Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
276results about How to "Solve excessive overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
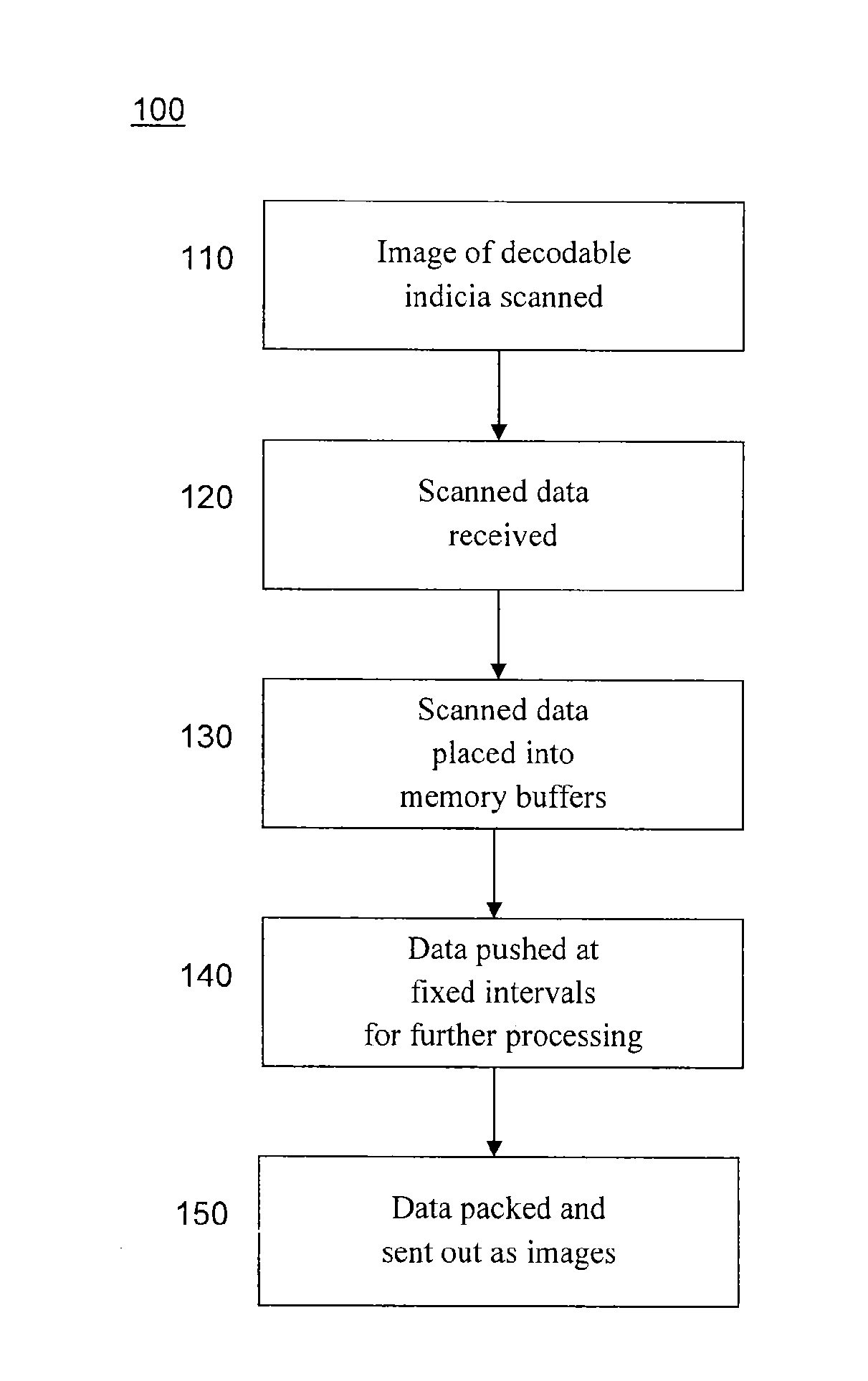
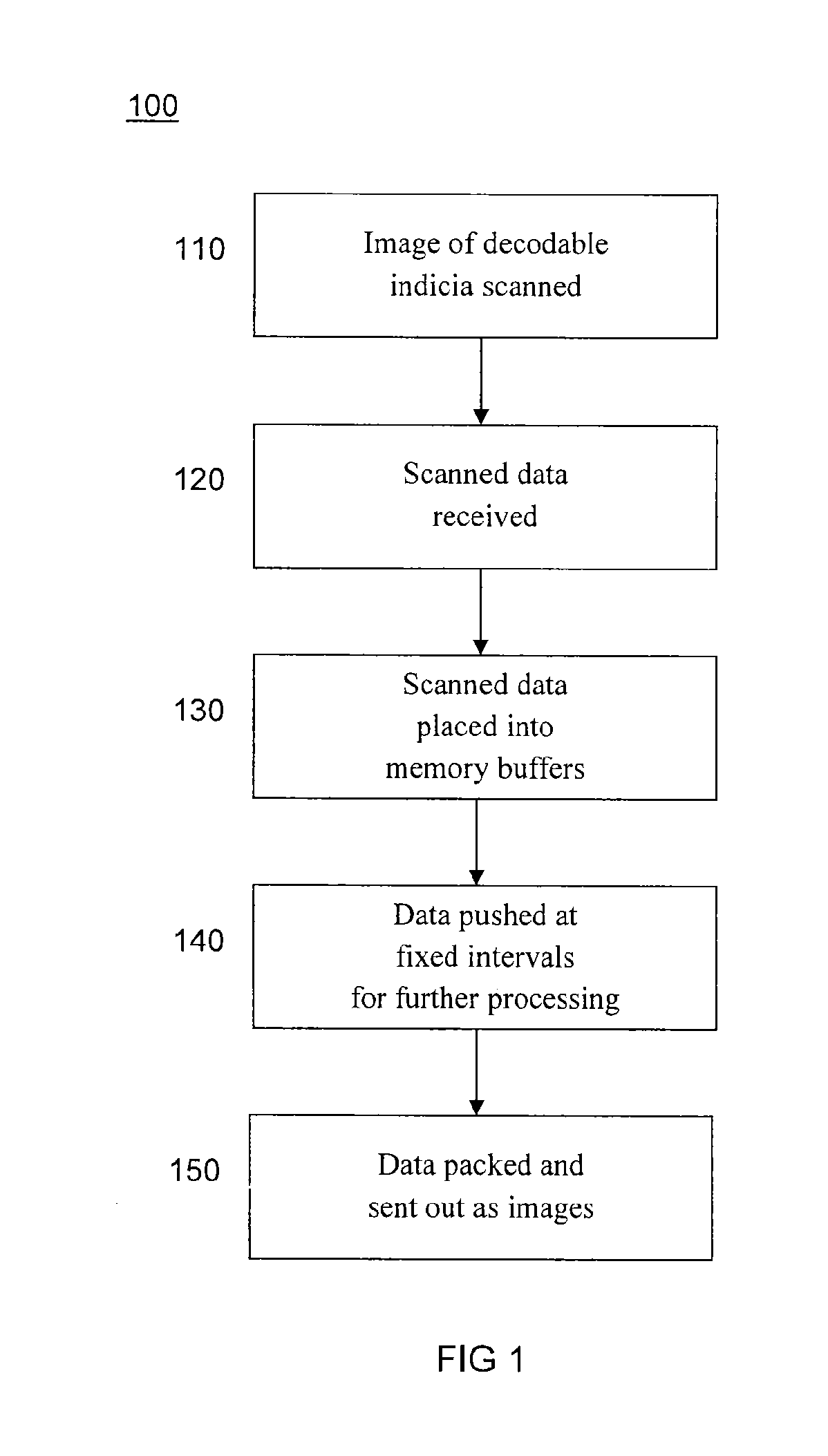
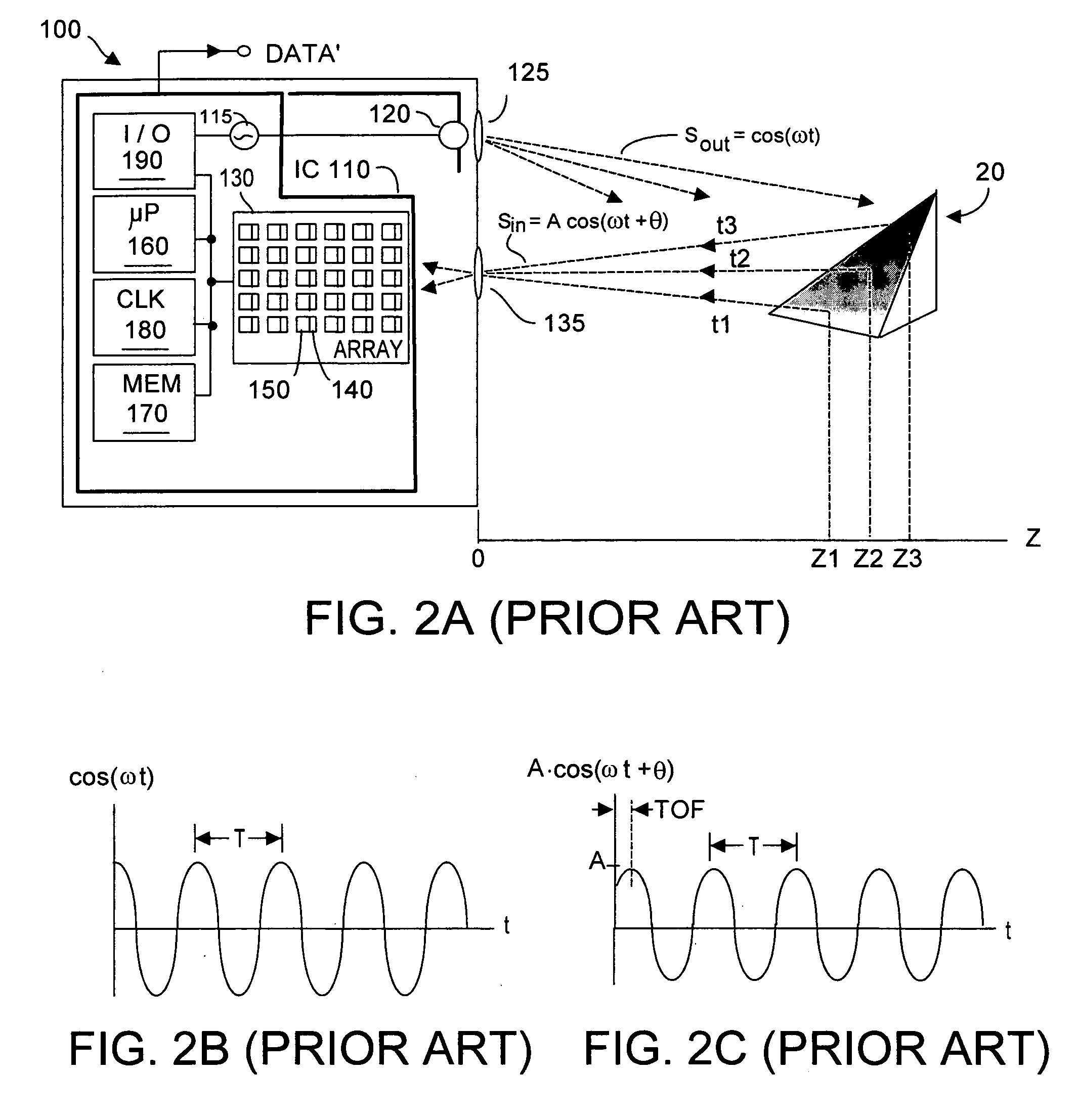
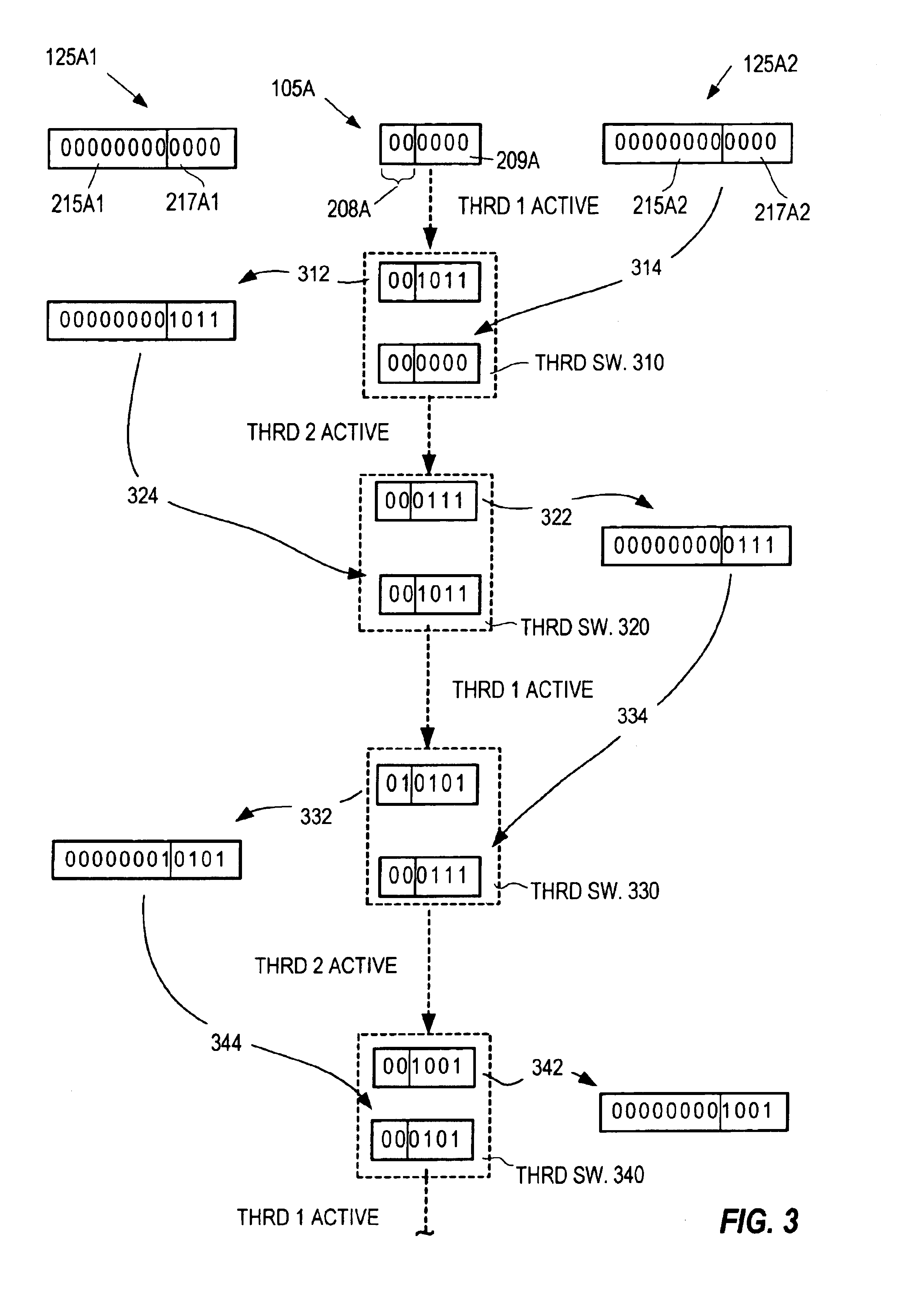
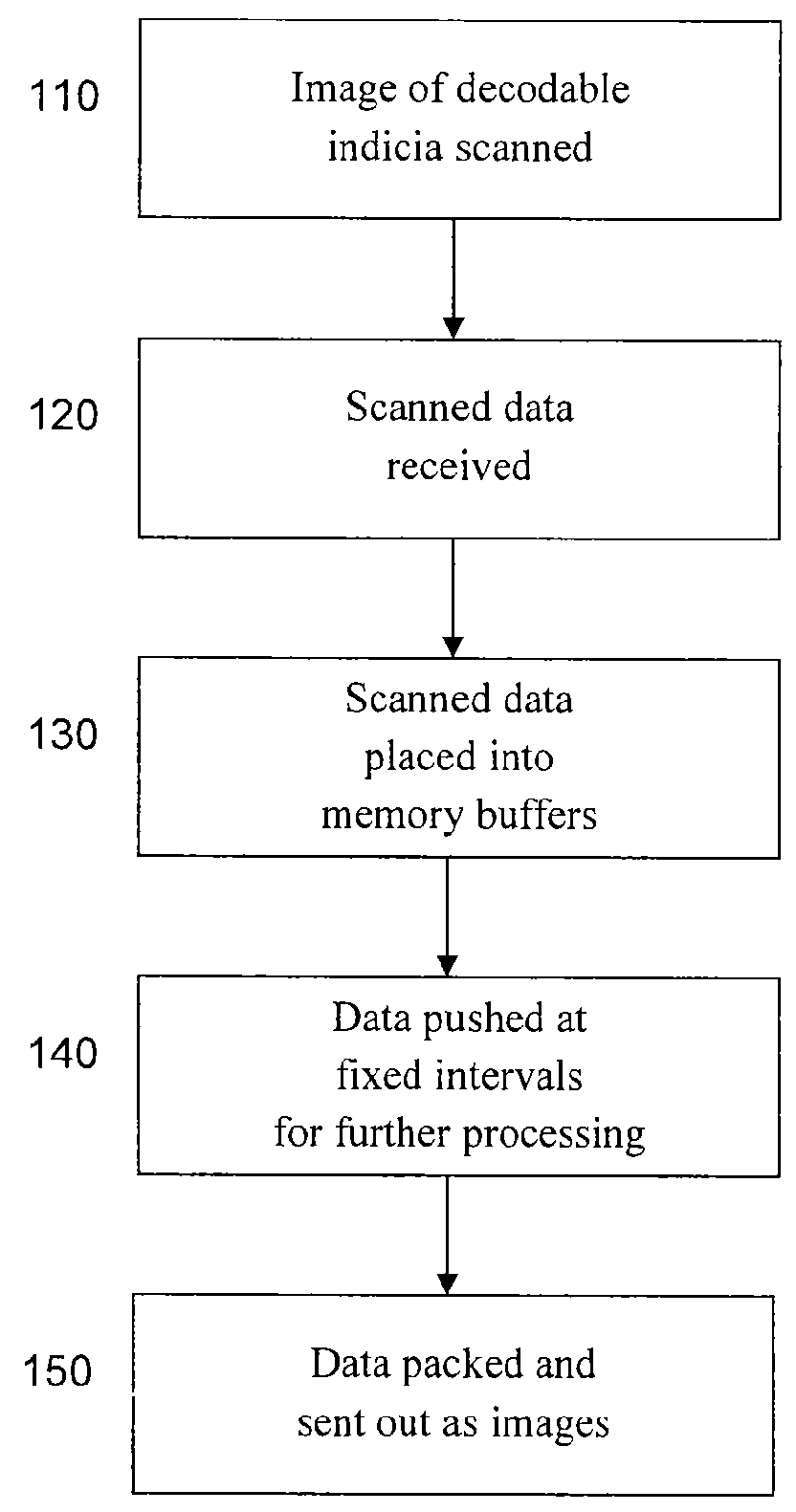
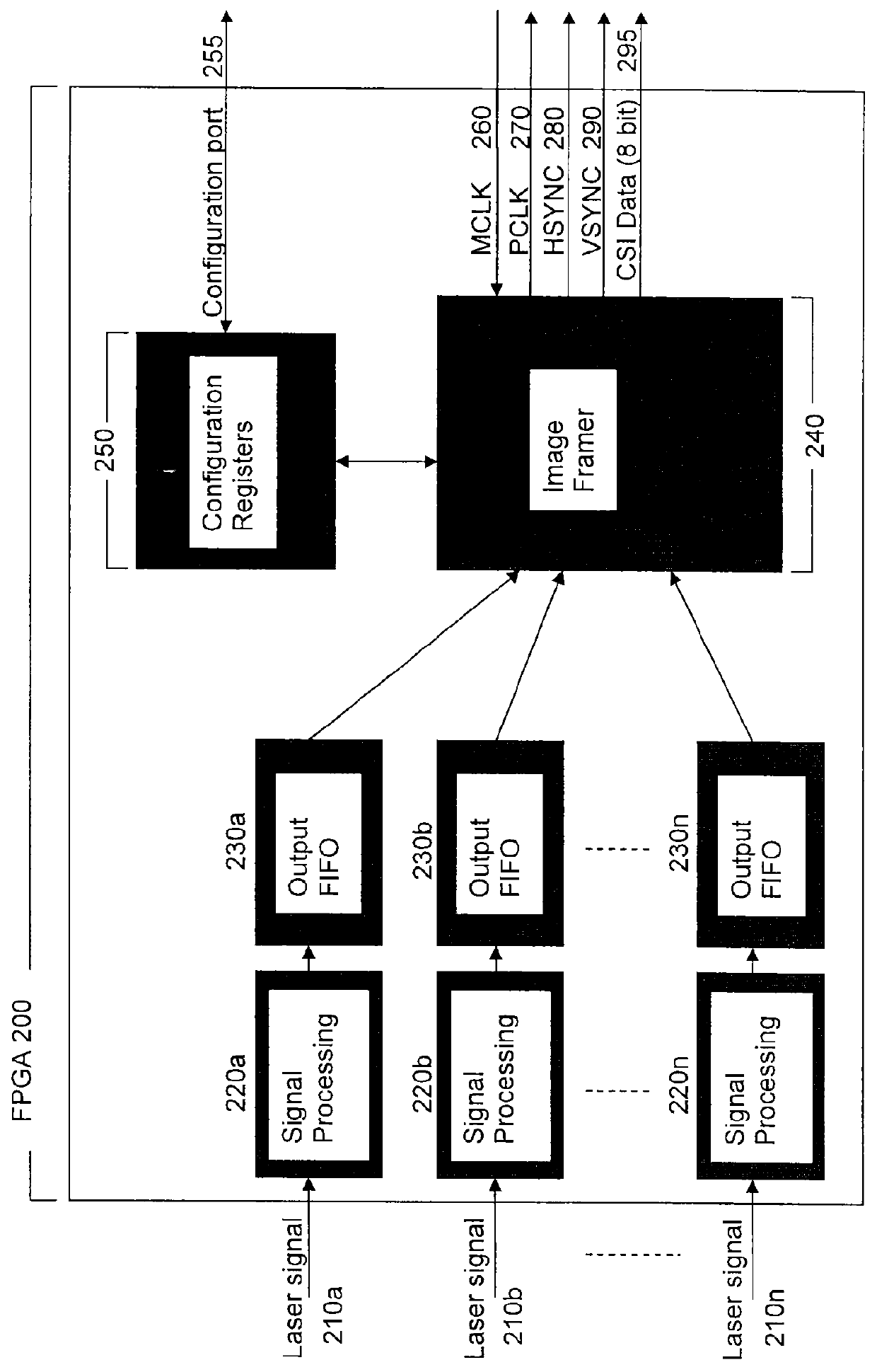
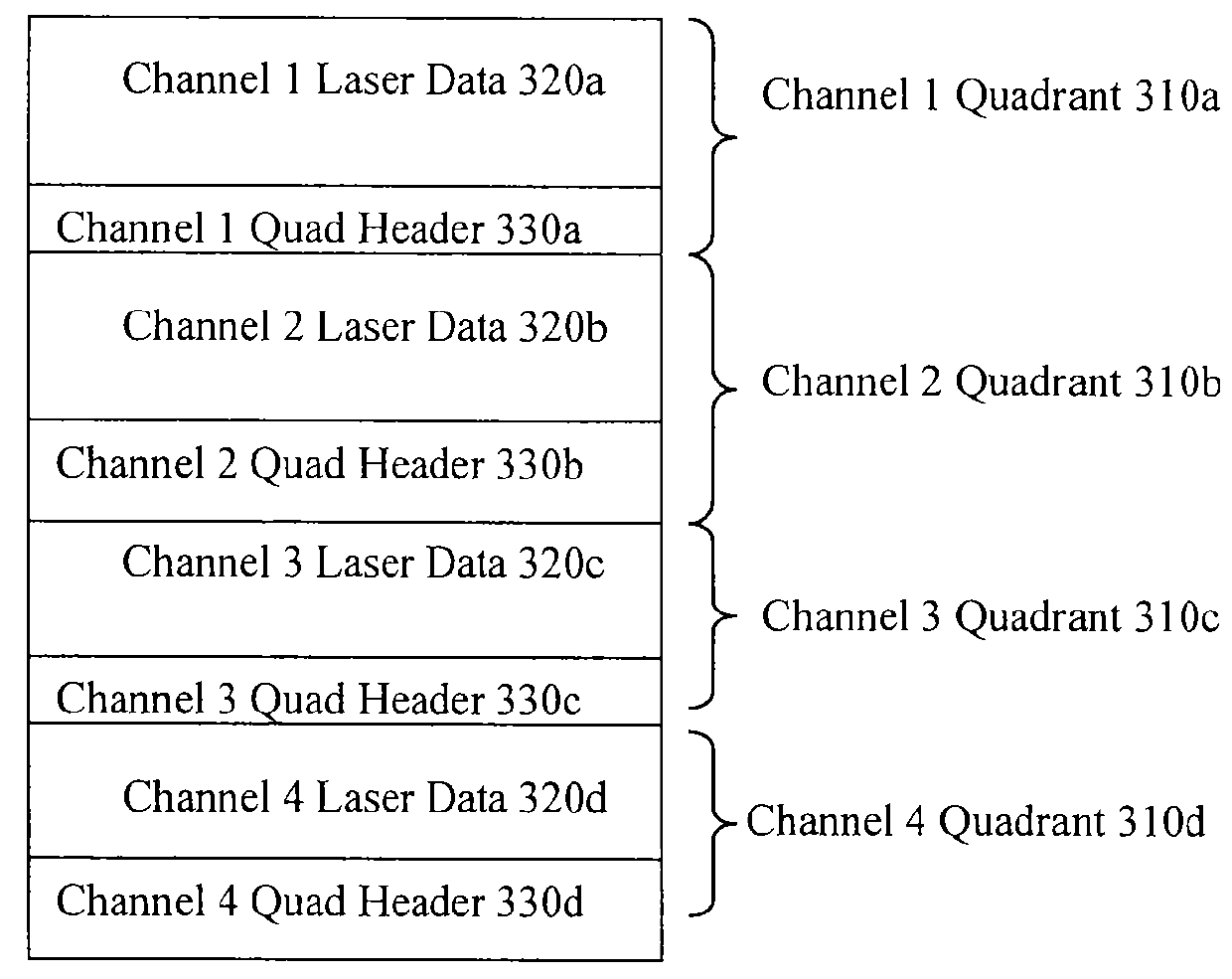
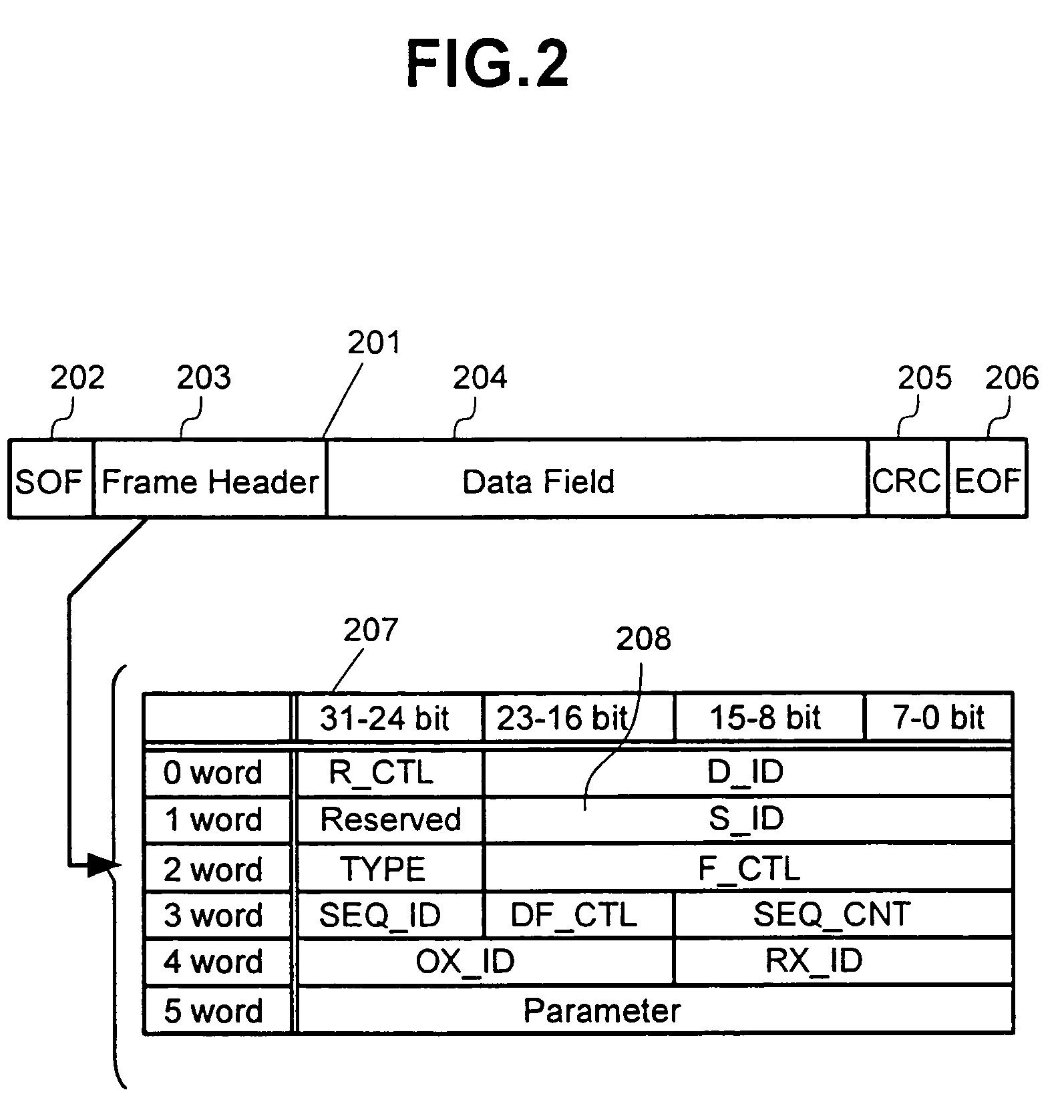
Method of using camera sensor interface to transfer multiple channels of scan data using an image format
ActiveUS20150053768A1Solve the slow scanning speedSolve excessive overheadCharacter and pattern recognitionRecord carriers used with machinesLaser scanningEngineering
Owner:HONEYWELL INT INC
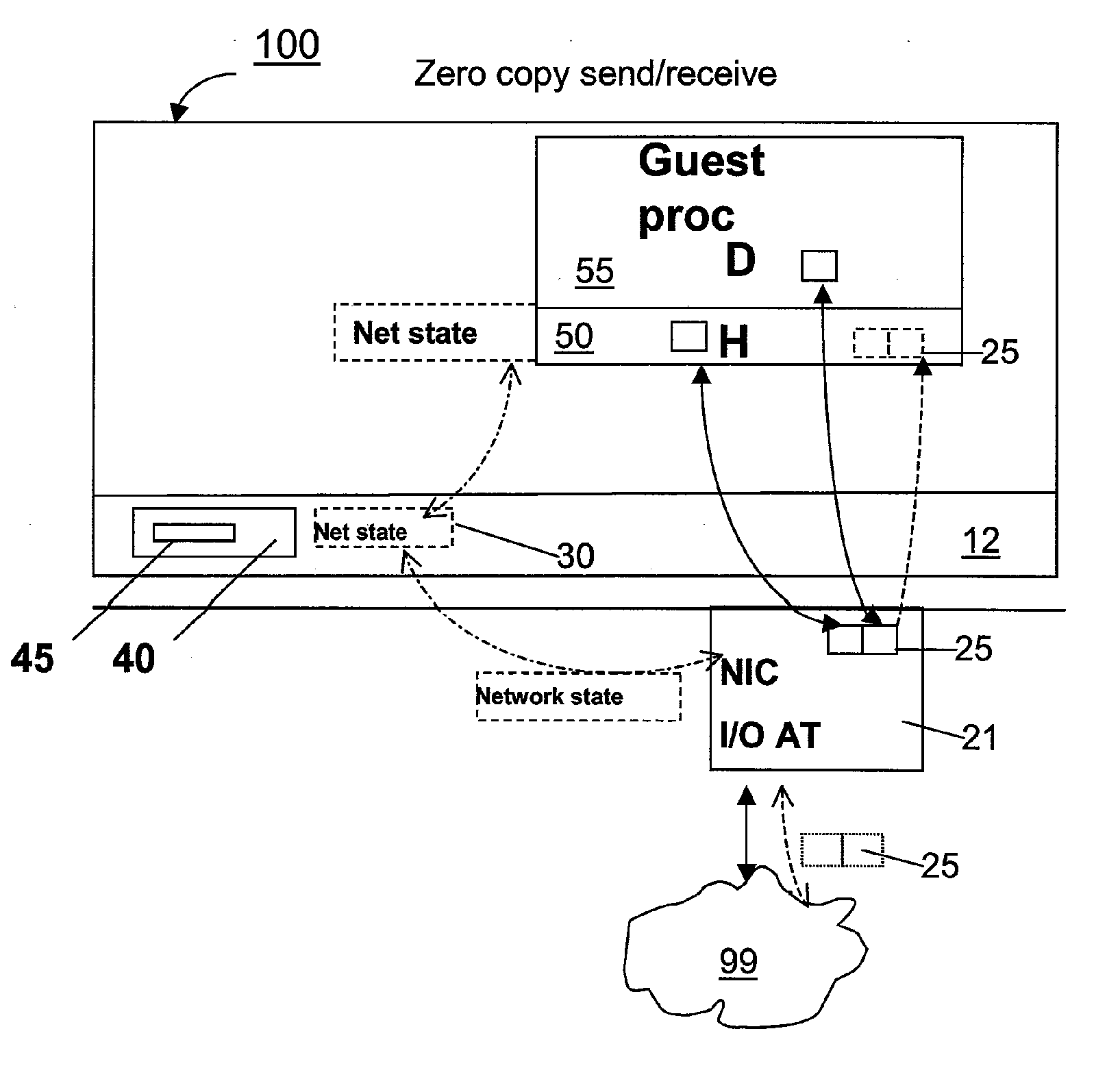
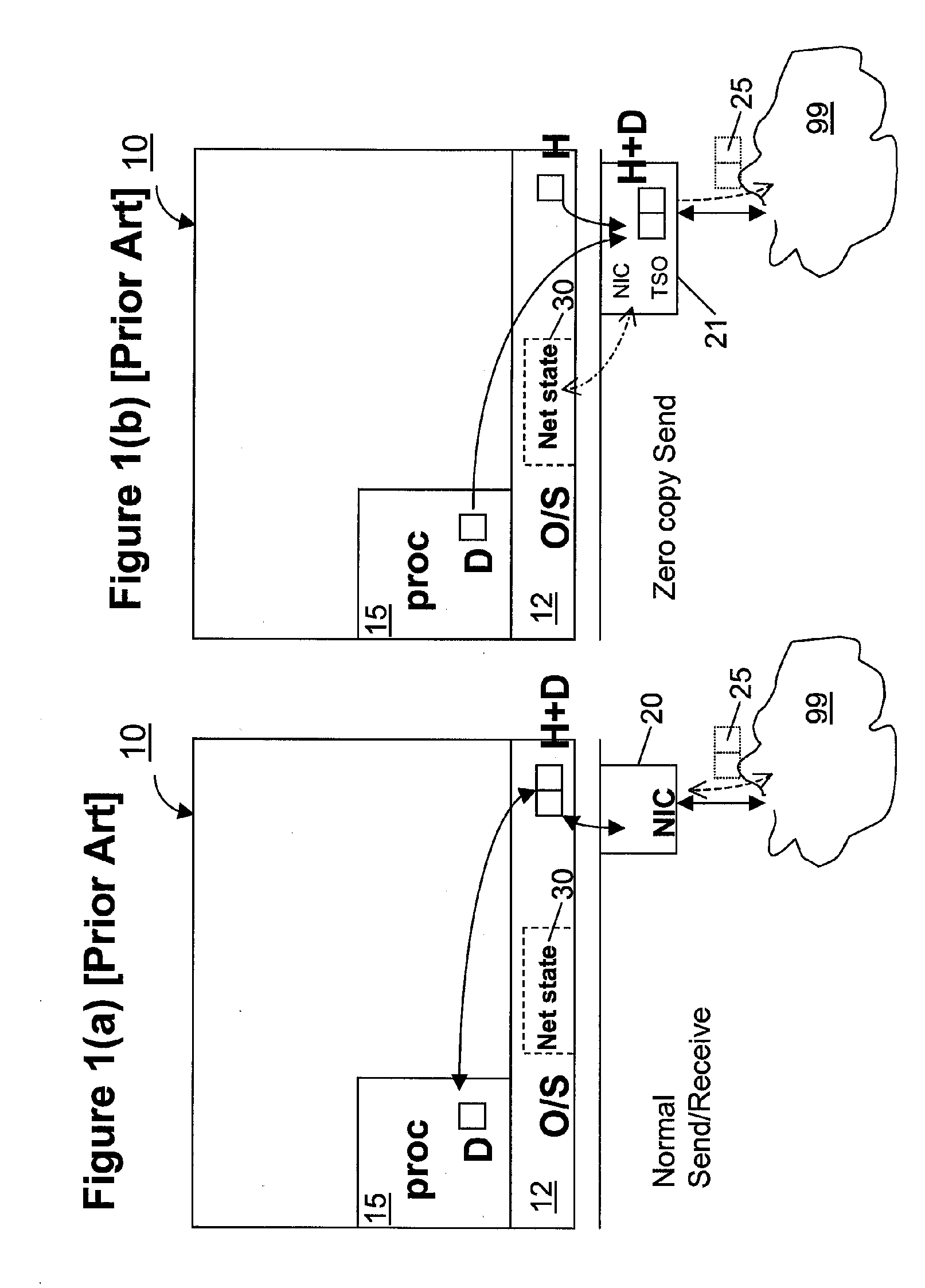
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
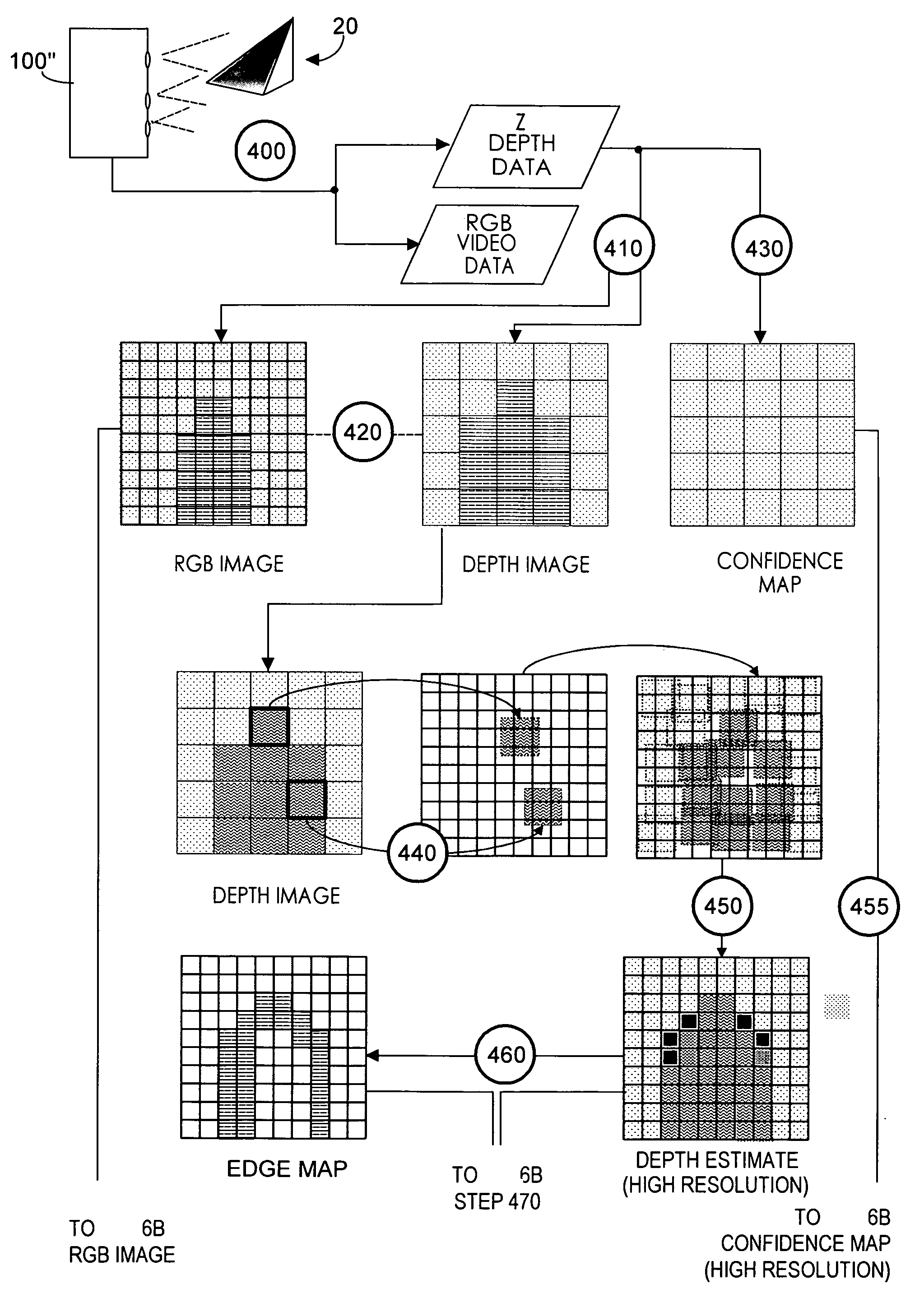
Video manipulation of red, green, blue, distance (RGB-Z) data including segmentation, up-sampling, and background substitution techniques
ActiveUS20110285910A1Improve resolutionEasy to processTelevision system detailsOptical rangefindersImage resolutionSignal characteristic
RGB-Z imaging systems acquire RGB data typically with a high X-Y resolution RGB pixel array, and acquire Z-depth data with an array of physically larger Z pixels having additive signal properties. In each acquired frame, RGB pixels are mapped to a corresponding Z pixel. Z image resolution is enhanced by identifying Z discontinuities and identifying corresponding RGB pixels where the Z discontinuities occur. Thus segmented data enables RGB background substitution, which preferably blends foreground pixel color and substitute background color. The segmented data also enables up-sampling in which a higher XY resolution Z image with accurate Z values is obtained. Up-sampling uses an equation set enabling assignment of accurate Z values to RGB pixels. Fixed acquisition frame rates are enabled by carefully culling bad Z data. Segmenting and up-sampling enhanced video effects and enable low cost, low Z resolution arrays to function comparably to higher quality, higher resolution Z arrays.
Owner:MICROSOFT TECH LICENSING LLC
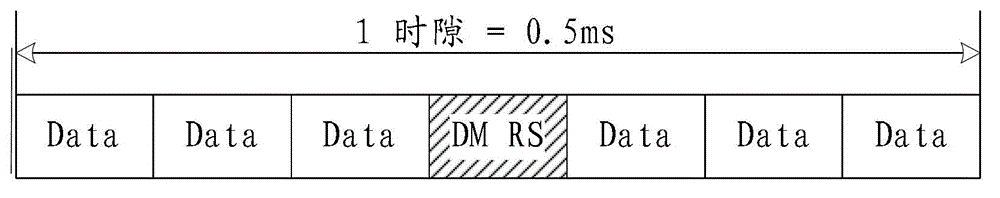
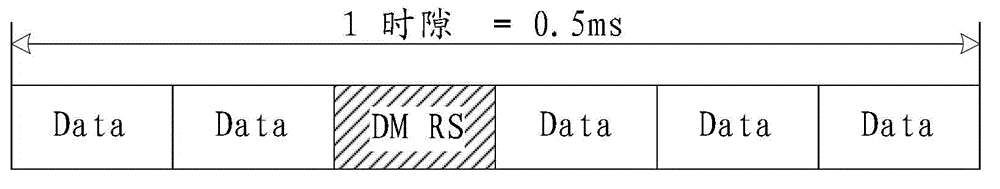
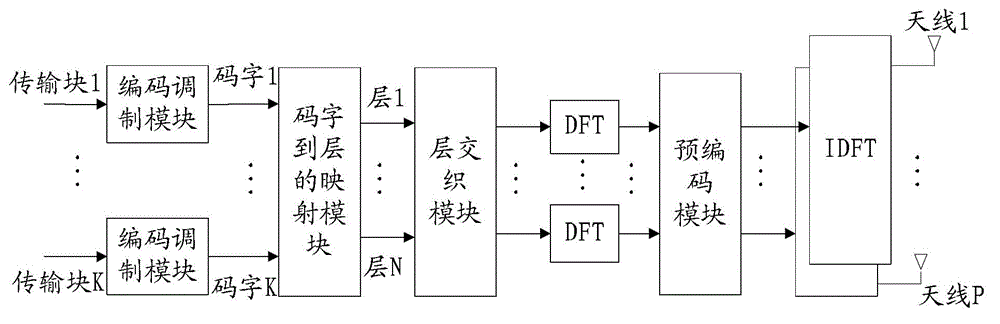
Uplink DMRS transmitting method, device and system/ Transmitting method, device and system used for uplink DMRS
ActiveCN103944665ASolve excessive overheadTransmission path divisionMulti-frequency code systemsTime domainDemodulation
The invention relates to the field of communication, provides an uplink DMRS (Demodulation Reference Signal) transmitting method, device and system and solves the problem that the time-frequency resource overhead of the uplink demodulation reference signal is excessive. The method comprises the steps that a base station configures a resource, a pattern or a parameter set required for transmitting the uplink DMRS for a user terminal; and the base station transmits or indicates the resource, the pattern or the parameter set required for transmitting the uplink DMRS to the user terminal via a bit domain or a high-level signaling of downlink control information. The resource, the pattern or the parameter set comprises a time domain position, a frequency domain position, a subframe configuration or a cycle, and a hopping mode. The technical scheme is applicable to a long term evolution system, and an uplink DMRS transmitting mechanism with the low time-frequency resource overhead is realized.
Owner:ZTE CORP
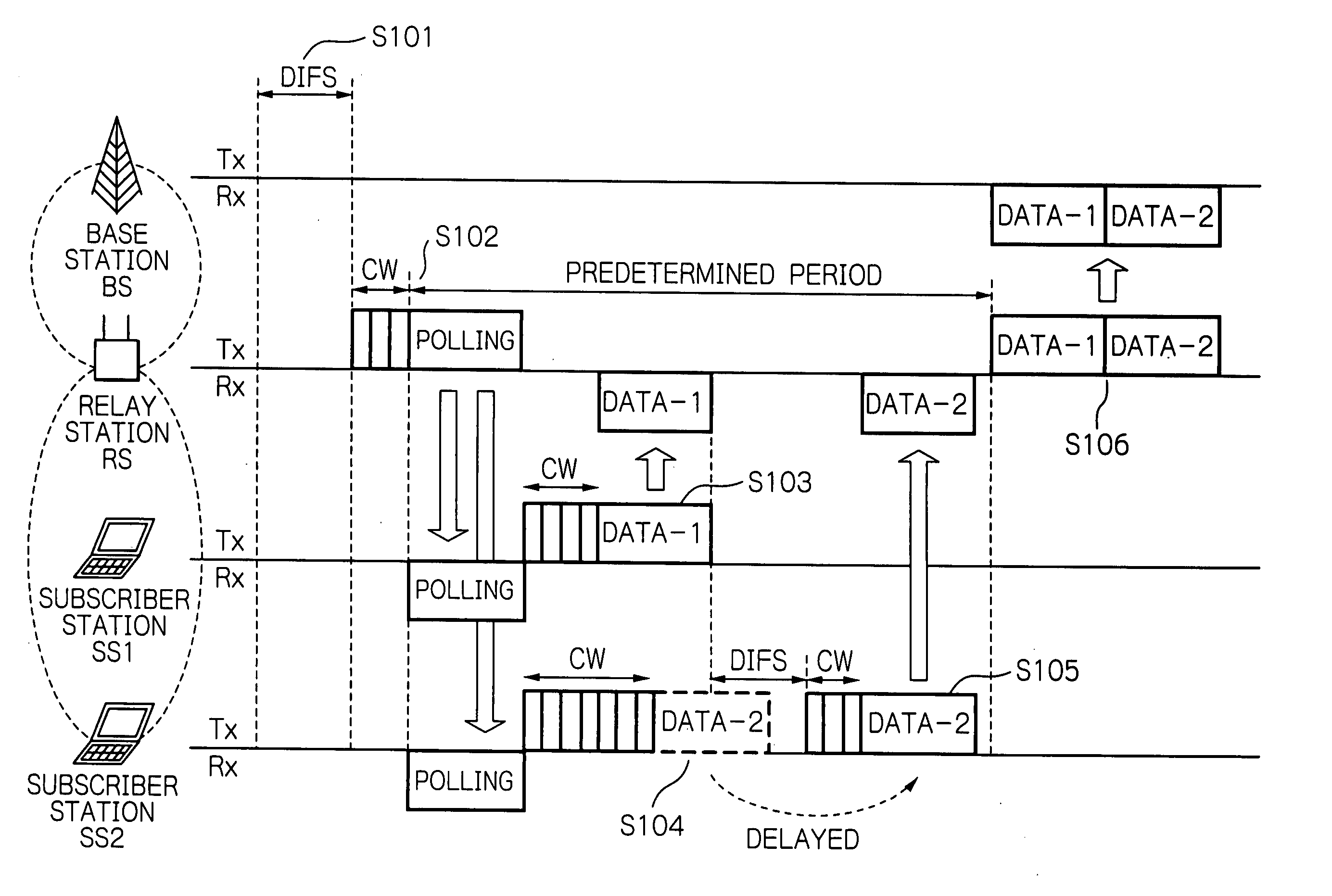
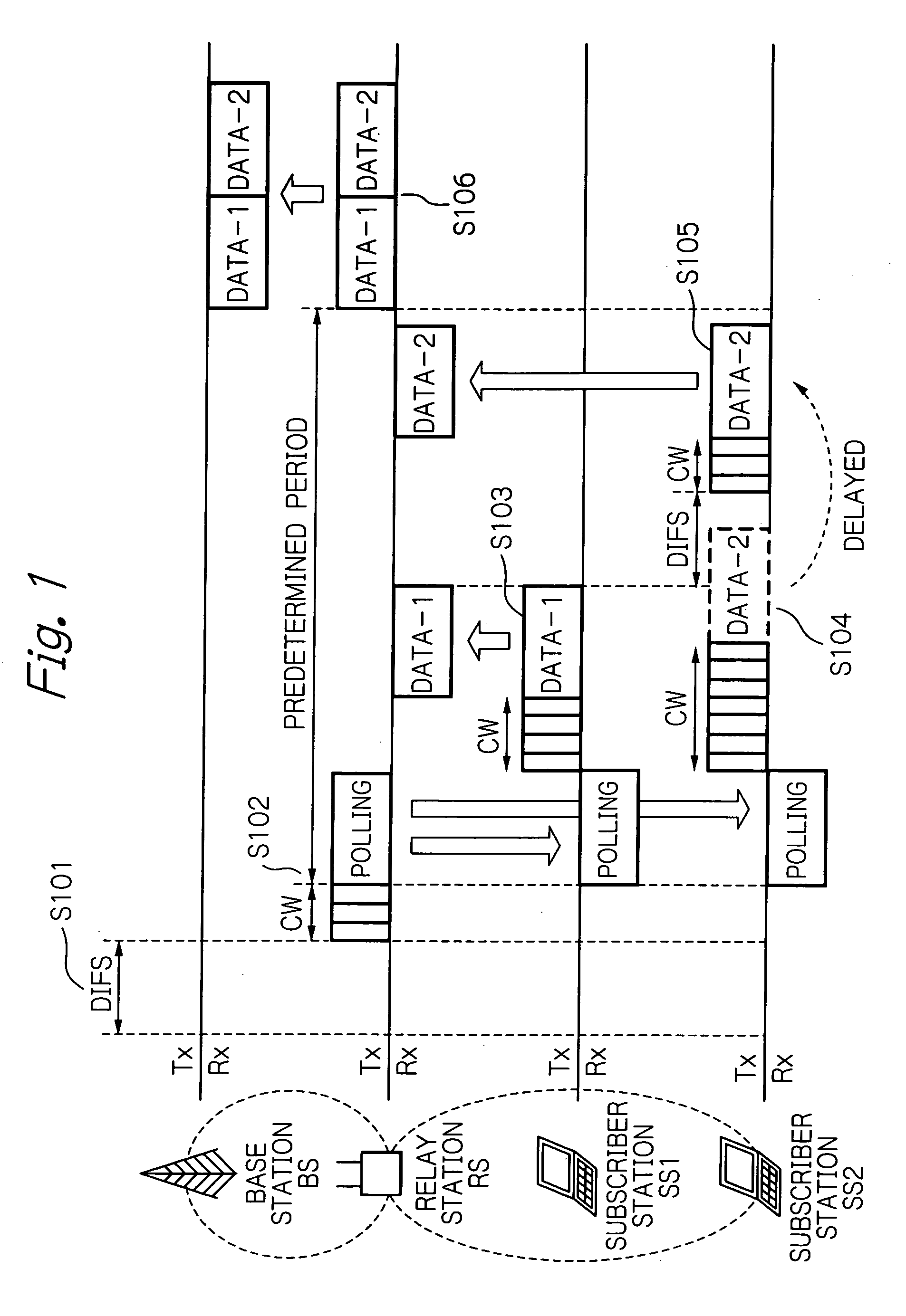
Method of medium access control for a wireless system and a relay station used in a wireless system
InactiveUS20060153132A1Wide coverage areaWide coverageTime-division multiplexRadio/inductive link selection arrangementsMedia access controlBroadcasting
The present invention relates to an method of medium access control for a wireless system that makes possible a subscriber station located out of coverage area of a base station communicate with the base station with the help of a relay station. The method includes broadcasting a polling packet by the relay station during the contention period, receiving the polling packet by the relayed subscriber station, transmitting a packet by the relayed subscriber station to the relay station during a predetermined period, and transmitting the packet to the base station by the relay station in the contention period after passing the predetermined period.
Owner:KDDI CORP
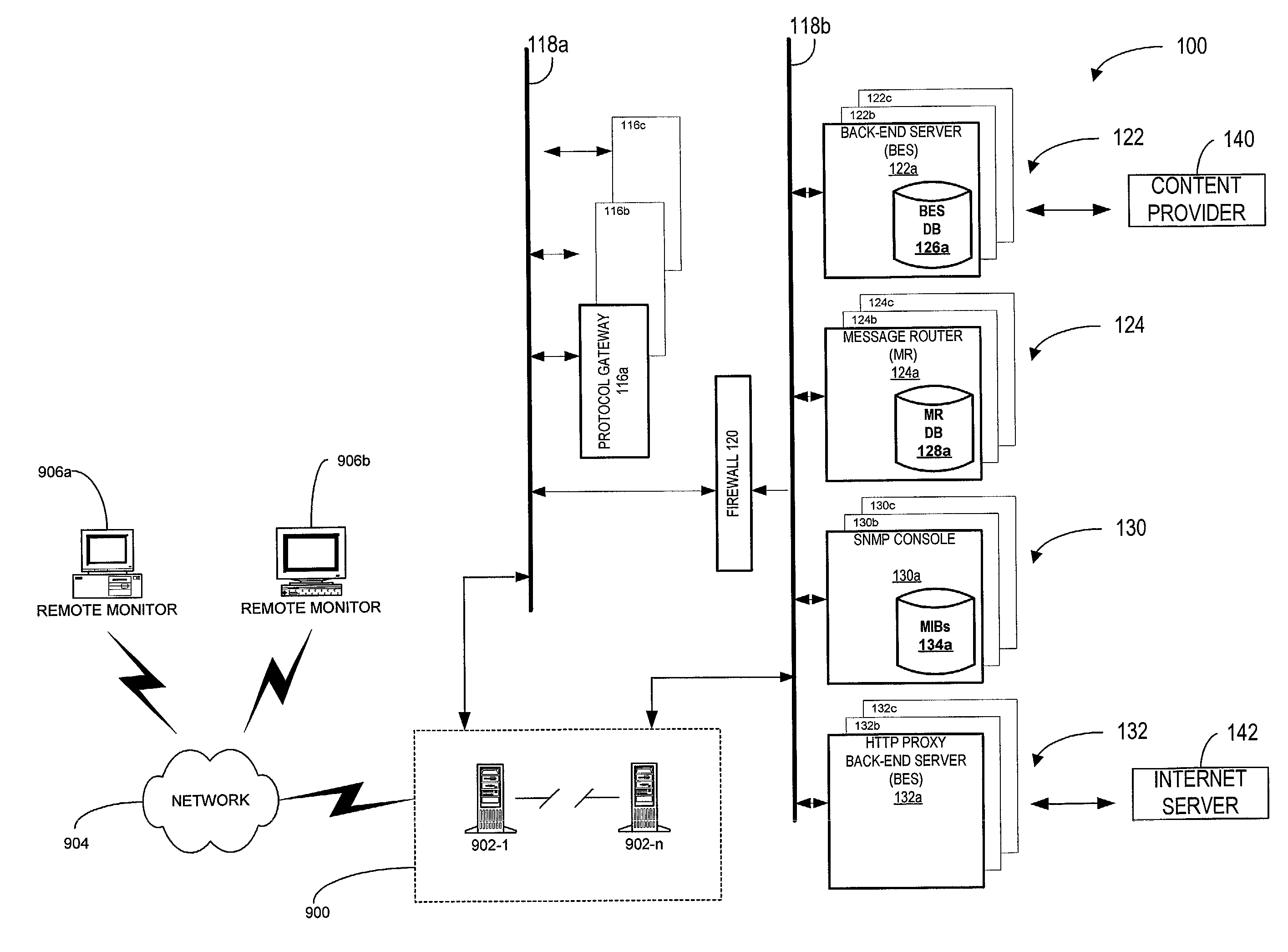
System and method to publish information from servers to remote monitor devices
InactiveUS7024474B2Easy to writeEfficient communicationError prevention/detection by using return channelDigital computer detailsWeb browserApplication software
To assist in monitoring the intelligent messaging network, a system and method for publishing logging and status information from the servers is provided. A list of available servers accessible for monitoring by persons, devices, and applications via a remote monitor device can be provided. The remote monitor device may forward selected servers from the list of available servers in which they are interested. Also, particular information about the selected servers can be requested. Access to certain servers and information may be restricted to those with authorization. Authorization can be verified by the use of digital certificates. The requested information can then be gathered and provided to authorized persons or devices. Typically, the information includes logging and status information from the servers. The information can be provided as an XML page and viewed using, for example, a standard web browser. Further, if the information is provided to the remote monitor device as an XML page, a standard XML parser may be used to extract particular information from the XML page.
Owner:TELECOMM SYST INC
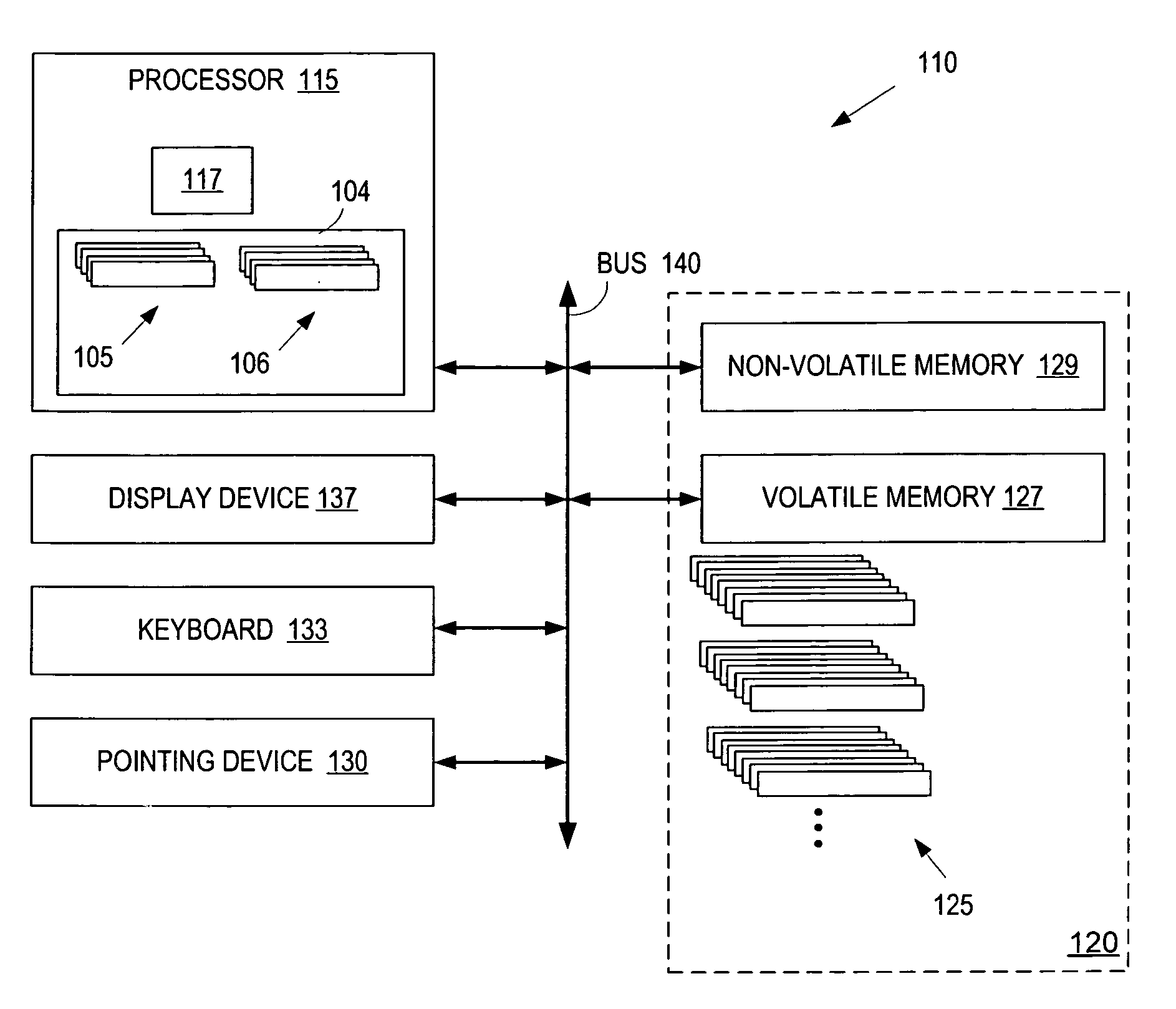
Method, apparatus and computer program product for efficient per thread performance information
InactiveUS6925424B2Solve excessive overheadAvoid interactionDigital computer detailsNuclear monitoringProcessor registerComputer science
A value in a counter on a processor is incremented for occurrences of a monitored event, providing a measured value for the event. The value of the counter register for a first thread is saved responsive to a switch from the first thread to a second thread. The value is saved in an accumulator in system memory. Then, responsive to a switch back to the first thread, the value for the first thread is restored from the accumulator. In this way, a counter may be read, and its value, for the first thread, for example, remains consistent despite any intervening thread switches. Since the counter register may be read directly, in the user state, this provides a faster and more consistent way to update performance counts.
Owner:IBM CORP
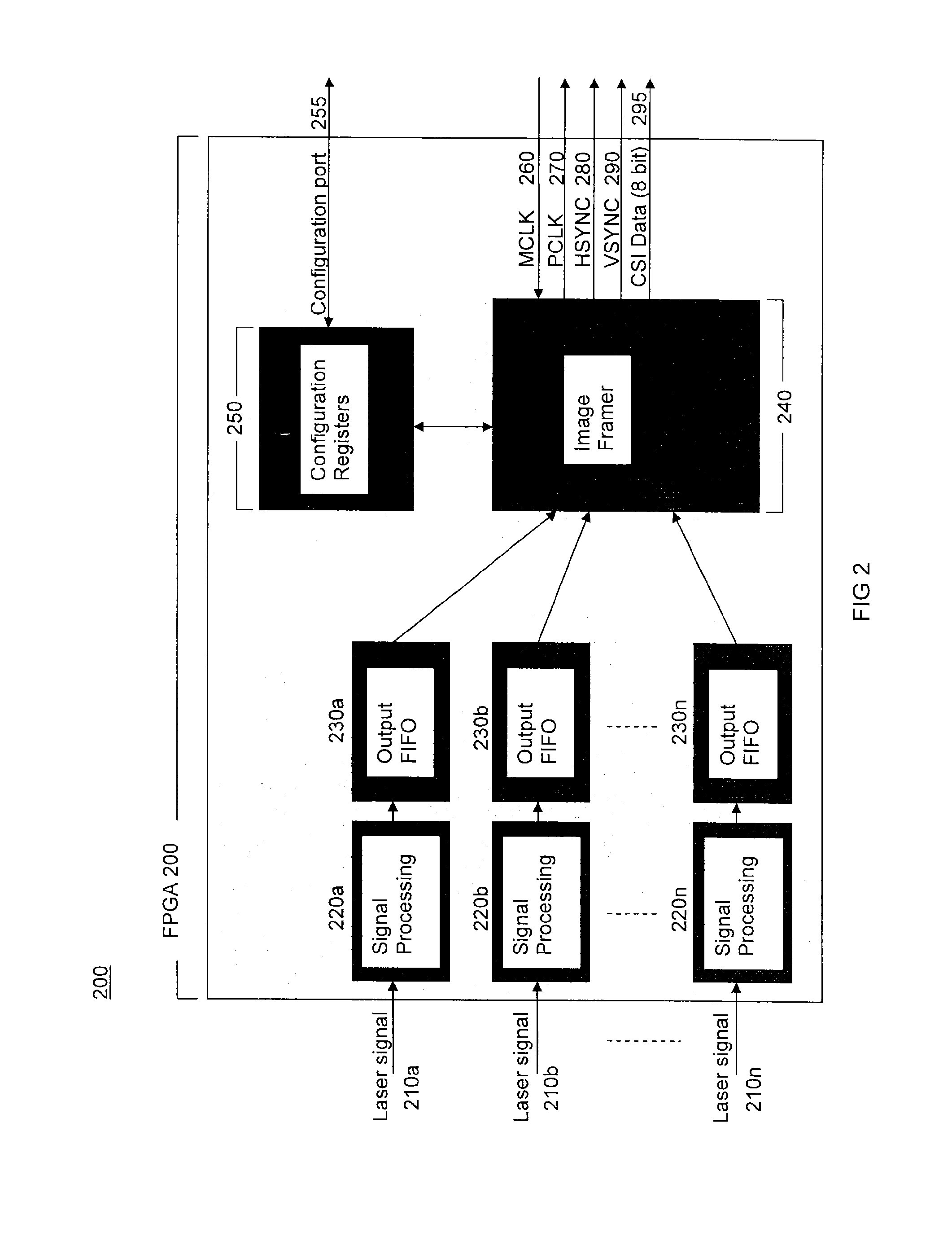
Method of using camera sensor interface to transfer multiple channels of scan data using an image format
ActiveUS9378403B2Solve the slow scanning speedSolve excessive overheadRecord carriers used with machinesSensing by electromagnetic radiationLaser scanningComputerized system
Owner:HONEYWELL INT INC
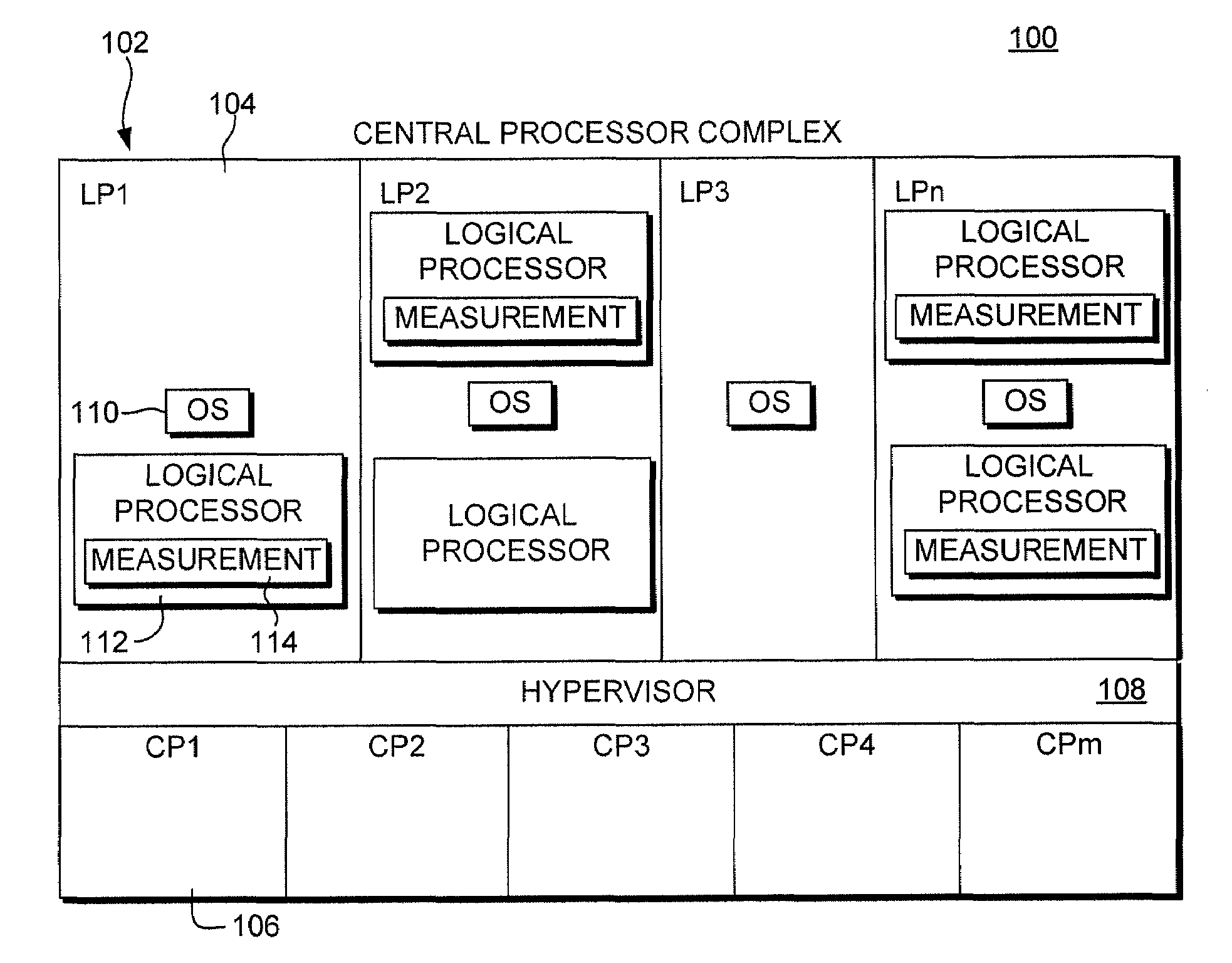
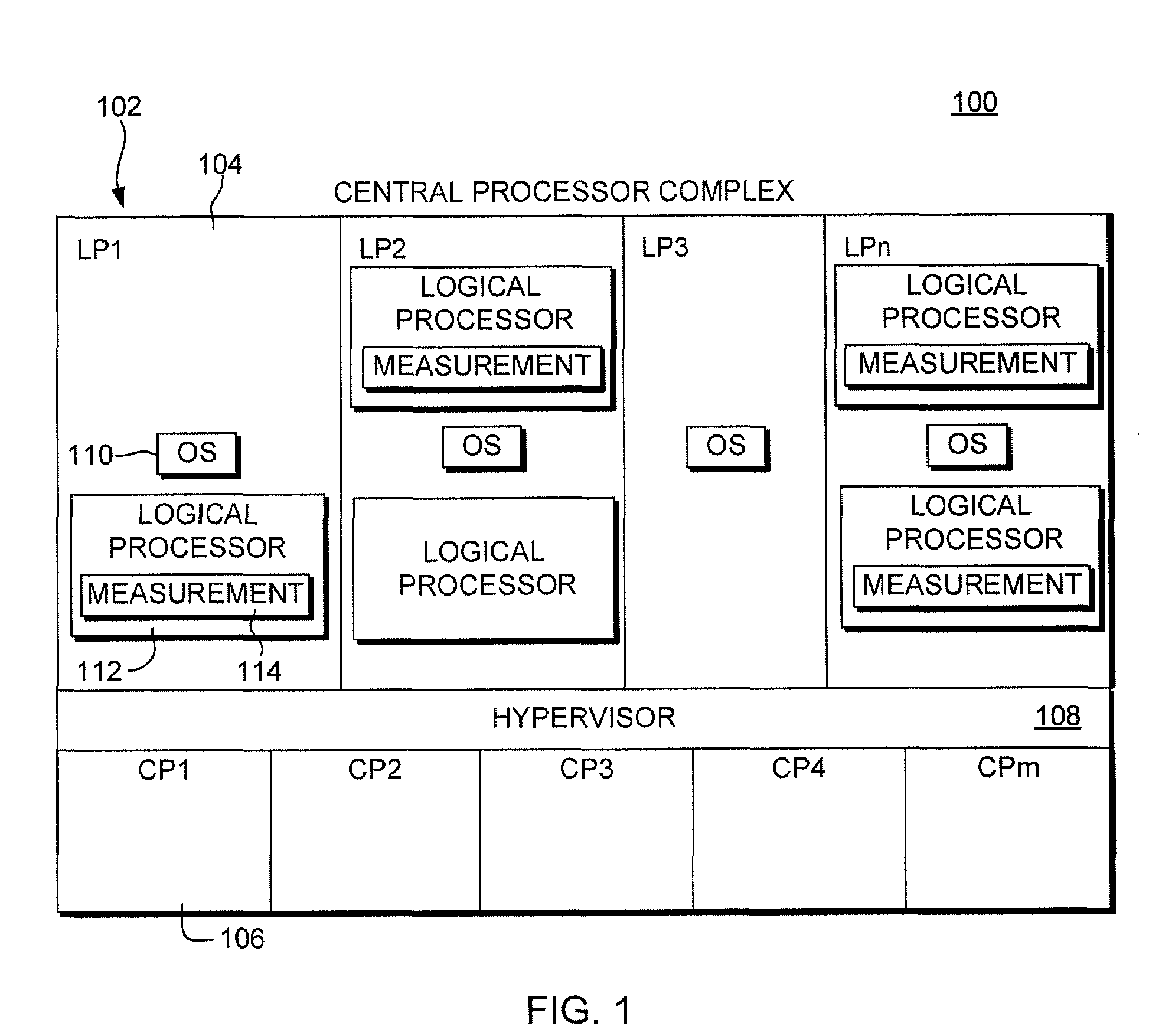
Virtualization of a central processing unit measurement facility
ActiveUS20100088771A1Less disruptiveLess effectiveDigital data processing detailsError detection/correctionVirtualizationComputer science
A central processing unit measurement facility is virtualized in order to support concurrent use of the facility by multiple guests executing within a virtual environment. Each guest of the environment has independent control over disablement / enablement of the facility for that guest.
Owner:IBM CORP
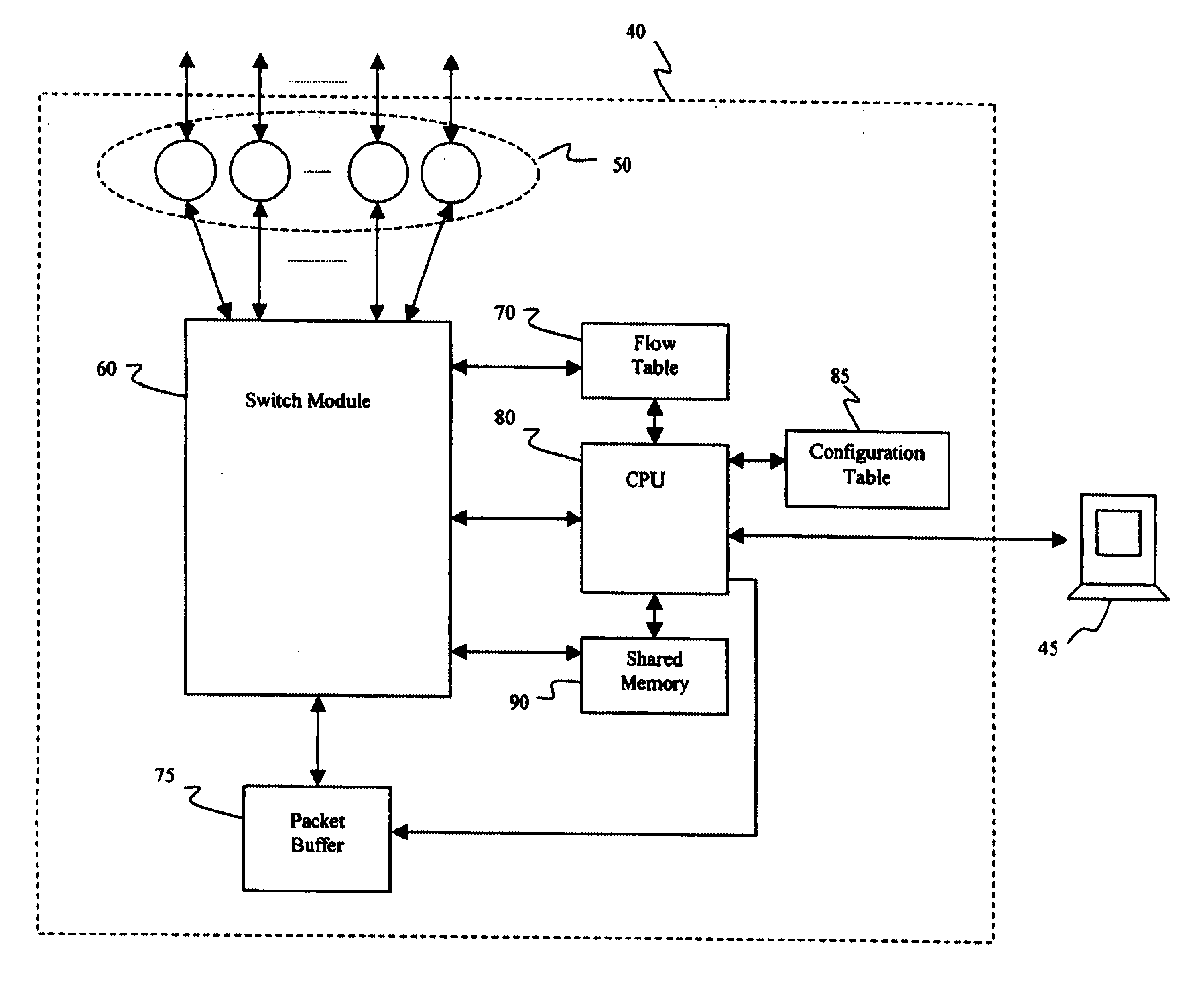
Method and apparatus for multiprotocol switching and routing
InactiveUS6876654B1Low implementation costPartly effectiveTime-division multiplexNetworks interconnectionMultiprotocol Label SwitchingWire speed
A packet forwarding method and apparatus performs multiprotocol routing (for IP and IPX protocols) and switching. Incoming data packets are examined and the flow (i.e., source and destination addresses and source and destination socket numbers) with which they are associated is determined. A flow table contains forwarding information that can be applied to the flow. If an entry is not present in the table for the particular flow, the packet is forwarded to the CPU to be processed. The CPU can then update the table with new forwarding information to be applied to all future packets belonging to the same flow. When the forwarding information is already present in the table, packets can thus be forwarded at wire speed. A dedicated ASIC is preferably employed to contain the table, as well as the engine for examining the packets and forwarding them according to the stored information. Decision-making tasks are thus more efficiently partitioned between the switch and the CPU so as to minimize processing overhead.
Owner:INTEL CORP
System and method for secure data transmission and storage
ActiveUS20170061138A1Easily and effectively utilizedReducing cost and complexityDigital data protectionSecuring communicationData transmissionData objects
Owner:GRID7 LLC
Using shrinkable read-once snapshots for online data backup
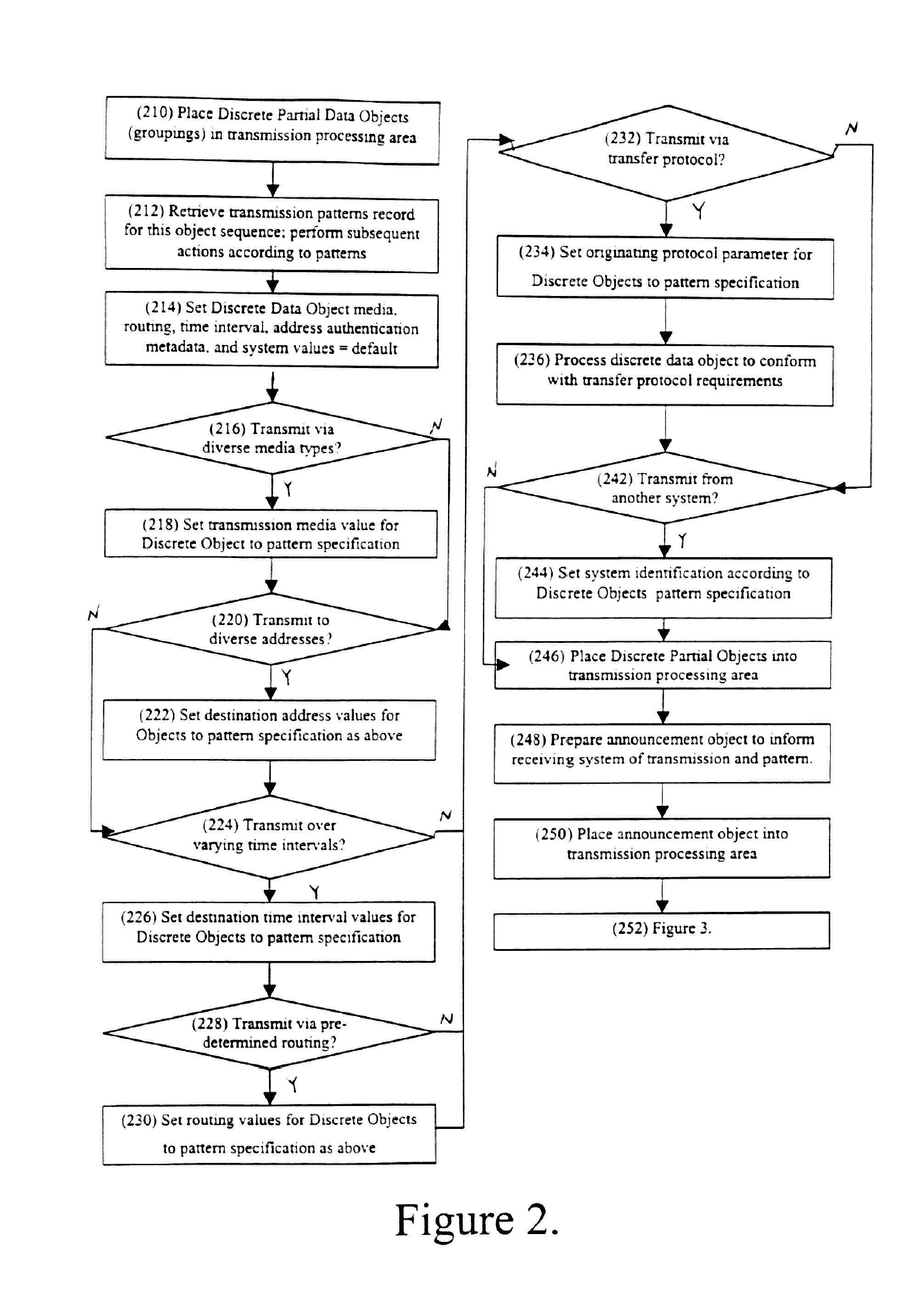
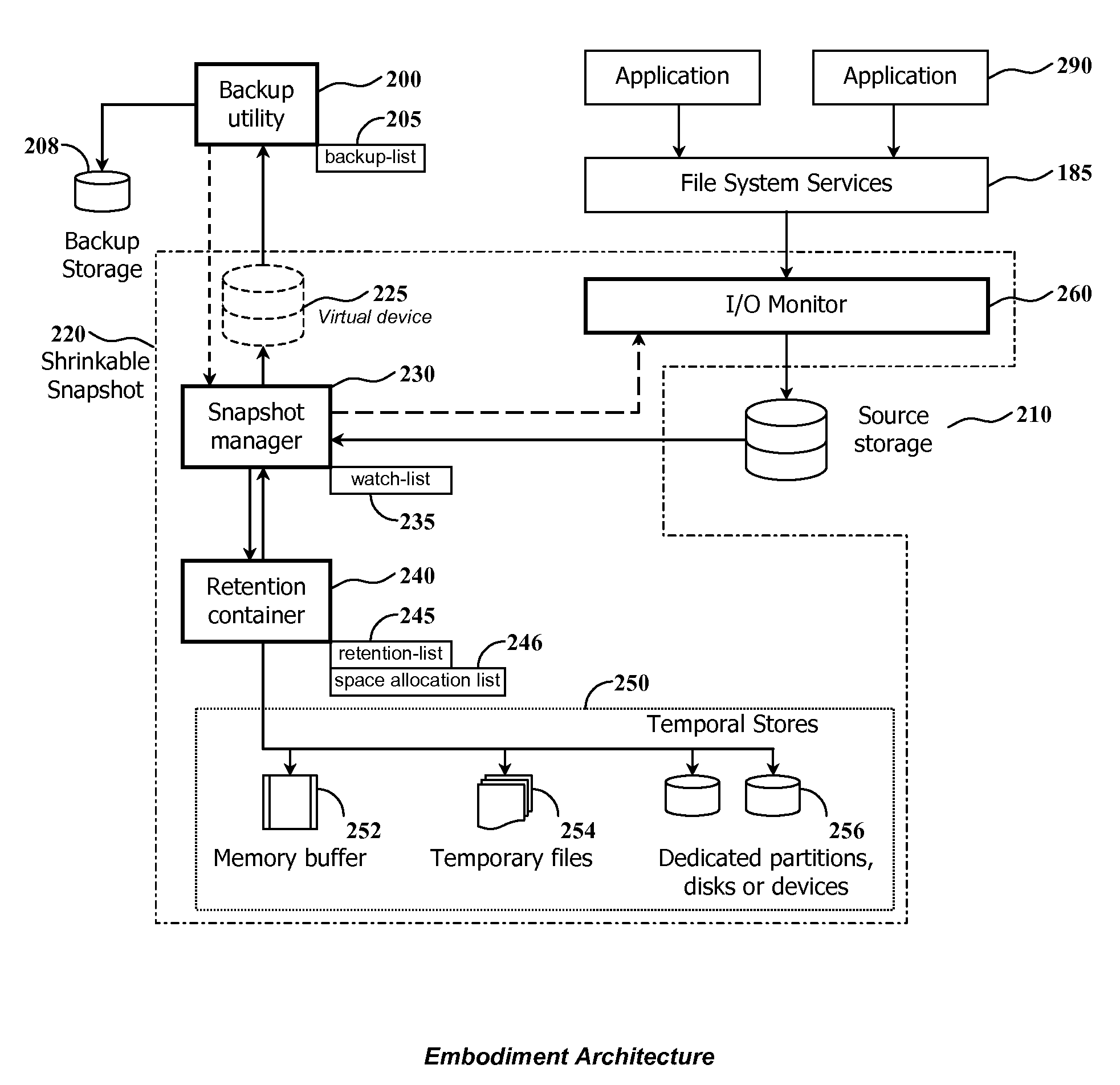
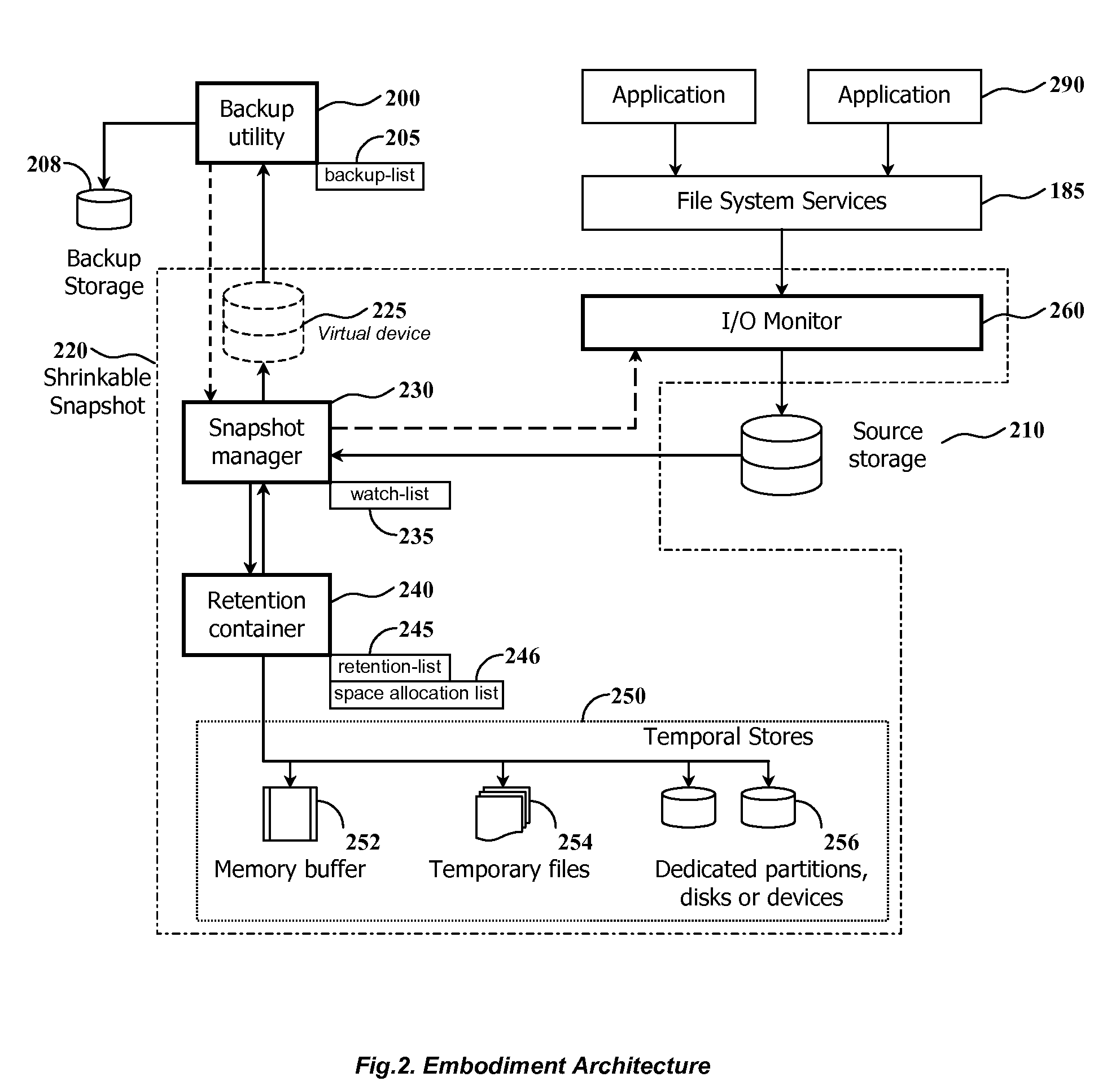
InactiveUS20080082593A1Improve performanceEasy to useDigital data information retrievalError detection/correctionRetention timeWatch list
The present invention discloses a method and system for snapshot-based online backup operations permitting reduced requirements to storage capacity and computational overhead for snapshot function.At the beginning of an online backup operation, the backup software system creates a snapshot of source data storage. The snapshot includes a watch-list used for identifying blocks of a source storage which are watched by snapshot management means for update. If a block included into the watch-list was requested for update, the snapshot management means preserve original contents of that block in a retention container for the purpose of temporary store. The retention container includes a set of temporal stores dedicated for transient storing of blocks until they are backed up.The essence of the invention is enabling to exclude blocks from the watch-list and the retention container at any moment within the period of snapshot operation. Therefore it is possible to exclude unnecessary blocks from the scope of blocks managed by the snapshot management means, for the purpose of preserving point-in-time data.Backed up blocks can be operatively excluded from the snapshot so that unchanged blocks are excluded from the watch-list and updated blocks are removed from the retention container. In the latter case temporal stores are shrunk as well. This technique allows to reduce progressively storage expenses and computational overheads required for maintenance of a snapshot being used in the online backup routine.When a volume-level online backup is performed the snapshot is switched to the read-once mode at the beginning of the data copying stage. A backup utility performs sequential read of blocks from the snapshot. The snapshot management means automatically exclude requested blocks from the scope of managed blocks.
Owner:PARAGON SOFTWARE GMBH
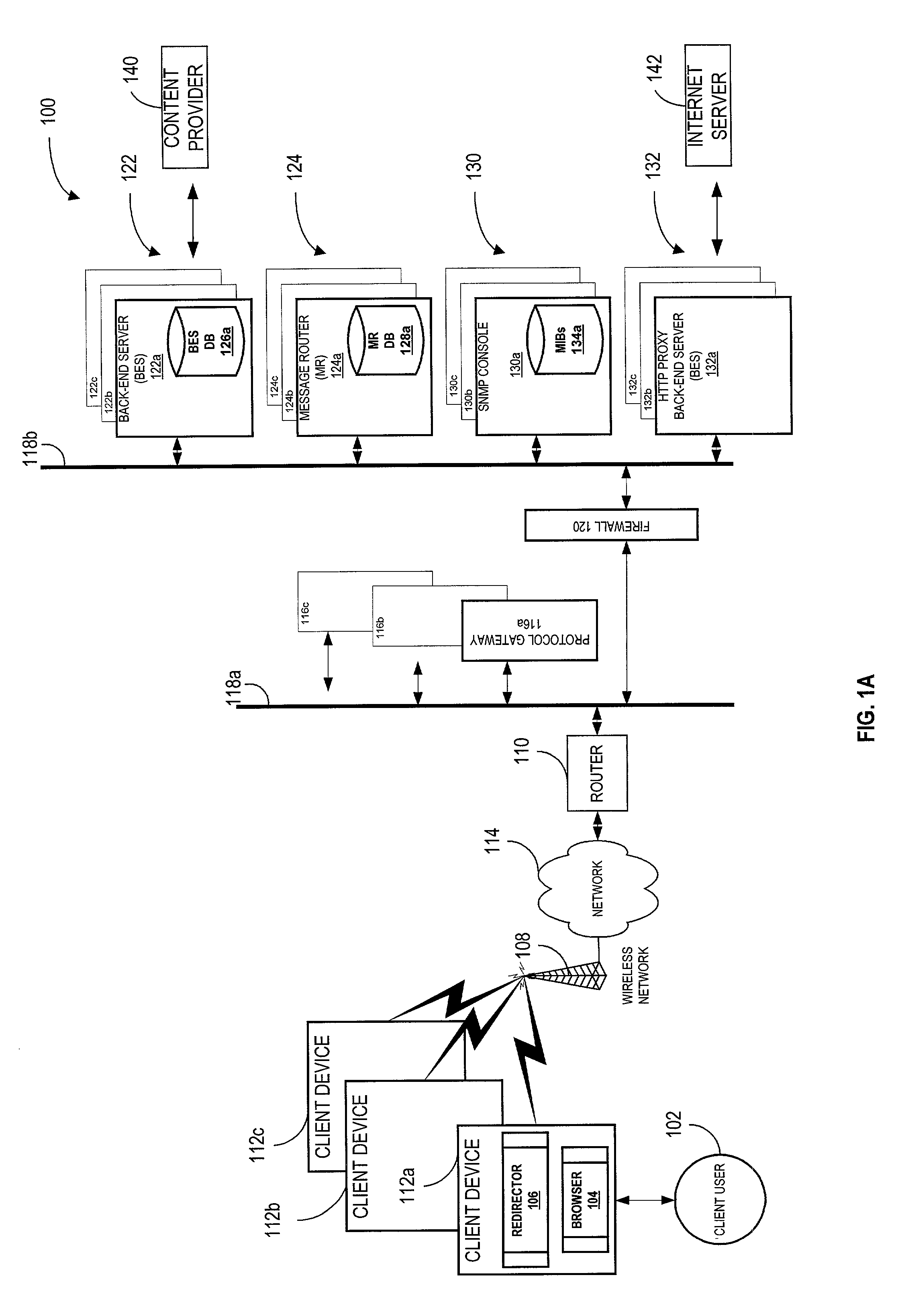
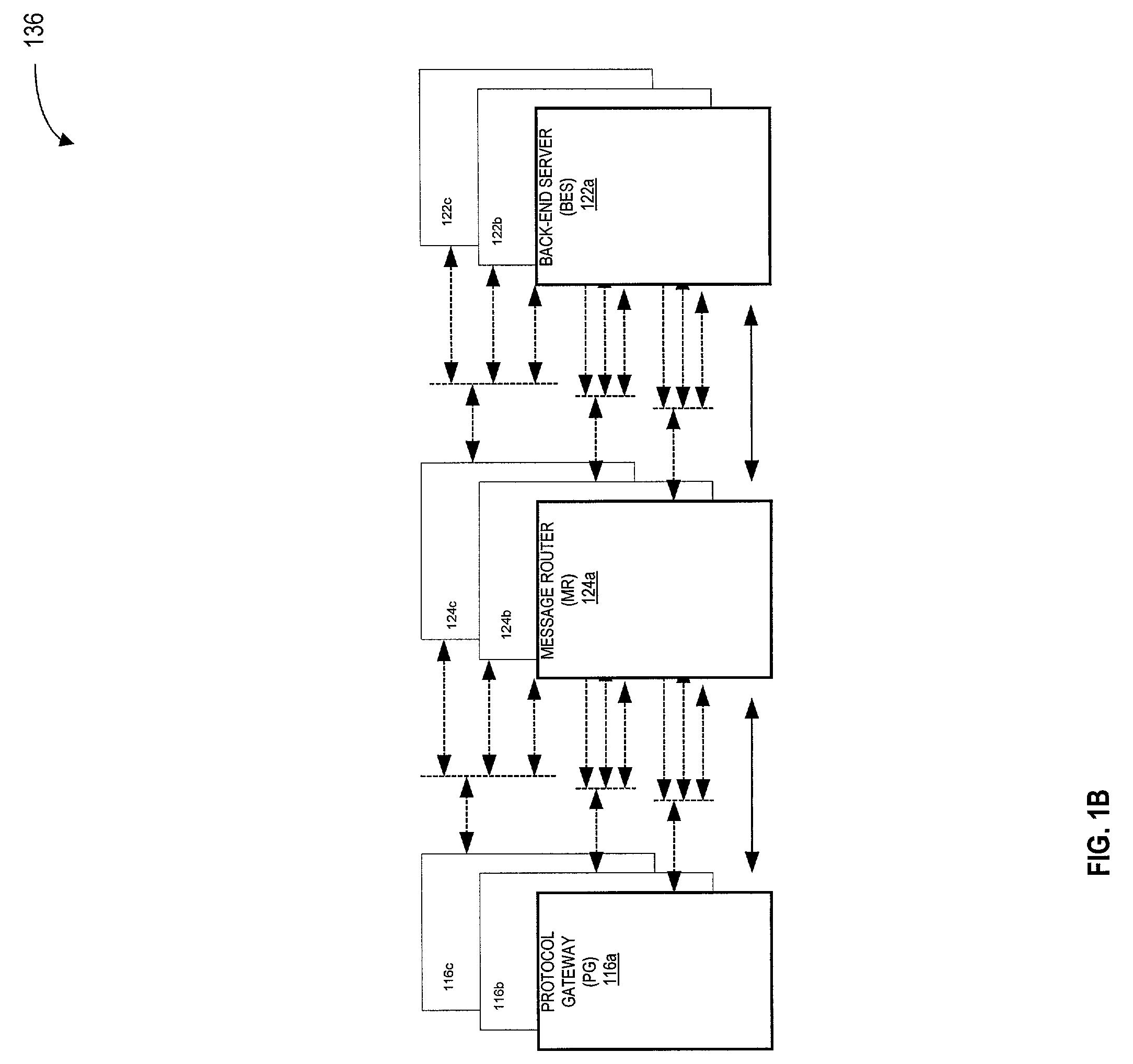
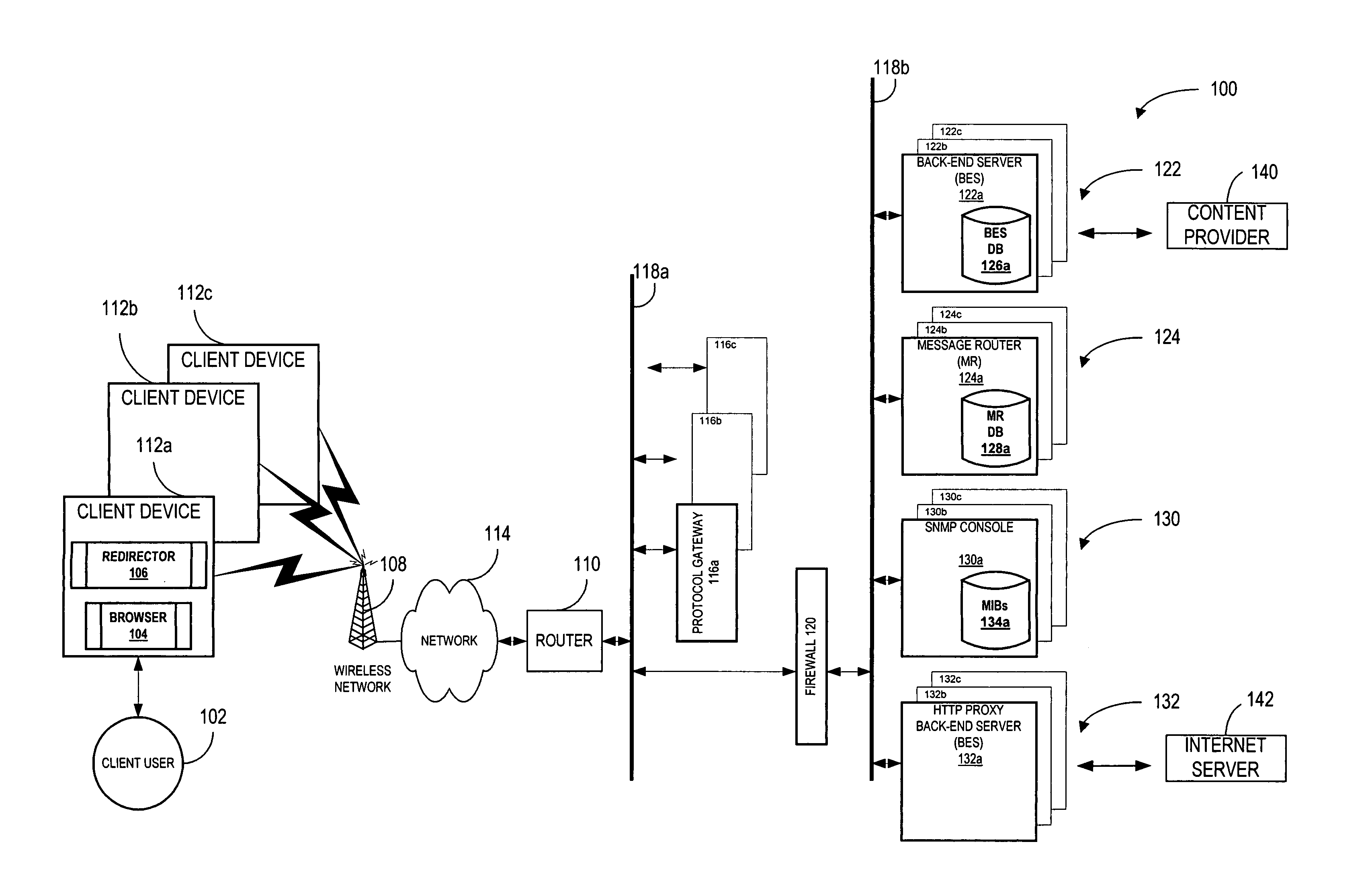
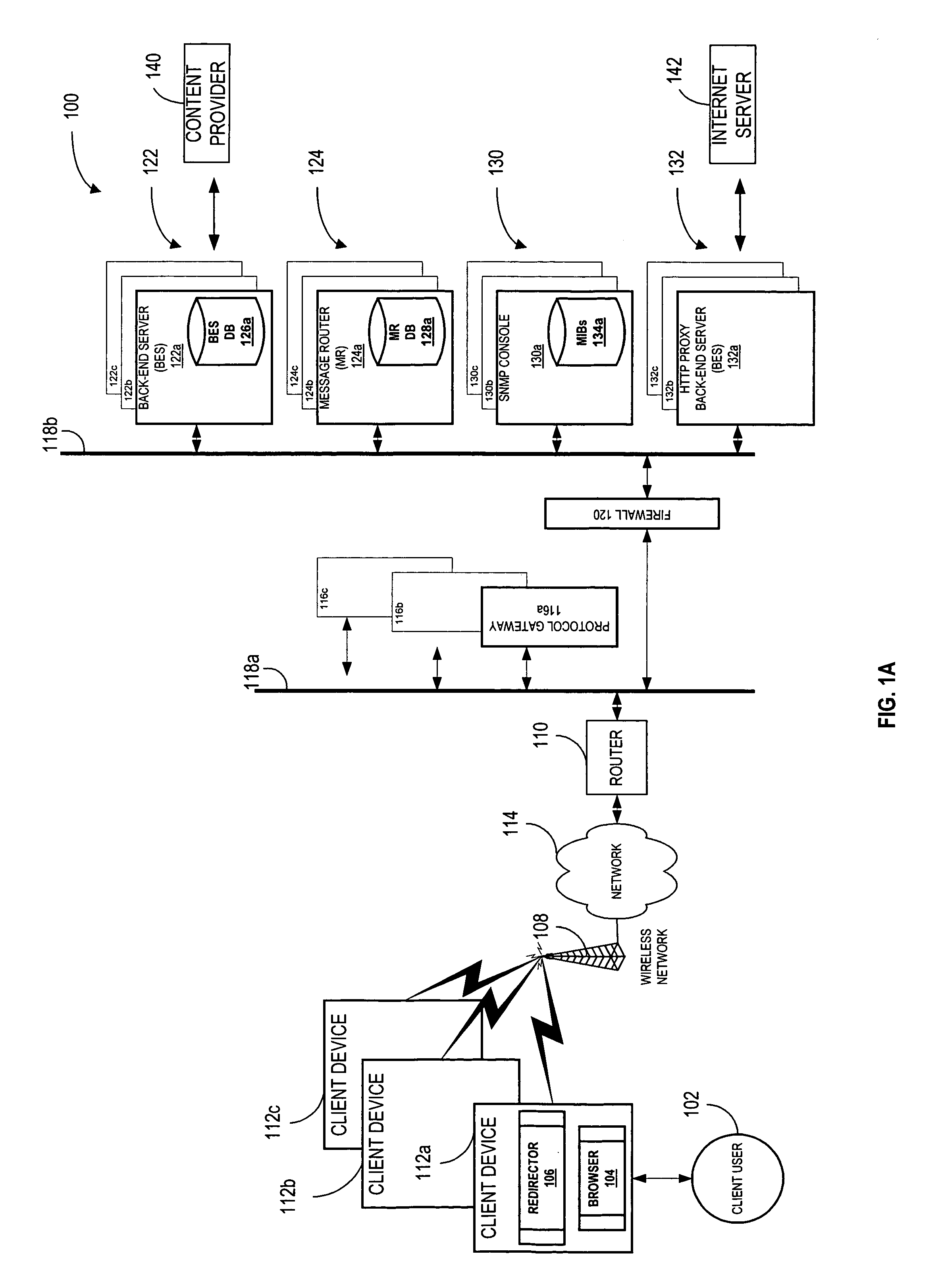
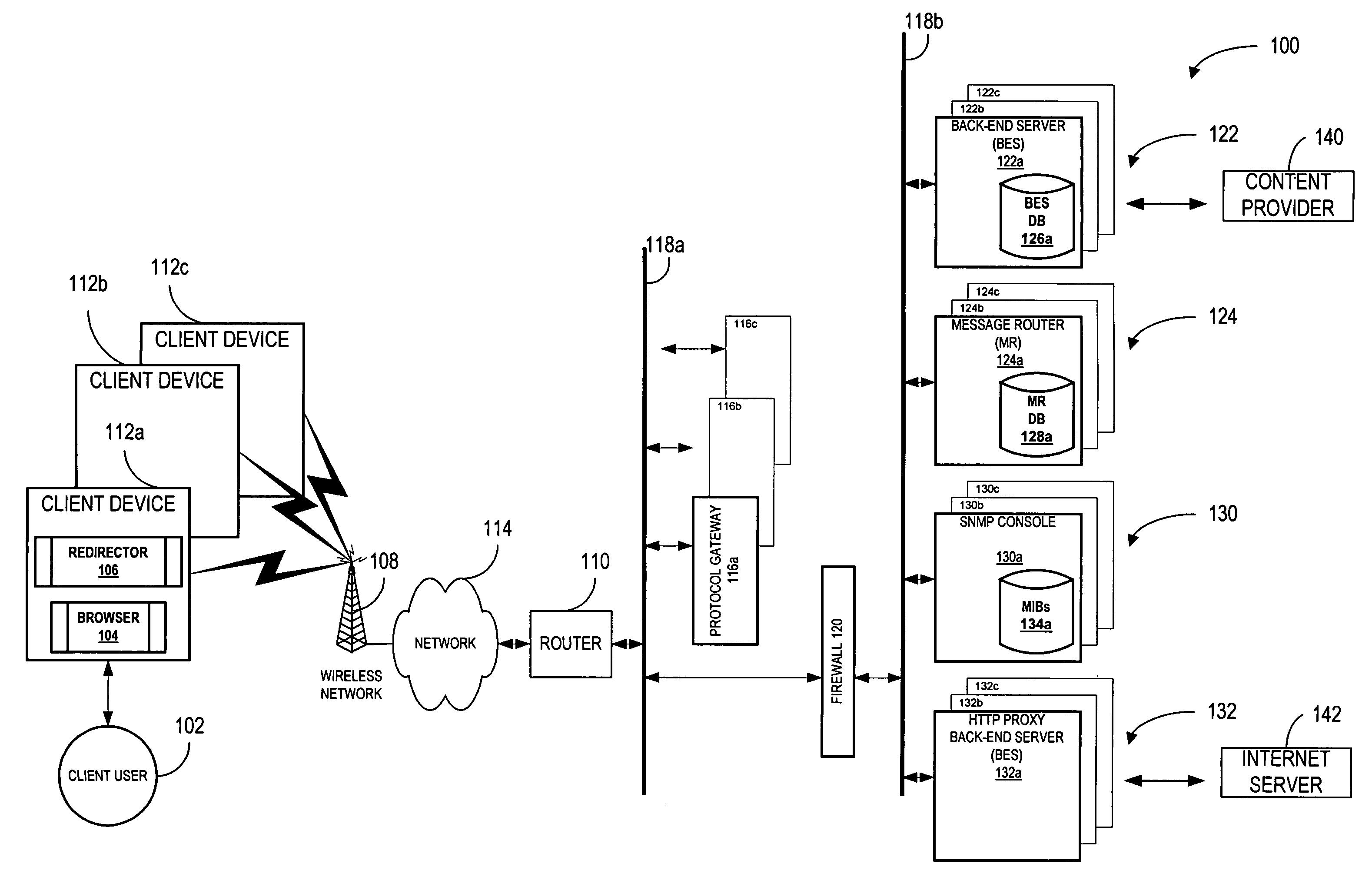
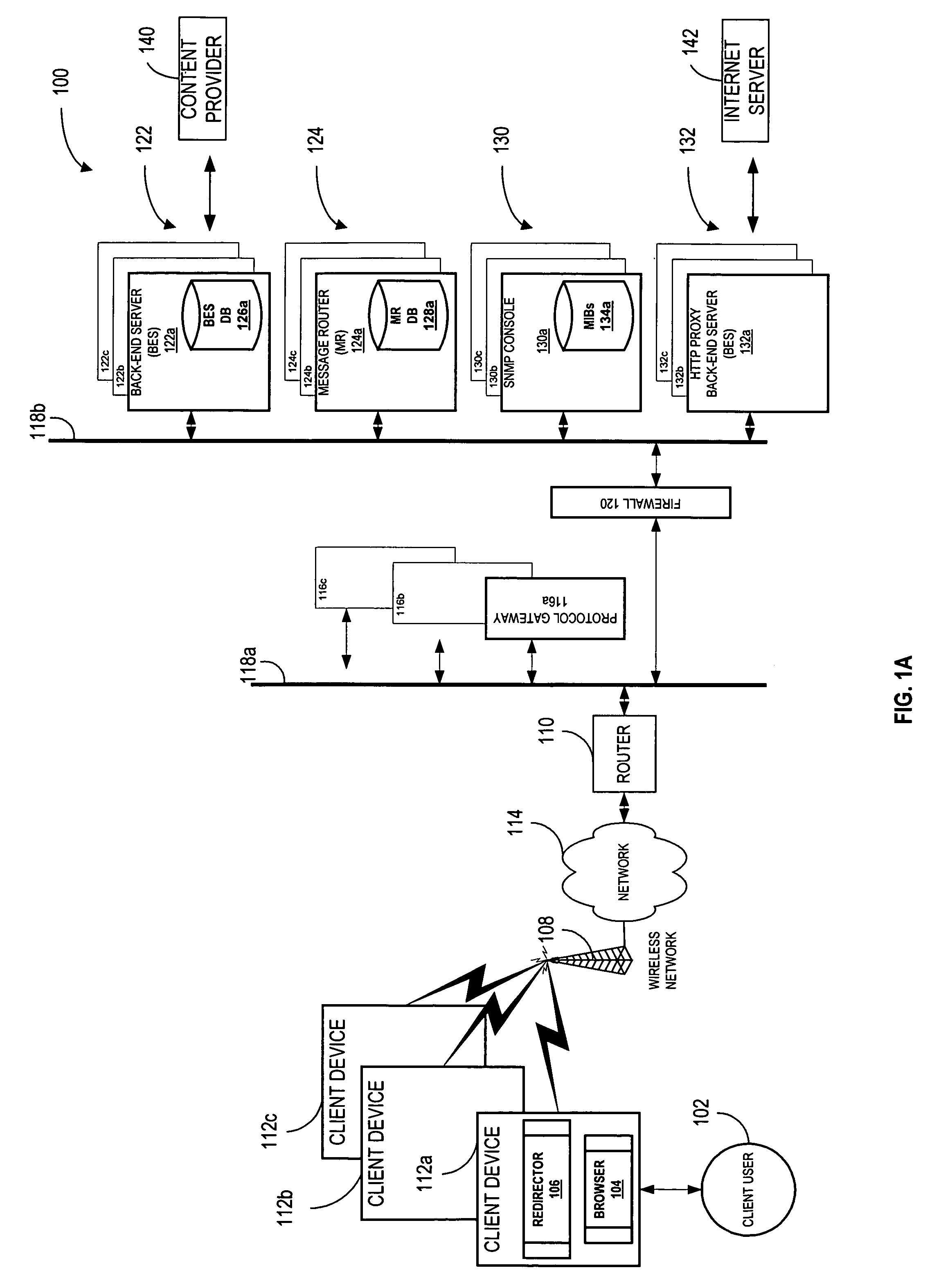
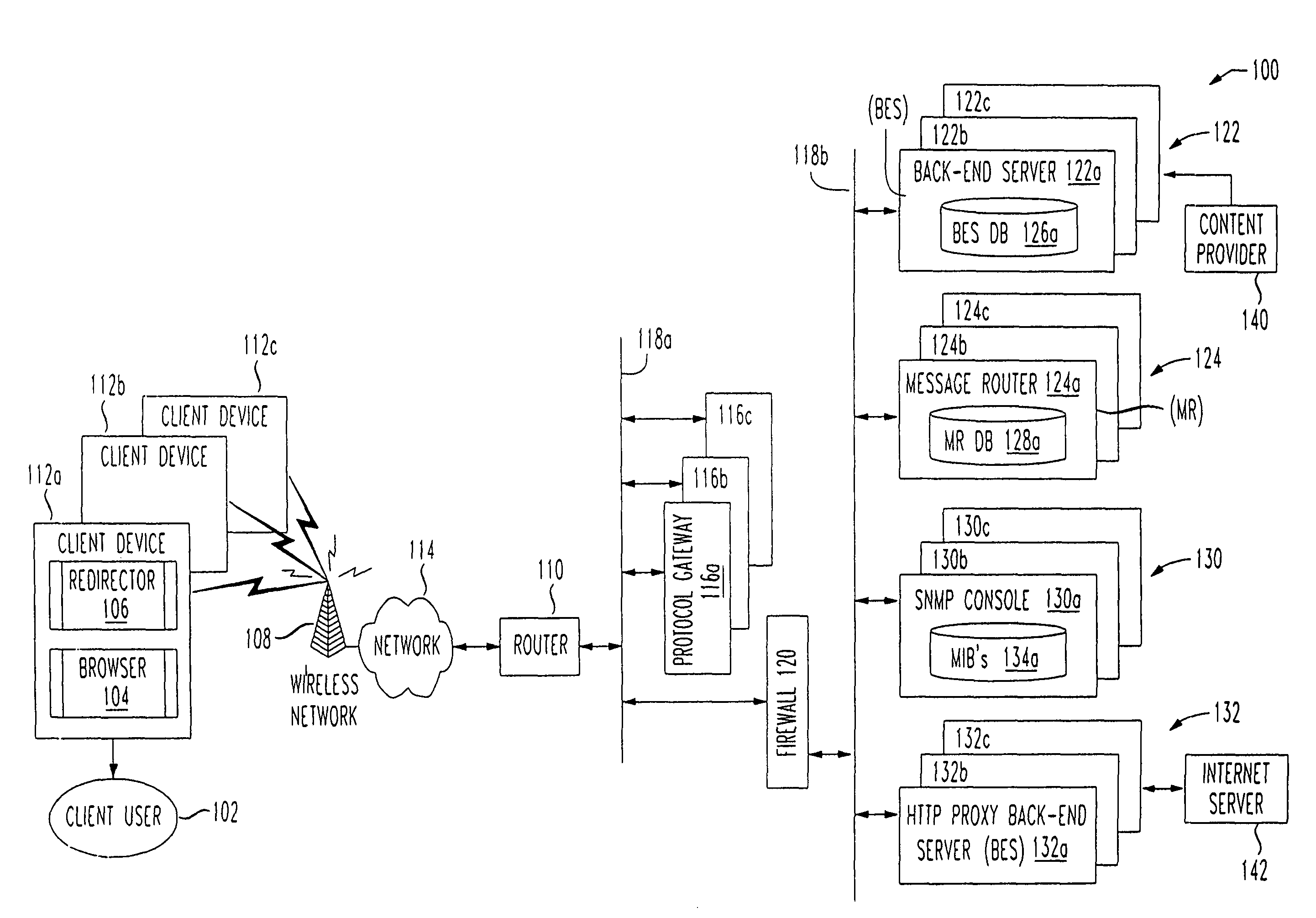
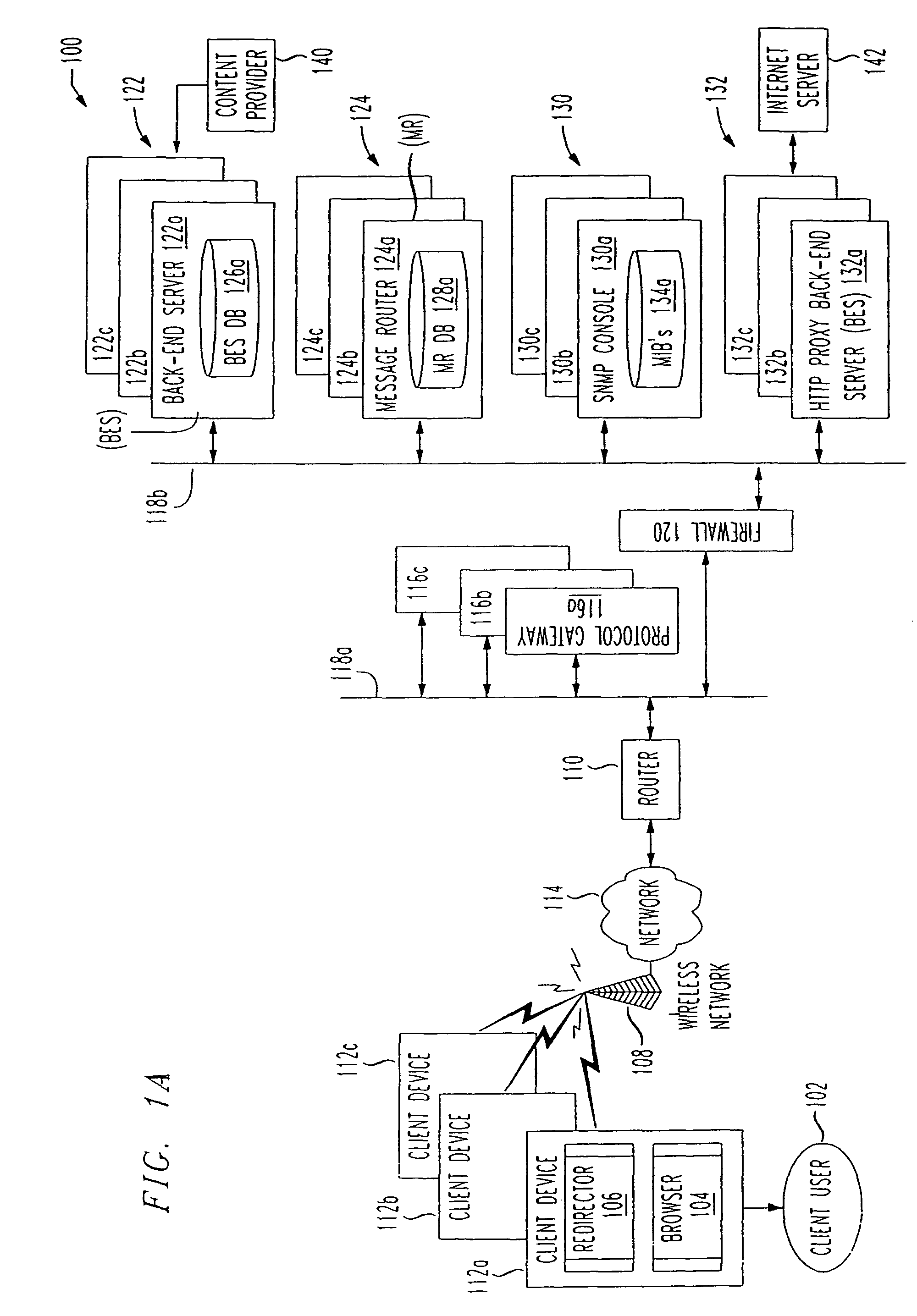
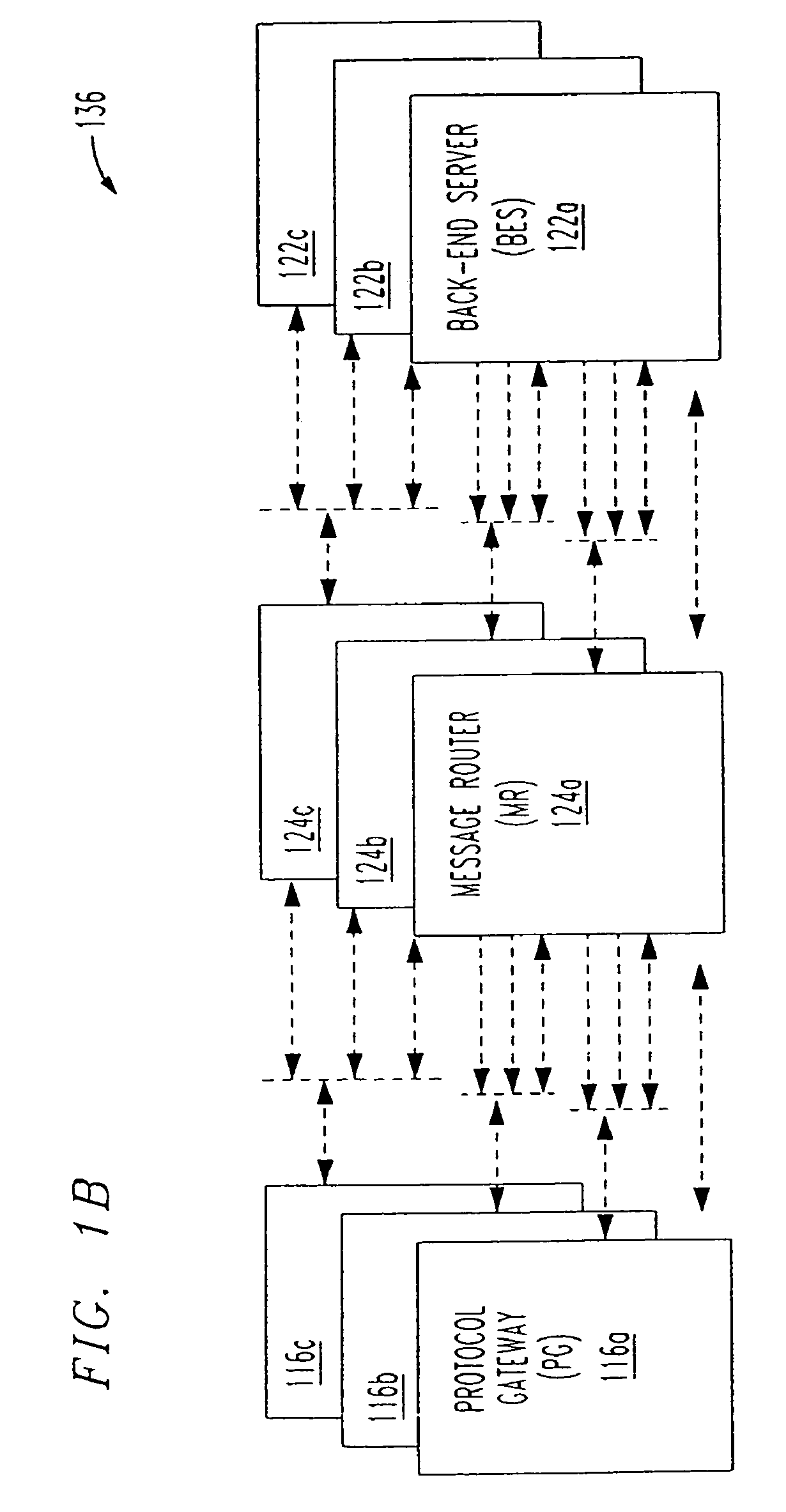
System and method for re-directing requests from browsers for communication over non-IP based networks
InactiveUS7003571B1Easy to writeEfficient communicationError prevention/detection by using return channelData switching by path configurationClient-sideWeb server
A method and system for deploying content to client applications is provided. Inbound messages are accepted from a client application running on a client device via a proxy IP / port. The inbound messages are packaged into an internal message format with an HTTP redirector. The packaged message is forwarded to a back-end server via a message router. A response is received form from a web server. The response is packaged into the internal message format with the back-end server. The response is then forwarded to the HTTP redirector via a message router. The response can then be transferred to the client application running on the client device, via the proxy IP / port.
Owner:TELECOMM SYST INC +1
Method, apparatus and computer program product for efficient, large counts of per thread performance events
InactiveUS6931354B2Maximum countSolve excessive overheadDigital computer detailsNuclear monitoringComputer scienceComputer program
Performance events are counted for a computing system. This includes designating a first processor counter as a low-order counter for counting a certain performance event encountered by the processor and associating with the first counter a second counter as a high-order counter. The first counter is incremented responsive to detecting the performance event for a first processing thread. Responsive to a second thread, an accumulator in system memory for the first thread and first and second counters is updated. Responsive to the first thread becoming active, values of the first and second counters are loaded from the accumulator. Responsive to a user call to read and return a combined value, a first instance of the second counter is read, then the first counter is read and a second instance of the second counter is read before returning the combined value.
Owner:INT BUSINESS MASCH CORP
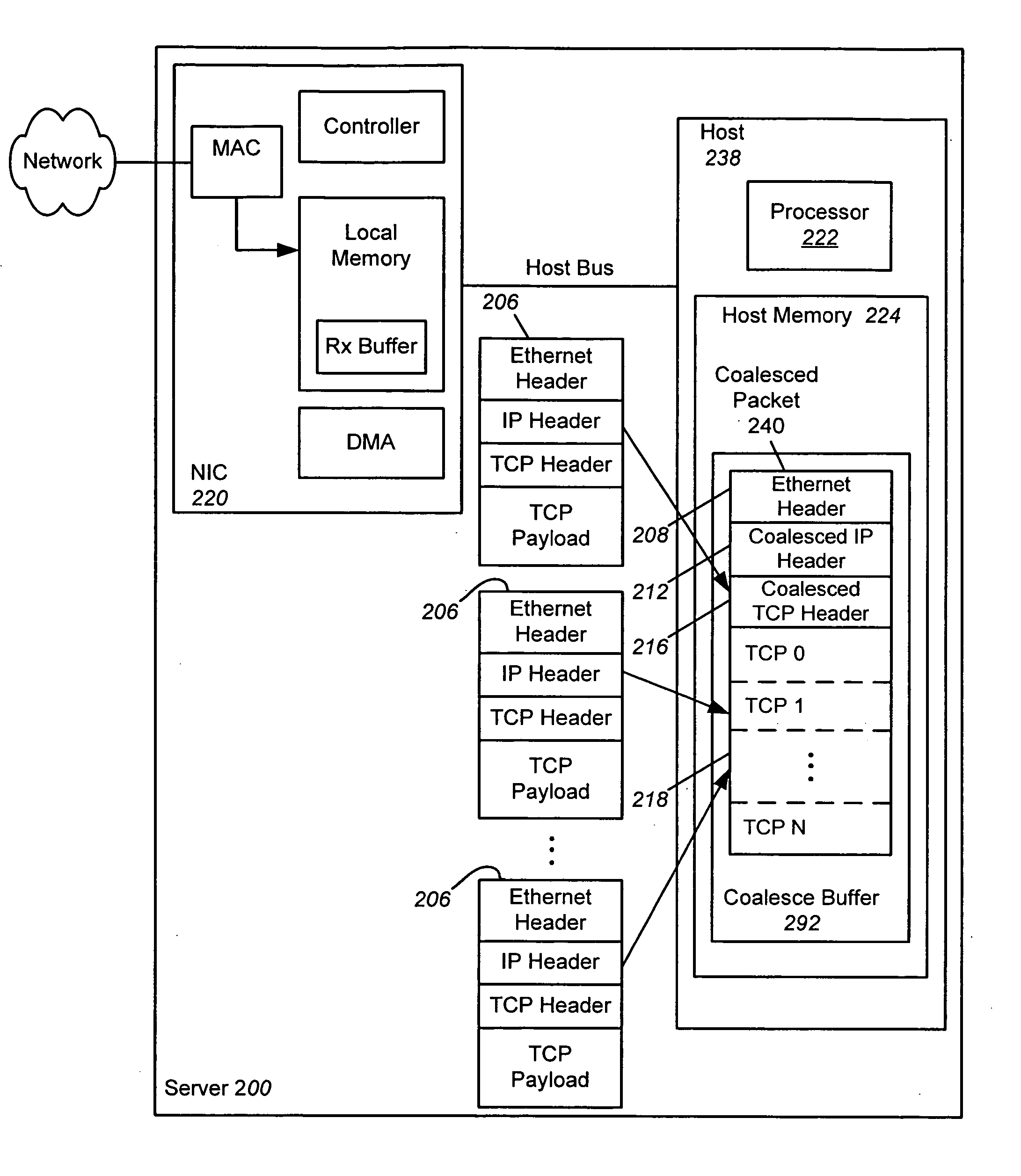
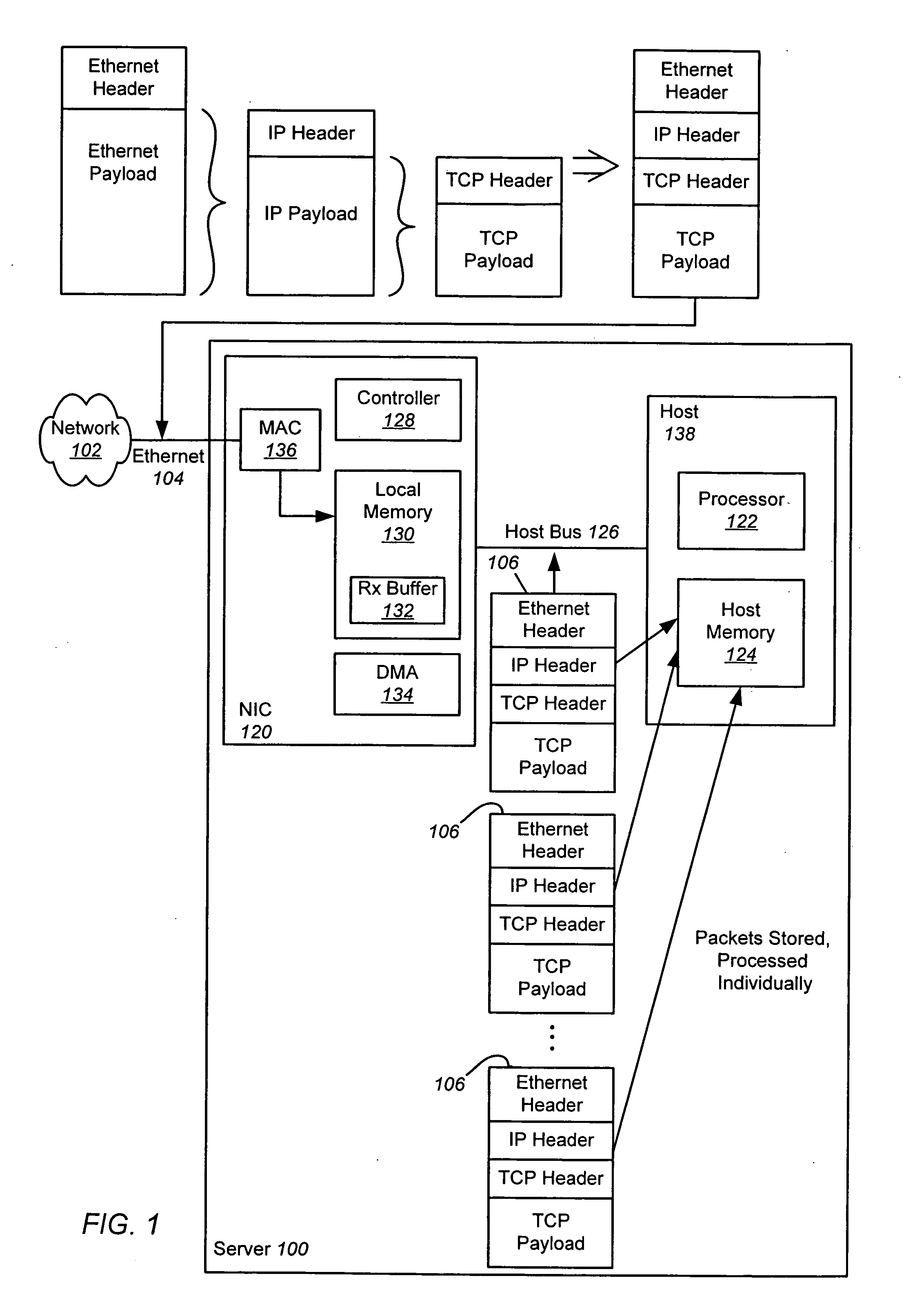
Receive coalescing and automatic acknowledge in network interface controller
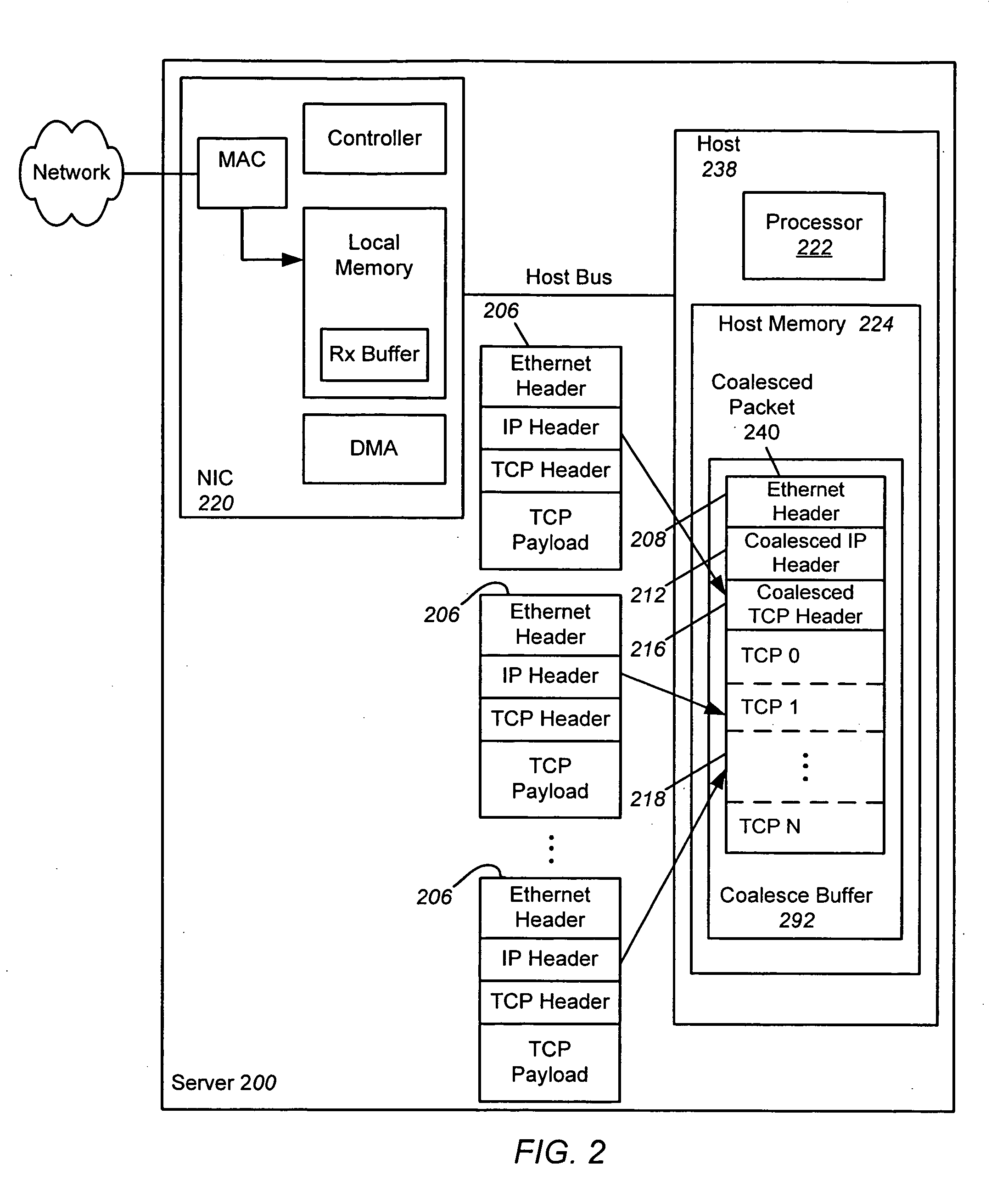
ActiveUS20070064737A1Reduce computational overheadImprove network performanceTime-division multiplexTransmissionHost memoryInternet Protocol
An apparatus and method is disclosed for reducing the computational overhead incurred by a host processor during packet processing and improving network performance by adding additional functionality to a Network Interface Controller (NIC). Under certain circumstances the NIC coalesces multiple receive packets into a single coalesced packet stored within a coalesce buffer in host memory. The coalesced packet includes an Ethernet header, a coalesced Internet Protocol (IP) header, a coalesced Transmission Control Protocol (TCP) header, and a coalesced TCP payload containing the TCP payloads of the multiple receive packets. By coalescing received packets into fewer larger coalesced packets within the host memory, the host software needed to process a receive packet will be invoked less often, meaning that less processor overhead is incurred in the host.
Owner:AVAGO TECH INT SALES PTE LTD
Training Signals for Selecting Antennas and Beams in Mimo Wireless Lans
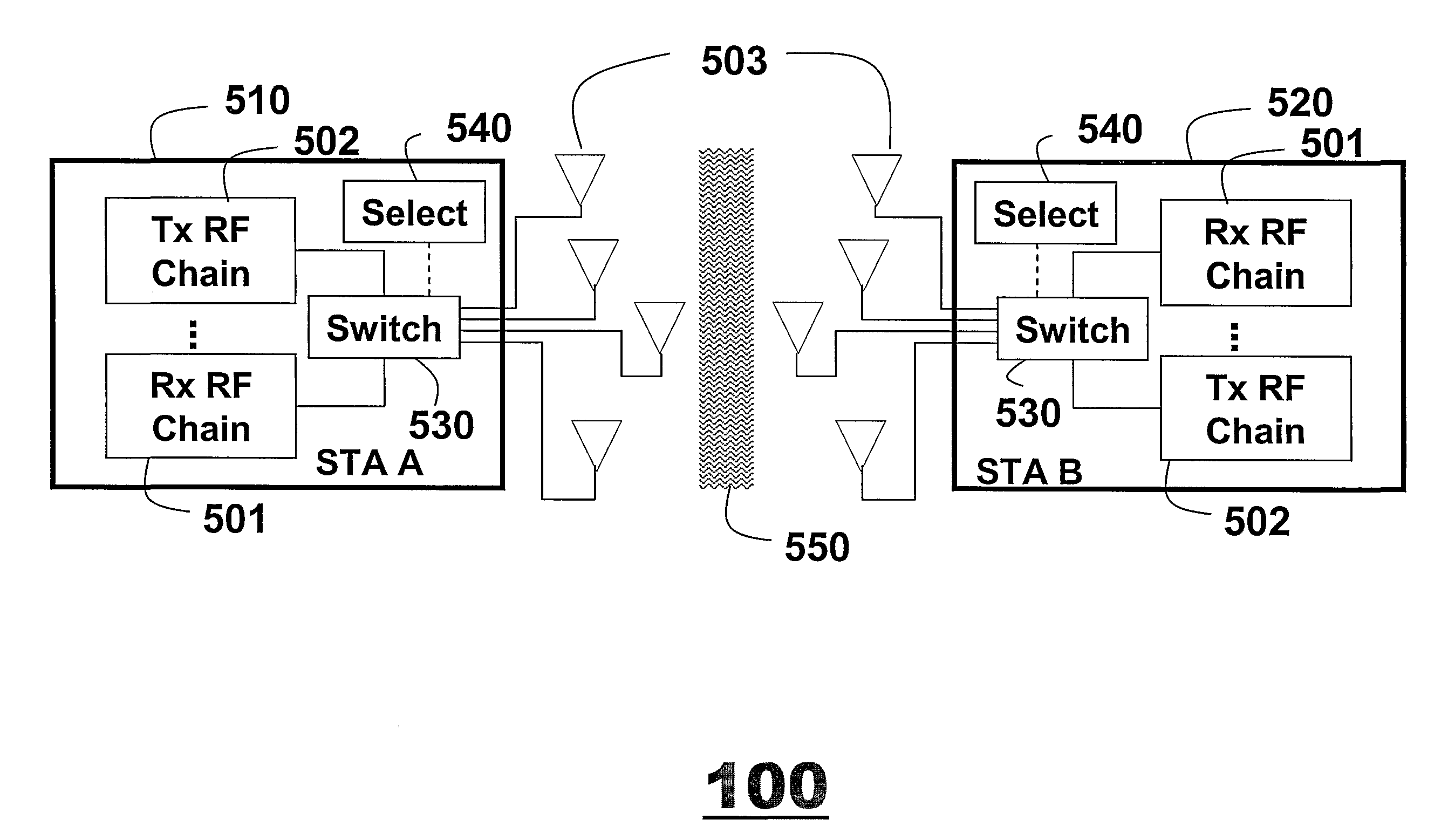
ActiveUS20080247370A1Solve excessive overheadImprove performanceSpecial service provision for substationMultiplex system selection arrangementsWireless lanLocal area network
A computer implemented method selects antennas in a multiple-input, multiple-output wireless local area network that includes multiple stations, and each station includes a set of antennas. Multiple consecutively transmitted sounding packets are received in a station. Each sounding packet corresponds to a different subset of the set of antennas. A channel matrix is estimated from the multiple consecutively transmitted sounding packets, and a subset of antennas is selected according to the channel matrix.
Owner:FREEDOM PATENTS LLC
Management and synchronization application for network file system
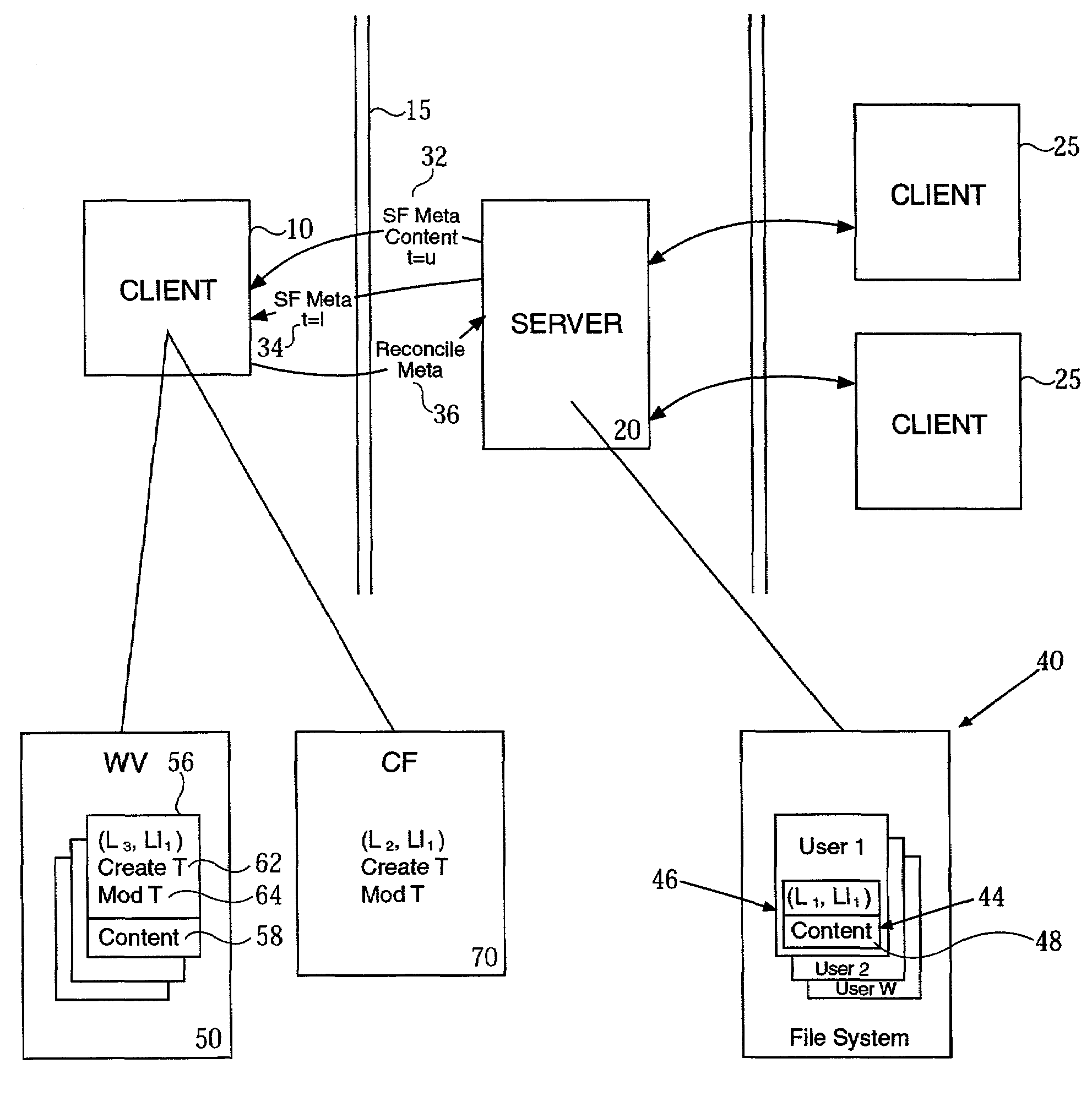
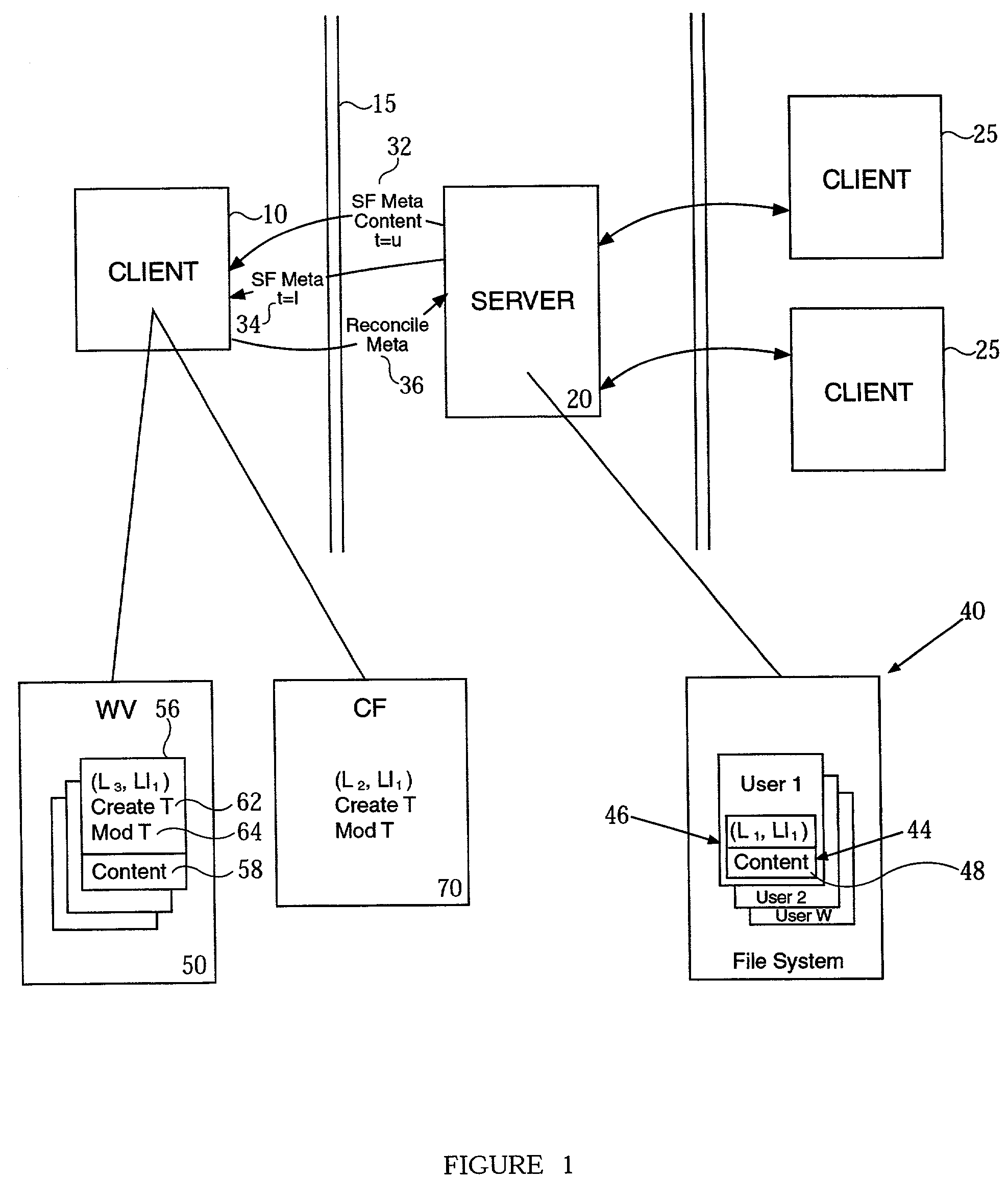
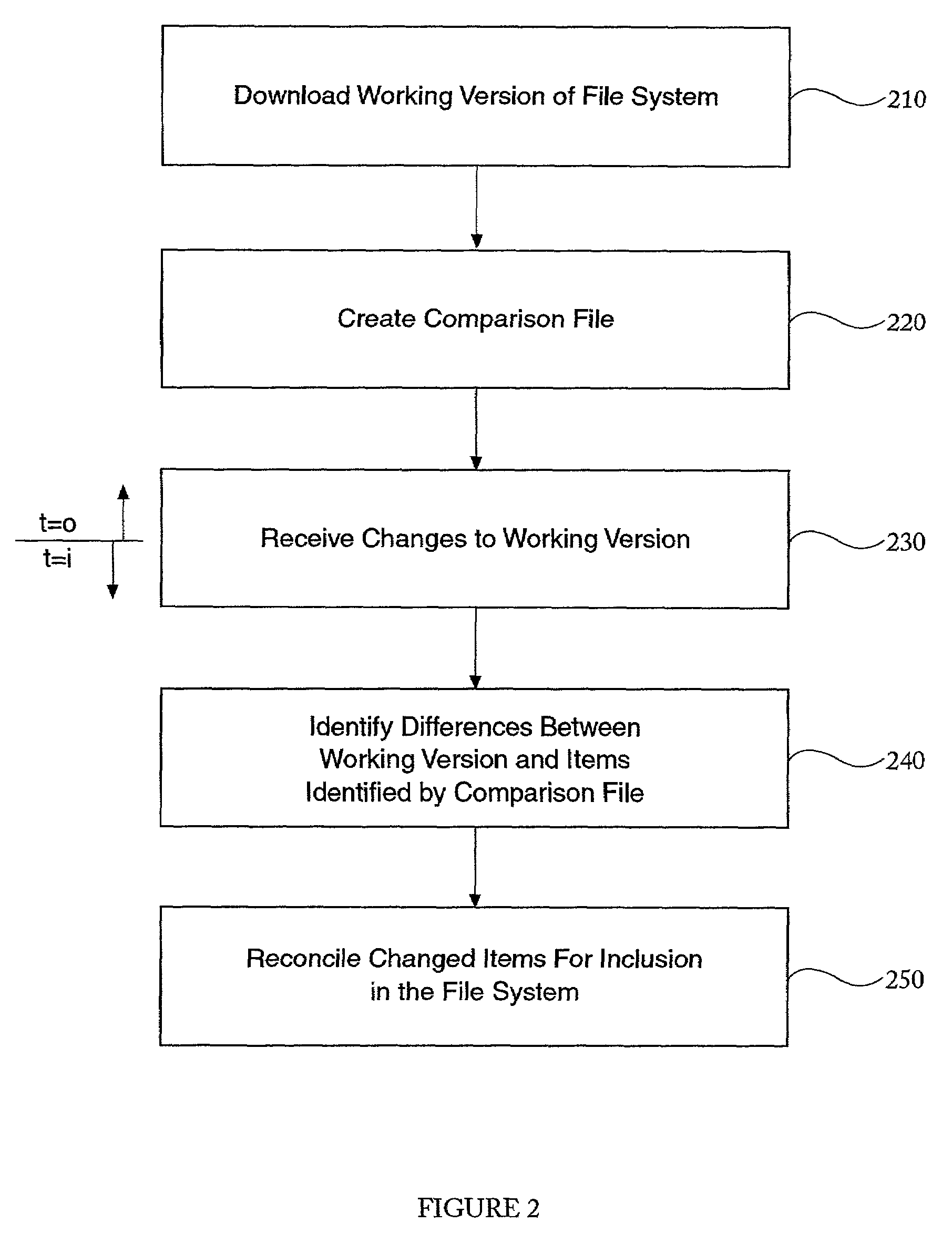
ActiveUS7711771B2Solve excessive overheadDigital data information retrievalDigital data processing detailsFile systemNetwork File System
An application is provided for managing files. Information about a file system is mapped to a comparison file. A working version is made from the file system. The application identify one or more operations were performed on the working version. The identified operations are recreated on the file system during a synchronization operation.
Owner:ORACLE INT CORP
Method for Sending and Detecting Downlink Control Information
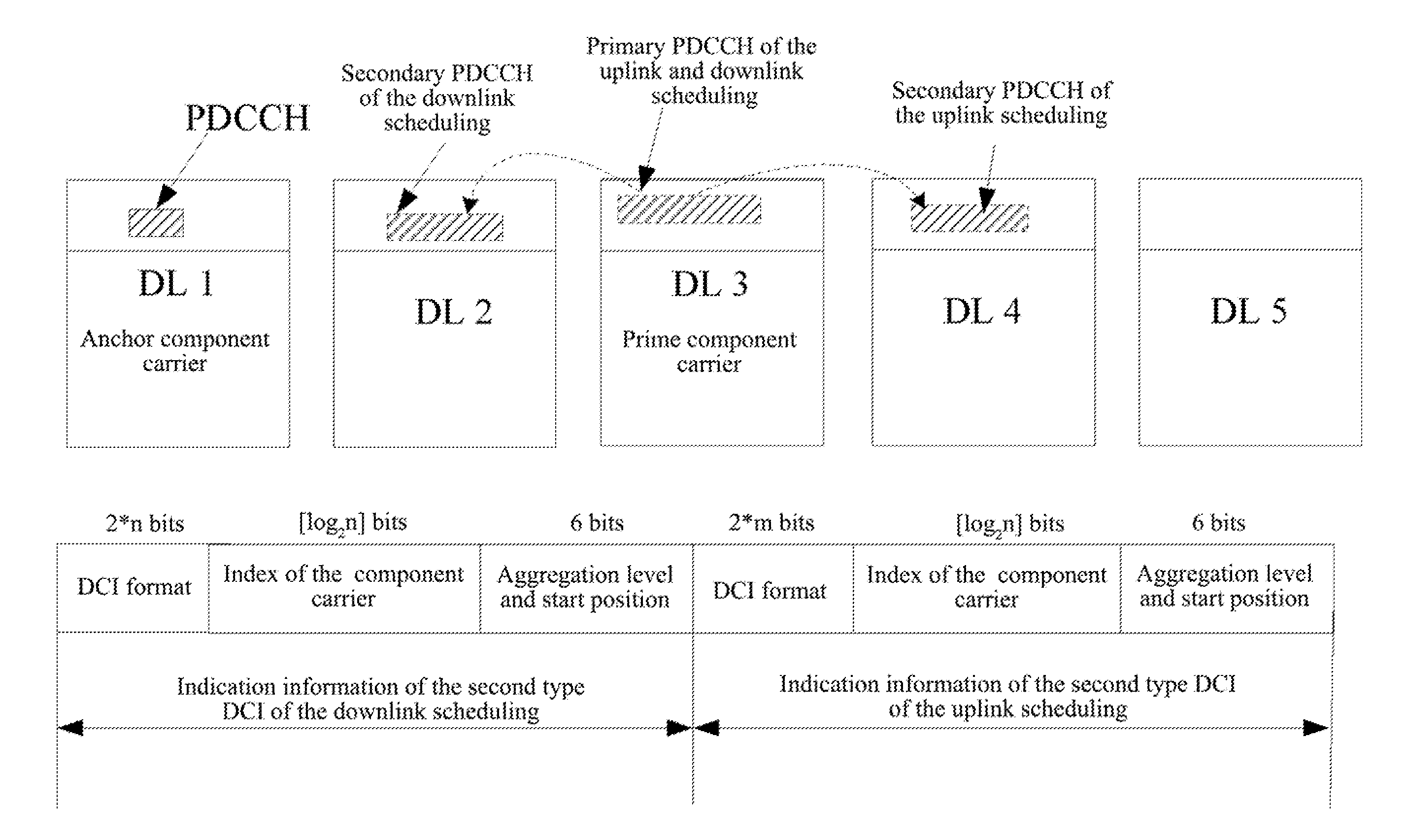
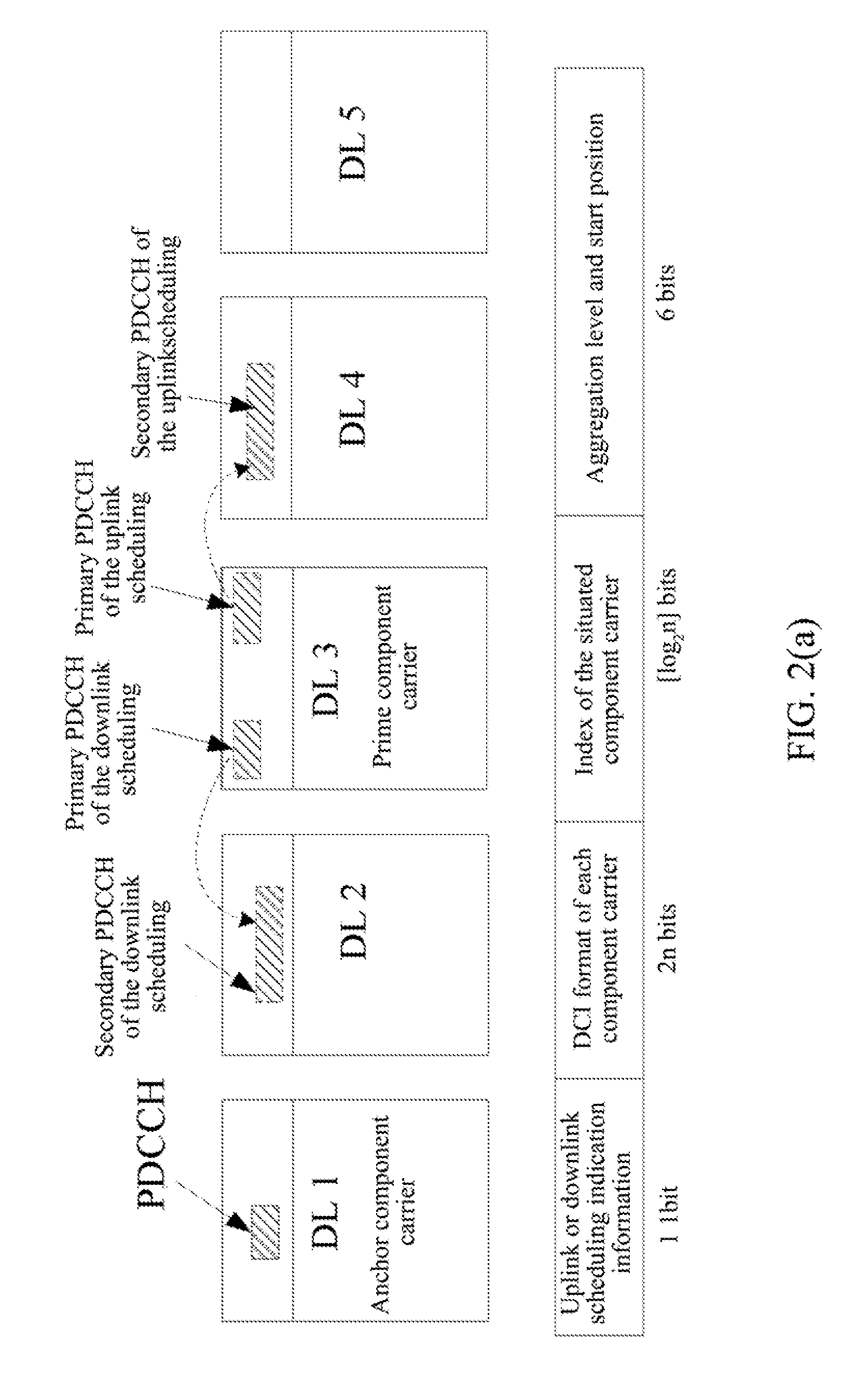
InactiveUS20120033627A1Low total numberLess signal overheadTransmission path divisionSignal allocationCarrier signalPower control
A method for sending and detecting downlink control information is provided. A base station carries the downlink control information in a physical downlink control channel, and sends said physical downlink control channel through component carriers. Said base station bears first type downlink control information on an anchor component carrier, and bears third type downlink control information on a prime component carrier, wherein said first type downlink control information bears one or more types of uplink scheduling information, downlink scheduling information and uplink power control information of its component carrier, said third type downlink control information bears indication information of the second type downlink control information which bears the uplink scheduling information and / or the downlink scheduling information of one or more component carriers. A terminal detects the first type downlink control information on the anchor component carries and detects the third type downlink control information on the prime component carrier.
Owner:ZTE CORP
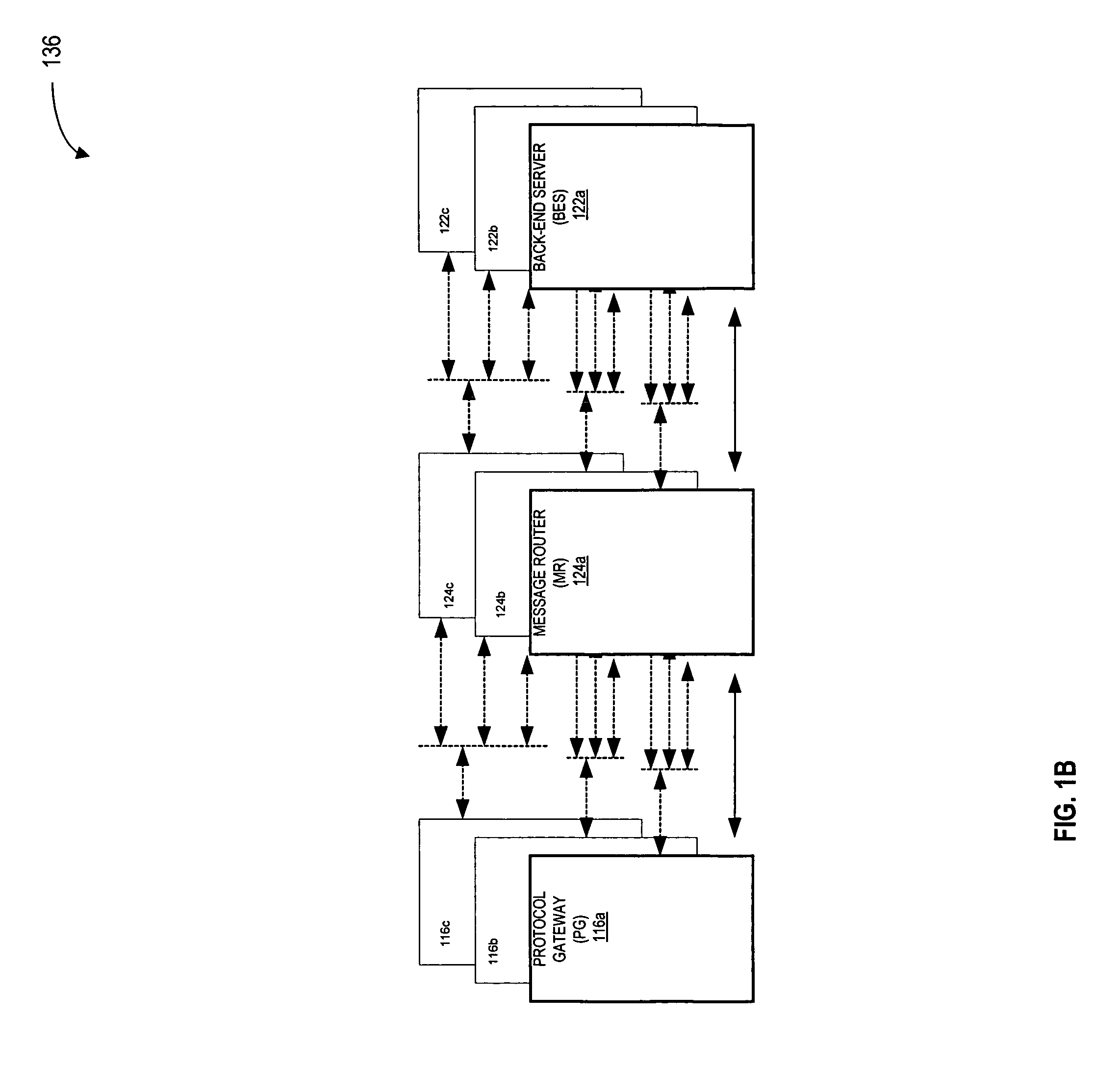
Message transfer using multiplexed connections in an open system interconnection transaction processing environment
InactiveUS20050193056A1Less complexSimpler connection creationMultiple digital computer combinationsSecuring communicationMessage lengthMultiplexing
Novel message formats for use in a distributed transaction environment are disclosed. Each message includes a message type field, a message length field, and a data field, typically in the foregoing order, and each field in the message has a fixed number of bytes. The message type and data length fields may be comprised of a single header. The data field may include novel groups of OSI TP PDUs where each grouping characterizes the content of the data in the PDU. A novel apparatus for use in a distributed transaction environment also is disclosed. The apparatus may include a peer processing machine and a multiplexed TCP / IP connection for exchanging messages with other peer processing machines in the distributed transaction environment.
Owner:UNISYS CORP
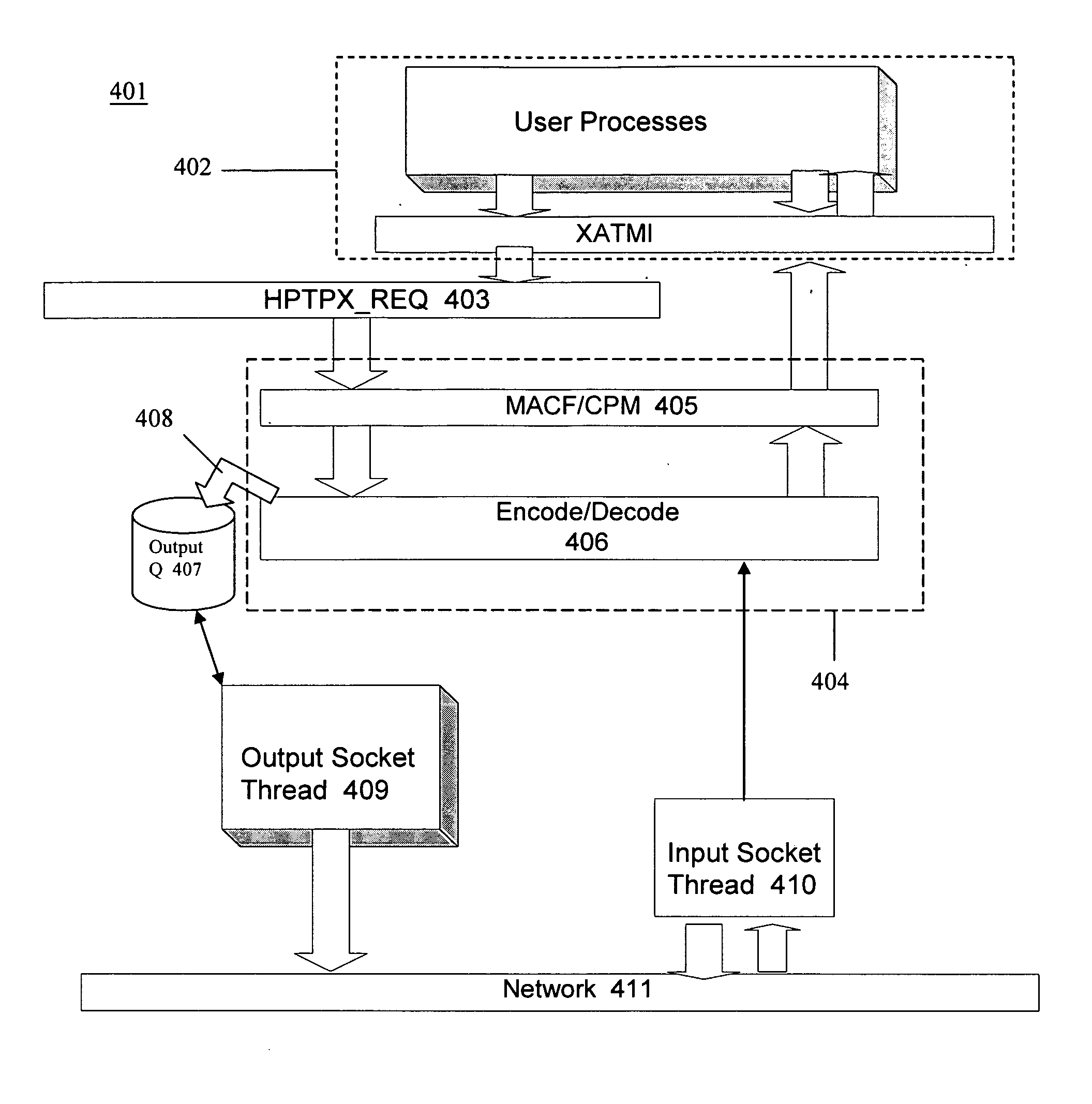
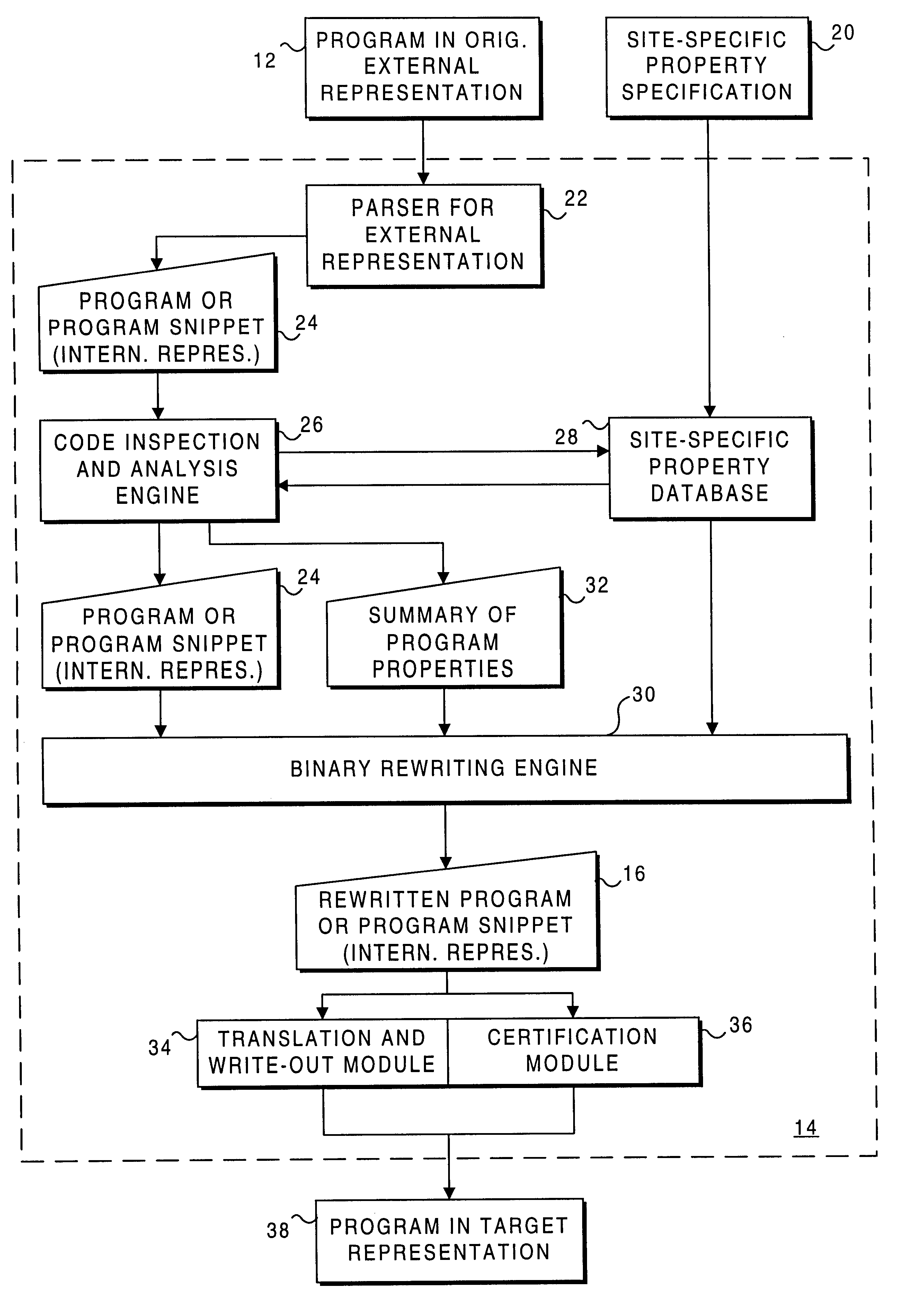
Process for rewriting executable content on a network server or desktop machine in order to enforce site specific properties
InactiveUS6865735B1Less processing overheadRun fastBinary to binaryMultiprogramming arrangementsProgram fragmentUnknown Source
A program or program snippet is rewritten to conform to site-specific properties prior to being executed by a target host. The program or program snippet directed to a target host from a known or unknown source is either intercepted by a server before reaching the target host or can be redirected from the target host to the server to effect its rewriting. The program is parsed in its external representation, converting it to an internal representation that is inspected and analyzed with reference to a site-specific properties database. A summary of the program's properties is then compared to the site-specific properties database by a binary rewriting engine, which produces a rewritten program in an internal representation. If appropriate, the program or program snippet is rewritten to convert it to a format suitable for execution on the target host. Furthermore, certifications may be added to the rewritten program to mark that the rewritten program obeys site-specific constraints. The rewriting service thus produces a program in an appropriate target representation that conforms to site-specific properties. These properties may relate to security, auditing, optimization, monitoring, threading, and / or management of the rewritten program.
Owner:UNIV OF WASHINGTON
System and method for providing unified transport and security protocols
InactiveUS20110099623A1Minimize delayFast and efficientMemory loss protectionError detection/correctionPacket lossMessage frame
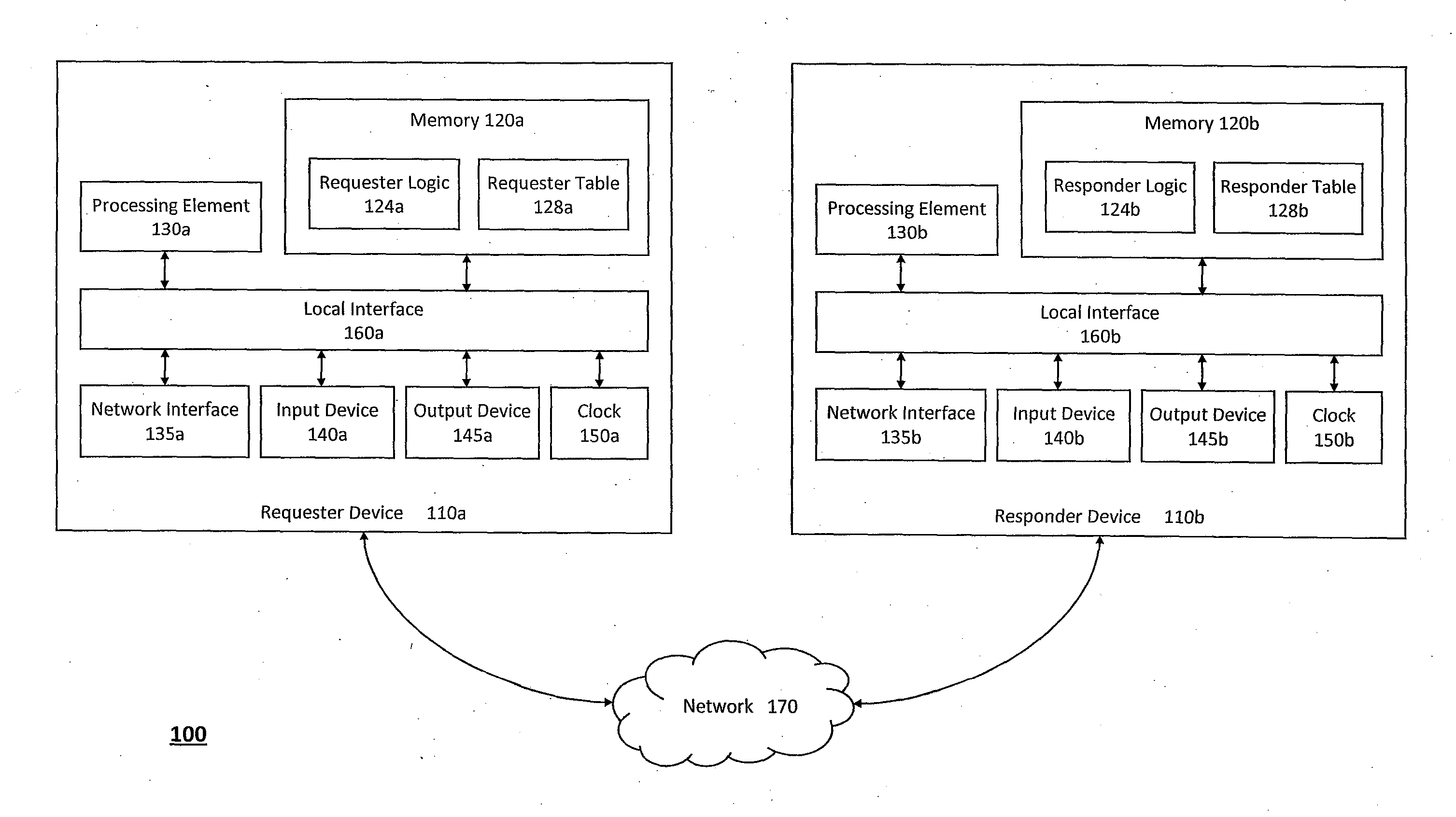
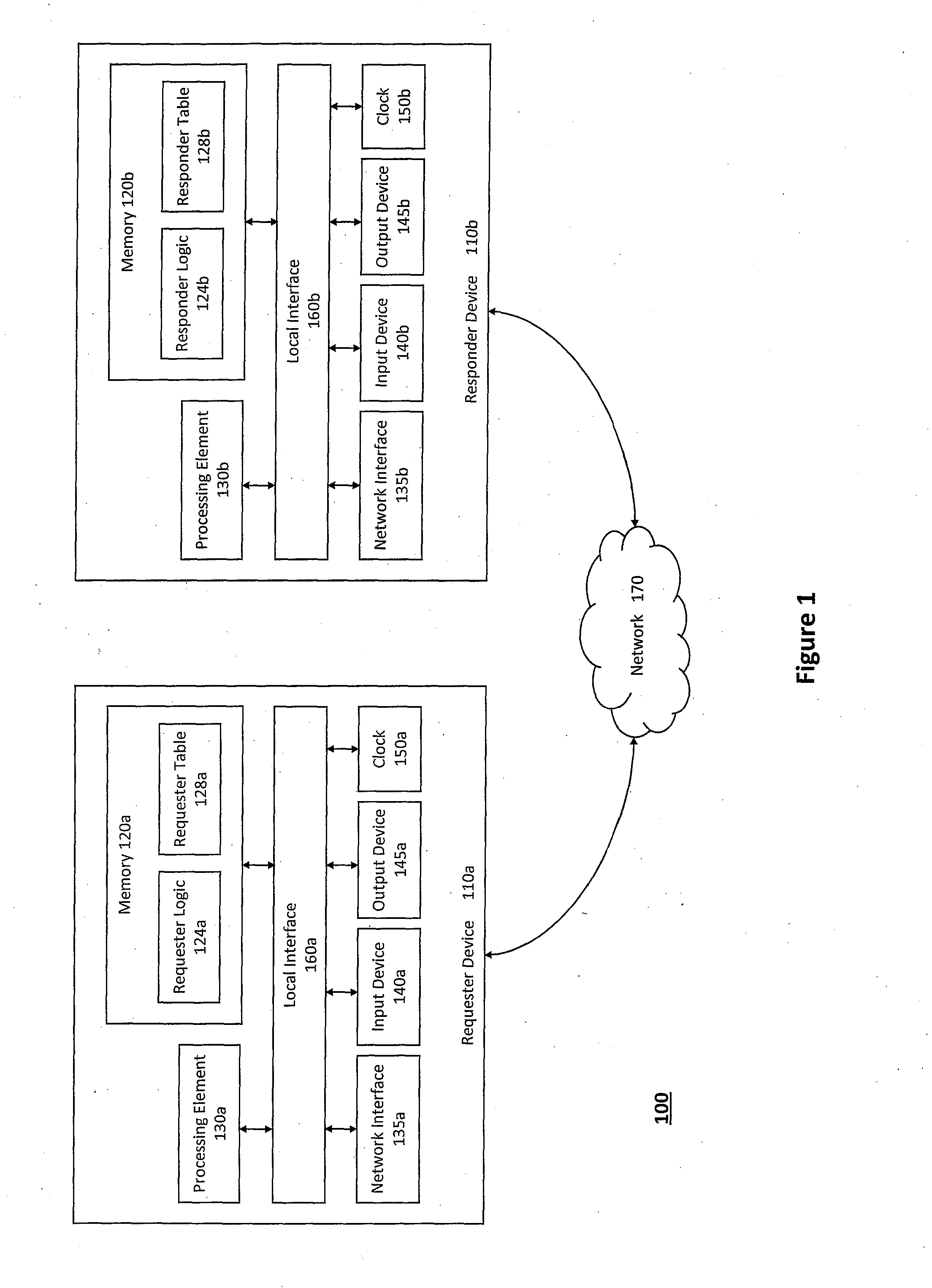
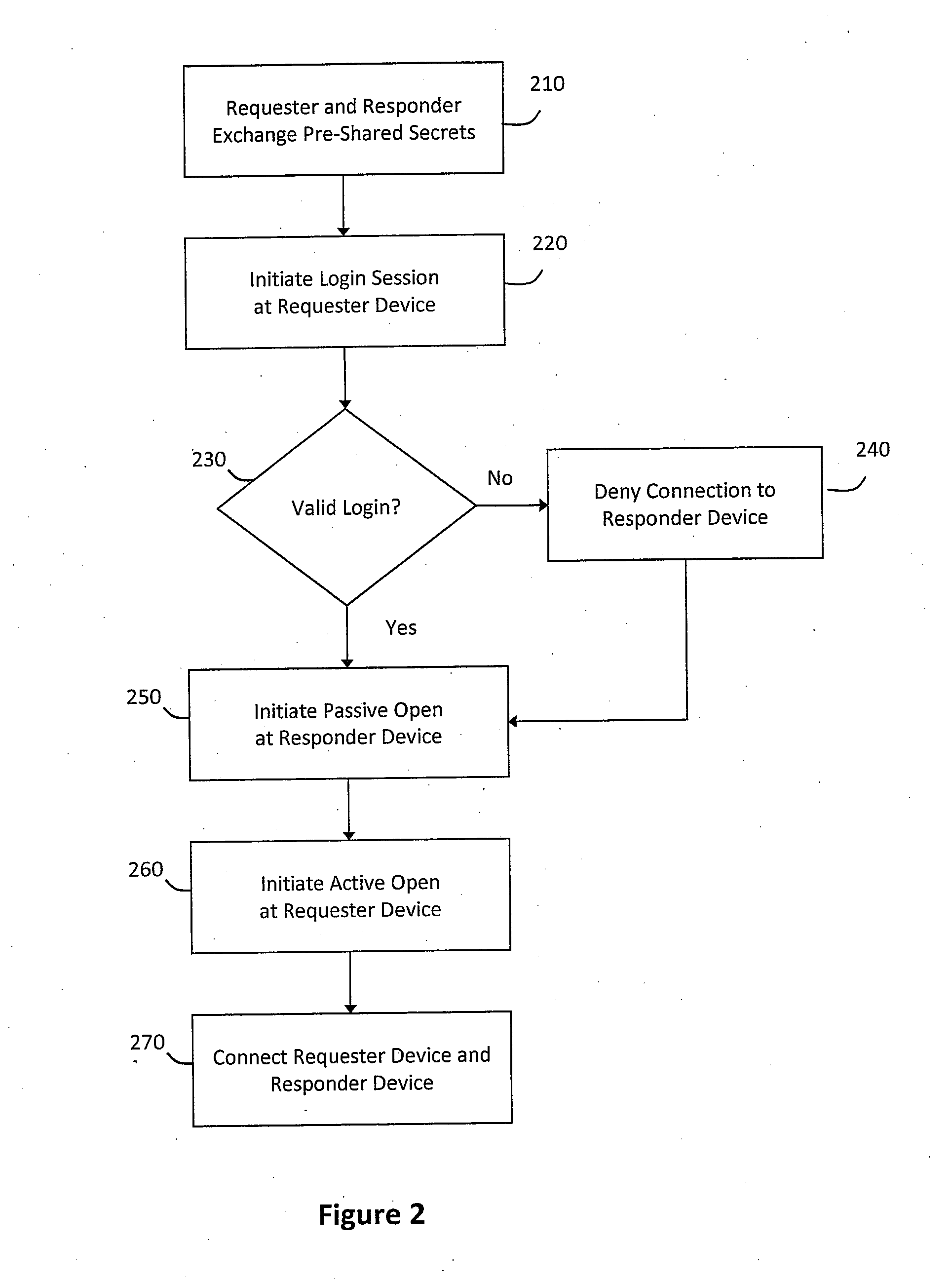
The system and method described herein may provide unified transport and security protocols. In particular, the unified transport and security protocols may include a Secure Frame Layer transport and security protocol that includes stages for initially configuring a requester device and a responder device, identifying the requester device and the responder device to one another, and authenticating message frames communicated between the requester device and the responder device. Additionally, the unified transport and security protocols may further include a Secure Persistent User Datagram Protocol that includes modes for processing message frames received at the requester device and the responder device, recovering the requester device in response to packet loss, retransmitting lost packets sent between the requester device and the responder device, and updating location information for the requester device to restore a communications session between the requester device and the responder device.
Owner:AUNIGMA NETWORK SECURITY CORP
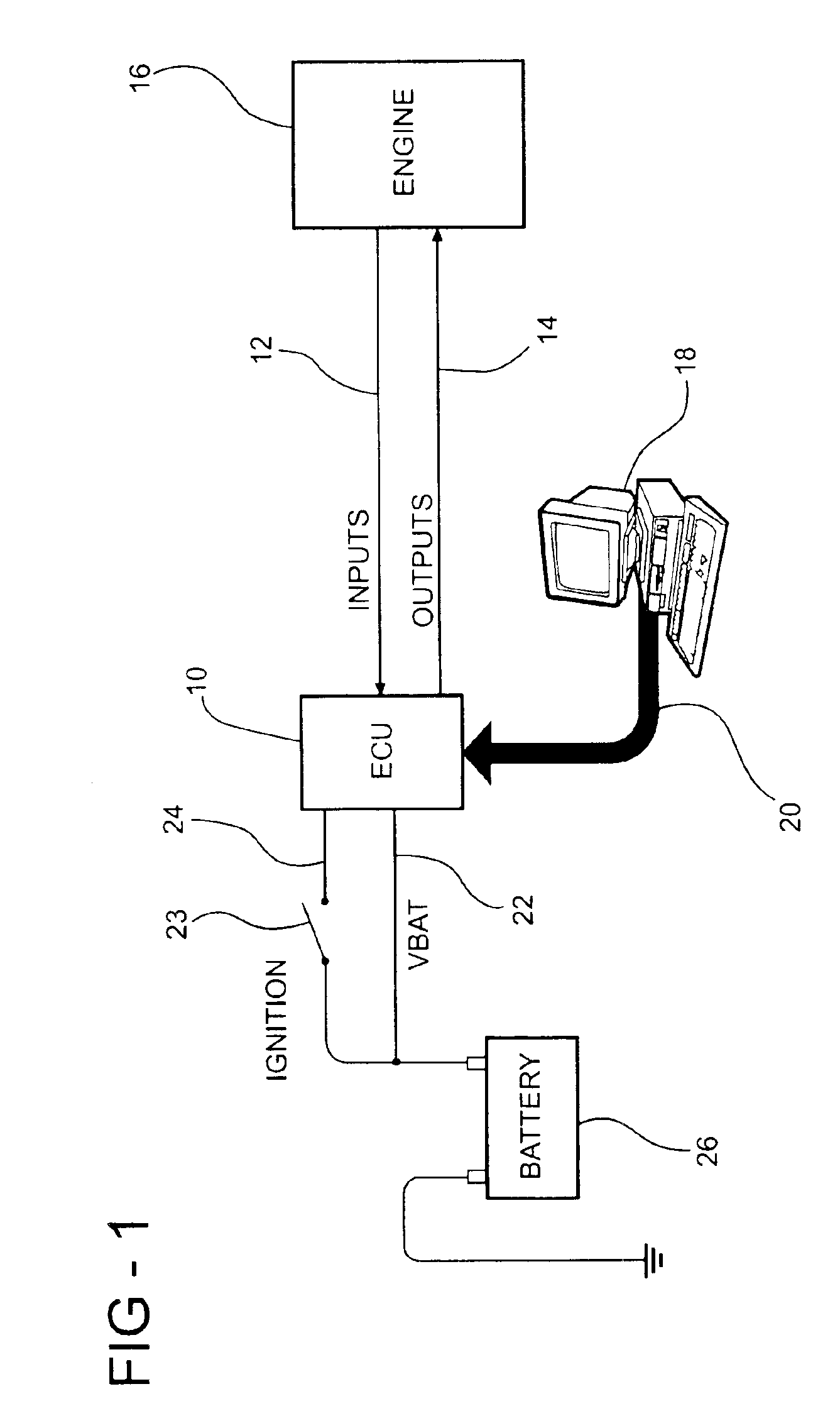
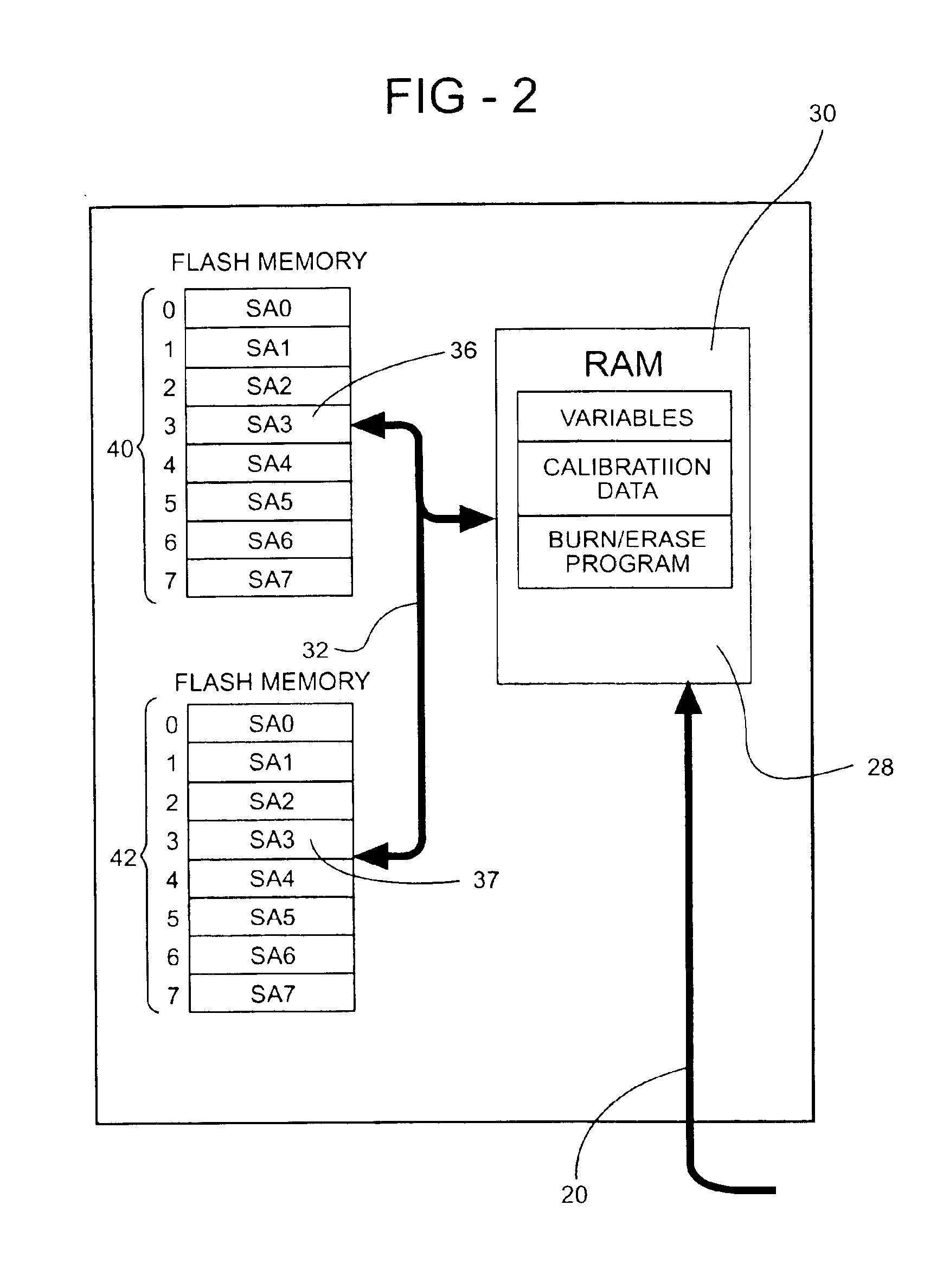
System and method for real time programmability of an engine control unit
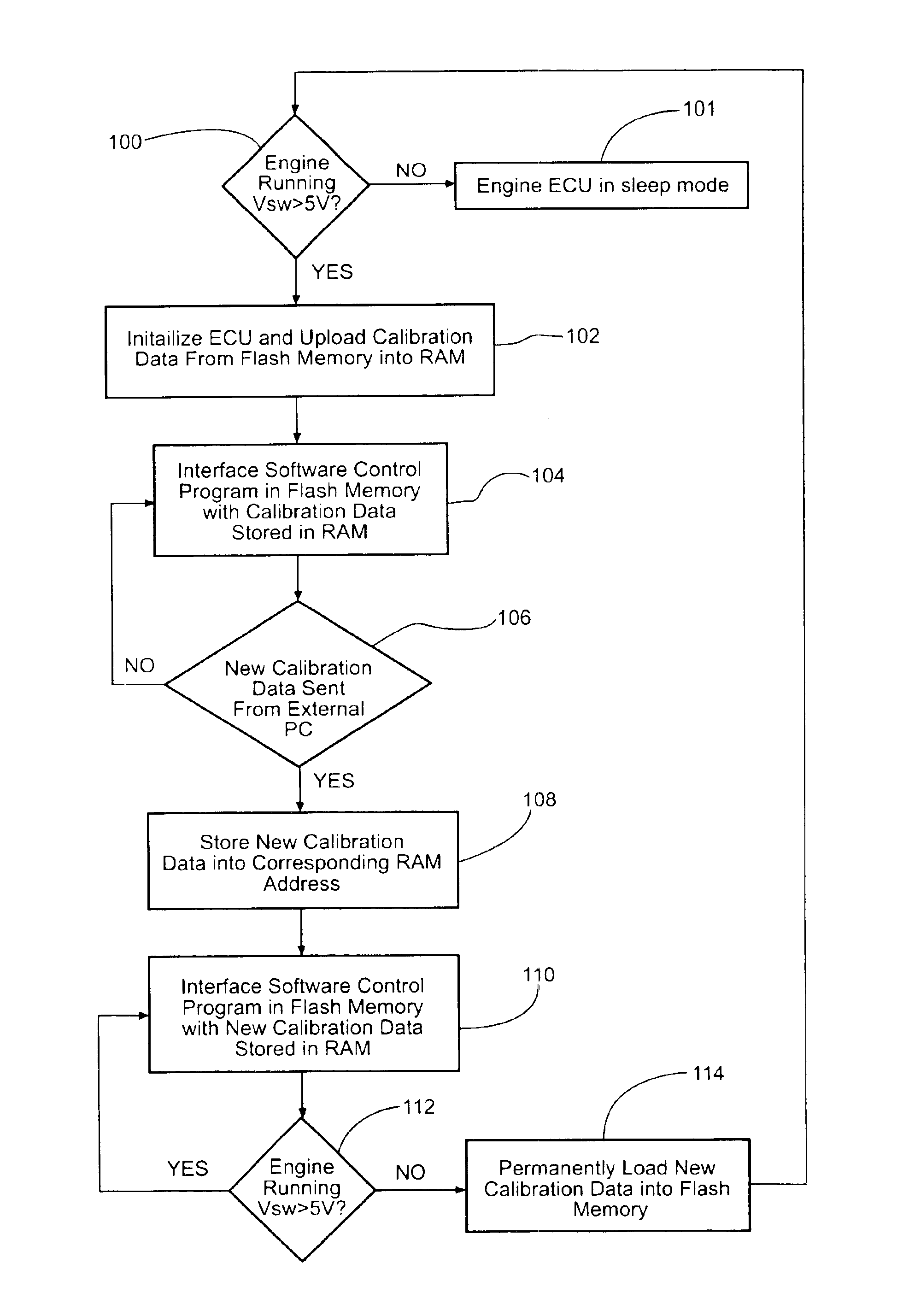
InactiveUS6928362B2Short amount of timeShorten development timeAnalogue computers for vehiclesElectrical controlComputer sciencePeripheral
A method for real time programmability of an engine electronic control unit (ECU). The present invention allows a user to update calibration data previously stored in memory in the engine ECU with new calibration data sent from an external device. The user can monitor the effects of the new calibration data on the engine instantaneously without having to wait for a period of time for the new calibration data to be permanently stored in the engine ECU's memory. To permanently store the new calibration data into the main memory, an erase / reprogram subroutine is uploaded from the main memory to a temporary memory. After the erase / reprogram subroutine is uploaded into the temporary memory location, the erase / reprogram subroutine will execute and permanently download the new calibration data into the main memory in response to a predetermined vehicle event.
Owner:MEANEY JOHN
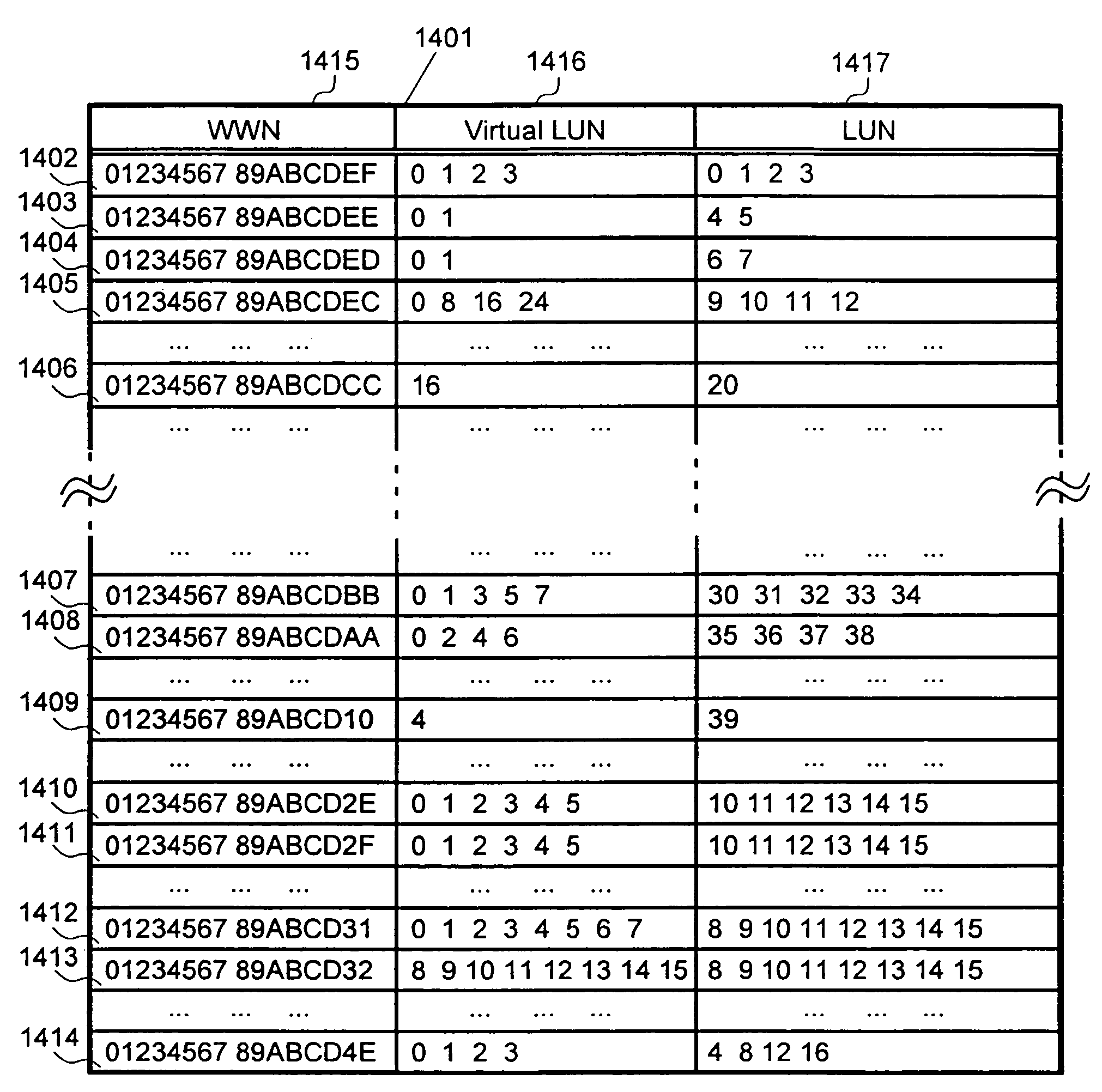
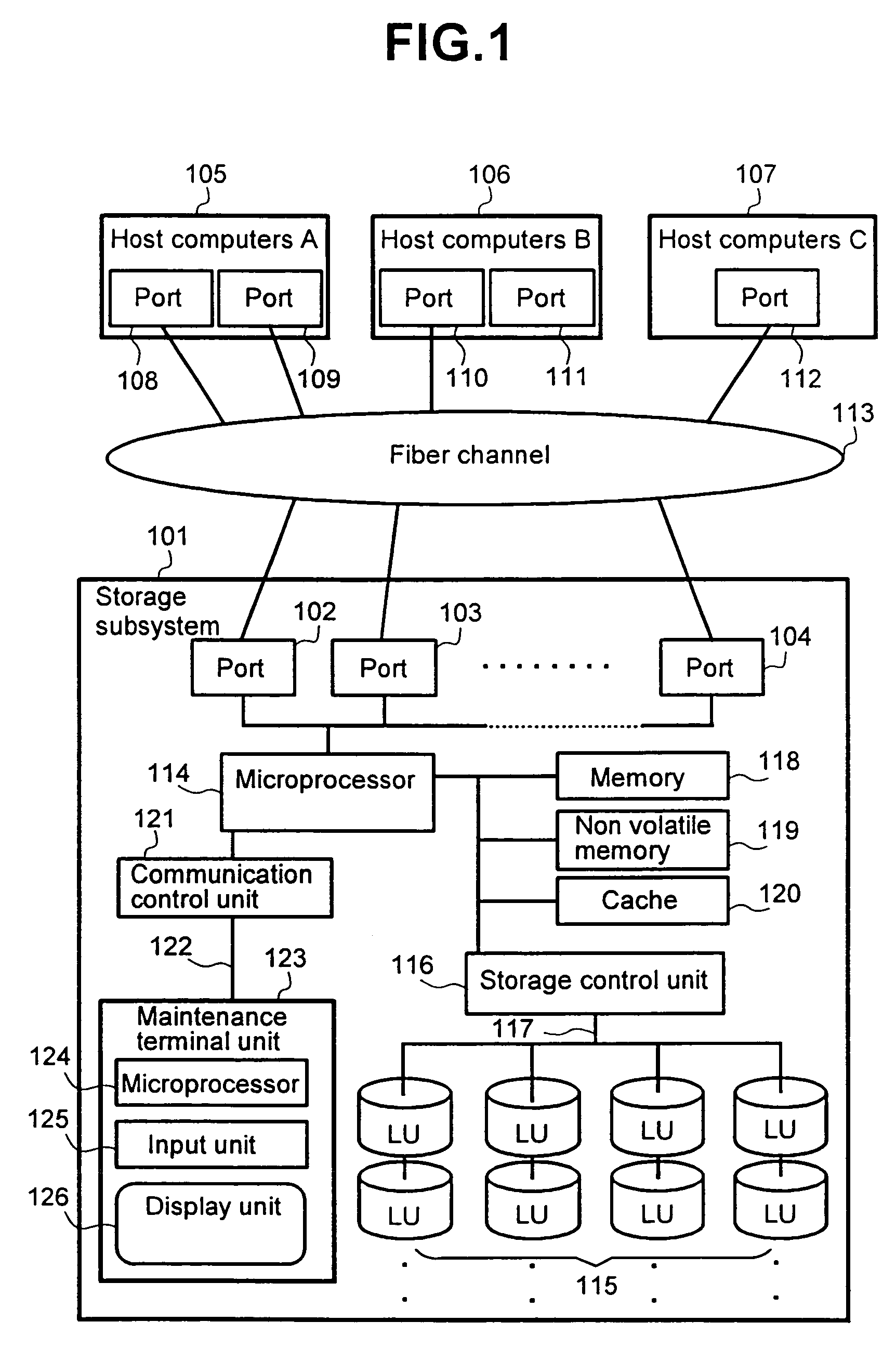
Security method and system for storage subsystem
InactiveUS7024410B2Prevent unauthorized accessImprove performanceInput/output to record carriersData processing applicationsAccessibilityOperating system
According to the present invention, techniques for performing security functions in computer storage subsystems in order to prevent illegal access by the host computers according to logical unit (LU) identity are provided. In representative embodiments management tables can be used to disclose the Logical Unit in the storage subsystem to the host computers in accordance with the users operational needs. In a specific embodiment, accessibility to a storage subsystem resource can be decided when an Inquiry Command is received, providing systems and apparatus wherein there is no further need to repeatedly determine accessibility for subsequent accesses to the Logical Unit. Many such embodiments can maintain relatively high performance, while providing robust security for each LU.
Owner:HITACHI LTD
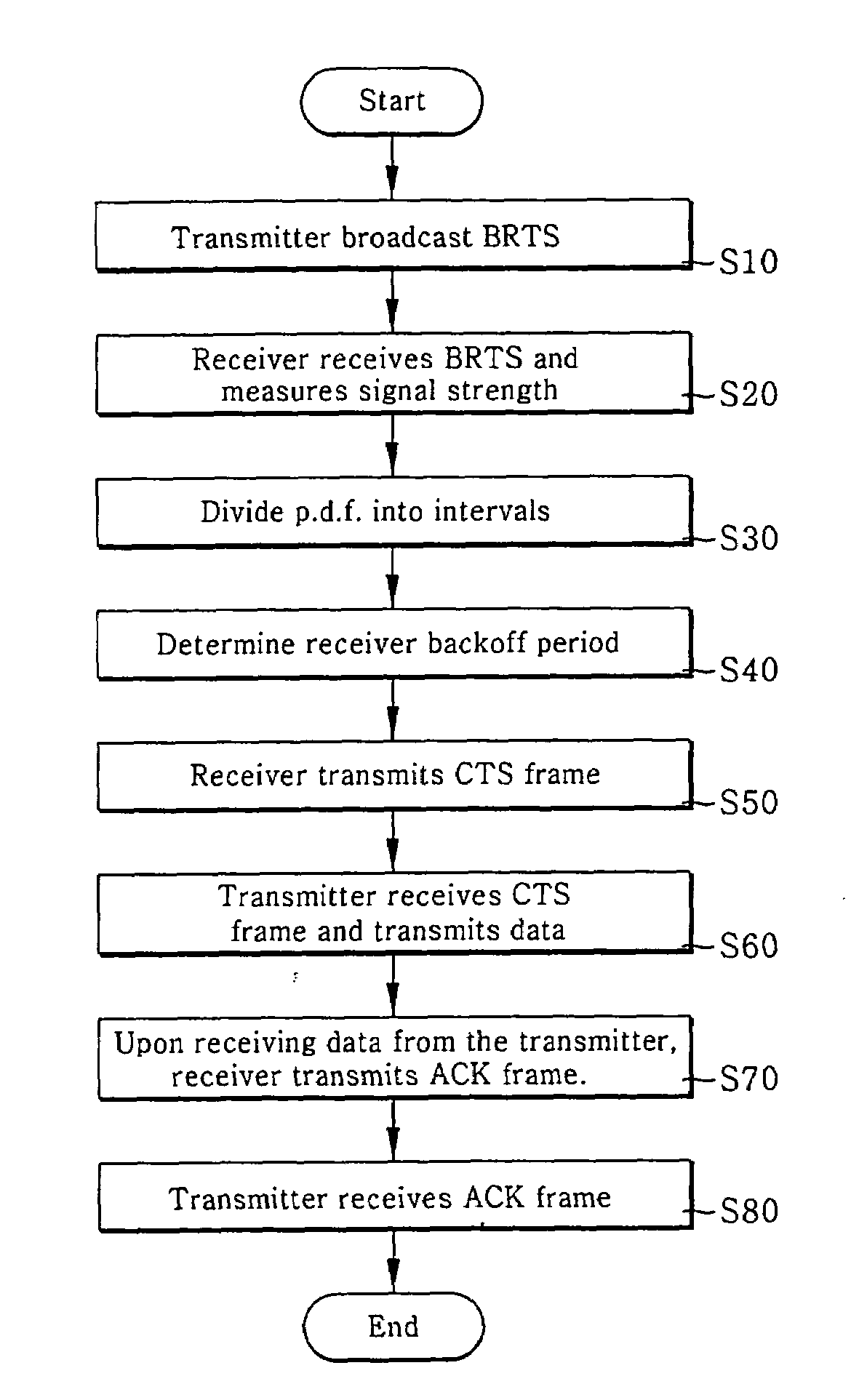
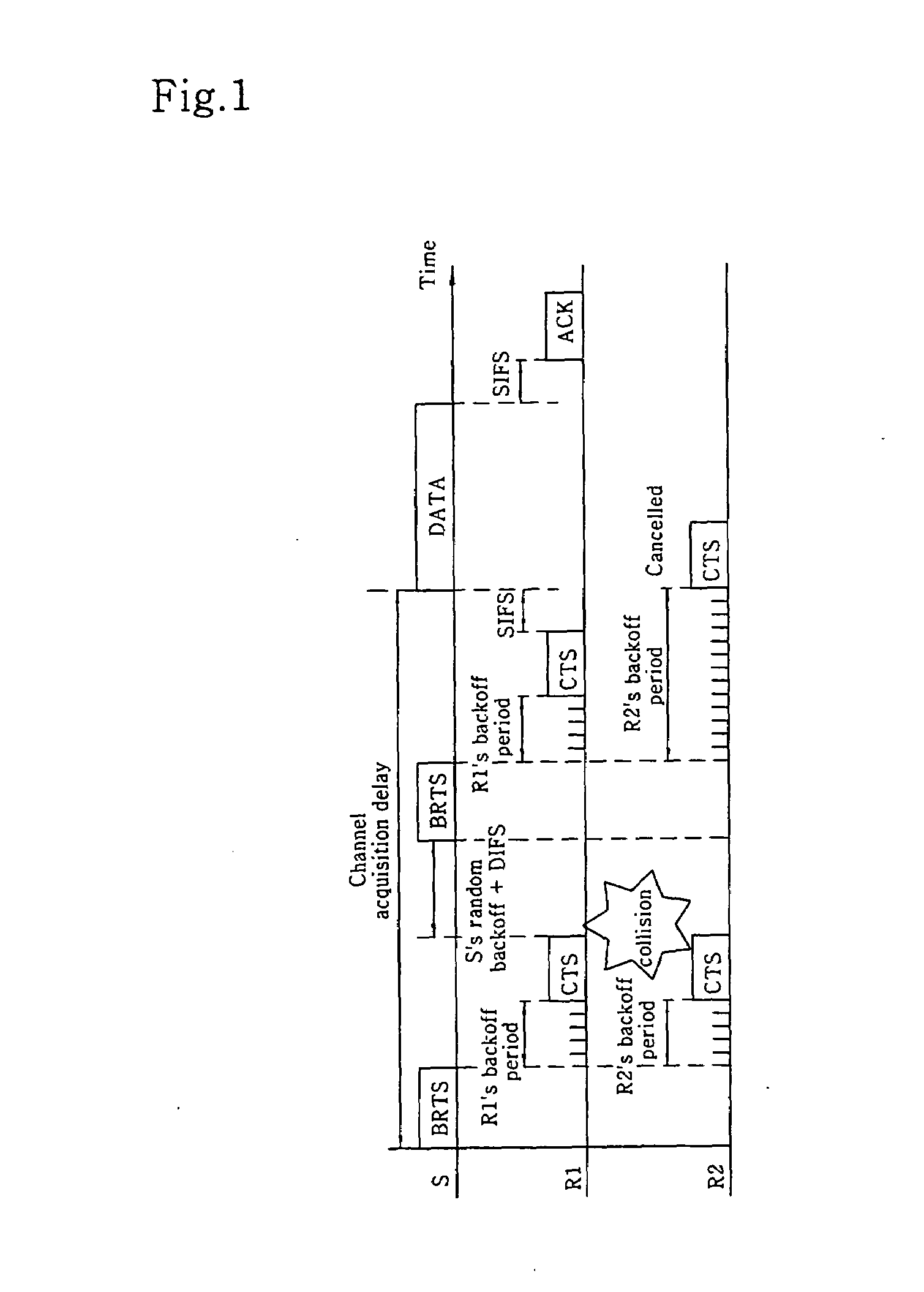
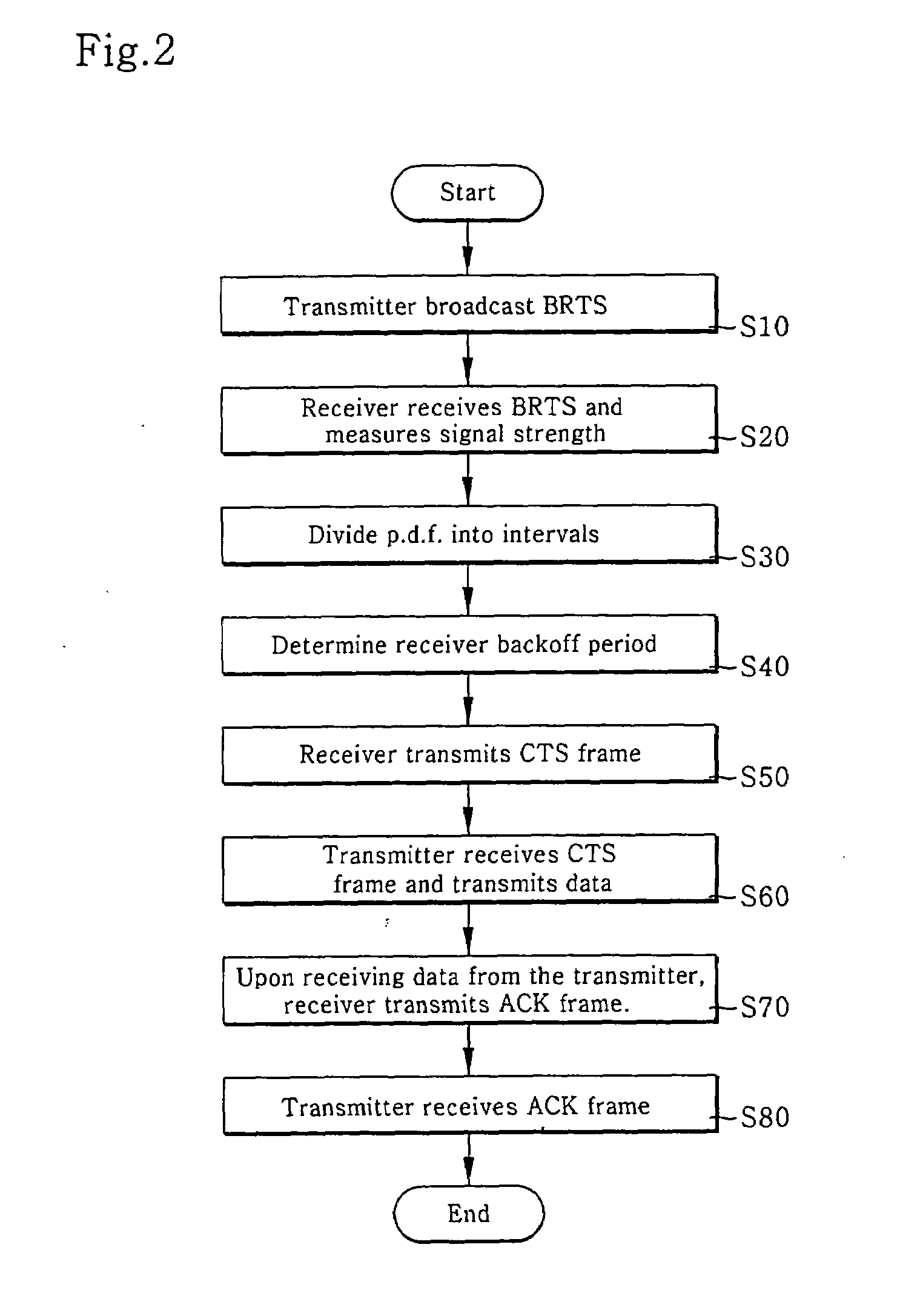
Distributed opportunistic scheduling in IEEE 802.11 wireless location area networks (WLANs)
InactiveUS20080063106A1Maximum multi-user diversity gainMaintaining probing overheadNetwork traffic/resource managementTime-division multiplexDelayed timeLocation area
A WLAN distributed / opportunistic scheduling (WDOS) method for acquiring a multi-user diversity gain is disclosed. The WDOS method allows a transmitter (i.e., a transmission user) to observe channel conditions of receivers (i.e., reception users), and commands the transmitter to transmit packets to a specific receiver having a relative good channel condition. The WDOS method uses a modified RTS / CTS exchange method to perform the channel probing. If the transmitter broadcasts the BRTS frame, each receiver transmits a CTS frame after the lapse of its backoff period. According to the reception signal strength distribution, the backoff delay time minimizes the number of CTS collisions irrespective of the number of receivers, reduces an amount of channel probing overheads, and maximizes a multi-user diversity gain. The better the relative channel condition, the lower the backoff delay time.
Owner:SEOUL NAT UNIV R&DB FOUND
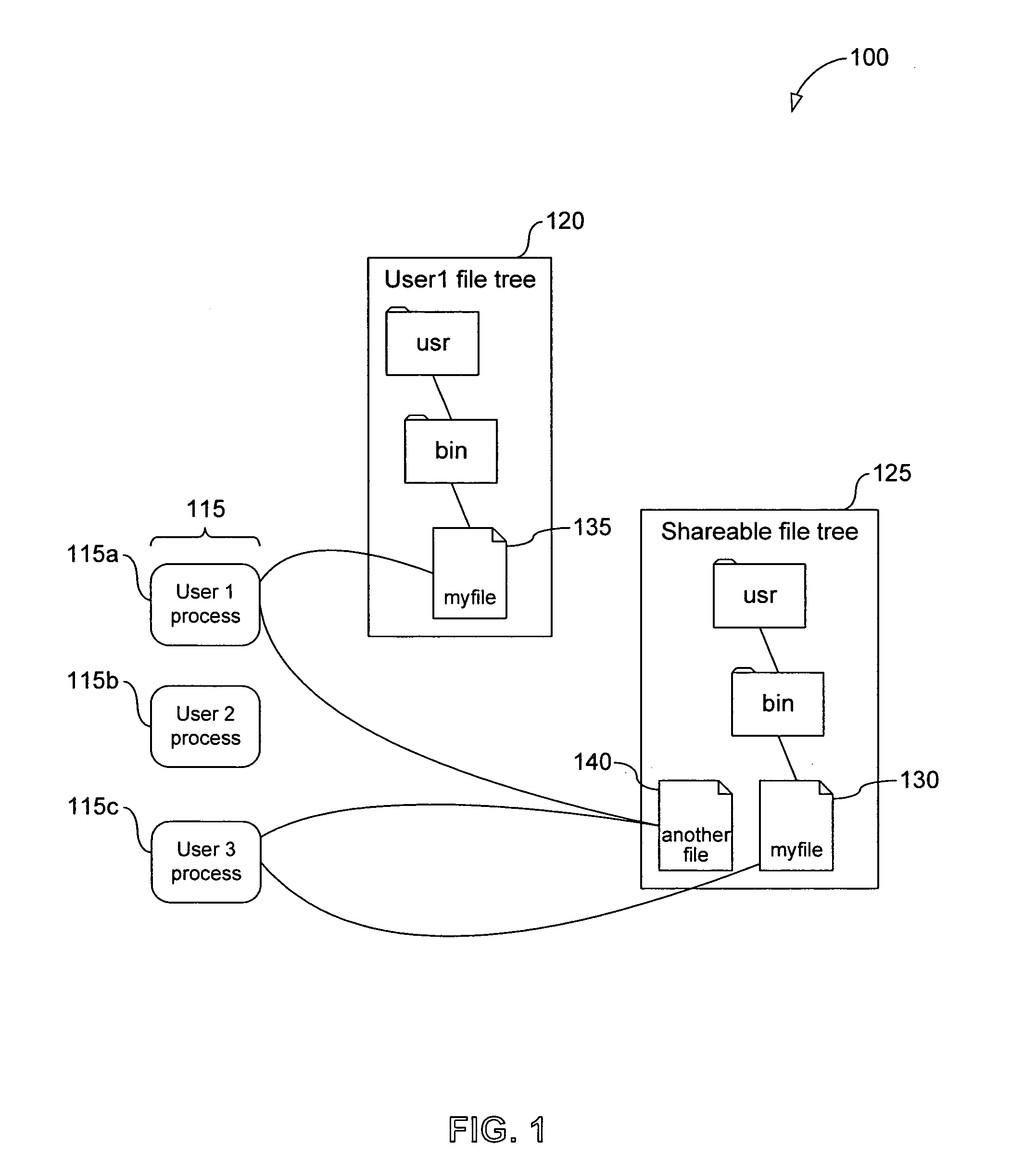
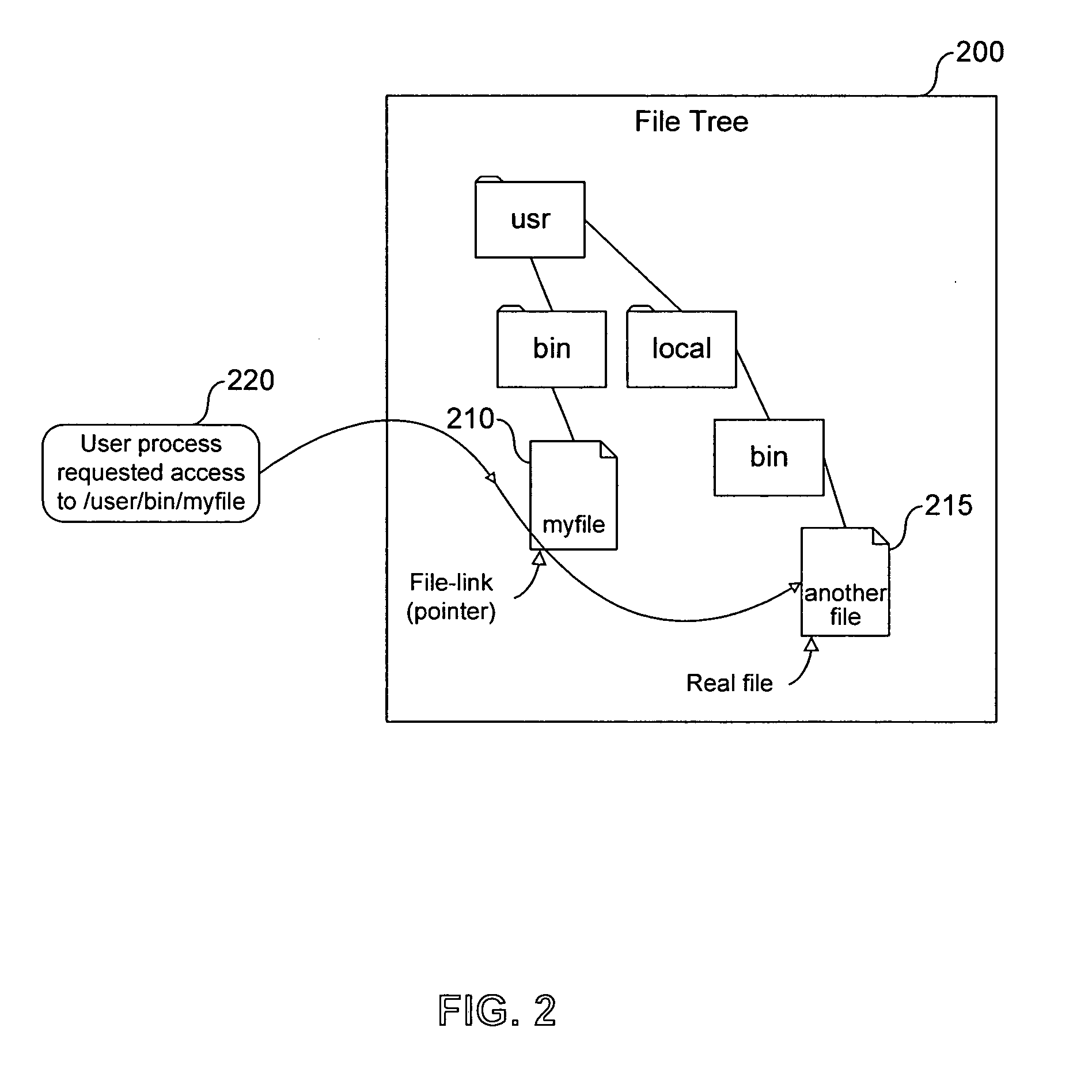
System, method and computer program product for multi-level file-sharing by concurrent users
ActiveUS7328225B1Efficient multi-user accessEfficient file sharingData processing applicationsSpecial data processing applicationsOperational systemFile size
A method of accessing a shareable computer file includes receiving a request to access the shareable computer file, retrieving a file ID from a stub file corresponding to the shareable computer file, retrieving a file name from a database corresponding to the file ID, accessing the shareable computer file if a user has not modified the shareable computer file, and accessing a modified copy of the shareable file stored in the stub file if the user has modified the shareable computer file. A database is generated in operating system space or accessed using the operating system, and includes file IDs and their corresponding file names for shareable computer files. The stub file is generated locally to correspond to the shareable computer file, and includes a modified copy of the shareable computer file if the shareable computer file has been modified, and a link to the shareable computer file if the shareable computer file has not been modified. If the shareable computer file has not been modified, a read-only operation retrieves any of file contents, file position and file size from the shareable computer file. File attributes relating to the shareable computer file can be retrieved from the stub file. The database is provided by the operating system for use by a Virtual Private Server.
Owner:VIRTUOZZO INT GMBH
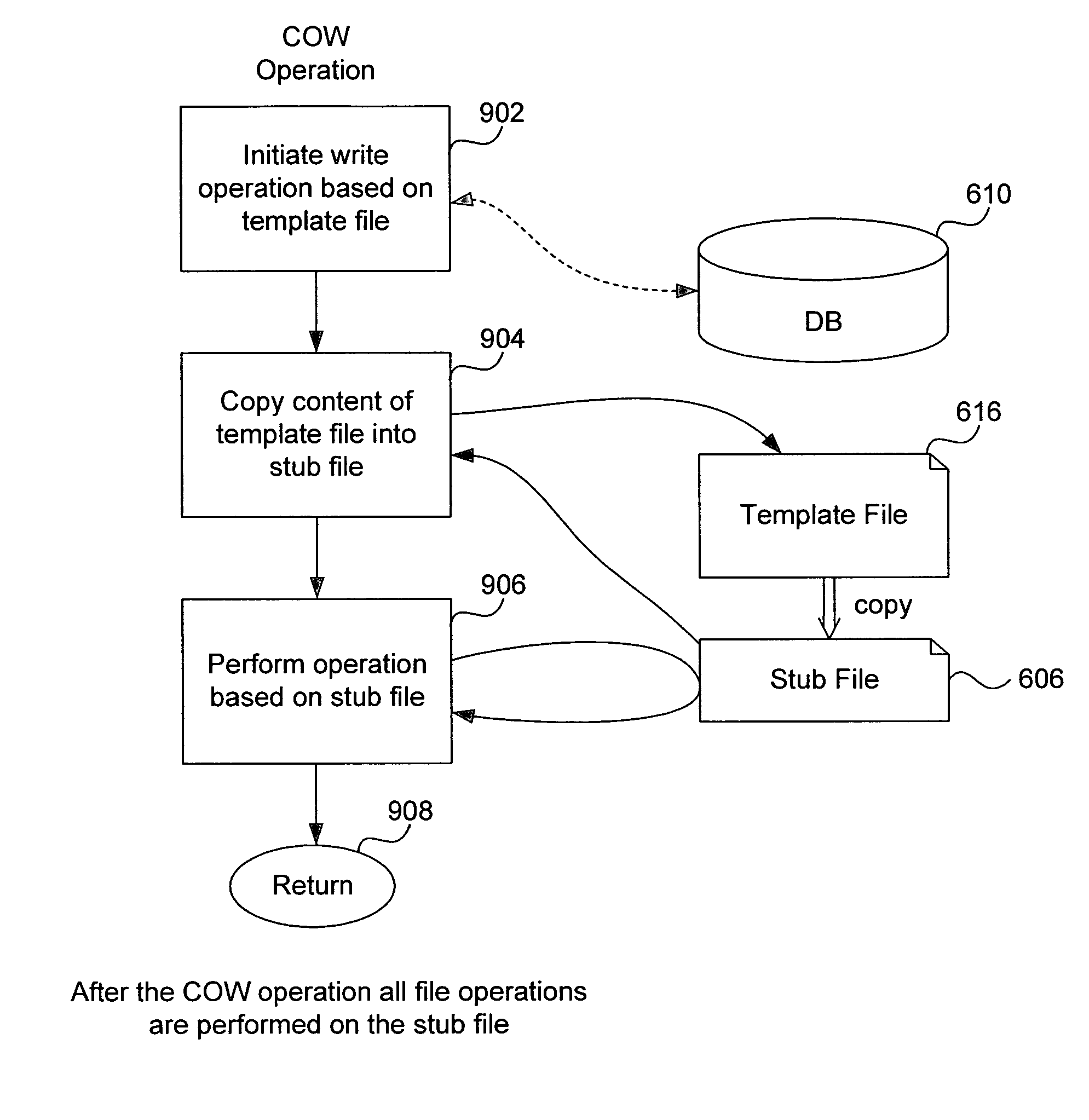
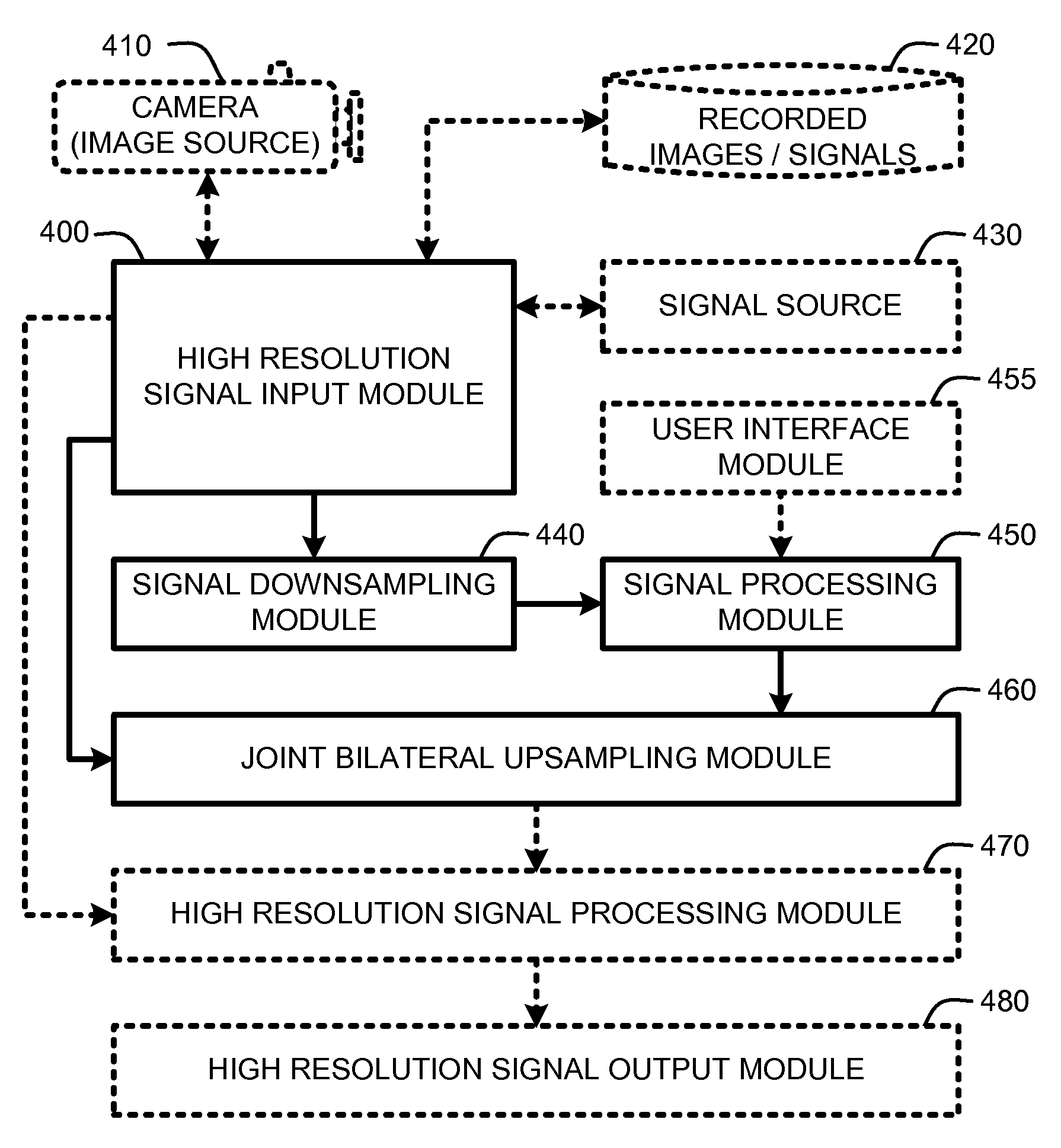
Joint bilateral upsampling
InactiveUS20080267494A1Less computational overhead and memorySolve excessive overheadGeometric image transformationCharacter and pattern recognitionImage resolutionLow resolution
A “Joint Bilateral Upsampler” uses a high-resolution input signal to guide the interpolation of a low-resolution solution set (derived from a downsampled version of the input signal) from low-to high-resolution. The resulting high-resolution solution set is then saved or applied to the original input signal to produce a high-resolution output signal. The high-resolution solution set is close to what would be produced directly from the input signal without downsampling. However, since the high-resolution solution set is constructed in part from a downsampled version of the input signal, it is computed using significantly less computational overhead and memory than a solution set computed directly from a high-resolution signal. Consequently, the Joint Bilateral Upsampler is advantageous for use in near real-time operations, in applications where user wait times are important, and in systems where computational costs and available memory are limited.
Owner:MICROSOFT TECH LICENSING LLC
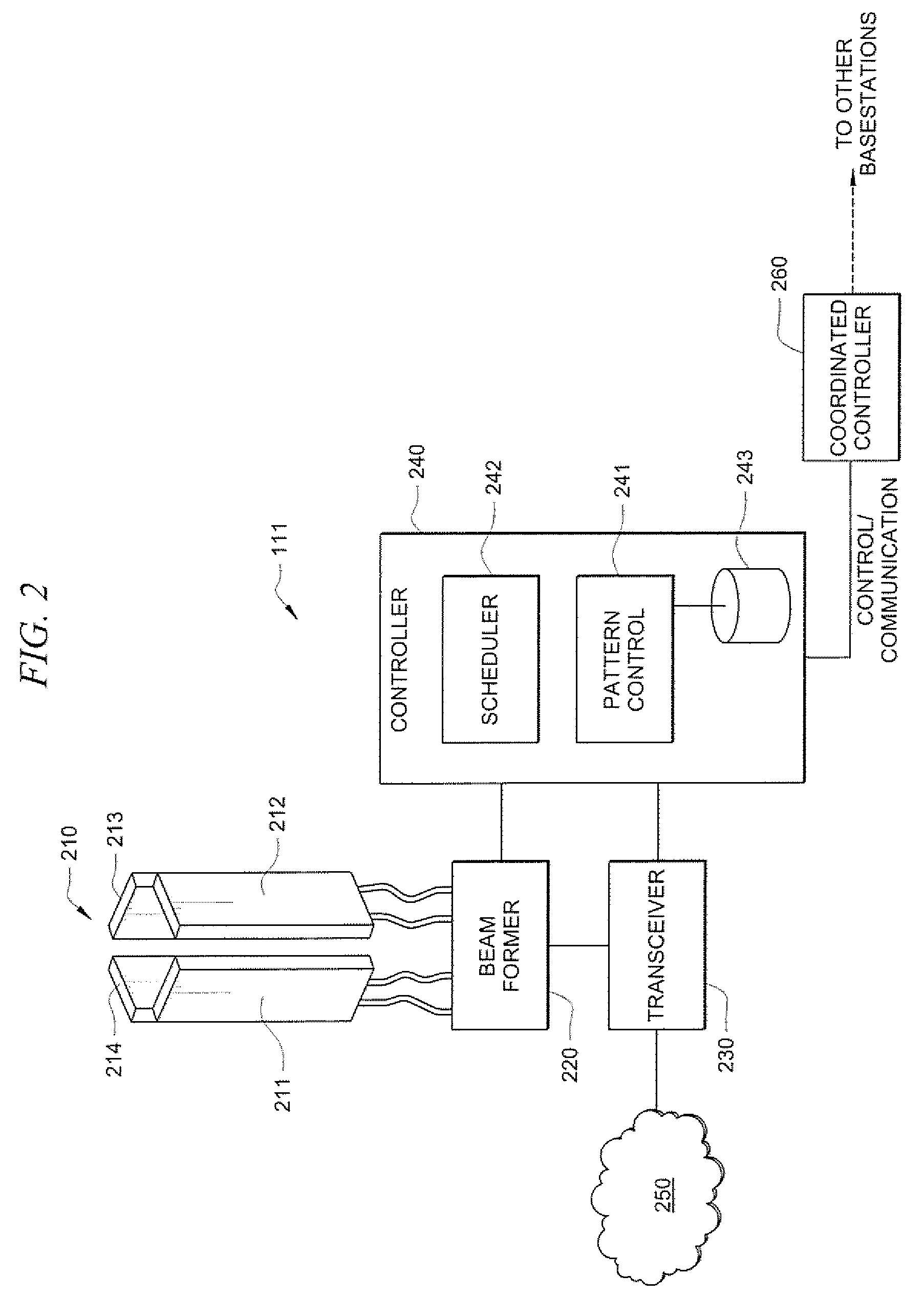
Systems and methods using antenna beam scanning for improved communications
ActiveUS20090005121A1Reduce processing requirementsReduce degradationAntenna arraysSubstation equipmentContinuous scanningCommunications system
Systems and methods which utilize antenna pattern or antenna beam scanning techniques to provide communication of payload traffic are shown. A base station radio is provided wireless communication links with a plurality of stations for communication of payload traffic between the base station and stations using a succession of antenna patterns. The antenna patterns are scanned in succession, such as randomly, quasi-randomly, sequentially, or according to a schedule. An antenna pattern scheduler may be used to implement antenna pattern scanning and traffic timing. Cooperative scheduling with respect to a plurality of base stations may be provided. Selection of the plurality of antenna patterns used by a base station is preferably adjusted from time to time, such as based upon environment, usage patterns, etcetera.
Owner:FIMAX TECH
Transmission of Information Relating to a Quality of Service
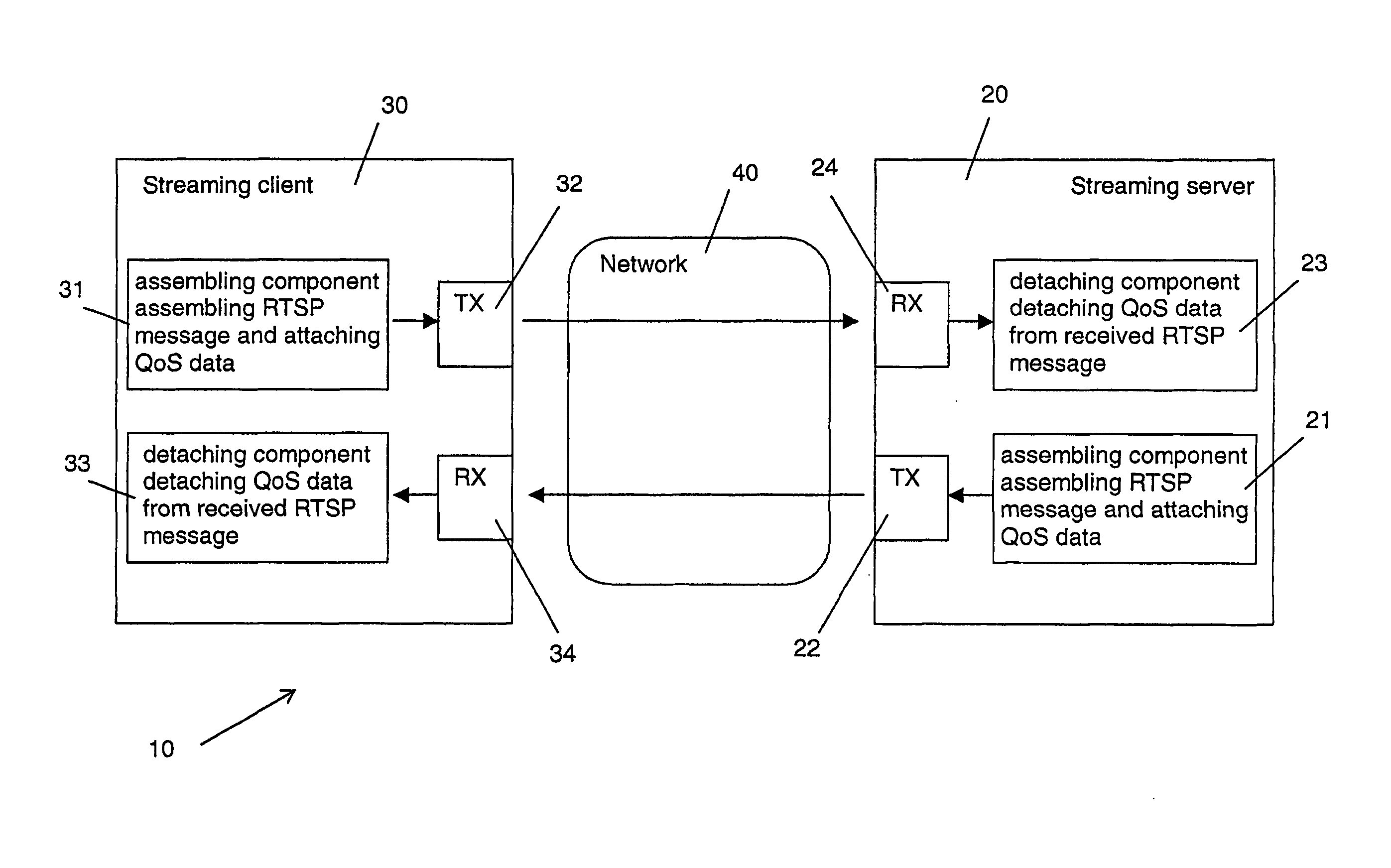
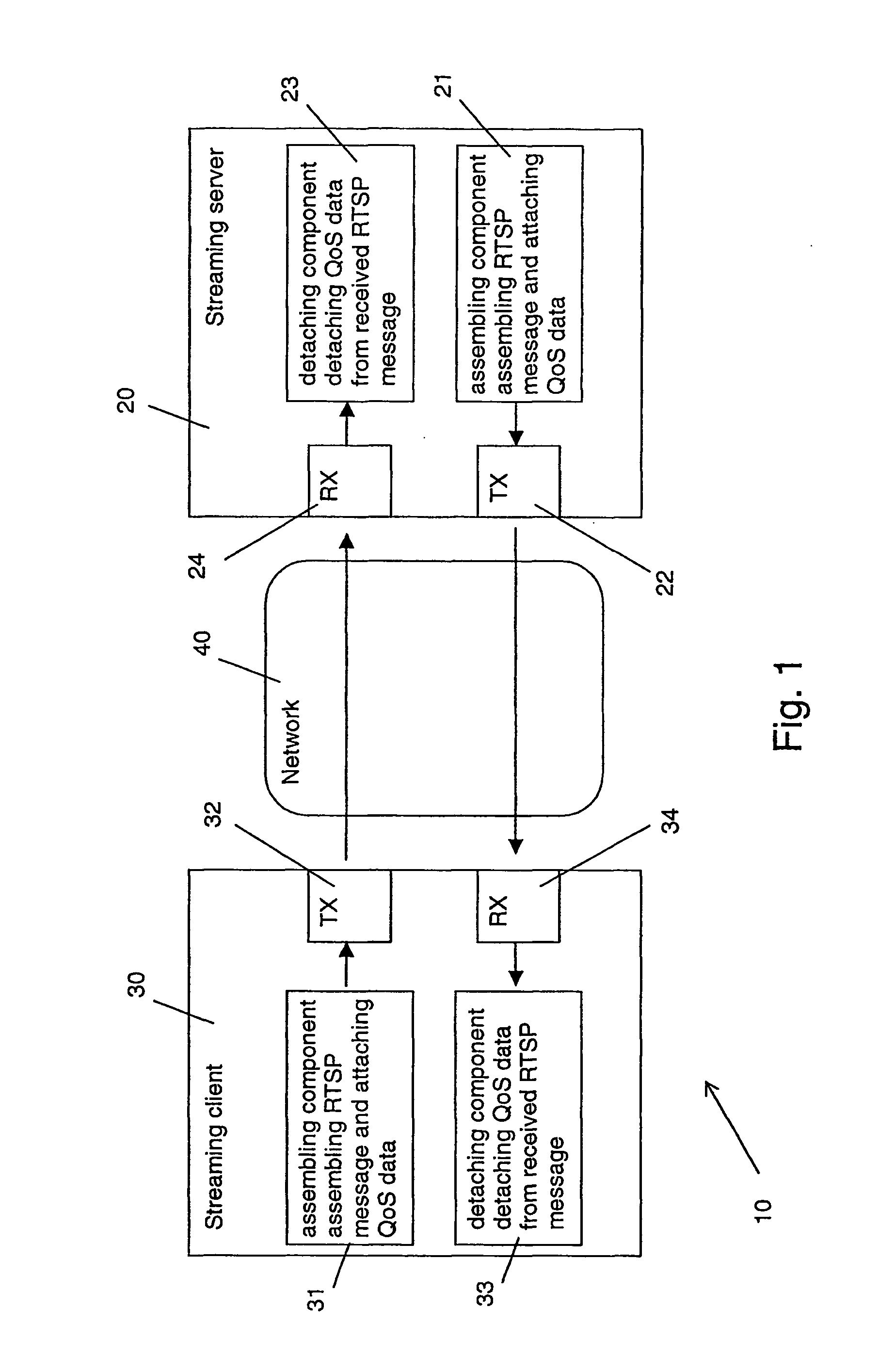
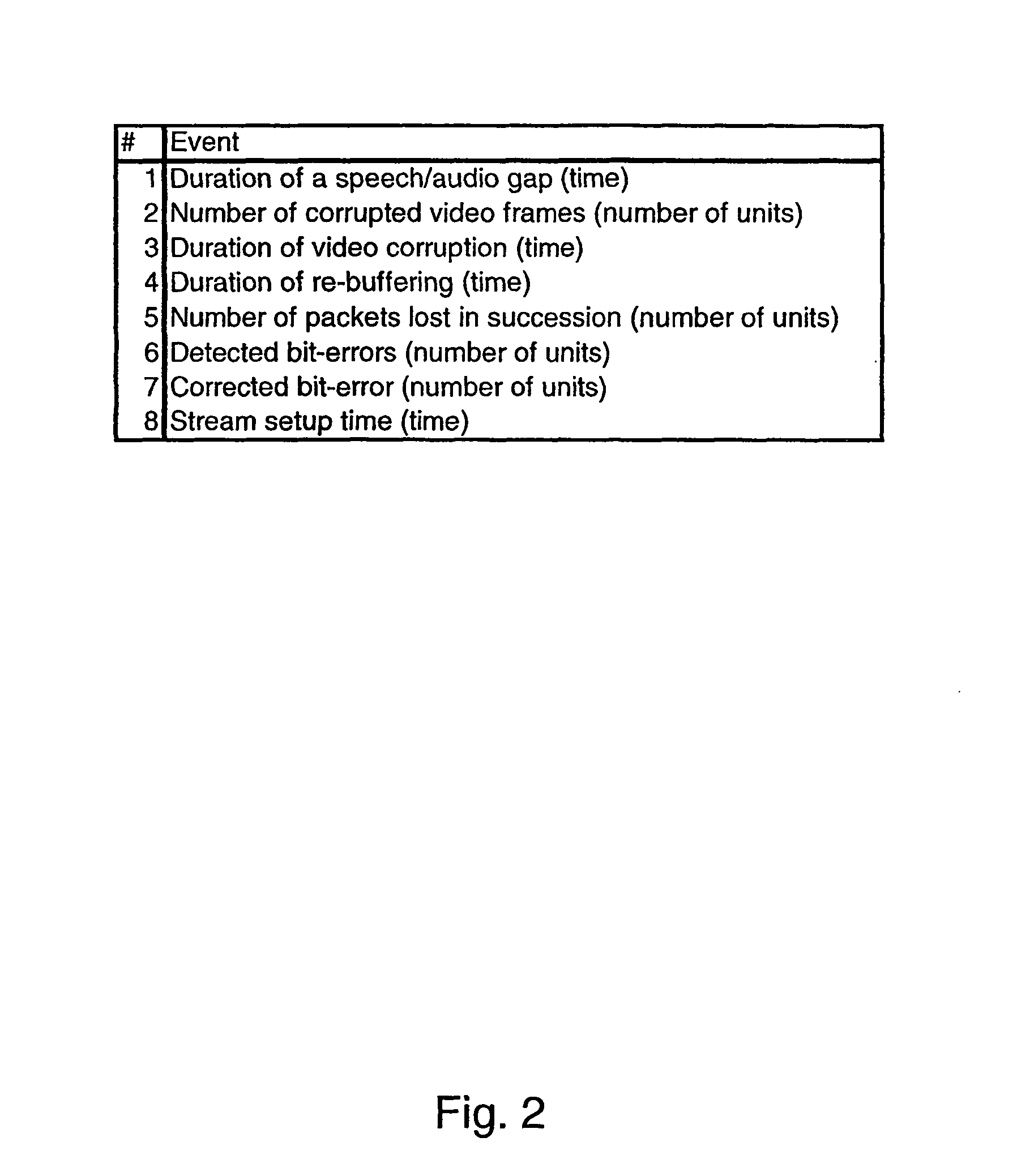
ActiveUS20080215704A1Quick SetupSolve excessive overheadMultiple digital computer combinationsData switching networksQuality of serviceInformation transmission
Methods of transmitting information relating to a quality of service are shown, which information is to be transmitted in at least one direction between a first device 30 and a second device 20. A first method comprises at least at one of the devices 20, 30 assembling a protocol message containing information other than the information relating to a quality of service and attaching the quality of service related information to the protocol message. A second method comprises forming the information relating to a quality of service inside at least one of a header field and an attribute of a protocol message. The disclosure relates equally to corresponding software codes, devices 20, 30, network elements and systems.
Owner:MICROSOFT TECH LICENSING LLC
Intelligent messaging network server interconnection
InactiveUS8090856B1Easy to writeEfficient communicationMultiple digital computer combinationsLink quality based transmission modificationMessage passingClient-side
An intelligent messaging network provides multiple software development kits (SDKs) to assist, e.g., engineers in developing client and server applications. The SDKs can contain a consistent set of application program interfaces (APIs) and a set of platform specific libraries for all intelligent messaging network supported platforms and networks. In addition to the SDKs, the intelligent messaging network can provide developers a resource kit including a set of tools to assist the developers when designing, implementing, and testing their client and server applications. The intelligent messaging network can provide a mobile client and server SDK environment to assist engineers developing client applications and servers. The SDKs can provide an easy to use APIs and a set of platform specific libraries to perform, e.g., compression, network management services, server-to-server communication, server registration / de-registration, and reliable message transport services.
Owner:TELECOMM SYST INC
System and method to publish information from servers to remote monitor devices
InactiveUS7970898B2Easy to writeEfficient communicationError prevention/detection by using return channelDigital computer detailsWeb browserAuthorization
To assist in monitoring the intelligent messaging network, a system and method for publishing logging and status information from the servers is provided. A list of available servers accessible for monitoring by persons, devices, and applications via a remote monitor device can be provided. The remote monitor device may forward selected servers from the list of available servers in which they are interested. Also, particular information about the selected servers can be requested. Access to certain servers and information may be restricted to those with authorization. Authorization can be verified by the use of digital certificates. The requested information can then be gathered and provided to authorized persons or devices. Typically, the information includes logging and status information from the servers. The information can be provided as an XML page and viewed using, for example, a standard web browser. Further, if the information is provided to the remote monitor device as an XML page, a standard XML parser may be used to extract particular information from the XML page.
Owner:TELECOMM SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com