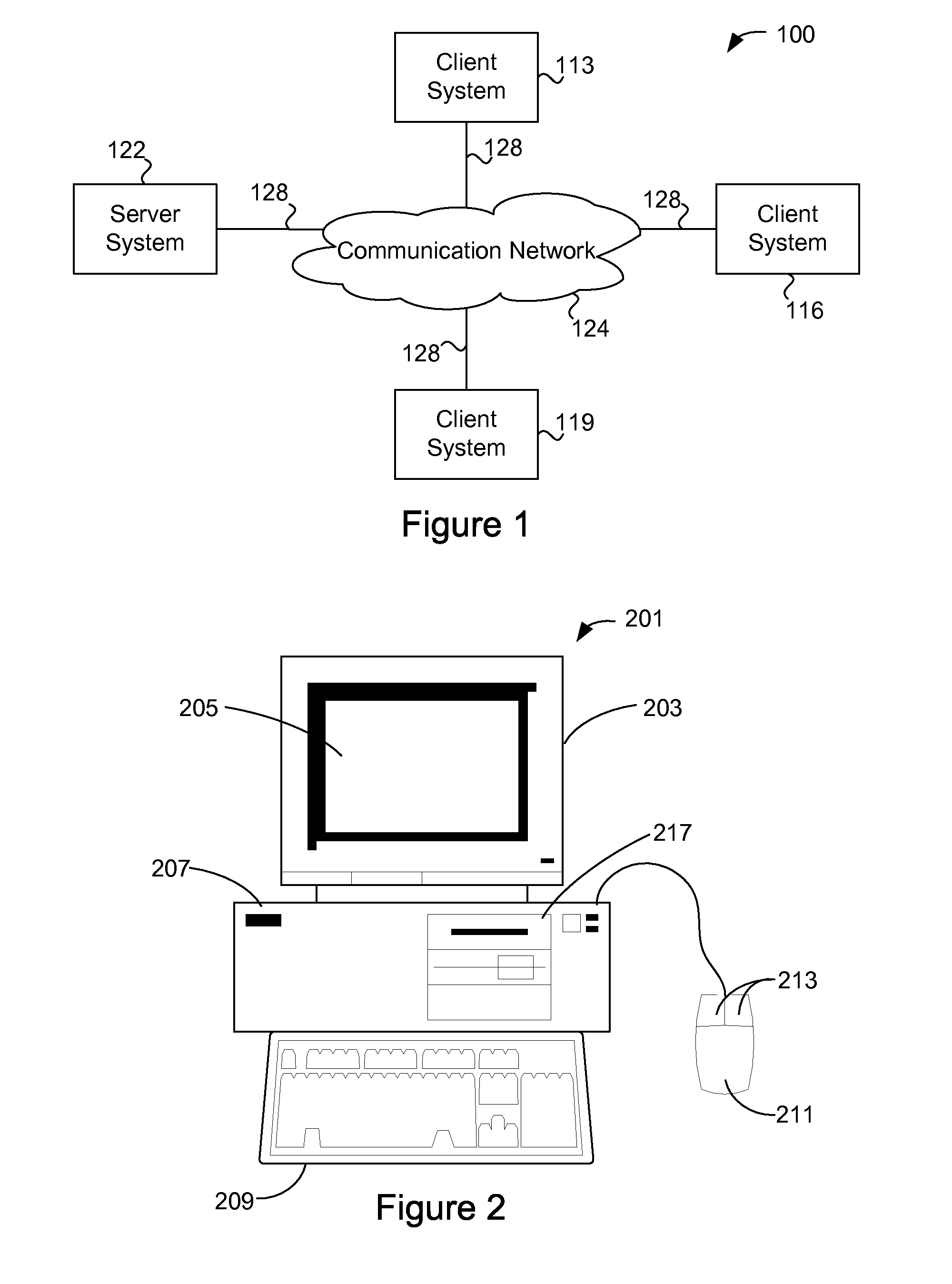
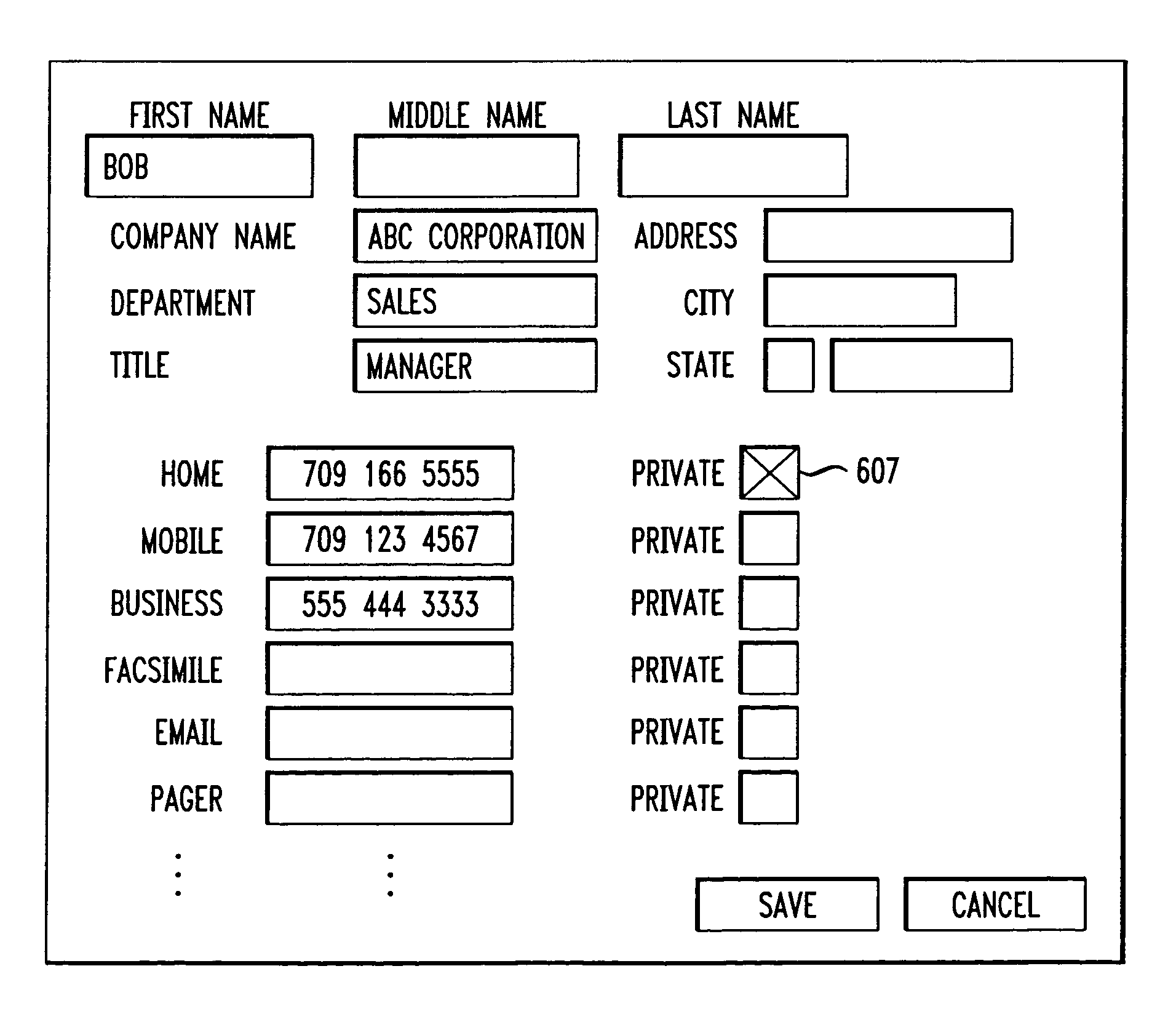
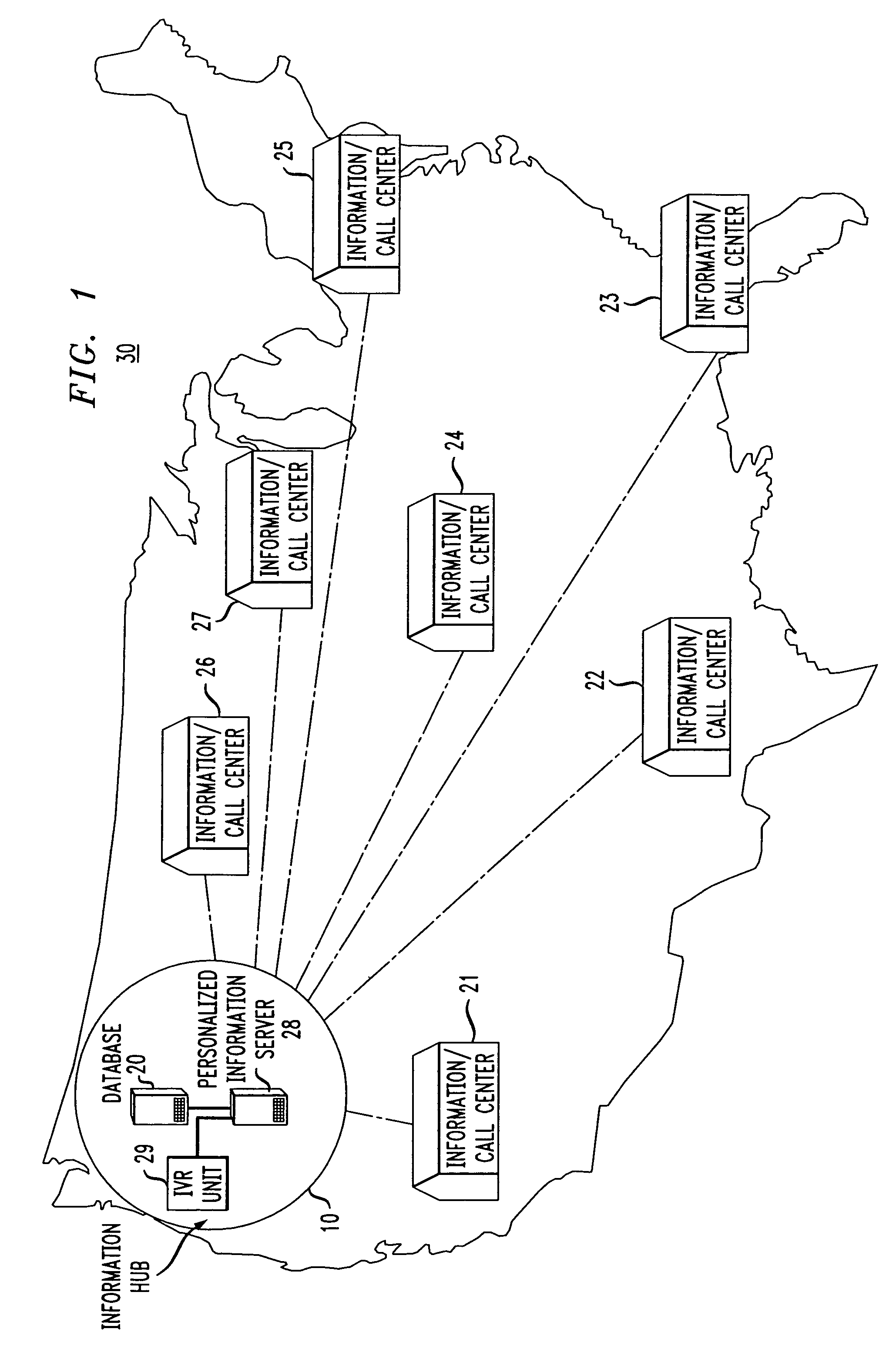
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
821results about "Graded-service arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
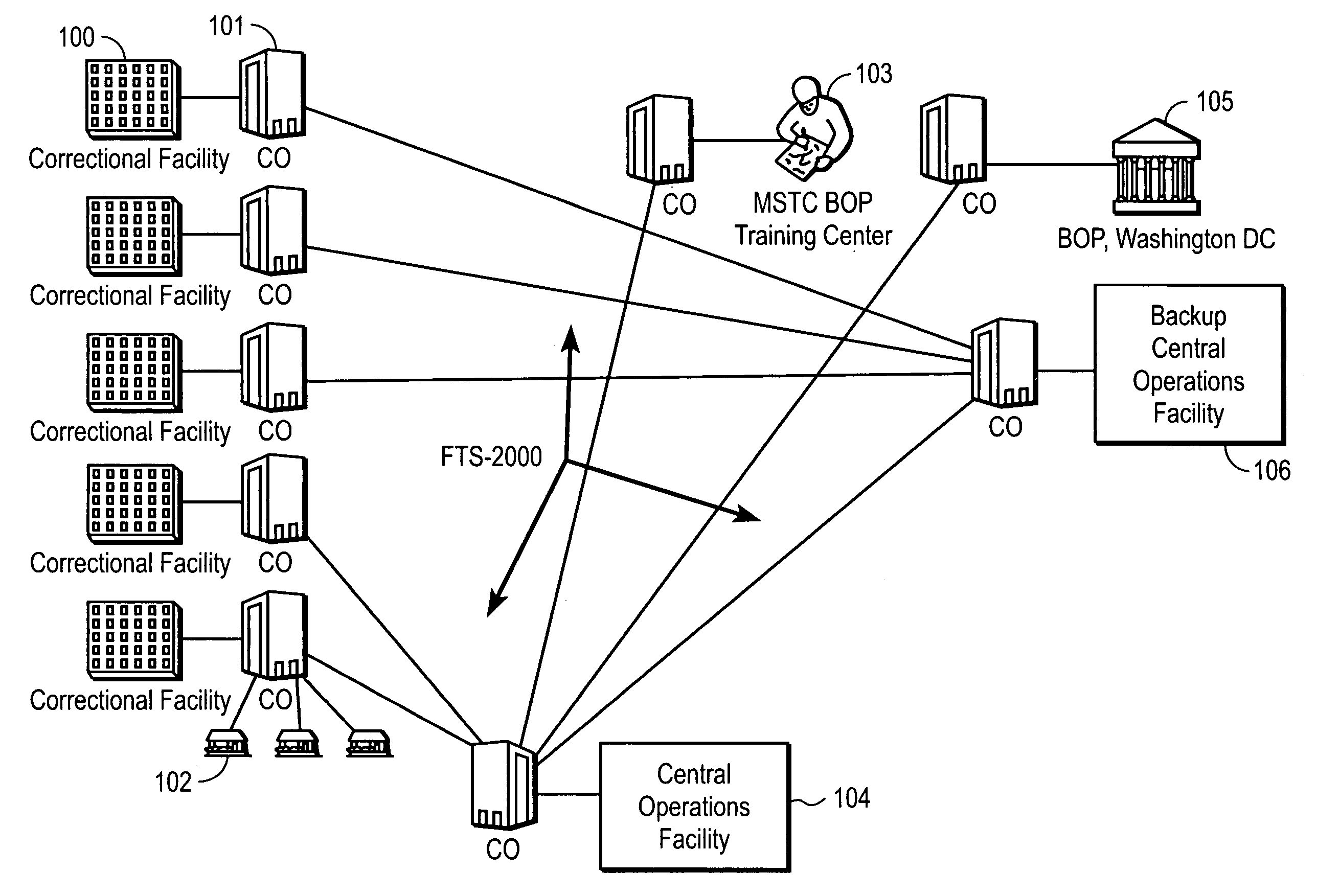
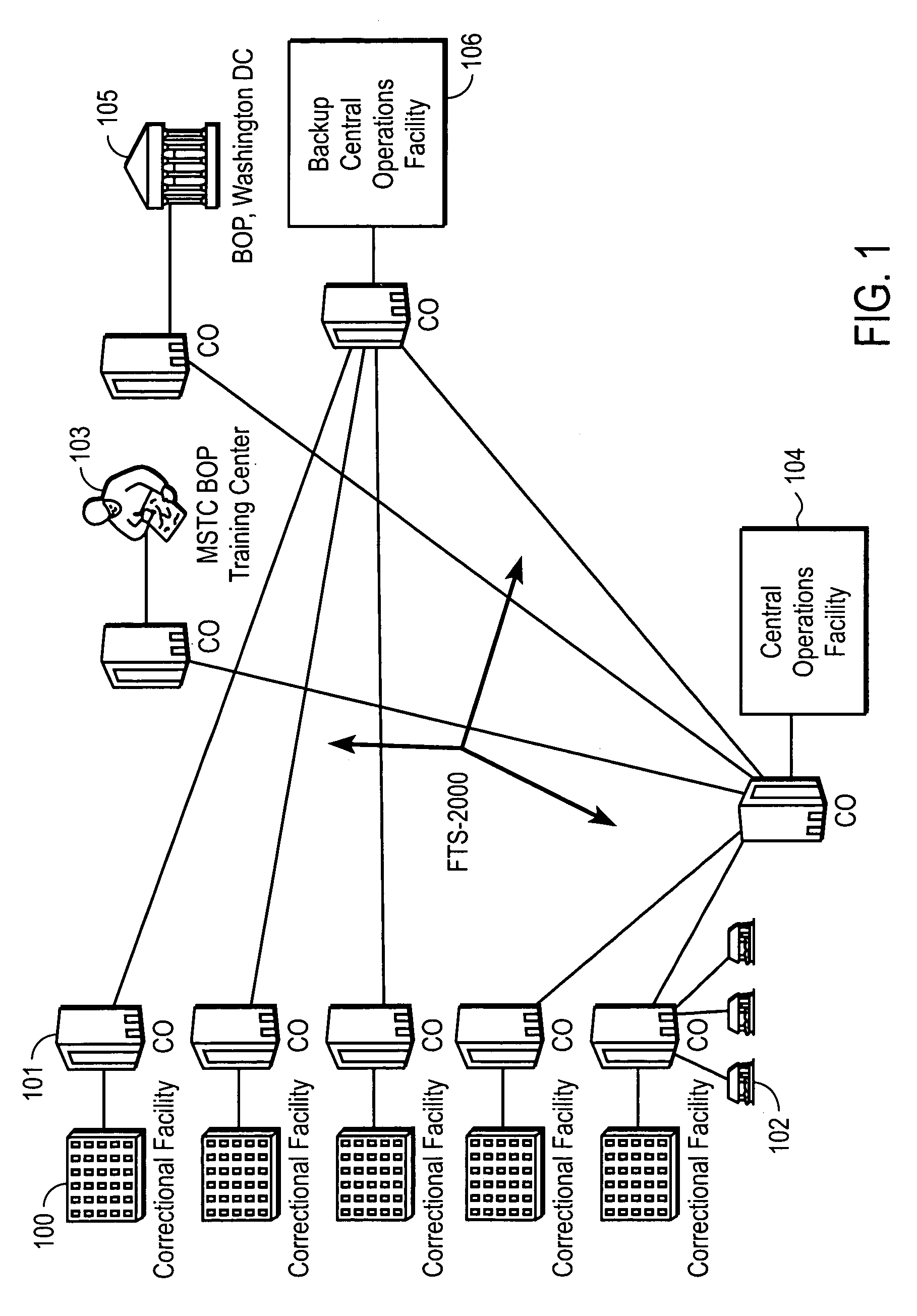
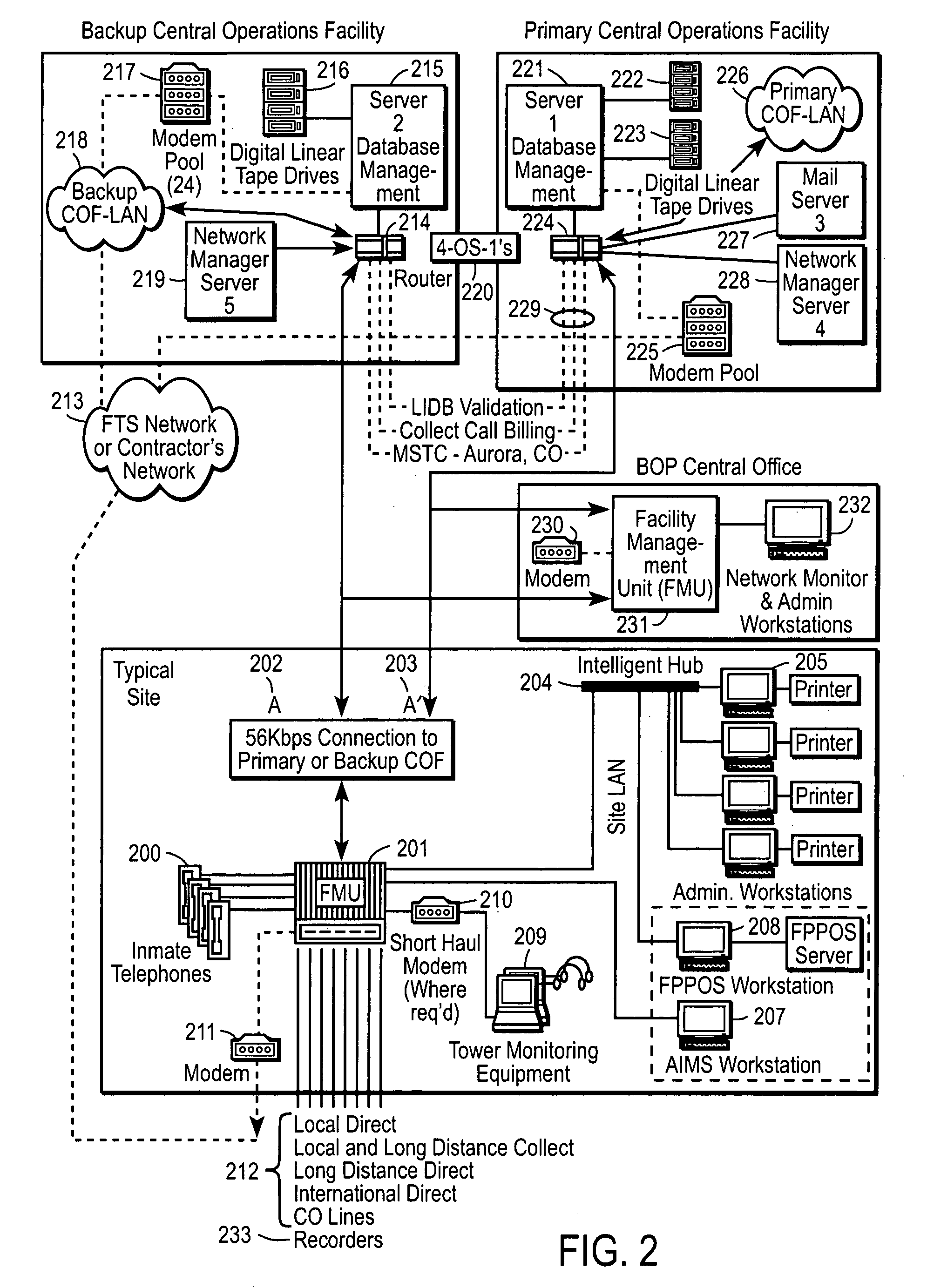
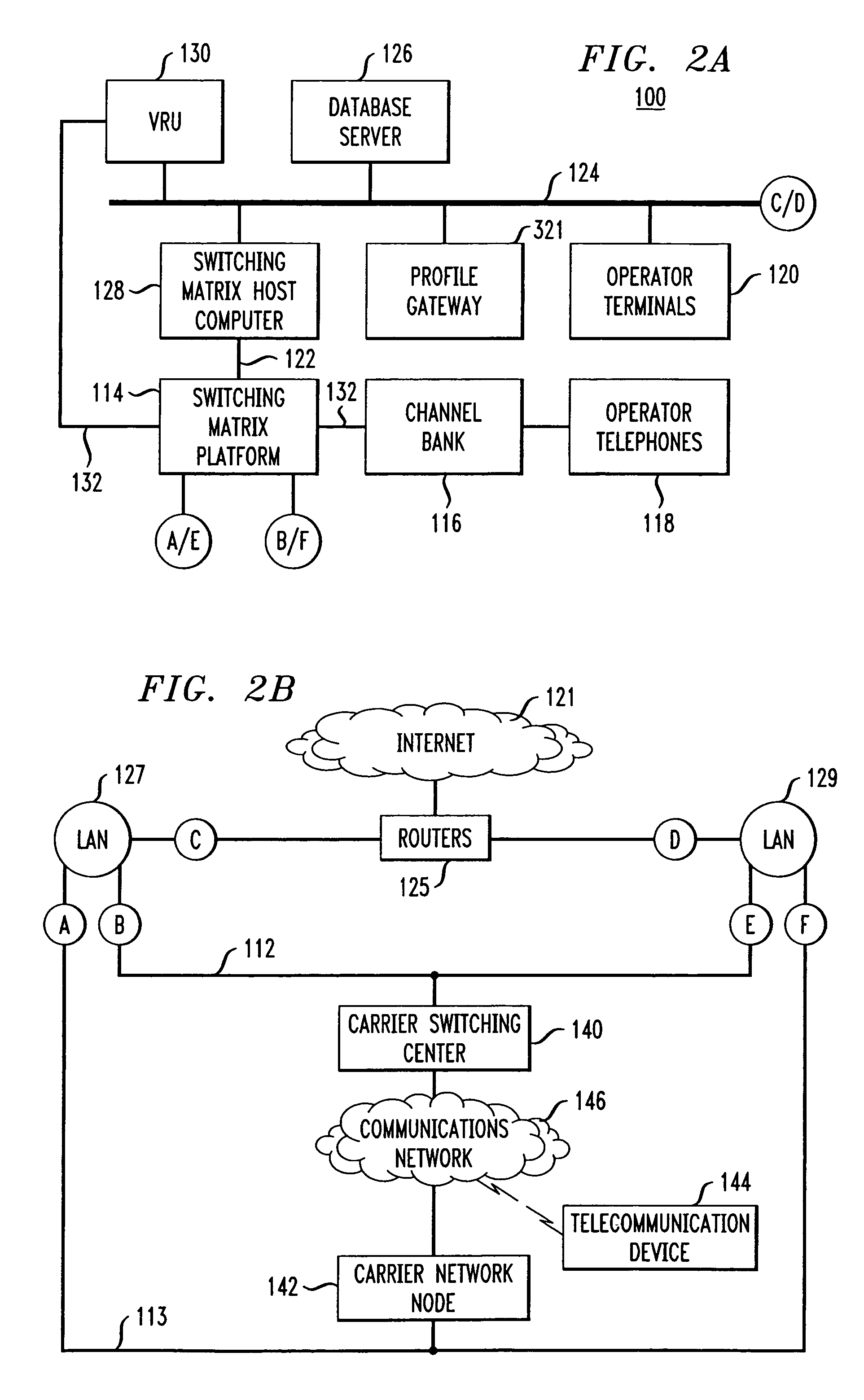
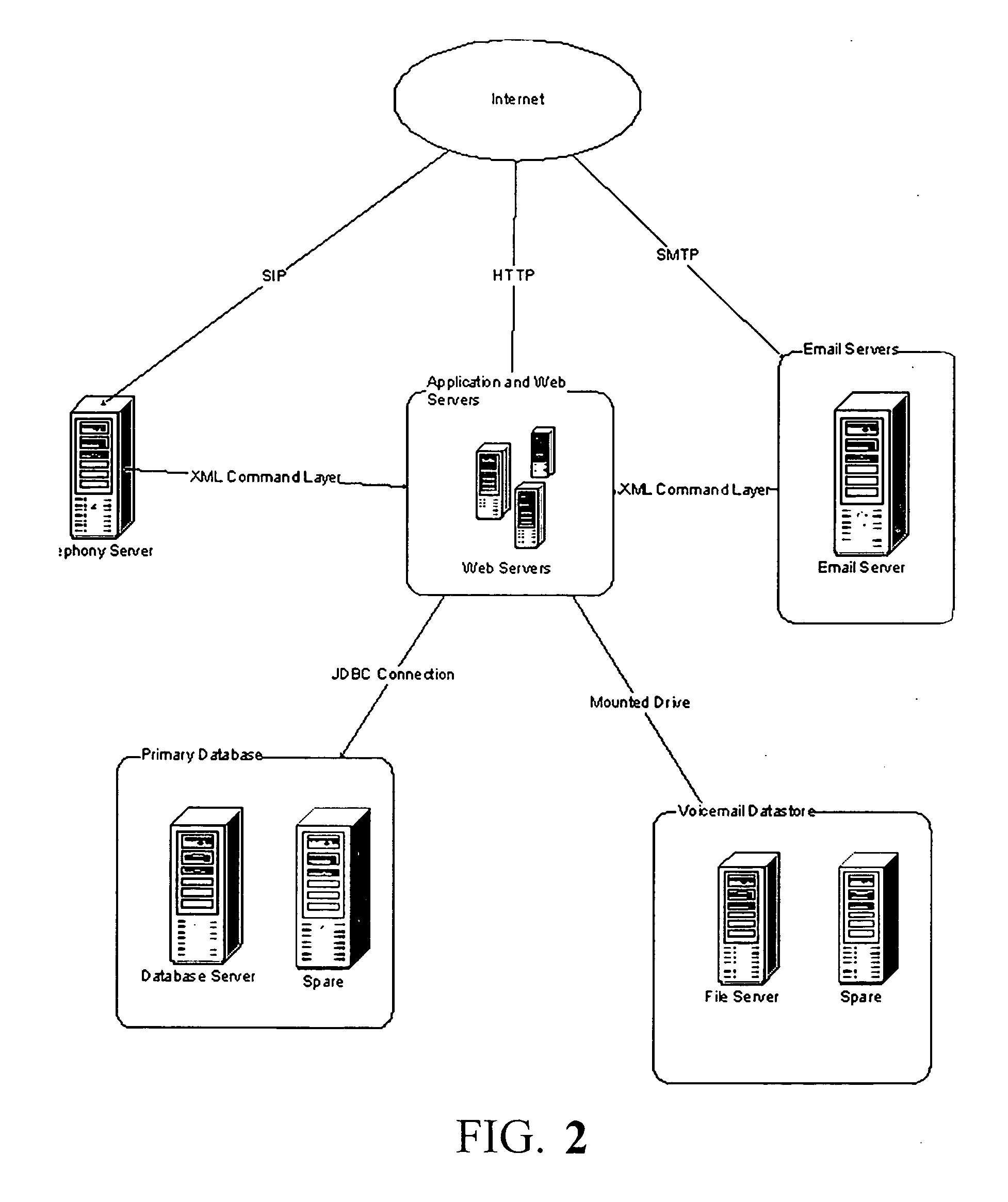
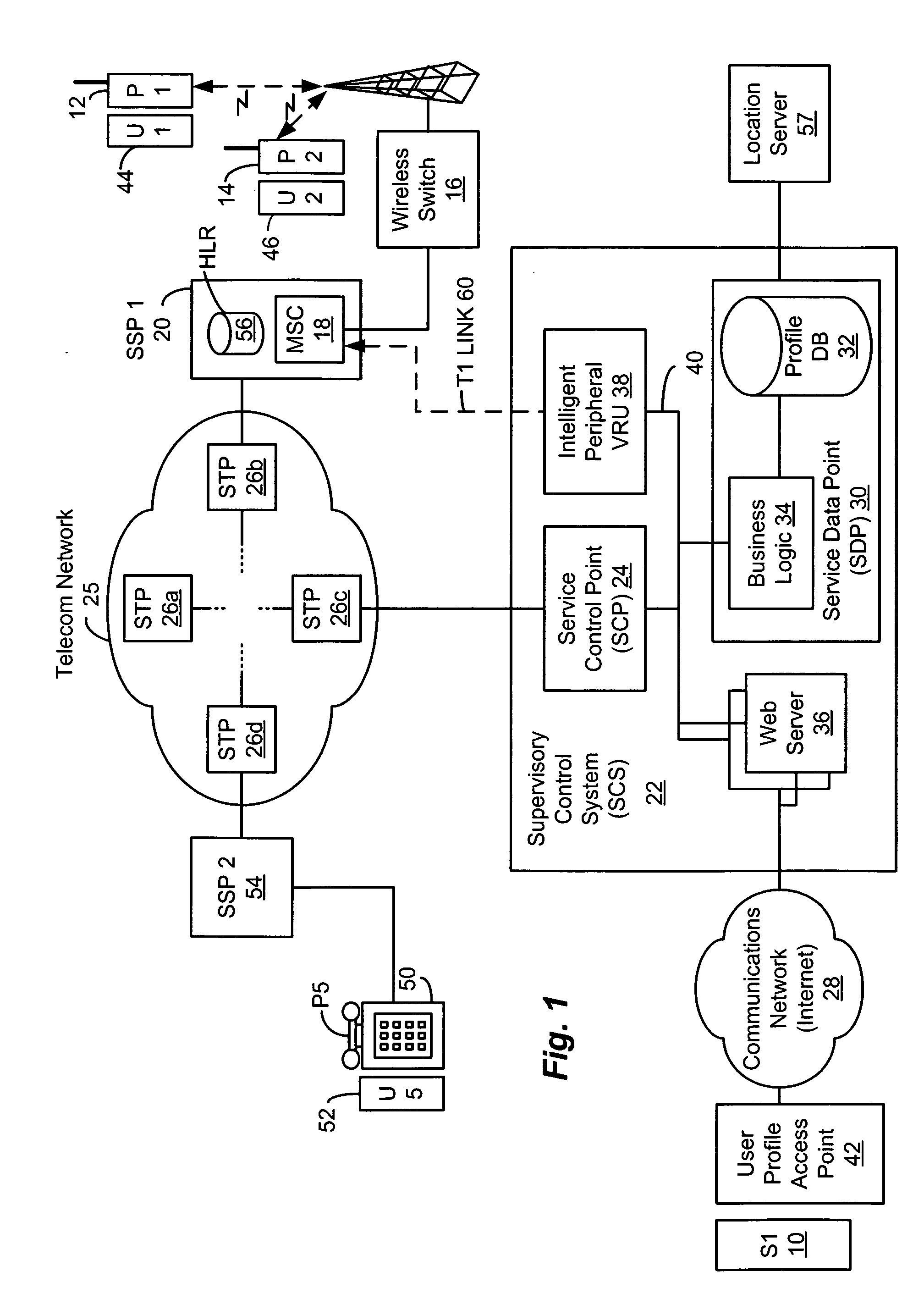
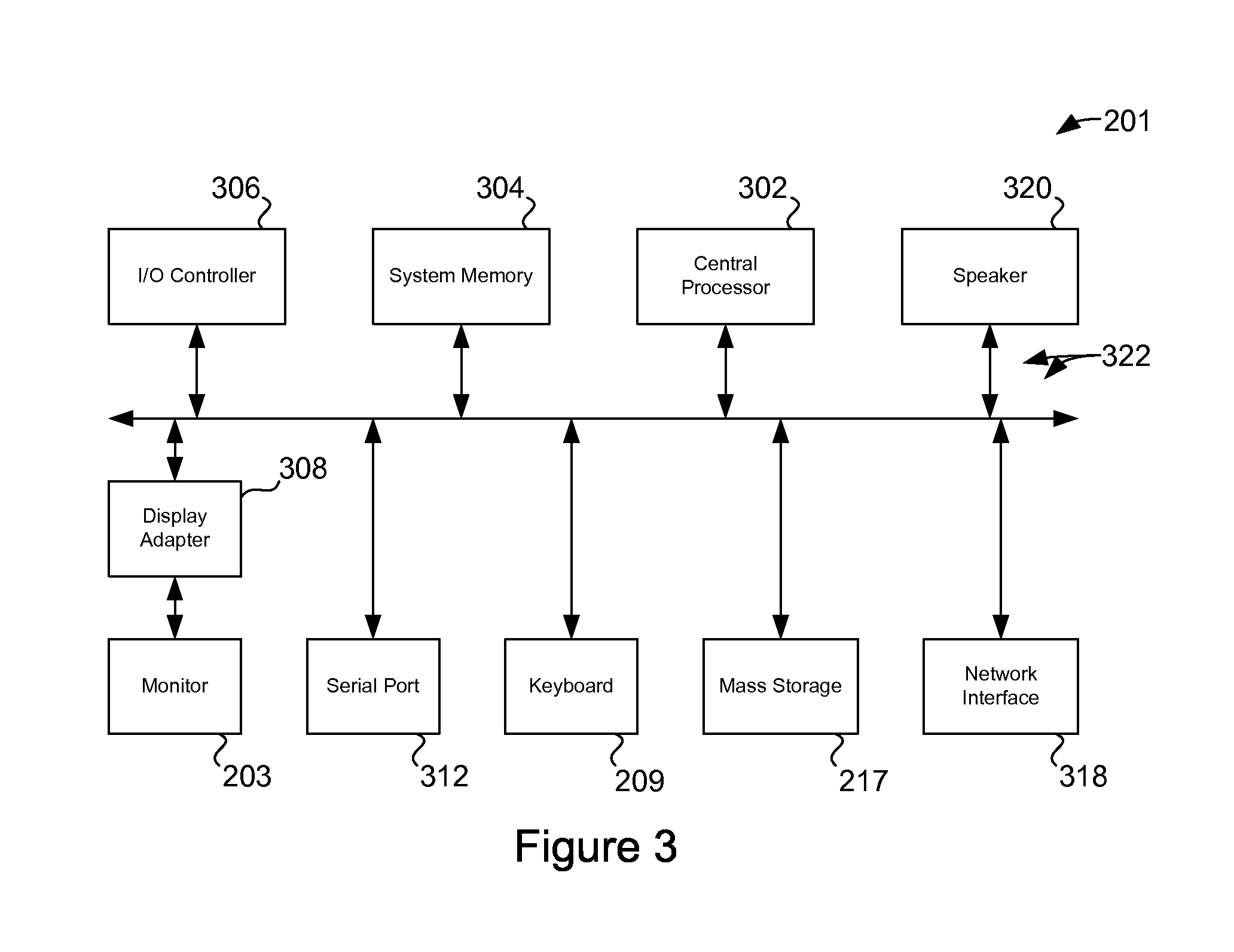
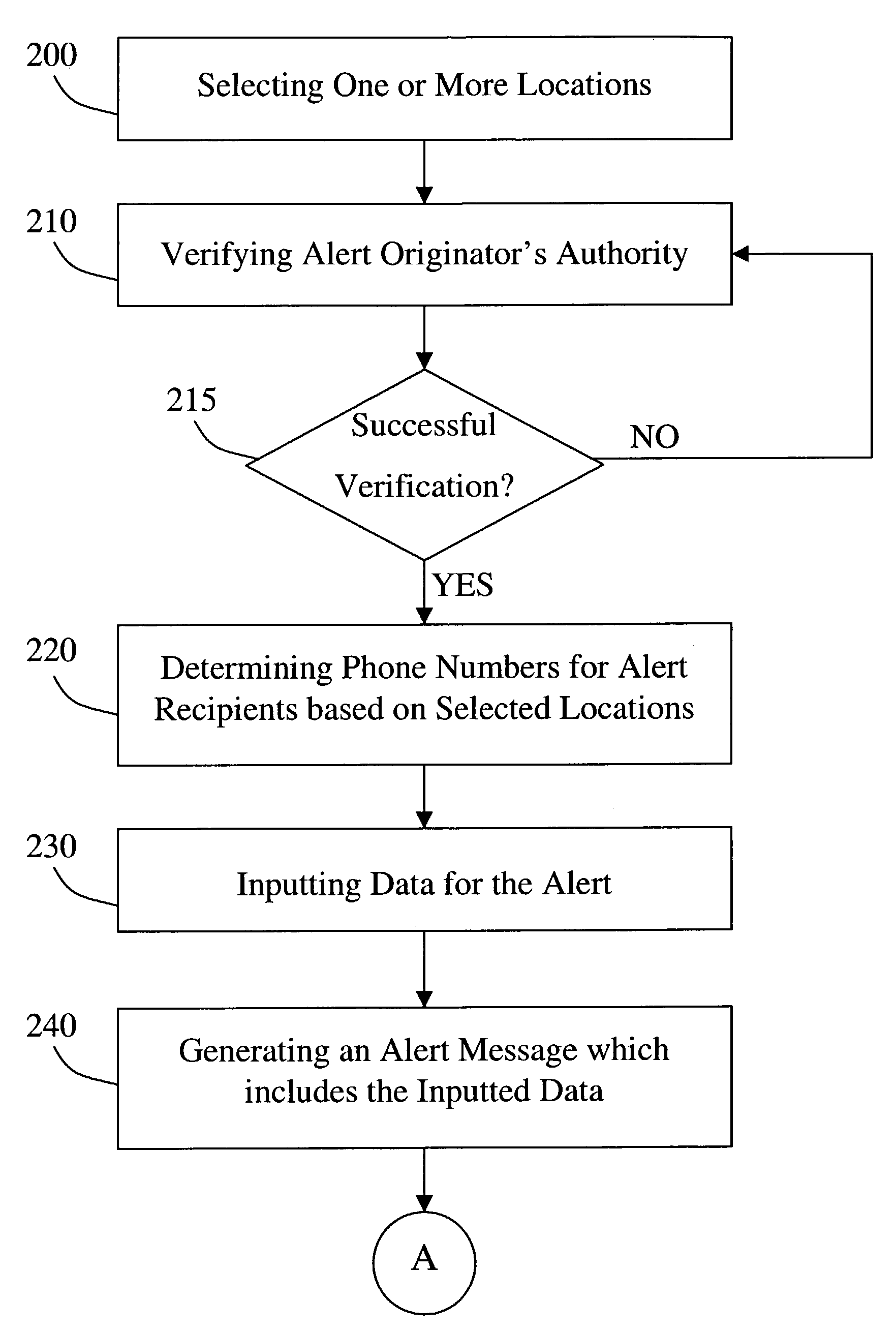
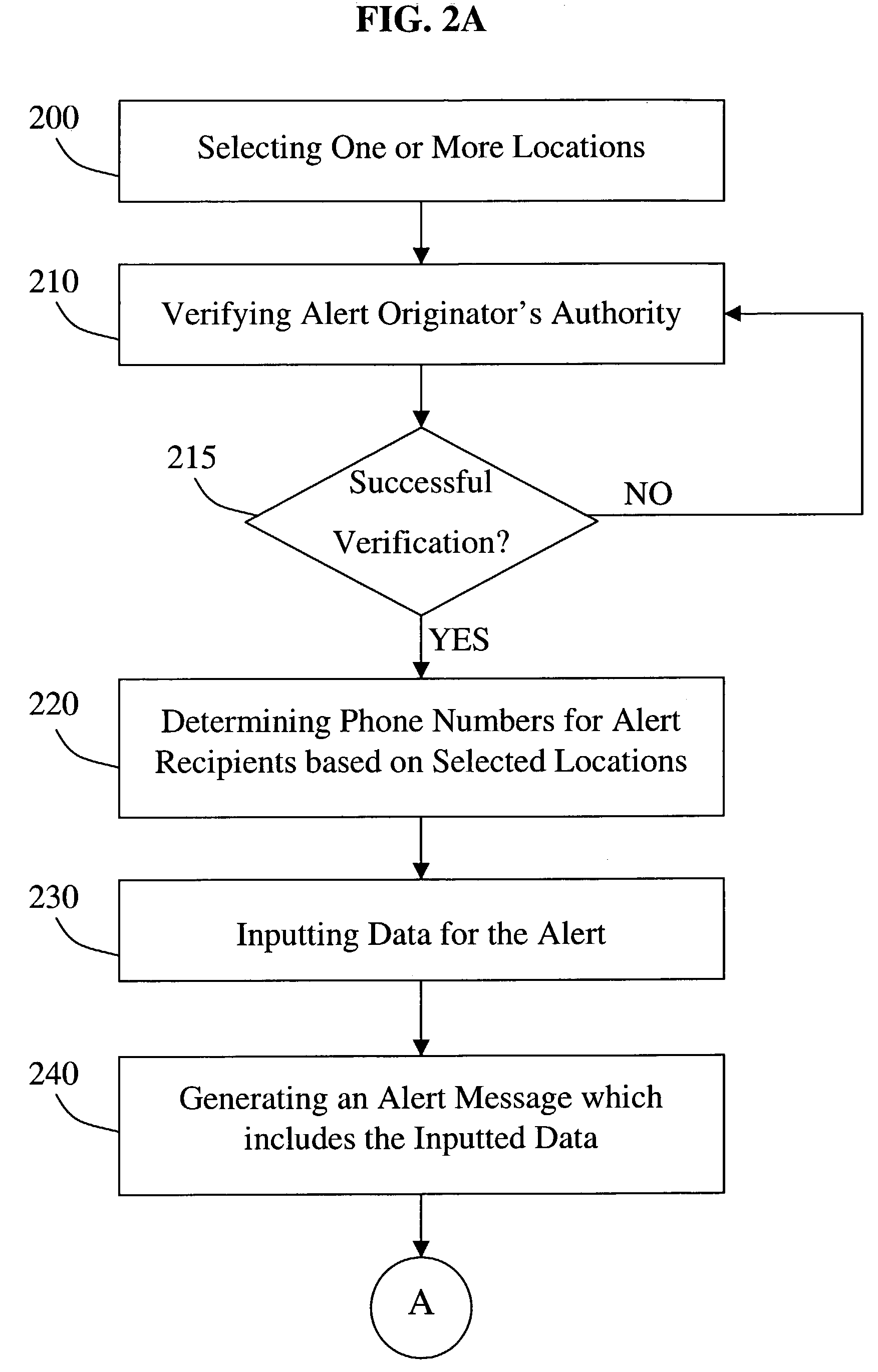
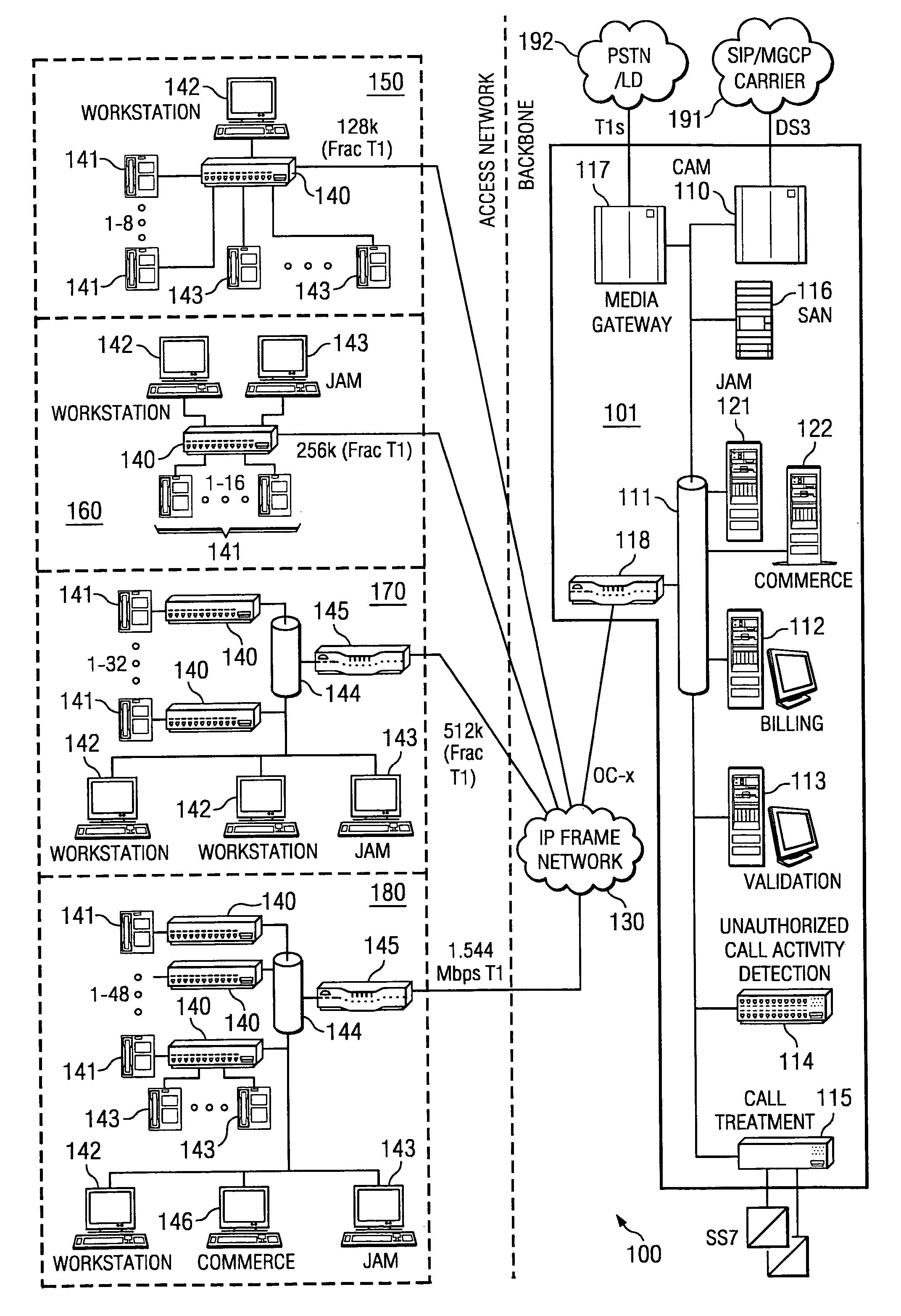
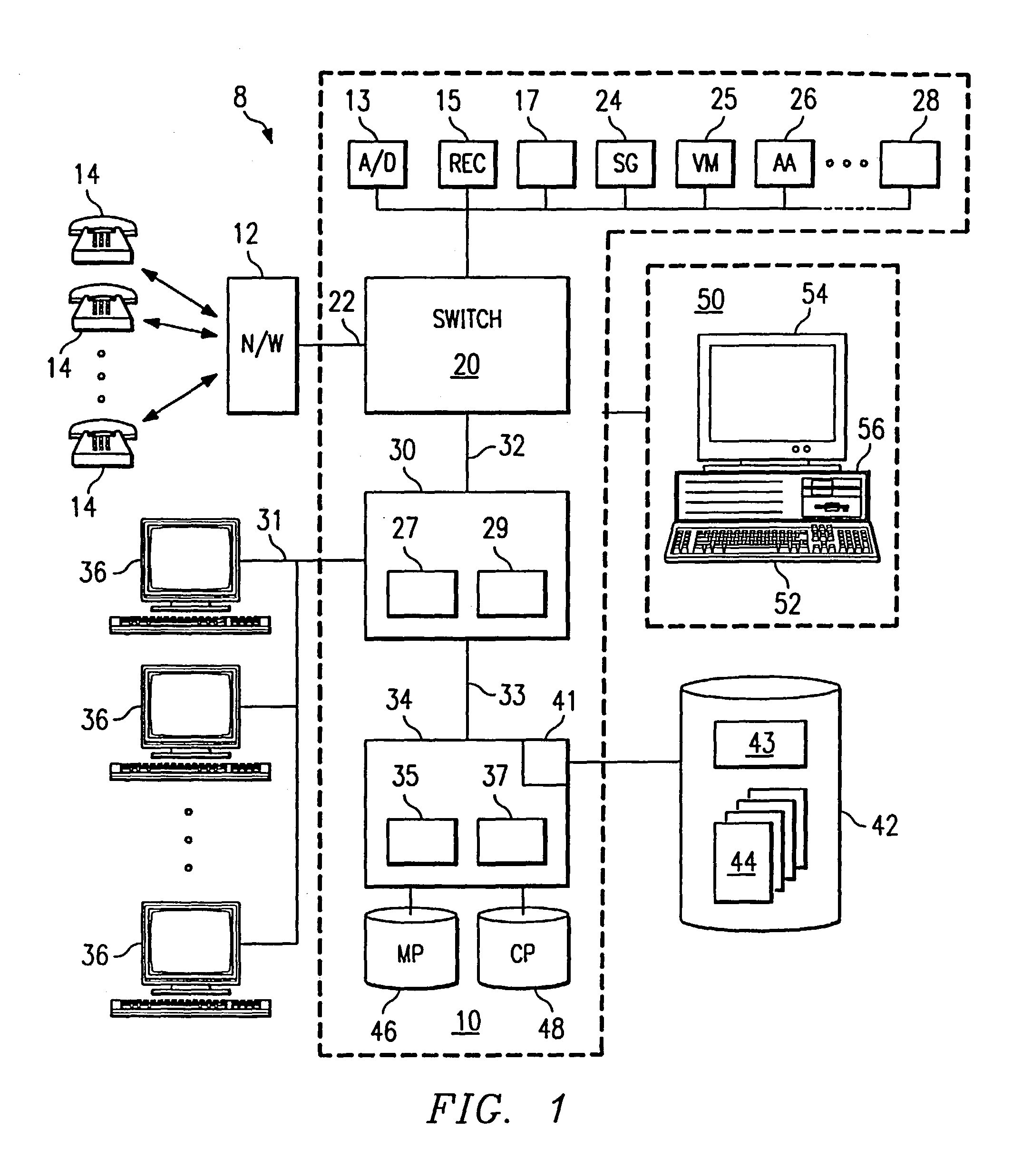
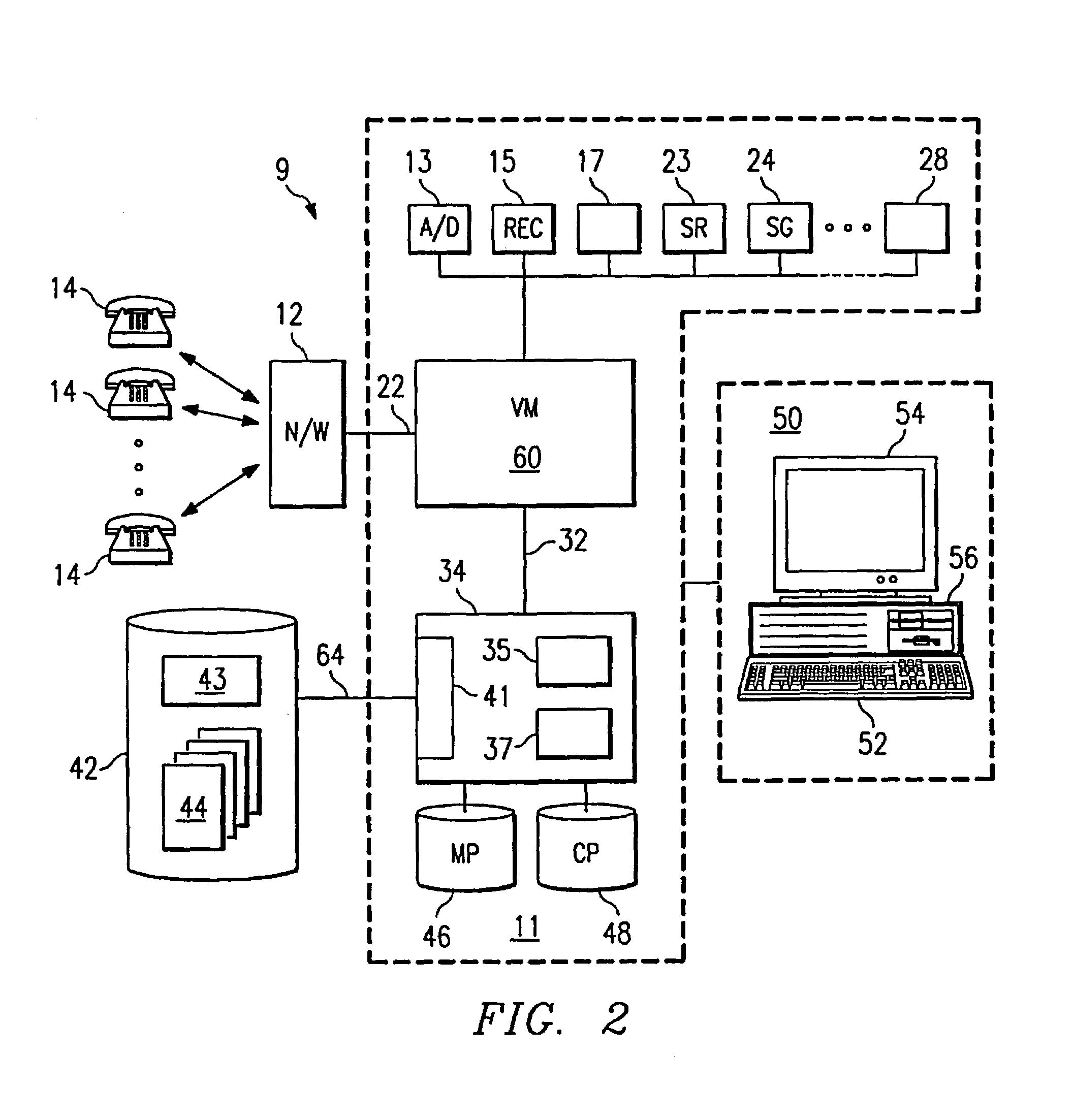
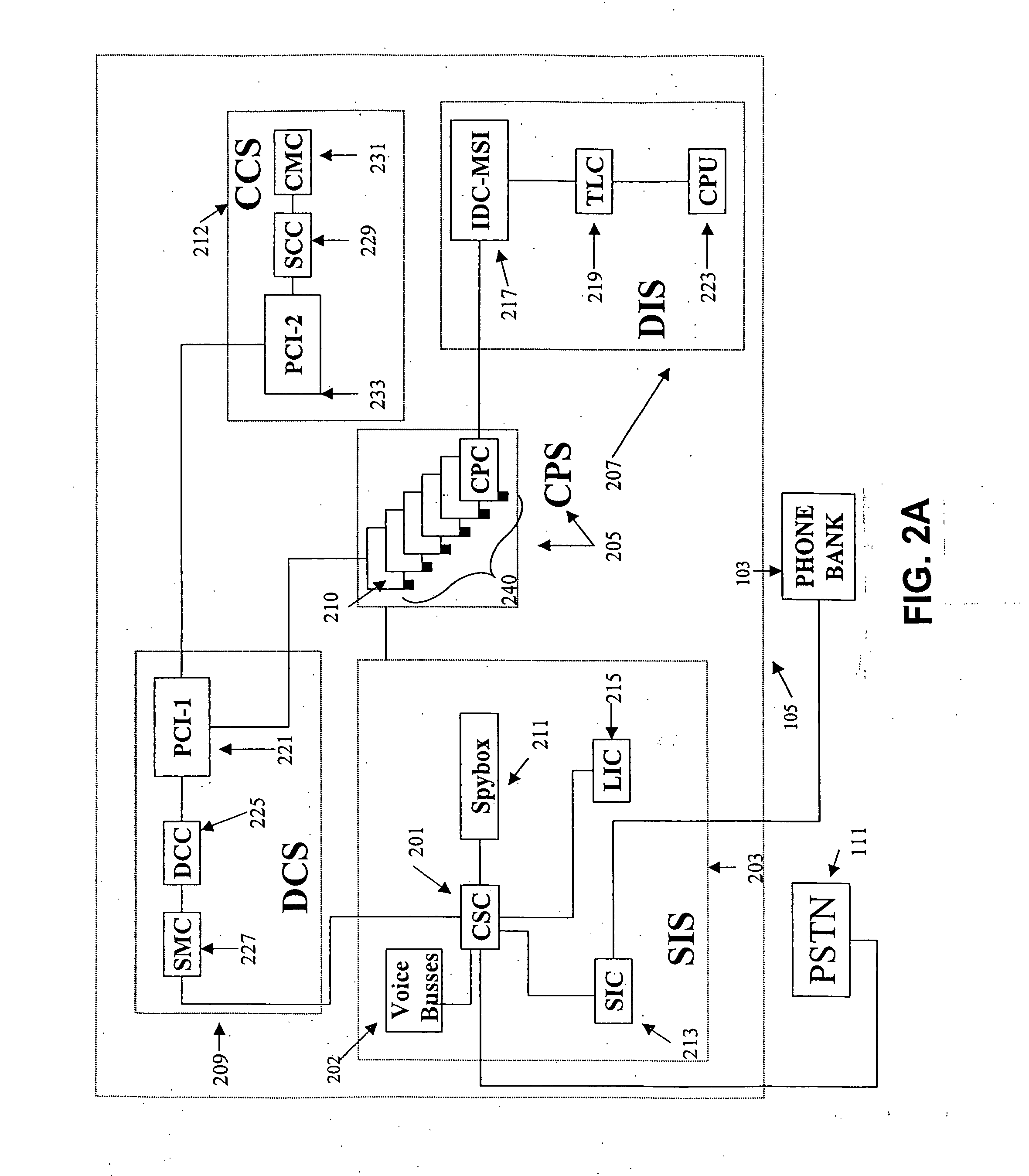
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
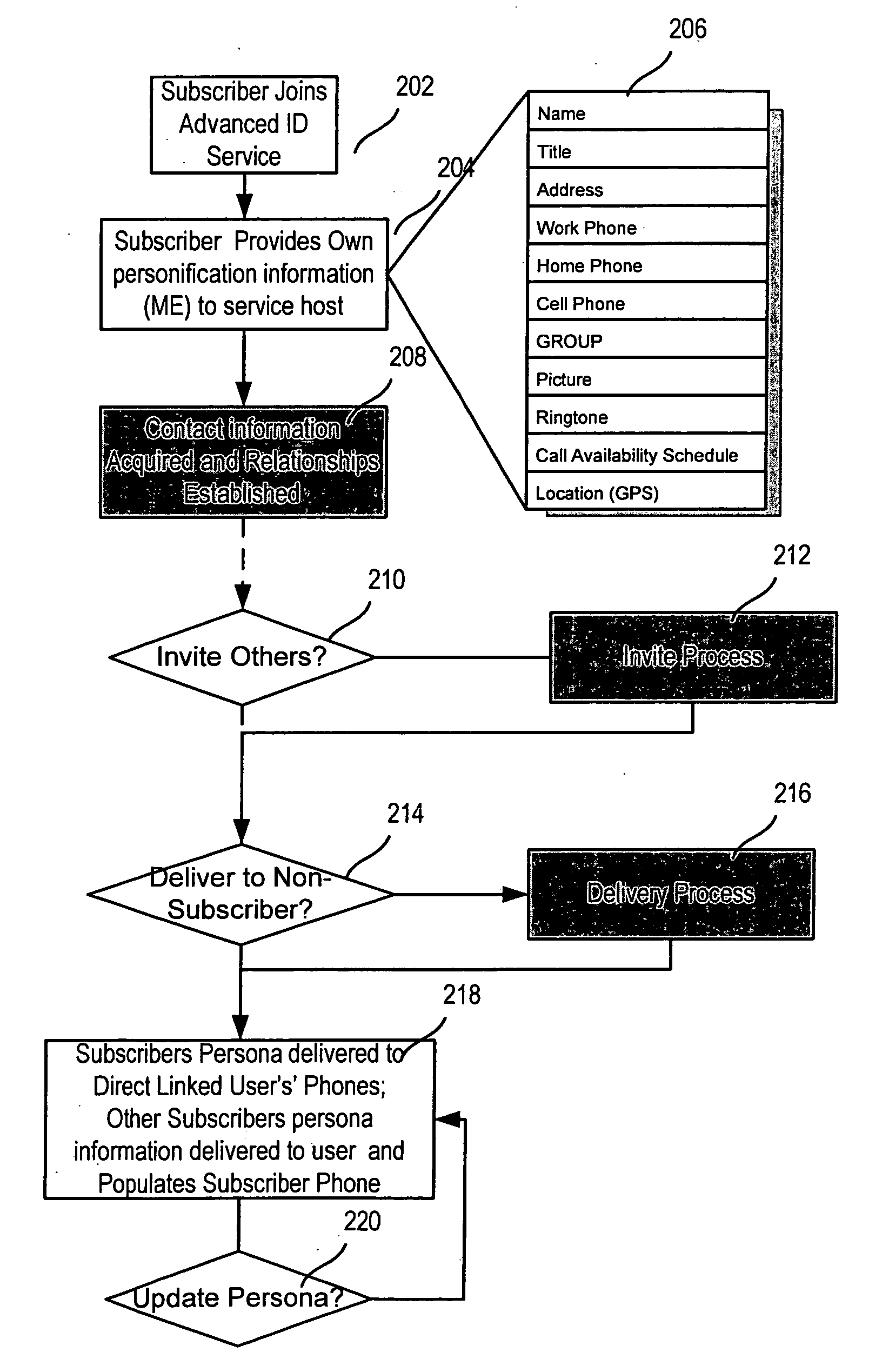
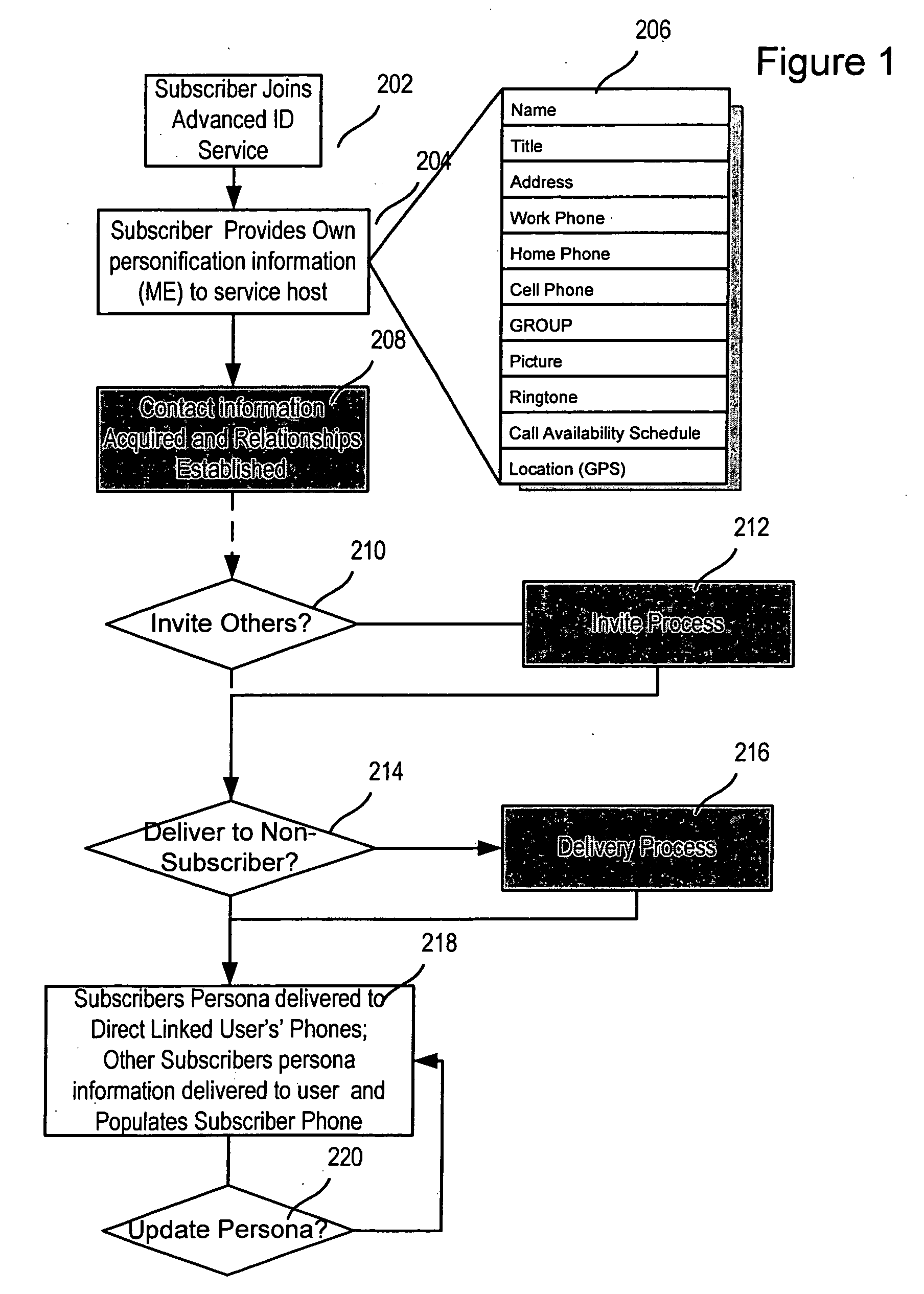
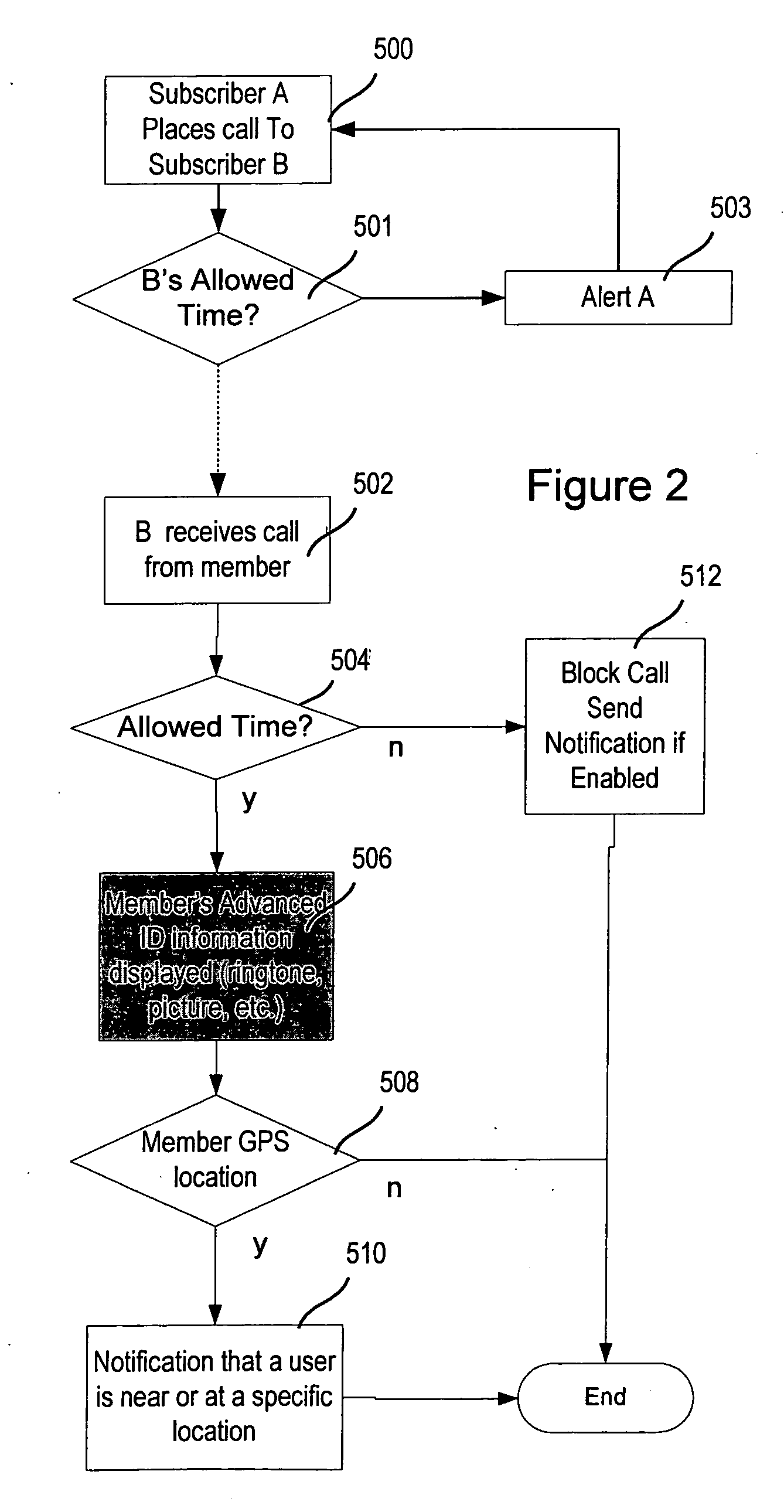
Advanced contact identification system
ActiveUS20060052091A1Special service for subscribersServices signallingAddress bookCommunication device
A system and method of advanced identification information to be created and distributed to users of wireless communication devices, such as mobile phones. Subscribers can define their own personas as collections of information which define the users. Subscribers can then publish their persona(s) to their friends' and associates' mobile phones, and update the others' address books with the subscriber's contact information. Users can specify different personas to be presented to different users.
Owner:SYNCHRONOSS TECH
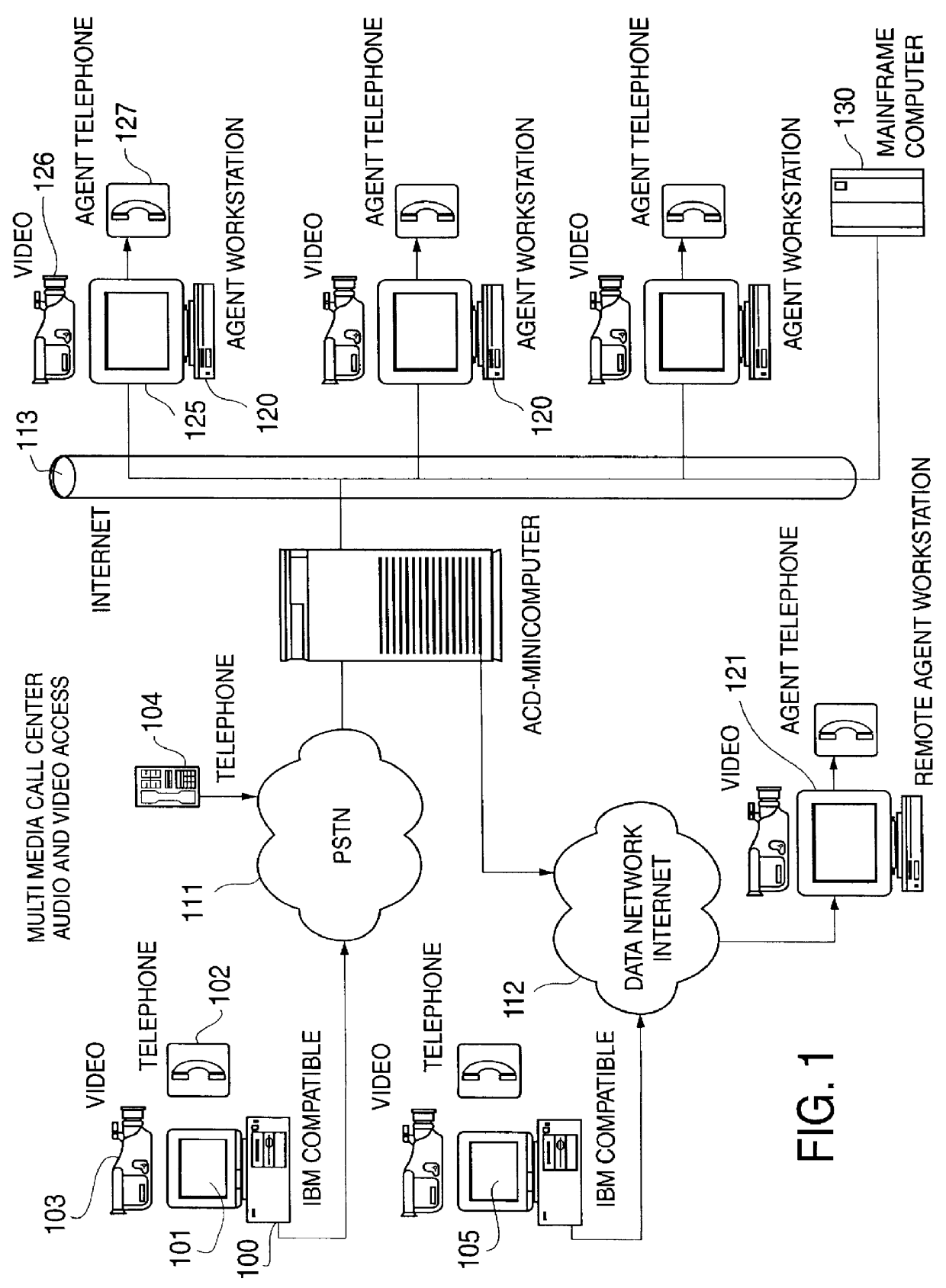
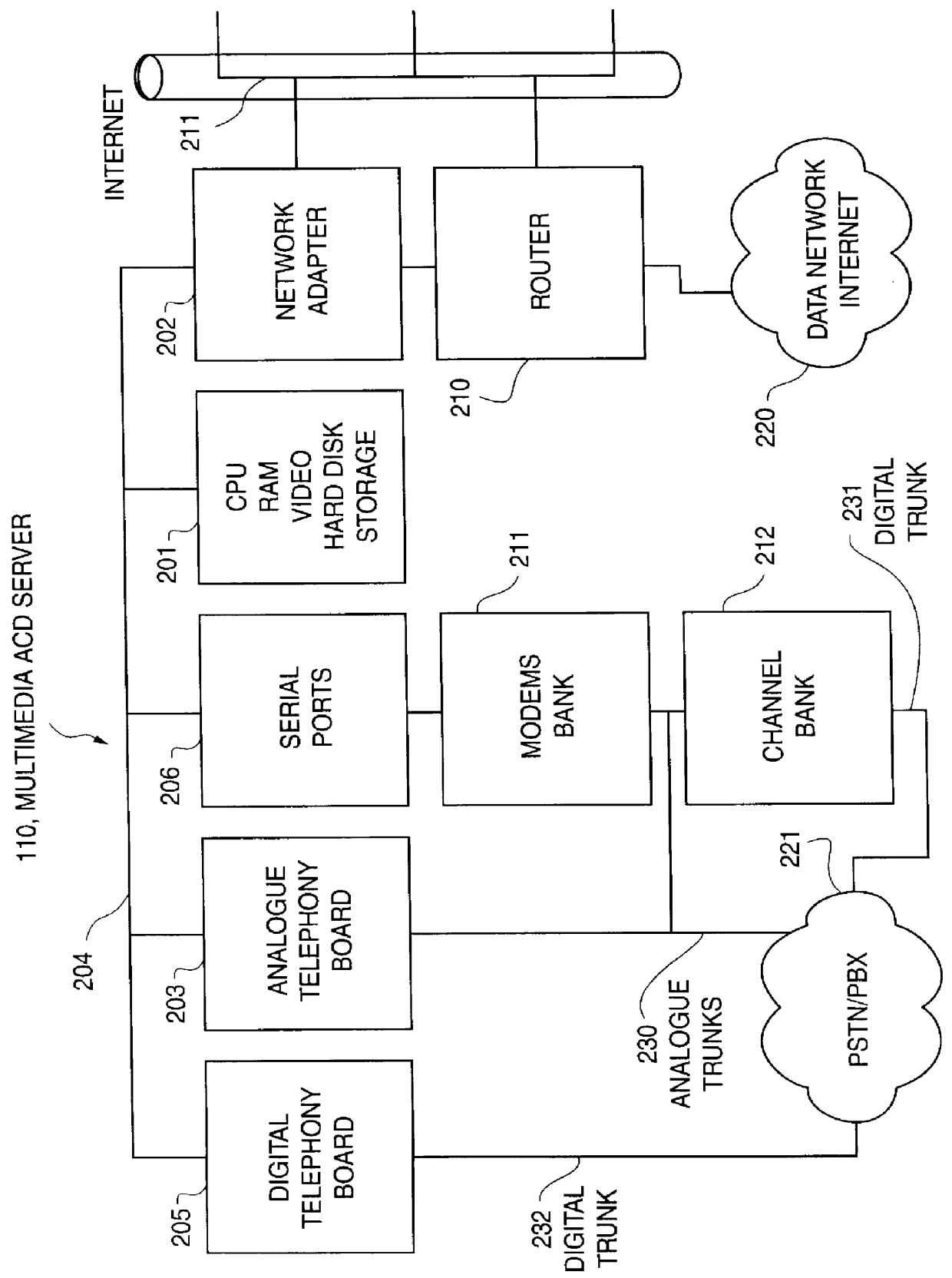
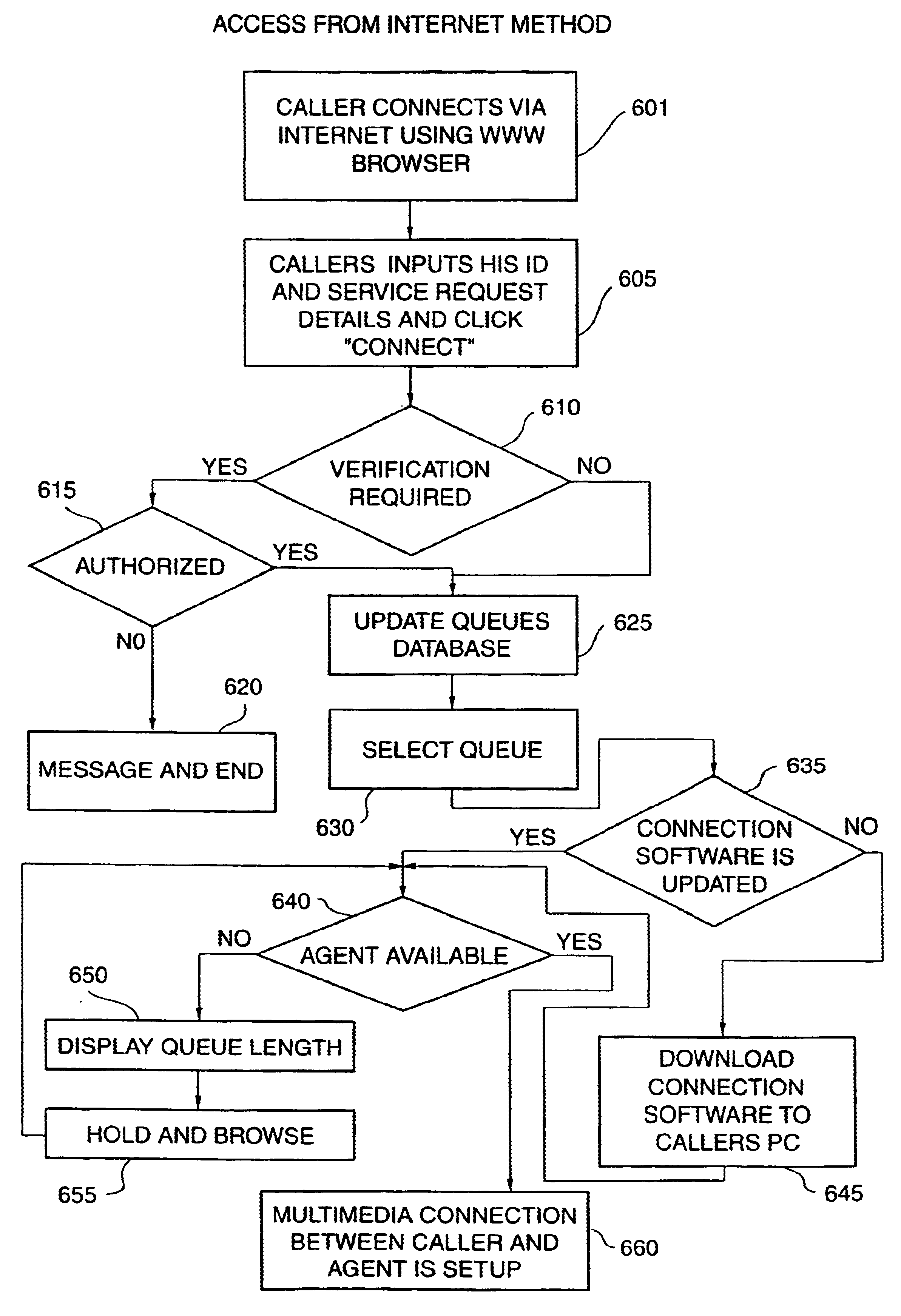
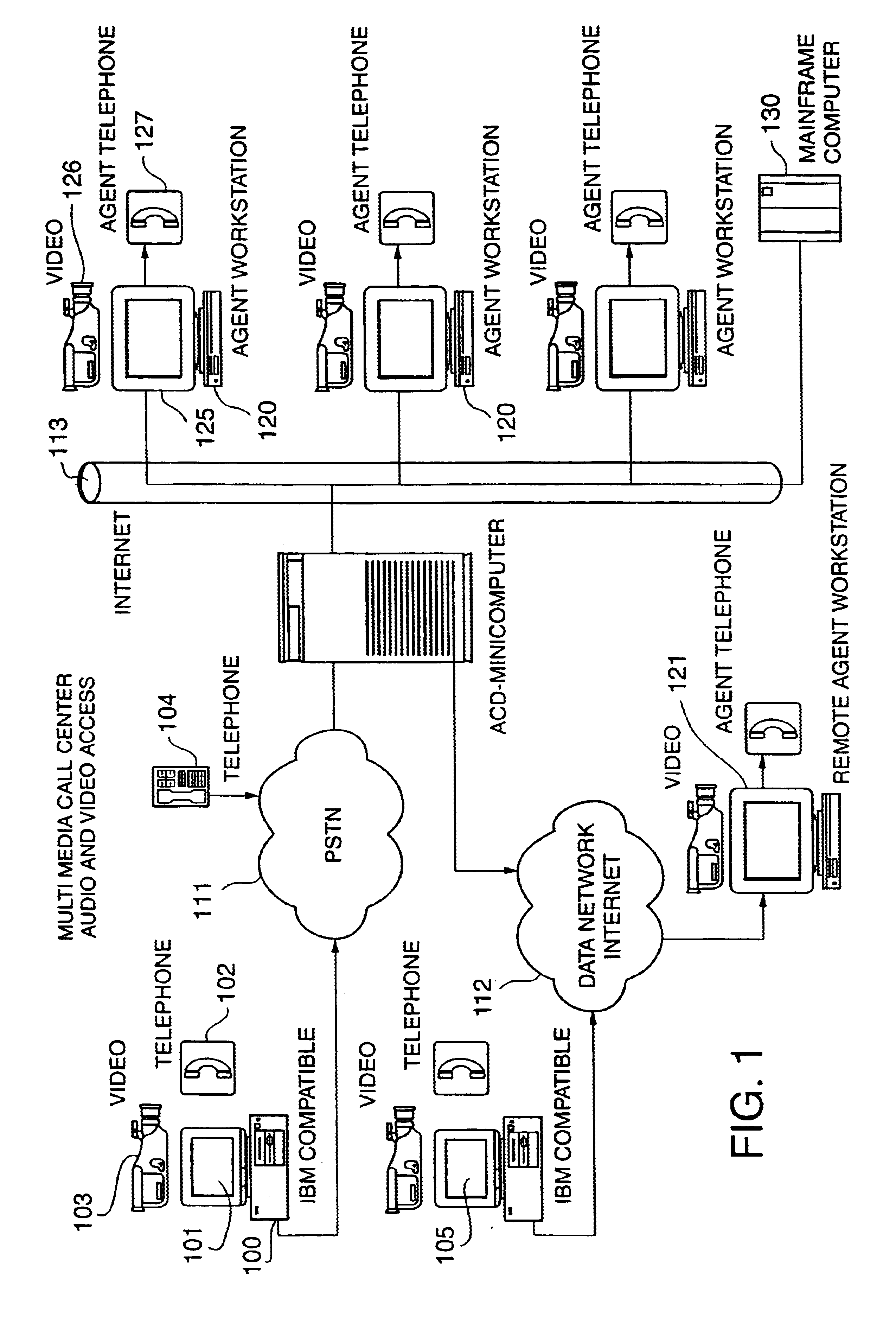
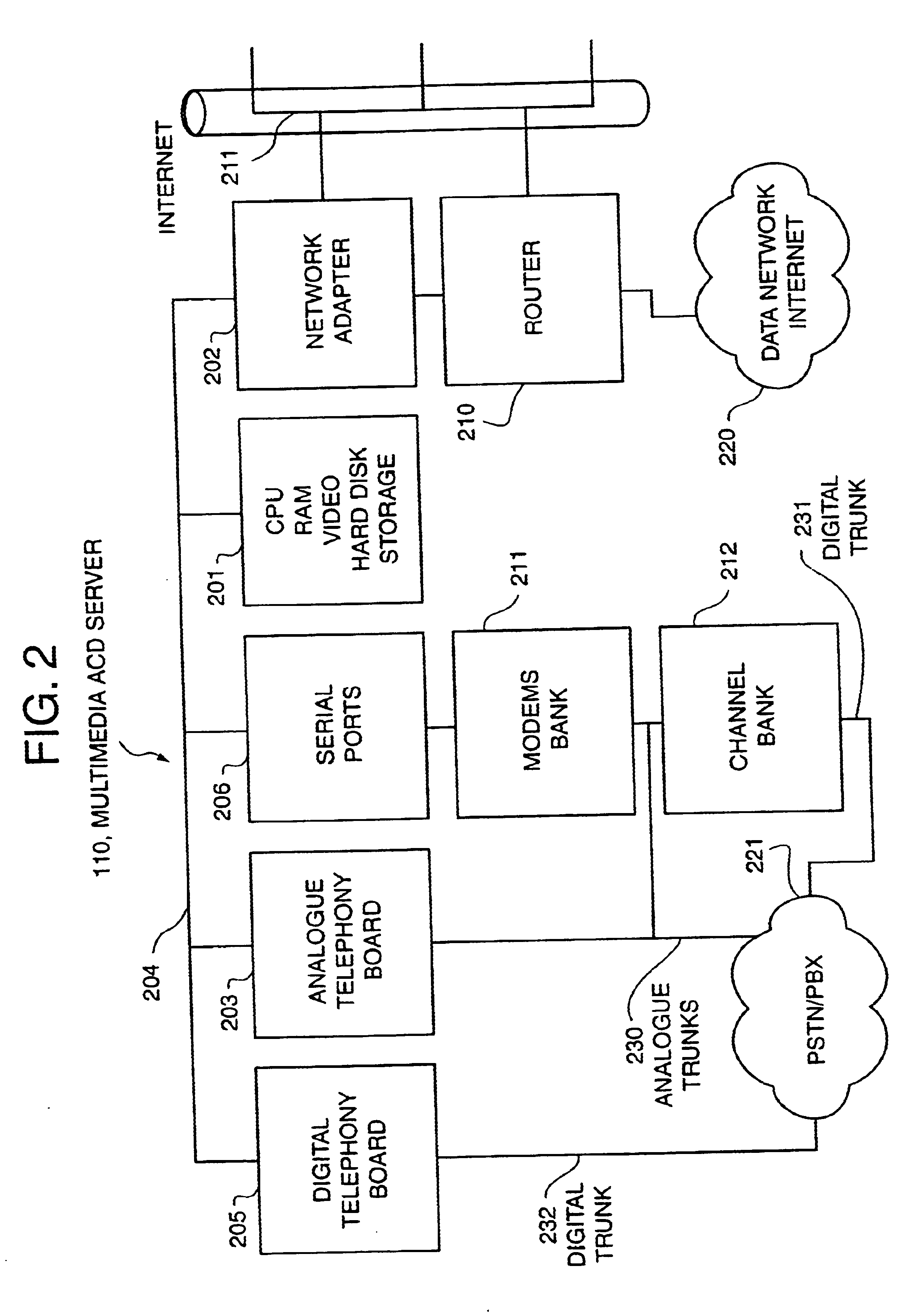
Multimedia telecommunication automatic call distribution system
InactiveUS6046762ATelevision system scanning detailsPicture reproducers using cathode ray tubesGeolocationConnection manager
A multimedia telecommunication automatic call distribution center which allows access to the call center via a plurality of access means, including telephone and data networks to provide simultaneous voice, data, and video access, and ensures effective transparent spreading of agents over different geographical locations. The automatic call distribution center of the present invention uses a multimedia automatic call distribution server acting as connection manager for data network callers and provides for automatic caller identification.
Owner:COSMO INC
System and method for the creation and automatic deployment of personalized, dynamic and interactive inbound and outbound voice services, with real-time interactive voice database queries
InactiveUS6885734B1Convenient transactionProvide informationData processing applicationsAutomatic call-answering/message-recording/conversation-recordingDatabase queryService bureau
The interactive delivery of voice serve messages communicating financial, personal or other news telecasts can be accessed at a subscriber's convenience on an inbound telephone, network enabled or other call. A voice service bureau may generate voice messages for individual subscribers according to their natural language queries. For instance, a subscriber may inquire “What was the closing Dow today” and the system converts the request to digital form, discriminates search terms, interrogates a database and annunciates to the call “The closing Dow was 11,000 today”. Responses to those or other inquiries may be delivered in real time or substantially real time.
Owner:MICROSTRATEGY
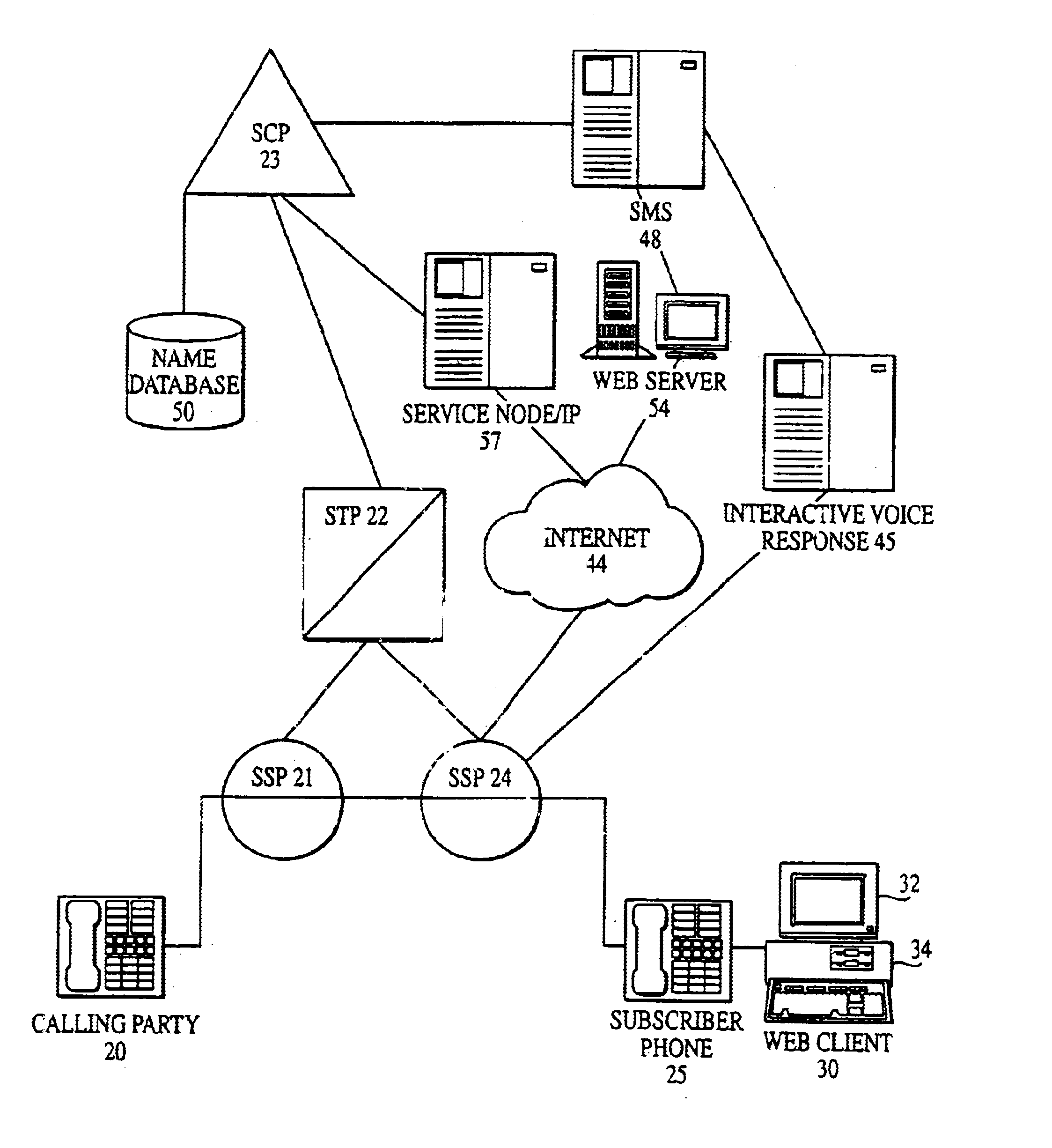
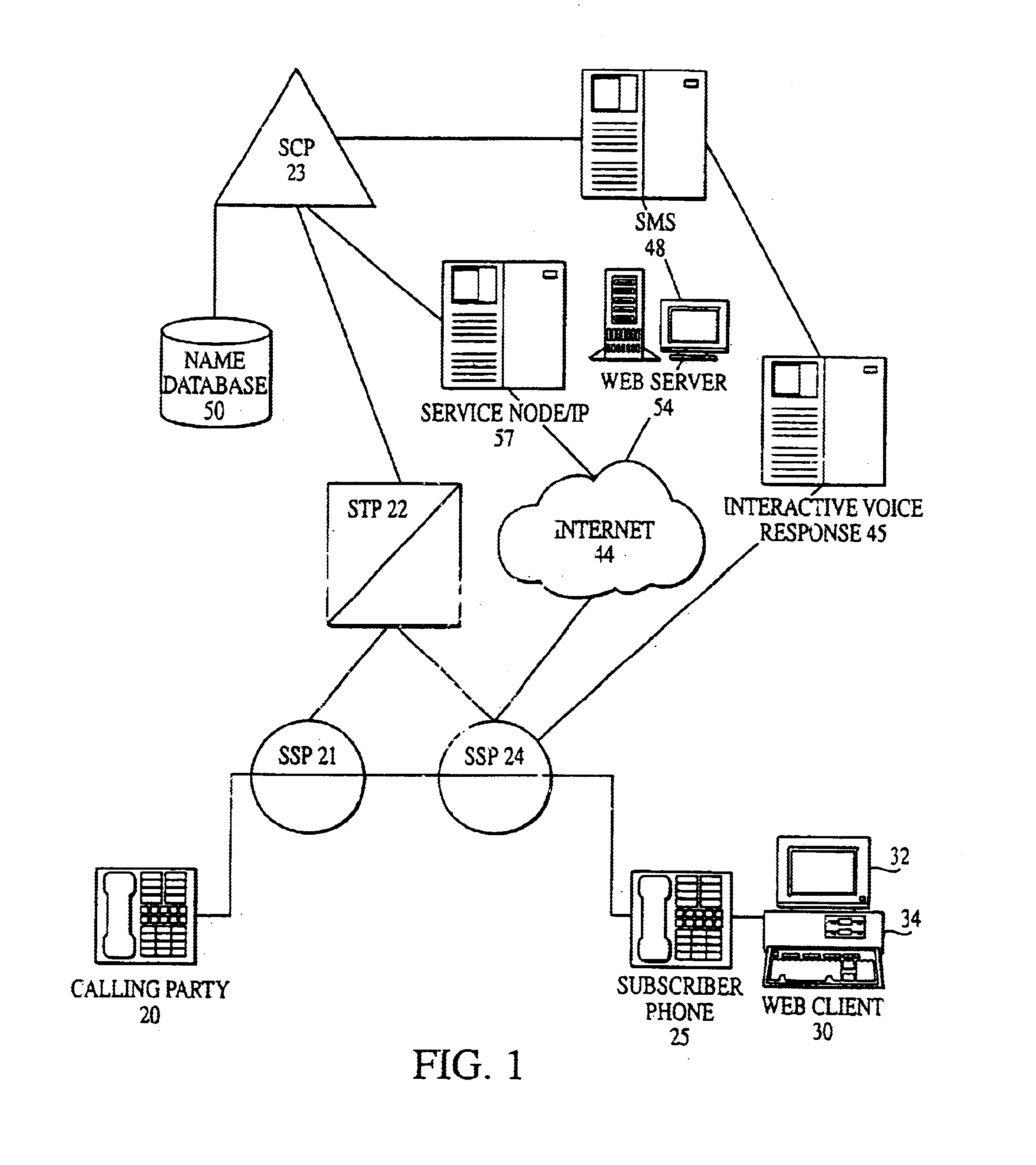
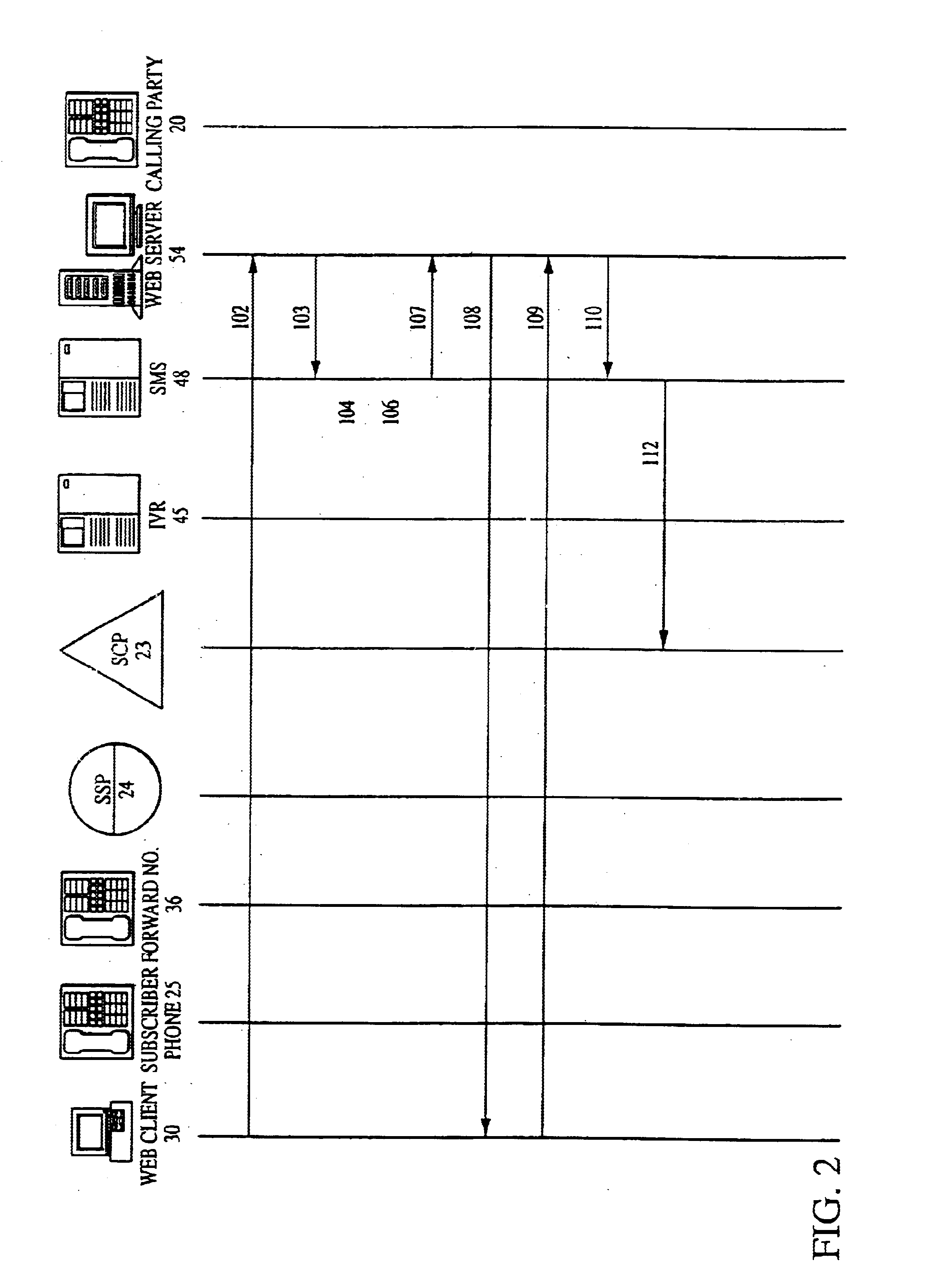
System and method for implementing and accessing call forwarding services
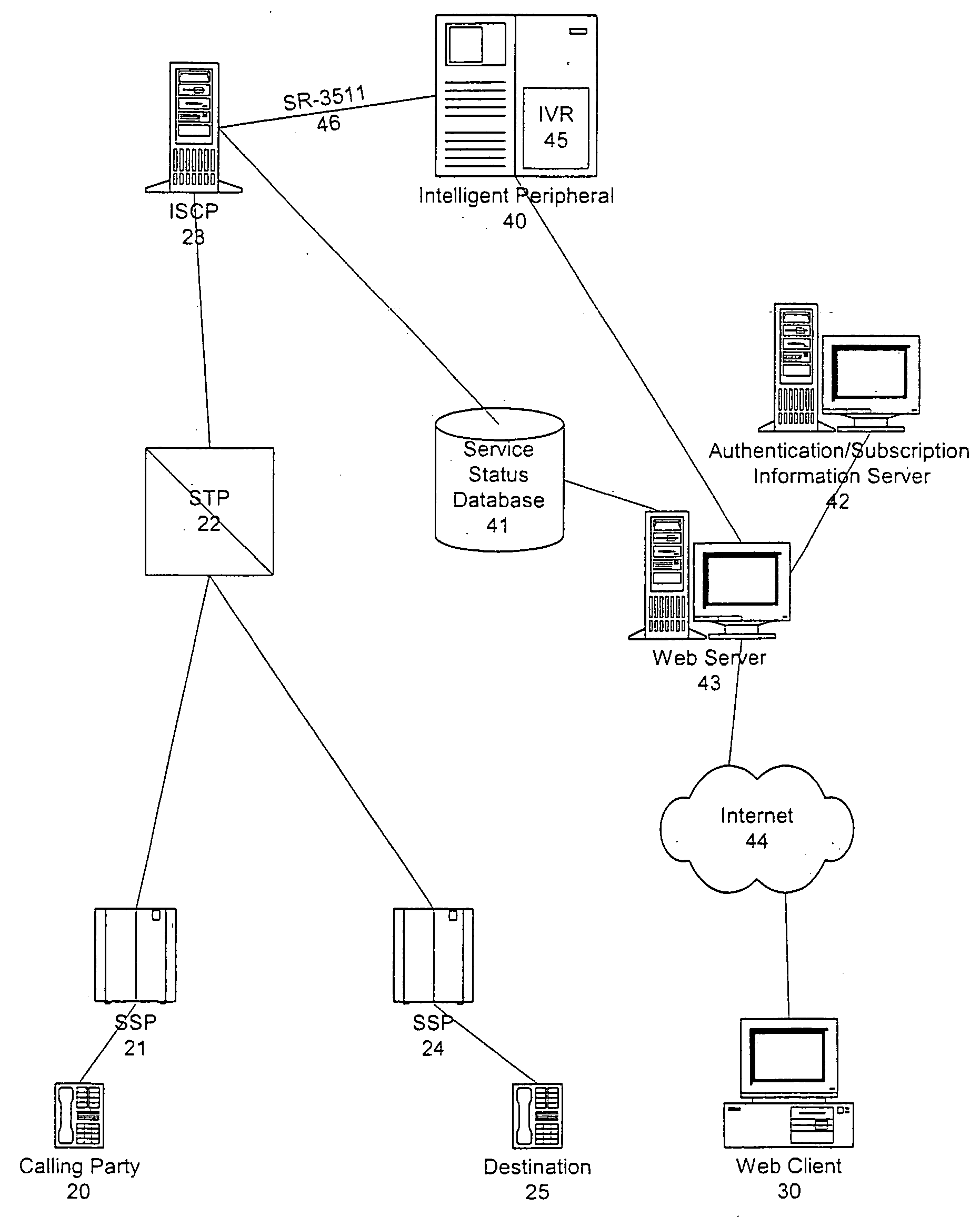
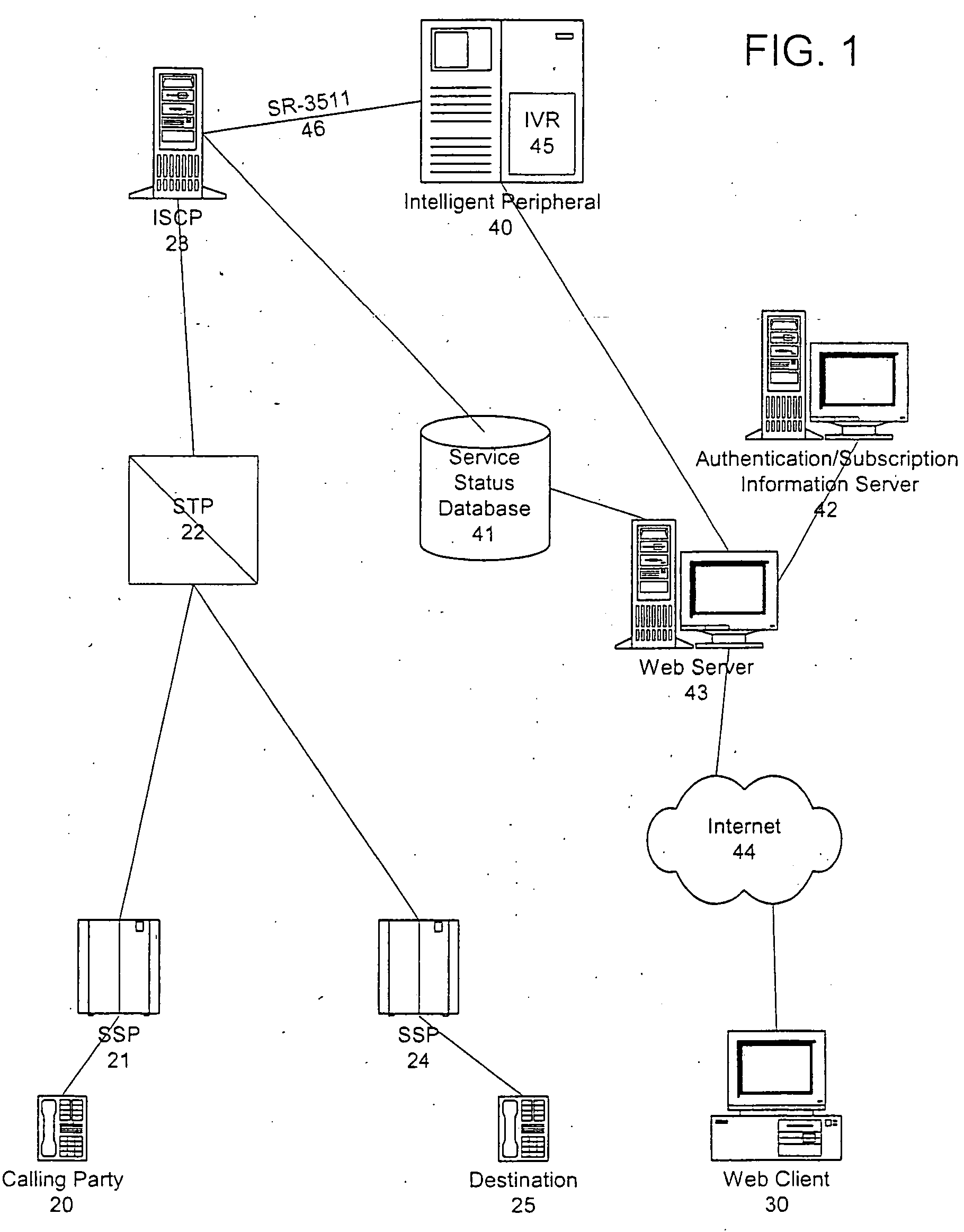
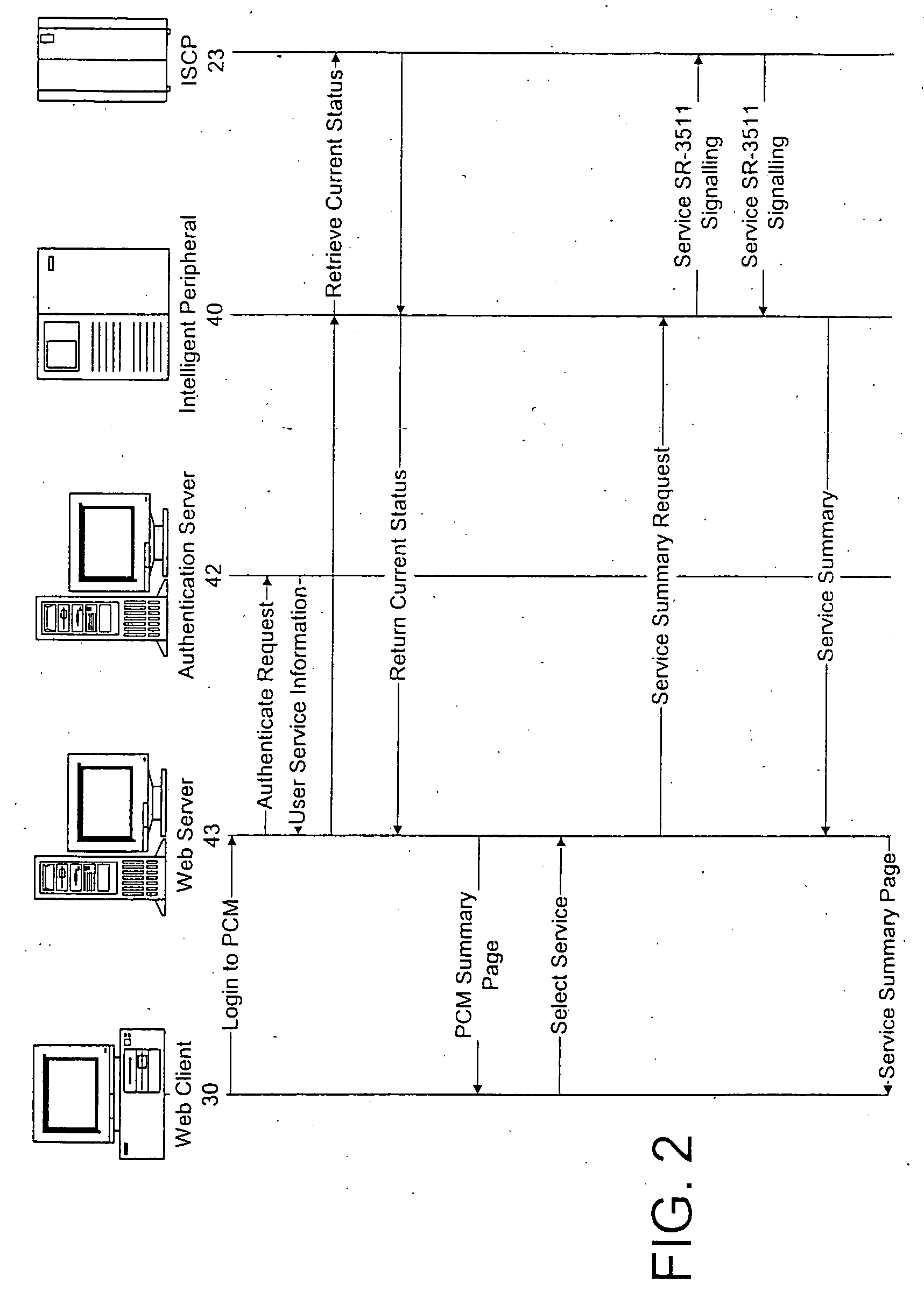
A system and method include implementing and accessing a subscriber's telecommunications services, using a graphical user interface (GUI) via the Internet, and an interactive voice response (IVR) system via the public switched telecommunications network (PSTN). The system and method enable a subscriber to review, schedule and modify call forwarding information stored and implemented by a service control-point (SCP) through a common server from any dual tone multi-frequency (DTMF) telephone and IVR system via the PSTN or any GUI and Web client via the Internet. The subscriber is able to build and edit call forwarding data, such as a scheduler and priority and rejection screening lists, by the GUI via the Internet for subsequent implementation.
Owner:AT&T LABS
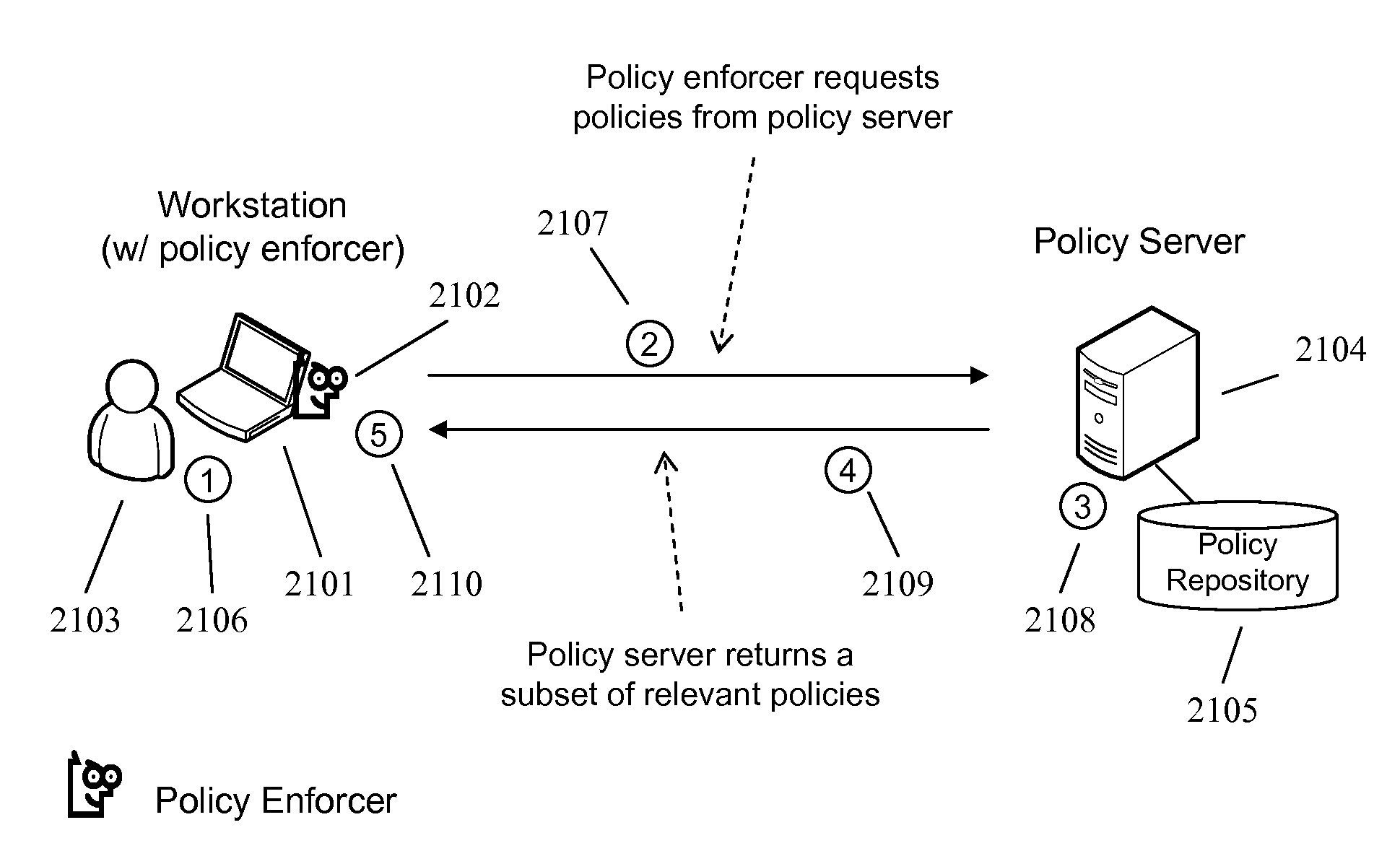
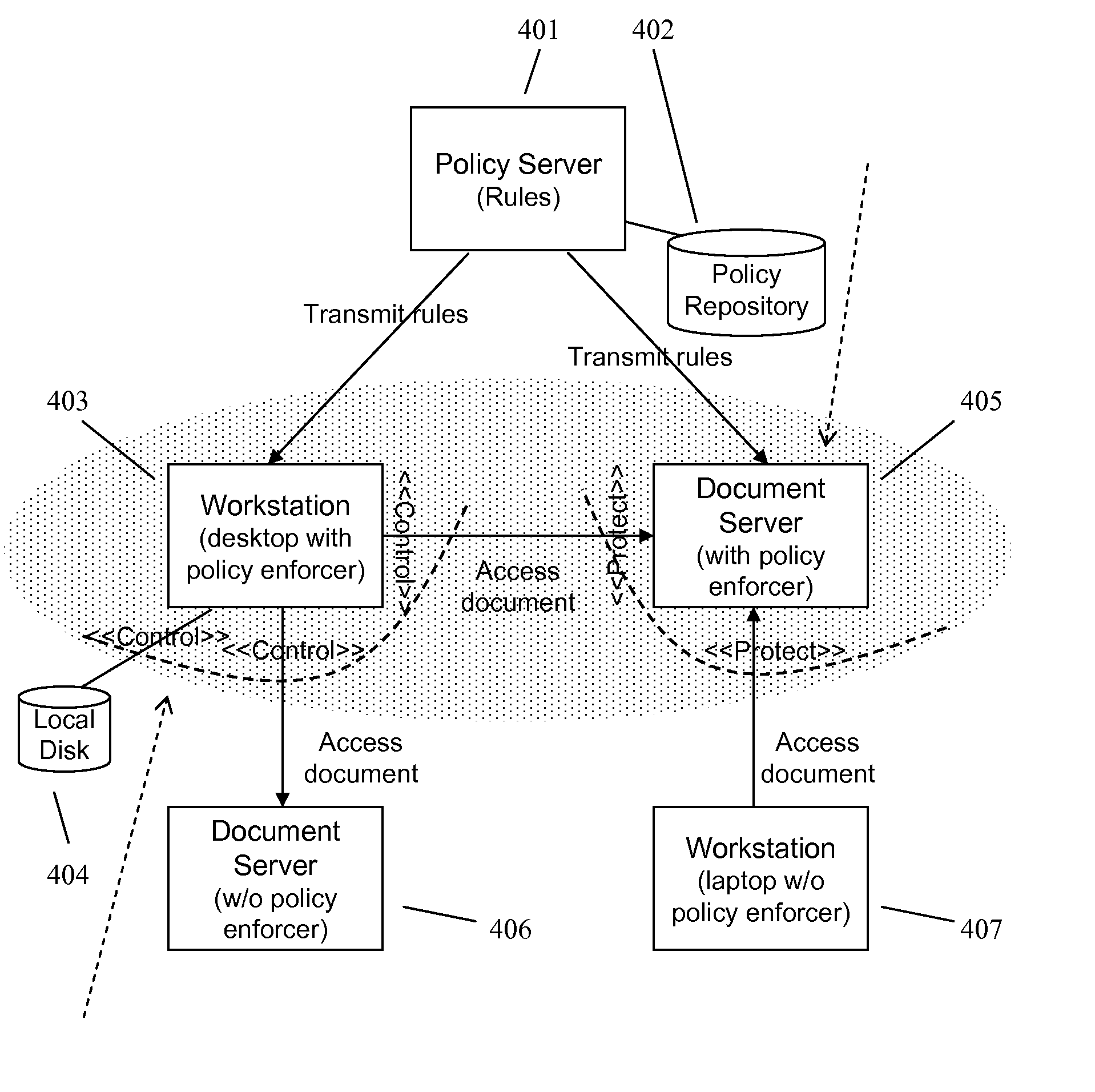
Techniques and System to Deploy Policies Intelligently
ActiveUS20070156659A1Reduce the amount requiredImprove execution speedDigital data processing detailsComputer security arrangementsSpace requirementsOperating system
In an information management system, relevant policies are deployed to targets while policies which are not relevant are not. By deploying relevant policies, this reduces the amount of space requirements at the target to store the policies and the amount of data that needs to be sent to the target. Also, execution speed at the target may increase since the target does not need to evaluate policies that are not relevant.
Owner:NEXTLABS
Technique for providing personalized information and communications services
InactiveUS7388950B2Efficient retrievalSame access rightSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingWeb browserFacsimile
A user may utilize a communication device, e.g., a wireless phone, mobile device or personal digital assistant (PDA), to contact an information / call center where an operator provides personalized information and communications services to the user in accordance with the invention. Such services include, e.g., providing listing information, contacts information, appointments information, etc. To provide effective connectivity, for example, when a user locates a phone number in his / her private directory using a web browser, the user may utilize a direct connect feature of the invention to initiate a phone call to the desired number over the Internet. In addition, the invention allows for delivery of the appointments information to the user not only via voice connection, but also SMS, email, facsimile, PDA, etc. It also allows for rendering a calendaring service in combination with such services as a TeleConcierge® service which helps the user to plan a future event, e.g., making a restaurant reservation. An appointment record concerning the future event is automatically incorporated into the user's calendar once it is successfully planned. To personalize the services, at least one profile associated with the user is used which specifies the subscribed services and the preferred ways of receiving them. For example, the profile may specify use of a special skilled operator, methods of delivery of information to the user, etc.
Owner:GRAPE TECH GROUP
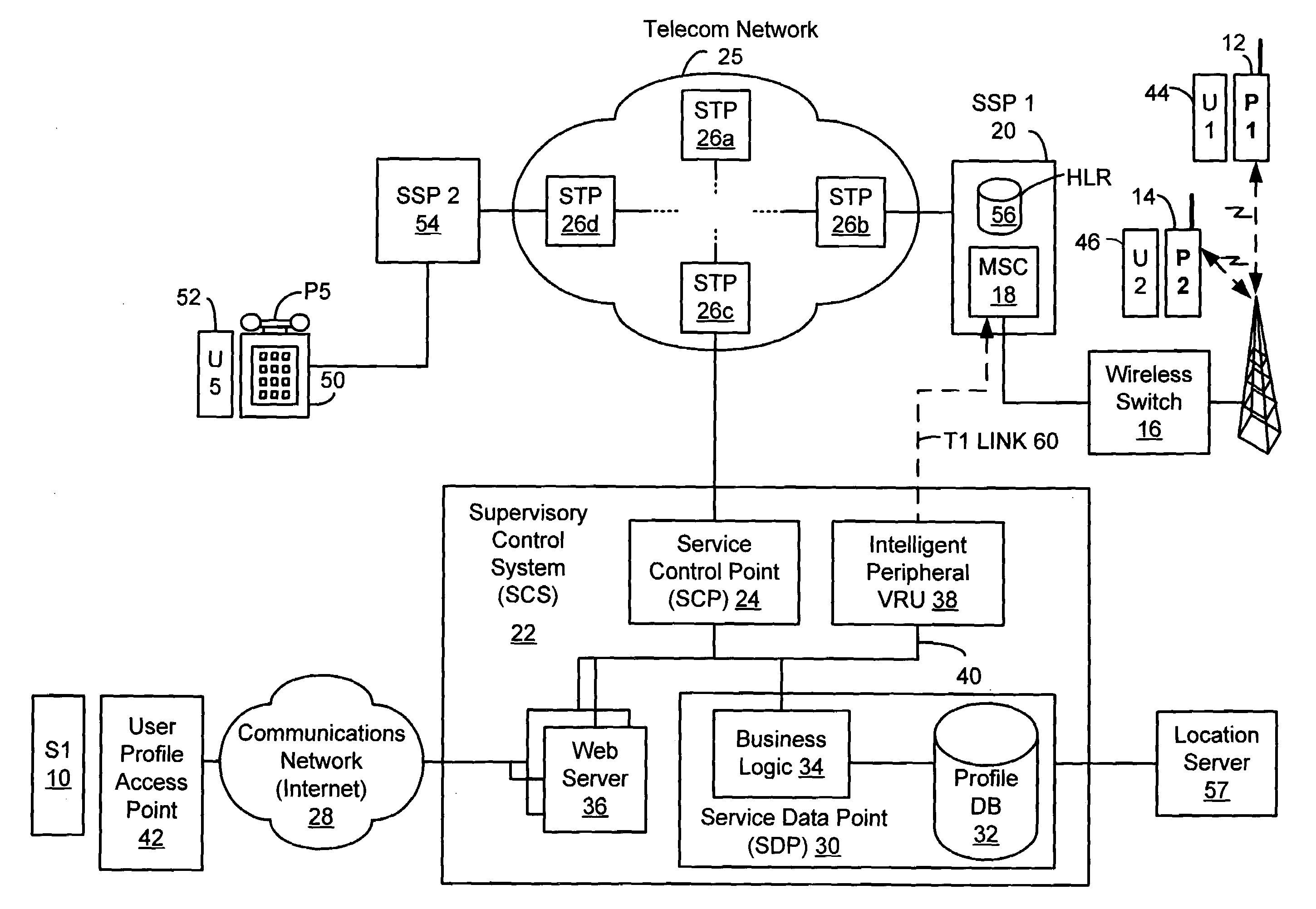
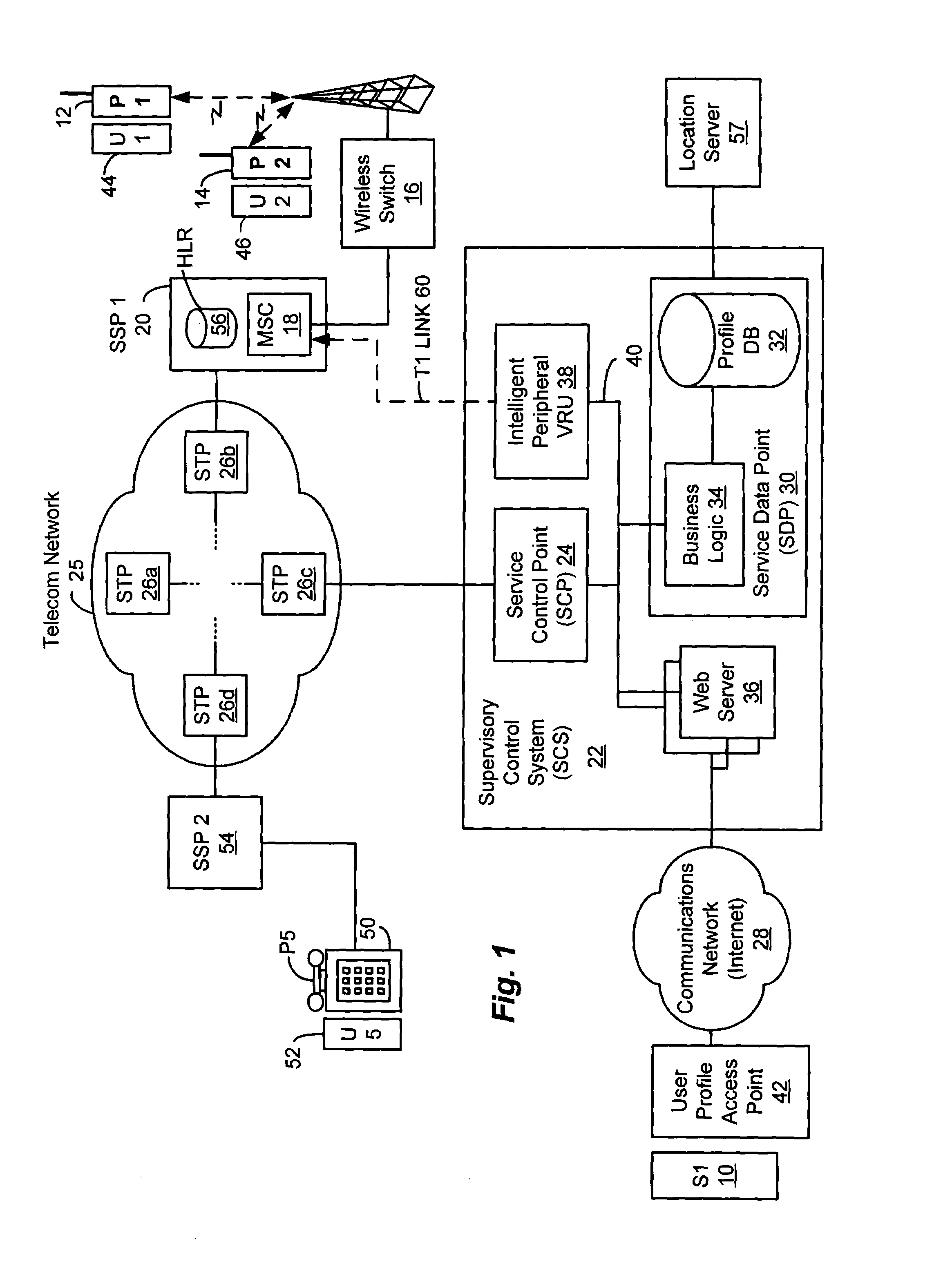
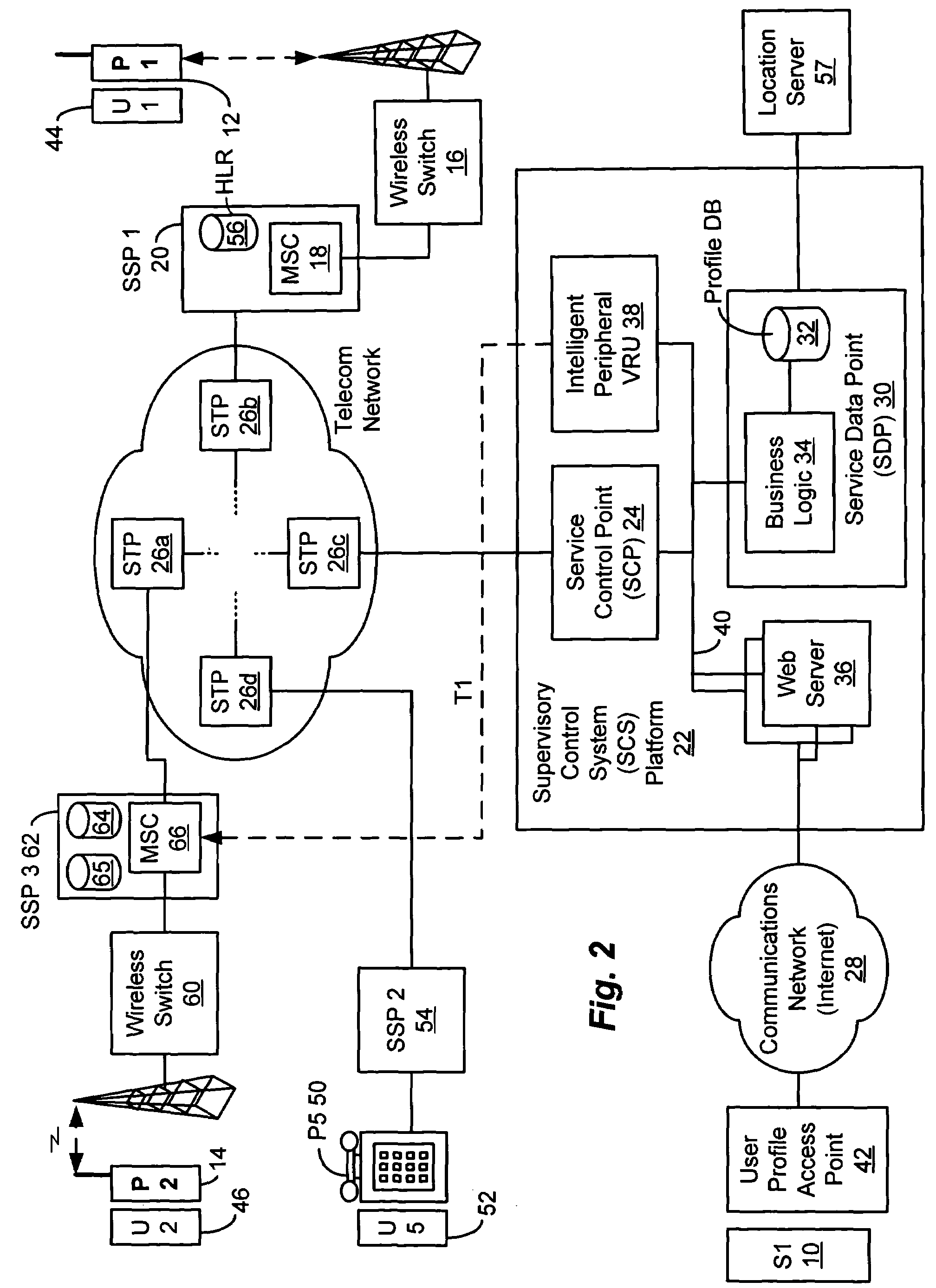
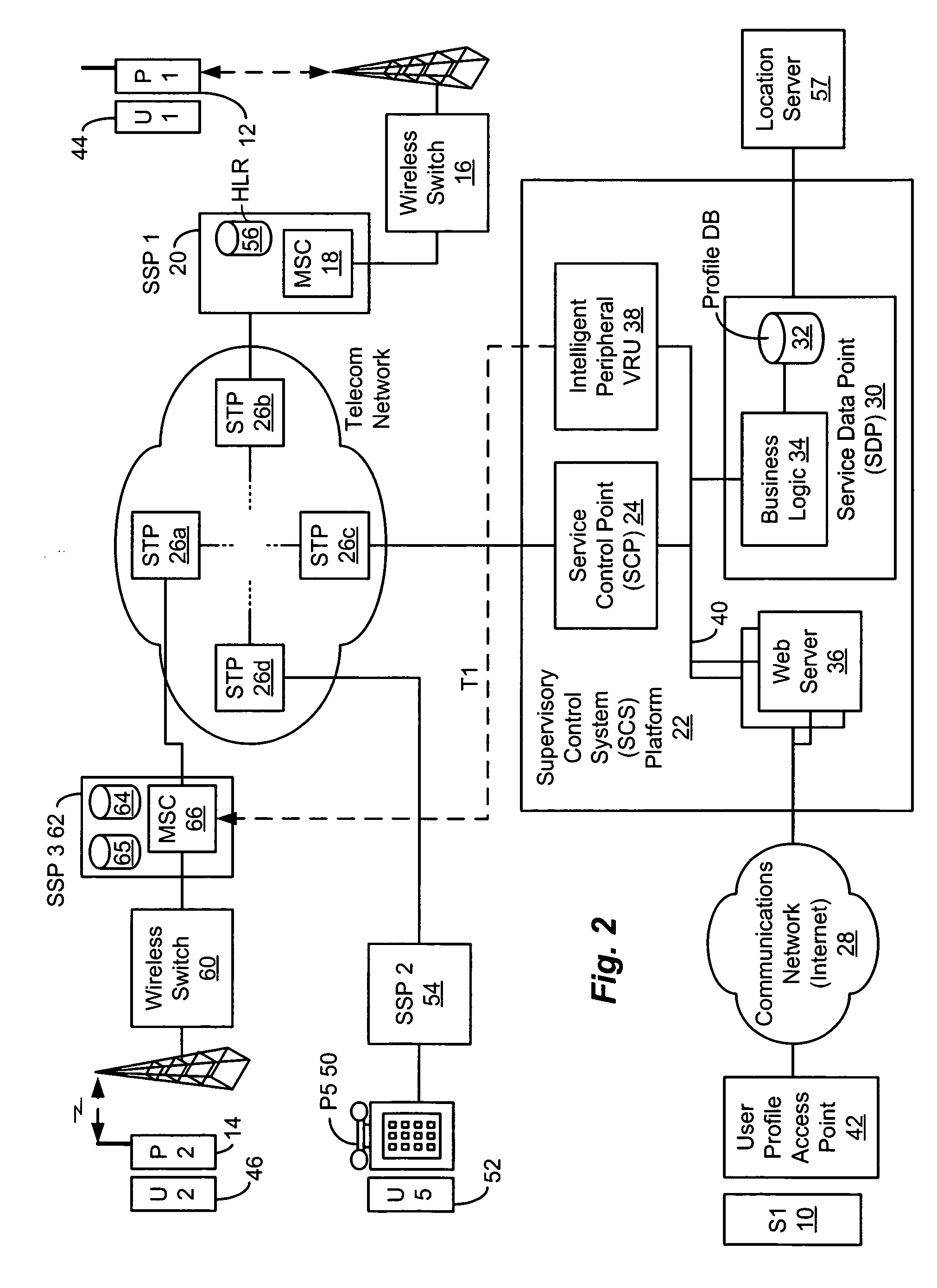
Method and system for providing supervisory control over wireless phone usage
InactiveUS7197321B2Reduce usageAccounting/billing servicesUnauthorised/fraudulent call preventionUser profileControl period
A system for controlling wireless phone usage enables a supervisor to establish user profiles for supervised users of wireless phones across a range of parameters which are stored in a user profile database. Such parameters may include one or more locations at which use of the wireless phone is restricted or permitted. In addition, restrictions on phone use may be provided based upon total phone usage within a specified control period, time periods, dates or days of the week during which phone use is restricted or permitted. One or more lists including numbers that are always-accessible may be provided and one or more lists including numbers that are never-accessible may also be provided. In the event a call does not satisfy predefined criteria, the call is blocked. Predetermined messages may be played to the called or calling party as applicable when a call is blocked. Boolean combinations of restrictions and permissive use criteria for the wireless phone may be specified to provide for flexibility when establishing use criteria for the wireless phone.
Owner:BOSTON COMM GROUP
Portable shopping and order fulfillment system
InactiveUS7040541B2Expand accessAdd supportCredit registering devices actuationCalling susbscriber number recording/indicationItem CollectionOrder fulfillment
The present invention relates to an improved order fulfillment system. The system is provided with improved data entry system for selecting items for purchase by a customer, and an improved item collection terminal and order delivery system. The portable terminal to be used for collecting of items is provided with an audio as well as video presentation means which are used to provide assistance to the to terminal user.
Owner:SYMBOL TECH LLC
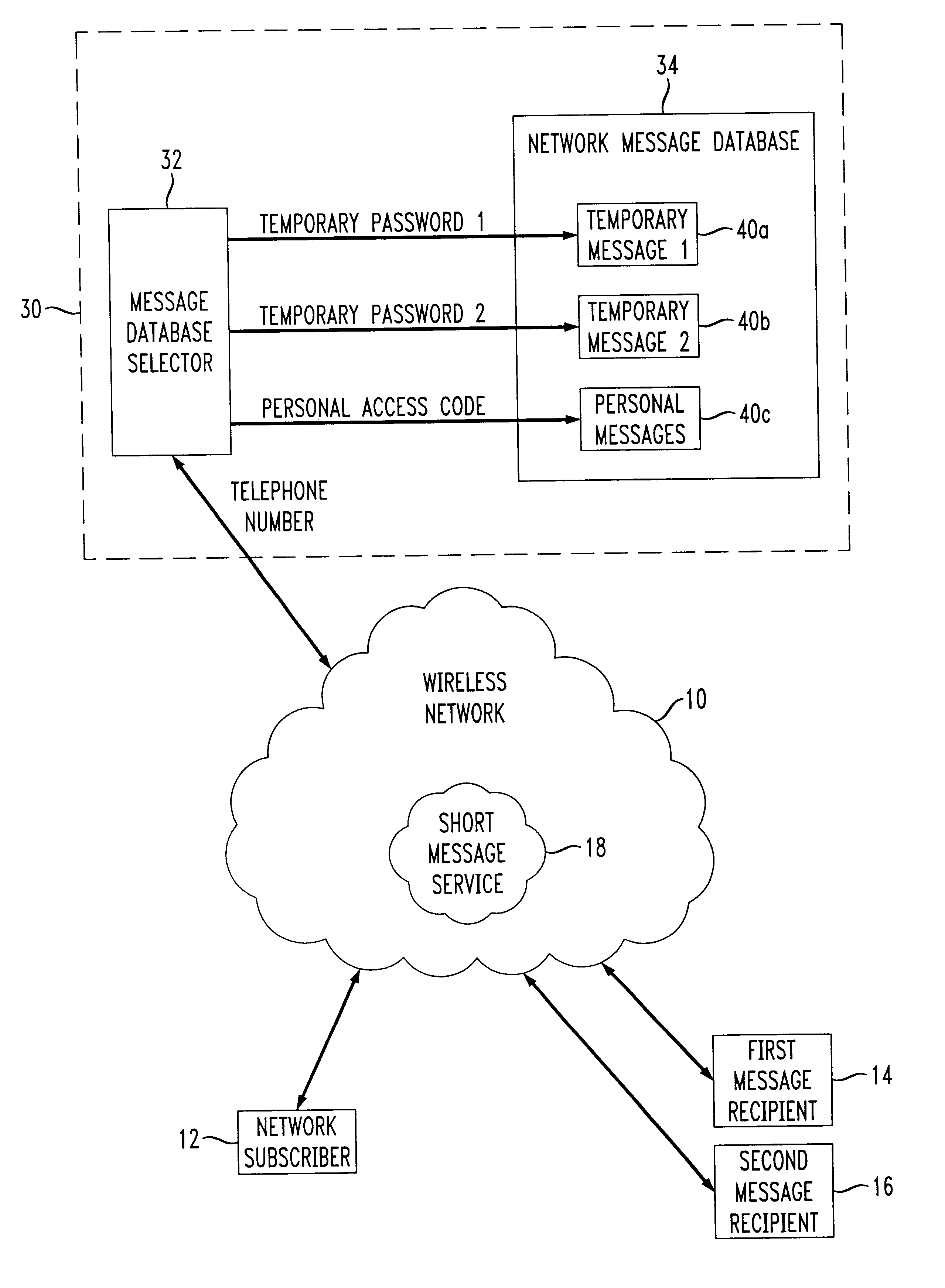
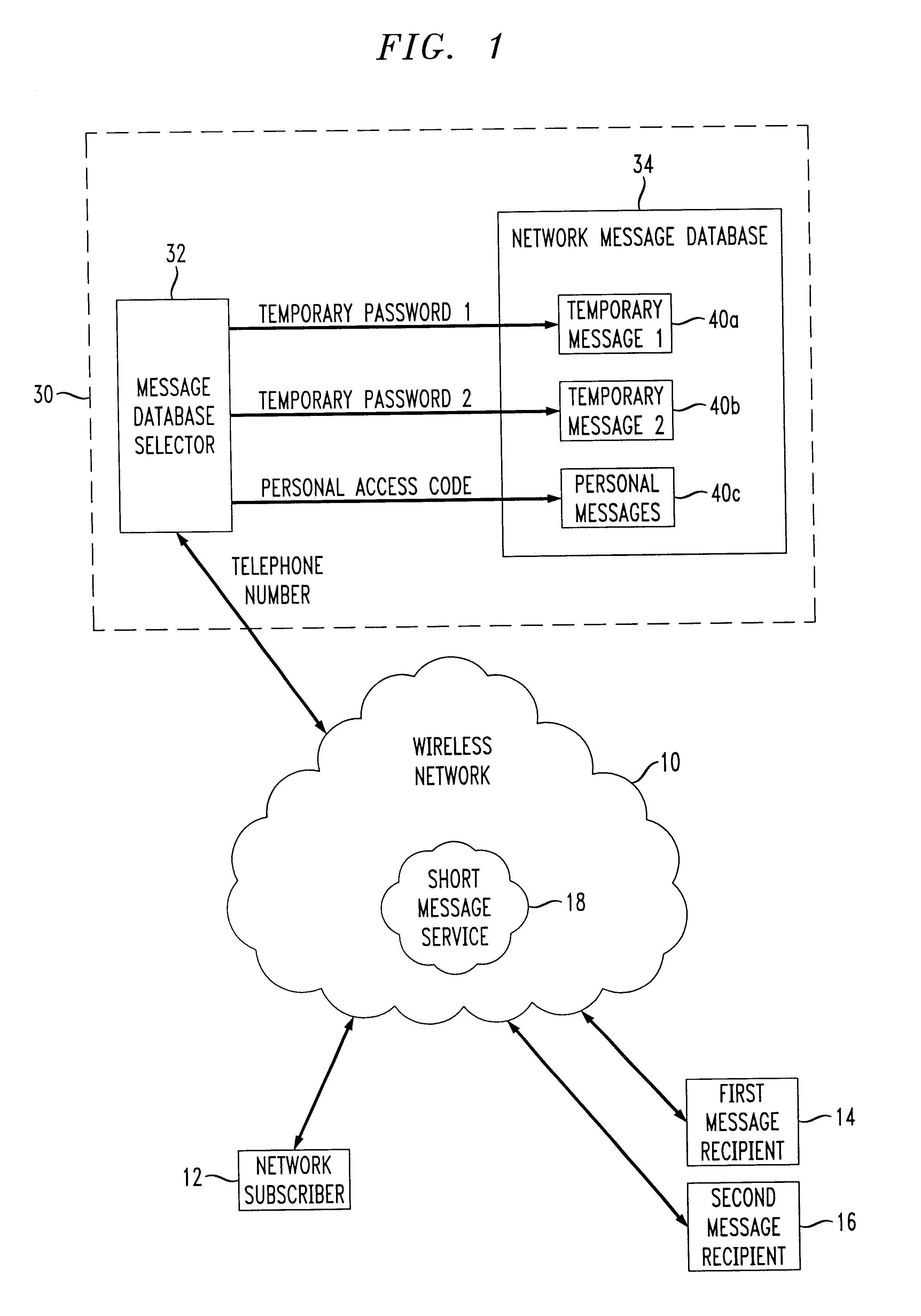
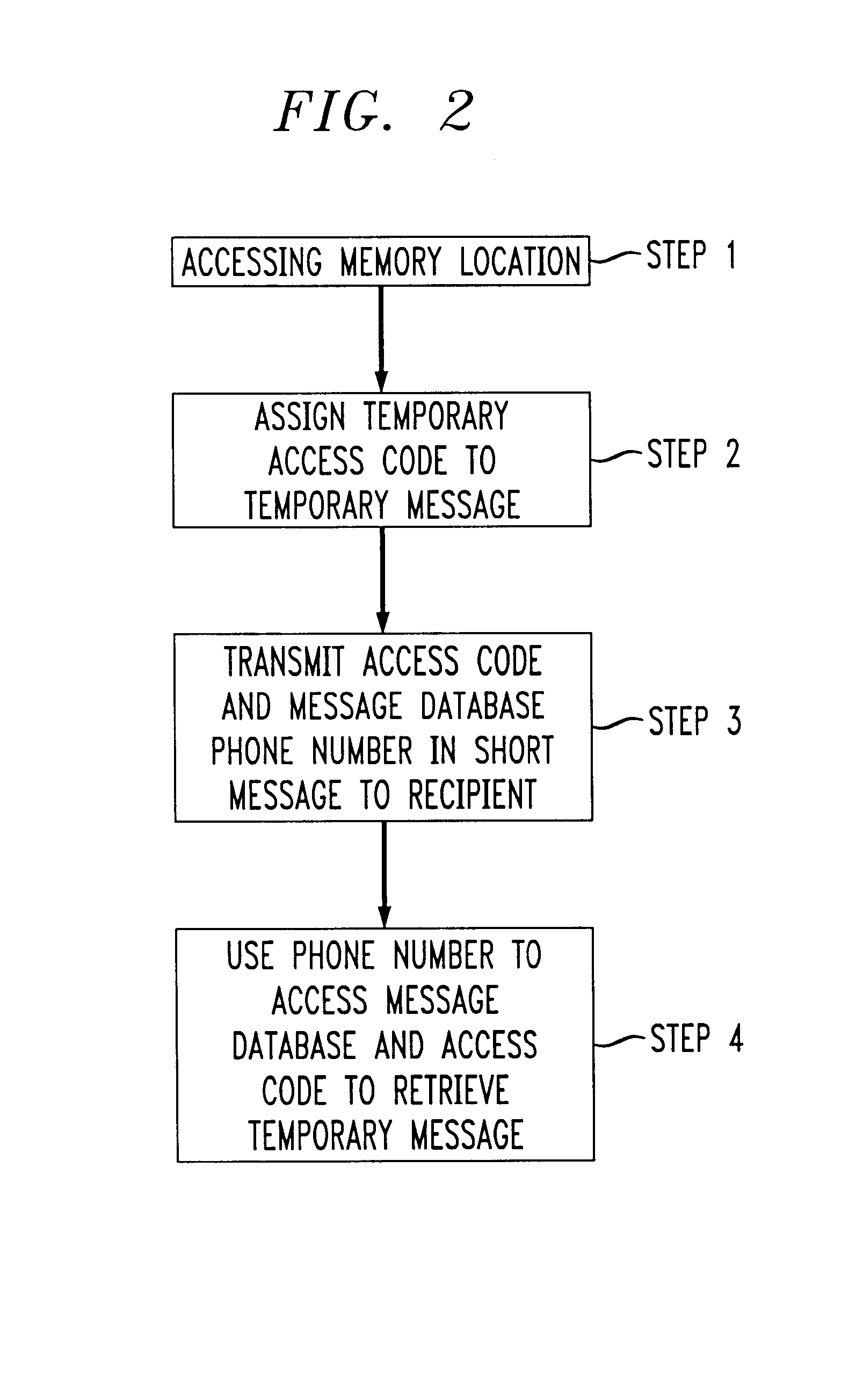
Internet voice & data messaging (IVDM) portal
InactiveUS20050041647A1Simple stepsEasy maintenanceSpecial service for subscribersGraded-service arrangementsPaymentToll-Free Number
An online voice messaging service that integrates all tools needed for an advertising sales representative to resell to their customers, in real time, a blind “ad box” including a temporary anonymous toll-free phone number with attached Internet Voice & Data Messaging (IVDM) service for collecting ad responses, such that the toll-free phone number can be incorporated into the text of the customer's advertisement as it is being booked. The software includes a portal or web interface that facilitates reselling of the service via a channel of resellers, such as media companies with sales representatives that have a service agreement with the service. The software also includes a separate portal for direct sales. Various value-added, user-options are provided including notifications of new messages, the ability to receive rental and / or credit applications, payments from customers, management of multiple ad boxes with one logon, and to retrieve messages as .wav files, emails as .txt files, and faxes as .pdf (or similar) files.
Owner:STINNIE DESMOND L
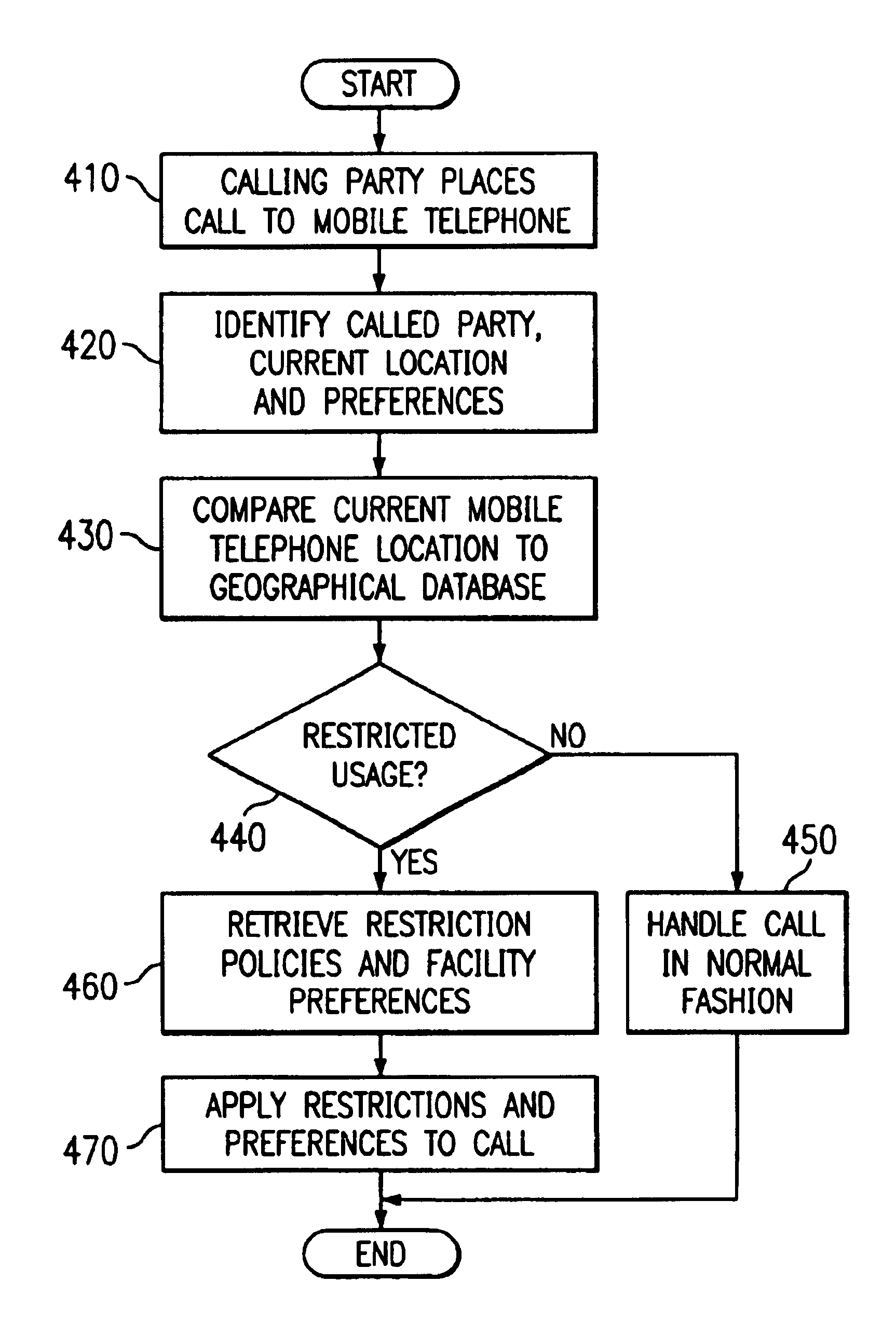
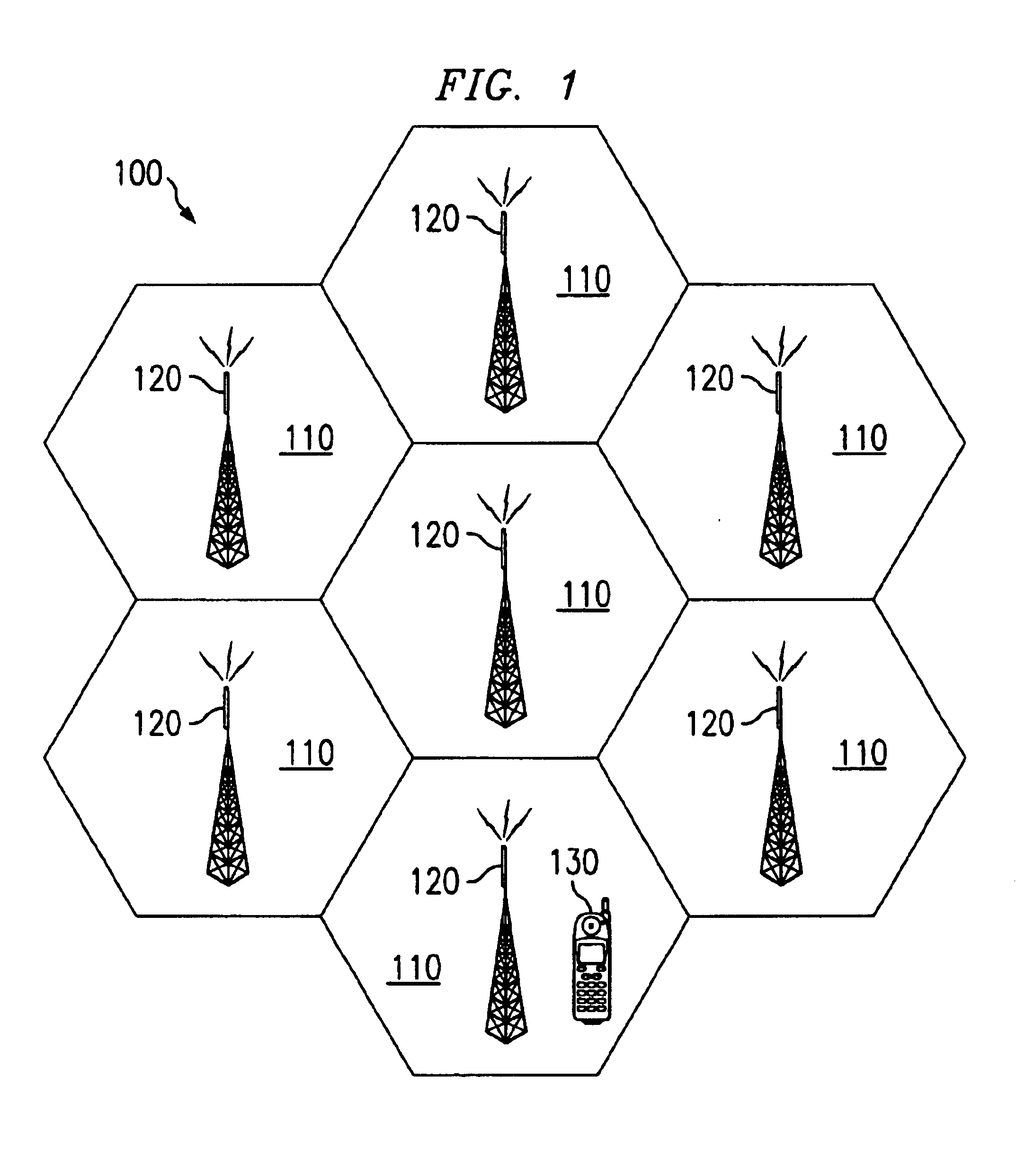
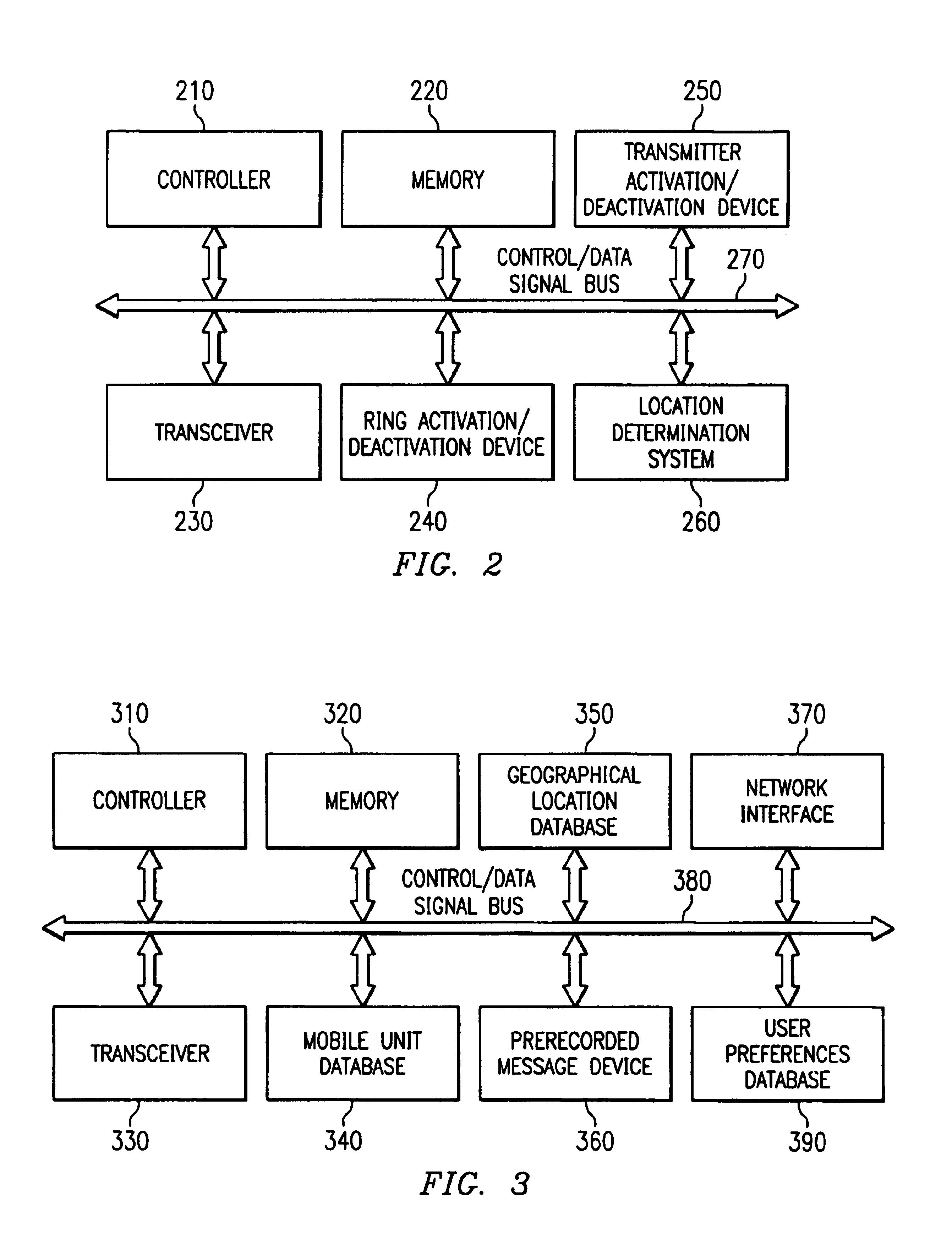
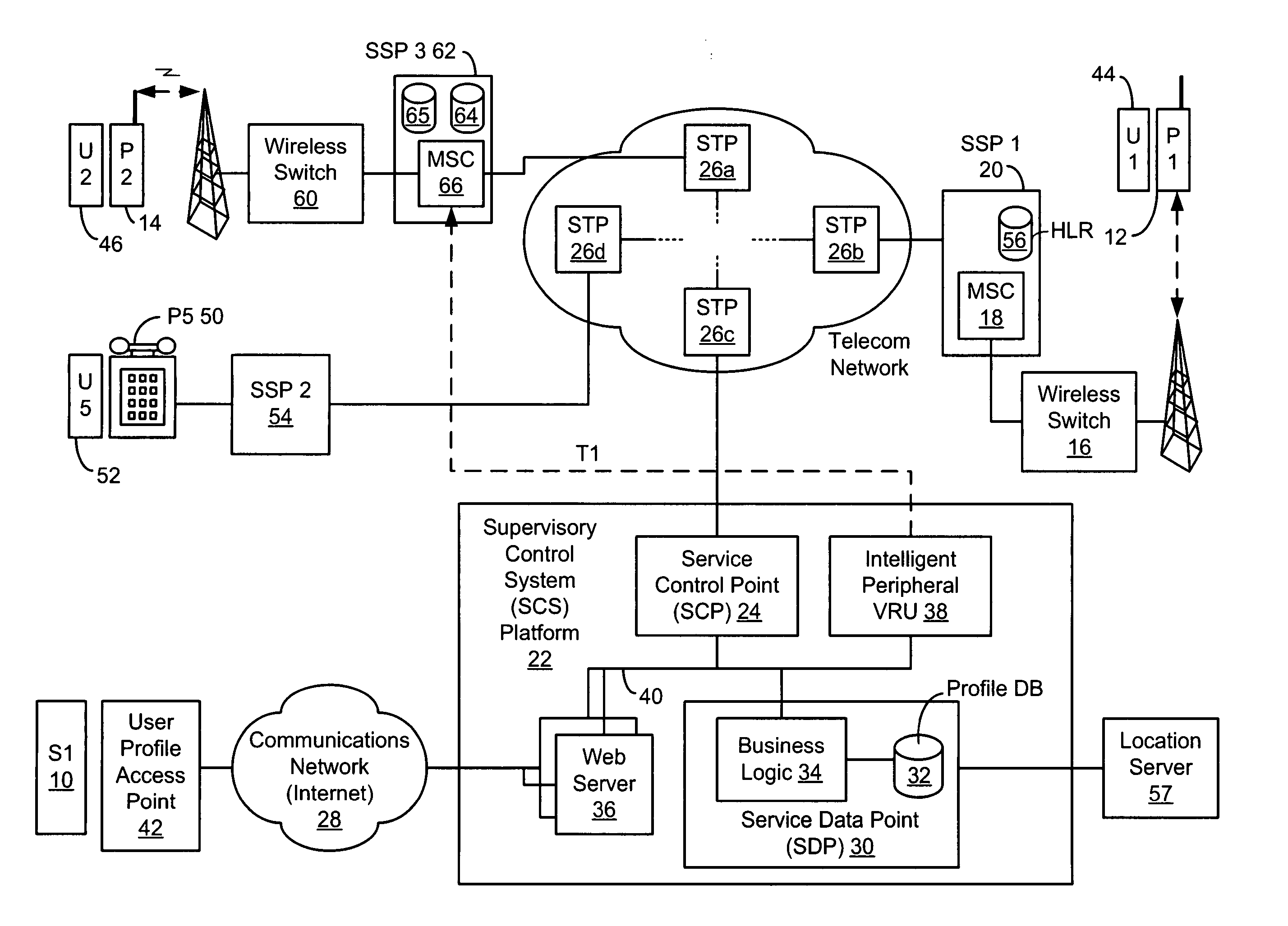
Apparatus and method for managing a mobile phone answering mode and outgoing message based on a location of the mobile phone
InactiveUS6937868B2Cordless telephonesAutomatic call-answering/message-recording/conversation-recordingPositioning systemMobile telephony
An apparatus and method for managing a mobile phone answering mode and outgoing message or other indicator based on a location of the mobile phone are provided. The apparatus and method make use of a location system to ascertain the current location of a mobile telephone being carried by a user. Based on the current location, the apparatus and method determine whether operation of the mobile telephone to receive and / or send calls should be restricted. In addition, the apparatus and method determine an appropriate outgoing message to be provided to calling parties while the mobile telephone is located in an area where use of the mobile telephone to receive calls is prohibited. The particular outgoing message provided is customized to the current location of the mobile telephone and optionally, the caller ID of the calling party.
Owner:IBM CORP
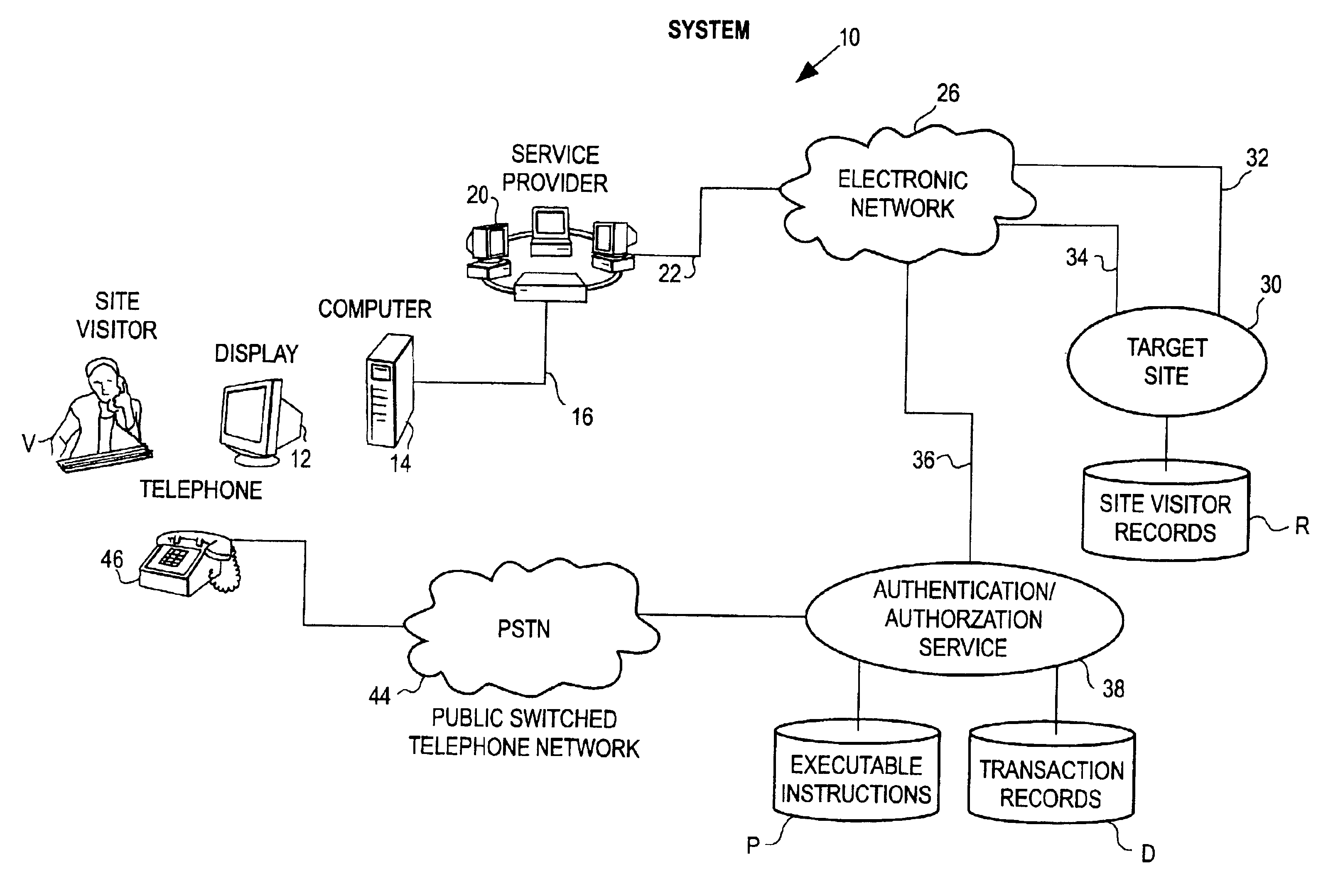
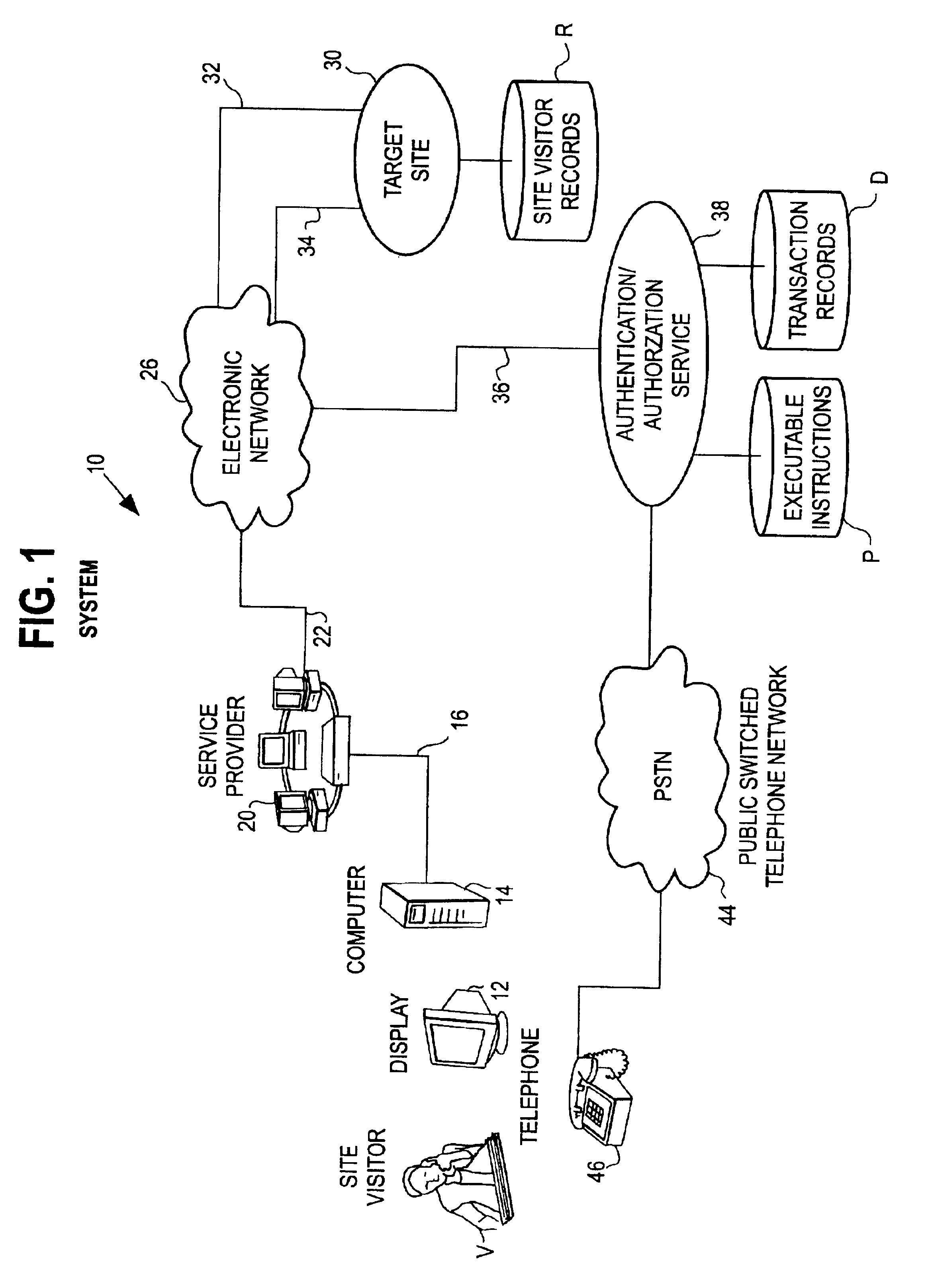
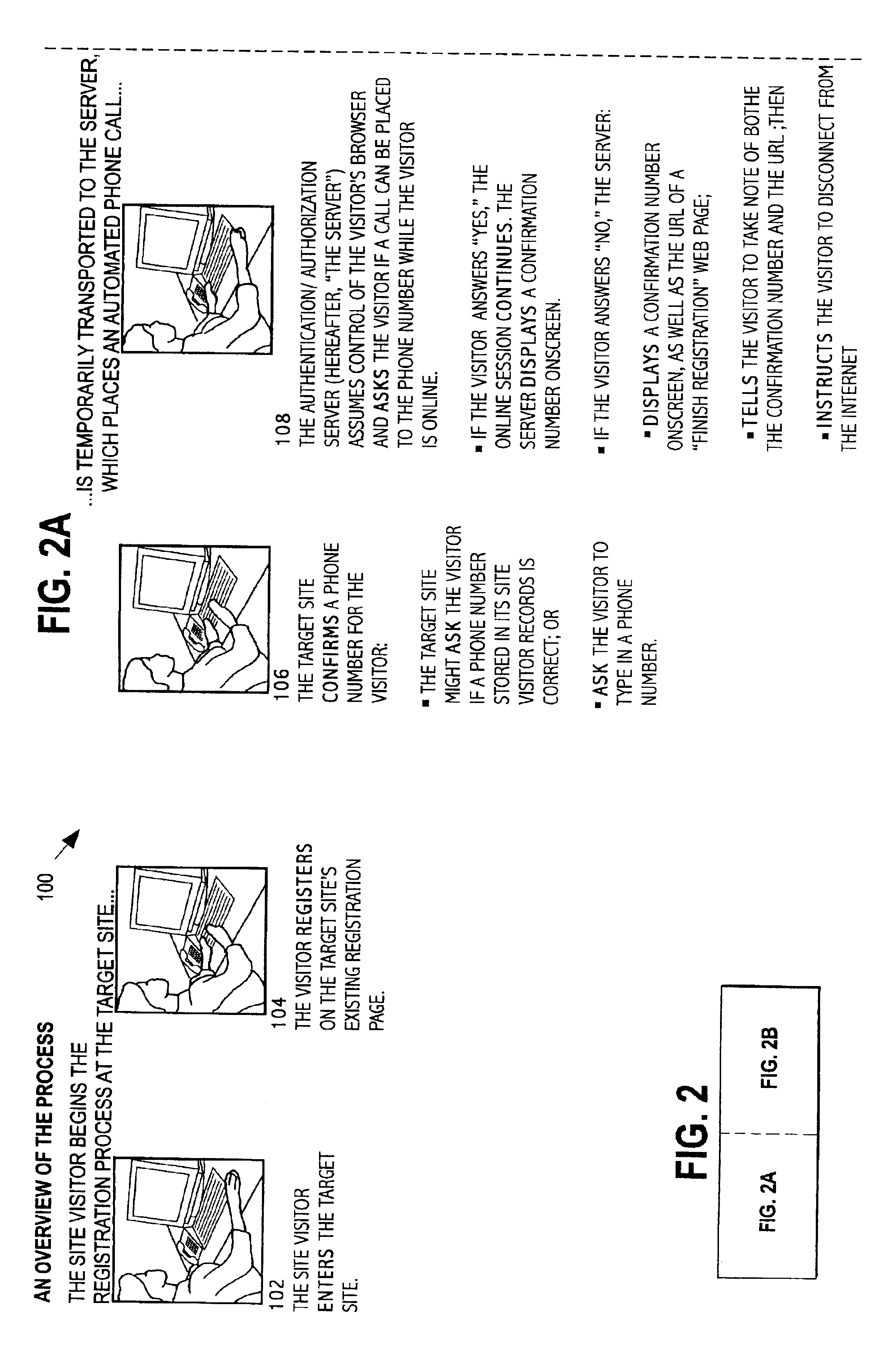
System and method of using the public switched telephone network in providing authentication or authorization for online transactions
InactiveUS6934858B2Quickly and reliably verifyingTelephone data network interconnectionsDigital data processing detailsTelecommunications linkThe Internet
An authentication or authorization system to facilitate electronic transactions uses simultaneous or substantially simultaneous communications on two different networks to verify a user's identity. When a user logs onto a site, via the internet, a telephone number, either pre-stored or obtained in real time from the visitor, where the visitor can be called essentially immediately is used to set up, via the switched telephone network another communication link. Where the user has multiple communication links available, the telephone call is automatically placed via the authentication or authorization software simultaneously while the user is on-line. In the event that the user has only a single communication link, that individual will have to log off temporarily for purposes of receiving the telephone call. Confirmatory information is provided via the internet to the user. The automatically placed telephone call requests that the user feed back this confirmatory information for verification purposes. The telephone number which is being called is adjacent to the user's internet terminal. The user's response, via the telephone network, can be compared to the originally transmitted confirmatory information to determine whether the authentication or authorization process should go forward.
Owner:PAYFONE
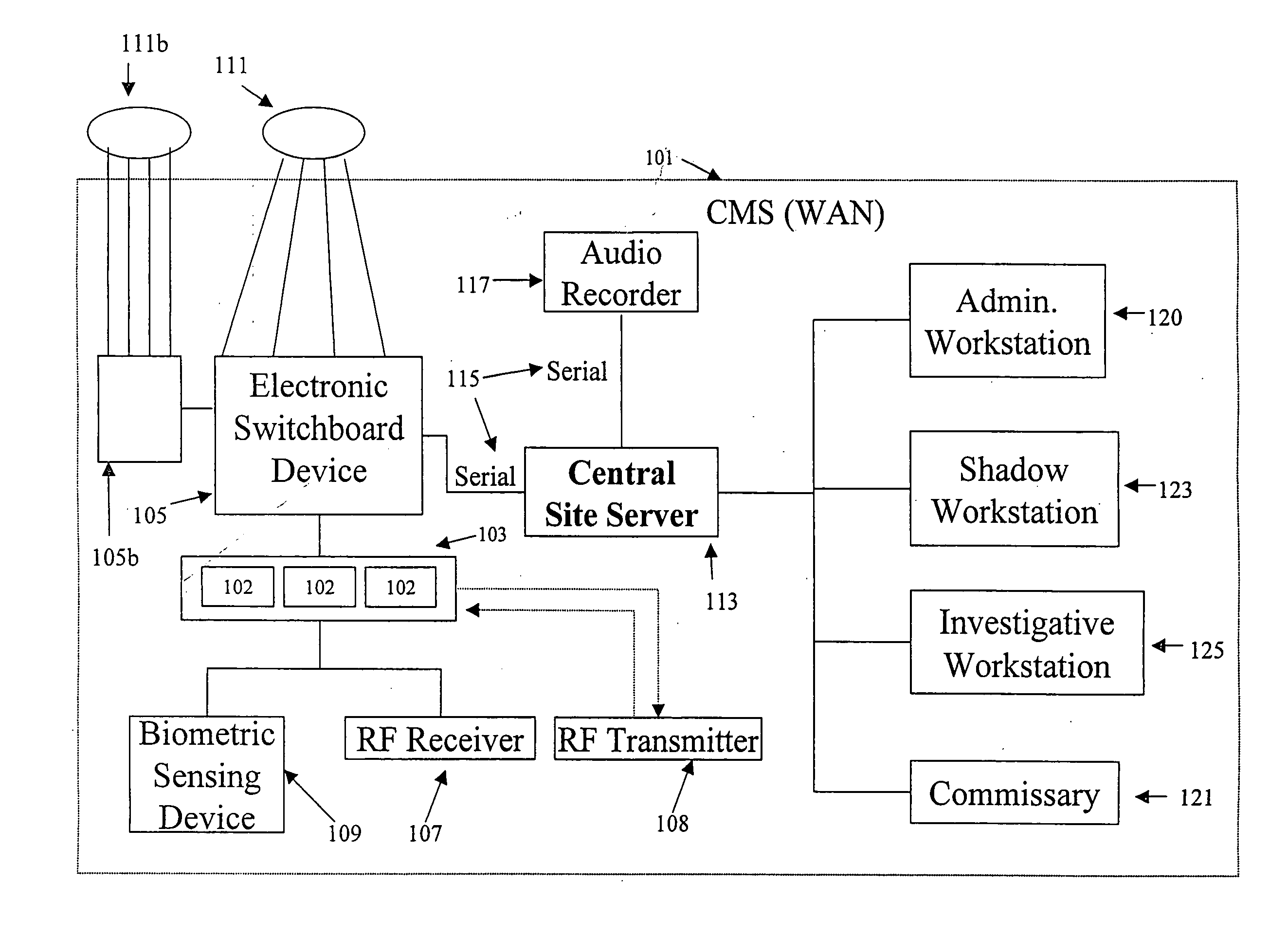
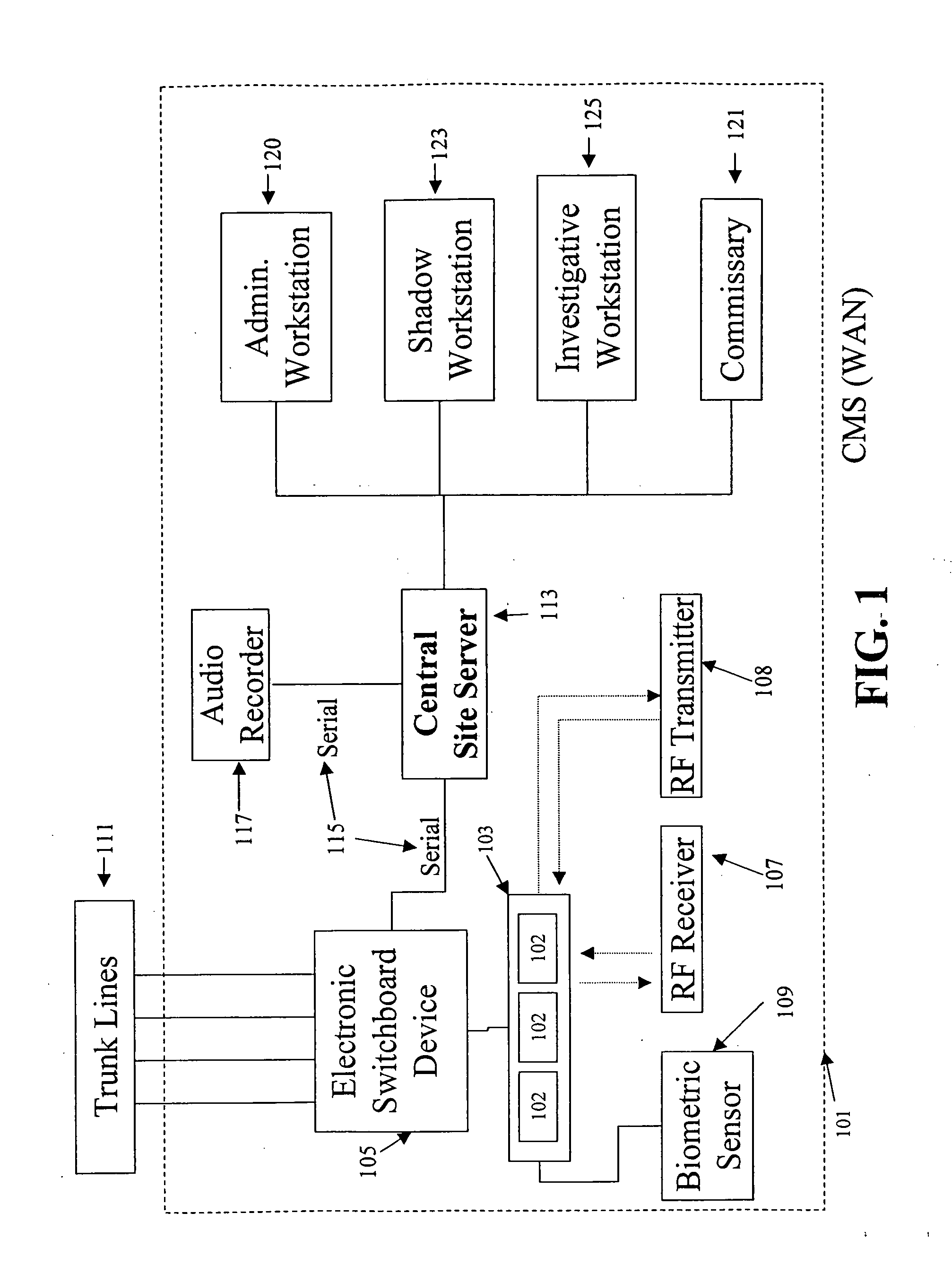
Multi-party conversation analyzer & logger
InactiveUS20140247926A1Combat useAutomatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsSpeech soundData library
In one aspect, the present invention facilitates the investigation of networks of criminals, by gathering associations between phone numbers, the names of persons reached at those phone numbers, and voice print data. In another aspect the invention automatically detects phone calls from a prison where the voiceprint of the person called matches the voiceprint of a past inmate. In another aspect the invention detects identity scams in prisons, by monitoring for known voice characteristics of likely imposters on phone calls made by prisoners. In another aspect, the invention automatically does speech-to-text conversion of phone numbers spoken within a predetermined time of detecting data indicative of a three-way call event while monitoring a phone call from a prison inmate. In another aspect, the invention automatically thwarts attempts of prison inmates to use re-dialing services. In another aspect, the invention automatically tags audio data retrieved from a database, by steganographically encoding into the audio data the identity of the official retrieving the audio data.
Owner:SECURUS TECH LLC
Multimedia telecommunication automatic call distribution system using internet/PSTN call routing
InactiveUS6614783B1Telephone data network interconnectionsAutomatic call-answering/message-recording/conversation-recordingThe InternetGeolocation
A multimedia telecommunication automatic call distribution center which allows access to the call center via a plurality of access means, including telephone and data networks to provide simultaneous voice, data, and video access, and ensures effective transparent spreading of agents over different geographical locations. The automatic call distribution center of the present invention uses a multimedia automatic call distribution server acting as connection manager for data network callers and provides for automatic caller identification.
Owner:COSMO INC
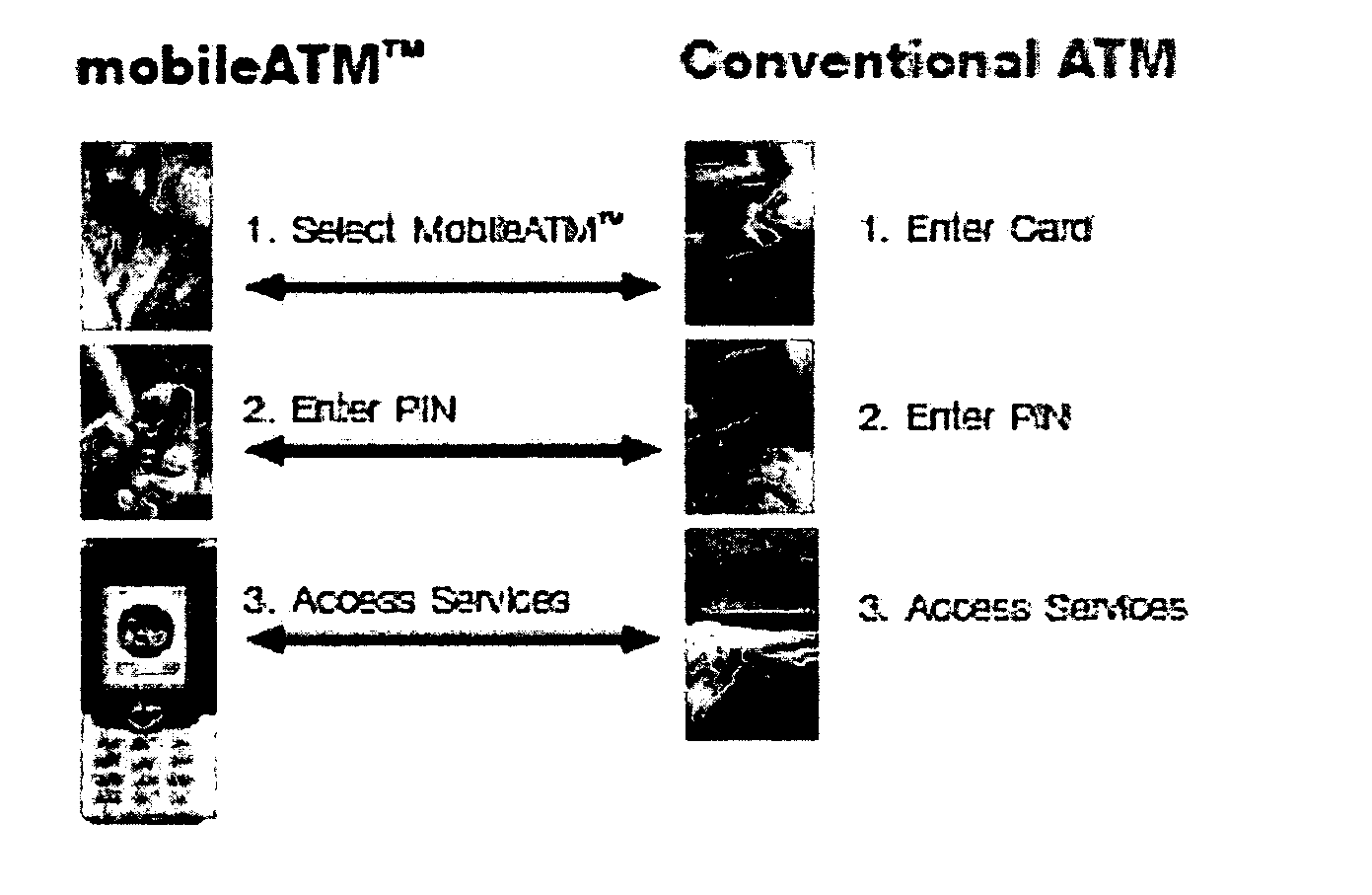
Electronic system for provision of banking services
ActiveUS20060136334A1Increased positional freedomWithout compromising securityComplete banking machinesFinanceElectronic systemsMobile telephony
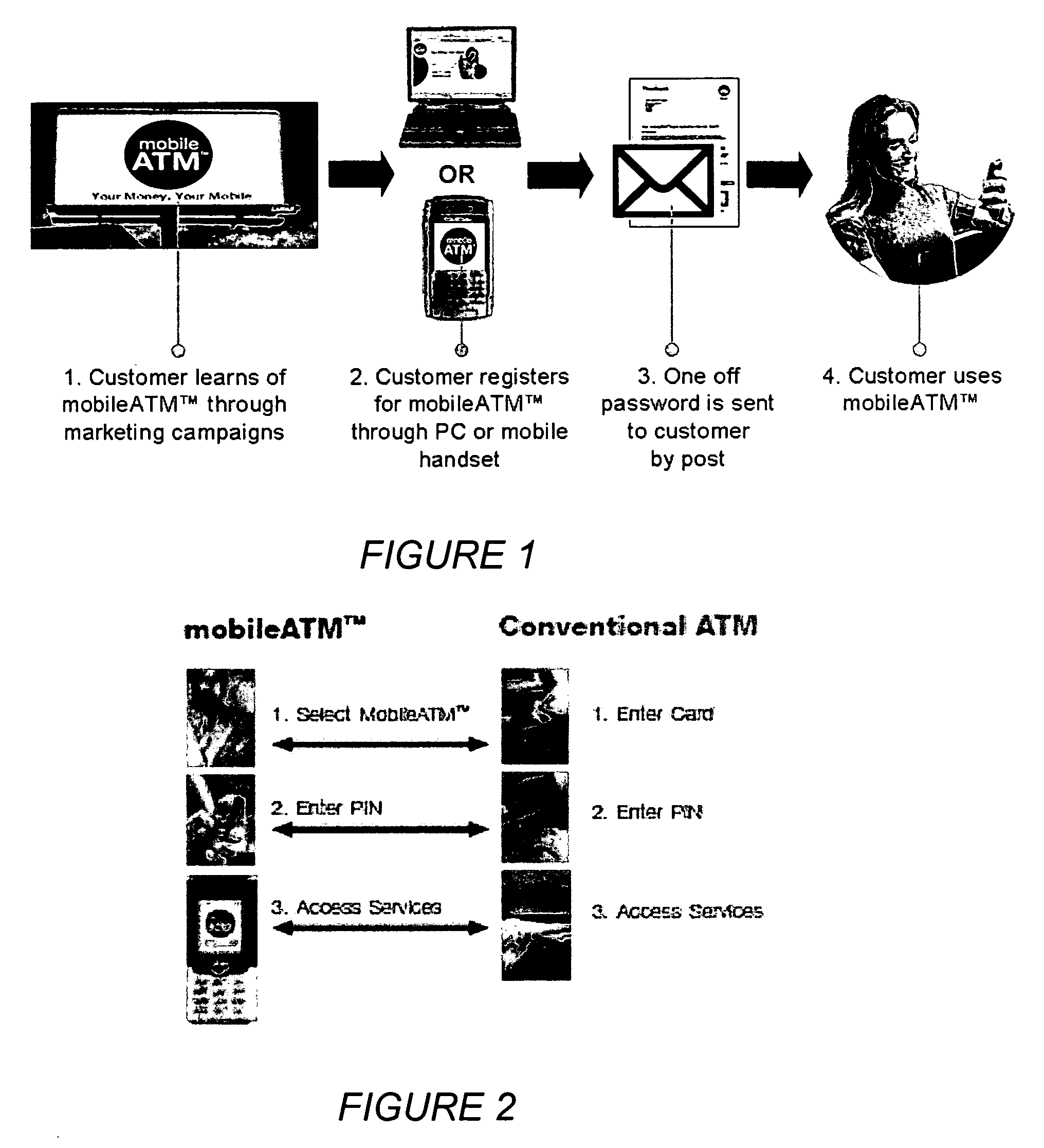
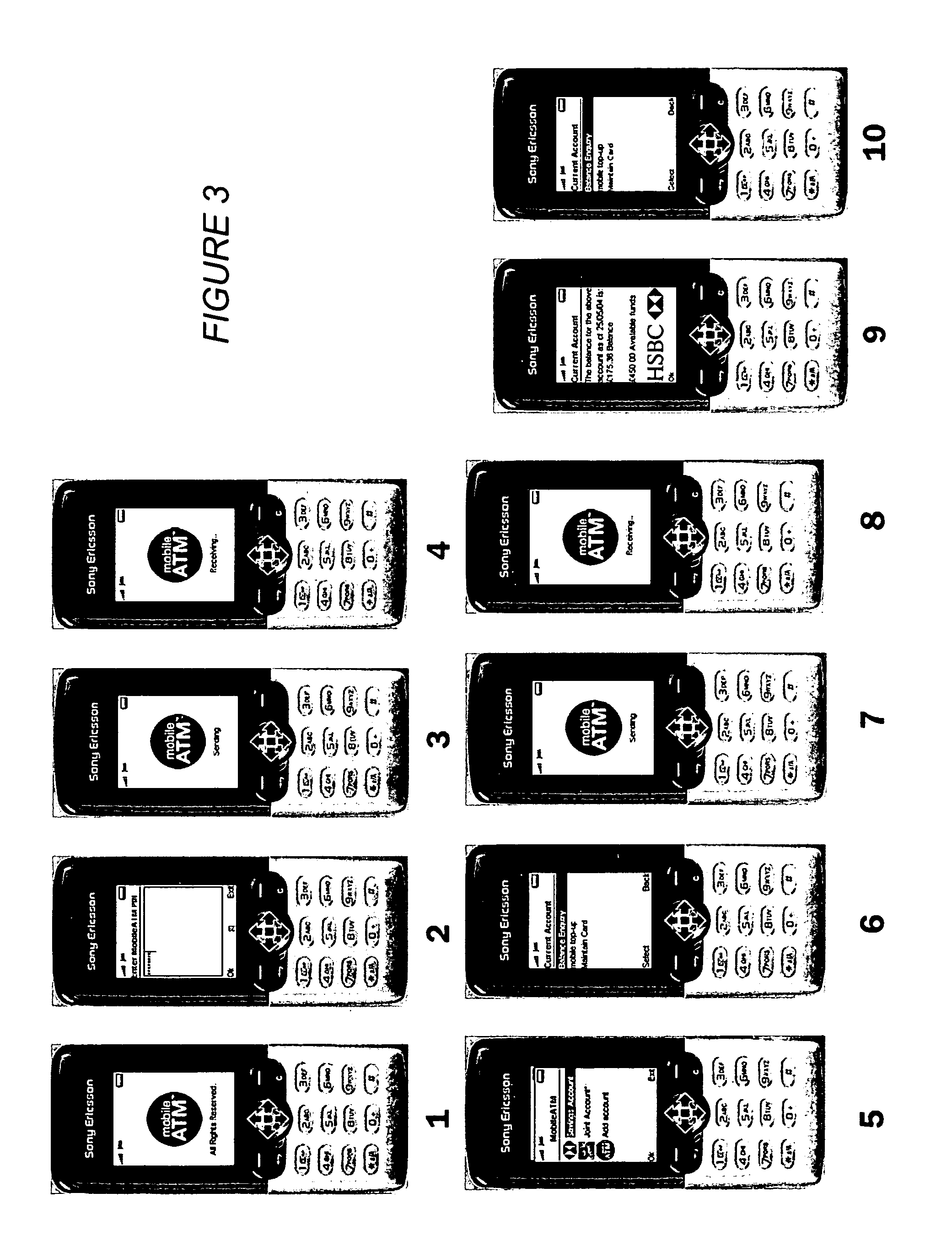
An electronic system providing banking services, comprises a server having a first interface for communication with user mobile telephony devices over a mobile telephone network; and a second interface for communication with an intermediary acting as a gateway to banking records of multiple banking organisations. The first interface is adapted to allow at least balance enquiry requests to be submitted to one of the multiple banking organisations by means of the intermediary and to provide at least balance enquiry replies for display on the user mobile telephony device. The invention provides the functions of the high street ATM using the mobile phone environment.
Owner:FISERV
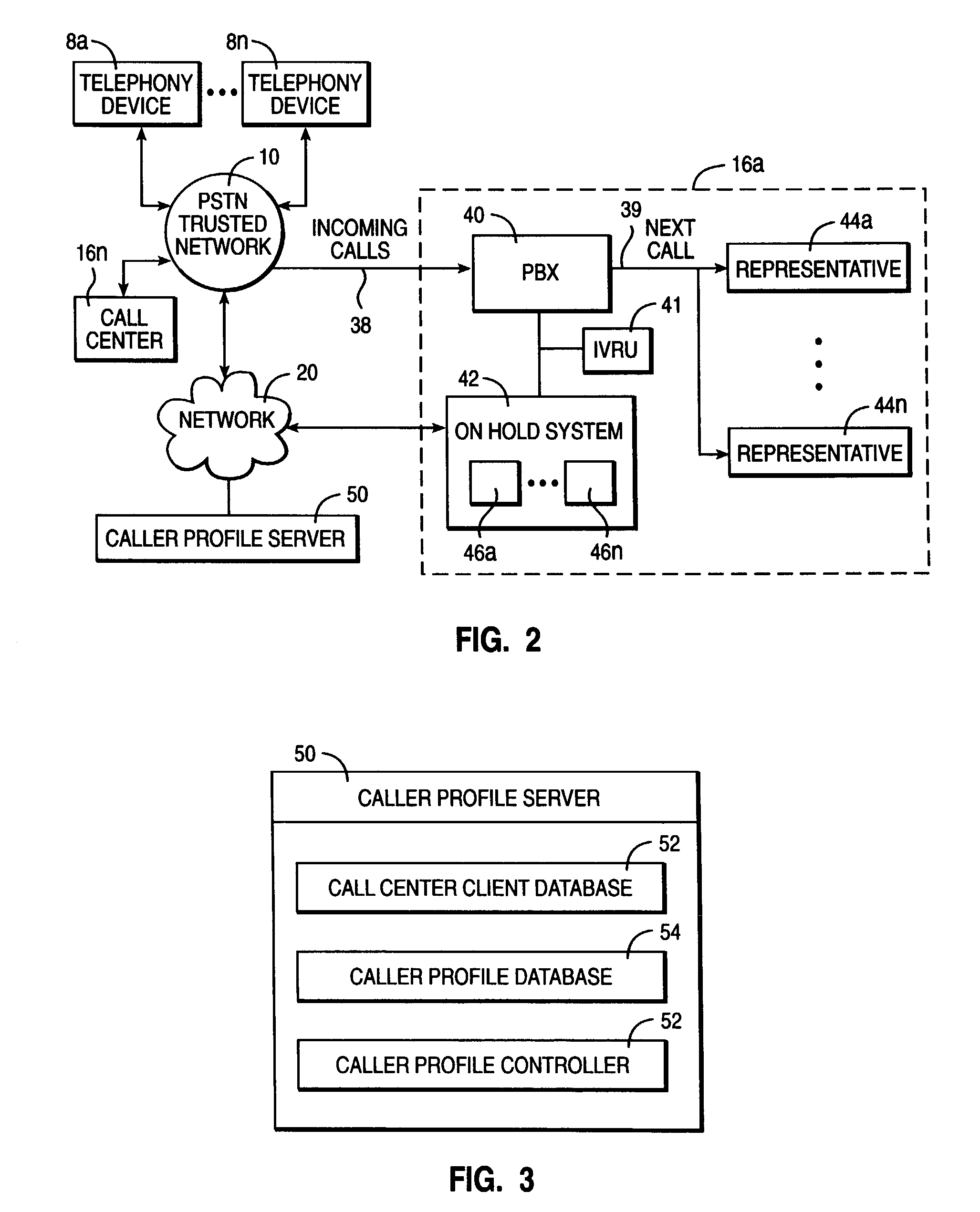
Managing caller profiles across multiple hold queues according to authenticated caller identifiers
InactiveUS7103172B2Television system scanning detailsAutomatic call-answering/message-recording/conversation-recordingUser identifierSpeech sound
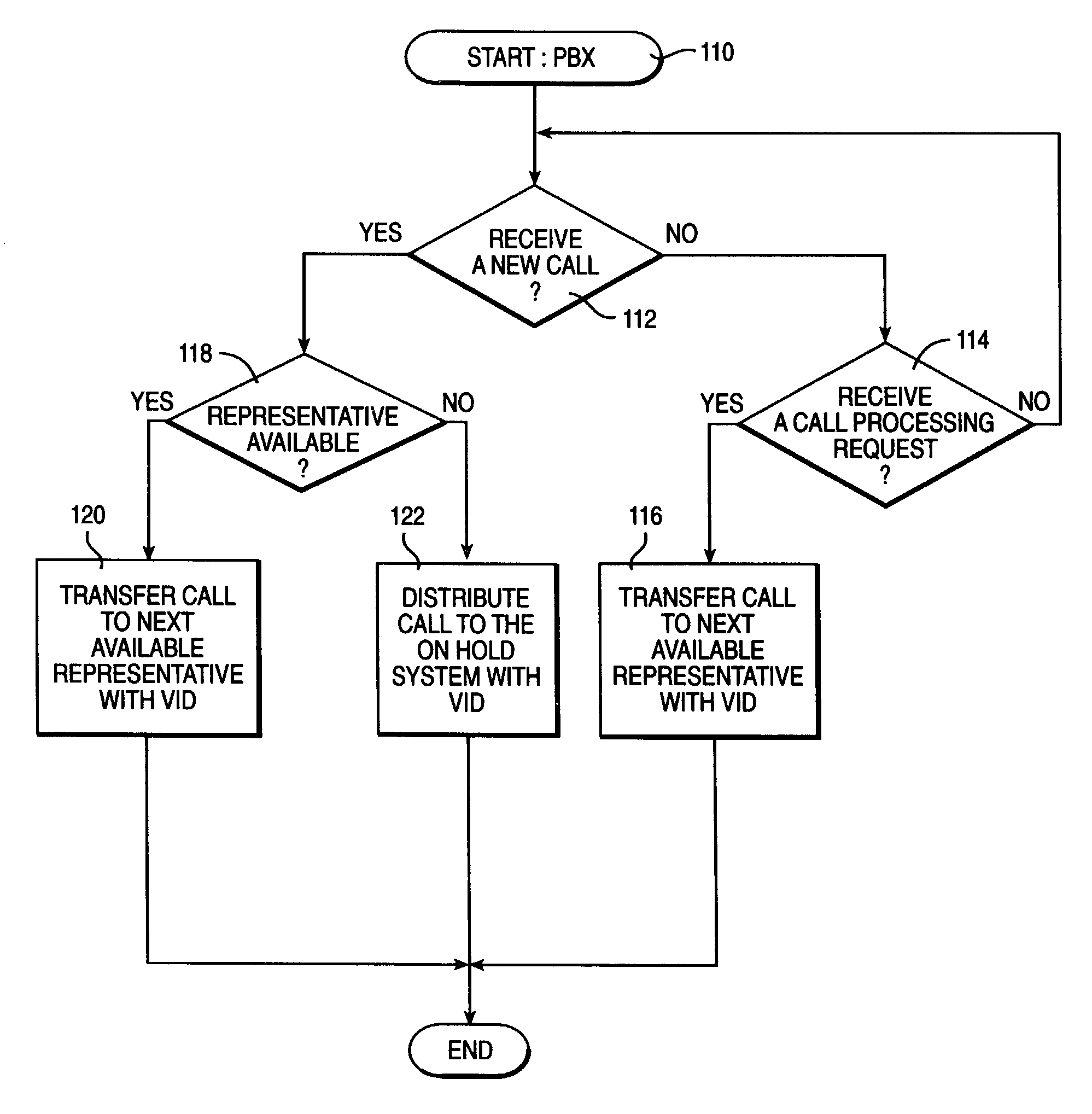
A method, system, and program for managing caller profiles across multiple hold queues according to authenticated caller identifiers are provided. An identity of a caller of a call received at an on hold system is authenticated. The call is then placed in a hold queue. A caller profile associated with the identity of the caller is retrieved, such that services available to the caller while on hold are specified according to the caller profile. In particular, the caller profile is preferably retrieved from at least one caller profile server according to the caller identifier, where the at least one caller profile server is accessible to multiple on hold systems. Further, the identity of a caller may be authenticated by authenticating a voice sample received from the caller, such that a single identity for the caller may be authenticated at multiple call centers.
Owner:IBM CORP
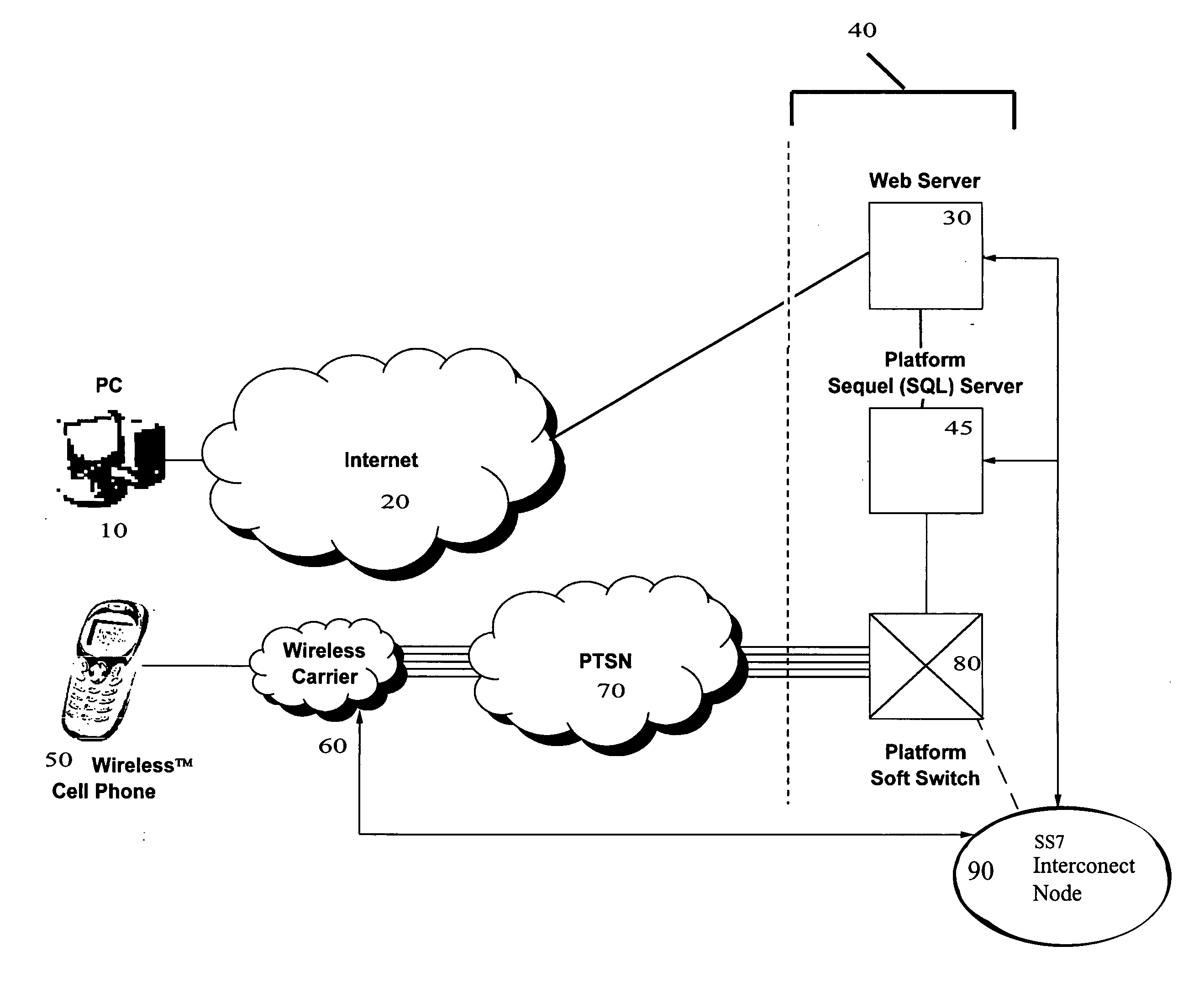
System and method for secure web-based mobile phone parental controls
InactiveUS20060293057A1Unwanted useGraded-service arrangementsRadio/inductive link selection arrangementsWeb siteSelf limiting
A wireless system and method for implementing call controls (such as parental controls) for wireless telephones via a call-intercept platform (including a soft switch and / or an SS7 interconnection node, and SQL database), and a conventional mobile phone that makes and receives all outgoing calls through the call intercept platform. The call intercept platform includes secure web server to provide a secure website point of entry for allowing parents to specify a ruleset of parental controls that is stored in the SQL database. Every outgoing call from the mobile phone is routed into the call-intercept platform, which logs the call, crosschecks the mobile phone and outgoing call number against the stored ruleset for that phone / user, and selectively screens te calls. Incoming calls are automatically forwarded from the wireless carrier to the call intercept platform and are logged, cross-checked and selectively screened. The secure web portal allows parents and guardians or other individuals who desire to self-limit call usage to thoroughly manage their dependent's or their own phone, inclusive of viewing calls, activating and deactivating controls, customizing controls, as well as purchasing prepaid minutes and managing their accounts.
Owner:CLOSECALL AMERICA
Method and system for providing supervisory control over wireless phone data usage
InactiveUS20050282559A1Reduce usageReduce in quantityAccounting/billing servicesSpecial service for subscribersByteUser profile
A system for controlling wireless phone usage enables a supervisor to establish user profiles for supervised users of wireless phones across a range of parameters, which are stored in a user profile database. Such parameters can include one or more locations, at which use of the wireless phone is restricted or permitted. In addition, restrictions on phone use, such as cumulative usage time, number of messages or number of bytes, can be provided based upon total phone usage within a specified control period, time periods, dates or days of the week during which phone use is restricted or permitted. One or more lists including numbers or other identifiers that are always-accessible can be provided, and one or more lists including numbers or other identifiers that are never-accessible can also be provided. In the event a call, message or browse does not satisfy predefined criteria, the communication attempt is blocked. Predetermined messages can be played or displayed to the called or calling party, as applicable, when a communication attempt is blocked. Boolean combinations of restrictions and permissive use criteria for the wireless phone can be specified to provide for flexibility when establishing use criteria for the wireless phone.
Owner:BOSTON COMM GROUP
Techniques and system to deploy policies intelligently
ActiveUS7716240B2Reduce the amount requiredImprove execution speedDigital data processing detailsComputer security arrangementsSpace requirementsOperating system
In an information management system, relevant policies are deployed to targets while policies which are not relevant are not. By deploying relevant policies, this reduces the amount of space requirements at the target to store the policies and the amount of data that needs to be sent to the target. Also, execution speed at the target may increase since the target does not need to evaluate policies that are not relevant.
Owner:NEXTLABS
Method and apparatus for providing access of messages to multiple recipients in cellular networks
InactiveUS6246871B1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersNetizenSpeech sound
Owner:NOKIA TECHNOLOGLES OY
Cellular messaging alert method and system
InactiveUS20040103158A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsGeolocationData mining
An efficient method and system for utilizing existing wireless communication devices and networks, such as cellular phones and carriers, as an underlying infrastructure in providing emergency information to a targeted percentage of the population in a specified geographical location, without requiring individuals to subscribe to an alerting service and without using information solicited from or provided by the intended recipients of the alert.
Owner:CMAS HLDG
Centralized call processing
InactiveUS7899167B1Reduce data communicationLower connection costsSpecial service provision for substationMultiplex system selection arrangementsData sharingCall routing
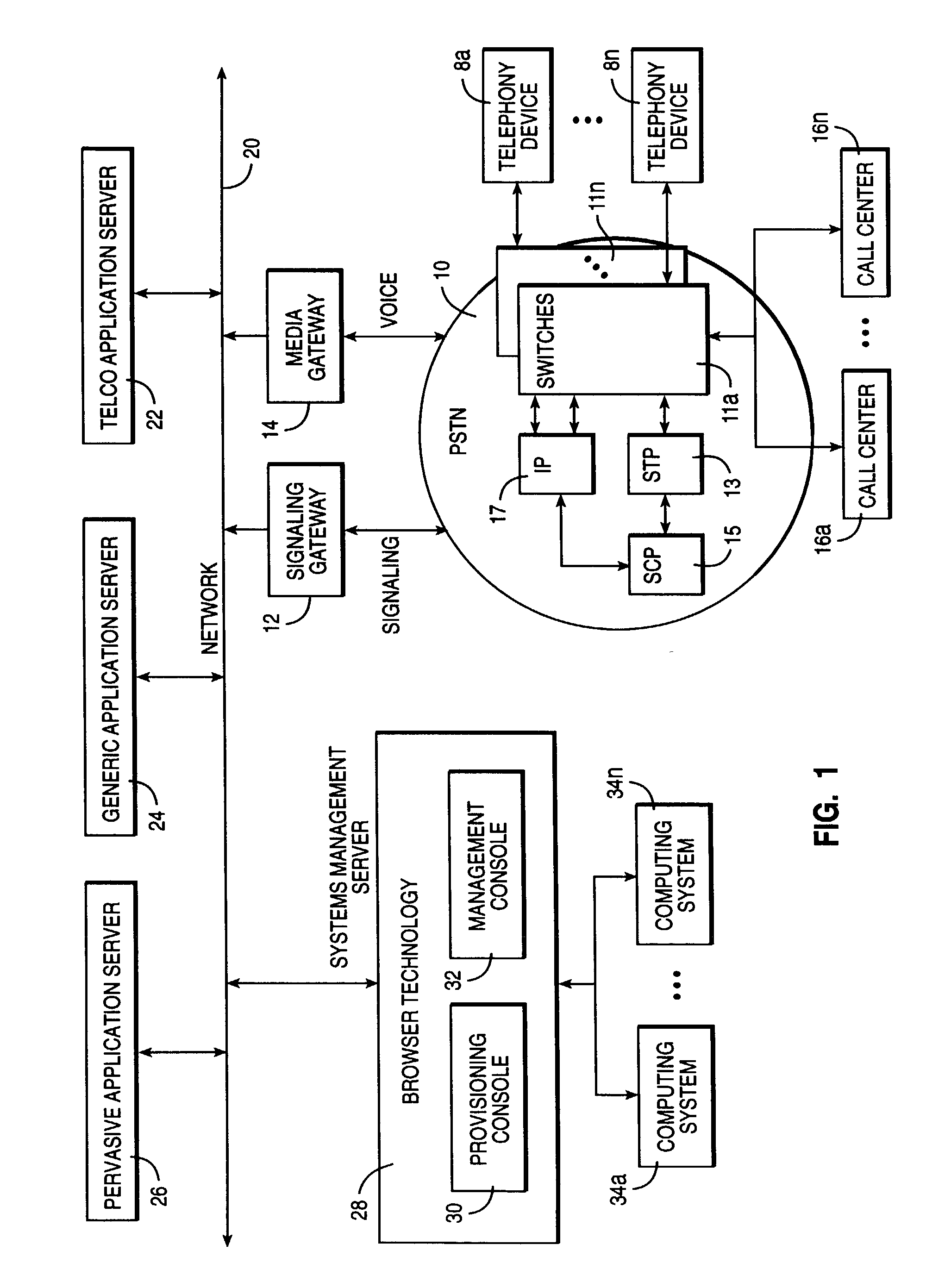
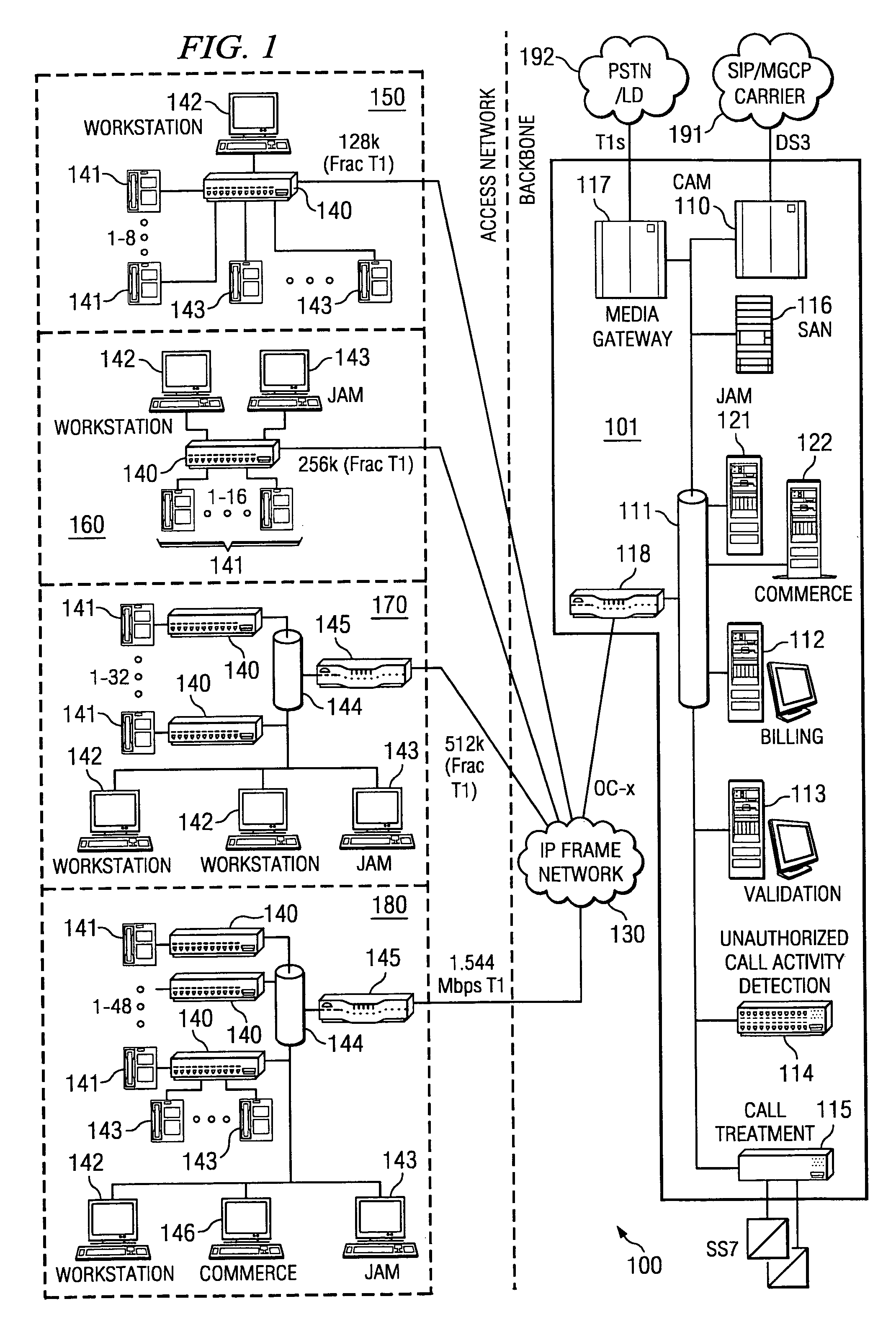
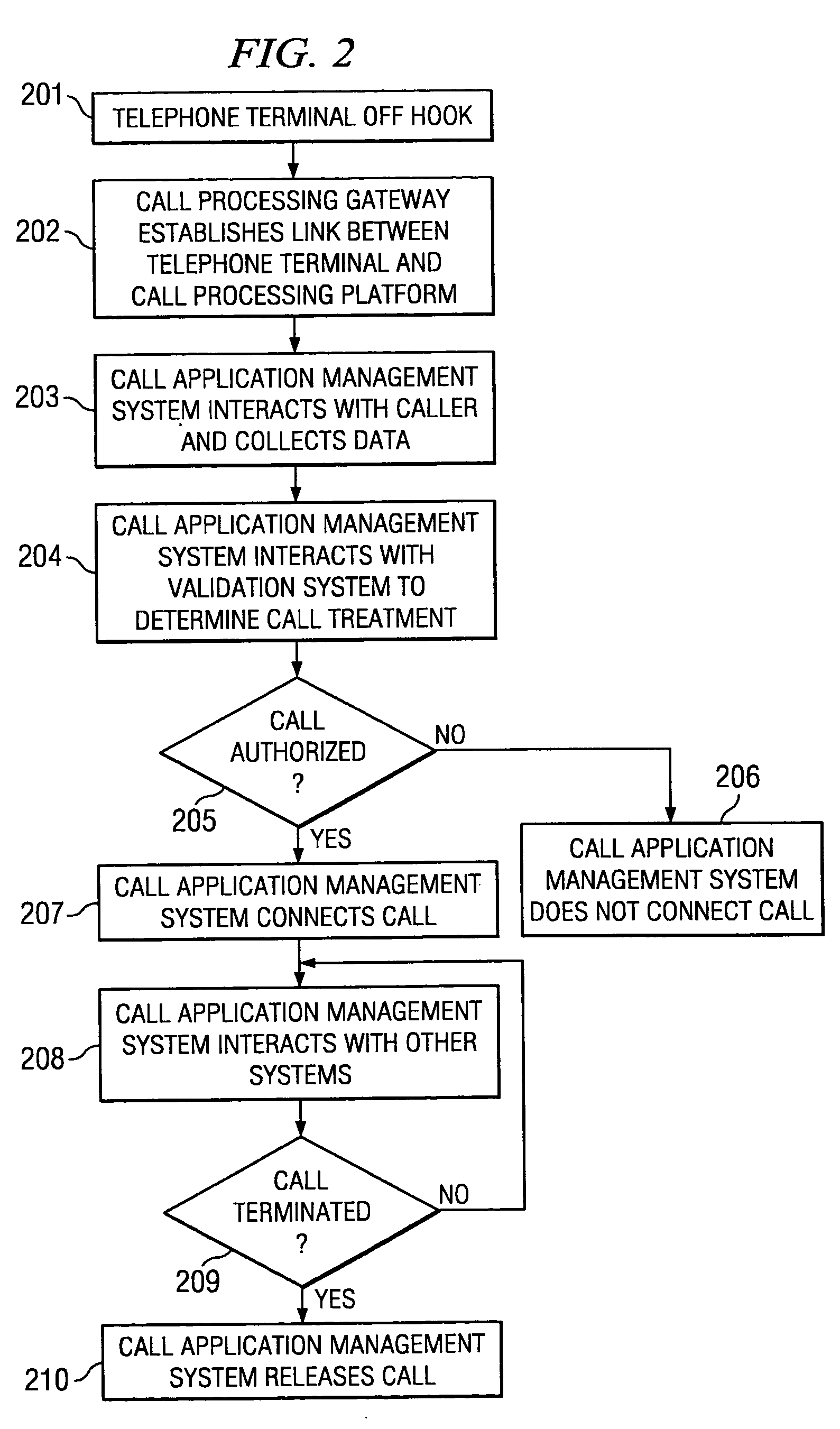
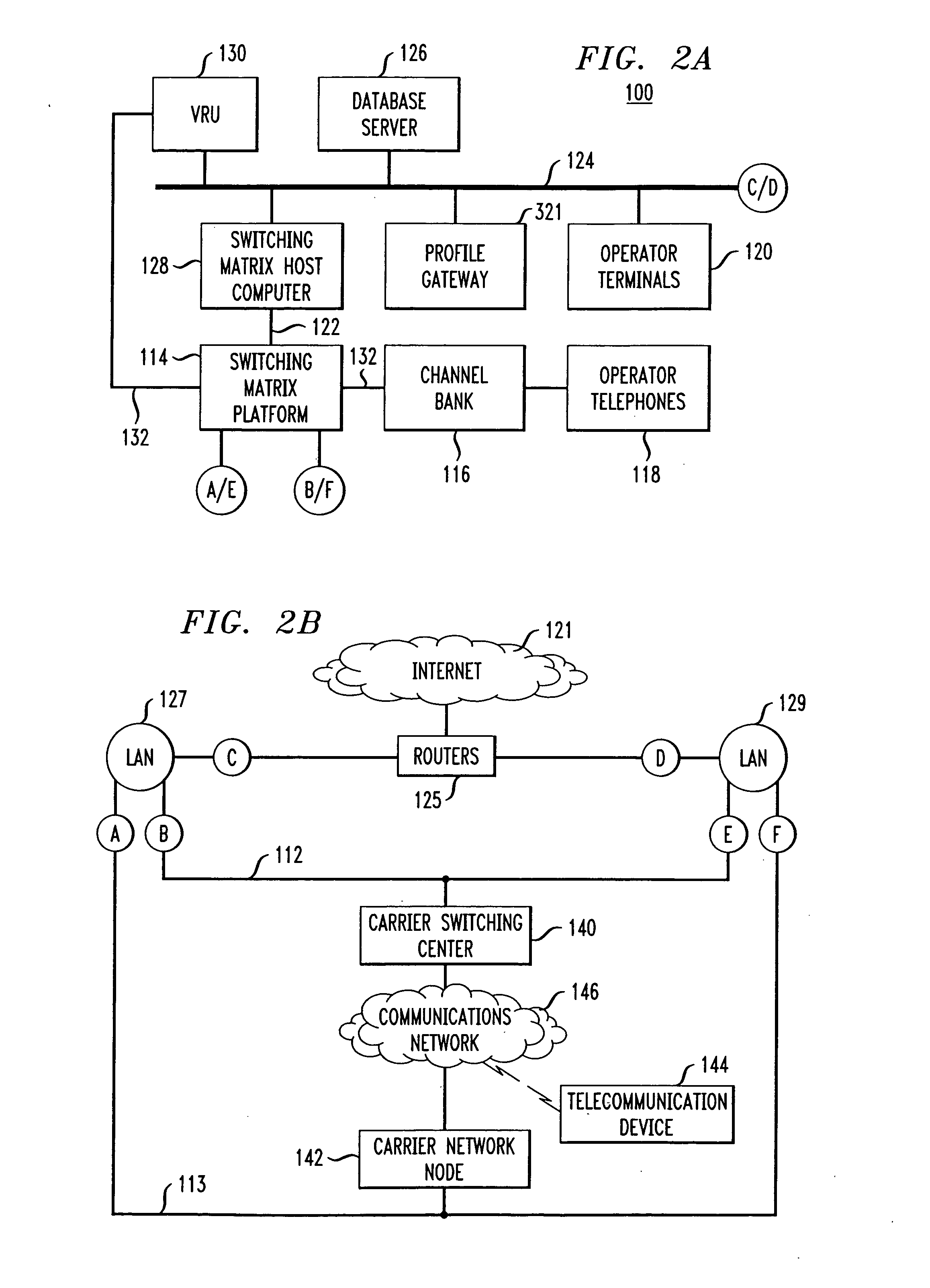
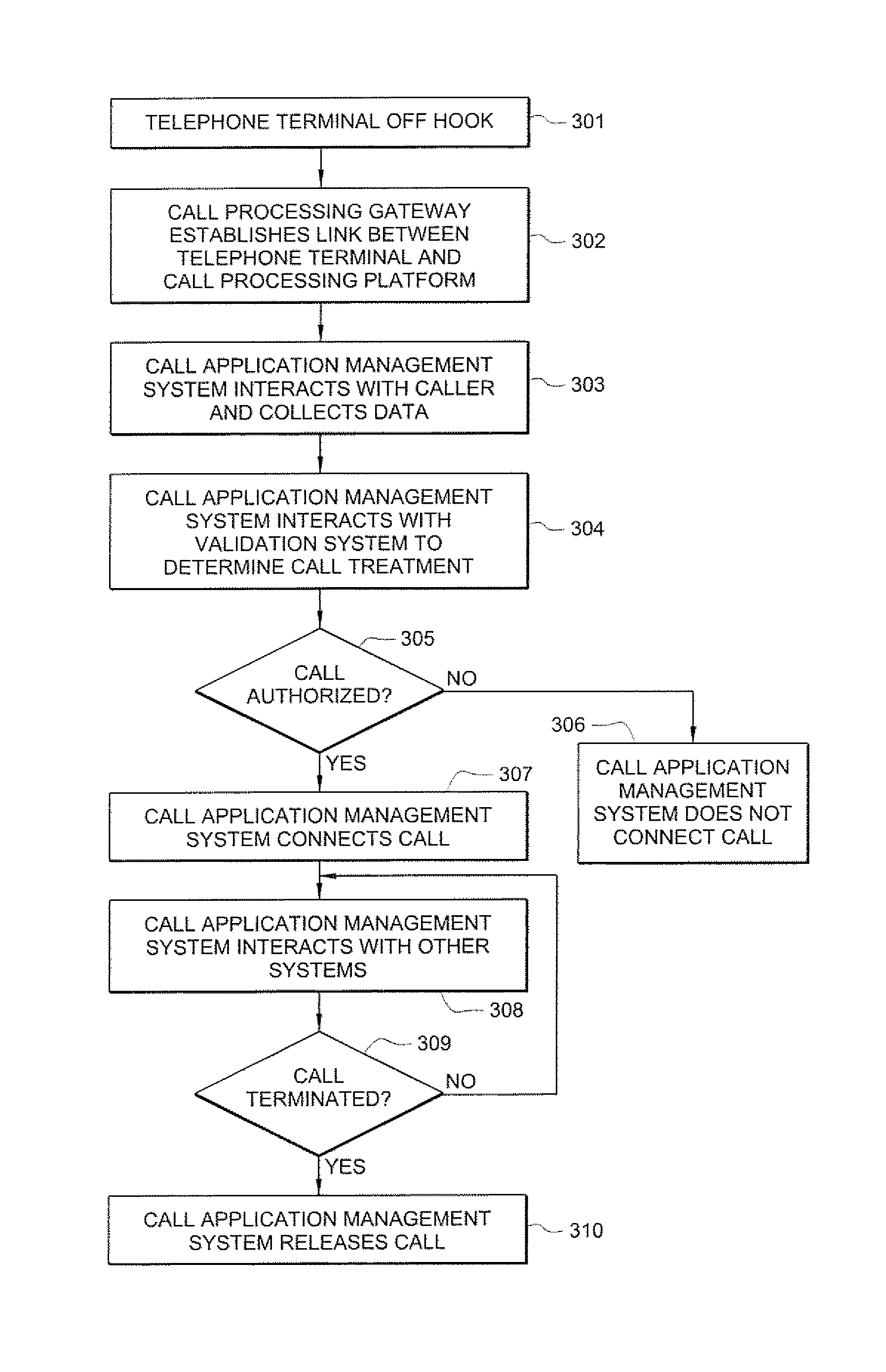
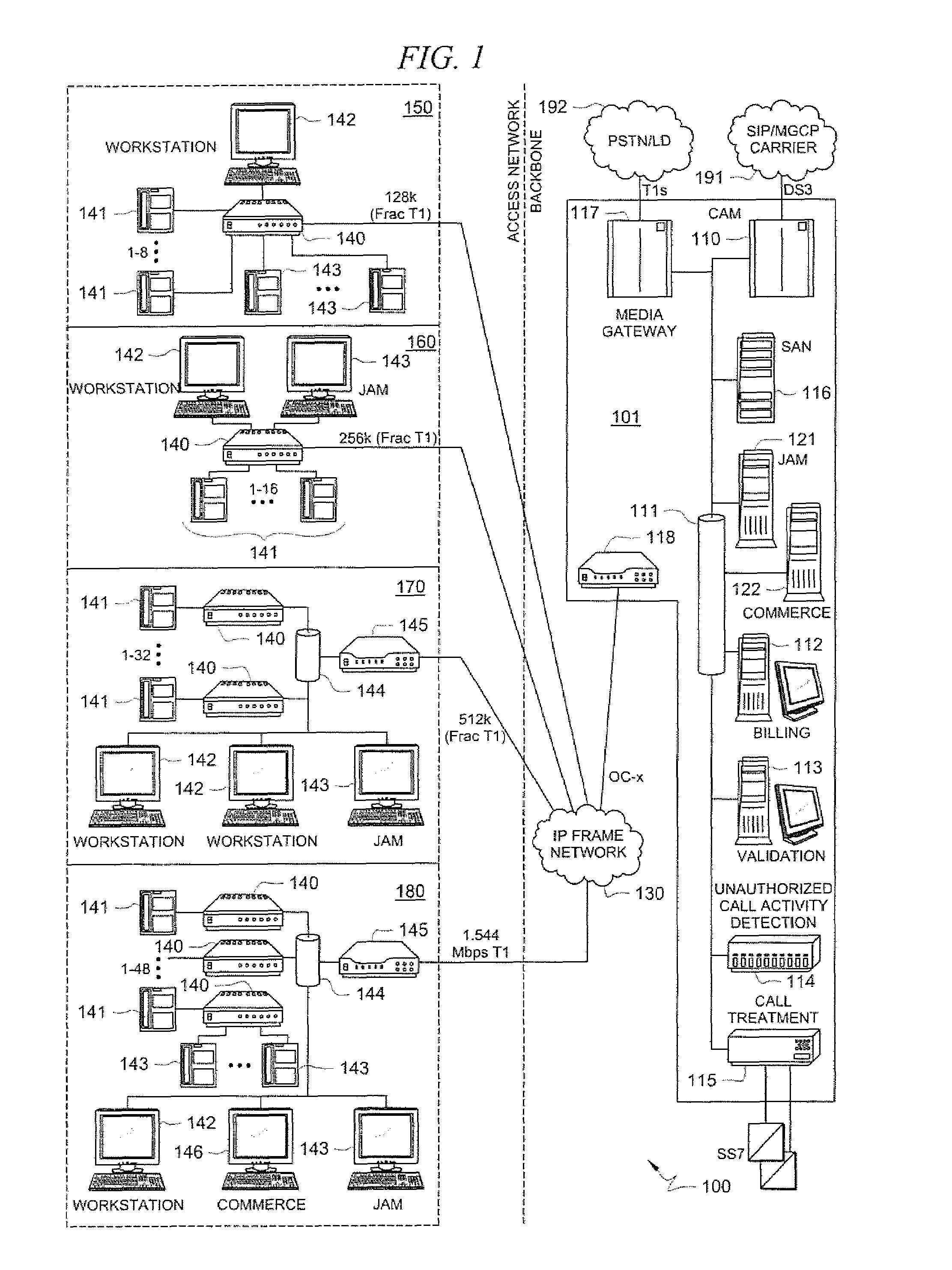
Disclosed are systems and methods which provide a centralized architecture for call processing. Embodiments utilize voice over Internet protocols (VoIP) to carry calls from a location at which calling services are provided to a centralized call processing platform providing call processing functionality, such as calling party identification, call validation, call routing, and connection to the public switched telephone network (PSTN). Call processing gateways may be utilized to provide plain old telephone service (POTS) analog line interfaces for use with a plurality of telephone sets disposed for use at a location and at least one wide area network (WAN) interface for providing high speed data communication to a centralized call processing platform. PSTN interfacing by a call processing platform may be provided as a VoIP connection to the PSTN and / or as POTS trunking. Call processing platforms may provide for data sharing, aggregation, and / or analysis across multiple facilities served.
Owner:SECURUS TECH LLC
Enhanced directory assistance service providing individual or group directories
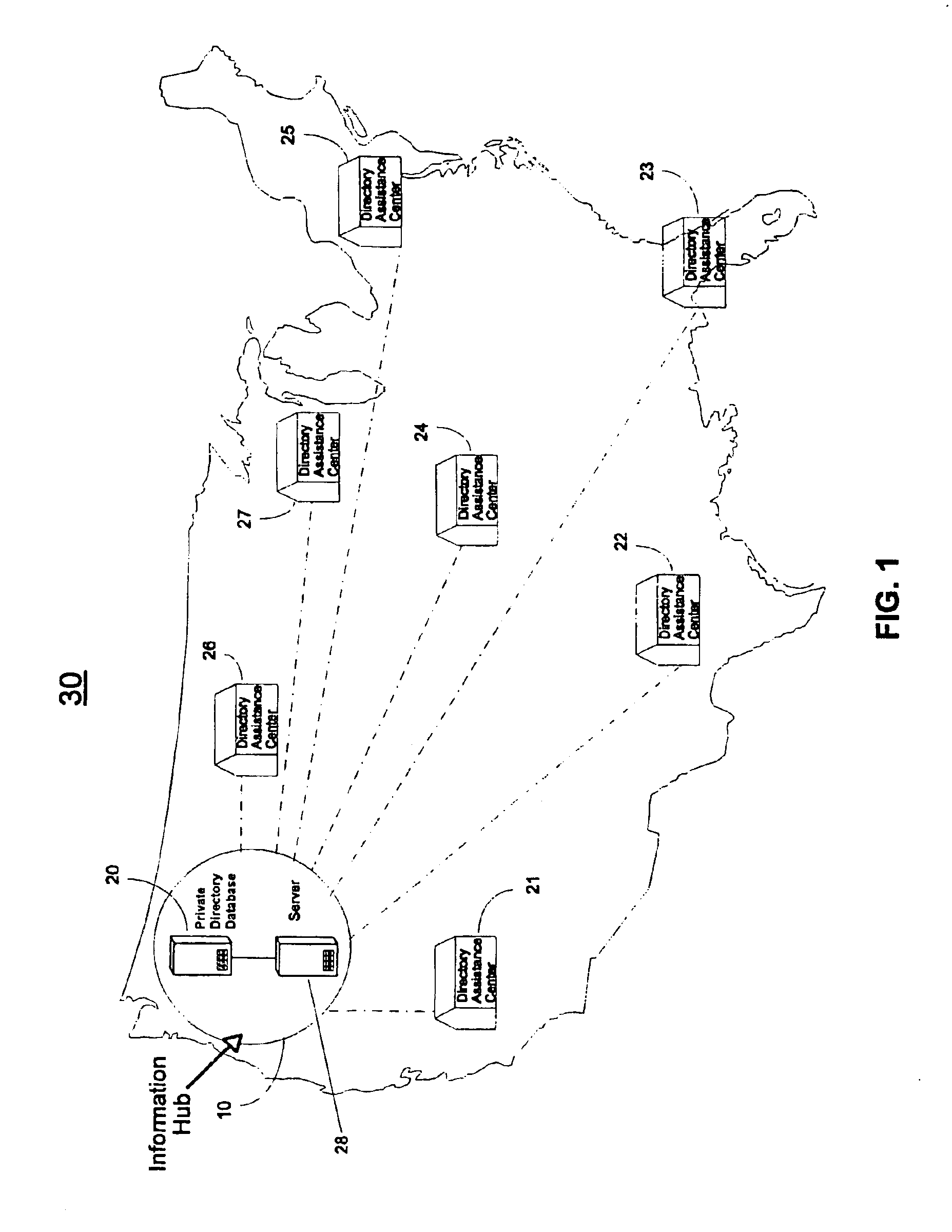
InactiveUS6870921B1Easy accessSpecial service for subscribersGraded-service arrangementsThe InternetDirectory service
Individuals and groups of individuals, such as corporations, are provided access to one or more private directories. The private directories can be edited by an administrator. Access to the private directories may be limited by administrators of the private directories. Access to private directories is provided via a connection to directory assistance providers. Directory service providers are capable of facilitating the administration of the private directories as well as connecting users of private directories to contacts in the private directories. Access to the private directory may be obtained via an internet connection.
Owner:GRAPE TECH GROUP
Registration, verification and notification system
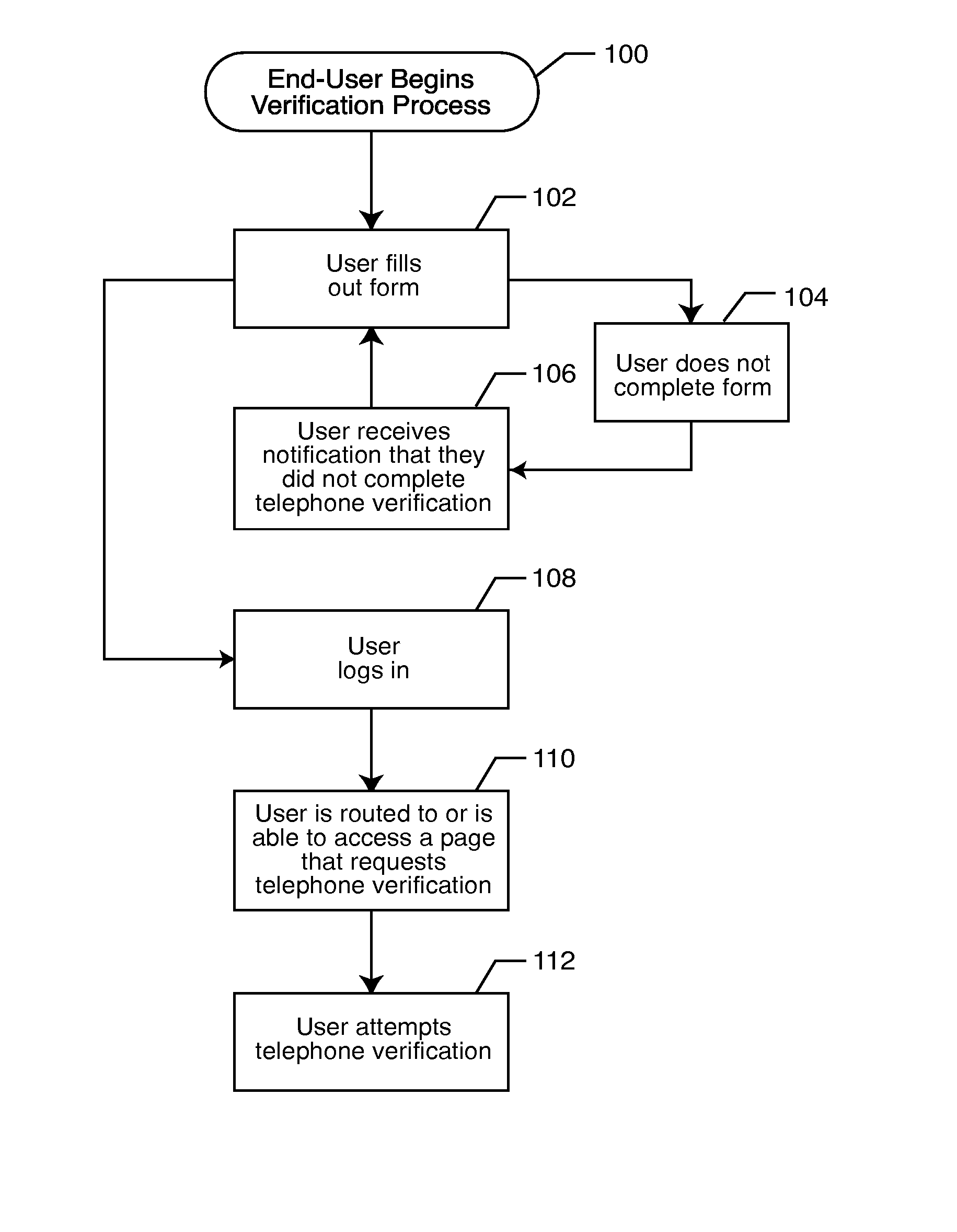
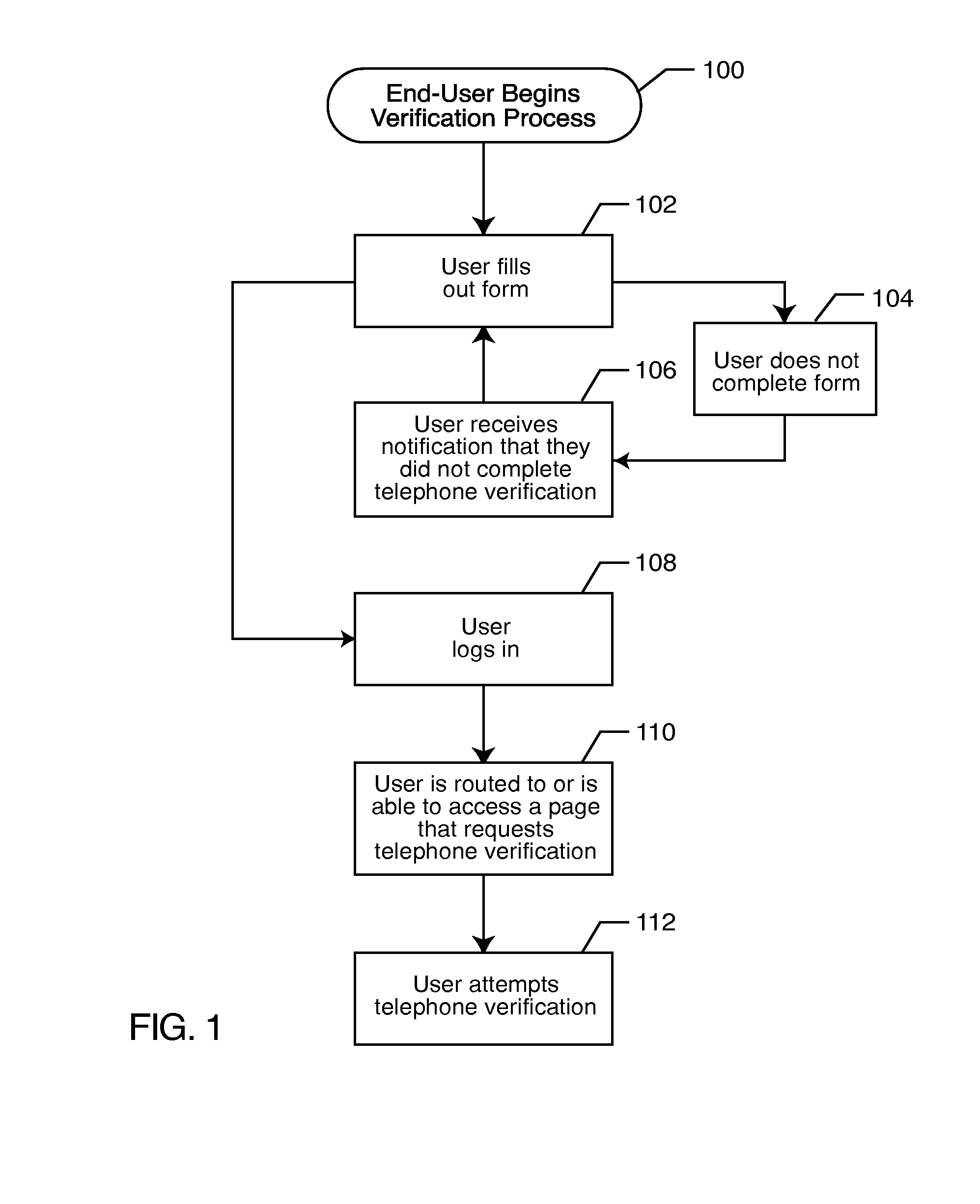
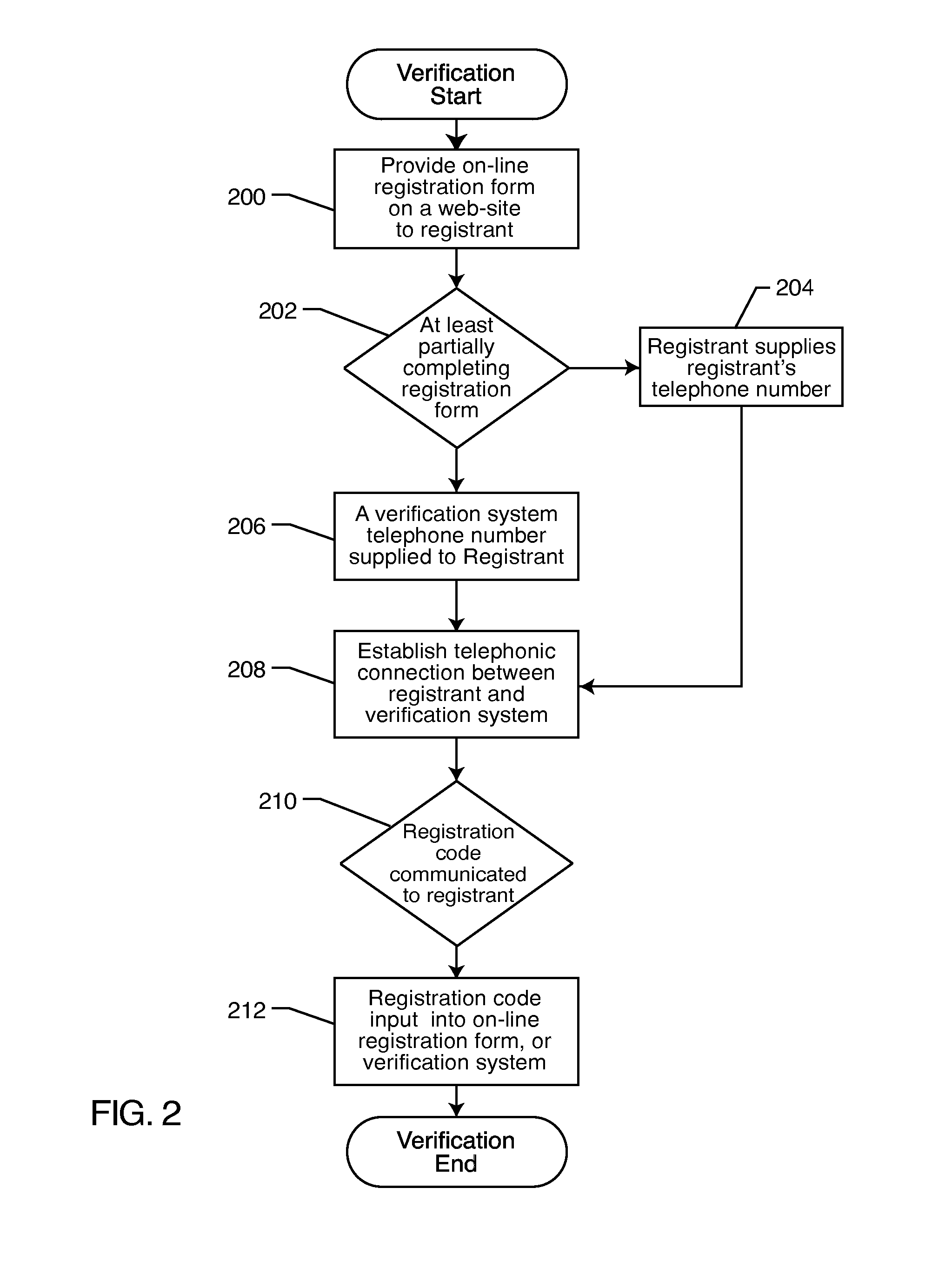
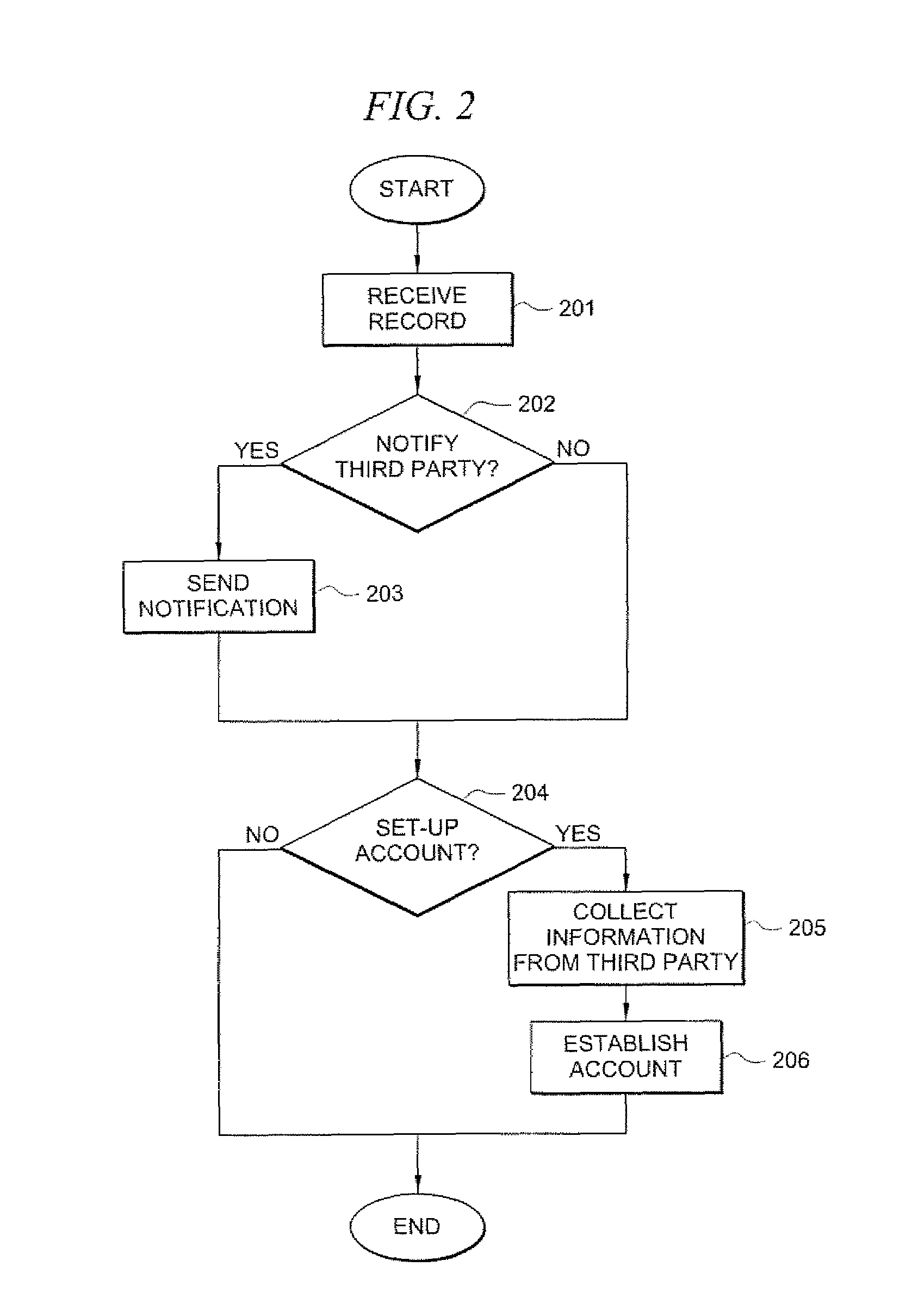
ActiveUS20080010687A1Digital data processing detailsUser identity/authority verificationVerification systemNotification system
A registrant provides at least one registrant electronic contact, such as a telephone number, during a registration process. The registrant's information may be compared to a database of such information. The registrant is verified by establishing a connection with the registrant via the registrant contact. The verification code is communicated to the registrant, which is input into an on-line form or a telephone verification system. Notification events are established, and the registrant is notified of the occurrence of a previously established notification event by establishing a connection with the registrant via the registrant contact.
Owner:TELESIGN CORP
Technique for providing personalized information and communications services
InactiveUS20050002510A1Efficient retrievalSame access rightAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersPersonalizationWeb browser
A user may utilize a communication device, e.g., a wireless phone, mobile device or personal digital assistant (PDA), to contact an information / call center where an operator provides personalized information and communications services to the user in accordance with the invention. Such services include, e.g., providing listing information, contacts information, appointments information, etc. To provide effective connectivity, for example, when a user locates a phone number in his / her private directory using a web browser, the user may utilize a direct connect feature of the invention to initiate a phone call to the desired number over the Internet. In addition, the invention allows for delivery of the appointments information to the user not only via voice connection, but also SMS, email, facsimile, PDA, etc. It also allows for rendering a calendaring service in combination with such services as a TeleConcierge® service which helps the user to plan a future event, e.g., making a restaurant reservation. An appointment record concerning the future event is automatically incorporated into the user's calendar once it is successfully planned. To personalize the services, at least one profile associated with the user is used which specifies the subscribed services and the preferred ways of receiving them. For example, the profile may specify use of a special skilled operator, methods of delivery of information to the user, etc.
Owner:GRAPE TECH GROUP
Inmate management and call processing systems and methods
InactiveUS7529357B1Reduce data communicationLower connection costsMultiplex system selection arrangementsSpecial service provision for substationThird partyHandling system
Disclosed are systems and methods that provide centralized or nodal inmate management and telephone call processing capabilities to controlled environment facilities. An inmate management and call processing system serves a plurality of facilities and includes an inmate information database. The database is shared across the facilities and contains inmate records that may be accessed and modified by each facility as the inmate is transferred among those facilities. Each inmate record may include, among other information, contact information of third parties whom may be notified of the inmate's arrest and / or subsequent transfers of the inmate to different facilities. The inmate management and telephone call processing system may use third party contact information to establish accounts used to charge calls or transactions made by an inmate while residing at the facility. Some systems may also provide call processing, video conferencing, e-mail, voicemail, and / or videomail applications, and the like to the facilities.
Owner:SECURUS TECH LLC
System and method for providing remote access to telecommunications services
InactiveUS20050141500A1Special service for subscribersCalling susbscriber number recording/indicationGraphicsGraphical user interface
A system and method are provided for reviewing and updating a subscriber's telecommunications services using a graphical user interface via multiple data networks. A data message is received at an intelligent peripheral from the graphical user interface via at least one of the data networks. The data message indicates a subscriber's desired update to a selected service. The data message is converted into a protocol compatible with a service control point. The converted data message is identical to a data message that the intelligent peripheral would create if the subscriber had entered the desired update via an interactive voice response system. The converted data message is transmitted to the service control point, which updates the service in accordance with the subscriber's update. Thus, the service is updated substantially contemporaneously with the request. Moreover, the subscriber retains the ability to update and review service data via the interactive voice response.
Owner:AT&T LABS
Authenticating a caller before providing the caller with access to one or more secured resources
InactiveUS7006605B1Improve accuracyImprove efficiencyMultiplex system selection arrangementsSpecial service for subscribersTelecommunicationsHandling system
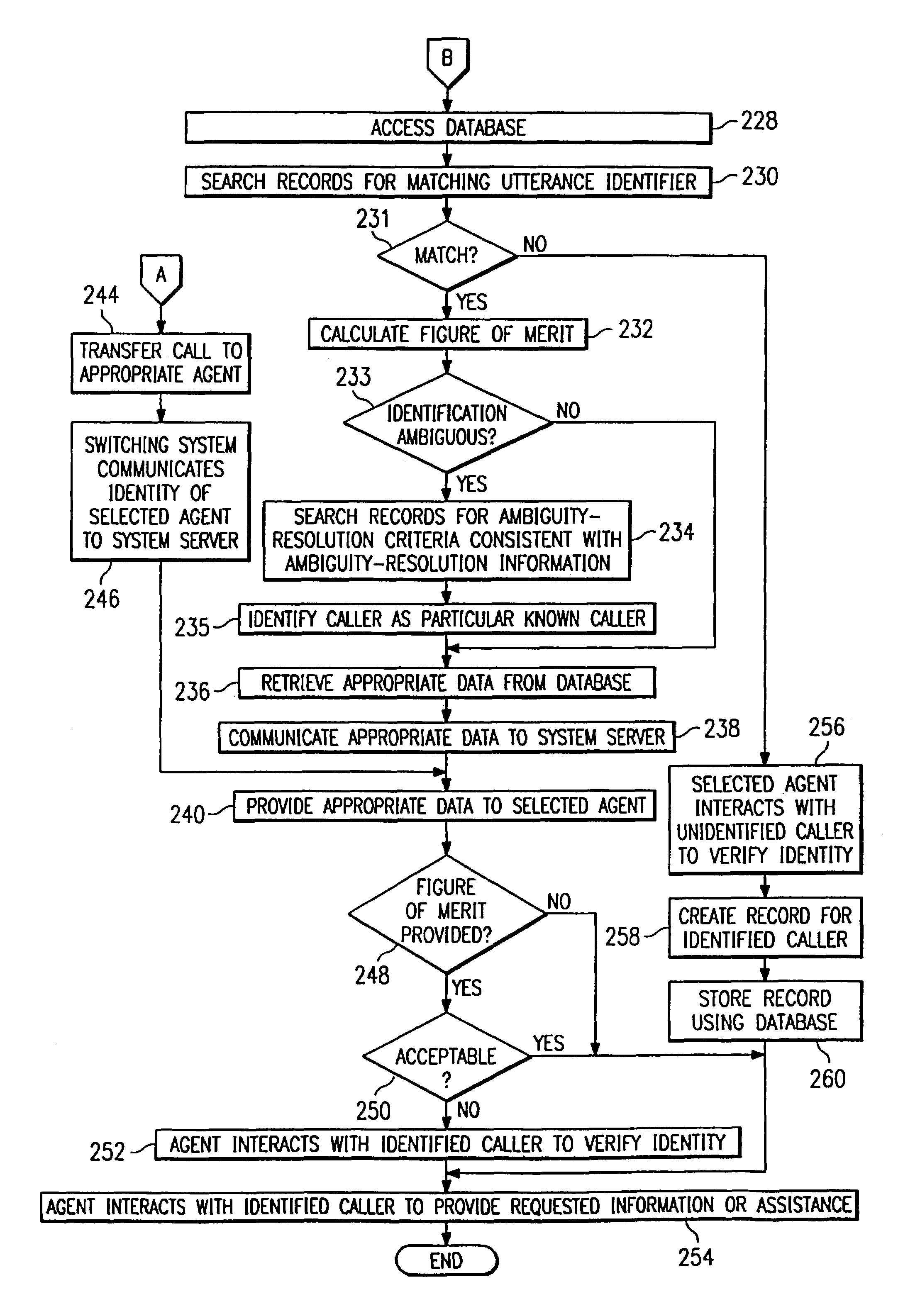
In one embodiment, a system authenticates a caller before providing the caller with access to one or more secured resources. Identification and verification data is stored during system enrollment of known persons. A processing system, in a current call initiated by a caller and prior to identification of the caller, receives voice-based information for the caller including a digital representation of a telephone number spoken by the caller in the current call, the received information including voice-based identification information and voice-based verification information for the caller. The processing system automatically compares the received identification information and the received verification information for the caller with the stored identification and verification data for known persons, respectively, to uniquely identify and verify the identity of the caller as a particular known person. The processing system authenticates the caller for access to the one or more secured resources in response.
Owner:ZARBANA DIGITAL FUND
Telecommunication call management and monitoring system with voiceprint verification
InactiveUS20050043014A1Accurate verificationEliminating system overloadTelevision system detailsUnauthorised/fraudulent call preventionPersonal identification numberMonitoring system
Disclosed is a secure telephone call management system for authenticating users of a telephone system in an institutional facility. Authentication of the users is accomplished by using a personal identification number, preferably in conjunction with speaker independent voice recognition and speaker dependent voice identification. When a user first enters the system, the user speaks his or her name which is used as a sample voice print. During each subsequent use of the system, the user is required to speak his or her name. Voice identification software is used to verify that the provided speech matches the sample voice print. The secure system includes accounting software to limit access based on funds in a user's account or other related limitations. Management software implements widespread or local changes to the system and can modify or set any number of user account parameters.
Owner:GLOBAL TELLINK
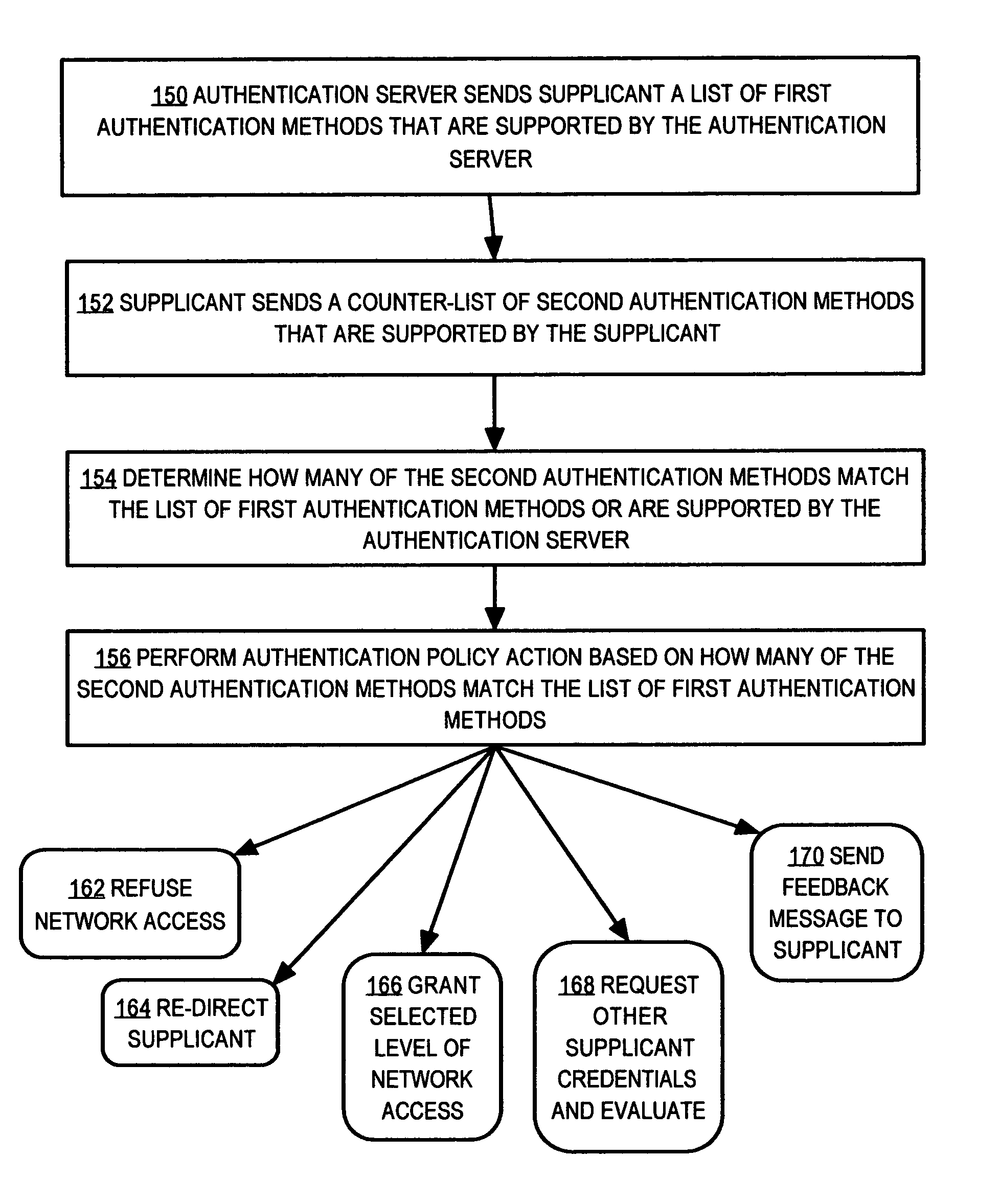
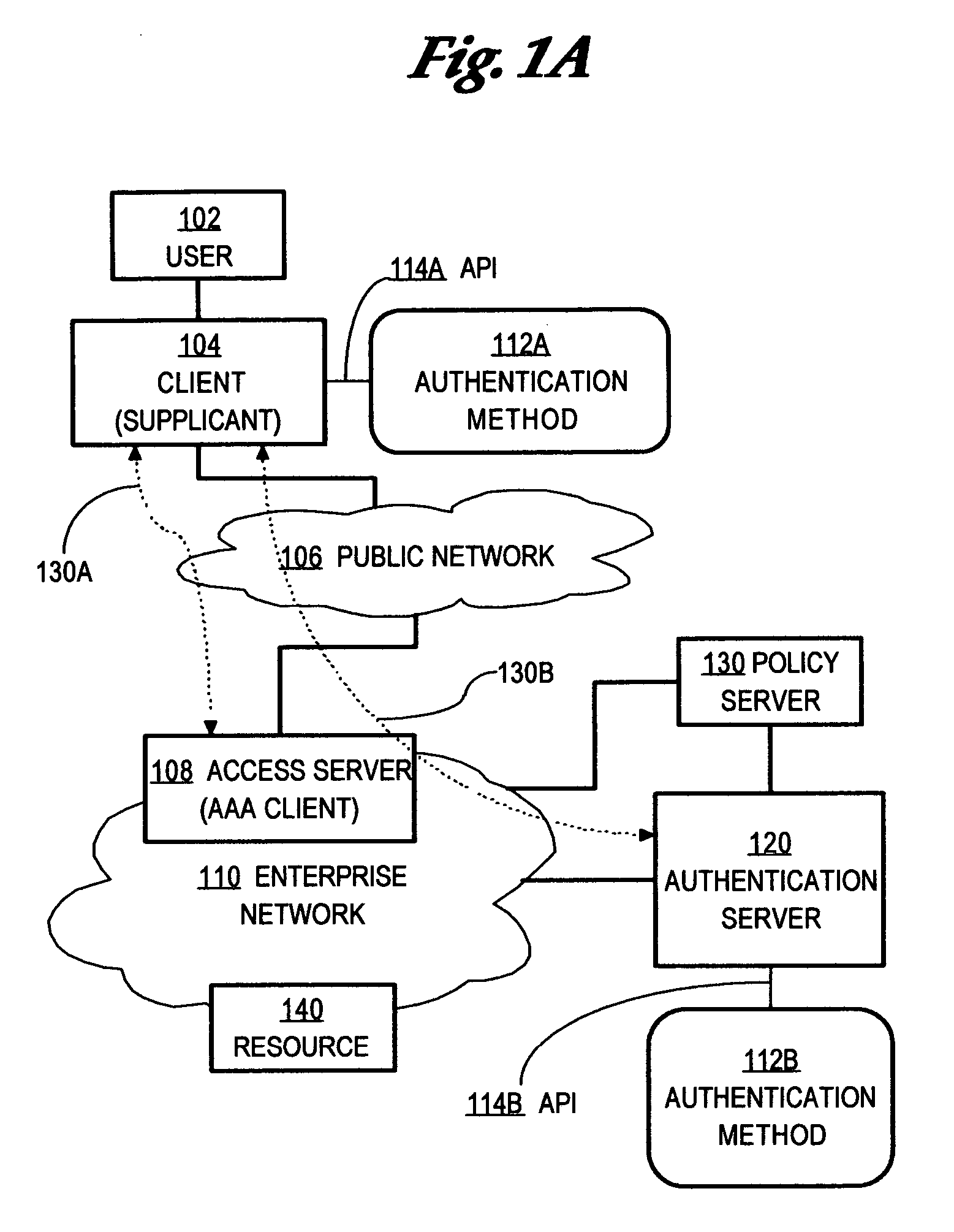
Method and apparatus for determining authentication capabilities
ActiveUS20060026671A1Public key for secure communicationDigital data processing detailsAuthentication serverClient-side
A method is disclosed for determining the authentication capabilities of a supplicant before initiating an authentication conversation with a client, for example, using Extensible Authentication Protocol (EAP). In one aspect, the method provides for sending, to a supplicant that is requesting access to a computer network subject to authentication of a user of the supplicant, a list of first authentication methods that are supported by an authentication server; receiving, from the supplicant, a counter-list of second authentication methods that are supported by the supplicant; determining how many second authentication methods in the counter-list match the first authentication methods; and performing an authentication policy action based on how many of the second authentication methods match the first authentication methods. Policy actions can include blocking access, re-directing to sources of acceptable authentication methods, granting one of several levels of network access, etc.
Owner:CISCO TECH INC
Popular searches
Current supply arrangements Manual exchanges Lock-out/secrecy provision Commmunication supplementary services Data switching by path configuration Wireless commuication services Network data management Picture reproducers with optical-mechanical scanning Picture reproducers using projection devices Picture reproducers using solid-state color display
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com