Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
872 results about "Software implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software Implementation. DEFINITION: The phase in the software life-cycle where the actual software is implemented. The result of this phase consists of source code, together with documentation to make the code more readable.
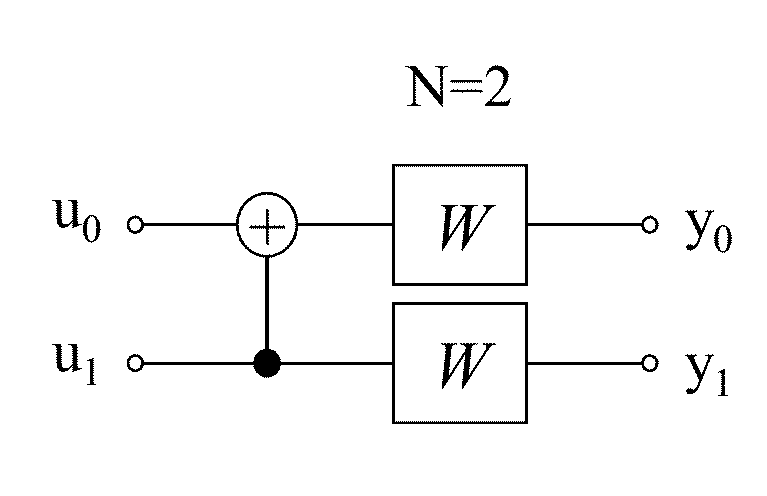
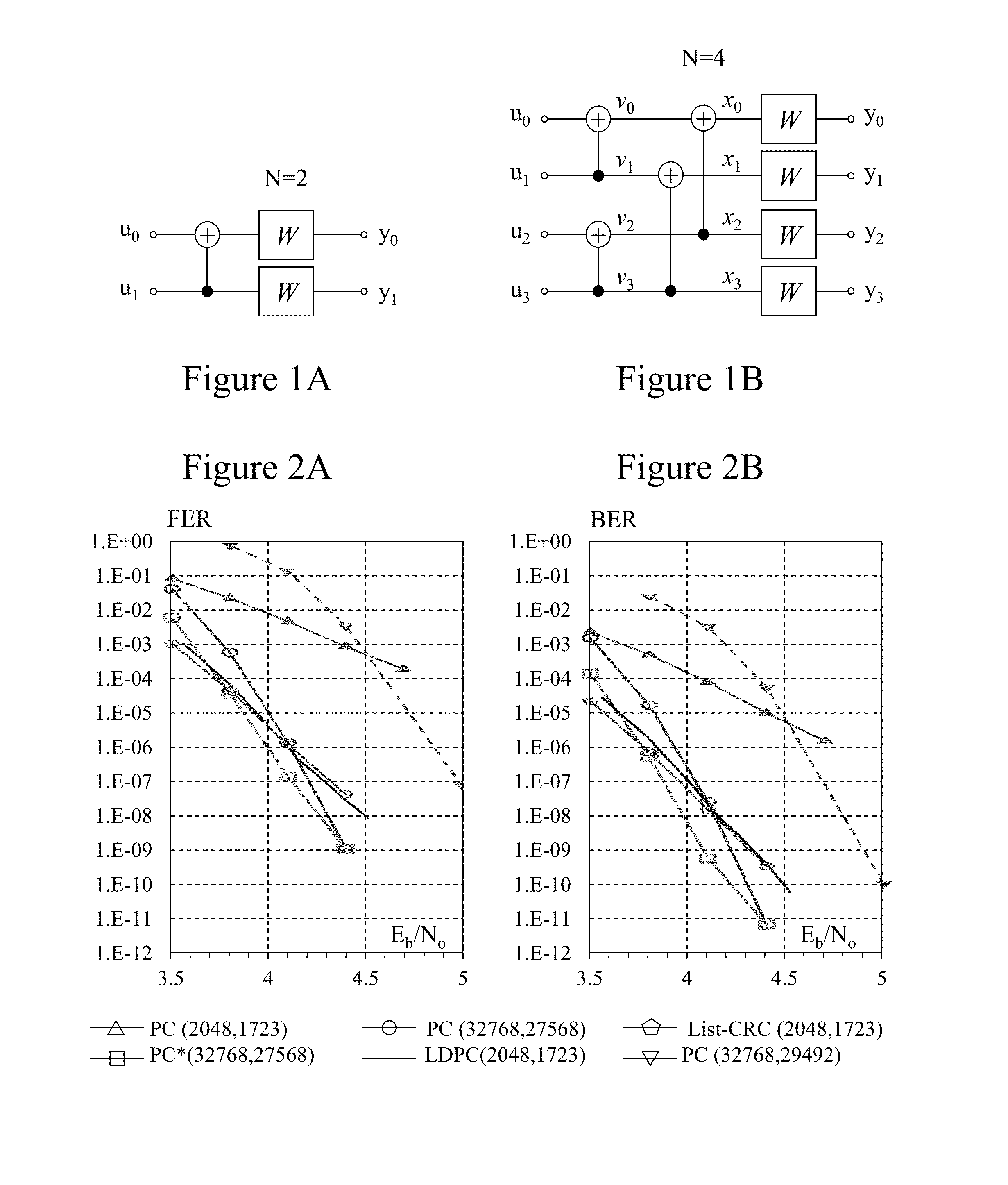
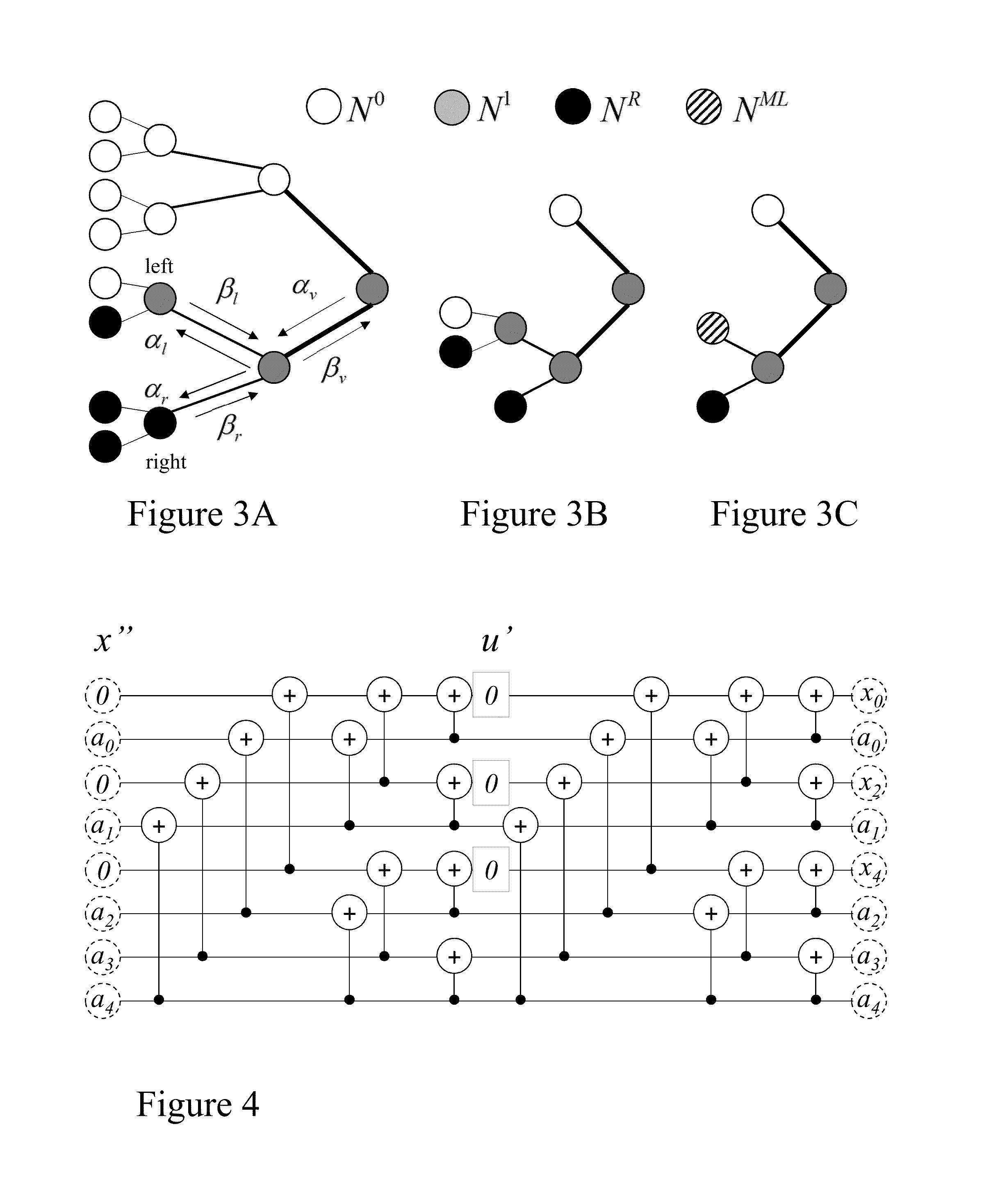
Flexible polar encoders and decoders
Modern communication systems must cope with varying channel conditions and differing throughput constraints. Polar codes despite being the first error-correcting codes with an explicit construction to achieve the symmetric capacity of memoryless channels are not currently employed against other older coding protocols such as low-density parity check (LDPC) codes as their performance at short / moderate lengths has been inferior and their decoding algorithm is serial leading to low decoding throughput. Accordingly techniques to address these issues are identified and disclosed including decoders that decode constituent codes without recursion and / or recognize classes of constituent directly decodable codes thereby increasing the decoder throughput. Flexible encoders and decoders supporting polar codes of any length up to a design maximum allow adaptive polar code systems responsive to communication link characteristics, performance, etc. whilst maximizing throughput. Further, designers are provided flexibility in implementing either hardware or software implementations.
Owner:POLAR TECH
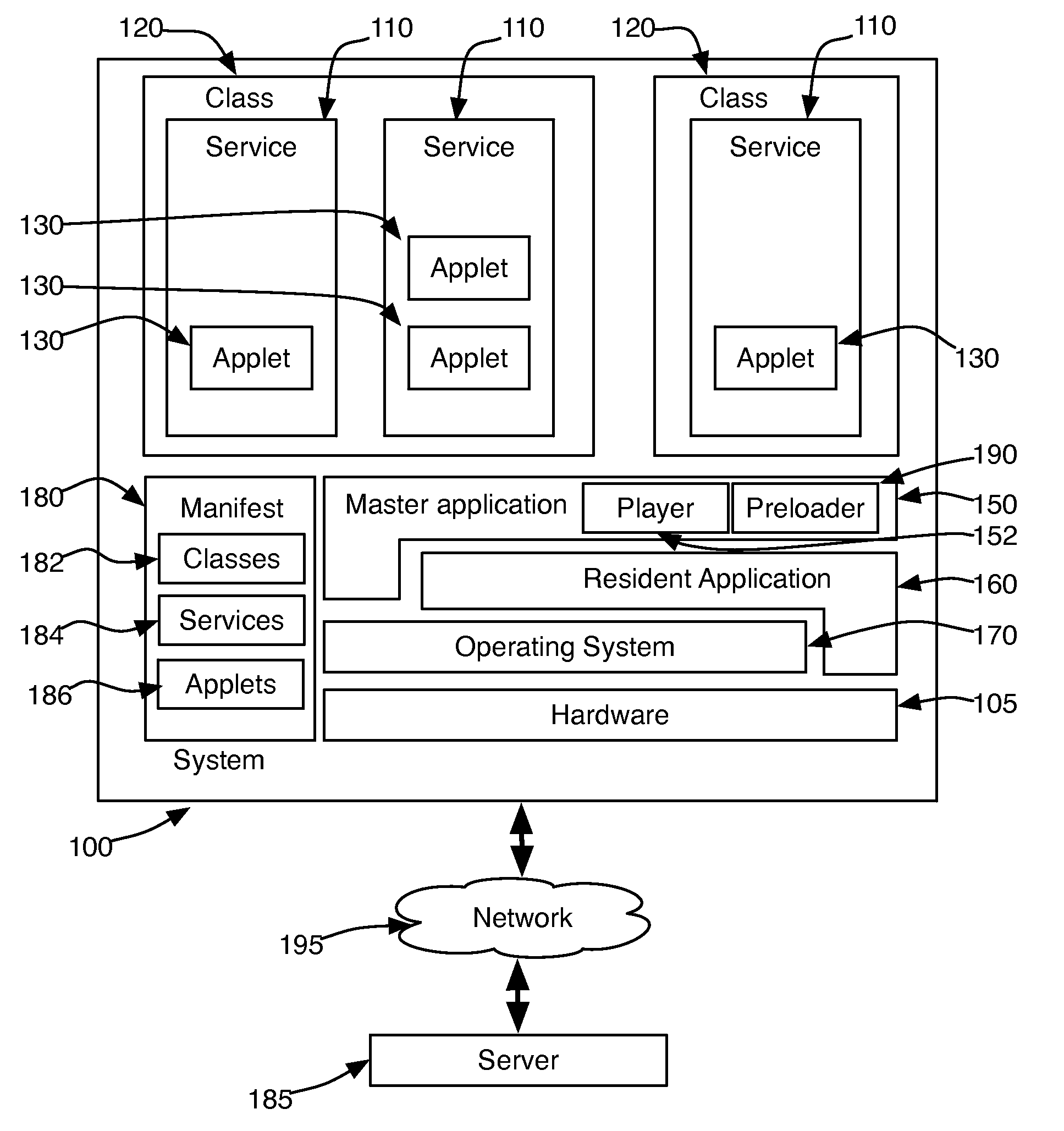
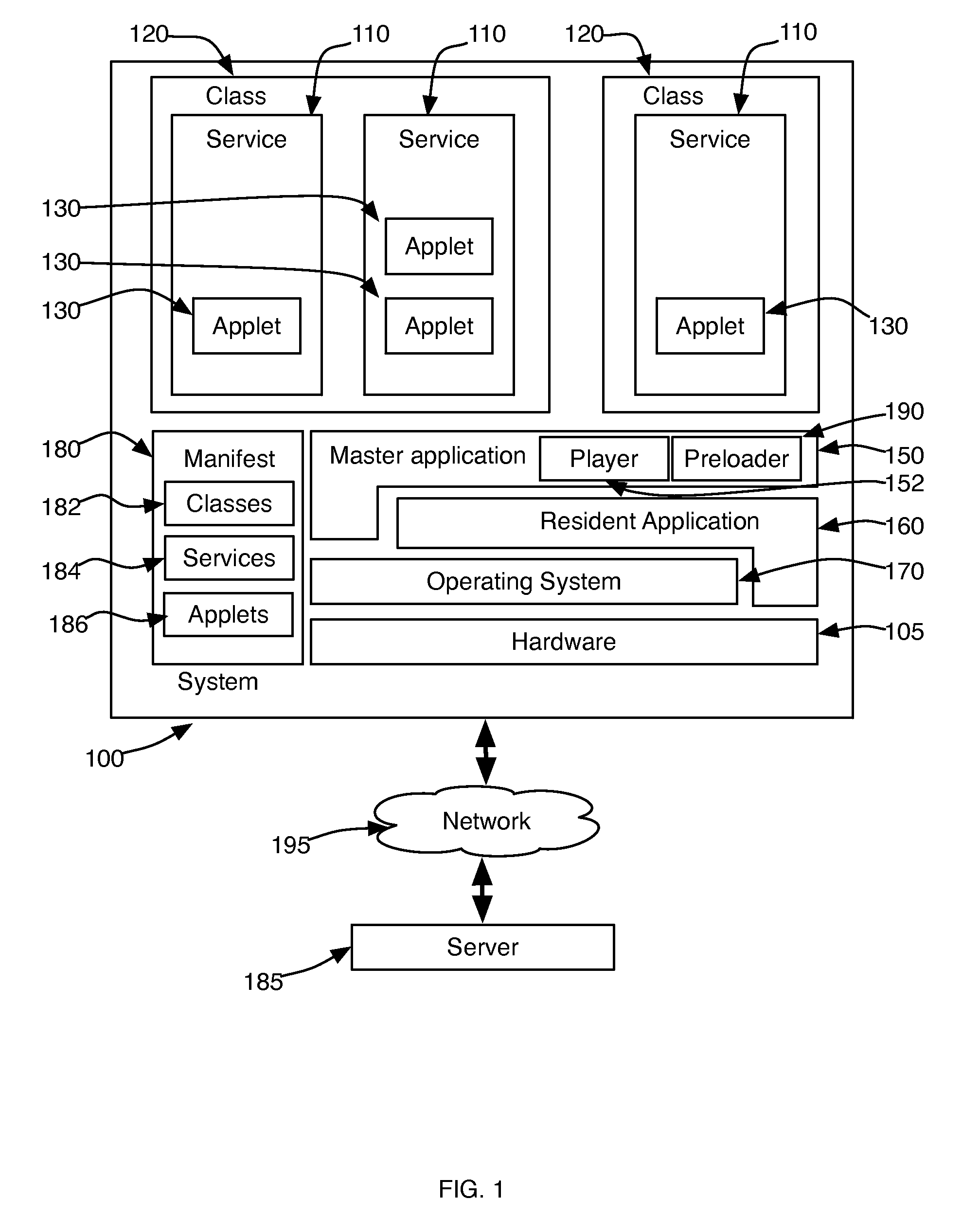
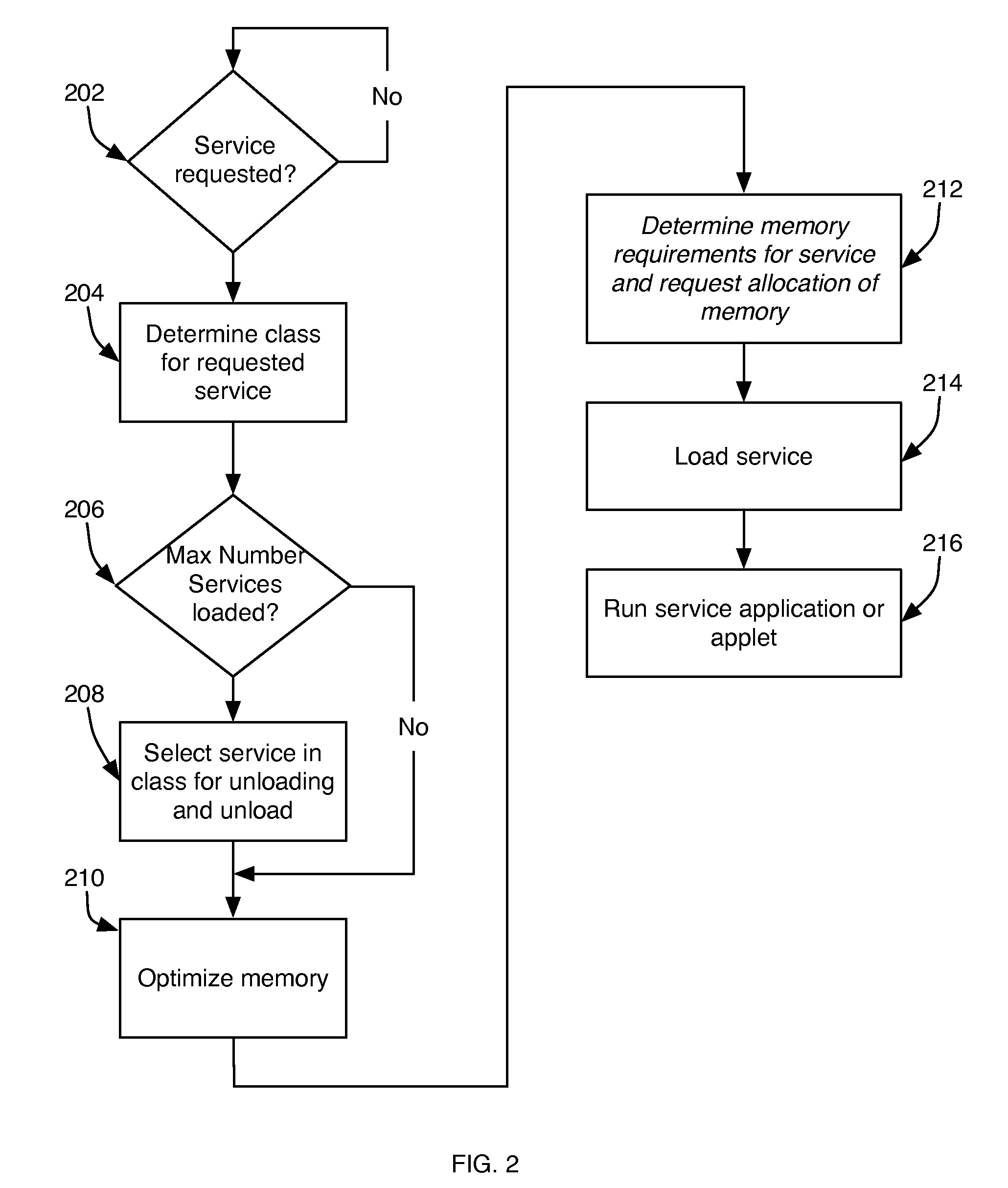
Management of Software Implemented Services in Processor-Based Devices
InactiveUS20090013157A1Reduce memory fragmentationShorten activation timeDigital computer detailsMultiprogramming arrangementsSatellite televisionApplication software
A service management system for devices with embedded processor systems manages use of memory by programs implementing the services by assigning services to classes and limiting the number of services per class that can be loaded into memory. Classes enable achieving predictable and stable system behavior, defining the services and service classes in a manifest that is downloaded to embedded devices operating on a network, such as a cable or satellite television network, telephone or computer network, and permit a system operator, administrator, or manager to manage the operation of the embedded devices while deploying new services implemented with applications downloaded from the network when the service is requested by a user.
Owner:BLUESTREAK TECH INC
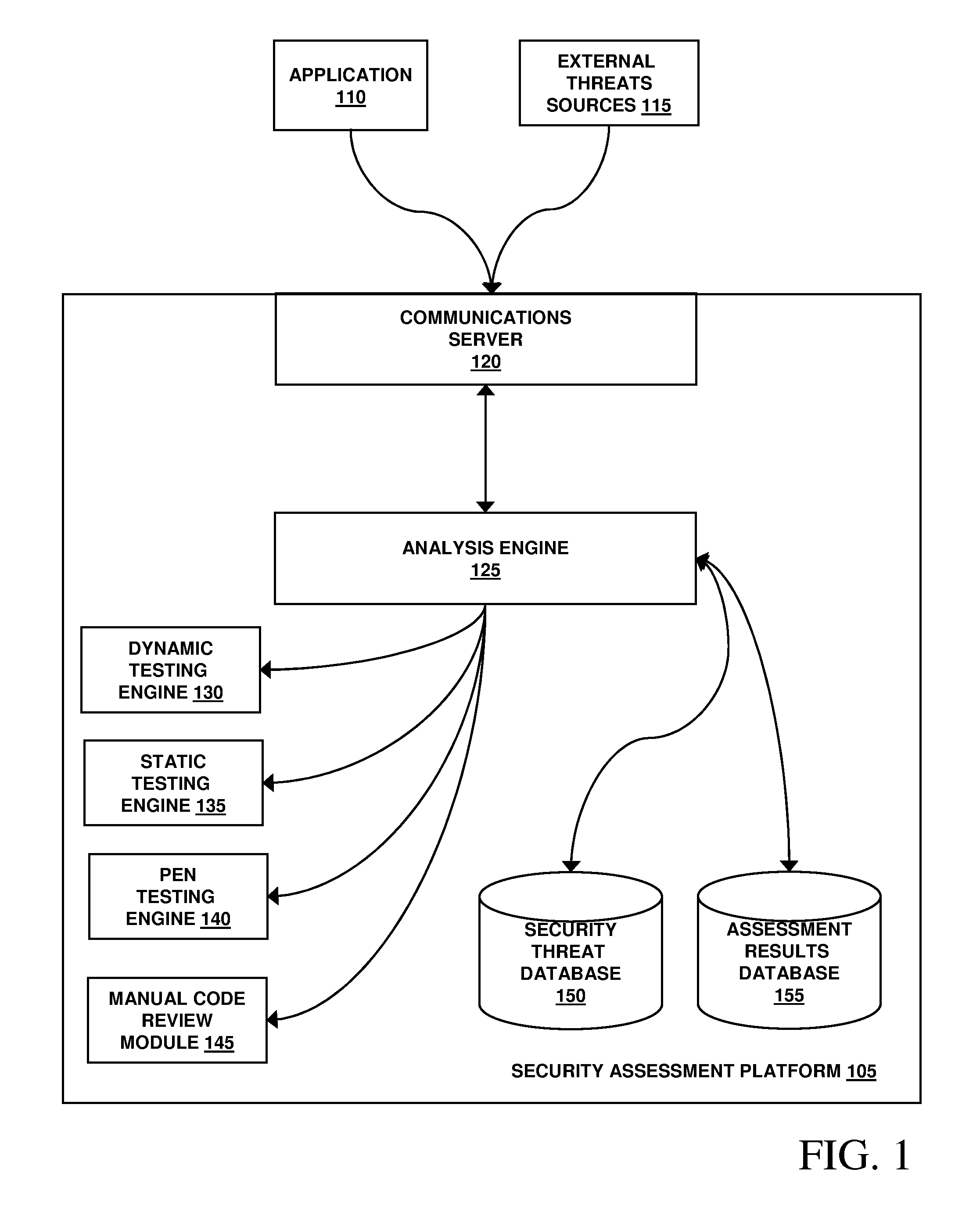
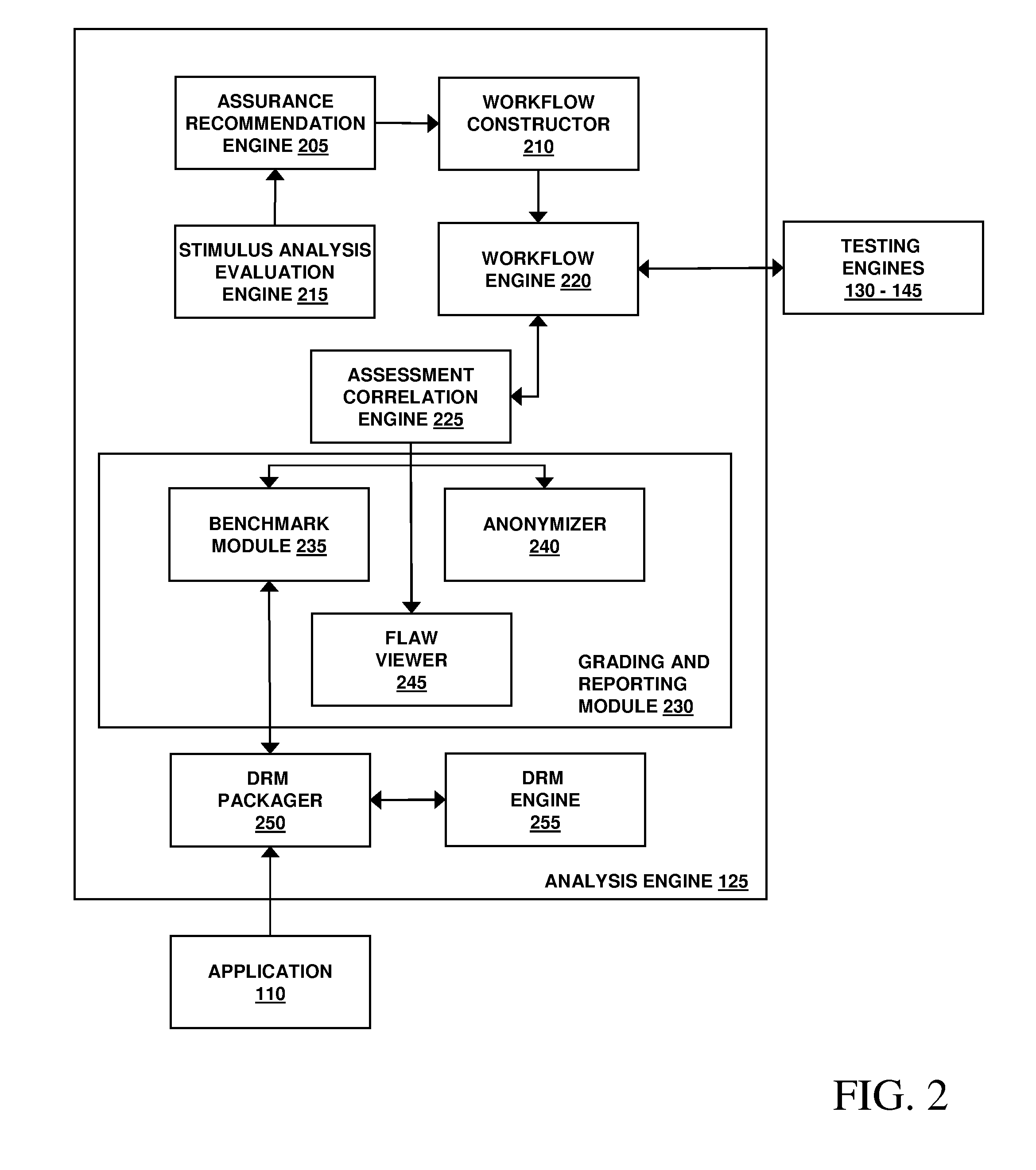
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
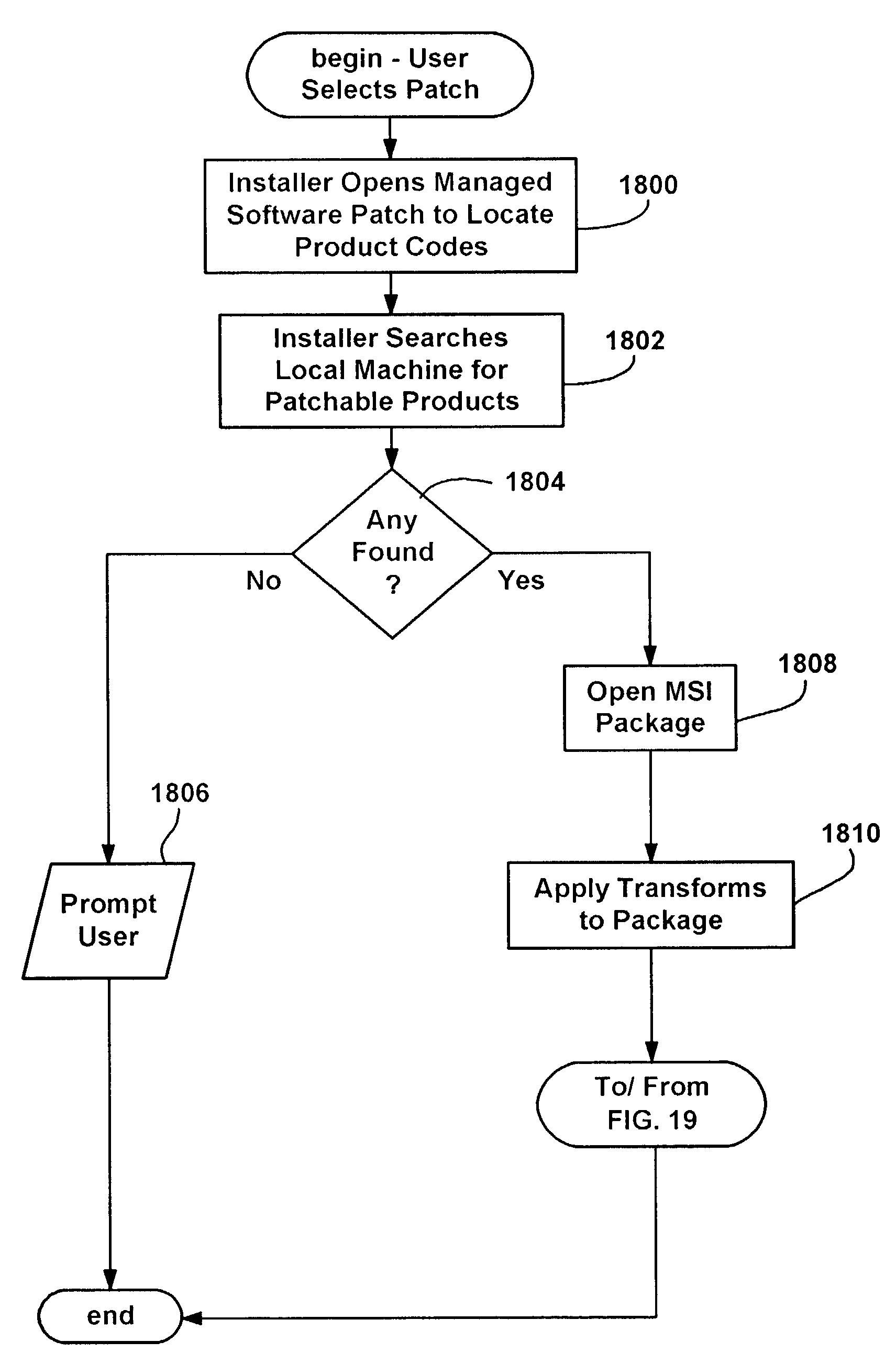
On demand patching of applications via software implementation installer mechanism
A method and mechanism for automatically patching software implementations such as applications as they are installed from an external source. A patch program is run for a software implementation that is advertised as available, or is otherwise available, though not yet installed (or fully installed). The mechanism maintains the patch information for that software implementation. Whenever the software implementation is installed, the mechanism determines that the software implementation has the patch information maintained therefor. The mechanism automatically applies the patch as part of the on-demand installation process. The patch may change the files, the values of registry entries and / or the installation logic associated with the software implementation.
Owner:MICROSOFT TECH LICENSING LLC
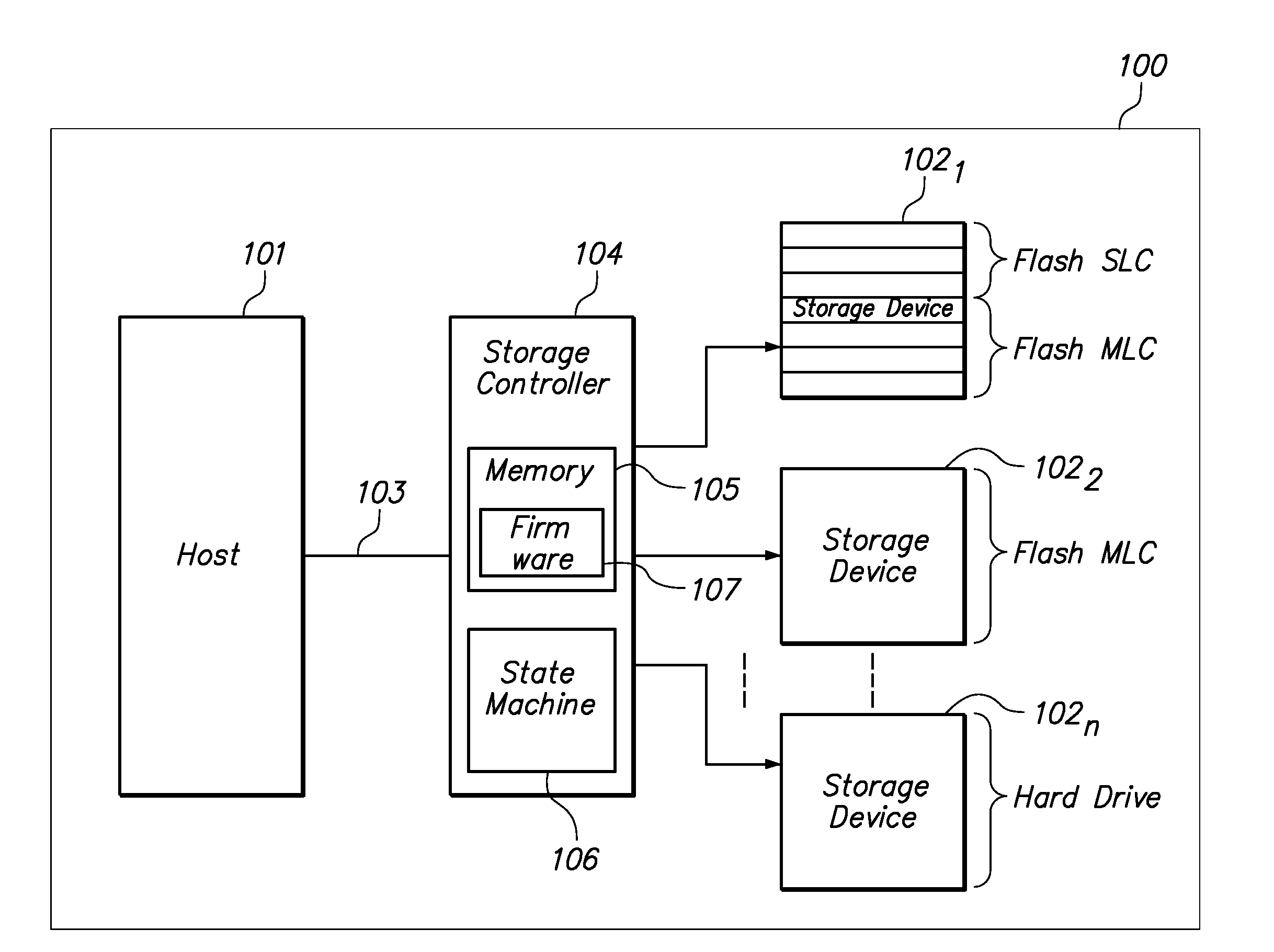
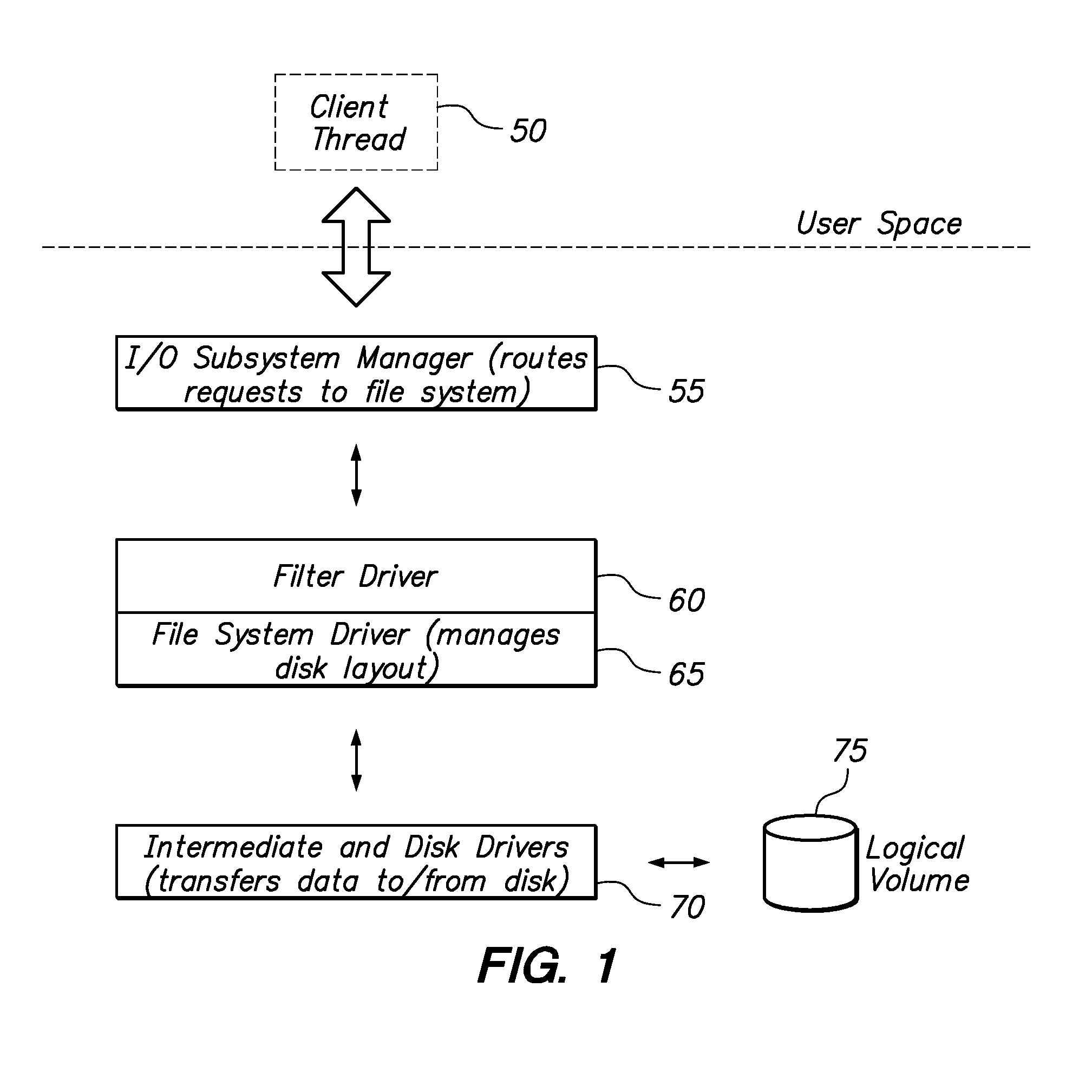
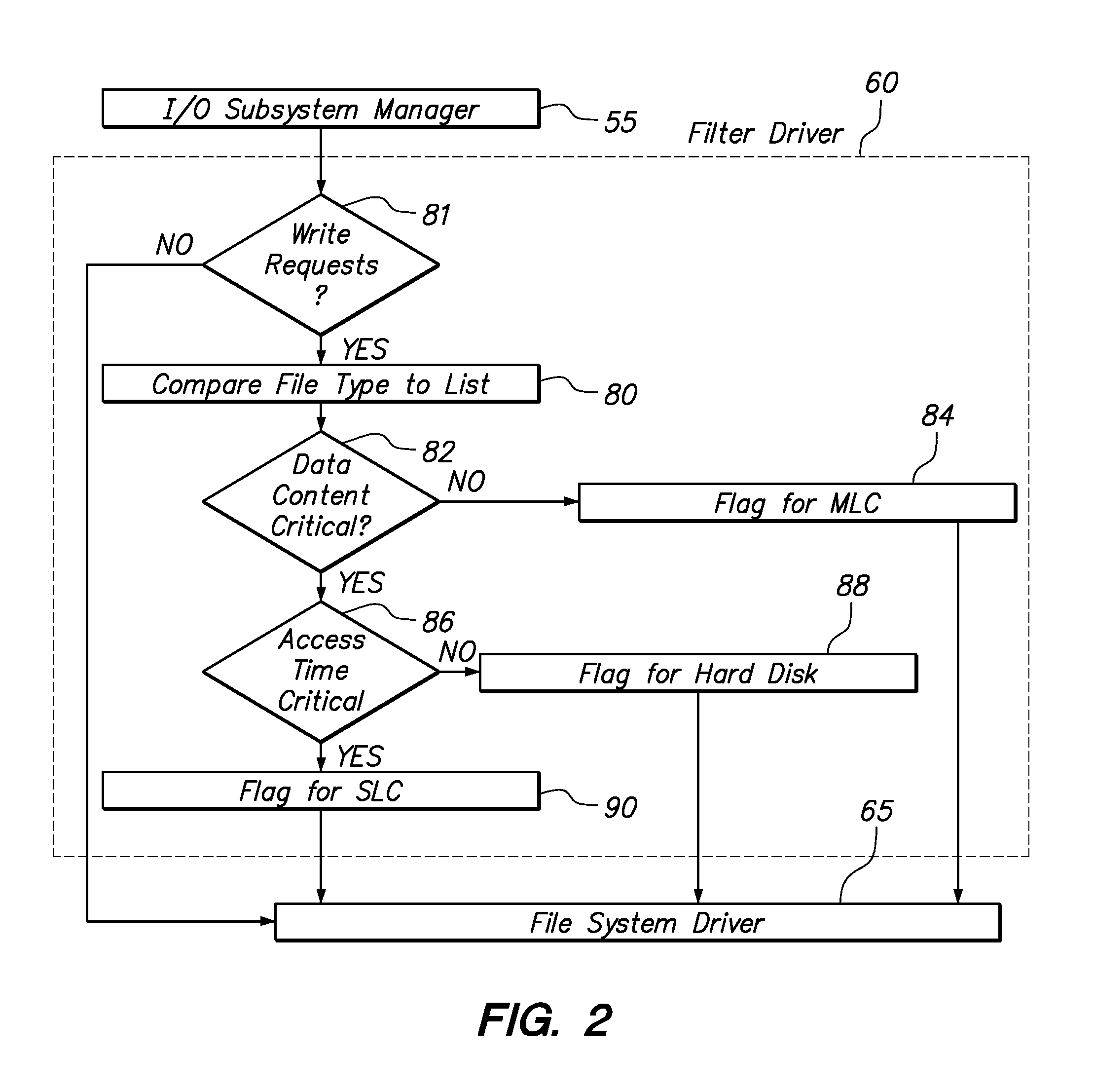
Smart Solid State Drive And Method For Handling Critical Files
InactiveUS20090043831A1Memory adressing/allocation/relocationInput/output processes for data processingControl storeComputerized system
A method and apparatus for dynamically distributing data to an appropriate storage device based on the significance of the data. In one embodiment the method determines the significance of a data file using the format of the data file. The method also includes identifying a storage device and memory location of the storage device to write the data. In a software implementation, a computer system employs a filter driver and / or a device driver to identify and store data files. In another embodiment, a storage controller includes a state machine that initiates and executes firmware to determine the data file format and also the storage device location.
Owner:MCM PORTFOLIO LLC
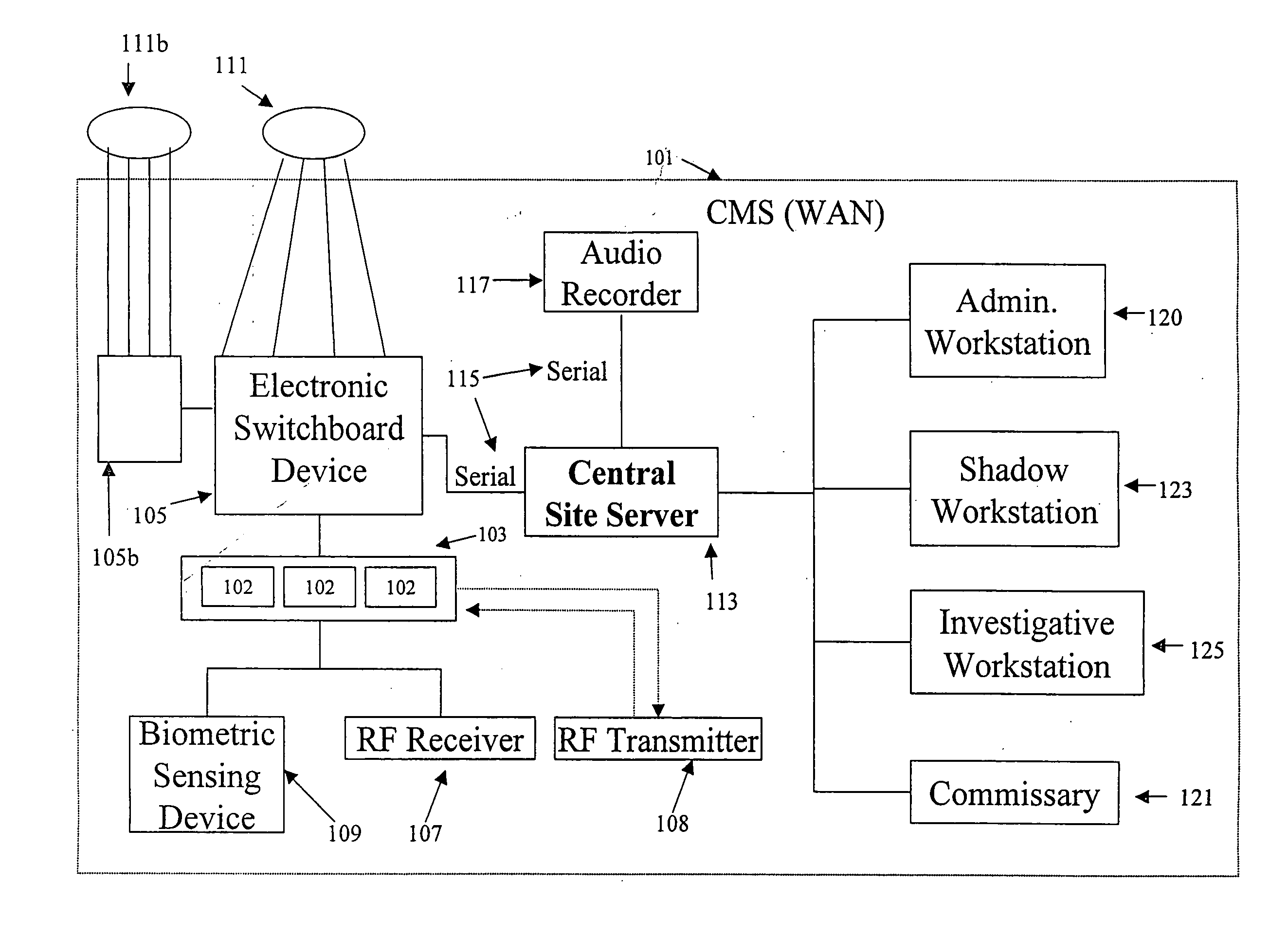
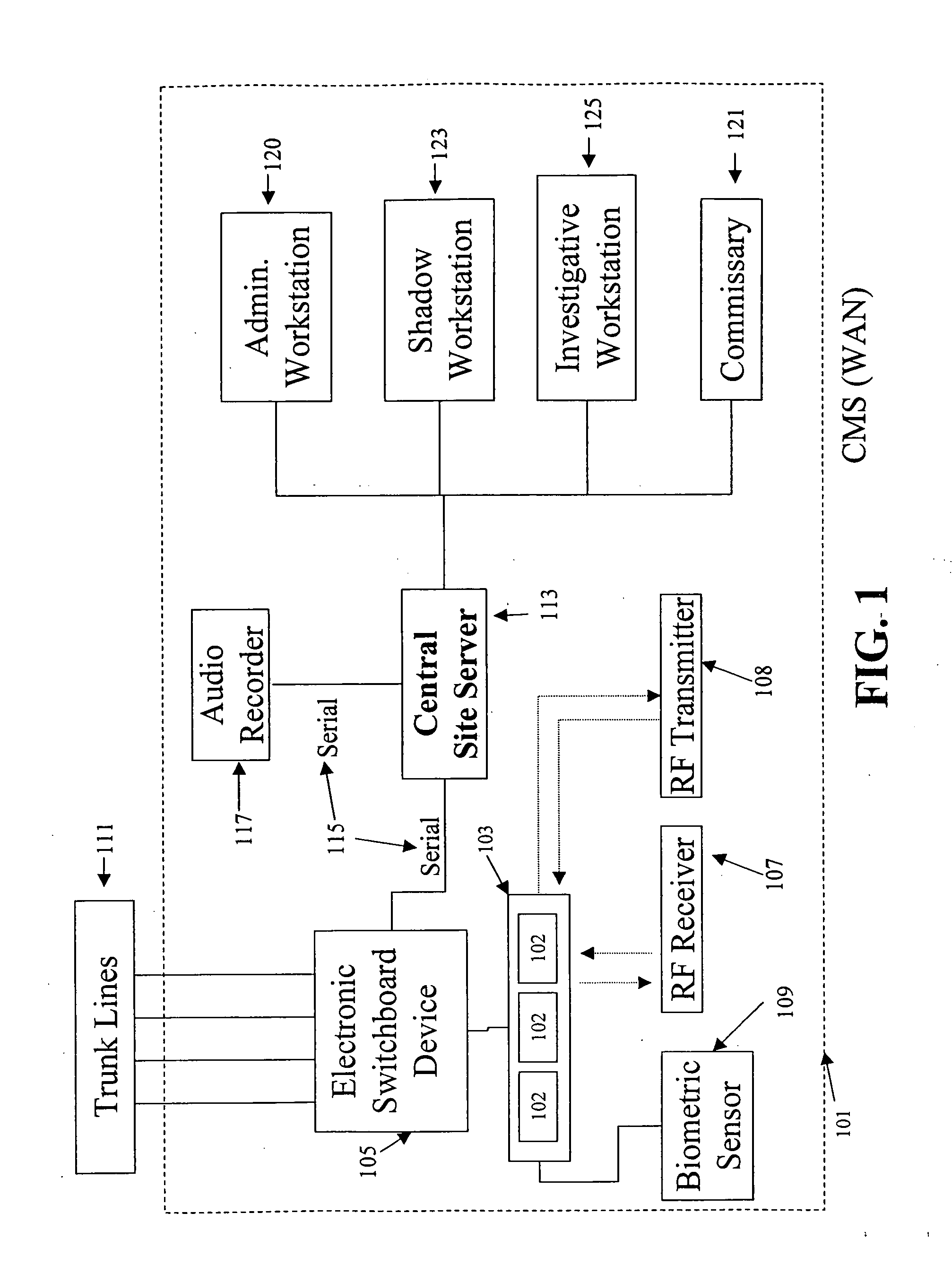
Telecommunication call management and monitoring system with voiceprint verification
InactiveUS20050043014A1Accurate verificationEliminating system overloadTelevision system detailsUnauthorised/fraudulent call preventionPersonal identification numberMonitoring system
Disclosed is a secure telephone call management system for authenticating users of a telephone system in an institutional facility. Authentication of the users is accomplished by using a personal identification number, preferably in conjunction with speaker independent voice recognition and speaker dependent voice identification. When a user first enters the system, the user speaks his or her name which is used as a sample voice print. During each subsequent use of the system, the user is required to speak his or her name. Voice identification software is used to verify that the provided speech matches the sample voice print. The secure system includes accounting software to limit access based on funds in a user's account or other related limitations. Management software implements widespread or local changes to the system and can modify or set any number of user account parameters.
Owner:GLOBAL TELLINK
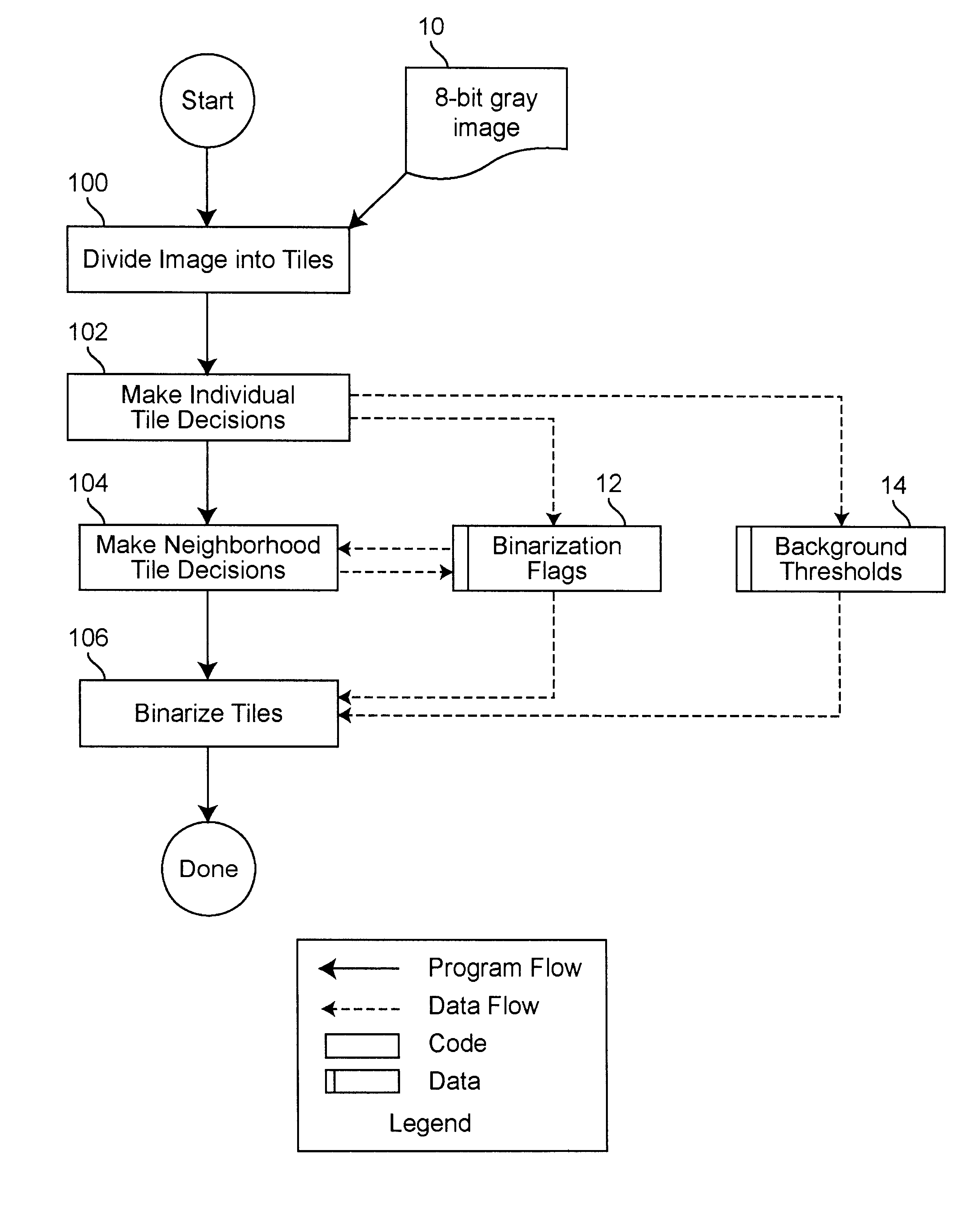
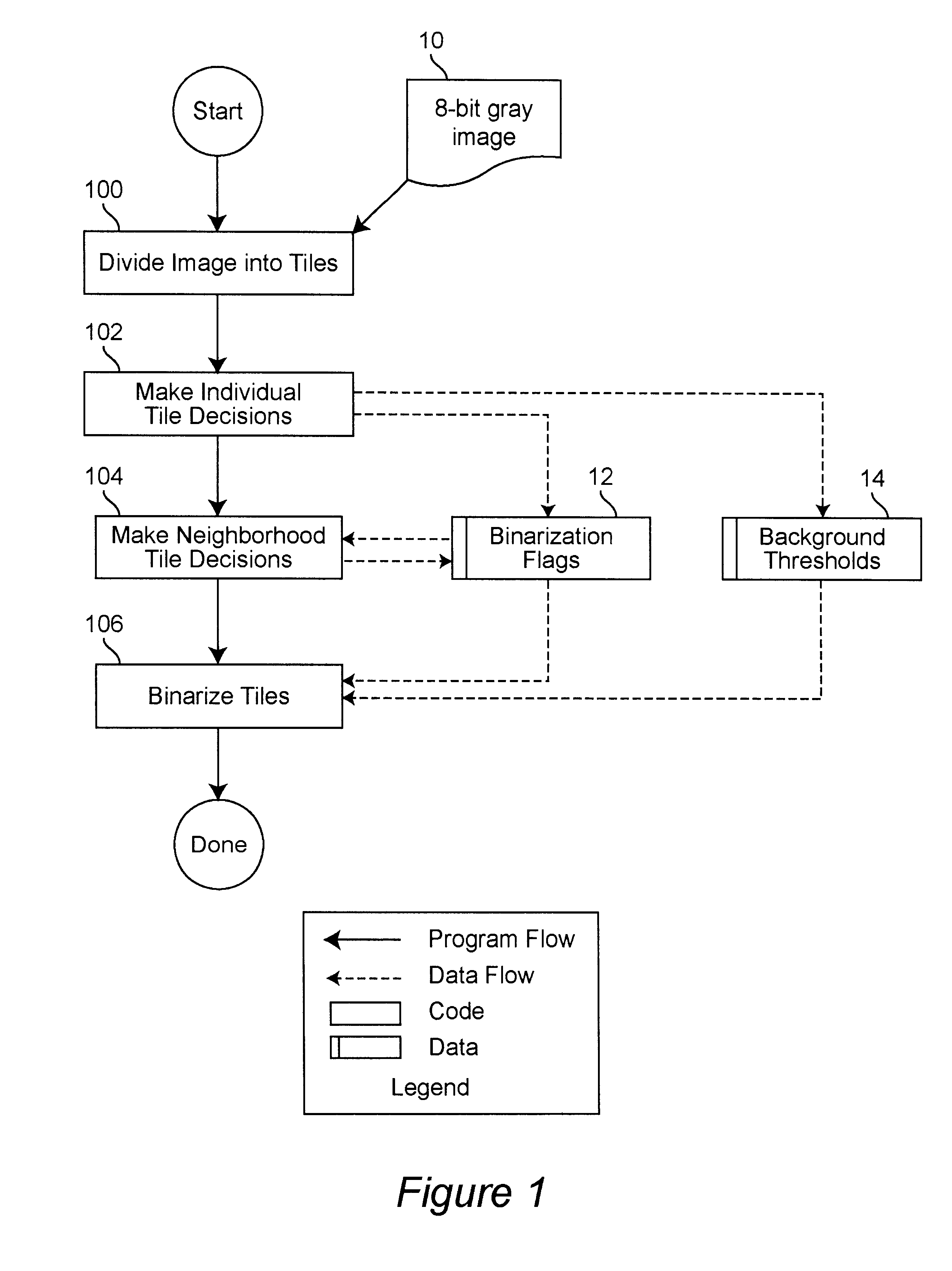
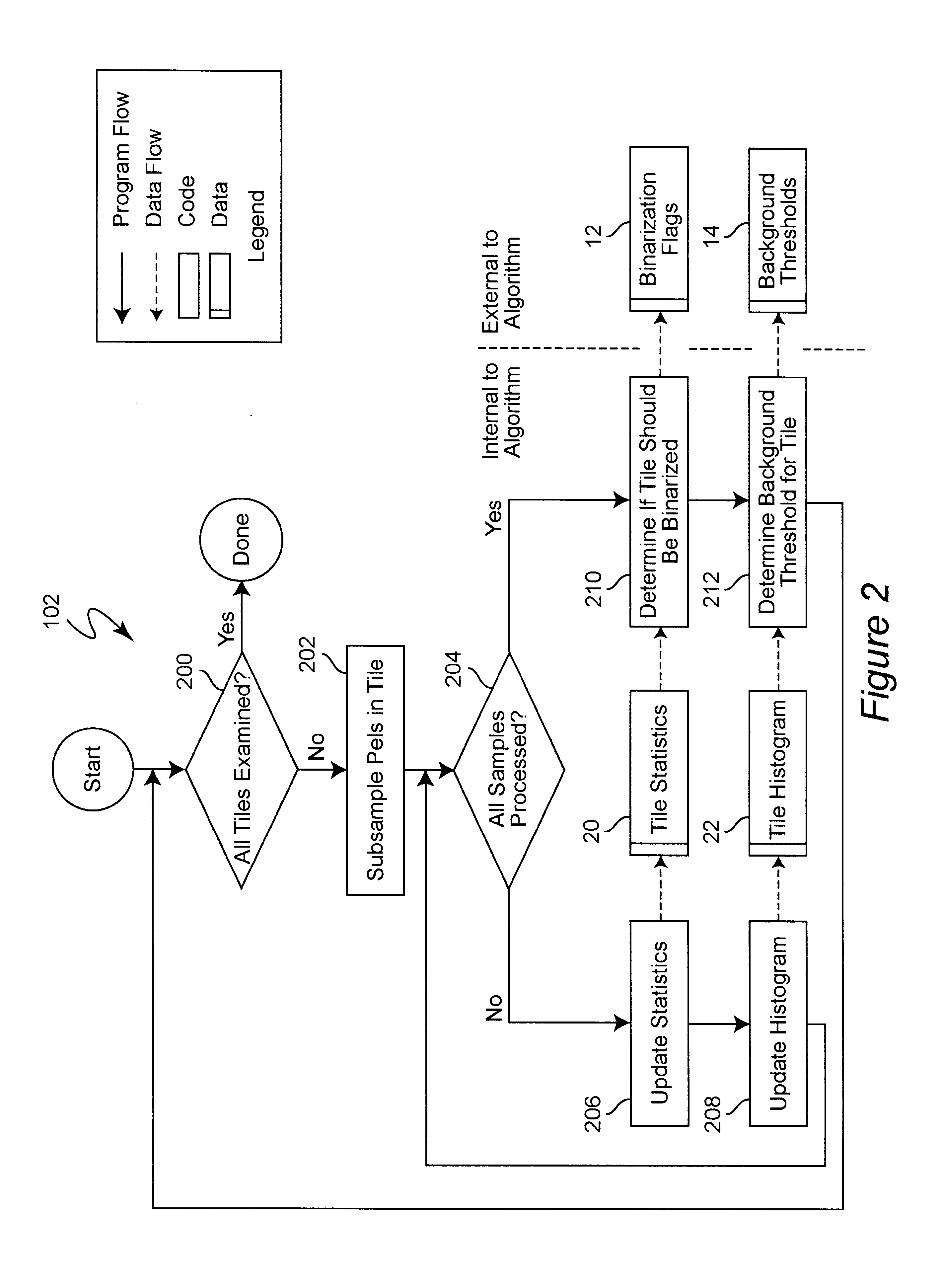
Real time binarization of gray images
InactiveUS6738496B1Promote resultsConvenient statisticsCharacter recognitionComputer visionGrayscale
A binarization method for gray address images which combines high quality and high speed. The method is designed specifically for efficient software implementation. Two binarization approaches, localized background thresholds and Laplacian edge enhancement, are combined into a process to enhance the strengths of the two methods and eliminate their weaknesses. The image is divided into tiles, making binarization decisions for each tile. Tile decisions are modified based on adjacent tile decisions and then the tiles are binarized. Binarization of pixels is performed by performing background thresholding and edge detection thresholding. Only pixels exceeding both thresholds are selected as "on".
Owner:LOCKHEED MARTIN CORP
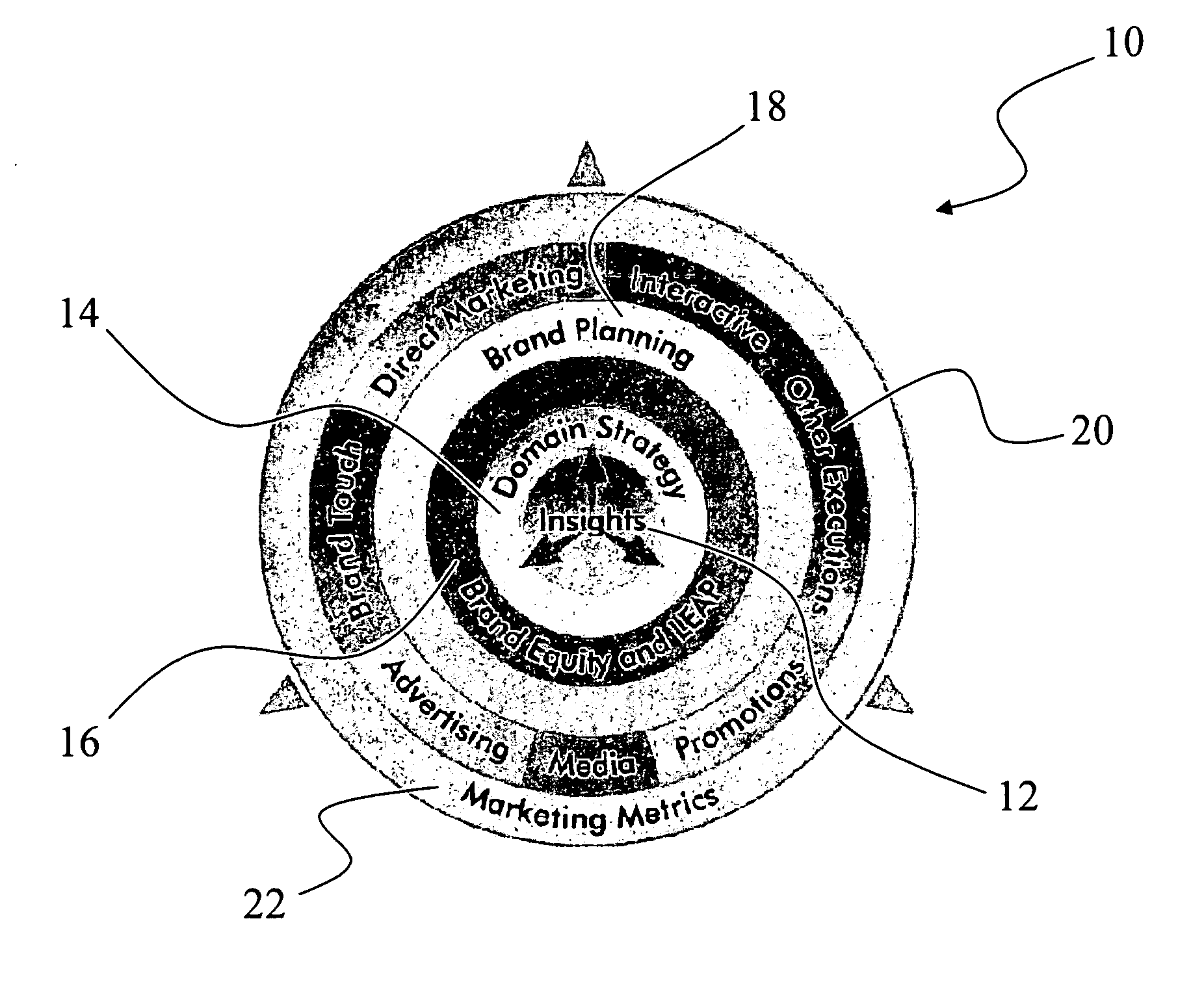
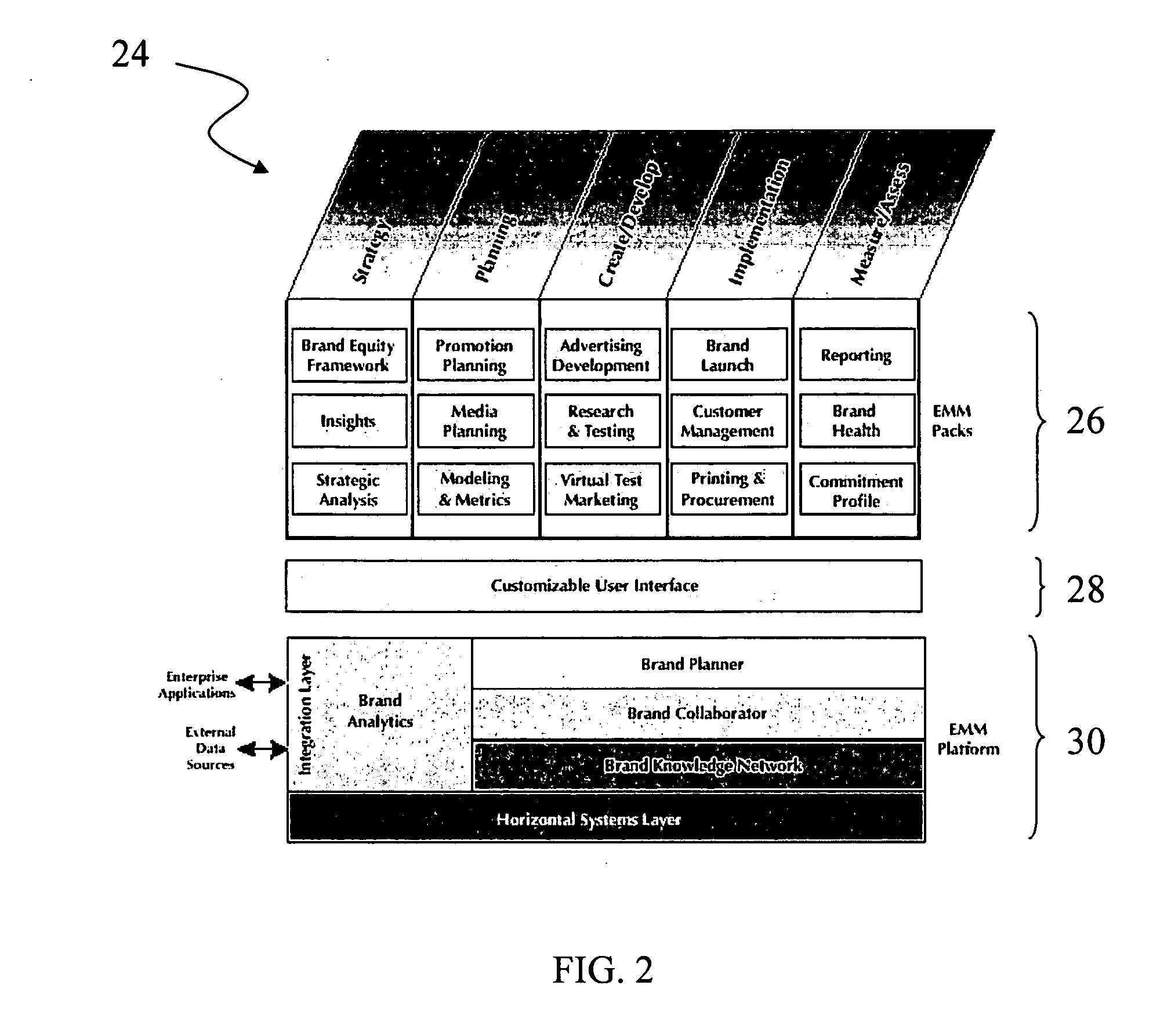
System, method and apparatus for modeling and utilizing metrics, processes and technology in marketing applications
InactiveUS20060085255A1Improve system efficiencyEasy to identifyMarketingManagement toolKnowledge management
A system, method and apparatus for modeling and utilizing metrics, processes and technology in marketing applications. According to multiple embodiments, the present invention includes marketing models, processes, metrics and software implementations and the integration thereof in marketing management tools for analysis of marketing functions and methodology. In one aspect the present invention provides for the strategic creation, nurturing and enhancement of brand equity as a metric of the marketing process.
Owner:EMM GROUP A NEVADA CORP
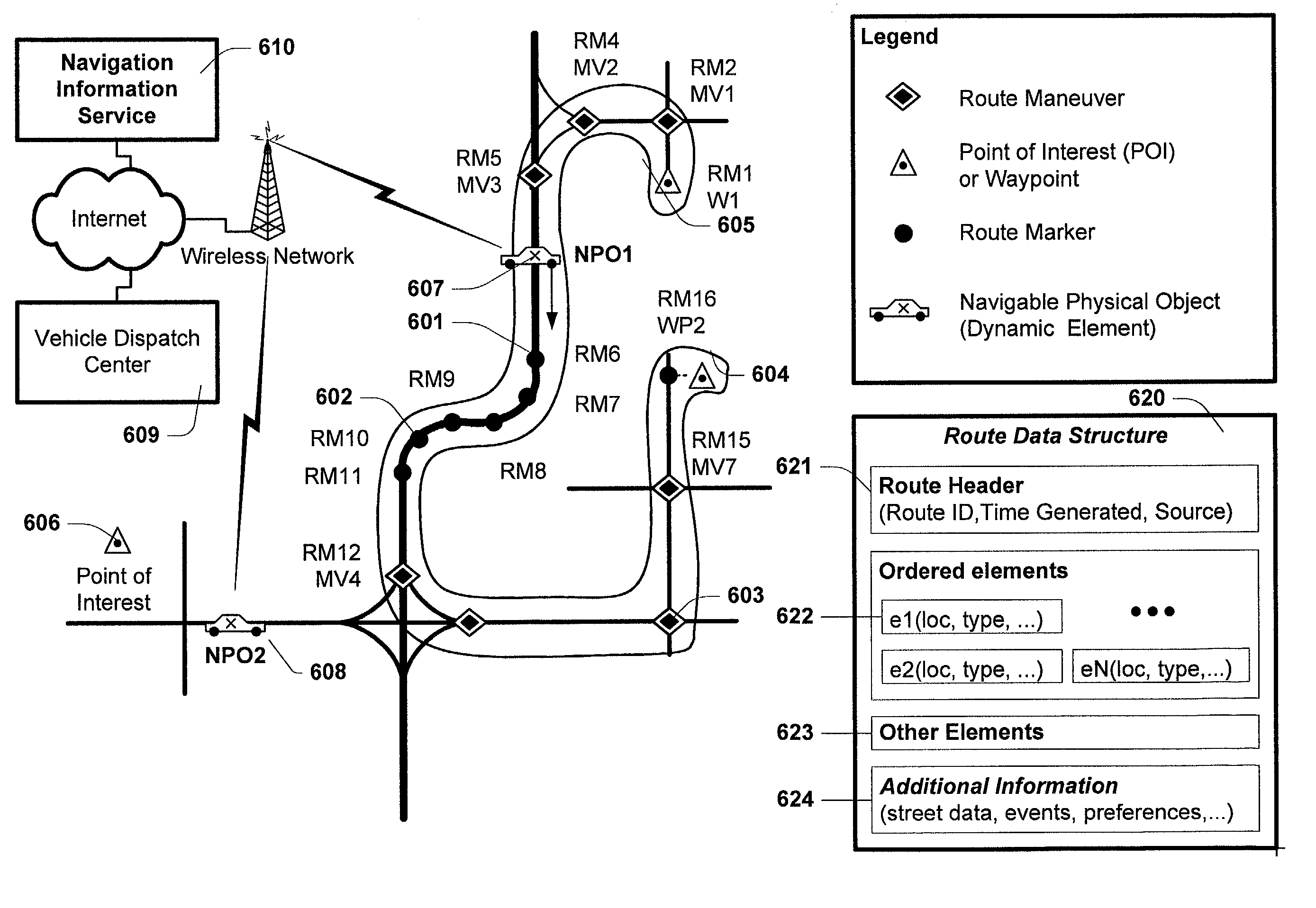
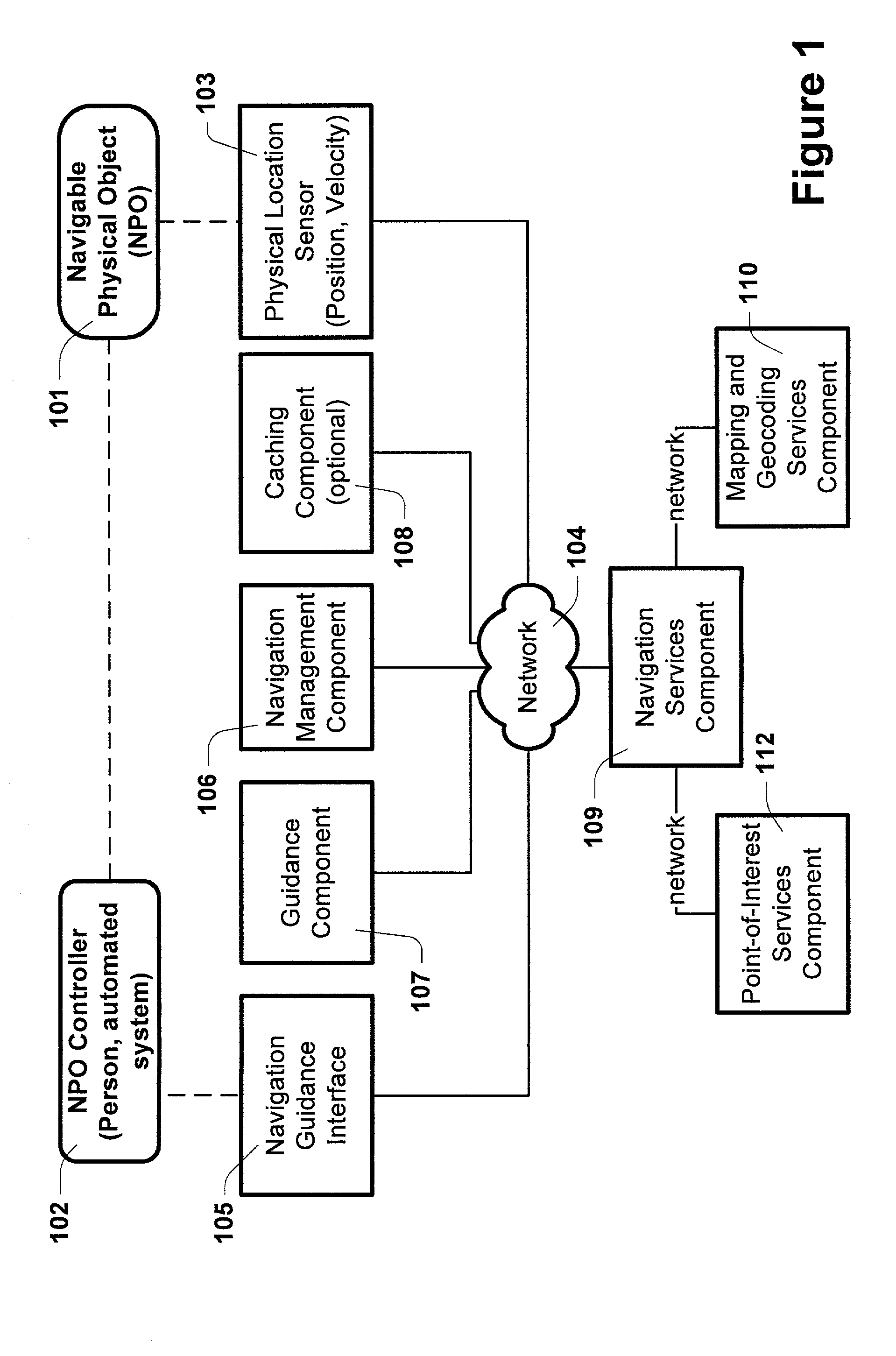
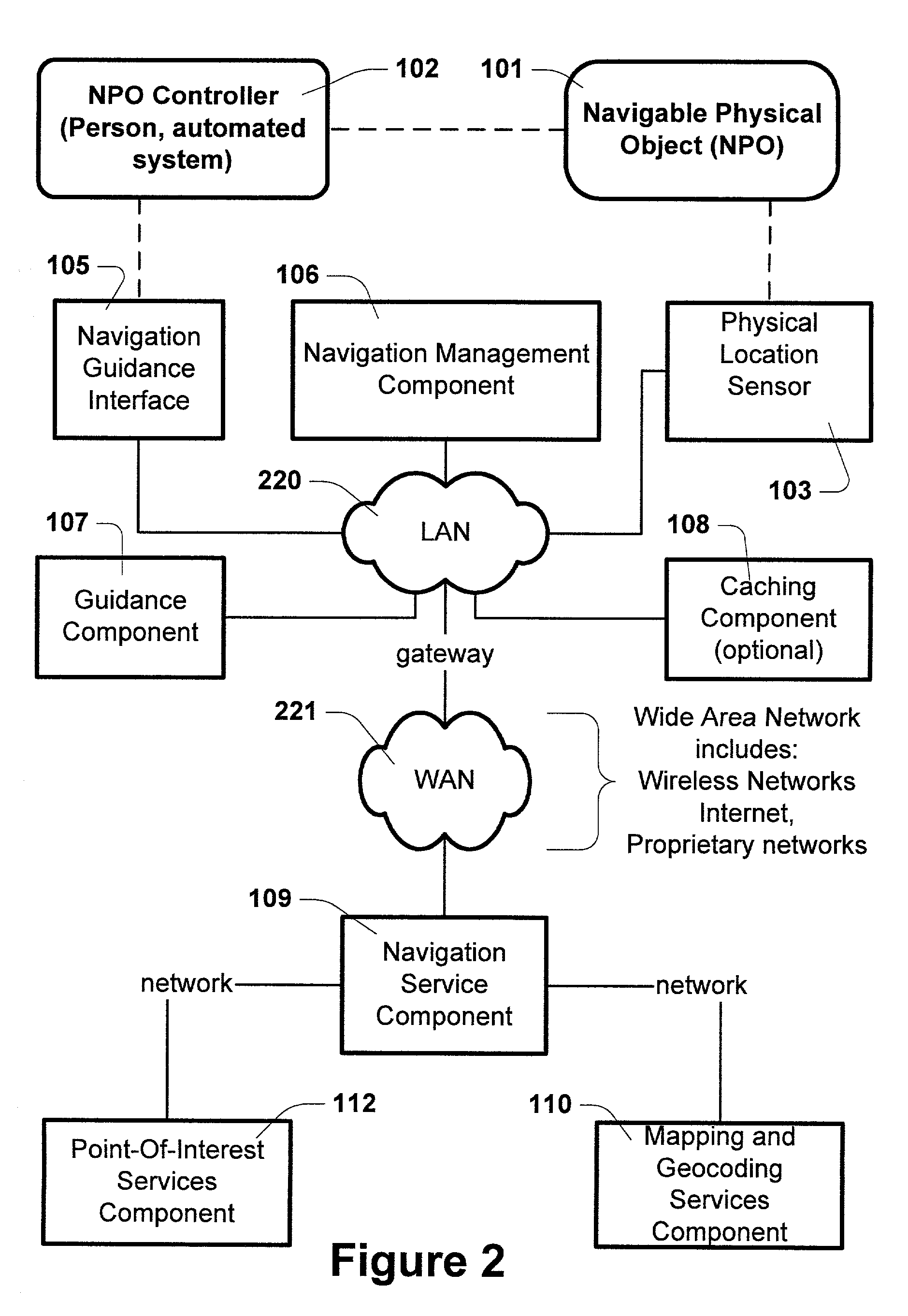
Method and system for distributed navigation and automated guidance
InactiveUS7149625B2Minimize network transactionReduce processInstruments for road network navigationRoad vehicles traffic controlGuidance systemHuman–machine interface
The present invention provides for distributed navigation and route guidance using networked computing devices. A computing device may host one or more navigation functional components. The location of a navigable object is sensed and communicated to associated navigation components in a communication network. The navigation components collectively provide guidance information to a navigable object controller. A navigable object controller directs the movement of an navigable object using guidance information to keep it on a specified route. The navigable object controller interacts with the distributed navigation system through an interface, which provides the appropriate presentation of guidance information and functions for the particular type of navigable object controller (e.g., human-machine interface, or system to system). The present invention provides the structures and methods for a flexible navigation and guidance system supporting a variety of network capabilities and computing devices using the same software implementation.
Owner:WRE HOL
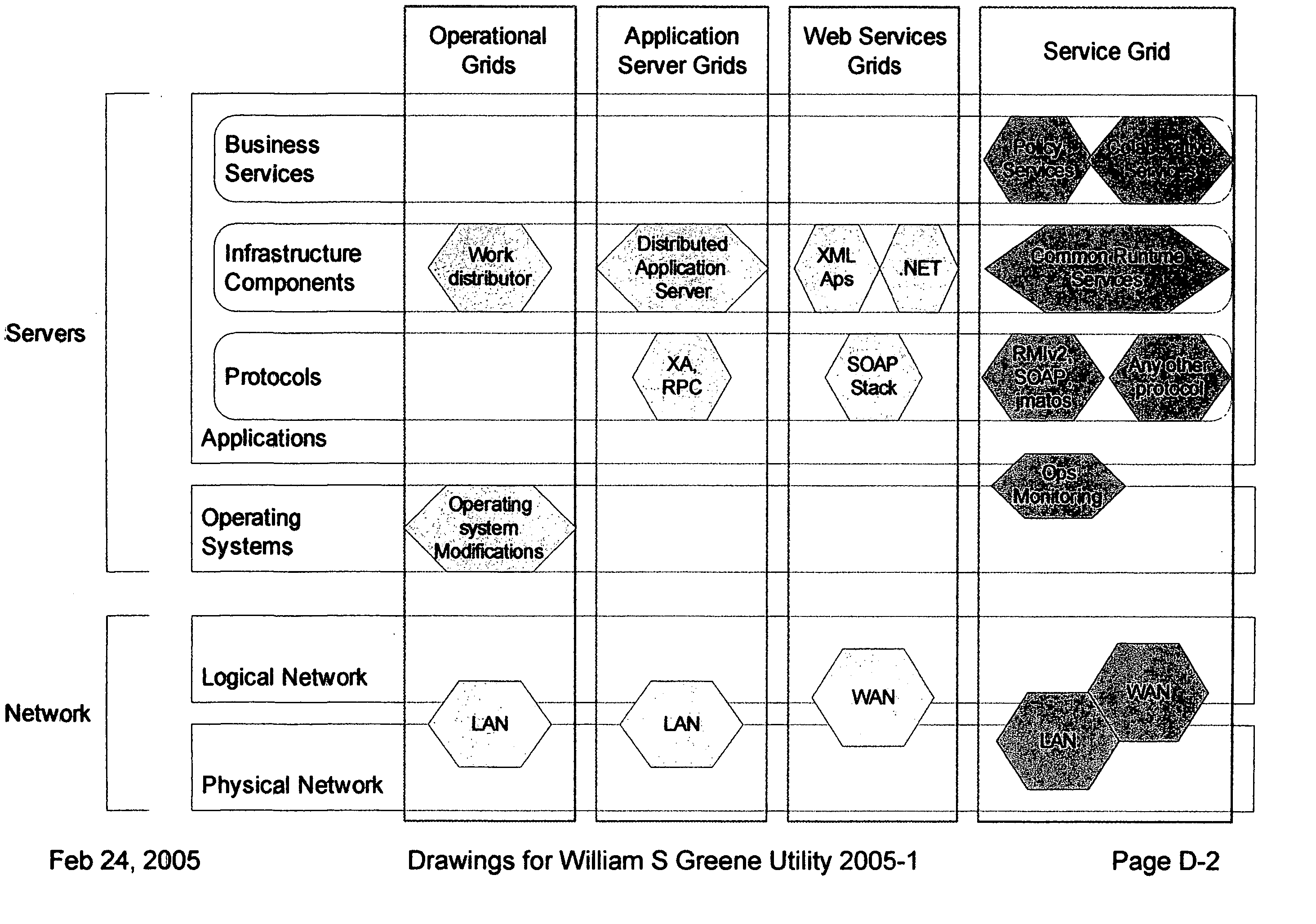
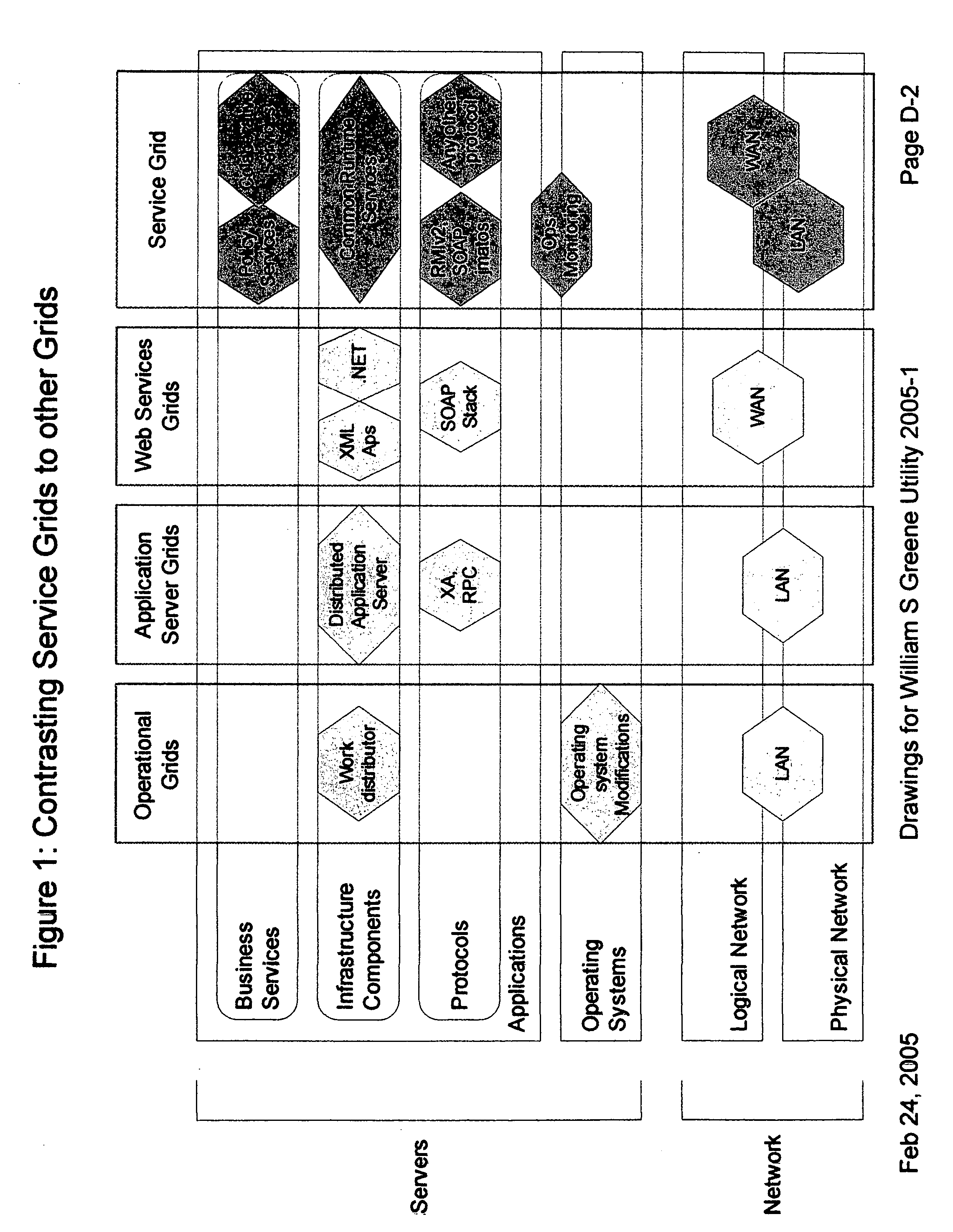
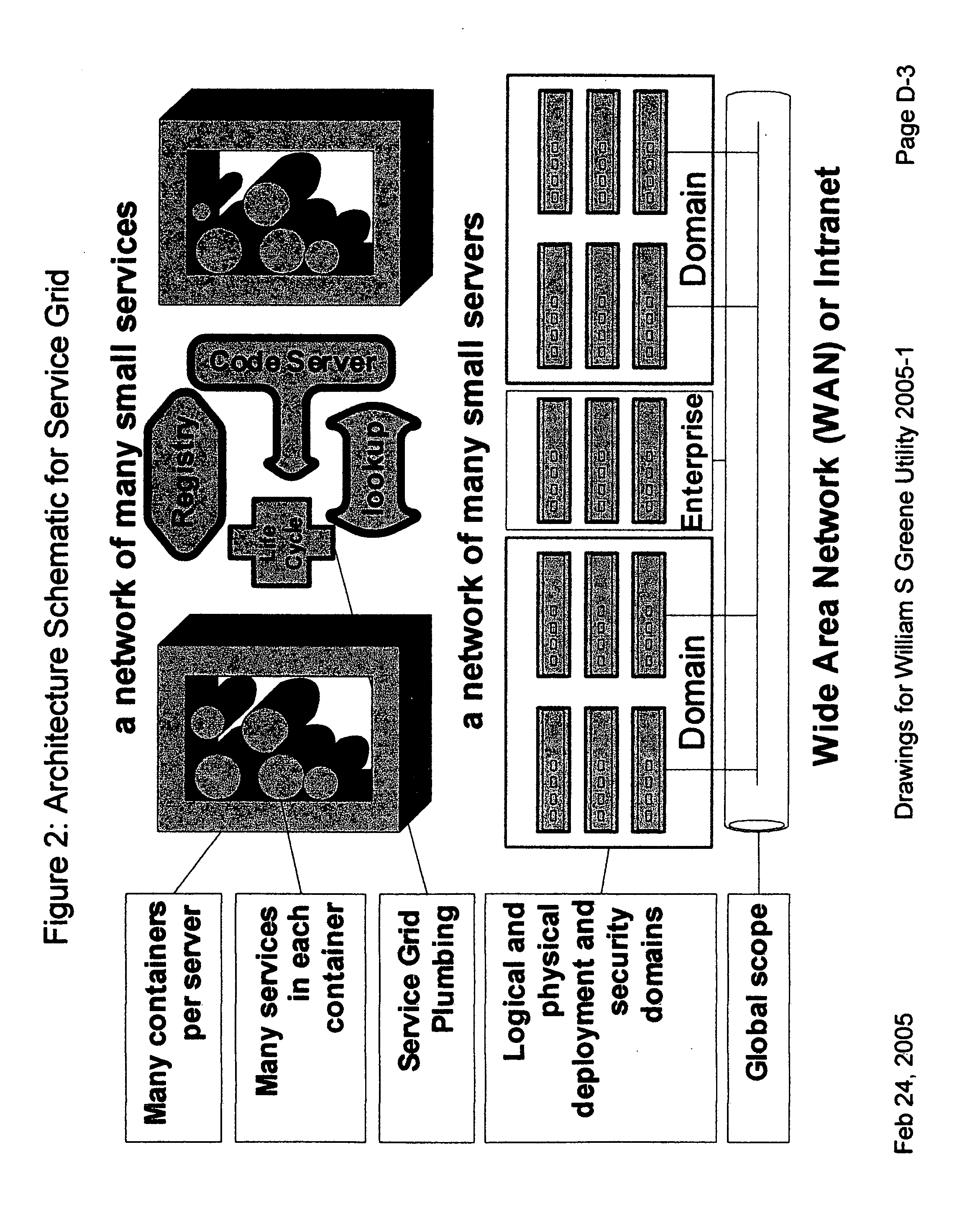
Providing secure data and policy exchange between domains in a multi-domain grid by use of a service ecosystem facilitating uses such as supply-chain integration with RIFD tagged items and barcodes
InactiveUS20050193222A1Simple methodImprove securityDigital data processing detailsMultiple digital computer combinationsSecurity domainRadio frequency
A system, method, and software implemented system of services provides enhanced security and management to multiple domain grids and allows intercommunications between the different grid domains providing for secure data exchange, policy exchange, and agent exchange between grids or grid domains. Via the exemplary example, utilizing the unique characteristics of the Service Grid and mobile agents, this is extended to provide enhanced security and management to supply chains: providing data exchange, policy exchange, and agent exchange between supply chain nodes and supply chain partners—facilitating enhanced methods of supply chain automation when using barcodes and Radio Frequency Identity (RFID) tags to identify and track goods through supply chains and consumer uses. Agents transport data and policy between supply-chain partners over an extranet, migrating across corporate boundaries and security domains, locating near where items are identified to provide local control, environmentally responsive policy, and ongoing permanent data capture & history.
Owner:GREENE WILLIAM SPROTT
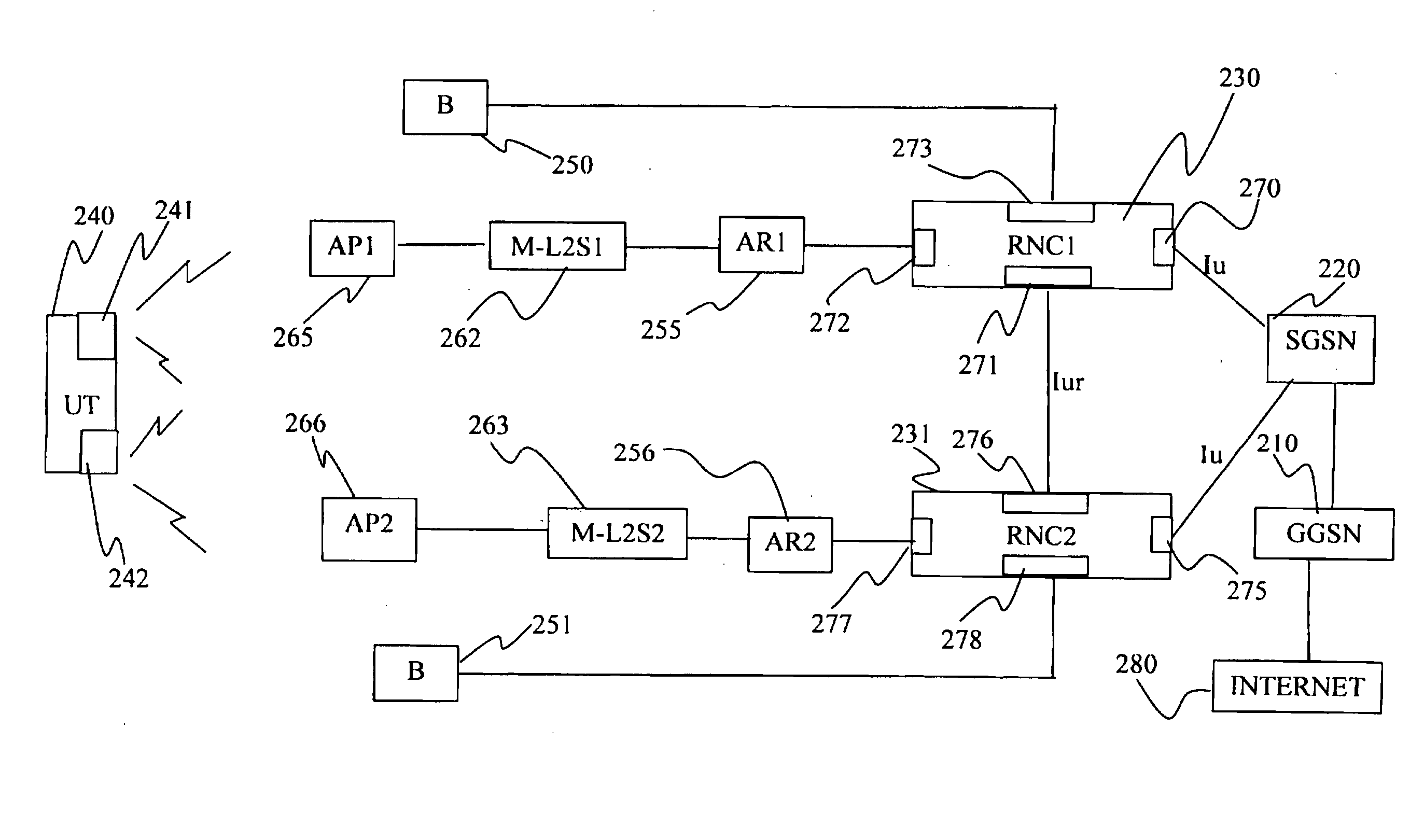
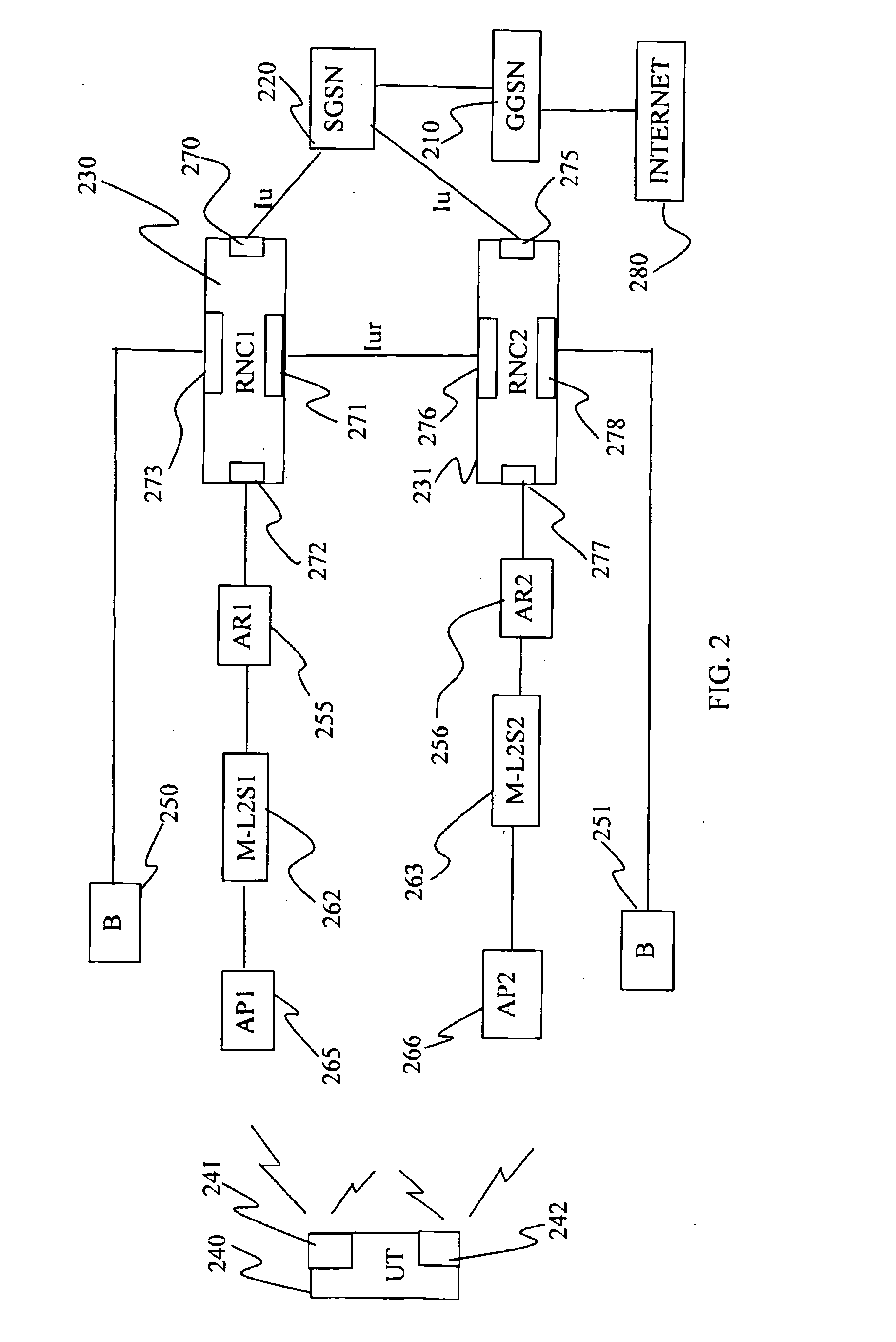
Means and Methods for Improving the Handover Characteristics of Integrated Radio Access Networks
InactiveUS20080205345A1Improve switching characteristicsMinimize data lossRadio/inductive link selection arrangementsWireless commuication servicesMessage typeRadio access network
The invention provides a method for assisting handover of a user terminal's, UT's, communication session in an integrated multi RAT network, said method to be carried out by an RNCI being installed in said network, said method comprising the following steps:— receiving a “Handover Candidate” message comprising a message type identifier information element identifying said message as being a “Handover Candidate” message and which message identifies said session and which message further identifies a candidate RNC of said network, wherein said candidate RNC constitutes an RNC handover candidate for said session,— establishing the identity of said RNC by investigating said message,— associating said communication session with said candidate RNC identified in the previous step. The invention provides an RNC1, RNC2, and software, realising the method according to the invention.
Owner:TELEFON AB LM ERICSSON (PUBL)
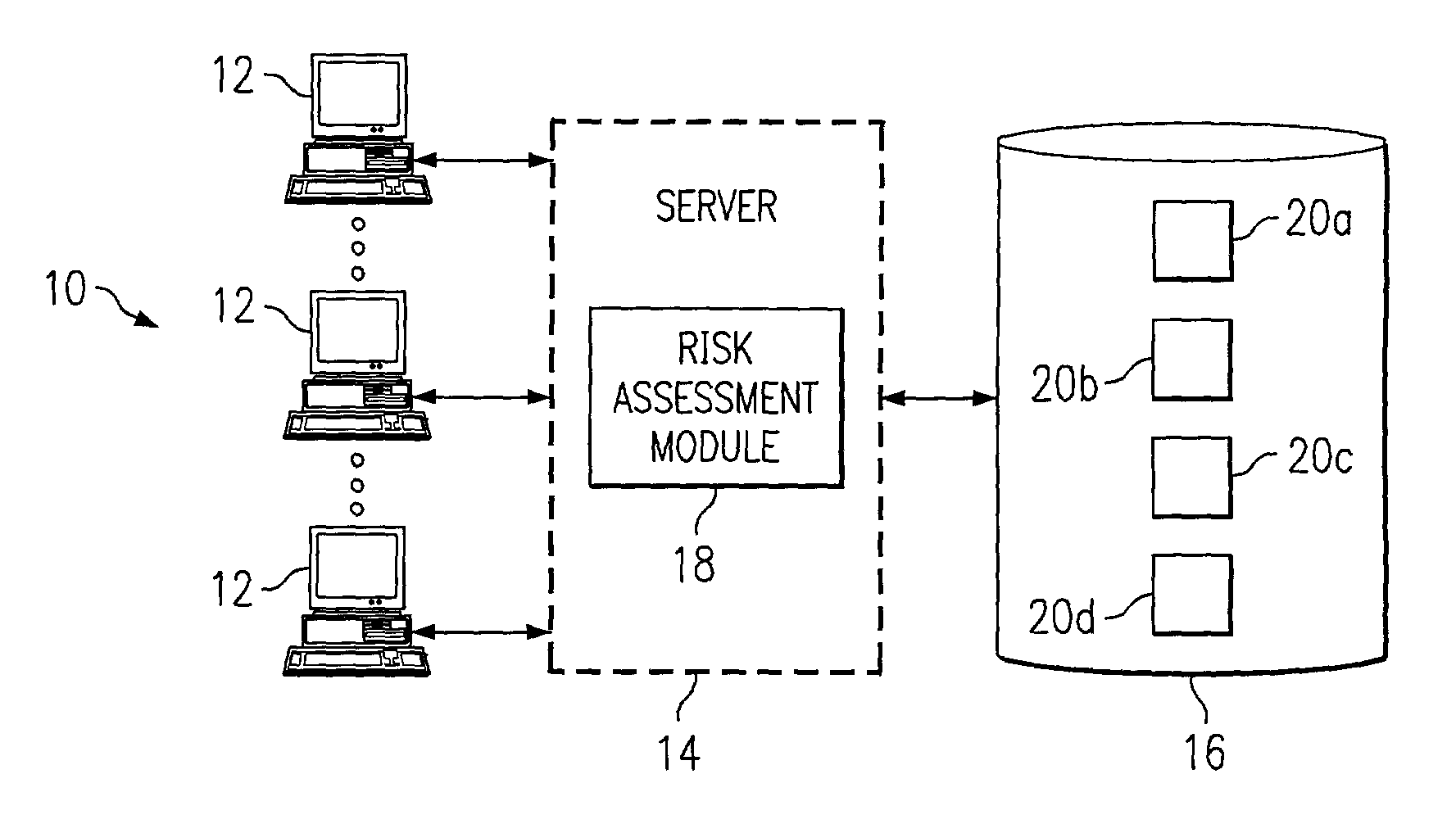
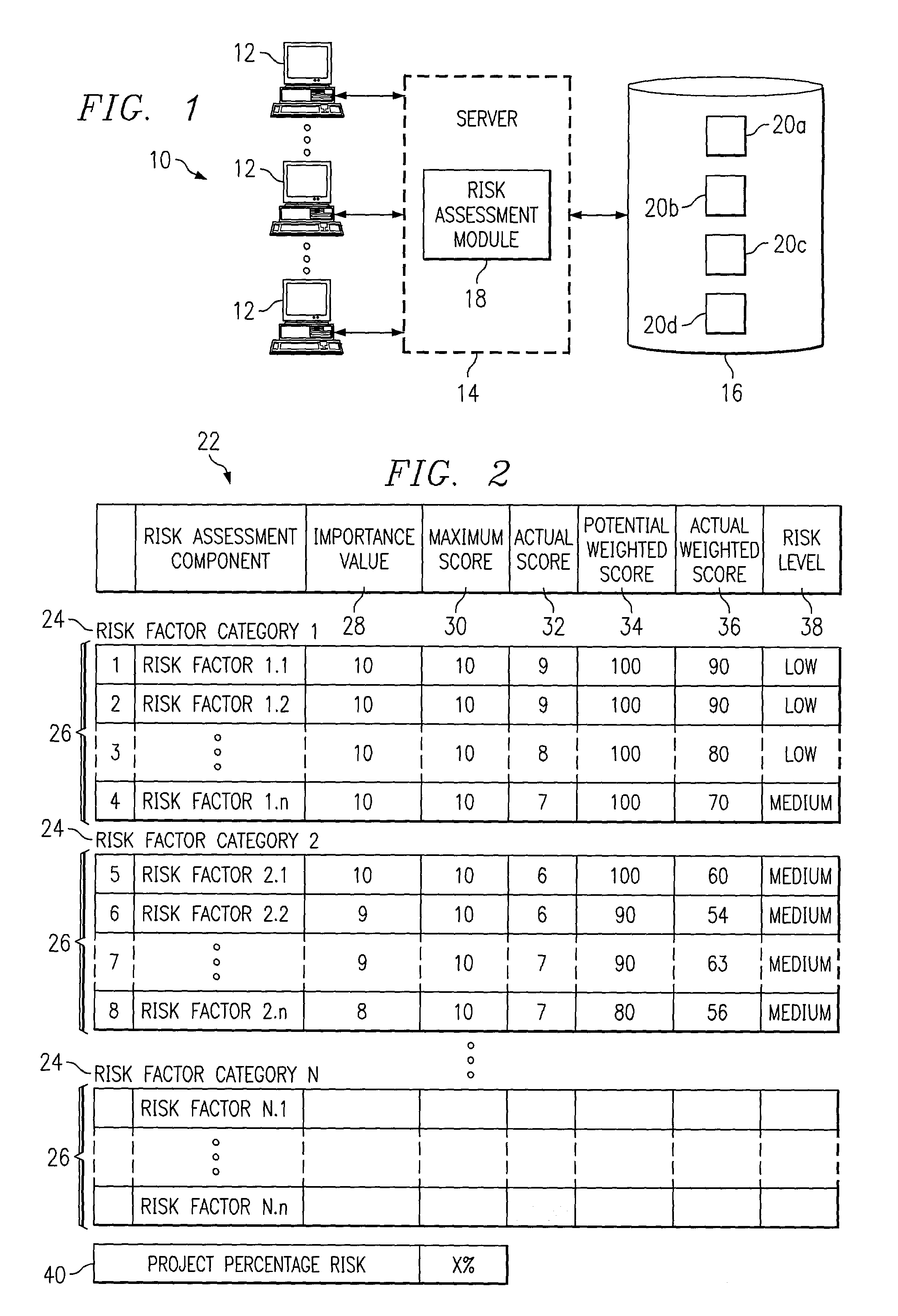
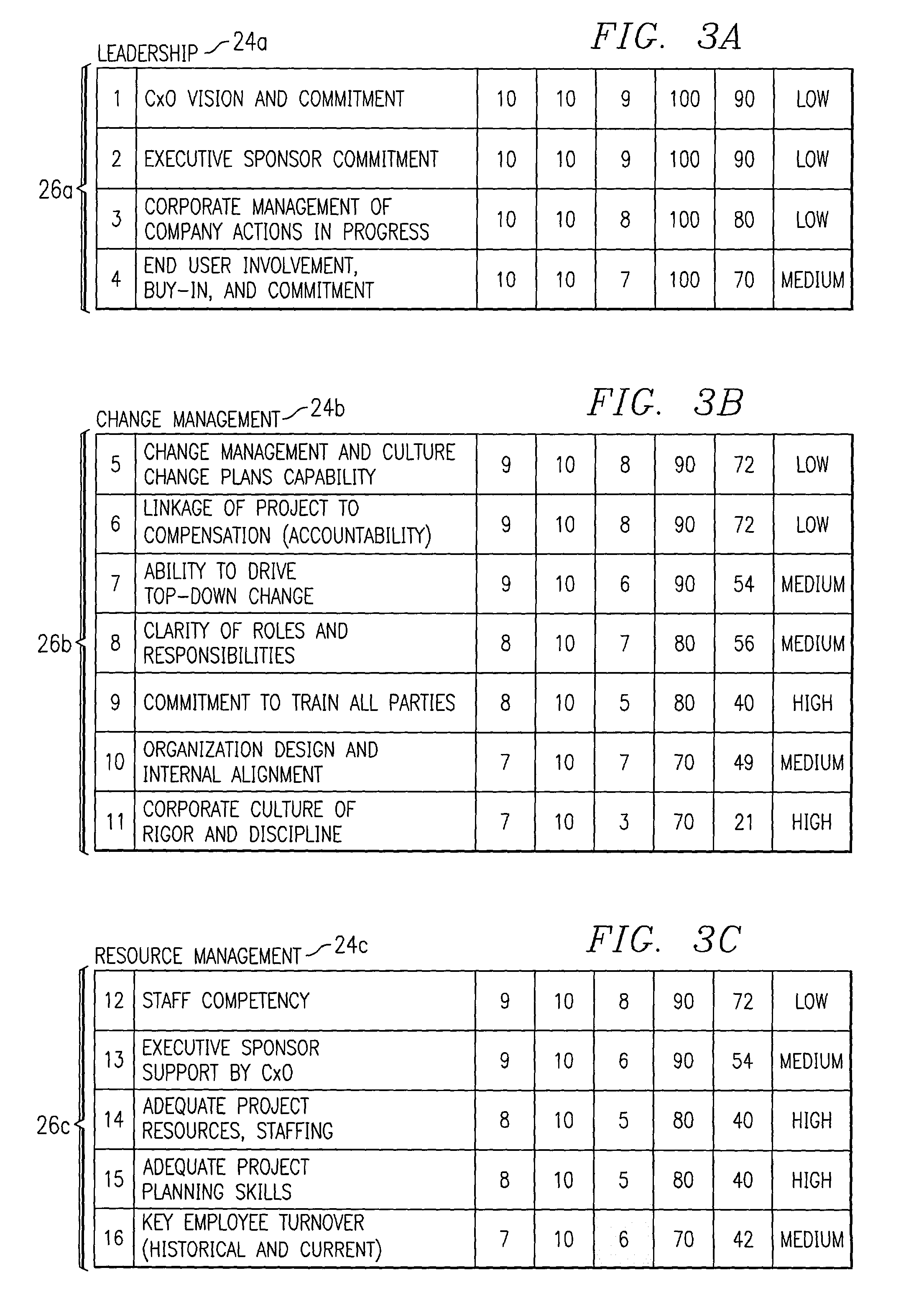
Generating a risk assessment regarding a software implementation project
InactiveUS7359865B1Disadvantages can be reduced eliminatedImplementation be reduced eliminatedFinanceResourcesRisk levelItem generation
A computer-implemented method for generating a risk assessment regarding a software implementation project includes accessing a previously specified importance value and maximum score for each of a multiple of risk factors. The importance value for each risk factor reflects experience of an implementing entity regarding the extent to which the factor may negatively impact a software implementation project if the factor is not adequately addressed, the importance value and maximum score for each factor being multiplied to define a potential weighted score for the factor. An actual score for a particular software implementation project is received for each factor based on an analysis specific to the particular project. An actual weighted score for the particular project is generated for each factor by multiplying the importance value and actual score for the factor, and a relationship between the potential weighted score and actual weighted score for each factor. A risk level for the particular project is assigned to each factor according to the relationship between the potential weighted score and the actual weighted score for the factor. The risk level for each factor represents an assessment regarding the extent to which the factor may negatively impact the particular project if the factor is not adequately addressed. A risk assessment is generated for the particular project including one or more of the assigned risk levels for the particular project for one or more corresponding factors.
Owner:BLUE YONDER GRP INC
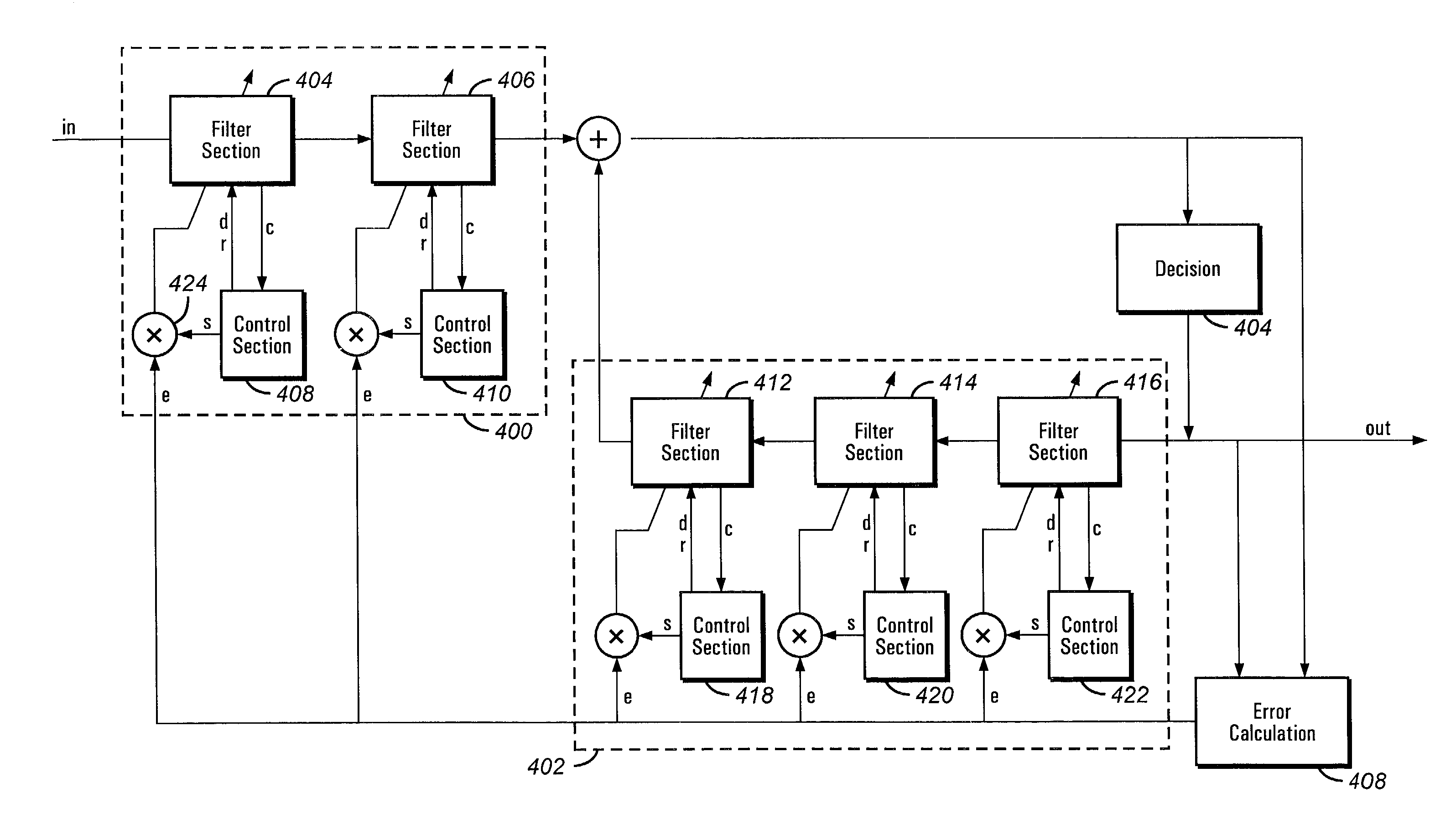
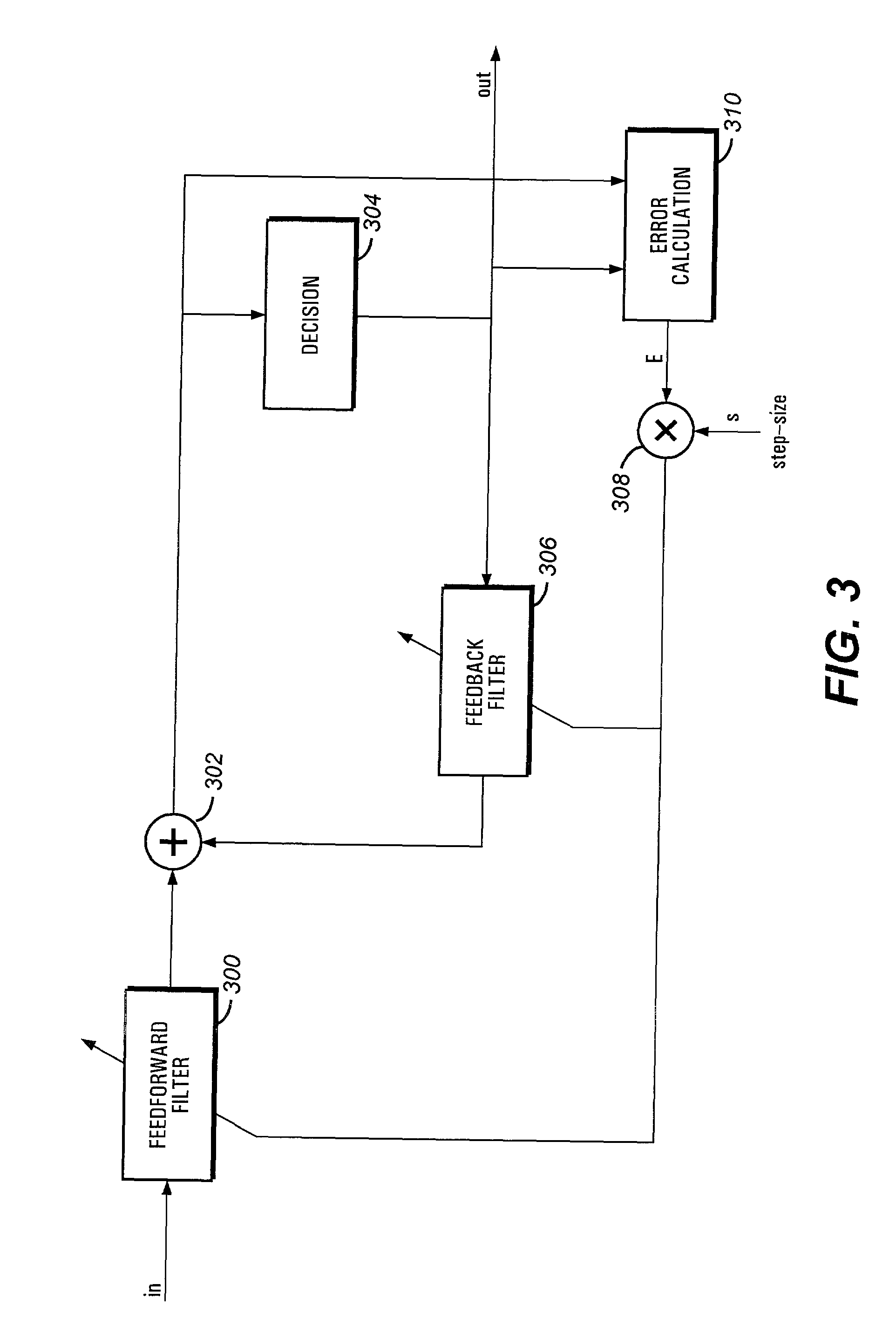
Convergence speed, lowering the excess noise and power consumption of equalizers
An equalizer for equalizing channel multi-path distortion includes digital filters. To improve the convergence speed and tracking ability of the equalizer while lowering noise and power consumption, the digital filters are divided into sections. Various parameters of the sections, such as step-size, shutdown and update rates can be controlled. Control of the various parameters can be realized either in software on an embedded or external processor or by dedicated hardware.
Owner:CONEXANT SYST INC
Hardware accelerated transactional memory system with open nested transactions
ActiveUS20100332538A1Well formedDigital data information retrievalDigital data processing detailsComputer hardwareSoftware lockout
Hardware assisted transactional memory system with open nested transactions. Some embodiments described herein implement a system whereby hardware acceleration of transactions can be accomplished by implementing open nested transaction in hardware which respect software locks such that a top level transaction can be implemented in software, and thus not be limited by hardware constraints typical when using hardware transactional memory systems.
Owner:MICROSOFT TECH LICENSING LLC
Network modeling system and method of simulating network operation with configurable node models
ActiveUS7765093B2Shorten speedFast executionAnalogue computers for electric apparatusDigital computer detailsGranularityModeling and simulation
Owner:HARRIS GLOBAL COMM INC
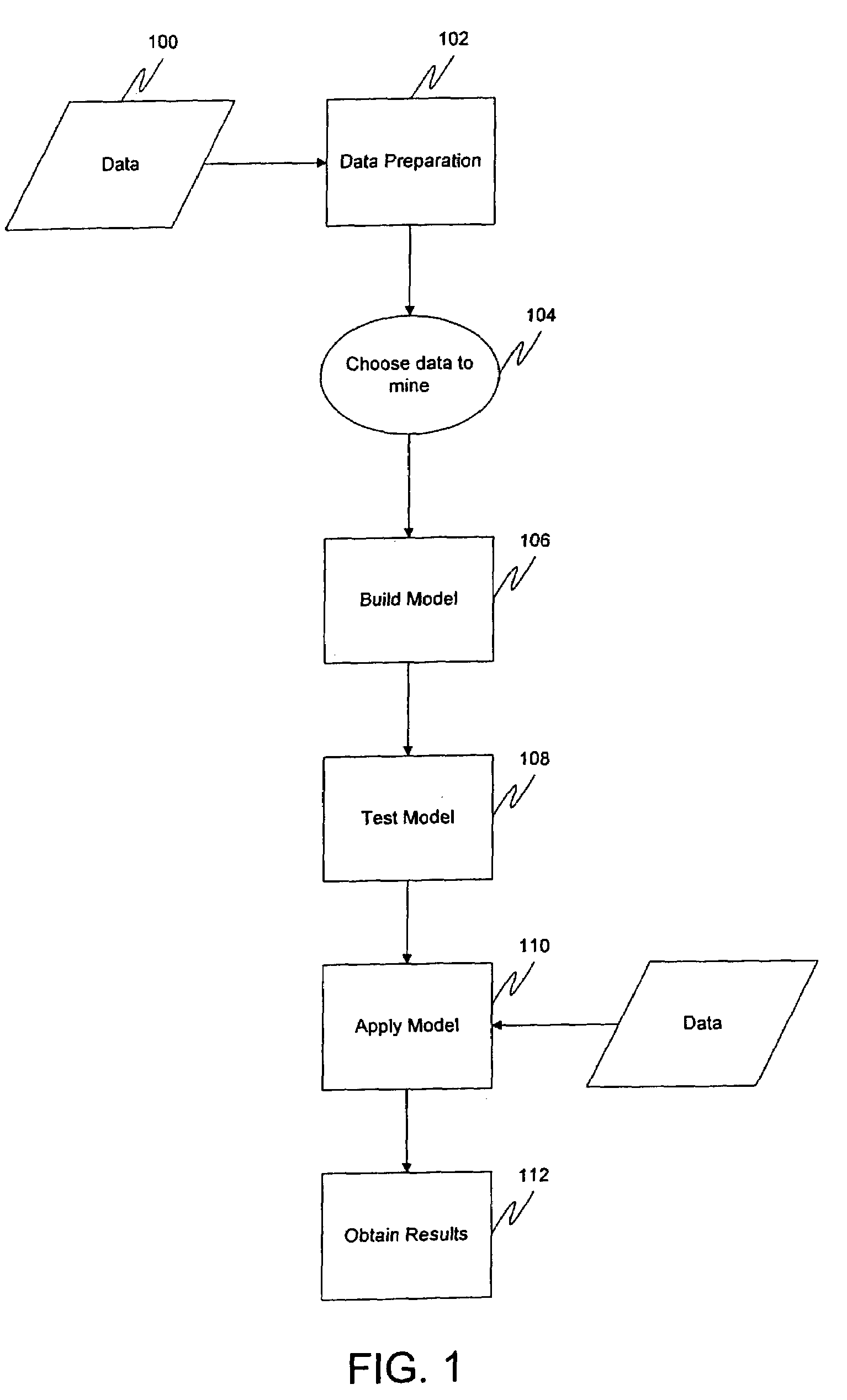
Data mining framework using a signature associated with an algorithm
ActiveUS7024417B1Digital data information retrievalData processing applicationsData dredgingData source
A framework is provided that enables data mining algorithms to be plugged into it without any change to algorithm software implementations, while still providing all the standard data mining tasks. It may be implemented by the data source provider. It also then allows for the complete separation of data storage and algorithms. When the user initiates a mining session and picks an algorithm for build task or a model for an apply or test task, the framework may become responsible for preparing a set of “prompts” to the user asking him to provide some expression which is specific to the particular kind of data the user is working with.
Owner:ORACLE INT CORP
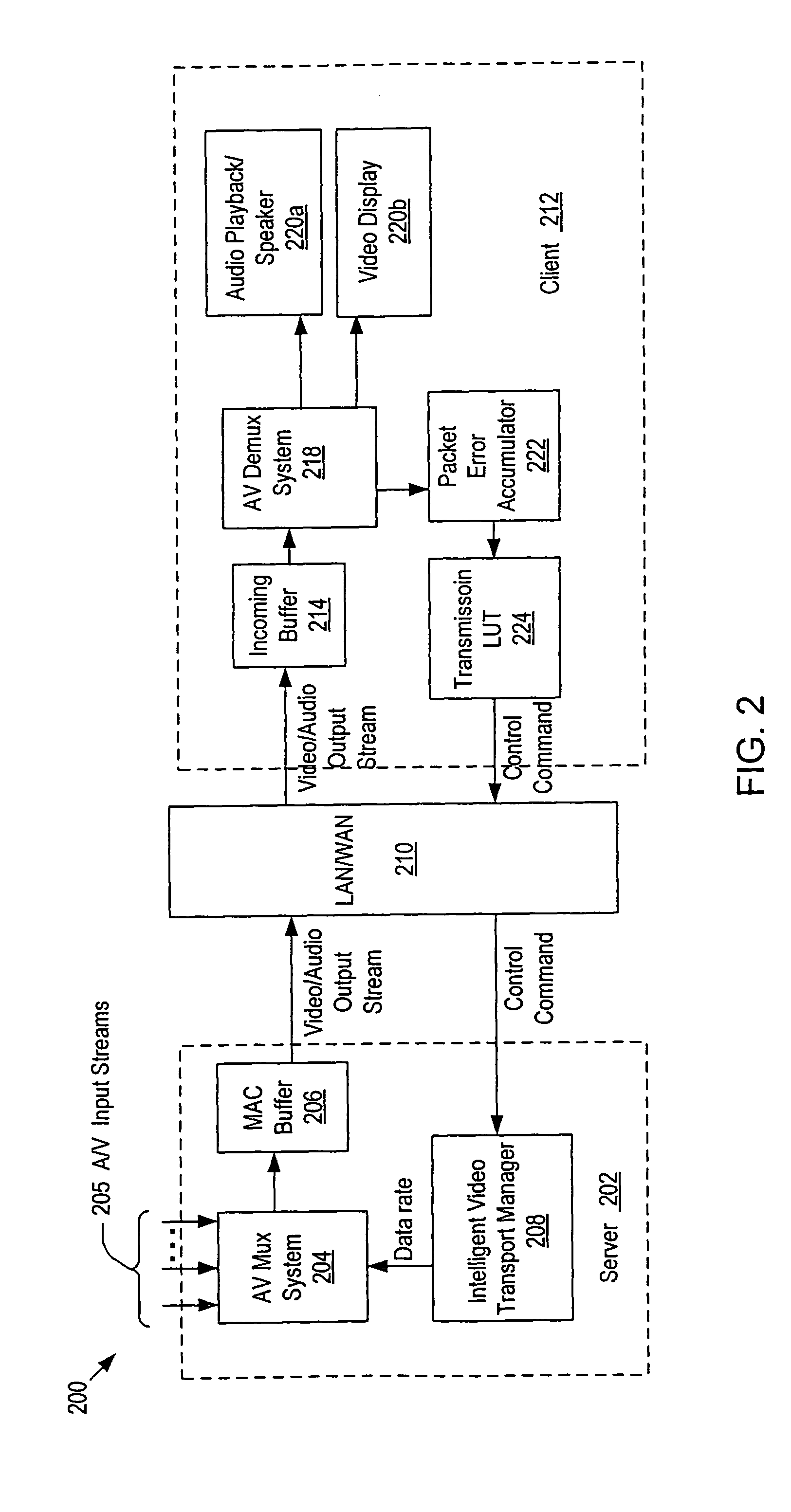
Adaptive media transport management for continuous media stream over LAN/WAN environment
InactiveUS7984179B1Simplify complexityReduce design costMultiple digital computer combinationsSelective content distributionData streamControl channel
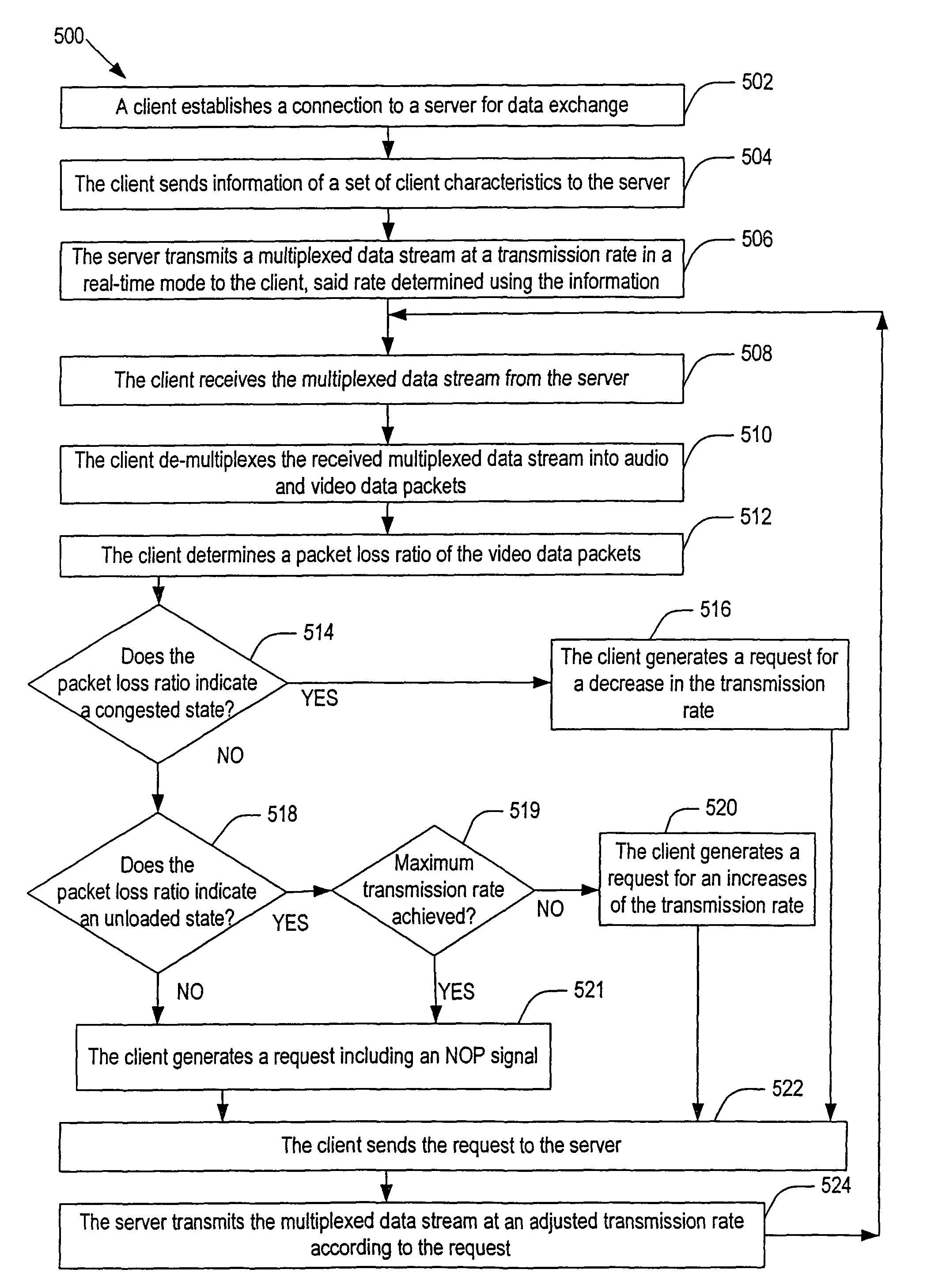
Methods and systems for transmitting compressed audio / video data streams across conventional networks or channels in real time. Each system employs the Adaptive Rate Control (ARC) technique that is based on the detection of defective packets and other influencing factors such as overall system performance, usage model and channel characteristics. To control data stream congestions in the channel and maintain the visual display quality above a certain level, the present invention exploits the human visual perception and adaptability to changing visual conditions. The ARC technique relies on the client's capacity for calculating the quality of video packets received from a server and sending information of a desired transmission rate to the server. This approach simplifies the hardware and software implementation complexity otherwise imposed on the server and reduces the overall design cost by shifting the burden of monitoring bandwidth and transmission control from the server to the client.
Owner:SEXTANT NAVIGATION
Cover plate for a mobile device having a push-through dial keypad
InactiveUS7133707B1Multiplex system selection arrangementsInterconnection arrangementsBiological activationMobile device
A dial keypad is provided for use with a mobile device having a keyboard. The keypad has a push-through, hinge-spring design that activates only one of two keyboard keys underlying a dial key and allows backlighting transmissivity. A translucent material can be used to allow the keyboard key backlighting to be coupled through to a top dial key. The keypad creates an aesthetically balanced dial keypad arrangement over a QWERTY keyboard. A preferable mechanical implementation allows backlighting and has an offset contact and spring design to activate one of the two underlying keys. This activation simplifies the software implementation for executing the dial number since the signal is coming from one address rather than having to make a determination of whether it is coming from one or two addresses. Moreover, the resulting dial key press has a standard single click feel.
Owner:BLACKBERRY LTD
Method and apparatus for performing antivirus tasks in a mobile wireless device
InactiveUS20060161985A1Loading and unloadingRestore accuratelyMemory loss protectionUnauthorized memory use protectionOperational systemApplication programming interface
Disclosed are techniques for performing an antivirus task in a mobile wireless device running an embedded operating system. In one embodiment, calls intended for an application programming interface (API) function code is redirected to an antivirus function code. The redirection to the antivirus function code may be performed by modifying a kernel structure to point to a modified entry list instead of an API entry list. The redirection to the antivirus function code may also be performed by modifying the API function code to allow the antivirus function code to execute before the API function code. The kernel structure or the API function code may be properly restored back to its original form. Software implementations of these techniques may be readily loaded and unloaded, and may not require re-installation of the embedded operating system.
Owner:TREND MICRO INC
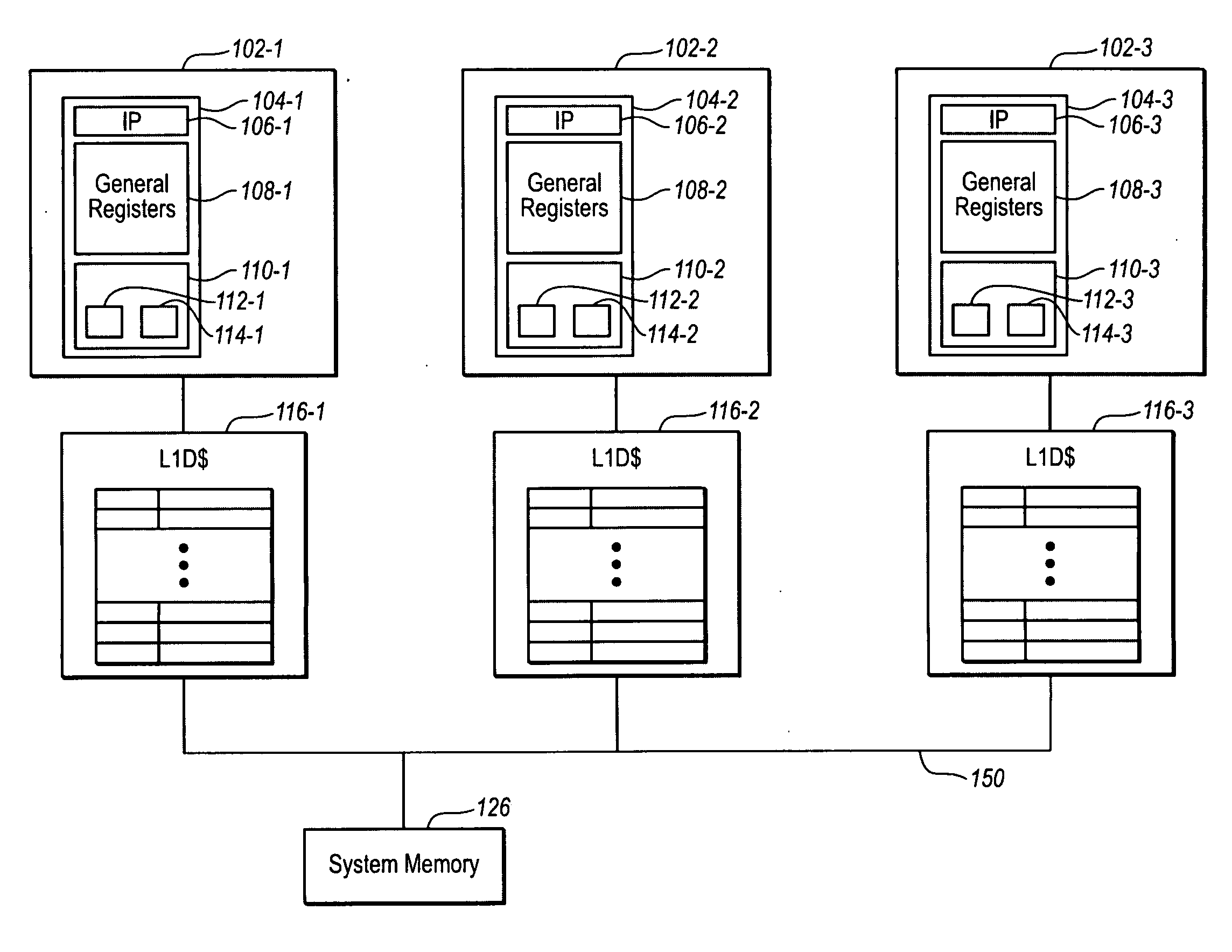
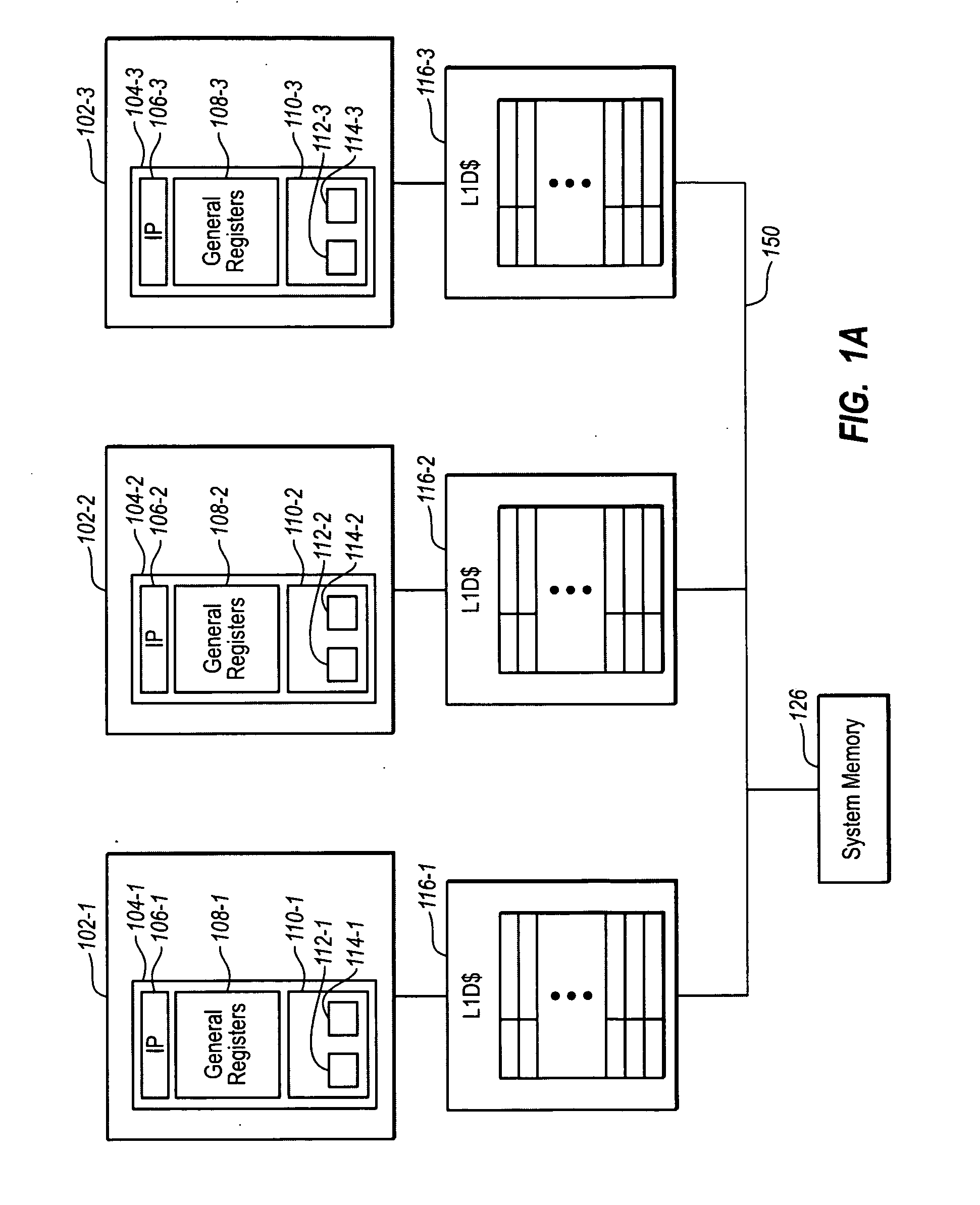
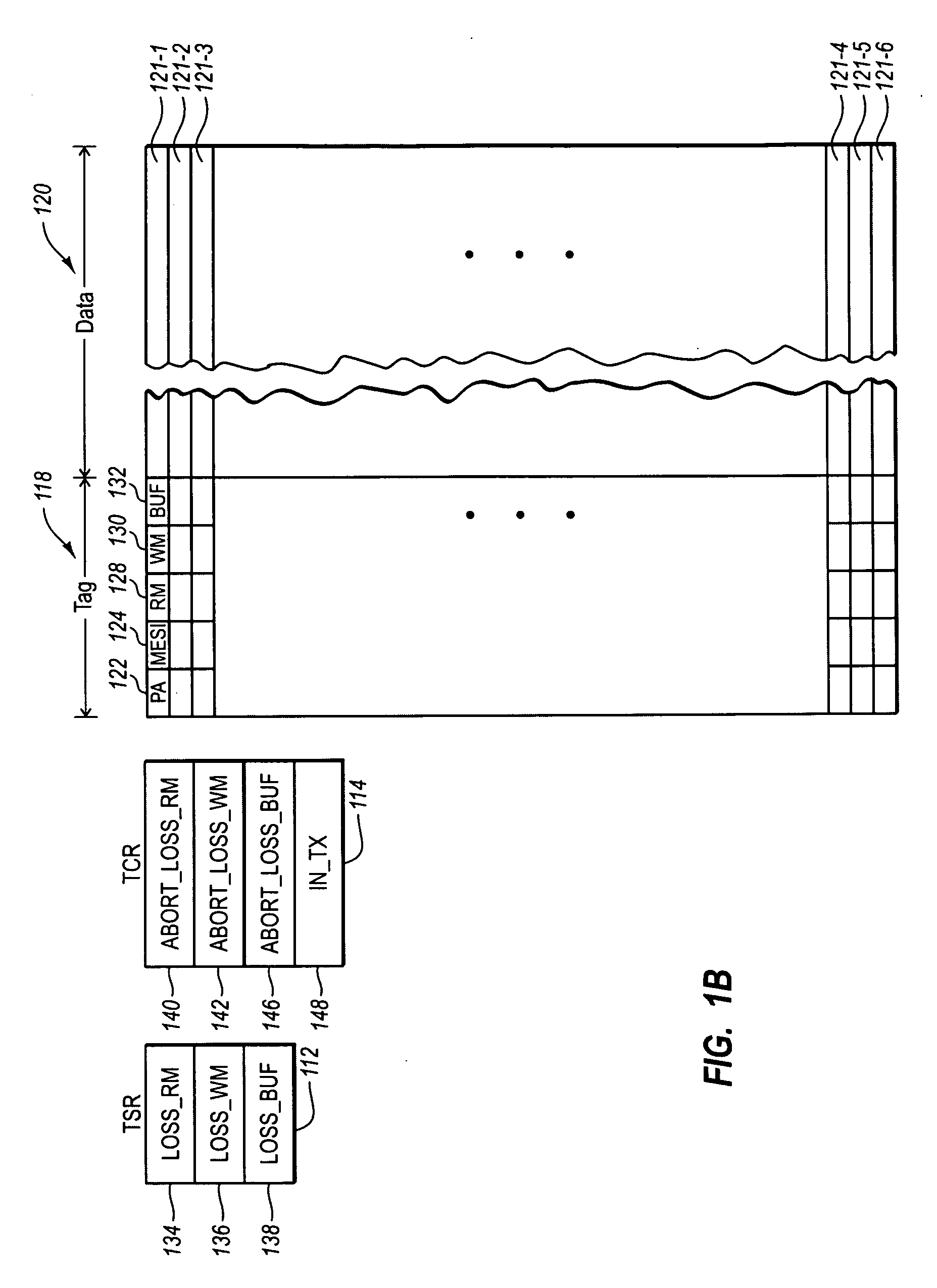
Software implementation of synchronous memory barriers
InactiveUS6996812B2Program synchronisationDigital computer detailsProcessor registerInter-processor interrupt
Selectively emulating sequential consistency in software improves efficiency in a multiprocessing computing environment. A writing CPU uses a high priority inter-processor interrupt to force each CPU in the system to execute a memory barrier. This step invalidates old data in the system. Each CPU that has executed a memory barrier instruction registers completion and sends an indicator to a memory location to indicate completion of the memory barrier instruction. Prior to updating the data, the writing CPU must check the register to ensure completion of the memory barrier execution by each CPU. The register may be in the form of an array, a bitmask, or a combining tree, or a comparable structure. This step ensures that all invalidates are removed from the system and that deadlock between two competing CPUs is avoided. Following validation that each CPU has executed the memory barrier instruction, the writing CPU may update the pointer to the data structure.
Owner:IBM CORP
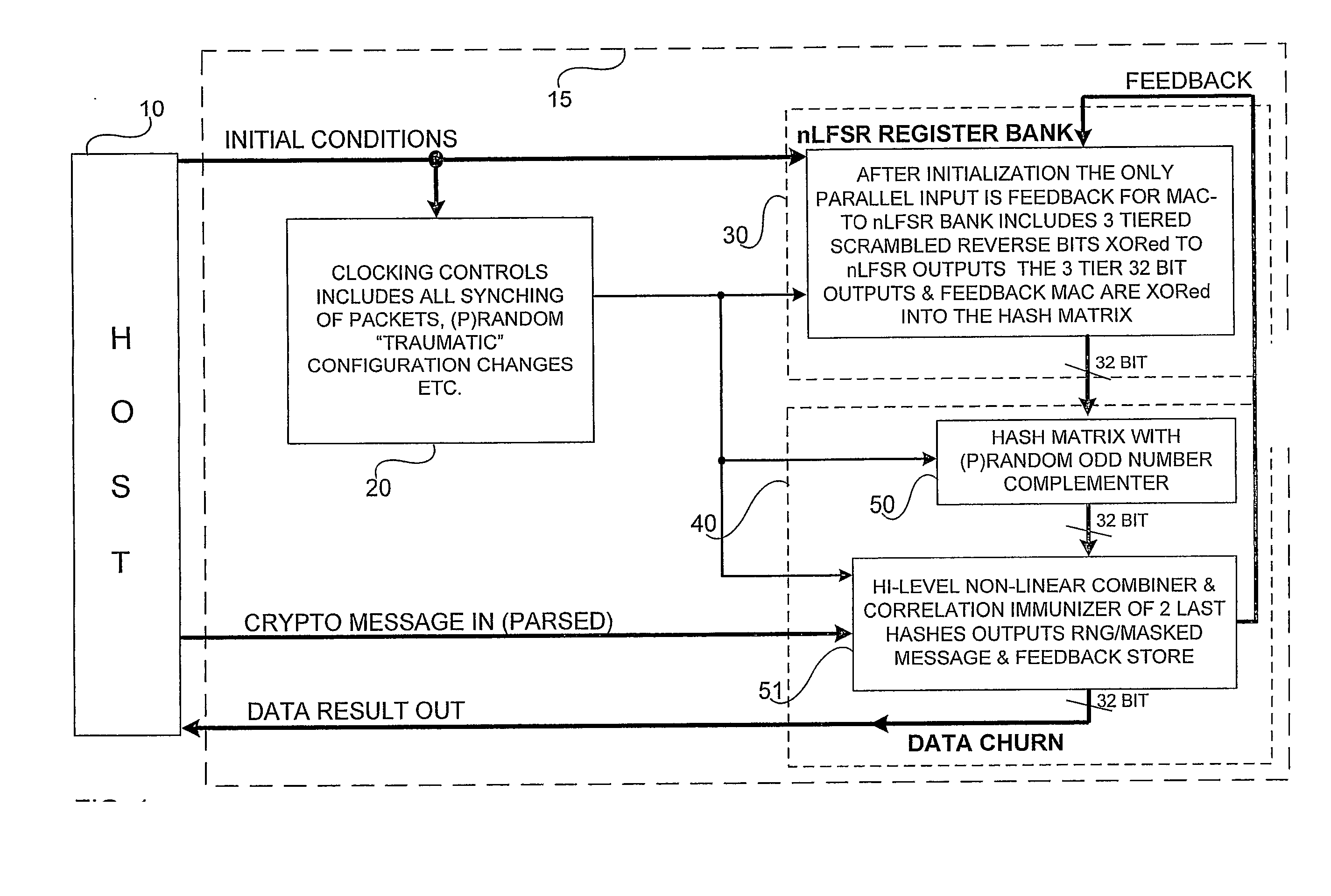
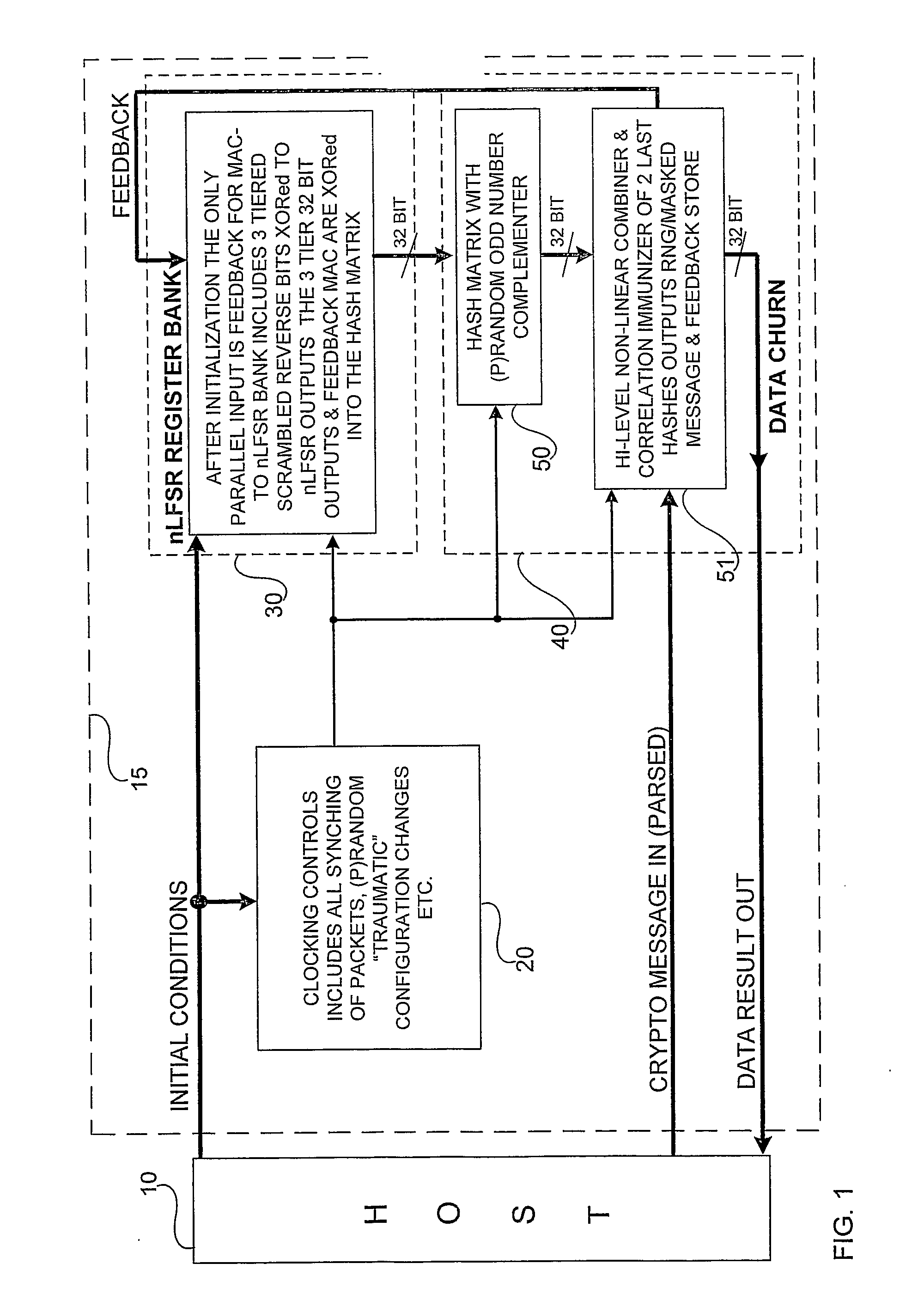
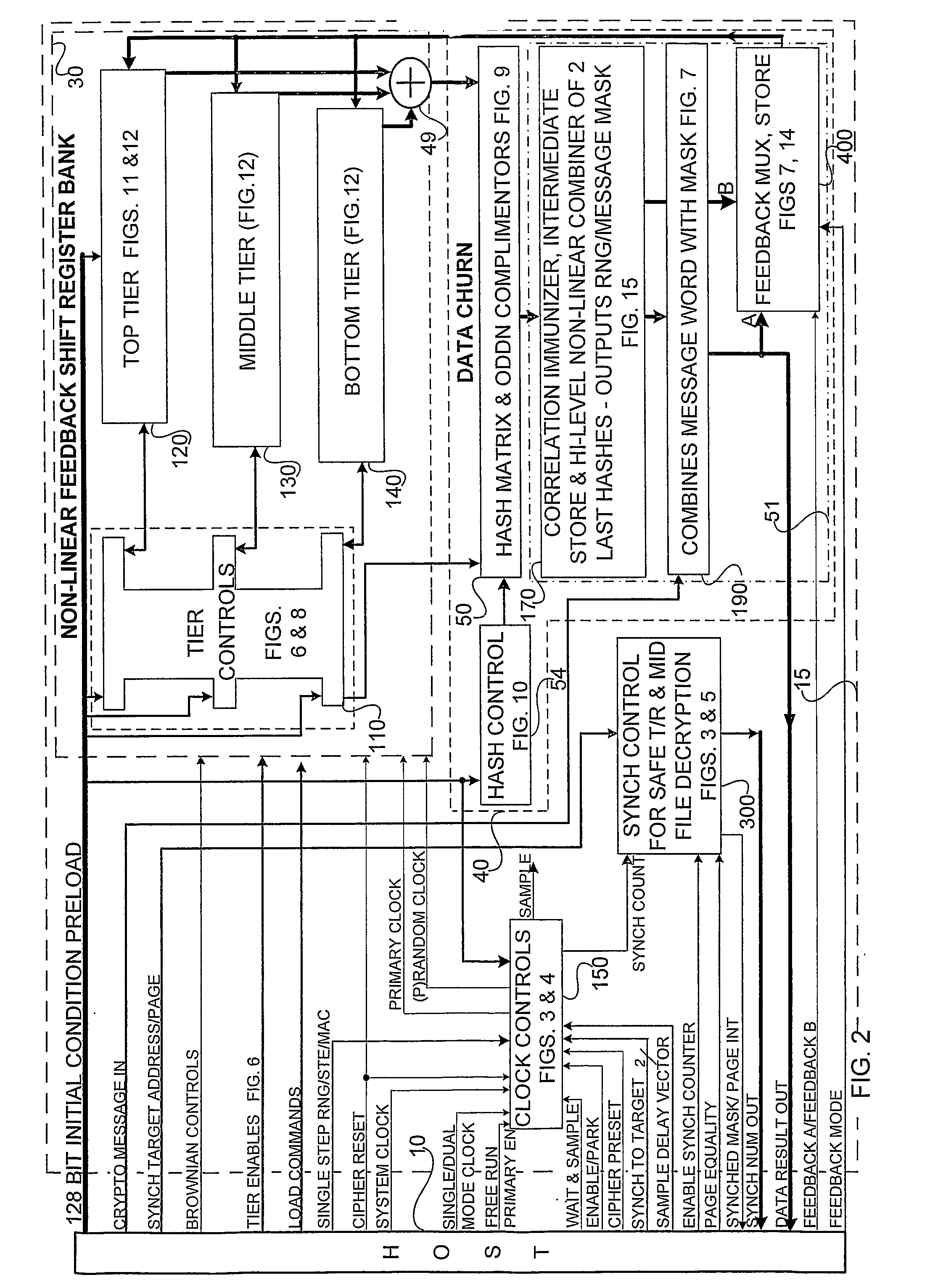
Accelerated Throughtput Synchronized Word Stream Cipher, Message Authenticator and Zero-Knowledge Output Random Number Generator
ActiveUS20070244951A1Small loss of entropyNecessary numberSynchronising transmission/receiving encryption devicesRandom number generatorsComputer hardwareFrame sequence
Systems and methods are disclosed, especially designed for very compact hardware implementations, to generate random number strings with a high level of entropy at maximum speed. For immediate deployment of software implementations, certain permutations have been introduced to maintain the same level of unpredictability which is more amenable to hi-level software programming, with a small time loss on hardware execution; typically when hardware devices communicate with software implementations. Particular attention has been paid to maintain maximum correlation immunity, and to maximize non-linearity of the output sequence. Good stream ciphers are based on random generators which have a large number of secured internal binary variables, which lead to the page synchronized stream ciphering. The method for parsed page synchronization which is presented is especially valuable for Internet applications, where occasionally frame sequences are often mixed. The large number of internal variables with fast diffusion of individual bits wherein the masked message is fed back into the machine variables is potentially ideal for message authentication procedures.
Owner:FORTRESS GB
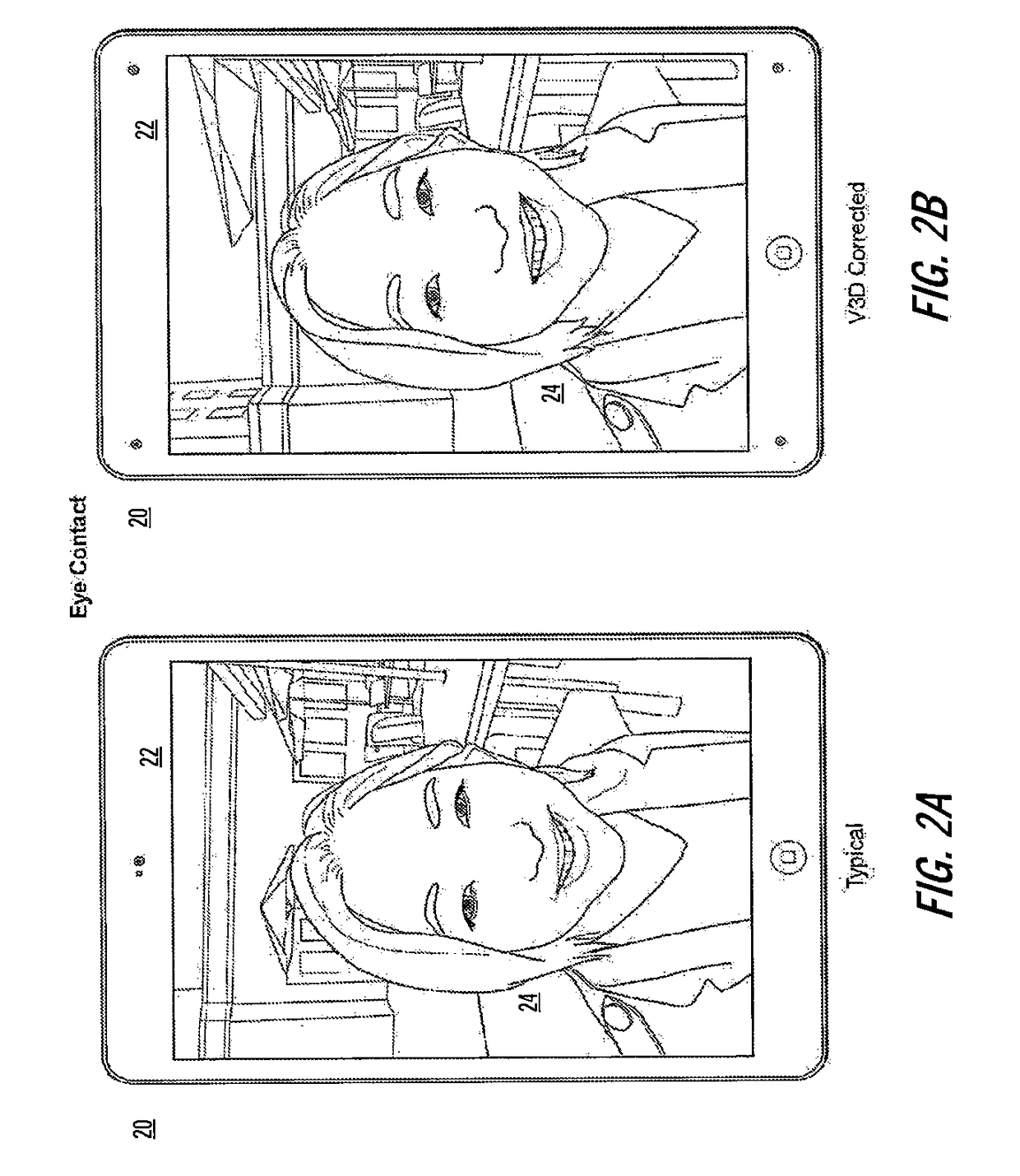
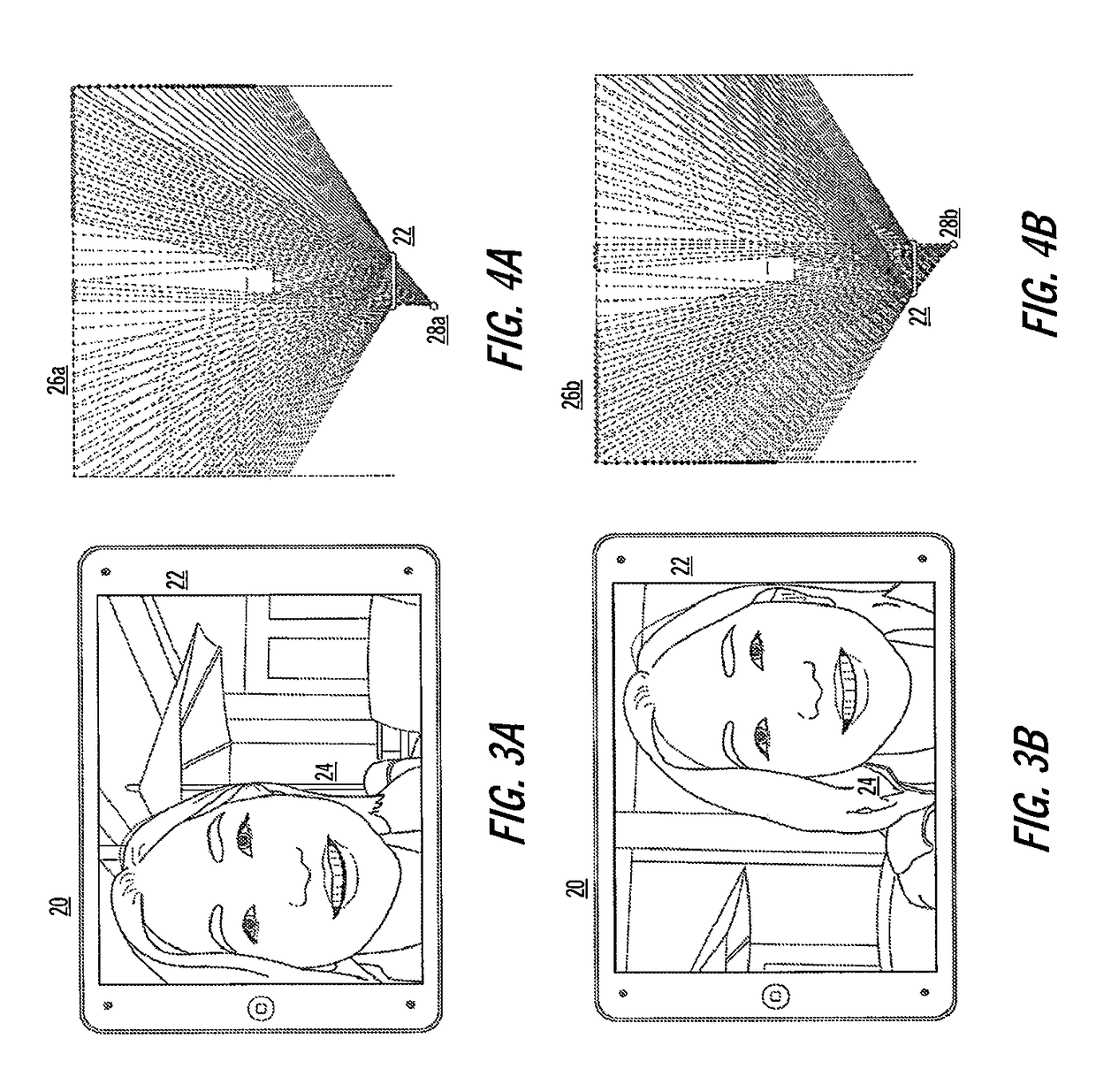
Virtual 3D methods, systems and software
ActiveUS20180307310A1Facilitate compositionEliminate the effects ofInput/output for user-computer interactionTelevision system detailsComputer graphics (images)Software
Methods, systems and computer program products (“software”) enable a virtual three-dimensional visual experience (referred to herein as “V3D”) videoconferencing and other applications, and capturing, processing and displaying of images and image streams.
Owner:MINE ONE GMBH
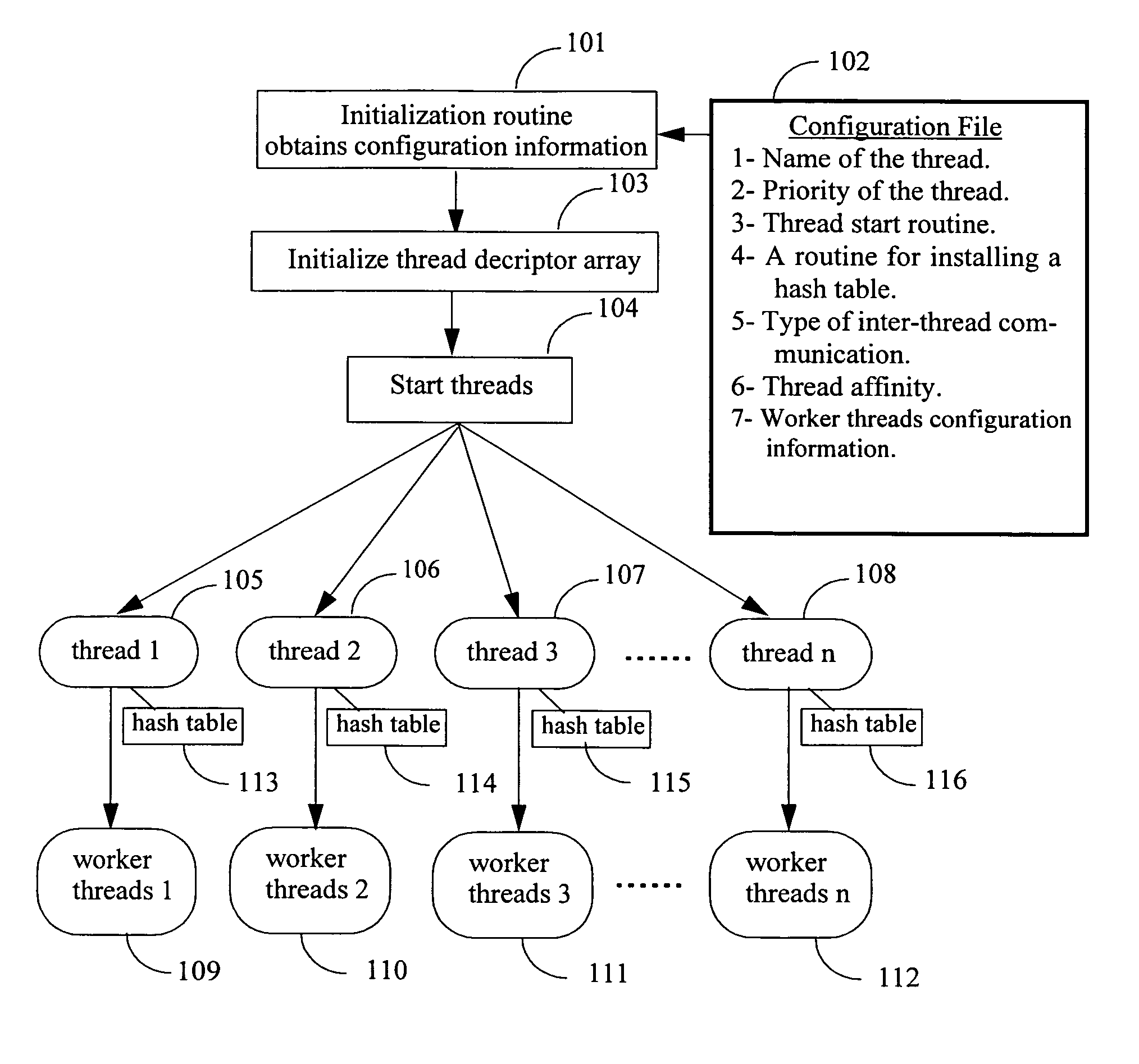
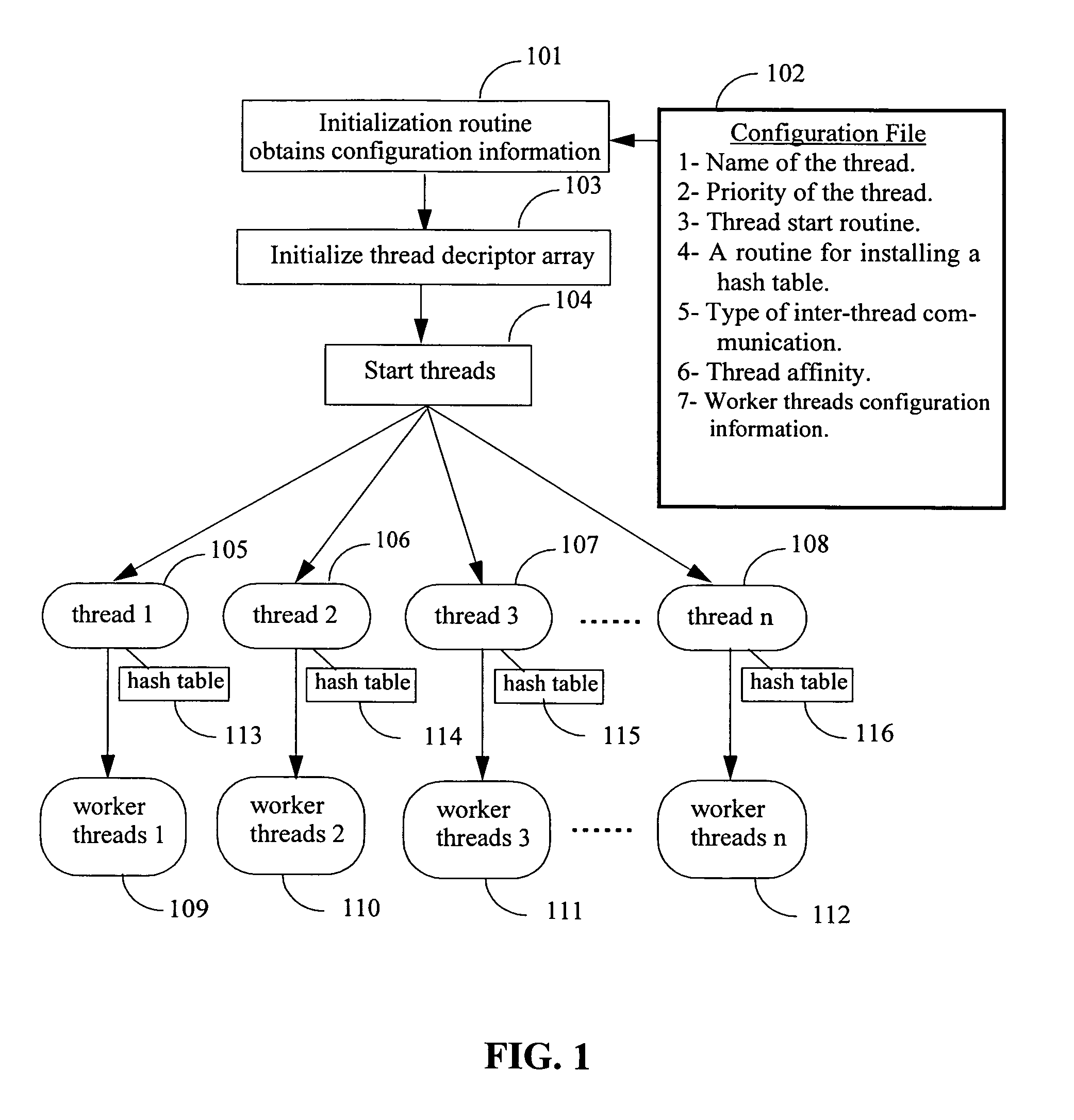
Method and system for managing lifecycles of deployed applications
Described is managing the changing of software implementations such as applications deployed to enterprise client users or machines. Precedence relationships between deployed applications are specified. To determine which applications to install for a given client, the precedence is applied to the subset of applications assigned or published to the client. At logon or machine reboot, an upgrade process evaluates the deployed applications and any upgrade relationships, setting applications for removal or installation. A user may also install an application that has been designated as optional. Also described is an application lifecycle model for replacing applications. For example, administrators can phase in upgrades as a pilot to a small group of users, roll out upgrades to a larger group, and then provide the application to all users. Upgrades may be mandatory or optional, and replaced programs may be removed and then replaced, or overlaid during installation.
Owner:MICROSOFT TECH LICENSING LLC
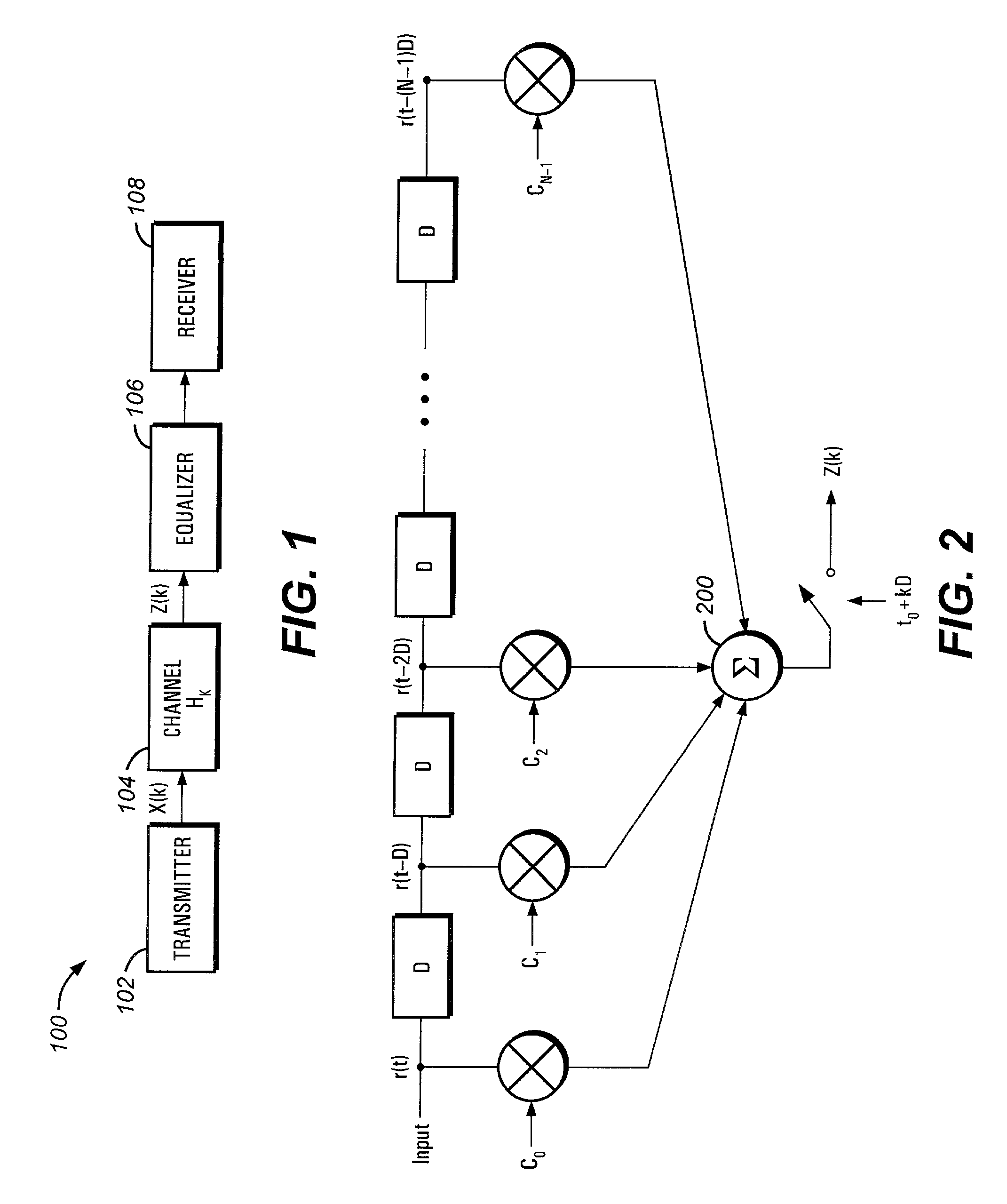
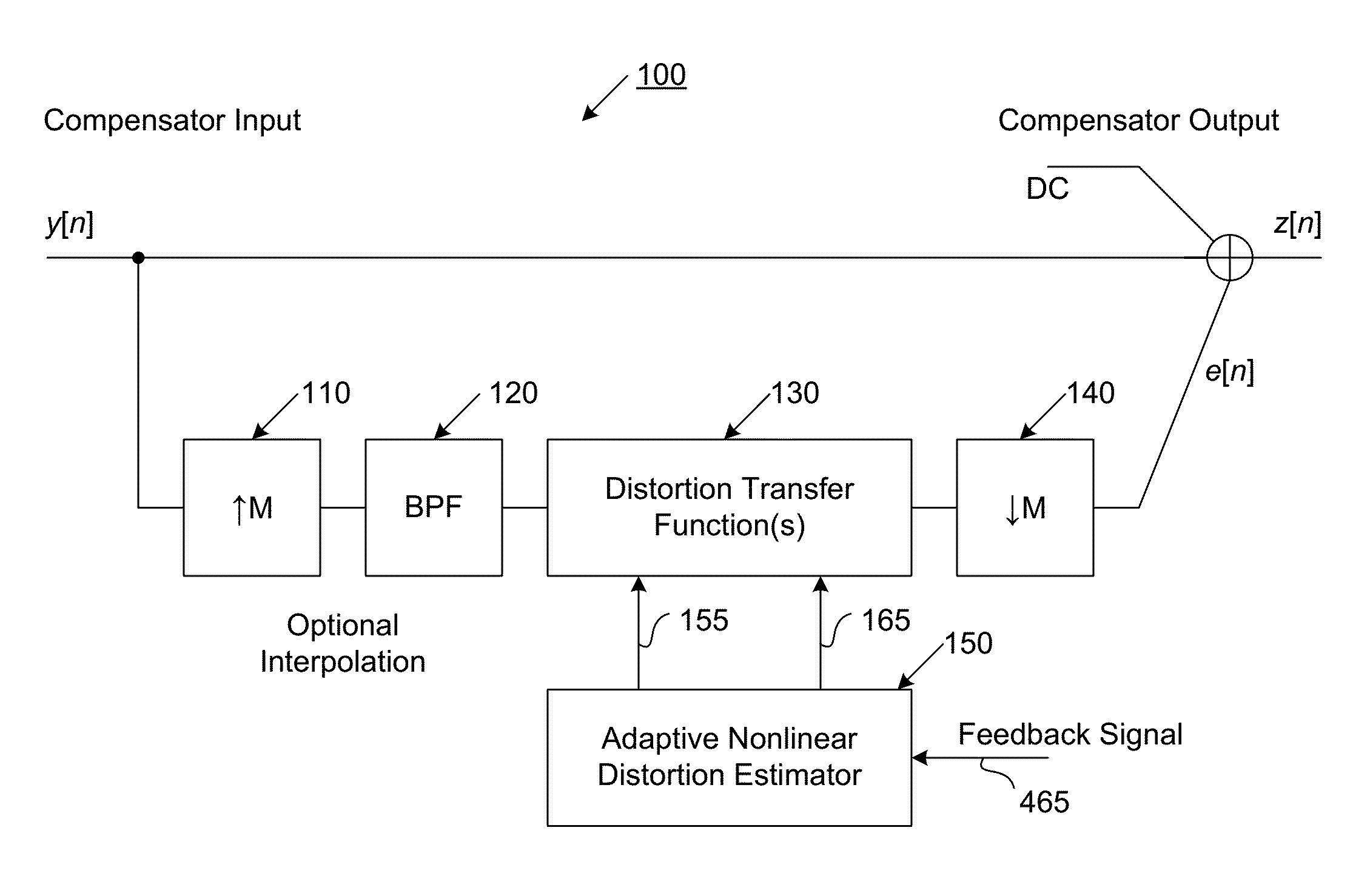
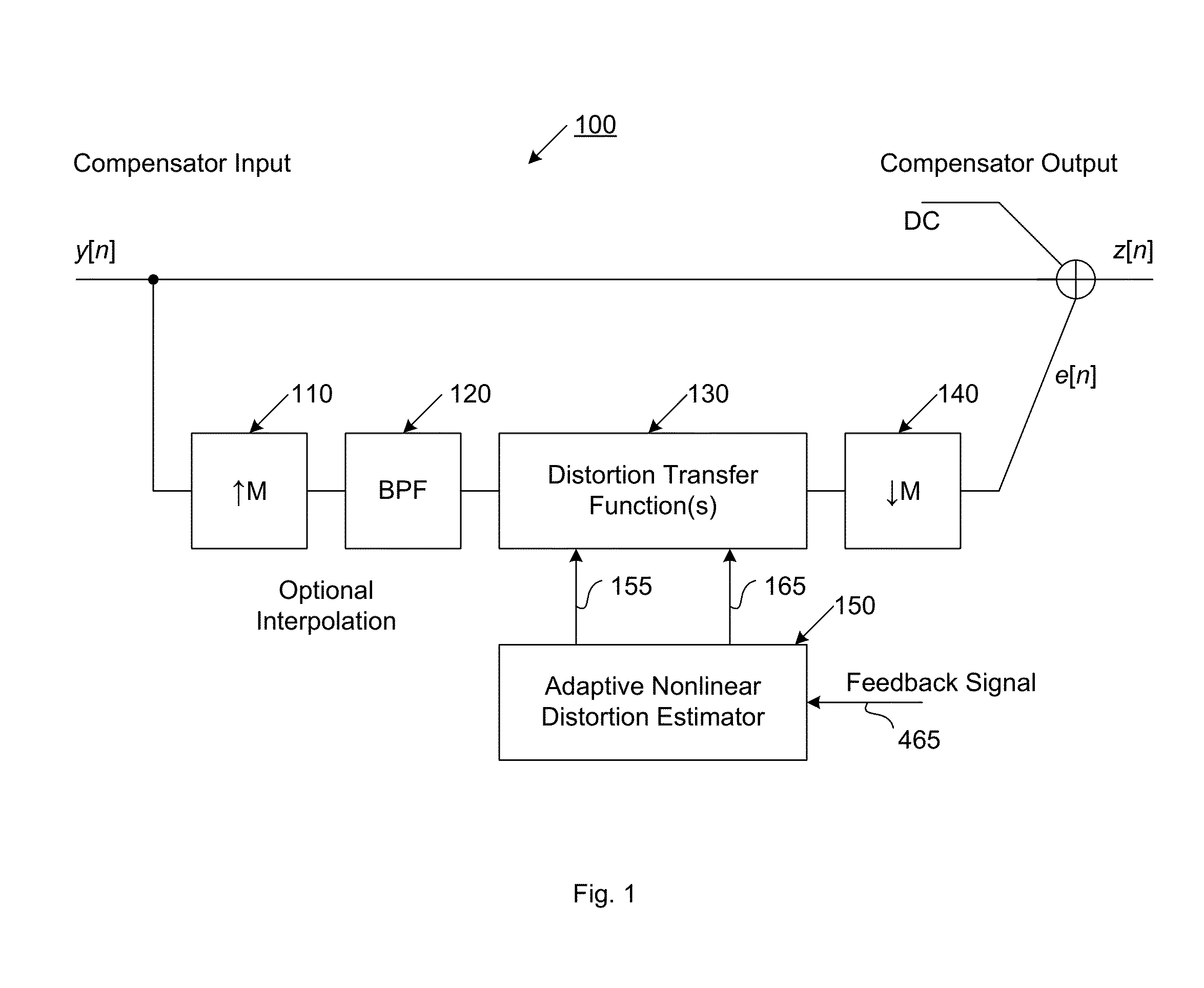
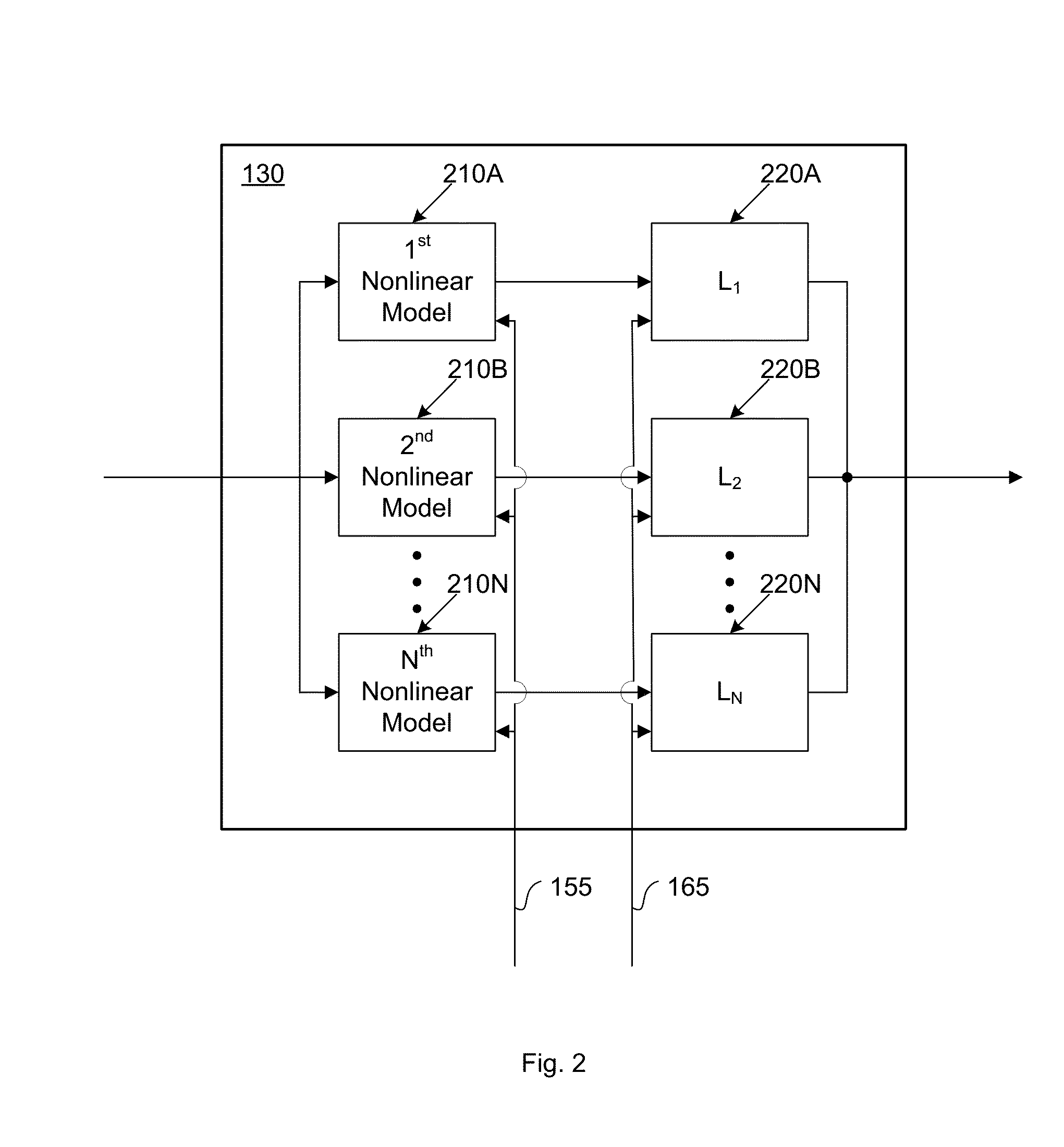
Compensator for removing nonlinear distortion
ActiveUS20160191020A1Easy to processReduce complexityChannel dividing arrangementsElectric signal transmission systemsNonlinear distortionComputation complexity
The present invention is a computationally-efficient compensator for removing nonlinear distortion. The compensator operates in a digital post-compensation configuration for linearization of devices or systems such as analog-to-digital converters and RF receiver electronics. The compensator also operates in a digital pre-compensation configuration for linearization of devices or systems such as digital-to-analog converters, RF power amplifiers, and RF transmitter electronics. The compensator effectively removes nonlinear distortion in these systems in a computationally efficient hardware or software implementation by using one or more factored multi-rate Volterra filters. Volterra filters are efficiently factored into parallel FIR filters and only the filters with energy above a prescribed threshold are actually implemented, which significantly reduces the complexity while still providing accurate results. For extremely wideband applications, the multi-rate Volterra filters are implemented in a demultiplexed polyphase configuration which performs the filtering in parallel at a significantly reduced data rate. The compensator is calibrated with an algorithm that iteratively subtracts an error signal to converge to an effective compensation signal. The algorithm is repeated for a multiplicity of calibration signals, and the results are used with harmonic probing to accurately estimate the Volterra filter kernels. The compensator improves linearization processing performance while significantly reducing the computational complexity compared to a traditional nonlinear compensator.
Owner:LINEARITY LLC
Methods, software and apparatus for detecting and neutralizing viruses from computer systems and networks
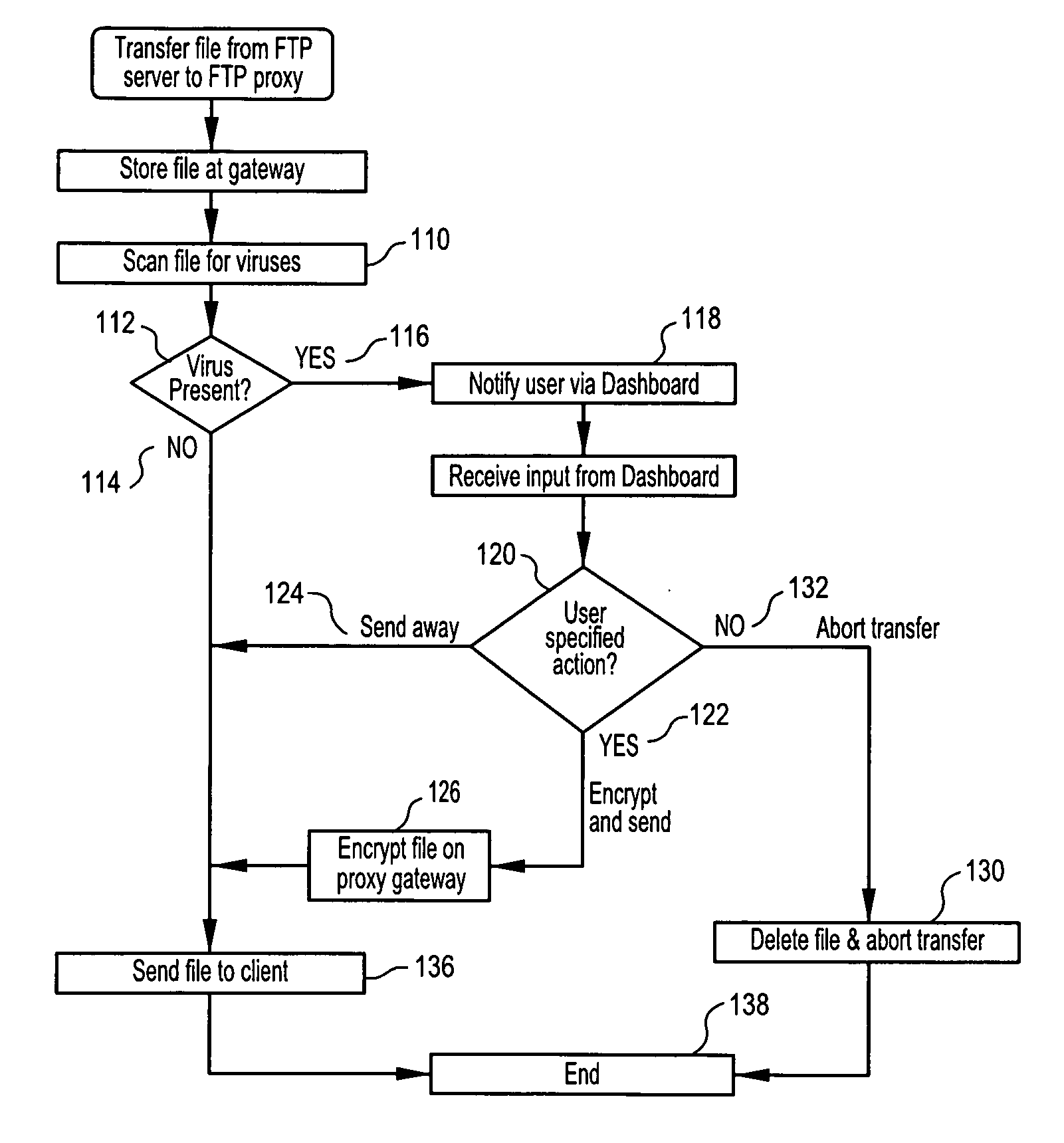
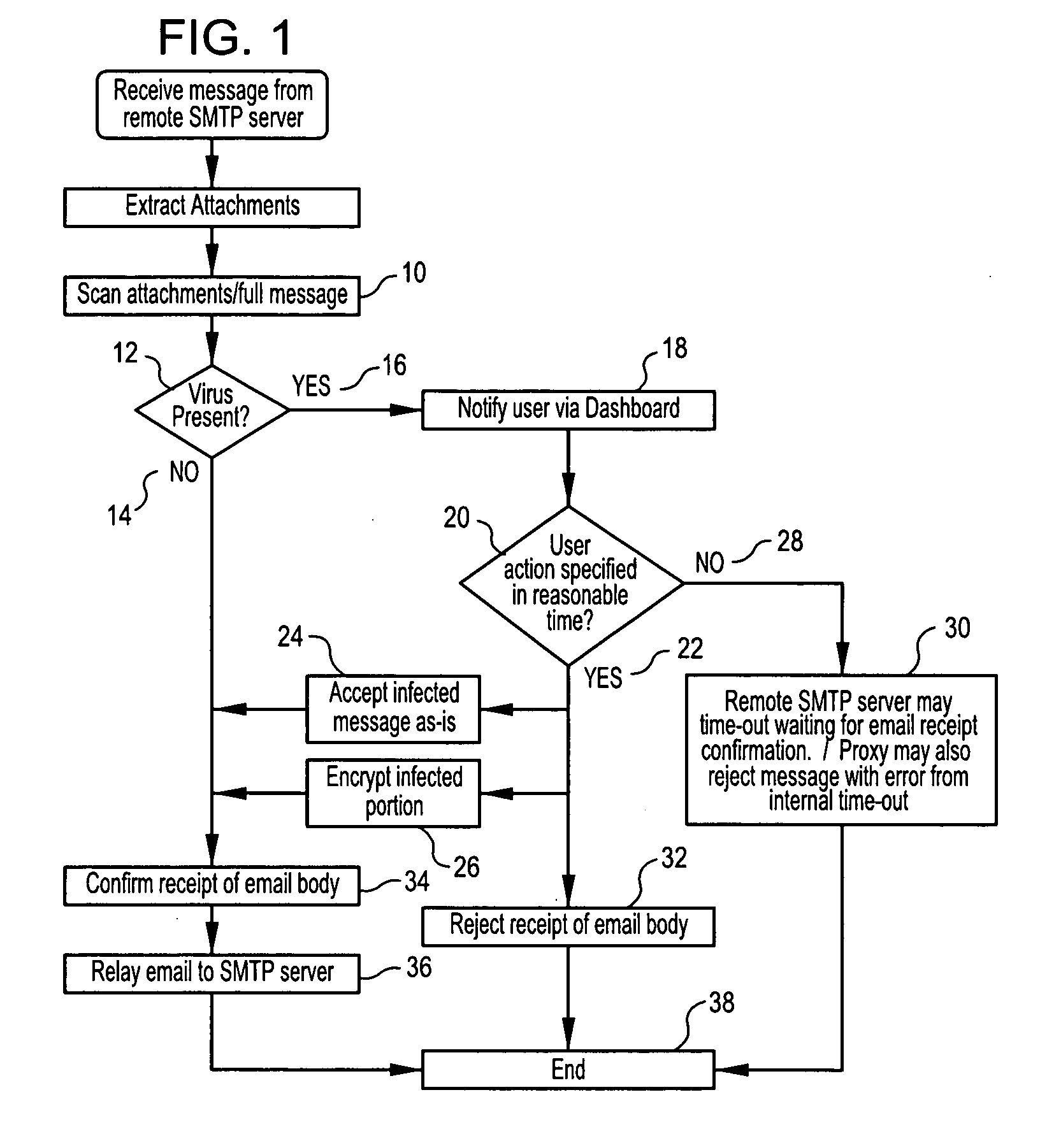
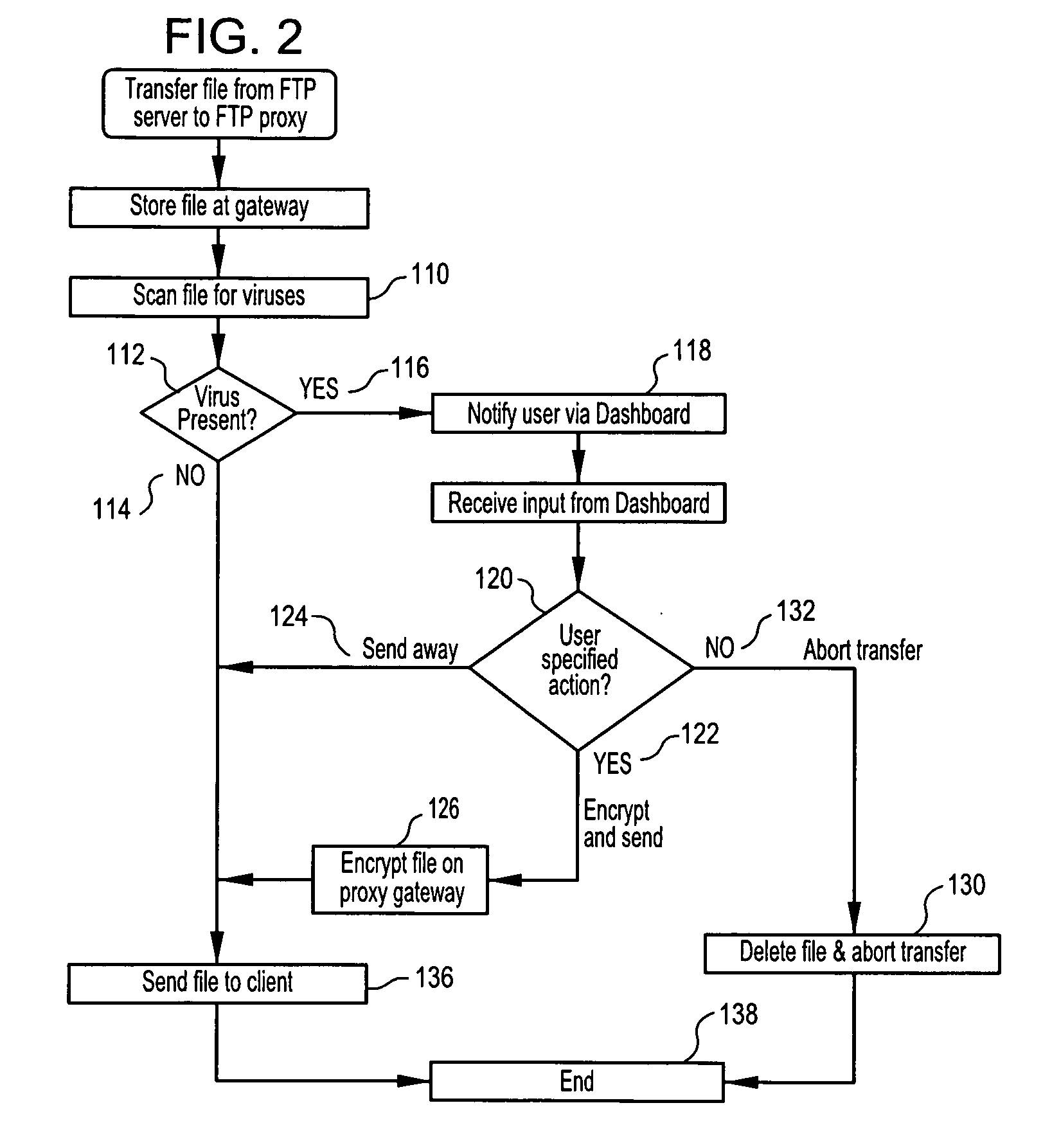
InactiveUS20080263670A1Minimizing chanceMitigating unwanted response time-outMemory loss protectionError detection/correctionData streamNetwork packet
Methods, software or computer programs, and apparatus for detecting viruses and mitigating their harm to computers communicating through a gateway node to another network are disclosed. Upon detection of a virus in an incoming data stream or plurality of data packets directed to a gateway device or node, the data requesting recipient is notified and provided with a plurality of pre-defined virus handling action options. If the recipient, or designated proxy, fails to select an action option, then a random selection is made. If a selection is made, then that selection, to the exclusion of other action options, is carried out. Thus, the recipient is empowered to dynamically select, as circumstances dictate and without future prejudice, the appropriate response upon detection of a particular virus. Action options may include data encryption and forwarding with recipient notification, or where email is the vector, attachment removal and location link insertion may be used. Software embodiments of the invention provide the machine readable instructions to carry out the methods according to the invention.
Owner:WIRESOFT OPERATING COMPANY
Application-level software watchdog timer
InactiveUS7000100B2Error detection/correctionData resettingCommunication interfaceOperational system
A software implementation of an application watchdog, comprising a restart service operating in the user mode and a watchdog driver operating in the kernel mode of a computer operating system. The driver incorporates a system thread configured to monitor a plurality of user applications operating in the user mode. The driver provides a first IOCTL signal interface for communicating control signals between the watchdog driver and one of the user applications and a second IOCTL signal interface for communicating control signals between the watchdog driver and the restart service. A communication interface exists for coordinating timer events with the operating system scheduler. If the system thread does not receive a message from one of said applications within an allotted period of time, the timer event alerts the watchdog driver that the allotted time has elapsed and the watchdog driver signals the restart service to restart that application.
Owner:HEWLETT PACKARD DEV CO LP
Sliding yardsticks fingerprint enrollment and verification system and method
InactiveUS6075876ALow costReduce memory requirementsCharacter and pattern recognitionComputer architectureImaging analysis
A fast position tolerant and economical fingerprint verification algorithm and software implementation is disclosed. The algorithm has very important advantages in comparison to existing fingerprint verification algorithms like minutia extraction or full image analysis based on a series of two dimensional fast Fourier transforms (FFT's) and two dimensional cross correlation in speed, compactness of the biocript and finger positioning for verification. It is based on a small "yardstick" pattern being moved inside the image to be verified, and when a match is found the rest of the verification process is started. The software code implements the algorithm in the most efficient way for utilization on a digital signal processor architecture. A main area of application is in fingerprint identification and verification, but it could be implemented with same success in other image verification systems like iris, eye, face etc., where two images should be compared. The algorithm is adaptive, so various false acceptance and false rejection coefficients could be utilized very easily. It also produces a very compact biocript, which leads to better memory utilization in fingerprint databases.
Owner:DRAGANOFF GEORGI HRISTOFF
Multi-threaded system for data management
InactiveUS8336056B1Easy to implementExpedites application developmentMultiprogramming arrangementsMemory systemsModularityData management
A multi-threaded system for data management and other computationally intensive applications. The invention takes advantage of multi-core processors to attain high performance. Multi-core processors provide high performance by executing programs in parallel. The amount of performance gained is strongly dependent on the software implementation. To take advantage of the multi-core architecture, applications should be multi-threaded. The invention provides a uniform, configurable, and a consistent multi-threaded software structure that increases performance by distribution of tasks and workload between threads and allocating threads to different processing units, so as to run programs in parallel. The uniform structure of the threads, the ease of configuring the software, and its modularity simplify execution of complex projects and expedite application development.
Owner:GADIR OMAR M A
Method and apparatus for authenticating a shipping transaction
InactiveUS6991174B2Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
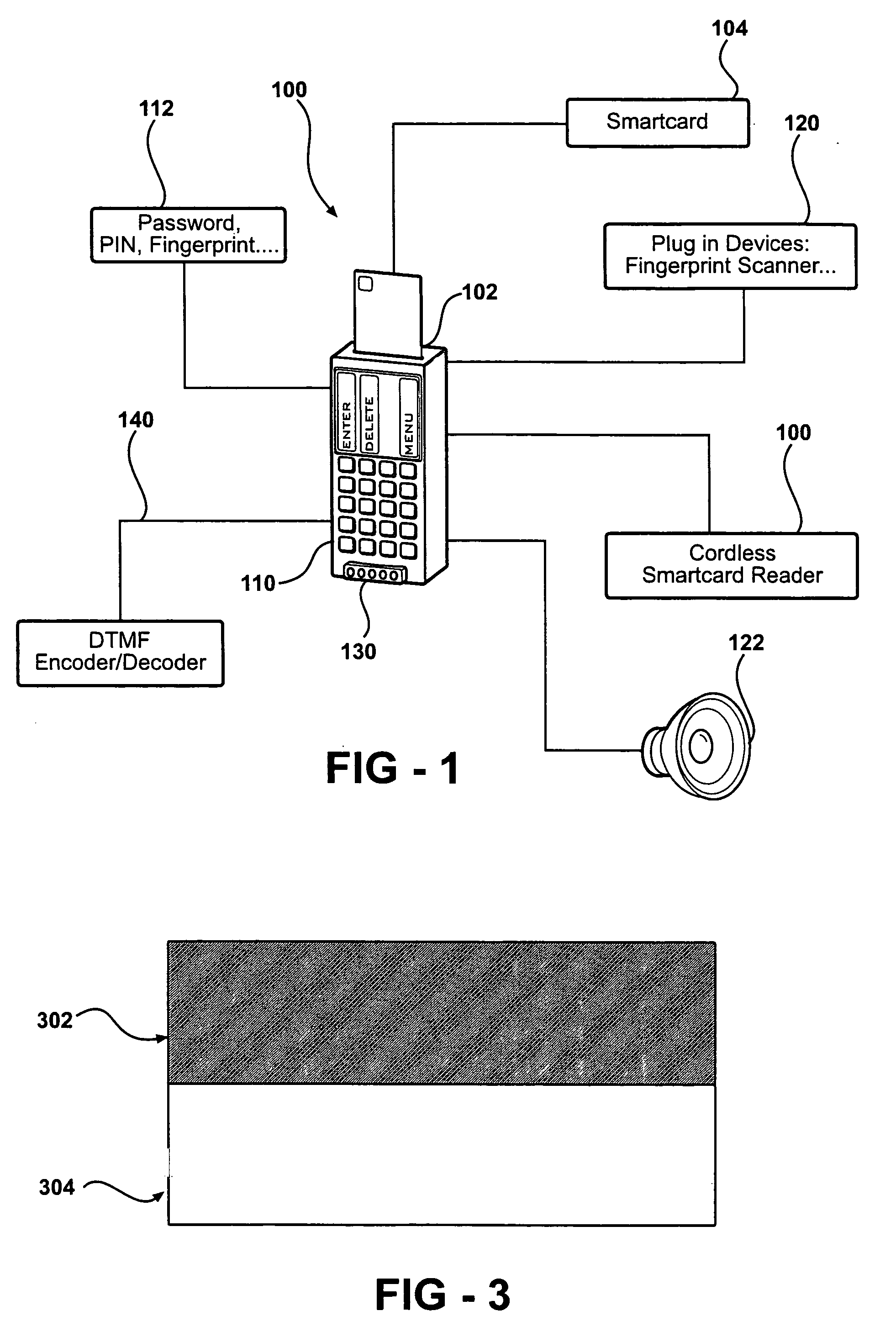
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. In essence, the device is a closed box with only two communication ports. The emulation of the device is therefore extremely complex due to the fact that it involves PKI and or identity-based encryption (IBE), key pair, elliptic curves encryption scheme, hardware serialization for communication and software implementation, in conjunction with a specific hardware embodiment and service usage infrastructure component that returns a response necessary for each unique transaction.
Owner:BRITE SMART
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com