Reduce lossesImprove efficiencyEfficient power electronics conversionDc-dc conversionDetector circuitsDual mode
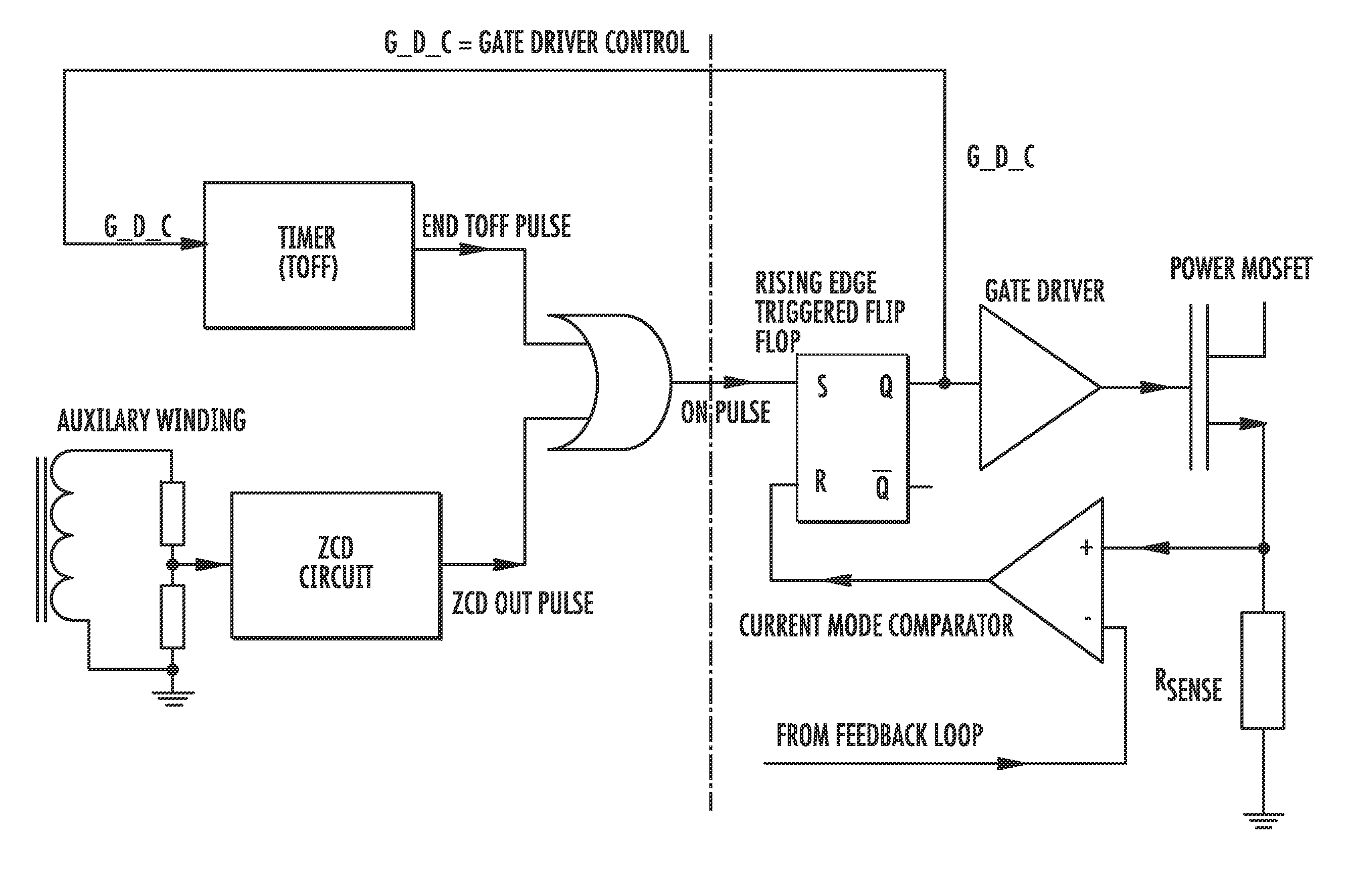
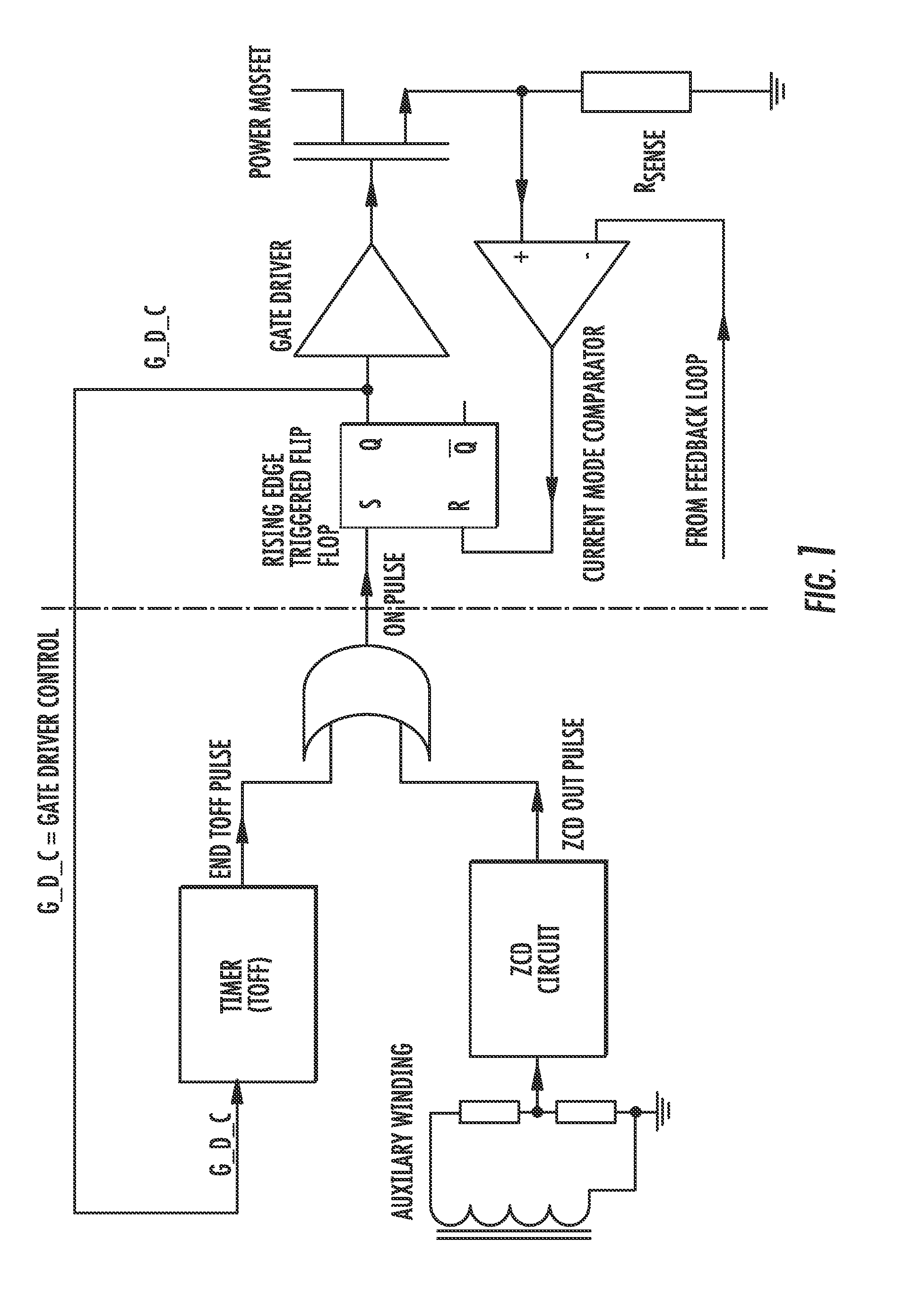
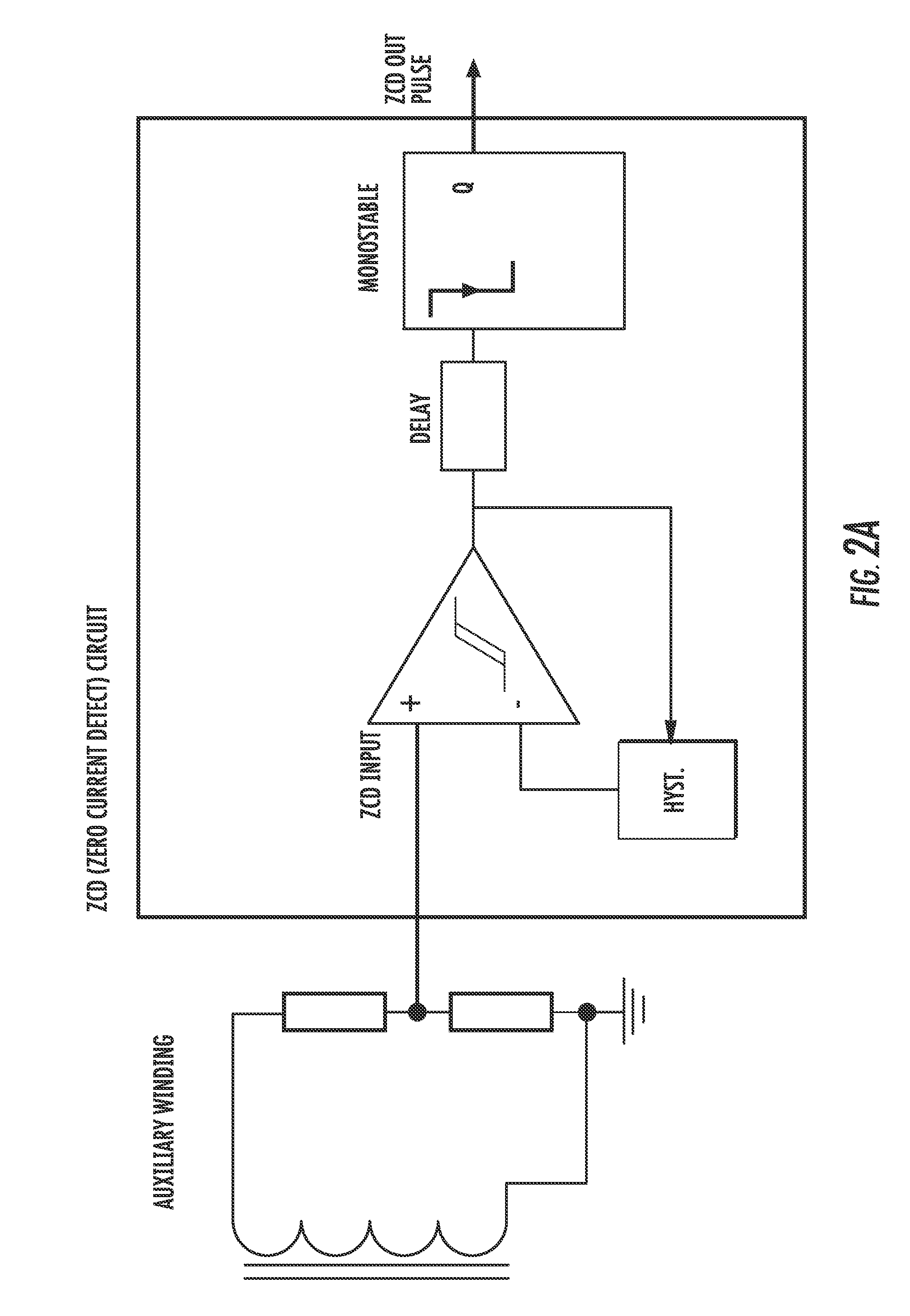
A DC-DC converter includes a power switching device and a mode control logic circuit to control the power switching device and generate an ON-pulse. A flip-flop is configured to be set by the mode control logic circuit. A current mode comparator is configured to reset the flip-flop and to compare a signal based upon current flowing through the power switching device with a signal based upon an output voltage of the dual mode flyback DC-DC converter. A transformer is driven by the current mode comparator. The mode control logic circuit includes a timer starting when a gate driver control signal applied to the power switching device turns the power switching device off and configured to generate a pulse when an off time interval elapses, a zero current detector circuit configured to sense a voltage on the transformer and generate a pulse when the voltage drops below a trigger threshold, and a combinatory logic circuit configured to compare pulse signals generated by the timer and the zero current detector circuit and generate the ON-pulse based thereupon.
Owner:STMICROELECTRONICS SRL
Fixed-frequency current mode converter and control method thereof
InactiveUS7230406B2Faster response to load transientRapid responseDc-dc conversionElectric variable regulationEngineeringInductor
A fixed-frequency current mode converter comprises a power stage to produce an inductor current and an output voltage, an error amplifier to generate an error signal from the difference between the output voltage and a reference voltage varied with the inductor current, a comparator to compare the error signal with a ramp signal varied with the inductor current to generate a comparison signal, and a PWM generator to generate a PWM signal in response to a fixed-frequency clock and the comparison signal to drive the power stage. A second comparator is further comprised to compare the error signal with a second reference voltage varied with the inductor current, and generates a second comparison signal to reset the clock when the error signal is lower than the second reference voltage.
Owner:RICHTEK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com