Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58 results about "Secure telephone" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
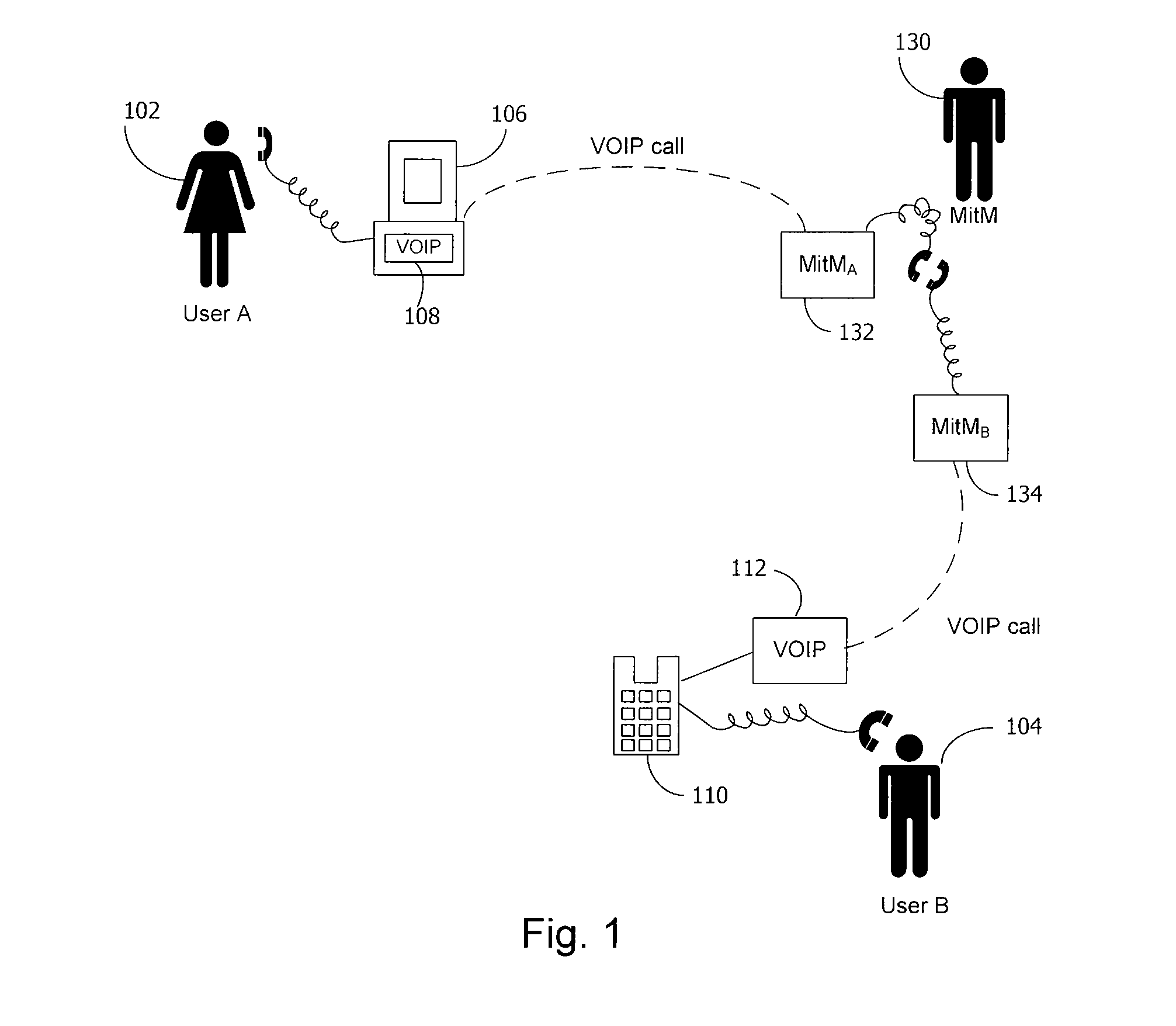
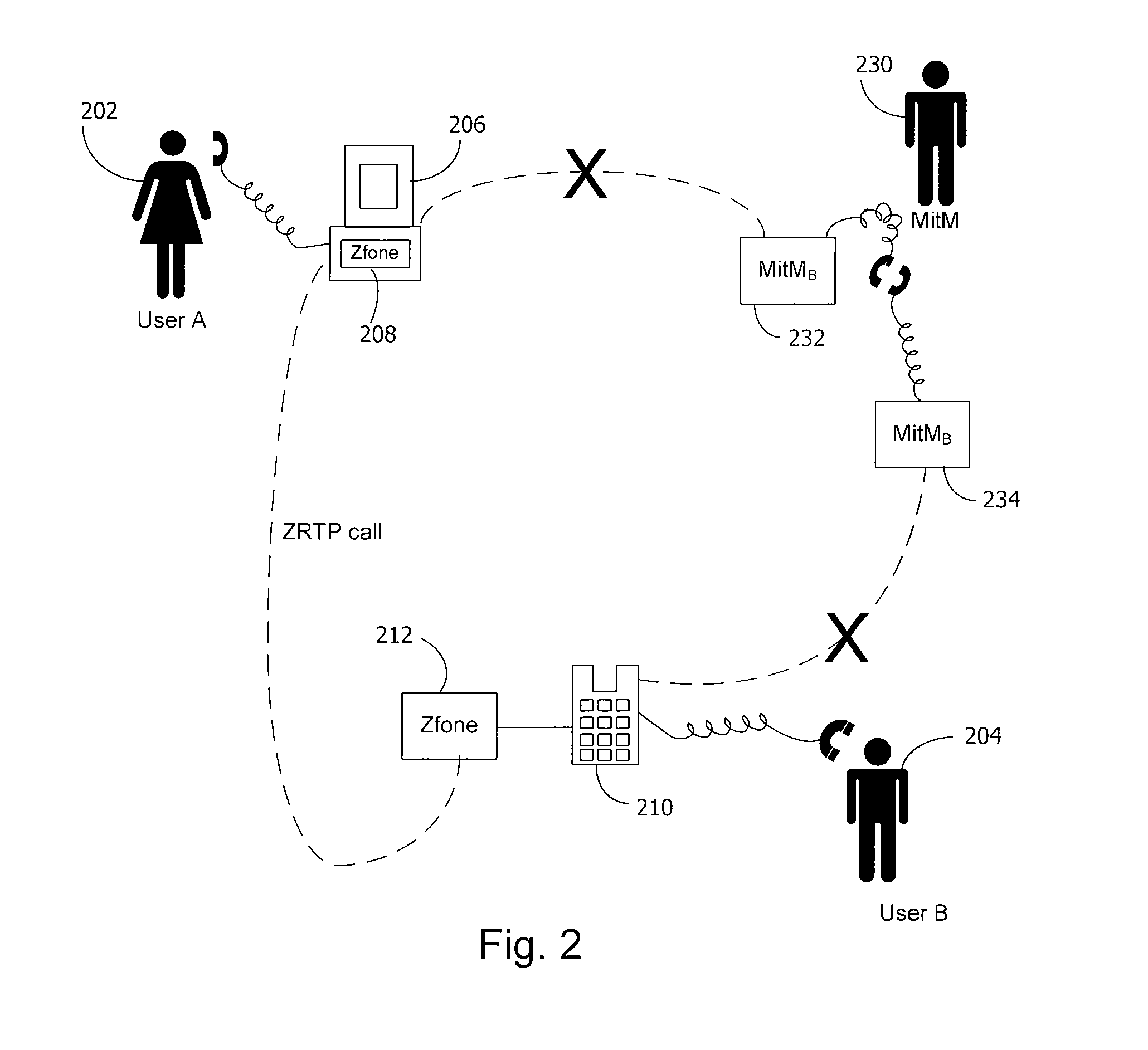
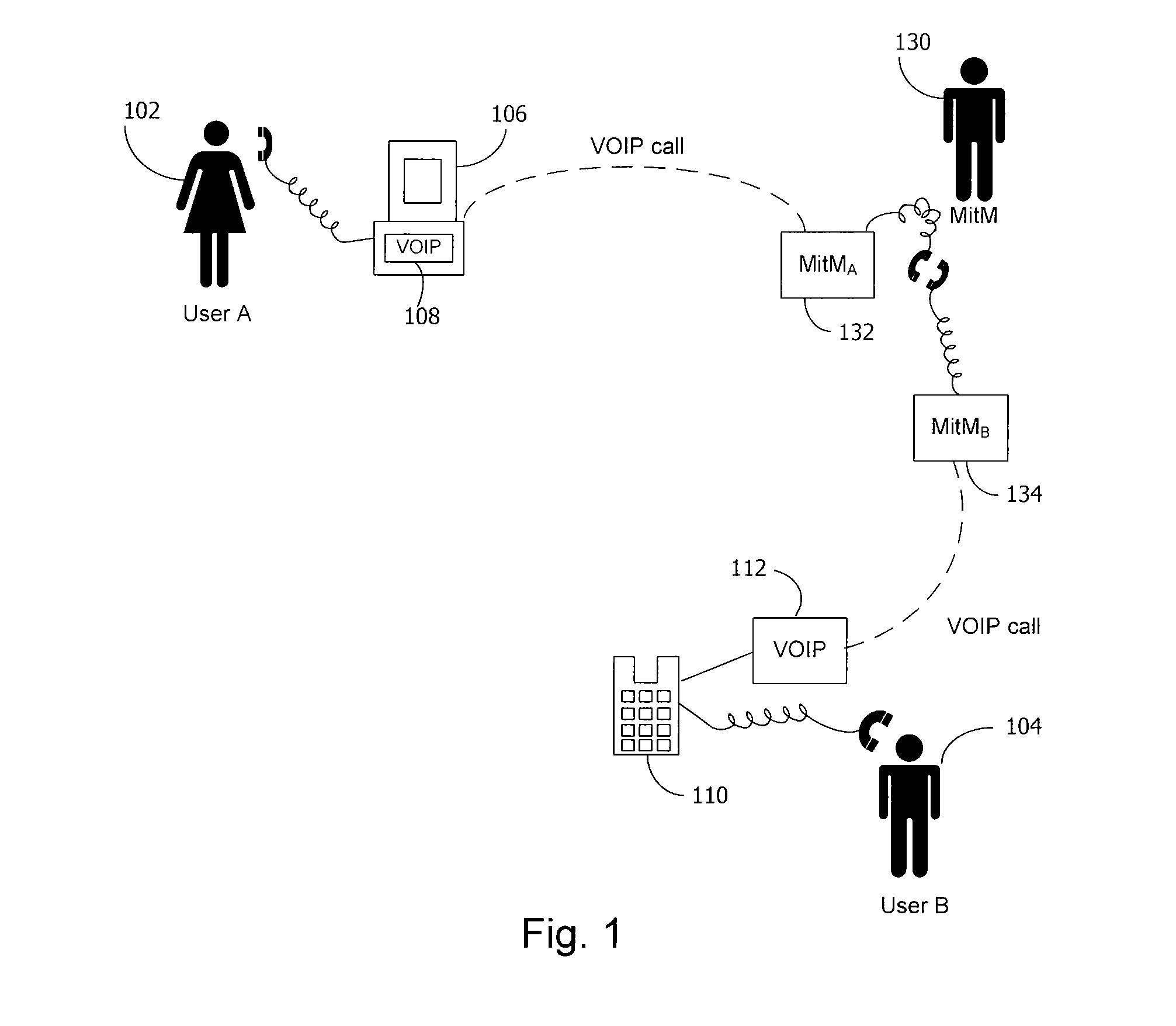
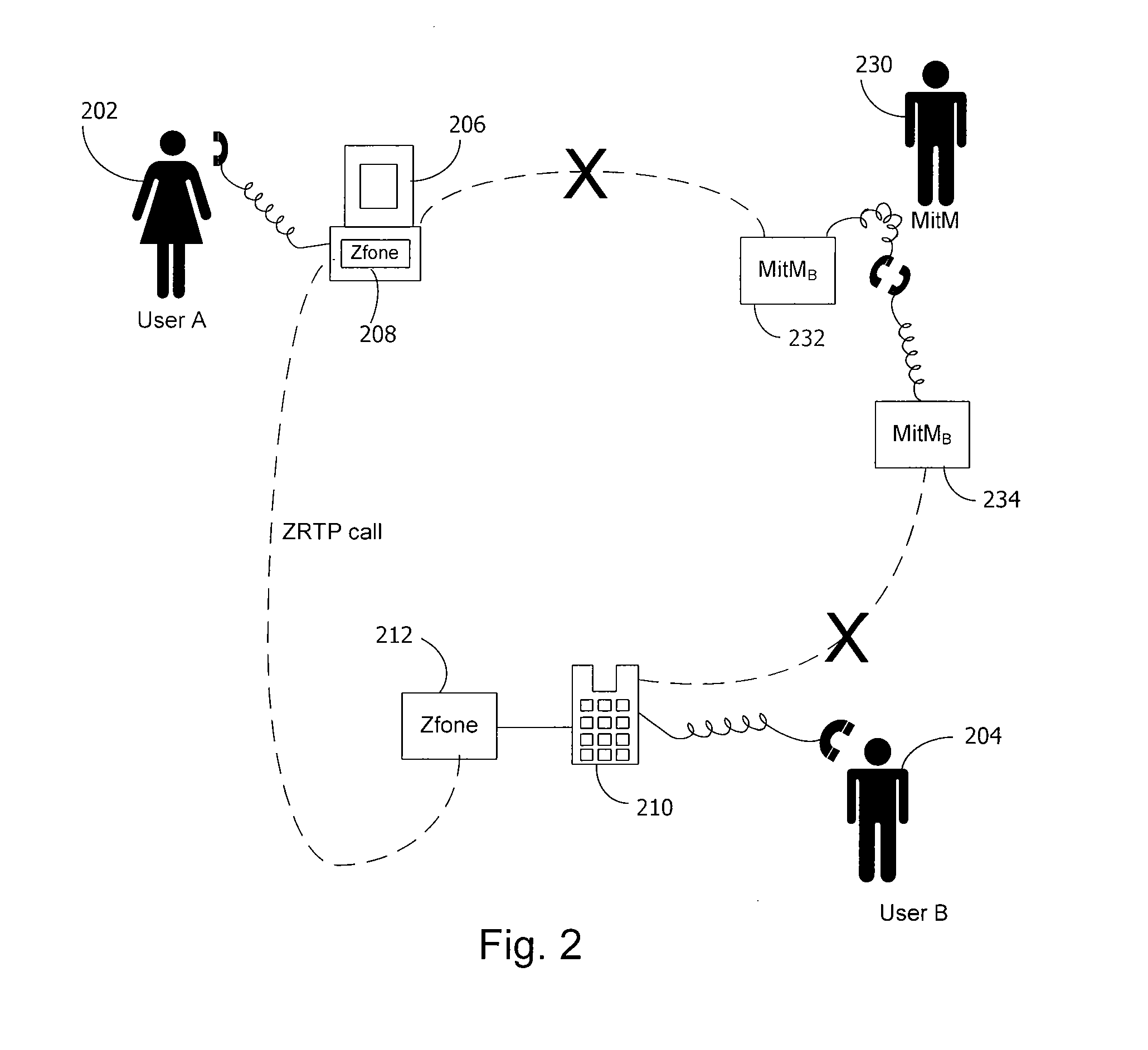
A secure telephone is a telephone that provides voice security in the form of end-to-end encryption for the telephone call, and in some cases also the mutual authentication of the call parties, protecting them against a man-in-the-middle attack. Concerns about massive growth of telephone tapping incidents led to growing demand for secure telephones.
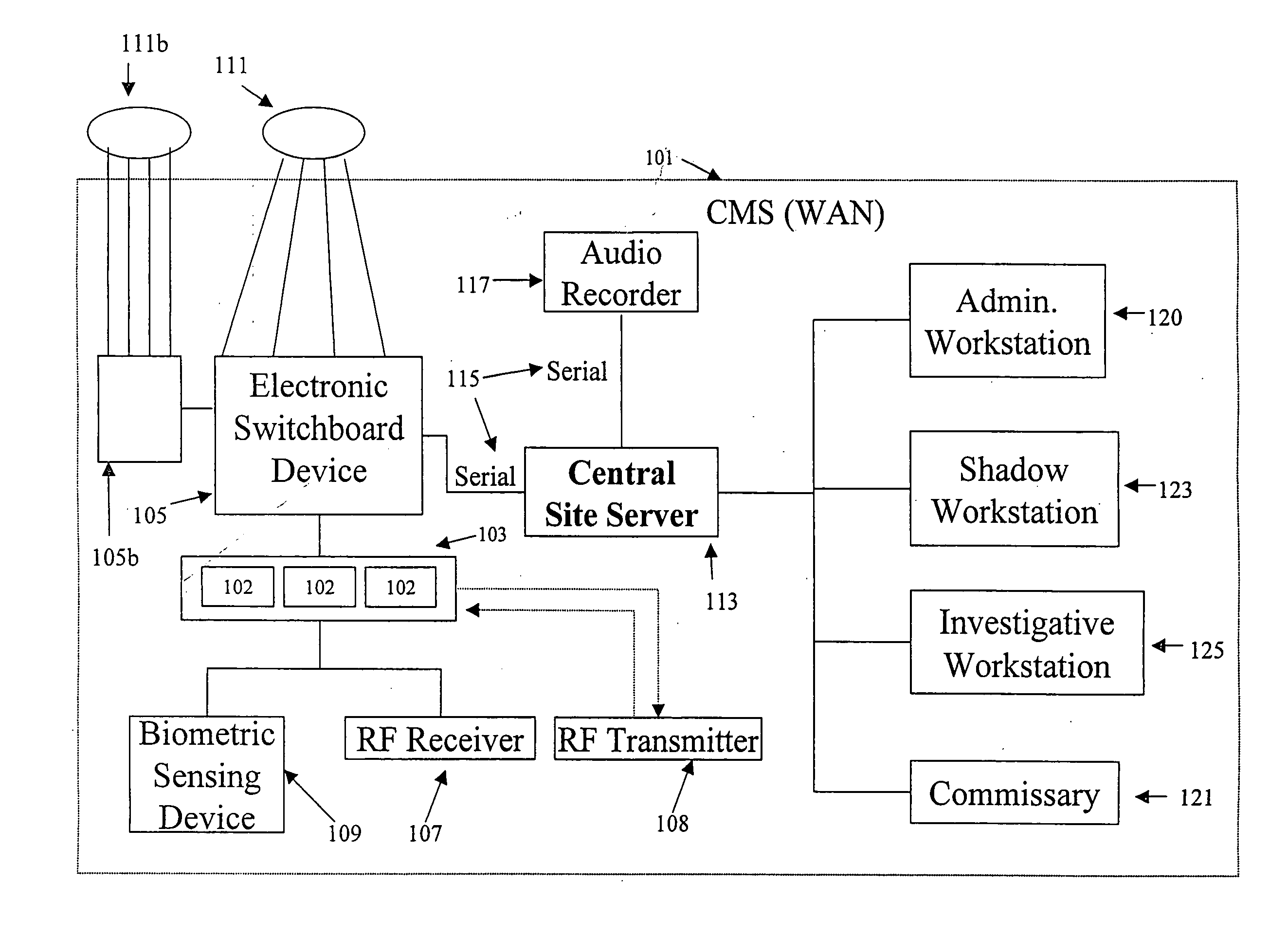
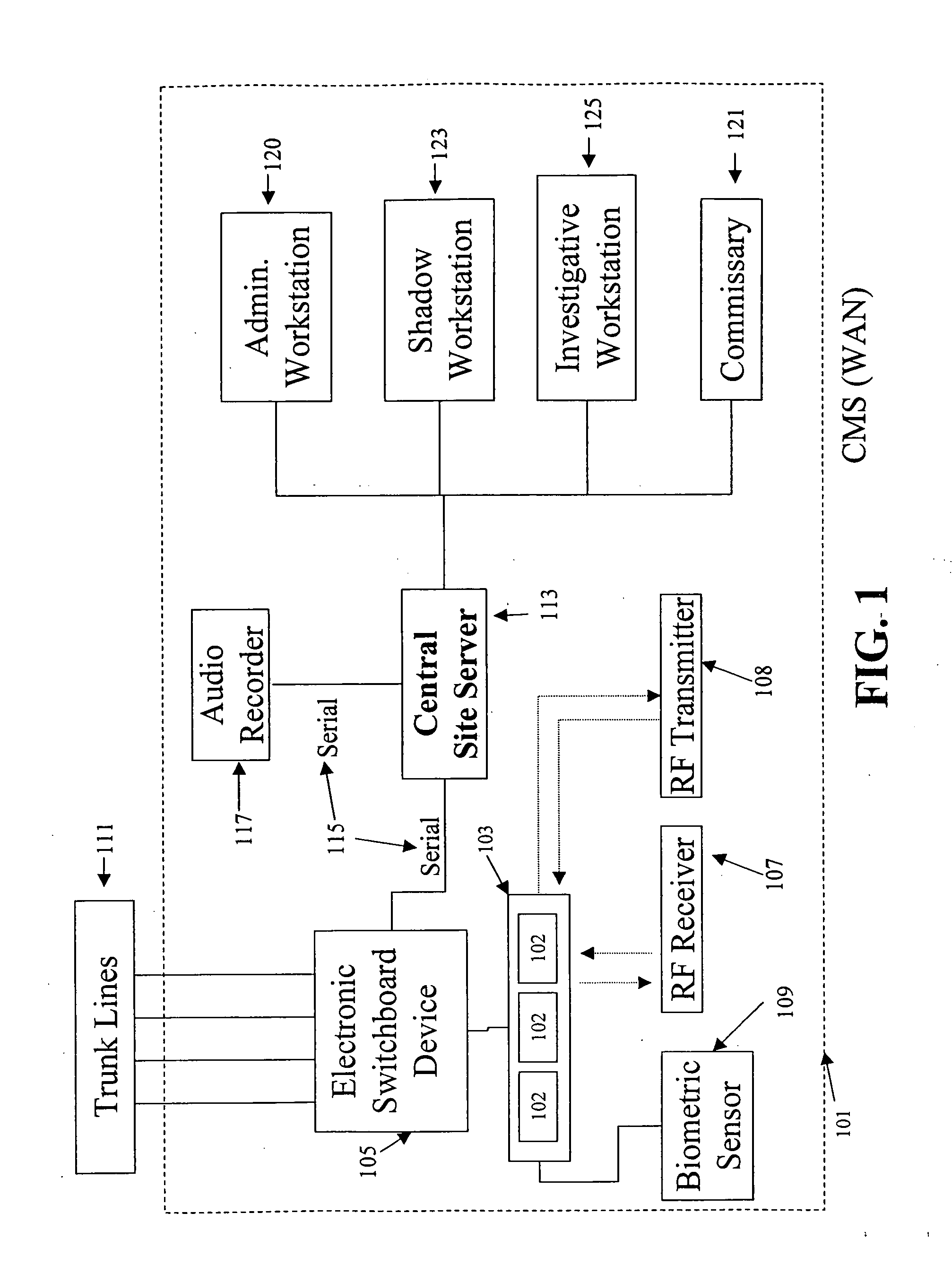
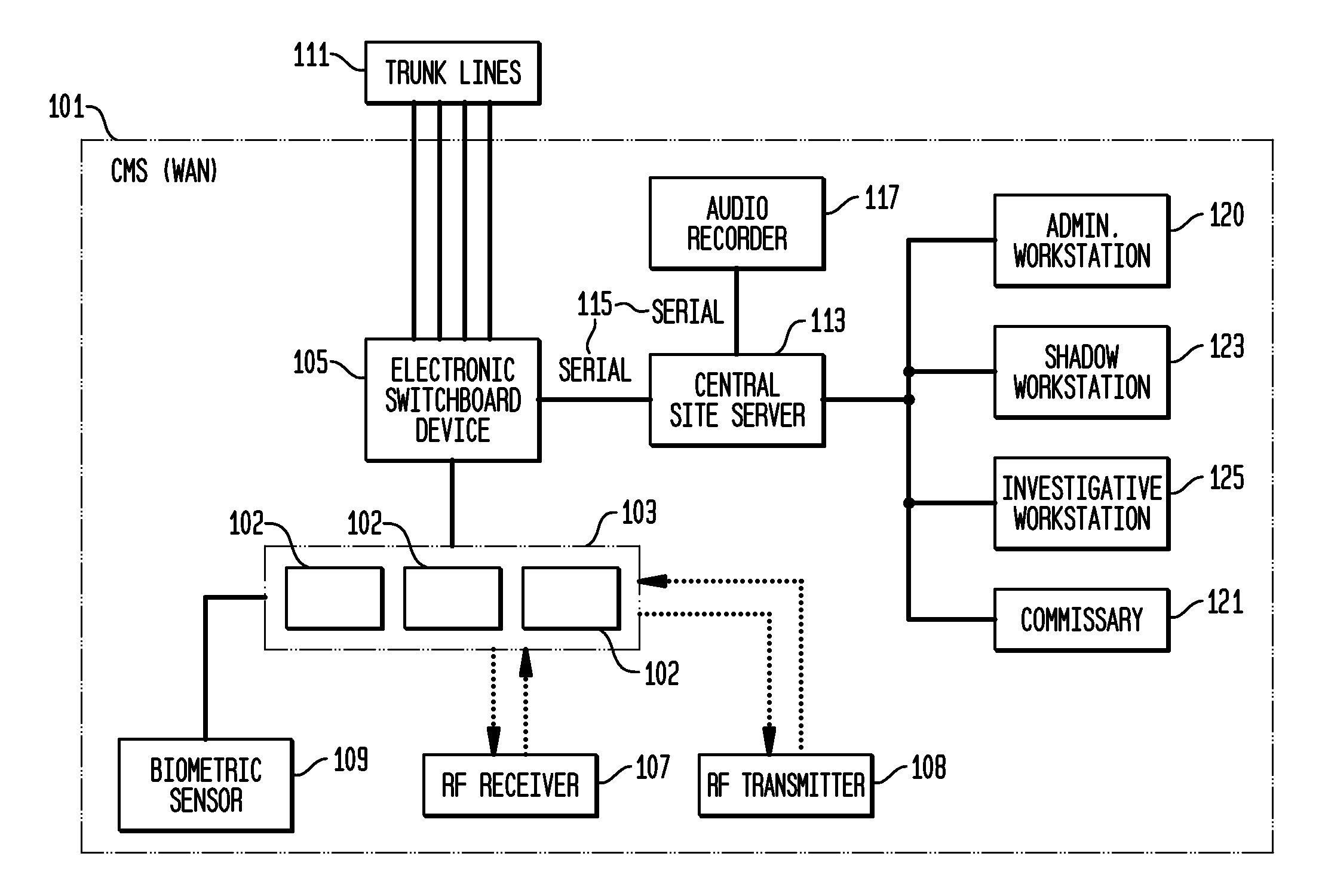
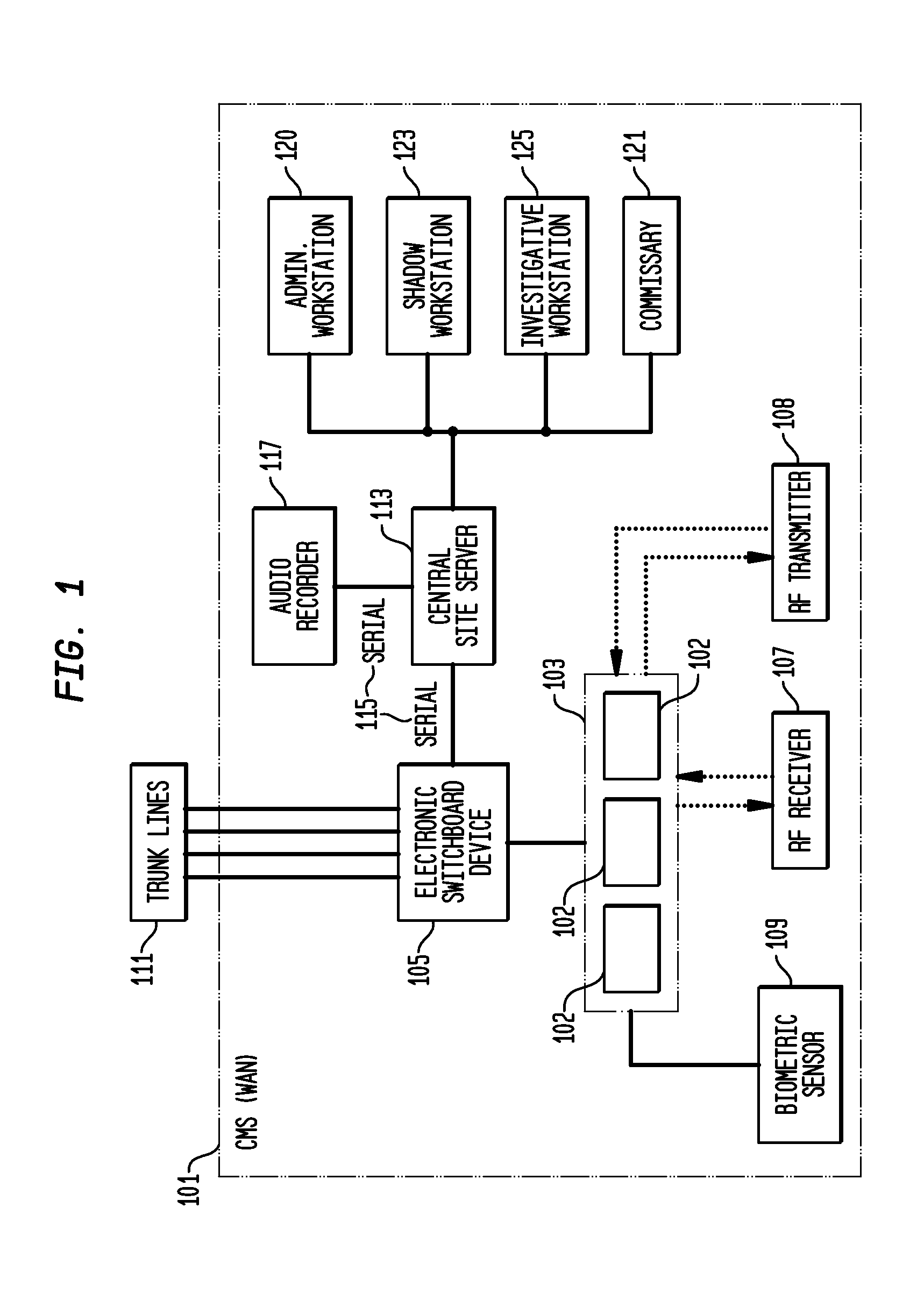
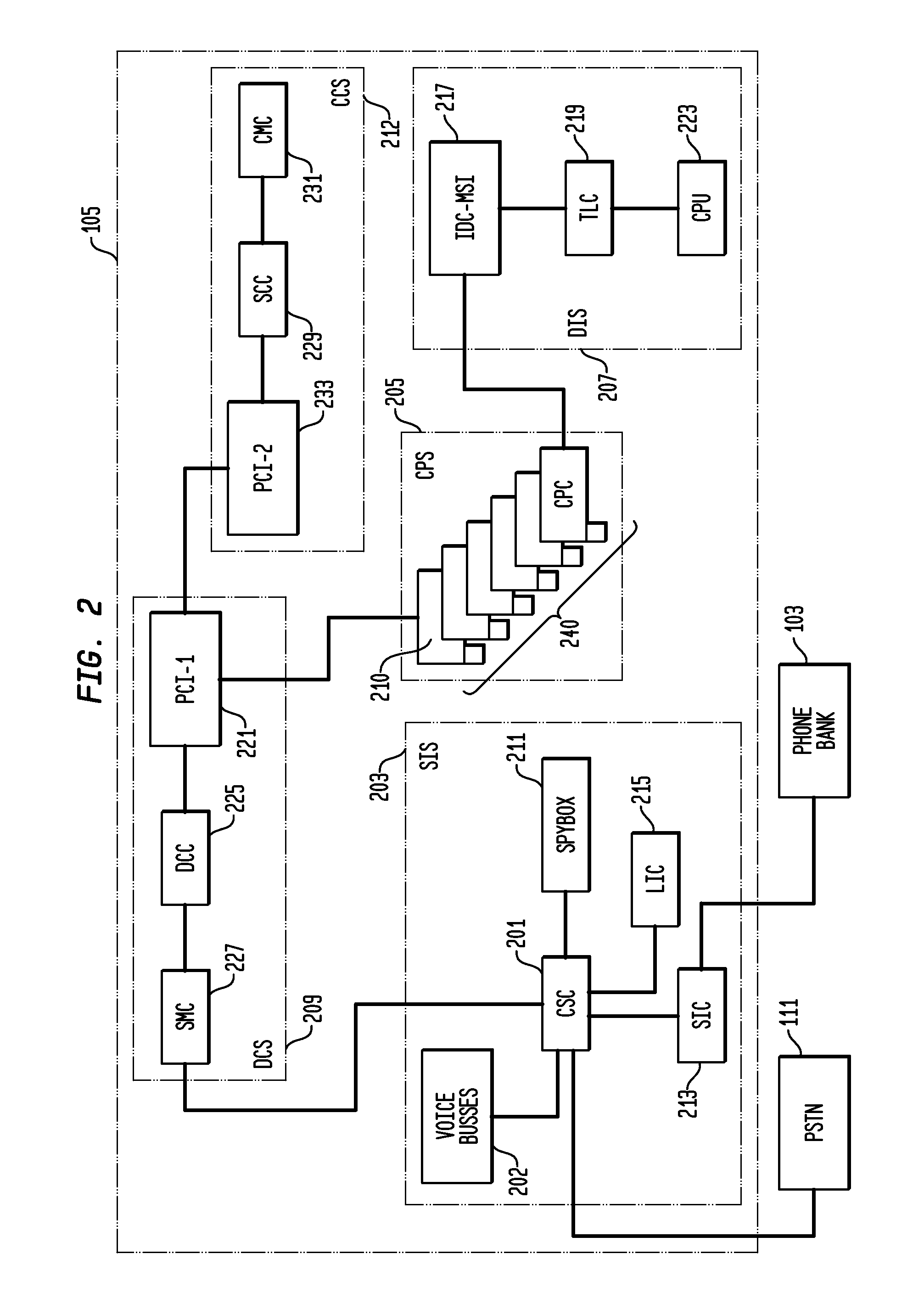
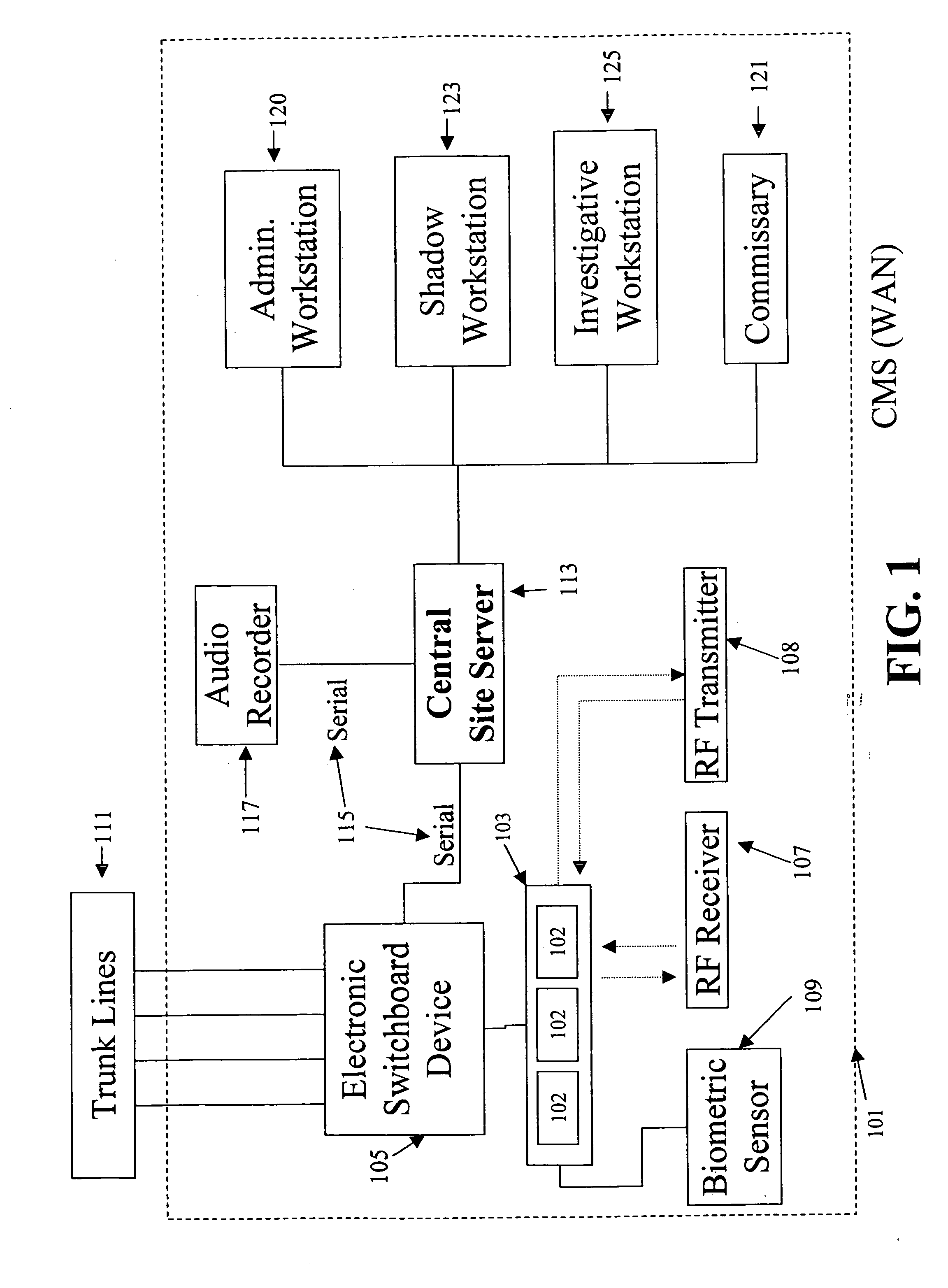
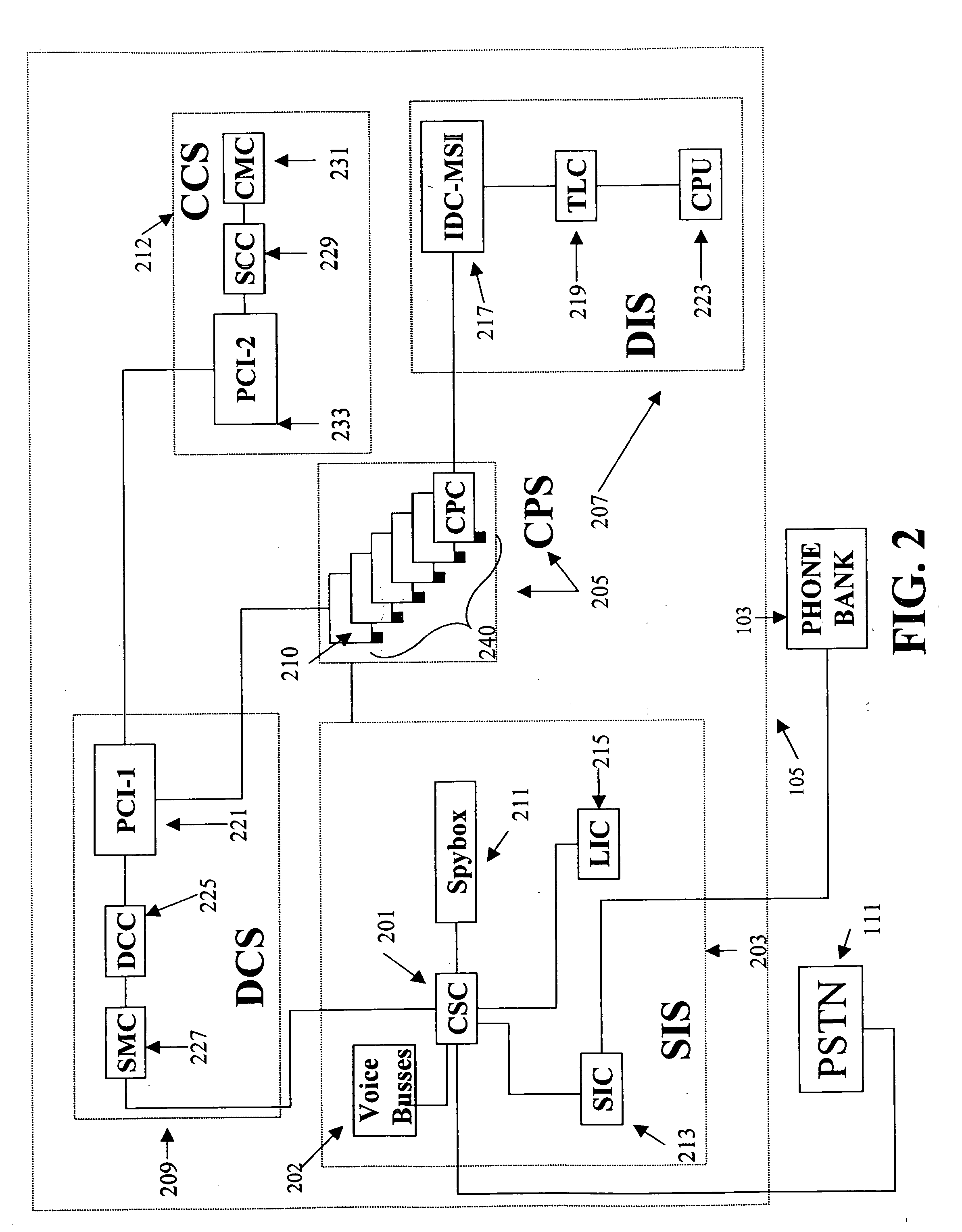
Telecommunication call management and monitoring system with voiceprint verification
InactiveUS20050043014A1Accurate verificationEliminating system overloadTelevision system detailsUnauthorised/fraudulent call preventionPersonal identification numberMonitoring system
Disclosed is a secure telephone call management system for authenticating users of a telephone system in an institutional facility. Authentication of the users is accomplished by using a personal identification number, preferably in conjunction with speaker independent voice recognition and speaker dependent voice identification. When a user first enters the system, the user speaks his or her name which is used as a sample voice print. During each subsequent use of the system, the user is required to speak his or her name. Voice identification software is used to verify that the provided speech matches the sample voice print. The secure system includes accounting software to limit access based on funds in a user's account or other related limitations. Management software implements widespread or local changes to the system and can modify or set any number of user account parameters.
Owner:GLOBAL TELLINK
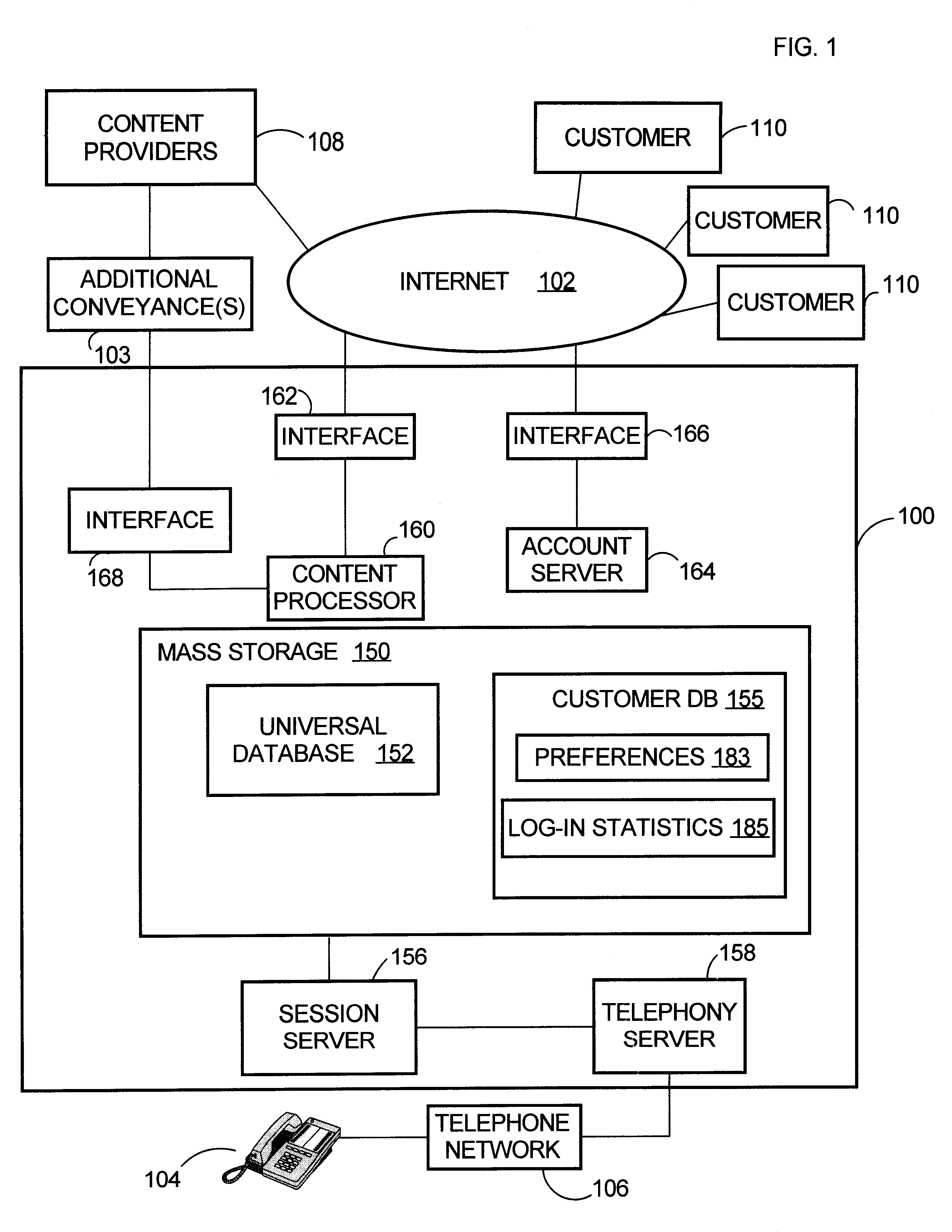
System and method for gathering, personalized rendering, and secure telephonic transmission of audio data
InactiveUS6529586B1Data processing applicationsAutomatic call-answering/message-recording/conversation-recordingPersonalizationThe Internet
An audio information delivery system collects electronic data via Internet or other conveyance, and responsive to customer inquiries, selectively retrieves data from local stores in areas of interest to the inquiring customers, formats the data, and transmits the data in audio form to the customers via their telephones. Initially, an information delivery agency makes advance arrangements with remotely located content providers to repeatedly obtain information of prescribed character. Agency computers continually gather digitally stored audio and text information from the predefined content providers and assemble the gathered information into a universal database. Separately, the agency enrolls a number of individual customers, which includes obtaining each customer's preferences regarding information content and playback order. Responsive to a telephone call from a registered customer, agency's computers retrieve the caller's pre-stored preferences and proceed to identify information in the universal database that pertains to the caller's subject matter preferences. After preparing vocalizations of the text information, agency computer equipment audibly presents the audio information and vocalizations to the caller in predetermined order via the caller's telephone connection. This is achieved, for example, by using an intermediate telephone network such as a wireless carrier network.
Owner:ORACLE INT CORP
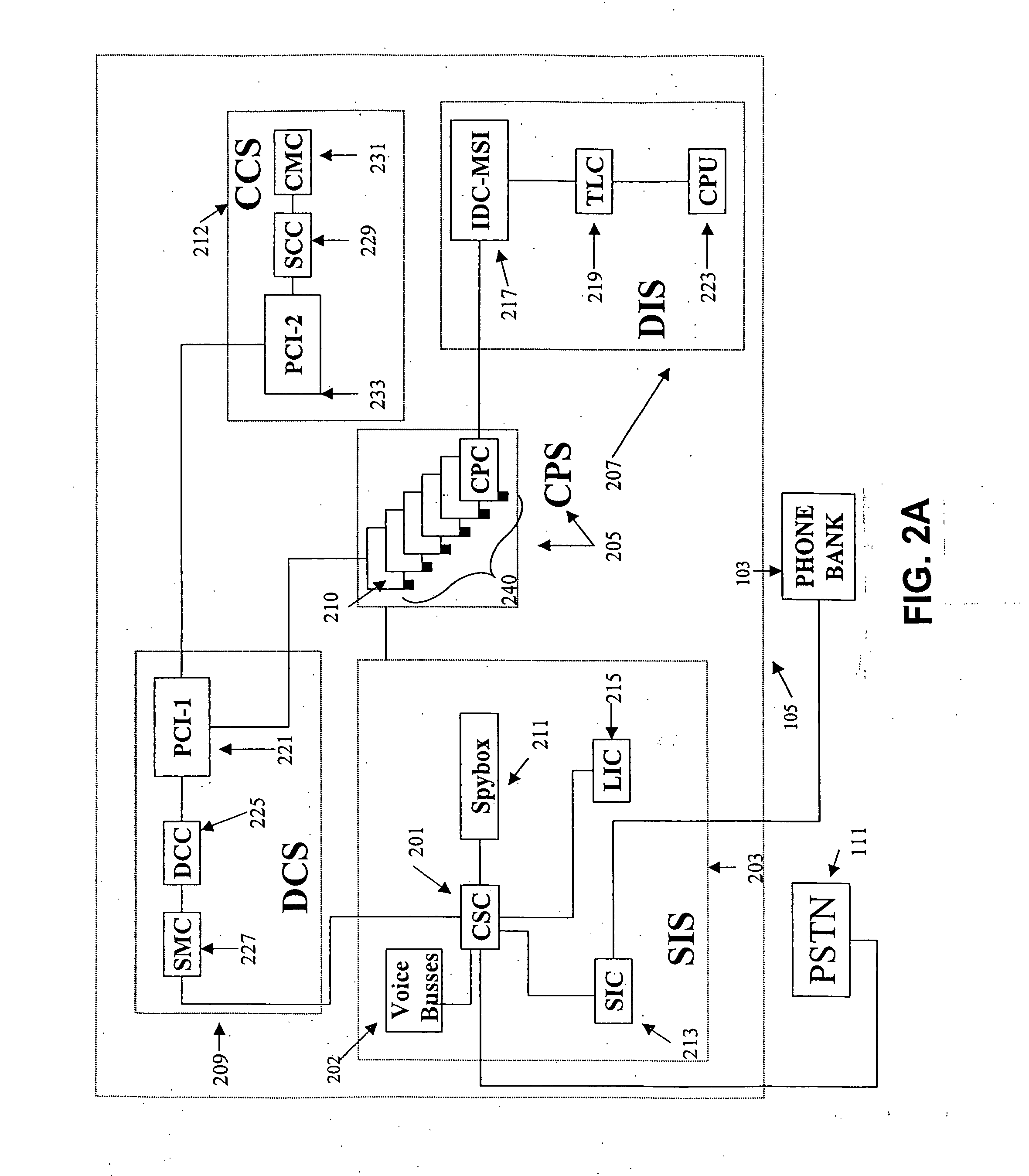
Telecommunication Call Management And Monitoring System With Voiceprint Verification
InactiveUS20110286585A1Efficient and reliableEliminating system overloadInterconnection arrangementsNetwork traffic/resource managementPersonal identification numberMonitoring system
A secure telephone call management system is provided for authenticating users of a telephone system in an institutional facility. Authentication of the users of the telephone call management system is accomplished by using a personal identification number, biometric means, and / or radio frequency means. The secure telephone call management system includes accounting software capable of limiting access to the system based on funds in a user's account, and includes management software capable of implementing widespread or local changes to the system. The system monitors a conversation in the telephone call to detect a presence of a first characteristic in audio of the conversation, and terminates the telephone call if the first characteristic does not match a second characteristic of biometric information of a user or a called party.
Owner:GLOBAL TELLINK
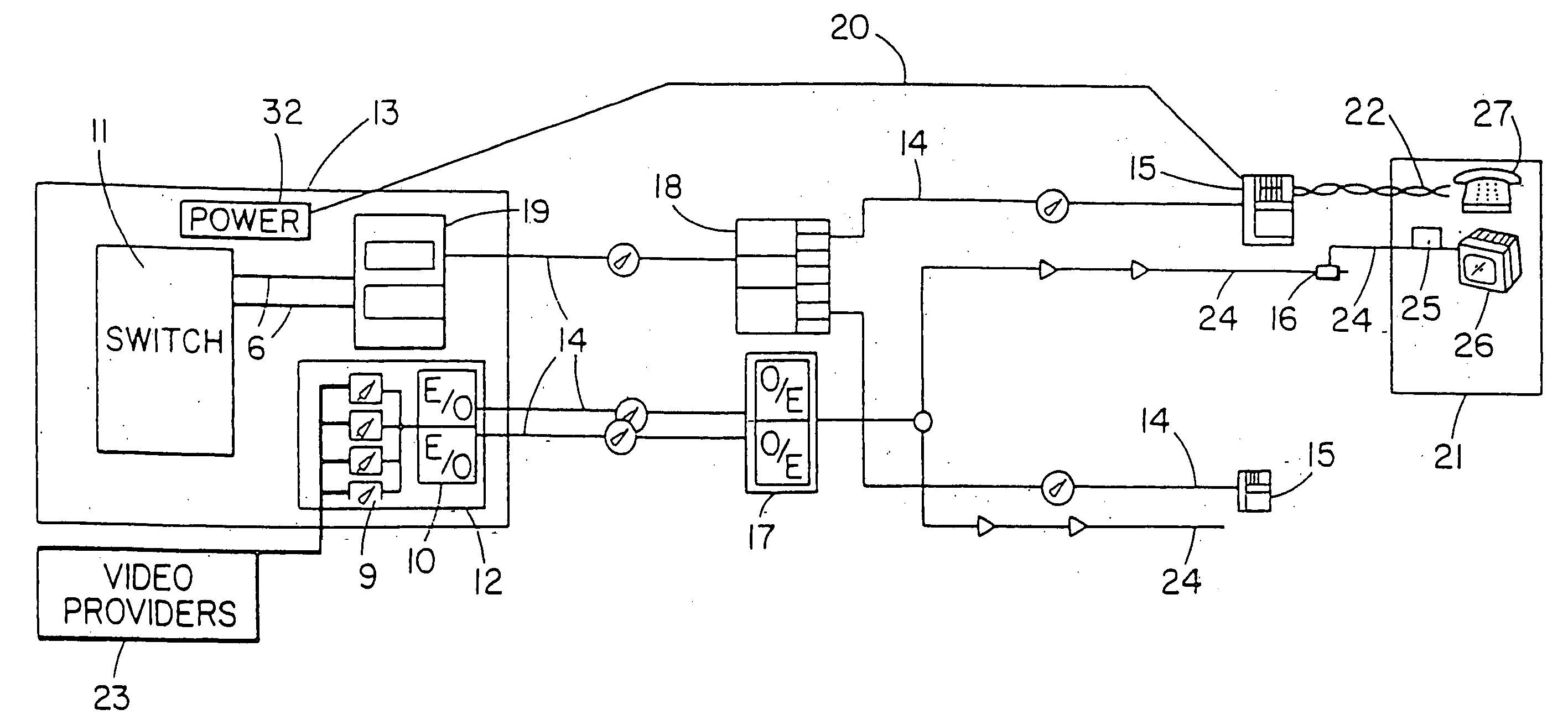
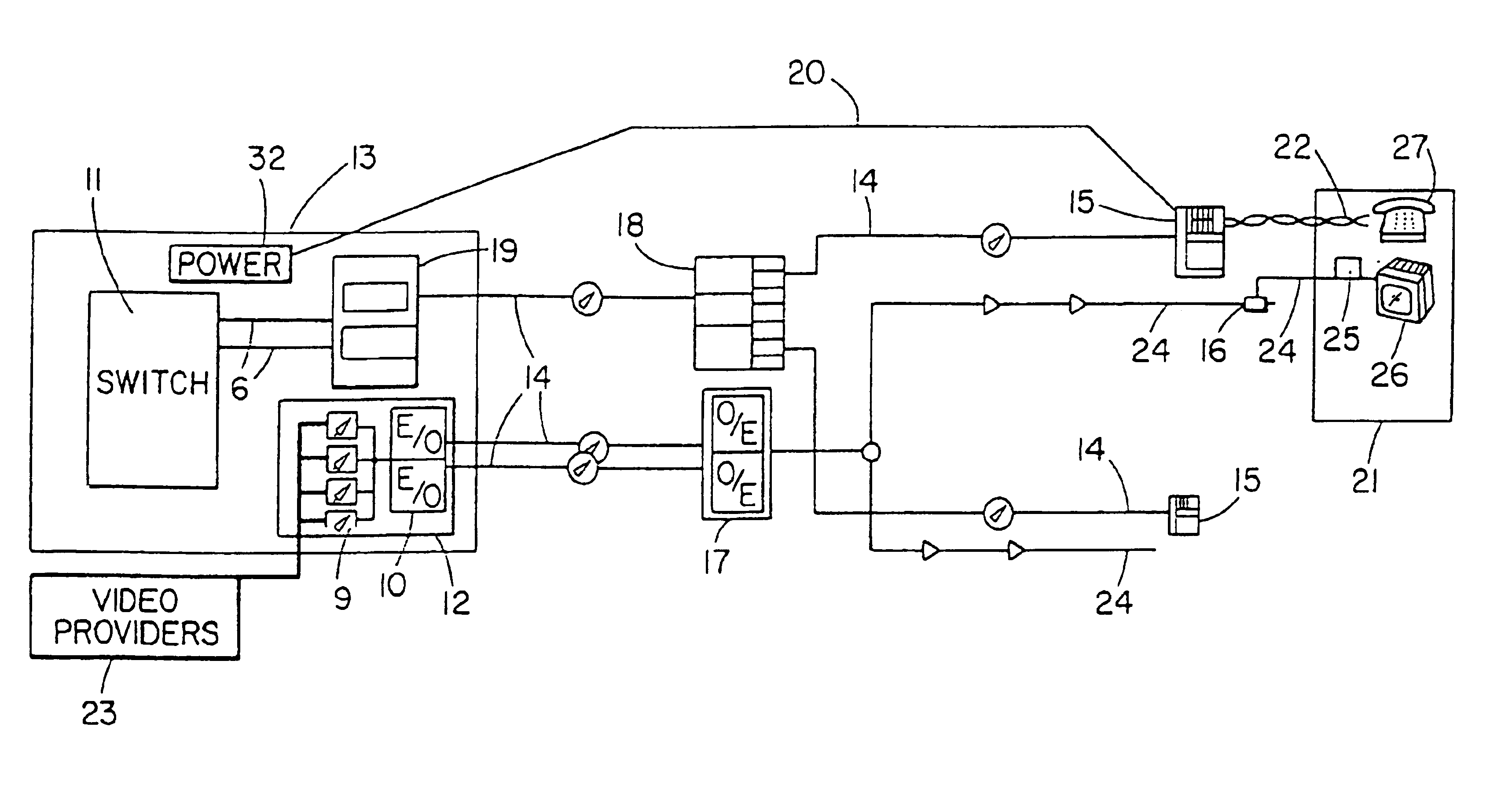
Method and apparatus for delivering secured telephony service in a hybrid coaxial cable network
InactiveUS20050034168A1Low costEliminate useInterconnection involving common lineBroadcast transmission systemsCoaxial cableInteractive video
A hybrid coaxial cable network employing interdiction to ensure privacy in telephony communications. The video and telephony signals are secured such that telephony and interactive video signals to and from a subscriber do not appear on the network at any other undesired subscriber location.
Owner:COMCAST MO GROUP
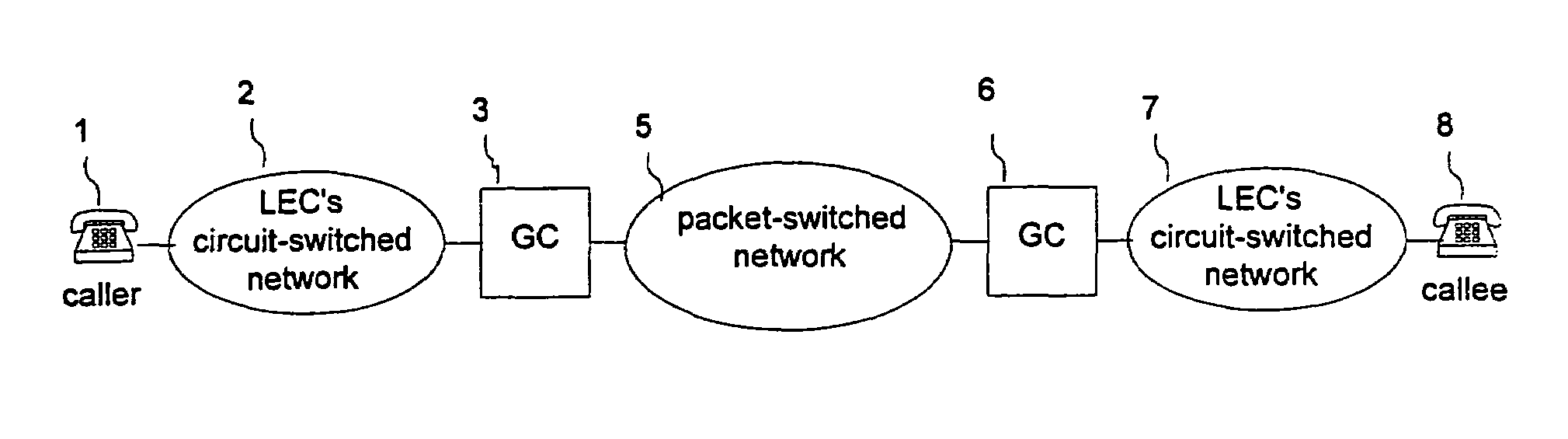
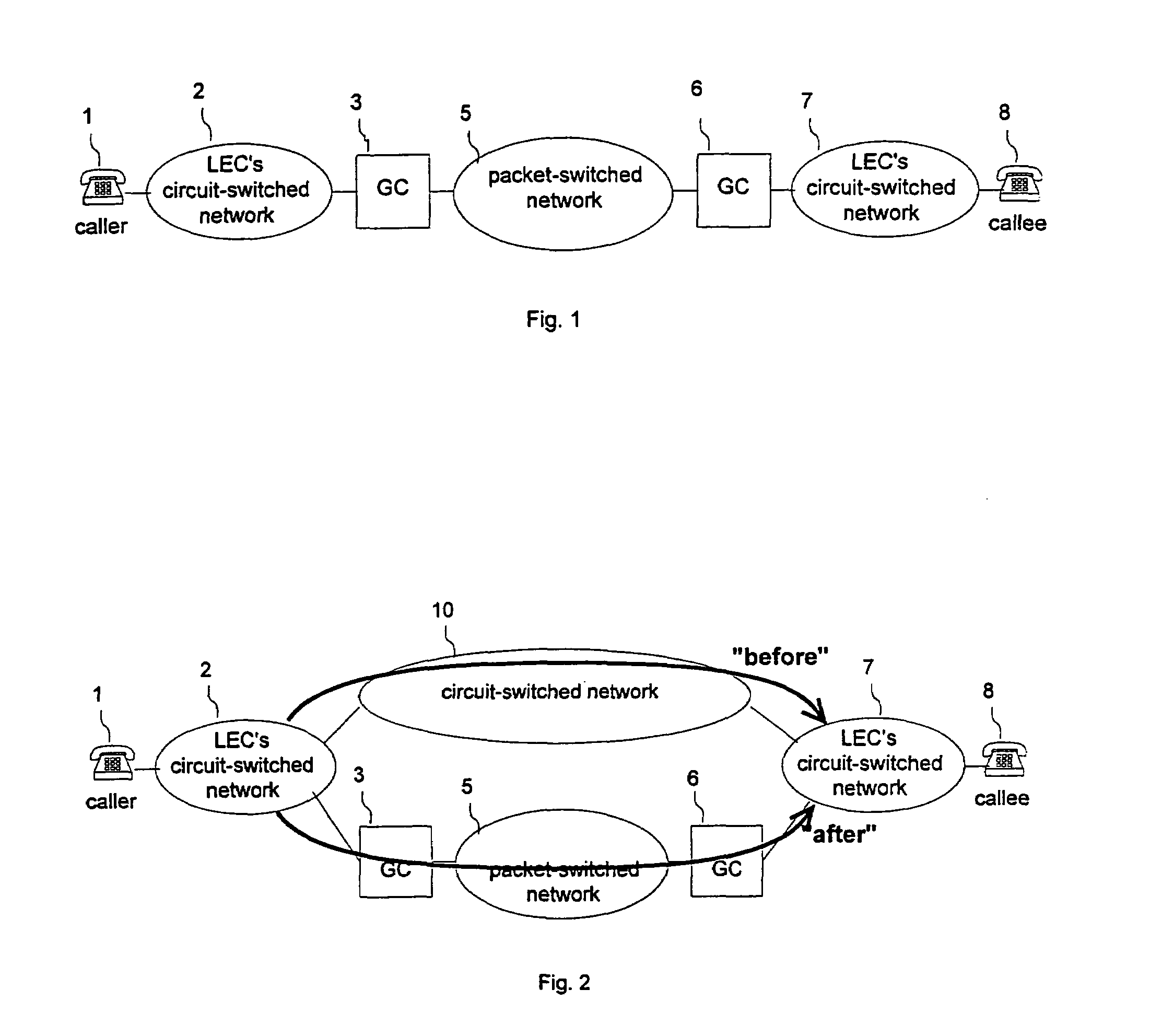
Hybrid packet-switched and circuit-switched telephony system
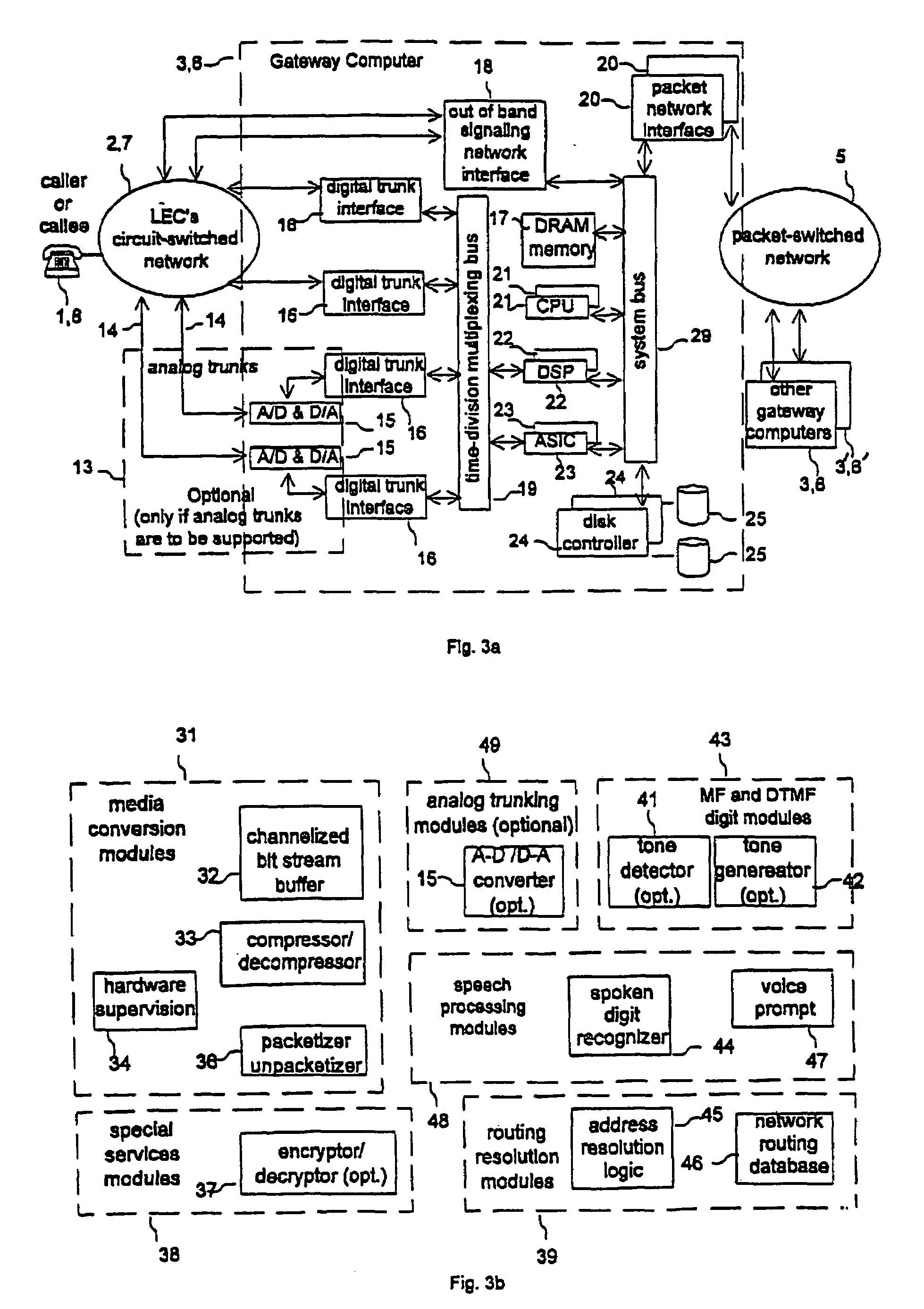
InactiveUS7336649B1Improve efficiencyImprove overall utilizationInterconnection arrangementsData switching by path configurationExchange networkSecure telephone
A hybrid telephony system with packet switching as well as circuit switching optimizes utilization of transport networks, and is accessible from any conventional telephone set. A call originating from a circuit-switched network is passed through a gateway computer to a backbone packet-switched network, and then through a second gateway computer to a second circuit-switched network where it terminates. The voice of both the originating party and the terminating party is converted to data packets by the near-end gateway computer and then converted back to voice by the far-end gateway computer. In an alternative scenario, the originating party uses a computer on the packet-switched network, which replaces the originating circuit-switched network and the originating computer. Powered by CPUs, DSPs, ASICs disks, telephony interfaces, and packet network interfaces, the gateway computers may have media conversion modules, speech processing modules and routing resolution modules, and are capable of translating telephony call signaling as well as voice between circuit-switched and packet-switched networks. Optionally, the gateway computers may also have analog trunking modules, MF and DTMF digit modules and special services modules, in order to support analog circuit-switched networks and secure telephone calls.
Owner:VERIZON PATENT & LICENSING INC
Method and system for key management in voice over internet protocol
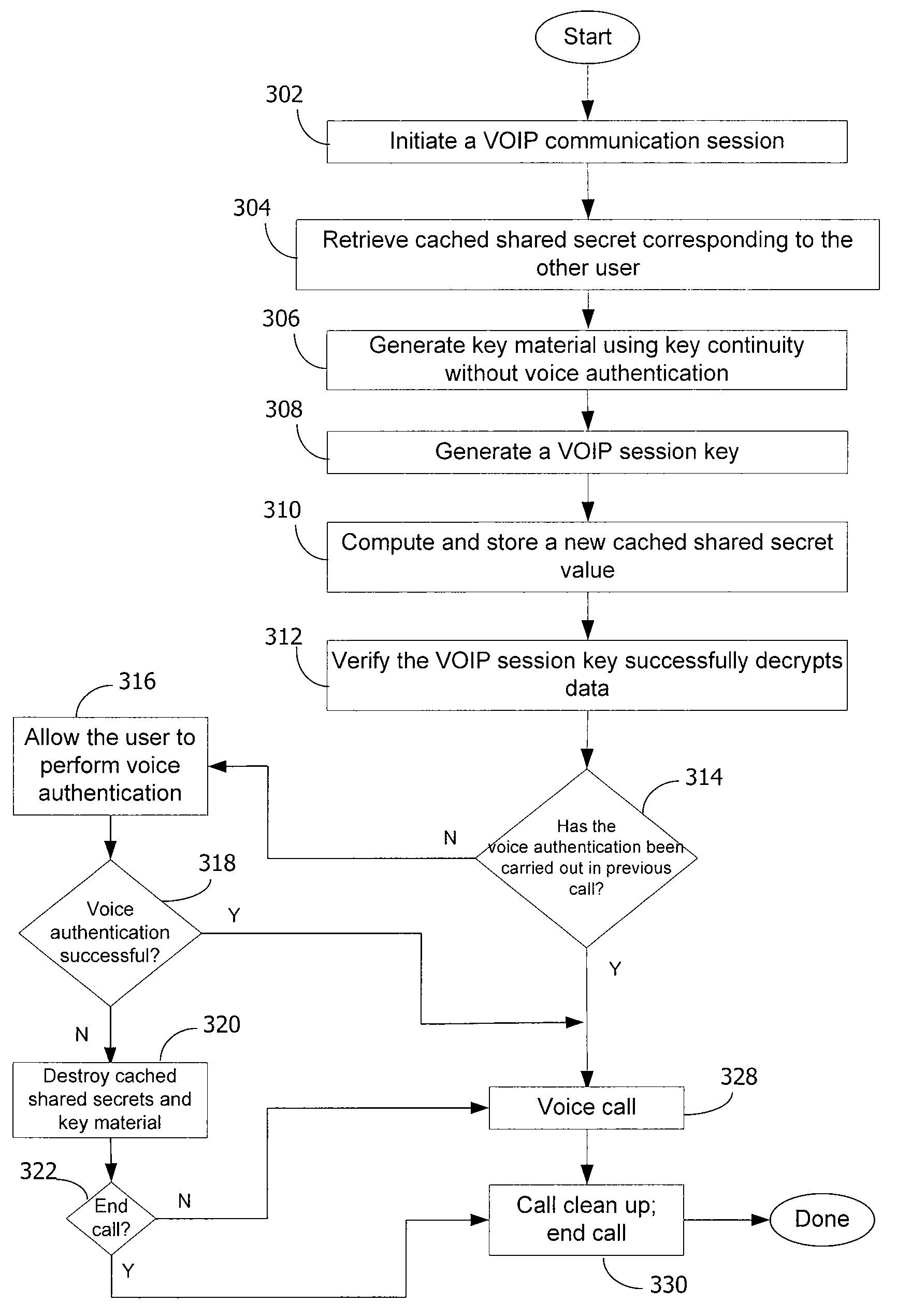
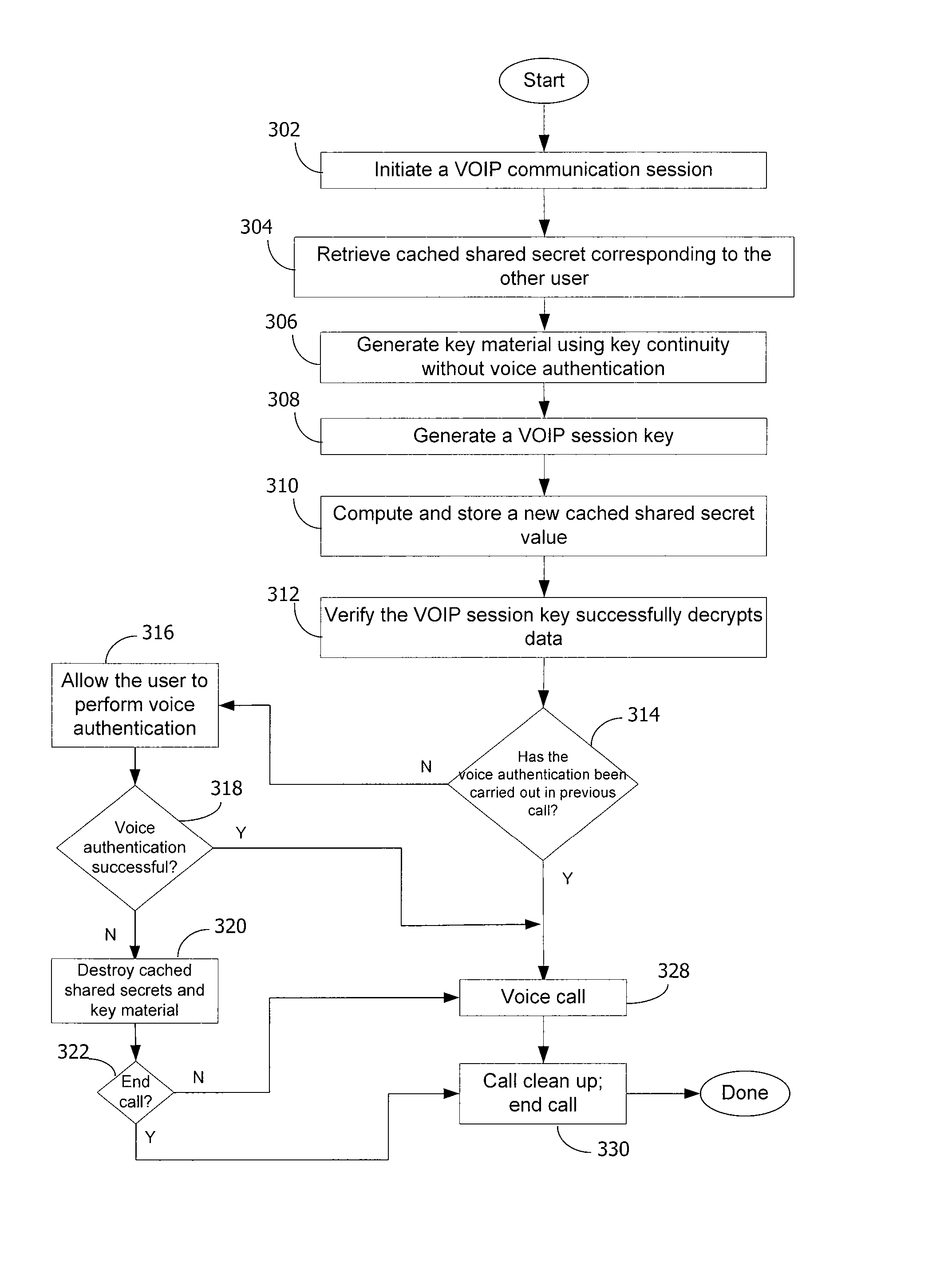
InactiveUS7730309B2Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
Method and system for key management in voice over internet protocol
InactiveUS20070157026A1Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
Multiple use secure transaction card
InactiveUS20060196929A1Acutation objectsPayment architectureMedical recordPersonal identification number
Diverse and or multiple functions are performed in a secure manner using a secure transaction card which validates a holder of the secure transaction card in accordance with a Personal Identification Number (PIN), generates, encrypts and transmits a pair of pseudo-random number sequences through a card reader to validate the card and generates, encrypts and transmits control signals or other information corresponding to a function comprising at least one of personal identity data, passport data, equipment control signals, an entry request to a secure area, medical records or access data therefor, note pad access data and secure telephone entry data in accordance with a protocol suitable for each function. One or more such functions can thus be performed in a secure manner from a single secure transaction card and selection, if needed, can be performed by a menu included in the secure transaction card.
Owner:IBM CORP
Secure telephony service appliance
ActiveUS8132001B1Limited accessInterconnection arrangementsDigital data processing detailsModem deviceLimited access
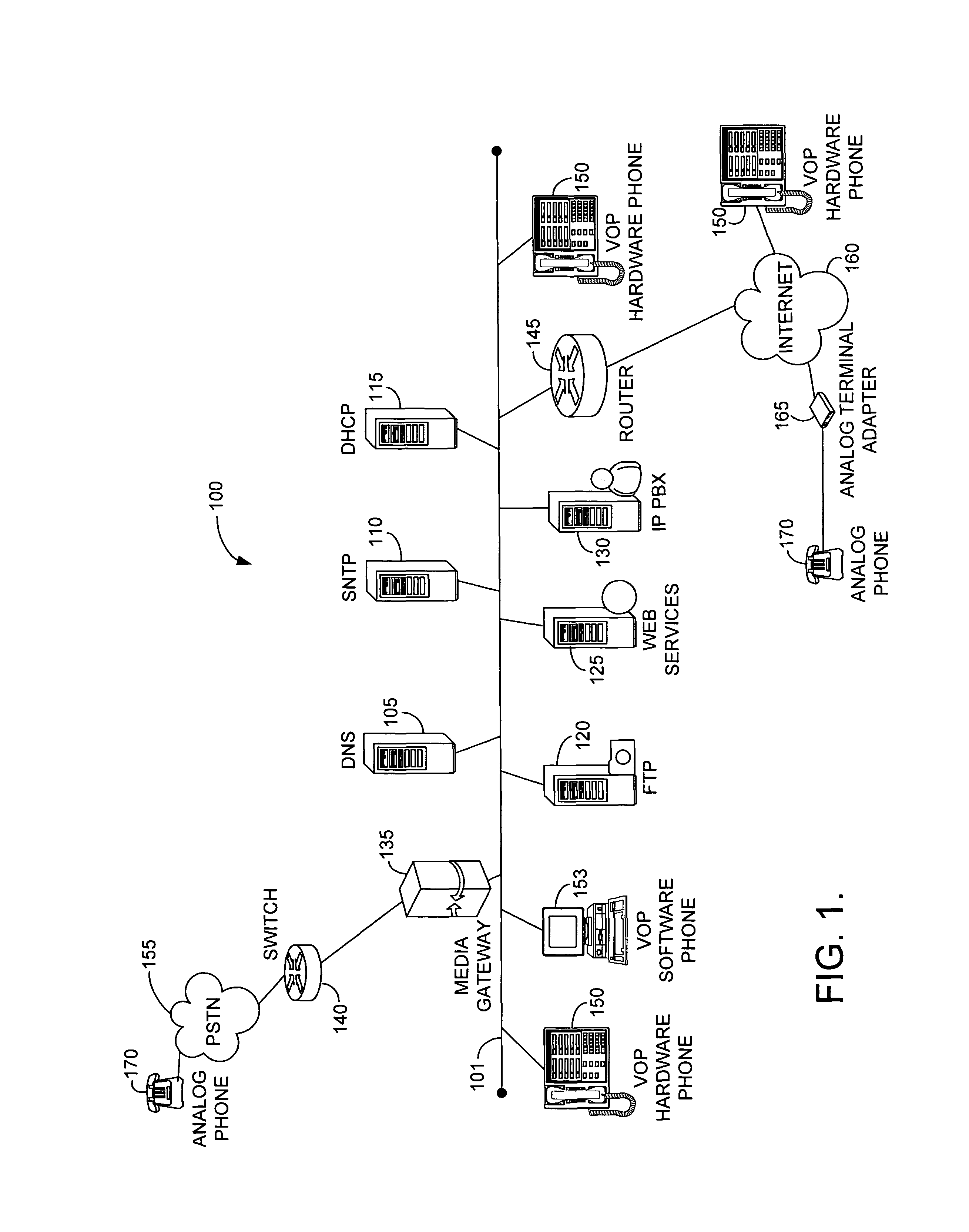
Secure telephony service appliances are created from computing devices. The computing devices have restricted access to their hardware and software. The computing devices perform VOP functions to other devices such as phones, modems, and adapters. Security vulnerabilities are reduced by implementing the computing devices as secure appliances for IP telephony.
Owner:T MOBILE INNOVATIONS LLC
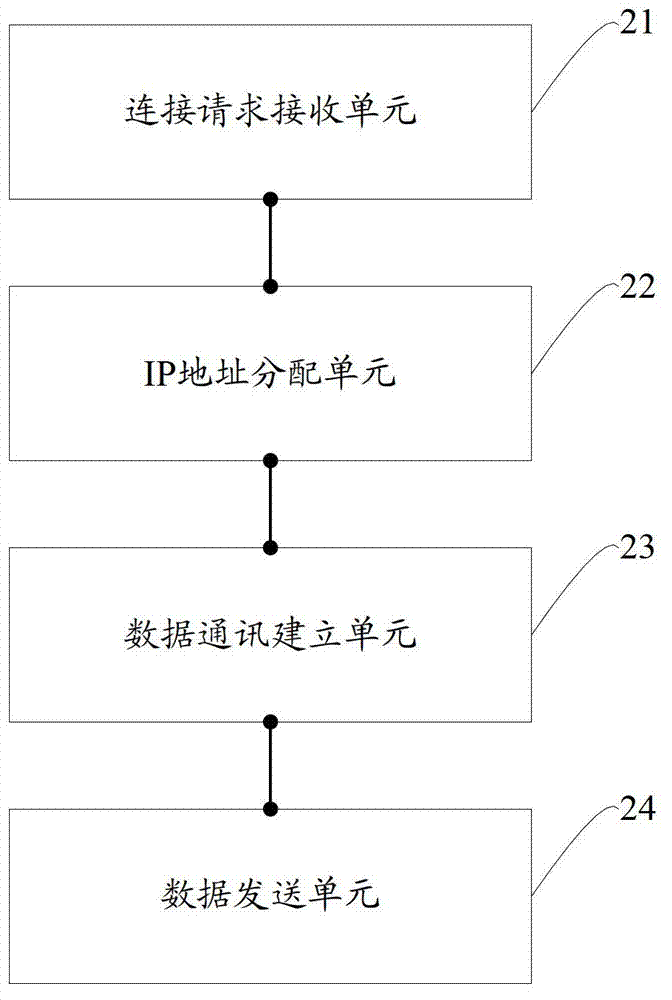
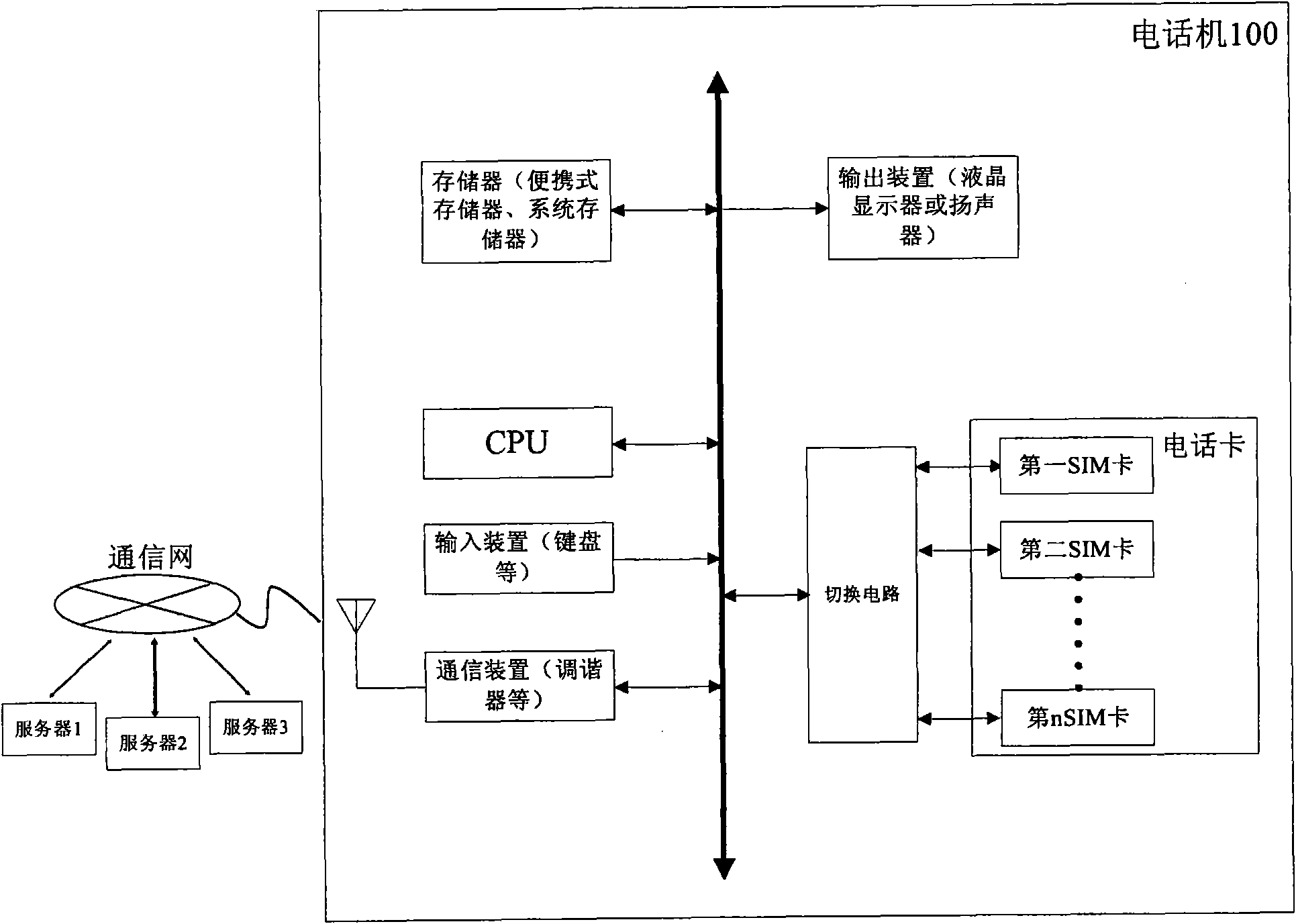
Data share method and mobile terminal
InactiveCN102882938ARealize data sharing functionHigh bandwidthConnection managementTransmissionTelecommunicationsIp address
The invention is applicable to the field of telephone communication. The invention provides a data share method and a mobile terminal. The method comprises the following steps: after opening a wireless local area network (WLAN) hotspot, a first telephone receives a WLAN connecting request sent by a second telephone, and the WLAN connecting request carries with a logo of the second telephone; after the WLAN connection between the first telephone and the second telephone is established successfully, an internet protocol (IP) address is distributed to the second telephone, the IP address marks the second telephone only; socket communication is built between the first telephone and the second telephone through the IP address; the first telephone receives the data obtaining request sent by the second telephone through the socket communication, and sends the data corresponding to the data obtaining request to the second telephone. According to the embodiment of the invention, the entire data sharing function can be fulfilled.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Telecommunication call management and monitoring system with voiceprint verification
InactiveUS8509736B2Eliminating system overloadInterconnection arrangementsNetwork traffic/resource managementPersonal identification numberMonitoring system
A secure telephone call management system is provided for authenticating users of a telephone system in an institutional facility. Authentication of the users of the telephone call management system is accomplished by using a personal identification number, biometric means, and / or radio frequency means. The secure telephone call management system includes accounting software capable of limiting access to the system based on funds in a user's account, and includes management software capable of implementing widespread or local changes to the system. The system monitors a conversation in the telephone call to detect a presence of a first characteristic in audio of the conversation, and terminates the telephone call if the first characteristic does not match a second characteristic of biometric information of a user or a called party.
Owner:GLOBAL TELLINK
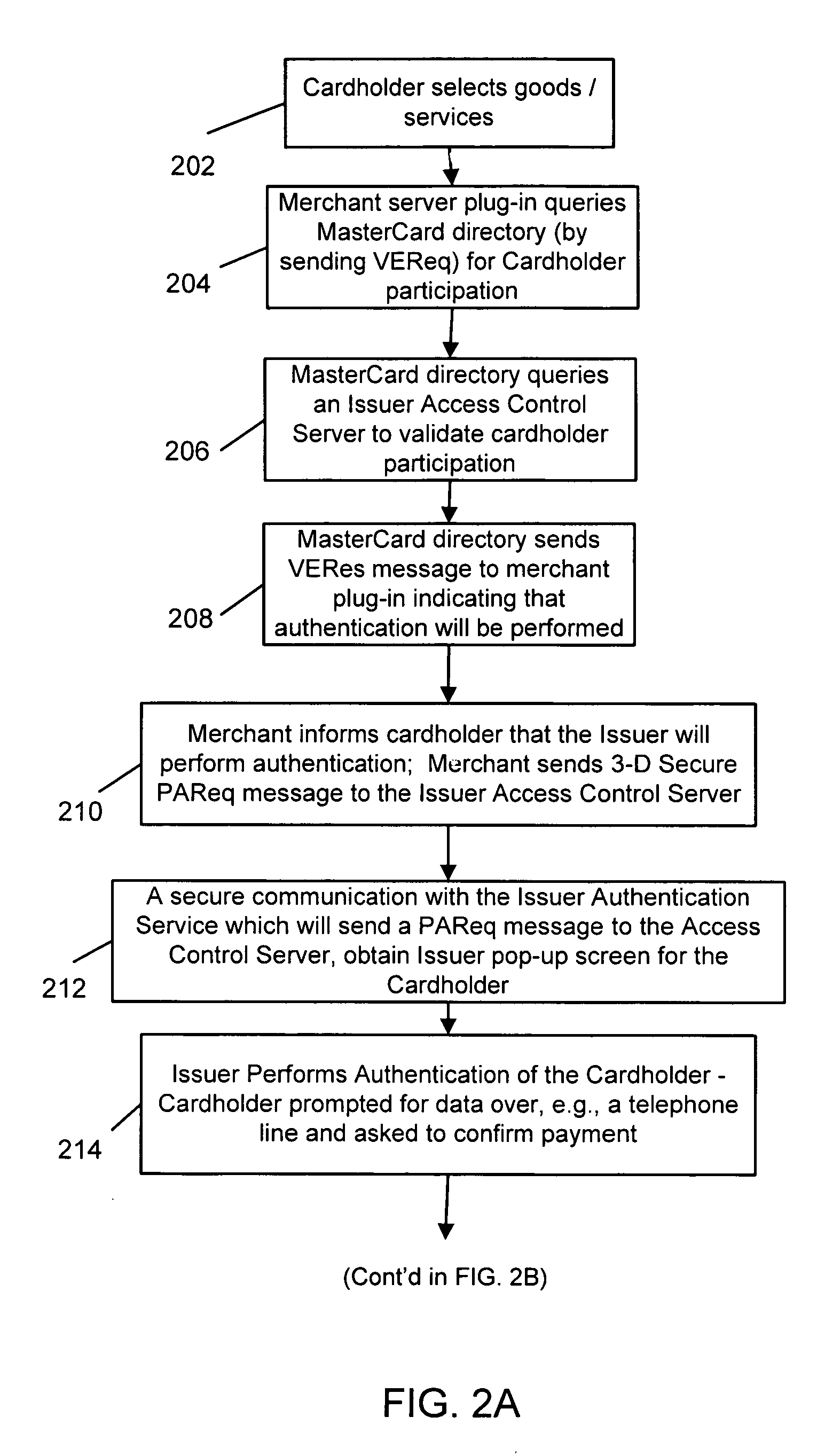
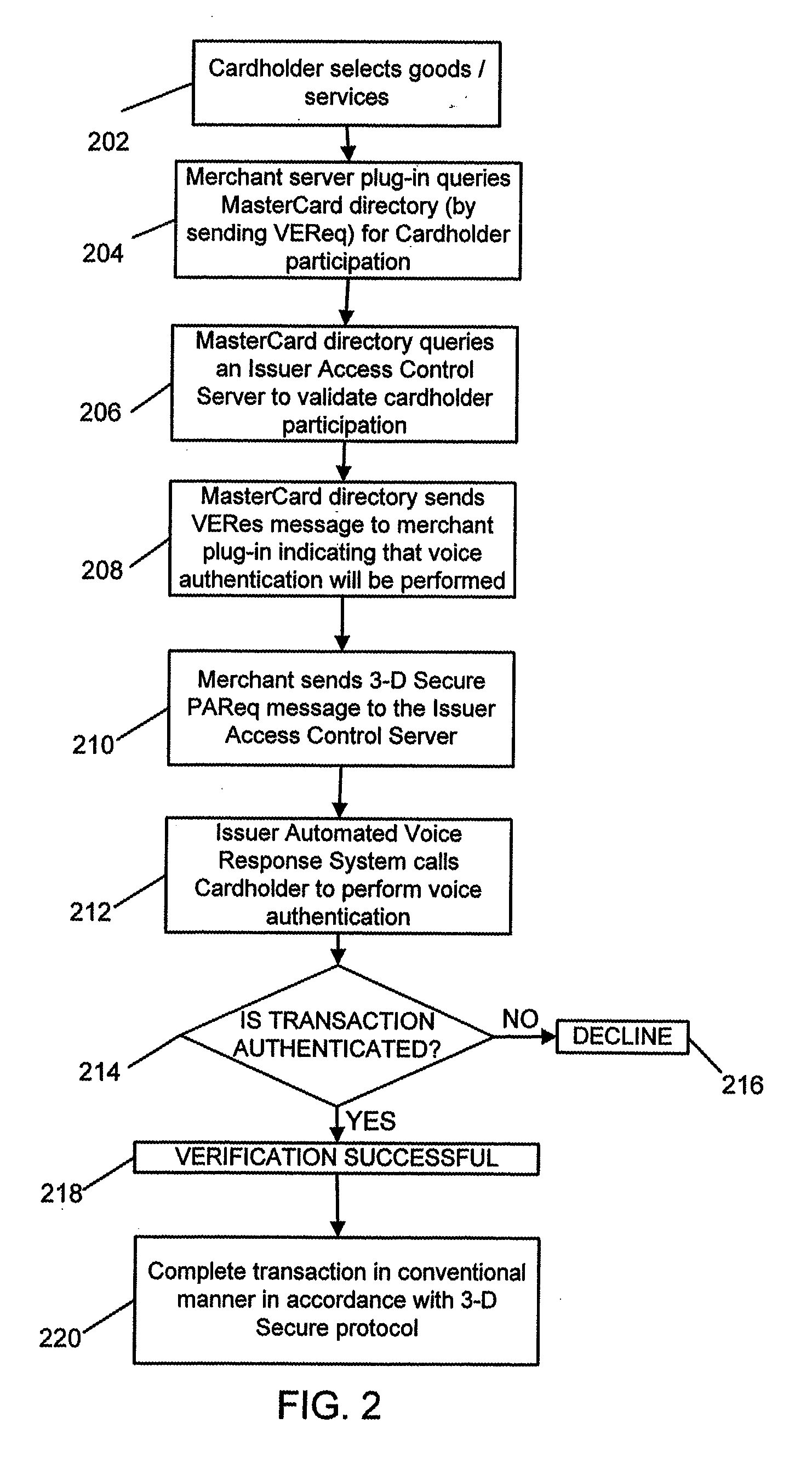
System and method for secure telephone and computer transactions
A secure electronic payment system and method for conducting a secure transaction using authentication is provided. A merchant's computer transmits an authorization request to an access control server. The access control obtains authentication to confirm the identity of the purchaser, via e.g., an electronic form or interactive voice response system. The access control server then transmits a response to the merchant's computer. If the purchaser is authorized to access the account, payment is processed by the merchant and the transaction is completed.
Owner:MASTERCARD INT INC
Telecommunication call management and monitoring system
InactiveUS20060285667A1Eliminating system overloadAccurate distanceOrganic active ingredientsTelevision system detailsPersonal identification numberMonitoring system
A secure telephone call management system is provided for authenticating users of a telephone system in an institutional facility. Authentication of the users of the telephone call management system is accomplished by using a personal identification number, biometric means, and / or radio frequency means. The secure telephone call management system includes accounting software capable of limiting access to the system based on funds in a user's account or other related limitations. The system includes management software capable of implementing widespread or local changes to the system and is further capable of modifying or setting any number of user account parameters.
Owner:GLOBAL TELLINK
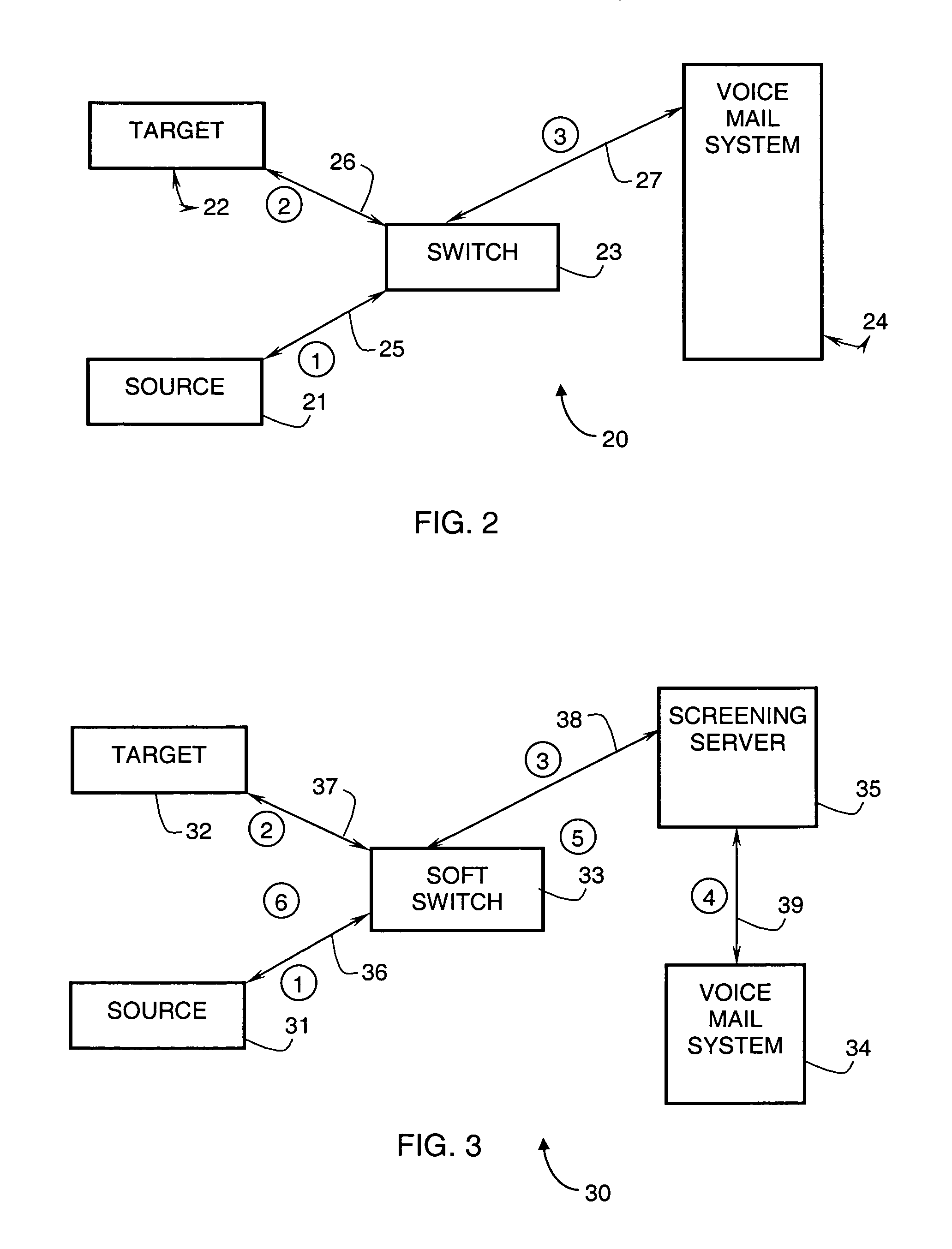
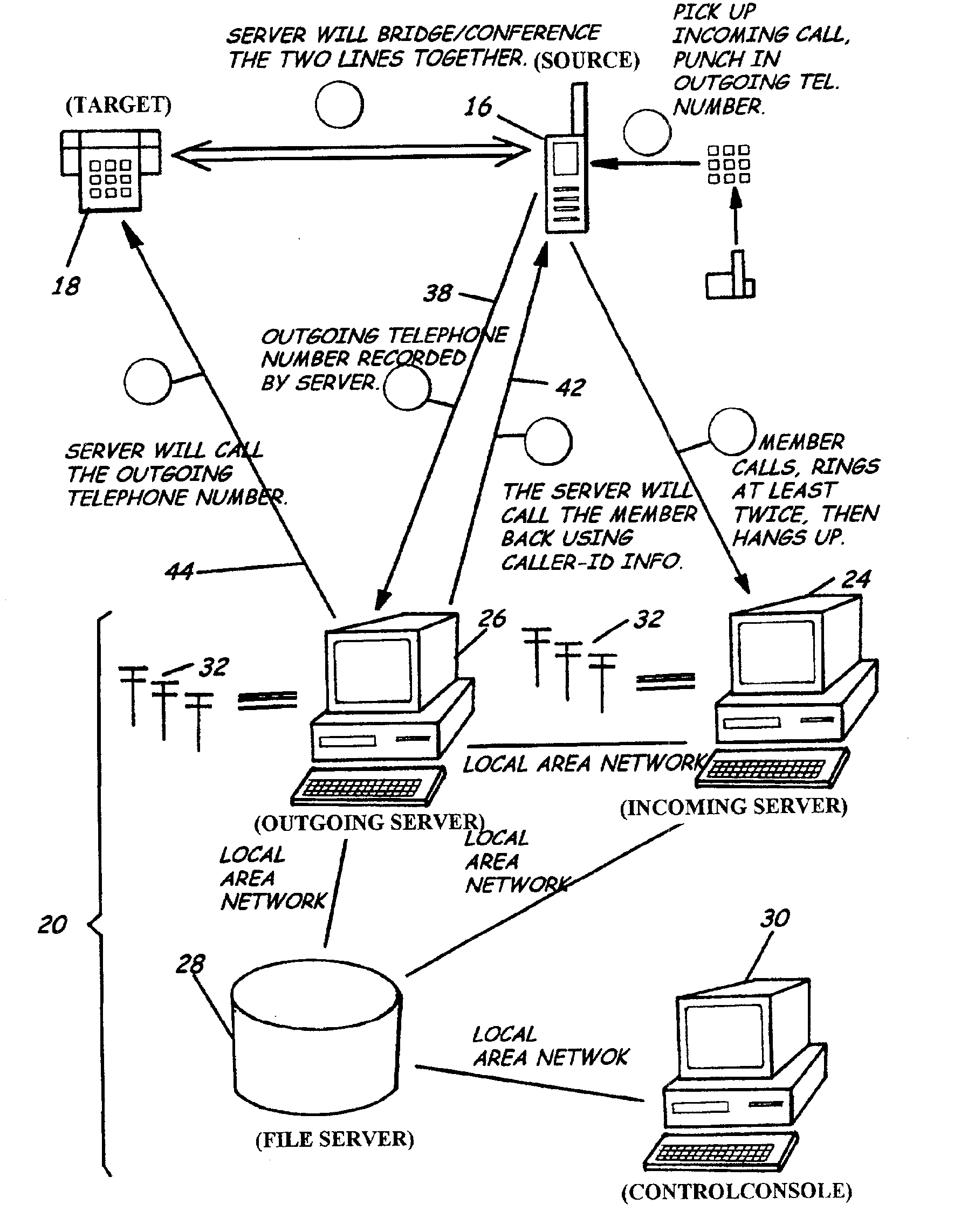
Method and system for providing a call answering service between a source telephone and a target telephone
ActiveUS7123697B2Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesSpeech soundSecure telephone
In a method and voice mail system for providing a call answering service between a source telephone and a target telephone, a voice mail system receives an unanswered call directed to the target telephone. If the target telephone is not busy, the voice mail system establishes an outgoing call to the target telephone and conveys to the source telephone a response having embedded media parameters identifying media ports of the voice mail system. In response to an accept call instruction received from the target telephone, the voice mail system terminates the response and bridges all media between the source telephone and the target telephone.
Owner:COMVERSE
System and method for secure telephone and computer transactions using voice authentication
A secure electronic payment system and method for conducting a secure transaction using voice authentication is provided. A merchant's computer transmits an authorization request to an access control server. The access control server places a telephone call to the purchaser and performs voice authentication to confirm the identity of the purchaser. The access control server then transmits a response to the merchant's computer. If the purchaser is authorized to access the account, payment is processed by the merchant and the transaction is completed.
Owner:MASTERCARD INT INC
Method and apparatus for delivering secured telephony service in a hybrid coaxial cable network
InactiveUS6862349B1Complete transparencyLow costBroadcast-related systemsInterconnection involving common lineCoaxial cableInteractive video
A hybrid coaxial cable network employing interdiction to ensure privacy in telephony communications. The video and telephony signals are secured such that telephony and interactive video signals to and from a subscriber do not appear on the network at any other undesired subscriber location.
Owner:COMCAST MO GROUP
Secure Phone Storage with Selective Transmission Functionality
InactiveUS20170323503A1Safe storageDistractionBuilding locksApparatus for meter-controlled dispensingEngineeringCharging station
Owner:GARCIA JORGE E
Telephone bridging method
InactiveUS6885856B2Low costSimple methodAccounting/billing servicesSpecial service for subscribersService provisionComputerized system
A method of reducing telephone usage charges billed by a telephone service provider for connecting a source telephone to a target telephone by communicating to a computer system the telephone number of the source telephone, and communicating to the computer system the telephone number of the target telephone, with the computer system originating a connection to the source telephone and originating a connection to the target telephone. The computer system then connects the source telephone to the target telephone. This connection is made such that a telephone service provider for the source telephone interprets the source telephone as a receiving telephone and bills the source telephone number at the discount rate for incoming calls for the telephone call. The computer system for this system may include a PBX system and computers capable of managing phone calls to and from the PBX system to accommodate both two party and multiple party calls.
Owner:CHANG SHENG INC
Secure telephone devices, systems and methods
InactiveUS20110135093A1Secret communicationSecuring communicationSecure communicationOperational system
Secure telephone devices, systems and methods are provided for carrying out secure communications utilizing a telephone device that includes cryptographic storage and processing components, the cryptographic processing components including intercepting and injecting capabilities for intercepting an incoming signal, cryptographically processing the signal and injecting the system for delivery to the output of the telephone device, wherein the system and method may utilize the telephone operating system, and wherein embodiments are provided where an exchange component regulates the cryptographic information so that users engaging in secure cryptographic communications do not need to provide encryption key information to each other.
Owner:CYBERSOFT
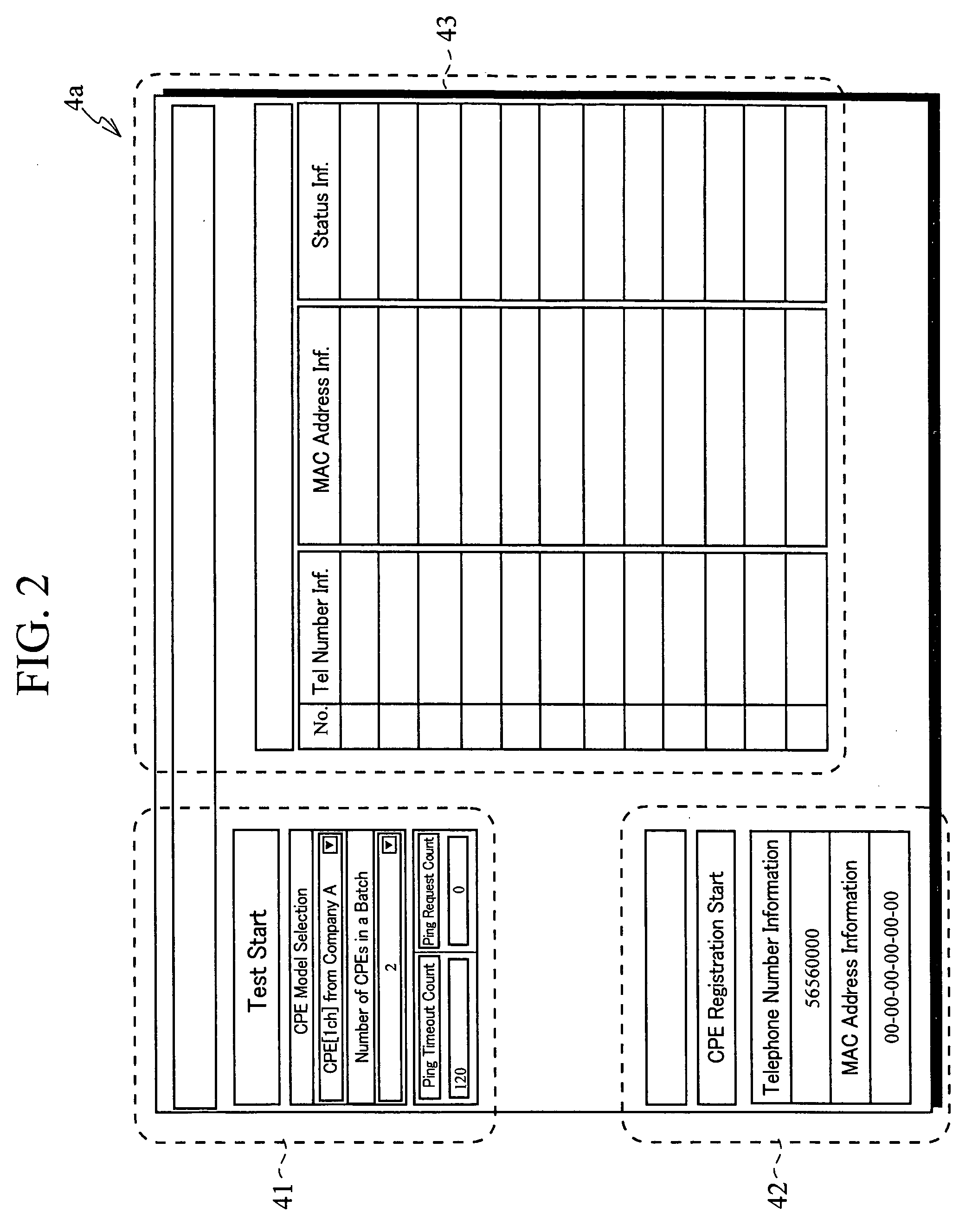
Voip Device Test System and Test Method
InactiveUS20080239971A1Improve efficiencyPossible to performError preventionTransmission systemsComputer hardwareIp address
An MAC address of each of devices under testing is entered. An IP address is assigned to each entered MAC address. The IP addresses and telephone numbers assigned to the devices and a failure test terminal are associated with one another and registered in a system server. Out of telephones connected to the devices, sets of two telephones are determined. For each set, a call is made from a first telephone connected to the device to a second telephone connected to another device. When the communication is established, a call is made from the called second telephone to the first telephone. If the communication is not established, communication with a telephone connected to the failure test terminal is tried. Thereby, adequate test on a large number of devices with simple operation is possible in performing an operation test on a VoIP device.
Owner:SOFTBANK BB CORP
Quantum secrete telephone
InactiveCN101827149AEnsure safetyImprove adaptabilityEavesdropping prevention circuitsSecret communicationTelephone communicationFeedback control
The invention relates to a quantum secrete telephone, which combines the quantum secrete communication with the current telephone communication and realizes secure telephone communication by encrypting / decrypting voice by use of an absolutely secure quantum codebook; the best advantage of the system is: by using FPGA as the control core, as the FPGA does not open the interface of the storage chip of the codebook, any behavior trying to attack a terminal so as to steal the codebook remotely is invalid. Compared with a common computer which has various bugs, the quantum secrete telephone is absolutely powerful guarantee for security. Moreover, along with development of FPGA technology, the current processing speed already reaches GHz level, thus a qualitative leap is made in both the processing speed for key selection and the precision and sensitivity for polarization feedback control; and besides, FPGA is further compatible with other coding schemes such as phase coding and entanglement coding and can work in a quantum key distribution system with higher working frequency with good adaptability.
Owner:SHANGHAI LANGYAN OPTOELECTRONICS TECH
System and method for secure telephone and computer transactions using voice authentication
A secure electronic payment system and method for conducting a secure transaction using voice authentication is provided. A merchant's computer transmits an authorization request to an access control server. The access control server places a telephone call to the purchaser and performs voice authentication to confirm the identity of the purchaser. The access control server then transmits a response to the merchant's computer. If the purchaser is authorized to access the account, payment is processed by the merchant and the transaction is completed.
Owner:MASTERCARD INT INC
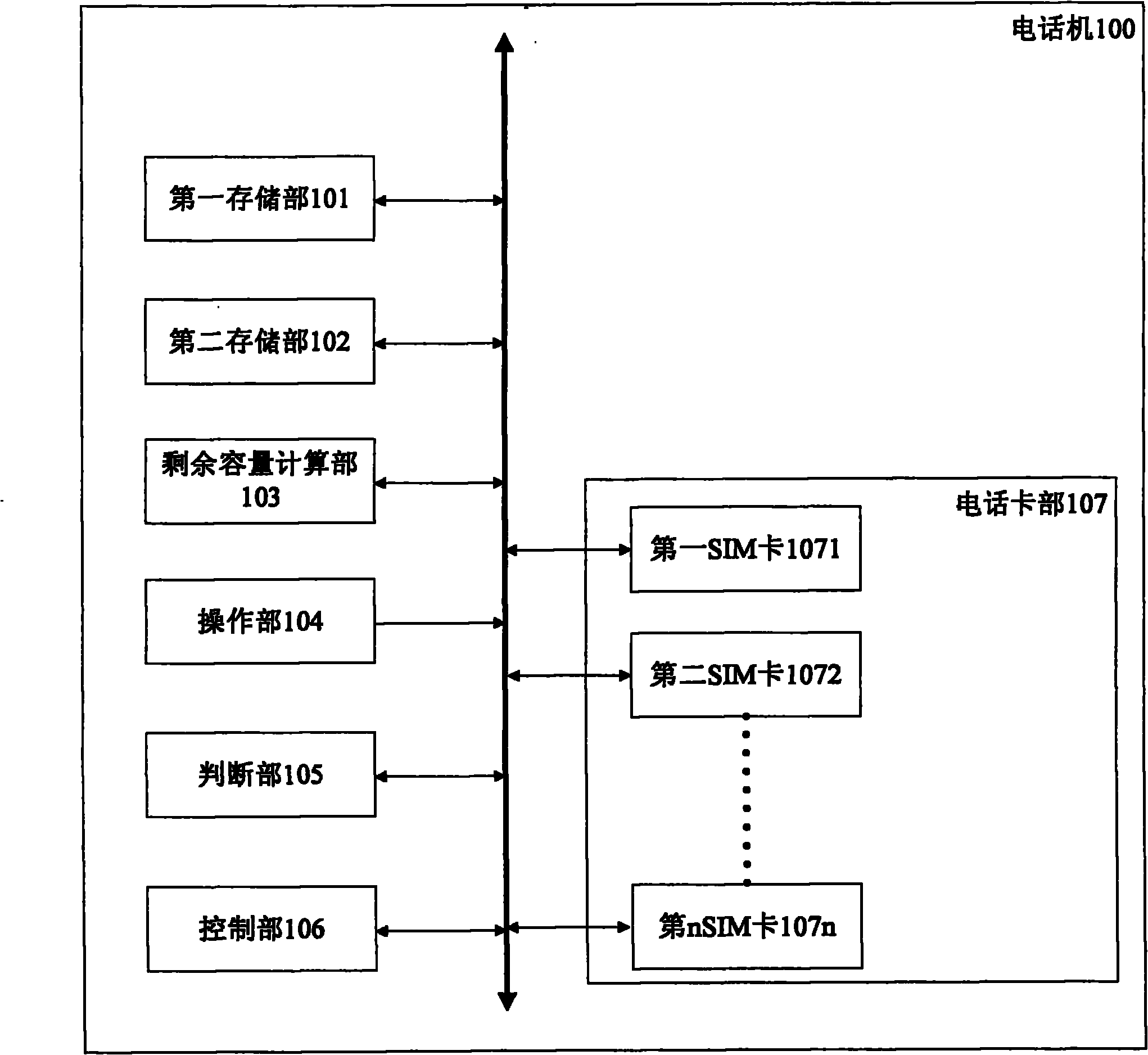
Telephone, vehicular hand-free telephone system and download method
InactiveCN102045434AReduce downloadsSubstation speech amplifiersPrepayment telephone systemsData capacityTelephone card
The invention provides a telephone, a vehicular hand-free telephone system and a download method. The telephone is provided with a plurality of telephone cards which respectively sign quota communication service, and the quota communication service can use data communication with specified capacity through quota in each prescribed period. When the residual capacity of the first telephone card of a control part of the telephone in the prescribed period is greater than the data capacity of downloaded and indicated content, the content is downloaded by using the data communication of the first telephone card. When the residual capacity of the first telephone card in the prescribed period is less than the data capacity of the downloaded and indicated content, the content is downloaded by using the data communication of a second telephone card under the condition that, the residual capacity of a plurality of telephone cards except the first telephone card in the prescribed period is greater than the data capacity of the downloaded and indicated content, and the second telephone card has the maximum residual capacity.
Owner:ALPINE ELECTRONICS INC
Secure telephone devices, systems and methods
InactiveUS20110135091A1Improve securityEfficient communicationSecret communicationSecuring communicationSecure communicationSecure telephone
Secure telephone devices, systems and methods are provided for carrying out secure communications utilizing a telephone device that includes cryptographic storage and processing components, the cryptographic processing components including intercepting and injecting capabilities for intercepting an incoming signal, cryptographically processing the signal and injecting the system for delivery to the output of the telephone device, wherein the system and method may utilize the telephone operating system, and wherein embodiments are provided where an exchange component regulates the cryptographic information so that users engaging in secure cryptographic communications do not need to provide encryption key information to each other.
Owner:CYBERSOFT
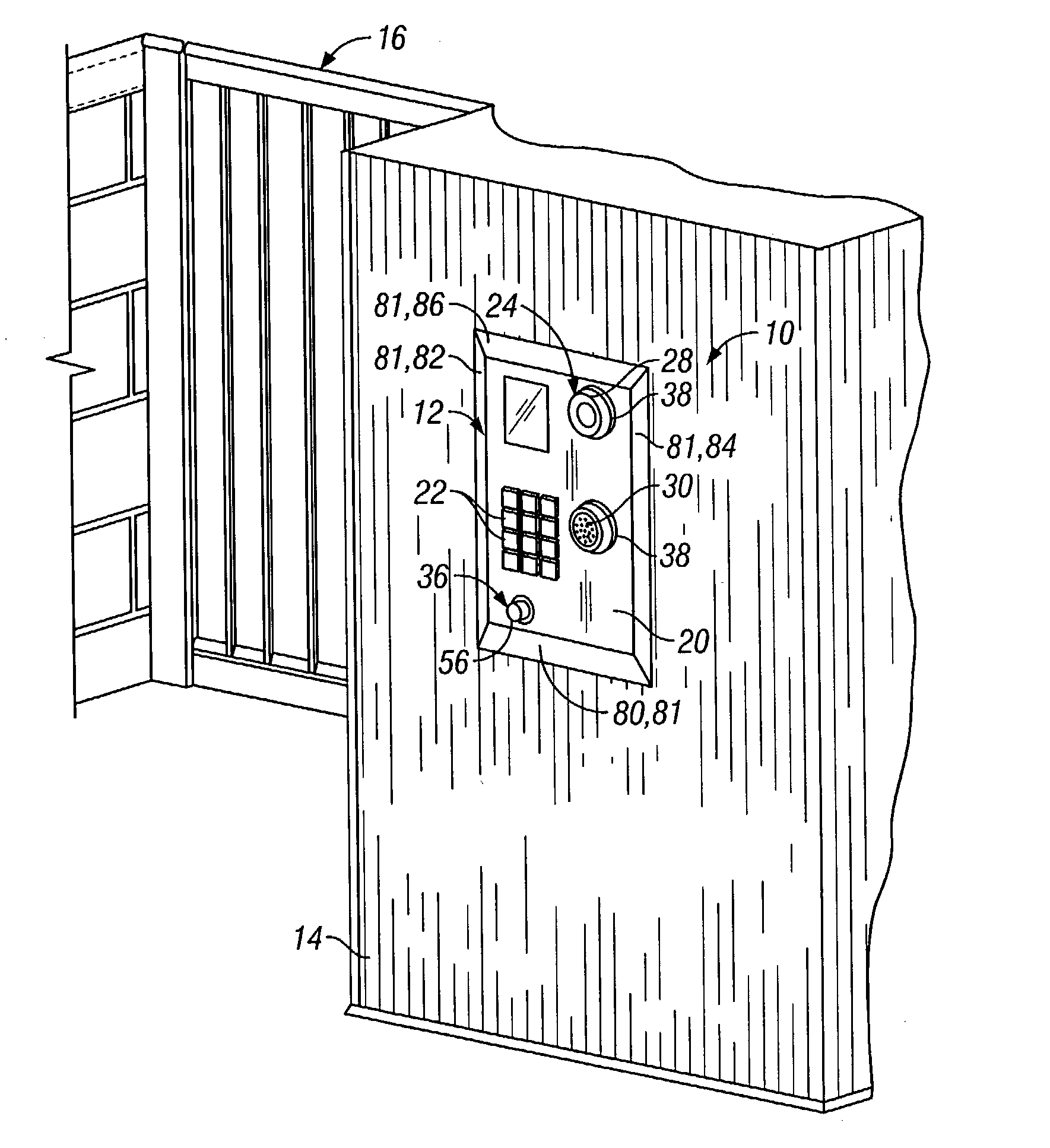
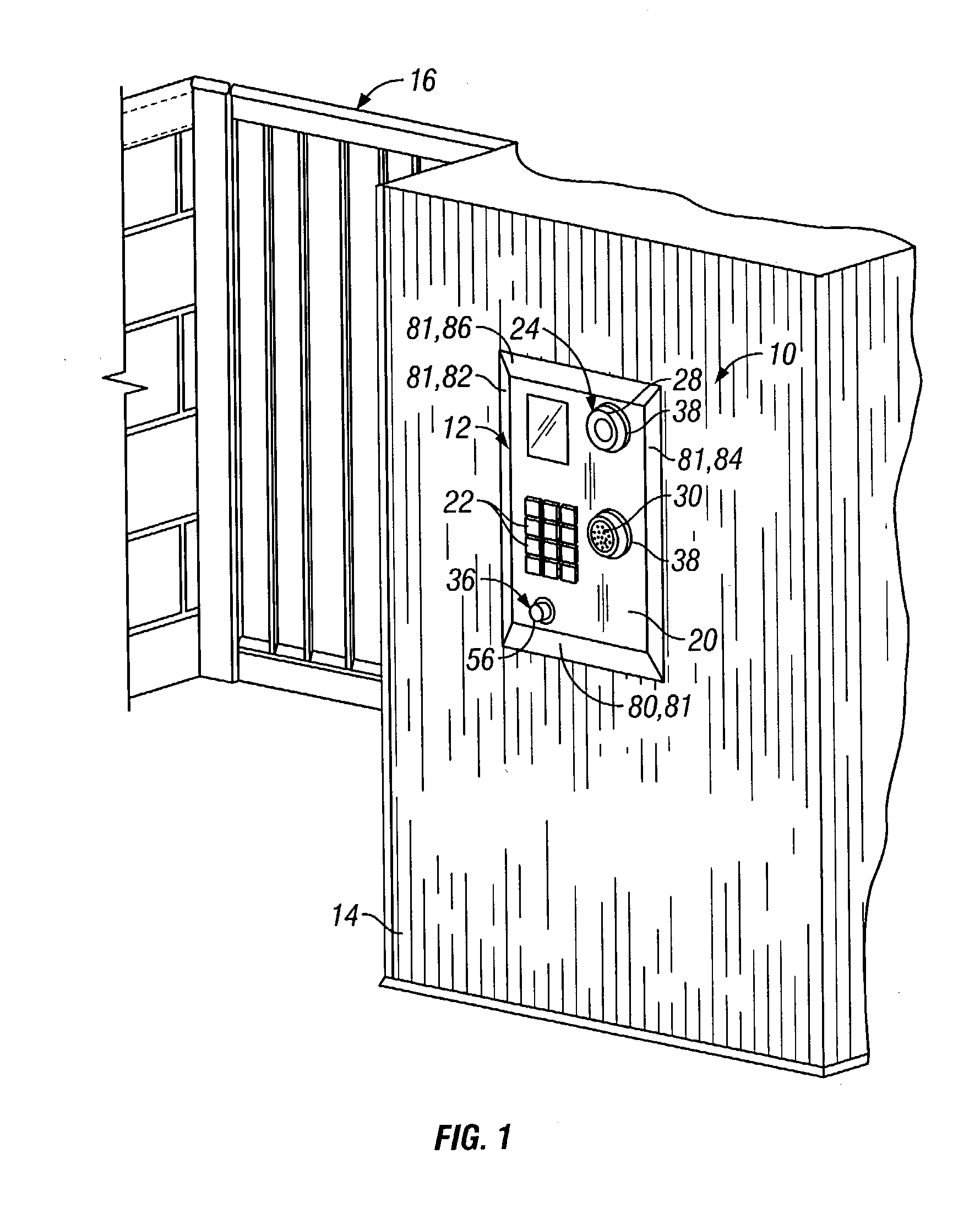
Abuse resistant tapered safety telephone
A telephone using conventional telephone mechanical and electrical components mounted within a telephone housing, typically mounted on a wall, with the earpiece and mouthpiece mounted to be protected by the telephone housing. The housing has a front face surrounded by tapered edges, which provide angled transitions from the front face to the mounting surface. To operate, the user pushes an on / off switch and places an ear next to the fixed earpiece. The telephone is designed for use in prisons, so inmates within a prison cannot hang themselves with a handset cord or break a handset and handset cord off for use as a weapon. The tapered edges restrict access to the abrupt sides of the rigid housing, so the phone does not protrude as a blunt object from the wall. The telephone, which may include a payphone escrow system, is also suitable for use in any high crime or remote public areas to reduce the potential for vandalism. The telephone design reduces the cost of maintenance by eliminating the need to fix and replace a telephone handset, or damaged housings.
Owner:TIP SYST HLDG CO
Large-scale telephone stored program control exchange set networking system and communication method thereof
InactiveCN102833437ADoes not affect normal useRealize networkingInterconnection arrangementsRouting tableStored program control
The invention discloses a large-scale telephone stored program control exchange set networking system and a communication method of the large-scale telephone stored program control exchange set networking system. The system comprises a calling management server and at least one telephone stored program control exchange, wherein each telephone stored program control exchange is connected with a corresponding IP (Internet Protocol) gateway and the calling management server in a manner of networking; an unified routing table is configured in the calling management server; each extension telephone of each telephone stored program control exchange has a unique extension telephone number in the routing table corresponding to PSTN (Public Switched Telephone Network) office number; once an external call incomes, the calling management server establishes the communication between the extension telephone of the calling party and the extension telephone of the called party based on the extension telephone number corresponding to the extension telephone of the called party and the PSTN office number. The system can be conveniently and quickly arranged without influencing the use of original service; the routing is unified; and internal telephone cornet allocating is carried out; the current equipment network can be utilized, so as to maximize the investment; the current PBX (private branch exchange) does not need to be replaced via IP-PBX equipment, so that the investment can be protected to the maximum extent; the system can be easily maintained and managed; in maintaining, the route of the whole network can be simply managed by maintaining the calling management server.
Owner:CTRIP COMP TECH SHANGHAI
Method for converting numbers of mobile phone and wire telephone
InactiveCN104158982AKeep dialing habitLow costNear-field transmissionSpecial service for subscribersCable telephonyComputer module
The invention provides a method for converting numbers of a mobile phone and a wire telephone, and belongs to the technical field of wireless communication. The method is realized by a Bluetooth relay gateway platform comprising a public switched telephone network (PSTN), a Bluetooth relay gateway and at least one Bluetooth terminal; a Bluetooth chip and a telephone circuit module are arranged in the Bluetooth relay gateway; the Bluetooth terminal is in wireless connection with the Bluetooth relay gateway through the Bluetooth chip; the Bluetooth chip is in wired connection with the PSTN through the telephone circuit module, and on the basis that the dial or incoming call attribution is determined, both-way communication between the Bluetooth terminal and the PSTN is realized by adding a telephone number conversion code before a telephone number. The method has the advantages that the communicate quality is stable and reliable, synchronization is facilitated, and phone bill is reduced.
Owner:TSINGHUA UNIV
Message relay system with message relay server
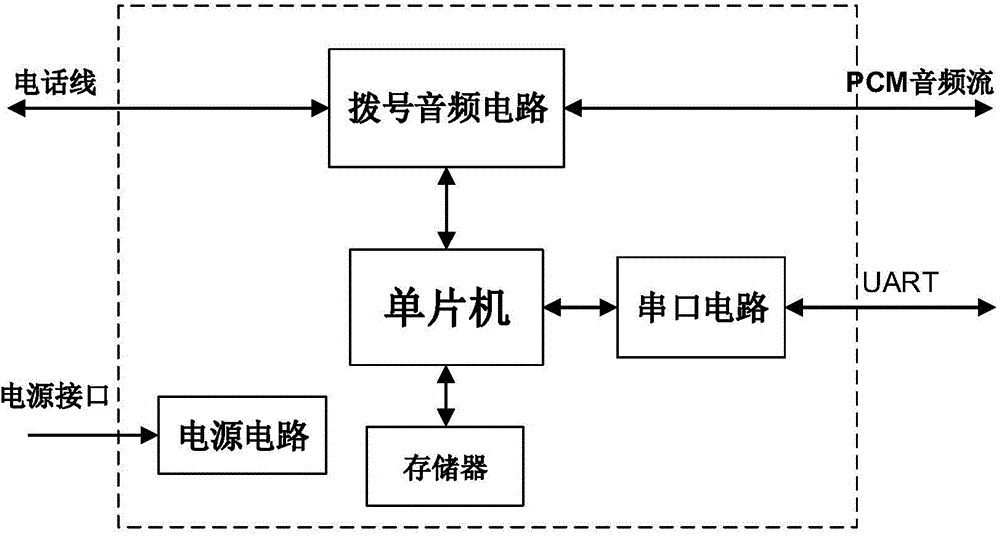
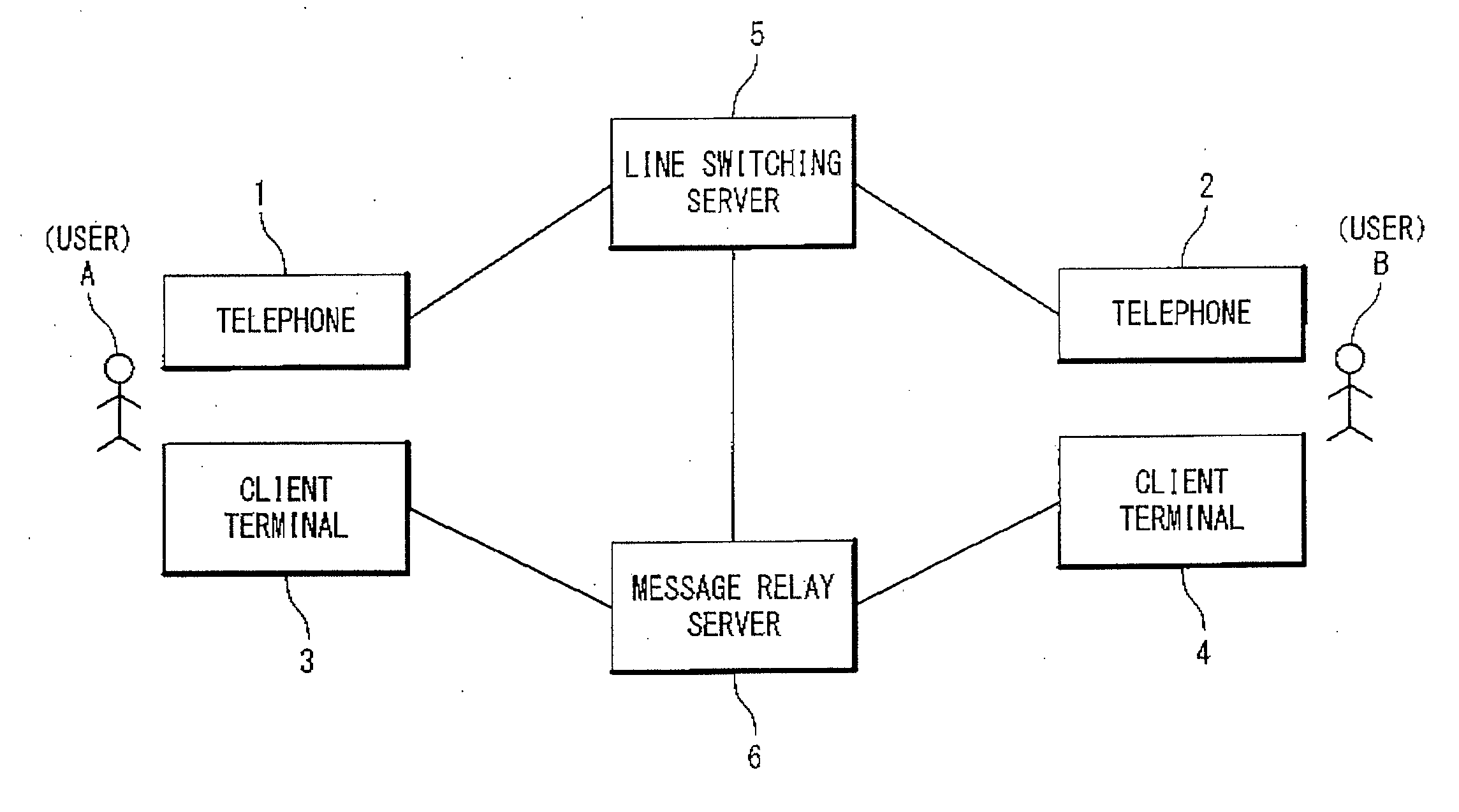
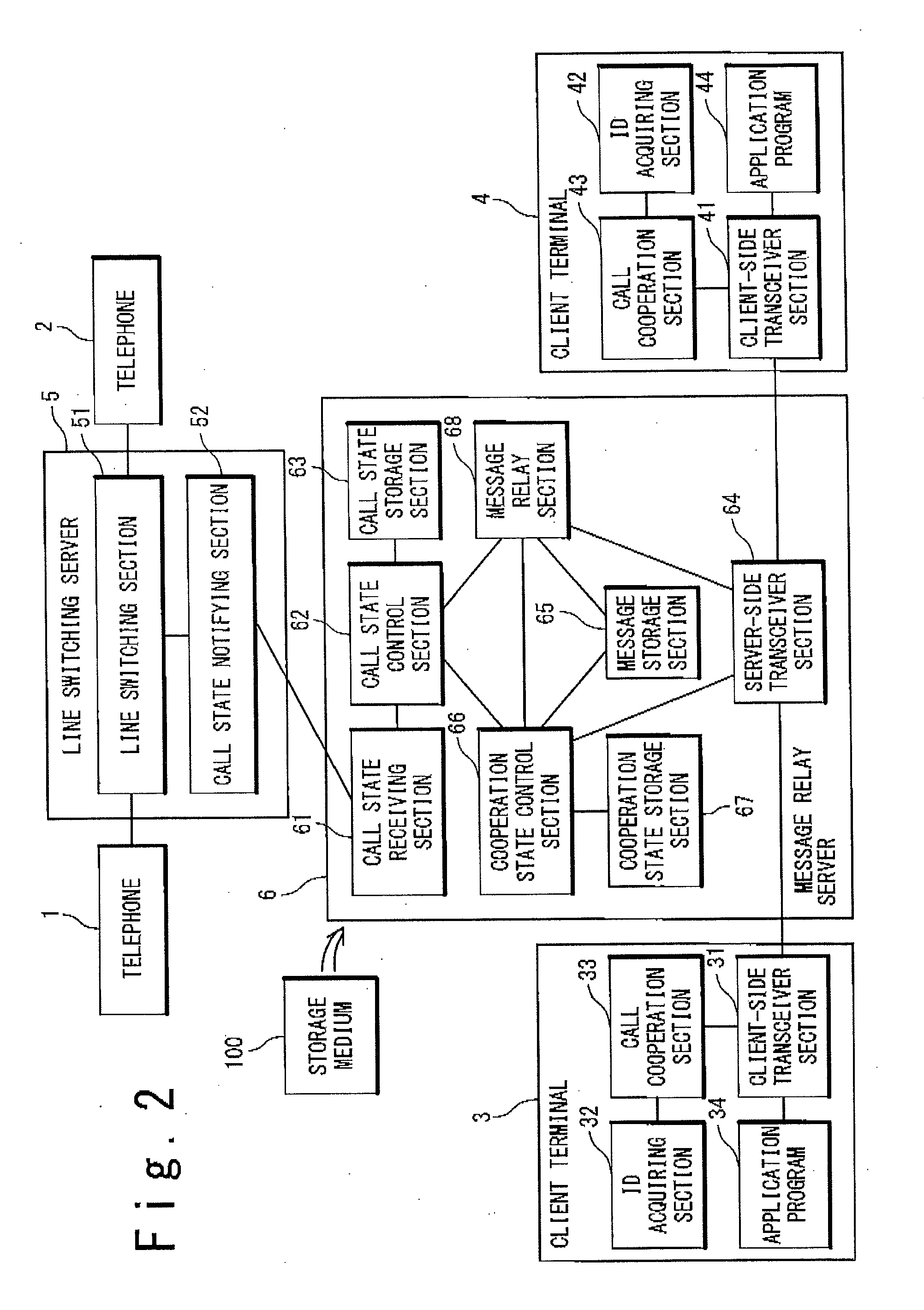
ActiveUS20100266108A1Easy to implementEasy to receiveAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersLine switchingSecure telephone
A message relay server includes; a call state control section configured to acquire a call state data which contains identification data of telephones, which perform a speech communication call, of a plurality of telephones from a line switching server which controls the speech communication call; a call state storage section configured to store the call state data for every the speech communication call; a message relay section configured to receive a message which includes the identification data of a first telephone of the plurality of telephones, from a first client terminal of the plurality of client terminals in cooperation with the first telephone, and specify a second telephone which performs the speech communication with the first telephone based on the identification data of the first telephone which is contained in the message and the call state data; and a message storage section configured to store the message and an identification data of the second telephone which are related to each other. The message relay section receives a message inquiry to acquire a message which includes the identification data of the second telephone from a second client terminal of the plurality of client terminals which is in cooperation with the second telephone, and transmits the stored message for the identifier data of the second telephone which is contained in the message inquiry to the second client terminal.
Owner:NEC CORP
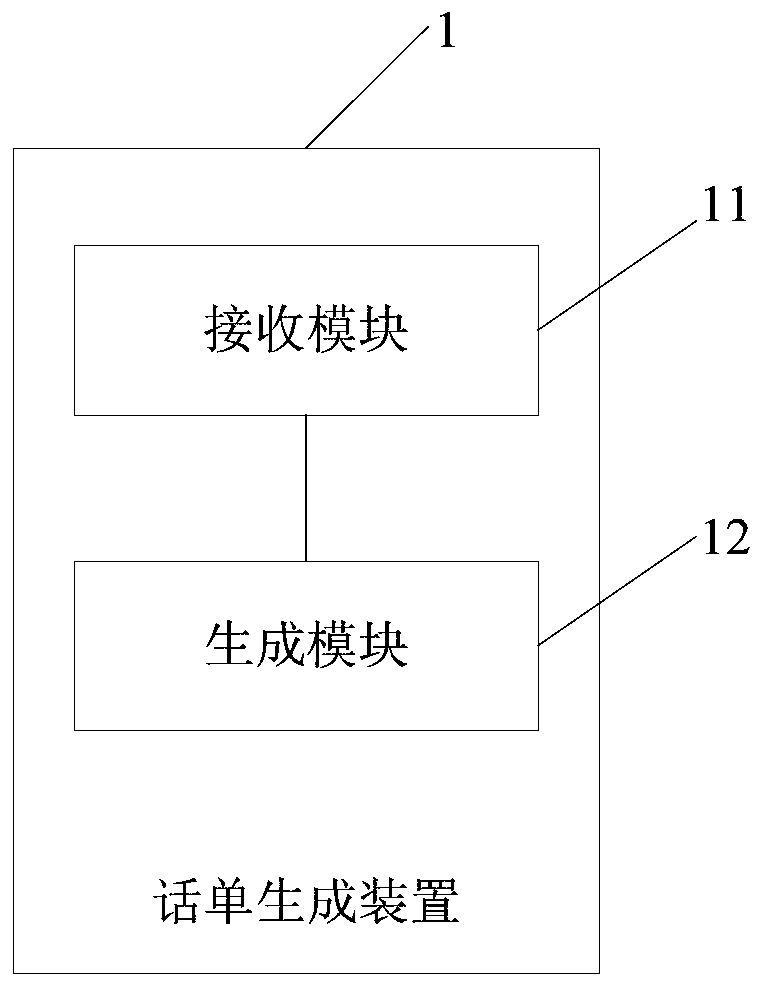
Call ticket generation method and system and call ticket generation server
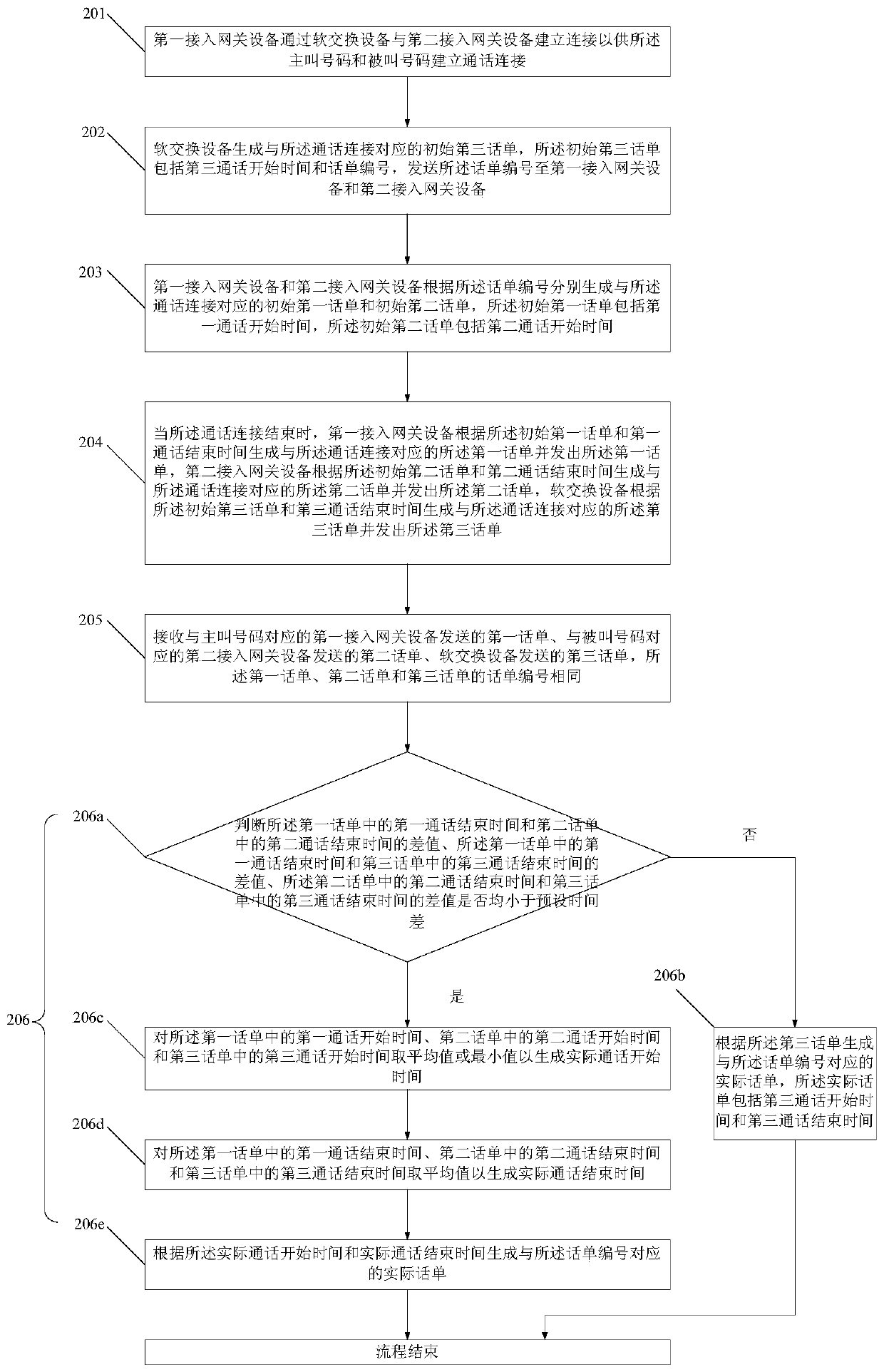
ActiveCN109714494AAvoid errorsHigh precisionTelephonic communicationTelecommunicationsSecure telephone
The invention discloses a call ticket generation method and system, and a call ticket generation server. The telephone bill generation method comprises the steps that a first telephone bill sent by first access gateway equipment corresponding to a calling number, a second telephone bill sent by second access gateway equipment corresponding to a called number and a third telephone bill sent by softswitching equipment are received, and the telephone bill numbers of the first telephone bill, the second telephone bill and the third telephone bill are the same; And an actual call ticket corresponding to the call ticket number is generated according to the first call ticket, the second call ticket and the third call ticket. According to the invention, the error and the call bill leakage betweenthe generated call bill and the actual call condition can be effectively avoided, so that the accuracy of call charging is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
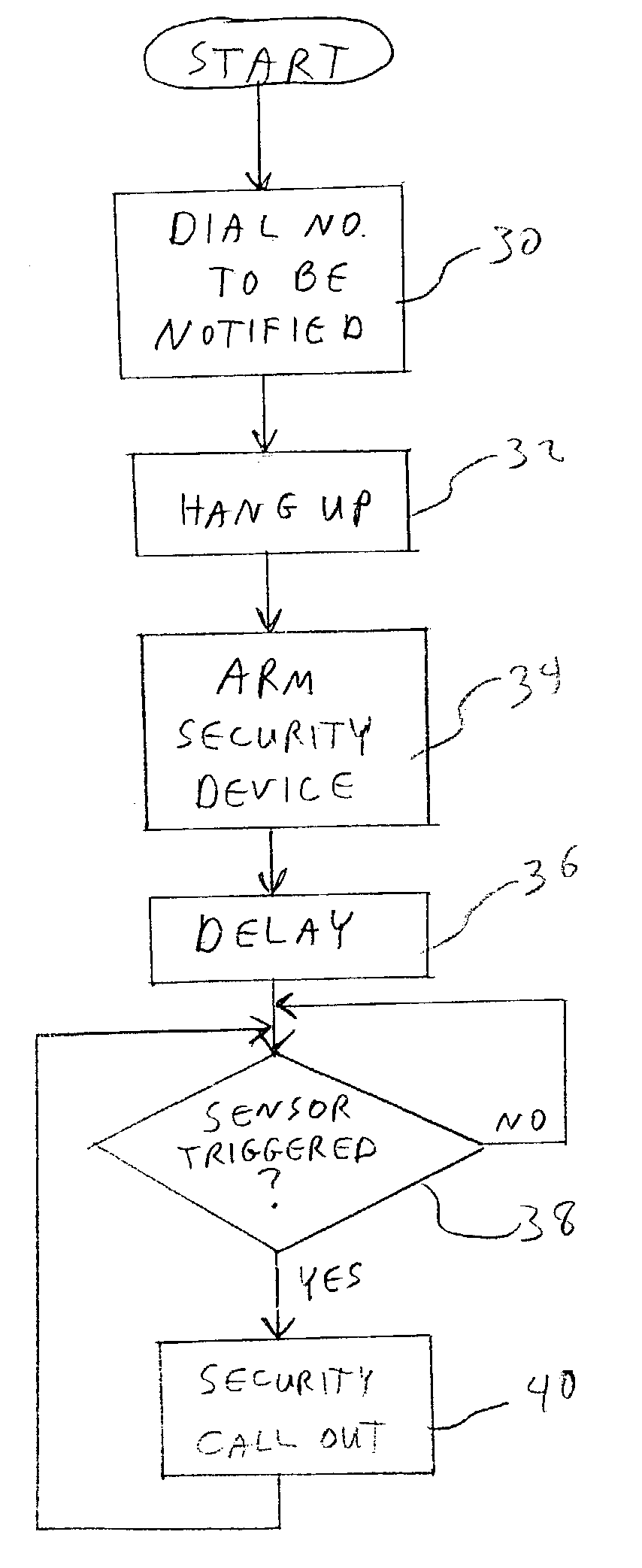
Security telephone
A telephone security device is built into a telephone unit. The device includes a sensor to detect an intrusion into the area in which the telephone is located. Upon detection of an event, the device places the telephone off hook, and triggers the redial feature of the telephone. This causes the telephone to redial the last number that had been called. The telephone then remains in the off hook condition for a delay interval to allow the recipient of the call to listen, via the telephone, for any sounds indication that an actual intrusion has occurred. In order to arm the security device, the user simply dials the number that is the intended recipient of the call, hang up, and switch on the sensor. Detection of a security event will then cause the last dialed number to be redialed.
Owner:GAREY WILLIAM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com