Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
66 results about "Watch list" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
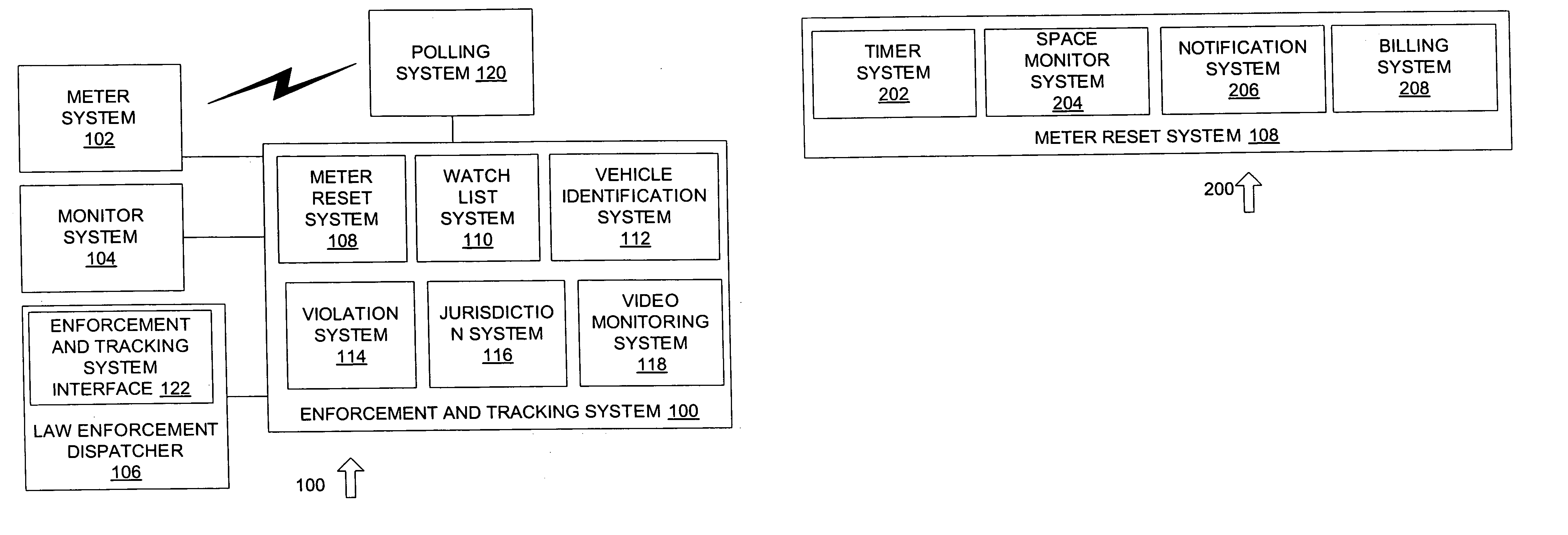
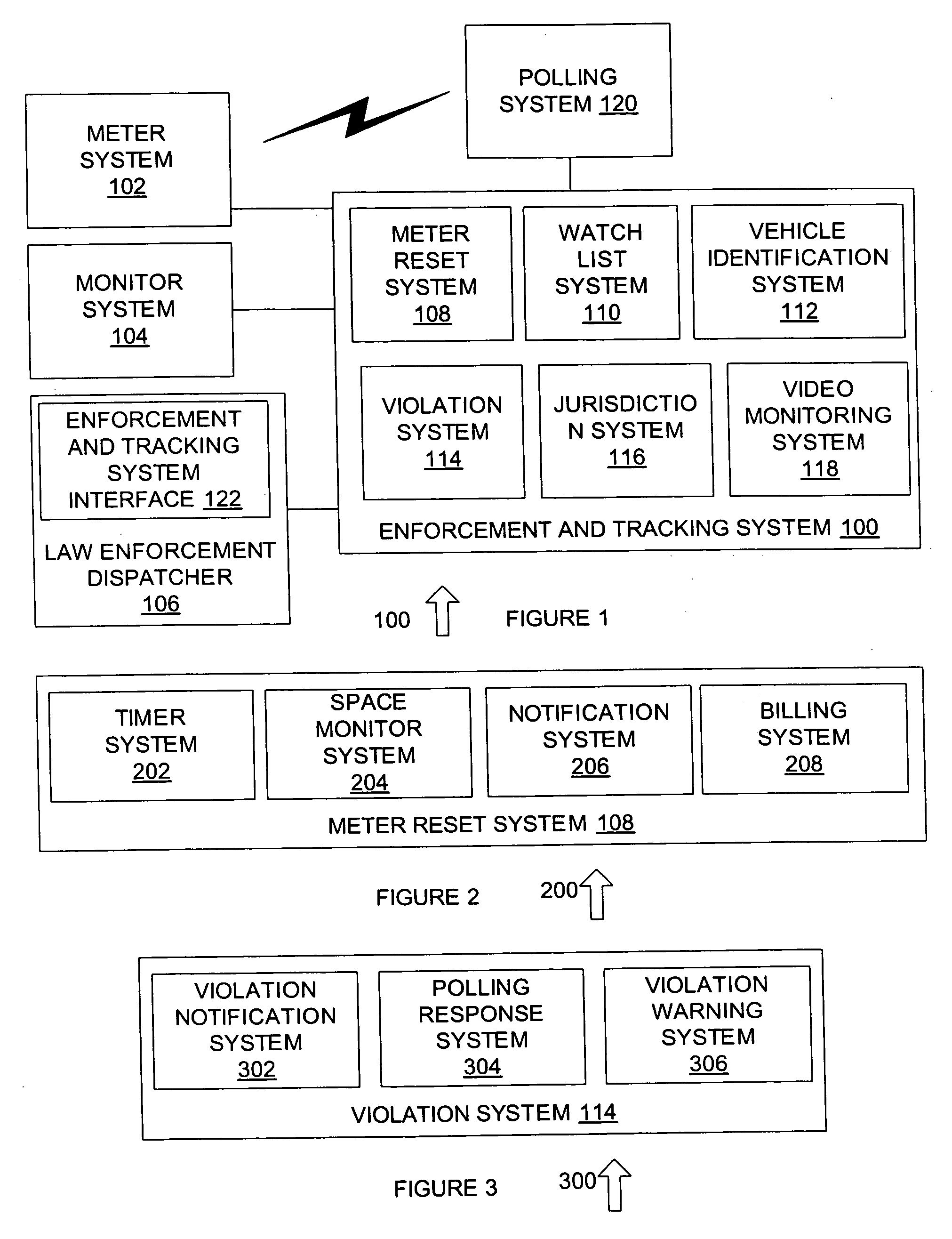
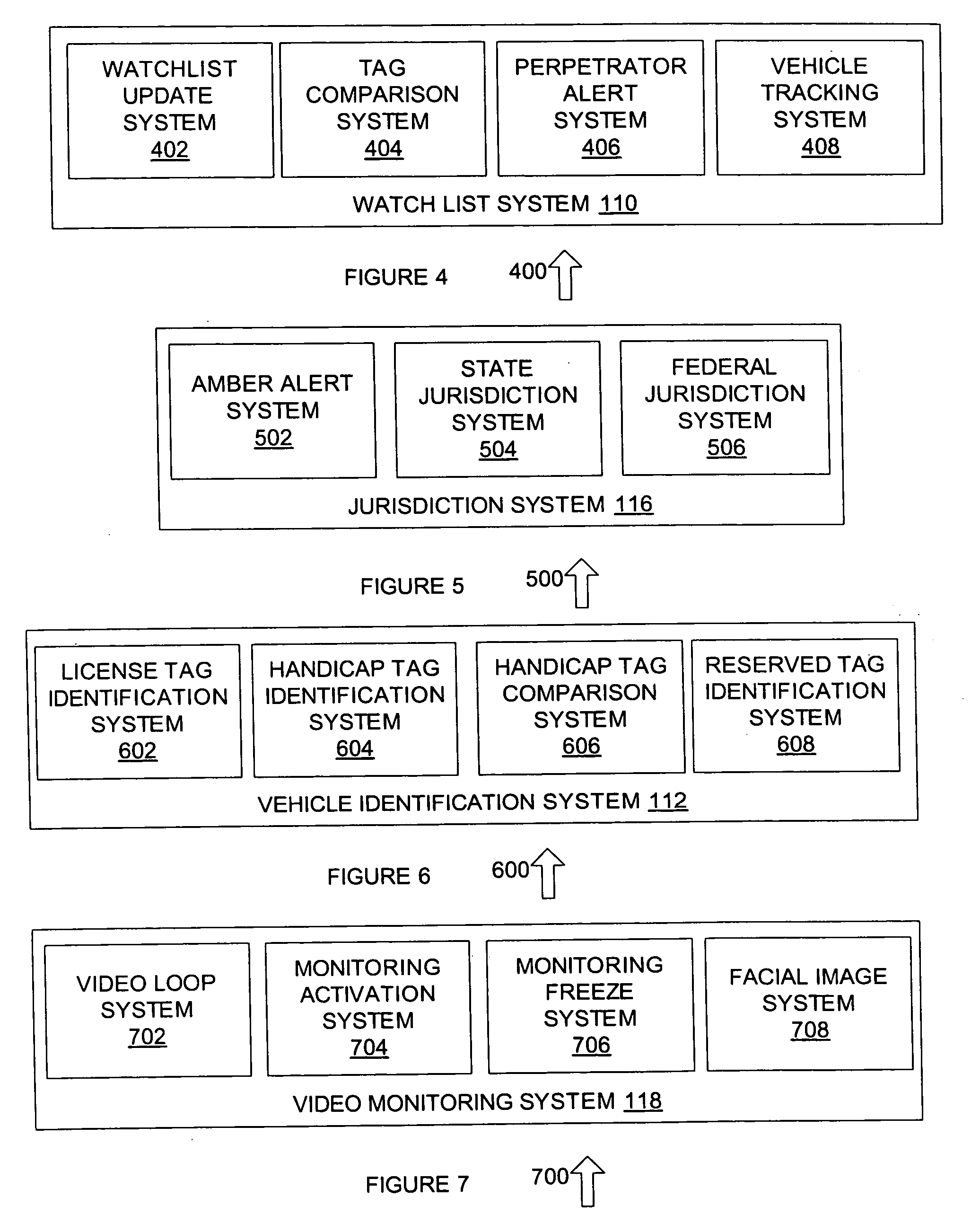
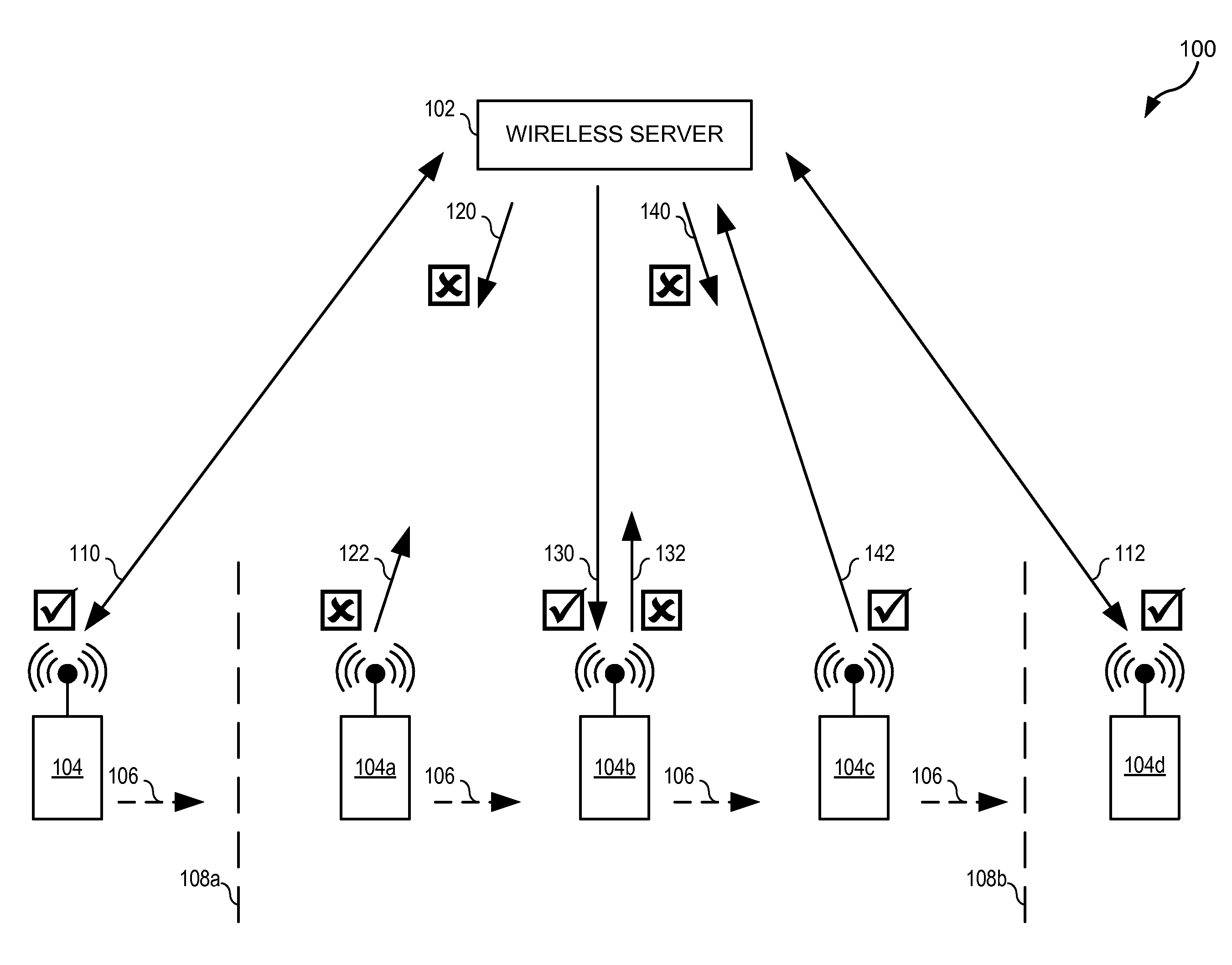
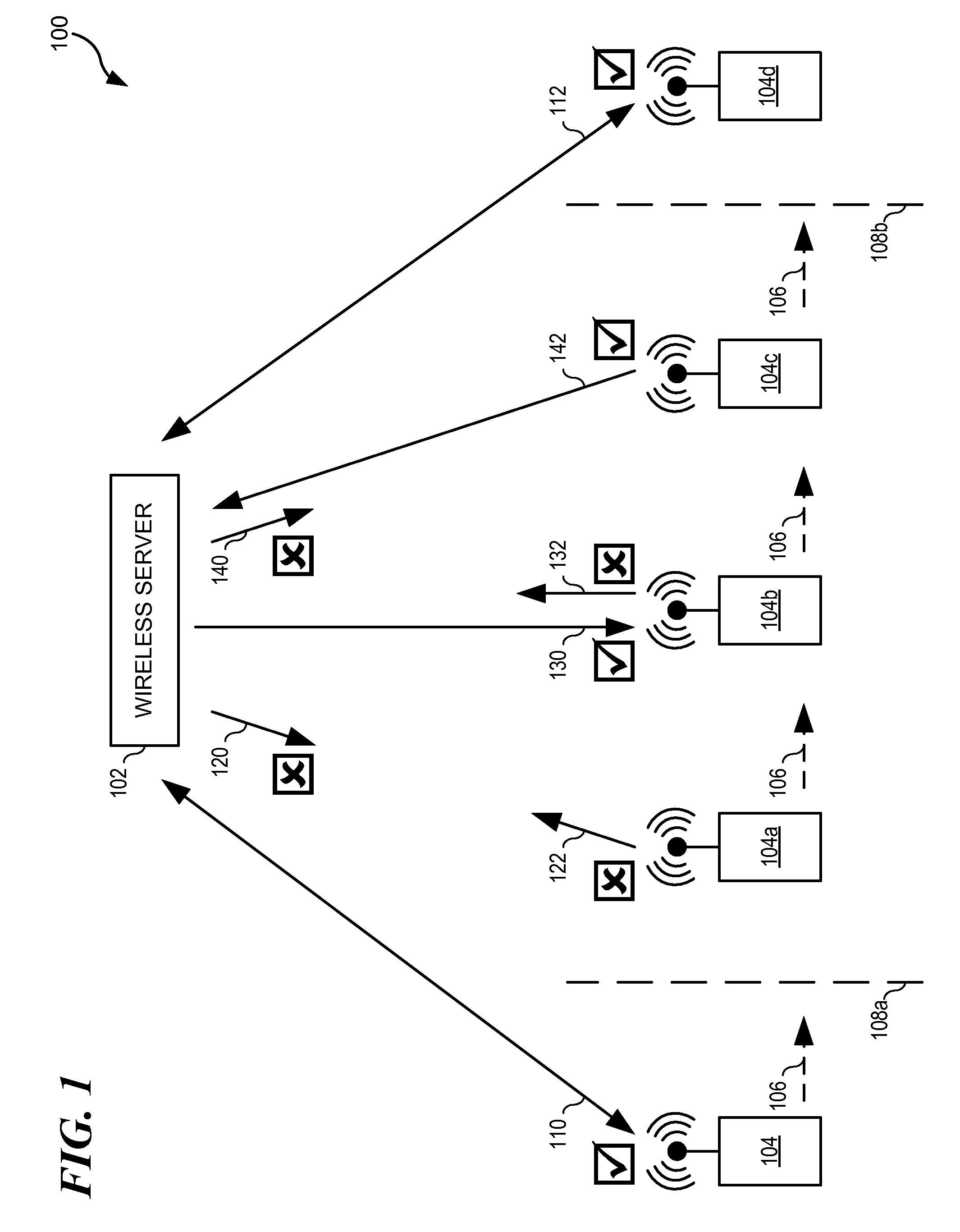
System for tracking suspicious vehicular activity
A system for monitoring and tracking vehicles in parking locations, public roadways and highway entrances and exits and other public vehicle access areas is provided, such as to monitor and track vehicles in parking spaces, public roadways and highways without the need for parking or traffic personnel. The system includes a meter system that generates image data of a vehicle in a parking space, public roadway and highway entrances and exits such as by creating an array of pixel data in a predetermined field of view that includes a vehicle identification tag and facial imaging. An enforcement and tracking system receives the image data and generates a vehicle license number, vehicle tag identification number and facial image from the image data, such as by analyzing the image data to identify the vehicle license number, vehicle tag identification number and facial image based on the expected location of the license tag, identification tag and field of view image data characteristics of the license tag, facial image or other suitable data. From the image data acquired, monitoring of parking spaces is performed and violation citations or notices are generated for errant vehicles in parking locations as well as notification to law enforcement and homeland security agencies of vehicles and facial images identified as being on a watch list.
Owner:MOTOROLA SOLUTIONS INC
Media content watch list systems and methods
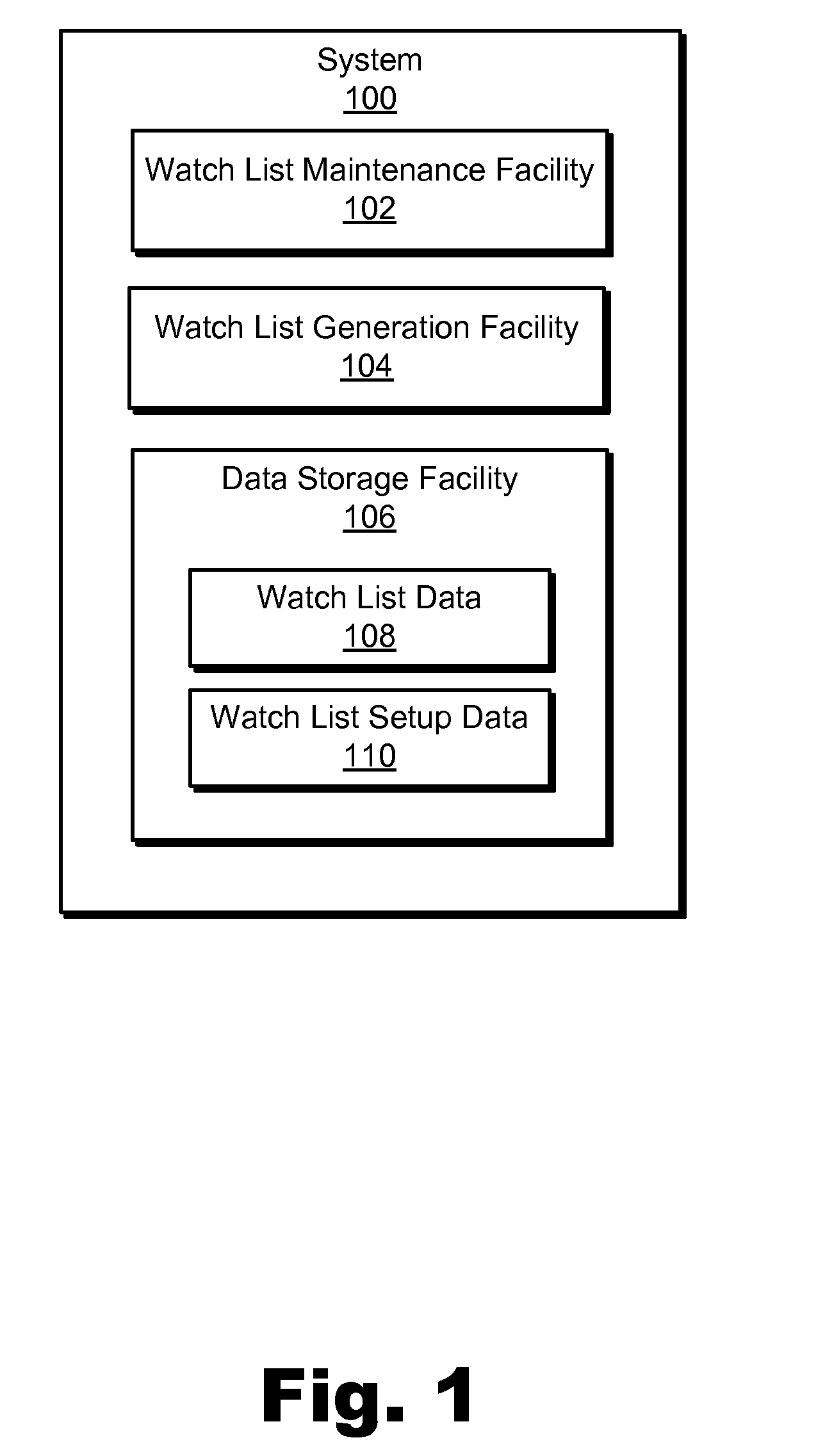
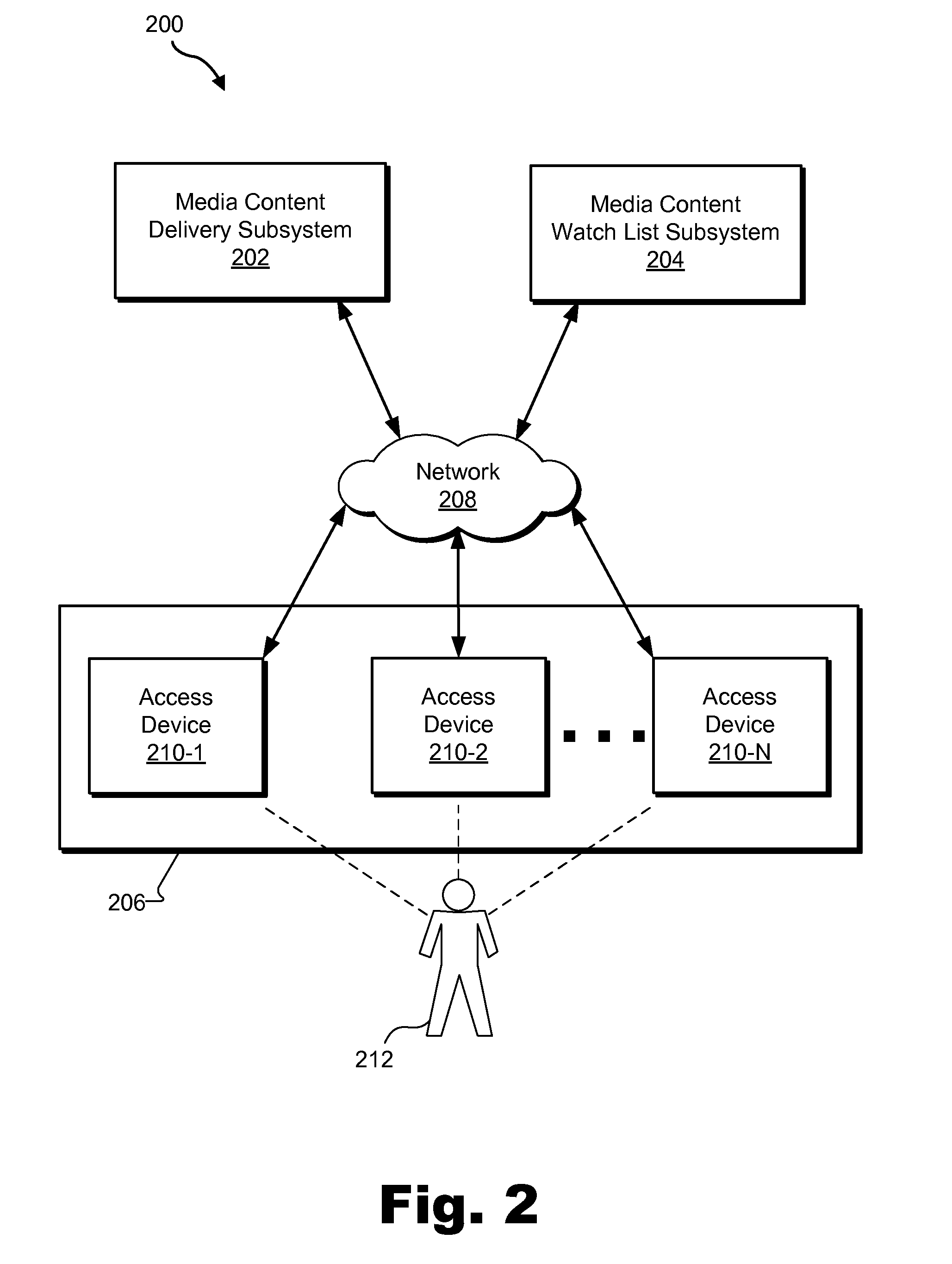
Exemplary media content watch list systems and methods are disclosed. An exemplary method includes a media content watch list subsystem maintaining media content watch list data representing a plurality of media content instances available for experiencing by a user, receiving a request for a media content watch list from a media content access device associated with the user, generating the media content watch list based on the media content watch list data and the request, and transmitting data representative of the media content watch list to the media content access device for presentation to the user. The maintaining of the media content watch list data includes updating the media content watch list data based on at least one predetermined non-watch-list-specific operation performed by the media content access device associated with the user. Corresponding systems and methods are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
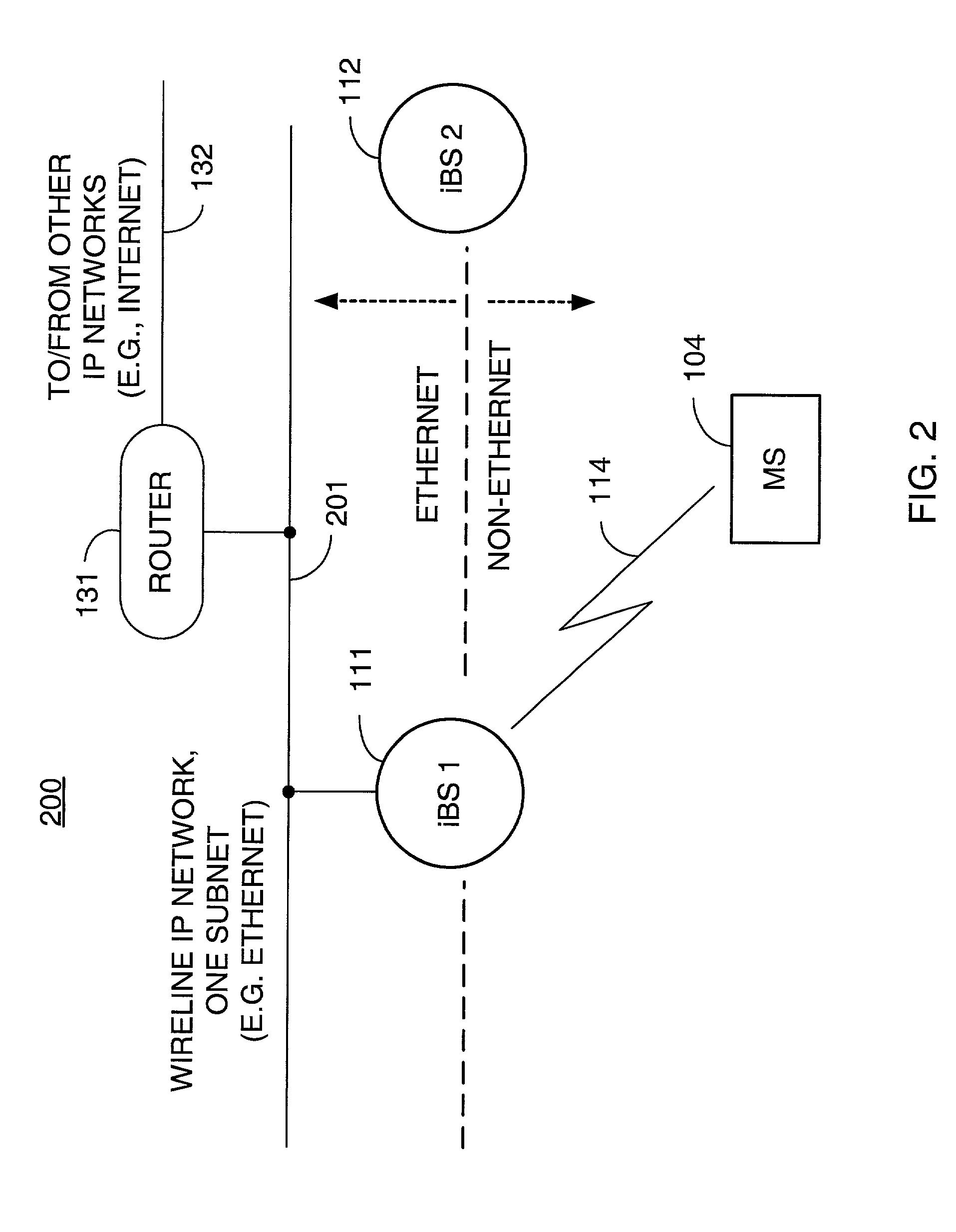
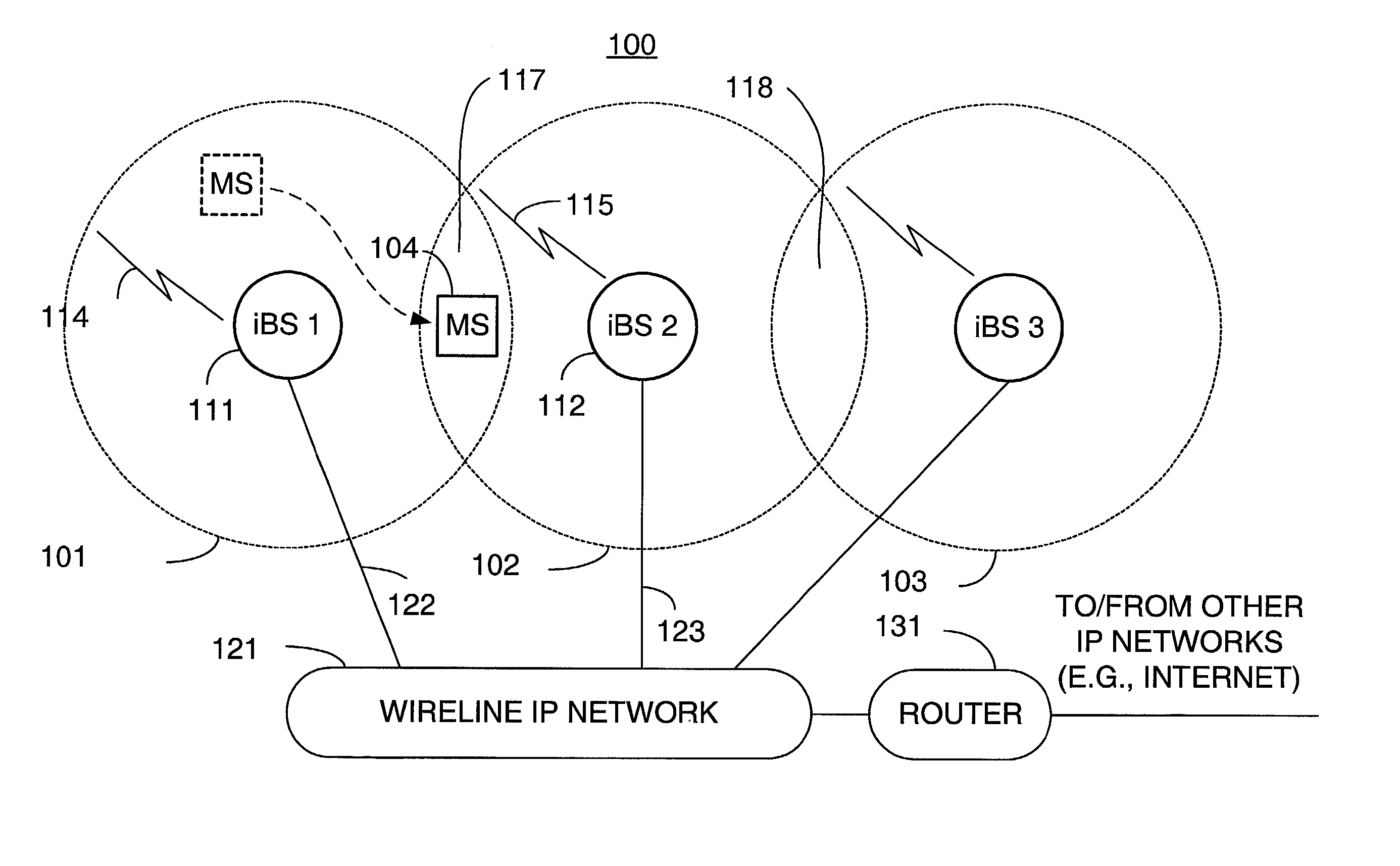
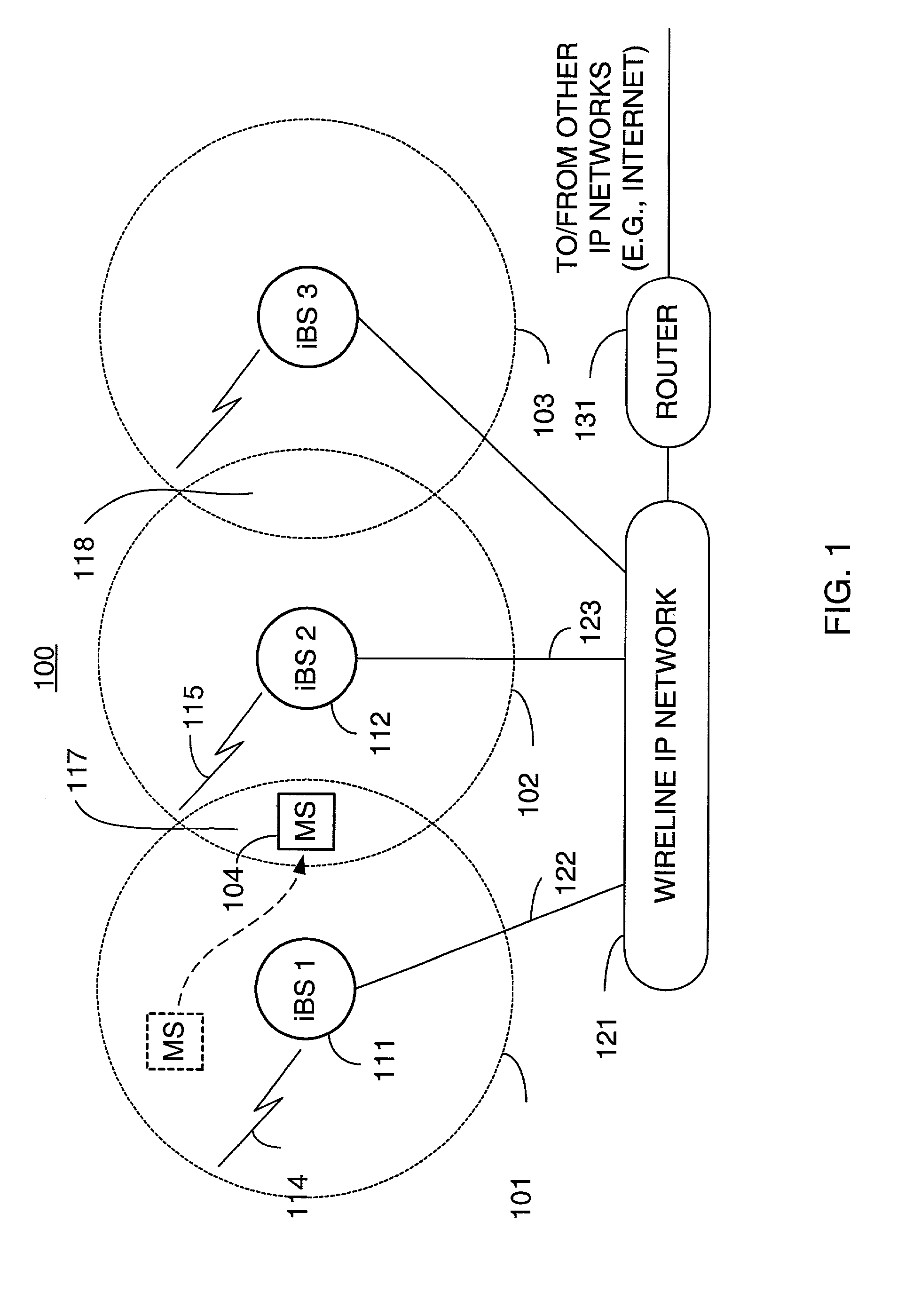
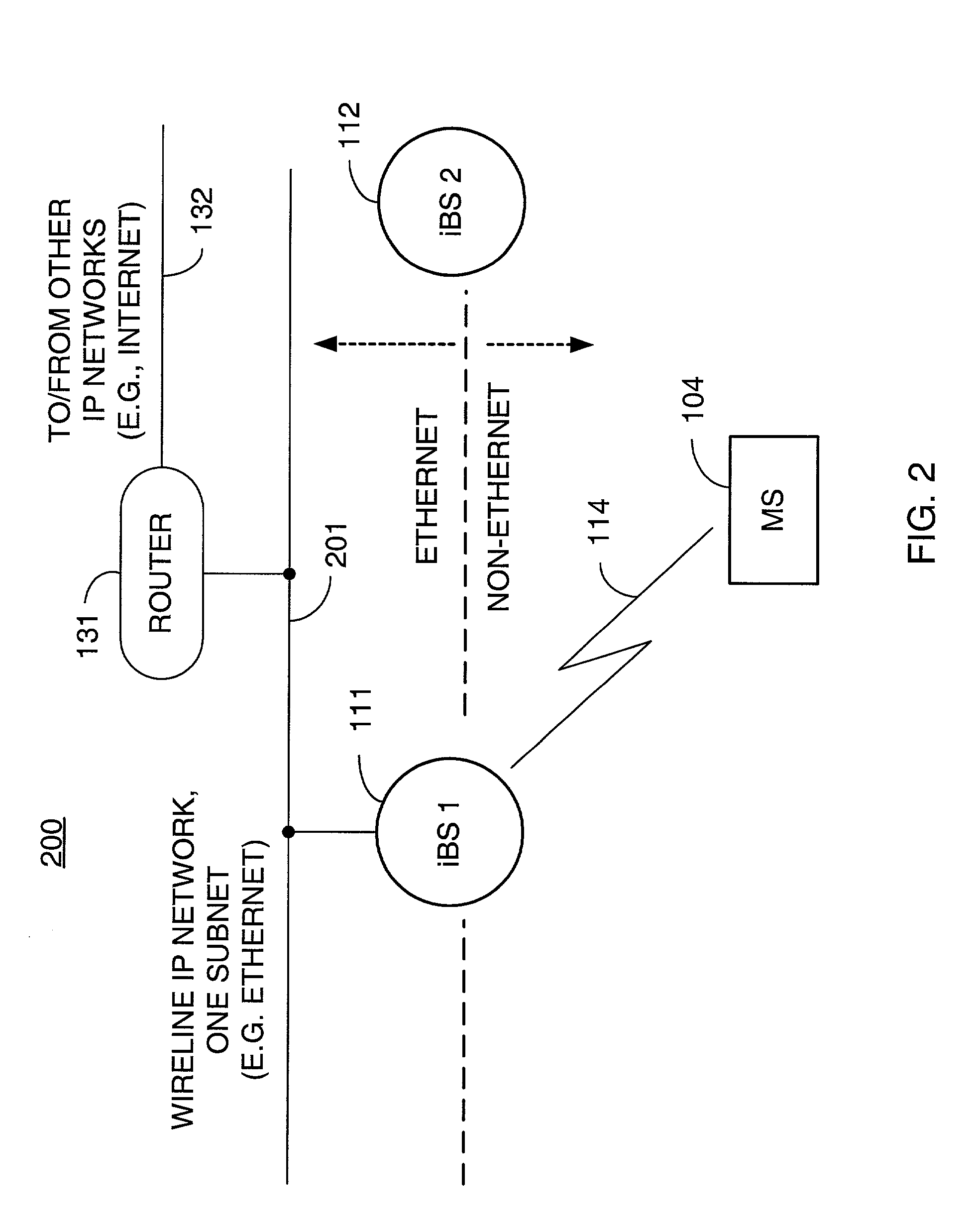
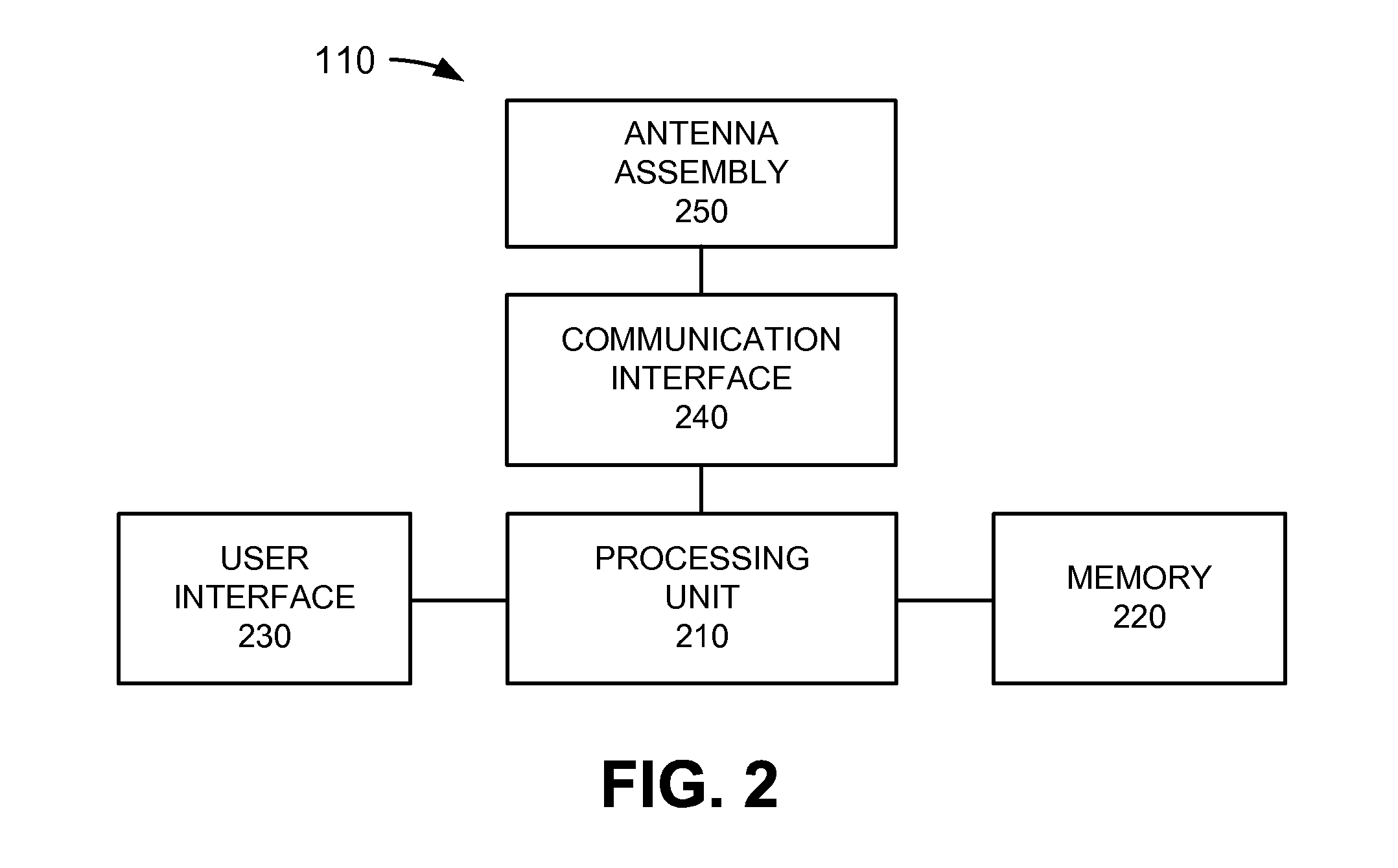
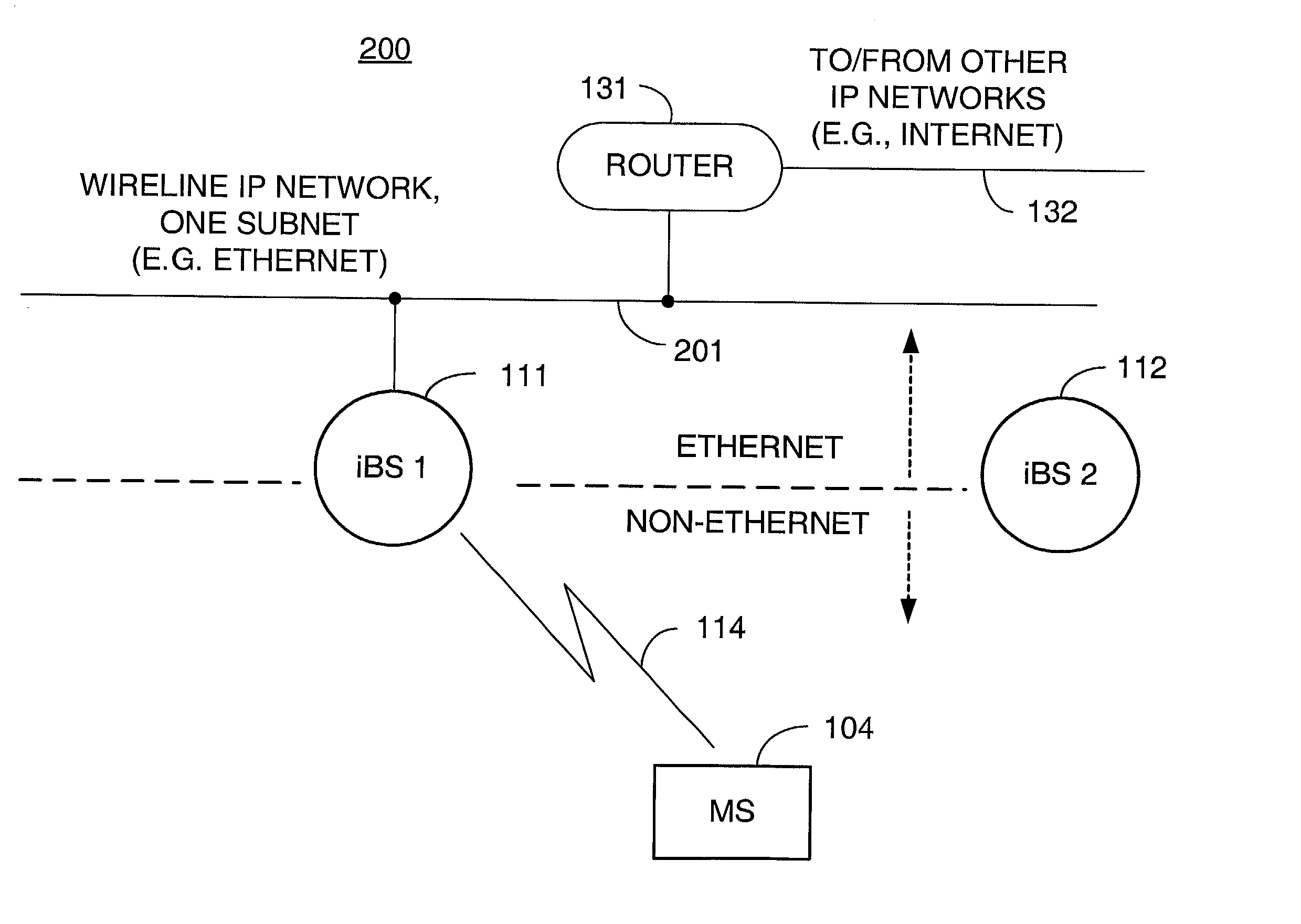
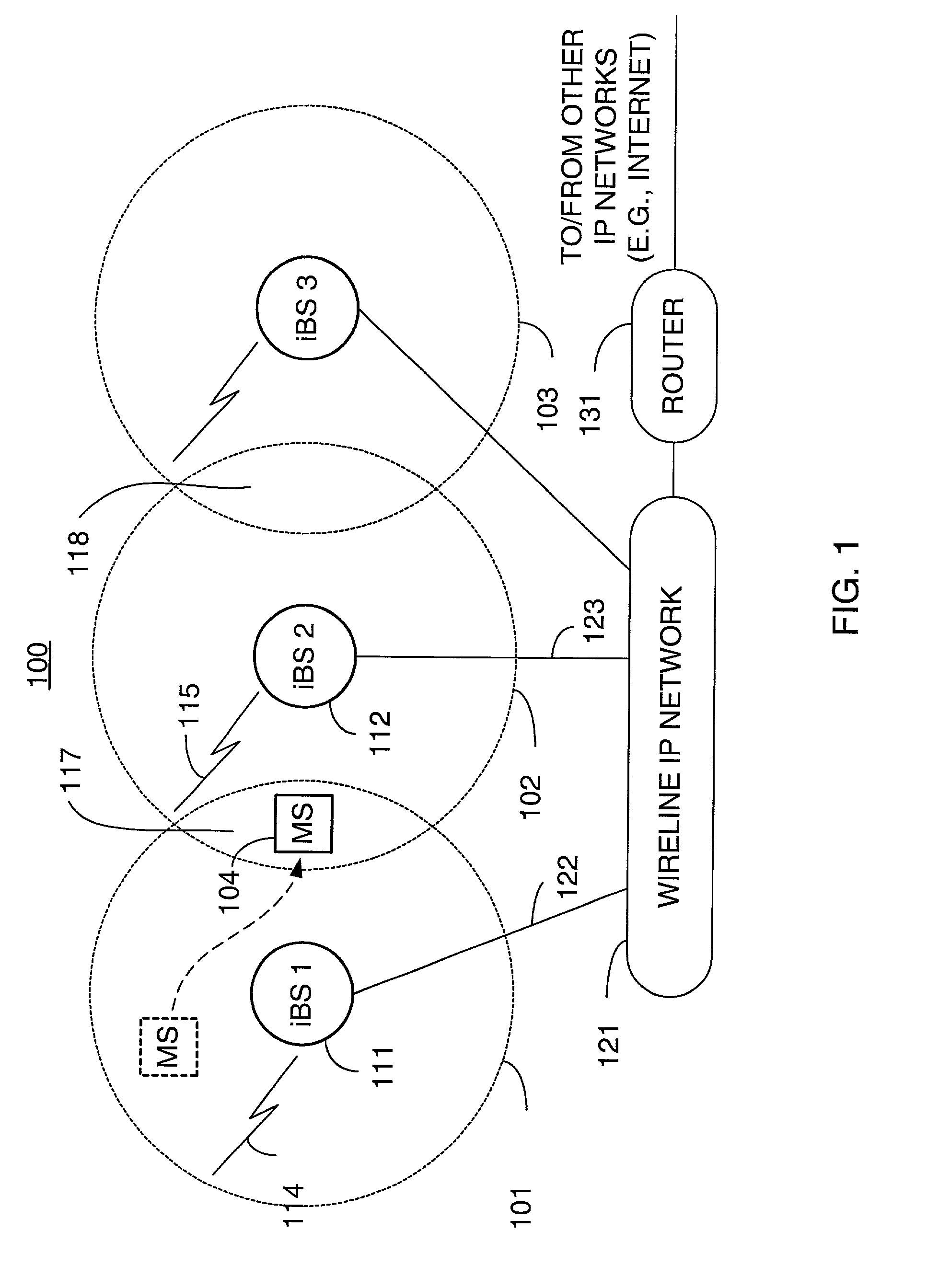
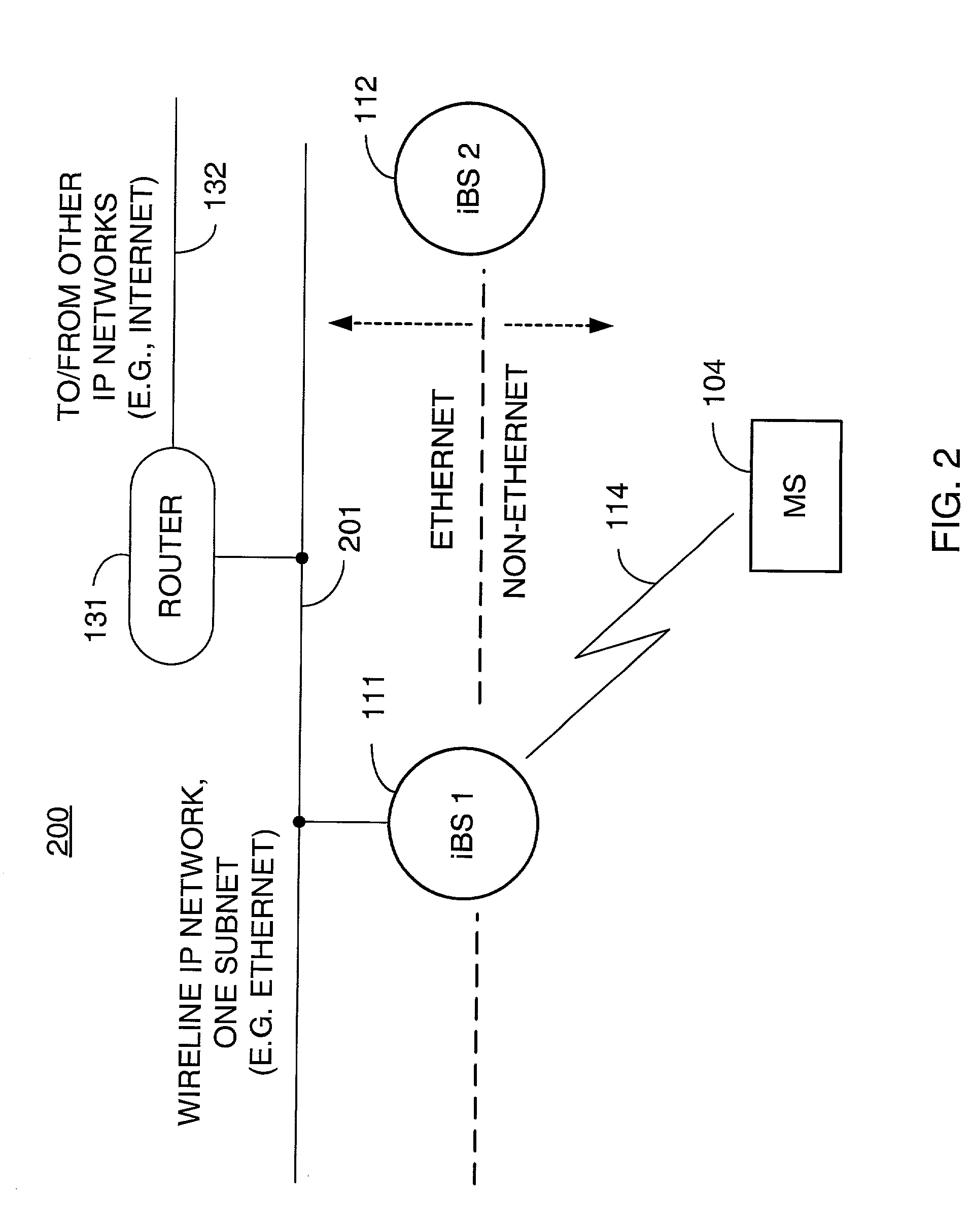
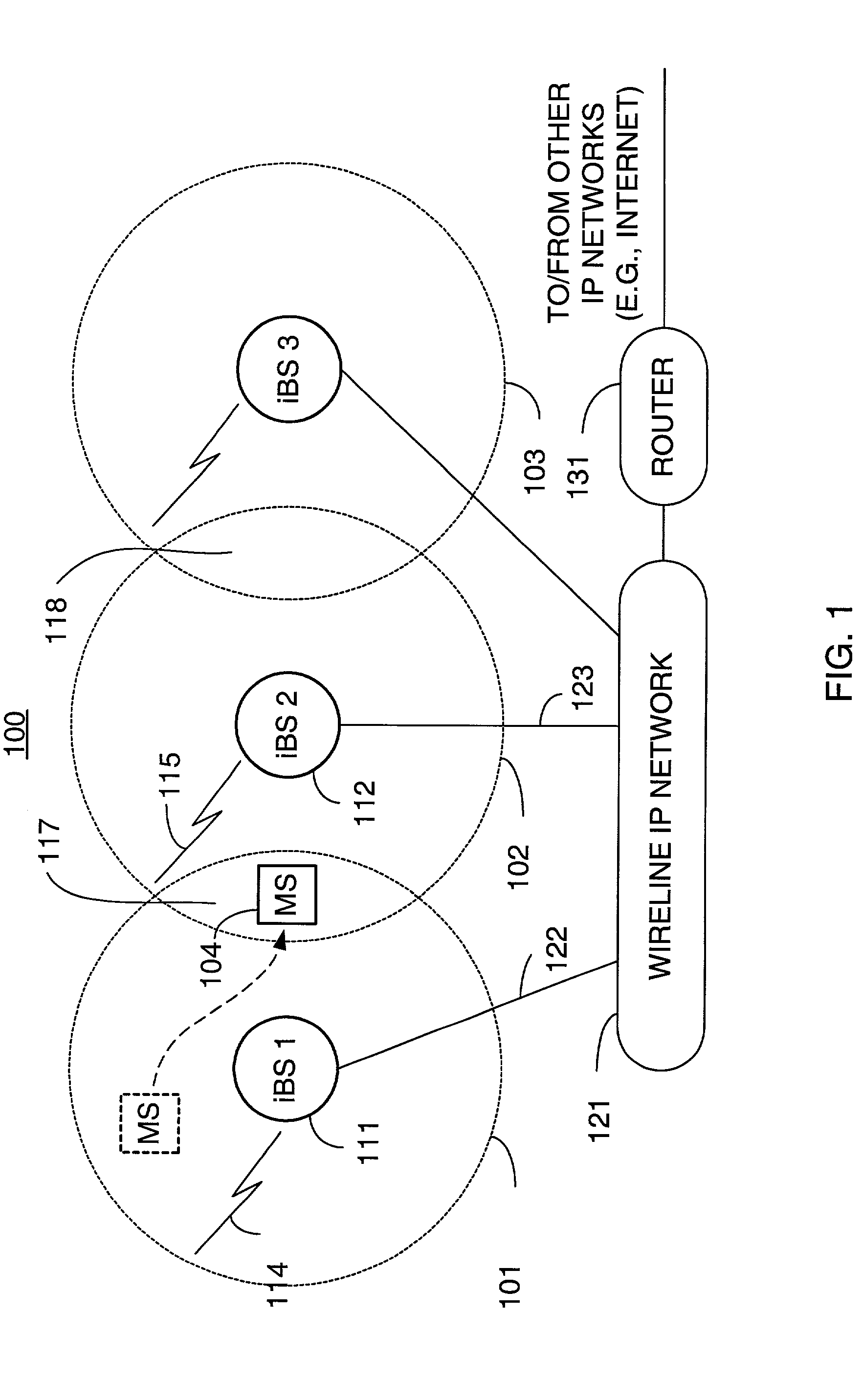
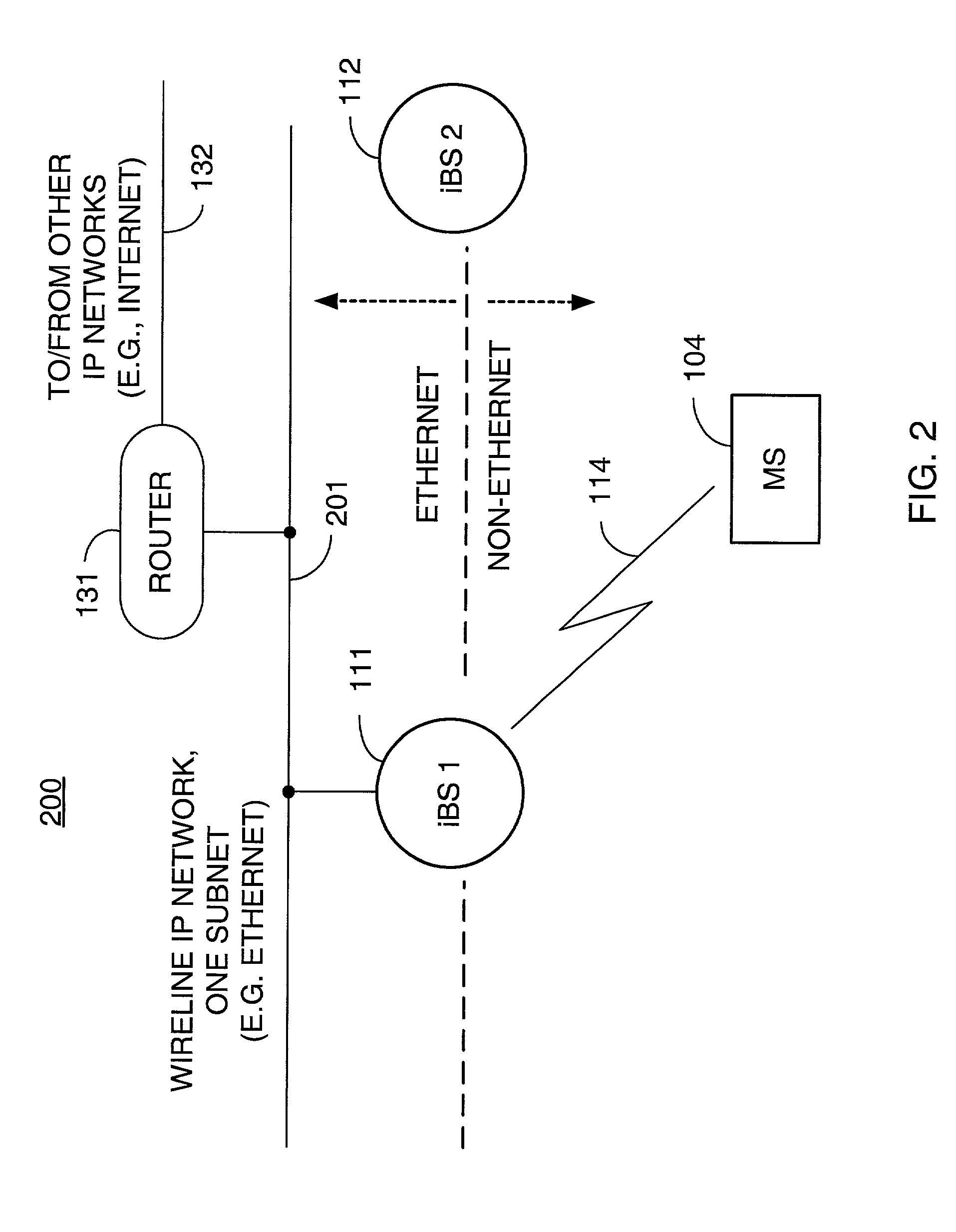
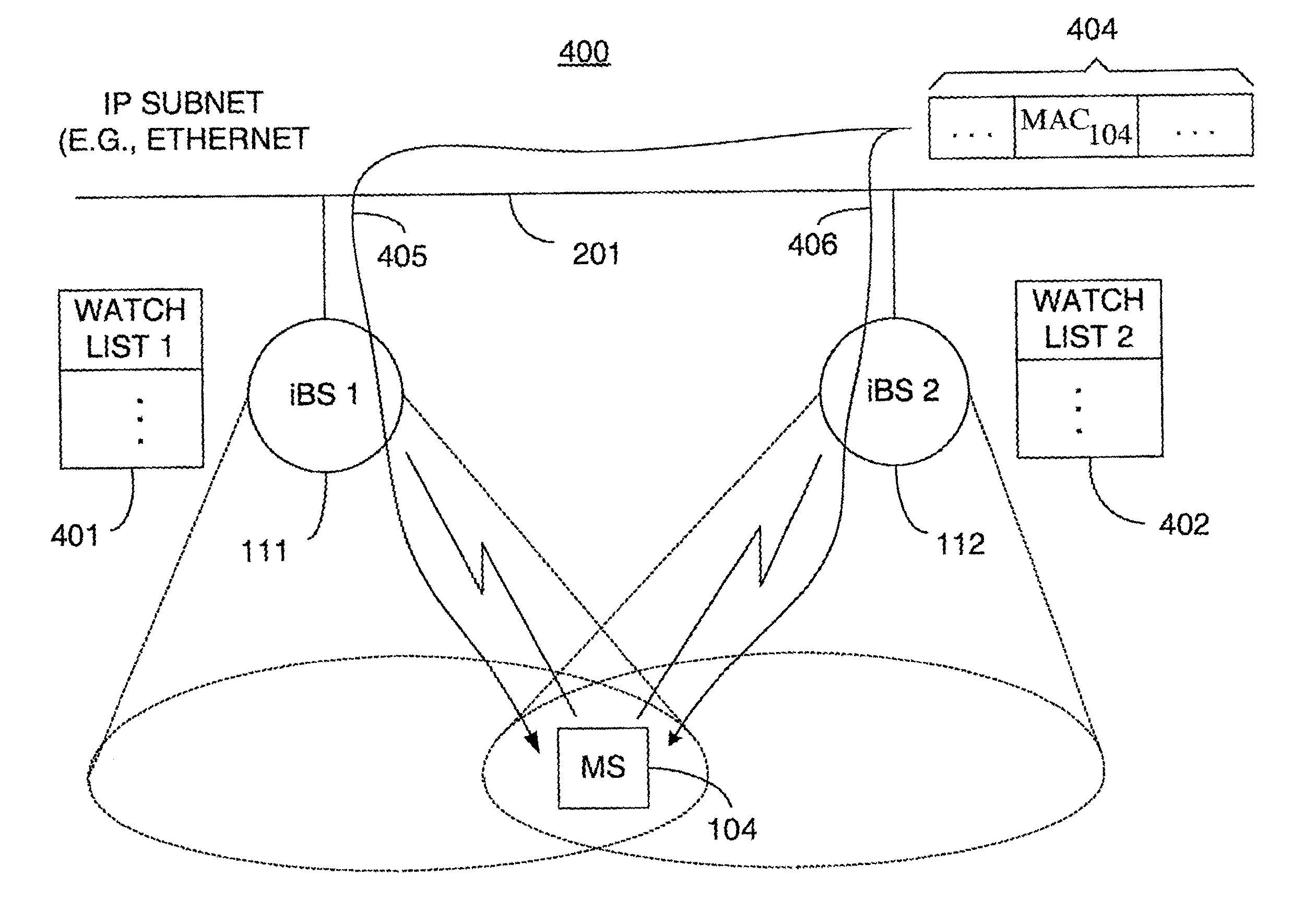
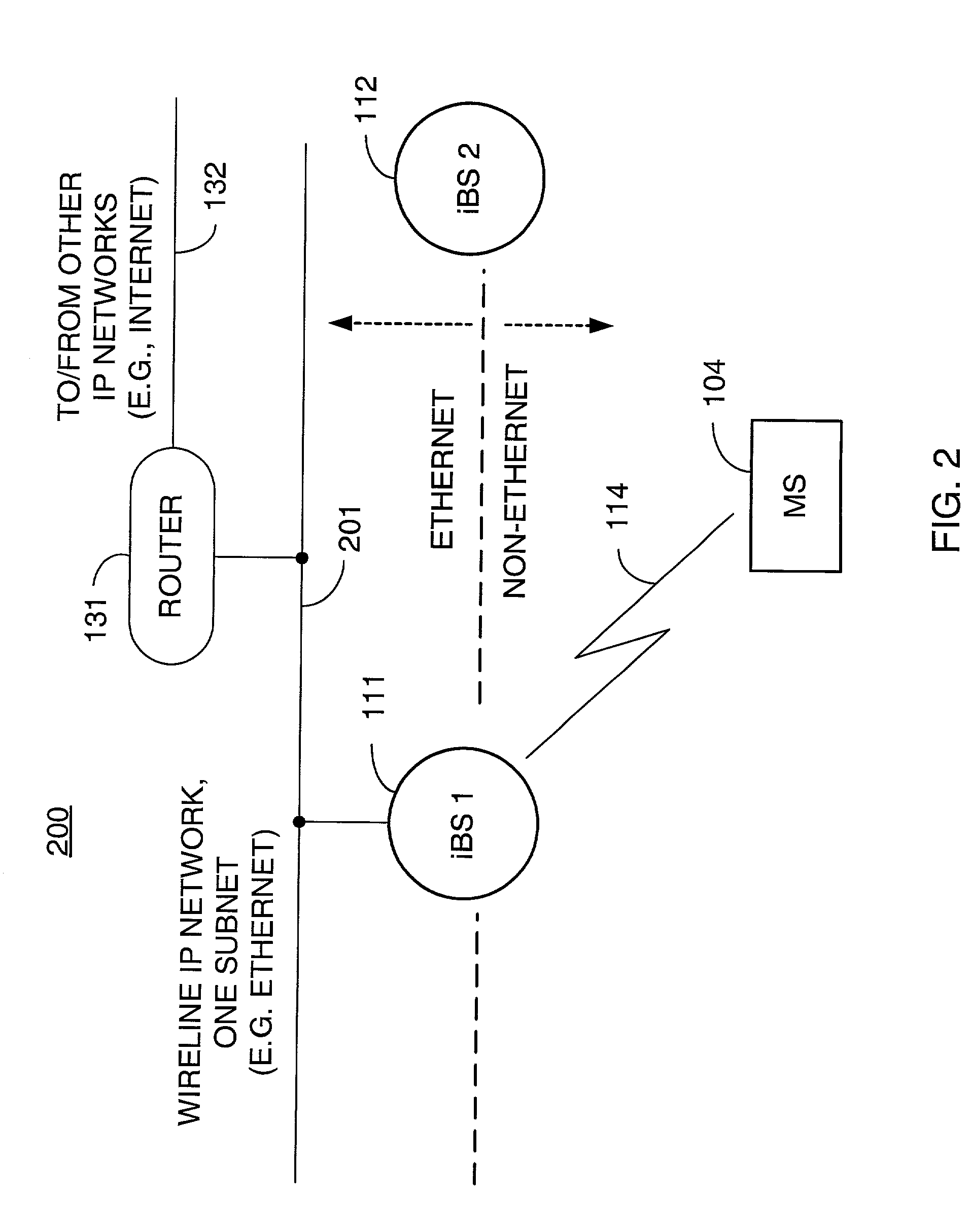
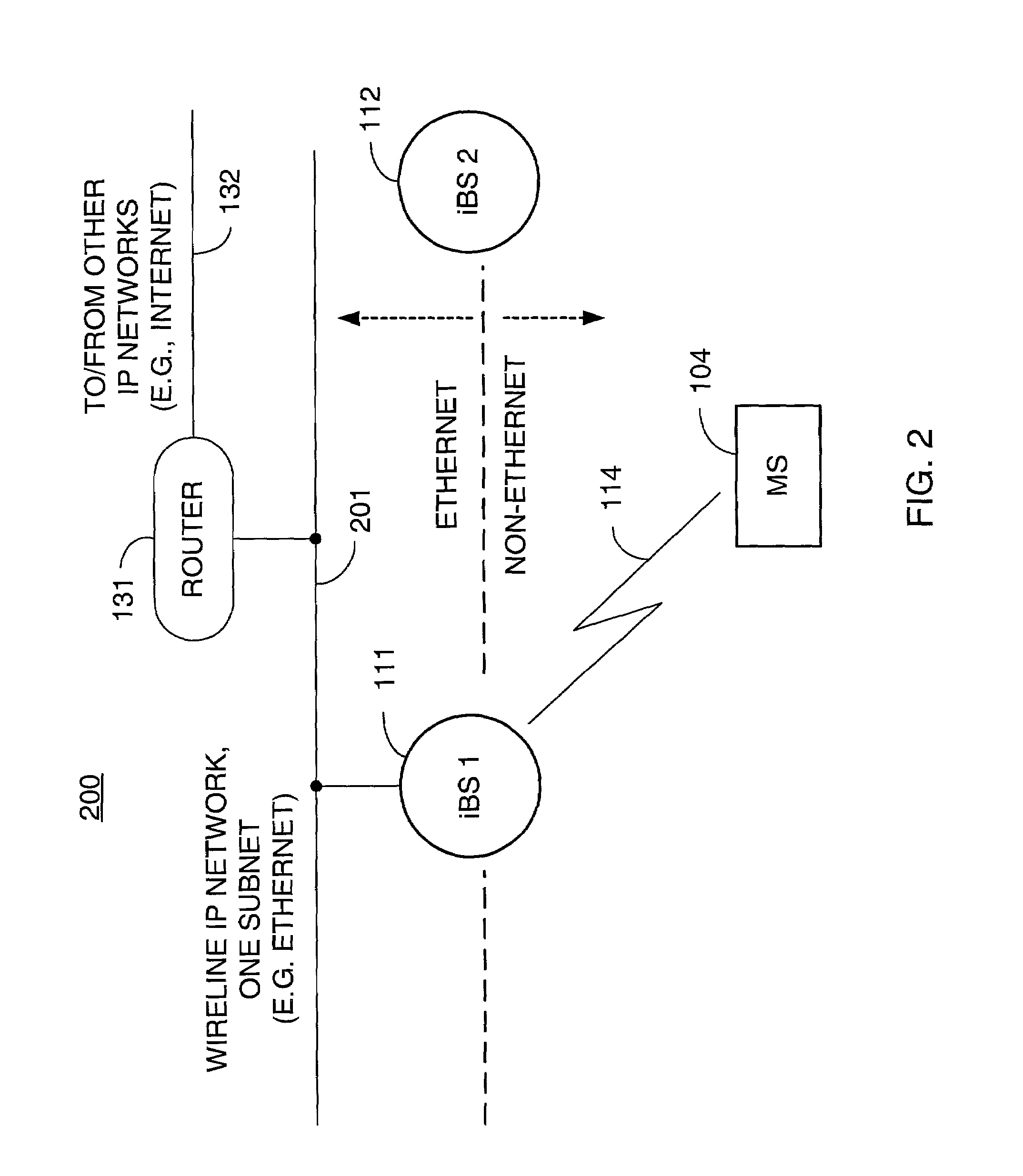
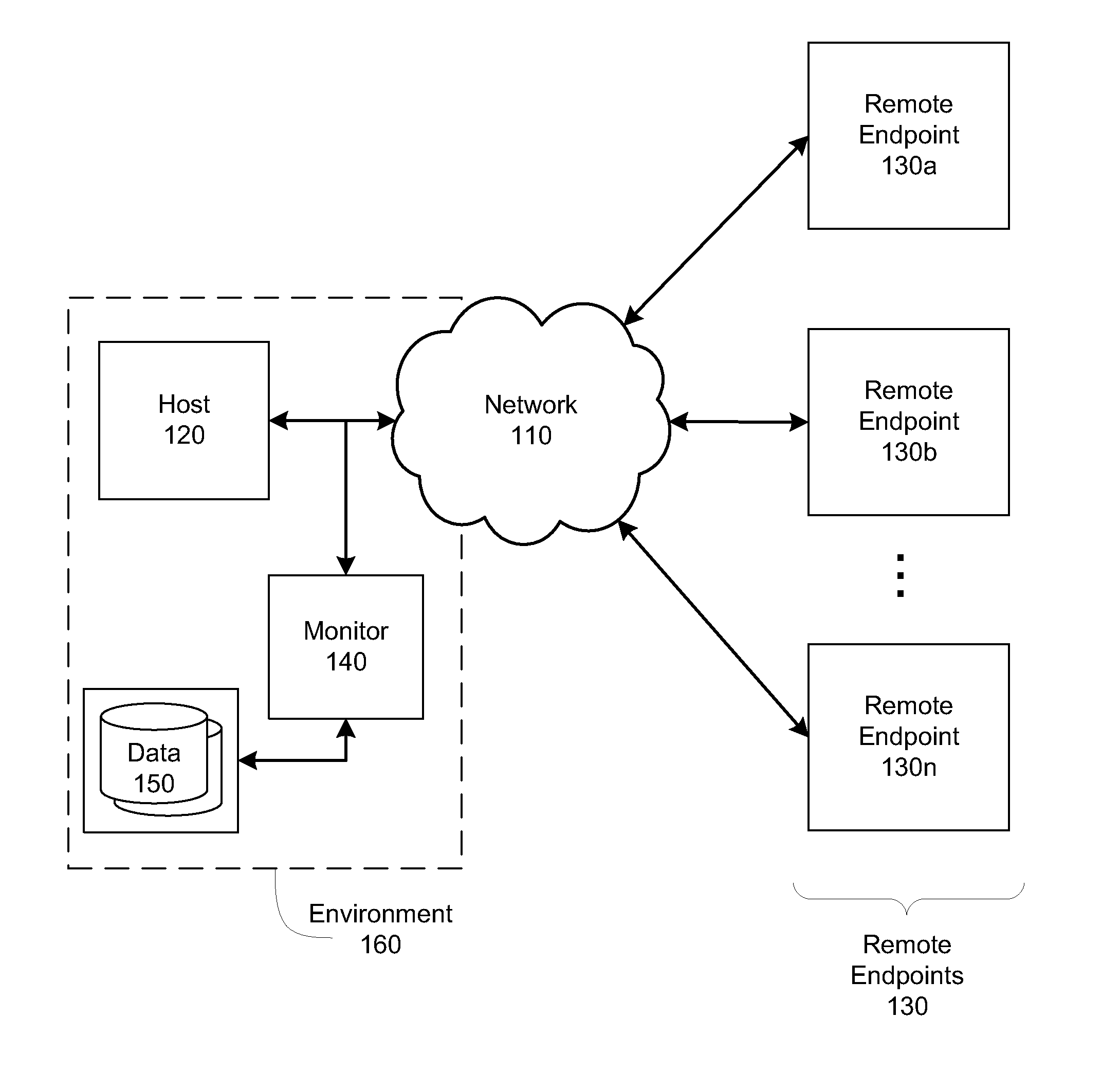
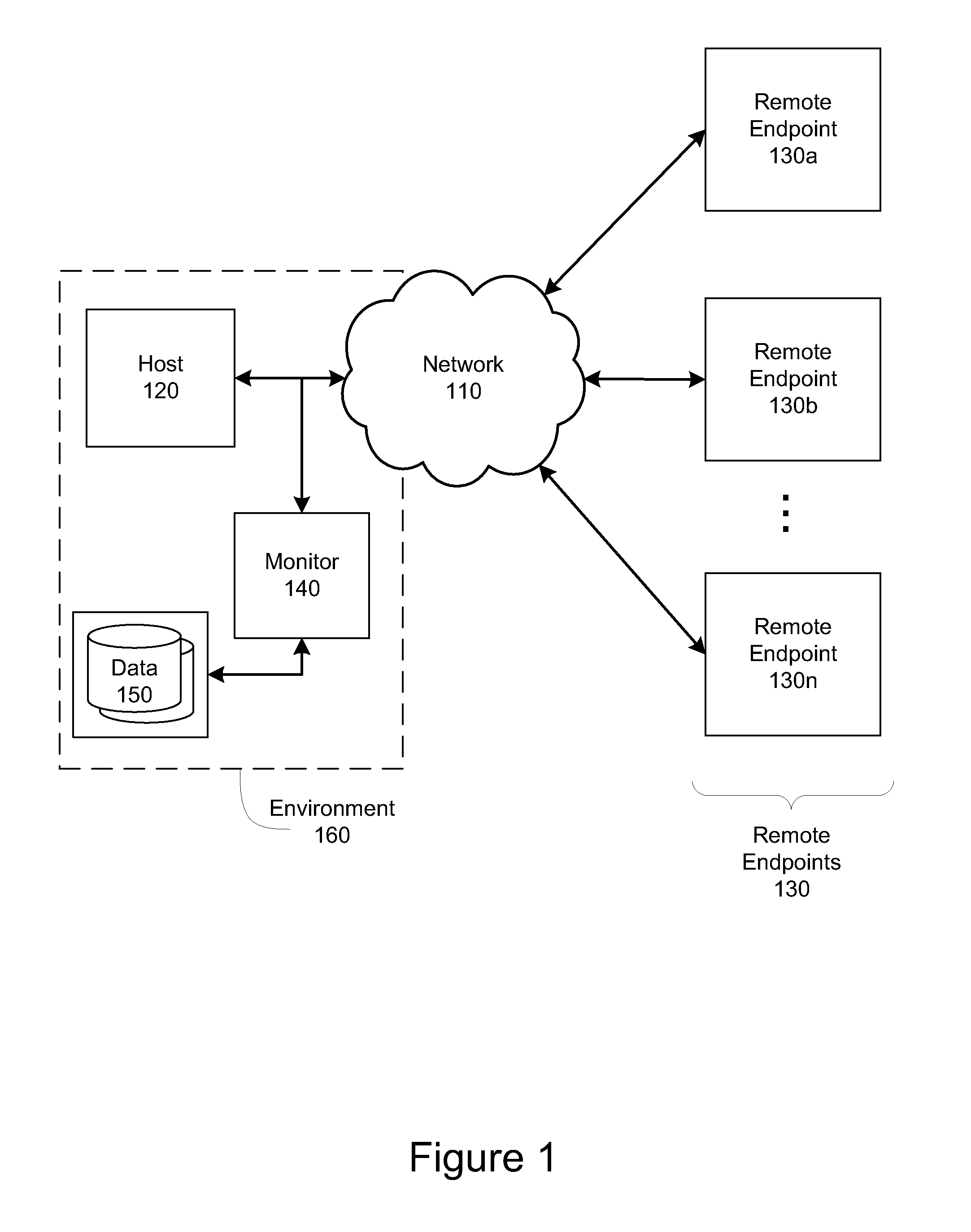
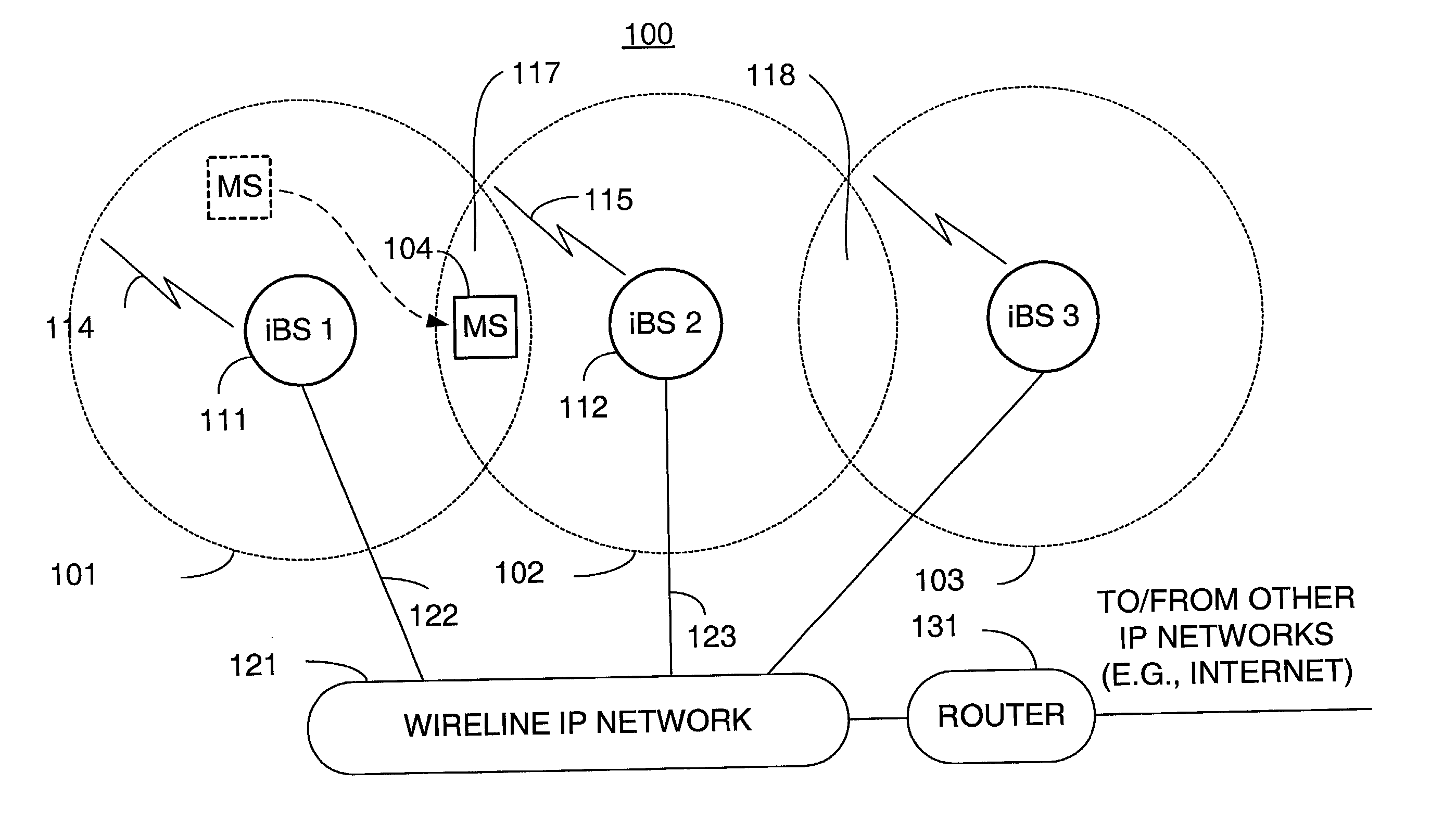
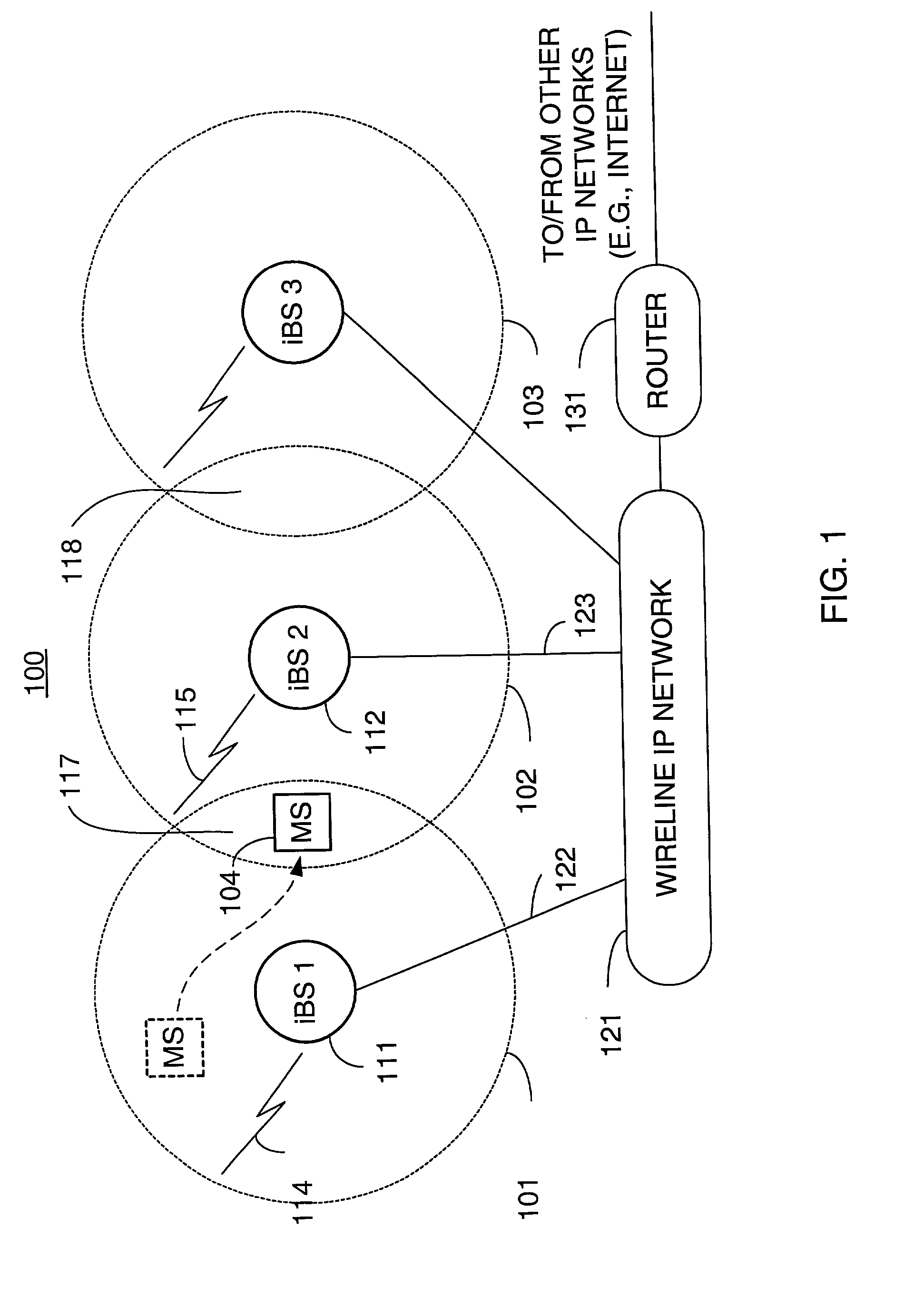
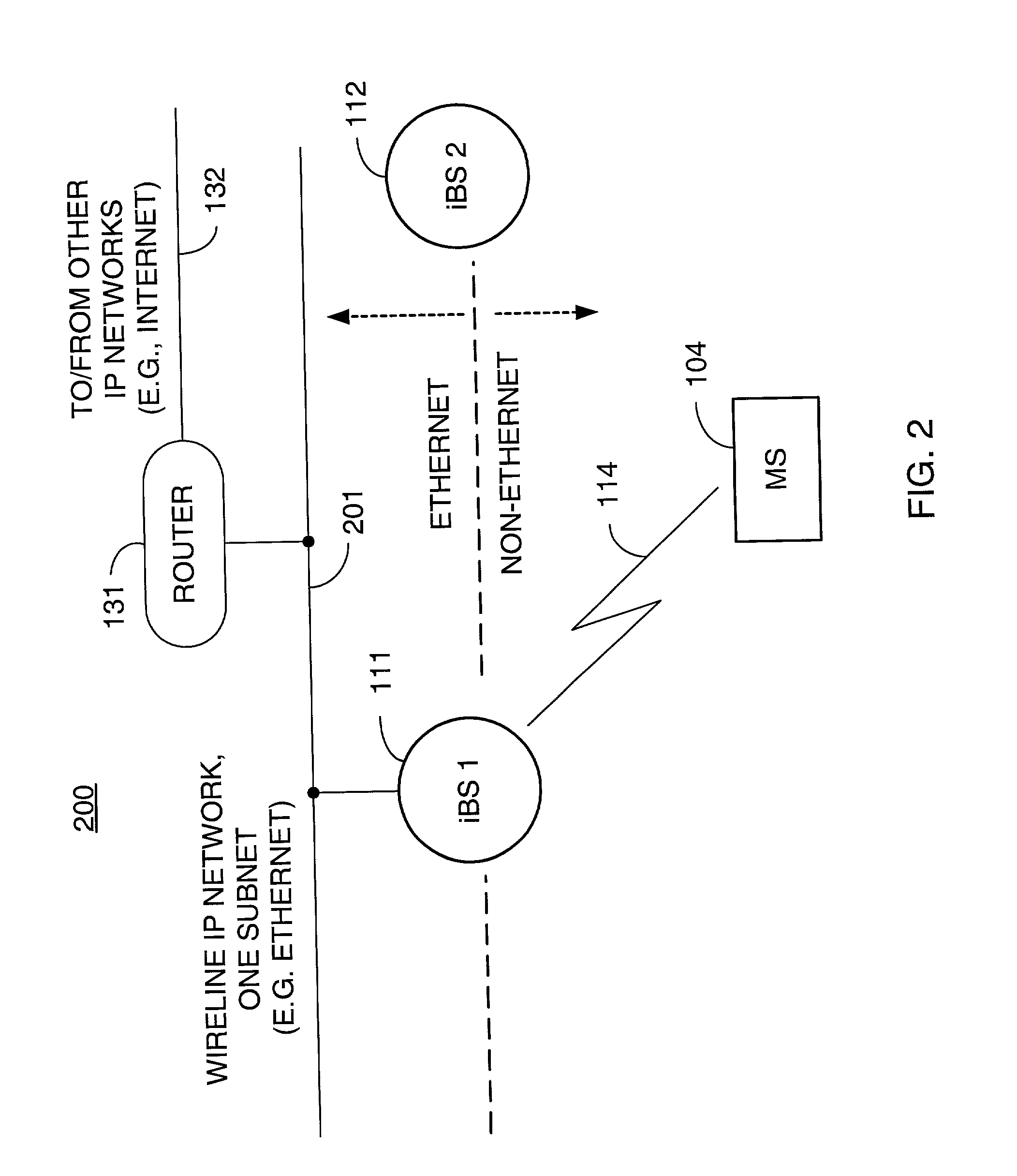
Packet distribution and selection in soft handoff for IP-based base stations among multiple subnets
ActiveUS20020191561A1Time-division multiplexData switching by path configurationWatch listMobile station
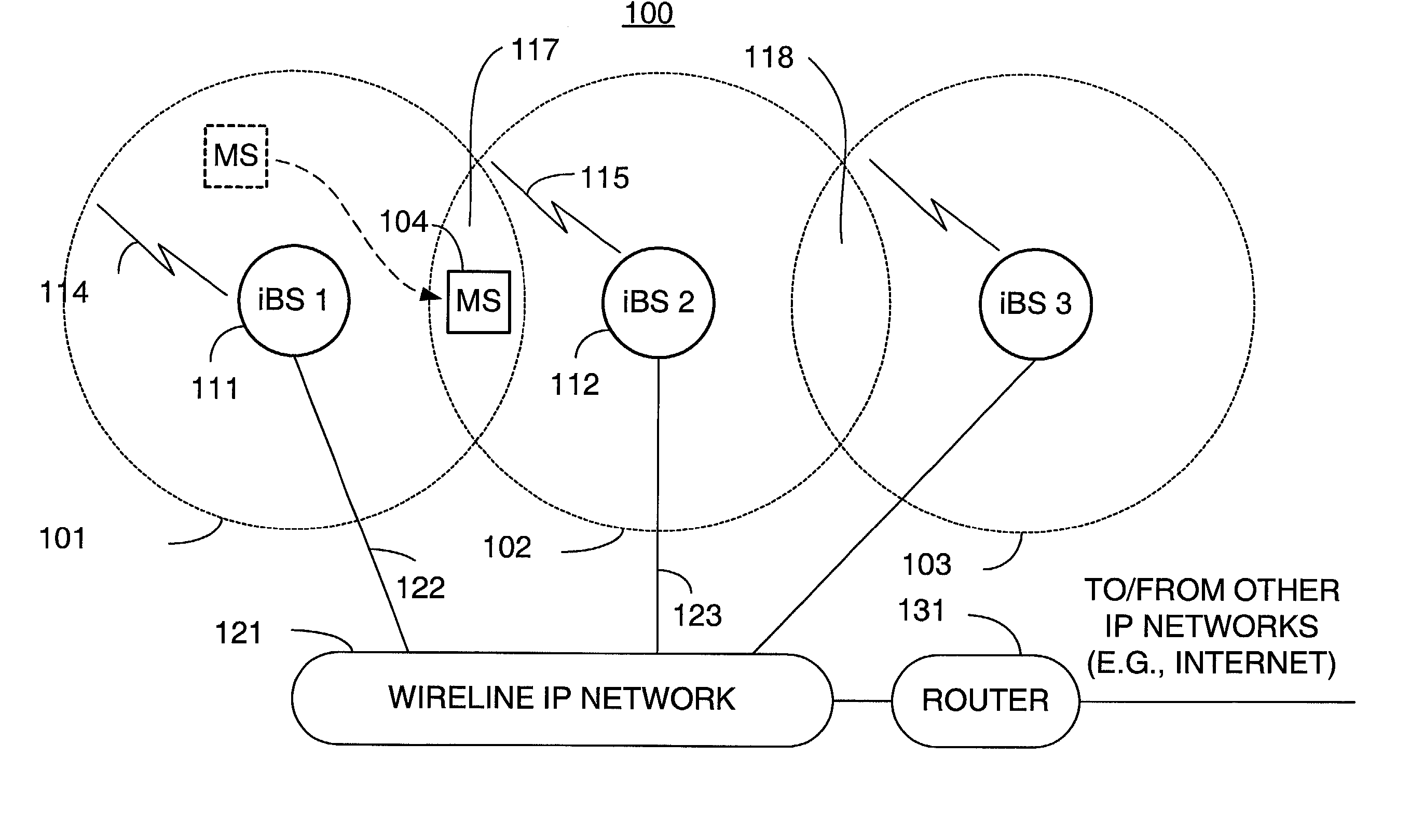
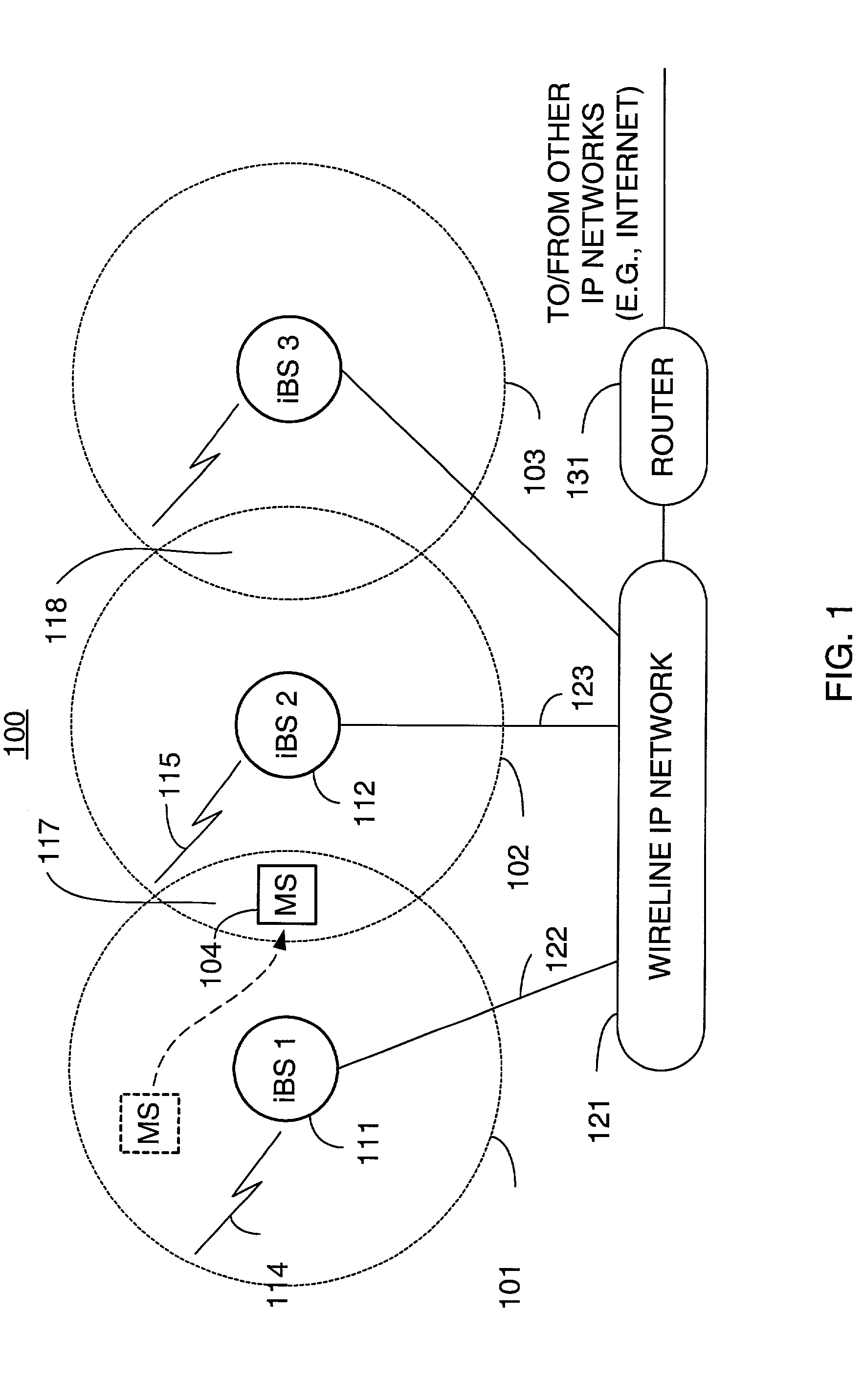
A technique for assigning an address ("shadow address") to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:FOUR BATONS WIRELESS LLC +1
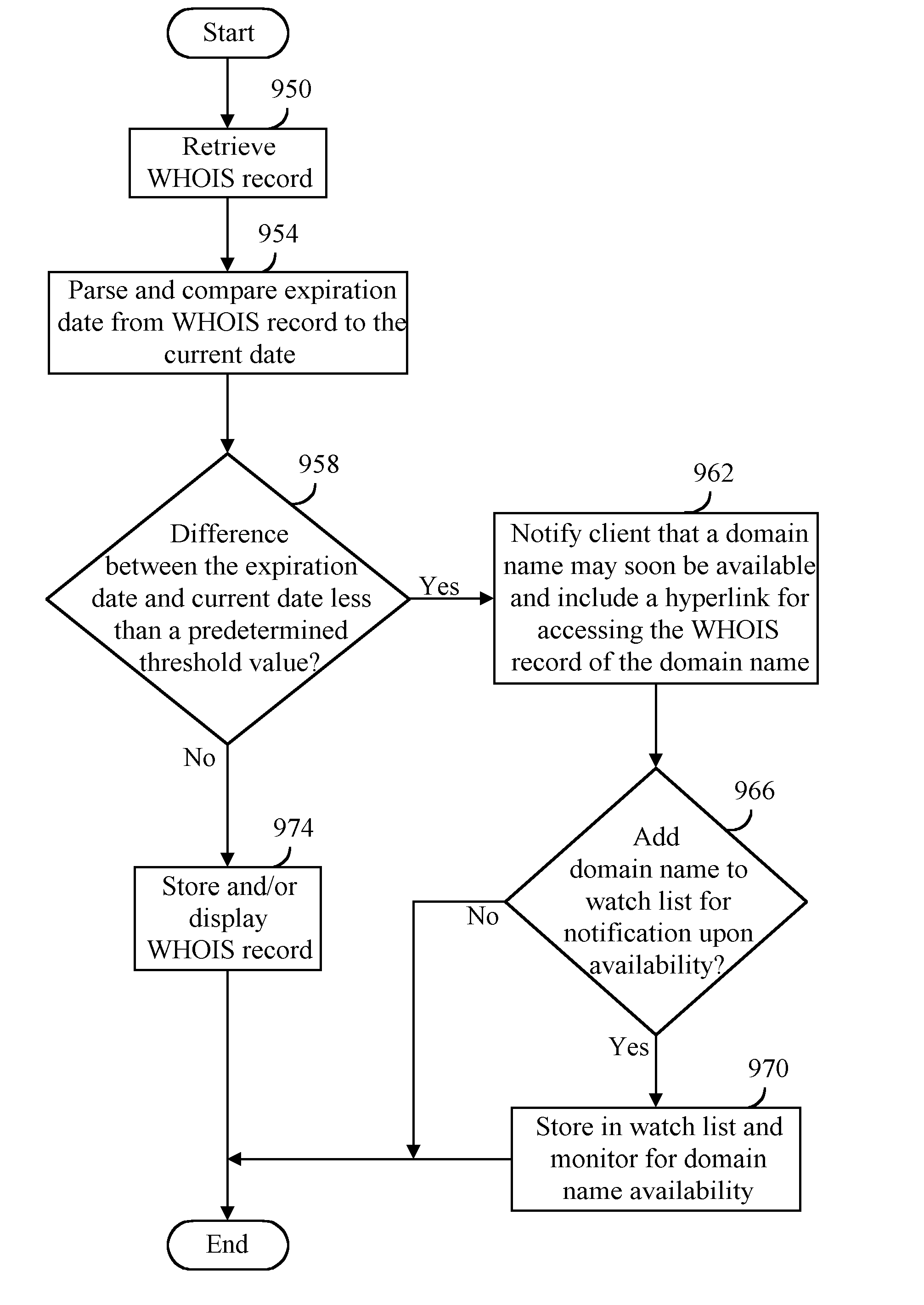
Method, product, and apparatus for enhancing resolution services, registration services, and search services
ActiveUS20080005342A1Minimize connection bandwidthMultiple digital computer combinationsTransmissionDomain nameWatch list
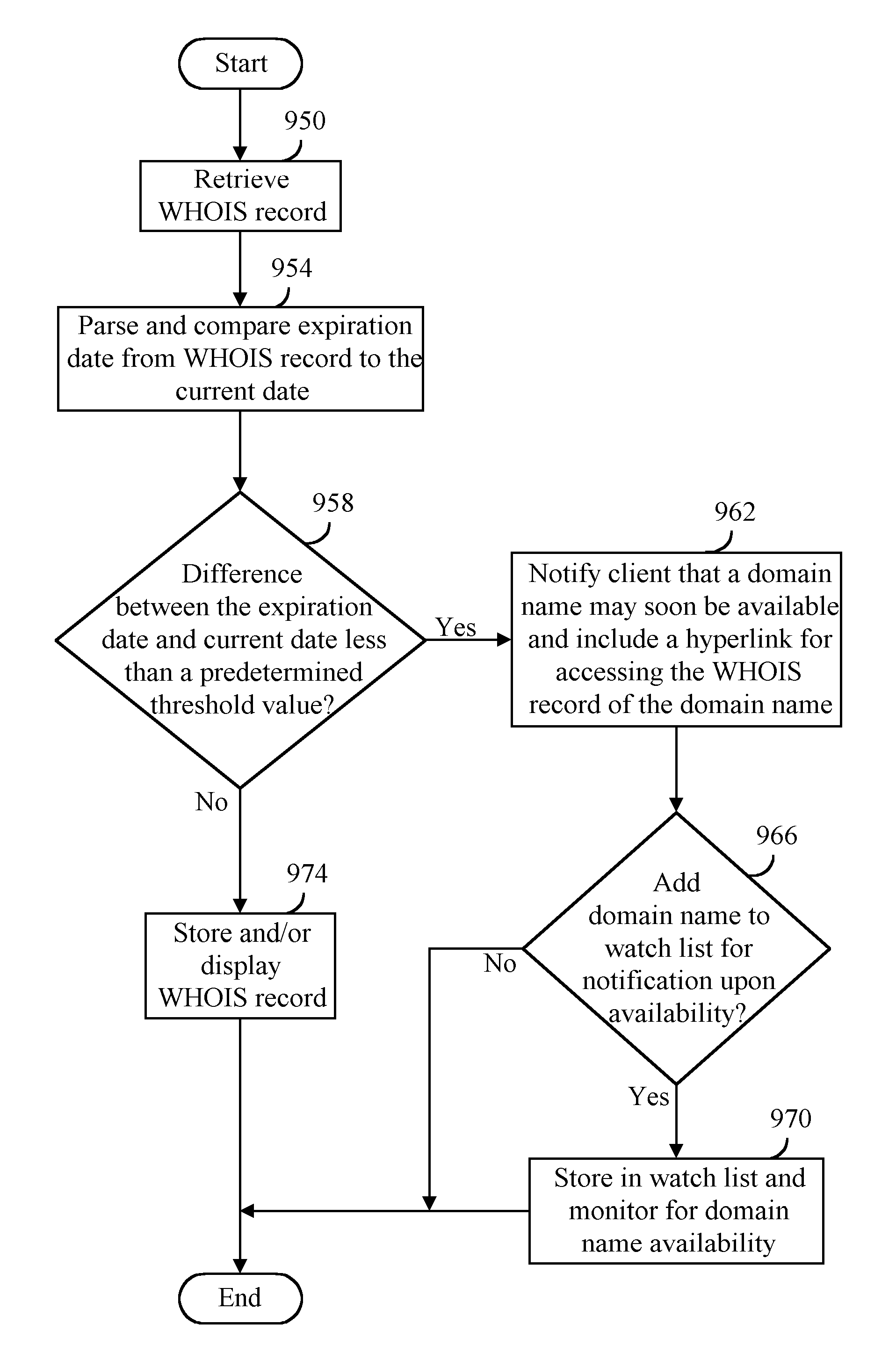
A WHOIS record of a domain name is retrieved at a first time, the WHOIS record including an expiry date of a second time, a time difference value can be calculated between the first time and the second time, and the time difference value provided to a user. Time difference value can be determined to satisfy at least one condition including a threshold value. An indication can be provided to the user that the at least one condition has been satisfied such as notifying the user of domain name expiration status, storing the domain name in a user expiration watch list, monitoring the domain name for expiration upon or after the second time, and attempting to register the domain name with a selected domain name registration provider after the second time or upon determining that either the domain name may soon be available for registration or available for registration. The WHOIS record can be retrieved in response to receiving or obtaining a request such as a resource location request, domain name resolution request, search engine request, WHOIS request, domain name availability request, and domain name registration request.
Owner:MEC MANAGEMENT LLC
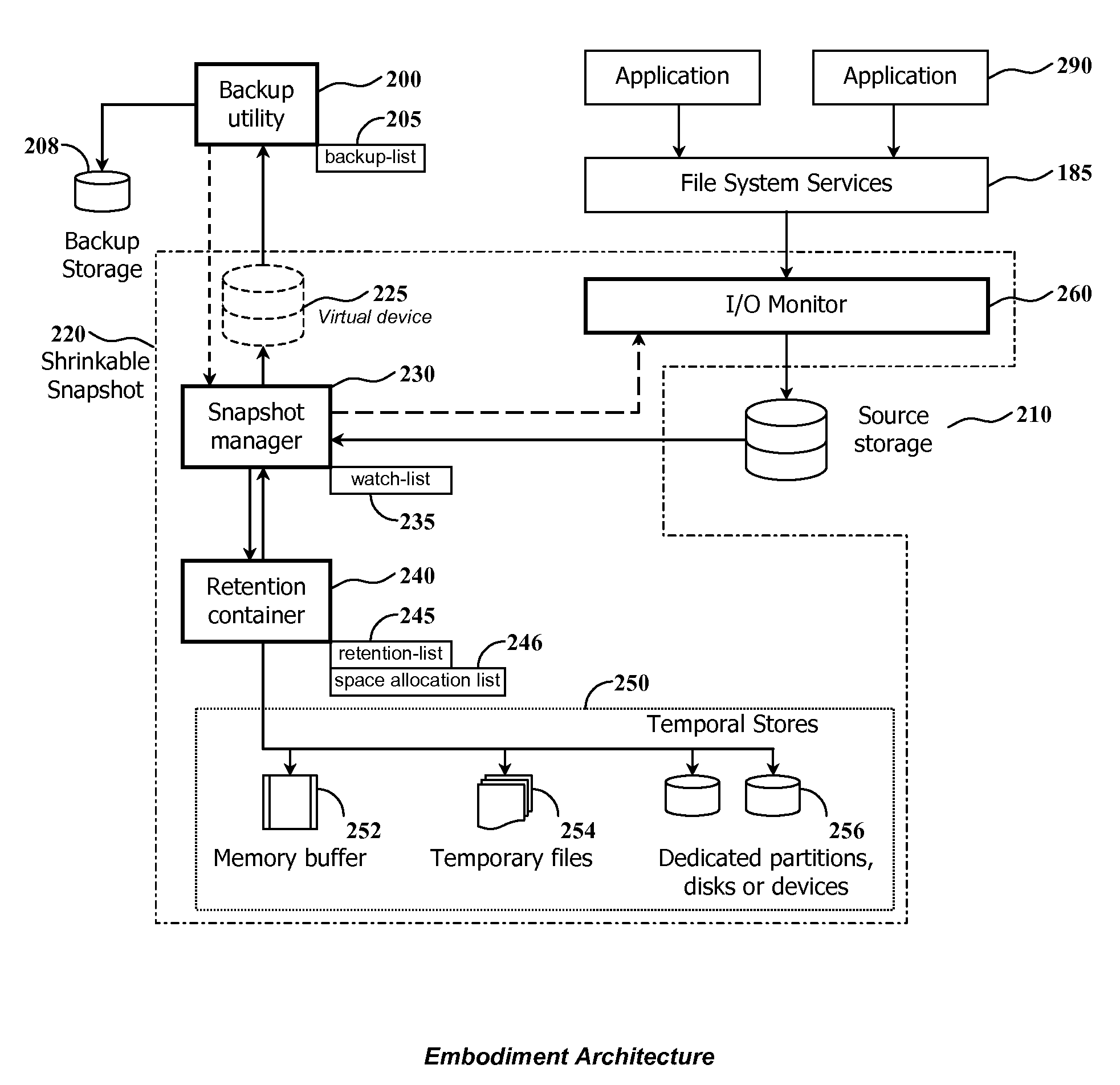
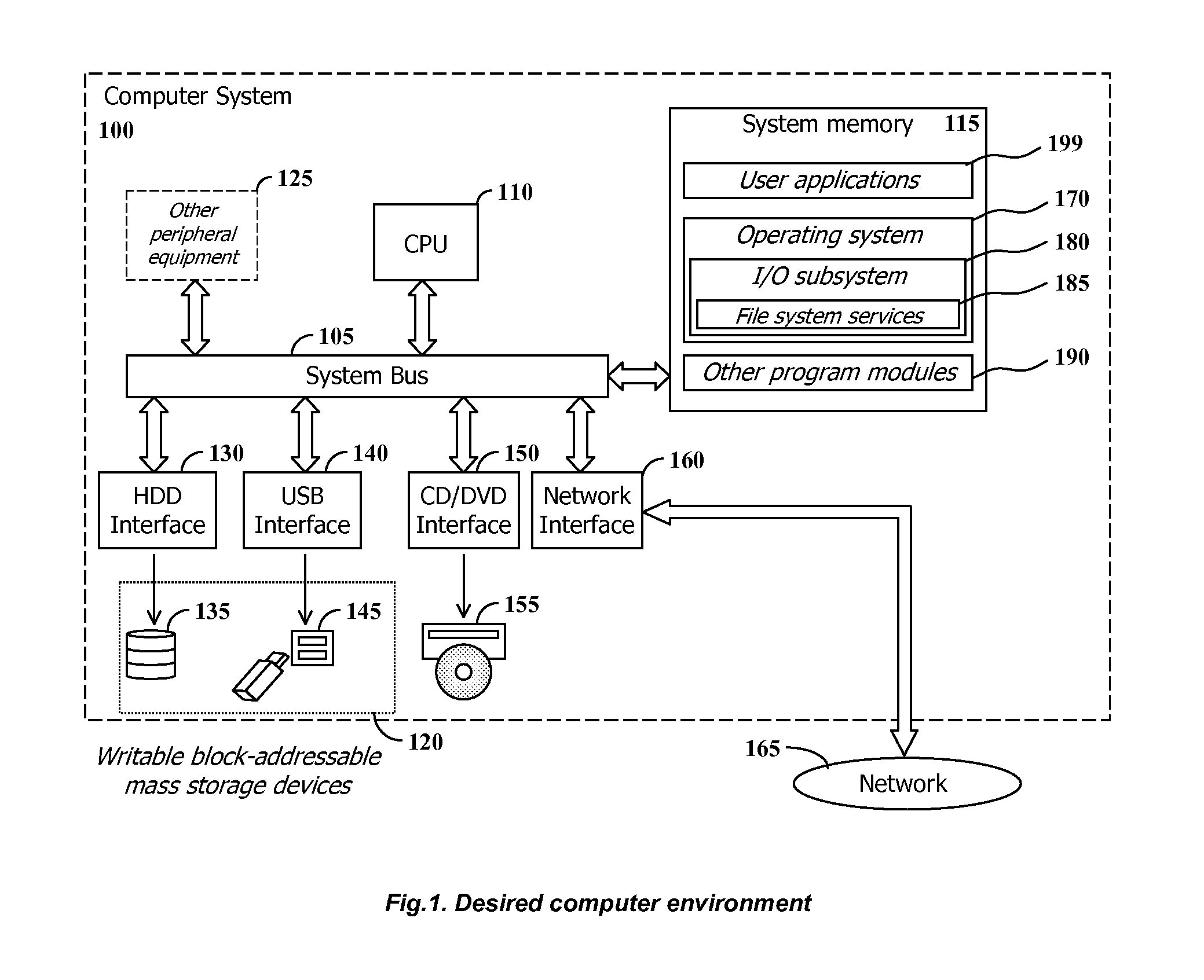
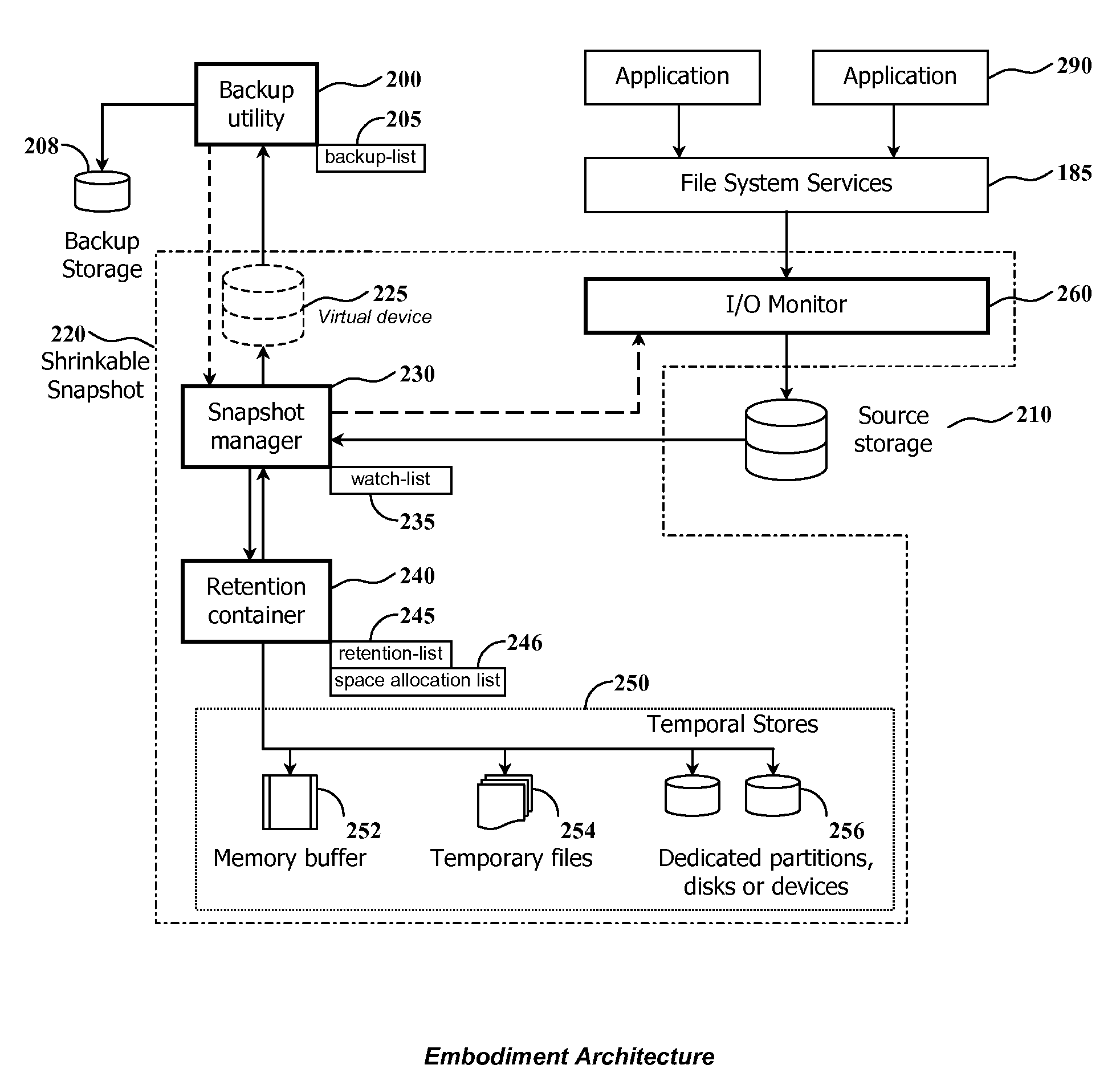
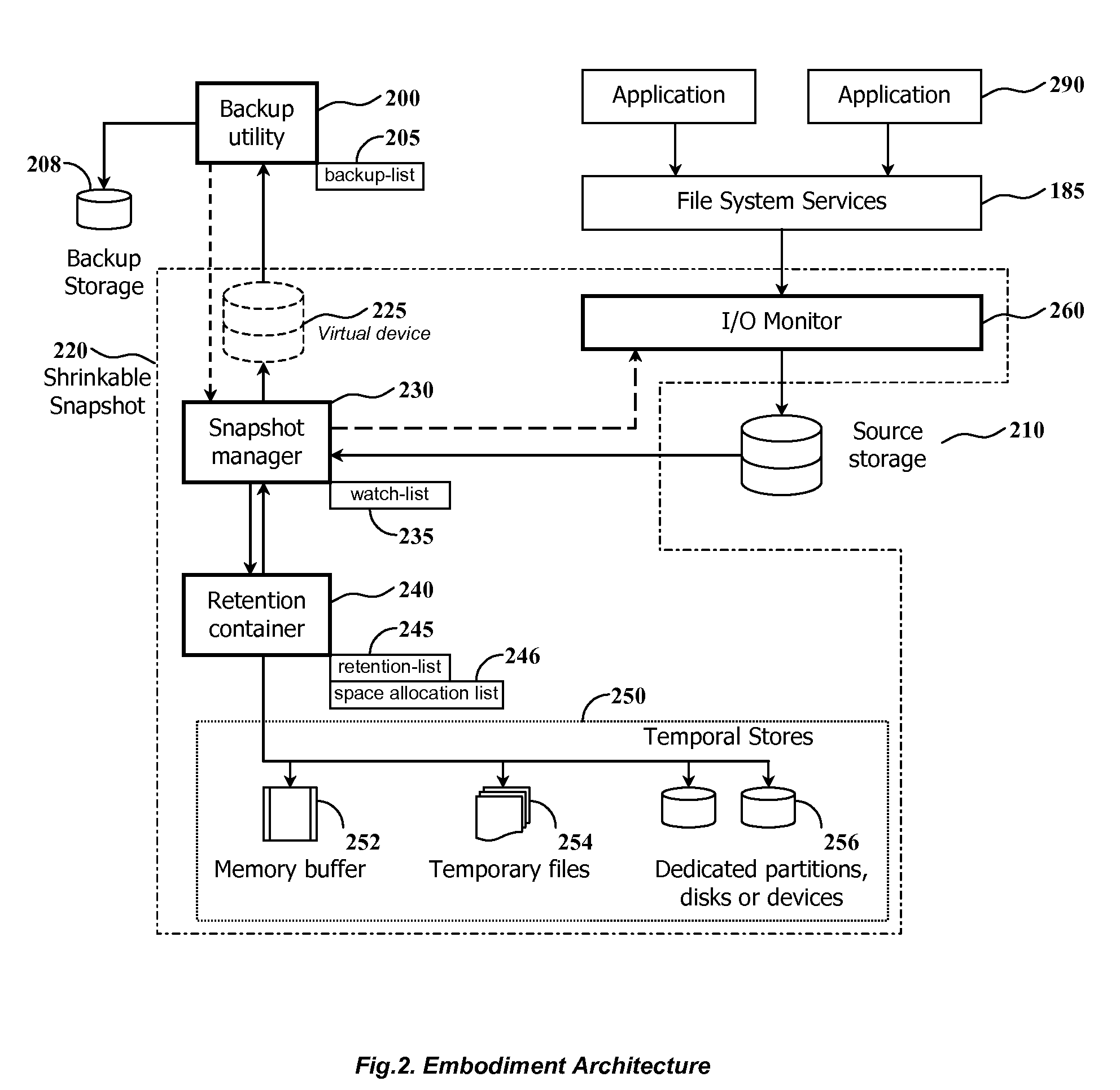
Using shrinkable read-once snapshots for online data backup
InactiveUS20080082593A1Improve performanceEasy to useDigital data information retrievalError detection/correctionRetention timeWatch list
The present invention discloses a method and system for snapshot-based online backup operations permitting reduced requirements to storage capacity and computational overhead for snapshot function.At the beginning of an online backup operation, the backup software system creates a snapshot of source data storage. The snapshot includes a watch-list used for identifying blocks of a source storage which are watched by snapshot management means for update. If a block included into the watch-list was requested for update, the snapshot management means preserve original contents of that block in a retention container for the purpose of temporary store. The retention container includes a set of temporal stores dedicated for transient storing of blocks until they are backed up.The essence of the invention is enabling to exclude blocks from the watch-list and the retention container at any moment within the period of snapshot operation. Therefore it is possible to exclude unnecessary blocks from the scope of blocks managed by the snapshot management means, for the purpose of preserving point-in-time data.Backed up blocks can be operatively excluded from the snapshot so that unchanged blocks are excluded from the watch-list and updated blocks are removed from the retention container. In the latter case temporal stores are shrunk as well. This technique allows to reduce progressively storage expenses and computational overheads required for maintenance of a snapshot being used in the online backup routine.When a volume-level online backup is performed the snapshot is switched to the read-once mode at the beginning of the data copying stage. A backup utility performs sequential read of blocks from the snapshot. The snapshot management means automatically exclude requested blocks from the scope of managed blocks.
Owner:PARAGON SOFTWARE GMBH
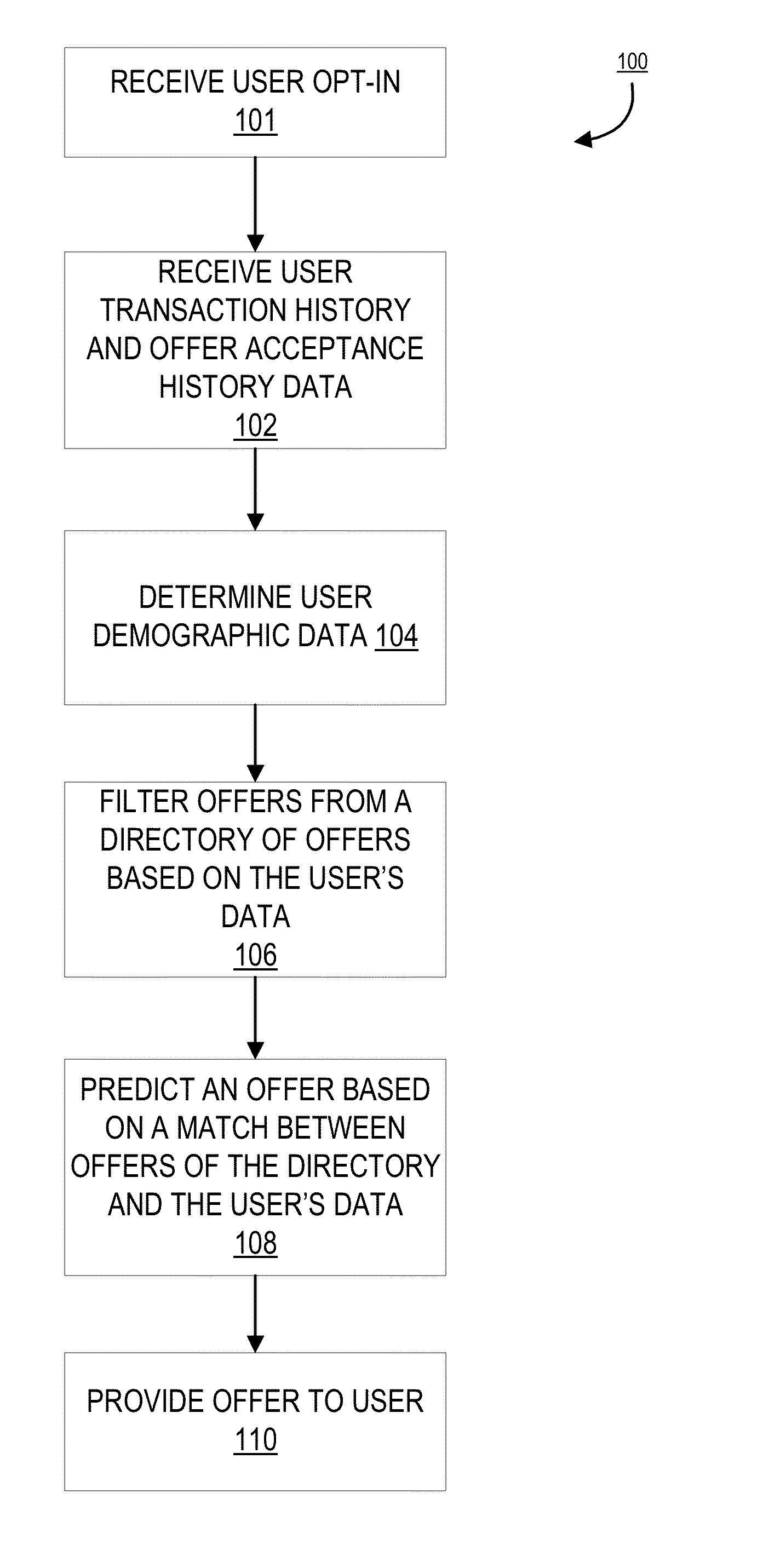
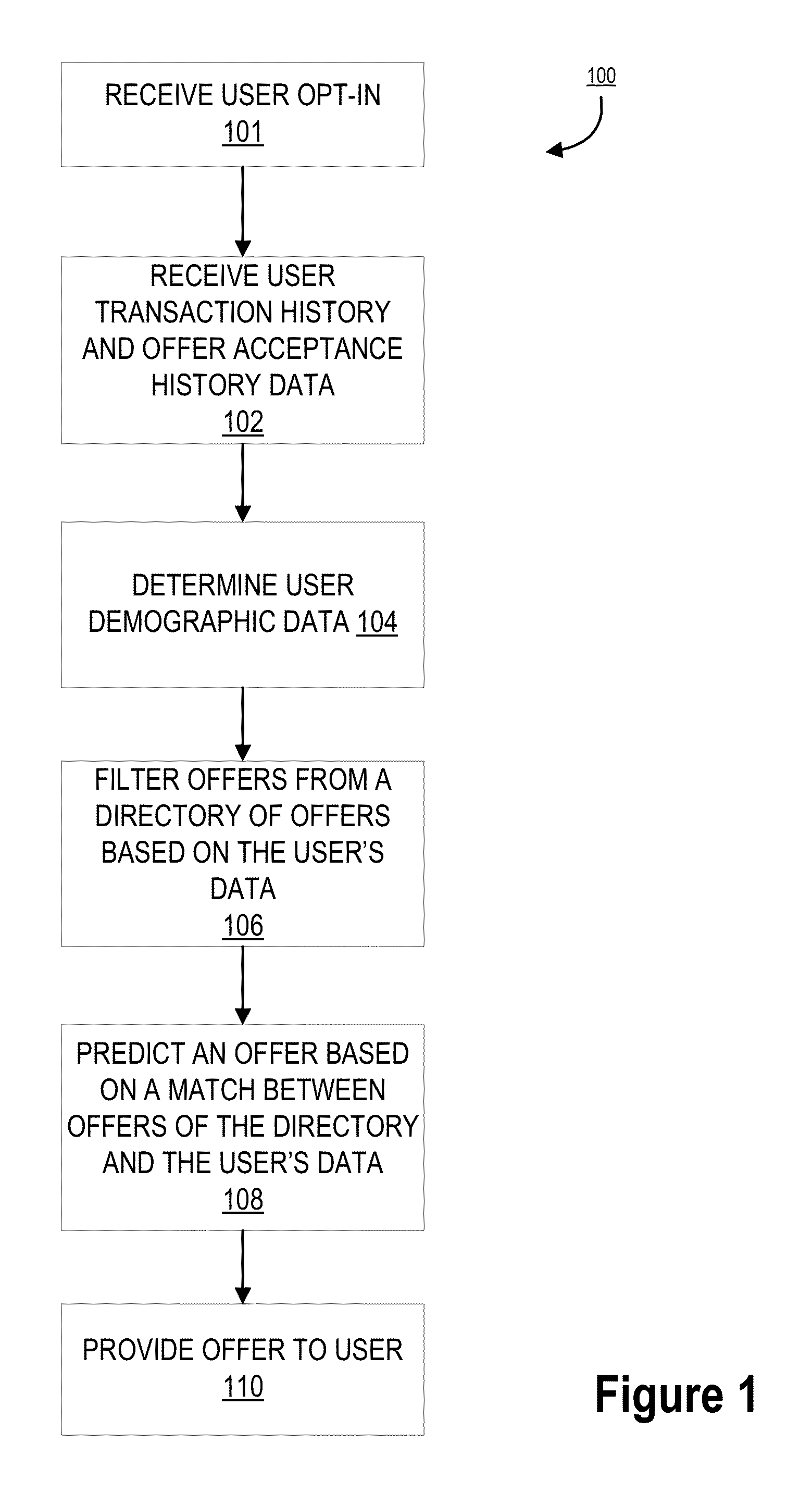
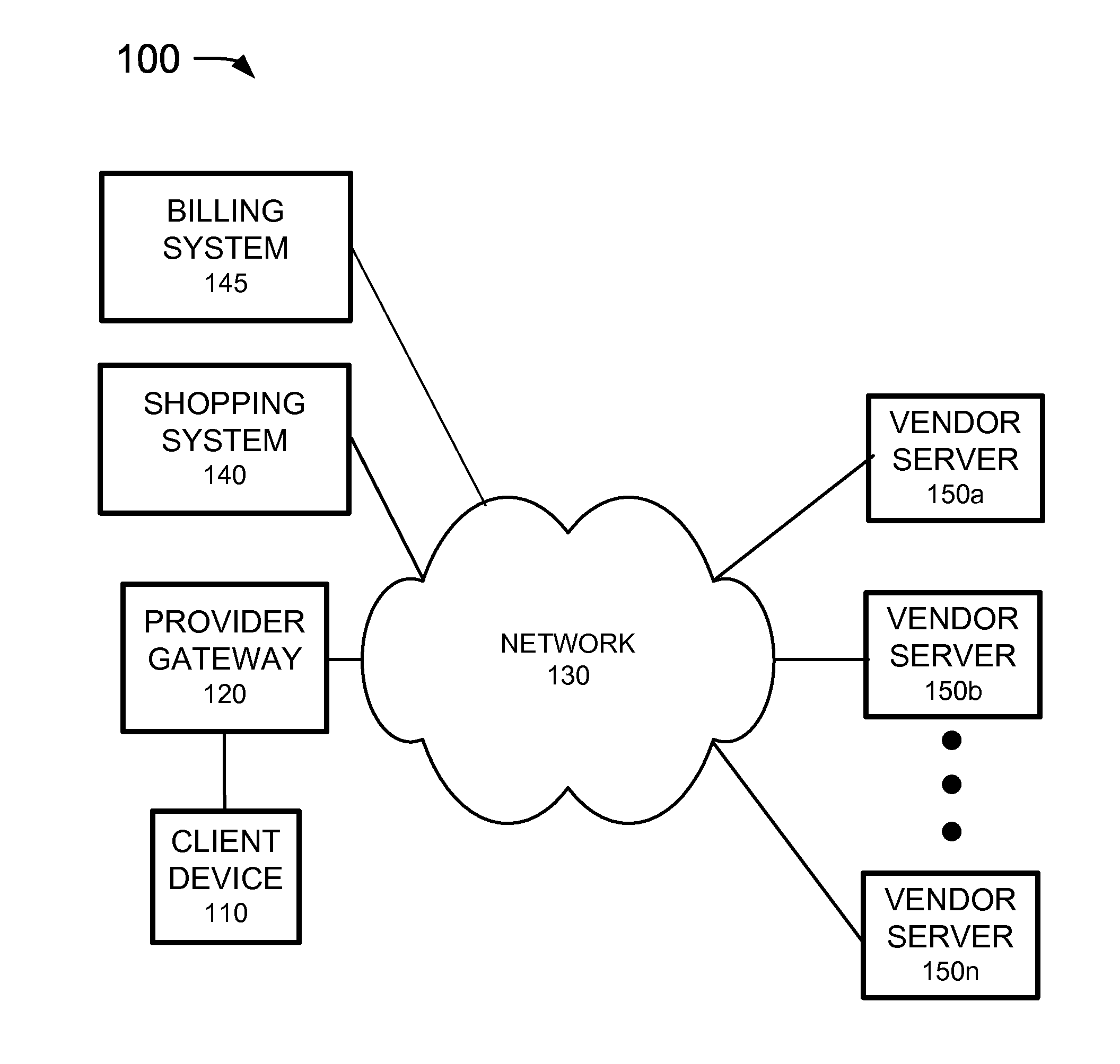
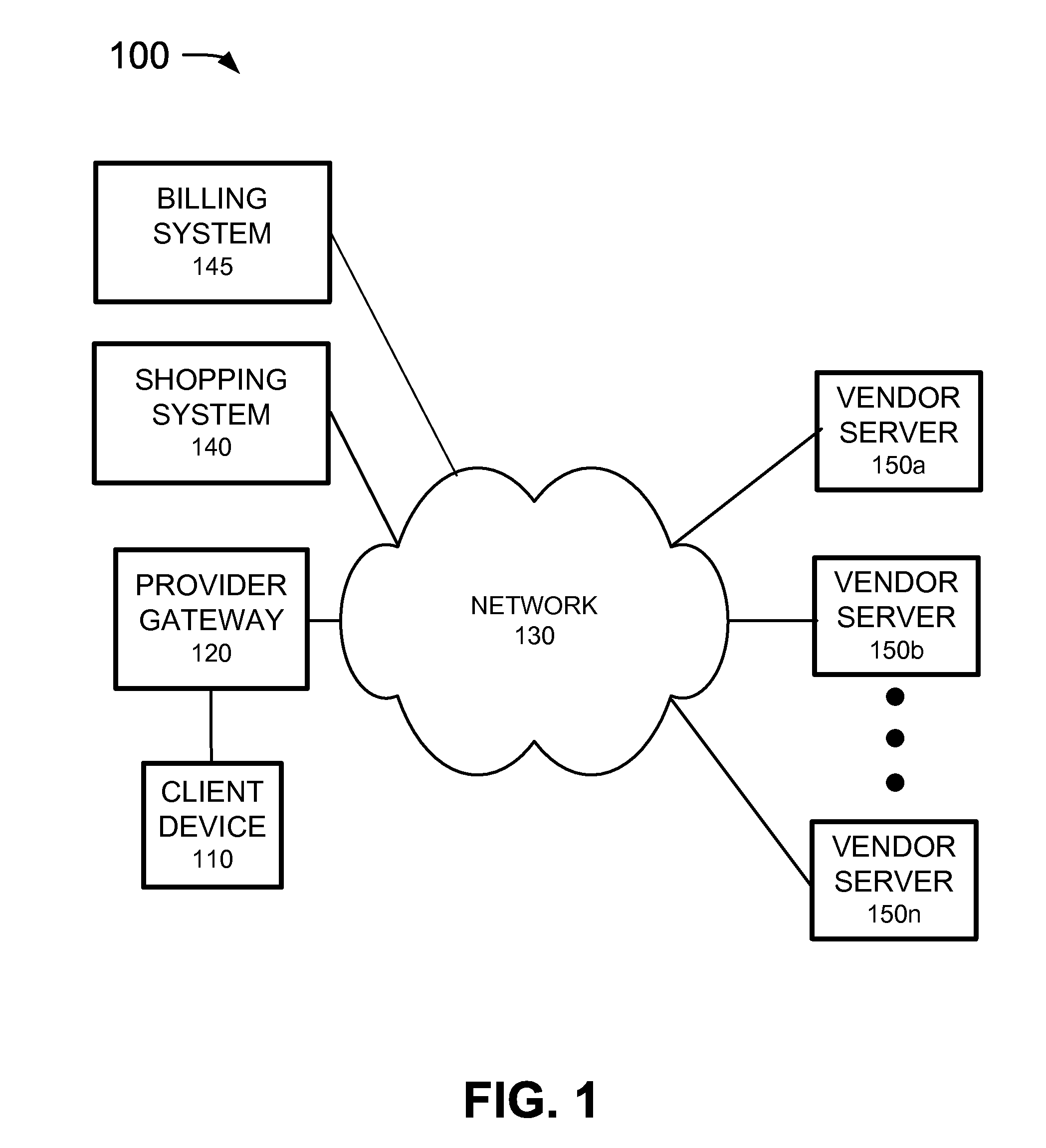
Optimizing offers based on user transaction history
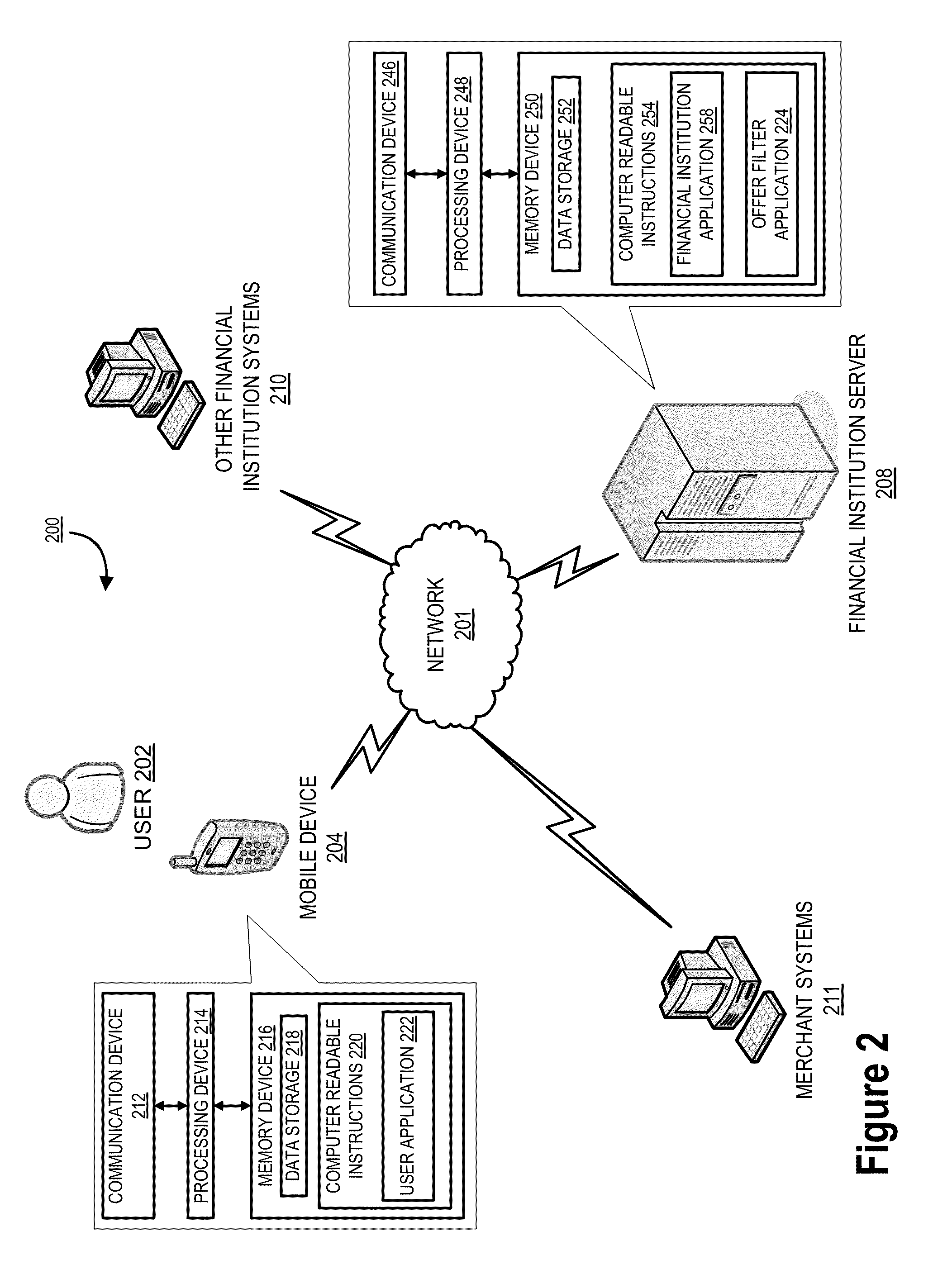
Embodiments of the invention are directed to a system, method, or computer program product for providing offers to purchase products or services to a user, the offers being tailored to the user. Embodiments of the invention allow a user to receive offers to purchase products based on the user's transaction history, offer acceptance history, demographic, or offers for products that the user wishes. In this way, the user receives offers for products that he / she may be interested in instead of having to find offers he / she is interested in by searching all the offers available to him / her. A financial institution may receive information regarding the user's transaction history, offer acceptance history, demographic, or watch list. This information may provide parameters for a filter to which offers may be provided to the user, such that the offers that are provided to the user may be of interest to him / her. Thus, the system may optimize the offers provided to the user to ensure that the offers the user receives are ones that he / she may have an interest in using to purchase a product or service.
Owner:BANK OF AMERICA CORP
Method, product, and apparatus for enhancing resolution services, registration services, and search services
InactiveUS8037168B2Minimize connection bandwidthError detection/correctionMultiple digital computer combinationsDomain nameWatch list
Owner:MEC MANAGEMENT LLC
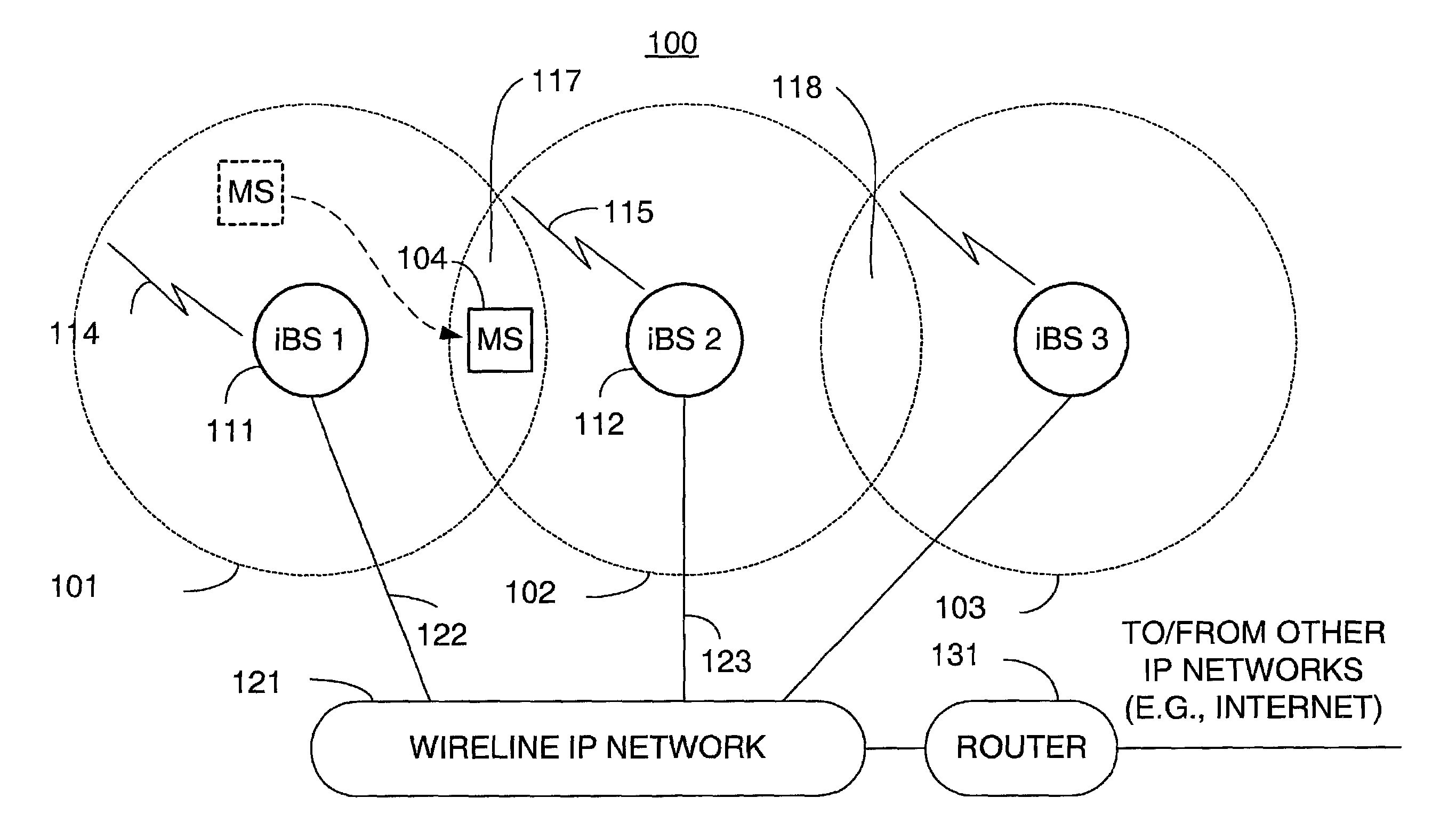
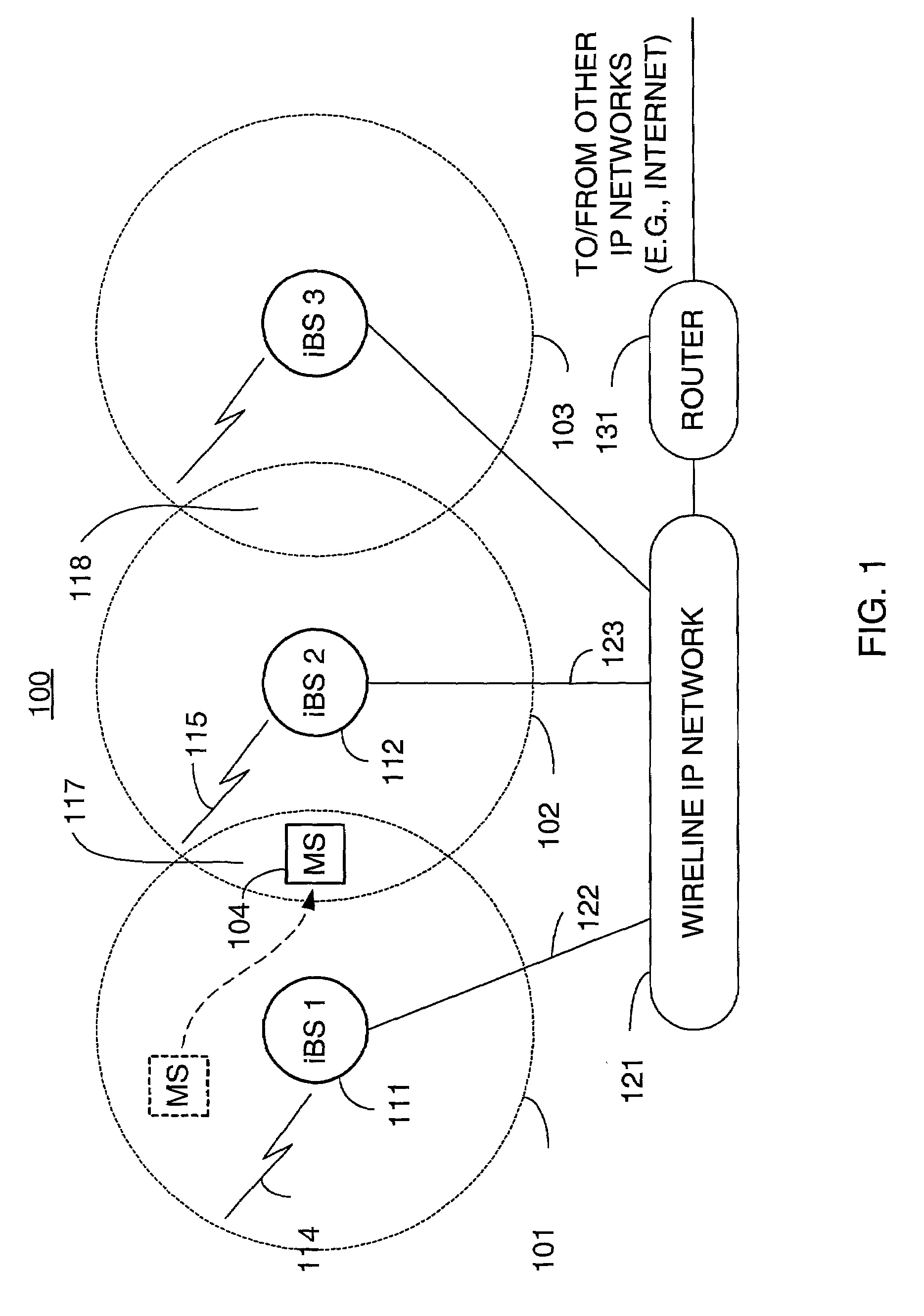
Network-layer and link-layer use of shadow addresses with IP-based base stations
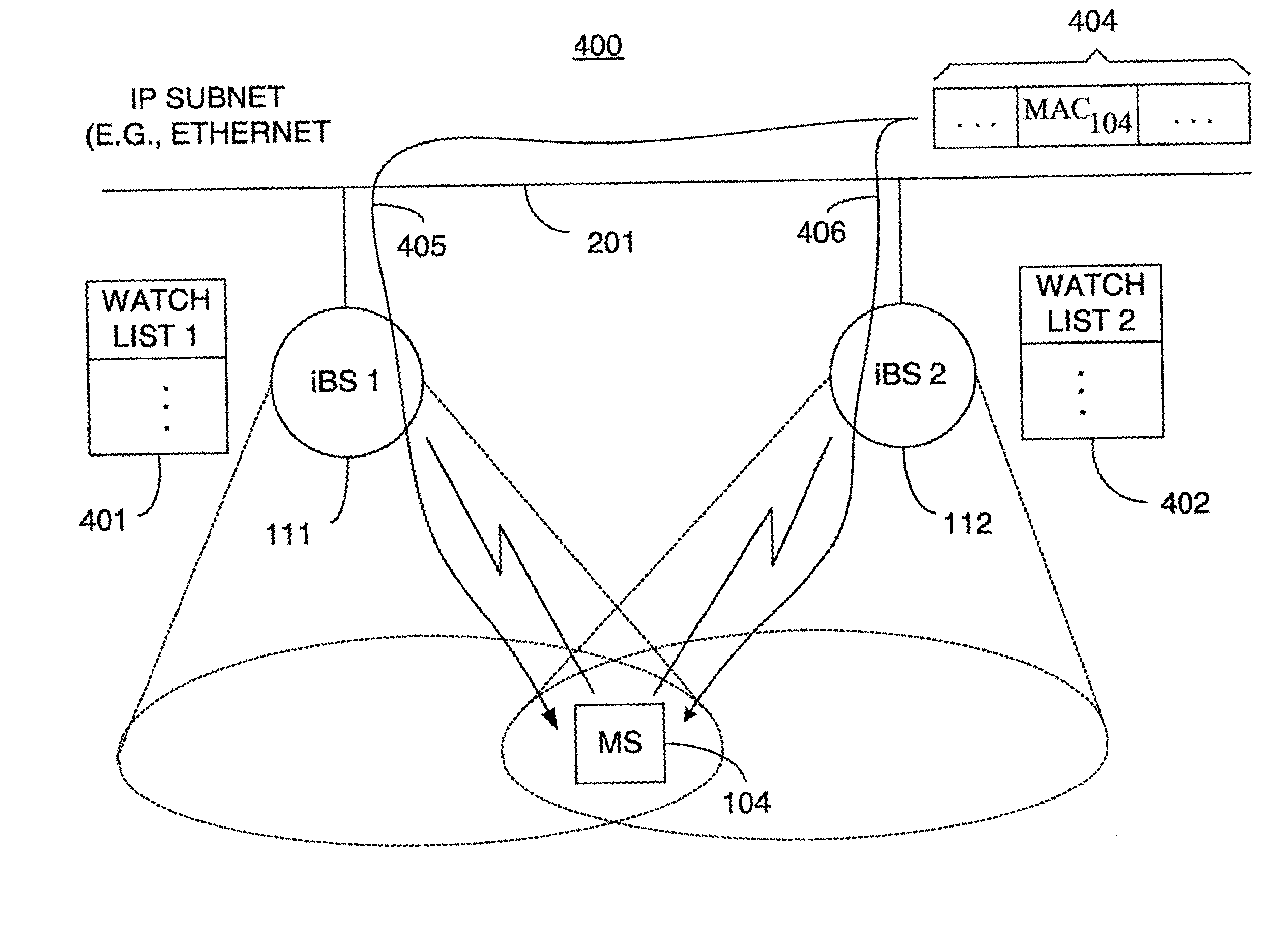
ActiveUS20020193116A1Data switching by path configurationWireless network protocolsWatch listMobile station
A technique for assigning an address ("shadow address") to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:TELCORDIA TECHNOLOGIES INC +1
Passive shopping service optimization
A shopping system may receive, from a user, a request to add information about an item to a watch list associated with the user; may receive, from the user, a price associated with the item; and may receive, from the user, a schedule associated with the item. The shopping system may identify a vendor offer associated with the item and associated with a particular vendor, where the vendor offer includes a price that is less than or equal to the received price, the identifying being based on the schedule associated with the item; and may provide a notification to the user, where the notification includes information about the identified vendor offer.
Owner:VERIZON PATENT & LICENSING INC
Distributed smooth handoff using shadow addresses in IP-based base stations
ActiveUS20020191560A1Time-division multiplexData switching by path configurationWatch listMobile station
A technique for assigning an address ("shadow address") to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:FOUR BATONS WIRELESS LLC +1
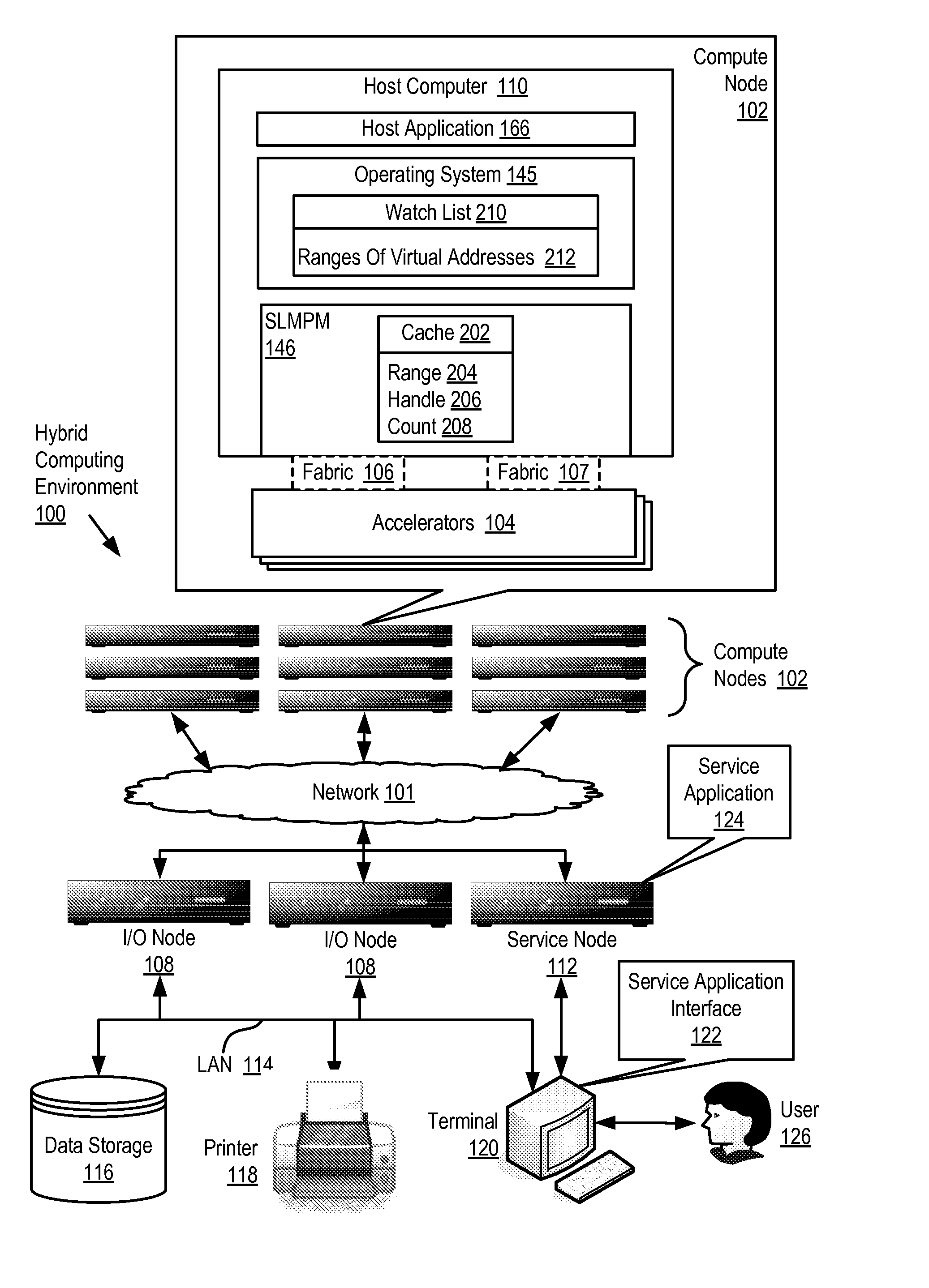
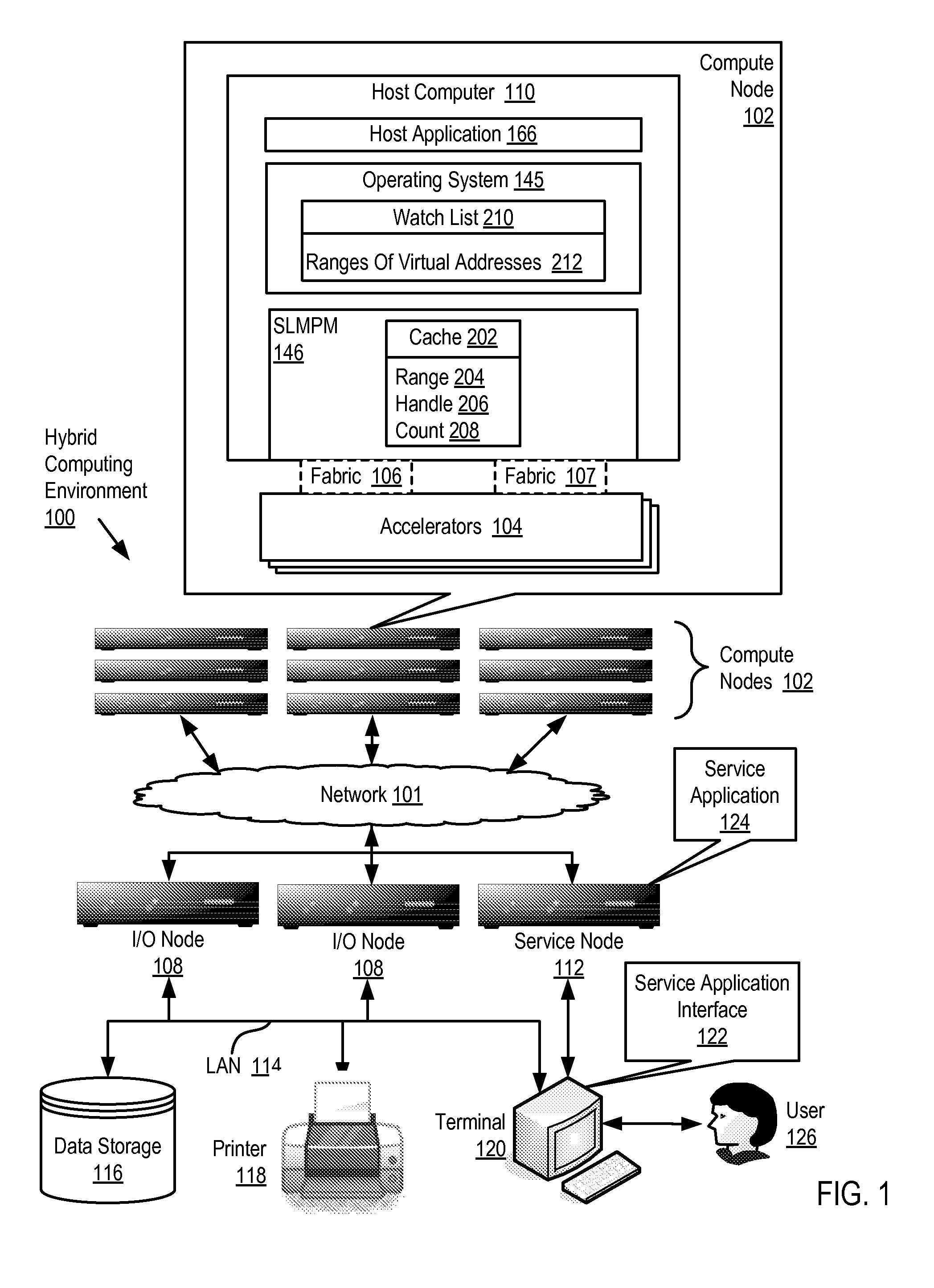
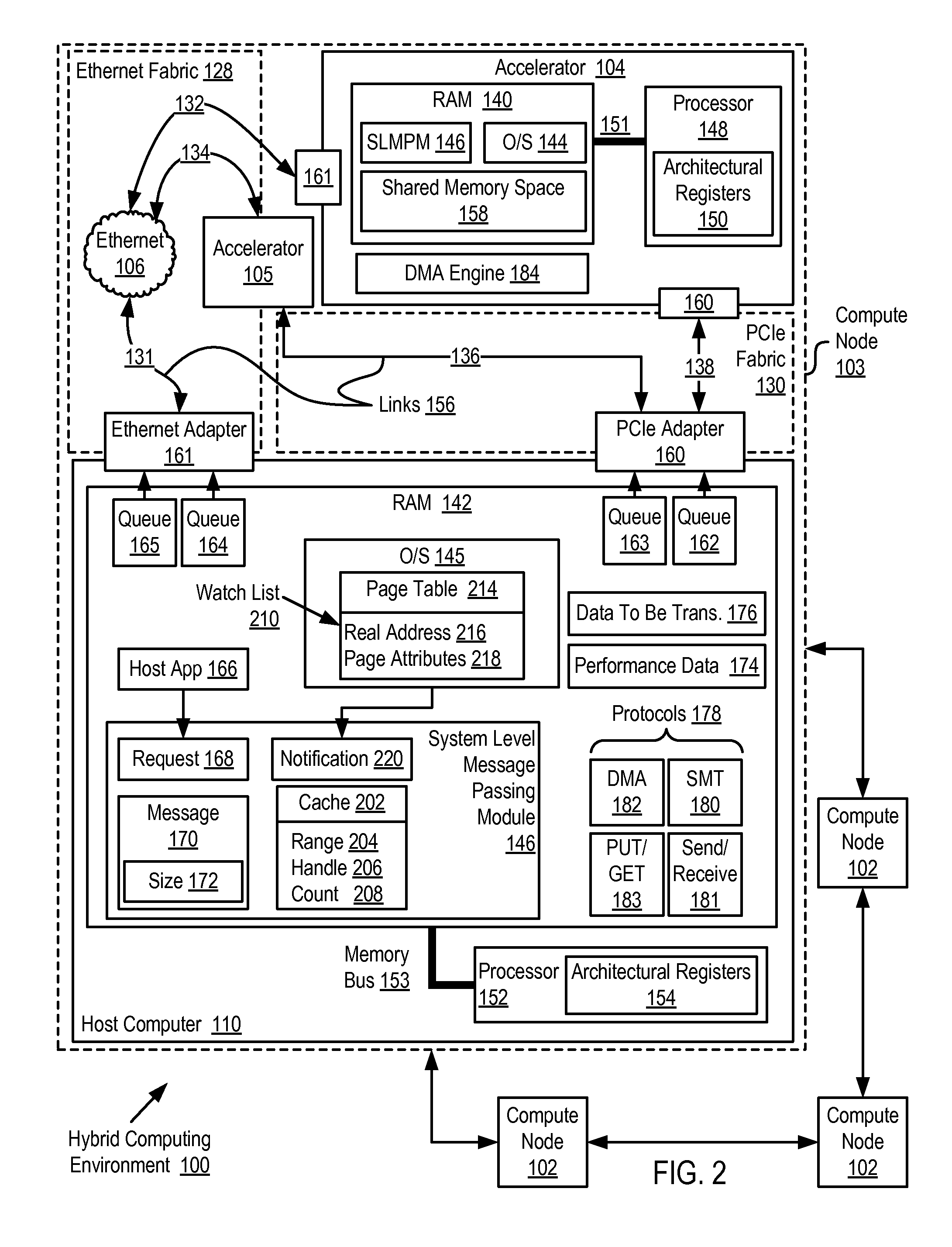
Administering Registered Virtual Addresses In A Hybrid Computing Environment Including Maintaining A Watch List Of Currently Registered Virtual Addresses By An Operating System
InactiveUS20100191917A1Memory adressing/allocation/relocationMicro-instruction address formationOperational systemWatch list
Administering registered virtual addresses in a hybrid computing environment that includes a host computer and an accelerator, the accelerator architecture optimized, with respect to the host computer architecture, for speed of execution of a particular class of computing functions, the host computer and the accelerator adapted to one another for data communications by a system level message passing module, where administering registered virtual addresses includes maintaining, by an operating system, a watch list of ranges of currently registered virtual addresses; upon a change in physical to virtual address mappings of a particular range of virtual addresses falling within the ranges included in the watch list, notifying the system level message passing module by the operating system of the change; and updating, by the system level message passing module, a cache of ranges of currently registered virtual addresses to reflect the change in physical to virtual address mappings.
Owner:IBM CORP
Packet distribution and selection in soft handoff for IP-based base stations among multiple subnets
ActiveUS7039028B2Time-division multiplexData switching by path configurationWatch listMobile station
A technique for assigning an address (“shadow address”) to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:FOUR BATONS WIRELESS LLC +1
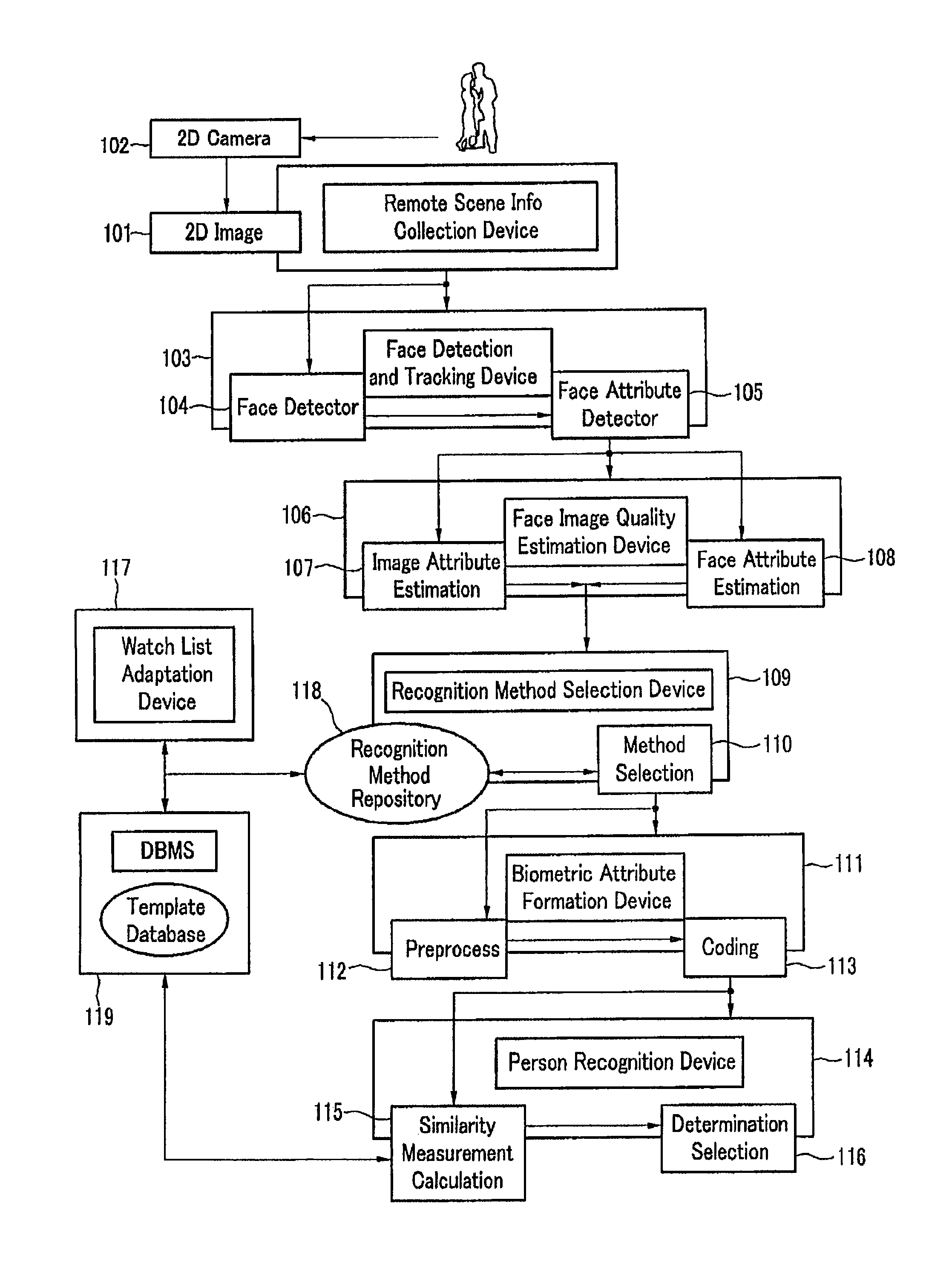
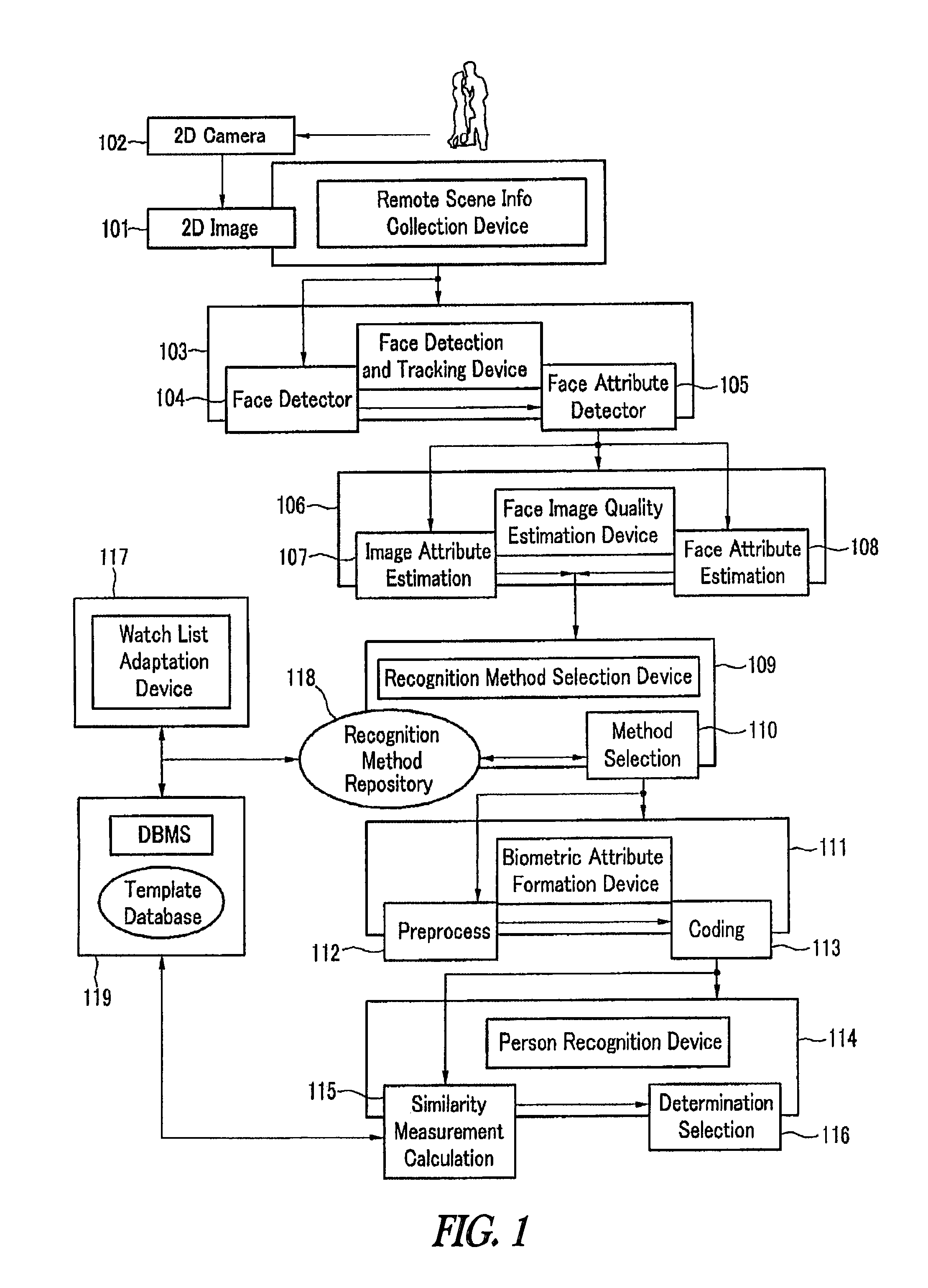
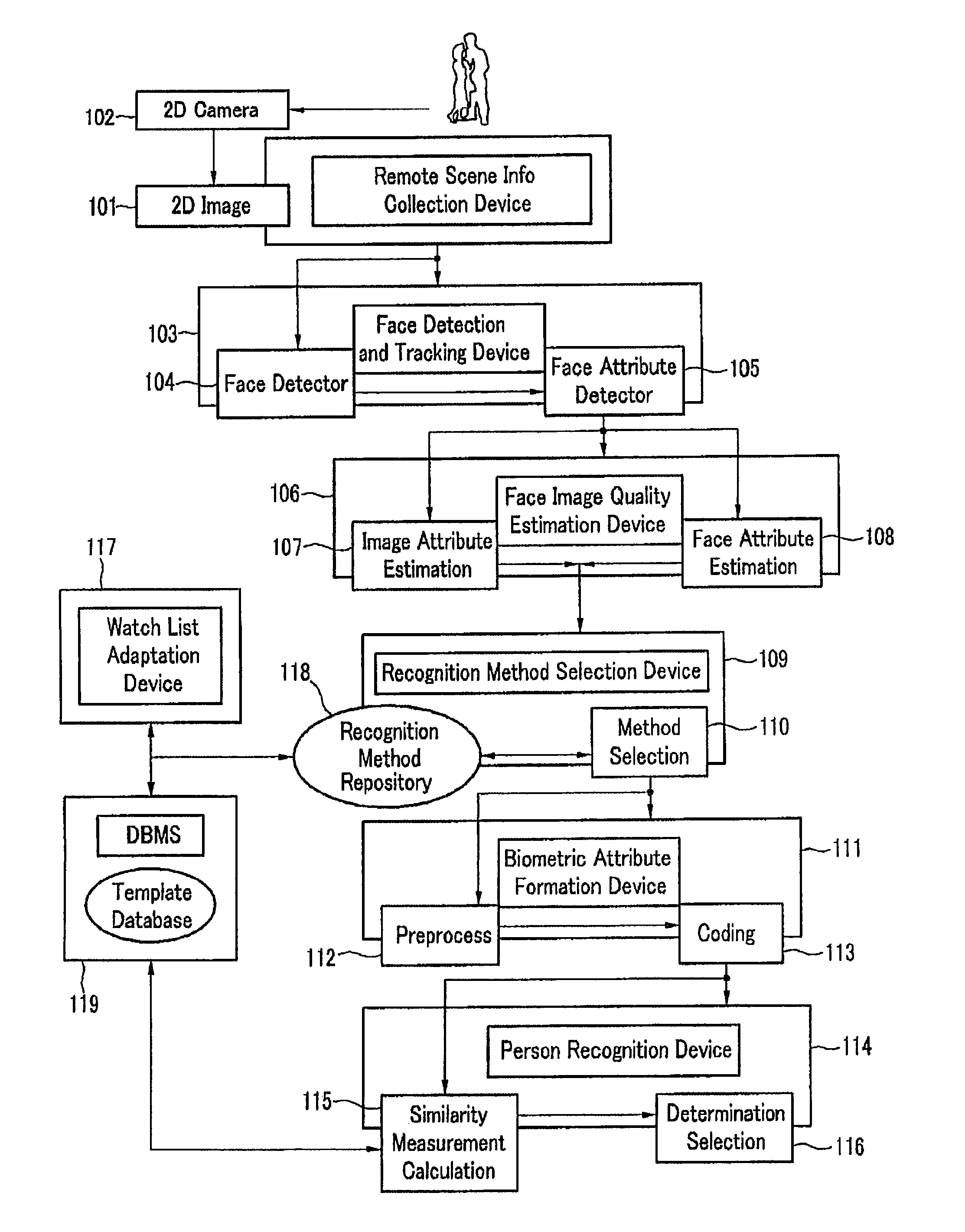
Method and system for automated face detection and recognition
ActiveUS20160086015A1Improve operational precisionImprove stabilityImage enhancementImage analysisFace detectionGraphics
The present invention relates to a figure recognition system and method for automatic detection, tracking and recognition of a human face image. 2D image data in the surveillance zone are remotely collected by using an optical sensor, the faces of all persons in the surveillance zone are detected, and corresponding positions are determined. The face is detected, the detected face's feature coordinate is estimated, and the detected face and the feature are tracked in the next frame while processing the video sequence. Image quality of each detected face is determined according to parameters of focus, brightness, contrast, and the presence of glasses. Recognition methods stored in the repository for each detected face are adjusted by considering the face image quality computation value, and a biometric feature set is generated by using the recognition method selected for each detected face. The figure is recognized according to the watch list by using the biometric feature generated by comparing each detected face and a template set stored in the database. A new user registration process is performed and the recognition method is adapted automatically by considering the watch list.
Owner:S1 CORP
System and method for improving mobile device safety by selectively disabling device features during unsafe operational conditions
InactiveUS20120028624A1Easy to understandAssess restrictionGraded-service arrangementsWatch listDevice status
A system for improving safe operation of mobile communication devices includes an operational module installable on a mobile communication device. The mobile communication device is able to communicate wirelessly over a mobile communications network and has a plurality of internal sensors, a plurality of external sensors, a user interface, and a plurality of communications modules. The operational module is able to monitor at least one of the internal sensors and the external sensors, to determine whether the mobile communication device state is one of a plurality of predetermined device states. The predetermined device states represent predetermined watch list operations, which are determined based on improving the safe operation of the mobile communication device. The operational module executes predetermined operations in the event the mobile communication device state is one of the plurality of predetermined device states, which include controlling operation of the user interface and at least one of the plurality of communications modules.
Owner:TCMD HLDG
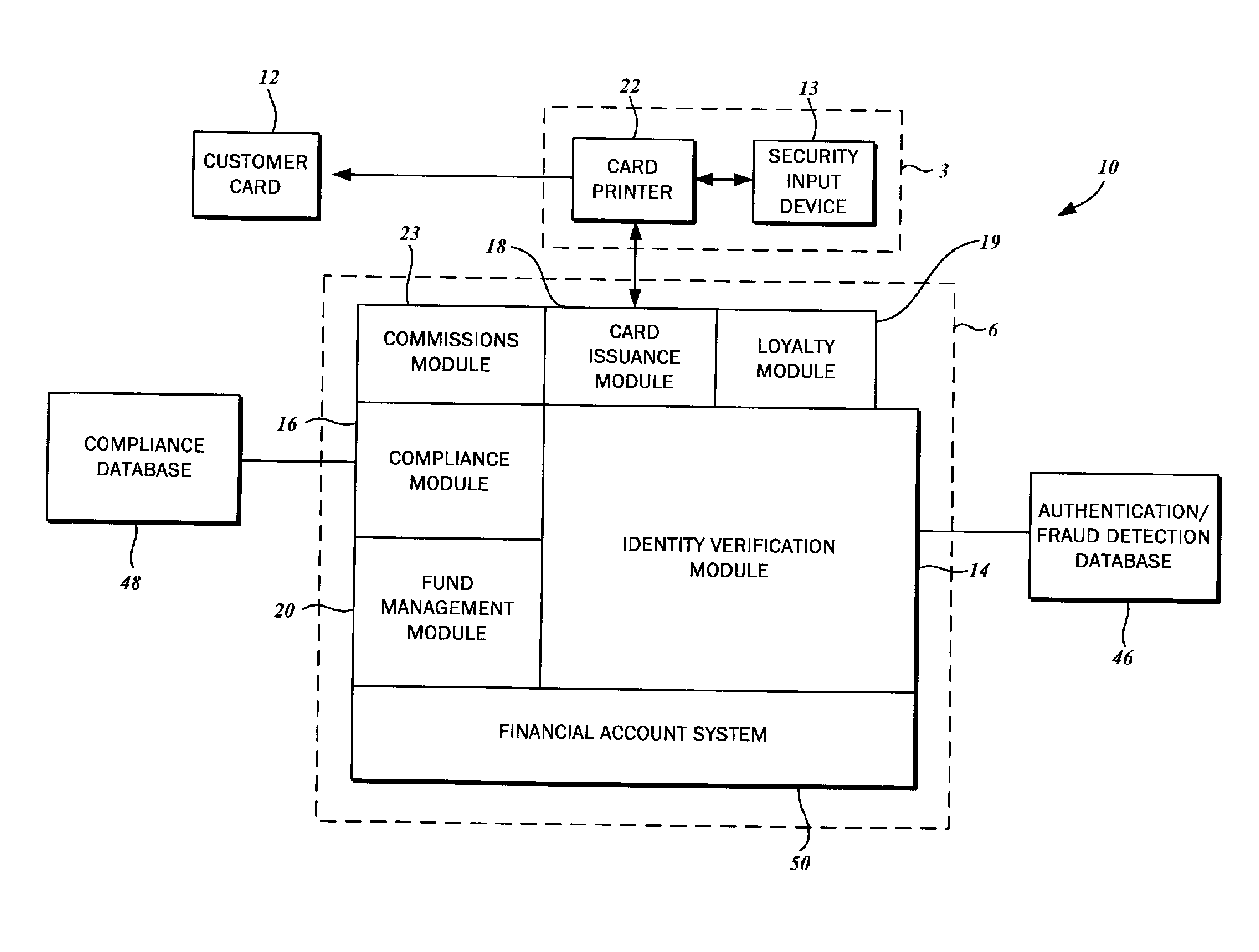
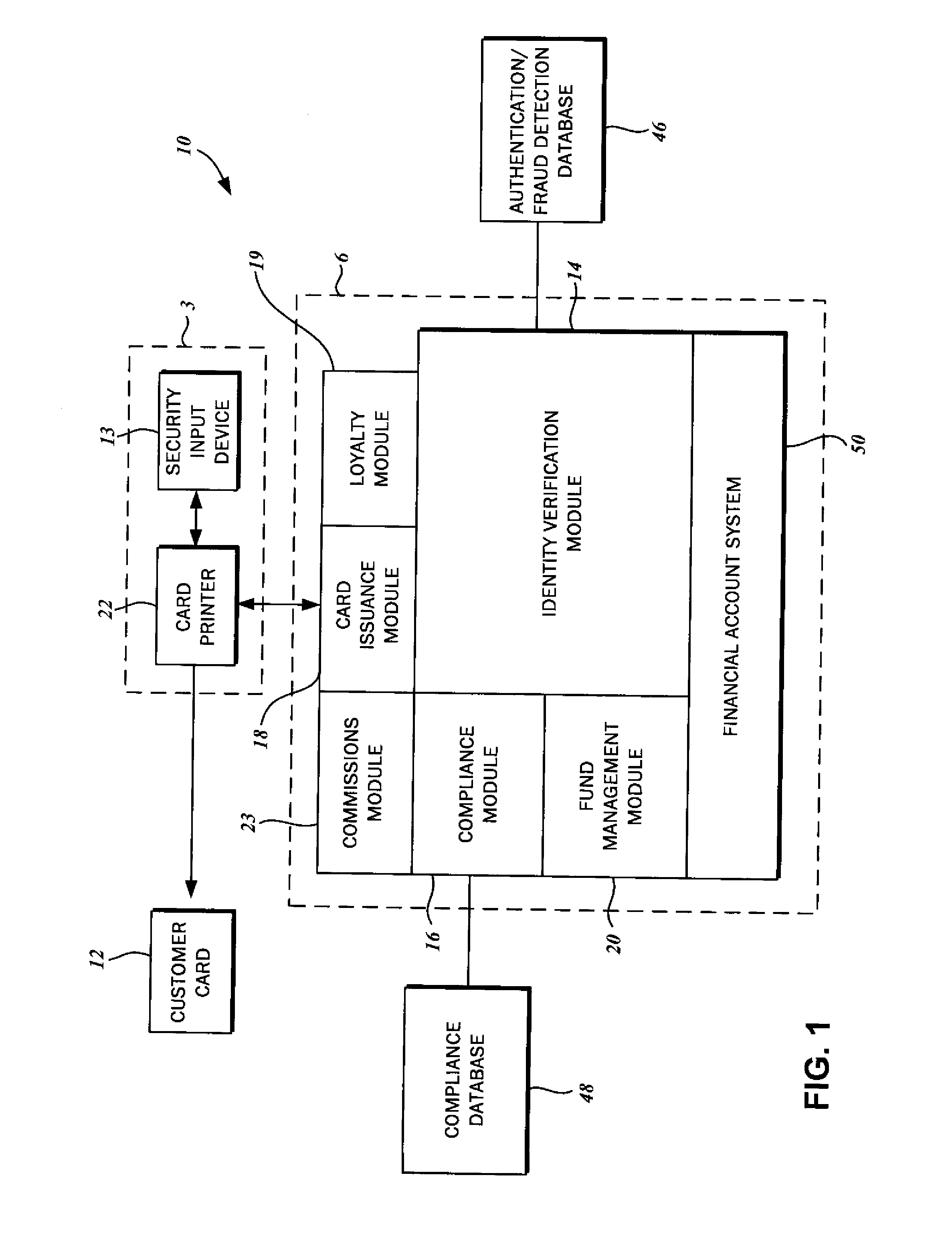
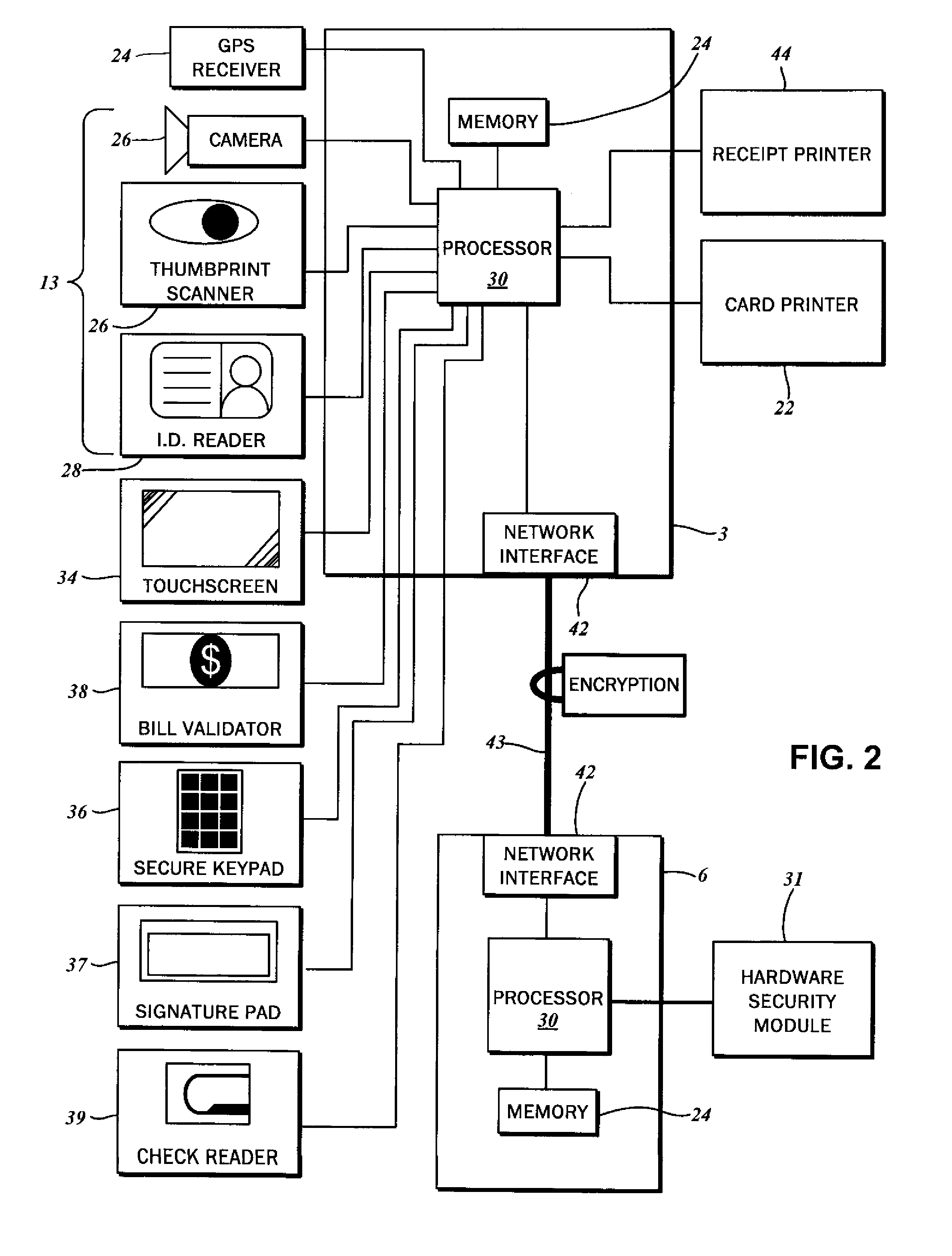
Method for verifying instant card issuance
There is disclosed a method for verifying instant card issuance. The method begins with receiving from a user an identification credential including personally identifying data. Then the method continues with authenticating the user based upon an evaluation of the personally identifying data against a fraud detection database. The identity of the user may be correlated to the identity specified in the identification credential. The user is then validated based upon an analysis of the personally identifying data against a compliance database including a list of prohibited identities or watch lists. The user is designated as authorized upon proper authentication and validation. The method concludes with dispensing a transaction card linked via a unique identifier to a financial account associated with the authorized user. The transaction card is imprinted with the unique identifier and a custom user-selected design.
Owner:UNICACHE INT
Distributed smooth handoff using shadow addresses in IP-based base stations
ActiveUS7075910B2Time-division multiplexData switching by path configurationWatch listMobile station
A technique for assigning an address (“shadow address”) to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:FOUR BATONS WIRELESS LLC +1
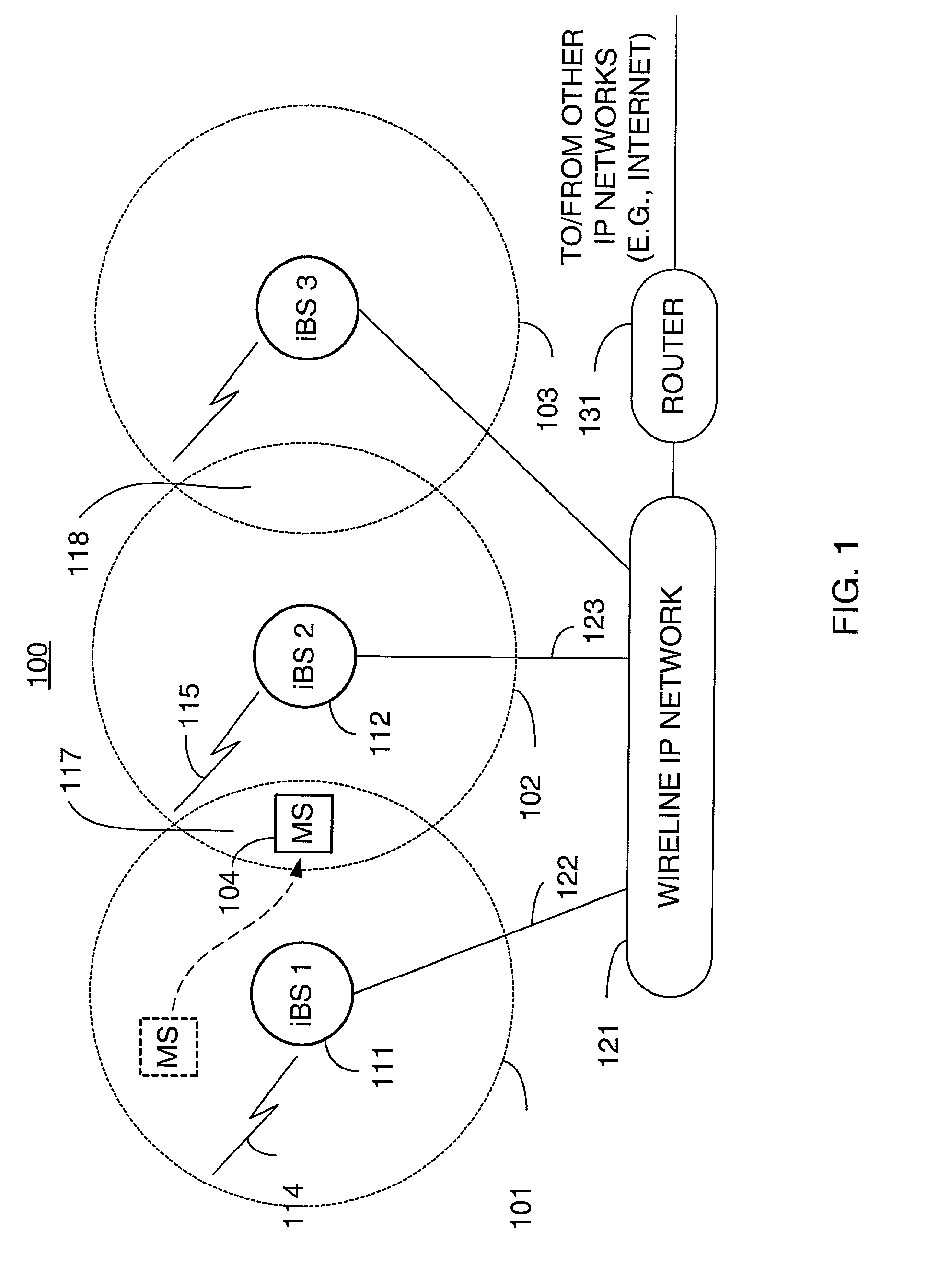
Distributed soft handoff among IP-based base stations
ActiveUS7002936B2Time-division multiplexData switching by path configurationWatch listMobile station
A technique for assigning an address (“shadow address”) to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:TELCORDIA TECHNOLOGIES INC
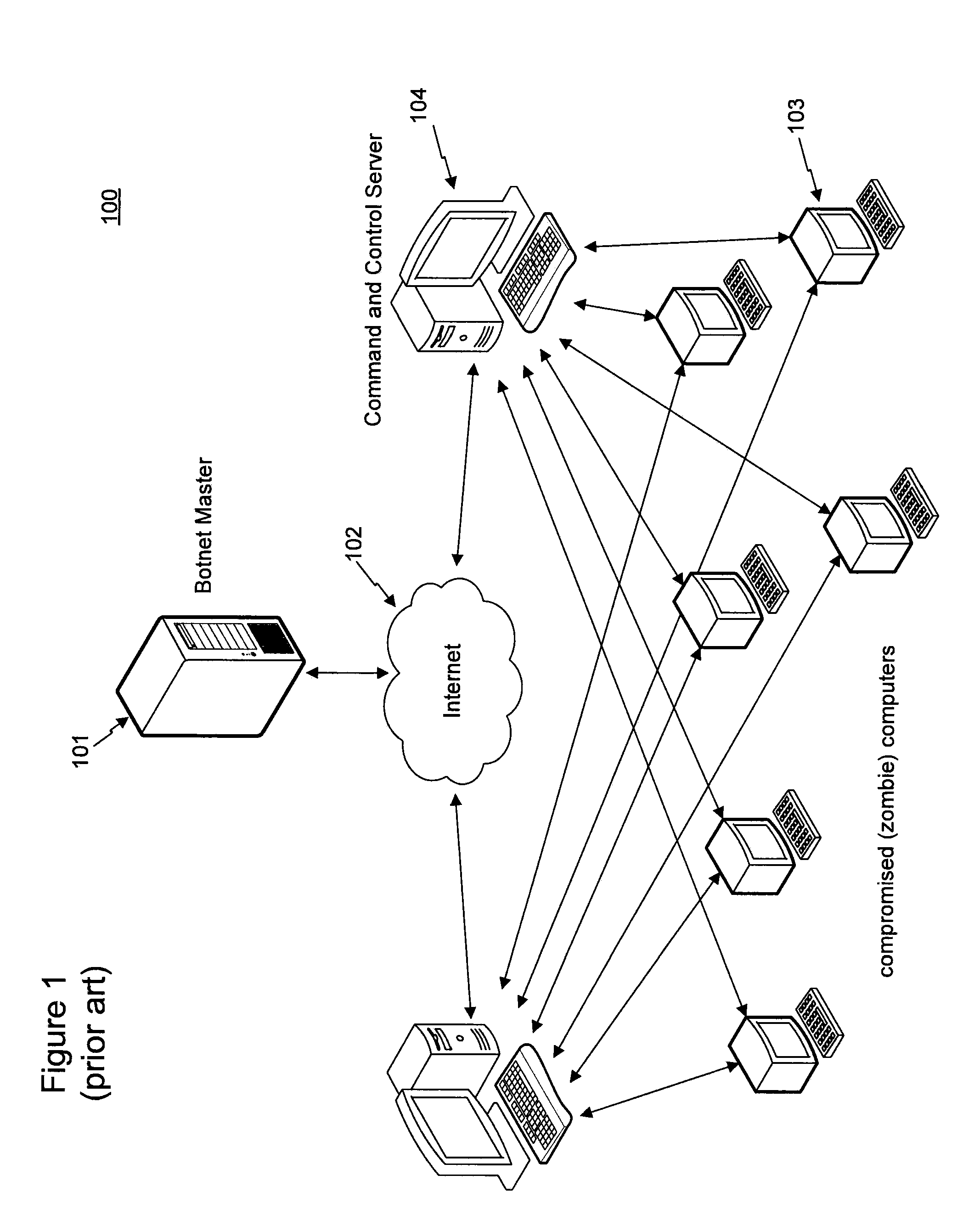
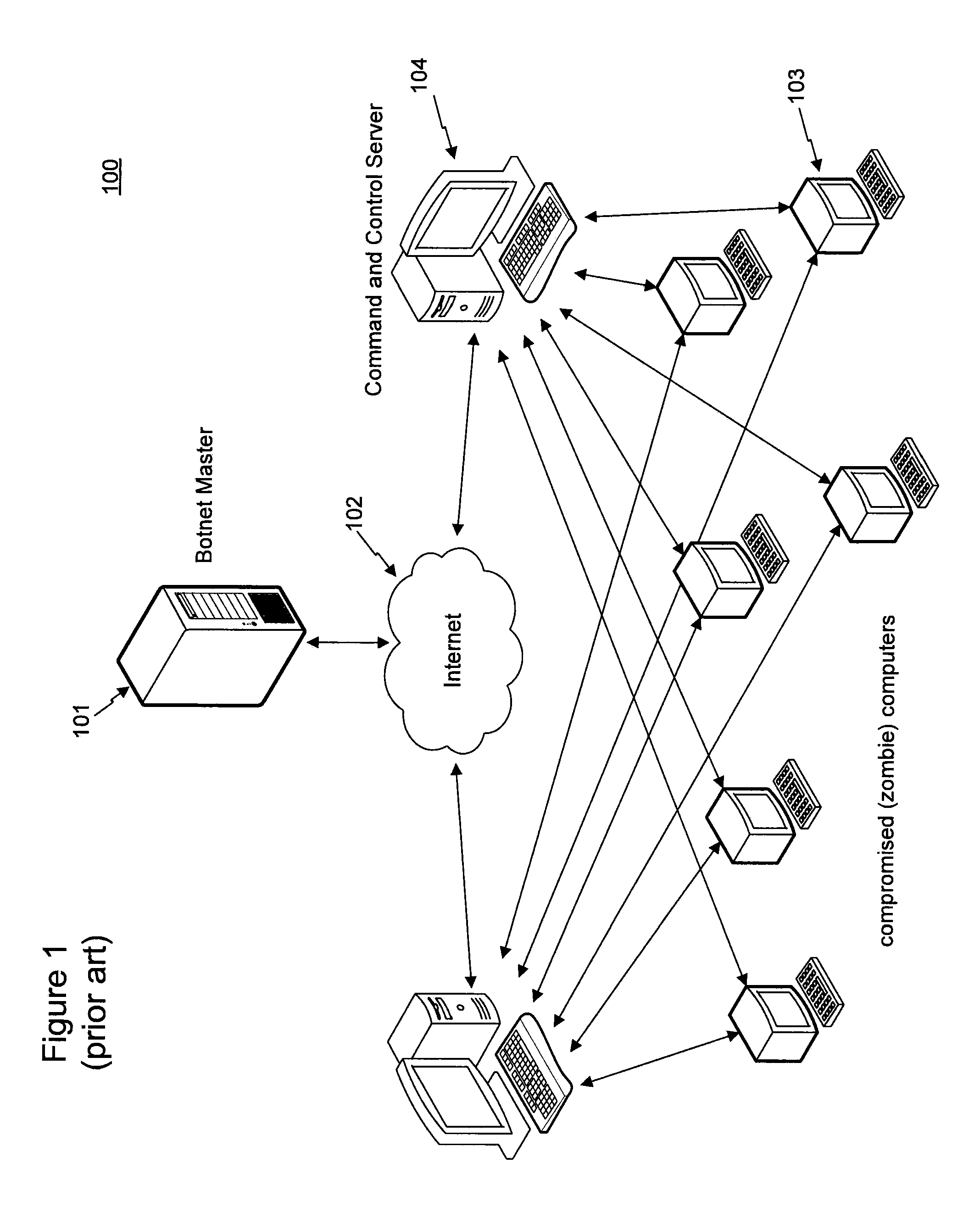
Methods and systems for reciprocal generation of watch-lists and malware signatures
ActiveUS20140317735A1Avoid accessMemory loss protectionError detection/correctionNetwork activityWatch list
The present disclosure is directed to methods and systems for reciprocal generation of watch-lists and traffic models characteristic of malicious network activity. In some aspects, the described methods and systems relate to maintaining data for recognition of malicious network activity. In general, the methods include monitoring network traffic; comparing endpoint data from monitored data packets to endpoints in a watch-list of network endpoints and comparing packet data from monitored data packets to traffic models in a catalog of traffic models characterizing malicious network activity; and determining, based on the comparisons, that a set of data packets comprise suspect network activity. The methods include adding a network endpoint to the watch-list when the determination is based on comparing packet data to a traffic model or adding a traffic model to the catalog when the determination is based on comparing endpoint data.
Owner:VMWARE INC
Distributed soft handoff among IP-based base stations
ActiveUS20020191558A1Time-division multiplexData switching by path configurationWatch listMobile station
A technique for assigning an address ("shadow address") to a mobile station that is compatible with the layer-2 address on the wireline network which serves the mobile station. The shadow address is then used as a wireline identifier for the destination address for frames ultimately destined for the mobile station. The shadow address is stored in a watch list for serving base stations, and any base station receiving a frame with a shadow address in its watch list process the frame to forward it the to mobile station. In this way, the shadow address facilitates carrying out soft handoff and smooth handoff.
Owner:TELCORDIA TECHNOLOGIES INC
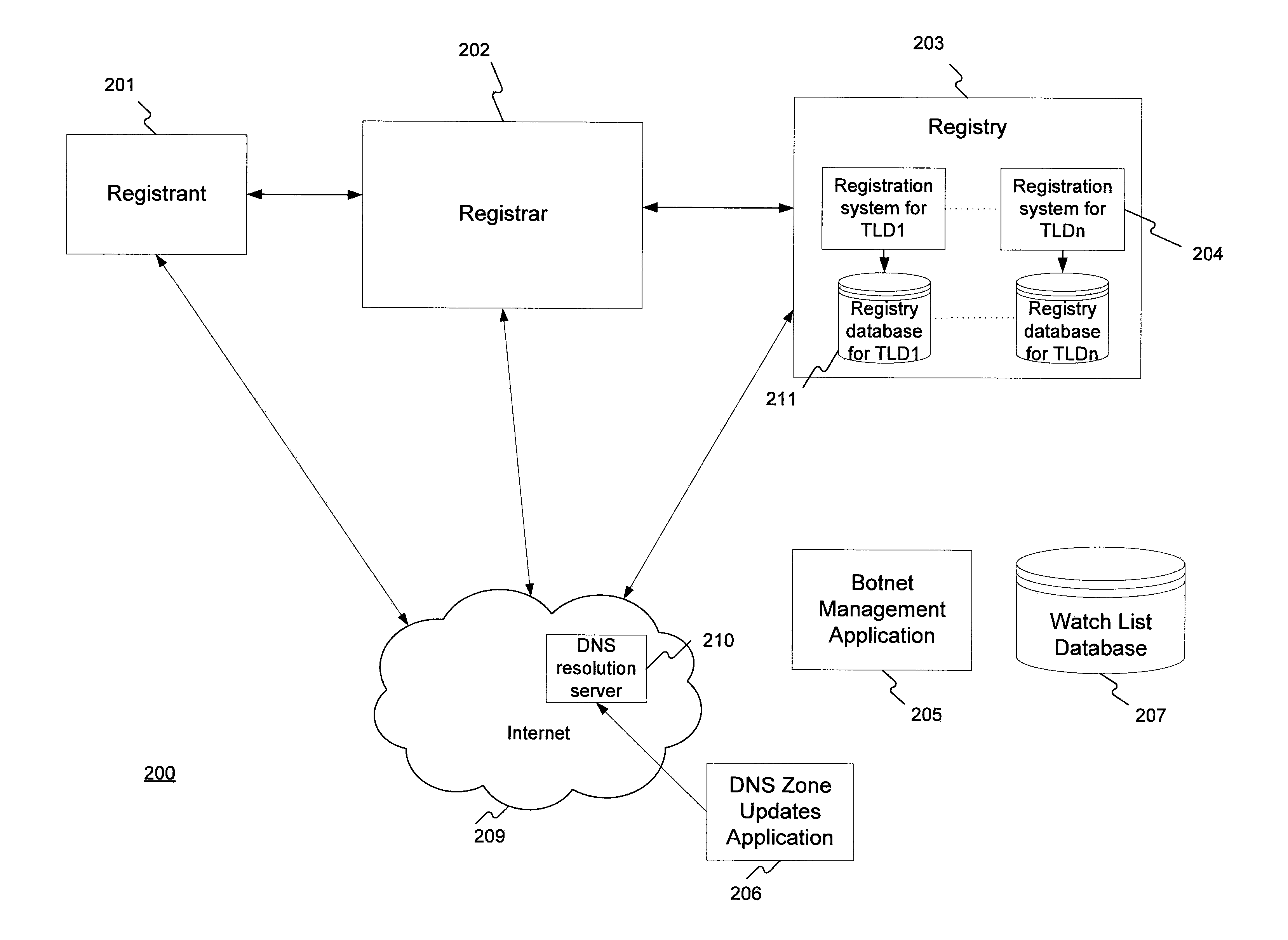
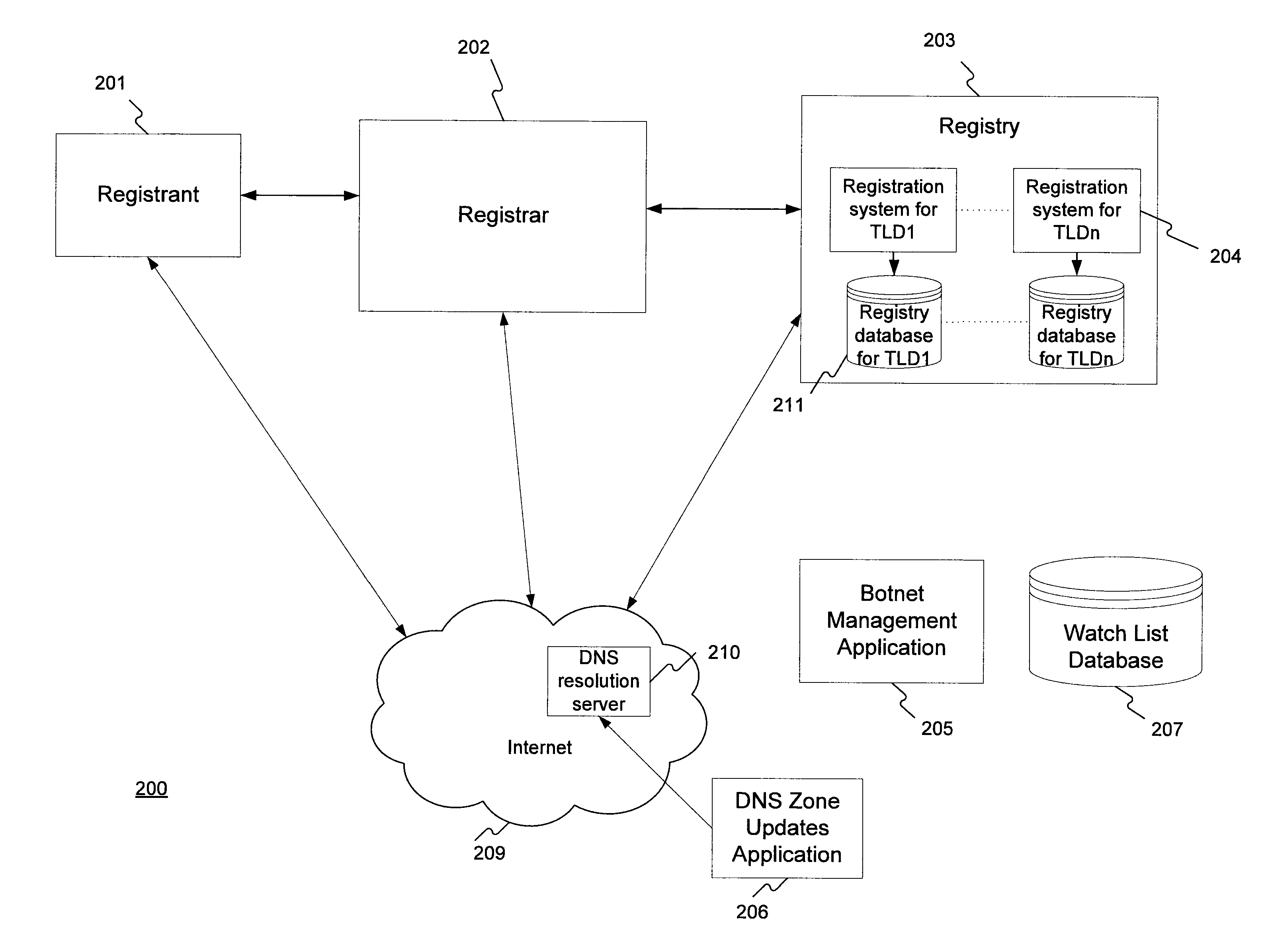
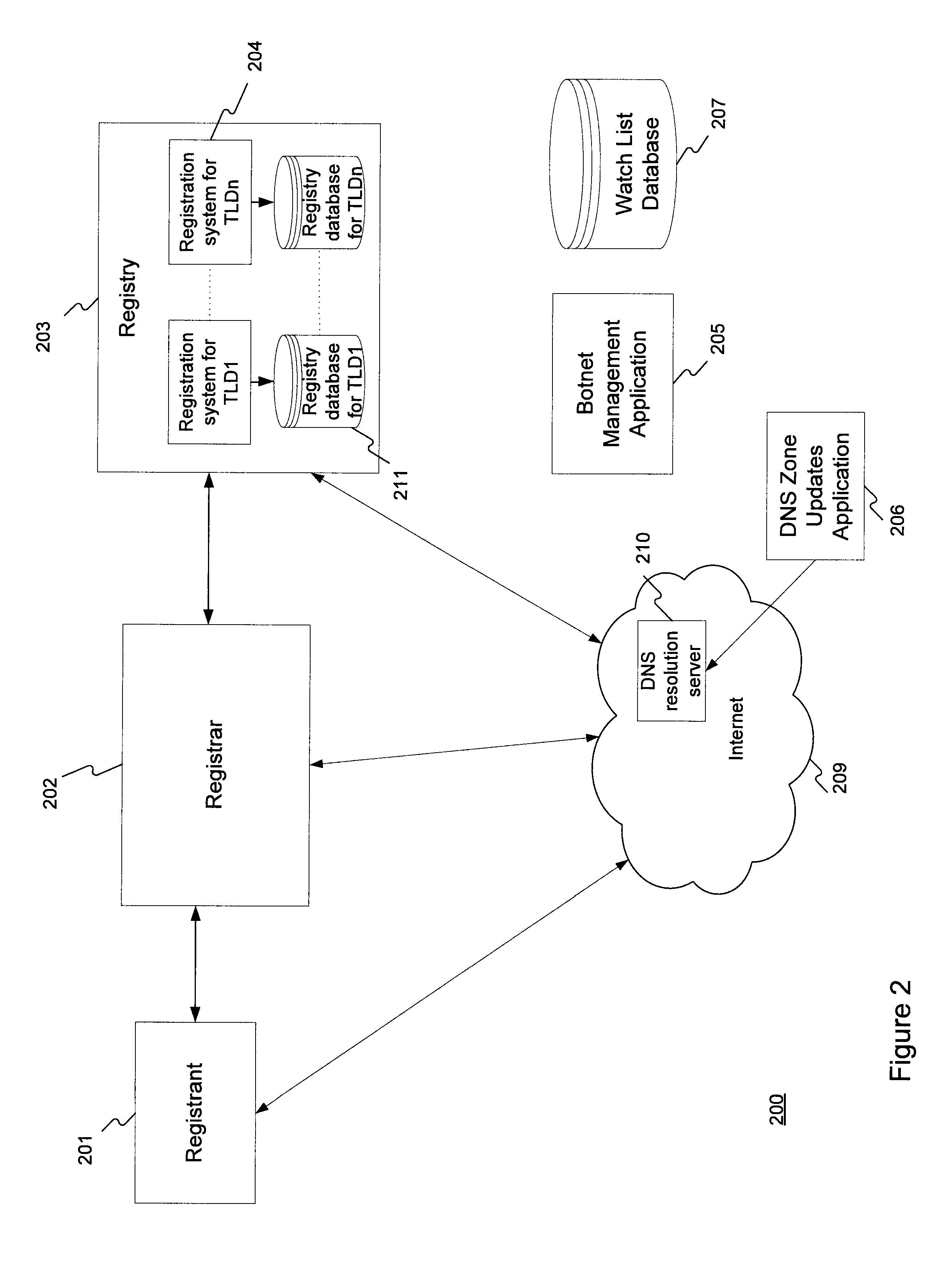
Method for administering a top-level domain
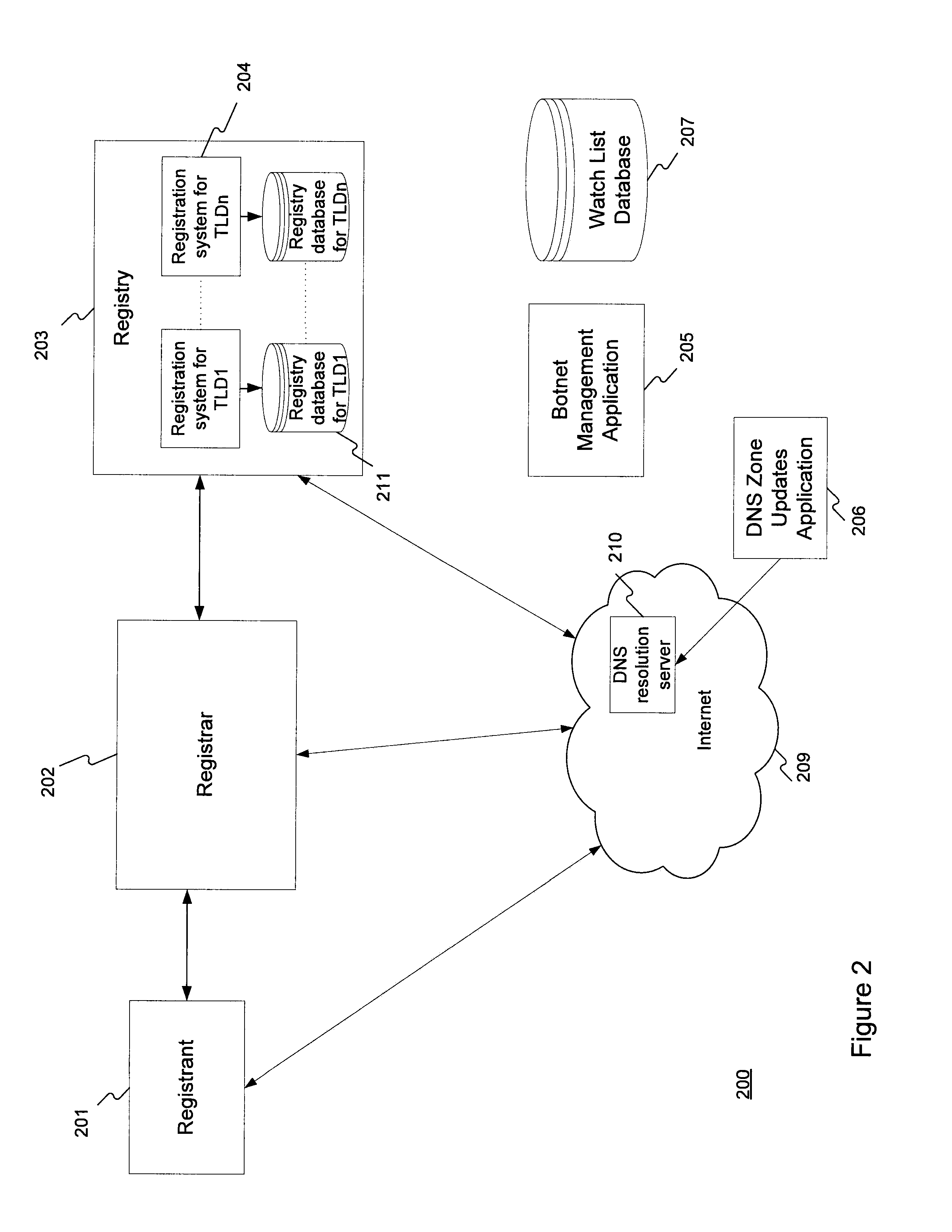
A method for administering a top-level domain by analyzing domain name registrations for requests for suspicious or malicious domain names. A request to register a domain name is received. The requested domain name's information may be stored in a registry database. The requested domain name may also be conditionally stored in the domain name system (DNS) zone. The requested domain name is compared to a list of botnet domain names stored in a watch list database. If the requested domain name corresponds to one of the botnet domain names, the requested domain name is prevented from being added to the DNS zone or is removed from the DNS zone, if it has already been stored there. The information regarding the requested domain name is stored in the registry database, even if the domain name does not ultimately stay in the DNS zone.
Owner:VERISIGN
Immigration control system
InactiveUS20130013527A1Facilitates immigration processReduce the amount of timeData processing applicationsIndividual entry/exit registersWatch listControl system
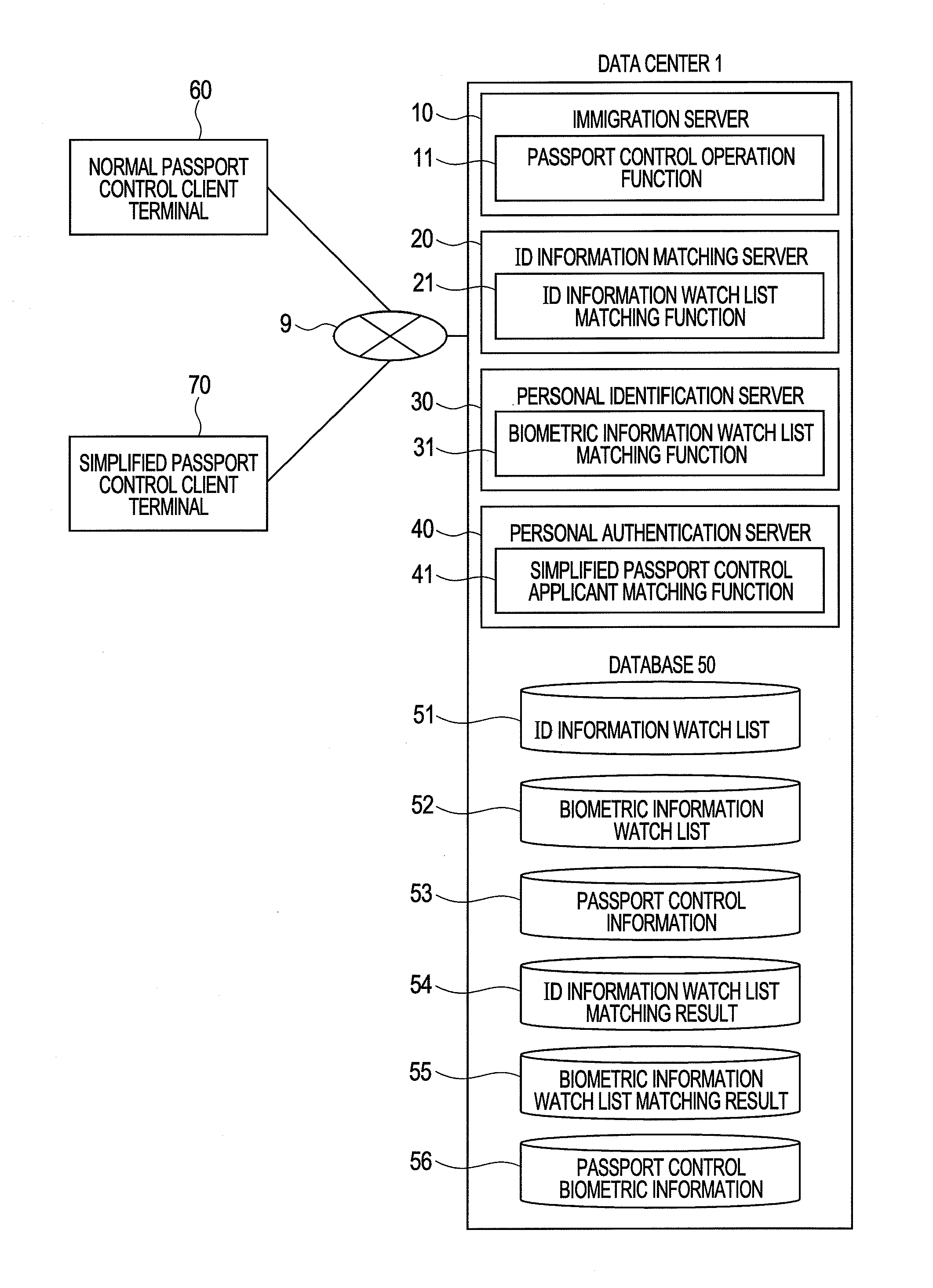
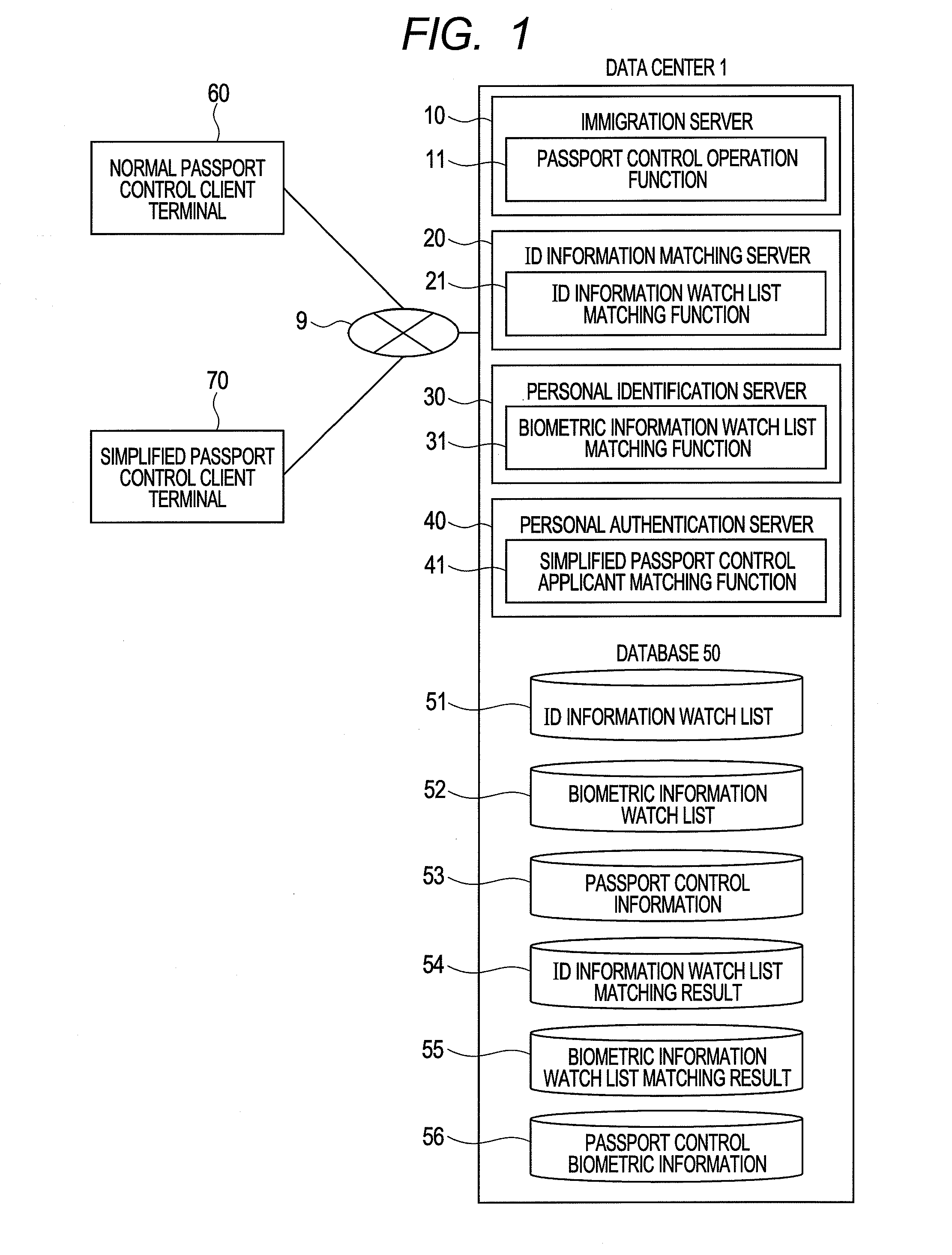
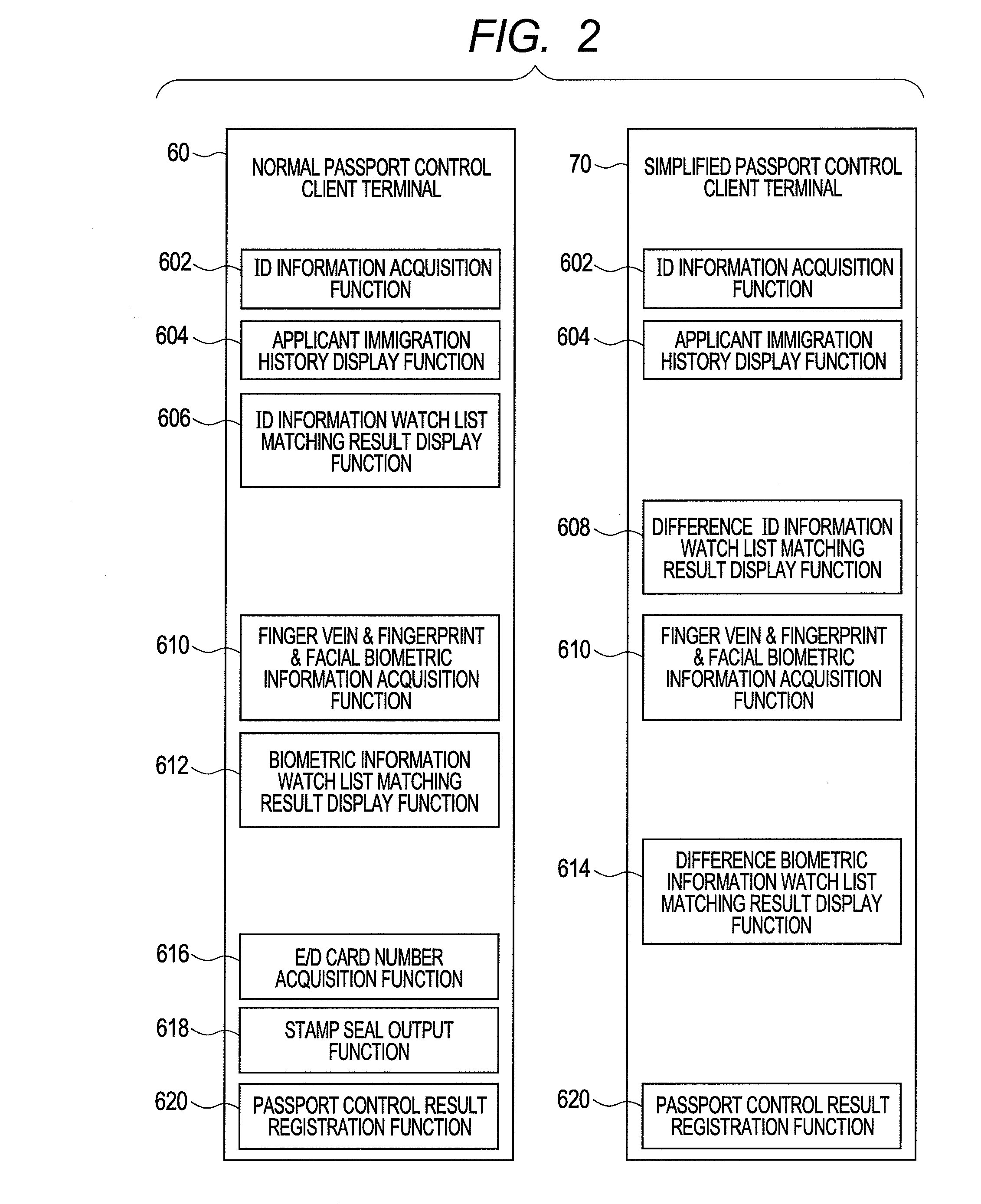
The present invention provides a system and a method for speeding up immigration. In first immigration, first biometric information is stored in a immigration biometric information DB. A normal immigration client terminal displays a first result of comparing an ID information watch list with a biometric information watch list. In subsequent second immigration, the first biometric information in the immigration biometric information DB is compared with second biometric information obtained by a simplified immigration client terminal. Then, the simplified immigration client terminal displays a second result of comparing the first biometric information with the watch list information that is added after the first comparison is done. Thus even if the number of registrations in a watch list database is large, a small amount of similar watch list information is displayed, reducing the time for checking the results by the operator.
Owner:HITACHI LTD
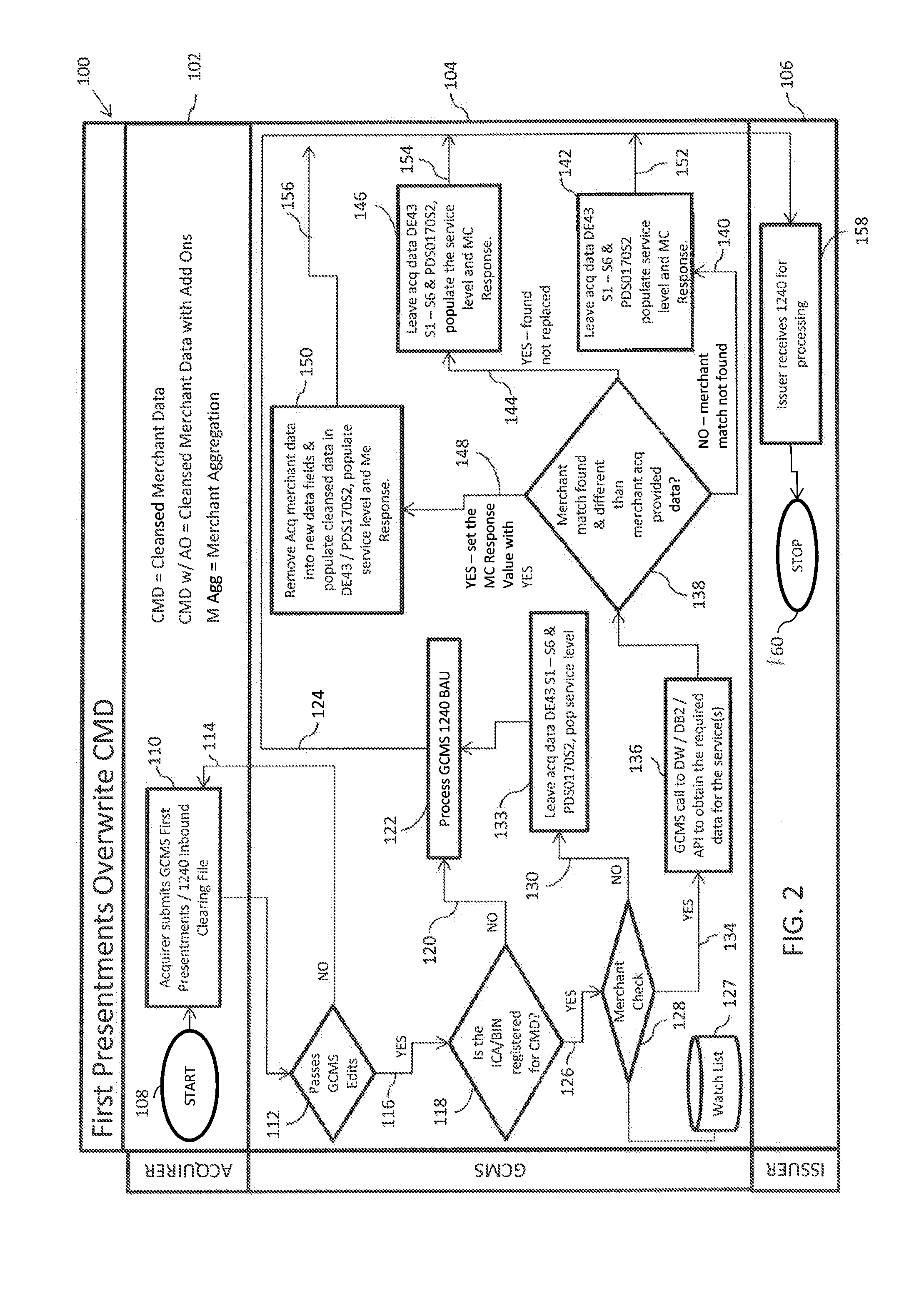
Merchant data cleansing in clearing record based on targeted merchants
InactiveUS20150032604A1Low costEasy to solveDigital data information retrievalFinanceThird partyWatch list
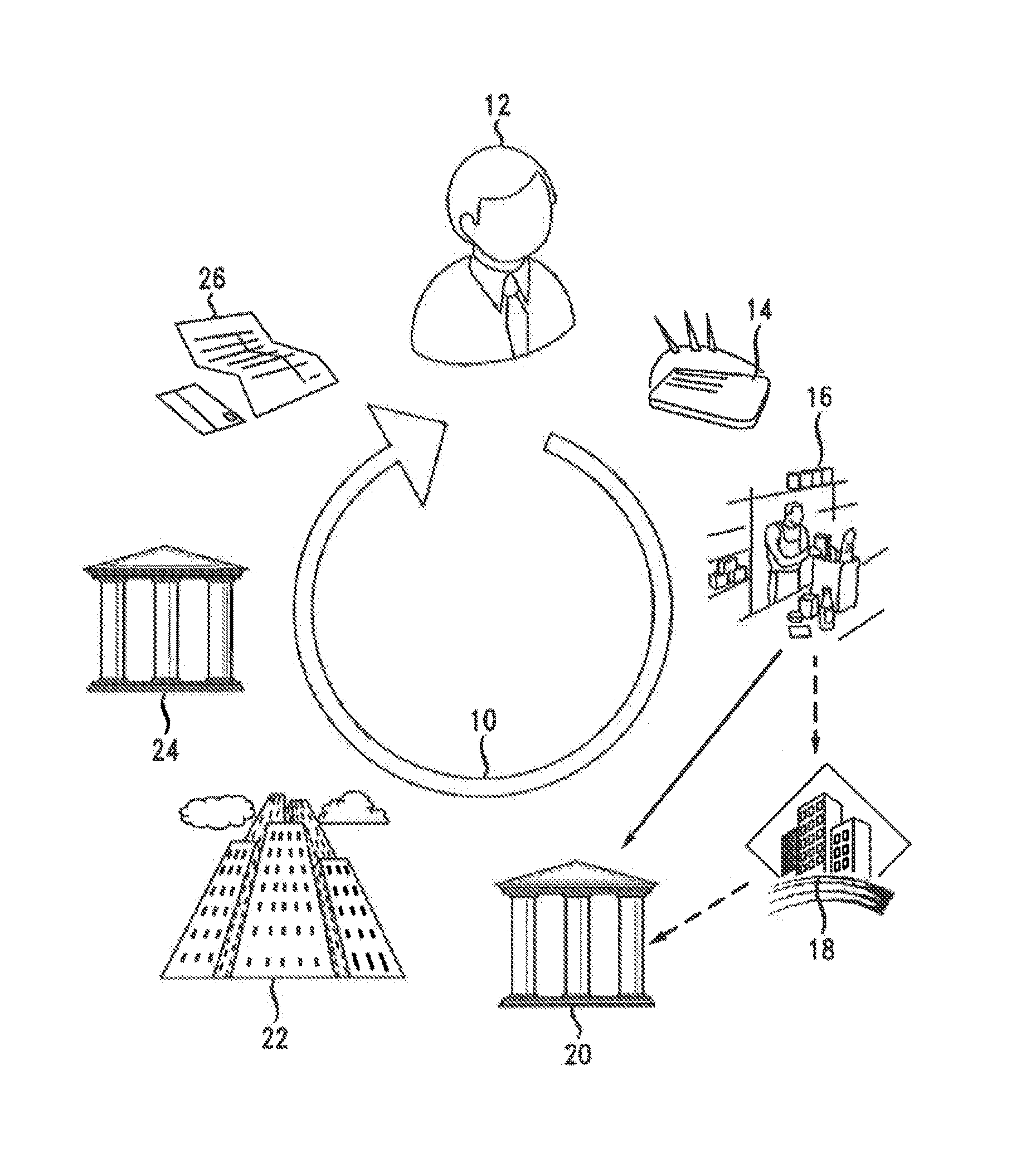
A network operator intermediates a cashless transaction by sending a payment device issuer an outbound clearing data file enriched with cleansed merchant data. Issuers that choose to participate in the merchant data cleansing service are provided with the cleansed, and optionally augmented, merchant information. Before providing the cleansed and / or augmented merchant information, a determination is made of whether a “do not recognize” call is likely, based upon a determination by a computing device of whether or not the merchant is on a “watch-list” of merchants. The “watch-list” is previously generated based upon one or several factors, including whether or not a minimum number or percentage of previous transactions have resulted in charge-backs, whether DNR transactions associated with the merchant were previously reported, or if an acquirer, issuer, or third-party payment provider recommends the merchant for inclusion.
Owner:MASTERCARD INT INC
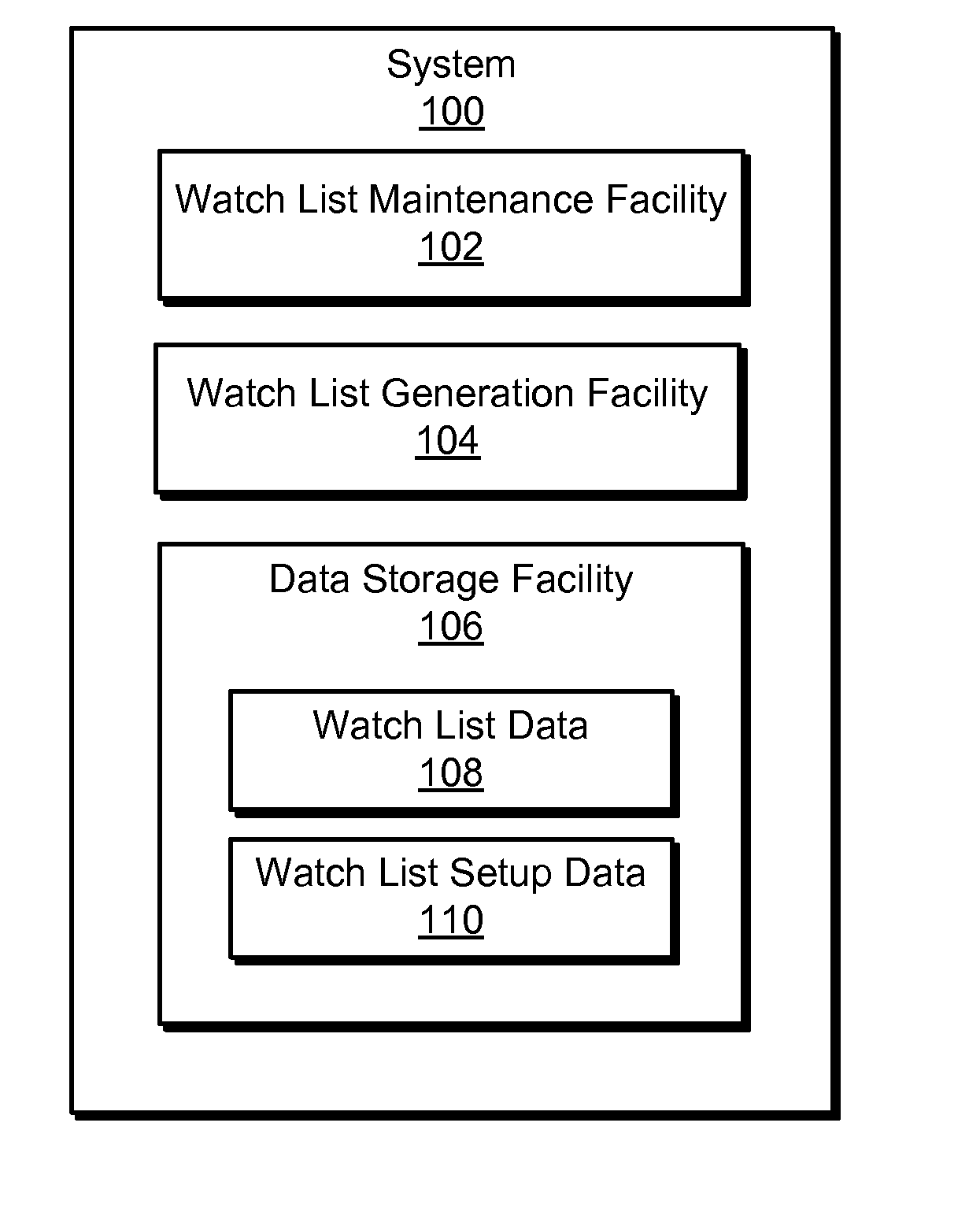
Method and system for building and maintenance watch lists
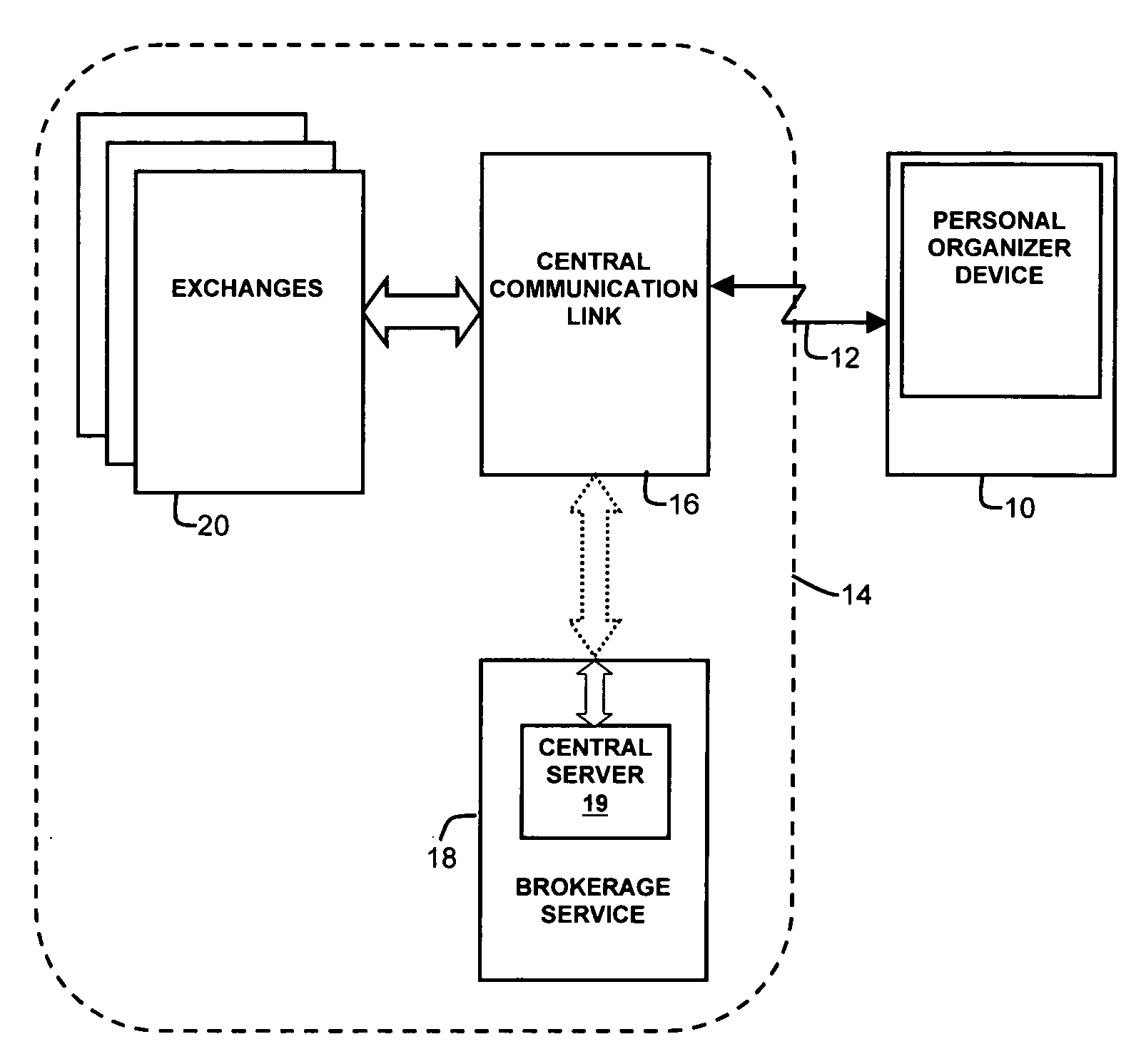
InactiveUS7333951B1Reduce storage capacityMore compactFinancePayment architecturePersonal organizerWatch list
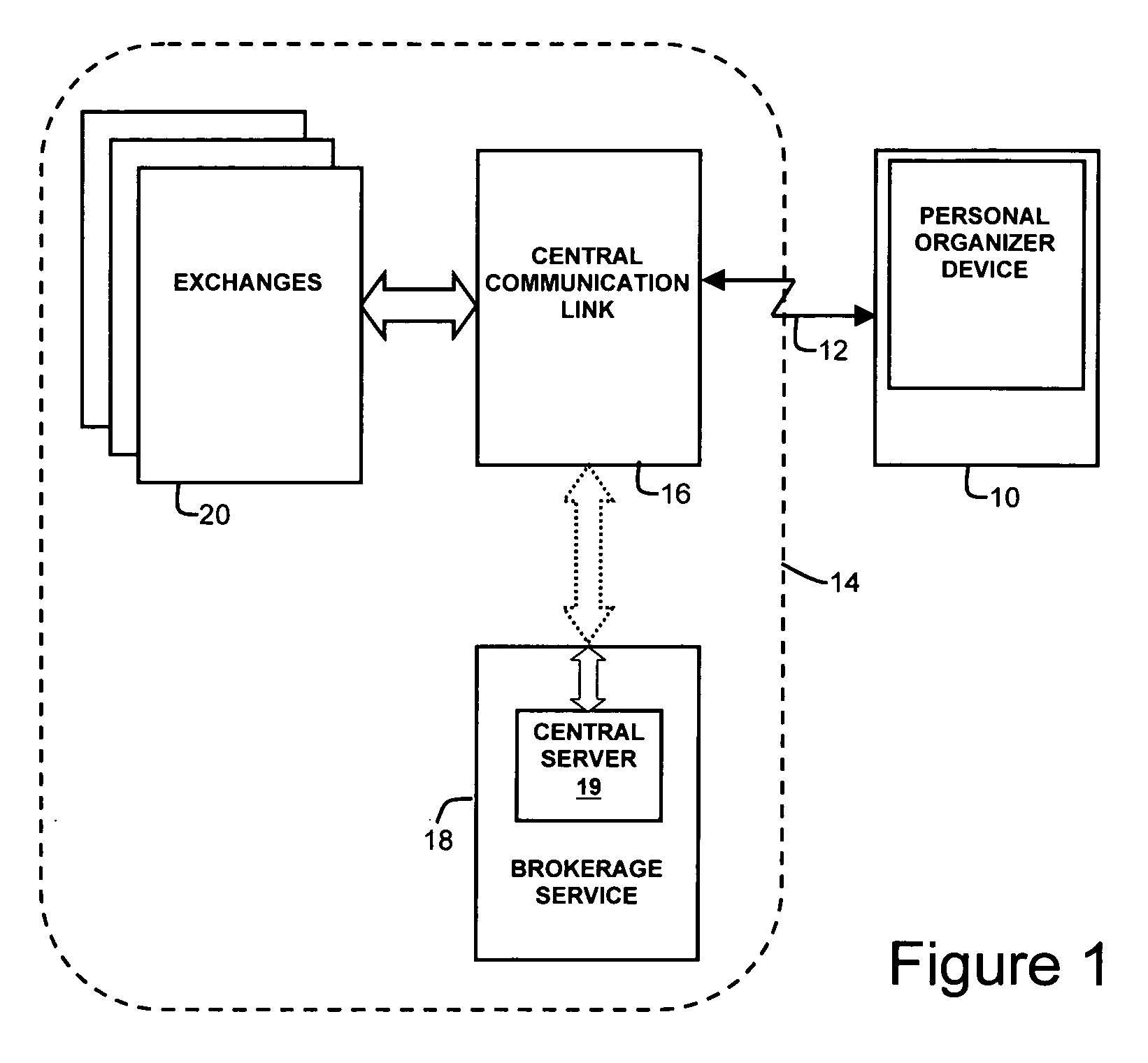
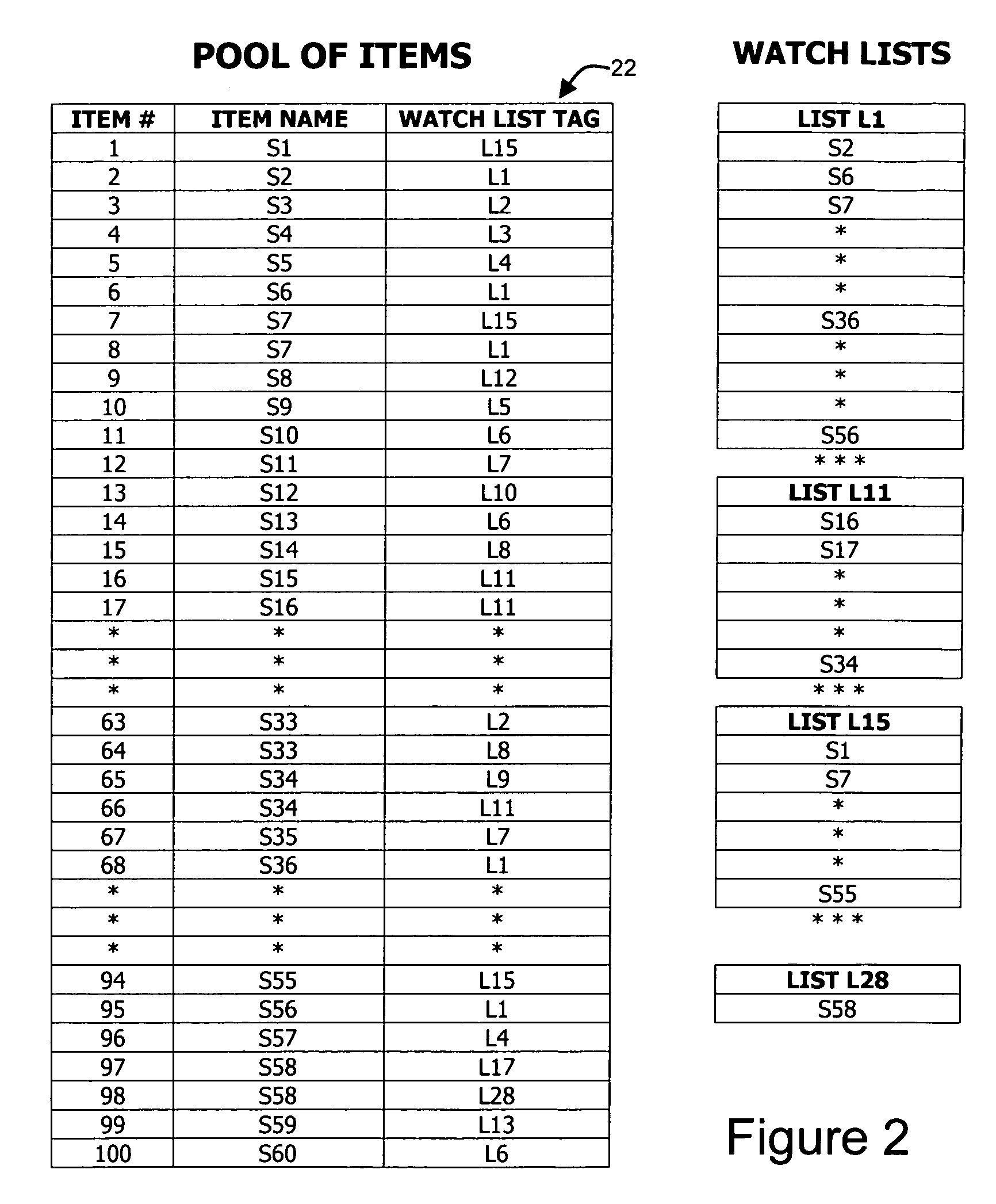
A method and apparatus for monitoring a items such as stocks and other securities, suitable for use in portable devices, such as personal organizers, wherein instead of separate watch lists, a pool of items being watched is maintained, and the total number of items which can be contained in the pool is intentionally limited to a predefined number, and further wherein each of the items in the pool includes an associated tag which defines a watch list to which it belongs, and the pool of the items being watched can be viewed simultaneously as one coherent collection, or specific watch lists can be displayed.
Owner:CHARLES SCHWAB & CO INC
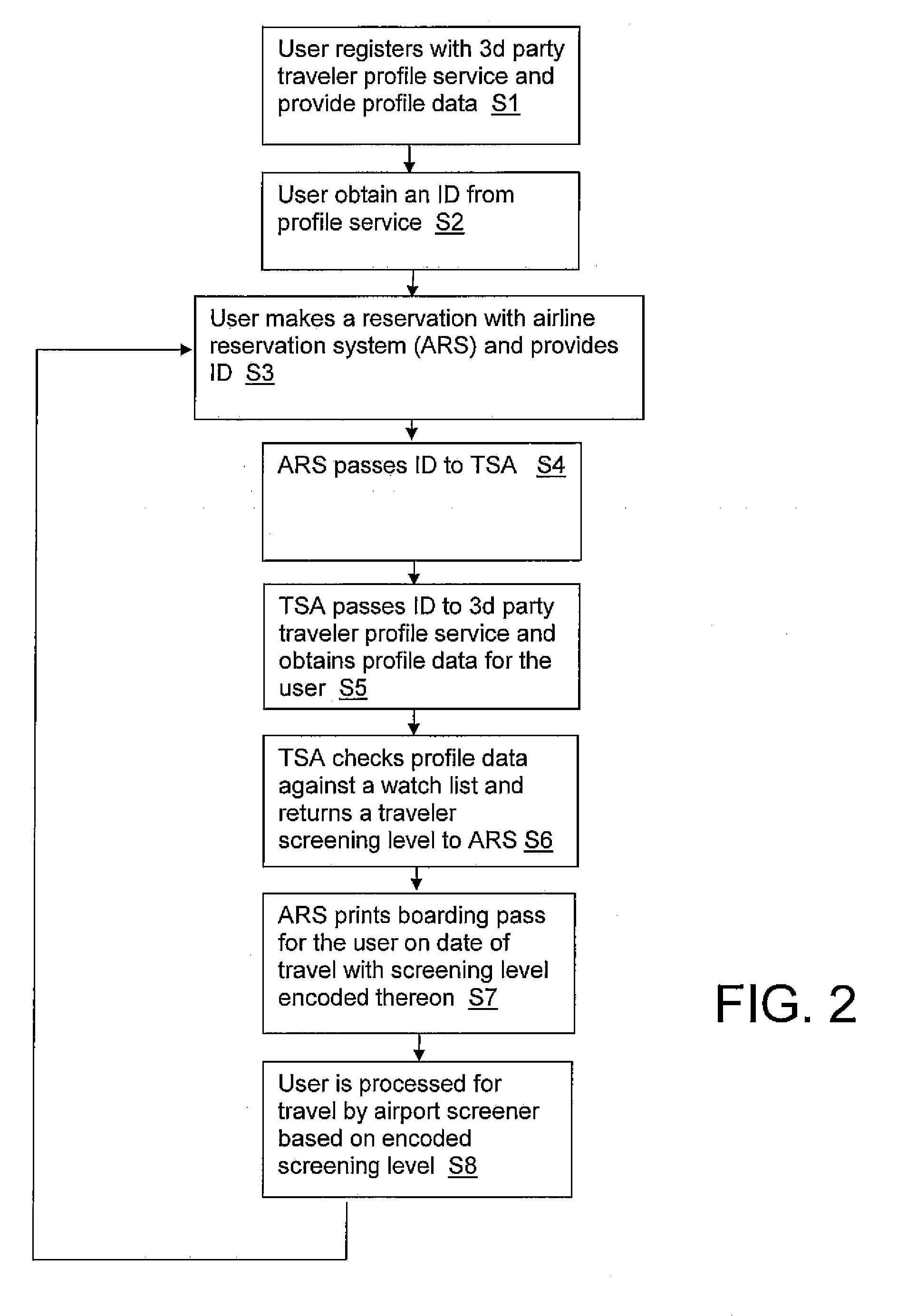
Passenger screening system
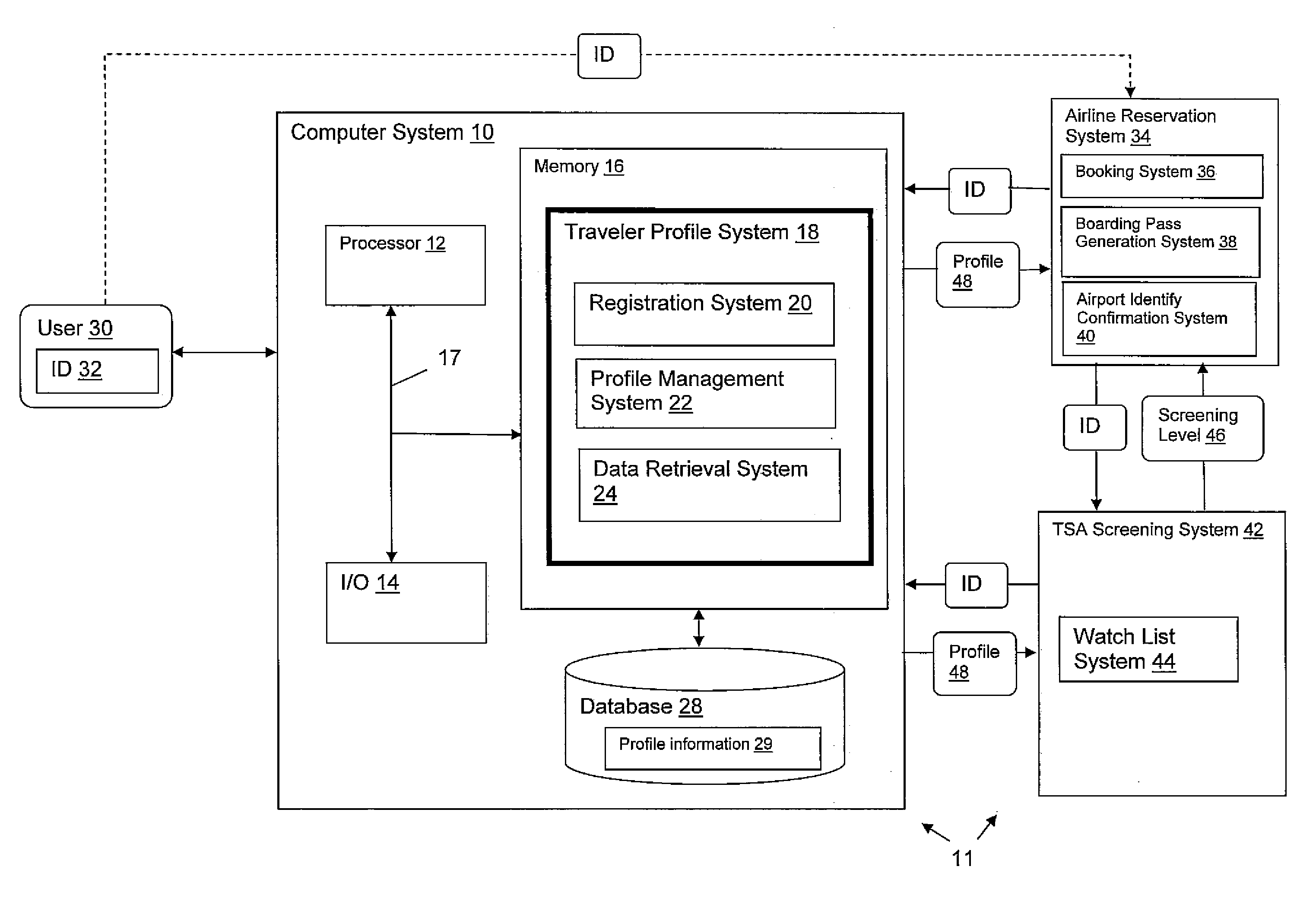
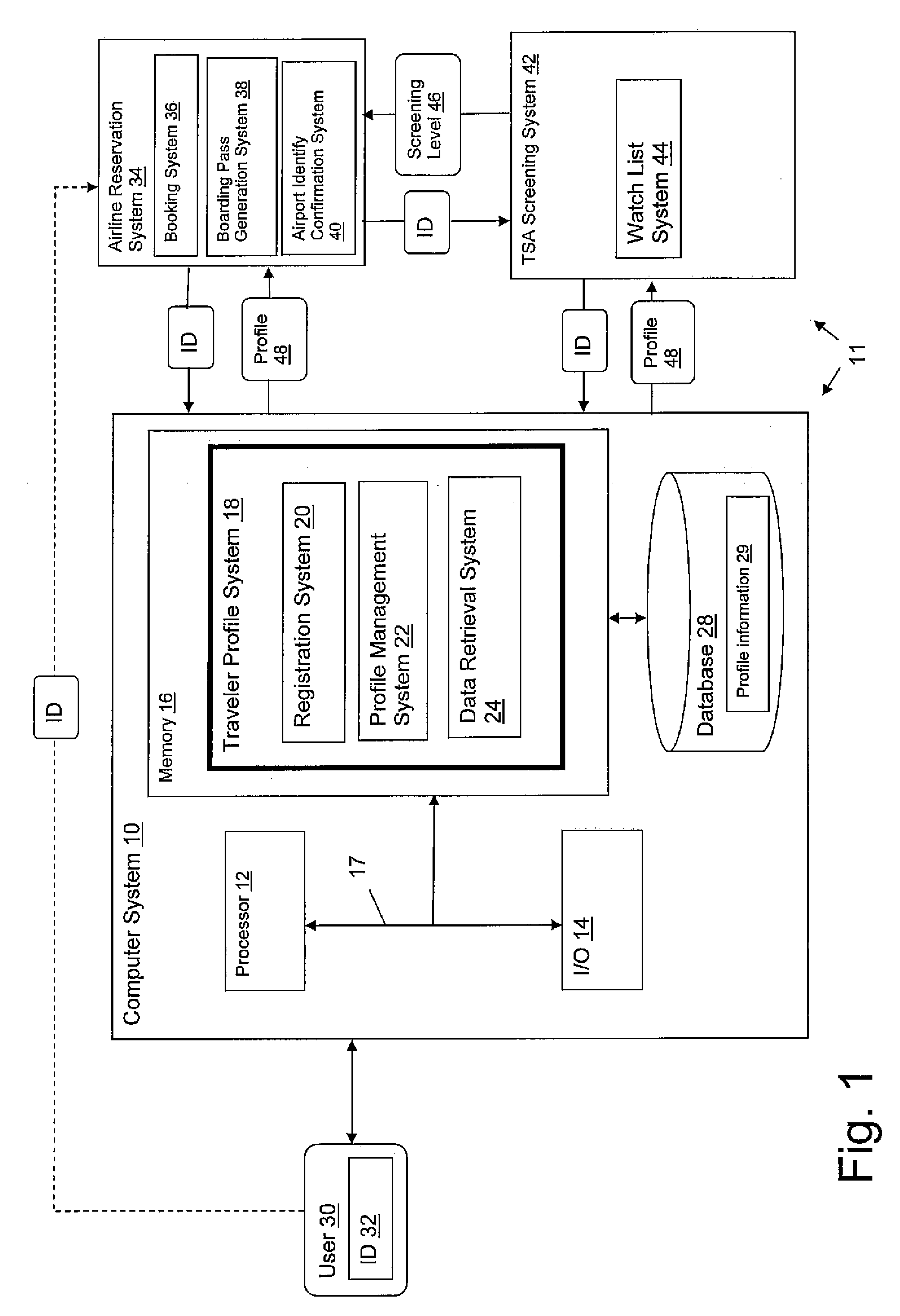
InactiveUS20090256675A1Electric signal transmission systemsDigital data processing detailsThird partyWatch list
A system, method and program product for providing passenger screening. A method is disclosed that includes: providing a third party service to collect profile information from a user and provide the user with a unique ID; submitting the unique ID from the user to a reservation system when the user books a reservation; passing the unique ID from the reservation system to a government agency; submitting the unique ID from the government agency to the third party service and returning associated profile information to the government agency; checking the associated profile information against a watch list within the government agency and generating a screening level for the user; and communicating the screening level to a screening agent.
Owner:KYNDRYL INC
System and/or method for handling recalled product purchases and/or return/warranty requests
ActiveUS20110119142A1Reduce maintenanceAccurate measurementHand manipulated computer devicesCoin-freed apparatus detailsWatch listWorld Wide Web
Certain exemplary embodiments described herein relate to the field of electronic registration (ER) of purchased products and, more particularly, to improved electronic registration techniques purchase-side and / or return-side handling of recalled items. Certain exemplary embodiments on the purchase-side may help to filter-out products that have recalled been before they are purchased. Certain exemplary embodiments on the return-side may help enable recall return overrides, thus facilitating the acceptance of recalled products even though they might not qualify under an original return / warranty policy. Advantageously, more and more recalled products may be filtered out of circulation through the use of purchase-side and / or return-side recall watch list checking techniques of certain exemplary embodiments. Such purchase-side and / or return-side recall watch list checking may be performed together with or separate from electronic registration techniques in different exemplary embodiments.
Owner:E2INTERACTIVE INC D B A E2INTERACTIVE
Adaptive object modeling and differential data ingestion for machine learning
ActiveUS20190347578A1Improve securityComputationally efficientComputer security arrangementsMachine learningData ingestionData set
A machine learning (ML)-based technique for user behavior analysis that detects when users deviate from expected behavior. A ML model is trained using training data derived from activity data from a first set of users. The model is refined in a computationally-efficient manner by identifying a second set of users that constitute a “watch list.” At a given time, a differential data ingestion operation is then performed to incorporate data for the second set of users into the training data, while also pruning at least a portion of the data set corresponding to data associated with any user included in the first set but not in the second set. These operations update the training data used for the machine learning. The machine learning model is then refined based on the updated training data that incorporates the activity data ingested from the users identified in the watch list.
Owner:IBM CORP
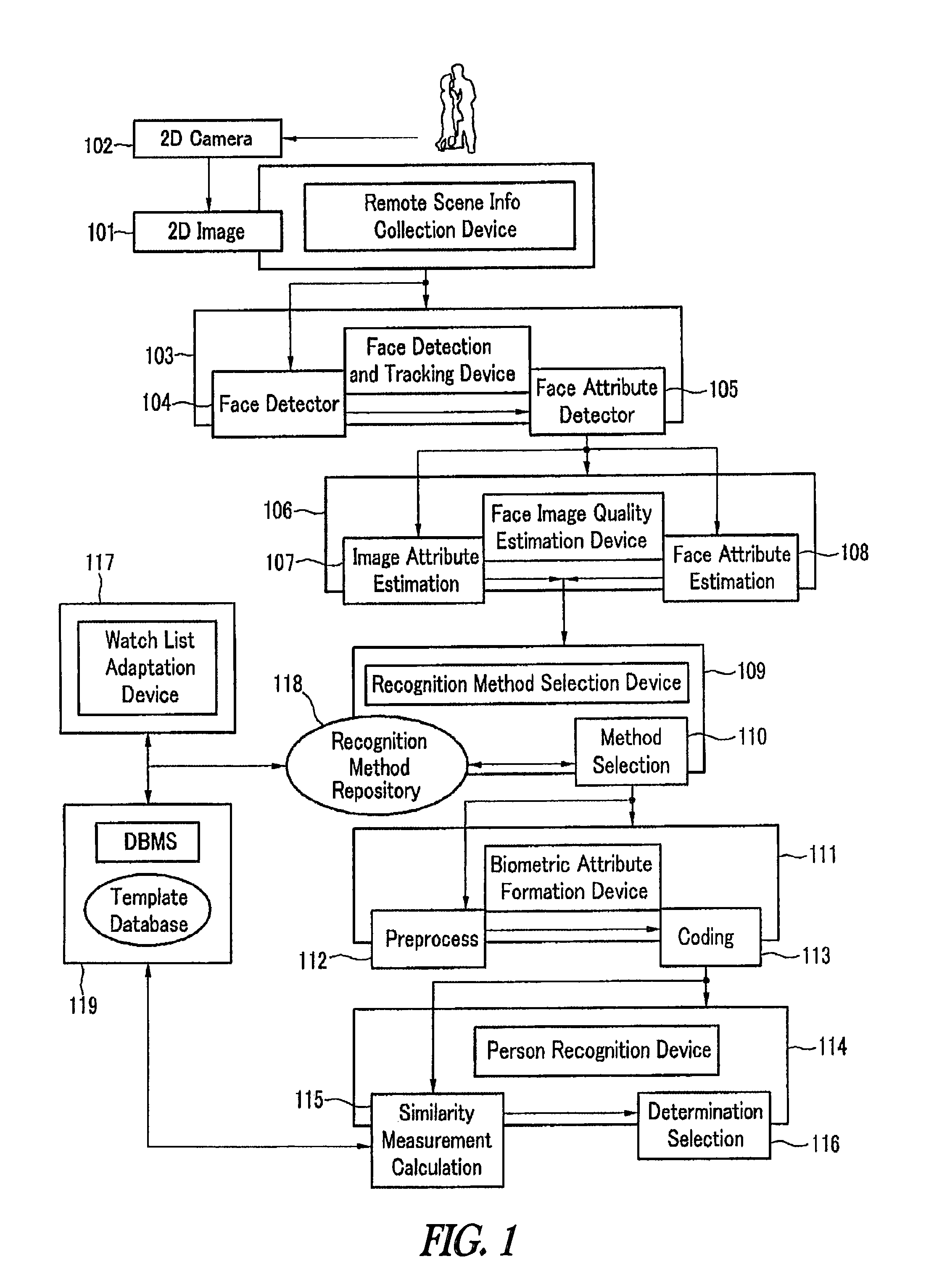
Method and system for automated face detection and recognition
ActiveUS9367730B2Improve operational precision and stabilityCancel noiseImage enhancementImage analysisFace detectionFeature set
The present invention relates to a figure recognition system and method for automatic detection, tracking and recognition of a human face image. 2D image data in the surveillance zone are remotely collected by using an optical sensor, the faces of all persons in the surveillance zone are detected, and corresponding positions are determined. The face is detected, the detected face's feature coordinate is estimated, and the detected face and the feature are tracked in the next frame while processing the video sequence. Image quality of each detected face is determined according to parameters of focus, brightness, contrast, and the presence of glasses. Recognition methods stored in the repository for each detected face are adjusted by considering the face image quality computation value, and a biometric feature set is generated by using the recognition method selected for each detected face. The figure is recognized according to the watch list by using the biometric feature generated by comparing each detected face and a template set stored in the database. A new user registration process is performed and the recognition method is adapted automatically by considering the watch list.
Owner:S1 CORP
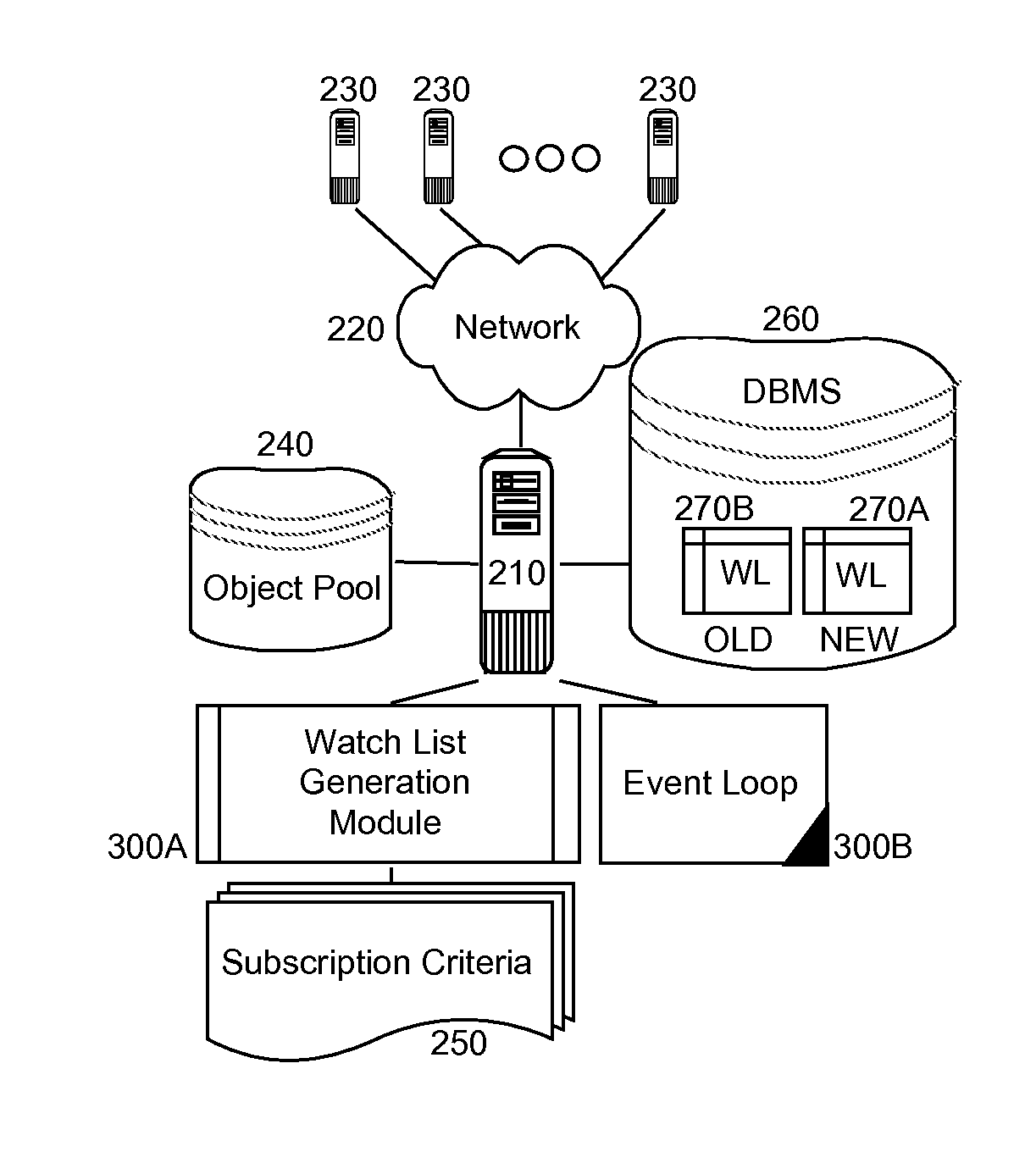
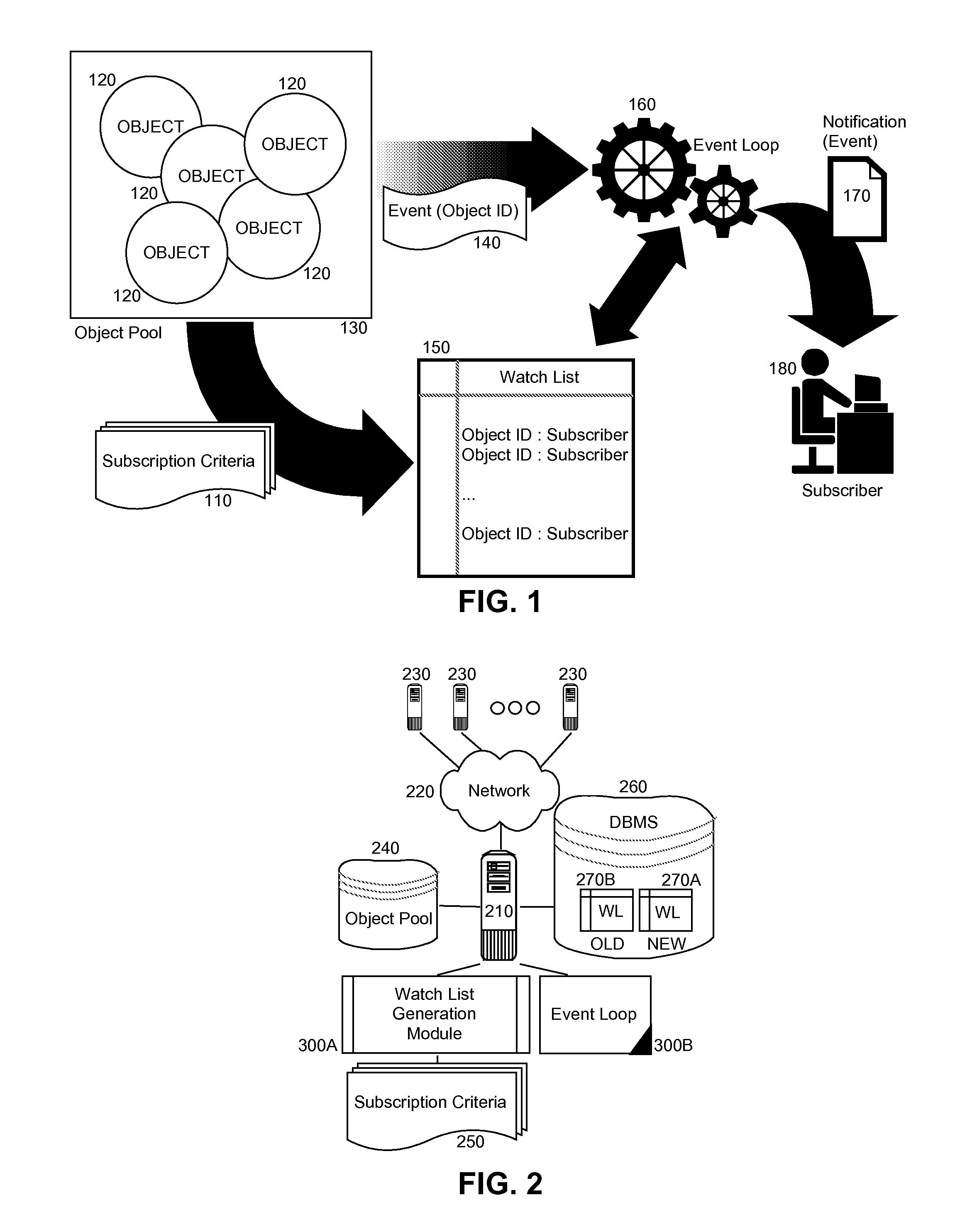
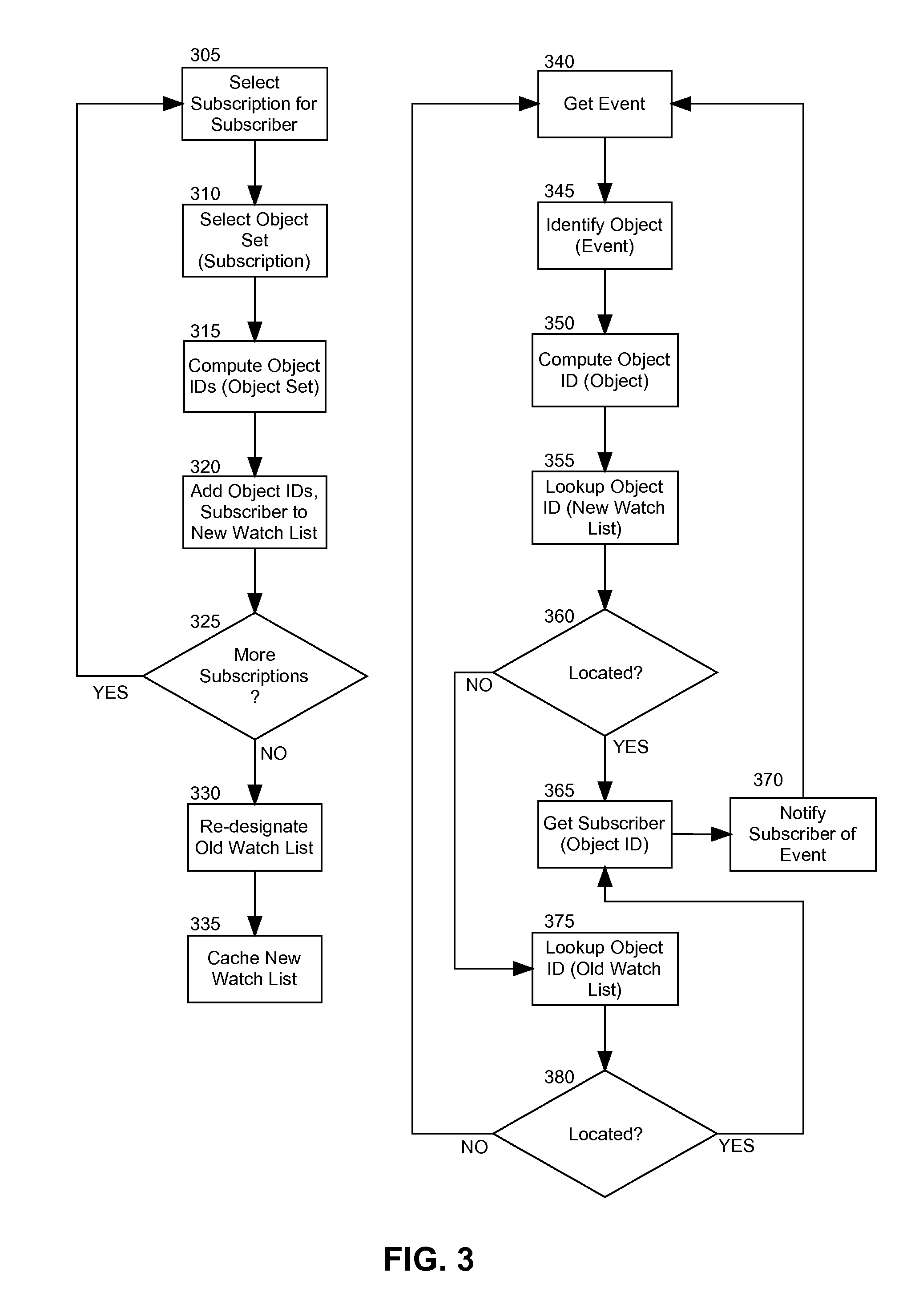
Subscription watch lists for event handling
Embodiments of the present invention provide a method, system and computer program product for watch list oriented processing of events in a multi-object event data processing system. In an embodiment of the invention, a method for watch list oriented processing of events in a multi-object event data processing system, can include pre-processing a set of subscriptions against a pool of objects monitored for events in the data processing system to produce a watch list of objects. The method further can include receiving events in the data processing system corresponding to different ones of the objects in the pool of objects. The method yet further can include comparing the received events to the watch list to determine which events pertain to objects referenced in the watch list. Finally, for each one of the received events, a notification can be forwarded to one or more subscribers corresponding to an object in the watch list matching an object implicated by the one of the received events.
Owner:IBM CORP
Method for administering a top-level domain
A method for administering a top-level domain by analyzing domain name registrations for requests for suspicious or malicious domain names. A request to register a domain name is received. The requested domain name's information may be stored in a registry database. The requested domain name may also be conditionally stored in the domain name system (DNS) zone. The requested domain name is compared to a list of botnet domain names stored in a watch list database. If the requested domain name corresponds to one of the botnet domain names, the requested domain name is prevented from being added to the DNS zone or is removed from the DNS zone, if it has already been stored there. The information regarding the requested domain name is stored in the registry database, even if the domain name does not ultimately stay in the DNS zone.
Owner:VERISIGN
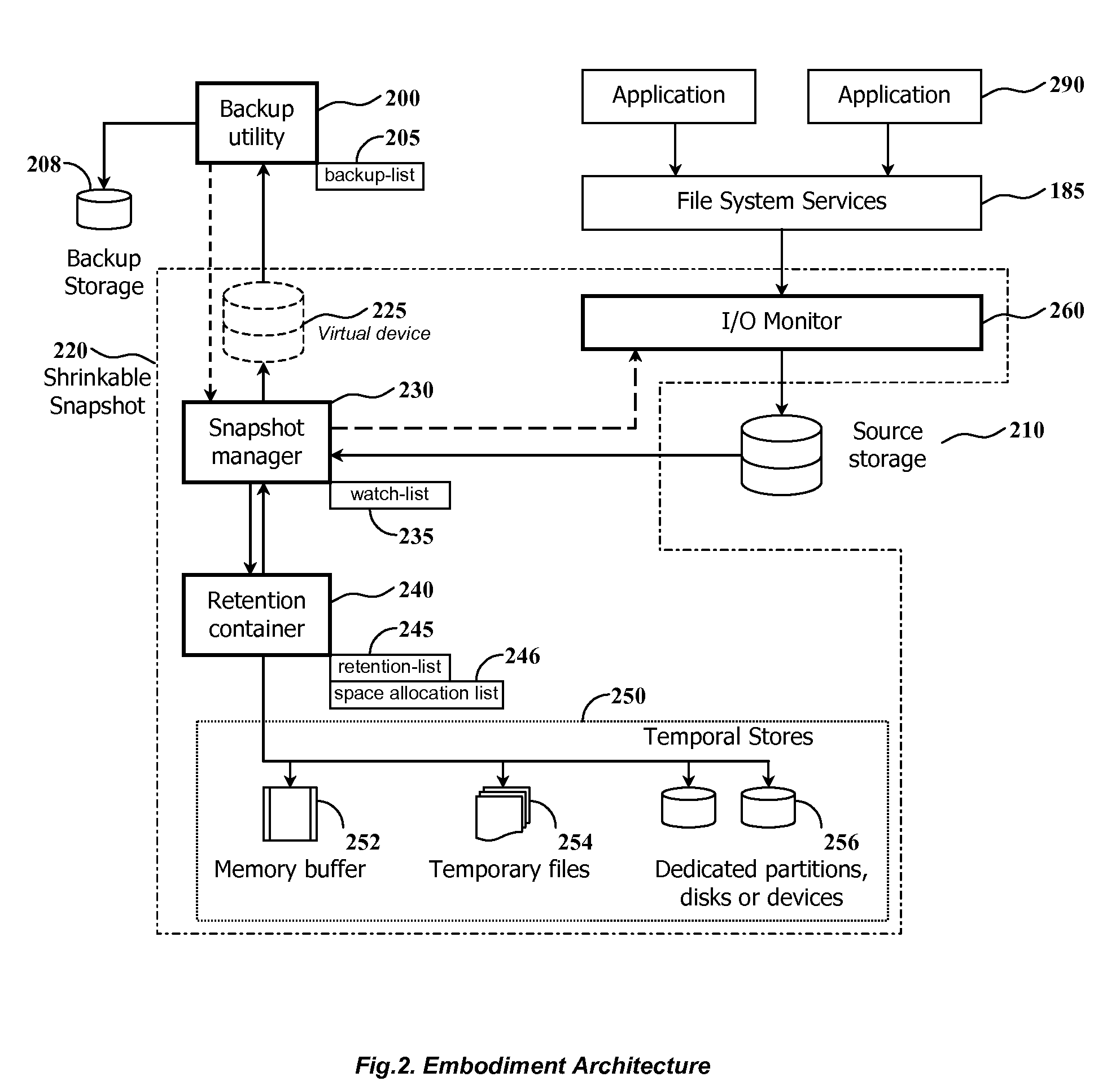
Method and system for shrinking a set of data using a differential snapshot, a watch-list structure along with identifying and retaining updated blocks
InactiveUS7680996B2Reduce expensesReduce overheadDigital data information retrievalError detection/correctionWatch listBackup software
At the beginning of an online backup operation, the backup software system creates a snapshot of source data storage. The snapshot includes a watch-list used for identifying blocks of a source storage which are watched by snapshot management means for update. If a block included into the watch-list was requested for update, the snapshot management means preserve original contents of that block in a retention container for the purpose of temporary store. The retention container includes a set of temporal stores dedicated for transient storing of blocks until they are backed up. Backed up blocks can be operatively excluded from the snapshot so that unchanged blocks are excluded from the watch-list and updated blocks are removed from the retention container.
Owner:PARAGON SOFTWARE GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com